| CHINA FOUNDATION.. | Panama | Panama | Panama Papers |
| CHINA FOUNDATION | Panama | Panama | Panama Papers |
| AMB CHINA | Not identified | Not identified | Offshore Leaks |
| CHINA LIMITED | Bahamas | | Bahamas Leaks |
| CHINA STORE | Aruba | | Paradise Papers |
| CHINA PACIFIC CONSTRUCTION (BVI) LIMITED-CHINA TREASURE | British Virgin Islands | Hong Kong | Panama Papers |
| THE CHINA CLUB CHINA INVESTMENT INCORPORATIONS) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA EVERGREEN INTERNATIONAL LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA MAINLAND INVESTMENTS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| VANGUARD CHINA HOLDINGS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA PROPERTY FUND LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA GEAR INTERNATIONAL LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| JOINDIN (CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA WISDOM INVESTMENT LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| RTI (CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA KEY INVESTMENTS LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA BROADBAND (BVI) CORP. | British Virgin Islands | Switzerland | Panama Papers |
| AEC CHINA LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA HOUSE HOLDINGS LIMITED | British Virgin Islands | Jersey | Panama Papers |
| CHINA BUSINESS COACHING LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA COL ENTERPRISES LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA RISE INVESTMENT LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA BASES (HOLDINGS) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| EURO-CHINA PROSPECTS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| SUPREME CHINA INTERNATIONAL LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA EYEWEAR CO. LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA CONCEPT MANAGEMENT LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA LAND PROPERTY LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA TELECOM (BVI) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA ASSOCIATES LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA DEVELOPMENT INTERNATIONAL CORPORATION | British Virgin Islands | Hong Kong | Panama Papers |
| TEXON CHINA HOLDINGS) LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA GOLD GROUP LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA PROSPEROUS INVESTMENTS LIMITED | British Virgin Islands | Isle of Man | Panama Papers |
| DORFORD (CHINA) LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| STANTEX CHINA LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA SUCCESS DEVELOPMENT LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| SPORTHATHLON CHINA LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA POWER HOLDINGS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA TREND LTD. | Samoa | Hong Kong | Panama Papers |
| UNISON GROUP (CHINA) LIMITED | Samoa | China | Panama Papers |
| FORTUNE HARDWARES (CHINA) INC. | Samoa | Hong Kong | Panama Papers |
| CHINA HYDRO COMPANY LIMITED | Samoa | Hong Kong | Panama Papers |
| CHINA RICH DEVELOPMENT LTD. | British Anguilla | Panama | Panama Papers |
| CHINA CHEN CO., LTD. | British Anguilla | Hong Kong | Panama Papers |
| CHINA JILONG GROUP CORPORATION | British Anguilla | Hong Kong | Panama Papers |
| OFFSHORE CONSULTANCY (CHINA) LTD. | Seychelles | Panama | Panama Papers |
| CHINA CONSULTANTS INTERNATIONAL LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA E-PHARM | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA FILM NETWORK LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA TALENT TRADING LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA ELEMENT INTERNATIONAL LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| GREENBACK CHINA HOLDING LTD | British Virgin Islands | Hong Kong | Panama Papers |
| SOLING CHINA) COMPANY LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA LIAISON LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| I-CHINA TECHNOLOGY, INC. | British Virgin Islands | Hong Kong | Panama Papers |
| EPL CHINA LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| ANGLO-CHINA LTD. | British Virgin Islands | Switzerland | Panama Papers |
| CHINA CONSULTANTS, INC. | British Virgin Islands | Hong Kong | Panama Papers |
| PICO INTERNATIONAL (CHINA) LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA GLORY INVESTMENTS LIMITED | British Virgin Islands | Isle of Man | Panama Papers |
| CHINA CLUB BEIJING LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| LUCKY CHINA) COMPANY LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CUSTOM COALS CHINA LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA LUCK LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| LOXLEY CHINA COMPANY LIMITED | British Virgin Islands | Isle of Man | Panama Papers |
| CHINA PLASTICS (H.K.) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA FOCUS INVESTMENTS LIMITED | British Virgin Islands | Isle of Man | Panama Papers |
| CHINA CENTURY PAPER LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| SIMSEN (CHINA) INVESTMENT LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA COSMOS HOLDINGS LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| T.A. CONSULTANTS (CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| SINO CENTURY (CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA LEGAL NETWORK.COM LTD. | British Virgin Islands | China | Panama Papers |
| VODATEL CHINA HOLDINGS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CELTERRA CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA OCEAN INTERNATIONAL LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| Main China Industrial Limited | Hong Kong | Panama | Panama Papers |
| CHINA SOURCE COMPANY LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA BRIGHT DEVELOPMENT LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| VODATEL CHINA LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA PEAK DEVELOPMENT LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA PU CORPORATION | British Virgin Islands | Taiwan | Panama Papers |
| NEW CHINA UNITED LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| KAM TAI (CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA GRAND PROPERTIES LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA FAME HOLDINGS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| EVERWING (CHINA) INVESTMENT LIMITED | British Virgin Islands | Isle of Man | Panama Papers |
| SHK CHINA INVESTMENT LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA FINANCE HOLDINGS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| BORNWELL CHINA INVESTMENTS LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| MULTIPLE CHINA HOLDINGS LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA DISTINCT INVESTMENTS LIMITED | British Virgin Islands | Isle of Man | Panama Papers |
| CHINA PRIME INVESTMENTS LIMITED | British Virgin Islands | Isle of Man | Panama Papers |
| China Card Services Ltd. | British Virgin Islands | Luxembourg | Panama Papers |
| QBM CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| BBI CHINA BEACH, LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA EAGLE LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA FOOD PROCESSING LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA GAIN CONSULTANTS LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA FOOD SERVICES LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA HONOR INTERNATIONAL LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| AWT CHINA LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| INTERNATIONAL INDUSTRIES (CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA RICH HOLDINGS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| MACRO CHINA LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA INFORMATION GROUP LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA TOP HOLDINGS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| FIRST CHINA CAPITAL LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA XINSHIDAI HOLDINGS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| IAA CHINA LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| Bioscor China Holding Ltd. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA VICTORY ENTERPRISES LIMITED | British Virgin Islands | Singapore | Panama Papers |
| SATORI INVESTMENTS (CHINA) LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| China Finance Limited | Samoa | Singapore | Panama Papers |
| CHINA WORLD TRADE CORPORATION | British Virgin Islands | Hong Kong | Panama Papers |
| ZHONGWANG CHINA INVESTMENT LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| GLOBAL ENTERPRISE CHINA LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| China Concrete Corporation | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA CHANCE LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA INDUSTRY (HK) LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA CHANCE ENTERPRISES LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| RICHWIN CHINA CORPORATION | British Virgin Islands | Hong Kong | Panama Papers |
| AO FREIGHT (CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| AEC CHINA HOLDINGS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| SEANA INTERNATIONAL (CHINA) LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| RAISER CHINA LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| ASHBY RECOVERIES (CHINA) LIMITED | British Virgin Islands | China | Panama Papers |
| CHESFER HOLDINGS ( CHINA ) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| ROAD & BRIDGE (CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA TOP INVESTMENT LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| SM CHINA CO., LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CENTRAL CHINA MINERALS LTD | British Virgin Islands | United Kingdom | Panama Papers |
| CHINA SOURCE HOLDINGS LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA PERFECT INTERNATIONAL LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA CHANCE LIMITED | Bahamas | Panama | Panama Papers |
| FIRST CHINA RESOURCES LTD. | Bahamas | Singapore | Panama Papers |
| MOSIA (CHINA) LIMITED | Seychelles | Hong Kong | Panama Papers |
| Nichiaka South China Limited | Seychelles | Hong Kong | Panama Papers |
| CHINA EAGLE HOLDINGS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA WISH GROUP LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| ELTRA CHINA LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| Clean Coal China Limited | British Virgin Islands | Panama | Panama Papers |
| China -I Limited | British Virgin Islands | United Kingdom | Panama Papers |
| CHINA WEALTH HOLDING LTD | British Virgin Islands | China | Panama Papers |
| West China Investment Limited | British Virgin Islands | Hong Kong | Panama Papers |
| GOLDHARVEST CHINA LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| China General Aviation Ltd. | British Virgin Islands | Hong Kong | Panama Papers |
| China Dream Equine Limited | British Virgin Islands | Singapore | Panama Papers |
| CHINA WINE INC. | Bahamas | Taiwan | Panama Papers |
| CHINA SEA MARITIME S.A. | Panama | Hong Kong | Panama Papers |
| Sunflower (CHINA) Investment Ltd. | British Virgin Islands | China | Panama Papers |
| UNITED CHINA INTERNATIONAL LIMITED | Bahamas | Hong Kong | Panama Papers |
| BEAUTY CHINA INTERNATIONAL LTD. | Seychelles | China | Panama Papers |
| BEAUTY CHINA MANAGEMENT LTD. | Seychelles | Panama | Panama Papers |
| NEW CHINA MANAGEMENT LTD. | Seychelles | Hong Kong | Panama Papers |
| CHINA WELFARE FOUNDATION LTD. | Niue | Taiwan | Panama Papers |
| CHINA FRANCHISES S.A. | Panama | Switzerland | Panama Papers |
| WINCO CHINA) LIMITED | Niue | Hong Kong | Panama Papers |
| CHINA FORTUNE INVESTMENTS LIMITED | British Virgin Islands | Isle of Man | Panama Papers |
| CHINA CAPITAL INVESTMENTS LIMITED | British Virgin Islands | Isle of Man | Panama Papers |
| NEWTOP (CHINA) INVESTMENT LTD. | Niue | Hong Kong | Panama Papers |
| CHINA TELECOM (TIANJIN) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| OCEAN CITY (CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA INDUSTRIAL HOLDINGS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| VIGERS CHINA LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA NEWMEDIA INC. | British Virgin Islands | Hong Kong | Panama Papers |
| TAKLAND SURVEYORS (CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| ZENITH HOTEL (CHINA) INC. | British Virgin Islands | Hong Kong | Panama Papers |
| UNITON CONSULTANT CHINA LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA PROPERTY ADVISORS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| Neo-China Investment Limited | British Virgin Islands | Hong Kong | Panama Papers |
| Neo-China Technology Limited | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA PEAK HOLDINGS LIMITED | British Virgin Islands | Jersey | Panama Papers |
| CHINA AVIATION INVESTMENT CORP. | British Virgin Islands | Hong Kong | Panama Papers |
| MEDICALAUNDRY INTERNATIONAL (CHINA) LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA CHANCE MANAGEMENT LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| GIGAMEDIA CHINA LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA REACH LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| RED HOUSE CHINA LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA CRYSTAL TRADING LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| ITOI China Inc. | British Virgin Islands | Hong Kong | Panama Papers |
| LEADING CHINA GROUP LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| China President Holding Ltd | British Virgin Islands | Hong Kong | Panama Papers |
| China Sea Holdings Limited | British Virgin Islands | Jersey | Panama Papers |
| TRIUMPH (CHINA) FINANCIAL LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| HENSE (CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA LIPU PAPER LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA CONIK TRADING LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA ORGANIC AGRICULTURE LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA MEDICAL FINANCE LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA STRATEGIC ALLIANCE LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| China Tea Holdings Ltd | British Virgin Islands | Singapore | Panama Papers |
| CARBON POSITIVE CHINA LIMITED | British Virgin Islands | Singapore | Panama Papers |
| CHINA WILL INVESTMENT LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| China Group Investors Limited | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA WISDOM DEVELOPMENT LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA FORAGE HOLDING LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA PURCHASE INC. | British Virgin Islands | China | Panama Papers |
| FARMER (CHINA) LIMITED | British Virgin Islands | China | Panama Papers |
| ALLIED CHINA INVESTMENTS LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA ORIGIN INVESTMENT LTD | British Virgin Islands | Hong Kong | Panama Papers |
| Heng Wei China Ltd. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA KOCODA TECHNOLOGY LTD | British Virgin Islands | China | Panama Papers |
| CHINA OCEAN ENTERPRISES LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| Rising Sun China Ltd. | British Virgin Islands | Hong Kong | Panama Papers |
| Sportscorp Management China Limited | British Virgin Islands | Hong Kong | Panama Papers |
| China Gold Reserve Limited | British Virgin Islands | Hong Kong | Panama Papers |
| China Square Industrial Limited | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA BAICAOTANG MEDICINE LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| China United Logistics Corporation | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA METAL INVESTMENT LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| NEW CHINA DOOR LTD | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA FULLBEST INTERNATIONAL LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| Sportscorp China Limited | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA COFFEE COMPANY LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA DOORMEDIA HOLDING LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA CHEN CO., LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| China Machinery Group Limited | Hong Kong | Hong Kong | Panama Papers |
| CHINA SKYWORK INVESTMENT LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA LUXE TRADING LIMITED | Hong Kong | Uruguay | Panama Papers |
| SUMCABLE (CHINA) CO., LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| MILLION CHINA INVESTMENTS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA FOCUS MOTORS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA STONE LIMITED | Hong Kong | Panama | Panama Papers |
| TRUE CHINA LIMITED | British Virgin Islands | Singapore | Panama Papers |
| CHINA BRIGHT TRANSPORTATION LIMITED | British Virgin Islands | Bahamas | Panama Papers |
| Sunrise Pharmaceuticals China, Ltd. | British Virgin Islands | Hong Kong | Panama Papers |
| Casa (China) Co., Ltd. | British Virgin Islands | China | Panama Papers |
| COMBEST CHINA) GROUP LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| China Tianhai Group Limited | British Virgin Islands | Hong Kong | Panama Papers |
| First China Enterprises Limited | Hong Kong | Switzerland | Panama Papers |
| China Glorious Capital Limited | British Virgin Islands | Hong Kong | Panama Papers |
| FOREVER CHINA LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA GATE GROUP LIMITED | British Virgin Islands | Isle of Man | Panama Papers |
| CHINA CONSULTANCY SERVICES LIMITED | British Virgin Islands | Guernsey | Panama Papers |
| CHINA WAVE INVESTMENTS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| UNION CHINA INTERNATIONAL LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA CENTURY HOLDINGS LIMITED | British Virgin Islands | Philippines | Panama Papers |
| CHINA CORE LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| HERITAGE NORTH CHINA LIMITED | British Virgin Islands | Guernsey | Panama Papers |
| CHINA BEST FOOD LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA CHANCE TRADING LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| AAFM CHINA) LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA TREND HOLDINGS LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA BPV CO., LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| Neo-China Development Limited | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA SHINE GROUP LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| ENRICH ENTERPRISES CHINA LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA DIGITAL HOLDING LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| BEL TRADE CHINA LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA VENTURE INTERNATIONAL LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA UNITED SECURITIES LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA GRAND INVESTMENT LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA PROSPECT INC. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA NET-PC LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA INSPECTION COMPANY LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| SiCOM China Limited | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA PEOPLE INTERNATIONAL LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| SATAREM CHINA LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA OCEAN LINE LTD. | British Virgin Islands | Singapore | Panama Papers |
| GREATER CHINA TECHNOLOGY LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| TECH TEAM CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA FUTURE CONSORTIUM LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| Tonix China Ltd. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA WISE DEVELOPMENT LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA PORTS TRANSPORTATION LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CNT HOLDINGS (CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| MAN CHINA CORP. | British Virgin Islands | Hong Kong | Panama Papers |
| WORTH CHINA CO., LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| YF GROUP (CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA SUNSHINE HOLDINGS LIMITED | British Virgin Islands | Singapore | Panama Papers |
| CHINA WHEEL GROUP LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| INTERNATIONAL HOUSE CHINA LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| M.POS (CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA SPIRIT LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| TIME WHEEL (CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| WILSON GROUP CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA MAGIC TRADING LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| GRAND CHINA INTERNATIONAL LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| ANGLOGOLD CHINA HOLDINGS LIMITED. | British Virgin Islands | Panama | Panama Papers |
| CHINA STONE INVESTMENTS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA INTERNET SERVICES CORPORATION | British Virgin Islands | Hong Kong | Panama Papers |
| FOREVER CHINA MANAGEMENT LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| Neo-China Property Limited | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA WISDOM MANAGEMENT LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| SOLARTRON MOBREY CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| AIC CHINA) ENTERPRISES LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA PAYMENT HOLDINGS LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| MICROFORM CHINA LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA LIUHE INVESTMENTS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| PVCG (CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| AMTRONIX CHINA LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA JOYCE INTERNATIONAL LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA FINE SPORTS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA WAVE LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA TALENT MANAGEMENT LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| HARTCOURT CHINA INC. | British Virgin Islands | Hong Kong | Panama Papers |
| Neo-China Management Limited | British Virgin Islands | Hong Kong | Panama Papers |
| BESTFOOD CHINA LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA API LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| China Financial Partners Ltd. | British Virgin Islands | Hong Kong | Panama Papers |
| China Project Shipping Limited | British Virgin Islands | Hong Kong | Panama Papers |
| China Yangtze Capital Corporation | British Virgin Islands | Hong Kong | Panama Papers |
| LMI-China Limited | British Virgin Islands | Hong Kong | Panama Papers |
| China Silk Ltd. | British Virgin Islands | China | Panama Papers |
| InternetSpeech China Ltd. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA REINV PARTNERS, L.P. | British Virgin Islands | Switzerland | Panama Papers |
| China Progress Investments Ltd | British Virgin Islands | Singapore | Panama Papers |
| China Streaming Co., Ltd. | British Virgin Islands | Hong Kong | Panama Papers |
| MAYA GROUP (CHINA) LIMITED | British Virgin Islands | China | Panama Papers |
| AMERICA CHINA INVESTMENT INC. | British Virgin Islands | Hong Kong | Panama Papers |
| China Museum Company Ltd. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA BAONENG GROUP LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA DIRECT LTD. | Bahamas | Hong Kong | Panama Papers |
| CHINA RISING INC. | Bahamas | Hong Kong | Panama Papers |
| CHINA ENERGY LIMITED | Samoa | Hong Kong | Panama Papers |
| CHINA STAR CORPORATION LIMITED | Bahamas | Isle of Man | Panama Papers |
| CHINA OCEAN DEVELOPMENT LTD. | Bahamas | Hong Kong | Panama Papers |
| CHINA LINE INTERNATIONAL LTD. | Bahamas | China | Panama Papers |
| Invest China Development Ltd | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA MARITIME SERVICES LTD | British Virgin Islands | Hong Kong | Panama Papers |
| China Blueberry Holdings Limited | British Virgin Islands | Hong Kong | Panama Papers |
| BEST CHINA ENTERPRISES LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| NAR China Group Limited | British Virgin Islands | Hong Kong | Panama Papers |
| GREATER CHINA CONSULTANTS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA TONGSHANG LTD | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA FALCON INTERNATIONAL LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| ALADDIN (CHINA) INTERNATIONAL LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| ASIA DEKOR (CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| South China Investment Limited | Hong Kong | Hong Kong | Panama Papers |
| China Escrow Services Inc. | British Virgin Islands | Hong Kong | Panama Papers |
| SHEEN CHINA HOLDINGS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| A.S.H. CHINA LIMITED | Hong Kong | Jersey | Panama Papers |
| China Wines Limited | British Virgin Islands | Hong Kong | Panama Papers |
| Ecoron (China) Limited | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA TOPPER LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| China Industrial Products Limited | British Virgin Islands | Hong Kong | Panama Papers |
| China United Communication Limited | British Virgin Islands | China | Panama Papers |
| China Freeze-Dry Inc. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA CINDA INVESTMENT LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA VITUP INVESTMENT LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA FANTASTIC GROUP LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| SILVER CHINA DEVELOPMENT LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA INVESTMENT CAPITAL LIMITED | British Virgin Islands | Singapore | Panama Papers |
| China Xinghuacun Wines Limited | British Virgin Islands | Hong Kong | Panama Papers |
| BAX (CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| China Dredger Group Limited | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA WAY HOLDINGS LIMITED | Bahamas | Hong Kong | Panama Papers |
| CHINA INDIGENOUS INC. | Bahamas | Guernsey | Panama Papers |
| COLONEL FOODS CHINA, LTD. | Bahamas | Hong Kong | Panama Papers |
| WAY CHINA ENTERPRISE LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| WIDER YACHT CHINA LIMITED | British Virgin Islands | Jersey | Panama Papers |
| DIAMOND TRADING CHINA LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| RICHTOY CHINA LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA PLUS LOGISTICS LTD | British Virgin Islands | Hong Kong | Panama Papers |
| China Dream Capital, LTD | British Virgin Islands | China | Panama Papers |
| CHINA TIDA LTD | British Virgin Islands | Hong Kong | Panama Papers |
| Peak China Property Ltd. | British Virgin Islands | Hong Kong | Panama Papers |
| SHINE RICH (CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA CONSTRUCTION AMERICA, INC. | Panama | Bahamas | Panama Papers |
| PYI CHINA HOLDING LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| SMART CHINA DEVELOPMENT LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| Hengqin China Investment Corporation | British Virgin Islands | Hong Kong | Panama Papers |
| Duet China Limited | British Virgin Islands | United Kingdom | Panama Papers |
| Prime Focus China Limited | British Virgin Islands | Hong Kong | Panama Papers |
| SIMZONE CHINA CO., LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| Great Trend (China) Limited | British Virgin Islands | Brazil | Panama Papers |
| GVA (China) Holdings Limited | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA PACIFIC MARITIME LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| Cumulative (China) Co., LTD | British Virgin Islands | Hong Kong | Panama Papers |
| China Africa Shipline Limited | Seychelles | Hong Kong | Panama Papers |
| China Investment Holdings Inc. | Seychelles | China | Panama Papers |
| GUTS ELECTROMECH CHINA LIMITED | Seychelles | Hong Kong | Panama Papers |
| RINCHEN INDUSTRIAL (CHINA) LIMITED | Seychelles | Hong Kong | Panama Papers |
| SUNTTON (CHINA) CO., LIMITED | Seychelles | Hong Kong | Panama Papers |
| BIZ CHINA LIMITED | Seychelles | Hong Kong | Panama Papers |
| CHINA NEW DEVELOPMENT LIMITED | Seychelles | Hong Kong | Panama Papers |
| CHINA POLYESTER PRODUCTS CORPORATION | Seychelles | Hong Kong | Panama Papers |
| CHINA SHANDONG GROUP LTD. | Seychelles | Hong Kong | Panama Papers |
| China Markets Group Limited | Seychelles | Thailand | Panama Papers |
| Silantes (China) Corporation | Seychelles | Hong Kong | Panama Papers |
| Eastern Fishing China Limited | Seychelles | Hong Kong | Panama Papers |
| Maxwise Production (China) Limited | Seychelles | Hong Kong | Panama Papers |
| CHINA LINK INTERNATIONAL LTD. | Seychelles | Hong Kong | Panama Papers |
| China Pacific Maritime Inc. | Seychelles | Hong Kong | Panama Papers |
| CHINA CAPITAL ENTERPRISES CORPORATION | Seychelles | Hong Kong | Panama Papers |
| FUMAN INTERNATIONAL (CHINA) LIMITED | Seychelles | China | Panama Papers |
| BRIGHTER CHINA INVESTMENT LIMITED | Seychelles | Hong Kong | Panama Papers |
| Chic Products (China) Ltd. | British Anguilla | Hong Kong | Panama Papers |
| CHINA ONO INTERNATIONAL LIMITED | British Anguilla | Hong Kong | Panama Papers |
| Aoshi International (China) Ltd. | British Anguilla | Hong Kong | Panama Papers |
| CHINA STAR CAPITAL LIMITED | Niue | Singapore | Panama Papers |
| CHINA FORUM LIMITED | Niue | Hong Kong | Panama Papers |
| CHINA UNITY DEVELOPMENT INC. | Niue | Hong Kong | Panama Papers |
| CHINA HOLDING MANAGEMENT S.A. | Niue | Lebanon | Panama Papers |
| FIAN (CHINA) INC. | Niue | Hong Kong | Panama Papers |
| TRINITY TECHNOLOGY CHINA LIMITED | Niue | Hong Kong | Panama Papers |
| GREAT CHINA INTERNATIONAL LIMITED | Niue | Hong Kong | Panama Papers |
| China Consultants Corporation | Samoa | China | Panama Papers |
| BEST CHINA INTERNATIONAL LIMITED | Samoa | Hong Kong | Panama Papers |
| CHINA INCORPORATIONS LIMITED | Samoa | China | Panama Papers |
| China Ruifeng Co., Ltd. | Samoa | Hong Kong | Panama Papers |
| China Sports Network Limited | Samoa | Hong Kong | Panama Papers |
| Longbridge Industrial (China) Ltd. | Samoa | Hong Kong | Panama Papers |
| CHINA HEALTH (USA) LIMITED | Nevada | Hong Kong | Panama Papers |
| CHINA PINE GROUP LTD. | Samoa | Hong Kong | Panama Papers |
| China Solutions Limited | Samoa | Hong Kong | Panama Papers |
| China Newsky Industry Ltd. | Samoa | Hong Kong | Panama Papers |
| CHINA JILONG GROUP CORPORATION | Samoa | Hong Kong | Panama Papers |
| China Concept International Limited | Samoa | China | Panama Papers |
| BOSEN (CHINA) HOLDING LIMITED | Nevada | Hong Kong | Panama Papers |
| INDO CHINA INVESTMENTS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA INTERNATIONAL LTD. | Samoa | Hong Kong | Panama Papers |
| TECTANE CHINA CORPORATION | Samoa | China | Panama Papers |
| CHINA HOLDING MANAGEMENT S.A. | Samoa | Lebanon | Panama Papers |
| GREAT CHINA INTERNATIONAL LIMITED | Samoa | Hong Kong | Panama Papers |
| CHINA UNITY DEVELOPMENT INC. | Samoa | Hong Kong | Panama Papers |
| ICE-TV (China) Ltd. | Samoa | China | Panama Papers |
| CHINA TOP GROUP LTD. | Samoa | Panama | Panama Papers |
| PASSION CHINA LIMITED | Samoa | Hong Kong | Panama Papers |
| CHINA FAITH LIMITED | Samoa | Hong Kong | Panama Papers |
| China Jiangsu International Corp. | Samoa | Hong Kong | Panama Papers |
| CONTAI (CHINA) INVESTMENT LIMITED | Samoa | Hong Kong | Panama Papers |
| China International Investment Ltd | Samoa | Hong Kong | Panama Papers |
| China Sports Technology Inc. | Samoa | Hong Kong | Panama Papers |
| China Sports Media Corporation | Samoa | Hong Kong | Panama Papers |
| ALLIED CHINA ENTERPRISES LIMITED | Samoa | Hong Kong | Panama Papers |
| VAST CHINA GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA SUPPLY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| American Food (China) Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Laser Computer (China) Limited | Labuan | Malaysia | Offshore Leaks |
| CHINA MIFENG TRADE CORP. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA PRIVILEGE INTERNATIONAL LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Ascott Holding (China) Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA HONOUR MANAGEMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| WILLIS PUBLICITY (CHINA) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA GLOBAL CONSTRUCTION LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA GOOD TECHNOLOGY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Communication Limited | Samoa | Samoa | Offshore Leaks |
| Just Do China Inc. | Samoa | Samoa | Offshore Leaks |
| HAITIAN (CHINA) INTERNATIONAL LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| WORLDTRADE (CHINA) LIMITED | Hong Kong | Not identified | Offshore Leaks |
| Destination China Co., Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA CONCEPT MANAGEMENT LIMITED | Samoa | Samoa | Offshore Leaks |
| China Asean Investment Inc. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| WEALTH CHINA TRADING LIMITED | Samoa | Samoa | Offshore Leaks |
| HANSCENT (CHINA) CO., LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| GC Investment (China) Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA BAY INVESTMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA CONCEPT GROUP LIMITED | Samoa | Samoa, Hong Kong | Offshore Leaks |
| COUNTRY HEIGHTS CHINA LTD | Labuan | Malaysia | Offshore Leaks |
| CHINA RIVER LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Smart Media Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| AMBER TOOLING CHINA LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA TRADER HOLDINGS LTD | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA SUPERSTRUCTURE CONSULTANCY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| PERFECT CHINA ENTERPRISES LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA INTERMODAL LTD | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA CONCEPTS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA WORLD INVESTORS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| ADI China Services Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA PROSPERITY HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA TRADE ENTERPRISES LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| SHINNING CHINA INVESTMENTS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Triumph (China) Financial Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA VIEW FINANCIAL LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA HARVEST HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| GRAND CHINA TRADING LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA JADE SECURITIES LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA SECURITIES INFRASTRUCTURE LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA SKY DEVELOPMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| MASTERLINE (CHINA) GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA COMMERCE LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| EASTVIEW (CHINA) GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| MOVIOLA (CHINA) PRODUCTIONS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA CHANNEL LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA LINK HOLDING LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA VIEW GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA FAITH SECURITIES LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA BRIGHT COMPANY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA STRENGTH INVESTMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA ASSETS INVESTMENTS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Che San (China) Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA HEALTH HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA DEVELOPMENT GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| GRAND CHINA HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CYBER CHINA INC. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China E-Net.com Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA RESOURCE PRODUCTS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Probability China Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA TOP GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA LINK TECHNOLOGIES LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| NEW CHINA SERVICES LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA DIRECT BUY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA NETWORKS EDUCATION LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA JADE INVESTMENT CORPORATION | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA GAS CONSTRUCTION LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA GRAND INTERNATIONAL LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| BERNARDO FASHIONS (CHINA) LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA DOLL LIMITED | British Virgin Islands | Cayman Islands, British Virgin Islands | Offshore Leaks |
| TRIGLOBAL CHINA HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| KMB (China) Holdings Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Concept International Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Media LLP Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA GAS PIPELINE LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Rhenfield (China) Investment Corporation | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA TIMES CONSULTANCY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA SMART HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA BIOTECHNOLOGY, INC. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China DongGuan Networks, Inc. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Transfield Resources (China) Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA STRATEGY CONSULTANCY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| RISE EXCEL (CHINA) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Entertainment Holdings Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA LOYAL DEVELOPMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| JOINT FAME (CHINA) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA CHEN HOLDINGS LIMITED | Hong Kong | Hong Kong | Offshore Leaks |
| CHINA PETROL INVESTMENTS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA LOYAL INTERNATIONAL LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA WIN OFFSHORE LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA LOYAL HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA JOY GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA FIELD HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA LEADER LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA MAX INVESTMENTS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA ELEGANT INVESTMENT LIMITED | British Virgin Islands | Cayman Islands, British Virgin Islands | Offshore Leaks |
| CHINA PACKAGING SOLUTIONS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA DYNASTY ASIA LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| FAME CHINA INTERNATIONAL LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Sunseeker China Co., Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA GAS INVESTMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| VAST CHINA DEVELOPMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| PARAMOUNT CHINA LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA BENEFIT GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China AIM Finance Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Coventive Holdings (China) Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA HONGDA HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| VIVID CHINA INVESTMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| i-vision China Inc. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| SUPREME CHINA TRADING LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Newway Investment Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Ventures Industrial Ltd | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA FAITH LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| PROFIT CHINA ENTERPRISES LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Amer-China Partners, Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA PORTAL LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA OLYMPIC INTERNATIONAL LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Anderson Land (China) Limited | Cayman Islands | Cayman Islands | Offshore Leaks |
| BEST CHINA GROUP INC. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| GREAT PALACE (CHINA) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA GOLF DEVELOPMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| GOLD ASCENT (CHINA) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| LOYAL CHINA HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Review Advisory Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA LEAP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Pinnacle Scientific (China) Corporation | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Construction System Inc. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| BILLION CHINA LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Green Paper, Inc. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Vitality Healthcare China Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Books International Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| ELITE CHINA LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| DRAGON LINK (CHINA) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA STRATEGY FINANCIAL LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA TIMES DEVELOPMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA FALCON LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA GIANT INTERNATIONAL LIMITED | Samoa | Samoa | Offshore Leaks |
| CHINA REGAL LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA BAY GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA ALLIANCE GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA SUCCESS INVESTMENTS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| MACROTEC China Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Fortune Capital Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| GOLDEN CHINA GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA EAGLE (ASIA) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA FAST DEVELOPMENT LIMITED | Samoa | Samoa | Offshore Leaks |
| HIROX CHINA CO., LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| ONSUN (CHINA) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| MAX CHINA INVESTMENTS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| IMA GROUP CHINA LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Infrastructure Group Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| ON GIANT (CHINA) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| BILLION KEEN (CHINA) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| GOOD CHINA INVESTMENTS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| INVEST CHINA GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA EXPRESSWAYS COMPANY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA FAST GROUP LIMITED | Samoa | Samoa | Offshore Leaks |
| YULON CHINA INVESTMENT LIMITED | Hong Kong | Hong Kong | Offshore Leaks |
| CHINA SOURCE INDUSTRIAL LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Semiconductor Materials Inc. | Cayman Islands | Cayman Islands | Offshore Leaks |
| Greater China Distribution Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA REGAL INVESTMENTS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Alpha International (China) Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA PRIVILEGE ENTERPRISES LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Daxin (China) Company Limited | Hong Kong | Hong Kong | Offshore Leaks |
| CHINA RAINBOW TECHNOLOGY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Sigma China Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| INNOFOAM CHINA LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Ao Jin China Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| TOP CHINA CONSULTANTS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| RICH ELEGANT (CHINA) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA MOON SHIPPING INC. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| HARRY CHINA LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA TIMES INVESTMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA BAND HOLDINGS LIMITED | Samoa | Samoa | Offshore Leaks |
| LOYAL CHINA MANAGEMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA CAPITAL INTERNATIONAL LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA ENERGY STRATEGIC LIMITED | Hong Kong | Hong Kong | Offshore Leaks |
| CHINA SUN GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| BILLION CHINA GROUP LIMITED | Samoa | Samoa, Cayman Islands | Offshore Leaks |
| BILLION CHINA INTERNATIONAL LIMITED | Samoa | Samoa | Offshore Leaks |
| REACHTOP TRADING (CHINA) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHANCE LINE (CHINA) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Mandra Forestry China Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Topmedia Co., Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Minerals Group Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| EQUIPE ELECTRONIC (CHINA) LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA MINERAL RESOURCES LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| INDUSTRIAL COMMUNICATIONS (CHINA) LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA RAINBOW INVESTMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| FLUVAL CHINA CO., LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Jingqiao Inc. | Cayman Islands | Cayman Islands | Offshore Leaks |
| Fortuna China Fund | Cayman Islands | Cayman Islands | Offshore Leaks |
| VAST CHINA TECHNOLOGY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Euro Resources China Limited | Hong Kong | Hong Kong | Offshore Leaks |
| VIVID CHINA GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Q-China Limited | Hong Kong | Hong Kong | Offshore Leaks |
| Proserv China Ltd. | Samoa | Samoa | Offshore Leaks |
| CHINA INTERACTIVE LIMITED | Marshall Islands | Marshall Islands | Offshore Leaks |
| CDC CAPITAL CHINA LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA DANTI ENTERPRISES LIMITED | Samoa | Samoa | Offshore Leaks |
| Era China Investment Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA WAVE INTERNATIONAL LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Panda Express China Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA REVIEW INVESTMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Qualisystems China Inc. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| SUNNY CHINA MANAGEMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Monorail (China) Development Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| SINO CHINA DEVELOPMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Print Distribution Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| MERCURY CHINA LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| LeeMAH China Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| EVER CHINA CORPORATION | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Energy Investment Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Times (BVI) Ltd. | British Virgin Islands | Cayman Islands, British Virgin Islands | Offshore Leaks |
| CHINA PALACE OVERSEAS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| ISA (China) Investment Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA MEDICINE (HOLDINGS) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| FMC Investment (China) Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA FINANCE NET LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA PETROLEUM LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Longflow (China) Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| WK China Technology Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CONCORD CHINA INTERNATIONAL LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Fixed Income Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Shangfu China Holdings Corp. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| iLink.net (China) Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA ELEGANT DEVELOPMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA GAS DEVELOPMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA HARBOUR INVESTMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA PROFIT ENTERPRISES LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA LINK PROPERTIES LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| SPARKLE CHINA DEVELOPMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| TOPBEST CHINA LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA KINGDOM INTERNATIONAL LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA EXPO LIMITED | British Virgin Islands | Cayman Islands, British Virgin Islands | Offshore Leaks |
| CHINA PARTNER LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| ETON CHINA LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA POINT INTERNATIONAL LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| ACTIVE CHINA LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Reader China Group Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| iAdvantage (China) Holdings Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA DRAGONCOM INVESTMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA LOYAL GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA HOPE INTERNATIONAL LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA SOUND DEVELOPMENT INC. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA SOURCES TECHNOLOGY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA PLAZA TRADINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA DELUXE SERVICES LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| G-Hanz China Limited | British Virgin Islands | British Virgin Islands, Cayman Islands | Offshore Leaks |
| VSC China Engineering Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA BRIDGE LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA POWER GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA RICH WORLDWIDE LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA WAVE HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA TECHNOLOGIES LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| FORTUNE CHINA GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA AUTOMATIVE COMPANY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| GFC CHINA LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA PROFIT INTERNATIONAL LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Roly China Investments Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA SYSTEM LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| MagicTech (China) Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA ECONOMIC DEVELOPMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Greater China Telecom Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Base Trading Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA TOWER INC. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA JET CLUB LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CYBER CHINA HOLDINGS INC. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Law Corporation | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA LAND TRADINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| ADMOMENTUM (CHINA)GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA EXPO INVESTMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| PHALANX CONSULTING (CHINA) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Putt-Putt China Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA VIEW INVESTMENTS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA BRIGHT INVESTMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA PROFIT GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA PROFIT INVESTMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Networks Inc. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Jet China Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA TOP CONSULTANTS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA LOGISTICS NETWORKS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| NEW CHINA CONSULTANTS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China ICG Inc. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Contests2win China Holdings Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Expert Development Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA ENTERPRISES HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| GRAND CHINA OVERSEAS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| NEW CHINA TRADING LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| MEGA CHINA SERVICES LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA SOURCES GROUP INC. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| DH CHINA CONSULTING LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| EQUITY CHINA GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| SINCERE CHINA INVESTMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Technic Essential (China) Limited | Not identified | Hong Kong, Not identified | Offshore Leaks |
| China Offshore Group Ltd. | Not identified | Hong Kong, Not identified | Offshore Leaks |
| China Bound Ltd. | Not identified | British Virgin Islands, China | Offshore Leaks |
| Felanda (China) Technology Limited | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| MASON CHINA ENTERPRISES LIMITED | Not identified | Hong Kong, Not identified | Offshore Leaks |
| China Trade Group Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China Broadcast.Com (BVI) Limited | Not identified | Not identified, Hong Kong | Offshore Leaks |
| China Point Group Limited | Not identified | Not identified, Hong Kong | Offshore Leaks |
| China Fortune Holdings Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China Invest Holdings S.A. | Not identified | Latvia, British Virgin Islands | Offshore Leaks |
| China Legend Company Limited | Not identified | Not identified, Hong Kong | Offshore Leaks |
| CHINA GROWTH CAPITAL LIMITED | Not identified | China, British Virgin Islands | Offshore Leaks |
| China General Trading Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China Creations Limited | Not identified | Not identified, Hong Kong | Offshore Leaks |
| NEWISH CHINA CO., LTD. | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| China One Capital Inc. | Not identified | British Virgin Islands, China | Offshore Leaks |
| WK China Technology Limited | Not identified | Not identified | Offshore Leaks |
| China Baolong Logistic Limited | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| China Communication Investment Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China Entrepreneurs Limited | Not identified | British Virgin Islands, China | Offshore Leaks |
| Pulse China Group Ltd. | Not identified | British Virgin Islands, China | Offshore Leaks |
| UNITED CHINA ORGANIZATION LIMITED | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| China Golf Apt. Corp. | Not identified | British Virgin Islands, United States | Offshore Leaks |
| CHINA GREAT MALLS LIMITED | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| China Jointa Group Limited | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| China Basic Industries Limited | Not identified | Not identified, United States | Offshore Leaks |
| Southern China Holdings Ltd. | Not identified | Not identified, Hong Kong | Offshore Leaks |
| China Interact Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| NORDIC CHINA INVESTMENTS LIMITED | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| United China Group Ltd. | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China Venture Associates Limited | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| Blue Angel (China) Limited | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| Xinhua Investments (China) Limited | Not identified | China, British Virgin Islands | Offshore Leaks |
| CHINA FUNGHIGARDEN INDUSTRIAL INC. | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China 4G Investment Ltd. | Not identified | British Virgin Islands, China | Offshore Leaks |
| CHINA 3G HOLDINGS LIMITED | Not identified | China, British Virgin Islands | Offshore Leaks |
| China SEACOT Co. Ltd. | Not identified | British Virgin Islands, China | Offshore Leaks |
| NORDIC CHINA HOLDINGS LIMITED | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China Top Finance Limited | Not identified | Not identified, Hong Kong | Offshore Leaks |
| WTO China Holdings Limited | Not identified | Hong Kong, Not identified | Offshore Leaks |
| China Perfect Corporation | Not identified | Hong Kong, Not identified | Offshore Leaks |
| USA-China Ventures Limited | Not identified | Not identified, Hong Kong | Offshore Leaks |
| China Offshore Ltd. | Not identified | Not identified, Hong Kong | Offshore Leaks |
| China Gateway Development Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| Great China Entertainment, Inc. | Not identified | United States, British Virgin Islands | Offshore Leaks |
| China Loft Ltd. | Not identified | Hong Kong, Not identified | Offshore Leaks |
| China Top Holdings Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| Media Explorer (China) Limited | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| CCI China Limited | Not identified | China, Not identified | Offshore Leaks |
| Metals China Limited | Not identified | Not identified, Hong Kong | Offshore Leaks |
| Access China Limited | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| CHINA TIDE INVESTMENT INC. | Not identified | British Virgin Islands, China | Offshore Leaks |
| China Hydroelectric Limited | Not identified | British Virgin Islands, China | Offshore Leaks |
| TRINITY INDUSTRY (CHINA) LIMITED | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| Silver Row China Limited | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| WMOBILE (CHINA) LIMITED | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| W.W. INDUSTRIAL (CHINA) LTD | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| EVER CHINA UNION LTD. | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| China Global Capital Ltd. | Not identified | Not identified, Hong Kong | Offshore Leaks |
| China United Group Ltd. | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| CHINA GROWELL LIMITED | Not identified | British Virgin Islands, China | Offshore Leaks |
| Navigator (China) Investment Limited | Not identified | Hong Kong, Not identified | Offshore Leaks |
| EBECA (CHINA) HOLDINGS LIMITED | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| China Universal Trading Limited | Not identified | Not identified, Hong Kong | Offshore Leaks |
| United China Industrial Limited | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| South China Ventures Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China Superred Technology Limited | Not identified | China, British Virgin Islands | Offshore Leaks |
| CHINA SUNERGY CO., LTD. | Not identified | British Virgin Islands, China | Offshore Leaks |
| CHINA NET SOLUTIONS LTD. | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| China Taxel Corporation | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| China Restaurant Holdings Ltd. | Not identified | British Virgin Islands, China | Offshore Leaks |
| SOIDO CHINA CORP. | Not identified | China, British Virgin Islands | Offshore Leaks |
| China Pack Co., Ltd. | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| West China Invest S.A. | Not identified | British Virgin Islands, Latvia | Offshore Leaks |
| China Butyl Rubber Limited | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| ECOPULP CHINA LTD. | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| Chequers Electronic (China) Limited | Not identified | Hong Kong, Not identified | Offshore Leaks |
| China Overseas Group Inc. | Not identified | Hong Kong, Not identified | Offshore Leaks |
| Belmont China Limited | Not identified | Not identified, Hong Kong | Offshore Leaks |
| China Treasury Holdings Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| Yishu Automotive (China) Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China Xiangxing International Limited | Not identified | China, British Virgin Islands | Offshore Leaks |
| China Donghui International Limited | Not identified | China, British Virgin Islands | Offshore Leaks |
| Red China Limited | Not identified | Hong Kong, Not identified | Offshore Leaks |
| Premium Land (China) Limited | Not identified | Hong Kong, Not identified | Offshore Leaks |
| China Intermedia Group Ltd. | Not identified | British Virgin Islands, China | Offshore Leaks |
| Excel (China) Partners Limited | Not identified | British Virgin Islands, China | Offshore Leaks |
| CHINA INDUSTRIAL MATERIALS LTD. | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| Policy China Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China Choice Capital Limited | Not identified | Not identified, Hong Kong | Offshore Leaks |
| China Cartoon Holdings Limited | Not identified | British Virgin Islands, China | Offshore Leaks |
| Neolith Group (China) Limited | Not identified | United States, Not identified | Offshore Leaks |
| Trans China Trade Ltd. | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China Peak International Limited | Not identified | Not identified, Hong Kong | Offshore Leaks |
| China Rich Holdings Limited | Not identified | Not identified | Offshore Leaks |
| China View Investments Ltd | Not identified | Not identified | Offshore Leaks |
| CHINA HJ CONSULTING LIMITED | Not identified | British Virgin Islands, China | Offshore Leaks |
| China Oilfield Services Limited | Not identified | Not identified | Offshore Leaks |
| CHINA FOREVER HOLDINGS LIMITED | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| Norasia (China) Ltd | Not identified | Not identified | Offshore Leaks |
| Faulding China Ltd | Not identified | Not identified | Offshore Leaks |
| Greater China Holdings Ltd | Not identified | Hong Kong | Offshore Leaks |
| China Xiangxing Group Limited | Not identified | British Virgin Islands, China | Offshore Leaks |
| Golden Pride China Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China Sales Group Limited | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| China Profits Marketing Limited | Not identified | Not identified, Hong Kong | Offshore Leaks |
| China Gateway Investment Limited | Not identified | Hong Kong, Not identified | Offshore Leaks |
| Sparkle China Development Limited | Not identified | Not identified | Offshore Leaks |
| Megastar Management (China) Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China Finance Ltd. | Not identified | Not identified, Panama | Offshore Leaks |
| Famar China Holdings Ltd. | Not identified | Not identified, China | Offshore Leaks |
| China Expert Development Limited | Not identified | Not identified | Offshore Leaks |
| CHINA INCORPORATIONS LIMITED ???????????? | Not identified | Not identified | Offshore Leaks |
| China Superstructure Consultancy Lt | Not identified | Not identified | Offshore Leaks |
| Chuang’s China Databank Limited | Not identified | Not identified | Offshore Leaks |
| Tengda (China) Corporation | Not identified | Hong Kong, Not identified | Offshore Leaks |
| CHINA TIDE CAPITAL LIMITED | Not identified | China, British Virgin Islands | Offshore Leaks |
| America China World | Not identified | Not identified | Offshore Leaks |
| CHINA TODAY GROUP LIMITED | Samoa | Samoa | Offshore Leaks |
| China Times Inc. | Not identified | Not identified | Offshore Leaks |
| China Retail Management LDC | Not identified | Not identified | Offshore Leaks |
| CHINA NEW MEDIA LIMITED | Samoa | Samoa | Offshore Leaks |
| CHINA TAIWAN HOLDING LIMITED | Samoa | Samoa | Offshore Leaks |
| CHINA ALLWAY CONSULTING LIMITED | Samoa | Samoa | Offshore Leaks |
| RICHTOY CHINA LIMITED | Samoa | Samoa | Offshore Leaks |
| China Field Investments Limited | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| Pricerite China Limited | Not identified | Not identified | Offshore Leaks |
| Raymond Chan (China) | Not identified | Not identified | Offshore Leaks |
| China Link Solutions Limited | Not identified | Not identified | Offshore Leaks |
| Fortuna China Fund | Not identified | Not identified | Offshore Leaks |
| Putt-Putt China Ltd | Not identified | Not identified | Offshore Leaks |
| KDS China Limited | Hong Kong | Hong Kong | Offshore Leaks |
| China Holdings Group Limited | Samoa | Samoa | Offshore Leaks |
| Pentad (China) Management Limited | Cook Islands | Not identified | Offshore Leaks |
| Embassy China Investments Limited | Cook Islands | Not identified | Offshore Leaks |
| Great China Global Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China Fen Limited | Samoa | Samoa | Offshore Leaks |
| China Rich Limited | Samoa | Samoa | Offshore Leaks |
| CHINA LEADER MANAGEMENT INC. | Cayman Islands | Cayman Islands | Offshore Leaks |
| Creative Electronics (China) Limited | Samoa | Samoa | Offshore Leaks |
| e-Logistic (China) Limited | Hong Kong | Not identified | Offshore Leaks |
| China A International Limited | Samoa | Samoa | Offshore Leaks |
| China Plus Ltd | Cayman Islands | Cayman Islands | Offshore Leaks |
| United China Holdings Ltd. | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| CHINA WAVE INVESTMENT LIMITED | Samoa | Samoa | Offshore Leaks |
| China Pharmacy Group Limited | Hong Kong | Hong Kong | Offshore Leaks |
| Heatandsave China Limited | Not identified | British Virgin Islands, China | Offshore Leaks |
| CHINA VALVE HOLDINGS LIMITED | Samoa | Samoa | Offshore Leaks |
| CHINA OPTICOM TELECOMMUNICATIONS LIMITED | Cayman Islands | Cayman Islands | Offshore Leaks |
| China Investment Worldwide Inc. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Fortuna China Growth Fund | Cayman Islands | Cayman Islands | Offshore Leaks |
| CHINA BESTSUPPLY LIMITED | Samoa | Samoa | Offshore Leaks |
| Majestic China Enterprises Limited | Samoa | Samoa | Offshore Leaks |
| Central China Enterprises Limited | Not identified | Not identified | Offshore Leaks |
| China Leader Management Inc. | Not identified | Not identified | Offshore Leaks |
| China Pacific Investments Limited | Cook Islands | Not identified | Offshore Leaks |
| CHINA INCORPORTAIONS LIMITED | Not identified | Not identified | Offshore Leaks |
| Companion-China Limited | Not identified | Not identified | Offshore Leaks |
| China Synthetic Rubber Corporation | Not identified | Not identified | Offshore Leaks |
| Dickson (China) Holdings Limited | Cook Islands | Not identified | Offshore Leaks |
| China-databank.com Limited | Cook Islands | Not identified | Offshore Leaks |
| China Infrastructure Investment Limited | Not identified | Not identified | Offshore Leaks |
| Hongkong China Consultancy Limited | Not identified | Not identified | Offshore Leaks |
| Fortuna China Growth Fund | Not identified | Not identified | Offshore Leaks |
| Motorola (China) Electronics Limited | Not identified | Not identified | Offshore Leaks |
| CHINA CORETECH CORPORATION | Cayman Islands | Cayman Islands | Offshore Leaks |
| Collamatrix China Corp. | Samoa | Samoa | Offshore Leaks |
| CHINA LEADER HOLDINGS INC. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA BAND MANAGEMENT LIMITED | Samoa | Samoa | Offshore Leaks |
| CHINA BRILLIANT MANAGEMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Dickson (China) Trading Limited | Cook Islands | Not identified | Offshore Leaks |
| Integrated (China) Corporation | Samoa | Samoa | Offshore Leaks |
| China Relation, Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA REGAL HOLDINGS INC. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA DELUXE INVESTMENTS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Oriental (China) Investment Limited | Cook Islands | Not identified | Offshore Leaks |
| CHINA GOOD GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Besco (China) Company Limited | Hong Kong | Hong Kong | Offshore Leaks |
| PORTCULLIS HOLDINGS (CHINA) LTD | Labuan | Malaysia | Offshore Leaks |
| Western China Resources Ltd | Cayman Islands | Cayman Islands | Offshore Leaks |
| CHINA KANGLI MEDICINE LIMITED | Hong Kong | Not identified | Offshore Leaks |
| Camco Ventures (China) Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA BESTAR LABORATORIES LTD. | Samoa | Samoa | Offshore Leaks |
| CHINA BOND INTERNATIONAL LTD. | Samoa | Samoa | Offshore Leaks |
| China Force Limited | Hong Kong | Hong Kong | Offshore Leaks |
| China Lions Development Limited | Hong Kong | Hong Kong | Offshore Leaks |
| China Vision Holding Limited | Samoa | Samoa | Offshore Leaks |
| China Profit Development Limited | Hong Kong | Hong Kong | Offshore Leaks |
| China Gas Holdings Limited | Not identified | Not identified | Offshore Leaks |
| China Elegant (Holdings) Limited | Not identified | Not identified | Offshore Leaks |
| CHINA HOME ENTERTAINMENT LIMITED | Hong Kong | Hong Kong | Offshore Leaks |
| CHINA FALCON INTERNATIONAL LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| PROMOTA CHINA LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| AXEND CHINA PTE LIMITED | Hong Kong | Hong Kong | Offshore Leaks |
| Greater China Association Inc. | Samoa | Samoa | Offshore Leaks |
| CHINA MOMENT COMPANY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA TODAY LIMITED | Samoa | Samoa | Offshore Leaks |
| China Bold Group Limited | Bahamas | | Bahamas Leaks |
| EXXONMOBIL CHINA (ORDOS) LIMITED | Bahamas | | Bahamas Leaks |
| EXXONMOBIL CHINA VENTURES LIMITED | Bahamas | | Bahamas Leaks |
| Central China Energy Limited | Bermuda | Bermuda | Paradise Papers |
| China Copper (Holdings) Limited | Bermuda | Bermuda | Paradise Papers |
| Wharf China Limited | Bermuda | Bermuda | Paradise Papers |
| China Partners Properties, Limited | Bermuda | Bermuda | Paradise Papers |
| China Stationery Limited | Bermuda | Bermuda | Paradise Papers |
| Gillette China Investment Ltd. | Bermuda | Bermuda | Paradise Papers |
| China Zhengda Sports Limited | Bermuda | Bermuda, China | Paradise Papers |
| Wilmar China (Bermuda) Limited | Bermuda | Bermuda, Singapore | Paradise Papers |
| China Green Technology Limited | Bermuda | Bermuda | Paradise Papers |
| China Unitek Group Limited | Bermuda | Bermuda | Paradise Papers |
| Genting Power China Limited | Bermuda | Bermuda | Paradise Papers |
| CHINA COKING COMPANY LIMITED | Bermuda | Bermuda | Paradise Papers |
| China Glass Holdings Limited | Bermuda | Bermuda, China, Hong Kong | Paradise Papers |
| China Paper Holdings Limited | Bermuda | Bermuda, China, Hong Kong, Singapore | Paradise Papers |
| FMG China Fund Ltd. | Bermuda | Bermuda | Paradise Papers |
| MEIBAN CHINA LTD. | Bermuda | Bermuda, Singapore | Paradise Papers |
| China Bridge, Ltd. | Bermuda | Bermuda, United States | Paradise Papers |
| CHINA STAR ENTERTAINMENT LIMITED | Bermuda | Bermuda, Hong Kong | Paradise Papers |
| China Point Limited | Bermuda | Bermuda | Paradise Papers |
| Reynolds International (China) Ltd. | Bermuda | Bermuda | Paradise Papers |
| China Pacific Merchants Ltd. | Bermuda | Bermuda | Paradise Papers |
| AXA China Region Limited | Bermuda | Bermuda, China, Hong Kong | Paradise Papers |
| China Central Properties Limited | Isle of Man | Hong Kong, Isle of Man | Paradise Papers |
| Renxin (China) Company Limited | Cayman Islands | Cayman Islands | Paradise Papers |
| China Mezzanine Capital Group | Cayman Islands | Cayman Islands, China | Paradise Papers |
| Xinming China Holdings Limited | Cayman Islands | Cayman Islands, China | Paradise Papers |
| China Commonwealthy Fund | Cayman Islands | Cayman Islands | Paradise Papers |
| China Vanguard Group Limited | Cayman Islands | Cayman Islands | Paradise Papers |
| China Candy Holdings Limited | Cayman Islands | Cayman Islands, China | Paradise Papers |
| Valuebed China Prospective Fund | Cayman Islands | Cayman Islands | Paradise Papers |
| CHINA METALS COMPANY LIMITED | Cayman Islands | Cayman Islands | Paradise Papers |
| ACHEM TECHNOLOGY CHINA | Cayman Islands | Cayman Islands | Paradise Papers |
| EHINFO CHINA HOLDING LTD. | Cayman Islands | Cayman Islands | Paradise Papers |
| China Fund Limited | Cayman Islands | Cayman Islands | Paradise Papers |
| CHINA INTERNATIONAL CAPITAL LIMITED | Cayman Islands | Cayman Islands | Paradise Papers |
| CHINA INVESTMENT (GLOBAL) LIMITED | Cayman Islands | Cayman Islands | Paradise Papers |
| China Lynx Holdings Limited | Cayman Islands | Cayman Islands | Paradise Papers |
| CHINA CENTURY CEMENT LIMITED | Bermuda | Bermuda, Hong Kong | Paradise Papers |
| China Cathay Tyre Limited | Bermuda | Bermuda | Paradise Papers |
| China Convergent Corporation Limited | Bermuda | Bermuda | Paradise Papers |
| GREATER CHINA HOLDINGS LIMITED | Bermuda | Bermuda, Hong Kong | Paradise Papers |
| CHINA BRILLIANCE INFRASTRUCTURE LIMITED | Bermuda | Bermuda | Paradise Papers |
| Schering-Plough (China) Limited | Bermuda | Bermuda, United States | Paradise Papers |
| China Enterprises Limited | Bermuda | Bermuda | Paradise Papers |
| CHINA AUTOMOTIVE COMPANY LIMITED | Bermuda | Bermuda | Paradise Papers |
| CHINA BRILLIANCE GROUP LIMITED | Bermuda | Bermuda | Paradise Papers |
| UNOCAL CHINA LIMITED | Bermuda | Bermuda | Paradise Papers |
| CHINA BREWERY HOLDINGS LIMITED | Bermuda | Bermuda | Paradise Papers |
| BRILLIANCE CHINA HOLDINGS LIMITED | Bermuda | Bermuda | Paradise Papers |
| GuocoLand (China) Limited | Bermuda | Bermuda, Singapore | Paradise Papers |
| China Bearing Holdings Limited | Bermuda | Bermuda, Hong Kong | Paradise Papers |
| China Internet Corporation Limited | Bermuda | Bermuda, Hong Kong | Paradise Papers |
| American Fidelity (China), Ltd. | Bermuda | Bermuda, United States | Paradise Papers |
| CHINA TELECOM LIMITED | Bermuda | Bermuda | Paradise Papers |
| Global China Investments Ltd. | Bermuda | Bermuda | Paradise Papers |
| Global China Holdings Ltd. | Bermuda | Bermuda | Paradise Papers |
| CHINA CONSTRUCTION HOLDINGS LIMITED | Bermuda | Bermuda, Hong Kong | Paradise Papers |
| China Consolidated Foods, Limited | Bermuda | | Paradise Papers |
| PRICOA China (Residential) Limited | Bermuda | Bermuda | Paradise Papers |
| China Homes Limited | Bermuda | Bermuda | Paradise Papers |
| PRICOA China (Warehouse) Limited | Bermuda | Bermuda | Paradise Papers |
| China Power Dynamics Ltd. | Bermuda | Bermuda | Paradise Papers |
| China Distri-Park Limited | Bermuda | Bermuda | Paradise Papers |
| HQI China Limited | Bermuda | Bermuda | Paradise Papers |
| China Household Holdings Limited | Bermuda | Bermuda, Hong Kong | Paradise Papers |
| China Innovationpay Group Limited | Bermuda | Bermuda, Hong Kong | Paradise Papers |
| APP China Group Limited | Bermuda | Bermuda | Paradise Papers |
| Burlington Resources China Limited | Bermuda | Bermuda, United States | Paradise Papers |
| China E-Net.com Limited | Bermuda | Bermuda, China, Hong Kong | Paradise Papers |
| China NewMedia Ltd. | Bermuda | Bermuda, Hong Kong | Paradise Papers |
| China PDA Limited | Bermuda | Bermuda, China | Paradise Papers |
| China Sourcing Ltd. | Bermuda | Bermuda, United States | Paradise Papers |
| China w-Metals Limited | Bermuda | Bermuda, Hong Kong | Paradise Papers |
| China Pipe Group Limited | Bermuda | Bermuda, Hong Kong | Paradise Papers |
| China LotSynergy Holdings Limited | Bermuda | Bermuda, Hong Kong | Paradise Papers |
| China Asean Resources Limited | Bermuda | Bermuda, Hong Kong | Paradise Papers |
| Digital China Holdings Limited | Bermuda | Bermuda, Hong Kong | Paradise Papers |
| CHINA COAST INVESTMENTS LIMITED | Cook Islands | Cook Islands | Paradise Papers |
| THE CHINA TRUST | Cook Islands | Cook Islands | Paradise Papers |
| MY CHINA TOWN | Malta | Malta | Paradise Papers |
| PARKDAN CHINA INVESTMENTS LTD | | | Pandora Papers |
| OCEAN CHINA MARITIME INC | | | Pandora Papers |
| PARKDAN CHINA INVESTMENTS LTD. | British Virgin Islands | British Virgin Islands | Pandora Papers |
| CHINA MICRO MEDICAL LIMITED | British Virgin Islands | British Virgin Islands | Pandora Papers |
| CHINA ART COMPANY LIMITED | Malta | Malta | Paradise Papers |
| CHINA HOLDING LIMITED | Malta | Malta | Paradise Papers |
| PARKROSE CHINA INVESTMENTS LTD. | British Virgin Islands | British Virgin Islands | Pandora Papers |
| China Trade Asia Limited | British Virgin Islands | British Virgin Islands | Pandora Papers |
| PARKDAN CHINA INVESTMENTS LTD. | British Virgin Islands | British Virgin Islands | Pandora Papers |
| CHINA CORD INVESTMENTS | Saint Kitts and Nevis | | Paradise Papers |
| CHINA SPRINGS INTERNATIONAL | Saint Kitts and Nevis | | Paradise Papers |
| CHINA AUSTRALIA CAPITAL LTD | British Virgin Islands | British Virgin Islands | Pandora Papers |
| CHINA AUSTRALIA CAPITAL LTD | British Virgin Islands | British Virgin Islands | Pandora Papers |
| CHINA XIANGHSHAN LTD | Malta | Malta | Paradise Papers |
| CHINA HARBOUR ENGINEERING COMPANY | Malta | Malta | Paradise Papers |
| GREEN CHINA DEVELOPMENT LTD | Malta | Malta | Paradise Papers |
| CHINA SYSTEMS (EUROPE) LIMITED | Malta | Malta | Paradise Papers |
| CHINA TOWN CATERERS LTD | Malta | Malta | Paradise Papers |
| MY CHINA TOWN LIMITED | Malta | Malta | Paradise Papers |
| CHINA AFRICA CORPORATION LIMITED | Malta | Malta | Paradise Papers |
| Askar China Malta Limited | Malta | Malta | Paradise Papers |
| BULK CHINA SHIPPING LTD | Malta | Malta | Paradise Papers |
| ANBAO CHINA COMPANY LIMITED | Malta | Malta | Paradise Papers |
| CHINA SPRING INTERNATIONAL LTD | Malta | Malta | Paradise Papers |
| CHINA TRADING CENTRE LIMITED | Malta | Malta | Paradise Papers |
| CHINA WHITE COMPANY LIMITED | Malta | Malta | Paradise Papers |
| MY CHINA TOWN LIMITED | Malta | Malta | Paradise Papers |
| SZ CHINA PROPERTIES LTD. | Saint Kitts and Nevis | | Paradise Papers |
| CAPITAL ENTERPRISES (CHINA) LIMITED | Saint Kitts and Nevis | | Paradise Papers |
| CHINA SERVICES LIMITED | Saint Kitts and Nevis | | Paradise Papers |
| CHINA BASE INC. | Saint Kitts and Nevis | | Paradise Papers |
| 888 Antique China Limited | Saint Kitts and Nevis | | Paradise Papers |
| China Stock Profile, Inc. | Saint Kitts and Nevis | | Paradise Papers |
| THE CHINA CONNECTION LIMITED | Saint Kitts and Nevis | | Paradise Papers |
| OSEM VENTURE (CHINA) INC. | Saint Kitts and Nevis | | Paradise Papers |
| CHINA GROVE, LTD. | Saint Kitts and Nevis | | Paradise Papers |
| CHINA CLIPPER HOLDINGS LTD | Saint Kitts and Nevis | | Paradise Papers |
| DYNAMIC CHINA CORP. | Saint Kitts and Nevis | | Paradise Papers |
| CHINA BELLE LLC | Saint Kitts and Nevis | | Paradise Papers |
| Star Bright China LLC | Saint Kitts and Nevis | | Paradise Papers |
| China Global Partners, LLC | Saint Kitts and Nevis | | Paradise Papers |
| China Coal Group Ltd. | Saint Kitts and Nevis | | Paradise Papers |
| China Capital P.T.C Inc. | Saint Kitts and Nevis | | Paradise Papers |
| Mi China Holdings, LTD | Saint Kitts and Nevis | | Paradise Papers |
| CHINA PETROLEUM PORT LTD. | Saint Kitts and Nevis | | Paradise Papers |
| Barnes China Investments Ltd. | Saint Kitts and Nevis | | Paradise Papers |
| China Sunshine Limited | Saint Kitts and Nevis | | Paradise Papers |
| CHINA WAY HOLDINGS LIMITED | Bahamas | | Bahamas Leaks |
| DEVON ENERGY CHINA, LTD. | Bahamas | | Bahamas Leaks |
| CHINA LINK LIMITED | Bahamas | | Bahamas Leaks |
| CHINA GOLD LIMITED | Bahamas | | Bahamas Leaks |
| CHINA PACK LTD | Bahamas | | Bahamas Leaks |
| CHINA FIRST HOLDINGS LIMITED | Bahamas | | Bahamas Leaks |
| NEW CHINA CO LTD | Bahamas | | Bahamas Leaks |
| CHINA ORIGINAL HOLDINGS LIMITED | Bahamas | | Bahamas Leaks |
| CHINA BLUE LTD. | Bahamas | | Bahamas Leaks |
| CHINA CASTLE INVESTMENTS LIMITED | Bahamas | | Bahamas Leaks |
| MBO (China) Limited | Bahamas | | Bahamas Leaks |
| China TNT, Inc. | Bahamas | | Bahamas Leaks |
| FIRST CHINA RESOURCES LTD. | Bahamas | | Bahamas Leaks |
| EXXONMOBIL CHINA UPSTREAM LIMITED | Bahamas | | Bahamas Leaks |
| CHINA TITANIUM & CHEMICALS CORP. | Bahamas | | Bahamas Leaks |
| Fine China Limited | Bahamas | | Bahamas Leaks |
| UNITED CHINA INTERNATIONAL LIMITED | Bahamas | | Bahamas Leaks |
| EXXONMOBIL CHINA (SICHUAN) LIMITED | Bahamas | | Bahamas Leaks |
| CHINA STAR HOLDINGS INC. | Bahamas | | Bahamas Leaks |
| ULTRA CHINA FUND LIMITED | Bahamas | | Bahamas Leaks |
| ARCO COAL CHINA INC. | Bahamas | | Bahamas Leaks |
| KERR-MCGEE CHINA LTD | Bahamas | | Bahamas Leaks |
| CHINA INDIGENAUS INC. | Bahamas | | Bahamas Leaks |
| GRAND CHINA DEVELOPMENT LIMITED | Bahamas | | Bahamas Leaks |
| CHINA SOUTHWEST LTD | Bahamas | | Bahamas Leaks |
| CHINA XUZHOU INC. | Bahamas | | Bahamas Leaks |
| CHINA RISING INC. | Bahamas | | Bahamas Leaks |
| China Motors Ltd. | Bahamas | | Bahamas Leaks |
| CHEVRON CHINA LIMITED | Bahamas | | Bahamas Leaks |
| CHINA ROSE INVESTMENTS LTD. | Bahamas | | Bahamas Leaks |
| CHINA PRIME INVESTMENTS LTD. | Bahamas | | Bahamas Leaks |
| CHINA EXCEED LIMITED | Bahamas | | Bahamas Leaks |
| CHINA WORLD INVESTMENTS LIMITED | Bahamas | | Bahamas Leaks |
| China Enterprises Limited | Bahamas | | Bahamas Leaks |
| China Vision SME, Ltd. | Bahamas | | Bahamas Leaks |
| INTER-MARKET CHINA LTD. | Bahamas | | Bahamas Leaks |
| PACIFIC MARINE CHINA LTD. | Bahamas | | Bahamas Leaks |
| CHINA SKY LIMITED | Bahamas | | Bahamas Leaks |
| PROUD CHINA HOLDINGS LTD. | Bahamas | | Bahamas Leaks |
| WTC China Holdings Limited | Bahamas | | Bahamas Leaks |
| CHINA INTERNATIONAL HOLDINGS, LTD. | Bahamas | | Bahamas Leaks |
| CHINA OCEAN DEVELOPMENT LTD | Bahamas | | Bahamas Leaks |
| GREATER CHINA TECHNOLOGY, INC. | Bahamas | | Bahamas Leaks |
| CHINA MERCHANT GROUP LTD | Bahamas | | Bahamas Leaks |
| CHUKKAR APPAREL CHINA, LTD. | Bahamas | | Bahamas Leaks |
| North China Shipping Limited | Bahamas | | Bahamas Leaks |
| StarCapital China Holding, Ltd. | Bahamas | | Bahamas Leaks |
| Wan-Fu China, Ltd. | Bahamas | | Bahamas Leaks |
| NEWFIELD CHINA HOLDING INC. | Bahamas | | Bahamas Leaks |
| China Bridge, Ltd. | Bahamas | | Bahamas Leaks |
| CHINA CHANCE LIMITED | Bahamas | | Bahamas Leaks |
| CHINA LIGHT LTD. | Bahamas | | Bahamas Leaks |
| CHINA GLOBAL LIMITED | Bahamas | | Bahamas Leaks |
| CHINA INVSTMENT MANAGEMENT CORP. | Bahamas | | Bahamas Leaks |
| CHINA DELIGHT LIMITED | Bahamas | | Bahamas Leaks |
| CHINA DIALOGUES NETWORK INCORPORATED | Bahamas | | Bahamas Leaks |
| MEGA CHINA LIMITED | Bahamas | | Bahamas Leaks |
| CHINA OVERSEAS FOUNDATION | Bahamas | | Bahamas Leaks |
| SOUTHWESTERN GOLD (CHINA) INC. | Bahamas | | Bahamas Leaks |
| CHINA DIRECT LIMITED | Bahamas | | Bahamas Leaks |
| CHINA MARK INVESTMENTS LIMITED | Bahamas | | Bahamas Leaks |
| PACIFIC CHINA GROUP LTD. | Bahamas | | Bahamas Leaks |
| TDI TRADING (CHINA) LIMITED | Bahamas | | Bahamas Leaks |
| AMERICAN CHINA DEVELOPMENT CORPORATION | Bahamas | | Bahamas Leaks |
| BRENCO OF CHINA LIMITED | Bahamas | | Bahamas Leaks |
| CHINA WORLDWIDE (BAHAMAS) LIMITED | Bahamas | | Bahamas Leaks |
| GREAT CHINA VENTURES LIMITED | Bahamas | | Bahamas Leaks |
| CHINA SYSTEMS HOLDINGS LTD | Bahamas | | Bahamas Leaks |
| CHINA DEVELOPMENT LTD | Bahamas | | Bahamas Leaks |
| CHINA SURGICAL DRESSINGS COMPANY | Bahamas | | Bahamas Leaks |
| CHINA ROSE LIMITED | Bahamas | | Bahamas Leaks |
| CHINA EQUITIES INTERNATIONAL LIMITED | Bahamas | | Bahamas Leaks |
| CHINA TOPSIDE LIMITED | Not identified | China, British Virgin Islands | Offshore Leaks |
| China Glass Holding Ltd. | Not identified | British Virgin Islands, China | Offshore Leaks |
| CHINA RESOURCE INDUSTRIAL LTD. | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| Skylight Financial (China) Ltd. | Not identified | British Virgin Islands, China | Offshore Leaks |
| CHINA EVERGREEN INDUSTRY CORPORATION | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| Adicomp China Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China SunJin Group Limited | Not identified | British Virgin Islands, China | Offshore Leaks |
| CHINA SEA RESOURCES LTD. | Not identified | British Virgin Islands, United States | Offshore Leaks |
| China Liuwei Holding Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China Nanotechnology Holding Inc. | Not identified | British Virgin Islands, China | Offshore Leaks |
| CHINA INVESTMENT CAPITAL LIMITED | Not identified | United Kingdom, British Virgin Islands | Offshore Leaks |
| Uptown China Limited | Not identified | United Kingdom, British Virgin Islands | Offshore Leaks |
| CHINA FURNITURE HOLDINGS LIMITED | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| HONG CHANG CHINA LIMITED | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| CHINA TOPRISE LIMITED | Not identified | China, British Virgin Islands | Offshore Leaks |
| ideaCulture China Limited | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| TRADEASY COMPANY (CHINA) LTD. | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| CHINA BASE METALS CORPORATION | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| Lindfield China Limited | Not identified | Not identified, Hong Kong | Offshore Leaks |
| China Optotech Co., Ltd. | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| Yerumedi Entertainment China Ltd. | Not identified | China, British Virgin Islands | Offshore Leaks |
| Pan China Co., Ltd. | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China Superstructure Consultancy Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China Offshore Investments Ltd. | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China Autocard Holdings Limited | Not identified | Hong Kong, Not identified | Offshore Leaks |
| Happy China Holding Ltd. | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| China Sports Management Limited | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| China Universal Capital Ltd. | Not identified | Not identified, Hong Kong | Offshore Leaks |
| CHINA INDUSTRIAL MANAGEMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| DIPLOMA (CHINA) HOLDINGS LIMITED | Not identified | China, British Virgin Islands | Offshore Leaks |
| TERANEX (CHINA) LTD. | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| Pro-Med China Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| BMT INTERNATIONAL (CHINA) LIMITED | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China Millennium Art, Ltd | Not identified | China, British Virgin Islands | Offshore Leaks |
| United China Investment Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA MEDICAL NET LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA TOP WORLDWIDE LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA WEBPHONE TECHNOLOGY LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Data Holdings Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA VENTURE TECHNOLOGY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA RAINBOW GROUP INC. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Dickson Construction (China) Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Roosevelt China Investments Corporation | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Siam Canadian (China) Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Alliance Investment Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| NovusAsia China Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| ASOKA (CHINA) COMPANY LTD | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Offshore Resources Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA STRATEGY HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| GAIN ASCENT (CHINA) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Semiconductor Technology Inc. | Cayman Islands | Cayman Islands | Offshore Leaks |
| China Elegance Resources Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| PEARL CHINA GROUP LIMITED | Samoa | Samoa | Offshore Leaks |
| CHINA CONTROLS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CINWIN CHINA LIMITED | Samoa | Samoa | Offshore Leaks |
| ALLIED SUPREME (CHINA) CORP. | Samoa | Cayman Islands, Samoa | Offshore Leaks |
| CHINA METALLURGICAL ENGINEERING CORPORATION | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| FAME CHINA GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| FAME CHINA INDUSTRIAL LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Six Seconds (China) Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| ABSOLUTELY CHINA LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA PINNACLE INDUSTRY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| APRIL China Holdings Limited | Hong Kong | Hong Kong | Offshore Leaks |
| CHINA SHENGYUAN INVESTMENT LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA ORIENTIR LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| SEASTAR GROUP (CHINA) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA ELEVATOR (GROUP) LTD. | Cayman Islands | Cayman Islands | Offshore Leaks |
| CHINA BABY LIMITED | Samoa | Samoa | Offshore Leaks |
| China Sport Investments Limited | Samoa | Samoa | Offshore Leaks |
| E Commerce China Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| TOPLINK LOGISTICS (CHINA) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA FUTURE INVESTMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| INNOSPORT CHINA LTD. | Samoa | Samoa | Offshore Leaks |
| BOHAI REFRACTORY CHINA LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA HEALTHCARE CORPORATION | Cayman Islands | Cayman Islands | Offshore Leaks |
| Rich China International Ltd. | Hong Kong | Not identified | Offshore Leaks |
| CHINA IPSC (HOLDINGS) LTD | Samoa | Samoa | Offshore Leaks |
| ACHEM TECHNOLOGY CHINA | Cayman Islands | Cayman Islands | Offshore Leaks |
| CHINA UNIQUE INDUSTRIAL LTD. | Samoa | Samoa | Offshore Leaks |
| CHINA WISDOM CO., LTD. | Samoa | Samoa | Offshore Leaks |
| China Prosperity Holdings Ltd | Not identified | Not identified | Offshore Leaks |
| China Solutions Limited | Not identified | Not identified | Offshore Leaks |
| Golden China Consultants Limited | Not identified | Not identified | Offshore Leaks |
| New World (China) Ltd | Not identified | Not identified | Offshore Leaks |
| Gateway China Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| CHINA HYDROPOWER GROUP LIMITED | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| CHINA CHARIOT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA SHANGHAI CAPITAL LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| PACIFIC CENTURY CHINA LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| POTEX CHINA INVESTMENTS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Jackley China Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA STORE N.V. | Aruba | | Paradise Papers |
| ESQUINA CHINA N.V. | Aruba | | Paradise Papers |
| CHINA TOWN SELFSERVICE | Aruba | | Paradise Papers |
| CHINA OVERSEAS ARUBA | Aruba | | Paradise Papers |
| CHINA WORLD RUGS N.V. | Aruba | | Paradise Papers |
| CHINA LIN HOLDING LIMITED | Seychelles | China, Seychelles | Paradise Papers |
| CHINA GLAZE CORPORATION | Seychelles | China, Seychelles | Paradise Papers |
| CHINA RETAIL CONCEPTS LIMITED | British Virgin Islands | British Virgin Islands, Hong Kong | Paradise Papers |
| China Haohan Holdings Limited | British Virgin Islands | British Virgin Islands, China | Paradise Papers |
| China Haohan Management Limited | British Virgin Islands | British Virgin Islands, China | Paradise Papers |
| Sunac China Holdings Limited | Cayman Islands | Cayman Islands | Paradise Papers |
| CHINA BIOPHARMACEUTICAL HOLDINGS LIMITED | Cayman Islands | Cayman Islands | Paradise Papers |
| Uniwisdom China Holdings Limited | Cayman Islands | Cayman Islands | Paradise Papers |
| China Orient Infrastructure Fund | Cayman Islands | Cayman Islands, China | Paradise Papers |
| CHINA VANADIUM INDUSTRY LIMITED | Cayman Islands | Cayman Islands | Paradise Papers |
| China Financial Management Limited | Cayman Islands | Cayman Islands | Paradise Papers |
| China Crystal Technologies Inc. | Cayman Islands | Cayman Islands | Paradise Papers |
| China Finance (Holdings) Limited | Cayman Islands | Cayman Islands | Paradise Papers |
| China Classics Group Limited | Cayman Islands | Cayman Islands | Paradise Papers |
| China Suppliers Co. Ltd. | Cayman Islands | Cayman Islands | Paradise Papers |
| Greenplum (Greater China) Limited | Cayman Islands | Cayman Islands | Paradise Papers |
| ZZZ-CHINA CORETECH CORPORATION | Cayman Islands | Cayman Islands | Paradise Papers |
| Panther China Fund | Cayman Islands | Cayman Islands, China | Paradise Papers |
| China Yinsheng QiQiao Fund | Cayman Islands | Cayman Islands, Hong Kong | Paradise Papers |
| China Stem Cells Ltd | Cayman Islands | Cayman Islands | Paradise Papers |
| China PowerTech Holdings Limited | Cayman Islands | Cayman Islands, Hong Kong | Paradise Papers |
| China Tiger Fund, Ltd. | Cayman Islands | Cayman Islands | Paradise Papers |
| LONGRUNNER CHINA GROWTH FUND | Cayman Islands | Cayman Islands | Paradise Papers |
| Branding China Group Limited | Cayman Islands | Cayman Islands, Hong Kong | Paradise Papers |
| China Haohan Group Limited | Cayman Islands | Cayman Islands, China | Paradise Papers |
| South China Growth Fund | Cayman Islands | Cayman Islands, China | Paradise Papers |
| INFA China Holdings Limited | Cayman Islands | Cayman Islands | Paradise Papers |
| Bohong China Growth Fund | Cayman Islands | Cayman Islands, China | Paradise Papers |
| Galaxy China Opportunities Fund | Cayman Islands | Cayman Islands | Paradise Papers |
| CHINA FISHERY GROUP LIMITED | Cayman Islands | Cayman Islands, Hong Kong | Paradise Papers |
| Ajisen (China) Holdings Limited | Cayman Islands | Cayman Islands, Hong Kong | Paradise Papers |
| China Hydroelectric Corporation | Cayman Islands | Cayman Islands, United States | Paradise Papers |
| China Pacific Services Corporation | Cayman Islands | Cayman Islands, Hong Kong | Paradise Papers |
| First China Opportunity Fund | Cayman Islands | Cayman Islands, Hong Kong | Paradise Papers |
| First China Partners Limited | Cayman Islands | Cayman Islands, China, Hong Kong | Paradise Papers |
| China Tianyi Holdings Limited | Cayman Islands | Cayman Islands | Paradise Papers |
| AEI China Power Limited | Cayman Islands | Cayman Islands | Paradise Papers |
| AEI China Gas Ltd. | Cayman Islands | Cayman Islands | Paradise Papers |
| Galaxy China Tactical Fund | Cayman Islands | Cayman Islands | Paradise Papers |
| China Art Development Ltd. | Cayman Islands | Cayman Islands | Paradise Papers |
| CHINA VILLAGE HOLDING VBA | Aruba | | Paradise Papers |
| CHEVRON CHINA LIMITED | Bahamas | Bahamas | Paradise Papers |
| FIRST NORTHERN CHINA LIMITED | Bahamas | | Bahamas Leaks |
| CHINA CHARITY FUND LIMITED | Bahamas | | Bahamas Leaks |
| CHINA RED ENTERPRISES LIMITED | Bahamas | | Bahamas Leaks |
| CHINA TIGER LIMITED | Bahamas | | Bahamas Leaks |
| CHINA MOUNTAIN HOLDINGS LIMITED | Bahamas | | Bahamas Leaks |
| CHINA TRINITY GROUP LIMITED | Bahamas | | Bahamas Leaks |
| CHINA HERO TRADING LIMITED | Bahamas | | Bahamas Leaks |
| FITNESS CONCEPT CHINA INC. | Bahamas | | Bahamas Leaks |
| COLONEL FOODS CHINA, LTD. | Bahamas | | Bahamas Leaks |
| CERRUTI (CHINA) LIMITED | Bahamas | | Bahamas Leaks |
| CHINA GAIN INTERNATIONAL LIMITED | Bahamas | | Bahamas Leaks |
| ESSO CHINA UPSTREAM LIMITED | Bahamas | | Bahamas Leaks |
| GRAND CHINA RESTAURANT INC. | Barbados | Barbados | Paradise Papers |
| GOLDEN CHINA ENTERPRISES LIMITED | Barbados | Barbados | Paradise Papers |
| CHINA INTERNATIONAL CORP. | Barbados | Barbados | Paradise Papers |
| POWERWAVE CHINA HOLDINGS SRL | Barbados | Barbados | Paradise Papers |
| TEXTRON CHINA HOLDINGS SRL | Barbados | Barbados | Paradise Papers |
| CHINA MANAGEMENT HOLDING SRL | Barbados | Barbados | Paradise Papers |
| BURRILL CHINA INVESTMENT SRL | Barbados | Barbados | Paradise Papers |
| BURRILL CHINA PARTNERS SRL | Barbados | Barbados | Paradise Papers |
| CHINA CONSTRUCTION COMPANY LIMITED | Bahamas | Bahamas | Paradise Papers |
| CHINA LINK LTD. | Barbados | Barbados | Paradise Papers |
| CHINA IMPEX CORPORATION | Barbados | Barbados | Paradise Papers |
| NEW CHINA GARDEN INC. | Barbados | Barbados | Paradise Papers |
| CHINA CHEF LTD. | Barbados | Barbados | Paradise Papers |
| CHINA EXPRESSWAYS COMPANY LIMITED | Barbados | Barbados | Paradise Papers |
| HUSKY OIL CHINA LTD. | Barbados | Barbados | Paradise Papers |
| CHINA SEA CRUISES INC. | Barbados | Barbados | Paradise Papers |
| ENGLISH CHINA HOUSE LIMITED | Bahamas | Bahamas | Paradise Papers |
| CHINA TEMPLE LIMITED | Bahamas | Bahamas | Paradise Papers |
| CHINA EMPEROR LIMITED, THE | Bahamas | Bahamas | Paradise Papers |
| BERNARDS CHINA & GIFTS LIMITED | Bahamas | Bahamas | Paradise Papers |
| GLOBAL PHOTOGRAPHIC (CHINA) INC. | Barbados | Barbados | Paradise Papers |
| AFCAN CHINA LIMITED | Barbados | Barbados | Paradise Papers |
| FLUENT CHINA HOLDINGS LIMITED | Barbados | Barbados | Paradise Papers |
| PLACER DOME (CHINA) LIMITED | Barbados | Barbados | Paradise Papers |
| CHINA HOTEL INVESTMENT LTD. | Barbados | Barbados | Paradise Papers |
| I.C.T.C. (CHINA) HOLDINGS CORPORATION | Barbados | Barbados | Paradise Papers |
| SENTIENT CHINA INVESTMENTS LTD | Barbados | Barbados | Paradise Papers |
| ENTREE CHINA HOLDINGS INC. | Barbados | Barbados | Paradise Papers |
| CHINA INTERNATIONAL CORP. | Barbados | Barbados | Paradise Papers |
| CERONE CHINA INTERNATIONAL LTD | Samoa | | Pandora Papers |
| ABACARE CHINA LIMITED | British Virgin Islands | British Virgin Islands | Pandora Papers |
| United China Opportunity Limited | British Virgin Islands | British Virgin Islands | Pandora Papers |
| China Assets Portfolio Limited | British Virgin Islands | British Virgin Islands | Pandora Papers |
| China Investment Advisory Limited | British Virgin Islands | British Virgin Islands | Pandora Papers |
| China PA Holdings Limited | British Virgin Islands | British Virgin Islands | Pandora Papers |
| China PA I Limited | British Virgin Islands | British Virgin Islands | Pandora Papers |
| China PA II Limited | British Virgin Islands | British Virgin Islands | Pandora Papers |
| PA China Investment Limited | British Virgin Islands | British Virgin Islands | Pandora Papers |
| Victory China Bright Limited | British Virgin Islands | British Virgin Islands | Pandora Papers |
| EQUITY CHINA INC. | British Virgin Islands | British Virgin Islands | Pandora Papers |
| EQUITY CHINA PARTNERS LIMITED | British Virgin Islands | British Virgin Islands | Pandora Papers |
| INTER-CHINA GROUP LIMITED | British Virgin Islands | British Virgin Islands | Pandora Papers |
| PACIFIC CHINA HOLDINGS LTD. | British Virgin Islands | British Virgin Islands | Pandora Papers |
| PAG China Investment Limited | British Virgin Islands | British Virgin Islands | Pandora Papers |
| CHINA VITALITY LIMITED | Hong Kong | | Pandora Papers |
| CYWORLD CHINA (HOLDINGS) LIMITED | Hong Kong | | Pandora Papers |
| FOUNT CHINA LIMITED | Hong Kong | | Pandora Papers |
| HANYU CHINA CO., LIMITED | Hong Kong | | Pandora Papers |
| NHN GREATER CHINA LIMITED | Hong Kong | | Pandora Papers |
| SENO CHINA LIMITED | Hong Kong | | Pandora Papers |
| SNOW CHINA LIMITED | Hong Kong | | Pandora Papers |
| NEO-CHINA ENERGY LIMITED [Neo-China Industrial Limited | British Virgin Islands | Hong Kong | Panama Papers |
| China Silicon Steel Holding Limited China Silicon Steel Holding Limited | Not identified | China, British Virgin Islands | Offshore Leaks |
| CHINA STAR HOLDINGS GROUP LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| UNION ADVERTISING (CHINA) COMPANY LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA PROSPEROUS INTERNATIONAL INVESTMENT LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA SUCCESS INTERNATIONAL HOLDINGS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA DEVELOPMENT FINANCE (SHENZHEN) CORPORATION | British Virgin Islands | Hong Kong | Panama Papers |
| COSMETIC CARE CHINA (HOLDINGS) LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA CONNECTION INTERNATIONAL INVESTMENT LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| YCH CHINA HOLDINGS (BVI) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA HOUSE OF TRADE LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| SOUTH CHINA PRODUCT CO. LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA MERCHANTS UNION BVI) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| GUANG LEE CHINA SECURITIES LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA PROPERTY FUND MANAGEMENT LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA SINGKONG INVESTMENT HOLDINGS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| GLOBAL INVESTMENTS (INDO-CHINA) LIMITED | British Virgin Islands | Guernsey | Panama Papers |
| CHINA FINANCE INVESTMENT HOLDINGS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA AIR BOSS HOLDINGS INC. | British Virgin Islands | Hong Kong | Panama Papers |
| FIRST EASTERN CHINA PROPERTIES LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| China Oceanwide Property Holdings Limited | British Virgin Islands | Hong Kong | Panama Papers |
| VIDEO-FILM PRODUCTIONS (CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA CHEM (QINGDAO) CO., LTD. | Samoa | Hong Kong | Panama Papers |
| Azad Collection (China) Co.,Ltd | Samoa | Hong Kong | Panama Papers |
| China Qiji Industry Co., Ltd. | British Anguilla | Hong Kong | Panama Papers |
| CHINA CABLEVISION INTERNET COMPANY LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| APEC (CHINA) ASSET MANAGEMENT LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| ASSOCIATED TOBACCO COMPANY (CHINA) LIMITED | British Virgin Islands | Switzerland | Panama Papers |
| GLOBAL TOTAL LOGISTICS (CHINA) LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA MARK SATELLITE TELEVISION LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| FIRST EASTERN CHINA INVESTMENT LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| GREAT CHINA INTERNATIONAL ENTERPRISES LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| VSC CHINA) INVESTMENTS HOLDINGS LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| YUEXIU PROPERTY CHINA) COMPANY LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| SSI CHINA RESOURCES PTY LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| TAUNUS PRINTING (CHINA) COMPANY LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| MAY FAIR PAINT (CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA DRAGON INTERNATIONAL (HOLDINGS) LIMITED | British Virgin Islands | United Kingdom | Panama Papers |
| AWT CHINA TRANSPORT INVESTMENT LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| UNITED ADVERTISING (CHINA) COMPANY LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA FOOD AND BEVERAGE INC. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA RICH INTERNATIONAL HOLDINGS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| LUK FOOK CHINA (B.V.I.) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA DRAGON INTERNATIONAL GROUP LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA CONCEPT METAL (BVI) LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| SOUTH CHINA INTERNATIONAL HOLDINGS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| SHKP (CHINA) CONSTRUCTION MANAGEMENT LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA GLORY INTERNATIONAL GROUP LTD. | British Virgin Islands | Taiwan | Panama Papers |
| METAL&MINING CAPITAL (CHINA) INC. | British Virgin Islands | Hong Kong | Panama Papers |
| REMARK CHINA AUTOMOTIVE DEVELOPMENT LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| MOSSACK FONSECA & CO. (CHINA) LTD. | British Virgin Islands | Panama | Panama Papers |
| CHINA CHEMICAL GROUP (HOLDINGS) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| AIR WORLD (CHINA) CO., LTD | Samoa | Hong Kong | Panama Papers |
| CHINA TAIYUAN (HOLDINGS) GROUP LTD | British Virgin Islands | Hong Kong | Panama Papers |
| YURI (CHINA) INTERNATIONAL HOLDINGS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA INTERNATIONAL ENERGY INVESTMENTS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| China Great Agriculture (Holding) Limited | British Virgin Islands | Hong Kong | Panama Papers |
| RED SUN GROUP (CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA AUTO TECHNOLOGY INVESTMENT LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA PGA TOUR HOLDINGS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| ALV CHINA & ASIA CAPITAL LTD. | British Virgin Islands | Thailand | Panama Papers |
| IT CHINA HOLDING CO., LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA TOC DECORATION HOLDINGS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA COAL TRADE CO LIMITED | British Virgin Islands | Jersey | Panama Papers |
| CHINA GROWING CHEMICAL CO., LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA JINHUI INTERNATIONAL COMPANY LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| SILVER DATATECH CHINA CO., LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA ELECTRONICS INTERNATIONAL GROUP LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| China Everbest Industrial Co., Ltd. | Seychelles | Hong Kong | Panama Papers |
| CHINA HOUSE-TECH INVESTMENT LIMITED | British Virgin Islands | Cyprus | Panama Papers |
| No.33 China Art Ltd | British Virgin Islands | China | Panama Papers |
| CHINA HENGWANG MINING CO., LTD. | British Virgin Islands | China | Panama Papers |
| WEALTH FAITH INDUSTRIAL (CHINA) LIMITED | British Virgin Islands | China | Panama Papers |
| HONOR LEGEND TECHNOLOGY (CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| FAITH SUN TECHNOLOGY (CHINA) LIMITED | Seychelles | China | Panama Papers |
| CHINA PHOS-CHEM TRANSPORTATION LTD. | Niue | Hong Kong | Panama Papers |
| CHINA BEIDA EDUCATION HOLDINGS LIMITED | Niue | Hong Kong | Panama Papers |
| CHINA CONCEPT INVESTMENT (BVI) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA INFRASTRUCTURE B.V.I.) COMPANY LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA FOODS INVESTMENT MANAGEMENT LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| KING BROTHERS & ASSOCIATES (CHINA) LTD. | British Virgin Islands | Switzerland | Panama Papers |
| HONG KONG CHINA FUNDS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA TREASURE HOLDING BVI) LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA SINGKONG DEVELOPMENT HOLDINGS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| SHKP (CHINA) PROJECTS MANAGEMENT LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| SOUTHERN CHINA RESOURCES GROUP INC. | British Virgin Islands | Belize | Panama Papers |
| TSE’S (CHINA CONCEPT) HOLDINGS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHEUNG KONG (CHINA INFRASTRUCTURE) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| KOPPEN YAN ZIMMERMANN (CHINA) INC. | British Virgin Islands | Hong Kong | Panama Papers |
| MEILIN (CHINA) HOLDING GROUP LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| HILLER PHARMA ( CHINA ) CO. LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| SUOANG INTERNATIONAL HOLDINGS (CHINA) CORPORATION | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA STARHOUSE TRADING CO., LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA NAKASENDO INTERNATIONAL GROUP LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| DIGITAL CHINA EPRO (BVI) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA STRATEGY & INVESTMENT GROUP LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA FINANCIAL ENGINEERING COMPANY LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA UNION INTERNATIONAL TECHNOLOGY INC. | British Virgin Islands | Hong Kong | Panama Papers |
| RISING SUN ENERGY (CHINA) LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA FRAME AND MIRROR, LTD. | British Virgin Islands | China | Panama Papers |
| CHINA NORTH DAIRY GROUP LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| SUNRISE CHINA TRADE COMPANY LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| NETPLUS GREATER CHINA COMPANY LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA MOBILE TEK HOLDING LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| China Wind Power Holdings Limited | British Virgin Islands | Hong Kong | Panama Papers |
| UNIBEST INTERNATIONAL GROUP (CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA EVERBRIGHT RESOURCES INVESTMENT LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| LENSO INTERNATIONAL (CHINA) HOLDING LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA VITUP HEALTHCARE HOLDINGS INC. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA SPORTS PROFESSIONAL NETWORK, INC. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA WIND POWER INVESTMENT LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA EUROPE TRADING COMPANY LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA AGRICULTURE RESOURCES INVESTMENT LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| China Sunshine Investment Co., Ltd. | British Virgin Islands | Hong Kong | Panama Papers |
| Green Global Licorice China Limited | British Virgin Islands | Hong Kong | Panama Papers |
| MAGN Media (China) Holdings Limited | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA CAPITAL RESOURCES HOLDINGS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| FORTUNE INVESTMENT (CHINA) CO., LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| China International Energy Group) Limited | British Virgin Islands | Hong Kong | Panama Papers |
| Black Tulip (China) Co., Ltd. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA ZHONG CHEN GROUP LIMITED | British Virgin Islands | China | Panama Papers |
| CHINA C-LINK HOLDING LTD | British Virgin Islands | Hong Kong | Panama Papers |
| China-Russia Trading Company Limited | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA TEAM ENTERPRISE COMPANY LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA OVERSEAS NEW ENERGY LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| China Steel Ball Holdings Ltd. | British Virgin Islands | Switzerland | Panama Papers |
| GAS INVESTMENT CHINA CO., LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| OILFIELD EQUIPMENT GROUP (CHINA) LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| Hands-On China Holdings Ltd. | British Virgin Islands | Hong Kong | Panama Papers |
| ET-CHINA TECHNICAL INTERNATIONAL LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| SHARESUN (CHINA) HOLDINGS CO. LTD. | British Virgin Islands | China | Panama Papers |
| GOLDEN LEAF CHINA HOLDINGS LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA INCORPORATIONS MANAGEMENT BVI) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| VICTOR CHU CHINA INVESTMENT LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA INVESTMENT INCORPORATIONS BVI) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA METALLURGICAL IMPORT & EXPORT CORPORATION | British Virgin Islands | Hong Kong | Panama Papers |
| TOP CHINA STRATEGY INVESTMENTS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA INTELLIGENT ELECTRONIC HOLDING LIMITED | British Virgin Islands | China | Panama Papers |
| ST. PATRICK’S INTERNATIONAL CHINA) LIMITED | British Virgin Islands | United Kingdom | Panama Papers |
| G P Enterprise China Limited | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA INTERNATIONAL CAPITAL HOLDINGS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| BRILLIANCE CHINA AUTOMOTIVE FINANCE LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA VENTURE CAPITAL COMPANY LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| UNITED MEDICAL SERVICES (CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA CEO INVESTMENT MANAGEMENT LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA DIESEL SUPPORT SERVICES LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| China India Alliance Center Limited | British Virgin Islands | Hong Kong | Panama Papers |
| SHEEN CHINA GROUP HOLDINGS INC. | British Virgin Islands | Hong Kong | Panama Papers |
| Welcome Group Investment (China) Limited | British Virgin Islands | Hong Kong | Panama Papers |
| TRANSACTION HOLDINGS (CHINA) CO., LTD | British Virgin Islands | Hong Kong | Panama Papers |
| NEW ERA FOUNDATION CHINA) LIMITED | Bahamas | Hong Kong | Panama Papers |
| ECS Tech (China) Co., Ltd. | British Virgin Islands | Hong Kong | Panama Papers |
| Saint Legends (China) Investment Limited | British Virgin Islands | Hong Kong | Panama Papers |
| Brothers Global China Investments Limited | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA CONFIDENCE WORLD LOGISTICS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| Feichi (China) Machinery Holdings Limited | British Virgin Islands | Hong Kong | Panama Papers |
| China Great Expectation Enterprises Ltd. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA EXPLORER TRAVEL SERVICE LTD. | British Virgin Islands | China | Panama Papers |
| China UniEntry Investment Co., Ltd | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA CHEN TEA CO., LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| China Energy Coal Co., Ltd. | British Virgin Islands | Hong Kong | Panama Papers |
| FANGWEI (CHINA) REFRACTORIES CO., LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| China Machine New Energy Corporation | British Virgin Islands | Hong Kong | Panama Papers |
| China Growth Partners Investment Ltd. | British Virgin Islands | Hong Kong | Panama Papers |
| DESHANG (CHINA) TRADING CO., LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| J & J (CHINA) GARMENT LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| China Universal Business Group Limited | British Virgin Islands | China | Panama Papers |
| China Impression International Holdings Limited | British Virgin Islands | China | Panama Papers |
| CHINA POWER CONSTRUCTION HOLDINGS CORPORATION | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA GREEN MUSIC UNION LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA OIL PRODUCTS GROUP LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| China Best Leasing Group Limited | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA OIL CAPITAL INVESTMENT LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| HILLS (CHINA) INVESTMENT CO., LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| Pastry Horizon (China) Co., Limited | British Virgin Islands | Hong Kong | Panama Papers |
| AGAPE CHINA TRAVEL SERVICE LTD. | British Virgin Islands | China | Panama Papers |
| China Heads Group (B.V.I.) Limited | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA ETONE BUSINESS INTELLIGENCE LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| SHUNAN CHINA) HEALTHCARE GROUP LIMITED | British Virgin Islands | China | Panama Papers |
| MOSSACK FONSECA & CO. (CHINA) LTD.. | British Virgin Islands | Panama | Panama Papers |
| China Fuel International Investment Limited | British Virgin Islands | China | Panama Papers |
| China Tuna Industry Holdings Limited | British Virgin Islands | China | Panama Papers |
| WtC (Way to China) Limited | British Virgin Islands | Hong Kong | Panama Papers |
| Properties (China) Investment Co., Ltd. | British Virgin Islands | Hong Kong | Panama Papers |
| CHUN SING CHINA INVESTMENT LIMITED | Bahamas | Hong Kong | Panama Papers |
| DI HWA ENTERPRISE (CHINA) LIMITED | Bahamas | Hong Kong | Panama Papers |
| CHINA GOLDEN INTERNATIONAL HOLDING LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA HUAYU INTERNATIONAL CO., LTD | British Virgin Islands | China | Panama Papers |
| American & China Studies Institution Ltd. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA CITY ASSET MANAGEMENT LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA-AFRICA INFRASTRUCTURE DESIGN LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| China Top Communication Co., Ltd. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA BAOSHENG INDUSTRIAL CO., LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CONTINENTAL CONSOLIDATORS (CHINA) CO. LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA GLORY MEDIA GROUP LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| China Mingxiang Energy Co., Limited | British Virgin Islands | China | Panama Papers |
| B&P Management (China) Corporation | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA HONGDA TRADE CO., LTD | British Virgin Islands | Hong Kong | Panama Papers |
| China Hourong Energy Co., Limited | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA RELIANCE INVESTMENT HOLDINGS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| First Internet Technology (China) Limited | British Virgin Islands | China | Panama Papers |
| CHINA CHENGTONG INDUSTRIAL CO., LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA XINDELONG CHEMICAL GROUP LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| China Yishu Electronics Group Limited | British Virgin Islands | Hong Kong | Panama Papers |
| Gopher China Special Opportunity Limited | British Virgin Islands | Hong Kong | Panama Papers |
| PAN-CHINA INVESTMENT HOLDINGS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| ASIA PROPERTY CHINA HOLDINGS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| Euclideon (China) Group Holding Limited | British Virgin Islands | China | Panama Papers |
| Gopher China S.O. Project Limited | British Virgin Islands | Hong Kong | Panama Papers |
| China Jiahe Energy Co., Ltd | British Virgin Islands | Hong Kong | Panama Papers |
| China Engineering Machinery Equipment Limited | Seychelles | Hong Kong | Panama Papers |
| CHINA HUAXIANG INTERNATIONAL CO., LTD. | Seychelles | China | Panama Papers |
| CHINA OVERSEAS FOUNDATION ASSOCIATION LIMITED | Niue | Hong Kong | Panama Papers |
| CHINA DAYUAN INDUSTRY CO., LTD. | Seychelles | China | Panama Papers |
| GRAND PROPERTY CONSULTANTS (CHINA) LIMITED | Niue | Hong Kong | Panama Papers |
| HKP China Motors Service Limited | Seychelles | Hong Kong | Panama Papers |
| China Great Logistics (Pty) Ltd. | Seychelles | Hong Kong | Panama Papers |
| SHUI FONG CHINA CO., LTD. | Seychelles | Hong Kong | Panama Papers |
| China Marsway International Co., Ltd. | Seychelles | Hong Kong | Panama Papers |
| CHINA ENERGY HOLDING CO., LTD. | Seychelles | Hong Kong | Panama Papers |
| CHINA ARTS INTERTRANS CO., LTD. | Seychelles | Hong Kong | Panama Papers |
| CHINA SUNLIGHT INDUSTRY CO.,LTD | Seychelles | Hong Kong | Panama Papers |
| EAST (CHINA) CONSTRUCTION MATERIAL LIMITED | Seychelles | Hong Kong | Panama Papers |
| CHINA RUNWIN LIGHTING CO., LTD. | Seychelles | Hong Kong | Panama Papers |
| DAF LOCKS CHINA CO., LTD. | Seychelles | Hong Kong | Panama Papers |
| FINE CHINA INTERNATIONAL INDUSTRIAL LIMITED | Seychelles | Hong Kong | Panama Papers |
| Annvita China Group Co., Ltd. | Seychelles | China | Panama Papers |
| FUJI (CHINA) HOLDINGS CO., LTD. | Seychelles | China | Panama Papers |
| CHINA BRIGHT INTERNATIONAL HOLDINGS S.A. | Niue | Hong Kong | Panama Papers |
| CHINA LIGHT ENGINEERING DEVELOPMENT LIMITED | Niue | Hong Kong | Panama Papers |
| GREATER CHINA INET GROUP INC. | Niue | Hong Kong | Panama Papers |
| EVER FORTUNE (CHINA) INVESTMENT LIMITED | Niue | Hong Kong | Panama Papers |
| KEYLAND INTERNATIONAL GROUP (CHINA) LIMITED | Niue | Hong Kong | Panama Papers |
| STRAIT HOLDINGS (CHINA) INVESTMENT LIMITED | Niue | Hong Kong | Panama Papers |
| CHINA STRATEGY & INVESTMENT GROUP LIMITED | Niue | Hong Kong | Panama Papers |
| CHINA TV PROGRAM AGENCY LTD. | Niue | Hong Kong | Panama Papers |
| CHINA ENTERPRISE INDUSTRIAL CO., LTD | Niue | Hong Kong | Panama Papers |
| CHINA EDUCATION INVESTMENT HOLDINGS LIMITED | Niue | Hong Kong | Panama Papers |
| SINO OCEAN ENTERPRISES (CHINA) LIMITED | Niue | Hong Kong | Panama Papers |
| NATIONAL GEM DEVELOPMENT (CHINA) LTD. | Niue | Hong Kong | Panama Papers |
| ENTERTAINMENT FRANCHISING GREATER CHINA LTD. | Niue | Hong Kong | Panama Papers |
| Kew Capital China Development Limited | Samoa | Hong Kong | Panama Papers |
| ANGLO-CHINA INTERNATIONAL TRADE S.A. | Panama | Jersey | Panama Papers |
| CHINA SPORTS UNITED INVESTMENT LIMITED | Samoa | Hong Kong | Panama Papers |
| CHINA SUCCEED TRADING CO., LTD. | Samoa | Hong Kong | Panama Papers |
| China South Recycling Co., Ltd. | Samoa | Hong Kong | Panama Papers |
| CHINA HUATONG INDUSTRY CO., LTD | Samoa | Hong Kong | Panama Papers |
| China Resources Group Co., Limited | Samoa | Hong Kong | Panama Papers |
| GOLDEN CHINA INTERNATIONAL HOLDINGS LIMITED | Niue | Hong Kong | Panama Papers |
| BSA M&E (CHINA) LIMITED | Niue | Hong Kong | Panama Papers |
| CHINA SUNRISE INVESTMENT CO., LIMITED | Samoa | Hong Kong | Panama Papers |
| CHINA MINING INVESTMENTS HOLDINGS LIMITED | Samoa | Hong Kong | Panama Papers |
| CHINA COAST FREIGHT CO., LTD. | Samoa | Hong Kong | Panama Papers |
| ACNTR (CHINA) TIRE CO., LTD. | Samoa | Hong Kong | Panama Papers |
| CHINA POWER INTERNATIONAL GROUP LIMITED | Samoa | Hong Kong | Panama Papers |
| RICHTUNE INTERNATIONAL (CHINA) CO., LIMITED | Samoa | Hong Kong | Panama Papers |
| CHINA BEST INVESTMENT DEVELOPMENT LIMITED | Samoa | Hong Kong | Panama Papers |
| CHINA SOURCING GROUP CO., LTD. | Samoa | Hong Kong | Panama Papers |
| St. City China H.K. Limited | Hong Kong | Hong Kong | Offshore Leaks |
| CHINA FORYOO CHAIN GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHANGING CHINA CULTURE EDUCATION CORPORATION | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA HONGYE INTERNATIONAL GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Saga-China Management Co., Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Regenerative Medicine Co., Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Plumbings & Hardwares Co., Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHANGING CHINA INVESTMENT HOLDINGS CORPORATION | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA GREAT WELL HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA FAST GROWTH FORESTRY LIMITED | Cayman Islands | Cayman Islands | Offshore Leaks |
| WICOM Technology (China) Co., Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Talent Found Capital Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA INTERNATIONAL MINING COMPANY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| ANGOLA-CHINA INVESTMENT CO. LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| NEWSTAR (CHINA) INDUSTRIAL CO., LTD | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| JOY PROPERTY CHINA II LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| LINK SINO CHEMICALS (CHINA) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA DIRECT MARKETING GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Asean Venture International Ltd | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA RESOURCES INVESTMENT HOLDINGS LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| DOUBLE-I DEVELOPMENT (CHINA) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| MINGSHENG INTERNATIONAL TRADE (CHINA) LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| ELITE CHINA INDUSTRIES CO., LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA GAS ENERGY INVESTMENTS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China E Pack International Inc. | Samoa | Samoa | Offshore Leaks |
| SMART & BROAD CHINA INVESTMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China E Pack Holding Inc. | Samoa | Samoa | Offshore Leaks |
| Sateri China (Hong Kong) Limited | Hong Kong | Hong Kong | Offshore Leaks |
| W & G (CHINA) HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Genesis GST CHINA Holdings Corporation | Samoa | Samoa | Offshore Leaks |
| China-Taiwan Industrial Holdings Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| KANGFULAI (CHINA) INVESTMENT CO., LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| South China Holdings Co., Ltd. | Samoa | Cayman Islands, Samoa | Offshore Leaks |
| CHINA BOKANG INVESTMENT MANAGEMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA MEDICAL DEVELOPMENT CO LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA HIGHWAY & BUILDING DEVELOPMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| WAH YUEN FOODS (CHINA) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| New World China Enterprises Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA PEACE INVESTMENTS GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| LOYAL BRIGHT (CHINA) HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| MAY FAIR (CHINA) FUND LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA FINANCE GROUP (ASIA) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| HITECH NIAGA INDO-CHINA LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA POWER HOLDINGS GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| GREATER CHINA INTERNATIONAL GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| NEW WORLD CHINA INDUSTRIAL LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA INVESTMENT HOLDING GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China E-Net Management Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA BIT INVESTMENT HOLDINGS LTD | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA TIME HOLDINGS GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| YesMobile China Development Company Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| New China Technology Licensing Inc. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Gas Development Group Limited. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA RESOURCES INVESTMENT GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Feiligao (China) Technology Company Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA SOUND INVESTMENT GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Core China Series Two Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Clinical Trials Centre Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA BRIGHT DEVELOPMENT GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA MOBILE TV HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Natural Gas Development Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA BLOOD SAFETY HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| MACAU PRIME PROPERTY (CHINA) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China International Education Investment Inc. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Industrial Investment Holdings Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Yulon China Investment Co., Ltd. | British Virgin Islands | British Virgin Islands, Cayman Islands | Offshore Leaks |
| China Commerce Development Co. Ltd. | Samoa | Samoa | Offshore Leaks |
| Global China Advertising Services Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Overseas Petroleum Co. Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA THOROUGHFARE INTERNATIONAL HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Greater China Environmental Protection Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA SUNLIGHT CAPITAL MANAGEMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Leader Management (BVI) Inc. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Tech Asset Management Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Smart Card Investment Inc. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA MINING INVESTMENT GROUP LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Dragon Petroleum Co., Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA CAREER ASSOCIATES CO., LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA TIMES MEDIA GROUP CORPORATION | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| BEST CHINA GLOBAL SERVICES LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA JIAMING ENTERPRISES INVESTMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Strategic Investment Capital Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| GUOLI (CHINA) EDUCATION ORGANIZATION LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA CITY NATURAL GAS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA RESOURCE UNITED DEVELOPMENT LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| QINGDAO SUNFINE (CHINA) CO., LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| EVERBRIGHT CONSTRUCTION INVESTMENT (CHINA) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA MORAL INTERNATIONAL HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA GUOMIN INVESTMENT HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Greater China Beverage Group Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA JINHUI GROUP COMPANY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| TOP CHINA FAR EAST LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA ELECTRONICS BROADBAND MEDIA LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA NATIONAL RESOURCE GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA NATIONAL ENERGY GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA ZHEJIANG PINNACLE INDUSTRY LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| JOY PROPERTY CHINA III LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA RUNFA OLEOCHEMICALS CO., LTD. | Samoa | Samoa | Offshore Leaks |
| CHINA HONOUR FAR EAST LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China NewTop Investment Co., Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| U.S.-CHINA INVESTMENT COMPANY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| MACAU PRIME INVESTMENT (CHINA) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Sud-Chemie China Holding Limited | Hong Kong | Hong Kong | Offshore Leaks |
| SINOTRAMP MARINE CHINA CO., LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| LOYAL WAY (CHINA) GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| FAME WAY (CHINA) GROUP INC. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA HUACHEN INTERNATIONAL CO., LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| South China Gas Holdings Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA WIND ENERGY GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| SOUTH ASIA PHARMACEUTICAL (CHINA) LIMITED | Labuan | Malaysia | Offshore Leaks |
| SUNBRIGHT LIGHTING (CHINA ) COMPANY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA BASE ENTERPRISE CO., LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA EAGLE FAR EAST LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA METAL INDUSTRY HOLDING LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Review Corporate Consultancy Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| JOY PROPERTY CHINA I LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA LINK TRADING GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA MARKET RESEARCH GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA EDUCATION INVESTMENT GROUP INC. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA FRANCHISE NET HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Gas International Trading Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Han Wind Energy China Ltd | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA YIJING SCIENCE RESEARCH LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Genesis GPT CHINA Holdings Corporation | Samoa | Samoa | Offshore Leaks |
| China Coal Energy Holdings Limited | Hong Kong | Hong Kong | Offshore Leaks |
| ANSHENG (CHINA) CAPITAL INVESTMENT LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA PRODUCTS CARE CO., LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| KA YAN CHINA INVESTMENTS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China City Gas Enterprises Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China International SOS Services Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHANG YUANG (CHINA) INVESTMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA AGRO CONSULTING COMPANY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| WebMD Greater China (BVI) Inc. | British Virgin Islands | British Virgin Islands, Cayman Islands | Offshore Leaks |
| CIRCLE (CHINA) INVESTMENT CO. LTD. | British Virgin Islands | Hong Kong, British Virgin Islands | Offshore Leaks |
| China Natural Gas Construction Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Expert Network Company Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA CONCORD ALLIANCE CO., LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA SCIENCES CONSERVATIONAL POWER LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Hai Pai Fishery (China) Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA GLOBAL LINK HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Fluoride Industries Holdings Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| VTION TECHNOLOGY (CHINA) COMPANY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Elegance Mining Company Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| ARTWAY PRODUCTS (CHINA) COMPANY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Greater China Group Holdings Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Oilfield Services (BVI) Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| SUPREME CHINA ASSETS MANAGEMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| HONG KONG CHINA TRADING LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA LAND & SKY INVESTMENTS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| ASIA-PAC CHINA PROPERTIES LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA PROFIT HOLDINGS GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA LINK INVESTMENT GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| SB China Venture (Holding) Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Great China Data Comm. Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA E-BUSINESS INVESTMENTS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA DIRECT MARKETING SERVICES LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA YANJING ENTERPRISES INVESTMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| SNACK SHOP (CHINA) INVESTMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA BRIGHT HOLDINGS GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Natural Gas Investment Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| SL&A Development (China) Inc. | British Virgin Islands | Cayman Islands, British Virgin Islands | Offshore Leaks |
| China City Gas Construction Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China E-Net Investment Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA LUXURIANCE JADE COMPANY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| New World China Genomics Inc | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Venture Investment Group Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Steel Case Co. Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China CEE (Holdings) Co., Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA GULF TRADING-W.L.L LIMITED | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| The Landmark Group (China) Ltd. | Not identified | Not identified, Hong Kong | Offshore Leaks |
| CHINA USKY INFORMATION TECHNOLOGY LIMITED | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| HK6 Investment China (BVI) Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China International Capital Group Ltd. | Not identified | Hong Kong, Not identified | Offshore Leaks |
| Phoenix Investment Group [China] Limited | Not identified | Hong Kong, Not identified | Offshore Leaks |
| China Orchid Energy Resources Limited | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| Smartech (China) Group Holdings Limited | Not identified | Not identified, Hong Kong | Offshore Leaks |
| Teksen Horizon Systems (China) Limited | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| Ectra Euro-China Trading Limited | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| China E-Access (BVI) Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China Star International Enterprise Ltd. | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| Vera Focus China Co., Ltd. | Not identified | British Virgin Islands, China | Offshore Leaks |
| China Packing Resources Corporation Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China Enterprise Investors Management Limited | Not identified | Hong Kong, Not identified | Offshore Leaks |
| E&L China Co., Ltd | Not identified | China, British Virgin Islands | Offshore Leaks |
| China Trade Service Holding Limited | Not identified | Not identified, Hong Kong | Offshore Leaks |
| CHINA MINMETALS RESOURCES COMPANY LIMITED | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China International Engineering Construction Corporation | Not identified | Hong Kong, Not identified | Offshore Leaks |
| China Electricity Development Management Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| CHINA FORTUNE CAPITAL MANAGEMENT LIMITED | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| Oracle Market Research (China) Ltd. | Not identified | Hong Kong, Not identified | Offshore Leaks |
| Pacific-China United Holdings Ltd. | Not identified | Hong Kong, Not identified | Offshore Leaks |
| China Sea Investment Group Ltd. | Not identified | Not identified, Hong Kong | Offshore Leaks |
| Energy Capital (China) Holdings Inc. | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| CHINA VIRTUAL TELECOM HOLDINGS LTD. | Not identified | British Virgin Islands, China | Offshore Leaks |
| China Tax & Business Consultants Limited | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| China World Trade Holdings Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China Venture Capital Management Inc. | Not identified | British Virgin Islands, China | Offshore Leaks |
| Growth Capital China Management Limited | Not identified | China, British Virgin Islands | Offshore Leaks |
| CHINA ORIENT OASIS INVESTMENT LIMITED | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| China Web Concept Company Ltd. | Not identified | Not identified, Hong Kong | Offshore Leaks |
| China House of Trade Limited | Not identified | Not identified, Hong Kong | Offshore Leaks |
| CHINA TREASURE INTERNATIONAL DEVELOP LIMITED | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| Ectra Euro-China Trade Limited | Not identified | Hong Kong, Not identified | Offshore Leaks |
| CHINA TZN (BVI) TOPRISE LIMITED | Not identified | British Virgin Islands, China | Offshore Leaks |
| Capkross (China) Petroleum Company Limited | Not identified | Not identified, Hong Kong | Offshore Leaks |
| East China Sea Investments Ltd. | Not identified | Not identified, United States | Offshore Leaks |
| FANGLIN MINERALS (CHINA) CO., LIMITED | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| CHINA UNION INTERNATIONAL TRADING LTD. | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| New China Telecom Group Ltd. | Not identified | Not identified, Canada | Offshore Leaks |
| ACCESS CHINA INVESTMENT COMPANY LTD. | Not identified | China, British Virgin Islands | Offshore Leaks |
| CHINA FIRE PROTECTION GROUP INC. | Not identified | China, British Virgin Islands | Offshore Leaks |
| China Medicare Investment Holdings Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| CHINA 9D DECORATION GROUP LIMITED | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China Oasis Regulate Sand Limited | Not identified | Hong Kong, Not identified | Offshore Leaks |
| China Base (Hong Kong) Limited | Not identified | Not identified | Offshore Leaks |
| China Finance Group (Asia) Ltd | Not identified | Not identified | Offshore Leaks |
| China Intellectual Property (H.K.) Limited | Not identified | Not identified | Offshore Leaks |
| CHINA TREASURY INTERNATIONAL DEVELOP LIMITED | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| Greater China Environmental Protection Ltd. | Not identified | Not identified | Offshore Leaks |
| Pacific Medical Group China Limited | Not identified | Not identified, Hong Kong | Offshore Leaks |
| China Advanced Mold International Corp. | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| CHINA ORIENT HOME COMPANY LIMITED | Hong Kong | Hong Kong | Offshore Leaks |
| CHINA GOLDEN GOOD (HOLDINGS) LIMITED | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China All Way Co., Ltd. | Not identified | Not identified | Offshore Leaks |
| CHINA SILVERTONE HOLDING CO., LTD. | Not identified | British Virgin Islands, China | Offshore Leaks |
| CHINA DRAGON INTERNATIONAL INVEST LIMITED | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China United Technologies Co., Ltd. | Not identified | China, British Virgin Islands | Offshore Leaks |
| CHINA REAL ESTATE INVESTMENT LIMITED | Samoa | Samoa | Offshore Leaks |
| China Eagle Group Co. Ltd. | Not identified | Not identified | Offshore Leaks |
| CHINA PROPERTY DEVELOPMENT INVESTMENTS LIMITED | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China Sci-Tech Holdings Limited | Not identified | Not identified | Offshore Leaks |
| China Environmental System Monitor Limited | Samoa | Samoa | Offshore Leaks |
| China Expert Net Company Limited | Hong Kong | Hong Kong | Offshore Leaks |
| New World China Land Limited | Not identified | Not identified | Offshore Leaks |
| SunChase International Group (China) Limited | Not identified | Not identified | Offshore Leaks |
| China North International Finance Limited | Cook Islands | Not identified | Offshore Leaks |
| China Silicon Village Holdings Limited | Samoa | Samoa | Offshore Leaks |
| CHINA COMMERCIAL LOGISTICS COMPANY LIMITED | Hong Kong | Hong Kong | Offshore Leaks |
| Bond Corporation International (China) Limited | Cook Islands | Cook Islands | Offshore Leaks |
| NEW WORLD ENTERPRISES (CHINA) LIMITED | Hong Kong | Not identified | Offshore Leaks |
| CHINA CONNECTIONS CENTRE CO., LIMITED | Cayman Islands | Cayman Islands | Offshore Leaks |
| Ronald Lu & Partners (China) Limited | Samoa | Samoa | Offshore Leaks |
| CHINA TOP INTERNATIONAL TRADING LIMITED | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China Petroleum (Overseas) International Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| LITE-ON TECHNOLOGY (CHINA) INC. | Samoa | Samoa, Cayman Islands | Offshore Leaks |
| China City Gas Investment Limited | Samoa | Samoa | Offshore Leaks |
| China Gas Development Group Limited | Samoa | Samoa | Offshore Leaks |
| Solomon China Investments Holdings Limited | Samoa | Samoa | Offshore Leaks |
| CHINA E-INTERNET TECHNOLOGIES LTD. | Samoa | Samoa | Offshore Leaks |
| CHINA ELITE CYBER (HOLDINGS) LIMITED | Cayman Islands | Cayman Islands | Offshore Leaks |
| CHINA INTERACTIVE (S) PTE. LTD. | Singapore | Singapore | Offshore Leaks |
| China Huaxin Group Company Ltd | Samoa | Samoa | Offshore Leaks |
| Rich China Industries Holdings Limited | Not identified | Not identified | Offshore Leaks |
| TES International Transport (China) Ltd. | Not identified | Not identified | Offshore Leaks |
| China Elite Cyber Information Limited | Not identified | Not identified | Offshore Leaks |
| Pentad Construction (China) Company Ltd | Cook Islands | Not identified | Offshore Leaks |
| The HongKong China (1996) Trust | Cook Islands | Not identified | Offshore Leaks |
| International Business Placement China Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA SINOSWEET HOLDINGS COMPANY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA MINING INVESTMENTS GROUP LIMITED | Samoa | Samoa | Offshore Leaks |
| CHINA MEDICARE INT’L CO., LTD | Samoa | Samoa | Offshore Leaks |
| CHINA VENTURE GROUP PTE LTD | Singapore | Singapore | Offshore Leaks |
| CHINA MINING MATERIAL HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Automotive Resources Asia (China) Ltd | Hong Kong | Not identified | Offshore Leaks |
| CHINA EVER SOFTWARE CO., LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Rich Construction Company Limited | Hong Kong | Not identified | Offshore Leaks |
| JOY PROPERTY CHINA IV LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Green China Assets Management Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Expert Project Company Limited | Hong Kong | Hong Kong | Offshore Leaks |
| B & J (CHINA) CO., LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China (EBH) Special Fiber Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Brilliance China Automotive Holdings Limited | Not identified | Not identified | Offshore Leaks |
| China City Gas Development Limited | Samoa | Samoa | Offshore Leaks |
| China & Taiwan Business Consulting Corp. | Not identified | Not identified | Offshore Leaks |
| China Resources (Holdings) Company Limited | Not identified | Not identified | Offshore Leaks |
| WEALTH FAITH INDUSTRIAL (CHINA) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| GENERIC PROTECTION CHINA EIGHT LTD. | Bahamas | | Bahamas Leaks |
| Structured China Guarantee One Ltd. | Bahamas | | Bahamas Leaks |
| STRUCTURED CHINA GUARANTEE TWO LTD. | Bahamas | | Bahamas Leaks |
| CHINA TOWN RESTAURANT AND NIGHTCLUB | Aruba | | Paradise Papers |
| China Angel Investment Management Limited | | British Virgin Islands | Paradise Papers |
| China Partners Capital Management, Limited | Bermuda | Bermuda | Paradise Papers |
| China Partners Property Management, Limited | Bermuda | Bermuda | Paradise Papers |
| China Partners Private Equity, Limited | Bermuda | Bermuda | Paradise Papers |
| IMC SHIPYARD HOLDINGS (CHINA) LTD | Bermuda | Bermuda, Singapore | Paradise Papers |
| China Kangda Food Company Limited | Bermuda | Bermuda, China, Hong Kong | Paradise Papers |
| CHINA DIGITAL CULTURE (GROUP) LIMITED | Bermuda | Bermuda, China | Paradise Papers |
| CHINA ALLIANCE TEXTILE HOLDINGS LIMITED | Bermuda | Bermuda, China | Paradise Papers |
| CHINA BEARING (BERMUDA) CO. LTD. | Bermuda | Bermuda, Singapore | Paradise Papers |
| PRINTEMPS CHINA DEPARTMENT STORES LIMITED | Bermuda | Bermuda, Hong Kong | Paradise Papers |
| China Distance Education Holdings Limited | Bermuda | Bermuda, China, Hong Kong | Paradise Papers |
| CHINA ASSET SOLUTION HOLDINGS LTD. | Bermuda | Bermuda, Hong Kong | Paradise Papers |
| Richly Field China Development Limited | Bermuda | Bermuda, Cayman Islands, Hong Kong | Paradise Papers |
| China Auto Electronics Group Limited | Bermuda | Bermuda, Hong Kong, Singapore | Paradise Papers |
| Unocal China New Ventures, Ltd. | Bermuda | Bermuda, United States | Paradise Papers |
| CHINA MERCHANTS (BERMUDA) COMPANY LIMITED | Bermuda | Bermuda, Hong Kong | Paradise Papers |
| China Merchants Holdings (Bermuda) Limited | Bermuda | Bermuda, Hong Kong | Paradise Papers |
| AXA China Region (Bermuda) Limited | Bermuda | Bermuda, China | Paradise Papers |
| China Copper Industrial Trading Limited | Hong Kong | Hong Kong | Paradise Papers |
| China Commodities Absolute Return Limited | Isle of Man | Isle of Man | Paradise Papers |
| China Jinqiao Properties Holdings Limited | Cayman Islands | Cayman Islands | Paradise Papers |
| WLR China Energy Associates, Ltd. | Cayman Islands | Cayman Islands | Paradise Papers |
| Zheng Yaonan (China) Investment Limited | Cayman Islands | Cayman Islands | Paradise Papers |
| China Commonwealthy Asset Management Limited | Cayman Islands | Cayman Islands | Paradise Papers |
| BOSHENG CHINA SPECIAL VALUE FUND | Cayman Islands | Cayman Islands | Paradise Papers |
| ZZZ-PLAYBOY CLUBS CHINA LTD | Cayman Islands | | Paradise Papers |
| ZZZ-CHINA FISHERY GROUP LIMITED | Cayman Islands | Cayman Islands | Paradise Papers |
| China Capital Management (Cayman) Limited | Cayman Islands | Cayman Islands | Paradise Papers |
| E-BILL (CHINA) HOLDING LTD. | Cayman Islands | Cayman Islands | Paradise Papers |
| China Hospital Group Investment Limited | Cayman Islands | Cayman Islands | Paradise Papers |
| China Global Capital Group Ltd | Cayman Islands | Cayman Islands | Paradise Papers |
| China Global Energy & Resources Ltd | Cayman Islands | Cayman Islands | Paradise Papers |
| GREATER CHINA UTILITIES FUND LIMITED | Cayman Islands | Cayman Islands | Paradise Papers |
| ZZZ-CHINA HOLYWELL INTERNATIONAL LIMITED | Cayman Islands | Cayman Islands | Paradise Papers |
| China Steel & Cement Holdings Limited | Bermuda | Bermuda | Paradise Papers |
| China Resources Gas Group Limited | Bermuda | Bermuda, Hong Kong | Paradise Papers |
| BRILLIANCE CHINA AUTOMOTIVE HOLDINGS LIMITED | Bermuda | Bermuda, United States | Paradise Papers |
| CHINA BRILLIANCE INDUSTRIAL HOLDINGS LIMITED | Bermuda | Bermuda | Paradise Papers |
| BRILLIANCE CHINA MACHINERY HOLDINGS LTD. | Bermuda | Bermuda | Paradise Papers |
| UNOCAL EAST CHINA SEA, LTD. | Bermuda | Bermuda | Paradise Papers |
| Tak Sing (China) Holdings Ltd. | Bermuda | Bermuda | Paradise Papers |
| China North Industries Investment Limited | Bermuda | Bermuda, Singapore | Paradise Papers |
| CHINA CENTURY CEMENT INTERNATIONAL LIMITED | Bermuda | Bermuda, Hong Kong | Paradise Papers |
| China Agri-Products Exchange Limited | Bermuda | Bermuda, Hong Kong, United Kingdom | Paradise Papers |
| WING TAI HOLDINGS (CHINA) LIMITED | Bermuda | Bermuda | Paradise Papers |
| China Nan Feng Group Limited | Bermuda | Bermuda, Hong Kong | Paradise Papers |
| China Toll Bridges & Roads Limited | Bermuda | Bermuda | Paradise Papers |
| APP China Finance (Bermuda) Limited | Bermuda | Bermuda, Indonesia | Paradise Papers |
| China Specialised Fibre Holdings Limited | Bermuda | Bermuda, Hong Kong | Paradise Papers |
| China Biotech Pharmaceutical Company Limited | Bermuda | Bermuda | Paradise Papers |
| Burlington Resources China Holdings Limited | Bermuda | Bermuda, United States | Paradise Papers |
| TerreNAP Data Centers (China), Ltd. | Bermuda | Bermuda, United States | Paradise Papers |
| Scientific Games China Holdings Ltd. | Bermuda | Bermuda, China | Paradise Papers |
| CHINA COMMUNICATIONS CONSTRUCTION COMPANY LIMITED | Malta | Malta | Paradise Papers |
| BARBADOS CHINA FRIENDSHIP ASSOCIATION INC. | Barbados | Barbados | Paradise Papers |
| BARBADOS CHINA CULTURAL CENTRE INC. | Barbados | Barbados | Paradise Papers |
| CHINA MEDICAL TEAM (BARBADOS) INC. | Barbados | Barbados | Paradise Papers |
| China Glass Trading Co., Ltd | | | Pandora Papers |
| SF&OC (HK, CHINA) LIMITED | | | Pandora Papers |
| Quickly (China) Holding Group Limited | British Virgin Islands | British Virgin Islands | Pandora Papers |
| CHINA PROSPER INVESTMENT GUARANTEE LIMITED | British Virgin Islands | British Virgin Islands | Pandora Papers |
| DEVELOPING EQUITIES CHINA INVESTMENTS LTD. | British Virgin Islands | British Virgin Islands | Pandora Papers |
| CHINA INTELLECTUAL PROPERTY INVESTMENT LTD | British Virgin Islands | British Virgin Islands | Pandora Papers |
| CHINA INTELLECTUAL PROPERTY INVESTMENT LTD | British Virgin Islands | British Virgin Islands | Pandora Papers |
| CHINA INTELLECTUAL PROPERTY INVESTMENT LTD | British Virgin Islands | British Virgin Islands | Pandora Papers |
| CHINA DESIGNER OUTLET MALL P.L.C. | Malta | Malta | Paradise Papers |
| CHINA MALTA INTERNATIONAL (C.M.I.) LIMITED | Malta | Malta | Paradise Papers |
| Nations Trust China Holdings Ltd. | Saint Kitts and Nevis | | Paradise Papers |
| GOLD DRAGON SERVICES (CHINA) LIMITED | Saint Kitts and Nevis | | Paradise Papers |
| CHINA TRADING INTERNATIONAL CORPORATION LC | Saint Kitts and Nevis | | Paradise Papers |
| China Trust Company International Limited | Saint Kitts and Nevis | | Paradise Papers |
| CHINA SHUANGJI CEMENT HOLDING LTD. | Saint Kitts and Nevis | | Paradise Papers |
| CHINA MEIYI FURNITURE CO. LTD. | Saint Kitts and Nevis | | Paradise Papers |
| DI HWA ENTERPRISE (CHINA) LIMITED | Bahamas | | Bahamas Leaks |
| PRIME CONSULTING (CHINA) COMPANY LTD | Bahamas | | Bahamas Leaks |
| CHINA HUANG CHAO COMPANY LTD. | Bahamas | | Bahamas Leaks |
| EXXONMOBIL CHINA (SHENZHEN) LNG LIMITED | Bahamas | | Bahamas Leaks |
| NORTHWEST CHINA OPPORTUNITIES FUND LIMITED | Bahamas | | Bahamas Leaks |
| GENERIC CHINA OBLIGATION T LTD. | Bahamas | | Bahamas Leaks |
| GENERIC CHINA OBLIGATION S LTD. | Bahamas | | Bahamas Leaks |
| GENERIC PROTECTION CHINA SIX LTD. | Bahamas | | Bahamas Leaks |
| Generic Protection China Seven Ltd. | Bahamas | | Bahamas Leaks |
| CHINA & BAHAMAS INTERNATIONAL INVESTMENT INCORPORATED | Bahamas | | Bahamas Leaks |
| EXXONMOBIL CHINA GAS PIPELINE LIMITED | Bahamas | | Bahamas Leaks |
| Generic China Obligation Q Ltd. | Bahamas | | Bahamas Leaks |
| CHINA CAPITAL MANAGEMENT COMPANY LTD. | Bahamas | | Bahamas Leaks |
| SOUTH CHINA SEAS TRADING CORPORATION | Bahamas | | Bahamas Leaks |
| Generic Protection China One Ltd. | Bahamas | | Bahamas Leaks |
| Anadarko China Merger Sub, Ltd. | Bahamas | | Bahamas Leaks |
| GENERIC PROTECTION CHINA TWO LTD. | Bahamas | | Bahamas Leaks |
| Generic Protection China Three Ltd. | Bahamas | | Bahamas Leaks |
| NEWFIELD CHINA EXPLORATION COMPANY LTD. | Bahamas | | Bahamas Leaks |
| GENERIC CHINA OBLIGATION U LTD. | Bahamas | | Bahamas Leaks |
| GENERIC CHINA OBLIGATION V LTD. | Bahamas | | Bahamas Leaks |
| Structured China Guarantee Three Ltd. | Bahamas | | Bahamas Leaks |
| GENERIC CHINA OBLIGATION Y LTD. | Bahamas | | Bahamas Leaks |
| GENERIC CHINA OBLIGATION Z LTD. | Bahamas | | Bahamas Leaks |
| Structured China Guarantee Four Ltd. | Bahamas | | Bahamas Leaks |
| Generic Protection China Four Ltd. | Bahamas | | Bahamas Leaks |
| GENERIC PROTECTION CHINA FIVE LTD. | Bahamas | | Bahamas Leaks |
| Generic Protection China Fourteen Ltd. | Bahamas | | Bahamas Leaks |
| ENDIAMA CHINA INTERNATIONAL HOLDING LIMITED | Bahamas | | Bahamas Leaks |
| ASIA PACIFIC HOLDINGS (CHINA) LIMITED | Bahamas | | Bahamas Leaks |
| JIA HONG MACHINERY (CHINA) LIMITED | Bahamas | | Bahamas Leaks |
| KERR-McGEE CHINA PETROLEUM LTD. | Bahamas | | Bahamas Leaks |
| CHUN SING CHINA INVESTMENT LIMITED | Bahamas | | Bahamas Leaks |
| SOUTH CHINA INVESTMENTS HOLDINGS LIMITED | Bahamas | | Bahamas Leaks |
| CHINA SYSTEMS NORTH AMERICA INC | Bahamas | | Bahamas Leaks |
| NEW ERA FOUNDATION (CHINA) LIMITED | Bahamas | | Bahamas Leaks |
| CHINA TZN (BVI ) SUNRISE LIMITED | Not identified | British Virgin Islands, China | Offshore Leaks |
| TAMC-China Management Co., Ltd. | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China Smart International Holdings Limited | Not identified | Not identified, Hong Kong | Offshore Leaks |
| CHINA STAR INDUSTRIAL GROUP LTD. | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| South China Sea Holdings Ltd. | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| Fat Lee (China) Company Limited | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| CHINA UNITED STAR COMPANY LTD. | Not identified | British Virgin Islands, China | Offshore Leaks |
| China Highland Capital Holdings Limited | Not identified | British Virgin Islands, China | Offshore Leaks |
| Pacific Great China Co. Ltd. | Not identified | Not identified, United States | Offshore Leaks |
| Kang Kang China Holdings Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| MAN SANG CHINA CO., LIMITED | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China Medi-Pharm Investment Inc. | Not identified | China, British Virgin Islands | Offshore Leaks |
| China International Trade Group Ltd. | Not identified | Not identified, Hong Kong | Offshore Leaks |
| Samson Paper (China) Licensing Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China PE Investment Federation Ltd. | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| HK-China International Trading Ltd. | Not identified | China, British Virgin Islands | Offshore Leaks |
| PAM & FRANK (CHINA) TRADING LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA TOP INTERNATIONAL INVESTMENTS LIMITED | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| Capital China Media Group Limited | Not identified | Not identified, Hong Kong | Offshore Leaks |
| China Consumable Goods Investment Corporation | Not identified | British Virgin Islands, China | Offshore Leaks |
| China-Victory Business Group Ltd. | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| Greater China Investment Group Ltd. | Not identified | Not identified, Hong Kong | Offshore Leaks |
| China Commerce Development Co. Ltd | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Multimedia Information (Group) Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Infotech Holdings Co. Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Eke Holdings (BVI) Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA GEO-GEOTECHNICAL ENGINEERING LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Youth Development Group Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA GAS INVESTMENT CONSTRUCTION LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA GAS INVESTMENT DEVELOPMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Sono Digital-Tech Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA HUANGJIN INVESTMENT COMPANY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA CENTURY HOLDINGS GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA REVIEW INVESTMENT HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| GREEN ENERGY RESOURCE (CHINA) CORPORATION | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA NOBLE CLASS TECHNOLOGIES LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA REVIEW FINANCIAL HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| TOP CHINA INTERNATIONAL HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA DISCOVERY ASSETS MANAGEMENT INC. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| TRAFFIC ENERGY (CHINA) INVESTMENT LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Aeronautical Technology Fund Limited | Cook Islands | Not identified | Offshore Leaks |
| Yuk Long Production (China) Limited | Samoa | Samoa | Offshore Leaks |
| China Resources International Holdings Limited | Samoa | Samoa | Offshore Leaks |
| STAR TELECOM OVERSEAS (CHINA) LIMITED | Hong Kong | Not identified | Offshore Leaks |
| China Elite Cyber Information Limited | Not identified | Not identified | Offshore Leaks |
| New China Business Consultant Company | Not identified | Not identified | Offshore Leaks |
| South China Commercial Corp. Ltd. | Not identified | Not identified | Offshore Leaks |
| Hang Ten (China) Group Ltd. | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| CHINA TRADE INVESTMENT GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| PAM & FRANK (CHINA) DEVELOPMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHEUNG SHING ENTERPRISES (CHINA) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA INVESTMENT HOLDINGS (BVI) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHEUNG SHING HOLDINGS (CHINA) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| NEW CHINA CONTROL SYSTEMS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| COOPERATIEVE VERENIGING NEW CHINA CLUB | Aruba | | Paradise Papers |
| CHINA WON DEPARTMENT STORE VOF | Aruba | | Paradise Papers |
| WLR China Energy CV, L.P. | Cayman Islands | Cayman Islands, United States | Paradise Papers |
| CYPRESS GREATER CHINA FUND L.P. | Cayman Islands | Cayman Islands | Paradise Papers |
| Morningside China TMT GP, L.P. | Cayman Islands | Cayman Islands | Paradise Papers |
| First China Opportunity Fund, L.P. | Cayman Islands | Cayman Islands, Hong Kong | Paradise Papers |
| CHINA NORTHERN OIL CO., LIMITED | British Virgin Islands | British Virgin Islands | Paradise Papers |
| CHINA GRAPHITE INVESTMENT CO., LIMITED | British Virgin Islands | British Virgin Islands, China | Paradise Papers |
| China Trend Asia Pacific Ltd | British Virgin Islands | British Virgin Islands, China | Paradise Papers |
| China Jinqiao Overseas Investments Limited | British Virgin Islands | British Virgin Islands, China | Paradise Papers |
| China Jinqiao International Investments Limited | British Virgin Islands | China | Paradise Papers |
| PCD China Real Estate Limited | British Virgin Islands | British Virgin Islands, Hong Kong | Paradise Papers |
| Bolina (China) Holding Co., Ltd. | British Virgin Islands | British Virgin Islands, China | Paradise Papers |
| CSV China Opportunities Fund, L.P. | British Virgin Islands | British Virgin Islands | Paradise Papers |
| Sunshine 100 China Holdings Ltd | Cayman Islands | Cayman Islands | Paradise Papers |
| ZZZ-ASKAR CHINA CAYMAN LTD | Cayman Islands | Cayman Islands | Paradise Papers |
| China Aluminum Cans Holdings Limited | Cayman Islands | Cayman Islands, Hong Kong | Paradise Papers |
| JAYHAWK CHINA FUND (CAYMAN) LTD. | Cayman Islands | Cayman Islands | Paradise Papers |
| China U-Ton Holdings Limited | Cayman Islands | Cayman Islands | Paradise Papers |
| Galaxy (China) Environmental Technology Ltd. | Cayman Islands | Cayman Islands | Paradise Papers |
| China Automobile Holding Group Limited | Cayman Islands | Cayman Islands | Paradise Papers |
| China Automobile Group Co., Limited | Cayman Islands | Cayman Islands | Paradise Papers |
| China Prosperity Investment Management Limited | Cayman Islands | Cayman Islands | Paradise Papers |
| IS China Strategy Balanced Fund | Cayman Islands | Cayman Islands, China | Paradise Papers |
| China Ludao Technology Company Limited | Cayman Islands | Cayman Islands, China | Paradise Papers |
| China Wood Optimization (Holding) Limited | Cayman Islands | Cayman Islands, Hong Kong | Paradise Papers |
| China Shi Quan Mining Ltd. | Cayman Islands | Cayman Islands, United States | Paradise Papers |
| China-USA Healthy Drinks Ltd. | Cayman Islands | Cayman Islands | Paradise Papers |
| China Zhongsheng Resources Holdings Limited | Cayman Islands | Cayman Islands, Hong Kong | Paradise Papers |
| Viva China & Macro Opportunity Fund | Cayman Islands | Cayman Islands, China | Paradise Papers |
| Xinchen China Power Holdings Limited | Cayman Islands | Cayman Islands, Hong Kong | Paradise Papers |
| KS China Premium Enterprise Fund | Cayman Islands | Cayman Islands, China | Paradise Papers |
| LONGAN CHINA VALUE SELECT FUND | Cayman Islands | Cayman Islands, China | Paradise Papers |
| Infore Capital China Growth Fund | Cayman Islands | Cayman Islands, China | Paradise Papers |
| CHINA HAINAN AGRICULTURE COMPANY LIMITED | Cayman Islands | Cayman Islands, China | Paradise Papers |
| New Vision China Fund SPC | Cayman Islands | Cayman Islands, Hong Kong | Paradise Papers |
| China U-Ton Holdings Limited | Cayman Islands | Cayman Islands | Paradise Papers |
| APS China A Share Fund | Cayman Islands | Cayman Islands | Paradise Papers |
| CHINA METAL INTERNATIONAL HOLDINGS INC. | Cayman Islands | Cayman Islands, Taiwan | Paradise Papers |
| China Linen Textile Industry, Ltd. | Cayman Islands | Cayman Islands | Paradise Papers |
| China High Growth Fund Limited | Cayman Islands | Cayman Islands, Hong Kong | Paradise Papers |
| Fuzon (China) Investment Holdings Limited | Cayman Islands | Cayman Islands, Hong Kong | Paradise Papers |
| CHINA INSTANT FOOD HOLDINGS LIMITED | Cayman Islands | Cayman Islands, Hong Kong | Paradise Papers |
| First China Partners Management, LLC | Cayman Islands | Cayman Islands, Hong Kong | Paradise Papers |
| Galaxy China Deep Value Fund | Cayman Islands | Cayman Islands, Hong Kong | Paradise Papers |
| JVSakk Opportunity Fund – Greater China | Cayman Islands | Cayman Islands | Paradise Papers |
| China Lumena New Materials Corp. | Cayman Islands | Cayman Islands, Hong Kong | Paradise Papers |
| South China Industries Limited ** INCOMPLETE ** | Cayman Islands | Cayman Islands, Hong Kong | Paradise Papers |
| China Electronic Technology Fund ** INCOMPLETE ** | Cayman Islands | Cayman Islands | Paradise Papers |
| China Gold Fund Ltd. ** INCOMPLETE ** | Cayman Islands | Cayman Islands | Paradise Papers |
| China Pipeline Holdings Ltd. ** INCOMPLETE ** | Cayman Islands | Cayman Islands, United States | Paradise Papers |
| China All Access (Holdings) Limited | Cayman Islands | Cayman Islands | Paradise Papers |
| GENERAL MINERAL (CHINA OROTON) LTD. | Bahamas | | Bahamas Leaks |
| SOUTH CHINA SEA HOLDINGS, LTD | Bahamas | | Bahamas Leaks |
| CHINA GATEWAY DEVELOPMENT COMPANY LIMITED | Bahamas | | Bahamas Leaks |
| CHINA ASSETS & STRATEGIC HOLDINGS LIMITED | Bahamas | | Bahamas Leaks |
| CHINA CARIBBEAN CONSTRUCTION COMPANY INC. | Barbados | Barbados | Paradise Papers |
| CHINA CARIBBEAN TRADE & DEVELOPMENT LTD | Barbados | Barbados | Paradise Papers |
| BAKER HUGHES CHINA HOLDINGS SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING I SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING II SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT I SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT II SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING IV SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT IV SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT III SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT VI SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT V SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING VII SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING V SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING VI SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT VII SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING III SRL | Barbados | Barbados | Paradise Papers |
| DAC CHINA DISTRESSED (BARBADOS), SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XI SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XII SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XIII SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XIV SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING VIII SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT IX SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING IX SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT X SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING X SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XI SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XII SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XIII SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XIV SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT VIII SRL | Barbados | Barbados | Paradise Papers |
| DAC CHINA OPPORTUNITY (BARBADOS), SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XVI SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XVII SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XVIII SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XV SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XVI SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XVII SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XVIII SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XV SRL | Barbados | Barbados | Paradise Papers |
| DAC CHINA HOTEL (BARBADOS) SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XIX SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XX SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XXI SRL | Barbados | Barbados | Paradise Papers |
| CATELLUS CHINA INVESTMENT I SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XIX SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XX SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XXI SRL | Barbados | Barbados | Paradise Papers |
| CATELLUS CHINA HOLDING I SRL | Barbados | Barbados | Paradise Papers |
| ATI ALLEGHENY CHINA HOLDINGS SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XXIII SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XXIV SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XXV SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XXVI SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XXVII SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XXVIII SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XXIX SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XXX SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XXXI SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XXXII SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XXXIII SRL | Barbados | Barbados | Paradise Papers |
| PH CHINA INVESTMENT II SRL | Barbados | Barbados | Paradise Papers |
| PH CHINA INVESTMENT III SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XXXVI SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XXXVII SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XXXVIII SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XXXIX SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XL SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XLI SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XLII SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XXIII SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XXIV SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XXV SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XXVI SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XXVII SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XXVIII SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XXIX SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XXX SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XXXI SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XXXII SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XXXIII SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING LXV SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING LXVI SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XXXVI SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XXXVII SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XXXVIII SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XXXIX SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XL SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XLI SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XLII SRL | Barbados | Barbados | Paradise Papers |
| DAC CHINA SOS (BARBADOS) SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING L SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING LII SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XLIX SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XLV SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XLVII SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XLIII SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XLIII SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING LXIV SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XLIX SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING LI SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XLVI SRL | Barbados | Barbados | Paradise Papers |
| PH CHINA INVESTMENT I SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XLVI SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XLV SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT L SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XLVII SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT LII SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT XLIV SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING XLIV SRL | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT LI SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA INVESTMENT (53) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA INVESTMENT (54) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA INVESTMENT (55) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA INVESTMENT (59) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA INVESTMENT (62) SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING LIII SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA HOLDING (54) SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING LV SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING LIX SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING LX SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING LXI SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING LXII SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA INVESTMENT (56) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA INVESTMENT (57) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA INVESTMENT (58) SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING LVII SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING LVIII SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING LVI SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA INVESTMENT (60) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA INVESTMENT (61) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA HOLDING (67) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA HOLDING (68) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA HOLDING (69) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA HOLDING (70) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA HOLDING (72) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA HOLDING (71) SRL | Barbados | Barbados | Paradise Papers |
| CHINA LOGISTICS HOLDING LXIII SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA HOLDING (64) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA HOLDING (65) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA HOLDING (66) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA INVESTMENT (69) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA INVESTMENT (70) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA INVESTMENT (71) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA INVESTMENT (72) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA INVESTMENT (63) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA INVESTMENT (64) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA INVESTMENT (65) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA INVESTMENT (67) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA INVESTMENT (66) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA INVESTMENT (68) SRL | Barbados | Barbados | Paradise Papers |
| JOY GLOBAL CHINA HOLDINGS SRL | Barbados | Barbados | Paradise Papers |
| CATELLUS CHINA HOLDING (10) SRL | Barbados | Barbados | Paradise Papers |
| CATELLUS CHINA INVESTMENT (6) SRL | Barbados | Barbados | Paradise Papers |
| CATELLUS CHINA HOLDING (5) SRL | Barbados | Barbados | Paradise Papers |
| CATELLUS CHINA HOLDING (9) SRL | Barbados | Barbados | Paradise Papers |
| CATELLUS CHINA HOLDING (11) SRL | Barbados | Barbados | Paradise Papers |
| CATELLUS CHINA HOLDING (6) SRL | Barbados | Barbados | Paradise Papers |
| CATELLUS CHINA HOLDING (2) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA HOLDING (81) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA INVESTMENT (78) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA INVESTMENT (74) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA HOLDING (78) SRL | Barbados | Barbados | Paradise Papers |
| CATELLUS CHINA INVESTMENT (10) SRL | Barbados | Barbados | Paradise Papers |
| CATELLUS CHINA INVESTMENT (8) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA HOLDING (79) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA HOLDING (77) SRL | Barbados | Barbados | Paradise Papers |
| CATELLUS CHINA INVESTMENT (9) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA INVESTMENT (81) SRL | Barbados | Barbados | Paradise Papers |
| CATELLUS CHINA INVESTMENT (4) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA INVESTMENT (77) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA INVESTMENT (79) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA INVESTMENT (80) SRL | Barbados | Barbados | Paradise Papers |
| CATELLUS CHINA INVESTMENT (11) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA HOLDING (80) SRL | Barbados | Barbados | Paradise Papers |
| CATELLUS CHINA INVESTMENT (3) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA HOLDING (76) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA INVESTMENT (73) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA HOLDING (74) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA HOLDING (75) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA HOLDING (73) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA HOLDING (82) SRL | Barbados | Barbados | Paradise Papers |
| CATELLUS CHINA INVESTMENT (5) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA INVESTMENT (82) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA INVESTMENT (75) SRL | Barbados | Barbados | Paradise Papers |
| CATELLUS CHINA INVESTMENT (2) SRL | Barbados | Barbados | Paradise Papers |
| CATELLUS CHINA HOLDING (7) SRL | Barbados | Barbados | Paradise Papers |
| CATELLUS CHINA HOLDING (8) SRL | Barbados | Barbados | Paradise Papers |
| PLD CHINA INVESTMENT (76) SRL | Barbados | Barbados | Paradise Papers |
| CATELLUS CHINA HOLDING (3) SRL | Barbados | Barbados | Paradise Papers |
| CATELLUS CHINA HOLDING (4) SRL | Barbados | Barbados | Paradise Papers |
| CATELLUS CHINA INVESTMENT (7) SRL | Barbados | Barbados | Paradise Papers |
| CHINA MINING MACHINERY GROUP SRL | Barbados | Barbados | Paradise Papers |
| SINKRO PRINTING INKS (CHINA) LIMITED | Barbados | Barbados | Paradise Papers |
| DIAMOND SHAMROCK CHINA PETROLEUM LIMITED | Bahamas | Bahamas | Paradise Papers |
| AAVID THERMALLOY CHINA HOLDINGS LIMITED | Barbados | Barbados | Paradise Papers |
| VALE CHINA HOLDINGS (BARBADOS) LIMITED | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA HOLDING I LTD. | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA HOLDING II LTD. | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT I LTD. | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA MANAGEMENT HOLDING LTD. | Barbados | Barbados | Paradise Papers |
| PROLOGIS CHINA INVESTMENT II LTD. | Barbados | Barbados | Paradise Papers |
| CHINA GRAND AUTOMOTIVE (BARBADOS) LIMITED | Barbados | Barbados | Paradise Papers |
| APREA CHINA INVESTMENTS 1 INC. | Barbados | Barbados | Paradise Papers |
| SENTIENT CHINA TITANIUM INVESTMENTS LTD. | Barbados | Barbados | Paradise Papers |
| E-COMMERCIAL (CHINA) HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Pandora Papers |
| China Pro Asset Management Ltd | British Virgin Islands | British Virgin Islands | Pandora Papers |
| China Shipbuilding and Exports Corporation | British Virgin Islands | British Virgin Islands | Pandora Papers |
| PA China Capital Partners Limited | British Virgin Islands | British Virgin Islands | Pandora Papers |
| PA China Equity Partners Limited | British Virgin Islands | British Virgin Islands | Pandora Papers |
| PA Guarantee (China) Holdings Limited | British Virgin Islands | British Virgin Islands | Pandora Papers |
| PAKA CONSUMER PRODUCTS (CHINA) LIMITED | British Virgin Islands | British Virgin Islands | Pandora Papers |
| CANTARA CHINA CONSULTING GROUP LIMITED | Hong Kong | | Pandora Papers |
| KOLON CHINA (HK) COMPANY LIMITED | Hong Kong | | Pandora Papers |
| NHN ENTERTAINMENT GREATER CHINA LIMITED | Hong Kong | | Pandora Papers |
| SK GLOBAL CHEMICAL CHINA LIMITED | Hong Kong | | Pandora Papers |
| SK GLOBAL CHEMICAL CHINA LIMITED | Hong Kong | | Pandora Papers |
| GREAT CHINA AQUATECH & MARKETING BVI) INC. | British Virgin Islands | Taiwan | Panama Papers |
| CHINA EXPORT FINANCE AND INVESTMENT CORPORATION | British Virgin Islands | Hong Kong | Panama Papers |
| NEW CHINA HONG KONG METALS (SUZHOU) LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA SOUTHERN COMM. CABLE CO. LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA SUCCESS INTERNATIONAL INVESTMENT (GROUP) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| KIN SUN PAPER FACTORY (CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA SCIENCE AND TECHNOLOGY FOUNDATION LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| ECTRAG EURO CHINA TRADE GROUP LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA SINGKONG MA LU DEVELOPMENT LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| FAR-EAST PACIFIC ENTERPRISES (CHINA) LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| FIRST EASTERN CHINA PROPERTIES (NANJING) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| China Changan Financial Industrial Group Limited | Samoa | Hong Kong | Panama Papers |
| CHINA-BASE INTERNATIONAL LOGISTICS CO., LTD. | British Anguilla | Hong Kong | Panama Papers |
| CHINA POWER INTERNATIONAL INVESTMENT GROUP LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA GOLD MINE INVESTMENT (BVI) LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA SINGKONG MENTOUGOU CEMENT INV’T LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA HI-TECH DEVELOPMENT MANAGEMENT LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| PEACE HILL ELECTRIC (CHINA) DEVELOPMENT CO. LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| AMERICAN DREAM PARKS & ENTERTAINMENT (CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHIMEXCO CHINA IMPORT & EXPORT COMPANY LTD. | British Virgin Islands | Switzerland | Panama Papers |
| CHINA YONG TONG GROUP CO., LTD. | British Virgin Islands | Switzerland | Panama Papers |
| China Environmental Energy Holdings Company Limited | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA RESOURCES TIANJIN INVESTMENT COMPANY LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| ACN REAL ESTATE ADVISORS (CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| International Auction Co. of China B.V.I.) Limited | British Virgin Islands | Hong Kong | Panama Papers |
| BUSINESS PROMOTION ASSOCIATION OF CHINA LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| China Baigong NGV Engineering (Group) Co., Ltd. | Samoa | Hong Kong | Panama Papers |
| CHINA COMMUNICATION INTERNATIONAL CRUISE HOLDING LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA TRANSPORT TELECOM BROADBAND NETWORK SERVICES LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| DEBARK INTERNATIONAL INDUSTRIAL (CHINA) CO., LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA INTERNATIONAL PETROLEUM HOLDING (GROUP) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA CLEAN ENERGY INVESTMENT COMPANY LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA VISION SPORTS & ENTERTAINMENT NETWORK LIMITED | Bahamas | Hong Kong | Panama Papers |
| JAPAN HOME CENTRE (CHINA) GROUP LIMITED | Seychelles | Hong Kong | Panama Papers |
| POLYTIC (CHINA) PROPERTIES INVESTMENT HOLDINGS LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| China Overseas Energy Investment Co., Ltd. | British Virgin Islands | China | Panama Papers |
| CHAMP GROUP INVESTMENT CAPITAL (CHINA) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| DAH-Star Logistics China) Co., Limited | British Virgin Islands | Hong Kong | Panama Papers |
| China Energy Resource Group Co. Ltd | British Virgin Islands | China | Panama Papers |
| China Intermodal Exposition Transportation Company Limited | Seychelles | Hong Kong | Panama Papers |
| CHINA P&H INTERNATIONAL GROUP LIMITED | Seychelles | China | Panama Papers |
| CHINA INTERNATIONAL FINANCIAL MERGING GROUP LIMITED | Niue | Hong Kong | Panama Papers |
| SUN HUNG KAI INFRASTRUCTURE (CHINA) HOLDINGS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA CANTON MANAGEMENT HONG KONG) LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA REALTY & RETAIL TRADE MARKET EMPOLDER CORP. | British Virgin Islands | Hong Kong | Panama Papers |
| WELLAGE (CHINA) SCIENCE & TECH. DEVELOPMENT CO., LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA MARK GARDEN PRODUCTS HOLDING LIMITED | British Virgin Islands | China | Panama Papers |
| CHINA SATELLITE TOWNSHIP DEVELOPMENT FOUNDATION COMPANY LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA XINYUAN REAL ESTATE HOLDINGS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA KAM LONG TEXTILE CO., LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| China New Century Investment Co., Ltd. | British Virgin Islands | China | Panama Papers |
| Great Dream Cartoon Investment (China) Co., Ltd. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA INTERNATIONAL PETROLEUM CHEMICAL DEVELOPMENT LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| Forever Flourish (China) Investment & Trading Group Ltd | British Virgin Islands | Hong Kong | Panama Papers |
| China Tea Industry Holding Co. Ltd | British Virgin Islands | China | Panama Papers |
| China Fertilizer Industry Import & Export Group Ltd. | British Virgin Islands | China | Panama Papers |
| Access-China Global Investment Group, Inc. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA ERA ENERGY POWER INVESTMENT LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA XING WANG INVESTMENT COMPANY LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| China Rui Hui Xiang Investment Holdings Inc. | British Virgin Islands | China | Panama Papers |
| CHINA FINE SPINNING HOLDING COMPANY LIMITED | British Virgin Islands | China | Panama Papers |
| CHINA SPECIAL COMMUNICATION (GROUP) CO., LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| FUJI ELECTRIC (CHINA) TECHNOLOGY SERVICE LIMITED | British Virgin Islands | China | Panama Papers |
| Israel China Advanced Technology Alliance Center Limited | British Virgin Islands | Hong Kong | Panama Papers |
| China Mobile Payment Technology Group Company Limited | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA E-PAY INVESTMENT GROUP CO., LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| RHEIN CHINA CAPITAL INVESTORS CO., LTD | British Virgin Islands | Hong Kong | Panama Papers |
| China Rural Cultural Museum Group Limited | British Virgin Islands | Hong Kong | Panama Papers |
| China Coal Water Mixture Industry Ltd | British Virgin Islands | China | Panama Papers |
| China Maintaining and Strengthening Group Limited | British Virgin Islands | China | Panama Papers |
| CHINA MEDIA COMMUNICATION (HOLDINGS) COMPANY LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| HONGKONG (CHINA) PETROCHEMICAL INTERNATIONAL ENGINEERING LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA MEDICAL INFORMATION INDUSTRY HOLDINGS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| God-bless China Investment Holding Corporation Limited | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA SKY TECH INDUSTRIAL DEVELOPMENT CO., LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| TONGGUANG HIGH-TECH ELECTRONIC (CHINA) CORPORATION | British Virgin Islands | Hong Kong | Panama Papers |
| CHIA TAI (CHINA) ENTERPRISES CO., LTD. | British Virgin Islands | China | Panama Papers |
| CHINA INDOOR AIR QUALITY CENTER LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CONTINENTAL AIR EXPRESS (CHINA) CO. LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| China Huishan Dairy Holdings International Limited | British Virgin Islands | Hong Kong | Panama Papers |
| IDEAL BATH (CHINA) HOLDING CO., LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| SKY INTERNATIONAL INVESTMENT GROUP (CHINA) LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA INTERNATIONAL MEDIA AND TELEVISION LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| EAST CHINA MARINE & CARGO SURVEYORS, INC. | British Virgin Islands | Hong Kong | Panama Papers |
| GUANGZHOU CONSTRUCTION & DEVELOPMENT HOLDINGS (CHINA) LIMITE | British Virgin Islands | Hong Kong | Panama Papers |
| POLY (CHINA) PROPERTIES INVESTMENT HOLDINGS LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA OASIS SAND CONTROL HOLDINGS LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| UNION CHINA ASSET INTERNATIONAL ORGANIZATION LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA WINE IMPORT GROUP HOLDINGS LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| GRAND CHINA WEALTH MANAGEMENT COMPANY LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA STAR AUTOMOTIVE TECHNOLOGY INVESTMENT COMPANY LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA INTERNATIONAL MANAGEMENT CONSULTING CO., LTD. | British Virgin Islands | Taiwan | Panama Papers |
| CHINA TOHIGH INTERNATIONAL HOLDINGS CO., LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA GUARD INVESTMENT HOLDING CO., LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA INTERNATIONAL FINANCE INVESTMENT GROUP CO., LTD | British Virgin Islands | Hong Kong | Panama Papers |
| China Blossom City (Holdings) Company Limited | British Virgin Islands | Hong Kong | Panama Papers |
| China National Metal Products Holdings Limited | British Virgin Islands | China | Panama Papers |
| O-LINE INVESTMENT (CHINA) CO., LTD | British Virgin Islands | Hong Kong | Panama Papers |
| China Refractory Industry Import & Export Group Ltd. | British Virgin Islands | China | Panama Papers |
| CHINA TOP BEIJING) TRADE DEVELOPMENT CO., LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA GREEN NATURE AGRICULTURE INVESTMENT CO. LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA COMPLETE TECHNOLOGY INTERNATIONAL CORPORATION LIMITED | Bahamas | Taiwan | Panama Papers |
| China Zhongyou Technology Holding Co., Ltd. | British Virgin Islands | China | Panama Papers |
| CHINA GUANGHUA INVESTMENT HOLDING GROUP LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| China Russia Chamber Commerce Company Limited | British Virgin Islands | Hong Kong | Panama Papers |
| China Fumin Asset Management Co., Ltd | British Virgin Islands | China | Panama Papers |
| CHINA EDUCATION TECHNOLOGY INVESTMENT HOLDINGS GROUP LTD | British Virgin Islands | China | Panama Papers |
| HILLER PHARMA (GREATER CHINA) CO. LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA ZHONG CHEN CAPITAL GROUP CO., LIMITED | British Virgin Islands | China | Panama Papers |
| Impact Creative (Greater China) Co. Ltd. | British Virgin Islands | Hong Kong | Panama Papers |
| Fashion Telecom Service (China) Co., Ltd. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA WINALL IMPORT&EXPORT GROUP CO., LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| China Ai Ying Si Group Ltd | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA EASTREACH INTERNATIONAL ENERGY GROUP CO., LIMITED | British Virgin Islands | China | Panama Papers |
| China Jingyin Huitong Finance Group Co., Ltd | British Virgin Islands | China | Panama Papers |
| Foresight Marine & Offshore Service (China) Ltd. | British Virgin Islands | Hong Kong | Panama Papers |
| Greater China Renewable Construction Materials Corp. | British Virgin Islands | China | Panama Papers |
| CHINA STATE CONSTRUCTION ENGINEERING CORPORATION LTD. | Panama | Bahamas | Panama Papers |
| Modern Green Development (China) Co., Limited | British Virgin Islands | China | Panama Papers |
| China Integrated Telecommunications Group Co. Limited | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA FIRST RESOURCES INVESTMENT CO., LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| China Sinotest Science & Technology Co., Ltd. | British Virgin Islands | Hong Kong | Panama Papers |
| China Hai Jiang Industrial Holdings Limited | British Virgin Islands | Hong Kong | Panama Papers |
| China O2O Business Group Co. Limited | British Virgin Islands | Hong Kong | Panama Papers |
| EAST TOWN INVESTMENT DEVELOPMENT (CHINA) CO., LIMITED | British Virgin Islands | China | Panama Papers |
| China Factory for Material Treatment Ltd. | British Virgin Islands | Gibraltar | Panama Papers |
| China Sequoia Pharmaceutical Group International Holdings Limited | British Virgin Islands | Hong Kong | Panama Papers |
| China Zhongyou Clean Energy Co., Ltd. | British Virgin Islands | China | Panama Papers |
| China City and Provincial Developments Group Limited | British Virgin Islands | Cyprus | Panama Papers |
| Green Resources (China) Investment Group Limited | British Virgin Islands | China | Panama Papers |
| CHINA INTERNATIONAL GENERAL AVIATION GROUP LTD | British Virgin Islands | China | Panama Papers |
| China Link Timber & Hardware Products Limited | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA SPLENDENT CULTURAL BRAND ACADEMY LIMITED | British Virgin Islands | China | Panama Papers |
| Hongkong China-Petroleum Everbright Group Limited | British Virgin Islands | China | Panama Papers |
| Top Wide China Holding Co., Ltd | British Virgin Islands | Hong Kong | Panama Papers |
| Longrich Technological Service (China) Co., Ltd. | British Virgin Islands | Hong Kong | Panama Papers |
| China Dream Film Culture Industry Limited | British Virgin Islands | Hong Kong | Panama Papers |
| China Sheng Rui Xuan Group LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA CULTURE PROPERTY INVESTMENT GROUP LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| China Fargo Investment and Consulting Limited | British Virgin Islands | Hong Kong | Panama Papers |
| MODERN GREEN LAND (CHINA) CO., LIMITED | British Virgin Islands | China | Panama Papers |
| China ZhongHui Investment Holding Group Limited | British Virgin Islands | Hong Kong | Panama Papers |
| JAVVA GREEN PROJECTS (CHINA) CO., LTD | British Anguilla | Hong Kong | Panama Papers |
| CHINA-EURO INTERNATIONAL TRADE COMPANY LTD. | Seychelles | Hong Kong | Panama Papers |
| (CHINA) INTERNATIONAL PETROLEUM TECHNOLOGY SERVICES LTD. | Seychelles | United Arab Emirates | Panama Papers |
| JOHN LEI (CHINA) INTERIOR DECORATION CO. LIMITED | Niue | Hong Kong | Panama Papers |
| TRIANGLE ELECTRIC EQUIP (CHINA) DEVELOP GROUP LTD. | Niue | Hong Kong | Panama Papers |
| CHINA NATIONAL CHEMICAL WESTZHONG IMP.EX COMPANY | Niue | Cyprus | Panama Papers |
| CHINA OVERSEAS CHINESE FOUNDATION ASSOCIATION LIMITED | Niue | Hong Kong | Panama Papers |
| AAAEO CHINA INT´L ENTERPRISE GROUP LTD. | Niue | Hong Kong | Panama Papers |
| BRITAIN YIKELONG LUBRICATING OIL (CHINA) CO., LIMITED | Niue | Hong Kong | Panama Papers |
| WCO OFFSHORE SERVICES (CHINA LEGAL & INVESTMENT) LIMITED | Niue | Hong Kong | Panama Papers |
| AR & W (CHINA) HOLDINGS COMPANY LIMITED | Niue | Hong Kong | Panama Papers |
| PING AN (CHINA) INTERNATIONAL INVESTMENT GROUP LTD. | Niue | Hong Kong | Panama Papers |
| JAPAN HOME CENTRE (CHINA) GROUP LIMITED | Niue | Panama | Panama Papers |
| China Art International Financial Investment Limited | Samoa | China | Panama Papers |
| CHINA-BASE NINGBO FOREIGN TRADE CO., LTD. | Samoa | Hong Kong | Panama Papers |
| China Brilliant Energy Source INT’L (Group) Limited | Samoa | Hong Kong | Panama Papers |
| China National Wencai Industry Company Limited | Samoa | Hong Kong | Panama Papers |
| US-CHINA ECONOMIC & TRADE EXCHANGE PROMOTION LTD. | Nevada | Hong Kong | Panama Papers |
| CHINA ECONOMIC DEVELOPMENT RESERCHER CENTER LLC | Nevada | China | Panama Papers |
| China Minerals Overseas Investment Group Ltd | Samoa | Hong Kong | Panama Papers |
| China Harbour International Construction Company Limited | Samoa | Hong Kong | Panama Papers |
| AR & W (China) Holdings Company Limited | Samoa | Hong Kong | Panama Papers |
| CHINA KUN PENG INTERNATIONAL GROUP LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Gold Cheever Capital Management Limited | Not identified | Not identified | Offshore Leaks |
| China Great Media Group Co., Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China BaiTong ZhengFang Capital Management Co., Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA MINING INTERNATIONAL INVESTMENT GROUP LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Q. R. PACIFIC (CHINA) CO., LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Information Network (Asia Pacific) Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA HEAVY INDUSTRY GROUP CO., LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Tanhoo International Brands Accessories Inc. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| United Success International Development (China) Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Science Biological Medicine Co., Limited | Cayman Islands | Cayman Islands | Offshore Leaks |
| US-CHINA INTERNATIONAL INVESTMENT HOLDING CO., LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Petroleum Gas Pipe Monitor Limited | Samoa | Samoa | Offshore Leaks |
| China Natural Gas Investment Group Limited | Samoa | Samoa | Offshore Leaks |
| China World Trade Center Holdings Limited | Samoa | Cayman Islands, Samoa | Offshore Leaks |
| China Flowers Science & Technology Investment Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Vision and Insight Great China Fund SPC | Not identified | Not identified | Offshore Leaks |
| China Fashion Brand International Co. Ltd. | Cayman Islands | Cayman Islands | Offshore Leaks |
| China Metal And Special Steel Co., Ltd. | Cayman Islands | Cayman Islands | Offshore Leaks |
| China Gold Cheever Capital Management Limited | Cayman Islands | Cayman Islands | Offshore Leaks |
| Asia Assets China Fund Management (I) Limited | Cayman Islands | Cayman Islands | Offshore Leaks |
| CHINA STEEL STRUCTURE INVESTMENT CO., LTD. | Samoa | Samoa, Cayman Islands | Offshore Leaks |
| AMERICAN CHINA MOULIN INVESTMENT (HK) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Lan Kwai Fong Great China Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| ASIA-PAC CHINA PROPERTIES (HUANAN) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Asia-Pac China Investment (Holdings) Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA INFRASTRUCTURE INVESTMENT HOLDINGS COMPANY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA ARMSTRONG INVESTMENT HOLDINGS COMPANY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| NEW WORLD MEDIA (CHINA) COMPANY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| WING KEUNG (CHINA) CONTRACTING & ENGINEERING COMPANY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| New World China Enterprises Investments Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| K Laser China Group Co., Ltd. | British Virgin Islands | British Virgin Islands, Cayman Islands | Offshore Leaks |
| Cathay International Biotechnology and Pharmaceutical (China) Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Global China Recruitment Media Services Co. Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Oilfield Services Eurasia (BVI) Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Roosevelt HuaSheng Capital Management Incorporated | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| WISE ARK MEDIA (CHINA) CO., LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Advanced Materials Processing (B.V.I.) Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China United Group Overseas Investment Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| MOBILE MEDIA (CHINA) HOLDING CO., LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| TIENS (China) Investment Holdings Group Overseas Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA MINERAL RESOURCES HOLDINGS CO., LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA EXPERT FINANCIAL HOLDINGS GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Good Family (China) Health Industrial Co., Ltd. | Cayman Islands | Cayman Islands | Offshore Leaks |
| CHINA FRANCHISE INVESTMENT HOLDING CO., LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Jian epayment (China) International Holdings Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Sing Tao News Corporation (China) Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| United Capital Investment China Venture II Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA SUN WAH AIRLINE GROUP COMPANY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA VISION AND MOVIES HOLDINGS LIMITED ?????????? | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA CITY NATURAL GAS DEVELOPMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Devon Business Consulting Co., Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| New World China Land Finance Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| KTB/UCI China Ventures I Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA CITY NATURAL GAS CONSTRUCTION LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| VERY POWER (CHINA) INVESTMENT CO., LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| TIENS (China) Investment Holdings Group Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| United Capital Investment China Venture IV Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA TIANDA HAITONG GROUP CO., LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA PETROLEUM INTERNATIONAL IMPORT AND EXPORT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA REVIEW FINANCIAL INVESTMENT DEVELOPMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| New World China Land Project Management Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Finance Prestige Invesment Group Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA MARK GARDEN PRODUCTS HOLDING LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA TAI RONG ENERGY HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| A&G INTERNATIONAL TRADING CHINA LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| New World China Land Project Management Limited | Hong Kong | Hong Kong | Offshore Leaks |
| China Highland International Holding Group Co., Ltd | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA XYJ FINANCIAL MANAGEMENT CHAIN LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Yellow River Television Asia Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| New World China Finance (BVI) Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| TIENS (China) Education Investment Holdings Group Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Asia Assets China Fund Management (108) Limited | Cayman Islands | Cayman Islands | Offshore Leaks |
| THE NEW CHINA HONG KONG HIGHWAY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| LITE-ON CHINA HOLDING CO. LTD. | British Virgin Islands | Cayman Islands, British Virgin Islands | Offshore Leaks |
| Brilliance China Auto Finance Co., Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Entertainment Investments Group Holdings Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Peng Cheng Finance Co., Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Korea Energy Development Company Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| BOND STREET MERCANTILE (CHINA) HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA COSMETICS IMPORT & EXPORT TRADING (HK) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA SHENZHOU UNITED TELECOMMUNICATIONS COMPANY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| LIONDEE INFORMATION GROUP (CHINA) INTERNATIONAL HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA ASIAN DEPARTMENT STORE CHAIN LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| United Capital Investment China Venture III Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| INDUSTRIAL AND COMMERCIAL BANK OF CHINA LIMITED | Singapore | Singapore | Offshore Leaks |
| CHINA LONGZHOU TECHNOLOGIES HOLDINGS CO. LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| SOLVEIGH GREATER CHINA (M&A) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Mining Finance Partners Co., Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Good Family (China) Holding Co., Ltd. | Cayman Islands | Cayman Islands | Offshore Leaks |
| FULL TEAM (CHINA) INDUSTRIAL DEVELOPMENT LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA DA SHAN LAN REAL ESTATE LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Gold Silver Group Company limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| GLOBAL NETWORK GROUP (CHINA) SERVICES LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| ROSE HOUSE CHINA HOLDINGS CO., LTD. | Samoa | Samoa | Offshore Leaks |
| CHINA GOLDEN DRAGON INTERNATIONAL TRADING COMPANY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA HUIZE TECHNIQUE & EQUIPMENT HOLDINGS INC. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| United Capital Investment China Venture VI Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA CORE ENTERPRISE GROUP HOLDING LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| GREATEAST INTERNATIONAL MINING (CHINA) HOLDING LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Hongkong China-Petroleum Everbright Group Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CAR-PLUS China Investment (Samoa) Co., Ltd. | Samoa | Cayman Islands, Samoa | Offshore Leaks |
| HONG ZHI (CHINA) EDUCATION FOUNDATION LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China 3i Management Consultancy Company Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA CITY GAS INVESTMENT HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA CITY NATURAL GAS INVESTMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA CITY NATURAL GAS HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA ELEGANCE MARINE SHIPPING COMPANY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| THE BETTER GREATER CHINA FOUNDATION LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Natural Gas Construction Holdings Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA IPTV INDUSTRY PARK HOLDINGS LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Natural Gas Development Holdings Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Oilfield Services Southeast Asia (BVI) Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA HEAVY MACHINE TOOL HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| GRAND ASIA (CHINA MEDIA) GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China City Gas Development Holdings Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| LAM SOON (CHINA) HOLDINGS COMPANY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA FOOD INVESTMENT HOLDINGS COMPANY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| HONG KONG TEAKWOOD WORKS (CHINA) LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA NONFERROUS METALS CYBERNETIC BUSINESS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA EMERGENCY (ASSISTANT SERVICES) ORGANISATION (INTERNATIONAL) LTD | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Electronic (B.V.I.) Holdings Co., Ltd. | British Virgin Islands | British Virgin Islands, Cayman Islands | Offshore Leaks |
| China Mobile Communications Technology Holdings Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA PHARMACEUTICAL PRODUCTS INVESTMENT HOLDINGS COMPANY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA YINHONG INTERNATIONAL TRUST CO., LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Business Investment and Holdings Co., Ltd. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA CONSTRUCTION MATERIALS INVESTMENT HOLDINGS COMPANY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Auto Frontier Equity LLP Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Global China Human Capital Management Holdings Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Global China Media Services Holdings Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Brightness World (China) Technology Education Limited | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| Eastern China International Development Co., Ltd. | Not identified | Hong Kong, Not identified | Offshore Leaks |
| CHINA MAGNESIUM RESEARCH & DEVELOPMENT CENTRE LIMITED | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| Sun Hung Kei (China) Electricity Development Limited | Not identified | Not identified, Hong Kong | Offshore Leaks |
| China Kind Environment Technologies Co. Ltd. | Not identified | British Virgin Islands, United States | Offshore Leaks |
| Yidanfeng (China) Food Technology Co. Ltd. | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| Investments In China United Services Co., Ltd. | Not identified | Not identified, Hong Kong | Offshore Leaks |
| China International Energy Investment Group Holdings Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China Oasis Regulate Sand Engineering Limited | Not identified | Not identified, Hong Kong | Offshore Leaks |
| China Century Asset Management Company Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China Pioneer Foundation & Capital Group Inc. | Not identified | Not identified, Hong Kong | Offshore Leaks |
| China Top (Overseas) Trading Co. Limited | Not identified | Hong Kong, Not identified | Offshore Leaks |
| CHINA OIL AND GRAIN SHIPPING CO., LIMITED | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| CHINA-AFRICA TRADE&INDUSTRY DEVELOPMENT CORPORATION | Not identified | China, British Virgin Islands | Offshore Leaks |
| Bio-Organic Food Industries China Limited | Not identified | Not identified, Hong Kong | Offshore Leaks |
| China Travel Alliance Group Co. Ltd. | Not identified | Not identified, Hong Kong | Offshore Leaks |
| Coca Suki Holdings (China) Company Limited | Not identified | Hong Kong, Not identified | Offshore Leaks |
| China Zone Multi-media Services Company Limited | Not identified | Hong Kong, Not identified | Offshore Leaks |
| China International Investment Group Co., Ltd. | Not identified | Not identified, United States | Offshore Leaks |
| China Global Trading Group Co., Ltd. | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| South China Petroleum Services Co., Ltd. | Not identified | Not identified, Hong Kong | Offshore Leaks |
| CHINA JOINT SHIPBUILDING TRADING CO., LIMITED | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| CHINA WARP CITY HOLDINGS GROUP SHARES LIMITED | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| China Display Electronic Technology Co., Ltd. | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| CHINA DRAGON YUANNAN PUER TEA LIMITED | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| China Nutrtion & Organic Products (CNOP) Co. Ltd. | Not identified | British Virgin Islands, China | Offshore Leaks |
| King Horn Holdings Investment (China) Company Limited | Not identified | Hong Kong, Not identified | Offshore Leaks |
| Towa Seiden Industrial (China) Co., Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China National Aviation Corporation (Group) Limited | Not identified | Not identified | Offshore Leaks |
| Jing Hua China Investment Consulting Co., Ltd. | Not identified | Not identified | Offshore Leaks |
| New World China Enterprises Projects Limited | Not identified | Not identified | Offshore Leaks |
| Sinar Mas Paper (China) Investment Co., Ltd | Not identified | Not identified | Offshore Leaks |
| Tian An China Investments Co. Ltd | Not identified | Not identified | Offshore Leaks |
| CHINA SONIX LIGHT INDUSTRIES CORP. LIMITED | Samoa | Samoa | Offshore Leaks |
| First Asia Merchants Greater China Limited | Samoa | Samoa | Offshore Leaks |
| China Civil Engineering Construction Co. (HK) Ltd | Not identified | Not identified | Offshore Leaks |
| China International Capital Services Co., Ltd | Not identified | Not identified | Offshore Leaks |
| Deloitte & Touche-China Practice Group (T040) ???????? | Not identified | Hong Kong | Offshore Leaks |
| CHINA NEW INDUSTRIAL MATERIAL TECHNOLOGY HOLDINGS LIMITED | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| CHINA LANSHI SPECIAL GLASS HOLDINGS LIMITED | Samoa | Samoa | Offshore Leaks |
| China Anti-Flooding System Monitor Limited | Samoa | Samoa | Offshore Leaks |
| NEW WORLD LIBERTY CHINA VENTURES LIMITED | Hong Kong | Not identified | Offshore Leaks |
| Clear Water Enviro Technologies China Limited | Samoa | Samoa | Offshore Leaks |
| China Natural Pharmaceutical Holdings Company Limited | Cayman Islands | Cayman Islands | Offshore Leaks |
| 21st Century China International Inv. Ltd | Cook Islands | Not identified | Offshore Leaks |
| CHINA STEEL GROUP (UK) CO., LIMITED | Samoa | Samoa | Offshore Leaks |
| HON CHUAN (CHINA) HOLDINGS CO., LTD. | Cayman Islands | Cayman Islands | Offshore Leaks |
| CHINA WEALTH ASSET MANAGEMENT (SAMOA) LIMITED | Samoa | Samoa | Offshore Leaks |
| New World Department Store China Limited | Not identified | Not identified | Offshore Leaks |
| GLOBAL ENERGY SUPPLIES TRADING (CHINA) PTE LTD | Singapore | Singapore | Offshore Leaks |
| CHINA YIWU INTERNATIONAL TRADING CO., LIMITED | Samoa | Samoa | Offshore Leaks |
| Vision and Insight Great China Fund SPC | Cayman Islands | Cayman Islands | Offshore Leaks |
| Vision and Insight Great China Fund SPC | Not identified | Not identified | Offshore Leaks |
| China Nonferrous Metals Holdings (Cook Islands) Limited | Cook Islands | Not identified | Offshore Leaks |
| Cathay International Properties (South China) Limited | Cook Islands | Not identified | Offshore Leaks |
| China Mansion (Shenzhen) International Development Company Limited | Samoa | Samoa | Offshore Leaks |
| CHIA TAI (CHINA) ENTERPRISES CO., LTD. | Samoa | Samoa | Offshore Leaks |
| SEA OASIS (CHINA) MARINE ENGINEERING CO., LTD | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Next-Gen Education Holding Inc. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA ONE HOLDING (HONG KONG) LIMITED | Samoa | Samoa | Offshore Leaks |
| NINGBO CHINA PLASTIC INT’L TRADE CO., LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Yung Shin China Holding Company Limited | Cayman Islands | Cayman Islands | Offshore Leaks |
| China Environmental Energy Protection Investment Limited | Samoa | Samoa | Offshore Leaks |
| SOUTH CHINA TIRE & RUBBER CO., LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Grand China Wealth Management Co., Ltd ???????????????? | Not identified | Not identified | Offshore Leaks |
| China United Garments MFG. (Samoa) Co., Ltd. | Samoa | Samoa, Cayman Islands | Offshore Leaks |
| China International Education Development Management Centre Limited | Samoa | Samoa | Offshore Leaks |
| Boma Carret China Investment Company Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| The China-America Capital Group Limited | Bermuda | Bermuda | Paradise Papers |
| CPCU Institute of Greater China, Ltd. | Bermuda | Bermuda | Paradise Papers |
| The LOMA Institute of Greater China, Ltd. | Bermuda | Bermuda, United States | Paradise Papers |
| Cleveland Bridge & Engineering Co. (China) Ltd. | Bermuda | Bermuda, United Kingdom | Paradise Papers |
| Unocal China Exploration Area 12-21, Ltd. | Bermuda | Bermuda, United States | Paradise Papers |
| Unocal China Exploration Area 20-14, Ltd. | Bermuda | Bermuda, United States | Paradise Papers |
| Unocal China Exploration Area 27-05, Ltd. | Bermuda | Bermuda, United States | Paradise Papers |
| AXA China Region Insurance Company (Bermuda) Limited | Bermuda | Bermuda, China | Paradise Papers |
| CHIA TAI (CHINA) AGRO-INDUSTRIAL LTD. | Bermuda | Bermuda, Hong Kong | Paradise Papers |
| CHINA ENTERTAINMENT AND LAND INVESTMENTS HOLDINGS LIMITED | Bermuda | Bermuda, Hong Kong | Paradise Papers |
| FULLGOAL CHINA ACCESS RQFII FUND SPC | Cayman Islands | Cayman Islands, China | Paradise Papers |
| CHINA INTERNATIONAL ECONOMIC CONSULTANTS (CAYMAN) COMPANY LIMITED | Cayman Islands | Cayman Islands | Paradise Papers |
| China Golden Phoenix International (Holdings) Limited | Cayman Islands | Cayman Islands | Paradise Papers |
| China Success Finance Group Holdings Limited | Cayman Islands | Cayman Islands | Paradise Papers |
| China Tailong Green Power Group Ltd. | Cayman Islands | Cayman Islands, China | Paradise Papers |
| Cosmo Lady (China) Holdings Company Limited | Cayman Islands | Cayman Islands | Paradise Papers |
| China Natural Gas For Vehicle Holdings Limited | Cayman Islands | Australia, Cayman Islands | Paradise Papers |
| CHINA JINJEE NEW ENERGY (CAYMAN) LIMITED | Cayman Islands | Cayman Islands, China | Paradise Papers |
| CHINA TA JING ASSET MANAGEMENT CO., LTD | Cayman Islands | Cayman Islands | Paradise Papers |
| China Energy Investment Fund Company Limited | Cayman Islands | Cayman Islands | Paradise Papers |
| ZZZ-Changfeng Axle (China) Co., Ltd. | Cayman Islands | Cayman Islands | Paradise Papers |
| China Stainless Steel Technology Holdings Ltd. | Cayman Islands | Cayman Islands | Paradise Papers |
| China Metal Regeneration Technology Holdings Ltd. | Cayman Islands | Cayman Islands | Paradise Papers |
| ZZZ-Jayhawk China Cayman Liquidating Fund, Ltd. | Cayman Islands | Cayman Islands | Paradise Papers |
| ZZZ-YUNG SHIN CHINA HOLDING COMPANY LIMITED | Cayman Islands | Cayman Islands | Paradise Papers |
| ZZZ-CHINA CONNECTIONS CENTRE CO. LIMITED | Cayman Islands | Cayman Islands | Paradise Papers |
| CHINA PEKING UNION MEDICAL & PHARMACEUTICAL LIMITED | Bermuda | Bermuda | Paradise Papers |
| CEFNA Greater China Investments Company Limited | Bermuda | Bermuda, Hong Kong | Paradise Papers |
| CHINA-HONGKONG PHOTO PRODUCTS HOLDINGS LIMITED | Bermuda | Bermuda | Paradise Papers |
| China Brilliance Medical & Pharmaceutical Holdings Limited | Bermuda | Bermuda | Paradise Papers |
| China Brilliance Automotive Components Group Limited | Bermuda | Bermuda | Paradise Papers |
| COSCO Lai Sun Infrastructure (China) Limited | Bermuda | Bermuda | Paradise Papers |
| ASIA PULP & PAPER COMPANY (CHINA) LTD. | Bermuda | Bermuda, Singapore | Paradise Papers |
| e hub (China) Information Technology Limited | Bermuda | Bermuda, China | Paradise Papers |
| Asia Global Crossing Holdings China Ltd. | Bermuda | Bermuda | Paradise Papers |
| CHINA RAILWAY FIRST GROUP (SAMOA) COMPANY LIMITED | Samoa | Samoa | Paradise Papers |
| THE CHINA NAVIGATION COMPANY PTE. LTD | Samoa | Samoa | Paradise Papers |
| Greater China Value Partners Fund SICAV p.l.c. | Malta | Malta | Paradise Papers |
| NEW CHINA PALACE CO (MALTA) LTD | Malta | Malta | Paradise Papers |
| CARIBBEAN-CHINA TRADE AND INVESTMENT PROMOTION CORP | British Virgin Islands | British Virgin Islands | Pandora Papers |
| MED-CHINA INTERNATIONAL TRADE CENTRE LIMITED | Malta | Malta | Paradise Papers |
| CHINA SHIPPING (MALTA) AGENCY CO. LTD. | Malta | Malta | Paradise Papers |
| MALTA-CHINA INVESTMENT CONSULTING COMPANY LIMITED | Malta | Malta | Paradise Papers |
| LY CHU TRANS-CHINA INTERTRADE (H.K.) LIMITED | Saint Kitts and Nevis | | Paradise Papers |
| EXXONMOBIL EXPLORATION AND PRODUCTION CHINA (SEOR) LIMITED | Bahamas | | Bahamas Leaks |
| EXXONMOBIL EXPLORATION AND PRODUCTION CHINA (EORC) LIMITED | Bahamas | | Bahamas Leaks |
| Structured China Gearing Certificate Five Ltd. | Bahamas | | Bahamas Leaks |
| STRUCTURED CHINA GEARING CERTIFICATE SIX LTD. | Bahamas | | Bahamas Leaks |
| NEW CHINA MD DOT COM CORPORATION | Bahamas | | Bahamas Leaks |
| STRUCTURED CHINA GEARING CERTIFICATE NINE LTD. | Bahamas | | Bahamas Leaks |
| 3CM CHINA GROWTH FUND I LTD. | Bahamas | | Bahamas Leaks |
| EXXONMOBIL CHINA TARIM BASIN GAS LIMITED | Bahamas | | Bahamas Leaks |
| CHINA VISION SPORTS & ENTERTAINMENT NETWORK LIMITED | Bahamas | | Bahamas Leaks |
| ST. ANDREW CHINA GROWTH FUND LTD | Bahamas | | Bahamas Leaks |
| CHINA COMPLETE TECHNOLOGY INTERNATIONAL CORPORATION LIMITED. | Bahamas | | Bahamas Leaks |
| EXXONMOBIL CHINA PETROLEUM & PETROCHEMICAL COMPANY LIMITED | Bahamas | | Bahamas Leaks |
| Creis China Investment Consultancy Co., Ltd. | Not identified | Hong Kong, Not identified | Offshore Leaks |
| Pacific Medical (China) Company Group Limited | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| China National Product Logistic Centre International Inc. | Not identified | Hong Kong, Not identified | Offshore Leaks |
| The China Britain Management Training Centre, Ltd. | Not identified | Not identified, Hong Kong | Offshore Leaks |
| CEO Clubs China Overseas Returnee Center Ltd. | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| China Broadcast International Exhibition Co., Ltd. | Not identified | Hong Kong, Not identified | Offshore Leaks |
| China Investment Consultants Group Co., Ltd | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| Greater China Investment Holding Co., Ltd. | Not identified | Hong Kong, Not identified | Offshore Leaks |
| New World China Land Nominee Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China New Century Telecommunications (BVI) Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Karl China Venture Capital Management Inc. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Pulp & Paper Investment Holdings Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA CITY NATURAL GAS INVESTMENT DEVELOPMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA CITY NATURAL GAS INVESTMENT CONSTRUCTION LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Huitong (Hong Kong) Company Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA PETROLEUM & NATURAL GAS INT’L INVESTMENT LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| United Capital Investment China Venture V Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| KTB/UCI China Ventures II Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Global Digital Trade (Greater China) Inc. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Art & Culture Investment (Holdings) Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA SANJIANGYUAN WATER OPERATION CO. LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Genesis Green Energy Service Great China Corporation | Samoa | Samoa | Offshore Leaks |
| PRIVATE VILLA HOLDINGS (CHINA) PTE. LTD. | Singapore | Singapore | Offshore Leaks |
| CROWN INDO-CHINA INVESTMENT COMPANY LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Asia Pacific China Infrastructure Holding Limited | Cook Islands | Not identified | Offshore Leaks |
| Greater China Herbs Development Company Limited | Hong Kong | Not identified | Offshore Leaks |
| CHINA FINANCIAL SERVICES INVESTMENT HOLDINGS COMPANY LIMITED | Hong Kong | Hong Kong | Offshore Leaks |
| Peter Pun Architectural Design (China) Limited | Samoa | Samoa | Offshore Leaks |
| CHINA STEEL STRUCTURE HOLDING CO., LTD. | Samoa | Samoa, Cayman Islands | Offshore Leaks |
| Yidanfeng (China) Food Services Co. Ltd. | Not identified | British Virgin Islands, Hong Kong | Offshore Leaks |
| GREATER CHINA FINANCIAL SERVICES GROUP INC. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Macro-Egg Group (China) Co., Ltd. | Not identified | Not identified, Hong Kong | Offshore Leaks |
| Morningside China TMT Top Up Fund, L.P. | Cayman Islands | Cayman Islands, Hong Kong | Paradise Papers |
| Morningside China TMT Special Opportunity Fund, L.P. | Cayman Islands | Cayman Islands | Paradise Papers |
| Morningside China TMT Fund III, L.P. | Cayman Islands | Cayman Islands | Paradise Papers |
| Morningside China TMT GP III, L.P. | Cayman Islands | Cayman Islands | Paradise Papers |
| WLR China Energy Infrastructure Fund L.P. | Cayman Islands | Cayman Islands, United States | Paradise Papers |
| Cowin China Growth Fund I, L.P. | Cayman Islands | Cayman Islands | Paradise Papers |
| Morningside China TMT Fund I, L.P. | Cayman Islands | Cayman Islands | Paradise Papers |
| Boxin China Growth Fund I L.P. | Cayman Islands | Cayman Islands | Paradise Papers |
| Morningside China TMT Affiliates Fund II, L.P. | Cayman Islands | Cayman Islands | Paradise Papers |
| Morningside China TMT GP II, L.P. | Cayman Islands | Cayman Islands | Paradise Papers |
| Morningside China TMT Fund II, L.P. | Cayman Islands | Cayman Islands | Paradise Papers |
| CHINA DIAO YU DAO WINE COMPANY LIMITED | Seychelles | China, Seychelles | Paradise Papers |
| JUNYING (CHINA) INVESTMENT MANAGEMENT COMPANY LIMITED | Seychelles | China, Seychelles | Paradise Papers |
| Eastern Energy Group (China) Co., Ltd. | Seychelles | Seychelles | Paradise Papers |
| ZHIHUA (CHINA) INDUSTRY & TRADE GROUP CO., LIMITED | British Virgin Islands | British Virgin Islands, China | Paradise Papers |
| China Global Mining Resources (BVI) Limited | British Virgin Islands | British Virgin Islands | Paradise Papers |
| PCD China Department Stores (Holdings) Limited | British Virgin Islands | British Virgin Islands, Hong Kong | Paradise Papers |
| Blue Zen Memorial Park (China) Limited | British Virgin Islands | British Virgin Islands | Paradise Papers |
| China Pre-Paid Legal Services Limited | Cayman Islands | Cayman Islands | Paradise Papers |
| Fullgoal China Mid-Small Cap Fund | Cayman Islands | Cayman Islands, China | Paradise Papers |
| JAYHAWK CHINA OFFSHORE FUND (CAYMAN) LTD. | Cayman Islands | Cayman Islands | Paradise Papers |
| China Grand Real Estate Co., Ltd | Cayman Islands | Cayman Islands | Paradise Papers |
| CHINA NEED EDUCATION GROUP HOLDINGS CO., LIMITED | Cayman Islands | Cayman Islands | Paradise Papers |
| JOINT CHINA VALUE INVESTMENT FUND LIMITED | Cayman Islands | Cayman Islands | Paradise Papers |
| CHINA RAIN GEAR HOLDING CO., LTD | Cayman Islands | Cayman Islands | Paradise Papers |
| King Tower China Growth Fund Co., Ltd. | Cayman Islands | Cayman Islands | Paradise Papers |
| Cypress Greater China Asset Management Limited | Cayman Islands | Cayman Islands | Paradise Papers |
| China Flavors and Fragrances Company Limited | Cayman Islands | Cayman Islands, China | Paradise Papers |
| China Yinsheng Asset Management (Cayman) Ltd. | Cayman Islands | Cayman Islands, Hong Kong | Paradise Papers |
| China Tian Lun Gas Holdings Limited | Cayman Islands | Cayman Islands, China | Paradise Papers |
| Galaxy Tianjin Gas China Fund SPC | Cayman Islands | Cayman Islands | Paradise Papers |
| Galaxy China High Performance Fund SPC | Cayman Islands | Cayman Islands | Paradise Papers |
| China Federated Automobile Dealership Group Limited | Cayman Islands | Cayman Islands, Hong Kong | Paradise Papers |
| Kai Shi China Holdings Company Limited | Cayman Islands | Cayman Islands, Hong Kong | Paradise Papers |
| Infore Capital China Growth Master Fund | Cayman Islands | Cayman Islands, China | Paradise Papers |
| South China Assets Management (Asia) Ltd. | Cayman Islands | Cayman Islands, China | Paradise Papers |
| LVGEM (China) Real Estate Investment Company Limited | Cayman Islands | Cayman Islands, Hong Kong | Paradise Papers |
| Synergis China Automotive Die Group Limited **INCOMPLETE** | Cayman Islands | Cayman Islands | Paradise Papers |
| Galaxy China Deep Value Fund SPC **INCOMPLETE** | Cayman Islands | Cayman Islands, Hong Kong | Paradise Papers |
| Galaxy China Deep Value Master Fund **INCOMPLETE** | Cayman Islands | Cayman Islands, Hong Kong | Paradise Papers |
| ANADIGICS China Holding Corporation, Inc.** INCOMPLETE** | Cayman Islands | Cayman Islands | Paradise Papers |
| China Agroforestry Low-Carbon Holdings Limited | Cayman Islands | Cayman Islands | Paradise Papers |
| FB Top Select China Columbus Fund | Cayman Islands | Cayman Islands | Paradise Papers |
| Pure Heart Investment Philosophy (China) Fund | Cayman Islands | Cayman Islands, Hong Kong | Paradise Papers |
| CHINA INTERNATIONAL EXCHANGE & DEVELOPMENT FUNDING, LTD. | Bahamas | | Bahamas Leaks |
| ESSO EXPLORATION AND PRODUCTION CHINA (BOHAI LIMITED) | Bahamas | | Bahamas Leaks |
| ESSO EXPLORATION AND PRODUCTION CHINA (XOHU LIMITED) | Bahamas | | Bahamas Leaks |
| ESSO EXPLORATION AND PRODUCTION CHINA (TARIM LIMITED) | Bahamas | | Bahamas Leaks |
| HUTCHISON CHINA MEDITECH ENTERPRISES (BAHAMAS) LIMITED | Bahamas | | Bahamas Leaks |
| CHINA DRAGON ENVIRONMENTAL DESIGN SERVICES, INC. | Bahamas | | Bahamas Leaks |
| CHINA ECONOMIC & TRADING CENTRE (BARBADOS) INC. | Barbados | Barbados | Paradise Papers |
| CHINA CITY CHINESE RESTAURANT CO. LTD. | Barbados | Barbados | Paradise Papers |
| CHINA STATE CONSTRUCTION ENGINEERING (BARBADOS) CORPORATION | Barbados | Barbados | Paradise Papers |
| CHINA REAL ESTATE PARTNERS I, LLC | Barbados | United States, Barbados | Paradise Papers |
| CHINA SHANXI CONSTRUCTION ENGINEERING (GROUP) CORP. | Barbados | Barbados, China | Paradise Papers |
| DAC CHINA REAL ESTATE (BARBADOS) SRL | Barbados | Barbados | Paradise Papers |
| TS CHINA FUND (BARBADOS) III SRL | Barbados | Barbados | Paradise Papers |
| TISHMAN SPEYER CHINA FUND (BARBADOS) SRL | Barbados | Barbados | Paradise Papers |
| SEQUOIA CAPITAL CHINA II HOLDINGS, SRL | Barbados | Barbados | Paradise Papers |
| SEQUOIA CAPITAL CHINA GROWTH I HOLDINGS, SRL | Barbados | Barbados | Paradise Papers |
| TS CHINA FUND (BARBADOS) II SRL | Barbados | Barbados | Paradise Papers |
| AL NPL CHINA INVESTMENT (BARBADOS) SRL | Barbados | Barbados | Paradise Papers |
| SEQUOIA CAPITAL CHINA II HOLDINGS II, SRL | Barbados | Barbados | Paradise Papers |
| PACIFIC ALLIANCE CHINA GROWTH FUND SRL | Barbados | Barbados | Paradise Papers |
| SHELL CHINA JILIN ENERGY HOLDING COMPANY LTD. | Barbados | Barbados | Paradise Papers |
| CAPITARETAIL CHINA DEVELOPMENTS (B) PTE. LTD. | Barbados | Barbados | Paradise Papers |
| CAPITARETAIL CHINA INVESTMENTS (B) PTE. LTD. | Barbados | Barbados | Paradise Papers |
| CAPITARETAIL CHINA INVESTMENTS (B) ALPHA PTE. LTD. | Barbados | Barbados | Paradise Papers |
| CAPITARETAIL CHINA INVESTMENTS (B) BETA PTE. LTD. | Barbados | Barbados | Paradise Papers |
| CAPITARETAIL CHINA INVESTMENTS (B) GAMMA PTE. LTD. | Barbados | Barbados | Paradise Papers |
| CANADA CHINA PROPERTY INVESTMENTS (BARBADOS) INC. | Barbados | Barbados | Paradise Papers |
| E-Commercial China Consulting Holdings Limited (CH | British Virgin Islands | British Virgin Islands | Pandora Papers |
| E-House (China) Capital Investment Management Ltd. | British Virgin Islands | British Virgin Islands | Pandora Papers |
| E-House (China) Information Technology Co., Ltd. | British Virgin Islands | British Virgin Islands | Pandora Papers |
| E-House (China) Information Technology Service Lim | British Virgin Islands | British Virgin Islands | Pandora Papers |
| E-House (China) International Property Development | British Virgin Islands | British Virgin Islands | Pandora Papers |
| CHINA NORTHEASTERN BUILDING MATERIALS CONSULTING L | British Virgin Islands | British Virgin Islands | Pandora Papers |
| Israel Technology Investments China 8, Limited | British Virgin Islands | British Virgin Islands | Pandora Papers |
| Israel Technology Investments China 9, Limited | British Virgin Islands | British Virgin Islands | Pandora Papers |
| EMPIRE CHINA INTERNATIONAL DEVELOPMENT CO., LTD | | | Pandora Papers |
| Nam Hing China Investment Holding Limited | British Virgin Islands | British Virgin Islands | Pandora Papers |
| PA China Fundamental Industry Investment Limited | British Virgin Islands | British Virgin Islands | Pandora Papers |
| WAI HING WAH ARCHITECTS (CHINA) LTD.(WITH CHINESE CH.) | British Virgin Islands | Hong Kong | Panama Papers |
| China Petroleum Kunlun Lubricating Oil Holding Group Co., Ltd | British Anguilla | China | Panama Papers |
| CHINA-BASE NINGBO GY FOREIGN TRADE CO., LTD. | British Anguilla | Hong Kong | Panama Papers |
| Asia Sports Media Limited – Ex – Greater China Consulting Group Limited | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA PROPERTY INFORMATION RESEARCH CENTRE LIMITED (WITH CHI | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA SCIENCE AND TECHNOLOGY INDUSTRIAL PARK SERVICES GROUP LIMITED | Samoa | Hong Kong | Panama Papers |
| CHINA CENTURY ORIENTAL HOTEL & TOURISM HOLDINGS (BVI) CO.LTD | British Virgin Islands | Hong Kong | Panama Papers |
| ZHEN HUA CHINA NATIONAL IMPORT & EXPORT CO., LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA SATELLITE TOWNSHIP DEVELOPMENT AND MANAGEMENT COMPANY LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| China International Science and Technology Industry Cooperation Alliance Limited | British Virgin Islands | Hong Kong | Panama Papers |
| U.K. INT’L DIGITAL INFO INDUSTRY GROUP (CHINA) HOLDINGS LTD. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA TIANFU DIGITAL MEDIA ENTERPRISES GROUP HOLDING) CORPORATION | British Virgin Islands | Hong Kong | Panama Papers |
| Canada China Technology Collaboration and Promotion Center Limited | British Virgin Islands | Hong Kong | Panama Papers |
| Panama China Centre for Promotion and Organizing International Trade S.A. | Panama | Hong Kong | Panama Papers |
| China Jewelry Art Investment and Development Co., Ltd. | British Virgin Islands | China | Panama Papers |
| China Three Sources International Investment Development Holdings Co., Ltd. | British Virgin Islands | Hong Kong | Panama Papers |
| CHINA HOST MOBILE INTERNET GREEN REAL ESTATE CO., LIMITED | British Virgin Islands | China | Panama Papers |
| China Civil Aircraft General Aviation Technology Development Co., Ltd. | British Virgin Islands | Hong Kong | Panama Papers |
| MODERN MOBILE INTERNET GREEN REAL ESTATE (CHINA) CO., LIMITED | British Virgin Islands | China | Panama Papers |
| China Metallurgical Industry & Heavy Machines Group Co. Ltd. | Seychelles | Hong Kong | Panama Papers |
| CHINA HEAVY DUTY TRUCK IMPORT&EXPORT CO., LTD | Seychelles | China | Panama Papers |
| North China Steel And Building Materials Co., Ltd | Seychelles | Hong Kong | Panama Papers |
| ZHEJIANG YIWU CHINA SMALL-COMMODITIES CITY TRADING CO., LIMITED | Seychelles | Hong Kong | Panama Papers |
| CHINA ROYAL DRAGON (GROUP) INTERNATIONAL HOLDING PTE., CO. | Niue | Hong Kong | Panama Papers |
| SENSEN INTERNATIONAL ECONOMICAL TRADE CULTURE CHINA GROUP CO | Niue | Hong Kong | Panama Papers |
| CHINA LU´S GROUP (H.K.) INVESTMENT & DEVELOPMENT LIMITED | Niue | Hong Kong | Panama Papers |
| YUANSHAN INVESTMENT MANAGEMENT LTD [CHIEF CHINA RESOURCES LIMITED | Samoa | Hong Kong | Panama Papers |
| China Star Steel Industrial And Trading Co., Ltd. | Samoa | Hong Kong | Panama Papers |
| CHINA LI SHI ZHEN CHINESE MEDICINE UNIVERSITY HOLDING LTD | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA CHANG JIANG CHEMICAL FERTILIZER (INTERNATIONAL) HOLDINGS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA SMALL AND MEDIUM ENTERPRISE DEVELOPMENT AND MANAGEMENT CORPORATION | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Energy Conservation & Environmental Protection Asia Assets Fund Limited | Cayman Islands | Cayman Islands | Offshore Leaks |
| CHINA GREEN & HENRY INT’L PETROLEUM INVESTMENT & DEVELOPMENT INC. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| BRILLIANT FORCE INTERNATIONAL CHINA HEATING SUPPLY HOLDINGS COMPANY LIMITED | Samoa | Samoa | Offshore Leaks |
| CHINA NATIONAL DEFENCE INVESTMENT CONSTRUCT HOLDING GROUP LTD | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA REVIEW HAI XIA CORPORATE EDUCATION GROUP LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Cathay International Pharma Manufacture and Distribution (China) Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA SECOND-HAND HOUSE TRANSACTION NETWORK HOLDINGS LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China World Trade Group Capital International Investment Co., Management Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Greater China Electronics Products Research and Development Limited | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| China Twin Dragon International Investment Holding (Group) Co., Limited | Not identified | Not identified, Hong Kong | Offshore Leaks |
| China Three Rivers Finance Investment Group Corporation Limited | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| Victory Road Partners – China Green Venture I, L.P. | Not identified | Not identified, United States | Offshore Leaks |
| CHINA-AMERICA VENTURE CAPITAL INTERNATIONAL GROUP CO. LIMITED | Not identified | Not identified, Hong Kong | Offshore Leaks |
| China Good Pastoral Group Int’l Finance Management Co. Ltd. | Not identified | Hong Kong, Not identified | Offshore Leaks |
| CHINA INTERNATIONAL CULTURE AND ARTS HOLDINGS COMPANY LIMITED | Cayman Islands | Cayman Islands | Offshore Leaks |
| Huangyan No.2 Canned Food Factory Zhejiang China Ltd | Samoa | Samoa | Offshore Leaks |
| China Nonferrous Metals Group (Hong Kong) Co. Ltd. | Not identified | Not identified | Offshore Leaks |
| Reliance China and Hong Kong Opportunity Fund Limited | Bermuda | Bermuda | Paradise Papers |
| CHINA CHONGQING INTERNATIONAL ECONOMIC AND TECHINCAL COOPERATIVE COMPANY | Malta | Malta | Paradise Papers |
| CHINA CHONGQING INTERNATIONAL CORPORATION FOR ECONOMIC &TECHNICAL COOPERATION | Malta | Malta | Paradise Papers |
| MALTA-CHINA INTERNATIONAL ECONOMIC TECHNIC COOPERATION CO. LTD. | Malta | Malta | Paradise Papers |
| EXXONMOBIL EXPLORATION AND PRODUCTION (SOUTH CHINA SEA) LIMITED | Bahamas | | Bahamas Leaks |
| RHODE ISLAND DEV. CORP FORMERLY US CHINA DEVELOPMENT CORP | Bahamas | | Bahamas Leaks |
| Yuke (China) Mining and Energy Investment Group Ltd. | Not identified | Hong Kong, British Virgin Islands | Offshore Leaks |
| HK NOFEMET (CHINA – CANADA – JAPAN) ALUMINIUM CURTAIN WALL ENGINEERING LTD. | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| CHINA FILM AND TELEVISION CULTURE MEDIA OVERSEAS LIMITED | British Virgin Islands | British Virgin Islands | Offshore Leaks |
| Morningside China TMT Fund III Co-Investment, L.P. | Cayman Islands | Cayman Islands | Paradise Papers |
| CHINA SUN VALLEY ENERGY APPLICATION TECHNOLOGY CO., LTD | Cayman Islands | Cayman Islands, United States | Paradise Papers |
| China High Speed Transmission Equipment Group Co., Ltd. | Cayman Islands | Cayman Islands | Paradise Papers |
| DOUBLE HAPPY BAR & RESTAURANT N.V. – NEW CHINA TOWN BAR & RESTAURANT | Aruba | | Paradise Papers |
| KERR-MCGEE CHINA PETROLEUM LTD. (FORMERLY) TRANSWORLD DRILLING | Bahamas | | Bahamas Leaks |
| SEQUOIA CAPITAL CHINA GROWTH I HOLDINGS II, SRL | Barbados | Barbados | Paradise Papers |
| CHINA NATIONAL COMPLETE PLANT IMPORT & EXPORT CORPORATION (BARBADOS) LTD. | Barbados | Barbados | Paradise Papers |
| CHINA JIANGSU INTERNATIONAL CORPORATION TRINIDAD AND TOBAGO LIMITED | Barbados | Trinidad and Tobago | Paradise Papers |
| E-House (China) Management Company Limited (易居(中国) | British Virgin Islands | British Virgin Islands | Pandora Papers |
| China Advising Company Ltd. (华保有限公司) | British Virgin Islands | British Virgin Islands | Pandora Papers |
| China Hua Rui International Petroleum Limited (中國華 | British Virgin Islands | British Virgin Islands | Pandora Papers |
| CHINA NATIONAL HEAVY DUTY TRUCK GROUP JINAN SPECIAL AUTOMOBILE CO.,LTD | Samoa | Hong Kong | Panama Papers |
| Winsway China) Petrochemicals Logistics Company Limited EX-WINSWAY GROUP ENTERPRISES LIMITED) [WINSWAY GROUP ENTERPRISES LIMITED | British Virgin Islands | Hong Kong | Panama Papers |
| Hong Kong China-Russia Economic Technology Communication and Co-ordination Company Limited | British Virgin Islands | Hong Kong | Panama Papers |
| AUSTRALIA CHINA HOLDINGS LIMITED 澳華控股有限公司 | Bermuda | Australia, Bermuda, Hong Kong | Paradise Papers |
| E-House China (Beijing) Holdings Limited (易居中國(北京) | British Virgin Islands | British Virgin Islands | Pandora Papers |
| E-House China (Tianjin) Holdings Limited (易居中國(天津) | British Virgin Islands | British Virgin Islands | Pandora Papers |
| CHINA ARK INTERNATIONAL LIMITED (中國ARK國際有限公司) | British Virgin Islands | British Virgin Islands | Pandora Papers |
| China Commercial Real Estate Group Limited (中国房商控股 | British Virgin Islands | British Virgin Islands | Pandora Papers |
| China Travel and Property Holdings Limited (中國旅遊地产 | British Virgin Islands | British Virgin Islands | Pandora Papers |
| BAOKU China Company Limited (宝库中国有限公司) | British Virgin Islands | British Virgin Islands | Pandora Papers |
| SINO CHINA COMPANY LIMITED (中港集團有限公司) | British Virgin Islands | British Virgin Islands | Pandora Papers |
| China Ruifeng Renewable Energy Holdings Limited 中國瑞風新能源控股有限公司 | Cayman Islands | Cayman Islands, China | Paradise Papers |
| China E-Real Estate Holdings Limited(中国房产电商控股有限公司) | British Virgin Islands | British Virgin Islands | Pandora Papers |









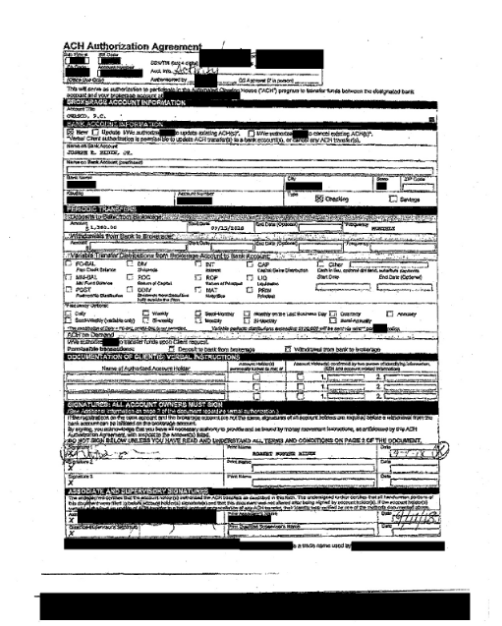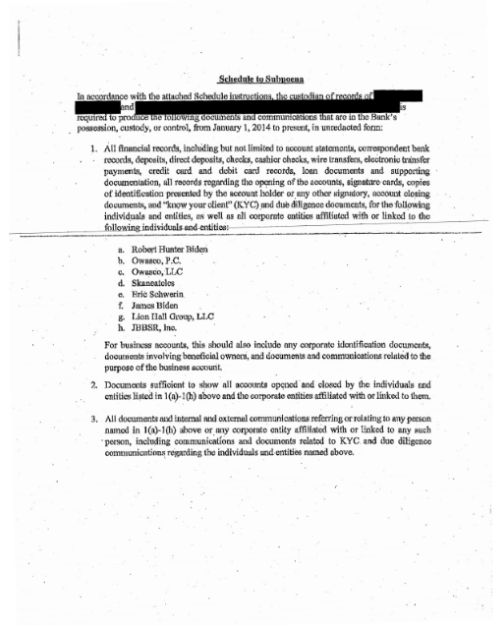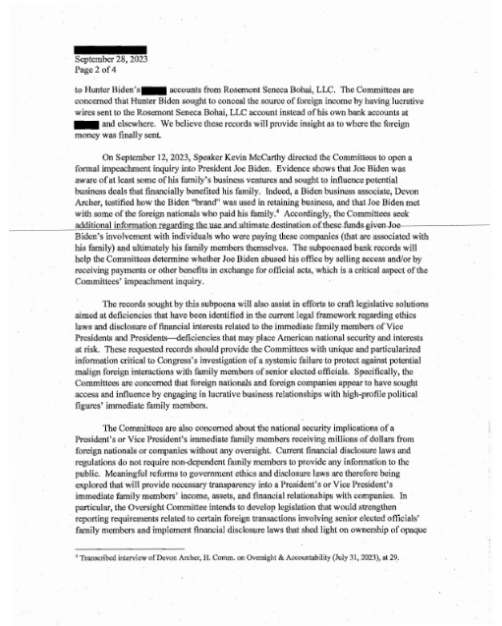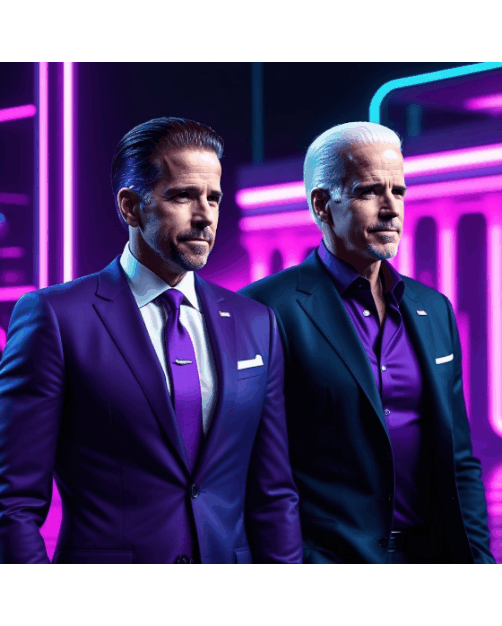





 March 23, 2023U.S.-China RelationsU.S. Seeks to Prevent China from Benefitting from $52 Billion Chips Funding
March 23, 2023U.S.-China RelationsU.S. Seeks to Prevent China from Benefitting from $52 Billion Chips Funding




















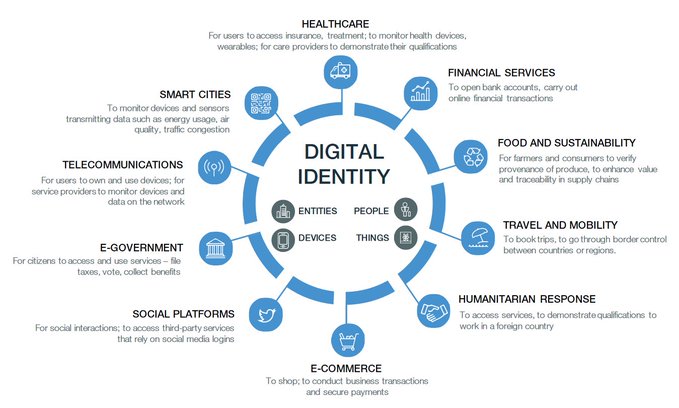

















































You must be logged in to post a comment.