Become a Patron!
True Information is the most valuable resource and we ask you to give back.
Tag: ebizz.tv
Stasi Children’s Television
Stasi Children’s Television
Yushchenko Poisoning Case -Viktor Yushchenko: Ukraine’s Ex-President On Being Poisoned
Become a Patron!
True Information is the most valuable resource and we ask you to give back.
Ukraine’s former president Viktor Yushchenko says he hopes Europe will wake up to the threat posed by Russia in the wake of the poisonings in Salisbury. Seventeen years ago Mr Yushchenko was taking on a presidential candidate favoured by Russia when he was poisoned with a dioxin, a toxic chemical.
KGB Psychological Warfare Techniques – Subversion & – Control Of Western Society
Watch Former KGB Spy, Professor Oleg Kalugin
The KGB Connections
Joseph Stalin & Lavrenty Beria – The Coup – Movie Excerpt
GET SMART – International Trailer With Steve Carell
Yushchenko Poisoning Case -Viktor Yushchenko: Ukraine’s Ex-President On Being Poisoned
Become a Patron!
True Information is the most valuable resource and we ask you to give back.
Ukraine’s former president Viktor Yushchenko says he hopes Europe will wake up to the threat posed by Russia in the wake of the poisonings in Salisbury. Seventeen years ago Mr Yushchenko was taking on a presidential candidate favoured by Russia when he was poisoned with a dioxin, a toxic chemical.
Stasi-Dioxin – The “NACHRICHTENDIENST” Searching For the Perfect Murder
Become a Patron!
True Information is the most valuable resource and we ask you to give back.
Evidence shows that such a perfect murder plotted by former Stasi agents is the cause of the death of German watchdog and journalist Heinz Gerlach.
The Ministry for State Security (German: Ministerium für Staatssicherheit (MfS), commonly known as the Stasi (IPA: [ˈʃtaziː]) (abbreviation German: Staatssicherheit, literally State Security), was the official state security service of East Germany. The MfS was headquartered in East Berlin, with an extensive complex in Berlin-Lichtenberg and several smaller facilities throughout the city. It was widely regarded as one of the most effective and repressive intelligence and secret police agencies in the world. The MfS motto was “Schild und Schwert der Partei” (Shield and Sword of the Party), that is the ruling Socialist Unity Party of Germany (SED).
Continue reading “Stasi-Dioxin – The “NACHRICHTENDIENST” Searching For the Perfect Murder”Stalin’s Secret Police: I
Stalin’s Secret Police: II
Stalin’s Secret Police: IV
Stalin’s Secret Police: V
Stalin’s Secret Police: VI
STASI – East Germany’s Secret Police -Germany’s Records Of Repression
Become a Patron!
True Information is the most valuable resource and we ask you to give back.
Sixty years after the Berlin Wall was erected, the spectre of the Stasi continues to loom over Germany.
STASI – East Germany’s Secret Police -The Fearsome POLITICAL POLICE That OVERCAME The KGB
STASI – East Germany’s Secret Police – Targeted By The STASI
Become a Patron!
True Information is the most valuable resource and we ask you to give back.
The Stasi spied on Silke Orphal and Ilona Seeber for years – after they applied to go to the West. Thirty years after the fall of the Berlin Wall, they both look back at their Stasi files. The Stasi files of Silke Orphal and Ilona Seeber include intercepted letters, official documents and countless reports by spies who meticulously noted everything about their lives, including the turning on and off of lights.
When Silke Orphal and Ilona Seeber, who were both ordinary typists at Neues Deutschland – the official newspaper of the Socialist Unity Party – applied to leave the GDR, it was considered scandalous. They were ostracized at work, threatened and subjected to interrogations that lasted hours. What did the experience do to them? How do they look back on that time today? A report by Axel Rowohlt.
STASI – East Germany’s Secret Police -Secret STASI Prison Berlin (GDR/East Germany) – 360° Video
STASI – East Germany’s Secret Police – Talk With Roland Jahn, Ex- Head Of The Stasi Archives
Staatsicherheitschef Erich Mielke – Eine Deutsche Karriere
Der „NACHRICHTENDIENST“ „GoMoPA“ – DIE CYBER-STASI DES 21. JAHRHUNDERTS
Become a Patron!
True Information is the most valuable resource and we ask you to give back.
“Worse than the Gestapo.” — Simon Wiesenthal, Nazi hunter
„Lauschen, spähen, schnüffeln: Vor 60 Jahren wurde die DDR-Staatssicherheit gegründet. Mehr als 91.000 hauptamtliche und doppelt so viele inoffizielle Mitarbeiter garantierten der SED die Macht. Ein Geheimdienst im klassischen Sinn war der Apparat nie, eher schon eine kriminelle Vereinigung mit tödlichen Methoden“, schreibt die angesehene Tageszeitung „DIE WELT“.
„Genau so verfährt auch der „NACHRICHTENDIENST“ „ GoMoPa“ , erläutert Rainer W. (Name wurde aus Sicherheitsgründen anonymisiert). Er war über mehrere Monate „inoffizieller“ Mitarbeiter des „NACHRICHTENDIENSTES“ „GoMoPa“, einem angeblichen Zusammenschluss jüdischer US-Rechtsanwälte namens Goldman, Morgenstern & Partner LLC, die noch nie jemand gesehen hat. Stattdessen sehen die Personen, die sich mit „GoMoPa“ beschäftigen nur die Totenkopfmaske stalinistischer STASI-Hacker, Erpresser und Cyberstalker.
Rainer W.: „Die eigentlichen Köpfe von „GoMoPa“ sind meiner Meinung nach wohl RA Jochen Resch und STASI-Oberst Ehrenfried Stelzer. Maurischat (ein Deckname) hat nicht das Format so eine Organisation aufzuziehen.“
Seit Jahren schon vesuchen die vorbestraften Serien-Kriminellen um das „Aushängeschild“ Klaus-Dieter Maurischat die deutsche Wirtschaft zu infiltrieren. Doch erst seit dem mutmasslichen Mord an Heinz Gerlach und den monatelangen Attacken gegen unser Haus sind viele Fakten recherchiert und zu Tage gekommen.
Vor allem über die Methoden des „NACHRICHTENDIENSTES“ – aber auch über dessen Hintermänner in Berlin, denn in New York existiert sowieso nur eine Briefkastenadresse und auch das „Büro“ in Berlin ist ein „virtuelles Regus-Büro“.
Die Fassade soll den „NACHRICHTENDIENST“ tarnen.
„DIE WELT“ schreibt: „40 Jahre lang, von der Gründung bis zu ihrer schrittweisen Auflösung zwischen Dezember 1989 und März 1990, war die Staatssicherheit der wichtigste Machtgarant der SED-Herrschaft. In dieser Zeit wucherte der Apparat immer mehr, bis schließlich mehr als 91.000 hauptamtliche Mitarbeiter für das MfS tätig waren.
Dieses Heer betreute eine Schattenarmee mit 189.000 „Inoffiziellen Mitarbeitern“ (IM). Statistisch gesehen kam in der DDR auf 55 erwachsene Bürger ein Vollzeit- oder Teilzeit-Stasi-Mann. Zum Vergleich: Im kommunistischen Polen lag das Verhältnis bei 1500 zu eins.
Der Apparat hat ungezählte Verbrechen zu verantworten. Darin folgte er seinen sowjetischen Vorbildern, der Tscheka (stolz nannten sich Stasi-Leute „Tschekisten“) und dem KGB. Vor allem aber prägte ein Mann das kriminelle Gebaren des MfS: Erich Mielke hatte sich schon als junger Mann 1931 als Attentäter in Berlin bewährt, als er im Auftrag der KPD zusammen mit einem Mittäter zwei Berliner Polizeioffiziere erschoss.
Der Doppelmörder konnte flüchten und führte im Spanischen Bürgerkrieg stalinistische Säuberungen in den eigenen Reihen durch. Im Sommer 1945 kehrte er nach Berlin zurück und übernahm sofort eine führende Position in der neu eingerichteten Polizei – interessanterweise in jenem Gebäude, das bis 1990 Sitz und Postanschrift der Staatssicherheit sein sollte.“
Zu den ungezählten Verrechen zählen Morde, Entführungen, Raub, Erpressung, Bespitzelung und jahrelange Gefängnishaft für Regime-Kritiker.
Jörg Berger flüchtete 1979 aus der DDR. Auch im Westen blieb die Stasi sein ständiger Begleiter. Jörg Berger berichtete vor seinem frühen Tod: „Nehmen wir den Fall des Spielers Lutz Eigendorf. Der war kurz vor mir geflüchtet und hat dann durch viel Medienpräsenz noch selbst dazu beigetragen, den Rummel anzufachen. Er starb bei einem Unfall auf der Autobahn, höchstwahrscheinlich hat ihn die Stasi vor seinem Tod geblendet. Entsprechendes findet sich jedenfalls in seiner Akte. Die Leute um Eigendorf waren die Leute, die ich auch um mich versammelt hatte. Dazu war er ein junger Spieler, ich ein gestandener Trainer. So hat man mir die Autoreifen zerstochen, auf der Autobahn löste sich ein Rad – und monatelang hatte ich Lähmungserscheinungen. Vermutlich von einer Bleivergiftung, die die Stasi initiiert hatte. Die haben mir wohl etwas in ein Getränk gemischt.“
„Der „Blitz“ traf Wilhelm van Ackern am 24. März 1955, kurz nach 22.30 Uhr – in Form von K.-o.-Tropfen in frisch gebrühtem Bohnenkaffee. Der vermeintliche Informant Fritz Weidmann hatte den 39-jährigen Fotohändler in eine konspirative Wohnung in der Kreuzberger Gneisenaustraße gelockt und ihm dort den vergifteten Kaffee serviert.
Nach wenigen Minuten wurde van Ackern übel; gestützt von Weidmann, verließ er die Wohnung. Doch auf der Straße erwartete ein weiterer Mann die beiden mit einem Wagen. Wilhelm van Ackern wurde im Schutz der Dunkelheit hineingestoßen und über die noch offene Sektorengrenze von West- nach Ost-Berlin ins Untersuchungsgefängnis Hohenschönhausen gefahren. Erst neuneinhalb Jahre später, teilweise verbüßt in der berüchtigten DDR-Sonderhaftanstalt Bautzen II, kam er frei und durfte zurück nach West-Berlin.“
Von Arsen bis Zyankali:
|
|
|
Dieter Baumann ist nicht totzukriegen. Nach einer zweijährigen Dopingsperre geht er jetzt wieder an den Start. 1999 eine positive Dopingprobe. Dass er sich selbst gedopt hat, glauben heute nur noch seine Feinde. Und Feinde aus der ehemaligen DDR hatte er genug: Dieter Baumann 1991: Dieter Baumann 1994: Dieter Baumann 1998: In Baumanns Zahnpasta fanden Kontrolleure das Dopingmittel Norandrostendion. Wie man Zahnpasta-Tuben mit Gift präpariert, kann man in den Stasiakten nachlesen: mit einem Glasröhrchen im hinteren Teil der Z-Tube. Die Zeitschrift „Laufzeit“ im Osten Berlins fragte ein Jahr vor Baumanns Dopingtest nach einem „Messias“ der Antidopingbewegung und beendete den Kommentar mit dem Satz: „Muß man sich angesichts morgendlicher Hochform eines Tages gar fragen: Ist meine Zahnpasta noch sauber?“ Laufzeit-Chef Wolfgang Weising, früher Leichtathletikautor bei der NVA-Zeitung „Volksarmee“ – sagte gegenüber report AUS MÜNCHEN, diese Formulierung sei Zufall gewesen. Baumann, das Opfer eines Komplotts? Selbst die Tübinger Kriminalpolizei schließt heute aus, dass sich Baumann selbst gedopt hat. Auch wissenschaftliche Untersuchungen belegen: Er konnte seine Zahnpasta nicht nachträglich manipuliert haben. Baumanns größte Entlastung: die Dosis war niemals leistungssteigernd. Baumann selbst will nicht öffentlich spekulieren, wer ihm das Dopingmittel unterjubelte. Es müsse aber jemand aus seinem engen Umfeld sein. Dieter Baumann, Olympiasieger 1992: Die Existenz von Kritikern vernichten, das war eine Aufgabe der Stasi. Der Rechtsmediziner Prof. Thomas Daldrup von der Universität Düsseldorf hat die sogenannte „Toxdat“-Studie der DDR untersucht – eine 900 Seiten starke Datenbank über Giftmordmöglichkeiten. Hier ist detailliert beschrieben wie sich selbst Laien Gifte beschaffen können und wie man einen Mord am besten verschleiert. Prof. Thomas Daldrup, Präsident Gesellschaft für Toxikologische und Forensische Chemie: Hinweise auf die Verschleierung provozierter Unfälle finden sich ebenfalls in Toxdat: „Vortäuschung von Verkehrsunfällen durch Auslösung von sekundenschneller Bewusstlosigkeit mittels Minigasgenerator in Belüftungsschächten von PKW.“ Da ist zum Beispiel der rätselhafte Verkehrsunfall des ehemaligen DDR-Fußballspielers Lutz Eigendorf im Jahr 1983. Vier Jahre zuvor war er nach einem Spiel in der Bundesrepublik nicht in die DDR zurückgekehrt. Er war ein leidenschaftlicher Autofahrer, seine Fahrweise risikovoll, das notierten die Spitzel der Stasi im Westen. Kurz vor seinem Verkehrsunfall stoppt die Stasi seine Fahrtzeit und die genaue Streckenführung seines täglichen Wegs vom Stadion nach Hause. Zum Unfallhergang tauchen vor zwei Jahren neue Hinweise auf. Wurde Eigendorf gezielt geblendet? In den Giftakten der Stasi heißt es: „verblitzen, Eigendorf“. Hatte man Eigendorf heimlich ein pupillenerweiterndes Mittel verabreicht? Die Staatsanwaltschaft Berlin kann Fragen dazu nicht beantworten, da eine Obduktion nicht angeordnet wurde, auch nach Auftauchen der neuen Stasidokumente nicht. Ein weiterer Fall: Fußballtrainer Jörg Berger liest seine Stasiakten. Nach seiner Flucht aus der DDR wurde der Star-Trainer ´79 zum Staatsfeind. Jörg Berger, Fußballtrainer Alemannia Aachen: Die Stasi wusste, dass Berger Angst hatte vor einem möglichen Auftragsmord, um weitere Fußballer vor einer Flucht abzuhalten: „BERGER bekundete angeblich (…), daß es ihm nicht so ergehen soll wie EIGENDORF.“ Die Stasi glaubte, dass Berger der Drahtzieher war für die Republikflucht mehrerer Fußballer. Als Berger dann Mitte der 80er Jahre als Trainer auf dem Sprung in die 1. Bundesliga war und sich die DDR-Sportler Falko Götz und Dirk Schlegel nach Westdeutschland absetzten, schien Berger für die DDR unerträglich zu werden. „Im operativen Vorgang ‚Ball’ wurde operativ herausgearbeitet, daß BERGER wesentlichen Anteil am Verrat von GÖTZ und SCHLEGEL hatte.“ Jörg Berger, Fußballtrainer, Alemannia Aachen: 1986 litt Berger unter rätselhaften Lähmungserscheinungen. Der Erklärungsversuch damals: eine Virusinfektion. Im Auftrag von report AUS MÜNCHEN hat der Rechtsmediziner Prof. Wolfgang Eisenmenger vor dem Hintergrund von Toxdat Bergers Krankenakten analysiert. Jetzt scheint festzustehen: Berger wurde vergiftet. Prof. Wolfgang Eisenmenger, Klinikum Innenstadt der Universität München, Institut für Rechtsmedizin: Die Anleitung, eine Arsenikvergiftung zu verschleiern – liefert ebenfalls wieder die DDR-Giftstudie Toxdat. Frühere Stasi-Mitarbeiter wollten auch ihn ausschalten, das glaubt der Bundestagsabgeordnete Hartmut Büttner aus Hannover. 1995 hatte er einen mysteriösen Autounfall, der ihn beinahe das Leben kostete. Nach der Wiedervereinigung hatte der Abgeordnete zu den Hintermännern der „Toxdat“-Studie recherchiert und sich sehr für die Offenlegung der Stasi-Akten durch die Gauck-Behörde eingesetzt. Hartmut Büttner, CDU-Bundestagsabgeordneter 1991: Als Büttner ´95 auf gerader, staubtrockener Straße verunglückte, findet keine Filigranuntersuchung des Wagens statt. Während er im Koma liegt, gibt die Polizei das Schrottauto frei. Eine Speditionsfirma zahlt dafür eilig das Sechsfache seines Werts. Büttner wurde mitgeteilt: Hartmut Büttner, CDU-Bundestagsabgeordneter: Viele Unfälle und Erkrankungen von ehemaligen DDR-Systemkritikern scheinen noch lange nicht geklärt. |
|||||||||||||||||||||||||||||||||||
Ebenso wie der Todesfall Heinz Gerlach zur Gänze aufgeklärt werden muss
„DIE WELT“ berichtet: „Mielkes Leute pfuschten in das Leben von Millionen DDR-Bürgern hinein, zerstörten berufliche oder private Hoffnungen und zersetzten routinemäßig ganze Familien. Außerdem schädigte die Stasi im Laufe der Jahrzehnte Hunderttausende Menschen in der SED-Diktatur vorsätzlich, brach unangepasste Charaktere mit psychischem Druck.
In jedem DDR-Bezirk unterhielt das MfS eigene Untersuchungshaftanstalten, in Potsdam zum Beispiel in der Lindenstraße 54/55. In Berlin gab es neben der Zentrale in Lichtenberg die Stasi-Bezirksverwaltung Berlin, die bis 1985 in einem ehemaligen Krankenhaus an der Prenzlauer Allee und danach in einem 100 Millionen DDR-Mark teuren Neubau am Tierpark Friedrichsfelde amtierte, und das große Sperrgebiet in Hohenschönhausen, wo neben einem Gefängnis auch das streng geheime NS-Archiv der Stasi und technische Abteilungen saßen.
Neben der alltäglichen Unterdrückung stehen die schweren Gewalttaten des MfS; sie umfassen praktisch alle Paragrafen des DDR-Strafgesetzbuchs. So verschleppten Stasi-Kommandos im Laufe der Zeit mindestens 500, vielleicht aber auch bis zu tausend Menschen in die DDR – westliche Agenten, Überläufer aus den eigenen Reihen und SED-Kritiker vor allem. Einige von ihnen, zum Beispiel der vormalige Volkspolizei-Chef Robert Bialek, überlebten die Verschleppung nicht; andere, wie die „Verräter“ Paul Rebenstock und Sylvester Murau, wurden nach manipulierten Prozessen hingerichtet.
Ein juristisch verbrämter Mord war die Hinrichtung des MfS-Hauptmanns Werner Teske 1981. Er hatte mit dem Gedanken gespielt, in den Westen überzulaufen, allerdings nie einen konkreten Versuch dazu unternommen. Obwohl selbst das scharfe DDR-Strafrecht die Todesstrafe nur für vollendeten schweren Landesverrat vorsah, den Teske unzweifelhaft nicht begangen hatte, wurde er im Leipziger Gefängnis durch Genickschuss getötet.
Auch direkte Mordanschläge beging die Stasi. So lauerte 1976 ein Spezialkommando der Stasi, die „Einsatzkompanie der Hauptabteilung I“, auf westlicher Seite der innerdeutschen Grenze dem Fluchthelfer Michael Gartenschläger auf. Er wollte dort eine Splittermine vom Typ SM-70 abmontieren, die berüchtigte „Selbstschussanlage“. Vier Männer der Einsatzkompanie erwarteten ihn und eröffneten sofort das Feuer, als der langjährige politische Gefangene an den Grenzzaun heranschlich. MfS-Generalleutnant Karl Kleinjung, der Chef der Hauptabteilung I, hatte zuvor befohlen, „den oder die Täter festzunehmen bzw. zu vernichten“.
Auch der Schweizer Fluchthelfer Hans Lenzlinger wurde wohl im Auftrag des MfS 1979 in seiner Züricher Wohnung erschossen. Vielleicht war Bruno Beater, der ranghöchste Stellvertreter Mielkes und Experte für „nasse Jobs“, in den Anschlag verwickelt; aufgeklärt wurde dieser Mord aber nie.
Nicht das befohlene Ziel erreichten dagegen Mordanschläge gegen andere Fluchthelfer. Kay Mierendorff, der Hunderten DDR-Bürgern gegen fünfstellige Summen in die Freiheit verhalf, bekam im Februar 1982 eine Briefbombe zugeschickt, die ihn schwer verletzte und bleibende Schäden hervorrief.
Einen anderen „Hauptfeind“ der SED, den Fluchthelfer Wolfgang Welsch, vergiftete ein in seinen Kreis eingeschleuster Stasi-Agent im Sommer 1981 mit dem extrem toxischen Schwermetall Thallium; den Tod von Welschs Ehefrau und ihrer Tochter nahm der Stasi-IM billigend in Kauf.
Geplant, aber wohl nicht ausgeführt worden sind Mordanschläge auf Rainer Hildebrandt, den Kopf der DDR-kritischen „Arbeitsgemeinschaft 13. August“, die von ihrem Haus am Checkpoint Charlie aus das Unrecht der Mauer unnachgiebig anprangerte, und auf den Friedrichshainer Pfarrer Rainer Eppelmann, der unter Erich Honecker zeitweise als „Staatsfeind Nummer eins“ der SED galt. Umstritten ist dagegen, ob der DDR-Fußballstar Lutz Eigendorf 1983 von der Stasi durch einen vorsätzlich herbeigeführten Autounfall ermordet wurde. Vieles spricht dafür; der letzte Beweis ist in den allerdings bisher nur zum Teil sachgerecht erschlossenen Akten der Birthler-Behörde nicht aufgetaucht.
Noch öfter als potenziell tödliche Methoden wandten die Stasi-Experten allerdings das Mittel der Erpressung an. In verschiedenen Hotels für westliche Touristen in der ganzen DDR waren über den Betten Kameras eingebaut; auf interessante Ausländer wurden gezielt Prostituierte der Stasi angesetzt, um sie später mit kompromittierenden Fotos erpressen zu können. Das Gleiche versuchte das MfS auch mit Heinrich Lummer, dem West-Berliner CDU-Politiker. Über Jahre hinweg pflegte er eine geheime Beziehung zu einer Ost-Berlinerin, die in Wirklichkeit wohl von Anfang an als Spitzel auf ihn angesetzt war. 1981/82 versuchte das MfS, Lummer zu erpressen, was aber misslang.
Rund 40 Jahre lang garantierte die Stasi als „Schild und Schwert der Partei“ die Existenz der SED-Diktatur. Doch manches misslang Mielkes Mannen auch. So erwies sich beispielsweise die Suche nach den Autoren eines anonymen, kritischen Aufrufs als erfolglos, der 1969 an der Humboldt-Universität auftauchte. Trotz enormen Aufwandes und Kosten von rund einer Million DDR-Mark konnte das MfS die Verantwortlichen, die Studenten Rainer Schottländer und Michael Müller, nie überführen. So wurde ihr Protest zum „teuersten Flugblatt der Welt“.“
Insider Rainer W.:“Genau diese Methodenw erden heute von „GoMoPa“ und deren Hintermännern weider angewandt – natürlich verfeinert und mit Internet-Cyberstalking-Taktiken garniert.
Hinzu kommt der systematische Rufmord via Google und mit falschen Gerüchten, Erpresseranrufen, Morddrohungen, Cyberattacken, Kontoplünderungen und die Zerstörung von Geschäftsbeziehung durch
Systematisch gestreutes Misstrauen. Nehmen Sie all dies zusammen, dann haben Sie die STASI von heute: den „NACHRICHTENDIENST“ „GoMoPa“.“
GoMoPa-Maurischat Cyberstalker- Dream Team – Live Video
Become a Patron!
True Information is the most valuable resource and we ask you to give back.
GoMoPa – Maurischat Cyberstalker Dream Team Live In Action
Remember – German Criminal Police Starts Allegedly Investigation Of „GoMoPa“ And Their Backers
Become a Patron!
True Information is the most valuable resource and we ask you to give back.

On our request the German criminal police (Kriminalpolizei) has opened new cases against the notorious “GoMoPa” organisation which already fled in the underground. Insiders say they have killed German journalist and watchdog Heinz Gerlach and their criminal record is bigger than the Encyclopedia – Britannica.
Continue reading “Remember – German Criminal Police Starts Allegedly Investigation Of „GoMoPa“ And Their Backers”Remember – New Criminal Police Action Against “GoMoPa” & Also Against Google
Become a Patron!
True Information is the most valuable resource and we ask you to give back.
Dear readers,
on our request the German criminal police (Kriminalpolizei) has opened new cases against the notorious “GoMoPa” organisation which already fled in the underground. Insiders say they have killed German journalist and watchdog Heinz Gerlach and their criminal record is bigger than the
Encyclopedia – Britannica
The case is also directed against Google, Germany, whilst supporting criminal action of “GoMoPa” for years and therefore give them the chance to blackmail successfull businessman. This case is therefore an example and will be followed by many others as far as we can project. Furthermore we will bring the case to the attention of the German lawyers community which will not tolerate such misconduct by Googles German legal representative Dr. Arndt Haller and we will bring the case to the attention of Google Inc in Mountain View, USA, and the American ministry of Justice to stop the Cyberstalkers once and for all.
Besides that many legal institutions, individuals and firms have already contacted us to help to clarify the death of Mr. Heinz Gerlach and to prosecute his murderers and their backers.
The case number is
ST/0148943/2011 My warmest regards Bernd Pulch
Stasi Children’s Television
Julian Assange – Why The World Needs WikiLeaks
WikiLeaks’ Julian Assange, Pt. 2
Politkovskaya Killer Identified
Seymour Hersh – Does Investigative Journalism Still Exist?
Journalist Murder Still Unsolved 25 Years On
King Kong vs Godzilla – Full Sci-Fi Action Movie – Michael Keith
Become a Patron!
True Information is the most valuable resource and we ask you to give back.
Watch #KingKongVsGodzilla Hollywood epic movie. Starring Michael Keith, Harry Holcombe, James Yagi, Tadao Takashima and Keji Sahaka. Directed by Ishirō Hondatch
The Nurse (1997) | Hollywood Thriller Movie – Lisa Zane, John Stockwell
Become a Patron!
True Information is the most valuable resource and we ask you to give back.
Watch #TheNurse 1997 Thriller movie. Starring Lisa Zane, John Stockwell, John Stockwell, Nancy Dussault and Sherrie Rose. Directed by Robert Malenfant. Music by Richard Bowers Produced by Richard Brandes #ActionThrillerMovie #HollywoodActionMovie #HollywoodThrillerMovie Synopsis A traumatized nurse plots revenge against a catatonic businessman, whom she blames for the death of her father. She integrates herself in to his family as his personal nurse and plots revenge by killing off his family members one by one.
Best of Charlie Chaplin – Best Moments – Charlie Chaplin Funny Moments
The Front Page -Steamboat Bill, Jr. (1928) | Silent Comedy Movie – Buster Keaton, Ernest Torrence
Become a Patron!
True Information is the most valuable resource and we ask you to give back.
How to Murder Your Wife (1965) – Romantic Comedy Movie – Jack Lemmon, Virna Lisi
Become a Patron!
True Information is the most valuable resource and we ask you to give back.
Watch #HowtoMurderYourWife 1965 Romantic Comedy movie.
Starring Jack Lemmon, Virna Lisi, Terry-Thomas, Claire Trevor, Sidney Blackmer and Max Showalter. Directed by Richard Quine Music by Neal Hefti Produced by George Axelrod
THE FRONT PAGE (1931) – Full Movie – Captioned
The Front Page – Wisconsin Calls For “Full Forensic Audit”
The Front Page – Chai Bisket Stories – Suhas
Become a Patron!
True Information is the most valuable resource and we ask you to give back.
An aspiring filmmaker narrates a highly complex story to a producer. As his story unfolds, we will find out if the narrator is successful in getting his story approved.
Starring Suhas & Sridhar
Directed by Filmian
Produced by Anurag & Sharath
Music by Karthik Rodriguez
Cinematography by Shreekar Khajandar
Editing by Pavan Kalyan
The Front Page – Trailer – Jack Lemmon – Walter Matthau
The Front Page – Full Movie
Become a Patron!
True Information is the most valuable resource and we ask you to give back.
Internet Journalism
Honoring Journalism’s Best – The Pulitzer
Frost Nixon Interview Watergate Tapes
Become a Patron!
True Information is the most valuable resource and we ask you to give back.
Investigative Journalism – WT Stead – The Father Of Investigative Journalism
Osher Forum: What Happened To Investigative Journalism?
Simon Bolivar – A Great Freedom Fighter
Tips From Bob Woodward On Investigative Journalism
Robert Redford, Bob Woodward, Carl Bernstein Discuss All The President’s Men At BAM
Great Conversations: Defending Human Rights
Thomas Jefferson’s Prophetic Wisdom
Abraham Lincoln – History Channel
Voltaire “Poème Sur Le Désastre De Lisbonne” French Poem Animaton
Jean-Jacques Rousseau And Social Contract – Rey Ty
The History Of Political Philosophy: Jean-Jacques Rousseau (Lecture 6,) By David Gordon
Martin Luther King Jr – I Have A Dream
Become a Patron!
True Information is the most valuable resource and we ask you to give back.
Great vision from a great leader
Kennedy – “I Am A Berliner – Ich Bin Ein Berliner”
We Choose To Go To The Moon
Ask Not What Your Country Can Do For You!
JFK – What Really Happened
John F. Kennedy Assassination
John F Kennedy’s Bodyguards Being Told To Stay Away From JFK
Oskar Schindler – Biography
Oskar Schindler – Part 7, A Martin Kent Documentary About Oskar Schindler
Become a Patron!
True Information is the most valuable resource and we ask you to give back.
Unforgotten Heroes
Biography – Need To Know – Nelson Mandela
Become a Patron!
True Information is the most valuable resource and we ask you to give back.
My favourite Politician
The Assassination of Abraham Lincoln
AN OVERVIEW OF THE HEAVY CYBERATTACKS ON OUR WEBSITES TO STOP THE TRUTH DONE BY THE SUSPECTS
These graphs below show the cyberattacks on our website initiated by the suspects we already mentioned and who even announced in an email that tehy would do this illegal internet crime. The email was by Otmar Knoll, Fairvesta, who announced the cybercrime. The suspected hackers are from “GoMoPa” and their thugs.
The graphs show the DDos attacks on our servers.
What is a DDos attack ?
Read here:
http://en.wikipedia.org/wiki/Denial-of-service_attack
These internet crimes are punished with longterm jail sentences and financial compensation..
Die untenstehenden Graphiken zeigen die Hackernagriffe auf unsere Webseiten, die seit Jahren durchgeführt werden im Ausschnitt. In einer Email an uns hat Otmar Knoll, Fairvesta, die Hackerangriffe, somit schwere Internetverbrechen angekündigt. Wir haben diese Emails bereits veröffentlicht. Mutmasslich arbeitet Otmar Knoll mit den üblichen Verdächtigen der “GoMoPa”, ihren Informanten und Hackern zusammen:
Die Graphiken zeigen die sogenannten DDos-Angriffe auf unsere Server.
Was ist eine DDos Attacke ?
http://de.wikipedia.org/wiki/Denial_of_Service
Lesen Sie hier:
Diese Vergehen werden mit langjährigen Freiheitsstrafen und Schadensersatz bestraft.
Unveiled – WikiLeaks Setting Another Trap for Journalists, NGOs
|
Public Intelligence – Ohio Fusion Center Report: Bath Salts and Officer Safety

(U//FOUO) The Ohio State Highway Patrol Criminal Intelligence Unit recently partnered with the Ohio Strategic Analysis and Information Center (SAIC) and gathered information regarding bath salts via a survey. The objective of the study was to assist Law Enforcement by creating an officer safety awareness product relating to the dangers of encountering people on bath salts.
(U//FOUO) A survey was distributed to law enforcement and 5 agencies responded back with pertinent information regarding the use and possession of bath salts. The agencies which contributed to this analysis are as follows:
Barberton Police Department, OH; Ohio State Highway Patrol; Powell Police Department, OH; Reynoldsburg Division of Police; and West Virginia State Police – Wheeling Division (Parcel Interdiction).
(U//FOUO) Information was obtained on 161 incidents involving bath salts.
(U//FOUO) OVERVIEW AND ANALYSIS OF RESULTS:
- Out of the 161 incidents reported, officers made 77 arrests involving bath salt use/possession. Many of the incidents occurred before legislation was passed; therefore mere possession was not criminal at the time of many of these reports.
- There were 27 use of force reports involving bath salts.
- There were 3 incidents that involved fleeing of suspects.
- 7 suspects were taken to hospital associated with bath salt use.
- 7 offenders were pinked slipped and taken to mental health facilities.
- There were 4 reports of deaths associated with bath salt use (Note: cause of death results did NOT find that bath salts use was the sole contributor in any of these deaths).
- There was 1 report of suicide; 2 suicide attempts; and 1 suicide threat involving bath salt use.
- Suspects reported paying approximately $20-$25 for bath salts.
- The offenders reported multiple ways of using bath salts including: snorting, injection with a needle syringe, and drinking the bath salts by mixing it with fluid.
- Many offenders admitted to combining bath salts with other drugs.
- When reported, most people said they got the bath salts from independently owned convenient stores and drive-thrus, gas stations or markets. A WV State Police (parcel narcotics interdiction) Officer reported that a prominent internet company is: Southern Burn LLC from South Carolina.
(U//FOUO) OFFICER SAFETY CONCERNS
- Use of force incidents included: use of Taser (3 incidents), hands on, escorts, restrained by medical professionals, and bean bag use.
- One “officer in trouble” call was reported, involving an officer fighting with a person on bath salts.
- Both officers in a Reynoldsburg Police case were surprised after a Taser was used on a suspect. They explained that the Taser was shot and the probes penetrated in the torso of the suspect, however it had minimal effects; the suspect fought through the electric current and rose to his feet.
- Injuries sustained to suspects included: bruises, cuts, Taser punctures, and minimal injuries from bean bag rounds.
- Officers sustained injuries including: injury to knee, injury to back, injury to groin, ankles, scrapes and bruises, and multiple injuries from strikes to the face.
- 2 officers and 7 offenders were taken to the hospital resulting from physical force.
- One incident involved the use of the SWAT team and another involved escalated use of force involving bean bag rounds.
(U//FOUO) PHYSIOLOGICAL REACTIONS FROM BATH SALT USE
- Suspects showed the following physical reactions to bath salts: Hyperventilation, cramps, dehydration, vomiting, shaking, loss of memory, pale, emaciated, jittery, lethargy, incoherent speech, rambling, rapid movement, rapid speech, disoriented, itchy skin, and several suspect admitted to a lack of sleep for multiple days.
- An offender described bath salts as giving him a “cocaine rush” and it being a very “intense” high.
- Witnesses described bath salt users as:
- Hostile, violent, unpredictable, out of control, paranoid, and reckless.
- Additional reports by Law Enforcement involving people on bath salts:
- Officer described one suspect as having unusual superhuman strength.
- Officer described suspect as shooting off the ground like a “flash of light.”
- One suspect bent the hinged handcuffs during the arrest.
- The following hallucinations were reported:
- A hit-skip offender said he saw a brick wall, which in turn caused a crash.
- A male, using bath salts, reported raccoons setting fire inside his home. As a result, he proceeded to destroy his home and used a hatchet to cut up his deck, while attempting to locate the fire-setting raccoons. He also believed the raccoons stole his cell phone.
- A male, using bath salts, believed he was being followed by police helicopters and police officers were using mirrors, snipers and different types of scopes to look through his walls. He called police requesting to negotiate with them, however there were no police at the residence when the call was made.
- During the course of speaking to an offender and officer reported, he yelled, “AT&T calling, may I help you, AT&T is calling, a million dollars, two black guys……it’s not a racial thing, it’s not a racial thing.”
- A bath salt user reported he hears voices; one voice was going to beat him with a ball bat.
- The domestic violence offender using bath salts reported his mother was practicing demonology & witchcraft and she was poisoning his food. He was arrested for choking her.
- DOWNLOAD THE ORIGINAL DOCUMENT HERE:
- OHSP-BathSalts
FEMEN – Topless Female Protest Group Set To Disrupt 2012 Euro Cup
Unveiled – Barclays Bank PLC Admits Misconduct Related to Submissions for the London InterBank Offered Rate and the Euro InterBank Offered Rate and Agrees to Pay $160 Million Penalty
WASHINGTON—Barclays Bank PLC, a financial institution headquartered in London, has entered into an agreement with the Department of Justice to pay a $160 million penalty to resolve violations arising from Barclays’ submissions for the London InterBank Offered Rate (LIBOR) and the Euro Interbank Offered Rate (EURIBOR), which are benchmark interest rates used in financial markets around the world, announced Assistant Attorney General Lanny A. Breuer of the Justice Department’s Criminal Division and Assistant Director in Charge James W. McJunkin of the FBI’s Washington Field Office.
As part of the agreement with the Department of Justice, Barclays has admitted and accepted responsibility for its misconduct set forth in a statement of facts that is incorporated into the agreement. According to the agreement, Barclays provided LIBOR and EURIBOR submissions that, at various times, were false because they improperly took into account the trading positions of its derivative traders, or reputational concerns about negative media attention relating to its LIBOR submissions. The Justice Department’s criminal investigation into the manipulation of LIBOR and EURIBOR by other financial institutions and individuals is ongoing. The agreement requires Barclays to continue cooperating with the department in its ongoing investigation.
“LIBOR and EURIBOR are critically important benchmark interest rates,” said Assistant Attorney General Breuer. “Because mortgages, student loans, financial derivatives, and other financial products rely on LIBOR and EURIBOR as reference rates, the manipulation of submissions used to calculate those rates can have significant negative effects on consumers and financial markets worldwide. For years, traders at Barclays encouraged the manipulation of LIBOR and EURIBOR submissions in order to benefit their financial positions; and, in the midst of the financial crisis, Barclays management directed that U.S. Dollar LIBOR submissions be artificially lowered. For this illegal conduct, Barclays is paying a significant price. To the bank’s credit, Barclays also took a significant step toward accepting responsibility for its conduct by being the first institution to provide extensive and meaningful cooperation to the government. Its efforts have substantially assisted the Criminal Division in our ongoing investigation of individuals and other financial institutions in this matter.”
“Barclays Bank’s illegal activity involved manipulating its submissions for benchmark interest rates in order to benefit its trading positions and the media’s perception of the bank’s financial health,” said Assistant Director in Charge McJunkin. “Today’s announcement is the result of the hard work of the FBI special agents, financial analysts, and forensic accountants as well as the prosecutors who dedicated significant time and resources to investigating this case.”
Barclays was one of the financial institutions that contributed rates used in the calculation of LIBOR and EURIBOR. The contributed rates are generally meant to reflect each bank’s assessment of the rates at which it could borrow unsecured interbank funds. For LIBOR, the highest and lowest 25 percent of contributed rates are excluded from the calculation and the remaining rates are averaged to calculate the fixed rates. For EURIBOR, the highest and lowest 15 percent are excluded, and the remaining 70 percent are averaged to calculate the fixed rates.
Futures, options, swaps, and other derivative financial instruments traded in the over-the-counter market and on exchanges worldwide are settled based on LIBOR. Further, mortgages, credit cards, student loans, and other consumer lending products often use LIBOR as a reference rate. According to the agreement, an individual bank’s LIBOR or EURIBOR submission cannot appropriately be influenced by the financial positions of its derivatives traders or the bank’s concerns about public perception of its financial health due to its LIBOR submissions.
According to the agreement, between 2005 and 2007, and then occasionally thereafter through 2009, certain Barclays traders requested that the Barclays LIBOR and EURIBOR submitters contribute rates that would benefit the financial positions held by those traders. The requests were made by traders in New York and London, via electronic messages, telephone conversations, and in-person conversations. The employees responsible for the LIBOR and EURIBOR submissions accommodated those requests on numerous occasions in submitting the bank’s contributions. On some occasions, Barclays’s submissions affected the fixed rates.
In addition, between August 2005 and May 2008, certain Barclays traders communicated with traders at other financial institutions, including other banks on the LIBOR and EURIBOR panels, to request LIBOR and EURIBOR submissions that would be favorable to their or their counterparts’ trading positions, according to the agreement.
When the requests of traders for favorable LIBOR and EURIBOR submissions were taken into account by the rate submitters, Barclays’ rate submissions were false and misleading.
Further, according to the agreement, between approximately August 2007 and January 2009, in response to initial and ongoing press speculation that Barclays’ high U.S. Dollar LIBOR submissions at the time might reflect liquidity problems at Barclays, members of Barclays management directed that Barclays’ dollar LIBOR submissions be lowered. This management instruction often resulted in Barclays’ submission of false rates that did not reflect its perceived cost of obtaining interbank funds. While the purpose of this particular conduct was to influence Barclays’ rate submissions, as opposed to the resulting fixes, there were some occasions when Barclays’ submissions affected the fixed rates.
The agreement and monetary penalty recognize Barclays’ extraordinary cooperation. Barclays made timely, voluntary, and complete disclosure of its misconduct. After government authorities began investigating allegations that banks had engaged in manipulation of benchmark interest rates, Barclays was the first bank to cooperate in a meaningful way in disclosing its conduct relating to LIBOR and EURIBOR. Barclays’ disclosure included relevant facts that at the time were not known to the government. Barclays’s cooperation has been extensive, in terms of the quality and type of information and assistance provided, and has been of substantial value in furthering the department’s ongoing criminal investigation. Barclays has made a commitment to future cooperation with the department and other government authorities in the United States and the United Kingdom.
Assistant Attorney General Breuer further stated, “As today’s agreement reflects, we are committed to holding companies accountable for their misconduct while, at the same time, giving meaningful credit to companies that provide full and valuable cooperation in our investigations.”
In addition, Barclays has implemented a series of compliance measures and will implement additional internal controls regarding its submission of LIBOR and EURIBOR contributions, as required by the Commodity Futures Trading Commission (CFTC). Barclays will also continue to be supervised and monitored by the FSA.
The agreement and monetary penalty further recognize certain mitigating factors to Barclays’ misconduct. At times, Barclays employees raised concerns with the British Bankers’ Association, the United Kingdom Financial Services Authority (FSA), the Bank of England, and the Federal Reserve Bank of New York in late 2007 and in 2008 that the Dollar LIBOR rates submitted by contributing banks, including Barclays, were too low and did not accurately reflect the market. Further, during this time, notwithstanding Barclays’s improperly low dollar LIBOR submissions, those submissions were often higher than the contributions used in the calculation of the fixed rates.
As a result of Barclays’s admission of its misconduct, its extraordinary cooperation, its remediation efforts and certain mitigating and other factors, the department agreed not to prosecute Barclays for providing false LIBOR and EURIBOR contributions, provided that Barclays satisfies its ongoing obligations under the agreement for a period of two years. The non-prosecution agreement applies only to Barclays and not to any employees or officers of Barclays or any other individuals.
In a related matter, the CFTC brought attempted manipulation and false reporting charges against Barclays, which the bank agreed to settle. The CFTC imposed a $200 million penalty and required Barclays to implement detailed measures designed to ensure the integrity and reliability of its benchmark interest rate submissions.
The FSA issued a final notice regarding its enforcement action against Barclays and has imposed a penalty of £59.5 million against it.
The case is being handled by Deputy Chief Daniel Braun, Assistant Chiefs Rebecca Rohr and Robertson Park, Trial Attorney Alexander Berlin, and Special Trial Attorney Luke Marsh of the Criminal Division’s Fraud Section. The investigation is being conducted by the FBI’s Washington Field Office, jointly with the Antitrust Division of the Department of Justice.
The Department acknowledges and expresses its appreciation for the significant assistance provided by the CFTC’s Division of Enforcement, which referred the conduct to the department, as well as the FSA’s Enforcement and Financial Crime Division.
This agreement is part of efforts underway by President Barack Obama’s Financial Fraud Enforcement Task Force. President Obama established the interagency Financial Fraud Enforcement Task Force to wage an aggressive, coordinated, and proactive effort to investigate and prosecute financial crimes. The task force includes representatives from a broad range of federal agencies, regulatory authorities, inspectors general and state and local law enforcement who, working together, bring to bear a powerful array of criminal and civil enforcement resources. The task force is working to improve efforts across the federal executive branch and, with state and local partners, to investigate and prosecute significant financial crimes, ensure just and effective punishment for those who perpetrate financial crimes, combat discrimination in the lending and financial markets, and recover proceeds for victims of financial crimes. For more information about the task force visit: http://www.stopfraud.gov.
TOP-SECRET from the FBI – Texas Resident Convicted on Charge of Attempted Use of Weapon of Mass Destruction
AMARILLO, TX—Khalid Ali-M Aldawsari, 22, a citizen of Saudi Arabia and resident of Lubbock, Texas, was convicted by a federal jury today on an indictment charging one count of attempted use of a weapon of mass destruction in connection with his purchase of chemicals and equipment necessary to make an improvised explosive device (IED) and his research of potential U.S. targets, including persons and infrastructure.
The verdict, which was reached in the Northern District of Texas, was announced by Sarah R. Saldaña, U.S. Attorney for the Northern District of Texas; Lisa Monaco, Assistant Attorney General for National Security; and Diego G. Rodriguez, Special Agent in Charge of the FBI Dallas Field Division.
Sentencing has been scheduled for October 9, 2012, in Amarillo. Aldawsari, who was lawfully admitted into the United States in 2008 on a student visa and was enrolled at South Plains College near Lubbock, faces a maximum sentence of life in prison and a $250,000 fine. He was arrested on February 23, 2011 on a criminal complaint and later charged in a March 9, 2011 federal indictment with attempting to use a weapon of mass destruction.
According to court documents and evidence presented during trial, at the time of his arrest last year, Aldawsari had been researching online how to construct an IED using several chemicals as ingredients. He had also acquired or taken a substantial step toward acquiring most of the ingredients and equipment necessary to construct an IED, and he had conducted online research of several potential U.S. targets, the affidavit alleges. In addition, he had allegedly described his desire for violent jihad and martyrdom in blog postings and a personal journal.
“While many people are responsible for thwarting Aldawsari’s threat and bringing him to justice, we owe a debt of gratitude to all the members of the North Texas Joint Terrorism Task Force, and especially to the hundreds of hardworking and dedicated FBI agents, analysts, linguists, and others,” said U.S. Attorney Saldaña. “Their efforts, coupled with the hard work and excellent cooperation from the Lubbock Police Department and the Texas Tech Police Department, are the reason we were able to stop this defendant from carrying out a catastrophic act of terrorism.”
“As this trial demonstrated, Aldawsari purchased ingredients to construct an explosive device and was actively researching potential targets in the United States. Thanks to the efforts of many agents, analysts, and prosecutors, this plot was thwarted before it could advance further,” said Assistant Attorney General Monaco. “This case serves as another reminder of the need for continued vigilance both at home and abroad.”
“Today’s guilty verdict shows how individuals in the United States with the intent to do harm can acquire the knowledge and materials necessary to carry out an attack,” said SAC Rodriguez. “Our success in locating and preventing Mr. Aldawsari from carrying out an attack is a result of cooperation within the law enforcement and intelligence communities, particularly, the North Texas Joint Terrorism Task Force, the Texas Tech Police Department, the Lubbock Police Department, and the Lubbock County Sheriff’s Office, but also a demonstration of information sharing across FBI divisions, as well as assistance from the community. I want to thank the dedicated agents, officers, and analysts; the computer forensics team; and linguists that worked diligently on this investigation, as well as prosecutors serving in the U.S. Attorney’s Office in the Northern District.”
The government presented evidence that on February 1, 2011, a chemical supplier reported to the FBI a suspicious attempted purchase of concentrated phenol by a man identifying himself as Khalid Aldawsari. Phenol is a toxic chemical with legitimate uses, but it can also be used to make the explosive trinitrophenol, also known as T.N.P., or picric acid. Ingredients typically used with phenol to make picric acid, or T.N.P., are concentrated sulfuric and nitric acids.
Aldawsari attempted to have the phenol order shipped to a freight company so it could be held for him there, but the freight company told Aldawsari that the order had been returned to the supplier and called the police. Later, Aldawsari falsely told the supplier he was associated with a university and wanted the phenol for “off-campus, personal research.” Frustrated by questions being asked over his phenol order, Aldawsari cancelled his order, placed an order with another company, and later e-mailed himself instructions for producing phenol. In December 2010, he had successfully purchased concentrated nitric and sulfuric acids.
Aldawsari used various e-mail accounts in researching explosives and targets and often sent e-mails to himself as part of this process. He e-mailed himself a recipe for picric acid, which was described in the e-mail as a “military explosive” and also e-mailed himself instructions on how to convert a cell phone into a remote detonator and how to prepare a booby-trapped vehicle using household items. Aldawsari also purchased many other items, including a Hazmat suit, a soldering iron kit, glass beakers and flasks, a stun gun, clocks, and a battery tester.
Excerpts from a journal found at Aldawsari’s residence indicated that he had been planning to commit a terrorist attack in the United States for years. One entry describes how Aldawsari sought and obtained a particular scholarship because it allowed him to come directly to the United States and helped him financially, which he said “will help tremendously in providing me with the support I need for Jihad.” The entry continues, “And now, after mastering the English language, learning how to build explosives and continuous planning to target the infidel Americans, it is time for Jihad.”
In another entry, Aldawsari wrote that he was near to reaching his goal and near to getting weapons to use against infidels and their helpers. He also listed a “synopsis of important steps” that included obtaining a forged U.S. birth certificate; renting a car; using different driver’s licenses for each car rented; putting bombs in cars and taking them to different places during rush hour; and leaving the city for a safe place.
Aldawsari conducted research on various targets and e-mailed himself information on these locations and people. One of the documents he sent himself, with the subject line listed as “Targets,” contained the names and home addresses of three American citizens who had previously served in the U.S. military and had been stationed for a time at Abu Ghraib prison in Iraq. In others, Aldawsari sent himself the names of 12 reservoir dams in Colorado and California and listed two categories of targets: hydroelectric dams and nuclear power plants. He also sent himself an e-mail titled “Tyrant’s House,” in which he listed the Dallas address for former President George W. Bush. Aldawsari also conducted research that indicated he considered using infant dolls to conceal explosives and the possible targeting of a nightclub with an explosive concealed in a backpack.
This case was investigated by the FBI’s Dallas Joint Terrorism Task Force, with assistance from the Lubbock Police Department and the Texas Tech Police Department. The prosecution is being handled by Assistant U.S. Attorneys Jeffrey R. Haag, Denise Williams, James T. Jacks, and Matthew J. Kacsmaryk and Trial Attorney David Cora from the Counterterrorism Section of the Justice Department’s National Security Division.
Murder at the Manor – Full Movie
TOP-SECRET – The Creation of the U.S. Spy Satellites
In September 1992 the Department of Defense acknowledged the existence of the National Reconnaissance Office (NRO), an agency established in 1961 to manage the development and operation of the nation’s reconnaissance satellite systems. The creation of the NRO was the result of a number of factors.
On May 1, 1960 Francis Gary Powers took off from Peshawar, Pakistan on the U-2 mission designated Operation GRAND SLAM. The flight was planned to take him over the heart of the Soviet Union and terminate at Bodo, Norway. The main target was Plesetsk, which communications intercepts had indicated might be the site of an ICBM facility.1 When the Soviet Union shot down his plane and captured him alive, they also forced President Dwight Eisenhower to halt aerial overflights of Soviet territory.
At that time the U.S. had two ongoing programs to produce satellite vehicles that could photograph Soviet territory. Such vehicles would allow far more frequent coverage than possible with manned aircraft. In addition, they would avoid placing the lives of pilots at risk and eliminate the risks of international incidents resulting from overflights.
The Air Force program, designated SAMOS, sought to develop a number of different satellite systems–including one that would radio its imagery back to earth and another that would return film capsules. The CIA program, CORONA, focused solely on developing a film return satellite.
However, both the CIA and Air Force programs were in trouble. Launch after launch in the CORONA program, eleven in all by May 1, 1960, eight of which carried cameras, had resulted in failure–the only variation was in the cause. Meanwhile, the SAMOS program was also experiencing difficulties, both with regard to hardware and program definition.2
Concerns over SAMOS led President Eisenhower to direct two groups to study both the technical aspects of the program as well as how the resulting system would be employed. The ultimate result was a joint report presented to the President and NSC on August 25, 1960.3
As a result of that meeting Eisenhower approved a first SAMOS launch in September, as well as reorientation of the program, with the development of high-resolution film-return systems being assigned highest priority while the electronic readout system would be pursued as a research project. With regard to SAMOS management, he ordered that the Air Force institute special management arrangements, which would involve a direct line of authority between the SAMOS project office and the Office of the Air Force Secretary, bypassing the Air Staff and any other intermediate layers of bureaucracy.4
Secretary of the Air Force Dudley C. Sharp wasted little time creating the recommended new structure and procedures. On August 31st Sharp signed Secretary of the Air Force Order 115.1, establishing the Office of Missile and Satellite Systems within his own office to help him manage the SAMOS project. With Order 116.1, Sharp created a SAMOS project office at the Los Angeles headquarters of the Air Force Ballistic Missile Division (AFBMD) as a field extension of the Office of the Secretary of the Air Force to carry out development of the satellite.5
The impact of the orders, in practice, was that the director of the SAMOS project would report directly to Under Secretary of the Air Force Joseph V. Charyk, who would manage it in the Secretary’s name. In turn, Charyk would report directly to the Secretary of Defense.6
The changes would not stop there. The urgency attached to developing a successful reconnaissance satellite led, ultimately, to the creation of a top secret program and organization to coordinate the entire national reconnaissance effort.
Several of the documents listed below also appear in either of two National Security Archive microfiche collections on U.S. intelligence. The U.S. Intelligence Community: Organization, Operations and Management: 1947-1989 (1990) and U.S. Espionage and Intelligence: Organization, Operations, and Management, 1947-1996 (1997) publish together for the first time recently declassified documents pertaining to the organizational structure, operations and management of the U.S. Intelligence Community over the last fifty years, cross-indexed for maximum accessibility. Together, these two sets reproduce on microfiche over 2,000 organizational histories, memoranda, manuals, regulations, directives, reports, and studies, totaling more than 50,000 pages of documents from the Office of the Director of Central Intelligence, the Central Intelligence Agency, National Reconnaissance Office, National Security Agency, Defense Intelligence Agency, military service intelligence organizations, National Security Council, and other official government agencies and organizations.
![]() Document 1
Document 1
Joseph Charyk, Memorandum for the Secretary of Defense
Management of the National Reconnaissance Program
24 July 1961
Top Secret
1 p.
The organizational changes resulting from the decisions of August 25, 1960 and their implementation left some unsatisfied. In particular, James Killian and Edwin Land, influential members of the President’s intelligence advisory board pushed for permanent and institutionalized collaboration between the CIA and Air Force. After the Kennedy administration took office the push to establish a permanent reconnaissance organization took on additional life. There was a strong feeling in the new administration, particularly by Secretary of Defense Robert McNamara and his deputy, Roswell Gilpatric, that a better, more formalized relationship was required.7
On July 24, 1961, Air Force Undersecretary Joseph Charyk sent a memorandum to McNamara attaching two possible memoranda of agreement for creation of a National Reconnaissance Program, along with some additional material.
![]() Document 2
Document 2
Memorandum of Understanding
Management of the National Reconnaissance Program (Draft)
20 July 1961
Top Secret
5 pp.
This memo specified establishment of a National Reconnaissance Program (NRP) consisting of “all satellite and overflight reconnaissance projects whether overt or covert,” and including “all photographic projects for intelligence, geodesy and mapping purposes, and electronic signal collection projects for electronic signal intelligence and communications intelligence.”
To manage the NRP, a National Reconnaissance Office (NRO) would be established on a covert basis. The NRO director (DNRO) would be the Deputy Director for Plans, CIA (at the time, Richard Bissell) while the Under Secretary of the Air Force would serve as Deputy Director (DDNRO). The DNRO would be responsible for the management of CIA activities, the DDNRO and the Air Force for Defense Department activities. The DoD, specifically the Air Force acting as executive agent, would be primarily responsible for technical program management, scheduling, vehicle operations, financial management and overt contract administration, while the CIA would be primarily responsible for targeting each satellite. The office would operate under streamlined management procedures similar to those established in August 1960 for SAMOS.
![]() Document 3
Document 3
Memorandum of Understanding
Management of the National Reconnaissance Program (Draft)
21 July 1961
Top Secret
4 pp.
This secondary memorandum was prepared at the suggestion of Defense Department General Counsel Cyrus Vance. It offered a quite different solution to the problem. As with the primary memo, it established a NRP covering both satellite and aerial reconnaissance operations. But rather than a jointly run program, it placed responsibility for management solely in the hands of a covertly appointed Special Assistant for Reconnaissance, to be selected by the Secretary of Defense. The office of the Special Assistant would handle the responsibilities assigned to the NRO in the other MOU. The CIA would “assist the Department of Defense by providing support as required in areas of program security, communications, and covert contract administration.”
![]() Document 4
Document 4
Memorandum
Pros and Cons of Each Solution
Not dated
Top Secret
2 pp.
The assessment of pros and cons favored the July 20 memorandum, listing five pros for the first solution and only two for the second. The first solution would consolidate responsibilities into a single program with relatively little disruption of established management, represented a proven solution, would require no overt organizational changes, would allow both agencies to retain authoritative voices in their areas of expertise, and provided a simplified management structure. The two cons noted were the division of program responsibility between two people, and that “successful program management depends upon mutual understanding and trust of the two people in charge of the NRO.” It would not be too long before that later observation would take on great significance.
In contrast, there were more cons than pros specified for the second solution. The only two points in its favor were the consolidation of reconnaissance activities into a single program managed by a single individual and the assignment of complete responsibility to the agency (DoD) with the most resources. Foremost of the six cons was the need for DoD to control and conduct large-scale covert operations, in as much as it was an entity “whose normal methods are completely foreign to this task.”
![]() Document 5
Document 5
Roswell Gilpatric, Letter to Allen Dulles
Management of the National Reconnaissance Program
6 September 1961
Top Secret
4 pp.
On July 28, 1961, four days after receiving Charyk’s memorandum and draft memoranda of understanding, McNamara instructed Air Force Undersecretary Joseph Charyk to continue discussions with the key officials and advisers in order to resolve any organizational difficulties that threatened to impede the satellite reconnaissance effort. The ultimate result was this letter from Deputy Secretary of Defense Roswell Gilpatric to Dulles, which confirmed “our agreement with respect to the setting up of the National Reconnaissance Program.”
The letter specified the creation of a NRP. It also established the NRO, a uniform security control system, and specified that the NRO would be directly responsive to the intelligence requirements and priorities specified by the United States Intelligence Board. It specified implementation of NRP programs assigned to the CIA through the Deputy Director for Plans. It designated the Undersecretary of the Air Force as the Defense Secretary’s Special Assistant for Reconnaissance, with full authority in DoD reconnaissance matters.
The letter contained no specific assignment of responsibilities to either the CIA or Defense Department, stating only that “The Directors of the National Reconnaissance Office will … insure that the particular talents, experience and capabilities within the Department of Defense and the Central Intelligence Agency are fully and most effectively utilized in this program.”
The letter provided for the NRO to be managed jointly by the Under Secretary of the Air Force and the CIA Deputy Director for Plans (at the time, still Richard Bissell). A May 1962 agreement between the CIA and Defense Department established a single NRO director. Joseph Charyk was named to the directorship shortly afterward.
![]() Document 6
Document 6
Joseph Charyk
Memorandum for NRO Program Directors/Director, NRO Staff
Organization and Functions of the NRO
23 July 1962
Top Secret
11 pp.
This memorandum represents the fundamental directive on the organization and functions of the NRO. In addition to the Director (there was no provision for a deputy director), there were four major elements to the NRO–the NRO staff and three program elements, designated A, B, and C. The staff’s functions included assisting the director in dealing with the USIB and the principal consumers of the intelligence collected.
The Air Force Office of Special Projects (the successor to the SAMOS project office) became NRO’s Program A. The CIA reconnaissance effort was designated Program B, while the Navy’s space reconnaissance effort, at the time consisting of the Galactic Radiation and Background (GRAB) satellite, whose radar ferret mission involved the collection of Soviet radar signals, became Program C. Although the GRAB effort was carried out by the Naval Research Laboratory, the director of the Office of Naval Intelligence would serve as Program C director until 1971.8
![]() Document 7
Document 7
Agreement between the Secretary of Defense and the Director of Central Intelligence on Management of the National Reconnaissance Program
13 March 1963
Top Secret
6 pp.
In December 1962, Joseph Charyk decided to leave government to become president of the COMSAT Corporation. By that time a number of disputes between the CIA and NRO had contributed to Charyk’s view that the position of the NRO and its director should be strengthened. During the last week of February 1963, his last week in office, he completed a revision of a CIA draft of a new reconnaissance agreement to replace the May 1962 agreement (which had replaced the September 6, 1961 agreement). Charyk took the revision to Deputy Secretary of Defense Roswell Gilpatric. It appears that some CIA-suggested changes were incorporated sometime after Charyk left office. On March 13, Gilpatric signed the slightly modified version on behalf of DoD. It was sent to the CIA that day and immediately approved by DCI John McCone, who had replaced Allen Dulles in November 1961.9
The new agreement, while it did not include all the elements Charyk considered important, did substantially strengthen the authority of the NRO and its director. It named the Secretary of Defense as the Executive Agent for the NRP. The program would be “developed, managed, and conducted in accordance with policies and guidance jointly agreed to by the Secretary of Defense and the Director of Central Intelligence.”
The NRO would manage the NRP “under the direction, authority, and control of the Secretary of Defense.” The NRO’s director would be selected by the Defense Secretary with the concurrence of the DCI, and report to the Defense Secretary. The NRO director was charged with presenting to the Secretary of Defense “all projects” for intelligence collection and mapping and geodetic information via overflights and the associated budgets, scheduling all overflight missions in the NRP, as well as engineering analysis to correct problems with collection systems. With regard to technical management, the DNRO was to “assign all project tasks such as technical management, contracting etc., to appropriate elements of the DoD and CIA, changing such assignments, and taking any such steps he may determine necessary to the efficient management of the NRP.”
![]() Document 8
Document 8
Department of Defense Directive Number TS 5105.23
Subject: National Reconnaissance Office
27 March 1964
Top Secret
4 pp.
This directive replaced the original June 1962 DoD Directive on the NRO, and remains in force today. The directive specifies the role of the Director of the NRO, the relationships between the NRO and other organizations, the director’s authorities, and security. It specified that documents or other material concerning National Reconnaissance Program matters would be handled within a special security system (known as the BYEMAN Control System).
![]() Document 9
Document 9
President’s Foreign Intelligence Advisory Board
Memorandum for the President
Subject: National Reconnaissance Program
2 May 1964
Top Secret
11 pp.
The 1963 CIA-DoD agreement on the NRP did not end the battles between the CIA and NRO–as some key CIA officials, including ultimately DCI John McCone, sought to reestablish a major role for the CIA in the satellite reconnaissance effort. The continuing conflict was examined by the PFIAB.
The board concluded that “the National Reconnaissance Program despite its achievements, has not yet reached its full potential.” The fundamental cause for the NRP’s shortcomings was “inadequacies in organizational structure.” In addition, there was no clear division of responsibilities and roles between the Defense Department, CIA, and the DCI.
The recommendations of the board represented a clear victory for the NRO and its director. The DCI should have a “large and important role” in establishing intelligence collection requirements and in ensuring that the data collected was effectively exploited, according to the board. In addition, his leadership would be a key factor in the work of the United States Intelligence Board relating to the scheduling of space and airborne reconnaissance missions.
But the board also recommended that President Johnson sign a directive which would assign to NRO’s Air Force component (the Air Force Office of Special Projects) systems engineering, procurement, and operation of all satellite reconnaissance systems.
![]() Document 10
Document 10
Agreement for Reorganization of the National Reconnaissance Program
13 August 1965
Top Secret
6 pp.
Despite the recommendations of the May 2, 1964 PFIAB report, which were challenged by DCI John McCone, no action was taken to solidify the position of the NRO and its director. Instead prolonged discussions over a new agreement continued into the summer of 1965. During this period the CIA continued work on what would become two key satellite programs–the HEXAGON/KH-9 imaging and RHYOLITE signals intelligence satellites.
In early August, Deputy Secretary of Defense Cyrus Vance and CIA official John Bross reached an understanding on a new agreement, and it was signed by Vice Adm. William F. Raborn (McCone’s successor) and Vance on August 13, 1965. It represented a significant victory for the CIA, assigning key decision-making authority to an executive committee, authority that was previously the prerogative of the NRO director as the agent of the Secretary of Defense.
The Secretary of Defense was to have “the ultimate responsibility for the management and operation of the NRO and the NRP,” and have the final power to approve the NRP budget. The Secretary also was empowered to make decisions when the executive committee could not reach agreement.
The DCI was to establish collection priorities and requirements for targeting NRP operations, as well as establish frequency of coverage, review the results obtained by the NRP and recommend steps for improving its results if necessary, serve on the executive committee, review and approve the NRP budget, and provide security policy guidance.
The NRP Executive Committee established by the agreement would consist of the DCI, Deputy Secretary of Defense, and Special Assistant to the President for Science and Technology. The committee was to recommend to the Secretary of Defense the “appropriate level of effort for the NRP,” approve or modify the consolidated NRP and its budget, approve the allocation of responsibility and the corresponding funds for research and exploratory development for new systems. It was instructed to insure that funds would be adequate to pursue a vigorous research and development program, involving both CIA and DoD. The executive committee was to assign development of sensors to the agency best equipped to handle the task.
The Director of the NRO would manage the NRO and execute the NRP “subject to the direction and control of the Secretary of Defense and the guidance of the Executive Committee.” His authority to initiate, improve, modify, redirect or terminate all research and development programs in the NRP, would be subject to review by the executive committee. He could demand that all agencies keep him informed about all programs undertaken as part of the NRP.
![]() Document 11
Document 11
Analysis of “A $1.5 Billion Secret in Sky” Washington Post, December 9, 1973
Not dated
Top Secret
33 pp.
Throughout the 1960s, the United States operation of reconnaissance satellites was officially classified, but well known among specialists and the press. However, it was not until January 1971 that the NRO’s existence was first disclosed by the media, when it was briefly mentioned in a New York Times article on intelligence and foreign policy.
A much more extensive discussion of the NRO appeared in the December 9, 1973 Washington Post as a result of the inadvertent mention of the reconnaissance office in a Congressional report. The NRO prepared this set of classified responses to the article, clearly intended for those in Congress who might be concerned about the article’s purported revelations about the NRO’s cost overruns and avoidance of Congressional oversight.
![]() Document 12
Document 12
E.C. Aldridge, Jr. (Director, NRO)
Letter to David L. Boren, Chairman,
Senate Select Committee on Intelligence
21 November 1988
Secret
3 pp.
The late 1980s saw the beginning of what eventually would be a wide-ranging restructuring of the NRO. In November 1988 NRO director Edward “Pete” Aldridge wrote to Senator David Boren, Chairman of the Senate Select Committee on Intelligence, concerning the findings of an extensive study (the NRO Restructure Study) of the organizational structure of the NRO.
Aldridge proceeded to report that, after having discussed the study’s recommendations with Secretary of Defense Frank Carlucci and Director of Central Intelligence William Webster, he was directing the development of plans to implement the recommendations. Specific changes would include the creation of a centralized systems analysis function “to conduct cross-system trades and simulations within the NRO,” creation of a “User Support” function to improve NRO support to intelligence community users as well as to the growing number of operational military users, and the dispersal of the NRO Staff to the new units, with the staff being replaced by a group of policy advisers. In addition, Aldridge foresaw the establishment of an interim facility “to house the buildup of the new functions and senior management.” The ultimate goal, projected for the 1991-92 period, would be the “collocation of all NRO elements [including the Los Angeles-based Air Force Office of Special Projects] . . . in the Washington, D.C. area.”
![]() Document 13
Document 13
Memorandum of Agreement
Subject: Organizational Restructure of the National Reconnaissance Office
15 December 1988
Secret
2 pp.
This memorandum of agreement, signed by the Director of the NRO and the directors of the NRO’s three programs commits them to the restructuring discussed in Edward Aldridge’s November 21 letter to Senator Boren.
Many changes recommended by Aldridge, who left office at the end of 1988, were considered by a 1989 NRO-sponsored review group and subsequently adopted.
![]() Document 14
Document 14
Report to the Director of Central Intelligence
DCI Task Force on The National Reconnaissance Office, Final Report
April 1992
Secret
35 pp.
This report was produced by a panel chaired by former Lockheed Corporation CEO Robert Fuhrman, whose members included both former and serving intelligence officials. It focused on a variety of issues other than current and possible future NRO reconnaissance systems. Among the issues it examined were mission, organizational structure, security and classification.
One of its most significant conclusions was that the Program A,B,C structure that had been instituted in 1962 (see Document 6) “does not enhance mission effectiveness” but “leads to counterproductive competition and makes it more difficult to foster loyalty and to maintain focus on the NRO mission.” As a result, the panel recommended that the NRO be restructured along functional lines with imagery and SIGINT directorates. This change was made even before the final version of the report was issued.
The report also noted that while the NRO’s existence was officially classified it was an “open secret” and that seeking to attempt to maintain such “open secrets … weakens the case for preserving ‘real’ secrets.” In addition, such secrecy limited the NRO’s ability to interact with customers and users. The group recommended declassifying the “fact of” the NRO, as well as providing information about the NRO’s mission, the identities of senior officials, headquarters locations, and the NRO as a joint Intelligence Community-Defense Department activity.
![]() Document 15
Document 15
National Security Directive 67
Subject: Intelligence Capabilities: 1992-2005
30 March 1992
Secret
2 pp.
NSD 67 directed a number of changes in U.S. intelligence organization and operations. Among those was implementation of the plan to restructure the NRO along functional lines–eliminating the decades old Program A (Air Force), B (CIA), and C (Navy) structure and replacing it with directorates for imaging, signals intelligence, and communication systems acquisition and operations–as recommended by the Fuhrman panel. As a result, Air Force, CIA, and Navy personnel involved in such activities would now work together rather than as part of distinct NRO components.
![]() Document 16
Document 16
Email message
Subject: Overt-Covert-DOS-REP-INPUT
27 July 1992
Secret
1 p.
In addition to the internal restructuring of the NRO, 1992 saw the declassification of the organization, as recommended by the Fuhrman report (Document 14), for a number of reasons–to facilitate interaction with other parts of the government, to make it easier for the NRO to support military operations, and in response to Congressional pressure to acknowledge the obvious. As part of the process of considering declassification NRO consulted Richard Curl, head of the Office of Intelligence Resources of the State Department’s Bureau of Intelligence and Research–the office which provides INR with expertise and support concerning technical collection systems. Curl recommended a low-key approach to declassification.
![]() Document 17
Document 17
Memorandum for Secretary of Defense, Director of Central Intelligence
Subject: Changing the National Reconnaissance Office (NRO) to an Overt Organization
30 July 1992
Secret
3 pp.
w/ attachments:
Document 17a: Mission of the NRO, 1 p.
Document 17b: Implications of Proposed Changes, 4 pp. (Two versions)
Version One
Version Two
These memos, from Director of the NRO Martin Faga, represent key documents in the declassification of the NRO. The memo noted Congressional pressure for declassification and that Presidential certification that declassification would result in “grave damage to the nation … would be difficult in this case.”
Faga reported that as a result of an NRO review he recommended declassifying the fact of NRO’s existence, issuing a brief mission statement, acknowledging the NRO as a joint DCI-Secretary of Defense endeavor, and identifying top level NRO officials. He also noted that his recommendations attempted to balance concerns about classifying information that realistically could not be protected, while maintaining an ability to protect matters believed to require continued protection.
Secretary of Defense Richard Cheney, DCI Robert Gates, and President Bush approved the recommendations in September and a three-paragraph memorandum to correspondents acknowledging the NRO and NRP was issued on September 18, 1992.
Document 17b comes in two versions, representing different security reviews. Material redacted from the first version includes provisions of National Security Directive 30 on space policy, expression of concern over “derived disclosures,” and the assessment that the “high degree of foreign acceptance of satellite reconnaissance, and the fact that we are not disclosing significant new data,” would not lead to any significant foreign reaction. Another redacted statement stated that “legislation . . . exempting all NRO operational files from [Freedom of Information Act] searches” was required.
![]() Document 18
Document 18
Final Report: National Reconnaissance Program Task Force for the Director of Central Intelligence
September 1992
Top Secret
15 pp.
The end of the Cold War and collapse of the Soviet Union required the U.S. intelligence community and NRO to reconsider how U.S. overhead reconnaissance systems were employed and what capabilities future systems should possess. To consider these questions DCI Robert Gates appointed a task force, chaired by his eventual successor, R. James Woolsey.
The final report considers future needs and collection methods, industrial base considerations, procurement policy considerations, international industrial issues, and transition considerations. Its recommendations included elimination of both some collection tasks as well as some entire types of present and planned collection systems.
![]() Document 19
Document 19
NRO Protection Review, “What is [BYEMAN]?”
6 November 1992
Top Secret
18 pp.
Traditionally, the designations of Sensitive Compartmented Information (SCI) compartments–such as UMBRA to indicate particularly sensitive communications intelligence and RUFF to intelligence based on satellite imagery–have themselves been classified. In recent years, however, the NSA and CIA have declassified a number of such terms and their meaning. One exception has been the term “BYEMAN”– the BYEMAN Control System being the security system used to protect information related to NRO collection systems (in contrast to their products) and other aspects of NRO activities, including budget and structure. Thus, the term BYEMAN has been deleted in the title of the document and throughout the study–although the term and its meaning has become known by specialists and conveys no information beyond the text of any particular document.
This study addresses the use of the BYEMAN classification within the NRO, its impact on contractors and other government personnel, and the consequences of the current application of the BYEMAN system. The study concludes that placing information in the highly restrictive BYEMAN channels (in contrast to classifying the information at a lower level) may unduly restrict its dissemination to individuals who have a legitimate need to know.
![]() Document 20
Document 20
NRO Strategic Plan
18 January 1993
Secret
19 pp.
A study headed by James Woolsey (Document 18), President Clinton’s first DCI, heavily influenced the contents of this early 1993 document. The plan’s introduction notes that while some collection tasks will no longer be handled by overhead reconnaissance the “uncertain nature of the world that is emerging from the end of the ‘cold war’ places a heavy premium on overhead reconnaissance.” At the same time, “this overhead reconnaissance challenge must be met in an era of a likely reduced national security budget.”
The strategic plan is described in the introduction, as “the ‘game plan’ to transition current overhead collection architectures into a more integrated, end-to-end architecture for improved global access and tasking flexibility.”
The document goes on to examine the strategic context for future NRO operations, NRO strategy, strategic objectives, and approaches to implementation. Strategic objectives include improving the responsiveness of NRO systems by developing an architecture that spans the entire collection and dissemination process, from the identification of requirements to dissemination of the data collected.
![]() Document 21
Document 21
National Reconnaissance Office: Collocation Construction Project, Joint DOD and CIA Review Report
November 1994
Unclassified
28 pp.
In an August 8, 1994 press conference, Senators Dennis DeConcini (D-Az.) and John Warner (R-Va.), the chairman and vice chairman of the Senate Select Committee on Intelligence accused the NRO of concealing from Congress the cost involved in building a new headquarters to house government and contractor employees. Previously NRO activities in the Washington area were conducted from the Pentagon and rented space in the Washington metropolitan area. The collocation and restructuring decisions of the late 1980s and early 1990s had resulted in a requirement for a new headquarters facility.10
The accusations were followed by hearings before both the Senate and House intelligence oversight committees–with House committee members defending the NRO and criticizing their Senate colleagues. While they noted that some of the documents presented by the NRO covering total costs were not presented with desirable clarity, the House members were more critical of the Senate committee for inattention to their committee work.11
This joint DoD and CIA review of the project, found “no intent to mislead Congress” but that “the NRO failed to follow Intelligence Community budgeting guidelines, applicable to all the intelligence agencies,” that would have caused the project to be presented as a “New Initiative,” and that the cost data provided by the NRO “were not presented in a consistent fashion and did not include a level of detail comparable to submissions for . . . intelligence community construction.”
![]() Document 22
Document 22
Memorandum for Director of Central Intelligence
Subject: Small Satellite Review Panel
Unclassified
July 1996
The concept of employing significantly smaller satellites for imagery collection was strongly advocated by Rep. Larry Combest during his tenure (1995-97) as chairman of the House Permanent Select Committee on Intelligence. As a result the DCI was instructed to appoint a panel of experts to review the issue.12
Panel members included former NRO directors Robert Hermann and Martin Faga; former NRO official and NSA director Lew Allen; scientist Sidney Drell and four others. The panel’s report supported a radical reduction in the size of most U.S. imagery satellites. The panel concluded that “now is an appropriate time to make a qualitative change in the systems architecture of the nation’s reconnaissance assets,” in part because “the technology and industrial capabilities of the country permit the creation of effective space systems that are substantially smaller and less costly than current systems.” Thus, the panel saw “the opportunity to move towards an operational capability for . . . imagery systems, that consists of an array of smaller, cheaper spacecraft in larger number with a total capacity which is at least as useful as those currently planned and to transport them to space with substantially smaller and less costly launch vehicles.”13
The extent to which those recommendations have influenced NRO’s Future Imagery Architecture plan is uncertain–although plans for large constellations of small satellites have not usually survived the budgetary process.
![]() Document 23
Document 23
Defining the Future of the NRO for the 21st Century, Final Report, Executive Summary
August 26, 1996
Unclassified
30 pp.
This report was apparently the first major outside review of the NRO conducted during the Clinton administration, and the first conducted after the NRO’s transformation to an overt institution and its restructuring were firmly in place.
Among those conducting the review were former Vice Chairman of the Joint Chiefs of Staff, Adm. David E. Jeremiah, former NRO director Martin Faga, and former Deputy Director of Central Intelligence John McMahon. Issues studied by the panel included, inter alia, the existence of a possible alternative to the NRO, NRO’s mission in the 21st Century, support to military operations, security, internal organization, and the relationship with NRO’s customers.
After reviewing a number of alternatives, the panel concluded that no other arrangement was superior for carrying out the NRO mission. It did, however, recommend, changes with regards to NRO’s mission and internal organization. The panel concluded that where the NRO’s current mission is “worldwide intelligence,” its future mission should be “global information superiority,” which “demands intelligence capabilities unimaginable just a few years ago.” The panel also recommended creation of a fourth NRO directorate, which was subsequently established, to focus solely on the development of advanced systems, in order to “increase the visibility and stature of technology innovation in the NRO.”
Notes
1. Michael R. Beschloss, Mayday: Eisenhower, Khrushchev and the U-2 Affair (New York: Harper & Row, 1986), pp.241-42; John Ranelagh, The Agency: The Rise and Decline of the CIA, From Wild Bill Donovan to William Casey (New York: Simon & Schuster, 1986), p. 319; Gregory W. Pedlow and Donald Welzenbach, The Central Intelligence Agency and Overhead Reconnaissance: The U-2 and OXCART Programs, 1954-1974 (Washington, D.C.: CIA, 1992), pp. 170-93.2. Kenneth Greer, “Corona,” Studies in Intelligence, Supplement 17, Spring 1973 in Kevin C. Ruffner (Ed.), CORONA: America’s First Satellite Program (Washington, D.C.: Central Intelligence Agency, 1995), pp. 3-40; Gen. Thomas D. White, Air Force Chief of Staff to General Thomas S. Power, Commander in Chief, Strategic Air Command, June 29, 1960, Thomas D. White Papers, Library of Congress, Box 34, Folder “2-15 SAC.”3. “Special Meeting of the National Security Council to be held in the Conference Room of the White House from 8:30 a.m. to 10 a.m., Thursday, August 25, 1960, undated, National Security Council Staff Papers, 1948-61, Executive Secretary’s Subject File Series, Box 15, Reconnaissance Satellites [1960], DDEL.
4. “Reconnaissance Satellite Program,” Action No.1-b at Special NSC Meeting on August 25, 1960, transmitted to the Secretary of Defense by Memo of September 1, 1960; G.B. Kistiakowsky to Allen Dulles, August 25, 1960, Special Assistant for Science and Technology, Box No. 15, Space [July-Dec 1960], DDEL.
5. Carl Berger, The Air Force in Space Fiscal Year 1961, (Washington, D.C.: Air Force Historical Liaison Office, 1966), pp.41-42; Secretary of the Air Force Order 115.1, “Organization and Functions of the Office of Missile and Satellite Systems,” August 31, 1960; Robert Perry, A History of Satellite Reconnaissance, Volume 5: Management of the National Reconnaissance Program, 1960-1965, (Washington, D.C., NRO, 1969), p. 20; Secretary of the Air Force Order 116.1, “The Director of the SAMOS Project,” August 31, 1960.
6. Perry, A History of Satellite Reconnaissance, Volume 5, p. 20.
7. Jeffrey T. Richelson, “Undercover in Outer Space: The Creation and Evolution of the NRO,” International Journal of Intelligence and Counterintelligence, 13, 3 (Fall 2000): 301-344.
8. Ibid.; GRAB: Galactic Radiation and Background (Washington, D.C.: NRL, 1997); Dwayne A. Day, “Listening from Above: The First Signals Intelligence Satellite,” Spaceflight, August 1999, pp. 339-347; NRO, Program Directors of the NRO: ABC&D, 1999.
9. Perry, A History of Satellite Reconnaissance, Volume 5, pp. 93, 96-97.
10. Pierre Thomas, “Spy Unit’s Spending Stuns Hill,” Washington Post, August 9, 1994, pp. A1, A6.
11. Walter Pincus, “Spy Agency Defended by House Panel,” Washington Post, August 12, 1994, p. A21; U.S. Congress, House Permanent Select Committee on Intelligence, NRO Headquarters Project (Washington, D.C.: U.S. Government Printing Office, 1995), pp. 3-4.
12. Walter Pincus, “Congress Debates Adding Smaller Spy Satellites to NRO’s Menu,” Washington Post, October 5, 1995, p. A14; Joseph C. Anselmo, “House, Senate at Odds Over Intel Small Sats,” Aviation Week & Space Technology, January 1, 1996, p. 19.
13. Small Satellite Review Panel, Memorandum for: Director of Central Intelligence, Subject: Small Satellite Review Panel, July 1996.
Revealed – Former CIA Officer Kiriakou Calls Leak Prosecution Selective, Vindictive
Former CIA officer John Kiriakou, who is charged with unauthorized disclosure of a covert officer’s identity and other classified information, says that the case against him is driven by government animosity, and that he is a target of selective prosecution.
“When White House aides leaked stories about the heroes who killed Osama Bin Laden, they were not prosecuted. When the Washington Post was granted access to the covert director of the CTC for a profile of those directing America’s ‘war on terror,’ no one was prosecuted,” his attorneys wrote in a newly disclosed motion for dismissal.
“But when John Kiriakou gave an interview where he admitted the United States used waterboarding and when he further opined that waterboarding was ineffective, the government went after him,” the motion stated.
“The United States has improperly selected him for prosecution based on his exercise of his constitutional rights and on the animus the United States holds toward him” while “the government has tolerated other disclosures because they resulted in press favorable to the government.”
A copy of the June 12 defense motion was cleared for public release yesterday.
In a separate motion for dismissal, Mr. Kiriakou’s attorneys challenged the constitutionality of the statutes under which he is being prosecuted, including the Intelligence Identities Protection Act and section 793(d) of the Espionage Act, which they argued are “unconstitutionally vague and overbroad.”
Furthermore, because overclassification is rampant, they said, the classification status of any particular information is not a reliable index of its sensitivity.
“The government’s acknowledged practice of over-classification means that not all classified information actually has the potential to damage national security if released…. The fact that information is classified does not actually clarify whether its disclosure… could cause any injury to the United States.”
A government response to the defense motions is due by July 2.
TMZ – Kate Upton — New TOPLESS Photos!!!
Anatoly S. Chernyaev Diary, 1972 – TOP-SECRET from the NSA
 click for full sizeFirst trip with Gorbachev. Chernyaev in Belgium, October 1972. |
Anatoly S. Chernyaev Diary, 1972
Soviet government official Anatoly Chernyaev records an insider’s view of the Brezhnev era
National Security Archive Electronic Briefing Book No. 379
| Translated and edited by Anna Melyakova and Svetlana Savranskaya “Anatoly Chernyaev’s diary is one of the great internal records of the Gorbachev years, a trove of irreplaceable observations about a turning point in history. There is nothing else quite like it, allowing the reader to sit at Gorbachev’s elbow at the time of perestroika and glasnost, experiencing the breakthroughs and setbacks. It is a major contribution to our understanding of this momentous period.” — David E. Hoffman, Pulitzer Prize-winning author of The Dead Hand “Remarkable diary …”
Washington, D.C., May 25, 2012 – Today the National Security Archive publishes excerpts from Anatoly S. Chernyaev’s diary of 1972 for the first time in English translation with edits and postscript by the author. While the diary for the Gorbachev years, 1985-1991, published before and widely used in scholarly work on the end of the Cold War provided a major source on the Gorbachev reforms, the earlier years of the diary give the reader a very rare window into the workings of the Brezhnev inner circle in the 1970s. The portrait of the Soviet leader Leonid Brezhnev, whom most Americans remember from his later years as frail and incomprehensible, emerges very differently from the earliest in the series of diaries donated by Anatoly Sergeyevich Chernyaev to the National Security Archive. In 1972, Chernyaev, deputy head of the International Department of the Central Committee, started keeping a systematic diary, recording his attendance at Politburo meetings, his participation in meetings at the state dacha in Zavidovo (where the experts and speechwriters met to draft speeches and reports for the General Secretary), visits abroad, and the daily life of a high-level Soviet apparatchik. In 1972, Brezhnev is a skillful negotiator, who prepares seriously for Richard Nixon’s first visit to Moscow, who discusses texts of his speeches with leading Moscow intellectuals whom he brought into his inner circle as speechwriters and consultants, who is essentially non-ideological in his dealings with foreign leaders-negotiating arms control and economic agreements with Nixon while the U.S. forces are bombing the Soviet communist ally Vietnam, preferring Georges Pompidou to the leader of French communists Georges Marchais, and”brainwashing” Pakistani leader Bhutto. The two most striking differences between the aging Brezhnev of the late 1970s-early 1980s and the Brezhnev of this diary are that the General Secretary is clearly in charge of the Politburo sessions and that he actively consults with leading experts and intellectuals, such as Georgy Arbatov, Nikolai Inozemtsev, Alexander Bovin and Chernyaev himself. Chernyaev’s daily duties are centered around the international communist movement, interactions with representatives from European communist parties. The reader sees Chernyaev’s emerging disillusionment with his work, which in comparison to real foreign policy, like preparation for Nixon’s visit, feels meaningless. Chernyaev comes to believe that “the Communist Movement right now is nothing more than an ideological addendum to our foreign policy,” and that the Soviet authority in the progressive movements in the world is shrinking: “nobody believes us anymore, no matter how we portray the Chinese and try to explain our Marxist-Leninist purity.” He sees the future in a different direction. After Nixon’s visit, Chernyaev is asked to draft Brezhnev’s speech on Soviet-American relations and thus is allowed to see all the materials from the meeting, including all transcripts of conversation. Impressed with the quality of interaction and the non-ideological spirit of it, Chernyaev anticipates a new era: “Be that as it may, but we’ve crossed the Rubicon. The great Rubicon of world history. These weeks of May 1972 will go down in history as the beginning of an era of convergence.” But the new era will only come thirteen years later. In 1972, he sees the first almost imperceptible sign from the future. In October 1972, he is asked to accompany first secretary of the Stavropol region on a trip to Belgium. This is where Chernyaev meets and spends time with Mikhail Gorbachev for the first time. Astonishingly, as Chernyaev later admits, he did not record this meeting in the diary at the time. Only photographs documented this auspicious meeting where Chernyaev sits on the left hand of the future Soviet leader, whose right hand he was destined to become in the late 1980s.
|
SECRET from Cryptome – FAA Sets Large ND Drone Training Airspace
|
TMZ – Kim Kardashian — The Great Ass Debate
Das neue “GoMoPa”-System der WordPress – Blogs oder “Der Bauer erkennt seine Schweine am Gang.”
Liebe Leser,
“GoMoPa” hat mit immer neuen WordPress-Blogs zwei Dinge vor:
– von negativen Meldungen abzulenken
– themenspezifische Angriffe zu starten.
Früher bediente sich die dubiose selbsternannte “Finanznachrichtenagentur” eines Blog-Netzwerkes aus teilweise fremden Blogs.
Scheinbar sind wohl diese Blogger auf Distanz zu der laut Eigenaussage “Financial Intelligence” gegangen.
Im Übrigen bedeutet Intelligence im Englischen Sprachgebrauch “Geheimdienst”.
Wohl kein Zufall – sieht man sich das STASI-Netzwerk um den STASI-Obersten Ehrenfried Stelzer, den “Ersten Kriminologen der DDR” an.
Wie schreibt “GoMoPa” so schön und ich darf die dubiosen Genossen hier – als Sohn eines Landwirtes, der auf dem Bauernhof groß geworden ist, – mit besonderer Freude zitieren: “Der Bauer erkennt seine Schweine am Gang !”
Eben…
Herzlichst Ihr
Bernd Pulch
Magister der Publizistik, Germanistik und Komparatistik
Leaked Video – Kim Kardashian Nude and Naughty for Playboy
TOP-SECRET from the FBI – Leader of Crips Gang Pleads Guilty in Virginia to Prostituting Eight Juveniles
ALEXANDRIA, VA—Justin Strom, aka “Jae,” “Jae Dee,” or “J-Dirt,” 26, of Lorton, Virginia, pleaded guilty today to recruiting at least eight juvenile girls to engage in commercial sex for his street gang’s prostitution business.
Neil H. MacBride, U.S. Attorney for the Eastern District of Virginia; Kenneth T. Cuccinelli, II, Attorney General of Virginia; Colonel David Rohrer, Fairfax County, Virginia Chief of Police; and Ronald T. Hosko, Special Agent in Charge of the FBI’s Washington Field Office Criminal Division, made the announcement after the plea was accepted by U.S. District Judge James C. Cacheris.
“For six years, Justin Strom profited from preying on teenage girls and others he recruited as prostitutes in a commercial sex ring,” said U.S. Attorney MacBride. “Strom is the fifth and final Underground Gangster Crips gang member to plead guilty to sex trafficking a juvenile—a very serious crime that carries a potential life sentence.”
“Justin Strom robbed these girls of their childhoods, their innocence, and their trust, and he did that in the most base, vile, and despicable way possible,” said Attorney General Cuccinelli. “Nothing can ever repair the damages Strom inflicted on his victims, but it’s our hope that today’s guilty plea will help them begin a path towards healing and moving forward.”
“Today, a fifth member of the Underground Gangster Crips pleaded guilty to strong-arming and pimping underage girls in the illegal sex trade—a trade that is taking place here in some of the most affluent neighborhoods in our nation,” said Special Agent in Charge Hosko. “These gang members admitted that they beat and intimidated young girls they met on the Internet or in Metro stops in our area. They preyed on some of the most vulnerable in our society, and today Justin Strom admitted to these crimes.”
“This gang-driven prostitution ring was a direct threat to the safety and welfare of young women,” said Chief Rohrer. “With the help of our federal partners, we will continue to work aggressively and consistently to rid Fairfax County of gang violence and criminal operations wherever and whenever we find it.”
Strom pleaded guilty to sex trafficking of a child, which carries a mandatory minimum of 10 years in prison and maximum penalty of life in prison. Sentencing is scheduled for September 14, 2012.
According to a statement of facts filed with his plea agreement and other court records, Strom is a member of the Underground Gangster Crips (UGC) set based in Fairfax County. From 2006 through March 2012, Strom misrepresented his identity online to recruit females—including juveniles—through online social networking sites such as Facebook, MySpace, and Datehookup and enticed the girls to use their good looks to earn money through prostitution. He and others posted numerous advertisements on Backpage, Craigslist, and other websites to solicit customers to pay to have sex with juvenile and adult prostitutes.
Strom admitted that he knowingly enticed at least eight juvenile girls to engage in prostitution for his business and that he received proceeds from this illicit conduct for approximately six years.
On March 28, 2012, Strom was among five members and associates of the UGC set based in Fairfax County charged with running a prostitution business that recruited and trafficked high school girls. Four previously pleaded guilty, and Strom’s guilty plea today marks the fifth and final conviction in this case.
Donyel Pier Dove, aka “Bleek,” 27, of Alexandria, Virginia, pleaded guilty on May 17, 2012 to sex trafficking of a juvenile. He also pleaded guilty to use of a firearm during a crime of violence in relation to two armed robberies of 7-11 stores in Manassas, Virginia, in March 2012 and to possession of a firearm by a convicted felon in Fairfax, which also occurred in March 2012. Dove faces a mandatory minimum penalty of five years and a maximum of life on the use of a firearm charge and a maximum of 10 years in prison on the possession of a firearm charge. He is scheduled to be sentenced on August 10, 2012 by U.S. District Judge Anthony J. Trenga.
On May 14, 2012, Henock Ghile, aka “Knots,” 23, of Springfield, Virginia, pleaded guilty to sex trafficking of a juvenile. In court, Ghile admitted that he was a UGC gang associate and that from May 2011 through September 2011, he transported two 17-year-old girls to work as prostitutes. Sentencing has been scheduled for August 3, 2012, before U.S. District Judge Claude M. Hilton.
On April 14, 2012, two others associated with the UGC prostitution operation—Michael Tavon Jefferies, aka “Loc,” 21, of Woodbridge, Virginia; and Christopher Sylvia, 23, of Springfield, Virginia—pleaded guilty to sex trafficking of a juvenile. Jefferies is scheduled to be sentenced on July 6, 2012 before U.S. District Judge Leonie M. Brinkema. Sylvia is scheduled for sentencing on July 20, 2012 before U.S. District Judge Gerald Bruce Lee.
This case was investigated by the Fairfax County Police Department and the FBI’s Washington Field Office, with assistance from the Northern Virginia Human Trafficking Task Force. Virginia Assistant Attorney General and Special Assistant U.S. Attorney Marc Birnbaum and Assistant U.S. Attorney Inayat Delawala are prosecuting the case on behalf of the United States.
Founded in 2004, the Northern Virginia Human Trafficking Task Force is a collaboration of federal, state, and local law enforcement agencies—along with non-governmental organizations—dedicated to combating human trafficking and related crimes.
Unveiled and Uncensored – Euro Cup FEMEN Protester Arrest
Video – Rihanna Is the Sexiest Woman Alive
Watch this exclusive Rihanna Esquire video set to “We Found Love,” then pick up the November issue of Esquire for more.
SECRET – New York Fusion Center Bulletin: Use of Cloned Vehicles in Terrorist or Criminal Operations

Criminals and terrorists have long used official vehicles, “cloned” vehicles (those painted/decorated to appear official), or seemingly legitimate vehicles (e.g. livery, maintenance or delivery) to circumvent security measures at targets of interest.
There have been numerous terrorist attacks overseas wherein operatives used police vehicles or ambulances (or vehicles painted to resemble same) to conceal improvised explosive devices. Within the US Homeland, the most common use of cloned official vehicles by criminals is for drug smuggling; however, at least one terrorist targeting New York envisioned misusing vehicles that would appear to be legitimate, in order to conduct an attack. Dhiren Barot, an al Qaeda operative involved in the 2004 Financial Centers Plot, allegedly plotted to detonate three limousines packed with explosives and gas cylinders in underground parking lots in Manhattan. While the limousines would not have masqueraded as “official vehicles” per se they would have appeared to be legitimately entering those parking structures.
Law enforcement officials and the general public should remain alert to potential fake or cloned official vehicles, with special attention near high-profile targets and mass gatherings at special events, such as upcoming Memorial Day and 4th of July holiday parades and celebrations, or large sporting events scheduled this summer across the State. These events provide the opportunity for terrorists to inflict mass casualties and evade detection by blending into large crowds.
Officials should also be mindful of locations where official vehicles may gain exclusive access, such as parking garages or loading docks proximate to potential targets of interest. Officials at such locations should know how to verify markings on any official vehicles likely to be present. Law enforcement outreach to security staff at these locations during routine patrols is encouraged.
DOWNLOAD THE ORIGINAL DOCUMENT HERE
TOP-SECRET from the FBI – Manhattan U.S. Attorney and FBI Assistant Director in Charge Announce 24 Arrests in Eight Countries as Part of International Cyber Crime Takedown
Preet Bharara, the United States Attorney for the Southern District of New York, and Janice K. Fedarcyk, the Assistant Director in Charge of the New York Field Office of the Federal Bureau of Investigation (FBI), announced today the largest coordinated international law enforcement action in history directed at “carding” crimes—offenses in which the Internet is used to traffic in and exploit the stolen credit card, bank account, and other personal identification information of hundreds of thousands of victims globally. Today’s coordinated action—involving 13 countries, including the United States—resulted in 24 arrests, including the domestic arrests of 11 individuals by federal and local authorities in the United States, and the arrests of 13 individuals abroad by foreign law enforcement in seven countries. In addition, the federal and local authorities and authorities overseas today conducted more than 30 subject interviews and executed more than 30 search warrants. Today’s coordinated actions result from a two-year undercover operation led by the FBI that was designed to locate cybercriminals, investigate and expose them, and disrupt their activities.
Eleven individuals were arrested today, and one last night, in the United States: Christian Cangeopol, a/k/a “404myth,” was arrested today in Lawrenceville, Georgia; Mark Caparelli, a/k/a “Cubby,” was arrested in San Diego, California; Sean Harper, a/k/a “Kabraxis314,” was arrested in Albuquerque, New Mexico; Alex Hatala, a/k/a “kool+kake,” was arrested in Jacksonville, Florida; Joshua Hicks, a/k/a “OxideDox,” was arrested in Bronx, New York; Michael Hogue, a/k/a “xVisceral,” was arrested in Tucson, Arizona; Mir Islam, a/k/a “JoshTheGod,” was arrested in Manhattan, New York; Peter Ketchum, a/k/a “IwearaMAGNUM,” was arrested in Pittsfield, Massachusetts; Steven Hansen, a/k/a “theboner1,” was arrested in Wisconsin, where he is currently serving a prison sentence on state charges. In addition, two minors, whose names will not be made public, were arrested by local authorities in Long Beach and Sacramento, California. Hicks and Islam will be presented later today before a magistrate judge in the Southern District of New York. The other federally arrested defendants will be presented before magistrate judges in the corresponding federal districts of arrest.
Another 13 individuals were arrested today in seven foreign countries. Eleven of those individuals were arrested as a result of investigations commenced in foreign jurisdictions based in part on information arising out of the undercover operation and provided by the FBI to foreign law enforcement. Those 11 arrests occurred in the United Kingdom (6 arrests), Bosnia (2), Bulgaria (1), Norway (1), and Germany (1). Two additional defendants were arrested today in foreign countries based on provisional arrest warrants obtained by the United States in connection with complaints unsealed today in the Southern District of New York. Those two individuals are Ali Hassan, a/k/a/ “Badoo,” who was arrested in Italy; and Lee Jason Juesheng, a/k/a “iAlert,” a/k/a “Jason Kato,” who was arrested in Japan. Australia, Canada, Denmark, and Macedonia conducted interviews, executed search warrants, or took other coordinated action in connection with today’s takedown.
Charges were also unsealed in the Southern District of New York against four additional defendants who remain at large.
Manhattan U.S. Attorney Preet Bharara said, “As the cyber threat grows more international, the response must be increasingly global and forceful. The coordinated law enforcement actions taken by an unprecedented number of countries around the world today demonstrate that hackers and fraudsters cannot count on being able to prowl the Internet in anonymity and with impunity, even across national boundaries. Clever computer criminals operating behind the supposed veil of the Internet are still subject to the long arm of the law.
The allegations unsealed today chronicle a breathtaking spectrum of cyber schemes and scams. As described in the charging documents, individuals sold credit cards by the thousands and took the private information of untold numbers of people. As alleged, the defendants casually offered every stripe of malware and virus to fellow fraudsters, even including software-enabling cyber voyeurs to hijack an unsuspecting consumer’s personal computer camera. To expose and prosecute individuals like the alleged cyber criminals charged today will continue to require exactly the kind of coordinated response and international cooperation that made today’s arrests possible.”
FBI Assistant Director in Charge Janice K. Fedarcyk said, “From New York to Norway and Japan to Australia, Operation Card Shop targeted sophisticated, highly organized cyber criminals involved in buying and selling stolen identities, exploited credit cards, counterfeit documents, and sophisticated hacking tools. Spanning four continents, the two-year undercover FBI investigation is the latest example of our commitment to rooting out rampant criminal behavior on the Internet.
Cyber crooks trade contraband and advance their schemes online with impunity, and they will only be stopped by law enforcement’s continued vigilance and cooperation. Today’s arrests cause significant disruption to the underground economy and are a stark reminder that masked IP addresses and private forums are no sanctuary for criminals and are not beyond the reach of the FBI.”
The following allegations are based on the Complaints unsealed today in Manhattan federal court:
Background on Carding Crimes
“Carding” refers to various criminal activities associated with stealing personal identification information and financial information belonging to other individuals—including the account information associated with credit cards, bank cards, debit cards, or other access devices—and using that information to obtain money, goods, or services without the victims’ authorization or consent. For example, a criminal might gain unauthorized access to (or “hack”) a database maintained on a computer server and steal credit card numbers and other personal information stored in that database. The criminal can then use the stolen information to, among other things, buy goods or services online; manufacture counterfeit credit cards by encoding them with the stolen account information; manufacture false identification documents (which can be used in turn to facilitate fraudulent purchases); or sell the stolen information to others who intend to use it for criminal purposes. Carding refers to the foregoing criminal activity generally and encompasses a variety of federal offenses, including, but not limited to, identification document fraud, aggravated identity theft, access device fraud, computer hacking, and wire fraud.
“Carding forums” are websites used by criminals engaged in carding (“carders”) to facilitate their criminal activity. Carders use carding forums to, among other things, exchange information related to carding, such as information concerning hacking methods or computer-security vulnerabilities that could be used to obtain personal identification information; and to buy and sell goods and services related to carding—for example, stolen credit or debit card account numbers, hardware for creating counterfeit credit or debit cards, or goods bought with compromised credit card or debit card accounts. Carding forums often permit users to post public messages—postings that can be viewed by all users of the site—sometimes referred to as threads. For example, a user who has stolen credit card numbers may post a public thread offering to sell the numbers. Carding forums also often permit users to communicate one-to-one through so-called private messages. Because carding forums are, in essence, marketplaces for illegal activities, access is typically restricted to avoid law enforcement surveillance. Typically, a prospective user seeking to join a carding forum can only do so if other, already established users vouch for him or her, or if he or she pays a sum of money to the operators of the carding forum. User accounts are typically identified by a username and access is restricted by password. Users of carding forums typically identify themselves on such forums using aliases or online nicknames (“nics”).
Individuals who use stolen credit card information to purchase goods on the Internet are typically reluctant to ship the goods to their own home addresses, for fear that law enforcement could easily trace the purchases. Accordingly, carders often seek out “drop addresses”—addresses with which they have no association, such as vacant houses or apartments—where carded goods can be shipped and retrieved without leaving evidence of their involvement in the shipment. Some individuals used carding forums to sell “drop services” to other forum members, usually in exchange for some form of compensation. One frequently used form of compensation is a “1-to-1” arrangement in which the carder wishing to ship to the drop must ship two of whatever items he has carded—one for the provider of the drop to forward to the carder and the other for the provider of the drop to keep as payment in kind for the carder’s use of the drop. Another frequently used compensation arrangement is for the carder and the drop provider to agree to resell the carded items shipped to the drop and to split the proceeds between them.
Background on the Undercover Operation
In June 2010, the FBI established an undercover carding forum called “Carder Profit” (the “UC Site”), enabling users to discuss various topics related to carding and to communicate offers to buy, sell, and exchange goods and services related to carding, among other things. Since individuals engaged in these unlawful activities on one of many other carding websites on the Internet, the FBI established the UC Site in an effort to identify these cybercriminals, investigate their crimes, and prevent harm to innocent victims. The UC Site was configured to allow the FBI to monitor and to record the discussion threads posted to the site, as well as private messages sent through the site between registered users. The UC Site also allowed the FBI to record the Internet protocol (IP) addresses of users’ computers when they accessed the site. The IP address is the unique number that identifies a computer on the Internet and allows information to be routed properly between computers.
Access to the UC Site, which was taken offline in May 2012, was limited to registered members and required a username and password to gain entry. Various membership requirements were imposed from time to time to restrict site membership to individuals with established knowledge of carding techniques or interest in criminal activity. For example, at times, new users were prevented from joining the site unless they were recommended by two existing users who had registered with the site or unless they paid a registration fee.
New users registering with the UC Site were required to provide a valid e-mail address as part of the registration process. The e-mail addresses entered by registered members of the site were collected by the FBI.
Harm Prevented by the Undercover Operation
In the course of the undercover operation, the FBI contacted multiple affected institutions and/or individuals to advise them of discovered breaches in order to enable them to take appropriate responsive and protective measures. In doing so, the FBI has prevented estimated potential economic losses of more than $205 million, notified credit card providers of over 411,000 compromised credit and debit cards, and notified 47 companies, government entities, and educational institutions of the breach of their networks.
The Charged Conduct
As alleged in the complaints unsealed today in the Southern District of New York, the defendants are charged with engaging in a variety of online carding offenses in which they sought to profit through, among other means, the sale of hacked victim account information, personal identification information, hacking tools, drop services, and other services that could facilitate carding activity.
Michael Hogue, a/k/a “xVisceral,” offered malware for sale, including remote access tools (RATs) that allowed the user to take over and remotely control the operations of an infected victim-computer. Hogue’s RAT, for example, enabled the user to turn on the web camera on victims’ computers to spy on them and to record every keystroke of the victim-computer’s user. If the victim visited a banking website and entered his or her user name and password, the key logging program could record that information, which could then be used to access the victim’s bank account. Hogue sold his RAT widely over the Internet, usually for $50 per copy and boasted that he had personally infected “50-100” computers with his RAT and that he’d sold it to others who had infected “thousands” of computers with malware. Hogue’s RAT infected computers in the United States, Canada, Germany, Denmark, Poland, and possibly other countries.
Jarand Moen Romtveit, a/k/a “zer0,” used hacking tools to steal information from the internal databases of a bank, a hotel, and various online retailers, and then sold the information to others. In February 2012, in return for a laptop computer, Romtveit sold credit card information to an individual he believed to be a fellow carder, but who, in fact, was an undercover FBI agent.
Mir Islam, a/k/a “JoshTheGod,” trafficked in stolen credit card information and possessed information for more than 50,000 credit cards. Islam also held himself out as a member of “UGNazi,” a hacking group that has claimed credit for numerous recent online hacks, and as a founder of “Carders.Org,” a carding forum on the Internet. Last night, Islam met in Manhattan with an individual he believed to be a fellow carder—but who, in fact, was an undercover FBI agent—to accept delivery of what Islam believed were counterfeit credit cards encoded with stolen credit card information. Islam was placed under arrest after he attempted to withdraw illicit proceeds from an ATM using one of the cards. Today, the FBI seized the web server for UGNazi.com and seized the domain name of Carders.org, taking both sites offline.
Steven Hansen, a/k/a “theboner1,” and Alex Hatala, a/k/a, “kool+kake,” sold stolen CVVs, a term used by carders to refer to credit card data that includes the name, address, and zip code of the card holder, along with the card number, expiration date, and security code printed on the card. Hatala advertised to fellow carders that he got “fresh” CVVs on a “daily” basis from hacking into “DBs [databases] around the world.”
Ali Hassan, a/k/a “Badoo,” also sold “fulls,” a term used by carders to refer to full credit card data including cardholder name, address, Social Security number, birthdate, mother’s maiden name, and bank account information. Hassan claimed to have obtained at least some of them by having hacked into an online hotel booking site.
Joshua Hicks, a/k/a “OxideDox,” and Lee Jason Jeusheng, a/k/a “iAlert, a/k/a “Jason Kato,” each sold “dumps,” which is a term used by carders to refer to stolen credit card data in a form in which the data is stored on the magnetic strips on the backs of credit cards. Hicks sold 15 credit card dumps in return for a camera and $250 in cash to a fellow carder who, unbeknownst to Hicks, was an undercover FBI agent. Hicks met the undercover agent in downtown Manhattan to consummate the sale. Similarly, Jeusheng sold 119 credit card dumps in return for three iPad 2s to a carder who was an undercover FBI agent. Jeusheng provided his shipping address in Japan to the undercover agent, which in part led to his identification and arrest.
Mark Caparelli, a/k/a “Cubby,” engaged in a so-called “Apple call-in” scheme in which he used stolen credit cards and social engineering skills to fraudulently obtain replacement products from Apple Inc., which he then resold for profit.The scheme involved Caparelli obtaining serial numbers of Apple products he had not bought. He would then call Apple with the serial number, claim the product was defective, arrange for a replacement product to be sent to an address he designated, and give Apple a stolen credit card number to charge if he failed to return the purportedly defective product. Caparelli sold and shipped four iPhone 4 cell phones that he had stolen through the Apple call-in scheme to an individual whom he believed to be a fellow-carder, but who, in fact, was an undercover FBI agent.
Sean Harper, a/k/a “Kabraxis314,” and Peter Ketchum, a/k/a “iwearaMAGNUM,” each sold drop services to other carders in return for money or carded merchandise. Harper provided drop addresses in Albuquerque, New Mexico, to which co-conspirators sent expensive electronics, jewelry, and clothing, among other things. Ketchum advertised drop locations “spread across multiple cities” in the United States and allegedly received and shipped carded merchandise including sunglasses and air purifiers, as well as synthetic marijuana.
Christian Cangeopol CANGEOPOL, a/k/a “404myth,” engaged in illegal “instoring” at Walmart to obtain Apple electronic devices with stolen credit cards. Instoring is a term used by carders to refer to using stolen credit card accounts to make in-store, as opposed to online, purchases of items using stolen credit card information and matching fake identifications. As part of the alleged scheme, Cangeopol and a co-conspirator used stolen credit card data to order electronic devices on Walmart’s website; in selecting a delivery option, they opted to have items delivered to various Walmart stores in Georgia; Cangeopol then picked up the items using a fake identification; Cangeopol and the co-conspirator then resold the carded electronics and split the proceeds.
* * *
The attached chart reflects the name, age, residence of, and pending charges against each individual charged in the Southern District of New York.
Mr. Bharara praised the outstanding investigative work of the FBI and its New York Cyber Crime Task Force, which is a federal, state, and local law enforcement task force combating cybercrime. Mr. Bharara also commended the U.S. Attorney’s offices in the following districts: New Mexico, Arizona, Delaware, Massachusetts, California (Central and Southern districts), Florida (Middle district), Georgia (Northern), as well as the Manhattan District Attorney’s Office. He also thanked the following domestic law enforcement partners for their assistance: the New York City Police Department; the Essex, Vermont Police Department; the Eaton, Ohio Police Department; the Butler County, Ohio Sheriff’s Office; the Cedar Bluff, Alabama Police Department; the Modesto, California Police Department; the Louisiana State Police; the Suffolk County, New York Police Department; the Bakersfield, California Police Department; the Kern County, California District Attorney’s Office; the Long Beach, California Police Department; the Louisville, Kentucky Metro Police Department; and the Nelson County, Kentucky Sheriff’s Office.
Mr. Bharara acknowledged and thanked the following international law enforcement agencies: the United Kingdom’s Serious Organised Crime Agency, Royal Military Police, Thames Valley Police, Greater Manchester Police, Leicestershire Police, Hertfordshire Police, and Wiltshire Police; the Australian Federal Police; Bosnia’s Republika Srpska Ministry of Interior; the Bulgarian Ministry of Interior, General Directorate for Combating Organized Crime; the Danish National Police; the Royal Canadian Mounted Police; the French National High-Tech Crime Unit (OCLCTIC) of the Central Directorate of the Police Judiciaire; the German Bundeskriminalamt (BKA); the Italian Polizia di Stato, Compartimento Polizia Postale e delle Comunicazioni; the National Police Agency of Japan, Tokyo Metropolitan Police Department (Cyber Crimes Control Division), Ministry of Justice of Japan, Tokyo High Prosecutors Office, and the Ministry of Foreign Affairs of Japan; the Macedonian Ministry of Interior, Department Against Organized Crime; and the Norwegian National Police for their efforts. He also thanked the Computer Crime and Intellectual Property Section of the Department of Justice, as well as the Office of International Affairs at the Department of Justice.
This case is being handled by the Office’s Complex Frauds Unit. AUSAs James Pastore, Serrin Turner, Timothy Howard, Rosemary Nidiry, Alexander Wilson, and Sarah McCallum are in charge of the prosecution.
The relevant charging documents can be found on the SDNY website at: http://www.justice.gov/usao/nys/pressreleases/index.html.
List of Arrested Defendants Charged in SDNY Complaints
|
Defendant |
SDNY Complaint Numer |
Residence |
Age |
Charges and Maximum Penalties |
| Christian Cangeopol, a/k/a “404myth” | 12 Mag. 1667 | Lawrenceville, Georgia | 19 |
|
| Mark Caparelli,
a/k/a “Cubby” |
12 Mag. 1640 | San Diego, California | 20 |
|
| Steven Hansen, a/k/a “theboner1” | 12 Mag. 1641 | Kentucky (in prison in Wisconsin) | 23 |
|
| Sean Harper, a/k/a “Kabraxis314” | 12 Mag. 1638 | Albuquerque, New Mexico | 23 |
|
| Ali Hassan, a/k/a “Mr Badoo,” a/k/a “Mr.Badoo,” a/k/a “Badoo” | 12 Mag. 1565 | Milan, Italy | 22 |
|
| Alex Hatala, a/k/a “kool+kake” | 12 Mag. 1669 | Jacksonville, Florida | 19 |
|
| Joshua Hicks, a/k/a “OxideDox” | 12 Mag. 1639 | Bronx, New York | 19 |
|
| Michael Hogue, a/k/a “xVisceral” | 12 Mag. 1632 | Tucson, Arizona | 21 |
|
| Lee Jason Juesheng, a/k/a “iAlert,” a/k/a “Jason Kato” | 12 Mag. 1605 | Tokyo, Japan | 23 |
|
| Peter Ketchum, Jr., a/k/a “iwearaMAGNUM” | 12 Mag. 1651 | Pittsfield, Massachusetts | 21 |
|
| Jarand Moen Romtveit, a/k/a “zer0,” a/k/a “zer0iq” | 12 Mag. 1656 | Porsgrunn, Norway | 25 |
|
| Mir Islam, a/k/a “JoshTheGod” | — | Bronx, New York | 18 |
|
ESQUIRE TV – Kate Upton and a Pair of Scissors
FEMEN Action against Ucraine Prostitution
CIA ALLOWED TO SUSTAIN COVER-UP OF BAY OF PIGS HISTORY
Washington, DC, June 26, 2012 – More than year after the National Security Archive sued the CIA to declassify the full “Official History of the Bay of Pigs Operation,” a U.S. District Court judge today sided with the Agency’s efforts to keep the last volume of the report secret in perpetuity. In her ruling, Judge Gladys Kessler accepted the CIA’s legal arguments that, because Volume V was a “draft” and never officially approved for inclusion in the Agency’s official history, it was exempt from declassification under the “deliberative process privilege” despite having been written over 30 years ago.
The National Security Archive called the decision “a regrettable blow to the right-to-know” and vowed to press the Obama administration to force the CIA to adhere to the President’s Executive Order 13526 that “no information shall remain classified indefinitely.”
The volume, titled “CIA’s Internal Investigations of the Bay of Pigs Operations,” was written by CIA historian Jack Pfeiffer in 1981. It forcefully critiqued the scathing investigative report written in the immediate aftermath of the paramilitary attack – by the CIA’s own Inspector General, Lyman Kirkpatrick – which held CIA planners fully responsible for the worst debacle in the Agency’s covert history. In court papers, CIA officials described Pfeiffer’s critique as “a polemic of recriminations against CIA officers who later criticized the operation.”
“When it comes to protecting its own, the CIA appears to have a double-standard on history,” said Peter Kornbluh who directs the National Security Archive’s Cuba Documentation Project which brought the FOIA lawsuit. Kornbluh noted that the CIA had no problem declassifying Volume IV of the official history–also a draft– in which Pfeiffer attacked both President Kennedy for his role in setting restrictions on the overt elements of what was supposed to be a covert, and “plausibly deniable,” operation, as well as Attorney General Robert Kennedy for his role in the Presidential commission, led by Gen. Maxwell Taylor, that investigated the failed invasion.
“Apparently, the CIA sees no problem in the American public reading a ‘polemic of recriminations’ against the White House,” according to Kornbluh. “But the CIA claims ‘historical accuracy’ as a reason to withhold documents critical of its own officials.”
In her ruling, Judge Kessler stated that “disclosure of a draft history would risk public release of inaccurate historical information.” She also cited the arguments of CIA Chief Historian David Robarge that “disclosure of Volume V would have a chilling effect on CIA’s current historians who would henceforth be inhibited from trying out innovative, unorthodox or unpopular interpretations in a draft manuscript.”
But the Archive characterized the CIA’s effort to cast itself as guardian of accurate and honest history as an exercise in cynicism. “The idea that the CIA can advance the cause of accurate historical analysis by hiding history from the peer review of the public is preposterous,” Kornbluh stated. He noted that it was the Agency’s selective declassification of the Pfeiffer volumes that fostered inaccurate historical information. “The real chilling effect of the CIA’s selective cover up is on the public’s ability to access and analyze the complete historical record on the Bay of Pigs.”
The Archive’s lawsuit did yield the release of Volumes I, II, and IV. Volume III was previously released under the Kennedy Assassination Records Act in 1998. Those four volumes can be read here.
Kate Upton and a Pair of Scissors – Esquire Video
Murder in the OC – Full Movie
TOP-SECRET – DoD Current and Projected Unmanned Aircraft Systems (UAS) Inventory Levels Through 2017
The following tables display the current Department of Defense unmanned aircraft systems (UAS) inventory levels (FY2012 budgeted inventory) and planned inventory through FY2017. The first table was taken from the recent Department of Defense Report to Congress on Future Unmanned Aircraft Systems Training, Operations, and Sustainability which was originally obtained and published by InsideDefense.com. The second table displays the total inventories by service.
UAS Inventory Levels (FY12 budgeted inventory with noted exception)
| Service Branch | UAS System Name | Current Inventory | FY12 | FY13 | FY14 | FY15 | FY16 | FY17 |
|---|---|---|---|---|---|---|---|---|
| Air Force | MQ-1B Predator | 163 | 152 | 141 | 130 | 121 | 115 | 110 |
| Air Force | MQ-9A Reaper | 70 | 96 | 135 | 167 | 199 | 229 | 256 |
| Air Force | RQ-4B Global Hawk* | 23 | 23 | 15 | 15 | 15 | 15 | 15 |
| Army | RQ-11B Raven | 5394 | 6294 | 6528 | 6717 | 6921 | 7074 | 7074 |
| Army | RQ-7B Shadow | 408 | 408 | 408 | 408 | 408 | 408 | 408 |
| Army | MQ-5B Hunter | 45 | 45 | 45 | 45 | 45 | 45 | 45 |
| Army | MQ-1C Gray Eagle | 19 | 45 | 74 | 110 | 138 | 152 | 152 |
| Navy | RQ-4A Global Hawk | 5 | 5 | 0 | 0 | 0 | 0 | 0 |
| Navy | MQ-4C BAMS | 0 | 0 | 2 | 2 | 5 | 9 | 13 |
| Navy | MQ-8B Firescout/TUAV | 5 | 9 | 14 | 18 | 25 | 32 | 37 |
| Navy | RQ-21A STUAS | 0 | 1 | 2 | 3 | 4 | 4 | 4 |
| Navy | RQ-21A Scan Eagle | 122 | 122 | 122 | 122 | 122 | 122 | 122 |
| Navy | X-47B UCAS-D | 2 | 2 | 2 | 2 | 0 | 0 | 0 |
| Navy | UCLASS | 0 | 0 | 0 | 0 | 2 | 2 | 4 |
| Marine Corps | RQ-7B Shadow | 52 | 52 | 52 | 52 | 52 | 52 | 52 |
| Marine Corps | RQ-21A STUAS | 8 | 8 | 8 | 23 | 48 | 73 | 100 |
* Reflects RQ-4B Block 20/40 invent0ry remaining after FY 2012 (Block 30 cancelled in President’s 2013 Budget submission).
UAS Total Inventory by Service
| Service Branch | Current Inventory | FY12 | FY13 | FY14 | FY15 | FY16 | FY17 |
|---|---|---|---|---|---|---|---|
| Air Force | 256 | 271 | 291 | 312 | 335 | 359 | 381 |
| Army | 5866 | 6792 | 7055 | 7280 | 7512 | 7679 | 7679 |
| Navy | 134 | 139 | 142 | 147 | 158 | 169 | 180 |
| Marine Corps | 60 | 60 | 60 | 75 | 100 | 125 | 152 |
| Total | 6316 | 7262 | 7548 | 7814 | 8105 | 8332 | 8392 |
TOP-SECRET from the FBI – Mortgage Rescue Business Owner Sentenced to 90 Months for Fraud
ALEXANDRIA, VA—Howard R. Shmuckler, 68, of Virginia Beach, Virginia, was sentenced today to 90 months in prison, followed by three years of supervised release, for running a fraudulent mortgage rescue business that received substantial fees but actually modified clients’ mortgages in only a few cases. The court ordered that this sentence be served consecutive to a 75-month federal sentence Shmuckler received on April 5, 2012 in the District of Columbia involving a counterfeit check scheme.
Neil H. MacBride, United States Attorney for the Eastern District of Virginia; James W. McJunkin, Assistant Director in Charge of the FBI’s Washington Field Office; Jon T. Rymer, Inspector General of the Federal Deposit Insurance Corporation (FDIC-OIG); and Christy Romero, Special Inspector General for the Troubled Asset Relief Program (SIGTARP); made the announcement after sentencing by United States District Judge Leonie M. Brinkema.
“Mr. Shmuckler is a cunning criminal who took advantage of distressed homeowners in desperate need of help,” said U.S. Attorney MacBride. “Today’s sentence should send a clear warning to other fraudsters of the heavy price they will pay for preying on vulnerable people looking for help to save their homes.”
“Mr. Schmuckler portrayed himself as a successful attorney and mortgage advisor who was able to rescue mortgages and provide relief to homeowners, but, in reality, he was a fraud,” said Assistance Director in Charge McJunkin. “The public should be wary of such individuals who offer a service or product that seems too good to be true. It probably is.”
“At a time when homeowners across the nation are struggling to keep their homes, Shmuckler actively targeted the most vulnerable of them with his mortgage modification scam,” said Special Inspector General Romero of SIGTARP. “Shmuckler exploited homeowners desperately seeking support through federal housing programs such as HAMP by essentially guaranteeing the homeowners mortgage modifications in exchange for an upfront fee. Shmuckler performed little, if any, service in return for the fees, and in many cases, the homeowners’ properties fell into foreclosure. SIGTARP and its partners in law enforcement will aggressively shut down these scams and hold their perpetrators accountable for their crimes.”
On April 10, 2012, Shmuckler pled guilty to six counts of wire fraud. According court records, Shmuckler, a convicted felon and disbarred attorney, owned and operated a Vienna, Virginia mortgage-rescue business known as The Shmuckler Group (TSG). From June 2008 through March 2009, TSG took in nearly $2.8 million from approximately 865 clients whose mortgages were in distress and who came to Shmuckler looking for relief. Shmuckler aggressively recruited new clients and pocketed their money while pretending he was successful, was an attorney, and that the business had restructured hundreds of mortgages, stopped hundreds of foreclosures, and negotiated hundreds of short sales. In reality, TSG was able to obtain relief for approximately 4.5 percent of its clients.
Court records indicate that Shmuckler instructed clients to terminate contact with their mortgage companies and to stop making payments to their lenders. TSG never facilitated a modification of the mortgages referenced in the statement of facts filed with his plea agreement.
This case was investigated by the FBI’s Washington Field Office, the FDIC-OIG, and SIGTARP. Assistant United States Attorneys Timothy D. Belevetz and Uzo Asonye are prosecuting the case on behalf of the United States.
A copy of this press release may be found on the website of the United States Attorney’s Office for the Eastern District of Virginia at http://www.justice.gov/usao/vae.
Unveiled – Mila Kunis: Exclusive Esquire Video of a Woman We Love
My Mothers Murder – Full Movie
Unveiled – TOP-SECRET – Obama Report on Global Deathcraft
Obama Report on Global Deathcraft
Banal dissimulation. Not a word about the dead and maimed, societies destroyed, waste and ineptitude, withholding secrets from the public. No sympathy for victims, no regret, no apology, no shame for deathcraft commerce and politics.
Coordinated reports on USG political promotion of more financial return and jobs through global deathcraft:
0427.pdf State Promotes Specially Designed Deathcrafts June 15, 2012 0426.pdf BIS Promotes Specially Designed Deathcrafts 2 June 15, 2012 0425.pdf BIS Promotes Specially Designed Deathcrafts 1 June 15, 2012 0423.htm ok US Promotes Jobs by Deathcraft June 15, 2012
The White House
Office of the Press Secretary
For Immediate Release
June 15, 2012
Presidential Letter — 2012 War Powers Resolution 6-Month Report
Dear Mr. Speaker: (Dear Mr. President:)
I am providing this supplemental consolidated report, prepared by my Administration and consistent with the War Powers Resolution (Public Law 93-148), as part of my efforts to keep the Congress informed about deployments of U.S. Armed Forces equipped for combat.
MILITARY OPERATIONS AGAINST AL-QA’IDA, THE TALIBAN, AND ASSOCIATED FORCES AND IN SUPPORT OF RELATED U.S. COUNTERTERRORISM (CT) OBJECTIVES
Since October 7, 2001, the United States has conducted combat operations in Afghanistan against al-Qa’ida terrorists, their Taliban supporters, and associated forces. In support of these and other overseas operations, the United States has deployed combat equipped forces to a number of locations in the U.S. Central, Pacific, European, Southern, and Africa Command areas of operation. Previously such operations and deployments have been reported, consistent with Public Law 107-40 and the War Powers Resolution, and operations and deployments remain ongoing. These operations, which the United States has carried out with the assistance of numerous international partners, have degraded al-Qa’ida’s capabilities and brought an end to the Taliban’s leadership of Afghanistan.
United States Armed Forces are now actively pursuing and engaging remaining al-Qa’ida and Taliban fighters in Afghanistan. The total number of U.S. forces in Afghanistan is approximately 90,000, of which more than 70,000 are assigned to the North Atlantic Treaty Organization (NATO)-led International Security Assistance Force (ISAF) in Afghanistan. In accordance with June 2011 Presidential guidance, the Department of Defense remains on track to achieve a Force Management Level of 68,000 U.S. forces by the end of this summer. After that, reductions will continue at a steady pace.
The U.N. Security Council most recently reaffirmed its authorization of ISAF for a 12-month period until October 13, 2012, in U.N. Security Council Resolution 2011 (October 12, 2011). The mission of ISAF, under NATO command and in partnership with the Government of the Islamic Republic of Afghanistan, is to prevent Afghanistan from once again becoming a safe haven for international terrorists. Fifty nations, including the United States and all 28 NATO Allies, contribute forces to ISAF. These forces, including U.S. “surge” forces deployed in late 2009 and 2010, broke Taliban momentum and trained additional Afghan National Security Forces (ANSF). The ANSF are now increasingly assuming responsibility for security on the timeline committed to at the 2010 NATO Summit in Lisbon by the United States, our NATO allies, ISAF partners, and the Government of Afghanistan.
United States Armed Forces are detaining in Afghanistan approximately 2,748 individuals under the Authorization for the Use of Military Force (Public Law 107-40) as informed by the laws of war. On March 9, 2012, the United States signed a Memorandum of Understanding with the Afghan government under which the United States is to transfer Afghan nationals detained by U.S. forces in Afghanistan to the custody and control of the Afghan government within 6 months. Efforts are underway to accomplish such transfers in a safe and humane manner.
The combat-equipped forces, deployed since January 2002 to Naval Base, Guantanamo Bay, Cuba, continue to conduct secure detention operations for the approximately 169 detainees at Guantanamo Bay under Public Law 107-40 and consistent with principles of the law of war.
In furtherance of U.S. efforts against members of al-Qa’ida, the Taliban, and associated forces, the United States continues to work with partners around the globe, with a particular focus on the U.S. Central Command’s area of responsibility. In this context, the United States has deployed U.S. combat-equipped forces to assist in enhancing the CT capabilities of our friends and allies, including special operations and other forces for sensitive operations in various locations around the world.
In Somalia, the U.S. military has worked to counter the terrorist threat posed by al-Qa’ida and al-Qa’ida-associated elements of al-Shabaab. In a limited number of cases, the U.S. military has taken direct action in Somalia against members of al-Qa’ida, including those who are also members of al-Shabaab, who are engaged in efforts to carry out terrorist attacks against the United States and our interests.
The U.S. military has also been working closely with the Yemeni government to operationally dismantle and ultimately eliminate the terrorist threat posed by al-Qa’ida in the Arabian Peninsula (AQAP), the most active and dangerous affiliate of al-Qa’ida today. Our joint efforts have resulted in direct action against a limited number of AQAP operatives and senior leaders in that country who posed a terrorist threat to the United States and our interests.
The United States is committed to thwarting the efforts of al-Qa’ida and its associated forces to carry out future acts of international terrorism, and we have continued to work with our CT partners to disrupt and degrade the capabilities of al-Qa’ida and its associated forces. As necessary, in response to the terrorist threat, I will direct additional measures against al-Qa’ida, the Taliban, and associated forces to protect
U.S. citizens and interests. It is not possible to know at this time the precise scope or the duration of the deployments of U.S. Armed Forces necessary to counter this terrorist threat to the United States. A classified annex to this report provides further information.
MILITARY OPERATIONS IN IRAQ
The United States completed its responsible withdrawal of U.S. forces from Iraq in December 2011, in accordance with the 2008 Agreement Between the United States of America and the Republic of Iraq on the Withdrawal of United States Forces from Iraq and the Organization of Their Activities during Their Temporary Presence in Iraq.
MILITARY OPERATIONS IN CENTRAL AFRICA
In October and November 2011, U.S. military personnel with appropriate combat equipment deployed to Uganda to serve as advisors to regional forces that are working to apprehend or remove Joseph Kony and other senior Lord’s Resistance Army (LRA) leaders from the battlefield, and to protect local populations. The total number of U.S. military personnel deployed for this mission, including those providing logistical and support functions, is approximately 90. United States forces are working with select partner nation forces to enhance cooperation, information-sharing and synchronization, operational planning, and overall effectiveness. Elements of these U.S. forces have deployed to forward locations in the LRA-affected areas of the Republic of South Sudan, the Democratic Republic of the Congo, and the Central African Republic to enhance regional efforts against the LRA. These forces, however, will not engage LRA forces except in self-defense. It is in the U.S. national security interest to help our regional partners in Africa to develop their capability to address threats to regional peace and security, including the threat posed by the LRA. The United States is pursuing a comprehensive strategy to help the governments and people of this region in their efforts to end the threat posed by the LRA and to address the impacts of the LRA’s atrocities.
MARITIME INTERCEPTION OPERATIONS
As noted in previous reports, the United States remains prepared to conduct maritime interception operations on the high seas in the areas of responsibility of each of the geographic combatant commands. These maritime operations are aimed at stopping the movement, arming, and financing of certain international terrorist groups, and also include operations aimed at stopping proliferation by sea of weapons of mass destruction and related materials. Additional information is provided in the classified annex.
HOSTAGE RESCUE OPERATIONS
As noted to you in my report of January 26, 2012, at my direction, on January 24, 2012, U.S. Special Operations Forces conducted a successful operation in Somalia to rescue Ms. Jessica Buchanan, a U.S. citizen who had been kidnapped by individuals linked to Somali pirate groups and financiers.
MILITARY OPERATIONS IN EGYPT
Approximately 693 military personnel are assigned to the U.S. contingent of the Multinational Force and Observers, which have been present in Egypt since 1981.
U.S.-NATO OPERATIONS IN KOSOVO
The U.N. Security Council authorized Member States to establish a NATO-led Kosovo Force (KFOR) in Resolution 1244 on June 10, 1999. The original mission of KFOR was to monitor, verify, and, when necessary, enforce compliance with the Military Technical Agreement between NATO and the then-Federal Republic of Yugoslavia (now Serbia), while maintaining a safe and secure environment. Today, KFOR deters renewed hostilities in cooperation with local authorities, bilateral partners, and international institutions. The principal military tasks of KFOR forces are to help maintain a safe and secure environment and to ensure freedom of movement throughout Kosovo.
Currently, 23 NATO Allies contribute to KFOR. Seven non-NATO countries also participate. The United States contribution to KFOR is approximately 817 U.S. military personnel out of the total strength of approximately 6,401 personnel, which includes a temporarily deployed Operational Reserve Force.
I have directed the participation of U.S. Armed Forces in all of these operations pursuant to my constitutional and statutory authority as Commander in Chief (including the authority to carry out Public Law 107-40 and other statutes) and as Chief Executive, as well as my constitutional and statutory authority to conduct the foreign relations of the United States. Officials of my Administration and I communicate regularly with the leadership and other Members of Congress with regard to these deployments, and we will continue to do so.
BARACK OBAMA
C-Cup 2012 – Comedy Central Germany HD – Model Football – UEFA EURO Soccer 2012
Cryptome – US Promotes Jobs by Deathcraft – SECRET
http://www.state.gov/r/pa/prs/ps/2012/06/192408.htm
Briefing on Department of State Efforts to Expand Defense Trade
Special Briefing
Andrew J. Shapiro
Assistant Secretary, Bureau of Political-Military Affairs
Via Teleconference
June 14, 2012
MR. TONER: Thank you so much. And thanks to everyone for joining us. Promoting U.S. businesses abroad and expanding U.S. exports our top priorities for the U.S. Department of State. And Assistant Secretary of State for Political and Military Affairs Andrew Shapiro joins us today to talk about how the Bureau of Political-Military Affairs is engaging with allies and partners to expand the defense trade that’s critical both to our national security as well as a part of our larger economic statecraft efforts on this Economic Statecraft Day.
Just before I hand it over to Assistant Secretary Shapiro, I just want to remind everybody this is an on-the-record briefing and you’ll have a chance for questions after he says a few words. So go ahead, Assistant Secretary.
ASSISTANT SECRETARY SHAPIRO: Thank you, Mark. And I’m delighted to be able to speak to you all today as part of Global Economic Statecraft Day. And as Mark noted, Global Economic Statecraft Day is a global event that we’re holding to highlight America’s commitment to put strengthening American jobs at the center of our foreign policy and to use diplomacy to advance America’s economic renewal. We’re using diplomatic tools to strengthen the economic foundations of America’s global leadership. And we are elevating the strategic role of economics, both in what we choose to prioritize and how we pursue solutions to some of the world’s most pressing challenges.
Our work in the Political-Military Bureau, to expand security cooperation with our allies and partners, is critical to America’s national security and economic prosperity. And it is also an important part of the State Department’s economic statecraft efforts. It also serves critical national security interests by helping allies and partners more capably secure their countries and contribute to international security efforts. And that’s a point that I want to emphasize. The purpose of our sales is to serve national security interests and that is a theme that runs through every sale that we conduct. We evaluate for how it will support U.S. national security and foreign policy interests.
So let me be clear about why the State Department oversees U.S. security cooperation, and that’s because security cooperation is fundamentally a foreign policy act. It is therefore the Secretary of State that is given the authority to oversee and authorize all arms sales in order to ensure they advance U.S. foreign policy.
The Bureau of Political-Military Affairs, which I oversee, implements the Secretary’s authority in this area and ensures that any assistance in the U.S Government – that the U.S. Government provides is fully in line with U.S. foreign policy. All sales and arms transfers are reviewed and assessed through the Conventional Arms Transfer Policy. This means we take into account political, military, economic, arms control, and human rights conditions in making decisions on the provisions of military equipment and the licensing of direct commercial sales to any country. We only allow a sale after we carefully examine issues like human rights, regional security, and nonproliferation concerns, and determine a sale is in the best foreign policy and national security interests of the United States.
Review and monitoring are also an integral part of our work. We work to make sure that items of U.S. origin are being used in the manner intended and are consistent with our legal obligations, foreign policy goals, and our values. If a license or transfer is approved, recipients are bound by end use restrictions and conditions. This grants U.S. Government officials full access to monitor how that defense article is being used throughout its lifetime. We also investigate all potential violations and take appropriate action depending on the nature and scope of the infraction.
Additionally, the transfer of items above a certain value requires the approval of Congress. We therefore work closely with Congress on all significant sales. The arm – to be quite frank, the arms transfer process sometimes causes consternation among our international partners who will gripe about onerous rules and procedures. And at times it makes countries, to be honest, reluctant to partner with the United States. But these safeguards are critical to our foreign policy, and I can assure you that they are aggressively enforced.
So therefore, what I think is remarkable is that despite our very high bar for approving transfers and our aggressive monitoring, more and more countries want to partner with the United States. At the State Department, when we deem that cooperating with an ally or partner in the security sector will advance our national security, we advocate tirelessly on behalf of U.S. companies abroad, and I think I have the frequent flyer miles to prove it.
It’s no longer just our ambassadors who promote U.S. security cooperation abroad. Senior State Department officials regularly advocate on behalf of the U.S. bidders on foreign government and foreign military procurements. We do so when we meet with officials on our travels abroad, on margins of international conferences, and in regular diplomatic correspondents to foreign government officials. And these efforts are having an impact. Despite the global economic strain, demand for U.S. defense products and services is stronger than ever.
Last week, we released the 655 Report, which is an annual report of defense articles and services that were authorized for export. This report focuses on direct commercial sales, and it showed that there was a more than $10 billion increase in Fiscal Year 2011 in items authorized for transfer. In 2011, the Directorate for Defense Trade Controls, which is part of the Political-Military Bureau, processed more than 83,000 licenses, the most ever. Today, I can confirm that this is already a record-breaking year for foreign military sales, which are government-to-government sales. We have already surpassed $50 billion in sales in Fiscal Year 2012. This represents at least a $20 billion increase over Fiscal Year 2011, and we still have more than a quarter of the fiscal year left.
To put this in context, Fiscal Year 2011 was a record-setting year at just over 30 billion. This fiscal year will be at least 70 percent greater than Fiscal Year 2011. These sales support tens of thousands of American jobs, which is welcome news for the economy.
So I’ll just take a minute or so to briefly outline why I think we are seeing such strong interest in U.S. systems. First, it’s because countries want to partner with the United States of America. This Administration has worked aggressively to improve America’s image abroad, to build new partnerships, and strengthen existing ones. We have seen tremendous growth and sales with developing countries and emerging powers such as Brazil and India, and this speaks volumes about our diplomatic efforts.
For a country to be willing to cooperate in the area of national defense, perhaps the most sensitive area for any nation, they have to be sure about the nature of the relationship with the United States. When a country buys an advanced U.S. defense system through our FMS, DCS, or Foreign Military Financing programs, they aren’t simply buying a product. They are also seeking a partnership with the United States. These programs both reinforce our diplomatic relations and establish a long-term security relationship.
The complex and technical nature of advanced defense systems frequently requires constant collaboration and interaction between countries over the life of that system, decades in many cases. This cooperation therefore helps build bilateral ties and creates strong incentives for recipient countries to maintain good relations with the United States. The fact that more countries want to deepen their defense trade partnership with the United States is a sign that our broader diplomatic efforts are having an impact.
For many countries, procurement decisions aren’t simply based on the specifications of the given system. Our advocacy helps demonstrate that the U.S. Government believes these sales are critical to our diplomatic relationship.
Second, countries want to buy the best. And to get the best, they rightly turn to U.S. defense systems. These systems are made in America, and the growth in defense sales abroad demonstrates the capabilities of American manufacturing and of American workers. This Administration has worked hard to support the U.S. defense industry abroad, because it supports our national security and supports jobs here at home.
For example, our agreement in December to expand our security cooperation with Saudi Arabia is projected to have a significant impact on the U.S. economy. According to industry experts, this agreement will support more than 50,000 American jobs. It will engage 600 suppliers in 44 states and provide $3.5 billion in annual economic impact to the U.S. economy. This will support jobs not only in the aerospace sector, but also on our manufacturing base and support chain, which are all crucial for sustaining our national defense.
Lastly, we are also working to improve our ability to cooperate with our partners. Nothing shows our commitment to expanding U.S. exports more than our export control reform efforts. The current system operates under laws written in the 1970s and was designed to address the challenges of the Cold War. It’s bad for U.S. business, it’s bad for enforcing our export control requirements, and it hurts our ability to prosecute those who violate U.S. export control laws.
The goals of our export control reform efforts are ultimately about making sure that our system protects the things it needs to protect. This will allow the U.S. Government to focus its limited resources on safeguarding and monitoring the most sensitive items. Our reform efforts will also allow us to streamline access to export-controlled items for our close allies. This will help improve interoperability with our allies as well as bolster our defense industrial base. And we are making substantial progress. We have almost finished our interagency work on all the list categories, and we’re working to have this process completed by the end of the year.
Another way we have worked to facilitate defense trade is through the defense trade treaties with the UK and Australia. This past April, the United States and UK signed an exchange of notes which brought the U.S.-UK Defense Trade Treaty into force. This treaty is the first of its kind and allows for the more efficient transfer of certain defense articles between the U.S. and UK. We’re also making progress in the implementation of the treaty with Australia, which we hope to be completed in the next year.
So with that, I’d be happy to take any questions.
MR. TONER: Okay. We’re ready to take any questions you might have now, Operator.
OPERATOR: Okay, thank you. We will now begin the question-and-answer session. If you would like to ask a question, please press *1. Please un-mute your phone and record your name clearly when prompted. If you need to withdraw your request, press *2. Again, to ask a question, it’s *1. It will be one moment, please, for the first question.
And our first question comes from Kate Brannen with Defense News.
QUESTION: Hi. I just wanted to clarify quickly a point and then ask a question. You said $50 billion in sales so far for 2012. Are those sales that the State Department has authorized? Is that the correct way to phrase it?
ASSISTANT SECRETARY SHAPIRO: Well, I believe that those are – and I’ll confirm this for you, but I believe that those are ones in which they’re authorized and the sales have been – the contracts have been negotiated.
QUESTION: Okay. And I was hoping to get an update on some of the changes the State Department has proposed to the Congressional notification process. I know there was some pushback on the Hill, and I was just curious what the current status is of – are you using that new notification process to inform Congress of sales?
ASSISTANT SECRETARY SHAPIRO: Yes, we are. And again, changes to the notification process were designed to ensure – to give Congress more information earlier than they’ve had it before, but also to provide some predictability to the length of the process and to identify which sales Congress has the most concerns about, so we’re able to address those concerns. But yes, we are proceeding with the new process.
QUESTION: Okay, thank you.
MR. TONER: Next question, please.
OPERATOR: And our next question comes from Eli Lake with Newsweek.
QUESTION: Hi. Thank you very much, Assistant Secretary. Could you break down in a little bit more detail what is responsible for this pretty significant uptick for what you anticipate for this fiscal year? Was it just more than the Saudi Arabia – can you get into that?
And if I can sneak in another one, how does the – these latest numbers kind of effect next month’s negotiations on, I guess, what would be a kind of global arms control – arms trade treaty?
ASSISTANT SECRETARY SHAPIRO: For your first question, obviously the sale to Saudi Arabia was very significant. It’s a sale worth $29.4 billion. And Saudi Arabia signed a letter of offer and acceptance in December for the sale, up to 84 advanced F-15SA fighter aircraft. It also includes upgrades of – to its current fleet of 70 F-15 aircraft, as well as munitions, spare parts, training, maintenance, and logistics. But this number also includes the sale of the Joint Strike Fighter to Japan, which is valued at approximately $10 billion.
In terms of the arms trade treaty, I’ll have to admit that’s not an issue that my bureau follows closely, and we work closely with our nonproliferation bureau led by Tom Countryman on this, so I’m going to allow – boot your question over to him and get you back an answer on that.
QUESTION: Thanks.
MR. TONER: All right. Next question, please.
OPERATOR: And next is Jen Dimascio with Aviation Week. And Jen, your line is open. Check your mute button.
QUESTION: Hello.
OPERATOR: Yes. Please continue.
QUESTION: Okay, sorry. I wanted to follow up on this record breaking year and kind of push it forward to next year. I mean, are you anticipating another record breaking year in FY13? And do you expect additional sales from countries like India?
ASSISTANT SECRETARY SHAPIRO: It’s too early to predict what FY13 will look like. Obviously, we’re going to continue to press and advocate for U.S. arms sales. We are hopeful that arms sales to India will increase. We’ve made tremendous progress in the relationship over the last decade. We went from nearly zero sales to about $8 billion in sales.
Going forward, there’s a number of tenders which we hope we’re successful on, including a tender for Apache helicopters. And we continue to advocate for them, and we’re hopeful that we’ll be successful on a number of sales over the coming year with India.
MR. TONER: All right. Next question please.
OPERATOR: And next is Austin Wright with Politico.
QUESTION: Hi. Can you give us a quick update on your efforts to push some export control reform initiatives through Congress? And there’s been some grumbling on the Hill, and I’m wondering if you think you’re going to make progress on this, given that many administrations have tried and have been unable to get these kind of reforms through the Hill.
ASSISTANT SECRETARY SHAPIRO: Right. Thanks. As you know, export control reform has many components, one of which is to revise both the State U.S. Munitions List and the Commerce Control List so that there is a clear distinction between what is controlled on each list. And our goal has been to complete the list reviews and publish the revised control list categories in proposed form this year and to both publish the revised categories in final form on a rolling basis, and that remains the goal. We’ve almost finished our interagency work on all the list categories, and we have people working from across our – the interagency working hard on this as we speak, and we are committed to meeting this goal.
I know that a lot of others have tried and failed and that there is skepticism that we can get this done, but let me be clear: Any speculation that export control reform is stalled is absolutely false. We’re making significant progress, interagency teams are making progress every day, and this has been a long, tough slide but we’re close to the finish line. And we published a number of categories and we have more in pipeline. We’re nearly halfway through rewriting the categories, and we have thus far briefed our Congressional committees on 13 categories.
QUESTION: Thank you.
MR. TONER: Great, thanks. Next questioner, please.
OPERATOR: And as a reminder, press *1 to ask a question. And next is Raymond Barrett with PAR.
QUESTION: Would you be able to expand on how completing that list and the categories and how maybe some of the individual categories might boost the domestic industry here in the States?
ASSISTANT SECRETARY SHAPIRO: Well, for example, we anticipate that – and Secretary Gates was quite eloquent in describing some of the challenges in our current export control reform system where a part or component for a previously approved aircraft would need a license. And it’s our hope that for those types of items, including thousands of parts and components, that once they move from the U.S. Munitions List to the Commerce Control List, it’ll improve the ability of our partners to acquire those parts and components (inaudible) it will streamline the system, make it easier for our partners to acquire those types of parts and components and help our manufacturing base as a result.
QUESTION: And also, just – you mentioned that the Defense Trade Cooperation Treaty with Australia might be done by the end of the year. Is that treaty going to be as extensive in nature as the one with the UK? As in – so if you can maybe compare the two.
And also, are there any other nations that you’re looking at signing a similar treaty with? Are there any ones that are (inaudible) proposed, that are next on the list after Australia?
ASSISTANT SECRETARY SHAPIRO: Well, there may be some minor differences in the text of the defense cooperation treaties between the UK and Australia. We anticipate that they will have the same broad impact in encouraging defense trade between both of our – between both the UK and Australia and the United States. And so we very much anticipate that this will have an impact.
What was your second question again?
QUESTION: Basically, who’s next? Okay, so –
ASSISTANT SECRETARY SHAPIRO: Oh. I’ll be quite clear. I testified before Congress that these would be – that we would not – that the Administration would not seek any further defense cooperation treaties. So any decision to reverse that will have to leave – be left to my successor.
QUESTION: All right.
ASSISTANT SECRETARY SHAPIRO: Okay.
QUESTION: Thank you.
OPERATOR: And our next question comes from Larry Shaughnessy from CNN.
QUESTION: Hello. This is Larry. My question is about the Secretary’s comments earlier this week alleging Russia is selling armed attack helicopters to Syria. How does the Department answer the Russian insistence that the U.S. is supplying crowd control weapons to places like Bahrain, and how do these issues differ?
ASSISTANT SECRETARY SHAPIRO: Well, I don’t have a lot to add to Toria’s response from yesterday where she – and today where she’s directly addressed this. But what I will say is it’s a totally specious comparison. Our – we have made clear that we’re not selling equipment to Bahrain now that can be used for internal security purposes until there is improvement on human rights; and whereas, as Secretary Clinton pointed out, the sales to Syria are directly implicated in attacking innocent people, innocent civilians. So we believe that that comparison does not hold water.
MR. TONER: Next question, please? And time for just a couple more, I think.
OPERATOR: Okay. And our next question comes from Adam Behsudi with Inside U.S. Trade.
QUESTION: Yes. Hi. I wanted to – you’d mentioned earlier that the goal on the export control reform would be to publish all the proposed rules this year and then final rules on a rolling basis. I mean, how many final categories or final rules for categories do you expect to be done this year, if any? And is there an effort to get more of that done based on the fact that it’s an election year, and maybe if there’s a change in administration this won’t be picked up as well by the next White House?
And then finally, what does the – in terms of Congressional pushback on wanting more notification on some of the categories that – on the items that are moving from one category to another, I mean, what is State Department doing in terms of working with Congress on their – on the 38 – Section 38(f) notification process?
ASSISTANT SECRETARY SHAPIRO: In response to your question, I’m not going to give you a precise estimate of how many will be published, because we do want to consult with Congress. And this will be a dialogue with Congress, and we want to make sure we have – take their concerns into account as we’re going through this system. And we intend to have robust consultations with Congress before we issue 38(f) notifications.
In terms of the timing, my view is by January of next year we’ll either be done or we’ll be so close to the goal line that it’ll just be up to the next administration to dive over the goal line and do a touchdown dance.
MR. TONER: Great, thank you. And I think it’s going to have to be our last question, unfortunately.
OPERATOR: And our last question comes from Jim Berger with Washington Trade Daily.
QUESTION: Yeah. Thank you. I guess – I don’t know – I don’t think you answered the second part of the previous question, but have you worked out a system with Congress on notifying as the products move from the Munitions List to the CCL? As I understand it, it’s such a large number, it’s very impractical to do it one by one.
ASSISTANT SECRETARY SHAPRIO: We’ve discussed – we are having discussion with Congress on each of the categories as they come up. And our goal, as I mentioned, is to have robust consultations with Congress. And we intend to follow the law regarding Congressional notification. And so we will provide the requisite notification for any of these changes to the United States Munitions List or Commerce Control List.
But this is – again, this is an iterative process. We are having discussions with Congress on a continuing basis about how best to provide them the information they need and solicit their input.
QUESTION: Thank you.
MR. TONER: Well, thank you all for joining us. And thanks certainly to Assistant Secretary Shapiro. Hope it was informative, and have a great afternoon.
PRN: 2012/990
TOP-SECRET – Former NYPD Officer Sentenced to 57 Months for Extortion and Criminal Civil Rights Violation
Earlier today, former New York City Police Officer Michael Daragjati was sentenced to nine months of imprisonment for violating the civil rights of an African-American man by falsely charging him with a crime, and a consecutive sentence of 48 months for threatening and assaulting another man whom Daragjati thought had stolen his snowplow equipment. The sentencing proceeding took place before United States District Judge William F. Kuntz, II.
The sentence was announced by Loretta E. Lynch, United States Attorney for the Eastern District of New York; Janice K. Fedarcyk, Assistant Director in Charge, Federal Bureau of Investigation, New York Field Office; and Raymond W. Kelly, Commissioner, New York City Police Department.
Daragjati was arrested on October 17, 2011 and has remained in custody since then. On January 24, 2012, Daragjati pleaded guilty to extortion and willfully violating the civil rights of the African-American victim.
As detailed in the sentencing letter filed by the government on June 20, 2012, on April 15, 2011, Daragjati falsely arrested an African-American man in Staten Island and fabricated charges against him, keeping the victim in jail for nearly two days. Soon after the incident, Daragjati was recorded telling a friend on the telephone that he had just “fried another n——-.” As also detailed in the government’s sentencing letter, on March 4, 2011, Daragjati and a group of associates assaulted and threatened a man in Staten Island in retaliation for the victim allegedly stealing Daragjati’s snowplow equipment. Daragjati later threatened to commit further acts of violence against the second victim if he went to the authorities.
“The sentence imposed today reflects the seriousness of the crimes committed by a former police officer—false arrest and imprisonment motivated by racial animus and engaging in vigilante justice. Crimes such as these erode the public’s confidence in our system of justice and will be met by the full resources of this office,” stated United States Attorney Lynch. Ms. Lynch expressed her grateful appreciation to the FBI and the NYPD Internal Affairs Bureau, the agencies responsible for leading the government’s investigation, and thanked the Richmond County District Attorney’s Office for its assistance.
The government’s case is being prosecuted by Assistant United States Attorney Paul Tuchmann.
Name Rank Serial Killer – Full Movie
FEMEN – Ukrainian Activists Go Topless In Prostitution Protest
TOP-SECRET from the NSA – Update: The Guatemalan Death Squad Diary and the Right to Truth
Washington, D.C., June 24, 2012 – On April 25, 2012, Kate Doyle, senior analyst and director of the Guatemala Documentation Project at the National Security Archive, provided expert witness testimony before the Inter-American Court of Human Rights in the case of the Diario Militar (Case 12.590, Gudiel Álvarez et al. (Diario Militar) vs. Guatemala) during the Court’s 45th Extraordinary Session held in Guayaquil, Ecuador. Doyle’s prepared testimony was followed by questioning by the Petitioners’ legal representatives, and nearly 45 minutes of questioning by the seven judges. The representatives for the State chose to not ask questions.
The following text is an excerpt of Doyle’s testimony. Slides referenced in testimony can be found in a copy of the power point presentation (9.08 MB).
25 April 2012
Guayaquil, Ecuador
To begin, the State of Guatemala has systematically hidden the information in its power about the internal armed conflict. The Guatemalan Army, the Police and the intelligence services are intrinsically opaque, secretive and closed institutions, and it has been almost impossible to gain access to their records. This policy of silence has survived the peace accords; it has survived the Historical Clarification Commission; and it continues today – despite the discovery of archives, the exhumations of clandestine cemeteries, the criminal convictions of perpetrators of human rights violations, and the unceasing demand for information by families of the disappeared.
In the 1980s, the State’s counterinsurgency strategy to kidnap, secretly detain, torture and execute men and women because of their political activities mobilized family members desperate to learn of the whereabouts of their loved ones. [SLIDE 1] They not only searched in hospitals, jails, cemeteries and morgues; they also directly confronted military officials and the chief of State. But the response was always the same: silence, ridicule, threats or worse.
That was also the experience of the Historical Clarification Commission (Comisión para el Esclarecimiento Histórico-CEH), [SLIDE 2], which from its earliest days tried to obtain information from State security agencies, but without success. I worked in collaboration with the commissioners and was witness to their frustration before the government’s repeated refusals to provide access to their archives. It had such an impact that in the final (twelfth) volume of their report the CEH reproduced dozens of letters between the three commissioners and the high command of the security institutions; letters that capture their exasperation in trying to obtain documents. [SLIDE 3] The letters also capture the implacable response of the authorities: No. There were no documents, documents did not exist, they had been destroyed, they had been lost, or they remained under the seal of national security.
During the very same week in which the CEH report was made public, in February 1999, the Military Logbook appeared. [SLIDE 4] The document was turned over to me and I made it public three months later in a press conference in Washington. It was exactly the kind of information sought repeatedly by the CEH, without success.
It was not until four years later that the first records of the Guatemalan Army emerged, with the dismantling of the Presidential General Staff ( Estado Mayor Presidencial-EMP) in 2003. It was a purged and fragmentary collection, and only recovered through the efforts of non-governmental organizations that insisted on copying them. Later the Human Rights Ombudsman (Procurador de Derechos Humanos-PDH) asked my organization to create a data base of the documents in order to facilitate access to them, but as far as I know there is still no public access to the database or the documents themselves.
We had our first real glimpse inside the State security apparatus during the conflict when the archives of the National Police were discovered in 2005. In fact employees of the PDH found them by accident during a visit to a police base in Guatemala City. [SLIDE 5] The accumulation of millions of pages of records was in a condition of extreme deterioration and abandon, hidden inside poorly maintained storage spaces. But after years of work to rescue, clean, organize and scan the documents, the archive is now fully accessible to the Guatemalan public without limit or restriction.
The Historical Archive of the National Police (Archivo Histórico de la Policía Nacional-AHPN) represents the entire documentary history generated by the National Police during more than 100 years. It contains an estimated eight linear kilometers of paper, videos, audiotapes, photographs, license plates, books and the ephemera of the revolutionary groups. Within the collection is every type of documentation: military and police plans for counterinsurgency operations [SLIDE 6], orders from the Director, political files on individuals [SLIDE 7], surveillance reports, interrogation transcripts [SLIDE 8], habeas corpus requests, telegrams, daily reports, circulars – many with the names and signatures of the officers in charge [SLIDE 9]. In short, it represents all of the paper necessary in order to make possible the flow of communications among the different National Police corps, and between the Police and other entities of the State, including the chief of State and the Army. To date, 2,530 documents have been found inside the AHPN with a direct relation to the captures registered in the Military Logbook.
Before the discovery of the archives, neither the families of the disappeared nor the CEH received a single page of these documents, despite their petitions to the State.
Today the Guatemalan Army’s policy of access regarding its own records continues to be a policy of denial. In 2009, the Defense Ministry responded to a judicial order that required it to produce four military documents as evidence in the genocide case, but it turned over only one complete record. The Ministry alleged that the others – including a key set of records relating to the 1982 counterinsurgency sweep called “Operation Sofía” – did not exist in its archives [SLIDE 10].
One month later, a person who requested anonymity gave me a package that contained the Operation Sofía documents, which I subsequently turned over to the Guatemalan Public Ministry. And that is how, in a national judicial process concerning crimes against humanity initiated in 2001, the petitioners did receive a Guatemalan document containing critical evidence – not from the institutions of the State that created it, but through my organization, a non-governmental group based in the United States.
Most recently, the Army responded to society’s demand for truth by opening a collection of “military archives” in June 2011. I have studied the archive – an unnecessarily difficult task, due to the lack of any index or guide – and I see no relevance in the documents to the study of the armed conflict. It is an apparently arbitrary collection, without any evident or transparent logic to its declassification, which contains thousands of pages of trivial and useless records that do not serve human rights investigators. Furthermore, according to the Ministry of Defense, there are no declassified records in the archive covering the most repressive period of the internal conflict, 1980-85.
The Army’s posture – and the legacy of silence about historic repression on the part of the State – has left survivors of the conflict and the family members of victims with less than nothing, with expectations raised by a peace process that to date has not resulted with the fundamental information they require: What happened and why? Who is responsible? And where are the disappeared?
Thank you.
Watch the recording of the Diario Militar hearing in three parts here, (in Spanish):
Playing With Fire – Full Movie
Unveiled – Euro 2012 Prostitution Focus in Ukraine
SECRET from Cryptome – Prez Orders Broadband Expansion Speed-Up
[Federal Register Volume 77, Number 119 (Wednesday, June 20, 2012)] [Presidential Documents] [Pages 36903-36906] From the Federal Register Online via the Government Printing Office [www.gpo.gov] [FR Doc No: 2012-15183] Presidential Documents Federal Register / Vol. 77, No. 119 / Wednesday, June 20, 2012 / Presidential Documents [[Page 36903]] Executive Order 13616 of June 14, 2012 Accelerating Broadband Infrastructure Deployment By the authority vested in me as President by the Constitution and the laws of the United States of America, including section 301 of title 3, United States Code, and in order to facilitate broadband deployment on Federal lands, buildings, and rights of way, federally assisted highways, and tribal and individual Indian trust lands (tribal lands), particularly in underserved communities, it is hereby ordered as follows: Section 1. Policy. Broadband access is essential to the Nation's global competitiveness in the 21st century, driving job creation, promoting innovation, and expanding markets for American businesses. Broadband access also affords public safety agencies the opportunity for greater levels of effectiveness and interoperability. While broadband infrastructure has been deployed in a vast majority of communities across the country, today too many areas still lack adequate access to this crucial resource. For these areas, decisions on access to Federal property and rights of way can be essential to the deployment of both wired and wireless broadband infrastructure. The Federal Government controls nearly 30 percent of all land in the United States, owns thousands of buildings, and provides substantial funding for State and local transportation infrastructure, creating significant opportunities for executive departments and agencies (agencies) to help expand broadband infrastructure. Sec. 2. Broadband Deployment on Federal Property Working Group. (a) In order to ensure a coordinated and consistent approach in implementing agency procedures, requirements, and policies related to access to Federal lands, buildings, and rights of way, federally assisted highways, and tribal lands to advance broadband deployment, there is established a Broadband Deployment on Federal Property Working Group (Working Group), to be co-chaired by representatives designated by the Administrator of General Services and the Secretary of Homeland Security (Co-Chairs) from their respective agencies, in consultation with the Director of the Office of Science and Technology Policy (Director) and in coordination with the Chief Performance Officer (CPO). (b) The Working Group shall be composed of: (i) a representative from each of the following agencies, and the Co- Chairs, all of which have significant ownership of, or responsibility for managing, Federal lands, buildings, and rights of way, federally assisted highways, and tribal lands (Broadband Member Agencies): (1) the Department of Defense; (2) the Department of the Interior; (3) the Department of Agriculture; (4) the Department of Commerce; (5) the Department of Transportation; (6) the Department of Veterans Affairs; and (7) the United States Postal Service; (ii) a representative from each of the following agencies or offices, to provide advice and assistance: [[Page 36904]] (1) the Federal Communications Commission; (2) the Council on Environmental Quality; (3) the Advisory Council on Historic Preservation; and (4) the National Security Staff; and (iii) representatives from such other agencies or offices as the Co-Chairs may invite to participate. (c) Within 1 year of the date of this order, the Working Group shall report to the Steering Committee on Federal Infrastructure Permitting and Review Process Improvement, established pursuant to Executive Order 13604 of March 22, 2012 (Improving Performance of Federal Permitting and Review of Infrastructure Projects), on the progress that has been made in implementing the actions mandated by sections 3 through 5 of this order. Sec. 3. Coordinating Consistent and Efficient Federal Broadband Procedures, Requirements, and Policies. (a) Each Broadband Member Agency, following coordination with other Broadband Member Agencies and interested non-member agencies, shall: (i) develop and implement a strategy to facilitate the timely and efficient deployment of broadband facilities on Federal lands, buildings, and rights of way, federally assisted highways, and tribal lands, that: (1) ensures a consistent approach across the Federal Government that facilitates broadband deployment processes and decisions, including by: avoiding duplicative reviews; coordinating review processes; providing clear notice of all application and other requirements; ensuring consistent interpretation and application of all procedures, requirements, and policies; supporting decisions on deployment of broadband service to those living on tribal lands consistent with existing statutes, treaties, and trust responsibilities; and ensuring the public availability of current information on these matters; (2) where beneficial and appropriate, includes procedures for coordination with State, local, and tribal governments, and other appropriate entities; (3) is coordinated with appropriate external stakeholders, as determined by each Broadband Member Agency, prior to implementation; and (4) is provided to the Co-Chairs within 180 days of the date of this order; and (ii) provide comprehensive and current information on accessing Federal lands, buildings, and rights of way, federally assisted highways, and tribal lands for the deployment of broadband facilities, and develop strategies to increase the usefulness and accessibility of this information, including ensuring such information is available online and in a format that is compatible with appropriate Government websites, such as the Federal Infrastructure Projects Dashboard created pursuant to my memorandum of August 31, 2011 (Speeding Infrastructure Development Through More Efficient and Effective Permitting and Environmental Review). (b) The activities conducted pursuant to subsection (a) of this section, particularly with respect to the establishment of timelines for permitting and review processes, shall be consistent with Executive Order 13604 and with the Federal Plan and Agency Plans to be developed pursuant to that order. (c) The Co-Chairs, in consultation with the Director and in coordination with the CPO, shall coordinate, review, and monitor the development and implementation of the strategies required by paragraph (a)(i) of this section. (d) Broadband Member Agencies may limit the information made available pursuant to paragraph (a)(ii) of this section as appropriate to accommodate national security, public safety, and privacy concerns. Sec. 4. Contracts, Applications, and Permits. (a) Section 6409 of the Middle Class Tax Relief and Job Creation Act of 2012 (Public Law 112-96) contains provisions addressing access to Federal property for the deployment of wireless broadband facilities, including requirements that the General Services [[Page 36905]] Administration (GSA) develop application forms, master contracts, and fees for such access. The GSA shall consult with the Working Group in developing these application forms, master contracts, and fees. (b) To the extent not already addressed by section 6409, each Broadband Member Agency with responsibility for managing Federal lands, buildings, or rights of way (as determined by the Co-Chairs) shall, in coordination with the Working Group and within 1 year of the date of this order, develop and use one or more templates for uniform contract, application, and permit terms to facilitate nongovernment entities' use of Federal property for the deployment of broadband facilities. The templates shall, where appropriate, allow for access by multiple broadband service providers and public safety entities. To ensure a consistent approach across the Federal Government and different broadband technologies, the templates shall, to the extent practicable and efficient, provide equal access to Federal property for the deployment of wireline and wireless facilities. Sec. 5. Deployment of Conduit for Broadband Facilities in Conjunction with Federal or Federally Assisted Highway Construction. (a) The installation of underground fiber conduit along highway and roadway rights of way can improve traffic flow and safety through implementation of intelligent transportation systems (ITS) and reduce the cost of future broadband deployment. Accordingly, within 1 year of the date of this order: (i) the Department of Transportation, in consultation with the Working Group, shall review dig once requirements in its existing programs and implement a flexible set of best practices that can accommodate changes in broadband technology and minimize excavations consistent with competitive broadband deployment; (ii) the Department of Transportation shall work with State and local governments to help them develop and implement best practices on such matters as establishing dig once requirements, effectively using private investment in State ITS infrastructure, determining fair market value for rights of way on federally assisted highways, and reestablishing any highway assets disturbed by installation; (iii) the Department of the Interior and other Broadband Member Agencies with responsibility for federally owned highways and rights of way on tribal lands (as determined by the Co-Chairs) shall revise their procedures, requirements, and policies to include the use of dig once requirements and similar policies to encourage the deployment of broadband infrastructure in conjunction with Federal highway construction, as well as to provide for the reestablishment of any highway assets disturbed by installation; (iv) the Department of Transportation, after outreach to relevant nonfederal stakeholders, shall review and, if necessary, revise its guidance to State departments of transportation on allowing for-profit or other entities to accommodate or construct, safely and securely maintain, and utilize broadband facilities on State and locally owned rights of way in order to reflect changes in broadband technologies and markets and to promote competitive broadband infrastructure deployment; and (v) the Department of Transportation, in consultation with the Working Group and the American Association of State Highway and Transportation Officials, shall create an online platform that States and counties may use to aggregate and make publicly available their rights of way laws and joint occupancy guidelines and agreements. (b) For the purposes of this section, the term ``dig once requirements'' means requirements designed to reduce the number and scale of repeated excavations for the installation and maintenance of broadband facilities in rights of way. Sec. 6. General Provisions. (a) This order shall be implemented consistent with all applicable laws, treaties, and trust obligations, and subject to the availability of appropriations. [[Page 36906]] (b) Nothing in this order shall be construed to impair or otherwise affect: (i) the authority granted by law to an executive department, agency, or the head thereof; or (ii) the functions of the Director of the Office of Management and Budget relating to budgetary, administrative, or legislative proposals. (c) Independent agencies are strongly encouraged to comply with this order. (d) This order is not intended to, and does not, create any right or benefit, substantive or procedural, enforceable at law or in equity by any party against the United States, its departments, agencies, or entities, its officers, employees, or agents, or any other person. (Presidential Sig.) THE WHITE HOUSE, Washington, June 14, 2012. [FR Doc. 2012-15183 Filed 6-19-12; 8:45 am] Billing code 3295-F2-P
TOP-SECRET – DHS-FBI Bulletin: Terrorist Interest in Attacking Theaters and Mass Gatherings

(U//FOUO) An early April 2012 suicide bombing of a theater in Somalia and a violent extremist communication advocating attacks on US theaters highlight terrorists’ continued interest in attacking such venues. Although we have no specific or credible information indicating that terrorists plan to attack theaters in the United States, terrorists may seek to emulate overseas attacks on theaters here in the United States because they have the potential to inflict mass casualties and cause local economic damage.
— (U//FOUO) On 4 April 2012, an al-Shabaab female suicide bomber detonated explosives at the National Theater in Mogadishu, Somalia during a speech by the Somali Prime Minister attended by multiple cabinet members. The bomber blended in with the audience until her attack, which targeted the VIPs in attendance.
— (U//FOUO) On 7 April 2012, an al-Qa‘ida-linked violent extremist urged others to emulate the 2002 Moscow theater hostage attack—in which Chechen terrorists seized the Dubrovka Theater and held over 800 people captive for three days until Russian security forces gassed the theater—by seizing crowded facilities in the United States, including movie theaters; taking hostages; and demanding the release of captured al-Qa‘ida-linked or -inspired violent extremists.
(U//FOUO) These recent instances demonstrate that mass gatherings such as those associated with theaters likely remain attractive terrorist targets. We encourage facility owners and operators, security personnel, and first responders to remain vigilant and report suspicious activities and behaviors that may indicate a potential attack.
(U//FOUO) Potential Suspicious Activity Indicators
— (U//FOUO) Persons in crowded areas wearing clothing that is unusually bulky or atypical for the season, possibly to conceal suicide explosives or weapons.
— (U//FOUO) Persons asking about theater security screening and evacuation procedures.
— (U//FOUO) Packages—possibly containing explosives—left unattended in open areas or hidden in trash receptacles, lockers, or similar containers.
— (U//FOUO) Suspicious or illegally parked vehicles near a theater or where crowds gather prior to or following performances and events.
Megapark 2012 – Sexy Russian Football Girls posing for C-Cup – Fussball EM – UEFA EURO 2012
TOP-SECRET from Cryptome – Julian Assange Casa Ecuador Embassy London
Julian Assange Casa Ecuador Embassy London
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict22.jpg)
A woman poses for a candid photograph alongside a protester wearing a Guy Fawkes mask and holding a sign reading ‘I’m Julian’ as he demonstrates outside the Ecuadorian embassy in London, on June 23, 2012, where Wikileaks founder Julian Assange is seeking political asylum. Ecuador today recalled its ambassador to Britain to discuss what to do about WikiLeaks founder Julian Assange, who has sought refuge in their diplomatic mission in London. Assange, an Australian national, sought refuge in the Ecuadoran embassy on June 19 and asked Quito to give him asylum as he seeks to avoid extradition to Sweden on allegations of rape, fearing Stockholm will turn him over to the United States. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict23.jpg)
Women walk past protest placards outside the Ecuadorian embassy in London, on June 23, 2012, where supporters of Wikileaks founder Julian Assange gathered to demonstrate. Ecuador today recalled its ambassador to Britain to discuss what to do about WikiLeaks founder Julian Assange, who has sought refuge in their diplomatic mission in London. Assange, an Australian national, sought refuge in the Ecuadoran embassy on June 19 and asked Quito to give him asylum as he seeks to avoid extradition to Sweden on allegations of rape, fearing Stockholm will turn him over to the United States. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict25.jpg)
Photographers take pictures of protesters showing their support for Julian Assange outside the Ecuadorian embassy on June 22, 2012 in London, England. Julian Assange, the founder of the WikiLeaks whistle-blowing website, has sought refuge in Ecuador’s London embassy to prevent him from being extradited to Sweden on allegations of rape and assault. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict26.jpg)
Protesters show their support for Julian Assange outside the Ecuadorian embassy on June 22, 2012 in London, England. Julian Assange, the founder of the WikiLeaks whistle-blowing website, has sought refuge in Ecuador’s London embassy to prevent him from being extradited to Sweden on allegations of rape and assault. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict27.jpg)
A British police officer stands guard outside the Ecuadorian Embassy, in London, Friday, June 22, 2012. WikiLeaks founder Julian Assange entered the embassy on Monday in an attempt to gain political asylum to prevent him from being extradited to Sweden to face allegations of sex crimes, which he denies. In a telephone interview with the Australian Broadcasting Corporation (ABC) from inside the embassy, the 40-year-old Australian said he did not know when the decision about his plea for asylum would be made. AP
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict24.jpg)
A man reads a book in front of a demonstration outside the Ecuadorian embassy in London, on June 22, 2012, where Wikileaks founder Julian Assange is seeking political asylum. President Rafael Correa said Ecuador would discuss WikiLeaks founder Julian Assange’s bid for asylum with other countries and did not want to ‘offend anyone,’ including Britain. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict21.jpg)
Sarah Saunders, a personal friend and contributor toward the bail of WikiLeaks founder Julian Assange, speaks to the media outside the Ecuadorian embassy in central London on June 21, 2012, where Assange is still holed up seeking political asylum. Assange will remain inside Ecuador’s embassy in London until his case is resolved, in a process that could take ‘hours or days’, a spokesman for the whistleblower website said June 21. Assange, 40, turned up in the embassy on June 19 and sought asylum in a dramatic bid to avoid extradition to Sweden over allegations of rape and sexual assault. Getty [Assange was reportedly housed most recently at the rural home of Sarah Saunders, a successful caterer.]
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/assange-ambassador.jpg)
Ecuadorian ambassador to London Ana Alban gets out of a car as she arrives at the embassy in central London on June 21, 2012 where Wikileaks founder Julian Assange is holed up while Ecuador consider his application for asylum. Ecuador’s president said Thursday his government would take its time in deciding whether to grant asylum to Julian Assange as the WikiLeaks founder spent a second night at its embassy in London. The 40-year-old Australian sparked a stand-off with British police after he turned up in the embassy on June 19 and asked for asylum in a dramatic bid to avoid extradition to Sweden over allegations of rape and sexual assault. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict18.jpg)
Police stand guard outside the Ecuadorian Embassy, London, Wednesday June 20, 2012. WikiLeaks chief Julian Assange has made a run for the Ecuadorean Embassy in London, seeking asylum in a long shot move that, if successful, would place him in a small, friendly South American country rather than in Sweden facing questioning about alleged sex crimes. Tuesday’s unexpected caper has added a new and bizarre twist to Assange’s increasingly desperate bid to avoid extradition to Scandinavia. AP
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict19.jpg)
Police patrol outside the Ecuadorian Embassy, London, Wednesday June 20, 2012. WikiLeaks chief Julian Assange has made a run for the Ecuadorean Embassy in London, seeking asylum in a long shot move that, if successful, would place him in a small, friendly South American country rather than in Sweden facing questioning about alleged sex crimes.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict20.jpg)
Police officers stand outside Ecuador’s embassy in London June 20, 2012. WikiLeaks’ founder Julian Assange has taken refuge in Ecuador’s embassy in London and asked for asylum, officials said on Tuesday, in a last-ditch bid to avoid extradition to Sweden over sex crime accusations. AP
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict17.jpg)
Police officers stand outside the Ecuadorian embassy in London Wednesday June 20, 2012 where the Wikileaks founder Julian Assange is seeking political asylum. Assange has made a run for the Ecuadorean Embassy in London, seeking asylum in a long shot move that, if successful, would place him in a small, friendly South American country rather than in Sweden facing questioning about alleged sex crimes. Tuesday’s unexpected caper has added a new and bizarre twist to Assange’s increasingly desperate bid to avoid extradition to Scandinavia. Reuters
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict13.jpg)
Supporters of WikiLeaks Founder Julian Assange gather outside Ecuador’s Embassy in central London June 20, 2012. Assange has taken refuge in Ecuador’s embassy in London and asked for asylum, officials said on Tuesday, in a last-ditch bid to avoid extradition to Sweden over sex crime accusations. Reuters
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict14.jpg)
Television crews and journalists gather outside the Ecuadorian Embassy (Background) in central London, on June 20, 2012, where Wikileaks founder Julian Assange is seeking political asylum as he fights extradition to Sweden over alleged sex crimes. Assange, who has sought political asylum inside the Ecuadorian embassy in London, has breached bail conditions and is subject to arrest, British police said Wednesday. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict15.jpg)
Supporters of Wikileaks founder Julian Assange rally with placards outside Ecuador’s embassy in central London on June 20, 2012, where Assange is seeking political asylum as he fights extradition to Sweden over alleged sex crimes. Assange, who last week exhausted all his legal options in Britain, walked into the embassy on June 19 and applied for political asylum, as time ran out in his marathon legal battle to avoid being sent to Sweden. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict16.jpg)
Demonstrators protest outside the Ecuadorian consulate on June 20, 2012 in London, England. Wikileaks Founder Julian Assange has sought asylum at the Ecuadorian embassy in Knightsbridge as he continues to fight against his possible extradition to Sweden over alleged sex crimes. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict2.jpg)
Ecuador’s Minister of Foreign Affairs Ricardo Patino (C), Vice Minister of Foreign Affairs Marco Albuja (R) and Undersecretary for North America and Europe, Paul Villagomez attend a news conference regarding WikiLeaks’ founder Julian Assange in Quito June 19, 2012. Assange is seeking asylum in Ecuador after arriving at the South American nation’s embassy in London, Ecuador’s foreign minister said on Tuesday, a move that may help the self-styled anti-secrecy crusader avoid extradition to Sweden. Reuters
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict3.jpg)
Members of the media gather outside Ecuador’s embassy where Wikileaks founder Julian Assange has sought political asylum, in London June 19, 2012. Assange is seeking asylum in Ecuador after arriving at the South American nation’s embassy in London, Ecuador’s foreign minister said on Tuesday, a move that may help the self-styled anti-secrecy crusader avoid extradition to Sweden. Reuters
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict4.jpg)
Members of the media gather outside Ecuador’s embassy where WikiLeaks founder Julian Assange has sought political asylum, in London June 19, 2012. Assange is seeking asylum in Ecuador after arriving at the South American nation’s embassy in London, Ecuador’s foreign minister said on Tuesday, a move that may help the self-styled anti-secrecy crusader avoid extradition to Sweden. Reuters
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict0.jpg)
A police officer gestures outside Ecuador’s embassy where WikiLeaks founder Julian Assange has sought political asylum, in London June 19, 2012. Assange is seeking asylum in Ecuador after arriving at the South American nation’s embassy in London, Ecuador’s foreign minister said on Tuesday, a move that may help the self-styled anti-secrecy crusader avoid extradition to Sweden. Reuters
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict1.jpg)
A police officer leaves Ecuador’s embassy where WikiLeaks founder Julian Assange has sought political asylum, in London June 19, 2012. Assange is seeking asylum in Ecuador after arriving at the South American nation’s embassy in London, Ecuador’s foreign minister said on Tuesday, a move that may help the self-styled anti-secrecy crusader avoid extradition to Sweden. Reuters
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict5.jpg)
Police officers stand outside Ecuador’s embassy where WikiLeaks founder Julian Assange has sought political asylum, in London June 19, 2012. Assange is seeking asylum in Ecuador after arriving at the South American nation’s embassy in London, Ecuador’s foreign minister said on Tuesday, a move that may help the self-styled anti-secrecy crusader avoid extradition to Sweden. Reuters
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict6.jpg)
Two men walk out of the Embassy of Ecuador in London, carrying legal books about diplomatic law , in London Tuesday, June 19, 2012. Embattled WikiLeaks chief Julian Assange took refuge Tuesday in Ecuador s embassy in London and is seeking political asylum, his organization and the South American nation s foreign minister said. Foreign Minister Ricardo Patino said the leftist government of President Rafael Correa was weighing the request. He did not indicate when a decision might be made. AP
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict7.jpg)
A general view of the Embassy of Ecuador in London Tuesday, June 19, 2012. Embattled WikiLeaks chief Julian Assange took refuge Tuesday in Ecuador s embassy in London and is seeking political asylum, his organization and the South American nation s foreign minister said. Foreign Minister Ricardo Patino said the leftist government of President Rafael Correa was weighing the request. He did not indicate when a decision might be made. AP
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict8.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict9.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict11.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict12.jpg)
FEMEN – Euro 2012 Prostitution
TOP-SECRET – Open Source Center Master Narratives Report: Muslim Communities of France

Understanding master narratives can be the difference between analytic anticipation and unwanted surprise, as well as the difference between communications successes and messaging gaffes. Master narratives are the historically grounded stories that reflect a community’s identity and experiences, or explain its hopes, aspirations, and concerns. These narratives help groups understand who they are and where they come from, and how to make sense of unfolding developments around them. As they do in all countries, effective communicators in France speaking to Muslim communities invoke master narratives in order to move audiences in a preferred direction. French influencers rely on their native familiarity with these master narratives to use them effectively. This task is considerably more challenging for US communicators and analysts because they must place themselves in the mindset of foreign audiences who believe stories that — from an American vantage point — may appear surprising, conspiratorial, or even outlandish.
This report serves as a resource for addressing this challenge in two ways. First, it surfaces a set of nine master narratives carefully selected based on their potency in the context of France’s Muslim communities, and their relevance to US strategic interests. Second, this report follows a consistent structure for articulating these narratives and explicitly identifies initial implications for US communicators and analysts. The set outlined here is not exhaustive: these nine master narratives represent a first step that communicators and analysts can efficiently apply to the specific messaging need or analytic question at hand. For seasoned experts on French Muslim communities, these narratives will already be familiar — the content contained in this report can be used to help check assumptions, surface tacit knowledge, and aid customer communications. For newcomers to European Islam accounts, these narratives offer deep insights into the stories and perceptions that shape French Muslim identity and worldviews that may otherwise take years to accumulate.
Some master narratives cut across broad stretches of the French Muslim populace, while others are held only by particular audience sub-segments. This study divides France’s Muslim communities into eight audience sub-segments that demonstrate how different master narratives resonate with different sections of the populace. Each of the nine master narratives aligns with one or more of the following segments: Cultural Muslims, Personal Practitioners, Civic Islamists, Wealthy Secularists, Old Guard, Strict Practitioners, Young Banlieuesards, and Indigènes (see the Appendix for a detailed description of these audience segments).
…
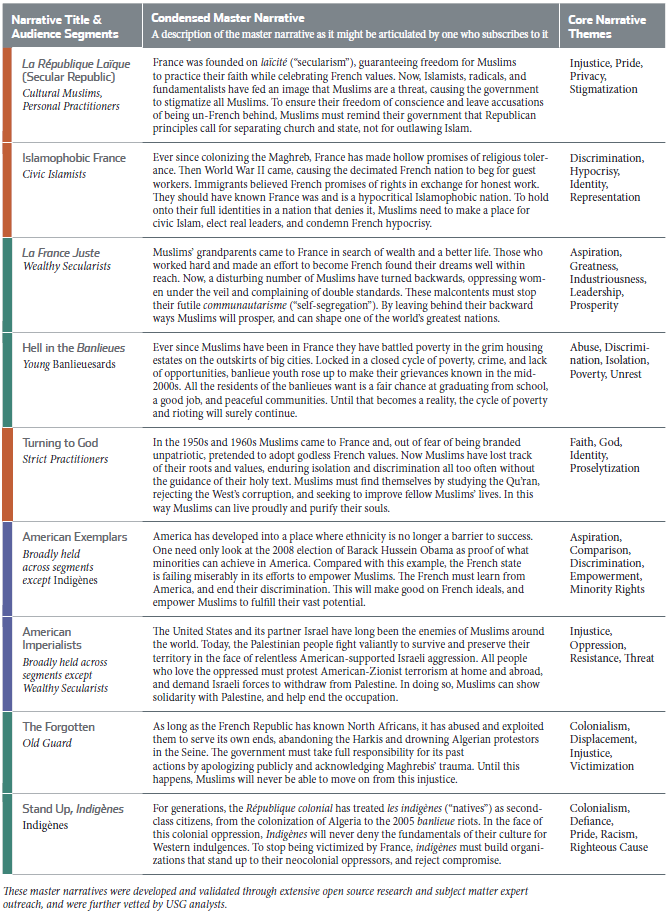
DOWNLOAD THE ORIGINAL DOCUMENT HERE
SECRET – FBI Releases 2011 Bank Crime Statistics
Today, the FBI released bank crime statistics for calendar year 2011. Between January 1, 2011 and December 31, 2011, there were 5,014 robberies, 60 burglaries, 12 larcenies, and seven extortions of financial institutions1 reported to law enforcement. The total 5,093 reported violations represent a decrease from 2010, during which 5,641 violations of the Federal Bank Robbery and Incidental Crimes Statute were reported.
Highlights of the report include:
- Of the 5,086 total reported bank robberies, burglaries, and larcenies, loot was taken in 4,534 incidents (89 percent). Loot was taken during two of the seven reported bank extortions.
- The total amount taken was valued at more than $38 million. More than $8 million was recovered and returned to financial institutions.
- During the reported bank robberies, burglaries, and larcenies, the following modus operandi were the most common: demand note (2,958 incidents); oral demand (2,678 incidents); weapon threatened (2,331 incidents); and firearm used (1,242 incidents). Of the seven reported extortions, perpetrators used or threatened the use of explosive devices during one incident and made threats by telephone during four incidents.2
- Acts of violence were committed during 201 of the reported robberies, burglaries, and larcenies. These acts included 70 instances involving the discharge of firearms, 116 instances involving assaults, and one instance involving an explosive device.3 No acts of violence occurred during the seven reported bank extortions.
- Acts of violence during the reported robberis, burglaries, and larcenies resulted in 88 injuries, 13 deaths, and 30 persons being taken hostage. No injuries, deaths, or hostage takings occurred during the reported bank extortions.
- Most violations occurred on Friday. Regardless of the day of the week, violations between the hours of 9:00 a.m. and 11:00 a.m. were the most common.
- Most violations occurred in the Southern region of the U.S., with 1,576 reported incidents.
These statistics were recorded as of April 24, 2012. Note that not all bank crimes are reported to the FBI, and therefore the report is not a complete statistical compilation of all bank crimes that occurred in the United States.
1 Financial institutions include commercial banks, mutual savings banks, savings and loan associations, and credit unions.
2 More than one modus operandi may have been used during an incident
3 One or more acts of violence may occur during an incident.
Chasing the Barefoot Bandit – Full Movie
TOP-SECRET – Open Source Center Master Narratives Country Report: Somalia

Understanding master narratives can be the difference between analytic anticipation and unwanted surprise, as well as the difference between communications successes and messaging gaffes. Master narratives are the historically grounded stories that reflect a community’s identity and experiences, or explain its hopes, aspirations, and concerns. These narratives help groups understand who they are and where they come from, and how to make sense of unfolding developments around them. As they do in all countries, effective communicators in Somalia invoke master narratives in order to move audiences in a preferred direction. Somali influencers rely on their native familiarity with these master narratives to use them effectively. This task is considerably more challenging for US communicators and analysts because they must place themselves in the mindset of foreign audiences who believe stories that — from an American vantage point — may appear surprising, conspiratorial, or even outlandish.
This report serves as a resource for addressing this challenge in two ways. First, it surfaces a set of eight master narratives carefully selected based on their potency in the Somali context and relevance to US strategic interests. Second, this report follows a consistent structure for articulating these narratives and explicitly identifies initial implications for US communicators and analysts. The set outlined here is not exhaustive: these eight master narratives represent a first step that communicators and analysts can efficiently apply to the specific messaging need or analytic question at hand. For seasoned Somali experts, these narratives will already be familiar — the content contained in this report can be used to help check assumptions, surface tacit knowledge, and aid customer communications. For newcomers to Somalia accounts, these narratives offer deep insights into the stories and perceptions that shape the Somali political context that may otherwise take years to accumulate.
Some master narratives cut across broad stretches of the Somali populace, while others are held only by particular audience segments. This study divides Somalia into six audience segments that demonstrate how different master narratives resonate with different sections of the populace. Each of the eight master narratives aligns with one or more of the following segments: Centralists, Regionalists, Somaliland Nationalists, Salafi Islamists, Sufi Islamists, and Moderate Islamists. (See the Appendix for a detailed description of these audience segments.) This audience segmentation is tailored specifically to surface important Somali master narratives and the interactions between them. Somali society is heavily influenced by longstanding clan structures, with some clan affiliations creating intractable intergroup conflict while other affiliations are more fluid in response to shifting political priorities. Some of the master narratives profiled in this report are deeply informed by clan dynamics, while others transcend clan allegiances altogether. Based on this, the audience segmentation is this report provides an additional lens for understanding competing and interconnected camps in Somali politics and society.
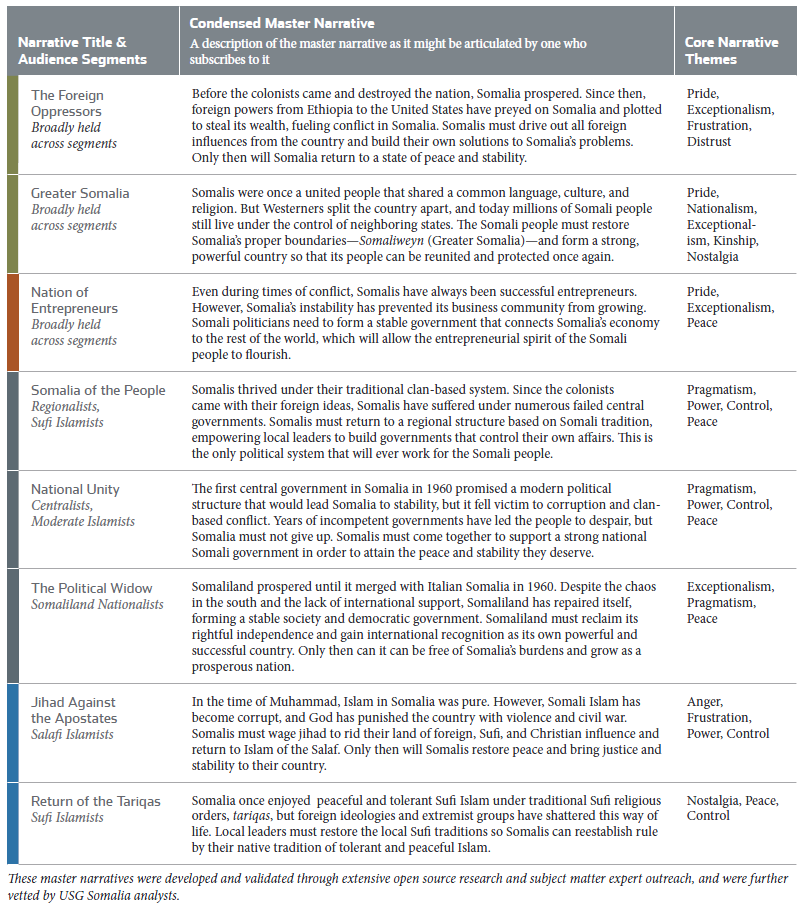
DOWNLOAD THE ORIGINAL DOCUMENT HERE
The FEMEN active in Poland – Uncensored
TOP-SECRET from the FBI – Texas Man Indicted for Threatening to Bomb Islamic Center in Murfreesboro
WASHINGTON—Javier Alan Correa, 24, of Corpus Christi, Texas, was indicted by a federal grand jury in Nashville, Tennesee, today and charged with violating the civil rights of members of a Murfreesboro, Tennessee mosque. Correa is charged in the Middle District of Tennessee with one count of intentionally obstructing by threat of force the free exercise of religious beliefs and one count of using an instrument of interstate commerce to communicate a threat to destroy a building by means of an explosive device. The indictment was announced today by Assistant Attorney General Thomas E. Perez for the Civil Rights Division; Jerry E. Martin, U.S. Attorney for the Middle District of Tennessee; and Aaron T. Ford, Special Agent in Charge of the Memphis Division of the FBI.
According to the indictment, on September 5, 2011, Correa called on a cell phone from Corpus Christi to the Islamic Center of Murfreesboro and left a threatening, explicative-ridden voice message saying, amongst other things, “On September 11, 2011, there’s going to be a bomb in the building.“
“The Department of Justice, the FBI, and our law enforcement partners intend to protect the rights afforded under the Constitution to all individuals, including the most basic right to exercise freedom of religious beliefs,” said Jerry E. Martin, U.S. Attorney of the Middle District of Tennessee. “The controversy and criminal activity surrounding the construction of this particular place of worship has impeded the ability of people to exercise that most basic right. We will continue to monitor the progress of construction and legal proceedings at the local level to insure these citizens are able to enjoy all basic liberties guaranteed under the Constitution.”
“The FBI is tasked with defending civil rights in the United States and takes very seriously its responsibilities to protect people of all religions from intimidation and violence,” said Aaron T. Ford, Special Agent in Charge of the Memphis Division of the FBI. “The FBI and our law enforcement partners pursued this investigation with great tenacity and will always strive to ensure those who attempt to take religious freedoms from others are brought to face justice.”
Correa faces a maximum penalty of 20 years for the count one and 10 years for count two of the indictment, as well as a fine of up to $250,000 for each offense.
This case was investigated by the FBI and is being prosecuted by Assistant U.S. Attorney Lee Deneke and Civil Rights Division Trial Attorney Adriana Vieco.
An indictment is merely an accusation. All persons are presumed innocent unless and until proven guilty and have the right to a trial, at which, the government must bear the burden of proof beyond a reasonable doubt.
Megapark 2012 – Micaela Schaefer | Fussball EM C-Cup | Mallorca GER-NED Deutschland Holland
The Shocking Truth – Nigel Farage: “Listen! The Whole Thing’s a Giant Ponzi Scheme!”
U.K. Independence Party Leader Nigel Farage on the causes of the financial crisis in Europe.
*You know an interview is gonna be good when it starts with Farage calling Barroso a deluded idiot and communist supporter of Mao.*
TOP-SECRET – Public Intelligence – ITU CWG-WCIT12 US Comments on Draft Proposals
The following document details comments of the U.S. delegation on a compilation of draft proposals for modifications to International Telecommunications Regulations (ITRs) under the International Telecommunication Union. The collection of draft proposals being commented on CWG-WCIT12 TEMPORARY DOCUMENT 36 (CWG-WCIT12/TD – 36) is also available.
| CWG-WCIT12 CONTRIBUTION 45 (CWG-WCIT12/C – 45) “U.S. comments on Temporary Document 36″ | 65 pages | August 24, 2011 | Download |
Der Mord an dem DDR-Reichsbahnminister durch die STASI und Mielke – Dokument
STASI DOKUMENT kann als PDF heruntergeladen werden
Megapark 2012 – Sexy Espania Backstage! Football Girls C-Cup | BH | Fussball EM
TOP-SECRET from the FBI – Another Assault Linked to Potomac River Rapist
he Metropolitan Police Department announced today that forensic evidence from a sexual assault that occurred on July 20, 1996 in the 4900 block of MacArthur Boulevard, NW has been linked to other sexual assaults and a murder committed by a single assailant who attacked women in the Washington, DC metropolitan area.
“We are asking for the public’s help in identifying and locating this violent offender who is responsible for numerous brutal attacks,” said Police Chief Cathy L. Lanier.
The Potomac River Rapist is wanted for a total of ten sexual assaults that occurred between May 1991 and August 1998, one of which resulted in a homicide in Washington, DC.
On August, 1, 1998, Christine Mirzayan, a 28-year-old intern, was sexually assaulted and murdered while walking to her residence in the Georgetown area. During the violent attack, she was struck multiple times in the head with a rock and her body was left yards from Canal Road. The other eight sexual assaults occurred in Montgomery County, Md.
“The 1996 assault in the 4900 block of MacArthur Boulevard, NW and the murder in 1998 occurred less than two miles apart – which could indicate that the offender may have ties to this area,” said Chief Lanier.
The case is being investigated by the Metropolitan Police Department, Montgomery County, Md., Police Department, and the FBI’s Washington Field Office with assistance from the U.S. Attorney’s Office for the District of Columbia.
In the 1996 assault, the subject is described as a black or black/Hispanic male, with a light to medium complexion and high, pronounced cheekbones.
Throughout the entire investigation, he has been described as being approximately 5’8” – 6’0” in height, with a muscular build, especially in his upper body. The individual was in his late 20s to early 30s at the time of the offenses. He was wearing a polo-type shirt and khaki pants, and has been described as neatly attired.
Most of the Maryland assaults followed a particular pattern. The assailant used a “blitz” attack by throwing a blanket or towel over the victim’s head. All of the sexual assault victims, with the exception of the Washington, DC attacks, were attacked in their homes or private residences. Both the DC sexual assault and murder victims were walking on sidewalks when they were pulled into wooded areas and sexually assaulted on a Saturday night.
The dates and locations of these assaults are:
|
Date |
Approximate Time |
Subdivision |
Location |
| Monday, May 6, 1991 | 8:00 p.m. – 11:00 p.m. | Washingtonian Woods | Gaithersburg, Md. |
| Thursday, Sept. 5, 1991 | 10:00 p.m. – 10:30p.m. | Watkins Meadows | Germantown, Md. |
| Thursday, Nov. 21, 1991 | 9:00 p.m. – 10:00 p.m. | Potomac Village/Downtown | Bethesda, Md. |
| Wednesday, Dec. 11, 1991 | 8:30 p.m. – 9:00 p.m. | Quince Orchard Knolls | North Potomac, Md. |
| Friday, Jan. 24, 1992 | 9:00 p.m. | Potomac Grove | North Potomac, Md. |
| Tuesday, March 8, 1994 | 7:00 p.m. – 8:00 p.m. | Highwood | Rockville, Md. |
| Saturday, July 20, 1996 | 8:30 p.m. – 8:45 p.m. | 4900 block of MacArthur Boulevard, NW | Washington, DC |
| Wednesday, Feb. 26, 1997 | 7:00 p.m. – 8:00 p.m. | Rock Creek Manor | Rockville, Md. |
| Friday, Nov. 14, 1997 | 7:30 p.m. – 8:00 p.m. | New Hampshire Avenue/Rt. 198 | Silver Spring, Md. |
| Saturday, Aug. 1, 1998 | 10:30 p.m. – 11:00 p.m. | 3600 block Canal Road, Georgetown | Washington, D.C. |
The public is asked to review the information and consider whether they know someone who generally fits this description, who lived or had ties to the area around the times of the assaults or who may have been known to spend considerable amounts of time in those areas.
People who know the suspect may not believe that he is capable of committing these crimes. He may not necessarily have a violent criminal history. Because investigators are in possession of DNA evidence that can either positively link the suspect to his crimes or exclude innocent parties, citizens should not hesitate to provide information, even if it is just the name of a potential suspect.
Law enforcement agencies are asking anyone with information to contact MPD at (202) 727-9099 or the FBI at 1-800-CALL-FBI (1-800-225-5324). Additionally, anonymous information may be submitted to the police department’s TEXT TIP LINE by text messaging 50411.
For more information about this investigation, go to http://fbi.gov/potomacriverrapist.
Composites below are of the same assailant from two separate incidents.
Funny – Ohio Police Describe Strange Hallucinations of Bath Salts Users
Last month the Ohio State Highway Patrol partnered with the Ohio Strategic Analysis and Information Center (SAIC) to survey local police departments about their encounters with suspects under the influence of bath salts. Since its release last month, the survey has been circulated by law enforcement around the country, discussed online in forums by concerned police officers and has even begun to garner press attention for its disturbing reports of the effects of the designer drug, including superhuman strength and highly bizarre hallucinations that often result in violent behavior.
According to the survey, suspects under the influence of bath salts display symptoms of “hyperventilation, cramps, dehydration, vomiting, shaking, loss of memory” or display “rapid movement, rapid speech.” Bath salts users often appear “disoriented … pale, emaciated, jittery,” have “itchy skin” and sometimes admit to not having slept for several days. Suspects under the influence of bath salts have also been reported by witnesses as being “hostile, violent, unpredictable, out of control, paranoid, and reckless.”
One section of the report offers several examples of hallucinations and irrational behavior exhibited by suspects using bath salts:
A male, using bath salts, reported raccoons setting fire inside his home. As a result, he proceeded to destroy his home and used a hatchet to cut up his deck, while attempting to locate the fire-setting raccoons. He also believed the raccoons stole his cell phone.A male, using bath salts, believed he was being followed by police helicopters and police officers were using mirrors, snipers and different types of scopes to look through his walls. He called police requesting to negotiate with them, however there were no police at the residence when the call was made. During the course of speaking to an offender and officer reported, he yelled, “AT&T calling, may I help you, AT&T is calling, a million dollars, two black guys……it’s not a racial thing, it’s not a racial thing.”
Another incident described in the report involved a man who was on bath salts and was arrested for choking his mother after he reportedly told officers that she had been “practicing demonology” and poisoning his food. These hallucinations can be increasingly dangerous as the survey found that bath salts often make people exhibit “unusual superhuman strength” and seemingly be resistant to pain. An incident reported by Reynoldsburg Police involved the use of a Taser against a subject where the “probes penetrated in the torso of the suspect,” yet the “suspect fought through the electric current and rose to his feet.”
Of course, it is unclear how many of these incidents are truly attributable to bath salts as the report notes that in approximately 50% of these incidents other narcotics were discovered on the suspect, including Marjijuana, Cocaine and prescription medication.
FEMEN activists strip in protest against UEFA EURO 2012
Daddy’s Girl – Full Movie
TOP-SECRET from the FBI – Hogsett Announces 30-Year Sentence for Woman Guilty of Production of Child Pornography
EVANSVILLE—“As a prosecutor, and as a parent, it is difficult to put into words damage done as a result of the horrific acts committed by these two people,” said Joseph H. Hogsett, the United States Attorney, while announcing today that Emma Dell Hodge, age 44, of Evansville, was sentenced to 30 years in prison this morning by Chief United States District Judge Richard L. Young. This follows Ms. Hodge’s May 2, 2012 guilty plea to the charges of production of sexually explicit material involving minors and conspiracy to produce sexually explicit material involving minors. Today’s decision also follows the sentencing of Larry Everett Hodge, Ms. Hodge’s spouse, to 115 years in prison several weeks ago.
“Our hope is that through this prosecution and the sentences handed down by Judge Young, justice has been given to the young victim in this case and the healing process can begin,” Hogsett stated.
In November 2010, the Evansville Police Department responded to a report of child abuse from a concerned individual who had been sent images depicting the sexual abuse of a minor on her cell phone. That individual indicated that she had received the images from Larry Everett Hodge. Child abuse detectives were contacted to initiate an investigation.
Detectives went to the Hodge residence to speak with the couple, at which point it was immediately apparent that both knew about the abuse of the child, later identified as an 8-year-old female. Larry Hodge admitted in an interview with law enforcement that he had engaged in oral sex with the victim and was arrested on charges of child molestation.
The full extent of the abuse was later established during an examination of a Memorex data storage disc taken during a search of the Hodge residence. Agents identified at least seven separate digital photography sessions and two videos that were saved on the disc by Larry Hodge, all of which depicted sexual abuse of the minor. Some of the videos and images depicted sexual abuse by Larry Hodge himself, while others depicted sexual abuse by Emma Dell Hodge.
Further investigation revealed that the couple had gained access to the child by volunteering to assist the child’s parents by caring for the child after school and at various other times. Larry Hodge has also admitted to distributing the images and videos of the victim to a co-defendant, George K. Jackson. A sentencing hearing in the matter of Jackson is expected later today before Judge Young.
According to Assistant U.S. Attorney Todd S. Shellenbarger, who prosecuted the case for the government, Chief Judge Young also imposed lifetime supervision following Emma Hodge’s release from prison. During the period of supervised release, Hodge must comply with all sex offender registration laws, must not have unsupervised contact with minors, and must submit to an examination of any computer devices she uses.
This case was the result of an investigation by the Evansville Police Department and the Federal Bureau of Investigation and was brought as part of the U.S. Attorney’s Project Safe Childhood, a nationwide initiative launched in May 2006 by the Department of Justice to combat the growing epidemic of child sexual exploitation and abuse.
Led by the United States Attorneys’ Offices and the Criminal Division’s Child Exploitation and Obscenity Section, Project Safe Childhood marshals federal, state, and local resources to locate, apprehend, and prosecute individuals who sexually exploit children, and to identify and rescue victims. For more information about Project Safe Childhood, please visit http://www.usdoj.gov/psc.
Megapark 2012 – Croatia! Penalty Shoot-Out. Sexy Football Girls – C-Cup | Fussball EM
TOP-SECRET from the FBI – Second Recruiter Convicted in City Nursing Scheme
HOUSTON—Gwendolyn Kay Frank, 43, of Houston, has entered a plea of guilty to conspiracy to violate the Anti-Kickback Statue for her role in role in the $45 million City Nursing health care scandal, United States Attorney Kenneth Magidson announced today.
The Anti-Kickback Statute prohibits referring beneficiaries to business that bill federal health care programs in return for payments. According to the plea agreement, Frank referred at least 28 Medicare beneficiaries to the owner of City Nursing in return for $24,500. City Nursing then billed Medicare for approximately $1,051,392 worth of services for those individuals which were not provided and received $712,052 in payments from Medicare and Medicaid.
Frank is the second recruiter to plead guilty to conspiracy to violate the Anti-Kickback Statue this month and one of a growing list of individuals convicted in the Houston-based City Nursing health care fraud conspiracy. Floyd Leslie Brooks, 45, of Houston, pleaded guilty earlier this month. The owner of City Nursing, Umawa Oke Imo, was convicted in May 2011 and sentenced to more than 27 years in federal prison for his role in the health care fraud conspiracy which included making cash payments to both Medicare beneficiaries and recruiters bringing Medicare beneficiaries to City Nursing.
Frank was permitted to remain on bond pending her sentencing hearing, set for September 14, 2012. At that time, she faces up to five years in prison and a $250,000 fine.
This case has been investigated by the FBI, Internal Revenue Service-Criminal Investigations, the Department of Health and Human Services-Office of Inspector General and the Texas Attorney General’s Office-Medicare Fraud Control Unit. Assistant United States Attorney Julie Redlinger is prosecuting the case.
Megapark 2012 – Sexy Russian Football Girls posing – C-Cup Fussball EM | Comedy Central
TOP-SECRET from Public Intelligence – ITU CWG-WCIT12 Draft Compilation of Proposals/Options
The following documents are compilations of draft proposals for modifications to International Telecommunications Regulations (ITRs) under the International Telecommunication Union. The current version of the proposed changes to the ITRs (CWG-WCIT12 Temporary Document 64) was recently leaked in response to a lack of publicly available information on the proposals. These documents help to provide background and context on the development of the current proposal.
| CWG-WCIT12 TEMPORARY DOCUMENT 43 (CWG-WCIT12/TD – 43) “Draft compilation of options” | 137 pages | November 24, 2011 | Download |
| CWG-WCIT12 TEMPORARY DOCUMENT 36 (CWG-WCIT12/TD – 36) “Draft compilation of proposals” | 53 pages | June 13, 2011 | Download |
FEMEN – Topless Female Protest Group Set To Disrupt 2012 Euro Cup
Dark Side of Paradise – Full Movie
The FBI – Manhattan U.S. Attorney and FBI Assistant Director in Charge Announce Guilty Plea of Expert Networking Firm Consultant to Insider Trading Conspiracy Charge
Preet Bharara, the United States Attorney for the Southern District of New York, and Janice K. Fedarcyk, the Assistant Director in Charge of the New York Field Office of the Federal Bureau of Investigation (FBI), announced that Alnoor Ebrahim pled guilty today in Manhattan federal court to one count of conspiracy to commit securities fraud and wire fraud in connection with an insider trading scheme in which Ebrahim, formerly an associate director of channel marketing at AT&T, provided material, non-public information to members of the investment community. The information concerned product sales for AT&T’s handset devices, including Apple Inc.’s iPhone and Research in Motion Limited’s Blackberry products. Ebrahim pled guilty before U.S. District Judge Paul J. Oetken.
According to the information, statements made during today’s guilty plea proceeding, and evidence from the trial of Ebrahim’s co-conspirator, James Fleishman:
Between 2008 and 2010, Ebrahim provided material, non-public information concerning, among other things, product sales information for AT&T’s handset devices, including Apple Inc.’s iPhone and Research in Motion Limited’s Blackberry products (the “inside information”), in breach of his duties of trust and loyalty to AT&T. Ebrahim and his co-conspirators used an “expert networking” firm (the “firm”) for the purpose of facilitating “consultation calls,” during which Ebrahim provided the inside information to firm clients. Many of the consultation calls in which Ebrahim provided the inside information were with employees of investment firms located in New York, New York. During this time period, the firm paid Ebrahim more than $180,000 for his consultation calls.
***
Ebrahim, 57, of Alpharetta, Georgia, pled guilty to one count of conspiracy to commit securities fraud and wire fraud. The conspiracy count carries a maximum sentence of five years in prison. Ebrahim also faces a maximum fine of $250,000, or twice the gross gain or loss from the offense on the conspiracy count, and agreed as part of his plea agreement to forfeit the proceeds he obtained as a result of the offense.
Ebrahim is scheduled to be sentenced by Judge Oetken on October 25, 2012 at 2:00 p.m.
Mr. Bharara praised the investigative work of the Federal Bureau of Investigation. He also thanked the U.S. Securities and Exchange Commission.
This case was brought in coordination with President Barack Obama’s Financial Fraud Enforcement Task Force, on which Mr. Bharara serves as a Co-Chair of the Securities and Commodities Fraud Working Group. President Obama established the interagency Financial Fraud Enforcement Task Force to wage an aggressive, coordinated, and proactive effort to investigate and prosecute financial crimes. The task force includes representatives from a broad range of federal agencies, regulatory authorities, inspectors general, and state and local law enforcement who, working together, bring to bear a powerful array of criminal and civil enforcement resources. The task force is working to improve efforts across the federal executive branch and, with state and local partners, to investigate and prosecute significant financial crimes, ensure just and effective punishment for those who perpetrate financial crimes, combat discrimination in the lending and financial markets, and recover proceeds for victims of financial crimes.
Assistant U.S. Attorneys Antonia M. Apps and Reed Brodsky are in charge of the prosecution.
Megapark 2012 – Schamlippen Deospray! Manolo No1 | Football Girls Fussball EM
Dark Voyage – Full Movie
TOP-SECRET – Restricted U.S. Army Psychological Operations Process Tactics, Techniques, and Procedures Manual

Field Manual (FM) 3-05.301 describes the tactics, techniques, and procedures (TTP) for the implementation of United States (U.S.) Army Psychological Operations (PSYOP) doctrine presented in the higher-level publication, FM 3-05.30, Psychological Operations. FM 3-05.301 provides general guidance for commanders, staffs, and Soldiers who plan and conduct PSYOP across the range of military operations. The TTP in this manual are presented within the framework of the seven-phase PSYOP process, a mainstay for effective PSYOP executed at the tactical, operational, and strategic levels.
FM 3-05.301 is the principal reference for the PSYOP process. The contents of this manual supersede the discussion of the PSYOP process in FM 3-05.302, Tactical Psychological Operations Tactics, Techniques, and Procedures (28 October 2005). Any mention of the PSYOP process in other preceding doctrine or training literature should be validated by the contents of FM 3-05.301. This manual incorporates updated organizational structures, terminology, and capabilities to provide PSYOP Soldiers with the latest guidance to support a broad range of missions. This manual describes procedures and strategies derived from applied scientific and academic disciplines in an effort to improve the efficacy of the PSYOP process. These TTP are designed to facilitate the successful execution of each phase of the process: planning; target audience analysis; series development; product development and design; approval; production, distribution, and dissemination; and evaluation.
The PSYOP community, in general, is the intended audience for this manual. Members of the tactical, regional, and dissemination PSYOP battalions should find the information particularly useful. Written to give PSYOP officers, noncommissioned officers (NCOs), enlisted Soldiers, and civilians standardized PSYOP doctrine, FM 3-05.301 is a comprehensive how-to guide that focuses on critical PSYOP tasks, duties, and responsibilities.
…
Behavior Modification
2-58. Behavior can be modified by changing the conditions or situations that lead up to the TA’s current behavior. Behavior can also be modified by the manipulation of the consequences of the TA’s current behavior or by introducing new consequences (rewards and punishments) a TA receives for engaging in a behavior.
2-59. Decreasing a behavior involves devaluing or reducing the positive consequences and increasing the value of the negative consequences a TA receives. Removing something desirable or pleasant to a TA that is currently reinforcing a behavior, or introducing something into the TA’s environment that it finds unpleasant, are ways of decreasing a behavior.
2-60. Increasing a behavior involves increasing the value of the positive consequences and decreasing the value of the negative consequences a TA receives. Introducing or emphasizing things in the TA’s environment that are desirable or pleasant when it engages in the desired behavior, or removing things that are unpleasant when it engages in the desired behavior, are ways of increasing a behavior.
…
Psychographics
2-66. Psychographics are psychological characteristics of a TA. These are internal psychological factors— attitudes, values, lifestyles, motivations, and opinions. Psychographics might include characteristics such as fears, loves, hates, cultural norms, and values. Psychographics are vulnerabilities because they provoke an emotional response from the TA that can be used to increase the effectiveness of a PSYOP argument or PSYACT. Although often difficult to derive from standard intelligence and open sources, they can prove to be very effective in persuasion.
2-67. Psychographics include the following:
• Fears: What does the TA fear?
• Hates: What does the TA hate?
• Anger: What angers the TA?
• Loves: What does the TA love?
• Shame or embarrassment: What does the TA consider shameful or embarrassing?
• What is the TA dissatisfied with? (What are its gripes?)
• What are the cultural norms? (How is the TA expected to act?)
• What does the TA value? (What is important to the TA?)
• What are the frustrations? (What does the TA want that it cannot get?)Some examples of psychographics include the following:
• Green Tribe fighters have a very acute fear of fire/being burned alive based upon past experiences while fighting the Ruskinian Army in the 1980s. The Ruskinians used incendiaries, to include napalm, on Green Tribe positions.
• TA considers any effeminate characteristics/actions by males to be very shameful/embarrassing. These actions include crying, caring for children, housework, and physical displays of affection, such as holding hands and hugging between men.
• Male members of the TA are expected to work outside the home and provide for their immediate family and often other elderly/infirm members of their extended family.
• Red Tribesmen in the Birmingville area are highly dissatisfied with the perceived lack of progress on the electrical distribution system in the city.
• TA places a high value on education and will make great sacrifices to ensure the best education for its children.…
Appeals
2-95. An appeal is the overall approach used to present the main argument. It is the flavor or tone of the argument. Appeals gain the TA members’ attention and maintain their interest throughout the argument. Appeals are selected based upon the conditions and vulnerabilities of the TA. For example, a TA that does not believe the government of its country is legitimate will not be swayed by an appeal to legitimacy, whereas a military TA may be greatly affected by an appeal to authority. The following is a list of general persuasive appeals commonly used in PSYOP:
• Legitimacy.
• Inevitability.
• In group-out group.
• Bandwagon.
• Nostalgia.
• Self-interest (gain/loss).2-96. Legitimacy appeals use law, tradition, historical continuity, or support of the people. The following are types of legitimacy appeals:
• Authority: An appeal to laws or regulations, or to people in superior positions in the social hierarchy. For example, the Uniform Code of Military Justice, NCOs and officers, police officers, parents, or government officials. The TA must recognize the authority for the appeal to work.
• Reverence: An appeal to a belief-teaching institution or individual that is revered or worshiped; for example, the Dalai Lama, the Roman Catholic Church, or even a sports figure such as Michael Jordan.
• Tradition: An appeal to that which the TA is already used to. It is behavior that is repeated continually without question. Why do people have turkey on Thanksgiving? Because it has always been that way.
• Loyalty: An appeal to groups to which the TA belongs. Examples are military units, family, or friends. This appeal is usually used to reinforce behavior that already occurs.2-97. Inevitability appeals most often rely on the emotion of fear, particularly fear of death, injury, or some other type of harm. For example, if a person does not surrender, he will die, or if a person does not pay his taxes, he will go to jail. It can also be an appeal to logic. Both require proof that the promised outcome will actually occur. Therefore, it is crucial that credibility be gained and maintained throughout
the argument.2-98. An in group-out group appeal seeks to divide a TA or separate two TAs. It creates an enemy of one group, and encourages the other group to rebel/discriminate against them. This appeal frequently points out major differences between TAs, or factions of a TA. If PSYOP cannot effectively portray the in group in a negative manner, the appeal will fail.
2-99. Bandwagon appeals play upon the TA’s need to belong or conform to group standards. The two main types of bandwagon appeal are an appeal to companionship and an appeal to conformity. Peer pressure is an example of the conformity type of bandwagon appeal.
2-100. Nostalgia appeals refer to how things were done in the past. This appeal can be used to encourage or discourage a particular behavior. In a positive light, it refers to the “good old days” and encourages the TA to behave in a manner that will return to those times. In the negative, it points out how things were bad in the past and how a change in behavior will avoid a repeat of those times.
2-101. Self-interest appeals are those that play directly to the wants and desires of the individuals that make up a TA. This type of appeal can play upon the TA’s vulnerability for acquisition, success, or status. A self-interest appeal can be presented in the form of a gain or loss. An appeal to loss would be exploiting the fact that if the TA does not engage in the desired behavior, PSYOP cannot satisfy a want. An appeal to gain would inform the TA that to satisfy a want, the TA must engage in a desired behavior.
Techniques
2-102. For the purposes of TAA, techniques refer to the specific methods used to present information to the TA. Effective persuasion techniques are based on the conditions affecting the TA and the type of information being presented. Determining the most effective technique or combination of techniques to persuade the TA is only accomplished through a cultivated understanding of the TA and its behavior.
2-103. Persuasion and influence are the primary tools of PSYOP. As such, PSYOP Soldiers must strive to become familiar with, and ultimately develop, tactical and technical proficiency in the use of persuasion techniques. The following are some specific techniques used to present supporting arguments to the TA:
• Glittering generalities. These are intense, emotionally appealing words so closely associated with highly valued concepts and beliefs that the appeals are convincing without being supported
by fact or reason. The appeals are directed toward such emotions as love of country and home, and desire for peace, freedom, glory, and honor.
• Transference. This technique projects positive or negative qualities of a person, entity, object, or value to another. It is generally used to transfer blame from one party in a conflict to another.
• Least of evils. This technique acknowledges that the COA being taken is perhaps undesirable, but emphasizes that any other COA would result in a worse outcome.
• Name-calling. Name-calling seeks to arouse prejudices in an audience by labeling the object of the propaganda as something the TA fears, loathes, or finds undesirable.
• Plain folks or common man. This approach attempts to convince the audience that the position noted in the PSYOP argument is actually the same as that of the TA. This technique is designed to win the confidence of the audience by communicating in the usual manner and style of the audience. Communicators use ordinary or common language, mannerisms, and clothes in face-to-face and other audiovisual communications when they attempt to identify their point of view with that of the average person.
• Testimonials. Testimonials are quotations (in and out of context) that are cited to support or reject a given policy, action, program, or personality. The reputation or the role of the individual giving the statement is exploited. There can be different types of testimonial authority. Official testimonials use endorsements or the approval of people in authority or well known in a particular field. Personal sources of testimonials may include hostile leaders, fellow soldiers, opposing leaders, famous scholars, writers, popular heroes, and other personalities.
• Insinuation. Insinuation is used to create or increase TA suspicions of ideas, groups, or individuals as a means of dividing the adversary. The PSYOP Soldier hints, suggests, and implies, but lets the TA draw its own conclusions.
• Presenting the other side. Some people in a TA believe that neither of the belligerents is entirely virtuous. To them, messages that express concepts solely in terms of right and wrong may not be credible. Agreement with minor aspects of the enemy’s point of view may overcome this cynicism.
• Simplification. In this technique, facts are reduced to either right, wrong, good, or evil. The technique provides simple solutions for complex problems and offers simplified interpretations of events, ideas, concepts, or personalities.
• Compare and contrast. Two or more ideas, issues, or choices are compared and differences between them are explained. This technique is effective if the TA has a needs conflict that must be resolved.
• Compare for similarities. Two or more ideas, issues, or objects are compared to try and liken one to the other. This technique tries to show that the desired behavior or attitude (SPO) is
similar to one that has already been accepted by the TA.
• Illustrations and narratives. An illustration is a detailed example of the idea that is being presented. It is an example that makes abstract or general ideas easier to comprehend. If it is in a story form, it is a narrative.
• Specific instances. These are a list of examples that help prove the point.
• Statistics. Statistics have a certain authority, but they must be clear enough to show the TA why they are relevant. In most cases, it is best to keep the statistical evidence simple and short so the TA can easily absorb it.
• Explanations. These are used when a term or idea is unfamiliar to the TA.Primary Influence Tactics
2-104. These primary influence tactics are widely applicable to many situations, cultures, and TAs. By using the appropriate influence tactics in products and actions, the persuasiveness of PSYOP will be magnified. The following are examples of primary influence tactics:
• Rewards and punishments: “If you do X, you will get Y,” or “if you do not do X, Y will happen to you.” Example: “Surrender, and you will be treated well; continue to fight, and you will be killed.”
• Expertise: “Speaking as an authority on the subject, I can tell you that rewards/punishments will occur if you do or do not do X.” Example: “Oil Minister Gregor (key communicator/expert) states that if rebel groups continue to sabotage oil pipelines, the national economy will be seriously affected.”
• Gifts: Giving something as a gift before requesting compliance. The idea is that the target will feel the need to reciprocate later. Example: “This well and cistern are a gift to the people of Birmingville from the coalition forces…demonstration of our good will and hope for mutual cooperation in the future.”
• Debt: Calling in past favors. Example: “Coalition forces have done a lot for Birmingville, Elder Chang: the new school, the well in the center of town… these insurgents are endangering all we have worked for together. We need your help in stopping these groups by reporting any information you and your people may discover.”
• Aversive stimulation: Continuous punishment, and the cessation of punishment, is contingent on compliance. Example: “We will continue to bomb your position unless you surrender immediately.”
• Moral appeal: Entails finding moral common ground, and then using the moral commitments of a person to obtain compliance. Example: “The killing of innocent civilians is wrong; please help the security forces stop this tragic loss of innocent life by reporting any information on terrorist activities.”
• Positive and negative self-feeling: “You will feel better/bad if you do X.” Example: “Become part of something bigger than yourself, know honor and take pride in your work…join the national security forces!”
• Positive and negative altercasting: “Good people do X / Bad people do Y.” Example: “Red Tribe members are brave and honorable people who care about the future of their country and are not intimidated by rebel groups. Call and report insurgent activity now on the coalition hotline.”
• Positive and negative esteem of others: “Other people will think highly/less of you if you do X.” Example: “Earn the respect of your friends and the pride of your family…join the Patriotsville National Guard now!”
• Fear: “Bad things will happen to you if you do X.” Example: “Only death and fire await those who continue to fight…surrender now.”
TOP-SECRET from the NSA – New Documents Spotlight Reagan-era Tensions over Pakistani Nuclear Program
|
Washington, D.C., June 18, 2012 – Tensions between the United States and Pakistan rose through the 1980s over intelligence reports that suggested to U.S. officials that Pakistani leader Zia ul-Haq had repeatedly lied to them about his country’s nuclear program, according to recently declassified records published today by the National Security Archive and the Nuclear Proliferation International History Project. Zia’s apparent mendacity posed an immediate challenge to U.S. nonproliferation goals, but also threatened the even higher priority of providing aid to Islamabad and to the Mujahedin resistance fighting Soviet forces in Afghanistan.
Preventing the spread of nuclear weapons has been a significant objective for U.S.presidents, but there have been instances when diplomatic and other interests have overridden concerns about nuclear proliferation. Israel since the late 1960s is one example and Pakistan during the 1980s is another. Concerned by new intelligence about the Pakistani nuclear program, in July 1982, the Reagan administration sent former CIA deputy director General Vernon Walters to meet secretly with Pakistani dictator General Muhammad Zia-ul-Haq. U.S. intelligence had detected an upswing of clandestine Pakistani efforts to procure nuclear weapons-related technology and unwanted publicity could jeopardize U.S. government economic and military aid to Pakistan, a key partnerin the secret war against Soviet forces in Afghanistan.
Confronted with the evidence, Zia acknowledged that the information “must be true,” but then denied everything, leading Walters to conclude that either Zia “did not know the facts” or was the “most superb and patriotic liar I have ever met.” While Zia restated earlier promises not to develop a nuclear weapon and made pledges to avoid specific nuclear “firebreaks,” officials from Secretary of State George Shultz on down would conclude time and time again, that Zia was breaking his word.
In 1986, Arms Control and Disarmament Agency (ACDA) director Kenneth Adelman wrote in a memorandum to the White House that Zia “has lied to us again,” and warned that failure to act would lead the General to conclude that he can “lie to us with impunity.” While the Reagan administration was concerned about nuclear proliferation, it gave a greater priority to securing aid to Pakistan so it could support the Afghan anti-Soviet insurgency. The White House and the State Department leadership hoped that building a strong bilateral relationship would dissuade Pakistan from building nuclear weapons.
Top levels of the U.S. government let relations with a friendly government supersede nonproliferation goals as long as there was no public controversy that could “embarrass” the President the documents show. Indeed, Reagan administration officials feared that if the Pakistanis had told them the “truth” about the purpose and scope of their nuclear activities, it would have made it impossible for the administration to certify to Congress that Pakistan was not developing nuclear weapons. On that certification rode the continued flow of aid to assist the Afghanistan resistance. For the sake of that aid, senior Reagan administration officials gave Pakistan much slack by obscuring its nuclear activities, but that they wrote about lying and “breaking … assurances” suggests that lack of trust and confidence was an important element in the U.S.-Pakistan relationship, as it is today.
Among the disclosures in today’s publication:
- By the early summer of 1981, State Department intelligence estimated that the Pakistanis were “probably capable of producing a workable device at this time,” although the Kahuta enrichment plant was unlikely to produce enough fissile material for a test until 1983.
- Pakistan was slated to acquire F-16 fighter-bombers from the U.S. That prospective sale troubled Indian leaders because a nuclear Pakistan with advanced fighter bombers would be a more formidable adversary.
- During the spring of 1982 U.S. diplomats and intelligence collectors found that Pakistani agents were trying to acquire “fabricated shapes” (metal hemispheres for producing nuclear explosive devices) and other sensitive technology for a nuclear program. Suggesting that Pakistan was starting to cross the line by building a nuclear weapon, these discoveries contributed to the decision to send former CIA deputy director Vernon Walters to meet secretly with General Zia in July and October 1982.
- During Walters’ October 1982 visit, Zia told him of his meeting with Saudi Arabia’s King Fahd who had told him that agents from an unspecified country had attempted to sell him a nuclear device for $250 million. Zia advised Fahd not to “touch the offer with a barge pole.”
- A controversial element in the F-16 sale was whether the U.S. would comply with Pakistani requests that it include the same radar system as the most advanced U.S. model. While top CIA officials warned that the Pakistanis were likely to share the technology with China, Secretary of State George Shultz and other officials believed, ironically, that denying Pakistani requests would make that country less responsive to U.S. nonproliferation goals.
- With Pakistan’s efforts to acquire sensitive technology continuing, in December 1982 Secretary of State Shultz warned President Reagan of the “overwhelming evidence that Zia has been breaking his assurances.” He also expressed concern that Pakistan would make sensitive nuclear technology available to “unstable Arab countries.”
- In June 1986 ACDA director Kenneth Adelman wrote that Zia has “lied to us again” about violations of agreements not to produce highly-enriched uranium above a five-percent level. If Washington did not apply real pressure it would reinforce Zia’s belief “that he can lie to us with impunity.”
- In the spring of 1987, senior State Department officials wrote that Pakistani nuclear development activities were proceeding apace and that General Zia was approaching a “threshold which he cannot cross without blatantly violating his pledge not to embarrass the President.”
Until 1990, after the Soviets had left Afghanistan, Washington never allowed events to reach a point where public controversy over Pakistani nuclear weapons activities could force a decision that to cut off aid and threaten Pakistan’s role as a go—between to the Afghan resistance. The tough sanctions that have been used against countries like Iran and North Korea were never given serious consideration because the Reagan administration believed that embracing close associates like Pakistan in a “broader bilateral relationship” could discourage them from testing a nuclear device. U.S. policymakers unsuccessfully tried to jawbone their Pakistani counterparts from enriching uranium and building a nuclear weapon.
The other side of U.S. policy was the organized multilateral effort, begun during the Carter administration, to prevent sensitive technology from reaching Pakistan. This largely consisted of efforts to persuade other nuclear suppliers to bar exports of dual-use technology. While international export controls could not stop the Pakistani program, U.S. officials believed that they could “delay” and even “set [it] back”. Those activities were at a high tempo during the early 1980s but whether they continued at the same pace during the rest of the decade is not clear. More declassifications may shed light on that.
The White House and the State Department worked successfully at offsetting Congressional pressures to impose tough nonproliferation standards, although arrests by the U.S. Customs Service raised inconvenient questions. The first major case was Nazir Ahmed Vaid’s arrest in June 1984 for trying to purchase nuclear weapons technology. U.S. government officials may have interfered in the case to minimize adverse publicity that could weaken Congressional support for aid to Pakistan. Nevertheless, Congressional pressure continued. In 1985, Senator John Glenn (D-Oh), among others, wanted the administration to certify, as a condition for further aid, that Pakistan neither possessed nor was developing a nuclear weapon. But the White House and its supporters in Congress won support for a weaker version: an amendment, supported by Senator Larry Pressler (R-SD), requiring annual certification that Pakistan did not possess a nuclear device and that U.S. aid would reduce the risk that Pakistan would acquire one. [1]
In 1986 Reagan certified that Pakistan was in compliance with the Pressler amendment, but months later participants in the Khan network were caught again. In July 1987 U.S. Customs officials arrested Arshad Pervez for trying to buy supplies for the Kahuta enrichment plant. Nevertheless, the administration insisted that nothing was amiss, arguing that it was too early to conclude the Pervez had official support in Pakistan. [2] Even after Pervez was convicted later that year, Reagan certified again that Pakistan did not possess a nuclear device, thereby ensuring that aid flowed without interruption. Congress, however, showed its concern by letting the five- year Symington amendment waiver expire, which temporarily halted “new commitments of aid.” When Congress reinstated a new waiver, it would be only for two-and-a- half years, instead of the six years that Reagan had proposed. 1990 would become a year of decision for future U.S. aid to Pakistan. [3]
This is the third in a series of Electronic Briefing Books on U.S. policy toward the Pakistani nuclear program. The first was on the Carter administration’s policy; the second was on the efforts to work with allies to prevent the export of sensitive technology to Pakistan. The National Security Archive has filed numerous declassification requests to U.S. government agencies on important developments during the 1970s, 80s, and early 1990s, and as significant material becomes declassified the Archive will update this series of EBBs.
READ THE DOCUMENTS
Document 1:”Reached a Dead End”
U.S. Department of State Cable 145139 to U.S. Embassy India [repeating cable sent to Embassy Pakistan], “Non-Proliferation in South [Asia],” 6 June 1979, Secret
Source: MDR request
By the spring of 1979, the Carter administration decided that it had “reached a dead end” in its efforts to stop the spread of nuclear technology to South Asia and that a “new strategy” was necessary to check the spread of nuclear weapons in the region. Given close security ties with Pakistan and concerns about that country’s stability, the State Department was not going to take a hard-line approach, such as embargoes. to force a nuclear roll-back. Thus, Washington would maintain “vigilance” to ensure that sensitive supplies did not reach Pakistan, but the administration no longer saw it possible to reverse Pakistan’s efforts to construct uranium enrichment facilities. More serious dangers were a South Asian nuclear arms race and the threat to U.S. nonproliferation policy which “will collapse under the weight of two additional nuclear-weapons states.” By playing the role of an “honest broker,” and offering appropriate inducements, Washington would make a “sincere attempt to convince South Asians that nuclear weapons are not a viable option.”
Three interrelated actions were necessary. Pakistan would have to be persuaded not to stage a “peaceful nuclear explosion,” along the line of India’s 1974 test, because that would push India to develop a nuclear arsenal and even consider preemptive action. The U.S. would have to seek assurances from Prime Minister Desai that India would not produce nuclear weapons. Finally, Washington would need China’s support, e.g. security assurances to India. To make these arrangements work, Washington would have sell nuclear fuel to India and lift the Symington amendment sanctions against Pakistan that the enrichment program had triggered. Policy success was by no means assured–China might not cooperate–and other uncertainties could complicate matters, for example, if Pakistan helped other Muslim states develop an “Islamic bomb.”
Document 2: “Two-Step Carrot-Stick Approach”
Anthony Lake, director, Policy Planning Staff, to Secretary of State Vance, “The Pakistan strategy and Future Choices,” 8 September 1979, Secret
Source: National Archives, Record Group 59, Records of Anthony Lake, box
The previous document was a marker for policy change, but carrying it out was difficult because of the difficulty of balancing “good relations” with Pakistan with global nonproliferation interests. Concerns about a nuclear test and the transfer of sensitive technology to other states had crystallized into a “no-test/no-transfer” approach, but Washington needed help from other Western aid donors to persuade General Zia’s government to accept those parameters. To try to forge an understanding with Pakistan, Lake describes a “two-step carrot-stick” approach, involving pressures by aid donors. As Lake’s report to Vance makes clear, there were significant divisions in the Carter administration over what “carrots” could be offered and under what conditions, for example, whether sale of F-16 fighter-jets could win the military’s support for scaling back the nuclear program, and how to deal with the Symington amendment. If the “two-step” approach failed Washington might have to consider a “third step” which could either be a resumption of pressure or a waiver of the Symington amendment in exchange for a no-test/no-transfer understanding.
The next month, Secretary of State Vance and Ambassador Gerard C. Smith met with Foreign Minister Shahi, warning him that a nuclear test would harm U.S. –Pakistani relations, with Smith arguing that Pakistan was “entering the valley of death” because India “can utterly destroy you.” Apparently Shahi responded that “he did not have to be a nuclear expert to understand that ‘the value of a nuclear capability lies in its possession, not in its use.” Smith soon traveled to Europe and discussed Pakistan with donor governments, but found little support for applying pressure. [4]
Document 3: “Set the Nuclear Issue Aside”
Secretary of Defense Harold Brown to Ambassador-at-Large Gerard C. Smith, 31 January 1980, enclosing excerpts from memoranda of conversations with Geng Biao and Deng Xiaoping, 7 and 8 January 1980, Top Secret
Source: FOIA release
The Soviet invasion of Afghanistan in December 1979 had an immediate impact on U.S. policy toward Pakistan as indicated by Secretary of Defense Brown’s talks with top Chinese officials. In light of the high priority of funneling aid through Islamabad to the anti-Soviet resistance and concern that Moscow might put Islamabad under pressure, interest in improved relations with Pakistan further lowered the nuclear issue’s priority, although efforts to block sensitive exports continued. As Brown explained to Deng, “we will set [the nuclear issue] aside for the time being and concentrated on strengthening Pakistan against possible Soviet action.” In other words, Cold War objectives had priority over nonproliferation concerns. [5] While Deng claimed that Beijing opposed Pakistan’s nuclear program, China and Pakistan had already developed a special nuclear relationship and ambivalence was evidence in Deng’s advice that the United States “not mention” the nuclear issue in talks with Pakistan.
Document 4: “Pakistan Will Not Give up This Program”
Bureau of Intelligence and Research, U.S. Department of State, “Pakistan and the US: Seeking Ways to Improve Relations,” Report 97-PA, 23 March 1981, Secret
Source: Department of State FOIA release, copy courtesy of Jeffrey Richelson
According to INR analysts, the Pakistani leadership wanted to improve relations with Washington and certainly get a bigger aid package than the “peanuts” offered by the Carter administration. Nevertheless, INR recommended caution about getting too close to General Zia; he would be gone someday and “too close a US tie … might harm future relations.” Moreover, better relations would not make the nuclear problem go away: “Pakistan will not give up this program.” There was some chance that Pakistanis could be persuaded not to test a device but this “would be difficult to accomplish.” The Indians might react badly if Washington gets too close to Pakistan: “they might well retaliate by moving closer to the Soviets.”
Document 5: A “Broader Bilateral Relationship”
Special Assistant for Nuclear Proliferation Intelligence, National Foreign Assessment Center, Central Intelligence Agency, to Resource Management Staff, Office of Program Assessment et al, “Request for Review of Draft Paper on the Security Dimension of Non-Proliferation,” 9 April 1981, Secret, excised copy
Source: MDR release
A new presidential administration wanted to put its own stamp on nonproliferation policy and the Department of State helped begin the process with a draft paper on the “security dimensions of nonproliferation.” Convinced that further spread of nuclear capabilities could have an adverse impact on U.S. security, the report emphasized the importance of perceptions of insecurity as a motive leading states to opt for a nuclear explosive program. While denial of sensitive technology and equipment remained “fundamental,” State Department officials believed that a “broader bilateral relationship” based on the integration of political incentives and security assistance could persuade friendly threshold states that they did not need nuclear weapons. By contrast, “more negative methods of dissuasion” would apply to countries which had poor relations with Washington.
The State Department’s review of threshold states, from Argentina and Brazil to Libya and Iraq, include a discussion of Pakistan, where the “broad bilateral relationship” approach was taken into account. The U.S. objective should be a “closer security relationship which builds confidence in us and makes the Paks feel more secure.” Such a relationship would be “more likely to provide Pakistan with incentives to forego, or at least delay, a nuclear test than any alternative approach.” Following the Carter administration, the Reagan team had minimal goals: preventing a Pakistani nuclear test, not dismantling the enrichment program, had become the key objective. Nevertheless, State’s politico-military analysts argued that Washington should not give the impression that was acquiescing in Pakistan nuclear activity: it was necessary to “lay down a marker” by making Pakistani officials understand the “political costs” of continuing a weapons program.
Document 6: More “Carrots and Sticks”
Lewis A. Dunn, Arms Control and Disarmament Agency, “Implications for U.S. Policy of a Pakistani Nuclear Test,” 11 June 1981, Secret
Source: FOIA release
Signs of the Reagan team’s emphasis on propitiating Islamabad are evident in a memorandum that incoming ACDA official Lewis Dunn had prepared just before he left Herman Kahn’s Hudson Institute. Seeing Pakistan as likely to test a weapon once it had enough fissile material (a test site had already been discovered [6]) Dunn believed that prospects for halting a test were “dimming.” If Pakistan did test, however, there could be a range of U.S. responses, but he favored a “muted” one, owing to regional security considerations and the importance of “holding down” Pakistani nuclear activities. In that regard, Dunn saw “carrots and sticks” as relevant; if Pakistan tested, offers of military assistance or civilian nuclear technology might discourage further nuclear activities. He identified no “sticks.” Dunn also believed it useful to encourage Indian-Pakistan dialogue and regional arms control measures (e.g., no first use pledges and confidence building activities). Pakistan did not test for years, but the Reagan administration would hope in vain that “yes” was the answer to one of Dunn’s questions: “Would the prospect of access to U.S. arms enhance Pakistani incentives for nuclear restraint?”
Document 7: “Probably Capable of Producing a Workable Device at this time”
Bureau of Intelligence and Research, U.S. Department of State, “India-Pakistani Views on a Nuclear Weapons Options and Potential Repercussions,” Report 169-AR, 25 June 1981, confidential
Source: Department of State FOIA release, copy courtesy of Jeffrey Richelson
This report provides an overview of the state of the Indian and the Pakistani nuclear programs, reviewing motivations, the technical situation, possible decisions to test, and the implications of a Pakistani test. According to INR, the Pakistanis are “probably capable of producing a workable device at this time,” but the Kahuta plant was unlikely to produce enough fissile material for a test until 1983. While the Indians had stated publicly that they were preparing their test site that declaration may have been for political effect because they may have wanted the Pakistanis make the “first move.” If Zia decided to do so, he would have to decide whether to risk worsening relations with Washington and a heightened regional nuclear arms race. Indira Gandhi would likely order retaliatory nuclear tests and quiet work on a weapons program. But if Pakistan went further and began an active nuclear weapons program, India was not likely to take risky preventive action because of the difficulty of taking out “Pakistan’s well-defended nuclear facilities” and the risk of “antagonizing China.” INR analysts opined that a nuclear South Asia would not be a stable region: “it is difficult to be optimistic that a stable, long-term mutual deterrence relationship would be established.”
Document 8: A “Great Security Threat” to India
Acting Special Assistant for Nuclear Proliferation Intelligence, National Foreign Assessment Center, to Director and Deputy Director of Central Intelligence, “Warning Report – Nuclear Proliferation,” 20 August 1981, Top Secret, Excised Copy
Source: Mandatory Review Request
An International Atomic Energy Agency report that Pakistan may have diverted plutonium from the Karachi nuclear power plant was raising questions about the adequacy of safeguards, but
Intelligence repots suggested that the Pakistanis “were not overly concerned.” More serious were the implications of U.S.-Pakistani discussions of the sale of advanced F-16 fighter-bombers as part of a larger U.S. aid package to secure Pakistan’s collaboration in the covert war against Soviet forces in Afghanistan. Indian Prime Minister Indira Gandhi worried that Pakistan’s nuclear program and its slated acquisition of F-16s posed a “great security threat” that raised the risk of war.
Document 9: The Danger of Indian Preventive Action
John N. McMahon, Deputy Director for National Foreign Assessment, to Ambassador Richard T. Kennedy,Under Secretary of State for Management, “Special National Intelligence Estimate on Indian Reactions to Nuclear Developments in Pakistan,” 21 September 1981, enclosing SNIE 31-32/81, Secret, excised copy
Source: FOIA release
The heightened Indian concerns about Pakistan discussed in the August “Warning Report” raised enough hackles in the Reagan administration for the CIA to produce a Special National Intelligence Estimate on the possibility of Indian preventive action against Pakistan’s nuclear program. While the estimators could not be sure, they believed that Prime Minister Gandhi would take a “wait-and-see” approach as to whether Pakistan 1) was going to test a device and 2) keep producing fissile material for weapons. India would have to decide whether to stage an “answering test” (for which preparatory work had already been undertaken), but also whether to take preventive action before Pakistan had a weapons stockpile.
Israel’s use of F-16s to destroy Iraq’s Osirak nuclear reactor in June 1981 and Washington’s announcement on 14 September of the F-16 sale to Pakistan made Indian defense officials wonder whether preventive action against nuclear facilities was necessary before Islamabad had the fighter-bombers (for which nuclear-capable versions existed). If India took such action it would have to face the prospect of a “severe” international reaction as well as the possibility that China might intervene on Pakistan’s behalf. One alternative for India was to develop a nuclear stockpile superior to Pakistan’s. That would take a high-level decision to produce nuclear weapons, while financial, technological, and other considerations might encourage Gandhi to move slowly. Nevertheless, the possibility that India (or even Israel) would take preventive action against the Pakistani nuclear program would be a continuing concern.
Document 10: “In All Probability We Would Choose to Cut off Assistance”
Secretary of State Alexander Haig to Senator Mark Hatfield (R-Or), 21 November 1981, Confidential
Source: State Department FOIA release
While concerned about what India might do, the Reagan administration focused on working with Pakistan to weaken the Soviet position in Afghanistan. Facilitating that involved a multi-billion military and economic aid package to Pakistan which included a five year waiver of the Symington amendment to eliminate automatic triggers that would cut aid if Washington detected evidence of nuclear weapons work. Nevertheless, Congress imposed some conditions, namely that aid would stop if Pakistan tested a nuclear weapon. To confirm that the administration was on board, Senator Mark Hatfield, who had long been concerned about nuclear proliferation, asked Secretary of State Alexander Haig how the U.S. government would react to a Pakistani nuclear test. Haig replied that “in all probability”, Washington would cut aid. Haig might have thought that there would be no problem because General Zia had assured Under Secretary of State James Buckley that he would not develop or test a nuclear weapon (See document 11A for that assurance). On human rights, another of Hatfield’s concerns, the Reagan administration was departing from the human rights emphasis of its predecessor. Haig would make no commitments because of Pakistan’s “limited tradition of representative government.”
Document 11: “Significant” Chinese Aid on Nuclear Design
Note for [name excised] from [name excised], “State/INR Request for Update of Pak SNIE, and Assessment of Argentine Nuclear Program,” 4 June 1982, Secret, excised copy
Source: CREST
A planned update of a Special National Intelligence Estimate concluded that the Pakistani nuclear program was keeping its momentum and that new evidence, apparently acquired by British intelligence, suggested a “significant” Chinese role, at least in providing assistance on weapons design. [7] CIA was apparently adjusting its earlier estimate—late 1982/1983-84–for the availability of fissile material for weapons. The implication was that a Pakistani test was not imminent, thus reducing pressure on India.
Document 12: Discoveries and Demarches
Terry Jones, Office of Nonproliferation and Export Policy, Department of State, to J. Devine et al., enclosing summaries of State Department cable traffic during 1981-1982 relating to demarches on attempted purchase of sensitive nuclear-related products, 17 June 1982
Source: State Department FOIA release
The Reagan administration gave Pakistan some slack, but it continued the campaign of demarches, begun under Jimmy Carter, to try to prevent the export of sensitive nuclear technology to Pakistan, among others. (See EBB “Demarches and Non-Papers”) As before, Pakistan was a special target of concern, but these summaries of State Department telegrams, some in the sensitive intelligence-related “Roger” channel, show that Washington was also trying to prevent sales of nuclear-related technology to a host of countries: Argentina, Brazil, China, India, Iraq, Israel, Korea, Libya, Romania, South Africa, and Syria. For example, cable traffic on Syria showed concern about Damascus’s interest in acquiring a research reactor, while messages on Libya show U.S. government efforts to discourage Belgian sale of a plant to produce uranium tetraflouride (the precursor to uranium hexaflouride, used for uranium enrichment).
The name A. Q. Khan was not mentioned in these cables, but his fingerprint showed up, for example, in the attempted purchases of electrical inverters (used for gas centrifuges). These attempts were probably by the Khan network. But the group of Pakistani agents seeking to purchase nuclear-related technology was broaderthan Khan’s. For example, the nuclear reprocessing technology program was directed by Pakistan Atomic Energy Commission chief Munir Ahmad Khan, who had a procurement network in Europe directedby S.A. Butt. The cable summaries for Pakistan showed a number of attempted and completed purchases by Pakistani agents from suppliers in a variety of countries, including Belgium, Finland, Japan, Sweden, andTurkey. Besides the inverters, agents were seeking such items as fabricated shapes” (metal hemispheres for producing nuclear explosive devices), coaxial cables, fuel chopping machines(to help reprocess plutonium), nuclear power plants, and “flash X-ray units”(diagnostic instrument used in tests of neutron initiators for nuclear weapons).[8] Suggesting that Pakistan was starting to cross the line into producing a nuclear weapon, these efforts raised alarm bells in Washington. [Updated 4 May 2012. Thanks to Mansoor Ahmed for information]
Documents 13A-B: “The Most Superb and Patriotic Liar”
A. U.S. Embassy Pakistan cable 10239 to State Department, “My First Meeting with President Zia,” 5 July 1982, Secret
B. U.S. Embassy Pakistan cable 10276 to State Department, “My Final Meeting with President Zia,” 6 July 1982, Secret
Source: State Department MDR release
Much needs to be learned about White House decision-making but evidently the alleged Pakistani efforts to purchase sensitive technology discussed above, and possibly the intelligence on Chinese weapon design assistance, prompted concern that Congress would find out and stop aid if it believed that Pakistan was developing a capability for a nuclear test. To keep the situation in check, Reagan sent General Vernon Walters, former Deputy Director of Central Intelligence and personal translator for U.S. presidents, among other high-level and sensitive positions, to take a presidential letter to General Zia. During their 4 July meeting, Walter told Zia that Washington had “incontrovertible intelligence” that Pakistani representatives had “transferred designs and specifications for nuclear weapons components to purchasing agents in several countries for the purpose of having these nuclear weapons components fabricated for Pakistan.” Under the law, Walters told Zia, the administration would have to inform the U.S. Congress. Zia denied everything: Pakistan did not have a weapons development program and repeated assurances made to Under Secretary of State James Buckley that Pakistan would not develop or test a nuclear weapon. Zia said that he was sure that no one was buying nuclear equipment, but he would check with his subordinates to be sure. Walter later commented: “either he really does not know or is the most superb and patriotic liar I have ever met.”
In what Walters saw as a diversion from the main discussion, the conversion turned to the problem of the IAEA inspection of the Karachi Nuclear Power Plant and recommendations on safeguards to prevent diversion of spent fuel. Zia repeated his earlier assurances on nuclear weapons and insisted that Pakistan would not “embarrass” the U.S. government. Walters reported that Zia “took the matter somewhat better than I had expected.”
The conversation the next day showed that Zia was a master of double-talk. Verbally, he admitted that U.S. intelligence was on to something: “The president must be right. Your information must be right. I accept its authenticity.” But he would not put that in writing and in a formal response to Reagan’s letter, Zia argued that the U.S. information was a “total fabrication.” This, Walter argued, was a matter of keeping “face”: what Zia was saying was “it did not happen but you can be sure it won’t happen again.” “I think he has the message,” Walter concluded, although he did not explain whether he believed that there would be any changes in Pakistani policy.
Documents 14A-B: “Word of Honor”
A. U.S. Embassy Pakistan cable 15696 to State Department, “Pakistan Nuclear Issue: Meeting with General Zia,” 17 October 1982, Secret
B. State Department cable 299499 to U.S. Embassy Islamabad, “Pakistan Nuclear Issue: Meeting with General Zia,” 25 October 1982, Secret
Source: State Department MDR release
What Zia said to Walters was irrelevant because U.S. intelligence detected continuing efforts to procure sensitive technology and materials (see next document). Thus, Walters returned to Islamabad for another demarche in October, to warn Zia that U.S. aid was in “grave jeopardy.” (see document 16 below). Walter showed drawings of Chinese-influenced nuclear weapons designs that U.S. intelligence had obtained, but Zia denied that there was anything untoward: Pakistan’s reprocessing and enrichment programs were entirely peaceful and there was “nothing” in the nuclear weapons field. Pakistan would do nothing that would jeopardize its aid and other relationships with Washington. Any information on clandestine nuclear activities, he suggested, had been concocted by Pakistan’s “enemies.” As for the items that Pakistan was allegedly attempting to procure, such as “spheres”, Zia argued, there was nothing that could not be produced internally. Walter said he would review the U.S. evidence, but observed that intelligence advisers had assured him that there was “no possibility of fabrication or disinformation.”
The delivery of the F-16s to Pakistan was nearing and Zia wanted to make sure that they were equipped with the ALR-69 radar warning receiver, the most advanced radar warning technology in the U.S. Air Force’s inventory. What had held up delivery was concern in Washington that Pakistan might give the Chinese access to this advanced technology. Walters said he would look into it.
Zia concluded the meeting with a story based on conversations with Saudi Arabia’s King Fahd. The latter had told him that agents from an unspecified country had attempted to sell a nuclear device to Saudi Arabia for $250 million. He had advised Fahd not to “touch the offer with a ‘barge pole.'”
In a follow-up message, prepared after he was back in Washington, Walters noted that at the end of the conversation, Zia had given his “word of honor” that Pakistan “will not develop a nuclear device or a weapon.”
Document 15A-B: “A Serious Blow to U.S. Worldwide Nonproliferation Efforts”
A. Excerpt from Intelligence Report, “Pakistan-US: Demarche on F-16 Equipment,” 8 November 1982, enclosed with memorandum from Deputy CIA Director John N. McMahon to Deputy Secretary of Defense Frank Carlucci, “Risk Assessment of the Sale of AN/ALR-69 Radar Warning Receiver to Pakistan,” 8 November 1982, with excerpt from National Intelligence Estimate on Pakistan attached, n.d., Secret
B. Henry S. Rowen, National Intelligence Council, to DDCI [Deputy Director of Central Intelligence McMahon], 19 November 1982, with attached memorandum from National Intelligence Council staffer [name excised], “Pakistan,” same date, Secret
Source: CREST
Whether the Pakistanis, and presumably the Chinese, should get access to advanced F-16 technology was hotly contested. CIA officials acknowledged that, despite an agreement not to disclose military information, the Pakistanis were likely to give Beijing access to the AN/ALR-radar warning system, especially if “major strains” in the U.S.-Pakistan relationship developed. Because ALR-69 technology would allow a “potential adversary” to use radar equipment to defeat an F-16, Deputy CIA Director McMahon advised against releasing it to Pakistan. Secretary of State George Shultz wanted to meet Pakistani requirements and an official at CIA’s National Intelligence Council, supported by Henry Rowen, provided supporting arguments. Sanguine about the risk of disclosure to Beijing, they argued that failure to supply the F-16 with “USAF radar” would deprive Washington of “leverage” that made possible General Walter’s access to Zia. Highly sanguine about the political influence associated with arms sales, CIA analysts argued that failure to meet Pakistani demands would constitute a “serious blow to U.S. worldwide nonproliferation efforts.” This optimistic view prevailed and the Air Force was constrained to provide the AN/ALR-69 to Pakistan. [9]
Document 16: “Overwhelming Evidence that Zia Has Been Breaking His Assurances”
Secretary of State George Schultz to President Reagan, “How Do We Make Use of the Zia Visit to Protect Our Strategic Interests in the Face of Pakistan’s Nuclear Weapons Activities,” 26 November 1982, Secret
Source: CREST
George Shultz probably saw the ALR-69 issue as a minor problem compared to the “overwhelming evidence that Zia has been breaking his assurances” on Pakistan’s nuclear weapons program, Shultz may have accepted the interpretation that Zia was a patriotic liar” but this raised a tough diplomatic problem because the General would soon be in Washington to meet President Reagan. Citing an interagency report on issues and options, Shultz saw high risks because good relations with Pakistan, especially while the war in Afghanistan was in progress, were a major strategic interest. Yet, if Pakistan continued its nuclear weapons work, Congress could cut off aid. Moreover, a South Asian nuclear arms race could destabilize the region, not to mention the dangers of Indian and/or Israeli preemptive action against Pakistan, and the possibility that the latter could transfer nuclear technology to “unstable Arab countries.”
Options presented to Reagan ranged from cutting off aid directly if Pakistan kept trying to procure sensitive technology to warning Zia that continued activities would “seriously jeopardize our security relationship.” Shultz did not make a recommendation in this paper, but he it was evident that he wanted to avoid action other than a warning so as not to jeopardize the relationship. Records of his talks with Zia on 6 December and Zia’s meeting with President Reagan the next day are not yet available, but the Kenneth Adelman memorandum produced below (see document 20) discloses that Reagan laid out specific parameters to Zia: no assembly or test of nuclear devices, no transfer of technology for such devices, no violation of international safeguards, and no unsafeguarded reprocessing. [10]
Document 17: “Punish an Indian Attack So Severely that it will be Deterred to Begin With”
Bureau of Intelligence and Research, U.S. Department of State, “Pakistan: Security Planning and the Nuclear Option,” Report 83-AR, 1983 [full date cut off copy], Limited Official Use
Source: Department of State FOIA release, copy courtesy of Jeffrey Richelson
Based on a contract study prepared by University of Illinois political scientist (presently affiliated with Brookings) Stephen P. Cohen, after he had made three visits to Pakistan, this report focuses on the Pakistani military’s approach to deterrence. While the Pakistani military had once emphasized the value of using force first, the danger of war with India has produced a strategic doctrine that stresses the “use of military force to deter an Indian attack.” This doctrinal shift was creating a consensus in the military on the value of a “modest, ‘limited’ [nuclear] weapons program.” Pakistani military leaders did not like nuclear weapons, but they believed that they would “enable them to do what their armored divisions and air force can no longer” do in conventional terms: “punish an Indian attack so severely that it will be deterred to begin with.”
On the problem of Pakistani command-and-control over nuclear weapons, the summary of Cohen’s report observed that “Pakistan’s military has done self-destructive things in the past, and one cannot assume that it will not do them in the future.” Yet with greater professionalism in the Army, it was not “likely to make [decisions on nuclear weapons] any more irresponsibility than other states confronted with the same perplexing set of security constraints.” Cohen did not believe that Washington could do much to reverse nuclearization in South Asia, but U.S. influence could help ensure that proliferation did not lead to greater instability, for example, by limiting the buildup of stockpiles and supporting regional “mutual balanced force reductions” arrangements.
Document 18: “Supplying Conventional Weapons … Can be a Positive Force Against Proliferation”
Hugh Montgomery, director, Bureau of Intelligence and Research, U.S. Department of State, to Ambassador Ronald Spiers, 17 February 1984, enclosing “India-Pakistan: Pressures for Nuclear Proliferation,” Report 778-AR, 10 February 1984, Limited Official Use
Source: Department of State FOIA release, copy courtesy of Jeffrey Richelson
This interesting review of the South Asian nuclear problem starts by exploring the India-Pakistan nuclear dynamic. If Pakistan tested a weapon, India might resist following through on a weapons option, but might begin a series of tests. Both countries could covertly begin a weapons program. Despite speculation about an Indian preemptive strike against Pakistani nuclear installations, such an occurrence was unlikely because of the serious risks for India, not least the spread of “deadly radiation poisoning.” While New Delhi had resisted internal pressures for weaponization, changes in the security environment could weaken resistance, for example, if relations with Beijing worsened or if Chinese-Soviet relations improved (which would make the Indians more worried about Moscow’s reliability). The INR analyst believed that Washington had the most “leverage” with Pakistan because of the latter’s dependence on U.S. supplies of conventional weapons. “Supplying conventional weapons to Pakistan can be a positive force against proliferation” because they “can give Pakistan sufficient confidence in its own security that it would find the nuclear option less attractive and unnecessary.” This may have been the basis of State Department thinking that not meeting Pakistani desiderata on such issues as the F-16 would be a blow to nuclear non-proliferation policy. The challenge, however, was to not over-arm Pakistan because that could threaten Indian security and “increase the danger of nuclear proliferation in South Asia.”
Document 19: Pakistan Has “Produced an Atomic Weapon”
Defense Intelligence Agency cable to [excised location], “Pakistan-China: Nuclear Weapons Production and Testing,” 7 December 1985, Secret, excised copy
Source: DIA FOIA release
Only months after Congress enacted the Pressler amendment, an intelligence source claimed that Pakistan with Chinese assistance had “produced an atomic weapon in early October.” DIA had received similar reports and was trying to confirm this one. That U.S. intelligence believed that Pakistan was producing enough HEU for at least one device becomes evident in the next document.
Document 20: “He Lied to Us Again”
Kenneth Adelman, director, Arms Control and Disarmament Agency, o Assistant to the President for National Security Affairs, “Pakistan’s Nuclear Weapons Programs and U.S. Security Assistance,” 16 June 1986, Top Secret
Source: MDR release
More declassification actions will elucidate what the United States discovered during 1982-1986 about the Pakistani nuclear program, the renewed efforts to prevent procurement of sensitive technology, and high-level pressures to discourage secret nuclear work, but this memorandum by ACDA director Adelman gives perspective on some developments after the Reagan-Zia meeting in late 1982. The points that President Reagan made to Zia in December 1982 were re-stated in a May 1984 “non-paper” and then refined the following September when Reagan informed Zia that enriching uranium above 5 percent would be just as problematic as unsafeguarded plutonium reprocessing. But Reagan never put serious pressure on Zia to comply.
According to Adelman, the Pakistanis had been producing enriched uranium above the five percent level and, after overcoming an important “hurdle,” were enriching uranium at levels high enough (presumably close to 90 percent) to produce “one or more nuclear devices.” Adelman insisted that Zia was lying to Washington about this and that these activities jeopardized U.S. aid to Pakistan. The problem was that Washington had only “jawboned” General Zia instead of applying real pressure, thus undermining Reagan’s credibility and reinforcing “Zia’s belief that he can lie to us with impunity.” This raised serious problems for Congressional approval of aid, not only for certifying that Pakistan did not “possess” an explosive device, but also for renewing the 1982 Foreign Assistance Act that had exempted Pakistan from more rigorous nonproliferation standards.
Adelman recommended the precise application of pressure—to give Zia the “stark choice” of continued aid or the enrichment program. The possibility that Zia might resist could make it necessary to “tough it out” with Congress to assure the continuity of aid. But Adelman thought it possible that pressure would work and that Zia would conclude that “payoff” of U.S. aid and military sales was too high to forego.
Document 21: “Annual certification … very problematic”
Briefing Book, “Visit of Prime Minister Junejo of Pakistan, July 15-21, 1986,” Secret
Source: MDR Release
With Prime Minister Junejo about to visit Washington ACDA director had suggested that the U.S. tell him that pending a policy review on the Pakistani nuclear program “all actions involving military sales” have been halted . But this harder-line view apparently found no takers because the State Department briefing book for the Junejo visit only suggested tacit threats, not the “stark choice” that Adelman had recommended, that certification was “very problematic” without “positive Pak actions to help convince the Congress” which meant “quiet Pak actions to restrain [the enrichment] program.”
On the status of the Pakistani program, the briefing book included an intelligence finding [page 39 of pdf] that if the Kahuta plant operated at capacity it could produce enough m for “several nuclear devices per year.” Nevertheless, it was “our assessment … that Pakistan does not possess a device.” The highest levels of the Department were taking the position that Pakistan was in compliance with the Pressler amendment.
Document 22: “Absolute Criticality … of Restraint”
State Department cable 229696 to U.S. Embassy France et al., “Visit of Pakistani Primin Mohammad Khan Junejo to Washington – 15-18 July 1986,” 23 July 1986, Secret
Source: MDR Release
The only record of the meetings with Junejo that is available so far is this telegram that went out to a number of embassies. Impressing administration officials who found him “astute and well briefed,” Junejo professed to be responsive to the U.S. emphasis on the “absolute criticality” of “restraint” in Pakistani nuclear activities. In meetings with the press, Junejo “specifically affirmed” commitment not to enrich uranium above the five percent level, but this would continue to be a problem.
Document 23: “He Has Approached a Threshold”
Fred McGoldrick, Acting Director, Office of Nonproliferation and Export Policy, to John Negroponte, Assistant Secretary of State for Environment, Oceans and Fisheries, “Pakistan,” 9 April 1987, Secret, enclosing memorandum from Richard Murphy, Assistant Secretary for Near East and South Asian Affairs, “Action Plan on Pakistan Nuclear And Security Problems,” to Secretary of State, n.d., Secret
Source: MDR Release
In the fall of 1986, Reagan certified Pakistan’s compliance with the Pressler amendment although it was manifest that U.S. aid was not preventing Pakistan from doing what it could to produce a nuclear device. With the White House’s request for a new assistance program under review, Congress was contemplating a shorter, two-year, waiver of the Symington amendment or possibly tying aid directly to a halt of enriched uranium production. In early 1987 the Pakistani nuclear program was getting in the news again—-statements by A.Q. Khan about a “nuclear weapons capability,” Zia declaring that “Pakistan can build a bomb whenever it wishes,” and a speech by Ambassador Dean Hinton stating that Pakistan’s nuclear efforts were “inconsistent” with a peaceful program—which could only raise Congressional objections to aid to Pakistan. [11] In this context, according to Assistant Secretary Murphy, the danger was that Zia “has approached a threshold which he cannot cross without blatantly violating his pledge not to embarrass the President.”
Arguing that the administration needed “to obtain specific actions demonstrating restraint,” Murphy acknowledged that Pakistan was “unlikely” to do so, especially because Zia had “not so far responded constructively” to previous requests. Nevertheless, he proposed an “action plan” that included a new demarche on enrichment and other “nuclear firebreaks,” a message to India also asking for “restraint,” a “Congressional game plan,” and a presidential envoy to “engage” both India and Pakistan in the nuclear issue.
With the U.S. considering sales of airborne early warning aircraft (AEW) to Pakistan, Richard Kennedy, the ambassador-at-large for nonproliferation matters, had suggested that Washington directly link the sales to “Pakistani action on nonproliferation,” but other officials opposed such linkage. Perhaps Murphy raised the issue to see if Shultz had any interest in pursuing it.
What action Shultz may have taken on Murphy’s proposal remains to be learned, but any pressure exerted was likely to have been weak. Later in 1987, Reagan certified that Pakistan did not possess a nuclear advice; the aid kept flowing.
NOTES
[1] Dennis Kux,The United States and Pakistan, 1947-2000: Disenchanted Allies (Washington, D.C.: Woodrow Wilson Center Press; Baltimore : Johns Hopkins University Press, 2001), 276-277; Adrian Levy and Catherine Scott-Clark, Deception: Pakistan, the United States, and the Secret Trade in Nuclear Weapons (New York: Walker & Co.: 2007), 116; David Armstrong and Joseph Trento, America and the Islamic Bomb: The Deadly Compromise (Hanover NH: Steerforth Press, 2007), 122-137.
[3] Kux, The United States and Pakistan, 282-286; Armstrong and Trento, America and the Islamic Bomb, 142-154, and Levy and Scott-Clark, Deception, 156-163.
[4] For details on the Shahi-Vance-Smith talks, see Kux, The United States and Pakistan. 240-241. For Smith’s report on his talks, see http://www.gwu.edu/~nsarchiv/nukevault/ebb333/index.htm, document 45.
[6] For detection of Pakistan’s test site, see Jeffrey Richelson, Spying on the Bomb: American Nuclear Intelligence from Nazi Germany to Iran and North Korea (New York: W.W. Norton, 2006), 341.
[7] David Albright, Peddling Peril: How the Secret Nuclear Trade Arms America’s Enemies (New York: Free Press, 2010), 50.
[8] For the Pakistani purchasing networks, see BrunoTertrais, “Not a ‘Wal-Mart’, but an ‘Imports-Exports Enterprise’: Understanding the Nature of the A.Q. Khan Network,”Strategic Insights (August 2007) http://www.nps.edu/Academics/centers/ccc/publications/OnlineJournal/2007/Aug/tertraisAug07.pdf . See also Albright, Peddling Peril, 48.
[9] T. V. Paul, “influence through Arms Transfers: Lessons from the US-Pakistani Relationship,” Asian Survey 32 (Dec. 1992), 1086.
[10] Shultz does not mention his 1982 meeting with Zia in his memoir, Turmoil and Triumph: My Years As Secretary of State (New York: Charles Scribner’s Sons, 1993), although at 493-494, he covers a 1984 discussion after Indira Gandhi’s funeral. Zia said that Pakistan was “nowhere near” building a nuclear weapon and that “We have no intention of making such a weapon.”
Dirty Little Secrets – Full Movie
FEMEN protests against UEFA EUROCUP 2012
Cryptome unveils Cyberwarhawks
Cyberwarhawks
http://www.hsgac.senate.gov/imo/media/doc/CYBER%20letter%20from%20top%20security%20guys.pdf
![[Image]](https://i0.wp.com/cryptome.org/2012/06/cyberwarhawks.jpg)
http://www.hsgac.senate.gov/issues/cybersecurity
United States Senate Homeland Security and Governmental Affairs Committee
Cybersecurity
Last February, in the 112th Congress, Senators Lieberman, Collins, and Carper introduced The Cybersecurity and Internet Freedom Act, S.413, which was very similar to the Cyber Space as a National Asset legislation. Since other committees had related legislation, Majority Leader Reid directed all committees of jurisdiction to come together and produce a single bill. That bill is the Cybersecurity Act of 2012, S. 2105, which was introduced February 14, 2012, by Senators Lieberman, Collins, Rockefeller, and Feinstein.
The measure would protect federal civilian systems and the systems of the nation’s most critical infrastructure, most ofs which is owned by the private sector. The Cybersecurity Act of 2012 is the result of months of negotiations with other Committees of jurisdiction; the energy, financial services, and chemical industries; national security and privacy and civil liberties groups; and a number of other government agencies. The Senate is expected to debate the measure in the coming weeks. Read letters of praise and support below.
The FBI against Cybercrimes
 |
|---|
Update on March 12, 2012: To assist victims affected by the DNSChanger malicious software, the FBI obtained a court order authorizing the Internet Systems Consortium (ISC) to deploy and maintain temporary clean DNS servers. This solution is temporary, providing additional time for victims to clean affected computers and restore their normal DNS settings. The clean DNS servers will be turned off on July 9, 2012, and computers still impacted by DNSChanger may lose Internet connectivity at that time. |
Operation Ghost Click
International Cyber Ring That Infected Millions of Computers Dismantled
11/09/11
Six Estonian nationals have been arrested and charged with running a sophisticated Internet fraud ring that infected millions of computers worldwide with a virus and enabled the thieves to manipulate the multi-billion-dollar Internet advertising industry. Users of infected machines were unaware that their computers had been compromised—or that the malicious software rendered their machines vulnerable to a host of other viruses.
Details of the two-year FBI investigation called Operation Ghost Click were announced today in New York when a federal indictment was unsealed. Officials also described their efforts to make sure infected users’ Internet access would not be disrupted as a result of the operation.
| FBI Statement: Janice Fedarcyk, New York Assistant Director in Charge
|
|---|
The indictment, said Janice Fedarcyk, assistant director in charge of our New York office, “describes an intricate international conspiracy conceived and carried out by sophisticated criminals.” She added, “The harm inflicted by the defendants was not merely a matter of reaping illegitimate income.”
Beginning in 2007, the cyber ring used a class of malware called DNSChanger to infect approximately 4 million computers in more than 100 countries. There were about 500,000 infections in the U.S., including computers belonging to individuals, businesses, and government agencies such as NASA. The thieves were able to manipulate Internet advertising to generate at least $14 million in illicit fees. In some cases, the malware had the additional effect of preventing users’ anti-virus software and operating systems from updating, thereby exposing infected machines to even more malicious software.
“They were organized and operating as a traditional business but profiting illegally as the result of the malware,” said one of our cyber agents who worked the case. “There was a level of complexity here that we haven’t seen before.”
DNS—Domain Name System—is a critical Internet service that converts user-friendly domain names, such as http://www.fbi.gov, into numerical addresses that allow computers to talk to each other. Without DNS and the DNS servers operated by Internet service providers, computer users would not be able to browse websites or send e-mail.
| Success Through Partnerships
A complex international investigation such as Operation Ghost Click could only have been successful through the strong working relationships between law enforcement, private industry, and our international partners. Announcing today’s arrests, Preet Bharara, (above left) U.S. Attorney for the Southern District of New York, praised the investigative work of the FBI, NASA’s Office of Inspector General (OIG), the Estonian Police and Border Guard Board, and he specially thanked the National High Tech Crime Unit of the Dutch National Police Agency. In addition, the FBI and NASA-OIG received assistance from multiple domestic and international private sector partners, including Georgia Tech University, Internet Systems Consortium, Mandiant, National Cyber-Forensics and Training Alliance, Neustar, Spamhaus, Team Cymru, Trend Micro, University of Alabama at Birmingham, and members of an ad hoc group of subject matter experts known as the DNS Changer Working Group (DCWG). |
|---|
DNSChanger was used to redirect unsuspecting users to rogue servers controlled by the cyber thieves, allowing them to manipulate users’ web activity. When users of infected computers clicked on the link for the official website of iTunes, for example, they were instead taken to a website for a business unaffiliated with Apple Inc. that purported to sell Apple software. Not only did the cyber thieves make money from these schemes, they deprived legitimate website operators and advertisers of substantial revenue.
The six cyber criminals were taken into custody yesterday in Estonia by local authorities, and the U.S. will seek to extradite them. In conjunction with the arrests, U.S. authorities seized computers and rogue DNS servers at various locations. As part of a federal court order, the rogue DNS servers have been replaced with legitimate servers in the hopes that users who were infected will not have their Internet access disrupted.
It is important to note that the replacement servers will not remove the DNSChanger malware—or other viruses it may have facilitated—from infected computers. Users who believe their computers may be infected should contact a computer professional. They can also find additional information in the links on this page, including how to register as a victim of the DNSChanger malware. And the FBI’s Office for Victim Assistance will provide case updates periodically at 877-236-8947.
Resources:
– Press release
– Statement by New York ADIC Janice Fedarcyk
– Learn more about DNSChanger malware and how it can affect your computer
– Check your computer’s DNS settings
– Register as a victim of the DNSChanger malware
– Cyber Crimes stories
Every Picture Tells a Story – Full Movie
The FBI – Former Corporate Chairman of Consulting Firm and Board of Director Rajat Gupta Found Guilty of Insider Trading in Manhattan Federal Court
Preet Bharara, the United States Attorney for the Southern District announced that Rajat K. Gupta, former corporate chairman of an international consulting firm and a member of the Boards of Directors of The Goldman Sachs Group Inc. (“Goldman Sachs”) and the Procter & Gamble Company (“P&G”), was found guilty today by a jury in Manhattan federal court of conspiracy and securities fraud crimes stemming from his involvement in an insider trading scheme with his business partner and friend, Raj Rajaratnam, the founder and former head of the Galleon Group.
Manhattan U.S. Attorney Preet Bharara stated, “Rajat Gupta once stood at the apex of the international business community. Today, he stands convicted of securities fraud. He achieved remarkable success and stature, but he threw it all away. Having fallen from respected insider to convicted inside trader, Mr. Gupta has now exchanged the lofty board room for the prospect of a lowly jail cell. Violating clear and sacrosanct duties of confidentiality, Mr. Gupta illegally provided a virtual open line into the board room for his benefactor and business partner, Raj Rajaratnam.
“Almost two years ago, we said that insider trading is rampant, and today’s conviction puts that claim into stark relief. It bears repeating that, in coordination with our extraordinary partners at the FBI, we will continue to pursue those who violate the securities laws, regardless of status, wealth, or influence. I thank the members of the jury for their time, attention, and service, and the dedicated career prosecutors from my office who so ably tried this case.”
According to the superseding indictment filed in Manhattan federal court, other court documents, statements made at trial, and court proceedings:
During all relevant times, Gupta and Rajaratnam maintained a close personal and business relationship. Among other things, Gupta described Rajaratnam as a close friend; Gupta invested his money in Galleon funds while he served as chairman of the international consulting firm; Gupta co-owned a fund of funds with Rajaratnam, which invested its money in Galleon funds; Gupta served as chairman of a $1.5 billion private equity firm called NSR in which Rajaratnam invested approximately $50 million and served on the investment committee; and Gupta was given the position of Chairman of Galleon International in 2008 and expected to receive 15 percent of that fund’s performance fees.
From 2007 through January 2009, Gupta repeatedly disclosed material, non-public information (“inside information”) that he acquired in his capacity as a member of the Board of Directors of Goldman Sachs, with the understanding that Rajaratnam would use the inside information to purchase and sell securities. Rajaratnam, in turn, caused the execution of transactions in the securities of Goldman Sachs on the basis of the inside information and shared the inside information with others at Galleon, thereby earning illegal profits, and illegally avoiding losses, of millions of dollars. On separate occasions that were proven at trial, Gupta gave Rajaratnam inside information that included highly sensitive and secret information. Illegal tips that were proven at trial include the following:
The September 23, 2008 Goldman Sachs Tip
The evidence at trial proved that, on September 23, 2008, within approximately 60 seconds after the conclusion of a Goldman Sachs telephonic board meeting in which the Board approved a $5 billion investment by Berkshire Hathaway, Gupta spoke with Rajaratnam. Immediately following the call, Rajaratnam directed two separate traders to purchase approximately $43 million of Goldman Sachs stock within minutes before the close of trading. During two court-authorized wiretapped conversations the following morning on September 24, 2008 between Rajaratnam and his principal trader and coconspirator, Ian Horowitz, Rajaratnam said that he received a call at 3:58 p.m. the day before telling him “something good’s gonna happen” at Goldman Sachs, that he directed the two traders to buy Goldman shares before the market closed, and that he could not yell this information out on Galleon’s trading floor. The evidence at trial showed that, based on Gupta’s illegal tip, Rajaratnam and co-conspirator Gary Rosenbach earned over $1 million in illegal profits.
The October 23, 2008 Goldman Sachs Tip
The evidence at trial proved that, on October 23, 2008, Gupta participated on a Goldman Sachs Board posting call during which he learned that Goldman Sachs was losing money for the quarter, which Goldman Sachs had never done since becoming a public company. Just 23 seconds after that call ended, Gupta called Rajaratnam. Following that call, at the first available opportunity after the stock market reopened, Rajaratnam started to sell his entire holdings in Goldman Sachs stock. Later that day, during a court-authorized wiretapped conversation, Rajaratnam explained to a senior portfolio manager at Galleon International that Rajaratnam had spoken with a member of the Board of Goldman Sachs and learned that Goldman Sachs was losing money during the quarter while Wall Street analysts expected the company to make money. The evidence at trial showed that, based on Gupta’s illegal tip, Rajaratnam was able to avoid losses of several million dollars.
* * *
Gupta, 63, of Westport, Connecticut, was found guilty of one count of conspiracy to commit securities fraud and three counts of securities fraud. He was acquitted on two securities fraud counts. The conspiracy count carries a maximum sentence of five years in prison and a maximum fine of the greater of $250,000 or twice the gross gain or loss from the offense. Each of the securities fraud counts carries a maximum sentence of 20 years in prison and a fine of $5 million. Gupta will be sentenced on October 18, 2012.
Rajaratnam was convicted in a jury trial on May 11, 2011 of 14 counts of conspiracy and securities fraud. He was sentenced on October 13, 2011 to 11 years in prison and was ordered to pay forfeiture in the amount of $53,816,434 and a $10 million fine.
Mr. Bharara praised the outstanding efforts of the FBI. He also thanked the SEC for its assistance in the investigation.
This case was brought in coordination with President Barack Obama’s Financial Fraud Enforcement Task Force, on which U.S. Attorney Bharara serves as a co-chair of the Securities and Commodities Fraud Working Group. President Obama established the interagency Financial Fraud Enforcement Task Force to wage an aggressive, coordinated, and proactive effort to investigate and prosecute financial crimes. The task force includes representatives from a broad range of federal agencies, regulatory authorities, inspectors general, and state and local law enforcement who, working together, bring to bear a powerful array of criminal and civil enforcement resources. The task force is working to improve efforts across the federal executive branch and, with state and local partners, to investigate and prosecute significant financial crimes, ensure just and effective punishment for those who perpetrate financial crimes, combat discrimination in the lending and financial markets, and recover proceeds for victims of financial crimes.
Assistant U.S. Attorneys Reed Brodsky and Richard C. Tarlowe are in charge of the prosecution.
– Statement by FBI New York Assistant Director in Charge Janice K. Fedarcyk on Gupta’s conviction
TOP-SECRET from the FBI – Economic Espionage
 |
|---|
| American industry and private sector businesses are the choice target of foreign intelligence agencies, criminals, and industry spies. The above image on the cost of economic espionage to the U.S. can currently be seen on digital billboards—courtesy of Clear Channel and Adams Outdoor Advertising—in several regions of the country with a concentration of high-tech research and development companies, laboratories, major industries, and national defense contractors. If you suspect economic espionage, report it to the FBI at tips.fbi.gov. | Download high-resolution image |
Economic Espionage
How to Spot a Possible Insider Threat
05/11/12
This past February, five individuals and five companies were charged with economic espionage and theft of trade secrets for their roles in a long-running effort to obtain information for the benefit of companies controlled by the government of the People’s Republic of China.

What Do They Want From Us? According to the latest economic espionage report to Congress from the Office of the National Counterintelligence Executive, although foreign collectors will remain interested in all aspects of U.S. economic activity and technology, they’re probably most interested in the following areas: – Information and communications technology, which form the backbone of nearly every other technology; – Business information that pertains to supplies of scarce natural resources or that provides global actors an edge in negotiations with U.S. businesses or the U.S. government; – Military technologies, particularly marine systems, unmanned aerial vehicles, and other aerospace/aeronautic technologies; and – Civilian and dual-use technologies in fast-growing sectors like clean energy, health care/pharmaceuticals, and agricultural technology. |
|---|
According to the superseding indictment, the PRC government was after information on chloride-route titanium dioxide (TiO2) production capabilities. TiO2 is a commercially valuable white pigment with numerous uses, including coloring paints, plastics, and paper. DuPont, a company based in Wilmington, Delaware, invented the chloride-route process for manufacturing TiO2 and invested heavily in research and development to improve the process over the years. In 2011, the company reported that its TiO2 trade secrets had been stolen.
Among the individuals charged in the case? Two long-time DuPont employees…one of whom pled guilty in fairly short order.
Foreign economic espionage against the U.S. is a significant and growing threat to our country’s economic health and security…and so is the threat from corporate insiders willing to carry it out.
And because we’re now in the digital age, insiders—who not so many years ago had to photocopy and smuggle mountains of documents out of their offices—can now share documents via e-mail or download them electronically on easy-to-hide portable devices.
Why do insiders do it? Lots of reasons, including greed or financial need, unhappiness at work, allegiance to another company or another country, vulnerability to blackmail, the promise of a better job, and/or drug or alcohol abuse.
How to stop them? Obviously, a strong organizational emphasis on personnel and computer security is key, and the FBI conducts outreach efforts with industry partners—like InfraGard—that offer a variety of security and counterintelligence training sessions, awareness seminars, and information.
| Successful Investigation of ‘Insiders’
– In Detroit, a car company employee copied proprietary documents, including some on sensitive designs, to an external hard drive…shortly before reporting for a new job with a competing firm in China. Details – In Indianapolis, an employee of an international agricultural business stole trade secrets on organic pesticides from his employer and shared them with individuals in China and Germany. Details In Boston, a technology company employee e-mailed an international consulate in that city and offered proprietary business information. He later provided pricing and contract data, customer lists, and names of other employees…to what turned out to be a federal undercover agent. Details All three subjects pled guilty. But in two of the three cases, the stolen secrets probably ended up in the hands of global businesses that will use them to attempt to gain an unfair competitive edge over the United States. Podcasts Gotcha: Special agent discusses 2010 economic espionage case. FBI, This Week: The FBI is seeing an increase in cases involving spying from foreign intelligence agencies, criminals, and others who wish America harm. |
|---|
You can help as well. In our experience, those who purloin trade secrets and other sensitive information from their own companies and sell them overseas exhibit certain behaviors that co-workers could have picked up on ahead of time, possibly preventing the information breaches in the first place. Many co-workers came forward only after the criminal was arrested. Had they reported those suspicions earlier, the company’s secrets may have been kept safe.
Here are some warning signs that MAY indicate that employees are spying and/or stealing secrets from their company:
- They work odd hours without authorization.
- Without need or authorization, they take proprietary or other information home in hard copy form and/or on thumb drives, computer disks, or e-mail.
- They unnecessarily copy material, especially if it’s proprietary or classified.
- They disregard company policies about installing personal software or hardware, accessing restricted websites, conducting unauthorized searches, or downloading confidential material.
- They take short trips to foreign countries for unexplained reasons.
- They engage in suspicious personal contacts with competitors, business partners, or other unauthorized individuals.
- They buy things they can’t afford.
- They are overwhelmed by life crises or career disappointments.
- They are concerned about being investigated, leaving traps to detect searches of their home or office or looking for listening devices or cameras.
If you suspect someone in your office may be committing economic espionage, report it to your corporate security officer and to your local FBI office, or submit a tip online at https://tips.fbi.gov/.
Megapark 2012 – Sexy Russian Football Girls posing – UEFA2012 EM – Video
Larry King Interview with Admiral General Aladeen – Sacha Barron Cohen Video
TOP-SECRET – Open Source Center North Korea Unusual Threats Signal Possible Action Against South Korea

North Korea’s recent threat to carry out “special actions” against the South is rare and seems intended to signal the regime’s resolve to move forward with some form of provocation. The threat, however, is unlike past warnings the regime has typically issued prior to military provocations, suggesting that the North might follow through with a move other than a conventional military attack. Significantly, some aspects of the warning appear to signal Pyongyang’s commitment to follow up on the “actions” in the near future.
North Korea on 23 April issued an unprecedented “notice” in the name of the Korean People’s Army (KPA) Supreme Command Special Operations Action Team. The toughly worded message — a response to what Pyongyang apparently viewed as provocative remarks recently made by ROK President Lee Myung-bak — contained an unusually vague warning against Seoul.
- The “notice” particularly took issue with President Lee’s recent comments on “strengthening” South Korea’s national “self-defense capabilities” (Yonhap, 19 April), which it characterized as an “extremely grave frenzy of provocation” and a “theory of striking” the North’s “supreme headquarters” (Pyongyang radio, 23 April). The message stated that the North’s “revolutionary armed forces” will take “special actions” against the “gang of traitors’ reckless” move, and emphasized that the “actions…will start soon” (Pyongyang radio, 23 April).
- This is only the second time the North has used the “special actions” formulation to threaten President Lee in an authoritative military pronouncement. Pyongyang just five days earlier used the same threat — albeit in a passive voice — in an authoritative KPA Supreme Command spokesman’s “statement,” which said that “special action measures will be taken” (Pyongyang radio, 18 April).
- The “notice” also contained a figurative reference to turning the “group of rats” — referring to the ROK leadership — into “ashes” within “three to four minutes” (Pyongyang radio, 23 April). The “ashes” formulation is on the low end of the rhetorical threat spectrum. Pyongyang in recent years has issued more direct and literal formulations to threaten Seoul, particiuarly following the Ch’o’nan sinking.
The threat to carry out “special actions” is ambiguous and not as definitive as warnings Pyongyang has issued in the lead-up to past military provocations, suggesting that the regime might be contemplating some form of action other than an actual military attack. The North’s typical rhetorical pattern prior to provocations is to signal in authoritative media that it has decided to act without divulging how, when, or where it will move.
- Prior to the sinking of Ch’o’nan, Pyongyang issued a more direct threat in the name of an authoritative KPA General Staff spokesman stating that it “will” respond to US ROK military drills with a “powerful military counteraction” (Pyongyang radio, 25 February 2010). Similarly, leading up to the Yo’np’yo’ng Island shelling, a statement by the spokesman for the North side’s delegation to North-South military talks warned that its Army “will counter” the South’s provocations with a “merciless physical retaliation” (KCNA, 29 October 2010).
Committing to Prompt Action
Although the recent threat was not as definitive as warnings the North issued in advance of past military provocations, the unusual use of the phrase “will start soon” in combination with the unique “special actions” formulation appears designed to signal that the regime is committed to following through with its warning.
- Pyongyang’s use of the term “soon” is unusually specific and categorical. The last time the North modified its threat with this term was in a less authoritative North-South Military Talks General-Level Representative “notice,” which warned that its “army will soon” take “corresponding decisive measures” in response to South Korea distributing leaflets to the North (Pyongyang radio, 10 April 2010). Unlike the most recent threat, however, this warning was preceded by a conditional phrase, which afforded the regime the flexibility to refrain from taking immediate action.
- Further underscoring its commitment to carry out its threat, the North broadcast the KPA “notice” to both domestic and external audiences. In addition, the North Korean radio and television carried the message at least two times a day for three days following the initial announcement.
DOWNLOAD THE ORIGINAL DOCUMENT HERE
Megapark 2012: Micaela Schaefer Fussball EM C-Cup – Mallorca Video
Family Affair – Full Movie
Uncensored – FEMEN Female Fighters
TOP-SECRET from the FBI – Former Chief Financial Officer of Taylor, Bean, & Whitaker Sentenced to 60 Months in Prison for Fraud Scheme
WASHINGTON—Delton de Armas, a former chief financial officer (CFO) of Taylor, Bean, & Whitaker Mortgage Corp. (TBW), was sentenced today to 60 months in prison for his role in a more than $2.9 billion fraud scheme that contributed to the failure of TBW.
De Armas was sentenced today by U.S. District Judge Leonie M. Brinkema in the Eastern District of Virginia. The sentence was announced today by Assistant Attorney General Lanny A. Breuer of the Criminal Division; U.S. Attorney Neil H. MacBride for the Eastern District of Virginia; Christy Romero, Special Inspector General, Office of the Special Inspector General for the Troubled Asset Relief Program (SIGTARP); Assistant Director in Charge James W. McJunkin of the FBI’s Washington Field Office; David A. Montoya, Inspector General of the Department of Housing and Urban Development (HUD-OIG); Jon T. Rymer, Inspector General of the Federal Deposit Insurance Corporation (FDIC-OIG); Steve A. Linick, Inspector General of the Federal Housing Finance Agency (FHFA-OIG); and Richard Weber, Chief of the Internal Revenue Service Criminal Investigation (IRS-CI).
De Armas, 41, of Carrollton, Texas, pleaded guilty in March to one count of conspiracy to commit bank and wire fraud and one count of making false statements.
“For years, Mr. de Armas, the CFO of one of the country’s largest private mortgage companies, helped defraud financial institutions by concealing from them billions of dollars in losses,” said Assistant Attorney General Breuer. “His lies and deceits contributed to the devastating losses suffered by major institutional investors. As a consequence for his crimes, he will now spend the next five years of his life behind bars.”
“As CFO, Mr. de Armas could have—and should have—put a stop to the massive fraud at TBW the moment he discovered it,” said U.S. Attorney MacBride. “Instead, he and others lied for years on end to investors, banks, regulators, and auditors and caused more than $2.4 billion in losses to major financial institutions.”
“Rather than blow the whistle on billions of dollars in fraud, de Armas chose to help conceal it,” said Special Inspector General Romero. “This CFO lied to investors, banks, regulators, and auditors to cover up the massive fraud scheme which resulted in the failure of both TBW and Colonial Bank. The court’s decision to sentence de Armas to five years in prison reflects the seriousness of his role as a gatekeeper within TBW and the contribution of his crime to our nation’s financial crisis.”
“The actions of Mr. De Armas and others resulted in the loss of billions of dollars to major financial institutions,” said Assistant Director in Charge McJunkin. “Today’s sentence serves as a warning to anyone who attempts to take advantage of investors and our banking system. Together with our law enforcement partners, the FBI will pursue justice for anyone involved in such fraudulent schemes.”
According to court documents, de Armas joined TBW in 2000 as its CFO and reported directly to its chairman, Lee Bentley Farkas, and later to its CEO, Paul Allen. He previously admitted in court that from 2005 through August 2009, he and other co-conspirators engaged in a scheme to defraud financial institutions that had invested in a wholly-owned lending facility called Ocala Funding. Ocala Funding obtained funds for mortgage lending for TBW from the sale of asset-backed commercial paper to financial institutions, including Deutsche Bank and BNP Paribas. The facility was managed by TBW and had no employees of its own.
According to court records, shortly after Ocala Funding was established, de Armas learned there were inadequate assets backing its commercial paper, a deficiency referred to internally at TBW as a “hole” in Ocala Funding. De Armas knew that the hole grew over time to more than $700 million. He learned from the CEO that the hole was more than $1.5 billion at the time of TBW’s collapse. De Armas admitted he was aware that, in an effort to cover up the hole and mislead investors, a subordinate who reported to him had falsified Ocala Funding collateral reports and periodically sent the falsified reports to financial institution investors in Ocala Funding and to other third parties. De Armas acknowledged that he and the CEO also deceived investors by providing them with a false explanation for the hole in Ocala Funding.
De Armas also previously admitted in court that he directed a subordinate to inflate an account receivable balance for loan participations in TBW’s financial statements. De Armas acknowledged that he knew that the falsified financial statements were subsequently provided to Ginnie Mae and Freddie Mac for their determination on the renewal of TBW’s authority to sell and service securities issued by them.
In addition, de Armas admitted in court to aiding and abetting false statements in a letter the CEO sent to the U.S. Department of Housing and Urban Development, through Ginnie Mae, regarding TBW’s audited financial statements for the fiscal year ending on March 31, 2009. De Armas reviewed and edited the letter, knowing it contained material omissions. The letter omitted that the delay in submitting the financial data was caused by concerns its independent auditor had raised about the financing relationship between TBW and Colonial Bank and its request that TBW retain a law firm to conduct an internal investigation. Instead, the letter falsely attributed the delay to a new acquisition and TBW’s switch to a compressed 11-month fiscal year.
“We are pleased to have joined our law enforcement colleagues in bringing Mr. de Armas to justice,” said Inspector General Rymer. “The former chief financial officer’s actions contributed to one of the largest bank frauds in the country and led to the demise of TBW. His punishment, along with the earlier sentencings of other co-conspirators involved in the Colonial Bank and TBW scheme, sends a clear message that those who abuse their positions of trust and seek to undermine the integrity of the financial services industry will be held accountable. We will continue to pursue such cases in the interest of ensuring the safety and soundness of our nation’s banks and the strength of the financial services industry as a whole.”
“Delton de Armas was a key player in the TBW fraud; the significant sentence of 60 months handed down today appropriately takes that role into account,” said Inspector General Linick.
In April 2011, a jury in the Eastern District of Virginia found Lee Bentley Farkas, the chairman of TBW, guilty of 14 counts of conspiracy, bank, securities, and wire fraud. On June 30, 2011, Judge Brinkema sentenced Farkas to 30 years in prison. In addition, six individuals have pleaded guilty for their roles in the fraud scheme, including: Paul Allen, former chief executive officer of TBW, who was sentenced to 40 months in prison; Raymond Bowman, former president of TBW, who was sentenced to 30 months in prison; Desiree Brown, former treasurer of TBW, who was sentenced to six years in prison; Catherine Kissick, former senior vice president of Colonial Bank and head of its Mortgage Warehouse Lending Division (MWLD), who was sentenced to eight years in prison; Teresa Kelly, former operations supervisor for Colonial Bank’s MWLD, who was sentenced to three months in prison; and Sean Ragland, a former senior financial analyst at TBW, who was sentenced to three months in prison.
The case is being prosecuted by Deputy Chief Patrick Stokes and Trial Attorney Robert Zink of the Criminal Division’s Fraud Section and Assistant U.S. Attorneys Charles Connolly and Paul Nathanson of the Eastern District of Virginia. This case was investigated by SIGTARP, FBI’s Washington Field Office, FDIC-OIG, HUD-OIG, FHFA-OIG, and the IRS-Criminal Investigation. The Financial Crimes Enforcement Network (FinCEN) of the Department of the Treasury also provided support in the investigation. The department would also like to acknowledge the substantial assistance of the SEC in the investigation of the fraud scheme.
This prosecution was brought in coordination with President Barack Obama’s Financial Fraud Enforcement Task Force. President Obama established the interagency Financial Fraud Enforcement Task Force to wage an aggressive, coordinated, and proactive effort to investigate and prosecute financial crimes. The task force includes representatives from a broad range of federal agencies, regulatory authorities, inspectors general, and state and local law enforcement who, working together, bring to bear a powerful array of criminal and civil enforcement resources. The task force is working to improve efforts across the federal executive branch and, with state and local partners, to investigate and prosecute significant financial crimes, ensure just and effective punishment for those who perpetrate financial crimes, combat discrimination in the lending and financial markets, and recover proceeds for victims of financial crimes.
Liebe Freunde von der STASI & CO
Sehr wenig verehrenswürdige STASI-“GoMoPa”-Freunde und deren Allierte,
vor 2 Jahren sagte ich, ich werde Euch outen und dies habe ich trotz all Eurer
Morddrohungen, Rufmorde und vieler anderer Schädigungen getan.
Und es kommt noch besser !
Die Vorfreude ist doch die schönste Freude !
Freuen wir uns doch alle !
Herzlichst
Bernd Pulch
Magister Artium, Publizistik, Germanistik, Komparatistik
Fatal Choice – Full Movie
Nach KGB-STASI-Art – FEMEN-Alexandra Shevchenko, Yana Zhdanova und Anna Bolshakova gekidnappt
-

Die Femen-Aktivistinnen Alexandra Shevchenko, Yana Zhdanova und Anna Bolshakova sind spurlos verschwunden:
Drei Mitglieder der ukrainischen Frauengruppe Femen sind in der Stadt Donezk spurlos verschwunden. Möglicherweise wurden sie entführt.
Eine Gruppe von 15 Männern habe die Aktivistinnen seit deren Ankunft in dem ostukrainischen EM-Spielort verfolgt, teilte die Organisation mit. In Donezk hatten die Frauen einen Protest gegen die Fußball-Europameisterschaft geplant.
Am Nachmittag sei der Kontakt zur Aktivistin Alexandra Shevchenko abgebrochen, teilte Femen am Freitagabend weiter mit. Eine Stunde später konnten dann auch Anna Bolshakova und Yana Zhdanovea nicht mehr erreicht werden.
Die örtliche Miliz suche nach den verschwundenen Frauen, meldete die Agentur Interfax.
Femen-Aktivistinnen hatten zuvor schon in Warschau und Kiew gegen Sextourismus und Prostitution demonstriert, vor den Stadien blank gezogen.
Am 10. Juni tauchten sie auf der Reeperbahn in Hamburg auf, nannten Prostitution eine neue Form des Faschismus.
Im Dezember 2011 wurden drei Femen-Mitglieder nach einer Protestaktion gegen den weißrussischen Präsidenten Alexander Lukaschenko aus Minsk verschleppt.
Bei Temperaturen um den Gefrierpunkt seien die Frauen in einem Wald mit Öl übergossen und mit dem Tode bedroht worden, hieß es seinerzeit. Die Aktivistinnen wurden nackt ausgesetzt, konnten aber wieder Kontakt zu ihrer Organisation aufnehmen.
Secret – Cryptome unveils – Shell Battles Fiction
To: <jya[at]pipeline.com>
From: Royal Dutch Shell plc. <alerts[at]shell.com>
Subject: Shell considers legal action following launch of fictitious international campaign
Date: Thu, 7 Jun 2012 21:48:37 +0200 (CEST)
[Images link to articready.com]
![[]](https://i0.wp.com/arcticready.com/PR-images/shell.gif)
![]()
![]() Shell considers legal action following launch of fictitious international campaign
Shell considers legal action following launch of fictitious international campaign
Lawyers operating on behalf of Royal Dutch Shell plc. (Shell) are considering formal action against unknown activists who staged a counterfeit campaign launch event at the Seattle Space Needle.
The groups released a stream of social media content, with the defamatory hashtag #shellfail, which deliberately misrepresents the safety of Shell’s drill rigs heading to the Arctic, and extensively violated Shell’s intellectual property rights.
Shell is monitoring the spread of potentially defamatory material on the internet and reporters are advised to avoid publishing such material.
These activists’ tactics stand in marked contrast to Shell’s transparency regarding the safety of Shell’s Arctic efforts. Earlier this week, Shell hosted Alaskan Governor Sean Parnell and Senator Lisa Murkowski on a safety tour of the Kulluk rig, during which the Senator and Governor were soundly impressed by the Kulluk’s cutting-edge safety mechanisms.
“We can confirm that this was not a Shell event. Activist groups are becoming increasingly desperate in their attempts to block our federally approved right to drill in the Arctic, and are resorting to ever more underhanded tactics,” said Curtis Smith, Shell Alaska Spokesman.
“These individuals choose to focus on the safety record of the rigs going to the Arctic, but there have been no accidents involving either vessel and both have been extensively upgraded in a recent $150 million overhaul. We stand confidently behind these measures, which is why we have gone beyond the federally-mandated liability cap of $75 million and have established a $12 billion escrow fund to mitigate any potential risks. Despite this deliberate attempt to frighten the public, it is clear and obvious that Shell takes safety extremely seriously.”
Journalists are also warned about a counterfeit website and European billboard campaign launched by the activists. The website, at www.ArcticReady.com, includes fake Let’s Go ads, a “Let’s Go Ad Generator,” and a children’s game.
“These people have gone to great lengths to mislead the public about the age and reliability of our Arctic vessels, and otherwise damage Shell’s credibility,” said Smith. “Shell can obviously not allow this sort of misinformation to proliferate, and we are taking the firmest legal measures against the perpetrators of this campaign.”
Enquiries
Shell Media Relations
US Press: 713-628-6047, usmedia[at]shell.com [links to: media[at]arcticready.com]
Notes
Royal Dutch Shell plc is incorporated in England and Wales, has its headquarters in The Hague and is listed on the London, Amsterdam, and New York stock exchanges. Shell companies have operations in more than 100 countries and territories with businesses including oil and gas exploration and production; production and marketing of Liquefied Natural Gas and Gas to Liquids; manufacturing, marketing and shipping of oil products and chemicals and renewable energy projects. For further information, visit www.shell.com
Cautionary note
The companies in which Royal Dutch Shell plc directly and indirectly owns investments are separate entities. In this document “Shell”, “Shell group” and “Royal Dutch Shell” are sometimes used for convenience where references are made to Royal Dutch Shell plc and its subsidiaries in general. Likewise, the words “we”, “us” and “our” are also used to refer to subsidiaries in general or to those who work for them. These expressions are also used where no useful purpose is served by identifying the particular company or companies. ”Subsidiaries”, “Shell subsidiaries” and “Shell companies” as used in this document refer to companies in which Royal Dutch Shell either directly or indirectly has control, by having either a majority of the voting rights or the right to exercise a controlling influence. The companies in which Shell has significant influence but not control are referred to as “associated companies” or “associates” and companies in which Shell has joint control are referred to as “jointly controlled entities”. In this document, associates and jointly controlled entities are also referred to as “equity-accounted investments”. The term “Shell interest” is used for convenience to indicate the dire ct and/or indirect (for example, through our 34% shareholding in Woodside Petroleum Ltd.) ownership interest held by Shell in a venture, partnership or company, after exclusion of all third-party interest. This document contains forward-looking statements concerning the financial condition, results of operations and businesses of Royal Dutch Shell. All statements other than statements of historical fact are, or may be deemed to be, forward-looking statements. Forward-looking statements are statements of future expectations that are based on management’s current expectations and assumptions and involve known and unknown risks and uncertainties that could cause actual results, performance or events to differ materially from those expressed or implied in these statements. Forward-looking statements include, among other things, statements concerning the potential exposure of Royal Dutch Shell to market risks and statements expressing management’s expectations, beliefs, estimates , forecasts, projections and assumptions. These forward-looking statements are identified by their use of terms and phrases such as ”anticipate”, ”believe”, ”could”, ”estimate”, ”expect”, ”intend”, ”may”, ”plan”, ”objectives”, ”outlook”, ”probably”, ”project”, ”will”, ”seek”, ”target”, ”risks”, ”goals”, ”should” and similar terms and phrases. There are a number of factors that could affect the future operations of Royal Dutch Shell and could cause those results to differ materially from those expressed in the forward-looking statements included in this document, including (without limitation): (a) price fluctuations in crude oil and natural gas; (b) changes in demand for the Group’s products; (c) currency fluctuations; (d) drilling and production results; (e) reserve estimates; (f) loss of market share and industry competition; (g) environmental and physical risks; (h) risks associated with the identification of suitable potential acquisit ion properties and targets, and successful negotiation and completion of such transactions; (i) the risk of doing business in developing countries and countries subject to international sanctions; (j) legislative, fiscal and regulatory developments including potential litigation and regulatory effects arising from recategorisation of reserves; (k) economic and financial market conditions in various countries and regions; (l) political risks, including the risks of expropriation and renegotiation of the terms of contracts with governmental entities, delays or advancements in the approval of projects and delays in the reimbursement for shared costs; and (m) changes in trading conditions. All forward-looking statements contained in this document are expressly qualified in their entirety by the cautionary statements contained or referred to in this section. Readers should not place undue reliance on forward-looking statements. Additional factors that may affect future results ar e contained in Royal Dutch Shell’s Annual Report and Form 20-F for the year ended December 31, 2009 (available at http://www.shell.com/investor and http://www.sec.gov – opens in new window). These factors also should be considered by the reader. Each forward-looking statement speaks only as of the date of this press release, 17 May, 2010. Neither Royal Dutch Shell nor any of its subsidiaries undertake any obligation to publicly update or revise any forward-looking statement as a result of new information, future events or other information. In light of these risks, results could differ materially from those stated, implied or inferred from the forward-looking statements contained in this document.
The United States Securities and Exchange Commission (SEC) permits oil and gas companies, in their filings with the SEC, to disclose only proved reserves that a company has demonstrated by actual production or conclusive formation tests to be economically and legally produc ible under existing economic and operating conditions. We use certain terms in this document that SEC’s guidelines strictly prohibit us from including in filings with the SEC. U.S. Investors are urged to consider closely the disclosure in our Form 20-F, File No 1-32575, available on the SEC website http://www.sec.gov – opens in new window. You can also obtain these forms from the SEC by calling 1-800-SEC-0330.
C-Cup 2012 – Comedy Central Germany
FEMEN – UEFA EURO 2012 – Uncensored – Le Carton Rouge
The FBI – Allen Stanford Gets 110 Years for Orchestrating $7 Billion Investment Fraud Scheme
HOUSTON—R. Allen Stanford, the former board of directors chairman of Stanford International Bank (SIB), has been sentenced to a total of 110 years in prison for orchestrating a 20-year investment fraud scheme in which he misappropriated $7 billion from SIB to finance his personal businesses.
The sentencing was announced by Assistant Attorney General Lanny A. Breuer of the Justice Department’s Criminal Division; U.S. Attorney Kenneth Magidson of the Southern District of Texas; FBI Assistant Director Kevin Perkins of the Criminal Investigative Division; Assistant Secretary of Labor for the Employee Benefits Security Administration Phyllis C. Borzi; Chief Postal Inspector Guy J. Cottrell; and Chief Richard Weber, Internal Revenue Service-Criminal Investigations (IRS-CI).
Stanford, 62, was convicted on 13 of 14 counts by a federal jury following a six-week trial before U.S. District Judge David Hittner and approximately three days of deliberation. The jury also found that 29 financial accounts located abroad and worth approximately $330 million were proceeds of Stanford’s fraud and should be forfeited.
Speaking on behalf of the victims in the case during the sentencing hearing today were Angie Shaw, the director and founder of the Stanford Victims Coalition, and Jaime Escalona, who represents Stanford victims from Latin America.
“Mr. Stanford, you took advantage of the trust that is placed in U.S. companies and caused losses that prevented families from being able to pay for medical and basic living expenses,” said Escalona.
“This was not a bloodless financial crime carried out on paper,” furthered Shaw. “It was and is an inconceivably heinous crime, and it has taken a staggering toll on the victims. Innocent investors from around the world sacrificed and saved for decades to build a solid foundation for their futures. That foundation crumbled beneath them when the news of the Stanford Financial Group Ponzi scheme became public. Many of the victims had lived the proverbial American Dream, only to have it snatched away from them in the name of greed.”
In handing down the sentence, Judge Hittner remarked that “this is one of the most egregious frauds ever presented to a trial jury in federal court.”
After considering all the evidence, including more than 350 victim impact letters that were sent to the court, Judge Hittner sentenced Stanford to 20 years for conspiracy to commit wire and mail fraud; 20 years on each of the four counts of wire fraud, as well as five years for conspiring to obstruct a U.S. Securities and Exchange Commission (SEC) investigation; and five years for obstruction of an SEC investigation. Those sentences will all run consecutively. He also received 20 years for each of the five counts of mail fraud and 20 years for conspiracy to commit money laundering, which will run concurrent to the other sentences imposed today, for a total sentence of 110 years.
As part of Stanford’s sentence, the court also imposed a personal money judgment of $5.9 billion, which is an ongoing obligation for Stanford to pay back the criminal proceeds. The court found that it would be impracticable to issue a restitution order at this time. However, all forfeited funds recovered by the United States will be returned to the fraud victims and credited against Stanford’s money judgment.
According to court documents and evidence presented at trial, the vehicle for Stanford’s fraud was SIB, an offshore bank Stanford owned based in Antigua and Barbuda that sold certificates of deposit (CDs) to depositors. Stanford began operating the bank in 1985 in Montserrat, the British West Indies, under the name Guardian International Bank. He moved the bank to Antigua in 1990 and changed its name to Stanford International Bank in 1994. SIB issued CDs that typically paid a premium over interest rates on CDs issued by U.S. banks. By 2008, the bank owed its CD depositors more than $8 billion.
According to SIB’s annual reports and marketing brochures, the bank purportedly invested CD proceeds in highly conservative, marketable securities, which were also highly liquid, meaning the bank could sell its assets and repay depositors very quickly. The bank also represented that all of its assets were globally diversified and overseen by money managers at top-tier financial institutions, with an additional level of oversight by SIB analysts based in Memphis, Tennessee.
As shown at trial, that purported investment strategy and management of the bank’s assets was followed for only about 10-15 percent of the bank’s assets. Stanford diverted billions in depositor funds into various companies that he owned personally, in the form of undisclosed “loans.” Stanford was thus able to continue the operations of his personal businesses, which ran at a net loss each year totaling hundreds of millions of dollars, at the expense of depositors. These businesses were concentrated primarily in the Caribbean and included restaurants, a cricket tournament, and various real estate projects. Evidence at trial established Stanford also used the misappropriated CD money to finance a lavish lifestyle, which included a 112-foot yacht and support vessels, six private planes, and gambling trips to Las Vegas.
According to evidence presented at trial, Stanford continued the scheme by using sales from new CDs to pay existing depositors who redeemed their CDs. In 2008, when the financial crisis caused a slump in new CD sales and record redemptions, Stanford lied about personally investing $741 million in additional funds into the bank to strengthen its capital base. To support that false announcement, Stanford’s internal accountants inflated on paper the value of a piece of real estate SIB had purchased for $63.5 million earlier in 2008 by 5,000 percent, to $3.1 billion, even though there were no independent appraisals or improvements to the property.
The trial evidence also showed that Stanford perpetuated his fraud by paying bribes from a Swiss slush fund at Societe Generale to C.A.S. Hewlett, SIB’s auditor (now deceased), and Leroy King, the then-head of the Antiguan Financial Services Regulatory Commission.
In addition to Stanford, a grand jury in the Southern District of Texas previously indicted several of his alleged co-conspirators, including: James Davis, the former chief financial officer; Laura Holt, the former chief investment officer; Gil Lopez, the former chief accounting officer; Mark Kuhrt, the former controller; and King. Davis has pleaded guilty and faces up to 30 years in prison under the terms of his plea agreement. The trial of Holt, Kuhrt, and Lopez, which was severed from Stanford’s trial, is scheduled to begin before Judge Hittner on September 10, 2012. They are presumed innocent unless and until convicted through due process of law.
The investigation was conducted by the FBI’s Houston Field Office; the U.S. Postal Inspection Service; IRS-CI; and the U.S. Department of Labor, Employee Benefits Security Administration. The case was prosecuted by Deputy Chief William Stellmach and Trial Attorney Andrew Warren of the Criminal Division’s Fraud Section, former Assistant U.S. Attorney (AUSA) Gregg Costa of the Southern District of Texas. AUSA Kristine Rollinson of the Southern District of Texas and Trial Attorney Kondi Kleinman of the Asset Forfeiture and Money Laundering Section in the Justice Department’s Criminal Division assisted with the forfeiture proceeding, and AUSA Jason Varnado and Fraud Section Jeffrey Goldberg assisted with the sentencing proceeding.
The Justice Department also wishes to thank several countries for their ongoing cooperation during the investigation and prosecution of Stanford and his co-conspirators, including the governments of Antigua and Barbuda, Switzerland, the Cook Islands, the United Kingdom, and the Isle of Man.
The Dictator On SNL ‘Saturday Night Live’ with Martin Scorsese – Video
TOP-SECRET from the FBI – Al Shabaab Associate Pleads Guilty in Manhattan
THE INVESTMENT MAGAZINE – THE ORIGINAL – Das INVESTMENT MAGAZIN – DAS ORIGINAL – Preet Bharara, the United States Attorney for the Southern District of New York; Janice K. Fedarcyk, the Assistant Director in Charge of the New York Field Office of the Federal Bureau of Investigation (“FBI”); and Raymond W. Kelly, the Police Commissioner of the City of New York (“NYPD”), announced that MOHAMED IBRAHIM AHMED pled guilty today to conspiring to provide material support to and receive military-type training from al Shabaab, a terrorist organization based in Somalia. The U.S. Department of State has designated al Shabaab as a Foreign Terrorist Organization. AHMED pled guilty before U.S. District Judge P. Kevin Castel.
Manhattan U.S. Attorney Preet Bharara said: “Mohamed Ibrahim Ahmed traveled a long way from his home in Sweden to Somalia, where he took up the cause of al Shabaab, a deadly terrorist organization and sworn enemy of the United States and its people. Protecting Americans from the threat of terrorism both at home and abroad is the highest priority of this office, and today’s plea is yet another victory in that fight.”
FBI Assistant Director in Charge Janice K. Fedarcyk said: “The guilty plea entered today, by a man so dedicated to a known terrorist group that he traveled to Somalia to train with al Shabaab and give them financial support, emphasizes the need for continued vigilance in the fight against terrorism worldwide. The FBI is committed to working with our law enforcement partners here and abroad to thwart would-be terrorists.”
NYPD Commissioner Raymond W. Kelly said: “This plea is important to the ongoing efforts by the NYPD and federal partners to deter terrorist organizations and their followers, who continue in their attempts to put New York City and the United States at risk.”
According to the superseding information filed today in Manhattan federal court and prior court filings:
In early 2009, AHMED left his home in Sweden and traveled to Somalia in order to support and receive military-type training from al Shabaab. Al Shabaab has used violent means to destabilize the government of Somalia and to force the withdrawal of foreign troops from the country. The group has recruited foreign fighters to join in its “holy war” in Somalia, resulting in men from other countries, including the United States, traveling there to engage in violent jihad. Al Shabaab has also made numerous public statements demonstrating its intent to harm the United States.
While in Somalia, AHMED contributed approximately 3,000 Euros to al Shabaab, received training and instruction with respect to bomb-making and bomb-detonation, and purchased an AK-47 rifle, additional magazines, and two grenades. AHMED subsequently provided the rifle and magazines to an al Shabaab military commander.
AHMED, 38, a native of Eritrea and a lawful resident of Sweden, was arrested in Nigeria in November 2009. On March 6, 2010, AHMED was transferred to the custody of the United States and subsequently transported to the Southern District of New York for prosecution.
AHMED pled guilty to one count of conspiracy to provide material support to a Foreign Terrorist Organization (al Shabaab) and one count of conspiracy to receive military-type training from a Foreign Terrorist Organization (al Shabaab). He faces a maximum sentence of 10 years in prison, and is scheduled to be sentenced by Judge Castel on November 2, 2012 at 11:30 a.m.
Mr. Bharara praised the outstanding investigative work of the New York-based Joint Terrorism Task Force—which principally consists of special agents of the FBI and detectives of the New York City Police Department. He also expressed gratitude to the U.S. Department of Justice’s National Security Division, the Office of International Affairs, and the U.S. Department of State for their extraordinary assistance in the case. Mr. Bharara also thanked the Governments of Sweden and Nigeria for their assistance in this matter.
This case is being handled by the Office’s Terrorism and International Narcotics Unit. Assistant United States Attorneys Benjamin Naftalis, John P. Cronan, Rachel P. Kovner, and Christopher LaVigne are in charge of the prosecution.
Reporting by Bernd Puzlch, Sarah Goodsmith, Bridget Gallagher and Tim Wilkinson
Follow The Money – Full Movie
TOP-SECRET – Open Source Center North Korea Propaganda Coverage of Party Representatives Conferences
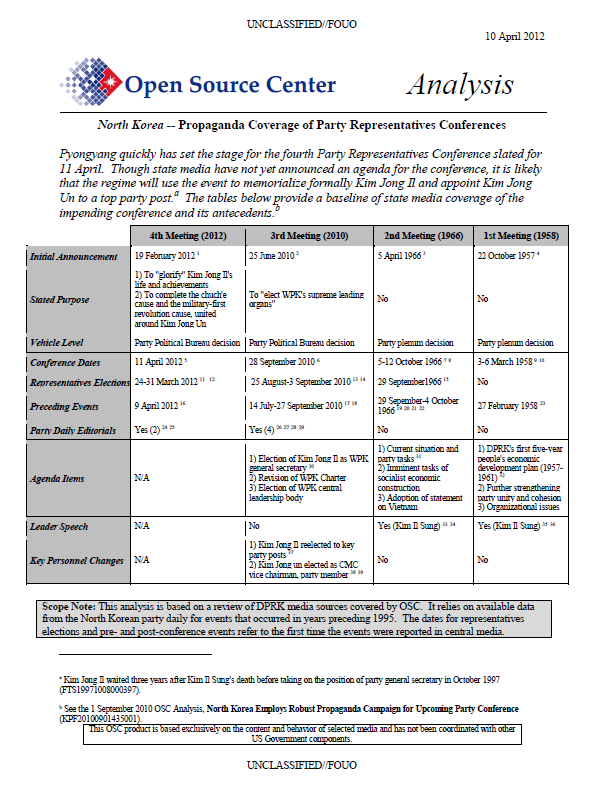
Pyongyang quickly has set the stage for the fourth Party Representatives Conference slated for 11 April. Though state media have not yet announced an agenda for the conference, it is likely that the regime will use the event to memorialize formally Kim Jong Il and appoint Kim Jong Un to a top party post. The tables below provide a baseline of state media coverage of the impending conference and its antecedents.
This analysis is based on a review of DPRK media sources covered by OSC. It relies on available data from the North Korean party daily for events that occurred in years preceding 1995. The dates for representatives elections and pre- and post-conference events refer to the first time the events were reported in central media.
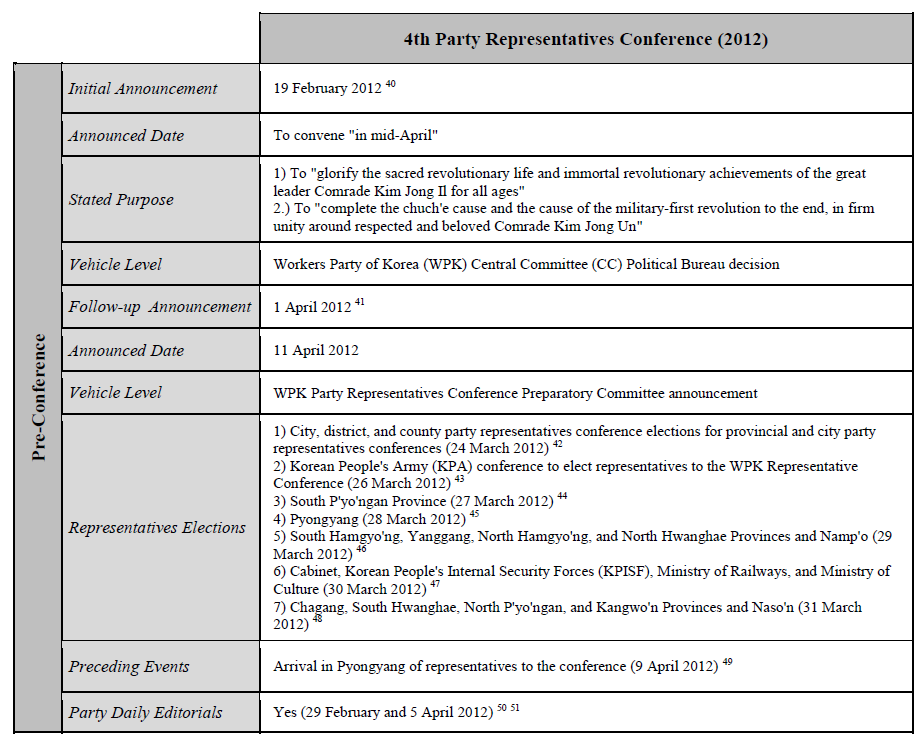
DOWNLOAD THE ORIGINAL DOCUMENT HERE
Uncensored – FEMEN against Police and Prostitution in Ucraine
Grave Injustice – Full Feature Movie
Cryptome unveils – Customs Sets New Spying Operations Records
[Federal Register Volume 77, Number 110 (Thursday, June 7, 2012)] [Notices] [Pages 33753-33758] From the Federal Register Online via the Government Printing Office [www.gpo.gov] [FR Doc No: 2012-13813] ======================================================================= ----------------------------------------------------------------------- DEPARTMENT OF HOMELAND SECURITY Office of the Secretary [Docket No. DHS-2011-0113] Privacy Act of 1974; Department of Homeland Security, U.S. Customs and Border Protection, DHS/CBP--017 Analytical Framework for Intelligence (AFI) System of Records AGENCY: Privacy Office, DHS. ACTION: Notice of Privacy Act system of records. ----------------------------------------------------------------------- SUMMARY: In accordance with the Privacy Act of 1974, the Department of Homeland Security proposes to establish a new Department of Homeland Security system of records titled, ``Department of Homeland Security, U.S. Customs and Border Protection, DHS/CBP--017 Analytical Framework for Intelligence (AFI) System of Records.'' This system of records will allow the Department of Homeland Security/U.S. Customs and Border Protection to improve border and national security by providing AFI users with a single platform for research, analysis, and visualization of large amounts of data from disparate sources and maintaining the final analysis or products in a single, searchable location for later use as well as appropriate dissemination. Additionally, the Department of Homeland Security is issuing a Notice of Proposed Rulemaking concurrent with this system of records elsewhere in the Federal Register. This newly established system will be included in the Department of Homeland Security's inventory of record systems. DATES: Submit comments on or before July 9, 2012. This new system will be effective July 9, 2012. ADDRESSES: You may submit comments, identified by docket number DHS- 2011-0113 by one of the following methods: Federal e-Rulemaking Portal: http://www.regulations.gov. Follow the instructions for submitting comments. Fax: 703-483-2999. Mail: Mary Ellen Callahan, Chief Privacy Officer, Privacy Office, Department of Homeland Security, Washington, DC 20528. Instructions: All submissions received must include the agency name and docket number for this rulemaking. All comments received will be posted without change to http://www.regulations.gov, including any personal information provided. Docket: For access to the docket to read background documents or comments received go to http://www.regulations.gov. FOR FURTHER INFORMATION CONTACT: For general questions please contact: Laurence E. Castelli (202-325-0280), CBP Privacy Officer, Office of International Trade, U.S. Customs and Border Protection, Mint Annex, 799 Ninth Street NW., Washington, DC 20229. For privacy issues please contact: Mary Ellen Callahan (703-235-0780), Chief Privacy Officer, Privacy Office, Department of Homeland Security, Washington, DC 20528. SUPPLEMENTARY INFORMATION: I. Background In accordance with the Privacy Act of 1974, 5 U.S.C. 552a, the Department of Homeland Security (DHS) U.S. Customs and Border Protection (CBP) proposes to establish a new DHS system of records titled, ``DHS/U.S. Customs and Border Protection, DHS/CBP--017 Analytical Framework for Intelligence (AFI) System of Records.'' CBP is publishing this SORN because AFI is a group of records under the control of CBP that contains personally identifiable information which is retrieved by a unique identifier. AFI enhances DHS's ability to identify, apprehend, and prosecute individuals who pose a potential law enforcement or security risk; and it aids in the enforcement of customs and immigration laws, and other laws enforced by DHS at the border. AFI is used for the purposes of: (1) Identifying individuals, associations, or relationships that may pose a potential law enforcement or security risk, targeting cargo that may present a threat, and assisting intelligence product users in the field in preventing the illegal entry of people and goods, or identifying other violations of law; (2) conducting additional research on persons and/or cargo to understand whether there are patterns or trends that could assist in the identification of potential law enforcement or security risks; and (3) sharing finished intelligence products developed in connection with the above purposes with DHS employees who have a need to know the analysis in the intelligence products in the performance of their official duties and who have appropriate clearances or permissions. Finished intelligence products are tactical, operational, and strategic law enforcement intelligence products that have been reviewed and approved for sharing with finished intelligence product users and authorities outside of DHS, pursuant to routine uses. To support its capability to efficiently query multiple data sources, AFI creates and maintains an index, which is a portion of the necessary and relevant data in existing operational DHS source systems, by ingesting this data through and from the Automated Targeting System (ATS) and other source systems. In addition to the index, AFI provides AFI analysts with different tools that assist in detecting trends, patterns, and emerging threats, and in identifying non-obvious relationships. AFI improves the efficiency and effectiveness of CBP's research and analysis process by providing a platform for the research, collaboration, approval, and publication of finished intelligence products. AFI provides a platform for preparing responses to requests for information (RFIs). AFI will centrally maintain the requests, the research based on those requests, and the response to those requests. AFI allows analysts to perform federated queries against external systems of record, including those of Department of State, the Department of Justice/FBI, as well as publicly and commercially available data sources, and eventually, classified data. AFI also enables an authorized user to search the Internet for additional information that may contribute to an intelligence gathering and analysis effort. AFI facilitates the sharing of finished intelligence products within DHS and tracks sharing outside of DHS. Two principal types of users will access AFI: DHS analysts and DHS finished intelligence product users. Analysts will use the system to obtain a more comprehensive view of data available to CBP, and then analyze and interpret that data using the visualization and collaboration tools [[Page 33754]] accessible in AFI. If an analyst finds actionable terrorist, law enforcement, or intelligence information, he may use relevant information to produce a report, create an alert, or take some other appropriate action within DHS's mission and authorities. In addition to using AFI as a workspace to analyze and interpret data, analysts may submit or respond to RFIs, assign tasks, or create finished intelligence products based on their research or in response to an RFI. Finished intelligence product users are officers, agents, and employees of DHS who have been determined to have a need to know the analysis in the intelligence products in the performance of their official duties and who have appropriate clearances or permissions. Finished intelligence product users will have more limited access to AFI, will not have access to the research space or tools, and will only view finished intelligence products that analysts published in AFI. Finished intelligence product users are not able to query the data from the source systems through AFI. AFI performs extensive auditing that records the search activities of all users to mitigate any risk of authorized users conducting searches for inappropriate purposes. AFI also requires that analysts re-certify annually any user-provided information marked as containing PII to ensure its continued relevance and accuracy. Analysts will be prompted to re-certify any documents that contain PII which are not related to a finished intelligence product. Information that is not re- certified is automatically purged from AFI. Account access is controlled by AFI passing individual user credentials to the originating system or through a previously approved certification process in another system in order to minimize the risk of unauthorized access. When an analyst conducts a search for products, AFI will only display those results that an individual user has permission to view. Consistent with DHS's information sharing mission, information stored in AFI may be shared consistent with the Privacy Act, including in accordance with the routine uses, and applicable laws as described below including sharing with other DHS components and appropriate federal, state, local, tribal, territorial, foreign, multilateral, or international government agencies. This sharing will only take place after DHS determines that the receiving component or agency has a need to know the information and the information will be used consistent with the Privacy Act, including the routine uses set forth in this SORN, in order to carry out national security, law enforcement, customs, immigration, intelligence, or other authorized functions. Additionally, DHS is issuing a Notice of Proposed Rulemaking to exempt this system of records from certain provisions of the Privacy Act, elsewhere in the Federal Register. This newly established system will be included in DHS' inventory of record systems. II. Privacy Act The Privacy Act embodies fair information practice principles in a statutory framework governing the means by which the U.S. Government collects, maintains, uses, and disseminates individuals' records. The Privacy Act applies to information that is maintained in a ``system of records.'' A ``system of records'' is a group of any records under the control of an agency for which information is retrieved by the name of an individual or by some identifying number, symbol, or other identifying particular assigned to the individual. In the Privacy Act, an individual is defined to encompass U.S. citizens and lawful permanent residents. As a matter of policy (Privacy Policy Guidance Memorandum 2007-1, most recently updated January 7, 2009), DHS extends administrative Privacy Act protections to all persons, regardless of citizenship, where a system of records maintains information on U.S. citizens and lawful permanent residents, as well as visitors. Individuals may request access to their own records that are maintained in a system of records in the possession or under the control of DHS by complying with DHS Privacy Act regulations, 6 CFR part 5. Below is the description of the DHS/CBP--017 Analytical Framework for Intelligence (AFI) System of Records. In accordance with 5 U.S.C. 552a(r), DHS has provided a report of this system of records to the Office of Management and Budget and to Congress. System of Records Department of Homeland Security (DHS)/CBP--017 Analytical Framework for Intelligence (AFI). System name: U.S. Customs and Border Protection (CBP) Analytical Framework for Intelligence (AFI). Security classification: Unclassified, Sensitive, Classified. System location: Records are maintained within the Information Technology system called the Analytical Framework for Intelligence (AFI) at the CBP Headquarters in Washington, DC, field offices, and in locations overseas where users are stationed. Categories of individuals covered by the system: 1. Persons who are the subject of, related to, or associated with the subject of a finished intelligence product. 2. Persons whose information is responsive to a request for information (RFI). 3. Persons whose information is maintained in CBP systems described under the ``Record Source Categories'' below that are being indexed by AFI, such as: A. Persons, including operators, crew and passengers, who seek to, or do in fact, enter, exit, or transit through the United States or through other locations where CBP maintains an enforcement or operational presence. B. Crew members traveling on commercial aircraft that fly over the United States. C. Persons who are employed in or who engage in any form of trade, the transit of goods intended to cross the United States border, or other commercial transaction related to the importation or exportation of merchandise. D. Persons who serve as booking agents, brokers, or other persons who provide information on behalf of persons seeking to enter, exit, or transit through the United States, or to enter, exit or transit goods through the United States. E. Owners of vehicles that cross the border. F. Persons whose data was received by the Department as the result of a memorandum of understanding or other information sharing agreement or arrangement because the information is relevant to the border security mission of the Department. G. Persons who were identified in a narrative report, prepared by an officer or agent, as being related to or associated with other persons who are alleged to be involved in, who are suspected of, or who have been arrested for violations of the laws enforced or administered by DHS. H. Persons who are alleged to be involved in, who are suspected of, who have been arrested for, or who are victims of violations of the laws enforced or administered by DHS. I. Persons with outstanding wants and warrants. J. Persons associated with matches to threshold targeting rules. K. Persons who may pose a national security, border security, or criminal threat to the United States. [[Page 33755]] L. Persons who seek to board an aircraft to travel internationally who have been identified by the Centers for Disease Control and Prevention (CDC), U.S. Health and Human Services, as ``No Boards'' because of a highly contagious communicable disease. M. Persons traveling across U.S. borders or through other locations where CBP maintains an enforcement or operational presence and who have a nexus to a law enforcement action. Categories of records in the system: AFI uses information from a variety of federal and commercial systems. If additional data is ingested and that additional data does not require amendment of the categories of records in this SORN, the PIA for AFI will be updated to reflect that information. The updated PIA can be found at www.dhs.gov/privacy. Information from such source systems is incorporated into AFI's five general categories of records: (1) Finished intelligence products: Intelligence products refer to tactical, operational, and strategic law enforcement intelligence products (hereinafter referred to as intelligence products). They include intelligence products that analysts have created based on their research and analysis of the source data contained in AFI and published in the system to make available as appropriate throughout CBP and DHS. (2) Requests for information (RFIs) and tasks and responses: This includes requests for information or tasks (generic requests for work to be performed) that have been submitted through AFI. AFI will also store the responses to RFIs and those responses will fall in the same category of records as the RFIs unless the AFI analyst determines that a response should be converted to a finished intelligence product and makes it available more broadly. (3) Projects: This includes projects created in AFI where an analyst can store source data for visualization and analysis and also share that information with other designated users. Projects may also contain analyst-compiled data from the source data described below and unfinished intelligence products that have not yet been published. (4) Index data: AFI ingests subsets or portions of data from the CBP and DHS systems described in ``Record Source Categories'' and creates an index of the searchable data elements, as described below in ``source data.'' This index will indicate which source system records match the search term used, when a response to a query is compiled. (5) Source data: AFI uses various types of data from CBP systems and other DHS systems as described in the individual system of records notices noted in ``Record Source Categories'' below. AFI also uses data from other federal agency systems and commercial data providers as noted in ``Record Source Categories.'' Data elements may include but are not limited to: a. Name. b. Alias. c. Addresses. d. Telephone and fax numbers. e. Tax ID number (e.g., Employer Identification Number (EIN) or Social Security Number (SSN), where available). f. Seizure number. g. Date and place of birth. h. Gender. i. Nationality. j. Citizenship. k. Physical characteristics, including biometrics where available (e.g., height, weight, race, eye and hair color, scars, tattoos, marks, fingerprints). l. Familial relationships and other contact information. m. Occupation and employment information. n. Information from documents used to verify the identity of individuals (e.g., driver's license, passport, visa, alien registration, citizenship card, border crossing card, birth certificate, certificate of naturalization, re-entry permit, military card, trusted traveler cards) including the: i. Type; ii. Number; iii. Date of issuance; and iv. Place of issuance. o. Travel information pertaining to individuals, including: i. Information derived from an Electronic System for Travel Authorization (ESTA) application (where applicable) or I-94 arrival/ departure information, where applicable; ii. Travel itinerary (e.g., Passenger Name Record (PNR)); Advance Passenger Information System (APIS) information; and land border records including information submitted in advance of arrival or departure); iii. Date of arrival or departure, and means of conveyance with associated identification (e.g., Vehicle Identification Number, year, make, model, registration); iv. Payment information; v. Any admissibility determination; and vi. Law enforcement data associated with an individual which is created by CBP or other government agencies. p. Information pertaining to the importation and exportation of cargo and/or property, including but not limited to bills of lading, manifests, commodity type, and inspection and examination results q. Identity and geospatial information obtained from commercial systems used to cross reference information contained in CBP systems Authority for maintenance of the system: Title II of the Homeland Security Act of 2002 (Pub. L. 107-296), as amended by the Intelligence Reform and Terrorism Prevention Act of 2004 (Pub. L. 108-458, 118 Stat. 3638); The Tariff Act of 1930, as amended; The Immigration and Nationality Act (``INA''), 8 U.S.C. 1101, et seq.; the Implementing Recommendations of the 9/11 Commission Act of 2007 (Pub. L. 110-53); the Antiterrorism and Effective Death Penalty Act of 1996 (Pub. L. 104-132, 110 Stat. 1214); SAFE Port Act of 2006 (Pub. L. 109-347); Aviation and Transportation Security Act of 2001 (Pub. L. 107-71); 6 U.S.C. 202. Purpose(s): The purpose of this system is to enhance DHS's ability to: Identify, apprehend, and/or prosecute individuals who pose a potential law enforcement or security risk; aid in the enforcement of the customs and immigration laws, and other laws enforced by DHS at the border; and enhance United States security. AFI uses data to: (1) Identify individuals, associations, or relationships that may pose a potential law enforcement or security risk, target cargo that may present a threat, and assist intelligence product users in the field in preventing the illegal entry of people and goods, or identifying other violations of law; (2) Allow analysts to conduct additional research on persons and/or cargo to understand whether there are patterns or trends that could identify potential law enforcement or security risks; and (3) Allow finished intelligence product users with a need to know to query or receive relevant finished intelligence products. Routine uses of records maintained in the system, including categories of users and the purposes of such uses: Source data are to be handled consistent with the published system of records notice as noted in ``Source Category Records.'' Source data that is not part of or incorporated into a finished intelligence product, a response to an RFI, project, or the index shall not be disclosed out of AFI. The routine uses below apply only to [[Page 33756]] finished intelligence products, responses to RFIs, projects, and responsive compilations of the index and only as explicitly stated in each routine use. In addition to those disclosures generally permitted under 5 U.S.C. 552a(b) of the Privacy Act, all or a portion of the AFI records contained in this system may be disclosed outside DHS as a routine use pursuant to 5 U.S.C. 552a(b)(3) as follows: A. To the Department of Justice (DOJ), including U.S. Attorney Offices, or other federal agency conducting litigation or in proceedings before any court, adjudicative or administrative body, when it is necessary to the litigation and one of the following is a party to the litigation or has an interest in such litigation: 1. DHS or any component thereof; 2. Any employee of DHS in his/her official capacity; 3. Any employee of DHS in his/her individual capacity where DOJ or DHS has agreed to represent the employee; or 4. The U.S. or any agency thereof, is a party to the litigation or has an interest in such litigation, and DHS determines that the records are both relevant and necessary to the litigation and the use of such records is compatible with the purpose for which DHS collected the records. This routine use applies to finished intelligence products, responses to RFIs, projects, and responsive compilations of the index. B. To a congressional office from the record of an individual in response to an inquiry from that congressional office made at the request of the individual to whom the record pertains. This routine use applies to finished intelligence products, responses to RFIs, projects, and responsive compilations of the index. C. To the National Archives and Records Administration (NARA) or other federal government agencies pursuant to records management inspections being conducted under the authority of 44 U.S.C. 2904 and 2906 and for records that NARA maintains as permanent records. This routine use applies to finished intelligence products, responses to RFIs, projects, and responsive compilations of the index. D. To an agency, organization, or individual for the purpose of performing audit or oversight operations as authorized by law, but only such information as is necessary and relevant to such audit or oversight function. This routine use applies to finished intelligence products, responses to RFIs, projects, and responsive compilations of the index. E. To appropriate agencies, entities, and persons when: 1. DHS suspects or has confirmed that the security or confidentiality of information in the system of records has been compromised; 2. DHS has determined that as a result of the suspected or confirmed compromise there is a risk of harm to economic or property interests, identity theft or fraud, or harm to the security or integrity of this system or other systems or programs (whether maintained by DHS or another agency or entity) or harm to the individuals that rely upon the compromised information; and 3. The disclosure made to such agencies, entities, and persons is reasonably necessary to assist in connection with DHS' efforts to respond to the suspected or confirmed compromise and prevent, minimize, or remedy such harm. This routine use applies to finished intelligence products, responses to RFIs, projects, and responsive compilations of the index. F. To contractors and their agents, grantees, experts, consultants, and others performing or working on a contract, service, grant, cooperative agreement, or other assignment for DHS, when necessary to accomplish an agency function related to this system of records. Individuals provided information under this routine use are subject to the same Privacy Act requirements and limitations on disclosure as are applicable to DHS officers and employees. This routine use applies to finished intelligence products, responses to RFIs, projects, and responsive compilations of the index. G. To the federal, state, local, tribal, or foreign government agencies or multilateral governmental organizations that submit an RFI, in order to identify individuals who present a risk to national security or to identify, apprehend, and/or prosecute individuals who are suspected of violating a law, where DHS has information responsive to the RFI and has determined that it is appropriate to provide that information in response to the RFI. This routine use applies to all responses to RFIs. H. To appropriate federal, state, local, tribal, or foreign governmental agencies or multilateral governmental organizations responsible for investigating or prosecuting the violations of, or for enforcing or implementing, a statute, rule, regulation, order, license, agreement, or treaty where DHS determines that the information would assist in the enforcement of civil or criminal laws. This routine use applies only to finished intelligence products. I. To appropriate federal, state, local, tribal, or foreign governmental agencies or multilateral governmental organizations for the purpose of protecting the vital health interests of a data subject or other persons (e.g. to assist such agencies or organizations in preventing exposure to or transmission of a communicable or quarantinable disease or to combat other significant public health threats; appropriate notice will be provided of any identified health threat or risk). This routine use applies only to finished intelligence products, responses to RFIs, and responsive compilations of the index. J. To a court, magistrate, or administrative tribunal in the course of presenting evidence, including disclosures to opposing counsel or witnesses in the course of civil or criminal discovery, litigation, or settlement negotiations, or in response to a subpoena from a court of competent jurisdiction. This routine use applies to all AFI records, which include finished intelligence products, responses to RFIs, projects, and responsive compilations of the index. K. To third parties during the course of a law enforcement investigation to the extent necessary to obtain information pertinent to the investigation. This routine use applies only to finished intelligence products. L. To a federal, state, local, tribal, or foreign governmental agency or multilateral governmental organization for the purpose of consulting with that agency or entity: (1) To assist in making a determination regarding redress for an individual in connection with the operations of a DHS component or program; (2) for the purpose of verifying the identity of an individual seeking redress in connection with the operations of a DHS component or program; or (3) for the purpose of verifying the accuracy of information submitted by an individual who has requested such redress on behalf of another individual. This routine use applies only to finished intelligence products and responses to RFIs. M. To appropriate federal, state, local, tribal, or foreign governmental agencies or multilateral governmental organizations when DHS reasonably believes there to be a threat or potential threat to national or international security for which the information may be relevant in countering the threat or potential threat. This routine use applies only to finished intelligence products. N. To a federal, state, tribal, or local agency, or other appropriate entity or [[Page 33757]] individual, or foreign governments, in order to provide relevant information related to intelligence, counterintelligence, or antiterrorism activities authorized by U.S. law, Executive Order, or other applicable national security directive. This routine use applies only to finished intelligence products. O. To an organization or individual in either the public or private sector, either foreign or domestic, where there is a reason to believe that the recipient is or could become the target of a particular terrorist activity or conspiracy, or where the information is relevant and necessary to the protection of life or property. This routine use applies only to finished intelligence products. P. To an appropriate federal, state, local, tribal, foreign, or international agency, if the information is relevant to a requesting agency's decision concerning the hiring or retention of an individual, or issuance of a security clearance, license, contract, grant, or other benefit, or if the information is relevant to a DHS decision concerning the hiring or retention of an employee, the issuance of a security clearance, the reporting of an investigation of an employee, the letting of a contract, or the issuance of a license, grant or other benefit. This routine use applies only to finished intelligence products. Q. To the news media and the public, with the approval of the Chief Privacy Officer in consultation with counsel, when there exists a legitimate public interest in the disclosure of the information or when disclosure is necessary to preserve confidence in the integrity of DHS or is necessary to demonstrate the accountability of DHS's officers, employees, or individuals covered by the system, except to the extent it is determined that release of the specific information in the context of a particular case would constitute an unwarranted invasion of personal privacy. This routine use applies only to finished intelligence products. Disclosure to consumer reporting agencies: None. Policies and practices for storing, retrieving, accessing, retaining, and disposing of records in the system: Storage: Records in this system are stored electronically or on paper in secure facilities in a locked drawer behind a locked door. The records are stored on magnetic disc, tape, digital media, and CD-ROM. Retrievability: Records may be retrieved by any search term, including name, personal identifier, date, subject matter or other criteria. Safeguards: Records in this system are safeguarded in accordance with applicable rules and policies, including all applicable DHS automated systems security and access policies. Two principal types of users will access AFI: DHS analysts and DHS finished intelligence product users. DHS Analysts will use the system to obtain a more comprehensive view of data available to CBP, and then analyze and interpret that data using the visualization and collaboration tools accessible in AFI. Finished intelligence product users are officers, agents, and employees of DHS who have been determined to have a need to know based on their job description and duties. Finished intelligence product users will have more limited access to AFI, will not have access to the research space or tools, and will only view finished tactical, operational, and strategic intelligence products that analysts published in AFI. Finished intelligence product users are not able to query the data from the source systems through AFI. If a finished intelligence product user requires the source data in order to take action or make a determination, he will be required to go to the source data to ensure that he is receiving the most accurate data available. Strict controls have been imposed to minimize the risk of compromising the information that is being stored. Access to AFI is limited to those individuals who have a need to know the information for the performance of their official duties and who have appropriate clearances or permissions. Retention and disposal: Source data contained in AFI that has not been incorporated into a finished intelligence product, response to an RFI, or project will follow the retention schedule set forth in the applicable source data system of records notice, as noted in ``Record Source Categories'' below. AFI projects that do not contain PII are retained for 30 years and are then deleted. Projects containing PII must be recertified annually for up to 30 years or the entire record is purged from the system. Requests for information (RFIs) and responses to RFIs, excluding finished intelligence products, are retained for 10 years and are then deleted. Finished intelligence products are retained in accordance with the NARA-approved record retention schedule by first maintaining the products as active in the system for a period of 20 years, and then transferring the records to the National Archives for permanent storage and retention. The index is maintained within AFI as a permanent feature. Any changes to source system records, or the addition or deletion of source system records, will be reflected in corresponding amendments to the AFI index as the index is routinely updated. Legacy indices that are part of a project, responses to RFI, or finished intelligence product are maintained as part of those records. System Manager and address: Director of Advanced Analytics & Intelligence Systems, Office of Intelligence and Investigative Liaison, U.S. Customs and Border Protection, Ronald Reagan Building and Director, Targeting and Analysis, Systems Program Office, Office of Information and Technology, U.S. Customs and Border Protection. Notification procedure: The Secretary of Homeland Security has exempted this system from the notification, access, and amendment procedures of the Privacy Act because it is a law enforcement system. These exemptions also apply to the extent that information in this system of records is recompiled or is created from information contained in other systems of records. To the extent that a record is exempted in a source system, the exemption will continue to apply. However, CBP will consider individual requests to determine whether or not information may be released. After conferring with the appropriate component or agency, as applicable, DHS may waive applicable exemptions in appropriate circumstances and where it would not appear to interfere with or adversely affect the law enforcement purposes of the systems from which the information is recompiled or in which it is contained. Additionally, CBP and DHS are not exempting any records that were ingested or indexed by AFI where the source system of records already provides access and/or amendment under the Privacy Act. Individuals seeking notification of and access to any record contained in this system of records, or seeking to contest its content, may submit a request in writing to the Headquarters or CBP's FOIA Officer, whose contact information can be found at http://www.dhs.gov/foia under ``contacts.'' If an individual believes more than one component [[Page 33758]] maintains Privacy Act records concerning him or her the individual may submit the request to the Chief Privacy Officer, Department of Homeland Security, 245 Murray Drive SW., Building 410, STOP-0655, Washington, DC 20528. When seeking records about yourself from this system of records or any other Departmental system of records your request must conform with the Privacy Act regulations set forth in 6 CFR part 5. You must first verify your identity, meaning that you must provide your full name, current address and date and place of birth. You must sign your request, and your signature must either be notarized or submitted under 28 U.S.C. 1746, a law that permits statements to be made under penalty of perjury as a substitute for notarization. While no specific form is required, you may obtain forms for this purpose from the Director, Disclosure and FOIA Operations, http://www.dhs.gov or 1-703-235-0790. In addition you must: Provide an explanation of why you believe the Department would have information on you; Identify which component(s) of the Department you believe may have the information about you; Specify when you believe the records would have been created; Provide any other information that will help the FOIA staff determine which DHS component agency may have responsive records; If your request is seeking records pertaining to another living individual, include a statement from that individual certifying his/her agreement for you to access his/her records. Without this bulleted information the component(s) may not be able to conduct an effective search, and your request may be denied due to lack of specificity or lack of compliance with applicable regulations. Record access procedures: See ``Notification procedure'' above. Contesting record procedures: See ``Notification procedure'' above. Record source categories: AFI receives records and incorporates portions of records into an index of those records. Records are incorporated from the following CBP and DHS systems: ATS (last SORN published at 72 FR 43650 (August 6, 2007)); APIS (last SORN published at 73 FR 68435 (November 18, 2008)); ESTA (last SORN published at 76 FR 67751 (November 2, 2011)); Border Crossing Information (BCI) (last SORN published at 73 FR 43457 (July 25, 2008)); TECS (last SORN published at 73 FR 77778 (December 19, 2008)); Nonimmigrant Information System (NIIS) (last SORN published at 73 FR 77739 (December 19, 2008)); Seized Asset Case Tracking System (SEACATS) (last SORN published at 73 FR 77764 (December 19, 2008)); Department of Homeland Security/All-030 Use of the Terrorist Screening Database System of Records (last SORN published at 76 FR 39408 (July 6, 2011)); Enterprise Management Information System--Enterprise Data Warehouse (EMIS-EDW), including: a. Arrival and Departure Form (I-94) information from the Nonimmigrant Information System (NIIS) (last SORN published at 73 FR 77739 (December 19, 2008)); b. Currency or Monetary Instruments Report (CMIR) obtained from TECS (last SORN for TECS published at 73 FR 77778 (December 19, 2008)); c. Apprehension information and National Security Entry-Exit Program (NSEERS) information from ENFORCE (last SORN published at 75 FR 23274 (May 3, 2010)); d. Seizure information from SEACATS (last SORN published at 73 FR 77764 (December 19, 2008)); e. Student and Exchange Visitor Information System (SEVIS) information (last SORN published at 75 FR 412 (January 5, 2010)); and AFI accesses records from the following agencies, but the records are not part of the index: Department of State; Department of Justice/FBI; Department of Treasury; and Commercial information from commercial data providers and geospatial data providers. Additionally, AFI permits analysts to upload and store any information from any source including public and commercial sources, which may be relevant to projects, responses to RFIs, or final intelligence products. Accepted requests for information may come from within or outside DHS where CBP determines it has responsive information and it is consistent with the purposes of this system. Exemptions claimed for the system: For index data and source data, as described under Categories of Records, to the extent that a record is exempted in a source system, the exemption will continue to apply. To the extent there is no exemption for giving access to a record under the source system, CBP will provide access to the information maintained in AFI. Finished intelligence products, RFIs, tasks, and responses, and projects, as described under Categories of Records, pursuant to 5 U.S.C. 552a(j)(2) of the Privacy Act, are exempt from the following provisions of the Privacy Act: 5 U.S.C. 552a(c)(3) and (4); (d); (e)(1), (e)(2), (e)(3), (e)(4)(G), (e)(4)(H), (e)(4)(I), (e)(5) and (e)(8); (f); and (g). Finished intelligence products, RFIs, tasks, and responses, and projects, as described under Categories of Records, pursuant to 5 U.S.C. 552a(k)(1) and (2), are exempt from the following provisions of the Privacy Act: 5 U.S.C. 552a(c)(3), (d), (e)(1), (e)(4)(G), (e)(4)(H), (e)(4)(I), and (f). Dated: June 4, 2012. Mary Ellen Callahan, Chief Privacy Officer, Department of Homeland Security. [FR Doc. 2012-13813 Filed 6-6-12; 8:45 am] BILLING CODE 9110-06-P
[Federal Register Volume 77, Number 110 (Thursday, June 7, 2012)] [Proposed Rules] [Pages 33683-33685] From the Federal Register Online via the Government Printing Office [www.gpo.gov] [FR Doc No: 2012-13815] ======================================================================= ----------------------------------------------------------------------- DEPARTMENT OF HOMELAND SECURITY Office of the Secretary 6 CFR Part 5 [Docket No. DHS-2011-0114] Privacy Act of 1974: Implementation of Exemptions; Department of Homeland Security, U.S. Customs and Border Protection, DHS/CBP--017 Analytical Framework for Intelligence (AFI) System of Records AGENCY: Privacy Office, DHS. ACTION: Notice of proposed rulemaking. ----------------------------------------------------------------------- SUMMARY: The Department of Homeland Security is giving concurrent notice of a newly established system of records pursuant to the Privacy Act of 1974 for the ``Department of Homeland Security/U.S. Customs and Border Protection--017 Analytical Framework for Intelligence (AFI) System of Records'' and this proposed rulemaking. In this proposed rulemaking, the Department proposes to exempt the system of records from one or more provisions of the Privacy Act because of criminal, civil, and administrative enforcement requirements. DATES: Comments must be received on or before July 9, 2012. ADDRESSES: You may submit comments, identified by docket number DHS- 2012-0114, by one of the following methods: Federal e-Rulemaking Portal: http://www.regulations.gov. Follow the instructions for submitting comments. Fax: 703-483-2999. Mail: Mary Ellen Callahan, Chief Privacy Officer, Privacy Office, Department of Homeland Security, Washington, DC 20528. Instructions: All submissions received must include the agency name and docket number for this notice. All comments received will be posted without change to http://www.regulations.gov, including any personal information provided. Docket: For access to the docket to read background documents or comments received, go to http://www.regulations.gov. FOR FURTHER INFORMATION CONTACT: For general questions please contact: Laurence E. Castelli (202-325-0280), CBP Privacy Officer, Office of International Trade, U.S. Customs and Border Protection, Mint Annex, 799 Ninth Street NW., Washington, DC 20229. For privacy issues please contact: Mary Ellen Callahan (703-235-0780), Chief Privacy Officer, Privacy Office, Department of Homeland Security, Washington, DC 20528. SUPPLEMENTARY INFORMATION: I. Background In accordance with the Privacy Act of 1974, 5 U.S.C. 552a, the Department of Homeland Security (DHS) U.S. Customs and Border Protection (CBP) proposes to establish a new DHS system of records titled, ``DHS/U.S. Customs and Border Protection, DHS/CBP--017 Analytical Framework for Intelligence (AFI) System of Records.'' AFI enhances DHS's ability to identify, apprehend, and prosecute individuals who pose a potential law enforcement or security risk; and aids in the enforcement of customs and immigration laws, and other laws enforced by DHS at the border. AFI is used for the purposes of: (1) Identifying individuals, associations, or relationships that may pose a potential law enforcement or security risk, targeting cargo that may present a threat, and assisting intelligence product users in the field in preventing the illegal entry of people and goods, or identifying other violations of law; (2) conducting additional research on persons and/or cargo to understand whether there are patterns or trends that could assist in the identification of potential law enforcement or security risks; and (3) sharing finished intelligence products developed in connection with the above purposes with DHS employees who have a need to know in the performance of their official duties and who have appropriate clearances or permissions. Finished intelligence products are tactical, operational, and strategic law enforcement intelligence products that have been reviewed and approved for sharing with finished intelligence product users and authorities outside of DHS, pursuant to routine uses. To support its capability to query, efficiently, multiple data sources, AFI creates and maintains an index, which is a portion of the necessary and relevant data in existing operational [[Page 33684]] DHS source systems, by ingesting this data through and from the Automated Targeting System (ATS) and those source systems. In addition to the index, AFI provides AFI analysts with different tools that assist in detecting trends, patterns, and emerging threats, and in identifying non-obvious relationships. AFI improves the efficiency and effectiveness of CBP's research and analysis process by providing a platform for the research, collaboration, approval, and publication of finished intelligence products. AFI provides a platform for preparing responses to requests for information (RFIs). AFI will centrally maintain the requests, the research based on those requests, and the response to those requests. AFI allows analysts to perform federated queries against external data sources, including the Department of State, the Department of Justice/ FBI, as well as publicly and commercially available data sources and, eventually, classified data. AFI also enables an authorized user to search the Internet for additional information that may contribute to an intelligence gathering and analysis effort. AFI facilitates the sharing of finished intelligence products within DHS and tracks sharing outside of DHS. Two principal types of users will access AFI: DHS analysts and DHS finished intelligence product users. Analysts will use the system to obtain a more comprehensive view of data available to CBP, and then analyze and interpret that data using the visualization and collaboration tools accessible in AFI. If an analyst finds actionable terrorist, law enforcement, or intelligence information, he may use relevant information to produce a report, create an alert, or take some other appropriate action within DHS's mission and authorities. In addition to using AFI as a workspace to analyze and interpret data, analysts may submit or respond to RFIs, assign tasks, or create finished intelligence products based on their research or in response to an RFI. Finished intelligence product users are officers, agents, and employees of DHS who have been determined to have a need to know in the performance of their official duties and who have appropriate clearances or permissions. Finished intelligence product users will have more limited access to AFI, will not have access to the research space or tools, and will only view finished intelligence products that analysts published in AFI. Finished intelligence product users are not able to query the data from the source systems through AFI. AFI performs extensive auditing that records the search activities of all users to mitigate any risk of authorized users conducting searches for inappropriate purposes. AFI also requires that analysts re-certify annually any user-provided information marked as containing PII to ensure its continued relevance and accuracy. Analysts will be prompted to re-certify any documents that maintain PII which are not related to a finished intelligence product. Information that is not re- certified is automatically purged from AFI. Account access is controlled by AFI passing individual user credentials to the originating system or through a previously approved certification process in another system in order to minimize the risk of unauthorized access. When an analyst conducts a search for products, AFI will only display those results that an individual user has permission to view. Consistent with DHS's information sharing mission, information stored in AFI may be shared consistent with the Privacy Act, including in accordance with the routine uses, and applicable laws as described below including sharing with other DHS components and appropriate federal, state, local, tribal, territorial, foreign, multilateral, or international government agencies. This sharing will only take place after DHS determines that the receiving component or agency has a need to know the information and the information will be used consistent with the Privacy Act, including the routine uses set forth in the SORN, in order to carry out national security, law enforcement, customs, immigration, intelligence, or other authorized functions. DHS is claiming exemptions from certain requirements of the Privacy Act for DHS/CBP--017 Analytical Framework for Intelligence (AFI) System of Records. Some information in AFI relates to official DHS national security, law enforcement, and immigration activities. The exemptions are required to preclude subjects from compromising an ongoing law enforcement, national security or fraud investigation; to avoid disclosure of investigative techniques; to protect the identities and physical safety of confidential informants and law enforcement personnel; and to ensure DHS's ability to obtain information from third parties and other sources. Pursuant to 5 U.S.C. 552a(j)(2), this system is exempted from the following provisions of the Privacy Act: 5 U.S.C. 552a(c)(3) and (c)(4); (d); (e)(1), (e)(2), (e)(3), (e)(4)(G), (e)(4)(H), (e)(5), (e)(8); (f); and (g). Additionally, pursuant to 5 U.S.C. 552a(k)(1) and (2) this system is exempted from the following provisions of the Privacy Act: 5 U.S.C 552a(c)(3); (d); (e)(1), (e)(4)(G), (e)(4)(H); and (f). Many of the functions in this system require retrieving records from law enforcement systems. Where a record received from another system has been exempted in that source system under 5 U.S.C. 552a(j)(2), (k)(1) and/or (k)(2), DHS will claim the same exemptions for those records that are claimed for the original primary systems of records from which they originated and claims any additional exemptions in accordance with this rule. The exemptions proposed here are standard for agencies where the information may contain investigatory materials compiled for law enforcement purposes. These exemptions are exercised by executive federal agencies. In appropriate circumstances, where compliance would not appear to interfere with or adversely affect the overall law enforcement process, the applicable exemptions may be waived on a case- by-case basis. A notice of system of records for DHS/CBP--017 Analytical Framework for Intelligence (AFI) is also published in this issue of the Federal Register. II. Privacy Act The Privacy Act embodies fair information practice principles in a statutory framework governing the means by which the U.S. Government collects, maintains, uses, and disseminates personally identifiable information. The Privacy Act applies to information that is maintained in a ``system of records.'' A ``system of records'' is a group of any records under the control of an agency from which information is retrieved by the name of the individual or by some identifying number, symbol, or other identifying particular assigned to the individual. In the Privacy Act, an individual is defined to encompass U.S. citizens and lawful permanent residents. As a matter of policy, DHS extends administrative Privacy Act protections to all persons, regardless of citizenship, where a system of records maintains information on both U.S. citizens and lawful permanent residents, as well as visitors. The Privacy Act allows government agencies to exempt systems of records from certain provisions of the Act. If an agency claims an exemption, however, it must issue a Notice of Proposed Rulemaking and a Final Rule to make clear to the public the reasons why a particular exemption is claimed. List of Subjects in 6 CFR Part 5 Freedom of information; Privacy. [[Page 33685]] For the reasons stated in the preamble, DHS proposes to amend Chapter I of Title 6, Code of Federal Regulations, as follows: PART 5--DISCLOSURE OF RECORDS AND INFORMATION 1. The authority citation for Part 5 continues to read as follows: Authority: Public Law 107-296, 116 Stat. 2135; (6 U.S.C. 101 et seq.); 5 U.S.C. 301. Subpart A also issued under 5 U.S.C. 552. Subpart B also issued under 5 U.S.C. 552a. 2. Add at the end of Appendix C to Part 5, the following new paragraph ``68'': Appendix C to Part 5--DHS Systems of Records Exempt From the Privacy Act * * * * * 68. The DHS/CBP--017 Analytical Framework for Intelligence (AFI) System of Records consists of electronic and paper records and will be used by DHS and its components. The DHS/CBP--017 Analytical Framework for Intelligence (AFI) System of Records is a repository of information held by DHS to enhance DHS's ability to: identify, apprehend, and/or prosecute individuals who pose a potential law enforcement or security risk; aid in the enforcement of the customs and immigration laws, and other laws enforced by DHS at the border; and enhance United States security. This system also supports certain other DHS programs whose functions include, but are not limited to, the enforcement of civil and criminal laws; investigations, inquiries, and proceedings there under; and national security and intelligence activities. The DHS/CBP--017 Analytical Framework for Intelligence (AFI) System of Records contains information that is collected by, on behalf of, in support of, or in cooperation with DHS and its components and may contain personally identifiable information collected by other federal, state, local, tribal, foreign, or international government agencies. The Secretary of Homeland Security has exempted this system from certain provisions of the Privacy Act as follows: Pursuant to 5 U.S.C. 552a(j)(2), the system is exempt from 5 U.S.C. 552a(c)(3) and (c)(4), (e)(1), (e)(2), (e)(3), (e)(4)(G), (e)(4)(H), (e)(4)(I), (e)(5), (e)(8), (f), and (g). Pursuant to 5 U.S.C. 552a(j)(2), the system (except for any records that were ingested by AFI where the source system of records already provides access and/or amendment under the Privacy Act) is exempt from 5 U.S.C. 552a(d)(1), (d)(2), (d)(3), and (d)(4). Pursuant to 5 U.S.C. 552a(k)(1), the system is exempt from 5 U.S.C. 552a(c)(3); (e)(1), (e)(4)(G), (e)(4)(H), (e)(4)(I); and (f). Pursuant to 5 U.S.C. 552a(k)(1), the system is exempt from (d)(1), (d)(2), (d)(3), and (d)(4). Pursuant to 5 U.S.C. 552a(k)(2), the system is exempt from 5 U.S.C. 552a(c)(3); (e)(1), (e)(4)(G), (e)(4)(H), (e)(4)(I); and (f). Pursuant to 5 U.S.C. 552a(k)(2), the system (except for any records that were ingested by AFI where the source system of records already provides access and/or amendment under the Privacy Act) is exempt from (d)(1), (d)(2), (d)(3), and (d)(4). Exemptions from these particular subsections are justified, on a case-by-case basis to be determined at the time a request is made, for the following reasons: (a) From subsection (c)(3) and (4) (Accounting for Disclosures) because release of the accounting of disclosures could alert the subject of an investigation of an actual or potential criminal, civil, or regulatory violation to the existence of that investigation and reveal investigative interest on the part of DHS as well as the recipient agency. Disclosure of the accounting would therefore present a serious impediment to law enforcement efforts and/or efforts to preserve national security. Disclosure of the accounting would also permit the individual who is the subject of a record to impede the investigation, to tamper with witnesses or evidence, and to avoid detection or apprehension, which would undermine the entire investigative process. (b) From subsection (d) (Access to Records) because access to the records contained in this system of records could inform the subject of an investigation of an actual or potential criminal, civil, or regulatory violation to the existence of that investigation and reveal investigative interest on the part of DHS or another agency. Access to the records could permit the individual who is the subject of a record to impede the investigation, to tamper with witnesses or evidence, and to avoid detection or apprehension. Amendment of the records could interfere with ongoing investigations and law enforcement activities and would impose an unreasonable administrative burden by requiring investigations to be continually reinvestigated. In addition, permitting access and amendment to such information could disclose security-sensitive information that could be detrimental to homeland security. (c) From subsection (e)(1) (Relevancy and Necessity of Information) because in the course of investigations into potential violations of federal law, the accuracy of information obtained or introduced occasionally may be unclear, or the information may not be strictly relevant or necessary to a specific investigation. In the interests of effective law enforcement and national security, it is appropriate to retain all information that may aid in establishing patterns of unlawful activity. (d) From subsection (e)(2) (Collection of Information from Individuals) because requiring that information be collected from the subject of an investigation would alert the subject to the nature or existence of the investigation, thereby interfering with that investigation and related law enforcement and national security activities. (e) From subsection (e)(3) (Notice to Individuals) because providing such detailed information could impede law enforcement and national security by compromising the existence of a confidential investigation or reveal the identity of witnesses or confidential informants. (f) From subsections (e)(4)(G), (e)(4)(H), and (e)(4)(I) (Agency Requirements) and (f) (Agency Rules), because portions of this system are exempt from the individual access provisions of subsection (d) for the reasons noted above, and therefore DHS is not required to establish requirements, rules, or procedures with respect to such access. Providing notice to individuals with respect to existence of records pertaining to them in the system of records or otherwise setting up procedures pursuant to which individuals may access and view records pertaining to themselves in the system would undermine investigative efforts and reveal the identities of witnesses, and potential witnesses, and confidential informants. (g) From subsection (e)(5) (Collection of Information) because with the collection of information for law enforcement purposes, it is impossible to determine in advance what information is accurate, relevant, timely, and complete. Compliance with subsection (e)(5) would preclude DHS agents from using their investigative training and exercise of good judgment to both conduct and report on investigations. (h) From subsection (e)(8) (Notice on Individuals) because compliance would interfere with DHS's ability to obtain, serve, and issue subpoenas, warrants, and other law enforcement mechanisms that may be filed under seal and could result in disclosure of investigative techniques, procedures, and evidence. (i) From subsection (g)(1) (Civil Remedies) to the extent that the system is exempt from other specific subsections of the Privacy Act. Dated: June 4, 2012. Mary Ellen Callahan, Chief Privacy Officer, Department of Homeland Security. [FR Doc. 2012-13815 Filed 6-6-12; 8:45 am] BILLING CODE 9110-06-P
The Dictator – Official Trailer Video
Haunted – Full Movie
TOP-SECRET – Open Source Center North Korea Kim Jong Un Party Leadership Analysis

Personnel moves at the recent Party Conference and spring session of the legislature — beyond Kim Jong Un’s assumption of the top slots — underscore the new leadership’s continued commitment to revitalizing the Party as an institution and its confidence in managing the system. Though state media billed the moves merely as filling vacancies, the leadership quietly elevated or replaced almost one-third of the ruling Political Bureau, many through unannounced retirements or dismissals. The personnel changes occurred in military, internal security, and economic organizations and are not clustered in one area. Though personnel were added to the National Defense Commission (NDC), its relationship to the Political Bureau and Central Military Commission (CMC) remains unclear.
Although foreign media reporting on the North’s 4th Party Conference and the subsequent gathering of the Supreme People’s Assembly (SPA) focused on Kim Jong Un’s taking the titles of first secretary of the Workers Party of Korea and first chairman of the NDC, the regime made significant personnel changes below Kim’s level.
These personnel moves build on steps that Kim Jong Il took in his final year to strengthen the Party, and they suggest that the new leadership also sees the Party as an important instrument of governance during the transition. The extent of the changes indicates that the new leadership is confident in its ability to manage the regime and its key stakeholders.
Almost half of the membership of the Political Bureau that Kim Jong Il put in place at the 3rd Party Conference in 2010 has shifted in one way or another. Four members moved up significantly. Seven appear to have been dismissed. One slipped significantly but still remains on the Political Bureau, and three have died, including Kim Jong Il (KCNA, 11 April).
Kim Jong Il began revitalizing the Party’s governing bodies in 2010, apparently as part of the effort to facilitate Kim Jong Un’s succession. The elder Kim called a Party Conference in September of that year, the first major Party meeting of its kind in almost 30 years (KCNA, 28 September 2010). Kim Jong Un debuted at the Conference, and the regime dramatically expanded the governing Political Bureau, which Kim Jong Il had allowed to atrophy since taking power in 1994.
…
Military/Security Balance
The leadership is continuing the trend of blurring the distinction between military and internal security personnel on the one hand and civilian Party leaders on the other. The reason for the blending is not clear, but the regime since 2010 has conferred general-officer rank on several regime civilians.
This time the regime named Choe Ryong Hae a vice marshal and put him in charge of the Army’s influential political affairs department, which Kim Jong Il’s trusted military advisor Jo Myong Rok once ran. Though not a professional soldier, Choe effectively now outranks Chief of Staff Ri Yong Ho, calling into question Ri’s influence.
At the same time, the regime has increased the percentage of military and internal security personnel on the Political Bureau to its highest level since before 1980. The two groups now make up more than a third of the total membership. In 2010, they represented a quarter of the group, which was the same share they had after the 1980 Party Congress.
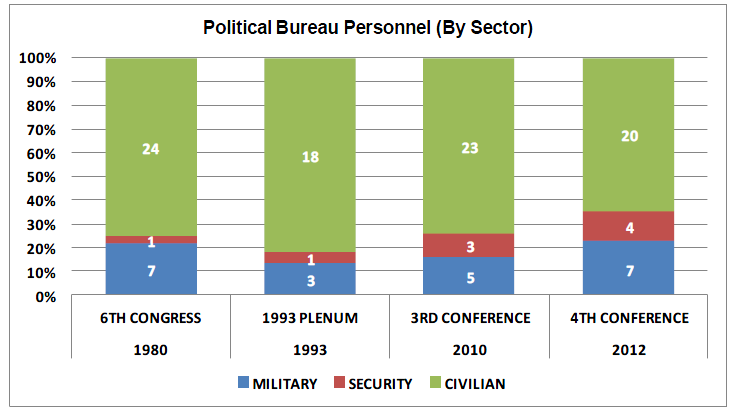

DOWNLOAD THE ORIGINAL DOCUMENT HERE
Soccer UEFA EURO 2012 Ucraine – FEMEN bare it all
House Of Secrets – Full Movie
TOP-SECRET from the FBI – ING Bank N.V. Agrees to Forfeit $619 Million for Illegal Transactions with Cuban and Iranian Entities
WASHINGTON—ING Bank N.V., a financial institution headquartered in Amsterdam, has agreed to forfeit $619 million to the Justice Department and the New York County District Attorney’s Office for conspiring to violate the International Emergency Economic Powers Act (IEEPA) and the Trading with the Enemy Act (TWEA) and for violating New York state laws by illegally moving billions of dollars through the U.S. financial system on behalf of sanctioned Cuban and Iranian entities. The bank has also entered into a parallel settlement agreement with the Treasury Department’s Office of Foreign Assets Control (OFAC).
The announcement was made by Lisa Monaco, Assistant Attorney General for National Security; Ronald C. Machen, U.S. Attorney for the District of Columbia; Assistant Attorney General Lanny A. Breuer of the Criminal Division; District Attorney Cyrus R. Vance, Jr. of the New York County District Attorney’s Office; James W. McJunkin, Assistant Director in Charge of the FBI Washington Field Office; Richard Weber, Chief, Internal Revenue Service (IRS) Criminal Investigation; and Adam J. Szubin, Director of the Office of Foreign Assets Control.
A criminal information was filed today in federal court in the District of Columbia charging ING Bank N.V. with one count of knowingly and willfully conspiring to violate the IEEPA and TWEA. ING Bank waived the federal indictment, agreed to the filing of the information, and has accepted responsibility for its criminal conduct and that of its employees. ING Bank agreed to forfeit $619 million as part of the deferred prosecution agreements reached with the Justice Department and the New York County District Attorney’s Office.
According to court documents, starting in the early 1990s and continuing until 2007, ING Bank violated U.S. and New York state laws by moving more than $2 billion illegally through the U.S. financial system—via more than 20,000 transactions—on behalf of Cuban and Iranian entities subject to U.S. economic sanctions. ING Bank knowingly and willfully engaged in this criminal conduct, which caused unaffiliated U.S. financial institutions to process transactions that otherwise should have been rejected, blocked, or stopped for investigation under regulations by OFAC relating to transactions involving sanctioned countries and parties.
“The fine announced today is the largest ever against a bank in connection with an investigation into U.S. sanctions violations and related offenses and underscores the national security implications of ING Bank’s criminal conduct. For more than a decade, ING Bank helped provide state sponsors of terror and other sanctioned entities with access to the U.S. financial system, allowing them to move billions of dollars through U.S. banks for illicit purchases and other activities,” said Assistant Attorney General Monaco. “I applaud the agents, analysts, and prosecutors who for years pursued this case.”
“Banks that try to skirt U.S. sanctions laws undermine the integrity of our financial system and threaten our national security,” said U.S. Attorney Machen. “When banks place their loyalty to sanctioned clients above their obligation to follow the law, we will hold them accountable. On more than 20,000 occasions, ING intentionally manipulated financial and trade transactions to remove references to Iran, Cuba, and other sanctioned countries and entities. Today’s $619 million forfeiture—the largest ever—holds ING accountable for its wrongdoing.”
“For years, ING Bank blatantly violated U.S. laws governing transactions involving Cuba and Iran and then used shell companies and other deceptive measures to cover up its criminal conduct,” said Assistant Attorney General Breuer. “Today’s resolution reflects a strong collaboration among federal and state law enforcement partners to hold ING accountable.”
“Investigations of financial institutions, businesses, and individuals who violate U.S. sanctions by misusing banks in New York are vitally important to national security and the integrity of our banking system,” said New York County District Attorney Vance. “These cases give teeth to sanctions enforcement, send a strong message about the need for transparency in international banking, and ultimately contribute to the fight against money laundering and terror financing. I thank our federal partners for their cooperation and assistance in pursuing this investigation.”
“Today, ING Bank was held accountable for their illegal actions involving the movement of more than $2 billion through the U.S. financial system on behalf of Cuban and Iranian entities subject to U.S. economic sanctions,” said FBI Assistant Director in Charge McJunkin. “Investigations of this type are complicated and demand significant time and dedication from agents, analysts and prosecutors. In this case, their steadfast tenacity brought this case through to today’s result, and we will continue to pursue these matters in diligent fashion.”
“In today’s environment of increasingly sophisticated financial markets, it’s critical that global institutions follow U.S. law, including sanctions against other countries,” said IRS Criminal Investigation Chief Weber. “The IRS is proud to share its world-renowned financial investigative expertise in this and other complex financial investigations. Creating new strategies and models of cooperation among our law enforcement partners to ensure international financial compliance is a top-priority of the IRS.”
“Our sanctions laws reflect core U.S. national security and foreign policy interests and OFAC polices them aggressively. Today’s historic settlement should serve as a clear warning to anyone who would consider profiting by evading U.S. sanctions,” said OFAC Director Szubin. “We commend our federal and state colleagues for their work on this important investigation.”
The Scheme
According to court documents, ING Bank committed its criminal conduct by, among other things, processing payments for ING Bank’s Cuban banking operations through its branch in Curaçao on behalf of Cuban customers without reference to the payments’ origin and by providing U.S. dollar trade finance services to sanctioned entities through misleading payment messages, shell companies, and the misuse of ING Bank’s internal suspense account.
Furthermore, ING Bank eliminated payment data that would have revealed the involvement of sanctioned countries and entities, including Cuba and Iran; advised sanctioned clients on how to conceal their involvement in U.S. dollar transactions; fabricated ING Bank endorsement stamps for two Cuban banks to fraudulently process U.S. dollar travelers’ cheques; and threatened to punish certain employees if they failed to take specified steps to remove references to sanctioned entities in payment messages.
According to court documents, this conduct occurred in various business units in ING Bank’s wholesale banking division and in locations around the world with the knowledge, approval, and encouragement of senior corporate managers and legal and compliance departments. Over the years, several ING Bank employees raised concerns to management about the bank’s sanctions violations. However, no action was taken.
For decades, the United States has employed sanctions and embargoes on Iran and Cuba. Financial transactions conducted by wire on behalf of Iranian or Cuban financial institutions have been subject to these U.S. sanctions. The TWEA prohibits U.S. persons from engaging in financial transactions involving or benefiting Cuba or Cuban nationals and prohibits attempts to evade or avoid these restrictions. IEEPA makes it a crime to willfully attempt to commit, conspire to commit, or aid and abet in the commission of any violations of the Iranian Transaction Regulations, which prohibit the exportation of any services from the United States to Iran and any attempts to evade or avoid these restrictions. IEEPA and TWEA regulations are administered by OFAC.
The Investigation
The Justice Department’s investigation into ING Bank arose out of ongoing investigations into the illegal export of goods from the United States to sanctioned countries, including Iran. For instance, ING processed payments on behalf of one customer, Aviation Services International B.V. (ASI), a Dutch aviation company which was the subject of a U.S. Commerce Department-initiated criminal investigation, through the United States for trade services relating to the procurement by ASI of dual-use U.S. aviation parts for ASI’s Iranian clients. The ING Bank investigation also resulted in part from a criminal referral from OFAC, which was conducting its own probe of ING Bank.
ING Bank’s forfeiture of $309.5 million to the United States and $309.5 million to the New York County District Attorney’s Office will settle forfeiture claims by the Department of Justice and the state of New York. In light of the bank’s remedial actions to date and its willingness to acknowledge responsibility for its actions, the Department will recommend the dismissal of the information in 18 months, provided ING Bank fully cooperates with, and abides by, the terms of the deferred prosecution agreement.
OFAC’s settlement agreement with ING deems the bank’s obligations to pay a civil settlement amount of $619 million to be satisfied by its payment of an equal amount to the Justice Department and the state of New York. OFAC’s settlement agreement further requires the bank to conduct a review of its policies and procedures and their implementation, taking a risk-based sampling of U.S. dollar payments, to ensure that its OFAC compliance program is functioning effectively to detect, correct, and report apparent sanctions violations to OFAC.
The case was prosecuted by Trial Attorney Jonathan C. Poling of the Justice Department’s National Security Division; Assistant U.S. Attorneys Ann H. Petalas and George P. Varghese, of the National Security Section of the U.S. Attorney’s Office for the District of Columbia; and Trial Attorney Matthew Klecka of the Criminal Division’s Asset Forfeiture and Money Laundering Section.
The case was investigated by the FBI’s Washington Field Office and the IRS-Criminal Investigation’s Washington Field Division, with assistance from the Treasury Department’s OFAC and the Commerce Department’s Bureau of Industry and Security.
The Department of Justice expressed its gratitude to Executive Assistant District Attorney, Chief of Investigation Division Adam Kaufmann; and Assistant District Attorneys Sally Pritchard and Garrett Lynch of the New York County District Attorney’s Office, Major Economic Crimes Bureau.
The Dictator (aka Sacha Baron Cohen) Responds To Oscar Ban – Video
Borat – You Will Never Get This – Comedy Video
In Too Deep – Full Movie
Unveiled by the NSA – Taylor Verdict Milestone for International Justice

Washington, D.C., June 12, 2012 – The former Liberian president Charles Taylor today became the first head of state since Nuremberg convicted by an international court for crimes against humanity, for his role in the decade-long Sierra Leone civil war; and his human rights abuses in Liberia from 1990 to 2003 were likely even more systematic, according to declassified U.S. government documents posted today by the National Security Archive at www.nsarchive.org.
The U.S. Embassy Monrovia began one Confidential 2003 report during Taylor’s last year in office by noting, “A few months ago, The Economist magazine dubbed Liberia as the worst place in the world. Things have declined since then.” The cable went on to report, “The Taylor regime is like a wounded shark feeding on its own entrails.”
A subsequent Confidential Embassy cable from June 2003 described the constant threat of Taylor’s “bully boys” and “security thugs”going on “a killing spree in Monrovia,” in reaction to the original 2003 indictment by the UN-backed Special Court for Sierra Leone, whose judgment was announced today in The Hague.
The CIA reported as early as February 1990 in its Africa Review – then classified at the Secret level and since released under the Freedom of Information Act to the Archive – that Taylor’s insurrection in northern Liberia against then-dictator Samuel Doe had generated a refugee crisis because of both “Army and rebel atrocities,” including “ethnic score-settling” and “deliberate attempt[s] to stir up tribal animosities.”
A subsequent CIA analysis in May 1990 provided a Taylor biography noting his “alleged large-scale theft of government funds and coup plotting” during his 1983 tenure in the Samuel Doe government, admitted that the CIA had previously “underestimated” Taylor’s leadership skills and likelihood of success against Doe, and predicted “the rebels would indiscriminately begin slaughtering Krahns [Doe’s ethnic base], seeking retribution for Army atrocities committed against their fellow Gio tribesmen.”
The Department of State’s Bureau of Intelligence and Research considered the question “Liberia: Genocide?” in a Secret 1996 assessment that described “wholesale killings of civilians” both by the Liberian armed forces and by the various militias including Taylor’s, prior to his assuming the presidency of Liberia in 1997.
The documents posted today were obtained by the Archive through the Freedom of Information Act, in a multi-year systematic requesting project in support of the 2006-2009 Liberian Truth and Reconciliation Commission, and in partnership with human rights advocates and investigators both in Liberia and internationally including the Robert F. Kennedy Memorial Center for Human Rights. Today’s posting also includes a detailed analysis – written by the Urban Morgan Institute for Human Rights at the University of Cincinnati Law School – of more than 1,000 declassified documents released through the Archive’s FOIA requests on specific atrocities committed during the Liberian wars.
DOCUMENTS
Document 1: Central Intelligence Agency, “Liberia: Doe Grapples With Dissident Incursion,” from the CIA’s Africa Review, Secret, February 16, 1990.
Source: Freedom of Information Act request.
This report, complete with an inset photograph of “Dissident Leader Charles Taylor,” warns that “Liberian President [Samuel] Doe’s hapless army remains unable to suppress a seven-week-old tribally based insurrection.” The CIA reports that the fighting had not yet threatened Doe’s immediate hold on power, but predicts that Liberia “will remain unstable… aggravating ethnic animosities, regional tensions, and US-Liberian relations.”
Document 2: Central Intelligence Agency, Undated Estimate circa 5/90-7/90, title redacted.
Source: Freedom of Information Act request.
The CIA estimates that President Doe “is almost certain to fall” to Charles Taylor. The Agency predicts that the regime change will “usher in a period of anarchy and ethnic bloodletting, especially in Monrovia.” This Estimate also includes a biography of Taylor, which describes him as an “Americo-Liberian descended from freed US slaves.” In 1983, he fled Liberia to the United States and was arrested in the US at the behest of the Liberian government. According to the CIA estimate, he escaped from jail and “a US warrant for his arrest is still active.”
Document 3: Defense Intelligence Agency, “Subject: [Redacted], Encampment, Disarmament, Demobilization Plan,” Confidential NoForn, October 19, 1993.
Source: Freedom of Information Act request.
This DIA cable summarizes the travails of Liberian child-soldiers and provides possible methods for their reintegration into society, in conjunction with the Liberian government and UNICEF. The cable reports that child-soldiers were employed by “all warring factions in Liberia” because children were “easily controlled and naturally obey adults.”
Document 4: Department of State Bureau of Intelligence and Research, “Liberia: Genocide?,” Intelligence Assessment, Secret, May 2, 1996.
Source: Freedom of Information Act request.
This Department of State assessment concludes that “it is difficult to determine to what extent the mass killings in Liberia…are genocidal.” The INR recounts that hundreds–if not thousands–of civilians had been killed by all sides during the civil war. The assessment hedges, “Ethnic hatred is deeply rooted and widespread in Liberia, but this does not necessarily equate to organized genocide.”
Document 5: Department of State, “Subject: Scenesetter for Ceasefire Talks/Roundtable and ICGL,” Confidential, April 29, 2003.
Source: Freedom of Information Act request.
As rebel groups in both the north and south advanced on Taylor in Monrovia, US Ambassador John W. Blaney warns the US Secretary of State Colin Powell that “Liberia is going into a dangerous national meltdown, including increasing ethnic violence and spreading humanitarian crisis.” He reports that, “Taylor is under intense pressure, but will cling to power longer because he fears the UN’s War Crimes Tribunal in Sierra Leone.” Blaney warns that the “wildfire of ethnic and tribal hatred may soon burn uncontrollably.” The ambassador cites an Economist article that dubbed Liberia “the worst place in the world,” and expounds, “things have declined since then.”
Document 6: Department of State, “Subject: Liberia’s Opposition Requests Immediate Peacekeeping Force, States Threats Increased Since Indictment,” Confidential, June 18, 2003.
Source: Freedom of Information Act request.
Two months after the previous cable, Taylor travelled to Accra, Ghana to participate in peace talks with opposition rebels. Upon Taylor’s return, Ambassador Blaney wrote that fighting had temporarily ended in Monrovia, but “politics may never again be business as usual, []unless and until a credible international stabilization force is established.” The ambassador recounts that Taylor’s “bully boys” continued to terrorize anyone they perceived as “anti-Taylor.” According to one Liberian source, “These militia boys just don’t care… They just start shooting everywhere, into the homes of people they think oppose their leader and innocent people get shot too.” In July of 2003, rebel groups launched an assault on Monrovia which forced Taylor into exile in Nigeria; in 2005, Liberia held elections widely regarded as free and fair.
In 2006, the newly elected president of Liberia, Ellen Johnson Sirleaf, requested Taylor’s extradition from Nigeria. Upon his arrival in Monrovia, Taylor was transferred to the custody of the United Nations and flown to Sierra Leone to stand trial at the Special Court for Sierra Leone for war crimes and crimes against humanity.
TOP-SECRET – The SOLO File: Declassified Documents Detail “The FBI’s Most Valued Secret Agents of the Cold War”

Washington, D.C., April 10, 2012 – The “FBI’s most valued secret agents of the Cold War,” brothers Morris and Jack Childs, together codenamed SOLO, reported back to J. Edgar Hoover starting in 1958 about face-to-face meetings with top Soviet and Chinese Communist leaders including Mao and Khrushchev, while couriering Soviet funds for the American Communist Party, according to newly declassified FBI files cited in the new book by Tim Weiner, Enemies: A History of the FBI (New York: Random House, 2012).
Highlights from the massive SOLO files (which total more than 6,941 pages in 45 volumes declassified in August 2011 and January 2012) appear on the National Security Archive’s Web site today at www.nsarchive.org, together with an overview by Tim Weiner and a new search function, powered by the Archive’s partnership with DocumentCloud, that enables full-text search of the entire SOLO file (instead of the 45 separate PDF searches required by the FBI’s Vault publication at http://vault.fbi.gov/solo).
For more on Enemies, see last night’s broadcast of The Daily Show with Jon Stewart, featuring Tim Weiner, and the reviews by The New York Times Book Review, The Guardian, and The Washington Post.
“SOLO” BY TIM WEINER
FBI Director J, Edgar Hoover’s most valued secret agent was a naturalized citizen of Russian/Ukrainian/Jewish origins named Morris Childs. He was the first and perhaps the only American spy to penetrate the Soviet Union and Communist China at the highest levels during the Cold War, including having face-to-face conversations with Nikita Khrushchev, Mao Zedong and others in a red-ribbon cast of Communist leaders.
The operation, codenamed SOLO, that the FBI built on his work (and that of his brother, Jack) posed great risks and the promise of greater rewards. The FBI’s first debriefings of Morris Childs were declassified in August 2011 in time for inclusion in the book Enemies. Even more SOLO debriefings and associated memos – upwards of 45 volumes and thousands of pages – emerged in January 2012.
Researchers have been requesting these documents for years, and with good reason. They are unique records of a crucial chapter in the history of American intelligence. They illuminate several mysteries of the Cold War, including the origins of Hoover’s hatred for Martin Luther King, some convincing reasons for Dwight Eisenhower’s decision to hold off on the CIA’s plans to invade Fidel Castro’s Cuba, and the beginnings of Richard Nixon’s thoughts about a détente with the Soviets.
Morris Childs was an important figure in the Communist Party of the United States in the 1930s and 1940s, serving as the editor of its newspaper, the Daily Worker. He and his brother Jack had fallen out with the Party in 1948. Three years later, the FBI approached him as part of a new program called TOPLEV, in which FBI agents tried to talk top-level Communist Party members and officials into becoming informants.
Childs became a Communist for the FBI. He rejoined the Party and rose higher and higher in its secret hierarchy. In the summer of 1957, the Party’s leaders proposed that he serve as their international emissary in an effort to reestablish direct political and financial ties with the Kremlin. If Moscow approved, Childs would be reporting to Hoover as the foreign secretary of the Communist Party of the United States.
The FBI’s intelligence chief, Al Belmont, could barely contain his excitement over Childs’ cooperation. If the operation succeeded, he told Hoover, “it would enhance tremendously the Bureau’s prestige as an intelligence agency.”
[See Document 1: Memorandum from A.H. Belmont to L.V. Boardman, “Courier System Between Communist Party, USA, and Communist Party, Soviet Union,” 30 August 1957. Source: http://vault.fbi.gov/solo/solo-part-01-of/view, page 17.]
On March 5, 1958, the FBI’s top intelligence officials agreed that the operation would work: the Bureau could “guide one of our informants into the position of being selected by the CPUSA as a courier between the Party in this country and the Soviet Union.”
[See Document 2: Memorandum from A.H. Belmont to L.V. Boardman, “Communist Party, USA, International Relations, Internal Security-C,” 5 March 1958. Source: http://vault.fbi.gov/solo/solo-part-01-of/view, page 1.]
On April 24, 1958, Childs boarded TWA Flight 824 to Paris, on the first leg of his long trip to Moscow, at the invitation of the Kremlin. He met the Party’s leaders over the course of eight weeks. He learned that his next stop would be Beijing. On July 6, 1958, he had an audience with Chairman Mao Zedong (see pages 13-16 of Document 3B) Was the United States planning to go to war in Southeast Asia? Mao asked. If so, China intended to fight to the death, as it had during the Korean War. “There may be many Koreas in Asia,” Mao predicted.
[See Documents 3A-B: A: Childs’ Account of his April 1958 Trip to Soviet Union and China. B: SAC, New York, to Director, FBI, 23 July 1958 [account of Child’s first trip as a double-agent] Source: http://vault.fbi.gov/solo/solo-part-02-of/view.]
Returning to Moscow that summer, conferring with leaders of the Party and the KGB, Morris received a formal invitation to attend the 21st Congress of the Communist Party of the Soviet Union, and he accepted promises of cash payments for the CPUSA that would come to $348,385 over the next few months. The money was delivered to Morris by a Soviet delegate to the United Nations at a restaurant in Queens, New York.
Though the trips exhausted him, leaving him a physically broken man, Morris Childs went abroad two or three times a year over the course of the next two decades. He undertook fifty- two international missions, befriending the world’s most powerful Communists. He controlled the income of the American Communist Party’s treasury and contributed to the formulation of its foreign policy. His work as SOLO was undetected by the KGB and kept secret from all but the most powerful American leaders.
[See Document 4: Clyde Tolson to the Director, 12 March 1959 [report on Child’s background, how he was recruited, and information from his most recent trip to Moscow] Source: http://vault.fbi.gov/solo/solo-part-11-of-17/view, p. 49.]
SOLO’s intelligence gave Hoover an unquestioned authority in the White House. The United States never had had a spy inside the high councils of the Soviet Union or the People’s Republic of China. Morris Childs would provide the U.S. government with insights no president had ever before possessed.
Hoover briefed President Eisenhower about the SOLO mission repeatedly from November 1958 onwards. For the next two years, Hoover sent summaries of his reporting directly to Eisenhower and Vice President Nixon. Hoover reported that the world’s most powerful Communists– Mao Zedong and Nikita Khrushchev– were at each other’s throats. The breach between Moscow and Beijing was a revelation to Eisenhower. The FBI director also reported that Moscow wanted the CPUSA to support the civil rights movement in the United States. The idea that communism and civil rights were connected through covert operations was electrifying to Hoover.
Hoover told the White House that SOLO had met with Anibal Escalante, a political leader of the newly victorious revolution in Cuba, a confidant to Fidel Castro and the Cuban Communist most highly regarded in Moscow. Escalante said that the Cubans knew the United States was planning a paramilitary attack to overthrow Castro. This reporting gave Eisenhower pause as he weighed the CIA’s proposal to invade the island with a force of anti-Castro Cubans undergoing training in Guatemala. He never approved the plan; that was left to President Kennedy, who went ahead with the disastrous Bay of Pigs invasion.
[See Document 5: Memoranda and Letters to Director/Naval Intelligence, Director/CIA, National Security Adviser, Secretary of State, and Vice President Nixon on Information from Anibal Escalante. Source: http://vault.fbi.gov/solo/solo-part-21-22-of/view]
Hoover reported directly to Nixon as the vice president prepared to go to Moscow in July 1959, where he would engage Khrushchev in a public discussion on the political and cultural merits of communism and capitalism. SOLO had met with the top Communist Party officials responsible for American affairs. Hoover distilled their thinking about the leading candidates in the 1960 presidential election.
Moscow liked Ike: he understood the meaning of war and he was willing to risk the chances of peace. But Senator Kennedy was judged as “inexperienced” and potentially dangerous. As for Nixon, the Communists thought he would be a capable president, though he was “cunning” and “ambitious.”
[See Document 6: SAC, New York, to Director, FBI, 13 March 1960 [report on Khrushchev’s imminent visit to France and on President Eisenhower’s prospective (later cancelled) trip to Soviet Union]. Source: http://vault.fbi.gov/solo/solo-part-19-20-of/view, pp. 93-98.]
Nixon learned from the SOLO debriefings that Moscow could conduct rational political discourse; a decade later, the lesson served him well as president when he sought détente with the Soviets.
[Adapted from Tim Weiner, Enemies: A History of the FBI, pp. 207-209]
MORE ABOUT SOLO
The SOLO records are an extraordinary new contribution to the history of the FBI and American intelligence. It is worth noting that prior to the new FBI releases, earlier scholars had made important contributions to knowledge of this FBI operation. Civil rights historian and assiduous FOIA requester David J.Garrow was the first researcher to discover the role of the Childs brothers as FBI double-agents. In his book, Martin Luther King and the FBI: from ‘Solo’ to Memphis (New York: W. W. Norton, 1981), Garrow sought to explain why J.Edgar Hoover and the Bureau were such “viciously negative” opponents of King. Garrow disclosed that the Childs brothers had provided information to the FBI on Stanley Levison, one of King’s key political advisers. Levison had been active in the U.S. Communist Party during the early 1950s but, as Childs reported, had left the organization because of its political irrelevance. Nevertheless, the FBI saw Levison as a Soviet agent and used his former political connections as leverage to force King to break with his adviser.
Following Garrow’s trail was the late John Barron, a former Naval intelligence officer turned journalist and later a full-time writer for Readers Digest who produced as full an account of “Operation Solo” as was possible in the 1990s. An expert on the KGB, Barron met numerous former Soviet agents. One day, Morris Childs and his wife turned up at Barron’s Washington, D.C. office. Recognizing the Childs’ importance, Barron wanted to tell Morris’ story and did so through interviews with the FBI case officers who had handled contacts with the Childs brothers and their associates. Barron had no access to the documents, but his book, Operation Solo: The FBI’s Man in the Kremlin (Regnery, 1996), provided the first detailed account of the rise of Morris Childs to an influential role in the U.S. Communist Party, why he secretly broke with the Party, when and how he started to work with the FBI, and how he used his party connections and recurrent travel to Moscow and Beijing to provide current intelligence on developments in those capitals.
– William Burr
THE DOCUMENTS
Archive staff have downloaded the SOLO files from the FBI site and launched them in DocumentCloud in order to get a higher-quality full-text (OCR) and keyword search capacity down to the individual page level. The following files correspond to the 45 volumes posted on the FBI’s Vault. To search the entire group, enter terms in the field below and press “Enter.” The results will take you to the correct volume. Repeat your search and the results will take you to the correct page with the term highlighted in yellow.
Justice in the Heartland – Full Movie
SECRET from Cryptome – Health Dept: Four $305K Data Apps Competitions
[Federal Register Volume 77, Number 110 (Thursday, June 7, 2012)] [Notices] [Pages 33737-33739] From the Federal Register Online via the Government Printing Office [www.gpo.gov] [FR Doc No: 2012-13819] ----------------------------------------------------------------------- DEPARTMENT OF HEALTH AND HUMAN SERVICES Announcement of Requirements and Registration for ``Blue Button Mash Up Challenge'' AGENCY: Office of the National Coordinator for Health Information Technology, HHS. Award Approving Official: Farzad Mostashari, National Coordinator for Health Information Technology. ACTION: Notice. ----------------------------------------------------------------------- SUMMARY: The Office of the National Coordinator for Health Information Technology (ONC) and the Department of Veterans Affairs are working to empower individuals to be partners in their health through health information technology (health IT). Giving patients access to information about them related to the care they receive from doctors and other healthcare providers is in itself valuable, but it is also important to enable patients to use that information to make informed decisions. Individuals should be able to access and use their basic health information together with other information to take action: To better understand their current health status, use decision support software to choose treatments, anticipate and consider the costs of different options, and target and modify the everyday behaviors that have the greatest impact on their health. Inspired by the well-known ``three- part aim'' for improvement of the health care system, this challenge requires participants to help individuals to take action based on combining their health information with additional information that puts it into a more meaningful context. The statutory authority for this challenge competition is Section 105 of the America COMPETES Reauthorization Act of 2010 (Pub. L. 111- 358). DATES: Effective on June 5, 2012. Challenge submission period ends September 5, 2012, 11:59 p.m. et. FOR FURTHER INFORMATION CONTACT: Adam Wong, 202-720-2866; Wil Yu, 202- 690-5920. SUPPLEMENTARY INFORMATION: [[Page 33738]] Subject of Challenge Competition This challenge builds on a prior Blue Button challenge to make personal health information more usable and meaningful for the individual consumer or patient. Apps must be platform neutral. The challenge is broken into two parts: 1. App Development: Entrants must submit an app that makes the best use of Blue Button downloaded personal health data and combines it with other types of data. Apps must include data from at least two of the three part aim categories below. 2. Reach: The app must be able to garner high patient engagement rates. Entrants will therefore have to demonstrate a partnership with a personal health information data holding organization (such as a provider, payor, or Personal Health Record vendor--see healthit.gov/pledge for a definition of a data holding organization) to achieve wide distribution among patients. Applying the Three Part Aim: To participate in the challenge, entrants must mash up Blue Button data--data about a patient which the patient can download directly using a health plan's, doctor's or hospital's Blue Button function--with information from two or more of the three part aim categories. Below are examples of types of contextual data that would qualify for purposes of this contest. Entrants can use data sets from the categories below or similar data sets. Components of the Three Part Aim Part 1: Better Care Interactions With the Healthcare System Assist individuals in choosing high quality care that is relevant to their individual needs by including ratings for physician comparisons, hospital comparisons, or other care quality data. Assist individuals in identifying providers, practices, and hospitals that are health information technology enabled by using information from CMS related to Meaningful Use or other sources. Support individuals in understanding their current state of health by combining clinical data and medical claims data to create a comprehensive list of the individual's medical conditions. Support individuals in understanding their current medication regimen by aggregating clinical data from doctors/hospitals, prescription claims data, and downloaded clinical data to create a single comprehensive list of medications. Part 2: Better Care for Oneself Outside of the Healthcare System Provide support to help an individual meet some of their personally stated health goals, (for example related to healthy eating, exercise, social support, or other virtual or geographically based resources). Provide an easily understood representation of an individual's health status in comparisons to others of a similar demographic (age, gender, ethnicity, or otherwise), and make recommendations for actionable things an individual could do toward better health outcomes based on their comparative health data. Extrapolate how healthy behavior change can lead to positive health outcomes over time (for example show potential weight loss and reduced risk of cardiac illness from adding two 30 minute walks per week) Part 3: Reduced Costs Provide information related to costs of relevant health care services (treatments, procedures, medication formularies, etc.) and/or financial savings likely to accrue from behavior changes. Create algorithms that exhibit cost savings to the individual and/or the health care system if the individual makes healthy living interventions, or different cost related choices in their health care. Eligibility Rules for Participating in the Competition To be eligible to win a prize under this challenge, an individual or entity-- (1) Shall have registered to participate in the competition under the rules promulgated by the Office of the National Coordinator for Health Information Technology. (2) Shall have complied with all the requirements under this section. (3) In the case of a private entity, shall be incorporated in and maintain a primary place of business in the United States, and in the case of an individual, whether participating singly or in a group, shall be a citizen or permanent resident of the United States. (4) May not be a Federal entity or Federal employee acting within the scope of their employment. (5) Shall not be an HHS employee working on their applications or submissions during assigned duty hours. (6) Shall not be an employee of Office of the National Coordinator for Health IT. (7) Federal grantees may not use Federal funds to develop COMPETES Act challenge applications unless consistent with the purpose of their grant award. (8) Federal contractors may not use Federal funds from a contract to develop COMPETES Act challenge applications or to fund efforts in support of a COMPETES Act challenge submission. An individual or entity shall not be deemed ineligible because the individual or entity used Federal facilities or consulted with Federal employees during a competition if the facilities and employees are made available to all individuals and entities participating in the competition on an equitable basis. Entrants must agree to assume any and all risks and waive claims against the Federal Government and its related entities, except in the case of willful misconduct, for any injury, death, damage, or loss of property, revenue, or profits, whether direct, indirect, or consequential, arising from my participation in this prize contest, whether the injury, death, damage, or loss arises through negligence or otherwise. Entrants must also agree to indemnify the Federal Government against third party claims for damages arising from or related to competition activities. Registration Process for Participants To register for this challenge participants should either: Access the www.challenge.gov Web site and search for the ``Blue Button Mash Up Challenge''. Access the ONC Investing in Innovation (i2) Challenge Web site at: [cir] http://www.health2con.com/devchallenge/challenges/onc-i2-challenges/. [cir] A registration link for the challenge can be found on the landing page under the challenge description. Amount of the Prize First Prize: $45,000. Second Prize: $20,000. Third Prize: $10,000. Awards may be subject to Federal income taxes and HHS will comply with IRS withholding and reporting requirements, where applicable. Payment of the Prize Prize will be paid by contractor. Basis Upon Which Winner Will Be Selected The ONC review panel will make selections based upon the following criteria: Effectively integrate Blue Button data that incorporates elements from two or more of the sections described [[Page 33739]] above (special consideration will be given to apps and tools that incorporate data from all three components of the three-part aim). Integrate patient-centered design and usability concepts to drive high patient adoption and engagement rates. Innovation--how is the data mashed up in innovative ways to contextualize the individual's Blue Button downloaded data. Provide a one page implementation plan for how this app solution will be implemented for scalability, including details for marketing and promotion. Existing or modified apps should show an uptake in their initial user base demonstrating the potential for market penetration based on Blue Button data contextualization capabilities. Additional Information Ownership of intellectual property is determined by the following: Each entrant retains title and full ownership in and to their submission. Entrants expressly reserve all intellectual property rights not expressly granted under the challenge agreement. By participating in the challenge, each entrant hereby irrevocably grants to Sponsor and Administrator a limited, non- exclusive, royalty free, worldwide, license and right to reproduce, publically perform, publically display, and use the Submission to the extent necessary to administer the challenge, and to publically perform and publically display the Submission, including, without limitation, for advertising and promotional purposes relating to the challenge. Authority: 15 U.S.C. 3719. Dated: May 31, 2012. Farzad Mostashari, National Coordinator for Health Information Technology. [FR Doc. 2012-13819 Filed 6-6-12; 8:45 am] BILLING CODE 4150-45-P
[Federal Register Volume 77, Number 110 (Thursday, June 7, 2012)] [Notices] [Pages 33739-33740] From the Federal Register Online via the Government Printing Office [www.gpo.gov] [FR Doc No: 2012-13826] ----------------------------------------------------------------------- DEPARTMENT OF HEALTH AND HUMAN SERVICES Announcement of Requirements and Registration for ``Health Data Platform Metadata Challenge'' AGENCY: Office of the National Coordinator for Health Information Technology, HHS. ACTION: Notice. ----------------------------------------------------------------------- Award Approving Official: Farzad Mostashari, National Coordinator for Health Information Technology. SUMMARY: As part of the HHS Open Government Plan, the HealthData.gov Platform (HDP) is a flagship initiative and focal point helping to establish learning communities that collaboratively evolve and mature the utility and usability of a broad range of health and human service data. HDP will deliver greater potential for new data driven insights into complex interactions of health and health care services. To augment the HDP effort, seven complementary challenges will encourage innovation around initial platform- and domain-specific priority areas, fostering opportunities to tap the creativity of entrepreneurs and productivity of developers. The ``Health Data Platform Metadata Challenge'' requests the application of existing voluntary consensus standards for metadata common to all open government data, and invites new designs for health domain specific metadata to classify datasets in our growing catalog, creating entities, attributes and relations that form the foundations for better discovery, integration and liquidity. The statutory authority for this challenge competition is Section 105 of the America COMPETES Reauthorization Act of 2010 (Pub. L. 111- 358). DATES: Effective on June 5, 2012. Challenge submission period ends October 2, 2012, 11:59 p.m. et. FOR FURTHER INFORMATION CONTACT: Adam Wong, 202-720-2866; Wil Yu, 202- 690-5920. SUPPLEMENTARY INFORMATION: Subject of Challenge Competition The W3C has a number of standard vocabulary recommendations for Linked Data publishers, defining cross domain semantic metadata of open government data, including concept schemes, provenance, statistics, organizations, people, data catalogs and their holdings, linked data assets, and geospatial data, in addition to the foundational standards of the Web of Data (such as HTTP, XML, RDF and various serializations, SPARQL, OWL, etc). Other voluntary consensus standards development organizations are also making valuable contributions to open standards for Linked Data publishers, such as the emerging GeoSPARQL standard from the Open Geospatial Consortium. In some cases, the entities and relations in these vocabulary standards are expressed using UML class diagrams as an abstract syntax, then automatically translated into various concrete syntaxes like XML Schemas and RDF Schemas, which also makes many of the standards from the Object Management Group easy to express as RDF Schemas, such as those that describe business motivation (including but not limited to vision, mission, strategies, tactics, goals, objectives), service orientation, process automation, systems integration, and other government specific standards. Oftentimes there exist domain specific standards organizations, with standards products that express domain specific entities and relations, such as those for the health or environmental sectors. The Data.gov PMO has recently stood up a site to collect these standards when expressed as RDF Schemas for use by the growing community of Government Linked Data publishers, which includes HHS/CMS, EPA, DOE/NREL, USDA, and the Library of Congress. The challenge winner will demonstrate the application of voluntary consensus and de facto cross domain and domain specific standards, using as many of the HHS datasets available on healthdata.gov as possible. There are two objectives: 1. Apply existing standards as RDF Schemas from voluntary consensus standards organizations (W3C, OMG, OGC, etc.) for expressing cross domain metadata that is common to all open government data. 2. Design new HHS domain specific metadata based on the data made available on healthdata.gov where no RDF Schema is otherwise given or available. When designing new metadata expressed as RDF Schemas, designers should: Leverage existing data dictionaries expressed as natural language in the creation of new conceptual schemas, as provided by domain authorities; Observe best practices for URI's schemes that is consistent with existing healthdata.gov work (such as the Clinical Quality Linked Data release from HDI 2011); and Organize related concepts into small, compose-able component vocabularies. Turtle syntax for RDFS and RDF is preferred. The contributed code will be given an open source license and managed by HHS on github.com, with copyright and attribution to the developer(s) as appropriate, and will ideally be used to populate vocab.data.gov. Eligibility Rules for Participating in the Competition To be eligible to win a prize under this challenge, an individual or entity-- (1) Shall have registered to participate in the competition under the rules promulgated by the Office of the [[Page 33740]] National Coordinator for Health Information Technology. (2) Shall have complied with all the requirements under this section. (3) In the case of a private entity, shall be incorporated in and maintain a primary place of business in the United States, and in the case of an individual, whether participating singly or in a group, shall be a citizen or permanent resident of the United States. (4) May not be a Federal entity or Federal employee acting within the scope of their employment. (5) Shall not be an HHS employee working on their applications or submissions during assigned duty hours. (6) Shall not be an employee of Office of the National Coordinator for Health IT. (7) Federal grantees may not use Federal funds to develop COMPETES Act challenge applications unless consistent with the purpose of their grant award. (8) Federal contractors may not use Federal funds from a contract to develop COMPETES Act challenge applications or to fund efforts in support of a COMPETES Act challenge submission. An individual or entity shall not be deemed ineligible because the individual or entity used Federal facilities or consulted with Federal employees during a competition if the facilities and employees are made available to all individuals and entities participating in the competition on an equitable basis. Entrants must agree to assume any and all risks and waive claims against the Federal Government and its related entities, except in the case of willful misconduct, for any injury, death, damage, or loss of property, revenue, or profits, whether direct, indirect, or consequential, arising from my participation in this prize contest, whether the injury, death, damage, or loss arises through negligence or otherwise. Entrants must also agree to indemnify the Federal Government against third party claims for damages arising from or related to competition activities. Registration Process for Participants To register for this challenge participants should either: Access the www.challenge.gov Web site and search for the ``Health Data Platform Metadata Challenge''. Access the ONC Investing in Innovation (i2) Challenge Web site at: [cir] http://www.health2con.com/devchallenge/challenges/onc-i2-challenges/. [cir] A registration link for the challenge can be found on the landing page under the challenge description. Amount of the Prize [ssquf] First Prize: $20,000. [ssquf] Second Prize: $10,000. [ssquf] Third Prize: $5,000. Awards may be subject to Federal income taxes and HHS will comply with IRS withholding and reporting requirements, where applicable. Payment of the Prize Prize will be paid by contractor. Basis Upon Which Winner Will Be Selected The ONC review panel will make selections based upon the following criteria: Metadata: The number of cross domain and domain specific voluntary consensus and defacto standard schemas, vocabularies or ontologies that are (re)used or designed and applied to HHS data on healthdata.gov. Data: The number of datasets that the standards based cross domain metadata and schema designed domain specific data is applied to. Linked Data: The solution should use best practices for the expression of metadata definitions and instance data identification, leveraging the relevant open standards, including but not limited to foundational standards (RDF, RDFS, SPARQL, OWL), and other defacto vocabularies and ontologies such as those listed here as required, with the expectation that existing standards will be reused to the fullest extent possible. Components: Leveraging software components that are already a part of the HDP is preferable, but other open source solutions may be used. Tools: Use of automation and round trip engineering that enable multiple concrete syntax realization from abstract syntax of cross domain and/or domain specific metadata is desirable, with no expectation that the tools must be open source or otherwise contributed to HDP as part of this challenge submission. Only newly designed domain specific RDF Schemas, their composition cross domain standards based RDF Schemas, and their application to various datasets are expected to be submitted for this challenge. Tool functionality may be highlighted to explain implementations as desired. Best practices: Where any new schemas and software code is created, they should exemplify design best practices and known software patterns, or otherwise establish them. Documentation: Articulation of design using well known architecture artifacts. Engagement: Willingness to participate in the community as a maintainer/committer after award. Additional Information The virtual machines and codebase outputs from innovations demonstrated by challenge participants will be made publically available through HHS Github repositories (see https://github.com/hhs/) as release candidates for further community refinement as necessary, including open source licensing and contributor attribution as appropriate. Authority: 15 U.S.C. 3719. Dated: May 31, 2012. Farzad Mostashari, National Coordinator for Health Information Technology. [FR Doc. 2012-13826 Filed 6-6-12; 8:45 am] BILLING CODE 4150-45-P
[Federal Register Volume 77, Number 110 (Thursday, June 7, 2012)] [Notices] [Pages 33740-33742] From the Federal Register Online via the Government Printing Office [www.gpo.gov] [FR Doc No: 2012-13830] ----------------------------------------------------------------------- DEPARTMENT OF HEALTH AND HUMAN SERVICES Announcement of Requirements and Registration for ``Health Data Platform Simple Sign-On Challenge'' AGENCY: Office of the National Coordinator for Health Information Technology, HHS. ACTION: Notice. ----------------------------------------------------------------------- Award Approving Official: Farzad Mostashari, National Coordinator for Health Information Technology. SUMMARY: As part of the HHS Open Government Plan, the HealthData.gov Platform (HDP) is a flagship initiative and focal point helping to establish learning communities that collaboratively evolve and mature the utility and usability of a broad range of health and human service data. HDP will deliver greater potential for new data driven insights into complex interactions of health and health care services. To augment the HDP effort, seven complementary challenges will encourage innovation around initial platform- and domain-specific priority areas, fostering opportunities to tap the creativity of entrepreneurs and productivity of developers. The ``Health Data Platform Simple Sign-On Challenge'' will improve community engagement by providing simplified sign on (SSO) for external users interacting across multiple HDP technology components, making it easier for community collaborators to contribute, leveraging new approaches to decentralized authentication. [[Page 33741]] The statutory authority for this challenge competition is Section 105 of the America COMPETES Reauthorization Act of 2010 (Pub. L. 111- 358). DATES: Effective on June 5, 2012. Challenge submission period ends October 2, 2012, 11:59 p.m. et. FOR FURTHER INFORMATION CONTACT: Adam Wong, 202-720-2866; Wil Yu, 202- 690-5920. SUPPLEMENTARY INFORMATION: Subject of Challenge Competition Healthdata.gov is leveraging a variety of open source infrastructure components including the Drupal 7 content management system, the CKAN data portal, the Solr search engine, and the community edition of the Virtuoso (as a RDF database and SPARQL endpoint query service). Going forward, the HDP team intends to realize an architecture similar to the Linked Data Integration Framework (LDIF) and leverage tools in the LOD2 stack where possible, beginning with Ontowiki to be used as Virtuoso editor, most likely followed by SILK for cross domain correlation. HDP would like to enable service requestors to be authenticated using WebID from the W3C. Some of the current and upcoming HDP infrastructure components support aspects of WebID functionality already while others do not. A number of WebID libraries are available, written in various languages. This challenge winner will present a replicable open source virtual machine environment demonstrating how HDP components (with an initial emphasis on Virtuoso,\1\ Drupal 7,\2\ CKAN,\3\ OntoWiki,\4\ and Solr,\5\) can provide and/or consume WebID's, contributing to simplified sign-on for humans and machines. The developer designs how their code might utilize each component as a WebID identity provider or relying party, presumably leveraging existing capabilities to the fullest extent possible. The end result will demonstrate seamless integration across a number of HDP components, without introducing any external service dependencies that couldn't be operated by HHS. The contributed code will be given an open source license and managed by HHS on github.com, with copyright and attribution to the developer(s) as appropriate. --------------------------------------------------------------------------- \1\ http://virtuoso.openlinksw.com/dataspace/dav/wiki/Main/. \2\ http://www.acquia.com/Drupal-7. \3\ http://ckan.org/. \4\ http://lod2.eu/Project/OntoWiki.html. \5\ http://lucene.apache.org/solr/. --------------------------------------------------------------------------- Eligibility Rules for Participating in the Competition To be eligible to win a prize under this challenge, an individual or entity-- (1) Shall have registered to participate in the competition under the rules promulgated by the Office of the National Coordinator for Health Information Technology. (2) Shall have complied with all the requirements under this section. (3) In the case of a private entity, shall be incorporated in and maintain a primary place of business in the United States, and in the case of an individual, whether participating singly or in a group, shall be a citizen or permanent resident of the United States. (4) May not be a Federal entity or Federal employee acting within the scope of their employment. (5) Shall not be an HHS employee working on their applications or submissions during assigned duty hours. (6) Shall not be an employee of Office of the National Coordinator for Health IT. (7) Federal grantees may not use Federal funds to develop COMPETES Act challenge applications unless consistent with the purpose of their grant award. (8) Federal contractors may not use Federal funds from a contract to develop COMPETES Act challenge applications or to fund efforts in support of a COMPETES Act challenge submission. An individual or entity shall not be deemed ineligible because the individual or entity used Federal facilities or consulted with Federal employees during a competition if the facilities and employees are made available to all individuals and entities participating in the competition on an equitable basis. Entrants must agree to assume any and all risks and waive claims against the Federal Government and its related entities, except in the case of willful misconduct, for any injury, death, damage, or loss of property, revenue, or profits, whether direct, indirect, or consequential, arising from my participation in this prize contest, whether the injury, death, damage, or loss arises through negligence or otherwise. Entrants must also agree to indemnify the Federal Government against third party claims for damages arising from or related to competition activities. Registration Process for Participants To register for this challenge participants should either: Access the www.challenge.gov Web site and search for the ``Health Data Platform Simple Sign-On Challenge''. Access the ONC Investing in Innovation (i2) Challenge Web site at: [cir] http://www.health2con.com/devchallenge/challenges/onc-i2-challenges/. [cir] A registration link for the challenge can be found on the landing page under the challenge description. Amount of the Prize First Prize: $20,000. Second Prize: $10,000. Third Prize: $5,000. Awards may be subject to Federal income taxes and HHS will comply with IRS withholding and reporting requirements, where applicable. Payment of the Prize Prize will be paid by contractor. Basis Upon Which Winner Will Be Selected The ONC review panel will make selections based upon the following criteria: Coverage: The more integrated components the better, with an emphasis on leverage existing work and capabilities of each component. Coupling: The level with which any integrated components can be removed without affecting the remaining component functionality. Performance: The lowest latency and best responsiveness of the component interactions as demonstrated by test cases. Elegance: How the design deals with both human and application agents that interact with different interfaces, and how each is managed across infrastructure components. Documentation: Articulation of design using well known architecture artifacts and executable test cases. Engagement: Willingness to participate in the community as a maintainer/committer after award. Additional Information The virtual machines and codebase outputs from innovations demonstrated by challenge participants will be made publically available through HHS Github repositories (see https://github.com/hhs/) as release candidates for further community refinement as necessary, including open source licensing and contributor attribution as appropriate. Authority: 15 U.S.C. 3719. [[Page 33742]] Dated: May 31, 2012. Farzad Mostashari, National Coordinator for Health Information Technology. [FR Doc. 2012-13830 Filed 6-6-12; 8:45 am] BILLING CODE 4150-45-P
[Federal Register Volume 77, Number 110 (Thursday, June 7, 2012)] [Notices] [Pages 33742-33745] From the Federal Register Online via the Government Printing Office [www.gpo.gov] [FR Doc No: 2012-13834] ----------------------------------------------------------------------- DEPARTMENT OF HEALTH AND HUMAN SERVICES Announcement of Requirements and Registration for ``My Air, My Health Challenge'' AGENCY: Office of the National Coordinator for Health Information Technology, HHS. National Institute of Environmental Health Sciences, National Institutes of Health, HHS. Award Approving Official: Farzad Mostashari, National Coordinator for Health Information Technology. ACTION: Notice. ----------------------------------------------------------------------- SUMMARY: Environmental and public health are closely related and complementary fields--and their future depends on a closer understanding of those connections. New portable sensors have the potential to transform the way we measure and interpret the influence of pollution on health. These technologies can provide a picture that is more detailed and more personal, with dramatic implications for health care, air quality oversight, and individuals' control over their own environments and health. The U.S. Environmental Protection Agency (EPA) and U.S. Department of Health and Human Service (HHS) [National Institute of Environmental Health Sciences (NIEHS) and Office of the National Coordinator for Health Information Technology (ONC)] envision a future in which powerful, affordable, and portable sensors provide a rich awareness of environmental quality, moment-to-moment physiological changes, and long-term health outcomes. Health care will be connected to the whole environment, improving diagnosis, treatment, and prevention at all levels. Many of the first steps toward this future have already been taken. Prototype projects have developed portable air quality and physiologic sensors, and experimental analysis tools for handling data that is higher quantity, but often lower quality, than more traditional monitoring techniques. The ``My Air, My Health Challenge'' aims to build on this foundation. We are seeking solutions that integrate data from portable physiological and air quality monitors, producing a combined picture that is meaningful and usable. The statutory authority for this challenge competition is Section 105 of the America COMPETES Reauthorization Act of 2010 (Pub. L. 111-358) and section 103 of the Clean Air Act, 42 U.S.C. 7403. This challenge addresses the mission of the NIEHS to conduct and support programs with respect to factors in the environment that affect human health, directly or indirectly. 42 U.S.C. 285. DATES: Phase 1: Effective on June 6, 2012. Submission period ends October 5, 2012, 11:59 p.m. et. Phase 2: Effective on November 19, 2012. Submission period ends May 19, 2013, 11:59 p.m. et. FOR FURTHER INFORMATION CONTACT: Denice Shaw, EPA, 202-564-1108; Adam Wong, ONC, 202-720-2866. SUPPLEMENTARY INFORMATION: Subject of Challenge Competition The ``My Air, My Health Challenge'' is a multidisciplinary call to innovators and software developers (``Solvers'') to enable near-real- time, location-specific monitoring and reporting of air pollutants and potentially related physiological parameters, using a personal/portable integrated system to assess connections between the two (``sensor systems''). The system must link air-pollutant concentrations with physiological data, provide geocoded and time-stamped files in an easy- to-use format, and transmit this data via existing networks to a central data repository provided by EPA and HHS. The challenge is structured in 2 phases: Phase 1--Project Plan (no more than 15 pages, not including appendices that may consist of diagrams/schematics, bibliography, and other supplementary materials). 1. Propose a plausible link between health outcomes and airborne pollutants (chemical species and/or particulates), and provide evidence to support a plausible and physiologically meaningful relationship between airborne pollutants and physiological metrics in a defined population. 2. Propose a prototype design and development plan for an integrated multi-sensor and data management system that may be easily worn or carried by individuals within the defined target community/ population. 3. Conceptualize data generation, management (may include processing & on-board storage), and transmission functionality of the device. 4. Propose a small-scale proof-of-concept study to validate the proposed prototype. 5. Study design process must include input from the target community/population. Phase 2--Proof-of-Concept Pilot Project. 6. Finalists attend an event for feedback, questions, and business/ entrepreneurial resources prepared by Challenge sponsors (EPA, HHS ONC, NIEHS). 7. Solvers develop the proposed prototype and execute experimental validation of the system to bring together data from personal air quality and physiological monitors, showing how these types of data and sensors can be integrated for practical use by health and environmental agencies, and by individual citizens. Proof-of-concept data must illustrate the accuracy and precision of the raw data and of any processed data produced by the system. Level of Focus for Health/Pollution connections: Systems must track airborne pollutants and physiological parameters for a known or plausible health-pollution link. Solvers must be able to justify their chosen combination with research citations and to optimize the air sampling parameters (volume, frequency, etc.) and physiological measurement parameters to provide resolution appropriate to the specific pollutant, or combination of pollutants, and related health implications. Challenge Sponsors will provide examples of such links for illustrative purposes (appended to the challenge announcement), but will not limit Solvers to these particular cases. Sensor development: Solvers are not expected to develop novel sensors for this challenge, but are not restricted to commercially available sensors. They may use sensors that are currently in the development or piloting stage, but must show that the sensor will be ready to use in functional tests--at least at a small scale--in time for the Phase 2 proof-of-concept demonstration. Instruments must be well characterized in terms of precision, accuracy and sensitivity. Integrated sensor systems must be able to transmit data to the central repository (in real time, or store and forward) using existing data networks (e.g. 3G, LTE, or WiFi), or able to connect with personal devices (e.g., smart phones) that have such capability. Solvers must enable appropriate calibration and error checking capabilities, although these need not be onboard the portable monitoring components. Data Requirements and Constraints: Data transmitted by the integrated devices to a centralized data repository must enable the following to be understood from transmitted data: 1. Indicators of device functionality, including any results of automated [[Page 33743]] system diagnostics, calibrations, or error logs 2. The device unique identifier, including any paired communication device identifier (particularly important if bidirectional communication functionality is proposed) 3. Date and time the data were collected/measurements made (start and end timestamp) 4. The location of the device during data collection (geocode)--if sampling occurs over several minutes or longer Solvers should consider that users may be using transportation and that analysis should ideally show locations between sample start and end 5. Raw measurement data (quantitative or semi-quantitative) as well as any processed data or combined 6. Quality control metrics indicating, for instance, whether the device is being worn/carried or functioning correctly. Error checking can occur either prior to or after data transmission, but is an essential component. The preferred data transmission file format is comma separated value (.csv) or variants thereof. Alternatively, encrypted binary files are also acceptable. Encryption keys/codes should be provided to the Challenge Sponsors so that data can be accessed at the central data repository. Pollutant Focus: Solvers will be required to include at least one air pollution metric--although at their discretion they may include multiple air pollution metrics and/or other environmental metrics such as noise level and UV exposure. The focus, however, will be on chemical and/or particulate air pollutants. Physiological Parameter Focus: Solvers will be required to include at least one physiological metric--although at their discretion they may include multiple physiological metrics and/or other person-oriented metrics such as behaviors and social interactions. The focus, however, will be on physical parameters (e.g., heart rate, breathing, pulse oxygenation), and their connection to pollutants. Physical Guidelines for Sensors: At least one component of the sensor system must be wearable or carryable, and all components should have a minimal burden and be minimally obtrusive. The overall sensor system must focus on personal and local metrics (i.e., measuring air quality in the immediate vicinity of the wearer). Wearable components must be the right size and weight for their target audience (e.g., no more than 300 g for a child). Sampling frequency and area must be appropriate to the pollutants and physiological metrics of interest, as well as to the context of data collection (e.g., by walkers, cyclists or passengers on public transportation). The sensor system must include an on-board data buffer for when network access is unavailable, and may also at the Solver's discretion include personal media to which data may be downloaded for permanent or temporary storage. Open source hardware and software are desired but not required. Measurement Guidelines for Sensors: Accuracy, detection limit, measurement range, and sensitivity of all sensors must be at sufficient resolution to record health-relevant changes in air pollutant(s) and physiological marker(s). If processing of the data is required in order to achieve this (e.g., normalization, increasing signal-to-noise ratios), the Solver must include the algorithm and its scientific basis (i.e., previously collected data and/or appropriate citations) in their report. Alternatively, centralized processing that enables parsing of local data, in order to increase data robustness and reduce false positive signals, may be used. If such an approach is determined to be useful, Solvers must outline suitable strategies and/or boundary criteria. In either case, solvers must communicate the overall uncertainty level of the final system output Community Involvement: The sensor system must address a need in a specific community or population. In addition to scientific evidence supporting that need, Solvers must also seek and document community input. Representatives of the affected community should provide feedback on the pilot project both during conceptualization (Phase 1), and throughout the pilot study (Phase 2). This is not intended to override the Solvers' scientific judgment on technical issues, but to ensure that the project is respectful of local knowledge, community identity, and needs. Projects must include feedback to the community regarding both technical success (e.g., whether sensors performed as planned) and results (e.g., any correlations found in the data). Scaling and Future Plans: While Phase 2 requires only a small-scale proof-of-concept project, final submissions for this phase must include a description of how the project could or will be extended and expanded. In general, Solvers are asked to propose concrete next steps that might be carried out with more time or resources available. Eligibility Rules for Participating in the Competition To be eligible to win a prize under this challenge, an individual or entity shall have complied with all the requirements under this section and Federal Register Notice. This challenge is open to any Solver who is (1) an individual or team of U.S. citizens or permanent residents of the United States who are 18 years of age and over, or (2) an entity incorporated in and maintaining a primary place of business in the United States. Foreign citizens can participate as employees of an entity that is properly incorporated in the U.S. and maintains a primary place of business in the U.S. Solvers may submit more than one entry. Eligibility for Phase 2 is conditional upon being selected as a Phase 1 Finalist. Eligibility for a prize award is contingent upon fulfilling all requirements set forth herein. An individual, team, or entity that is currently on the Excluded Parties List (https://www.epls.gov/) will not be selected as a Finalist or Winner. Employees of EPA, HHS, and the reviewers or any other company or individual involved with the design, production, execution, or distribution of the challenge and their immediate family (spouse, parents and step-parents, siblings and step-siblings, and children and step-children) and household members (people who share the same residence at least three (3) months out of the year) are not eligible to participate. An individual or entity may not be a Federal entity or Federal employee acting within the scope of their employment. Federal employees seeking to participate in this challenge outside the scope of their employment should consult their ethics official prior to developing a submission. An individual or entity shall not be deemed ineligible because the individual or entity used Federal facilities or consulted with Federal employees during a competition if the facilities and employees are made available to all individuals and entities participating in the competition on an equitable basis. Federal grantees may not use Federal funds to develop COMPETES Act challenge applications unless consistent with the purpose of their grant award. (Grantees should consult with their cognizant Grants Management Official to make this determination.) Federal contractors may not use Federal funds from a contract to develop COMPETES Act challenge applications or to fund efforts in support of a COMPETES Act challenge submission. [[Page 33744]] Liability and Indemnification: By participating in this competition, Solvers agree to assume any and all risks and waive claims against the Federal Government and its related entities, except in the case of willful misconduct, for any injury, death, damage, or loss of property, revenue, or profits, whether direct, indirect, or consequential, arising from participation in this competition, whether the injury, death, damage, or loss arises through negligence or otherwise. By participating in this competition, Solvers agree to indemnify the Federal Government against third party claims for damages arising from or related to competition activities. Insurance: Based on the subject matter of the competition, the type of work that it will possibly require, as well as an analysis of the likelihood of any claims for death, bodily injury, or property damage, or loss potentially resulting from competition participation, Solvers are not required to obtain liability insurance or demonstrate financial responsibility in order to participate in this competition. Registration Process for Participants To register for this challenge participants may do any of the following: [ssquf] Access the www.challenge.gov Web site and search for the ``My Air, My Health Challenge''. [ssquf] Access the ONC Investing in Innovation (i2) Challenge Web site at: [cir] http://www.health2con.com/devchallenge/challenges/onc-i2-challenges/. [cir] A registration link for the challenge can be found on the landing page under the challenge description. [ssquf] Access the Innocentive challenge Web site at www.innocentive.com/myairmyhealth. Amount of the Prize [ssquf] Phase 1: $15,000 each for up to four Finalists who are selected to move on to Phase 2. [ssquf] Phase 2: $100,000 to the Winner. Awards may be subject to Federal income taxes. Payment of the Prize HHS and EPA prizes awarded under this competition will be paid by electronic funds transfer and may be subject to Federal income taxes. HHS and EPA will comply with the Internal Revenue Service withholding and reporting requirements, where applicable. Basis Upon Which Winner Will Be Selected The review panel will make selections based upon the following criteria in Phase 1: [ssquf] Strength of evidence and/or argumentation regarding the linkage between air pollutant and physiological effect. [ssquf] Potential significance of technology and eventual benefit to target population(s). [ssquf] Viability of proposed sensor technologies to detect and quantify pollutants and their effects, and provide physiologically relevant health and air quality data. [ssquf] Viability of the proposed data reporting technology (communication to a centralized data repository provided by EPA and HHS) [ssquf] Viability of the proposed project plan. [ssquf] Viability of the proposed instrument design as a wearable/ portable device. [ssquf] Viability of the proposed proof-of-concept study (low complexity is preferred). [ssquf] Appropriate use of community input in designing proof-of- concept study. The review panel will make selections based upon the following criteria in Phase 2: [ssquf] Sensors: Successful technical collection of both health and environmental data [ssquf] Data Reporting: Successful formatting and transmission of data [ssquf] Data processing and evaluation [ssquf] Community Involvement and Interaction Additional Information Intellectual Property Rights: Upon submission, each Solver warrants that he or she is the sole author and owner of the work, that the work is wholly original with the Solver (or is an improved version of an existing work that the Solver has sufficient rights to use--including the substantial improvement of existing open-source work) and that it does not infringe any copyright or any other rights of any third party of which Solver is aware. Each Solver also warrants that the work is free of malware. (a) Copyright. By participating in this competition, each Solver hereby grants to the Federal government an irrevocable, paid-up, royalty-free, nonexclusive worldwide license to reproduce, distribute copies, display, create derivative works, and publicly post, link to, and share, the work or parts thereof, including any parts for which it has obtained rights from a third party, in any medium, for Federal purposes. User warrants that it has obtained rights to any parts of the work not authored by Solver adequate to convey the aforementioned license. (b) Inventions. Finalists hereby grant to the Federal government a nonexclusive, nontransferable, irrevocable, paid-up license to practice or have practiced for or on behalf of the United States any invention throughout the world made by Finalists that, if patented, would cover the submission or its use. Privacy, Data Security, Ethics, and Compliance Solvers are required to identify and address privacy and security issues in their proposed projects, and describe specific solutions for meeting them. In addition to complying with appropriate policies, procedures, and protections for data that ensures all privacy requirements and institutional policies are met, use of data should not allow the identification of the individual from whom the data was collected. Solvers are responsible for compliance with all applicable federal, state, local, and institutional laws, regulations, and policy. These may include, but are not limited to, HIPAA, HHS Protection of Human Subjects regulations, and FDA regulations. If approvals (e.g., from Institutional Review Boards) will be required to initiate project activities in Phase 2, it is recommended that solvers apply for approval at or before the Phase 1 submission deadline. The following links are intended as a starting point for addressing regulatory requirements, but should not be interpreted as a complete list of resources on these issues: HIPAA Main link: http://www.hhs.gov/ocr/privacy/index.html. Summary of the HIPAA Privacy Rule: http://www.hhs.gov/ocr/privacy/hipaa/understanding/summary/index.html. Summary of the HIPAA Privacy Rule: http://www.hhs.gov/ocr/privacy/hipaa/understanding/summary/index.html. Summary of the HIPAA Security Rule: http://www.hhs.gov/ocr/privacy/hipaa/understanding/srsummary.html. Human Subjects--HHS Office for Human Research Protections: http://www.hhs.gov/ohrp/index.html. Protection of Human Subjects Regulations: http://www.hhs.gov/ohrp/humansubjects/guidance/45cfr46.html. Policy & Guidance: http://www.hhs.gov/ohrp/policy/index.html. Institutional Review Boards & Assurances: http://www.hhs.gov/ohrp/assurances/index.html. [[Page 33745]] Human Subjects--FDA Clinical Trials: http://www.fda.gov/ScienceResearch/SpecialTopics/RunningClinicalTrials/ default.htm. Office of Good Clinical Practice: http://www.fda.gov/AboutFDA/CentersOffices/OfficeofMedicalProductsand Tobacco/OfficeofScienceandHealthCoordination/ucm2018191. Consumer Protection--FTC Bureau of Consumer Protection: http://business.ftc.gov/privacy-and-security. Authority: 15 U.S.C. 3719. Dated: May 31, 2012. Farzad Mostashari, National Coordinator for Health Information Technology. [FR Doc. 2012-13834 Filed 6-6-12; 8:45 am] BILLING CODE 4150-45-P
Last Chance for Justice – Full Movie
TOP-SECRET – Open Source Center Analysis of North Korea Joint Ventures With Foreign Partners 2004-2011

OSC has identified more than 350 joint ventures in North Korea in a search of open source information. For the 88 ventures for which we have investment amount data, the aggregate total of reported foreign investment from 2004 to 2011 amounted to $2.32 billion, with roughly half of that going toward ventures in the mining sector. Firms from China account for 75% of the joint venture partners for which partner country is known, followed by firms from South Korea, Japan, and Europe. Of the joint ventures for which we found location information, most show a Pyongyang address. The remaining are concentrated at seven locales in other parts of the country.
The main vehicle for private foreign investors to conduct large-scale business in North Korea is a joint venture with a local partner, judging from available open sources. DPRK law permits other types of foreign direct investment, but all of the investments made by foreign firms we found in our research were either equity or contractual joint ventures.
North Korean joint ventures, like other companies in North Korea, appear to be largely staffed by Koreans and operate under the constraints of the North Korean system. Majority ownership of joint ventures, however, appears to be primarily in the hands of the foreign partners: eight of the 12 joint ventures for which we have ownership share information are controlled by overseas firms, and the remaining four are split 50-50 (Table 1). Directorships and presidencies of North Korean joint ventures are often held by an officer of the foreign company.
OSC has identified 351 North Korean joint ventures with partner companies from around the world and in a range of industries (Table 2). More than 260 of these joint ventures have been active as recently as 2004.
…
Chinese Involvement Preeminent
Partner firms in North Korean joint ventures have come from Asia, Europe, Oceania, and North America (Table 2), but Chinese firms are the dominant investors.
- China accounts for 205 of the joint ventures we found. Japan with 15 and South Korea with 10 are a distant second and third.
- European companies from Italy, the United Kingdom, Netherlands, and Germany are engaged in joint ventures in North Korea, focusing on finance and technology.
- Egyptian and Thai firms do not sponsor many JVs, but their partnerships are crucial to North Korea’s domestic communications network — managing the country’s mobile telephone network and Internet services, respectively.
The share of Chinese firms as a total of new North Korean joint venture starts appears to be sharply increasing. Out of the JVs for which we know country of investor and start date, only four in ten had Chinese investors before 2004. From then until the end of 2011, however, Chinese firms represent about 87 percent of JVs started, 148 of the 167 in this set.
- Most of the Chinese firms that we found with specific location data were from the northeast provinces of Liaoning and Jilin, both of which share long borders with North Korea (Figure 3). Companies based in Shandong, Beijing, and Tianjin are also major players in joint ventures.
When compared with their investment in other destinations, though, Chinese firms’ investment in North Korea is small. Even firms from Liaoning Province — despite their proximity to the DPRK — sent almost 99% of their outbound investment from 2006-2011 to destinations other than North Korea, according to a provincial government record of private outlays (Table 4).
…
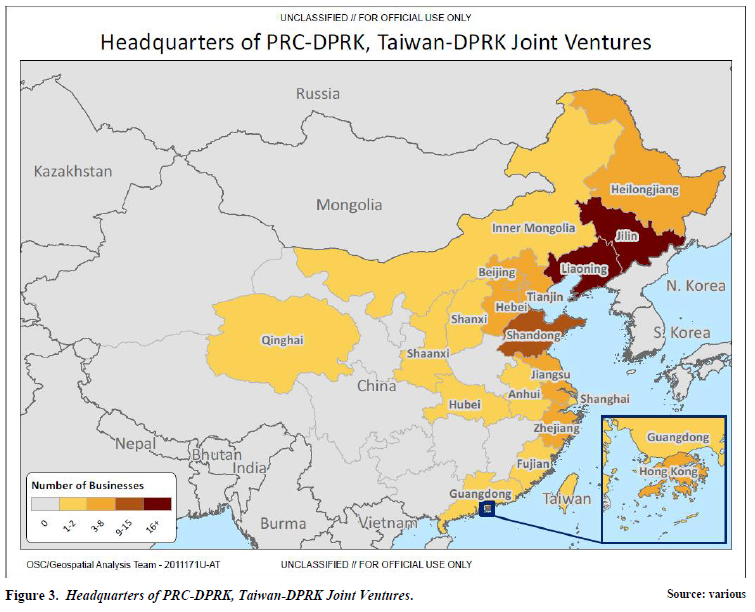
DOWNLOAD THE ORIGINAL FILE HERE
Lies and Whispers – Full Movie
MfS und sowjetischer KGB

Das Ministerium für Staatssicherheit (MfS) wurde unter strenger Anleitung sowjetischer Geheimdienste (NKWD, MGB bzw. KGB) aufgebaut und hat bis fast zum Ende eng mit ihnen zusammengearbeitet. Die Unterordnung unter sowjetische Dienste wurde seit 1957 gelockert, aber das KGB hatte gegenüber den DDR-Genossen grundsätzlich das erste und das letzte Wort. Mielke selbst bezeichnete (1981) das MfS als “Kampfabteilung der ruhmreichen sowjetischen Tscheka” (Sammelbegriff für die sowjetische Geheimpolizei).
Agierte das KGB ursprünglich als Teil der Besatzungsmacht, die sich keinen vertraglichen Bindungen durch ihren Kooperationspartner in der SBZ/DDR unterziehen musste, so wurde der völkerrechtliche Status der DDR ab Mitte der 50er Jahre aufgewertet. Auch die Beziehungen zwischen den Diensten wurden auf vertragliche Ebene gestellt. Zumindest die Form von Konsultationen und Vereinbarungen wurde nun beachtet. Auf dieser Website finden Sie Dokumente, in denen sich die Beziehung zwischen MfS und KGB entsprechend niedergeschlagen hat: Verträge über die Zusammenarbeit beider Geheimdienste wie jener vom 6. Dezember 1973, “Protokolle” über die Zusammenarbeit, die faktisch Arbeitsvereinbarungen waren, und Aufzeichnungen zu Treffen zwischen den Spitzen des MfS und des KGB.
Die Dokumentation ist entstanden im Zusammenhang mit einem Vorhaben mit dem History and Public Policy Project des Woodrow Wilson Center in Washington. Mit diesem Gemeinschaftsvorhaben verschiedener Archive in ehemaligen sowjetischen Satellitenstaaten wird versucht, die weitgehende Unzugänglichkeit der KGB-Akten in Russland (wenngleich etliche KGB-Dokumente an anderer Stelle zu finden sind) für westliche Forscher auszugleichen. Es wird den Spuren nachgegangen, die der KGB in den heute besser zugänglichen Archiven seiner “Bruderorgane” hinterlassen hat.
QUELLE: BStU
Hier ist das Original-Dokument zum Download:
Cryptome – GAO: State Dept Assess Counter-IED in Pakistan
DOWNLAOD THE ORIGINAL FILE HERE
Live to Tell Full Moon – Full Movie
TOP-SECRET – U.S. Marine Corps Intelligence Activity Afghanistan Culture Card


TOP-SECRET from the FBI – Chicago Man Sentenced to Over Seven Years in Prison for Attempting to Provide Funds to Support al Qaeda in Pakistan
CHICAGO—A Chicago man who personally provided hundreds of dollars to an alleged terrorist leader with whom he had met in his native Pakistan, was sentenced today to 7.5 years in federal prison for attempting to provide additional funds to the same individual after learning he was working with al Qaeda. The defendant, Raja Lahrasib Khan, a Chicago taxi driver and native of Pakistan who became a naturalized U.S. citizen in 1988, pleaded guilty in February to one count of attempting to provide material support to a foreign terrorist organization, following his arrest in March 2010.
Khan, 58, of the city’s north side, displayed “toxic altruism” U.S. District Judge James Zagel said in imposing the 90-month sentence, followed by lifetime supervised release, in Federal Court in Chicago. In addition, the judge said it was a “profoundly aggravating factor” that Khan’s crime occurred after he voluntarily chose to become a naturalized U.S. citizen.
Although Khan’s actual donations (approximately $500 to $550) and attempted donation ($1,000) were, relatively speaking, not incredibly substantial amounts, donations need not be large to be of assistance to terrorist organizations, the government argued, and the judge noted as well.
Khan’s plea agreement called for an agreed sentence of between five and eight years in prison, and it requires Khan to cooperate with the government in any matter in which he is called upon to assist through the termination of his sentence and any period of supervised release.
The sentence was announced by Patrick J. Fitzgerald, United States Attorney for the Northern District of Illinois, and Robert D. Grant, Special Agent in Charge of the Chicago Office of the Federal Bureau of Investigation.
Khan, who was born and resided in the Azad Kashmir region of Pakistan before immigrating to the United States in the late 1970s, admitted that he met with Ilyas Kashmiri, a leader of the Kashmir independence movement, in Pakistan in the early to mid-2000s and again in 2008. At the time of the second meeting, Khan knew or had reason to believe that Kashmiri was working with al Qaeda, in addition to leading attacks against the Indian government in the Kashmir region. During their 2008 meeting, Kashmiri told Khan that Osama bin Laden was alive, healthy, and giving orders, and Khan gave Kashmiri approximately 20,000 Pakistani rupees (approximately $200 to $250), which he intended Kashmiri to use to support attacks against India.
On November 23, 2009, Khan sent approximately 77,917 rupees (approximately $930) from Chicago to an individual in Pakistan, via Western Union, and then directed the individual by phone to give Kashmiri approximately 25,000 rupees (approximately $300). Although Khan intended the funds to be used by Kashmiri to support attacks against India, he was also aware that Kashmiri was working with al Qaeda.
In February and March 2010, Khan participated in several meetings with an undercover law enforcement agent who posed as someone interested in sending money to Kashmiri to purchase weapons and ammunition, but only if Kashmiri was working with al Qaeda, as well as sending individuals into Pakistan to receive military-style training so they could conduct attacks against U.S. forces and interests. On March 17, 2010, the undercover agent provided Khan with $1,000, which Khan agreed to provide to Kashmiri. Khan then gave the funds to his son, who was traveling from the United States to the United Kingdom, intending to later retrieve the money from his son in the U.K. and subsequently provide it to Kashmiri in Pakistan.
On March 23, 2010, Khan’s son arrived at an airport in the U.K. and a search by U.K. law enforcement officials yielded seven of the 10 $100 bills that the undercover agent had provided to Khan. After learning of his son’s detention, Khan attempted to end his involvement in the scheme to provide funds to Kashmiri by requesting an urgent meeting with another individual who was also present at Khan’s earlier meetings with the undercover agent. During their meeting, Khan demanded to return the undercover agent’s funds by providing $800 to this other individual.
The investigation was conducted by the Chicago FBI Joint Terrorism Task Force, with particular assistance from the Chicago Police Department, the Illinois State Police, and the Department of Homeland Security’s U.S. Customs and Border Protection and U.S. Immigration and Customs Enforcement.
The government is being represented by Assistant U.S. Attorneys Christopher Veatch and Heather McShain and DOJ trial attorney Joseph Kaster, of the Counterterrorism Section of the Justice Department’s National Security Division.
Live to Tell Hunting Humans – Full Movie
APPENDIX: STASI-NAMEN ALPHABETISCH BUCHSTABE EH-EI – STASI-NAMES IN ALPHABETICAL ORDER – EH-EI
Die Liste wurde bereits früher hier publiziert:
http://stasiopfer.de/component/option,com_simpleboard/Itemid,/func,view/id,993815828/catid,4/
Vom “Stasiopfer”-Angebot führt ein Link zu einer Website in den USA (www.jya.com), die sich auch mit den Praktiken von Geheimdiensten beschäftigt. Dort findet sich die “Fipro-Liste”, das detaillierte “Finanzprojekt” der Stasi, angefertigt in den letzten Tagen der DDR, um die Rentenansprüche der rund 100 000 hauptamtlichen Mitarbeiter des MfS auch nach dem Zusammenbruch des Systems belegen zu können. Die “Fipro-Liste” ist seit langem bekannt und diente Anfang der neunziger Jahre etwa zur Identifizierung der so genannten OibE – Offiziere im besonderen Einsatz. Diese Liste „Offiziere im besonderen Einsatz“im Jahre 1991 erschien in der “taz. Die Echtheit kann beim BStU überprüft werden.
Siehe u.a. http://www.spiegel.de/spiegel/print/d-22539439.html
Auf Druck ehemaliger STASI-Leute und Ihrer Genossen wurde die Liste aus dem Verkehr gezogen.
Hier ist sie wieder:
230950519015;94;30;00;;EHBRECHT, BAERBEL:;;;20640,00
250456402215;97;17;00;;EHBRECHT, HARALD:;;;21390,00
291049530085;98;83;00;;EHE, GABRIELE:;;;19465,80
040647420314;18;29;00;;EHE, GUENTER:;;;24187,50
070767412228;18;31;00;;EHEBRECHT, JOERG:;;;9825,00
090970429728;18;32;00;;EHLE, HENRIK:;;;2795,00
070658518525;09;00;40;;EHLE, ROSWITHA:;;;16155,08
080466500717;94;03;00;;EHLERS, CLAUDIA:;;;14782,87
210957402313;96;15;22;;EHLERS, HENDRICK:;;;25012,50
250563406828;94;03;00;;EHLERS, KERSTEN:;;;16720,00
240248411919;07;03;00;;EHLERS, KLAUS:;;;16272,50
050951404115;94;03;00;;EHLERS, MANFRED:;;;20160,00
110962400891;60;90;00;;EHLERS, NORBERT:;;;
110962400891;60;90;00;;EHLERS, NORBERT:;;;16210,00
200954515030;08;80;00;;EHLERT, ANNETTE:;;;18847,01
270459513218;02;31;00;;EHLERT, BIRGIT:;;;17741,93
100946416210;09;06;00;;EHLERT, DETLEF:;;;20640,00
031050415016;08;80;00;;EHLERT, EGON-MICHAEL:;;;20340,00
270469413018;08;00;56;;EHLERT, ENRICO:;;;13175,00
030667403416;03;69;00;;EHLERT, ENRICO:;;;9600,00
081251423915;96;15;25;;EHLERT, ERNST-GUENTER:;;;31740,00
070271402528;18;28;00;;EHLERT, GUIDO:;;;2720,00
160970413014;08;00;50;;EHLERT, GUIDO:;;;2700,00
150867430191;97;22;00;;EHLERT, KARSTEN:;;;8950,00
150661530146;30;84;00;;EHLERT, KATHRIN:;;;10667,55
240352403417;98;82;00;;EHLERT, KLAUS-DIETRICH:;;;26220,00
030264430081;15;65;00;;EHLERT, LUTZ:;;;17242,50
210946401526;97;06;00;;EHLERT, MANFRED:;;;24000,00
210670416726;18;33;00;;EHLERT, MARCO:;;;6958,87
240846411417;07;00;53;;EHLERT, MICHAEL:;;;25500,00
081056430167;15;03;00;;EHLERT, REINHARD:;;;20191,77
051157421537;10;77;00;;EHLICH, RONALD:;;;29565,16
220271407020;18;33;00;;EHLING, STEFAN:;;;2795,00
200571403015;99;43;00;;EHLKE, RICARDO:;;;2870,00
040151400715;01;55;00;;EHM, EBERHARD:;;;21097,50
181057400857;97;01;00;;EHM, MANFRED:;;;25530,00
020456400857;97;01;00;;EHM, THOMAS:;;;29517,50
031258419710;09;20;00;;EHMCKE, JOHANNES:;;;21344,00
060667409815;18;80;00;;EHME, SILVIO:;;;15636,00
010360404416;15;08;00;;EHMER, HARTMUT:;;;3105,00
090254417718;10;20;00;;EHMER, RALF:;;;33840,00
280942429728;94;03;00;;EHMIG, HARALD:;;;26250,00
060155404826;04;00;43;;EHMIG, VOLKER:;;;18975,00
220670426210;18;34;00;;EHMKE, ANDRE:;;;6705,00
160769426913;96;15;14;;EHMKE, ANDREAS:;;;8300,00
190451402724;02;80;00;;EHMKE, HELMUT:;;;19080,00
140431402721;02;80;00;;EHMKE, KURT:;;;19125,00
140656402749;02;51;00;;EHMKE, LOTHAR:;;;20125,00
030267402713;18;41;30;;EHMKE, MAIK:;;;13932,00
010365500626;01;19;69;;EHMKE, MARITA:;;;9574,43
040444401527;99;43;00;;EHMKE, WILFRIED:;;;24750,00
010369419614;18;33;00;;EHMUELLER, DIRK:;;;9675,00
130469424038;13;69;00;;EHNERT, CARSTEN:;;;9675,00
130469424011;13;69;00;;EHNERT, INGOLF:;;;9675,00
240870427339;18;32;00;;EHNERT, TINO:;;;2795,00
170142407216;90;65;40;4025/79,;EHRCKE, HANS-JU(E)RGEN;1090;WELSESTR.2;
170142407216;90;65;40;4025/79,;EHRCKE, HANS-JU(E)RGEN;1090;WELSESTR.2;
201166410048;07;07;00;;EHRECKE, HENRY:;;;9872,00
031245415323;07;00;48;;EHRECKE, JOACHIM:;;;25500,00
280453412212;07;18;00;;EHRECKE, NORBERT:;;;27360,00
150143421214;03;54;00;;EHREKE, LOUIS-FERDINAND:;;;26250,00
260869430109;99;53;00;;EHRENBERG, BERT:;;;8300,00
220662413444;08;80;00;;EHRENBERG, JO(E)RG:;;;15510,00
040962513916;08;80;00;;EHRENBERG, KARIN:;;;2498,84
050460413420;99;43;00;;EHRENBERG, LUTZ:;;;23402,50
040158512234;30;83;00;;EHRENBERG, NICOLE:;;;6938,38
261269413924;18;32;00;;EHRENBERG, NORBERT:;;;9510,00
261137429713;98;18;00;;EHRENBERG, RICHARD:;;;39750,00
250947409518;05;09;00;V/447/88, :;EHRENBERG, ROLLAND;1200;AURORAHU(E)GEL 10;
250947409518;05;09;00;V/447/88, :;EHRENBERG, ROLLAND;1200;AURORAHU(E)GEL 10;
220338407528;05;65;00;;EHRENBERG, SIEGFRIED:;;;22937,50
221259430206;15;09;00;;EHRENBERG, SIEGFRIED:;;;22080,00
020142419328;10;00;51;;EHRENBERG, VOLKER:;;;29250,00
091147402718;99;77;00;;EHRENBOTH, WOLFGANG:;;;20250,00
280568414314;18;71;20;;EHRENFORTH, UWE:;;;14250,00
200566403838;05;69;00;;EHRENREICH, FRANCO:;;;9675,00
220552529761;98;83;00;;EHRENSBERGER, CAROLA:;;;18480,00
091161430010;98;82;00;;EHRENSPERGER, CARSTEN:;;;16830,00
251030430029;95;45;00;;EHRENSPERGER, GUENTER:;;;25500,00
200366430217;17;00;00;;EHRENSPERGER, JENS:;;;15876,00
050855429742;94;03;00;;EHRENSPERGER, UWE:;;;19024,00
060368424628;18;80;00;;EHRENTRAUT, FRANK:;;;9600,00
050669426927;14;69;00;;EHRENTRAUT, GUENTER:;;;12085,00
300342406114;04;60;00;;EHRENTRAUT, KLAUS-DETLEF:;;;20160,00
040354429737;99;43;00;;EHRESMANN, RALF-DIETER:;;;25200,00
240434414718;13;69;00;;EHRET, GEORG:;;;30500,00
150745515381;08;53;00;;EHRET, MARLIT:;;;20570,00
210645415334;08;60;00;;EHRET, RONALD:;;;31875,00
251153414715;94;03;00;;EHRET, VOLKHARDT:;;;27720,00
231260430165;98;82;00;;EHRHARDT, ANDRE:;;;18554,66
080160530075;18;80;00;;EHRHARDT, ANGELIKA:;;;15620,00
010248419319;11;00;42;;EHRHARDT, ARND:;;;29520,00
070445430052;15;65;00;;EHRHARDT, BERND:;;;25625,00
040942406128;04;06;00;;EHRHARDT, DIETER:;;;23937,50
020142430092;98;54;00;;EHRHARDT, EHRENFRIED:;;;27600,00
280261417828;09;08;00;;EHRHARDT, FERNANDO:;;;19455,00
240848411816;17;00;00;;EHRHARDT, FRANK:;;;32250,00
220969418725;99;13;00;;EHRHARDT, FRANK:;;;8855,00
231053415317;08;00;40;;EHRHARDT, HANS-GUENTER:;;;23460,00
150455418524;10;51;00;;EHRHARDT, HARTMUT:;;;21027,50
270226430024;15;99;00;;EHRHARDT, HEINZ:;;;46500,00
010933418621;10;00;48;;EHRHARDT, HELMUT:;;;19875,00
290252418414;07;06;00;;EHRHARDT, HUBERT:;;;20340,00
080967426519;18;34;00;;EHRHARDT, JENS:;;;9825,00
020758415333;94;03;00;;EHRHARDT, JOERG:;;;22712,50
310138429713;98;83;00;;EHRHARDT, KLAUS:;;;27750,00
090246418710;10;00;49;;EHRHARDT, LOTHAR:;;;27000,00
271070404835;18;35;00;;EHRHARDT, MAIK:;;;2795,00
131246418639;10;06;00;;EHRHARDT, MANFRED:;;;23250,00
280948504813;18;80;00;;EHRHARDT, MARITA:;;;16905,00
090269419919;18;33;00;;EHRHARDT, MARKUS:;;;10289,52
070851417419;94;11;00;;EHRHARDT, MARTIN:;;;21097,50
191061409546;97;08;00;;EHRHARDT, MICHAEL:;;;16830,00
080770418427;07;06;00;;EHRHARDT, MIKE:;;;3557,10
181070409522;18;80;00;;EHRHARDT, MIKE:;;;2945,00
180668407121;18;35;00;;EHRHARDT, OLE:;;;9825,00
300744413229;08;55;00;;EHRHARDT, RALF:;;;21750,00
120955409512;97;08;00;;EHRHARDT, RALF:;;;22662,50
160658417117;99;43;00;;EHRHARDT, RALPH:;;;22597,50
190551519831;11;00;42;;EHRHARDT, REGINA:;;;19508,85
190948419927;99;12;00;;EHRHARDT, ROLF:;;;24000,00
040170420316;18;33;00;;EHRHARDT, SVEN:;;;9510,00
081056517764;17;00;00;;EHRHARDT, SYLVIA:;;;17657,06
050362406147;04;80;00;;EHRHARDT, THOMAS:;;;15840,00
230370420318;94;65;00;;EHRHARDT, THOMAS:;;;9670,00
030667419610;11;00;45;;EHRHARDT, TORSTEN:;;;11587,10
141068408911;18;77;00;;EHRHARDT, TORSTEN:;;;9782,50
220164420123;94;03;00;;EHRHARDT, UDO:;;;14850,00
250761407119;95;45;00;;EHRHARDT, ULRICH:;;;17985,00
100864430051;97;07;00;;EHRHARDT, UWE:;;;16830,00
011156415366;97;01;00;;EHRHARDT, UWE-ROLAND:;;;20125,00
190366414114;08;19;00;;EHRHARDT, VOLKER:;;;15268,00
230547404816;18;00;50;;EHRHARDT, WOLFGANG:;;;25500,00
300141429715;94;65;00;;EHRICH, EUGEN:;;;33000,00
251144429712;18;35;00;;EHRICH, HEINZ:;;;26250,00
060141416228;09;06;00;;EHRICH, HELMUT:;;;21250,00
090450415322;08;06;00;;EHRICH, JOACHIM:;;;25200,00
121249414116;12;06;00;;EHRICH, KARL:;;;21453,63
010756520325;99;53;00;;EHRICH, KERSTIN:;;;19299,97
240351414122;99;43;00;;EHRICH, KLAUS:;;;19736,25
260845415369;08;00;61;;EHRICH, KLAUS-ULRICH:;;;36000,00
230969405915;18;33;00;;EHRICH, MAIK:;;;6921,77
200668417317;98;83;00;;EHRICH, MARIO:;;;14382,00
120955415349;99;13;00;;EHRICH, STEFAN:;;;22520,00
211269415318;08;69;00;;EHRICH, SVEN:;;;11930,00
130444429713;15;00;45;;EHRICKE, JOACHIM:;;;27750,00
201059415345;30;80;00;;EHRIG, ANDREAS:;;;12200,00
290645528235;14;40;00;;EHRIG, BRIGITTE:;;;19560,00
200338428224;14;08;00;;EHRIG, DIETMAR:;;;36000,00
240329415313;05;02;00;;EHRIG, EBERHARD:;;;19018,75
010851415320;99;10;00;;EHRIG, JUERGEN:;;;26580,00
171069413971;98;83;00;;EHRIG, THOMAS:;;;10035,00
050354429226;14;00;56;;EHRIG, THOMAS:;;;27360,00
190444428213;14;00;40;;EHRIG, VOLKER:;;;40500,00
301029428223;30;34;00;;EHRIG, WOLFGANG:;;;24120,00
200370406922;99;43;00;;EHRING, FRANK:;;;6780,00
100850514537;99;77;00;;EHRING, HANNELORE:;;;22284,39
131239406939;99;43;00;;EHRING, HANS-JOACHIM:;;;24750,00
090743506922;99;43;00;;EHRING, HELGA:;;;20250,00
130951414524;99;77;00;;EHRING, MATTHIAS:;;;30960,00
050853415312;97;08;00;;EHRING, RAINER:;;;23040,00
151165403812;18;25;00;;EHRKE, JOERN:;;;17251,50
130756403416;99;13;00;;EHRKE, KLAUS-PETER:;;;20671,25
101055403015;99;43;00;;EHRKE, RUDOLF:;;;18112,50
061064408922;09;06;22;;EHRKE, SVEN:;;;16170,00
121151526224;10;00;51;;EHRLER, ELVI:;;;20160,00
091049409545;06;08;00;;EHRLER, ROLF:;;;24300,00
140351427320;10;00;43;;EHRLER, WOLFGANG:;;;28290,00
200231428224;14;08;00;;EHRLICH, ACHIM:;;;23250,00
191262422122;99;26;00;;EHRLICH, BERND:;;;16885,00
200946530126;98;82;00;;EHRLICH, BRIGITTE:;;;17280,00
030867411859;18;35;00;;EHRLICH, DIRK:;;;9675,00
191269428236;18;40;00;;EHRLICH, FRANK:;;;9555,00
021061417712;09;08;00;;EHRLICH, FRANK:;;;4860,00
010944429721;94;03;00;;EHRLICH, FRANK:;;;30287,50
020351425070;13;18;00;;EHRLICH, GERT:;;;27195,00
260861406921;97;06;00;;EHRLICH, GERT:;;;21006,00
171041429736;99;43;00;;EHRLICH, GUENTER:;;;33000,00
131043421715;12;00;51;;EHRLICH, HANSJOACHIM:;;;25687,50
200459413416;99;43;00;;EHRLICH, HELGE:;;;18891,93
081038421814;12;26;00;;EHRLICH, HORST:;;;23937,50
010256419714;11;20;00;;EHRLICH, JOACHIM:;;;23800,00
070569412251;18;35;00;;EHRLICH, JOERG:;;;9555,00
020248423819;97;01;00;;EHRLICH, KARL-HEINZ:;;;28500,00
140150422144;12;09;00;;EHRLICH, KNUT:;;;23040,00
010832418227;14;51;00;;EHRLICH, LOTHAR:;;;26250,00
060753522742;13;20;00;;EHRLICH, MARGITTA:;;;18967,93
280162420319;97;01;00;;EHRLICH, MATTHIAS:;;;21784,54
231060417724;18;35;00;;EHRLICH, MIKE:;;;19910,00
050442429736;15;03;00;;EHRLICH, PETER:;;;32437,50
020463413410;98;83;00;;EHRLICH, RALF:;;;18315,00
120265406920;94;03;00;;EHRLICH, RALF:;;;18782,50
241146405635;30;62;00;;EHRLICH, ROLF:;;;20160,00
240546411116;97;01;00;;EHRLICH, RUEDIGER:;;;13915,32
031268430024;18;32;00;;EHRLICH, STEFAN:;;;9389,52
080965427729;96;15;22;;EHRLICH, STEFFEN:;;;15604,50
210968424817;13;00;52;;EHRLICH, THOMAS:;;;8300,00
200368418414;18;31;00;;EHRLICH, THOMAS:;;;9775,00
111167417744;97;06;00;;EHRLICH, UWE:;;;14100,00
091059420211;10;06;00;;EHRLICH, UWE:;;;19320,00
271163426814;14;00;47;;EHRLICH, WILK:;;;14135,00
290842406122;04;51;00;;EHRLICH, WOLFGANG:;;;23250,00
280156519929;97;01;00;;EHRLICHER, DAGMAR:;;;17416,75
050370420029;18;34;00;;EHRSAM, ANDREAS:;;;6705,00
211046416719;97;08;00;;EHRSAM, PETER:;;;21960,00
021261416220;09;08;00;;EHRSAM, ROLAND:;;;19596,50
101146529713;98;82;00;;EHRT, ANGELA:;;;19760,09
180952513124;12;96;67;;EHRT, HELGA:;;;17922,83
310857424994;13;08;00;;EHRT, KARL-DIETRICH:;;;21332,50
241044430127;98;83;00;;EHRT, RAINER:;;;23250,00
111169421819;18;33;00;;EHRT, THOMAS:;;;9600,00
120752411428;04;06;00;;EHRT, UDO:;;;26640,00
270870424215;13;69;00;;EHSER, MATTHIAS:;;;6780,00
Live to Tell Kidnap on Highway – Full Movie
TOP-SECRET – State Dept Brett McGurk – WSJ Gina Chon Emails
|
Uncensored – FEMEN activists strip in protest against Euro 2012
SECRET – FBI-NGIC Gang Criminal Activity Expanding Into Juvenile Prostitution

DETAILS:
(U//FOUO) The National Gang Intelligence Center (NGIC) and the FBI’s Crimes Against Children Unit (CACU) assesses with medium confidence that gang activity is expanding towards juvenile prostitution primarily for its steady financial rewards and perceived low risk of law enforcement interaction. Historically, prison, street and outlaw motorcycle gangs profit from drug distribution and have recently become involved in non-traditional criminal activity such as mortgage fraud and identity theft. Some gangs appear to be diversifying their income by reducing or eliminating drug trafficking activities in favor of juvenile prostitution.
Key Findings:
• (U//FOUO) Juvenile prostitution is expanding as an additional source of income for many gangs, primarily for its high and steady financial rewards and perceived low risk of apprehension and punishment.
• (U//FOUO) Gang members and associates target young, vulnerable, and often runaway girls to recruit them into prostitution, while also sexually exploiting female gang member associates to capitalize on financial opportunities. Gang members and associates recruit and exploit juveniles at detention centers, public housing units, shopping malls, schools, flea markets, sporting events, and through telephone chat lines.
• (U) Gang control techniques include the use of violence, sexual assault, branding, and manipulation of victims in furtherance of their enterprise.
• (U//FOUO) Consistent with current trends in juvenile prostitution, gang members use the Internet to recruit, advertise and exploit victims of juvenile prostitution through modern technology due to the perceived anonymity of cyberspace.…
(U) As observed with traditional pimps, gang control techniques include the use of violence, sexual assault, branding, and manipulation of victims to commit other crimes in furtherance of the gang. Gang members provide security, transport the victims to the dates, and schedule appointments often exploiting the victims for free sex. As part of efforts by the pimp to remove himself from direct prostitution operations and shift culpability away from himself, juvenile victims – some of them female gang members and associates – may be forced to advertise for the business, solicit customers, schedule appointments, and collect money for the gang.
• (U) As of November 2011, MS-13 gang members would prostitute victims, whose ages ranged from 15 to 17, on numerous occasions while providing other gang members with free sexual encounters. The gang members also manipulated the victims into obtaining clients, scheduling prostitution appointments, transporting juvenile females to appointments, and collecting money.
• (U) In October 2011, an MS-13 member in Springfield, Virginia, was arrested for operating a prostitution ring involving juvenile runaway girls. The MS-13 member, who allegedly recruited customers and provided security for their appointments, is also accused of threatening the girls and physically assaulting them if they did not want to have sex with clients. He also carried a machete for security duties and had sex with the juvenile girls free of charge.
• (U//FOUO) According to June 2011 FBI reporting, MS-13 gang members in the Washington, DC metropolitan area brandedd their prostitutes’ bodies with “M” and “S” gang symbols using knives and razors to show ownership.
• (U//LES) In December 2010, a suspected Bloods gang member in Toledo, Ohio, allegedly prostituted a 14-year old juvenile female member of the Bloods gang, and girlfriend of the Bloods member. The Bloods member reportedly hosted parties at his home where he forced the victim to have sex with other partygoers, while assaulting the victim and preventing her from leaving.(U//FOUO) Consistent with current juvenile prostitution trends, gang members and pimps are using the Internet to recruit, advertise, and exploit their victims. Some authorities suggest that gangs are enticed into Internet prostitution by the potentially large profits derived from forcing their victims to prostitute themselves online, in addition to the convenience and anonymity of cyberspace, which often makes prostitution difficult for authorities to detect. The ease of Internet advertising and the use of smart phones have also afforded gangs a larger clientele and recruitment base.
• (U) In November 2011, two members of the Crips gang in Oceanside, California, were sentenced to 10 years in federal prison for the sex trafficking children – mostly runaways – and forcing them into prostitution. Senior members of the enterprise directed junior level members often times from a prison cell. The gang used Internet websites such as Facebook, Twitter, and Craigslist to advertise their victims and find customers.
• (U//FOUO) As of November 2011 an identified Gangster Disciples pimp, with a violent criminal history, recruited juvenile victims through facebook.com, and advertised them on backpage.com, a known escort website.
• (U//LES) February 2011 FBI reporting indicates that several pimps allegedly associated with the Bloods, are operating an underage sex trafficking and prostitution ring in New Orleans, Louisiana and Memphis, Tennessee. The pimps photographed female juvenile victims and posted their photos on Internet websites and message boards to attract customers. The websites included myredbook.com, backpage.com, poshlistings.com, myproviderguide.com, mypreviews.com, cheatingboards.com, and cityvibe.com.OUTLOOK:
(U//FOUO) The NGIC and CACU assesses with medium confidence that based on trends observed in the past several years, gangs will continue to expand their involvement in juvenile prostitution, while in some instances, minimizing their involvement in traditional drug distribution activities. The NGIC and CACU further assesses with medium confidence that rival gang members will likely cross jurisdictions and collaborate with each other when motivated by the financial gain incurred from juvenile prostitution activity. The exploitation of juvenile victims for prostitution will likely continue to be popular with gang members in as much as gang members are opportunistic criminals. However, proposed changes in legislation to increase the punishment from a misdemeanor to a felony for solicitation of a minor, as proposed in Virginia, may impact gang involvement in this type of criminal activity.
DOWNLOAD THE ORIGINAL DOCUMENT HERE
The Guessing Game – Full Movie
FBI – Three Attorneys and One Former Attorney Plead Guilty in Manhattan Federal Court for Participating in $66 Million Mortgage Fraud Scheme
Preet Bharara, the United States Attorney for the Southern District of New York, announced that attorneys Jacquelyn Torado, Neal Sultzer, and Kevin Hymes and former attorney Michael Schlussel pled guilty to conspiring to commit wire fraud and bank fraud in connection with a $66 million mortgage fraud scheme involving over 100 home mortgage loans for residential properties in the New York City area, Westchester County, Dutchess County, and Long Island. Sultzer, Schlussel, and Hymes pled guilty today, and Torado pled guilty yesterday before U.S. District Judge Robert P. Patterson.
Manhattan U.S. Attorney Preet Bharara said, “In helping to perpetrate this massive mortgage fraud scheme, these individuals exploited their trusted positions as attorneys. And Michael Schlussel went a step further, representing himself as an attorney in good standing, when, in fact, he was not. With their guilty pleas, they now stand convicted for the roles they played in undermining the integrity of the mortgage industry and the legal profession.”
According to the indictment previously filed in Manhattan federal court, as well as statements made in public proceedings:
First Class Equities (FCE), a/k/a Thunder Funding, a/k/a TAT Mutual Capital, was a mortgage brokerage firm with offices located in Oceanside and Old Westbury, New York. In August 2011, 14 individuals were charged in connection with their roles in a massive mortgage fraud scheme, including FCE’s owner and president, loan officers, attorneys, and one disbarred lawyer. As part of the scheme, FCE arranged home sales between “straw buyers”—people who posed as home buyers, but who had no intention of living in, or paying for, the mortgaged properties—and homeowners who were often people in financial distress and willing to sell their homes. Loan officers at FCE recruited straw buyers—many of whom were paid—and obtained mortgage loans on their behalf by submitting fraudulent applications to banks and lenders that made false representations about the straw buyers’ net worth, employment, income, and plans to live in the properties.
After approving the loans, the lenders sent the mortgage proceeds to attorneys who were involved in these transactions, including Torado, Sultzer, Hymes, and another attorney. Torado, Sultzer, Hymes, and Schlussel, acting on behalf of the fourth attorney involved in the scheme, would then appear at real estate closings and distribute the loan proceeds. Schlussel held himself out as an attorney, but in fact, he had previously been disbarred and was not licensed to practice law. He and the other attorneys submitted false statements to the lenders about how they were distributing the loan proceeds and made illicit payments, typically totalling tens of thousands of dollars or more per transaction, from the loan proceeds to themselves and to other members of the conspiracy.
In addition, Torado and Schlussel caused false documents to be provided to lenders in order to obtain home equity lines of credit, or second mortgages, on properties purchased through straw buyers the same day, the proceeds of which Torado distributed among certain members of the conspiracy.
***
Torado, 42, of Westbury, New York, pled guilty to one count of conspiracy to commit wire fraud and bank fraud and faces a maximum sentence of 30 years in prison. In connection with her plea, Torado agreed to forfeit $6,554,842. She will be sentenced by Judge Patterson on September 13, 2012 at 4:00 p.m.
Sultzer, 61, of Plainview, New York, pled guilty to one count of conspiracy to commit wire fraud and bank fraud and faces a maximum sentence of 30 years in prison. In connection with his plea, Sultzer agreed to forfeit $10,689,500. He will be sentenced by Judge Patterson on October 1, 2012 at 4:00 p.m.
Schlussel, 50, of Merrick, New York, pled guilty to one count of conspiracy to commit wire fraud and bank fraud, and faces a maximum sentence of 30 years in prison. In connection with his plea, Schlussel agreed to forfeit $5,878,442. He will be sentenced by Judge Patterson on September 24, 2012 at 4:00 p.m.
Hymes, 39, of Armonk, New York, pled guilty to one count of conspiracy to commit wire fraud and bank fraud and faces a maximum sentence of 30 years in prison. In connection with his plea, Hymes agreed to forfeit $7,606,500. He will be sentenced by Judge Patterson on September 27, 2012 at 4:00 p.m.
In addition to Torado, Sultzer, Schlussel, and Hymes, five other defendants charged in the scheme—Canino, Pandora Bacon, Michael Charles, James Vignola, and Henry Richards—have also pled guilty and are awaiting sentencing.
Charges are still pending against the remaining five defendants—Ian Katz, Omar Guzman, Robert Thornton, Michael Raphan, and Ralph Delgiorno—who are presumed innocent unless and until proven guilty. The trial for any remaining defendants is scheduled to begin on July 2, 2012.
Mr. Bharara praised the FBI for its outstanding work in the investigation.
This case was brought in coordination with President Barack Obama’s Financial Fraud Enforcement Task Force, on which Mr. Bharara serves as a co-chair of the Securities and Commodities Fraud Working Group. President Obama established the interagency Financial Fraud Enforcement Task Force to wage an aggressive, coordinated, and proactive effort to investigate and prosecute financial crimes. The task force includes representatives from a broad range of federal agencies, regulatory authorities, inspectors general, and state and local law enforcement who, working together, bring to bear a powerful array of criminal and civil enforcement resources. The task force is working to improve efforts across the federal executive branch and, with state and local partners, to investigate and prosecute significant financial crimes, ensure just and effective punishment for those who perpetrate financial crimes, combat discrimination in the lending and financial markets, and recover proceeds for victims of financial crimes.
This matter is being handled by the Office’s Complex Frauds Unit. Assistant U.S. Attorneys Nicole Friedlander, Andrew Goldstein, and Niketh Velamoor are in charge of the criminal case.
The Killing Fields – Full Movie
TOP-SECRET – CIA Prepares Iraq Pullback
CIA Prepares Iraq Pullback
U.S. Presence Has Grown Contentious; Backers Favor Focus on Terror Hot Spots
By SIOBHAN GORMAN And ADAM ENTOUS
The Central Intelligence Agency is preparing to cut its presence in Iraq to less than half of wartime levels, according to U.S. officials familiar with the planning, a move that is largely a result of challenges the CIA faces operating in a country that no longer welcomes a major U.S. presence.
Under the plans being considered, the CIA’s presence in Iraq would be reduced to 40% of wartime levels, when Baghdad was the largest CIA station in the world with more than 700 agency personnel, officials said.
The CIA had already begun to pull back in Iraq since the height of the war, officials said. But the drawdown, coming six months after the departure of American military forces, would be significant. The officials declined to provide exact numbers, give a breakdown of levels of analysts versus covert operators or say where agency workers would be redeployed, all of which are classified.
Proponents of the change say the CIA can make better use of its personnel in other areas. Those could include emerging terrorist hot spots such as Yemen, home to the al Qaeda affiliate the U.S. considers to pose the greatest threat to the homeland, and Mali, where an unstable government has fanned concerns.
The move comes amid worries over possible gaps in U.S. intelligence about the threat posed by al Qaeda in Iraq. Administration officials, diplomats and intelligence analysts have in recent weeks debated whether the militant organization is a growing threat after an internal government report pointed to a rise in the number of attacks this year, officials said.
The plan would also reduce the U.S. intelligence presence in the region as neighboring Syria appears to be verging on civil war. Al Qaeda in Iraq is also sending fighters to Syria to battle the Assad regime, Pentagon officials say.
The spy drawdown is part of a broader shift in U.S.-Iraq relations, with Washington moving to scale back diplomatic and training missions in the country. But it illustrates the limits of the Obama administration’s national-security strategy, as it steers away from ground wars and toward smaller operations that combine intelligence and special-operations capabilities.
Such a strategy relies heavily on cooperation from host governments, and as the CIA’s Iraq experience shows, cooperation can wane even where the U.S. has invested billions of dollars and lost thousands of lives.
The Iraqi government, including Iraq’s intelligence service, has scaled back its counterterrorism cooperation with the U.S. as it asserts its sovereignty, U.S. officials say.
“If you don’t have that cooperation, you are probably wasting the resources you are allocating there and not accomplishing much,” said Paul Pillar, a former top CIA Near East analyst.
Backers of the drawdown say al Qaeda in Iraq doesn’t pose a direct threat to the U.S. “This is what success is supposed to be like,” said a senior U.S. official who has worked closely with the Iraqis. “Of course we don’t want to have the same number of people after all U.S. troops go home that we had at the height of the war.”
A senior Obama administration official said the U.S. is in the process of “right-sizing” its presence in Iraq. Both President Barack Obama and Iraqi Prime Minister Nouri al-Maliki have “made very clear that we’re going to continue to have a close and strong security partnership,” this official said.
The planned reductions at the CIA represent a major shift from the approach under consideration just six months ago. Late last year, the CIA and Pentagon were considering several options for CIA and special-operations commandos to team up in Iraq, according to current and former officials. One option was to have special-operations forces operate under covert CIA authority, similar to the arrangement used in the raid that killed Osama bin Laden in Pakistan.
“There was a general consensus,” said a former intelligence official, “that there was a need for this in Iraq.”
But as it became clear that the U.S. would withdraw all troops and that the Iraqi government was less inclined to accept an expansive CIA-special operations role, those plans were tabled. “It’s not going to happen,” said a U.S. official.
Iraq requires CIA officers to make appointments to meet with officials who were previously easily accessible, one of several obstacles that add to a mood of growing distance between the sides. The result is a degraded U.S. awareness about the activities of al Qaeda in Iraq, particularly at a tactical level, officials said.
“Half of our situational awareness is gone,” said one U.S. official.
Iraqi officials said they continue to cooperate with the U.S. on counterterrorism. Hassan Kokaz, deputy head of the Iraqi Ministry of Interior’s intelligence service, said the U.S. may be adjusting to the new “state-to-state” relationship between the countries since the military withdrawal in December.
“We have asked them to wear civilian clothes and not military uniforms and to be searched when they visit Iraqi institutions,” he said. “Perhaps they are not used to this.”
In the northern oil city of Kirkuk, police are pursuing al Qaeda-linked militants without needing U.S. special-operations forces or the CIA, said Gen. Sarhad Qadir, a local police commander.
Another senior Iraqi security official, however, said Iraqis don’t have the necessary surveillance and other technical capabilities. Iraqi forces also are plagued by clashing sectarian and political loyalties, the official added. “We need the Americans because they were able to work with all the [Iraqi] forces without exception,” he said.
The CIA drawdown would recalibrate the agency’s responsibility in the country away from counterterrorism operations and back toward traditional intelligence collection, with a sharpened focus on neighboring Iran, officials say. Baghdad will remain one of the agency’s largest stations, they say; Kabul is currently the largest.
The plan comes with risks, however, because al Qaeda in Iraq still presents a threat to the region.
“A further diplomatic or intelligence drawdown in Iraq could jeopardize U.S. national security down the road if al Qaeda in Iraq is able to sustain—or increase—its activity,” said Seth Jones, a Rand Corp. counterterrorism specialist who has written extensively about al Qaeda. “The concern is that al Qaeda is able to use its Iraq branch to destabilize other countries in the region, and they are able to facilitate the movement of foreign fighters.”
Al Qaeda in Iraq’s activities against the regime of Syrian President Bashar al-Assad also complicates the U.S. government’s ability to support the opposition, Pentagon officials say.
A recent assessment by the National Counterterrorism Center, the U.S. intelligence community’s central clearinghouse for counterterrorism analysis, pointed to an uptick in attacks by al Qaeda’s Iraq affiliate since the U.S. troop withdrawal in December, according to officials briefed on the document’s contents.
During high-level Obama administration discussions last month, some senior counterterrorism officials seized on the NCTC assessment as evidence of a growing threat from al Qaeda in Iraq, touching off a debate about the dangers posed by the group, officials said. A spokesman refused to comment on questions about the report.
Recent U.S. intelligence reports show the number of attacks have risen this year to 25 per month, compared with an average of 19 for each month last year, according to a person familiar with them.
But officials disagree over the significance of this increase, and questioned the value of focusing on attacks in such a limited time frame.
James Jeffrey, who served as U.S. ambassador to Iraq until last week, said the figures being cited were misleading.
“Significant attacks are continuing to drop and, most importantly, casualties are way down,” Ambassador Jeffrey said in an interview before his Iraq rotation ended. “Everything I know points to an organization—al Qaeda in Iraq—under extraordinary stress.”
The Lost Children – Full Movie
TOP-SECRET – FEMEN Topless protest in Warsaw ahead of Euro 2012 kick off
SECRET – LulzSec Sneak Preview of Files to be Released
|
SECRET from the NSA – NSA: Defense Against Drive-By Downloads
DOWNLOAD THE ORIGINAL FILE HERE
Studie-Rechtsextremus in der Ära Honecker und Mielke – STASI
The Lost Night – Full Movie
TOP-SECRET from the FBI – Hells Angels Members and Associates Arrested on 91-Count Federal RICO Indictment
COLUMBIA, SC—United States Attorney Bill Nettles and Special Agent in Charge David A. Thomas of the Federal Bureau of Investigation stated that 19 individuals were arrested today after the return of a 91-count indictment charging members and associates of the Rock Hell City Nomad Chapter of the Hells Angels with racketeering and racketeering conspiracy (RICO-18 U.S.C. §1962), narcotics violations (21 U.S.C. §§ 841, 846), Hobbs Act robbery (18 U.S.C. §1951), money laundering (18 U.S.C. §1956), and firearm violations [18 U.S.C. §§ 922 and 924; 26 U.S.C. §§ 5861(d), 5845(a)(7), and 5871]. Those arrested were Daniel Eugene Bifield, a/k/a Diamond Dan (Leesville); Mark William Baker, a/k/a Lightning (Lancaster); David Channing Oiler, a/k/a Gravel Dave (Lancaster); Bruce James Long, a/k/a Bruce-Bruce (West Columbia); Richard Thrower, a/k/a Little Mark, Rat (Lancaster); David Pryor, a/k/a Yard Owl (York); James Frederick Keach, Jr., a/k/a Big Fred (Pelion); Frank Enriquez, Jr., a/k/a Big Frank (Rock Hill); Donald Boersma, a/k/a Brooklyn Donnie (Clover); Lisa Ellen Bifield, a/k/a Lisa Ellen Meyers, Lisa Ellen Stockton (Leesville); Johanna Looper, a/k/a JoJo (York); Kerry Chitwood (Gastonia, North Carolina); Carlos Hernandez (Charlotte, North Carolina); Ronald Dean Byrum, Jr., a/k/a Big Ron (Gastonia, North Carolina); Trent Allen Brown (West Columbia); Bruce Ranson Wilson, a/k/a Diesel (Swansea); Thomas McManus Plyler, a/k/a Uncle Tom (Rock Hill); Jamie Hobbs Long (Lancaster); and Somying Anderson, a/k/a Ying (West Columbia).
The arrest warrants were served along with the execution of 23 search warrants in North and South Carolina. During today’s operation, law enforcement seized methamphatamine, cocaine, marijuana, pills, and approximately 100 firearms, including two automatic machine guns. Special Agent in Charge David Thomas stated, “The significance of the extensive and long-term investigative efforts that resulted in the arrests today represent the FBI’s continuing commitment to the dismantling of organized criminal organizations. By working in a joint environment with federal, state, and local counterparts, we send a clear message that such pervasive criminal activities will not be tolerated.”
These arrests follow a two-year interagency investigation by the South Carolina Hells Angels Task Force (SCHATF). Assisting in the investigation and today’s operation were the Federal Bureau of Investigation-Columbia and Charlotte Field Divisions; Bureau of Alcohol, Tobacco, Firearms, and Explosives; Lexington County Sheriff’s Department; Lexington Police Department; Rock Hill Police Department; York County Sheriff’s Office; Lancaster County Sheriff’s Office; State Law Enforcement Division; Gastonia, Police Department; Charlotte-Mecklenburg Police Department; Gaston County Sheriff’s Office; and North Carolina State Bureau of Investigation.
United States Attorney Bill Nettles commended the inter-agency cooperation, saying, “Today’s arrests and seizures are an important step in our ongoing fight against criminal gangs operating in South Carolina. This investigation is also another example of what can be accomplished through a close partnership among local, state, and federal law enforcement agencies.” The case will be prosecuted by Assistant United States Attorney Jay N. Richardson.
The United States Attorney stated that all charges in this indictment are merely accusations and that all defendants are presumed innocent until and unless proven guilty.
The One Who Got Away – Full Movie
TOP-SECRET – How to Conduct Psychological Operations

Psychological operations (PSYOP) have long been used by militaries around the world to coerce populations into acting in a manner favorable to their mission objective. The product of these operations, which is commonly called propaganda when distributed by enemy forces, is a mixture of complex social research, art direction and psychological theory designed to manipulate its unsuspecting recipient into modifying their behavior in a way favorable to those conducting the PSYOP. The message conveyed through a PSYOP can often stray into deeply emotional and personal territory that is intended to trigger a profound psychological response. For example, U.S. and British troops fighting in Italy and France during World War II were subjected to a barrage of leaflets distributed by German forces describing the futility of their mission, encouraging them to take the “POW life insurance policy” and instructing them that their girlfriends back home were being taken advantage of by Jewish businessmen. The methodology behind these persuasive psychological tactics is described in detail in U.S. Army FM 3-05.301 Psychological Operations Process Tactics, Techniques, and Procedures, which provides fascinating insight into the methods used by PSYOP soldiers to modify the behavior of targeted populations.
FM 3-05.301 is described as the “principal reference for the PSYOP process” detailing “procedures and strategies derived from applied scientific and academic disciplines in an effort to improve the efficacy” of PSYOP. The manual includes everything from analyzing target audiences to tactical strategies for influencing populations. There are guides for production and dissemination of pamphlets, newspapers, magazines and video propaganda designed to influence target audiences and facilitate mission objectives. An appendix to the manual even includes complex instructions on the aerial dissemination of PSYOP leaflets, including tables for calculating the altitude and wind’s effect on the range of dispersal.
In order to influence populations more effectively, FM 3-05.301 provides PSYOP soldiers with helpful tips to produce effective and professional PSYOP packages. A section of the manual focuses entirely on aesthetic symmetry, formal balance and how to capitalize on sequential eye movements that “follow an established logical sequence of shapes, colors, and numbers or letters” in the layout of PSYOP publications. Detailed descriptions of the process for assessing target audiences (TA) and their susceptibility to specific arguments or sentiments are also included. A section titled “Psychographics” provides examples of psychological motivations to utilize in the production of PSYOP material:
- Fears: What does the TA fear?
- Hates: What does the TA hate?
- Anger: What angers the TA?
- Loves: What does the TA love?
- Shame or embarrassment: What does the TA consider shameful or embarrassing?
- What is the TA dissatisfied with? (What are its gripes?)
- What are the cultural norms? (How is the TA expected to act?)
- What does the TA value? (What is important to the TA?)
- What are the frustrations? (What does the TA want that it cannot get?)
An example of a PSYOP leaflet distributed in Iraq describing terrorists’ indiscriminate use of force, including against children.
Once the TA of a PSYOP is determined, the manual describes methods for properly appealing to the interests of the audience by utilizing legitimacy, tradition, reverence and other emotional responses to coerce audience members. Nostalgia can be used to “encourage or discourage a particular behavior” by referring to the “good old days” encouraging the TA to “behave in a manner that will return to those times.” Self-interest can also be used to “play directly to the wants and desires of the individuals that make up a TA.” Or, a PSYOP may appeal to “the TA’s need to belong or conform to group standards” through either companionship or conformity utilizing “peer pressure.”
To further the emotional appeals of the argument presented in a PSYOP product, FM 3-05.301 recommends utilizing a variety of rhetorical tools so that PSYOP soldiers can “become familiar with, and ultimately develop, tactical and technical proficiency in the use of persuasion techniques.” For example, the use of “glittering generalities” or “intense, emotionally appealing words so closely associated with highly valued concepts and beliefs that the appeals are convincing without being supported by fact or reason. The appeals are directed toward such emotions as love of country and home, and desire for peace, freedom, glory, and honor.” Name-calling “seeks to arouse prejudices in an audience by labeling the object of the propaganda as something the TA fears, loathes, or finds undesirable.” Transference “projects positive or negative qualities of a person, entity, object, or value to another.” FM 3-05.301 also includes a list of “primary influence tactics”:
- Rewards and punishments: “If you do X, you will get Y,” or “if you do not do X, Y will happen to you.” Example: “Surrender, and you will be treated well; continue to fight, and you will be killed.”
- Expertise: “Speaking as an authority on the subject, I can tell you that rewards/punishments will occur if you do or do not do X.” Example: “Oil Minister Gregor (key communicator/expert) states that if rebel groups continue to sabotage oil pipelines, the national economy will be seriously affected.”
- Gifts: Giving something as a gift before requesting compliance. The idea is that the target will feel the need to reciprocate later. Example: “This well and cistern are a gift to the people of Birmingville from the coalition forces…demonstration of our good will and hope for mutual cooperation in the future.”
- Debt: Calling in past favors. Example: “Coalition forces have done a lot for Birmingville, Elder Chang: the new school, the well in the center of town… these insurgents are endangering all we have worked for together. We need your help in stopping these groups by reporting any information you and your people may discover.”
- Aversive stimulation: Continuous punishment, and the cessation of punishment, is contingent on compliance. Example: “We will continue to bomb your position unless you surrender immediately.”
- Moral appeal: Entails finding moral common ground, and then using the moral commitments of a person to obtain compliance. Example: “The killing of innocent civilians is wrong; please help the security forces stop this tragic loss of innocent life by reporting any information on terrorist activities.”
- Positive and negative self-feeling: “You will feel better/bad if you do X.” Example: “Become part of something bigger than yourself, know honor and take pride in your work…join the national security forces!”
- Positive and negative altercasting: “Good people do X / Bad people do Y.” Example: “Red Tribe members are brave and honorable people who care about the future of their country and are not intimidated by rebel groups. Call and report insurgent activity now on the coalition hotline.”
- Positive and negative esteem of others: “Other people will think highly/less of you if you do X.” Example: “Earn the respect of your friends and the pride of your family…join the Patriotsville National Guard now!”
- Fear: “Bad things will happen to you if you do X.” Example: “Only death and fire await those who continue to fight…surrender now.”
Each of these tactics is designed to further the intensity of the PSYOP argument and, thus, increase its chance of influencing its TA. Behavioral change in the TA is the ultimate goal off these activities, “challenging or emphasizing beliefs” and manipulating “existing consequences or introducing new ones” to affect the target and exploit vulnerabilities in their psychological makeup.
see
The Preachers Wife – Full Movie
FEMEN Set To Disrupt 2012 Euro Cup
TOP-SECRET – Former Jersey City Construction Project Superintendent Sentenced to Prison for Social Security Disability Scam
NEWARK—The former project superintendent on a Jersey City, New Jersey high-rise construction project was sentenced today to six months in prison and six months of home confinement for a scheme in which he hid his employment so he could continue to receive Social Security disability payments, U.S. Attorney Paul J. Fishman announced.
Pasquale Zinna, 44, of Hackettstown, New Jersey, previously pleaded guilty to two counts of the indictment against him: Social Security disability fraud and structuring financial transactions. His wife, Janeen Zinna, 43, was also sentenced today—to two years’ probation with the special condition of 100 hours of community service. She previously pleaded guilty to a superseding information charging her with misprision of her husband’s Social Security fraud. U.S. District Court Judge Katharine S. Hayden imposed the sentences today in Newark federal court.
According to documents filed in this case and statements made in court:
In 1999, Pasquale Zinna filed an application for disability insurance benefits with the Social Security Administration (SSA), claiming that, as of March 15, 1996, he was disabled and unable to work due to a back injury. By filing the application, Pasquale Zinna agreed to notify the SSA if there was any improvement in his medical condition or if he regained the ability to work.
Beginning in September 2005, Pasquale Zinna was the project superintendent for 160 Broadway Concrete, a sub-contractor at the high-rise construction project at 77 Hudson Street in Jersey City. He failed to report his return to work to Social Security and concealed his employment at Broadway Concrete by having his paychecks issued to him in the names of other individuals, including his wife. Janeen Zinna admitted during her guilty plea that she filed a joint federal income tax return with her husband for 2007 which claimed income received from Broadway Concrete was for work she performed.
Pasquale Zinna also admitted to making a series of cash withdrawals from his joint checking account with his wife at Commerce Bank, now TD Bank, in order to avoid the bank’s reporting requirement for financial transactions in excess of $10,000.
In addition to the prison term, Judge Hayden sentenced Pasquale Zinna to three years of supervised release. He was also ordered to pay $101,753 in restitution to the Social Security Administration and to forfeit $98,000 involved in the illegal financial transactions. Janeen Zinna was also held responsible for the restitution. The defendants paid these obligations in full at today’s proceeding.
Four New York men have also pleaded guilty to a wide range of fraud and other offenses stemming from their involvement in the Jersey City construction project between 2007 and 2008.
Rocco Mazzaferro, 64, of Brooklyn, New York, and Vincenzo Genovese, 75, of Staten Island, New York, pleaded guilty November 22, 2011 to conspiracy to commit wire fraud. Vincenzo Genovese also pleaded guilty to one count of conspiracy to embezzle pension benefits.
Anselmo Genovese, 44, of Staten Island, New York, pleaded guilty December 16, 2011 to two counts of making unlawful labor payments.
Eric Haynberg, 46, of New York, pleaded guilty December 16, 2011, to a superseding information charging him with misprision of the wire fraud committed by Mazzaferro and Vincenzo Genovese.
The sentencings of Mazzaferro and Vincenzo Genovese are currently scheduled for July 10, and July 12, 2012, respectively. Sentencing for Eric Haynberg is currently scheduled for June 7, 2012, and for Anselmo Genovese on July 11, 2012.
U.S. Attorney Fishman credited special agents of the FBI, under the direction of Special Agent in Charge Michael B. Ward in Newark; and Department of Labor’s Office of Inspector General, Office of Labor Racketeering and Fraud Investigations, under the direction of Special Agent in Charge Robert L. Panella for the New York Region, for the investigation leading to the arrests and charges. He also thanked the IRS, under the direction of Acting Special Agent in Charge JoAnn S. Zuniga; and the SSA Office of the Inspector General, under the direction of Edward J. Ryan, New York Field Division, for their work on this case, and the U.S. Department of Labor, Employee Benefits Security Administration, for its assistance.
The government is represented by Assistant U.S. Attorney Leslie F. Schwartz of the U.S. Attorney’s Office Economic Crimes Unit in Newark.
The Producers Story – Full Movie
TOP-SECRET – NSA: PDF Redaction with Adobe Acrobat Pro X
The Untold Story of Caylee Anthony – Full Movie
TOP-SECRET – Open Source Center North Korea Unusual Threats Signal Possible Action Against South Korea

North Korea’s recent threat to carry out “special actions” against the South is rare and seems intended to signal the regime’s resolve to move forward with some form of provocation. The threat, however, is unlike past warnings the regime has typically issued prior to military provocations, suggesting that the North might follow through with a move other than a conventional military attack. Significantly, some aspects of the warning appear to signal Pyongyang’s commitment to follow up on the “actions” in the near future.
North Korea on 23 April issued an unprecedented “notice” in the name of the Korean People’s Army (KPA) Supreme Command Special Operations Action Team. The toughly worded message — a response to what Pyongyang apparently viewed as provocative remarks recently made by ROK President Lee Myung-bak — contained an unusually vague warning against Seoul.
- The “notice” particularly took issue with President Lee’s recent comments on “strengthening” South Korea’s national “self-defense capabilities” (Yonhap, 19 April), which it characterized as an “extremely grave frenzy of provocation” and a “theory of striking” the North’s “supreme headquarters” (Pyongyang radio, 23 April). The message stated that the North’s “revolutionary armed forces” will take “special actions” against the “gang of traitors’ reckless” move, and emphasized that the “actions…will start soon” (Pyongyang radio, 23 April).
- This is only the second time the North has used the “special actions” formulation to threaten President Lee in an authoritative military pronouncement. Pyongyang just five days earlier used the same threat — albeit in a passive voice — in an authoritative KPA Supreme Command spokesman’s “statement,” which said that “special action measures will be taken” (Pyongyang radio, 18 April).
- The “notice” also contained a figurative reference to turning the “group of rats” — referring to the ROK leadership — into “ashes” within “three to four minutes” (Pyongyang radio, 23 April). The “ashes” formulation is on the low end of the rhetorical threat spectrum. Pyongyang in recent years has issued more direct and literal formulations to threaten Seoul, particiuarly following the Ch’o’nan sinking.
The threat to carry out “special actions” is ambiguous and not as definitive as warnings Pyongyang has issued in the lead-up to past military provocations, suggesting that the regime might be contemplating some form of action other than an actual military attack. The North’s typical rhetorical pattern prior to provocations is to signal in authoritative media that it has decided to act without divulging how, when, or where it will move.
- Prior to the sinking of Ch’o’nan, Pyongyang issued a more direct threat in the name of an authoritative KPA General Staff spokesman stating that it “will” respond to US ROK military drills with a “powerful military counteraction” (Pyongyang radio, 25 February 2010). Similarly, leading up to the Yo’np’yo’ng Island shelling, a statement by the spokesman for the North side’s delegation to North-South military talks warned that its Army “will counter” the South’s provocations with a “merciless physical retaliation” (KCNA, 29 October 2010).
Committing to Prompt Action
Although the recent threat was not as definitive as warnings the North issued in advance of past military provocations, the unusual use of the phrase “will start soon” in combination with the unique “special actions” formulation appears designed to signal that the regime is committed to following through with its warning.
- Pyongyang’s use of the term “soon” is unusually specific and categorical. The last time the North modified its threat with this term was in a less authoritative North-South Military Talks General-Level Representative “notice,” which warned that its “army will soon” take “corresponding decisive measures” in response to South Korea distributing leaflets to the North (Pyongyang radio, 10 April 2010). Unlike the most recent threat, however, this warning was preceded by a conditional phrase, which afforded the regime the flexibility to refrain from taking immediate action.
- Further underscoring its commitment to carry out its threat, the North broadcast the KPA “notice” to both domestic and external audiences. In addition, the North Korean radio and television carried the message at least two times a day for three days following the initial announcement.
DOWNOAD THE ORIGINAL FILE HERE
Mighty Derringer – TOP SECRET – U.S. Nuclear Terrorism Exercise Leaves Indianapolis in “Ruins”

Washington, D.C., May 29, 2012 – A secret exercise in 1986 by a U.S. government counter-terrorist unit uncovered a host of potential problems associated with disrupting a nuclear terrorist plot in the United States. Declassified documents released under the Freedom of Information Act (FOIA) and posted today by the National Security Archive offer the first detailed public look at the inner workings of the agencies, military units and other U.S. entities responsible for protecting the country from a terrorist nuclear attack.
Today’s posting consists of over 60 documents related to MIGHTY DERRINGER, an exercise that focused on Indianapolis in December 1986. The materials provide background on the creation, in 1974-1975, of the Nuclear Emergency Search Team (NEST), a group assigned to respond to plausible threats of nuclear terrorism or extortion. Today, NEST (now the Nuclear Emergency Support Team) conducts exercises to assess its capability to respond to the possible presence of a terrorist device and test the ability of NEST and critical cooperating organizations (including military units)to work together.
While the MIGHTY DERRINGER exercise and resulting documents are over two decades old, the institutions participating in the exercise retain their roles today, and the issues confronting them in 1986 are similar to the ones that they would face in responding to a nuclear threat in 2012 (and beyond).
This posting is notable for being the first publication of documents that provide in-depth exposure into all aspects of such an exercise – including the state-of-play at key points and the array of issues involved in disabling terrorist devices. Of particular interest are references to the participation of the Joint Special Operations Command and Delta Force – mirroring the role they would have in a real-world incident. In addition, after-action reports reveal the assorted problems that can arise in coordinating the response to a nuclear terrorist threat among a large number of organizations.
* * * *
THE MIGHTY DERRINGER EXERCISE
In late January and early February 2012, members of the Department of Energy’s Nuclear Emergency Support Team (NEST) patrolled Lucas Oil Stadium as well as surrounding areas of Indianapolis as a precautionary measure in advance of Super Bowl XLVI. An initial survey to gather information on background levels of radiation was followed by an actual search for signatures associated with either a nuclear explosive device or a radiation dispersal device (a ‘dirty bomb’).1 Fortunately, none was found.
Over twenty-five years earlier, for a few days in early December 1986, NEST personnel also patrolled Indianapolis, also in search of a nuclear device. That search was triggered by an intelligence report that suggested that an Improvised Nuclear Device (IND) might have been smuggled into the city by terrorists. With the assistance of the Delta Force, U.S. personnel were able to recover and disable the device in a fictitious neighboring country; unfortunately the Indianapolis device exploded and 20 square blocks in downtown Indianapolis were completely destroyed.
As it happens, the terrorist group, the intelligence report, and the detonation were fictional – elements of a NEST exercise designated MIGHTY DERRINGER, one of a number of tests designed to anticipate and prevent the potential real-world catastrophe of a terrorist nuclear strike in a major American city. Documents published today by the National Security Archive provide newly declassified details on how the MIGHTY DERRINGER exercise unfolded and how the participants later evaluated it.
This is the most extensive set of declassified documents on any nuclear counterterrorism exercise, covering every phase of the response, from concept to critiques, and it offers valuable insights into a world that is usually hidden from public scrutiny. Among the disclosures:
§ The role of the top secret Joint Special Operations Command’s Delta Force in carrying out the assault on the terrorist cell in the fictional country of Montrev.
§ Descriptions of the different types of disablement techniques U.S. forces utilize – emergency destruct, standard destruction, and hard entry.
§ Assessments of the coordination problems and different perspectives of agencies that would be involved in a real-world response.
The instruction to establish NEST, known until 2002 as the Nuclear Emergency Search Team, took the form of a November 18, 1974 memo from Maj. Gen. Ernest Graves, the Atomic Energy Commission’s assistant general manager for military application, to Mahlon Gates, the manager of the commission’s Nevada Operations Office. (Document 1). Gates was “directed and authorized” to assume responsibility for the planning and execution of field operations employing AEC radiation detection systems for the “search and identification of lost or stolen nuclear weapons and special nuclear materials, bomb threats, and radiation dispersal threats.”
Personnel for NEST would come from AEC’s nuclear weapons laboratories – Lawrence Livermore, Sandia, and Los Alamos – as well as key AEC contractors. Almost all those individuals would continue in their regular positions full-time and become part of a NEST effort when required.
What inspired Graves’ memo was an incident that had taken place in May of that year. The Federal Bureau of Investigation received a letter demanding $200,000. Failure to comply would result in the detonation of a nuclear bomb somewhere in Boston. Personnel and equipment were quickly assembled and transported to Griffiss Air Force Base in Rome, New York. But before the team could make it to the threatened city, the crisis receded when no-one came to pick up the $200,000 in phony bills left at the designated site. 2
But the incident and the difficulties involved in responding to the threat convinced senior leaders that there was a need for a dedicated capability to deal with any attempt at nuclear extortion or nuclear terrorism. From its inception, NEST devoted considerable time and effort to conducting exercises designed to allow the team to test its readiness, procedures, and equipment in a variety of scenarios. In addition, since confronting a nuclear threat would involve not only NEST but a multitude of organizations, exercises provided an opportunity to identify potential problems in interagency cooperation.
MIGHTY DERRINGER was a particularly notable exercise in exploring the organizational, governmental, and technical problems that might arise in responding to a nuclear terrorist threat. While the existence of MIGHTY DERRINGER has been reported previously, the documents obtained by the National Security Archive and posted in this briefing book provide far more detail than previously available on the scenario, results, and after-action assessments of the assorted organizations involved. Since NEST and these other government entities are still critical components of America’s counter-terrorist capability, these records are valuable for the insight they offer into how a current-day nuclear detection operation would unfold and particularly what kinds of problems might be encountered.3
The exercise took place in two locations – Camp Atterbury, Indiana, near Indianapolis, and Area A-25 of the Energy Department’s Nevada Test Site – which corresponded to the two locations involved in the exercise scenario. One of the those locations was Indianapolis while the other was the country of ‘Montrev’ – a rather transparent fictional version of Mexico (since Montrev shared a border with the United States, its capital city was ‘Montrev City’, and its primary security agency was the Directorate for Federal Security – the same as Mexico’s).
Montrev was the initial focus of the exercise, with a terrorist group commanded by “Gooch” threatening to detonate an improvised nuclear device (IND) near the country’s Bullatcha oil field. According to the scenario, terrorists had stolen the devices from a new nuclear weapons state. Eventually, the participants discovered that that there was a second nuclear device and it appeared that it was being infiltrated into the United States, possibly with Pittsburgh as a target – although it was subsequently determined that the target was Indianapolis. While U.S. forces (with Delta Force assistance) were able to recover and disable the device in Montrev, Indianapolis experienced a 1 kiloton nuclear detonation that resulted in “total devastation over a 20 square block area.” (Document 38) The scenario had originally posited a successful disarming, but the exercise controllers decided to introduce a new element.
The scenario allowed for all aspects of a possible response to a nuclear terrorist/extortionist threat to be practiced – from initial assessment of the threat to the management of the “consequences” of a detonation. The documents posted cover, with varying detail, the core aspects of a response – intelligence collection, technical and behavioral assessments, search, access/defeat of terrorist forces, recovery of a device, diagnostics, hazards and effects estimation, disablement and damage limitation, safe transportation of the device, and consequence management of a detonation. In addition, they also concern a variety of important aspects of a response – including security, command and control, communications, logistics, radiological measurement and containment, weather forecasting, public information, and interaction with local officials.
The documents also identify the large number of organizations involved in the exercise. There is NEST and the organizations that contributed members or capabilities – including Lawrence Livermore National Laboratory, Los Alamos National Laboratory, and contractor EG&G. Additional organizations whose participation is evident include the State Department, Central Intelligence Agency, Federal Bureau of Investigation, Joint Special Operations Command, Special Forces Operation Detachment – Delta (Delta Force), several military explosive ordnance disposal units (from the Army and Navy), the Federal Radiological Monitoring and Assessment Center, the Environmental Protection Agency, and the Federal Emergency Management Agency.
Beyond detailing participants and describing different aspects of the exercise and static plans, some of the documents (the ‘Sitreps’- Document 19, Document 23, Document 32) provide a more dynamic view of the state of play at various points in the exercise. In addition, the post-exercise critiques provide different individual and institutional perspectives as to either the realism of the exercise or what the exercise revealed about strengths and weaknesses of the then current U.S. ability to respond to a nuclear terrorist threat.
Thus, Vic Berkinklau, an engineer with the Atomic Energy Commission, in addition to describing MIGHTY DERRINGER as an “Excellent, well managed exercise,” had an additional eight observations which concerned subjects such as uncertainty as to the number of NEST personnel needed in Montrev, the relationship between NEST and the Explosive Ordinance Disposal (EOD) team, and the need for more detailed analysis of the consequences of a nuclear detonation in a populated area (Document 43). L.J. Wolfson of the Navy Explosive Ordnance Disposal Technical Center contributed an eight-page single-spaced analysis concerning a variety of topics, including the nuclear device, assessment and intelligence, command and control and disablement. He observed (Document 47) that “there is too great a prevalence to believe what might, and probably is, very inconclusive intelligence information” and that “the entire operation was slowed and overburdened by the number of personnel involved.”
Commenting on the terrorism phase of the exercise (Document 50), William Chambers, NEST member and site controller for the Indianapolis component of the exercise, wrote that liaison between the FBI’s Hostage Rescue Team, NEST, and EOD personnel was “excellent” but that “the joint procedures for withdrawing the HRT and survivors, securing the perimeter, and clearing access to the device need clarification.” An unattributed comment (Document 66) suggested that the Delta Force players did not appreciate the “gravity of dealing with a nuclear device.”
In the subsequent twenty-five years, NEST and other organizations concerned with nuclear terrorism have conducted a significant number of exercises – particularly following the attacks of September 11, 2001.4 However, because of its scale and scope MIGHTY DERRINGER remains one of the more notable nuclear counterterrorism exercises.
The Energy Department is keeping secret significant aspects of MIGHTY DERRINGER, but more may be learned about the exercise and the State Department’s role in it from the response to a pending request. Moreover, files on MIGHTY DERRINGER at the Ronald Reagan Presidential Library will eventually be declassified and shed light on the National Security Council’s role.
(Note: A list of abbreviations used in the documents appears below.)
READ THE DOCUMENTS
Background
Document 1: Ernest Graves, Assistant General Manager for Military Application, Atomic Energy Commission, to M.E. Gates, Nevada Operations, “Responsibility for Search and Detection Operations,” November 18, 1974. Secret.
Source: Department of Energy FOIA Release
With this memo General Graves assigned Gates and the AEC’s Nevada Operations Office responsibility for search and detection operations with respect to lost and stolen nuclear weapons and special nuclear material as well as responding to nuclear bomb and radiation dispersal threats. The memo became the basis for the creation of the Nuclear Emergency Search Team (NEST).
Document 2: Director of Central Intelligence, IIM 76-002, The Likelihood of the Acquisition of Nuclear Weapons by Terrorist Groups for Use Against the United States, January 8, 1976. Secret.
Source: CIA FOIA Release.
An interagency group of intelligence analysts explored the constraints on the exploitation of nuclear explosives, attitudes and behavior toward the United States, means of acquiring nuclear explosives, the ways in which nuclear devices might be used against the United States, and the capabilities of existing terrorist groups. While the authors considered it unlikely that the U.S. would be the target of a nuclear terrorist attack “in the next year or two,” they also noted that, in the longer term, “we would expect a corresponding erosion of the constraints against terrorist use of nuclear explosives.”
Document 3: Energy Research and Development Administration, “Nuclear Emergency Search Team (NEST),” n.d. (but 1977). Unclassified.
Source: Energy Research and Development Administration
NEST began its existence as an unacknowledged government organization, but in 1977 it was concluded that NEST would have to interact with local law enforcement and political authorities in dealing with nuclear threats, and thus its existence would need to be acknowledged. This fact sheet, distributed to the press by ERDA, was the means by which NEST’s existence was quietly announced.
Document 4: E.J. Dowdy, C.N. Henry, R.D. Hastings, S.W. France, LA-7108, Nuclear Detector Suitcase for the Nuclear Emergency Search Team, February 1978. Unclassified.
Source: Los Alamos National Laboratory
This technical paper describes one piece of equipment designed specifically for NEST personnel – a portable Neutron Detection system that could be carried in any vehicle. The paper describes the detectors, the electronics, and the operations.
Document 5: Director of Central Intelligence, NIE 6-86, The Likelihood of Nuclear Acts by Terrorist Groups, April 1986, Secret, excised copy
Source: Mandatory Review Request; release by Interagency Security Classification Appeals Panel.
This estimate examined several incentives and constraints with regard to nuclear terrorism – including the availability of nuclear information, material, and trained personnel; changing levels of protection for nuclear weapons and other sources of nuclear/radioactive material; and terrorist capabilities and motivations (including possible state support to nuclear terrorism). The authors concluded that there was only a “low to very low” probability of nuclear terrorism that involved detonation of an improvised nuclear device or nuclear weapon – or the dispersal of radioactive material in a way that would threaten mass casualties or produce widespread contamination.
Preparations
Document 6: William Hoover, Deputy Assistant Secretary of Energy for Defense Programs, to DCI William Casey, 23 September 1985, with CIA routing memos, Confidential
Source: CREST, National Archives II
A senior Energy Department official informed Director of Central Intelligence William J. Casey of the Department’s conclusion on the need for a large-scale nuclear exercise in the early 1987 fiscal year and requested the CIA’s participation.
Document 7: Robert B. Oakley, State Department Counter-Terrrorism Center, to Executive Secretary Nicholas Platt, MIGHTY DERRINGER Exercise Planning,” 4 April 1986, with memorandum to Vice Admiral John Poindexter attached, Confidential
Source: State Department FOIA release
This memorandum, from the head of the State Department’s Counter-Terrorism Center, along with that attached memo to the president’s national security adviser, described the level of State Department participation in MIGHTY DERRINGER.
Document 8: Peter Borg, State Department Counter-Terrorism Center, to Richard Kennedy et al., “Exercise MIGHTY DERRINGER,” 6 October 1986, Secret
Source: State Department FOIA release
A number of State Department officials were recipients of this secret memo, which informed them of the nature of MIGHTY DERRINGER, when it would take place, some requirements for the exercise to be realistic, and the State Department’s participation.
The Exercise
Document 9: Don McMaster, Behavioral Assessment Report/PLC, n.d. [circa 2 December 1986], Incomplete copy, Secret
Source: Energy Department FOIA release
This behavioral assessment mirrors the earliest phases of responding to an actual threat, especially trying to assess its credibility. It discusses the reliability of a source, motivations of other key figures in the terrorist group, and concludes that a credible threat exists to both the United States and ‘Montrev.’
Document 10: F.W. Jessen, Lawrence Livermore National Laboratory, “Summary Assessment,” 2 December 1986, Secret, Incomplete copy
Source: Energy Department FOIA release
This assessment, conducted at Lawrence Livermore, where much of the credibility assessment effort has been located, reports that the available information suggests that the terrorist group possesses two improvised nuclear devices but that LLNL and Los Alamos National Laboratory disagree over the technical credibility of the threat.
Document 11: “Aggregate Assessment – – One Hour – – Of Threat Message and Sketch,”
n.d., Secret, Page 1 only
Source: Energy Department FOIA release
The title of this memo indicates that a sketch of a device was included with the threat message. Technical experts had already begun to draw conclusions about the device in Montrev as well as the implications for finding a second device in the United States.
Document 12: Thomas R. Clark, Manager, Nevada Operations Office, Department of Energy, “NEST Alert Status,” 3 December 1986, Confidential, excised copy
Source: Energy Department FOIA release
This message, from a Department of Energy manager, informs NEST participants at key laboratories and contractors that NEST is on “alert.” The Department of State has received a threat and the Department of Energy has been asked to evaluate it. Other actions have been taken.
Document 13: “Security Plan for NEST Retrograde Operation, December 1986,” n.d., Secret
Source: Energy Department FOIA release
The plan described in this document notes the classification levels and types of information involved in the exercise as well as measures for the protection of cryptological matter and classified documents.
Document 14: Peter Mygatt, Exercise Mighty Derringer, “Chronological Media Play, ‘Site City,’ Beginning 12/7/86,” n.d., Secret
Source: Energy Department FOIA release
The MIGHTY DERRINGER scenario writers assumed that if it was a real-world event, part of it would be visible and covered extensively by the media. This document summarizes reports of fictional news services and television stations as well as interaction between the media and FBI and Department of Energy.
Document 15: NEST On-Scene Commander, Subject: Event Mighty Derringer Sitrep No. 1 OCONUS, Prepared at 00:15 PST on 12/06/86, Secret
Source: Energy Department FOIA release
The first Situation Report (Sitrep) of the part of the exercise that takes place in Montrev summarizes the current situation (including the number of personnel in country) as well as
the status of a variety of subjects – including command and control, intelligence, disablement, and weather.
Document 16: W. Rogers, NEST Paramedic Coordinator, to V. Withirill, N.T.S.O, “MIGHTY DERRINGER, MEDICAL EMERGECY RESPONSE,” 6 December 1986, Secret
Source: Energy Department FOIA release
This memo reports that MIGHTY DERRINGER was being conducted in area A-25 of the Nevada Test Site and would involve approximately 450 people. It focuses on “areas of responsibility … and those assets available” in the event of an actual medical emergency.
Document 17: “NEST Evacuation Plan,” n.d., Secret
Source: Energy Department FOIA release
This plan addresses the evacuation of NEST personnel and equipment from Montrev City in the event of a nuclear detonation at the nearby Bullatcha Refinery No. 5. It focuses on execution, logistics, and command and control.
Document 18: NEST On-Scene Coordinator/Exercise Mighty Derringer, to Director, Emergency Management Team, DOE-EDC, Washington, D.C., Event Mighty Derringer Sitrep No. 2, Prepared at 1100 PST 6 December 1986, Secret
Source: Energy Department FOIA release
This report updates the Sitrep that had been prepared just after midnight on December 6 and reports on the significant developments that had occurred during the day. It covers thirteen different topics, and provides significant details of the terrorist site in Montrev, a summary of the behavioral assessment based on communications intelligence, and an assessment of the device. It notes that a “second nuclear device may be enroute [to] CONUS” and there is no confidence that the device is one-point safe, that is, the risk of an accidental nuclear detonation had to be taken into account (to be one-point safe there must be less than 1 in one million probability of producing a nuclear yield exceeding the equivalent of 4 pounds of TNT when the high explosive inside the weapon is detonated at any single point).
Document 19: NEST On-Scene Coordinator /Exercise Mighty Derringer, to Director, Emergency Management Team, DOE-EDC, Washington, D.C., Subject: Event Mighty Derringer Sitrep No. 3, Prepared at 00:10, on 12/07/86, Secret
Source: Energy Department FOIA release
This Sitrep prepared an about one hour after Sitrep No. 2, notes that “prestaging of equipment for access has been completed.”
Document 20: Assessment/McMaster, to Standard Distribution, “IRT Intelligence Summary 061200-062400,” 7 December 1986 02:30, Secret
Source: Energy Department FOIA release
This assessment reports on attempts to determine the presence of a nuclear device at the terrorist site, the movements of the terrorist group’s leader, the weapons and equipment possessed by the group, and a conclusion regarding the capability of Montrev’s armed forces to secure the terrorist site.
Document 21: Assessment/McMaster, to Standard Distribution, “Status Montrev Forces,” 7 December 1986 05:30, Secret
Source: Energy Department FOIA release
The status of Montrev’s forces is reported in this memo, which is based on information received from the Defense Intelligence Agency. It discusses their location, vehicle lift capability, and maintenance issues.
Document 22: CN1 to All, “Mighty Derringer,” 7 December 1986 8:44, Secret
Source: Energy Department FOIA release
This memo conveys a report from the IWS news service on events in Montrev.
Document 23: NEST On-Scene Coordinator, Subject: Event Mighty Derringer, Sitrep No. 4, OCONUS, Prepared at 09:40 on 12/07/86, Secret
Source: Energy Department FOIA release
This Sitrep indicates a successful assault by forces of the Joint Special Operations Command, resulting in their control of both the north and south sites that had been under terrorist control. It reports on the status of the nuclear device and the initial implementation of the emergency disablement plan.
Document 24: Summary Assessment to Standard Distribution, “Summary Assessment,” 7 December 1986 10:30, Secret
Source: Energy Department FOIA release
The technical assessment has been entirely redacted from this document, but the operational and behavioral assessments have been released in their entirety. They note that “The adversary has set up the Montrev situation in such a way that if and when he surfaces in CONUS and makes an explicit threat and demand, he must be taken seriously.”
Document 25a: CN1 to All, “Mighty Derringer,” 7 December 1986 12:28, Secret
Document 25b: CN1 to All, “Mighty Derringer,” 7 December 1986 13:07, Secret
Document 25c: CN1 to All, “Mighty Derringer,” 7 December 1986 15:48, Secret
Source: Energy Department FOIA release
These bulletins convey various media reports of developments in Montrev, including the presence of NEST personnel.
Document 26: Assessment/F. Kloverstrom to Standard Distribution, “Results of examination of containers found in south building,” 7 December 1986 18:10, Secret
Source: Energy Department FOIA release
This memo reports on the discovery, after the assault, of two containers, which appear to contain radioactive material.
Document 27: Jim Boyer, “Suggested Procedure for Joint DOE/Montrev News Releases,” 7 December 1986, Secret
Source: Energy Department FOIA release
Among the recommendations in this short memo are obtaining input from the Montrev Ministry of Information “to get an idea of what El Presidente will approve,” developing a cover for the NEST operation, but preparing to admit NEST participation during the last phase of the operation.
Document 28: “Time Line/Event/Decision Sequence,” 8 December 1986 19:00, Secret
Source: Energy Department FOIA release
This document focuses on the essential steps in disabling the nuclear device seized in Montrev and limiting damage. Thus, it addresses access, diagnostics, disablement, damage limitation, and hazards and effects.
Document 29: “Damage Limitation Containment Implementation,”8 December 1986, Secret
Source: Energy Department FOIA release
This eight-page memo has been almost completely redacted but the opening paragraph notes the location of the Montrev device and that its location presents a “formidable problem” but that all participants reached a common conclusion for the solution.
Document 30: “Hazards and Effects Analysis Prior to Montrev Disablement,” n.d. [8 December 1986?], Secret
Source: Energy Department FOIA release
This three-paragraph memo notes that hazard predictions (involving fallout dose and exposure rates) considered a variety of possible yields, wind projections, and the vulnerability of “the small village of Taco Caliente.”
Document 31: A/I [Assessment & Intelligence] Behavioral, “Booby Traps/Tamper Proof,” n.d. [8 December 1986?], Secret
Source: Energy Department FOIA release
This assessment focuses on the likelihood that the terrorist group and its leader would have installed booby traps to prevent tampering with the nuclear device seized in Montrev. It notes the implications of the extensive anti-personnel attack defenses around the area.
Document 32: James K. Magruder, On-Scene Commander, to Director, Emergency Management Team, DOE-EOC, Washington, D.C, Event Mighty Derringer Sitrep No. 7, 8 December 1986 23:00, Secret
Source: Energy Department FOIA release
This Sitrep notes presumed deadlines for nuclear device detonation and a proposed disablement schedule, the number of personnel on site, an extensive report on current intelligence, and that an “emergency destruct plan has been prepared.”
Document 33: Assessment & Intelligence/F. Jessen to Standard Distribution, “A&I Summary/8 December 2130,” 8 December 1986, Secret
Source: Energy Department FOIA release
This assessment notes the credibility of a threat message claiming the existence of a second nuclear device based on experimental measurements of the device seized in Montrev. The memo’s contents suggest a U.S. target for the second device.
Document 34: J.A. Morgan, Disablement Team Leader, to On-Scene Commander, “Disablement Plan,” 9 December 1986, Secret
Source: Energy Department FOIA release
The memo includes a computer sketch of the terrorist nuclear device and the disablement method, as well as the reentry and evacuation plans – all of which have been redacted.
Document 35: “Exercise Mighty Derringer Post-Event Plan to Safe and Remove the Device,” circa 9 December 1986, Secret
Source: Energy Department FOIA release
This heavily-redacted memo covers four topics – the situation, mission, execution, and administration and logistics. The released portion notes that disablement action had been completed and that an intact physics package had been recovered.
Document 36: “NEST Demobilization Plan,” 10 December 1986, Secret
Source: Energy Department FOIA release
This memo marks plans for the ending the exercise – specifying the responsibilities of the individual organizations, procedures for transportation to the airport and the loading of aircraft, and command and control.
Document 37: Assessment/M. Miron, to Standard Distribution, “Resemblance of Montrev Device to Tahoe Bomb,” 9 December 1986 20:35, Secret
Source: Energy Department FOIA release
In 1980, a sophisticated improvised (non-nuclear) explosive device placed at Harvey’s Wagon Wheel Casino did substantial damage when disablement efforts failed. The memo suggests that publicly available information about the device may have been employed to construct the Montrev device.
Document 38: Cal Wood, Livermore National Laboratory, to Bob Nelson, Controller Team Leader, “Preliminary Evaluation of Players’ Device Estimate,” 10 December 1986, Secret
Source: Energy Department FOIA release
This heavily redacted memo notes that “the diagnostic techniques used by the team produced a rather good estimate of both the materials present and their configuration.”
Document 39: Director FEMA to National Security Council, “Situation Report on MONTREV/Indianapolis Terrorist Situation,” 11 December 1986 17:00 EST, Secret
Source: Energy Department FOIA release
The FEMA director begins with the observation that “At 0700, 11 December 1986, a nuclear detonation occurred in the City of Indianapolis” devastating 20 square blocks. He does not describe the type of damage produced, for example, whether the detonation led to any fires, or the extent to which it caused local fallout hazards. The FEMA director then describes the consequence management phase of the exercise, including involvement of state and federal authorities and agencies.
Critiques
Document 40: Carl Henry, Los Alamos National Laboratory, “Mighty Derringer Report,” 2 February 1987, enclosing comments by Ray D. Duncan, n.d., Secret
Source: Energy Department FOIA release
Some weeks after the exercise, Los Alamos official Carl Henry sent a large package of commentary on MIGHTY DERRINGER, which is presented below, piece by piece, except for the critique by Ray D. Duncan,which is attached to the Henry memorandum. Duncan, a manager at the Nevada Test Site, produced an extensive review which raised a number of issues, including the “unusual challenges” MIGHTY DERRINGER raised for NEST if it was ever deployed to a foreign country for a “covert operation.” Perhaps some incident during the exercise led him to the recommendation for educational training for Delta Force and the Joint Special Operations Command so that their members “understand the potential consequences of moving or unintentionally shooting an IND [improvised nuclear device].”
Document 41: Untitled, unattributed document, Secret, incomplete
Source: Energy Department FOIA release
This critique gives some detail on how the NEST group entered Montrev during the crisis. The State Department had created an approved access list and a simulated Montrev consulate processed the players when they entered the country. When players realized that they had forgotten some equipment, they were easily able to retrieve it as it was only 65 miles away. The commentator noted that in a “real world situation, the NEST contingent could be thousands of miles away from necessary equipment or supplies.”
Document 42: Eric Schuld to Bob Nelson, “Comments on Mighty Derringer – OCONUS Issues,” n.d., Secret
Source: Energy Department FOIA release
Schuld listed issues brought up by the “Outside Continental United States” exercise. For example, the JSOC solved its problem through a “quick assault” that created problems for other organizations in the exercise.
Document 43: Vic Berniklau to Bob Nelson, “Issues/Major Observations/Lessons Learned,” n.d., Secret
Source: Energy Department FOIA release
Like many of the commentators, Berniklau saw the exercise as “excellent” and “well managed,” but he raised problems that others also brought up, such as fragmentation of information and “confusion.”
Document 44: T.T. Scolman, Comments, n.d., Secret
Source: Energy Department FOIA release
Scolman, whose role was “Commander for Science,” also saw an information management problem and pointed to other concerns, such as lack of support staff.
Document 45: Richard F. Smale, HSE, to Carl Henry/Bill Chambers, “First Impressions: Mighty Derringer: Consequence Phase,” n.d., Classification unknown
Source: Energy Department FOIA release
The “consequence phase” referred to the aftermath of the nuclear detonation in Indianapolis. Smale saw “great things” in the exercise, such as its technical organization, but he pointed to concerns such as the failure to present information that would be accessible to a non-technical audience and the lack of time to “develop good fallout plots.”
Document 46: L J. O’Neill, “Exercise Impressions,” 9 December 1986, Secret
Source: Energy Department FOIA release
O’Neill was impressed by the participation of “foreign speaking actors” which helped the participants to enter “wholeheartedly into the play.”
Document 47: L.J. Wolfson to R. Nelson, “Exercise Mighty Derringer,” 10 December 1986, Classificaion unknown, excised copy
Source: Energy Department FOIA release
Like O’Neill, Wolfson pointed to the “good actor play,” especially by the actor who had the role of Montrev’s “El General.” Nevertheless, he argued that “too many people” slowed down the operation.
Document 48: William Nelson, Mighty Derringer Washington Controller, to Captain Ronald St. Martin, National Security Council, “Mighty Derringer Meeting at FBI Headquarters, 12 December 1986, Classification unknown
Source: Energy Department FOIA release
The discussion at FBI headquarters on organizational issues produced a consensus on the need for a White House-designated “leader,” possibly at the cabinet level, responsible for managing post-nuclear disaster recovery activities.
Document 49: Kathy S. Gant, Emergency Technology Program, Oak Ridge National Laboratory, to William Chambers, Los Alamos National Laboratory, 17 December 1986, enclosing “Comments on Exercise Mighty Derringer,” 18 December 1986, Classification unknown
Source: Energy Department FOIA release
Seeing a need for better integration of the consequences phase into MIGHTY DERRINGER, Gant emphasized the need for state and local actors to play a stronger role in such exercises to give them greater realism. Her discussion of the Federal Radiological Response Plan led to a recommendation that NEST staffers play a role in post-incident field monitoring of radiation hazards because they would be the “first available federal personnel.”
Document 50: William H. Chambers, CONUS Site Controller, to Carl Henry, Chief Controller, “‘Quick Look,’ Report, Mighty Derringer CONUS,” 19 December 1986, Secret
Source: Energy Department FOIA release
Chambers provided some detail on the role of the Indianapolis nuclear detonation in MIGHTY DERRINGER. According to the script, the device had been “rendered-safe,” but the exercise leaders “deviated” from the script by improvising a “simulated nuclear detonation.”
Document 51: Zolin Burson, EG&G Energy Measurements, to Carl Henry, 29 December 1986, Secret
Source: Energy Department FOIA release
Like Gant, Burson pointed to the need for more involvement by state and local actors in such exercises, suggesting that “if the real Governor and Mayor” had been present, “they would have had a much stronger influence.”
Document 52: Richard F. Smale, Associate Group Leader, to Jesse Aragon, HSE Division Leader, “Trip Report December 7 to 13, Camp Atterbury (Indianapolis), Indiana,” 7 January 1987, Secret
Source: Energy Department FOIA release
Smale provides more detail on the role of nuclear devices in the exercise scenario, noting that “terrorists had stolen two … from a developing nuclear capable country.” He also observed that “when control of the device had been obtained, the NEST scientists could have disabled it.”
Document 53: Thomas S. Dahlstrom, EG&G Measurements, to William H. Chambers, Carl Henry, and Norm Bailey, “Mighty Derringer Observations,” 13 January 1987, Classification unknown, excised copy
Source: Energy Department FOIA release
After noting that his “overall reaction” was “quite positive,” Dahlstrom believed that “confusion” emanated from a basic problem: the players did “not comprehend the complexity of an OCONUS deployment – specifically how the State Department controls the matter.”
Document 54: F. Jessen/LLNL to G. Allen and W. Adams/NVO, “Mighty Derringer Critique,” 16 December 1986, Rev[ised] 13 January 1987, Secret, excised copy
Source: Energy Department FOIA release
Jessen pointed to a number of problems, for example, that “many of the participating agencies were not serious players,” the “unrealistic background information” on the “fictitious” countries and people, “bad guidance on the use of existing proliferant country data,” and failure to recognize that “information to be assessed related to intelligence reports of a nuclear terrorist threat.” Especially disturbing was the relocation of the command post to a “safe location,” while NEST personnel were not notified”: “the blatant lack of concern for [their] safety … is inexcusable.”
Document 55: Julie A. Orcutt/HSE, Los Alamos National Laboratory, to Jesse Aragon, HSE Division Leader, “Trip Report: Mighty Derringer Exercise, Montrev Site,” 13 January 1987, Secret
Source: Energy Department FOIA release
During the exercise, the on-scene commander at Indianapolis had decided against building a “containment structure” to prevent the spread of hazardous material because of the risks. That meant, however, that plutonium would be scattered about which presented dangers of “lung doses.” Los Alamos staffer Julie Orcutt recommended the provision of more anti-contamination equipment, such as foam mitigation, to reduce dangers to officials entering the blast area.
Document 56: J. Doyle to Gylan C. Allen, “EG&G Comments for Mighty Derringer,” 14 January 1987, Classification unknown, excised, incomplete copy
Source: Energy Department FOIA release
Noting that the exercise provided “very valuable training,” Doyle saw such problems as the “sheer magnitude” in numbers of players, cramped space, and inadequate communications staffing.
Document 57: G.C. Allen, USDOE/NVO, “Mighty Derringer: Comments and Observations,” 15 January 15, 1987, Classification unknown, excised copy
Source: Energy Department FOIA release
Among the shortcomings cited in Allen’s rather critical evaluation were poor communications and weaknesses in interagency coordination.
Document 58: William E. Nelson, Emergency Response, Lawrence Livermore National Laboratory, to Carl Henry, Los Alamos National Laboratory, “‘Quick Look,’ Report, Mighty Derringer,” 21 January 1987, Secret, excised copy
Source: Energy Department FOIA release
Jumping the gun was a weakness cited in Nelson’s critique: players “did not wait for establishment of credibility before acting,” which made a “shambles of an orderly assessment of information.” He also observed that NEST search team “escorts” needed “experience in covert operations” to “prevent inadvertent acts that would alert terrorists.” Nelson’s report included a number of observations made by other participants.
Document 59: J. Strickfadden, LANL, to Bob Nelson, “Mighty Derringer Comments,” n.d., Secret
Source: Energy Department FOIA release
The overall positive evaluation – the “most realistic exercise ever conducted by the NEST community” – included some criticisms, such as “chaotic” operations at the Working Point [WP] and a shambolic state of affairs at the “reentry” point (detonation zone).
Document 60: Milt Madsen (Monitor) to Bob Nelson, “Mighty Derringer Observations,” n.d., Secret, excised, incomplete copy
Source: Energy Department FOIA release
Madsen’s comments included suggestions for future improvements in NEST’s organization: for example, to avoid fragmented committee operations, NEST needed a technical program manager.
Document 61: Peter Mygatt, “Mighty Derringer – Media Play Report,” n.d., Secret
Source: Energy Department FOIA release
Energy Department spokesperson Mygatt’s evaluation of the player’s management of the media was generally positive, although he saw a few failings, e.g., the Joint Information Center never called a news conference, “which is unheard of in an emergency.”.
Document 62: Walter Nervik, Senior Command Controller, to Robert M. Nelson, Exercise Mighty Derringer Controller, “Lessons Learned,” n.d., Secret
Source: Energy Department FOIA release
An official at Lawrence Livermore Laboratory, Nervik wondered who would provide security after JSOC operatives attacked the terrorists in an overseas environment. Special forces personnel would leave the scene but the NEST would still need security resources.
Document 63: Walter Nervik to Bob Nelson, “Lessons Learned,” n.d., Secret
Source: Energy Department FOIA release
Nervik was critical in another evaluation: the NEST team was far too large, players were complacent about a nuclear threat, there were no “penalties” for making a mistake, and playing conditions were “unreal.” With respect to the latter point, the fact that the Montrev phase of the exercise occurred on U.S.-controlled territory, (the Nevada Test Site), “severely limits the stress placed on players in unfamiliar surroundings, dealing with strangers, and relying on untested sources of support.” Nervik also saw a danger that participants would see exercises as “more of a game than a serious test of all facets of the NEST capabilities.”
Document 64: Jack Campbell, Public Information, to Robert M. Nelson, Exercise Mighty Derringer Controller, n.d., Secret
Source: Energy Department FOIA release
Campbell pointed to a weakness: higher level officials did not really “play.” For example, after the JSOC assault, the State Department left Montrev, even though “lives of American correspondents were in jeopardy.” Another surprise was that the Department of Energy NEST team did not establish a “public affairs” function, although in real life such a group would be highly active.
Document 65: “Mighty Derringer 86,” unattributed, n.d., Secret, excised copy
Source: Energy Department FOIA release
These handwritten notes raised several issues, such as the interaction between EOD and the Delta force players and the impact of the “play” in the United States on decisions in the OCONUS (Montrev) activity. One impact was that a “risky” disablement option was taken in Montrev in order to preserve evidence to help raise the chance for a successful operation in “site city” (Indianapolis).
Document 66: “Mighty Derringer,” unattributed, n.d., Secret, excised copy
Source: Energy Department FOIA release
Handwritten notes by another player raised basic organizational issues. The absence of a “chain of command” prior to the deployment made it unclear who EOD worked for. A serious concern was that the Delta Force players did not appreciate the “gravity of dealing with a nuclear device,” an issue suggested by other reports (see document 41).
Document 67: “Mighty Derringer Search Planning,” unattributed, n.d., Secret, excised copy
Source: Energy Department FOIA release
This document provides a review of organizational arrangements established for the device search in Indianapolis.
Document 68: “Communications Observations (Site City),” unattributed, n.d., Classification unknown
Source: Energy Department FOIA release
This review of communications systems concluded that this was the “best NEST communications exercise that I have observed.”
Document 69: Second page of fax to Carl Henry, unattributed document, n.d., Classification unknown
Source: Energy Department FOIA release
This critique points to operational security (OPSEC) as the “real” problem, noting that players had organizational logos on their clothing and that “loose talk” in hotels and bars was “particularly bad.”
ABBREVIATIONS
CONUS Continental United States
EG&G Edgerton, Germeshausen, and Grier
EOC Emergency Operations Center
EOD Explosive Ordnance Disposal
EODTECHCTR Explosive Ordnance Disposal Technical Center (Navy)
ERDA Energy Research and Development Administration
EST Emergency Support Team
FBI Federal Bureau of Investigation
FCP Forward Control Point
FEMA Federal Emergency Management Agency
FRMAC Federal Radiation Monitoring Assessment Center
HRT Hostage Response Team
IND Improved Nuclear Device
JNACC Joint Nuclear Accident Coordination Center
JSOC Joint Special Operations Command
LANL Los Alamos National Laboratory
LLNL Lawrence Livermore National Laboratory
NEST Nuclear Emergency Search Team
NVO Nevada Operations Office
OCONUS Outside the Continental United States
OSC On-Scene Commander
REECo Reynolds Electrical Engineering Corporation
SAC Special-Agent-in Charge (FBI)
SFOD Special Forces Operational Detachment – Delta
SITREP Situation Report
TOC Tactical Operations Center
WP Working Point
Former Jersey City Construction Project Superintendent Sentenced to Prison for Social Security Disability Scam
NEWARK—The former project superintendent on a Jersey City, New Jersey high-rise construction project was sentenced today to six months in prison and six months of home confinement for a scheme in which he hid his employment so he could continue to receive Social Security disability payments, U.S. Attorney Paul J. Fishman announced.
Pasquale Zinna, 44, of Hackettstown, New Jersey, previously pleaded guilty to two counts of the indictment against him: Social Security disability fraud and structuring financial transactions. His wife, Janeen Zinna, 43, was also sentenced today—to two years’ probation with the special condition of 100 hours of community service. She previously pleaded guilty to a superseding information charging her with misprision of her husband’s Social Security fraud. U.S. District Court Judge Katharine S. Hayden imposed the sentences today in Newark federal court.
According to documents filed in this case and statements made in court:
In 1999, Pasquale Zinna filed an application for disability insurance benefits with the Social Security Administration (SSA), claiming that, as of March 15, 1996, he was disabled and unable to work due to a back injury. By filing the application, Pasquale Zinna agreed to notify the SSA if there was any improvement in his medical condition or if he regained the ability to work.
Beginning in September 2005, Pasquale Zinna was the project superintendent for 160 Broadway Concrete, a sub-contractor at the high-rise construction project at 77 Hudson Street in Jersey City. He failed to report his return to work to Social Security and concealed his employment at Broadway Concrete by having his paychecks issued to him in the names of other individuals, including his wife. Janeen Zinna admitted during her guilty plea that she filed a joint federal income tax return with her husband for 2007 which claimed income received from Broadway Concrete was for work she performed.
Pasquale Zinna also admitted to making a series of cash withdrawals from his joint checking account with his wife at Commerce Bank, now TD Bank, in order to avoid the bank’s reporting requirement for financial transactions in excess of $10,000.
In addition to the prison term, Judge Hayden sentenced Pasquale Zinna to three years of supervised release. He was also ordered to pay $101,753 in restitution to the Social Security Administration and to forfeit $98,000 involved in the illegal financial transactions. Janeen Zinna was also held responsible for the restitution. The defendants paid these obligations in full at today’s proceeding.
Four New York men have also pleaded guilty to a wide range of fraud and other offenses stemming from their involvement in the Jersey City construction project between 2007 and 2008.
Rocco Mazzaferro, 64, of Brooklyn, New York, and Vincenzo Genovese, 75, of Staten Island, New York, pleaded guilty November 22, 2011 to conspiracy to commit wire fraud. Vincenzo Genovese also pleaded guilty to one count of conspiracy to embezzle pension benefits.
Anselmo Genovese, 44, of Staten Island, New York, pleaded guilty December 16, 2011 to two counts of making unlawful labor payments.
Eric Haynberg, 46, of New York, pleaded guilty December 16, 2011, to a superseding information charging him with misprision of the wire fraud committed by Mazzaferro and Vincenzo Genovese.
The sentencings of Mazzaferro and Vincenzo Genovese are currently scheduled for July 10, and July 12, 2012, respectively. Sentencing for Eric Haynberg is currently scheduled for June 7, 2012, and for Anselmo Genovese on July 11, 2012.
U.S. Attorney Fishman credited special agents of the FBI, under the direction of Special Agent in Charge Michael B. Ward in Newark; and Department of Labor’s Office of Inspector General, Office of Labor Racketeering and Fraud Investigations, under the direction of Special Agent in Charge Robert L. Panella for the New York Region, for the investigation leading to the arrests and charges. He also thanked the IRS, under the direction of Acting Special Agent in Charge JoAnn S. Zuniga; and the SSA Office of the Inspector General, under the direction of Edward J. Ryan, New York Field Division, for their work on this case, and the U.S. Department of Labor, Employee Benefits Security Administration, for its assistance.
The government is represented by Assistant U.S. Attorney Leslie F. Schwartz of the U.S. Attorney’s Office Economic Crimes Unit in Newark.
The Whole Truth – Full Movie
TOP-SECRET – NSA: Apple iOS5 Devices Security Configuration
DOWNLOAD THE ORIGINAL FILE HERE
SECURE – Washington Airports Electronic Security Systems
SECRET – Zero Human Terrain System: Firing, Budget
DOWNLOAD THE ORGINAL DOCUMENT HERE
Thou Shalt Not Kill – Full Movie
TOP-SECRET – SEC Plan To End Extraordinary Market Volatility
|
[Federal Register Volume 77, Number 109 (Wednesday, June 6, 2012)] [Notices] [Pages 33498-33522] From the Federal Register Online via the Government Printing Office [www.gpo.gov] [FR Doc No: 2012-13653] ======================================================================= ----------------------------------------------------------------------- SECURITIES AND EXCHANGE COMMISSION [Release No. 34-67091; File No. 4-631] Joint Industry Plans; Order Approving, on a Pilot Basis, the National Market System Plan To Address Extraordinary Market Volatility by BATS Exchange, Inc., BATS Y-Exchange, Inc., Chicago Board Options Exchange, Incorporated, Chicago Stock Exchange, Inc., EDGA Exchange, Inc., EDGX Exchange, Inc., Financial Industry Regulatory Authority, Inc., NASDAQ OMX BX, Inc., NASDAQ OMX PHLX LLC, The Nasdaq Stock Market LLC, National Stock Exchange, Inc., New York Stock Exchange LLC, NYSE MKT LLC, and NYSE Arca, Inc. May 31, 2012. I. Introduction On April 5, 2011, NYSE Euronext, on behalf of New York Stock Exchange LLC (``NYSE''), NYSE Amex LLC (``NYSE Amex''),\1\ and NYSE Arca, Inc. (``NYSE Arca''), and the following parties to the proposed National Market System Plan: BATS Exchange, Inc., BATS Y-Exchange, Inc., Chicago Board Options Exchange, Incorporated (``CBOE''), Chicago Stock Exchange, Inc., EDGA Exchange, Inc., EDGX Exchange, Inc., Financial Industry Regulatory Authority, Inc., NASDAQ OMX BX, Inc., NASDAQ OMX PHLX LLC, the [[Page 33499]] Nasdaq Stock Market LLC, and National Stock Exchange, Inc. (collectively with NYSE, NYSE MKT, and NYSE Arca, the ``Participants''), filed with the Securities and Exchange Commission (the ``Commission'') pursuant to Section 11A of the Securities Exchange Act of 1934 (``Act''),\2\ and Rule 608 thereunder,\3\ a proposed Plan to Address Extraordinary Market Volatility (as amended, the ``Plan'').\4\ A copy of the Plan is attached as Exhibit A hereto. The Participants requested that the Commission approve the Plan as a one- year pilot.\5\ The Plan was published for comment in the Federal Register on June 1, 2011.\6\ The Commission received eighteen comment letters in response to the proposal.\7\ On September 27, 2011, the Commission extended the deadline for Commission action on the Plan and designated November 28, 2011 as the new date by which the Commission would be required to take action.\8\ The Commission found that such extension was appropriate in order to provide sufficient time to consider and take action on the Plan, in light of, among other things, the comments received on the proposal.\9\ On November 2, 2011, the Participants to the Plan, other than CBOE, responded to the comment letters and proposed changes to the Plan that were subsequently reflected in an amendment.\10\ On November 18, 2011, the Participants consented to the Commission's request that the deadline for Commission action on the Plan be extended an additional three months, to February 29, 2012.\11\ On February 27, 2012, the Participants consented to the Commission's request that the deadline for Commission action on the Plan be extended an additional three months, to May 31, 2012.\12\ On May 24, 2012, the Participants submitted an amendment that proposed several changes to the Plan.\13\ This order approves the Plan, as amended, on a one-year pilot basis. --------------------------------------------------------------------------- \1\ On May 14, 2012, NYSE Amex filed a proposed rule change on an immediately effective basis to change its name to NYSE MKT LLC (``NYSE MKT''). See Securities Exchange Act Release No. 67037 (May 21, 2012) (SR-NYSEAmex-2012-32). \2\ 15 U.S.C. 78k-1. \3\ 17 CFR 242.608. \4\ See Letter from Janet M. McGinness, Senior Vice President, Legal and Corporate Secretary, NYSE Euronext, to Elizabeth M. Murphy, Secretary, Commission, dated April 5, 2011 (``Transmittal Letter''). \5\ Id. at 1. \6\ See Securities Exchange Act Release No. 64547 (May 25, 2011), 76 FR 31647 (``Notice''). \7\ See Letter from Steve Wunsch, Wunsch Auction Associates, LLC, to Elizabeth M. Murphy, Secretary, Commission, dated June 2, 2011 (``Wunsch Letter''); Letter from Peter J. Driscoll, Investment Professional, Chicago, IL, to Elizabeth M. Murphy, Secretary, Commission, dated June 17, 2011 (``Driscoll Letter''); Letter from Stuart J. Kaswell, Executive Vice President & Managing Director, General Counsel, Managed Funds Association (``MFA''), to Elizabeth M. Murphy, Secretary, Commission, dated June 21, 2011 (``MFA Letter''); Letter from George U. Sauter, Managing Director and Chief Investment Officer, The Vanguard Group, Inc. (``Vanguard''), to Elizabeth M. Murphy, Secretary, Commission, dated June 22, 2011 (``Vanguard Letter''); Letter from Karrie McMillan, General Counsel, Investment Company Institute (``ICI''), to Elizabeth M. Murphy, Secretary, Commission, dated June 22, 2011 (``ICI Letter''); Letter from Manisha Kimmel, Executive Director, Financial Information Forum (``FIF''), to Elizabeth M. Murphy, Secretary, Commission, dated June 22, 2011 (``FIF Letter''); Letter from Craig S. Donohue, Chief Executive Officer, CME Group Inc., to Elizabeth M. Murphy, Secretary, Commission, dated June 22, 2011 (``CME Letter''); Letter from Joseph N. Cangemi, Chairman, and Jim Toes, President and Chief Executive Officer, Security Traders Association, to Elizabeth M. Murphy, Secretary, Commission, dated June 22, 2011 (``STA Letter''); Letter from Leonard J. Amoruso, General Counsel, Knight Capital Group, Inc. (``Knight''), to Elizabeth M. Murphy, Secretary, Commission, dated June 22, 2011 (``Knight Letter); Letter from Ann L. Vlcek, Managing Director and Associate General Counsel, Securities Industry and Financial Markets Association (``SIFMA''), to Elizabeth M. Murphy, Secretary, Commission, dated June 22, 2011 (``SIFMA Letter''); Letter from Jamie Selway, Managing Director, and Patrick Chi, Chief Compliance Officer, ITG Inc., to Elizabeth M. Murphy, Secretary, Commission, dated June 23, 2011 (``ITG Letter''); Letter from Jose Marques, Managing Director and Global Head of Electronic Equity Trading, Deutsche Bank Securities Inc. (``Deutsche Bank''), to Elizabeth M. Murphy, Secretary, Commission, dated June 23, 2011 (``Deutsche Bank Letter''); Letter from Kimberly Unger, Esq., Executive Director, The Security Traders Association of New York, Inc., to Elizabeth M. Murphy, Secretary, Commission, dated June 23, 2011 (``STANY Letter''); Letter from James J. Angel, Ph.D., CFA, Associate Professor of Finance, Georgetown University, McDonough School of Business, to Commission, dated June 24, 2011 (``Angel Letter''); Letter from John A. McCarthy, General Counsel, GETCO, to Elizabeth M. Murphy, Secretary, Commission, dated June 24, 2011 (``GETCO Letter''); Letter from Andrew C. Small, Executive Director and General Counsel, Scottrade, Inc., to Elizabeth M. Murphy, Secretary, Commission, dated July 5, 2011 (``Scottrade Letter''); Letter from Peter Skopp, President, Molinete Trading Inc., to Elizabeth M. Murphy, Secretary, Commission, dated July 19, 2011 (``Molinete Letter''); and Letter from Sal Arnuk, Joe Saluzzi, and Paul Zajac, Themis Trading, LLC, to Elizabeth M. Murphy, Secretary, Commission (``Themis Letter''). Copies of all comments received on the proposed Plan are available on the Commission's Web site, located at http://www.sec.gov/comments/4-631/4-631.shtml. Comments are also available for Web site viewing and printing in the Commission's Public Reference Room, 100 F Street, NE., Washington, DC 20549, on official business days between the hours of 10:00 a.m. and 3:00 p.m. ET. \8\ See Securities Exchange Act Release No. 65410 (September 27, 2011), 76 FR 61121 (Oct. 3, 2011). \9\ Id. \10\ See Letter from Janet M. McGinness, Senior Vice President, Legal and Corporate Secretary, NYSE Euronext, to Elizabeth M. Murphy, Secretary, Commission, dated November 2, 2011 (``Response Letter''). \11\ See Letter from Janet M. McGinness, Senior Vice President and Corporate Secretary, NYSE Euronext, to Elizabeth M. Murphy, Secretary, Commission, dated November 18, 2011. \12\ See Letter from Janet M. McGinness, Senior Vice President and Corporate Secretary, NYSE Euronext, to Elizabeth M. Murphy, Secretary, Commission, dated February 27, 2012. \13\ See Letter from Janet M. McGinness, Senior Vice President, Legal and Corporate Secretary, NYSE Euronext, to Elizabeth M. Murphy, Secretary, Commission, dated May 24, 2012 (``Amendment''). --------------------------------------------------------------------------- II. Background On May 6, 2010, the U.S. equity markets experienced a severe disruption.\14\ Among other things, the prices of a large number of individual securities suddenly declined by significant amounts in a very short time period, before suddenly reversing to prices consistent with their pre-decline levels. This severe price volatility led to a large number of trades being executed at temporarily depressed prices, including many that were more than 60% away from pre-decline prices and were broken by the exchanges and FINRA. The Commission was concerned that events such as those that occurred on May 6 could seriously undermine the integrity of the U.S. securities markets. Accordingly, Commission staff has worked with the exchanges and FINRA since that time to identify and assess the causes and contributing factors of the May 6 market disruption \15\ and to fashion policy responses that will help prevent a recurrence. --------------------------------------------------------------------------- \14\ The events of May 6 are described more fully in a joint report by the staffs of the Commodity Futures Trading Commission (``CFTC'') and the Commission. See Report of the Staffs of the CFTC and SEC to the Joint Advisory Committee on Emerging Regulatory Issues, ``Findings Regarding the Market Events of May 6, 2010,'' dated September 30, 2010, available at http://www.sec.gov/news/studies/2010/marketevents-report.pdf. \15\ Id. --------------------------------------------------------------------------- One such response to the events of May 6, 2010, was the development of the single-stock circuit breaker pilot program, which was implemented through a series of rule filings by the Exchanges and FINRA. This pilot was introduced in three stages, beginning in June 2010. In the first stage, the Commission approved, on an accelerated basis, proposed rule changes by the Exchanges and FINRA to pause trading during periods of extraordinary market volatility in stocks included in Standard & Poor's 500 index.\16\ In the second stage, the Commission approved the Exchanges' and FINRA's proposals to add securities included in the Russell 1000 index, as well as specified exchange traded products (``ETPs''), to the pilot.\17\ In the third stage, the [[Page 33500]] Commission approved the Exchanges' and FINRA's proposals to add all remaining NMS stocks, as defined in Rule 600(b)(47) of Regulation NMS under the Act (``NMS Stocks'') \18\ to the pilot.\19\ The Exchanges and FINRA each subsequently filed, on an immediately effective basis, proposals to exempt all rights and warrants from the pilot.\20\ The single-stock circuit breaker pilot is currently set to expire on July 31, 2012.\21\ --------------------------------------------------------------------------- \16\ See Securities Exchange Act Release Nos. 62252 (June 10, 2010), 75 FR 34186 (June 16, 2010) (File Nos. SR-BATS-2010-014; SR- EDGA-2010-01; SR-EDGX-2010-01; SR-BX-2010-037; SR-ISE-2010-48; SR- NYSE-2010-39; SR-NYSEAmex-2010-46; SR-NYSEArca-2010-41; SR-NASDAQ- 2010-061; SR-CHX-2010-10; SR-NSX-2010-05; and SR-CBOE-2010-047); 62251 (June 10, 2010), 75 FR 34183 (June 16, 2010) (SR-FINRA-2010- 025). \17\ See Securities Exchange Act Release Nos. 62884 (September 10, 2010), 75 FR 56618 (September 16, 2010) (File Nos. SR-BATS-2010- 018; SR-BX-2010-044; SR-CBOE-2010-065; SR-CHX-2010-14; SR-EDGA-2010- 05; SR-EDGX-2010-05; SR-ISE-2010-66; SR-NASDAQ-2010-079; SR-NYSE- 2010-49; SR-NYSEAmex-2010-63; SR-NYSEArca-2010-61; and SR-NSX-2010- 08); and Securities Exchange Act Release No. 62883 (September 10, 2010), 75 FR 56608 (September 16, 2010) (SR-FINRA-2010-033). \18\ 17 CFR 242.600(b)(47). \19\ See Securities Exchange Act Release No. 64735 (June 23, 2011), 76 FR 38243 (June 29, 2011) (File Nos. SR-BATS-2011-016; SR- BYX-2011-011; SR-BX-2011-025; SR-CBOE-2011-049; SR-CHX-2011-09; SR- EDGA-2011-15; SR-EDGX-2011-14; SR-FINRA-2011-023; SR-ISE-2011-028; SR-NASDAQ-2011-067; SR-NYSE-2011-21; SR-NYSEAmex-2011-32; SR- NYSEArca-2011-26; SR-NSX-2011-06; SR-Phlx-2011-64). \20\ See, e.g., Securities Exchange Act Release No. 65810 (November 23, 2011) 76 FR 74080 (November 30, 2011) (SR-NYSE-2011- 57). \21\ See, e.g., Securities Exchange Act Release No. 66134 (January 11, 2012), 77 FR 2592 (January 18, 2012) (SR-NYSE-2011-68). In addition to the trading pause pilot for individual securities, the Commission and the SROs also implemented other regulatory responses to the events of May 6, 2010. For example, the Commission approved proposed rule changes that set forth clearer standards and reduced the discretion of self-regulatory organizations with respect to breaking erroneous trades. See e.g., Securities Exchange Act Release No. 62886 (September 10, 2010), 75 FR 56613 (September 16, 2010). Further, the Commission approved proposed rule changes that enhanced the minimum quoting standards for equity market makers to require that they post continuous two- sided quotations within a designated percentage of the inside market to eliminate market maker ``stub quotes'' that are so far away from the prevailing market that they are clearly not intended to be executed. See Securities Exchange Act Release No. 63255 (November 5, 2010), 75 FR 69484 (November 12, 2010). --------------------------------------------------------------------------- The Plan is intended to replace the single-stock circuit breaker pilot that is currently in place. III. Description of the Proposal The Participants filed the Plan to create a market-wide limit up- limit down mechanism that is intended to address extraordinary market volatility in NMS Stocks.\22\ The Plan sets forth procedures that provide for market-wide limit up-limit down requirements that would be designed to prevent trades in individual NMS Stocks from occurring outside of the specified price bands.\23\ These limit up-limit down requirements would be coupled with trading pauses, as defined in Section I(X) of the Plan, to accommodate more fundamental price moves (as opposed to erroneous trades or momentary gaps in liquidity). --------------------------------------------------------------------------- \22\ See Section I(H) of the Plan. \23\ As set forth in Section V of the Plan, the price bands would consist of a Lower Price Band and an Upper Price Band for each NMS Stock. The price bands would be based on a Reference Price that equals the arithmetic mean price of Eligible Reported Transactions for the NMS stock over the immediately preceding five-minute period. As defined in the proposed Plan, Eligible Reported Transactions would have the meaning prescribed by the Operating Committee for the proposed Plan, and generally mean transactions that are eligible to update the sale price of an NMS Stock. --------------------------------------------------------------------------- As set forth in Section V of the Plan, the price bands would consist of a Lower Price Band and an Upper Price Band for each NMS Stock.\24\ The price bands would be calculated by the Securities Information Processors (``SIPs'' or ``Processors'') responsible for consolidation of information for an NMS Stock pursuant to Rule 603(b) of Regulation NMS under the Act.\25\ Those price bands would be based on a Reference Price \26\ for each NMS Stock that equals the arithmetic mean price of Eligible Reported Transactions for the NMS Stock over the immediately preceding five-minute period. The price bands for an NMS Stock would be calculated by applying the Percentage Parameter for such NMS Stock to the Reference Price, with the Lower Price Band being a Percentage Parameter \27\ below the Reference Price, and the Upper Price Band being a Percentage Parameter above the Reference Price. Between 9:30 a.m. and 9:45 a.m. ET and 3:35 p.m. and 4:00 p.m. ET, the price bands would be calculated by applying double the Percentage Parameters. --------------------------------------------------------------------------- \24\ Capitalized terms used herein but not otherwise defined shall have the meaning ascribed to such terms in the Plan. \25\ 17 CFR 242.603(b). The Plan refers to this entity as the Processor. \26\ See Section I(T) of the Plan. \27\ As initially proposed by the Participants, the Percentage Parameters for Tier 1 NMS Stocks (i.e., stocks in the S&P 500 Index or Russell 1000 Index and certain ETPs) with a Reference Price of $1.00 or more would be five percent and less than $1.00 would be the lesser of (a) $0.15 or (b) 75 percent. The Percentage Parameters for Tier 2 NMS Stocks (i.e., all NMS Stocks other than those in Tier 1) with a Reference Price of $1.00 or more would be 10 percent and less than $1.00 would be the lesser of (a) $0.15 or (b) 75 percent. The Percentage Parameters for a Tier 2 NMS Stock that is a leveraged ETP would be the applicable Percentage Parameter set forth above multiplied by the leverage ratio of such product. On May 24, 2012, the Participants amended the Plan to create a 20% price band for Tier 1 and Tier 2 stocks with a Reference Price of $0.75 or more and up to and including $3.00. The Percentage Parameter for stocks with a Reference Price below $0.75 would be the lesser of (a) $0.15 or (b) 75 percent. --------------------------------------------------------------------------- The Processors would also calculate a Pro-Forma Reference Price for each NMS Stock on a continuous basis during Regular Trading Hours. If a Pro-Forma Reference Price did not move by one percent or more from the Reference Price in effect, no new price bands would be disseminated, and the current Reference Price would remain the effective Reference Price. If the Pro-Forma Reference Price moved by one percent or more from the Reference Price in effect, the Pro-Forma Reference Price would become the Reference Price, and the Processors would disseminate new price bands based on the new Reference Price. Each new Reference Price would remain in effect for at least 30 seconds. When one side of the market for an individual security is outside the applicable price band, the Processors would be required to disseminate such National Best Bid \28\ or National Best Offer \29\ with an appropriate flag identifying it as non-executable. When the other side of the market reaches the applicable price band, the market for an individual security would enter a Limit State,\30\ and the Processors would be required to disseminate such National Best Offer or National Best Bid with an appropriate flag identifying it as a Limit State Quotation.\31\ All trading would immediately enter a Limit State if the National Best Offer equals the Lower Limit Band and does not cross the National Best Bid, or the National Best Bid equals the Upper Limit Band and does not cross the National Best Offer. Trading for an NMS Stock would exit a Limit State if, within 15 seconds of entering the Limit State, all Limit State Quotations were executed or canceled in their entirety. If the market did not exit a Limit State within 15 seconds, then the Primary Listing Exchange would declare a five-minute trading pause, which would be applicable to all markets trading the security. --------------------------------------------------------------------------- \28\ 17 CFR 242.600(b)(42). See also Section I(G) of the Plan. \29\ Id. \30\ A stock enters the Limit State if the National Best Offer equals the Lower Price Band and does not cross the National Best Bid, or the National Best Bid equals the Upper Price Band and does not cross the National Best Offer. See Section VI(A) of the Plan. \31\ See Section I(D) of the Plan. --------------------------------------------------------------------------- These limit up-limit down requirements would be coupled with trading pauses \32\ to accommodate more fundamental price moves (as opposed to erroneous trades or momentary gaps in liquidity). As set forth in more detail in [[Page 33501]] the Plan, all trading centers \33\ in NMS Stocks, including both those operated by Participants and those operated by members of Participants, would be required to establish, maintain, and enforce written policies and procedures that are reasonably designed to comply with the limit up-limit down and trading pause requirements specified in the Plan. --------------------------------------------------------------------------- \32\ The primary listing market would declare a trading pause in an NMS Stock; upon notification by the primary listing market, the Processor would disseminate this information to the public. No trades in that NMS Stock could occur during the trading pause, but all bids and offers may be displayed. See Section VII(A) of the Plan. \33\ As defined in Section I(W) of the Plan, a trading center shall have the meaning provided in Rule 600(b)(78) of Regulation NMS under the Act. --------------------------------------------------------------------------- Under the Plan, all trading centers would be required to establish, maintain, and enforce written policies and procedures reasonably designed to prevent the display of offers below the Lower Price Band and bids above the Upper Price Band for an NMS Stock. The Processors would disseminate an offer below the Lower Price Band or bid above the Upper Price Band that nevertheless inadvertently may be submitted despite such reasonable policies and procedures, but with an appropriate flag identifying it as non-executable; such bid or offer would not be included in National Best Bid or National Best Offer calculations. In addition, all trading centers would be required to develop, maintain, and enforce policies and procedures reasonably designed to prevent trades at prices outside the price bands, with the exception of single-priced opening, reopening, and closing transactions on the Primary Listing Exchange. As proposed, the Plan would be implemented as a one-year pilot program in two Phases. Phase I of the Plan would be implemented immediately following the initial date of Plan operations; Phase II of the Plan would commence six months after the initial date of the Plan or such earlier date as may be announced by the Processors with at least 30 days' notice. Phase I of the Plan would apply only to Tier 1 NMS Stocks, as defined in Appendix A of the Plan. During Phase I of the Plan, the first Price Bands would be calculated and disseminated 15 minutes after the start of Regular Trading Hours, no Price Bands would be calculated and disseminated less than 30 minutes before the end of Regular Trading Hours, and trading would not enter a Limit State less than 25 minutes before the end of Regular Trading Hours. In Phase II, the Plan would fully apply to all NMS Stocks beginning at 9:30 a.m. and ending at 4:00 p.m. each trading day. As stated by the Participants in the Plan, the limit up-limit down mechanism is intended to reduce the negative impacts of sudden, unanticipated price movements in NMS Stocks,\34\ thereby protecting investors and promoting a fair and orderly market.\35\ In particular, the Plan is designed to address the type of sudden price movements that the market experienced on the afternoon of May 6, 2010.\36\ --------------------------------------------------------------------------- \34\ 17 CFR 242.600(b)(47). \35\ See Transmittal Letter, supra note 4. \36\ The limit up-limit down mechanism set forth in the proposed Plan would replace the existing single-stock circuit breaker pilot. See e.g., Securities Exchange Act Release Nos. 62251 (June 10, 2010), 75 FR 34183 (June 16, 2010) (SR-FINRA-2010-025); 62883 (September 10, 2010), 75 FR 56608 (September 16, 2010) (SR-FINRA- 2010-033). --------------------------------------------------------------------------- IV. Comment Letters and Response Letter The Commission received 18 comment letters on the proposed Plan.\37\ Many commenters generally supported the Plan,\38\ while others indicated that they did not oppose the Plan and its intended goals, but raised concerns regarding specific details on the terms of the Plan.\39\ A few commenters opposed \40\ the Plan and suggested different alternatives to achieve the intended goal of the Plan. The Participants responded to the comments regarding the proposal.\41\ --------------------------------------------------------------------------- \37\ See supra note 7. \38\ See MFA Letter at 1; Vanguard Letter at 1; ICI Letter at 1; STA Letter at 1; Knight Letter at 1; SIFMA Letter at 1; ITG Letter at 1; Deutsche Bank Letter at 1; STANY Letter at 1; GETCO Letter at 1. \39\ See Driscoll Letter at 1; FIF Letter at 1; Angel Letter at 1 (stating that the proposed Plan is an improvement over the current single stock circuit breaker pilot); Scottrade Letter at 1 and 5 (supporting the goals of the proposed Plan, but stating that it believes that more work needs to be done before it can support the proposed Plan); Themis Letter at 1 (commending the efforts of the proposed Plan); Molinete Letter at 1. \40\ See Wunsch Letter at 1; CME Group Letter at 1-2 (supporting the proposed Plan's fundamental goal of promoting fair and orderly markets and mitigating the negative impacts of sudden and extraordinary price movements in NMS stocks, but stating that the proposed Plan sets forth an overly complicated and insufficiently coordinated structure that, in a macro-liquidity event, will have the unintended consequence of undermining rather than promoting liquidity). \41\ See Response Letter, supra note 10. --------------------------------------------------------------------------- A. Reference Price Calculation As proposed in the Plan, the Processors would be responsible for calculating and disseminating the applicable Price Bands as provided for in Section V of the Plan. The Processors for each NMS stock would calculate and disseminate to the public a Lower Price Band and an Upper Price Band during regular trading hours, as defined in Section I(R) of the Plan, for such NMS Stock. The Price Bands would be based on a Reference Price for each NMS Stock that equals the arithmetic mean price of Eligible Reported Transactions \42\ for the NMS stock over the immediately preceding five-minute period (except for periods following openings and reopenings).\43\ The Price Bands for an NMS Stock would be calculated by applying the Percentage Parameter \44\ for such NMS Stock to the Reference Price, with the lower Price Band being a Percentage Parameter below the Reference Price, and the upper Price Band being a Percentage Parameter above the Reference Price. Some commenters expressed concern about the complexity involved in calculating the Reference Price.\45\ --------------------------------------------------------------------------- \42\ As defined in the proposed Plan, Eligible Reported Transactions shall have the meaning prescribed by the Operating Committee for the proposed Plan, and generally mean transactions that are eligible to update the sale price of an NMS Stock. \43\ See infra, Section III.G. for a discussion on the application of the Price Bands at the open and close of the trading day. \44\ As defined in Section (I)(M) of the proposed Plan, the ``Percentage Parameter'' means the percentages for each tier of NMS Stocks set forth in Appendix A of the Plan. As such, the Percentage Parameters for Tier 1 NMS Stocks with a Reference Price of $1.00 or more would be 5%, and the Percentage Parameters for Tier 2 NMS Stocks with a Reference Price of $1.00 or more would be 10%. For Tier 1 and Tier 2 NMS Stocks with a Reference Price less than $0.75, the Percentage Parameters would be the lesser of $0.15 or 75%. The Percentage Parameters for a Tier 2 NMS Stock that is a leveraged exchange-traded product would be the applicable Percentage Parameter multiplied by the leverage ratio of such product. \45\ See Angel Letter at 4; GETCO Letter at 3-4; MFA Letter at 5; Molinete Letter at 1-2 (stating that it is not clear whether the trades used to calculate the Reference Price are weighted by volume, or if this is a strict average of the trade prices reported); Themis Letter at 1. See also SIFMA Letter at 8 (noting that if the market price for an NMS Stock moves by less than one percent, the Price Bands will not change and, as a result, the limit up and limit down prices will be closer to four percent than five percent over the prevailing market price because a new Reference Price will only be disseminated if there is a change of one percent or more in the Pro- Forma Reference Price over the then prevailing Reference Price). --------------------------------------------------------------------------- Commenters suggested alternative ways to calculate the Reference Price. In its letter, one commenter suggested simplifying the Reference Price calculation by ``calculating a new Reference Price on regular 30 second intervals, regardless of whether it has changed by 1%'' and noted that ``[t]his simplification also obviates the definition of a Pro-Forma Reference Price.''\46\ That commenter also recommended calculating the Reference Prints with a volume weighted average price rather than an arithmetic average price, which would remove the possibility of market participants splitting orders in different ways to affect the calculation of the Reference Price.\47\ Another commenter stated that [[Page 33502]] the Participants should consider using the opening price of a stock as the Reference Price because it would be much simpler than the calculation that the Participants proposed.\48\ Another commenter stated that the Participants should consider using the prior day's closing price as a static Reference Price, rather than constantly updating the Reference Price throughout the trading day, noting that this would be similar to how the futures markets calculate their limit up-limit down Price Bands.\49\ --------------------------------------------------------------------------- \46\ See MFA Letter at 5. \47\ Id. \48\ See Angel Letter 4. \49\ See GETCO Letter at 3-4. See also SIFMA Letter at 9 (requesting that the Participants clarify how Price Bands will apply to stocks with prices that cross the one dollar threshold during intra-day trading); Molinete Letter at 3-4 (stating its belief that changes in Price Band calculations throughout the trading day can create problems). --------------------------------------------------------------------------- Commenters also stated that certain types of trades should be exempted from the Plan and thus the calculation of the Reference Price. Three commenters noted that certain Regulation NMS-exempt trades should be exempt from the Plan because they are unrelated to the last sale of a stock.\50\ More specifically, one commenter stated that ``trading centers should be permitted to execute orders internally at prices outside of the specified Price Bands if the executions comply [with certain Regulation NMS exemptions].'' \51\ That commenter noted that most Regulation NMS exemptions ``have corresponding sale conditions that identify those trades as being not eligible for last sale.'' \52\ Another commenter stated that certain block facilitation trades should be exempted from the Plan.\53\ That commenter argued that block facilitation trades tend to stabilize the market because a block positioner is committing capital to absorb a large trading interest that would otherwise impact the market for the underlying stock of the block order.\54\ Finally, two commenters suggested that trades that are executed outside of the current Price Bands be exempt from Reference Price calculations.\55\ --------------------------------------------------------------------------- \50\ See e.g., FIF Letter at 1-2; Deutsche Bank Letter at 3; SIFMA Letter at 2-4. \51\ See FIF Letter at 1-2 (listing the exemptions found in Rule 611(a)--non-convertible preferred securities; Rule 611(b)(2)--not regular way; Rule 611(b)(7)--benchmark derivatively priced; Rule 611(b)(9)--stopped stock; Rule 611(d)--qualified contingent trades; Rule 611(d)--error correction; Rule 611(d)--print protection). \52\ Id. \53\ See Deutsche Bank Letter at 3 (stating that ``it is critical for a block facilitator to execute outside a band when the market is moving rapidly or it will lose the ability to trade effectively for its client.'') See also FIF Letter at 2 (requesting an impact analysis on the printing of block transactions accompanied by a Regulation NMS sweep as well as block transactions printed without ISO modifiers in adherence with Regulation NMS FAQ 3.23). \54\ Id. \55\ See MFA Letter at 6 (recommend that the Plan include a more explicit definition for which prints are included in calculating a Reference Price); STANY Letter at 2 (noting that clearly erroneous transactions may still occur, and thus suggesting that trades that are executed outside the then existing price bands not be included in the calculation of the Reference Price). --------------------------------------------------------------------------- The Participants noted that alternatives were considered when the Plan was being drafted, but the Participants determined that something more dynamic would be preferable, and that the five percent level is more therefore appropriate, particularly for highly liquid stocks.\56\ Moreover, the Participants stated that the proposed one percent requirement would help to reduce quote traffic but still provide for appropriate adjustments of Reference Prices in a rapidly moving market.\57\ The Participants also stated that using the arithmetic average would reduce the impact of any erroneous trades that may be included in the calculation of the Reference Price.\58\ --------------------------------------------------------------------------- \56\ See Response Letter at 4. \57\ The Participants are not proposing to amend the Plan with respect to the calculation of the Reference Price. However, in an effort to keep a rapidly-moving market aware of the current price bands, the Processor would republish the existing price bands every 15 seconds. See Response Letter at 5. \58\ Id. --------------------------------------------------------------------------- As discussed in greater detail below, the Participants recently amended the Plan to clarify that the Reference Price used in determining which Percentage Parameter is applicable during the trading day would be based on the closing price of the subject security on the Primary Listing Exchange on the previous trading day or, if no closing price exists, the last sale on the Primary Listing Exchange reported by the Processors. The Participants also amended the Plan to permit certain transactions to execute outside of the price bands. Specifically, the Participants proposed that transactions that are exempt under Rule 611 of Regulation NMS,\59\ and which do not update the last sale price (except if solely because the transaction was reported late), should be allowed to execute outside of the price bands.\60\ As part of the amendment, the Participants also proposed to exclude rights and warrants from the Plan, consistent with the current single-stock circuit breaker pilot.\61\ --------------------------------------------------------------------------- \59\ 17 CFR 242.611. \60\ See Amendment, supra note 13. \61\ Id. --------------------------------------------------------------------------- B. Display of Offers Below the Lower Price Band and Bids Above the Upper Price Band As proposed in the Plan, offers below the Lower Price Band and bids above the Upper Price Band would not be displayed on the consolidated tape. One commenter disagreed with this aspect of the Plan and stated that all quotes should be displayed, but marked as non-executable if outside the Price Bands.\62\ That commenter stated that preventing the display of quotes outside the Price Bands could lead to unusual side effects and that a broker-dealer entering an order on behalf of a customer should have the option of re-pricing or posting the order in accordance with the customer's wishes, rather than a market center re- pricing non-executable orders to a Price Band.\63\ Another commenter stated that displaying certain non-accessible quotes that are the result ``of an altered price discovery process will have greater negative implications for investor confidence'' because the only trades than can be executed during a Limit State ``do not represent the true equilibrium of supply and demand.'' \64\ --------------------------------------------------------------------------- \62\ See MFA Letter at 2-3. \63\ See id. \64\ See Driscoll Letter at 3. --------------------------------------------------------------------------- The Participants noted that under the Plan, all trading centers would be required to establish, maintain, and enforce written policies and procedures reasonably designed to prevent the display of offers below the Lower Price Band and bids above the Upper Price Band for an NMS Stock.\65\ When one side of the market for an individual security is outside the applicable Price Band, the Processors would be required to disseminate such National Best Bid or National Best Offer with an appropriate flag identifying it as non-executable. When the other side of the market reaches the applicable Price Band, the market for an individual security would enter a Limit State, and the Processor would be required to disseminate such National Best Offer or National Best Bid with an appropriate flag identifying it as a Limit State Quotation. The Participants stated that after considering whether more quotes should be displayed as unexecutable, they determined that any potential benefits arising from such practice would be outweighed by the risk of investor confusion. As a result, the Participants did not believe that the Plan should be amended to permit all quotes outside the Price Bands to be displayed. The Participants stated that they would continue to review this issue and could [[Page 33503]] revisit it after gaining experience during the pilot.\66\ --------------------------------------------------------------------------- \65\ See Response Letter at 4. \66\ Id. --------------------------------------------------------------------------- C. Criteria for Entering the Limit State As set forth in Section VI of the Plan, when one side of the market for an individual security is outside the applicable Price Band (i.e., when the National Best Bid \67\ is below the Lower Limit Band or the National Best Offer \68\ is above the Upper Limit Band for an NMS Stock), the Processors would be required to disseminate such National Best Bid or National Best Offer with an appropriate flag identifying it as non-executable. When the other side of the market reaches the applicable Price Band (i.e., when the National Best Offer is equal to the Lower Limit Band or the National Best Bid is equal to the Upper Limit Band for an NMS Stock), the market for an individual security would enter a Limit State,\69\ and the Processors would be required to disseminate such National Best Offer or National Best Bid with an appropriate flag identifying it as a Limit State Quotation.\70\ --------------------------------------------------------------------------- \67\ 17 CFR 242.600(b)(42). See also Section I(G) of the Plan. \68\ Id. \69\ As set forth in Section VI(B) of the Plan, when trading for an NMS Stock enters a Limit State, the Processor shall cease calculating and disseminating updated Reference Prices and Price Bands for the NMS Stock until either trading exits the Limit State or trading resumes with an opening or re-opening as provided in Section V of the proposed Plan. \70\ See Section I(D) of the Plan. --------------------------------------------------------------------------- Commenters expressed concern that requiring the National Best Bid or Offer (``NBBO'') to be equal to, but not necessarily cross the applicable Price Band in order to enter a Limit State could create some unusual market discrepancies.\71\ One commenter stated that ``it does not make sense for a Limit State to be triggered if the national best bid or offer equals a price band, but not if the national best bid or offer has crossed a price band [because the] same rationale for entering a Limit State exists in either case.'' \72\ Instead, the commenters suggested that if either the best bid or offer is outside the Price Band, the market should enter the Limit State. --------------------------------------------------------------------------- \71\ See MFA Letter at 6 (stating that ``buyers may not submit orders if the Upper Price Band is sufficiently far away from the market'' and recommending that ``if either the best bid or ask is outside the Price Band, the market enters a Limit State and has 5 seconds to readjust before a Trading Halt''); Deutsche Bank Letter at 4. \72\ See Deutsche Bank Letter at 4 (emphasis in original). --------------------------------------------------------------------------- One commenter expressed concern about a scenario where a stock is effectively not trading, but still has not entered a Limit State--for example, where the National Best Bid is below the Lower Price Band, and is thus non-executable, while the National Best Offer remains within the price bands. Since, in this example, the offer has not hit the Lower Price Band, the Limit State has not yet been triggered; however, the market for that stock is essentially one-sided, as the bid cannot be executed against. Since the Limit State has not yet been triggered, the concern is that the market could remain in this condition for an indefinite period of time.\73\ --------------------------------------------------------------------------- \73\ See Molinete Letter at 2-3 (discussing a situation where the market may not enter a Limit State due to a market order against an illiquid book that would execute against a quote that is outside the applicable price bands). --------------------------------------------------------------------------- In the situation where a stock is effectively not trading, i.e., because the National Best Bid is below the Lower Price Band, but the National Best Offer is still within the price bands and thus the Limit State would not be triggered, the Participants responded that the National Best Offer would generally follow the National Best Bid downwards, and sellers would be willing to offer the stock at the Lower Price Band, triggering the Limit State.\74\ The Participants also responded that, alternatively, the reference price may be recalculated due to transactions occurring in the previous five minutes. This could adjust the price bands downwards, potentially bringing the National Best Bid within the price bands, at which time it may be executed against.\75\ The Participants represented that they would monitor these situations during the pilot and consider modifications to the Plan structure if needed.\76\ --------------------------------------------------------------------------- \74\ See Response Letter at 5. \75\ Id. \76\ Id. --------------------------------------------------------------------------- As discussed below, in response to commenters' concerns, the Participants recently amended the Plan to create a manual override function where the National Best Bid (Offer) for a security is below (above) the Lower (Upper) Price Band, and the security has not entered the Limit State. With this provision, the Primary Listing Exchange has the ability to initiate a trading pause for a stock in this situation.\77\ --------------------------------------------------------------------------- \77\ See Amendment, supra note 13. --------------------------------------------------------------------------- D. Order Handling During the Limit State As set forth in the Plan, all trading centers \78\ in NMS Stocks, including both those operated by Participants and those operated by members of Participants, would be required to establish, maintain, and enforce written policies and procedures that are reasonably designed to comply with the limit up-limit down and trading pause requirements specified in the Plan. Some commenters stated that clarifications are necessary regarding the Commission's Order Handling Rules so that they could be applied uniformly across all market centers once the Plan is in effect.\79\ One commenter noted that market centers would benefit from guidance on best industry standards for handling customer orders during the periods of time when securities are in a Limit State, as well as periods when trading in a security restarts after a trading pause.\80\ --------------------------------------------------------------------------- \78\ As defined in Section I(W) of the Plan, a trading center shall have the meaning provided in Rule 600(b)(78) of Regulation NMS under the Exchange Act. \79\ See STA Letter at 3; SIFMA Letter at 6 (stating that the proposal contemplates that broker-dealers may delay, reprice or reject ``held'' orders, thus implicating the limit order display rule as well as best execution requirements); Angel Letter at 4 (requesting the clarification of best execution requirements during the Limit State). \80\ See STA Letter at 3. --------------------------------------------------------------------------- E. Duration of the Limit State By the terms of the Plan, trading for an NMS Stock would exit a Limit State if, within 15 seconds of entering the Limit State, the entire size of all Limit State Quotations is executed or cancelled. If the market does not exit a Limit State within 15 seconds, then the Primary Listing Exchange would declare a five-minute trading pause pursuant to Section VII of the Plan. Two commenters suggested that the Plan should contemplate a longer Limit State than 15 seconds, such as 30 seconds, because a shorter time period would trigger too many trading pauses.\81\ One commenter advocated for a longer Limit State ``[b]ecause the price bands should eliminate significant erroneous trades, and trading halts interfere with the natural interaction of orders and the price discovery process.'' \82\ That commenter stated that halts should thus ``be limited to extraordinary circumstances.'' \83\ Another commenter noted that ``15 seconds is not a sufficient amount of time for most investors to digest information about a limit state condition and to react to the information.'' \84\ These commenters believe that a 30 second Limit State would provide a more sufficient opportunity for market participants to provide liquidity to the market of an NMS Stock. These [[Page 33504]] commenters stated that, at a minimum, the timeframe should not be shortened from the proposed 15 seconds. --------------------------------------------------------------------------- \81\ See Vanguard Letter at 2; ICI Letter at 2. One commenter stated it would serve the public to understand why 15 seconds was chosen for the Limit State condition, as opposed to 30 seconds, or perhaps 60 seconds. See Themis Letter at 1. \82\ See Vanguard Letter at 2. \83\ Id. \84\ See ICI Letter at 2. --------------------------------------------------------------------------- Other commenters proposed shortening the length of the Limit State to 5 seconds, suggesting that this would be ample time for the market to replenish the necessary liquidity given the technological advances in modern trading.\85\ One commenter stated that a shorter Limit State is preferable because a longer Limit State could lead to wider spreads and uncertainty in the options markets.\86\ Another commenter stated that retail investors may wonder why their orders had not been executed.\87\ --------------------------------------------------------------------------- \85\ See SIFMA Letter at 5-6; MFA Letter at 6; and Scottrade Letter at 2. \86\ See SIFMA Letter at 5. \87\ See Scottrade Letter at 2 (stating its confidence that stocks that enter the Limit State Quotation erroneously will be addressed within a 5 second threshold, allowing the security to continue trading). --------------------------------------------------------------------------- In response, the Participants stated that the 15-second Limit State should be long enough to reasonably attract additional available liquidity without recourse to a trading pause, while short enough to reasonably limit any market uncertainty that might accompany a Limit State.\88\ The Participants represented that, during the pilot period, they will continue to review the length of the Limit State and consider whether, based on that experience, it should be lengthened or shortened.\89\ --------------------------------------------------------------------------- \88\ See Response Letter at 6. \89\ Id. --------------------------------------------------------------------------- F. Criteria for Exiting a Limit State Under the Plan, trading for an NMS Stock would exit a Limit State if within 15 seconds of entering the Limit State, the entire size of all Limit State Quotations is executed or cancelled. Some commenters proposed alternative criteria for exiting a Limit State. One commenter expressed concern ``that the exit from a Limit State is arbitrary and may be easily manipulated * * * [because] it's not clear to market participants from moment to moment whether a trading pause will be declared or whether the Price Bands will suddenly be adjusted. Exiting a Limit State would depend upon the timing of an order that could clear out the Limit State quotation and when a new limit order arrives at the Limit State quotation.'' \90\ Another commenter suggested that in order to reestablish an orderly market, that the Plan should require a new bid and a new offer that are executable before the expiration of a Limit State period.\91\ Another commenter stated that the conditions for exiting a Limit State are not clearly defined in the Plan and further clarifications are necessary.\92\ --------------------------------------------------------------------------- \90\ See MFA Letter at 5. \91\ See SIFMA Letter at 6. \92\ See Molinete Letter at 3. --------------------------------------------------------------------------- The Participants declined to amend the Plan to address these concerns, noting in the Response Letter that adding a requirement that a new executable bid or offer be entered before exiting a Limit State raises the question of who would be obligated to enter such a bid or offer.\93\ Moreover, the Participants stated that depending on the price movements during the five minutes prior to entering the Limit State, the Reference Price may have moved, thus moving the Price Bands.\94\ The Participants noted that in such a case, executable bids and offers may become available simply by virtue of the recalculated Price Bands. --------------------------------------------------------------------------- \93\ Id. \94\ Id. --------------------------------------------------------------------------- G. Application of the Price Bands at the Open and Close During Phase I of the Plan's implementation time period, the terms of the Plan would apply only to Tier 1 NMS Stocks, as defined in Appendix A of the Plan, and the first Price Bands would be calculated and disseminated 15 minutes after the start of Regular Trading Hours, as specified in Section V(A) of the Plan, and no Price Bands would be calculated and disseminated less than 30 minutes before the end of Regular Trading Hours. In Phase II, the Plan would fully apply to all NMS Stocks beginning at 9:30 a.m. ET and ending at 4:00 p.m. ET of each trading day. Some commenters expressed concerns about the application of the Price Bands at the opening of the trading day. One commenter stated that the approach proposed in Phase I--the first Price Bands would be calculated and disseminated 15 minutes after the start of Regular Trading Hours, and no Price Bands would be calculated and disseminated less than 30 minutes before the end of Regular Trading Hours--should apply to both phases of the Plan.\95\ Another commenter agreed that the Plan should not be in effect during the first five minutes of the trading day because price information is critical at that time.\96\ That commenter also stated that any regulatory gap during this time period could be filled by the clearly erroneous trade rules, which it proposed should only be in effect during the first five (and last five) minutes of the trading day.\97\ Rather than placing a specific time limit on the opening, another commenter asserted that it would benefit the market if Price Bands were not established until a single opening price occurs at the Primary Listing Exchange.\98\ However, one commenter stated that the Price Bands should be in effect for the entire trading day because long-term investors may appreciate this simplicity.\99\ --------------------------------------------------------------------------- \95\ See SIFMA Letter at 8. The commenter also requested clarification on whether it is true that there may be no Price Bands in effect for an NMS Stock during the first five minutes if the Opening Price for the stock does not occur on the Primary Market within that period because there will be no Reference Price under such circumstance. See id. \96\ See Knight Letter at 3. \97\ Id. \98\ See Scottrade Letter at 2. \99\ See Themis Letter at 1. --------------------------------------------------------------------------- Commenters also expressed concerns about the application of the Price Bands at the close of the trading day. Six commenters opposed applying the Price Bands at the close of the trading day.\100\ These commenters described the close of the trading day as a critical part of the trading day \101\ and argued that under the terms of the Plan, exchanges could have inconsistent closing times as a result of a trading pause.\102\ According to these commenters, keeping track of various closing times could have serious negative effects for market participants attempting to close positions or hedge by the end of the day.\103\ Alternatively, one commenter suggested that if there is a disruptive event immediately prior to the close, regular-way trading and the closing auction should be extended to make sure the closing price is accurate.\104\ --------------------------------------------------------------------------- \100\ Six commenters generally advocated for the Plan not being in effect during the final 10 minutes of the trading day, i.e., 3:50 p.m. to 4:00 p.m. ET. See FIF Letter at 5; Deutsche Bank Letter at 2 and 4; Knight Letter at 3; SIFMA Letter at 2; ITG Letter at 2; Scottrade Letter at 2-3. Two of these commenters suggested that it would be ideal to suspend the operation of the Plan from 3:35 p.m. to 4:00 p.m. ET. See ITG Letter at 2; Scottrade Letter at 2-3. \101\ See e.g., Knight Letter at 3. \102\ See e.g., FIF Letter at 5 (stating that exchanges could have different closing times as a result of trading pauses); Deutsche Bank Letter at 2 (advocating for consistent closing times across all of the exchanges). \103\ See Deutsche Bank Letter at 2. \104\ See Angel Letter at 5. --------------------------------------------------------------------------- The Participants stated in the Response Letter that they believe that the proposed doubling of the Percentage Parameters around the opening and closing periods is appropriate in light of the increased volatility at those times, and that no adjustment to the timing or levels of the Price Bands should be made to the Plan until experience is gained from both Phases I and II.\105\ --------------------------------------------------------------------------- \105\ See Response Letter at 4. --------------------------------------------------------------------------- [[Page 33505]] H. Reopenings on the Primary Listing Exchange Under the terms of the Plan, following a trading pause in an NMS Stock, and if the Primary Listing Exchange has not declared a Regulatory Halt, the next Reference Price would be the Reopening Price on the Primary Listing Exchange if such Reopening Price occurs within ten minutes after the beginning of the trading pause, and subsequent Reference Prices shall be determined in the manner prescribed for normal openings, as specified in Section V(B)(1) of the Plan. One commenter stated, instead of this provision, exchanges could compete for the five to ten minute exclusive window to reopen an issue.\106\ The commenter suggested reviewing trading volumes and awarding the reopening rights to the venue with the most average daily volume over the review period.\107\ --------------------------------------------------------------------------- \106\ See Driscoll Letter at 2-3. \107\ Id. at 4. --------------------------------------------------------------------------- I. Classification and Treatment of Tier 2 Stocks Pursuant to the Plan, Tier 1 NMS Stocks would include all NMS Stocks included in the S&P 500 Index, the Russell 1000 Index, and the exchange-traded products listed on Schedule 1 to the Plan's Appendix. Tier 2 NMS Stocks would include all NMS Stocks other than those in Tier 1. The Percentage Parameters for Tier 2 NMS Stocks with a Reference Price of $1.00 or more would be 10% and the Percentage Parameters for Tier 2 NMS Stocks with a Reference Price less than $1.00 would be the lesser of (a) $0.15 or (b) 75%. One commenter stated that a 10% price band may be too restrictive for some Tier 2 stocks and suggested that the Participants reduce the number of Tier 2 stocks to a test group.\108\ That commenter also stated that a 10% price band may be too restrictive for thinly traded stocks.\109\ Another commenter proposed the creation of a Tier 3 for stocks with a sufficiently low average daily volume (``ADV'') and wide bid-offer spreads.\110\ That commenter stated that the originally proposed limit up-limit down parameters may be unsuitable for these types of low-liquidity stocks and that they may require a higher percentage parameter.\111\ --------------------------------------------------------------------------- \108\ See MFA Letter at 4. \109\ Id. (for example, the commenter suggested that reopening rights be awarded to the trading venue with the most average daily volume over the review period). \110\ See Knight Letter at 3. \111\ Id. --------------------------------------------------------------------------- As discussed below, the Participants recently amended the Plan to create a 20% price band for Tier 1 and Tier 2 stocks with a Reference Price equal to $0.75 and up to and including $3.00. The Participants also proposed a conforming amendment for Tier 1 and Tier 2 stocks with a Reference Price less than $0.75. The Percentage Parameters for these stocks shall be the lesser of (a) $0.15 or (b) 75%.\112\ As initially proposed, those Percentage Parameters would have applied to Tier 1 and Tier 2 stocks with a Reference Price less than $1.00. --------------------------------------------------------------------------- \112\ See Amendment, supra note 13. --------------------------------------------------------------------------- J. Treatment and Impact of the Plan on Exchange Traded Products (ETPs) The Commission also received comments on the scope of the Plan as it applies to ETPs. ICI stated that all ETFs should be included in the pilot on an expedited basis.\113\ Vanguard seconded this idea and noted that the original list of ETPs was created when the Commission, FINRA, and the exchanges had to act quickly following the market events of May 6, 2010.\114\ --------------------------------------------------------------------------- \113\ See ICI Letter at 2-3. \114\ See Vanguard Letter at 2. --------------------------------------------------------------------------- MFA suggested that there could be unintended consequences of the Plan on ETFs (or derivatives) because the spreads in such products could increase due to uncertainty in the underlying security, i.e., if the components of an ETF are subject to Limit States or trading pauses, quotes in the ETF would widen accordingly, potentially causing the ETF itself to enter a Limit State.\115\ According to MFA, index arbitragers may decline to trade because of uncertainty if they do not have a way to hedge risk.\116\ --------------------------------------------------------------------------- \115\ See MFA Letter at 6. \116\ Id. --------------------------------------------------------------------------- In response, the Participants noted that the proposed phases of the Plan appropriately focus on trading characteristics and volatility rather than instrument type, and that including only certain ETPs in Tier 1 was consistent with scope of the current single-stock circuit breaker pilot.\117\ --------------------------------------------------------------------------- \117\ See Response Letter at 9. --------------------------------------------------------------------------- As discussed below, the Participants recently amended the Plan to require a review and update, on a semi-annual basis, of the list of ETPs included in Tier I of the Plan, and re-stated the criteria by which ETPs would be selected for inclusion in Tier I. K. Coordination of the Plan With Other Volatility Moderating Mechanisms Five commenters noted that the Plan implicates other volatility moderating mechanisms that currently exist \118\ and requested that the interaction of the Plan with these existing mechanisms be clarified.\119\ The commenters stated that the Plan could interact with the single-stock circuit breaker pilot,\120\ the Regulation SHO circuit breaker,\121\ and the exchange-specific volatility guards.\122\ One commenter stated that ``simultaneous triggering of two or more of these speed bumps during times of heightened market volatility could cause confusion and uncertainty unless there is a scheme in place for handing multiple triggers.'' \123\ One commenter advocated that as the Participants implement the Plan, the Commission phase out: (1) The NYSE LRPs; (2) the Nasdaq Volatility Guard; (3) the Regulation SHO alternative uptick rule; and (4) the single-stock circuit breakers.\124\ Two commenters also requested that the Commission amend clearly erroneous rules so the presumption is that trades executed within the Price Band are not subject to being broken.\125\ --------------------------------------------------------------------------- \118\ See Scottrade Letter at 3; STANY Letter at 4; Knight Letter at 2-3; SIFMA Letter at 6-7; CME Letter at 1 and 3 (noting that the proposed Plan would replace the existing single-stock circuit breaker pilot program currently in effect); FIF Letter at 5 (noting that under the single-stock circuit breaker pilot, exchanges deal with held orders differently). \119\ See e.g., Scottrade Letter at 3. \120\ See e.g., Scottrade Letter at 3; STANY Letter at 4; FIF Letter at 5. \121\ See e.g., STANY Letter at 4; \122\ See e.g., STANY Letter at 4; Knight Letter at 2-3. \123\ See STANY Letter at 4. \124\ See Knight Letter at 1. \125\ See SIFMA Letter at 6-7; STANY Letter at 4. See also Knight Letter at 3 (Knight stated that clearly erroneous rules should only operate during the first and last five minutes of the trading day and that there is also a utility in extending the clearly erroneous rules to after-hours trading). --------------------------------------------------------------------------- Another commenter stated that the Plan does not consider how it would interact with the market-wide circuit breakers being evaluated by the Commission and the U.S. Commodity Futures Trading Commission.\126\ This commenter stated that single-stock circuit breaker halts may affect products across markets, and may undermine rather than promote liquidity during market disruptions.\127\ Moreover, according to this commenter, halting individual securities without a market-wide halt would, in the case of an index, impair the calculation of that index, which would have cross-market effects. This commenter concluded that market-wide circuit breakers, coupled with automated volatility and risk management functionality, i.e., price bands, protection points, order quantity [[Page 33506]] protections, and stop logic functionality, would be the better alternative.\128\ --------------------------------------------------------------------------- \126\ See CME Letter at 2-3. \127\ Id. at 3. \128\ Id. --------------------------------------------------------------------------- The Participants noted that some commenters requested that the Participants amend their rules to provide that an execution within a Price Band could not be deemed a clearly erroneous execution. The Participants responded that, while it may be useful to do so and that a key benefit of the limit up-limit down mechanism should be the prevention of clearly erroneous executions, the clearly erroneous trade rules are separate from the Plan and as such the Participants would consider such a change on a separate track.\129\ --------------------------------------------------------------------------- \129\ See Response Letter at 7. --------------------------------------------------------------------------- L. Coordination and Impact on Other Markets Commenters also expressed opinions regarding the impact of the Plan on other markets, e.g., options,\130\ futures,\131\ and foreign markets.\132\ One commenter suggested that in the options markets, the proposed Limit State for an NMS Stock could create uncertainty and result in wider spreads on the related option.\133\ In its letter, that commenter stated that option traders hedge option transactions with the underlying security, so that a Limit State could impact hedging activity as well. This commenter suggested that options market-makers may be unwilling to be subject to normal market-making requirements and minimum quoting widths when the underlying security is in a Limit State. Moreover, options markets do not have uniform clearly erroneous standards. Accordingly, when the underlying security is in a Limit State, some options exchanges may reject all options market orders, while other exchanges may reject only orders on the same side of the market that caused the Limit State.\134\ --------------------------------------------------------------------------- \130\ See SIFMA Letter at 7; STANY Letter at 3-4. \131\ See e.g., CME Group Letter, supra note 38. \132\ See Angel Letter at 5 (stating that policy makers should consider how foreign markets address issues of extraordinary market volatility). \133\ See STANY Letter at 3-4. \134\ Id. --------------------------------------------------------------------------- The Participants responded that the Plan will generally benefit the market for NMS Stocks and protect investors and should not be delayed while further consideration is given to coordination with options and futures markets.\135\ The Participants also stated their belief that the Plan strikes appropriate balance in the areas noted. Because the Plan would be adopted as a pilot, the Participants represented that they would have an opportunity to further consider the commenters' suggestions above after gaining experience with the Plan. --------------------------------------------------------------------------- \135\ See Response Letter at 7. --------------------------------------------------------------------------- M. Role of the Processors The Processors are fundamental to the operation of the Plan. In short, the single plan processor responsible for consolidation of information for an NMS Stock would be responsible for calculating and disseminating the applicable Price Bands as well as marking certain quotations as non-executable. One commenter stated that the SIPs should run test data to prove that they are up to the tasks required by them under the terms of the Plan.\136\ Another commenter questioned the ability of the SIPs to perform the tasks because under the Plan, SIPs would be producing data rather than merely passing through data to the markets for the first time.\137\ Another commenter stated that the SIPs should have mechanisms to determine when they have invalid or delayed market data and thus the ability to halt the dissemination of the Price Bands accordingly.\138\ Finally, because SIP data is slower than data disseminated directly by an exchange, one commenter questioned whether participants co-located to an exchange could calculate Price Band information faster than the rest of the market and use this information to their advantage.\139\ --------------------------------------------------------------------------- \136\ See STA Letter at 4. \137\ See STANY Letter at 5. See also FIF Letter at 5 (noting that it is possible that a trade will be executed at a price within the Price Bands, but will be reported to the SIP after the Price Band has moved and potentially should be studied.) \138\ See SIFMA Letter at 9. \139\ See Themis Letter at 1-2. --------------------------------------------------------------------------- The Participants responded that the Processor is well-suited to carrying out its responsibilities under the Plan and the Participants will monitor the Processor's performance during the pilot.\140\ --------------------------------------------------------------------------- \140\ See Response Letter at 8. --------------------------------------------------------------------------- N. Operating Committee Composition Section III(C) of the Plan provides for each Participant to designate an individual to represent the Participant as a member of an Operating Committee.\141\ No later than the initial date of the Plan, the Operating Committee would be required to designate one member of the Operating Committee to act as the Chair of the Operating Committee. The Operating Committee would monitor the procedures established pursuant to the Plan and advise the Participants with respect to any deficiencies, problems, or recommendations as the Operating Committee may deem appropriate. While the Plan generally provides that amendments to the Plan shall be unanimous, any recommendation for an amendment to the Plan from the Operating Committee that receives an affirmative vote of at least two-thirds of the Participants, but is less than unanimous, would be submitted to the Commission as a request for an amendment to the Plan initiated by the Commission under Rule 608 of Regulation NMS under the Act.\142\ --------------------------------------------------------------------------- \141\ See Section I(J) of the proposed Plan. \142\ 17 CFR 242.608. --------------------------------------------------------------------------- Two commenters suggested that the Operating Committee be supplemented by an advisory committee, made up of a cross-section of users, investors, and agents in the marketplace, that would report to the Operating Committee.\143\ One of these commenters stated that this would achieve due process for the both review and recommendations of altering the Plan.\144\ In the spirit of transparency, the other commenter recommended that the minutes of the Plan committee meetings be made available to interested parties.\145\ Two additional commenters recommended that industry representatives who are not parties to the Plan be added to the Operating Committee of the Plan.\146\ --------------------------------------------------------------------------- \143\ See STA Letter at 4-5; SIFMA Letter at 7. \144\ See STA Letter at 5. \145\ See SIFMA Letter at 7. \146\ See STANY Letter at 5-6; Driscoll Letter at 4 (recommending diverse representation of all key trading groups, retail order execution representation, institutional buy-side representation, representatives of various trading venues and representation of those who focus on small capitalization securities). --------------------------------------------------------------------------- The Participants initially responded that a non-voting advisory committee is unnecessary.\147\ Except with respect to the addition of new Participants to the Plan, the Participants stated that any proposed change in, addition to, or deletion from the Plan would have to be effected by means of a written amendment to the Plan that (1) sets forth the change, addition, or deletion; (2) is executed on behalf of each Participant; and (3) is approved by the SEC pursuant to, or otherwise becomes effective under, Rule 608 of Regulation NMS under the Exchange Act. Thus, any person affected by changes to the Plan would have notice and an opportunity to comment as part of the SEC approval process in accordance with Rule 608.\148\ --------------------------------------------------------------------------- \147\ See Response Letter at 7. \148\ Id. --------------------------------------------------------------------------- As discussed below, however, the Participants recently proposed an amendment to the Plan to create an Advisory Committee to the Operating Committee. Members of the Advisory Committee would have the right to submit their view on Plan matters to the [[Page 33507]] Operating Committee prior to a decision by the Operating Committee on such matters. Such matters may include, but would not be limited to, proposed material amendments to the Plan. The Operating Committee would be required to select at least one representative from each of the following categories to be members of the Advisory Committee: (i) A broker-dealer with a substantial retail investor customer base, (ii) a broker-dealer with a substantial institutional investor customer base, (iii) an alternative trading system, and (iv) an investor.\149\ --------------------------------------------------------------------------- \149\ See Amendment, supra note 13. --------------------------------------------------------------------------- O. Withdrawal of Participants From the Plan Section IX of the Plan provides that a Participant may withdraw from the Plan upon obtaining approval from the Commission and upon providing not less than 30 days written notice to the other participants. Four commenters expressed concern about the withdrawal provision and suggested that Commission require FINRA and all trading centers to participate in the Plan because withdrawal could create problems if only some market centers are part of the Plan.\150\ --------------------------------------------------------------------------- \150\ See FIF Letter at 5; SIFMA Letter at 7; STANY Letter at 5; Molinete Letter at 3. --------------------------------------------------------------------------- P. Implementation Time-Period The Participants proposed that the initial date of the Plan operations be 120 calendar days following the publication of the Commission's order approving the Plan in the Federal Register. The Participants would implement that Plan as a one-year pilot program in two Phases, consistent with Section VIII of the Plan. Phase I of Plan implementation would apply immediately following the initial date of Plan operations; Phase II of the Plan would commence six months after the initial date of the Plan or such earlier date as may be announced by the Processor with at least 30 days notice. As discussed below, the Participants recently proposed an amendment to the Plan that included a new implementation date of February 4, 2013. One commenter stated that the Plan should be implemented as quickly as possible.\151\ Another commenter recommended an implementation date of 12 months instead of 120 days,\152\ while another commenter stated that the Plan should be implemented no earlier than the second quarter of 2012.\153\ --------------------------------------------------------------------------- \151\ See Vanguard Letter at 2. See also ICI Letter at 3 (recommending that ETPs be included in the pilot on an expedited basis). \152\ See FIF Letter at 5-6. \153\ See SIFMA Letter at 9. See also Molinete Letter at 5 (stating that the 120-day implementation time period is too ambitious). --------------------------------------------------------------------------- Prior to the implementation of Phase II of the Plan, one commenter recommended that the Participants analyze empirical evidence derived from Phase I.\154\ Another commenter recommended that the Participants seek comment before implementing the Plan on a permanent basis.\155\ Yet another commenter stated that the Commission should have to approve Phase II of the Plan prior to its implementation.\156\ --------------------------------------------------------------------------- \154\ See Deutsche Bank Letter at 4. \155\ See SIFMA Letter at 9. \156\ See STANY Letter at 7. --------------------------------------------------------------------------- Q. Comments on Rule-Making Process of the Plan The Participants filed the Plan with the Commission pursuant to Section 11A of the Act \157\ and Rule 608 thereunder.\158\ The Commission solicited comments on the Plan from interested persons. One commenter stated that the process for the creation of a new NMS plan circumvented the formal notice and comment process provided for in The Administrative Procedure Act.\159\ The commenter stated that the existence of confidentiality agreements among the Participants in developing the proposal has negative implications for transparency in the rulemaking process.\160\ --------------------------------------------------------------------------- \157\ 15 U.S.C. 78k-1. \158\ 17 CFR 242.608. \159\ Pub. Law 79-404, 5 U.S.C. 500 et seq. See Driscoll Letter at 1. \160\ Id (stating that the narrow focus of the group that developed the regulation may have also allowed some opportunities to increase competition between exchanges to have been overlooked). --------------------------------------------------------------------------- Another commenter questioned whether there is a need for a Commission rule instead of an NMS plan and stated that ongoing and direct involvement of the Commission will be important to efficient and effective resolution of interpretive questions relating to the Plan and the reasonable policies and procedures.\161\ The same commenter also stated that self-regulatory organizations will need to adopt rules specifying how they plan to handle orders that have been routed to them when such orders present display or execution issues under the Plan.\162\ --------------------------------------------------------------------------- \161\ See SIFMA Letter at 7. \162\ Id. at 9. --------------------------------------------------------------------------- Finally, one commenter stated that a cost-benefit analysis of the Plan should be conducted to address the anticipated costs of implementing the Plan, the parties that would pay for new systems, whether processors would be allowed to charge more than their costs for the new data components of the consolidated feeds, and the incremental benefits that would be incurred over the existing trading pause rules if the Plan were approved.\163\ --------------------------------------------------------------------------- \163\ See Scottrade Letter at 4. --------------------------------------------------------------------------- V. Amendment to the Plan On May 24, 2012, in response to the comments received on the proposed Plan, the Participants submitted an amendment that proposed several changes to the Plan.\164\ First, the participants proposed to amend the Plan to allow transactions that are exempt under Rule 611 of Regulation NMS \165\, and which do not update the last sale price (except if solely because the transaction was reported late), to execute outside of the price bands.\166\ --------------------------------------------------------------------------- \164\ See Amendment, supra note 13. \165\ 17 CFR 242.611. \166\ See Amendment, supra note 13. --------------------------------------------------------------------------- Second, the Participants proposed to amend the Plan to provide for a 20% price band for Tier 1 and Tier 2 stocks with a Reference Price equal to $0.75 and up to and including $3.00. The Participants also proposed a conforming amendment for Tier 1 and Tier 2 stocks with a Reference Price less than $0.75. The Percentage Parameters for these stocks would be the lesser of (a) $0.15 or (b) 75%.\167\ As initially proposed, those Percentage Parameters would apply to Tier 1 and Tier 2 stocks with a Reference Price less than $1.00. --------------------------------------------------------------------------- \167\ Id. --------------------------------------------------------------------------- Third, the Participants proposed to amend the Plan to exclude rights and warrants from the Plan, consistent with the current single- stock circuit breaker pilot.\168\ --------------------------------------------------------------------------- \168\ Id. --------------------------------------------------------------------------- Fourth, the Participants proposed to amend the Plan to provide for the creation of an Advisory Committee to the Operating Committee. As set forth in greater detail in the amendment, the Operating Committee would be required to select at least one representative from each of the following categories to be members of the Advisory Committee: (i) A broker-dealer with a substantial retail investor customer base, (ii) a broker-dealer with a substantial institutional investor customer base, (iii) an alternative trading system, and (iv) an investor.\169\ Members of the Advisory Committee would have the right to submit their view on Plan matters to the Operating Committee prior to a decision by the Operating Committee on such matters. Such matters could include, but would not be limited to, proposed material amendments to the Plan. --------------------------------------------------------------------------- \169\ Id. --------------------------------------------------------------------------- Fifth, the Participants proposed to amend the Plan to provide for a manual [[Page 33508]] override functionality when, for example, the National Best Bid for an NMS Stock is below the Lower Price Band, the NMS Stock has not entered the Limit State, and the Primary Listing Exchange has determined that trading in that stock has sufficiently deviated from its normal trading characteristics such that a trading pause would promote the Plan's core purpose of addressing extraordinary market volatility. Upon making this determination, the Primary Listing Exchange would have the ability to declare a trading pause in that stock.\170\ --------------------------------------------------------------------------- \170\ Id. --------------------------------------------------------------------------- Sixth, the Participants proposed a new implementation date of February 4, 2013. The Participants stated that this date would provide appropriate time to develop and test the technology necessary to implement the Plan, including market-wide testing. Finally, the Participants proposed to amend the Plan to require the Participants to review and update, on a semi-annual basis, the list of ETPs included in Tier I of the Plan, and re-stated the criteria by which ETPs would selected for inclusion in Tier I.\171\ --------------------------------------------------------------------------- \171\ For example, ETPs, including inverse ETPs, that trade over $2,000,000 consolidated average daily volume would be included in Tier I, as would ETPs that do not meet this volume criterion, but track similar benchmarks. --------------------------------------------------------------------------- The Participants also proposed technical changes to the Plan. For example, the Participants clarified that Regular Trading Hours could end earlier than 4:00 p.m. ET in the case of an early scheduled close. The Participants also provided that Participants may re-transmit the price bands calculated and disseminated by the Processor. Finally, the Participants clarified that the Reference Price used in determining which Percentage Parameter is applicable during the trading day would be based on the closing price of the subject security on the Primary Listing Exchange on the previous trading day or, if no closing price exists, the last sale on the Primary Listing Exchange reported by the Processor. The Participants also proposed to amend the Plan in order to collect and provide to the Commission various data and analysis throughout the duration of the pilot period. Specifically, the Participants will provide summary statistics to the Commission, including data covering how often stocks enter the Limit State, and how often stocks enter a trading pause as a result of the limit up-limit down mechanism. The Participants will also examine certain parameters of the limit up-limit down mechanism, including the appropriateness of the proposed price bands, and the appropriateness of the duration of the Limit State. Finally, the Participants will provide raw data to the Commission, including the record of every limit price, the record of every Limit State, and the record of every trading pause. VI. Discussion and Commission Findings A. Section 11A of the Act In 1975, Congress directed the Commission, through the enactment of Section 11A of the Act,\172\ to facilitate the establishment of a national market system to link together the individual markets that trade securities. Congress found the development of a national market system to be in the public interest and appropriate for the protection of investors and the maintenance of fair and orderly markets to assure fair competition among the exchange markets.\173\ Section 11A(a)(3)(B) of the Act directs the Commission, ``by rule or order, to authorize or require self-regulatory organizations to act jointly with respect to matters as to which they share authority under this title in planning, developing, operating, or regulating a national market system (or a subsystem thereof) or one or more facilities.'' \174\ The Commission's approval of a national market system plan is required to be conditioned upon a finding that the plan is ``necessary or appropriate in the public interest, for the protection of investors and the maintenance of fair and orderly markets, to remove impediments to, and perfect the mechanism of, a national market system, or otherwise in furtherance of the purposes of the Act.'' \175\ --------------------------------------------------------------------------- \172\ 15 U.S.C. 78k-1. \173\ 15 U.S.C. 78k-1(a)(1)(C). \174\ 15 U.S.C. 78k-1(a)(3)(B). \175\ 17 CFR 242.608(b)(2). See also 15 U.S.C. 78k-1(a). --------------------------------------------------------------------------- After carefully considering the proposed Plan and the issues raised by the comment letters, the Commission has determined to approve the Plan, as amended by the Participants, pursuant to Section 11A(a)(3)(B) of the Act \176\ and Rule 608.\177\ The Commission believes that the Plan is reasonably designed to prevent potentially harmful price volatility, including severe volatility of the kind that occurred on May 6, 2010.\178\ The Plan should thereby help promote the goals of investor protection and fair and orderly markets. The Commission also believes that the Plan is a prudent replacement of the single-stock circuit breaker that is currently in effect, and that it is appropriately being introduced on a pilot basis. The pilot period will allow the public, the Participants, and the Commission to assess the operation of the Plan and whether the Plan should be modified prior to approval on a permanent basis. --------------------------------------------------------------------------- \176\ 15 U.S.C. 78k-1(a)(3)(B). \177\ 17 CFR 242.608. In approving this Plan, the Commission has considered the proposed rule's impact on efficiency, competition, and capital formation. See 15 U.S.C. 78c(f). \178\ The Commission and the Participants have conducted simulations on historical data to examine how a limit up-limit down mechanism might work. The simulations generally support the structure of the proposal. In particular, the proposal would reduce, but not eliminate, extreme short-term price changes, and would not result in an excessive number of trading pauses. Commission staff, for example, conducted a simulation that suggested that the percentage limits should be larger at the open and close and that the percentage limits should be larger for lower priced stocks. In addition, the simulation suggested that most trades occurring outside of the bands are reversed quickly, providing support for the notion that a limit state may help avoid unnecessary trading pauses. The simulation also showed that an average of slightly more than one large index stock would have a trading pause every four days, based on the structure of the simulation, which was not the same as the proposed structure. A follow-up analysis using the proposed structure showed that only one large index stock would have a trading pause in the three months analyzed. The NYSE staff also simulated the proposed limit up-limit down mechanism to examine how the mechanism would have worked on May 6th, 2010. Given time constraints, the simulation was limited to the price band aspect of the proposal and did not consider the limit state or trading pause provisions of the proposal. This simulation suggested that the price bands alone would have reduced the size of the flash crash significantly, but stocks would still have experienced large five-minute declines. For example, on May 6th, Accenture experienced a five-minute decline of 99.98%. The simulation suggests that if there had been price bands in place on May 6th, the most extreme five-minute decline in Accenture might have been 6.43%. While the Commission recognizes that this is still a significant decline, it would have much less than the actual decline. The NYSE simulation also examined the ability of the limit up- limit down price bands to reduce extreme positive and negative returns. In the Tier 1 stocks priced more than $1.00, the price bands would eliminate five-minute returns more extreme than 10% and -10%. The price bands would reduce but not eliminate these extreme five-minute returns in other stocks. A sensitivity analysis comparing the proposed price limit percentages to alternative ones suggested that the proposed bands behave at least as well as the alternatives examined. --------------------------------------------------------------------------- As discussed above, commenters raised a variety of thoughtful concerns about the proposal and recommended certain changes. Some of the recommended changes were incorporated in the Amendment. As discussed further below, other comments raised important issues that are difficult to evaluate fully in the absence of practical experience with the Plan. These issues will warrant close consideration during the pilot period. The Commission believes that it is consistent with the Act to approve the [[Page 33509]] Plan on a pilot basis at this time because the Plan reflects the considered judgments of the Participants on operational issues and clearly represents a significant step forward that builds upon the experience with the current single-stock circuit breaker. The limit up- limit down mechanism set forth in the Plan approved today and the single-stock circuit breaker are broadly similar in some respects. For example, both mechanisms calculate a reference price that is based on a rolling five-minute price band, and both mechanisms incorporate a five- minute trading pause, followed by a reopening auction on the Primary Listing Exchange. The Plan, however, provides a more finely calibrated mechanism than that of the current single-stock circuit breaker. For example, the single-stock circuit breaker is triggered by trades that occur at or outside of the price band, and erroneous trades have triggered trading halts throughout the current pilot. In contrast, under the Plan, all trading centers in NMS stocks, including both those operated by Participants and those operated by members of Participants, are required to establish policies and procedures that are reasonably designed to prevent trades at prices outside of the price bands. In addition, quotes outside of the price bands will be marked as non- executable. Given that trades should not occur outside of the price bands, the Commission believes that the Plan is reasonably designed to reduce the number of erroneous trades in comparison to the current single-stock circuit breaker. Moreover, Limit States under the Plan (and, ultimately, trading pauses) will be triggered by movements in the National Best Bid or the National Best Offer, rather than single trades. These quoting-based triggers are designed to be more stable and reliable indicators of a significant market event than the single trades that currently can trigger a single stock circuit breaker. The result of this change should be to reduce the frequency of Limit States (and, ultimately, trading pauses) to those circumstances that truly warrant a check on continuous trading. In contrast to the current single-stock circuit breaker, the Plan also features a fifteen-second Limit State that precedes a trading pause. In those instances where the movement of, for example, the National Best Bid below the Lower Price Band is due to a momentary gap in liquidity, rather than a fundamental price move, the Limit State is reasonably designed to allow the market to quickly correct and resume normal trading, without resorting to a trading pause. Because a Limit State, rather than a trading pause, may be sufficient to resolve some of these scenarios, the corresponding price bands can be narrower than in the single-stock circuit breaker. As such, the Commission believes that the Plan is reasonably designed to be a more finely calibrated mechanism than the current single-stock circuit breaker in guarding against market volatility.\179\ --------------------------------------------------------------------------- \179\ The Commission also finds that the Plan is consistent with the requirements of Rule 602 under Regulation NMS. Under that rule, bids and offers must be firm, i.e., brokers and dealers are obligated to execute any order to buy or sell a subject security presented to it by another broker or dealer at a price at least as favorable to such buyer or seller as that broker or dealer's published bid or published offer in any amount up to its published quotation size. Similarly, the best bids and offers collected by national securities exchanges must also be firm. See 17 CFR 242.602. However, Rule 602(a)(3)(i) relieves exchanges of their obligation to collect and make available bids and offers (which are firm) if the existence of ``unusual market conditions'' makes those bids and offers no longer accurately reflective of the current state of the market. This provision also relieves brokers and dealers of their corresponding obligation to submit firm quotes. The Commission believes that, when the National Best Bid (Offer) crosses the Lower (Upper) Price Band, and such quote becomes non-executable, an unusual market condition exists for purposes of Rule 602. To the extent that this scenario constitutes an unusual market condition, the broker or dealer could submit a quote that is outside of the applicable price band, and is thus not firm (as it is non- executable), and the exchange could collect and display such quote, without violating Rule 602. The Commission notes, however, that the firmness requirement continues to apply to quotes at or within the price bands that are submitted by brokers or dealers and collected by exchanges, as such quotes are executable. --------------------------------------------------------------------------- While the price bands in the Plan are reasonably designed to be more finely calibrated than the current single-stock circuit breaker, the Commission notes that the Plan is also designed to accommodate more fundamental price moves, albeit in a manner that lessens the velocity of such moves. In this regard, the Commission notes that the Plan provides that the price bands shall not apply to single-priced re- openings, which allows for the stock to enter a trading pause and reopen at a price that is potentially significantly above or below its previous price. The Commission finds that this mechanism is reasonably designed to allow for more fundamental price moves to occur. To the extent that a reopening only may occur following a five-minute trading pause, however, the Plan is still reasonably designed to reduce the velocity of more significant price moves. The Amendment improves the initial proposal by addressing a number of concerns raised by commenters. Specifically, it excludes transactions that are exempt under Rule 611 of Regulation NMS and do not update the last sale price (except if solely because the transaction was reported late), from the requirement that such transactions occur within the price bands. This exclusion addresses commenters' concerns that such transactions often are executed at prices unrelated to the current market and do not have the capacity to initiate or exacerbate volatility. In response to the concerns of commenters about the potential for bids or offers in an NMS stock to become unexecutable without triggering a Limit State, the Amendment authorizes the Primary Listing Exchange manually to declare a trading pause in these circumstances. This mechanism should help ensure that the market for a stock does not remain impaired for an indefinite period of time, while providing the Primary Listing Exchange with the discretion to determine whether such impairment is inconsistent with the stock's normal trading characteristics. The Amendment assigns wider price bands for Tier 1 and Tier 2 securities that are priced between $0.75 and $3.00 that are reasonably designed to reflect more appropriately the characteristics of stocks that trade in that price range. Similarly, the Amendment excludes all rights and warrants from the Plan, which reflects the trading characteristics of such securities and is consistent with the scope of the current single-stock circuit breaker pilot. The Amendment's provision for evaluating, on a semi-annual basis, the ETPs that are included in Tier I helps assure that ETPs meeting the criteria for inclusion are appropriately included in Tier I, and vice versa. The Amendment also extends the implementation date to February 4, 2013. This extension of time should provide appropriate time to develop and test the technology necessary to implement the Plan, including market-wide testing. Finally, in response to concerns expressed by commenters, the Amendment establishes an Advisory Committee to the Operating Committee composed of a broad cross-section of market participants. The Advisory Committee members will have the right to submit their views on Plan matters to the Operating Committee and thereby engage in the ongoing assessment of Plan operations and formulation of future proposed amendments to the Plan. One serious concern raised by comments was the interaction between the limit up-limit down mechanism and the market-wide circuit breakers that apply across all securities and securities-related products, particularly [[Page 33510]] during a ``macro market event'' that affects a large number of securities and securities-related products. The Commission is approving separately today on a pilot basis SRO proposals to revise these market- wide circuit breakers and make them more meaningful in today's high- speed electronic markets.\180\ These SRO rules include both tighter parameters and shorter halt periods. The Commission recognizes the potential for limit up-limit down trading halts in many securities to affect both the calculation of broader indexes and the trading in products related to such indexes. Nevertheless, it believes that the need for protection against extraordinary volatility in individual equities is essential for both investors in such listed equities and for their listed companies. Accordingly, it is approving the Plan on a pilot basis, but welcomes comments during the pilot period on ways that the Plan could be improved to address potential problems in its interaction with market-wide circuit breakers. The Commission also is accepting comment during the pilot period for the market-wide circuit breakers on ways to improve them to address this question on their interaction with the Plan. --------------------------------------------------------------------------- \180\ See Securities Exchange Act Release No. 67090 (May 31, 2012) (File Nos. SR-BATS-2011-038; SR-BYX-2011-025; SR-BX-2011-068; SR-CBOE-2011-087; SR-C2-2011-024; SR-CHX-2011-30; SR-EDGA-2011-31; SR-EDGX-2011-30; SR-FINRA-2011-054; SR-ISE-2011-61; SR-NASDAQ-2011- 131; SR-NSX-2011-11; SR-NYSE-2011-48; SR-NYSEAmex-2011-73; SR- NYSEArca-2011-68; SR-Phlx-2011-129). --------------------------------------------------------------------------- The Commission notes that the Participants did not amend the Plan to incorporate some of the recommendations to modify the operational details of the Plan, including the duration of the Limit State, the calculation of the Reference Price, the application of the price bands at the open and the close, the criteria required to enter and exit the Limit State, and the display of quotes outside of the price bands. The Commission recognizes the thoughtfulness of the comments that put forward such recommendations, and indeed believes they raise valid concerns that warrant close scrutiny during the pilot period. At this time, however, the Commission believes that it is consistent with the Act to accept the considered collective judgment of the Participants on these complex issues, particularly given their expertise and responsibility for operating markets on a daily basis.\181\ --------------------------------------------------------------------------- \181\ The Commission notes that one of the concerns of requiring the National Best Offer (Bid) to trigger the Limit Down (Up) may be partially alleviated by one of the amendments to the Plan. Specifically, if the National Best Bid is outside of the lower price band and is thus non-executable, while the offer remains within the price bands, the stated concern is that the market for that stock is impaired, perhaps for an indefinite period of time, while the stock has not entered the Limit State. The Commission believes that the addition of a manual override, as proposed by the Participants in the amendment to the Plan, may, at least partially, alleviate this concern. --------------------------------------------------------------------------- Approving the Plan on a pilot basis will allow the Participants and the public to gain valuable practical experience with Plan operations during the pilot period. This experience should prove invaluable in assessing whether further modifications of the Plan are necessary or appropriate prior to final approval. The Participants also have agreed to provide the Commission with a significant amount of data bearing on operational questions that should assist the Commission in its evaluation of Plan operations. Finally, the Commission welcomes additional comments, and empirical evidence, on the Plan during the pilot period to further assist it in its evaluation of the Plan. Of course, any final approval of the Plan would require a proposed amendment of the Plan, and such amendment will provide an opportunity for public comment prior to further Commission action. To the extent that the Participants did not amend the Plan to reflect other operational or procedural concerns, the Commission believes that those suggestions and concerns were generally considered by the Participants in developing a uniform proposal that would not be excessively complicated and yet could still provide important benefits to the markets. For example, one commenter noted that allowing the primary listing market to control the re-opening process in the first five minutes following a trading pause may confer a competitive advantage upon that market. The Commission notes that this aspect of the Plan is consistent with the current procedure for re-opening the market following a trading pause that has been triggered under the single-stock circuit breaker pilot. Another commenter suggested that a market-wide limit up-limit down mechanism was more appropriately developed through Commission rulemaking than through an NMS plan. While a Commission rulemaking may be an appropriate means for developing such a mechanism, the Commission believes that an NMS plan, which was the means selected by the Participants here, is equally appropriate, particularly given the Participants' expertise in the trading characteristics in individual securities and the operation of market systems. Some commenters expressed concern over the provision in the Plan governing withdrawal of Participants from the Plan. The Commission notes that withdrawing from the Plan would require an amendment to the Plan, and Commission approval of that amendment. Given the importance of applying a limit up-limit down mechanism uniformly throughout the market, the Commission would anticipate approving such withdrawal from the Plan only if the Participant seeking to withdraw from the Plan ceased to trade NMS securities. One commenter suggested that a cost-benefit analysis of the Plan should be conducted. The Commission notes that market participants are welcome to submit additional comments and empirical evidence during the pilot period with respect to, among other things, the operation of the limit up-limit down mechanism, its effectiveness in achieving its intended goals, and the costs associated therewith. The Commission will take such comments into account in considering whether to approve any amendment, in accordance with Rule 608 of Regulation NMS, that proposes to make the Plan permanent. As such, the Commission believes that the Plan is consistent with the Act, notwithstanding such comments, and that it is reasonably designed to achieve its objective of reducing extraordinary market volatility. Given that the Plan is being approved on a pilot basis, the Commission expects that the Participants will monitor the scope and operation of the Plan and study the data produced during that time with respect to such issues, and will propose any modifications to the Plan that may be necessary or appropriate. Similarly, the Commission expects that the Participants will propose any modifications to the Plan that may be necessary or appropriate in response to the data being gathered by the Participants during the pilot.\182\ --------------------------------------------------------------------------- \182\ The Commission notes that some of the comments focused on the relation between the Plan, and other, exchange-specific volatility mechanisms, including the NYSE Liquidity Replenishment Points, and the Nasdaq Volatility Guard. While a stated purpose of the Plan is to replace the current single-stock circuit breaker, the Commission is also aware of the potential for unnecessary complexity that could result if the Plan were adopted, and exchange-specific volatility mechanisms were retained. To this end, the Commission expects that, upon implementation of the Plan, such exchange- specific volatility mechanisms would be discontinued by the respective exchanges. In that regard, the Commission notes that one such mechanism, the Nasdaq Volatility Guard, is currently set to expire on the earlier of July 31, 2012, or the date on which the Plan is approved by the Commission. See Securities Exchange Act Release No. 66275 (January 30, 2012), 77 FR 5606 (February 3, 2012) (SR-Nasdaq-2012-019). --------------------------------------------------------------------------- [[Page 33511]] VII. Conclusion It is therefore ordered, pursuant to Sections 11A of the Act,\183\ and the rules thereunder, that the Plan (File No. 4-631), as amended, is approved on a one-year pilot basis and declared effective, and the Participants are authorized to act jointly to implement the Plan as a means of facilitating a national market system. --------------------------------------------------------------------------- \183\ 15 U.S.C. 78k-1. By the Commission. Elizabeth M. Murphy, Secretary. Exhibit A Plan To Address Extraordinary Market Volatility Submitted to the Securities and Exchange Commission Pursuant to Rule 608 of Regulation NMS Under the Securities Exchange Act of 1934 Table of Contents Section Page Preamble....................................................... 1 I. Definitions................................................. 2 II. Parties.................................................... 4 III. Amendments to Plan........................................ 7 IV. Trading Center Policies and Procedures..................... 8 V. Price Bands................................................. 9 VI. Limit Up-Limit Down Requirements........................... 12 VII. Trading Pauses............................................ 14 VIII. Implementation........................................... 15 IX. Withdrawal from Plan....................................... 16 X. Counterparts and Signatures................................. 16 Appendix A--Percentage Parameters.............................. 18 Appendix A--Schedule 1......................................... 21 Appendix B--Data............................................... 33 Preamble The Participants submit to the SEC this Plan establishing procedures to address extraordinary volatility in NMS Stocks. The procedures provide for market-wide limit up-limit down requirements that prevent trades in individual NMS Stocks from occurring outside of the specified Price Bands. These limit up-limit down requirements are coupled with Trading Pauses to accommodate more fundamental price moves. The Plan procedures are designed, among other things, to protect investors and promote fair and orderly markets. The Participants developed this Plan pursuant to Rule 608(a)(3) of Regulation NMS under the Exchange Act, which authorizes the Participants to act jointly in preparing, filing, and implementing national market system plans. I. Definitions (A) ``Eligible Reported Transactions'' shall have the meaning prescribed by the Operating Committee and shall generally mean transactions that are eligible to update the last sale price of an NMS Stock. (B) ``Exchange Act'' means the Securities Exchange Act of 1934, as amended. (C) ``Limit State'' shall have the meaning provided in Section VI of the Plan. (D) ``Limit State Quotation'' shall have the meaning provided in Section VI of the Plan. (E) ``Lower Price Band'' shall have the meaning provided in Section V of the Plan. (F) ``Market Data Plans'' shall mean the effective national market system plans through which the Participants act jointly to disseminate consolidated information in compliance with Rule 603(b) of Regulation NMS under the Exchange Act. (G) ``National Best Bid'' and ``National Best Offer'' shall have the meaning provided in Rule 600(b)(42) of Regulation NMS under the Exchange Act. (H) ``NMS Stock'' shall have the meaning provided in Rule 600(b)(47) of Regulation NMS under the Exchange Act. (I) ``Opening Price'' shall mean the price of a transaction that opens trading on the Primary Listing Exchange, or, if the Primary Listing Exchange opens with quotations, the midpoint of those quotations. (J) ``Operating Committee'' shall have the meaning provided in Section III(C) of the Plan. (K) ``Participant'' means a party to the Plan. (L) ``Plan'' means the plan set forth in this instrument, as amended from time to time in accordance with its provisions. (M) ``Percentage Parameter'' shall mean the percentages for each tier of NMS Stocks set forth in Appendix A of the Plan. (N) ``Price Bands'' shall have the meaning provided in Section V of the Plan. (O) ``Primary Listing Exchange'' shall mean the Participant on which an NMS Stock is listed. If an NMS Stock is listed on more than one Participant, the Participant on which the NMS Stock has been listed the longest shall be the Primary Listing Exchange. (P) ``Processor'' shall mean the single plan processor responsible for the consolidation of information for an NMS Stock pursuant to Rule 603(b) of Regulation NMS under the Exchange Act. (Q) ``Pro-Forma Reference Price'' shall have the meaning provided in Section V(A)(2) of the Plan. (R) ``Regular Trading Hours'' shall have the meaning provided in Rule 600(b)(64) of Regulation NMS under the Exchange Act. For purposes of the Plan, Regular Trading Hours can end earlier than 4:00 p.m. ET in the case of an early scheduled close. (S) ``Regulatory Halt'' shall have the meaning specified in the Market Data Plans. (T) ``Reference Price'' shall have the meaning provided in Section V of the Plan. (U) ``Reopening Price'' shall mean the price of a transaction that reopens [[Page 33512]] trading on the Primary Listing Exchange following a Trading Pause or a Regulatory Halt, or, if the Primary Listing Exchange reopens with quotations, the midpoint of those quotations. (V) ``SEC'' shall mean the United States Securities and Exchange Commission. (W) ``Straddle State'' shall have the meaning provided in Section VII(A)(2) of the Plan. (X) ``Trading center'' shall have the meaning provided in Rule 600(b)(78) of Regulation NMS under the Exchange Act. (Y) ``Trading Pause'' shall have the meaning provided in Section VII of the Plan. (Z) ``Upper Price Band'' shall have the meaning provided in Section V of the Plan. II. Parties (A) List of Parties The parties to the Plan are as follows: (1) BATS Exchange, Inc., 8050 Marshall Drive, Lenexa, Kansas 66214. (2) BATS Y-Exchange, Inc., 8050 Marshall Drive, Lenexa, Kansas 66214. (3) Chicago Board Options Exchange, Incorporated, 400 South LaSalle Street, Chicago, Illinois 60605. (4) Chicago Stock Exchange, Inc., 440 South LaSalle Street, Chicago, Illinois 60605. (5) EDGA Exchange, Inc., 545 Washington Boulevard, Sixth Floor, Jersey City, NJ 07310. (6) EDGX Exchange, Inc., 545 Washington Boulevard, Sixth Floor, Jersey City, NJ 07310. (7) Financial Industry Regulatory Authority, Inc., 1735 K Street, NW., Washington, DC 20006. (8) NASDAQ OMX BX, Inc., One Liberty Plaza, New York, New York 10006. (9) NASDAQ OMX PHLX LLC, 1900 Market Street, Philadelphia, Pennsylvania 19103. (10) The Nasdaq Stock Market LLC, 1 Liberty Plaza, 165 Broadway, New York, NY 10006. (11) National Stock Exchange, Inc., 101 Hudson, Suite 1200, Jersey City, NJ 07302. (12) New York Stock Exchange LLC, 11 Wall Street, New York, New York 10005. (13) NYSE MKT LLC, 20 Broad Street, New York, New York 10005. (14) NYSE Arca, Inc., 100 South Wacker Drive, Suite 1800, Chicago, IL 60606. (B) Compliance Undertaking By subscribing to and submitting the Plan for approval by the SEC, each Participant agrees to comply with and to enforce compliance, as required by Rule 608(c) of Regulation NMS under the Exchange Act, by its members with the provisions of the Plan. To this end, each Participant shall adopt a rule requiring compliance by its members with the provisions of the Plan, and each Participant shall take such actions as are necessary and appropriate as a participant of the Market Data Plans to cause and enable the Processor for each NMS Stock to fulfill the functions set forth in this Plan. (C) New Participants The Participants agree that any entity registered as a national securities exchange or national securities association under the Exchange Act may become a Participant by: (1) becoming a participant in the applicable Market Data Plans; (2) executing a copy of the Plan, as then in effect; (3) providing each then-current Participant with a copy of such executed Plan; and (4) effecting an amendment to the Plan as specified in Section III(B) of the Plan. (D) Advisory Committee (1) Formation. Notwithstanding other provisions of this Plan, an Advisory Committee to the Plan shall be formed and shall function in accordance with the provisions set forth in this section. (2) Composition. Members of the Advisory Committee shall be selected for two-year terms as follows: (A) Advisory Committee Selections. By affirmative vote of a majority of the Participants, the Participants shall select at least one representatives from each of the following categories to be members of the Advisory Committee: (1) A broker-dealer with a substantial retail investor customer base; (2) a broker-dealer with a substantial institutional investor customer base; (3) an alternative trading system; and (4) an investor. (3) Function. Members of the Advisory Committee shall have the right to submit their views to the Operating Committee on Plan matters, prior to a decision by the Operating Committee on such matters. Such matters shall include, but not be limited to, proposed material amendments to the Plan. (4) Meetings and Information. Members of the Advisory Committee shall have the right to attend meetings of the Operating Committee and to receive any information concerning Plan matters; provided, however, that the Operating Committee may meet in executive session if, by affirmative vote of a majority of the Participants, the Operating Committee determines that an item of Plan business requires confidential treatment. III. Amendments to Plan (A) General Amendments Except with respect to the addition of new Participants to the Plan, any proposed change in, addition to, or deletion from the Plan shall be effected by means of a written amendment to the Plan that: (1) Sets forth the change, addition, or deletion; (2) is executed on behalf of each Participant; and, (3) is approved by the SEC pursuant to Rule 608 of Regulation NMS under the Exchange Act, or otherwise becomes effective under Rule 608 of Regulation NMS under the Exchange Act. (B) New Participants With respect to new Participants, an amendment to the Plan may be effected by the new national securities exchange or national securities association executing a copy of the Plan, as then in effect (with the only changes being the addition of the new Participant's name in Section II(A) of the Plan) and submitting such executed Plan to the SEC for approval. The amendment shall be effective when it is approved by the SEC in accordance with Rule 608 of Regulation NMS under the Exchange Act or otherwise becomes effective pursuant to Rule 608 of Regulation NMS under the Exchange Act. (C) Operating Committee (1) Each Participant shall select from its staff one individual to represent the Participant as a member of an Operating Committee, together with a substitute for such individual. The substitute may participate in deliberations of the Operating Committee and shall be considered a voting member thereof only in the absence of the primary representative. Each Participant shall have one vote on all matters considered by the Operating Committee. No later than the initial date of Plan operations, the Operating Committee shall designate one member of the Operating Committee to act as the Chair of the Operating Committee. (2) The Operating Committee shall monitor the procedures established pursuant to this Plan and advise the Participants with respect to any deficiencies, problems, or recommendations as the Operating Committee may deem appropriate. The Operating Committee shall establish specifications and procedures for the implementation and operation of the Plan that are consistent with the provisions of this Plan and the Appendixes thereto. With respect to [[Page 33513]] matters in this paragraph, Operating Committee decisions shall be approved by a simple majority vote. (3) Any recommendation for an amendment to the Plan from the Operating Committee that receives an affirmative vote of at least two- thirds of the Participants, but is less than unanimous, shall be submitted to the SEC as a request for an amendment to the Plan initiated by the Commission under Rule 608 of Regulation NMS. IV. Trading Center Policies and Procedures All trading centers in NMS Stocks, including both those operated by Participants and those operated by members of Participants, shall establish, maintain, and enforce written policies and procedures that are reasonably designed to comply with the limit up-limit down requirements specified in Sections VI of the Plan, and to comply with the Trading Pauses specified in Section VII of the Plan. V. Price Bands (A) Calculation and Dissemination of Price Bands (1) The Processor for each NMS stock shall calculate and disseminate to the public a Lower Price Band and an Upper Price Band during Regular Trading Hours for such NMS Stock. The Price Bands shall be based on a Reference Price for each NMS Stock that equals the arithmetic mean price of Eligible Reported Transactions for the NMS stock over the immediately preceding five-minute period (except for periods following openings and reopenings, which are addressed below). If no Eligible Reported Transactions for the NMS Stock have occurred over the immediately preceding five-minute period, the previous Reference Price shall remain in effect. The Price Bands for an NMS Stock shall be calculated by applying the Percentage Parameter for such NMS Stock to the Reference Price, with the Lower Price Band being a Percentage Parameter below the Reference Price, and the Upper Price Band being a Percentage Parameter above the Reference Price. The Price Bands shall be calculated during Regular Trading Hours. Between 9:30 a.m. and 9:45 a.m. ET, and 3:35 p.m. and 4:00 p.m. ET, or in the case of an early scheduled close, during the last 25 minutes of trading before the early scheduled close, the Price Bands shall be calculated by applying double the Percentage Parameters set forth in Appendix A. If a Reopening Price does not occur within ten minutes after the beginning of a Trading Pause, the Price Band, for the first 30 seconds following the reopening after that Trading Pause, shall be calculated by applying triple the Percentage Parameters set forth in Appendix A. (2) The Processor shall calculate a Pro-Forma Reference Price on a continuous basis during Regular Trading Hours, as specified in Section V(A)(1) of the Plan. If a Pro-Forma Reference Price has not moved by 1% or more from the Reference Price currently in effect, no new Price Bands shall be disseminated, and the current Reference Price shall remain the effective Reference Price. When the Pro-Forma Reference Price has moved by 1% or more from the Reference Price currently in effect, the Pro-Forma Reference Price shall become the Reference Price, and the Processor shall disseminate new Price Bands based on the new Reference Price; provided, however, that each new Reference Price shall remain in effect for at least 30 seconds. (B) Openings (1) Except when a Regulatory Halt is in effect at the start of Regular Trading Hours, the first Reference Price for a trading day shall be the Opening Price on the Primary Listing Exchange in an NMS Stock if such Opening Price occurs less than five minutes after the start of Regular Trading Hours. During the period less than five minutes after the Opening Price, a Pro-Forma Reference Price shall be updated on a continuous basis to be the arithmetic mean price of Eligible Reported Transactions for the NMS Stock during the period following the Opening Price (including the Opening Price), and if it differs from the current Reference Price by 1% or more shall become the new Reference Price, except that a new Reference Price shall remain in effect for at least 30 seconds. Subsequent Reference Prices shall be calculated as specified in Section V(A) of the Plan. (2) If the Opening Price on the Primary Listing Exchange in an NMS Stock does not occur within five minutes after the start of Regular Trading Hours, the first Reference Price for a trading day shall be the arithmetic mean price of Eligible Reported Transactions for the NMS Stock over the preceding five minute time period, and subsequent Reference Prices shall be calculated as specified in Section V(A) of the Plan. (C) Reopenings (1) Following a Trading Pause in an NMS Stock, and if the Primary Listing Exchange has not declared a Regulatory Halt, the next Reference Price shall be the Reopening Price on the Primary Listing Exchange if such Reopening Price occurs within ten minutes after the beginning of the Trading Pause, and subsequent Reference Prices shall be determined in the manner prescribed for normal openings, as specified in Section V(B)(1) of the Plan. If such Reopening Price does not occur within ten minutes after the beginning of the Trading Pause, the first Reference Price following the Trading Pause shall be equal to the last effective Reference Price before the Trading Pause. Subsequent Reference Prices shall be calculated as specified in Section V(A) of the Plan. (2) Following a Regulatory Halt, the next Reference Price shall be the Opening or Reopening Price on the Primary Listing Exchange if such Opening or Reopening Price occurs within five minutes after the end of the Regulatory Halt, and subsequent Reference Prices shall be determined in the manner prescribed for normal openings, as specified in Section V(B)(1) of the Plan. If such Opening or Reopening Price has not occurred within five minutes after the end of the Regulatory Halt, the Reference Price shall be equal to the arithmetic mean price of Eligible Reported Transactions for the NMS Stock over the preceding five minute time period, and subsequent Reference Prices shall be calculated as specified in Section V(A) of the Plan. VI. Limit Up-Limit Down Requirements (A) Limitations on Trades and Quotations Outside of Price Bands (1) All trading centers in NMS Stocks, including both those operated by Participants and those operated by members of Participants, shall establish, maintain, and enforce written policies and procedures that are reasonably designed to prevent trades at prices that are below the Lower Price Band or above the Upper Price Band for an NMS Stock. Single-priced opening, reopening, and closing transactions on the Primary Listing Exchange, however, shall be excluded from this limitation. In addition, any transaction that both does not update the last sale price (except if solely because the transaction was reported late) and is excepted or exempt from Rule 611 under Regulation NMS shall be excluded from this limitation. (2) When a National Best Bid is below the Lower Price Band or a National Best Offer is above the Upper Price Band for an NMS Stock, the Processor shall disseminate such National Best Bid or National Best Offer with an appropriate flag identifying it as non-executable. When a National Best Offer is equal to [[Page 33514]] the Lower Price Band or a National Best Bid is equal to the Upper Price Band for an NMS Stock, the Processor shall distribute such National Best Bid or National Best Offer with an appropriate flag identifying it as a ``Limit State Quotation''. (3) All trading centers in NMS Stocks, including both those operated by Participants and those operated by members of Participants, shall establish, maintain, and enforce written policies and procedures that are reasonably designed to prevent the display of offers below the Lower Price Band and bids above the Upper Price Band for an NMS Stock. The Processor shall disseminate an offer below the Lower Price Band or bid above the Upper Price Band that may be submitted despite such reasonable policies and procedures, but with an appropriate flag identifying it as non-executable; provided, however, that any such bid or offer shall not be included in National Best Bid or National Best Offer calculations. (B) Entering and Exiting a Limit State (1) All trading for an NMS Stock shall immediately enter a Limit State if the National Best Offer equals the Lower Price Band and does not cross the National Best Bid, or the National Best Bid equals the Upper Price Band and does not cross the National Best Offer. (2) When trading for an NMS Stock enters a Limit State, the Processor shall disseminate this information by identifying the relevant quotation (i.e., a National Best Offer that equals the Lower Price Band or a National Best Bid that equals the Upper Price Band) as a Limit State Quotation. At this point, the Processor shall cease calculating and disseminating updated Reference Prices and Price Bands for the NMS Stock until either trading exits the Limit State or trading resumes with an opening or re-opening as provided in Section V. (3) Trading for an NMS Stock shall exit a Limit State if, within 15 seconds of entering the Limit State, the entire size of all Limit State Quotations are executed or cancelled. (4) If trading for an NMS Stock exits a Limit State within 15 seconds of entry, the Processor shall immediately calculate and disseminate updated Price Bands based on a Reference Price that equals the arithmetic mean price of Eligible Reported Transactions for the NMS Stock over the immediately preceding five-minute period (including the period of the Limit State). (5) If trading for an NMS Stock does not exit a Limit State within 15 seconds of entry, the Limit State will terminate when the Primary Listing Exchange declares a Trading Pause pursuant to Section VII of the Plan. If trading for an NMS Stock is in a Limit State at the end of Regular Trading Hours, the Limit State will terminate when the Primary Listing Exchange executes a closing transaction in the NMS Stock or five minutes after the end of Regular Trading Hours, whichever is earlier. VII. Trading Pauses (A) Declaration of Trading Pauses (1) If trading for an NMS Stock does not exit a Limit State within 15 seconds of entry during Regular Trading Hours, then the Primary Listing Exchange shall declare a Trading Pause for such NMS Stock and shall notify the Processor. (2) The Primary Listing Exchange may also declare a Trading Pause for an NMS Stock when an NMS Stock is in a Straddle State, which is when National Best Bid (Offer) is below (above) the Lower (Upper) Price Band and the NMS Stock is not in a Limit State, and trading in that NMS Stock deviates from normal trading characteristics such that declaring a Trading Pause would support the Plan's goal to address extraordinary market volatility. The Primary Listing Exchange shall develop policies and procedures for determining when it would declare a Trading Pause in such circumstances. If a Trading Pause is declared for an NMS Stock under this provision, the Primary Listing Exchange shall notify the Processor. (3) The Processor shall disseminate Trading Pause information to the public. No trades in an NMS Stock shall occur during a Trading Pause, but all bids and offers may be displayed. (B) Reopening of Trading During Regular Trading Hours (1) Five minutes after declaring a Trading Pause for an NMS Stock, and if the Primary Listing Exchange has not declared a Regulatory Halt, the Primary Listing Exchange shall attempt to reopen trading using its established reopening procedures. The Trading Pause shall end when the Primary Listing Exchange reports a Reopening Price. (2) The Primary Listing Exchange shall notify the Processor if it is unable to reopen trading in an NMS Stock for any reason other than a significant order imbalance and if it has not declared a Regulatory Halt. The Processor shall disseminate this information to the public, and all trading centers may begin trading the NMS Stock at this time. (3) If the Primary Listing Exchange does not report a Reopening Price within ten minutes after the declaration of a Trading Pause in an NMS Stock, and has not declared a Regulatory Halt, all trading centers may begin trading the NMS Stock. (4) When trading begins after a Trading Pause, the Processor shall update the Price Bands as set forth in Section V(C)(1) of the Plan. (C) Trading Pauses Within Five Minutes of the End of Regular Trading Hours (1) If a Trading Pause for an NMS Stock is declared less than five minutes before the end of Regular Trading Hours, the Primary Listing Exchange shall attempt to execute a closing transaction using its established closing procedures. All trading centers may begin trading the NMS Stock when the Primary Listing Exchange executes a closing transaction. (2) If the Primary Listing Exchange does not execute a closing transaction within five minutes after the end of Regular Trading Hours, all trading centers may begin trading the NMS Stock. VIII. Implementation (A) Phase I (1) Phase I of Plan implementation shall apply immediately following the initial date of Plan operations. (2) During Phase I, the Plan shall apply only to the Tier 1 NMS Stocks identified in Appendix A of the Plan. (3) During Phase I, the first Price Bands for a trading day shall be calculated and disseminated 15 minutes after the start of Regular Trading Hours as specified in Section (V)(A) of the Plan. No Price Bands shall be calculated and disseminated less than 30 minutes before the end of Regular Trading Hours, and trading shall not enter a Limit State less than 25 minutes before the end of Regular Trading Hours. (B) Phase II--Full Implementation Six months after the initial date of Plan operations, or such earlier date as may be announced by the Processor with at least 30 days notice, the Plan shall fully apply (i) to all NMS Stocks; and (ii) beginning at 9:30 a.m. ET, and ending at 4:00 p.m. ET each trading day, or earlier in the case of an early scheduled close or if the Processor disseminates a closing trade for the Primary Listing Exchange. (C) Pilot The Plan shall be implemented on a one-year pilot basis. IX. Withdrawal from Plan If a Participant obtains SEC approval to withdraw from the Plan, such Participant may withdraw from the Plan [[Page 33515]] at any time on not less than 30 days' prior written notice to each of the other Participants. At such time, the withdrawing Participant shall have no further rights or obligations under the Plan. X. Counterparts and Signatures The Plan may be executed in any number of counterparts, no one of which need contain all signatures of all Participants, and as many of such counterparts as shall together contain all such signatures shall constitute one and the same instrument. IN WITNESS THEREOF, this Plan has been executed as of the--day of-- ------2012 by each of the parties hereto. BATS EXCHANGE, INC. BY:-------------------------------------------------------------------- BATS Y-EXCHANGE, INC. BY:-------------------------------------------------------------------- CHICAGO BOARD OPTIONS EXCHANGE, INCORPORATED BY:-------------------------------------------------------------------- CHICAGO STOCK EXCHANGE, INC. BY:-------------------------------------------------------------------- EDGA EXCHANGE, INC. BY:-------------------------------------------------------------------- EDGX EXCHANGE, INC. BY:-------------------------------------------------------------------- FINANCIAL INDUSTRY REGULATORY AUTHORITY, INC. BY:-------------------------------------------------------------------- NASDAQ OMX BX, INC. BY:-------------------------------------------------------------------- NASDAQ OMX PHLX LLC BY:-------------------------------------------------------------------- THE NASDAQ STOCK MARKET LLC BY:-------------------------------------------------------------------- NATIONAL STOCK EXCHANGE, INC. BY:-------------------------------------------------------------------- NEW YORK STOCK EXCHANGE LLC BY:-------------------------------------------------------------------- NYSE MKT LLC BY:-------------------------------------------------------------------- NYSE ARCA, INC. BY:-------------------------------------------------------------------- Appendix A--Percentage Parameters I. Tier 1 NMS Stocks (1) Tier 1 NMS Stocks shall include all NMS Stocks included in the S&P 500 Index, the Russell 1000 Index, and the exchange-traded products (``ETP'') listed on Schedule 1 to this Appendix. Schedule 1 to the Appendix will be reviewed and updated semi-annually based on the fiscal year by the Primary Listing Exchange to add ETPs that meet the criteria, or delete ETPs that are no longer eligible. To determine eligibility for an ETP to be included as a Tier 1 NMS Stock, all ETPs across multiple asset classes and issuers, including domestic equity, international equity, fixed income, currency, and commodities and futures will be identified. Leveraged ETPs will be excluded and the list will be sorted by notional consolidated average daily volume (``CADV''). The period used to measure CADV will be from the first day of the previous fiscal half year up until one week before the beginning of the next fiscal half year. Daily volumes will be multiplied by closing prices and then averaged over the period. ETPs, including inverse ETPs, that trade over $2,000,000 CADV will be eligible to be included as a Tier 1 NMS Stock. To ensure that ETPs that track similar benchmarks but that do not meet this volume criterion do not become subject to pricing volatility when a component security is the subject of a trading pause, non- leveraged ETPs that have traded below this volume criterion, but that track the same benchmark as an ETP that does meet the volume criterion, will be deemed eligible to be included as a Tier 1 NMS Stock. The semi-annual updates to Schedule 1 do not require an amendment to the Plan. The Primary Listing Exchanges will maintain the updated Schedule 1 on their respective Web sites. (2) The Percentage Parameters for Tier 1 NMS Stocks with a Reference Price more than $3.00 shall be 5%. (3) The Percentage Parameters for Tier 1 NMS Stocks with a Reference Price equal to $0.75 and up to and including $3.00 shall be 20%. (4) The Percentage Parameters for Tier 1 NMS Stocks with a Reference Price less than $0.75 shall be the lesser of (a) $0.15 or (b) 75%. (5) The Reference Price used for determining which Percentage Parameter shall be applicable during a trading day shall be based on the closing price of the NMS Stock on the Primary Listing Exchange on the previous trading day, or if no closing price exists, the last sale on the Primary Listing Exchange reported by the Processor. II. Tier 2 NMS Stocks (1) Tier 2 NMS Stocks shall include all NMS Stocks other than those in Tier 1, provided, however, that all rights and warrants are excluded from the Plan. (2) The Percentage Parameters for Tier 2 NMS Stocks with a Reference Price more than $3.00 shall be 10%. (3) The Percentage Parameters for Tier 2 NMS Stocks with a Reference Price equal to $0.75 and up to and including $3.00 shall be 20%. (4) The Percentage Parameters for Tier 2 NMS Stocks with a Reference Price less than $0.75 shall be the lesser of (a) $0.15 or (b) 75%. (5) Notwithstanding the foregoing, the Percentage Parameters for a Tier 2 NMS Stock that is a leveraged ETP shall be the applicable Percentage Parameter set forth in clauses (2), (3), or (4) above, multiplied by the leverage ratio of such product. (6) The Reference Price used for determining which Percentage Parameter shall be applicable during a trading day shall be based on the closing price of the NMS Stock on the Primary Listing Exchange on the previous trading day, or if no closing price exists, the last sale on the Primary Listing Exchange reported by the Processor. Appendix A--Schedule 1 ------------------------------------------------------------------------ Symbol Name ------------------------------------------------------------------------ AAVX......................... ETRACS Daily Short 1-Month S&P 500 VIX Futures ETN AAXJ......................... iShares MSCI All Country Asia ex Japan Index Fund ACWI......................... iShares MSCI ACWI Index Fund ACWX......................... iShares MSCI ACWI ex US Index Fund AGG.......................... iShares Barclays Aggregate Bond Fund AGZ.......................... iShares Barclays Agency Bond Fund ALD.......................... WisdomTree Asia Local Debt Fund AMJ.......................... JPMorgan Alerian MLP Index ETN AMLP......................... Alerian MLP ETF BAB.......................... PowerShares Build America Bond Portfolio BDG.......................... PowerShares DB Base Metals Long ETN BIK.......................... SPDR S&P BRIC 40 ETF BIL.......................... SPDR Barclays Capital 1-3 Month T-Bill ETF BIV.......................... Vanguard Intermediate-Term Bond ETF BKF.......................... iShares MSCI BRIC Index Fund BKLN......................... PowerShares Senior Loan Portfolio BLV.......................... Vanguard Long-Term Bond ETF BND.......................... Vanguard Total Bond Market ETF BNO.......................... United States Brent Oil Fund LP BOND......................... Pimco Total Return ETF BOS.......................... PowerShares DB Base Metals Short ETN [[Page 33516]] BRF.......................... Market Vectors Brazil Small-Cap ETF BSV.......................... Vanguard Short-Term Bond ETF BWX.......................... SPDR Barclays Capital International Treasury Bond ETF BXDB......................... Barclays ETN+short B Leveraged ETN Linked to S&P 500 CEW.......................... WisdomTree Dreyfus Emerging Currency Fund CFT.......................... iShares Barclays Credit Bond Fund CIU.......................... iShares Barclays Intermediate Credit Bond Fund CLY.......................... iShares 10+ Year Credit Bond Fund CORN......................... Teucrium Corn Fund CSJ.......................... iShares Barclays 1-3 Year Credit Bond Fund CVY.......................... Guggenheim Multi-Asset Income ETF CWB.......................... SPDR Barclays Capital Convertible Securities ETF CWI.......................... SPDR MSCI ACWI ex-US ETF CYB.......................... WisdomTree Dreyfus Chinese Yuan Fund DBA.......................... PowerShares DB Agriculture Fund DBB.......................... PowerShares DB Base Metals Fund DBC.......................... PowerShares DB Commodity Index Tracking Fund DBE.......................... PowerShares DB Energy Fund DBO.......................... PowerShares DB Oil Fund DBP.......................... PowerShares DB Precious Metals Fund DBV.......................... PowerShares DB G10 Currency Harvest Fund DEM.......................... WisdomTree Emerging Markets Equity Income Fund DGL.......................... PowerShares DB Gold Fund DGS.......................... WisdomTree Emerging Markets SmallCap Dividend Fund DGZ.......................... PowerShares DB Gold Short ETN DHS.......................... WisdomTree Equity Income Fund DIA.......................... SPDR Dow Jones Industrial Average ETF Trust DJCI......................... E-TRACS UBS AG Dow Jones-UBS Commodity Index Total Return ETN DJP.......................... iPath Dow Jones-UBS Commodity Index Total Return ETN DLN.......................... WisdomTree LargeCap Dividend Fund DOG.......................... ProShares Short Dow30 DON.......................... WisdomTree MidCap Dividend Fund DOO.......................... WisdomTree International Dividend Ex- Financials Fund DTN.......................... WisdomTree Dividend Ex-Financials Fund DVY.......................... iShares Dow Jones Select Dividend Index Fund DWM.......................... WisdomTree DEFA Fund DWX.......................... SPDR S&P International Dividend ETF DXJ.......................... WisdomTree Japan Hedged Equity Fund ECH.......................... iShares MSCI Chile Investable Market Index Fund ECON......................... EGShares Emerging Markets Consumer ETF EDIV......................... SPDR S&P Emerging Markets Dividend ETF EDV.......................... Vanguard Extended Duration Treasury ETF EEB.......................... Guggenheim BRIC ETF EEM.......................... iShares MSCI Emerging Markets Index Fund EFA.......................... iShares MSCI EAFE Index Fund EFG.......................... iShares MSCI EAFE Growth Index EFV.......................... iShares MSCI EAFE Value Index EFZ.......................... ProShares Short MSCI EAFE EIDO......................... iSHARES MSCI Indonesia Investable Market Index Fund ELD.......................... WisdomTree Emerging Markets Local Debt Fund ELR.......................... SPDR Dow Jones Large Cap ETF EMB.......................... iShares JPMorgan USD Emerging Markets Bond Fund EMLC......................... Market Vectors Emerging Markets Local Currency Bond ETF EMM.......................... SPDR Dow Jones Mid Cap ETF EPHE......................... iShares MSCI Philippines Investable Market Index Fund EPI.......................... WisdomTree India Earnings Fund EPP.......................... iShares MSCI Pacific ex-Japan Index Fund EPU.......................... iShares MSCI All Peru Capped Index Fund ERUS......................... iShares MSCI Russia Capped Index Fund EUM.......................... ProShares Short MSCI Emerging Markets EWA.......................... iShares MSCI Australia Index Fund EWC.......................... iShares MSCI Canada Index Fund EWD.......................... iShares MSCI Sweden Index Fund EWG.......................... iShares MSCI Germany Index Fund EWH.......................... iShares MSCI Hong Kong Index Fund EWI.......................... iShares MSCI Italy Index Fund EWJ.......................... iShares MSCI Japan Index Fund EWL.......................... iShares MSCI Switzerland Index Fund EWM.......................... iShares MSCI Malaysia Index Fund EWP.......................... iShares MSCI Spain Index Fund EWQ.......................... iShares MSCI France Index Fund EWS.......................... iShares MSCI Singapore Index Fund [[Page 33517]] EWT.......................... iShares MSCI Taiwan Index Fund EWU.......................... iShares MSCI United Kingdom Index Fund EWW.......................... iShares MSCI Mexico Investable Market Index Fund EWX.......................... SPDR S&P Emerging Markets SmallCap ETF EWY.......................... iShares MSCI South Korea Index Fund EWZ.......................... iShares MSCI Brazil Index Fund EZA.......................... iShares MSCI South Africa Index Fund EZU.......................... iShares MSCI EMU Index Fund FBT.......................... First Trust NYSE Arca Biotechnology Index Fund FCG.......................... First Trust ISE-Revere Natural Gas Index Fund FDL.......................... First Trust Morningstar Dividend Leaders Index FDN.......................... First Trust Dow Jones Internet Index Fund FEX.......................... First Trust Large Cap Core AlphaDEX Fund FEZ.......................... SPDR EURO STOXX 50 ETF FGD.......................... First Trust DJ Global Select Dividend Index Fund FLAT......................... iPath US Treasury Flattener ETN FNX.......................... First Trust Mid Cap Core AlphaDEX Fund FRI.......................... First Trust S&P REIT Index Fund FVD.......................... First Trust Value Line Dividend Index Fund FXA.......................... CurrencyShares Australian Dollar Trust FXB.......................... CurrencyShares British Pound Sterling Trust FXC.......................... CurrencyShares Canadian Dollar Trust FXD.......................... First Trust Consumer Discretionary AlphaDEX Fund FXE.......................... CurrencyShares Euro Trust FXF.......................... CurrencyShares Swiss Franc Trust FXG.......................... First Trust Consumer Staples AlphaDEX Fund FXH.......................... First Trust Health Care AlphaDEX Fund FXI.......................... iShares FTSE China 25 Index Fund FXL.......................... First Trust Technology AlphaDEX Fund FXU.......................... First Trust Utilities AlphaDEX Fund FXY.......................... CurrencyShares Japanese Yen Trust FXZ.......................... First Trust Materials AlphaDEX Fund GAZ.......................... iPath Dow Jones-UBS Natural Gas Subindex Total Return ETN GCC.......................... GreenHaven Continuous Commodity Index Fund GDX.......................... Market Vectors Gold Miners ETF GDXJ......................... Market Vectors Junior Gold Miners ETF GIY.......................... Guggenheim Enhanced Core Bond ETF GLD.......................... SPDR Gold Shares GMF.......................... SPDR S&P Emerging Asia Pacific ETF GNR.......................... SPDR S&P Global Natural Resources ETF GOVT......................... iShares Barclays U.S. Treasury Bond Fund GSG.......................... iShares S&P GSCI Commodity Indexed Trust GSP.......................... iPath GSCI Total Return Index ETN GSY.......................... Guggenheim Enhanced Short Duration Bond ETF GVI.......................... iShares Barclays Intermediate Government/ Credit Bond Fund GWX.......................... SPDR S&P International Small Cap ETF GXC.......................... SPDR S&P China ETF GXG.......................... Global X FTSE Colombia 20 ETF HAO.......................... Guggenheim China Small Cap ETF HDGE......................... Active Bear ETF/The HDV.......................... iShares High Dividend Equity Fund HYD.......................... Market Vectors High Yield Municipal Index ETF HYG.......................... iShares iBoxx $ High Yield Corporate Bond Fund HYS.......................... PIMCO 0-5 Year High Yield Corporate Bond Index Fund IAU.......................... iShares Gold Trust IBB.......................... iShares Nasdaq Biotechnology Index Fund ICF.......................... iShares Cohen & Steers Realty Majors Index Fund ICI.......................... iPath Optimized Currency Carry ETN IDU.......................... iShares Dow Jones US Utilities Sector Index Fund IDV.......................... iShares Dow Jones International Select Dividend Index Fund IDX.......................... Market Vectors Indonesia Index ETF IEF.......................... iShares Barclays 7-10 Year Treasury Bond Fund IEI.......................... iShares Barclays 3-7 Year Treasury Bond Fund IEO.......................... iShares Dow Jones US Oil & Gas Exploration & Production Index Fund IEV.......................... iShares S&P Europe 350 Index Fund IEZ.......................... iShares Dow Jones US Oil Equipment & Services Index Fund IGE.......................... iShares S&P North American Natural Resources Sector Index Fund IGF.......................... iShares S&P Global Infrastructure Index Fund IGOV......................... iShares S&P/Citigroup International Treasury Bond Fund IGS.......................... ProShares Short Investment Grade Corporate IGV.......................... iShares S&P North American Technology- Software Index Fund IHE.......................... iShares Dow Jones US Pharmaceuticals Index Fund [[Page 33518]] IHF.......................... iShares Dow Jones US Healthcare Providers Index Fund IHI.......................... iShares Dow Jones US Medical Devices Index Fund IJH.......................... iShares S&P MidCap 400 Index Fund IJJ.......................... iShares S&P MidCap 400/BARRA Value Index Fund IJK.......................... iShares S&P MidCap 400 Growth Index Fund IJR.......................... iShares S&P SmallCap 600 Index Fund IJS.......................... iShares S&P SmallCap 600 Value Index Fund IJT.......................... iShares S&P SmallCap 600/BARRA Growth Index Fund ILF.......................... iShares S&P Latin America 40 Index Fund INDA......................... iShares MSCI India Index Fund INDY......................... iShares S&P India Nifty 50 Index Fund INP.......................... iPath MSCI India Index ETN IOO.......................... iShares S&P Global 100 Index Fund IPE.......................... SPDR Barclays Capital TIPS ETF ITB.......................... iShares Dow Jones US Home Construction Index Fund ITM.......................... Market Vectors Intermediate Municipal ETF IVE.......................... iShares S&P 500 Value Index Fund IVOO......................... Vanguard S&P Mid-Cap 400 ETF IVOP......................... iPath Inverse S&P 500 VIX Short-Term FuturesTM ETN II IVV.......................... iShares S&P 500 Index Fund/US IVW.......................... iShares S&P 500 Growth Index Fund IWB.......................... iShares Russell 1000 Index Fund IWC.......................... iShares Russell Microcap Index Fund IWD.......................... iShares Russell 1000 Value Index Fund IWF.......................... iShares Russell 1000 Growth Index Fund IWM.......................... iShares Russell 2000 Index Fund IWN.......................... iShares Russell 2000 Value Index Fund IWO.......................... iShares Russell 2000 Growth Index Fund IWP.......................... iShares Russell Midcap Growth Index Fund IWR.......................... iShares Russell Midcap Index Fund IWS.......................... iShares Russell Midcap Value Index Fund IWV.......................... iShares Russell 3000 Index Fund IWW.......................... iShares Russell 3000 Value Index Fund IWY.......................... iShares Russell Top 200 Growth Index Fund IWZ.......................... iShares Russell 3000 Growth Index Fund IXC.......................... iShares S&P Global Energy Sector Index Fund IXG.......................... iShares S&P Global Financials Sector Index Fund IXJ.......................... iShares S&P Global Healthcare Sector Index Fund IXN.......................... iShares S&P Global Technology Sector Index Fund IXP.......................... iShares S&P Global Telecommunications Sector Index Fund IYC.......................... iShares Dow Jones US Consumer Services Sector Index Fund IYE.......................... iShares Dow Jones US Energy Sector Index Fund IYF.......................... iShares Dow Jones US Financial Sector Index Fund IYG.......................... iShares Dow Jones US Financial Services Index Fund IYH.......................... iShares Dow Jones US Healthcare Sector Index Fund IYJ.......................... iShares Dow Jones US Industrial Sector Index Fund IYK.......................... iShares Dow Jones US Consumer Goods Sector Index Fund IYM.......................... iShares Dow Jones US Basic Materials Sector Index Fund IYR.......................... iShares Dow Jones US Real Estate Index Fund IYT.......................... iShares Dow Jones Transportation Average Index Fund IYW.......................... iShares Dow Jones US Technology Sector Index Fund IYY.......................... iShares Dow Jones US Index Fund IYZ.......................... iShares Dow Jones US Telecommunications Sector Index Fund JJC.......................... iPath Dow Jones-UBS Copper Subindex Total Return ETN JJG.......................... iPath Dow Jones-UBS Grains Subindex Total Return ETN JNK.......................... SPDR Barclays Capital High Yield Bond ETF JXI.......................... iShares S&P Global Utilities Sector Index Fund JYN.......................... iPath JPY/USD Exchange Rate ETN KBE.......................... SPDR S&P Bank ETF KBWB......................... PowerShares KBW Bank Portfolio KIE.......................... SPDR S&P Insurance ETF KOL.......................... Market Vectors Coal ETF KRE.......................... SPDR S&P Regional Banking ETF KXI.......................... iShares S&P Global Consumer Staples Sector Index Fund LAG.......................... SPDR Barclays Capital Aggregate Bond ETF LQD.......................... iShares iBoxx Investment Grade Corporate Bond Fund LTPZ......................... PIMCO 15+ Year US TIPS Index Fund LWC.......................... SPDR Barclays Capital Long Term Corporate BondETF MBB.......................... iShares Barclays MBS Bond Fund MBG.......................... SPDR Barclays Capital Mortgage Backed Bond ETF MCHI......................... iShares MSCI China Index Fund MDY.......................... SPDR S&P MidCap 400 ETF Trust [[Page 33519]] MGC.......................... Vanguard Mega Cap 300 ETF MGK.......................... Vanguard Mega Cap 300 Growth ETF MINT......................... PIMCO Enhanced Short Maturity Strategy Fund MLPI......................... UBS E-TRACS Alerian MLP Infrastructure ETN MLPN......................... Credit Suisse Cushing 30 MLP Index ETN MOO.......................... Market Vectors Agribusiness ETF MUB.......................... iShares S&P National Municipal Bond Fund MXI.......................... iShares S&P Global Materials Sector Index Fund MYY.......................... ProShares Short MidCap 400 NKY.......................... MAXIS Nikkei 225 Index Fund ETF OEF.......................... iShares S&P 100 Index Fund OIH.......................... Market Vectors Oil Service ETF OIL.......................... iPath Goldman Sachs Crude Oil Total Return Index ETN PALL......................... ETFS Physical Palladium Shares PBJ.......................... Powershares Dynamic Food & Beverage Portfolio PCEF......................... PowerShares CEF Income Composite Portfolio PCY.......................... PowerShares Emerging Markets Sovereign Debt Portfolio PDP.......................... Powershares DWA Technical Leaders Portfolio PEY.......................... PowerShares High Yield Equity Dividend Achievers Portfolio PFF.......................... iShares S&P US Preferred Stock Index Fund PFM.......................... PowerShares Dividend Achievers Portfolio PGF.......................... PowerShares Financial Preferred Portfolio PGX.......................... PowerShares Preferred Portfolio PHB.......................... PowerShares Fundamental High Yield Corporate Bond Portfolio PHO.......................... PowerShares Water Resources Portfolio PHYS......................... Sprott Physical Gold Trust PID.......................... PowerShares International Dividend Achievers Portfolio PIE.......................... PowerShares DWA Emerging Markets Technical Leaders Portfolio PIN.......................... PowerShares India Portfolio PJP.......................... Powershares Dynamic Pharmaceuticals Portfolio PLW.......................... PowerShares 1-30 Laddered Treasury Portfolio PPH.......................... Market Vectors Pharmaceutical ETF PPLT......................... ETFS Platinum Trust PRF.......................... Powershares FTSE RAFI US 1000 Portfolio PRFZ......................... PowerShares FTSE RAFI US 1500 Small-Mid Portfolio PSLV......................... Sprott Physical Silver Trust PSP.......................... PowerShares Global Listed Private Equity Portfolio PSQ.......................... ProShares Short QQQ PVI.......................... PowerShares VRDO Tax Free Weekly Portfolio PXH.......................... PowerShares FTSE RAFI Emerging Markets Portfolio PZA.......................... PowerShares Insured National Municipal Bond Portfolio QQQ.......................... Powershares QQQ Trust Series 1 REM.......................... iShares FTSE NAREIT Mortgage Plus Capped Index Fund REMX......................... Market Vectors Rare Earth/Strategic Metals ETF REZ.......................... iShares FTSE NAREIT Residential Plus Capped Index Fund RFG.......................... Guggenheim S&P Midcap 400 Pure Growth ETF RJA.......................... ELEMENTS Linked to the Rogers International Commodity Index--Agri Tot Return RJI.......................... ELEMENTS Linked to the Rogers International Commodity Index--Total Return RJN.......................... ELEMENTS Linked to the Rogers International Commodity Index--Energy To Return RJZ.......................... ELEMENTS Linked to the Rogers International Commodity Index--Metals Tot Return RPG.......................... Guggenheim S&P 500 Pure Growth ETF RSP.......................... Guggenheim S&P 500 Equal Weight ETF RSX.......................... Market Vectors Russia ETF RTH.......................... Market Vectors Retail ETF RWM.......................... ProShares Short Russell 2000 RWO.......................... SPDR Dow Jones Global Real Estate ETF RWR.......................... SPDR Dow Jones REIT ETF RWX.......................... SPDR Dow Jones International Real Estate ETF RYH.......................... Guggenheim S&P 500 Equal Weight Healthcare ETF SAGG......................... Direxion Daily Total Bond Market Bear 1x Shares SCHA......................... Schwab US Small-Cap ETF SCHB......................... Schwab US Broad Market ETF SCHD......................... Schwab US Dividend Equity ETF SCHE......................... Schwab Emerging Markets Equity ETF SCHF......................... Schwab International Equity ETF SCHG......................... Schwab U.S. Large-Cap Growth ETF SCHH......................... Schwab U.S. REIT ETF SCHM......................... Schwab U.S. Mid-Cap ETF SCHO......................... Schwab Short-Term U.S. Treasury ETF SCHP......................... Schwab U.S. TIPs ETF SCHR......................... Schwab Intermediate-Term U.S. Treasury ETF SCHV......................... Schwab U.S. Large-Cap Value ETF [[Page 33520]] SCHX......................... Schwab US Large-Cap ETF SCHZ......................... Schwab U.S. Aggregate Bond ETF SCPB......................... SPDR Barclays Capital Short Term Corporate Bond ETF SCZ.......................... iShares MSCI EAFE Small Cap Index Fund SDY.......................... SPDR S&P Dividend ETF SEF.......................... ProShares Short Financials SGG.......................... iPath Dow Jones-UBS Sugar Subindex Total Return ETN SGOL......................... ETFS Gold Trust SH........................... ProShares Short S&P 500 SHM.......................... SPDR Nuveen Barclays Capital Short Term Municipal Bond ETF SHV.......................... iShares Barclays Short Treasury Bond Fund SHY.......................... iShares Barclays 1-3 Year Treasury Bond Fund SIL.......................... Global X Silver Miners ETF SIVR......................... ETFS Physical Silver Shares SJB.......................... ProShares Short High Yield SJNK......................... SPDR Barclays Capital Short Term High Yield Bond ETF SLV.......................... iShares Silver Trust SLX.......................... Market Vectors Steel Index Fund SMH.......................... Market Vectors Semiconductor ETF SOXX......................... iShares PHLX SOX Semiconductor Sector Index Fund SPLV......................... PowerShares S&P 500 Low Volatility Portfolio SPY.......................... SPDR S&P 500 ETF Trust SPYG......................... SPDR S&P 500 Growth ETF SPYV......................... SPDR S&P 500 Value ETF STIP......................... iShares Barclays 0-5 Year TIPS Bond Fund STPP......................... iPath US Treasury Steepener ETN STPZ......................... PIMCO 1-5 Year US TIPS Index Fund SUB.......................... iShares S&P Short Term National AMT-Free Municipal Bond Fund SVXY......................... ProShares Short VIX Short-Term Futures ETF TAN.......................... Guggenheim Solar ETF TBF.......................... ProShares Short 20+ Year Treasury TBX.......................... ProShares Short 7-10 Treasury TFI.......................... SPDR Nuveen Barclays Capital Municipal Bond ETF THD.......................... iShares MSCI Thailand Index Fund TIP.......................... iShares Barclays TIPS Bond Fund TLH.......................... iShares Barclays 10-20 Year Treasury Bond Fund TLT.......................... iShares Barclays 20+ Year Treasury Bond Fund TUR.......................... iShares MSCI Turkey Index Fund UDN.......................... PowerShares DB US Dollar Index Bearish Fund UGA.......................... United States Gasoline Fund LP UNG.......................... United States Natural Gas Fund LP URA.......................... Global X Uranium ETF USCI......................... United States Commodity Index Fund USL.......................... United States 12 Month Oil Fund LP USO.......................... United States Oil Fund LP UUP.......................... PowerShares DB US Dollar Index Bullish Fund VAW.......................... Vanguard Materials ETF VB........................... Vanguard Small-Cap ETF VBK.......................... Vanguard Small-Cap Growth ETF VBR.......................... Vanguard Small-Cap Value ETF VCIT......................... Vanguard Intermediate-Term Corporate Bond ETF VCLT......................... Vanguard Long-Term Corporate Bond ETF VCR.......................... Vanguard Consumer Discretionary ETF VCSH......................... Vanguard Short-Term Corporate Bond ETF VDC.......................... Vanguard Consumer Staples ETF VDE.......................... Vanguard Energy ETF VEA.......................... Vanguard MSCI EAFE ETF VEU.......................... Vanguard FTSE All-World ex-US ETF VFH.......................... Vanguard Financials ETF VGK.......................... Vanguard MSCI European ETF VGT.......................... Vanguard Information Technology ETF VHT.......................... Vanguard Health Care ETF VIG.......................... Vanguard Dividend Appreciation ETF VIIX......................... VelocityShares VIX Short Term ETN VIOO......................... Vanguard S&P Small-Cap 600 ETF VIS.......................... Vanguard Industrials ETF VIXM......................... ProShares VIX Mid-Term Futures ETF VIXY......................... ProShares VIX Short-Term Futures ETF VMBS......................... Vanguard Mortgage-Backed Securities ETF VNM.......................... Market Vectors Vietnam ETF VNQ.......................... Vanguard REIT ETF VO........................... Vanguard Mid-Cap ETF [[Page 33521]] VOE.......................... Vanguard Mid-Cap Value Index Fund/Closed- end VONE......................... Vanguard Russell 1000 VONG......................... Vanguard Russell 1000 Growth ETF VONV......................... Vanguard Russell 1000 Value VOO.......................... Vanguard S&P 500 ETF VOOG......................... Vanguard S&P 500 Growth ETF VOOV......................... Vanguard S&P 500 Value ETF VOT.......................... Vanguard Mid-Cap Growth Index Fund/Closed- end VOX.......................... Vanguard Telecommunication Services ETF VPL.......................... Vanguard MSCI Pacific ETF VPU.......................... Vanguard Utilities ETF VQT.......................... Barclays ETN+ ETNs Linked to the S&P 500 Dynamic VEQTORTM TotaL Return Index VSS.......................... Vanguard FTSE All World ex-US Small-Cap ETF VT........................... Vanguard Total World Stock Index Fund ETF VTHR......................... Vanguard Russell 3000 VTI.......................... Vanguard Total Stock Market ETF VTV.......................... Vanguard Value ETF VTWG......................... Vanguard Russell 2000 Growth VTWO......................... Vanguard Russell 2000 VTWV......................... Vanguard Russell 2000 Value VUG.......................... Vanguard Growth ETF VV........................... Vanguard Large-Cap ETF VWO.......................... Vanguard MSCI Emerging Markets ETF VXAA......................... ETRACS 1-Month S&P 500 VIX Futures ETN VXEE......................... ETRACS 5-Month S&P 500 VIX Futures ETN VXF.......................... Vanguard Extended Market ETF VXUS......................... Vanguard Total International Stock ETF VXX.......................... iPATH S&P 500 VIX Short-Term Futures ETN VXZ.......................... iPATH S&P 500 VIX Mid-Term Futures ETN VYM.......................... Vanguard High Dividend Yield ETF VZZB......................... iPath Long Enhanced S&P 500 VIX Mid-Term FuturesTM ETN II WDTI......................... WisdomTree Managed Futures Strategy Fund WIP.......................... SPDR DB International Government Inflation-Protected Bond ETF XBI.......................... SPDR S&P Biotech ETF XES.......................... SPDR S&P Oil & Gas Equipment & Services ETF XHB.......................... SPDR S&P Homebuilders ETF XIV.......................... VelocityShares Daily Inverse VIX Short Term ETN XLB.......................... Materials Select Sector SPDR Fund XLE.......................... Energy Select Sector SPDR Fund XLF.......................... Financial Select Sector SPDR Fund XLG.......................... Guggenheim Russell Top 50 ETF XLI.......................... Industrial Select Sector SPDR Fund XLK.......................... Technology Select Sector SPDR Fund XLP.......................... Consumer Staples Select Sector SPDR Fund XLU.......................... Utilities Select Sector SPDR Fund XLV.......................... Health Care Select Sector SPDR Fund XLY.......................... Consumer Discretionary Select Sector SPDR Fund XME.......................... SPDR S&P Metals & Mining ETF XOP.......................... SPDR S&P Oil & Gas Exploration & Production ETF XPH.......................... SPDR S&P Pharmaceuticals ETF XRT.......................... SPDR S&P Retail ETF XSD.......................... SPDR S&P Semiconductor ETF XXV.......................... iPath Inverse S&P 500 VIX Short-Term Futures ETN ZROZ......................... PIMCO 25+ Year Zero Coupon US Treasury Index Fund ------------------------------------------------------------------------ Appendix B--Data Unless otherwise specified, the following data shall be collected and transmitted to the SEC in an agreed-upon format on a monthly basis, to be provided 30 calendar days following month end. Unless otherwise specified, the Primary Listing Exchanges shall be responsible for collecting and transmitting the data to the SEC. Data collected in connection with Sections II(E)-(G) below shall be transmitted to the SEC with a request for confidential treatment under the Freedom of Information Act. 5 U.S.C. 552, and the SEC's rules and regulations thereunder. I. Summary Statistics A. Frequency with which NMS Stocks enter a Limit State. Such summary data shall be broken down as follows: 1. Partition stocks by category a. Tier 1 non-ETP issues >$3.00 b. Tier 1 non-ETP issues > =$0.75 and =$3.00 c. Tier 1 non-ETP issues <$0.75 d. Tier 1 non-leveraged ETPs in each of above categories e. Tier 1 leveraged ETPs in each of above categories f. Tier 2 non-ETPs in each of above categories g. Tier 2 non-leveraged ETPs in each of above categories h. Tier 2 leveraged ETPs in each of above categories 2. Partition by time of day a. Opening (prior to 9:45 a.m. ET) b. Regular (between 9:45 a.m. ET and 3:35 p.m. ET) c. Closing (after 3:35 p.m. ET) d. Within five minutes of a Trading Pause re-open or IPO open [[Page 33522]] 3. Track reasons for entering a Limit State, such as: a. Liquidity gap -price reverts from a Limit State Quotation and returns to trading within the Price Bands b. Broken trades c. Primary Listing Exchange manually declares a Trading Pause pursuant to Section (VII)(2) of the Plan d. Other B. Determine (1), (2) and (3) for when a Trading Pause has been declared for an NMS Stock pursuant to the Plan. II. Raw Data (all Participants, except A-E, which are for the Primary Listing Exchanges only) A. Record of every Straddle State. 1. Ticker, date, time entered, time exited, flag for ending with Limit State, flag for ending with manual override. 2. Pipe delimited with field names as first record. B. Record of every Price Band 1. Ticker, date, time at beginning of Price Band, Upper Price Band, Lower Price Band 2. Pipe delimited with field names as first record C. Record of every Limit State 1. Ticker, date, time entered, time exited, flag for halt 2. Pipe delimited with field names as first record D. Record of every Trading Pause or halt 1. Ticker, date, time entered, time exited, type of halt (i.e., regulatory halt, non-regulatory halt, Trading Pause pursuant to the Plan, other) 2. Pipe delimited with field names as first record E. Data set or orders entered into reopening auctions during halts or Trading Pauses 1. Arrivals, Changes, Cancels, shares, limit/market, side, Limit State side 2. Pipe delimited with field name as first record F. Data set of order events received during Limit States G. Summary data on order flow of arrivals and cancellations for each 15-second period for discrete time periods and sample stocks to be determined by the SEC in subsequent data requests. Must indicate side(s) of Limit State. 1. Market/marketable sell orders arrivals and executions a. Count b. Shares c. Shares executed 2. Market/marketable buy orders arrivals and executions a. Count b. Shares c. Shares executed 3. Count arriving, volume arriving and shares executing in limit sell orders above NBBO mid-point 4. Count arriving, volume arriving and shares executing in limit sell orders=NBBO mid-point (non-marketable) 5. Count arriving, volume arriving and shares executing in limit buy orders above NBBO mid-point (non-marketable) 6. Count arriving, volume arriving and shares executing in limit buy orders below NBBO mid-point 7. Count and volume arriving of limit sell orders priced at or above NBBO+$0.05 8. Count and volume arriving of limit buy orders priced at or below NBBO-$0.05 9. Count and volume of (iii-viii) for cancels 10. Include: Ticker, date, time at start, time of Limit State, data item fields, last sale prior to 1-minute period (null if no trades today), range during 15-second period, last trade during 15-second period III. At Least Two Months Prior to the End of the Pilot Period, All Participants Shall Provide to the SEC Assessments Relating to Impact of the Plan and Calibration of the Percentage Parameters as Follows: A. Assess the statistical and economic impact on limit order book of approaching Price Bands. B. Assess the statistical and economic impact of the Price Bands on erroneous trades. C. Assess the statistical and economic impact of the appropriateness of the Percentage Parameters used for the Price Bands. D. Assess whether the Limit State is the appropriate length to allow for liquidity replenishment when a Limit State is reached because of a temporary liquidity gap. E. Evaluate concerns from the options markets regarding the statistical and economic impact of Limit States on liquidity and market quality in the options markets. (Participants that operate options exchange should also prepare such assessment reports.) F. Assess whether the process for entering a Limit State should be adjusted and whether Straddle States are problematic. G. Assess whether the process for exiting a Limit State should be adjusted. H. Assess whether the Trading Pauses are too long or short and whether the reopening procedures should be adjusted. [FR Doc. 2012-13653 Filed 6-5-12; 8:45 am] BILLING CODE 8011-01-P
Unmasking A Killer – Full Movie
TOP-SECRET – The Case of the Mysterious Khalid Sheikh Mohammed in Guantanamo Bay Photos

Last month, nearly a dozen photos purporting to show alleged al-Qaeda mastermind Khalid Sheikh Mohammed posing serenely inside the internment facility at Guantanamo Bay were posted on a popular Jihadist forum. The photos depict what appears to be Mohammed sitting in a variety of poses in clothing similar to what is worn by detainees at the internment facility in Guantanamo Bay. Two of the photos also depict other detainees being held at Guantanamo.
On May 24 the U.S. military told NBC news that they were investigating the photos to determine whether or not they had been digitally manipulated. The next day an article from AFP quoted Pentagon spokesman Lieutenant-Colonel Todd Breasseale as saying the “recent photos of Khalid Sheikh Mohammad, et al, that have surfaced on the Internet represent a very poor effort at digital manipulation . . . clearly using the official work of the ICRC — approved for release by the US government — in order to deceive and rally those inclined toward radicalism.”
Some of the photos do appear to be manipulated. However, several photos appear to be genuine depictions of Mohammed and other detainees. Confusing the issue further, many media outlets do not seem to understand that there were several photos released and have instead focused upon a single photo from the collection that appears to be manipulated.
In order to further analysis of the photos, Public Intelligence has reproduced all of the photos and made them available for download in a high-resolution format. Let us know what your opinions are on the authenticity of the photos in the comment section below, via email or by using our encrypted contact form.
Here’s a quick look at some of the photos from the collection:
Vegas Heat – Full Movie
Private Needhams War – Full Movie
TOP-SECRET – Beware of Imitators by Al Qa’ida Secretary
Redemption Song – Full Movie
SECRET – Unmarked Aircraft at Dulles Airport Identified
| FAA aircraft registration records show that the three Vision Airlines aircraft below are owned by International Bank of Commerce, Vision Asset Co. LLC and Wells Fargo Bank Northwest NA Trustee. Vision Asset Co. LLC is the financial unit which handles aircraft leasing for Vision Airlines. A 27 May 2010 document (in German):
http://www.docstoc.com/docs/40561767/Globaler-Airline-Newsletter-von-Berlinspotterde
http://www.airlineinfo.com/Sites/DailyAirline/web-content/ostdocket2009/ost090120.html
http://www.airlineinfo.com/Sites/DailyAirline/web-content/ostpdf74/134.pdf
2 June 2012. Add links to photos of the very faintly marked aircraft in use for international flights as distinguished from Vision Airlines domestic US flights which have prominent markings:
1 June 2012. A4 sends:
1 June 2012. A3 sends:
1 June 2012. The aircraft are discussed here, with links to photos:
1 June 2012. A2 sends:
A3 sends: Those planes are 767-200s rather than 737s. [If Vision Airlines, the three are 2-767s and 1-737.] 31 May 2012. A sends:
31 May 2012 Unmarked Aircraft at Dulles Airport Shepherd Johnson sends: When I flew out of Dulles on May 13, 2012, these two unmarked Boeing 737s were sitting in an area just south of the C terminal on the tarmac at Dulles. These aircraft don’t have a “N” number or any other FAA identification. When I returned two weeks later they were in the same position. Any ideas?
|
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/dulles-mystery/pict22.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/dulles-mystery/pict23.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/dulles-mystery/pict24.jpg) |
Enlarging and sharpening the full resolution photo of a very faint number, the aircraft below is Vision Airlines N769VA.![[Image]](https://i0.wp.com/cryptome.org/2012-info/dulles-mystery/pict35.jpg)
|
| Following aerial views from Bing.com/mapshttp://binged.it/N1RvPY |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/dulles-mystery/pict31.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/dulles-mystery/pict30.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/dulles-mystery/pict29.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/dulles-mystery/pict27.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/dulles-mystery/pict28.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/dulles-mystery/pict25.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/dulles-mystery/pict26.jpg) |
Screenplay for Murder – Full Movie
FEMEN Protest EURO 2012 – Uncensored
FEMEN Protest EURO 2012
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-euro2012/pict18.jpg)
An activist of Ukrainian women’s movement FEMEN wearing a penis costume stands in position on a flower bed in the form of EURO 2012 mascots Slavek and Slavko in Independence Square in Kiev on May 31, 2012. The protest was held to oppose the staging of the Euro 2012 football championships in the Ukraine. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-euro2012/pict20.jpg)
An activist of Ukrainian women’s movement FEMEN wearing a penis costume stands in position on a flower bed in the form of EURO 2012 mascots Slavek and Slavko as another activist sprays a slogan on the grass in Independence Square in Kiev on May 31, 2012. The protest was held to oppose the staging of the Euro 2012 football championships in the Ukraine. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-euro2012/pict11.jpg)
Police detain activists of Ukrainian women’s movement FEMEN during a protest on a flower bed in the form of EURO 2012 mascots Slavek and Slavko as another activist sprays a slogan on the grass in Independence Square in Kiev on May 31, 2012. The protest was held to oppose the staging of the Euro 2012 football championships in the Ukraine. Getty [Woman appears to have a cellphone in pants.]
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-euro2012/pict12.jpg)
Police detain an activist of Ukrainian women’s movement FEMEN during a protest on a flower bed in the form of EURO 2012 mascots Slavek and Slavko as another activist sprays a slogan on the grass in Independence Square in Kiev on May 31, 2012. The protest was held to oppose the staging of the Euro 2012 football championships in the Ukraine. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-euro2012/pict13.jpg)
Police detain an activist of Ukrainian women’s movement FEMEN during a protest on a flower bed in the form of EURO 2012 mascots Slavek and Slavko as another activist sprays a slogan on the grass in Independence Square in Kiev on May 31, 2012. The protest was held to oppose the staging of the Euro 2012 football championships in the Ukraine. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-euro2012/pict16.jpg)
Police detain an activist of Ukrainian women’s movement FEMEN during a protest on a flower bed in the form of EURO 2012 mascots Slavek and Slavko as another activist sprays a slogan on the grass in Independence Square in Kiev on May 31, 2012. The protest was held to oppose the staging of the Euro 2012 football championships in the Ukraine. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-euro2012/pict17.jpg)
Police detain an activist of Ukrainian women’s movement FEMEN during a protest on a flower bed in the form of EURO 2012 mascots Slavek and Slavko as another activist sprays a slogan on the grass in Independence Square in Kiev on May 31, 2012. The protest was held to oppose the staging of the Euro 2012 football championships in the Ukraine. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-euro2012/pict32.jpg)
Police detain activists of Ukrainian women’s movement FEMEN during a protest on a flower bed in the form of EURO 2012 mascots Slavek and Slavko as another activist sprays a slogan on the grass in Independence Square in Kiev on May 31, 2012. The protest was held to oppose the staging of the Euro 2012 football championships in the Ukraine. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-euro2012/pict33.jpg)
Police detain activists of Ukrainian women’s movement FEMEN during a protest on a flower bed in the form of EURO 2012 mascots Slavek and Slavko as another activist sprays a slogan on the grass in Independence Square in Kiev on May 31, 2012. The protest was held to oppose the staging of the Euro 2012 football championships in the Ukraine. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-euro2012/pict14.jpg)
Police detain activists of Ukrainian women’s movement FEMEN during a protest on a flower bed in the form of EURO 2012 mascots Slavek and Slavko as another activist sprays a slogan on the grass in Independence Square in Kiev on May 31, 2012. The protest was held to oppose the staging of the Euro 2012 football championships in the Ukraine. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-euro2012/pict15.jpg)
Police detain activists of Ukrainian women’s movement FEMEN during a protest on a flower bed in the form of EURO 2012 mascots Slavek and Slavko as another activist sprays a slogan on the grass in Independence Square in Kiev on May 31, 2012. The protest was held to oppose the staging of the Euro 2012 football championships in the Ukraine.
TOP-SECRET – Open Source Center Status of Syrian Uprising, Regime Cohesion May 2012

Conflict between government and opposition forces continued during the week, generally following the established pattern of government military attacks and security raids against centers of opposition, on the one hand, and ambushes and bombings by opposition forces on the other. The Syrian conflict also continued to spark clashes in neighboring Lebanon. Further turmoil among the top leadership of the opposition Syrian National Council (SNC) reflected the opposition’s continued difficulty in unifying ranks. Syria and the United Nations traded accusations on the subject of human-rights violations.
Update on Clashes
Reports from opposition sources transmitted via Arab media — such as the influential, London-based, pan-Arab daily Al-Sharq al-Awsat — described widespread clashes between government and opposition in and around several major population centers. Opposition sources typically claimed that government forces killed dozens of individuals in various daily assaults, though such claims remain impossible to verify.
- Government forces reportedly used artillery and helicopters during bombardments in Al-Rastan, Homs, Idlib Province, and villages near Aleppo.
- Clashes were also reported in a southwestern district of Damascus and specifically on 23 May in the city of Aleppo, the scene of antigovernment demonstrations. Various opposition sources described the Aleppo protests as comprising “1,500,” “tens,” or “hundreds” of thousands of demonstrators.
- A large car bomb, apparently targeting military intelligence facilities, exploded in the eastern town of Dayr al-Zawr on 19 May, resulting in several deaths. Another deadly bomb attack occurred in the Damascus neighborhood of Qabun during the night of 21-22 May.
Reports of clashes transmitted by the state-run SANA news agency followed a familiar pattern of branding opposition attacks as terrorist in nature and hinting of foreign support.
- SANA reported several deadly attacks by “armed terrorist groups,” typically against isolated security forces, such as border guards.
- It also reported military engineers’ success in disarming a number of “terrorist” bombs.
- According to SANA, security forces discovered a “terrorist” weapons-manufacturing warehouse in Homs and intercepted several “Tunisian terrorists” attempting to infiltrate into Syria from Turkey.
More Clashes in Lebanon
Clashes between pro-Syrian Government and pro-Syrian opposition factions continued in
Lebanon, and a number of Lebanese Shiites were abducted in Syria under unclear
circumstances.
- Following a week of clashes in Tripoli between Sunnis hostile to the Syrian regime and Alawite regime supporters, fighting broke out in Beirut during the night of 21-22 May, reportedly resulting in two deaths.
- Ahmad Abd-al-Wahib, a Sunni cleric belonging to the pro-Syria 14 March alliance, was killed under disputed circumstances by Lebanese Army troops at a security checkpoint in northern Lebanon on 20 May.
- Approximately one dozen Lebanese Shiites, said to be pilgrims returning to Lebanon via Syria from Iran, were seized at gunpoint in Aleppo on 22 May. Family members and Syrian state media blamed the assault on the Free Syrian Army (FSA), but the FSA denied all responsibility and accused the Syrian Government of staging the incident.
Crisis Within SNC
The SNC formally accepted the resignation of Burhan Ghalyun, who had been reelected president on 15 May, and announced a new presidential election on 9-10 June. Ghalyun resigned under pressure from critics within the SNC who accused him of monopolizing power and failing to support properly the uprising.
Mutual Accusations Regarding Human-Rights Violations
In a report addressed to the UN Human Rights Council on 20 May, the Syrian Foreign and Expatriates Ministry charged that Syria is the victim of human-rights violations, both through “direct killing operations” by “armed terrorist groups” and through “the sanctions imposed by the countries, which are funding, backing, and hosting these groups.”
In a report released on 24 May, the UN’s Independent Commission of Inquiry on Syria charged that the Syrian Army and security services were responsible for most of the human-rights violations documented by the commission, both in the form of direct attacks against individuals and the “systematic denial” of food, water, and medical care.
DOWNLOAD THE ORIGINAL DOCUMENT HERE
Secrets Lies and Alibis – Full Movie
CONFIDENTIAL by Cryptome – LulzSec Sneak Preview of Files to be Released
Shootout at The Hills – Full Movie
TOP-SECRET – CEO and Head Trader of Bankrupt Sentinel Management Indicted in Alleged $500 Million Fraud Scheme
CHICAGO—The chief executive officer and the head trader of the bankrupt Sentinel Management Group Inc. were indicted on federal fraud charges for allegedly defrauding more than 70 customers of more than $500 million before the firm collapsed in August 2007, federal law enforcement officials announced today. Sentinel, which was located in suburban Northbrook, managed short-term cash investments of futures commission merchants, commodity pools, hedge funds, at least one pension fund, and other customers. The defendants, Eric A. Bloom and Charles K. Mosley, allegedly misappropriated securities belonging to customers by using them as collateral for a loan that Sentinel obtained from Bank of New York Mellon Corp. (BoNY) that was in part used to purchase millions of dollars worth of high-risk, illiquid securities not for customers, but for a trading portfolio maintained for the benefit of Sentinel’s officers, including Mosley, Bloom, certain Bloom family members, and corporations controlled by the Bloom family.
Bloom, the president and CEO of Sentinel who was responsible for its day-to-day operations, allegedly misled customers four days before Sentinel declared bankruptcy by blaming Sentinel’s financial problems on the “liquidity crisis” and “investor fear and panic” when he knew that the actual reasons for Sentinel’s financial problems were its purchase of high-risk, illiquid securities; excessive use of leverage; and the resulting indebtedness on the BoNY credit line, which had a balance exceeding $415 million on August 13, 2007. Sentinel declared bankruptcy on August 17, 2007.
Bloom, 47, of Northbrook, and Mosley, 48, of Vernon Hills, will be arraigned on a date yet to be scheduled in U.S. District Court in Chicago. They were each charged with 18 counts of wire fraud, one count of securities fraud, and one count of making false statements to an employee pension plan in a 20-count indictment that was returned by a federal grand jury yesterday. The indictment seeks forfeiture of more than $500 million.
The case is one of the largest criminal financial fraud cases ever prosecuted in federal court in Chicago. The indictment was announced by Patrick J. Fitzgerald, United States Attorney for the Northern District of Illinois; Robert D. Grant, Special Agent in Charge of the Chicago Office of the Federal Bureau of Investigation; and James Vanderberg, Special Agent in Charge of the U.S. Department of Labor Office of Inspector General in Chicago. Also assisting in the investigation were the Labor Department’s Employee Benefits Security Administration, the Commodity Futures Trading Commission, and the Securities and Exchange Commission. The CFTC and the SEC filed separate civil enforcement lawsuits following the collapse of Sentinel, which remains in bankruptcy proceedings.
According to the indictment, between January 2003 and August 2007, Bloom and Mosley fraudulently obtained and retained under management more than $500 million of customers’ funds by falsely representing the risks associated with investing with Sentinel, the use of customers’ funds and securities, the value of customers’ investments, and the profitability of investing with Sentinel. Bloom and Mosley allegedly used customers’ securities invested in Sentinel’s “125 Portfolio” and its “Prime Portfolio” as collateral for its credit line with BoNY to purchase millions of dollars worth of high-risk, illiquid securities, some of which were collateralized debt obligations (CDOs). Mosley allegedly purchased the CDOs from two brokerage firms and received substantial personal benefits from those firms in the form of gifts, vacations, expensive tickets to sporting events, and parties.
The indictment alleges that Bloom and Mosley lied about customers’ investments and engaged in an undisclosed trading strategy with Sentinels’ own “House Portfolio,” which they traded for the benefit of themselves and Bloom family members. In addition to his salary, Mosley received an annual bonus based on the profitability of the House Portfolio. The undisclosed trading strategy included extensive leverage and a high concentration of CDOs that was inconsistent with the representations Bloom and Mosley made to customers regarding separate investment portfolios. The undisclosed strategy affected all customers, regardless of the trading portfolio in which they were invested, because the defendants allegedly used customers’ securities as collateral when they borrowed money from the BoNY and so-called “repo” lenders and then used the borrowed money to carry out the undisclosed trading strategy. (Under a repurchase agreement, known as a “repo,” a party such as Sentinel, effectively a borrower, sold securities to a counterparty, effectively a lender, with an agreement to repurchase the securities at a later date.)
“The use of their customers’ securities as collateral allowed the defendants to borrow more money than Sentinel otherwise could, subjected the customer securities to potential legal claims by creditors, and allowed the defendants to employ leverage to the extent that Sentinel itself, and all of the customer portfolios, were at increased risk of adverse market movements and insolvency,” the indictment states.
As part of the fraud scheme, Bloom and Mosley allegedly falsely represented to customers the returns generated by the securities in each Sentinel portfolio. Rather than giving customers the actual returns generated by a particular portfolio, the defendants on a daily basis pooled the trading results for all of Sentinel’s portfolios and then allocated the returns to the various portfolios as they saw fit, the indictment alleges. To conceal the scheme, to encourage customers to invest additional funds, and to otherwise lull customers, Bloom and Mosley on a daily basis allegedly caused false and misleading account statements to be created and distributed to customers, including via e-mail. These account statements reported returns earned by customers without disclosing that the returns actually were allocated by the defendants and were not the result of the market performance of the customers’ particular portfolios. The account statements also listed the purported value of securities being held by each portfolio without disclosing that the securities were being used as collateral for Sentinel’s loan from BoNY. The daily account statements were also misleading in that many of them, particularly those issued in July and August 2007, contained incorrect securities and inflated values of certain securities, the indictment alleges.
In July and August 2007, when Bloom and Mosley knew that Sentinel was approaching insolvency and that defaulting on the over-$400 million bank line of credit was a real possibility, they allegedly caused millions of dollars in investments in Sentinel to be obtained and retained by concealing Sentinel’s true financial condition from customers.
Each count of wire fraud carries a maximum penalty of 20 years in prison and a $250,000 fine, or, alternatively, a fine totaling twice the loss to any victim or twice the gain to the defendant, whichever is greater, and restitution is mandatory. Securities fraud and making false statements to a pension plan each carry a maximum penalty of five years in prison and a $250,000 fine. If convicted, the court must impose a reasonable sentence under federal statutes and the advisory United States Sentencing Guidelines.
The government is being represented by Assistant U.S. Attorneys Clifford C. Histed and Patrick M. Otlewski.
The investigation falls under the umbrella of the Financial Fraud Enforcement Task Force, which includes representatives from a broad range of federal agencies, regulatory authorities, inspectors general, and state and local law enforcement who, working together, bring to bear a powerful array of criminal and civil enforcement resources. The task force is working to improve efforts across the federal executive branch and, with state and local partners, to investigate and prosecute significant financial crimes, ensure just and effective punishment for those who perpetrate financial crimes, combat discrimination in the lending and financial markets, and recover proceeds for victims of financial crimes. For more information on the task force, visit http://www.stopfraud.gov.
An indictment contains only charges and is not evidence of guilt. The defendants are presumed innocent and are entitled to a fair trial at which the government has the burden of proving guilt beyond a reasonable doubt.
Soccer Moms Confidential – Full Movie
TIO-SECRET from the FBI – Leader of MS-13 Gang Sentenced to 50 Years in Prison for Sex Trafficking Multiple Teens
ALEXANDRIA, VA—Rances Ulices Amaya, 24, also known as “Murder” and “Blue,” was sentenced today to 50 years in prison for recruiting girls as young as 14 from middle schools, high schools, and homeless shelters in Northern Virginia and forcing them to engage commercial sex acts on behalf of MS-13.
Neil H. MacBride, U.S. Attorney for the Eastern District of Virginia, and James W. McJunkin, Assistant Director in Charge of the FBI’s Washington Field Office, made the announcement after sentencing by U.S. District Judge Anthony J. Trenga.
“Rances Amaya’s gang name was ‘Murder,’ and in a real sense, he killed the hopes and dreams of teenage girls whom he systematically and sadistically victimized,” said U.S. Attorney MacBride. “He told these girls that he owned them and that he would hurt their loved ones if they didn’t comply. They were his sex slaves, and that slavery goes to the heart of the heinous crime of sex trafficking. These girls have traumatic scars that will last a lifetime, and Mr. Amaya is justly going to spend the rest of his productive life paying for his crimes.”
“Today’s sentencing demonstrates the commitment of law enforcement and the judicial system to combat juvenile prostitution and human trafficking in Northern Virginia,” said Assistant Director in Charge McJunkin. “Together with our partner agencies, we will continue to pursue individuals such as Mr. Amaya who ruthlessly exploit vulnerable young girls for sex and money.”
Amaya was convicted by a jury on February 23, 2012 of conspiracy and three counts of sex trafficking of a child. According to court records and evidence at trial, Amaya joined MS-13 when he was a teenager and later became a “shot caller” for his MS-13 clique, the Guanacos Lokotes Salvatruchas. MS-13 gave him the gang monikers “Murder” and “Blue,” and he bears multiple MS-13 tattoos on his hands and arms.
In 2009, Amaya joined forces with an MS-13 associate who was already prostituting underage girls. Amaya used the violent reputation of MS-13 to ensure that sex customers paid for the sex and did not lure the underage victims away. He also used his MS-13 contacts to find sex customers and would offer free sex with the victims and a cut of the profits for any gang member who provided customers or underage girls. Amaya and his co-conspirator sought out illegal aliens as customers because they believed illegal aliens were unlikely to call the police. Amaya would hand out his telephone number at construction sites and convenience stores frequented by day laborers from Latin America.
Victims were required to have sex with eight to 10 paying customers per day, sometimes seven days per week. Some of the customers were sex addicts and repeat customers who paid daily for the sex. At night, after the paying customers were finished, Amaya would invite his fellow MS-13 members to have sex with the girls. Sometimes, to punish victims, the gang would “run a train” on a victim, which meant that multiple gang members would have sex with the victim in rapid succession. Amaya and other gang members also raped the victims both for their enjoyment and to “groom” them for the sex trafficking scheme.
Besides raping them to keep the victims compliant, Amaya would provide them with cigarettes, alcohol, marijuana, and other drugs. The evidence showed that Amaya prostituted five victims who were between the ages of 14 and 17 years old. The jury heard that using underage girls had two advantages: customers preferred young girls, and Amaya found them easier to manipulate and control. In addition, there was always an implicit threat of violence insofar as the victims knew that Amaya was MS-13, and he frequently carried a machete with him, MS-13’s weapon of choice. Amaya also struck at least one of the victims in the face.
The sex acts took place at motels, hotels, houses, apartments, and cars in Washington, D.C. and the Northern Virginia area. In particular, Amaya frequented a few hotels in Falls Church, Virginia, and many of the customers were solicited from convenience stores in the Culmore and Chirilagua neighborhoods of Northern Virginia.
Amaya charged between $30 and $120 for about 20 minutes of sex with the victims. Customers were required to pay more for “unusual” sex acts. The proceeds of the prostitution were used to purchase narcotics, alcoholic beverages, and to support MS-13 in the United States and El Salvador.
Amaya is the fourth MS-13 member to be convicted of sex trafficking children in the Eastern District of Virginia.
This case was investigated by the FBI’s Washington Field Office and the Fairfax County Gang Unit, with assistance from the Northern Virginia Human Trafficking Task Force. Assistant U.S. Attorney G. Zachary Terwilliger and Special Assistant U.S. Attorney Michael J. Frank are prosecuting the case on behalf of the United States.
Founded in 2004, the Northern Virginia Human Trafficking Task Force is a collaboration of federal, state, and local law enforcement agencies—along with non-governmental organizations—dedicated to combating human trafficking and related crimes.
A copy of this press release may be found on the website of the U.S. Attorney’s Office for the Eastern District of Virginia at http://www.justice.gov/usao/vae.
SECRET – 14 Anon Hackers Seized Data Discovery Process
DOWNLOAD THE ORIGINAL DOCUMENT HERE
Taken The Amber Dubois Story – Full Movie
Crytome – Arab Americans Seek Disadvantaged Minority Help
|
CONFIDENTIAL – Bilderberg Meeting 2012 Protest Photos
Bilderberg Meeting 2012 Protest Photos
Westfields Marriott Conference Center, Chantilly, VA
Bing.com/maps
![[Image]](https://i0.wp.com/cryptome.org/2012-info/bilderberg-2012/pict52.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/bilderberg-2012/pict44.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/bilderberg-2012/pict55.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/bilderberg-2012/pict45.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/bilderberg-2012/pict46.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/bilderberg-2012/pict47.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/bilderberg-2012/pict48.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/bilderberg-2012/pict49.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/bilderberg-2012/pict50.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/bilderberg-2012/pict51.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/bilderberg-2012/pict56.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/bilderberg-2012/pict57.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/bilderberg-2012/pict36.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/bilderberg-2012/pict37.jpg) Alex Jones, Radio-TV host, infowars.com, at center with megaphone.
Alex Jones, Radio-TV host, infowars.com, at center with megaphone.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/bilderberg-2012/pict38.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/bilderberg-2012/pict39.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/bilderberg-2012/pict40.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/bilderberg-2012/pict41.jpg) Alex Jones
Alex Jones
![[Image]](https://i0.wp.com/cryptome.org/2012-info/bilderberg-2012/pict42.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/bilderberg-2012/pict54.jpg) Concealed license plate.
Concealed license plate.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/bilderberg-2012/pict43.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/bilderberg-2012/pict53.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/bilderberg-2012/pict58.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/bilderberg-2012/pict59.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/bilderberg-2012/pict60.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/bilderberg-2012/pict61.jpg)
Temptation – Full Movie
SECRET – Special Operations Forces Chemical, Biological, Radiological, and Nuclear Operations Manual

ield Manual (FM) 3-05.132 is an Army special operations forces (ARSOF) Tier 2 publication. The acronym ARSOF represents Special Forces (SF), Rangers (RGR), special operations aviation (SOA), Psychological Operations (PSYOP), and Civil Affairs (CA)—all supported by the Sustainment Brigade (Special Operations) (Airborne) (SB[SO][A]).
PURPOSE
FM 3-05.132 serves as a reference document for ARSOF commanders and staff, training developers, and doctrine developers throughout the United States Army Special Operations Command (USASOC). It provides commanders with doctrinal considerations for organizing their individual CBRN operations and putting them into action to accomplish missions.
SCOPE
This publication describes ARSOF CBRN missions and tasks for the chemical reconnaissance detachment (CRD), chemical decontamination detachments (CDDs), ARSOF CBRN reconnaissance and survey operations, decontamination and reconnaissance teams (DRTs), and ARSOF sensitive site exploitation (SSE), and discusses reachback capability. This publication provides a basis for understanding the requirements of individual special operations forces (SOF) personnel operating in CBRN environments, as well as the requirements of ARSOF staff planners across the range of military operations. The manual also provides guidance for commanders who determine force structure, equipment, material, and operational requirements necessary to conduct SOF CBRN missions described herein.
…
ARSOF CBRN MISSION
1-1. The United States Special Operations Command (USSOCOM) is responsible for synchronizing planning for global operations against terrorist networks, which it does in coordination with other combatant commands, the Services, and, as directed, appropriate United States (U.S.) government agencies. As directed, USSOCOM executes global operations against terrorist networks. As a subordinate unit, the USASOC has an important role in CWMD operations and recognizes that the probability of operating in a CBRN environment exists; therefore, ARSOF must specifically organize, train, and equip to be successful in a CBRN mission. The term CBRN environment includes the deliberate, accidental employment, or threat of CBRN weapons and attacks with CBRN or toxic industrial materials (TIMs). ARSOF CBRN forces provide CBRN reconnaissance, surveillance, and exploitation support for SOF in support of strategic, operational, and tactical objectives in all environments (permissive, uncertain, and hostile) to support the geographic and functional combatant commanders’ (CCDRs’) intent and objectives. This section defines the relationships between ARSOF core tasks and the military mission areas identified in the NMS-CWMD and describes how ARSOF CBRN units support the execution of the ARSOF core tasks across the spectrum of combating weapons of mass destruction (CWMD) operations (Figure 1-1, page 1-2). Joint Publication (JP) 3-40, Combating Weapons of Mass Destruction, Chapters 1 and 4, provide a complete description of the NMS-CWMD.
PASSIVE DEFENSE
1-2. ARSOF units are capable of providing a wide range of specialized support to CWMD operations but are generally not resourced to conduct large-scale CWMD operations. As such, the CBRN capabilities within ARSOF are mostly used for passive defense and to support the execution of ARSOF core tasks. CBRN capabilities are aligned with the four subtasks of CBRN passive defense: sense, shape, shield, and sustain. In addition to minimizing the vulnerability to and effects of WMD attacks, the ARSOF CBRN capabilities also minimize vulnerability to the effects of TIM accidents or events.
…
BIOLOGICAL AGENTS
1-46. The North Atlantic Treaty Organization (NATO) defines a biological agent as a microorganism (or its toxin) that causes disease or deterioration of material. Biological agents are generally directed against the respiratory system to maximize the organism’s ability to diffuse directly into the bloodstream and bodily tissue. Individual protective equipment (IPE) generally provides protection against a biological warfare (BW) attack. Generally, biological warfare agents (BWAs) may be classified into the following broad groups:
- Pathogens. Microorganisms that produce disease in humans, animals, or plants (for example, protozoa, fungi, bacteria, rickettsia, and viruses).
- Toxins. Any toxic substance that can be produced by a living organism.
1-47. Most organisms are naturally occurring and can be found in almost any environment. Without proper hygiene and appropriate prophylactic measures, they have the capability to rapidly cause incapacitating or lethal illness. When used as a warfare agent, biological agents can be disseminated in aerosol form, by vectors such as mosquitoes and ticks, or through contaminated food or water. JP 3-11 provides additional biological agent operational planning considerations.
RADIOLOGICAL AGENTS
1-48. Nuclear threats are associated with the explosive detonation of special nuclear material. The radiological agent (RA) threat deals with radiation hazards and radioactive materials that may be in more common use. The threat of low-level radiation exists in all operations. This threat can exist in certain expended rounds (depleted uranium), damaged or destroyed equipment, or contaminated shrapnel. It also may occur from inadequate nuclear waste disposal, deterioration of nuclear power facilities, damage to facilities that routinely use radioactive material or sources, and the direct use of radioactive materials or compounds by an adversary (terrorism). Specialized detection equipment is required to detect lower levels of radiation.
NUCLEAR WEAPONS
1-49. Nuclear weapons are similar to conventional weapons insofar as their destructive action is due mainly to blast or shock. However, nuclear explosions can be millions of times more powerful than the largest conventional detonations. For the release of a given amount of energy, the material mass required for a nuclear explosion would be much less than that of a conventional explosion. The radiation effects of a nuclear explosion are divided into two categories: initial and residual. A nuclear detonation produces its damaging effects through four primary ways: blast, thermal radiation, ionizing radiation, and electromagnetic pulse (EMP).
Blast
1-50. The blast wave created by an explosion produces a shock front that travels rapidly away from the fireball, behaving like a moving wall of highly compressed air (approximately 900 miles per hour [mph]). When this blast wave strikes the surface of the earth, it is reflected back, causing a second wave to be formed. The second wave will eventually merge with the first wave (called Mach effect), and the overpressure will essentially double. Winds generated by the blast of the weapon could reach several hundred mph at ground zero (GZ), and be as high as 70 mph as far as 6 miles away.
Thermal Radiation
1-51. Immediately after a detonation, weapon residues emit primary thermal radiation (X-rays) that are absorbed within a few feet of air. This energy then reemits from the fireball as thermal radiation consisting of ultraviolet, visible, and infrared rays. The following thermal pulses result from that detonation:
- First pulse. It lasts about a second, has high temperatures, and can cause flash blindness or retinal burns.
- Second pulse. It lasts about 10 seconds, carries about 99 percent of the thermal radiation energy, and causes skin burns and fires.
Ionizing Radiation
1-52. The two radioactivity hazards from a nuclear detonation are ionizing radiation and fallout. Ionizing radiation (x-rays, gamma rays, and neutrons) is emitted within the first minute of the detonation. Fallout is the residual radiation product distributed in the air by a nuclear detonation.
Electromagnetic Pulse
1-53. An electromagnetic signal produced by a nuclear detonation is commonly known as EMP. EMP-induced currents and voltages can cause electronic component equipment failure, affecting a wide range of electric and communication equipment, global positioning systems, command control nodes, vehicle ignition systems, avionics, and fire control systems.
TOXIC INDUSTRIAL MATERIALS
1-54. Although less lethal than current CW agents, industrial materials are often available in enormous quantities, do not require expensive research programs, are easily mass-produced, do not violate the Chemical Weapons Convention, and can still produce mass casualties. TIMs could be released from industrial plants or storage depots through battle damage, as consequence of a strike against a particular facility, or as a desperation measure during military operations. They could also be used as improvised chemical weapons and have potential for inclusion in clandestine programs or contingency plans. Note: IPE does not protect against all TIMs. For example, IPE will not protect the wearer from ammonia-based or chlorine-based industrial chemicals.
RIOT CONTROL AGENTS
1-55. Riot control agents (RCAs) are chemicals that produce temporary irritating or disabling effects when in contact with the eye or when inhaled. Generally used in the control of violent disorders, RCAs can be effectively used to contaminate terrain and to cause degrading effects on individuals, requiring them to use IPE for protection. U.S. policy does not classify RCAs as CW agents. Presidential Executive Order (EO) 11850, Renunciation of Certain Uses in War of Chemical Herbicides and Riot Control Agents, establishes the national policy for the use of RCAs by U.S. forces in combat.
DOWNLOAD THE ORIGINAL DOCUMENT HERE
TOP-SECRET from the FBI – Leader of MS-13 Gang Sentenced to 50 Years in Prison for Sex Trafficking Multiple Teens
ALEXANDRIA, VA—Rances Ulices Amaya, 24, also known as “Murder” and “Blue,” was sentenced today to 50 years in prison for recruiting girls as young as 14 from middle schools, high schools, and homeless shelters in Northern Virginia and forcing them to engage commercial sex acts on behalf of MS-13.
Neil H. MacBride, U.S. Attorney for the Eastern District of Virginia, and James W. McJunkin, Assistant Director in Charge of the FBI’s Washington Field Office, made the announcement after sentencing by U.S. District Judge Anthony J. Trenga.
“Rances Amaya’s gang name was ‘Murder,’ and in a real sense, he killed the hopes and dreams of teenage girls whom he systematically and sadistically victimized,” said U.S. Attorney MacBride. “He told these girls that he owned them and that he would hurt their loved ones if they didn’t comply. They were his sex slaves, and that slavery goes to the heart of the heinous crime of sex trafficking. These girls have traumatic scars that will last a lifetime, and Mr. Amaya is justly going to spend the rest of his productive life paying for his crimes.”
“Today’s sentencing demonstrates the commitment of law enforcement and the judicial system to combat juvenile prostitution and human trafficking in Northern Virginia,” said Assistant Director in Charge McJunkin. “Together with our partner agencies, we will continue to pursue individuals such as Mr. Amaya who ruthlessly exploit vulnerable young girls for sex and money.”
Amaya was convicted by a jury on February 23, 2012 of conspiracy and three counts of sex trafficking of a child. According to court records and evidence at trial, Amaya joined MS-13 when he was a teenager and later became a “shot caller” for his MS-13 clique, the Guanacos Lokotes Salvatruchas. MS-13 gave him the gang monikers “Murder” and “Blue,” and he bears multiple MS-13 tattoos on his hands and arms.
In 2009, Amaya joined forces with an MS-13 associate who was already prostituting underage girls. Amaya used the violent reputation of MS-13 to ensure that sex customers paid for the sex and did not lure the underage victims away. He also used his MS-13 contacts to find sex customers and would offer free sex with the victims and a cut of the profits for any gang member who provided customers or underage girls. Amaya and his co-conspirator sought out illegal aliens as customers because they believed illegal aliens were unlikely to call the police. Amaya would hand out his telephone number at construction sites and convenience stores frequented by day laborers from Latin America.
Victims were required to have sex with eight to 10 paying customers per day, sometimes seven days per week. Some of the customers were sex addicts and repeat customers who paid daily for the sex. At night, after the paying customers were finished, Amaya would invite his fellow MS-13 members to have sex with the girls. Sometimes, to punish victims, the gang would “run a train” on a victim, which meant that multiple gang members would have sex with the victim in rapid succession. Amaya and other gang members also raped the victims both for their enjoyment and to “groom” them for the sex trafficking scheme.
Besides raping them to keep the victims compliant, Amaya would provide them with cigarettes, alcohol, marijuana, and other drugs. The evidence showed that Amaya prostituted five victims who were between the ages of 14 and 17 years old. The jury heard that using underage girls had two advantages: customers preferred young girls, and Amaya found them easier to manipulate and control. In addition, there was always an implicit threat of violence insofar as the victims knew that Amaya was MS-13, and he frequently carried a machete with him, MS-13’s weapon of choice. Amaya also struck at least one of the victims in the face.
The sex acts took place at motels, hotels, houses, apartments, and cars in Washington, D.C. and the Northern Virginia area. In particular, Amaya frequented a few hotels in Falls Church, Virginia, and many of the customers were solicited from convenience stores in the Culmore and Chirilagua neighborhoods of Northern Virginia.
Amaya charged between $30 and $120 for about 20 minutes of sex with the victims. Customers were required to pay more for “unusual” sex acts. The proceeds of the prostitution were used to purchase narcotics, alcoholic beverages, and to support MS-13 in the United States and El Salvador.
Amaya is the fourth MS-13 member to be convicted of sex trafficking children in the Eastern District of Virginia.
This case was investigated by the FBI’s Washington Field Office and the Fairfax County Gang Unit, with assistance from the Northern Virginia Human Trafficking Task Force. Assistant U.S. Attorney G. Zachary Terwilliger and Special Assistant U.S. Attorney Michael J. Frank are prosecuting the case on behalf of the United States.
Founded in 2004, the Northern Virginia Human Trafficking Task Force is a collaboration of federal, state, and local law enforcement agencies—along with non-governmental organizations—dedicated to combating human trafficking and related crimes.
A copy of this press release may be found on the website of the U.S. Attorney’s Office for the Eastern District of Virginia at http://www.justice.gov/usao/vae.
The Country Club Murders – Full Movie
CONFIDENTIAL – SE Prosecution Authority: The Assange Matter
|
FEMEN in Italy
The Dog Trainer The Heiress and The Bodyguard – Full Movie
The Dog Trainer The Heiress and The Bodyguard – Full Movie – Part 2
Public Intelligence – Rebuild Your Local Economy With the Drone Industry
y 27, 2012 in Featured
U.S. Air Force First Lieutenant Greg Sundbeck (L), and Dr. Gregory Parker, Micro Air Vehicle team leader, observe a test flight of a U.S. Air Force drone in the microaviary lab at Wright Patterson Air Force Base in Dayton, Ohio, July 11, 2011. REUTERS/Skip Peterson
Public Intelligence
Is your state in need of a growth industry that can employ large numbers of people and contribute to the local economy? You may want to consider expanding your state’s role in the drone industry. It may sound like an unusual way to rebuild local economies, but that’s just what a number of states around the country have decided to do. Ohio, in particular, has made attracting the drone industry a major component of its statewide economic strategy, hoping to encourage local economic growth and create jobs by making the state the premier location for drone testing and research in the U.S. To further these efforts, the State of Ohio has worked with several business development groups to create the Ohio Unmanned Aircraft Systems (UAS) Initiative to promote the state’s prominent role in the drone industry. The potential job growth presented by the Ohio UAS Initiative makes it a priority for the state, which has lost more than 369,097 manufacturing jobs in the last decade.
The Ohio UAS Initiative aims to make Ohio “the destination of choice for all UAS researchers, developers, manufacturers, suppliers, trainers and educators.” At a roundtable conference held earlier this year, proponents of the initiative argued that Ohio is uniquely positioned to be the national leader for future development in the drone industry. A talking points card instructs proponents of the Ohio UAS Initiative that the state has “assets that support all facets of UAS development and operations” and wants to become the leading center of innovation and collaboration in the drone industry. According to the Ohio Aerospace & Business Aviation Advisory Council, aerospace and defense is one of Ohio’s top industries, employing more than 100,000 people in the state. Unlike many of Ohio’s other industries, the market for both commercial and military drones, which already is valued at approximately $4.5 billion a year, is seen as rapidly expanding and set to double in value by 2019. The rush to build Ohio’s image as a center of drone production and testing has even led a local community college to offer certificate programs in the technical maintenance and piloting of drones. The college has already created the first non-military UAS simulation center for training pilots of unmanned aircraft and it has plans to make the first National Center for UAS Training and Certification.
A presentation slide for the Ohio UAS Initiative describes talking points for proponents of the initiative to help emphasize Ohio’s position in the drone industry.
A major partner in the Ohio UAS Initiative is the Air Force Research Laboratory (AFRL) which is headquartered at Wright-Patterson Air Force Base just outside of Dayton, Ohio. The AFRL plays a leading role in the design of drone technology for the Air Force and sees the area as an ideal location for testing and development efforts aimed at integrating drones into the National Airspace System (NAS). Since 2009, the AFRL has been working with the Federal Aviation Administration (FAA) on a Next Generation Air Traffic System capable of integrating drones safely and efficiently into the NAS. Last March, several government agencies produced a UAS Research and Development Roadmap addressing long-term goals for incorporating drones into the NAS by funding research on improved sense and avoid capabilities and efforts to obtain a dedicated frequency range for ground control data links. The problems of frequency allocation and mid-air collision are significant obstacles to the widespread use of drones within the domestic airspace and a primary goal of the Ohio UAS Initiative is to create an “enduring relationship” with the FAA for testing and development that addresses these challenges. In fact, the prospect of long-term economic growth from the expanding drone industry is so appealing to Ohio that the state legislature recently passed a resolution affirming the state’s intent to to form a lasting partnership with the FAA for drone testing and research. The text of the resolution states that in “the next 15 years, more than 23,000 jobs could be created in the United States as a result of integration of Unmanned Aerial Systems in the National Airspace System, according to the Association of Unmanned Vehicle Systems International (AUVSI).”
In order to clear the way for increased drone testing and research in Ohio, the Dayton Development Coalition and Science Applications International Corporation (SAIC), a major defense contractor with substantial operations in Dayton, are conducting a multi-year study led by “senior executives of military and civilian stakeholder organizations.” The Ohio Airspace Strategic Integration Study (OASIS) will help to generate “short and long term safe, secure and efficient solutions for military UAS airspace requirements in collaboration with all stakeholders within the national airspace system.”
Many of the companies participating in efforts to increase Ohio’s involvement in the drone industry, including SAIC, are also members of the drone industry trade group AUVSI, which works to promote the interests of drone manufacturers around the world. A spokesman for the AUVSI recently told Salon that the organization is initiating a P.R. campaign to counter negative perceptions of drones, particularly on topics related to privacy and their use in targeted killings overseas. The campaign will reportedly include advertising aimed at promoting positive applications of drone technology in disaster response and other humanitarian situations. Presumably, the potential for economic growth and job creation in local economies will continue to remain one of the drone industry’s most attractive attributes as they seek to create a more positive public image. As an increasingly large number of states around the U.S. face severe economic problems, you may soon see the drone industry coming to a city near you.
The Facebook Detectives – Full Movie
The Girl Who Knew Too Much – Full Movie
DER STASI-MORD AN HEINZ GERLACH WEIL ER DAS STASI KOMPLOTT DURCHSCHAUTE
The Godfathers Daughter – Full Movie
Opfer – Die mutmassliche Hackordnung der Neo-STASI
SECRET – Sabu Interview by James Ball
Sabu Interview July2011
Sabu gave me this log of a private IRC not long after it occurred. It’s an “off the record” conversation between him and a correspondent from The Guardian. I don’t remember exactly what his reason was for giving it to me, other than that he said it was an example of “bad journalism” or some such thing (I don’t necessarily agree with that assessment). I’ve just recently found it again in my Google Docs, and since I no longer have any reason to keep it private, I’m putting it up for the benefit of those who are trying to get a better sense of what was going on with this guy during the time that he was secretly working as an FBI informant. At this point, he would have been under the quiet supervision of his handlers for nearly two months.
The context is that he’s being approached by this journalist who’s interested in doing a piece on the fact that he’d changed his Twitter logo to a representation of the Hamas flag. Apparently, this journalist had seen something written by th3j35t3r in which that particular genius figured out that Sabu’s Hamas flag logo was a logo of the Hamas flag. In the course of the discussion, several things come up that are especially interesting in hindsight.
Ever since March 6th, when Sabu’s status was made public, there have been questions about how much of a role the FBI played in a number of things that Sabu did, and how many of those things were done in pursuit of a larger strategy to weaken the movement. The recent release of Parmy Olsen’s “We Are Anonymous,” which is derived from interviews with a number of major participants, is already bringing a renewed degree of attention to those questions. One specific question that I still have is why Sabu began to regularly frequent my group’s IRC two months before the “Lulzsec indictments” and my own FBI raid occurred, and whether or not certain things he did there – including bullying a real activist and Project PM regular, Alexander Hanff, who worked for Privacy International, DDOSing Privacy International’s server, and then later denying he had done any such thing when called on it – were done in pursuit of a wider policy of disruption. We really could have done without having an FBI asset pull that kind of shit against one of our actual participants.
Anyway, here’s the convo between Sabu and the journalist:
-Barrett Brown
Project PM
irc.project-pm.org
— Log opened Fri Jul 29 13:24:07 2011
13:24 -!- Irssi: Starting query in anonops with jamesrbuk
13:24 <jamesrbuk> As requested ? hi
13:24 <SABU> hi
13:24 <SABU> I am confused by your Q/A regarding a trolls “research”
13:25 <SABU> there’s no other evidence or research to suggest I have any ties with hamas or any other terrorist group
13:25 <SABU> so are you really writing about a non-story? or was the Q/A just out of curiosity?
13:25 <jamesrbuk> Jester’s got a known agenda, and anything said is taken in that context
13:25 <jamesrbuk> But
13:26 <jamesrbuk> Given he has evidenced ? to an extent ? links from your twitter account to particular websites and individuals
13:26 <jamesrbuk> it’s worth setting out, with the context of who he is and your response
13:26 <jamesrbuk> alongside updates from the Shetlands arrest etc
13:27 <SABU> thats fine, but, the research he presents is
13:27 <SABU> google “hamas flag”
13:28 <SABU> and ties me to a PUBLIC FIGURE / RAPPER
13:28 <SABU> the rapper in question beast1333 is someone that believes in reverse symbolism etc. to say he has any ties to terrorism would be to say he has any ties to the freemason society
13:28 <SABU> and thats pure shit
13:28 <SABU> as for myself, I’ve repeately, dozens of times explained why I have used the flag as my avatar
13:29 <SABU> so take this opportunity to clear up any confusion or questions you may have. but rest assured I have no ties at all to terrorism
13:30 <jamesrbuk> Why not the Palestinian flag as opposed to Hamas?
13:30 <jamesrbuk> Hamas have some pretty extreme views
13:31 <SABU> because thats not the point I am making
13:31 <SABU> the united states and israel pushed the people of gaza to democratically choose a government
13:31 <SABU> they chose hamas
13:31 <SABU> then the united states and israely denies to accept the government of gaza as the true government of gaza
13:31 <SABU> is this not hypocratic of our democratic ideals?
13:31 <jamesrbuk> But at the West Bank they chose Fatah ? there’s an aspect of decision-making there, right?
13:31 <SABU> its only democracy unless we believe/say so
13:32 <SABU> and israel/us did not object to fatah
13:32 <SABU> so using fatah does not convey my point
13:32 <SABU> I know you’re a smart gent and you know the point I am making
13:33 <jamesrbuk> so it’s purely related to the fact Israel/US don’t recognise HGamas at democratically legitimate (but do recognise Fatah), rather than any supporting of their views?
13:35 <jamesrbuk> Because you can see why someone ? especially coming from the Jester’s POV ? would be concerned: Anon has moved from Goatse to attacks first on private security, then into systems like NATO. Escalation, plus a shift to security-related targets
13:36 <jamesrbuk> Where would a line be drawn? At what point *would* it start to benefit extremist/violent anti-Western groups/agendas?
13:36 <SABU> I’m sure/win 392
13:36 <SABU> one moment wrong window
13:37 <jamesrbuk> And even if people like the Jester totally wrong ? in your view ? surely you can see why the shift in targets over the last few months would paint a picture?
13:38 <SABU> to your first question yes exactly. good to see you get the idea.
13:39 <SABU> everything else: this is a non-story, its not even news-worthy. I’ve seen your other work so I’m curious why all of a sudden you’re focusing on this topic. Truth is we’re not doing anything pro-religious, thus mitigating the idea that we are tied to any islamic groups.
13:40 <SABU> we’ve helped many countries and peoples with different operations and nothing has been tied to terrorist activities. as soon as Jester posts a screen shot of “hamas flag” and ties it to my avatar all of a sudden thoughts jump out the window
13:41 <jamesrbuk> You know I’m following it closely ? I’m trying to udnerstand the extent to which you think about how it looks to someone, say, in the US who’s a strong patriot and sees sites like the CIA or NATO hacked.
13:41 <SABU> and honestly who gives a fuck if jester thinks what? Is he the common people? is he some sort of authority on what we are think en masse ? as far as I know he’s some random guy who DoSes sites (including an American shared web host last week that took down a Church, which no one thought to write about oddly).
13:41 <jamesrbuk> To most people who read it, they don’t think it’s just a website or DDOS, they worry about state secrets
13:43 <SABU> in order for us to understand how a real patriot would behave and think we need to know what a true patriot is: the forefathers of the united states of america were revolutionaries and extremists who at all costs (boston tea party et al) did what they had to do to expose and eventually expunge the crown from control
13:44 <SABU> for examle^
13:44 <SABU> example rather
13:44 <SABU> so, you have to look at this several ways
13:44 <jamesrbuk> Okay, so what’s your limit? What’s too much/too far?
13:44 <jamesrbuk> What’s the goal?
13:45 <SABU> I’m not giving you an interview, or to be quoted by the way. we are talking like two gentlemen
13:45 <SABU> but the goals? are stated in our press releases
13:45 <SABU> every press release discusses exactly the point of each operation
13:45 <SABU> for example, in the case of #antisec we have clearly stated we are focusing on security companies and government affiliates with poor security standards
13:45 <SABU> in the process exposing corruption when found
13:46 <SABU> in less than one month of antisec’s existence it has exposed 3-4 major federal contractors for the u.s.
13:46 <jamesrbuk> But surely there’s a wider point? You refer to the US founding fathers ? their operations were part of a wider plan.
13:47 <jamesrbuk> Is there a tagrety you wouldn’t go for/info you wouldn’t release if found?
13:48 <SABU> I think all of that is somewhat obvious? #antisec is targeting government and security corruption
13:48 <SABU> anonymous is involved in a myriad of operations from oporlando where they fought against the cops arresting people feeding the homeless
13:49 <SABU> to massive operations liek operation freedom / payback
13:49 <SABU> lulzsec is dead and ceases to exist so answering questions about that is irrelevant
13:50 <jamesrbuk> What kind of op would be the limit for you, though, personally?
13:50 <SABU> also I’m unsure if you know this but we came out very very strong against the terrorist act in Oslo, getting thousands of retweets of our message of solidarity with norway and its victims
13:50 <jamesrbuk> You’re the lightning rod at the moment, especially with Topiary off the scene atm.
13:50 <SABU> so again I really don’t see the newsworthyness in this
13:50 <SABU> the problem with your question is this
13:51 <SABU> I’m sure you’re sitting there thinking I’m avoiding the question
13:51 <SABU> but the actual answer is
13:51 <SABU> anonymous is a collective. when its massive and full of irc users on this one network (we’re not even talking about other anonymous networks) there are a lot of different operations
13:52 <SABU> it is up to you as the individual to choose with operations you will partake in or not
13:52 <SABU> for example, there are operations here I won’t get involved in because it simply doesnt interest me
13:52 <SABU> you might have an operation that is about the “doxing” of people. I don’t go around doxing people so I woulnd’t join it
13:52 <SABU> unlike my foes who sit on google all day googling peoples names hoping to dox them
13:52 <SABU> so _that_ is my personal limit
13:53 <jamesrbuk> Is not doxing a matter of it not interesting you, or a problem with it on principle?
13:53 <SABU> and again no disrespect to you but this is not an interview nor do I want to be quoted. this is a conversation between men and I hope my answers help you
13:54 <SABU> yes I do not like doxing, I think it is vile and sick because at the end of the day you never know if the person you dox is innocent or your target
13:54 <SABU> and if you go off and get an innocent person raided or killed
13:54 <SABU> then you’re liable for those consequences
13:54 <jamesrbuk> If we do something I’m likely to use part of the twitter reply as a quote, may use some of what is said here to shape a story without quoting.
13:54 <SABU> plus you get innocent people harrassed for no reason.
13:54 <SABU> thanks.
13:55 <jamesrbuk> Do you worry about the same when releasing email caches, though? WikiLeaks now takes names out of basically everything it puts out for that concern
13:57 <SABU> I can’t speak regarding lulzsec because it is now dead, and anything it did at this point is irrelevant. if you refer to us for example releasing 90k intelligence community logins for the military then I can discuss that
13:58 <SABU> in the case of the booz allan hamilton hack we as a collective expose a billion dollar company as a weak entry point into the united states military and intelligence community
13:58 <jamesrbuk> Was thinking largely of HBGary ? which clearly had stuff of public interest/import within it, but lots of irrelevent stuff ? and also NATO/The Sun, which I assume still have the potential to appear
13:59 <SABU> by posting the logins scoured through the initial attack we focus our point on the loss of confidentiality of our intelligence/military community as a result of BAHs lax security policy
14:01 <SABU> HBGary was a special case: 1) it was a company that had a focus of pushing this idea of social network doxing. in essence they were planning to sell the idea of mass doxing to the government/FBI/MET(eventually I’m sure). though, a few minutes ago you and I have just discussed our position regarding doxing. the fact that hbgary had produced any sort of research against anonymous using these invalid doxing techniques and were willing to go uut of their way to publicly discuss that case we had to make sure their technology was nothing more than incorrect assumption, FUD and bluff
14:01 <SABU> still writing patience …
14:02 <SABU> as for the release of their emails this was a decision that was made by a group of people, not myself specifically, so I can’t give you their perspective on the release of the emails but I can assure you the point of erleasing the emails was to expose hbgary as a whole
14:02 <SABU> because im sure you have read their emails
14:02 <SABU> and I’m sure you noticed a LOT OF CORRUPTION
14:02 <SABU> there was no way to expose that sort of corruption in one day where there were several gigabytes of emails
14:03 <jamesrbuk> Well, I was named (very peripherally) in the HBGary doc..
14:04 <SABU> nice
14:06 <SABU> now
14:06 <SABU> to continue with your question
14:06 <SABU> TheSun emails are safeguarded and won’t be released unless sifted through. AT the moment we are a bit too busy to focus on them so they’ll sit there until things can be handled correctly
14:06 <SABU> I’m sure you realize anonymous evolves
14:07 <SABU> otherwise we would have dropped the emails
14:07 <SABU> we realize there are potential sources that need protections in those archives
14:07 <jamesrbuk> Yes. Often strikes me as a similar evolution in some ways to WL
14:08 <SABU> now NATO
14:09 <SABU> if you google back a bit you’ll find a decleration of “war” by NATO to hackers world wide
14:09 <SABU> and because of that I’m sure we won’t be the last to own them
14:09 <SABU> until they take that ridiculous assertion down from their archives
14:11 <jamesrbuk> ah
14:12 <SABU> how are you feeling so far?
14:13 <SABU> am I sounding like an islamic extremist still?
14:14 <jamesrbuk> The charge is that it’s being used as a channel to move people/hackers towards extremism ? to that mode of thinking, your not sounding like an Islamic extremist could be taken as evidence. It’s the problem with the internet/conspiracies: they’re unflasifiable
14:14 <jamesrbuk> But I think it’s reasonably known I’m interested in anon/hacktivism/etc in a much wider sense than just that particular line
14:15 <jamesrbuk> Next thing I look at is likely to be the criminilization of dissent ? penalties towards protest/disruption online and how they compare (usually much more severe) to street protests etc
14:16 <SABU> yeah
14:16 <jamesrbuk> Anyway, I need to go and write some pieces. As a quick question ? is there any on-the-record comment you want to make re “Topiary”s arrest and continued detention?
14:17 <SABU> That it be recognized that if it in fact is Topiary, he is to be considered a political prisoner and his rights should be respected. The community stands behind all political prisoners across the world, and Topiary is one of them.
14:17 <SABU> thanks mate
14:17 <jamesrbuk> No worries if not
14:17 <SABU> recognizes*
14:17 <SABU> not recognized
14:18 <jamesrbuk> Cheers. Give me a shout on Twitter etc if you want to chat.
14:20 <SABU> I will. mention me when your story is up I’d like to read it. and I’ll RT it for people to see it
14:20 <SABU> direct traffic to it etc.
14:20 <SABU> wait
14:20 <SABU> you’re @ the guardian yes?
14:22 <jamesrbuk> There’s a chance the quote won’t appear as it might be taken as confirmation the guy arrested *is* Topiary, so would be contempt of court
14:22 <jamesrbuk> I am
14:22 <SABU> well
14:23 <SABU> so make it this then
14:23 <SABU> eh, it kills it
14:23 <SABU> pass a message to charles though: “you’re a twat”
14:23 <SABU> I would thoroughly appreciate it
14:24 <SABU> ❤
— Log closed Fri Jul 29 14:29:16 2011
— Log opened Fri Jul 29 15:22:22 2011
15:22 -!- jamesrbuk [jamesrbuk@AN-8ap.uh9.r3rabr.IP] has quit [Connection closed]
— Log closed Fri Jul 29 15:28:16 2011
TOP-SECRET – Arab Americans Seek Disadvantaged Minority Help
|
A Killer Among Us – Full Movie
One of the FBI’s top criminal profilers — takes you inside the minds of America’s most notorious killers
Solved ~ The Rivalry – Full Movie
25-year-old waitress Corey Parker is found dead in her apartment bedroom with over 100 stab wounds to her body. After two long years of intense investigation, detectives finally zero in on a suspect.
CONFIDENTIAL – Role of Liar “q” Between LulzSec and WikiLeaks
Gangland – The Filthy Few – Hells Angels of Seattle – Full Movie
TOP-SECRET – Fukushima Daiichi Nuclear Power Station 12-0528

FEMEN uncensored – Anti-Putin protesters strip off
TOP-SECRET – 2012 Bilderberg Meeting Participant List
The following press release and participants list was obtained from the official website of Bilderberg Meetings. Participant lists from nearly every Bilderberg Meeting since 1954 are also available as well as tax returns for the non-profit U.S.-based corporation American Friends of Bilderberg from 2007 – 2010.
BILDERBERG MEETINGS
Chantilly, Virginia, USA
31 May-3 June 2012
LIST OF PARTICIPANTS
| FRA | Castries, Henri de | Chairman and CEO, AXA Group |
| DEU | Ackermann, Josef | Chairman of the Management Board and the Group Executive Committee, Deutsche Bank AG |
| GBR | Agius, Marcus | Chairman, Barclays plc |
| USA | Ajami, Fouad | Senior Fellow, The Hoover Institution, Stanford University |
| USA | Alexander, Keith B. | Commander, US Cyber Command; Director, National Security Agency |
| INT | Almunia, Joaquín | Vice-President – Commissioner for Competition, European Commission |
| USA | Altman, Roger C. | Chairman, Evercore Partners |
| PRT | Amado, Luís | Chairman, Banco Internacional do Funchal (BANIF) |
| NOR | Andresen, Johan H. | Owner and CEO, FERD |
| FIN | Apunen, Matti | Director, Finnish Business and Policy Forum EVA |
| TUR | Babacan, Ali | Deputy Prime Minister for Economic and Financial Affairs |
| PRT | Balsemão, Francisco Pinto | President and CEO, Impresa; Former Prime Minister |
| FRA | Baverez, Nicolas | Partner, Gibson, Dunn & Crutcher LLP |
| FRA | Béchu, Christophe | Senator, and Chairman, General Council of Maine-et-Loire |
| BEL | Belgium, H.R.H. Prince Philippe of | |
| TUR | Berberoğlu, Enis | Editor-in-Chief, Hürriyet Newspaper |
| ITA | Bernabè, Franco | Chairman and CEO, Telecom Italia |
| GBR | Boles, Nick | Member of Parliament |
| SWE | Bonnier, Jonas | President and CEO, Bonnier AB |
| NOR | Brandtzæg, Svein Richard | President and CEO, Norsk Hydro ASA |
| AUT | Bronner, Oscar | Publisher, Der Standard Medienwelt |
| SWE | Carlsson, Gunilla | Minister for International Development Cooperation |
| CAN | Carney, Mark J. | Governor, Bank of Canada |
| ESP | Cebrián, Juan Luis | CEO, PRISA; Chairman, El País |
| AUT | Cernko, Willibald | CEO, UniCredit Bank Austria AG |
| FRA | Chalendar, Pierre André de | Chairman and CEO, Saint-Gobain |
| DNK | Christiansen, Jeppe | CEO, Maj Invest |
| RUS | Chubais, Anatoly B. | CEO, OJSC RUSNANO |
| CAN | Clark, W. Edmund | Group President and CEO, TD Bank Group |
| GBR | Clarke, Kenneth | Member of Parliament, Lord Chancellor and Secretary of Justice |
| USA | Collins, Timothy C. | CEO and Senior Managing Director, Ripplewood Holdings, LLC |
| ITA | Conti, Fulvio | CEO and General Manager, Enel S.p.A. |
| USA | Daniels, Jr., Mitchell E. | Governor of Indiana |
| USA | DeMuth, Christopher | Distinguished Fellow, Hudson Institute |
| USA | Donilon, Thomas E. | National Security Advisor, The White House |
| GBR | Dudley, Robert | Group Chief Executive, BP plc |
| ITA | Elkann, John | Chairman, Fiat S.p.A. |
| DEU | Enders, Thomas | CEO, Airbus |
| USA | Evans, J. Michael | Vice Chairman, Global Head of Growth Markets, Goldman Sachs & Co. |
| AUT | Faymann, Werner | Federal Chancellor |
| DNK | Federspiel, Ulrik | Executive Vice President, Haldor Topsøe A/S |
| USA | Ferguson, Niall | Laurence A. Tisch Professor of History, Harvard University |
| GBR | Flint, Douglas J. | Group Chairman, HSBC Holdings plc |
| CHN | Fu, Ying | Vice Minister of Foreign Affairs |
| IRL | Gallagher, Paul | Former Attorney General; Senior Counsel |
| USA | Gephardt, Richard A. | President and CEO, Gephardt Group |
| GRC | Giannitsis, Anastasios | Former Minister of Interior; Professor of Development and International Economics, University of Athens |
| USA | Goolsbee, Austan D. | Professor of Economics, University of Chicago Booth School of Business |
| USA | Graham, Donald E. | Chairman and CEO, The Washington Post Company |
| ITA | Gruber, Lilli | Journalist – Anchorwoman, La 7 TV |
| INT | Gucht, Karel de | Commissioner for Trade, European Commission |
| NLD | Halberstadt, Victor | Professor of Economics, Leiden University; Former Honorary Secretary General of Bilderberg Meetings |
| USA | Harris, Britt | CIO, Teacher Retirement System of Texas |
| USA | Hoffman, Reid | Co-founder and Executive Chairman, LinkedIn |
| CHN | Huang, Yiping | Professor of Economics, China Center for Economic Research, Peking University |
| USA | Huntsman, Jr., Jon M. | Chairman, Huntsman Cancer Foundation |
| DEU | Ischinger, Wolfgang | Chairman, Munich Security Conference; Global Head Government Relations, Allianz SE |
| RUS | Ivanov, Igor S. | Associate member, Russian Academy of Science; President, Russian International Affairs Council |
| FRA | Izraelewicz, Erik | CEO, Le Monde |
| USA | Jacobs, Kenneth M. | Chairman and CEO, Lazard |
| USA | Johnson, James A. | Vice Chairman, Perseus, LLC |
| USA | Jordan, Jr., Vernon E. | Senior Managing Director, Lazard |
| USA | Karp, Alexander | CEO, Palantir Technologies |
| USA | Karsner, Alexander | Executive Chairman, Manifest Energy, Inc |
| FRA | Karvar, Anousheh | Inspector, Inter-ministerial Audit and Evaluation Office for Social, Health, Employment and Labor Policies |
| RUS | Kasparov, Garry | Chairman, United Civil Front (of Russia) |
| GBR | Kerr, John | Independent Member, House of Lords |
| USA | Kerry, John | Senator for Massachusetts |
| TUR | Keyman, E. Fuat | Director, Istanbul Policy Center and Professor of International Relations, Sabanci University |
| USA | Kissinger, Henry A. | Chairman, Kissinger Associates, Inc. |
| USA | Kleinfeld, Klaus | Chairman and CEO, Alcoa |
| TUR | Koç, Mustafa | Chairman, Koç Holding A.Ş. |
| DEU | Koch, Roland | CEO, Bilfinger Berger SE |
| INT | Kodmani, Bassma | Member of the Executive Bureau and Head of Foreign Affairs, Syrian National Council |
| USA | Kravis, Henry R. | Co-Chairman and Co-CEO, Kohlberg Kravis Roberts & Co. |
| USA | Kravis, Marie-Josée | Senior Fellow, Hudson Institute |
| INT | Kroes, Neelie | Vice President, European Commission; Commissioner for Digital Agenda |
| USA | Krupp, Fred | President, Environmental Defense Fund |
| INT | Lamy, Pascal | Director-General, World Trade Organization |
| ITA | Letta, Enrico | Deputy Leader, Democratic Party (PD) |
| ISR | Levite, Ariel E. | Nonresident Senior Associate, Carnegie Endowment for International Peace |
| USA | Li, Cheng | Director of Research and Senior Fellow, John L. Thornton China Center, Brookings Institution |
| USA | Lipsky, John | Distinguished Visiting Scholar, Johns Hopkins University |
| USA | Liveris, Andrew N. | President, Chairman and CEO, The Dow Chemical Company |
| DEU | Löscher, Peter | President and CEO, Siemens AG |
| USA | Lynn, William J. | Chairman and CEO, DRS Technologies, Inc. |
| GBR | Mandelson, Peter | Member, House of Lords; Chairman, Global Counsel |
| USA | Mathews, Jessica T. | President, Carnegie Endowment for International Peace |
| DEN | Mchangama, Jacob | Director of Legal Affairs, Center for Political Studies (CEPOS) |
| CAN | McKenna, Frank | Deputy Chair, TD Bank Group |
| USA | Mehlman, Kenneth B. | Partner, Kohlberg Kravis Roberts & Co. |
| GBR | Micklethwait, John | Editor-in-Chief, The Economist |
| FRA | Montbrial, Thierry de | President, French Institute for International Relations |
| PRT | Moreira da Silva, Jorge | First Vice-President, Partido Social Democrata (PSD) |
| USA | Mundie, Craig J. | Chief Research and Strategy Officer, Microsoft Corporation |
| DEU | Nass, Matthias | Chief International Correspondent, Die Zeit |
| NLD | Netherlands, H.M. the Queen of the | |
| ESP | Nin Génova, Juan María | Deputy Chairman and CEO, Caixabank |
| IRL | Noonan, Michael | Minister for Finance |
| USA | Noonan, Peggy | Author, Columnist, The Wall Street Journal |
| FIN | Ollila, Jorma | Chairman, Royal Dutch Shell, plc |
| USA | Orszag, Peter R. | Vice Chairman, Citigroup |
| GRC | Papalexopoulos, Dimitri | Managing Director, Titan Cement Co. |
| NLD | Pechtold, Alexander | Parliamentary Leader, Democrats ’66 (D66) |
| USA | Perle, Richard N. | Resident Fellow, American Enterprise Institute |
| NLD | Polman, Paul | CEO, Unilever PLC |
| CAN | Prichard, J. Robert S. | Chair, Torys LLP |
| ISR | Rabinovich, Itamar | Global Distinguished Professor, New York University |
| GBR | Rachman, Gideon | Chief Foreign Affairs Commentator, The Financial Times |
| USA | Rattner, Steven | Chairman, Willett Advisors LLC |
| CAN | Redford, Alison M. | Premier of Alberta |
| CAN | Reisman, Heather M. | CEO, Indigo Books & Music Inc. |
| DEU | Reitzle, Wolfgang | CEO & President, Linde AG |
| USA | Rogoff, Kenneth S. | Professor of Economics, Harvard University |
| USA | Rose, Charlie | Executive Editor and Anchor, Charlie Rose |
| USA | Ross, Dennis B. | Counselor, Washington Institute for Near East Policy |
| POL | Rostowski, Jacek | Minister of Finance |
| USA | Rubin, Robert E. | Co-Chair, Council on Foreign Relations; Former Secretary of the Treasury |
| NLD | Rutte, Mark | Prime Minister |
| ESP | Sáenz de Santamaría Antón, Soraya | Vice President and Minister for the Presidency |
| NLD | Scheffer, Paul | Professor of European Studies, Tilburg University |
| USA | Schmidt, Eric E. | Executive Chairman, Google Inc. |
| AUT | Scholten, Rudolf | Member of the Board of Executive Directors, Oesterreichische Kontrollbank AG |
| FRA | Senard, Jean-Dominique | CEO, Michelin Group |
| USA | Shambaugh, David | Director, China Policy Program, George Washington University |
| INT | Sheeran, Josette | Vice Chairman, World Economic Forum |
| FIN | Siilasmaa, Risto | Chairman of the Board of Directors, Nokia Corporation |
| USA | Speyer, Jerry I. | Chairman and Co-CEO, Tishman Speyer |
| CHE | Supino, Pietro | Chairman and Publisher, Tamedia AG |
| IRL | Sutherland, Peter D. | Chairman, Goldman Sachs International |
| USA | Thiel, Peter A. | President, Clarium Capital / Thiel Capital |
| TUR | Timuray, Serpil | CEO, Vodafone Turkey |
| DEU | Trittin, Jürgen | Parliamentary Leader, Alliance 90/The Greens |
| GRC | Tsoukalis, Loukas | President, Hellenic Foundation for European and Foreign Policy |
| FIN | Urpilainen, Jutta | Minister of Finance |
| CHE | Vasella, Daniel L. | Chairman, Novartis AG |
| INT | Vimont, Pierre | Executive Secretary General, European External Action Service |
| GBR | Voser, Peter | CEO, Royal Dutch Shell plc |
| SWE | Wallenberg, Jacob | Chairman, Investor AB |
| USA | Warsh, Kevin | Distinguished Visiting Fellow, The Hoover Institution, Stanford University |
| GBR | Wolf, Martin H. | Chief Economics Commentator, The Financial Times |
| USA | Wolfensohn, James D. | Chairman and CEO, Wolfensohn and Company |
| CAN | Wright, Nigel S. | Chief of Staff, Office of the Prime Minister |
| USA | Yergin, Daniel | Chairman, IHS Cambridge Energy Research Associates |
| INT | Zoellick, Robert B. | President, The World Bank Group |
| Rapporteurs | ||
| GBR | Bredow, Vendeline von | Business Correspondent, The Economist |
| GBR | Wooldridge, Adrian D. | Foreign Correspondent, The Economist |
Press Release
Bilderberg Meetings
The 60th Bilderberg Meeting will be held in Chantilly, Virginia, USA from 31 May – 3 June 2012. The Conference will deal mainly with political, economic and societal issues like Transatlantic Relations, Evolution of the Political Landscape in Europe and the US, Austerity and Growth in Developed Economies, Cyber Security, Energy Challenges, the Future of Democracy, Russia, China and the Middle East.
Approximately 145 participants will attend of whom about two-thirds come from Europe and the balance from North America and other countries. About one-third is from government and politics, and two-thirds are from finance, industry, labor, education, and communications. The meeting is private in order to encourage frank and open discussion.
Bilderberg takes its name from the hotel in Holland, where the first meeting took place in May 1954. That pioneering meeting grew out of the concern expressed by leading citizens on both sides of the Atlantic that Western Europe and North America were not working together as closely as they should on common problems of critical importance. It was felt that regular, off-the-record discussions would help create a better understanding of the complex forces and major trends affecting Western nations in the difficult post-war period.
The Cold War has now ended. But in practically all respects there are more, not fewer, common problems – from trade to jobs, from monetary policy to investment, from ecological challenges to the task of promoting international security. It is hard to think of any major issue in either Europe or North America whose unilateral solution would not have repercussions for the other.
Thus the concept of a European-American forum has not been overtaken by time. The dialogue between these two regions is still – even increasingly – critical.
What is unique about Bilderberg as a forum is the broad cross-section of leading citizens that are assembled for nearly three days of informal and off-the-record discussion about topics of current concern especially in the fields of foreign affairs and the international economy; the strong feeling among participants that in view of the differing attitudes and experiences of the Western nations, there remains a clear need to further develop an understanding in which these concerns can be accommodated; the privacy of the meetings, which has no purpose other than to allow participants to speak their minds openly and freely.
In short, Bilderberg is a small, flexible, informal and off-the-record international forum in which different viewpoints can be expressed and mutual understanding enhanced.
Bilderberg’s only activity is its annual Conference. At the meetings, no resolutions are proposed, no votes taken, and no policy statements issued. Since 1954, fifty-nine conferences have been held. The names of the participants are made available to the press. Participants are chosen for their experience, their knowledge, and their standing; all participants attend Bilderberg in a private and not an official capacity.
For further inf
M – Full Movie
** IMDB #58 Best Movie Of All Time ** in High Def
M – Eine Stadt sucht einen Moerder (1931)
When the police in a German city are unable to catch a child-murderer, other criminals join in the manhunt.
This film is nothing less than a masterpiece.
It is a highly structured and stylized film about a serial killer.
It created the serial kill genre, which includes such entries as Psycho and Silence of the Lambs.
Alfred Hitchcock (the director of Psycho) was a disciple of Lang as were Jacques Tourneur (The Leopard Man (1943)) and Michael Powell (Peeping Tom (1960)).
M was not only the originator of the genre, but arguably remains it preeminent entry.
Highly recommended for those in the mood for a Hitchcockian-style thriller with a great performance by Peter Lorre and great story-telling technique by Fritz Lang
CYBER-STASI – Stockton Man Sentenced to Almost Five Years in Prison for Identity Theft
SACRAMENTO, CA—Michael Garcia, 39, of Stockton, was sentenced today by United States District Judge Morrison C. England Jr. to 57 months in prison for fraud in connection with computers and in connection with an access device, United States Attorney Benjamin B. Wagner announced.
According to court documents, Garcia was employed as a technician by a contractor that provided information technology (IT) assistance to third parties. While employed there, Garcia accessed the computer servers of a law firm and an accountant firm without their knowledge or authorization and downloaded the personal information of more than 1,450 clients and employees. Garcia maintained this information on his computer and elsewhere.
According to court documents, Garcia and others used this personal and financial information to make counterfeited identification documents including driver’s licenses and military identification. They used the information to open bank accounts, draft bank checks, make cash withdrawals, obtain loans and lines of credit, and make unauthorized purchases. Additionally, Garcia accompanied others who wore stolen U.S. Customs and Border Protection uniforms to carry out certain fraudulent transactions, such as cashing checks, in the belief that the uniforms gave them more credibility. When arrested, Garcia possessed counterfeit California driver’s licenses, one of which bore his photo but with the name of a victim. The loss is more than $136,000.
Today in court, an employee of the accounting firm where Garcia unlawfully accessed the personal financial information told of the severe hardship suffered by the firm because of Garcia’s actions, as well as the personal toll she experienced because of Garcia’s breach of trust. Judge England commented that identity theft cases, particularly those where there has been an abuse of trust, negatively affect many lives.
This case was the product of an extensive investigation by the Federal Bureau of Investigation and the San Joaquin County Sheriff’s Department. Assistant United States Attorneys Todd Pickles and Robin Taylor prosecuted the case.
Gangland – Capitol Killers – MS-13 – Full Movie
Toxdat-Opfer belegen die Mordpläne und Morde der STASI – The Original STASI Murder Documents
Gangland – Shoot To Kill – Florencia 13 – Full Movie
CONFIDENTIAL – The Real Sabu from We Are Anonymous
DOWNLOAD THE ORIGINAL DOCUMENT HERE
Gangland – Better Off Dead – Ñetas – Full Movie
Unveiled – 142 WikiLeaks Cables Citing SIMO Code for CIA
142 WikiLeaks Cables Citing SIMO Code for CIA
SIMO-CIA.zip 142 WikiLeaks Cables Citing SIMO Code for CIA May 31, 2012
Examples of WikiLeaks Cables Showing Use of Code Word SIMO for CIA or C/SIMO for Chief of Station (Thanks to @Nin_99 and @Wikileaks for link to Taz.de)
http://cablesearch.org/cable/view.php?id=05LJUBLJANA808&hl=C%2FSIMO
1. (S) On November 23, DCM, C/SIMO, and PolMiloff delivered reftel demarche and presentation to MFA Director for Policy Planning and Multilateral Policy (A/S equivalent) Stanislav Rascan, Security Department Head Stanislav Vidovic, and Security Department staffer Rina Pavlin Gnidovec. During the course of C/SIMO’s presentation, Vidovic asked whether the documents shown in the PowerPoint were from Iran, whether the test facility pictured in the diagram was a detonation site or a monitoring facility, and whether IC projections included a timeline for completion of a usable nuclear weapon. C/SIMO responded by noting the documents were from Iran, the diagram featured in the presentation depicted a monitoring facility 10 km removed from the detonation site, and that no known concrete timeline for weaponization existed. Vidovic also asked whether it is the U.S. assessment that Iran is building a nuclear weapon for defensive purposes or whether it has aggressive intentions. C/SIMO underscored the possibility that Iran could use a nuclear weapon preemptively, though it might choose to do so through another state or non-state organization.
http://cablesearch.org/cable/view.php?id=06TOKYO5624&hl=SIMO
8. (S) U.S. participants:
– Assistant Secretary Randall Fort
– INR/NEA Chief John Merrill
– Embassy SIMO Representative Constance Taube
– Political Officer Keith Jordan (control officer)
– Political Officer Evan Reade (notetaker)
http://cablesearch.org/cable/view.php?id=08BELGRADE1108&hl=SIMO
1. (S/NF) The GOT on January 12 passed to SIMO the names of US Embassy officers found on a piece of paper at one of the sites used by “Salafist” terror suspects (reftels). SIMO is reporting this information through other channels.
http://cablesearch.org/cable/view.php?id=06KUWAIT4653&hl=SIMO
2. (S/NF) SIMO noted continuing robust information exchange with Kuwait State Security (KSS) and Kuwait Military Intelligence (KMI) on a range of issues including Iraq, Iran and Hezbollah. KSS and KMI continue to expend substantial resources on force protection efforts for U.S. personnel and convoys. SIMO Chief said U.S.-provided training had increased this year through his organization. He cited the GOK need to improve capabilities across the board, particularly tradecraft and technical capabilities. DATT noted that following the initial phase of DIA-funded human intelligence training, Kuwait will likely pursue further training through private contractors.
For many more instances search for “SIMO” at Cablesearch.org (SIMO will be highlighted in yellow. Ignore its use as a proper name.)
TOP-SECRET – U.S. Army Afghanistan Human Terrain Teams Map April 2012
The following map depicts the approximate locations, members and national affiliations of every human terrain team operating in Afghanistan as part of the U.S. Army’s Human Terrain System. The information is accurate as of April 3, 2012.
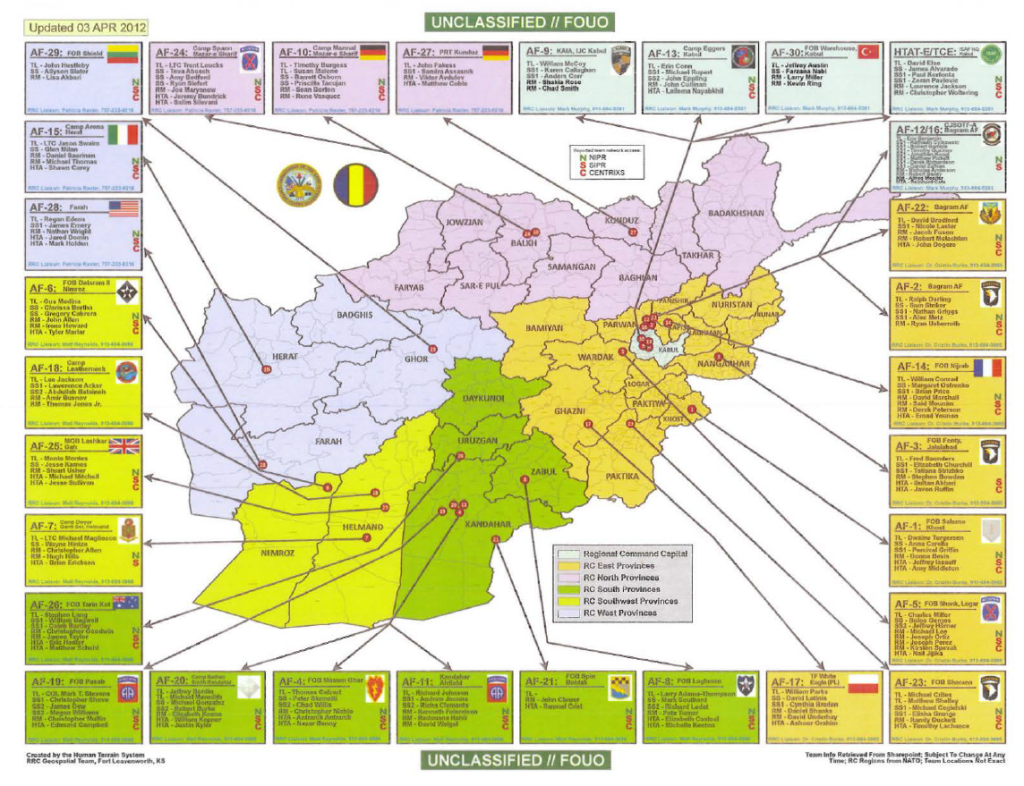
Gangland – Valley of Death – New Mexican Mafia – Full Movie
Cryptome – Anonymous Battles Media Gorgons
Anonymous Battles Media Gorgons, May 26, 2012
By John Young “Cryptome” (New York, NY)
This review is from: We Are Anonymous: Inside the Hacker World of LulzSec, Anonymous, and the Global Cyber Insurgency (Hardcover)
We Are Anonymous portrays the battle unfolding for control of the Internet era as insurgent skills and techniques for cyber and real world challenges are invented, shared and applied in a struggle with armies of governments, commerce and institutions accustomed to collusive domination.
Parmy Olson’s highly informative account based on extensive interviews, IRC chats, emails of celebrated nics of Anonymous, LulzSec and other subversive inititatives demonstrates that these well-publicized skirmishes are only a small part of a much greater conflict underway between agile, swarming, anarchic, proficient dissidents and heirarchical, sclerotic, bloated and inept authorities worldwide.
This is a amply resourced book to learn about a rapidly spreading under-culture undermining the over-culture, to enjoy its Encyclopedia Dramatica humor, to be infected by its gutsy courage, for appreciating its generous, bountiful, defiant lulz.
Above all, though, this rollicking narrative of misbehavior and disobedience can inspire opposition to the pretentious, ponderous, manipulative ideology of using the Internet to enforce knowledge consumption manufactured by gov, com, edu and org.
This volume shows that the prime force working both sides of the contest is opportunistic multi-headed media gorgon of journalism, film, documentaries, scholarship and personal data aggregating — social engineering, egging on, flattering, seducing, lying, betraying, cheating, double-crossing, promising fame, notoriety and gratification — deploying the traditional means and methods of uniquely privileged spies operating outside the rules of engagement, claiming the high ground above the battleground from their own protected overlook to broadcast beguiling events as they fabricate and churn opinion, news and knowledge.
Succumb to the allure of publicity gorgons and be packaged for sale to your enemies.
The gorgons are legion. Expect them to promote suspicion. This should make U mad.
__________
Apropos:
From a New York Times review of Buzz Bissinger’s latest book:
In a line that’s as slashing as anything in Janet Malcolm’s book “The Journalist and the Murderer,” he says: “All writers silently soak up despair for our own advantage; like dogs rolling in the guts of dead animals, the stink of others makes us giddy. We deny it but we lie in denying it.”
http://en.wikipedia.org/wiki/The_Journalist_and_the_Murderer
The Journalist and the Murderer is an examination of the professional choices that shape a work of non-fiction, as well as a rumination on the morality that underpins the journalistic enterprise. The journalist in question is the author Joe McGinniss; the murderer is the former Special Forces Captain Jeffery MacDonald, who became the subject of McGinniss’ 1983 book Fatal Vision.
When Malcolm’s work first appeared in March 1989, as a two-part serialization in The New Yorker magazine, it caused a sensation, becoming the occasion for wide-ranging debate within the news industry.
Malcolm’s thesis, and the most widely quoted passage from The Journalist and the Murderer, is presented in the book’s opening paragraph: “Every journalist who is not too stupid or too full of himself to notice what is going on knows that what he does is morally indefensible.” She continues:
He is a kind of confidence man, preying on people’s vanity, ignorance or loneliness, gaining their trust and betraying them without remorse. Like the credulous widow who wakes up one day to find the charming young man and all her savings gone, so the consenting subject of a piece of nonfiction learns—when the article or book appears—his hard lesson. Journalists justify their treachery in various ways according to their temperaments. The more pompous talk about freedom of speech and “the public’s right to know”; the least talented talk about Art; the seemliest murmur about earning a living.”Anonymous Battles Media Gorgons, May 26, 2012
By John Young “Cryptome” (New York, NY)
This review is from: We Are Anonymous: Inside the Hacker World of LulzSec, Anonymous, and the Global Cyber Insurgency (Hardcover)
We Are Anonymous portrays the battle unfolding for control of the Internet era as insurgent skills and techniques for cyber and real world challenges are invented, shared and applied in a struggle with armies of governments, commerce and institutions accustomed to collusive domination.
Parmy Olson’s highly informative account based on extensive interviews, IRC chats, emails of celebrated nics of Anonymous, LulzSec and other subversive inititatives demonstrates that these well-publicized skirmishes are only a small part of a much greater conflict underway between agile, swarming, anarchic, proficient dissidents and heirarchical, sclerotic, bloated and inept authorities worldwide.
This is a amply resourced book to learn about a rapidly spreading under-culture undermining the over-culture, to enjoy its Encyclopedia Dramatica humor, to be infected by its gutsy courage, for appreciating its generous, bountiful, defiant lulz.
Above all, though, this rollicking narrative of misbehavior and disobedience can inspire opposition to the pretentious, ponderous, manipulative ideology of using the Internet to enforce knowledge consumption manufactured by gov, com, edu and org.
This volume shows that the prime force working both sides of the contest is opportunistic multi-headed media gorgon of journalism, film, documentaries, scholarship and personal data aggregating — social engineering, egging on, flattering, seducing, lying, betraying, cheating, double-crossing, promising fame, notoriety and gratification — deploying the traditional means and methods of uniquely privileged spies operating outside the rules of engagement, claiming the high ground above the battleground from their own protected overlook to broadcast beguiling events as they fabricate and churn opinion, news and knowledge.
Succumb to the allure of publicity gorgons and be packaged for sale to your enemies.
The gorgons are legion. Expect them to promote suspicion. This should make U mad.
__________
Apropos:
From a New York Times review of Buzz Bissinger’s latest book:
In a line that’s as slashing as anything in Janet Malcolm’s book “The Journalist and the Murderer,” he says: “All writers silently soak up despair for our own advantage; like dogs rolling in the guts of dead animals, the stink of others makes us giddy. We deny it but we lie in denying it.”
http://en.wikipedia.org/wiki/The_Journalist_and_the_Murderer
The Journalist and the Murderer is an examination of the professional choices that shape a work of non-fiction, as well as a rumination on the morality that underpins the journalistic enterprise. The journalist in question is the author Joe McGinniss; the murderer is the former Special Forces Captain Jeffery MacDonald, who became the subject of McGinniss’ 1983 book Fatal Vision.
When Malcolm’s work first appeared in March 1989, as a two-part serialization in The New Yorker magazine, it caused a sensation, becoming the occasion for wide-ranging debate within the news industry.
Malcolm’s thesis, and the most widely quoted passage from The Journalist and the Murderer, is presented in the book’s opening paragraph: “Every journalist who is not too stupid or too full of himself to notice what is going on knows that what he does is morally indefensible.” She continues:
He is a kind of confidence man, preying on people’s vanity, ignorance or loneliness, gaining their trust and betraying them without remorse. Like the credulous widow who wakes up one day to find the charming young man and all her savings gone, so the consenting subject of a piece of nonfiction learns—when the article or book appears—his hard lesson. Journalists justify their treachery in various ways according to their temperaments. The more pompous talk about freedom of speech and “the public’s right to know”; the least talented talk about Art; the seemliest murmur about earning a living.”
Gangland – Road Warriros – Full Movie
TOP-SECRET – Assange Extradition Appeal Judgement
FEMEN – Topless Activists Seize Euro 2012 Trophy
Topless members of the Femen radical feminist group seized the Euro 2012 football trophy on display in Ukraine to protest against the increase of sex tourism in the former Soviet republic.
TOP-SECRET – NSA Crypto Shaping of Computer Industry
DOWNLOAD THE ORIGINAL DOCUMENT HERE
Gangland – Wild Boyz – Full Movie
Gangland – Death Before Dishonor – Full Movie
TOP-SECRET – NSA Crypto Shaping of Data Encryption Standard
DOWNLOAD THE ORIGINAL DOCUMENT HERE
Gangland ~ Evil Breed – Full Movie
Gangland tells the inside stories of some of America’s most notorious street gangs.
TOP-SECRET – CIA: US Psychological Warfare Doctrinal Program
DOWNLOAD THE ORIGINAL DOCUMENT HERE
Gangland ~ Behind Enemy Lines – Full Movie
TOP-SECRET – Fukushima Daiichi Nuclear Power Station 12-0526
28 May 2012
TEPCO video of the 26 May 2012 tour shown below:http://photo.tepco.co.jp/en/date/2012/201205-e/120526-01e.html
TEPCO high-resolution photos of the tour:
http://photo.tepco.co.jp/en/date/2012/201205-e/120528_01e.html
http://photo.tepco.co.jp/en/date/2012/201205-e/120528-02e.html
27 May 2012
Fukushima Daiichi Nuclear Power Station 26 May 2012
These photos are reduced to half-size of the originals. The 16 full-size originals:
http://cryptome.org/2012-info/daiichi-12-0526/daiichi-12-0526.zip (18.4MB)
TEPCO report on structural stability of Unit 4, 25 May 2012:
http://www.tepco.co.jp/en/nu/fukushima-np/images/handouts_120525_05-e.pdf
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict19.jpg)
Cryptome Nuclear Power Plant and WMD series: http://cryptome.org/nppw-series.htm
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict3.jpg) Media persons and Tokyo Electric Power Co. employees look at the company’s tsunami-crippled Fukushima Dai-Ichi nuclear power plant during a press tour in Okuma town, Fukushima prefecture, Japan, Saturday, May 26, 2012. (Tomohiro Ohsumi, Pool) Media persons and Tokyo Electric Power Co. employees look at the company’s tsunami-crippled Fukushima Dai-Ichi nuclear power plant during a press tour in Okuma town, Fukushima prefecture, Japan, Saturday, May 26, 2012. (Tomohiro Ohsumi, Pool) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict15.jpg) Reactor buildings from left to right, the No. 1, the No. 2, the No. 3 and the No. 4, are seen during a press tour at Tokyo Electric Power Co.’s (TEPCO) Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. (Tomohiro Ohsumi, Pool) Reactor buildings from left to right, the No. 1, the No. 2, the No. 3 and the No. 4, are seen during a press tour at Tokyo Electric Power Co.’s (TEPCO) Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. (Tomohiro Ohsumi, Pool) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict0.jpg) Members of the media and Tokyo Electric Power Co. employees walk in front of the No. 4 reactor building, rear, crippled by the March 11 earthquake and tsunami, at the utility company’s Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. (Tomohiro Ohsumi, Pool) Members of the media and Tokyo Electric Power Co. employees walk in front of the No. 4 reactor building, rear, crippled by the March 11 earthquake and tsunami, at the utility company’s Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. (Tomohiro Ohsumi, Pool) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict12.jpg) The damaged No. 4 reactor building stands at Tokyo Electric Power Co.’s Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. Japanese Environment and Nuclear Minister Goshi Hosono, accompanied by the media, has visited the crippled Fukushima Dai-ichi nuclear power plant to inspect a reactor building and its spent fuel pool at the center of safety concerns. (Tomohiro Ohsumi, Pool) The damaged No. 4 reactor building stands at Tokyo Electric Power Co.’s Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. Japanese Environment and Nuclear Minister Goshi Hosono, accompanied by the media, has visited the crippled Fukushima Dai-ichi nuclear power plant to inspect a reactor building and its spent fuel pool at the center of safety concerns. (Tomohiro Ohsumi, Pool) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict11.jpg) Goshi Hosono, Japan’s environment and nuclear minister, third from left, wearing a red helmet, along with members of the media, walks on the No. 4 reactor building at Tokyo Electric Power Co.’s (TEPCO) Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. Japan’s environment and nuclear minister Hosono visited the tsunami-crippled nuclear power plant Saturday to inspect a spent fuel pool at the center of safety concerns. (Tomohiro Ohsumi, Pool) Goshi Hosono, Japan’s environment and nuclear minister, third from left, wearing a red helmet, along with members of the media, walks on the No. 4 reactor building at Tokyo Electric Power Co.’s (TEPCO) Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. Japan’s environment and nuclear minister Hosono visited the tsunami-crippled nuclear power plant Saturday to inspect a spent fuel pool at the center of safety concerns. (Tomohiro Ohsumi, Pool) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict16.jpg) Goshi Hosono, Japan’s environment and nuclear minister, inspects the No. 4 reactor building at Tokyo Electric Power Co.’s Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima Prefecture, Japan, Saturday, May 26, 2012. The visit by Hosono, apparently aimed at demonstrating the safety of the facility, came amid renewed concerns about conditions at the plant’s No. 4 reactor after its operator reported a bulging of the building’s wall. (Toshiaki Shimizu, Japan Pool) [Yellow reactor containment dome at center background.] Goshi Hosono, Japan’s environment and nuclear minister, inspects the No. 4 reactor building at Tokyo Electric Power Co.’s Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima Prefecture, Japan, Saturday, May 26, 2012. The visit by Hosono, apparently aimed at demonstrating the safety of the facility, came amid renewed concerns about conditions at the plant’s No. 4 reactor after its operator reported a bulging of the building’s wall. (Toshiaki Shimizu, Japan Pool) [Yellow reactor containment dome at center background.] |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict2.jpg) Workers walk in front of the No. 4 reactor building at Tokyo Electric Power Co.’s tsunami-crippled Fukushima Dai-Ichi nuclear power plant in Okuma town, Fukushima prefecture, Japan, Saturday, May 26, 2012. (Tomohiro Ohsumi, Pool) Workers walk in front of the No. 4 reactor building at Tokyo Electric Power Co.’s tsunami-crippled Fukushima Dai-Ichi nuclear power plant in Okuma town, Fukushima prefecture, Japan, Saturday, May 26, 2012. (Tomohiro Ohsumi, Pool) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict7.jpg) An inside view of the damaged No. 4 reactor building is seen at Tokyo Electric Power Co.’s tsunami-crippled Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. (Toshiaki Shimizu, Japan Pool) An inside view of the damaged No. 4 reactor building is seen at Tokyo Electric Power Co.’s tsunami-crippled Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. (Toshiaki Shimizu, Japan Pool) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict8.jpg) The inside of the tsunami-crippled No. 4 reactor building is seen during a press tour at Tokyo Electric Power Co.’s (TEPCO) Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima Prefecture, Japan, Saturday, May 26, 2012.(Toshiaki Shimizu, Japan Pool) The inside of the tsunami-crippled No. 4 reactor building is seen during a press tour at Tokyo Electric Power Co.’s (TEPCO) Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima Prefecture, Japan, Saturday, May 26, 2012.(Toshiaki Shimizu, Japan Pool) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict5.jpg) Japan’s Environment and Nuclear Minister Goshi Hosono, second from left, inspects a pool containing spent fuel rods inside the No. 4 reactor building at Tokyo Electric Power Co. ‘s tsunami-crippled Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima Prefecture, Japan, Saturday, May 26, 2012. The pool, located at the top of the building above the reactor, remains one of the plant’s biggest risks due to its vulnerability to earthquakes. (Toshiaki Shimizu, Japan Pool) Japan’s Environment and Nuclear Minister Goshi Hosono, second from left, inspects a pool containing spent fuel rods inside the No. 4 reactor building at Tokyo Electric Power Co. ‘s tsunami-crippled Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima Prefecture, Japan, Saturday, May 26, 2012. The pool, located at the top of the building above the reactor, remains one of the plant’s biggest risks due to its vulnerability to earthquakes. (Toshiaki Shimizu, Japan Pool) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict6.jpg) A pool for spent fuel rods is seen inside the No. 4 reactor building of Tokyo Electric Power Co.’s tsunami-crippled Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. The pool, located at the top of the building above the reactor, remains one of the plant’s biggest risks due to its vulnerability to earthquakes. (Toshiaki Shimizu, Japan Pool) A pool for spent fuel rods is seen inside the No. 4 reactor building of Tokyo Electric Power Co.’s tsunami-crippled Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. The pool, located at the top of the building above the reactor, remains one of the plant’s biggest risks due to its vulnerability to earthquakes. (Toshiaki Shimizu, Japan Pool) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict10.jpg) The No. 3 reactor building is seen at Tokyo Electric Power Co.’s (TEPCO) Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. Japan’s environment and nuclear minister, accompanied by the media, visited the tsunami-crippled nuclear power plant Saturday to inspect a spent fuel pool at the center of safety concerns. (Tomohiro Ohsumi, Pool) The No. 3 reactor building is seen at Tokyo Electric Power Co.’s (TEPCO) Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. Japan’s environment and nuclear minister, accompanied by the media, visited the tsunami-crippled nuclear power plant Saturday to inspect a spent fuel pool at the center of safety concerns. (Tomohiro Ohsumi, Pool) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict4.jpg) The No. 1, left, and the No. 2, reactor buildings are seen during a press tour at the tsunami-crippled Fukushima Dai-ichi nuclear power plant of Tokyo Electric Power Co. (TEPCO) in Okuma, Fukushima Prefecture, Japan, Saturday, May 26, 2012. (Tomohiro Ohsumi, Pool) The No. 1, left, and the No. 2, reactor buildings are seen during a press tour at the tsunami-crippled Fukushima Dai-ichi nuclear power plant of Tokyo Electric Power Co. (TEPCO) in Okuma, Fukushima Prefecture, Japan, Saturday, May 26, 2012. (Tomohiro Ohsumi, Pool) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict13.jpg) Workers carry out radiation screening on a bus for a media tour at Tokyo Electric Power Co. (TEPCO) ‘s Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, on Saturday, May 26, 2012. Japan’s environment and nuclear minister, accompanied by the media, visited the tsunami-crippled nuclear power plant Saturday to inspect a spent fuel pool at the center of safety concerns. (Tomohiro Ohsumi, Pool) Workers carry out radiation screening on a bus for a media tour at Tokyo Electric Power Co. (TEPCO) ‘s Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, on Saturday, May 26, 2012. Japan’s environment and nuclear minister, accompanied by the media, visited the tsunami-crippled nuclear power plant Saturday to inspect a spent fuel pool at the center of safety concerns. (Tomohiro Ohsumi, Pool) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict14.jpg) A worker carries out radiation screening on a bus for a media tour at Tokyo Electric Power Co. (TEPCO) ‘s Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, on Saturday, May 26, 2012. (Tomohiro Ohsumi, Pool) A worker carries out radiation screening on a bus for a media tour at Tokyo Electric Power Co. (TEPCO) ‘s Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, on Saturday, May 26, 2012. (Tomohiro Ohsumi, Pool) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict9.jpg) A worker walks through the building used as crisis management headquarters at the tsunami-crippled Fukushima Dai-ichi nuclear power plant of Tokyo Electric Power Co.’s (TEPCO) in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. (Tomohiro Ohsumi, Pool) A worker walks through the building used as crisis management headquarters at the tsunami-crippled Fukushima Dai-ichi nuclear power plant of Tokyo Electric Power Co.’s (TEPCO) in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. (Tomohiro Ohsumi, Pool) |
Gangland ~ Blood River – Full Movie
TOP-SECRET – We Are Anonymous Index of Informants
DOWNLOAD THE ORIGINAL DOCUMENT HERE
Gangland – Clash of The Crips – Full Movie
TOP-SECRET – Criminals and Hacktivists May Use 2012 Summer Olympics as Platform for Cyberattacks

Executive Overview
(U) Major social events such as the World Cup, Super Bowl, and Olympics have typically drawn the interest of cyber criminals and hacktivists. Open source reporting indicated that China was subjected to approximately 12 million online attacks per day during the 2008 Summer Olympics in Beijing. Two months after the closing ceremony for the 2008 Games, cyber criminals began launching campaigns using 2012 London Summer Olympic themes. Reporting last year indicates some groups are also preparing attacks linked to the 2014 Winter Games in Sochi, Russia.
(U) Scams, malware campaigns and attacks will continue to grow in scale and complexity as the 27 July opening ceremony in London draws near. Event organizers, sponsors and British authorities continue to increase their physical and cybersecurity awareness as the event approaches. Information systems supporting the Games, transport infrastructure, law enforcement communications, financial operations and similar will become prime targets for criminals. A collective of approximately eighty-seven UK banks exercised their ability to withstand cyber attacks last November. Olympic organizers anticipated cyber threats and began testing their cybersecurity posture during ‘technical rehearsals’ by running scenarios from their Technology Operations Center (TOC) situated on Canary Wharf. The TOC will be manned with over one hundred personnel continuously monitoring critical applications, such as the Commentator Information System, organizers’ intranet, and a telecom infrastructure encompassing 900 servers, 1,000 network and security devices, and 9,500 computers. In addition, British law enforcement organizations have been collaborating with the U.S. Secret Service and other industry experts to understand attack vectors, detection methods and mitigation strategies to combat the threat. However, the cyber implications are more expansive than localized attacks against systems and encompass globally distributed Olympic-themed malware, spam campaigns and scams.
(U) There are eleven global sponsors of the 2012 Olympic Games: Coca-Cola, Acer, Atos, Dow, General Electric, McDonalds, Omega, Panasonic, Proctor & Gamble, Samsung, and VISA. These sponsors include a variety of companies, some of which are Critical Infrastructure Key Resources (CIKR) or Information Sharing Analysis Center (ISAC) members. The actions or creditability of the sponsors may become targets for cyber criminals or hacktivists. The purpose of this bulletin is to provide a strategic outlook for the 2012 Summer Olympic Games and similar events to assist partners in detecting and mitigating related attacks.
…
Technical Details
(U) Disruption of Operations: Protestors could choose to disrupt the Games using cyber or physical means. Typical methods of cyber disruption include a denial of service (DOS) or distributed denial of service (DDOS) attack, which may be the result of a physical or cyber action, and causes an interruption of business operations against a network, website or other resources. With an IT staff of over five thousand (approximately half are volunteers), there is potential for insider attacks during the Olympics which could cause a DOS, this bulletin will focus on a DOS or DDOS achievable through technological means only. DDOS attacks are typically launched using a botnet and the ability to bring down a target depends on three variables:
- Type of DDOS: Certain styles of DDOS attacks are more effective than others, depending on the type of DDOS attacks. DDOS attacks typically manipulate the way systems communicate.
- Size of the botnet: A large botnet spanning multiple network blocks and geographic locations is more difficult to mitigate than a small, group of attackers concentrating on a single target.
- Resiliency of the target infrastructure: The ability of an organization to withstand a robust DDOS attack depends on the infrastructure and technology solutions in place (routers, firewalls, ISPs, etc).
(U) Attackers motivated by ideals are considered hacktivist and a wide spectrum of events may at as a flashpoint for their attacks. Criminals or hacktivists utilizing DDOS attacks or web defacements may be motivated by ideological or financial objectives. For example, in February, a group of Iranian hackers dubbed the “Cocain (sic) Warriors” took credit for defacing the official website of the National Olympic Committee of Azerbaijan and the website of Azerbaijan Airlines. The actors left an anti-Israeli political message about Azerbaijan and Israel’s recent increased cooperation and arms deal. Israel recently announced that it was selling $1.6 billion in arms to Azerbaijan, a move that upset both Armenia and Iran. The text of the defacement was political, with likely intentions to reach as broad an audience as possible and amplify the message by targeting an Olympics-related national-level website. The following are examples of things which may incite hacktivists to launch attacks during the Olympics:
- Olympic organizer issued warnings about stringent enforcement of limiting photography, digital recordings and general publishing of Olympic activities. This warning included prohibition of content being posted to social media sites. It is possible that tight enforcement of copyright infringement laws during the games may also prompt cyber reactions.
- The recent controversy over stadium panels provided by Dow. Critics have tried to block the installation of the panels because of the Dow links to Union Carbide, which was accused of the 1984 gas leak in Bhopal, India. These pre-game criticisms by activists may translate to physical protests or cyber actions.
- Hacktivists have consistently attacked websites and networks of countries ‘perceived’ as violating human rights, especially countries that endorse policies that limit access to digital content. As a result, countries banning or controlling Internet access to Olympic Games will also likely draw the attention of global hacktivists.
- Hacktivists may rally around an unforeseen cause, such as the emergence of a news story surrounding the Olympics or Olympics sponsors that hacktivists find offensive or that conforms to their ideological platform (e.g. allegations of corporate malfeasance, environmental damage, corruption, etc.).
(U) Information Theft: The second type of attack would have a goal of information theft. This information could be used to grant a competitive edge to a company, individual or other entity. This type of attack may be facilitated by an insider or a remote attacker exfiltrating data through a system compromise. Criminals seeking competitive advantage often use spearphishing to penetrate a network. Spearphishing is an email-based attack where tailored emails containing malicious attachments or links are sent to key personnel identified during reconnaissance operations. These emails are especially convincing because they appear to be sent from a legitimate source. The highly customized nature of spearphishing emails and employment of spoofed email addresses make it extremely difficult to mitigate at the email gateway. In addition, advanced attackers understand how to bypass email filters and antivirus software so that the payload can be delivered successfully. Adversaries may target Olympic personnel to gain access to engineering schematics, scoring technologies, competitor information, ticketing systems, or similar targets.
…
Future Outlook
(U) The 2014 Winter Olympics to be held in Sochi, Russia, have prompted (and will likely prompt more) attention to controversial issues and Russia’s role in the region. Sochi is located on the Black Sea and borders the North Caucasus region. The North Caucasus is part of the Russian Federation and is comprised of several smaller republics, many ethnic groups and a rich cultural legacy wracked by war, intermittent violence and competing claims to power. Legacies surrounding land claims and ethnic sovereignty issues in the Caucasus have been ongoing for centuries, and they continue to the current day with wars having occurred in the last few decades, particularly in the early 1990s in Chechnya and between Georgia and South Ossetia as recently as 2008. This demonstrates that political beliefs (or reactions to such speech) are often expressed via cyber means in the region.
(U) Pro-Olympic Cyber Attacks: The construction of the 2014 Olympics facilities near the UNESCO protected Caucasus Biosphere Reserve and Sochi National Park has drawn criticisms from global environmental groups, as well as local Sochi news organizations. These Sochi news portals came under attack in late 2010 because of their vocal opposition to the Olympic construction. It is unknown who perpetrated this series of attacks, but their choice of targets indicates the attacker was possibly attempting to subdue opposition.
(U) Hacktivism: Hacktivists (Anonymous Kavkaz) purporting to be part of the larger Anonymous collective vowed to attack MegaFon on May 21, 2012 as part of ‘Operation BlackHole’. MegaFon is Russia’s second largest mobile phone operator in Russia and one of the national sponsors for the 2014 Winter Olympics, to be held in Sochi, Russia. The Adiga actors expressed outrage about the location of the Olympics in Sochi, Russia, as they believe that the Olympic complex is being built upon mass graves from the Circassian genocide. The attack date is significant, as Circassians commemorate the Circassian-Russian War every year on May 21, the day that Circassia was annexed by the Russians and as a remembrance of the genocide that the Circassians believed occurred at the hands of the Russians.
(U) Anonymous Kavkaz (aka Adiga Hackers) started a Twitter feed on Feb. 25 and have only updated it twice, with just a handful of followers as of this writing. The true affiliation with the larger Anonymous group seems unlikely because:
- Anonymous Kavkaz does not appear to be active in the main communications channels, where they would be most likely to make connections with more capable actors.
- Anonymous Kavkaz’s Facebook presence is more geared toward ethnic, religious and political grievances in the Caucasus than with traditional Anonymous causes.
(U) The group purports to have attacked and disabled (exact means unknown) the server of the Russian Commercial Bank (a subsidiary of another Russian bank, the VTB Bank) on March 29, 2012. According to a website monitoring service, the bank’s website was having problems, but it is unclear what the issues were or if they were related to the alleged attack.
(U) Politically motivated actors from this region vary in ability, but the Russian e-crime underground offers advanced capabilities that could be sought out by North Caucasus hacktivists. Similarly, the Adiga hackers could seek more skilled Anonymous-associated actors for assistance, but thus far they have not been observed communicating in known Anonymous communications channels. This could be good indication that they are only peripheral, aspirational actors. It is possible the Adiga hackers only adopted the Anonymous moniker in an attempt to gain legitimacy and anchor their somewhat obscure cause in the framework of a larger movement to attract more followers or participants.
(U) This is the first time Russia has hosted the Olympics (the 1980 Olympic Games were held in the USSR) and officials are actively monitoring the region for any indication of unrest. Russia has recently deployed military forces to the North Caucasus as part of a broader effort to stabilize the region in the lead-up to the 2014 Olympics.
(U) Although each host country will face unique challenges, the majority of cyber threats will remain consistent as officials begin preparations for the 2016 (Rio de Janeiro, Brazil) and 2018 (Pyeongchang, South Korea) Olympic Games. DHS and partners should continue to coordinate with impacted CIKR partners while promoting awareness campaigns to minimize malware infections.
DOWNLOAD THE ORIGINAL DOCUMENT HERE
Gangland ~ Gangsta Killers – Full Movie
Bullets over Boston: The Irish Mob – Full Movie
Pablo Escobar – King of Cocaine – Full Movie
Incorporating never before-seen archival footage, home movies and interviews with family members, journalists and law enforcement officials, this tells the story of the twisted Robin Hood who founded the Medellin cartel cocaine smuggling organization and became the first billionaire criminal in South America.
APPENDIX: STASI-NAMEN ALPHABETISCH BUCHSTABE BS-BU – STASI NAMES IN ALPHABETICAL ORDER BS-BU
Die Liste wurde bereits früher hier publiziert:
http://stasiopfer.de/component/option,com_simpleboard/Itemid,/func,view/id,993815828/catid,4/
Vom “Stasiopfer”-Angebot führt ein Link zu einer Website in den USA (www.jya.com), die sich auch mit den Praktiken von Geheimdiensten beschäftigt. Dort findet sich die “Fipro-Liste”, das detaillierte “Finanzprojekt” der Stasi, angefertigt in den letzten Tagen der DDR, um die Rentenansprüche der rund 100 000 hauptamtlichen Mitarbeiter des MfS auch nach dem Zusammenbruch des Systems belegen zu können. Die “Fipro-Liste” ist seit langem bekannt und diente Anfang der neunziger Jahre etwa zur Identifizierung der so genannten OibE – Offiziere im besonderen Einsatz. Diese Liste „Offiziere im besonderen Einsatz“im Jahre 1991 erschien in der “taz. Die Echtheit kann beim BStU überprüft werden.
Siehe u.a. http://www.spiegel.de/spiegel/print/d-22539439.html
Auf Druck ehemaliger STASI-Leute und Ihrer Genossen wurde die Liste aus dem Verkehr gezogen.
Hier ist sie wieder:
090471423014;18;35;00;;BRA(E)CKLEIN, JO(E)RG:;;;2795,00
190435415322;13;00;41;K, 4232/86:;BRA(E)NDEL, LOTHAR;4090;GARTENSTADTSTR. 4;
190435415322;13;00;41;K, 4232/86:;BRA(E)NDEL, LOTHAR;4090;GARTENSTADTSTR. 4;
150359412122;07;00;59;;BRA(E)SE, UDO:;;;22080,00
060769426819;18;31;00;;BRA(E)UER, HOLM:;;;9510,00
031170413111;18;35;00;;BRA(E)UER, OLAF:;;;2795,00
060269415021;18;34;00;;BRA(E)UNER, JO(E)RG:;;;9675,00
160170408225;18;33;00;;BRA(E)UNIG, JO(E)RG:;;;9510,00
150569419728;18;31;00;;BRA(E)UNLICH, HEIKO:;;;9600,00
180470414836;18;33;00;;BRA(E)UNLICH, TOBIAS:;;;6958,87
060468418313;18;33;00;;BRA(E)UTIGAM, JENS:;;;9825,00
190768428922;18;31;00;;BRA(E)UTIGAM, MICHAEL:;;;9648,38
220269425027;18;33;00;;BRA(E)UTIGAM, SVEN:;;;9675,00
181270424938;18;32;00;;BRA(E)UTIGAM, UWE:;;;2795,00
130965400916;01;69;00;;BRAASCH, KARSTEN:;;;15898,50
091165402711;97;08;00;;BRAATZ, ANDREAS:;;;18179,00
260940403112;03;00;42;;BRAATZ, ECKHARD:;;;28080,00
261052505721;04;09;00;;BRAATZ, ELKE:;;;20160,00
151038402729;30;44;00;;BRAATZ, GUENTER:;;;15570,00
300333422120;12;40;00;;BRAATZ, RUDOLF:;;;38250,00
120270411521;07;06;00;;BRAATZ, THOMAS:;;;12460,00
150271422211;18;28;00;;BRAATZ, THOMAS:;;;2720,00
070365403716;97;08;00;;BRAATZ, UWE:;;;17682,50
100557430174;15;18;00;;BRABAND, CARSTEN:;;;22990,00
250255429737;15;02;00;;BRABAND, HENRY:;;;25080,00
111153529817;15;77;00;;BRABAND, ILONA:;;;0,00
241053428221;18;35;00;;BRABANDT, BERTHOLD:;;;25200,00
181252415376;13;80;00;;BRABANT, BERND:;;;20405,00
201239529710;97;01;00;;BRABANT, CHRISTA:;;;19575,00
080139416411;09;06;00;;BRABANT, HEINRICH:;;;19620,00
291037429764;98;20;00;;BRABANT, HEINZ:;;;30937,50
300449426334;99;99;99;::;BRABANT, JOACHIM;1140;MARCHWITZASTR. 3;
300449426334;99;99;99;::;BRABANT, JOACHIM;1140;MARCHWITZASTR. 3;
210357415401;99;02;00;;BRABANT, PETER:;;;23345,00
311261430095;94;65;00;;BRABANT, PETER:;;;18150,00
030162530049;30;84;00;;BRABANT, SIMONE:;;;12321,24
150363430112;15;02;00;;BRABETZ, HEIKO:;;;14850,00
140371403457;03;69;00;;BRACH, ANDREAS:;;;2870,00
051159406154;05;06;00;;BRACH, HARTMUT:;;;17710,00
110637528226;98;27;00;;BRACHAUS, GISELA:;;;23760,00
310540429711;97;06;00;;BRACHAUS, KLAUS:;;;27375,00
290531429730;15;40;00;;BRACHLOW, HERBERT:;;;28500,00
110652529817;30;74;00;;BRACHMANN, DORIS:;;;23262,86
230652413423;04;11;00;;BRACHMANN, HANS-DIETER:;;;26520,00
021165426226;14;40;00;;BRACHMANN, TILO:;;;5263,20
180764401811;02;80;00;;BRACHMANN, WILFRIED:;;;14148,00
210947404438;04;18;00;;BRACHOLD, HERBERT:;;;20872,50
310547412234;07;00;40;;BRACHWITZ, DETLEV:;;;19320,00
200269412287;99;02;00;;BRACHWITZ, GERO:;;;9600,00
300457504515;04;00;41;;BRACHWITZ, ILONA:;;;17595,00
051269413128;18;32;00;;BRACHWITZ, JO(E)RG:;;;9510,00
261042512215;96;15;05;;BRACHWITZ, KRISTINA:;;;26104,16
280752402110;99;43;00;;BRACK, HANS-JUERGEN:;;;19440,00
260639419318;10;00;43;;BRACK, HELMUT:;;;22250,00
220758416412;09;08;00;;BRACK, LUTZ:;;;17595,00
080342429728;94;65;00;;BRACK, MANFRED:;;;23250,00
120760411524;07;00;48;;BRACK, UWE:;;;18013,53
010152404614;04;00;43;;BRACKLOW, EBERHARD:;;;27300,00
210533430054;18;28;00;;BRACKLOW, SIEGFRIED:;;;28500,00
120251404713;17;00;00;;BRACKMANN, GUENTER:;;;25920,00
270162509541;97;06;00;;BRACKROCK, ANDREA:;;;14997,25
151150430068;96;15;00;650/75/11, :;BRADA, WOLFGANG;1130;FRANKFURTER ALLEE 128;
151150430068;96;15;00;650/75/11, :;BRADA, WOLFGANG;1130;FRANKFURTER ALLEE 128;
040469422025;18;32;00;;BRADATSCH, TIMO:;;;9675,00
210655426918;18;35;00;;BRADE, ANDREAS:;;;22350,00
240960530081;99;77;00;;BRADE, ANGELA:;;;19636,77
291157404318;04;51;00;;BRADE, DIRK:;;;20700,00
050535429727;15;53;00;;BRADE, FRED:;;;35250,00
180434430097;18;28;00;;BRADE, GERHARD:;;;27375,00
280665430252;97;08;00;;BRADE, HEIKO:;;;17384,00
061059430025;97;22;00;;BRADE, INGO:;;;18630,00
110768425067;18;32;00;;BRADE, JO(E)RG:;;;9675,00
300170428922;99;43;00;;BRADE, MARIO:;;;9600,00
111268407238;18;35;00;;BRADE, OLIVER:;;;9600,00
230851400211;96;15;21;;BRADE, PETER:;;;25761,38
210742424929;94;11;00;271/68, :;BRADE, ROLF;1600;HERDERSTR. 6;
210742424929;94;11;00;271/68, :;BRADE, ROLF;1600;HERDERSTR. 6;
070336524914;13;26;00;;BRADE, ROSWITHA:;;;25375,00
250748417734;09;08;00;;BRADEL, WOLFGANG:;;;24480,00
100662414811;30;47;00;;BRADEMANN, FRANK:;;;16830,00
060669400830;01;02;00;;BRADEMANN, JENS:;;;8550,00
300344400824;17;00;00;;BRADEMANN, JUERGEN:;;;31680,00
280758415318;08;00;50;;BRADL, ACHIM:;;;16912,50
030562430194;96;15;10;;BRADLER, THORSTEN:;;;18090,00
040669407321;05;69;00;;BRADTKE, MICHAEL:;;;9510,00
240769407421;99;40;00;;BRADTKE, UDO:;;;8300,00
180656529738;94;65;00;;BRAEHMER, IRIS:;;;18529,85
261049404516;18;25;00;;BRAEKOW, ERHARD:;;;27750,00
131256516224;97;07;00;;BRAEKOW, UTE:;;;19046,74
060458404129;97;08;00;;BRAEMER, JOERG:;;;20412,50
270953404113;18;29;00;;BRAEMER, KLAUS-DIETER:;;;23280,00
160254411915;07;00;54;;BRAEMER, LOTHAR:;;;26640,00
260953407411;05;00;40;;BRAEMER, UWE:;;;26640,00
311049516211;99;41;00;;BRAEMING, ILONA:;;;27000,00
280648429751;98;84;00;;BRAEMING, RAINER:;;;22687,50
060238427417;14;06;00;;BRAENDEL, ARMIN:;;;22437,50
260141529712;99;49;00;;BRAENLICH, DORIS:;;;27250,00
191069409129;06;69;00;;BRAENZEL, THOMAS:;;;9510,00
191169500712;01;96;31;;BRAESEL, ANKA:;;;2297,58
071169430025;15;69;00;;BRAESEL, MATHIAS:;;;9510,00
250943407611;05;00;40;;BRAETSCH, UWE:;;;25562,50
090552506444;98;82;00;;BRAETZ, MONIKA:;;;22916,37
120248409214;04;12;00;;BRAEUER, DIETER:;;;21000,00
201065429217;18;33;00;;BRAEUER, DIRK:;;;14110,04
131128430012;99;02;00;;BRAEUER, GERD:;;;37500,00
270437430059;30;47;00;;BRAEUER, GUENTER:;;;20880,00
310843429751;97;06;00;;BRAEUER, HERBERT:;;;24000,00
220263426213;02;00;44;;BRAEUER, INGOLF:;;;19140,00
151256424985;97;17;00;;BRAEUER, JUERGEN:;;;21332,50
171163430057;15;00;49;;BRAEUER, KARSTEN:;;;17572,50
280464426716;14;80;00;;BRAEUER, MATHIAS:;;;15482,50
310557415121;96;15;25;;BRAEUER, MICHAEL:;;;25884,00
180661423823;13;00;43;;BRAEUER, PETER:;;;16142,50
170955513024;99;77;00;;BRAEUER, SABINE:;;;10394,09
270853426219;97;29;00;;BRAEUER, STEFFEN:;;;26640,00
191155527711;30;49;00;;BRAEUER, STEFFI:;;;11382,21
241065426346;94;03;00;;BRAEUER, SVEN:;;;11016,00
270546407210;30;42;00;;BRAEUER, UDO:;;;19440,00
140160425074;13;08;00;;BRAEUER, VOLKER:;;;15592,50
041244428260;99;78;00;;BRAEUER, WILFRIED:;;;25975,00
150469528230;14;53;00;;BRAEUNIG, ANNETT:;;;12205,00
071252429754;30;47;00;;BRAEUNIG, BERND:;;;24120,00
190532429718;99;40;00;;BRAEUNIG, GERHARD:;;;28500,00
270153429718;96;15;13;;BRAEUNIG, HANS-JUERGEN:;;;25530,00
040940530061;98;83;00;;BRAEUNIG, HELGA:;;;23040,00
040851503344;30;84;00;;BRAEUNIG, ILONA:;;;21390,00
200551529753;96;15;31;;BRAEUNIG, INGRID:;;;25920,00
010242424512;13;00;49;;BRAEUNIG, JUERGEN:;;;27000,00
081144422714;04;26;00;;BRAEUNIG, KLAUS-JUERGEN:;;;23187,50
250249428228;30;80;00;;BRAEUNIG, REINER:;;;22590,00
200149528226;14;30;00;;BRAEUNIG, SONJA:;;;16610,00
231249524937;30;80;00;;BRAEUNIG, SONJA:;;;21045,00
310371417444;09;69;00;;BRAEUNIG, SWEN:;;;3928,06
110461422013;98;84;00;;BRAEUNIG, ULF:;;;18610,96
150667430189;15;18;00;;BRAEUNIGER, OLAF:;;;14819,00
190750420017;11;00;43;;BRAEUNING, HUBERTUS:;;;29160,00
030851528315;30;84;00;;BRAEUNING, MARGIT:;;;15101,16
051155414210;07;08;00;;BRAEUNING, ROLF:;;;17077,50
160163430109;98;81;00;;BRAEUNLICH, FRANK:;;;16830,00
100568413716;97;22;00;;BRAEUNLICH, FRANK:;;;14994,00
130652424976;60;90;00;;BRAEUNLICH, GERD:;;;
130652424976;60;90;00;;BRAEUNLICH, GERD:;;;18917,01
140440429731;98;84;00;;BRAEUNLICH, JUERGEN:;;;30187,50
190639418218;10;00;40;;BRAEUNLICH, KLAUS:;;;25500,00
270261430126;97;06;00;;BRAEUNLICH, WOLFRAM:;;;18232,50
141039506926;99;43;00;;BRAEUNLING, ANNEMARIE:;;;20625,00
231047413411;97;01;00;;BRAEUNLING, EBERHARD:;;;27750,00
120451421817;99;02;00;;BRAEUNLING, GUENTER:;;;28980,00
080342406913;99;43;00;;BRAEUNLING, WILFRIED:;;;21750,00
041070417739;97;01;00;;BRAEUTIGAM, ANDRE:;;;3070,16
180457423623;17;00;00;;BRAEUTIGAM, ANDREAS:;;;18285,00
200950517717;09;40;00;;BRAEUTIGAM, BRIGITTE:;;;19050,20
041244417748;09;51;00;;BRAEUTIGAM, ERNST:;;;27000,00
191043406114;04;06;00;;BRAEUTIGAM, GOETZ:;;;22437,50
251029420210;11;00;47;;BRAEUTIGAM, GUENTER:;;;27000,00
290753408310;06;14;00;;BRAEUTIGAM, HANS-HENNING:;;;18457,50
061150409315;10;06;00;;BRAEUTIGAM, HELMUT:;;;22475,00
111046430053;18;27;00;;BRAEUTIGAM, HOLGER:;;;27750,00
300347429729;97;06;00;;BRAEUTIGAM, JOERGEN:;;;26250,00
191169430048;99;02;00;;BRAEUTIGAM, MARCO:;;;13880,00
160748429779;15;00;41;;BRAEUTIGAM, PETER:;;;33120,00
010369408544;12;69;00;;BRAEUTIGAM, RONALD:;;;12412,26
301269428230;14;69;00;;BRAEUTIGAM, STEFFEN:;;;12085,00
270749423931;99;13;00;;BRAEUTIGAM, WOLFRAM:;;;27060,00
280868430041;18;35;00;;BRAEUTIGAMM, HENRY:;;;10600,00
210963402619;02;00;49;;BRAHM, FRANK:;;;19965,00
130647402510;02;53;00;;BRAHM, GERHARD:;;;27000,00
090866402648;01;00;48;;BRAHM, RENE:;;;12035,00
031170401516;02;06;00;;BRAHM, THOMAS:;;;3510,00
190469402511;02;06;00;;BRAHM, THORSTEN:;;;13175,00
130171524626;13;07;00;;BRAJER, KATHRIN:;;;3220,00
271256409546;06;03;00;;BRAMER, SIEGFRIED:;;;17490,00
280170415114;98;82;00;;BRAMIG, RENE:;;;10376,13
120769403918;18;35;00;;BRAMMER, ANDREAS:;;;10035,00
140271416453;18;80;00;;BRAND, AXEL:;;;2945,00
130635429716;97;06;00;;BRAND, EBERHARD:;;;37500,00
020134529711;97;06;00;;BRAND, EDITH:;;;25375,00
180764421812;12;55;00;;BRAND, EGBERT:;;;16170,00
010359417789;09;15;00;;BRAND, FRANK:;;;17974,00
050152421816;12;00;52;;BRAND, GUNTER:;;;25200,00
070558508936;04;55;00;;BRAND, HEIKE:;;;18669,32
200170413749;99;43;00;;BRAND, JAN:;;;9510,00
281069408512;98;82;00;;BRAND, JOERG:;;;10376,13
280970409927;18;35;00;;BRAND, MARIO:;;;2795,00
160241428224;14;00;40;;BRAND, ROLAND:;;;26820,00
290370413016;05;69;00;;BRAND, STEFAN:;;;9910,00
300870421828;18;34;00;;BRAND, STEFFEN:;;;6736,77
190569417534;18;33;00;;BRAND, THOMAS:;;;9600,00
130755423626;04;53;00;;BRAND, WOLFRAM:;;;24150,00
100857516025;11;77;00;;BRANDAU, MARITTA:;;;16708,73
271169413248;08;00;44;;BRANDAU, SVEN:;;;8300,00
170153416011;11;06;00;;BRANDAU, WOLFGANG:;;;24782,50
281052402720;02;55;00;;BRANDECKER, DIETER:;;;20160,00
220969402715;17;00;00;;BRANDENBURG, AXEL:;;;8300,00
241169427036;94;03;00;;BRANDENBURG, BERND:;;;9630,00
281252405213;30;63;00;;BRANDENBURG, BERND:;;;14100,00
010359400514;01;06;27;;BRANDENBURG, DIETMAR:;;;18457,50
061152424914;13;15;00;;BRANDENBURG, HANS:;;;10002,57
230940522819;96;15;22;;BRANDENBURG, HILDEGARD:;;;24480,00
090267409928;07;06;00;;BRANDENBURG, INGO:;;;16832,32
110171431114;15;69;00;;BRANDENBURG, INGO:;;;2925,64
090663506922;30;72;00;;BRANDENBURG, JANA:;;;13860,00
110139402110;02;19;00;;BRANDENBURG, KLAUS:;;;29250,00
080965403428;97;08;00;;BRANDENBURG, LUTZ:;;;16470,00
031164422775;94;65;00;;BRANDENBURG, LUTZ:;;;17985,00
301035422725;97;22;00;;BRANDENBURG, MANFRED:;;;27937,50
020966404356;18;28;00;;BRANDENBURG, RENE:;;;16686,00
100244429746;99;43;00;;BRANDENBURG, ROLF:;;;27000,00
240164430063;94;03;00;;BRANDENBURG, THOMAS:;;;19800,00
300669430036;18;33;00;;BRANDENBURG, TINO:;;;6816,29
260942425008;13;07;00;;BRANDENBURGER, KLAUS:;;;25216,68
030565405912;04;00;40;;BRANDENBURGER, OLAF:;;;16665,00
141058523924;13;55;00;;BRANDENBURGER, PETRA:;;;16088,13
180656411545;07;51;00;;BRANDES, GERALD:;;;17710,00
230251428915;14;18;00;;BRANDHOFF, MANFRED:;;;25200,00
140855420018;96;15;26;;BRANDIES, JUERGEN:;;;21780,00
020855519724;96;15;26;;BRANDIES, SABINE:;;;17940,00
231268407410;18;35;00;;BRANDIS, ANDRE:;;;10900,00
140465402615;02;06;00;;BRANDIS, DIRK:;;;16500,00
130364407426;97;22;00;;BRANDIS, GERD:;;;17423,09
290565411846;07;00;53;;BRANDL, RALF:;;;14355,00
150168408411;18;35;00;;BRANDL, TONI:;;;9675,00
200458428288;14;00;57;;BRANDL, UWE:;;;20355,00
260753409113;06;65;00;;BRANDL, WERNER:;;;20040,00
210360413415;08;00;46;;BRANDL, WILFRIED:;;;22110,00
111266421511;12;09;00;;BRANDNER, ANDREAS:;;;11016,00
260443429717;97;06;00;;BRANDNER, GERD:;;;26250,00
011149422779;12;00;40;;BRANDNER, HARALD:;;;23200,00
080562425112;99;09;00;;BRANDNER, HENNING:;;;18425,00
080468430310;99;77;00;;BRANDNER, JENS:;;;14319,00
080468430302;97;06;00;;BRANDNER, MARKO:;;;15021,00
180669402138;99;43;00;;BRANDSTAEDTER, DIRK:;;;13575,00
020446402111;02;06;00;;BRANDSTAEDTER, SIEGMAR:;;;23250,00
080329406118;17;00;00;;BRANDSTAETER, SIEGFRIED:;;;33000,00
021240408918;06;60;00;;BRANDT, ALBRECHT:;;;23250,00
290828430011;97;06;00;;BRANDT, ALWIN:;;;39750,00
010162400617;04;06;00;;BRANDT, ANDREAS:;;;18260,00
050558402121;02;51;00;;BRANDT, ARNOLD:;;;16560,00
151246503719;17;00;00;;BRANDT, BAERBEL:;;;20625,00
080471526145;97;06;00;;BRANDT, BEATRICE:;;;4900,00
031052424936;94;03;00;;BRANDT, BERND:;;;25200,00
140157502737;30;47;00;;BRANDT, BIRKA:;;;17693,00
060739530076;97;17;00;;BRANDT, BRIGITTE:;;;21750,00
031243406415;04;80;00;;BRANDT, BURCKHARD:;;;26625,00
200856505015;18;77;00;;BRANDT, CHRISTIANE:;;;18975,00
270257409914;15;03;00;;BRANDT, CLAUS-DIETER:;;;20010,00
290453527641;94;30;00;;BRANDT, DAGMAR:;;;19664,33
281266406727;99;14;00;;BRANDT, DIEGO:;;;14375,00
090647413910;08;08;00;;BRANDT, DIETER:;;;17687,50
040552402711;99;40;00;;BRANDT, DIETER:;;;21375,00
010962430136;18;71;20;;BRANDT, DIETMAR:;;;14685,00
110355407119;18;78;00;;BRANDT, DIETRICH:;;;20280,00
151168412255;18;35;00;;BRANDT, DIRK:;;;9825,00
251045500827;01;80;00;;BRANDT, DORIT:;;;15660,57
101251416411;09;00;44;;BRANDT, EBERHARD:;;;23760,00
091058410628;07;03;00;;BRANDT, FRANK:;;;19200,66
240852404029;03;00;49;;BRANDT, GERT:;;;22320,00
190937429724;99;26;00;;BRANDT, GUENTER:;;;28500,00
291051426316;99;55;00;;BRANDT, GUNTER:;;;24960,00
070535403912;03;00;48;;BRANDT, HANS-DIETER:;;;18375,00
150653410718;07;43;00;;BRANDT, HANS-HELMUT:;;;23040,00
130848414411;08;00;56;;BRANDT, HANS-JUERGEN:;;;17192,50
061152411419;17;00;00;;BRANDT, HANS-PETER:;;;19440,00
040749409116;99;40;00;;BRANDT, HANS-ULRICH:;;;27360,00
240843403710;17;00;00;;BRANDT, HARTMUT:;;;18285,00
051259406119;94;03;00;;BRANDT, HEIKO:;;;18345,00
241166403119;03;00;42;;BRANDT, HEINO:;;;2236,00
230236429717;98;18;00;;BRANDT, HELMUT:;;;35250,00
280369407525;97;01;00;;BRANDT, HENRY:;;;3674,19
031256430246;15;00;41;;BRANDT, HOLGER:;;;26162,50
220539429731;96;15;22;;BRANDT, HORST:;;;27187,50
281147403216;03;06;00;;BRANDT, JOACHIM:;;;21750,00
291062413027;08;80;00;;BRANDT, JOCHEN:;;;16170,00
120364430109;96;15;22;;BRANDT, JUERGEN:;;;15510,00
060552400618;01;06;27;;BRANDT, KARL:;;;18227,50
290961400719;18;32;00;;BRANDT, KARSTEN:;;;23100,00
140958411915;30;48;00;;BRANDT, KARSTEN:;;;18240,00
290556509518;99;10;00;;BRANDT, KERSTIN:;;;21900,00
110344413011;07;55;00;;BRANDT, KLAUS:;;;20125,00
070870430619;15;69;00;;BRANDT, MAREK:;;;2925,64
020239529718;99;02;00;;BRANDT, MARIA:;;;24000,00
050155529734;98;83;00;;BRANDT, MARION:;;;15720,26
040869412272;07;06;00;;BRANDT, MATTHIAS:;;;8592,10
091260401514;99;43;00;;BRANDT, MICHAEL:;;;17647,02
200558414529;08;51;00;;BRANDT, PETER:;;;19492,50
011149420319;11;14;00;;BRANDT, PETER:;;;24462,50
250466422017;97;22;00;;BRANDT, PETER:;;;17251,50
010252526328;98;83;00;;BRANDT, PETRA:;;;21600,00
290449415321;08;08;00;;BRANDT, RAINER:;;;23875,00
200945430051;15;08;00;;BRANDT, RAINER:;;;24000,00
041068428332;97;22;00;;BRANDT, RICO:;;;9875,00
030847416417;09;00;44;;BRANDT, ROBERT:;;;21562,50
301068424436;18;31;00;;BRANDT, RONNY:;;;9675,00
270869419822;07;69;00;;BRANDT, SILVIO:;;;8302,58
100271426858;18;32;00;;BRANDT, STEFFEN:;;;6958,87
270169430035;96;15;22;;BRANDT, STEPHAN:;;;9555,00
290170411227;18;34;00;;BRANDT, SVEN:;;;9510,00
050970428251;18;31;00;;BRANDT, SYLVIO:;;;6705,00
240463402134;02;08;00;;BRANDT, THILO:;;;16252,50
200969403111;18;38;00;;BRANDT, THOMAS:;;;9510,00
300964402628;02;09;00;;BRANDT, TORSTEN:;;;16720,00
130353429718;99;14;00;;BRANDT, UDO:;;;24300,00
180735402719;02;26;00;;BRANDT, ULRICH:;;;23250,00
260256502739;99;55;00;;BRANDT, UTE:;;;19969,19
200770400730;18;35;00;;BRANDT, VOLKER:;;;3475,00
120933429715;95;45;00;;BRANDT, WALTER:;;;21750,00
191155405917;04;06;00;;BRANDT, WILFRIED:;;;18842,50
250136429718;99;02;00;;BRANDT, WILFRIED:;;;31125,00
190455405631;30;47;00;;BRANDT, WILFRIED:;;;26840,00
270158411410;07;09;00;;BRANDT, WOLFGANG:;;;21102,50
120149402412;12;18;00;;BRANDT, WOLFGANG:;;;23712,50
151051400824;01;14;00;;BRANDT, WOLFGANG:;;;20520,00
270953409117;99;40;00;;BRANDT, WOLFGANG:;;;25530,00
090655419036;99;43;00;;BRANDTNER, MANFRED:;;;25875,00
250660407515;97;01;00;;BRANDTNER, THOMAS:;;;23712,50
151064430280;96;15;13;;BRANDWEIN, MICHAEL:;;;16500,00
251239530127;99;77;00;;BRANKE, HELGA:;;;41040,00
241039430288;94;65;00;;BRANKE, JUERGEN:;;;27750,00
190446409518;06;02;00;;BRANKE, KLAUS:;;;28312,50
070630430011;97;07;00;;BRANKE, KURT:;;;27000,00
140154402714;30;54;00;;BRANNYS, GEORG:;;;24620,00
211166427412;99;43;00;;BRANSTNER, JENS:;;;15714,00
210749420517;12;07;00;;BRANZ, KLAUS:;;;29625,00
190449410813;07;00;49;;BRASA, GUENTER:;;;27360,00
110970412243;07;06;00;;BRASACK, GUNAR:;;;3557,10
290148410615;07;06;00;;BRASCHE, KLAUS-DIETER:;;;21187,50
070350429796;15;08;00;;BRASCHING, DIETER:;;;22413,01
180263530068;15;19;00;;BRASE, SIMONE:;;;14912,98
011069427625;18;34;00;;BRASE, SWEN:;;;6876,77
260371422443;12;09;00;;BRASOW, RAMON:;;;2700,00
010329430018;97;08;00;;BRASSAT, ALFRED:;;;5437,50
070261400852;01;15;00;;BRASSAT, FRANK:;;;18312,00
140569400868;01;69;00;;BRASSAT, RONALD:;;;6671,61
021270400220;01;69;00;;BRASSEN, ANDREAS:;;;2896,61
111254421215;96;15;00;3039/82, M:;BRATE, ANDREAS;1142;MAX-HERRMANN-STR. 4;
111254421215;96;15;00;3039/82, M:;BRATE, ANDREAS;1142;MAX-HERRMANN-STR. 4;
210637413216;08;51;00;;BRATFISCH, FRITZ:;;;24000,00
120964419018;10;65;00;;BRATFISCH, PASQUALE:;;;12925,00
161253419311;97;01;00;;BRATGE, HANS-JUERGEN:;;;27360,00
280536409529;06;08;00;;BRATKE, ALFRED:;;;28250,00
021267422736;10;00;51;;BRATKE, MAIK:;;;13032,00
240366408024;06;51;00;;BRATKE, THOMAS:;;;16645,50
010554426314;13;00;40;;BRATTIG, ANDREAS:;;;18179,59
300959402244;99;43;00;;BRATZ, DETLEF:;;;21332,50
020760502225;98;27;00;;BRATZ, MANUELA:;;;21142,50
130644428010;14;18;00;;BRATZ, ROLAND:;;;26250,00
200952506915;99;49;00;;BRAUCHLER, DORIS:;;;17825,00
210751403732;17;00;00;;BRAUCHMANN, BERND:;;;30960,00
070652503015;17;00;00;;BRAUCHMANN, INGRID:;;;18199,95
111157403728;03;53;00;;BRAUCHMANN, RALF:;;;22440,00
040650524018;99;09;00;;BRAUER, BAERBEL:;;;25920,00
150358422791;12;00;40;;BRAUER, BERND:;;;22080,00
110554420527;12;00;42;;BRAUER, BERND:;;;26640,00
140762430137;98;83;00;;BRAUER, BJOERN:;;;17270,00
011240502518;97;01;00;;BRAUER, BRIGITTE:;;;20250,00
040552505112;18;77;00;;BRAUER, DORIS:;;;21362,21
311041529720;99;43;00;;BRAUER, ERIKA:;;;22125,00
200166412233;60;90;00;;BRAUER, FRANK:;;;
200166412233;60;90;00;;BRAUER, FRANK:;;;13630,00
120250417117;09;06;00;;BRAUER, GOTTFRIED:;;;21000,00
190843400816;94;65;00;;BRAUER, GUENTER:;;;24000,00
080341429734;99;43;00;;BRAUER, GUENTHER:;;;21750,00
090248429747;94;65;00;;BRAUER, HANS-JOACHIM:;;;27750,00
290965509535;06;09;00;;BRAUER, HEIKE:;;;12762,58
170169402714;01;69;00;;BRAUER, HEIKO:;;;13250,00
180266406206;04;06;00;;BRAUER, HOLGER:;;;16281,00
190933406138;97;08;00;;BRAUER, HORST:;;;28500,00
120962407224;97;01;00;;BRAUER, JAN:;;;16335,00
181169409514;97;22;00;;BRAUER, JENS:;;;6757,50
031265413018;17;00;00;;BRAUER, JOERG:;;;13345,50
271254429746;97;08;00;;BRAUER, KLAUS-PETER:;;;21700,00
250158530147;99;09;00;;BRAUER, MARTINA:;;;14916,87
250451419325;99;09;00;;BRAUER, MICHAEL:;;;28320,00
250933430068;60;90;00;;BRAUER, PETER:;;;
250933430068;60;90;00;;BRAUER, PETER:;;;23520,00
300839413045;08;00;42;;BRAUER, RUDOLF:;;;34560,00
180937429717;94;03;00;;BRAUER, SIEGFRIED:;;;21000,00
241260530122;15;80;00;;BRAUER, SILVIA:;;;14171,58
090163402529;94;03;00;;BRAUER, TORSTEN:;;;18810,00
270737402519;02;06;00;;BRAUER, WILLY:;;;21000,00
201161406197;04;08;00;;BRAUER, WOLFGANG:;;;15744,00
010234509225;30;56;00;;BRAUMANN, ILSE:;;;13680,00
220769410710;18;35;00;;BRAUMANN, RALF:;;;6736,77
250248412216;05;06;00;;BRAUMANN, ROLF-DIETER:;;;19500,00
040751410319;07;12;00;;BRAUMANN, ULRICH:;;;21060,00
071268406936;18;31;00;;BRAUN, ANDRE:;;;9825,00
271251426611;94;03;00;;BRAUN, ANDRE:;;;24900,00
310861409578;06;00;40;;BRAUN, ANDREAS:;;;17325,00
280963413119;99;43;00;;BRAUN, ANDREAS:;;;16260,48
100469404611;99;43;00;;BRAUN, ANDREAS:;;;9600,00
170154422720;30;57;00;;BRAUN, ANDREAS:;;;16080,00
240569528923;14;00;54;;BRAUN, ANETT:;;;13275,00
181252527319;94;03;00;;BRAUN, ANNEROSE:;;;20872,50
150641406930;99;43;00;;BRAUN, BERND:;;;21625,00
191061500876;01;51;00;;BRAUN, BIANCA:;;;16716,07
270846528225;14;08;00;;BRAUN, BIRGIT:;;;21387,50
091049504411;03;53;00;;BRAUN, BRIGITTE:;;;23840,00
030743506928;99;43;00;;BRAUN, BRIGITTE:;;;19172,37
071047506917;99;43;00;;BRAUN, BRIGITTE:;;;20182,50
220728404111;99;43;00;;BRAUN, BRUNO:;;;21750,00
070643428228;99;26;00;;BRAUN, CLAUS-DIETER:;;;24125,00
190355421319;98;84;00;;BRAUN, DIETER:;;;22140,00
280758428215;99;43;00;;BRAUN, DIETMAR:;;;18630,00
060130504118;99;43;00;;BRAUN, DORA:;;;17940,00
090639429728;98;19;00;;BRAUN, EDGAR:;;;51750,00
091053404317;97;17;00;;BRAUN, EDWIN:;;;22320,00
070546411416;07;07;00;;BRAUN, ERNST-ERIK:;;;28020,00
280762502510;02;00;44;;BRAUN, EVELYN:;;;13767,07
091148428012;30;51;00;;BRAUN, FRANK:;;;15120,00
281260521839;98;85;00;;BRAUN, GABRIELA:;;;17283,64
281036417754;98;19;00;;BRAUN, GERHARD:;;;25200,00
190756403728;99;43;00;;BRAUN, GERO:;;;21390,00
310844404310;94;30;00;;BRAUN, HANS-JOACHIM:;;;27750,00
151053417160;11;02;00;;BRAUN, HANS-JOERG:;;;25200,00
110149426714;97;06;00;;BRAUN, HARALD:;;;23360,00
120338430068;99;53;00;;BRAUN, HARRI:;;;25920,00
271154417748;09;40;00;;BRAUN, HEINZ:;;;23250,00
080665429239;14;08;00;;BRAUN, HENDRIK:;;;15322,00
100636403713;03;99;00;;BRAUN, HORST:;;;42750,00
100565403723;03;18;00;;BRAUN, INGO:;;;21120,00
190170500424;18;80;00;;BRAUN, JANA:;;;13730,00
151168422744;17;00;00;;BRAUN, JENS:;;;8300,00
020653424719;13;00;51;;BRAUN, JOCHEN:;;;25200,00
240362421010;12;65;00;;BRAUN, JU(E)RGEN:;;;17022,50
200251413943;08;00;61;;BRAUN, JUERGEN:;;;17077,50
140154421317;99;40;00;;BRAUN, JUERGEN:;;;25320,00
260441529714;15;07;00;;BRAUN, KARIN:;;;16838,64
160952411816;07;80;00;;BRAUN, KARL-HEINZ:;;;18000,00
181062430102;99;51;00;;BRAUN, KARSTEN:;;;17820,00
051243429738;97;06;00;;BRAUN, KLAUS:;;;20500,00
121249404313;03;02;00;;BRAUN, MANFRED:;;;29250,00
040637428216;14;11;00;;BRAUN, MANFRED:;;;26312,50
040244406913;99;43;00;;BRAUN, MANFRED:;;;24000,00
071064402714;02;14;00;;BRAUN, MARIO:;;;15840,00
090267403120;98;82;00;;BRAUN, MATHIAS:;;;17490,00
041264430085;99;02;00;;BRAUN, MICHAEL:;;;18205,00
061064406142;04;06;00;;BRAUN, MIKE:;;;15268,00
050670400046;98;19;00;;BRAUN, MIRKO:;;;3620,00
101069429224;18;31;00;;BRAUN, MIRKO:;;;9600,00
080150504623;99;77;00;;BRAUN, MONIKA:;;;21600,00
080854429713;98;83;00;;BRAUN, PETER:;;;19237,50
240166421320;98;19;00;;BRAUN, RAINER:;;;11016,00
241159417715;99;53;00;;BRAUN, RALF:;;;18343,26
271262402535;02;80;00;;BRAUN, RENE:;;;16190,04
090970414411;18;33;00;;BRAUN, ROLAND:;;;2795,00
080237528214;14;51;00;;BRAUN, SIEGLINDE:;;;19965,00
010169500418;18;78;00;;BRAUN, SILKE:;;;14025,00
100269413935;18;34;00;;BRAUN, STEFFEN:;;;9675,00
050271423128;18;38;00;;BRAUN, STEFFEN:;;;2795,00
130770424723;18;35;00;;BRAUN, SVEN:;;;6705,00
210369417738;18;32;00;;BRAUN, THOMAS:;;;10725,00
280569426210;18;33;00;;BRAUN, TINO:;;;6958,87
201058400619;01;69;00;;BRAUN, UWE:;;;21792,50
070238428224;14;02;00;;BRAUN, WALTER:;;;30750,00
310534429723;99;14;00;;BRAUN, WERNER:;;;37500,00
010845422727;12;08;00;;BRAUN, WOLF-DIETER:;;;22125,00
290770409411;18;28;00;;BRAUNE, ANDRE:;;;2720,00
210767410814;07;06;00;;BRAUNE, FRITZ-GUENTER:;;;16175,23
301053414219;06;08;00;;BRAUNE, GUENTER:;;;17422,50
140235429724;97;17;00;;BRAUNE, HEINZ:;;;41250,00
271064428240;14;14;00;;BRAUNE, JENS:;;;16170,00
070271400864;01;69;00;;BRAUNE, JENS:;;;2896,61
280543529713;97;17;00;;BRAUNE, JUTTA:;;;24562,50
191270409817;18;32;00;;BRAUNE, MARCO:;;;2795,00
230264412322;30;62;00;;BRAUNE, MARIO:;;;14685,00
070552424926;94;11;00;;BRAUNE, RALPH:;;;22942,50
210366415315;97;08;00;;BRAUNE, RENE:;;;16960,53
080260412228;99;02;00;;BRAUNE, THOMAS:;;;23045,00
200655414512;11;20;00;;BRAUNE, UWE:;;;23460,00
260869430061;99;43;00;;BRAUNEIS, UWE:;;;9510,00
261161409237;06;69;00;;BRAUNER, DIETMAR:;;;16967,50
181146424519;13;20;00;;BRAUNER, MANFRED:;;;24000,00
310742524514;13;77;00;;BRAUNER, VIKTORIA:;;;14677,42
180751417742;09;01;00;;BRAUNER, WERNER:;;;24480,00
140252429806;96;15;11;;BRAUNERT, HANS-JOACHIM:;;;33120,00
110462430103;96;15;21;;BRAUNERT, MATTHIAS:;;;17490,00
220734530085;15;80;00;;BRAUNGARDT, ELFRIEDE:;;;20375,00
160757430122;94;65;00;;BRAUNGARDT, VOLKER:;;;19008,39
120471415713;08;69;00;;BRAUNGART, STEFFEN:;;;3220,00
080955408532;18;77;00;;BRAUNS, ANDREAS:;;;21409,03
250154413111;97;08;00;;BRAUNS, LOTHAR:;;;22500,00
080757419716;97;08;00;;BRAUNSBERGER, DETLEF:;;;17595,00
020851500719;01;96;31;;BRAUNSCHWEIG, ANGELIKA:;;;17806,45
021049423810;94;03;00;;BRAUNSCHWEIG, ECKHARD:;;;24000,00
300949523835;98;83;00;;BRAUNSCHWEIG, HEIDI:;;;18802,50
150369408928;18;32;00;;BRAUNSCHWEIG, JENS:;;;9675,00
230442429718;99;43;00;;BRAUNSCHWEIG, JUERGEN:;;;22500,00
240549400711;01;96;31;;BRAUNSCHWEIG, SIEGBERT:;;;18000,00
120338415351;08;02;00;;BRAUTZSCH, PETER:;;;25500,00
120571427623;18;32;00;;BRAUTZSCH, STEFFEN:;;;2795,00
231166427613;95;45;00;;BRAUTZSCH, UWE:;;;15714,00
241267415338;99;43;00;;BRAUTZSCH, WOLFGANG:;;;14025,00
090252528318;14;96;00;;BRECHEIS, MONIKA:;;;19440,00
260759406431;04;00;45;;BRECHLIN, FRED:;;;21330,00
070652408915;98;19;00;;BRECHLIN, GERT:;;;25530,00
290649406438;04;55;00;;BRECHLIN, HELMUT:;;;20072,58
070344406168;04;30;00;;BRECHLIN, KLAUS-PETER:;;;24000,00
300744416219;09;77;00;;BRECHLING, BERNHARD:;;;37620,00
110964402778;18;71;20;;BRECHOT, TORSTEN:;;;21010,00
170968401339;01;06;26;;BRECHT, ANDREAS:;;;9510,00
220759410127;99;43;00;;BRECHT, FRANK:;;;22252,50
161257410111;99;43;00;;BRECHT, HOLGER:;;;21390,00
210950412228;07;08;00;;BRECKAU, JUERGEN:;;;20160,00
280848412217;07;06;00;;BRECKAU, WOLFGANG:;;;23812,50
201148422010;96;15;22;;BREDACK, ROLAND:;;;27300,00
200157501517;02;06;00;;BREDDIN, ANNELIE:;;;17834,27
011254402518;02;65;00;;BREDDIN, HERBERT:;;;19440,00
081163402516;07;06;00;;BREDDIN, MATTHIAS:;;;17325,00
061061413216;08;00;44;;BREDDIN, PETER:;;;18590,00
150561402526;97;01;00;;BREDDIN, ROLAND:;;;24210,00
311250407519;05;06;00;;BREDE, ECKHARD:;;;22320,00
171170403815;18;35;00;;BREDENDIEK, TINO:;;;6705,00
080259530016;18;80;00;;BREDERECK, KARIN:;;;16039,44
281257500711;30;83;00;;BREDEREKE, KARIN:;;;14263,44
140741406170;04;11;00;;BREDERLOW, ROLAND:;;;30375,00
240468530063;97;06;00;;BREDIS, CHRISTINE:;;;11420,93
210334402712;02;11;00;;BREDIS, MANFRED:;;;33750,00
280265415328;94;65;00;;BREDIS, TORSTEN:;;;16830,00
120946518514;10;06;00;;BREDOW, CHRISTINE:;;;21756,77
131144418515;10;00;46;;BREDOW, HORST:;;;24312,50
151051401958;03;00;41;;BREDOW, LOTHAR:;;;25200,00
220470404834;18;33;00;;BREDOW, MICHAEL:;;;2720,00
191262430114;15;07;00;;BREEDE, DIETMAR:;;;15675,00
250261401917;02;00;43;;BREESE, HARTMUT:;;;18232,50
230446530039;97;22;00;;BREETZ, BRIGITTE:;;;20625,00
200439430067;97;22;00;;BREETZ, GUENTER:;;;20187,50
040448401313;03;51;00;;BREETZKE, KLAUS:;;;23400,00
131167419713;18;33;00;;BREHM, FRANK:;;;10800,00
140368419829;11;69;00;;BREHM, GERD:;;;9675,00
180366420216;97;06;00;;BREHM, GERHARD:;;;16200,00
230752419013;10;00;40;;BREHM, HARTMUT:;;;24480,00
261048400812;94;11;00;;BREHM, HEINZ:;;;34500,00
140367430129;97;22;00;;BREHM, KARSTEN:;;;15876,00
200470417119;09;69;00;;BREHM, MARCO:;;;9510,00
120571410813;18;34;00;;BREHM, MIKE:;;;2795,00
080669420223;18;28;00;;BREHM, OLAF:;;;6792,09
230744422028;07;06;00;;BREHM, WOLFGANG:;;;26250,00
160753417414;97;06;00;;BREHME, HARALD:;;;25920,00
220256414222;99;51;00;;BREHME, RALF:;;;22400,00
290158407444;97;08;00;;BREHME, RENE:;;;22080,00
110469405218;18;34;00;;BREHMEL, THOMAS:;;;9675,00
181158404128;96;15;05;;BREHMER, FRED:;;;18862,50
210754529912;99;49;00;;BREHMER, GABRIELE:;;;1126,61
200150429890;15;03;00;;BREHMER, GERD:;;;24571,67
270235404119;03;40;00;;BREHMER, GERD:;;;17048,75
070235429715;96;15;15;;BREHMER, HERBERT:;;;33000,00
180942429746;99;40;00;;BREHMER, INGO:;;;26250,00
160942529714;99;43;00;;BREHMER, JUTTA:;;;19843,24
050553410122;04;80;00;;BREHMER, KARL-HEINZ:;;;18720,00
050140429714;15;22;00;;BREHMER, PETER:;;;27000,00
140537504128;03;40;00;;BREHMER, RENATE:;;;14886,77
100134422738;96;15;25;;BREHMER, WOLFGANG:;;;25500,00
190869410326;07;69;00;;BREIER, BERND:;;;2911,13
180266417757;18;32;00;;BREIER, DETLEF:;;;18396,00
270837415325;08;08;00;;BREINIG, KLAUS-PETER:;;;26250,00
010563400634;01;00;42;;BREINLINGER, FRANK:;;;17820,00
150967400619;01;00;49;;BREINLINGER, JENS:;;;12775,00
040369407020;94;03;00;;BREIT, RALF:;;;9510,00
300359400843;96;15;13;;BREITBARTH, JENS-UWE:;;;19347,50
240358417721;09;00;40;;BREITBARTH, LUTZ:;;;17820,00
240140400820;99;40;00;;BREITBARTH, MANFRED:;;;21937,50
070661500828;99;77;00;;BREITBARTH, MARION:;;;18070,34
231062400811;01;69;00;;BREITBARTH, PETER:;;;15620,00
120130430077;18;25;00;;BREITBARTH, RICHARD:;;;28500,00
080962430084;94;65;00;;BREITBARTH, STEFFEN:;;;16170,00
130940500814;99;40;00;;BREITBARTH, URSULA:;;;20032,50
290549416911;09;06;00;;BREITBARTH, WILFRIED:;;;25125,00
260641429718;99;12;00;;BREITE, MANFRED:;;;23937,50
240154524971;97;01;00;;BREITE, SUSANNE:;;;19313,80
120759404212;03;14;00;;BREITENFELD, WOLF-DIETER:;;;15181,50
281255400215;01;00;42;;BREITENFELDT, DETLEF:;;;22440,00
060658408546;98;83;00;;BREITENSTEIN, FRANK:;;;20182,50
071052411728;07;26;00;;BREITENSTEIN, HORST:;;;20010,00
050363412258;97;06;00;;BREITENSTEIN, RONALD:;;;14650,40
110156414738;99;43;00;;BREITER, HANS-GUENTER:;;;19320,00
080458413226;98;82;00;;BREITER, PETER:;;;18227,50
200569426218;18;34;00;;BREITFELD, GISO:;;;9675,00
230557404828;99;02;00;;BREITFELD, HANS:;;;24150,00
250268415115;08;69;00;;BREITFELD, UWE:;;;9875,00
110367530173;96;15;06;;BREITFELDT, INES:;;;13675,00
101238406120;04;06;00;;BREITGOFF, KLAUS:;;;24000,00
200835418211;10;00;44;;BREITHAUPT, KARL-HEINZ:;;;19875,00
291133416218;09;06;00;;BREITHAUPT, WALTER:;;;21583,36
071053419051;99;40;00;;BREITHECKER, GERO:;;;24225,00
250263522114;12;96;67;;BREITING, INA:;;;15757,50
061259422118;94;03;00;;BREITING, PETER:;;;22770,00
190450423646;14;18;00;;BREITKOPF, RAINER:;;;29625,00
290260405912;97;07;00;;BREITKREUTZ, BORIS:;;;17030,00
100854406111;04;00;40;;BREITKREUTZ, GERHARD:;;;19800,00
121041429730;98;82;00;;BREITKREUZ, HORST:;;;20625,00
301068411221;18;35;00;;BREITLAUCH, DIRK:;;;9675,00
090935417756;09;12;00;;BREITLAUCH, WERNER:;;;26250,00
140762415148;99;40;00;;BREITMANN, GOETZ:;;;19415,00
140762415121;15;69;00;;BREITMANN, JOST:;;;17077,50
210141522435;99;43;00;;BREITREITER, HELGA:;;;23250,00
280240422417;95;45;00;;BREITREITER, KARL-HELMUT:;;;37500,00
091270421228;18;33;00;;BREITREITER, THOMAS:;;;2720,00
051050421211;99;99;99;::;BREITREITER, UWE;1140;BA(E)RENSTEINSTR. 6;
051050421211;99;99;99;::;BREITREITER, UWE;1140;BA(E)RENSTEINSTR. 6;
070746530030;30;83;00;;BREITSCHUH, GISELA:;;;18060,00
190750429767;30;47;00;;BREITSCHUH, JUERGEN:;;;17280,00
310367413934;08;07;00;;BREITSCHWERDT, GOTTHARD:;;;15390,00
010344516610;97;01;00;;BREITSPRECHER, CHRISTEL:;;;21000,00
211268405230;04;69;00;;BREITSPRECHER, DIRK:;;;9675,00
160571418440;98;83;00;;BREITSPRECHER, JOERG-DIETMAR:;;;3020,00
200556403623;18;32;00;;BREITSPRECHER, JUERGEN:;;;18630,00
010571414120;18;28;00;;BREITSPRECHER, MARCO:;;;2720,00
061057430152;94;65;00;;BREITSPRECHER, PETER:;;;19665,00
261263403610;03;80;00;;BREITSPRECHER, RAINER:;;;15592,50
041144416617;09;00;45;;BREITSPRECHER, SIEGFRIED:;;;29250,00
180968413814;18;32;00;;BREITUNG, JENS:;;;9675,00
131270428212;18;35;00;;BREITZKE, ANDRE:;;;2795,00
291148401326;01;02;00;;BREITZKE, ROLF:;;;26162,50
240169403435;03;69;00;;BREMER, ANDREAS:;;;9510,00
240169411427;18;31;00;;BREMER, ANDREAS:;;;9600,00
130655503610;03;14;00;;BREMER, BRITTA:;;;17681,17
080139429722;15;69;00;;BREMER, DIETER:;;;33000,00
270450402431;02;00;47;;BREMER, DIETER:;;;16920,00
280868402411;02;69;00;;BREMER, HEIKO:;;;9555,00
110763530140;30;83;00;;BREMER, IRIS:;;;12197,15
260164430088;98;84;00;;BREMER, JENS:;;;18095,00
200234429716;96;15;14;;BREMER, KARL-HEINZ:;;;22500,00
220436404216;03;09;00;;BREMER, KURT:;;;24750,00
070249401713;94;03;00;;BREMER, MANFRED:;;;26220,00
120670429720;99;40;00;;BREMER, MIRKO:;;;2870,00
261249403913;03;26;00;;BREMER, ROBERT:;;;22275,00
020643402428;02;18;00;;BREMER, WILFRIED:;;;29250,00
160654403316;03;14;00;;BREMER, WOLFGANG:;;;18480,00
270562400836;01;19;69;;BREMERKAMP, FALK:;;;19305,00
140840510117;07;00;44;;BREMERT, ILSE:;;;22500,00
090138410113;07;00;44;;BREMERT, KLAUS:;;;18875,00
040460530011;99;77;00;;BREMERT, UTE:;;;19140,00
200251416116;05;03;00;;BREMME, KLAUS-DIETER:;;;22275,00
140555419031;10;55;00;;BREMME, WOLFGANG:;;;20100,00
151259517554;30;61;00;;BREMMERT, KATHRIN:;;;10696,78
250244430054;07;51;00;;BREMSE, JUERGEN:;;;22500,00
050963409538;99;02;00;;BRENDAHL, THOMAS:;;;19470,00
140459421713;10;00;51;;BRENDEL, ALEXANDER:;;;12675,00
151158425079;30;36;00;;BRENDEL, ANDREAS:;;;18487,00
220352507912;99;02;00;;BRENDEL, INGEBORG:;;;24480,49
090468407515;05;19;00;;BRENDEL, JOERG:;;;9872,00
010153421520;06;15;00;;BRENDEL, JUERGEN:;;;26400,00
090945428918;14;00;54;;BRENDEL, JUERGEN:;;;26640,00
070553504119;06;55;00;;BRENDEL, JUTTA:;;;21480,00
301146429719;97;22;00;;BRENDEL, KLAUS:;;;20625,00
060146430045;15;08;00;;BRENDEL, PETER:;;;24000,00
160353506119;30;56;00;;BRENDEL, URSULA:;;;13530,00
131246428212;99;02;00;;BRENDEL, WERNER:;;;27375,00
191254422712;12;00;40;;BRENDEL, WOLFGANG:;;;20700,00
100238404315;97;06;00;;BRENDEMUEHL, HELMUT:;;;24562,50
080868420517;18;32;00;;BRENDLER, ANDREAS:;;;6958,87
140651422257;98;85;00;;BRENDLER, ARNDT:;;;19440,00
310338404510;96;15;22;;BRENDLER, JOACHIM:;;;30000,00
090170404522;18;34;00;;BRENDLER, RENE:;;;10810,00
260960404518;97;01;00;;BRENDLER, STEFAN:;;;22934,35
051168400512;17;00;00;;BRENDTNER, JOERG:;;;8950,00
230342400512;01;07;00;4733/88, :;BRENDTNER, WERNER;2520;HERMANN-MATERN-STR. 16;
230342400512;01;07;00;4733/88, :;BRENDTNER, WERNER;2520;HERMANN-MATERN-STR. 16;
180152407614;15;09;00;;BRENNECKE, BURKHARDT:;;;26100,00
040569407615;97;06;00;;BRENNECKE, JOERG:;;;13750,00
240837411917;97;97;11;;BRENNECKE, ROLF:;;;35250,00
010647411525;04;19;00;;BRENNECKE, ROLF-DIETER:;;;23545,00
041137511915;94;03;00;;BRENNECKE, SIGRID:;;;22927,09
250142430061;18;40;00;;BRENNER, HEINZ:;;;24750,00
200553428219;14;00;41;;BRENNER, JUERGEN:;;;25200,00
180460402516;02;18;00;;BRENNER, LUTZ:;;;9120,00
050160430181;15;80;00;;BRENNER, WOLF-EKKEHARD:;;;17940,00
220449524727;96;15;31;;BRENNIG, BRIGITTE:;;;21600,00
040250429804;97;01;00;;BRENNIG, KLAUS:;;;29250,00
090451503420;03;41;00;;BRENTFUEHRER, MARLIES:;;;19980,00
171147403411;03;09;00;;BRENTFUEHRER, UWE:;;;24000,00
110947410610;97;01;00;;BRENZ, GERT-JOACHIM:;;;35250,00
201051411518;12;06;00;;BRESCH, HANS:;;;21975,00
280355511014;07;06;00;;BRESCH, KARIN:;;;19320,00
090254411017;07;06;00;;BRESCH, PETER:;;;20160,00
140248400816;30;43;00;;BRESEMANN, HANS-PETER:;;;17876,00
050649400228;99;12;00;;BRESEMANN, KLAUS:;;;32530,65
280155400248;99;12;00;;BRESEMANN, VOLKER:;;;21700,00
210571400892;01;06;22;;BRESIEN, MICHAEL:;;;2896,61
210160430069;15;20;00;;BRESKI, JUERGEN:;;;24150,00
230358525053;13;53;00;;BRESLER, ANKE:;;;16431,32
220647424911;13;65;00;;BRESLER, CLAUS:;;;26250,00
110856424320;13;26;00;;BRESLER, DIETMAR:;;;22965,50
300852520320;11;12;00;;BRESLER, ILONA:;;;20180,00
200867424958;18;41;30;;BRESLER, MICHAEL:;;;13200,00
160951420315;11;00;40;;BRESLER, NORBERT:;;;25200,00
180551417721;09;00;40;;BRESSA, KLAUS-DETLEF:;;;26400,00
150939402115;02;06;00;;BRESSEL, DIETER:;;;26250,00
290358530308;94;30;00;;BRESSEL, TATJANA:;;;16239,79
110758408810;94;03;00;;BRESSEM, HARALD:;;;22597,50
230553403713;94;65;00;;BRESSIN, HELMUT:;;;19440,00
070468430127;98;27;00;;BRESSLER, FRANK:;;;14332,00
210334530060;96;15;11;;BRESSLER, LIESELOTTE:;;;22620,00
290734429714;99;43;00;;BRESTRICH, WOLFGANG:;;;27000,00
230456421215;12;00;48;;BRESZLER, HANS-JUERGEN:;;;16276,50
280651426527;04;00;42;;BRESZLER, KLAUS:;;;21485,81
291142429715;99;43;00;;BRETERNITZ, DIETER:;;;24000,00
300955412218;08;20;00;;BRETERNITZ, FRED:;;;23975,00
310768413927;18;40;00;;BRETERNITZ, JO(E)RG:;;;10155,00
300463430217;99;77;00;;BRETERNITZ, UWE:;;;17572,50
290149418432;99;55;00;;BRETERNITZ, WILFRIED:;;;25500,00
241142429728;97;06;00;;BRETFELD, HERMANN:;;;24000,00
200941428229;14;02;00;;BRETFELD, KLAUS:;;;28500,00
251053429223;14;65;00;;BRETSCHNEIDER, CHRISTIAN:;;;19860,00
140548428220;96;15;18;;BRETSCHNEIDER, CHRISTIAN:;;;27360,00
250458430148;99;02;00;;BRETSCHNEIDER, DETLEF:;;;21562,50
030934429718;97;01;00;;BRETSCHNEIDER, DIETER:;;;27750,00
050158421817;12;06;00;;BRETSCHNEIDER, DIETER:;;;19320,00
290663427016;14;51;00;;BRETSCHNEIDER, DIRK:;;;17792,50
250371403622;18;29;30;;BRETSCHNEIDER, DIRK:;;;3070,16
060635429723;94;03;00;;BRETSCHNEIDER, EBERHARDT:;;;24000,00
171239429723;94;30;00;;BRETSCHNEIDER, EGON:;;;26750,00
101144425005;30;47;00;;BRETSCHNEIDER, FRANZ:;;;28780,00
270668421010;18;32;00;;BRETSCHNEIDER, GERALD:;;;9675,00
080268417760;18;35;00;;BRETSCHNEIDER, GERD:;;;10775,00
150542429774;99;77;00;;BRETSCHNEIDER, GERT:;;;24000,00
141036426218;14;03;00;;BRETSCHNEIDER, GUENTER:;;;23250,00
181255422715;94;65;00;;BRETSCHNEIDER, GUENTER:;;;17595,00
250844406728;05;00;41;;BRETSCHNEIDER, GUNTER:;;;27540,00
090455425028;13;20;00;;BRETSCHNEIDER, HARALD:;;;24880,00
150438530071;99;40;00;;BRETSCHNEIDER, HELGA:;;;17595,00
191152529770;30;83;00;;BRETSCHNEIDER, ILONA:;;;17432,26
130930530024;98;83;00;;BRETSCHNEIDER, ILSE:;;;19170,00
290959429213;15;19;00;;BRETSCHNEIDER, INGO:;;;21560,00
211068421818;18;33;00;;BRETSCHNEIDER, JAN:;;;9675,00
211165430214;97;08;00;;BRETSCHNEIDER, JAN:;;;16656,50
290867427210;14;08;00;182, :;BRETSCHNEIDER, JENS;9271;AM HANG 3;
290867427210;14;08;00;182, :;BRETSCHNEIDER, JENS;9271;AM HANG 3;
091069420928;18;34;00;;BRETSCHNEIDER, JO(E)RG:;;;10500,00
080168506731;05;00;40;;BRETSCHNEIDER, KERSTIN:;;;14382,00
160251400612;05;00;41;;BRETSCHNEIDER, KLAUS:;;;24140,00
251258408944;06;65;00;;BRETSCHNEIDER, MICHAEL:;;;17825,00
010943530369;98;83;00;;BRETSCHNEIDER, MONIKA:;;;20309,36
040668409819;18;31;00;;BRETSCHNEIDER, NICO:;;;9825,00
120257520010;97;22;00;;BRETSCHNEIDER, REGINA:;;;17448,10
140135422728;12;03;00;;BRETSCHNEIDER, SIEGFRIED:;;;31437,50
031151429783;99;43;00;;BRETSCHNEIDER, THOMAS:;;;23040,00
260165426232;14;00;47;;BRETSCHNEIDER, TORSTEN:;;;18881,00
250366530221;96;15;14;;BRETSCHNEIDER, UTA:;;;12920,00
220570415119;18;31;00;;BRETSCHNEIDER, VOLKER:;;;6705,00
070268406712;05;69;00;;BRETSCHNER, JOERG:;;;9675,00
230559407010;11;18;00;;BRETTIN, BODO:;;;20189,00
300156517718;99;02;00;;BRETTIN, PETRA:;;;20137,98
240954429710;94;94;00;;BRETTIN, RALF:;;;29670,00
050358407016;05;08;00;;BRETTIN, UWE:;;;20240,00
020951409314;06;00;45;;BRETTSCHNEIDER, GU(E)NTER:;;;21065,00
301146422410;12;00;47;;BRETTSCHNEIDER, HANS:;;;21812,50
050543427916;30;34;00;;BRETTSCHNEIDER, RAINER:;;;23200,00
121053406413;18;80;00;;BRETZKE, KLAUS-DIETER:;;;19980,00
101135429717;15;08;00;;BREU, DIETER:;;;27187,50
070369503212;03;09;00;;BREU, KERSTIN:;;;13000,00
050242429731;98;18;00;;BREUCKER, PETER:;;;30750,00
270869430044;18;32;00;;BREUCKER, TORSTEN:;;;9510,00
030334429722;97;08;00;;BREUDEL, GUENTER:;;;28500,00
271063406410;04;00;42;;BREUER, ANDREAS:;;;16227,00
131068430044;99;02;00;;BREUER, CARSTEN:;;;14475,00
160244429724;99;40;00;;BREUER, FRANK:;;;40312,50
240352429799;97;01;00;;BREUER, HARTMUT:;;;21700,00
310838408219;06;00;42;;BREUER, HEINZ:;;;26875,00
120641429713;97;17;00;;BREUER, HEINZ:;;;28500,00
050167421712;99;12;00;;BREUER, JAN:;;;15606,00
050458420330;97;08;00;;BREUER, JUERGEN:;;;17940,00
070665408228;99;43;00;;BREUER, KLAUS:;;;15463,50
191147419614;11;03;00;;BREUER, LOTHAR:;;;26875,02
250461421728;99;43;00;;BREUER, MARIO:;;;17820,00
280959411815;04;06;00;;BREUER, REINER:;;;19952,50
150465430236;98;83;00;;BREUER, RONALD:;;;16623,00
140431429721;98;83;00;;BREUER, WALTER:;;;21750,00
031048405310;04;00;45;;BREUHAHN, JOACHIM:;;;23760,00
150554504823;04;00;45;;BREUHAHN, SIGRID:;;;18912,82
080643429756;97;06;00;;BREUL, BERND:;;;24000,00
270768411928;18;33;00;;BREUM, JO(E)RG:;;;10575,00
210369408313;18;32;00;;BREUNINGER, JO(E)RG:;;;9675,00
150953426519;14;51;00;;BREY, WOLFGANG:;;;29111,62
260747517716;09;06;00;;BREYER, ILONA:;;;22000,00
041242429737;99;43;00;;BREYER, JUERGEN:;;;21750,00
140546417720;09;09;00;;BREYER, LOTHAR:;;;33187,50
250735430067;96;15;05;;BREYER, LOTHAR:;;;28500,00
190539529711;96;15;12;;BREYER, MONIKA:;;;24155,65
191052429799;99;43;00;;BREYER, ULRICH:;;;24480,00
240251417166;09;51;00;;BREYER, WILFRID:;;;21240,00
160968411212;18;33;00;;BREYMANN, NICO:;;;9600,00
171234405319;04;00;49;;BREYVOGEL, OTTMAR:;;;19560,48
300829407522;05;00;40;;BREZINSKI, HORST:;;;27000,00
221149402722;02;00;45;;BREZMANN, GERHARD:;;;23402,50
040142429786;98;50;00;;BRIEBSCH, EBERHARD:;;;37500,00
230461430247;94;03;00;;BRIEBSCH, ERIK:;;;17160,00
110169430075;98;84;00;;BRIEBSCH, RONALD:;;;14425,00
091061419033;10;08;00;;BRIEGER, ANDREE:;;;17820,00
280755406715;97;22;00;;BRIEGER, KLAUS-DIETER:;;;27700,00
251157528226;99;13;00;;BRIEGER, MARGITTA:;;;17531,75
280257427126;99;13;00;;BRIEGER, STEPHAN:;;;21390,00
261261430092;98;85;00;;BRIEN, JOERG:;;;17820,00
071259430061;97;08;00;;BRIEN, MICHAEL:;;;21026,52
160862530221;97;08;00;;BRIEN, UTE:;;;16169,10
140534429732;99;43;00;;BRIEN, WERNER:;;;27750,00
050747430068;30;58;00;;BRIER, ARMIN:;;;17760,48
280346425018;13;00;40;;BRIER, KARL-HEINZ:;;;33187,50
240266422814;60;90;00;;BRIER, ROLAND:;;;
240266422814;60;90;00;;BRIER, ROLAND:;;;15732,00
211148530117;30;84;00;;BRIER, SIGRID:;;;16560,00
170954424046;30;47;00;;BRIESE, ANDREAS:;;;18758,67
010158424034;30;32;00;;BRIESE, HOLGER:;;;13923,15
190869410414;07;18;00;;BRIESE, JENS:;;;8300,00
200956403710;30;58;00;;BRIESE, JUERGEN:;;;16934,00
141149400217;01;80;00;;BRIESE, JUERGEN:;;;22320,00
250861506114;03;15;00;;BRIESE, KAREN:;;;16665,00
280259530012;30;80;00;;BRIESE, PETRA:;;;3182,90
020952529748;30;76;00;;BRIESE, SIGRID:;;;9465,64
040351408316;06;60;00;;BRIESEMANN, BERND:;;;20182,50
070668408311;97;01;00;;BRIESEMANN, DIRK:;;;8812,50
080456500027;99;40;00;;BRIESEMEISTER, EIKE:;;;18329,19
250656400847;18;32;00;;BRIESEMEISTER, HARALD:;;;29670,00
010345408013;18;33;00;;BRIESEMEISTER, KLAUS:;;;23040,00
240956506134;30;47;00;;BRIESENICK, ILONA:;;;20233,50
110659404013;03;11;00;;BRIESKORN, BERND:;;;19320,00
220363406412;04;14;00;;BRIESKORN, RENE:;;;16170,00
180341406418;04;00;42;;BRIESKORN, WOLFGANG:;;;29250,00
240639417760;09;00;40;;BRIESNER, GERD:;;;30000,00
131142517712;09;60;00;;BRIESNER, RENATE:;;;20750,00
150433405714;04;00;52;;BRIEST, FRITZ:;;;18250,00
250969425068;18;35;00;;BRIEST, HANS-JOERG:;;;10287,08
090860403156;30;62;00;;BRIETZKE, PETER:;;;15251,00
160351429762;30;55;00;;BRILLAT, BERND:;;;3600,00
050752404411;99;12;00;;BRINCKMANN, UWE:;;;21395,00
080659530023;96;15;11;;BRINGER, GABRIELE:;;;17808,29
150358430070;99;26;00;;BRINGER, KLAUS-DIETER:;;;19745,00
261059430013;96;15;14;;BRINGEZU, MARIO:;;;21562,50
010446430041;96;15;07;;BRINGMANN, MATTHIAS:;;;29520,00
200832406928;30;50;00;;BRINGMANN, OTTO:;;;18720,00
070455415315;08;80;00;;BRINK, MATTHIAS:;;;17940,00
270144421327;97;06;00;;BRINKE, FRANK:;;;24000,00
150253510015;07;06;00;;BRINKE, HELGA:;;;20104,00
251232400821;97;01;00;;BRINKEL, GEORG:;;;25687,50
101269400848;01;06;20;;BRINKHOFF, FRANK:;;;12650,00
060161420312;09;03;00;;BRINKMANN, ANDREAS:;;;19277,50
030562430231;98;83;00;;BRINKMANN, BERND:;;;18397,50
040144429747;99;43;00;;BRINKMANN, DETLEF:;;;27750,00
020842429738;98;82;00;;BRINKMANN, GERHARD:;;;17398,39
300751429755;94;03;00;;BRINKMANN, HANS-JOERG:;;;20870,00
110958402747;18;71;25;;BRINKMANN, JOERG:;;;20182,50
080654403244;18;71;10;;BRINKMANN, LOTHAR:;;;20160,00
270371415744;18;33;00;;BRINKMANN, MARKO:;;;2795,00
250251400216;01;06;27;;BRINKMANN, MARTIN:;;;19740,00
110567530143;99;53;00;;BRINKMANN, PETRA:;;;16470,00
240652529812;99;53;00;;BRINKMANN, REGINA:;;;26634,82
010441530051;98;83;00;;BRINKMANN, RUTH:;;;19440,00
311230530018;99;09;00;;BRINKMANN, SIEGLINDE:;;;23250,00
110230430016;97;01;00;;BRINKMANN, WILLY:;;;24750,00
190160409221;99;43;00;;BRITZE, FRANK:;;;21332,50
250166409224;99;43;00;;BRITZE, STEFFEN:;;;16038,00
140858411811;05;00;43;;BRIX, ERHARD:;;;21780,00
180966406119;17;00;00;;BRIX, THORSTEN:;;;9872,00
111253414734;99;14;00;;BRIXEL, HEINZ:;;;27360,00
260755503736;99;09;00;;BRIXEL, SIGRID:;;;17860,29
180965404138;99;14;00;;BRO(E)CKER, FRED:;;;11169,00
090670404422;18;32;00;;BRO(E)CKER, JO(E)RG:;;;2795,00
150466513922;18;80;00;;BRO(E)CKERT, ANNETTE:;;;15660,00
220969413123;18;31;00;;BRO(E)DEL, HOLGER:;;;9510,00
030863424927;08;80;00;;BRO(E)DEL, STEFFEN:;;;15294,59
230263424938;07;06;00;;BRO(E)DNER, KARSTEN:;;;17820,00
140467413967;99;55;00;;BRO(E)MEL, STEFFEN:;;;16092,00
150670406411;18;35;00;;BRO(E)SECKE, ANDRE:;;;6705,00
261154417757;09;20;00;;BROAETER, HANS-JUERGEN:;;;23312,50
031137429736;99;09;00;;BROCK, DIETER:;;;28500,00
270230506917;99;43;00;;BROCK, GISELA:;;;20625,00
160559412222;01;03;00;;BROCK, HOLGER:;;;17997,50
101053406917;99;43;00;;BROCK, KLAUS-DIETER:;;;19440,00
050758410847;94;03;00;;BROCK, REINER:;;;21390,00
120470422743;18;33;00;;BROCK, STEFFEN:;;;9986,44
190733514513;08;96;00;;BROCKE, ANITA:;;;17460,00
111038517749;09;14;00;;BROCKE, MARGARETE:;;;18572,50
290168406445;17;00;00;;BROCKE, TOM:;;;8950,00
150756417744;97;01;00;;BROCKE, UDO:;;;25530,00
030358517719;09;07;00;;BROCKE, VERA:;;;17223,17
080271412119;18;33;00;;BROCKEL, ANDREAS:;;;2795,00
121268400852;18;35;00;;BROCKHAUSEN, JENS:;;;9327,00
081068402112;02;69;00;;BROCKHOFF, PETER:;;;9875,00
241155402428;02;00;47;;BROCKMANN, BERND:;;;22770,00
270257411926;07;00;57;;BROCKMANN, HELMUT:;;;15525,00
030550405012;04;08;00;;BROCKMANN, JOACHIM:;;;22500,00
041162400619;30;61;00;;BROCKMANN, JOERG:;;;14355,00
290962420914;12;00;44;;BROCKMANN, OLAF:;;;13932,00
260237400884;01;06;23;;BROCKMANN, WINFRIED:;;;24000,00
250259408538;97;08;00;;BROCKSCH, ULLRICH:;;;22080,00
310538522722;12;08;00;;BROD, MARGA:;;;17940,00
110959411442;07;00;53;;BRODA, MARIO:;;;22770,00
170948430060;15;08;00;;BRODDA, WILFRIED:;;;23760,00
290948522762;94;30;00;;BRODE, CHRISTINE:;;;20640,00
141062423918;99;43;00;;BRODE, DETLEF:;;;17600,00
101248429748;94;30;00;;BRODE, HARTMUT:;;;22770,00
171067430065;94;30;00;;BRODE, STEPHAN:;;;8950,00
010953402723;02;03;00;;BRODEHL, PETER:;;;24480,00
130841429725;97;08;00;;BRODEHL, ROLF-WERNER:;;;26250,00
250338529717;96;15;10;;BRODEHL, SIEGRID:;;;21937,50
110568430144;99;02;00;;BRODEHL, UWE:;;;14994,00
120754410111;94;03;00;;BRODIEN, GERNOT:;;;20010,00
260168412266;18;32;00;;BRODMANN, DIRK:;;;10621,77
071250520052;30;37;00;;BRODOWSKI, BIANKA:;;;16686,00
240868408542;06;00;46;;BRODOWSKI, THOMAS:;;;12825,00
310147420016;30;37;00;;BRODOWSKI, WOLFRAM:;;;20160,00
130129420313;11;00;40;;BRODRECHT, GERHARD:;;;23250,00
030542419617;11;51;00;;BRODRECHT, JUERGEN:;;;21000,00
181148428927;97;01;00;;BROECKEL, KLAUS:;;;23040,00
200968430097;15;80;00;;BROECKER, RAINER:;;;14750,00
120344429717;97;08;00;;BROECKER, ULRICH:;;;25500,00
240451430058;98;84;00;;BROEDE, WOLFGANG:;;;20100,00
260568413954;99;43;00;;BROEDEL, JOERG:;;;13500,00
040566513922;08;19;00;;BROEDEL, PETRA:;;;13179,42
120252424214;99;02;00;;BROEDNER, INGO:;;;26547,50
020761428119;14;80;00;;BROEDNER, LUTZ:;;;16472,50
311056428113;99;13;00;;BROEDNER, NORBERT:;;;19665,00
010564430085;18;29;30;;BROEGE, AXEL:;;;11220,00
020338430094;18;71;20;;BROEGE, WOLFGANG:;;;24150,00
190166409919;07;00;50;;BROEHL, THOMAS:;;;14812,50
130440411110;07;00;51;;BROEKER, ROLF:;;;29250,00
191057413980;08;20;00;;BROEMEL, INGOLF:;;;23205,00
081268419330;05;69;00;;BROEMEL, SILVIO:;;;9675,00
080357430115;98;18;00;;BROEMME, ANDREAS:;;;26392,50
010230530019;99;02;00;;BROEMME, ILSE:;;;24750,00
060941415426;08;00;40;;BROEMME, JUERGEN:;;;27750,00
051156530141;99;53;00;;BROEMME, MARGRET:;;;21551,13
111231429724;99;09;00;;BROEMME, RUDI:;;;33000,00
190254417513;97;29;00;;BROEMMER, EGBERT:;;;23940,00
070753526339;99;77;00;;BROEMMER, GABRIELE:;;;31680,00
290668415129;08;14;00;;BROEMMLING, DIRK:;;;12130,00
010368402327;97;08;00;;BROER, ANDREAS:;;;15221,00
091030430010;97;08;00;;BROESE, HEINZ:;;;28500,00
270654520720;99;77;00;;BROESE, KARIN:;;;22770,00
241231530051;97;06;00;;BROESE, MARGARETE:;;;21375,00
190848411514;07;06;00;;BROESEL, GUENTER:;;;20562,50
020653511222;07;80;00;;BROESEL, HELGA:;;;18000,00
031233505110;30;54;00;;BROESICKE, JOHANNA:;;;22680,00
091036405115;30;54;00;;BROESICKE, WOLFGANG:;;;26700,00
161139429719;99;43;00;;BROETZMANN, HANS-JOACHIM:;;;23187,50
190241406110;17;00;00;;BROHMANN, WILLI:;;;20700,00
040548402719;02;00;49;;BROMBACH, GUENTER:;;;24375,00
110537400823;01;55;00;;BROMBERG, FRITZ:;;;22500,00
051060408424;97;29;00;;BROMBERG, JOERG:;;;24062,90
220867404218;03;00;44;;BROMBERG, MAIK:;;;13982,00
100247424617;99;02;00;;BROMME, HANS-WERNER:;;;27360,00
241068423618;99;43;00;;BROMME, JOERG:;;;9825,00
240452424610;14;80;00;;BROMME, KARL-HEINZ:;;;14372,13
201132430032;15;20;00;;BRONDER, MANFRED:;;;37500,00
220939530054;15;00;41;;BRONDER, MARLIS:;;;23937,50
170170421314;18;35;00;;BRONDER, TIMO:;;;9600,00
280168409815;07;08;00;;BRONESKE, HARALD:;;;11758,00
260959404115;99;43;00;;BRONEWSKI, WERNER:;;;16830,00
050459422792;12;06;00;;BRONNER, UWE:;;;19780,00
220769418915;10;06;00;;BRONST, THOMAS:;;;12555,00
190645411522;07;06;00;;BROSCH, EDUARD:;;;21687,50
311041429711;99;51;00;;BROSCH, FRITZ:;;;26250,00
250435502719;02;65;00;;BROSCH, HANNA:;;;19500,00
160755402718;02;02;00;;BROSCH, PETER:;;;22080,00
051056430071;99;51;00;;BROSCH, PETER:;;;24725,00
010358430113;99;09;00;;BROSCH, RAINER:;;;22252,50
160169404411;98;85;00;;BROSCHE, FRANK:;;;9675,00
021249413414;13;00;43;;BROSCHE, FRANK:;;;26910,00
180537504415;03;00;40;;BROSCHE, HELENE:;;;16031,25
210566422843;12;65;00;;BROSCHE, KLAUS:;;;14580,00
251232422721;12;60;00;;BROSCHE, RUDOLF:;;;36000,00
040261422771;12;20;00;;BROSCHE, RUDOLF:;;;19745,00
241260530026;94;03;00;;BROSCHIES, MARINA:;;;16847,50
290739408912;06;00;54;;BROSE, GUENTER:;;;29700,00
100657411819;07;00;56;;BROSE, HARALD:;;;22942,50
151058430225;94;11;00;;BROSE, NORBERT:;;;21275,00
210371407619;18;32;00;;BROSE, STEFFEN:;;;2795,00
040171408423;18;32;00;;BROSE, STEFFEN:;;;2795,00
191161403715;03;07;00;;BROSE, UWE:;;;21120,00
161124430012;96;15;14;;BROSE, WALTER:;;;33000,00
180268424838;99;43;00;;BROSGE, SVEN:;;;9600,00
261255412218;94;03;00;;BROSIG, FRANK-ULRICH:;;;20010,00
030661404127;96;15;12;;BROSIG, STEFFEN:;;;20278,79
211069427111;14;69;00;;BROSIG, TORSTEN:;;;12085,00
041149524940;13;20;00;;BROSINSKY, ANGELA:;;;21540,00
231065503736;05;08;00;;BROSINSKY, CORNELIA:;;;7598,31
270968403746;99;43;00;;BROSINSKY, JAN:;;;14425,00
120467403728;05;80;00;;BROSINSKY, RENE:;;;15390,00
250462408525;15;15;00;;BROSIUS, BURKHARD:;;;21450,00
180334429726;99;43;00;;BROSIUS, HERBERT:;;;24750,00
140759406910;94;65;00;;BROSIUS, THOMAS:;;;17745,00
290847529711;99;40;00;;BROSK, BAERBEL:;;;22687,50
010348429725;97;06;00;;BROSK, WOLFGANG:;;;24750,00
240336429748;94;03;00;;BROSKE, HORST:;;;27750,00
221060413628;98;84;00;;BROSOWSKY, HANS-ULRICH:;;;17700,00
050347400812;01;65;00;;BROSTOWSKI, DETLEF:;;;21270,82
230459430088;30;61;00;;BROSY, JOERG:;;;16575,00
310149407616;05;03;00;;BROSZ, GERD:;;;26250,00
190933530067;97;08;00;;BROSZAT, CHRISTEL:;;;19125,00
110632430078;97;08;00;;BROSZAT, HANS-GUENTER:;;;21750,00
140957404844;04;00;50;;BROSZIO, THOMAS:;;;16215,00
230741410814;10;07;00;;BROSZMANN, HARALD:;;;30750,00
101167410324;08;69;00;;BROTHUHN, ULF:;;;6025,00
091236416214;09;00;43;;BROTMEYER, ROLF:;;;28937,50
240270406120;04;18;00;;BROXTERMANN, ANDREAS:;;;2700,00
120747406130;04;41;00;;BROXTERMANN, JUERGEN:;;;31500,00
200443518520;99;40;00;;BROYER, EDELTRAUT:;;;22125,00
010470419328;97;22;00;;BROYER, HEIKO:;;;9930,00
110136418520;95;60;12;;BROYER, KLAUS:;;;33000,00
060670415036;18;33;00;;BRU(E)CKNER, DIRK:;;;9551,61
111270426534;18;35;00;;BRU(E)CKNER, ENRICO:;;;2795,00
130968417334;18;80;00;;BRU(E)CKNER, JENS:;;;9825,00
100169428910;18;33;00;;BRU(E)CKNER, JO(E)RG:;;;2720,00
051035407219;18;25;00;;BRU(E)CKNER, KARL-HEINZ:;;;28687,50
141161419711;11;00;41;;BRU(E)CKNER, KLAUS:;;;15510,00
211062407513;04;00;54;;BRU(E)CKNER, STEFFEN:;;;21065,00
220571403320;18;33;00;;BRU(E)CKNER, STEFFEN:;;;2795,00
060968429246;18;32;00;;BRU(E)CKNER, SVEN:;;;9675,00
261168428916;18;32;00;;BRU(E)CKNER, TINO:;;;10025,00
220968424920;18;31;00;;BRU(E)DGAM, HENRY:;;;9600,00
090368406160;18;31;00;;BRU(E)GGEMANN, GERRIT:;;;9825,00
190770430634;18;31;00;;BRU(E)HL, JENS:;;;2795,00
110663402715;96;15;00;4361/84, M:;BRU(E)NING, FALK;1095;WARNEMU(E)NDER STR. 16;
110663402715;96;15;00;4361/84, M:;BRU(E)NING, FALK;1095;WARNEMU(E)NDER STR. 16;
141270427518;18;32;00;;BRU(E)NING, STEFAN:;;;2795,00
230668415036;18;34;00;;BRU(E)SCHKE, JENS:;;;10375,00
250955429738;30;47;00;;BRUCH, PETER:;;;23805,00
021061402123;02;08;00;;BRUCHE, DIETMAR:;;;18590,00
270859402111;02;26;00;;BRUCHE, JUERGEN:;;;20010,00
130362501718;02;26;00;;BRUCHE, PETRA:;;;10687,34
130970427347;18;40;00;;BRUCHHOLD, LUTZ:;;;6736,77
200655422723;12;26;00;;BRUCHHOLZ, HANS-PETER:;;;20412,50
280152403814;12;00;58;;BRUCHMANN, DETLEF:;;;23460,00
270752421814;12;41;00;;BRUCHMANN, FRANK:;;;31680,00
210538429722;97;06;00;;BRUCHMANN, PETER:;;;27125,00
070353518516;12;08;00;;BRUCHMANN, WALTRAUD:;;;2300,00
230662530084;99;77;00;;BRUCHMUELLER, HEIKE:;;;14594,95
040162414741;99;14;00;;BRUCHMUELLER, UWE:;;;20401,34
260556409915;95;60;24;;BRUCKE, ANDRE:;;;25600,00
050371431117;18;33;00;;BRUCKELT, STEFAN:;;;2795,00
180552506929;99;43;00;;BRUCKER, URSULA:;;;9987,75
091134429719;97;06;00;;BRUCKERT, ARTUR:;;;27595,84
300564410119;96;15;26;;BRUCKERT, TORSTEN:;;;16912,50
100662403629;99;02;00;;BRUCKHOFF, FRANK:;;;19085,00
060633403618;03;00;45;;BRUCKHOFF, HERBERT:;;;26250,00
090570400715;99;77;00;;BRUCKHOFF, MARIO:;;;2915,97
230465503116;03;80;00;;BRUCKSCH, CORINNA:;;;10611,40
120456522123;12;00;43;;BRUCKSCH, MARTINA:;;;5528,21
200340422112;12;00;54;;BRUCKSCH, WERNER:;;;27000,00
190737403116;03;00;50;;BRUCKSCH, WOLF-DIETER:;;;36000,00
060550413917;08;08;00;;BRUDER, KLAUS-DIETER:;;;18450,00
211033430052;18;27;30;;BRUDER, SIEGFRIED:;;;27000,00
051034529716;96;15;11;;BRUDER, SIGRID:;;;21937,50
041131403825;03;02;00;;BRUDNICKI, BRUNO:;;;17666,66
090370403823;97;06;00;;BRUDNICKI, DIRK:;;;9600,00
010268412237;07;06;00;;BRUDNICKI, JENS:;;;11600,00
100166417730;09;00;40;;BRUECK, JENS:;;;18764,40
091068420010;09;69;00;;BRUECK, STEFFEN:;;;9700,00
011243530055;30;47;00;;BRUECKHAENDLER, GITTA:;;;24140,00
070651507524;05;06;00;;BRUECKL, HANNELORE:;;;20040,00
170142507540;05;29;00;;BRUECKL, INGRID:;;;22500,00
121041407515;05;00;50;;BRUECKL, UWE:;;;25500,00
250264415126;97;01;00;;BRUECKMANN, HARTMUT:;;;10560,00
100163417719;94;03;00;;BRUECKMANN, MARIO:;;;18480,00
040362506915;99;77;00;;BRUECKMANN, STEFFI:;;;17796,11
020854421813;12;40;00;;BRUECKNER, ANDREAS:;;;22165,00
100268426814;99;02;00;;BRUECKNER, ANDREAS:;;;9872,00
290359506924;05;80;00;;BRUECKNER, BAERBEL:;;;17250,00
280852418419;97;01;00;;BRUECKNER, BERND:;;;31520,04
061148411926;99;43;00;;BRUECKNER, BERND:;;;27000,00
140240507213;18;29;00;;BRUECKNER, BRIGITTE:;;;19440,00
100250408538;97;22;00;;BRUECKNER, CHRISTIAN:;;;25500,00
061260530116;96;15;12;;BRUECKNER, DANIELA:;;;13895,95
091066426611;14;69;00;;BRUECKNER, DANIELO:;;;13860,00
150445421025;04;06;00;;BRUECKNER, DIETMAR:;;;23250,00
210869407317;99;43;00;;BRUECKNER, FRANK:;;;8350,00
231257422789;99;40;00;;BRUECKNER, FRANK:;;;22770,00
070260418516;94;03;00;;BRUECKNER, FRANK:;;;21562,50
261157419715;97;22;00;;BRUECKNER, GEORG:;;;24840,00
060552429218;01;80;00;;BRUECKNER, GUNTER:;;;18720,00
260642513612;99;40;00;;BRUECKNER, HANNELORE:;;;26815,00
110337520310;11;77;00;;BRUECKNER, HELLA:;;;25500,00
291252412228;07;08;00;;BRUECKNER, HENNING:;;;22320,00
070450411710;98;84;00;;BRUECKNER, HERBERT:;;;21532,50
071049515024;08;78;00;;BRUECKNER, ISABELLA:;;;20880,00
220165427415;99;43;00;;BRUECKNER, JENS:;;;16830,00
280747415013;08;64;00;;BRUECKNER, JOACHIM:;;;24750,00
220767419711;17;00;00;;BRUECKNER, JOERG:;;;8950,00
101046512914;18;96;00;;BRUECKNER, KAROLA:;;;19262,50
180653402715;02;00;48;;BRUECKNER, KLAUS:;;;25200,00
230267408927;06;69;00;;BRUECKNER, LARS:;;;11016,00
190333429715;99;53;00;;BRUECKNER, LOTHAR:;;;32062,50
010254418515;10;11;00;;BRUECKNER, LUTZ:;;;26640,00
071055422238;96;15;21;;BRUECKNER, LUTZ:;;;21822,50
120127418413;97;01;00;;BRUECKNER, MANFRED:;;;33500,04
021146421825;12;08;00;;BRUECKNER, MANFRED:;;;27000,00
050669415355;01;69;00;;BRUECKNER, MARCO:;;;6806,61
030635429726;97;06;00;;BRUECKNER, MARTIN:;;;23000,00
210657407438;18;29;00;;BRUECKNER, MATTHIAS:;;;24092,50
071156417745;99;55;00;;BRUECKNER, MICHAEL:;;;19435,00
151070413444;97;22;00;;BRUECKNER, MICHAEL:;;;3772,33
120753417792;09;12;00;;BRUECKNER, MICHAEL:;;;23220,00
220753428027;12;06;00;;BRUECKNER, PETER:;;;19040,00
151060501328;30;81;00;;BRUECKNER, RAMONA:;;;11491,54
011239413614;99;40;00;;BRUECKNER, ROBERT:;;;27000,00
140332420318;11;06;00;;BRUECKNER, ROLAND:;;;26250,00
141255429742;30;47;00;;BRUECKNER, ROLAND:;;;24942,50
210257417717;99;13;00;;BRUECKNER, RUEDIGER:;;;21045,00
130236530323;98;83;00;;BRUECKNER, RUTH:;;;18360,00
270939407211;94;03;00;;BRUECKNER, SIEGFRIED:;;;27750,00
061269419748;97;06;00;;BRUECKNER, STEFAN:;;;15150,00
070455403410;97;01;00;;BRUECKNER, STEFFEN:;;;25290,00
190270418428;99;43;00;;BRUECKNER, STEFFEN:;;;6780,00
230470419752;11;69;00;;BRUECKNER, STEPHAN:;;;2720,00
200369426512;14;69;00;;BRUECKNER, SVEN:;;;12675,00
011268415328;18;35;00;;BRUECKNER, SVEN:;;;10725,00
090468430125;99;77;00;;BRUECKNER, THOMAS:;;;9872,00
230464412300;97;01;00;;BRUECKNER, TINO:;;;16775,00
180571419644;99;43;00;;BRUECKNER, TORSTEN:;;;2870,00
241266400628;98;82;00;;BRUECKNER, VOLKER:;;;14946,00
050930407448;99;02;00;;BRUECKNER, WILLY:;;;42375,00
101164415330;08;08;00;;BRUEDER, MICHAEL:;;;16753,50
070945427714;13;51;00;;BRUEDERLEIN, BERND:;;;27000,00
150452506414;97;01;00;;BRUEGERT, CHRISTIANE:;;;18682,88
150354401328;04;43;00;;BRUEGERT, DETLEF:;;;21600,00
190951411256;98;20;00;;BRUEGGEMANN, DETLEF:;;;25080,00
021057408557;94;03;00;;BRUEGGEMANN, STEFFEN:;;;21332,50
300647406115;30;40;00;;BRUEGGENKAMP, DETLEV:;;;23320,00
200540403610;03;65;00;;BRUEGGER, SIEGFRIED:;;;22437,50
280658403416;99;55;00;;BRUEGGERT, HANS-JUERGEN:;;;18083,75
031254401919;02;00;43;;BRUEGGERT, RAINER:;;;22080,00
080966402726;94;03;00;;BRUEGGMANN, CAROL:;;;15498,00
050244502728;02;18;00;;BRUEGGMANN, EDELTRAUD:;;;17167,77
010236402712;02;02;00;;BRUEGGMANN, HARRY:;;;27000,00
280751513230;98;19;00;;BRUEGMANN, GISELA:;;;22030,00
181231429728;99;43;00;;BRUEHL, GERHARD:;;;27750,00
291070421115;99;43;00;;BRUEHL, HEIKO:;;;2480,32
020245521026;98;83;00;;BRUEHL, ILONA:;;;19780,00
240643421025;98;20;00;;BRUEHL, JUERGEN:;;;25920,00
131153427210;97;22;00;;BRUEHL, JUERGEN:;;;20880,00
121235429747;99;77;00;;BRUEHL, KURT:;;;20316,53
190657430050;94;03;00;;BRUEHL, MARIO:;;;21332,50
101257506127;99;77;00;;BRUEHL, MARTINA:;;;19043,66
290145429732;97;01;00;;BRUEHL, PETER:;;;30750,00
081239412228;07;78;00;;BRUEHL, PETER:;;;33750,00
130158406182;99;02;00;;BRUEHL, UWE:;;;25875,00
200834429736;98;83;00;;BRUEHL, WALTER:;;;23250,00
261264412914;94;03;00;;BRUEHMANN, PETER:;;;17050,00
151055403627;15;00;43;;BRUEHNING, ERHARD:;;;24092,50
310553406420;08;20;00;;BRUEMMER, HANS-JOACHIM:;;;22080,00
270960413624;96;15;10;;BRUENECKE, FRANK:;;;19305,00
171254512226;07;78;00;;BRUENING, BIRGIT:;;;17464,92
210532430044;13;99;01;;BRUENING, CLAUS:;;;42750,00
060468400615;01;00;49;;BRUENING, DIRK:;;;13785,00
250447411910;07;19;00;;BRUENING, GERHARD:;;;27000,00
141048507410;98;20;00;;BRUENING, HEIDEMARIE:;;;19993,63
230568406116;04;69;00;;BRUENING, HEIKO:;;;9875,00
180448401828;02;19;00;;BRUENING, HEINZ:;;;25875,00
081253407417;99;43;00;;BRUENING, JUERGEN:;;;25860,00
090941402219;02;08;00;;BRUENING, KLAUS:;;;19718,75
090463427736;30;59;00;;BRUENING, RALPH:;;;15180,00
231046411414;94;30;00;;BRUENING, REINHARD:;;;26562,50
251270400638;98;18;00;;BRUENING, ULF:;;;2700,00
050266400896;01;18;00;;BRUENKMANN, UWE:;;;15974,00
070851427019;14;22;00;;BRUENLER, HARRY:;;;23040,00
121169418328;94;30;00;;BRUENNER, DIRK:;;;2700,00
061146418315;10;00;45;;BRUENNER, HANS-DIETER:;;;24480,00
081244500724;30;81;00;;BRUENNER, RENATE:;;;16200,00
140139505918;97;06;00;;BRUESEHABER, GERDA:;;;22320,00
160942405914;99;40;00;;BRUESEHABER, GUENTER:;;;27750,00
250966400893;18;41;30;;BRUESEHABER, JAN:;;;14168,00
081050403416;03;20;00;;BRUESER, BODO:;;;22892,50
070641428929;97;06;00;;BRUESEWITZ, PETER:;;;24000,00
210961406747;98;85;00;;BRUESKE, HANS-JUERGEN:;;;18480,00
211051429741;30;62;00;;BRUESSAU, MICHAEL:;;;15903,75
261142506111;17;00;00;;BRUESSEL, HEIDI:;;;21000,00
280858428124;14;00;60;;BRUESSEL, ULLRICH:;;;12161,25
300154400022;01;55;00;;BRUESSOW, BERNHARD:;;;16867,50
020366515351;97;01;00;;BRUESSOW, GRIT:;;;13217,31
100950409910;95;45;00;;BRUESSOW, KLAUS:;;;26460,00
041262400712;97;01;00;;BRUESSOW, MARIO:;;;16038,00
240652400517;01;19;00;;BRUEST, HANS-JOACHIM:;;;21620,00
150469403729;18;32;00;;BRUGGER, THOMAS:;;;9313,50
031048402419;18;80;00;;BRUHN, DIETER:;;;20812,50
040747417120;09;26;00;;BRUHN, HEINZ-JUERGEN:;;;26437,50
270247401812;02;00;42;;BRUHN, ROLF:;;;30750,00
281150401318;96;15;00;650/75/39, :;BRUHN, SIEGFRIED;2520;ALEKSIS-KIVI-STR. 29;
281150401318;96;15;00;650/75/39, :;BRUHN, SIEGFRIED;2520;ALEKSIS-KIVI-STR. 29;
061068414713;94;03;00;;BRUHN, TORSTEN:;;;13175,00
200250400817;01;00;40;;BRUHN, WOLFGANG:;;;25500,00
060353406128;04;06;00;;BRUHNS, ULF-PETER:;;;20711,62
240664403627;03;14;00;;BRUKSCH, ANDREAS:;;;15840,00
130768413726;18;35;00;;BRUMBY, MAIK:;;;9675,00
290942530032;99;77;00;;BRUMM, DORIS:;;;27000,00
060440422740;12;00;40;;BRUMM, GERHARD:;;;26250,00
250369430074;17;00;00;;BRUMM, HOLGER:;;;8950,00
011158405110;15;80;00;;BRUMM, JUERGEN:;;;18227,50
210560400870;01;06;25;;BRUMM, NORBERT:;;;17680,00
180155418618;94;03;00;;BRUMME, KLAUS-PETER:;;;22647,50
300562416226;09;06;00;;BRUMMER, HEIKO:;;;17380,00
010268403218;03;69;00;;BRUMMUND, DIRK:;;;10575,00
020135402739;02;53;00;;BRUMMUND, EGON:;;;27375,00
250863402749;99;02;00;;BRUMMUND, JU(E)RGEN:;;;19415,00
290862402727;94;30;00;;BRUMMUND, MICHAEL:;;;17847,50
081268430038;99;43;00;;BRUNA, ANDREAS:;;;13575,00
140147530064;99;43;00;;BRUNA, GUDRUN:;;;20706,00
230844429729;99;43;00;;BRUNA, WOLFGANG:;;;27750,00
160359522224;98;83;00;;BRUNK, BIRGIT:;;;17585,39
010253429749;15;20;00;;BRUNK, ECKART:;;;23715,00
280955401310;97;17;00;;BRUNK, HEINZ:;;;20010,00
020969404415;94;03;00;;BRUNK, KARSTEN:;;;9510,00
180349401320;98;82;00;;BRUNK, KLAUS-DIETER:;;;24337,50
190559403841;03;80;00;;BRUNK, KLAUS-DIETER:;;;16675,00
190847403715;97;08;00;;BRUNK, MANFRED:;;;27000,00
140253403720;03;14;00;;BRUNK, REINHARD:;;;18480,00
210360524940;30;63;00;;BRUNKAL, ELKE:;;;10916,33
280355425052;30;63;00;;BRUNKAL, KARL-HEINZ:;;;15510,00
210370429752;94;03;00;;BRUNKOW, BIRK:;;;2700,00
190342429733;99;26;00;;BRUNKOW, HANS-PETER:;;;39750,00
010240529716;98;20;00;;BRUNKOW, INGRID:;;;23125,00
050150406428;04;00;42;;BRUNKOW, KLAUS:;;;25860,00
020560508913;30;84;00;;BRUNN, DANIELA:;;;12738,97
280550413428;30;63;00;;BRUNN, HELMUT:;;;17280,00
031239430092;15;06;00;;BRUNN, LOTHAR:;;;26250,00
300155515315;99;40;00;;BRUNNE, PETRA:;;;20842,50
280954423825;99;40;00;;BRUNNE, RALF:;;;23400,00
210163400893;97;01;00;;BRUNNENMEIER, STEFFEN:;;;16335,00
270259422717;12;08;00;;BRUNNER, ANDREAS:;;;19952,50
231244530078;99;12;00;;BRUNNER, ANKE:;;;21600,00
220260406129;04;06;00;;BRUNNER, AXEL:;;;19665,00
071055529836;96;15;04;;BRUNNER, CARMEN:;;;19492,50
010553501829;02;03;00;;BRUNNER, CHRISTA:;;;11757,08
010247411518;07;00;54;;BRUNNER, DIETER:;;;27937,50
021047410418;02;00;42;;BRUNNER, DIETER:;;;22500,00
020366430024;98;27;00;;BRUNNER, DIRK:;;;15876,00
260238418410;97;06;00;;BRUNNER, GOTTFRIED:;;;21266,66
070847422725;12;00;47;;BRUNNER, HANS-JUERGEN:;;;25117,50
010951429818;97;08;00;;BRUNNER, HEINZ:;;;18942,50
070369428224;18;38;00;;BRUNNER, INGO:;;;9675,00
120765430214;96;15;25;;BRUNNER, JAN:;;;19150,50
210169427229;18;33;00;;BRUNNER, JENS:;;;10500,00
061152428210;14;15;00;;BRUNNER, JUERGEN:;;;24832,50
030239429724;99;09;00;;BRUNNER, KLAUS:;;;29250,00
260429430017;96;15;00;1920/75, J:;BRUNNER, MANFRED;1144;TETEROWER RING 86;
260429430017;96;15;00;1920/75, J:;BRUNNER, MANFRED;1144;TETEROWER RING 86;
050170429352;94;03;00;;BRUNNER, MARKO:;;;10335,00
040438430233;60;90;00;;BRUNNER, THEO:;;;
040438430233;60;90;00;;BRUNNER, THEO:;;;30600,00
010766420125;11;69;00;;BRUNNER, TORSTEN:;;;15876,00
190942405233;03;18;00;;BRUNNER, WERNER:;;;27000,00
280736414218;08;00;54;;BRUNNERT, HILMAR:;;;23343,01
260639410815;07;06;00;;BRUNNERT, JUERGEN:;;;24187,50
070670409823;18;33;00;;BRUNNGRA(E)BER, MAREK:;;;6958,87
240369410023;18;31;00;;BRUNOW, RALF:;;;9675,00
050662522799;96;15;00;6555/82, J:;BRUNS, BEATE;1140;BA(E)RENSTEINSTR. 8;
050662522799;96;15;00;6555/82, J:;BRUNS, BEATE;1140;BA(E)RENSTEINSTR. 8;
100571409523;05;69;00;;BRUNS, HENRY:;;;2870,00
160858405938;97;08;00;;BRUNS, MICHAEL:;;;18601,25
110570421116;12;69;00;;BRUNS, STEFFEN:;;;9830,00
210951508811;30;83;00;;BRUNS, SYBILLE:;;;20359,55
020348410820;99;55;00;;BRUNS, WALTER:;;;24000,00
031268403632;18;35;00;;BRUNS, WOLFGANG:;;;9675,00
301057413934;97;01;00;;BRUNSCH, JUERGEN:;;;29760,00
240543411110;07;00;51;;BRUNSCH, KLAUS-DIETER:;;;24750,00
150166413911;15;07;00;;BRUNSCH, OLAF:;;;18414,00
020853409812;07;18;00;;BRUNSENDORF, DIETER:;;;24480,00
191154511435;07;41;00;;BRUNSENDORF, GUDRUN:;;;19440,00
300852409825;07;00;41;;BRUNSENDORF, LOTHAR:;;;23460,00
290153402716;02;06;00;;BRUNST, HOLGER:;;;20160,00
060270403714;18;34;00;;BRUNST, STEFAN:;;;6705,00
230358430062;15;80;00;;BRUNTSCH, DETLEF:;;;17935,02
260862407010;18;38;00;;BRUSAK, DIRK:;;;20161,43
070268501568;97;06;00;;BRUSCH, ANNETT:;;;9783,34
151063400119;01;00;45;;BRUSCH, HOLGER:;;;15592,50
050657400113;99;12;00;;BRUSCH, MANFRED:;;;20815,00
051165401528;01;60;00;;BRUSE, DIRK:;;;14835,00
211040501517;01;06;22;;BRUSE, GERDA:;;;16296,30
150646400810;01;65;00;;BRUSE, GERHARD:;;;20625,00
070638403413;03;65;00;;BRUSE, HANS-ULRICH:;;;25687,50
140948401510;97;06;00;;BRUSE, PAUL:;;;24000,00
020741430086;30;84;00;;BRUSENDORF, WOLFGANG:;;;16560,00
100357421716;12;06;00;;BRUSSIG, ROLAND:;;;19492,50
070736421711;12;00;51;;BRUSSIG, SIEGFRIED:;;;16847,50
220260523624;14;00;56;;BRUSSOG, BIRGIT:;;;14948,75
081148529711;94;30;00;;BRUST, MARION:;;;21157,25
021046429715;99;43;00;;BRUST, UDO:;;;26187,50
210137429713;99;02;00;;BRUTKE, RUDOLF:;;;36008,06
011153429746;30;47;00;;BRUTSCHIN, SIEGBERT:;;;23090,00
120140411216;07;08;00;;BRUTTLOFF, HANS-JOACHIM:;;;21750,00
120249430066;30;47;00;;BRYCHCY, MICHAEL:;;;29280,00
091052407014;05;08;00;;BRYKCZYNSKI, JOERG:;;;18749,03
060571512244;07;96;00;;BRYLLA, KERSTIN:;;;3220,00
140250412226;07;06;00;;BRYLLA, KLAUS-DIETER:;;;21720,00
140853412217;07;06;00;;BRYLLA, WOLFGANG:;;;20160,00
180842421827;94;03;00;;BRYLSKI, JUERGEN:;;;24000,00
231269407228;05;69;00;;BRYM, RAINER:;;;2870,00
020858406418;30;58;00;;BRZAKALA, JUERGEN:;;;16445,00
170160413628;06;00;50;;BRZANK, RAINER:;;;19800,00
161250413213;08;00;44;;BRZEZINSKI, JU(E)RGEN:;;;19800,00
130655417528;09;00;51;;BRZEZINSKI, LUTZ:;;;27967,50
200239402731;30;44;00;;BRZEZOWSKA, ALFRED:;;;15120,00
251243412211;07;51;00;;BRZOSKA, INGBERT:;;;21750,00
280542512215;07;40;00;;BRZOSKA, MARGA:;;;26437,50
091056518520;10;51;00;;BRZUSKA, DAGMAR:;;;18917,50
090956407215;05;80;00;;BRZYSKI, BODO:;;;16905,00
040743530388;18;77;00;;BSDUREK, RENATE:;;;23040,00
SECRET – The FBI – Chinese National Charged with Illegal Export of Sensitive Technology to China
BOSTON—A Chinese national in Massachusetts on business was arrested for illegally supplying U.S. origin parts to end-users in China in violation of U.S. export laws.
Qiang Hu, a/k/a Johnson Hu, 47, was charged in a complaint with conspiracy to violate the Export Administration Regulations and the International Emergency Economic Powers Act. The complaint, originally filed on May 18, was unsealed after Hu’s arrest at his hotel in North Andover yesterday.
The complaint alleges that Hu has been the sales manager at MKS Instruments Shanghai Ltd. (MKS-Shanghai) since 2008. MKS-Shanghai is the Shanghai sales office of MKS Instruments Inc. (MKS), which is headquartered in Andover. Hu’s employment gave him access to MKS-manufactured parts, including export-controlled pressure-measuring sensors (manometer types 622B, 623B, 626A, 626B, 627B, 722A, and 722B), which are commonly known as pressure transducers. Pressure transducers are export controlled because they are used in gas centrifuges to enrich uranium and produce weapons-grade uranium.
The complaint alleges that beginning in 2007, Hu and others caused thousands of MKS pressure transducers worth millions of dollars to be exported from the United States and delivered to unauthorized end-users using export licenses that were fraudulently obtained from the U.S. Department of Commerce. The complaint alleges that Hu and his co-conspirators used two primary means of deception to export the pressure transducers. First, the conspirators used licenses issued to legitimate MKS business customers to export the pressure transducers to China and then caused the parts to be delivered to other end-users who were not themselves named on the export licenses or authorized to receive the parts. Second, the conspirators obtained export licenses in the name of a front company and then used these fraudulently obtained licenses to export the parts to China, where they were delivered to the actual end-users.
MKS is not a target of the government’s investigation into these matters.
Hu remains in custody and is scheduled for a detention hearing on May 31 at 11 a.m. If convicted, he faces a maximum sentence of 20 years in federal prison, to be followed by up to three years of supervised release, and a $1 million fine.
United States Attorney Carmen M. Ortiz; Richard DesLauriers, Special Agent in Charge of the Federal Bureau of Investigation, Boston Field Office; Bruce M. Foucart, Special Agent in Charge of U.S. Immigration and Customs Enforcement’s Office of Homeland Security Investigations in Boston; and John J. McKenna, Special Agent in Charge of the U.S. Department of Commerce, Office of Export Enforcement, Boston Field Office made the announcement today. The case is being prosecuted by Assistant U.S. Attorneys William D. Weinreb and B. Stephanie Siegmann in Ortiz’s Antiterrorism and National Security Unit.
The details contained in the complaint are allegations. The defendant is presumed to be innocent unless and until proven guilty beyond a reasonable doubt in a court of law.
TOP-SECRET from the FBI – Jury Convicts Naser Jason Abdo on All Counts in Connection with Texas Bomb Plot
WACO, TX—A jury this afternoon in Waco convicted 22-year-old Naser Jason Abdo on federal charges in connection with a July 2011 bomb plot in Killeen, Texas. The conviction was announced by U.S. Attorney Robert Pitman and FBI Special Agent in Charge Armando Fernandez.
The jury convicted Abdo of one count of attempted use of a weapon of mass destruction; one count of attempted murder of officers or employees of the United States; two counts of possession of a firearm in furtherance of a federal crime of violence; and two counts of possession of a destructive device in furtherance of a federal crime of violence.
Testimony presented at trial revealed that on July 27, 2011, Abdo unlawfully attempted to create and detonate a bomb in an attempt to kill, with pre-meditation and malice aforethought, members of the uniformed services of the United States and to shoot survivors of said detonation with a firearm. Evidence further revealed that Abdo did knowingly possess a .40 caliber semiautomatic pistol while carrying out his plot.
“It’s important to note that this plot was interrupted and a potential tragedy prevented because an alert citizen notified law enforcement of suspicious activity, triggering prompt investigation and intervention. While we in law enforcement will be aggressive in investigating and prosecuting people like Mr. Abdo, we depend on the vigilance of the public in helping ensure the safety of the community,” said U.S. Attorney Robert Pitman.
Officers with the Killeen Police Department arrested Abdo on July 27, 2011. At the time of his arrest, the defendant, an absent without leave (AWOL) soldier from Fort Campbell, Kentucky, was in possession of the handgun, plus instructions on how to build a bomb as well as bomb making components. Testimony during the trial revealed that Abdo intended to detonate the destructive device inside an unspecified restaurant frequented by soldiers from Fort Hood.
“This verdict confirms the collective efforts by all of our partners on the FBI’s Joint Terrorism Task Force (JTTF) to address terrorism in any shape or form, whether it be by one or by many,” said FBI Special Agent in Charge Armando Fernandez.
Abdo remains in federal custody. He faces up to life in federal prison for the attempted use of a weapon of mass destruction charge; up to 20 years in federal prison for the attempted murder charge; a mandatory 30 years in prison for each possession of a destructive device in furtherance of a federal crime of violence charge; and a mandatory five years in federal prison for each possession of a firearm in furtherance of a federal crime of violence charge. Sentencing is scheduled for 9:00 a.m. on July 20, 2012 before U.S. District Judge Walter S. Smith.
This case is being investigated by agents with the FBI, together with U.S. Army Criminal Investigation Command; Bureau of Alcohol, Tobacco, Firearms, and Explosives; Killeen Police Department; and the Texas Department of Public Safety.
Assistant U.S. Attorneys Mark Frazier and Gregg Sofer of the Western District of Texas and Trial Attorney Larry Schneider of the Justice Department’s Counterterrorism Section are prosecuting this case on behalf of the government.
The Two Escobars – Full Movie
Plot Summary for
The Two Escobars – [HD] (2010)
Pablo Escobar was the richest, most powerful drug kingpin in the world, ruling the Medellín Cartel with an iron fist. Andres Escobar was the biggest soccer star in Colombia. The two were not related, but their fates were inextricably-and fatally-intertwined. Pablo’s drug money had turned Andres’ national team into South American champions, favored to win the 1994 World Cup in Los Angeles. It was there, in a game against the U.S., that Andres committed one of the most shocking mistakes in soccer history, scoring an “own goal” that eliminated his team from the competition and ultimately cost him his life. The Two Escobars is a riveting examination of the intersection of sports, crime, and politics. For Colombians, soccer was far more than a game: their entire national identity rode on the success or failure of their team. Jeff and Michael Zimbalist’s fast and furious documentary plays out on an ever-expanding canvas, painting a fascinating portrait of Pablo, Andres, and a country in the grips of a violent, escalating civil war. Written by David Ansen, Los Angeles Film Festival
SECRET – CIA: US Psychological Warfare Doctrinal Program
DOWNLOAD THE ORIGINAL DOCUMENT HERE
Joseph D. Pistone aka “Donnie Brasco” – Full Movie
Joseph Dominick Pistone, alias Donnie Brasco, (born September 17, 1939), is a former FBI agent who worked undercover for six years infiltrating the Bonanno crime family and to a lesser extent the Colombo crime family, two of the Five Families of the Mafia in New York City.[1][2] Pistone was an FBI agent for 17 years and is considered to be an FBI legend.[3]
Pistone was a pioneer for deep long-term undercover work. J. Edgar Hoover originally did not want FBI agents to work undercover because it could be a dirty job and might end up tainting the agents, but Pistone’s work helped convince the FBI that using undercover agents instead of just using informants was a crucial tool in law enforcement.
Pistone was born in Erie, Pennsylvania and grew up in Paterson, New Jersey. He graduated from Paterson State College (now William Paterson University) with a B.A. in elementary education social studies in 1965, then worked as a teacher for one year before taking a position at the Office of Naval Intelligence. Pistone joined the FBI in 1969; after serving in a variety of roles, he was transferred to New York in 1974 and assigned to the truck hijacking squad.
His ability to drive 18-wheel trucks and bulldozers led to being chosen for what would become his first undercover operation, infiltrating a gang stealing heavy vehicles and equipment. His penetration of the group led to the arrest of over 30 people along the Eastern Seaboard in February 1976 – described at the time as one of the largest and most profitable theft rings ever broken in America. The name Donald (“Donnie”) Brasco was chosen to be Pistone’s alias.
Pistone was born in Erie, Pennsylvania and grew up in Paterson, New Jersey. He graduated from Paterson State College (now William Paterson University) with a B.A. in elementary education social studies in 1965, then worked as a teacher for one year before taking a position at the Office of Naval Intelligence. Pistone joined the FBI in 1969; after serving in a variety of roles, he was transferred to New York in 1974 and assigned to the truck hijacking squad.
His ability to drive 18-wheel trucks and bulldozers led to being chosen for what would become his first undercover operation, infiltrating a gang stealing heavy vehicles and equipment. His penetration of the group led to the arrest of over 30 people along the Eastern Seaboard in February 1976 – described at the time as one of the largest and most profitable theft rings ever broken in America. The name Donald (“Donnie”) Brasco was chosen to be Pistone’s alias.
[edit]Operation Donnie Brasco (1976–1981)
Pistone was selected to be an undercover agent because he was of Sicilian heritage, was fluent in Italian and was acquainted with the mob from growing up in New Jersey. He also said that he did not perspire under pressure and was aware of the Mafia’s codes of conduct and system. The operation was given the code name “Sun-Apple” after the locations of its two simultaneous operations: Miami (“Sunny Miami”) and New York (“The Big Apple”). After extensive preparation including FBI gemology classes and again using the alias Donnie Brasco, he went undercover as an expert jewel thief.
In September 1976, Pistone walked out of the FBI office and did not return for the next six years. The FBI erased Pistone’s history (making it seem like he never existed) and anyone who called asking for him would be told that no one by that name was employed there. His co-workers, friends and informants had no idea what had happened to him. Pistone stated that it was not the original aim to penetrate the Mafia; rather, the focus was to be on a group of people fencing stolen property from the large number of truck hijackings taking place each day in New York (five to six a day). It was intended that the undercover operation last for around six months.
TOP-SECRET – FBI Inspire Magazine Encourages the Use of Wildfires in Jihad

(U//FOUO) The Denver Division of the FBI is releasing this report to raise the awareness of local and state law enforcement partners and public safety officials about the possible threat of wildfires.
(U//FOUO) Al-Qaida in the Arabian Peninsula (AQAP) has released issue 9 of its English-language “Inspire” Magazine. There is a portion of the magazine dedicated to attacking the United States by starting wildfires. The article instructs the audience to look for two necessary factors for a successful wildfire, which are dryness and high winds to help spread the fire. Specific fire conditions that are likely to spread fire quickly are Pinewood, crownfires (where the trees and branches are close together), and steep slope fires (fire spreads faster going up a slope).
(U//FOUO) Inspire magazine lists instructions for igniting a forest fire. The list of required materials include quick inflammable material (1/3 of a liter of gasoline), and a material with slow and long lasting inflammation (foam). The article continues to instruct the reader about how to prepare an ember bomb, which consists of gasoline soaked foam that is ignited by a timer. The article advises the reader to use thirty ember bombs, placed in the tops of trees about a third into the forest, opposite the wind.
(U//FOUO) Throughout Colorado, conditions are favorable for wildfires. Colorado’s forests have been impacted by the mountain pine beetle, and the plains regions are extremely dry. Continuous stands of dead lodgepole pine with dead needles in the crowns (typically lasting 2 to 3 years after a successful fire) will support running crown fires under the right weather conditions.
The Real Goodfella Henry Hill – Full Movie
Doc about henry hill shows what he is doing today and he talks about life in the mob
The Gambinos: First Family of Crime – Full Movie
TOP-SECRET from the FBI – Texas Man Sentenced to Prison for Support to al Qaeda
HOUSTON—Barry Walter Bujol, Jr., a 30-year-old Hempstead, Texas resident and former student at Prairie View A&M University, has been sentenced to serve 20 years in federal prison, U.S. Attorney for the Southern District of Texas Kenneth Magidson announced today, along with Lisa Monaco, Assistant Attorney General for National Security. Bujol was convicted November 14, 2011 of attempting to provide material support to al Qaeda in the Arabian Peninsula (AQAP), a designated foreign terrorist organization.
Just moments ago, U.S. District Judge David Hittner handed Bujol the statutory maximum sentence, ordering him to serve 180 months in prison for attempting to provide material support to AQAP and 60 months in prison for aggravated identity theft, which will be served consecutively, for a total sentence of 240 months in prison.
“We do not take matters of potential national security lightly,” said U.S. Attorney Magidson. “This case and its successful resolution represents our commitment to making our communities a safer place to live.”
Bujol requested a bench trial before Judge Hittner, which lasted nearly four days, during which he acted as his own attorney. The United States presented a total of 325 trial exhibits and 12 witnesses, which resulted in Bujol’s convictions for both attempt to provide material support or resources to a designated foreign terrorist organization as well as aggravated identity theft.
Evidence revealed Bujol had asked Anwar Al-Aulaqi, a now-deceased Yemeni-American AQAP associate, for advice on raising money for the “mujahideen” without attracting police attention and on his duty as a Muslim to make “violent jihad.” Al-Aulaqi replied by sending Bujol a document entitled “42 Ways of Supporting Jihad,” which asserted that “‘jihad’ is the greatest deed in Islam…[and] obligatory on every Muslim.” Court records indicated the “jihad” Al-Aulaqi advocated involved violence and killing.
In 2009, Bujol made three attempts to depart the United States for the Middle East, but law enforcement, believing these were Bujol’s efforts to make “violent jihad,” thwarted him each time he tried to leave. Bujol eventually told a confidential source he desired to fight with the “mujahideen.” The source testified at trial, explaining that each time he told Bujol he would be joining AQAP, Bujol replied by saying, “God willing” in Arabic.
To prove his worth to the source and AQAP, Bujol performed numerous purported “training exercises,” often involving surveillance detection and covert means of communication. Moreover, Bujol repeatedly told the source that AQAP should attack the human beings essential to operate military unmanned aerial vehicles (UAVs) instead of attacking the UAVs themselves. Bujol suggested multiple targets, including one in the Southern District of Texas.
Bujol was arrested on May 30, 2010 after boarding a ship docked at the Port of Houston. He believed the ship was bound for Algeria, where he would stay at an al Qaeda safe house before continuing on to Yemen. Bujol intended to stow away to join AQAP and to deliver items to AQAP that a confidential source had given him. The items included two public access restricted military manuals, global position system receivers, pre-paid international calling cards, SIM cards, and approximately 2,000 in Euros, among other items. Bujol secured these items in his baggage and quickly boarded the ship. Minutes after stowing away in a room on board the ship, agents took him into custody without incident.
Simultaneously, agents executed a search warrant on his apartment and his laptop computer. On the computer, agents found a home-made video montage of still photographs, including images of Osama bin Laden, Najibullah Zazi, and multiple armed “mujahideen” fighters, which Bujol narrated. On the video, which was offered into evidence at trial, he addressed his words to his wife, explaining that he had left her suddenly and without forewarning to pursue “jihad.” Bujol told her he would likely not see her until the afterlife.
The aggravated identity theft charge, of which he was also convicted, stemmed from a false transportation worker identity card (purporting to be a card issued by the Transportation Security Administration) that Bujol possessed to access the Port of Houston. Bujol supplied the confidential source with a passport photo and a false name and the source used these materials to acquire the false card for use in the sting operation. On the night of the operation, Bujol used the false card to gain access to the port.
Bujol has been in federal custody since his May 30, 2010, where he will remain pending transfer to a U.S. Bureau of Prisons facility to be determined in the near future.
This multi-agency investigation was conducted by the U.S. Attorney’s Office for the Southern District of Texas, the Department of Justice’s Counterterrorism Section, the FBI’s Joint Terrorism Task Force in Bryan, Texas—comprised of the Brazos County, Texas Sheriff’s Office; the Texas A&M University Police Department; the Bryan Police Department; the U.S. Secret Service;, the Waller County, Texas Sheriff’s Office; and the College, Texas Station Police Department. Other investigating agencies were the Houston FBI Joint Terrorism Task Force, the Prairie View A&M University Department of Public Safety, the New Jersey State Police, the Coast Guard Investigative Service, Homeland Security Investigations, Houston Police Department, and the Canada Border Services Agency.
The case was prosecuted by Assistant U.S. Attorneys Mark McIntyre and Craig Feazel, as well as Garrett Heenan, Trial Attorney from the Counterterrorism Section of the Justice Department’s National Security Division, and former Assistant U.S. Attorney Mark W. White, III.
Al Capone: The Untouchable Legend – Full Movie
Al Capone: The Untouchable Legend is a new one-hour biography of the most notorious gangster in history. On January 17th, 1999, Al Capone would have celebrated his 100th birthday. His exploits in the early part of the century have inspired authors, journalists and filmmakers. Myths have always been woven around the figure of Al Capone. Born in Brooklyn, he began his career in crime as protege to New York underworld boss Frankie Yale in the early 1920’s, and then moved to Chicago where he made himself a multi-millionaire from the protection business, gambling, brothels, and speakeasies. He is most infamous for planning the massacre of seven members of a rival gang on Valentine’s Day in 1929. This was also the year the Justice Department named Eliot Ness to form a special crime-busting squad which came to be known as “The Untouchables.” In 1931 Alphonse Capone was convicted on income tax evasion and began an eleven year sentence in the Federal Prison on Alcatraz Island. Capone died in 1947 and is buried in Chicago’s Mount Carmel Cemetery.
But who really was this man? How did this child of Neapolitan immigrants become the most legendary gangster of the “Roaring Twenties.” Using historical film footage, movie scenes, and dramatic recreations filmed on location in Chicago, Brooklyn, Ellis Island, Florida’s Palm Island, and Alcatraz, Al Capone: The Untouchable Legend not only depicts the rise and fall of “Scarface,” but also looks behind the myths at the private family man. Interviews with Capone’s nephew Harry Hart, and with Capone experts John Binder, Dennis Hoffman and William Balsamo all help to illuminate the social and economic milieu of the ’20s and ’30s that led to the rise of the “Mafia.”
Inside The Mafia- The Godfathers – Full Movie
Aryan Brotherhood – Full Movie
SECRET – CIA: Origin of the CIA Medical Office
DOWNLOAD THE ORIGINAL DOCUMENT
MS 13 – The Worlds Most Dangerous Gang – Full Movie
SECRET – CIA: Guerilla Warfare Psychological Operations
DOWNLOAD THE ORIGINAL DOCUMENT HERE
Russian Prison System – Full Movie
TOP-SECRET – Chicago Police NATO Summit Media and Reporter’s Guidelines
The following “media guidance” paper from the Chicago Police Department was obtained and published by the Illinois News Broadcasters Association. The paper states that a number of routine activities for credentialed journalists, such as passing behind police lines, will not be allowed. The paper also includes a number of ominous warnings about not getting arrested and how no special rights will be afforded journalists if they are arrested.
NOT INTENDED FOR GENERAL DISTRIBUTION.
FOR MEDIA GUIDANCE ONLY.
Debra Kirby, chief of the Chicago Police Department Office of International Relations, said it is not the intent of Chicago Police to limit or otherwise interfere with coverage of protests and other events related to the NATO summit. The department anticipates that members of the media will be accompanying protesters.
Kirby said the department is not endorsing a formal embedding policy (reporters/crews will not be assigned to tag along with specific police units).
The department is cognizant that not everyone covering the protests has a NATO or Chicago Police credential. Kirby said credentials from other jurisdictions will be honored, and she recommends that they be worn on a lanyard. At the same time, she is also aware that those who did so in New York encountered problems from protesters; doing so in such circumstances is a judgment call. If there is any question, reporters will be allowed to pull credentials from their pockets to show to police on the street. Information will be released through two joint incident command centers, effective Friday.
– U.S. Secret Service (Security-related information and arrest tallies): (312) 469-1440
– City/OEMC: (312) 746-9454
– Chicago Police News Affairs (generally for non-NATO-related information): (312) 745-6110
In addition, she said that Chicago Police lieutenants and captains “on the ground” will have access to most information. At minimum, OEMC will host one briefing a day on activities relating to the summit at OEMC headquarters, 1411 W. Madison St., probably in the evening. She said information will be relayed to news desks with sufficient time to set up. More will be scheduled if events warrant, but Kirby does not know that it would be the wisest use of a news organization’s staff to place someone at OEMC full-time. News Affairs Director Melissa Stratton is checking to see if the briefings can be webcast. She said that media access generally will be the same as public access. Credentials will, however, allow media personnel access to media-only areas. No “cutting” in and out of police lines will be permitted, or “going up against their backs.” Those who follow protesters onto private property to document their actions are also will be subject to arrest if laws are broken.
Any member of the media who is arrested will have to go through the same booking process as anyone else. Release of equipment depends on what part the equipment played in the events that led to the arrest.
There will not be any quick personal recognizance bond just for media members. Kirby said that the Chicago Police Department does not intend to “break ground” in terms of enforcing the Illinois eavesdropping law. In short, police will not interfere if we videotape or record audio of police activities, including arrests. Likewise, she says the department has no intention of “kettling” protesters as they did on Chicago Avenue during antiwar protests in 2003; there will be plenty of warning by loudspeaker to clear or avoid specific areas before arrests are undertaken; however, those reporters who choose to disregard such warnings are subject to arrest. To date, the department has seen no evidence that protesters are turning on media representatives as happened in New York. She urges media to keep safety in mind and to “not become the story.”
If there is a problem, Office of News Affairs Director Melissa Stratton can be reached through Chicago Police News Affairs.
Chicago Police command will be broken down by sector, and the department has made efforts to provide media parking for large planned events. These parking zones are effective from 8 p.m. Friday until 6 p.m. Monday. They include:
Petrillo/Grant Park/Art Institute events:
– Columbus Drive: Both curbs from Jackson to Monroe, but not blocking the entrance to the Art Institute.
South of Loop/River
– 9th Street: both curbs, Wabash to Michigan
– Upper Randolph: south curb, Columbus to Field Drive
Nurses Rally (only on Friday)
– Randolph, south curb, Clark to LaSalle
– Clark, east curb, Randolph to Lake
North of River
– East Lake Shore Dr.: north curb, mid-block to inner LSD
– Mies Van Der Rohe Ct.: west curb, Chicago to Pearson
– Upper Cityfront Plaza Dr.: west curb, North Water to Illinois (no satellite trucks)
McCormick Place/end of protest
– Cermak Road: south curb, State to Clark
– 24th Street, both curbs, State to Federal
The National Nurses’ Union has control of the parking area for the Friday rally and concert. On Sunday, the CANG8 protest group will set up the media bullpen. In addition, police say they will attempt to set up media parking and bullpen locations along march routes as they determine what is happening.
WHILE PARKING AREAS WILL HAVE POLICE AT THE PERMIETER, POLICE WILL NOT BE CHECKING TO ASSURE THAT CONTENTS ARE SECURE. MEDIA ORGANIZATIONS ARE RESPONSIBLE FOR MAKING CERTAIN THAT VEHICLES AND THEIR CONTENTS ARE SECURE.
The Sunday march steps off at 2 p.m. and is anticipated to take two hours and 15 minutes to cover the 2.64 miles. On Sunday, no risers will be provided at Cermak/Michigan in the bullpen area for the concluding ceremonies of the big march. Cameras will have to shoot over one another. Space is constrained at the end of the march for the general public. Parking Sunday will be at Cermak/State and dispersal of the crowd will be to the west. Kirby does NOT recommend that reporters who march along the parade route try to get into the media bullpen at the end of the march; she said it will be possible, but it will not be easy to do so.
If a suspicious package is found or an area is cordoned off because of a potential bomb, the area cleared will depend on the threat that is posed. Media will be allowed as close as possible, but that is an event-by-event call.
Reporters who carry backpacks should be prepared to show their content to police. You may be asked to fire up and demonstrate any equipment that does not look familiar to officers.
Those who have negotiated parking on private property should inform CPD News Affairs if they have not already done so. Police may check to make certain that vehicles are parked on private property with consent of the owner. Unmarked vehicles should have Chicago Police news media vehicle identification cards displayed at all times. It is the intent of Chicago Police to provide close access, with direct vision and contact with those entering and leaving events/marches/rallies. But police emphasized that those who choose to walk amid the protesters are “on your own.” The department cannot guarantee the safety of those who do so and cannot guaranteed that they can extract any reporter who ends up the target of protesters.
Repeatedly, the speakers stressed that the rights of the media are the same as those of the general public.
Police say if a street is “stripped” of parking, and no parking is allowed for the general public, outside of the aforementioned locations, it is done for a reason. KIRBY STRONGLY SUGGESTS THAT VANS AND CARS BE SENT WITH DRIVERS SO THAT IF WORKING PRESS MEMBERS MUST LEAVE THE VEHICLE, IT REMAINS ATTENDED. She said Chicago Police will not hesitate to tow city-owned vehicles if they are in “stripped” areas, so media representatives should expect to be cut no slack with live trucks or other vehicles that are parked where prohibited.
The Russian Mafia – Full Movie – The History Channel
APPENDIX: STASI-NAMEN ALPHABETISCH BUCHSTABE BRA-BS – STASI NAMES IN ALPHABETICAL ORDER BRA-BS
see more at http://www.victims-opfer.com
Die Liste wurde bereits früher hier publiziert:
http://stasiopfer.de/component/option,com_simpleboard/Itemid,/func,view/id,993815828/catid,4/
Vom “Stasiopfer”-Angebot führt ein Link zu einer Website in den USA (www.jya.com), die sich auch mit den Praktiken von Geheimdiensten beschäftigt. Dort findet sich die “Fipro-Liste”, das detaillierte “Finanzprojekt” der Stasi, angefertigt in den letzten Tagen der DDR, um die Rentenansprüche der rund 100 000 hauptamtlichen Mitarbeiter des MfS auch nach dem Zusammenbruch des Systems belegen zu können. Die “Fipro-Liste” ist seit langem bekannt und diente Anfang der neunziger Jahre etwa zur Identifizierung der so genannten OibE – Offiziere im besonderen Einsatz. Diese Liste „Offiziere im besonderen Einsatz“im Jahre 1991 erschien in der “taz. Die Echtheit kann beim BStU überprüft werden.
Siehe u.a. http://www.spiegel.de/spiegel/print/d-22539439.html
Auf Druck ehemaliger STASI-Leute und Ihrer Genossen wurde die Liste aus dem Verkehr gezogen.
Hier ist sie wieder:
090471423014;18;35;00;;BRA(E)CKLEIN, JO(E)RG:;;;2795,00
190435415322;13;00;41;K, 4232/86:;BRA(E)NDEL, LOTHAR;4090;GARTENSTADTSTR. 4;
190435415322;13;00;41;K, 4232/86:;BRA(E)NDEL, LOTHAR;4090;GARTENSTADTSTR. 4;
150359412122;07;00;59;;BRA(E)SE, UDO:;;;22080,00
060769426819;18;31;00;;BRA(E)UER, HOLM:;;;9510,00
031170413111;18;35;00;;BRA(E)UER, OLAF:;;;2795,00
060269415021;18;34;00;;BRA(E)UNER, JO(E)RG:;;;9675,00
160170408225;18;33;00;;BRA(E)UNIG, JO(E)RG:;;;9510,00
150569419728;18;31;00;;BRA(E)UNLICH, HEIKO:;;;9600,00
180470414836;18;33;00;;BRA(E)UNLICH, TOBIAS:;;;6958,87
060468418313;18;33;00;;BRA(E)UTIGAM, JENS:;;;9825,00
190768428922;18;31;00;;BRA(E)UTIGAM, MICHAEL:;;;9648,38
220269425027;18;33;00;;BRA(E)UTIGAM, SVEN:;;;9675,00
181270424938;18;32;00;;BRA(E)UTIGAM, UWE:;;;2795,00
130965400916;01;69;00;;BRAASCH, KARSTEN:;;;15898,50
091165402711;97;08;00;;BRAATZ, ANDREAS:;;;18179,00
260940403112;03;00;42;;BRAATZ, ECKHARD:;;;28080,00
261052505721;04;09;00;;BRAATZ, ELKE:;;;20160,00
151038402729;30;44;00;;BRAATZ, GUENTER:;;;15570,00
300333422120;12;40;00;;BRAATZ, RUDOLF:;;;38250,00
120270411521;07;06;00;;BRAATZ, THOMAS:;;;12460,00
150271422211;18;28;00;;BRAATZ, THOMAS:;;;2720,00
070365403716;97;08;00;;BRAATZ, UWE:;;;17682,50
100557430174;15;18;00;;BRABAND, CARSTEN:;;;22990,00
250255429737;15;02;00;;BRABAND, HENRY:;;;25080,00
111153529817;15;77;00;;BRABAND, ILONA:;;;0,00
241053428221;18;35;00;;BRABANDT, BERTHOLD:;;;25200,00
181252415376;13;80;00;;BRABANT, BERND:;;;20405,00
201239529710;97;01;00;;BRABANT, CHRISTA:;;;19575,00
080139416411;09;06;00;;BRABANT, HEINRICH:;;;19620,00
291037429764;98;20;00;;BRABANT, HEINZ:;;;30937,50
300449426334;99;99;99;::;BRABANT, JOACHIM;1140;MARCHWITZASTR. 3;
300449426334;99;99;99;::;BRABANT, JOACHIM;1140;MARCHWITZASTR. 3;
210357415401;99;02;00;;BRABANT, PETER:;;;23345,00
311261430095;94;65;00;;BRABANT, PETER:;;;18150,00
030162530049;30;84;00;;BRABANT, SIMONE:;;;12321,24
150363430112;15;02;00;;BRABETZ, HEIKO:;;;14850,00
140371403457;03;69;00;;BRACH, ANDREAS:;;;2870,00
051159406154;05;06;00;;BRACH, HARTMUT:;;;17710,00
110637528226;98;27;00;;BRACHAUS, GISELA:;;;23760,00
310540429711;97;06;00;;BRACHAUS, KLAUS:;;;27375,00
290531429730;15;40;00;;BRACHLOW, HERBERT:;;;28500,00
110652529817;30;74;00;;BRACHMANN, DORIS:;;;23262,86
230652413423;04;11;00;;BRACHMANN, HANS-DIETER:;;;26520,00
021165426226;14;40;00;;BRACHMANN, TILO:;;;5263,20
180764401811;02;80;00;;BRACHMANN, WILFRIED:;;;14148,00
210947404438;04;18;00;;BRACHOLD, HERBERT:;;;20872,50
310547412234;07;00;40;;BRACHWITZ, DETLEV:;;;19320,00
200269412287;99;02;00;;BRACHWITZ, GERO:;;;9600,00
300457504515;04;00;41;;BRACHWITZ, ILONA:;;;17595,00
051269413128;18;32;00;;BRACHWITZ, JO(E)RG:;;;9510,00
261042512215;96;15;05;;BRACHWITZ, KRISTINA:;;;26104,16
280752402110;99;43;00;;BRACK, HANS-JUERGEN:;;;19440,00
260639419318;10;00;43;;BRACK, HELMUT:;;;22250,00
220758416412;09;08;00;;BRACK, LUTZ:;;;17595,00
080342429728;94;65;00;;BRACK, MANFRED:;;;23250,00
120760411524;07;00;48;;BRACK, UWE:;;;18013,53
010152404614;04;00;43;;BRACKLOW, EBERHARD:;;;27300,00
210533430054;18;28;00;;BRACKLOW, SIEGFRIED:;;;28500,00
120251404713;17;00;00;;BRACKMANN, GUENTER:;;;25920,00
270162509541;97;06;00;;BRACKROCK, ANDREA:;;;14997,25
151150430068;96;15;00;650/75/11, :;BRADA, WOLFGANG;1130;FRANKFURTER ALLEE 128;
151150430068;96;15;00;650/75/11, :;BRADA, WOLFGANG;1130;FRANKFURTER ALLEE 128;
040469422025;18;32;00;;BRADATSCH, TIMO:;;;9675,00
210655426918;18;35;00;;BRADE, ANDREAS:;;;22350,00
240960530081;99;77;00;;BRADE, ANGELA:;;;19636,77
291157404318;04;51;00;;BRADE, DIRK:;;;20700,00
050535429727;15;53;00;;BRADE, FRED:;;;35250,00
180434430097;18;28;00;;BRADE, GERHARD:;;;27375,00
280665430252;97;08;00;;BRADE, HEIKO:;;;17384,00
061059430025;97;22;00;;BRADE, INGO:;;;18630,00
110768425067;18;32;00;;BRADE, JO(E)RG:;;;9675,00
300170428922;99;43;00;;BRADE, MARIO:;;;9600,00
111268407238;18;35;00;;BRADE, OLIVER:;;;9600,00
230851400211;96;15;21;;BRADE, PETER:;;;25761,38
210742424929;94;11;00;271/68, :;BRADE, ROLF;1600;HERDERSTR. 6;
210742424929;94;11;00;271/68, :;BRADE, ROLF;1600;HERDERSTR. 6;
070336524914;13;26;00;;BRADE, ROSWITHA:;;;25375,00
250748417734;09;08;00;;BRADEL, WOLFGANG:;;;24480,00
100662414811;30;47;00;;BRADEMANN, FRANK:;;;16830,00
060669400830;01;02;00;;BRADEMANN, JENS:;;;8550,00
300344400824;17;00;00;;BRADEMANN, JUERGEN:;;;31680,00
280758415318;08;00;50;;BRADL, ACHIM:;;;16912,50
030562430194;96;15;10;;BRADLER, THORSTEN:;;;18090,00
040669407321;05;69;00;;BRADTKE, MICHAEL:;;;9510,00
240769407421;99;40;00;;BRADTKE, UDO:;;;8300,00
180656529738;94;65;00;;BRAEHMER, IRIS:;;;18529,85
261049404516;18;25;00;;BRAEKOW, ERHARD:;;;27750,00
131256516224;97;07;00;;BRAEKOW, UTE:;;;19046,74
060458404129;97;08;00;;BRAEMER, JOERG:;;;20412,50
270953404113;18;29;00;;BRAEMER, KLAUS-DIETER:;;;23280,00
160254411915;07;00;54;;BRAEMER, LOTHAR:;;;26640,00
260953407411;05;00;40;;BRAEMER, UWE:;;;26640,00
311049516211;99;41;00;;BRAEMING, ILONA:;;;27000,00
280648429751;98;84;00;;BRAEMING, RAINER:;;;22687,50
060238427417;14;06;00;;BRAENDEL, ARMIN:;;;22437,50
260141529712;99;49;00;;BRAENLICH, DORIS:;;;27250,00
191069409129;06;69;00;;BRAENZEL, THOMAS:;;;9510,00
191169500712;01;96;31;;BRAESEL, ANKA:;;;2297,58
071169430025;15;69;00;;BRAESEL, MATHIAS:;;;9510,00
250943407611;05;00;40;;BRAETSCH, UWE:;;;25562,50
090552506444;98;82;00;;BRAETZ, MONIKA:;;;22916,37
120248409214;04;12;00;;BRAEUER, DIETER:;;;21000,00
201065429217;18;33;00;;BRAEUER, DIRK:;;;14110,04
131128430012;99;02;00;;BRAEUER, GERD:;;;37500,00
270437430059;30;47;00;;BRAEUER, GUENTER:;;;20880,00
310843429751;97;06;00;;BRAEUER, HERBERT:;;;24000,00
220263426213;02;00;44;;BRAEUER, INGOLF:;;;19140,00
151256424985;97;17;00;;BRAEUER, JUERGEN:;;;21332,50
171163430057;15;00;49;;BRAEUER, KARSTEN:;;;17572,50
280464426716;14;80;00;;BRAEUER, MATHIAS:;;;15482,50
310557415121;96;15;25;;BRAEUER, MICHAEL:;;;25884,00
180661423823;13;00;43;;BRAEUER, PETER:;;;16142,50
170955513024;99;77;00;;BRAEUER, SABINE:;;;10394,09
270853426219;97;29;00;;BRAEUER, STEFFEN:;;;26640,00
191155527711;30;49;00;;BRAEUER, STEFFI:;;;11382,21
241065426346;94;03;00;;BRAEUER, SVEN:;;;11016,00
270546407210;30;42;00;;BRAEUER, UDO:;;;19440,00
140160425074;13;08;00;;BRAEUER, VOLKER:;;;15592,50
041244428260;99;78;00;;BRAEUER, WILFRIED:;;;25975,00
150469528230;14;53;00;;BRAEUNIG, ANNETT:;;;12205,00
071252429754;30;47;00;;BRAEUNIG, BERND:;;;24120,00
190532429718;99;40;00;;BRAEUNIG, GERHARD:;;;28500,00
270153429718;96;15;13;;BRAEUNIG, HANS-JUERGEN:;;;25530,00
040940530061;98;83;00;;BRAEUNIG, HELGA:;;;23040,00
040851503344;30;84;00;;BRAEUNIG, ILONA:;;;21390,00
200551529753;96;15;31;;BRAEUNIG, INGRID:;;;25920,00
010242424512;13;00;49;;BRAEUNIG, JUERGEN:;;;27000,00
081144422714;04;26;00;;BRAEUNIG, KLAUS-JUERGEN:;;;23187,50
250249428228;30;80;00;;BRAEUNIG, REINER:;;;22590,00
200149528226;14;30;00;;BRAEUNIG, SONJA:;;;16610,00
231249524937;30;80;00;;BRAEUNIG, SONJA:;;;21045,00
310371417444;09;69;00;;BRAEUNIG, SWEN:;;;3928,06
110461422013;98;84;00;;BRAEUNIG, ULF:;;;18610,96
150667430189;15;18;00;;BRAEUNIGER, OLAF:;;;14819,00
190750420017;11;00;43;;BRAEUNING, HUBERTUS:;;;29160,00
030851528315;30;84;00;;BRAEUNING, MARGIT:;;;15101,16
051155414210;07;08;00;;BRAEUNING, ROLF:;;;17077,50
160163430109;98;81;00;;BRAEUNLICH, FRANK:;;;16830,00
100568413716;97;22;00;;BRAEUNLICH, FRANK:;;;14994,00
130652424976;60;90;00;;BRAEUNLICH, GERD:;;;
130652424976;60;90;00;;BRAEUNLICH, GERD:;;;18917,01
140440429731;98;84;00;;BRAEUNLICH, JUERGEN:;;;30187,50
190639418218;10;00;40;;BRAEUNLICH, KLAUS:;;;25500,00
270261430126;97;06;00;;BRAEUNLICH, WOLFRAM:;;;18232,50
141039506926;99;43;00;;BRAEUNLING, ANNEMARIE:;;;20625,00
231047413411;97;01;00;;BRAEUNLING, EBERHARD:;;;27750,00
120451421817;99;02;00;;BRAEUNLING, GUENTER:;;;28980,00
080342406913;99;43;00;;BRAEUNLING, WILFRIED:;;;21750,00
041070417739;97;01;00;;BRAEUTIGAM, ANDRE:;;;3070,16
180457423623;17;00;00;;BRAEUTIGAM, ANDREAS:;;;18285,00
200950517717;09;40;00;;BRAEUTIGAM, BRIGITTE:;;;19050,20
041244417748;09;51;00;;BRAEUTIGAM, ERNST:;;;27000,00
191043406114;04;06;00;;BRAEUTIGAM, GOETZ:;;;22437,50
251029420210;11;00;47;;BRAEUTIGAM, GUENTER:;;;27000,00
290753408310;06;14;00;;BRAEUTIGAM, HANS-HENNING:;;;18457,50
061150409315;10;06;00;;BRAEUTIGAM, HELMUT:;;;22475,00
111046430053;18;27;00;;BRAEUTIGAM, HOLGER:;;;27750,00
300347429729;97;06;00;;BRAEUTIGAM, JOERGEN:;;;26250,00
191169430048;99;02;00;;BRAEUTIGAM, MARCO:;;;13880,00
160748429779;15;00;41;;BRAEUTIGAM, PETER:;;;33120,00
010369408544;12;69;00;;BRAEUTIGAM, RONALD:;;;12412,26
301269428230;14;69;00;;BRAEUTIGAM, STEFFEN:;;;12085,00
270749423931;99;13;00;;BRAEUTIGAM, WOLFRAM:;;;27060,00
280868430041;18;35;00;;BRAEUTIGAMM, HENRY:;;;10600,00
210963402619;02;00;49;;BRAHM, FRANK:;;;19965,00
130647402510;02;53;00;;BRAHM, GERHARD:;;;27000,00
090866402648;01;00;48;;BRAHM, RENE:;;;12035,00
031170401516;02;06;00;;BRAHM, THOMAS:;;;3510,00
190469402511;02;06;00;;BRAHM, THORSTEN:;;;13175,00
130171524626;13;07;00;;BRAJER, KATHRIN:;;;3220,00
271256409546;06;03;00;;BRAMER, SIEGFRIED:;;;17490,00
280170415114;98;82;00;;BRAMIG, RENE:;;;10376,13
120769403918;18;35;00;;BRAMMER, ANDREAS:;;;10035,00
140271416453;18;80;00;;BRAND, AXEL:;;;2945,00
130635429716;97;06;00;;BRAND, EBERHARD:;;;37500,00
020134529711;97;06;00;;BRAND, EDITH:;;;25375,00
180764421812;12;55;00;;BRAND, EGBERT:;;;16170,00
010359417789;09;15;00;;BRAND, FRANK:;;;17974,00
050152421816;12;00;52;;BRAND, GUNTER:;;;25200,00
070558508936;04;55;00;;BRAND, HEIKE:;;;18669,32
200170413749;99;43;00;;BRAND, JAN:;;;9510,00
281069408512;98;82;00;;BRAND, JOERG:;;;10376,13
280970409927;18;35;00;;BRAND, MARIO:;;;2795,00
160241428224;14;00;40;;BRAND, ROLAND:;;;26820,00
290370413016;05;69;00;;BRAND, STEFAN:;;;9910,00
300870421828;18;34;00;;BRAND, STEFFEN:;;;6736,77
190569417534;18;33;00;;BRAND, THOMAS:;;;9600,00
130755423626;04;53;00;;BRAND, WOLFRAM:;;;24150,00
100857516025;11;77;00;;BRANDAU, MARITTA:;;;16708,73
271169413248;08;00;44;;BRANDAU, SVEN:;;;8300,00
170153416011;11;06;00;;BRANDAU, WOLFGANG:;;;24782,50
281052402720;02;55;00;;BRANDECKER, DIETER:;;;20160,00
220969402715;17;00;00;;BRANDENBURG, AXEL:;;;8300,00
241169427036;94;03;00;;BRANDENBURG, BERND:;;;9630,00
281252405213;30;63;00;;BRANDENBURG, BERND:;;;14100,00
010359400514;01;06;27;;BRANDENBURG, DIETMAR:;;;18457,50
061152424914;13;15;00;;BRANDENBURG, HANS:;;;10002,57
230940522819;96;15;22;;BRANDENBURG, HILDEGARD:;;;24480,00
090267409928;07;06;00;;BRANDENBURG, INGO:;;;16832,32
110171431114;15;69;00;;BRANDENBURG, INGO:;;;2925,64
090663506922;30;72;00;;BRANDENBURG, JANA:;;;13860,00
110139402110;02;19;00;;BRANDENBURG, KLAUS:;;;29250,00
080965403428;97;08;00;;BRANDENBURG, LUTZ:;;;16470,00
031164422775;94;65;00;;BRANDENBURG, LUTZ:;;;17985,00
301035422725;97;22;00;;BRANDENBURG, MANFRED:;;;27937,50
020966404356;18;28;00;;BRANDENBURG, RENE:;;;16686,00
100244429746;99;43;00;;BRANDENBURG, ROLF:;;;27000,00
240164430063;94;03;00;;BRANDENBURG, THOMAS:;;;19800,00
300669430036;18;33;00;;BRANDENBURG, TINO:;;;6816,29
260942425008;13;07;00;;BRANDENBURGER, KLAUS:;;;25216,68
030565405912;04;00;40;;BRANDENBURGER, OLAF:;;;16665,00
141058523924;13;55;00;;BRANDENBURGER, PETRA:;;;16088,13
180656411545;07;51;00;;BRANDES, GERALD:;;;17710,00
230251428915;14;18;00;;BRANDHOFF, MANFRED:;;;25200,00
140855420018;96;15;26;;BRANDIES, JUERGEN:;;;21780,00
020855519724;96;15;26;;BRANDIES, SABINE:;;;17940,00
231268407410;18;35;00;;BRANDIS, ANDRE:;;;10900,00
140465402615;02;06;00;;BRANDIS, DIRK:;;;16500,00
130364407426;97;22;00;;BRANDIS, GERD:;;;17423,09
290565411846;07;00;53;;BRANDL, RALF:;;;14355,00
150168408411;18;35;00;;BRANDL, TONI:;;;9675,00
200458428288;14;00;57;;BRANDL, UWE:;;;20355,00
260753409113;06;65;00;;BRANDL, WERNER:;;;20040,00
210360413415;08;00;46;;BRANDL, WILFRIED:;;;22110,00
111266421511;12;09;00;;BRANDNER, ANDREAS:;;;11016,00
260443429717;97;06;00;;BRANDNER, GERD:;;;26250,00
011149422779;12;00;40;;BRANDNER, HARALD:;;;23200,00
080562425112;99;09;00;;BRANDNER, HENNING:;;;18425,00
080468430310;99;77;00;;BRANDNER, JENS:;;;14319,00
080468430302;97;06;00;;BRANDNER, MARKO:;;;15021,00
180669402138;99;43;00;;BRANDSTAEDTER, DIRK:;;;13575,00
020446402111;02;06;00;;BRANDSTAEDTER, SIEGMAR:;;;23250,00
080329406118;17;00;00;;BRANDSTAETER, SIEGFRIED:;;;33000,00
021240408918;06;60;00;;BRANDT, ALBRECHT:;;;23250,00
290828430011;97;06;00;;BRANDT, ALWIN:;;;39750,00
010162400617;04;06;00;;BRANDT, ANDREAS:;;;18260,00
050558402121;02;51;00;;BRANDT, ARNOLD:;;;16560,00
151246503719;17;00;00;;BRANDT, BAERBEL:;;;20625,00
080471526145;97;06;00;;BRANDT, BEATRICE:;;;4900,00
031052424936;94;03;00;;BRANDT, BERND:;;;25200,00
140157502737;30;47;00;;BRANDT, BIRKA:;;;17693,00
060739530076;97;17;00;;BRANDT, BRIGITTE:;;;21750,00
031243406415;04;80;00;;BRANDT, BURCKHARD:;;;26625,00
200856505015;18;77;00;;BRANDT, CHRISTIANE:;;;18975,00
270257409914;15;03;00;;BRANDT, CLAUS-DIETER:;;;20010,00
290453527641;94;30;00;;BRANDT, DAGMAR:;;;19664,33
281266406727;99;14;00;;BRANDT, DIEGO:;;;14375,00
090647413910;08;08;00;;BRANDT, DIETER:;;;17687,50
040552402711;99;40;00;;BRANDT, DIETER:;;;21375,00
010962430136;18;71;20;;BRANDT, DIETMAR:;;;14685,00
110355407119;18;78;00;;BRANDT, DIETRICH:;;;20280,00
151168412255;18;35;00;;BRANDT, DIRK:;;;9825,00
251045500827;01;80;00;;BRANDT, DORIT:;;;15660,57
101251416411;09;00;44;;BRANDT, EBERHARD:;;;23760,00
091058410628;07;03;00;;BRANDT, FRANK:;;;19200,66
240852404029;03;00;49;;BRANDT, GERT:;;;22320,00
190937429724;99;26;00;;BRANDT, GUENTER:;;;28500,00
291051426316;99;55;00;;BRANDT, GUNTER:;;;24960,00
070535403912;03;00;48;;BRANDT, HANS-DIETER:;;;18375,00
150653410718;07;43;00;;BRANDT, HANS-HELMUT:;;;23040,00
130848414411;08;00;56;;BRANDT, HANS-JUERGEN:;;;17192,50
061152411419;17;00;00;;BRANDT, HANS-PETER:;;;19440,00
040749409116;99;40;00;;BRANDT, HANS-ULRICH:;;;27360,00
240843403710;17;00;00;;BRANDT, HARTMUT:;;;18285,00
051259406119;94;03;00;;BRANDT, HEIKO:;;;18345,00
241166403119;03;00;42;;BRANDT, HEINO:;;;2236,00
230236429717;98;18;00;;BRANDT, HELMUT:;;;35250,00
280369407525;97;01;00;;BRANDT, HENRY:;;;3674,19
031256430246;15;00;41;;BRANDT, HOLGER:;;;26162,50
220539429731;96;15;22;;BRANDT, HORST:;;;27187,50
281147403216;03;06;00;;BRANDT, JOACHIM:;;;21750,00
291062413027;08;80;00;;BRANDT, JOCHEN:;;;16170,00
120364430109;96;15;22;;BRANDT, JUERGEN:;;;15510,00
060552400618;01;06;27;;BRANDT, KARL:;;;18227,50
290961400719;18;32;00;;BRANDT, KARSTEN:;;;23100,00
140958411915;30;48;00;;BRANDT, KARSTEN:;;;18240,00
290556509518;99;10;00;;BRANDT, KERSTIN:;;;21900,00
110344413011;07;55;00;;BRANDT, KLAUS:;;;20125,00
070870430619;15;69;00;;BRANDT, MAREK:;;;2925,64
020239529718;99;02;00;;BRANDT, MARIA:;;;24000,00
050155529734;98;83;00;;BRANDT, MARION:;;;15720,26
040869412272;07;06;00;;BRANDT, MATTHIAS:;;;8592,10
091260401514;99;43;00;;BRANDT, MICHAEL:;;;17647,02
200558414529;08;51;00;;BRANDT, PETER:;;;19492,50
011149420319;11;14;00;;BRANDT, PETER:;;;24462,50
250466422017;97;22;00;;BRANDT, PETER:;;;17251,50
010252526328;98;83;00;;BRANDT, PETRA:;;;21600,00
290449415321;08;08;00;;BRANDT, RAINER:;;;23875,00
200945430051;15;08;00;;BRANDT, RAINER:;;;24000,00
041068428332;97;22;00;;BRANDT, RICO:;;;9875,00
030847416417;09;00;44;;BRANDT, ROBERT:;;;21562,50
301068424436;18;31;00;;BRANDT, RONNY:;;;9675,00
270869419822;07;69;00;;BRANDT, SILVIO:;;;8302,58
100271426858;18;32;00;;BRANDT, STEFFEN:;;;6958,87
270169430035;96;15;22;;BRANDT, STEPHAN:;;;9555,00
290170411227;18;34;00;;BRANDT, SVEN:;;;9510,00
050970428251;18;31;00;;BRANDT, SYLVIO:;;;6705,00
240463402134;02;08;00;;BRANDT, THILO:;;;16252,50
200969403111;18;38;00;;BRANDT, THOMAS:;;;9510,00
300964402628;02;09;00;;BRANDT, TORSTEN:;;;16720,00
130353429718;99;14;00;;BRANDT, UDO:;;;24300,00
180735402719;02;26;00;;BRANDT, ULRICH:;;;23250,00
260256502739;99;55;00;;BRANDT, UTE:;;;19969,19
200770400730;18;35;00;;BRANDT, VOLKER:;;;3475,00
120933429715;95;45;00;;BRANDT, WALTER:;;;21750,00
191155405917;04;06;00;;BRANDT, WILFRIED:;;;18842,50
250136429718;99;02;00;;BRANDT, WILFRIED:;;;31125,00
190455405631;30;47;00;;BRANDT, WILFRIED:;;;26840,00
270158411410;07;09;00;;BRANDT, WOLFGANG:;;;21102,50
120149402412;12;18;00;;BRANDT, WOLFGANG:;;;23712,50
151051400824;01;14;00;;BRANDT, WOLFGANG:;;;20520,00
270953409117;99;40;00;;BRANDT, WOLFGANG:;;;25530,00
090655419036;99;43;00;;BRANDTNER, MANFRED:;;;25875,00
250660407515;97;01;00;;BRANDTNER, THOMAS:;;;23712,50
151064430280;96;15;13;;BRANDWEIN, MICHAEL:;;;16500,00
251239530127;99;77;00;;BRANKE, HELGA:;;;41040,00
241039430288;94;65;00;;BRANKE, JUERGEN:;;;27750,00
190446409518;06;02;00;;BRANKE, KLAUS:;;;28312,50
070630430011;97;07;00;;BRANKE, KURT:;;;27000,00
140154402714;30;54;00;;BRANNYS, GEORG:;;;24620,00
211166427412;99;43;00;;BRANSTNER, JENS:;;;15714,00
210749420517;12;07;00;;BRANZ, KLAUS:;;;29625,00
190449410813;07;00;49;;BRASA, GUENTER:;;;27360,00
110970412243;07;06;00;;BRASACK, GUNAR:;;;3557,10
290148410615;07;06;00;;BRASCHE, KLAUS-DIETER:;;;21187,50
070350429796;15;08;00;;BRASCHING, DIETER:;;;22413,01
180263530068;15;19;00;;BRASE, SIMONE:;;;14912,98
011069427625;18;34;00;;BRASE, SWEN:;;;6876,77
260371422443;12;09;00;;BRASOW, RAMON:;;;2700,00
010329430018;97;08;00;;BRASSAT, ALFRED:;;;5437,50
070261400852;01;15;00;;BRASSAT, FRANK:;;;18312,00
140569400868;01;69;00;;BRASSAT, RONALD:;;;6671,61
021270400220;01;69;00;;BRASSEN, ANDREAS:;;;2896,61
111254421215;96;15;00;3039/82, M:;BRATE, ANDREAS;1142;MAX-HERRMANN-STR. 4;
111254421215;96;15;00;3039/82, M:;BRATE, ANDREAS;1142;MAX-HERRMANN-STR. 4;
210637413216;08;51;00;;BRATFISCH, FRITZ:;;;24000,00
120964419018;10;65;00;;BRATFISCH, PASQUALE:;;;12925,00
161253419311;97;01;00;;BRATGE, HANS-JUERGEN:;;;27360,00
280536409529;06;08;00;;BRATKE, ALFRED:;;;28250,00
021267422736;10;00;51;;BRATKE, MAIK:;;;13032,00
240366408024;06;51;00;;BRATKE, THOMAS:;;;16645,50
010554426314;13;00;40;;BRATTIG, ANDREAS:;;;18179,59
300959402244;99;43;00;;BRATZ, DETLEF:;;;21332,50
020760502225;98;27;00;;BRATZ, MANUELA:;;;21142,50
130644428010;14;18;00;;BRATZ, ROLAND:;;;26250,00
200952506915;99;49;00;;BRAUCHLER, DORIS:;;;17825,00
210751403732;17;00;00;;BRAUCHMANN, BERND:;;;30960,00
070652503015;17;00;00;;BRAUCHMANN, INGRID:;;;18199,95
111157403728;03;53;00;;BRAUCHMANN, RALF:;;;22440,00
040650524018;99;09;00;;BRAUER, BAERBEL:;;;25920,00
150358422791;12;00;40;;BRAUER, BERND:;;;22080,00
110554420527;12;00;42;;BRAUER, BERND:;;;26640,00
140762430137;98;83;00;;BRAUER, BJOERN:;;;17270,00
011240502518;97;01;00;;BRAUER, BRIGITTE:;;;20250,00
040552505112;18;77;00;;BRAUER, DORIS:;;;21362,21
311041529720;99;43;00;;BRAUER, ERIKA:;;;22125,00
200166412233;60;90;00;;BRAUER, FRANK:;;;
200166412233;60;90;00;;BRAUER, FRANK:;;;13630,00
120250417117;09;06;00;;BRAUER, GOTTFRIED:;;;21000,00
190843400816;94;65;00;;BRAUER, GUENTER:;;;24000,00
080341429734;99;43;00;;BRAUER, GUENTHER:;;;21750,00
090248429747;94;65;00;;BRAUER, HANS-JOACHIM:;;;27750,00
290965509535;06;09;00;;BRAUER, HEIKE:;;;12762,58
170169402714;01;69;00;;BRAUER, HEIKO:;;;13250,00
180266406206;04;06;00;;BRAUER, HOLGER:;;;16281,00
190933406138;97;08;00;;BRAUER, HORST:;;;28500,00
120962407224;97;01;00;;BRAUER, JAN:;;;16335,00
181169409514;97;22;00;;BRAUER, JENS:;;;6757,50
031265413018;17;00;00;;BRAUER, JOERG:;;;13345,50
271254429746;97;08;00;;BRAUER, KLAUS-PETER:;;;21700,00
250158530147;99;09;00;;BRAUER, MARTINA:;;;14916,87
250451419325;99;09;00;;BRAUER, MICHAEL:;;;28320,00
250933430068;60;90;00;;BRAUER, PETER:;;;
250933430068;60;90;00;;BRAUER, PETER:;;;23520,00
300839413045;08;00;42;;BRAUER, RUDOLF:;;;34560,00
180937429717;94;03;00;;BRAUER, SIEGFRIED:;;;21000,00
241260530122;15;80;00;;BRAUER, SILVIA:;;;14171,58
090163402529;94;03;00;;BRAUER, TORSTEN:;;;18810,00
270737402519;02;06;00;;BRAUER, WILLY:;;;21000,00
201161406197;04;08;00;;BRAUER, WOLFGANG:;;;15744,00
010234509225;30;56;00;;BRAUMANN, ILSE:;;;13680,00
220769410710;18;35;00;;BRAUMANN, RALF:;;;6736,77
250248412216;05;06;00;;BRAUMANN, ROLF-DIETER:;;;19500,00
040751410319;07;12;00;;BRAUMANN, ULRICH:;;;21060,00
071268406936;18;31;00;;BRAUN, ANDRE:;;;9825,00
271251426611;94;03;00;;BRAUN, ANDRE:;;;24900,00
310861409578;06;00;40;;BRAUN, ANDREAS:;;;17325,00
280963413119;99;43;00;;BRAUN, ANDREAS:;;;16260,48
100469404611;99;43;00;;BRAUN, ANDREAS:;;;9600,00
170154422720;30;57;00;;BRAUN, ANDREAS:;;;16080,00
240569528923;14;00;54;;BRAUN, ANETT:;;;13275,00
181252527319;94;03;00;;BRAUN, ANNEROSE:;;;20872,50
150641406930;99;43;00;;BRAUN, BERND:;;;21625,00
191061500876;01;51;00;;BRAUN, BIANCA:;;;16716,07
270846528225;14;08;00;;BRAUN, BIRGIT:;;;21387,50
091049504411;03;53;00;;BRAUN, BRIGITTE:;;;23840,00
030743506928;99;43;00;;BRAUN, BRIGITTE:;;;19172,37
071047506917;99;43;00;;BRAUN, BRIGITTE:;;;20182,50
220728404111;99;43;00;;BRAUN, BRUNO:;;;21750,00
070643428228;99;26;00;;BRAUN, CLAUS-DIETER:;;;24125,00
190355421319;98;84;00;;BRAUN, DIETER:;;;22140,00
280758428215;99;43;00;;BRAUN, DIETMAR:;;;18630,00
060130504118;99;43;00;;BRAUN, DORA:;;;17940,00
090639429728;98;19;00;;BRAUN, EDGAR:;;;51750,00
091053404317;97;17;00;;BRAUN, EDWIN:;;;22320,00
070546411416;07;07;00;;BRAUN, ERNST-ERIK:;;;28020,00
280762502510;02;00;44;;BRAUN, EVELYN:;;;13767,07
091148428012;30;51;00;;BRAUN, FRANK:;;;15120,00
281260521839;98;85;00;;BRAUN, GABRIELA:;;;17283,64
281036417754;98;19;00;;BRAUN, GERHARD:;;;25200,00
190756403728;99;43;00;;BRAUN, GERO:;;;21390,00
310844404310;94;30;00;;BRAUN, HANS-JOACHIM:;;;27750,00
151053417160;11;02;00;;BRAUN, HANS-JOERG:;;;25200,00
110149426714;97;06;00;;BRAUN, HARALD:;;;23360,00
120338430068;99;53;00;;BRAUN, HARRI:;;;25920,00
271154417748;09;40;00;;BRAUN, HEINZ:;;;23250,00
080665429239;14;08;00;;BRAUN, HENDRIK:;;;15322,00
100636403713;03;99;00;;BRAUN, HORST:;;;42750,00
100565403723;03;18;00;;BRAUN, INGO:;;;21120,00
190170500424;18;80;00;;BRAUN, JANA:;;;13730,00
151168422744;17;00;00;;BRAUN, JENS:;;;8300,00
020653424719;13;00;51;;BRAUN, JOCHEN:;;;25200,00
240362421010;12;65;00;;BRAUN, JU(E)RGEN:;;;17022,50
200251413943;08;00;61;;BRAUN, JUERGEN:;;;17077,50
140154421317;99;40;00;;BRAUN, JUERGEN:;;;25320,00
260441529714;15;07;00;;BRAUN, KARIN:;;;16838,64
160952411816;07;80;00;;BRAUN, KARL-HEINZ:;;;18000,00
181062430102;99;51;00;;BRAUN, KARSTEN:;;;17820,00
051243429738;97;06;00;;BRAUN, KLAUS:;;;20500,00
121249404313;03;02;00;;BRAUN, MANFRED:;;;29250,00
040637428216;14;11;00;;BRAUN, MANFRED:;;;26312,50
040244406913;99;43;00;;BRAUN, MANFRED:;;;24000,00
071064402714;02;14;00;;BRAUN, MARIO:;;;15840,00
090267403120;98;82;00;;BRAUN, MATHIAS:;;;17490,00
041264430085;99;02;00;;BRAUN, MICHAEL:;;;18205,00
061064406142;04;06;00;;BRAUN, MIKE:;;;15268,00
050670400046;98;19;00;;BRAUN, MIRKO:;;;3620,00
101069429224;18;31;00;;BRAUN, MIRKO:;;;9600,00
080150504623;99;77;00;;BRAUN, MONIKA:;;;21600,00
080854429713;98;83;00;;BRAUN, PETER:;;;19237,50
240166421320;98;19;00;;BRAUN, RAINER:;;;11016,00
241159417715;99;53;00;;BRAUN, RALF:;;;18343,26
271262402535;02;80;00;;BRAUN, RENE:;;;16190,04
090970414411;18;33;00;;BRAUN, ROLAND:;;;2795,00
080237528214;14;51;00;;BRAUN, SIEGLINDE:;;;19965,00
010169500418;18;78;00;;BRAUN, SILKE:;;;14025,00
100269413935;18;34;00;;BRAUN, STEFFEN:;;;9675,00
050271423128;18;38;00;;BRAUN, STEFFEN:;;;2795,00
130770424723;18;35;00;;BRAUN, SVEN:;;;6705,00
210369417738;18;32;00;;BRAUN, THOMAS:;;;10725,00
280569426210;18;33;00;;BRAUN, TINO:;;;6958,87
201058400619;01;69;00;;BRAUN, UWE:;;;21792,50
070238428224;14;02;00;;BRAUN, WALTER:;;;30750,00
310534429723;99;14;00;;BRAUN, WERNER:;;;37500,00
010845422727;12;08;00;;BRAUN, WOLF-DIETER:;;;22125,00
290770409411;18;28;00;;BRAUNE, ANDRE:;;;2720,00
210767410814;07;06;00;;BRAUNE, FRITZ-GUENTER:;;;16175,23
301053414219;06;08;00;;BRAUNE, GUENTER:;;;17422,50
140235429724;97;17;00;;BRAUNE, HEINZ:;;;41250,00
271064428240;14;14;00;;BRAUNE, JENS:;;;16170,00
070271400864;01;69;00;;BRAUNE, JENS:;;;2896,61
280543529713;97;17;00;;BRAUNE, JUTTA:;;;24562,50
191270409817;18;32;00;;BRAUNE, MARCO:;;;2795,00
230264412322;30;62;00;;BRAUNE, MARIO:;;;14685,00
070552424926;94;11;00;;BRAUNE, RALPH:;;;22942,50
210366415315;97;08;00;;BRAUNE, RENE:;;;16960,53
080260412228;99;02;00;;BRAUNE, THOMAS:;;;23045,00
200655414512;11;20;00;;BRAUNE, UWE:;;;23460,00
260869430061;99;43;00;;BRAUNEIS, UWE:;;;9510,00
261161409237;06;69;00;;BRAUNER, DIETMAR:;;;16967,50
181146424519;13;20;00;;BRAUNER, MANFRED:;;;24000,00
310742524514;13;77;00;;BRAUNER, VIKTORIA:;;;14677,42
180751417742;09;01;00;;BRAUNER, WERNER:;;;24480,00
140252429806;96;15;11;;BRAUNERT, HANS-JOACHIM:;;;33120,00
110462430103;96;15;21;;BRAUNERT, MATTHIAS:;;;17490,00
220734530085;15;80;00;;BRAUNGARDT, ELFRIEDE:;;;20375,00
160757430122;94;65;00;;BRAUNGARDT, VOLKER:;;;19008,39
120471415713;08;69;00;;BRAUNGART, STEFFEN:;;;3220,00
080955408532;18;77;00;;BRAUNS, ANDREAS:;;;21409,03
250154413111;97;08;00;;BRAUNS, LOTHAR:;;;22500,00
080757419716;97;08;00;;BRAUNSBERGER, DETLEF:;;;17595,00
020851500719;01;96;31;;BRAUNSCHWEIG, ANGELIKA:;;;17806,45
021049423810;94;03;00;;BRAUNSCHWEIG, ECKHARD:;;;24000,00
300949523835;98;83;00;;BRAUNSCHWEIG, HEIDI:;;;18802,50
150369408928;18;32;00;;BRAUNSCHWEIG, JENS:;;;9675,00
230442429718;99;43;00;;BRAUNSCHWEIG, JUERGEN:;;;22500,00
240549400711;01;96;31;;BRAUNSCHWEIG, SIEGBERT:;;;18000,00
120338415351;08;02;00;;BRAUTZSCH, PETER:;;;25500,00
120571427623;18;32;00;;BRAUTZSCH, STEFFEN:;;;2795,00
231166427613;95;45;00;;BRAUTZSCH, UWE:;;;15714,00
241267415338;99;43;00;;BRAUTZSCH, WOLFGANG:;;;14025,00
090252528318;14;96;00;;BRECHEIS, MONIKA:;;;19440,00
260759406431;04;00;45;;BRECHLIN, FRED:;;;21330,00
070652408915;98;19;00;;BRECHLIN, GERT:;;;25530,00
290649406438;04;55;00;;BRECHLIN, HELMUT:;;;20072,58
070344406168;04;30;00;;BRECHLIN, KLAUS-PETER:;;;24000,00
300744416219;09;77;00;;BRECHLING, BERNHARD:;;;37620,00
110964402778;18;71;20;;BRECHOT, TORSTEN:;;;21010,00
170968401339;01;06;26;;BRECHT, ANDREAS:;;;9510,00
220759410127;99;43;00;;BRECHT, FRANK:;;;22252,50
161257410111;99;43;00;;BRECHT, HOLGER:;;;21390,00
210950412228;07;08;00;;BRECKAU, JUERGEN:;;;20160,00
280848412217;07;06;00;;BRECKAU, WOLFGANG:;;;23812,50
201148422010;96;15;22;;BREDACK, ROLAND:;;;27300,00
200157501517;02;06;00;;BREDDIN, ANNELIE:;;;17834,27
011254402518;02;65;00;;BREDDIN, HERBERT:;;;19440,00
081163402516;07;06;00;;BREDDIN, MATTHIAS:;;;17325,00
061061413216;08;00;44;;BREDDIN, PETER:;;;18590,00
150561402526;97;01;00;;BREDDIN, ROLAND:;;;24210,00
311250407519;05;06;00;;BREDE, ECKHARD:;;;22320,00
171170403815;18;35;00;;BREDENDIEK, TINO:;;;6705,00
080259530016;18;80;00;;BREDERECK, KARIN:;;;16039,44
281257500711;30;83;00;;BREDEREKE, KARIN:;;;14263,44
140741406170;04;11;00;;BREDERLOW, ROLAND:;;;30375,00
240468530063;97;06;00;;BREDIS, CHRISTINE:;;;11420,93
210334402712;02;11;00;;BREDIS, MANFRED:;;;33750,00
280265415328;94;65;00;;BREDIS, TORSTEN:;;;16830,00
120946518514;10;06;00;;BREDOW, CHRISTINE:;;;21756,77
131144418515;10;00;46;;BREDOW, HORST:;;;24312,50
151051401958;03;00;41;;BREDOW, LOTHAR:;;;25200,00
220470404834;18;33;00;;BREDOW, MICHAEL:;;;2720,00
191262430114;15;07;00;;BREEDE, DIETMAR:;;;15675,00
250261401917;02;00;43;;BREESE, HARTMUT:;;;18232,50
230446530039;97;22;00;;BREETZ, BRIGITTE:;;;20625,00
200439430067;97;22;00;;BREETZ, GUENTER:;;;20187,50
040448401313;03;51;00;;BREETZKE, KLAUS:;;;23400,00
131167419713;18;33;00;;BREHM, FRANK:;;;10800,00
140368419829;11;69;00;;BREHM, GERD:;;;9675,00
180366420216;97;06;00;;BREHM, GERHARD:;;;16200,00
230752419013;10;00;40;;BREHM, HARTMUT:;;;24480,00
261048400812;94;11;00;;BREHM, HEINZ:;;;34500,00
140367430129;97;22;00;;BREHM, KARSTEN:;;;15876,00
200470417119;09;69;00;;BREHM, MARCO:;;;9510,00
120571410813;18;34;00;;BREHM, MIKE:;;;2795,00
080669420223;18;28;00;;BREHM, OLAF:;;;6792,09
230744422028;07;06;00;;BREHM, WOLFGANG:;;;26250,00
160753417414;97;06;00;;BREHME, HARALD:;;;25920,00
220256414222;99;51;00;;BREHME, RALF:;;;22400,00
290158407444;97;08;00;;BREHME, RENE:;;;22080,00
110469405218;18;34;00;;BREHMEL, THOMAS:;;;9675,00
181158404128;96;15;05;;BREHMER, FRED:;;;18862,50
210754529912;99;49;00;;BREHMER, GABRIELE:;;;1126,61
200150429890;15;03;00;;BREHMER, GERD:;;;24571,67
270235404119;03;40;00;;BREHMER, GERD:;;;17048,75
070235429715;96;15;15;;BREHMER, HERBERT:;;;33000,00
180942429746;99;40;00;;BREHMER, INGO:;;;26250,00
160942529714;99;43;00;;BREHMER, JUTTA:;;;19843,24
050553410122;04;80;00;;BREHMER, KARL-HEINZ:;;;18720,00
050140429714;15;22;00;;BREHMER, PETER:;;;27000,00
140537504128;03;40;00;;BREHMER, RENATE:;;;14886,77
100134422738;96;15;25;;BREHMER, WOLFGANG:;;;25500,00
190869410326;07;69;00;;BREIER, BERND:;;;2911,13
180266417757;18;32;00;;BREIER, DETLEF:;;;18396,00
270837415325;08;08;00;;BREINIG, KLAUS-PETER:;;;26250,00
010563400634;01;00;42;;BREINLINGER, FRANK:;;;17820,00
150967400619;01;00;49;;BREINLINGER, JENS:;;;12775,00
040369407020;94;03;00;;BREIT, RALF:;;;9510,00
300359400843;96;15;13;;BREITBARTH, JENS-UWE:;;;19347,50
240358417721;09;00;40;;BREITBARTH, LUTZ:;;;17820,00
240140400820;99;40;00;;BREITBARTH, MANFRED:;;;21937,50
070661500828;99;77;00;;BREITBARTH, MARION:;;;18070,34
231062400811;01;69;00;;BREITBARTH, PETER:;;;15620,00
120130430077;18;25;00;;BREITBARTH, RICHARD:;;;28500,00
080962430084;94;65;00;;BREITBARTH, STEFFEN:;;;16170,00
130940500814;99;40;00;;BREITBARTH, URSULA:;;;20032,50
290549416911;09;06;00;;BREITBARTH, WILFRIED:;;;25125,00
260641429718;99;12;00;;BREITE, MANFRED:;;;23937,50
240154524971;97;01;00;;BREITE, SUSANNE:;;;19313,80
120759404212;03;14;00;;BREITENFELD, WOLF-DIETER:;;;15181,50
281255400215;01;00;42;;BREITENFELDT, DETLEF:;;;22440,00
060658408546;98;83;00;;BREITENSTEIN, FRANK:;;;20182,50
071052411728;07;26;00;;BREITENSTEIN, HORST:;;;20010,00
050363412258;97;06;00;;BREITENSTEIN, RONALD:;;;14650,40
110156414738;99;43;00;;BREITER, HANS-GUENTER:;;;19320,00
080458413226;98;82;00;;BREITER, PETER:;;;18227,50
200569426218;18;34;00;;BREITFELD, GISO:;;;9675,00
230557404828;99;02;00;;BREITFELD, HANS:;;;24150,00
250268415115;08;69;00;;BREITFELD, UWE:;;;9875,00
110367530173;96;15;06;;BREITFELDT, INES:;;;13675,00
101238406120;04;06;00;;BREITGOFF, KLAUS:;;;24000,00
200835418211;10;00;44;;BREITHAUPT, KARL-HEINZ:;;;19875,00
291133416218;09;06;00;;BREITHAUPT, WALTER:;;;21583,36
071053419051;99;40;00;;BREITHECKER, GERO:;;;24225,00
250263522114;12;96;67;;BREITING, INA:;;;15757,50
061259422118;94;03;00;;BREITING, PETER:;;;22770,00
190450423646;14;18;00;;BREITKOPF, RAINER:;;;29625,00
290260405912;97;07;00;;BREITKREUTZ, BORIS:;;;17030,00
100854406111;04;00;40;;BREITKREUTZ, GERHARD:;;;19800,00
121041429730;98;82;00;;BREITKREUZ, HORST:;;;20625,00
301068411221;18;35;00;;BREITLAUCH, DIRK:;;;9675,00
090935417756;09;12;00;;BREITLAUCH, WERNER:;;;26250,00
140762415148;99;40;00;;BREITMANN, GOETZ:;;;19415,00
140762415121;15;69;00;;BREITMANN, JOST:;;;17077,50
210141522435;99;43;00;;BREITREITER, HELGA:;;;23250,00
280240422417;95;45;00;;BREITREITER, KARL-HELMUT:;;;37500,00
091270421228;18;33;00;;BREITREITER, THOMAS:;;;2720,00
051050421211;99;99;99;::;BREITREITER, UWE;1140;BA(E)RENSTEINSTR. 6;
051050421211;99;99;99;::;BREITREITER, UWE;1140;BA(E)RENSTEINSTR. 6;
070746530030;30;83;00;;BREITSCHUH, GISELA:;;;18060,00
190750429767;30;47;00;;BREITSCHUH, JUERGEN:;;;17280,00
310367413934;08;07;00;;BREITSCHWERDT, GOTTHARD:;;;15390,00
010344516610;97;01;00;;BREITSPRECHER, CHRISTEL:;;;21000,00
211268405230;04;69;00;;BREITSPRECHER, DIRK:;;;9675,00
160571418440;98;83;00;;BREITSPRECHER, JOERG-DIETMAR:;;;3020,00
200556403623;18;32;00;;BREITSPRECHER, JUERGEN:;;;18630,00
010571414120;18;28;00;;BREITSPRECHER, MARCO:;;;2720,00
061057430152;94;65;00;;BREITSPRECHER, PETER:;;;19665,00
261263403610;03;80;00;;BREITSPRECHER, RAINER:;;;15592,50
041144416617;09;00;45;;BREITSPRECHER, SIEGFRIED:;;;29250,00
180968413814;18;32;00;;BREITUNG, JENS:;;;9675,00
131270428212;18;35;00;;BREITZKE, ANDRE:;;;2795,00
291148401326;01;02;00;;BREITZKE, ROLF:;;;26162,50
240169403435;03;69;00;;BREMER, ANDREAS:;;;9510,00
240169411427;18;31;00;;BREMER, ANDREAS:;;;9600,00
130655503610;03;14;00;;BREMER, BRITTA:;;;17681,17
080139429722;15;69;00;;BREMER, DIETER:;;;33000,00
270450402431;02;00;47;;BREMER, DIETER:;;;16920,00
280868402411;02;69;00;;BREMER, HEIKO:;;;9555,00
110763530140;30;83;00;;BREMER, IRIS:;;;12197,15
260164430088;98;84;00;;BREMER, JENS:;;;18095,00
200234429716;96;15;14;;BREMER, KARL-HEINZ:;;;22500,00
220436404216;03;09;00;;BREMER, KURT:;;;24750,00
070249401713;94;03;00;;BREMER, MANFRED:;;;26220,00
120670429720;99;40;00;;BREMER, MIRKO:;;;2870,00
261249403913;03;26;00;;BREMER, ROBERT:;;;22275,00
020643402428;02;18;00;;BREMER, WILFRIED:;;;29250,00
160654403316;03;14;00;;BREMER, WOLFGANG:;;;18480,00
270562400836;01;19;69;;BREMERKAMP, FALK:;;;19305,00
140840510117;07;00;44;;BREMERT, ILSE:;;;22500,00
090138410113;07;00;44;;BREMERT, KLAUS:;;;18875,00
040460530011;99;77;00;;BREMERT, UTE:;;;19140,00
200251416116;05;03;00;;BREMME, KLAUS-DIETER:;;;22275,00
140555419031;10;55;00;;BREMME, WOLFGANG:;;;20100,00
151259517554;30;61;00;;BREMMERT, KATHRIN:;;;10696,78
250244430054;07;51;00;;BREMSE, JUERGEN:;;;22500,00
050963409538;99;02;00;;BRENDAHL, THOMAS:;;;19470,00
140459421713;10;00;51;;BRENDEL, ALEXANDER:;;;12675,00
151158425079;30;36;00;;BRENDEL, ANDREAS:;;;18487,00
220352507912;99;02;00;;BRENDEL, INGEBORG:;;;24480,49
090468407515;05;19;00;;BRENDEL, JOERG:;;;9872,00
010153421520;06;15;00;;BRENDEL, JUERGEN:;;;26400,00
090945428918;14;00;54;;BRENDEL, JUERGEN:;;;26640,00
070553504119;06;55;00;;BRENDEL, JUTTA:;;;21480,00
301146429719;97;22;00;;BRENDEL, KLAUS:;;;20625,00
060146430045;15;08;00;;BRENDEL, PETER:;;;24000,00
160353506119;30;56;00;;BRENDEL, URSULA:;;;13530,00
131246428212;99;02;00;;BRENDEL, WERNER:;;;27375,00
191254422712;12;00;40;;BRENDEL, WOLFGANG:;;;20700,00
100238404315;97;06;00;;BRENDEMUEHL, HELMUT:;;;24562,50
080868420517;18;32;00;;BRENDLER, ANDREAS:;;;6958,87
140651422257;98;85;00;;BRENDLER, ARNDT:;;;19440,00
310338404510;96;15;22;;BRENDLER, JOACHIM:;;;30000,00
090170404522;18;34;00;;BRENDLER, RENE:;;;10810,00
260960404518;97;01;00;;BRENDLER, STEFAN:;;;22934,35
051168400512;17;00;00;;BRENDTNER, JOERG:;;;8950,00
230342400512;01;07;00;4733/88, :;BRENDTNER, WERNER;2520;HERMANN-MATERN-STR. 16;
230342400512;01;07;00;4733/88, :;BRENDTNER, WERNER;2520;HERMANN-MATERN-STR. 16;
180152407614;15;09;00;;BRENNECKE, BURKHARDT:;;;26100,00
040569407615;97;06;00;;BRENNECKE, JOERG:;;;13750,00
240837411917;97;97;11;;BRENNECKE, ROLF:;;;35250,00
010647411525;04;19;00;;BRENNECKE, ROLF-DIETER:;;;23545,00
041137511915;94;03;00;;BRENNECKE, SIGRID:;;;22927,09
250142430061;18;40;00;;BRENNER, HEINZ:;;;24750,00
200553428219;14;00;41;;BRENNER, JUERGEN:;;;25200,00
180460402516;02;18;00;;BRENNER, LUTZ:;;;9120,00
050160430181;15;80;00;;BRENNER, WOLF-EKKEHARD:;;;17940,00
220449524727;96;15;31;;BRENNIG, BRIGITTE:;;;21600,00
040250429804;97;01;00;;BRENNIG, KLAUS:;;;29250,00
090451503420;03;41;00;;BRENTFUEHRER, MARLIES:;;;19980,00
171147403411;03;09;00;;BRENTFUEHRER, UWE:;;;24000,00
110947410610;97;01;00;;BRENZ, GERT-JOACHIM:;;;35250,00
201051411518;12;06;00;;BRESCH, HANS:;;;21975,00
280355511014;07;06;00;;BRESCH, KARIN:;;;19320,00
090254411017;07;06;00;;BRESCH, PETER:;;;20160,00
140248400816;30;43;00;;BRESEMANN, HANS-PETER:;;;17876,00
050649400228;99;12;00;;BRESEMANN, KLAUS:;;;32530,65
280155400248;99;12;00;;BRESEMANN, VOLKER:;;;21700,00
210571400892;01;06;22;;BRESIEN, MICHAEL:;;;2896,61
210160430069;15;20;00;;BRESKI, JUERGEN:;;;24150,00
230358525053;13;53;00;;BRESLER, ANKE:;;;16431,32
220647424911;13;65;00;;BRESLER, CLAUS:;;;26250,00
110856424320;13;26;00;;BRESLER, DIETMAR:;;;22965,50
300852520320;11;12;00;;BRESLER, ILONA:;;;20180,00
200867424958;18;41;30;;BRESLER, MICHAEL:;;;13200,00
160951420315;11;00;40;;BRESLER, NORBERT:;;;25200,00
180551417721;09;00;40;;BRESSA, KLAUS-DETLEF:;;;26400,00
150939402115;02;06;00;;BRESSEL, DIETER:;;;26250,00
290358530308;94;30;00;;BRESSEL, TATJANA:;;;16239,79
110758408810;94;03;00;;BRESSEM, HARALD:;;;22597,50
230553403713;94;65;00;;BRESSIN, HELMUT:;;;19440,00
070468430127;98;27;00;;BRESSLER, FRANK:;;;14332,00
210334530060;96;15;11;;BRESSLER, LIESELOTTE:;;;22620,00
290734429714;99;43;00;;BRESTRICH, WOLFGANG:;;;27000,00
230456421215;12;00;48;;BRESZLER, HANS-JUERGEN:;;;16276,50
280651426527;04;00;42;;BRESZLER, KLAUS:;;;21485,81
291142429715;99;43;00;;BRETERNITZ, DIETER:;;;24000,00
300955412218;08;20;00;;BRETERNITZ, FRED:;;;23975,00
310768413927;18;40;00;;BRETERNITZ, JO(E)RG:;;;10155,00
300463430217;99;77;00;;BRETERNITZ, UWE:;;;17572,50
290149418432;99;55;00;;BRETERNITZ, WILFRIED:;;;25500,00
241142429728;97;06;00;;BRETFELD, HERMANN:;;;24000,00
200941428229;14;02;00;;BRETFELD, KLAUS:;;;28500,00
251053429223;14;65;00;;BRETSCHNEIDER, CHRISTIAN:;;;19860,00
140548428220;96;15;18;;BRETSCHNEIDER, CHRISTIAN:;;;27360,00
250458430148;99;02;00;;BRETSCHNEIDER, DETLEF:;;;21562,50
030934429718;97;01;00;;BRETSCHNEIDER, DIETER:;;;27750,00
050158421817;12;06;00;;BRETSCHNEIDER, DIETER:;;;19320,00
290663427016;14;51;00;;BRETSCHNEIDER, DIRK:;;;17792,50
250371403622;18;29;30;;BRETSCHNEIDER, DIRK:;;;3070,16
060635429723;94;03;00;;BRETSCHNEIDER, EBERHARDT:;;;24000,00
171239429723;94;30;00;;BRETSCHNEIDER, EGON:;;;26750,00
101144425005;30;47;00;;BRETSCHNEIDER, FRANZ:;;;28780,00
270668421010;18;32;00;;BRETSCHNEIDER, GERALD:;;;9675,00
080268417760;18;35;00;;BRETSCHNEIDER, GERD:;;;10775,00
150542429774;99;77;00;;BRETSCHNEIDER, GERT:;;;24000,00
141036426218;14;03;00;;BRETSCHNEIDER, GUENTER:;;;23250,00
181255422715;94;65;00;;BRETSCHNEIDER, GUENTER:;;;17595,00
250844406728;05;00;41;;BRETSCHNEIDER, GUNTER:;;;27540,00
090455425028;13;20;00;;BRETSCHNEIDER, HARALD:;;;24880,00
150438530071;99;40;00;;BRETSCHNEIDER, HELGA:;;;17595,00
191152529770;30;83;00;;BRETSCHNEIDER, ILONA:;;;17432,26
130930530024;98;83;00;;BRETSCHNEIDER, ILSE:;;;19170,00
290959429213;15;19;00;;BRETSCHNEIDER, INGO:;;;21560,00
211068421818;18;33;00;;BRETSCHNEIDER, JAN:;;;9675,00
211165430214;97;08;00;;BRETSCHNEIDER, JAN:;;;16656,50
290867427210;14;08;00;182, :;BRETSCHNEIDER, JENS;9271;AM HANG 3;
290867427210;14;08;00;182, :;BRETSCHNEIDER, JENS;9271;AM HANG 3;
091069420928;18;34;00;;BRETSCHNEIDER, JO(E)RG:;;;10500,00
080168506731;05;00;40;;BRETSCHNEIDER, KERSTIN:;;;14382,00
160251400612;05;00;41;;BRETSCHNEIDER, KLAUS:;;;24140,00
251258408944;06;65;00;;BRETSCHNEIDER, MICHAEL:;;;17825,00
010943530369;98;83;00;;BRETSCHNEIDER, MONIKA:;;;20309,36
040668409819;18;31;00;;BRETSCHNEIDER, NICO:;;;9825,00
120257520010;97;22;00;;BRETSCHNEIDER, REGINA:;;;17448,10
140135422728;12;03;00;;BRETSCHNEIDER, SIEGFRIED:;;;31437,50
031151429783;99;43;00;;BRETSCHNEIDER, THOMAS:;;;23040,00
260165426232;14;00;47;;BRETSCHNEIDER, TORSTEN:;;;18881,00
250366530221;96;15;14;;BRETSCHNEIDER, UTA:;;;12920,00
220570415119;18;31;00;;BRETSCHNEIDER, VOLKER:;;;6705,00
070268406712;05;69;00;;BRETSCHNER, JOERG:;;;9675,00
230559407010;11;18;00;;BRETTIN, BODO:;;;20189,00
300156517718;99;02;00;;BRETTIN, PETRA:;;;20137,98
240954429710;94;94;00;;BRETTIN, RALF:;;;29670,00
050358407016;05;08;00;;BRETTIN, UWE:;;;20240,00
020951409314;06;00;45;;BRETTSCHNEIDER, GU(E)NTER:;;;21065,00
301146422410;12;00;47;;BRETTSCHNEIDER, HANS:;;;21812,50
050543427916;30;34;00;;BRETTSCHNEIDER, RAINER:;;;23200,00
121053406413;18;80;00;;BRETZKE, KLAUS-DIETER:;;;19980,00
101135429717;15;08;00;;BREU, DIETER:;;;27187,50
070369503212;03;09;00;;BREU, KERSTIN:;;;13000,00
050242429731;98;18;00;;BREUCKER, PETER:;;;30750,00
270869430044;18;32;00;;BREUCKER, TORSTEN:;;;9510,00
030334429722;97;08;00;;BREUDEL, GUENTER:;;;28500,00
271063406410;04;00;42;;BREUER, ANDREAS:;;;16227,00
131068430044;99;02;00;;BREUER, CARSTEN:;;;14475,00
160244429724;99;40;00;;BREUER, FRANK:;;;40312,50
240352429799;97;01;00;;BREUER, HARTMUT:;;;21700,00
310838408219;06;00;42;;BREUER, HEINZ:;;;26875,00
120641429713;97;17;00;;BREUER, HEINZ:;;;28500,00
050167421712;99;12;00;;BREUER, JAN:;;;15606,00
050458420330;97;08;00;;BREUER, JUERGEN:;;;17940,00
070665408228;99;43;00;;BREUER, KLAUS:;;;15463,50
191147419614;11;03;00;;BREUER, LOTHAR:;;;26875,02
250461421728;99;43;00;;BREUER, MARIO:;;;17820,00
280959411815;04;06;00;;BREUER, REINER:;;;19952,50
150465430236;98;83;00;;BREUER, RONALD:;;;16623,00
140431429721;98;83;00;;BREUER, WALTER:;;;21750,00
031048405310;04;00;45;;BREUHAHN, JOACHIM:;;;23760,00
150554504823;04;00;45;;BREUHAHN, SIGRID:;;;18912,82
080643429756;97;06;00;;BREUL, BERND:;;;24000,00
270768411928;18;33;00;;BREUM, JO(E)RG:;;;10575,00
210369408313;18;32;00;;BREUNINGER, JO(E)RG:;;;9675,00
150953426519;14;51;00;;BREY, WOLFGANG:;;;29111,62
260747517716;09;06;00;;BREYER, ILONA:;;;22000,00
041242429737;99;43;00;;BREYER, JUERGEN:;;;21750,00
140546417720;09;09;00;;BREYER, LOTHAR:;;;33187,50
250735430067;96;15;05;;BREYER, LOTHAR:;;;28500,00
190539529711;96;15;12;;BREYER, MONIKA:;;;24155,65
191052429799;99;43;00;;BREYER, ULRICH:;;;24480,00
240251417166;09;51;00;;BREYER, WILFRID:;;;21240,00
160968411212;18;33;00;;BREYMANN, NICO:;;;9600,00
171234405319;04;00;49;;BREYVOGEL, OTTMAR:;;;19560,48
300829407522;05;00;40;;BREZINSKI, HORST:;;;27000,00
221149402722;02;00;45;;BREZMANN, GERHARD:;;;23402,50
040142429786;98;50;00;;BRIEBSCH, EBERHARD:;;;37500,00
230461430247;94;03;00;;BRIEBSCH, ERIK:;;;17160,00
110169430075;98;84;00;;BRIEBSCH, RONALD:;;;14425,00
091061419033;10;08;00;;BRIEGER, ANDREE:;;;17820,00
280755406715;97;22;00;;BRIEGER, KLAUS-DIETER:;;;27700,00
251157528226;99;13;00;;BRIEGER, MARGITTA:;;;17531,75
280257427126;99;13;00;;BRIEGER, STEPHAN:;;;21390,00
261261430092;98;85;00;;BRIEN, JOERG:;;;17820,00
071259430061;97;08;00;;BRIEN, MICHAEL:;;;21026,52
160862530221;97;08;00;;BRIEN, UTE:;;;16169,10
140534429732;99;43;00;;BRIEN, WERNER:;;;27750,00
050747430068;30;58;00;;BRIER, ARMIN:;;;17760,48
280346425018;13;00;40;;BRIER, KARL-HEINZ:;;;33187,50
240266422814;60;90;00;;BRIER, ROLAND:;;;
240266422814;60;90;00;;BRIER, ROLAND:;;;15732,00
211148530117;30;84;00;;BRIER, SIGRID:;;;16560,00
170954424046;30;47;00;;BRIESE, ANDREAS:;;;18758,67
010158424034;30;32;00;;BRIESE, HOLGER:;;;13923,15
190869410414;07;18;00;;BRIESE, JENS:;;;8300,00
200956403710;30;58;00;;BRIESE, JUERGEN:;;;16934,00
141149400217;01;80;00;;BRIESE, JUERGEN:;;;22320,00
250861506114;03;15;00;;BRIESE, KAREN:;;;16665,00
280259530012;30;80;00;;BRIESE, PETRA:;;;3182,90
020952529748;30;76;00;;BRIESE, SIGRID:;;;9465,64
040351408316;06;60;00;;BRIESEMANN, BERND:;;;20182,50
070668408311;97;01;00;;BRIESEMANN, DIRK:;;;8812,50
080456500027;99;40;00;;BRIESEMEISTER, EIKE:;;;18329,19
250656400847;18;32;00;;BRIESEMEISTER, HARALD:;;;29670,00
010345408013;18;33;00;;BRIESEMEISTER, KLAUS:;;;23040,00
240956506134;30;47;00;;BRIESENICK, ILONA:;;;20233,50
110659404013;03;11;00;;BRIESKORN, BERND:;;;19320,00
220363406412;04;14;00;;BRIESKORN, RENE:;;;16170,00
180341406418;04;00;42;;BRIESKORN, WOLFGANG:;;;29250,00
240639417760;09;00;40;;BRIESNER, GERD:;;;30000,00
131142517712;09;60;00;;BRIESNER, RENATE:;;;20750,00
150433405714;04;00;52;;BRIEST, FRITZ:;;;18250,00
250969425068;18;35;00;;BRIEST, HANS-JOERG:;;;10287,08
090860403156;30;62;00;;BRIETZKE, PETER:;;;15251,00
160351429762;30;55;00;;BRILLAT, BERND:;;;3600,00
050752404411;99;12;00;;BRINCKMANN, UWE:;;;21395,00
080659530023;96;15;11;;BRINGER, GABRIELE:;;;17808,29
150358430070;99;26;00;;BRINGER, KLAUS-DIETER:;;;19745,00
261059430013;96;15;14;;BRINGEZU, MARIO:;;;21562,50
010446430041;96;15;07;;BRINGMANN, MATTHIAS:;;;29520,00
200832406928;30;50;00;;BRINGMANN, OTTO:;;;18720,00
070455415315;08;80;00;;BRINK, MATTHIAS:;;;17940,00
270144421327;97;06;00;;BRINKE, FRANK:;;;24000,00
150253510015;07;06;00;;BRINKE, HELGA:;;;20104,00
251232400821;97;01;00;;BRINKEL, GEORG:;;;25687,50
101269400848;01;06;20;;BRINKHOFF, FRANK:;;;12650,00
060161420312;09;03;00;;BRINKMANN, ANDREAS:;;;19277,50
030562430231;98;83;00;;BRINKMANN, BERND:;;;18397,50
040144429747;99;43;00;;BRINKMANN, DETLEF:;;;27750,00
020842429738;98;82;00;;BRINKMANN, GERHARD:;;;17398,39
300751429755;94;03;00;;BRINKMANN, HANS-JOERG:;;;20870,00
110958402747;18;71;25;;BRINKMANN, JOERG:;;;20182,50
080654403244;18;71;10;;BRINKMANN, LOTHAR:;;;20160,00
270371415744;18;33;00;;BRINKMANN, MARKO:;;;2795,00
250251400216;01;06;27;;BRINKMANN, MARTIN:;;;19740,00
110567530143;99;53;00;;BRINKMANN, PETRA:;;;16470,00
240652529812;99;53;00;;BRINKMANN, REGINA:;;;26634,82
010441530051;98;83;00;;BRINKMANN, RUTH:;;;19440,00
311230530018;99;09;00;;BRINKMANN, SIEGLINDE:;;;23250,00
110230430016;97;01;00;;BRINKMANN, WILLY:;;;24750,00
190160409221;99;43;00;;BRITZE, FRANK:;;;21332,50
250166409224;99;43;00;;BRITZE, STEFFEN:;;;16038,00
140858411811;05;00;43;;BRIX, ERHARD:;;;21780,00
180966406119;17;00;00;;BRIX, THORSTEN:;;;9872,00
111253414734;99;14;00;;BRIXEL, HEINZ:;;;27360,00
260755503736;99;09;00;;BRIXEL, SIGRID:;;;17860,29
180965404138;99;14;00;;BRO(E)CKER, FRED:;;;11169,00
090670404422;18;32;00;;BRO(E)CKER, JO(E)RG:;;;2795,00
150466513922;18;80;00;;BRO(E)CKERT, ANNETTE:;;;15660,00
220969413123;18;31;00;;BRO(E)DEL, HOLGER:;;;9510,00
030863424927;08;80;00;;BRO(E)DEL, STEFFEN:;;;15294,59
230263424938;07;06;00;;BRO(E)DNER, KARSTEN:;;;17820,00
140467413967;99;55;00;;BRO(E)MEL, STEFFEN:;;;16092,00
150670406411;18;35;00;;BRO(E)SECKE, ANDRE:;;;6705,00
261154417757;09;20;00;;BROAETER, HANS-JUERGEN:;;;23312,50
031137429736;99;09;00;;BROCK, DIETER:;;;28500,00
270230506917;99;43;00;;BROCK, GISELA:;;;20625,00
160559412222;01;03;00;;BROCK, HOLGER:;;;17997,50
101053406917;99;43;00;;BROCK, KLAUS-DIETER:;;;19440,00
050758410847;94;03;00;;BROCK, REINER:;;;21390,00
120470422743;18;33;00;;BROCK, STEFFEN:;;;9986,44
190733514513;08;96;00;;BROCKE, ANITA:;;;17460,00
111038517749;09;14;00;;BROCKE, MARGARETE:;;;18572,50
290168406445;17;00;00;;BROCKE, TOM:;;;8950,00
150756417744;97;01;00;;BROCKE, UDO:;;;25530,00
030358517719;09;07;00;;BROCKE, VERA:;;;17223,17
080271412119;18;33;00;;BROCKEL, ANDREAS:;;;2795,00
121268400852;18;35;00;;BROCKHAUSEN, JENS:;;;9327,00
081068402112;02;69;00;;BROCKHOFF, PETER:;;;9875,00
241155402428;02;00;47;;BROCKMANN, BERND:;;;22770,00
270257411926;07;00;57;;BROCKMANN, HELMUT:;;;15525,00
030550405012;04;08;00;;BROCKMANN, JOACHIM:;;;22500,00
041162400619;30;61;00;;BROCKMANN, JOERG:;;;14355,00
290962420914;12;00;44;;BROCKMANN, OLAF:;;;13932,00
260237400884;01;06;23;;BROCKMANN, WINFRIED:;;;24000,00
250259408538;97;08;00;;BROCKSCH, ULLRICH:;;;22080,00
310538522722;12;08;00;;BROD, MARGA:;;;17940,00
110959411442;07;00;53;;BRODA, MARIO:;;;22770,00
170948430060;15;08;00;;BRODDA, WILFRIED:;;;23760,00
290948522762;94;30;00;;BRODE, CHRISTINE:;;;20640,00
141062423918;99;43;00;;BRODE, DETLEF:;;;17600,00
101248429748;94;30;00;;BRODE, HARTMUT:;;;22770,00
171067430065;94;30;00;;BRODE, STEPHAN:;;;8950,00
010953402723;02;03;00;;BRODEHL, PETER:;;;24480,00
130841429725;97;08;00;;BRODEHL, ROLF-WERNER:;;;26250,00
250338529717;96;15;10;;BRODEHL, SIEGRID:;;;21937,50
110568430144;99;02;00;;BRODEHL, UWE:;;;14994,00
120754410111;94;03;00;;BRODIEN, GERNOT:;;;20010,00
260168412266;18;32;00;;BRODMANN, DIRK:;;;10621,77
071250520052;30;37;00;;BRODOWSKI, BIANKA:;;;16686,00
240868408542;06;00;46;;BRODOWSKI, THOMAS:;;;12825,00
310147420016;30;37;00;;BRODOWSKI, WOLFRAM:;;;20160,00
130129420313;11;00;40;;BRODRECHT, GERHARD:;;;23250,00
030542419617;11;51;00;;BRODRECHT, JUERGEN:;;;21000,00
181148428927;97;01;00;;BROECKEL, KLAUS:;;;23040,00
200968430097;15;80;00;;BROECKER, RAINER:;;;14750,00
120344429717;97;08;00;;BROECKER, ULRICH:;;;25500,00
240451430058;98;84;00;;BROEDE, WOLFGANG:;;;20100,00
260568413954;99;43;00;;BROEDEL, JOERG:;;;13500,00
040566513922;08;19;00;;BROEDEL, PETRA:;;;13179,42
120252424214;99;02;00;;BROEDNER, INGO:;;;26547,50
020761428119;14;80;00;;BROEDNER, LUTZ:;;;16472,50
311056428113;99;13;00;;BROEDNER, NORBERT:;;;19665,00
010564430085;18;29;30;;BROEGE, AXEL:;;;11220,00
020338430094;18;71;20;;BROEGE, WOLFGANG:;;;24150,00
190166409919;07;00;50;;BROEHL, THOMAS:;;;14812,50
130440411110;07;00;51;;BROEKER, ROLF:;;;29250,00
191057413980;08;20;00;;BROEMEL, INGOLF:;;;23205,00
081268419330;05;69;00;;BROEMEL, SILVIO:;;;9675,00
080357430115;98;18;00;;BROEMME, ANDREAS:;;;26392,50
010230530019;99;02;00;;BROEMME, ILSE:;;;24750,00
060941415426;08;00;40;;BROEMME, JUERGEN:;;;27750,00
051156530141;99;53;00;;BROEMME, MARGRET:;;;21551,13
111231429724;99;09;00;;BROEMME, RUDI:;;;33000,00
190254417513;97;29;00;;BROEMMER, EGBERT:;;;23940,00
070753526339;99;77;00;;BROEMMER, GABRIELE:;;;31680,00
290668415129;08;14;00;;BROEMMLING, DIRK:;;;12130,00
010368402327;97;08;00;;BROER, ANDREAS:;;;15221,00
091030430010;97;08;00;;BROESE, HEINZ:;;;28500,00
270654520720;99;77;00;;BROESE, KARIN:;;;22770,00
241231530051;97;06;00;;BROESE, MARGARETE:;;;21375,00
190848411514;07;06;00;;BROESEL, GUENTER:;;;20562,50
020653511222;07;80;00;;BROESEL, HELGA:;;;18000,00
031233505110;30;54;00;;BROESICKE, JOHANNA:;;;22680,00
091036405115;30;54;00;;BROESICKE, WOLFGANG:;;;26700,00
161139429719;99;43;00;;BROETZMANN, HANS-JOACHIM:;;;23187,50
190241406110;17;00;00;;BROHMANN, WILLI:;;;20700,00
040548402719;02;00;49;;BROMBACH, GUENTER:;;;24375,00
110537400823;01;55;00;;BROMBERG, FRITZ:;;;22500,00
051060408424;97;29;00;;BROMBERG, JOERG:;;;24062,90
220867404218;03;00;44;;BROMBERG, MAIK:;;;13982,00
100247424617;99;02;00;;BROMME, HANS-WERNER:;;;27360,00
241068423618;99;43;00;;BROMME, JOERG:;;;9825,00
240452424610;14;80;00;;BROMME, KARL-HEINZ:;;;14372,13
201132430032;15;20;00;;BRONDER, MANFRED:;;;37500,00
220939530054;15;00;41;;BRONDER, MARLIS:;;;23937,50
170170421314;18;35;00;;BRONDER, TIMO:;;;9600,00
280168409815;07;08;00;;BRONESKE, HARALD:;;;11758,00
260959404115;99;43;00;;BRONEWSKI, WERNER:;;;16830,00
050459422792;12;06;00;;BRONNER, UWE:;;;19780,00
220769418915;10;06;00;;BRONST, THOMAS:;;;12555,00
190645411522;07;06;00;;BROSCH, EDUARD:;;;21687,50
311041429711;99;51;00;;BROSCH, FRITZ:;;;26250,00
250435502719;02;65;00;;BROSCH, HANNA:;;;19500,00
160755402718;02;02;00;;BROSCH, PETER:;;;22080,00
051056430071;99;51;00;;BROSCH, PETER:;;;24725,00
010358430113;99;09;00;;BROSCH, RAINER:;;;22252,50
160169404411;98;85;00;;BROSCHE, FRANK:;;;9675,00
021249413414;13;00;43;;BROSCHE, FRANK:;;;26910,00
180537504415;03;00;40;;BROSCHE, HELENE:;;;16031,25
210566422843;12;65;00;;BROSCHE, KLAUS:;;;14580,00
251232422721;12;60;00;;BROSCHE, RUDOLF:;;;36000,00
040261422771;12;20;00;;BROSCHE, RUDOLF:;;;19745,00
241260530026;94;03;00;;BROSCHIES, MARINA:;;;16847,50
290739408912;06;00;54;;BROSE, GUENTER:;;;29700,00
100657411819;07;00;56;;BROSE, HARALD:;;;22942,50
151058430225;94;11;00;;BROSE, NORBERT:;;;21275,00
210371407619;18;32;00;;BROSE, STEFFEN:;;;2795,00
040171408423;18;32;00;;BROSE, STEFFEN:;;;2795,00
191161403715;03;07;00;;BROSE, UWE:;;;21120,00
161124430012;96;15;14;;BROSE, WALTER:;;;33000,00
180268424838;99;43;00;;BROSGE, SVEN:;;;9600,00
261255412218;94;03;00;;BROSIG, FRANK-ULRICH:;;;20010,00
030661404127;96;15;12;;BROSIG, STEFFEN:;;;20278,79
211069427111;14;69;00;;BROSIG, TORSTEN:;;;12085,00
041149524940;13;20;00;;BROSINSKY, ANGELA:;;;21540,00
231065503736;05;08;00;;BROSINSKY, CORNELIA:;;;7598,31
270968403746;99;43;00;;BROSINSKY, JAN:;;;14425,00
120467403728;05;80;00;;BROSINSKY, RENE:;;;15390,00
250462408525;15;15;00;;BROSIUS, BURKHARD:;;;21450,00
180334429726;99;43;00;;BROSIUS, HERBERT:;;;24750,00
140759406910;94;65;00;;BROSIUS, THOMAS:;;;17745,00
290847529711;99;40;00;;BROSK, BAERBEL:;;;22687,50
010348429725;97;06;00;;BROSK, WOLFGANG:;;;24750,00
240336429748;94;03;00;;BROSKE, HORST:;;;27750,00
221060413628;98;84;00;;BROSOWSKY, HANS-ULRICH:;;;17700,00
050347400812;01;65;00;;BROSTOWSKI, DETLEF:;;;21270,82
230459430088;30;61;00;;BROSY, JOERG:;;;16575,00
310149407616;05;03;00;;BROSZ, GERD:;;;26250,00
190933530067;97;08;00;;BROSZAT, CHRISTEL:;;;19125,00
110632430078;97;08;00;;BROSZAT, HANS-GUENTER:;;;21750,00
140957404844;04;00;50;;BROSZIO, THOMAS:;;;16215,00
230741410814;10;07;00;;BROSZMANN, HARALD:;;;30750,00
101167410324;08;69;00;;BROTHUHN, ULF:;;;6025,00
091236416214;09;00;43;;BROTMEYER, ROLF:;;;28937,50
240270406120;04;18;00;;BROXTERMANN, ANDREAS:;;;2700,00
120747406130;04;41;00;;BROXTERMANN, JUERGEN:;;;31500,00
200443518520;99;40;00;;BROYER, EDELTRAUT:;;;22125,00
010470419328;97;22;00;;BROYER, HEIKO:;;;9930,00
110136418520;95;60;12;;BROYER, KLAUS:;;;33000,00
060670415036;18;33;00;;BRU(E)CKNER, DIRK:;;;9551,61
111270426534;18;35;00;;BRU(E)CKNER, ENRICO:;;;2795,00
130968417334;18;80;00;;BRU(E)CKNER, JENS:;;;9825,00
100169428910;18;33;00;;BRU(E)CKNER, JO(E)RG:;;;2720,00
051035407219;18;25;00;;BRU(E)CKNER, KARL-HEINZ:;;;28687,50
141161419711;11;00;41;;BRU(E)CKNER, KLAUS:;;;15510,00
211062407513;04;00;54;;BRU(E)CKNER, STEFFEN:;;;21065,00
220571403320;18;33;00;;BRU(E)CKNER, STEFFEN:;;;2795,00
060968429246;18;32;00;;BRU(E)CKNER, SVEN:;;;9675,00
261168428916;18;32;00;;BRU(E)CKNER, TINO:;;;10025,00
220968424920;18;31;00;;BRU(E)DGAM, HENRY:;;;9600,00
090368406160;18;31;00;;BRU(E)GGEMANN, GERRIT:;;;9825,00
190770430634;18;31;00;;BRU(E)HL, JENS:;;;2795,00
110663402715;96;15;00;4361/84, M:;BRU(E)NING, FALK;1095;WARNEMU(E)NDER STR. 16;
110663402715;96;15;00;4361/84, M:;BRU(E)NING, FALK;1095;WARNEMU(E)NDER STR. 16;
141270427518;18;32;00;;BRU(E)NING, STEFAN:;;;2795,00
230668415036;18;34;00;;BRU(E)SCHKE, JENS:;;;10375,00
250955429738;30;47;00;;BRUCH, PETER:;;;23805,00
021061402123;02;08;00;;BRUCHE, DIETMAR:;;;18590,00
270859402111;02;26;00;;BRUCHE, JUERGEN:;;;20010,00
130362501718;02;26;00;;BRUCHE, PETRA:;;;10687,34
130970427347;18;40;00;;BRUCHHOLD, LUTZ:;;;6736,77
200655422723;12;26;00;;BRUCHHOLZ, HANS-PETER:;;;20412,50
280152403814;12;00;58;;BRUCHMANN, DETLEF:;;;23460,00
270752421814;12;41;00;;BRUCHMANN, FRANK:;;;31680,00
210538429722;97;06;00;;BRUCHMANN, PETER:;;;27125,00
070353518516;12;08;00;;BRUCHMANN, WALTRAUD:;;;2300,00
230662530084;99;77;00;;BRUCHMUELLER, HEIKE:;;;14594,95
040162414741;99;14;00;;BRUCHMUELLER, UWE:;;;20401,34
260556409915;95;60;24;;BRUCKE, ANDRE:;;;25600,00
050371431117;18;33;00;;BRUCKELT, STEFAN:;;;2795,00
180552506929;99;43;00;;BRUCKER, URSULA:;;;9987,75
091134429719;97;06;00;;BRUCKERT, ARTUR:;;;27595,84
300564410119;96;15;26;;BRUCKERT, TORSTEN:;;;16912,50
100662403629;99;02;00;;BRUCKHOFF, FRANK:;;;19085,00
060633403618;03;00;45;;BRUCKHOFF, HERBERT:;;;26250,00
090570400715;99;77;00;;BRUCKHOFF, MARIO:;;;2915,97
230465503116;03;80;00;;BRUCKSCH, CORINNA:;;;10611,40
120456522123;12;00;43;;BRUCKSCH, MARTINA:;;;5528,21
200340422112;12;00;54;;BRUCKSCH, WERNER:;;;27000,00
190737403116;03;00;50;;BRUCKSCH, WOLF-DIETER:;;;36000,00
060550413917;08;08;00;;BRUDER, KLAUS-DIETER:;;;18450,00
211033430052;18;27;30;;BRUDER, SIEGFRIED:;;;27000,00
051034529716;96;15;11;;BRUDER, SIGRID:;;;21937,50
041131403825;03;02;00;;BRUDNICKI, BRUNO:;;;17666,66
090370403823;97;06;00;;BRUDNICKI, DIRK:;;;9600,00
010268412237;07;06;00;;BRUDNICKI, JENS:;;;11600,00
100166417730;09;00;40;;BRUECK, JENS:;;;18764,40
091068420010;09;69;00;;BRUECK, STEFFEN:;;;9700,00
011243530055;30;47;00;;BRUECKHAENDLER, GITTA:;;;24140,00
070651507524;05;06;00;;BRUECKL, HANNELORE:;;;20040,00
170142507540;05;29;00;;BRUECKL, INGRID:;;;22500,00
121041407515;05;00;50;;BRUECKL, UWE:;;;25500,00
250264415126;97;01;00;;BRUECKMANN, HARTMUT:;;;10560,00
100163417719;94;03;00;;BRUECKMANN, MARIO:;;;18480,00
040362506915;99;77;00;;BRUECKMANN, STEFFI:;;;17796,11
020854421813;12;40;00;;BRUECKNER, ANDREAS:;;;22165,00
100268426814;99;02;00;;BRUECKNER, ANDREAS:;;;9872,00
290359506924;05;80;00;;BRUECKNER, BAERBEL:;;;17250,00
280852418419;97;01;00;;BRUECKNER, BERND:;;;31520,04
061148411926;99;43;00;;BRUECKNER, BERND:;;;27000,00
140240507213;18;29;00;;BRUECKNER, BRIGITTE:;;;19440,00
100250408538;97;22;00;;BRUECKNER, CHRISTIAN:;;;25500,00
061260530116;96;15;12;;BRUECKNER, DANIELA:;;;13895,95
091066426611;14;69;00;;BRUECKNER, DANIELO:;;;13860,00
150445421025;04;06;00;;BRUECKNER, DIETMAR:;;;23250,00
210869407317;99;43;00;;BRUECKNER, FRANK:;;;8350,00
231257422789;99;40;00;;BRUECKNER, FRANK:;;;22770,00
070260418516;94;03;00;;BRUECKNER, FRANK:;;;21562,50
261157419715;97;22;00;;BRUECKNER, GEORG:;;;24840,00
060552429218;01;80;00;;BRUECKNER, GUNTER:;;;18720,00
260642513612;99;40;00;;BRUECKNER, HANNELORE:;;;26815,00
110337520310;11;77;00;;BRUECKNER, HELLA:;;;25500,00
291252412228;07;08;00;;BRUECKNER, HENNING:;;;22320,00
070450411710;98;84;00;;BRUECKNER, HERBERT:;;;21532,50
071049515024;08;78;00;;BRUECKNER, ISABELLA:;;;20880,00
220165427415;99;43;00;;BRUECKNER, JENS:;;;16830,00
280747415013;08;64;00;;BRUECKNER, JOACHIM:;;;24750,00
220767419711;17;00;00;;BRUECKNER, JOERG:;;;8950,00
101046512914;18;96;00;;BRUECKNER, KAROLA:;;;19262,50
180653402715;02;00;48;;BRUECKNER, KLAUS:;;;25200,00
230267408927;06;69;00;;BRUECKNER, LARS:;;;11016,00
190333429715;99;53;00;;BRUECKNER, LOTHAR:;;;32062,50
010254418515;10;11;00;;BRUECKNER, LUTZ:;;;26640,00
071055422238;96;15;21;;BRUECKNER, LUTZ:;;;21822,50
120127418413;97;01;00;;BRUECKNER, MANFRED:;;;33500,04
021146421825;12;08;00;;BRUECKNER, MANFRED:;;;27000,00
050669415355;01;69;00;;BRUECKNER, MARCO:;;;6806,61
030635429726;97;06;00;;BRUECKNER, MARTIN:;;;23000,00
210657407438;18;29;00;;BRUECKNER, MATTHIAS:;;;24092,50
071156417745;99;55;00;;BRUECKNER, MICHAEL:;;;19435,00
151070413444;97;22;00;;BRUECKNER, MICHAEL:;;;3772,33
120753417792;09;12;00;;BRUECKNER, MICHAEL:;;;23220,00
220753428027;12;06;00;;BRUECKNER, PETER:;;;19040,00
151060501328;30;81;00;;BRUECKNER, RAMONA:;;;11491,54
011239413614;99;40;00;;BRUECKNER, ROBERT:;;;27000,00
140332420318;11;06;00;;BRUECKNER, ROLAND:;;;26250,00
141255429742;30;47;00;;BRUECKNER, ROLAND:;;;24942,50
210257417717;99;13;00;;BRUECKNER, RUEDIGER:;;;21045,00
130236530323;98;83;00;;BRUECKNER, RUTH:;;;18360,00
270939407211;94;03;00;;BRUECKNER, SIEGFRIED:;;;27750,00
061269419748;97;06;00;;BRUECKNER, STEFAN:;;;15150,00
070455403410;97;01;00;;BRUECKNER, STEFFEN:;;;25290,00
190270418428;99;43;00;;BRUECKNER, STEFFEN:;;;6780,00
230470419752;11;69;00;;BRUECKNER, STEPHAN:;;;2720,00
200369426512;14;69;00;;BRUECKNER, SVEN:;;;12675,00
011268415328;18;35;00;;BRUECKNER, SVEN:;;;10725,00
090468430125;99;77;00;;BRUECKNER, THOMAS:;;;9872,00
230464412300;97;01;00;;BRUECKNER, TINO:;;;16775,00
180571419644;99;43;00;;BRUECKNER, TORSTEN:;;;2870,00
241266400628;98;82;00;;BRUECKNER, VOLKER:;;;14946,00
050930407448;99;02;00;;BRUECKNER, WILLY:;;;42375,00
101164415330;08;08;00;;BRUEDER, MICHAEL:;;;16753,50
070945427714;13;51;00;;BRUEDERLEIN, BERND:;;;27000,00
150452506414;97;01;00;;BRUEGERT, CHRISTIANE:;;;18682,88
150354401328;04;43;00;;BRUEGERT, DETLEF:;;;21600,00
190951411256;98;20;00;;BRUEGGEMANN, DETLEF:;;;25080,00
021057408557;94;03;00;;BRUEGGEMANN, STEFFEN:;;;21332,50
300647406115;30;40;00;;BRUEGGENKAMP, DETLEV:;;;23320,00
200540403610;03;65;00;;BRUEGGER, SIEGFRIED:;;;22437,50
280658403416;99;55;00;;BRUEGGERT, HANS-JUERGEN:;;;18083,75
031254401919;02;00;43;;BRUEGGERT, RAINER:;;;22080,00
080966402726;94;03;00;;BRUEGGMANN, CAROL:;;;15498,00
050244502728;02;18;00;;BRUEGGMANN, EDELTRAUD:;;;17167,77
010236402712;02;02;00;;BRUEGGMANN, HARRY:;;;27000,00
280751513230;98;19;00;;BRUEGMANN, GISELA:;;;22030,00
181231429728;99;43;00;;BRUEHL, GERHARD:;;;27750,00
291070421115;99;43;00;;BRUEHL, HEIKO:;;;2480,32
020245521026;98;83;00;;BRUEHL, ILONA:;;;19780,00
240643421025;98;20;00;;BRUEHL, JUERGEN:;;;25920,00
131153427210;97;22;00;;BRUEHL, JUERGEN:;;;20880,00
121235429747;99;77;00;;BRUEHL, KURT:;;;20316,53
190657430050;94;03;00;;BRUEHL, MARIO:;;;21332,50
101257506127;99;77;00;;BRUEHL, MARTINA:;;;19043,66
290145429732;97;01;00;;BRUEHL, PETER:;;;30750,00
081239412228;07;78;00;;BRUEHL, PETER:;;;33750,00
130158406182;99;02;00;;BRUEHL, UWE:;;;25875,00
200834429736;98;83;00;;BRUEHL, WALTER:;;;23250,00
261264412914;94;03;00;;BRUEHMANN, PETER:;;;17050,00
151055403627;15;00;43;;BRUEHNING, ERHARD:;;;24092,50
310553406420;08;20;00;;BRUEMMER, HANS-JOACHIM:;;;22080,00
270960413624;96;15;10;;BRUENECKE, FRANK:;;;19305,00
171254512226;07;78;00;;BRUENING, BIRGIT:;;;17464,92
210532430044;13;99;01;;BRUENING, CLAUS:;;;42750,00
060468400615;01;00;49;;BRUENING, DIRK:;;;13785,00
250447411910;07;19;00;;BRUENING, GERHARD:;;;27000,00
141048507410;98;20;00;;BRUENING, HEIDEMARIE:;;;19993,63
230568406116;04;69;00;;BRUENING, HEIKO:;;;9875,00
180448401828;02;19;00;;BRUENING, HEINZ:;;;25875,00
081253407417;99;43;00;;BRUENING, JUERGEN:;;;25860,00
090941402219;02;08;00;;BRUENING, KLAUS:;;;19718,75
090463427736;30;59;00;;BRUENING, RALPH:;;;15180,00
231046411414;94;30;00;;BRUENING, REINHARD:;;;26562,50
251270400638;98;18;00;;BRUENING, ULF:;;;2700,00
050266400896;01;18;00;;BRUENKMANN, UWE:;;;15974,00
070851427019;14;22;00;;BRUENLER, HARRY:;;;23040,00
121169418328;94;30;00;;BRUENNER, DIRK:;;;2700,00
061146418315;10;00;45;;BRUENNER, HANS-DIETER:;;;24480,00
081244500724;30;81;00;;BRUENNER, RENATE:;;;16200,00
140139505918;97;06;00;;BRUESEHABER, GERDA:;;;22320,00
160942405914;99;40;00;;BRUESEHABER, GUENTER:;;;27750,00
250966400893;18;41;30;;BRUESEHABER, JAN:;;;14168,00
081050403416;03;20;00;;BRUESER, BODO:;;;22892,50
070641428929;97;06;00;;BRUESEWITZ, PETER:;;;24000,00
210961406747;98;85;00;;BRUESKE, HANS-JUERGEN:;;;18480,00
211051429741;30;62;00;;BRUESSAU, MICHAEL:;;;15903,75
261142506111;17;00;00;;BRUESSEL, HEIDI:;;;21000,00
280858428124;14;00;60;;BRUESSEL, ULLRICH:;;;12161,25
300154400022;01;55;00;;BRUESSOW, BERNHARD:;;;16867,50
020366515351;97;01;00;;BRUESSOW, GRIT:;;;13217,31
100950409910;95;45;00;;BRUESSOW, KLAUS:;;;26460,00
041262400712;97;01;00;;BRUESSOW, MARIO:;;;16038,00
240652400517;01;19;00;;BRUEST, HANS-JOACHIM:;;;21620,00
150469403729;18;32;00;;BRUGGER, THOMAS:;;;9313,50
031048402419;18;80;00;;BRUHN, DIETER:;;;20812,50
040747417120;09;26;00;;BRUHN, HEINZ-JUERGEN:;;;26437,50
270247401812;02;00;42;;BRUHN, ROLF:;;;30750,00
281150401318;96;15;00;650/75/39, :;BRUHN, SIEGFRIED;2520;ALEKSIS-KIVI-STR. 29;
281150401318;96;15;00;650/75/39, :;BRUHN, SIEGFRIED;2520;ALEKSIS-KIVI-STR. 29;
061068414713;94;03;00;;BRUHN, TORSTEN:;;;13175,00
200250400817;01;00;40;;BRUHN, WOLFGANG:;;;25500,00
060353406128;04;06;00;;BRUHNS, ULF-PETER:;;;20711,62
240664403627;03;14;00;;BRUKSCH, ANDREAS:;;;15840,00
130768413726;18;35;00;;BRUMBY, MAIK:;;;9675,00
290942530032;99;77;00;;BRUMM, DORIS:;;;27000,00
060440422740;12;00;40;;BRUMM, GERHARD:;;;26250,00
250369430074;17;00;00;;BRUMM, HOLGER:;;;8950,00
011158405110;15;80;00;;BRUMM, JUERGEN:;;;18227,50
210560400870;01;06;25;;BRUMM, NORBERT:;;;17680,00
180155418618;94;03;00;;BRUMME, KLAUS-PETER:;;;22647,50
300562416226;09;06;00;;BRUMMER, HEIKO:;;;17380,00
010268403218;03;69;00;;BRUMMUND, DIRK:;;;10575,00
020135402739;02;53;00;;BRUMMUND, EGON:;;;27375,00
250863402749;99;02;00;;BRUMMUND, JU(E)RGEN:;;;19415,00
290862402727;94;30;00;;BRUMMUND, MICHAEL:;;;17847,50
081268430038;99;43;00;;BRUNA, ANDREAS:;;;13575,00
140147530064;99;43;00;;BRUNA, GUDRUN:;;;20706,00
230844429729;99;43;00;;BRUNA, WOLFGANG:;;;27750,00
160359522224;98;83;00;;BRUNK, BIRGIT:;;;17585,39
010253429749;15;20;00;;BRUNK, ECKART:;;;23715,00
280955401310;97;17;00;;BRUNK, HEINZ:;;;20010,00
020969404415;94;03;00;;BRUNK, KARSTEN:;;;9510,00
180349401320;98;82;00;;BRUNK, KLAUS-DIETER:;;;24337,50
190559403841;03;80;00;;BRUNK, KLAUS-DIETER:;;;16675,00
190847403715;97;08;00;;BRUNK, MANFRED:;;;27000,00
140253403720;03;14;00;;BRUNK, REINHARD:;;;18480,00
210360524940;30;63;00;;BRUNKAL, ELKE:;;;10916,33
280355425052;30;63;00;;BRUNKAL, KARL-HEINZ:;;;15510,00
210370429752;94;03;00;;BRUNKOW, BIRK:;;;2700,00
190342429733;99;26;00;;BRUNKOW, HANS-PETER:;;;39750,00
010240529716;98;20;00;;BRUNKOW, INGRID:;;;23125,00
050150406428;04;00;42;;BRUNKOW, KLAUS:;;;25860,00
020560508913;30;84;00;;BRUNN, DANIELA:;;;12738,97
280550413428;30;63;00;;BRUNN, HELMUT:;;;17280,00
031239430092;15;06;00;;BRUNN, LOTHAR:;;;26250,00
300155515315;99;40;00;;BRUNNE, PETRA:;;;20842,50
280954423825;99;40;00;;BRUNNE, RALF:;;;23400,00
210163400893;97;01;00;;BRUNNENMEIER, STEFFEN:;;;16335,00
270259422717;12;08;00;;BRUNNER, ANDREAS:;;;19952,50
231244530078;99;12;00;;BRUNNER, ANKE:;;;21600,00
220260406129;04;06;00;;BRUNNER, AXEL:;;;19665,00
071055529836;96;15;04;;BRUNNER, CARMEN:;;;19492,50
010553501829;02;03;00;;BRUNNER, CHRISTA:;;;11757,08
010247411518;07;00;54;;BRUNNER, DIETER:;;;27937,50
021047410418;02;00;42;;BRUNNER, DIETER:;;;22500,00
020366430024;98;27;00;;BRUNNER, DIRK:;;;15876,00
260238418410;97;06;00;;BRUNNER, GOTTFRIED:;;;21266,66
070847422725;12;00;47;;BRUNNER, HANS-JUERGEN:;;;25117,50
010951429818;97;08;00;;BRUNNER, HEINZ:;;;18942,50
070369428224;18;38;00;;BRUNNER, INGO:;;;9675,00
120765430214;96;15;25;;BRUNNER, JAN:;;;19150,50
210169427229;18;33;00;;BRUNNER, JENS:;;;10500,00
061152428210;14;15;00;;BRUNNER, JUERGEN:;;;24832,50
030239429724;99;09;00;;BRUNNER, KLAUS:;;;29250,00
260429430017;96;15;00;1920/75, J:;BRUNNER, MANFRED;1144;TETEROWER RING 86;
260429430017;96;15;00;1920/75, J:;BRUNNER, MANFRED;1144;TETEROWER RING 86;
050170429352;94;03;00;;BRUNNER, MARKO:;;;10335,00
040438430233;60;90;00;;BRUNNER, THEO:;;;
040438430233;60;90;00;;BRUNNER, THEO:;;;30600,00
010766420125;11;69;00;;BRUNNER, TORSTEN:;;;15876,00
190942405233;03;18;00;;BRUNNER, WERNER:;;;27000,00
280736414218;08;00;54;;BRUNNERT, HILMAR:;;;23343,01
260639410815;07;06;00;;BRUNNERT, JUERGEN:;;;24187,50
070670409823;18;33;00;;BRUNNGRA(E)BER, MAREK:;;;6958,87
240369410023;18;31;00;;BRUNOW, RALF:;;;9675,00
050662522799;96;15;00;6555/82, J:;BRUNS, BEATE;1140;BA(E)RENSTEINSTR. 8;
050662522799;96;15;00;6555/82, J:;BRUNS, BEATE;1140;BA(E)RENSTEINSTR. 8;
100571409523;05;69;00;;BRUNS, HENRY:;;;2870,00
160858405938;97;08;00;;BRUNS, MICHAEL:;;;18601,25
110570421116;12;69;00;;BRUNS, STEFFEN:;;;9830,00
210951508811;30;83;00;;BRUNS, SYBILLE:;;;20359,55
020348410820;99;55;00;;BRUNS, WALTER:;;;24000,00
031268403632;18;35;00;;BRUNS, WOLFGANG:;;;9675,00
301057413934;97;01;00;;BRUNSCH, JUERGEN:;;;29760,00
240543411110;07;00;51;;BRUNSCH, KLAUS-DIETER:;;;24750,00
150166413911;15;07;00;;BRUNSCH, OLAF:;;;18414,00
020853409812;07;18;00;;BRUNSENDORF, DIETER:;;;24480,00
191154511435;07;41;00;;BRUNSENDORF, GUDRUN:;;;19440,00
300852409825;07;00;41;;BRUNSENDORF, LOTHAR:;;;23460,00
290153402716;02;06;00;;BRUNST, HOLGER:;;;20160,00
060270403714;18;34;00;;BRUNST, STEFAN:;;;6705,00
230358430062;15;80;00;;BRUNTSCH, DETLEF:;;;17935,02
260862407010;18;38;00;;BRUSAK, DIRK:;;;20161,43
070268501568;97;06;00;;BRUSCH, ANNETT:;;;9783,34
151063400119;01;00;45;;BRUSCH, HOLGER:;;;15592,50
050657400113;99;12;00;;BRUSCH, MANFRED:;;;20815,00
051165401528;01;60;00;;BRUSE, DIRK:;;;14835,00
211040501517;01;06;22;;BRUSE, GERDA:;;;16296,30
150646400810;01;65;00;;BRUSE, GERHARD:;;;20625,00
070638403413;03;65;00;;BRUSE, HANS-ULRICH:;;;25687,50
140948401510;97;06;00;;BRUSE, PAUL:;;;24000,00
020741430086;30;84;00;;BRUSENDORF, WOLFGANG:;;;16560,00
100357421716;12;06;00;;BRUSSIG, ROLAND:;;;19492,50
070736421711;12;00;51;;BRUSSIG, SIEGFRIED:;;;16847,50
220260523624;14;00;56;;BRUSSOG, BIRGIT:;;;14948,75
081148529711;94;30;00;;BRUST, MARION:;;;21157,25
021046429715;99;43;00;;BRUST, UDO:;;;26187,50
210137429713;99;02;00;;BRUTKE, RUDOLF:;;;36008,06
011153429746;30;47;00;;BRUTSCHIN, SIEGBERT:;;;23090,00
120140411216;07;08;00;;BRUTTLOFF, HANS-JOACHIM:;;;21750,00
120249430066;30;47;00;;BRYCHCY, MICHAEL:;;;29280,00
091052407014;05;08;00;;BRYKCZYNSKI, JOERG:;;;18749,03
060571512244;07;96;00;;BRYLLA, KERSTIN:;;;3220,00
140250412226;07;06;00;;BRYLLA, KLAUS-DIETER:;;;21720,00
140853412217;07;06;00;;BRYLLA, WOLFGANG:;;;20160,00
180842421827;94;03;00;;BRYLSKI, JUERGEN:;;;24000,00
231269407228;05;69;00;;BRYM, RAINER:;;;2870,00
020858406418;30;58;00;;BRZAKALA, JUERGEN:;;;16445,00
170160413628;06;00;50;;BRZANK, RAINER:;;;19800,00
161250413213;08;00;44;;BRZEZINSKI, JU(E)RGEN:;;;19800,00
130655417528;09;00;51;;BRZEZINSKI, LUTZ:;;;27967,50
200239402731;30;44;00;;BRZEZOWSKA, ALFRED:;;;15120,00
251243412211;07;51;00;;BRZOSKA, INGBERT:;;;21750,00
280542512215;07;40;00;;BRZOSKA, MARGA:;;;26437,50
091056518520;10;51;00;;BRZUSKA, DAGMAR:;;;18917,50
090956407215;05;80;00;;BRZYSKI, BODO:;;;16905,00
040743530388;18;77;00;;BSDUREK, RENATE:;;;23040,00
Inside the Yakuza- GANGLAND TOKYO Crime Lords of Tokyo – Full Movie
Lost Worlds – Secret Cities of the A-Bomb – Full Movie
TOPSECRET from the FBI – West New York Mayor, Son Arrested for Hacking
NEWARK—The mayor of West New York, New Jersey and his son were arrested today for allegedly hacking into an e-mail account and website associated with a movement to recall the mayor, U.S. Attorney Paul J. Fishman announced.
Felix Roque, 55, of Hudson County, and Joseph Roque, 22, of Passaic County, are charged by complaint with gaining unauthorized access to computers in furtherance of causing damage to protected computers; causing damage to protected computers; and conspiracy to commit those crimes. Felix and Joseph Roque are scheduled to appear this afternoon before U.S. Magistrate Judge Mark S. Falk in Newark federal court.
“In this case, the elected leader of West New York and his son allegedly hacked into computers to intimidate constituents who were simply using the Internet to exercise their Constitutional rights to criticize the government,” U.S. Attorney Fishman said. “We will continue to investigate and prosecute those who illegally hack into computers and disable websites with the goal of suppressing the exercise of that right.”
“This case illustrates two primary concerns of law enforcement, the violation of public trust and cyber intrusion,” FBI Special Agent in Charge Michael B. Ward said. “In this instance, an elected official conspired to hack into a website and e-mail account. It’s incredibly disappointing that resources have to be diverted from protecting the U.S. against cyber intrusions targeting critical infrastructure, federally funded research, and military technology to address a public official intruding into computer systems to further a political agenda.”
According to the criminal complaint unsealed today:
In early February 2012, a Hudson County resident and public official anonymously established and moderated an Internet website, http://www.recallroque.com, to post commentary and criticism of Mayor Felix Roque and his administration. On February 6 2012, Mayor Roque and his son, Joseph Roque, schemed to hack into and take down the website and to identify, intimidate, and harass those who operated and were associated with the website.
By the late afternoon of February 8, 2012, Joseph Roque had successfully hacked into various online accounts used in connection with the recall website. Joseph Roque then used that access to disable the website. Mayor Roque harassed and attempted to intimidate several individuals whom he had learned were associated with the recall website.
The conspiracy charge and the charge of gaining unauthorized access to a computer in furtherance of causing damage to protected computers are each punishable by a maximum potential penalty of five years in prison and a fine of up to $250,000. The charge of causing damage to protected computers carries a maximum potential penalty of one year in prison and a fine of up to $250,000.
U.S. Attorney Fishman credited special agents of the FBI under the direction of Special Agent in Charge Michael B. Ward in Newark with the investigation leading to the arrests.
The government is represented by Assistant U.S. Attorneys Seth Kosto of the U.S. Attorney’s Office Computer Hacking and Intellectual Property Section of the Office’s Economic Crimes Unit and Barbara Llanes of the Special Prosecutions Division in Newark.
The charges and allegations contained in the complaint are merely accusations, and the defendants are considered innocent unless and until proven guilty.
Secret Superpower Aircraft – Spy planes – Full Movie – The History Channel
TOP-SECRET – (U//LES) FBI Domestic Terrorism Operations Unit Introduction to Sovereign Citizens

Sovereign citizens believe the government is operating outside of its jurisdiction and generally do not recognize federal, state, or local laws, policies, or governmental regulations. They subscribe to a number of conspiracy theories, including a prevalent theory which states the United States Government (USG) became bankrupt and began using citizens as collateral in trade agreements with foreign governments. They believe secret bank accounts exist at the United States (US) Department of the Treasury. These accounts can be accessed using Internal Revenue Service (IRS), Universal Commercial Code (UCC), and fraudulent financial documents.
Sovereign citizens are known to travel the country conducting training seminars on debt elimination schemes. The seminars focus on obtaining funds from a secret “Strawman” account using legitimate IRS forms, UCC forms, and fraudulent financial documents. Sovereign citizens believe once the documentation is filed, they gain access to their “Strawman” account with the Treasury Department.
The purpose of this primer is to assist law enforcement in the identification of sovereign citizen extremist activity to prevent, detect, and/or deter acts associated with sovereign citizen criminal activity.
…
POSSIBLE INDICATORS OF SOVEREIGN CITIZEN ACTIVITY
Some or all of the following may provide an indication of sovereign activity. However it is important to note these activities may also be indicative of lawful, innocent conduct and in some instances may constitute the exercise of rights guaranteed by the United States Constitution. For these reasons, these indicators should be considered in the context of other suspicious behavior and the totality of the circumstances in which they are observed or reported.
- Documentation may be mailed and addressed to the Secretary of the Treasury Department or the Depository Trust Company
- Documentation includes an “Apostille Number”
- Documents contain the phrase “Accepted for Value”
- Documents are notarized, even if not required
- International postage rates is applied even for domestic mailings
- All paperwork will be mailed using registered mail
- Stamps will be affixed near the signature line or at the bottom corner of the page
- Name written in all capital letters
- Example: JOHN SMITH
- Name will be written last name : first name
- Example: Smith: John or Smith: Family of John
- Zip codes enclosed in brackets
- Example: [11233]
- Presence of thumbprints on documents,
- Typically in red or blue ink
- Typically on or near a signature or seal
- “SLS” may follow signature
- “SLS” stands for “Sovereign Living Soul”
…
Generally, sovereign citizens do not operate as a group or have an established leadership hierarchy. Rather, they act independently or in loosely affiliated groups which come together for training, to assist with paperwork, and to socialize based on sovereign ideology. Sovereign citizens often refer to themselves as “Freemen.” [Note: The use of the word “Freemen” does not inherently indicate a connection to any specific group, however, some use the term “Freemen” in their group name. Others may indicate they are a “free man,” meaning free from government control.]
Sovereign citizens believe the USG is illegitimate and has drifted away from the true intent of the Constitution. As a result, the USG is not perceived to be acting in the interest of the American people. These groups generally do not adhere to federal, state, or local laws. Some sovereign citizens believe federal and state officials have no real authority and will only recognize the local sheriff’s department as the only legitimate government official. Other law enforcement officials are viewed as being oppressive and illegitimate.
Individuals who adhere to this ideology believe their status as a sovereign citizen exempts them from US laws and the US tax system. They believe the US Federal Reverse System, the Treasury Department, and banking systems are illegitimate. Therefore, one of the perceived “benefits” of being a sovereign citizen is not paying federal or state taxes.
Sovereign citizens view the USG as bankrupt and without tangible assets; therefore, the USG is believed to use citizens to back US currency. Sovereign citizens believe the USG operates solely on a credit system using American citizens as collateral. Sovereign citizens exploit this belief by filing fraudulent financial documents charging their debt to the Treasury Department. In addition, they routinely engage in mortgage, credit card, tax, and loan fraud.
Soviet Top Secret Weapons – Full Movie
For the entire period of the Cold War, a large proportion of the Soviet Union’s economy and massive scientific establishment was dedicated to the development and refinement of new and better weapons. During the 50s and 60s, the Soviet government’s paranoia about Western technical superiority was at its height.
UNVEILED – Hillary Clinton Addresses Special Forces Gala
ADM MCRAVEN: Thank you, Steve. Well, good evening, everyone, and welcome to tonight’s gala dinner. Before I begin, please join me in a round of applause for the staff of the Tampa Convention Center and the action officers from USSOCOM who worked so very hard to make this event a great success. (Applause.)
To our international guests, our local, state, and national leaders, our guests from industry, and the National Defense Industrial Association, thank you for making this event a priority in your busy schedule, and for your continued support to Special Operations.
Now I have the great privilege of introducing our guest speaker, a woman who has spent virtually her entire life in the service of our country and in the service of the greater international community. She was the first lady of the state of Arkansas, the first lady of the United States, a U.S. senator from the great state of New York, and since 2009, she has held the position as the U.S. Secretary of State.
In a Time Magazine article last month, she was named one of the top 100 most influential people in the world. In that Time article, the former Secretary of Defense, Bob Gates, said of her, and I quote, “In a world that is ever more complex, turbulent, and dangerous, Secretary Clinton has made a singular contribution to strengthening this country’s relationships with allies, partners, and friends, rallying other countries to join us in dealing with challenges to the global order from Libya to Iran to the South China Sea, and reaching out to the people in scores continue – in scores of countries to demonstrate that America cares about them.”
No Secretary in recent memory has had to deal with more international challenges than the war in Iraq and Afghanistan, to the Arab Spring, to the always difficult and challenging North Korea and Iran. In spite of these challenges, she has made incredible strides in safeguarding democratic reforms in Burma, advancing women’s rights around the globe, and reshaping the State Department to align the incredible power of our diplomats, the civilian power, with our already strong military power.
Secretary Clinton is beloved by the men and women in the U.S. military. She is our type of lady – a woman of uncompromising integrity who won’t back down from a good fight, particularly when it comes to matters of principle, a leader who is passionate about the welfare of the world’s less privileged, the disenfranchised, and the downtrodden, and a Secretary who deeply cares for her people and who is an incredibly strong supporter of our men and women in uniform.
Over the last few years, I have had several opportunities to work with Secretary Clinton on some of the United States’s most sensitive military missions. In each case, she listened intently to my advice. In each case, she was instrumental in the final decisions. And in each and every case, she never, ever wavered from her commitment to the American people. She is, without a doubt, one of the finest public servants ever to serve this great nation.
Ladies and gentlemen, please join me in welcoming the United States Secretary of State, The Honorable Hillary Rodham Clinton. (Applause.)
SECRETARY CLINTON: Good evening. Good evening. It is a great honor for me to be here with you this evening. I want to thank Admiral McRaven for that introduction, but far more than that, for his remarkable service to our country, from leading an underwater demolition SEAL platoon to heading the Joint Special Operations Command. He’s doing a terrific job as the ninth commander of the United States Special Operations Command. (Applause.) Many of you know, as Admiral McRaven knows, that it takes real guts to run a mission deep into hostile territory, full of potential dangers. And of course, I’m talking about the White House Correspondents’ Dinner. (Laughter.)
I am pleased to be here with so many representatives to this conference from 90 countries around the world. Your participation is a testament to the important partnerships, and I am grateful that you are here. Because we face common challenges, we face common threats, and they cannot be contained by borders and boundaries.
You know that extremist networks squeezed in one country migrate to others. Terrorist propaganda from a cell in Yemen can incite attacks as far away as Detroit or Delhi. A flu in Macao can become an epidemic in Miami. Technology and globalization have made our countries and our communities interdependent and interconnected. And today’s threats have become so complex, fast-moving, and cross-cutting that no one nation could ever hope to solve them alone.
From the first days of this Administration, we have worked to craft a new approach to our national security that reflects this changing landscape, starting with better integrating the three Ds of our foreign policy and national security: diplomacy, development, and defense. And we call it smart power.
And I have been privileged to work with two secretaries of Defense, Bob Gates and Leon Panetta, and two chairmen of the Joint Chiefs of Staff, Mike Mullen and Marty Dempsey, who understood and valued the role of diplomacy and development, who saw that we need to work to try to prevent conflict, help rebuild shattered societies, and lighten the load on our military.
For my part, first as a senator serving on the Armed Services Committee and now as Secretary of State, I have seen and admired the extraordinary service and sacrifice of our men and women in uniform. So we have made it a priority to have our soldiers, diplomats, and development experts work hand-in-hand across the globe. And we are getting better at coordinating budgets and bureaucracies in Washington as well.
To my mind, Special Operations Forces exemplify the ethic of smart power – fast and flexible, constantly adapting, learning new languages and cultures, dedicated to forming partnerships where we can work together. And we believe that we should work together wherever we can, and go it alone when we must. This model is delivering results.
Admiral McRaven talks about two mutually reinforcing strategies for Special Operations: the direct and the indirect. Well, we all know about the direct approach. Just ask the al-Qaida leaders who have been removed from the battlefield.
But not enough attention is paid to the quiet, persistent work Special Operations Forces are doing every single day along with many of you to build our joint capacity. You are forging relationships in key communities, and not just with other militaries, but also with civil society. You are responding to natural disasters and alleviating humanitarian suffering.
Now, some might ask what does all this have to do with your core mission of war fighting? Well, we’ve learned – and it’s been a hard lesson in the last decade – we’ve learned that to defeat a terror network, we need to attack its finances, recruitment, and safe havens. We also need to take on its ideology and diminish its appeal, particularly to young people. And we need effective international partners in both government and civil society who can extend this effort to all the places where terrorists hide and plot their attacks.
This is part of the smart power approach to our long fight against terrorism. And so we need Special Operations Forces who are as comfortable drinking tea with tribal leaders as raiding a terrorist compound. We also need diplomats and development experts who understand modern warfare and are up to the job of being your partners.
One of our senior Foreign Service officers, Karen Williams, is serving here in Tampa on Admiral McRaven’s staff. And under an agreement finalized this year, we are nearly doubling the number of military and Foreign Service officers who will be exchanged between the Departments of State and Defense. (Applause.) We know we need to better understand each other, and we know that through that better understanding there is even more we can do together.
When I served on the Senate Armed Services Committee, I was impressed by the Pentagon’s Quadrennial Defense Reviews, called the QDR, which guided plans and priorities every four years. So when I became Secretary of State, I launched the first-ever Quadrennial Diplomacy and Development Review, and we call it the QDDR. Through it, we are overhauling the State Department and USAID to become more operational, more strategic in our use of resources and personnel, more expeditionary, and more focused on transnational threats.
Let me highlight a few examples. As part of the QDDR, we created a new Bureau of Conflict and Stabilization Operations that is working to put into practice lessons learned over the past decade and institutionalize a civilian surge capacity to deal with crises and hotspots.
Experts from this new bureau are working closely with Special Operations Forces around the world. I’ll give you, though, just this one example from Central Africa, where we are working together to help our African partners pursue Joseph Kony and the Lord’s Resistance Army. In fact, they were on the ground a few months before our troops arrived, building relationships in local communities. And because of their work, village chiefs and other leaders are actively encouraging defections from the Lord’s Resistance Army. Just a few weeks ago, our civilians and troops together helped one community set up its own radio station that is now broadcasting “come home” messages to the fighters. Our diplomats also saw that the UN staff in the region could be useful partners. So they worked through our team in Washington and New York to obtain new authorities for the UN officials on the ground and then link them up directly with our Special Operations Forces to share expertise and improve coordination. Now, this mission isn’t finished yet, but you can begin to see the potential when soldiers and diplomats live in the same camps and eat the same MREs. That is smart power in action.
Here’s another example. We know we need to do a better job contesting the online space, media websites and forums where al-Qaida and its affiliates spread their propaganda and recruit followers. So at the State Department, we’ve launched a new interagency Center for Strategic Counterterrorism Communications. It’s housed at the State Department, but it draws on experts from the intelligence community and the Defense Department, including Special Operations Forces.
The nerve center in Washington is linking up to military and civilian teams around the world and serving as a force multiplier for our embassies’ communications efforts. Together, we are working to pre-empt, discredit, and outmaneuver extremist propagandists. A digital outreach team of tech savvy specialists – fluent in Urdu, Arabic, Somali – is already patrolling the web and using social media and other tools to expose the inherent contradictions in al-Qaida’s propaganda and also bring to light the abuses committed by al-Qaida, particularly the continuing brutal attacks on Muslim civilians.
For example, a couple of weeks ago, al-Qaida’s affiliate in Yemen began an advertising campaign on key tribal web sites bragging about killing Americans and trying to recruit new supporters. Within 48 hours, our team plastered the same sites with altered versions of the ads that showed the toll al-Qaida attacks have taken on the Yemeni people. And we can tell that our efforts are starting to have an impact, because we monitor the extremists venting their frustration and asking their supporters not to believe everything they read on the Internet. (Applause.)
Now, this kind of ideological battle is slow and incremental, but I think it’s critical to our efforts, because what sustains al-Qaida and its terrorist affiliates is the steady flow of new recruits. They replace the terrorists you kill or capture so that they can plan new attacks. This is not about winning a popularity contest, but it is a simple fact that achieving our objectives is easier with more friends and fewer enemies. And I believe passionately that the truth is our friend. Exposing the lies and evil that rests at the heart of the terrorist narrative is absolutely to our advantage.
Now, we’ve also changed the way we do business on the civilian side to be better partners to you in the military. As part of our reorganization, we’ve created a full Counterterrorism Bureau at the State Department that is spearheading a diplomatic campaign around the world to increase local capacity of governments and to deny terrorists the space and financing they need to plan and carry out attacks.
This fits right in with the purpose of this conference: deepening international cooperation against terrorism and other shared challenges. As the threat from al-Qaida becomes more diffuse and distributed, shifting from the core to the affiliates, it is even more important to forge close ties with the governments and communities on the front lines and to help build up their counterterrorism capacity. After all, they often are better positioned than we are to provide services to their people, disrupt plots, and prosecute extremists, and they certainly often bear the brunt of terrorist attacks. So we need to build an international counterterrorism network that is as nimble and adaptive as our adversaries’. Admiral McRaven helped establish the NATO Special Operations Forces Coordination Centre, so I know he understands how important this is.
Each year, the State Department trains nearly 7,000 police, prosecutors, and counterterrorism officials from more than 60 countries, including frontline states like Yemen and Pakistan. We’re expanding our work with civil society organizations in specific terrorist hotspots – particular villages, prisons, and schools – to try to disrupt the process of radicalization by creating jobs, promoting religious tolerance, amplifying the voices of the victims of terrorism.
This whole effort goes hand-in-glove with the work of Special Operations Forces to train elite troops in places like the Philippines, Colombia, and Afghanistan under the Army Special Forces motto: By, with, and through. You’re doing this in one form or another in more than 100 countries around the world. And this work gives you a chance to develop a deeper understanding of local culture and customs, to learn the human domain as well as the physical terrain.
I’m impressed by the work of your Cultural Support Teams, highly-trained female Special Operations Forces who engage with local populations in sensitive areas like Afghanistan. This is part of our National Action Plan on Women, Peace, and Security that was developed jointly by the Departments of State, Defense, and others to capitalize on the contributions women everywhere can make to resolving conflicts and improving security. Around the world today, women are refusing to sit on the sidelines while extremism undermines their communities, steals their sons, kills their husbands, and destroys family after family. (Applause.) They’re joining police forces in Afghanistan. They’re writing newspaper articles in Yemen. They’re forming organizations such as Sisters Against Violent Extremism that has now spread to 17 countries. And we are committed to working with these women and doing everything we can to support their efforts as well.
We have to keep our international cooperation going and growing at every level. Next week I’ll be heading to Europe, and I’ll end up in Istanbul for the second meeting of the new Global Counterterrorism Forum, which we helped launch last year. Turkey and the United States serve as the founding co-chairs, and we’ve been joined by nearly 30 other nations. Together, we’re working to identify threats and weaknesses like porous borders, unchecked propaganda, and then devise solutions and mobilize resources. For example, the UAE has agreed to host a new center to develop best practices for countering extremism and radicalization.
Now, some of you in this room have come great distances to be here because you understand that we need a global effort to defeat a global terrorist network. And I thank you for that recognition and for your commitment.
I want to say just a final word about American Special Forces and to thank the admiral and every member of the United States Special Operations Forces who are here today – Army Rangers and Special Forces soldiers, Navy SEALs and Marine special operators, Air Force commandos, every one of you. So much of what you do, both the tremendous successes and the terrible sacrifices, will never be known by the citizens we serve. But I know what you do, and so do others who marvel and appreciate what it means for you to serve.
We’ve just passed the one-year anniversary of the raid that killed Usama bin Ladin. (Applause.) And I well remember those many hours in the Situation Room, the small group that was part of the planning and decision-making process with Admiral McRaven sitting there at the table with us. And I certainly remember that day. We were following every twist and turn of that mission. It was a day of stress and emotion, concern and commitment. I couldn’t help but think of all the people that I represented as a senator from New York serving on 9/11 and how much they and all of us deserved justice for our friends and our loved ones. I was thinking about America and how important it was to protect our country from another attack. But mostly, I was thinking of the men in the helicopters, praying for their safety as they risked their lives on that moonless Pakistani night.
And one thing that I am always proud of and that I hope is conveyed to our visitors and partners around the world: When you meet our special operators or when you meet members of our military or our diplomats and development experts, you will see every shade of skin color, every texture of hair, every color of eye. And if you spend a little time talking and getting to know that man or woman, you will find different parentage, different ethnicity, different religions, because we are Americans. And as Americans, we have a special opportunity and obligation in this interdependent, interconnected world to stand up for the universal rights and dignity of every person; to protect every man, woman, and child from the kind of senseless violence that terrorism inflicts; and also, frankly, to model.
In many places where we go, I as a Secretary of State or our special forces as members of our military, we see ancient disputes between tribes, ethnicities, religions, sex of the same religion, men and women. Just about every possible category is used all too often to separate people instead of finding common ground. If we have learned nothing in the last decade, we should certainly have learned that the terrorists are equal opportunity killers. They want to inflict terror on everyone who does not see the world from their particular narrow, outdated, dead-end worldview.
When you are pursuing a mission in partnership or on behalf of your own country, let us remember that we are on the right side of history. We are on the side of right. Your service is making the world safer for people to be who they are, to live their lives in peace and harmony. That is going to be the challenge of the 21st century. Will we once and for all recognize our common humanity and stand together against the forces of darkness or not? I’m betting we will. And I think it’s a pretty good bet, knowing that our Special Operations Forces and their partners are at the point of that spear.
Thank you for all that you do, not only to keep us safe and protect our ways of life but to demonstrate unequivocally that the world will not tolerate being undermined by those who refuse to recognize that we are truly one world of humanity that deserves the opportunity to pursue our rights and opportunities for a better life. I am very proud to be here to thank you. Thank you for keeping our nation safe and strong. Thank you for working to keep other nations safe and strong. Thank you for helping us build the world that our children deserve.
Thank you all very much. (Applause.)
MODERATOR: Ladies and gentlemen, the commander will now present our guest of honor with a token of our appreciation.
ADM MCRAVEN: Madam Secretary, a small token of our appreciation for joining us here tonight. This is, as you quickly noted, our version of Excalibur, the sword and the stone. And of course, as legend has it, only the wisest and the bravest can pull the sword from the stone. My guess is it will come out easily in your hand. So thank you very much, ma’am, for joining us here tonight. Thank you very much.
SECRETARY CLINTON: Thank you so much, Admiral. (Applause.)
Video – Barely legal – Uncensored – FEMEN Bare All in Kiev Protest
The Nazi Secret Weapons Project – Full Movie
Nazi Technology – Full Movie by the History Channel
Hitler’s Secret Science – Full Movie
Sinking Hitlers Supership – Full Movie – National Geographic
CONFIDENTIAL – Measuring the Human Factor of Cyber Security
DOWNLOAD THE ORGINAL DOCUMENT HERE
The Most Courageous Raid of WWII – BBC – Full Movie
Lord Ashdown, a former special forces commando, tells the story of the ‘Cockleshell Heroes’, who led one of the most daring and audacious commando raids of World War II.
In 1942, Britain was struggling to fight back against Nazi Germany. Lacking the resources for a second front, Churchill encouraged innovative and daring new methods of combat. Enter stage left, Blondie Hasler.
With a unit of twelve Royal Marine commandos, Major Blondie Hasler believed his ‘cockleshell’ canoe could be effectively used in clandestine attacks on the enemy. Their brief was to navigate the most heavily defended estuary in Europe, to dodge searchlights, machine-gun posts and armed river-patrol craft 70 miles downriver, and then to blow up enemy shipping in Bordeaux harbour.
Lord Ashdown recreates parts of the raid and explains how this experience was used in preparing for one of the greatest land invasions in history, D-day.
Rise And Fall Of The Third Reich – Full Movie
Rise And Fall Of The Third Reich
Escape from Sobibor – Full Movie
Escape from Sobibor tells the story of the Jews who could escape from the most secret camp of the German during WW II: Sobibor
Protest – FEMEN rings the bell: Naked activists defend women’s right for Abortion
Cryptome – Person Search in Large-Area Video Spying
DOWNLOAD THE ORGINAL DOCUMENT HERE
Uncensored – FEMEN Euro Cup Protest Video
CONFIDENTIAL – Deloitte Study on Economic Impact of the NATO Summit on the City of Chicago

The following study was commissioned by World Business Chicago, the parent organization of the group hosting the upcoming NATO Summit. The study estimates an injection of $128 million into the local economy of Chicago as a result of the summit. Economists have questioned the accuracy of these numbers, which do not take into account a number of factors including potential damage to the city as well as widespread business closures in and around downtown Chicago.
On May 20-21, 2012, Chicago will host the 25th North Atlantic Treaty Organization (NATO) Summit – the first NATO Summit in the U.S. held outside of Washington, DC. Delegations from 28 NATO Member Countries, 24 International Security Assistance Force (ISAF) Partner Countries, and six other nations and international organizations will participate in the Summit. The Summit will bring economic benefits in the form of spending, tax revenues, employment, hotel guests, tourism, and broader global attention. Over 7,500 delegates and 7,300 staff, press, and other dignitaries are expected to attend the Summit. In addition, planning for the Summit prompted visits and spending by delegations during advance trips to Chicago. Building on the momentum of the Summit, many Chicago organizations have planned events that will generate additional economic impacts for the City. These ancillary events are expected to draw thousands of additional speakers, staff, attendees, and members of the media.
The scope of this analysis is limited to the City of Chicago proper, and all impacts described refer to the City and not to the larger Cook County, Chicago Metropolitan Statistical Area, or the State of Illinois.
Summary:
- The Summit and its planning phases will inject an estimated $123.0 million into the City of Chicago economy; the City will receive over 18,300 Summit attendees and staff, contributing more than 44,000 room nights.
- Ancillary events will add an estimated $5.2 million, 2,900 additional out-of-town visitors, and more than 5,300 room nights to the City of Chicago economy.
- The City will accrue an additional $3.0 million in fiscal impacts through tax receipts. This does not include any State or County taxes.
- In total, the Summit will result in an estimated $128.2 million in total impacts to the City of Chicago, $3.0 million in local tax revenues, over 21,200 visitors, 49,300 hotel nights, and close to 2,200 temporary jobs in the City of Chicago. These impacts are summarized in Figure 1 above.
In addition to the quantitative impacts described in this report, Chicago is likely to experience other, less tangible effects from the Summit. These include immediate and long term international attention, reinforcement of Chicago’s brand as a world class city, and elevation of Chicago’s role as host for future global events. At an international event of this scale, protests or other unscheduled disruptions may also occur, which could result in mixed media attention; however, the value of exposure is difficult to estimate reliably and was not within the scope of this analysis.
DOWNLOAD THE ORIGINAL DOCUMENT HERE
Cryptome unveils Drone Crew Photos
|
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict110.jpg) US Air Force (USAF) maintenance personnel assigned to the 12th Expeditionary Reconnaissance Squadron (ERS), check the maintenance log for a RQ-4A Global Hawk high-altitude, long-endurance unmanned aerial reconnaissance system while preparing for a mission at a forward location, while deployed in support of Operation ENDURING FREEDOM. Pictured left-to-right, USAF (Major) Greg Hataway, Staff Sergeant (SSGT) Kelvin Rasor, and MAJ John D’ortona. Photographer’s Name: SSGT Reynaldo Ramon, USAF. Date Shot: 6/30/2002 US Air Force (USAF) maintenance personnel assigned to the 12th Expeditionary Reconnaissance Squadron (ERS), check the maintenance log for a RQ-4A Global Hawk high-altitude, long-endurance unmanned aerial reconnaissance system while preparing for a mission at a forward location, while deployed in support of Operation ENDURING FREEDOM. Pictured left-to-right, USAF (Major) Greg Hataway, Staff Sergeant (SSGT) Kelvin Rasor, and MAJ John D’ortona. Photographer’s Name: SSGT Reynaldo Ramon, USAF. Date Shot: 6/30/2002 |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict107.jpg) Chuck Gardner, systems engineer(front), and Patrick Didier, senior crew technician, both from Northrop Grumman Ryan Aeronautical Center, check the systems on a Global Hawk unmanned aerial vehicle after its arrival at Langley Air Force Base, Va., June 21, 2001. The aircraft flew non-stop from Edwards Air Force, California in support of the Supreme Allied Commander, Atlantic (SACLANT) Seminar taking place at Langley. (Photo by TSgt Jack Braden) (Released). Date Shot: 6/21/2001 Chuck Gardner, systems engineer(front), and Patrick Didier, senior crew technician, both from Northrop Grumman Ryan Aeronautical Center, check the systems on a Global Hawk unmanned aerial vehicle after its arrival at Langley Air Force Base, Va., June 21, 2001. The aircraft flew non-stop from Edwards Air Force, California in support of the Supreme Allied Commander, Atlantic (SACLANT) Seminar taking place at Langley. (Photo by TSgt Jack Braden) (Released). Date Shot: 6/21/2001 |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict106.jpg) Sitting at the controls, Maj. George Barth, a pilot from the 31st Test and Evaluation Squadron, Edwards Air Force Base, Calif., flies the Global Hawk May 14, 2001, from inside the Mission Control Element, at Edinburgh Air Force Base, Australia, in support of Exercise Tandem Thrust. The Global Hawk is a jet powered Unmanned Aerial Vehicle (UAV) designed as a Reconnaissance and Surveillance vehicle with a wing span equal to a Boeing 737, flying at altitudes of up to 65,000 feet for more than 24 hours and capable of searching an area of more than 40,000 square miles. The Global Hawk is deployed to Australia from April to June 2001, flying more than a dozen missions. These missions will include sorties in support of Tandem Thrust as well as maritime, littoral, land surveillance and stand off reconnaissance capabilities. The Global Hawk completed its first successful maiden flight in February 1998. Currently there are five U.S. Air Force Global Hawks which have logged over 60 flights and have clocked more than 600 hours, with it’s biggest challenge to date the non-stop Trans-Pacific flight from Edwards to Edinburgh. Tandem Thrust 2001 is a combined U.S., Australian and Canadian military training exercise. This biannual exercise is being held in the vicinity of Shoalwater Bay training area, Queensland, More than 27,000 soldiers, sailors, airmen and marines are participating, with Canadian units taking part as opposing forces. The purpose of Exercise Tandem Thrust is to train for crisis action planningand execution of contingency response operations. (U.S. Air Force photo by Staff Sgt. Jeremy T. Lock) (Released). Date Shot: 5/14/2001 Sitting at the controls, Maj. George Barth, a pilot from the 31st Test and Evaluation Squadron, Edwards Air Force Base, Calif., flies the Global Hawk May 14, 2001, from inside the Mission Control Element, at Edinburgh Air Force Base, Australia, in support of Exercise Tandem Thrust. The Global Hawk is a jet powered Unmanned Aerial Vehicle (UAV) designed as a Reconnaissance and Surveillance vehicle with a wing span equal to a Boeing 737, flying at altitudes of up to 65,000 feet for more than 24 hours and capable of searching an area of more than 40,000 square miles. The Global Hawk is deployed to Australia from April to June 2001, flying more than a dozen missions. These missions will include sorties in support of Tandem Thrust as well as maritime, littoral, land surveillance and stand off reconnaissance capabilities. The Global Hawk completed its first successful maiden flight in February 1998. Currently there are five U.S. Air Force Global Hawks which have logged over 60 flights and have clocked more than 600 hours, with it’s biggest challenge to date the non-stop Trans-Pacific flight from Edwards to Edinburgh. Tandem Thrust 2001 is a combined U.S., Australian and Canadian military training exercise. This biannual exercise is being held in the vicinity of Shoalwater Bay training area, Queensland, More than 27,000 soldiers, sailors, airmen and marines are participating, with Canadian units taking part as opposing forces. The purpose of Exercise Tandem Thrust is to train for crisis action planningand execution of contingency response operations. (U.S. Air Force photo by Staff Sgt. Jeremy T. Lock) (Released). Date Shot: 5/14/2001 |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict105.jpg) Portrait of Systems Test Engineer Chuck Gardner, (left), and Avionics Technician Brent Bremer, from Northrop Grumman Edwards Air Force Base, California, as they pre-flight the RQ-4A Global Hawk at RAAF Base Edinburgh, Adelaide, Australia, in support of Exercise TANDEM THRUST 01. Able to cover more than 40,000 square miles, the jet powered Unmanned Aerial Vehicle (UAV) RQ-4A Global Hawk has a wing span of 116 feet, equal to a Boeing 737, able to fly up to 65,000 feet and loiter for more than 24 hours. The Global Hawk deployed to Australia from April to June 2001, flying more than a dozen missions. This Global Hawk completed its biggest challenge to date the non-stop Trans-Pacific flight from Edwards to Edinburgh to support TANDEM THRUST 01. TANDEM THRUST 2001 a combined US, Australian, and Canadian military exercise for crisis action planning and execution of contingency response operations. The biannual exercise is held in the vicinity of Shoalwater Bay training area in Queensland, Australia. Photographer’s Name: SSGT JEREMY LOCK, USAF. Date Shot: 5/13/2001 Portrait of Systems Test Engineer Chuck Gardner, (left), and Avionics Technician Brent Bremer, from Northrop Grumman Edwards Air Force Base, California, as they pre-flight the RQ-4A Global Hawk at RAAF Base Edinburgh, Adelaide, Australia, in support of Exercise TANDEM THRUST 01. Able to cover more than 40,000 square miles, the jet powered Unmanned Aerial Vehicle (UAV) RQ-4A Global Hawk has a wing span of 116 feet, equal to a Boeing 737, able to fly up to 65,000 feet and loiter for more than 24 hours. The Global Hawk deployed to Australia from April to June 2001, flying more than a dozen missions. This Global Hawk completed its biggest challenge to date the non-stop Trans-Pacific flight from Edwards to Edinburgh to support TANDEM THRUST 01. TANDEM THRUST 2001 a combined US, Australian, and Canadian military exercise for crisis action planning and execution of contingency response operations. The biannual exercise is held in the vicinity of Shoalwater Bay training area in Queensland, Australia. Photographer’s Name: SSGT JEREMY LOCK, USAF. Date Shot: 5/13/2001 |
|
Eichmann (2007) – Full Movie
Adolf Eichmann was a German Nazi and SS-Obersturmbannführer (Lieutenant Colonel) and one of the major organizers of the Holocaust. Because of his organizational talents and ideological reliability, Eichmann was charged by Obergruppenführer (General) Reinhard Heydrich with the task of facilitating and managing the logistics of mass deportation of Jews to ghettos and extermination camps in German-occupied Eastern Europe.
Read the rest at Wikipedia http://en.wikipedia.org/wiki/Adolf_Eichmann
Conspiracy – Full BBC Movie about the notorious “Wannsee Conference”
Conspiracy “Wansee Conference” of January 1942 was the real beginning of the Holocaust In the sublime surroundings of a German country house, the assembled mingle for drinks, enjoy a first class buffet lunch and debate whether execution or sterilisation is the most efficient option of eliminating an entire race of people.
Is about the bureacratic genesis of the Holocaust. It shows, in more or less real time, a fictionalized version of a real-life conference of 15 officials from the SS/SD, Gestapo, Railway Ministry, Interior Ministry, Government General, and Ministry of Justice, which was chaired by Reinhard Heydrich and organized by Adolf Eichmann.
As a movie, however, it is really a study in the essential amorality of bureacracy and, to use a tired phrase, the banality of evil.
Credit must be given to Kenneth Branagh who propels the entire piece with one of the best portrayals on screen in memory. He is utterly convincing in the role of a man who epitomises the classic definition of evil: not just the doing of wrong, but the perversion of the human spirit so that it no longer has any perception of the good.
http://en.wikipedia.org/wiki/Kenneth_Branagh
http://en.wikipedia.org/wiki/Stanley_Tucci
http://en.wikipedia.org/wiki/Colin_Firth
http://www.imdb.com/title/tt0266425/
http://en.wikipedia.org/wiki/Conspiracy_(2001_film)
http://en.wikipedia.org/wiki/Nazi
http://en.wikipedia.org/wiki/Holocaust
http://en.wikipedia.org/wiki/BBC
http://en.wikipedia.org/wiki/HBO_Films
Cryptome unveils Drone Photos
|
|
|
Superman: Requiem – Official – Full Movie – Fan Made
Official uncut theatrical version of Gene Fallaize’s ‘Superman: Requiem’ fan film, starring Martin Richardson, Stacy Sobieski, Paul Khanna, Serena Lorien, and Jack O’Halloran.
Superman is the world’s greatest super hero, and law enforcement across the globe has come to rely on him to deal with some of the major tasks that face society. When the Man of Steel loses some of his powers after an evil villain attacks him with Kryptonite though, he must overcome his obstacles and prove he really is a super man.
Superman: Requiem is a high-value fan-film that depicts the life of Superman several years after the events of Superman Returns, and takes into account the events of Superman (1978), Superman II (1980) and Superman Returns (2006), and focuses on an event by an evil villain who attempts to make Superman lose his powers.
The film was conceived in 2011 by producer Gene Fallaize who decided to he was going to make an independent Superman fan-film, and wrote the first draft of the script in less than a week. Fallaize brought Tony Cook on board to co-produce the project to allow him the freedom and time to direct the project.
The film was released globally online on 11.11.11 after a red carpet World Premiere in London’s Odeon Covent Garden.
For more information visit http://www.themanofsteelisback.com or facebook.com/supermanrequiem
CONFIDENTIAL – DHS Domestic Terrorism and Homegrown Violent Extremism Lexicon
The following document is an updated version of a 2009 “Domestic Extremism Lexicon” produced by the Department of Homeland Security’s Office of Intelligence and Analysis. The list of terms has been substantially reduced and does not include a number of controversial terms from the first version, such as “alternative media” and “direct action.” This version was obtained and published by a blogger associated with PJ Media.
![]()
![]()
![]()
Spider Man – Full Movie
When bitten by a genetically modified spider, a nerdy, shy, and awkward high school student gains spider-like abilities that he eventually must use to fight evil as a superhero after tragedy befalls his family.
TOP-SECRET – Open Source Center Social Media Accounts Promoting Jihadist Attacks in Syria

OSC has recently observed two Facebook pages and a popular blog that promote the recently established Syrian jihadist group Al-Nusrah Front and jihadist attacks in Syria. As these pages are the top results for a Google search in Arabic of “Al-Nusrah Front,” they are likely to be visited by Arabic-speaking Internet users interested in the group. Observed activity on these pages suggests expanding interest in Al-Nusrah Front.
The two Facebook pages — Insaru Jabhat al-Nusrah li-Ahl al-Sham and Jabhat al-Nusrah l-Ahal al-Sham – and a Syria-focused jihadist blog — Ansar al-Sham Network — have become the top three Arabic-language Google search results for “Al-Nusrah Front,” a Syrian jihadist group first announced in Januaryi that has claimed several attacks against regime targets there. This suggests the pages are becoming primary locations for Arabic-language materialglorifying Al-Nusrah Front.
- All three pages host Al-Nusrah Front’s official statements and the Facebook pages have been observed to further promote it by posting graphics, banners, and video compilations devoted to it.
- The pages all attempt to incite anger at the Al-Asad regime, with Insaru Jabhat al-Nusrah li-Ahl al-Sham posting content such as photographs of children reportedly killed in Syria and Jabhat al-Nusrah l-Ahal al-Sham and Ansar al-Sham Network prominently displaying articles and videos on Syrian “martyrs.”
- The Facebook pages also encourage attacks in Syria, by hosting basic military training materials, such as an instructional sniper video found on Insaru Jabhat al-Nusrah li-Ahl al-Sham. Similarly, Jabhat al-Nusrah l-Ahal al-Sham posts instructions for detonating a bomb without using a telephone trigger.
Facebook Activity Suggests Increasing Interest in Al-Nusrah Front
Although, thus far, users have indicated approval of the Facebook pages — by clicking the “like” buttons — relatively few times, the trend is increasing, suggesting heightened interest in Al-Nusrah Front. Statistics on readership of the pages are not available.
- As of 2 May, Insaru Jabhat al-Nusrah li-Ahl al-Sham readers have clicked “like” 481 times, and Jabhat al-Nusrah l-Ahal al-Sham users have done so 344 times.
- However, marking a substantial increase, during the week ending on 27 April, Insaru Jabhat al-Nusrah li-Ahl al-Sham received 143 “likes,” with 202 “people talking about” it. In contrast, during the week ending on 30 March –the earliest period for which data is available – the page received only 47 “likes,” with 60 users “talking about it.”
- Jabhat al-Nusrah l-Ahal al-Sham has experienced similar growth in activity. During the week ending on 27 April, it received 57 “likes” with 48 “people talking about” it, up substantially from 25 “likes” and 25 “people talking about it” in the week ending on 30 March.
The blog Ansar al-Sham Network reported between 33,000 and 78,000 views between 27 April and 5 May. Although it is not clear how the site calculates traffic, it appears to count visits on a daily, rather than cumulative basis. This high viewership offers further evidence of online interest in Al-Nusrah Front.
Unveiled – Opposition Parties Claim Karzai is Strengthening the Taliban to Consolidate Political Power

Dr. Abdullah Abdullah, center, head of the National Coalition of Afghanistan (NCA). Prominent members of the NCA and other rival parties have stated that they believe Afghan President Hamid Karzai is strengthening the Taliban in an effort to bolster his own power. Photo via Ariana News.
Public Intelligence
A recent report from the Director of National Intelligence’s Open Source Center (OSC) indicates that opposition parties increasingly believe that Afghan President Hamid Karzai is strengthening the Taliban in an effort to bolster his own political power. The report also assesses that members of Karzai’s camp may be willing to work with militant forces to prevent rival political parties from gaining influence.
Prominent members of two major opposition parties, the National Coalition of Afghanistan (NCA) and the National Front of Afghanistan (NFA), have expressed concern about Karzai’s connection with Taliban militants. At a meeting of the NFA leadership in Kabul in early April, former Vice President Ahmad Zia Massoud warned that the government is “working toward strengthening the terrorist groups” and that this being facilitated by “senior government leaders” who are “trying to facilitate the penetration of the Taliban into the security forces.”
A prominent member of the NCA former parliament speaker Mohmmad Yunos Qanuni recently stated in an interview with a Afghan news outlet that “Karzai’s thoughts are more inclined toward the Taliban than our lot [anti-Taliban forces],” adding that “individuals with pro-Taliban orientations have more of an impact on the president’s mind.” Qanuni made similar claims in an address to the youth wing of the NCA in April, warning that in an effort to perpetuate their rule, the government leadership is trying to “facilitate the return of terrorism and the Taliban.”
The author of the OSC report assesses that the “Afghan Government’s backing of the Taliban’s opening of an office in Qatar and the Afghan ambassador to Pakistan’s suggestive remarks, in a 3 April interview with UK’s Guardian newspaper, that negotiations would lead to the Taliban’s participation in presidential elections suggests that at least some in Karzai’s camp may be willing to court the militants to countervail the anti-Taliban forces’ influence.” The report also states that a merger between the NCA and NFA is likely before the 2014 elections, creating “two political, and possibly even militarized, rival clusters” that could have negative effects on the future stability of Afghanistan.
The Transporter 2 (2005) – Full Movie
TOP-SECRET from the FBI – Seattle Financial Advisor Indicted in $46 Million Investment Fraud Scheme
A long-time Seattle financial advisor was indicted today by a federal grand jury with 23 criminal counts, including wire fraud, money laundering and investment advisor fraud, announced U.S. Attorney Jenny A. Durkan. Mark F. Spangler, 57, of Seattle is accused of diverting investor money from accounts he managed to risky start-up ventures in which he or his investment firm had an ownership interest. Spangler allegedly diverted more than $46 million to two companies, one of which is now shut down after failing to generate any positive revenue. Those who invested in the funds managed by Spangler, as part of The Spangler Group Inc.(TSG), were not told that their money was being invested in risky start-up companies. Spangler and several of his companies went into receivership last year. Today, the Securities and Exchange Commission filed a civil suit against Spangler as well. Spangler is scheduled to appear in U.S. District Court in Seattle on May 18, 2012 at 2:30.
“The Department of Justice is making the prosecution of financial fraud a top priority,” said U.S. Attorney Durkan. “These investors lost millions to a man they trusted to safeguard their resources. We are working closely with the SEC to ensure Mr. Spangler is held accountable for his fraud.”
The six investors described in the indictment were told their funds were conservatively invested in publicly traded companies and in bonds. Spangler allegedly provided them misleading statements over time, falsely describing the value of their accounts and how the money was invested. When investors sought to liquidate their holdings, Spangler was unable to provide them any funds, because the money had been funneled to the high risk start-up ventures that were not profitable.
According to the indictment, Spangler established a variety of funds as early as 1998 to pool investor money to buy publicly traded stocks and bonds. Spangler co-founded the two startup companies in the early 2000s—Tamarac Inc. in 2000 and TeraHop Networks Inc. in 2002. Tamarac Inc. is headquartered in Seattle and provides software to financial planners. TeraHop Networks Inc. is headquartered in Georgia and manufactured wireless devices used to monitor the location and activity of people and physical assets such as construction equipment. TeraHop has ceased operation. Spangler not only failed to disclose to his investors that he was diverting significant amounts of their funds to TeraHop and Tamarac, but he also failed to disclose that he was involved in the management of these companies, had an ownership interest in Tamarac, and was receiving payments from both companies. The indictment contains an order of forfeiture, which will be used to try to recover assets for the investors.
The case is being investigated by the FBI and Internal Revenue Service Criminal Investigation (IRS-CI).
The case is being prosecuted by Assistant United States Attorneys Mike Lang and Carl Blackstone.
For additional information please contact Emily Langlie, Public Affairs Officer for the United States Attorney’s Office, at (206) 553-4110 or Emily.Langlie@USDOJ.Gov.
Jason Statham – Killer Elite – Full Movie
RED ANGEL – FULL MOVIE
Resident Evil Apocalypse – Full Movie
Resident Evil Degeneration – Full Movie
Resident Evil 4 – Feature Film
Uncensored – Resident Evil Extinction – Full Movie HD
One Million Years BC -Full Movie
TOP-SECRET – Open Source Center Changes in Afghan Political Landscape Leading Up to 2014

Open source reporting indicates the Afghan political landscape, presently dominated by four political groupings and a number of prominent politicians, is likely to undergo further changes in the lead-up to the presidential elections and withdrawal of ISAF forces in 2014. Differing views of the Taliban threat as ISAF withdraws is likely to help drive the realignment and consolidation of political forces. This realignment may result in two major groupings: President Hamid Karzai and allies keen on working with the Taliban versus former anti-Taliban forces and others opposed to the government’s alleged appeasement toward the militants. Such consolidation would likely lead the emerging generation of younger leaders to choose between joining one of the groupings or risk being marginalized at the national level. Four main political groupings — Karzai’s camp, the National Front of Afghanistan (NFA), the National Coalition of Afghanistan (NCA), and the Truth and Justice Party (TJP) — are currently dominating the Afghan political scene (See Appendix for more details on key figures and positions of the four groups).
- Karzai’s camp is currently the dominant group but is a tenuous alliance of convenience among elements of former anti-Taliban forces, Hezb-e Islami (HI), and the Pashtun nationalist Afghan Mellat Party (AMP).
- The NFA was launched in November 2011 by former Karzai allies who now oppose many of his policies. It features some prominent anti-Taliban figures, including Hazara leader Mohammad Mohaqeq, Uzbek leader Abdul Rashid Dostum, and former Vice President Ahmad Zia Massoud (Daily Afghanistan, 12 November 2011).
- The NCA was created in December 2011 as a successor to the Coalition for Change and Hope and is led by former Foreign Minister Abdullah Abdullah and former parliament speaker Mohmmad Yunos Qanuni. Like NFA, it opposes Karzai and features some prominent anti-Taliban leaders (Bokhdinews, 22 December 2011).
- The TJP was launched in early November 2011 by a number of former cabinet ministers and lawmakers who lost their seats in the 2010 parliamentary elections, including former Minister of Rural Development Mohammad Ihsan Zia and former Interior Minister Mohammad Hanif Atmar. It is the weakest of the four main groupings and does not oppose Karzai’s policies as strongly as the NFA or NCA. (Pajhwok Afghan News, 3 November 2011; Kabulpress, 20 November 2011).
In addition, there are a handful of prominent Afghan figures with links to some of these groupings, although currently they do not formally belong to any of them: Balkh Governor, Atta Mohammad Nur, Nangarhar Governor Gol Agha Sherzai, former intelligence chief Amrullah Saleh, Badakhshan MP Fawzia Koofi, Kabul MP Ramazan Bashardost, and Nangarhar MP Abdul Zaher Qadir.
…
Growing concerns about the Taliban threat and its role in post-2014 Afghanistan may consolidate the political landscape around two political, and possibly even militarized, rival clusters.
- A merger of the NFA and NCA at some point before or during 2014 is possible, given their similar political agendas and common anti-Taliban roots. Both groups have called for parliamentary government and elected governors and are suspicious of reconciliation with the Taliban. The differences between them seem to be mainly of a personal nature at the leadership level. Massoud indicated recently that NFA and NCA would “merge soon” to which Abdullah responded by saying that NCA “have not yet decided on merger with [NFA]” (Bokhdinews, 17, 20 January). NCA might pursue the idea of merger more favorably after Abdullah’s rotating leadership ends, since Qanuni has expressed desire for a “grand national umbrella” to confront the looming Taliban threat (Jomhornews, 1 April).
- In an 11 March gathering, former anti-Taliban leaders from a cross-section of the major political clusters, including Karzai’s camp, urged unity and even military preparedness among the anti-Taliban forces. Karzai ally MP Abdurrab Rasul Sayyaf said: “Be very careful that we should not be undermined from within under the divisive pretexts of ethnicity, region, and language; we should preserve this united body at any cost.” He warned the anti-Taliban forces not to “sit unconcerned about the future; do not be totally oblivious and unaware about today and post-2014 and thereabouts.” (Tolonews, 11 March). Massoud suggested that the anti-Taliban forces should revive their “military structures” in anticipation of ISAF withdrawal (Jabha-e Melli, 12 March).
Should the NFA and NCA unify and attract major anti-Taliban leaders among Karzai’s allies, the remainder of the Karzai camp may rely increasingly on HI and some level of cooperation even from the Taliban to remain politically relevant.
- In the context of his remarks to deny reports that the insurgent group Hezb-e Islami Gulbuddin (HIG) had severed negotiations with the government, HIG chief negotiator Ghairat Bahir effectively endorsed Karzai’s leadership by saying that “from our perspective Hamid Karzai is the president of Afghanistan” (Bokhdinews, 29 January).
- Similarly, the Afghan Government’s backing of the Taliban’s opening of an office in Qatar and the Afghan ambassador to Pakistan’s suggestive remarks, in a 3 April interview with UK’s Guardian newspaper, that negotiations would lead to the Taliban’s participation in presidential elections suggests that at least some in Karzai’s camp may be willing to court the militants to countervail the anti-Taliban forces’ influence (Hewad, 7 April; Hasht-e Sobh, 8, 9 April).
- State-run newspaper Hewad issued a strongly worded editorial against a 5 May 2011 opposition rally and approvingly quoted a former Taliban leader’s denunciatory words, perhaps portending the dichotomization of politics along pro- and anti-Taliban lines (7 May 2011).
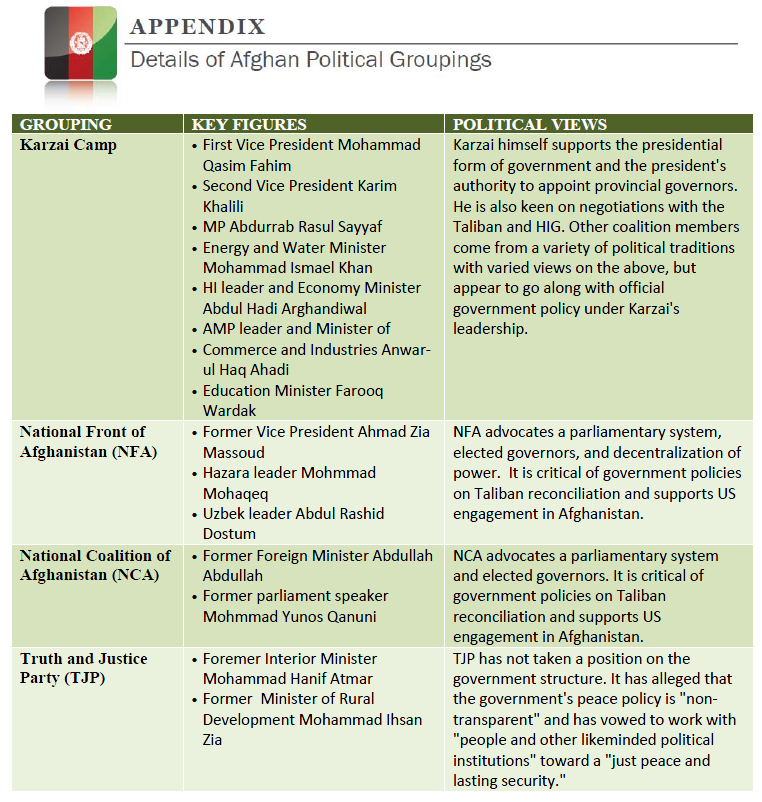
DOWNLOAD THE ORIGINAL DOCUMENT HERE














![[Image]](https://i0.wp.com/cryptome.org/2012/06/wikileaks-trap1.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012/06/wikileaks-trap2.jpg)












 “Today, with the flip of a switch, the FBI and our partners dismantled the Rove criminal enterprise. Thanks to the collective effort across the U.S. and in Estonia, six leaders of the criminal enterprise have been arrested and numerous servers operated by the criminal organization have been disabled. Additionally, thanks to a coordinated effort of trusted industry partners, a mitigation plan commenced today, beginning with the replacement of rogue DNS servers with clean DNS servers to keep millions online, while providing ISPs the opportunity to coordinate user remediation efforts.”
“Today, with the flip of a switch, the FBI and our partners dismantled the Rove criminal enterprise. Thanks to the collective effort across the U.S. and in Estonia, six leaders of the criminal enterprise have been arrested and numerous servers operated by the criminal organization have been disabled. Additionally, thanks to a coordinated effort of trusted industry partners, a mitigation plan commenced today, beginning with the replacement of rogue DNS servers with clean DNS servers to keep millions online, while providing ISPs the opportunity to coordinate user remediation efforts.” 


![[Image]](https://i0.wp.com/cryptome.org/2012/06/mcgurk-chon/chon-mcgurk-sfc.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012/06/mcgurk-chon/pict0.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012/06/mcgurk-chon/pict1.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012/06/mcgurk-chon/pict2.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012/06/mcgurk-chon/pict3.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012/06/mcgurk-chon/pict4.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012/06/mcgurk-chon/pict5.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012/06/mcgurk-chon/pict6.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012/06/mcgurk-chon/pict7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012/06/mcgurk-chon/pict8.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012/06/lulzsec-sneak-preview.jpg)







![[Image]](https://i0.wp.com/cryptome.org/2012-info/dulles-mystery/pict21.jpg)



















![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict170.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict171.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict172.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict173.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict168.jpg) Israeli soldiers control the Skylark drone during a drill on January 16, 2012 near Bat Shlomo, Israel. The Skylark can carry a camera payload of up to 1kg, has an operational ceiling of 15,000ft and allows users to monitor any designated point within a 15km radius. The Skylark unit consists of a ground control element and three drones, which provide battalion-level commanders with real-time information. Getty
Israeli soldiers control the Skylark drone during a drill on January 16, 2012 near Bat Shlomo, Israel. The Skylark can carry a camera payload of up to 1kg, has an operational ceiling of 15,000ft and allows users to monitor any designated point within a 15km radius. The Skylark unit consists of a ground control element and three drones, which provide battalion-level commanders with real-time information. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict169.jpg) A technician supporting U.S. Navy SEAL Team 18 works on a UAV, an unmanned aerial vehicle, before a demonstration of combat skills at the National Navy UDT-SEAL Museum in Fort Pierce, Florida November 11, 2011. The demonstration for the public is part of a Veteran’s Day celebration and the annual reunion at the Museum. The drone is equipped with cameras for surveillance. Reuters
A technician supporting U.S. Navy SEAL Team 18 works on a UAV, an unmanned aerial vehicle, before a demonstration of combat skills at the National Navy UDT-SEAL Museum in Fort Pierce, Florida November 11, 2011. The demonstration for the public is part of a Veteran’s Day celebration and the annual reunion at the Museum. The drone is equipped with cameras for surveillance. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict167.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict104.jpg) Adam Stock, the lead pilot for 29 Palms Unmanned Aerial Systems, out of Twentynine Palms, California, pilots a ScanEagle unmanned aerial vehicle at Fort Hunter Liggett, Calif., May 19, 2011, in support of Global Medic 2011 and Warrior 91 11-01. Global Medic is a joint field training exercise for theater aeromedical evacuation system and ground medical components designed to replicate all aspects of combat medical service support. Warrior 91 11-01 was a tactical exercise in which U.S. Service members responded to simulated enemy attacks as part of Global Medic 2011 . (U.S. Air Force photo by Staff Sgt. Donald R. Allen/Released). Date Shot: 5/19/2011
Adam Stock, the lead pilot for 29 Palms Unmanned Aerial Systems, out of Twentynine Palms, California, pilots a ScanEagle unmanned aerial vehicle at Fort Hunter Liggett, Calif., May 19, 2011, in support of Global Medic 2011 and Warrior 91 11-01. Global Medic is a joint field training exercise for theater aeromedical evacuation system and ground medical components designed to replicate all aspects of combat medical service support. Warrior 91 11-01 was a tactical exercise in which U.S. Service members responded to simulated enemy attacks as part of Global Medic 2011 . (U.S. Air Force photo by Staff Sgt. Donald R. Allen/Released). Date Shot: 5/19/2011![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict166.jpg) U.S. Soldiers with the 10th Special Forces Group fly an RQ-7B Shadow unmanned aerial vehicle at Hurlburt Field, Fla., from inside their ground control station March 7, 2011, during Emerald Warrior 2011. Emerald Warrior is an annual two-week joint/combined tactical exercise sponsored by U.S. Special Operations Command designed to leverage lessons learned from operations Iraqi and Enduring Freedom to provide trained and ready forces to combatant commanders. (U.S. Air Force photo by Staff Sgt. Andy M. Kin/Released). Date Shot: 3/7/2011
U.S. Soldiers with the 10th Special Forces Group fly an RQ-7B Shadow unmanned aerial vehicle at Hurlburt Field, Fla., from inside their ground control station March 7, 2011, during Emerald Warrior 2011. Emerald Warrior is an annual two-week joint/combined tactical exercise sponsored by U.S. Special Operations Command designed to leverage lessons learned from operations Iraqi and Enduring Freedom to provide trained and ready forces to combatant commanders. (U.S. Air Force photo by Staff Sgt. Andy M. Kin/Released). Date Shot: 3/7/2011![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict165.jpg) U.S. Airmen with the 380th Expeditionary Aircraft Maintenance Squadron prepare an RQ-4A Global Hawk unmanned aerial vehicle aircraft for takeoff at an undisclosed location in Southwest Asia Dec. 2, 2010. (U.S. Air Force photo by Staff Sgt. Eric Harris/Released). Date Shot: 12/2/2010
U.S. Airmen with the 380th Expeditionary Aircraft Maintenance Squadron prepare an RQ-4A Global Hawk unmanned aerial vehicle aircraft for takeoff at an undisclosed location in Southwest Asia Dec. 2, 2010. (U.S. Air Force photo by Staff Sgt. Eric Harris/Released). Date Shot: 12/2/2010![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict164.jpg) U.S. Airmen with the 380th Aircraft Maintenance Squadron prepare an RQ-4 Global Hawk unmanned aerial vehicle for its first launch from an undisclosed base in Southwest Asia Nov. 27, 2010. The RQ-4 was designed for intelligence, surveillance and reconnaissance. (U.S. Air Force photo by Staff Sgt. Eric Harris/Released). Date Shot: 11/27/2010
U.S. Airmen with the 380th Aircraft Maintenance Squadron prepare an RQ-4 Global Hawk unmanned aerial vehicle for its first launch from an undisclosed base in Southwest Asia Nov. 27, 2010. The RQ-4 was designed for intelligence, surveillance and reconnaissance. (U.S. Air Force photo by Staff Sgt. Eric Harris/Released). Date Shot: 11/27/2010![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict163.jpg) U.S. Marine Corps unmanned aerial vehicle (UAV) mechanics assigned to Marine Unmanned Aerial Vehicle Squadron (VMU) 3 work on an RQ-7B Shadow UAV during Enhanced Mojave Viper at Marine Corps Air Ground Combat Center Twentynine Palms, Calif., Aug. 3, 2010. Enhanced Mojave Viper is a combined exercise that prepares Marines for deployments. (U.S. Marine Corps photo by Lance Cpl. Michael C. Nerl/Released). Date Shot: 8/3/2010
U.S. Marine Corps unmanned aerial vehicle (UAV) mechanics assigned to Marine Unmanned Aerial Vehicle Squadron (VMU) 3 work on an RQ-7B Shadow UAV during Enhanced Mojave Viper at Marine Corps Air Ground Combat Center Twentynine Palms, Calif., Aug. 3, 2010. Enhanced Mojave Viper is a combined exercise that prepares Marines for deployments. (U.S. Marine Corps photo by Lance Cpl. Michael C. Nerl/Released). Date Shot: 8/3/2010![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict162.jpg) Civilian employees with Fleet Readiness Center East perform maintenance and corrosion assessments on two MQ-8B Fire Scout unmanned aerial vehicles at Marine Corps Air Station Cherry Point, N.C., May 14, 2010. (U.S. Navy photo by David R. Hooks/Released). Date Shot: 5/14/2010
Civilian employees with Fleet Readiness Center East perform maintenance and corrosion assessments on two MQ-8B Fire Scout unmanned aerial vehicles at Marine Corps Air Station Cherry Point, N.C., May 14, 2010. (U.S. Navy photo by David R. Hooks/Released). Date Shot: 5/14/2010![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict161.jpg) U.S. Air Force Master Sgt. Jennifer Oberg, background, a communications maintenance instructor, and Senior Airman Raquel Martinez, foreground, check a ground control station during training at March Air Reserve Base, Calif., April 19, 2010. Both are assigned to the 163rd Maintenance Group at March. The California Air National Guard unit is primarily involved in Predator unmanned aerial vehicle missions. (U.S. Air Force photo by Val Gempis/Released). Date Shot: 4/19/2010
U.S. Air Force Master Sgt. Jennifer Oberg, background, a communications maintenance instructor, and Senior Airman Raquel Martinez, foreground, check a ground control station during training at March Air Reserve Base, Calif., April 19, 2010. Both are assigned to the 163rd Maintenance Group at March. The California Air National Guard unit is primarily involved in Predator unmanned aerial vehicle missions. (U.S. Air Force photo by Val Gempis/Released). Date Shot: 4/19/2010![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict160.jpg) U.S. Air Force Tech. Sgt. Ron Zechman, a predator sensor operator, and Maj. Jeff Bright, a predator pilot and detachment commander of the 432nd Wing out of Creech Air Force Base, Nev., go over pre-flight check lists for an RQ-1 Predator unmanned aerial vehicle at Aeropuerto Rafael Hernandez outside Aguadilla, Puerto Rico, Jan. 28, 2010. Airmen from Creech AFB are providing 24-hour-a-day full-motion video in real time to international relief workers on the ground in order to speed humanitarian aid to remote and cut-off areas of the Haiti following the earthquake Jan. 12, 2010. (U.S. Air Force photo by Tech. Sgt. James Harper/Released). Date Shot: 1/21/2010
U.S. Air Force Tech. Sgt. Ron Zechman, a predator sensor operator, and Maj. Jeff Bright, a predator pilot and detachment commander of the 432nd Wing out of Creech Air Force Base, Nev., go over pre-flight check lists for an RQ-1 Predator unmanned aerial vehicle at Aeropuerto Rafael Hernandez outside Aguadilla, Puerto Rico, Jan. 28, 2010. Airmen from Creech AFB are providing 24-hour-a-day full-motion video in real time to international relief workers on the ground in order to speed humanitarian aid to remote and cut-off areas of the Haiti following the earthquake Jan. 12, 2010. (U.S. Air Force photo by Tech. Sgt. James Harper/Released). Date Shot: 1/21/2010![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict158.jpg) U.S. Air Force Maj. Jeff Bright, a predator pilot from the 432nd Wing out of Creech Air Force Base, Nev., goes over a pre-flight check list for an RQ-1 Predator unmanned aerial vehicle at Aeropuerto Rafael Hernandez outside Aguadilla, Puerto Rico, Jan. 28, 2010. Airmen from Creech AFB are providing 24-hour-a-day full-motion video in real time to international relief workers on the ground in order to speed humanitarian aid to remote and cut-off areas of the Haiti following the earthquake Jan. 12, 2010. (U.S. Air Force photo by Tech. Sgt. James Harper/Released). Date Shot: 1/21/2010
U.S. Air Force Maj. Jeff Bright, a predator pilot from the 432nd Wing out of Creech Air Force Base, Nev., goes over a pre-flight check list for an RQ-1 Predator unmanned aerial vehicle at Aeropuerto Rafael Hernandez outside Aguadilla, Puerto Rico, Jan. 28, 2010. Airmen from Creech AFB are providing 24-hour-a-day full-motion video in real time to international relief workers on the ground in order to speed humanitarian aid to remote and cut-off areas of the Haiti following the earthquake Jan. 12, 2010. (U.S. Air Force photo by Tech. Sgt. James Harper/Released). Date Shot: 1/21/2010![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict157.jpg) Predator pilot Jonathon Johnson, an air interdiction agent for the U.S. Customs and Border Protection, enters the ground control station for the Predator B unmanned aerial systems (UAS) April 3, 2009, at the U.S. Customs and Border Protection UAS operations center at Grand Forks Air Force Base, N.D. The Predator is a new high-tech tool being used to help in flood fight planning for the first time in North Dakota. It has been recording flood imagery, which is being used for positioning of National Guard flood fighting personnel and resources. (DoD photo by Senior Master Sgt. David H. Lipp, U.S. Air Force/Released). Date Shot: 4/3/2009
Predator pilot Jonathon Johnson, an air interdiction agent for the U.S. Customs and Border Protection, enters the ground control station for the Predator B unmanned aerial systems (UAS) April 3, 2009, at the U.S. Customs and Border Protection UAS operations center at Grand Forks Air Force Base, N.D. The Predator is a new high-tech tool being used to help in flood fight planning for the first time in North Dakota. It has been recording flood imagery, which is being used for positioning of National Guard flood fighting personnel and resources. (DoD photo by Senior Master Sgt. David H. Lipp, U.S. Air Force/Released). Date Shot: 4/3/2009![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict155.jpg) Predator pilot Jonathon Johnson, left, an air interdiction agent for the U.S. Customs and Border Protection, pilots a Predator aircraft in the ground control station for the Predator B unmanned aerial systems (UAS) April 3, 2009, at the U.S. Customs and Border Protection UAS operations center at Grand Forks Air Force Base, N.D., as UAS instructor pilot Bob Concannon operates the sensor controls. The Predator is a new high-tech tool being used to help in flood fight planning for the first time in North Dakota. It has been recording flood imagery, which is being used for positioning of National Guard flood fighting personnel and resources. (DoD photo by Senior Master Sgt. David H. Lipp, U.S. Air Force/Released). Date Shot: 4/3/2009
Predator pilot Jonathon Johnson, left, an air interdiction agent for the U.S. Customs and Border Protection, pilots a Predator aircraft in the ground control station for the Predator B unmanned aerial systems (UAS) April 3, 2009, at the U.S. Customs and Border Protection UAS operations center at Grand Forks Air Force Base, N.D., as UAS instructor pilot Bob Concannon operates the sensor controls. The Predator is a new high-tech tool being used to help in flood fight planning for the first time in North Dakota. It has been recording flood imagery, which is being used for positioning of National Guard flood fighting personnel and resources. (DoD photo by Senior Master Sgt. David H. Lipp, U.S. Air Force/Released). Date Shot: 4/3/2009![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict154.jpg) Predator pilot and instructor Michael Nelson, of the University of North Dakota, pilots a Predator in the ground control station for the Predator B unmanned aerial systems (UAS) April 3, 2009, at the U.S. Customs and Border Protection UAS operations center at Grand Forks Air Force Base, N.D. The Predator is a new high-tech tool being used to help in flood fight planning for the first time in North Dakota. It has been recording flood imagery, which is being used for positioning of National Guard flood fighting personnel and resources. (DoD photo by Senior Master Sgt. David H. Lipp, U.S. Air Force/Released). Date Shot: 4/3/2009
Predator pilot and instructor Michael Nelson, of the University of North Dakota, pilots a Predator in the ground control station for the Predator B unmanned aerial systems (UAS) April 3, 2009, at the U.S. Customs and Border Protection UAS operations center at Grand Forks Air Force Base, N.D. The Predator is a new high-tech tool being used to help in flood fight planning for the first time in North Dakota. It has been recording flood imagery, which is being used for positioning of National Guard flood fighting personnel and resources. (DoD photo by Senior Master Sgt. David H. Lipp, U.S. Air Force/Released). Date Shot: 4/3/2009![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict153.jpg) U.S. Army Pfc. Shawn Miller, left, and Sgt. 1st Class Wayne Davidson, both with Brigade Special Troops Battalion, 3rd Brigade Combat Team, 82nd Airborne Division, prepare equipment needed to operate a Raven unmanned aerial vehicle system at Joint Security Station Loyalty in eastern Baghdad, Iraq, March 25, 2009. (U.S. Army photo by Staff Sgt. James Selesnick/Released). Date Shot: 3/25/2009
U.S. Army Pfc. Shawn Miller, left, and Sgt. 1st Class Wayne Davidson, both with Brigade Special Troops Battalion, 3rd Brigade Combat Team, 82nd Airborne Division, prepare equipment needed to operate a Raven unmanned aerial vehicle system at Joint Security Station Loyalty in eastern Baghdad, Iraq, March 25, 2009. (U.S. Army photo by Staff Sgt. James Selesnick/Released). Date Shot: 3/25/2009![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict152.jpg) U.S. Army Pfc. Shawn Miller, from Brigade Special Troops Battalion, 3rd Brigade Combat Team, 82nd Airborne Division, processes information gathered from a Raven unmanned aerial vehicle system, at Joint Security Station Loyalty, in eastern Baghdad, Iraq, March 25, 2009. (U.S. Army photo by Staff Sgt. James Selesnick/Released). Date Shot: 3/25/2009
U.S. Army Pfc. Shawn Miller, from Brigade Special Troops Battalion, 3rd Brigade Combat Team, 82nd Airborne Division, processes information gathered from a Raven unmanned aerial vehicle system, at Joint Security Station Loyalty, in eastern Baghdad, Iraq, March 25, 2009. (U.S. Army photo by Staff Sgt. James Selesnick/Released). Date Shot: 3/25/2009![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict151.jpg) U.S. Air Force Maj. John Chesser operates the controls of an MQ-9 Reaper unmanned aerial vehicle cockpit during a demonstration at Joint Base Balad, Iraq, on Aug. 1, 2008. The Reaper is designed as a hunter-killer, capable of loitering over targets for long periods of time and delivering laser-guided ordnance. Chesser is a Reaper pilot with the 46th Expeditionary Reconnaissance and Attack Squadron. DoD photo by Staff Sgt. Don Branum, U.S. Air Force. (Released). Date Shot: 8/1/2008
U.S. Air Force Maj. John Chesser operates the controls of an MQ-9 Reaper unmanned aerial vehicle cockpit during a demonstration at Joint Base Balad, Iraq, on Aug. 1, 2008. The Reaper is designed as a hunter-killer, capable of loitering over targets for long periods of time and delivering laser-guided ordnance. Chesser is a Reaper pilot with the 46th Expeditionary Reconnaissance and Attack Squadron. DoD photo by Staff Sgt. Don Branum, U.S. Air Force. (Released). Date Shot: 8/1/2008![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict150.jpg) U.S. Air Force Tech. Sgt. Justin Michaels, of 3rd Special Operations Command, Cannon Air Force Base, N.M., guides a ground control station (GCS) as other Airmen from his unit lower the station into place July 21, 2008. The GCS will serve as a cockpit for Predator/Reaper unmanned aerial vehicles. (U.S. Air Force photo by Airman 1st Class James R. Bell/Released). Date Shot: 7/21/2008
U.S. Air Force Tech. Sgt. Justin Michaels, of 3rd Special Operations Command, Cannon Air Force Base, N.M., guides a ground control station (GCS) as other Airmen from his unit lower the station into place July 21, 2008. The GCS will serve as a cockpit for Predator/Reaper unmanned aerial vehicles. (U.S. Air Force photo by Airman 1st Class James R. Bell/Released). Date Shot: 7/21/2008![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict149.jpg) U.S. Air Force Staff Sgt. Robert Moore, right, describes his every action to Airman 1st Class Carrie Smith during the setup of a Vehicle Test Controller for a RQ-1 Global Hawk unmanned aerial vehicle June 16, 2008, at Beale Air Force Base, Calif. They are with the 9th Aircraft Maintenance Squadron. (U.S. Air Force photo by Lance Cheung/Released). Date Shot: 6/16/2008
U.S. Air Force Staff Sgt. Robert Moore, right, describes his every action to Airman 1st Class Carrie Smith during the setup of a Vehicle Test Controller for a RQ-1 Global Hawk unmanned aerial vehicle June 16, 2008, at Beale Air Force Base, Calif. They are with the 9th Aircraft Maintenance Squadron. (U.S. Air Force photo by Lance Cheung/Released). Date Shot: 6/16/2008![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict148.jpg) U.S. Air Force Airman 1st Class Evan Barnhart assists Senior Airman Stephen Simeone as she controls an unmanned aerial vehicle at Patrol Base Meade, Iraq, Jan. 21, 2008, while providing armed reconnaissance over watch in Southern Arab Jabour, Iraq. Simeone and Barnhart are both joint terminal attack controllers from Fort Stewart, Ga., and are deployed with the 2nd Brigade Combat Team, 3rd Infantry Division. (U.S. Air Force photo by Master Sgt. Andy Dunaway) (Released). Date Shot: 1/21/2008
U.S. Air Force Airman 1st Class Evan Barnhart assists Senior Airman Stephen Simeone as she controls an unmanned aerial vehicle at Patrol Base Meade, Iraq, Jan. 21, 2008, while providing armed reconnaissance over watch in Southern Arab Jabour, Iraq. Simeone and Barnhart are both joint terminal attack controllers from Fort Stewart, Ga., and are deployed with the 2nd Brigade Combat Team, 3rd Infantry Division. (U.S. Air Force photo by Master Sgt. Andy Dunaway) (Released). Date Shot: 1/21/2008![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict147.jpg) Royal Air Force Maj. Kevin Gambold monitors and pilots an MQ-1 Predator unmanned aerial vehicle at Ali Air Base, Iraq, Jan. 10, 2008. Gambold is the commander the 361st Expeditionary Reconnaissance Squadron and deployed from the 15th Reconnaissance Squadron, Creech Air Force Base, Nev., through a military personnel exchange program. (U.S. Air Force photo by Airman 1st Class Jonathan Snyder) (Released). Date Shot: 1/10/2008
Royal Air Force Maj. Kevin Gambold monitors and pilots an MQ-1 Predator unmanned aerial vehicle at Ali Air Base, Iraq, Jan. 10, 2008. Gambold is the commander the 361st Expeditionary Reconnaissance Squadron and deployed from the 15th Reconnaissance Squadron, Creech Air Force Base, Nev., through a military personnel exchange program. (U.S. Air Force photo by Airman 1st Class Jonathan Snyder) (Released). Date Shot: 1/10/2008![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict146.jpg) U.S. Air Force Senior Airman Logan Abrams, right, a Joint Tactical Air Control Party journeyman (JTAC in training), talks with his Army counterparts who are operating a Shadow unmanned aerial vehicle from Forward Operating Base Kalsu, Iraq, June 25, 2007. The Army Shadow is being used to provide real time video surveillance of a suspected explosives laden roadway south of Baghdad. Abrams takes information from the shadow back to his JTAC, Tech. Sgt. Mike Cmelik, who is controlling a B-1 Lancer aircraft to drop 13,500 pounds of ordinance on the roadway. This bombing mission severed a suspected main supply route used by Iraqi insurgents to bring accelerants from the south into the Baghdad area. (U.S. Air Force photo by Master Sgt. Jim Varhegyi/Released). Date Shot: 6/25/2007
U.S. Air Force Senior Airman Logan Abrams, right, a Joint Tactical Air Control Party journeyman (JTAC in training), talks with his Army counterparts who are operating a Shadow unmanned aerial vehicle from Forward Operating Base Kalsu, Iraq, June 25, 2007. The Army Shadow is being used to provide real time video surveillance of a suspected explosives laden roadway south of Baghdad. Abrams takes information from the shadow back to his JTAC, Tech. Sgt. Mike Cmelik, who is controlling a B-1 Lancer aircraft to drop 13,500 pounds of ordinance on the roadway. This bombing mission severed a suspected main supply route used by Iraqi insurgents to bring accelerants from the south into the Baghdad area. (U.S. Air Force photo by Master Sgt. Jim Varhegyi/Released). Date Shot: 6/25/2007![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict144.jpg) FORWARD OPERATING BASE KALSU, Iraq — U.S. Air Force Tech. Sgt. Andrea Patterson, one of three battlefield weatherman assigned to forward operating base (FOB) Kalsu south of Baghdad, Iraq, provides a weather brief to U.S. Army soldiers controlling Shadow Unmanned Aerial Vehicles (UAVs) for the U.S. Army’s 2nd Battalion, 3rd Combat Aviation Brigade, 3rd Infantry Division, Monday, June 25, 2007. Sergeant Patterson, and her fellow Air Force weather forecasters, provide 24 hour a day weather updates to the various U. S. Army 3rd Infantry Division’s operations occurring in the Triangle of Death area. The instantaneous weather information the battlefield weathermen are able to provide are critical to the success, and to the safety of the 3rd ID’s ground and aviation operations. Though Sergeant Patterson is attached to the 3rd ID she officially falls under the recently formed 3rd Expeditionary Weather Squadron headquartered on Camp Victory, Baghdad, Iraq. She is deployed from Detachment 6, 7th Weather Squadron, Wiesbaden, Germany. (U.S. Air Force photo by Master Sgt. Jim Varhegyi)(released). Date Shot: 6/25/2007
FORWARD OPERATING BASE KALSU, Iraq — U.S. Air Force Tech. Sgt. Andrea Patterson, one of three battlefield weatherman assigned to forward operating base (FOB) Kalsu south of Baghdad, Iraq, provides a weather brief to U.S. Army soldiers controlling Shadow Unmanned Aerial Vehicles (UAVs) for the U.S. Army’s 2nd Battalion, 3rd Combat Aviation Brigade, 3rd Infantry Division, Monday, June 25, 2007. Sergeant Patterson, and her fellow Air Force weather forecasters, provide 24 hour a day weather updates to the various U. S. Army 3rd Infantry Division’s operations occurring in the Triangle of Death area. The instantaneous weather information the battlefield weathermen are able to provide are critical to the success, and to the safety of the 3rd ID’s ground and aviation operations. Though Sergeant Patterson is attached to the 3rd ID she officially falls under the recently formed 3rd Expeditionary Weather Squadron headquartered on Camp Victory, Baghdad, Iraq. She is deployed from Detachment 6, 7th Weather Squadron, Wiesbaden, Germany. (U.S. Air Force photo by Master Sgt. Jim Varhegyi)(released). Date Shot: 6/25/2007![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict143.jpg) A representative with the Insitu, Inc., on board the Military Sealift Command afloat prepositioning ship USNS Stockham (T-AK 3017), operates a Scan Eagle Unmanned Aerial Vehicle over the Solomon Islands April 17, 2007. The scan eagle is assessing earthquake and tsunami damage that struck the island. (U.S. Navy photo by Mass Communication Specialist Second Class Andrew Meyers/Released). Date Shot: 4/17/2007
A representative with the Insitu, Inc., on board the Military Sealift Command afloat prepositioning ship USNS Stockham (T-AK 3017), operates a Scan Eagle Unmanned Aerial Vehicle over the Solomon Islands April 17, 2007. The scan eagle is assessing earthquake and tsunami damage that struck the island. (U.S. Navy photo by Mass Communication Specialist Second Class Andrew Meyers/Released). Date Shot: 4/17/2007![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict142.jpg) U.S. Air Force Capt. Michael Edmonston, left, and Airman 1st Class Stephen Sadler, both of the 46th Expeditionary Reconnaissance Squadron, work together to remotely operate a Predator MQ-1 unmanned aerial vehicle at Balad Air Base, Iraq, Nov. 5, 2006. The Predators are used to provide surveillance and are equipped with AGM-114 Hellfire missiles. (U.S. Air Force photo by Airman 1st Class Chad Kellum) (Released). Date Shot: 11/5/2006
U.S. Air Force Capt. Michael Edmonston, left, and Airman 1st Class Stephen Sadler, both of the 46th Expeditionary Reconnaissance Squadron, work together to remotely operate a Predator MQ-1 unmanned aerial vehicle at Balad Air Base, Iraq, Nov. 5, 2006. The Predators are used to provide surveillance and are equipped with AGM-114 Hellfire missiles. (U.S. Air Force photo by Airman 1st Class Chad Kellum) (Released). Date Shot: 11/5/2006![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict141.jpg) Peter Bale, Director of Business Development, readies an Aerosonde Unmanned Aerial Vehicle (UAV) for a test flight at Naval Air Station Key West, Fla., on Sept. 7, 2006. The remote-piloted UAV is designed to gather critical, near surface data on active hurricanes. (U.S. Navy photo by Mass Communication Specialist 2nd Class Timothy Cox) (Released). Date Shot: 9/7/2006
Peter Bale, Director of Business Development, readies an Aerosonde Unmanned Aerial Vehicle (UAV) for a test flight at Naval Air Station Key West, Fla., on Sept. 7, 2006. The remote-piloted UAV is designed to gather critical, near surface data on active hurricanes. (U.S. Navy photo by Mass Communication Specialist 2nd Class Timothy Cox) (Released). Date Shot: 9/7/2006![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict140.jpg) Kris Kokkely, an advanced tactical systems engineer for Boeing, watches his computer screen as data and video streams back from a ScanEagle unmanned aerial vehicle (UAV) as it flies over Yodaville training range on Marine Corps Air Station Yuma, Ariz., June 19, 2006, for Desert Talon. ScanEagle is a UAV system that is designed to provide persistent intelligence, surveillance and reconnaissance data, battle damage assessment and communications relay. (U.S. Marine Corps photo by Cpl. Michael P. Snody) (Released). Date Shot: 7/19/2006
Kris Kokkely, an advanced tactical systems engineer for Boeing, watches his computer screen as data and video streams back from a ScanEagle unmanned aerial vehicle (UAV) as it flies over Yodaville training range on Marine Corps Air Station Yuma, Ariz., June 19, 2006, for Desert Talon. ScanEagle is a UAV system that is designed to provide persistent intelligence, surveillance and reconnaissance data, battle damage assessment and communications relay. (U.S. Marine Corps photo by Cpl. Michael P. Snody) (Released). Date Shot: 7/19/2006![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict139.jpg) U.S. Air Force Capt. Michael J. Conte, Unmanned Aerial Vehicle (UAV) pilot assigned to the 46th Expeditionary Strike and Reconnaissance Squadron, Nellis Air Force Base, Nev., prepares for the nights UAV mission from Balad Air Base, Iraq, July 8, 2006. (U.S. Air Force photo by Master Sgt. Jonathan F. Doti/Released). Date Shot: 7/8/2006
U.S. Air Force Capt. Michael J. Conte, Unmanned Aerial Vehicle (UAV) pilot assigned to the 46th Expeditionary Strike and Reconnaissance Squadron, Nellis Air Force Base, Nev., prepares for the nights UAV mission from Balad Air Base, Iraq, July 8, 2006. (U.S. Air Force photo by Master Sgt. Jonathan F. Doti/Released). Date Shot: 7/8/2006![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict138.jpg) On 21 June 2006, Maj Toby Buchan, from Spencertown, NY, of Marine Unmanned Aerial Vehicle Squadron 2 (VMU-2) gives the clearance to fly to a Pioneer Unmanned Aerial Vehicle (UAV)before it departs on a mission in Al Taqaddum, Iraq. VMU-2 is deployed with IMEF (FWD) in support of in support of Operation Iraqi Freedom in the Al Anbar Province of Iraq (MNF-W) to develop the Iraqi security force, facilitate the development of official rule of law through democratic government, and continue the development of a market based economy centered on Iraqi reconstruction. .Official USMC Photo by Sergeant Jennifer L. Jones.060621-M-AK780-023.(RELEASED). Date Shot: 6/21/2006
On 21 June 2006, Maj Toby Buchan, from Spencertown, NY, of Marine Unmanned Aerial Vehicle Squadron 2 (VMU-2) gives the clearance to fly to a Pioneer Unmanned Aerial Vehicle (UAV)before it departs on a mission in Al Taqaddum, Iraq. VMU-2 is deployed with IMEF (FWD) in support of in support of Operation Iraqi Freedom in the Al Anbar Province of Iraq (MNF-W) to develop the Iraqi security force, facilitate the development of official rule of law through democratic government, and continue the development of a market based economy centered on Iraqi reconstruction. .Official USMC Photo by Sergeant Jennifer L. Jones.060621-M-AK780-023.(RELEASED). Date Shot: 6/21/2006![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict137.jpg) Pfc. Jonathan Machado, from HHB 3rd Battalion, 320th Field Artillery Regiment, 101st Airborne Division, operates a remote control for the Raven Unmanned Aerial Vehicle (UAV) from a safe location. The Raven is used to support land warfare operations and surveillance of the area. The 101st Airborne Division is currently deployed in the Tikrit area in support of the operation. FOB REMAGEN (U.S. Army photo by Spc. Teddy Wade) (Released). Date Shot: 4/21/2006
Pfc. Jonathan Machado, from HHB 3rd Battalion, 320th Field Artillery Regiment, 101st Airborne Division, operates a remote control for the Raven Unmanned Aerial Vehicle (UAV) from a safe location. The Raven is used to support land warfare operations and surveillance of the area. The 101st Airborne Division is currently deployed in the Tikrit area in support of the operation. FOB REMAGEN (U.S. Army photo by Spc. Teddy Wade) (Released). Date Shot: 4/21/2006![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict134.jpg) John T. Nicholson, Boeing Phantom Works Field Service Representative and Stewart Errico the Boeing ScanEagle, an unmanned aerial vehicle, secures the aircraft so it can be stored for the evening at Asad, Iraq, July 13, 2005. These men are civilian contractors that work with the U.S. Marines Unmanned Aerial Vehicle Squadron Two. (U.S. Marine Corps photo by Lance Cpl. Dustin S. Schaefer/Released). Date Shot: 7/12/2005
John T. Nicholson, Boeing Phantom Works Field Service Representative and Stewart Errico the Boeing ScanEagle, an unmanned aerial vehicle, secures the aircraft so it can be stored for the evening at Asad, Iraq, July 13, 2005. These men are civilian contractors that work with the U.S. Marines Unmanned Aerial Vehicle Squadron Two. (U.S. Marine Corps photo by Lance Cpl. Dustin S. Schaefer/Released). Date Shot: 7/12/2005![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict133.jpg) Todd Alexander, a support engineer from the Insitu Group, Boeing Corporation, maneuvers a Scan Eagle unmanned aerial vehicle from a remote location during an urban warfare exercise at Indian Springs Auxiliary Air Field, Nev., on May 4, 2005. Scan Eagle flies at low altitudes while taking video surveillance and it feeds images directly to security forces personnel in the field. (U.S. Air Force photo by Master Sgt. Robert W. Valenca) (Released). Date Shot: 5/4/2005
Todd Alexander, a support engineer from the Insitu Group, Boeing Corporation, maneuvers a Scan Eagle unmanned aerial vehicle from a remote location during an urban warfare exercise at Indian Springs Auxiliary Air Field, Nev., on May 4, 2005. Scan Eagle flies at low altitudes while taking video surveillance and it feeds images directly to security forces personnel in the field. (U.S. Air Force photo by Master Sgt. Robert W. Valenca) (Released). Date Shot: 5/4/2005![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict132.jpg) U.S. Air Force Capt. Andy Beitz (left), a student pilot, and Airman 1st Class Stephanie Barroso, a student sensor operator, practice operating an MQ-1 Predator Unmanned Aerial Vehicle (UAV) during training inside the Ground Control Station Cell at Indian Springs Auxiliary Field, Nev., on April 26, 2005. (U.S. Air Force photo by Tech. Sgt. Kevin J. Gruenwald) (Released). Date Shot: 4/26/2005
U.S. Air Force Capt. Andy Beitz (left), a student pilot, and Airman 1st Class Stephanie Barroso, a student sensor operator, practice operating an MQ-1 Predator Unmanned Aerial Vehicle (UAV) during training inside the Ground Control Station Cell at Indian Springs Auxiliary Field, Nev., on April 26, 2005. (U.S. Air Force photo by Tech. Sgt. Kevin J. Gruenwald) (Released). Date Shot: 4/26/2005![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict131.jpg) U.S. Air Force 1st Lt. Adam Twitchell, an Intelligence Officer and Operations Cell Mission Coordinator from the 11th Reconnaissance Squadron, Indian Springs Auxiliary Field, Nev., reviews local training plans during a MQ-1 Predator Unmanned Aerial Vehicle (UAV) mission over Nevada on April 2, 2005. (U.S. Air Force Photo by Tech. Sgt. Kevin J. Gruenwald) (Released). Date Shot: 4/2/2005
U.S. Air Force 1st Lt. Adam Twitchell, an Intelligence Officer and Operations Cell Mission Coordinator from the 11th Reconnaissance Squadron, Indian Springs Auxiliary Field, Nev., reviews local training plans during a MQ-1 Predator Unmanned Aerial Vehicle (UAV) mission over Nevada on April 2, 2005. (U.S. Air Force Photo by Tech. Sgt. Kevin J. Gruenwald) (Released). Date Shot: 4/2/2005![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict130.jpg) A U.S. Contractor (left), a U.S. Marine Corps 1st Lt. (second from left), a U.S. Marine Corps 1st Sgt. (second from right), and an U.S. Air Force Col. (right) stand around a Unmanned Aerial Vehicle that is on display at Camp Fallujah, Al Anbar Province, Iraq, on Dec. 4, 2004, that will be shown to U.S. Marine Corps Gen. James L. Jones, Supreme Allied Commander, Europe, and Commander, U.S. European Command, and U.S. Marine Corps Sgt. Maj. Alford L. McMichael, Senior Non-Commissioned Officer, Allied Command Operations, who are visiting with U.S. military service members who all participated in Operation Al Fajr, which was conducted during Operation Iraqi Freedom. (U.S. Marine Corps photo by Gunnery Sgt. Robert Blankenship) (Released). Date Shot: 12/4/2004
A U.S. Contractor (left), a U.S. Marine Corps 1st Lt. (second from left), a U.S. Marine Corps 1st Sgt. (second from right), and an U.S. Air Force Col. (right) stand around a Unmanned Aerial Vehicle that is on display at Camp Fallujah, Al Anbar Province, Iraq, on Dec. 4, 2004, that will be shown to U.S. Marine Corps Gen. James L. Jones, Supreme Allied Commander, Europe, and Commander, U.S. European Command, and U.S. Marine Corps Sgt. Maj. Alford L. McMichael, Senior Non-Commissioned Officer, Allied Command Operations, who are visiting with U.S. military service members who all participated in Operation Al Fajr, which was conducted during Operation Iraqi Freedom. (U.S. Marine Corps photo by Gunnery Sgt. Robert Blankenship) (Released). Date Shot: 12/4/2004![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict124.jpg) US Air Force (USAF) 46th Expeditionary Aerial Reconnaissance Squadron (EARS) Predator pilots, Captain (CPT) John “Disco” Songer and Airman 1st Class (A1C) Stephanie L. “Princess” Schulte operate individual Predator Unmanned Aerial Vehicles (UAV) using remote controls at Balad Air Base (AB), Iraq (IRQ), in support of Operation IRAQI FREEDOM. Photographer’s Name: SSGT COHEN A. YOUNG, USAF. Date Shot: 7/2/2004
US Air Force (USAF) 46th Expeditionary Aerial Reconnaissance Squadron (EARS) Predator pilots, Captain (CPT) John “Disco” Songer and Airman 1st Class (A1C) Stephanie L. “Princess” Schulte operate individual Predator Unmanned Aerial Vehicles (UAV) using remote controls at Balad Air Base (AB), Iraq (IRQ), in support of Operation IRAQI FREEDOM. Photographer’s Name: SSGT COHEN A. YOUNG, USAF. Date Shot: 7/2/2004![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict129.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict123.jpg) US Air Force (USAF) 46th Expeditionary Aerial Reconnaissance Squadron (EARS) Crew Chief, Staff Sergeant (SSGT) Sean Pietre and Senior Airman (SRA) Rothschild Pierre-Louis III unload a rocket from a Predator Unmanned Aerial Vehicle (UAV) at Balad Air Base (AB), Iraq (IRQ), in support of Operation IRAQI FREEDOM. Photographer’s Name: SSGT COHEN A. YOUNG, USAF. Date Shot: 7/2/2004
US Air Force (USAF) 46th Expeditionary Aerial Reconnaissance Squadron (EARS) Crew Chief, Staff Sergeant (SSGT) Sean Pietre and Senior Airman (SRA) Rothschild Pierre-Louis III unload a rocket from a Predator Unmanned Aerial Vehicle (UAV) at Balad Air Base (AB), Iraq (IRQ), in support of Operation IRAQI FREEDOM. Photographer’s Name: SSGT COHEN A. YOUNG, USAF. Date Shot: 7/2/2004![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict122.jpg) US Air Force (USAF) Staff Sergeant (SSGT) David Miranda, a Dedicated Crew Chief on the MQ-1L Predator Unmanned Aerial Vehicle (UAV), inspects an engine during a Preventative Maintenance Inspection (PMI). Miranda is assigned to the 46th Expeditionary Reconnaissance Squadron (ERS) at Balad Air Base (AB), Iraq (IRQ). Photographer’s Name: TSGT SCOTT REED, USAF. Date Shot: 6/10/2004
US Air Force (USAF) Staff Sergeant (SSGT) David Miranda, a Dedicated Crew Chief on the MQ-1L Predator Unmanned Aerial Vehicle (UAV), inspects an engine during a Preventative Maintenance Inspection (PMI). Miranda is assigned to the 46th Expeditionary Reconnaissance Squadron (ERS) at Balad Air Base (AB), Iraq (IRQ). Photographer’s Name: TSGT SCOTT REED, USAF. Date Shot: 6/10/2004![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict121.jpg) US Air Force (USAF) Crew Chief with the 46th Reconnaissance Squadron (RS), Staff Sergeant (SGT) James Barr (right), starts up the engine of a Predator MQ-1 Unmanned Aerial Vehicle (UAV) during a functional check while Senior Airman (SRA) Christipher Dewey observes the engine performance. Photographer’s Name: SSGT PRENTICE COLTER, USAF. Date Shot: 5/26/2004
US Air Force (USAF) Crew Chief with the 46th Reconnaissance Squadron (RS), Staff Sergeant (SGT) James Barr (right), starts up the engine of a Predator MQ-1 Unmanned Aerial Vehicle (UAV) during a functional check while Senior Airman (SRA) Christipher Dewey observes the engine performance. Photographer’s Name: SSGT PRENTICE COLTER, USAF. Date Shot: 5/26/2004![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict120.jpg) US Air Force (USAF) Staff Sergeant (SSGT) Michael Gonzales, a Crew Chief for the 46th Expeditionary Reconnaissance Squadron (ERS), unscrews the engine of a Predator Unmanned Aerial Vehicle (UAV) for repairs at Balad Air Base (AB), Iraq (IRQ), in support of Operation IRAQI FREEDOM. Photographer’s Name: SSGT CHYRECE E. LEWIS, USAF. Date Shot: 2/10/2004
US Air Force (USAF) Staff Sergeant (SSGT) Michael Gonzales, a Crew Chief for the 46th Expeditionary Reconnaissance Squadron (ERS), unscrews the engine of a Predator Unmanned Aerial Vehicle (UAV) for repairs at Balad Air Base (AB), Iraq (IRQ), in support of Operation IRAQI FREEDOM. Photographer’s Name: SSGT CHYRECE E. LEWIS, USAF. Date Shot: 2/10/2004![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict119.jpg) US Air Force (USAF) Staff Sergeant (SSGT) Tracy Jones, left and SSGT Jeffery Hicks, Crew Chiefs for the 46th Expeditionary Reconnaissance Squadron (ERS), sign-off preflight documents for the RQ-1 Predator Unmanned Aerial Vehicle (UAV), before its mission from Balad Air Base (AB), Iraq, in support of Operation IRAQI FREEDOM. Photographer’s Name: SSGT CHYRECE LEWIS, USAF. Date Shot: 1/31/2004
US Air Force (USAF) Staff Sergeant (SSGT) Tracy Jones, left and SSGT Jeffery Hicks, Crew Chiefs for the 46th Expeditionary Reconnaissance Squadron (ERS), sign-off preflight documents for the RQ-1 Predator Unmanned Aerial Vehicle (UAV), before its mission from Balad Air Base (AB), Iraq, in support of Operation IRAQI FREEDOM. Photographer’s Name: SSGT CHYRECE LEWIS, USAF. Date Shot: 1/31/2004![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict118.jpg) US Air Force (USAF) Staff Sergeant (SSGT) Jeffrey Hicks, left and Senior Airman (SRA) John Fanning, with the 46th Expeditionary Reconnaissance Squadron (ERS), perform a post flight check on their RQ-1 Predator Unmanned Aerial Vehicle (UAV) at Tallil Air Base (AB), Iraq, in support of OPERATION IRAQI FREEDOM. Photographer’s Name: SSGT SUZANNE M. JENKINS, USAF. Date Shot: 1/19/2004
US Air Force (USAF) Staff Sergeant (SSGT) Jeffrey Hicks, left and Senior Airman (SRA) John Fanning, with the 46th Expeditionary Reconnaissance Squadron (ERS), perform a post flight check on their RQ-1 Predator Unmanned Aerial Vehicle (UAV) at Tallil Air Base (AB), Iraq, in support of OPERATION IRAQI FREEDOM. Photographer’s Name: SSGT SUZANNE M. JENKINS, USAF. Date Shot: 1/19/2004![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict117.jpg) The Joint Unmanned Aerial Vehicle (UAV) Experiment Program consists of British and Israeli contractors working together controlling the UAV for experimental purposes during a Combat Search and Rescue (CSAR) training exercise at Fallon Naval Air Station (NAS), Nevada (NV), during exercise DESERT RESCUE XI. Here two British contractors view a low-resolution strip map, which covers a large area provided by the electrical optical and infrared camera, installed in the UAV during a surveillance and reconnaissance mission. The exercise is a joint service Combat Search and Rescue (CSAR) training exercise hosted by the Naval Strike and Warfare Center, designed to simulate downed aircrews, enabling CSAR related missions to experiment with new techniques in realistic scenarios. Photographer’s Name: SSGT REYNALDO RAMON, USAF. Date Shot: 8/13/2003
The Joint Unmanned Aerial Vehicle (UAV) Experiment Program consists of British and Israeli contractors working together controlling the UAV for experimental purposes during a Combat Search and Rescue (CSAR) training exercise at Fallon Naval Air Station (NAS), Nevada (NV), during exercise DESERT RESCUE XI. Here two British contractors view a low-resolution strip map, which covers a large area provided by the electrical optical and infrared camera, installed in the UAV during a surveillance and reconnaissance mission. The exercise is a joint service Combat Search and Rescue (CSAR) training exercise hosted by the Naval Strike and Warfare Center, designed to simulate downed aircrews, enabling CSAR related missions to experiment with new techniques in realistic scenarios. Photographer’s Name: SSGT REYNALDO RAMON, USAF. Date Shot: 8/13/2003![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict116.jpg) A contracted worker operates to controls of a Hunter Joint Tactical Unmanned Aerial Vehicle (UAV), as it prepares for a experimental flight during a Combat Search and Rescue (CSAR) training exercise at Fallon Naval Air Station (NAS), Nevada (NV), during exercise DESERT RESCUE XI. The Hunter is an Israeli multi-role short-range UAV system in service with the US Army (USA). The exercise is a joint service Combat Search and Rescue (CSAR) training exercise hosted by the Naval Strike and Warfare Center, designed to simulate downed aircrews, enabling CSAR related missions to experiment with new techniques in realistic scenarios. Photographer’s Name: SSGT REYNALDO RAMON, USAF. Date Shot: 8/13/2003
A contracted worker operates to controls of a Hunter Joint Tactical Unmanned Aerial Vehicle (UAV), as it prepares for a experimental flight during a Combat Search and Rescue (CSAR) training exercise at Fallon Naval Air Station (NAS), Nevada (NV), during exercise DESERT RESCUE XI. The Hunter is an Israeli multi-role short-range UAV system in service with the US Army (USA). The exercise is a joint service Combat Search and Rescue (CSAR) training exercise hosted by the Naval Strike and Warfare Center, designed to simulate downed aircrews, enabling CSAR related missions to experiment with new techniques in realistic scenarios. Photographer’s Name: SSGT REYNALDO RAMON, USAF. Date Shot: 8/13/2003![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict113.jpg) Sergeant (SGT) Carlos Carrasco (left) and USMC of Reading PA and Sgt Carlos Carrasco, both from 3rd Light Armored Reconnaissance (LAR) Battalion, operate the wearable ground control station for the “Dragon Eye” Unmanned Aerial Vehicle (UAV) at Camp Ripper, Kuwait during Operation ENDURING FREEDOM. Photographer’s Name: LCPL Kenneth E. Madden, USMC. Date Shot: 3/7/2003
Sergeant (SGT) Carlos Carrasco (left) and USMC of Reading PA and Sgt Carlos Carrasco, both from 3rd Light Armored Reconnaissance (LAR) Battalion, operate the wearable ground control station for the “Dragon Eye” Unmanned Aerial Vehicle (UAV) at Camp Ripper, Kuwait during Operation ENDURING FREEDOM. Photographer’s Name: LCPL Kenneth E. Madden, USMC. Date Shot: 3/7/2003![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict111.jpg) US Marine Corps (USMC) Corporal (CPL) John Rocha, Marine Unmanned Aerial Vehicle Squadron-1 (VMU-1), Twentynine Palms, California (CA), at the controls of the GCS-2000 Ground Control Station (GCS) that operates an unmanned air vehicle (UAV) from the flightline near Camp Workhorse during Operation ENDURING FREEDOM. Photographer’s Name: LCPL ALICIA M. ANDERSON, USMC. Date Shot: 2/25/2003
US Marine Corps (USMC) Corporal (CPL) John Rocha, Marine Unmanned Aerial Vehicle Squadron-1 (VMU-1), Twentynine Palms, California (CA), at the controls of the GCS-2000 Ground Control Station (GCS) that operates an unmanned air vehicle (UAV) from the flightline near Camp Workhorse during Operation ENDURING FREEDOM. Photographer’s Name: LCPL ALICIA M. ANDERSON, USMC. Date Shot: 2/25/2003![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict112.jpg) US Marine Corps (USMC) Marines from Marine Unmanned Aerial Vehicle Squadron-1 (VMU-1), Twentynine Palms, California (CA), and VMU-2, Cherry Point, North Carolina (NC), lunch together during a construction break of a runway near Camp Workhorse during Operation ENDURING FREEDOM. Photographer’s Name: LCPL ALICIA M. ANDERSON, USMC. Date Shot: 2/25/2003
US Marine Corps (USMC) Marines from Marine Unmanned Aerial Vehicle Squadron-1 (VMU-1), Twentynine Palms, California (CA), and VMU-2, Cherry Point, North Carolina (NC), lunch together during a construction break of a runway near Camp Workhorse during Operation ENDURING FREEDOM. Photographer’s Name: LCPL ALICIA M. ANDERSON, USMC. Date Shot: 2/25/2003![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict115.jpg) US Air Force (USAF) Senior Airman (SRA) Amy Hodges, Airborne Surveillance Radar System Technician assigned to the 438th Expeditionary Force Protection Squadron (EFPS) waits for final Global Positioning Systems (GPS) data before launching a US Air Force (USAF) “Desert Hawk” Force Protection Airborne Surveillance (FPAS), Unmanned Aerial Vehicle (UAV), while deployed at forward location during Operation ENDURING FREEDOM. Photographer’s Name: SSGT William Greer, USAF. Date Shot: 10/4/2002
US Air Force (USAF) Senior Airman (SRA) Amy Hodges, Airborne Surveillance Radar System Technician assigned to the 438th Expeditionary Force Protection Squadron (EFPS) waits for final Global Positioning Systems (GPS) data before launching a US Air Force (USAF) “Desert Hawk” Force Protection Airborne Surveillance (FPAS), Unmanned Aerial Vehicle (UAV), while deployed at forward location during Operation ENDURING FREEDOM. Photographer’s Name: SSGT William Greer, USAF. Date Shot: 10/4/2002![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict114.jpg) US Army (USA) Specialist (SPC) Dan Sawicki, 972nd Military Police (MP) Company, operates the controls of a US Air Force (USAF) “Desert Hawk” Force Protection Airborne Surveillance (FPAS), Unmanned Aerial Vehicle (UAV), while deployed at forward location during Operation ENDURING FREEDOM. Photographer’s Name: SSGT William Greer, USAF. Date Shot: 10/4/2002
US Army (USA) Specialist (SPC) Dan Sawicki, 972nd Military Police (MP) Company, operates the controls of a US Air Force (USAF) “Desert Hawk” Force Protection Airborne Surveillance (FPAS), Unmanned Aerial Vehicle (UAV), while deployed at forward location during Operation ENDURING FREEDOM. Photographer’s Name: SSGT William Greer, USAF. Date Shot: 10/4/2002![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict109.jpg) Staff Sgt. Brian Fox, VTC operator (Vehicle Test Controller) of the 12th ERS (Expeditionary Reconnaissance Squadron), uses a computer interface to provide flight instructions to the Global Hawk on June 30, 2002. The RQ-4A Global Hawk is a high-altitude, long-endurance unmanned aerial reconnaissance system designed to provide military field commanders with high resolution, near-real-time imagery of large geographic areas. (U.S. Air Force photo by Staff Sgt. Reynaldo Ramon) (Released). Date Shot: 6/30/2002
Staff Sgt. Brian Fox, VTC operator (Vehicle Test Controller) of the 12th ERS (Expeditionary Reconnaissance Squadron), uses a computer interface to provide flight instructions to the Global Hawk on June 30, 2002. The RQ-4A Global Hawk is a high-altitude, long-endurance unmanned aerial reconnaissance system designed to provide military field commanders with high resolution, near-real-time imagery of large geographic areas. (U.S. Air Force photo by Staff Sgt. Reynaldo Ramon) (Released). Date Shot: 6/30/2002![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict108.jpg) Terry Collins, an L3 employee out of Edwards Air Force Base, checks the uplinks and downlinks for satellite communication with the Global Hawk on June 30, 2002. The RQ-4A Global Hawk is a high-altitude, long-endurance unmanned aerial reconnaissance system designed to provide military field commanders with high resolution, near-real-time imagery of large geographic areas. (U.S. Air Force photo by Staff Sgt. Reynaldo Ramon) (Released). Date Shot: 6/30/2002
Terry Collins, an L3 employee out of Edwards Air Force Base, checks the uplinks and downlinks for satellite communication with the Global Hawk on June 30, 2002. The RQ-4A Global Hawk is a high-altitude, long-endurance unmanned aerial reconnaissance system designed to provide military field commanders with high resolution, near-real-time imagery of large geographic areas. (U.S. Air Force photo by Staff Sgt. Reynaldo Ramon) (Released). Date Shot: 6/30/2002![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict35.jpg) In this March, 28, 2012, photo, an Arcti Copter 5 drone flies over a waterfront park in Berkeley, Calif. Interest in the domestic use of drones is surging among public agencies and private citizens alike, including a thriving subculture of amateur hobbyists, even as the prospect of countless tiny but powerful eyes circling in the skies raises serious privacy concerns. (Eric Risberg)
In this March, 28, 2012, photo, an Arcti Copter 5 drone flies over a waterfront park in Berkeley, Calif. Interest in the domestic use of drones is surging among public agencies and private citizens alike, including a thriving subculture of amateur hobbyists, even as the prospect of countless tiny but powerful eyes circling in the skies raises serious privacy concerns. (Eric Risberg)![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict36.jpg) In this March, 28, 2012, photo, Mark Harrison, left, and Andreas Oesterer, right, watch as a Ritewing Zephyr II drone lifts off at a waterfront park in Berkeley, Calif. Interest in the domestic use of drones is surging among public agencies and private citizens alike, including a thriving subculture of amateur hobbyists, even as the prospect of countless tiny but powerful eyes circling in the skies raises serious privacy concerns. (Eric Risberg)
In this March, 28, 2012, photo, Mark Harrison, left, and Andreas Oesterer, right, watch as a Ritewing Zephyr II drone lifts off at a waterfront park in Berkeley, Calif. Interest in the domestic use of drones is surging among public agencies and private citizens alike, including a thriving subculture of amateur hobbyists, even as the prospect of countless tiny but powerful eyes circling in the skies raises serious privacy concerns. (Eric Risberg)![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict90.jpg) A quadrocopter drone equipped with a camera stands on display at the Zeiss stand on the first day of the CeBIT 2012 technology trade fair on March 6, 2012 in Hanover, Germany. CeBIT 2012, the world’s largest information technology trade fair, will run from March 6-10, and advances in cloud computing and security are major features this year. Getty
A quadrocopter drone equipped with a camera stands on display at the Zeiss stand on the first day of the CeBIT 2012 technology trade fair on March 6, 2012 in Hanover, Germany. CeBIT 2012, the world’s largest information technology trade fair, will run from March 6-10, and advances in cloud computing and security are major features this year. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict89.jpg) A drone equipped with cameras and sensors flies over a simulation of a contaminated area during a training exercise of a nuclear accident following an earthquake in the region of the nuclear site of Cadarache, January 17, 2012. Reuters
A drone equipped with cameras and sensors flies over a simulation of a contaminated area during a training exercise of a nuclear accident following an earthquake in the region of the nuclear site of Cadarache, January 17, 2012. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict88.jpg) Israeli soldiers dismantle the Skylark drone during a drill on January 16, 2012 near Bat Shlomo, Israel. The Skylark can carry a camera payload of up to 1kg, has an operational calking of 15,000ft and allows users to monitor any designated point within a 15km radius. The Skylark unit consists of a ground control element and three drones, which provide battalion-level commanders with real-time information. Getty
Israeli soldiers dismantle the Skylark drone during a drill on January 16, 2012 near Bat Shlomo, Israel. The Skylark can carry a camera payload of up to 1kg, has an operational calking of 15,000ft and allows users to monitor any designated point within a 15km radius. The Skylark unit consists of a ground control element and three drones, which provide battalion-level commanders with real-time information. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict87.jpg) A TV drone flies beside Canada’s Erick Guay during the second practice of the men’s Alpine skiing World Cup downhill race at the Lauberhorn in Wengen, January 12, 2012. Reuters
A TV drone flies beside Canada’s Erick Guay during the second practice of the men’s Alpine skiing World Cup downhill race at the Lauberhorn in Wengen, January 12, 2012. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict86.jpg) Advanced Defense Technology Centre engineer Fumiyuki Sato demonstrates his spherical observation drone at the opening of the annual Digital Contents Expo in Tokyo on October 20, 2011. The Japanese defence researcher has invented a spherical observation drone that can fly down narrow alleys, hover on the spot, take off vertically and bounce along the ground. Getty
Advanced Defense Technology Centre engineer Fumiyuki Sato demonstrates his spherical observation drone at the opening of the annual Digital Contents Expo in Tokyo on October 20, 2011. The Japanese defence researcher has invented a spherical observation drone that can fly down narrow alleys, hover on the spot, take off vertically and bounce along the ground. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict84.jpg) President of French far-right party Front national (FN) and candidate for the 2012 French presidential election Marine Le Pen looks at a drone helicopter at the stand of French company Eden as she visits on October 19, 2011 in Paris, at the the France’s Milipol global security trade fair on October 18, 2011 in Paris. Milipol Paris 2011, welcoming more than 1,000 exhibiting companies from 43 countries, runs until October 21. Getty
President of French far-right party Front national (FN) and candidate for the 2012 French presidential election Marine Le Pen looks at a drone helicopter at the stand of French company Eden as she visits on October 19, 2011 in Paris, at the the France’s Milipol global security trade fair on October 18, 2011 in Paris. Milipol Paris 2011, welcoming more than 1,000 exhibiting companies from 43 countries, runs until October 21. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict85.jpg) This Sept. 2011 photo provided by Vanguard Defense Industries, shows a ShadowHawk drone with Montgomery County, Texas, SWAT team members. Civilian cousins of the unmanned military aircraft that have been tracking and killing terrorists in the Middle East and Asia are being sought by police departments, border patrols, power companies, news organizations and others who want a bird?s-eye view. AP
This Sept. 2011 photo provided by Vanguard Defense Industries, shows a ShadowHawk drone with Montgomery County, Texas, SWAT team members. Civilian cousins of the unmanned military aircraft that have been tracking and killing terrorists in the Middle East and Asia are being sought by police departments, border patrols, power companies, news organizations and others who want a bird?s-eye view. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict41.jpg) A Pakistani villager holds a wreckage of a suspected surveillance drone which is crashed in Pakistani border town of Chaman along the Afghanistan border in Pakistan on Thursday, Aug 25, 2011. Suspected US surveillance drone crashes in Pakistan military area near border with Afghanistan. (Shah Khalid)
A Pakistani villager holds a wreckage of a suspected surveillance drone which is crashed in Pakistani border town of Chaman along the Afghanistan border in Pakistan on Thursday, Aug 25, 2011. Suspected US surveillance drone crashes in Pakistan military area near border with Afghanistan. (Shah Khalid)![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict83.jpg) A maple seed is seen on the hand of Craig Stoneking, bottom, project manager at Lockheed Martin Advance Technology Laboratories, as engineer David Sharp holds the company’s new drone, Wednesday, Aug. 10, 2011, in Southampton, N.J. The unmanned, one-winged flight machine is based on the flight of maple seeds that twirl down from trees during the spring. AP
A maple seed is seen on the hand of Craig Stoneking, bottom, project manager at Lockheed Martin Advance Technology Laboratories, as engineer David Sharp holds the company’s new drone, Wednesday, Aug. 10, 2011, in Southampton, N.J. The unmanned, one-winged flight machine is based on the flight of maple seeds that twirl down from trees during the spring. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict42.jpg) Pakistani officials collect remains of a Pakistan Navy unmanned aerial vehicle (UAV) which crashed outside an oil refinery in Karachi, Pakistan on Tuesday, July 19, 2011. According to a Pakistan Navy official, the accident was caused by a bird hit. No casualties were reported. (Shakil Adil)
Pakistani officials collect remains of a Pakistan Navy unmanned aerial vehicle (UAV) which crashed outside an oil refinery in Karachi, Pakistan on Tuesday, July 19, 2011. According to a Pakistan Navy official, the accident was caused by a bird hit. No casualties were reported. (Shakil Adil)![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict80.jpg) Dr. Gregory Parker, Micro Air Vehicle team leader, holds a small winged drone that resembles an insect, in the U.S. Air Force Micro Air Vehicles lab at Wright Patterson Air Force Base in Dayton, Ohio, July 11, 2011. The Micro Air Vehicles unit of the Air Force Research Laboratory at Wright Patterson AFB is developing small military drones, with the goal of making them so small that they resemble small birds and insects, including some that will have moving wings. The mission is to develop MAVs that can find, track and target adversaries while operating in complex urban environments. The engineers are using a variety of small helicopters and drones in the lab to develop the programs and software. Testing takes place in a controlled indoor lab where the team flies the MAVs and then gathers data to analyze for further development. Reuters
Dr. Gregory Parker, Micro Air Vehicle team leader, holds a small winged drone that resembles an insect, in the U.S. Air Force Micro Air Vehicles lab at Wright Patterson Air Force Base in Dayton, Ohio, July 11, 2011. The Micro Air Vehicles unit of the Air Force Research Laboratory at Wright Patterson AFB is developing small military drones, with the goal of making them so small that they resemble small birds and insects, including some that will have moving wings. The mission is to develop MAVs that can find, track and target adversaries while operating in complex urban environments. The engineers are using a variety of small helicopters and drones in the lab to develop the programs and software. Testing takes place in a controlled indoor lab where the team flies the MAVs and then gathers data to analyze for further development. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict81.jpg) A model of an insect size U.S. Air Force drone is held by a member of the Micro Air Vehicles team of the Air Force Research Laboratory, which is developing small drones at Wright Patterson Air Force Base in Dayton, Ohio, July 11, 2011. Reuters
A model of an insect size U.S. Air Force drone is held by a member of the Micro Air Vehicles team of the Air Force Research Laboratory, which is developing small drones at Wright Patterson Air Force Base in Dayton, Ohio, July 11, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict82.jpg) A computer controlled U.S. Air Force drone prepares to lift off for a test flight of in the Micro Air Vehicles lab at Wright Patterson Air Force Base in Dayton, Ohio, July 11, 2011. Reuters
A computer controlled U.S. Air Force drone prepares to lift off for a test flight of in the Micro Air Vehicles lab at Wright Patterson Air Force Base in Dayton, Ohio, July 11, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict43.jpg) This product image provided by Parrot, shows the AR.Drone. Parrot, a company known more for its Bluetooth hands-free car speakerphones, has launched a small, unmanned aircraft that can be controlled using an iPhone or another of Apple Inc.’s Wi-Fi-enabled gadgets, including the iPod Touch and the iPad.(Parrot)
This product image provided by Parrot, shows the AR.Drone. Parrot, a company known more for its Bluetooth hands-free car speakerphones, has launched a small, unmanned aircraft that can be controlled using an iPhone or another of Apple Inc.’s Wi-Fi-enabled gadgets, including the iPod Touch and the iPad.(Parrot)![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict37.jpg) This undated handout photo provided by the U.S. Air Force shows a MQ-9 Reaper, armed with GBU-12 Paveway II laser guided munitions and AGM-114 Hellfire missiles, piloted by Col. Lex Turner during a combat mission over southern Afghanistan. (Lt. Col.. Leslie Pratt, US Air Force)
This undated handout photo provided by the U.S. Air Force shows a MQ-9 Reaper, armed with GBU-12 Paveway II laser guided munitions and AGM-114 Hellfire missiles, piloted by Col. Lex Turner during a combat mission over southern Afghanistan. (Lt. Col.. Leslie Pratt, US Air Force)![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict40.jpg) This undated photo provided by U.S. Customs and Border Protection shows an unmanned drone used to patrol the U.S.-Canadian border. The planes, which are based out of North Dakota, are now venturing as far as Eastern Washington on their patrols. (U.S. Customs and Border Protection)
This undated photo provided by U.S. Customs and Border Protection shows an unmanned drone used to patrol the U.S.-Canadian border. The planes, which are based out of North Dakota, are now venturing as far as Eastern Washington on their patrols. (U.S. Customs and Border Protection)![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict44.jpg) U.S. Navy Boatswain’s Mate 3rd Class Christian Riddle, left, and Boatswain’s Mate 2nd Class Dante Galati secure a recovered Air Force BQM-74C Chukar III aerial target drone to a crane aboard USS Tortuga (LSD 46) after an at-sea exercise for Cooperation Afloat Readiness and Training (CARAT) 2011 in the South China Sea June 11, 2011. CARAT is a series of bilateral exercises held annually in Southeast Asia to strengthen relationships and enhance force readiness. (U.S. Navy photo by Mass Communication Specialist 2nd Class Katerine Noll/Released)
U.S. Navy Boatswain’s Mate 3rd Class Christian Riddle, left, and Boatswain’s Mate 2nd Class Dante Galati secure a recovered Air Force BQM-74C Chukar III aerial target drone to a crane aboard USS Tortuga (LSD 46) after an at-sea exercise for Cooperation Afloat Readiness and Training (CARAT) 2011 in the South China Sea June 11, 2011. CARAT is a series of bilateral exercises held annually in Southeast Asia to strengthen relationships and enhance force readiness. (U.S. Navy photo by Mass Communication Specialist 2nd Class Katerine Noll/Released)![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict78.jpg) An X-47B Unmanned Combat Air System Demonstrator (UCAS-D) completes its first flight at Edwards Air Force Base, Calif., Feb. 4, 2011. The UCAS-D program will demonstrate the capability of an autonomous, low-observable unmanned aircraft to perform carrier launches and recoveries. (DoD photo courtesy of Northrop Grumman/Released). Date Shot: 2/4/2011
An X-47B Unmanned Combat Air System Demonstrator (UCAS-D) completes its first flight at Edwards Air Force Base, Calif., Feb. 4, 2011. The UCAS-D program will demonstrate the capability of an autonomous, low-observable unmanned aircraft to perform carrier launches and recoveries. (DoD photo courtesy of Northrop Grumman/Released). Date Shot: 2/4/2011
![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict79.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict91.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict77.jpg) U.S. Army Sgt. Brian Curd, and Spc. Nicholas Boxley, both combat engineers, from Echo Company, 1st Battalion, 68th Armor Regiment, 3rd Advise and Assist Brigade, 4th Infantry Division, prepare the RQ-16A Tarantula Hawk unmanned aerial vehicle, for operation, at Basra province, Iraq, Dec. 1, 2010. Although, T-Hawk requires a great deal of maintenance, the capabilities it provides are well worth the time spent. (U.S. Army photo by 2nd Lt. Matthew Fumagalli/Released). Date Shot: 12/1/2010
U.S. Army Sgt. Brian Curd, and Spc. Nicholas Boxley, both combat engineers, from Echo Company, 1st Battalion, 68th Armor Regiment, 3rd Advise and Assist Brigade, 4th Infantry Division, prepare the RQ-16A Tarantula Hawk unmanned aerial vehicle, for operation, at Basra province, Iraq, Dec. 1, 2010. Although, T-Hawk requires a great deal of maintenance, the capabilities it provides are well worth the time spent. (U.S. Army photo by 2nd Lt. Matthew Fumagalli/Released). Date Shot: 12/1/2010![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict76.jpg) Engineers, from left, Daniel Braun, Eric Sanchez and David Barney, with Space and Naval Warfare Systems Command Systems Center Pacific, perform pre-deployment inspections on Littoral Battlespace Sensing Unmanned Undersea Vehicles aboard the oceanographic survey ship USNS Pathfinder (T-AGS 60) while portside in San Diego, Calif., Oct. 21, 2010. Each vehicle hosts a payload suite of sensors that will measure the physical characteristics of the water column as it routinely descends and ascends in the ocean. (U.S. Navy photo by Rick Naystatt/Released). Date Shot: 10/21/2010
Engineers, from left, Daniel Braun, Eric Sanchez and David Barney, with Space and Naval Warfare Systems Command Systems Center Pacific, perform pre-deployment inspections on Littoral Battlespace Sensing Unmanned Undersea Vehicles aboard the oceanographic survey ship USNS Pathfinder (T-AGS 60) while portside in San Diego, Calif., Oct. 21, 2010. Each vehicle hosts a payload suite of sensors that will measure the physical characteristics of the water column as it routinely descends and ascends in the ocean. (U.S. Navy photo by Rick Naystatt/Released). Date Shot: 10/21/2010![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict75.jpg) U.S. Navy Aerographer’s Mate Airman Alex Boston, left, and Aerographer’s Mate 3rd Class Ryan Thuecks, right, both assigned to the Naval Oceanography Mine Warfare Center, and Ana Ziegler, with the Office of Naval Research, deploy an unmanned underwater vehicle during exercise Frontier Sentinel in the northern Atlantic Ocean June 9, 2010. The annual joint maritime homeland security exercise involved the Canadian navy, the U.S. Navy and Coast Guard, and federal, state, and local agencies in the detection, assessment and response to maritime security threats. (U.S. Navy photo by Wayne Stigstedt/Released). Date Shot: 6/9/2010
U.S. Navy Aerographer’s Mate Airman Alex Boston, left, and Aerographer’s Mate 3rd Class Ryan Thuecks, right, both assigned to the Naval Oceanography Mine Warfare Center, and Ana Ziegler, with the Office of Naval Research, deploy an unmanned underwater vehicle during exercise Frontier Sentinel in the northern Atlantic Ocean June 9, 2010. The annual joint maritime homeland security exercise involved the Canadian navy, the U.S. Navy and Coast Guard, and federal, state, and local agencies in the detection, assessment and response to maritime security threats. (U.S. Navy photo by Wayne Stigstedt/Released). Date Shot: 6/9/2010![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict74.jpg) U.S. Navy Sonar Technician Surface 1st Class Bryson Menke and Mineman 3rd Class Michael Darcy, both stationed with Explosive Ordnance Disposal Mobile Unit (EODMU) 1, prepare to deploy an unmanned underwater vehicle April 22, 2010, in the Persian Gulf. EODMU-1 and USS Dextrous (MCM 13) are conducting drills. (U.S. Navy photo by Mass Communication Specialist 2nd Class Ja’lon A. Rhinehart/Released). Date Shot: 4/22/2010
U.S. Navy Sonar Technician Surface 1st Class Bryson Menke and Mineman 3rd Class Michael Darcy, both stationed with Explosive Ordnance Disposal Mobile Unit (EODMU) 1, prepare to deploy an unmanned underwater vehicle April 22, 2010, in the Persian Gulf. EODMU-1 and USS Dextrous (MCM 13) are conducting drills. (U.S. Navy photo by Mass Communication Specialist 2nd Class Ja’lon A. Rhinehart/Released). Date Shot: 4/22/2010![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict73.jpg) Danielle Bryant, right, an oceanographer from the Naval Oceanographic Office (NAVOCEANO), establishes a satellite connection to the Glider Operations Center at NAVOCEANO before launching the seaglider unmanned underwater vessel from the Military Sealift Command oceanographic survey ship USNS Henson (T-AGS 63) March 24, 2010, in the Atlantic Ocean. The vessel is designed to collect physical oceanography data in deep water. Henson is under way off the coast of Fortaleza, Brazil, for Oceanographic-Southern Partnership Station 2010 conducting survey demonstrations with the Brazilian Directorate of Hydrograph and Navigation. Oceanographic-Southern Partnership Station is an oceanographic surveying and information exchange program between subject matter experts with partner nations in the U.S. Southern Command area of responsibility. (U.S. Navy photo by Mass Communication Specialist 2nd Class Lily Daniels/Released). Date Shot: 3/24/2010
Danielle Bryant, right, an oceanographer from the Naval Oceanographic Office (NAVOCEANO), establishes a satellite connection to the Glider Operations Center at NAVOCEANO before launching the seaglider unmanned underwater vessel from the Military Sealift Command oceanographic survey ship USNS Henson (T-AGS 63) March 24, 2010, in the Atlantic Ocean. The vessel is designed to collect physical oceanography data in deep water. Henson is under way off the coast of Fortaleza, Brazil, for Oceanographic-Southern Partnership Station 2010 conducting survey demonstrations with the Brazilian Directorate of Hydrograph and Navigation. Oceanographic-Southern Partnership Station is an oceanographic surveying and information exchange program between subject matter experts with partner nations in the U.S. Southern Command area of responsibility. (U.S. Navy photo by Mass Communication Specialist 2nd Class Lily Daniels/Released). Date Shot: 3/24/2010![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict72.jpg) U.S. Navy Sonar Technician (Surface) 2nd Class Brad Goss, right, and Sonar Technician (Surface) 1st Class Anthony Craig, left, from the Littoral Combat Ship Anti-Submarine Warfare (LCS ASW) Mission Package detachment, operate an unmanned surface vehicle (USV) in the waters of the Narragansett Bay, R.I., Feb. 16, 2010. The Naval Undersea Warfare Center Division Newport is developing the USV for future LCS ASW operations. (U.S. Navy photo/Released). Date Shot: 2/16/2010
U.S. Navy Sonar Technician (Surface) 2nd Class Brad Goss, right, and Sonar Technician (Surface) 1st Class Anthony Craig, left, from the Littoral Combat Ship Anti-Submarine Warfare (LCS ASW) Mission Package detachment, operate an unmanned surface vehicle (USV) in the waters of the Narragansett Bay, R.I., Feb. 16, 2010. The Naval Undersea Warfare Center Division Newport is developing the USV for future LCS ASW operations. (U.S. Navy photo/Released). Date Shot: 2/16/2010![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict96.jpg) U.S. Navy Mineman Seaman James Raper pushes the mine neutralization vehicle (MNV) of the mine countermeasures ship USS Defender (MCM 2) into its cradle Nov. 24, 2009, in the Yellow Sea. An MNV is a remote-controlled, unmanned submarine that uses a video camera to confirm the presence of underwater mines. Defender is participating in exercise Clear Horizon, an annual exercise conducted with the Republic of Korea Navy, that is one of the largest international mine counter-measures exercises in the world. (U.S. Navy photo by Mass Communication Specialist 1st Class Richard Doolin/Released). Date Shot: 11/24/2009
U.S. Navy Mineman Seaman James Raper pushes the mine neutralization vehicle (MNV) of the mine countermeasures ship USS Defender (MCM 2) into its cradle Nov. 24, 2009, in the Yellow Sea. An MNV is a remote-controlled, unmanned submarine that uses a video camera to confirm the presence of underwater mines. Defender is participating in exercise Clear Horizon, an annual exercise conducted with the Republic of Korea Navy, that is one of the largest international mine counter-measures exercises in the world. (U.S. Navy photo by Mass Communication Specialist 1st Class Richard Doolin/Released). Date Shot: 11/24/2009![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict97.jpg) The U.S Air Force Academy’s Viking 300 aircraft, an unmanned aerial system, flies over Camp Red Devil at Fort Carson, Colo., July 22, 2009. The Air Force Academy is the first military service academy to begin integrating unmanned aerial systems into its curriculum. (U.S. Air Force photo by Mike Kaplan/Released). Date Shot: 7/23/2009
The U.S Air Force Academy’s Viking 300 aircraft, an unmanned aerial system, flies over Camp Red Devil at Fort Carson, Colo., July 22, 2009. The Air Force Academy is the first military service academy to begin integrating unmanned aerial systems into its curriculum. (U.S. Air Force photo by Mike Kaplan/Released). Date Shot: 7/23/2009![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict98.jpg) An Unmanned Little Bird helicopter, a smaller version of the manned A/MH-6M Little Bird helicopter, is tested and evaluated by personnel from the U.S. Marine Corps’ Warfighting Laboratory at Marine Corps Combat Development Command, Quantico, Va., June 16, 2009, in Bridgeport, Calif., during Javelin Thrust-09. Marine Forces Reserve, headquartered in New Orleans, is conducting Javelin Thrust-09 at six locations throughout the Western United States. The combined arms exercise showcases a range of combat and logistics capabilities and allows leaders to assess the operational readiness of participating units. More than 2,000 reserve- and active-component Marines, Sailors, Soldiers and Airmen are training simultaneously in support of the exercise. (U.S. Marine Corps photo by Chief Warrant Officer Keith A. Stevenson/Released). Date Shot: 6/16/2009
An Unmanned Little Bird helicopter, a smaller version of the manned A/MH-6M Little Bird helicopter, is tested and evaluated by personnel from the U.S. Marine Corps’ Warfighting Laboratory at Marine Corps Combat Development Command, Quantico, Va., June 16, 2009, in Bridgeport, Calif., during Javelin Thrust-09. Marine Forces Reserve, headquartered in New Orleans, is conducting Javelin Thrust-09 at six locations throughout the Western United States. The combined arms exercise showcases a range of combat and logistics capabilities and allows leaders to assess the operational readiness of participating units. More than 2,000 reserve- and active-component Marines, Sailors, Soldiers and Airmen are training simultaneously in support of the exercise. (U.S. Marine Corps photo by Chief Warrant Officer Keith A. Stevenson/Released). Date Shot: 6/16/2009![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict99.jpg) Dirk D. Reum, a robotic systems engineer, conducts a systems check of a robotic unmanned ground vehicle (RUGV) June 13, 2009, in Hawthorne, Nev., before making it available for test training with U.S. Marine Corps infantrymen of India Company, 3rd Battalion, 23rd Marine Regiment, 4th Marine Division, during exercise Javelin Thrust 2009. The RUGV has a payload capacity of 1,400 pounds. Javelin Thrust showcases a wide range of combat and logistics capabilities, and allows leaders to assess the operational readiness of participating units. More than 3,000 reserve and active component Marines and members of the Navy, Army and Air National Guard will train during the combined arms exercise at six locations throughout the Western United States. (U.S. Marine Corps photo by Chief Warrant Officer 2 Keith A. Stevenson/Released). Date Shot: 6/13/2009
Dirk D. Reum, a robotic systems engineer, conducts a systems check of a robotic unmanned ground vehicle (RUGV) June 13, 2009, in Hawthorne, Nev., before making it available for test training with U.S. Marine Corps infantrymen of India Company, 3rd Battalion, 23rd Marine Regiment, 4th Marine Division, during exercise Javelin Thrust 2009. The RUGV has a payload capacity of 1,400 pounds. Javelin Thrust showcases a wide range of combat and logistics capabilities, and allows leaders to assess the operational readiness of participating units. More than 3,000 reserve and active component Marines and members of the Navy, Army and Air National Guard will train during the combined arms exercise at six locations throughout the Western United States. (U.S. Marine Corps photo by Chief Warrant Officer 2 Keith A. Stevenson/Released). Date Shot: 6/13/2009![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict100.jpg) The Heron TP medium altitude long endurance unmanned aerial vehicle takes off from Comalapa International Airport in San Salvador, El Salvador, May 21, 2009, during a counter drug operations support mission. The Heron is part of an unmanned aircraft system deployed to El Salvador to support Project Monitoreo, a month-long evaluation initiative to assess the suitability of using unmanned aircraft for counterdrug missions in the United States Southern Command area. (U.S. Army photo by Jose Ruiz/Released). Date Shot: 5/21/2009
The Heron TP medium altitude long endurance unmanned aerial vehicle takes off from Comalapa International Airport in San Salvador, El Salvador, May 21, 2009, during a counter drug operations support mission. The Heron is part of an unmanned aircraft system deployed to El Salvador to support Project Monitoreo, a month-long evaluation initiative to assess the suitability of using unmanned aircraft for counterdrug missions in the United States Southern Command area. (U.S. Army photo by Jose Ruiz/Released). Date Shot: 5/21/2009![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict101.jpg) The U.S. Navy and Spatial Integrated Systems Inc. demonstrate a fully autonomous Unmanned Surface Vehicle (USV) near Fort Monroe, Va., Jan. 14, 2009. The USV uses its autonomous maritime navigation systems to patrol and detect intruders. (U.S. Navy photo by Mass Communication Specialist Seaman Apprentice Joshua Adam Nuzzo/Released). Date Shot: 1/14/2009
The U.S. Navy and Spatial Integrated Systems Inc. demonstrate a fully autonomous Unmanned Surface Vehicle (USV) near Fort Monroe, Va., Jan. 14, 2009. The USV uses its autonomous maritime navigation systems to patrol and detect intruders. (U.S. Navy photo by Mass Communication Specialist Seaman Apprentice Joshua Adam Nuzzo/Released). Date Shot: 1/14/2009![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict93.jpg) U.S. Navy Lt. Timothy Stanford, a graduate student at University of Wisconsin, tests his Autonomous Unmanned Vehicle (AUV) prior to competing in the Association for Unmanned Vehicle Society International’s (AUVSI) 11th annual competition in San Diego, Calif., Aug. 1, 2008. AUVSI, in cooperation with the Space and Naval Warfare Systems Center, hosts the event to encourage young engineers and scientists to consider careers developing AUV technologies for the U.S. Navy. (U.S. Navy photo by Mass Communication Specialist 2nd Class Brian Gaines/Released). Date Shot: 8/1/2008
U.S. Navy Lt. Timothy Stanford, a graduate student at University of Wisconsin, tests his Autonomous Unmanned Vehicle (AUV) prior to competing in the Association for Unmanned Vehicle Society International’s (AUVSI) 11th annual competition in San Diego, Calif., Aug. 1, 2008. AUVSI, in cooperation with the Space and Naval Warfare Systems Center, hosts the event to encourage young engineers and scientists to consider careers developing AUV technologies for the U.S. Navy. (U.S. Navy photo by Mass Communication Specialist 2nd Class Brian Gaines/Released). Date Shot: 8/1/2008![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict94.jpg) Fox News reporter Phil Keating interviews U.S. Navy Capt. Robert Dishman, the Persistent Maritime Unmanned Aircraft Systems Program Office 262 Program Manager, in front of the Skyship 600 blimp at Naval Air Station Key West, Fla., July 10, 2008. The lighter-than-air vehicle is in Key West for six weeks to conduct a series of maritime surveillance evaluations. The joint airship experiment between the U.S. Navy and Coast Guard emphasizes the cooperative strategy for 21st century seapower among the sea services. (U.S. Navy photo by Mass Communication Specialist 2nd Class Rachel McMarr/Released). Date Shot: 7/10/2008
Fox News reporter Phil Keating interviews U.S. Navy Capt. Robert Dishman, the Persistent Maritime Unmanned Aircraft Systems Program Office 262 Program Manager, in front of the Skyship 600 blimp at Naval Air Station Key West, Fla., July 10, 2008. The lighter-than-air vehicle is in Key West for six weeks to conduct a series of maritime surveillance evaluations. The joint airship experiment between the U.S. Navy and Coast Guard emphasizes the cooperative strategy for 21st century seapower among the sea services. (U.S. Navy photo by Mass Communication Specialist 2nd Class Rachel McMarr/Released). Date Shot: 7/10/2008![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict38.jpg) An unmanned aerial vehicle’s Predator Hellfire missile is shown on a simulator’s virtual camera at the March Air Reserve Base in Riverside County, Calif., June 25, 2008. As the U.S. military scrambles to get more robotic warplanes like the Predator drone aloft, it is confronting an unexpected adversary: human error. (Damian Dovarganes)
An unmanned aerial vehicle’s Predator Hellfire missile is shown on a simulator’s virtual camera at the March Air Reserve Base in Riverside County, Calif., June 25, 2008. As the U.S. military scrambles to get more robotic warplanes like the Predator drone aloft, it is confronting an unexpected adversary: human error. (Damian Dovarganes)![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict95.jpg) Secretary of Defense Robert M. Gates learns how to operate an unmanned ground vehicle during a tour of the future combat systems facility at Fort Bliss, Texas, May 1, 2008. (Department of Defense photo by Cherie Cullen/Released). Date Shot: 5/1/2008
Secretary of Defense Robert M. Gates learns how to operate an unmanned ground vehicle during a tour of the future combat systems facility at Fort Bliss, Texas, May 1, 2008. (Department of Defense photo by Cherie Cullen/Released). Date Shot: 5/1/2008![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict92.jpg) A Condor unmanned aerial vehicle sits on top of its carrying case before flying during Atlantic Strike V at the air-ground training complex in Avon Park, Fla., April 17, 2007. Atlantic Strike is a U.S. Central Command Air Forces initiative and the only joint, tactical-level, urban, close air support training event dedicated to supporting the war on terror. (U.S. Air Force photo by Staff Sgt. Stephen Otero) (Released). Date Shot: 4/17/2007
A Condor unmanned aerial vehicle sits on top of its carrying case before flying during Atlantic Strike V at the air-ground training complex in Avon Park, Fla., April 17, 2007. Atlantic Strike is a U.S. Central Command Air Forces initiative and the only joint, tactical-level, urban, close air support training event dedicated to supporting the war on terror. (U.S. Air Force photo by Staff Sgt. Stephen Otero) (Released). Date Shot: 4/17/2007![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict71.jpg) US Marine Corps (USMC) Marines, 15th Marine Expeditionary Unit (MEU) show the US Navy (USN) Sailors aboard the USN Wasp Class Amphibious Assault Ship USS BOXER (LHD 4) the “Silver Fox” Unmanned Aerial Vehicle (UAV). The 15th MEU and the BOXER are part of Expeditionary Strike Group (ESG) 5 which is currently participating in their Composite Training Unit Exercise (COMPTUEX) off the coast of Southern California. U.S. Navy photo by Mass Communication Specialist Third Class Noel Danseco (RELEASED). Date Shot: 7/16/2006
US Marine Corps (USMC) Marines, 15th Marine Expeditionary Unit (MEU) show the US Navy (USN) Sailors aboard the USN Wasp Class Amphibious Assault Ship USS BOXER (LHD 4) the “Silver Fox” Unmanned Aerial Vehicle (UAV). The 15th MEU and the BOXER are part of Expeditionary Strike Group (ESG) 5 which is currently participating in their Composite Training Unit Exercise (COMPTUEX) off the coast of Southern California. U.S. Navy photo by Mass Communication Specialist Third Class Noel Danseco (RELEASED). Date Shot: 7/16/2006![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict70.jpg) Engineers check the structure after the test flights of the Navy-built Guardian Griffin unmanned aerial vehicle (UAV). The flights demonstrated its capability to support U.S. joint forces with missions ranging from convoy escort and port security to combat patrol. U.S. Navy photo by Mr. John Joyce (RELEASED). Date Shot: 5/18/2006
Engineers check the structure after the test flights of the Navy-built Guardian Griffin unmanned aerial vehicle (UAV). The flights demonstrated its capability to support U.S. joint forces with missions ranging from convoy escort and port security to combat patrol. U.S. Navy photo by Mr. John Joyce (RELEASED). Date Shot: 5/18/2006![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict69.jpg) The Proteus aircraft takes off from Mojave Airfield near Edwards Air Force Base, Calif., on May 9, 2006. It carries the pod that eventually will contain the radar that will be used on the Global Hawk unmanned aerial vehicle. A year of testing, that will be conducted by the 851st Electronic Testing Group, will begin in September once the radar is installed on Proteus. (U.S. Air Force photo) (Released). Date Shot: 5/9/2006
The Proteus aircraft takes off from Mojave Airfield near Edwards Air Force Base, Calif., on May 9, 2006. It carries the pod that eventually will contain the radar that will be used on the Global Hawk unmanned aerial vehicle. A year of testing, that will be conducted by the 851st Electronic Testing Group, will begin in September once the radar is installed on Proteus. (U.S. Air Force photo) (Released). Date Shot: 5/9/2006![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict68.jpg) Northrop Grumman’s RQ-8A Fire Scout Vertical Takeoff and Landing Tactical Unmanned Aerial Vehicle (VTUAV) test fires the second of two Mark (MK) 66 2.75-inch unguided rockets during weapons testing at Arizona’s Yuma Proving Grounds. The Fire Scout has the ability to autonomously take off and land from any aviation-capable warship and at unprepared landing zones, with an on-station endurance of over four hours. The Fire Scout system is capable of continuous operations, providing coverage at 110 nautical miles from the launch site. Utilizing a baseline payload that includes electro-optical/infrared sensors and a laser rangefinder/designator the Fire Scout can find and identify tactical targets, track and designate targets, accurately provide targeting data to strike platforms, employ precision weapons, and perform battle damage assessment. Photographer’s Name: TIM PAYNTER, CIV. Date Shot: 7/25/2005
Northrop Grumman’s RQ-8A Fire Scout Vertical Takeoff and Landing Tactical Unmanned Aerial Vehicle (VTUAV) test fires the second of two Mark (MK) 66 2.75-inch unguided rockets during weapons testing at Arizona’s Yuma Proving Grounds. The Fire Scout has the ability to autonomously take off and land from any aviation-capable warship and at unprepared landing zones, with an on-station endurance of over four hours. The Fire Scout system is capable of continuous operations, providing coverage at 110 nautical miles from the launch site. Utilizing a baseline payload that includes electro-optical/infrared sensors and a laser rangefinder/designator the Fire Scout can find and identify tactical targets, track and designate targets, accurately provide targeting data to strike platforms, employ precision weapons, and perform battle damage assessment. Photographer’s Name: TIM PAYNTER, CIV. Date Shot: 7/25/2005![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict67.jpg) U.S. Air Force Tech. Sgt. Patrick Vasquez, a Force Protection Airborne Surveillance System (FPASS) operator from the 99th Security Forces Group, prepares to release a Desert Hawk unmanned aerial vehicle during an urban warfare training at Indian Springs Auxiliary Air Field, Nev., on May 4, 2005. The Desert Hawk gives real-time video surveillance to FPASS operators who in turn are able to instantly relay enemy force locations to the troops in the field. (U.S. Air Force photo by Master Sgt. Robert W. Valenca) (Released). Date Shot: 5/4/2005
U.S. Air Force Tech. Sgt. Patrick Vasquez, a Force Protection Airborne Surveillance System (FPASS) operator from the 99th Security Forces Group, prepares to release a Desert Hawk unmanned aerial vehicle during an urban warfare training at Indian Springs Auxiliary Air Field, Nev., on May 4, 2005. The Desert Hawk gives real-time video surveillance to FPASS operators who in turn are able to instantly relay enemy force locations to the troops in the field. (U.S. Air Force photo by Master Sgt. Robert W. Valenca) (Released). Date Shot: 5/4/2005![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict65.jpg) A U.S. Air Force BQM-167A Unmanned Aerial Vehicle (UAV) is launched from Tyndall Air Force Base, Fla., on Dec. 22, 2004. The BQM-167A is powered by a ventrally mounted turbojet engine. It can be air or ground launched, and can carry the full range of current target payloads, including radar enhancers, countermeasures, scoring devices, and towed targets. (USAF Photo by Bruce Hoffman, CIV) (Released). Date Shot: 12/22/2004
A U.S. Air Force BQM-167A Unmanned Aerial Vehicle (UAV) is launched from Tyndall Air Force Base, Fla., on Dec. 22, 2004. The BQM-167A is powered by a ventrally mounted turbojet engine. It can be air or ground launched, and can carry the full range of current target payloads, including radar enhancers, countermeasures, scoring devices, and towed targets. (USAF Photo by Bruce Hoffman, CIV) (Released). Date Shot: 12/22/2004![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict64.jpg) A Boeing ScanEagle Unmanned Aerial Vehicle (UAV) sits on top of a table during a demonstration at Indian Springs Auxiliary Field, N.V., on Dec. 18, 2004. The U.S. military uses the four-foot-long UAV as a forward observer to monitor enemy concentrations, vehicle and personnel movement, buildings and terrain in Iraq. (USAF Photo by Tech. Sgt. Kevin J.Gruenwald) (Released). Date Shot: 12/18/2004 [Engine and propeller unit is rotated 90-degrees for service.]
A Boeing ScanEagle Unmanned Aerial Vehicle (UAV) sits on top of a table during a demonstration at Indian Springs Auxiliary Field, N.V., on Dec. 18, 2004. The U.S. military uses the four-foot-long UAV as a forward observer to monitor enemy concentrations, vehicle and personnel movement, buildings and terrain in Iraq. (USAF Photo by Tech. Sgt. Kevin J.Gruenwald) (Released). Date Shot: 12/18/2004 [Engine and propeller unit is rotated 90-degrees for service.]
![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict66.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict63.jpg) U.S. Air Force maintenance personnel prepare to push Global Hawk Air Vehicle Number 3 (AV-3) into its hanger after its 400th mission at an undisclosed location in support of Operation Iraqi Freedom on Nov. 8, 2004. The Global Hawk is an unmanned aerial vehicle designed for surveillance and reconnaissance. (USAF Photo by Tech. Sgt. Erik Gudmundson) (Released). Date Shot: 11/8/2004
U.S. Air Force maintenance personnel prepare to push Global Hawk Air Vehicle Number 3 (AV-3) into its hanger after its 400th mission at an undisclosed location in support of Operation Iraqi Freedom on Nov. 8, 2004. The Global Hawk is an unmanned aerial vehicle designed for surveillance and reconnaissance. (USAF Photo by Tech. Sgt. Erik Gudmundson) (Released). Date Shot: 11/8/2004![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict62.jpg) An AGM-114 Hellfire missile hung on the rail of an US Air Force (USAF) MQ-1L Predator Unmanned Aerial Vehicle (UAV) is inscribed with, “IN MEMORY OF HONORABLE RONALD REAGAN.” Photographer’s Name: TSGT SCOTT REED, USAF. Date Shot: 6/10/2004
An AGM-114 Hellfire missile hung on the rail of an US Air Force (USAF) MQ-1L Predator Unmanned Aerial Vehicle (UAV) is inscribed with, “IN MEMORY OF HONORABLE RONALD REAGAN.” Photographer’s Name: TSGT SCOTT REED, USAF. Date Shot: 6/10/2004![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict61.jpg) Tracked and wheeled versions of the Gladiator Tactical Unmanned Ground Vehicles (TUGV) take a forward position to determine security of the area. The Gladiators are taking part in a live fire exercise with 1st Battalion, 2nd Marines (1/2), Bravo Company (B CO), Marine Corps Base (MCB) Camp Lejeune, North Carolina (NC), at Range 400 aboard Marine Air Ground Task Force Training Command (MAGTF-TC), Twentynine Palms, California (CA). Photographer’s Name: LCPL PATRICK GREEN, USMC. Date Shot: 1/14/2004
Tracked and wheeled versions of the Gladiator Tactical Unmanned Ground Vehicles (TUGV) take a forward position to determine security of the area. The Gladiators are taking part in a live fire exercise with 1st Battalion, 2nd Marines (1/2), Bravo Company (B CO), Marine Corps Base (MCB) Camp Lejeune, North Carolina (NC), at Range 400 aboard Marine Air Ground Task Force Training Command (MAGTF-TC), Twentynine Palms, California (CA). Photographer’s Name: LCPL PATRICK GREEN, USMC. Date Shot: 1/14/2004![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict60.jpg) Lt. Col. George Biondi, Director of Operations for the 82nd Aerial Targets Squadron, Tyndall Air Force Base, Florida, flies this QF-4 “Rhino” as a safety chase on the wing of a remote-controlled unmanned QF-4 “Rhino” full-scale aerial target drone after a Combat Archer Air-to-Air Weapons System Evaluation Program mission over the Gulf of Mexico. The QF-4 Phantom II, affectionately known as the “Rhino”, is used as a threat-representative unmanned target for live-fire test and evaluation missions. It maintains the basic flight envelope capabilities of the original F-4, and can also be flown manned for workup and remote controller training missions. United States Air Force QF-4’s are flown by the 82nd Aerial Targets Squadron from Tyndall Air Force Base, Florida and Holloman Air Force Base, New Mexico. (U.S. Air Force photo Tech. Sgt. Michael Ammons) (Released). Date Shot: 9/16/2003
Lt. Col. George Biondi, Director of Operations for the 82nd Aerial Targets Squadron, Tyndall Air Force Base, Florida, flies this QF-4 “Rhino” as a safety chase on the wing of a remote-controlled unmanned QF-4 “Rhino” full-scale aerial target drone after a Combat Archer Air-to-Air Weapons System Evaluation Program mission over the Gulf of Mexico. The QF-4 Phantom II, affectionately known as the “Rhino”, is used as a threat-representative unmanned target for live-fire test and evaluation missions. It maintains the basic flight envelope capabilities of the original F-4, and can also be flown manned for workup and remote controller training missions. United States Air Force QF-4’s are flown by the 82nd Aerial Targets Squadron from Tyndall Air Force Base, Florida and Holloman Air Force Base, New Mexico. (U.S. Air Force photo Tech. Sgt. Michael Ammons) (Released). Date Shot: 9/16/2003![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict59.jpg) A VMU-2’s Unmanned Air Vehicle (UAV) is ready for launch off a Pneumatic Launcher on the desert floor. Photographer’s Name: LCPL RICHARD W. COURT, USAF. Date Shot: 3/9/2003
A VMU-2’s Unmanned Air Vehicle (UAV) is ready for launch off a Pneumatic Launcher on the desert floor. Photographer’s Name: LCPL RICHARD W. COURT, USAF. Date Shot: 3/9/2003![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict58.jpg) Chief of Naval Operations (CNO) Admiral Vern Clark listens to Steve Castelin of NAVSEA Coastal Systems Station, as he talks about the future of unmanned aerial vehicles (UAV) such as the Blue Fin currently displayed on Nov. 26, 2002. The CNO is in Panama City, Fla., to see new technology hardware and to visit with local area community leaders. (U.S. Navy photo by Chief Photographer’s Mate Johnny Bivera) (RELEASED). Date Shot: 11/26/2002
Chief of Naval Operations (CNO) Admiral Vern Clark listens to Steve Castelin of NAVSEA Coastal Systems Station, as he talks about the future of unmanned aerial vehicles (UAV) such as the Blue Fin currently displayed on Nov. 26, 2002. The CNO is in Panama City, Fla., to see new technology hardware and to visit with local area community leaders. (U.S. Navy photo by Chief Photographer’s Mate Johnny Bivera) (RELEASED). Date Shot: 11/26/2002![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict57.jpg) A RQ-1L Predator UAV (Unmanned Aerial Vehicle) from the 57th Wing Operations Group, Nellis AFB, NV sits in a maintenance bunker at a forward operating airbase in the ENDURING FREEDOM area. The Predator is a medium-altitude, long-endurance, unmanned aerial vehicle system used for reconnaissance, surveillance and target acquisition and is in Afghanistan in direct support of Operation ENDURING FREEDOM. Photographer’s Name: CWO2 William D. Crow, USMC. Date Shot: 2/14/2002
A RQ-1L Predator UAV (Unmanned Aerial Vehicle) from the 57th Wing Operations Group, Nellis AFB, NV sits in a maintenance bunker at a forward operating airbase in the ENDURING FREEDOM area. The Predator is a medium-altitude, long-endurance, unmanned aerial vehicle system used for reconnaissance, surveillance and target acquisition and is in Afghanistan in direct support of Operation ENDURING FREEDOM. Photographer’s Name: CWO2 William D. Crow, USMC. Date Shot: 2/14/2002![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict56.jpg) Operations Specialist 1st Class Guy Hurkmans of Escanaba, Mich., assigned to Destroyer Squadron 50 (DESRON50), Naval Support Activity, Bahrain manually launches an Unmanned Air Vehicle (UAV) during a flight test that is being conducted in support of Maritime Interception Operations (MIO) on Jan. 6, 2002. (U.S. Navy photo by Photographer’s Mate 1st Class Ted Banks) (Released). Date Shot: 1/6/2002
Operations Specialist 1st Class Guy Hurkmans of Escanaba, Mich., assigned to Destroyer Squadron 50 (DESRON50), Naval Support Activity, Bahrain manually launches an Unmanned Air Vehicle (UAV) during a flight test that is being conducted in support of Maritime Interception Operations (MIO) on Jan. 6, 2002. (U.S. Navy photo by Photographer’s Mate 1st Class Ted Banks) (Released). Date Shot: 1/6/2002![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict54.jpg) Army personnel walkout and position the Hunter UAV (Unmanned Aerial Vehicle) for takeoff at Petrovec Airfield, Skopje, Macedonia, in support of TASK FORCE HARVEST. The role of TASK FORCE HARVEST is to collect arms and ammunition voluntarily turned over by ethnic Albanian insurgents, and thereby helps to build confidence in the broader peace process suggested by the President of former Yugoslav Republic of Macedonia. The Hunter UAV plays a key role in helping NATO troops by surveying and looking for any changes in the local area that might hinder the peacekeeping mission. Photographer’s Name: SSGT JOCELYN M. BROUSSARD, USAF. Date Shot: 9/13/2001
Army personnel walkout and position the Hunter UAV (Unmanned Aerial Vehicle) for takeoff at Petrovec Airfield, Skopje, Macedonia, in support of TASK FORCE HARVEST. The role of TASK FORCE HARVEST is to collect arms and ammunition voluntarily turned over by ethnic Albanian insurgents, and thereby helps to build confidence in the broader peace process suggested by the President of former Yugoslav Republic of Macedonia. The Hunter UAV plays a key role in helping NATO troops by surveying and looking for any changes in the local area that might hinder the peacekeeping mission. Photographer’s Name: SSGT JOCELYN M. BROUSSARD, USAF. Date Shot: 9/13/2001![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict53.jpg) The new Dragon Eye Unmanned Arial Reconnaissance Vehicle sits partially disassembled prior to a demonstration given to commanders during Kernal Blitz Experimental aboard Camp Pendleton, Calif., on June 23, 2001. The Dragon Eye is controlled line of site via computer and can transmit real time video imagery back to the operator. (U.S. Marine Corps photo by Sgt. John Vannucci) (Released) Date Shot: 6/23/2001
The new Dragon Eye Unmanned Arial Reconnaissance Vehicle sits partially disassembled prior to a demonstration given to commanders during Kernal Blitz Experimental aboard Camp Pendleton, Calif., on June 23, 2001. The Dragon Eye is controlled line of site via computer and can transmit real time video imagery back to the operator. (U.S. Marine Corps photo by Sgt. John Vannucci) (Released) Date Shot: 6/23/2001![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict52.jpg) The Global Hawk heads back towards its hanger after doing preflight checks before going on a twenty four hour mission out of Edinburgh Air Force Base in Adelaide, South Australia, in support of Exercise Tandem Thrust. The Global Hawk is a jet powered Unmanned Aerial Vehicle (UAV) designed as a Reconnaissance and Surveillance vehicle with a wing span equal to a Boeing 737, flying at altitudes of up to 65,000 feet for more than 24 hours and capable of searching an area of more than 40,000 square miles. The Global Hawk is deployed to Australia from April to June 2001, flying more than a dozen missions. These missions will include sorties in support of Tandem Thrust as well as maritime, littoral, land surveillance and stand off reconnaissance capabilities. The Global Hawk completed its first successful maiden flight in February 1998. Currently there are five U.S. Air Force Global Hawks which have logged over 60 flights and have clocked more than 600 hours, with it’s biggest challenge to date the non-stop Trans-Pacific flight from Edwards AFB CA to Edinburgh AFB South Australia. Exercise Tandem Thrust 2001 is a combined United States and Australian military training exercise. This biennial exercise is being held in the vicinity of Shoalwater Bay Training Area, Queensland, Australia. More than 27,000 Soldiers, Sailors, Airmen and Marines are participating, with Canadian units taking part as opposing forces. The purpose of Exercise Tandem Thrust is to train for crisis action planning and execution of contingency response operations. Photograph CLEARED FOR RELEASE by Lt. Col .Pat Bolibrzuch, Australian Deployment Commander, Global Hawk Program Office and Wing Commander Brett Newell, Deputy Director Emerging Systems, Aerospace Development Branch. U.S. Navy Photo by PH3 J. Smith (Released). Photographer’s Name: PH3 JENNIFER A. SMITH. Date Shot: 5/13/2001
The Global Hawk heads back towards its hanger after doing preflight checks before going on a twenty four hour mission out of Edinburgh Air Force Base in Adelaide, South Australia, in support of Exercise Tandem Thrust. The Global Hawk is a jet powered Unmanned Aerial Vehicle (UAV) designed as a Reconnaissance and Surveillance vehicle with a wing span equal to a Boeing 737, flying at altitudes of up to 65,000 feet for more than 24 hours and capable of searching an area of more than 40,000 square miles. The Global Hawk is deployed to Australia from April to June 2001, flying more than a dozen missions. These missions will include sorties in support of Tandem Thrust as well as maritime, littoral, land surveillance and stand off reconnaissance capabilities. The Global Hawk completed its first successful maiden flight in February 1998. Currently there are five U.S. Air Force Global Hawks which have logged over 60 flights and have clocked more than 600 hours, with it’s biggest challenge to date the non-stop Trans-Pacific flight from Edwards AFB CA to Edinburgh AFB South Australia. Exercise Tandem Thrust 2001 is a combined United States and Australian military training exercise. This biennial exercise is being held in the vicinity of Shoalwater Bay Training Area, Queensland, Australia. More than 27,000 Soldiers, Sailors, Airmen and Marines are participating, with Canadian units taking part as opposing forces. The purpose of Exercise Tandem Thrust is to train for crisis action planning and execution of contingency response operations. Photograph CLEARED FOR RELEASE by Lt. Col .Pat Bolibrzuch, Australian Deployment Commander, Global Hawk Program Office and Wing Commander Brett Newell, Deputy Director Emerging Systems, Aerospace Development Branch. U.S. Navy Photo by PH3 J. Smith (Released). Photographer’s Name: PH3 JENNIFER A. SMITH. Date Shot: 5/13/2001![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict51.jpg) The Broad-area Unmanned Responsive Resupply Operations (BURRO) is used in conjunction with the Slice Multi-Task Boat (only flight deck is seen) for providing over the horizon sea-based logistics. The BURRO (also known as the KAMAN K-1200 K-MAX Helicopter) is also used for resupplying ships at sea. It is currently on the flightdeck of the Slice Boat (Prototype) at Coast Guard Island in Oakland, California, due to its participation in Fleet Battle Experiment Echo. Also seen in the frame is a right side front view of the U.S. Coast Guard High Endurance Cutter, USCGC SHERMAN, (WHEC-720). This mission is in direct support of Urban Warrior ’99. Photographer’s Name: LCPL Christopher L. Vallee. Date Shot: 3/19/1999
The Broad-area Unmanned Responsive Resupply Operations (BURRO) is used in conjunction with the Slice Multi-Task Boat (only flight deck is seen) for providing over the horizon sea-based logistics. The BURRO (also known as the KAMAN K-1200 K-MAX Helicopter) is also used for resupplying ships at sea. It is currently on the flightdeck of the Slice Boat (Prototype) at Coast Guard Island in Oakland, California, due to its participation in Fleet Battle Experiment Echo. Also seen in the frame is a right side front view of the U.S. Coast Guard High Endurance Cutter, USCGC SHERMAN, (WHEC-720). This mission is in direct support of Urban Warrior ’99. Photographer’s Name: LCPL Christopher L. Vallee. Date Shot: 3/19/1999![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict50.jpg) The Navtec, Incorporated Owl MKII Unmanned Surface Vehicle (USV) glides stealthly through the waters of Mile Hammock Bay, New River during a demonstration to highlight it’s marine reconnaissance capabilities to the Riverine Insertion Operation Exercise (RIOEX) ’98 participants. The Owl MKII is funded by the Office of Naval Research (ONR) and is remote-controlled from a small shoreline control station by Brad Dowling, a Navtec, Inc. electronics engineer, at Camp Lejeune, North Carolina, during the Riverine Insertion Operation Exercise (RIOEX) ’98. Photographer’s Name: LCPL T.A. Pope, USMC. Date Shot: 5/14/1998
The Navtec, Incorporated Owl MKII Unmanned Surface Vehicle (USV) glides stealthly through the waters of Mile Hammock Bay, New River during a demonstration to highlight it’s marine reconnaissance capabilities to the Riverine Insertion Operation Exercise (RIOEX) ’98 participants. The Owl MKII is funded by the Office of Naval Research (ONR) and is remote-controlled from a small shoreline control station by Brad Dowling, a Navtec, Inc. electronics engineer, at Camp Lejeune, North Carolina, during the Riverine Insertion Operation Exercise (RIOEX) ’98. Photographer’s Name: LCPL T.A. Pope, USMC. Date Shot: 5/14/1998![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict49.jpg) The Dragon Drone Unmanned Aerial Vehicle was on display at the MOUT (Military Operations in Urban Terrain) facility during LOE 1 (Limited Objective Experiment 1). Urban Warrior is the U.S. Marine Corps Warfighting Laboratory’s series of limited objective experiments examining new urban tactics and experimental technologies. Photographer’s Name: Sgt. Jason J. Bortz. Date Shot: 1/23/1998
The Dragon Drone Unmanned Aerial Vehicle was on display at the MOUT (Military Operations in Urban Terrain) facility during LOE 1 (Limited Objective Experiment 1). Urban Warrior is the U.S. Marine Corps Warfighting Laboratory’s series of limited objective experiments examining new urban tactics and experimental technologies. Photographer’s Name: Sgt. Jason J. Bortz. Date Shot: 1/23/1998![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict48.jpg) US Marine Corps Air Ground Combat Center (MCAGCC). A “Night Owl”, or RQ-2A Pioneer, surveillance Unmanned Aerial Vehicle (UAV) is launched from its twin rail catapult mounted on a 5-ton truck. This launch is conducted by the Cherry Point Marine Base, Squadron-2, part of Combined Arms Exercise (CAX) 5-97 at Airfield Seagle. Photographer’s Name: LCPL E. J. Young. Date Shot: 4/14/1997
US Marine Corps Air Ground Combat Center (MCAGCC). A “Night Owl”, or RQ-2A Pioneer, surveillance Unmanned Aerial Vehicle (UAV) is launched from its twin rail catapult mounted on a 5-ton truck. This launch is conducted by the Cherry Point Marine Base, Squadron-2, part of Combined Arms Exercise (CAX) 5-97 at Airfield Seagle. Photographer’s Name: LCPL E. J. Young. Date Shot: 4/14/1997![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict47.jpg) A close up front view of the fuselage section from the wreckage of a Predator Unmanned Aerial Vehicle (UAV) laying on a hillside in the Russian sector of the Multinational Division North (MDN) area of operations. Photographer’s Name: SSG Edward W. Nino. Date Shot: 10/1/1996
A close up front view of the fuselage section from the wreckage of a Predator Unmanned Aerial Vehicle (UAV) laying on a hillside in the Russian sector of the Multinational Division North (MDN) area of operations. Photographer’s Name: SSG Edward W. Nino. Date Shot: 10/1/1996![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict46.jpg) A civilian contractor tests the unmanned submersible Deep Drone aboard a US Navy ship. The sonar device is being used during salvage operations for downed Korean Air Lines Flight 007 (KAL 007). The commercial jet was shot down by Soviet aircraft over Sakhalin Island in the Sea of Japan on August 30, 1983. All 269 passengers and crewmen were killed. PH1 Fel Barbante, USN
A civilian contractor tests the unmanned submersible Deep Drone aboard a US Navy ship. The sonar device is being used during salvage operations for downed Korean Air Lines Flight 007 (KAL 007). The commercial jet was shot down by Soviet aircraft over Sakhalin Island in the Sea of Japan on August 30, 1983. All 269 passengers and crewmen were killed. PH1 Fel Barbante, USN
You must be logged in to post a comment.