
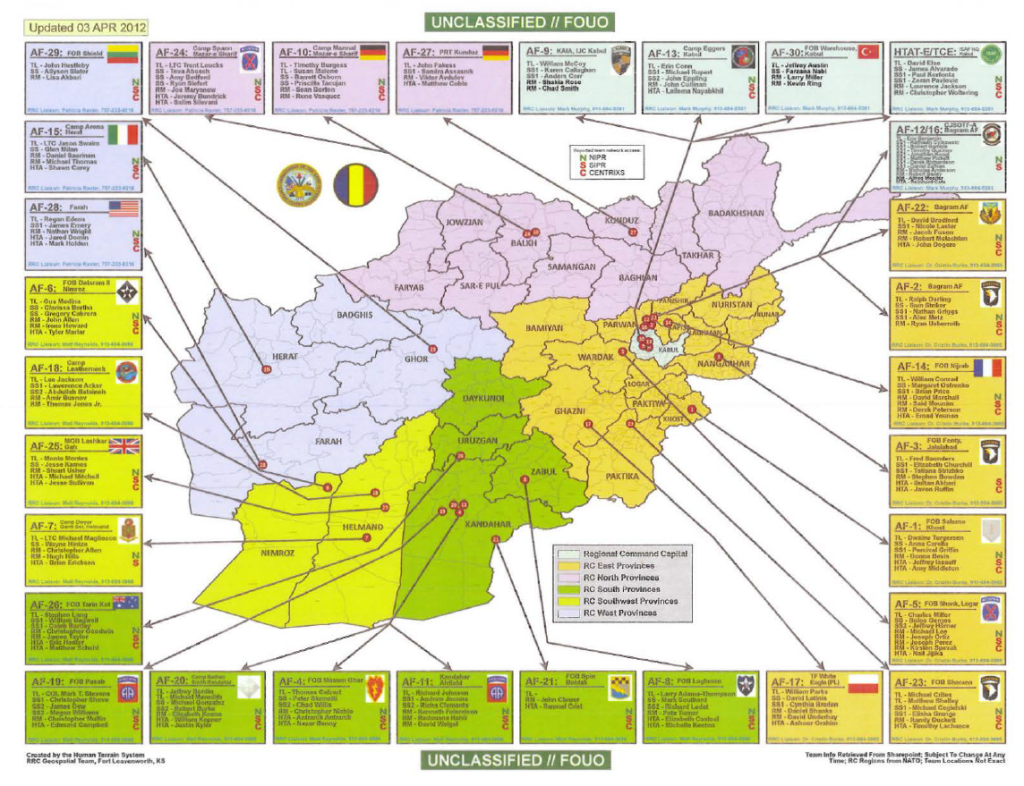
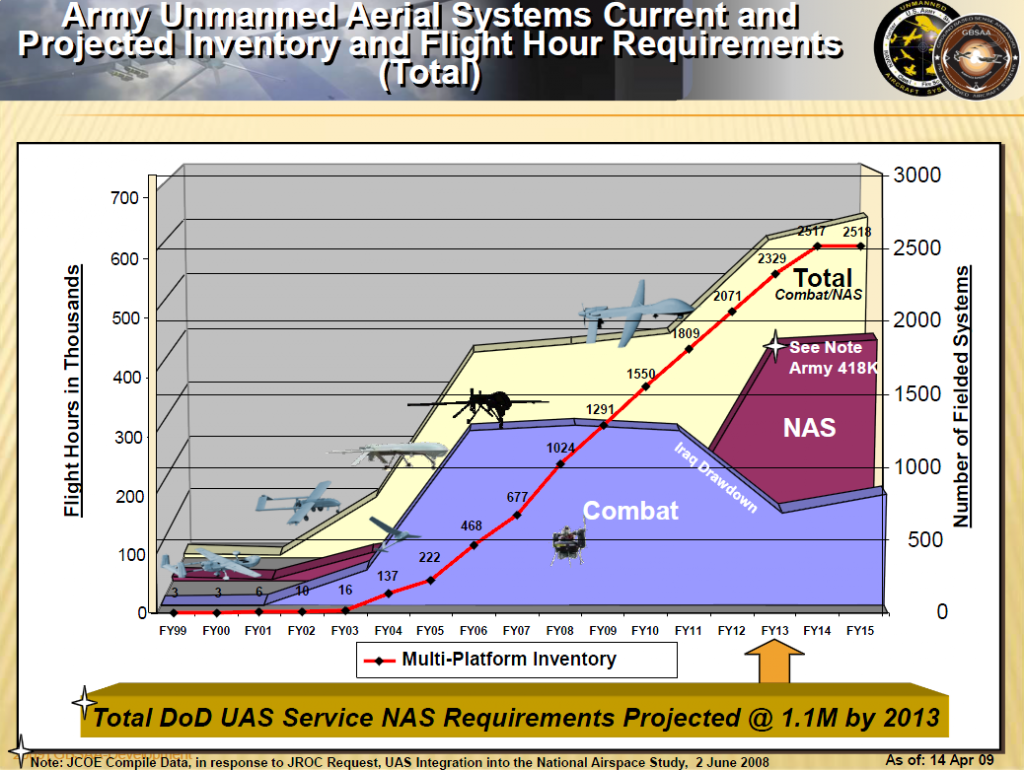
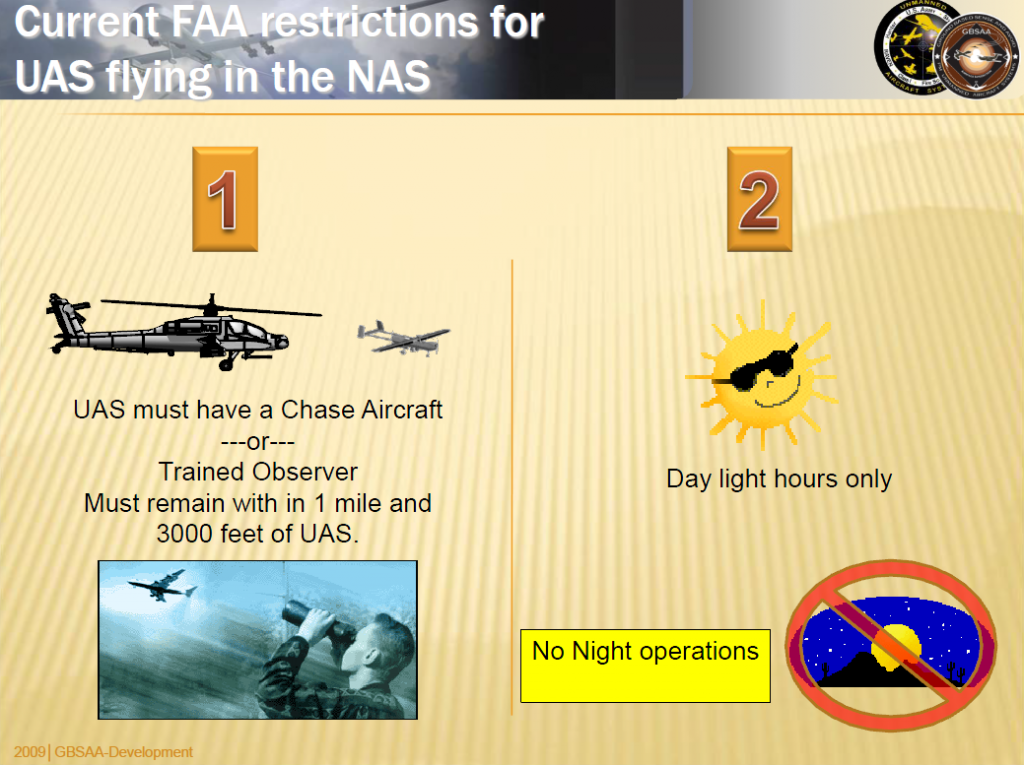
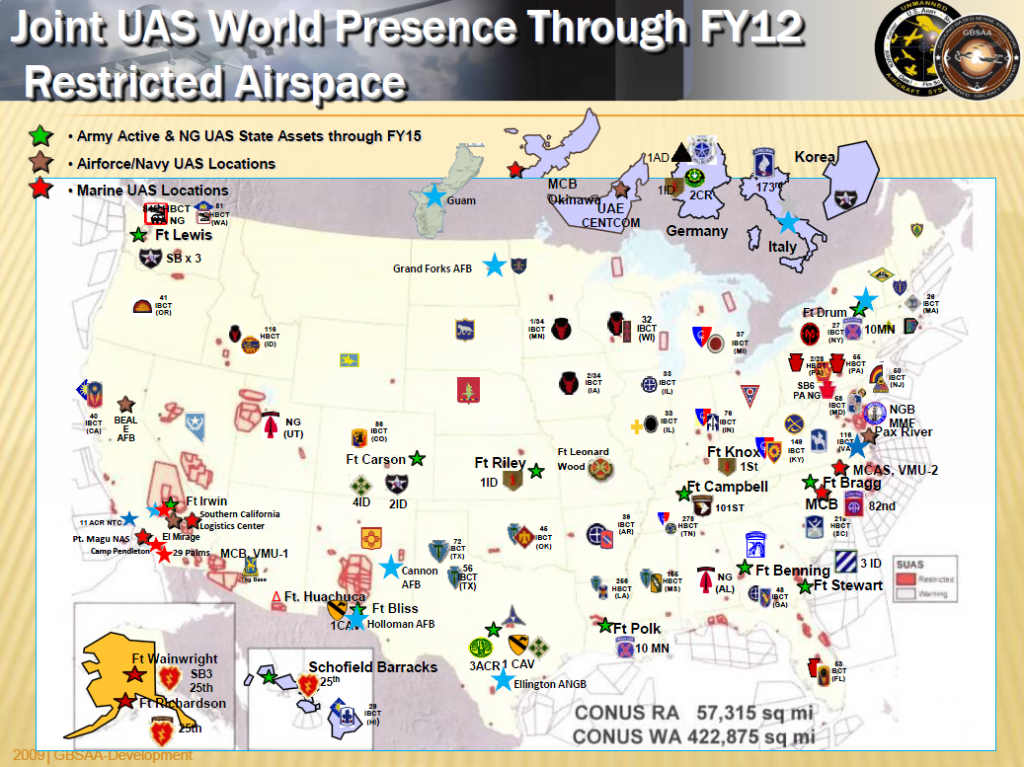
see more at http://www.victims-opfer.com
Die Liste wurde bereits früher hier publiziert:
Vom “Stasiopfer”-Angebot führt ein Link zu einer Website in den USA (www.jya.com), die sich auch mit den Praktiken von Geheimdiensten beschäftigt. Dort findet sich die “Fipro-Liste”, das detaillierte “Finanzprojekt” der Stasi, angefertigt in den letzten Tagen der DDR, um die Rentenansprüche der rund 100 000 hauptamtlichen Mitarbeiter des MfS auch nach dem Zusammenbruch des Systems belegen zu können. Die “Fipro-Liste” ist seit langem bekannt und diente Anfang der neunziger Jahre etwa zur Identifizierung der so genannten OibE – Offiziere im besonderen Einsatz. Diese Liste „Offiziere im besonderen Einsatz“im Jahre 1991 erschien in der “taz. Die Echtheit kann beim BStU überprüft werden.
Siehe u.a. http://www.spiegel.de/spiegel/print/d-22539439.html
Auf Druck ehemaliger STASI-Leute und Ihrer Genossen wurde die Liste aus dem Verkehr gezogen.
Hier ist sie wieder:
090471423014;18;35;00;;BRA(E)CKLEIN, JO(E)RG:;;;2795,00
190435415322;13;00;41;K, 4232/86:;BRA(E)NDEL, LOTHAR;4090;GARTENSTADTSTR. 4;
190435415322;13;00;41;K, 4232/86:;BRA(E)NDEL, LOTHAR;4090;GARTENSTADTSTR. 4;
150359412122;07;00;59;;BRA(E)SE, UDO:;;;22080,00
060769426819;18;31;00;;BRA(E)UER, HOLM:;;;9510,00
031170413111;18;35;00;;BRA(E)UER, OLAF:;;;2795,00
060269415021;18;34;00;;BRA(E)UNER, JO(E)RG:;;;9675,00
160170408225;18;33;00;;BRA(E)UNIG, JO(E)RG:;;;9510,00
150569419728;18;31;00;;BRA(E)UNLICH, HEIKO:;;;9600,00
180470414836;18;33;00;;BRA(E)UNLICH, TOBIAS:;;;6958,87
060468418313;18;33;00;;BRA(E)UTIGAM, JENS:;;;9825,00
190768428922;18;31;00;;BRA(E)UTIGAM, MICHAEL:;;;9648,38
220269425027;18;33;00;;BRA(E)UTIGAM, SVEN:;;;9675,00
181270424938;18;32;00;;BRA(E)UTIGAM, UWE:;;;2795,00
130965400916;01;69;00;;BRAASCH, KARSTEN:;;;15898,50
091165402711;97;08;00;;BRAATZ, ANDREAS:;;;18179,00
260940403112;03;00;42;;BRAATZ, ECKHARD:;;;28080,00
261052505721;04;09;00;;BRAATZ, ELKE:;;;20160,00
151038402729;30;44;00;;BRAATZ, GUENTER:;;;15570,00
300333422120;12;40;00;;BRAATZ, RUDOLF:;;;38250,00
120270411521;07;06;00;;BRAATZ, THOMAS:;;;12460,00
150271422211;18;28;00;;BRAATZ, THOMAS:;;;2720,00
070365403716;97;08;00;;BRAATZ, UWE:;;;17682,50
100557430174;15;18;00;;BRABAND, CARSTEN:;;;22990,00
250255429737;15;02;00;;BRABAND, HENRY:;;;25080,00
111153529817;15;77;00;;BRABAND, ILONA:;;;0,00
241053428221;18;35;00;;BRABANDT, BERTHOLD:;;;25200,00
181252415376;13;80;00;;BRABANT, BERND:;;;20405,00
201239529710;97;01;00;;BRABANT, CHRISTA:;;;19575,00
080139416411;09;06;00;;BRABANT, HEINRICH:;;;19620,00
291037429764;98;20;00;;BRABANT, HEINZ:;;;30937,50
300449426334;99;99;99;::;BRABANT, JOACHIM;1140;MARCHWITZASTR. 3;
300449426334;99;99;99;::;BRABANT, JOACHIM;1140;MARCHWITZASTR. 3;
210357415401;99;02;00;;BRABANT, PETER:;;;23345,00
311261430095;94;65;00;;BRABANT, PETER:;;;18150,00
030162530049;30;84;00;;BRABANT, SIMONE:;;;12321,24
150363430112;15;02;00;;BRABETZ, HEIKO:;;;14850,00
140371403457;03;69;00;;BRACH, ANDREAS:;;;2870,00
051159406154;05;06;00;;BRACH, HARTMUT:;;;17710,00
110637528226;98;27;00;;BRACHAUS, GISELA:;;;23760,00
310540429711;97;06;00;;BRACHAUS, KLAUS:;;;27375,00
290531429730;15;40;00;;BRACHLOW, HERBERT:;;;28500,00
110652529817;30;74;00;;BRACHMANN, DORIS:;;;23262,86
230652413423;04;11;00;;BRACHMANN, HANS-DIETER:;;;26520,00
021165426226;14;40;00;;BRACHMANN, TILO:;;;5263,20
180764401811;02;80;00;;BRACHMANN, WILFRIED:;;;14148,00
210947404438;04;18;00;;BRACHOLD, HERBERT:;;;20872,50
310547412234;07;00;40;;BRACHWITZ, DETLEV:;;;19320,00
200269412287;99;02;00;;BRACHWITZ, GERO:;;;9600,00
300457504515;04;00;41;;BRACHWITZ, ILONA:;;;17595,00
051269413128;18;32;00;;BRACHWITZ, JO(E)RG:;;;9510,00
261042512215;96;15;05;;BRACHWITZ, KRISTINA:;;;26104,16
280752402110;99;43;00;;BRACK, HANS-JUERGEN:;;;19440,00
260639419318;10;00;43;;BRACK, HELMUT:;;;22250,00
220758416412;09;08;00;;BRACK, LUTZ:;;;17595,00
080342429728;94;65;00;;BRACK, MANFRED:;;;23250,00
120760411524;07;00;48;;BRACK, UWE:;;;18013,53
010152404614;04;00;43;;BRACKLOW, EBERHARD:;;;27300,00
210533430054;18;28;00;;BRACKLOW, SIEGFRIED:;;;28500,00
120251404713;17;00;00;;BRACKMANN, GUENTER:;;;25920,00
270162509541;97;06;00;;BRACKROCK, ANDREA:;;;14997,25
151150430068;96;15;00;650/75/11, :;BRADA, WOLFGANG;1130;FRANKFURTER ALLEE 128;
151150430068;96;15;00;650/75/11, :;BRADA, WOLFGANG;1130;FRANKFURTER ALLEE 128;
040469422025;18;32;00;;BRADATSCH, TIMO:;;;9675,00
210655426918;18;35;00;;BRADE, ANDREAS:;;;22350,00
240960530081;99;77;00;;BRADE, ANGELA:;;;19636,77
291157404318;04;51;00;;BRADE, DIRK:;;;20700,00
050535429727;15;53;00;;BRADE, FRED:;;;35250,00
180434430097;18;28;00;;BRADE, GERHARD:;;;27375,00
280665430252;97;08;00;;BRADE, HEIKO:;;;17384,00
061059430025;97;22;00;;BRADE, INGO:;;;18630,00
110768425067;18;32;00;;BRADE, JO(E)RG:;;;9675,00
300170428922;99;43;00;;BRADE, MARIO:;;;9600,00
111268407238;18;35;00;;BRADE, OLIVER:;;;9600,00
230851400211;96;15;21;;BRADE, PETER:;;;25761,38
210742424929;94;11;00;271/68, :;BRADE, ROLF;1600;HERDERSTR. 6;
210742424929;94;11;00;271/68, :;BRADE, ROLF;1600;HERDERSTR. 6;
070336524914;13;26;00;;BRADE, ROSWITHA:;;;25375,00
250748417734;09;08;00;;BRADEL, WOLFGANG:;;;24480,00
100662414811;30;47;00;;BRADEMANN, FRANK:;;;16830,00
060669400830;01;02;00;;BRADEMANN, JENS:;;;8550,00
300344400824;17;00;00;;BRADEMANN, JUERGEN:;;;31680,00
280758415318;08;00;50;;BRADL, ACHIM:;;;16912,50
030562430194;96;15;10;;BRADLER, THORSTEN:;;;18090,00
040669407321;05;69;00;;BRADTKE, MICHAEL:;;;9510,00
240769407421;99;40;00;;BRADTKE, UDO:;;;8300,00
180656529738;94;65;00;;BRAEHMER, IRIS:;;;18529,85
261049404516;18;25;00;;BRAEKOW, ERHARD:;;;27750,00
131256516224;97;07;00;;BRAEKOW, UTE:;;;19046,74
060458404129;97;08;00;;BRAEMER, JOERG:;;;20412,50
270953404113;18;29;00;;BRAEMER, KLAUS-DIETER:;;;23280,00
160254411915;07;00;54;;BRAEMER, LOTHAR:;;;26640,00
260953407411;05;00;40;;BRAEMER, UWE:;;;26640,00
311049516211;99;41;00;;BRAEMING, ILONA:;;;27000,00
280648429751;98;84;00;;BRAEMING, RAINER:;;;22687,50
060238427417;14;06;00;;BRAENDEL, ARMIN:;;;22437,50
260141529712;99;49;00;;BRAENLICH, DORIS:;;;27250,00
191069409129;06;69;00;;BRAENZEL, THOMAS:;;;9510,00
191169500712;01;96;31;;BRAESEL, ANKA:;;;2297,58
071169430025;15;69;00;;BRAESEL, MATHIAS:;;;9510,00
250943407611;05;00;40;;BRAETSCH, UWE:;;;25562,50
090552506444;98;82;00;;BRAETZ, MONIKA:;;;22916,37
120248409214;04;12;00;;BRAEUER, DIETER:;;;21000,00
201065429217;18;33;00;;BRAEUER, DIRK:;;;14110,04
131128430012;99;02;00;;BRAEUER, GERD:;;;37500,00
270437430059;30;47;00;;BRAEUER, GUENTER:;;;20880,00
310843429751;97;06;00;;BRAEUER, HERBERT:;;;24000,00
220263426213;02;00;44;;BRAEUER, INGOLF:;;;19140,00
151256424985;97;17;00;;BRAEUER, JUERGEN:;;;21332,50
171163430057;15;00;49;;BRAEUER, KARSTEN:;;;17572,50
280464426716;14;80;00;;BRAEUER, MATHIAS:;;;15482,50
310557415121;96;15;25;;BRAEUER, MICHAEL:;;;25884,00
180661423823;13;00;43;;BRAEUER, PETER:;;;16142,50
170955513024;99;77;00;;BRAEUER, SABINE:;;;10394,09
270853426219;97;29;00;;BRAEUER, STEFFEN:;;;26640,00
191155527711;30;49;00;;BRAEUER, STEFFI:;;;11382,21
241065426346;94;03;00;;BRAEUER, SVEN:;;;11016,00
270546407210;30;42;00;;BRAEUER, UDO:;;;19440,00
140160425074;13;08;00;;BRAEUER, VOLKER:;;;15592,50
041244428260;99;78;00;;BRAEUER, WILFRIED:;;;25975,00
150469528230;14;53;00;;BRAEUNIG, ANNETT:;;;12205,00
071252429754;30;47;00;;BRAEUNIG, BERND:;;;24120,00
190532429718;99;40;00;;BRAEUNIG, GERHARD:;;;28500,00
270153429718;96;15;13;;BRAEUNIG, HANS-JUERGEN:;;;25530,00
040940530061;98;83;00;;BRAEUNIG, HELGA:;;;23040,00
040851503344;30;84;00;;BRAEUNIG, ILONA:;;;21390,00
200551529753;96;15;31;;BRAEUNIG, INGRID:;;;25920,00
010242424512;13;00;49;;BRAEUNIG, JUERGEN:;;;27000,00
081144422714;04;26;00;;BRAEUNIG, KLAUS-JUERGEN:;;;23187,50
250249428228;30;80;00;;BRAEUNIG, REINER:;;;22590,00
200149528226;14;30;00;;BRAEUNIG, SONJA:;;;16610,00
231249524937;30;80;00;;BRAEUNIG, SONJA:;;;21045,00
310371417444;09;69;00;;BRAEUNIG, SWEN:;;;3928,06
110461422013;98;84;00;;BRAEUNIG, ULF:;;;18610,96
150667430189;15;18;00;;BRAEUNIGER, OLAF:;;;14819,00
190750420017;11;00;43;;BRAEUNING, HUBERTUS:;;;29160,00
030851528315;30;84;00;;BRAEUNING, MARGIT:;;;15101,16
051155414210;07;08;00;;BRAEUNING, ROLF:;;;17077,50
160163430109;98;81;00;;BRAEUNLICH, FRANK:;;;16830,00
100568413716;97;22;00;;BRAEUNLICH, FRANK:;;;14994,00
130652424976;60;90;00;;BRAEUNLICH, GERD:;;;
130652424976;60;90;00;;BRAEUNLICH, GERD:;;;18917,01
140440429731;98;84;00;;BRAEUNLICH, JUERGEN:;;;30187,50
190639418218;10;00;40;;BRAEUNLICH, KLAUS:;;;25500,00
270261430126;97;06;00;;BRAEUNLICH, WOLFRAM:;;;18232,50
141039506926;99;43;00;;BRAEUNLING, ANNEMARIE:;;;20625,00
231047413411;97;01;00;;BRAEUNLING, EBERHARD:;;;27750,00
120451421817;99;02;00;;BRAEUNLING, GUENTER:;;;28980,00
080342406913;99;43;00;;BRAEUNLING, WILFRIED:;;;21750,00
041070417739;97;01;00;;BRAEUTIGAM, ANDRE:;;;3070,16
180457423623;17;00;00;;BRAEUTIGAM, ANDREAS:;;;18285,00
200950517717;09;40;00;;BRAEUTIGAM, BRIGITTE:;;;19050,20
041244417748;09;51;00;;BRAEUTIGAM, ERNST:;;;27000,00
191043406114;04;06;00;;BRAEUTIGAM, GOETZ:;;;22437,50
251029420210;11;00;47;;BRAEUTIGAM, GUENTER:;;;27000,00
290753408310;06;14;00;;BRAEUTIGAM, HANS-HENNING:;;;18457,50
061150409315;10;06;00;;BRAEUTIGAM, HELMUT:;;;22475,00
111046430053;18;27;00;;BRAEUTIGAM, HOLGER:;;;27750,00
300347429729;97;06;00;;BRAEUTIGAM, JOERGEN:;;;26250,00
191169430048;99;02;00;;BRAEUTIGAM, MARCO:;;;13880,00
160748429779;15;00;41;;BRAEUTIGAM, PETER:;;;33120,00
010369408544;12;69;00;;BRAEUTIGAM, RONALD:;;;12412,26
301269428230;14;69;00;;BRAEUTIGAM, STEFFEN:;;;12085,00
270749423931;99;13;00;;BRAEUTIGAM, WOLFRAM:;;;27060,00
280868430041;18;35;00;;BRAEUTIGAMM, HENRY:;;;10600,00
210963402619;02;00;49;;BRAHM, FRANK:;;;19965,00
130647402510;02;53;00;;BRAHM, GERHARD:;;;27000,00
090866402648;01;00;48;;BRAHM, RENE:;;;12035,00
031170401516;02;06;00;;BRAHM, THOMAS:;;;3510,00
190469402511;02;06;00;;BRAHM, THORSTEN:;;;13175,00
130171524626;13;07;00;;BRAJER, KATHRIN:;;;3220,00
271256409546;06;03;00;;BRAMER, SIEGFRIED:;;;17490,00
280170415114;98;82;00;;BRAMIG, RENE:;;;10376,13
120769403918;18;35;00;;BRAMMER, ANDREAS:;;;10035,00
140271416453;18;80;00;;BRAND, AXEL:;;;2945,00
130635429716;97;06;00;;BRAND, EBERHARD:;;;37500,00
020134529711;97;06;00;;BRAND, EDITH:;;;25375,00
180764421812;12;55;00;;BRAND, EGBERT:;;;16170,00
010359417789;09;15;00;;BRAND, FRANK:;;;17974,00
050152421816;12;00;52;;BRAND, GUNTER:;;;25200,00
070558508936;04;55;00;;BRAND, HEIKE:;;;18669,32
200170413749;99;43;00;;BRAND, JAN:;;;9510,00
281069408512;98;82;00;;BRAND, JOERG:;;;10376,13
280970409927;18;35;00;;BRAND, MARIO:;;;2795,00
160241428224;14;00;40;;BRAND, ROLAND:;;;26820,00
290370413016;05;69;00;;BRAND, STEFAN:;;;9910,00
300870421828;18;34;00;;BRAND, STEFFEN:;;;6736,77
190569417534;18;33;00;;BRAND, THOMAS:;;;9600,00
130755423626;04;53;00;;BRAND, WOLFRAM:;;;24150,00
100857516025;11;77;00;;BRANDAU, MARITTA:;;;16708,73
271169413248;08;00;44;;BRANDAU, SVEN:;;;8300,00
170153416011;11;06;00;;BRANDAU, WOLFGANG:;;;24782,50
281052402720;02;55;00;;BRANDECKER, DIETER:;;;20160,00
220969402715;17;00;00;;BRANDENBURG, AXEL:;;;8300,00
241169427036;94;03;00;;BRANDENBURG, BERND:;;;9630,00
281252405213;30;63;00;;BRANDENBURG, BERND:;;;14100,00
010359400514;01;06;27;;BRANDENBURG, DIETMAR:;;;18457,50
061152424914;13;15;00;;BRANDENBURG, HANS:;;;10002,57
230940522819;96;15;22;;BRANDENBURG, HILDEGARD:;;;24480,00
090267409928;07;06;00;;BRANDENBURG, INGO:;;;16832,32
110171431114;15;69;00;;BRANDENBURG, INGO:;;;2925,64
090663506922;30;72;00;;BRANDENBURG, JANA:;;;13860,00
110139402110;02;19;00;;BRANDENBURG, KLAUS:;;;29250,00
080965403428;97;08;00;;BRANDENBURG, LUTZ:;;;16470,00
031164422775;94;65;00;;BRANDENBURG, LUTZ:;;;17985,00
301035422725;97;22;00;;BRANDENBURG, MANFRED:;;;27937,50
020966404356;18;28;00;;BRANDENBURG, RENE:;;;16686,00
100244429746;99;43;00;;BRANDENBURG, ROLF:;;;27000,00
240164430063;94;03;00;;BRANDENBURG, THOMAS:;;;19800,00
300669430036;18;33;00;;BRANDENBURG, TINO:;;;6816,29
260942425008;13;07;00;;BRANDENBURGER, KLAUS:;;;25216,68
030565405912;04;00;40;;BRANDENBURGER, OLAF:;;;16665,00
141058523924;13;55;00;;BRANDENBURGER, PETRA:;;;16088,13
180656411545;07;51;00;;BRANDES, GERALD:;;;17710,00
230251428915;14;18;00;;BRANDHOFF, MANFRED:;;;25200,00
140855420018;96;15;26;;BRANDIES, JUERGEN:;;;21780,00
020855519724;96;15;26;;BRANDIES, SABINE:;;;17940,00
231268407410;18;35;00;;BRANDIS, ANDRE:;;;10900,00
140465402615;02;06;00;;BRANDIS, DIRK:;;;16500,00
130364407426;97;22;00;;BRANDIS, GERD:;;;17423,09
290565411846;07;00;53;;BRANDL, RALF:;;;14355,00
150168408411;18;35;00;;BRANDL, TONI:;;;9675,00
200458428288;14;00;57;;BRANDL, UWE:;;;20355,00
260753409113;06;65;00;;BRANDL, WERNER:;;;20040,00
210360413415;08;00;46;;BRANDL, WILFRIED:;;;22110,00
111266421511;12;09;00;;BRANDNER, ANDREAS:;;;11016,00
260443429717;97;06;00;;BRANDNER, GERD:;;;26250,00
011149422779;12;00;40;;BRANDNER, HARALD:;;;23200,00
080562425112;99;09;00;;BRANDNER, HENNING:;;;18425,00
080468430310;99;77;00;;BRANDNER, JENS:;;;14319,00
080468430302;97;06;00;;BRANDNER, MARKO:;;;15021,00
180669402138;99;43;00;;BRANDSTAEDTER, DIRK:;;;13575,00
020446402111;02;06;00;;BRANDSTAEDTER, SIEGMAR:;;;23250,00
080329406118;17;00;00;;BRANDSTAETER, SIEGFRIED:;;;33000,00
021240408918;06;60;00;;BRANDT, ALBRECHT:;;;23250,00
290828430011;97;06;00;;BRANDT, ALWIN:;;;39750,00
010162400617;04;06;00;;BRANDT, ANDREAS:;;;18260,00
050558402121;02;51;00;;BRANDT, ARNOLD:;;;16560,00
151246503719;17;00;00;;BRANDT, BAERBEL:;;;20625,00
080471526145;97;06;00;;BRANDT, BEATRICE:;;;4900,00
031052424936;94;03;00;;BRANDT, BERND:;;;25200,00
140157502737;30;47;00;;BRANDT, BIRKA:;;;17693,00
060739530076;97;17;00;;BRANDT, BRIGITTE:;;;21750,00
031243406415;04;80;00;;BRANDT, BURCKHARD:;;;26625,00
200856505015;18;77;00;;BRANDT, CHRISTIANE:;;;18975,00
270257409914;15;03;00;;BRANDT, CLAUS-DIETER:;;;20010,00
290453527641;94;30;00;;BRANDT, DAGMAR:;;;19664,33
281266406727;99;14;00;;BRANDT, DIEGO:;;;14375,00
090647413910;08;08;00;;BRANDT, DIETER:;;;17687,50
040552402711;99;40;00;;BRANDT, DIETER:;;;21375,00
010962430136;18;71;20;;BRANDT, DIETMAR:;;;14685,00
110355407119;18;78;00;;BRANDT, DIETRICH:;;;20280,00
151168412255;18;35;00;;BRANDT, DIRK:;;;9825,00
251045500827;01;80;00;;BRANDT, DORIT:;;;15660,57
101251416411;09;00;44;;BRANDT, EBERHARD:;;;23760,00
091058410628;07;03;00;;BRANDT, FRANK:;;;19200,66
240852404029;03;00;49;;BRANDT, GERT:;;;22320,00
190937429724;99;26;00;;BRANDT, GUENTER:;;;28500,00
291051426316;99;55;00;;BRANDT, GUNTER:;;;24960,00
070535403912;03;00;48;;BRANDT, HANS-DIETER:;;;18375,00
150653410718;07;43;00;;BRANDT, HANS-HELMUT:;;;23040,00
130848414411;08;00;56;;BRANDT, HANS-JUERGEN:;;;17192,50
061152411419;17;00;00;;BRANDT, HANS-PETER:;;;19440,00
040749409116;99;40;00;;BRANDT, HANS-ULRICH:;;;27360,00
240843403710;17;00;00;;BRANDT, HARTMUT:;;;18285,00
051259406119;94;03;00;;BRANDT, HEIKO:;;;18345,00
241166403119;03;00;42;;BRANDT, HEINO:;;;2236,00
230236429717;98;18;00;;BRANDT, HELMUT:;;;35250,00
280369407525;97;01;00;;BRANDT, HENRY:;;;3674,19
031256430246;15;00;41;;BRANDT, HOLGER:;;;26162,50
220539429731;96;15;22;;BRANDT, HORST:;;;27187,50
281147403216;03;06;00;;BRANDT, JOACHIM:;;;21750,00
291062413027;08;80;00;;BRANDT, JOCHEN:;;;16170,00
120364430109;96;15;22;;BRANDT, JUERGEN:;;;15510,00
060552400618;01;06;27;;BRANDT, KARL:;;;18227,50
290961400719;18;32;00;;BRANDT, KARSTEN:;;;23100,00
140958411915;30;48;00;;BRANDT, KARSTEN:;;;18240,00
290556509518;99;10;00;;BRANDT, KERSTIN:;;;21900,00
110344413011;07;55;00;;BRANDT, KLAUS:;;;20125,00
070870430619;15;69;00;;BRANDT, MAREK:;;;2925,64
020239529718;99;02;00;;BRANDT, MARIA:;;;24000,00
050155529734;98;83;00;;BRANDT, MARION:;;;15720,26
040869412272;07;06;00;;BRANDT, MATTHIAS:;;;8592,10
091260401514;99;43;00;;BRANDT, MICHAEL:;;;17647,02
200558414529;08;51;00;;BRANDT, PETER:;;;19492,50
011149420319;11;14;00;;BRANDT, PETER:;;;24462,50
250466422017;97;22;00;;BRANDT, PETER:;;;17251,50
010252526328;98;83;00;;BRANDT, PETRA:;;;21600,00
290449415321;08;08;00;;BRANDT, RAINER:;;;23875,00
200945430051;15;08;00;;BRANDT, RAINER:;;;24000,00
041068428332;97;22;00;;BRANDT, RICO:;;;9875,00
030847416417;09;00;44;;BRANDT, ROBERT:;;;21562,50
301068424436;18;31;00;;BRANDT, RONNY:;;;9675,00
270869419822;07;69;00;;BRANDT, SILVIO:;;;8302,58
100271426858;18;32;00;;BRANDT, STEFFEN:;;;6958,87
270169430035;96;15;22;;BRANDT, STEPHAN:;;;9555,00
290170411227;18;34;00;;BRANDT, SVEN:;;;9510,00
050970428251;18;31;00;;BRANDT, SYLVIO:;;;6705,00
240463402134;02;08;00;;BRANDT, THILO:;;;16252,50
200969403111;18;38;00;;BRANDT, THOMAS:;;;9510,00
300964402628;02;09;00;;BRANDT, TORSTEN:;;;16720,00
130353429718;99;14;00;;BRANDT, UDO:;;;24300,00
180735402719;02;26;00;;BRANDT, ULRICH:;;;23250,00
260256502739;99;55;00;;BRANDT, UTE:;;;19969,19
200770400730;18;35;00;;BRANDT, VOLKER:;;;3475,00
120933429715;95;45;00;;BRANDT, WALTER:;;;21750,00
191155405917;04;06;00;;BRANDT, WILFRIED:;;;18842,50
250136429718;99;02;00;;BRANDT, WILFRIED:;;;31125,00
190455405631;30;47;00;;BRANDT, WILFRIED:;;;26840,00
270158411410;07;09;00;;BRANDT, WOLFGANG:;;;21102,50
120149402412;12;18;00;;BRANDT, WOLFGANG:;;;23712,50
151051400824;01;14;00;;BRANDT, WOLFGANG:;;;20520,00
270953409117;99;40;00;;BRANDT, WOLFGANG:;;;25530,00
090655419036;99;43;00;;BRANDTNER, MANFRED:;;;25875,00
250660407515;97;01;00;;BRANDTNER, THOMAS:;;;23712,50
151064430280;96;15;13;;BRANDWEIN, MICHAEL:;;;16500,00
251239530127;99;77;00;;BRANKE, HELGA:;;;41040,00
241039430288;94;65;00;;BRANKE, JUERGEN:;;;27750,00
190446409518;06;02;00;;BRANKE, KLAUS:;;;28312,50
070630430011;97;07;00;;BRANKE, KURT:;;;27000,00
140154402714;30;54;00;;BRANNYS, GEORG:;;;24620,00
211166427412;99;43;00;;BRANSTNER, JENS:;;;15714,00
210749420517;12;07;00;;BRANZ, KLAUS:;;;29625,00
190449410813;07;00;49;;BRASA, GUENTER:;;;27360,00
110970412243;07;06;00;;BRASACK, GUNAR:;;;3557,10
290148410615;07;06;00;;BRASCHE, KLAUS-DIETER:;;;21187,50
070350429796;15;08;00;;BRASCHING, DIETER:;;;22413,01
180263530068;15;19;00;;BRASE, SIMONE:;;;14912,98
011069427625;18;34;00;;BRASE, SWEN:;;;6876,77
260371422443;12;09;00;;BRASOW, RAMON:;;;2700,00
010329430018;97;08;00;;BRASSAT, ALFRED:;;;5437,50
070261400852;01;15;00;;BRASSAT, FRANK:;;;18312,00
140569400868;01;69;00;;BRASSAT, RONALD:;;;6671,61
021270400220;01;69;00;;BRASSEN, ANDREAS:;;;2896,61
111254421215;96;15;00;3039/82, M:;BRATE, ANDREAS;1142;MAX-HERRMANN-STR. 4;
111254421215;96;15;00;3039/82, M:;BRATE, ANDREAS;1142;MAX-HERRMANN-STR. 4;
210637413216;08;51;00;;BRATFISCH, FRITZ:;;;24000,00
120964419018;10;65;00;;BRATFISCH, PASQUALE:;;;12925,00
161253419311;97;01;00;;BRATGE, HANS-JUERGEN:;;;27360,00
280536409529;06;08;00;;BRATKE, ALFRED:;;;28250,00
021267422736;10;00;51;;BRATKE, MAIK:;;;13032,00
240366408024;06;51;00;;BRATKE, THOMAS:;;;16645,50
010554426314;13;00;40;;BRATTIG, ANDREAS:;;;18179,59
300959402244;99;43;00;;BRATZ, DETLEF:;;;21332,50
020760502225;98;27;00;;BRATZ, MANUELA:;;;21142,50
130644428010;14;18;00;;BRATZ, ROLAND:;;;26250,00
200952506915;99;49;00;;BRAUCHLER, DORIS:;;;17825,00
210751403732;17;00;00;;BRAUCHMANN, BERND:;;;30960,00
070652503015;17;00;00;;BRAUCHMANN, INGRID:;;;18199,95
111157403728;03;53;00;;BRAUCHMANN, RALF:;;;22440,00
040650524018;99;09;00;;BRAUER, BAERBEL:;;;25920,00
150358422791;12;00;40;;BRAUER, BERND:;;;22080,00
110554420527;12;00;42;;BRAUER, BERND:;;;26640,00
140762430137;98;83;00;;BRAUER, BJOERN:;;;17270,00
011240502518;97;01;00;;BRAUER, BRIGITTE:;;;20250,00
040552505112;18;77;00;;BRAUER, DORIS:;;;21362,21
311041529720;99;43;00;;BRAUER, ERIKA:;;;22125,00
200166412233;60;90;00;;BRAUER, FRANK:;;;
200166412233;60;90;00;;BRAUER, FRANK:;;;13630,00
120250417117;09;06;00;;BRAUER, GOTTFRIED:;;;21000,00
190843400816;94;65;00;;BRAUER, GUENTER:;;;24000,00
080341429734;99;43;00;;BRAUER, GUENTHER:;;;21750,00
090248429747;94;65;00;;BRAUER, HANS-JOACHIM:;;;27750,00
290965509535;06;09;00;;BRAUER, HEIKE:;;;12762,58
170169402714;01;69;00;;BRAUER, HEIKO:;;;13250,00
180266406206;04;06;00;;BRAUER, HOLGER:;;;16281,00
190933406138;97;08;00;;BRAUER, HORST:;;;28500,00
120962407224;97;01;00;;BRAUER, JAN:;;;16335,00
181169409514;97;22;00;;BRAUER, JENS:;;;6757,50
031265413018;17;00;00;;BRAUER, JOERG:;;;13345,50
271254429746;97;08;00;;BRAUER, KLAUS-PETER:;;;21700,00
250158530147;99;09;00;;BRAUER, MARTINA:;;;14916,87
250451419325;99;09;00;;BRAUER, MICHAEL:;;;28320,00
250933430068;60;90;00;;BRAUER, PETER:;;;
250933430068;60;90;00;;BRAUER, PETER:;;;23520,00
300839413045;08;00;42;;BRAUER, RUDOLF:;;;34560,00
180937429717;94;03;00;;BRAUER, SIEGFRIED:;;;21000,00
241260530122;15;80;00;;BRAUER, SILVIA:;;;14171,58
090163402529;94;03;00;;BRAUER, TORSTEN:;;;18810,00
270737402519;02;06;00;;BRAUER, WILLY:;;;21000,00
201161406197;04;08;00;;BRAUER, WOLFGANG:;;;15744,00
010234509225;30;56;00;;BRAUMANN, ILSE:;;;13680,00
220769410710;18;35;00;;BRAUMANN, RALF:;;;6736,77
250248412216;05;06;00;;BRAUMANN, ROLF-DIETER:;;;19500,00
040751410319;07;12;00;;BRAUMANN, ULRICH:;;;21060,00
071268406936;18;31;00;;BRAUN, ANDRE:;;;9825,00
271251426611;94;03;00;;BRAUN, ANDRE:;;;24900,00
310861409578;06;00;40;;BRAUN, ANDREAS:;;;17325,00
280963413119;99;43;00;;BRAUN, ANDREAS:;;;16260,48
100469404611;99;43;00;;BRAUN, ANDREAS:;;;9600,00
170154422720;30;57;00;;BRAUN, ANDREAS:;;;16080,00
240569528923;14;00;54;;BRAUN, ANETT:;;;13275,00
181252527319;94;03;00;;BRAUN, ANNEROSE:;;;20872,50
150641406930;99;43;00;;BRAUN, BERND:;;;21625,00
191061500876;01;51;00;;BRAUN, BIANCA:;;;16716,07
270846528225;14;08;00;;BRAUN, BIRGIT:;;;21387,50
091049504411;03;53;00;;BRAUN, BRIGITTE:;;;23840,00
030743506928;99;43;00;;BRAUN, BRIGITTE:;;;19172,37
071047506917;99;43;00;;BRAUN, BRIGITTE:;;;20182,50
220728404111;99;43;00;;BRAUN, BRUNO:;;;21750,00
070643428228;99;26;00;;BRAUN, CLAUS-DIETER:;;;24125,00
190355421319;98;84;00;;BRAUN, DIETER:;;;22140,00
280758428215;99;43;00;;BRAUN, DIETMAR:;;;18630,00
060130504118;99;43;00;;BRAUN, DORA:;;;17940,00
090639429728;98;19;00;;BRAUN, EDGAR:;;;51750,00
091053404317;97;17;00;;BRAUN, EDWIN:;;;22320,00
070546411416;07;07;00;;BRAUN, ERNST-ERIK:;;;28020,00
280762502510;02;00;44;;BRAUN, EVELYN:;;;13767,07
091148428012;30;51;00;;BRAUN, FRANK:;;;15120,00
281260521839;98;85;00;;BRAUN, GABRIELA:;;;17283,64
281036417754;98;19;00;;BRAUN, GERHARD:;;;25200,00
190756403728;99;43;00;;BRAUN, GERO:;;;21390,00
310844404310;94;30;00;;BRAUN, HANS-JOACHIM:;;;27750,00
151053417160;11;02;00;;BRAUN, HANS-JOERG:;;;25200,00
110149426714;97;06;00;;BRAUN, HARALD:;;;23360,00
120338430068;99;53;00;;BRAUN, HARRI:;;;25920,00
271154417748;09;40;00;;BRAUN, HEINZ:;;;23250,00
080665429239;14;08;00;;BRAUN, HENDRIK:;;;15322,00
100636403713;03;99;00;;BRAUN, HORST:;;;42750,00
100565403723;03;18;00;;BRAUN, INGO:;;;21120,00
190170500424;18;80;00;;BRAUN, JANA:;;;13730,00
151168422744;17;00;00;;BRAUN, JENS:;;;8300,00
020653424719;13;00;51;;BRAUN, JOCHEN:;;;25200,00
240362421010;12;65;00;;BRAUN, JU(E)RGEN:;;;17022,50
200251413943;08;00;61;;BRAUN, JUERGEN:;;;17077,50
140154421317;99;40;00;;BRAUN, JUERGEN:;;;25320,00
260441529714;15;07;00;;BRAUN, KARIN:;;;16838,64
160952411816;07;80;00;;BRAUN, KARL-HEINZ:;;;18000,00
181062430102;99;51;00;;BRAUN, KARSTEN:;;;17820,00
051243429738;97;06;00;;BRAUN, KLAUS:;;;20500,00
121249404313;03;02;00;;BRAUN, MANFRED:;;;29250,00
040637428216;14;11;00;;BRAUN, MANFRED:;;;26312,50
040244406913;99;43;00;;BRAUN, MANFRED:;;;24000,00
071064402714;02;14;00;;BRAUN, MARIO:;;;15840,00
090267403120;98;82;00;;BRAUN, MATHIAS:;;;17490,00
041264430085;99;02;00;;BRAUN, MICHAEL:;;;18205,00
061064406142;04;06;00;;BRAUN, MIKE:;;;15268,00
050670400046;98;19;00;;BRAUN, MIRKO:;;;3620,00
101069429224;18;31;00;;BRAUN, MIRKO:;;;9600,00
080150504623;99;77;00;;BRAUN, MONIKA:;;;21600,00
080854429713;98;83;00;;BRAUN, PETER:;;;19237,50
240166421320;98;19;00;;BRAUN, RAINER:;;;11016,00
241159417715;99;53;00;;BRAUN, RALF:;;;18343,26
271262402535;02;80;00;;BRAUN, RENE:;;;16190,04
090970414411;18;33;00;;BRAUN, ROLAND:;;;2795,00
080237528214;14;51;00;;BRAUN, SIEGLINDE:;;;19965,00
010169500418;18;78;00;;BRAUN, SILKE:;;;14025,00
100269413935;18;34;00;;BRAUN, STEFFEN:;;;9675,00
050271423128;18;38;00;;BRAUN, STEFFEN:;;;2795,00
130770424723;18;35;00;;BRAUN, SVEN:;;;6705,00
210369417738;18;32;00;;BRAUN, THOMAS:;;;10725,00
280569426210;18;33;00;;BRAUN, TINO:;;;6958,87
201058400619;01;69;00;;BRAUN, UWE:;;;21792,50
070238428224;14;02;00;;BRAUN, WALTER:;;;30750,00
310534429723;99;14;00;;BRAUN, WERNER:;;;37500,00
010845422727;12;08;00;;BRAUN, WOLF-DIETER:;;;22125,00
290770409411;18;28;00;;BRAUNE, ANDRE:;;;2720,00
210767410814;07;06;00;;BRAUNE, FRITZ-GUENTER:;;;16175,23
301053414219;06;08;00;;BRAUNE, GUENTER:;;;17422,50
140235429724;97;17;00;;BRAUNE, HEINZ:;;;41250,00
271064428240;14;14;00;;BRAUNE, JENS:;;;16170,00
070271400864;01;69;00;;BRAUNE, JENS:;;;2896,61
280543529713;97;17;00;;BRAUNE, JUTTA:;;;24562,50
191270409817;18;32;00;;BRAUNE, MARCO:;;;2795,00
230264412322;30;62;00;;BRAUNE, MARIO:;;;14685,00
070552424926;94;11;00;;BRAUNE, RALPH:;;;22942,50
210366415315;97;08;00;;BRAUNE, RENE:;;;16960,53
080260412228;99;02;00;;BRAUNE, THOMAS:;;;23045,00
200655414512;11;20;00;;BRAUNE, UWE:;;;23460,00
260869430061;99;43;00;;BRAUNEIS, UWE:;;;9510,00
261161409237;06;69;00;;BRAUNER, DIETMAR:;;;16967,50
181146424519;13;20;00;;BRAUNER, MANFRED:;;;24000,00
310742524514;13;77;00;;BRAUNER, VIKTORIA:;;;14677,42
180751417742;09;01;00;;BRAUNER, WERNER:;;;24480,00
140252429806;96;15;11;;BRAUNERT, HANS-JOACHIM:;;;33120,00
110462430103;96;15;21;;BRAUNERT, MATTHIAS:;;;17490,00
220734530085;15;80;00;;BRAUNGARDT, ELFRIEDE:;;;20375,00
160757430122;94;65;00;;BRAUNGARDT, VOLKER:;;;19008,39
120471415713;08;69;00;;BRAUNGART, STEFFEN:;;;3220,00
080955408532;18;77;00;;BRAUNS, ANDREAS:;;;21409,03
250154413111;97;08;00;;BRAUNS, LOTHAR:;;;22500,00
080757419716;97;08;00;;BRAUNSBERGER, DETLEF:;;;17595,00
020851500719;01;96;31;;BRAUNSCHWEIG, ANGELIKA:;;;17806,45
021049423810;94;03;00;;BRAUNSCHWEIG, ECKHARD:;;;24000,00
300949523835;98;83;00;;BRAUNSCHWEIG, HEIDI:;;;18802,50
150369408928;18;32;00;;BRAUNSCHWEIG, JENS:;;;9675,00
230442429718;99;43;00;;BRAUNSCHWEIG, JUERGEN:;;;22500,00
240549400711;01;96;31;;BRAUNSCHWEIG, SIEGBERT:;;;18000,00
120338415351;08;02;00;;BRAUTZSCH, PETER:;;;25500,00
120571427623;18;32;00;;BRAUTZSCH, STEFFEN:;;;2795,00
231166427613;95;45;00;;BRAUTZSCH, UWE:;;;15714,00
241267415338;99;43;00;;BRAUTZSCH, WOLFGANG:;;;14025,00
090252528318;14;96;00;;BRECHEIS, MONIKA:;;;19440,00
260759406431;04;00;45;;BRECHLIN, FRED:;;;21330,00
070652408915;98;19;00;;BRECHLIN, GERT:;;;25530,00
290649406438;04;55;00;;BRECHLIN, HELMUT:;;;20072,58
070344406168;04;30;00;;BRECHLIN, KLAUS-PETER:;;;24000,00
300744416219;09;77;00;;BRECHLING, BERNHARD:;;;37620,00
110964402778;18;71;20;;BRECHOT, TORSTEN:;;;21010,00
170968401339;01;06;26;;BRECHT, ANDREAS:;;;9510,00
220759410127;99;43;00;;BRECHT, FRANK:;;;22252,50
161257410111;99;43;00;;BRECHT, HOLGER:;;;21390,00
210950412228;07;08;00;;BRECKAU, JUERGEN:;;;20160,00
280848412217;07;06;00;;BRECKAU, WOLFGANG:;;;23812,50
201148422010;96;15;22;;BREDACK, ROLAND:;;;27300,00
200157501517;02;06;00;;BREDDIN, ANNELIE:;;;17834,27
011254402518;02;65;00;;BREDDIN, HERBERT:;;;19440,00
081163402516;07;06;00;;BREDDIN, MATTHIAS:;;;17325,00
061061413216;08;00;44;;BREDDIN, PETER:;;;18590,00
150561402526;97;01;00;;BREDDIN, ROLAND:;;;24210,00
311250407519;05;06;00;;BREDE, ECKHARD:;;;22320,00
171170403815;18;35;00;;BREDENDIEK, TINO:;;;6705,00
080259530016;18;80;00;;BREDERECK, KARIN:;;;16039,44
281257500711;30;83;00;;BREDEREKE, KARIN:;;;14263,44
140741406170;04;11;00;;BREDERLOW, ROLAND:;;;30375,00
240468530063;97;06;00;;BREDIS, CHRISTINE:;;;11420,93
210334402712;02;11;00;;BREDIS, MANFRED:;;;33750,00
280265415328;94;65;00;;BREDIS, TORSTEN:;;;16830,00
120946518514;10;06;00;;BREDOW, CHRISTINE:;;;21756,77
131144418515;10;00;46;;BREDOW, HORST:;;;24312,50
151051401958;03;00;41;;BREDOW, LOTHAR:;;;25200,00
220470404834;18;33;00;;BREDOW, MICHAEL:;;;2720,00
191262430114;15;07;00;;BREEDE, DIETMAR:;;;15675,00
250261401917;02;00;43;;BREESE, HARTMUT:;;;18232,50
230446530039;97;22;00;;BREETZ, BRIGITTE:;;;20625,00
200439430067;97;22;00;;BREETZ, GUENTER:;;;20187,50
040448401313;03;51;00;;BREETZKE, KLAUS:;;;23400,00
131167419713;18;33;00;;BREHM, FRANK:;;;10800,00
140368419829;11;69;00;;BREHM, GERD:;;;9675,00
180366420216;97;06;00;;BREHM, GERHARD:;;;16200,00
230752419013;10;00;40;;BREHM, HARTMUT:;;;24480,00
261048400812;94;11;00;;BREHM, HEINZ:;;;34500,00
140367430129;97;22;00;;BREHM, KARSTEN:;;;15876,00
200470417119;09;69;00;;BREHM, MARCO:;;;9510,00
120571410813;18;34;00;;BREHM, MIKE:;;;2795,00
080669420223;18;28;00;;BREHM, OLAF:;;;6792,09
230744422028;07;06;00;;BREHM, WOLFGANG:;;;26250,00
160753417414;97;06;00;;BREHME, HARALD:;;;25920,00
220256414222;99;51;00;;BREHME, RALF:;;;22400,00
290158407444;97;08;00;;BREHME, RENE:;;;22080,00
110469405218;18;34;00;;BREHMEL, THOMAS:;;;9675,00
181158404128;96;15;05;;BREHMER, FRED:;;;18862,50
210754529912;99;49;00;;BREHMER, GABRIELE:;;;1126,61
200150429890;15;03;00;;BREHMER, GERD:;;;24571,67
270235404119;03;40;00;;BREHMER, GERD:;;;17048,75
070235429715;96;15;15;;BREHMER, HERBERT:;;;33000,00
180942429746;99;40;00;;BREHMER, INGO:;;;26250,00
160942529714;99;43;00;;BREHMER, JUTTA:;;;19843,24
050553410122;04;80;00;;BREHMER, KARL-HEINZ:;;;18720,00
050140429714;15;22;00;;BREHMER, PETER:;;;27000,00
140537504128;03;40;00;;BREHMER, RENATE:;;;14886,77
100134422738;96;15;25;;BREHMER, WOLFGANG:;;;25500,00
190869410326;07;69;00;;BREIER, BERND:;;;2911,13
180266417757;18;32;00;;BREIER, DETLEF:;;;18396,00
270837415325;08;08;00;;BREINIG, KLAUS-PETER:;;;26250,00
010563400634;01;00;42;;BREINLINGER, FRANK:;;;17820,00
150967400619;01;00;49;;BREINLINGER, JENS:;;;12775,00
040369407020;94;03;00;;BREIT, RALF:;;;9510,00
300359400843;96;15;13;;BREITBARTH, JENS-UWE:;;;19347,50
240358417721;09;00;40;;BREITBARTH, LUTZ:;;;17820,00
240140400820;99;40;00;;BREITBARTH, MANFRED:;;;21937,50
070661500828;99;77;00;;BREITBARTH, MARION:;;;18070,34
231062400811;01;69;00;;BREITBARTH, PETER:;;;15620,00
120130430077;18;25;00;;BREITBARTH, RICHARD:;;;28500,00
080962430084;94;65;00;;BREITBARTH, STEFFEN:;;;16170,00
130940500814;99;40;00;;BREITBARTH, URSULA:;;;20032,50
290549416911;09;06;00;;BREITBARTH, WILFRIED:;;;25125,00
260641429718;99;12;00;;BREITE, MANFRED:;;;23937,50
240154524971;97;01;00;;BREITE, SUSANNE:;;;19313,80
120759404212;03;14;00;;BREITENFELD, WOLF-DIETER:;;;15181,50
281255400215;01;00;42;;BREITENFELDT, DETLEF:;;;22440,00
060658408546;98;83;00;;BREITENSTEIN, FRANK:;;;20182,50
071052411728;07;26;00;;BREITENSTEIN, HORST:;;;20010,00
050363412258;97;06;00;;BREITENSTEIN, RONALD:;;;14650,40
110156414738;99;43;00;;BREITER, HANS-GUENTER:;;;19320,00
080458413226;98;82;00;;BREITER, PETER:;;;18227,50
200569426218;18;34;00;;BREITFELD, GISO:;;;9675,00
230557404828;99;02;00;;BREITFELD, HANS:;;;24150,00
250268415115;08;69;00;;BREITFELD, UWE:;;;9875,00
110367530173;96;15;06;;BREITFELDT, INES:;;;13675,00
101238406120;04;06;00;;BREITGOFF, KLAUS:;;;24000,00
200835418211;10;00;44;;BREITHAUPT, KARL-HEINZ:;;;19875,00
291133416218;09;06;00;;BREITHAUPT, WALTER:;;;21583,36
071053419051;99;40;00;;BREITHECKER, GERO:;;;24225,00
250263522114;12;96;67;;BREITING, INA:;;;15757,50
061259422118;94;03;00;;BREITING, PETER:;;;22770,00
190450423646;14;18;00;;BREITKOPF, RAINER:;;;29625,00
290260405912;97;07;00;;BREITKREUTZ, BORIS:;;;17030,00
100854406111;04;00;40;;BREITKREUTZ, GERHARD:;;;19800,00
121041429730;98;82;00;;BREITKREUZ, HORST:;;;20625,00
301068411221;18;35;00;;BREITLAUCH, DIRK:;;;9675,00
090935417756;09;12;00;;BREITLAUCH, WERNER:;;;26250,00
140762415148;99;40;00;;BREITMANN, GOETZ:;;;19415,00
140762415121;15;69;00;;BREITMANN, JOST:;;;17077,50
210141522435;99;43;00;;BREITREITER, HELGA:;;;23250,00
280240422417;95;45;00;;BREITREITER, KARL-HELMUT:;;;37500,00
091270421228;18;33;00;;BREITREITER, THOMAS:;;;2720,00
051050421211;99;99;99;::;BREITREITER, UWE;1140;BA(E)RENSTEINSTR. 6;
051050421211;99;99;99;::;BREITREITER, UWE;1140;BA(E)RENSTEINSTR. 6;
070746530030;30;83;00;;BREITSCHUH, GISELA:;;;18060,00
190750429767;30;47;00;;BREITSCHUH, JUERGEN:;;;17280,00
310367413934;08;07;00;;BREITSCHWERDT, GOTTHARD:;;;15390,00
010344516610;97;01;00;;BREITSPRECHER, CHRISTEL:;;;21000,00
211268405230;04;69;00;;BREITSPRECHER, DIRK:;;;9675,00
160571418440;98;83;00;;BREITSPRECHER, JOERG-DIETMAR:;;;3020,00
200556403623;18;32;00;;BREITSPRECHER, JUERGEN:;;;18630,00
010571414120;18;28;00;;BREITSPRECHER, MARCO:;;;2720,00
061057430152;94;65;00;;BREITSPRECHER, PETER:;;;19665,00
261263403610;03;80;00;;BREITSPRECHER, RAINER:;;;15592,50
041144416617;09;00;45;;BREITSPRECHER, SIEGFRIED:;;;29250,00
180968413814;18;32;00;;BREITUNG, JENS:;;;9675,00
131270428212;18;35;00;;BREITZKE, ANDRE:;;;2795,00
291148401326;01;02;00;;BREITZKE, ROLF:;;;26162,50
240169403435;03;69;00;;BREMER, ANDREAS:;;;9510,00
240169411427;18;31;00;;BREMER, ANDREAS:;;;9600,00
130655503610;03;14;00;;BREMER, BRITTA:;;;17681,17
080139429722;15;69;00;;BREMER, DIETER:;;;33000,00
270450402431;02;00;47;;BREMER, DIETER:;;;16920,00
280868402411;02;69;00;;BREMER, HEIKO:;;;9555,00
110763530140;30;83;00;;BREMER, IRIS:;;;12197,15
260164430088;98;84;00;;BREMER, JENS:;;;18095,00
200234429716;96;15;14;;BREMER, KARL-HEINZ:;;;22500,00
220436404216;03;09;00;;BREMER, KURT:;;;24750,00
070249401713;94;03;00;;BREMER, MANFRED:;;;26220,00
120670429720;99;40;00;;BREMER, MIRKO:;;;2870,00
261249403913;03;26;00;;BREMER, ROBERT:;;;22275,00
020643402428;02;18;00;;BREMER, WILFRIED:;;;29250,00
160654403316;03;14;00;;BREMER, WOLFGANG:;;;18480,00
270562400836;01;19;69;;BREMERKAMP, FALK:;;;19305,00
140840510117;07;00;44;;BREMERT, ILSE:;;;22500,00
090138410113;07;00;44;;BREMERT, KLAUS:;;;18875,00
040460530011;99;77;00;;BREMERT, UTE:;;;19140,00
200251416116;05;03;00;;BREMME, KLAUS-DIETER:;;;22275,00
140555419031;10;55;00;;BREMME, WOLFGANG:;;;20100,00
151259517554;30;61;00;;BREMMERT, KATHRIN:;;;10696,78
250244430054;07;51;00;;BREMSE, JUERGEN:;;;22500,00
050963409538;99;02;00;;BRENDAHL, THOMAS:;;;19470,00
140459421713;10;00;51;;BRENDEL, ALEXANDER:;;;12675,00
151158425079;30;36;00;;BRENDEL, ANDREAS:;;;18487,00
220352507912;99;02;00;;BRENDEL, INGEBORG:;;;24480,49
090468407515;05;19;00;;BRENDEL, JOERG:;;;9872,00
010153421520;06;15;00;;BRENDEL, JUERGEN:;;;26400,00
090945428918;14;00;54;;BRENDEL, JUERGEN:;;;26640,00
070553504119;06;55;00;;BRENDEL, JUTTA:;;;21480,00
301146429719;97;22;00;;BRENDEL, KLAUS:;;;20625,00
060146430045;15;08;00;;BRENDEL, PETER:;;;24000,00
160353506119;30;56;00;;BRENDEL, URSULA:;;;13530,00
131246428212;99;02;00;;BRENDEL, WERNER:;;;27375,00
191254422712;12;00;40;;BRENDEL, WOLFGANG:;;;20700,00
100238404315;97;06;00;;BRENDEMUEHL, HELMUT:;;;24562,50
080868420517;18;32;00;;BRENDLER, ANDREAS:;;;6958,87
140651422257;98;85;00;;BRENDLER, ARNDT:;;;19440,00
310338404510;96;15;22;;BRENDLER, JOACHIM:;;;30000,00
090170404522;18;34;00;;BRENDLER, RENE:;;;10810,00
260960404518;97;01;00;;BRENDLER, STEFAN:;;;22934,35
051168400512;17;00;00;;BRENDTNER, JOERG:;;;8950,00
230342400512;01;07;00;4733/88, :;BRENDTNER, WERNER;2520;HERMANN-MATERN-STR. 16;
230342400512;01;07;00;4733/88, :;BRENDTNER, WERNER;2520;HERMANN-MATERN-STR. 16;
180152407614;15;09;00;;BRENNECKE, BURKHARDT:;;;26100,00
040569407615;97;06;00;;BRENNECKE, JOERG:;;;13750,00
240837411917;97;97;11;;BRENNECKE, ROLF:;;;35250,00
010647411525;04;19;00;;BRENNECKE, ROLF-DIETER:;;;23545,00
041137511915;94;03;00;;BRENNECKE, SIGRID:;;;22927,09
250142430061;18;40;00;;BRENNER, HEINZ:;;;24750,00
200553428219;14;00;41;;BRENNER, JUERGEN:;;;25200,00
180460402516;02;18;00;;BRENNER, LUTZ:;;;9120,00
050160430181;15;80;00;;BRENNER, WOLF-EKKEHARD:;;;17940,00
220449524727;96;15;31;;BRENNIG, BRIGITTE:;;;21600,00
040250429804;97;01;00;;BRENNIG, KLAUS:;;;29250,00
090451503420;03;41;00;;BRENTFUEHRER, MARLIES:;;;19980,00
171147403411;03;09;00;;BRENTFUEHRER, UWE:;;;24000,00
110947410610;97;01;00;;BRENZ, GERT-JOACHIM:;;;35250,00
201051411518;12;06;00;;BRESCH, HANS:;;;21975,00
280355511014;07;06;00;;BRESCH, KARIN:;;;19320,00
090254411017;07;06;00;;BRESCH, PETER:;;;20160,00
140248400816;30;43;00;;BRESEMANN, HANS-PETER:;;;17876,00
050649400228;99;12;00;;BRESEMANN, KLAUS:;;;32530,65
280155400248;99;12;00;;BRESEMANN, VOLKER:;;;21700,00
210571400892;01;06;22;;BRESIEN, MICHAEL:;;;2896,61
210160430069;15;20;00;;BRESKI, JUERGEN:;;;24150,00
230358525053;13;53;00;;BRESLER, ANKE:;;;16431,32
220647424911;13;65;00;;BRESLER, CLAUS:;;;26250,00
110856424320;13;26;00;;BRESLER, DIETMAR:;;;22965,50
300852520320;11;12;00;;BRESLER, ILONA:;;;20180,00
200867424958;18;41;30;;BRESLER, MICHAEL:;;;13200,00
160951420315;11;00;40;;BRESLER, NORBERT:;;;25200,00
180551417721;09;00;40;;BRESSA, KLAUS-DETLEF:;;;26400,00
150939402115;02;06;00;;BRESSEL, DIETER:;;;26250,00
290358530308;94;30;00;;BRESSEL, TATJANA:;;;16239,79
110758408810;94;03;00;;BRESSEM, HARALD:;;;22597,50
230553403713;94;65;00;;BRESSIN, HELMUT:;;;19440,00
070468430127;98;27;00;;BRESSLER, FRANK:;;;14332,00
210334530060;96;15;11;;BRESSLER, LIESELOTTE:;;;22620,00
290734429714;99;43;00;;BRESTRICH, WOLFGANG:;;;27000,00
230456421215;12;00;48;;BRESZLER, HANS-JUERGEN:;;;16276,50
280651426527;04;00;42;;BRESZLER, KLAUS:;;;21485,81
291142429715;99;43;00;;BRETERNITZ, DIETER:;;;24000,00
300955412218;08;20;00;;BRETERNITZ, FRED:;;;23975,00
310768413927;18;40;00;;BRETERNITZ, JO(E)RG:;;;10155,00
300463430217;99;77;00;;BRETERNITZ, UWE:;;;17572,50
290149418432;99;55;00;;BRETERNITZ, WILFRIED:;;;25500,00
241142429728;97;06;00;;BRETFELD, HERMANN:;;;24000,00
200941428229;14;02;00;;BRETFELD, KLAUS:;;;28500,00
251053429223;14;65;00;;BRETSCHNEIDER, CHRISTIAN:;;;19860,00
140548428220;96;15;18;;BRETSCHNEIDER, CHRISTIAN:;;;27360,00
250458430148;99;02;00;;BRETSCHNEIDER, DETLEF:;;;21562,50
030934429718;97;01;00;;BRETSCHNEIDER, DIETER:;;;27750,00
050158421817;12;06;00;;BRETSCHNEIDER, DIETER:;;;19320,00
290663427016;14;51;00;;BRETSCHNEIDER, DIRK:;;;17792,50
250371403622;18;29;30;;BRETSCHNEIDER, DIRK:;;;3070,16
060635429723;94;03;00;;BRETSCHNEIDER, EBERHARDT:;;;24000,00
171239429723;94;30;00;;BRETSCHNEIDER, EGON:;;;26750,00
101144425005;30;47;00;;BRETSCHNEIDER, FRANZ:;;;28780,00
270668421010;18;32;00;;BRETSCHNEIDER, GERALD:;;;9675,00
080268417760;18;35;00;;BRETSCHNEIDER, GERD:;;;10775,00
150542429774;99;77;00;;BRETSCHNEIDER, GERT:;;;24000,00
141036426218;14;03;00;;BRETSCHNEIDER, GUENTER:;;;23250,00
181255422715;94;65;00;;BRETSCHNEIDER, GUENTER:;;;17595,00
250844406728;05;00;41;;BRETSCHNEIDER, GUNTER:;;;27540,00
090455425028;13;20;00;;BRETSCHNEIDER, HARALD:;;;24880,00
150438530071;99;40;00;;BRETSCHNEIDER, HELGA:;;;17595,00
191152529770;30;83;00;;BRETSCHNEIDER, ILONA:;;;17432,26
130930530024;98;83;00;;BRETSCHNEIDER, ILSE:;;;19170,00
290959429213;15;19;00;;BRETSCHNEIDER, INGO:;;;21560,00
211068421818;18;33;00;;BRETSCHNEIDER, JAN:;;;9675,00
211165430214;97;08;00;;BRETSCHNEIDER, JAN:;;;16656,50
290867427210;14;08;00;182, :;BRETSCHNEIDER, JENS;9271;AM HANG 3;
290867427210;14;08;00;182, :;BRETSCHNEIDER, JENS;9271;AM HANG 3;
091069420928;18;34;00;;BRETSCHNEIDER, JO(E)RG:;;;10500,00
080168506731;05;00;40;;BRETSCHNEIDER, KERSTIN:;;;14382,00
160251400612;05;00;41;;BRETSCHNEIDER, KLAUS:;;;24140,00
251258408944;06;65;00;;BRETSCHNEIDER, MICHAEL:;;;17825,00
010943530369;98;83;00;;BRETSCHNEIDER, MONIKA:;;;20309,36
040668409819;18;31;00;;BRETSCHNEIDER, NICO:;;;9825,00
120257520010;97;22;00;;BRETSCHNEIDER, REGINA:;;;17448,10
140135422728;12;03;00;;BRETSCHNEIDER, SIEGFRIED:;;;31437,50
031151429783;99;43;00;;BRETSCHNEIDER, THOMAS:;;;23040,00
260165426232;14;00;47;;BRETSCHNEIDER, TORSTEN:;;;18881,00
250366530221;96;15;14;;BRETSCHNEIDER, UTA:;;;12920,00
220570415119;18;31;00;;BRETSCHNEIDER, VOLKER:;;;6705,00
070268406712;05;69;00;;BRETSCHNER, JOERG:;;;9675,00
230559407010;11;18;00;;BRETTIN, BODO:;;;20189,00
300156517718;99;02;00;;BRETTIN, PETRA:;;;20137,98
240954429710;94;94;00;;BRETTIN, RALF:;;;29670,00
050358407016;05;08;00;;BRETTIN, UWE:;;;20240,00
020951409314;06;00;45;;BRETTSCHNEIDER, GU(E)NTER:;;;21065,00
301146422410;12;00;47;;BRETTSCHNEIDER, HANS:;;;21812,50
050543427916;30;34;00;;BRETTSCHNEIDER, RAINER:;;;23200,00
121053406413;18;80;00;;BRETZKE, KLAUS-DIETER:;;;19980,00
101135429717;15;08;00;;BREU, DIETER:;;;27187,50
070369503212;03;09;00;;BREU, KERSTIN:;;;13000,00
050242429731;98;18;00;;BREUCKER, PETER:;;;30750,00
270869430044;18;32;00;;BREUCKER, TORSTEN:;;;9510,00
030334429722;97;08;00;;BREUDEL, GUENTER:;;;28500,00
271063406410;04;00;42;;BREUER, ANDREAS:;;;16227,00
131068430044;99;02;00;;BREUER, CARSTEN:;;;14475,00
160244429724;99;40;00;;BREUER, FRANK:;;;40312,50
240352429799;97;01;00;;BREUER, HARTMUT:;;;21700,00
310838408219;06;00;42;;BREUER, HEINZ:;;;26875,00
120641429713;97;17;00;;BREUER, HEINZ:;;;28500,00
050167421712;99;12;00;;BREUER, JAN:;;;15606,00
050458420330;97;08;00;;BREUER, JUERGEN:;;;17940,00
070665408228;99;43;00;;BREUER, KLAUS:;;;15463,50
191147419614;11;03;00;;BREUER, LOTHAR:;;;26875,02
250461421728;99;43;00;;BREUER, MARIO:;;;17820,00
280959411815;04;06;00;;BREUER, REINER:;;;19952,50
150465430236;98;83;00;;BREUER, RONALD:;;;16623,00
140431429721;98;83;00;;BREUER, WALTER:;;;21750,00
031048405310;04;00;45;;BREUHAHN, JOACHIM:;;;23760,00
150554504823;04;00;45;;BREUHAHN, SIGRID:;;;18912,82
080643429756;97;06;00;;BREUL, BERND:;;;24000,00
270768411928;18;33;00;;BREUM, JO(E)RG:;;;10575,00
210369408313;18;32;00;;BREUNINGER, JO(E)RG:;;;9675,00
150953426519;14;51;00;;BREY, WOLFGANG:;;;29111,62
260747517716;09;06;00;;BREYER, ILONA:;;;22000,00
041242429737;99;43;00;;BREYER, JUERGEN:;;;21750,00
140546417720;09;09;00;;BREYER, LOTHAR:;;;33187,50
250735430067;96;15;05;;BREYER, LOTHAR:;;;28500,00
190539529711;96;15;12;;BREYER, MONIKA:;;;24155,65
191052429799;99;43;00;;BREYER, ULRICH:;;;24480,00
240251417166;09;51;00;;BREYER, WILFRID:;;;21240,00
160968411212;18;33;00;;BREYMANN, NICO:;;;9600,00
171234405319;04;00;49;;BREYVOGEL, OTTMAR:;;;19560,48
300829407522;05;00;40;;BREZINSKI, HORST:;;;27000,00
221149402722;02;00;45;;BREZMANN, GERHARD:;;;23402,50
040142429786;98;50;00;;BRIEBSCH, EBERHARD:;;;37500,00
230461430247;94;03;00;;BRIEBSCH, ERIK:;;;17160,00
110169430075;98;84;00;;BRIEBSCH, RONALD:;;;14425,00
091061419033;10;08;00;;BRIEGER, ANDREE:;;;17820,00
280755406715;97;22;00;;BRIEGER, KLAUS-DIETER:;;;27700,00
251157528226;99;13;00;;BRIEGER, MARGITTA:;;;17531,75
280257427126;99;13;00;;BRIEGER, STEPHAN:;;;21390,00
261261430092;98;85;00;;BRIEN, JOERG:;;;17820,00
071259430061;97;08;00;;BRIEN, MICHAEL:;;;21026,52
160862530221;97;08;00;;BRIEN, UTE:;;;16169,10
140534429732;99;43;00;;BRIEN, WERNER:;;;27750,00
050747430068;30;58;00;;BRIER, ARMIN:;;;17760,48
280346425018;13;00;40;;BRIER, KARL-HEINZ:;;;33187,50
240266422814;60;90;00;;BRIER, ROLAND:;;;
240266422814;60;90;00;;BRIER, ROLAND:;;;15732,00
211148530117;30;84;00;;BRIER, SIGRID:;;;16560,00
170954424046;30;47;00;;BRIESE, ANDREAS:;;;18758,67
010158424034;30;32;00;;BRIESE, HOLGER:;;;13923,15
190869410414;07;18;00;;BRIESE, JENS:;;;8300,00
200956403710;30;58;00;;BRIESE, JUERGEN:;;;16934,00
141149400217;01;80;00;;BRIESE, JUERGEN:;;;22320,00
250861506114;03;15;00;;BRIESE, KAREN:;;;16665,00
280259530012;30;80;00;;BRIESE, PETRA:;;;3182,90
020952529748;30;76;00;;BRIESE, SIGRID:;;;9465,64
040351408316;06;60;00;;BRIESEMANN, BERND:;;;20182,50
070668408311;97;01;00;;BRIESEMANN, DIRK:;;;8812,50
080456500027;99;40;00;;BRIESEMEISTER, EIKE:;;;18329,19
250656400847;18;32;00;;BRIESEMEISTER, HARALD:;;;29670,00
010345408013;18;33;00;;BRIESEMEISTER, KLAUS:;;;23040,00
240956506134;30;47;00;;BRIESENICK, ILONA:;;;20233,50
110659404013;03;11;00;;BRIESKORN, BERND:;;;19320,00
220363406412;04;14;00;;BRIESKORN, RENE:;;;16170,00
180341406418;04;00;42;;BRIESKORN, WOLFGANG:;;;29250,00
240639417760;09;00;40;;BRIESNER, GERD:;;;30000,00
131142517712;09;60;00;;BRIESNER, RENATE:;;;20750,00
150433405714;04;00;52;;BRIEST, FRITZ:;;;18250,00
250969425068;18;35;00;;BRIEST, HANS-JOERG:;;;10287,08
090860403156;30;62;00;;BRIETZKE, PETER:;;;15251,00
160351429762;30;55;00;;BRILLAT, BERND:;;;3600,00
050752404411;99;12;00;;BRINCKMANN, UWE:;;;21395,00
080659530023;96;15;11;;BRINGER, GABRIELE:;;;17808,29
150358430070;99;26;00;;BRINGER, KLAUS-DIETER:;;;19745,00
261059430013;96;15;14;;BRINGEZU, MARIO:;;;21562,50
010446430041;96;15;07;;BRINGMANN, MATTHIAS:;;;29520,00
200832406928;30;50;00;;BRINGMANN, OTTO:;;;18720,00
070455415315;08;80;00;;BRINK, MATTHIAS:;;;17940,00
270144421327;97;06;00;;BRINKE, FRANK:;;;24000,00
150253510015;07;06;00;;BRINKE, HELGA:;;;20104,00
251232400821;97;01;00;;BRINKEL, GEORG:;;;25687,50
101269400848;01;06;20;;BRINKHOFF, FRANK:;;;12650,00
060161420312;09;03;00;;BRINKMANN, ANDREAS:;;;19277,50
030562430231;98;83;00;;BRINKMANN, BERND:;;;18397,50
040144429747;99;43;00;;BRINKMANN, DETLEF:;;;27750,00
020842429738;98;82;00;;BRINKMANN, GERHARD:;;;17398,39
300751429755;94;03;00;;BRINKMANN, HANS-JOERG:;;;20870,00
110958402747;18;71;25;;BRINKMANN, JOERG:;;;20182,50
080654403244;18;71;10;;BRINKMANN, LOTHAR:;;;20160,00
270371415744;18;33;00;;BRINKMANN, MARKO:;;;2795,00
250251400216;01;06;27;;BRINKMANN, MARTIN:;;;19740,00
110567530143;99;53;00;;BRINKMANN, PETRA:;;;16470,00
240652529812;99;53;00;;BRINKMANN, REGINA:;;;26634,82
010441530051;98;83;00;;BRINKMANN, RUTH:;;;19440,00
311230530018;99;09;00;;BRINKMANN, SIEGLINDE:;;;23250,00
110230430016;97;01;00;;BRINKMANN, WILLY:;;;24750,00
190160409221;99;43;00;;BRITZE, FRANK:;;;21332,50
250166409224;99;43;00;;BRITZE, STEFFEN:;;;16038,00
140858411811;05;00;43;;BRIX, ERHARD:;;;21780,00
180966406119;17;00;00;;BRIX, THORSTEN:;;;9872,00
111253414734;99;14;00;;BRIXEL, HEINZ:;;;27360,00
260755503736;99;09;00;;BRIXEL, SIGRID:;;;17860,29
180965404138;99;14;00;;BRO(E)CKER, FRED:;;;11169,00
090670404422;18;32;00;;BRO(E)CKER, JO(E)RG:;;;2795,00
150466513922;18;80;00;;BRO(E)CKERT, ANNETTE:;;;15660,00
220969413123;18;31;00;;BRO(E)DEL, HOLGER:;;;9510,00
030863424927;08;80;00;;BRO(E)DEL, STEFFEN:;;;15294,59
230263424938;07;06;00;;BRO(E)DNER, KARSTEN:;;;17820,00
140467413967;99;55;00;;BRO(E)MEL, STEFFEN:;;;16092,00
150670406411;18;35;00;;BRO(E)SECKE, ANDRE:;;;6705,00
261154417757;09;20;00;;BROAETER, HANS-JUERGEN:;;;23312,50
031137429736;99;09;00;;BROCK, DIETER:;;;28500,00
270230506917;99;43;00;;BROCK, GISELA:;;;20625,00
160559412222;01;03;00;;BROCK, HOLGER:;;;17997,50
101053406917;99;43;00;;BROCK, KLAUS-DIETER:;;;19440,00
050758410847;94;03;00;;BROCK, REINER:;;;21390,00
120470422743;18;33;00;;BROCK, STEFFEN:;;;9986,44
190733514513;08;96;00;;BROCKE, ANITA:;;;17460,00
111038517749;09;14;00;;BROCKE, MARGARETE:;;;18572,50
290168406445;17;00;00;;BROCKE, TOM:;;;8950,00
150756417744;97;01;00;;BROCKE, UDO:;;;25530,00
030358517719;09;07;00;;BROCKE, VERA:;;;17223,17
080271412119;18;33;00;;BROCKEL, ANDREAS:;;;2795,00
121268400852;18;35;00;;BROCKHAUSEN, JENS:;;;9327,00
081068402112;02;69;00;;BROCKHOFF, PETER:;;;9875,00
241155402428;02;00;47;;BROCKMANN, BERND:;;;22770,00
270257411926;07;00;57;;BROCKMANN, HELMUT:;;;15525,00
030550405012;04;08;00;;BROCKMANN, JOACHIM:;;;22500,00
041162400619;30;61;00;;BROCKMANN, JOERG:;;;14355,00
290962420914;12;00;44;;BROCKMANN, OLAF:;;;13932,00
260237400884;01;06;23;;BROCKMANN, WINFRIED:;;;24000,00
250259408538;97;08;00;;BROCKSCH, ULLRICH:;;;22080,00
310538522722;12;08;00;;BROD, MARGA:;;;17940,00
110959411442;07;00;53;;BRODA, MARIO:;;;22770,00
170948430060;15;08;00;;BRODDA, WILFRIED:;;;23760,00
290948522762;94;30;00;;BRODE, CHRISTINE:;;;20640,00
141062423918;99;43;00;;BRODE, DETLEF:;;;17600,00
101248429748;94;30;00;;BRODE, HARTMUT:;;;22770,00
171067430065;94;30;00;;BRODE, STEPHAN:;;;8950,00
010953402723;02;03;00;;BRODEHL, PETER:;;;24480,00
130841429725;97;08;00;;BRODEHL, ROLF-WERNER:;;;26250,00
250338529717;96;15;10;;BRODEHL, SIEGRID:;;;21937,50
110568430144;99;02;00;;BRODEHL, UWE:;;;14994,00
120754410111;94;03;00;;BRODIEN, GERNOT:;;;20010,00
260168412266;18;32;00;;BRODMANN, DIRK:;;;10621,77
071250520052;30;37;00;;BRODOWSKI, BIANKA:;;;16686,00
240868408542;06;00;46;;BRODOWSKI, THOMAS:;;;12825,00
310147420016;30;37;00;;BRODOWSKI, WOLFRAM:;;;20160,00
130129420313;11;00;40;;BRODRECHT, GERHARD:;;;23250,00
030542419617;11;51;00;;BRODRECHT, JUERGEN:;;;21000,00
181148428927;97;01;00;;BROECKEL, KLAUS:;;;23040,00
200968430097;15;80;00;;BROECKER, RAINER:;;;14750,00
120344429717;97;08;00;;BROECKER, ULRICH:;;;25500,00
240451430058;98;84;00;;BROEDE, WOLFGANG:;;;20100,00
260568413954;99;43;00;;BROEDEL, JOERG:;;;13500,00
040566513922;08;19;00;;BROEDEL, PETRA:;;;13179,42
120252424214;99;02;00;;BROEDNER, INGO:;;;26547,50
020761428119;14;80;00;;BROEDNER, LUTZ:;;;16472,50
311056428113;99;13;00;;BROEDNER, NORBERT:;;;19665,00
010564430085;18;29;30;;BROEGE, AXEL:;;;11220,00
020338430094;18;71;20;;BROEGE, WOLFGANG:;;;24150,00
190166409919;07;00;50;;BROEHL, THOMAS:;;;14812,50
130440411110;07;00;51;;BROEKER, ROLF:;;;29250,00
191057413980;08;20;00;;BROEMEL, INGOLF:;;;23205,00
081268419330;05;69;00;;BROEMEL, SILVIO:;;;9675,00
080357430115;98;18;00;;BROEMME, ANDREAS:;;;26392,50
010230530019;99;02;00;;BROEMME, ILSE:;;;24750,00
060941415426;08;00;40;;BROEMME, JUERGEN:;;;27750,00
051156530141;99;53;00;;BROEMME, MARGRET:;;;21551,13
111231429724;99;09;00;;BROEMME, RUDI:;;;33000,00
190254417513;97;29;00;;BROEMMER, EGBERT:;;;23940,00
070753526339;99;77;00;;BROEMMER, GABRIELE:;;;31680,00
290668415129;08;14;00;;BROEMMLING, DIRK:;;;12130,00
010368402327;97;08;00;;BROER, ANDREAS:;;;15221,00
091030430010;97;08;00;;BROESE, HEINZ:;;;28500,00
270654520720;99;77;00;;BROESE, KARIN:;;;22770,00
241231530051;97;06;00;;BROESE, MARGARETE:;;;21375,00
190848411514;07;06;00;;BROESEL, GUENTER:;;;20562,50
020653511222;07;80;00;;BROESEL, HELGA:;;;18000,00
031233505110;30;54;00;;BROESICKE, JOHANNA:;;;22680,00
091036405115;30;54;00;;BROESICKE, WOLFGANG:;;;26700,00
161139429719;99;43;00;;BROETZMANN, HANS-JOACHIM:;;;23187,50
190241406110;17;00;00;;BROHMANN, WILLI:;;;20700,00
040548402719;02;00;49;;BROMBACH, GUENTER:;;;24375,00
110537400823;01;55;00;;BROMBERG, FRITZ:;;;22500,00
051060408424;97;29;00;;BROMBERG, JOERG:;;;24062,90
220867404218;03;00;44;;BROMBERG, MAIK:;;;13982,00
100247424617;99;02;00;;BROMME, HANS-WERNER:;;;27360,00
241068423618;99;43;00;;BROMME, JOERG:;;;9825,00
240452424610;14;80;00;;BROMME, KARL-HEINZ:;;;14372,13
201132430032;15;20;00;;BRONDER, MANFRED:;;;37500,00
220939530054;15;00;41;;BRONDER, MARLIS:;;;23937,50
170170421314;18;35;00;;BRONDER, TIMO:;;;9600,00
280168409815;07;08;00;;BRONESKE, HARALD:;;;11758,00
260959404115;99;43;00;;BRONEWSKI, WERNER:;;;16830,00
050459422792;12;06;00;;BRONNER, UWE:;;;19780,00
220769418915;10;06;00;;BRONST, THOMAS:;;;12555,00
190645411522;07;06;00;;BROSCH, EDUARD:;;;21687,50
311041429711;99;51;00;;BROSCH, FRITZ:;;;26250,00
250435502719;02;65;00;;BROSCH, HANNA:;;;19500,00
160755402718;02;02;00;;BROSCH, PETER:;;;22080,00
051056430071;99;51;00;;BROSCH, PETER:;;;24725,00
010358430113;99;09;00;;BROSCH, RAINER:;;;22252,50
160169404411;98;85;00;;BROSCHE, FRANK:;;;9675,00
021249413414;13;00;43;;BROSCHE, FRANK:;;;26910,00
180537504415;03;00;40;;BROSCHE, HELENE:;;;16031,25
210566422843;12;65;00;;BROSCHE, KLAUS:;;;14580,00
251232422721;12;60;00;;BROSCHE, RUDOLF:;;;36000,00
040261422771;12;20;00;;BROSCHE, RUDOLF:;;;19745,00
241260530026;94;03;00;;BROSCHIES, MARINA:;;;16847,50
290739408912;06;00;54;;BROSE, GUENTER:;;;29700,00
100657411819;07;00;56;;BROSE, HARALD:;;;22942,50
151058430225;94;11;00;;BROSE, NORBERT:;;;21275,00
210371407619;18;32;00;;BROSE, STEFFEN:;;;2795,00
040171408423;18;32;00;;BROSE, STEFFEN:;;;2795,00
191161403715;03;07;00;;BROSE, UWE:;;;21120,00
161124430012;96;15;14;;BROSE, WALTER:;;;33000,00
180268424838;99;43;00;;BROSGE, SVEN:;;;9600,00
261255412218;94;03;00;;BROSIG, FRANK-ULRICH:;;;20010,00
030661404127;96;15;12;;BROSIG, STEFFEN:;;;20278,79
211069427111;14;69;00;;BROSIG, TORSTEN:;;;12085,00
041149524940;13;20;00;;BROSINSKY, ANGELA:;;;21540,00
231065503736;05;08;00;;BROSINSKY, CORNELIA:;;;7598,31
270968403746;99;43;00;;BROSINSKY, JAN:;;;14425,00
120467403728;05;80;00;;BROSINSKY, RENE:;;;15390,00
250462408525;15;15;00;;BROSIUS, BURKHARD:;;;21450,00
180334429726;99;43;00;;BROSIUS, HERBERT:;;;24750,00
140759406910;94;65;00;;BROSIUS, THOMAS:;;;17745,00
290847529711;99;40;00;;BROSK, BAERBEL:;;;22687,50
010348429725;97;06;00;;BROSK, WOLFGANG:;;;24750,00
240336429748;94;03;00;;BROSKE, HORST:;;;27750,00
221060413628;98;84;00;;BROSOWSKY, HANS-ULRICH:;;;17700,00
050347400812;01;65;00;;BROSTOWSKI, DETLEF:;;;21270,82
230459430088;30;61;00;;BROSY, JOERG:;;;16575,00
310149407616;05;03;00;;BROSZ, GERD:;;;26250,00
190933530067;97;08;00;;BROSZAT, CHRISTEL:;;;19125,00
110632430078;97;08;00;;BROSZAT, HANS-GUENTER:;;;21750,00
140957404844;04;00;50;;BROSZIO, THOMAS:;;;16215,00
230741410814;10;07;00;;BROSZMANN, HARALD:;;;30750,00
101167410324;08;69;00;;BROTHUHN, ULF:;;;6025,00
091236416214;09;00;43;;BROTMEYER, ROLF:;;;28937,50
240270406120;04;18;00;;BROXTERMANN, ANDREAS:;;;2700,00
120747406130;04;41;00;;BROXTERMANN, JUERGEN:;;;31500,00
200443518520;99;40;00;;BROYER, EDELTRAUT:;;;22125,00
010470419328;97;22;00;;BROYER, HEIKO:;;;9930,00
110136418520;95;60;12;;BROYER, KLAUS:;;;33000,00
060670415036;18;33;00;;BRU(E)CKNER, DIRK:;;;9551,61
111270426534;18;35;00;;BRU(E)CKNER, ENRICO:;;;2795,00
130968417334;18;80;00;;BRU(E)CKNER, JENS:;;;9825,00
100169428910;18;33;00;;BRU(E)CKNER, JO(E)RG:;;;2720,00
051035407219;18;25;00;;BRU(E)CKNER, KARL-HEINZ:;;;28687,50
141161419711;11;00;41;;BRU(E)CKNER, KLAUS:;;;15510,00
211062407513;04;00;54;;BRU(E)CKNER, STEFFEN:;;;21065,00
220571403320;18;33;00;;BRU(E)CKNER, STEFFEN:;;;2795,00
060968429246;18;32;00;;BRU(E)CKNER, SVEN:;;;9675,00
261168428916;18;32;00;;BRU(E)CKNER, TINO:;;;10025,00
220968424920;18;31;00;;BRU(E)DGAM, HENRY:;;;9600,00
090368406160;18;31;00;;BRU(E)GGEMANN, GERRIT:;;;9825,00
190770430634;18;31;00;;BRU(E)HL, JENS:;;;2795,00
110663402715;96;15;00;4361/84, M:;BRU(E)NING, FALK;1095;WARNEMU(E)NDER STR. 16;
110663402715;96;15;00;4361/84, M:;BRU(E)NING, FALK;1095;WARNEMU(E)NDER STR. 16;
141270427518;18;32;00;;BRU(E)NING, STEFAN:;;;2795,00
230668415036;18;34;00;;BRU(E)SCHKE, JENS:;;;10375,00
250955429738;30;47;00;;BRUCH, PETER:;;;23805,00
021061402123;02;08;00;;BRUCHE, DIETMAR:;;;18590,00
270859402111;02;26;00;;BRUCHE, JUERGEN:;;;20010,00
130362501718;02;26;00;;BRUCHE, PETRA:;;;10687,34
130970427347;18;40;00;;BRUCHHOLD, LUTZ:;;;6736,77
200655422723;12;26;00;;BRUCHHOLZ, HANS-PETER:;;;20412,50
280152403814;12;00;58;;BRUCHMANN, DETLEF:;;;23460,00
270752421814;12;41;00;;BRUCHMANN, FRANK:;;;31680,00
210538429722;97;06;00;;BRUCHMANN, PETER:;;;27125,00
070353518516;12;08;00;;BRUCHMANN, WALTRAUD:;;;2300,00
230662530084;99;77;00;;BRUCHMUELLER, HEIKE:;;;14594,95
040162414741;99;14;00;;BRUCHMUELLER, UWE:;;;20401,34
260556409915;95;60;24;;BRUCKE, ANDRE:;;;25600,00
050371431117;18;33;00;;BRUCKELT, STEFAN:;;;2795,00
180552506929;99;43;00;;BRUCKER, URSULA:;;;9987,75
091134429719;97;06;00;;BRUCKERT, ARTUR:;;;27595,84
300564410119;96;15;26;;BRUCKERT, TORSTEN:;;;16912,50
100662403629;99;02;00;;BRUCKHOFF, FRANK:;;;19085,00
060633403618;03;00;45;;BRUCKHOFF, HERBERT:;;;26250,00
090570400715;99;77;00;;BRUCKHOFF, MARIO:;;;2915,97
230465503116;03;80;00;;BRUCKSCH, CORINNA:;;;10611,40
120456522123;12;00;43;;BRUCKSCH, MARTINA:;;;5528,21
200340422112;12;00;54;;BRUCKSCH, WERNER:;;;27000,00
190737403116;03;00;50;;BRUCKSCH, WOLF-DIETER:;;;36000,00
060550413917;08;08;00;;BRUDER, KLAUS-DIETER:;;;18450,00
211033430052;18;27;30;;BRUDER, SIEGFRIED:;;;27000,00
051034529716;96;15;11;;BRUDER, SIGRID:;;;21937,50
041131403825;03;02;00;;BRUDNICKI, BRUNO:;;;17666,66
090370403823;97;06;00;;BRUDNICKI, DIRK:;;;9600,00
010268412237;07;06;00;;BRUDNICKI, JENS:;;;11600,00
100166417730;09;00;40;;BRUECK, JENS:;;;18764,40
091068420010;09;69;00;;BRUECK, STEFFEN:;;;9700,00
011243530055;30;47;00;;BRUECKHAENDLER, GITTA:;;;24140,00
070651507524;05;06;00;;BRUECKL, HANNELORE:;;;20040,00
170142507540;05;29;00;;BRUECKL, INGRID:;;;22500,00
121041407515;05;00;50;;BRUECKL, UWE:;;;25500,00
250264415126;97;01;00;;BRUECKMANN, HARTMUT:;;;10560,00
100163417719;94;03;00;;BRUECKMANN, MARIO:;;;18480,00
040362506915;99;77;00;;BRUECKMANN, STEFFI:;;;17796,11
020854421813;12;40;00;;BRUECKNER, ANDREAS:;;;22165,00
100268426814;99;02;00;;BRUECKNER, ANDREAS:;;;9872,00
290359506924;05;80;00;;BRUECKNER, BAERBEL:;;;17250,00
280852418419;97;01;00;;BRUECKNER, BERND:;;;31520,04
061148411926;99;43;00;;BRUECKNER, BERND:;;;27000,00
140240507213;18;29;00;;BRUECKNER, BRIGITTE:;;;19440,00
100250408538;97;22;00;;BRUECKNER, CHRISTIAN:;;;25500,00
061260530116;96;15;12;;BRUECKNER, DANIELA:;;;13895,95
091066426611;14;69;00;;BRUECKNER, DANIELO:;;;13860,00
150445421025;04;06;00;;BRUECKNER, DIETMAR:;;;23250,00
210869407317;99;43;00;;BRUECKNER, FRANK:;;;8350,00
231257422789;99;40;00;;BRUECKNER, FRANK:;;;22770,00
070260418516;94;03;00;;BRUECKNER, FRANK:;;;21562,50
261157419715;97;22;00;;BRUECKNER, GEORG:;;;24840,00
060552429218;01;80;00;;BRUECKNER, GUNTER:;;;18720,00
260642513612;99;40;00;;BRUECKNER, HANNELORE:;;;26815,00
110337520310;11;77;00;;BRUECKNER, HELLA:;;;25500,00
291252412228;07;08;00;;BRUECKNER, HENNING:;;;22320,00
070450411710;98;84;00;;BRUECKNER, HERBERT:;;;21532,50
071049515024;08;78;00;;BRUECKNER, ISABELLA:;;;20880,00
220165427415;99;43;00;;BRUECKNER, JENS:;;;16830,00
280747415013;08;64;00;;BRUECKNER, JOACHIM:;;;24750,00
220767419711;17;00;00;;BRUECKNER, JOERG:;;;8950,00
101046512914;18;96;00;;BRUECKNER, KAROLA:;;;19262,50
180653402715;02;00;48;;BRUECKNER, KLAUS:;;;25200,00
230267408927;06;69;00;;BRUECKNER, LARS:;;;11016,00
190333429715;99;53;00;;BRUECKNER, LOTHAR:;;;32062,50
010254418515;10;11;00;;BRUECKNER, LUTZ:;;;26640,00
071055422238;96;15;21;;BRUECKNER, LUTZ:;;;21822,50
120127418413;97;01;00;;BRUECKNER, MANFRED:;;;33500,04
021146421825;12;08;00;;BRUECKNER, MANFRED:;;;27000,00
050669415355;01;69;00;;BRUECKNER, MARCO:;;;6806,61
030635429726;97;06;00;;BRUECKNER, MARTIN:;;;23000,00
210657407438;18;29;00;;BRUECKNER, MATTHIAS:;;;24092,50
071156417745;99;55;00;;BRUECKNER, MICHAEL:;;;19435,00
151070413444;97;22;00;;BRUECKNER, MICHAEL:;;;3772,33
120753417792;09;12;00;;BRUECKNER, MICHAEL:;;;23220,00
220753428027;12;06;00;;BRUECKNER, PETER:;;;19040,00
151060501328;30;81;00;;BRUECKNER, RAMONA:;;;11491,54
011239413614;99;40;00;;BRUECKNER, ROBERT:;;;27000,00
140332420318;11;06;00;;BRUECKNER, ROLAND:;;;26250,00
141255429742;30;47;00;;BRUECKNER, ROLAND:;;;24942,50
210257417717;99;13;00;;BRUECKNER, RUEDIGER:;;;21045,00
130236530323;98;83;00;;BRUECKNER, RUTH:;;;18360,00
270939407211;94;03;00;;BRUECKNER, SIEGFRIED:;;;27750,00
061269419748;97;06;00;;BRUECKNER, STEFAN:;;;15150,00
070455403410;97;01;00;;BRUECKNER, STEFFEN:;;;25290,00
190270418428;99;43;00;;BRUECKNER, STEFFEN:;;;6780,00
230470419752;11;69;00;;BRUECKNER, STEPHAN:;;;2720,00
200369426512;14;69;00;;BRUECKNER, SVEN:;;;12675,00
011268415328;18;35;00;;BRUECKNER, SVEN:;;;10725,00
090468430125;99;77;00;;BRUECKNER, THOMAS:;;;9872,00
230464412300;97;01;00;;BRUECKNER, TINO:;;;16775,00
180571419644;99;43;00;;BRUECKNER, TORSTEN:;;;2870,00
241266400628;98;82;00;;BRUECKNER, VOLKER:;;;14946,00
050930407448;99;02;00;;BRUECKNER, WILLY:;;;42375,00
101164415330;08;08;00;;BRUEDER, MICHAEL:;;;16753,50
070945427714;13;51;00;;BRUEDERLEIN, BERND:;;;27000,00
150452506414;97;01;00;;BRUEGERT, CHRISTIANE:;;;18682,88
150354401328;04;43;00;;BRUEGERT, DETLEF:;;;21600,00
190951411256;98;20;00;;BRUEGGEMANN, DETLEF:;;;25080,00
021057408557;94;03;00;;BRUEGGEMANN, STEFFEN:;;;21332,50
300647406115;30;40;00;;BRUEGGENKAMP, DETLEV:;;;23320,00
200540403610;03;65;00;;BRUEGGER, SIEGFRIED:;;;22437,50
280658403416;99;55;00;;BRUEGGERT, HANS-JUERGEN:;;;18083,75
031254401919;02;00;43;;BRUEGGERT, RAINER:;;;22080,00
080966402726;94;03;00;;BRUEGGMANN, CAROL:;;;15498,00
050244502728;02;18;00;;BRUEGGMANN, EDELTRAUD:;;;17167,77
010236402712;02;02;00;;BRUEGGMANN, HARRY:;;;27000,00
280751513230;98;19;00;;BRUEGMANN, GISELA:;;;22030,00
181231429728;99;43;00;;BRUEHL, GERHARD:;;;27750,00
291070421115;99;43;00;;BRUEHL, HEIKO:;;;2480,32
020245521026;98;83;00;;BRUEHL, ILONA:;;;19780,00
240643421025;98;20;00;;BRUEHL, JUERGEN:;;;25920,00
131153427210;97;22;00;;BRUEHL, JUERGEN:;;;20880,00
121235429747;99;77;00;;BRUEHL, KURT:;;;20316,53
190657430050;94;03;00;;BRUEHL, MARIO:;;;21332,50
101257506127;99;77;00;;BRUEHL, MARTINA:;;;19043,66
290145429732;97;01;00;;BRUEHL, PETER:;;;30750,00
081239412228;07;78;00;;BRUEHL, PETER:;;;33750,00
130158406182;99;02;00;;BRUEHL, UWE:;;;25875,00
200834429736;98;83;00;;BRUEHL, WALTER:;;;23250,00
261264412914;94;03;00;;BRUEHMANN, PETER:;;;17050,00
151055403627;15;00;43;;BRUEHNING, ERHARD:;;;24092,50
310553406420;08;20;00;;BRUEMMER, HANS-JOACHIM:;;;22080,00
270960413624;96;15;10;;BRUENECKE, FRANK:;;;19305,00
171254512226;07;78;00;;BRUENING, BIRGIT:;;;17464,92
210532430044;13;99;01;;BRUENING, CLAUS:;;;42750,00
060468400615;01;00;49;;BRUENING, DIRK:;;;13785,00
250447411910;07;19;00;;BRUENING, GERHARD:;;;27000,00
141048507410;98;20;00;;BRUENING, HEIDEMARIE:;;;19993,63
230568406116;04;69;00;;BRUENING, HEIKO:;;;9875,00
180448401828;02;19;00;;BRUENING, HEINZ:;;;25875,00
081253407417;99;43;00;;BRUENING, JUERGEN:;;;25860,00
090941402219;02;08;00;;BRUENING, KLAUS:;;;19718,75
090463427736;30;59;00;;BRUENING, RALPH:;;;15180,00
231046411414;94;30;00;;BRUENING, REINHARD:;;;26562,50
251270400638;98;18;00;;BRUENING, ULF:;;;2700,00
050266400896;01;18;00;;BRUENKMANN, UWE:;;;15974,00
070851427019;14;22;00;;BRUENLER, HARRY:;;;23040,00
121169418328;94;30;00;;BRUENNER, DIRK:;;;2700,00
061146418315;10;00;45;;BRUENNER, HANS-DIETER:;;;24480,00
081244500724;30;81;00;;BRUENNER, RENATE:;;;16200,00
140139505918;97;06;00;;BRUESEHABER, GERDA:;;;22320,00
160942405914;99;40;00;;BRUESEHABER, GUENTER:;;;27750,00
250966400893;18;41;30;;BRUESEHABER, JAN:;;;14168,00
081050403416;03;20;00;;BRUESER, BODO:;;;22892,50
070641428929;97;06;00;;BRUESEWITZ, PETER:;;;24000,00
210961406747;98;85;00;;BRUESKE, HANS-JUERGEN:;;;18480,00
211051429741;30;62;00;;BRUESSAU, MICHAEL:;;;15903,75
261142506111;17;00;00;;BRUESSEL, HEIDI:;;;21000,00
280858428124;14;00;60;;BRUESSEL, ULLRICH:;;;12161,25
300154400022;01;55;00;;BRUESSOW, BERNHARD:;;;16867,50
020366515351;97;01;00;;BRUESSOW, GRIT:;;;13217,31
100950409910;95;45;00;;BRUESSOW, KLAUS:;;;26460,00
041262400712;97;01;00;;BRUESSOW, MARIO:;;;16038,00
240652400517;01;19;00;;BRUEST, HANS-JOACHIM:;;;21620,00
150469403729;18;32;00;;BRUGGER, THOMAS:;;;9313,50
031048402419;18;80;00;;BRUHN, DIETER:;;;20812,50
040747417120;09;26;00;;BRUHN, HEINZ-JUERGEN:;;;26437,50
270247401812;02;00;42;;BRUHN, ROLF:;;;30750,00
281150401318;96;15;00;650/75/39, :;BRUHN, SIEGFRIED;2520;ALEKSIS-KIVI-STR. 29;
281150401318;96;15;00;650/75/39, :;BRUHN, SIEGFRIED;2520;ALEKSIS-KIVI-STR. 29;
061068414713;94;03;00;;BRUHN, TORSTEN:;;;13175,00
200250400817;01;00;40;;BRUHN, WOLFGANG:;;;25500,00
060353406128;04;06;00;;BRUHNS, ULF-PETER:;;;20711,62
240664403627;03;14;00;;BRUKSCH, ANDREAS:;;;15840,00
130768413726;18;35;00;;BRUMBY, MAIK:;;;9675,00
290942530032;99;77;00;;BRUMM, DORIS:;;;27000,00
060440422740;12;00;40;;BRUMM, GERHARD:;;;26250,00
250369430074;17;00;00;;BRUMM, HOLGER:;;;8950,00
011158405110;15;80;00;;BRUMM, JUERGEN:;;;18227,50
210560400870;01;06;25;;BRUMM, NORBERT:;;;17680,00
180155418618;94;03;00;;BRUMME, KLAUS-PETER:;;;22647,50
300562416226;09;06;00;;BRUMMER, HEIKO:;;;17380,00
010268403218;03;69;00;;BRUMMUND, DIRK:;;;10575,00
020135402739;02;53;00;;BRUMMUND, EGON:;;;27375,00
250863402749;99;02;00;;BRUMMUND, JU(E)RGEN:;;;19415,00
290862402727;94;30;00;;BRUMMUND, MICHAEL:;;;17847,50
081268430038;99;43;00;;BRUNA, ANDREAS:;;;13575,00
140147530064;99;43;00;;BRUNA, GUDRUN:;;;20706,00
230844429729;99;43;00;;BRUNA, WOLFGANG:;;;27750,00
160359522224;98;83;00;;BRUNK, BIRGIT:;;;17585,39
010253429749;15;20;00;;BRUNK, ECKART:;;;23715,00
280955401310;97;17;00;;BRUNK, HEINZ:;;;20010,00
020969404415;94;03;00;;BRUNK, KARSTEN:;;;9510,00
180349401320;98;82;00;;BRUNK, KLAUS-DIETER:;;;24337,50
190559403841;03;80;00;;BRUNK, KLAUS-DIETER:;;;16675,00
190847403715;97;08;00;;BRUNK, MANFRED:;;;27000,00
140253403720;03;14;00;;BRUNK, REINHARD:;;;18480,00
210360524940;30;63;00;;BRUNKAL, ELKE:;;;10916,33
280355425052;30;63;00;;BRUNKAL, KARL-HEINZ:;;;15510,00
210370429752;94;03;00;;BRUNKOW, BIRK:;;;2700,00
190342429733;99;26;00;;BRUNKOW, HANS-PETER:;;;39750,00
010240529716;98;20;00;;BRUNKOW, INGRID:;;;23125,00
050150406428;04;00;42;;BRUNKOW, KLAUS:;;;25860,00
020560508913;30;84;00;;BRUNN, DANIELA:;;;12738,97
280550413428;30;63;00;;BRUNN, HELMUT:;;;17280,00
031239430092;15;06;00;;BRUNN, LOTHAR:;;;26250,00
300155515315;99;40;00;;BRUNNE, PETRA:;;;20842,50
280954423825;99;40;00;;BRUNNE, RALF:;;;23400,00
210163400893;97;01;00;;BRUNNENMEIER, STEFFEN:;;;16335,00
270259422717;12;08;00;;BRUNNER, ANDREAS:;;;19952,50
231244530078;99;12;00;;BRUNNER, ANKE:;;;21600,00
220260406129;04;06;00;;BRUNNER, AXEL:;;;19665,00
071055529836;96;15;04;;BRUNNER, CARMEN:;;;19492,50
010553501829;02;03;00;;BRUNNER, CHRISTA:;;;11757,08
010247411518;07;00;54;;BRUNNER, DIETER:;;;27937,50
021047410418;02;00;42;;BRUNNER, DIETER:;;;22500,00
020366430024;98;27;00;;BRUNNER, DIRK:;;;15876,00
260238418410;97;06;00;;BRUNNER, GOTTFRIED:;;;21266,66
070847422725;12;00;47;;BRUNNER, HANS-JUERGEN:;;;25117,50
010951429818;97;08;00;;BRUNNER, HEINZ:;;;18942,50
070369428224;18;38;00;;BRUNNER, INGO:;;;9675,00
120765430214;96;15;25;;BRUNNER, JAN:;;;19150,50
210169427229;18;33;00;;BRUNNER, JENS:;;;10500,00
061152428210;14;15;00;;BRUNNER, JUERGEN:;;;24832,50
030239429724;99;09;00;;BRUNNER, KLAUS:;;;29250,00
260429430017;96;15;00;1920/75, J:;BRUNNER, MANFRED;1144;TETEROWER RING 86;
260429430017;96;15;00;1920/75, J:;BRUNNER, MANFRED;1144;TETEROWER RING 86;
050170429352;94;03;00;;BRUNNER, MARKO:;;;10335,00
040438430233;60;90;00;;BRUNNER, THEO:;;;
040438430233;60;90;00;;BRUNNER, THEO:;;;30600,00
010766420125;11;69;00;;BRUNNER, TORSTEN:;;;15876,00
190942405233;03;18;00;;BRUNNER, WERNER:;;;27000,00
280736414218;08;00;54;;BRUNNERT, HILMAR:;;;23343,01
260639410815;07;06;00;;BRUNNERT, JUERGEN:;;;24187,50
070670409823;18;33;00;;BRUNNGRA(E)BER, MAREK:;;;6958,87
240369410023;18;31;00;;BRUNOW, RALF:;;;9675,00
050662522799;96;15;00;6555/82, J:;BRUNS, BEATE;1140;BA(E)RENSTEINSTR. 8;
050662522799;96;15;00;6555/82, J:;BRUNS, BEATE;1140;BA(E)RENSTEINSTR. 8;
100571409523;05;69;00;;BRUNS, HENRY:;;;2870,00
160858405938;97;08;00;;BRUNS, MICHAEL:;;;18601,25
110570421116;12;69;00;;BRUNS, STEFFEN:;;;9830,00
210951508811;30;83;00;;BRUNS, SYBILLE:;;;20359,55
020348410820;99;55;00;;BRUNS, WALTER:;;;24000,00
031268403632;18;35;00;;BRUNS, WOLFGANG:;;;9675,00
301057413934;97;01;00;;BRUNSCH, JUERGEN:;;;29760,00
240543411110;07;00;51;;BRUNSCH, KLAUS-DIETER:;;;24750,00
150166413911;15;07;00;;BRUNSCH, OLAF:;;;18414,00
020853409812;07;18;00;;BRUNSENDORF, DIETER:;;;24480,00
191154511435;07;41;00;;BRUNSENDORF, GUDRUN:;;;19440,00
300852409825;07;00;41;;BRUNSENDORF, LOTHAR:;;;23460,00
290153402716;02;06;00;;BRUNST, HOLGER:;;;20160,00
060270403714;18;34;00;;BRUNST, STEFAN:;;;6705,00
230358430062;15;80;00;;BRUNTSCH, DETLEF:;;;17935,02
260862407010;18;38;00;;BRUSAK, DIRK:;;;20161,43
070268501568;97;06;00;;BRUSCH, ANNETT:;;;9783,34
151063400119;01;00;45;;BRUSCH, HOLGER:;;;15592,50
050657400113;99;12;00;;BRUSCH, MANFRED:;;;20815,00
051165401528;01;60;00;;BRUSE, DIRK:;;;14835,00
211040501517;01;06;22;;BRUSE, GERDA:;;;16296,30
150646400810;01;65;00;;BRUSE, GERHARD:;;;20625,00
070638403413;03;65;00;;BRUSE, HANS-ULRICH:;;;25687,50
140948401510;97;06;00;;BRUSE, PAUL:;;;24000,00
020741430086;30;84;00;;BRUSENDORF, WOLFGANG:;;;16560,00
100357421716;12;06;00;;BRUSSIG, ROLAND:;;;19492,50
070736421711;12;00;51;;BRUSSIG, SIEGFRIED:;;;16847,50
220260523624;14;00;56;;BRUSSOG, BIRGIT:;;;14948,75
081148529711;94;30;00;;BRUST, MARION:;;;21157,25
021046429715;99;43;00;;BRUST, UDO:;;;26187,50
210137429713;99;02;00;;BRUTKE, RUDOLF:;;;36008,06
011153429746;30;47;00;;BRUTSCHIN, SIEGBERT:;;;23090,00
120140411216;07;08;00;;BRUTTLOFF, HANS-JOACHIM:;;;21750,00
120249430066;30;47;00;;BRYCHCY, MICHAEL:;;;29280,00
091052407014;05;08;00;;BRYKCZYNSKI, JOERG:;;;18749,03
060571512244;07;96;00;;BRYLLA, KERSTIN:;;;3220,00
140250412226;07;06;00;;BRYLLA, KLAUS-DIETER:;;;21720,00
140853412217;07;06;00;;BRYLLA, WOLFGANG:;;;20160,00
180842421827;94;03;00;;BRYLSKI, JUERGEN:;;;24000,00
231269407228;05;69;00;;BRYM, RAINER:;;;2870,00
020858406418;30;58;00;;BRZAKALA, JUERGEN:;;;16445,00
170160413628;06;00;50;;BRZANK, RAINER:;;;19800,00
161250413213;08;00;44;;BRZEZINSKI, JU(E)RGEN:;;;19800,00
130655417528;09;00;51;;BRZEZINSKI, LUTZ:;;;27967,50
200239402731;30;44;00;;BRZEZOWSKA, ALFRED:;;;15120,00
251243412211;07;51;00;;BRZOSKA, INGBERT:;;;21750,00
280542512215;07;40;00;;BRZOSKA, MARGA:;;;26437,50
091056518520;10;51;00;;BRZUSKA, DAGMAR:;;;18917,50
090956407215;05;80;00;;BRZYSKI, BODO:;;;16905,00
040743530388;18;77;00;;BSDUREK, RENATE:;;;23040,00
















 h
h![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict19.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict3.jpg) Media persons and Tokyo Electric Power Co. employees look at the company’s tsunami-crippled Fukushima Dai-Ichi nuclear power plant during a press tour in Okuma town, Fukushima prefecture, Japan, Saturday, May 26, 2012. (Tomohiro Ohsumi, Pool)
Media persons and Tokyo Electric Power Co. employees look at the company’s tsunami-crippled Fukushima Dai-Ichi nuclear power plant during a press tour in Okuma town, Fukushima prefecture, Japan, Saturday, May 26, 2012. (Tomohiro Ohsumi, Pool)![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict15.jpg) Reactor buildings from left to right, the No. 1, the No. 2, the No. 3 and the No. 4, are seen during a press tour at Tokyo Electric Power Co.’s (TEPCO) Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. (Tomohiro Ohsumi, Pool)
Reactor buildings from left to right, the No. 1, the No. 2, the No. 3 and the No. 4, are seen during a press tour at Tokyo Electric Power Co.’s (TEPCO) Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. (Tomohiro Ohsumi, Pool)![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict0.jpg) Members of the media and Tokyo Electric Power Co. employees walk in front of the No. 4 reactor building, rear, crippled by the March 11 earthquake and tsunami, at the utility company’s Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. (Tomohiro Ohsumi, Pool)
Members of the media and Tokyo Electric Power Co. employees walk in front of the No. 4 reactor building, rear, crippled by the March 11 earthquake and tsunami, at the utility company’s Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. (Tomohiro Ohsumi, Pool)![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict12.jpg) The damaged No. 4 reactor building stands at Tokyo Electric Power Co.’s Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. Japanese Environment and Nuclear Minister Goshi Hosono, accompanied by the media, has visited the crippled Fukushima Dai-ichi nuclear power plant to inspect a reactor building and its spent fuel pool at the center of safety concerns. (Tomohiro Ohsumi, Pool)
The damaged No. 4 reactor building stands at Tokyo Electric Power Co.’s Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. Japanese Environment and Nuclear Minister Goshi Hosono, accompanied by the media, has visited the crippled Fukushima Dai-ichi nuclear power plant to inspect a reactor building and its spent fuel pool at the center of safety concerns. (Tomohiro Ohsumi, Pool)![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict11.jpg) Goshi Hosono, Japan’s environment and nuclear minister, third from left, wearing a red helmet, along with members of the media, walks on the No. 4 reactor building at Tokyo Electric Power Co.’s (TEPCO) Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. Japan’s environment and nuclear minister Hosono visited the tsunami-crippled nuclear power plant Saturday to inspect a spent fuel pool at the center of safety concerns. (Tomohiro Ohsumi, Pool)
Goshi Hosono, Japan’s environment and nuclear minister, third from left, wearing a red helmet, along with members of the media, walks on the No. 4 reactor building at Tokyo Electric Power Co.’s (TEPCO) Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. Japan’s environment and nuclear minister Hosono visited the tsunami-crippled nuclear power plant Saturday to inspect a spent fuel pool at the center of safety concerns. (Tomohiro Ohsumi, Pool)![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict16.jpg) Goshi Hosono, Japan’s environment and nuclear minister, inspects the No. 4 reactor building at Tokyo Electric Power Co.’s Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima Prefecture, Japan, Saturday, May 26, 2012. The visit by Hosono, apparently aimed at demonstrating the safety of the facility, came amid renewed concerns about conditions at the plant’s No. 4 reactor after its operator reported a bulging of the building’s wall. (Toshiaki Shimizu, Japan Pool) [Yellow reactor containment dome at center background.]
Goshi Hosono, Japan’s environment and nuclear minister, inspects the No. 4 reactor building at Tokyo Electric Power Co.’s Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima Prefecture, Japan, Saturday, May 26, 2012. The visit by Hosono, apparently aimed at demonstrating the safety of the facility, came amid renewed concerns about conditions at the plant’s No. 4 reactor after its operator reported a bulging of the building’s wall. (Toshiaki Shimizu, Japan Pool) [Yellow reactor containment dome at center background.]![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict2.jpg) Workers walk in front of the No. 4 reactor building at Tokyo Electric Power Co.’s tsunami-crippled Fukushima Dai-Ichi nuclear power plant in Okuma town, Fukushima prefecture, Japan, Saturday, May 26, 2012. (Tomohiro Ohsumi, Pool)
Workers walk in front of the No. 4 reactor building at Tokyo Electric Power Co.’s tsunami-crippled Fukushima Dai-Ichi nuclear power plant in Okuma town, Fukushima prefecture, Japan, Saturday, May 26, 2012. (Tomohiro Ohsumi, Pool)![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict7.jpg) An inside view of the damaged No. 4 reactor building is seen at Tokyo Electric Power Co.’s tsunami-crippled Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. (Toshiaki Shimizu, Japan Pool)
An inside view of the damaged No. 4 reactor building is seen at Tokyo Electric Power Co.’s tsunami-crippled Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. (Toshiaki Shimizu, Japan Pool)![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict8.jpg) The inside of the tsunami-crippled No. 4 reactor building is seen during a press tour at Tokyo Electric Power Co.’s (TEPCO) Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima Prefecture, Japan, Saturday, May 26, 2012.(Toshiaki Shimizu, Japan Pool)
The inside of the tsunami-crippled No. 4 reactor building is seen during a press tour at Tokyo Electric Power Co.’s (TEPCO) Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima Prefecture, Japan, Saturday, May 26, 2012.(Toshiaki Shimizu, Japan Pool)![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict5.jpg) Japan’s Environment and Nuclear Minister Goshi Hosono, second from left, inspects a pool containing spent fuel rods inside the No. 4 reactor building at Tokyo Electric Power Co. ‘s tsunami-crippled Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima Prefecture, Japan, Saturday, May 26, 2012. The pool, located at the top of the building above the reactor, remains one of the plant’s biggest risks due to its vulnerability to earthquakes. (Toshiaki Shimizu, Japan Pool)
Japan’s Environment and Nuclear Minister Goshi Hosono, second from left, inspects a pool containing spent fuel rods inside the No. 4 reactor building at Tokyo Electric Power Co. ‘s tsunami-crippled Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima Prefecture, Japan, Saturday, May 26, 2012. The pool, located at the top of the building above the reactor, remains one of the plant’s biggest risks due to its vulnerability to earthquakes. (Toshiaki Shimizu, Japan Pool)![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict6.jpg) A pool for spent fuel rods is seen inside the No. 4 reactor building of Tokyo Electric Power Co.’s tsunami-crippled Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. The pool, located at the top of the building above the reactor, remains one of the plant’s biggest risks due to its vulnerability to earthquakes. (Toshiaki Shimizu, Japan Pool)
A pool for spent fuel rods is seen inside the No. 4 reactor building of Tokyo Electric Power Co.’s tsunami-crippled Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. The pool, located at the top of the building above the reactor, remains one of the plant’s biggest risks due to its vulnerability to earthquakes. (Toshiaki Shimizu, Japan Pool)![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict10.jpg) The No. 3 reactor building is seen at Tokyo Electric Power Co.’s (TEPCO) Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. Japan’s environment and nuclear minister, accompanied by the media, visited the tsunami-crippled nuclear power plant Saturday to inspect a spent fuel pool at the center of safety concerns. (Tomohiro Ohsumi, Pool)
The No. 3 reactor building is seen at Tokyo Electric Power Co.’s (TEPCO) Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. Japan’s environment and nuclear minister, accompanied by the media, visited the tsunami-crippled nuclear power plant Saturday to inspect a spent fuel pool at the center of safety concerns. (Tomohiro Ohsumi, Pool)![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict4.jpg) The No. 1, left, and the No. 2, reactor buildings are seen during a press tour at the tsunami-crippled Fukushima Dai-ichi nuclear power plant of Tokyo Electric Power Co. (TEPCO) in Okuma, Fukushima Prefecture, Japan, Saturday, May 26, 2012. (Tomohiro Ohsumi, Pool)
The No. 1, left, and the No. 2, reactor buildings are seen during a press tour at the tsunami-crippled Fukushima Dai-ichi nuclear power plant of Tokyo Electric Power Co. (TEPCO) in Okuma, Fukushima Prefecture, Japan, Saturday, May 26, 2012. (Tomohiro Ohsumi, Pool)![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict13.jpg) Workers carry out radiation screening on a bus for a media tour at Tokyo Electric Power Co. (TEPCO) ‘s Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, on Saturday, May 26, 2012. Japan’s environment and nuclear minister, accompanied by the media, visited the tsunami-crippled nuclear power plant Saturday to inspect a spent fuel pool at the center of safety concerns. (Tomohiro Ohsumi, Pool)
Workers carry out radiation screening on a bus for a media tour at Tokyo Electric Power Co. (TEPCO) ‘s Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, on Saturday, May 26, 2012. Japan’s environment and nuclear minister, accompanied by the media, visited the tsunami-crippled nuclear power plant Saturday to inspect a spent fuel pool at the center of safety concerns. (Tomohiro Ohsumi, Pool)![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict14.jpg) A worker carries out radiation screening on a bus for a media tour at Tokyo Electric Power Co. (TEPCO) ‘s Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, on Saturday, May 26, 2012. (Tomohiro Ohsumi, Pool)
A worker carries out radiation screening on a bus for a media tour at Tokyo Electric Power Co. (TEPCO) ‘s Fukushima Dai-ichi nuclear power plant in Okuma, Fukushima prefecture, Japan, on Saturday, May 26, 2012. (Tomohiro Ohsumi, Pool)![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0526/pict9.jpg) A worker walks through the building used as crisis management headquarters at the tsunami-crippled Fukushima Dai-ichi nuclear power plant of Tokyo Electric Power Co.’s (TEPCO) in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. (Tomohiro Ohsumi, Pool)
A worker walks through the building used as crisis management headquarters at the tsunami-crippled Fukushima Dai-ichi nuclear power plant of Tokyo Electric Power Co.’s (TEPCO) in Okuma, Fukushima prefecture, Japan, Saturday, May 26, 2012. (Tomohiro Ohsumi, Pool)




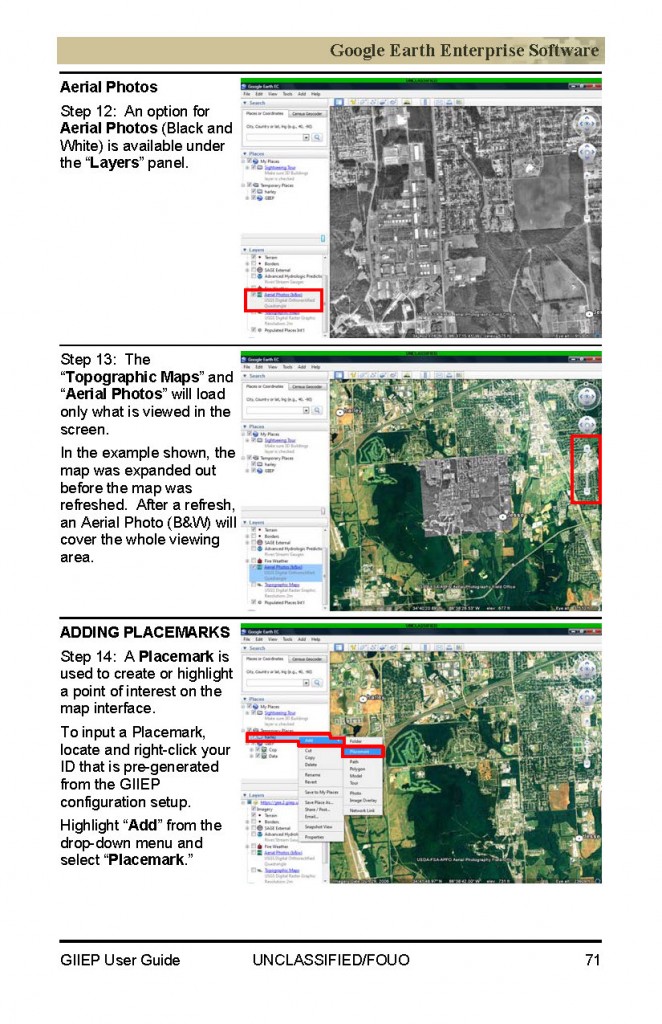




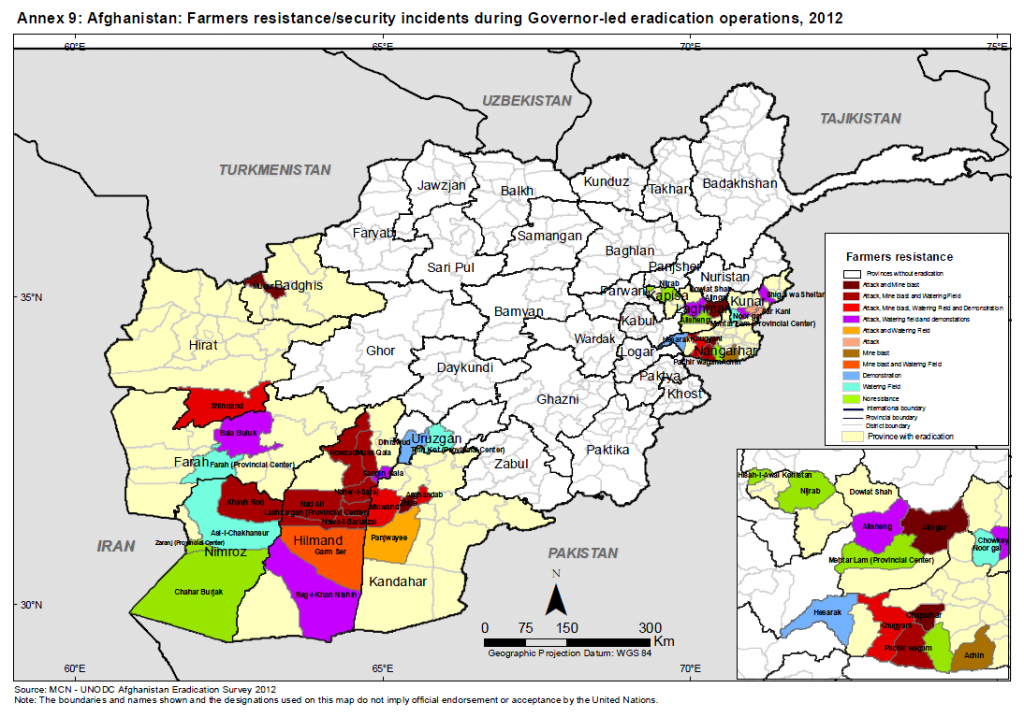


![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict170.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict171.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict172.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict173.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict168.jpg) Israeli soldiers control the Skylark drone during a drill on January 16, 2012 near Bat Shlomo, Israel. The Skylark can carry a camera payload of up to 1kg, has an operational ceiling of 15,000ft and allows users to monitor any designated point within a 15km radius. The Skylark unit consists of a ground control element and three drones, which provide battalion-level commanders with real-time information. Getty
Israeli soldiers control the Skylark drone during a drill on January 16, 2012 near Bat Shlomo, Israel. The Skylark can carry a camera payload of up to 1kg, has an operational ceiling of 15,000ft and allows users to monitor any designated point within a 15km radius. The Skylark unit consists of a ground control element and three drones, which provide battalion-level commanders with real-time information. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict169.jpg) A technician supporting U.S. Navy SEAL Team 18 works on a UAV, an unmanned aerial vehicle, before a demonstration of combat skills at the National Navy UDT-SEAL Museum in Fort Pierce, Florida November 11, 2011. The demonstration for the public is part of a Veteran’s Day celebration and the annual reunion at the Museum. The drone is equipped with cameras for surveillance. Reuters
A technician supporting U.S. Navy SEAL Team 18 works on a UAV, an unmanned aerial vehicle, before a demonstration of combat skills at the National Navy UDT-SEAL Museum in Fort Pierce, Florida November 11, 2011. The demonstration for the public is part of a Veteran’s Day celebration and the annual reunion at the Museum. The drone is equipped with cameras for surveillance. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict167.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict104.jpg) Adam Stock, the lead pilot for 29 Palms Unmanned Aerial Systems, out of Twentynine Palms, California, pilots a ScanEagle unmanned aerial vehicle at Fort Hunter Liggett, Calif., May 19, 2011, in support of Global Medic 2011 and Warrior 91 11-01. Global Medic is a joint field training exercise for theater aeromedical evacuation system and ground medical components designed to replicate all aspects of combat medical service support. Warrior 91 11-01 was a tactical exercise in which U.S. Service members responded to simulated enemy attacks as part of Global Medic 2011 . (U.S. Air Force photo by Staff Sgt. Donald R. Allen/Released). Date Shot: 5/19/2011
Adam Stock, the lead pilot for 29 Palms Unmanned Aerial Systems, out of Twentynine Palms, California, pilots a ScanEagle unmanned aerial vehicle at Fort Hunter Liggett, Calif., May 19, 2011, in support of Global Medic 2011 and Warrior 91 11-01. Global Medic is a joint field training exercise for theater aeromedical evacuation system and ground medical components designed to replicate all aspects of combat medical service support. Warrior 91 11-01 was a tactical exercise in which U.S. Service members responded to simulated enemy attacks as part of Global Medic 2011 . (U.S. Air Force photo by Staff Sgt. Donald R. Allen/Released). Date Shot: 5/19/2011![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict166.jpg) U.S. Soldiers with the 10th Special Forces Group fly an RQ-7B Shadow unmanned aerial vehicle at Hurlburt Field, Fla., from inside their ground control station March 7, 2011, during Emerald Warrior 2011. Emerald Warrior is an annual two-week joint/combined tactical exercise sponsored by U.S. Special Operations Command designed to leverage lessons learned from operations Iraqi and Enduring Freedom to provide trained and ready forces to combatant commanders. (U.S. Air Force photo by Staff Sgt. Andy M. Kin/Released). Date Shot: 3/7/2011
U.S. Soldiers with the 10th Special Forces Group fly an RQ-7B Shadow unmanned aerial vehicle at Hurlburt Field, Fla., from inside their ground control station March 7, 2011, during Emerald Warrior 2011. Emerald Warrior is an annual two-week joint/combined tactical exercise sponsored by U.S. Special Operations Command designed to leverage lessons learned from operations Iraqi and Enduring Freedom to provide trained and ready forces to combatant commanders. (U.S. Air Force photo by Staff Sgt. Andy M. Kin/Released). Date Shot: 3/7/2011![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict165.jpg) U.S. Airmen with the 380th Expeditionary Aircraft Maintenance Squadron prepare an RQ-4A Global Hawk unmanned aerial vehicle aircraft for takeoff at an undisclosed location in Southwest Asia Dec. 2, 2010. (U.S. Air Force photo by Staff Sgt. Eric Harris/Released). Date Shot: 12/2/2010
U.S. Airmen with the 380th Expeditionary Aircraft Maintenance Squadron prepare an RQ-4A Global Hawk unmanned aerial vehicle aircraft for takeoff at an undisclosed location in Southwest Asia Dec. 2, 2010. (U.S. Air Force photo by Staff Sgt. Eric Harris/Released). Date Shot: 12/2/2010![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict164.jpg) U.S. Airmen with the 380th Aircraft Maintenance Squadron prepare an RQ-4 Global Hawk unmanned aerial vehicle for its first launch from an undisclosed base in Southwest Asia Nov. 27, 2010. The RQ-4 was designed for intelligence, surveillance and reconnaissance. (U.S. Air Force photo by Staff Sgt. Eric Harris/Released). Date Shot: 11/27/2010
U.S. Airmen with the 380th Aircraft Maintenance Squadron prepare an RQ-4 Global Hawk unmanned aerial vehicle for its first launch from an undisclosed base in Southwest Asia Nov. 27, 2010. The RQ-4 was designed for intelligence, surveillance and reconnaissance. (U.S. Air Force photo by Staff Sgt. Eric Harris/Released). Date Shot: 11/27/2010![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict163.jpg) U.S. Marine Corps unmanned aerial vehicle (UAV) mechanics assigned to Marine Unmanned Aerial Vehicle Squadron (VMU) 3 work on an RQ-7B Shadow UAV during Enhanced Mojave Viper at Marine Corps Air Ground Combat Center Twentynine Palms, Calif., Aug. 3, 2010. Enhanced Mojave Viper is a combined exercise that prepares Marines for deployments. (U.S. Marine Corps photo by Lance Cpl. Michael C. Nerl/Released). Date Shot: 8/3/2010
U.S. Marine Corps unmanned aerial vehicle (UAV) mechanics assigned to Marine Unmanned Aerial Vehicle Squadron (VMU) 3 work on an RQ-7B Shadow UAV during Enhanced Mojave Viper at Marine Corps Air Ground Combat Center Twentynine Palms, Calif., Aug. 3, 2010. Enhanced Mojave Viper is a combined exercise that prepares Marines for deployments. (U.S. Marine Corps photo by Lance Cpl. Michael C. Nerl/Released). Date Shot: 8/3/2010![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict162.jpg) Civilian employees with Fleet Readiness Center East perform maintenance and corrosion assessments on two MQ-8B Fire Scout unmanned aerial vehicles at Marine Corps Air Station Cherry Point, N.C., May 14, 2010. (U.S. Navy photo by David R. Hooks/Released). Date Shot: 5/14/2010
Civilian employees with Fleet Readiness Center East perform maintenance and corrosion assessments on two MQ-8B Fire Scout unmanned aerial vehicles at Marine Corps Air Station Cherry Point, N.C., May 14, 2010. (U.S. Navy photo by David R. Hooks/Released). Date Shot: 5/14/2010![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict161.jpg) U.S. Air Force Master Sgt. Jennifer Oberg, background, a communications maintenance instructor, and Senior Airman Raquel Martinez, foreground, check a ground control station during training at March Air Reserve Base, Calif., April 19, 2010. Both are assigned to the 163rd Maintenance Group at March. The California Air National Guard unit is primarily involved in Predator unmanned aerial vehicle missions. (U.S. Air Force photo by Val Gempis/Released). Date Shot: 4/19/2010
U.S. Air Force Master Sgt. Jennifer Oberg, background, a communications maintenance instructor, and Senior Airman Raquel Martinez, foreground, check a ground control station during training at March Air Reserve Base, Calif., April 19, 2010. Both are assigned to the 163rd Maintenance Group at March. The California Air National Guard unit is primarily involved in Predator unmanned aerial vehicle missions. (U.S. Air Force photo by Val Gempis/Released). Date Shot: 4/19/2010![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict160.jpg) U.S. Air Force Tech. Sgt. Ron Zechman, a predator sensor operator, and Maj. Jeff Bright, a predator pilot and detachment commander of the 432nd Wing out of Creech Air Force Base, Nev., go over pre-flight check lists for an RQ-1 Predator unmanned aerial vehicle at Aeropuerto Rafael Hernandez outside Aguadilla, Puerto Rico, Jan. 28, 2010. Airmen from Creech AFB are providing 24-hour-a-day full-motion video in real time to international relief workers on the ground in order to speed humanitarian aid to remote and cut-off areas of the Haiti following the earthquake Jan. 12, 2010. (U.S. Air Force photo by Tech. Sgt. James Harper/Released). Date Shot: 1/21/2010
U.S. Air Force Tech. Sgt. Ron Zechman, a predator sensor operator, and Maj. Jeff Bright, a predator pilot and detachment commander of the 432nd Wing out of Creech Air Force Base, Nev., go over pre-flight check lists for an RQ-1 Predator unmanned aerial vehicle at Aeropuerto Rafael Hernandez outside Aguadilla, Puerto Rico, Jan. 28, 2010. Airmen from Creech AFB are providing 24-hour-a-day full-motion video in real time to international relief workers on the ground in order to speed humanitarian aid to remote and cut-off areas of the Haiti following the earthquake Jan. 12, 2010. (U.S. Air Force photo by Tech. Sgt. James Harper/Released). Date Shot: 1/21/2010![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict158.jpg) U.S. Air Force Maj. Jeff Bright, a predator pilot from the 432nd Wing out of Creech Air Force Base, Nev., goes over a pre-flight check list for an RQ-1 Predator unmanned aerial vehicle at Aeropuerto Rafael Hernandez outside Aguadilla, Puerto Rico, Jan. 28, 2010. Airmen from Creech AFB are providing 24-hour-a-day full-motion video in real time to international relief workers on the ground in order to speed humanitarian aid to remote and cut-off areas of the Haiti following the earthquake Jan. 12, 2010. (U.S. Air Force photo by Tech. Sgt. James Harper/Released). Date Shot: 1/21/2010
U.S. Air Force Maj. Jeff Bright, a predator pilot from the 432nd Wing out of Creech Air Force Base, Nev., goes over a pre-flight check list for an RQ-1 Predator unmanned aerial vehicle at Aeropuerto Rafael Hernandez outside Aguadilla, Puerto Rico, Jan. 28, 2010. Airmen from Creech AFB are providing 24-hour-a-day full-motion video in real time to international relief workers on the ground in order to speed humanitarian aid to remote and cut-off areas of the Haiti following the earthquake Jan. 12, 2010. (U.S. Air Force photo by Tech. Sgt. James Harper/Released). Date Shot: 1/21/2010![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict157.jpg) Predator pilot Jonathon Johnson, an air interdiction agent for the U.S. Customs and Border Protection, enters the ground control station for the Predator B unmanned aerial systems (UAS) April 3, 2009, at the U.S. Customs and Border Protection UAS operations center at Grand Forks Air Force Base, N.D. The Predator is a new high-tech tool being used to help in flood fight planning for the first time in North Dakota. It has been recording flood imagery, which is being used for positioning of National Guard flood fighting personnel and resources. (DoD photo by Senior Master Sgt. David H. Lipp, U.S. Air Force/Released). Date Shot: 4/3/2009
Predator pilot Jonathon Johnson, an air interdiction agent for the U.S. Customs and Border Protection, enters the ground control station for the Predator B unmanned aerial systems (UAS) April 3, 2009, at the U.S. Customs and Border Protection UAS operations center at Grand Forks Air Force Base, N.D. The Predator is a new high-tech tool being used to help in flood fight planning for the first time in North Dakota. It has been recording flood imagery, which is being used for positioning of National Guard flood fighting personnel and resources. (DoD photo by Senior Master Sgt. David H. Lipp, U.S. Air Force/Released). Date Shot: 4/3/2009![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict155.jpg) Predator pilot Jonathon Johnson, left, an air interdiction agent for the U.S. Customs and Border Protection, pilots a Predator aircraft in the ground control station for the Predator B unmanned aerial systems (UAS) April 3, 2009, at the U.S. Customs and Border Protection UAS operations center at Grand Forks Air Force Base, N.D., as UAS instructor pilot Bob Concannon operates the sensor controls. The Predator is a new high-tech tool being used to help in flood fight planning for the first time in North Dakota. It has been recording flood imagery, which is being used for positioning of National Guard flood fighting personnel and resources. (DoD photo by Senior Master Sgt. David H. Lipp, U.S. Air Force/Released). Date Shot: 4/3/2009
Predator pilot Jonathon Johnson, left, an air interdiction agent for the U.S. Customs and Border Protection, pilots a Predator aircraft in the ground control station for the Predator B unmanned aerial systems (UAS) April 3, 2009, at the U.S. Customs and Border Protection UAS operations center at Grand Forks Air Force Base, N.D., as UAS instructor pilot Bob Concannon operates the sensor controls. The Predator is a new high-tech tool being used to help in flood fight planning for the first time in North Dakota. It has been recording flood imagery, which is being used for positioning of National Guard flood fighting personnel and resources. (DoD photo by Senior Master Sgt. David H. Lipp, U.S. Air Force/Released). Date Shot: 4/3/2009![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict154.jpg) Predator pilot and instructor Michael Nelson, of the University of North Dakota, pilots a Predator in the ground control station for the Predator B unmanned aerial systems (UAS) April 3, 2009, at the U.S. Customs and Border Protection UAS operations center at Grand Forks Air Force Base, N.D. The Predator is a new high-tech tool being used to help in flood fight planning for the first time in North Dakota. It has been recording flood imagery, which is being used for positioning of National Guard flood fighting personnel and resources. (DoD photo by Senior Master Sgt. David H. Lipp, U.S. Air Force/Released). Date Shot: 4/3/2009
Predator pilot and instructor Michael Nelson, of the University of North Dakota, pilots a Predator in the ground control station for the Predator B unmanned aerial systems (UAS) April 3, 2009, at the U.S. Customs and Border Protection UAS operations center at Grand Forks Air Force Base, N.D. The Predator is a new high-tech tool being used to help in flood fight planning for the first time in North Dakota. It has been recording flood imagery, which is being used for positioning of National Guard flood fighting personnel and resources. (DoD photo by Senior Master Sgt. David H. Lipp, U.S. Air Force/Released). Date Shot: 4/3/2009![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict153.jpg) U.S. Army Pfc. Shawn Miller, left, and Sgt. 1st Class Wayne Davidson, both with Brigade Special Troops Battalion, 3rd Brigade Combat Team, 82nd Airborne Division, prepare equipment needed to operate a Raven unmanned aerial vehicle system at Joint Security Station Loyalty in eastern Baghdad, Iraq, March 25, 2009. (U.S. Army photo by Staff Sgt. James Selesnick/Released). Date Shot: 3/25/2009
U.S. Army Pfc. Shawn Miller, left, and Sgt. 1st Class Wayne Davidson, both with Brigade Special Troops Battalion, 3rd Brigade Combat Team, 82nd Airborne Division, prepare equipment needed to operate a Raven unmanned aerial vehicle system at Joint Security Station Loyalty in eastern Baghdad, Iraq, March 25, 2009. (U.S. Army photo by Staff Sgt. James Selesnick/Released). Date Shot: 3/25/2009![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict152.jpg) U.S. Army Pfc. Shawn Miller, from Brigade Special Troops Battalion, 3rd Brigade Combat Team, 82nd Airborne Division, processes information gathered from a Raven unmanned aerial vehicle system, at Joint Security Station Loyalty, in eastern Baghdad, Iraq, March 25, 2009. (U.S. Army photo by Staff Sgt. James Selesnick/Released). Date Shot: 3/25/2009
U.S. Army Pfc. Shawn Miller, from Brigade Special Troops Battalion, 3rd Brigade Combat Team, 82nd Airborne Division, processes information gathered from a Raven unmanned aerial vehicle system, at Joint Security Station Loyalty, in eastern Baghdad, Iraq, March 25, 2009. (U.S. Army photo by Staff Sgt. James Selesnick/Released). Date Shot: 3/25/2009![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict151.jpg) U.S. Air Force Maj. John Chesser operates the controls of an MQ-9 Reaper unmanned aerial vehicle cockpit during a demonstration at Joint Base Balad, Iraq, on Aug. 1, 2008. The Reaper is designed as a hunter-killer, capable of loitering over targets for long periods of time and delivering laser-guided ordnance. Chesser is a Reaper pilot with the 46th Expeditionary Reconnaissance and Attack Squadron. DoD photo by Staff Sgt. Don Branum, U.S. Air Force. (Released). Date Shot: 8/1/2008
U.S. Air Force Maj. John Chesser operates the controls of an MQ-9 Reaper unmanned aerial vehicle cockpit during a demonstration at Joint Base Balad, Iraq, on Aug. 1, 2008. The Reaper is designed as a hunter-killer, capable of loitering over targets for long periods of time and delivering laser-guided ordnance. Chesser is a Reaper pilot with the 46th Expeditionary Reconnaissance and Attack Squadron. DoD photo by Staff Sgt. Don Branum, U.S. Air Force. (Released). Date Shot: 8/1/2008![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict150.jpg) U.S. Air Force Tech. Sgt. Justin Michaels, of 3rd Special Operations Command, Cannon Air Force Base, N.M., guides a ground control station (GCS) as other Airmen from his unit lower the station into place July 21, 2008. The GCS will serve as a cockpit for Predator/Reaper unmanned aerial vehicles. (U.S. Air Force photo by Airman 1st Class James R. Bell/Released). Date Shot: 7/21/2008
U.S. Air Force Tech. Sgt. Justin Michaels, of 3rd Special Operations Command, Cannon Air Force Base, N.M., guides a ground control station (GCS) as other Airmen from his unit lower the station into place July 21, 2008. The GCS will serve as a cockpit for Predator/Reaper unmanned aerial vehicles. (U.S. Air Force photo by Airman 1st Class James R. Bell/Released). Date Shot: 7/21/2008![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict149.jpg) U.S. Air Force Staff Sgt. Robert Moore, right, describes his every action to Airman 1st Class Carrie Smith during the setup of a Vehicle Test Controller for a RQ-1 Global Hawk unmanned aerial vehicle June 16, 2008, at Beale Air Force Base, Calif. They are with the 9th Aircraft Maintenance Squadron. (U.S. Air Force photo by Lance Cheung/Released). Date Shot: 6/16/2008
U.S. Air Force Staff Sgt. Robert Moore, right, describes his every action to Airman 1st Class Carrie Smith during the setup of a Vehicle Test Controller for a RQ-1 Global Hawk unmanned aerial vehicle June 16, 2008, at Beale Air Force Base, Calif. They are with the 9th Aircraft Maintenance Squadron. (U.S. Air Force photo by Lance Cheung/Released). Date Shot: 6/16/2008![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict148.jpg) U.S. Air Force Airman 1st Class Evan Barnhart assists Senior Airman Stephen Simeone as she controls an unmanned aerial vehicle at Patrol Base Meade, Iraq, Jan. 21, 2008, while providing armed reconnaissance over watch in Southern Arab Jabour, Iraq. Simeone and Barnhart are both joint terminal attack controllers from Fort Stewart, Ga., and are deployed with the 2nd Brigade Combat Team, 3rd Infantry Division. (U.S. Air Force photo by Master Sgt. Andy Dunaway) (Released). Date Shot: 1/21/2008
U.S. Air Force Airman 1st Class Evan Barnhart assists Senior Airman Stephen Simeone as she controls an unmanned aerial vehicle at Patrol Base Meade, Iraq, Jan. 21, 2008, while providing armed reconnaissance over watch in Southern Arab Jabour, Iraq. Simeone and Barnhart are both joint terminal attack controllers from Fort Stewart, Ga., and are deployed with the 2nd Brigade Combat Team, 3rd Infantry Division. (U.S. Air Force photo by Master Sgt. Andy Dunaway) (Released). Date Shot: 1/21/2008![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict147.jpg) Royal Air Force Maj. Kevin Gambold monitors and pilots an MQ-1 Predator unmanned aerial vehicle at Ali Air Base, Iraq, Jan. 10, 2008. Gambold is the commander the 361st Expeditionary Reconnaissance Squadron and deployed from the 15th Reconnaissance Squadron, Creech Air Force Base, Nev., through a military personnel exchange program. (U.S. Air Force photo by Airman 1st Class Jonathan Snyder) (Released). Date Shot: 1/10/2008
Royal Air Force Maj. Kevin Gambold monitors and pilots an MQ-1 Predator unmanned aerial vehicle at Ali Air Base, Iraq, Jan. 10, 2008. Gambold is the commander the 361st Expeditionary Reconnaissance Squadron and deployed from the 15th Reconnaissance Squadron, Creech Air Force Base, Nev., through a military personnel exchange program. (U.S. Air Force photo by Airman 1st Class Jonathan Snyder) (Released). Date Shot: 1/10/2008![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict146.jpg) U.S. Air Force Senior Airman Logan Abrams, right, a Joint Tactical Air Control Party journeyman (JTAC in training), talks with his Army counterparts who are operating a Shadow unmanned aerial vehicle from Forward Operating Base Kalsu, Iraq, June 25, 2007. The Army Shadow is being used to provide real time video surveillance of a suspected explosives laden roadway south of Baghdad. Abrams takes information from the shadow back to his JTAC, Tech. Sgt. Mike Cmelik, who is controlling a B-1 Lancer aircraft to drop 13,500 pounds of ordinance on the roadway. This bombing mission severed a suspected main supply route used by Iraqi insurgents to bring accelerants from the south into the Baghdad area. (U.S. Air Force photo by Master Sgt. Jim Varhegyi/Released). Date Shot: 6/25/2007
U.S. Air Force Senior Airman Logan Abrams, right, a Joint Tactical Air Control Party journeyman (JTAC in training), talks with his Army counterparts who are operating a Shadow unmanned aerial vehicle from Forward Operating Base Kalsu, Iraq, June 25, 2007. The Army Shadow is being used to provide real time video surveillance of a suspected explosives laden roadway south of Baghdad. Abrams takes information from the shadow back to his JTAC, Tech. Sgt. Mike Cmelik, who is controlling a B-1 Lancer aircraft to drop 13,500 pounds of ordinance on the roadway. This bombing mission severed a suspected main supply route used by Iraqi insurgents to bring accelerants from the south into the Baghdad area. (U.S. Air Force photo by Master Sgt. Jim Varhegyi/Released). Date Shot: 6/25/2007![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict144.jpg) FORWARD OPERATING BASE KALSU, Iraq — U.S. Air Force Tech. Sgt. Andrea Patterson, one of three battlefield weatherman assigned to forward operating base (FOB) Kalsu south of Baghdad, Iraq, provides a weather brief to U.S. Army soldiers controlling Shadow Unmanned Aerial Vehicles (UAVs) for the U.S. Army’s 2nd Battalion, 3rd Combat Aviation Brigade, 3rd Infantry Division, Monday, June 25, 2007. Sergeant Patterson, and her fellow Air Force weather forecasters, provide 24 hour a day weather updates to the various U. S. Army 3rd Infantry Division’s operations occurring in the Triangle of Death area. The instantaneous weather information the battlefield weathermen are able to provide are critical to the success, and to the safety of the 3rd ID’s ground and aviation operations. Though Sergeant Patterson is attached to the 3rd ID she officially falls under the recently formed 3rd Expeditionary Weather Squadron headquartered on Camp Victory, Baghdad, Iraq. She is deployed from Detachment 6, 7th Weather Squadron, Wiesbaden, Germany. (U.S. Air Force photo by Master Sgt. Jim Varhegyi)(released). Date Shot: 6/25/2007
FORWARD OPERATING BASE KALSU, Iraq — U.S. Air Force Tech. Sgt. Andrea Patterson, one of three battlefield weatherman assigned to forward operating base (FOB) Kalsu south of Baghdad, Iraq, provides a weather brief to U.S. Army soldiers controlling Shadow Unmanned Aerial Vehicles (UAVs) for the U.S. Army’s 2nd Battalion, 3rd Combat Aviation Brigade, 3rd Infantry Division, Monday, June 25, 2007. Sergeant Patterson, and her fellow Air Force weather forecasters, provide 24 hour a day weather updates to the various U. S. Army 3rd Infantry Division’s operations occurring in the Triangle of Death area. The instantaneous weather information the battlefield weathermen are able to provide are critical to the success, and to the safety of the 3rd ID’s ground and aviation operations. Though Sergeant Patterson is attached to the 3rd ID she officially falls under the recently formed 3rd Expeditionary Weather Squadron headquartered on Camp Victory, Baghdad, Iraq. She is deployed from Detachment 6, 7th Weather Squadron, Wiesbaden, Germany. (U.S. Air Force photo by Master Sgt. Jim Varhegyi)(released). Date Shot: 6/25/2007![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict143.jpg) A representative with the Insitu, Inc., on board the Military Sealift Command afloat prepositioning ship USNS Stockham (T-AK 3017), operates a Scan Eagle Unmanned Aerial Vehicle over the Solomon Islands April 17, 2007. The scan eagle is assessing earthquake and tsunami damage that struck the island. (U.S. Navy photo by Mass Communication Specialist Second Class Andrew Meyers/Released). Date Shot: 4/17/2007
A representative with the Insitu, Inc., on board the Military Sealift Command afloat prepositioning ship USNS Stockham (T-AK 3017), operates a Scan Eagle Unmanned Aerial Vehicle over the Solomon Islands April 17, 2007. The scan eagle is assessing earthquake and tsunami damage that struck the island. (U.S. Navy photo by Mass Communication Specialist Second Class Andrew Meyers/Released). Date Shot: 4/17/2007![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict142.jpg) U.S. Air Force Capt. Michael Edmonston, left, and Airman 1st Class Stephen Sadler, both of the 46th Expeditionary Reconnaissance Squadron, work together to remotely operate a Predator MQ-1 unmanned aerial vehicle at Balad Air Base, Iraq, Nov. 5, 2006. The Predators are used to provide surveillance and are equipped with AGM-114 Hellfire missiles. (U.S. Air Force photo by Airman 1st Class Chad Kellum) (Released). Date Shot: 11/5/2006
U.S. Air Force Capt. Michael Edmonston, left, and Airman 1st Class Stephen Sadler, both of the 46th Expeditionary Reconnaissance Squadron, work together to remotely operate a Predator MQ-1 unmanned aerial vehicle at Balad Air Base, Iraq, Nov. 5, 2006. The Predators are used to provide surveillance and are equipped with AGM-114 Hellfire missiles. (U.S. Air Force photo by Airman 1st Class Chad Kellum) (Released). Date Shot: 11/5/2006![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict141.jpg) Peter Bale, Director of Business Development, readies an Aerosonde Unmanned Aerial Vehicle (UAV) for a test flight at Naval Air Station Key West, Fla., on Sept. 7, 2006. The remote-piloted UAV is designed to gather critical, near surface data on active hurricanes. (U.S. Navy photo by Mass Communication Specialist 2nd Class Timothy Cox) (Released). Date Shot: 9/7/2006
Peter Bale, Director of Business Development, readies an Aerosonde Unmanned Aerial Vehicle (UAV) for a test flight at Naval Air Station Key West, Fla., on Sept. 7, 2006. The remote-piloted UAV is designed to gather critical, near surface data on active hurricanes. (U.S. Navy photo by Mass Communication Specialist 2nd Class Timothy Cox) (Released). Date Shot: 9/7/2006![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict140.jpg) Kris Kokkely, an advanced tactical systems engineer for Boeing, watches his computer screen as data and video streams back from a ScanEagle unmanned aerial vehicle (UAV) as it flies over Yodaville training range on Marine Corps Air Station Yuma, Ariz., June 19, 2006, for Desert Talon. ScanEagle is a UAV system that is designed to provide persistent intelligence, surveillance and reconnaissance data, battle damage assessment and communications relay. (U.S. Marine Corps photo by Cpl. Michael P. Snody) (Released). Date Shot: 7/19/2006
Kris Kokkely, an advanced tactical systems engineer for Boeing, watches his computer screen as data and video streams back from a ScanEagle unmanned aerial vehicle (UAV) as it flies over Yodaville training range on Marine Corps Air Station Yuma, Ariz., June 19, 2006, for Desert Talon. ScanEagle is a UAV system that is designed to provide persistent intelligence, surveillance and reconnaissance data, battle damage assessment and communications relay. (U.S. Marine Corps photo by Cpl. Michael P. Snody) (Released). Date Shot: 7/19/2006![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict139.jpg) U.S. Air Force Capt. Michael J. Conte, Unmanned Aerial Vehicle (UAV) pilot assigned to the 46th Expeditionary Strike and Reconnaissance Squadron, Nellis Air Force Base, Nev., prepares for the nights UAV mission from Balad Air Base, Iraq, July 8, 2006. (U.S. Air Force photo by Master Sgt. Jonathan F. Doti/Released). Date Shot: 7/8/2006
U.S. Air Force Capt. Michael J. Conte, Unmanned Aerial Vehicle (UAV) pilot assigned to the 46th Expeditionary Strike and Reconnaissance Squadron, Nellis Air Force Base, Nev., prepares for the nights UAV mission from Balad Air Base, Iraq, July 8, 2006. (U.S. Air Force photo by Master Sgt. Jonathan F. Doti/Released). Date Shot: 7/8/2006![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict138.jpg) On 21 June 2006, Maj Toby Buchan, from Spencertown, NY, of Marine Unmanned Aerial Vehicle Squadron 2 (VMU-2) gives the clearance to fly to a Pioneer Unmanned Aerial Vehicle (UAV)before it departs on a mission in Al Taqaddum, Iraq. VMU-2 is deployed with IMEF (FWD) in support of in support of Operation Iraqi Freedom in the Al Anbar Province of Iraq (MNF-W) to develop the Iraqi security force, facilitate the development of official rule of law through democratic government, and continue the development of a market based economy centered on Iraqi reconstruction. .Official USMC Photo by Sergeant Jennifer L. Jones.060621-M-AK780-023.(RELEASED). Date Shot: 6/21/2006
On 21 June 2006, Maj Toby Buchan, from Spencertown, NY, of Marine Unmanned Aerial Vehicle Squadron 2 (VMU-2) gives the clearance to fly to a Pioneer Unmanned Aerial Vehicle (UAV)before it departs on a mission in Al Taqaddum, Iraq. VMU-2 is deployed with IMEF (FWD) in support of in support of Operation Iraqi Freedom in the Al Anbar Province of Iraq (MNF-W) to develop the Iraqi security force, facilitate the development of official rule of law through democratic government, and continue the development of a market based economy centered on Iraqi reconstruction. .Official USMC Photo by Sergeant Jennifer L. Jones.060621-M-AK780-023.(RELEASED). Date Shot: 6/21/2006![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict137.jpg) Pfc. Jonathan Machado, from HHB 3rd Battalion, 320th Field Artillery Regiment, 101st Airborne Division, operates a remote control for the Raven Unmanned Aerial Vehicle (UAV) from a safe location. The Raven is used to support land warfare operations and surveillance of the area. The 101st Airborne Division is currently deployed in the Tikrit area in support of the operation. FOB REMAGEN (U.S. Army photo by Spc. Teddy Wade) (Released). Date Shot: 4/21/2006
Pfc. Jonathan Machado, from HHB 3rd Battalion, 320th Field Artillery Regiment, 101st Airborne Division, operates a remote control for the Raven Unmanned Aerial Vehicle (UAV) from a safe location. The Raven is used to support land warfare operations and surveillance of the area. The 101st Airborne Division is currently deployed in the Tikrit area in support of the operation. FOB REMAGEN (U.S. Army photo by Spc. Teddy Wade) (Released). Date Shot: 4/21/2006![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict134.jpg) John T. Nicholson, Boeing Phantom Works Field Service Representative and Stewart Errico the Boeing ScanEagle, an unmanned aerial vehicle, secures the aircraft so it can be stored for the evening at Asad, Iraq, July 13, 2005. These men are civilian contractors that work with the U.S. Marines Unmanned Aerial Vehicle Squadron Two. (U.S. Marine Corps photo by Lance Cpl. Dustin S. Schaefer/Released). Date Shot: 7/12/2005
John T. Nicholson, Boeing Phantom Works Field Service Representative and Stewart Errico the Boeing ScanEagle, an unmanned aerial vehicle, secures the aircraft so it can be stored for the evening at Asad, Iraq, July 13, 2005. These men are civilian contractors that work with the U.S. Marines Unmanned Aerial Vehicle Squadron Two. (U.S. Marine Corps photo by Lance Cpl. Dustin S. Schaefer/Released). Date Shot: 7/12/2005![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict133.jpg) Todd Alexander, a support engineer from the Insitu Group, Boeing Corporation, maneuvers a Scan Eagle unmanned aerial vehicle from a remote location during an urban warfare exercise at Indian Springs Auxiliary Air Field, Nev., on May 4, 2005. Scan Eagle flies at low altitudes while taking video surveillance and it feeds images directly to security forces personnel in the field. (U.S. Air Force photo by Master Sgt. Robert W. Valenca) (Released). Date Shot: 5/4/2005
Todd Alexander, a support engineer from the Insitu Group, Boeing Corporation, maneuvers a Scan Eagle unmanned aerial vehicle from a remote location during an urban warfare exercise at Indian Springs Auxiliary Air Field, Nev., on May 4, 2005. Scan Eagle flies at low altitudes while taking video surveillance and it feeds images directly to security forces personnel in the field. (U.S. Air Force photo by Master Sgt. Robert W. Valenca) (Released). Date Shot: 5/4/2005![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict132.jpg) U.S. Air Force Capt. Andy Beitz (left), a student pilot, and Airman 1st Class Stephanie Barroso, a student sensor operator, practice operating an MQ-1 Predator Unmanned Aerial Vehicle (UAV) during training inside the Ground Control Station Cell at Indian Springs Auxiliary Field, Nev., on April 26, 2005. (U.S. Air Force photo by Tech. Sgt. Kevin J. Gruenwald) (Released). Date Shot: 4/26/2005
U.S. Air Force Capt. Andy Beitz (left), a student pilot, and Airman 1st Class Stephanie Barroso, a student sensor operator, practice operating an MQ-1 Predator Unmanned Aerial Vehicle (UAV) during training inside the Ground Control Station Cell at Indian Springs Auxiliary Field, Nev., on April 26, 2005. (U.S. Air Force photo by Tech. Sgt. Kevin J. Gruenwald) (Released). Date Shot: 4/26/2005![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict131.jpg) U.S. Air Force 1st Lt. Adam Twitchell, an Intelligence Officer and Operations Cell Mission Coordinator from the 11th Reconnaissance Squadron, Indian Springs Auxiliary Field, Nev., reviews local training plans during a MQ-1 Predator Unmanned Aerial Vehicle (UAV) mission over Nevada on April 2, 2005. (U.S. Air Force Photo by Tech. Sgt. Kevin J. Gruenwald) (Released). Date Shot: 4/2/2005
U.S. Air Force 1st Lt. Adam Twitchell, an Intelligence Officer and Operations Cell Mission Coordinator from the 11th Reconnaissance Squadron, Indian Springs Auxiliary Field, Nev., reviews local training plans during a MQ-1 Predator Unmanned Aerial Vehicle (UAV) mission over Nevada on April 2, 2005. (U.S. Air Force Photo by Tech. Sgt. Kevin J. Gruenwald) (Released). Date Shot: 4/2/2005![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict130.jpg) A U.S. Contractor (left), a U.S. Marine Corps 1st Lt. (second from left), a U.S. Marine Corps 1st Sgt. (second from right), and an U.S. Air Force Col. (right) stand around a Unmanned Aerial Vehicle that is on display at Camp Fallujah, Al Anbar Province, Iraq, on Dec. 4, 2004, that will be shown to U.S. Marine Corps Gen. James L. Jones, Supreme Allied Commander, Europe, and Commander, U.S. European Command, and U.S. Marine Corps Sgt. Maj. Alford L. McMichael, Senior Non-Commissioned Officer, Allied Command Operations, who are visiting with U.S. military service members who all participated in Operation Al Fajr, which was conducted during Operation Iraqi Freedom. (U.S. Marine Corps photo by Gunnery Sgt. Robert Blankenship) (Released). Date Shot: 12/4/2004
A U.S. Contractor (left), a U.S. Marine Corps 1st Lt. (second from left), a U.S. Marine Corps 1st Sgt. (second from right), and an U.S. Air Force Col. (right) stand around a Unmanned Aerial Vehicle that is on display at Camp Fallujah, Al Anbar Province, Iraq, on Dec. 4, 2004, that will be shown to U.S. Marine Corps Gen. James L. Jones, Supreme Allied Commander, Europe, and Commander, U.S. European Command, and U.S. Marine Corps Sgt. Maj. Alford L. McMichael, Senior Non-Commissioned Officer, Allied Command Operations, who are visiting with U.S. military service members who all participated in Operation Al Fajr, which was conducted during Operation Iraqi Freedom. (U.S. Marine Corps photo by Gunnery Sgt. Robert Blankenship) (Released). Date Shot: 12/4/2004![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict124.jpg) US Air Force (USAF) 46th Expeditionary Aerial Reconnaissance Squadron (EARS) Predator pilots, Captain (CPT) John “Disco” Songer and Airman 1st Class (A1C) Stephanie L. “Princess” Schulte operate individual Predator Unmanned Aerial Vehicles (UAV) using remote controls at Balad Air Base (AB), Iraq (IRQ), in support of Operation IRAQI FREEDOM. Photographer’s Name: SSGT COHEN A. YOUNG, USAF. Date Shot: 7/2/2004
US Air Force (USAF) 46th Expeditionary Aerial Reconnaissance Squadron (EARS) Predator pilots, Captain (CPT) John “Disco” Songer and Airman 1st Class (A1C) Stephanie L. “Princess” Schulte operate individual Predator Unmanned Aerial Vehicles (UAV) using remote controls at Balad Air Base (AB), Iraq (IRQ), in support of Operation IRAQI FREEDOM. Photographer’s Name: SSGT COHEN A. YOUNG, USAF. Date Shot: 7/2/2004![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict129.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict110.jpg) US Air Force (USAF) maintenance personnel assigned to the 12th Expeditionary Reconnaissance Squadron (ERS), check the maintenance log for a RQ-4A Global Hawk high-altitude, long-endurance unmanned aerial reconnaissance system while preparing for a mission at a forward location, while deployed in support of Operation ENDURING FREEDOM. Pictured left-to-right, USAF (Major) Greg Hataway, Staff Sergeant (SSGT) Kelvin Rasor, and MAJ John D’ortona. Photographer’s Name: SSGT Reynaldo Ramon, USAF. Date Shot: 6/30/2002
US Air Force (USAF) maintenance personnel assigned to the 12th Expeditionary Reconnaissance Squadron (ERS), check the maintenance log for a RQ-4A Global Hawk high-altitude, long-endurance unmanned aerial reconnaissance system while preparing for a mission at a forward location, while deployed in support of Operation ENDURING FREEDOM. Pictured left-to-right, USAF (Major) Greg Hataway, Staff Sergeant (SSGT) Kelvin Rasor, and MAJ John D’ortona. Photographer’s Name: SSGT Reynaldo Ramon, USAF. Date Shot: 6/30/2002![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict107.jpg) Chuck Gardner, systems engineer(front), and Patrick Didier, senior crew technician, both from Northrop Grumman Ryan Aeronautical Center, check the systems on a Global Hawk unmanned aerial vehicle after its arrival at Langley Air Force Base, Va., June 21, 2001. The aircraft flew non-stop from Edwards Air Force, California in support of the Supreme Allied Commander, Atlantic (SACLANT) Seminar taking place at Langley. (Photo by TSgt Jack Braden) (Released). Date Shot: 6/21/2001
Chuck Gardner, systems engineer(front), and Patrick Didier, senior crew technician, both from Northrop Grumman Ryan Aeronautical Center, check the systems on a Global Hawk unmanned aerial vehicle after its arrival at Langley Air Force Base, Va., June 21, 2001. The aircraft flew non-stop from Edwards Air Force, California in support of the Supreme Allied Commander, Atlantic (SACLANT) Seminar taking place at Langley. (Photo by TSgt Jack Braden) (Released). Date Shot: 6/21/2001![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict106.jpg) Sitting at the controls, Maj. George Barth, a pilot from the 31st Test and Evaluation Squadron, Edwards Air Force Base, Calif., flies the Global Hawk May 14, 2001, from inside the Mission Control Element, at Edinburgh Air Force Base, Australia, in support of Exercise Tandem Thrust. The Global Hawk is a jet powered Unmanned Aerial Vehicle (UAV) designed as a Reconnaissance and Surveillance vehicle with a wing span equal to a Boeing 737, flying at altitudes of up to 65,000 feet for more than 24 hours and capable of searching an area of more than 40,000 square miles. The Global Hawk is deployed to Australia from April to June 2001, flying more than a dozen missions. These missions will include sorties in support of Tandem Thrust as well as maritime, littoral, land surveillance and stand off reconnaissance capabilities. The Global Hawk completed its first successful maiden flight in February 1998. Currently there are five U.S. Air Force Global Hawks which have logged over 60 flights and have clocked more than 600 hours, with it’s biggest challenge to date the non-stop Trans-Pacific flight from Edwards to Edinburgh. Tandem Thrust 2001 is a combined U.S., Australian and Canadian military training exercise. This biannual exercise is being held in the vicinity of Shoalwater Bay training area, Queensland, More than 27,000 soldiers, sailors, airmen and marines are participating, with Canadian units taking part as opposing forces. The purpose of Exercise Tandem Thrust is to train for crisis action planningand execution of contingency response operations. (U.S. Air Force photo by Staff Sgt. Jeremy T. Lock) (Released). Date Shot: 5/14/2001
Sitting at the controls, Maj. George Barth, a pilot from the 31st Test and Evaluation Squadron, Edwards Air Force Base, Calif., flies the Global Hawk May 14, 2001, from inside the Mission Control Element, at Edinburgh Air Force Base, Australia, in support of Exercise Tandem Thrust. The Global Hawk is a jet powered Unmanned Aerial Vehicle (UAV) designed as a Reconnaissance and Surveillance vehicle with a wing span equal to a Boeing 737, flying at altitudes of up to 65,000 feet for more than 24 hours and capable of searching an area of more than 40,000 square miles. The Global Hawk is deployed to Australia from April to June 2001, flying more than a dozen missions. These missions will include sorties in support of Tandem Thrust as well as maritime, littoral, land surveillance and stand off reconnaissance capabilities. The Global Hawk completed its first successful maiden flight in February 1998. Currently there are five U.S. Air Force Global Hawks which have logged over 60 flights and have clocked more than 600 hours, with it’s biggest challenge to date the non-stop Trans-Pacific flight from Edwards to Edinburgh. Tandem Thrust 2001 is a combined U.S., Australian and Canadian military training exercise. This biannual exercise is being held in the vicinity of Shoalwater Bay training area, Queensland, More than 27,000 soldiers, sailors, airmen and marines are participating, with Canadian units taking part as opposing forces. The purpose of Exercise Tandem Thrust is to train for crisis action planningand execution of contingency response operations. (U.S. Air Force photo by Staff Sgt. Jeremy T. Lock) (Released). Date Shot: 5/14/2001![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict105.jpg) Portrait of Systems Test Engineer Chuck Gardner, (left), and Avionics Technician Brent Bremer, from Northrop Grumman Edwards Air Force Base, California, as they pre-flight the RQ-4A Global Hawk at RAAF Base Edinburgh, Adelaide, Australia, in support of Exercise TANDEM THRUST 01. Able to cover more than 40,000 square miles, the jet powered Unmanned Aerial Vehicle (UAV) RQ-4A Global Hawk has a wing span of 116 feet, equal to a Boeing 737, able to fly up to 65,000 feet and loiter for more than 24 hours. The Global Hawk deployed to Australia from April to June 2001, flying more than a dozen missions. This Global Hawk completed its biggest challenge to date the non-stop Trans-Pacific flight from Edwards to Edinburgh to support TANDEM THRUST 01. TANDEM THRUST 2001 a combined US, Australian, and Canadian military exercise for crisis action planning and execution of contingency response operations. The biannual exercise is held in the vicinity of Shoalwater Bay training area in Queensland, Australia. Photographer’s Name: SSGT JEREMY LOCK, USAF. Date Shot: 5/13/2001
Portrait of Systems Test Engineer Chuck Gardner, (left), and Avionics Technician Brent Bremer, from Northrop Grumman Edwards Air Force Base, California, as they pre-flight the RQ-4A Global Hawk at RAAF Base Edinburgh, Adelaide, Australia, in support of Exercise TANDEM THRUST 01. Able to cover more than 40,000 square miles, the jet powered Unmanned Aerial Vehicle (UAV) RQ-4A Global Hawk has a wing span of 116 feet, equal to a Boeing 737, able to fly up to 65,000 feet and loiter for more than 24 hours. The Global Hawk deployed to Australia from April to June 2001, flying more than a dozen missions. This Global Hawk completed its biggest challenge to date the non-stop Trans-Pacific flight from Edwards to Edinburgh to support TANDEM THRUST 01. TANDEM THRUST 2001 a combined US, Australian, and Canadian military exercise for crisis action planning and execution of contingency response operations. The biannual exercise is held in the vicinity of Shoalwater Bay training area in Queensland, Australia. Photographer’s Name: SSGT JEREMY LOCK, USAF. Date Shot: 5/13/2001![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict123.jpg) US Air Force (USAF) 46th Expeditionary Aerial Reconnaissance Squadron (EARS) Crew Chief, Staff Sergeant (SSGT) Sean Pietre and Senior Airman (SRA) Rothschild Pierre-Louis III unload a rocket from a Predator Unmanned Aerial Vehicle (UAV) at Balad Air Base (AB), Iraq (IRQ), in support of Operation IRAQI FREEDOM. Photographer’s Name: SSGT COHEN A. YOUNG, USAF. Date Shot: 7/2/2004
US Air Force (USAF) 46th Expeditionary Aerial Reconnaissance Squadron (EARS) Crew Chief, Staff Sergeant (SSGT) Sean Pietre and Senior Airman (SRA) Rothschild Pierre-Louis III unload a rocket from a Predator Unmanned Aerial Vehicle (UAV) at Balad Air Base (AB), Iraq (IRQ), in support of Operation IRAQI FREEDOM. Photographer’s Name: SSGT COHEN A. YOUNG, USAF. Date Shot: 7/2/2004![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict122.jpg) US Air Force (USAF) Staff Sergeant (SSGT) David Miranda, a Dedicated Crew Chief on the MQ-1L Predator Unmanned Aerial Vehicle (UAV), inspects an engine during a Preventative Maintenance Inspection (PMI). Miranda is assigned to the 46th Expeditionary Reconnaissance Squadron (ERS) at Balad Air Base (AB), Iraq (IRQ). Photographer’s Name: TSGT SCOTT REED, USAF. Date Shot: 6/10/2004
US Air Force (USAF) Staff Sergeant (SSGT) David Miranda, a Dedicated Crew Chief on the MQ-1L Predator Unmanned Aerial Vehicle (UAV), inspects an engine during a Preventative Maintenance Inspection (PMI). Miranda is assigned to the 46th Expeditionary Reconnaissance Squadron (ERS) at Balad Air Base (AB), Iraq (IRQ). Photographer’s Name: TSGT SCOTT REED, USAF. Date Shot: 6/10/2004![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict121.jpg) US Air Force (USAF) Crew Chief with the 46th Reconnaissance Squadron (RS), Staff Sergeant (SGT) James Barr (right), starts up the engine of a Predator MQ-1 Unmanned Aerial Vehicle (UAV) during a functional check while Senior Airman (SRA) Christipher Dewey observes the engine performance. Photographer’s Name: SSGT PRENTICE COLTER, USAF. Date Shot: 5/26/2004
US Air Force (USAF) Crew Chief with the 46th Reconnaissance Squadron (RS), Staff Sergeant (SGT) James Barr (right), starts up the engine of a Predator MQ-1 Unmanned Aerial Vehicle (UAV) during a functional check while Senior Airman (SRA) Christipher Dewey observes the engine performance. Photographer’s Name: SSGT PRENTICE COLTER, USAF. Date Shot: 5/26/2004![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict120.jpg) US Air Force (USAF) Staff Sergeant (SSGT) Michael Gonzales, a Crew Chief for the 46th Expeditionary Reconnaissance Squadron (ERS), unscrews the engine of a Predator Unmanned Aerial Vehicle (UAV) for repairs at Balad Air Base (AB), Iraq (IRQ), in support of Operation IRAQI FREEDOM. Photographer’s Name: SSGT CHYRECE E. LEWIS, USAF. Date Shot: 2/10/2004
US Air Force (USAF) Staff Sergeant (SSGT) Michael Gonzales, a Crew Chief for the 46th Expeditionary Reconnaissance Squadron (ERS), unscrews the engine of a Predator Unmanned Aerial Vehicle (UAV) for repairs at Balad Air Base (AB), Iraq (IRQ), in support of Operation IRAQI FREEDOM. Photographer’s Name: SSGT CHYRECE E. LEWIS, USAF. Date Shot: 2/10/2004![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict119.jpg) US Air Force (USAF) Staff Sergeant (SSGT) Tracy Jones, left and SSGT Jeffery Hicks, Crew Chiefs for the 46th Expeditionary Reconnaissance Squadron (ERS), sign-off preflight documents for the RQ-1 Predator Unmanned Aerial Vehicle (UAV), before its mission from Balad Air Base (AB), Iraq, in support of Operation IRAQI FREEDOM. Photographer’s Name: SSGT CHYRECE LEWIS, USAF. Date Shot: 1/31/2004
US Air Force (USAF) Staff Sergeant (SSGT) Tracy Jones, left and SSGT Jeffery Hicks, Crew Chiefs for the 46th Expeditionary Reconnaissance Squadron (ERS), sign-off preflight documents for the RQ-1 Predator Unmanned Aerial Vehicle (UAV), before its mission from Balad Air Base (AB), Iraq, in support of Operation IRAQI FREEDOM. Photographer’s Name: SSGT CHYRECE LEWIS, USAF. Date Shot: 1/31/2004![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict118.jpg) US Air Force (USAF) Staff Sergeant (SSGT) Jeffrey Hicks, left and Senior Airman (SRA) John Fanning, with the 46th Expeditionary Reconnaissance Squadron (ERS), perform a post flight check on their RQ-1 Predator Unmanned Aerial Vehicle (UAV) at Tallil Air Base (AB), Iraq, in support of OPERATION IRAQI FREEDOM. Photographer’s Name: SSGT SUZANNE M. JENKINS, USAF. Date Shot: 1/19/2004
US Air Force (USAF) Staff Sergeant (SSGT) Jeffrey Hicks, left and Senior Airman (SRA) John Fanning, with the 46th Expeditionary Reconnaissance Squadron (ERS), perform a post flight check on their RQ-1 Predator Unmanned Aerial Vehicle (UAV) at Tallil Air Base (AB), Iraq, in support of OPERATION IRAQI FREEDOM. Photographer’s Name: SSGT SUZANNE M. JENKINS, USAF. Date Shot: 1/19/2004![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict117.jpg) The Joint Unmanned Aerial Vehicle (UAV) Experiment Program consists of British and Israeli contractors working together controlling the UAV for experimental purposes during a Combat Search and Rescue (CSAR) training exercise at Fallon Naval Air Station (NAS), Nevada (NV), during exercise DESERT RESCUE XI. Here two British contractors view a low-resolution strip map, which covers a large area provided by the electrical optical and infrared camera, installed in the UAV during a surveillance and reconnaissance mission. The exercise is a joint service Combat Search and Rescue (CSAR) training exercise hosted by the Naval Strike and Warfare Center, designed to simulate downed aircrews, enabling CSAR related missions to experiment with new techniques in realistic scenarios. Photographer’s Name: SSGT REYNALDO RAMON, USAF. Date Shot: 8/13/2003
The Joint Unmanned Aerial Vehicle (UAV) Experiment Program consists of British and Israeli contractors working together controlling the UAV for experimental purposes during a Combat Search and Rescue (CSAR) training exercise at Fallon Naval Air Station (NAS), Nevada (NV), during exercise DESERT RESCUE XI. Here two British contractors view a low-resolution strip map, which covers a large area provided by the electrical optical and infrared camera, installed in the UAV during a surveillance and reconnaissance mission. The exercise is a joint service Combat Search and Rescue (CSAR) training exercise hosted by the Naval Strike and Warfare Center, designed to simulate downed aircrews, enabling CSAR related missions to experiment with new techniques in realistic scenarios. Photographer’s Name: SSGT REYNALDO RAMON, USAF. Date Shot: 8/13/2003![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict116.jpg) A contracted worker operates to controls of a Hunter Joint Tactical Unmanned Aerial Vehicle (UAV), as it prepares for a experimental flight during a Combat Search and Rescue (CSAR) training exercise at Fallon Naval Air Station (NAS), Nevada (NV), during exercise DESERT RESCUE XI. The Hunter is an Israeli multi-role short-range UAV system in service with the US Army (USA). The exercise is a joint service Combat Search and Rescue (CSAR) training exercise hosted by the Naval Strike and Warfare Center, designed to simulate downed aircrews, enabling CSAR related missions to experiment with new techniques in realistic scenarios. Photographer’s Name: SSGT REYNALDO RAMON, USAF. Date Shot: 8/13/2003
A contracted worker operates to controls of a Hunter Joint Tactical Unmanned Aerial Vehicle (UAV), as it prepares for a experimental flight during a Combat Search and Rescue (CSAR) training exercise at Fallon Naval Air Station (NAS), Nevada (NV), during exercise DESERT RESCUE XI. The Hunter is an Israeli multi-role short-range UAV system in service with the US Army (USA). The exercise is a joint service Combat Search and Rescue (CSAR) training exercise hosted by the Naval Strike and Warfare Center, designed to simulate downed aircrews, enabling CSAR related missions to experiment with new techniques in realistic scenarios. Photographer’s Name: SSGT REYNALDO RAMON, USAF. Date Shot: 8/13/2003![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict113.jpg) Sergeant (SGT) Carlos Carrasco (left) and USMC of Reading PA and Sgt Carlos Carrasco, both from 3rd Light Armored Reconnaissance (LAR) Battalion, operate the wearable ground control station for the “Dragon Eye” Unmanned Aerial Vehicle (UAV) at Camp Ripper, Kuwait during Operation ENDURING FREEDOM. Photographer’s Name: LCPL Kenneth E. Madden, USMC. Date Shot: 3/7/2003
Sergeant (SGT) Carlos Carrasco (left) and USMC of Reading PA and Sgt Carlos Carrasco, both from 3rd Light Armored Reconnaissance (LAR) Battalion, operate the wearable ground control station for the “Dragon Eye” Unmanned Aerial Vehicle (UAV) at Camp Ripper, Kuwait during Operation ENDURING FREEDOM. Photographer’s Name: LCPL Kenneth E. Madden, USMC. Date Shot: 3/7/2003![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict111.jpg) US Marine Corps (USMC) Corporal (CPL) John Rocha, Marine Unmanned Aerial Vehicle Squadron-1 (VMU-1), Twentynine Palms, California (CA), at the controls of the GCS-2000 Ground Control Station (GCS) that operates an unmanned air vehicle (UAV) from the flightline near Camp Workhorse during Operation ENDURING FREEDOM. Photographer’s Name: LCPL ALICIA M. ANDERSON, USMC. Date Shot: 2/25/2003
US Marine Corps (USMC) Corporal (CPL) John Rocha, Marine Unmanned Aerial Vehicle Squadron-1 (VMU-1), Twentynine Palms, California (CA), at the controls of the GCS-2000 Ground Control Station (GCS) that operates an unmanned air vehicle (UAV) from the flightline near Camp Workhorse during Operation ENDURING FREEDOM. Photographer’s Name: LCPL ALICIA M. ANDERSON, USMC. Date Shot: 2/25/2003![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict112.jpg) US Marine Corps (USMC) Marines from Marine Unmanned Aerial Vehicle Squadron-1 (VMU-1), Twentynine Palms, California (CA), and VMU-2, Cherry Point, North Carolina (NC), lunch together during a construction break of a runway near Camp Workhorse during Operation ENDURING FREEDOM. Photographer’s Name: LCPL ALICIA M. ANDERSON, USMC. Date Shot: 2/25/2003
US Marine Corps (USMC) Marines from Marine Unmanned Aerial Vehicle Squadron-1 (VMU-1), Twentynine Palms, California (CA), and VMU-2, Cherry Point, North Carolina (NC), lunch together during a construction break of a runway near Camp Workhorse during Operation ENDURING FREEDOM. Photographer’s Name: LCPL ALICIA M. ANDERSON, USMC. Date Shot: 2/25/2003![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict115.jpg) US Air Force (USAF) Senior Airman (SRA) Amy Hodges, Airborne Surveillance Radar System Technician assigned to the 438th Expeditionary Force Protection Squadron (EFPS) waits for final Global Positioning Systems (GPS) data before launching a US Air Force (USAF) “Desert Hawk” Force Protection Airborne Surveillance (FPAS), Unmanned Aerial Vehicle (UAV), while deployed at forward location during Operation ENDURING FREEDOM. Photographer’s Name: SSGT William Greer, USAF. Date Shot: 10/4/2002
US Air Force (USAF) Senior Airman (SRA) Amy Hodges, Airborne Surveillance Radar System Technician assigned to the 438th Expeditionary Force Protection Squadron (EFPS) waits for final Global Positioning Systems (GPS) data before launching a US Air Force (USAF) “Desert Hawk” Force Protection Airborne Surveillance (FPAS), Unmanned Aerial Vehicle (UAV), while deployed at forward location during Operation ENDURING FREEDOM. Photographer’s Name: SSGT William Greer, USAF. Date Shot: 10/4/2002![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict114.jpg) US Army (USA) Specialist (SPC) Dan Sawicki, 972nd Military Police (MP) Company, operates the controls of a US Air Force (USAF) “Desert Hawk” Force Protection Airborne Surveillance (FPAS), Unmanned Aerial Vehicle (UAV), while deployed at forward location during Operation ENDURING FREEDOM. Photographer’s Name: SSGT William Greer, USAF. Date Shot: 10/4/2002
US Army (USA) Specialist (SPC) Dan Sawicki, 972nd Military Police (MP) Company, operates the controls of a US Air Force (USAF) “Desert Hawk” Force Protection Airborne Surveillance (FPAS), Unmanned Aerial Vehicle (UAV), while deployed at forward location during Operation ENDURING FREEDOM. Photographer’s Name: SSGT William Greer, USAF. Date Shot: 10/4/2002![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict109.jpg) Staff Sgt. Brian Fox, VTC operator (Vehicle Test Controller) of the 12th ERS (Expeditionary Reconnaissance Squadron), uses a computer interface to provide flight instructions to the Global Hawk on June 30, 2002. The RQ-4A Global Hawk is a high-altitude, long-endurance unmanned aerial reconnaissance system designed to provide military field commanders with high resolution, near-real-time imagery of large geographic areas. (U.S. Air Force photo by Staff Sgt. Reynaldo Ramon) (Released). Date Shot: 6/30/2002
Staff Sgt. Brian Fox, VTC operator (Vehicle Test Controller) of the 12th ERS (Expeditionary Reconnaissance Squadron), uses a computer interface to provide flight instructions to the Global Hawk on June 30, 2002. The RQ-4A Global Hawk is a high-altitude, long-endurance unmanned aerial reconnaissance system designed to provide military field commanders with high resolution, near-real-time imagery of large geographic areas. (U.S. Air Force photo by Staff Sgt. Reynaldo Ramon) (Released). Date Shot: 6/30/2002![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-crew/pict108.jpg) Terry Collins, an L3 employee out of Edwards Air Force Base, checks the uplinks and downlinks for satellite communication with the Global Hawk on June 30, 2002. The RQ-4A Global Hawk is a high-altitude, long-endurance unmanned aerial reconnaissance system designed to provide military field commanders with high resolution, near-real-time imagery of large geographic areas. (U.S. Air Force photo by Staff Sgt. Reynaldo Ramon) (Released). Date Shot: 6/30/2002
Terry Collins, an L3 employee out of Edwards Air Force Base, checks the uplinks and downlinks for satellite communication with the Global Hawk on June 30, 2002. The RQ-4A Global Hawk is a high-altitude, long-endurance unmanned aerial reconnaissance system designed to provide military field commanders with high resolution, near-real-time imagery of large geographic areas. (U.S. Air Force photo by Staff Sgt. Reynaldo Ramon) (Released). Date Shot: 6/30/2002![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict35.jpg) In this March, 28, 2012, photo, an Arcti Copter 5 drone flies over a waterfront park in Berkeley, Calif. Interest in the domestic use of drones is surging among public agencies and private citizens alike, including a thriving subculture of amateur hobbyists, even as the prospect of countless tiny but powerful eyes circling in the skies raises serious privacy concerns. (Eric Risberg)
In this March, 28, 2012, photo, an Arcti Copter 5 drone flies over a waterfront park in Berkeley, Calif. Interest in the domestic use of drones is surging among public agencies and private citizens alike, including a thriving subculture of amateur hobbyists, even as the prospect of countless tiny but powerful eyes circling in the skies raises serious privacy concerns. (Eric Risberg)![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict36.jpg) In this March, 28, 2012, photo, Mark Harrison, left, and Andreas Oesterer, right, watch as a Ritewing Zephyr II drone lifts off at a waterfront park in Berkeley, Calif. Interest in the domestic use of drones is surging among public agencies and private citizens alike, including a thriving subculture of amateur hobbyists, even as the prospect of countless tiny but powerful eyes circling in the skies raises serious privacy concerns. (Eric Risberg)
In this March, 28, 2012, photo, Mark Harrison, left, and Andreas Oesterer, right, watch as a Ritewing Zephyr II drone lifts off at a waterfront park in Berkeley, Calif. Interest in the domestic use of drones is surging among public agencies and private citizens alike, including a thriving subculture of amateur hobbyists, even as the prospect of countless tiny but powerful eyes circling in the skies raises serious privacy concerns. (Eric Risberg)![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict90.jpg) A quadrocopter drone equipped with a camera stands on display at the Zeiss stand on the first day of the CeBIT 2012 technology trade fair on March 6, 2012 in Hanover, Germany. CeBIT 2012, the world’s largest information technology trade fair, will run from March 6-10, and advances in cloud computing and security are major features this year. Getty
A quadrocopter drone equipped with a camera stands on display at the Zeiss stand on the first day of the CeBIT 2012 technology trade fair on March 6, 2012 in Hanover, Germany. CeBIT 2012, the world’s largest information technology trade fair, will run from March 6-10, and advances in cloud computing and security are major features this year. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict89.jpg) A drone equipped with cameras and sensors flies over a simulation of a contaminated area during a training exercise of a nuclear accident following an earthquake in the region of the nuclear site of Cadarache, January 17, 2012. Reuters
A drone equipped with cameras and sensors flies over a simulation of a contaminated area during a training exercise of a nuclear accident following an earthquake in the region of the nuclear site of Cadarache, January 17, 2012. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict88.jpg) Israeli soldiers dismantle the Skylark drone during a drill on January 16, 2012 near Bat Shlomo, Israel. The Skylark can carry a camera payload of up to 1kg, has an operational calking of 15,000ft and allows users to monitor any designated point within a 15km radius. The Skylark unit consists of a ground control element and three drones, which provide battalion-level commanders with real-time information. Getty
Israeli soldiers dismantle the Skylark drone during a drill on January 16, 2012 near Bat Shlomo, Israel. The Skylark can carry a camera payload of up to 1kg, has an operational calking of 15,000ft and allows users to monitor any designated point within a 15km radius. The Skylark unit consists of a ground control element and three drones, which provide battalion-level commanders with real-time information. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict87.jpg) A TV drone flies beside Canada’s Erick Guay during the second practice of the men’s Alpine skiing World Cup downhill race at the Lauberhorn in Wengen, January 12, 2012. Reuters
A TV drone flies beside Canada’s Erick Guay during the second practice of the men’s Alpine skiing World Cup downhill race at the Lauberhorn in Wengen, January 12, 2012. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict86.jpg) Advanced Defense Technology Centre engineer Fumiyuki Sato demonstrates his spherical observation drone at the opening of the annual Digital Contents Expo in Tokyo on October 20, 2011. The Japanese defence researcher has invented a spherical observation drone that can fly down narrow alleys, hover on the spot, take off vertically and bounce along the ground. Getty
Advanced Defense Technology Centre engineer Fumiyuki Sato demonstrates his spherical observation drone at the opening of the annual Digital Contents Expo in Tokyo on October 20, 2011. The Japanese defence researcher has invented a spherical observation drone that can fly down narrow alleys, hover on the spot, take off vertically and bounce along the ground. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict84.jpg) President of French far-right party Front national (FN) and candidate for the 2012 French presidential election Marine Le Pen looks at a drone helicopter at the stand of French company Eden as she visits on October 19, 2011 in Paris, at the the France’s Milipol global security trade fair on October 18, 2011 in Paris. Milipol Paris 2011, welcoming more than 1,000 exhibiting companies from 43 countries, runs until October 21. Getty
President of French far-right party Front national (FN) and candidate for the 2012 French presidential election Marine Le Pen looks at a drone helicopter at the stand of French company Eden as she visits on October 19, 2011 in Paris, at the the France’s Milipol global security trade fair on October 18, 2011 in Paris. Milipol Paris 2011, welcoming more than 1,000 exhibiting companies from 43 countries, runs until October 21. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict85.jpg) This Sept. 2011 photo provided by Vanguard Defense Industries, shows a ShadowHawk drone with Montgomery County, Texas, SWAT team members. Civilian cousins of the unmanned military aircraft that have been tracking and killing terrorists in the Middle East and Asia are being sought by police departments, border patrols, power companies, news organizations and others who want a bird?s-eye view. AP
This Sept. 2011 photo provided by Vanguard Defense Industries, shows a ShadowHawk drone with Montgomery County, Texas, SWAT team members. Civilian cousins of the unmanned military aircraft that have been tracking and killing terrorists in the Middle East and Asia are being sought by police departments, border patrols, power companies, news organizations and others who want a bird?s-eye view. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict41.jpg) A Pakistani villager holds a wreckage of a suspected surveillance drone which is crashed in Pakistani border town of Chaman along the Afghanistan border in Pakistan on Thursday, Aug 25, 2011. Suspected US surveillance drone crashes in Pakistan military area near border with Afghanistan. (Shah Khalid)
A Pakistani villager holds a wreckage of a suspected surveillance drone which is crashed in Pakistani border town of Chaman along the Afghanistan border in Pakistan on Thursday, Aug 25, 2011. Suspected US surveillance drone crashes in Pakistan military area near border with Afghanistan. (Shah Khalid)![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict83.jpg) A maple seed is seen on the hand of Craig Stoneking, bottom, project manager at Lockheed Martin Advance Technology Laboratories, as engineer David Sharp holds the company’s new drone, Wednesday, Aug. 10, 2011, in Southampton, N.J. The unmanned, one-winged flight machine is based on the flight of maple seeds that twirl down from trees during the spring. AP
A maple seed is seen on the hand of Craig Stoneking, bottom, project manager at Lockheed Martin Advance Technology Laboratories, as engineer David Sharp holds the company’s new drone, Wednesday, Aug. 10, 2011, in Southampton, N.J. The unmanned, one-winged flight machine is based on the flight of maple seeds that twirl down from trees during the spring. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict42.jpg) Pakistani officials collect remains of a Pakistan Navy unmanned aerial vehicle (UAV) which crashed outside an oil refinery in Karachi, Pakistan on Tuesday, July 19, 2011. According to a Pakistan Navy official, the accident was caused by a bird hit. No casualties were reported. (Shakil Adil)
Pakistani officials collect remains of a Pakistan Navy unmanned aerial vehicle (UAV) which crashed outside an oil refinery in Karachi, Pakistan on Tuesday, July 19, 2011. According to a Pakistan Navy official, the accident was caused by a bird hit. No casualties were reported. (Shakil Adil)![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict80.jpg) Dr. Gregory Parker, Micro Air Vehicle team leader, holds a small winged drone that resembles an insect, in the U.S. Air Force Micro Air Vehicles lab at Wright Patterson Air Force Base in Dayton, Ohio, July 11, 2011. The Micro Air Vehicles unit of the Air Force Research Laboratory at Wright Patterson AFB is developing small military drones, with the goal of making them so small that they resemble small birds and insects, including some that will have moving wings. The mission is to develop MAVs that can find, track and target adversaries while operating in complex urban environments. The engineers are using a variety of small helicopters and drones in the lab to develop the programs and software. Testing takes place in a controlled indoor lab where the team flies the MAVs and then gathers data to analyze for further development. Reuters
Dr. Gregory Parker, Micro Air Vehicle team leader, holds a small winged drone that resembles an insect, in the U.S. Air Force Micro Air Vehicles lab at Wright Patterson Air Force Base in Dayton, Ohio, July 11, 2011. The Micro Air Vehicles unit of the Air Force Research Laboratory at Wright Patterson AFB is developing small military drones, with the goal of making them so small that they resemble small birds and insects, including some that will have moving wings. The mission is to develop MAVs that can find, track and target adversaries while operating in complex urban environments. The engineers are using a variety of small helicopters and drones in the lab to develop the programs and software. Testing takes place in a controlled indoor lab where the team flies the MAVs and then gathers data to analyze for further development. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict81.jpg) A model of an insect size U.S. Air Force drone is held by a member of the Micro Air Vehicles team of the Air Force Research Laboratory, which is developing small drones at Wright Patterson Air Force Base in Dayton, Ohio, July 11, 2011. Reuters
A model of an insect size U.S. Air Force drone is held by a member of the Micro Air Vehicles team of the Air Force Research Laboratory, which is developing small drones at Wright Patterson Air Force Base in Dayton, Ohio, July 11, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict82.jpg) A computer controlled U.S. Air Force drone prepares to lift off for a test flight of in the Micro Air Vehicles lab at Wright Patterson Air Force Base in Dayton, Ohio, July 11, 2011. Reuters
A computer controlled U.S. Air Force drone prepares to lift off for a test flight of in the Micro Air Vehicles lab at Wright Patterson Air Force Base in Dayton, Ohio, July 11, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict43.jpg) This product image provided by Parrot, shows the AR.Drone. Parrot, a company known more for its Bluetooth hands-free car speakerphones, has launched a small, unmanned aircraft that can be controlled using an iPhone or another of Apple Inc.’s Wi-Fi-enabled gadgets, including the iPod Touch and the iPad.(Parrot)
This product image provided by Parrot, shows the AR.Drone. Parrot, a company known more for its Bluetooth hands-free car speakerphones, has launched a small, unmanned aircraft that can be controlled using an iPhone or another of Apple Inc.’s Wi-Fi-enabled gadgets, including the iPod Touch and the iPad.(Parrot)![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict37.jpg) This undated handout photo provided by the U.S. Air Force shows a MQ-9 Reaper, armed with GBU-12 Paveway II laser guided munitions and AGM-114 Hellfire missiles, piloted by Col. Lex Turner during a combat mission over southern Afghanistan. (Lt. Col.. Leslie Pratt, US Air Force)
This undated handout photo provided by the U.S. Air Force shows a MQ-9 Reaper, armed with GBU-12 Paveway II laser guided munitions and AGM-114 Hellfire missiles, piloted by Col. Lex Turner during a combat mission over southern Afghanistan. (Lt. Col.. Leslie Pratt, US Air Force)![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict40.jpg) This undated photo provided by U.S. Customs and Border Protection shows an unmanned drone used to patrol the U.S.-Canadian border. The planes, which are based out of North Dakota, are now venturing as far as Eastern Washington on their patrols. (U.S. Customs and Border Protection)
This undated photo provided by U.S. Customs and Border Protection shows an unmanned drone used to patrol the U.S.-Canadian border. The planes, which are based out of North Dakota, are now venturing as far as Eastern Washington on their patrols. (U.S. Customs and Border Protection)![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict44.jpg) U.S. Navy Boatswain’s Mate 3rd Class Christian Riddle, left, and Boatswain’s Mate 2nd Class Dante Galati secure a recovered Air Force BQM-74C Chukar III aerial target drone to a crane aboard USS Tortuga (LSD 46) after an at-sea exercise for Cooperation Afloat Readiness and Training (CARAT) 2011 in the South China Sea June 11, 2011. CARAT is a series of bilateral exercises held annually in Southeast Asia to strengthen relationships and enhance force readiness. (U.S. Navy photo by Mass Communication Specialist 2nd Class Katerine Noll/Released)
U.S. Navy Boatswain’s Mate 3rd Class Christian Riddle, left, and Boatswain’s Mate 2nd Class Dante Galati secure a recovered Air Force BQM-74C Chukar III aerial target drone to a crane aboard USS Tortuga (LSD 46) after an at-sea exercise for Cooperation Afloat Readiness and Training (CARAT) 2011 in the South China Sea June 11, 2011. CARAT is a series of bilateral exercises held annually in Southeast Asia to strengthen relationships and enhance force readiness. (U.S. Navy photo by Mass Communication Specialist 2nd Class Katerine Noll/Released)![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict78.jpg) An X-47B Unmanned Combat Air System Demonstrator (UCAS-D) completes its first flight at Edwards Air Force Base, Calif., Feb. 4, 2011. The UCAS-D program will demonstrate the capability of an autonomous, low-observable unmanned aircraft to perform carrier launches and recoveries. (DoD photo courtesy of Northrop Grumman/Released). Date Shot: 2/4/2011
An X-47B Unmanned Combat Air System Demonstrator (UCAS-D) completes its first flight at Edwards Air Force Base, Calif., Feb. 4, 2011. The UCAS-D program will demonstrate the capability of an autonomous, low-observable unmanned aircraft to perform carrier launches and recoveries. (DoD photo courtesy of Northrop Grumman/Released). Date Shot: 2/4/2011
![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict79.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict91.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict77.jpg) U.S. Army Sgt. Brian Curd, and Spc. Nicholas Boxley, both combat engineers, from Echo Company, 1st Battalion, 68th Armor Regiment, 3rd Advise and Assist Brigade, 4th Infantry Division, prepare the RQ-16A Tarantula Hawk unmanned aerial vehicle, for operation, at Basra province, Iraq, Dec. 1, 2010. Although, T-Hawk requires a great deal of maintenance, the capabilities it provides are well worth the time spent. (U.S. Army photo by 2nd Lt. Matthew Fumagalli/Released). Date Shot: 12/1/2010
U.S. Army Sgt. Brian Curd, and Spc. Nicholas Boxley, both combat engineers, from Echo Company, 1st Battalion, 68th Armor Regiment, 3rd Advise and Assist Brigade, 4th Infantry Division, prepare the RQ-16A Tarantula Hawk unmanned aerial vehicle, for operation, at Basra province, Iraq, Dec. 1, 2010. Although, T-Hawk requires a great deal of maintenance, the capabilities it provides are well worth the time spent. (U.S. Army photo by 2nd Lt. Matthew Fumagalli/Released). Date Shot: 12/1/2010![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict76.jpg) Engineers, from left, Daniel Braun, Eric Sanchez and David Barney, with Space and Naval Warfare Systems Command Systems Center Pacific, perform pre-deployment inspections on Littoral Battlespace Sensing Unmanned Undersea Vehicles aboard the oceanographic survey ship USNS Pathfinder (T-AGS 60) while portside in San Diego, Calif., Oct. 21, 2010. Each vehicle hosts a payload suite of sensors that will measure the physical characteristics of the water column as it routinely descends and ascends in the ocean. (U.S. Navy photo by Rick Naystatt/Released). Date Shot: 10/21/2010
Engineers, from left, Daniel Braun, Eric Sanchez and David Barney, with Space and Naval Warfare Systems Command Systems Center Pacific, perform pre-deployment inspections on Littoral Battlespace Sensing Unmanned Undersea Vehicles aboard the oceanographic survey ship USNS Pathfinder (T-AGS 60) while portside in San Diego, Calif., Oct. 21, 2010. Each vehicle hosts a payload suite of sensors that will measure the physical characteristics of the water column as it routinely descends and ascends in the ocean. (U.S. Navy photo by Rick Naystatt/Released). Date Shot: 10/21/2010![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict75.jpg) U.S. Navy Aerographer’s Mate Airman Alex Boston, left, and Aerographer’s Mate 3rd Class Ryan Thuecks, right, both assigned to the Naval Oceanography Mine Warfare Center, and Ana Ziegler, with the Office of Naval Research, deploy an unmanned underwater vehicle during exercise Frontier Sentinel in the northern Atlantic Ocean June 9, 2010. The annual joint maritime homeland security exercise involved the Canadian navy, the U.S. Navy and Coast Guard, and federal, state, and local agencies in the detection, assessment and response to maritime security threats. (U.S. Navy photo by Wayne Stigstedt/Released). Date Shot: 6/9/2010
U.S. Navy Aerographer’s Mate Airman Alex Boston, left, and Aerographer’s Mate 3rd Class Ryan Thuecks, right, both assigned to the Naval Oceanography Mine Warfare Center, and Ana Ziegler, with the Office of Naval Research, deploy an unmanned underwater vehicle during exercise Frontier Sentinel in the northern Atlantic Ocean June 9, 2010. The annual joint maritime homeland security exercise involved the Canadian navy, the U.S. Navy and Coast Guard, and federal, state, and local agencies in the detection, assessment and response to maritime security threats. (U.S. Navy photo by Wayne Stigstedt/Released). Date Shot: 6/9/2010![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict74.jpg) U.S. Navy Sonar Technician Surface 1st Class Bryson Menke and Mineman 3rd Class Michael Darcy, both stationed with Explosive Ordnance Disposal Mobile Unit (EODMU) 1, prepare to deploy an unmanned underwater vehicle April 22, 2010, in the Persian Gulf. EODMU-1 and USS Dextrous (MCM 13) are conducting drills. (U.S. Navy photo by Mass Communication Specialist 2nd Class Ja’lon A. Rhinehart/Released). Date Shot: 4/22/2010
U.S. Navy Sonar Technician Surface 1st Class Bryson Menke and Mineman 3rd Class Michael Darcy, both stationed with Explosive Ordnance Disposal Mobile Unit (EODMU) 1, prepare to deploy an unmanned underwater vehicle April 22, 2010, in the Persian Gulf. EODMU-1 and USS Dextrous (MCM 13) are conducting drills. (U.S. Navy photo by Mass Communication Specialist 2nd Class Ja’lon A. Rhinehart/Released). Date Shot: 4/22/2010![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict73.jpg) Danielle Bryant, right, an oceanographer from the Naval Oceanographic Office (NAVOCEANO), establishes a satellite connection to the Glider Operations Center at NAVOCEANO before launching the seaglider unmanned underwater vessel from the Military Sealift Command oceanographic survey ship USNS Henson (T-AGS 63) March 24, 2010, in the Atlantic Ocean. The vessel is designed to collect physical oceanography data in deep water. Henson is under way off the coast of Fortaleza, Brazil, for Oceanographic-Southern Partnership Station 2010 conducting survey demonstrations with the Brazilian Directorate of Hydrograph and Navigation. Oceanographic-Southern Partnership Station is an oceanographic surveying and information exchange program between subject matter experts with partner nations in the U.S. Southern Command area of responsibility. (U.S. Navy photo by Mass Communication Specialist 2nd Class Lily Daniels/Released). Date Shot: 3/24/2010
Danielle Bryant, right, an oceanographer from the Naval Oceanographic Office (NAVOCEANO), establishes a satellite connection to the Glider Operations Center at NAVOCEANO before launching the seaglider unmanned underwater vessel from the Military Sealift Command oceanographic survey ship USNS Henson (T-AGS 63) March 24, 2010, in the Atlantic Ocean. The vessel is designed to collect physical oceanography data in deep water. Henson is under way off the coast of Fortaleza, Brazil, for Oceanographic-Southern Partnership Station 2010 conducting survey demonstrations with the Brazilian Directorate of Hydrograph and Navigation. Oceanographic-Southern Partnership Station is an oceanographic surveying and information exchange program between subject matter experts with partner nations in the U.S. Southern Command area of responsibility. (U.S. Navy photo by Mass Communication Specialist 2nd Class Lily Daniels/Released). Date Shot: 3/24/2010![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict72.jpg) U.S. Navy Sonar Technician (Surface) 2nd Class Brad Goss, right, and Sonar Technician (Surface) 1st Class Anthony Craig, left, from the Littoral Combat Ship Anti-Submarine Warfare (LCS ASW) Mission Package detachment, operate an unmanned surface vehicle (USV) in the waters of the Narragansett Bay, R.I., Feb. 16, 2010. The Naval Undersea Warfare Center Division Newport is developing the USV for future LCS ASW operations. (U.S. Navy photo/Released). Date Shot: 2/16/2010
U.S. Navy Sonar Technician (Surface) 2nd Class Brad Goss, right, and Sonar Technician (Surface) 1st Class Anthony Craig, left, from the Littoral Combat Ship Anti-Submarine Warfare (LCS ASW) Mission Package detachment, operate an unmanned surface vehicle (USV) in the waters of the Narragansett Bay, R.I., Feb. 16, 2010. The Naval Undersea Warfare Center Division Newport is developing the USV for future LCS ASW operations. (U.S. Navy photo/Released). Date Shot: 2/16/2010![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict96.jpg) U.S. Navy Mineman Seaman James Raper pushes the mine neutralization vehicle (MNV) of the mine countermeasures ship USS Defender (MCM 2) into its cradle Nov. 24, 2009, in the Yellow Sea. An MNV is a remote-controlled, unmanned submarine that uses a video camera to confirm the presence of underwater mines. Defender is participating in exercise Clear Horizon, an annual exercise conducted with the Republic of Korea Navy, that is one of the largest international mine counter-measures exercises in the world. (U.S. Navy photo by Mass Communication Specialist 1st Class Richard Doolin/Released). Date Shot: 11/24/2009
U.S. Navy Mineman Seaman James Raper pushes the mine neutralization vehicle (MNV) of the mine countermeasures ship USS Defender (MCM 2) into its cradle Nov. 24, 2009, in the Yellow Sea. An MNV is a remote-controlled, unmanned submarine that uses a video camera to confirm the presence of underwater mines. Defender is participating in exercise Clear Horizon, an annual exercise conducted with the Republic of Korea Navy, that is one of the largest international mine counter-measures exercises in the world. (U.S. Navy photo by Mass Communication Specialist 1st Class Richard Doolin/Released). Date Shot: 11/24/2009![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict97.jpg) The U.S Air Force Academy’s Viking 300 aircraft, an unmanned aerial system, flies over Camp Red Devil at Fort Carson, Colo., July 22, 2009. The Air Force Academy is the first military service academy to begin integrating unmanned aerial systems into its curriculum. (U.S. Air Force photo by Mike Kaplan/Released). Date Shot: 7/23/2009
The U.S Air Force Academy’s Viking 300 aircraft, an unmanned aerial system, flies over Camp Red Devil at Fort Carson, Colo., July 22, 2009. The Air Force Academy is the first military service academy to begin integrating unmanned aerial systems into its curriculum. (U.S. Air Force photo by Mike Kaplan/Released). Date Shot: 7/23/2009![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict98.jpg) An Unmanned Little Bird helicopter, a smaller version of the manned A/MH-6M Little Bird helicopter, is tested and evaluated by personnel from the U.S. Marine Corps’ Warfighting Laboratory at Marine Corps Combat Development Command, Quantico, Va., June 16, 2009, in Bridgeport, Calif., during Javelin Thrust-09. Marine Forces Reserve, headquartered in New Orleans, is conducting Javelin Thrust-09 at six locations throughout the Western United States. The combined arms exercise showcases a range of combat and logistics capabilities and allows leaders to assess the operational readiness of participating units. More than 2,000 reserve- and active-component Marines, Sailors, Soldiers and Airmen are training simultaneously in support of the exercise. (U.S. Marine Corps photo by Chief Warrant Officer Keith A. Stevenson/Released). Date Shot: 6/16/2009
An Unmanned Little Bird helicopter, a smaller version of the manned A/MH-6M Little Bird helicopter, is tested and evaluated by personnel from the U.S. Marine Corps’ Warfighting Laboratory at Marine Corps Combat Development Command, Quantico, Va., June 16, 2009, in Bridgeport, Calif., during Javelin Thrust-09. Marine Forces Reserve, headquartered in New Orleans, is conducting Javelin Thrust-09 at six locations throughout the Western United States. The combined arms exercise showcases a range of combat and logistics capabilities and allows leaders to assess the operational readiness of participating units. More than 2,000 reserve- and active-component Marines, Sailors, Soldiers and Airmen are training simultaneously in support of the exercise. (U.S. Marine Corps photo by Chief Warrant Officer Keith A. Stevenson/Released). Date Shot: 6/16/2009![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict99.jpg) Dirk D. Reum, a robotic systems engineer, conducts a systems check of a robotic unmanned ground vehicle (RUGV) June 13, 2009, in Hawthorne, Nev., before making it available for test training with U.S. Marine Corps infantrymen of India Company, 3rd Battalion, 23rd Marine Regiment, 4th Marine Division, during exercise Javelin Thrust 2009. The RUGV has a payload capacity of 1,400 pounds. Javelin Thrust showcases a wide range of combat and logistics capabilities, and allows leaders to assess the operational readiness of participating units. More than 3,000 reserve and active component Marines and members of the Navy, Army and Air National Guard will train during the combined arms exercise at six locations throughout the Western United States. (U.S. Marine Corps photo by Chief Warrant Officer 2 Keith A. Stevenson/Released). Date Shot: 6/13/2009
Dirk D. Reum, a robotic systems engineer, conducts a systems check of a robotic unmanned ground vehicle (RUGV) June 13, 2009, in Hawthorne, Nev., before making it available for test training with U.S. Marine Corps infantrymen of India Company, 3rd Battalion, 23rd Marine Regiment, 4th Marine Division, during exercise Javelin Thrust 2009. The RUGV has a payload capacity of 1,400 pounds. Javelin Thrust showcases a wide range of combat and logistics capabilities, and allows leaders to assess the operational readiness of participating units. More than 3,000 reserve and active component Marines and members of the Navy, Army and Air National Guard will train during the combined arms exercise at six locations throughout the Western United States. (U.S. Marine Corps photo by Chief Warrant Officer 2 Keith A. Stevenson/Released). Date Shot: 6/13/2009![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict100.jpg) The Heron TP medium altitude long endurance unmanned aerial vehicle takes off from Comalapa International Airport in San Salvador, El Salvador, May 21, 2009, during a counter drug operations support mission. The Heron is part of an unmanned aircraft system deployed to El Salvador to support Project Monitoreo, a month-long evaluation initiative to assess the suitability of using unmanned aircraft for counterdrug missions in the United States Southern Command area. (U.S. Army photo by Jose Ruiz/Released). Date Shot: 5/21/2009
The Heron TP medium altitude long endurance unmanned aerial vehicle takes off from Comalapa International Airport in San Salvador, El Salvador, May 21, 2009, during a counter drug operations support mission. The Heron is part of an unmanned aircraft system deployed to El Salvador to support Project Monitoreo, a month-long evaluation initiative to assess the suitability of using unmanned aircraft for counterdrug missions in the United States Southern Command area. (U.S. Army photo by Jose Ruiz/Released). Date Shot: 5/21/2009![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict101.jpg) The U.S. Navy and Spatial Integrated Systems Inc. demonstrate a fully autonomous Unmanned Surface Vehicle (USV) near Fort Monroe, Va., Jan. 14, 2009. The USV uses its autonomous maritime navigation systems to patrol and detect intruders. (U.S. Navy photo by Mass Communication Specialist Seaman Apprentice Joshua Adam Nuzzo/Released). Date Shot: 1/14/2009
The U.S. Navy and Spatial Integrated Systems Inc. demonstrate a fully autonomous Unmanned Surface Vehicle (USV) near Fort Monroe, Va., Jan. 14, 2009. The USV uses its autonomous maritime navigation systems to patrol and detect intruders. (U.S. Navy photo by Mass Communication Specialist Seaman Apprentice Joshua Adam Nuzzo/Released). Date Shot: 1/14/2009![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict93.jpg) U.S. Navy Lt. Timothy Stanford, a graduate student at University of Wisconsin, tests his Autonomous Unmanned Vehicle (AUV) prior to competing in the Association for Unmanned Vehicle Society International’s (AUVSI) 11th annual competition in San Diego, Calif., Aug. 1, 2008. AUVSI, in cooperation with the Space and Naval Warfare Systems Center, hosts the event to encourage young engineers and scientists to consider careers developing AUV technologies for the U.S. Navy. (U.S. Navy photo by Mass Communication Specialist 2nd Class Brian Gaines/Released). Date Shot: 8/1/2008
U.S. Navy Lt. Timothy Stanford, a graduate student at University of Wisconsin, tests his Autonomous Unmanned Vehicle (AUV) prior to competing in the Association for Unmanned Vehicle Society International’s (AUVSI) 11th annual competition in San Diego, Calif., Aug. 1, 2008. AUVSI, in cooperation with the Space and Naval Warfare Systems Center, hosts the event to encourage young engineers and scientists to consider careers developing AUV technologies for the U.S. Navy. (U.S. Navy photo by Mass Communication Specialist 2nd Class Brian Gaines/Released). Date Shot: 8/1/2008![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict94.jpg) Fox News reporter Phil Keating interviews U.S. Navy Capt. Robert Dishman, the Persistent Maritime Unmanned Aircraft Systems Program Office 262 Program Manager, in front of the Skyship 600 blimp at Naval Air Station Key West, Fla., July 10, 2008. The lighter-than-air vehicle is in Key West for six weeks to conduct a series of maritime surveillance evaluations. The joint airship experiment between the U.S. Navy and Coast Guard emphasizes the cooperative strategy for 21st century seapower among the sea services. (U.S. Navy photo by Mass Communication Specialist 2nd Class Rachel McMarr/Released). Date Shot: 7/10/2008
Fox News reporter Phil Keating interviews U.S. Navy Capt. Robert Dishman, the Persistent Maritime Unmanned Aircraft Systems Program Office 262 Program Manager, in front of the Skyship 600 blimp at Naval Air Station Key West, Fla., July 10, 2008. The lighter-than-air vehicle is in Key West for six weeks to conduct a series of maritime surveillance evaluations. The joint airship experiment between the U.S. Navy and Coast Guard emphasizes the cooperative strategy for 21st century seapower among the sea services. (U.S. Navy photo by Mass Communication Specialist 2nd Class Rachel McMarr/Released). Date Shot: 7/10/2008![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict38.jpg) An unmanned aerial vehicle’s Predator Hellfire missile is shown on a simulator’s virtual camera at the March Air Reserve Base in Riverside County, Calif., June 25, 2008. As the U.S. military scrambles to get more robotic warplanes like the Predator drone aloft, it is confronting an unexpected adversary: human error. (Damian Dovarganes)
An unmanned aerial vehicle’s Predator Hellfire missile is shown on a simulator’s virtual camera at the March Air Reserve Base in Riverside County, Calif., June 25, 2008. As the U.S. military scrambles to get more robotic warplanes like the Predator drone aloft, it is confronting an unexpected adversary: human error. (Damian Dovarganes)![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict95.jpg) Secretary of Defense Robert M. Gates learns how to operate an unmanned ground vehicle during a tour of the future combat systems facility at Fort Bliss, Texas, May 1, 2008. (Department of Defense photo by Cherie Cullen/Released). Date Shot: 5/1/2008
Secretary of Defense Robert M. Gates learns how to operate an unmanned ground vehicle during a tour of the future combat systems facility at Fort Bliss, Texas, May 1, 2008. (Department of Defense photo by Cherie Cullen/Released). Date Shot: 5/1/2008![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict92.jpg) A Condor unmanned aerial vehicle sits on top of its carrying case before flying during Atlantic Strike V at the air-ground training complex in Avon Park, Fla., April 17, 2007. Atlantic Strike is a U.S. Central Command Air Forces initiative and the only joint, tactical-level, urban, close air support training event dedicated to supporting the war on terror. (U.S. Air Force photo by Staff Sgt. Stephen Otero) (Released). Date Shot: 4/17/2007
A Condor unmanned aerial vehicle sits on top of its carrying case before flying during Atlantic Strike V at the air-ground training complex in Avon Park, Fla., April 17, 2007. Atlantic Strike is a U.S. Central Command Air Forces initiative and the only joint, tactical-level, urban, close air support training event dedicated to supporting the war on terror. (U.S. Air Force photo by Staff Sgt. Stephen Otero) (Released). Date Shot: 4/17/2007![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict71.jpg) US Marine Corps (USMC) Marines, 15th Marine Expeditionary Unit (MEU) show the US Navy (USN) Sailors aboard the USN Wasp Class Amphibious Assault Ship USS BOXER (LHD 4) the “Silver Fox” Unmanned Aerial Vehicle (UAV). The 15th MEU and the BOXER are part of Expeditionary Strike Group (ESG) 5 which is currently participating in their Composite Training Unit Exercise (COMPTUEX) off the coast of Southern California. U.S. Navy photo by Mass Communication Specialist Third Class Noel Danseco (RELEASED). Date Shot: 7/16/2006
US Marine Corps (USMC) Marines, 15th Marine Expeditionary Unit (MEU) show the US Navy (USN) Sailors aboard the USN Wasp Class Amphibious Assault Ship USS BOXER (LHD 4) the “Silver Fox” Unmanned Aerial Vehicle (UAV). The 15th MEU and the BOXER are part of Expeditionary Strike Group (ESG) 5 which is currently participating in their Composite Training Unit Exercise (COMPTUEX) off the coast of Southern California. U.S. Navy photo by Mass Communication Specialist Third Class Noel Danseco (RELEASED). Date Shot: 7/16/2006![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict70.jpg) Engineers check the structure after the test flights of the Navy-built Guardian Griffin unmanned aerial vehicle (UAV). The flights demonstrated its capability to support U.S. joint forces with missions ranging from convoy escort and port security to combat patrol. U.S. Navy photo by Mr. John Joyce (RELEASED). Date Shot: 5/18/2006
Engineers check the structure after the test flights of the Navy-built Guardian Griffin unmanned aerial vehicle (UAV). The flights demonstrated its capability to support U.S. joint forces with missions ranging from convoy escort and port security to combat patrol. U.S. Navy photo by Mr. John Joyce (RELEASED). Date Shot: 5/18/2006![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict69.jpg) The Proteus aircraft takes off from Mojave Airfield near Edwards Air Force Base, Calif., on May 9, 2006. It carries the pod that eventually will contain the radar that will be used on the Global Hawk unmanned aerial vehicle. A year of testing, that will be conducted by the 851st Electronic Testing Group, will begin in September once the radar is installed on Proteus. (U.S. Air Force photo) (Released). Date Shot: 5/9/2006
The Proteus aircraft takes off from Mojave Airfield near Edwards Air Force Base, Calif., on May 9, 2006. It carries the pod that eventually will contain the radar that will be used on the Global Hawk unmanned aerial vehicle. A year of testing, that will be conducted by the 851st Electronic Testing Group, will begin in September once the radar is installed on Proteus. (U.S. Air Force photo) (Released). Date Shot: 5/9/2006![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict68.jpg) Northrop Grumman’s RQ-8A Fire Scout Vertical Takeoff and Landing Tactical Unmanned Aerial Vehicle (VTUAV) test fires the second of two Mark (MK) 66 2.75-inch unguided rockets during weapons testing at Arizona’s Yuma Proving Grounds. The Fire Scout has the ability to autonomously take off and land from any aviation-capable warship and at unprepared landing zones, with an on-station endurance of over four hours. The Fire Scout system is capable of continuous operations, providing coverage at 110 nautical miles from the launch site. Utilizing a baseline payload that includes electro-optical/infrared sensors and a laser rangefinder/designator the Fire Scout can find and identify tactical targets, track and designate targets, accurately provide targeting data to strike platforms, employ precision weapons, and perform battle damage assessment. Photographer’s Name: TIM PAYNTER, CIV. Date Shot: 7/25/2005
Northrop Grumman’s RQ-8A Fire Scout Vertical Takeoff and Landing Tactical Unmanned Aerial Vehicle (VTUAV) test fires the second of two Mark (MK) 66 2.75-inch unguided rockets during weapons testing at Arizona’s Yuma Proving Grounds. The Fire Scout has the ability to autonomously take off and land from any aviation-capable warship and at unprepared landing zones, with an on-station endurance of over four hours. The Fire Scout system is capable of continuous operations, providing coverage at 110 nautical miles from the launch site. Utilizing a baseline payload that includes electro-optical/infrared sensors and a laser rangefinder/designator the Fire Scout can find and identify tactical targets, track and designate targets, accurately provide targeting data to strike platforms, employ precision weapons, and perform battle damage assessment. Photographer’s Name: TIM PAYNTER, CIV. Date Shot: 7/25/2005![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict67.jpg) U.S. Air Force Tech. Sgt. Patrick Vasquez, a Force Protection Airborne Surveillance System (FPASS) operator from the 99th Security Forces Group, prepares to release a Desert Hawk unmanned aerial vehicle during an urban warfare training at Indian Springs Auxiliary Air Field, Nev., on May 4, 2005. The Desert Hawk gives real-time video surveillance to FPASS operators who in turn are able to instantly relay enemy force locations to the troops in the field. (U.S. Air Force photo by Master Sgt. Robert W. Valenca) (Released). Date Shot: 5/4/2005
U.S. Air Force Tech. Sgt. Patrick Vasquez, a Force Protection Airborne Surveillance System (FPASS) operator from the 99th Security Forces Group, prepares to release a Desert Hawk unmanned aerial vehicle during an urban warfare training at Indian Springs Auxiliary Air Field, Nev., on May 4, 2005. The Desert Hawk gives real-time video surveillance to FPASS operators who in turn are able to instantly relay enemy force locations to the troops in the field. (U.S. Air Force photo by Master Sgt. Robert W. Valenca) (Released). Date Shot: 5/4/2005![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict65.jpg) A U.S. Air Force BQM-167A Unmanned Aerial Vehicle (UAV) is launched from Tyndall Air Force Base, Fla., on Dec. 22, 2004. The BQM-167A is powered by a ventrally mounted turbojet engine. It can be air or ground launched, and can carry the full range of current target payloads, including radar enhancers, countermeasures, scoring devices, and towed targets. (USAF Photo by Bruce Hoffman, CIV) (Released). Date Shot: 12/22/2004
A U.S. Air Force BQM-167A Unmanned Aerial Vehicle (UAV) is launched from Tyndall Air Force Base, Fla., on Dec. 22, 2004. The BQM-167A is powered by a ventrally mounted turbojet engine. It can be air or ground launched, and can carry the full range of current target payloads, including radar enhancers, countermeasures, scoring devices, and towed targets. (USAF Photo by Bruce Hoffman, CIV) (Released). Date Shot: 12/22/2004![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict64.jpg) A Boeing ScanEagle Unmanned Aerial Vehicle (UAV) sits on top of a table during a demonstration at Indian Springs Auxiliary Field, N.V., on Dec. 18, 2004. The U.S. military uses the four-foot-long UAV as a forward observer to monitor enemy concentrations, vehicle and personnel movement, buildings and terrain in Iraq. (USAF Photo by Tech. Sgt. Kevin J.Gruenwald) (Released). Date Shot: 12/18/2004 [Engine and propeller unit is rotated 90-degrees for service.]
A Boeing ScanEagle Unmanned Aerial Vehicle (UAV) sits on top of a table during a demonstration at Indian Springs Auxiliary Field, N.V., on Dec. 18, 2004. The U.S. military uses the four-foot-long UAV as a forward observer to monitor enemy concentrations, vehicle and personnel movement, buildings and terrain in Iraq. (USAF Photo by Tech. Sgt. Kevin J.Gruenwald) (Released). Date Shot: 12/18/2004 [Engine and propeller unit is rotated 90-degrees for service.]
![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict66.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict63.jpg) U.S. Air Force maintenance personnel prepare to push Global Hawk Air Vehicle Number 3 (AV-3) into its hanger after its 400th mission at an undisclosed location in support of Operation Iraqi Freedom on Nov. 8, 2004. The Global Hawk is an unmanned aerial vehicle designed for surveillance and reconnaissance. (USAF Photo by Tech. Sgt. Erik Gudmundson) (Released). Date Shot: 11/8/2004
U.S. Air Force maintenance personnel prepare to push Global Hawk Air Vehicle Number 3 (AV-3) into its hanger after its 400th mission at an undisclosed location in support of Operation Iraqi Freedom on Nov. 8, 2004. The Global Hawk is an unmanned aerial vehicle designed for surveillance and reconnaissance. (USAF Photo by Tech. Sgt. Erik Gudmundson) (Released). Date Shot: 11/8/2004![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict62.jpg) An AGM-114 Hellfire missile hung on the rail of an US Air Force (USAF) MQ-1L Predator Unmanned Aerial Vehicle (UAV) is inscribed with, “IN MEMORY OF HONORABLE RONALD REAGAN.” Photographer’s Name: TSGT SCOTT REED, USAF. Date Shot: 6/10/2004
An AGM-114 Hellfire missile hung on the rail of an US Air Force (USAF) MQ-1L Predator Unmanned Aerial Vehicle (UAV) is inscribed with, “IN MEMORY OF HONORABLE RONALD REAGAN.” Photographer’s Name: TSGT SCOTT REED, USAF. Date Shot: 6/10/2004![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict61.jpg) Tracked and wheeled versions of the Gladiator Tactical Unmanned Ground Vehicles (TUGV) take a forward position to determine security of the area. The Gladiators are taking part in a live fire exercise with 1st Battalion, 2nd Marines (1/2), Bravo Company (B CO), Marine Corps Base (MCB) Camp Lejeune, North Carolina (NC), at Range 400 aboard Marine Air Ground Task Force Training Command (MAGTF-TC), Twentynine Palms, California (CA). Photographer’s Name: LCPL PATRICK GREEN, USMC. Date Shot: 1/14/2004
Tracked and wheeled versions of the Gladiator Tactical Unmanned Ground Vehicles (TUGV) take a forward position to determine security of the area. The Gladiators are taking part in a live fire exercise with 1st Battalion, 2nd Marines (1/2), Bravo Company (B CO), Marine Corps Base (MCB) Camp Lejeune, North Carolina (NC), at Range 400 aboard Marine Air Ground Task Force Training Command (MAGTF-TC), Twentynine Palms, California (CA). Photographer’s Name: LCPL PATRICK GREEN, USMC. Date Shot: 1/14/2004![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict60.jpg) Lt. Col. George Biondi, Director of Operations for the 82nd Aerial Targets Squadron, Tyndall Air Force Base, Florida, flies this QF-4 “Rhino” as a safety chase on the wing of a remote-controlled unmanned QF-4 “Rhino” full-scale aerial target drone after a Combat Archer Air-to-Air Weapons System Evaluation Program mission over the Gulf of Mexico. The QF-4 Phantom II, affectionately known as the “Rhino”, is used as a threat-representative unmanned target for live-fire test and evaluation missions. It maintains the basic flight envelope capabilities of the original F-4, and can also be flown manned for workup and remote controller training missions. United States Air Force QF-4’s are flown by the 82nd Aerial Targets Squadron from Tyndall Air Force Base, Florida and Holloman Air Force Base, New Mexico. (U.S. Air Force photo Tech. Sgt. Michael Ammons) (Released). Date Shot: 9/16/2003
Lt. Col. George Biondi, Director of Operations for the 82nd Aerial Targets Squadron, Tyndall Air Force Base, Florida, flies this QF-4 “Rhino” as a safety chase on the wing of a remote-controlled unmanned QF-4 “Rhino” full-scale aerial target drone after a Combat Archer Air-to-Air Weapons System Evaluation Program mission over the Gulf of Mexico. The QF-4 Phantom II, affectionately known as the “Rhino”, is used as a threat-representative unmanned target for live-fire test and evaluation missions. It maintains the basic flight envelope capabilities of the original F-4, and can also be flown manned for workup and remote controller training missions. United States Air Force QF-4’s are flown by the 82nd Aerial Targets Squadron from Tyndall Air Force Base, Florida and Holloman Air Force Base, New Mexico. (U.S. Air Force photo Tech. Sgt. Michael Ammons) (Released). Date Shot: 9/16/2003![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict59.jpg) A VMU-2’s Unmanned Air Vehicle (UAV) is ready for launch off a Pneumatic Launcher on the desert floor. Photographer’s Name: LCPL RICHARD W. COURT, USAF. Date Shot: 3/9/2003
A VMU-2’s Unmanned Air Vehicle (UAV) is ready for launch off a Pneumatic Launcher on the desert floor. Photographer’s Name: LCPL RICHARD W. COURT, USAF. Date Shot: 3/9/2003![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict58.jpg) Chief of Naval Operations (CNO) Admiral Vern Clark listens to Steve Castelin of NAVSEA Coastal Systems Station, as he talks about the future of unmanned aerial vehicles (UAV) such as the Blue Fin currently displayed on Nov. 26, 2002. The CNO is in Panama City, Fla., to see new technology hardware and to visit with local area community leaders. (U.S. Navy photo by Chief Photographer’s Mate Johnny Bivera) (RELEASED). Date Shot: 11/26/2002
Chief of Naval Operations (CNO) Admiral Vern Clark listens to Steve Castelin of NAVSEA Coastal Systems Station, as he talks about the future of unmanned aerial vehicles (UAV) such as the Blue Fin currently displayed on Nov. 26, 2002. The CNO is in Panama City, Fla., to see new technology hardware and to visit with local area community leaders. (U.S. Navy photo by Chief Photographer’s Mate Johnny Bivera) (RELEASED). Date Shot: 11/26/2002![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict57.jpg) A RQ-1L Predator UAV (Unmanned Aerial Vehicle) from the 57th Wing Operations Group, Nellis AFB, NV sits in a maintenance bunker at a forward operating airbase in the ENDURING FREEDOM area. The Predator is a medium-altitude, long-endurance, unmanned aerial vehicle system used for reconnaissance, surveillance and target acquisition and is in Afghanistan in direct support of Operation ENDURING FREEDOM. Photographer’s Name: CWO2 William D. Crow, USMC. Date Shot: 2/14/2002
A RQ-1L Predator UAV (Unmanned Aerial Vehicle) from the 57th Wing Operations Group, Nellis AFB, NV sits in a maintenance bunker at a forward operating airbase in the ENDURING FREEDOM area. The Predator is a medium-altitude, long-endurance, unmanned aerial vehicle system used for reconnaissance, surveillance and target acquisition and is in Afghanistan in direct support of Operation ENDURING FREEDOM. Photographer’s Name: CWO2 William D. Crow, USMC. Date Shot: 2/14/2002![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict56.jpg) Operations Specialist 1st Class Guy Hurkmans of Escanaba, Mich., assigned to Destroyer Squadron 50 (DESRON50), Naval Support Activity, Bahrain manually launches an Unmanned Air Vehicle (UAV) during a flight test that is being conducted in support of Maritime Interception Operations (MIO) on Jan. 6, 2002. (U.S. Navy photo by Photographer’s Mate 1st Class Ted Banks) (Released). Date Shot: 1/6/2002
Operations Specialist 1st Class Guy Hurkmans of Escanaba, Mich., assigned to Destroyer Squadron 50 (DESRON50), Naval Support Activity, Bahrain manually launches an Unmanned Air Vehicle (UAV) during a flight test that is being conducted in support of Maritime Interception Operations (MIO) on Jan. 6, 2002. (U.S. Navy photo by Photographer’s Mate 1st Class Ted Banks) (Released). Date Shot: 1/6/2002![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict54.jpg) Army personnel walkout and position the Hunter UAV (Unmanned Aerial Vehicle) for takeoff at Petrovec Airfield, Skopje, Macedonia, in support of TASK FORCE HARVEST. The role of TASK FORCE HARVEST is to collect arms and ammunition voluntarily turned over by ethnic Albanian insurgents, and thereby helps to build confidence in the broader peace process suggested by the President of former Yugoslav Republic of Macedonia. The Hunter UAV plays a key role in helping NATO troops by surveying and looking for any changes in the local area that might hinder the peacekeeping mission. Photographer’s Name: SSGT JOCELYN M. BROUSSARD, USAF. Date Shot: 9/13/2001
Army personnel walkout and position the Hunter UAV (Unmanned Aerial Vehicle) for takeoff at Petrovec Airfield, Skopje, Macedonia, in support of TASK FORCE HARVEST. The role of TASK FORCE HARVEST is to collect arms and ammunition voluntarily turned over by ethnic Albanian insurgents, and thereby helps to build confidence in the broader peace process suggested by the President of former Yugoslav Republic of Macedonia. The Hunter UAV plays a key role in helping NATO troops by surveying and looking for any changes in the local area that might hinder the peacekeeping mission. Photographer’s Name: SSGT JOCELYN M. BROUSSARD, USAF. Date Shot: 9/13/2001![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict53.jpg) The new Dragon Eye Unmanned Arial Reconnaissance Vehicle sits partially disassembled prior to a demonstration given to commanders during Kernal Blitz Experimental aboard Camp Pendleton, Calif., on June 23, 2001. The Dragon Eye is controlled line of site via computer and can transmit real time video imagery back to the operator. (U.S. Marine Corps photo by Sgt. John Vannucci) (Released) Date Shot: 6/23/2001
The new Dragon Eye Unmanned Arial Reconnaissance Vehicle sits partially disassembled prior to a demonstration given to commanders during Kernal Blitz Experimental aboard Camp Pendleton, Calif., on June 23, 2001. The Dragon Eye is controlled line of site via computer and can transmit real time video imagery back to the operator. (U.S. Marine Corps photo by Sgt. John Vannucci) (Released) Date Shot: 6/23/2001![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict52.jpg) The Global Hawk heads back towards its hanger after doing preflight checks before going on a twenty four hour mission out of Edinburgh Air Force Base in Adelaide, South Australia, in support of Exercise Tandem Thrust. The Global Hawk is a jet powered Unmanned Aerial Vehicle (UAV) designed as a Reconnaissance and Surveillance vehicle with a wing span equal to a Boeing 737, flying at altitudes of up to 65,000 feet for more than 24 hours and capable of searching an area of more than 40,000 square miles. The Global Hawk is deployed to Australia from April to June 2001, flying more than a dozen missions. These missions will include sorties in support of Tandem Thrust as well as maritime, littoral, land surveillance and stand off reconnaissance capabilities. The Global Hawk completed its first successful maiden flight in February 1998. Currently there are five U.S. Air Force Global Hawks which have logged over 60 flights and have clocked more than 600 hours, with it’s biggest challenge to date the non-stop Trans-Pacific flight from Edwards AFB CA to Edinburgh AFB South Australia. Exercise Tandem Thrust 2001 is a combined United States and Australian military training exercise. This biennial exercise is being held in the vicinity of Shoalwater Bay Training Area, Queensland, Australia. More than 27,000 Soldiers, Sailors, Airmen and Marines are participating, with Canadian units taking part as opposing forces. The purpose of Exercise Tandem Thrust is to train for crisis action planning and execution of contingency response operations. Photograph CLEARED FOR RELEASE by Lt. Col .Pat Bolibrzuch, Australian Deployment Commander, Global Hawk Program Office and Wing Commander Brett Newell, Deputy Director Emerging Systems, Aerospace Development Branch. U.S. Navy Photo by PH3 J. Smith (Released). Photographer’s Name: PH3 JENNIFER A. SMITH. Date Shot: 5/13/2001
The Global Hawk heads back towards its hanger after doing preflight checks before going on a twenty four hour mission out of Edinburgh Air Force Base in Adelaide, South Australia, in support of Exercise Tandem Thrust. The Global Hawk is a jet powered Unmanned Aerial Vehicle (UAV) designed as a Reconnaissance and Surveillance vehicle with a wing span equal to a Boeing 737, flying at altitudes of up to 65,000 feet for more than 24 hours and capable of searching an area of more than 40,000 square miles. The Global Hawk is deployed to Australia from April to June 2001, flying more than a dozen missions. These missions will include sorties in support of Tandem Thrust as well as maritime, littoral, land surveillance and stand off reconnaissance capabilities. The Global Hawk completed its first successful maiden flight in February 1998. Currently there are five U.S. Air Force Global Hawks which have logged over 60 flights and have clocked more than 600 hours, with it’s biggest challenge to date the non-stop Trans-Pacific flight from Edwards AFB CA to Edinburgh AFB South Australia. Exercise Tandem Thrust 2001 is a combined United States and Australian military training exercise. This biennial exercise is being held in the vicinity of Shoalwater Bay Training Area, Queensland, Australia. More than 27,000 Soldiers, Sailors, Airmen and Marines are participating, with Canadian units taking part as opposing forces. The purpose of Exercise Tandem Thrust is to train for crisis action planning and execution of contingency response operations. Photograph CLEARED FOR RELEASE by Lt. Col .Pat Bolibrzuch, Australian Deployment Commander, Global Hawk Program Office and Wing Commander Brett Newell, Deputy Director Emerging Systems, Aerospace Development Branch. U.S. Navy Photo by PH3 J. Smith (Released). Photographer’s Name: PH3 JENNIFER A. SMITH. Date Shot: 5/13/2001![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict51.jpg) The Broad-area Unmanned Responsive Resupply Operations (BURRO) is used in conjunction with the Slice Multi-Task Boat (only flight deck is seen) for providing over the horizon sea-based logistics. The BURRO (also known as the KAMAN K-1200 K-MAX Helicopter) is also used for resupplying ships at sea. It is currently on the flightdeck of the Slice Boat (Prototype) at Coast Guard Island in Oakland, California, due to its participation in Fleet Battle Experiment Echo. Also seen in the frame is a right side front view of the U.S. Coast Guard High Endurance Cutter, USCGC SHERMAN, (WHEC-720). This mission is in direct support of Urban Warrior ’99. Photographer’s Name: LCPL Christopher L. Vallee. Date Shot: 3/19/1999
The Broad-area Unmanned Responsive Resupply Operations (BURRO) is used in conjunction with the Slice Multi-Task Boat (only flight deck is seen) for providing over the horizon sea-based logistics. The BURRO (also known as the KAMAN K-1200 K-MAX Helicopter) is also used for resupplying ships at sea. It is currently on the flightdeck of the Slice Boat (Prototype) at Coast Guard Island in Oakland, California, due to its participation in Fleet Battle Experiment Echo. Also seen in the frame is a right side front view of the U.S. Coast Guard High Endurance Cutter, USCGC SHERMAN, (WHEC-720). This mission is in direct support of Urban Warrior ’99. Photographer’s Name: LCPL Christopher L. Vallee. Date Shot: 3/19/1999![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict50.jpg) The Navtec, Incorporated Owl MKII Unmanned Surface Vehicle (USV) glides stealthly through the waters of Mile Hammock Bay, New River during a demonstration to highlight it’s marine reconnaissance capabilities to the Riverine Insertion Operation Exercise (RIOEX) ’98 participants. The Owl MKII is funded by the Office of Naval Research (ONR) and is remote-controlled from a small shoreline control station by Brad Dowling, a Navtec, Inc. electronics engineer, at Camp Lejeune, North Carolina, during the Riverine Insertion Operation Exercise (RIOEX) ’98. Photographer’s Name: LCPL T.A. Pope, USMC. Date Shot: 5/14/1998
The Navtec, Incorporated Owl MKII Unmanned Surface Vehicle (USV) glides stealthly through the waters of Mile Hammock Bay, New River during a demonstration to highlight it’s marine reconnaissance capabilities to the Riverine Insertion Operation Exercise (RIOEX) ’98 participants. The Owl MKII is funded by the Office of Naval Research (ONR) and is remote-controlled from a small shoreline control station by Brad Dowling, a Navtec, Inc. electronics engineer, at Camp Lejeune, North Carolina, during the Riverine Insertion Operation Exercise (RIOEX) ’98. Photographer’s Name: LCPL T.A. Pope, USMC. Date Shot: 5/14/1998![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict49.jpg) The Dragon Drone Unmanned Aerial Vehicle was on display at the MOUT (Military Operations in Urban Terrain) facility during LOE 1 (Limited Objective Experiment 1). Urban Warrior is the U.S. Marine Corps Warfighting Laboratory’s series of limited objective experiments examining new urban tactics and experimental technologies. Photographer’s Name: Sgt. Jason J. Bortz. Date Shot: 1/23/1998
The Dragon Drone Unmanned Aerial Vehicle was on display at the MOUT (Military Operations in Urban Terrain) facility during LOE 1 (Limited Objective Experiment 1). Urban Warrior is the U.S. Marine Corps Warfighting Laboratory’s series of limited objective experiments examining new urban tactics and experimental technologies. Photographer’s Name: Sgt. Jason J. Bortz. Date Shot: 1/23/1998![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict48.jpg) US Marine Corps Air Ground Combat Center (MCAGCC). A “Night Owl”, or RQ-2A Pioneer, surveillance Unmanned Aerial Vehicle (UAV) is launched from its twin rail catapult mounted on a 5-ton truck. This launch is conducted by the Cherry Point Marine Base, Squadron-2, part of Combined Arms Exercise (CAX) 5-97 at Airfield Seagle. Photographer’s Name: LCPL E. J. Young. Date Shot: 4/14/1997
US Marine Corps Air Ground Combat Center (MCAGCC). A “Night Owl”, or RQ-2A Pioneer, surveillance Unmanned Aerial Vehicle (UAV) is launched from its twin rail catapult mounted on a 5-ton truck. This launch is conducted by the Cherry Point Marine Base, Squadron-2, part of Combined Arms Exercise (CAX) 5-97 at Airfield Seagle. Photographer’s Name: LCPL E. J. Young. Date Shot: 4/14/1997![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict47.jpg) A close up front view of the fuselage section from the wreckage of a Predator Unmanned Aerial Vehicle (UAV) laying on a hillside in the Russian sector of the Multinational Division North (MDN) area of operations. Photographer’s Name: SSG Edward W. Nino. Date Shot: 10/1/1996
A close up front view of the fuselage section from the wreckage of a Predator Unmanned Aerial Vehicle (UAV) laying on a hillside in the Russian sector of the Multinational Division North (MDN) area of operations. Photographer’s Name: SSG Edward W. Nino. Date Shot: 10/1/1996![[Image]](https://i0.wp.com/cryptome.org/2012-info/drone-photos/pict46.jpg) A civilian contractor tests the unmanned submersible Deep Drone aboard a US Navy ship. The sonar device is being used during salvage operations for downed Korean Air Lines Flight 007 (KAL 007). The commercial jet was shot down by Soviet aircraft over Sakhalin Island in the Sea of Japan on August 30, 1983. All 269 passengers and crewmen were killed. PH1 Fel Barbante, USN
A civilian contractor tests the unmanned submersible Deep Drone aboard a US Navy ship. The sonar device is being used during salvage operations for downed Korean Air Lines Flight 007 (KAL 007). The commercial jet was shot down by Soviet aircraft over Sakhalin Island in the Sea of Japan on August 30, 1983. All 269 passengers and crewmen were killed. PH1 Fel Barbante, USN


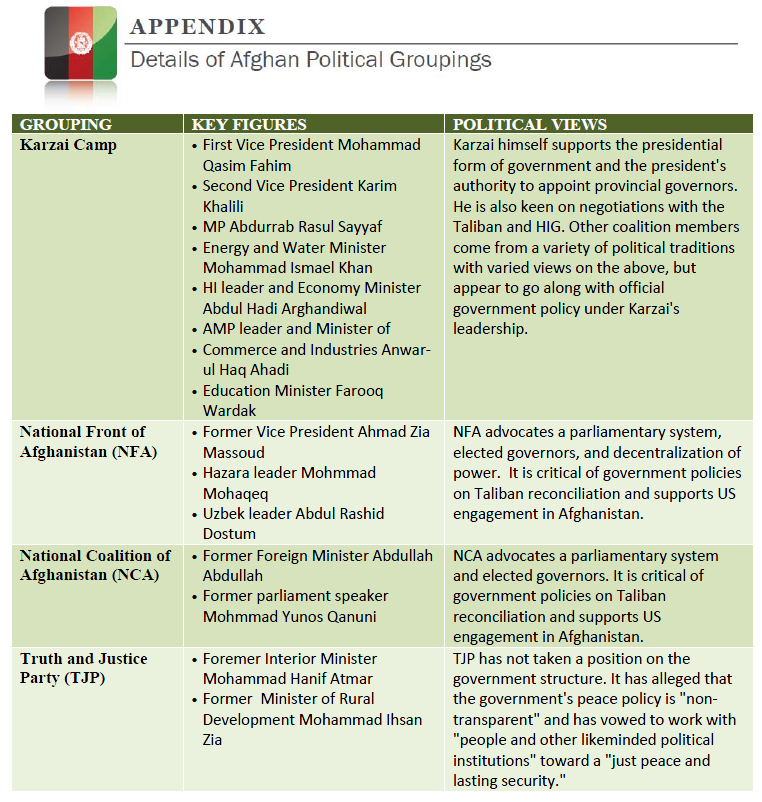










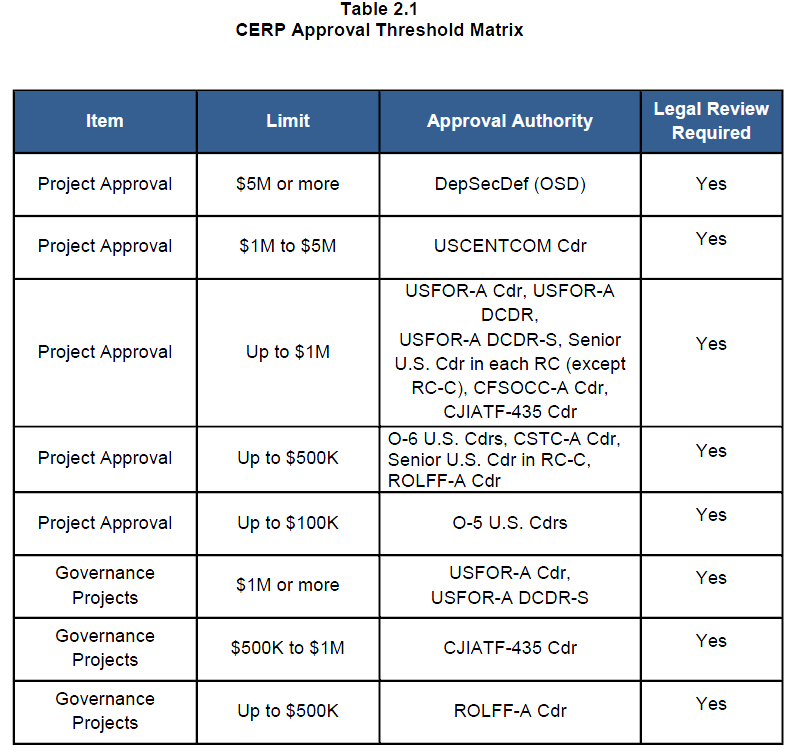


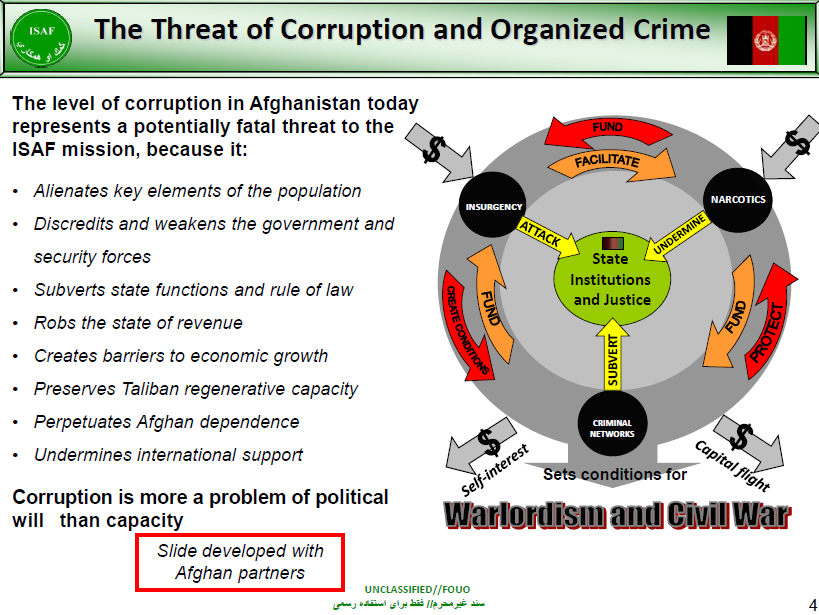
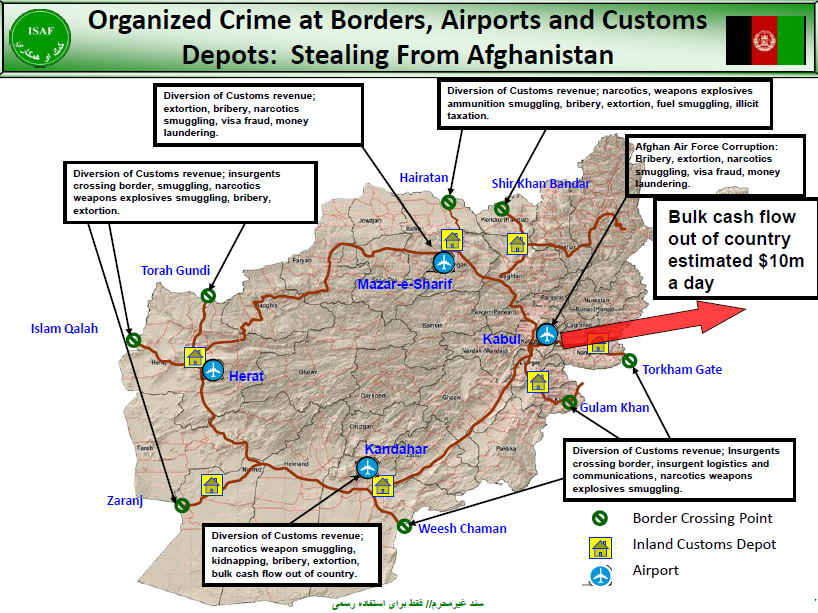
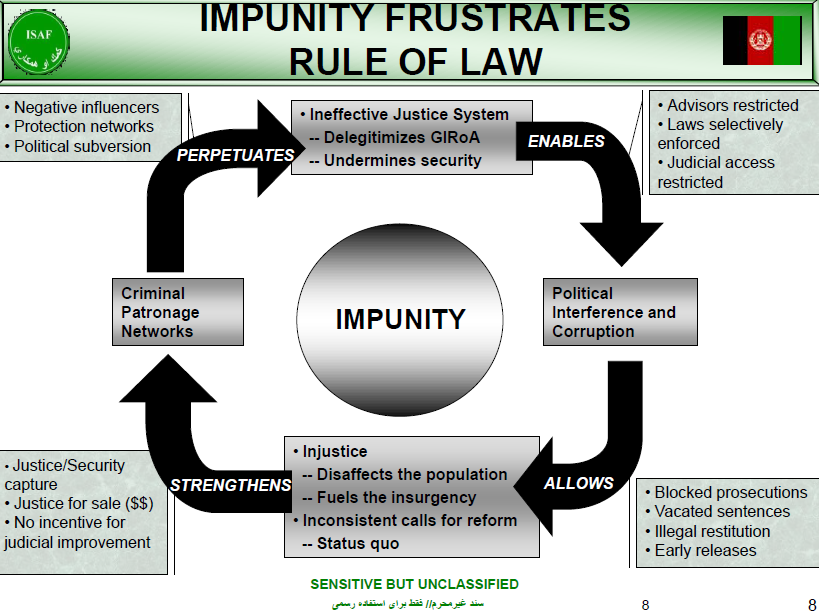



















![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-mayday-2012/pict21.jpg) A demonstrator grimaces after she was pepper sprayed by Israeli troops during a protest calling for the release prisoners jailed in Israel outside the Ofer military prison, near the West Bank city of Ramallah, Tuesday May 1, 2012. (Majdi Mohammed)
A demonstrator grimaces after she was pepper sprayed by Israeli troops during a protest calling for the release prisoners jailed in Israel outside the Ofer military prison, near the West Bank city of Ramallah, Tuesday May 1, 2012. (Majdi Mohammed)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-mayday-2012/pict7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-mayday-2012/pict0.jpg) A female protester associated with the Occupy Wall Street movement is arrested while marching through traffic in lower Manhattan on May 1, 2012 in New York City. May 1st, Labor Day, is a traditional day of global protest in sympathy with union and leftist politics. Getty
A female protester associated with the Occupy Wall Street movement is arrested while marching through traffic in lower Manhattan on May 1, 2012 in New York City. May 1st, Labor Day, is a traditional day of global protest in sympathy with union and leftist politics. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-mayday-2012/pict18.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-mayday-2012/pict1.jpg) An Occupy demonstrator confronts a police officer during rally in the streets as part of a nation-wide May Day protest in Oakland, California May 1, 2012. Reuters
An Occupy demonstrator confronts a police officer during rally in the streets as part of a nation-wide May Day protest in Oakland, California May 1, 2012. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-mayday-2012/pict8.jpg) An Israeli soldier restrains a Palestinian protester, grimacing after being hit by ‘skunk’ liquid after she was forced down from atop an Israeli military vehicle where she stood waving her national flag, during a protest by some 300 people outside Ofer military prison near the West Bank city of Ramallah on May 1, 2012 in a show of support for prisoners held in Israeli jails. Clashes erupted between stone-throwing youths and the Israeli army, who fired tear gas, rubber bullets and a foul-smelling liquid known as ‘skunk’ to break up the demonstration. Getty
An Israeli soldier restrains a Palestinian protester, grimacing after being hit by ‘skunk’ liquid after she was forced down from atop an Israeli military vehicle where she stood waving her national flag, during a protest by some 300 people outside Ofer military prison near the West Bank city of Ramallah on May 1, 2012 in a show of support for prisoners held in Israeli jails. Clashes erupted between stone-throwing youths and the Israeli army, who fired tear gas, rubber bullets and a foul-smelling liquid known as ‘skunk’ to break up the demonstration. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-mayday-2012/pict22.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-mayday-2012/pict25.jpg) Members of Occupy DC and union activists chant slogans in front of the White House during a May Day protest in Washington on May 1, 2012. More than 20 arrests were reported in various cities, including 10 at Los Angeles international airport and others in Oakland and Seattle, where shop windows were smashed. Getty
Members of Occupy DC and union activists chant slogans in front of the White House during a May Day protest in Washington on May 1, 2012. More than 20 arrests were reported in various cities, including 10 at Los Angeles international airport and others in Oakland and Seattle, where shop windows were smashed. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-mayday-2012/pict2.jpg) Protesters associated with the Occupy Wall Street movement march through traffic in lower Manhattan on May 1, 2012 in New York City. May 1st, Labor Day, is a traditional day of global protest in sympathy with union and leftist politics. Getty
Protesters associated with the Occupy Wall Street movement march through traffic in lower Manhattan on May 1, 2012 in New York City. May 1st, Labor Day, is a traditional day of global protest in sympathy with union and leftist politics. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-mayday-2012/pict3.jpg) Riot police charge during clashes between police and mostly left-wing protesters in the May Day demonstrations on May 1, 2012 in Hamburg, Germany. May 1st, also known as Labor Day, is a traditional day of global protest in sympathy with union and leftist politics. Getty
Riot police charge during clashes between police and mostly left-wing protesters in the May Day demonstrations on May 1, 2012 in Hamburg, Germany. May 1st, also known as Labor Day, is a traditional day of global protest in sympathy with union and leftist politics. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-mayday-2012/pict24.jpg) Indian laborers shots slogans during a rally to mark May Day in Ahmadabad, India, Tuesday, May 1, 2012. Placards in Gujarati read, ” strictly enforce all labor laws in the state”, bottom left and ” Pay Rupees 500 as monthly allowance to workers of the non-organized sector”, bottom right. (Ajit Solanki)
Indian laborers shots slogans during a rally to mark May Day in Ahmadabad, India, Tuesday, May 1, 2012. Placards in Gujarati read, ” strictly enforce all labor laws in the state”, bottom left and ” Pay Rupees 500 as monthly allowance to workers of the non-organized sector”, bottom right. (Ajit Solanki)![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-mayday-2012/pict9.jpg) Occupy Wall Street protesters picket during a May Day rally in front of the Bank of America buidling on May 1, 2012 in New York City. Demonstrators have called for nation-wide May Day strikes to protest economic inequality and political corruption. Getty
Occupy Wall Street protesters picket during a May Day rally in front of the Bank of America buidling on May 1, 2012 in New York City. Demonstrators have called for nation-wide May Day strikes to protest economic inequality and political corruption. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-mayday-2012/pict10.jpg) Bahraini Shiite Muslim women take part in a Labour Day pro-democracy protest in the Manama suburb of Sanabis on May 1, 2012. Hundreds of demonstrators took to the streets of Shiite villages in Bahrain to demand being reinstated in jobs from which they were fired during last year’s uprising, witnesses said. Getty
Bahraini Shiite Muslim women take part in a Labour Day pro-democracy protest in the Manama suburb of Sanabis on May 1, 2012. Hundreds of demonstrators took to the streets of Shiite villages in Bahrain to demand being reinstated in jobs from which they were fired during last year’s uprising, witnesses said. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-mayday-2012/pict31.jpg) A Bahraini anti-government protester runs from riot police dispersing a Labor Day demonstration in support of people fired from their jobs for political activity Tuesday, May 1, 2012, in Sitra, Bahrain, southeast of the capital of Manama. Also on Tuesday, a jailed Bahraini rights activist will not end his nearly three-months hunger strike despite a court-ordered review of his conviction and life sentence, his wife said, as sporadic clashes broke out around the Gulf kingdom. (Hasan Jamal)
A Bahraini anti-government protester runs from riot police dispersing a Labor Day demonstration in support of people fired from their jobs for political activity Tuesday, May 1, 2012, in Sitra, Bahrain, southeast of the capital of Manama. Also on Tuesday, a jailed Bahraini rights activist will not end his nearly three-months hunger strike despite a court-ordered review of his conviction and life sentence, his wife said, as sporadic clashes broke out around the Gulf kingdom. (Hasan Jamal)![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-mayday-2012/pict11.jpg) Kashmiri Muslim woman workers of Accredited Social Health Activist (ASHA) shouts slogans against the government on May Day in Srinagar India, Tuesday, May 1, 2012. May Day moved beyond its roots as an international workers’ holiday to a day of international protest Tuesday, with rallies throughout Asia demanding wage increases and marches planned across Europe over government-imposed austerity measures. AP
Kashmiri Muslim woman workers of Accredited Social Health Activist (ASHA) shouts slogans against the government on May Day in Srinagar India, Tuesday, May 1, 2012. May Day moved beyond its roots as an international workers’ holiday to a day of international protest Tuesday, with rallies throughout Asia demanding wage increases and marches planned across Europe over government-imposed austerity measures. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-mayday-2012/pict13.jpg) Students and workers carry red flags during a May Day protest in central Athens May 1, 2012. Thousands of workers across southern Europe protested against spending cuts in annual May Day rallies on Tuesday, before weekend elections in Greece and France where voters are expected to punish leaders for austerity. Reuters
Students and workers carry red flags during a May Day protest in central Athens May 1, 2012. Thousands of workers across southern Europe protested against spending cuts in annual May Day rallies on Tuesday, before weekend elections in Greece and France where voters are expected to punish leaders for austerity. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-mayday-2012/pict14.jpg) In this photograph taken by AP Images for AIDS Healthcare Foundation, AIDS Healthcare Foundation, National Guestworkers Alliance, Act Up Philadelphia and Metropolitan Community Church of Philadelphia protest outside of the Hershey’s annual shareholder meeting on Tuesday, May 1, 2012, in Hershey, Penn. AP
In this photograph taken by AP Images for AIDS Healthcare Foundation, AIDS Healthcare Foundation, National Guestworkers Alliance, Act Up Philadelphia and Metropolitan Community Church of Philadelphia protest outside of the Hershey’s annual shareholder meeting on Tuesday, May 1, 2012, in Hershey, Penn. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-mayday-2012/pict15.jpg) Cambodian protesters chain their hands as they block the road in front of Cambodia’s National Assembly in Phnom Penh, Cambodia, Tuesday, May 1, 2012. The demonstrators on Tuesday began what they said would be a week-long protest to pressure the government for the titles. They said they were residents of Phnom Penh’s Boueng Kak lake area whose land was awarded by the government to a Chinese company to be redeveloped commercially. AP
Cambodian protesters chain their hands as they block the road in front of Cambodia’s National Assembly in Phnom Penh, Cambodia, Tuesday, May 1, 2012. The demonstrators on Tuesday began what they said would be a week-long protest to pressure the government for the titles. They said they were residents of Phnom Penh’s Boueng Kak lake area whose land was awarded by the government to a Chinese company to be redeveloped commercially. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-mayday-2012/pict16.jpg) A Bangladeshi veiled woman participates in a march to celebrate May Day in Dhaka, Bangladesh, Tuesday, May 1, 2012. May Day moved beyond its roots as an international workers’ holiday to a day of international protest Tuesday, with rallies throughout Asia demanding wage increases and marches planned across Europe over government-imposed austerity measures. AP
A Bangladeshi veiled woman participates in a march to celebrate May Day in Dhaka, Bangladesh, Tuesday, May 1, 2012. May Day moved beyond its roots as an international workers’ holiday to a day of international protest Tuesday, with rallies throughout Asia demanding wage increases and marches planned across Europe over government-imposed austerity measures. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-mayday-2012/pict23.jpg) Supporters of the Lebanese Communist party, wave Lebanese flags with the Communist sign printed on them and chant slogans against the Lebanese government, during a demonstration to mark Labor Day, in Beirut, Lebanon, Tuesday, May 1, 2012. More than 3000 members of the Lebanese Communist party marched in Beirut Streets to mark May Day, using the occasion to protest the worsening economic conditions in the country. (Bilal Hussein)
Supporters of the Lebanese Communist party, wave Lebanese flags with the Communist sign printed on them and chant slogans against the Lebanese government, during a demonstration to mark Labor Day, in Beirut, Lebanon, Tuesday, May 1, 2012. More than 3000 members of the Lebanese Communist party marched in Beirut Streets to mark May Day, using the occasion to protest the worsening economic conditions in the country. (Bilal Hussein)![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-mayday-2012/pict19.jpg) Protesters block traffic on 42nd Street and 6th Avenue, Tuesday, May 1, 2012 in New York. Hundreds of activists with a variety of causes spread out over New York City Tuesday on International Workers Day, or May Day, with Occupy Wall Street members leading a charge against financial institutions. (Mary Altaffer)
Protesters block traffic on 42nd Street and 6th Avenue, Tuesday, May 1, 2012 in New York. Hundreds of activists with a variety of causes spread out over New York City Tuesday on International Workers Day, or May Day, with Occupy Wall Street members leading a charge against financial institutions. (Mary Altaffer)![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-mayday-2012/pict20.jpg) A coalition of activists join Occupy Wall Street in a May Day march from Bryant Park on Tuesday, May 1, 2012 in New York. Hundreds of activists with a variety of causes spread out over New York City on International Workers Day, or May Day, with Occupy Wall Street members leading a charge against financial institutions. (Bebeto Matthews)
A coalition of activists join Occupy Wall Street in a May Day march from Bryant Park on Tuesday, May 1, 2012 in New York. Hundreds of activists with a variety of causes spread out over New York City on International Workers Day, or May Day, with Occupy Wall Street members leading a charge against financial institutions. (Bebeto Matthews)![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-mayday-2012/pict26.jpg) May Day moved beyond its roots as an international workers’ holiday to a day of international protest Tuesday, with rallies throughout Asia demanding wage increases and marches planned across Europe over government-imposed austerity measures.Thousands of workers protested in the Philippines, Indonesia and Taiwan and other Asian nations, with the demand for wage hikes amid soaring oil prices a common theme.
May Day moved beyond its roots as an international workers’ holiday to a day of international protest Tuesday, with rallies throughout Asia demanding wage increases and marches planned across Europe over government-imposed austerity measures.Thousands of workers protested in the Philippines, Indonesia and Taiwan and other Asian nations, with the demand for wage hikes amid soaring oil prices a common theme.![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-mayday-2012/pict27.jpg) A protester is arrested during a May Day march and protest in Portland, Ore., Tuesday, May 1, 2012. Hundreds of activists across the U.S. joined the worldwide May Day protests on Tuesday, with Occupy Wall Street members in several cities leading demonstrations and in some cases clashing with police. (Don Ryan)
A protester is arrested during a May Day march and protest in Portland, Ore., Tuesday, May 1, 2012. Hundreds of activists across the U.S. joined the worldwide May Day protests on Tuesday, with Occupy Wall Street members in several cities leading demonstrations and in some cases clashing with police. (Don Ryan)![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-mayday-2012/pict28.jpg) A demonstrator, who wished not to give her name, stands in front of the Georgia Capitol for a May Day immigration rally Tuesday, May 1, 2012, in Atlanta. The May Day rally at the Capitol Tuesday that organizers called a “historic coming together” of immigrants and working people was significantly smaller than in recent years, drawing only about 100 people. (David Goldman)
A demonstrator, who wished not to give her name, stands in front of the Georgia Capitol for a May Day immigration rally Tuesday, May 1, 2012, in Atlanta. The May Day rally at the Capitol Tuesday that organizers called a “historic coming together” of immigrants and working people was significantly smaller than in recent years, drawing only about 100 people. (David Goldman)![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-mayday-2012/pict29.jpg) Protesters march through the streets, Tuesday, May 1, 2012 in New York. Hundreds of activists with a variety of causes spread out over New York City Tuesday on International Workers Day, or May Day, with Occupy Wall Street members leading a charge against financial institutions. (Mary Altaffer)
Protesters march through the streets, Tuesday, May 1, 2012 in New York. Hundreds of activists with a variety of causes spread out over New York City Tuesday on International Workers Day, or May Day, with Occupy Wall Street members leading a charge against financial institutions. (Mary Altaffer)

![[Image]](https://i0.wp.com/cryptome.org/2012-info/osama-shrine2/pict34.jpg) Children play on the demolished site of a compound of Osama bin Laden in Abbottabad May 1, 2012. Al Qaeda leader bin Laden was killed almost a year ago, on May 2, 2011, by a United States special operations military unit in a raid on his compound in Abbottabad. Reuters
Children play on the demolished site of a compound of Osama bin Laden in Abbottabad May 1, 2012. Al Qaeda leader bin Laden was killed almost a year ago, on May 2, 2011, by a United States special operations military unit in a raid on his compound in Abbottabad. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/osama-shrine2/pict30.jpg) This two-picture combo shows from top to bottom: Pakistani men walk through a path in a field next to the house where al-Qaida leader Osama bin Laden was caught and killed in Abbottabad, Pakistan, May 5, 2011; A Pakistani woman and a girl walk through a path in a field next to the demolished house where al-Qaida leader Osama bin Laden was caught and killed in Abbottabad, Pakistan, Sunday, April 29, 2012.
This two-picture combo shows from top to bottom: Pakistani men walk through a path in a field next to the house where al-Qaida leader Osama bin Laden was caught and killed in Abbottabad, Pakistan, May 5, 2011; A Pakistani woman and a girl walk through a path in a field next to the demolished house where al-Qaida leader Osama bin Laden was caught and killed in Abbottabad, Pakistan, Sunday, April 29, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/osama-shrine2/pict31.jpg) A Pakistani woman and a girl walk through a path in a field next to the demolished house where al-Qaida leader Osama bin Laden was caught and killed in Abbottabad, Pakistan, Sunday, April 29, 2012. A year after the U.S. raid that killed Osama bin Laden, al-Qaida is hobbled and hunted, too busy surviving for the moment to carry out another Sept. 11-style attack on U.S. soil. (Muhammed Muheisen)
A Pakistani woman and a girl walk through a path in a field next to the demolished house where al-Qaida leader Osama bin Laden was caught and killed in Abbottabad, Pakistan, Sunday, April 29, 2012. A year after the U.S. raid that killed Osama bin Laden, al-Qaida is hobbled and hunted, too busy surviving for the moment to carry out another Sept. 11-style attack on U.S. soil. (Muhammed Muheisen)![[Image]](https://i0.wp.com/cryptome.org/2012-info/osama-shrine2/pict28.jpg) In this Sunday, April 29, 2012 photo, a Pakistani boy tries to break a concrete block as he and other children look for iron from the demolished compound of Osama bin Laden, in Abbottabad, Pakistan. One year since U.S. commandos flew into this army town and killed Osama bin Laden, Pakistan has tried to close one of the most notorious chapters in its history. The compound that housed him for six years was razed to the ground, and the wives and children who shared the hideaway were flown to Saudi Arabia just last week. (Muhammed Muheisen)
In this Sunday, April 29, 2012 photo, a Pakistani boy tries to break a concrete block as he and other children look for iron from the demolished compound of Osama bin Laden, in Abbottabad, Pakistan. One year since U.S. commandos flew into this army town and killed Osama bin Laden, Pakistan has tried to close one of the most notorious chapters in its history. The compound that housed him for six years was razed to the ground, and the wives and children who shared the hideaway were flown to Saudi Arabia just last week. (Muhammed Muheisen)![[Image]](https://i0.wp.com/cryptome.org/2012-info/osama-shrine2/pict29.jpg) In a Sunday, April 29, 2012 photo, Pakistani girls, center, walk at the demolished compound of Osama bin Laden, in Abbottabad, Pakistan. One year since U.S. commandos flew into this army town and killed Osama bin Laden, Pakistan has tried to close one of the most notorious chapters in its history. The compound that housed him for six years was razed to the ground, and the wives and children who shared the hideaway were flown to Saudi Arabia just last week. (Muhammed Muheisen)
In a Sunday, April 29, 2012 photo, Pakistani girls, center, walk at the demolished compound of Osama bin Laden, in Abbottabad, Pakistan. One year since U.S. commandos flew into this army town and killed Osama bin Laden, Pakistan has tried to close one of the most notorious chapters in its history. The compound that housed him for six years was razed to the ground, and the wives and children who shared the hideaway were flown to Saudi Arabia just last week. (Muhammed Muheisen)![[Image]](https://i0.wp.com/cryptome.org/2012-info/osama-shrine2/pict32.jpg) This photograph taken on April 25, 2012, shows a Pakistani labourer working at a house in front the site of the demolished compound of slain Al-Qaeda leader Osama bin Laden in northern Abbottabad, ahead of bin Laden’s first death anniversary. The Pakistani intelligence services provided the United States with information that was helpful in learning more about the compound where Osama bin Laden was killed, a US official said on April 28. Getty
This photograph taken on April 25, 2012, shows a Pakistani labourer working at a house in front the site of the demolished compound of slain Al-Qaeda leader Osama bin Laden in northern Abbottabad, ahead of bin Laden’s first death anniversary. The Pakistani intelligence services provided the United States with information that was helpful in learning more about the compound where Osama bin Laden was killed, a US official said on April 28. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/osama-shrine2/pict33.jpg) This photograph taken on April 25, 2012, shows a Pakistani boy swinging a cricket bat at the site of the demolished compound of slain Al-Qaeda leader Osama bin Laden, in northern Abbottabad ahead of bin Laden’s first death anniversary. The Pakistani intelligence services provided the United States with information that was helpful in learning more about the compound where Osama bin Laden was killed, a US official said on April 28. Getty
This photograph taken on April 25, 2012, shows a Pakistani boy swinging a cricket bat at the site of the demolished compound of slain Al-Qaeda leader Osama bin Laden, in northern Abbottabad ahead of bin Laden’s first death anniversary. The Pakistani intelligence services provided the United States with information that was helpful in learning more about the compound where Osama bin Laden was killed, a US official said on April 28. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/osama-shrine2/pict35.jpg) This photograph taken on April 25, 2012, shows local Pakistani residents walking past the site of the demolished compound of slain Al-Qaeda leader Osama bin Laden, in northern Abbottabad ahead of bin Laden’s first death anniversary. The Pakistani intelligence services provided the United States with information that was helpful in learning more about the compound where Osama bin Laden was killed, a US official said on April 28. Getty
This photograph taken on April 25, 2012, shows local Pakistani residents walking past the site of the demolished compound of slain Al-Qaeda leader Osama bin Laden, in northern Abbottabad ahead of bin Laden’s first death anniversary. The Pakistani intelligence services provided the United States with information that was helpful in learning more about the compound where Osama bin Laden was killed, a US official said on April 28. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/osama-shrine2/pict36.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/osama-shrine2/pict37.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/osama-shrine2/pict38.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/osama-shrine2/pict39.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/osama-shrine2/pict40.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012/04/cia-john3/pict27.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012/04/cia-john3/pict26.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012/04/cia-john3/pict25.jpg)

You must be logged in to post a comment.