Month: January 2012
TOP-SECRET – WikiLeaks Confidentiality/Non-Disclosure Agreement



TOP SECRET – Financial Crimes Law Enforcement/Subpoena Contacts List
Unveiled – The Most Technologically Secure Super Bowl Ever
TOP-SECRET – (U//FOUO) Los Angeles Fusion Center: Steganography Intelligence Bulletin

(U//FOUO) Steganography—the practice of concealing data within a carrier—may be used to obscure malicious or criminal information and activity from law enforcement. While steganography dates to the fifth century BC, it has long been regarded as, and remains, one of the most advanced forms of clandestine communication. In modern usage, the Internet allows accessibility to, and broad dissemination of, steganography tools, and its application continues to evolve with technology. Understanding steganography in its current state is essential to its identification and detection.
(U) Detection
(U//FOUO) Detecting steganography is challenging; in fact, determining whether media contains extraneous data is nearly impossible. Generally, detection occurs only through direct knowledge of its existence, evidence of steganography tools, or chance. Some indicators of steganography may include:
• (U//FOUO) Conspicuous and unusual sharing of digital media files via peer-to-peer (P2P) clients, e-mail, or uploads to Web sites
• (U//FOUO) Repeated sharing of the same file
• (U//FOUO) Possession of steganography software, or visiting sites known to contain steganography
• (U//FOUO) Sharing of content that is inconsistent with a subject’s life, such as pictures of children when he or she is not known to have any
• (U//FOUO) Possession of two or more copies of a file that do not look/sound identical, that is, the same image but of varying sizes and hash values
• (U//FOUO) Presence of files whose large size is unusual for the type of content
• (U//FOUO) Possession of books or articles on—or, expression of interest in—cryptography or steganography(U) Note that traditional security devices (for example, firewalls) do not detect steganography; a file containing a concealed message presents as a legitimate file.
(U) Tools for Detection
(U) Steganalysis, the method of detecting steganography and destroying the hidden message, is possible through free online tools. Deciphering and viewing the original message is challenging without the encryption keys, and some detection software may only identify steganography within a specific medium.
(U) Illicit Uses of Steganography
(U) Covert Communication
(U) Steganography can be used to hide communication behind seemingly innocuous files to pass messages without fear of detection.
• (U) According to an indictment unsealed in June 2010, an accused Russian spy network in New York began to use steganography as early as 2005. After a raid on the home of an alleged spy, law enforcement found a program on a computer that allowed group members to embed data in images on publicly available Web sites.
• (U//FOUO) The second issue of The Technical Mujahid details the benefits of using steganography over encryption; the magazine includes instructions for and examples of steganography.(U) Concealing Illicit Activity
(U//FOUO) Criminals use steganography to hide materials or information for the purpose of
• (U) Trafficking in child pornography
• (U) Committing fraud
• (U) Evading government censorship abroad
• (U) Conducting industrial espionage(U) VoIP Steganography
(U) Voice over Internet Protocol (VoIP) steganography, also known as network steganography, is one example of adaption to new technology. Use of a proprietary VoIP service eliminates the need for a carrier to conceal data, and extends the message length. The longer the conversation or data exchange, the longer or more detailed the hidden message can be. The brief time period the VoIP data exists for makes this nearly impossible to detect or prevent.
DOWNLOAD ORIGINAL DOCUMENT HERE
FEMEN UNCENSORED – Stop Davos! 3
FEMEN UNCENSORED – Stop Davos! 2
FEMEN UNCENSORED – Stop Davos
CONFIDENTIAL – The FBI – The Chicago Mafia Down but Not Out
06/27/11

“Members of the mob will go to almost any lengths to carry out their criminal activity,” said Special Agent Ted McNamara, a veteran investigator who supervises the La Cosa Nostra (LCN) organized crime squad in our Chicago Field Office.
Calabrese, Sr., was sentenced to life in prison in 2009 for his role in 18 gangland slayings in the Chicago area dating back to 1970. His arrest—along with 13 others—was part of one of the most successful organized crime cases in FBI history, an eight-year investigation called Operation Family Secrets.
Because of the Family Secrets case—in which Calabrese’s son testified against him—“the Chicago mob does not have the power and influence it once had,” McNamara said. “But the mob still operates, and its members still represent a potentially serious criminal threat.”
Unlike New York’s infamous Five Families, the Chicago mob consists of only one family, often referred to as the “Outfit.” It is organized under a variety of crews that engage in various criminal activities. A portion of the crews’ illegal gains goes to the Outfit’s top bosses.
“New York gets most of the attention regarding LCN,” McNamara said, “but historically, going back to the days of Al Capone, Chicago LCN has always been a player, particularly in places like Las Vegas.”
Unlike their New York counterparts, the Outfit has traditionally stayed away from drug trafficking, preferring instead crimes such as loan-sharking and online gambling operations and capitalizing on other profitable vices. One of the reasons it is so difficult to completely stamp out mob activity, McNamara said, is that over time the crews have insinuated themselves into unions and legitimate businesses.
“Typically they get into running restaurants and other legal businesses that they can use to hide money gained from their illicit activities,” McNamara explained. “Over the years the Outfit has learned that killing people brings too much heat from law enforcement. Today they might not even beat up a businessman who doesn’t pay back a debt,” he added. Instead, they take a piece of his business, and then, over time, exercise more and more control over the company.
The Family Secrets case, which began in 1999 and resulted in the indictment of 14 subjects in 2005 for racketeering and murder, dealt a crushing blow to the Chicago mob. “Our goal now,” McNamara said, “is to keep them from gaining strength again. We’ve got them down, and we’ve got to keep them down.”
He noted that some of the mobsters currently in jail as a result of numerous prosecutions will be getting out in the next few years, and they will be under pressure to start making money again for the Outfit’s top bosses.
“As long as there is money to be made from criminal activity,” McNamara said, “these guys will never stop. So we need to continue to be vigilant and take the long view. The work we do on the LCN squad requires a lot of patience.”
The FBI reports about the Sicilian Mafia
Italian Organized Crime
 |
Since their appearance in the 1800s, the Italian criminal societies known as the Mafia have infiltrated the social and economic fabric of Italy and now impact the world. They are some of the most notorious and widespread of all criminal societies.
There are several groups currently active in the U.S.: the Sicilian Mafia; the Camorra or Neapolitan Mafia; the ’Ndrangheta or Calabrian Mafia; and the Sacra Corona Unita or United Sacred Crown.
We estimate the four groups have approximately 25,000 members total, with 250,000 affiliates worldwide. There are more than 3,000 members and affiliates in the U.S., scattered mostly throughout the major cities in the Northeast, the Midwest, California, and the South. Their largest presence centers around New York, southern New Jersey, and Philadelphia.
Their criminal activities are international with members and affiliates in Canada, South America, Australia, and parts of Europe. They are also known to collaborate with other international organized crime groups from all over the world, especially in drug trafficking.
The major threats to American society posed by these groups are drug trafficking and money laundering. They have been involved in heroin trafficking for decades. Two major investigations that targeted Italian organized crime drug trafficking in the 1980s are known as the “French Connection” and the “Pizza Connection.”
These groups don’t limit themselves to drug running, though. They’re also involved in illegal gambling, political corruption, extortion, kidnapping, fraud, counterfeiting, infiltration of legitimate businesses, murders, bombings, and weapons trafficking. Industry experts in Italy estimate that their worldwide criminal activity is worth more than $100 billion annually.
A Long History
These enterprises evolved over the course of 3,000 years during numerous periods of invasion and exploitation by numerous conquering armies in Italy. Over the millennia, Sicilians became more clannish and began to rely on familial ties for safety, protection, justice, and survival.
An underground secret society formed initially as resistance fighters against the invaders and to exact frontier vigilante justice against oppression. A member was known as a “Man Of Honor,” respected and admired because he protected his family and friends and kept silent even unto death.
Sicilians weren’t concerned if the group profited from its actions because it came at the expense of the oppressive authorities. These secret societies eventually grew into the Mafia.
Since the 1900s, thousands of Italian organized crime figures—mostly Sicilian Mafiosi—have come illegally to this country. Many who fled here in the early 1920s helped establish what is known today as La Cosa Nostra or the American Mafia.
Charles “Lucky” Luciano, a Mafioso from Sicily, came to the U.S. during this era and is credited for making the American La Cosa Nostra what it is today. Luciano structured the La Cosa Nostra after the Sicilian Mafia. When Luciano was deported back to Italy in 1946 for operating a prostitution ring, he became a liaison between the Sicilian Mafia and La Cosa Nostra.
Sicilian Mafia (based in Sicily)
The Sicilian Mafia formed in the mid-1800s to unify the Sicilian peasants against their enemies. In Sicily, the word Mafia tends to mean “manly.” The Sicilian Mafia changed from a group of honorable Sicilian men to an organized criminal group in the 1920s.
In the 1950s, Sicily enjoyed a massive building boom. Taking advantage of the opportunity, the Sicilian Mafia gained control of the building contracts and made millions of dollars. Today, the Sicilian Mafia has evolved into an international organized crime group. Some experts estimate it is the second largest organization in Italy.
The Sicilian Mafia specializes in heroin trafficking, political corruption, and military arms trafficking—and is also known to engage in arson, frauds, counterfeiting, and other racketeering crimes. With an estimated 2,500 Sicilian Mafia affiliates it is the most powerful and most active Italian organized crime group in the U.S.
The Sicilian Mafia is infamous for its aggressive assaults on Italian law enforcement officials. In Sicily the term “Excellent Cadaver” is used to distinguish the assassination of prominent government officials from the common criminals and ordinary citizens killed by the Mafia. High-ranking victims include police commissioners, mayors, judges, police colonels and generals, and Parliament members.
On May 23, 1992, the Sicilian Mafia struck Italian law enforcement with a vengeance. At approximately 6 p.m., Italian Magistrate Giovanni Falcone, his wife, and three police body guards were killed by a massive bomb. Falcone was the director of Criminal Affairs in Rome. The bomb made a crater 30 feet in diameter in the road. The murders became known as the Capaci Massacre.
Less than two months later, on July 19, the Mafia struck Falcone’s newly named replacement, Judge Paolo Borsellino in Palermo, Sicily. Borsellino and five bodyguards were killed outside the apartment of Borsellino’s mother when a car packed with explosives was detonated by remote control.
Under Judge Falcone’s tenure the FBI and Italian law enforcement established a close working relationship aimed at dismantling Italian organized crime groups operating in both countries. That relationship has intensified since then.
Camorra or Neapolitan Mafia (based in Naples)
The word “Camorra” means gang. The Camorra first appeared in the mid-1800s in Naples, Italy, as a prison gang. Once released, members formed clans in the cities and continued to grow in power. The Camorra has more than 100 clans and approximately 7,000 members, making it the largest of the Italian organized crime groups.
In the 1970s, the Sicilian Mafia convinced the Camorra to convert their cigarette smuggling routes into drug smuggling routes with the Sicilian Mafia’s assistance. Not all Camorra leaders agreed, leading to the Camorra Wars that cost 400 lives. Opponents of drug trafficking lost the war.
The Camorra made a fortune in reconstruction after an earthquake ravaged the Campania region in 1980. Now it specializes in cigarette smuggling and receives payoffs from other criminal groups for any cigarette traffic through Italy. The Camorra is also involved in money laundering, extortion, alien smuggling, robbery, blackmail, kidnapping, political corruption, and counterfeiting.
It is believed that nearly 200 Camorra affiliates reside in this country, many of whom arrived during the Camorra Wars.
’Ndrangheta or Calabrian Mafia (based in Calabria)
The word “’Ndrangheta” comes from the Greek meaning courage or loyalty. The ’Ndrangheta formed in the 1860s when a group of Sicilians was banished from the island by the Italian government. They settled in Calabria and formed small criminal groups.
There are about 160 ’Ndrangheta cells with roughly 6,000 members. They specialize in kidnapping and political corruption, but also engage in drug trafficking, murder, bombings, counterfeiting, gambling, frauds, thefts, labor racketeering, loansharking, and alien smuggling.
Cells are loosely connected family groups based on blood relationships and marriages. In the U.S., there are an estimated 100-200 members and associates, primarily in New York and Florida.
Sacra Corona Unita or United Sacred Crown (based in the Puglia region)
Law enforcement became aware of the Sacra Corona Unita in the late 1980s. Like other groups, it started as a prison gang. As its members were released, they settled in the Puglia region in Italy and continued to grow and form links with other Mafia groups. The Sacra Corona Unita is headquartered in Brindisi, located in the southeastern region of Puglia.
The Sacra Corona Unita consists of about 50 clans with approximately 2,000 members and specializes in smuggling cigarettes, drugs, arms, and people. It is also involved in money laundering, extortion, and political corruption. The organization collects payoffs from other criminal groups for landing rights on the southeast coast of Italy, a natural gateway for smuggling to and from post-Communist countries like Croatia, Yugoslavia, and Albania.
Very few Sacra Corona Unita members have been identified in the U.S., although some individuals in Illinois, Florida, and New York have links to the organization.
La Cosa Nostra is the foremost organized criminal threat to American society. Literally translated into English it means “this thing of ours.” It is a nationwide alliance of criminals—linked by blood ties or through conspiracy—dedicated to pursuing crime and protecting its members.
La Cosa Nostra, or the LCN as it is known by the FBI, consists of different “families” or groups that are generally arranged geographically and engaged in significant and organized racketeering activity. It is also known as the Mafia, a term used to describe other organized crime groups.
The LCN is most active in the New York metropolitan area, parts of New Jersey, Philadelphia, Detroit, Chicago, and New England. It has members in other major cities and is involved in international crimes.
History of La Cosa Nostra
Although La Cosa Nostra has its roots in Italian organized crime, it has been a separate organization for many years. Today, La Cosa Nostra cooperates in various criminal activities with different criminal groups that are headquartered in Italy.
Giuseppe Esposito was the first known Sicilian Mafia member to emigrate to the U.S. He and six other Sicilians fled to New York after murdering the chancellor and a vice chancellor of a Sicilian province and 11 wealthy landowners. He was arrested in New Orleans in 1881 and extradited to Italy.
New Orleans was also the site of the first major Mafia incident in this country. On October 15, 1890, New Orleans Police Superintendent David Hennessey was murdered execution-style. Hundreds of Sicilians were arrested, and 19 were eventually indicted for the murder. An acquittal generated rumors of widespread bribery and intimidated witnesses. Outraged citizens of New Orleans organized a lynch mob and killed 11 of the 19 defendants. Two were hanged, nine were shot, and the remaining eight escaped.
The American Mafia has evolved over the years as various gangs assumed—and lost—dominance over the years: the Black Hand gangs around 1900; the Five Points Gang in the 1910s and ‘20s in New York City; Al Capone’s Syndicate in Chicago in the 1920s. By the end of the ‘20s, two primary factions had emerged, leading to a war for control of organized crime in New York City.
The murder of faction leader Joseph Masseria brought an end to the gang warfare, and the two groups united to form the organization now dubbed La Cosa Nostra. It was not a peaceful beginning: Salvatore Maranzano, the first leader of La Cosa Nostra, was murdered within six months.
Charles “Lucky” Luciano became the new leader. Maranzano had established the La Cosa Nostra code of conduct, set up the “family” divisions and structure, and established procedures for resolving disputes. Luciano set up the “Commission” to rule all La Cosa Nostra activities. The Commission included bosses from six or seven families.
Luciano was deported back to Italy in 1946 based on his conviction for operating a prostitution ring. There, he became a liaison between the Sicilian Mafia and La Cosa Nostra.
Other Historical Highlights:
1951: A U.S. Senate committee led by Democrat Estes Kefauver of Tennessee determined that a “sinister criminal organization” known as the Mafia operated in this nation.
1957: The New York State Police uncovered a meeting of major LCN figures from around the country in the small upstate New York town of Apalachin. Many of the attendees were arrested. The event was the catalyst that changed the way law enforcement battles organized crime.
1963: Joseph Valachi became the first La Cosa Nostra member to provide a detailed looked inside the organization. Recruited by FBI agents, Valachi revealed to a U.S. Senate committee numerous secrets of the organization, including its name, structure, power bases, codes, swearing-in ceremony, and members of the organization.
Today, La Cosa Nostra is involved in a broad spectrum of illegal activities: murder, extortion, drug trafficking, corruption of public officials, gambling, infiltration of legitimate businesses, labor racketeering, loan sharking, prostitution, pornography, tax-fraud schemes, and stock manipulation schemes.
Named after legendary boss Vito Genovese, the Genovese crime family was once considered the most powerful organized crime family in the nation. Members and their numerous associates engaged in drug trafficking, murder, assault, gambling, extortion, loansharking, labor racketeering, money laundering, arson, gasoline bootlegging, and infiltration of legitimate businesses.
Genovese family members are also involved in stock market manipulation and other illegal frauds and schemes as evidenced by the recent FBI investigation code named “Mobstocks.”
The Genovese crime family has its roots in the Italian criminal groups in New York controlled by Joseph Masseria in the 1920s. The family history is rife with murder, violence, and greed.
Early History—Masseria and Maranzano
Masseria sparked the so-called “Castellammarese War” in 1928 when he tried to gain control of organized crime across the country. The war ended in 1931 when Salvatore Maranzano conspired with Masseria’s top soldier, Charles “Lucky” Luciano, to have Masseria killed. Maranzano emerged as the most powerful Mafia boss in the nation, setting up five separate criminal groups in New York and calling himself “Boss of Bosses.”
Two of the most powerful La Cosa Nostra families—known today as the Genovese and Gambino families—emerged from Maranzano’s restructuring efforts. Maranzano named Luciano the first boss of what would later be known as the Genovese family. Luciano showed his appreciation less than five months later by sending five men dressed as police officers to Maranzano’s office to murder him.
Luciano, Costello, and Genovese
With Maranzano out of the way, Luciano become the most powerful Mafia boss in America and used his position to run La Cosa Nostra like a major corporation. He set up the LCN Commission, or ruling body, composed of seven bosses, and divided the different rackets among the families.
In 1936, Luciano was sentenced to 30 to 50 years in prison. Ten years later, he was released from prison and deported to Italy, never to return. When he was convicted, Frank Costello became acting boss because Genovese—then just an underboss—had fled to Italy to avoid a murder charge. His return to the states was cleared when a key witness against him was poisoned and the charges were dropped.
Costello led the family for approximately 20 years until May of 1957 when Genovese took control by sending soldier Vincent “the Chin” Gigante to murder him. Costello survived the attack but relinquished control of the family to Genovese. Attempted murder charges against Gigante were dismissed when Costello refused to identify him as the shooter.
In 1959, it was Genovese’s turn to go to prison following a conviction of conspiracy to violate narcotics laws. He received a 15-year sentence but continued to run the family through his underlings from his prison cell in Atlanta, Georgia.
Valachi Sings—and Lombardo Leads
About this time, Joseph Valachi, a “made man,” was sent to the same prison as Genovese on a narcotics conviction. Labeled an informer, Valachi survived three attempts on his life behind bars. Still in prison in 1962, he killed a man he thought Genovese had sent to kill him. He was sentenced to life for the murder.
The sentencing was a turning point for Valachi, who decided to cooperate with the U.S. government. On September 27, 1963, he appeared before the U.S. Senate Permanent Subcommittee on Investigations and testified that he was a member of a secret criminal society in the U.S. known as La Cosa Nostra.
In 1969, several years after Valachi began cooperating with the FBI, Vito Genovese died in his prison cell. By then the Genovese family was under the control of Philip “Benny Squint” Lombardo. Unlike the bosses before him, Lombardo preferred to rule behind his underboss. His first, Thomas Eboli, was murdered in 1972. Lombardo promoted Frank “Funzi” Tieri, and later Anthony “Fat Tony” Salerno as his front men.
Throughout the 1980s, the Genovese family hierarchy went through several changes. Tieri, recognized on the street as the Genovese family boss in the late 1970s, was convicted for operating a criminal organization through a pattern of racketeering that included murder and extortion.
Salerno then fronted as boss until he had stroke in 1981. In 1985, Salerno and the bosses of the other four New York families were convicted for operating a criminal enterprise—the LCN Commission. Lombardo, his two captains in prison and his health failing, turned full control of the Genovese family over to Gigante—the man who tried to kill Costello 30 years earlier.
Fish on the Hook
In 1986, a second member turned against the Genovese family when Vincent “Fish” Cafaro, a soldier and right-hand-man to Anthony Salerno, decided to cooperate with the FBI and testify. According to Cafaro’s sworn statement, Gigante ran the family from behind the scenes while pretending to be mentally ill. Cafaro said this behavior helped further insulate Gigante from authorities while he ran the Genovese family’s criminal activities.
Gigante’s odd behavior and mumbling while he walked around New York’s East Village in a bathrobe earned him the nickname “the Odd Father.” After an FBI investigation, Gigante was convicted of racketeering and murder conspiracy in December 1997 and sentenced to 12 years. Another FBI investigation led to his indictment on January 17, 2002, accusing him of continuing to run the Genovese family from prison. He pled guilty to obstruction of justice in 2003.
Gigante died in prison in December 2005 in the same federal hospital where Gambino family leader John Gotti had died in 2002.
The Italian American Working Group
Over the years, FBI investigations have revealed how organized criminal groups have proliferated and impacted much of the world. Partnerships with foreign law enforcement agencies are essential to combat global organized crime groups.
Among the partnerships the FBI is involved with is the Italian American Working Group, which meets every year. The group addresses organized crime, cyber crime, money laundering, international terrorism, illegal immigration, cooperating witnesses, drug smuggling, art theft, extradition matters, and cigarette smuggling. The U.S. and Italy take turns hosting the meetings.
Labor racketeering is the domination, manipulation, and control of a labor movement in order to affect related businesses and industries. It can lead to the denial of workers’ rights and inflicts an economic loss on the workers, business, industry, insurer, or consumer.
The historical involvement of La Cosa Nostra in labor racketeering has been thoroughly documented:
- More than one-third of the 58 members arrested in 1957 at the Apalachin conference in New York listed their employment as “labor” or “labor-management relations.”
- Three major U.S. Senate investigations have documented La Cosa Nostra’s involvement in labor racketeering. One of these, the McClellan Committee, in the late-1950s, found systemic racketeering in both the International Brotherhood of Teamsters and the Hotel Employees and Restaurant Employees International Union.
- In 1986, the President’s Council on Organized Crime reported that five major unions—including the Teamsters and the Laborers International Union of North America—were dominated by organized crime.
- In the early 1980s, former Gambino Family Boss Paul Castellano was overheard saying, “Our job is to run the unions.”
Labor racketeering has become one of La Cosa Nostra’s fundamental sources of profit, national power, and influence.
FBI investigations over the years have clearly demonstrated that labor racketeering costs the American public millions of dollars each year through increased labor costs that are eventually passed on to consumers.
Labor unions provide a rich source for organized criminal groups to exploit: their pension, welfare, and health funds. There are approximately 75,000 union locals in the U.S., and many of them maintain their own benefit funds. In the mid-1980s, the Teamsters controlled more than 1,000 funds with total assets of more than $9 billion.
Labor racketeers attempt to control health, welfare, and pension plans by offering “sweetheart” contracts, peaceful labor relations, and relaxed work rules to companies, or by rigging union elections.
Labor law violations occur primarily in large cities with both a strong industrial base and strong labor unions, like New York, Buffalo, Chicago, Cleveland, Detroit, and Philadelphia. These cities also have a large presence of organized crime figures.
We have several investigative techniques to root out labor law violations: electronic surveillance, undercover operations, confidential sources, and victim interviews. We also have numerous criminal and civil statutes to use at our disposal, primarily through the Racketeer Influenced and Corrupt Organization (RICO) Statute.
The civil provisions of the RICO statute have proven to be very powerful weapons, especially the consent decrees. They are often more productive because they attack the entire corrupt entity instead of imprisoning individuals, who can easily be replaced with other organized crime members or associates.
Consent decrees are most effective when there is long-term, systemic corruption at virtually every level of a labor union by criminal organizations. A civil RICO complaint and subsequent consent decree can restore democracy to a corrupt union by imposing civil remedies designed to eliminate such corruption and deter its re-emergence.
The Teamsters are the best example of how efficiently the civil RICO process can be used. For decades, the Teamsters has been substantially controlled by La Cosa Nostra. In recent years, four of eight Teamster presidents were indicted, yet the union continued to be controlled by organized crime elements. The government has been fairly successful at removing the extensive criminal influence from this 1.4 million-member union by using the civil process.
We work closely with the Office of Labor Racketeering in the Department of Labor and with the U.S. Attorneys’ offices in investigating violations of labor law.
CONFIDENTIAL – Hellenic Air Force F-16C/D Flight Manuals
Confidential from the FBI – Cargo Theft How a Memphis Task Force Combats a Costly Problem
fter many hours on the road, the long-haul driver pulled his tractor-trailer into a Tennessee truck stop for a break and a hot meal. But by the time he looked over the menu, a crew of professional thieves had made off with his rig and all its contents.
|
Partnerships Make a Difference In 2005, two large pharmaceutical companies were the victims of major cargo thefts at the same truck stop within a short time period, and each had no idea what had happened to the other. When they found out later, a meeting was called among pharmaceutical industry leaders, and the concept of a security coalition was born. The coalition would consist not only of industry members but also law enforcement. Today, the Pharmaceutical Cargo Security Coalition shares information about thefts and best practices for reducing risk, according to Charles Forsaith, director of supply chain security for Purdue Pharma Technologies, who coordinates the coalition. “We educate everyone in our industry,” said Forsaith, “and we work together with law enforcement to stop these crimes. That partnership has yielded a measurable decline in cargo theft.” In 2008, for example, the pharmaceutical industry reported losses of 16 full trailer loads each valued in excess of $1 million. In 2011, Forsaith said, there were only four such losses valued over $1 million. In 2008, the odds of recovering a lost load were 31 percent. Today, he said, with the help of GPS tracking devices and a strong working relationship with law enforcement, the odds for recovery are better than 65 percent. “We realized that we couldn’t put a stop to these crimes on our own,” he said. “In addition to educating our industry, we knew we needed buy-in from law enforcement, and we have been extremely pleased working with the FBI’s cargo theft task forces.” |
|---|
Cargo theft is a multi-billion-dollar criminal enterprise in the U.S., and the FBI has seven task forces located around the country to combat the problem. In the Memphis region, according to Special Agent Conrad Straube, coordinator of the Memphis Cargo Theft Task Force, “there is an average of one cargo theft every day of the year.”
Memphis—located along major interstate highways and home to a variety of product distribution centers—is a hot spot for cargo theft. The thieves steal trucks with trailers or just the trailers and their contents. Often, goods are stolen from distribution center warehouses or even from moving rail cars.
On a recent day, Straube and his task force partners from the Memphis Police Department, Shelby County Sheriff’s Office, and the U.S. Marshals Service were on the road, following up on leads at truck stops and other locations in and around Memphis. The task force is busy—and successful. From January 2011 to the end of September, it recovered more than $1.5 million in stolen cargo and vehicles.
Task force member Barry Clark, a detective with the Shelby County Sheriff’s Office, explained that some of the theft crews are so organized that each member has his own specialty, from the break-in artist who can steal a rig in seconds to professional drivers, surveillance experts, and the guys who know how to defeat the specialized devices that lock trailers carrying extremely valuable loads. “This is their business,” Clark said. “And they are good at it.”
Crew leaders know where to find willing buyers, too—from small mom and pop stores who don’t ask questions when they buy at prices below wholesale to online merchants who may or may not know they are purchasing stolen goods.
Although many crews target specific cargo such as electronics and pharmaceuticals—always in demand and easy to sell—other thieves steal whatever they can get their hands on. Straube and his team have recovered stolen trailers full of dog food, hair dryers, lawn mower engines, and even popsicles.
“When you talk about the victims of cargo theft,” Straube explained, “beyond the trucking companies and manufacturers, you have to include all consumers. Because when these items are stolen, it eventually drives up the cost of merchandise for everybody.”
 |
|
|---|---|
| Podcast: Special agent discusses cargo theft. |
Cargo theft is also a “gateway” crime, said Special Agent Eric Ives, a program manager in our Criminal Investigative Division at FBI Headquarters who coordinates major theft investigations from a national perspective. “Groups that do these crimes are often funding other illegal activities, like buying drugs or weapons. And compared to many crimes,” Ives added, “cargo theft is highly profitable and not particularly dangerous.”
Conrad agreed, adding that thieves often rob warehouses on a Friday night, and by the time the crime is discovered and reported Monday morning, the stolen merchandise may already be on a store shelf or auctioned online.
That’s why our task forces—comprised of local, state, and federal law enforcement—and our partnerships with private industry (see sidebar) are critical in the fight against these costly crimes, Ives said. “Cargo theft is a sophisticated and organized enterprise,” he added, “and we take this threat very seriously.”
Uncensored – Femen topless protest : ‘Gangsta party in Davos’
Three topless Ukrainian protesters were detained on Saturday while trying to break into an invitation-only gathering of international CEOs and political leaders to call attention to the needs of the world’s poor. After a complicated journey to reach the heavily guarded Swiss resort town of Davos, the women arrived at the entrance to the congress centre where the World Economic Forum takes place every year. With temperatures around freezing in the snow-filled town, they took off their tops and climbed a fence before being detained. Davos police spokesman Thomas Hobi said the three women were taken to the police station and their papers were checked. The activists are from the group Femen, which has become popular in Ukraine for staging small, half-naked protests to highlight a range of issues including oppression of political opposition. They have also conducted protests in some other countries.
TOP-SECRET – Anti-Counterfeiting Trade Agreement (ACTA) Final Version May 2011

The Parties to this Agreement,
Noting that effective enforcement of intellectual property rights is critical to sustaining economic growth across all industries and globally;
Noting further that the proliferation of counterfeit and pirated goods, as well as of services that distribute infringing material, undermines legitimate trade and sustainable development of the world economy, causes significant financial losses for right holders and for legitimate businesses, and, in some cases, provides a source of revenue for organized crime and otherwise poses risks to the public;
Desiring to combat such proliferation through enhanced international cooperation and more effective international enforcement;
Intending to provide effective and appropriate means, complementing the TRIPS Agreement, for the enforcement of intellectual property rights, taking into account differences in their respective legal systems and practices;
Desiring to ensure that measures and procedures to enforce intellectual property rights do not themselves become barriers to legitimate trade;
Desiring to address the problem of infringement of intellectual property rights, including infringement taking place in the digital environment, in particular with respect to copyright or related rights, in a manner that balances the rights and interests of the relevant right holders, service providers, and users;
Desiring to promote cooperation between service providers and right holders to address relevant infringements in the digital environment;
Desiring that this Agreement operates in a manner mutually supportive of international enforcement work and cooperation conducted within relevant international organizations;
Recognizing the principles set forth in the Doha Declaration on the TRIPS Agreement and Public Health, adopted on 14 November 2001, at the Fourth WTO Ministerial Conference;
Hereby agree as follows:
…
pirated copyright goods means any goods which are copies made without the consent of the right holder or person duly authorized by the right holder in the country of production and which are made directly or indirectly from an article where the making of that copy would have constituted an infringement of a copyright or a related right under the law of the country in which the procedures set forth in Chapter II (Legal Framework for Enforcement of Intellectual Property Rights) are invoked;
…
ARTICLE 9: DAMAGES
1. Each Party shall provide that, in civil judicial proceedings concerning the enforcement of intellectual property rights, its judicial authorities have the authority to order the infringer who, knowingly or with reasonable grounds to know, engaged in infringing activity to pay the right holder damages adequate to compensate for the injury the right holder has suffered as a result of the infringement. In determining the
amount of damages for infringement of intellectual property rights, a Party’s judicial authorities shall have the authority to consider, inter alia, any legitimate measure of value the right holder submits, which may include lost profits, the value of the infringed goods or services measured by the market price, or the suggested retail price.2. At least in cases of copyright or related rights infringement and trademark counterfeiting, each Party shall provide that, in civil judicial proceedings, its judicial authorities have the authority to order the infringer to pay the right holder the infringer’s profits that are attributable to the infringement. A Party may presume those profits to be the amount of damages referred to in paragraph 1.
…
ARTICLE 11: INFORMATION RELATED TO INFRINGEMENT
Without prejudice to its law governing privilege, the protection of confidentiality of information sources, or the processing of personal data, each Party shall provide that, in civil judicial proceedings concerning the enforcement of intellectual property rights, its judicial authorities have the authority, upon a justified request of the right holder, to order the infringer or, in the alternative, the alleged infringer, to provide to the right holder or to the judicial authorities, at least for the purpose of collecting evidence, relevant information as provided for in its applicable laws and regulations that the infringer or alleged infringer possesses or controls. Such information may include information regarding any person involved in any aspect of the infringement or alleged infringement and regarding the means of production or the channels of distribution of the infringing or allegedly infringing goods or services, including the identification of third persons alleged to be involved in the production and distribution of such goods or services and of their channels of distribution.
…
ARTICLE 19: DETERMINATION AS TO INFRINGEMENT
Each Party shall adopt or maintain procedures by which its competent authorities may determine, within a reasonable period after the initiation of the procedures described in Article 16 (Border Measures), whether the suspect goods infringe an intellectual property right.
ARTICLE 20: REMEDIES
1. Each Party shall provide that its competent authorities have the authority to order the destruction of goods following a determination referred to in Article 19 (Determination as to Infringement) that the goods are infringing. In cases where such goods are not destroyed, each Party shall ensure that, except in exceptional circumstances, such goods are disposed of outside the channels of commerce in such a manner as to avoid any harm to the right holder.
2. In regard to counterfeit trademark goods, the simple removal of the trademark unlawfully affixed shall not be sufficient, other than in exceptional cases, to permit release of the goods into the channels of commerce.
3. A Party may provide that its competent authorities have the authority to impose administrative penalties following a determination referred to in Article 19 (Determination as to Infringement) that the goods are infringing.
DOWNLOAD ORIGINAL DOCUMENT HERE
Uncensored – FEMEN.— Woman Power.Missions.Goals.Actions.
FEMEN. Woman Power.
WE ARE THE WOMEN’S MOVEMENT
We unite young women basing on the principles of social awareness and activism, intellectual and cultural development.
We recognise the European values of freedom, equality and comprehensive development of a person irrespective of the gender.
We build up a national image of feminity, maternity and beauty based on the Euro-Athlantic Women’s Movements experience.
We set up brand new standards of the civil movement in Ukraine.
We have worked out our own unique form of a civil self-expression based on courage, creativity, efficiency and shock.
We demonstrate that the civil movements can influence the public opinion and lobby the interests of a target group.
We plan to become the biggest and the most influential feminist movement in Europe.
OUR MISSION
The mission of the “FEMEN” Movement is to create the most favorable conditions for the young women to join up into a social group with the general idea of the mutual support and social responsibility, helping to reveal the talents of each member of the Movement.
OUR GOALS
To react and influence the acute social issues of the Ukrainian society, especially those that directly touch upon the interests of the Ukrainian Women.
To counteract actively the negative tendencies endangering physical and mental health of the Ukrainian women community.
Inform the society of the Ukrainian women’s issues and problems.
To develop leadership, intellectual and moral qualities of the young women in Ukraine.
To build up the image of Ukraine, the country with great opportunities for women.
To establish cooperation with other international women’s organizations to carry out the large-scale international programmes on the territory of Ukraine.
OUR ACTIONS
Subway — Movement – Life: The Joint Action with Kyiv underground authorities targeted on improving the image of the underground.
No Water in the Tap — I Wash in Maydan: Action against hot water cut offs in Kyiv hostels.
Ukraine is not a Brothel: The national programme aimed at fighting against the sexual tourism in Ukraine.
A Letter to the Minister: The Appeal to the governmental authorities with the demands to impose sanctions on sexual tourism in Ukraine on the legislation level.
Bromide Deactivation Action: The Picket outside the Turkish Republic Embassy. Turkish citizen are the most active sexual tourists in our country.
Dirty Games: The Action against the pre-term parliamentary elections in Ukraine.
Civil Solidarity Action A Rescue Buoy: The action in support of the Ukrainian sailors held hostage by Somalia Pirates.
No More Games, Mr Gainer: The Action within the frames of the Sex Tourtism Fighting Programme held at the National Security Service Office Building and targeted on the citizen of the USA, Mr David Gainer, the organizer of the sex-tours to Ukraine. There was a letter sent to the Foreign Office and Consulate with the demands to start the investigation and deportation of the man.
OUR PROGRAMMES
“Ukraine is not a Brothel”: The National Programme targeted at fighting against the sex-tourism in Ukraine.
“Sex is not for Sale”: The Programme to fight against sex and porn industry in Ukraine.
“MATER FEST”: The first international festival of a modern women culture.
«Kyiv Glam Sprint 2009»: The Ukrainian analogue of the international movement “Race on high hills”.
“The Green Mile”: The Programme to abolish the lifetime sentence for women in Ukraine.
Emergency programme: The Programme of immediate reacting on the acute issues that includes street actions and performances.
The following mass media reported on the FEMEN actions:
Der Spiegel
Die Welt
Independent.ie
Korrespondent.net
Gelf Magazine
Korrespondent
Kyiv Post
Jetzt.de
OUR CONTACTS
Anna Gutsol
+3 8(097) 96 71 753
anna.hutsol@mail.ru
TOP-SECRET – NSA Review of Information for the Public
TOP-SECRET – Documents Detail CIA, MI6 Relationship With Qaddafi

This image provided by Human Rights Watch on Saturday, Sept. 3, 2011 shows part of a secret document dated June 19, 2003 discovered by Human Rights Watch in Tripoli, Libya, detailing a meeting regarding a CIA visit to Libya’s WMD programs. The CIA and other Western intelligence agencies worked closely with the ousted regime of Moammar Gadhafi, sharing tips and cooperating in handing over terror suspects for interrogation to a regime known to use torture, according to a trove of security documents discovered after the fall of Tripoli. The revelations provide new details on the West’s efforts to turn Libya’s mercurial leader from foe to ally and provide an embarrassing example of the U.S. administration’s collaboration with authoritarian regimes in the war on terror. (AP Photo/Human Rights Watch)
Libya: secret dossier reveals Gaddafi’s UK spy links
A cache of papers found at the intelligence headquarters dating from the time it was run by Moussa Koussa, who later became foreign minister and defected in March, showed Libya was handed Islamist opposition members as part of the CIA’s “extraordinary rendition” programme.
MI6 also provided extensive information to the Libyan authorities of opponents living in Britain.
The British intelligence services seem to have been more circumspect than their American colleagues, however. Often the files, which were found by Human Rights Watch and shown to The Sunday Telegraph, suggest they restricted themselves to confirming information already known to the Libyans.
It also shows one reason for the co-operation – MI6′s belief that Libyan Islamists were playing a central role in funding and supporting al-Qaeda, often via contacts in Iran.
MI6 and the CIA were instrument in the attempts by former Prime Minister Tony Blair to bring Col Gaddafi “in from the cold”, started at the time the alleged Lockerbie bombers were handed over for trial in The Hague.
In return for compensating victims of the Lockerbie bombing and other terrorist outrages, and surrendering its programme for weapons of mass destruction, diplomatic relations were resumed and sanctions dropped.
The documents give details of how much further subsequent co-operation went between Libya and the West. They confirm that Abdulhakim Belhadj, now leader of the Tripoli Military Council under the rebel government, was flown by the CIA to Libya for interrogation and imprisonment in 2004.

Documents with photographs and details of people wanted by the Libyan External Security office are seen in the abandoned office where Muammar Gaddafi’s former spy chief and foreign minister Moussa Koussa was based in Tripoli September 3, 2011. Documents found in the abandoned office of Gaddafi’s intelligence chief indicate the U.S. and British spy agencies helped the fallen strongman persecute Libyan dissidents, Human Rights Watch said on Saturday. The documents were uncovered by the human rights activist group in Koussa’s abandoned offices.

A list of telephone interceptions by the Libyan External Security office is seen at the abandoned office of Muammar Gaddafi’s former spy chief and foreign minister Moussa Koussa in Tripoli September 3, 2011. Documents found in the abandoned office of Gaddafi’s intelligence chief indicate the U.S. and British spy agencies helped the fallen strongman persecute Libyan dissidents, Human Rights Watch said on Saturday. The documents were uncovered by the human rights activist group in Koussa’s abandoned offices.

This image provided by Human Rights Watch on Saturday, Sept. 3, 2011, shows a secret document dated April 15, 2004 discovered by Human Rights Watch in Tripoli, Libya, detailing a request for Libya to take custody of a terrorist suspect known as “Shaykh Musa.” The CIA and other Western intelligence agencies worked closely with the ousted regime of Moammar Gadhafi, sharing tips and cooperating in handing over terror suspects for interrogation to a regime known to use torture, according to a trove of security documents discovered after the fall of Tripoli. The revelations provide new details on the West’s efforts to turn Libya’s mercurial leader from foe to ally and provide an embarrassing example of the U.S. administration’s collaboration with authoritarian regimes in the war on terror.
TOP-SECRET – (U//FOUO) DHS-FBI-USSS 2012 State of the Union Address Joint Threat Assessment

(U//FOUO) This Joint Threat Assessment (JTA) addresses potential threats to the President’s delivery of the State of the Union address at the US Capitol on 24 January 2012.
(U) This information is intended to support federal, state, territorial, tribal, and local government agencies and authorities and other entities in developing and prioritizing protective and support measures relating to an existing or emerging threat to homeland security.
(U//FOUO) The information in this assessment is current as of 9 January 2012. Unless otherwise noted, this JTA uses the FBI definition of terms, which may differ from the definitions used by DHS.
…
(U) Key Findings
(U//FOUO) We have no specific or credible information indicating a threat to the US Capitol or the National Capital Region (NCR) to coincide with the 2012 State of the Union address. We assess, however, that al-Qa‘ida and its affiliates and allies remain committed to attacking the Homeland and, as of February 2010, al-Qa‘ida identified the NCR and the State of the Union address itself as important targets, presumably for attacks. Moreover, homegrown violent extremists (HVEs) as well as lone offenders could view the event as an attractive target, offering the means to inflict casualties and garner extensive media coverage. Detecting homeland plots involving HVEs and lone offenders continues to challenge law enforcement and intelligence agencies due to the operational independence of the perpetrators, which can reduce or eliminate preoperational indicators.
(U//FOUO) Robust event security at the US Capitol might cause would-be attackers to engage less secure targets within the NCR during the State of the Union address in order to leverage the media attention and symbolism associated with the address.
…
(U) Intelligence Gaps
(U//FOUO) Are international terrorist groups or their affiliates and allies plotting to attack the US Capitol or the NCR during the State of the Union address?
(U//FOUO) Are domestic extremists planning to disrupt the State of the Union address by targeting entities associated with the US Government, including the US Capitol?
(U//FOUO) Are unidentified HVEs, inspired by international terrorist groups, planning to attack the US Capitol or the NCR during the State of the Union address?
(U//FOUO) Are unidentified lone offenders plotting to attack the US Capitol or the NCR during the State of the Union address?
(U//FOUO) Will peaceful demonstrations in the area of the US Capitol or within the NCR be exploited by violent actors who will pose a risk to officer safety during the State of the Union address?
DOWNLOAD ORIGINAL DOCUMENT HERE
UNCENSORED – FEMEN Protests at World Economic Forum
|
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-wef/pict6.jpg) Activists of the Ukrainian feminist nudity group FEMEN clash with Swiss police during a protest at the 42nd Annual Meeting of the World Economic Forum, WEF, in Davos, Switzerland, Saturday, Jan. 28, 2012. (Jean-Christophe Bott) Activists of the Ukrainian feminist nudity group FEMEN clash with Swiss police during a protest at the 42nd Annual Meeting of the World Economic Forum, WEF, in Davos, Switzerland, Saturday, Jan. 28, 2012. (Jean-Christophe Bott) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-wef/pict7.jpg) EDS NOTE NUDITY Topless Ukrainian protesters demonstrate at the entrance to the congress center where the World Economic Forum takes place in Davos, Switzerland Saturday, Jan. 28, 2012. The activists are from the group Femen, which has have become popular in Ukraine for staging small, half-naked protests against a range of issues including oppression of political opposition. (Anja Niedringhaus) EDS NOTE NUDITY Topless Ukrainian protesters demonstrate at the entrance to the congress center where the World Economic Forum takes place in Davos, Switzerland Saturday, Jan. 28, 2012. The activists are from the group Femen, which has have become popular in Ukraine for staging small, half-naked protests against a range of issues including oppression of political opposition. (Anja Niedringhaus) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-wef/pict5.jpg) Topless Ukrainian protesters climb up a fence at the entrance to the congress center where the World Economic Forum takes place in Davos, Switzerland Saturday, Jan. 28, 2012. The activists are from the group Femen, which has have become popular in Ukraine for staging small, half-naked protests against a range of issues including oppression of political opposition. (Anja Niedringhaus) Topless Ukrainian protesters climb up a fence at the entrance to the congress center where the World Economic Forum takes place in Davos, Switzerland Saturday, Jan. 28, 2012. The activists are from the group Femen, which has have become popular in Ukraine for staging small, half-naked protests against a range of issues including oppression of political opposition. (Anja Niedringhaus) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-wef/pict4.jpg) EDS NOTE NUDITY – Topless Ukrainian protesters demonstrate at the entrance to the congress center where the World Economic Forum takes place in Davos, Saturday, Jan. 28, 2012. The activists are from the group Femen, which has become popular in Ukraine for staging small, half-naked protests against a range of issues including oppression of political opposition. (Anja Niedringhaus) EDS NOTE NUDITY – Topless Ukrainian protesters demonstrate at the entrance to the congress center where the World Economic Forum takes place in Davos, Saturday, Jan. 28, 2012. The activists are from the group Femen, which has become popular in Ukraine for staging small, half-naked protests against a range of issues including oppression of political opposition. (Anja Niedringhaus) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-wef/pict3.jpg) EDS NOTE NUDITY- A topless Ukrainian protester is arrested by Swiss police after climbing up a fence at the entrance to the congress center where the World Economic Forum takes place in Davos, Saturday, Jan. 28, 2012. The activists are from the group Femen, which has become popular in Ukraine for staging small, half-naked protests against a range of issues including oppression of political opposition. (Anja Niedringhaus) EDS NOTE NUDITY- A topless Ukrainian protester is arrested by Swiss police after climbing up a fence at the entrance to the congress center where the World Economic Forum takes place in Davos, Saturday, Jan. 28, 2012. The activists are from the group Femen, which has become popular in Ukraine for staging small, half-naked protests against a range of issues including oppression of political opposition. (Anja Niedringhaus) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-wef/pict2.jpg) Topless Ukrainian protesters demonstrate at the entrance to the congress center where the World Economic Forum takes place in Davos, Switzerland Saturday, Jan. 28, 2012. The activists are from the group Femen, which has have become popular in Ukraine for staging small, half-naked protests against a range of issues including oppression of political opposition. (Anja Niedringhaus) Topless Ukrainian protesters demonstrate at the entrance to the congress center where the World Economic Forum takes place in Davos, Switzerland Saturday, Jan. 28, 2012. The activists are from the group Femen, which has have become popular in Ukraine for staging small, half-naked protests against a range of issues including oppression of political opposition. (Anja Niedringhaus) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-wef/pict0.jpg) A topless Ukrainian protester is arrested by Swiss police after climbing up a fence at the entrance to the congress center where the World Economic Forum takes place in Davos, Switzerland Saturday, Jan. 28, 2012. The activists are from the group Femen, which has have become popular in Ukraine for staging small, half-naked protests against a range of issues including oppression of political opposition. (Anja Niedringhaus) A topless Ukrainian protester is arrested by Swiss police after climbing up a fence at the entrance to the congress center where the World Economic Forum takes place in Davos, Switzerland Saturday, Jan. 28, 2012. The activists are from the group Femen, which has have become popular in Ukraine for staging small, half-naked protests against a range of issues including oppression of political opposition. (Anja Niedringhaus) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-wef/pict1.jpg) Topless Ukrainian protesters demonstrate at the entrance to the congress center where the World Economic Forum takes place in Davos, Saturday, Jan. 28, 2012. The activists are from the group Femen, which has have become popular in Ukraine for staging small, half-naked protests against a range of issues including oppression of political opposition. (Anja Niedringhaus) Topless Ukrainian protesters demonstrate at the entrance to the congress center where the World Economic Forum takes place in Davos, Saturday, Jan. 28, 2012. The activists are from the group Femen, which has have become popular in Ukraine for staging small, half-naked protests against a range of issues including oppression of political opposition. (Anja Niedringhaus) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-wef/pict11.jpg) An activist from Ukrainian feminist group FEMEN shouts slogans as she is arrested by Swiss police during a topless protest on January 28, 2012, against the World Economic Forum (WEF) annual meeting on January 28, 2012 in the Swiss resort of Davos. Getty An activist from Ukrainian feminist group FEMEN shouts slogans as she is arrested by Swiss police during a topless protest on January 28, 2012, against the World Economic Forum (WEF) annual meeting on January 28, 2012 in the Swiss resort of Davos. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-wef/pict10.jpg) An activist from Ukrainian feminist group FEMEN shouts slogans as she is arrested by Swiss police during a topless protest on January 28, 2012, against the World Economic Forum (WEF) annual meeting on January 28, 2012 in the Swiss resort of Davos. Getty An activist from Ukrainian feminist group FEMEN shouts slogans as she is arrested by Swiss police during a topless protest on January 28, 2012, against the World Economic Forum (WEF) annual meeting on January 28, 2012 in the Swiss resort of Davos. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-wef/pict9.jpg) Attivist from Ukrainian feminist group ‘ Femen ‘ is arrested by Swiss police as they make a topless protest on January 28, 2012, against the World Economic Forum (WEF) in the center of the Swiss resort of Davos. The global elite has talked itself into an upbeat frame of mind as the Davos forum nears its climax on Saturday, but the Greek debt crisis still hangs heavily over proceedings. Getty Attivist from Ukrainian feminist group ‘ Femen ‘ is arrested by Swiss police as they make a topless protest on January 28, 2012, against the World Economic Forum (WEF) in the center of the Swiss resort of Davos. The global elite has talked itself into an upbeat frame of mind as the Davos forum nears its climax on Saturday, but the Greek debt crisis still hangs heavily over proceedings. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-wef/pict8.jpg) EDS NOTE : NUDITY – A member of the Ukrainian FEMEN women’s rights group is detained by policemen after a protest at the 42nd Annual Meeting of the World Economic Forum, WEF, in Davos, Switzerland, Saturday, Jan. 28, 2012. In freezing temperatures three topless Ukrainian protesters were detained Saturday while climbing a security fence outside the economic forum to draw attention to the needs of the world’s poor. The protesters had their papers checked and will be released later from custody. EDS NOTE : NUDITY – A member of the Ukrainian FEMEN women’s rights group is detained by policemen after a protest at the 42nd Annual Meeting of the World Economic Forum, WEF, in Davos, Switzerland, Saturday, Jan. 28, 2012. In freezing temperatures three topless Ukrainian protesters were detained Saturday while climbing a security fence outside the economic forum to draw attention to the needs of the world’s poor. The protesters had their papers checked and will be released later from custody. |
TOP-SECRET-Bilderberg Meetings Participant Lists 1954-2011
The following represents a nearly complete list of participants and attendees of Bilderberg Meetings from 1954-2011. It will be updated over time as more information is acquired. If you have any additional information, including copies of official participant lists, please contact us or upload them using our secure online submission form.
| Meeting Time | Meeting Location | Participant List | Agenda |
|---|---|---|---|
| May 29-31, 1954 | Hotel de Bilderberg Osterbeek, Netherlands |
Unofficial | Unofficial |
| March 18-20, 1955 | Barbizon, France | ||
| September 23-25, 1955 | Garmisch-Partenkirchen, Germany | ||
| May 11-13, 1956 | Fredenborg, Denmark | ||
| February 15-17, 1957 | St. Simons Island Conference, USA | Unofficial | Unofficial |
| September 13-15, 1958 | Buxton Conference, England | Incomplete | Unofficial |
| September 18-20, 1959 | Çinar Hotel Yeşilköy, Istanbul, Turkey |
||
| May 28-29, 1960 | Palace Hotel Bürgenstock, Nidwalden, Switzerland | ||
| April 21-23, 1961 | Manoir St. Castin Lac-Beauport, Quebec, Quebec, Canada | ||
| May 18-20, 1962 | Grand Hotel Saltsjöbaden Saltsjöbaden, Sweden | ||
| March 29-31, 1963 | Cannes, France | Unofficial | Unofficial |
| March 20-22, 1964 | Williamsburg Conference, Virginia, USA | Unofficial | Unofficial |
| April 2-4, 1965 | Villa D’Este Conference, Italy | Unofficial | Unofficial |
| April 2-4, 1966 | Nassauer Hof Hotel Wiesbaden Wiesbaden, West Germany | Unofficial | Unofficial |
| March 31-April 2, 1967 | Cambridge, United Kingdom | Unofficial | Unofficial |
| April 26-28, 1968 | Mont Tremblant, Canada | Unofficial | Unofficial |
| May 9-11, 1969 | Hotel Marienlyst Helsingør, Denmark |
Unofficial | Unofficial |
| April 17-19, 1970 | Grand Hotel Quellenhof Bad Ragaz Conference, Sweden |
Unofficial | Unofficial |
| April 23-25, 1971 | Woodstock Inn Woodstock, Vermont, U.S.A. |
Unofficial | Unofficial |
| April 21-23, 1972 | La Reserve di Knokke-Heist Knokke, Belgium |
Unofficial | Unofficial |
| May 11-13, 1973 | Grand Hotel Saltsjöbaden Saltsjöbaden, Sweden |
Unofficial | Unofficial |
| April 19-21, 1974 | Hotel Mont d’Arbois Megeve, France |
Unofficial | Unofficial |
| April 25-27, 1975 | Golden Dolphin Hotel Çeşme, İzmir, Turkey | Unofficial | Unofficial |
| April 1976 | The Homestead Hot Springs, Virginia, United States |
||
| April 22-24, 1977 | Paramount Imperial Hotel Torquay, United Kingdom | Unofficial | Unofficial |
| April 21-23, 1978 | Chauncey Conference Center Princeton, New Jersey, United States |
Unofficial | Unofficial |
| April 27-29, 1979 | Grand Hotel Sauerhof Baden bei Wien, Austria | Unofficial | Unofficial |
| April 18-20, 1980 | Dorint Sofitel Quellenhof Aachen Aachen, West Germany |
Unofficial | Unofficial |
| May 15-17, 1981 | Palace Hotel Bürgenstock, Nidwalden, Switzerland |
Unofficial | Unofficial |
| April 14-16, 1982 | Rica Park Hotel Sandefjord Sandefjord, Norway |
Unofficial | Unofficial |
| May 13-15, 1983 | Château Montebello Montebello, Quebec, Canada | Unofficial | Unofficial |
| May 11-13, 1984 | Grand Hotel Saltsjöbaden Saltsjöbaden, Sweden | Unofficial | Unofficial |
| May 10-12, 1985 | Doral Arrowwood Hotel Rye Brook, New York, United States | Unofficial | Unofficial |
| April 25-27, 1986 | Gleneagles Hotel Gleneagles, Auchterarder, United Kingdom | Unofficial | Unofficial |
| April 24-26, 1987 | Villa d’Este Cernobbio, Italy |
Unofficial | Unofficial |
| June 3-5, 1988 | Interalpen-Hotel Tyrol Telfs-Buchen, Austria | Unofficial | Unofficial |
| May 12-14, 1989 | Gran Hotel de La Toja Isla de La Toja, Spain | Unofficial | Unofficial |
| May 10-13, 1990 | Harrison Conference Center Glen Cove, New York, United States |
Unofficial | Unofficial |
| June 6-9, 1991 | Baden-Baden, Germany | Unofficial | Unofficial |
| May 21-24, 1992 | Evian-les-Bains, France | Unofficial | Unofficial |
| April 22-25, 1993 | Nafsika Astir Palace Hotel Vouliagmeni, Greece |
Unofficial | Unofficial |
| June 2-5, 1994 | Helsinki, Finland | Unofficial | Unofficial |
| June 8-11, 1995 | Zurich, Switzerland | Unofficial | Unofficial |
| May 30 – June 2, 1996 | The Kingbridge Centre in King City, Ontario, Canada | Unofficial | Unofficial |
| June 12-15, 1997 | PineIsle Resort, Atlanta, U.S.A. | Unofficial | Unofficial |
| May 14-17, 1998 | Turnberry Hotel, Ayrshire, Scotland | Unofficial | Unofficial |
| June 3-6, 1999 | Caesar Park Hotel Penha Longa Hotel Caesar Park Penha Longa,Sintra, Portugal |
Unofficial | Unofficial |
| June 1-3, 2000 | Chateau Du Lac Hotel Brussels, Belgium |
Unofficial | Unofficial |
| May 24-27, 2001 | Hotel Stenungsbaden Stenungsund, Sweden |
Unofficial | Unofficial |
| May 30 – June 2, 2002 | Westfields Marriott Chantilly, Virginia, U.S.A. |
Unofficial | Unofficial |
| May 15-18, 2003 | Trianon Palace Hotel Versaille, France |
Unofficial | Unofficial |
| June 3-6, 2004 | Grand Hotel des Iles Borromees Stressa, Italy |
Unofficial | Unofficial |
| May 5-8, 2005 | Dorint Sofitel Seehotel Überfahrt Rottach-Egern, Germany |
Unofficial | Unofficial |
| June 8-11, 2006 | Brookstreet Hotel Ottawa, Canada | Unofficial | |
| June 3 – May 31, 2007 | Ritz-Carlton Hotel Istanbul, Turkey |
Official | |
| June 5-8, 2008 | Westfields Marriott Chantilly, Virginia, USA |
Official | |
| May 14-17, 2009 | Astir Palace Vouliagmeni, Greece |
Official | |
| June 3-6, 2010 | Hotel Dolce Sitges, Spain |
Official | |
| June 9-12, 2011 | Hotel Suvretta House, St. Moritz, Switzerland | Official |
TOP-SECRET-(U//FOUO) U.S. Army Female Suicide Bombers Report
TOP-SECRET-(U//FOUO) Afghanistan Human Terrain Team AF-24 Quarterly Report Summer 2011

COMMERCE (Security, Drought, and Prices) by DR Burke
Drought is taking its toll on farmers in the western areas of RC north. The first sign appeared in early spring. Realizing that the grazing land was going to be insufficient to support their flocks, farmers began slaughtering more of their sheep than usual. This, in turn, produced a temporary glut of lamb and a drop in what the farmer could expect from each animal. Faced with insufficient grazing land, some farmers are opting to move their animals to higher ground and to fields that can still provide a bit of nourishment for their hungry animals. Farmers in Jowzjan, for example, are moving their sheep down into Faryab. If current conditions worsen, flare-ups over common grazing lands may occur; local farmers may be unwilling to share valuable terrain with those they view as intruders.
All the farmers we have spoken with have noted the dramatic downturn in the yield of all crops, especially the all-important wheat harvest. Drought has severely diminished this year’s wheat harvest in the west of RC-North and escalated the price for flour for the average consumer. In response to a worsening economy, a few farmers have planted small fields of poppies, a crop that can tolerate dry conditions much better than wheat, watermelon, grapes, and tomatoes, the typical cash crops of the region. The poppy farmers are hoping, no doubt, that the lucrative profits from a small amount of opium will offset the shortfall of other crops. Some farmers have gone to Iran or sent their sons to Iran to seek jobs in construction in order to support their families, leaving behind villages even more vulnerable to insurgent influence. Without sufficient food for their families, other military aged men will, no doubt, be more susceptible to offers from insurgent leaders.
…
GOVERNANCE by DR Burke:
Local governance in rural Afghanistan is not simple. Older customary local assemblies operate alongside GIRoA officials, Community Development Councils (CDC’s), and insurgent groups. Although we speak of insurgent governments as “shadow governments,” they rarely exist in the shadows for those over whom they wield power. In villages where insurgents continue to exercise control, the insurgents and not GIRoA perform traditional governmental functions; they levy taxes, resolve disputes (they are, in many villages the only law in town), and maintain local defense forces.
Western Powers have invested their hope and their treasure in inventing a new form of local control: Community District Councils that come out of the National Solidarity Program (NSP). Managed by the Ministry of Rural Rehabilitation and Development (MRRD) with funds from NGO’s and from the World Bank, these organizations set priorities for the expenditure of donor money and oversee contracts. Although they offer an alternative to the indiscriminate funding of the past that encouraged favoritism and corruption, these organizations have little authority except when it comes to the stewardship of outside money. As those development funds begin to dry up, will CDC’s vanish? Can they be further empowered?
Customary organizations like shuras, on the other hand, continue in many rural areas to function as they have for generations raising collective concerns and resolving disputes. In districts like Ghormach insurgents have exerted considerable influence on these local shuras. In the last few months we have learned a good deal about these governing bodies. We recommend that ISAF forces use these local shuras as vehicles through which they can engage villagers and increase security. Our efforts have focused on obtaining information for our brigade, battalion, and companies located in Ghormach and Qeysar that identifies individuals with whom they may want to engage.
DOWNLOAD ORGINAL FILE HERE
TOP-SECRET – (U//FOUO) Joint Publication 3-15.1 Counter-Improvised Explosive Device Operations


(U) This publication provides joint doctrine for planning and executing counter-improvised explosive device (C-IED) operations. It outlines responsibilities, provides command and control considerations, discusses organizational options, details the C-IED process and attack the network methodology, and introduces models for coordinating with C-IED supporting organizations.
(U) This publication has been prepared under the direction of the Chairman of the Joint Chiefs of Staff. It sets forth joint doctrine to govern the activities and performance of the Armed Forces of the United States in joint operations, and provides the doctrinal basis for the planning and conduct of joint C-IED operations. It provides military guidance for the exercise of authority by combatant commanders and other joint force commanders (JFCs) and prescribes joint doctrine for operations, education, and training. It provides military guidance for use by the Armed Forces in preparing their appropriate plans. It is not the intent of this publication to restrict the authority of the JFC from organizing the force and executing the mission in a manner the JFC deems most appropriate to ensure unity of effort in the accomplishment of the overall objective.
…
3. (U) Attacking the Network—General Considerations
(U) While attacking the adversary’s network is a complex, time-consuming task, raising the adversaries’ cost of IED employment to unacceptable levels can be accomplished through a focused, continuous series of operations designed to disrupt the people, places, processes, and materials that support the IEDs’ design, supply, and employment chain. However, C-IED operations must be accomplished within the context of successfully targeting the broader adversary infrastructure.
a. (FOUO) There is no guaranteed method of defining and codifying targetable activities and major components of an IED network. To avoid detection and attack, adversary networks camouflage and constantly revise, or adapt, their TTP. At the highest echelons, the leadership rarely communicates openly and generally uses trusted aides and couriers to provide broad guidance to subordinates and direct the network. At the lowest echelons, the local cell members are detectable, targetable, and replaceable. Therefore, eliminating individuals only provides temporary and limited solutions to countering IED threats. But as networks function and move resources (information, money, supplies, recruits) from the highest to the lowest echelons, these activities are detectable and targetable. Disrupting the flow of resources is the most reliable way of neutralizing the adversary’s use of IEDs. While ideology may produce recruits, they have to eat, obtain weapons, travel, and build, transport, and emplace bombs. Personnel can be replaced, but
the adversary’s logistical infrastructure and materials often take more time.
DOWNLOAD ORIGINAL DOCUMENT HERE
# “GoMoPa”- Opfer # DIE PERVERSEN METHODEN DER “GoMoPa”- SCHEISSHAUSFLIEGEN (Eigenbezeichnung und Eigenbeschreibung)
CONFIDENTIAL – US State Department Telephone Directory 2012
DIE WELT ÜBER DIE DIFFAMIERUNGSMETHODEN DER STASI – VORBILD FÜR “GoMoPa”
DIE PLEITE-FIRMEN DER FINGIERTEN SCHEISSHAUSFLIEGEN-“GoMoPa” (Eigenbezeichnung) SEIT JAHREN INSOLVENT
CONFIDENTIAL – FBI MegaUpload Search Photos and Video
Hi.
4 FBI agents took part in the Megaupload Search. They are still in NZ.
Here are Flickr Photos from the Search. 2 pictures are from inside the villa. The cars in the garage etc., and from the court yesterday.
FBI Operation in Kim Schmitz Dotcom House NZ – Flicker Photos
http://www.flickr.com/photos/32368051[at]N08/sets/72157625312230860/
USA v. Convicted Hacker Kim Schmitz Kim Dotcom – Indictment
http://www.4law.co.il/mega5112.pdf
Videos are here from the court etc.
New Zealand TV : MegaUpload Piracy Arrest 23/1/12 Hacker Kim Schmitz Dotcom
http://www.youtube.com/watch?v=WC47dn0LnnQ
China Brasil Germany TVs : MegaUpload Piracy Arrest 23/1/12 Hacker Kim Schmitz Dotcom
http://www.youtube.com/watch?v=86pT7r4RcYg
A French Blogger Already Killed me Yesterday hehehe…
http://nanojv.wordpress.com/2012/01/23/boaz-guttman-attentat/
VIDEO- LAPD, Special Forces Conduct Urban Operations Exercise Over Downtown LA
Military helicopters will be flying high and dipping low above the skies of Los Angeles Thursday as part of a special operations training program.
Sky2 captured dramatic maneuvers Wednesday night as a Blackhawk helicopter and four other OH-6 helicopters – or “little birds” – flew over the city.
The Blackhawk hovered over the U.S. Bank building before it made a practice drop-off at a nearby park.
At one point, our cameras captured a soldier sitting with his legs dangling outside a chopper.
Throughout the exercise, the five rotorcrafts were staged at Dodger Stadium.
The LAPD says the purpose of the training is, in part, to ensure the military’s ability to operate in urban environments.
DIE GIFTSTUDIE “TOXDAT” DES RESCH-PROTEGE´S STASI-OBERST EHRENFRIED STELZER
Unveield – Corruption scandal shakes Vatican as internal letters leaked
The Vatican was shaken by a corruption scandal Thursday after an Italian television investigation said a former top official had been transferred against his will after complaining about irregularities in awarding contracts.
The show “The Untouchables” on the respected private television network La 7 Wednesday night showed what it said were several letters that Archbishop Carlo Maria Vigano, who was then deputy-governor of Vatican City, sent to superiors, including Pope Benedict, in 2011 about the corruption.
The Vatican issued a statement Thursday criticizing the “methods” used in the journalistic investigation. But it confirmed that the letters were authentic by expressing “sadness over the publication of reserved documents.”
As deputy governor of the Vatican City for two years from 2009 to 2011, Vigano was the number two official in a department responsible for maintaining the tiny city-state’s gardens, buildings, streets, museums and other infrastructure.
Vigano, currently the Vatican’s ambassador in Washington, said in the letters that when he took the job in 2009 he discovered a web of corruption, nepotism and cronyism linked to the awarding of contracts to outside companies at inflated prices.
In one letter, Vigano tells the pope of a smear campaign against him (Vigano) by other Vatican officials who wanted him transferred because they were upset that he had taken drastic steps to save the Vatican money by cleaning up its procedures.
“Holy Father, my transfer right now would provoke much disorientation and discouragement in those who have believed it was possible to clean up so many situations of corruption and abuse of power that have been rooted in the management of so many departments,” Vigano wrote to the pope on March 27, 2011.
In another letter to the pope on April 4, 2011, Vigano says he discovered the management of some Vatican City investments was entrusted to two funds managed by a committee of Italian bankers “who looked after their own interests more than ours.”
LOSS OF $2.5 MILLION, 550,000 EURO NATIVITY SCENE
Vigano says in the same letter that in one single financial transaction in December, 2009, “they made us lose two and a half million dollars.”
The program interviewed a man it identified as a member of the bankers’ committee who said Vigano had developed a reputation as a “ballbreaker” among companies that had contracts with the Vatican, because of his insistence on transparency and competition.
The man’s face was blurred on the transmission and his voice was distorted in order to conceal his identity.
In one of the letters to the pope, Vigano said Vatican-employed maintenance workers were demoralized because “work was always given to the same companies at costs at least double compared to those charged outside the Vatican.”
For example, when Vigano discovered that the cost of the Vatican’s larger than life nativity scene in St Peter’s Square was 550,000 euros in 2009, he chopped 200,000 euros off the cost for the next Christmas, the program said.
Even though, Vigano’s cost-cutting and transparency campaign helped turned Vatican City’s budget from deficit to surplus during his tenure, in 2011 unsigned articles criticizing him as inefficient appeared in the Italian newspaper Il Giornale.
On March 22, 2011, Vatican Secretary of State Cardinal Tarcisio Bertone informed Vigano that he was being removed from his position, even though it was to have lasted until 2014.
Five days later he wrote to Bertone complaining that he was left “dumbfounded” by the ouster and because Bertone’s motives for his removal were identical to those published in an anonymous article published against him in Il Giornale that month.
In early April, Vigano went over Bertone’s head again and wrote directly to the pope, telling him that he had worked hard to “eliminate corruption, private interests and dysfunction that are widespread in various departments.”
He also tells the pope in the same letter that “no-one should be surprised about the press campaign against me” because he tried to root out corruption and had made enemies.
Despite his appeals to the pope that a transfer, even if it meant a promotion, “would be a defeat difficult for me to accept,” Vigano was named ambassador to Washington in October of last year after the sudden death of the previous envoy to the United States.
In its statement, the Vatican said the journalistic investigation had treated complicated subjects in a “partial and banal way” and could take steps to defend the “honor of morally upright people” who loyally serve the Church.
The statement said that today’s administration was a continuation of the “correct and transparent management that inspired Monsignor Vigano.”
CONFIDENTIAL – Information Operations Are Now “Inform and Influence Activities”

The U.S. Army’s doctrine on information operations is getting an overhaul and a new name to reflect the changing nature of military operations. Information operations, which has traditionally included fields such as psychological operations and military deception, will now be incorporated into “Inform and Influence Operations” and changes to the doctrine will be reflected in an updated field manual to be released in 2012. The changes are in response to fundamental shifts in U.S. Army information operations that emphasize the increasingly integrated role of U.S. forces in stability operations and counterinsurgency.
The sometimes controversial field of information operations focuses on military control and manipulation of the information environment operating in a battlespace. According to a 2003 manual from the Joint Chiefs of Staff, “Information operations (IO) are described as the integrated employment of electronic warfare (EW), computer network operations (CNO), psychological operations (PSYOP), military deception (MILDEC), and operations security (OPSEC), in concert with specified supporting and related capabilities, to influence, disrupt, corrupt, or usurp adversarial human and automated decision making while protecting our own.” When a revised version of the Army manual on operations (FM-3) was released in 2010, the revisions vastly changed the nature of military information operations. Several of the revisions were brought about after there was public and congressional controversy surrounding the issue of whether certain military tactics constituted “traditional military action” or “covert action.” Some of the tactics, such as military information support operations (MISO), formerly referred to as psychological operations (PSYOP), require the military to lie about the source of material or “delay recognition” of its origin. The 2010 U.S. Army War College Information Operations Primer states that “the military’s activities to influence target audiences outside combat zones has sparked debate over whether these activities should properly fall under the Department of State. These questions have caused additional media interest and Congressional scrutiny, and in cases have resulted in reduced funding for military IO efforts.”
A draft version of the U.S. Army’s new manual obtained by Public Intelligence defines “Inform and Influence activities” as the “integration of designated information-related capabilities in order to synchronize themes, messages, and actions with operations to inform U.S. and global audiences, influence foreign audiences, and affect adversary and enemy decisionmaking.” The manual provides a more holistic approach to information operations designed to emphasize the nature of every soldiers’ actions on the information environment of a given operation. It describes “information fratricide” as “employing information-related capabilities operations elements in a way that causes effects in the information environment that impede the conduct of friendly operations or adversely affect friendly forces.”
The ability to “influence” a population is defined in the manual as causing audiences to “think or behave in a manner favorable to the commander’s objectives” which results from “applying perception management to affect the target’s emotions, motives, and reasoning.” This can include inform and influence activities that support offensive operations, such as “destroying” which uses “lethal and nonlethal means to physically render enemy information useless or information systems ineffective unless reconstituted.” The manual also includes a number of newer concepts related to information operations, such as “cyber electromagnetic activities” which “seize, retain, and exploit advantages in cyberspace and the electromagnetic spectrum” enabling “Army forces to retain freedom of action while denying freedom of action to enemies and adversaries.”
SEE DRAFT HERE
STASILAND – True Stories – The Book by Anna Funder
 Stasiland: Oh Wasn’t it so Terrible – True Stories from Behind the Berlin Wall (Stasiland: Ach, war es nicht so schrecklich – Wahre Geschichten von hinter der Berliner Mauer by Anna Funder is a polyvocal text about individuals who resisted the East German regime, and others who worked for its secret police, the Stasi. It tells the story of what it was like to work for the Stasi, and describes how those who did so now come to terms, or not, with their pasts.
Stasiland: Oh Wasn’t it so Terrible – True Stories from Behind the Berlin Wall (Stasiland: Ach, war es nicht so schrecklich – Wahre Geschichten von hinter der Berliner Mauer by Anna Funder is a polyvocal text about individuals who resisted the East German regime, and others who worked for its secret police, the Stasi. It tells the story of what it was like to work for the Stasi, and describes how those who did so now come to terms, or not, with their pasts.
Funder, an Australian, found that Germans often resorted to stereotypes in describing the Ossis, the German nickname for those who lived in East Germany, dismissing questions about civil resistance. She used classified ads to reach former members of the Stasi and anti-Stasi organizations and interviewed them extensively.[1]
Chris Mitchell of Spike Magazine called it “an essential insight into the totalitarian regime”.[2] Giles MacDonogh wrote in The Guardian that the culture of informants and moral capitulations “comes wonderfully to life in Funder’s racy account”.[1]
Stasiland has been published in fifteen countries and translated into a dozen different languages. It was shortlisted for many awards in the UK and Australia, among them the Age Book of the Year Awards, the Queensland Premier’s Literary Awards, the Guardian First Book Award 2003, the South Australian Festival Awards for Literature (Innovation in Writing) 2004, the Index Freedom of Expression Awards 2004, and the W.H. Heinemann Award 2004. In June 2004 it was awarded the world’s biggest prize for non-fiction, the Samuel Johnson Prize.
Stasiland is being developed for the stage by The National Theatre in London.
Notes
- ^ a b Giles MacDonogh (June 7, 2003). “The spy’s the limit: Giles MacDonogh is gripped by personal histories of Stasi rule in Anna Funder’s Stasiland”. London: The Guardian. Retrieved 2007-07-14.
- ^ “Anna Funder: Stasiland”. Spike Magazine. August 2004. Retrieved 2007-07-14.
References
- Funder, Anna (2003). Stasiland: Stories from behind the Berlin Wall. London: Granta. ISBN 9781862076556. OCLC 55891480.
- Byrnes, Sholto; Tonkin, Boyd (2004-06-18). “Anna Funder: Inside the real Room 101” (html). London: The Independent. Retrieved 2008-02-02.
Stalisland – Germany – Video
Everyone knows about the Nazis camps of Auschwitz and Dachau. But few are aware of the systemic oppression that went on under the Stasis. Now some ex-Stasis agents are trying to re-write history.
“I won’t apologise for anything. I can only apologise for not having worked more efficiently”, states former Stasi spy Peter Wolter. He maintains that the thousands of people tortured and imprisoned were; “quite rightly punished”. Along with other ex-agents, Wolter is campaigning to have a museum documenting the suffering of prisoners in Stasi prisons closed. As Anna Funder, author of ‘Stasiland’ states; “these were people writing doctoral theses on how to destroy a soul”. Now thousands of ordinary Germans who had their lives destroyed by the Stasis fear their suffering will be negated.
Betreff: STASI-Stalking und Erpressung
Süddeutsche Zeitung über die kriminellen Machenschaften der “GoMoPa”
Kim Dotcom starring in Kimble goes Monaco # 2
One year later Kimble wants to go and visit the Monaco Grand Prix once more! So guess what, he invited his friends again, now even a bigger group and they drive off in the most expensive cars you can imagine for a $10.000.000+ weekend in Monaco!
Kimble, also known as Kim Dotcom is currently being indicted for copyright fraud as owner of Megaupload.
“Kimble Goes Monaco Part II,” like all sequels, strains to top its predecessor; it’s the Teflon Don to Part I’s Port of Miami. More Ferraris! More hangers-on! A more lavish steam-table banquet! A champagne-spritzing Saint Tropez lingerie party! A Trap-a-Holics-style announcer peppering his German-language narration with stray English phrases like “all-inclusive,” “The boys are in town!,” “Kim-pire,” and “Fireworks, DJ, laser show!” Kim-posse members like Keiwan, Matthias and Gitta return, but they’re preceded in the credits—which borrow the theme music and wipe effects from Dynasty’s opening sequence by some new faces. Here’s Finn Batato, who would go on to become Megaupload’s chief marketing officer; he was arrested on Thursday, too. (The indictment names him as part of the overall MegaConspiracy but also specifically charges him with having circulated Megaupload links to infringing copies of the movies My Blueberry Nights and Dan in Real Life and Louis Armstrong’s recording of the song “We Have All The Time In The World,” which anyone attuned to the James Bondian aspects of this case will recognize as a soundtrack cut from On Her Majesty’s Secret Service.)
Here, too, and all over the video, is Frank Lämmermann, sort of a German Jean-Ralphio type with a towering head of shellacked ich-bin-un-zany-comedian hair, acting as de facto master of ceremonies. Lämmermann was apparently a presenter on the German music/entertainment network Viva at the time, and went on to conquer America with an appearance on Pauly Shore’s TBS series Minding the Store, which Google indicates was a thing that existed. A German message-board poster once said of Lämmermann, “For, instead of encouraging you to laugh stimulates only! Apart from that the guy is so annoying that one feels after a short time to give him the urge to become one with the baseball bat.” We’re pretty sure we agree; although his presence as host frees up Schmitz himself to drink out of a punchbowl and whip his male associates’ bare asses with a belt, it lends a self-conscious, Billionaires Gone Wild vibe to the proceedings, especially when Lämmermann is walking around with a shotgun mic interviewing women about their nipples.
Like the Jersey Shore kids returning to Karma, the Kimble Clan returns to the Autobahn, to the zuper-yacht, and eventually to Jimmy*z. They’ve been coming to this same party for years, and in no way is that depressing! The party continues back on the yacht—fireworks, DJ, lasershow!—and at some point Keiwan, egged on by other party guests, eats a whole onion. In a way, we’re lucky that all Kim went on to do was change his name to “Dotcom” and (allegedly) aid in the file-sharing-abetted downfall of the content industry; there’s a sociopathic emptiness to the proceedings on display in this second video. This is the party you have before you have the party where you rent out an island and hunt humans for sport.
Kim Dotcom starring in Kimble goes Monaco #1
Kimble, our internethero goes to Monaco with his friends, spending a good $10.000.000 during one Formula 1 weekend!
Kimble, also known as Kim Dotcom is currently being indicted for copyright fraud as owner of Megaupload.
It’s not every day that you encounter a real-life practitioner of Bond-villainous ostentation like Kim Schmitz, aka Kim Dotcom, founder of the now-shuttered file-hosting network Megaupload. The German-Finnish hacker-turned-accused-copyright-infringement-magnate was arrested last Thursday by New Zealand police acting in cooperation with the FBI; he and his business associates, referred to, awesomely, as “the MegaConspiracy” in an indictment filed on January 5th in U.S. District Court, are being charged with “criminal copyright infringement and money laundering on a massive scale with estimated harm to copyright holders well in excess of $500,000,000 and reported income in excess of $175,000,000.” In happier times, Schmitz raced in the Gumball Rally and bankrolled lavish fireworks displays for his adopted homeland of New Zealand and star-studded music videos featuring artists like will.i.am (literally) singing Megaupload’s praises; shortly before his arrest, he became the world’s top-ranked Call of Duty: Modern Warfare 3 player, sitting at #1 on the game’s “Kills” and “Free-for-all” leaderboards as of three weeks ago. He was busted the day before his 38th birthday, at a $30 million rented mansion north of Auckland; he was allegedly hiding in a panic room with a sawed-off shotgun, like any innocent person celebrating a birthday.
Schmitz is six-foot-six, per Wikipedia, and weighs 285 pounds. He looks like Augustus Gloop grown up all muah-ha-ha; basically, the US government and the entertainment industry could not have asked for a better Dr. Evil figure to help them dramatize the inherent nefariousness of copyright infringement, unless Kim had been so kind as to pose for pictures stroking a fluffy white cat. The indictment (posted as a PDF here) is 72 pages long and packed with amazing details. The list of assets the authorities are looking to seize includes 59 different bank accounts, a $15,000 Devon Works Tread 1 watch made of bulletproof polycarbonate (described on Devon Works’ Website as “a big, bold sexy declaration of independence from the status quo”), a statue of the Predator, and a fleet of luxury cars, including Mercedes-Benzes with license plates reading “GOOD,” “EVIL,” “CEO,” “MAFIA,” “GOD,” “STONED,” “POLICE,” “HACKER” and “GUILTY.” (Some perspective: When Time Magazine profiled Napster cofounder and original file-sharing gangsta Shawn Fanning twelve years ago, he was driving a “newly customized” Mazda RX-7.)
Commissioning vanity plates to trumpet your Internet-outlaw status on a fleet of Benzes is crazy, but it’s by no means out of character for Dotcom. Way back at the dawn of this century, when he was merely a hacker-turned-entrepreneur known as “Kimble,” before he was arrested in Bangkok and fined ¬100,000 for embezzlement and insider trading, he made some endlessly entertaining video documentaries celebrating a cash-incinerating lifestyle that looks, in retrospect, like a dress rehearsal for the hyperindulged-international-superpirate role the US government has accused him of playing.
You can find both “Kimble Goes to Monaco” and “Kimble Goes to Monaco Part II” on Google Video. They’re in German, without subtitles, but you’ll get the gist: Look at how much fun we’re having. Imagine how much it costs.
Uncensored Video – Femen of Ukraine
Our God is woman, our mission is protest, our weapons are bare breasts!
簡介
FEMEN (Ukrainian:Фемен) is a Ukrainian protest group based in Kiev, founded in 2008. The organisation became internationally known for organizing topless protests against sex tourists, international marriage agencies, sexism and other social, national and international ills. Some of the goals of the organisation are: “To develop leadership, intellectual and moral qualities of the young women in Ukraine” and “To build up the image of Ukraine, the country with great opportunities for women”. As of late April 2010 the organisation is contemplating becoming a political party to run for seats in the next Ukrainian parliamentary election.
History
The movement was founded in 2008 by Anna Hutsol (born 1983, most FEMEN members are younger) after she became attuned to the sad stories of Ukrainian woman duped by false promises from abroad: “I set up FEMEN because I realised that there was a lack of women activists in our society; Ukraine is male-oriented and women take a passive role.” Since then the organization has staged noticeable erotically-flavored rallies (among others) near the building of the Cabinet of Ministers, at Maidan Nezalezhnosti, the Turkish embassy in Ukraine and in front of the Iranian embassy to oppose the expected execution of Sakineh Mohammadi Ashtiani.
The goals of the organization is “to shake women in Ukraine, making them socially active; to organize in 2017 a women’s revolution.”
FEMEN justifies its provocative methods stating “This is the only way to be heard in this country. If we staged simple protests with banners, then our claims would not have been noticed”. The organisation plans to become the biggest and the most influential feminist movement in Europe.
Exposed – Mitt Romney’s Tax Returns 2010-2011

Willard M and Ann D Romney Estimated 1040 for 2011
104 pages
Download original document here
Willard M and Ann D Romney 1040 for 2010 203 pages
Download original document here
The Ann and Mitt Romney 1995 Family Trust 1041 for 2010 81 page
The Ann D. Romney Blind Trust 1041 for 2010 83 pages
The W. Mitt Romney Blind Trust 1041 for 2010 37 pages
The Tyler Foundation 990 from 2010 39 pages
The word ‘Stasi’ has become ‘a global synonym for the secret police terrors of communism’.
The East German State Security Service, commonly known as the Stasi, was founded in February 1950. For forty years, the Stasi maintained a frightening reputation for surveillance, infiltration and terror, leading Historian Timothy Garton Ash to comment that the word ‘Stasi’ has become ‘a global synonym for the secret police terrors of communism’. The tentacles of Stasi power and influence were so far reaching that it was recently revealed that the Stasi had even compiled a secret dossier on Erich Honecker, leader of the GDR 1971 – 1989; using information obtained about Honecker’s attempts to collaborate with the Nazis during the Second World War to force him to resign in October 1989. In January 1990, shortly after the collapse of communism in the GDR, crowds of protestors stormed and occupied the Stasi headquarters in Berlin; an act symbolising the people’s victory over one of the greatest evils of state socialism in the GDR. The Stasi kept meticulous records about those placed under surveillance, with over 180km of shelved Stasi files surviving the collapse of the GDR. In the post-communist years this information was declassified and between 1992 and 2011 an estimated 2.75 individuals have requested access to their files. In many instances people discovered that people they had trusted – family members, close friends, neighbours and work colleagues – had worked as informants for the Stasi. In this article, guest author David Cook explores the key role played by Stasi informers in the GDR, considering the motivations of those who agreed to work with the Stasi and the impact of popular participation on wider society.
Living with the Enemy: Informing the Stasi in the GDR.
By David Cook.
The German Democratic Republic (GDR) was the golden child of the Soviet Union, often portrayed as the torch bearer for the communist system around the world. Yet its people still could not be allowed the freedom to air their individual opinions, the views of the state were final and absolute, and to contradict the party was considered no less serious a crime than treason itself. A powerful police organ was needed to keep the people in check, a progenitor of fear that would bend the populace to the will of the state. In the GDR the Ministerium für Staatssicherheit (MfS), commonly known as the Stasi, was the tool used to attempt to mould the East German people to the Communist Party’s (SED) requirements. However, police and party pressure alone is not enough to oppress an entire country; popular participation is ultimately key to any regime’s survival. In the case of the GDR, its own people helped to maintain the party’s power through their role as police informers. Informers played a crucial role, acting as a vital cog in the vast machinery of the East German police state; both responding to and perpetuating the climate of fear that permeated throughout East German society.
By 1989, when the Berlin Wall collapsed and communism in East Germany came to an end, it is estimated that the MfS had 97,000 official employees as well as approximately 173,000 unofficial informers. Roughly this translated as a ratio of one agent per 63 of the population, a position far in advance of the Soviet Union’s KGB, that even at its height could only manage one per 5830 people (Figures taken from Anna Funder, Stasiland, Granta: 2004). The Stasi amounted to a small army infiltrating the very fabric of the communist regime, whose sole purpose was the surveillance and repression of the East German people. Fear of the state – and of the Stasi as a tool of state control – was widespread, and this terror was used as a vital tool in the creation of a malleable citizenry.
 The Stasi motto ‘Schild und Schwert der Partei’ declared its intention to act as the ‘Shield and Sword’ of the Communist Party in East Germany.
The Stasi motto ‘Schild und Schwert der Partei’ declared its intention to act as the ‘Shield and Sword’ of the Communist Party in East Germany.
There were a variety of things that could bring a person to the attention of the Stasi. Once the MfS had targeted a suspect the goal was often to engender self-doubt in that person, to prevent them from living any semblance of a normal life, and if indeed they were guilty of some form of ‘subversion’, to encourage them to further implicate and discredit themselves. Ulrike Poppe was one such individual whose work in dissident peace and feminist movements were deemed to be a threat to the stability of communist East Germany by the Stasi. Between 1973 – 1989, Poppe was arrested a total of 14 times. For 15 years she was placed under surveillance, followed by her own personal MfS agent and subjected to daily harassment. In this way the Stasi undermined their targets’ self-confidence and peace of mind, rather than physically beating them. Although physical coercion was employed by the Stasi, the evidence indicates that they often preferred to utilise more ‘subtle’ (but equally effective) means of psychological torture. Isolation, sleep deprivation, disorientation, humiliation, restriction of food and water and ominous threats against the subject and their families combined with promises of leniency if they ‘confessed’ were all commonly cited interrogation tactics. The MfS was not concerned with human rights and paid no more than lip service to the notion of a democratic legal process and legitimate trials, as illustrated by the head of the Stasi, Erich Mielke, who maintained a policy of: ‘Execution, if necessary without a court verdict.’
One victim’s memories of Hohenschönhausen, the feared Stasi prison in East Berlin:
For the police state to function fully however, participation from amongst the populace was key. Their vital tool here was to be the Inofizelle Mitarbeiter (I.M). IMs were unofficial collaborators who informed on work colleagues, friends, and even their own spouses. Informers were a part of everyday life, supplying the Stasi with the banal trivialities that they deemed necessary to neutralise their targets. During the lifespan of the communist regime in East Germany it is estimated from existing archival material that there were up to 500,000 informers active at various times. Or more starkly one in 30 of the population had worked for the Stasi by the fall of the GDR. Informers were controlled by their own special department, HA IX (Main Department 9), often referred to as ‘the centre of the inquisition.’
People were not often willing informers however, and it would be wrong to accuse the majority of East Germans of freely consenting to work with the Stasi. Motives for becoming an informer appear to be numerous, and this topic has provided the basis for many historical works. Yet as crucial as they were to the oppression of the population, what drove so many East Germans to inform on their own people? Robert Gellately in his article, Denunciation in 20th Century Germany, posits a view of a ‘culture of denunciation’ that was a hangover from the Nazi period. People became I.Ms for a number of reasons in his view: for personal gain; so visits to the West would be granted; from a desire to change the system from within; or in the majority of cases through blackmail and coercion by the Stasi. Fear then, was also used as a tool to recruit informers from the general populace.
Timothy Garton Ash’s book, The File, is based on his own personal Stasi file as he tracks down and talks to many of those that informed on him, noting the motivations behind their actions. Each of the informers exhibits differing reasons for their collaboration, all of which are covered by Gellately’s theory. ‘Michaela’ was an art director and as such was encouraged to inform on those the Stasi deemed interesting in order to make her job easier. Visas enabling visits to art exhibits in the West or much needed budget increases could be obtained in exchange for information. Whilst ‘Michalea’ was an example of someone working for the police state for personal gain, two other examples in Garton Ash’s book were recruited through blackmail. ‘Schuldt’ was persuaded to become an informer due to fear of his homosexuality being made public and his life ruined; ‘Smith’ on the other hand collaborated to prove his innocence in the face of accusations of being a Western spy. In this way the Stasi was able to build up a frighteningly vast network of informers utilised to collate data on anyone deemed of interest to the state.
 Stasi Files Department, Berlin. The Stasi kept meticulous files on all individuals under surveillance, the majority of which survived the collapse of communism and are now accesible to the public.
Stasi Files Department, Berlin. The Stasi kept meticulous files on all individuals under surveillance, the majority of which survived the collapse of communism and are now accesible to the public.
Fear, as illustrated in the cases of ‘Smith’ and ‘Schuldt’, was the most powerful weapon possessed by the Stasi. It was a weapon they utilised freely, creating large networks of informers and ensuring the system survived. The MfS were the source of this fear in society at large, creating a resigned conformity amongst the masses that kept them subordinate to the whims of the SED. This is the crucial role played by the security apparatus in a truly repressive police state. Without the conformity of the lower levels of society the system would have collapsed. The majority of the population learned, from a dread of the consequences, to live with this authority in return for living a semblance of a peaceful life. Reicker, Schwarz and Schneider describe the day to day life of a GDR citizen as such: ‘The daily lie, which everyone participated in to some extent … Once you learn to accept the big political lie you allow yourself little lies in other places. Unconsciously.’ It was this willingness by the German population to be subjected to authority, and the all powerful nature of the MfS, that Funder argues led to the relatively low level dissident movement within the GDR.
Everyday life was pervaded by the party ideology, the individual was disregarded and the regime elevated above it. Virtually no corner of life was left untouched by the influence of the party and its ‘guard dog’, the Stasi. The security apparatus infiltrated and manipulated the educational sector; determining who could study at university and which subjects were ‘suitable’ for academic research and teaching, with almost a quarter of staff at the East German Humboldt university in the Stasi’s employ. All communication in and out of the communist state was monitored and intercepted by the MfS. In East Berlin, 25 phone stations enabled the tapping of up to 20,000 calls simultaneously. Figures show that 2,300 telegrams a day were read by the Stasi in 1983 alone. Interception of packages also proved to be a favoured method of state security, and one that provided rich dividends. Estimates taken from surviving archival material put the figure of currency seized by the MfS as equalling 32.8 million DM. (Figures taken from Mike Dennis, The Stasi: Myth and Reality, Longman: 2003)
Life was controlled by the MfS and the SED, with all methods utilised to prevent contact with the western world. People adapt however, and East Germans developed ‘coping mechanisms’. Secret codes and gestures were developed to indicate when known Stasi informers or operatives were nearby. Even today the terror of the MfS remains a powerful force in the everyday life of former GDR citizens, acting as a kind of ‘wall in the mind’. Claudia Rusch, the daughter of an East German dissident, leaves no doubt as to the GDR’s status as a police state in her description of life under the former regime:
“That was the real strength of the state security; to produce the effect that millions of people behaved towards one another with anxiety, self-control and suspicion. They ensured that if you told a political joke you automatically lowered your voice. Anticipatory obedience spread through every sinew of society and intimidated a whole nation”.
(Claudia Rusch, quoted in Mary Fulbrook, The People’s State, Yale University Press: 2005)
The people of East Germany were browbeaten by the Stasi’s propagation of fear, its far reaching tentacles spread through society in the form of informers hidden in plain sight. Any person deemed of particular interest had an MfS file which would contain an almost minute-by-minute account of the suspect’s life, from which the MfS could create any motive for action they deemed necessary. Fear pervaded all aspects of life in the GDR, the population cowed by the threat of MfS reprisal, unable to build the foundations for an opposition movement. In the pursuit of blanket surveillance of the population, the Stasi gained a terrifying level of power over the East German people and could manipulate them at their whim. Agents of the state were everywhere, in the workplace, the classroom and even sleeping in the same bed. In this way conformity was enforced through implicit, rather than explicit terror.
About the Author:
David Cook has just completed his BA (Hons) in History at Swansea University, graduating with first-class honours in July 2011. During the final year of his study he specialised in the study of Cold War Eastern Europe. Following university David plans to travel, before eventually undertaking a Masters degree in History.
For more information on this topic see:
Timothy Garton Ash, The File: A Personal History, (London: Atlantic Books, 2009)
Mary Fulbrook, Anatomy of a Dictatorship: Inside the GDR 1949-1989, (Oxford: Oxford University Press, 1995)
Mary Fulbrook, The People’s State: East German Society from Hitler to Hoenecker, (London:YaleUniversity Press, 2005)
Anna Funder, Stasiland: Stories From Behind the Berlin Wall, (London: Granta Books, 2004)
Robert Gellately, Denunciations in 20th Century Germany: Aspects of Self-Policing in the Third Reich and the German Democratic Republic
OPFER: MORD-DROHUNG DER NEO-STASI AN UNS WG STASI-LISTE MIT KLARNAMEN
TOP-SECRET – The FBI – Closing in on the Barker/Karpis Gang
 |
|---|
| The Barkers were heavily armed at a cottage near Lake Weir, Florida where they engaged in a shootout with Bureau agents in 1935. The weapons above were seized following the gunfight. |
In January 1935—77 years ago this month—more than a dozen Bureau agents surrounded a quaint two-story home on Lake Weir, Florida. Within moments, a fierce shoot-out erupted. It didn’t go well for the heavily armed criminals inside.

The Bremer Investigation A total of 25 individuals were convicted in connection with the Edward Bremer kidnapping, including seven who harbored members of the Barker/Karpis gang. Six of those convicted received life sentences, and three were killed resisting arrest, including Russell Gibson, Fred Barker (above), and Kate “Ma” Barker. |
|---|
For the Bureau of Investigation—just six months away from being renamed the FBI—the firefight was a continuation of a busy year of battling gangsters. In 1934, notorious public enemies like John Dillinger, “Pretty Boy” Floyd, and “Baby Face” Nelson had fallen at the hands of Bureau agents. Heading into 1935, the top priority was to put a dangerous gang—led by the wily Alvin “Creepy” Karpis and a pair of Barker brothers—out of business.
The gang got the Bureau’s attention through two high-profile kidnappings. The second targeted a wealthy banker named Edward George Bremer, Jr., who was snatched in St. Paul, Minnesota on January 17, 1934. Bremer was released three weeks later after his family paid $200,000 in ransom. Although he couldn’t identify the culprits, Bremer provided many clues. A key break came when the fingerprint of Arthur “Doc” or “Dock” Barker, a known criminal, turned up on an empty gas can found by a local police officer along the kidnapping route. Soon, a number of Barker’s confederates—including his brother Fred, Karpis, Harry Campbell, Fred Goetz, Russell Gibson, Volney Davis, and others—were linked to the crime.
The hunt was on, but the gang had a head start. They had split up and begun crisscrossing the country—with some even fleeing to Cuba. Three went as far as to undergo back-room plastic surgeries to conceal their fingerprints and identities. Others passed the ransom loot back and forth and looked for ways to launder the bills.
 |
|
|---|---|
| View Gallery |
In late September, Fred Barker and Campbell registered under fake names at the El Commodore Hotel in Miami. Joining them was Fred’s mother—Kate “Ma” Barker, who was known to help her criminal sons. When Fred asked for a quiet place to live, the hotel manager told him of a friend’s cottage for rent on the nearby Lake Weir. The Barkers moved there in November.
In December, Doc Barker was tracked by Bureau investigators to a home in Chicago. On January 8, Doc was arrested without incident. Later that night, several associates of Russell Gibson were also apprehended. Heavily armed and wearing a bullet-proof vest, Gibson tried to fight it out but was mortally wounded. Searching the apartment, agents found powerful firearms and loads of ammunition. And, tellingly, a map of Florida—with Lake Weir circled. Agents soon located the cottage hideout.
Shortly after 5 a.m. on January 16, 1935, a group of agents led by Earl Connelly surrounded the house and demanded the Barkers’ surrender. No response. They waited 15 minutes and called again. Again, no answer. Following another call for surrender and more silence, agents shot some tear gas grenades at the windows of the house. Someone in the house shouted, “All right, go ahead,” then machine-gun fire blasted from the upstairs window.
The agents responded with volleys of their own; more gunfire erupted from the house. Over the next hour, intermittent shots came from the home, and agents returned fire. By 10:30 a.m., all firing had stopped. Both Ma and Fred, it was soon learned, were dead.
The Barkers were history, but the cunning Karpis was still on the loose. How we caught up with him is another story that we’ll tell in the coming months.
BETREFF: Stellen Sie sich vor Frau “Beate P” eng verwandt mit ihrem Wettbewerber Thomas P. “ermittelt seit Jahren gegen Sie!
Liebe Leser,
seit geraumer Zeit versucht eine Staatsdienerin gegen mich vorzugehen..
Seit mindestens 2006 wird all dies gegen mich (die “GoMoPa” Stalker gegen mich Seiten) kolportiert in self-full-filling prophecy
Beate P.*** (Name auf Anfrage anonymisiert).
Ich habe meine Gesellschaftsanteile an der Immobilien Zeitung GmbH an Thomas P*** (selber Name) verkauft.
(Name auf Anfrage anonymisiert).
Seitdem wir die STASI-Connections aufgedeckt haben, geht die betreffende Staatsdienerin. gegen mich verstärkt vor.
Zu dieser Stunde gebe ich Ihnen hierzu weiter keinen Kommentar.
Sie steht mutmasslich in enger Verbindung mit RA Resch, dessen STASI-Verbindungen offenkundig sind und selbst von ihm bestätigt wurden.
Sie hat gleichzeitig seit langem Kenntnis von allen Stalker Sites gegen mich und allen anderen miesen Tricks, den Rufmorden auch gegen viele andere Unternehmen und unternimmt mutmasslich nichts hierzu. Damit deckt sie mutmasslich die Täter und ermöglicht Ihnen mutmasslich weitere Verbrechen.
Bernd Pulch, Magister Artium, Publizistik, Germanistik, Komparastistk,
Für Rückfragen stehe ich Ihnen jederzeit zur Verfügung.
TOP-SECRET – Information Operations, Electronic Warfare, and Cyberwar

This report describes the emerging areas of information operations, electronic warfare, and cyberwar in the context of U.S. national security. It also suggests related policy issues of potential interest to Congress. For military planners, the control of information is critical to military success, and communications networks and computers are of vital operational importance. The use of technology to both control and disrupt the flow of information has been generally referred to by several names: information warfare, electronic warfare, cyberwar, netwar, and Information Operations (IO). Currently, IO activities are grouped by the Department of Defense (DOD) into five core capabilities: (1) Psychological Operations, (2) Military Deception, (3) Operational Security, (4) Computer Network Operations, and (5) Electronic Warfare. Current U.S. military doctrine for IO now places increased emphasis on Psychological Operations, Computer Network Operations, and Electronic Warfare, which includes use of non-kinetic electromagnetic pulse (EMP) weapons, and nonlethal weapons for crowd control. However, as high technology is increasingly incorporated into military functions, the boundaries between all five IO core capabilities are becoming blurred.
DOD has noted that military functions involving the electromagnetic spectrum take place in what is now called the cyber domain, similar to air, land, and sea. This cyber domain is the responsibility of the new Air Force Cyber Command and includes cyberwarfare, electronic warfare, and protection of U.S. critical infrastructure networks that support telecommunications systems, utilities, and transportation.
…
Control of information has always been part of military operations, and the U.S. Strategic Command views information operations as a core military competency, with new emphasis on (1) use of electromagnetic energy, (2) cyber operations, and (3) use of psychological operations to manipulate an adversary’s perceptions. Department of Defense (DOD) officials now consider cyberspace to be a domain forwarfare, similar to air, space, land, and sea.
The DOD views information itself as both a weapon and a target in warfare. In addition, Psychological Operations (PSYOP) provides the ability to rapidly disseminate persuasive information to directly influence the decisionmaking of diverse audiences, and is seen as a means for deterring aggression, and important for undermining the leadership and popular support for terrorist organizations. However, new technologies for military IO also create new national security policy issues, including (1) consideration of psychological operations used to affect friendly nations or domestic audiences; and (2) possible accusations against the U.S. of war crimes if offensive military computer operations or electronic warfare tools severely disrupt critical civilian computer systems, or the systems of non-combatant nations.
…
At the same time, the civilian Al Jazeera news network, based in Qatar, beams its messages to well over 35 million viewers in the Middle East, and is considered by many to be a “market competitor” for U.S. PSYOP. Terrorist groups can also use the Internet to quickly place their own messages before an international audience. Some observers have stated that the U.S. will continue to lose ground in the global media wars until it develops a coordinated strategic communications strategy to counter competitive civilian news media, such as Al Jazeera.
…
Domination of the Electromagnetic Spectrum.
DOD now emphasizes maximum control of the entire electromagnetic spectrum, including the capability to disrupt all current and future communication systems, sensors, and weapons systems. This may include: (1) navigation warfare, including methods for offensive space operations where global positioning satellites may be disrupted; or, (2) methods to control adversary radio systems; and, (3) methods to place false images onto radar systems, block directed energy weapons, and misdirect unmanned aerial vehicles (UAVs) or robots operated by adversaries.
…
Homeland security reportedly will also be a large part of the Cyber Command’s responsibility, including protection of telecommunications systems, utilities, and transportation. Several issues to be considered may include: (1) what kind of educational skills, technical skills, and training are needed for staff at the Cyber Command; and (2), what kind of career path can be offered to those in the Air Force who want to participate in defending the new cyber domain.
MAULKORB BEI DER STASI ? !
BUCHT-TIP – aus Georg Herbstritt Alles rechtens bei der Stasi? Die Strafverfahren bundesdeutscher Gerichte gegen MfS-Mitarbeiter
Das Ministerium für Staatssicherheit (MfS) hat entscheidend dazu beigetragen, dass vielen DDR-Bürgern grundlegende Menschen- und Bürgerrechte vorenthalten blieben, und MfS-Mitarbeiter haben sich in großem Umfang strafbarer Methoden bedient. Das ist weitgehend unstrittig. Doch als die MfS-Straftaten in den neunziger Jahren endlich juristisch geahndet werden konnten, war die Enttäuschung am Ende groß: Gerade einmal 251 Personen wurden wegen Straftaten angeklagt, die sie im Auftrag des MfS begangen hatten; unter ihnen 182 hauptamtliche und 42 inoffizielle MfS-Mitarbeiter. Zwei Drittel der Strafverfahren endeten entweder mit Freispruch oder ohne ein Urteil, lediglich ein Drittel der Angeklagten wurde verurteilt, wobei die Strafen äußerst milde ausfielen. Nur ein MfS-Offizier sowie zwei inoffizielle Mitarbeiter (IM) mussten eine Haftstrafe antreten; ersterer wegen Beihilfe zum Mord, ein IM wegen dreifachen Mordversuchs, ein anderer IM wegen Beihilfe zum versuchten Mord.
„Die strafrechtliche Aufarbeitung des MfS-Unrechts ist zu großen Teilen erfolglos gewesen“, lautet denn auch das Fazit von Roland Schißau in seinem hier zu besprechenden Buch, und er schreibt weiter: „Das Unternehmen, die Taten des MfS mit den Mitteln des Strafrechts umfassend zu ahnden, hat sich trotz umfangreicher Strafverfolgungsaktivitäten der Ermittlungsbehörden als nicht durchführbar erwiesen.“
Die Enttäuschung hierüber führt immer wieder zu unsachlicher und unfundierter Kritik an den Justizbehörden. Wer sich mit solcher Polemik nicht zufrieden geben will, sondern verstehen und begreifen möchte, warum die Justiz so und nicht anders handelte, dem sei die Arbeit von Schißau nachdrücklich empfohlen. Schißaus Arbeit entstand als Dissertation im Rahmen des groß angelegten Projekts „Strafjustiz und DDR-Unrecht“ bei den Strafrechtsprofessoren Klaus Marxen und Gerhard Werle an der Berliner Humboldt-Universität. Aus dem umfangreichen Themenkomplex der juristischen Aufarbeitung von DDR-Systemkriminalität nahm er die Deliktgruppe „MfS-Unrecht“ in den Blick. Dabei gab es faktisch Überschneidungen mit anderen Deliktgruppen des DDR-Unrechts wie den Misshandlungen in Haftanstalten, der Denunziation oder der Spionage, worauf Schißau deutlich hinweist. So bezieht er auch Anklageschriften aus den Spionagestrafverfahren in seine Untersuchung und seine Statistik mit ein, konkret die Anklagen gegen Günther Kratsch, weil diesem neben der MfS-Hauptabteilung II (Spionageabwehr) auch die Abteilung M (Postkontrolle) unterstand, Horst Männchen, der als Leiter der Hauptabteilung III (Funkaufklärung) auch für Telefonüberwachung verantwortlich war, sowie die früheren Leiter der Hauptabteilung VIII (Ermittlungen), Albert Schubert und Karli Coburger, wegen den von Mitarbeitern ihrer Abteilung begangenen Mordversuche außerhalb der DDR. Unklar bleibt, warum das 1997 ergangene Urteil gegen den langjährigen Leiter der Hauptverwaltung A (HV A) des MfS (Auslandsspionage), Markus Wolf, nicht einbezogen wird. Denn Wolf wurde 1997 unter anderem wegen der unerlaubten Festnahme Georg Angerers im Jahr 1959 verurteilt, und der Fall Angerer wird in Schißaus Buch als ein Beispiel für MfS-Unrecht vorgestellt.
Schißaus Arbeit ist klar strukturiert. Einleitend präsentiert er einige Basisdaten zum MfS, stellt die verschiedenen Justizbehörden vor, die mit der Ahndung von DDR-Unrecht befasst waren und erörtert die allgemeinen rechtlichen Voraussetzungen der Strafverfolgung. Sodann behandelt er kapitelweise die verschiedenen Fallgruppen von MfS-Straftaten: Abhören von Telefongesprächen, Öffnen von Briefsendungen, Entnahme von Geld- und Wertgegenständen aus Postsendungen, heimliches Betreten fremder Räumlichkeiten, Preisgabe von Informationen aus Mandats- und Patientenverhältnissen, Tötungsdelikte, Verschleppungen aus der Bundesrepublik in die DDR, Verrat und Denunziation, Drangsalierungen zur Aussageerzwingung, unerlaubte Festnahmen, Repressalien gegenüber Ausreiseantragstellern sowie sonstige Taten. In jedem Kapitel geht er nach einem einheitlichen Muster vor: Er skizziert zunächst konkrete, historische Fälle, also „Tathandlungen“, beschreibt dann den Verlauf der Strafverfahren, um dann ausGeorg
Herbstritt
Alles rechtens bei der Stasi?
Die Strafverfahren bundesdeutscher Gerichte gegen MfS-Mitarbeiter
Roland Schißau: Strafverfahren wegen MfS-Unrechts. Die Strafprozesse bundesdeutscher Gerichte gegen ehemalige Mitarbeiter des Ministeriums für Staatssicherheit der DDR (= Berliner Juristische Universitätsschriften, Strafrecht, Bd. 22.)
Berlin: Berliner Wissenschaftsverlag, 2006,
361 Seiten. 44,65 EUR. ISBN 978-3-8305-1140-3.
71
H
orch und Guck 1/2008 | Heft 59
führlich die juristische bzw. strafrechtliche Entscheidungsfindung darzulegen. Dem schließt sich jeweils ein Kommentar des Verfassers an. Verschiedene Statistiken am Ende des Bandes ermöglichen eine schnelle Übersicht über die Strafverfahren; ihr Wert besteht auch darin, dass sie die Daten aus den einzelnen Bundesländern unter einheitlichen Kriterien zusammenführen.
Insgesamt wird das Buch den selbst gesteckten Zielen gerecht: Tatsachengrundlagen zu bieten sowie die Justizaktivitäten in einer für dieses Thema bislang nicht vorgelegten Vollständigkeit offenzulegen und kritisch zu würdigen, um die Leser in die Lage zu versetzen, sich ein eigenes Urteil über diese Fragen zu bilden.
Bemerkenswert ist vor allem die offene und direkte Art, in der der Autor Gerichtsentscheidungen kritisiert und mitunter direkt als „falsch“ bezeichnet und verdeutlicht, welche Entscheidung die bestehende Rechtslage eigentlich erfordert hätte. Mehrfach thematisiert er auch die markanten regionalen Unterschiede bei der Strafverfolgung und richtet an die besonders zurückhaltenden Staatsanwaltschaften in Brandenburg und Mecklenburg-Vorpommern die Frage, ob sie nicht das berechtigte Interesse der Opfer an einer gerichtlichen Befassung mit den MfS-Taten vernachlässigten. In vielen Fällen kann er aber auch nur die rechtlichen Probleme erläutern, die einer Strafverfolgung im Wege standen: So konnten verschiedene Delikte wie Öffnen von Briefsendungen oder heimliches Betreten der Wohnung einfach deshalb nicht geahndet werden, weil die Justiz in diesen Fällen nur dann aktiv werden darf, wenn die Opfer innerhalb einer sehr kurzes Frist selbst einen Strafantrag stellen, wozu es aber bis auf eine Ausnahme nicht kam. Andere Delikte wie die Verletzung des Post- und Fernmeldegeheimnisses waren nach DDR-Strafgesetzbuch nur für Postmitarbeiter mit Strafe bedroht. Hinzu kamen überlastete Gerichte und nicht fachkundige Richter, während das Problem der Verjährung faktisch kaum eine Rolle spielte.
Deutlich wird aus all dem, dass die geringe Zahl der Verurteilungen keineswegs einen Freibrief für die ehemaligen MfS-Mitarbeiter darstellt. Den wenigen Urteilen kommt nach Ansicht von Schißau deshalb vor allem symbolische Bedeutung zu, weil sie die auch juristisch begründete Aussage erlauben, dass sich das MfS strafbarer Methoden bediente.
Als Jurist erkennt Schißau den Wert der Strafverfahren auch darin, dass eine gerichtliche Klärung bestimmter Sachverhalte herbeigeführt wurde, was den gesamten Aufarbeitungsprozess voranbrachte, auch wenn es kaum zu Urteilen kam. Beispielsweise war das Oberlandesgericht (OLG) Dresden zu der Entscheidung gelangt, dass MfS-Mitarbeiter keinen „Verbotsirrtum“ für sich beanspruchen könnten; zumal als Hochschulabsolventen seien sie sehr wohl in der Lage gewesen, die Rechtswidrigkeit ihres Handelns zu erkennen, so das OLG Dresden. Schißau bescheinigt der Justiz in seinem Fazit letztlich ein rechtlich einwandfreies Vorgehen ohne politisch motivierten Verfolgungseifer; insbesondere seien keine Sonderstraftatbestände konstruiert worden. Künftige Diskussionen über den Einsatz des Strafrechts könnten nun auf einer fundierten sachlichen Grundlage geführt werden.
Für den juristischen Laien bietet Schißaus Buch die Möglichkeit, juristische Argumentationsgänge zu einem wichtigen zeithistorischen Thema kennenzulernen. Manche Ausführungen sind indes schwer verständlich, weil Schißau die Inhalte der Paragraphen, mit denen er argumentiert, nicht erläutert. Lediglich die einschlägigen Bestimmungen aus der Strafprozessordnung und dem Strafgesetzbuch der DDR druckt er im Anhang ab; dasselbe hätte man sich für die bundesdeutschen Vorschriften gewünscht. Äußerst lückenhaft ist das Sach- und Namensregister am Ende des Bandes ausgefallen. Bedauerlich ist, dass sich das Buch ausschließlich auf juristischem Terrain bewegt und die Möglichkeiten nicht nutzt, die sich aus der Nähe zur Zeitgeschichtsschreibung ergeben. Praktisch wirkt sich das unter anderem dahingehend aus, dass die zeithistorische Literatur zur MfS-Geschichte weitestgehend unberücksichtigt bleibt. Einige Feststellungen über das MfS sowie über zeithistorische Sachverhalte sind deshalb unzutreffend; beispielsweise kann man der Postkontrolle des MfS nicht bescheinigen, dass sie „vornehmlich Aufgaben der Spionageabwehr“ wahrnahm.
Parallel zu Schißaus Dissertation erschien im Rahmen des Projekts „Strafjustiz und DDR-Unrecht“ ein Doppelband mit mehreren einschlägigen Anklageschriften und Gerichtsurteilen. Es wäre wünschenswert, wenn auch die übrigen Anklageschriften und Gerichtsurteile, die im Rahmen des Projekts zusammengetragen wurden, der zeitgeschichtlichen Forschung zur Verfügung gestellt würden. Von einem interdisziplinären Ansatz könnten Juristen und Historiker gleichermaßen
profitieren. GH
2.440 Seiten Informationen zu einem Spott-Preis!
Die HORCH-UND-GUCK-CD-ROM mit den Heften 1 – 30 (1/1992 – 2/2000)
Die CD-ROM kostet 20,– € (für Abonnenten 10,– €, für Institutionen 50,– €)
und kann bei uns bestellt werden:
H
ORCH UND GUCK, Winsstraße 60, 10405 Berlin
Telefon: +49 (0) 30 / 88 55 21 70, E-Mail: info@buergerkomitee.org
Georg Herbstritt,
geb. l965 in Schluchsee. Historiker,
l994-98 wiss. Mitarbeiter des LStU in Schwerin und seit l999 in der Abt. Bildung und Forschung der BStU. Zuletzt publ.: Bundesbürger im Dienst der DDR-Spionage, Göttingen 2007.
Scheinberg-Indictment-Anklageschrift im Original: MANHATTAN U.S. ATTORNEY CHARGES PRINCIPALS OF THREE LARGEST INTERNET POKER COMPANIES WITH BANK FRAUD, ILLEGAL GAMBLING OFFENSES AND LAUNDERING BILLIONS IN ILLEGAL GAMBLING PROCEEDS
After the indictment of the founder of PokerStars, Isai Scheinberg, by the U.S. Department of Justice on “Black Friday,” many in the business and poker communities are asking, “Who is Isai Scheinberg?” An article in a Canadian newspaper attempts to answer that question.
The Toronto Globe and Mail presented an article written by Colin Freeze that covers much of what is known about Scheinberg. Freeze looks at the Scheinbergs as an “Internet Age equivalent of the Bronfmans, the Montreal clan who famously parlayed U.S. Prohibition laws into a billion-dollar booze business.” The Bronfmans owned Seagram’s during the Prohibition Era of the early 20th century.
Freeze details the April 15 indictment of Scheinberg and Paul Tate of PokerStars as well as the founders of Full Tilt Poker and Absolute Poker before delving into what effect the shutdown of poker in the United States will mean for the company.
“Win or lose, PokerStars’ luck has already soured fast,” Freeze wrote in his article. “Gone already are millions of paying American customers, a number of lucrative television contracts, and the nascent partnership with Wynn Resorts. Operations in other jurisdictions – including Europe, where it is partly licensed, and Canada, where it is not – should help PokerStars weather the U.S. shutdown, albeit in a diminished form.”
So what is known about Scheinberg and how did he reach such lofty heights with PokerStars? According to the Globe and Mail, Scheinberg got his start in the computer industry as a programmer with IBM in Canada. While working in the computer industry, Scheinberg showed an interest in poker.
According to the Hendon Mob database, Scheinberg competed at the 1996 World Series of Poker, earning a 25th place finish in a $2,500 No Limit Hold’em event. Two years later, he made the final table in a $1,000 No Limit Hold’em tournament at the United States Poker Championships in Atlantic City. Scheinberg would eventually bow out of the tournament in eighth place against a table that featured poker pros like Men “The Master” Nguyen and Kevin Song.
Perhaps these brushes with the poker world were what planted the seed for what would become Scheinberg’s greatest success – or his greatest pain. As the 21st century dawned, Scheinberg created PYR Software, a company that Forbes described in a February 2010 article as “a software development company that helps customers worldwide to retain industry leadership.” The real reason for the development of PYR Software, however, was to facilitate an idea in Scheinberg’s head.
In March 2001, PokerStars went active, offering internet poker to a quietly growing worldwide market. Over the next five years, the gaming site became one of the major players in the online poker industry. By 2006, the growth of the company led Scheinberg to float the idea of holding an initial public offering (IPO). Political activity in that same year, however, changed his mind and led PokerStars onto the path it has reached today.
The passage of the Unlawful Internet Gambling Enforcement Act in 2006 shut down the IPO rumblings, as PokerStars continued to offer its wares to American customers. The reason for this was simple: with the major players in the industry such as PartyPoker and 888 leaving the market due to their publicly traded status, PokerStars would be able to snare a sizeable chunk of the American market.
Over the past five years, PokerStars became the preeminent leader in online poker, with a reported value of around $10 billion.
The 65-year-old Scheinberg and his family do not actively court media attention, although Scheinberg has occasionally stepped to the poker tables. In 2008, he played in one of the preliminary events during the PokerStars European Poker Tour Grand Final. In a €1,000 No Limit Hold’em tournament, Scheinberg finished eighth, but many in the audience had no clue that the founder of the site they played at was in such close proximity.
The future for Scheinberg is murky at best. Due to the indictment, Scheinberg and his family may never set foot on North American soil because of extradition treaties among the U.S., Mexico, and Canada. MANX Radio, the radio station of the Isle of Man where PokerStars’ headquarters are located, reports that the legal team for PokerStars is already ramping up, stating to a reporter from the station that they will “robustly” defend Scheinberg and Paul Tate against the charges in the United States.
Letztes Jahr haben die US-Behörden bekanntlich die Webseiten von PokerStars, Full Tilt, UB und Absolute Poker gesperrt. Es wurde Anklage gegen die Betreiber und deren Mitarbeiter erhoben. PokerOlymp hat die 51-seitige Anklageschrift unter die Lupe genommen und erklärt den Lesern, was genau die Behörden den Online-Pokerräumen vorwerfen.
 Preet Bhrara, Verfasser der Anklage
Preet Bhrara, Verfasser der Anklage
Juristisch gesehen ist eine Anklageschrift das Dokument, mit der die Strafverfolgungsbehörden einen Fall vor Gericht bringen.
Sie hat grundsätzlich zwei Funktionen, zum einen den oder die Angeklagten über die ihnen vorgeworfenen Taten zu informieren und zum anderen die Festlegung des Prozessgegenstandes in sachlicher und personaler Hinsicht.
Die vorgeworfenen Delikte und Handlungen
Zum Vorwurf wird den Angeklagten die Unterwanderung des Unlawful Internet Gambling Enforcement Act von 2006, das Betreiben illegaler Glücksspiel-Unternehmen, organisierter Bankbetrug und organisierte Geldwäsche gemacht. Hierfür sind Geldstrafen und Gefängnisstrafen bis zu 30 Jahre vorgesehen.
Bereits in der Einleitung macht United States Attorney Preet Bhrara klar, worum es geht. Er benennt zunächst PokerStars, Full Tilt und AP/UB als die führenden Online-Poker-Unternehmen in den USA seit 2006. Die Unternehmen hätten mindestens von November 2006 bis März 2011 agiert. Als Verantwortliche benennt er die Angeklagten Isai Scheinberg, Raymond Bitar, Scott Tom, Brent Beckley, Nelson Burtnick, Paul Tate, Ryan Lang, Bradley Franzen, Ira Rubin, Chad Elie und John Campos.
Die angeblichen Methoden der Täuschung
Dann geht es direkt ans Eingemachte: Der Staatsanwalt führt aus, dass in den USA seit Einführung des UIGEA den Banken verboten sei, Transaktionen im Zusammenhang mit Online-Glücksspiel durchzuführen. Die Angeklagten hätten im Tatzeitraum betrügerische Methoden verwendet, diese Restriktionen zu umgehen und so mehrere Milliarden Dollar von US-Bürgern aus illegalem Glücksspiel erhalten. Zu diesem Zweck seien US-Banken und andere Stellen direkt und indirekt getäuscht worden.
Hierzu hätten sich die Pokerräume unter anderem so genannter ‘payment-processors’ bedient, deren Aufgabe es gewesen sei, die wahre Natur die Geldströme gegenüber den Banken zu verschleiern. Hierzu seien Scheinfirmen und eigens zu dem Zweck erstellte Webseiten benutzt worden. Die Angeklagten Ryan Lang, Bradley Franzen, Ira Rubin und Chad Elie hätten als solche “payment processors” im Auftrag der Gaming-Unternehmen fungiert.
Dann listet die Anklage über mehrere Seiten detailliert die Angeklagten auf und welche Funktion sie bei den jeweiligen Pokerräumen ausüben. Der Fokus liegt hier insbesondere auf Isai Scheinberg, der als Gründer von PokerStars benannt wird und auf Raymond Bitar, dem Gründer von Full Tilt.
PartyPoker und der UIGEA
Es wird ausführlich die Einführung des UIGEA im Jahr 2006 beschrieben und dass es seitdem ein “federal crime” sei, als Online-Glücksspiel-Unternehmen wissentlich Zahlungen zu empfangen oder weiterzuleiten, die aus illegalem Glücksspiel stammen oder für dieses bestimmt sind.
Es wird auch erwähnt, dass der größte damalige Pokerraum wegen dem UIGEA seine Dienste in den USA eingestellt hatte. Gemeint ist PartyPoker, obwohl das Unternehmen in der Anklage nicht ausdrücklich benannt wird. Die jetzt im Fokus der Ermittlungen stehenden Pokerräume hätten aber weitergemacht, so hätte beispielsweise Absolute Poker damals verlauten lassen, dass sie “eine private Organisation seien, die gemäß ihrem Geschäftsmodell viel Flexibilität und Kreativität genieße.”
Die Methoden im Detail
Dann geht es weiter und es werden die Methoden beschrieben, die PokerStars, Full Tilt und UB/AP angeblich dazu verwendeten, die Banken über die illegale Natur der Geldtransaktionen hinwegzutäuschen und die Geldströme aus den USA heraus hin zu den Firmensitzen in Übersee zu leiten.
Es ist zum einen die Rede davon, dass Visa und Mastercard spezifische “transaction codes” für Online-Gambling-Vorgänge eingeführt hätten. So sei es für die Banken leicht gewesen, Vorgänge, die mit Online-Glücksspiel zu tun haben, zu blockieren. Die Angeklagten hätten dies aber umgangen, indem sie den Vorgängen falsche “transaction codes” zugeordnet hätten. Hierdurch hätten sie die Banken über die wahre Natur der Vorgänge getäuscht. Allein zu diesem Zweck sei ein Netz von Scheinfirmen, z. B. Online-Blumenläden oder Online-Tierfutter-Händler, aufgebaut worden.
Von Zeit zu Zeit seien diese Scheinfirmen jedoch entdeckt worden. Für diesen Fall hätten die Angeklagten jedoch zahllose Ersatzunternehmen parat gehabt, z. B. http://www.petfoodstore.biz oder http://www.beddingsuperstore.tv, die bei Bedarf eingesprungen seien. Daneben seien so genannte “pre-paid credit cards” zu Verschleierung benutzt worden. Diese konnte man angeblich ohne verdächtigen “transaction code” aufladen.
Auch im Wege des “e-check processing” seien Zahlungen mit Hilfe von Scheinfirmen verschleiert worden. Die Scheinfirmen hätten Konten eröffnet und so unrechtmäßig den Geldfluss zwischen den Online-Gambling-Unternehmen und den Banken ermöglicht. Vor allem die angeklagten “payment-processors” Ryan Lang und Bradley Franzen hätten hierfür von den Online-Pokerräumen hohe Beträge erhalten. Auch der Angeklagte Ira Rubin hätte beispielsweise Mitte 2008 dutzende Scheinfirmen aufgebaut, darunter Fahrrad-, Juwelen-, Bekleidungs- und Golfhändler.
Teilweise hätten die Spieler das gemerkt und seien auf die ‘komischen’ Namen der Scheinhändler auf ihren Kontoauszügen aufmerksam geworden. So hätten zwei Spieler im März 2009 sogar versucht, bei ‘oneshopcenter.com’ und ‘mygolflocation.com’ Waren zu erwerben. Hierauf hätten sie Antwort von PokerStars bekommen und nicht von den betreffenden Websites.
Daneben werden in der Anklage noch weitere angeblich benutzte Techniken zur Verschleierung der illegalen Geldtransaktionen beschrieben. Besonders schwer wiegt der Vorwurf, es seien “Multi-Millionen-Investitionen” geflossen, um Banken unter eigene Kontrolle zu bringen.
Die Konsequenzen
Im Ergebnis sollen die Angeklagten mehrere Milliarden Dollar an den Staat zahlen. Es werden auch detailliert die Konten beschrieben, auf denen das Geld momentan zu finden ist. Vor allem die Vorwürfe organisierte Geldwäsche und organisierter Bankbetrug wiegen sehr schwer. Für diese Delikte sieht das amerikanische Rechtssystem hohe Strafen vor, bei Geldwäsche ist gibt es maximal 20, bei Bankbetrug bis zu 30 Jahre Gefängnis.
Die Höhe der in Rede stehenden Summen, der lange Tatbegehungszeitraum und die hohe Strafandrohung machen den Ernst der Lage deutlich. Kennern des amerikanischen Rechtssystems zufolge, ist in dem Verfahren nicht mit besonders viel Milde des Staates zu rechnen. Immerhin ist Anurag Dikshit als einer der Gründer von PartyPoker seinerzeit zur Zahlung einer Strafe in Höhe von 300 Millionen Dollar verurteilt worden. Und das obwohl PartyPoker seinen Betrieb in den USA nach dem Inkrafttreten des UIGEA nachweislich eingestellt hatte. Lange war unklar, ob der Milliardär nicht sogar zusätzlich eine Gefängnisstrafe antreten muss.
Wir möchten darauf hinweisen, dass dies nur eine grobe Übersicht der 51-seitigen Anklageschrift darstellt, die notwendigerweise nicht alle Aspekte im Detail abdecken kann. Wir hoffen dennoch, unseren Lesern die Tatvorwürfe etwas näher gebracht zu haben.
HIER KÖNNEN SIE DIE ANKLAGESCHRIFT IM ORIGINAL DOWNLOADEN
UNCENSORED – FEMEN.— Woman Power.
CONFIDENTIAL – U.S. Army FM 3-13 Inform and Influence Activities Draft Manual

INFORM AND INFLUENCE ACTIVITIES DEFINED
1-1. Inform and influence activities is the integration of designated information-related capabilities in order to synchronize themes, messages, and actions with operations to inform U.S. and global audiences, influence foreign audiences, and affect adversary and enemy decisionmaking.
INTEGRATE INFORMATION-RELATED CAPABILITIES
1-2. All assets and capabilities at a commander’s disposal have the capacity to inform and influence selected audiences to varying degrees. While specific assets termed as “information-related capabilities” are information-centric in mission and purpose, others are standard capabilities that inform and influence officers use for planning to support commanders’ information strategy and mission objectives. The primary information-related capabilities that support inform and influence activities typically include, but are not limited to, public affairs, military information support operations, combat camera, Soldier and leader engagement, civil affairs, cyber electromagnetic activities, counterintelligence, operations security, military deception, and others so designated by a commander. In addition to the primary information-related capabilities, there are operational capabilities not solely designed to inform or influence that commanders can designate to assist in achieving mission objectives, such as maneuver forces, engineers, and medical units. Success depends on commanders and staffs effectively employing all available operational assets to best shape the information environment.
SYNCHRONIZE THEMES, MESSAGES, AND ACTIONS WITH OPERATIONS
1-3. Commanders synchronize themes, messages, and actions with operations to inform and influence the various audiences within their area of operations and area of interest. Audiences include groups, organizations, and individuals. Synchronization of themes, messages, and actions promotes and shapes the attitudes, values, beliefs, and behaviors of the audiences in the area of operations while marginalizing or defeating adversary or enemy information efforts towards the same. Synchronization supports the commander’s operational goals by aligning words with deeds to avoid message confusion or information fratricide. Information fratricide is the result of employing information-related capabilities operations elements in a way that causes effects in the information environment that impede the conduct of friendly operations or adversely affect friendly forces.
1-4. Soldiers’ actions are among the most potent factors in successfully executing inform and influence activities. Visible actions coordinated with carefully chosen, truthful words influence audiences more than uncoordinated or contradictory actions and words. All audiences—local and regional as well as adversary and enemy—compare the friendly force’s message with its actions. Consistency contributes to the success of friendly operations by building trust and reinforcing credibility. Conversely, if actions and messages are inconsistent, friendly forces lose credibility. Loss of credibility makes land forces vulnerable to enemy and adversary propaganda or counter-messaging and places Army forces at a disadvantage. Aligning inform and influence activities with the overall operation ensures that messages are consistent with forces’ actions to amplify the credibility of those messages.
…
MILITARY DECEPTION
3-12. Military deception involves actions executed to deliberately mislead adversary military, paramilitary, or violent extremist organization decisionmakers. This information-related capability intends the adversary to take specific actions (or inactions) that contribute to accomplishment of the friendly mission. Military deception does not fall under the direct purview of the G-7 (S-7) but is considered a primary influencing capability of inform and influence activities. Military deception consists of counterdeception, deception in support of operations security, and tactical deception.
3-13. Counterdeception contributes to situational understanding by protecting friendly human and automated decisionmaking from adversary deception. Counterdeception strives to make Army commanders aware of adversary deception activities so they can formulate informed and coordinated responses.
3-14. A deception in support of operations security protects friendly operations, personnel, programs, equipment, and other assets against foreign intelligence security services collection. It creates multiple false indicators. These indicators confuse the adversary or enemy. Sometimes they make friendly intentions harder for the adversary or enemy intelligence gathering apparatus to interpret. Often it limits the adversary or enemy’s ability to collect accurate intelligence on friendly forces.
…
CYBER ELECTROMAGNETIC ACTIVITIES
3-16. Cyber electromagnetic activities seize, retain, and exploit advantages in cyberspace and the electromagnetic spectrum. The result enables Army forces to retain freedom of action while denying freedom of action to enemies and adversaries, thereby enabling the overall operation. For more information on cyber electromagnetic operations, see FM 3-36.
3-17. Although inform and influence activities and cyber electromagnetic activities are interrelated, each requires a uniquely different skill set to perform the required processes effectively. Ultimately both work towards contributing to affecting personal cognition, and both activities are able to mutually support one another. Therefore, cyber electromagnetic activities is considered an information-related capability that must be synchronized and integrated through inform and influence activities. Not only can it reinforce messaging efforts by providing additional means for message distribution, but it is also incorporated to execute or support offensive and defensive operational planning against an adversary or enemy audience.
DOWNLOAD ORIGINAL DOCUMENT HERE
EXPERTE KNABE – STASI-Seilschaft schiesst gegen Berliner Justizminister-Parallele zum Fall Minister Stelter
CONFIDENTIAL – Number of Corrupt Russian Officials Doubled

The number of corruption-related crimes involving top government officials and large bribes increased 100% in 2010 year-on-year, Russian Interior Minister Rashid Nurgaliyev said on Thursday.
“Criminal proceedings were launched against some 10,000 officials, one-third of them were started for taking brides,” Nurgaliyev said at a session of a Russian presidential council for combating corruption.
More than 20 top Russian officials were brought to trial last year compared with half that number in 2009. “Such cases almost doubled,” Nurgaliyev said adding that corruption remains an issue of concern despite efforts taken by the government.
Nurgaliyev said the Russian Interior Ministry plans to speed up efforts to combat corruption. He said the main focus will be made on detecting corruption-related crimes among businessmen and also ministry officials themselves.
Russian President Dmitry Medvedev launched a wholesale reform to clean up corruption but admitted earlier that his anti-corruption drive had so far yielded few practical results.
The Berlin-based non-governmental anti-corruption organization Transparency International has persistently rated Russia as one of the most corrupt nations in the world. In the 2009 Corruption Perception Index, Russia was ranked 146 out of 180 countries, with a ranking below countries like Togo, Pakistan and Libya.
President Dmitry Medvedev gave prosecutors three months to verify income declarations filed by government officials as part of his drive to stamp out Russia’s rampant corruption.
“You hear that they all have palaces in the countryside and the declarations they make” are tiny, Medvedev told a government meeting on corruption in the Kremlin today. “Let’s check it all. If there are discrepancies, prepare proposals on the accountability of these people.”
Medvedev, who called corruption a threat to national security, has pushed for government officials to make their income declarations public and wants new legislation that will dramatically increase fines for taking bribes. Russia is the world’s most corrupt major economy, according to Berlin-based Transparency International’s 2010 Corruption Perceptions Index released in October. It ranked 154th among 178 countries.
Among new proposals, bribes under 25,000 rubles ($832) will entail either a fine of 25 times to 50 times the amount, or a jail term of up to three years and a fine. Bribes of over a million rubles will carry a fine of between 80 times and 100 times the sum or a jail term of up to 15 years plus a fine.
“We have to find a way to undermine the material interest in bribe taking,” Medvedev’s aide Larisa Brycheva told reporters after the meeting. Anti-corruption amendments to more than a dozen laws will be sent to the State Duma, the lower chamber of parliament, by the end of the month, she said.
UNCENSORED – Belarus Protest Photos
![[Image]](https://i0.wp.com/cryptome.org/info/belarus-protest/pict64.jpg) Belarus plainclothes policemen detain protesters during an action “Revolution via social network” in Minsk, Belarus, Wednesday, June 29, 2011. Police in Belarus have violently quashed a peaceful anti-government rally, detaining dozens of people protesting the authoritarian regime of President Alexander Lukashenko. (Sergei Grits) Belarus plainclothes policemen detain protesters during an action “Revolution via social network” in Minsk, Belarus, Wednesday, June 29, 2011. Police in Belarus have violently quashed a peaceful anti-government rally, detaining dozens of people protesting the authoritarian regime of President Alexander Lukashenko. (Sergei Grits) |
![[Image]](https://i0.wp.com/cryptome.org/info/belarus-protest/pict63.jpg) Belarus plainclothes policemen detain a protester during an action “Revolution via social network” in Minsk, Belarus, Wednesday, June 29, 2011. Police in Belarus have violently quashed a peaceful anti-government rally, detaining dozens of people protesting the authoritarian regime of President Alexander Lukashenko. (Sergei Grits) Belarus plainclothes policemen detain a protester during an action “Revolution via social network” in Minsk, Belarus, Wednesday, June 29, 2011. Police in Belarus have violently quashed a peaceful anti-government rally, detaining dozens of people protesting the authoritarian regime of President Alexander Lukashenko. (Sergei Grits) |
![[Image]](https://i0.wp.com/cryptome.org/info/belarus-protest/pict68.jpg) Belarus plainclothes policemen detain protesters during an action “Revolution via social network” in Minsk, Belarus, Wednesday, June 29, 2011. Police in Belarus have violently quashed a peaceful anti-government rally, detaining dozens of people protesting the authoritarian regime of President Alexander Lukashenko. Belarus plainclothes policemen detain protesters during an action “Revolution via social network” in Minsk, Belarus, Wednesday, June 29, 2011. Police in Belarus have violently quashed a peaceful anti-government rally, detaining dozens of people protesting the authoritarian regime of President Alexander Lukashenko.![[Image]](https://i0.wp.com/cryptome.org/info/belarus-protest/pict69.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/info/belarus-protest/pict72.jpg) Detained protesters show V-signs as they sit in a police van during an action “Revolution via social network” in Minsk, Belarus, Wednesday, June 29, 2011. Police in Belarus have violently quashed a peaceful anti-government rally, detaining dozens of people protesting the authoritarian regime of President Alexander Lukashenko. (Sergei Grits) Detained protesters show V-signs as they sit in a police van during an action “Revolution via social network” in Minsk, Belarus, Wednesday, June 29, 2011. Police in Belarus have violently quashed a peaceful anti-government rally, detaining dozens of people protesting the authoritarian regime of President Alexander Lukashenko. (Sergei Grits) |
![[Image]](https://i0.wp.com/cryptome.org/info/belarus-protest/pict60.jpg) A detained protester showsa V-sign as he sits in a police van during an action “Revolution via social network” in Minsk, Belarus, Wednesday, June 29, 2011. Police in Belarus have violently quashed a peaceful anti-government rally, detaining dozens of people protesting the authoritarian regime of President Alexander Lukashenko. (Sergei Grits) A detained protester showsa V-sign as he sits in a police van during an action “Revolution via social network” in Minsk, Belarus, Wednesday, June 29, 2011. Police in Belarus have violently quashed a peaceful anti-government rally, detaining dozens of people protesting the authoritarian regime of President Alexander Lukashenko. (Sergei Grits) |
![[Image]](https://i0.wp.com/cryptome.org/info/belarus-protest/pict58.jpg) Belarus plainclothes policemen detain a protester during an action “Revolution via social network” in Minsk, Belarus, Wednesday, June 29, 2011. Police in Belarus have violently quashed a peaceful anti-government rally, detaining dozens of people protesting the authoritarian regime of President Alexander Lukashenko. (Sergei Grits) Belarus plainclothes policemen detain a protester during an action “Revolution via social network” in Minsk, Belarus, Wednesday, June 29, 2011. Police in Belarus have violently quashed a peaceful anti-government rally, detaining dozens of people protesting the authoritarian regime of President Alexander Lukashenko. (Sergei Grits) |
![[Image]](https://i0.wp.com/cryptome.org/info/belarus-protest/pict66.jpg) Belarus plainclothes policemen detain a protester during an action “Revolution via social network” in Minsk, Belarus, Wednesday, June 29, 2011. Police in Belarus have violently quashed a peaceful anti-government rally, detaining dozens of people protesting the authoritarian regime of President Alexander Lukashenko. (Sergei Grits) Belarus plainclothes policemen detain a protester during an action “Revolution via social network” in Minsk, Belarus, Wednesday, June 29, 2011. Police in Belarus have violently quashed a peaceful anti-government rally, detaining dozens of people protesting the authoritarian regime of President Alexander Lukashenko. (Sergei Grits) |
![[Image]](https://i0.wp.com/cryptome.org/info/belarus-protest/pict67.jpg) A Belarus plainclothes policeman, left, detains protesters during an action “Revolution via social network” in Minsk, Belarus, Wednesday, June 29, 2011. Police in Belarus have violently quashed a peaceful anti-government rally, detaining dozens of people protesting the authoritarian regime of President Alexander Lukashenko. (Sergei Grits) A Belarus plainclothes policeman, left, detains protesters during an action “Revolution via social network” in Minsk, Belarus, Wednesday, June 29, 2011. Police in Belarus have violently quashed a peaceful anti-government rally, detaining dozens of people protesting the authoritarian regime of President Alexander Lukashenko. (Sergei Grits) |
![[Image]](https://i0.wp.com/cryptome.org/info/belarus-protest/pict57.jpg) A woman protects her husband from a plainclothes policeman, left, during an action “Revolution via social network” in Minsk, Belarus, Wednesday, June 29, 2011. Police in Belarus have violently quashed a peaceful anti-government rally, detaining dozens of people protesting the authoritarian regime of President Alexander Lukashenko. (Sergei Grits) A woman protects her husband from a plainclothes policeman, left, during an action “Revolution via social network” in Minsk, Belarus, Wednesday, June 29, 2011. Police in Belarus have violently quashed a peaceful anti-government rally, detaining dozens of people protesting the authoritarian regime of President Alexander Lukashenko. (Sergei Grits) |
![[Image]](https://i0.wp.com/cryptome.org/info/belarus-protest/pict59.jpg) A woman argues with plainclothes policemen as they push back protesters during an action “Revolution via social network” in Minsk, Belarus, Wednesday, June 29, 2011. Police in Belarus have violently quashed a peaceful anti-government rally, detaining dozens of people protesting the authoritarian regime of President Alexander Lukashenko. (Sergei Grits) A woman argues with plainclothes policemen as they push back protesters during an action “Revolution via social network” in Minsk, Belarus, Wednesday, June 29, 2011. Police in Belarus have violently quashed a peaceful anti-government rally, detaining dozens of people protesting the authoritarian regime of President Alexander Lukashenko. (Sergei Grits) |
![[Image]](https://i0.wp.com/cryptome.org/info/belarus-protest/pict71.jpg) Belarus plainclothes policemen push back protesters during an action “Revolution via social network” in Minsk, Belarus, Wednesday, June 29, 2011. Police in Belarus have violently quashed a peaceful anti-government rally, detaining dozens of people protesting the authoritarian regime of President Alexander Lukashenko. (Sergei Grits) Belarus plainclothes policemen push back protesters during an action “Revolution via social network” in Minsk, Belarus, Wednesday, June 29, 2011. Police in Belarus have violently quashed a peaceful anti-government rally, detaining dozens of people protesting the authoritarian regime of President Alexander Lukashenko. (Sergei Grits) |
![[Image]](https://i0.wp.com/cryptome.org/info/belarus-protest/pict62.jpg) Youths applaud as they participate in a peaceful rally to protest the authoritarian regime of President Alexander Lukashenko, Minsk, Belarus, Wednesday, June 29, 2011. Belarusian police violently dispersed a peaceful rally Wednesday by thousands of people protesting the authoritarian regime of President Alexander Lukashenko and the country’s worst financial crisis since the fall of the Soviet Union two decades ago. (Sergei Grits) Youths applaud as they participate in a peaceful rally to protest the authoritarian regime of President Alexander Lukashenko, Minsk, Belarus, Wednesday, June 29, 2011. Belarusian police violently dispersed a peaceful rally Wednesday by thousands of people protesting the authoritarian regime of President Alexander Lukashenko and the country’s worst financial crisis since the fall of the Soviet Union two decades ago. (Sergei Grits) |
TOP-SECRET – Guantanamo 10th Anniversary Photos
Guantanamo Prison 24 January 2010![[Image]](https://i0.wp.com/cryptome.org/2012-info/gitmo-10/pict18.jpg) |
|
High-value Detainee Units 6, top left, and 5, top right.![[Image]](https://i0.wp.com/cryptome.org/2012-info/gitmo-10/pict16.jpg) |
|
Detainee Hearing Court![[Image]](https://i0.wp.com/cryptome.org/2012-info/gitmo-10/pict0.jpg) |
|
|
|
2010 |
|
|
|
|
2009 |
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/gitmo-10/pict12.jpg) FILE – In this June 1, 2009 file photo, reviewed by the U.S. military, Chinese Uighur detainees, who at the time were cleared for release, show a home-made note to visiting members of the media in Camp Iguana detention facility at the Guantanamo Bay U.S. Naval Base in Cuba. FILE – In this June 1, 2009 file photo, reviewed by the U.S. military, Chinese Uighur detainees, who at the time were cleared for release, show a home-made note to visiting members of the media in Camp Iguana detention facility at the Guantanamo Bay U.S. Naval Base in Cuba. |
|
|
|
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/gitmo-10/pict6.jpg) FILE – In this May 14, 2009 file photo, reviewed by the U.S. military, detainees pray before dawn near a fence of razor-wire inside Camp 4 detention facility at the Guantanamo Bay U.S. Naval Base in Cuba. FILE – In this May 14, 2009 file photo, reviewed by the U.S. military, detainees pray before dawn near a fence of razor-wire inside Camp 4 detention facility at the Guantanamo Bay U.S. Naval Base in Cuba. |
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/gitmo-10/pict14.jpg) FILE – In this May 13, 2009 file photo, reviewed by the U.S. military, a detainee stands at his cell window yelling after seeing a group of journalists who were visiting Camp 5 maximum-security detention facility at the Guantanamo Bay U.S. Naval Base in Cuba. FILE – In this May 13, 2009 file photo, reviewed by the U.S. military, a detainee stands at his cell window yelling after seeing a group of journalists who were visiting Camp 5 maximum-security detention facility at the Guantanamo Bay U.S. Naval Base in Cuba. |
|
2008 |
|
|
|
|
2007 |
|
|
|
|
2006 |
|
|
|
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/gitmo-10/pict13.jpg) FILE – In this Dec. 4, 2006 file photo, reviewed by a U.S. Department of Defense official, a detainee shields his face as he peers out through the so-called “bean hole” which is used to pass food and other items into detainee cells, in Camp Delta detention facility at the Guantanamo Bay U.S. Naval Base in Cuba. FILE – In this Dec. 4, 2006 file photo, reviewed by a U.S. Department of Defense official, a detainee shields his face as he peers out through the so-called “bean hole” which is used to pass food and other items into detainee cells, in Camp Delta detention facility at the Guantanamo Bay U.S. Naval Base in Cuba. |
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/gitmo-10/pict5.jpg) FILE – In this Sept. 19, 2006 file photo, reviewed by a U.S. Department of Defense official, a detainee stands at a fence holding Islamic prayer beads in Camp Delta detention facility at the Guantanamo Bay U.S. Naval Base in Cuba. FILE – In this Sept. 19, 2006 file photo, reviewed by a U.S. Department of Defense official, a detainee stands at a fence holding Islamic prayer beads in Camp Delta detention facility at the Guantanamo Bay U.S. Naval Base in Cuba. |
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/gitmo-10/pict8.jpg) FILE – In this Sept. 19, 2006 file photo, reviewed by a U.S. Department of Defense official, military personnel stand inside the brand new Camp 6 maximum security detention facility at the Guantanamo Bay U.S. Naval Base in Cuba. FILE – In this Sept. 19, 2006 file photo, reviewed by a U.S. Department of Defense official, military personnel stand inside the brand new Camp 6 maximum security detention facility at the Guantanamo Bay U.S. Naval Base in Cuba. |
|
2004 |
|
|
|
|
2002 |
|
|
|
|
|
|
Believed Terrorist al’Qaeda of the Arabian Peninsula (AQAP) – statements as mirror
Inspire Magazine Series
A sends:
Please mirror the following documents on cryptome.org. They are all of the English language magazines titled “Inspire”, authored by al’Qaeda of the Arabian Peninsula (AQAP), put out to date.
If possible, it would be helpful for you to also have a single page that will be kept up to date in the future, listing all volumes that have been published.
inspire-1.pdf (31.6MB)
inspire-2.pdf (41.6MB)
inspire-3.pdf (5.5MB)
inspire-4.pdf (15.7MB)
inspire-5.pdf (6.5MB)
inspire-6.pdf (19.5MB)
inspire-7.pdf (28.9MB)
Uncensored – Women Protest Worldwide Photos 11
|
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest11/pict23.jpg) Members of the Turkish Communist Party (TKP) chant slongans against French president during a protest outside the French consulate in Istanbul, on January 24, 2012. The French Senate on Monday approved, by 127 votes to 86, the measure which makes it an offence punishable by jail in France to deny that the 1915 massacre of Armenians by Ottoman Turk forces amounted to genocide. French President Nicolas Sarkozy, whose right-wing UMP party put forward the bill, now has sign it into law. Getty Members of the Turkish Communist Party (TKP) chant slongans against French president during a protest outside the French consulate in Istanbul, on January 24, 2012. The French Senate on Monday approved, by 127 votes to 86, the measure which makes it an offence punishable by jail in France to deny that the 1915 massacre of Armenians by Ottoman Turk forces amounted to genocide. French President Nicolas Sarkozy, whose right-wing UMP party put forward the bill, now has sign it into law. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest11/pict24.jpg) Monica a German trucker gestures on the Turin highway during a truckers’ protest against the government’s deregulation plans in Turin January 23, 2012. Truckers blocked roads throughout Italy and taxi drivers resumed a strike on Monday as opposition mounted to fuel tax rises and economic reforms aimed at opening up competition in protected sectors including transport and pharmacies. Reuters Monica a German trucker gestures on the Turin highway during a truckers’ protest against the government’s deregulation plans in Turin January 23, 2012. Truckers blocked roads throughout Italy and taxi drivers resumed a strike on Monday as opposition mounted to fuel tax rises and economic reforms aimed at opening up competition in protected sectors including transport and pharmacies. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest11/pict25.jpg) Pro-life activists protest at the March for Life rally on January 23, 2012 in Washington, DC. Pro-life activists gather each year to protest on the anniversary of the Roe v. Wade Supreme Court decision that legalized abortion. Getty Pro-life activists protest at the March for Life rally on January 23, 2012 in Washington, DC. Pro-life activists gather each year to protest on the anniversary of the Roe v. Wade Supreme Court decision that legalized abortion. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest11/pict26.jpg) An ‘Occupy WEF’ protester cuts firewood during a protest against the World Economic Forum (WEF) at the Swiss resort of Davos on January 23, 2012. Some 1,600 economic and political leaders, including 40 heads of states and governments, will be asked to urgently find ways to reform a capitalist system that has been described as ‘outdated and crumbling as they converge at eastern Switzerland’s chic ski station of Davos for the 42nd edition of the five-day World Economic Forum (WEF) which opens on January 25, 2012. Getty An ‘Occupy WEF’ protester cuts firewood during a protest against the World Economic Forum (WEF) at the Swiss resort of Davos on January 23, 2012. Some 1,600 economic and political leaders, including 40 heads of states and governments, will be asked to urgently find ways to reform a capitalist system that has been described as ‘outdated and crumbling as they converge at eastern Switzerland’s chic ski station of Davos for the 42nd edition of the five-day World Economic Forum (WEF) which opens on January 25, 2012. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest11/pict27.jpg) Members of a leftist Turkish party waves party flags and hold a banner reading ‘Armenian allegations are part of a new Treaty of Sevres (which would have divided Turkey) by the USA and EU’ as they protest outside the French embassy in Ankara on January 23, 2012. Turkey threatened France with new sanctions over a bill criminalising the denial of the Armenian genocide as the French Senate prepared to vote on the legislation. Getty Members of a leftist Turkish party waves party flags and hold a banner reading ‘Armenian allegations are part of a new Treaty of Sevres (which would have divided Turkey) by the USA and EU’ as they protest outside the French embassy in Ankara on January 23, 2012. Turkey threatened France with new sanctions over a bill criminalising the denial of the Armenian genocide as the French Senate prepared to vote on the legislation. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest11/pict2.jpg) Cambodian victims hold a demonstration to mark the third anniversary of a forced eviction in the Dey Krahorm community, Tuesday, Jan. 24, 2012, in Phnom Penh, Cambodia. Three years ago residents were forcibly evicted from their homes and told by local authorities that the land was owned by others. (Heng Sinith) Cambodian victims hold a demonstration to mark the third anniversary of a forced eviction in the Dey Krahorm community, Tuesday, Jan. 24, 2012, in Phnom Penh, Cambodia. Three years ago residents were forcibly evicted from their homes and told by local authorities that the land was owned by others. (Heng Sinith) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest11/pict3.jpg) AIDS protestors are seen outside the FDA building on Monday Jan. 23, 2012, in Silver Spring, MD. (Larry French) AIDS protestors are seen outside the FDA building on Monday Jan. 23, 2012, in Silver Spring, MD. (Larry French) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest11/pict1.jpg) A Hungarian protestor covers her mouth with a mask during a protest in support of the largest opposition radio station ‘Klub Radio’ which recently lost its radio frequency in Budapest, Hungary, Sunday, Jan. 22, 2012. Thousands gathered to protest against the government’s controversial media law and to help the ‘Klub Radio’. (Bela Szandelszky) A Hungarian protestor covers her mouth with a mask during a protest in support of the largest opposition radio station ‘Klub Radio’ which recently lost its radio frequency in Budapest, Hungary, Sunday, Jan. 22, 2012. Thousands gathered to protest against the government’s controversial media law and to help the ‘Klub Radio’. (Bela Szandelszky) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest11/pict28.jpg) The Ladies in White, a group of family members of imprisoned dissidents, protest during their weekly march in Havana January 22, 2012. The opposition group “Ladies in White” accused the Cuban government on Sunday of “murdering” by neglect a 31-year-old dissident who died last week following a hunger strike in prison. Ladies in White leader Berta Soler said Wilman Villar Mendoza died because the government did not respect his rights and that he was only the latest such victim to die for the same reason. Reuters The Ladies in White, a group of family members of imprisoned dissidents, protest during their weekly march in Havana January 22, 2012. The opposition group “Ladies in White” accused the Cuban government on Sunday of “murdering” by neglect a 31-year-old dissident who died last week following a hunger strike in prison. Ladies in White leader Berta Soler said Wilman Villar Mendoza died because the government did not respect his rights and that he was only the latest such victim to die for the same reason. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest11/pict4.jpg) Anti-government protesters shout as they carry portraits of several prisoners during a rally organized by the pro-democracy 20th February movement in Casablanca, Morocco, Sunday, Jan. 22 2012. Like the rest of the region, Morocco was once shaken by pro-democracy protests but the king has succeeded in blunting them by holding early elections and amending the constitution and the numbers of protesters have dwindled. Anti-government protesters shout as they carry portraits of several prisoners during a rally organized by the pro-democracy 20th February movement in Casablanca, Morocco, Sunday, Jan. 22 2012. Like the rest of the region, Morocco was once shaken by pro-democracy protests but the king has succeeded in blunting them by holding early elections and amending the constitution and the numbers of protesters have dwindled. |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest11/pict5.jpg) Demonstrators, dressed as workers, holds a sign that reads in Spanish ‘I don’t want apartheids in Chile’ during a protest in support of maids and workers outside the gated community “El Algarrobal II” in Chicureo, Chile, Saturday, Jan. 21, 2012. According to community rules, workers are forbidden to walk along the residential development. Demonstrators, dressed as workers, holds a sign that reads in Spanish ‘I don’t want apartheids in Chile’ during a protest in support of maids and workers outside the gated community “El Algarrobal II” in Chicureo, Chile, Saturday, Jan. 21, 2012. According to community rules, workers are forbidden to walk along the residential development. |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest11/pict30.jpg) Topless activists of Ukraine’s protest group Femen punch reporters in front of the Bulgarian Parliament in Sofia, on Saturday, Jan 21, 2012. Ukrainian female rights activists FEMEN staged a protest in Sofia against the domestic violence on women and children and against human trafficking. (Valentina Petrova) Topless activists of Ukraine’s protest group Femen punch reporters in front of the Bulgarian Parliament in Sofia, on Saturday, Jan 21, 2012. Ukrainian female rights activists FEMEN staged a protest in Sofia against the domestic violence on women and children and against human trafficking. (Valentina Petrova) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest11/pict7.jpg) An anti-government protester holds a banner that reads ‘I love democracy’ while posing in front of a group of riot police in combat gear in Bucharest, Romania, early Saturday, Jan. 21, 2012. Police on Sunday clashed with a small contingent of around 1,000 protesters in the capital, after demonstrations against austerity measures turned violent. (Vadim Ghirda) An anti-government protester holds a banner that reads ‘I love democracy’ while posing in front of a group of riot police in combat gear in Bucharest, Romania, early Saturday, Jan. 21, 2012. Police on Sunday clashed with a small contingent of around 1,000 protesters in the capital, after demonstrations against austerity measures turned violent. (Vadim Ghirda) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest11/pict8.jpg) Occupy protester Julie Searle chains herself to fellow protesters blocking a Bank of America branch entrance on Friday, Jan. 20, 2012, in San Francisco. Anti-Wall Street demonstrators across the U.S. planned rallies Friday in front of banks and courthouses. (Noah Berger) Occupy protester Julie Searle chains herself to fellow protesters blocking a Bank of America branch entrance on Friday, Jan. 20, 2012, in San Francisco. Anti-Wall Street demonstrators across the U.S. planned rallies Friday in front of banks and courthouses. (Noah Berger) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest11/pict9.jpg) Children chant slogans during an anti-Syrian regime demonstration at the mountain resort town of Zabadani, Syria, near the Lebanese border, on Friday Jan. 20, 2012. President Bashar Assad’s forces attacked Zabadani, some 17 miles (27 kilometers) west of the capital, for six days, sparking fierce fighting that involved heavy bombardments and clashes with army defectors. Children chant slogans during an anti-Syrian regime demonstration at the mountain resort town of Zabadani, Syria, near the Lebanese border, on Friday Jan. 20, 2012. President Bashar Assad’s forces attacked Zabadani, some 17 miles (27 kilometers) west of the capital, for six days, sparking fierce fighting that involved heavy bombardments and clashes with army defectors. |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest11/pict10.jpg) Protesters hold signs that read in Spanish “English get out of Malvinas” outside the British embassy in Buenos Aires, Argentina, Friday Jan. 20, 2012. A small crowd of demonstrators turned out Friday after British Prime Minister David Cameron accused Argentina of being “much more than colonialist” for asserting its claims to the islands. Protesters hold signs that read in Spanish “English get out of Malvinas” outside the British embassy in Buenos Aires, Argentina, Friday Jan. 20, 2012. A small crowd of demonstrators turned out Friday after British Prime Minister David Cameron accused Argentina of being “much more than colonialist” for asserting its claims to the islands. |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest11/pict11.jpg) A demonstrator chants as she holds up a poster with the image of Chile’s Interior Minister Rodrigo Hinzpeter, during a protest against a proposed plan on new ways to crack down on unauthorized social protests, in Santiago, Chile, Thursday Jan. 19, 2012. “Hinzpeter Law,” had included enabling police to seize images from media without court orders but Hinzpeter is backing away from that idea. A demonstrator chants as she holds up a poster with the image of Chile’s Interior Minister Rodrigo Hinzpeter, during a protest against a proposed plan on new ways to crack down on unauthorized social protests, in Santiago, Chile, Thursday Jan. 19, 2012. “Hinzpeter Law,” had included enabling police to seize images from media without court orders but Hinzpeter is backing away from that idea. |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest11/pict12.jpg) Half naked and caged activists of the animal rights group ‘Igualdad Animal’ (Equality Animal) symbolically sit in cages to denounce the slaying of animals to make fur coats, in Barcelona, Spain, Thursday, Jan. 19, 2012. (Manu Fernandez) Half naked and caged activists of the animal rights group ‘Igualdad Animal’ (Equality Animal) symbolically sit in cages to denounce the slaying of animals to make fur coats, in Barcelona, Spain, Thursday, Jan. 19, 2012. (Manu Fernandez) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest11/pict13.jpg) Bulgarian environmental activist wears a gas mask and carries Bulgarian national flag during a protest in Sofia, on Wednesday, Jan 18, 2012. Though the Bulgarian parliament banned on Wednesday shale oil and gas exploration through hydraulic fracturing or fracking hundreds activists gathered to protest against the environmental policy of the government. (Valentina Petrova) Bulgarian environmental activist wears a gas mask and carries Bulgarian national flag during a protest in Sofia, on Wednesday, Jan 18, 2012. Though the Bulgarian parliament banned on Wednesday shale oil and gas exploration through hydraulic fracturing or fracking hundreds activists gathered to protest against the environmental policy of the government. (Valentina Petrova) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest11/pict14.jpg) Israeli Ethiopian girls have their faces painted as they take part in a demonstration against racism and discrimination in Jerusalem, Wednesday, Jan. 18, 2012. Thousands of young Ethiopian immigrants and other supporters gathered on Wednesday outside the Israeli parliament, to protest what they say is racism directed at them. (Sebastian Scheiner) Israeli Ethiopian girls have their faces painted as they take part in a demonstration against racism and discrimination in Jerusalem, Wednesday, Jan. 18, 2012. Thousands of young Ethiopian immigrants and other supporters gathered on Wednesday outside the Israeli parliament, to protest what they say is racism directed at them. (Sebastian Scheiner) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest11/pict15.jpg) An anti-government protester draped in a Bahraini flag argues with riot police who told her to go inside as police dispersed a banned demonstration Wednesday, Jan. 18, 2012, in Manama, Bahrain. Opposition groups, led by al-Wefaq society, had called for a march through central Manama, but turned the protest into a sit-in when police who turned out in large numbers blocked their way. An anti-government protester draped in a Bahraini flag argues with riot police who told her to go inside as police dispersed a banned demonstration Wednesday, Jan. 18, 2012, in Manama, Bahrain. Opposition groups, led by al-Wefaq society, had called for a march through central Manama, but turned the protest into a sit-in when police who turned out in large numbers blocked their way. |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest11/pict16.jpg) Workers demonstrate at the request of the CGT union (General Confederation of Work), in Marseille, southern France, Wednesday, Jan. 18, 2012, against what they describe as anti social government measures. Labor unions insist workers shouldn’t have to pay the cost of the financial crisis at a time when many French companies are still making profits, and accuse unpopular conservative leader President Nicolas Sarkozy of putting together a slap-dash solution ahead of elections. Workers demonstrate at the request of the CGT union (General Confederation of Work), in Marseille, southern France, Wednesday, Jan. 18, 2012, against what they describe as anti social government measures. Labor unions insist workers shouldn’t have to pay the cost of the financial crisis at a time when many French companies are still making profits, and accuse unpopular conservative leader President Nicolas Sarkozy of putting together a slap-dash solution ahead of elections. |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest11/pict17.jpg) Occupy London protesters chant anti-corporate slogans as they gather on the steps of St. Paul’s Cathedral, in central London, Wednesday, Jan. 18, 2012. Britain’s High Court decided Wednesday, Occupy London protest camp an be evicted from outside St. Paul’s Cathedral. (Lefteris Pitarakis) Occupy London protesters chant anti-corporate slogans as they gather on the steps of St. Paul’s Cathedral, in central London, Wednesday, Jan. 18, 2012. Britain’s High Court decided Wednesday, Occupy London protest camp an be evicted from outside St. Paul’s Cathedral. (Lefteris Pitarakis) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest11/pict18.jpg) Occupy Congress protesters arrives for a day of demonstrations and activities on Capitol Hill in Washington, Tuesday, Jan. 17, 2012. (J. Scott Applewhite) Occupy Congress protesters arrives for a day of demonstrations and activities on Capitol Hill in Washington, Tuesday, Jan. 17, 2012. (J. Scott Applewhite) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest11/pict19.jpg) Protester, holds a black cross to symbolically mourn the death of PSI (Private Sector Involvement) and CDS (Credit Default Swaps) during a rally in central Athens, Tuesday, Jan. 17, 2012. Strikes and demonstrations over austerity measures hit the Greek capital of Athens on Tuesday, as international debt inspectors returned to resume their scrutiny of the country’s reforms. (Dimitri Messinis) Protester, holds a black cross to symbolically mourn the death of PSI (Private Sector Involvement) and CDS (Credit Default Swaps) during a rally in central Athens, Tuesday, Jan. 17, 2012. Strikes and demonstrations over austerity measures hit the Greek capital of Athens on Tuesday, as international debt inspectors returned to resume their scrutiny of the country’s reforms. (Dimitri Messinis) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest11/pict20.jpg) International Indignados movement demonstrators chash with Italian police officers as they try to move out of St. Peter’s Square at the Vatican, in Rome, Saturday, Jan. 13, 2012. The Indignados staged a sit-in and tried to place tents and climb the Vatican Christmas tree as a protest. (Andrew Medichini) International Indignados movement demonstrators chash with Italian police officers as they try to move out of St. Peter’s Square at the Vatican, in Rome, Saturday, Jan. 13, 2012. The Indignados staged a sit-in and tried to place tents and climb the Vatican Christmas tree as a protest. (Andrew Medichini) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest11/pict21.jpg) Border guards, fire brigade officers and prison guards blow horns as they protest demanding monthly wage increases of 300 zlotys (US dollar 85, euro 66) , just like those recently given to the police and armed forces, in Warsaw, Poland, Thursday, Jan. 12, 2012. Similar protests took place simultaneously in Warsaw, Gdansk, Poznan and Wroclaw, the four Polish towns that will host the Euro 2012 soccer championships games. (Alik Keplicz) Border guards, fire brigade officers and prison guards blow horns as they protest demanding monthly wage increases of 300 zlotys (US dollar 85, euro 66) , just like those recently given to the police and armed forces, in Warsaw, Poland, Thursday, Jan. 12, 2012. Similar protests took place simultaneously in Warsaw, Gdansk, Poznan and Wroclaw, the four Polish towns that will host the Euro 2012 soccer championships games. (Alik Keplicz) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest11/pict22.jpg) Indigenous women rest after protesting the Conga gold and silver mining project in Cajamarca, Peru, Tuesday Jan. 3, 2012. Demonstrators in Peru resumed their protests against plans to develop a $4.8 billion gold mine, saying they fear the mine will will taint their water and affect a major aquifer. The mine is majority owned by U.S.-based Newmont Mining Corp. (Karel Navarro) Indigenous women rest after protesting the Conga gold and silver mining project in Cajamarca, Peru, Tuesday Jan. 3, 2012. Demonstrators in Peru resumed their protests against plans to develop a $4.8 billion gold mine, saying they fear the mine will will taint their water and affect a major aquifer. The mine is majority owned by U.S.-based Newmont Mining Corp. (Karel Navarro) |
ORIGINAL ANKLAGESCHRIFT GEGEN KIM DOTCOM, MEGAUPLOAD LIMITED, VESTOR LIMITED, FINN BATATO, JULIUS BENCKO, SVEN ECHTERNACH, MATHIAS ORTMANN, ANDRUS NOMM, and BRAM VAN DER KOLK,
DOWNLOAD INDICTMENT AS PDF ABOVE
Exclusive Photos – Kim Schmitz and Megauploads Photos from the FBI investigation

FBI & Investigations

FBI & Investigations

FBI & Investigations

FBI & Investigations

FBI & Investigations

FBI & Investigations

FBI & Investigations

FBI & Investigations

FBI & Investigations

FBI & Investigations

FBI & Investigations

FBI & Investigations

FBI & Investigations
FBI & Investigations
FBI Director Louis Freeh in FBI HQ With 2 Israeli Investigators.Second Left
Robert Goldstein.Second Right Oren Shalev.Both from the Israel National Anti Fraud Unit.During Investigation in US.Photo:FBI

FBI & Investigations
FBI & Investigations
Spies Arrested by FBI.
Exposed – Original Kim Schmitz and Megauploads Photos from the FBI investigation – Home and Cars

FBI & Investigations

FBI & Investigations

FBI & Investigations

FBI & Investigations

FBI & Investigations

FBI & Investigations

FBI & Investigations

FBI & Investigations

FBI & Investigations

FBI & Investigations

FBI & Investigations
STASI – Mit der Lizenz zum Töten und Rufmorden
TOP-SECRET – John Kiriakou Former CIA Officer Torture Leak Criminal Complaint
DIE ABSURDEN BEHAUPTUNGEN DER STASI-STALKER UND IHRER KOMPLIZEN
Liebe Leser,
STASI war schon immer absurd, kriminell, aber auch lächerlich und dumm.
Das zeigt sich auch gerade wieder an den Neo-STASI-STALKERN der “GoMoPa”.
Erst bin ich kein Akademiker, dann wieder doch, dann wird eine Meridian Capital-Webseite plump gefälscht, um mich zu belasten, dann sollen wir angeblich eine “rumänische Domain” und eine “mobile Bank” besitzen.
Hallo, gehts noch, Genossen STASI-STALKER ?
Zuviel Rotkäppchen-Sekt gemischt mit Methyl-Akohol getrunken ?
Wir haben weder das Eine noch das Andere.
Der eigentliche Skandal sind aber nicht nur die Neo-STASI, die STASI-STALKER und ihre dumm-dreisten Rufmorde und mutmasslich auch Morde, sondern ihre Komplizen, Zuträger und Informanten in der Immobilien- und Justizszene, denen wir auf die Spur gekommen sind.
Das wird alles ans Tageslicht kommen !
Herzlichst Ihr
Bernd Pulch, Magister Artium der Publizistik, Germanistik und Komparatistik
PS: All diese Zusammenhänge sind schon viel zu vielen Insidern bekannt, als das dies noch vertuscht werden kann.
DAS KINDERPORTAL MIT “SEXUAL-AUFKLÄRUNG” DER NEO-STASI “GoMoPa”
Featured CIA Stories – The National Committee for Free Europe, 1949
On June 1, 1949, a group of prominent American businessmen, lawyers, and philanthropists – including Allen Dulles, who would become Director of Central Intelligence in 1953 – launched the National Committee for Free Europe (NCFE) at a press release in New York. Only a handful of people knew that NCFE was actually the public face of an innovative “psychological warfare” project undertaken by the Central Intelligence Agency (CIA). That operation – which soon gave rise to Radio Free Europe – would become one of the longest running and successful covert action campaigns ever mounted by the United States.
 George Kennan of the Department of State could be considered the godfather of NCFE. He – more than any other official – pressed the National Security Council to reorganize covert action planning and management. This resulted in the creation of the Office of Policy Coordination (OPC) at the CIA in September 1948 and the appointment of the visionary OSS veteran Frank G. Wisner as its chief.
George Kennan of the Department of State could be considered the godfather of NCFE. He – more than any other official – pressed the National Security Council to reorganize covert action planning and management. This resulted in the creation of the Office of Policy Coordination (OPC) at the CIA in September 1948 and the appointment of the visionary OSS veteran Frank G. Wisner as its chief.
Kennan proposed that OPC work through an “American freedom committee” in dealing with anti-Communist émigré groups in the United States to develop operations abroad. The idea was to fund selected émigrés in their activities to demonstrate that the newly imposed Soviet-style dictatorships in Eastern Europe oppressed the aspirations of their people. NCFE was the American umbrella for these exiled European figures in the United States, raising private funds through Crusade for Freedom to supplement CIA funding and organizing exile activities to reach back to their occupied homelands.
From the start, Wisner and OPC regarded NCFE as one of their signature operations. As the Cold War reached perhaps its most dangerous phase, NCFE and other projects (such as the Congress for Cultural Freedom, 1950, and Radio Liberty, which began broadcasts to the Soviet Union in 1953) rallied anti-Communist intellectuals, politicians, and activists to fight the Soviets in a contest for the peoples’ “minds and loyalties.”
NCFE soon gave rise to its more famous progeny, Radio Free Europe, which began broadcasting behind the Iron Curtain on July 4, 1950. Radio Free Europe aired programs to Eastern Europe in six languages. For decades, it was a beacon of hope to people who had otherwise lost access to the outside world.
CIA subsidies to the Free Europe Committee (NCFE’s later name) ended in 1971, after Sen. Clifford P. Case (R-NJ) revealed that it received covert assistance. After that date, Radio Free Europe was publicly funded by Congressional appropriation through the presidentially appointed Board for International Broadcasting. RFE merged with Radio Liberty (RL) in 1976 in a new non-profit corporation, RFE/RL, INc. Oversight was assumed in 1995 by the Broadcasting Board of Governors, responsible for all non-military U.S. international broadcasting.
RFE/RL broadcasts today to 21 countries in 28 languages, including Iran, Iraq, Afghanistan, Pakistan, and Russia.
TOP-SECRET from the FBI – Former CIA Officer John Kiriakou Charged with Disclosing Covert Officer’s Identity and Other Classified Information to Journalists and Lying to CIA’s Publications Review Board
ALEXANDRIA, VA—A former CIA officer, John Kiriakou, was charged today with repeatedly disclosing classified information to journalists, including the name of a covert CIA officer and information revealing the role of another CIA employee in classified activities, Justice Department officials announced. The charges result from an investigation that was triggered by a classified defense filing in January 2009, which contained classified information the defense had not been given through official government channels, and, in part, by the discovery in the spring of 2009 of photographs of certain government employees and contractors in the materials of high-value detainees at Guantanamo Bay, Cuba. The investigation revealed that on multiple occasions, one of the journalists to whom Kiriakou is alleged to have illegally disclosed classified information, in turn, disclosed that information to a defense team investigator, and that this information was reflected in the classified defense filing and enabled the defense team to take or obtain surveillance photographs of government personnel. There are no allegations of criminal activity by any members of the defense team for the detainees.
Kiriakou, 47, of Arlington, Va., was a CIA intelligence officer between 1990 and 2004, serving at headquarters and in various classified overseas assignments. He is scheduled to appear at 2 p.m. today before U.S. Magistrate Judge John F. Anderson in federal court in Alexandria.
Kiriakou was charged with one count of violating the Intelligence Identities Protection Act for allegedly illegally disclosing the identity of a covert officer and two counts of violating the Espionage Act for allegedly illegally disclosing national defense information to individuals not authorized to receive it. Kiriakou was also charged with one count of making false statements for allegedly lying to the Publications Review Board of the CIA in an unsuccessful attempt to trick the CIA into allowing him to include classified information in a book he was seeking to publish.
The four-count criminal complaint, which was filed today in the Eastern District of Virginia, alleges that Kiriakou made illegal disclosures about two CIA employees and their involvement in classified operations to two journalists on multiple occasions between 2007 and 2009. In one case, revealing the employee’s name as a CIA officer disclosed classified information as the employee was and remains covert (identified in the complaint as “Covert Officer A”). In the second case, Kiriakou allegedly disclosed the name and contact information of an employee, identified in the complaint as “Officer B,” whose participation in an operation to capture and question terrorism subject Abu Zubaydah in 2002 was then classified. Kiriakou’s alleged disclosures occurred prior to a June 2008 front-page story in The New York Times disclosing Officer B’s alleged role in the Abu Zubaydah operation.
“Safeguarding classified information, including the identities of CIA officers involved in sensitive operations, is critical to keeping our intelligence officers safe and protecting our national security,” said Attorney General Eric Holder. “Today’s charges reinforce the Justice Department’s commitment to hold accountable anyone who would violate the solemn duty not to disclose such sensitive information.”
Patrick J. Fitzgerald, United States Attorney for the Northern District of Illinois, who was appointed Special Attorney in 2010 to supervise the investigation, said: “I want to thank the Washington Field Office of the FBI and the team of attorneys assigned to this matter for their hard work and dedication to tracing the sources of the leaks of classified information.” Mr. Fitzgerald announced the charges with James W. McJunkin, Assistant Director in Charge of the Washington Field Office of the Federal Bureau of Investigation, and they thanked the Central Intelligence Agency for its very substantial assistance in the investigation, as well as the Air Force Office of Special Investigations for its significant assistance.
“Protecting the identities of America’s covert operatives is one of the most important responsibilities of those who are entrusted with roles in our nation’s intelligence community. The FBI and our intelligence community partners work diligently to hold accountable those who violate that special trust,” said Mr. McJunkin.
The CIA filed a crimes report with the Justice Department on March 19, 2009, prior to the discovery of the photographs and after reviewing the Jan. 19, 2009, classified filing by defense counsel for certain detainees with the military commission then responsible for adjudicating charges. The defense filing contained information relating to the identities and activities of covert government personnel, but prior to Jan. 19, 2009, there had been no authorized disclosure to defense counsel of the classified information. The Justice Department’s National Security Division, working with the FBI, began the investigation. To avoid the risk of encountering a conflict of interest because of the pending prosecutions of some of the high-value detainees, Mr. Fitzgerald was assigned to supervise the investigation conducted by a team of attorneys from the Southern District of New York, the Northern District of Illinois, and the Counterespionage Section of the National Security Division who were not involved in pending prosecutions of the detainees.
According to the complaint affidavit, the investigation determined that no laws were broken by the defense team as no law prohibited defense counsel from filing a classified document under seal outlining for a court classified information they had learned during the course of their investigation. Regarding the 32 pages of photographs that were taken or obtained by the defense team and provided to the detainees, the investigation found no evidence the defense attorneys transmitting the photographs were aware of, much less disclosed, the identities of the persons depicted in particular photographs and no evidence that the defense team disclosed other classified matters associated with certain of those individuals to the detainees. The defense team did not take photographs of persons known or believed to be current covert officers. Rather, defense counsel, using a technique known as a double-blind photo lineup, provided photograph spreads of unidentified individuals to their clients to determine whether they recognized anyone who may have participated in questioning them. No law or military commission order expressly prohibited defense counsel from providing their clients with these photo spreads.
Further investigation, based in part on e-mails recovered from judicially-authorized search warrants served on two e-mail accounts associated with Kiriakou, allegedly revealed that:
- Kiriakou disclosed to Journalist A the name of Covert Officer A and the fact that Covert Officer A was involved in a particular classified operation. The journalist then provided the defense investigator with the full name of the covert CIA employee;
- Kiriakou disclosed or confirmed to Journalists A, B, and C the then-classified information that Officer B participated in the Abu Zubaydah operation and provided two of those journalists with contact information for Officer B, including a personal e-mail address. One of the journalists subsequently provided the defense investigator with Officer B’s home telephone number, which the investigator used to identify and photograph Officer B; and
- Kiriakou lied to the CIA regarding the existence and use of a classified technique, referred to as a “magic box,” in an unsuccessful effort to trick the CIA into allowing him to publish information about the classified technique in a book.
Upon joining the CIA in 1990 and on multiple occasions in following years, Kiriakou signed secrecy and non-disclosure agreements not to disclose classified information to unauthorized individuals.
Regarding Covert Officer A, the affidavit details a series of e-mail communications between Kiriakou and Journalist A in July and August 2008. In an exchange of e-mails on July 11, 2008, Kiriakou allegedly illegally confirmed for Journalist A that Covert Officer A, whose first name only was exchanged at that point, was “the team leader on [specific operation].” On August 18, 2008, Journalist A sent Kiriakou an e-mail asking if Kiriakou could pick out Covert Officer A’s last name from a list of names Journalist A provided in the e-mail. On Aug. 19, 2008, Kiriakou allegedly passed the last name of Covert Officer A to Journalist A by e-mail, stating “It came to me last night.” Covert Officer A’s last name had not been on the list provided by Journalist A. Later that same day, approximately two hours later, Journalist A sent an e-mail to the defense investigator that contained Covert Officer A’s full name. Neither Journalist A, nor any other journalist to the government’s knowledge, has published the name of Covert Officer A.
At the time of Kiriakou’s allegedly unauthorized disclosures to Journalist A, the identification of Covert Officer A as “the team leader on [specific operation]” was classified at the Top Secret/Sensitive Compartmented Information (SCI) level because it revealed both Covert Officer A’s identity and his association with the CIA’s Rendition, Detention, and Interrogation (RDI) Program relating to the capture, detention, and questioning of terrorism subjects. The defense investigator was able to identify Covert Officer A only after receiving the e-mail from Journalist A, and both Covert Officer A’s name and association with the RDI Program were included in the January 2009 classified defense filing. The defense investigator told the government that he understood from the circumstances that Covert Officer A was a covert employee and, accordingly, did not take his photograph. No photograph of Covert Officer A was recovered from the detainees at Guantanamo.
In a recorded interview last Thursday, FBI agents told Kiriakou that Covert Officer A’s name was included in the classified defense filing. The affidavit states Kiriakou said, among other things, “How the heck did they get him? . . . [First name of Covert Officer A] was always undercover. His entire career was undercover.” Kiriakou further stated that he never provided Covert Officer A’s name or any other information about Covert Officer A to any journalist and stated “Once they get the names, I mean this is scary.”
Regarding Officer B, the affidavit states that he worked overseas with Kiriakou on an operation to locate and capture Abu Zubaydah, and Officer B’s association with the RDI Program and the Abu Zubaydah operation in particular were classified until that information was recently declassified to allow the prosecution of Kiriakou to proceed.
In June 2008, The New York Times published an article by Journalist B entitled “Inside the Interrogation of a 9/11 Mastermind,” which publicly identified Officer B and reported his alleged role in the capture and questioning of Abu Zubaydah—facts which were then classified. The article attributed other information to Kiriakou as a source, but did not identify the source(s) who disclosed or confirmed Officer B’s identity. The charges allege that at various times prior to publication of the article, Kiriakou provided Journalist B with personal information regarding Officer B, knowing that Journalist B was seeking to identify and locate Officer B. In doing so, Kiriakou allegedly confirmed classified information that Officer B was involved in the Abu Zubaydah operation. For example, Kiriakou allegedly e-mailed Officer B’s phone number and personal e-mail address to Journalist B, who attempted to contact Officer B via his personal e-mail in April and May 2008. Officer B had provided his personal e-mail address to Kiriakou, but not to Journalist B or any other journalist. Subsequently, Kiriakou allegedly revealed classified information by confirming for Journalist B additional information that an individual with Officer B’s name, who was associated with particular contact information that Journalist B had found on a website, was located in Pakistan in March 2002, which was where and when the Abu Zubaydah operation took place.
After The New York Times article was published, Kiriakou sent several e-mails denying that he was the source for information regarding Officer B, while, at the same time, allegedly lying about the number and nature of his contacts with Journalist B. For example, in an e-mail dated June 30, 2008, Kiriakou told Officer B that Kiriakou had spoken to the newspaper’s ombudsman after the article was published and said that the use of Officer B’s name was “despicable and unnecessary” and could put Officer B in danger. Kiriakou also denied that he had cooperated with the article and claimed that he had declined to talk to Journalist B, except to say that he believed the article absolutely should not mention Officer B’s name. “[W]hile it might not be illegal to name you, it would certainly be immoral,” Kiriakou wrote to Officer B, according to the affidavit.
From at least November 2007 through November 2008, Kiriakou allegedly provided Journalist A with Officer B’s personal contact information and disclosed to Journalist A classified information revealing Officer B’s association with the RDI Program. Just as Journalist A had disclosed to the defense investigator classified information that Kiriakou allegedly imparted about Covert Officer A, Journalist A, in turn, provided the defense investigator information that Kiriakou had disclosed about Officer B. For example, in an e-mail dated April 10, 2008, Journalist A provided the defense investigator with Officer B’s home phone number, which, in light of Officer B’s common surname, allowed the investigator to quickly and accurately identify Officer B and photograph him. Both Officer B’s name and his association with the RDI Program were included in the January 2009 classified defense filing, and four photographs of Officer B were among the photos recovered at Guantanamo.
In the same recorded interview with FBI agents last week, Kiriakou said he “absolutely” considered Officer B’s association with the Abu Zubaydah operation classified, the affidavit states. Kiriakou also denied providing any contact information for Officer B or Officer B’s association with the Abu Zubaydah operation to Journalists A and B prior to publication of the June 2008 New York Times article. When specifically asked whether he had anything to do with providing Officer B’s name or other information about Officer B to Journalist B prior to the article, Kiriakou stated “Heavens no.”
As background, the affidavit states that sometime prior to May 22, 2007, Kiriakou disclosed to Journalist C classified information regarding Officer B’s association with Abu Zubaydah operation, apparently while collaborating on a preliminary book proposal. A footnote states that Journalist C is not the coauthor of the book Kiriakou eventually published.
Prior to publication of his book, The Reluctant Spy: My Secret Life in the CIA’s War on Terror, Kiriakou submitted a draft manuscript in July 2008 to the CIA’s Publication Review Board (PRB). In an attempt to trick the CIA into allowing him to publish information regarding a classified investigative technique, Kiriakou allegedly lied to the PRB by falsely claiming that the technique was fictional and that he had never heard of it before. In fact, according to a transcript of a recorded interview conducted in August 2007 to assist Kiriakou’s coauthor in drafting the book, Kiriakou described the technique, which he referred to as the “magic box,” and told his coauthor that the CIA had used the technique in the Abu Zubaydah operation. The technique was also disclosed in the June 2008 New York Times article and referred to as a “magic box.”
In his submission letter to the PRB, Kiriakou flagged the reference to a device called a “magic box,” stating he had read about it in the newspaper article but added that the information was “clearly fabricated,” as he was unaware of and had used no such device. The affidavit contains the contents of an August 2008 e-mail that Kiriakou sent his coauthor admitting that he lied to the PRB in an attempt to include classified information in the book. The PRB subsequently informed Kiriakou that the draft manuscript contained classified information that he could not use, and information regarding the technique that Kiriakou included in the manuscript remained classified until it was recently declassified to allow Kiriakou’s prosecution to proceed.
Upon conviction, the count charging illegal disclosure of Covert Officer A’s identity to a person not authorized to receive classified information carries a maximum penalty of five years in prison, which must be imposed consecutively to any other term of imprisonment; the two counts charging violations of the Espionage Act each carry a maximum term of 10 years in prison; and making false statements carries a maximum prison term of five years. Each count carries a maximum fine of $250,000.
A complaint contains only allegations and is not evidence of guilt. The defendant is presumed innocent and is entitled to a fair trial at which the government has the burden of proving guilt beyond a reasonable doubt.
The government is being represented in court by Assistant U.S. Attorneys Iris Lan (Southern District of New York) and Mark E. Schneider (Northern District of Illinois), and DOJ trial attorney Ryan Fayhee, of the Counterespionage Section of the National Security Division. Assistant U.S. Attorney Lisa Owings (Eastern District of Virginia) will assist in the matter under local court rules.
STASI damals und heute – Anleitung und Praxis der Entführung, Mord und Totschlag
STASI UND RAF-MORD – Der Fall Rohwedder
10.000 Euro Belohnung für Aufklärung eines STASI-Mordes
TOP-SECRET – (U//FOUO) DoD Global Information Grid 2.0 Concept of Operations

Executive Summary
Achieving and maintaining the information advantage as a critical element of national power requires the concentrated effort of the entire Department of Defense (DoD) to provide a seamless information environment optimized for the warfighter.
Operational experiences in Iraq and Afghanistan support the continued need to eliminate barriers to information sharing that currently exist on DoD’s multiple networks. A concerted effort to unify the networks into a single information environment providing timely information to commanders will improve command and control, thus increasing our speed of action. Providing an information technology (IT) / National Security Systems (NSS) infrastructure that is accessible anywhere and anytime is key to ensuring the agility of the Department and allowing our most valuable resources, our people, nearly instant access to the information they need to make decisions in the execution of their missions. In turn, the Global Information Grid (GIG) must be designed and optimized to support warfighting functions of advantaged and disadvantaged users, to include mission partners, across the full range of military and National Security operations in any operational environment. The GIG must also be resilient and able to support the missions despite attacks by sophisticated adversaries.
The operational concept of GIG 2.0 is depicted in Figure 1, and builds upon net-centric concepts as articulated in DoD Information Enterprise Architecture (DIEA) Version 1.0 (April 2008).
Furthermore, GIG 2.0 is founded upon the following 5 characteristics which are further discussed in section 2.7: Global Authentication, Access Control, and Directory Services Information and Services ―From the Edge‖ Joint Infrastructure Common Policies and Standards Unity of Command.
GIG 2.0 will facilitate mission accomplishment by providing tactical services ―from the edge‖ in support of the warfighter. The warfighter tactical edge user solutions must work in austere deployed environments. Today many IT services and systems are designed to work in a robust IT environment and often do not scale down to the deployed user. This separation between home station and deployed capabilities requires the user to transition from garrison IT services to tactical IT services, often losing functionality in the deployed environment. This document presents the GIG 2.0 Concept of Operations (CONOPS) as it relates to five key critical characteristics of the GIG and their relationship to the DoD Joint Capability Areas (JCA).

DOWNLOAD ORIGINAL DOCUMENT HERE
Dokumentiert – STASI-Morde – Hinrichtungen in der DDR
Die Todesstrafe war eines der größten Geheimnisse der DDR: Vor 20 Jahren schaffte das Politbüro Exekutionen ab. SED-Chef Honecker ging es dabei nicht um Humanismus und Menschenrechte – der Diktator brauchte den Goodwill des Westens, um seinen maroden Staat am Leben zu halten.
Die wahrscheinlich letzte Hinrichtung in Deutschland fand am 26. Juni 1981 in der DDR, in der Hinrichtungsstätte im Gefängnis in der Alfred-Kästner-Straße, Leipzig, statt: Der 39-jährige Stasi-Hauptmann Dr. Werner Teske, dem vorgeworfen wurde, sich mit Akten in den Westen absetzen zu wollen (Spionagetatbestand), wurde durch den “unerwarteten Nahschuss” hingerichtet. Hierbei verkündete der Staatsanwalt dem völlig Ahnungslosen die beiden Sätze “Das Gnadengesuch ist abgelehnt. Ihre Hinrichtung steht unmittelbar bevor.” Daraufhin trat der letzte deutsche Henker, Hermann Lorenz, unbemerkt von hinten heran und schoss Teske ohne weitere Umschweife mit einer Armeepistole in den Hinterkopf. Lorenz hat auf diese Weise etwa zwanzig Hinrichtungen vollstreckt und wurde später zum Major befördert.
Das letzte nicht-militärische Todesurteil in der DDR wurde am 15. September 1972 an dem Kindermörder Erwin Hagedorn aus Eberswalde vollzogen.
INOFFIZIELL GING UND GEHT DAS MORDEN WEITER – ICH SAGE NUR DIOXIN
TOP-SECRET – Japanese Government Denied Existence of Document on Fukushima Worst-Case Scenario

The government buried a worst-case scenario for the Fukushima nuclear crisis that was drafted last March and kept it under wraps until the end of last year, sources in the administration said Saturday.
After the document was shown to a small, select group of senior government officials at the prime minister’s office in late March, the administration of then Prime Minister Naoto Kan decided to quietly bury it, the sources said.
“When the document was presented (in March), a discussion ensued about keeping its existence secret,” a government source said.
In order to deny its existence, the government treated it as a personal document of Japan Atomic Energy Commission Chairman Shunsuke Kondo, who authored it, until the end of December, the sources said.
It was only then that it was actually recognized as an official government document, they said.
“The content was so shocking that we decided to treat it as if it didn’t exist,” a senior government official said.
A private-sector panel investigating the disaster at the Fukushima No. 1 nuclear plant intends to examine whether the government tried to manipulate information during its handling of the crisis.
he document was dated March 25, 2011, two weeks after the massive earthquake and tsunami triggered the country’s worst nuclear crisis. It was premised on a scenario in which all plant workers had to be evacuated due to a rise in radiation levels after a hydrogen explosion damaged a containment vessel encasing the plan’s No. 1 reactor.
The document said that should such a case occur, residents within a radius of 170 kilometers or more of the plant would be forced to move out, while those within a radius of 250 km of the plant, including Tokyo, would be allowed to leave if they wish.
“It contained such shocking content that we decided to treat it as if it never existed,” a senior government official said.
Another government source said, “When the document was presented, there was a discussion about the choice of keeping the existence of the document itself secret.”
Kan admitted the existence of a worst case scenario in September, while the government of his successor, Prime Minister Yoshihiko Noda, decided to treat the document as a Cabinet Office document after some parts of it were reported in December.
Unveiled – Bail Ruling to Come for Dotcom in New Zealand
Kim Dotcom and his co-defendants in the Megaupload case appeared in an Auckland court Monday, which heard arguments over their bail requests. Dotcom’s lawyer said his client was innocent of internet piracy and money laundering charges. (Jan. 23)
Current Status of Fukushima Daiichi Nuclear Power Station by photographs
DOWNLOAD ORIGINAL FILE HERE
STASI-AGENTEN MIT GEHEIMCODES TEIL 16-STASI AGENTS WITH SECRET CODES PART 16
 010468410172;99;99;99;;::;;;7575,00
010468410172;99;99;99;;::;;;7575,00
250768415330;99;99;99;;::;;;7575,00
221169411538;99;99;99;;::;;;7575,00
150369401312;99;99;99;;::;;;7575,00
141169403212;99;99;99;;::;;;7575,00
070570408217;99;99;99;;::;;;7575,00
020537425052;99;99;99;;::;;;7548,39
021268400619;99;99;99;;::;;;7575,00
160168402414;99;99;99;;::;;;7483,71
271269428236;99;99;99;;::;;;7561,29
020667415311;99;99;99;;::;;;7560,00
250866400837;99;99;99;;::;;;7560,00
230170413236;99;99;99;;::;;;7550,00
030169407545;99;99;99;;::;;;7550,00
280667418521;99;99;99;;::;;;7550,00
041169402246;99;99;99;;::;;;7575,00
070966407616;99;99;99;;::;;;7425,00
231066422727;99;99;99;;::;;;7425,00
121067430270;99;99;99;;::;;;7425,00
200567420314;99;99;99;;::;;;7425,00
291267430242;99;99;99;;::;;;7425,00
270667430169;99;99;99;;::;;;7425,00
180666430176;99;99;99;;::;;;7425,00
250768406717;99;99;99;;::;;;7486,13
080967403720;99;99;99;;::;;;7425,00
140263404022;99;99;99;;::;;;7425,00
051067422798;99;99;99;;::;;;7425,00
020568408546;99;99;99;;::;;;7425,00
010358400862;99;99;99;;::;;;7417,50
150267416214;99;99;99;;::;;;7400,00
040368429228;99;99;99;;::;;;7400,00
290268413933;99;99;99;;::;;;7200,00
100766430330;99;99;99;;::;;;7425,00
100533530146;99;99;99;;::;;;7440,00
201169419312;99;99;99;;::;;;7595,00
210644408810;99;99;99;;::;;;7481,86
150568418512;99;99;99;;::;;;7480,00
171164417727;99;99;99;;::;;;7480,00
161255429724;99;99;99;;::;;;7475,00
300332402726;99;99;99;;::;;;7470,00
131267401326;99;99;99;;::;;;7425,00
090568412215;99;99;99;;::;;;7452,50
290962408915;99;99;99;;::;;;7425,00
231069424015;99;99;99;;::;;;7436,13
200857416217;99;99;99;;::;;;7431,25
020265404417;99;99;99;;::;;;7429,00
210866411513;99;99;99;;::;;;7425,00
150568430255;99;99;99;;::;;;7425,00
310368430103;99;99;99;;::;;;7425,00
040568411014;99;99;99;;::;;;7486,13
300538416824;99;99;99;;::;;;7466,66
280966400938;99;99;99;;::;;;7729,55
140666430305;99;99;99;;::;;;7750,00
140468414718;99;99;99;;::;;;7750,00
130429530012;99;99;99;;::;;;7750,00
040866430184;99;99;99;;::;;;7750,00
040437507622;99;99;99;;::;;;7750,00
290864407310;99;99;99;;::;;;7749,00
060268400899;99;99;99;;::;;;7729,55
020568401547;99;99;99;;::;;;7729,55
270162407318;99;99;99;;::;;;7755,00
011267400837;99;99;99;;::;;;7729,55
270568400212;99;99;99;;::;;;7729,55
010167400042;99;99;99;;::;;;7729,55
191267400766;99;99;99;;::;;;7729,55
150467400268;99;99;99;;::;;;7729,55
130641502713;99;99;99;;::;;;7583,34
070368401329;99;99;99;;::;;;7729,55
101066413710;99;99;99;;::;;;7800,00
241267422917;99;99;99;;::;;;6600,00
010168406446;99;99;99;;::;;;6600,00
131266413747;99;99;99;;::;;;7800,00
030468421216;99;99;99;;::;;;7800,00
130168413028;99;99;99;;::;;;7800,00
300368429250;99;99;99;;::;;;7800,00
211166428247;99;99;99;;::;;;7750,00
180446420312;99;99;99;;::;;;7800,00
111137530041;99;99;99;;::;;;7750,00
261129506918;99;99;99;;::;;;7786,45
270638512229;99;99;99;;::;;;7786,09
230268427548;99;99;99;;::;;;7775,00
171126412212;99;99;99;;::;;;7775,00
040457409536;99;99;99;;::;;;7762,50
160954518414;99;99;99;;::;;;7755,00
031067401323;99;99;99;;::;;;7729,55
201067403432;99;99;99;;::;;;7800,00
200429530013;99;99;99;;::;;;7625,00
060767411410;99;99;99;;::;;;7685,00
311267400719;99;99;99;;::;;;7684,55
100365406735;99;99;99;;::;;;7684,50
251166417747;99;99;99;;::;;;7683,71
100153415373;99;99;99;;::;;;7680,00
080569402415;99;99;99;;::;;;7677,50
170168406756;99;99;99;;::;;;7729,55
200729430014;99;99;99;;::;;;7631,25
280927415395;99;99;99;;::;;;7687,50
250468418919;99;99;99;;::;;;7625,00
080929407536;99;99;99;;::;;;7622,91
101266413037;99;99;99;;::;;;7614,00
211233511519;99;99;99;;::;;;7600,80
081267402748;99;99;99;;::;;;7600,00
291167401719;99;99;99;;::;;;7400,00
260769410012;99;99;99;;::;;;7640,00
160461402624;99;99;99;;::;;;7700,00
030468400861;99;99;99;;::;;;7729,55
280468429228;99;99;99;;::;;;7729,55
260667401326;99;99;99;;::;;;7729,55
110767407326;99;99;99;;::;;;7725,00
040368408523;99;99;99;;::;;;7725,00
040463411114;99;99;99;;::;;;7713,75
010138411519;99;99;99;;::;;;7687,50
220551426349;99;99;99;;::;;;7700,00
130930430023;99;99;99;;::;;;7687,50
070863409117;99;99;99;;::;;;7700,00
050568412112;99;99;99;;::;;;7700,00
020868410410;99;99;99;;::;;;7700,00
260866405338;99;99;99;;::;;;7690,00
101028430034;99;99;99;;::;;;7687,50
290128430029;99;99;99;;::;;;7687,50
200166430175;99;99;99;;::;;;7594,00
150261419633;99;99;99;;::;;;7711,91
070658530030;99;99;99;;::;;;7299,63
300667409524;99;99;99;;::;;;7400,00
101267413418;99;99;99;;::;;;7320,00
290529422775;99;99;99;;::;;;7312,50
171142429719;99;99;99;;::;;;7312,50
110332400811;99;99;99;;::;;;7312,50
120967424947;99;99;99;;::;;;7308,06
310567419329;99;99;99;;::;;;7320,00
120568405132;99;99;99;;::;;;7300,00
090966400236;99;99;99;;::;;;7320,00
011166409111;99;99;99;;::;;;7295,17
301166415330;99;99;99;;::;;;7295,00
200268425035;99;99;99;;::;;;7295,00
080468400824;99;99;99;;::;;;7295,00
300636407219;99;99;99;;::;;;7294,35
280331427010;99;99;99;;::;;;7287,50
110954429811;99;99;99;;::;;;7302,50
110468421216;99;99;99;;::;;;7325,00
050768426818;99;99;99;;::;;;7350,00
221167402435;99;99;99;;::;;;7345,00
291067414547;99;99;99;;::;;;7345,00
080267412132;99;99;99;;::;;;7344,00
301266414714;99;99;99;;::;;;7344,00
290366403640;99;99;99;;::;;;7344,00
130167409510;99;99;99;;::;;;7320,00
190268413038;99;99;99;;::;;;7325,00
201167426711;99;99;99;;::;;;7258,06
221267407938;99;99;99;;::;;;7325,00
211167421020;99;99;99;;::;;;7325,00
120966418318;99;99;99;;::;;;7325,00
220767428044;99;99;99;;::;;;7325,00
041165430274;99;99;99;;::;;;7325,00
020967430302;99;99;99;;::;;;7325,00
110966417164;99;99;99;;::;;;7344,00
290866413052;99;99;99;;::;;;7200,00
011267430075;99;99;99;;::;;;7207,26
100234506111;99;99;99;;::;;;7204,16
310867413623;99;99;99;;::;;;7200,00
310867410318;99;99;99;;::;;;7200,00
310867424939;99;99;99;;::;;;7200,00
310168420533;99;99;99;;::;;;7200,00
240168413113;99;99;99;;::;;;7278,87
300468430128;99;99;99;;::;;;7200,00
070666415366;99;99;99;;::;;;7225,00
280767412215;99;99;99;;::;;;7200,00
280567420536;99;99;99;;::;;;7200,00
290667417763;99;99;99;;::;;;7200,00
271267424717;99;99;99;;::;;;7200,00
290268400833;99;99;99;;::;;;7200,00
281267426236;99;99;99;;::;;;7200,00
300867403426;99;99;99;;::;;;7200,00
050632500812;99;99;99;;::;;;7250,00
230967420214;99;99;99;;::;;;7350,00
160867420531;99;99;99;;::;;;7257,00
230767411014;99;99;99;;::;;;7255,81
300338429727;99;99;99;;::;;;7250,00
290268407066;99;99;99;;::;;;7250,00
220831503716;99;99;99;;::;;;7250,00
080264430132;99;99;99;;::;;;7208,00
050745422419;99;99;99;;::;;;7250,00
050268413244;99;99;99;;::;;;7225,00
040242529725;99;99;99;;::;;;7250,00
031242530043;99;99;99;;::;;;7250,00
280268409556;99;99;99;;::;;;7225,00
251066402513;99;99;99;;::;;;7225,00
210867406134;99;99;99;;::;;;7225,00
121067404152;99;99;99;;::;;;7225,00
120126409515;99;99;99;;::;;;7274,19
100832530277;99;99;99;;::;;;7250,00
160367400147;99;99;99;;::;;;7400,00
210368422412;99;99;99;;::;;;7400,00
110267419013;99;99;99;;::;;;7400,00
181267417745;99;99;99;;::;;;7400,00
091268407515;99;99;99;;::;;;7400,00
180667418611;99;99;99;;::;;;7400,00
090567401514;99;99;99;;::;;;7400,00
041066400838;99;99;99;;::;;;7400,00
071167400615;99;99;99;;::;;;7400,00
120367424978;99;99;99;;::;;;7400,00
070766430344;99;99;99;;::;;;7400,00
151267400727;99;99;99;;::;;;7400,00
061267430169;99;99;99;;::;;;7400,00
230667402110;99;99;99;;::;;;7400,00
041167409428;99;99;99;;::;;;7400,00
091266409517;99;99;99;;::;;;7350,00
171167430054;99;99;99;;::;;;7400,00
010568401919;99;99;99;;::;;;7400,00
030966416727;99;99;99;;::;;;7400,00
030766430153;99;99;99;;::;;;7400,00
020867425039;99;99;99;;::;;;7400,00
260667406717;99;99;99;;::;;;7400,00
020468405313;99;99;99;;::;;;7400,00
260667405810;99;99;99;;::;;;7400,00
110667424989;99;99;99;;::;;;7400,00
241267407426;99;99;99;;::;;;7400,00
220667424062;99;99;99;;::;;;7400,00
240966430030;99;99;99;;::;;;7400,00
150965421838;99;99;99;;::;;;7400,00
241067407624;99;99;99;;::;;;7400,00
240268430121;99;99;99;;::;;;7400,00
130665400113;99;99;99;;::;;;7400,00
230167430019;99;99;99;;::;;;7400,00
180767430095;99;99;99;;::;;;7400,00
020168416248;99;99;99;;::;;;7400,00
040367424994;99;99;99;;::;;;7370,00
310766402722;99;99;99;;::;;;7375,00
081266430077;99;99;99;;::;;;7375,00
250666425044;99;99;99;;::;;;7375,00
150838529715;99;99;99;;::;;;7375,00
291167402519;99;99;99;;::;;;7375,00
240566422015;99;99;99;;::;;;7375,00
220368409516;99;99;99;;::;;;7400,00
010367403133;99;99;99;;::;;;7375,00
080767427728;99;99;99;;::;;;7388,71
250167421823;99;99;99;;::;;;7362,90
190367415434;99;99;99;;::;;;7360,00
260867428216;99;99;99;;::;;;7360,00
120767400019;99;99;99;;::;;;7350,00
261046416044;99;99;99;;::;;;7350,00
280268427412;99;99;99;;::;;;7400,00
040867419630;99;99;99;;::;;;7375,00
280167418816;99;99;99;;::;;;7400,00
300668401516;99;99;99;;::;;;7400,00
161066418452;99;99;99;;::;;;7400,00
281167416217;99;99;99;;::;;;7400,00
240766417712;99;99;99;;::;;;7400,00
200967430060;99;99;99;;::;;;7400,00
180168430093;99;99;99;;::;;;7400,00
081166400823;99;99;99;;::;;;7375,00
230168420314;99;99;99;;::;;;7400,00
151066407017;99;99;99;;::;;;7375,00
271167404727;99;99;99;;::;;;7400,00
260766406456;99;99;99;;::;;;7400,00
241267416736;99;99;99;;::;;;7400,00
241266430106;99;99;99;;::;;;7400,00
040967415397;99;99;99;;::;;;7396,77
131267424616;99;99;99;;::;;;7395,00
110867415323;99;99;99;;::;;;7350,00
151067407318;99;99;99;;::;;;7400,00
030168405716;99;99;99;;::;;;6600,00
020667423813;99;99;99;;::;;;6600,00
070568407127;99;99;99;;::;;;6600,00
030268406142;99;99;99;;::;;;6600,00
070667407915;99;99;99;;::;;;6600,00
030267428278;99;99;99;;::;;;6600,00
070668428216;99;99;99;;::;;;6600,00
070867418424;99;99;99;;::;;;6600,00
070368422787;99;99;99;;::;;;6600,00
030168407017;99;99;99;;::;;;6600,00
070467403426;99;99;99;;::;;;6600,00
021067424219;99;99;99;;::;;;6600,00
070467405616;99;99;99;;::;;;6600,00
021067403610;99;99;99;;::;;;6600,00
061267430142;99;99;99;;::;;;6600,00
021066410616;99;99;99;;::;;;6600,00
030167424720;99;99;99;;::;;;6600,00
030168415324;99;99;99;;::;;;6600,00
160568408516;99;99;99;;::;;;6640,00
070868409212;99;99;99;;::;;;6625,00
241067406429;99;99;99;;::;;;6625,00
240867422748;99;99;99;;::;;;6625,00
311267407312;99;99;99;;::;;;6622,00
230666414814;99;99;99;;::;;;6615,00
030168416212;99;99;99;;::;;;6600,00
250429430026;99;99;99;;::;;;6604,84
061167428117;99;99;99;;::;;;6600,00
030268401923;99;99;99;;::;;;6600,00
070568427216;99;99;99;;::;;;6600,00
030168426226;99;99;99;;::;;;6600,00
070767409539;99;99;99;;::;;;6600,00
030168417741;99;99;99;;::;;;6600,00
070867413957;99;99;99;;::;;;6600,00
011229430015;99;99;99;;::;;;6612,90
060667422833;99;99;99;;::;;;6600,00
060468419332;99;99;99;;::;;;6600,00
020666408910;99;99;99;;::;;;6600,00
060468428212;99;99;99;;::;;;6600,00
020568402515;99;99;99;;::;;;6600,00
060468409310;99;99;99;;::;;;6600,00
020767430076;99;99;99;;::;;;6600,00
061167425012;99;99;99;;::;;;6600,00
020766423827;99;99;99;;::;;;6600,00
021166418420;99;99;99;;::;;;6600,00
020667405738;99;99;99;;::;;;6600,00
060568422782;99;99;99;;::;;;6600,00
020766416010;99;99;99;;::;;;6600,00
060667414219;99;99;99;;::;;;6600,00
020568416220;99;99;99;;::;;;6600,00
060267406148;99;99;99;;::;;;6800,00
060467415356;99;99;99;;::;;;6600,00
061067416223;99;99;99;;::;;;6600,00
090568413947;99;99;99;;::;;;6653,33
021067410538;99;99;99;;::;;;6600,00
061267430353;99;99;99;;::;;;6600,00
021167424929;99;99;99;;::;;;6600,00
070168427428;99;99;99;;::;;;6600,00
020967426936;99;99;99;;::;;;6600,00
020966422837;99;99;99;;::;;;6600,00
020967427111;99;99;99;;::;;;6600,00
060468414515;99;99;99;;::;;;6600,00
020967411945;99;99;99;;::;;;6600,00
060867425035;99;99;99;;::;;;6600,00
021167408216;99;99;99;;::;;;6600,00
060965407914;99;99;99;;::;;;6600,00
020966416031;99;99;99;;::;;;6600,00
060967427134;99;99;99;;::;;;6600,00
021067423611;99;99;99;;::;;;6600,00
061066409822;99;99;99;;::;;;6600,00
270368422046;99;99;99;;::;;;6775,00
240468400867;99;99;99;;::;;;6800,00
280168429218;99;99;99;;::;;;6800,00
260767408517;99;99;99;;::;;;6800,00
260767403011;99;99;99;;::;;;6800,00
200468413127;99;99;99;;::;;;6795,00
220666413927;99;99;99;;::;;;6775,00
140941530336;99;99;99;;::;;;6758,40
270967417740;99;99;99;;::;;;6775,00
210568407321;99;99;99;;::;;;6800,00
240568402413;99;99;99;;::;;;6775,00
270767407513;99;99;99;;::;;;6775,00
151167424828;99;99;99;;::;;;6775,00
141267404518;99;99;99;;::;;;6775,00
230767413714;99;99;99;;::;;;6762,90
200568414258;99;99;99;;::;;;6640,00
160567430164;99;99;99;;::;;;6775,00
111268418914;99;99;99;;::;;;6800,00
220167424410;99;99;99;;::;;;6800,00
060268430043;99;99;99;;::;;;6800,00
200367421718;99;99;99;;::;;;6800,00
051167408926;99;99;99;;::;;;6800,00
171067411411;99;99;99;;::;;;6800,00
050568415372;99;99;99;;::;;;6800,00
031067412946;99;99;99;;::;;;6800,00
041067401314;99;99;99;;::;;;6800,00
150766407435;99;99;99;;::;;;6800,00
040766424334;99;99;99;;::;;;6800,00
221266405615;99;99;99;;::;;;6800,00
031267425020;99;99;99;;::;;;6800,00
190167420124;99;99;99;;::;;;6800,00
120767407317;99;99;99;;::;;;6800,00
110867429215;99;99;99;;::;;;6800,00
021067421042;99;99;99;;::;;;6755,00
141167422874;99;99;99;;::;;;6800,00
110468400538;99;99;99;;::;;;6700,00
210568428253;99;99;99;;::;;;6745,00
120632430085;99;99;99;;::;;;6741,94
150862430213;99;99;99;;::;;;6737,50
120760511023;99;99;99;;::;;;6728,10
200967406810;99;99;99;;::;;;6725,00
190653429829;99;99;99;;::;;;6720,00
140866428015;99;99;99;;::;;;6760,00
211066424919;99;99;99;;::;;;6700,00
240167401321;99;99;99;;::;;;6747,17
050924417738;99;99;99;;::;;;6691,81
070568402422;99;99;99;;::;;;6675,00
160767410117;99;99;99;;::;;;6675,00
140468413811;99;99;99;;::;;;6675,00
231070418819;99;99;99;;::;;;6660,00
060168404323;99;99;99;;::;;;6600,00
100168400414;99;99;99;;::;;;6700,00
291027428012;99;99;99;;::;;;6750,00
080168419910;99;99;99;;::;;;6750,00
141127430028;99;99;99;;::;;;6750,00
300129412216;99;99;99;;::;;;6750,00
140445430088;99;99;99;;::;;;6750,00
290435417115;99;99;99;;::;;;6750,00
120733409541;99;99;99;;::;;;6750,00
291166421718;99;99;99;;::;;;6745,00
171138507227;99;99;99;;::;;;6750,00
081166426839;99;99;99;;::;;;6745,00
280927430018;99;99;99;;::;;;6750,00
220842430057;99;99;99;;::;;;6750,00
120924412217;99;99;99;;::;;;6750,00
110526420028;99;99;99;;::;;;6750,00
070329426910;99;99;99;;::;;;6750,00
031226420311;99;99;99;;::;;;6750,00
230568408023;99;99;99;;::;;;6650,00
280429424926;99;99;99;;::;;;6750,00
040368424021;99;99;99;;::;;;6600,00
060766424973;99;99;99;;::;;;6600,00
011066406933;99;99;99;;::;;;6600,00
040168421520;99;99;99;;::;;;6600,00
011067427357;99;99;99;;::;;;6600,00
040468410137;99;99;99;;::;;;6600,00
011067415321;99;99;99;;::;;;6600,00
011067409829;99;99;99;;::;;;6600,00
010867416037;99;99;99;;::;;;6600,00
040268407523;99;99;99;;::;;;6600,00
011067408316;99;99;99;;::;;;6600,00
040168422128;99;99;99;;::;;;6600,00
010468429252;99;99;99;;::;;;6600,00
031066413736;99;99;99;;::;;;6600,00
010568422816;99;99;99;;::;;;6600,00
031267408052;99;99;99;;::;;;6600,00
040468415149;99;99;99;;::;;;6600,00
010867411156;99;99;99;;::;;;6600,00
010867409320;99;99;99;;::;;;6600,00
040767410110;99;99;99;;::;;;6600,00
010967430127;99;99;99;;::;;;6600,00
040766424959;99;99;99;;::;;;6600,00
010967416923;99;99;99;;::;;;6600,00
040667405314;99;99;99;;::;;;6600,00
040368411212;99;99;99;;::;;;6600,00
040568422215;99;99;99;;::;;;6600,00
010568406146;99;99;99;;::;;;6600,00
040568417328;99;99;99;;::;;;6600,00
010967416835;99;99;99;;::;;;6600,00
040767411914;99;99;99;;::;;;6600,00
011066414829;99;99;99;;::;;;6600,00
040168424975;99;99;99;;::;;;6600,00
010967427710;99;99;99;;::;;;6600,00
011066418619;99;99;99;;::;;;6600,00
010268412296;99;99;99;;::;;;6600,00
010267402117;99;99;99;;::;;;6600,00
030967426222;99;99;99;;::;;;6600,00
010267416447;99;99;99;;::;;;6600,00
030767410023;99;99;99;;::;;;6600,00
010368427110;99;99;99;;::;;;6600,00
030867429231;99;99;99;;::;;;6600,00
010468427310;99;99;99;;::;;;6600,00
030967421210;99;99;99;;::;;;6600,00
030967417414;99;99;99;;::;;;6600,00
030866415049;99;99;99;;::;;;6600,00
030568412253;99;99;99;;::;;;6600,00
100368416816;99;99;99;;::;;;7125,00
280866416625;99;99;99;;::;;;7400,00
010367402536;99;99;99;;::;;;6600,00
030568422785;99;99;99;;::;;;6600,00
010168405718;99;99;99;;::;;;6600,00
010667400866;99;99;99;;::;;;6600,00
040866424024;99;99;99;;::;;;6600,00
031267403411;99;99;99;;::;;;6600,00
010568413119;99;99;99;;::;;;6600,00
031267405310;99;99;99;;::;;;6600,00
010468410113;99;99;99;;::;;;6600,00
031067408939;99;99;99;;::;;;6600,00
030967424710;99;99;99;;::;;;6600,00
030967404824;99;99;99;;::;;;6600,00
010368416438;99;99;99;;::;;;6600,00
030766422778;99;99;99;;::;;;6600,00
010667402538;99;99;99;;::;;;6600,00
030766403614;99;99;99;;::;;;6600,00
010367417754;99;99;99;;::;;;6600,00
030767412125;99;99;99;;::;;;6600,00
010367417738;99;99;99;;::;;;6600,00
031267407017;99;99;99;;::;;;6600,00
010467403114;99;99;99;;::;;;6600,00
020268400884;99;99;99;;::;;;6600,00
020468419029;99;99;99;;::;;;6600,00
051266401711;99;99;99;;::;;;6600,00
020267404824;99;99;99;;::;;;6600,00
051166427017;99;99;99;;::;;;6600,00
020468400838;99;99;99;;::;;;6600,00
051167413039;99;99;99;;::;;;6600,00
050368414228;99;99;99;;::;;;6600,00
050766417758;99;99;99;;::;;;6600,00
051067425024;99;99;99;;::;;;6600,00
050867425001;99;99;99;;::;;;6600,00
011267418412;99;99;99;;::;;;6600,00
050668409519;99;99;99;;::;;;6600,00
011267414825;99;99;99;;::;;;6600,00
050667422033;99;99;99;;::;;;6600,00
040667424937;99;99;99;;::;;;6600,00
020468428320;99;99;99;;::;;;6600,00
020568420916;99;99;99;;::;;;6600,00
020867427544;99;99;99;;::;;;6600,00
060268413526;99;99;99;;::;;;6600,00
020667422837;99;99;99;;::;;;6600,00
060267407116;99;99;99;;::;;;6600,00
020867409215;99;99;99;;::;;;6600,00
060268404734;99;99;99;;::;;;6600,00
050967408022;99;99;99;;::;;;6600,00
060367409514;99;99;99;;::;;;6600,00
020368430028;99;99;99;;::;;;6600,00
060367405337;99;99;99;;::;;;6600,00
020568424722;99;99;99;;::;;;6600,00
060168430329;99;99;99;;::;;;6600,00
020468413938;99;99;99;;::;;;6600,00
051267412244;99;99;99;;::;;;6600,00
020468426931;99;99;99;;::;;;6600,00
011167425068;99;99;99;;::;;;6600,00
020568417418;99;99;99;;::;;;6600,00
050168424210;99;99;99;;::;;;6600,00
050168413933;99;99;99;;::;;;6600,00
010867407528;99;99;99;;::;;;6600,00
050268411820;99;99;99;;::;;;6600,00
010767410519;99;99;99;;::;;;6600,00
050168422426;99;99;99;;::;;;6600,00
010967409838;99;99;99;;::;;;6600,00
011267411413;99;99;99;;::;;;6600,00
010766424927;99;99;99;;::;;;6600,00
020168424416;99;99;99;;::;;;6600,00
010966415312;99;99;99;;::;;;6600,00
041067412275;99;99;99;;::;;;6600,00
010965428947;99;99;99;;::;;;6600,00
040866400516;99;99;99;;::;;;6600,00
010766419319;99;99;99;;::;;;6600,00
010268422056;99;99;99;;::;;;6600,00
041267413715;99;99;99;;::;;;6600,00
050367424969;99;99;99;;::;;;6600,00
050368405110;99;99;99;;::;;;6600,00
011167409316;99;99;99;;::;;;6600,00
050568428229;99;99;99;;::;;;6600,00
011166420118;99;99;99;;::;;;6600,00
050567412276;99;99;99;;::;;;6600,00
011267422219;99;99;99;;::;;;6600,00
020168419721;99;99;99;;::;;;6600,00
020168400414;99;99;99;;::;;;6600,00
041167424919;99;99;99;;::;;;6600,00
020168409523;99;99;99;;::;;;6600,00
050367416037;99;99;99;;::;;;6600,00
020168411113;99;99;99;;::;;;6600,00
050568426311;99;99;99;;::;;;6600,00
020168426315;99;99;99;;::;;;6600,00
050168406418;99;99;99;;::;;;6600,00
010967401967;99;99;99;;::;;;6600,00
050367406162;99;99;99;;::;;;6600,00
090666420016;99;99;99;;::;;;7000,00
010268409214;99;99;99;;::;;;7000,00
120167406118;99;99;99;;::;;;7000,00
111067421711;99;99;99;;::;;;7000,00
110568413926;99;99;99;;::;;;7000,00
110567402539;99;99;99;;::;;;7000,00
110268420518;99;99;99;;::;;;7000,00
041067427119;99;99;99;;::;;;7000,00
091167411232;99;99;99;;::;;;7000,00
120568427913;99;99;99;;::;;;7000,00
090167406113;99;99;99;;::;;;7000,00
080568430035;99;99;99;;::;;;7000,00
070440412218;99;99;99;;::;;;7000,00
060568412242;99;99;99;;::;;;7000,00
060766427728;99;99;99;;::;;;7000,00
240867419637;99;99;99;;::;;;7000,00
101066430019;99;99;99;;::;;;7000,00
031267413732;99;99;99;;::;;;7000,00
290735507518;99;99;99;;::;;;6960,00
190967422865;99;99;99;;::;;;7000,00
181228430015;99;99;99;;::;;;7000,00
180830430021;99;99;99;;::;;;7000,00
180567409523;99;99;99;;::;;;7000,00
171267424954;99;99;99;;::;;;7000,00
120568408018;99;99;99;;::;;;7000,00
170967417419;99;99;99;;::;;;7000,00
010168430294;99;99;99;;::;;;7000,00
160368407420;99;99;99;;::;;;7000,00
031166414517;99;99;99;;::;;;7000,00
130667414850;99;99;99;;::;;;7000,00
030268402774;99;99;99;;::;;;7000,00
120766424510;99;99;99;;::;;;7000,00
020867425100;99;99;99;;::;;;7000,00
040667404020;99;99;99;;::;;;7000,00
040467430208;99;99;99;;::;;;7000,00
010667419049;99;99;99;;::;;;6975,00
230967410817;99;99;99;;::;;;6975,00
230967428259;99;99;99;;::;;;6975,00
241066403111;99;99;99;;::;;;6975,00
271167401542;99;99;99;;::;;;6975,00
280567410127;99;99;99;;::;;;6975,00
040767409216;99;99;99;;::;;;6975,00
050430430019;99;99;99;;::;;;7000,00
021167417737;99;99;99;;::;;;6975,00
150368419617;99;99;99;;::;;;6975,00
010667404242;99;99;99;;::;;;6975,00
200867400040;99;99;99;;::;;;6975,00
090568412282;99;99;99;;::;;;6966,13
220766400859;99;99;99;;::;;;6966,00
200965412117;99;99;99;;::;;;6966,00
131252417755;99;99;99;;::;;;6960,00
040368430085;99;99;99;;::;;;6975,00
200230503819;99;99;99;;::;;;6993,95
111167408928;99;99;99;;::;;;7000,00
130168402513;99;99;99;;::;;;7000,00
120368418318;99;99;99;;::;;;7000,00
120368420530;99;99;99;;::;;;7000,00
140168403224;99;99;99;;::;;;7000,00
010268410338;99;99;99;;::;;;7000,00
050167422053;99;99;99;;::;;;6975,00
170168420718;99;99;99;;::;;;7000,00
171167407436;99;99;99;;::;;;6975,00
230367417134;99;99;99;;::;;;6990,00
090568418916;99;99;99;;::;;;6990,00
270566405650;99;99;99;;::;;;6988,74
051166422742;99;99;99;;::;;;6975,00
061167413046;99;99;99;;::;;;6975,00
081155412220;99;99;99;;::;;;6975,00
241267430124;99;99;99;;::;;;7000,00
010268417548;99;99;99;;::;;;7000,00
120153425019;99;99;99;;::;;;7038,97
200967402510;99;99;99;;::;;;7050,00
180367412250;99;99;99;;::;;;7050,00
080767402619;99;99;99;;::;;;7050,00
080468413916;99;99;99;;::;;;7050,00
070668405516;99;99;99;;::;;;7050,00
120767405522;99;99;99;;::;;;7045,00
130468404123;99;99;99;;::;;;7017,74
040660415368;99;99;99;;::;;;7040,00
091066423824;99;99;99;;::;;;7060,00
190967428036;99;99;99;;::;;;7025,00
190368421318;99;99;99;;::;;;7025,00
180566430048;99;99;99;;::;;;7025,00
140667400116;99;99;99;;::;;;7025,00
270768404816;99;99;99;;::;;;7022,24
191067410329;99;99;99;;::;;;7000,00
250861400811;99;99;99;;::;;;7040,00
240867419020;99;99;99;;::;;;7075,00
081267405324;99;99;99;;::;;;7125,00
071167416617;99;99;99;;::;;;7125,00
080462416622;99;99;99;;::;;;7122,50
231040407246;99;99;99;;::;;;6800,00
291268421831;99;99;99;;::;;;7110,00
230570402333;99;99;99;;::;;;7110,00
230750510315;99;99;99;;::;;;7050,00
110470418219;99;99;99;;::;;;7110,00
270367400427;99;99;99;;::;;;7050,00
190668400826;99;99;99;;::;;;7075,00
131066415318;99;99;99;;::;;;7075,00
080468424930;99;99;99;;::;;;7075,00
040168416422;99;99;99;;::;;;7075,00
270267430290;99;99;99;;::;;;7066,93
171067422786;99;99;99;;::;;;7060,00
281059408025;99;99;99;;::;;;7012,50
130470413926;99;99;99;;::;;;7110,00
250767420322;99;99;99;;::;;;7000,00
250468419321;99;99;99;;::;;;7000,00
210967428920;99;99;99;;::;;;7000,00
250168408014;99;99;99;;::;;;7000,00
210467415023;99;99;99;;::;;;7000,00
240967420547;99;99;99;;::;;;7000,00
200467430275;99;99;99;;::;;;7000,00
111168409316;99;99;99;;::;;;7019,35
200667424216;99;99;99;;::;;;7000,00
220368424011;99;99;99;;::;;;7000,00
200168410717;99;99;99;;::;;;7000,00
250368422128;99;99;99;;::;;;7000,00
200168405336;99;99;99;;::;;;7000,00
241067424918;99;99;99;;::;;;7000,00
221267403822;99;99;99;;::;;;7000,00
250767401746;99;99;99;;::;;;7000,00
230268403423;99;99;99;;::;;;7000,00
270866427528;99;99;99;;::;;;7000,00
130468419341;99;99;99;;::;;;7003,63
300568421712;99;99;99;;::;;;7000,00
300568424614;99;99;99;;::;;;7000,00
300467426813;99;99;99;;::;;;7000,00
290967403312;99;99;99;;::;;;7000,00
290666403837;99;99;99;;::;;;7000,00
211167426331;99;99;99;;::;;;7000,00
271066514716;99;99;99;;::;;;7000,00
250866422737;99;99;99;;::;;;7000,00
270667403427;99;99;99;;::;;;7000,00
270667407014;99;99;99;;::;;;7000,00
260368406127;99;99;99;;::;;;7000,00
220567430174;99;99;99;;::;;;7000,00
220567401517;99;99;99;;::;;;7000,00
250667428271;99;99;99;;::;;;7000,00
160168410828;99;99;99;;::;;;7120,00
290343516212;99;99;99;;::;;;7000,00
270168409525;99;99;99;;::;;;6845,00
211265415353;99;99;99;;::;;;6850,00
060967404717;99;99;99;;::;;;6850,00
290967420323;99;99;99;;::;;;6850,00
250568423619;99;99;99;;::;;;6850,00
290567418515;99;99;99;;::;;;6850,00
220168417511;99;99;99;;::;;;6850,00
030667404523;99;99;99;;::;;;6800,00
310568417544;99;99;99;;::;;;6845,00
201167419052;99;99;99;;::;;;6875,00
230967426616;99;99;99;;::;;;6845,00
200368420522;99;99;99;;::;;;6845,00
140666428221;99;99;99;;::;;;6845,00
070568420321;99;99;99;;::;;;6840,00
101063424510;99;99;99;;::;;;6806,25
310556417512;99;99;99;;::;;;6900,00
150767428115;99;99;99;;::;;;6850,00
030468418615;99;99;99;;::;;;6895,00
190667428210;99;99;99;;::;;;6900,00
150655407512;99;99;99;;::;;;6900,00
111267407623;99;99;99;;::;;;6900,00
100741519013;99;99;99;;::;;;6895,16
290468415028;99;99;99;;::;;;6895,00
250268416724;99;99;99;;::;;;6895,00
010368418812;99;99;99;;::;;;6862,80
070666401925;99;99;99;;::;;;6895,00
190427422717;99;99;99;;::;;;6875,00
010165404314;99;99;99;;::;;;6888,50
130166400813;99;99;99;;::;;;6885,00
211264427037;99;99;99;;::;;;6885,00
111168426810;99;99;99;;::;;;6876,13
240740529716;99;99;99;;::;;;6875,00
230427412213;99;99;99;;::;;;6875,00
281267401338;99;99;99;;::;;;6800,00
120468421522;99;99;99;;::;;;6895,00
071167425054;99;99;99;;::;;;6800,00
090268413814;99;99;99;;::;;;6800,00
191267403246;99;99;99;;::;;;6800,00
080368421046;99;99;99;;::;;;6800,00
180767402537;99;99;99;;::;;;6800,00
080568401517;99;99;99;;::;;;6800,00
160368414524;99;99;99;;::;;;6800,00
280967430063;99;99;99;;::;;;6800,00
150168402757;99;99;99;;::;;;6800,00
211067400126;99;99;99;;::;;;6800,00
070867406714;99;99;99;;::;;;6800,00
060966421232;99;99;99;;::;;;6800,00
110867422056;99;99;99;;::;;;6800,00
120433429719;99;99;99;;::;;;6937,50
070467403223;99;99;99;;::;;;6800,00
120568430119;99;99;99;;::;;;6800,00
071167413723;99;99;99;;::;;;6800,00
110667400012;99;99;99;;::;;;6800,00
020766407018;99;99;99;;::;;;6800,00
280468416910;99;99;99;;::;;;6800,00
020767402411;99;99;99;;::;;;6800,00
261266401530;99;99;99;;::;;;6800,00
020468430244;99;99;99;;::;;;6800,00
260667416915;99;99;99;;::;;;6800,00
201067401525;99;99;99;;::;;;6800,00
260666406184;99;99;99;;::;;;6800,00
090468422803;99;99;99;;::;;;6800,00
230967426229;99;99;99;;::;;;6800,00
110268421035;99;99;99;;::;;;6800,00
230168401519;99;99;99;;::;;;6800,00
100866420316;99;99;99;;::;;;6800,00
220767400818;99;99;99;;::;;;6800,00
091067406719;99;99;99;;::;;;6800,00
140367406137;99;99;99;;::;;;6800,00
010468401524;99;99;99;;::;;;6800,00
040967406159;99;99;99;;::;;;6920,00
120866418919;99;99;99;;::;;;6925,00
061267413414;99;99;99;;::;;;6925,00
020167415032;99;99;99;;::;;;6925,00
020167415331;99;99;99;;::;;;6925,00
100967417124;99;99;99;;::;;;6920,00
100867411956;99;99;99;;::;;;6920,00
311067407027;99;99;99;;::;;;6920,00
180568410526;99;99;99;;::;;;6925,00
291167416910;99;99;99;;::;;;6920,00
040567407224;99;99;99;;::;;;6920,00
270468413235;99;99;99;;::;;;6920,00
110268413115;99;99;99;;::;;;6920,00
270367417413;99;99;99;;::;;;6920,00
240468402723;99;99;99;;::;;;6920,00
041267400826;99;99;99;;::;;;6920,00
211224407218;99;99;99;;::;;;6937,50
230528430066;99;99;99;;::;;;6937,50
080457430171;99;99;99;;::;;;6900,00
030328419042;99;99;99;;::;;;6937,50
200630430049;99;99;99;;::;;;6937,50
101043429728;99;99;99;;::;;;6937,50
190429430024;99;99;99;;::;;;6937,50
140667407211;99;99;99;;::;;;6925,00
120730430011;99;99;99;;::;;;6937,50
010367430123;99;99;99;;::;;;6925,00
110435429713;99;99;99;;::;;;6937,50
290345430084;99;99;99;;::;;;6933,34
151266414254;99;99;99;;::;;;6925,00
220168411523;99;99;99;;::;;;6925,00
210667403836;99;99;99;;::;;;6925,00
270229412219;99;99;99;;::;;;6937,50
160542429730;99;99;99;;::;;;6937,50
050468415367;99;99;99;;::;;;6920,00
150767403217;99;99;99;;::;;;6920,00
050667417322;99;99;99;;::;;;6920,00
130467412236;99;99;99;;::;;;6920,00
211266412912;99;99;99;;::;;;6920,00
160467412946;99;99;99;;::;;;6920,00
141266424015;99;99;99;;::;;;6920,00
051167408029;99;99;99;;::;;;6920,00
050568408420;99;99;99;;::;;;6920,00
300168419648;99;99;99;;::;;;6920,00
041167418519;99;99;99;;::;;;6920,00
291167400812;99;99;99;;::;;;6920,00
221167411411;99;99;99;;::;;;6920,00
110329530025;99;99;99;;::;;;6937,50
250634517710;99;99;99;;::;;;6905,24
080568424612;99;99;99;;::;;;6912,50
251267421112;99;99;99;;::;;;6920,00
150468408018;99;99;99;;::;;;6920,00
200568417520;99;99;99;;::;;;6920,00
090667430160;99;99;99;;::;;;6920,00
210168411815;99;99;99;;::;;;6920,00
090468405720;99;99;99;;::;;;6920,00
300467424017;99;99;99;;::;;;6900,65
081167408034;99;99;99;;::;;;6920,00
190668411824;99;99;99;;::;;;6920,00
080767424738;99;99;99;;::;;;6920,00
080568427717;99;99;99;;::;;;6920,00
130867413131;99;99;99;;::;;;6920,00
090967401943;99;99;99;;::;;;6920,00
070767402521;99;99;99;;::;;;6920,00
080667418111;99;99;99;;::;;;6920,00
231266413438;99;99;99;;::;;;6920,00
130367430111;99;99;99;;::;;;6920,00
151264424715;99;99;99;;::;;;6920,00
010158450080;97;07;00;;::;;;0,00
110761406146;94;11;00;;::;;;20295,00
310161401727;94;11;00;;::;;;19477,50
120870423817;90;65;40;;::;;;8955,00
190261402328;94;11;00;;::;;;18252,50
140857419061;94;11;00;;::;;;21850,00
101069422786;90;65;40;;::;;;2700,00
140161406131;94;11;00;;::;;;19636,13
241263401326;94;11;00;;::;;;16720,00
030552518328;94;11;00;;::;;;16652,50
100847404011;94;11;00;;::;;;24562,50
050762400078;00;00;00;;::;;;0,00
050442415115;00;00;00;;::;;;0,00
070667400019;00;00;00;;::;;;0,00
120259410317;00;00;00;;::;;;0,00
060548416211;00;00;00;;::;;;0,00
120962400436;00;00;00;;::;;;0,00
070156420827;00;00;00;;::;;;0,00
041028430016;00;00;00;;::;;;0,00
130268400873;00;00;00;;::;;;0,00
020768424911;00;00;00;;::;;;0,00
020465406134;00;00;00;;::;;;0,00
080457430139;00;00;00;;::;;;0,00
100565500427;00;00;00;;::;;;0,00
181229406121;00;00;00;;::;;;0,00
120147406145;00;00;00;;::;;;0,00
180966415402;00;00;00;;::;;;0,00
110829516211;00;00;00;;::;;;0,00
180562400423;00;00;00;;::;;;0,00
101251429714;00;00;00;;::;;;0,00
171259405112;00;00;00;;::;;;0,00
130129406124;00;00;00;;::;;;0,00
140654400838;00;00;00;;::;;;0,00
100948413427;00;00;00;;::;;;26125,00
140546417536;00;00;00;;::;;;0,00
090940415114;00;00;00;;::;;;0,00
131251512275;00;00;00;;::;;;0,00
090367413238;00;00;00;;::;;;0,00
081160423629;00;00;00;;::;;;0,00
020658504515;00;00;00;;::;;;0,00
080662528776;00;00;00;;::;;;0,00
100336411228;00;00;00;;::;;;0,00
050845414731;00;00;00;;::;;;5125,00
070367400615;00;00;00;;::;;;680,00
140270400214;00;00;00;;::;;;680,00
180362418610;00;00;00;;::;;;1292,50
230769405339;00;00;00;;::;;;2177,66
300968415346;00;00;00;;::;;;2355,00
280169430325;00;00;00;;::;;;2400,00
091166510028;00;00;00;;::;;;3396,87
010739429140;00;00;00;;::;;;0,00
051065500123;00;00;00;;::;;;4545,96
010767400118;00;00;00;;::;;;0,00
200868400237;00;00;00;;::;;;5600,00
240153405110;00;00;00;;::;;;6716,00
210369405710;00;00;00;;::;;;8850,00
110166430125;00;00;00;;::;;;9197,00
191066500410;00;00;00;;::;;;9695,18
251062511114;00;00;00;;::;;;13083,79
300462413431;00;00;00;;::;;;15812,50
260633500828;00;00;00;;::;;;3750,00
020253429828;00;00;00;;::;;;0,00
010264424310;00;00;00;;::;;;0,00
040926530065;00;00;00;;::;;;0,00
010330406138;00;00;00;;::;;;0,00
151027530258;00;00;00;;::;;;0,00
010662430046;00;00;00;;::;;;0,00
150958503720;00;00;00;;::;;;0,00
151256407325;00;00;00;;::;;;0,00
290370425447;00;00;00;;::;;;680,00
160250420929;00;00;00;;::;;;0,00
030642407613;00;00;00;;::;;;0,00
160751429817;00;00;00;;::;;;0,00
020349411956;00;00;00;;::;;;0,00
010168400415;00;00;00;;::;;;0,00
020159516917;00;00;00;;::;;;0,00
010668526524;00;00;00;;::;;;0,00
010765404422;00;00;00;;::;;;0,00
030868400019;00;00;00;;::;;;0,00
011068415016;00;00;00;;::;;;0,00
020836430142;00;00;00;;::;;;0,00
150320500010;00;00;00;;::;;;0,00
300648426820;00;00;00;;::;;;0,00
240447402222;00;00;00;;::;;;0,00
230852424928;00;00;00;;::;;;0,00
231065410310;00;00;00;;::;;;0,00
230565401512;00;00;00;;::;;;0,00
230442513418;00;00;00;;::;;;0,00
220660511200;00;00;00;;::;;;0,00
240564512244;00;00;00;;::;;;0,00
150252417759;00;00;00;;::;;;0,00
241134405144;00;00;00;;::;;;0,00
141262500850;00;00;00;;::;;;0,00
141253401519;00;00;00;;::;;;0,00
220265400623;00;00;00;;::;;;0,00
270463406116;00;00;00;;::;;;0,00
270471406431;00;00;00;;::;;;0,00
270767428015;00;00;00;;::;;;0,00
270652511433;00;00;00;;::;;;0,00
070663423635;00;00;00;;::;;;0,00
150333400115;00;00;00;;::;;;0,00
260360401516;00;00;00;;::;;;0,00
220152517315;00;00;00;;::;;;0,00
220145410819;00;00;00;;::;;;0,00
091251424730;00;00;00;;::;;;0,00
100256407616;00;00;00;;::;;;0,00
261236400617;00;00;00;;::;;;0,00
261157440741;00;00;00;;::;;;0,00
260952416615;00;00;00;;::;;;0,00
240764430235;00;00;00;;::;;;0,00
260248429711;00;00;00;;::;;;0,00
310750405136;00;00;00;;::;;;0,00
260351510315;00;00;00;;::;;;0,00
260264410818;00;00;00;;::;;;0,00
251160430326;00;00;00;;::;;;0,00
250526400216;00;00;00;;::;;;0,00
250521406117;00;00;00;;::;;;0,00
250359411718;00;00;00;;::;;;0,00
250366407215;00;00;00;;::;;;0,00
250266415445;00;00;00;;::;;;0,00
260466414825;00;00;00;;::;;;0,00
071162401512;00;00;00;;::;;;0,00
271045422011;00;00;00;;::;;;0,00
210244415018;00;00;00;;::;;;0,00
200963401537;00;00;00;;::;;;0,00
100363442214;00;00;00;;::;;;0,00
090451524694;00;00;00;;::;;;0,00
060951412245;00;00;00;;::;;;0,00
110328421513;00;00;00;;::;;;0,00
210862430055;00;00;00;;::;;;0,00
200853413115;00;00;00;;::;;;0,00
150662509218;00;00;00;;::;;;0,00
110963400623;00;00;00;;::;;;0,00
100856412275;00;00;00;;::;;;0,00
190669411113;00;00;00;;::;;;0,00
091265430189;00;00;00;;::;;;0,00
190451427913;00;00;00;;::;;;0,00
161256400210;00;00;00;;::;;;0,00
190264430252;00;00;00;;::;;;0,00
190867412256;00;00;00;;::;;;0,00
261251442110;00;00;00;;::;;;0,00
280960407522;00;00;00;;::;;;0,00
291048400836;00;00;00;;::;;;0,00
290931530125;00;00;00;;::;;;0,00
300862402141;00;00;00;;::;;;0,00
271034434121;00;00;00;;::;;;0,00
291056430154;00;00;00;;::;;;0,00
280254504229;00;00;00;;::;;;0,00
291031417711;00;00;00;;::;;;0,00
210356424015;00;00;00;;::;;;0,00
300170412226;00;00;00;;::;;;0,00
190562430357;00;00;00;;::;;;0,00
300862430089;00;00;00;;::;;;0,00
281161403423;00;00;00;;::;;;0,00
310554414713;00;00;00;;::;;;0,00
281056421128;00;00;00;;::;;;0,00
311260412223;00;00;00;;::;;;0,00
090964410828;00;00;00;;::;;;0,00
060567400012;00;00;00;;::;;;0,00
051262405918;00;00;00;;::;;;0,00
280556430173;00;00;00;;::;;;0,00
191064401312;00;00;00;;::;;;0,00
130637430147;90;65;40;;1/72,;;;0,00
261030400718;01;00;50;;1022/84, :;;;29250,00
151140430208;96;15;00;;1029/67, J:;;;26937,50
080630430248;96;15;00;;1041/67, M:;;;30158,33
230232430067;15;00;41;;1041/70, :;;;25995,83
290455415379;96;15;00;;1043/84, A:;;;19745,00
120636430234;96;15;00;;1046/67, M:;;;26375,00
110163405936;96;15;00;;1047/82, M:;;;17820,00
290350403611;90;65;40;;1058/86, :;;;22511,29
080861413445;96;15;00;;1078/81, F:;;;2800,00
091033429736;96;15;00;;1087/84, U:;;;27300,00
220351530117;96;15;00;;109/78, J:;;;21161,85
020728401344;01;00;47;;1110/73, :;;;22500,00
220441500114;01;18;00;;1119/79, :;;;20722,50
031141429712;96;15;00;;112/76, M:;;;25500,00
270541426834;96;15;00;;113/74, L:;;;22820,00
300358406426;96;15;00;;113/75, F:;;;19745,00
310828405620;15;18;00;;1143/70, :;;;24480,00
151060428220;90;65;40;;1153/86, :;;;19430,00
260666406125;90;65;40;;1159/89, :;;;15326,84
280267426223;90;65;40;;1160/89, :;;;15108,00
050666422787;90;65;40;;1161/89, :;;;16291,90
310352419719;96;15;00;;121/69/35, AB:;;;25677,16
070152408513;96;15;00;;1226/70, F:;;;21833,22
220538430132;96;15;00;;12487/60, A:;;;25500,00
120644430103;94;11;00;;1276/73, :;;;25080,00
250240430348;96;15;00;;128/68, F:;;;23062,50
060129429237;96;15;00;;12904/60, U:;;;35250,00
210351402124;15;06;00;;1299/85, :;;;24960,00
141038430077;96;15;00;;1305/68, P:;;;30000,00
270734430039;96;15;00;;13222/60, X:;;;27000,00
210739430260;96;15;00;;1331/63, T:;;;24750,00
291132429711;15;18;00;;1341/83, :;;;27052,08
210361505629;96;15;00;;1346/85/1, F:;;;8731,70
100730430013;96;15;00;;1347/85, F:;;;42000,00
230833430118;96;15;00;;1348/85, F:;;;37500,00
111142530150;96;15;00;;1351/89, N:;;;19980,00
260344413437;15;06;00;;1352/75, :;;;30000,00
270461430155;90;65;40;;1356/84, :;;;18480,00
050645422745;96;15;00;;136/71, J:;;;21390,00
140232430076;96;15;00;;1362/60, J:;;;25746,65
260857416035;96;15;00;;1371/77, F:;;;21040,00
120743406432;96;15;00;;1381/89, M:;;;31580,00
160747421011;96;15;00;;1382/89, M:;;;30625,00
160544430102;96;15;00;;1391/86, M:;;;30000,00
110130400821;01;06;00;;1397/86, :;;;29250,00
150860426915;96;15;00;;1433/85, J:;;;2900,00
070141426716;14;00;54;;1435/89, *:;;;33750,00
040454419085;96;15;00;;1439/89, F:;;;16280,00
110444417749;96;15;00;;1472/87, F:;;;30135,00
041250430068;96;15;00;;1476/87, F:;;;34980,00
250253417118;96;15;00;;1477/87, F:;;;26400,00
091251416247;96;15;00;;1478/87, F:;;;35040,00
230245424010;15;00;47;;1484/82, :;;;25854,17
200241419823;96;15;00;;1492/86, F:;;;33000,00
250537422752;96;15;00;;1498/87, F:;;;36450,00
190457430021;90;65;40;;1508/80,;;;0,00
210252429882;90;65;40;;1514/75,;;;0,00
041150424015;94;11;00;;1515/75, :;;;23200,00
161156409832;96;15;00;;1525/75, F:;;;23100,00
270248400715;96;15;00;;1528/87, M:;;;30000,00
290147429728;96;15;00;;1529/87, M:;;;30000,00
180730430198;96;15;00;;153/72, J:;;;28500,00
300532400821;01;18;00;;1530/70, :;;;25200,00
070750424548;96;15;00;;1530/87, M:;;;31282,50
191243413925;96;15;00;;1531/87, M:;;;37500,00
271151500722;94;11;00;;1533/87, M:;;;16038,00
220259427213;90;65;40;;1548/80,;;;0,00
130159404111;90;65;40;;1549/80,;;;0,00
251056417754;90;65;40;;1551/80,;;;0,00
200650422791;96;15;00;;1555/87, F:;;;27840,00
021252402118;96;15;00;;1565/86, M:;;;28800,00
120244409524;96;15;00;;1566/86, M:;;;30750,00
250552417329;96;15;00;;157/85, M:;;;28000,00
030232404823;96;15;00;;1573/85, K:;;;33000,00
040861403419;96;15;00;;1577/86, F:;;;18421,00
071152408948;06;40;00;;1587/87, :;;;24150,00
280244403416;96;15;00;;1587/87, F:;;;30750,00
290530430027;96;15;00;;1593/86, U:;;;35250,00
130736400736;96;15;00;;1594/75, M:;;;26250,00
111159403617;90;65;40;;1598/81,;;;0,00
050742420311;94;11;00;;1601/68, :;;;26250,00
080230426354;96;15;00;;1601/75, M:;;;27000,00
281050426913;96;15;00;;1603/75, M:;;;23265,00
200454500510;90;65;40;;1603/76,;;;0,00
290946406944;90;65;40;;1604/76,;;;0,00
141152404817;90;65;40;;1607/76,;;;0,00
300754401520;94;11;00;;1607/88, :;;;21600,00
140161500224;94;11;00;;1607/88/1, :;;;16252,50
061039401366;01;00;44;;1608/70, :;;;23040,00
270240430215;90;65;40;;1608/76,;;;0,00
071054400731;94;11;00;;1608/88, :;;;25290,00
220952529242;94;11;00;;1608/88/1, :;;;18000,00
100130430132;96;15;00;;1610/69, B:;;;33000,00
160236430282;96;15;00;;1611/69, Q:;;;30750,00
270941430170;90;65;40;;1611/76,;;;0,00
171052426346;14;08;00;;163, :;;;1980,00
270951416612;96;15;00;;1635/84, O:;;;28080,00
280943429738;96;15;00;;1640/88, F:;;;31491,93
140764430317;90;65;40;;1642/85, :;;;17850,00
120644430066;96;15;00;;1643/68, O:;;;27750,00
101047430080;96;15;00;;1644/69, F:;;;25200,00
300459424973;94;11;00;;1649/82, :;;;20625,00
270136430047;96;15;00;;1653/87, F:;;;35250,00
260265402721;96;15;00;;1656/69/2, P:;;;11220,00
220349427719;14;08;00;;166, :;;;1920,00
040342400611;96;15;00;;166/77, M:;;;30000,00
220355427213;14;08;00;;167, :;;;1920,00
200747409817;96;15;00;;167/78, K:;;;25920,00
060249420720;96;15;00;;1670/84, J:;;;23100,00
241045406815;96;15;00;;1671/87, F:;;;34800,00
180437529711;96;15;00;;1672/84, A:;;;22687,50
240740429715;96;15;00;;1675/84, C:;;;25500,00
120341529712;96;15;00;;1675/84/1, C:;;;21000,00
290951406113;96;15;00;;1679/88, E:;;;25530,00
161051427321;14;08;00;;168, :;;;1860,00
200761423615;96;15;00;;1680/88, F:;;;17016,00
200131430175;96;15;00;;1685/87, F:;;;39900,00
201142430132;90;65;40;;1687/76,;;;0,00
120653426237;14;08;00;;169, :;;;1860,00
281051421719;90;65;40;;1690/76,;;;0,00
300152402139;90;65;40;;1692/76,;;;0,00
200945403424;94;11;00;;17/71, :;;;24750,00
150256413739;94;11;00;;1709/89, :;;;22252,50
220830400838;01;18;00;;171/70, :;;;23250,00
030158430133;94;11;00;;1710/89, :;;;21844,43
240460409525;94;11;00;;1711/89, :;;;21762,50
100160411223;94;11;00;;1712/89, :;;;21562,50
180558519819;94;11;00;;1712/89/1, :;;;10780,00
161162423825;94;11;00;;1713/89, :;;;18656,79
230156412210;96;15;00;;1715/89, M:;;;26125,00
241164407618;96;15;00;;1716/89, T:;;;11220,00
140562422036;14;08;00;;172, :;;;1292,50
021258403824;96;15;00;;1738/87, F:;;;26730,00
120260503625;96;15;00;;1738/87/1, F:;;;8706,48
021066428285;14;08;00;;174, :;;;1215,00
261151421726;96;15;00;;174/79, M:;;;26640,00
280651422817;96;15;00;;1746/89, E:;;;28325,80
130547417782;94;11;00;;1748/75, :;;;24000,00
251141416238;01;06;00;;1748/89, :;;;27000,00
020867419616;14;08;00;;175, :;;;13860,00
091152428242;96;15;00;;175/75, F:;;;25817,50
300640428266;96;15;00;;1750/72, M:;;;30000,00
161052426929;90;65;40;;1753/80,;;;0,00
170151428270;14;08;00;;176, :;;;1687,50
190145419915;94;11;00;;176/72, :;;;24000,00
040944404820;96;15;00;;1762/89, N:;;;28500,00
150249426814;90;65;40;;1763/76,;;;0,00
230562514212;96;15;00;;1763/88, E:;;;15952,66
111140430164;90;65;40;;1769/71,;;;0,00
130355528322;14;08;00;;177, :;;;1351,25
230357430087;90;65;40;;1775/78,;;;0,00
160649424833;96;15;00;;1779/71, F:;;;26910,00
150341428222;14;08;00;;178, :;;;1750,00
110357415403;90;65;40;;1787/81,;;;0,00
160857401919;90;65;40;;1788/78,;;;0,00
041154426325;14;08;00;;179, :;;;1495,00
271138406926;94;11;00;;179/78, :;;;24750,00
030537430213;96;15;00;;18/67, S:;;;28500,00
130261427416;14;08;00;;180, :;;;1408,75
040938402749;96;15;00;;180/73, M:;;;33120,00
220135430082;90;65;40;;1807/72,;;;0,00
061058426614;14;08;00;;181, :;;;1667,50
140528430198;96;15;00;;181/73, M:;;;28500,00
170159413137;94;11;00;;1819/87, :;;;21390,00
290867427210;14;08;00;;182, :;;;13244,00
101241428953;94;11;00;;182/70, :;;;24000,00
060936429719;96;15;00;;1826/88, A:;;;30000,00
260528430143;96;15;00;;18264/60, Y:;;;36750,00
260156401914;90;65;40;;1840/79,;;;0,00
260259530137;94;11;00;;1844/88, :;;;19616,55
260529430129;96;15;00;;18500/60, F:;;;33000,00
240534430061;96;15;00;;18554/60, T:;;;28687,50
200631430171;96;15;00;;18556/60, E:;;;27750,00
200557430017;90;65;40;;1856/86, :;;;19830,00
161235430066;96;15;00;;1858/89, F:;;;32062,50
111037430211;96;15;00;;186/77, J:;;;28500,00
060744401543;96;15;00;;1863/89, M:;;;34920,00
090356402410;90;65;40;;1864/78,;;;0,00
090151425045;96;15;00;;1864/89, M:;;;27720,00
230230530064;94;11;00;;1866/69/2, :;;;20880,00
100137430178;94;11;00;;1868/69, :;;;33000,00
141150400839;96;15;00;;1870/87, L:;;;25530,00
070356415336;96;15;00;;1881/88, A:;;;24056,59
260752411019;90;65;40;;1883/81,;;;0,00
010555528320;90;65;40;;1884/81,;;;0,00
240451530032;90;65;40;;1885/81,;;;0,00
240438400866;01;18;00;;189/71, :;;;23040,00
260459412231;94;11;00;;1894/87, :;;;21390,00
260162512266;94;11;00;;1894/87/1, :;;;17490,00
120151428128;96;15;00;;19/76, F:;;;15697,50
160459420532;96;15;00;;19/81, F:;;;19305,00
090148400824;96;15;00;;1902/72, F:;;;27600,00
210145422773;94;11;00;;1903/72, :;;;24000,00
080448402128;94;11;00;;1904/72, :;;;24000,00
100851417712;96;15;00;;1904/73, F:;;;27600,00
270951418423;90;65;40;;1906/71,;;;0,00
280434430044;15;18;00;;1911/78, :;;;21248,00
110743417722;96;15;00;;192/73, X:;;;25380,00
260429430017;96;15;00;;1920/75, J:;;;34092,06
101149530218;90;65;40;;1922/76,;;;0,00
281153429789;90;65;40;;1926/76,;;;0,00
300451424987;96;15;00;;1938/75, F:;;;13800,00
250327406113;96;15;00;;19522/60, X:;;;26250,00
121054417747;96;15;00;;1960/75, M:;;;25920,00
130133430047;96;15;00;;19666/60, E:;;;29250,00
100738529720;96;15;00;;19666/60/1, E:;;;25500,00
150241415133;96;15;00;;1967/64, A:;;;27750,00
271259400416;90;65;40;;1985/79,;;;0,00
090651429245;90;65;40;;1988/76,;;;0,00
121037404434;96;15;00;;1990/72, M:;;;25200,00
130254419725;90;65;40;;1990/76,;;;0,00
260743430066;90;65;40;;1991/69,;;;0,00
300445424948;96;15;00;;1996/73, A:;;;23760,00
110749530101;90;65;40;;1997/77,;;;0,00
230455425003;90;65;40;;1999/77,;;;0,00
270941407632;15;19;00;;1O91/79, :;;;26424,00
031141410616;96;15;00;;200/66, F:;;;30000,00
141154524927;90;65;40;;2002/87, :;;;6130,34
090846423628;90;65;40;;2006/67,;;;0,00
240746414717;90;65;40;;2007/67,;;;0,00
280246420316;90;65;40;;2009/67,;;;0,00
180547408718;90;65;40;;2010/67,;;;0,00
300355413110;90;65;40;;2012/78,;;;0,00
240160530219;90;65;40;;2015/80,;;;0,00
140353403824;94;11;00;;2026/86, :;;;24480,00
110353401944;90;65;40;;2028/79,;;;0,00
090947424814;96;15;00;;2032/72, J:;;;22980,00
101235407611;94;11;00;;2046/64, :;;;26250,00
160160430082;96;15;00;;205/84, F:;;;20642,50
240239406130;90;65;40;;2075/76,;;;0,00
260563426713;90;65;40;;2080/82,;;;0,00
141043419614;96;15;00;;209/81, F:;;;30750,00
250351416426;94;11;00;;2093/72, :;;;23040,00
110650428262;90;65;40;;2094/72,;;;0,00
290633429731;96;15;00;;21/77, F:;;;32214,58
120146430151;96;15;00;;2105/73, O:;;;27202,50
190828430021;96;15;00;;2110/73, Z:;;;35250,00
020659430183;96;15;00;;2110/84, F:;;;21820,31
150843425048;96;15;00;;2111/72, F:;;;27600,00
281137424961;96;15;00;;2111/73, A:;;;24937,50
090446426811;90;65;40;;2112/66,;;;0,00
160551417731;96;15;00;;2112/72, F:;;;26580,00
160951429715;96;15;00;;2113/72, F:;;;24500,00
151053416942;96;15;00;;2113/89, E:;;;25530,00
161146428116;90;65;40;;2114/66,;;;0,00
120145427129;96;15;00;;2124/89, F:;;;36937,50
200458430046;90;65;40;;2129/78,;;;0,00
131239430066;96;15;00;;2133/73, A:;;;8864,91
121129430146;96;15;00;;2142/73, L:;;;25500,00
061166425109;96;15;00;;2143/86, A:;;;11016,00
070326430076;96;15;00;;2148/72, U:;;;33000,00
130834400860;01;02;00;;2162/88, :;;;28500,00
240451421346;96;15;00;;2163/73, F:;;;26910,00
190853429743;96;15;00;;2164/73, F:;;;23402,50
150434430225;15;20;00;;219/76, :;;;27739,58
101157422778;90;65;40;;2195/82,;;;0,00
060731403216;96;15;00;;221/75, M:;;;24750,00
190136530240;96;15;00;;2221/70, J:;;;24000,00
190250421355;96;15;00;;2224/86, O:;;;31500,00
071037430058;94;11;00;;2233/66, :;;;24000,00
221038422763;96;15;00;;2245/73, M:;;;35250,00
090130507519;96;15;00;;225/78, U:;;;23250,00
280841400897;01;29;00;;2254/84, :;;;26250,00
250452429787;96;15;00;;2256/73, F:;;;26910,00
080950414757;96;15;00;;2257/70, F:;;;27600,00
301146430082;96;15;00;;2259/73, M:;;;26820,00
240941430077;94;11;00;;2260/66, :;;;24000,00
250444429744;90;65;40;;2262/87, :;;;21750,00
100261530096;96;15;00;;2264/86, U:;;;17118,00
260953406435;96;15;00;;227/85, F:;;;26162,50
120650409239;90;65;40;;2279/74/1,;;;0,00
240647506915;90;65;40;;2286/74,;;;0,00
270236404815;96;15;00;;2295/70, U:;;;27750,00
150751422034;96;15;00;;23/77, F:;;;24420,00
230354427421;94;11;00;;2305/85, :;;;23040,00
300456408943;96;15;00;;2306/74, F:;;;21807,50
271149426332;90;65;40;;2309/73,;;;0,00
220947401340;96;15;00;;231/75, M:;;;25500,00
120249420722;96;15;00;;231/78, J:;;;24322,50
240531429719;96;15;00;;2310/88, E:;;;37500,00
070736529722;96;15;00;;2310/88/1, E:;;;21750,00
280654420219;96;15;00;;2311/88, O:;;;24660,00
050753407526;90;65;40;;2319/84, :;;;21135,00
250136422751;96;15;00;;2332/73, M:;;;25200,00
020752429830;96;15;00;;234/73, F:;;;25920,00
110137430150;94;11;00;;235/65, :;;;35250,00
270357406112;96;15;00;;235/79, M:;;;22990,00
121054407311;96;15;00;;2354/88, M:;;;27700,00
060444415396;96;15;00;;2355/88, M:;;;37500,00
030134430075;96;15;00;;2367/73, U:;;;31680,00
241235425099;94;11;00;;237/70, :;;;24750,00
141052403614;96;15;00;;237/73, F:;;;28740,00
040256429215;96;15;00;;2378/88, F:;;;25000,00
171150412212;94;11;00;;2382/74, :;;;23040,00
270443516414;94;11;00;;239/85, :;;;21750,00
160632530058;94;11;00;;2390/70, :;;;22500,00
171247413916;96;15;00;;2394/85, J:;;;27360,00
290756410619;90;65;40;;2403/78,;;;0,00
310153419054;94;11;00;;2414/88, :;;;25200,00
161055417737;94;11;00;;2415/88, :;;;20850,00
140261417743;94;11;00;;2416/88, :;;;20770,00
060661430146;94;11;00;;2417/88, :;;;17820,00
291252418515;96;15;00;;2427/74, F:;;;25702,50
140347515328;96;15;00;;2428/79, O:;;;17796,25
140247415418;96;15;00;;2429/79, O:;;;28800,00
061053422235;96;15;00;;2429/88, M:;;;28080,00
121140430163;90;65;40;;2437/60,;;;0,00
030131429714;94;11;00;;246/77, :;;;24000,00
040857430115;96;15;00;;2472/79, F:;;;19800,00
280854429832;96;15;00;;2477/75, F:;;;20350,00
020638402722;96;15;00;;2477/85, F:;;;38700,00
260934429711;96;15;00;;2481/88, F:;;;22687,50
040838530268;96;15;00;;2481/88/1, F:;;;21312,50
150250429780;96;15;00;;2482/88, F:;;;28380,00
231057406928;90;65;40;;2487/77,;;;0,00
060444403635;94;11;00;;2496/74, :;;;24000,00
140434427115;96;15;00;;250/81, M:;;;31500,00
200952427117;96;15;00;;2501/77, F:;;;25160,00
140952427254;96;15;00;;2503/77, F:;;;26392,50
071246430097;96;15;00;;2505/65, G:;;;21000,00
110250422048;96;15;00;;2511/77, M:;;;28080,00
150254418616;96;15;00;;2518/88, F:;;;28020,00
061126430149;96;15;00;;252/74, U:;;;29250,00
250253422777;90;65;40;;2528/82,;;;0,00
160159421023;94;11;00;;2528/88, :;;;22080,00
251256521046;96;15;00;;2528/88/1, F:;;;20074,92
091248419818;90;65;40;;255/73,;;;0,00
111148430118;96;15;00;;2553/80, P:;;;28800,00
030546430047;15;00;41;;2562/80, :;;;23785,83
030459522744;94;11;00;;2563/86, :;;;16353,75
260556424912;90;65;40;;2564/86, :;;;21210,00
200252406147;96;15;00;;2565/88, O:;;;28800,00
250362404412;90;65;40;;2567/87, :;;;16665,00
040851422421;96;15;00;;2570/79, O:;;;25702,50
181251414523;96;15;00;;2576/77, F:;;;24420,00
190932430144;96;15;00;;2580/65, K:;;;35812,50
051141430260;90;65;40;;2582/65,;;;0,00
270831405628;96;15;00;;2588/77, P:;;;20250,00
080758400822;96;15;00;;2592/80, F:;;;24150,00
140555422126;96;15;00;;2596/79, J:;;;21102,50
180439430205;96;15;00;;2607/84, F:;;;31500,00
201058422738;96;15;00;;2611/84, F:;;;20625,00
080363430285;96;15;00;;2612/84, F:;;;16800,00
220659430091;96;15;00;;2613/84, E:;;;20700,00
270761430042;96;15;00;;2614/84, F:;;;11220,00
040854429776;96;15;00;;2616/80, U:;;;20325,00
190744430139;90;65;40;;2626/65,;;;0,00
250529430015;96;15;00;;2637/77, S:;;;28687,50
270862410032;96;15;00;;2637/84, M:;;;14245,00
110853422741;96;15;00;;2639/79, J:;;;21540,00
240238429736;96;15;00;;2649/80, F:;;;44400,00
130850424934;94;11;00;;2649/82, :;;;23040,00
030440529727;96;15;00;;2650/80, F:;;;26400,00
160961430218;96;15;00;;2657/80, M:;;;16852,35
221144407516;96;15;00;;2660/79, M:;;;26937,50
041144405344;01;00;50;;2678/70, :;;;25637,50
280458412246;96;15;00;;2686/79, F:;;;12760,00
310129430165;96;15;00;;269/68, P:;;;30000,00
151157424947;96;15;00;;2691/80, F:;;;23460,00
130548414313;94;11;00;;270/74, :;;;23187,50
130656429715;96;15;00;;2708/78, F:;;;24365,00
210742424929;94;11;00;;271/68, :;;;24750,00
140247424939;90;65;40;;271/74,;;;0,00
211264413946;90;65;40;;2729/86, :;;;16335,00
240355421127;96;15;00;;2729/89, A:;;;27400,00
190754403433;96;15;00;;2730/89, F:;;;16280,00
151051416818;94;11;00;;2741/77, :;;;23040,00
150648411214;94;11;00;;2747/79, :;;;24000,00
060739424986;96;15;00;;2756/84, G:;;;27750,00
260953529857;96;15;00;;2758/78, J:;;;17681,25
250739530233;94;11;00;;2758/89, :;;;21750,00
100164412223;94;11;00;;2759/89, :;;;16704,03
210262413235;96;15;00;;2766/84, F:;;;14245,00
160267400027;96;15;00;;2767/89, F:;;;8262,00
300959406915;96;15;00;;2769/84, F:;;;24150,00
250652429802;96;15;00;;2769/87, F:;;;25530,00
280865430257;96;15;00;;2778/76/1, T:;;;11067,00
020852522776;96;15;00;;2779/84, O:;;;18794,02
030551426819;96;15;00;;2784/72, U:;;;23700,00
050653407422;96;15;00;;2784/73, F:;;;25530,00
260258424244;94;11;00;;2794/87, :;;;21562,50
180254423922;94;11;00;;2795/87, :;;;23040,00
150255421219;94;11;00;;2797/87, :;;;22720,00
021234430086;96;15;00;;2806/78, F:;;;37500,00
151258404611;94;11;00;;2806/89, :;;;20642,50
230752418336;90;65;40;;2808/79,;;;0,00
160961502517;96;15;00;;2816/80, O:;;;15446,82
180355429899;96;15;00;;2817/80, M:;;;26780,00
240239415379;96;15;00;;2824/84, X:;;;30000,00
270248529738;01;08;00;;2832/85, :;;;25500,00
160464400835;96;15;00;;2833/87, M:;;;21228,22
030467403438;96;15;00;;2842/89, J:;;;12929,00
300352515402;96;15;00;;2850/78, J:;;;21045,00
200343406433;96;15;00;;2856/80, M:;;;23250,00
040664424966;96;15;00;;2858/84, F:;;;11220,00
030629406712;96;15;00;;2859/68, M:;;;25920,00
230362430153;96;15;00;;2859/84, U:;;;17509,94
041050428246;96;15;00;;2879/78, J:;;;21505,00
110743430257;94;11;00;;288/67, :;;;24000,00
080151426372;94;11;00;;2895/77, :;;;23360,00
110739417770;94;11;00;;2899/68, :;;;26250,00
180644430140;90;65;40;;2900/66,;;;0,00
130241424023;90;65;40;;2901/66,;;;0,00
200759430066;96;15;00;;2912/78, F:;;;22715,00
200138430063;96;15;00;;2929/61, F:;;;30750,00
131257430166;90;65;40;;2955/79,;;;0,00
120459430099;90;65;40;;2958/79,;;;0,00
220258415325;90;65;40;;2959/79,;;;0,00
060356402413;96;15;00;;2963/78, F:;;;21065,00
260857412237;90;65;40;;2966/79,;;;0,00
130341410614;96;15;00;;2968/87, M:;;;31500,00
160641510614;96;15;00;;2969/87, M:;;;21000,00
190252422773;96;15;00;;2970/87, M:;;;26910,00
080753429247;96;15;00;;2972/76, F:;;;21065,00
030267407522;90;65;40;;2976/86, :;;;15876,00
270439430108;15;18;00;;2978/81, :;;;28960,00
080349414414;96;15;00;;2987/77, J:;;;24420,00
180240417724;96;15;00;;2990/76, M:;;;27000,00
200739425083;96;15;00;;30/70, A:;;;24375,00
051260430052;90;65;40;;3002/80,;;;0,00
111150428930;15;20;00;;3003/84, :;;;24633,55
080938422850;96;15;00;;3009/89, M:;;;26250,00
Diese Liste beinhaltet die Namen von 90.598 Mitarbeitern des Ministeriums für Staatssicherheit der DDR. Die Liste ist nicht vollständig. Insbesondere Mitarbeiter der Führungsebene sind nicht enthalten.
This is a list of 90.598 members of the secret police of East Germany (Ministry for State Security), the list isn’t complete, because the most of the high Officiers lieke Colonel and higher have destroyed the personal Informations in the last days of Eastern Germany.
| Listen der Stasimitarbeiter-hier findest Du sie! Was bedeuten die Zahlen? |
| 1.Listen der Stasi-Diensteinheiten! Bem.:hier kannst du die Nr.(6-stellig) der Dienststellen heraussuchen. 2.Liste der Stasi-Mitarbeiter (Hauptamtlich) Bem.:Hoffentlich hast Du einen guten Rechner, denn die Liste ist erschreckend lang. Die ersten 6 Ziffern sind das Geburtsdatum + die nächsten 6 Ziffern = Dienstausweisnummer! Die zwei Ziffern hinter dem Geburtsdatum geben das Geschlecht an: 41 und 42 = Männlich, 51 und 52 = Weiblich! Wichtig für suchen und finden, sind die sechs Ziffern in den Semikolon vor den Namen: z.B. ;07;00;44; ! Das ist die Nummer der Dienststelle ! Also du suchst in der Liste der Dienststellen, die Nummer der Dienststelle, die Dich interessiert. Damit gehst Du in die Liste der Mitarbeiter und suchst Dir alle Mitarbeiter der entsprechenden Dienststelle heraus. Ich habe das für mein Wohnort getan und so alle Mitarbeiter gefunden. Ob die Liste Vollständig ist kann ich nicht einschätzen, aber zumindest er/kannte ich einige Exverräter vom Namen her. 3.Liste der OibE (Offiziere im besonderen Einsatz) |
Warum mich die Neo-STASI zum Nummer 1 Feind erklärt hat und “liquidieren” will
Liebe Leser,
nachdem wir die STASI-Listen veröffentlichen und damit entschieden gegen die Neo-STASI und deren bislang getarnte Verbündete auch in der Gesellschaft, der Legislative und der Justiz vorgehen, nehmen die Morddrohungen und die Erpressungen sowie die Rufmorde vor allem der Neo STASI-“GoMoMoPa” gegen mich zu.
Keine Sorge.
Wer mich kennt, weiss, dass dies mich nicht stoppen wird.
Einer muss diesen Job machen.
Herzlichst Ihr
Bernd Pulch, MA
DIE STASI STALKER UND GEWOHNHEITSVERBRECHER DER STASI-“GoMoPA” in Dokumenten
Exposed – Kim Schmitz aka dotcom and MegaUpload Photos in the Court of New Zealand
![[Image]](https://i0.wp.com/cryptome.org/2012-info/megaupload/pict73.jpg) Megaupload.com employees Bram van der Kolk, also known as Bramos, left, Finn Batato,second from left, Mathias Ortmann and founder, former CEO and current chief innovation officer of Megaupload.com Kim Dotcom (also known as Kim Schmitz and Kim Tim Jim Vestor), right, appear in North Shore District Court in Auckland, New Zealand, Friday, Jan. 20, 2012. Megaupload.com employees Bram van der Kolk, also known as Bramos, left, Finn Batato,second from left, Mathias Ortmann and founder, former CEO and current chief innovation officer of Megaupload.com Kim Dotcom (also known as Kim Schmitz and Kim Tim Jim Vestor), right, appear in North Shore District Court in Auckland, New Zealand, Friday, Jan. 20, 2012. |
 German Internet millionaire Kim Schmitz arrives for. a trial at a district court in Munich in these May 27, 2002 file photos. New Zealand police broke through electronic locks and cut their way into a mansion safe room to arrest the alleged kingpin of an international Internet copyright theft case and seize millions of dollars worth of cars, artwork and other goods. German national Schmitz, also known as Kim Dotcom, was one of four men arrested in Auckland on January 20, 2012, in an investigation of the Megaupload.com website led by the U.S. Federal Bureau of Investigation. Reuters German Internet millionaire Kim Schmitz arrives for. a trial at a district court in Munich in these May 27, 2002 file photos. New Zealand police broke through electronic locks and cut their way into a mansion safe room to arrest the alleged kingpin of an international Internet copyright theft case and seize millions of dollars worth of cars, artwork and other goods. German national Schmitz, also known as Kim Dotcom, was one of four men arrested in Auckland on January 20, 2012, in an investigation of the Megaupload.com website led by the U.S. Federal Bureau of Investigation. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/megaupload/pict75.jpg) In this April 30, 2007 file photo, attorney Robert Bennett speaks in Washington. Bennett, one of the nation’s most prominent defense lawyers will represent file-sharing website Megaupload on charges that the company used its popular site to orchestrate a massive piracy scheme that enabled millions of illegal downloads of movies and other content. (J. Scott Applewhite) In this April 30, 2007 file photo, attorney Robert Bennett speaks in Washington. Bennett, one of the nation’s most prominent defense lawyers will represent file-sharing website Megaupload on charges that the company used its popular site to orchestrate a massive piracy scheme that enabled millions of illegal downloads of movies and other content. (J. Scott Applewhite) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/megaupload/pict72.jpg) Tow trucks wait to remove vehicles from Kim Dotcom’s house in Coatesville, north west of Auckland, New Zealand Friday, Jan. 20, 2012. Police arrested founder Kim Dotcom and three employees of Megaupload.com, a giant Internet file-sharing site, on U.S. accusations that they facilitated millions of illegal downloads of films, music and other content costing copyright holders at least $500 million in lost revenue. (Natalie Slade) Tow trucks wait to remove vehicles from Kim Dotcom’s house in Coatesville, north west of Auckland, New Zealand Friday, Jan. 20, 2012. Police arrested founder Kim Dotcom and three employees of Megaupload.com, a giant Internet file-sharing site, on U.S. accusations that they facilitated millions of illegal downloads of films, music and other content costing copyright holders at least $500 million in lost revenue. (Natalie Slade) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/megaupload/pict78.jpg) A general view shows the Dotcom Mansion, home of Megaupload founder Kim Dotcom, in Coatesville, Auckland, January 21, 2012. The U.S. government shut down the Megaupload.com content sharing website, charging its founders and several employees with massive copyright infringement, the latest skirmish in a high-profile battle against piracy of movies and music. The U.S. Department of Justice announced the indictment and arrests of four company executives in New Zealand on Friday as debate over online piracy reaches fever pitch in Washington where lawmakers are trying to craft tougher legislation. Reuters A general view shows the Dotcom Mansion, home of Megaupload founder Kim Dotcom, in Coatesville, Auckland, January 21, 2012. The U.S. government shut down the Megaupload.com content sharing website, charging its founders and several employees with massive copyright infringement, the latest skirmish in a high-profile battle against piracy of movies and music. The U.S. Department of Justice announced the indictment and arrests of four company executives in New Zealand on Friday as debate over online piracy reaches fever pitch in Washington where lawmakers are trying to craft tougher legislation. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/megaupload/pict79.jpg) A broken intercom system is seen after a police raid at Dotcom Mansion, home of accused Kim Dotcom, who founded the Megaupload.com site and ran it from the $30 million mansion in Coatesville, Auckland January 21, 2012. The U.S. government shut down the Megaupload.com content sharing website, charging its founders and several employees with massive copyright infringement, the latest skirmish in a high-profile battle against piracy of movies and music. New Zealand police on Friday raided a mansion in Auckland and arrested Kim Dotcom, also known as Kim Schmitz, 37, a German national with New Zealand residency. Reuters A broken intercom system is seen after a police raid at Dotcom Mansion, home of accused Kim Dotcom, who founded the Megaupload.com site and ran it from the $30 million mansion in Coatesville, Auckland January 21, 2012. The U.S. government shut down the Megaupload.com content sharing website, charging its founders and several employees with massive copyright infringement, the latest skirmish in a high-profile battle against piracy of movies and music. New Zealand police on Friday raided a mansion in Auckland and arrested Kim Dotcom, also known as Kim Schmitz, 37, a German national with New Zealand residency. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/megaupload/pict77.jpg) An entrance to Megaupload’s office at a hotel in Hong Kong is seen in this Hong Kong government handout photo released late January 20, 2012. The Hong Kong government said on Friday over HK$300 million ($38.4 million) worth of proceeds from Megaupload were seized in the country in joint operations by Hong Kong customs and U.S. authorities. The U.S. government shut down the Megaupload.com content sharing website, charging its founders and several employees with massive copyright infringement, the latest skirmish in a high-profile battle against piracy of movies and music. Reuters An entrance to Megaupload’s office at a hotel in Hong Kong is seen in this Hong Kong government handout photo released late January 20, 2012. The Hong Kong government said on Friday over HK$300 million ($38.4 million) worth of proceeds from Megaupload were seized in the country in joint operations by Hong Kong customs and U.S. authorities. The U.S. government shut down the Megaupload.com content sharing website, charging its founders and several employees with massive copyright infringement, the latest skirmish in a high-profile battle against piracy of movies and music. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/megaupload/pict74.jpg) In this photo taken Friday, Jan. 20,2012, provided by the Government Information Service in Hong Kong, large-scale high-speed servers set up at Megaupload’s office are shown inside a hotel room in Hong Kong. Customs officials said they seized more than $42.5 million in assets from the Hong Kong based company. The U.S. government shut down Megaupload’s file-sharing website on Thursday, alleging that the company facilitated illegal downloads of copyrighted movies and other content. In this photo taken Friday, Jan. 20,2012, provided by the Government Information Service in Hong Kong, large-scale high-speed servers set up at Megaupload’s office are shown inside a hotel room in Hong Kong. Customs officials said they seized more than $42.5 million in assets from the Hong Kong based company. The U.S. government shut down Megaupload’s file-sharing website on Thursday, alleging that the company facilitated illegal downloads of copyrighted movies and other content. |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/megaupload/pict76.jpg) A masked hacker, part of the Anonymous group, hacks the French presidential Elysee Palace website on January 20, 2012 near the eastern city of Lyon. Anonymous, which briefly knocked the FBI and Justice Department websites offline in retaliation for the US shutdown of file-sharing site Megaupload, is a shadowy group of international hackers with no central hierarchy. On the left screen, an Occupy mask is seen. Getty A masked hacker, part of the Anonymous group, hacks the French presidential Elysee Palace website on January 20, 2012 near the eastern city of Lyon. Anonymous, which briefly knocked the FBI and Justice Department websites offline in retaliation for the US shutdown of file-sharing site Megaupload, is a shadowy group of international hackers with no central hierarchy. On the left screen, an Occupy mask is seen. Getty |
The FBI reports – Human Trafficking Prevention
 |
|---|
| Human trafficking victims can be found in many job locations and industries. |
Human Trafficking Prevention
Help Us Identify Potential Victims
01/20/12
For the young Ukrainians, it was a dream come true—the promise of well-paying jobs and free room and board in the United States. Once they arrived, however, it quickly turned into a nightmare. They were forced to endure 16-plus hour workdays, usually with no pay. Their living conditions were wretched, with up to 10 workers in often-unfurnished apartments or row houses. And they faced intimidation, threats of physical harm, or actual violence to keep them in line.

Human Trafficking Myths Be aware of these enduring myths about human trafficking: Myth: Trafficking must involve the crossing of borders. Myth: U.S. citizens can’t be trafficked. Myth: Victims know what they are getting into or have chances to escape. Myth: Victims are never paid. Myth: Victims never have freedom of movement. One last note: human trafficking is often confused with alien smuggling, which includes those who consent to smuggling to get across a border illegally. |
|---|
Members of the organized criminal enterprise responsible for these workers’ misery were ultimately identified and charged in a conspiracy to operate a human trafficking scheme. But, as we observe National Slavery and Human Trafficking Prevention Month, we’re reminded that there are still thousands of victims in the U.S.—and millions worldwide—being forced into both legal and illegal activities.
Human trafficking generates billions of dollars of profit each year, making it one of the world’s fastest growing criminal activities. The FBI investigates it as a priority under our civil rights program, but we see human trafficking activities in other investigative areas as well, including organized crime, crimes against children, and gangs.
To address the threat, we work cases with our local, state, federal, and international partners and participate in approximately 70 multi-agency human trafficking task forces. We also offer our counterparts—as well as non-governmental organizations, including non-profits—human trafficking awareness training. And to help get a better handle on human trafficking within the U.S., the FBI’s Uniform Crime Reporting program plans to start collecting human trafficking data from law enforcement in 2013.
Many of our human trafficking cases are based on information from our partners and from criminal sources, but we also can and do receive tips from the public.
That’s where you come in. Please keep your eyes out for the following indicators that suggest the possibility of human trafficking:
- Individuals who have no contact with friends or family and no access to identification documents, bank accounts, or cash;
- Workplaces where psychological manipulation and control are used;
- Homes or apartments with inhumane living conditions;
- People whose communications and movements are always monitored or who have moved or rotated through multiple locations in a short amount of time;
- Places where locks and fences are positioned to confine occupants; and
- Workers who have excessively long and unusual hours, are unpaid or paid very little, are unable take breaks or days off and have unusual work restrictions, and/or have unexplained work injuries or signs of untreated illness or disease.
Bear in mind: human trafficking victims can be found in many job locations and industries—including factories, restaurants, elder care facilities, hotels, housekeeping, child-rearing, agriculture, construction and landscaping, food processing, meat-packing, cleaning services…as well as the commercial sex industry.
And here’s one more thing to consider: while the majority of human trafficking victims in our investigations are from other countries and may speak little or no English, approximately 33 percent of victims are Americans. They come from a variety of groups that are vulnerable to coercive tactics—like minors, certain immigrant populations, the homeless, substance abusers, the mentally challenged and/or minimally educated, and those who come from cultures that historically distrust law enforcement or who have little or no experience with the legal system.
If you suspect human trafficking activities, do us and the victims a big favor: call the National Human Trafficking Resource Center at 1-888-3737-888 or contact the FBI through our Tips webpage.
TOP-SECRET from the FBI – Former Chicago Lawyer Sentenced to 15 Years in Prison for Mortgage Fraud Involving at Least 102 Fraudulent Bailouts
CHICAGO—A former Chicago lawyer was sentenced to 15 years in federal prison for engaging in mortgage and bankruptcy fraud schemes involving a so-called “mortgage bailout” program that purported to “rescue” financially distressed homeowners but instead tricked victims into relinquishing title to their homes and declaring bankruptcy. The defendant, Norton Helton, participated in at least 102 fraudulent mortgage bailout transactions and more than a dozen fraudulent bankruptcies in 2004 and 2005. He was ordered to pay more than $3.2 million in mandatory restitution to various lenders and financial institutions that were not repaid by the borrowers or fully recovered through subsequent foreclosure sales, federal law enforcement officials announced today.
Helton, 50, of Atlanta and formerly of Chicago, was sentenced Wednesday by U.S. District Judge Samuel Der-Yeghiayan in federal court in Chicago. He was ordered to begin serving his sentence in June.
Helton and two co-defendants, Charles White and Felicia Ford, were convicted of multiple fraud counts following a five-week trial in June and July 2010. White, 43, of Chicago, was sentenced late last year to more than 22 years in prison, while Ford, 39, of Chicago, is awaiting sentencing next month.
White owned and operated Eyes Have Not Seen (EHNS), which purported to offer insolvent homeowners mortgage bailout services that would prevent them from losing their homes in foreclosure by selling their property to third-party investors for whom the defendants fraudulently obtained mortgage financing. The victim-clients were assured they could continue living in their homes rent and mortgage-free for a year while they attempted to eliminate their debt and repair their credit. EHNS misled clients concerning the operation of the purported program. In particular, victim-clients were not told that their homes were, in fact, being sold to third parties and that ENHS would strip their homes of any available equity at the time of sale, which EHNS did. Instead, ENHS clients were told that they were only temporarily transferring their homes and would preserve their ownership rights.
Helton was recruited by White to represent ENHS participants at the real estate transactions it orchestrated. The victim-clients typically met Helton for the first time at the closings at which they sold their homes. Helton worked to placate individuals who questioned the program and to dissuade them from retaining independent legal advice. He received above-market legal fees for appearing at closings at which he did little more than guide victim-clients through the paperwork that sold their homes with EHNS receiving all of the profits from the sale. Helton further used the ENHS real estate closings to recruit prospective bankruptcy clients, informing them that bankruptcy would serve as a component of the bailout program. Helton subsequently filed more than a dozen bankruptcy petitions for victim-clients that omitted any reference to their recent EHNS property sales.
In addition to participating in ENHS’s bailout program, Helton attempted to implement his own mortgage bailout program through Diamond Management of Chicago, Inc., a foreclosure avoidance company comparable to EHNS. Helton marketed Diamond’s bailout program and his bankruptcy services as part of a “credit repair” system.
Patrick J. Fitzgerald, United States Attorney for the Northern District of Illinois, announced the sentence today with Robert D. Grant, Special Agent in Charge of the Chicago Office of the Federal Bureau of Investigation; Barry McLaughlin, Special Agent in Charge of the U.S. Housing and Urban Development Office of Inspector General in Chicago; and Thomas P. Brady, Inspector in Charge of the U.S. Postal Inspection Service in Chicago. The U.S. Trustee Program, a Justice Department component that oversees administration of bankruptcy cases and private trustees, also assisted in the investigation.
The government is being represented by Assistant U.S. Attorneys Joel Hammerman and Mark E. Schneider.
The case is part of a continuing effort to investigate and prosecute mortgage fraud in northern Illinois and nationwide under the umbrella of the interagency Financial Fraud Enforcement Task Force, which was established to lead an aggressive, coordinated, and proactive effort to investigate and prosecute financial crimes. For more information on the task force, visit: http://www.StopFraud.go
UNCENSORED – FEMEN Protest against Radioactiviyt in Ucraine

Egyptian Revolution Protest Manual (How to Protest Intelligently)

This document is an Arabic manual for Egyptian protesters circulated via email and in hard copy prior to the protests on Friday January 28, 2010. For background on the document and English translations of selected portions, see The Atlantic’s article Egyptian Activists’ Action Plan: Translated.
DOWNLOAD ORIGINAL DOCUMENT HERE
TOP-SECRET – Faces of Torture: Egyptian State Security Officers Photos and Names

The following set of photos and names has been publicly posted to other sites, including Cryptome. However, with the recent confirmation that Flickr removed and censored these photos, we wish to ensure that this information reaches as many people as possible. We are also aware that this site is visited frequently by members of the Egyptian government and the International Criminal Court.
When we stormed State Security Police headquarters in Nasr City, which hosted one of Mubarak’s largest torture facilities, on Saturday I found two DVDs in one of the offices, both titled “أرشيف السادة ضباط الجهاز” The Agency Officers’ Archive. The DVDs included profile pictures of State Security officers, organized in folders. Each folder had the officers’ name. Some however did not have the names. There were also sub folders that included pictures of those officers in social events like weddings.
I don’t know what was the purpose of these two DVDs, but I sincerely thank the State Security officials who gave us this present on a golden plate. I initially uploaded the profile pictures to this flickr set and added them to the Piggipedia. But unfortunately, flickr censored the pictures on grounds of “copyrights infringement”!
With the help of ANONYMOUS and other bloggers in Egypt and abroad, I re-uploaded the pictures to the cyberspace, and they are now hosted on several sites.
I urge you all to circulate them. And if you have any more information about those officers please come forward.
Each member of SS has to be brought to justice. This was an agency devoted to spying, surveillance, torture and murder. Every member of this organization from the informer all the way up to the generals should be prosecuted. SS has to be dissolved. It cannot be “restructured” like what the current PM is calling for.
Although those torturers violated our private lives on a daily basis, bugging our phones, offices, and even our bedrooms, I will respect the privacy of their families and will not publish the photos of their social events that included family members.
Download .zip file containing all images (417 MB)
Download .pdf file containing all images (26 MB)
Names of Officers Whose Photos are Contained in the File
- Ahmad el-Badawi
- Ahmad Fathi
- Ahmad Raafat
- Ahmad Raoof
- Ahmed Atef
- Ahmed el-Azzazi
- Ali Allam
- Amgad Ezz Eddin
- Amr Abdel Moula
- Amr L’Assar
- Assem Esmat
- Ayman el-Banna
- Ayman el-Rashidi
- Ehab el-Gheryani
- Fahd Abul Kheir
- Hani Talaat
- Hassan Abdel Rahman
- Hassan Tantawi
- Hisham Abu Gheida
- Hisham el-Baradei
- Hisham el-Dafrawi
- Hossam Wahdan
- Kamal el-Sayyed
- Khaled el-Taweel
- Khaled Moussa
- Khaled Shaker
- Magdi el-Masri
- Maged Mostafa
- Mahmoud el-Rashidi
- Mahmoud el-Zeini
- Mohamed Abdel Kareem
- Mohamed Abul Wafa
- Mohamed el-Morshedi
- Mohamed el-Samanoudi
- Mohamed el-Zamak
- Mohamed Hanafi
- Mohamed Mahmoud Barghash
- Mohamed Safwat
- Mohamed Taher
- Mohamed Yehia
- Mortada Ibrahim
- Motassem Ghoneim
- Rashad Ghoneim
- Rushdi el-Qamari
- Salah Hegazi
- Salah Salama
- Sherif el-Bahei
- Sherif Shabana
- Shoman
- Tarek el-Bahnassawi
- Tarek el-Mouggi
- Tarek el-Rakaybi
Photos of 168 officers whose names are not known are also contained in the file.
FEMEN of Ukraine, the courageous sisters – Uncensored Movie leaked
Three Ukrainian FEMEN activists have allegedly been kidnapped by Belarusian KGB officers who threatened the protesters with knives, cut their hair and then left the women alone in the woods, says the movement’s webpage.
The activists disappeared on Monday in the Belarusian capital, Minsk, after protesting in front of the KGB building against the country’s long-ruling president, Aleksandr Lukashenko.
“From 6 pm Kiev time, the connection with the FEMEN activists has been lost, and one hour later all their mobile phones appeared to be switched off,” a statement on the movement’s webpage said.
Later one of the missing women, Irina Shevchenko, managed to get access to a phone. The activist told her colleagues she had been detained by the police and KGB officers at Minsk railway station, together with two other FEMEN protesters.
“We were blindfolded and put into a bus,” Shevchenko said. “Then they took us to the woods, poured oil over us, forced us to undress — threatening to set fire to us or stab us with knives. They later used those knives to cut our hair.”
Then the activists were left alone in the woods, with no clothes or documents. The girls made a long journey on foot before finding help in a small village which turned out to be deep in the Belarusian outback.
In their blog, the movement’s leaders called on locals to help the activists hide from the police until Ukrainian embassy staff managed to rescue them.
Earlier the movement announced that its camerawoman, Kitty Green, who has Australian citizenship, was detained together with two local journalists. The women were released from detention several hours later; Green was deported to Vilnius, Lithuania.
An official of Belarus State Border Committee, Aleksandr Tushchenko, told Interfax that the committee had no information on the arrest of the FEMEN activists.
The Belarusian Foreign Ministry also denied detaining the FEMEN protesters, nor have they confirmed that they are aware of the activists’ whereabouts.
During their anti-Lukashenko protest, the topless activists chanted, “Long live Belarus!” One of them was made up as President Lukashenko.
December 19 is the anniversary of an unauthorized opposition rally that took place in Minsk in 2010 following presidential elections which was brutally dispersed by police, with many protesters beaten up and arrested.
The FEMEN movement is not notorious for politically-motivated naked protests held at home in Ukraine and in countries throughout Europe, including Vatican City. One of their latest actions was held in the Russian capital, Moscow, in front of the Cathedral of Christ the Savior.
Revealed – Anonymous Hacks Public Intelligence in “Friendly Audit”

On January 16, 2012 an unauthorized party associated with the hacktivist collective Anonymous gained access to this site’s web server. The attacker gained root access and posted a number of versions of a photo of a naked man. These images were used to deface the front of the site in multiple locations and contained the message “WAS HERE WITH 0DAY, ONLY SHIT I FOUND BAD WAS U LOGGING IN FROM A DSL CONNECTION… THEN AGAIN U BOUGHT THIS SERVER WITH UR PERSONAL CARD SO U CAN BE DOX’D… LEFT U THESE COX AS A FRIENDLY REMINDER THAT YOUR BOX CAN BE PWNED AT ALL TIMES…” The attackers then manipulated configuration files for the server which caused an error message to appear to visitors of the site. This state persisted for approximately eight hours blocking access to the site before it was later fixed by the attacker, who left a longer explanation for the hack in the server’s root directory.
Though the hackers were fairly polite and we do not believe that there is any current threat to our users, we have disabled our submissions form and will not be accepting new information at the moment. We have also disabled some of the user features on the site, which were more a remnant of a previous phase of this site’s operation and served little practical value. If you, at any point, have had an account on this site with a password that is also used elsewhere, you should change it. The hackers claim that they did not look into our database to retrieve this information. However, you would be wise to protect against that possibility.
We feel that this action by Anonymous was misguided. While we understand their desire to demonstrate their ability to “penetrate” anything, their defacement of this platform was unnecessary. This site has functioned for several years now as a vital source of information that is concealed and restricted from the general public. Large amounts of people in all walks of life utilize its resources. At the time of the defacement, this site was serving several files as source material for articles in publications around the world, including information on the automated scanning of license plates and other forms of public surveillance in Germany, the Department of Defense’s Non-Lethal Weapons Reference Book which received a large amount of coverage in Russia and Eastern Europe after it was reported on by the BBC, and a particularly frank Marine Corps handbook that describes the CIA’s history of funding the Mujahideen via the Pakistani ISI. Because of the defacement, many people visiting the site were then confronted with pictures of naked men which may have dissuaded them from accessing the extremely important information contained in these documents.
We’ve never professed to be extremely adept technologically, nor have we ever claimed to be creating a massively secure system for the submission of high-profile leaks. In fact, we hate “leaks” in general and we try to avoid using the word as much as possible. Leaking implies an accident, like something that escaped through a crack or water passing through a sieve. How can you leak something that should never have been secret in the first place? We are simply average, humble people who are trying to inform ourselves and others about the world in which we live. Nearly every piece of information on this site is something that was obtained from a publicly-accessible source using means available to any member of the public. We have published this material using open-source software in an attempt to inform others and demonstrate the potential for public action in the sphere of intelligence and media.
And so, if we are to create anything lasting, we must work together towards a society where everyone can express themselves freely and share information openly. We must not attack one another, for this only undermines the legitimacy of our cause. If we are to live in a world where knowledge truly is free, we must act with the gravity that this freedom demands. Anarchy is not chaos, it is self-governance.
sorry for this but we consider u friendly so i just left a message and wiped /var/log there was nothing u could do against this breach, this was just to remind you that we can breach anything and so can the enemy :) be careful what u do, improve ur OPSEC maybe buy the server/hosting with a temp card and access is via Tor try and remove links from ur personal life from this service :) keep up the good work and hope u enjoy the cox :D cheers #antisec PS: i didnt steal any of ur credentials neither i even look into the mysql db, i dont know any of ur passwords though u should change them of course. this was a direct root via a 0day we have :) it was not ur fault... i just thought that i should leave u this message apart from the cox so u get a feel what penetration looks like... our enemies dont leave messages ;)
Mord an Benno Ohnesorg unter STASI-Aufsicht und Beihilfe der Berliner Polizei
STASI-AGENTEN MIT GEHEIMCODES TEIL 17-STASI AGENTS WITH SECRET CODES PART 17
see more info at http://www.victims-opfer.com
Die Liste wurde bereits früher hier publiziert:
http://stasiopfer.de/component/option,com_simpleboard/Itemid,/func,view/id,993815828/catid,4/
Vom “Stasiopfer”-Angebot führt ein Link zu einer Website in den USA (www.jya.com), die sich auch mit den Praktiken von Geheimdiensten beschäftigt. Dort findet sich die “Fipro-Liste”, das detaillierte “Finanzprojekt” der Stasi, angefertigt in den letzten Tagen der DDR, um die Rentenansprüche der rund 100 000 hauptamtlichen Mitarbeiter des MfS auch nach dem Zusammenbruch des Systems belegen zu können. Die “Fipro-Liste” ist seit langem bekannt und diente Anfang der neunziger Jahre etwa zur Identifizierung der so genannten OibE – Offiziere im besonderen Einsatz. Diese Liste „Offiziere im besonderen Einsatz“im Jahre 1991 erschien in der “taz. Die Echtheit kann beim BStU überprüft werden.
Siehe u.a. http://www.spiegel.de/spiegel/print/d-22539439.html
Auf Druck ehemaliger STASI-Leute und Ihrer Genossen wurde die Liste aus dem Verkehr gezogen.
Hier ist sie wieder:
130942401510;01;19;69;;3011/86, :;;;24750,00
070254529797;96;15;00;;3020/76/26, M:;;;2359,86
300361430128;96;15;00;;3020/76/9, M:;;;20315,16
200561406925;90;65;40;;3022/84,;;;0,00
220360519913;96;15;00;;3022/89, A:;;;17077,50
180331429712;96;15;00;;3032/82, J:;;;33000,00
180140430104;96;15;00;;3039/62, F:;;;27000,00
111254421215;96;15;00;;3039/82, M:;;;24150,00
250438430255;96;15;00;;304/80, M:;;;35250,00
070445429713;94;11;00;;3046/66, :;;;25500,00
120343420219;15;00;41;;3047/80, :;;;23689,17
241160430079;96;15;00;;3051/89, E:;;;20196,00
230653403446;96;15;00;;3057/89, F:;;;14025,00
140459424922;96;15;00;;3062/78, F:;;;18480,00
300640401522;01;19;69;;3062/85, :;;;26250,00
160636517790;96;15;00;;3073/89, K:;;;20631,05
140356429886;90;65;40;;3077/83, :;;;22080,00
191049429763;90;65;40;;3078/83,;;;0,00
140857418210;90;65;40;;3079/80,;;;0,00
310760404030;90;65;40;;3079/83, :;;;19737,50
140251422792;96;15;00;;3097/77, A:;;;22080,00
180757406411;90;65;40;;3100/80,;;;0,00
270652406414;94;11;00;;311/80, :;;;22400,00
090468424913;96;15;00;;3118/89, S:;;;12929,00
100833430032;96;15;00;;3121/64, L:;;;25500,00
070834416449;96;15;00;;3127/78, H:;;;17595,00
230233516436;96;15;00;;3127/78/1, H:;;;16905,00
181245429737;96;15;00;;3136/89, F:;;;21000,00
090649529722;96;15;00;;3137/89, F:;;;20766,25
070860518916;96;15;00;;3153/89, F:;;;17097,10
161231429746;96;15;00;;3156/89, E:;;;40312,50
121039529724;96;15;00;;3156/89/1, E:;;;25500,00
140752422766;96;15;00;;3166/78, J:;;;22022,50
091150523617;96;15;00;;3167/78, U:;;;18720,00
110766409223;96;15;00;;3170/89, Q:;;;13329,00
200351505722;96;15;00;;318/78, E:;;;17940,00
220248429731;94;11;00;;3212/77, :;;;24000,00
290651430066;96;15;00;;3254/84, E:;;;23940,00
040154401721;94;11;00;;3256/84, :;;;20460,00
241142430219;96;15;00;;326/73, F:;;;30750,00
281160404352;96;15;00;;3261/84, F:;;;7917,00
150430430092;96;15;00;;327/73, F:;;;33900,00
191053403427;96;15;00;;327/81, M:;;;23460,00
111162430026;15;20;00;;3299/88, :;;;18810,00
260539402420;96;15;00;;3317/84, M:;;;30000,00
120332404512;96;15;00;;3321/71, U:;;;33000,00
190237419402;96;15;00;;3323/86, J:;;;35250,00
260754415136;96;15;00;;3328/86, A:;;;23760,00
041135401325;01;19;00;;3335/75, :;;;27750,00
220646530114;90;65;40;;3339/78,;;;0,00
151163408011;96;15;00;;3341/86, S:;;;11220,00
240351510317;96;15;00;;3353/86, F:;;;21102,50
050446419025;96;15;00;;337/77, O:;;;24322,50
100351530081;96;15;00;;338/81, J:;;;17203,00
020765430021;96;15;00;;3383/85, Q:;;;9200,00
220860409518;94;11;00;;3385/84, :;;;18932,50
240747424028;94;11;00;;3386/71, :;;;24000,00
230356419011;90;65;40;;3388/76,;;;0,00
260457401715;90;65;40;;3389/76,;;;0,00
280948429710;94;11;00;;339/73, :;;;24000,00
040249530200;96;15;00;;339/73/2, E:;;;22260,00
160556400859;90;65;40;;3390/76,;;;0,00
220156413927;90;65;40;;3391/76,;;;0,00
270747401544;01;00;40;;3391/89, :;;;27000,00
251054414517;90;65;40;;3392/76,;;;0,00
230737430142;96;15;00;;340/81, F:;;;35250,00
090859430149;96;15;00;;3400/89, F:;;;18161,45
180262421038;96;15;00;;3407/84, F:;;;7224,00
100456510335;90;65;40;;3412/78,;;;0,00
150637425039;96;15;00;;3419/84, O:;;;35250,00
110237524912;96;15;00;;3419/84/1, O:;;;23418,75
101067413528;96;15;00;;3453/86, O:;;;9872,00
270160407517;94;11;00;;3455/86, :;;;20010,00
271251427729;94;11;00;;3457/86, :;;;20880,00
130759503236;96;15;00;;3458/84, N:;;;18543,75
120651415024;94;11;00;;3458/86, :;;;19965,00
150657413211;96;15;00;;3462/79, F:;;;18561,00
030844430061;96;15;00;;3467/86, L:;;;29000,00
081054416425;96;15;00;;3470/85, M:;;;23040,00
160156405941;90;65;40;;3472/76,;;;0,00
280456422774;90;65;40;;3473/76,;;;0,00
240755428256;90;65;40;;3474/76,;;;0,00
230357424429;90;65;40;;3475/76,;;;0,00
230436400820;01;00;50;;3477/73, :;;;26250,00
211141415394;96;15;00;;3478/65, A:;;;25200,00
230542428296;96;15;00;;3478/84, J:;;;26467,50
250753408912;90;65;40;;3490/83,;;;0,00
150930430136;90;65;40;;350/73,;;;0,00
310361430055;90;65;40;;3501/85, :;;;18645,00
281232430171;96;15;00;;3502/61, T:;;;26250,00
071056422774;90;65;40;;3503/87, :;;;20010,00
200364430328;90;65;40;;3507/86, :;;;16665,00
290450415396;96;15;00;;353/77, A:;;;27750,00
110960428225;96;15;00;;3543/81, F:;;;20217,50
181153417720;96;15;00;;3547/82, M:;;;28740,00
131153407527;96;15;00;;3548/82, M:;;;28740,00
271147418814;90;65;40;;3557/78,;;;0,00
071254422425;96;15;00;;3561/88, E:;;;22080,00
180958422741;96;15;00;;3573/82, F:;;;20460,00
190464403435;96;15;00;;3581/88, M:;;;9896,00
060657430119;96;15;00;;3594/74, F:;;;22605,00
200430430044;94;11;00;;3597/81, :;;;23250,00
050532522117;96;15;00;;3599/82, H:;;;16380,00
220643407110;96;15;00;;36/77, M:;;;33000,00
110144430060;96;15;00;;360/68, L:;;;28500,00
250655406411;96;15;00;;361/74, F:;;;26220,00
230956416420;90;65;40;;3619/77,;;;0,00
280150429762;90;65;40;;3622/77,;;;0,00
280130404517;96;15;00;;3627/74, A:;;;33000,00
220835429736;96;15;00;;364/77, U:;;;28500,00
060367414727;96;15;00;;3641/88, O:;;;8450,00
310736415389;96;15;00;;3659/64, M:;;;26250,00
210729430048;96;15;00;;3665/60/1, U:;;;37500,00
061153519712;96;15;00;;3670/88, F:;;;24702,58
031253416430;96;15;00;;3671/88, M:;;;25935,00
070642419362;96;15;00;;3672/88, M:;;;30750,00
131255402727;96;15;00;;3673/88, M:;;;24840,00
140260417119;96;15;00;;3683/81, J:;;;18425,00
200956414137;90;65;40;;3685/82,;;;0,00
101140430245;90;65;40;;3686/64,;;;0,00
031248418618;94;11;00;;3700/73, :;;;24000,00
100649413953;94;11;00;;3701/73, :;;;23040,00
241049428114;94;11;00;;3702/73, :;;;26437,50
030738418819;94;11;00;;3704/73, :;;;24000,00
250634430201;90;65;40;;3705/73,;;;0,00
270257416436;90;65;40;;3705/77,;;;0,00
130535430146;90;65;40;;3706/73,;;;0,00
201254416917;96;15;00;;372/73, F:;;;21065,00
030852420023;96;15;00;;3721/88, F:;;;26212,50
280951529755;96;15;00;;3721/88/1, F:;;;23368,21
100947430145;90;65;40;;3723/80,;;;0,00
110832430101;96;15;00;;3730/66, K:;;;28125,00
090566430217;96;15;00;;3732/87, O:;;;11067,00
191165422737;96;15;00;;3734/88, Y:;;;11067,00
120245428233;96;15;00;;3757/87, F:;;;31950,00
120447419028;90;65;40;;376/69,;;;0,00
240643426811;96;15;00;;3760/87, U:;;;31292,90
090841400718;01;09;00;;3762/82, :;;;31500,00
310152429760;94;11;00;;3763/88, :;;;23760,00
240754507622;96;15;00;;3763/88/1, F:;;;18480,00
260843418718;94;11;00;;377/69, :;;;24375,00
280962422136;96;15;00;;3776/85, F:;;;11220,00
210632429729;96;15;00;;3776/87, F:;;;34200,00
090852400836;01;00;40;;379/88, :;;;22202,50
021263422245;96;15;00;;3791/85, F:;;;11220,00
160760404814;94;11;00;;3814/85, :;;;19357,50
130457401314;90;65;40;;3819/79,;;;0,00
210150409522;96;15;00;;3820/85, F:;;;28463,70
041251508728;96;15;00;;3820/85/1, F:;;;23880,00
141049418647;90;65;40;;3822/77,;;;0,00
051150430043;90;65;40;;3823/77,;;;0,00
230248415355;96;15;00;;3823/86, M:;;;29250,00
241152420727;96;15;00;;3848/81, M:;;;24480,00
130552400811;96;15;00;;3849/81, M:;;;29520,00
100850409112;96;15;00;;3855/85, F:;;;27600,00
201238412211;01;18;00;;3862/81, :;;;24000,00
290639419016;96;15;00;;3871/87, F:;;;40762,50
150846522732;96;15;00;;3876/86, M:;;;23250,00
310548411719;90;65;40;;3883/76,;;;0,00
240856403410;90;65;40;;3884/76,;;;0,00
121059418212;96;15;00;;3887/83, E:;;;22160,32
140941430175;96;15;00;;389/74, A:;;;23040,00
251256413029;90;65;40;;3891/76,;;;0,00
161057416236;96;15;00;;3891/83, F:;;;20150,00
181158430027;90;65;40;;3892/79,;;;0,00
280452400738;90;65;40;;3893/77,;;;0,00
310143417522;90;65;40;;3894/77,;;;0,00
120333530289;96;15;00;;3899/63, U:;;;31500,00
231262530063;96;15;00;;3899/86, U:;;;13484,32
110866430177;96;15;00;;3900/85, M:;;;11016,00
051166403429;96;15;00;;3901/85, M:;;;11016,00
100751424958;96;15;00;;3904/86, F:;;;26852,50
200952529877;96;15;00;;3904/86/1, F:;;;19829,48
100743400833;96;15;00;;3906/83, M:;;;29300,00
050748405016;96;15;00;;3914/85, A:;;;24840,00
300664416913;96;15;00;;3925/86, F:;;;11220,00
230939424912;96;15;00;;3932/87, M:;;;32250,00
180468413412;96;15;00;;3948/86, M:;;;9872,00
290358407510;94;11;00;;3957/83, :;;;21562,50
060854402758;94;11;00;;3959/83, :;;;22267,50
210554404146;96;15;00;;3961/83, M:;;;24480,00
060957406911;96;15;00;;3962/83, N:;;;21957,34
220643409538;96;15;00;;3972/86, M:;;;30000,00
110563530277;96;15;00;;3973/81, O:;;;8003,75
140450414832;96;15;00;;3974/87, J:;;;25067,50
191154410714;96;15;00;;398/76, F:;;;25920,00
260739429732;96;15;00;;3997/85, N:;;;23787,50
200151407538;96;15;00;;4006/76, F:;;;28275,00
290326430281;96;15;00;;401/73, P:;;;30000,00
180640430143;96;15;00;;4010/70, E:;;;24750,00
170142407216;90;65;40;;4025/79,;;;0,00
271136400758;01;00;46;;4028/86, :;;;23250,00
200556405821;90;65;40;;4029/79,;;;0,00
271248522776;90;65;40;;4038/79,;;;0,00
251250514718;96;15;00;;4040/88, F:;;;19387,74
040653429972;96;15;00;;4049/88, O:;;;26220,00
100262400218;90;65;40;;4050/82,;;;0,00
280658402413;96;15;00;;4054/81, F:;;;21242,00
300349430088;90;65;40;;4054/85, :;;;23437,50
260554428928;96;15;00;;4055/88, O:;;;24420,00
280356416027;94;11;00;;407/78, :;;;20700,00
210553427717;90;65;40;;4070/79,;;;0,00
280547401514;01;19;69;;4080/86, :;;;25500,00
250638400739;01;19;00;;4081/86, :;;;24750,00
030135413621;96;15;00;;4083/81, M:;;;23935,49
031256406203;94;11;00;;409/81, :;;;21562,50
180143416412;94;11;00;;410/70, :;;;27000,00
270236429748;94;11;00;;410/81, :;;;23250,00
090935429714;15;06;00;;4101/77, :;;;35812,50
200259402739;90;65;40;;4107/79,;;;0,00
100842422712;90;65;40;;4110/79,;;;0,00
221051425053;94;11;00;;412/77, :;;;23040,00
260148411426;96;15;00;;4128/83, M:;;;30960,00
060838522784;96;15;00;;4139/88, M:;;;24000,00
250457403615;90;65;40;;4142/79,;;;0,00
250953430030;90;65;40;;4146/79,;;;0,00
230240430227;96;15;00;;415/81, F:;;;30750,00
220841405730;94;11;00;;416/70, :;;;24000,00
110845413917;94;11;00;;417/70/1, :;;;24750,00
260347513919;94;11;00;;417/70/2, :;;;21750,00
100636400846;01;18;00;;417/71, :;;;25200,00
180239412280;15;18;00;;417/79, :;;;26624,58
260156403418;96;15;00;;417/86, O:;;;26030,00
291256429246;94;11;00;;4170/83, :;;;21390,00
211053429761;96;15;00;;4174/88, A:;;;27360,00
080151429848;96;15;00;;4189/89, F:;;;11782,50
190751516213;96;15;00;;4189/89/1, F:;;;22130,00
110647407516;96;15;00;;419/81, M:;;;26250,00
230653429742;96;15;00;;4198/81, L:;;;17508,75
161154429821;15;18;00;;4199/80, :;;;23552,00
250135430063;96;15;00;;4207/84, O:;;;34075,00
100657406913;96;15;00;;421/79, F:;;;25012,50
280150404514;96;15;00;;4216/84, F:;;;30000,00
030351400833;96;15;00;;422/87, F:;;;24735,00
141065407614;96;15;00;;423/88, M:;;;11067,00
190159430138;96;15;00;;424/82, M:;;;23460,00
061034430264;96;15;00;;4242/60, J:;;;24304,16
100667425069;90;65;40;;4244/87, *:;;;15912,00
300554408728;96;15;00;;425/79, F:;;;20460,00
290847415028;90;65;40;;4254/77,;;;0,00
230845404814;96;15;00;;4270/78, N:;;;25875,00
111149517717;96;15;00;;4270/78/1, N:;;;21000,00
280446413428;96;15;00;;4273/89, M:;;;30180,00
190667530151;96;15;00;;4274/89, M:;;;13800,00
300161417762;96;15;00;;4276/83, J:;;;17712,00
210936430155;96;15;00;;4283/88, F:;;;30750,00
290455424515;96;15;00;;4288/81, F:;;;27100,00
220258530200;96;15;00;;4288/81/1, F:;;;19112,68
261160506174;96;15;00;;4293/84, J:;;;0,00
100950404730;96;15;00;;4297/89, F:;;;24882,50
231157519022;96;15;00;;4298/89, F:;;;18904,52
110937430140;96;15;00;;43/63, L:;;;24750,00
190363421837;96;15;00;;4311/84, M:;;;14245,00
070737429731;90;65;40;;4324/87, :;;;27000,00
250458408418;90;65;40;;4325/87, :;;;19082,50
121039430126;96;15;00;;4331/86, F:;;;34200,00
270252422722;96;15;00;;4349/84, O:;;;28800,00
211240524238;90;65;40;;4354/77,;;;0,00
110663402715;96;15;00;;4361/84, M:;;;1200,00
120545413412;90;65;40;;4378/77,;;;0,00
101148405642;90;65;40;;4379/77,;;;0,00
300766430222;96;15;00;;4383/86, F:;;;11016,00
160535430143;96;15;00;;4391/83, M:;;;27750,00
051152429839;15;06;00;;4392/76, :;;;21900,00
110558428024;96;15;00;;44/81, F:;;;18468,00
110535429710;96;15;00;;440/87, U:;;;23250,00
030958429253;96;15;00;;4416/80, F:;;;23100,00
060650406124;94;11;00;;4417/84, :;;;23040,00
281258425004;96;15;00;;4463/84, F:;;;22250,00
280957520217;96;15;00;;4463/84/1, F:;;;17595,00
250647424994;90;65;40;;447/74,;;;0,00
230951403612;90;65;40;;448/74,;;;0,00
080556401325;94;11;00;;448/80, :;;;20872,50
290553420227;96;15;00;;4484/84, F:;;;26910,00
240448413417;94;11;00;;4484/87, :;;;24000,00
140339504514;96;15;00;;45/80, F:;;;24687,50
060235412260;96;15;00;;4509/62, J:;;;27000,00
190956416646;96;15;00;;4527/87, A:;;;24150,00
151236430157;90;65;40;;454/73,;;;0,00
240132430157;90;65;40;;4550/77,;;;0,00
090558428213;90;65;40;;4551/77,;;;0,00
310137426940;96;15;00;;4553/85, H:;;;28860,00
200256505812;96;15;00;;4561/87, U:;;;16200,00
120648411428;90;65;40;;4565/77,;;;0,00
130749408921;90;65;40;;4566/77,;;;0,00
161236430113;90;65;40;;4568/77,;;;0,00
070839420244;96;15;00;;458/63, A:;;;33925,00
080241530261;94;11;00;;4586/85, :;;;24000,00
160751407538;96;15;00;;4598/87, F:;;;34100,65
220430530123;96;15;00;;46/72, U:;;;20820,00
221260417711;96;15;00;;4609/80, J:;;;19560,00
110349500413;96;15;00;;4640/89, M:;;;16445,00
080557430056;96;15;00;;4644/80, J:;;;20815,00
101167405314;90;65;40;;4649/87, *:;;;9150,00
111049410111;96;15;00;;465/74, F:;;;24322,50
090544405010;96;15;00;;4651/85, M:;;;27360,00
110770431220;96;15;00;;4666/89, :;;;2700,00
220342400863;96;15;00;;4674/89, M:;;;29250,00
031250429762;96;15;00;;4675/85, A:;;;28567,50
291056427617;96;15;00;;4681/79, F:;;;23805,00
030450407520;96;15;00;;4683/79, M:;;;25200,00
260451412122;96;15;00;;4691/89, L:;;;25530,00
030650428238;96;15;00;;4692/89, L:;;;25702,50
200943430090;96;15;00;;47/73, F:;;;30750,00
070157418411;96;15;00;;4700/89, F:;;;8085,00
021054501932;94;11;00;;4701/89, :;;;17312,50
100258419055;94;11;00;;4705/85, :;;;20700,00
271258406816;94;11;00;;4706/85, :;;;20400,00
070338404836;96;15;00;;4710/80, L:;;;23437,50
240557403138;90;65;40;;4711/78,;;;0,00
150555409537;90;65;40;;4712/78,;;;0,00
230839429724;96;15;00;;4718/88, F:;;;36185,08
181043529713;96;15;00;;4718/88/1, F:;;;24372,58
140342400011;96;15;00;;4719/88, F:;;;33300,00
030653408910;96;15;00;;4729/89, M:;;;28520,00
180466400896;90;65;00;;4732/87, :;;;16038,00
230342400512;01;07;00;;4733/88, :;;;36000,00
290360530091;96;15;00;;475/78, J:;;;16084,23
031247424426;96;15;00;;476/88, A:;;;26820,00
030861408528;90;65;40;;4768/81,;;;0,00
220358425029;94;11;00;;479/83, :;;;21390,00
230555417115;94;11;00;;480/83, :;;;22087,50
100557428250;96;15;00;;4848/80, F:;;;22605,00
130762403623;90;65;40;;4864/81,;;;0,00
170137400810;01;07;00;;4909/75, :;;;26250,00
030365413010;90;65;40;;4909/86, :;;;18150,00
150859413148;96;15;00;;491/80, F:;;;18452,00
160842401529;01;00;48;;4910/75, :;;;23040,00
120559413413;94;11;00;;492/87, :;;;20700,00
141059513031;96;15;00;;492/87/1, F:;;;18630,00
280156425084;94;11;00;;493/87, :;;;20480,00
070364411124;90;65;40;;4933/86, :;;;18030,00
101043424935;96;15;00;;494/69, F:;;;23460,00
210560411828;94;11;00;;494/87, :;;;20625,00
220556418516;90;65;40;;4952/77,;;;0,00
131154413216;96;15;00;;496/77, U:;;;26520,00
300652429848;15;07;00;;4977/79, :;;;28800,00
150658402733;94;11;00;;498/86, :;;;20642,50
280659523612;94;11;00;;498/86/1, :;;;0,00
221251406156;96;15;00;;4980/88, O:;;;20034,00
200148502112;94;11;00;;499/70/2, :;;;21900,00
240948421827;96;15;00;;499/87, F:;;;34137,50
100354429800;96;15;00;;4998/87, F:;;;26640,00
241063430034;96;15;00;;5000/87, F:;;;19800,00
131156502626;96;15;00;;5002/87, F:;;;18687,73
110448422764;90;65;40;;5003/80,;;;0,00
250737530088;90;65;40;;5004/80,;;;0,00
151137530152;96;15;00;;5009/87, D:;;;11808,00
160155529758;96;15;00;;5010/87, U:;;;16183,92
261038400819;01;06;00;;5011/86, :;;;28500,00
301154412212;90;65;40;;5015/85, :;;;21418,71
111059420559;90;65;40;;5016/85, :;;;20240,00
090560404624;90;65;40;;5019/85, :;;;19110,00
210562406117;96;15;00;;5026/84, F:;;;19800,00
181163420317;96;15;00;;503/82, M:;;;11220,00
180365413436;90;65;40;;5032/89, :;;;20460,00
231137415349;90;65;40;;5039/76,;;;0,00
160457407529;90;65;40;;5040/76,;;;0,00
310354421839;96;15;00;;5042/86, N:;;;22770,00
111050422750;96;15;00;;505/83, O:;;;29200,00
250957402715;90;65;40;;5075/77,;;;0,00
180656429227;90;65;40;;5095/77,;;;0,00
041152410418;94;11;00;;5125/85, :;;;23760,00
090747413459;90;65;40;;5133/76,;;;0,00
270147403714;96;15;00;;514/87, F:;;;32250,00
280242530374;90;65;40;;5150/88, :;;;17595,00
050539429724;90;65;40;;5151/88, :;;;24750,00
210563406928;90;65;40;;5152/88, :;;;16170,00
171052506944;90;65;40;;5153/88, :;;;15977,21
150360430053;90;65;40;;5154/88, :;;;17250,00
230856522795;90;65;40;;5155/88, *:;;;18840,35
110369430117;90;65;40;;5156/88, :;;;13210,00
240335530238;96;15;00;;5181/84, U:;;;22712,50
080256522213;96;15;00;;5182/84, M:;;;15318,71
161268430054;90;65;40;;5189/88, :;;;11610,00
110232407223;96;15;00;;5192/86, M:;;;26250,00
150765403416;96;15;00;;5196/84, F:;;;7429,00
120756424998;90;65;40;;5219/84, :;;;21562,50
150265430020;90;65;40;;5221/84, :;;;16699,50
160158419028;90;65;40;;5261/82,;;;0,00
141265419812;96;15;00;;5265/85, Q:;;;11101,00
100348401916;96;15;00;;527/88, M:;;;29520,00
300538429721;96;15;00;;528/88, M:;;;30750,00
280937400920;01;06;00;;5283/78, :;;;27000,00
100156424937;96;15;00;;529/88, M:;;;26985,00
040639400831;01;19;69;;5293/88, :;;;29250,00
201242427520;96;15;00;;530/88, M:;;;31680,00
300762406161;94;11;00;;5310/88, :;;;18480,00
250158415341;94;11;00;;5311/88, :;;;20700,00
121261403356;94;11;00;;5312/88, :;;;20460,00
041252400428;94;11;00;;5313/88, :;;;20880,00
141249403220;15;00;46;;5320/88, :;;;22320,00
190156413818;90;65;40;;5327/80,;;;0,00
201249426256;90;65;40;;5340/84, :;;;22817,50
060151422234;15;18;00;;5340/87, :;;;27588,00
240260402118;94;11;00;;5346/85, :;;;19110,00
200163406954;96;15;00;;5361/89, F:;;;14371,67
210566509535;96;15;00;;5361/89/1, F:;;;5726,67
270661516842;96;15;00;;5362/89, F:;;;13867,23
120166415135;90;65;40;;5391/86, :;;;11016,00
191264400736;96;15;00;;5423/88, S:;;;11084,00
160644425095;96;15;00;;544/88, F:;;;33000,00
050247524914;96;15;00;;544/88/02, F:;;;22054,15
150339501320;96;15;00;;5478/88, F:;;;21687,50
290333400822;01;18;00;;549/60, :;;;26250,00
290739416218;96;15;00;;551/86, F:;;;30000,00
140835400896;01;00;40;;552/75, :;;;23250,00
070138400937;01;06;00;;553/75, :;;;23250,00
200259416428;90;65;40;;5547/88, :;;;17235,00
101062400728;90;65;40;;5558/83, :;;;17160,00
140265412253;90;65;40;;5561/83, :;;;16830,00
190843404120;01;00;49;;5577/81, :;;;14081,73
250641430082;96;15;00;;5602/86, L:;;;28500,00
250454429860;96;15;00;;5630/86, A:;;;23100,00
020842405314;01;00;50;;5678/84, :;;;24420,00
030842422746;96;15;00;;5681/86, M:;;;35250,00
080756425006;96;15;00;;5693/81, A:;;;22440,00
040153422790;96;15;00;;5693/83, F:;;;28800,00
090153418527;96;15;00;;574/72, F:;;;26640,00
251057403928;96;15;00;;5743/84, M:;;;24782,50
270732401322;01;18;00;;5749/79, :;;;23250,00
130943430073;96;15;00;;5764/81, D:;;;26937,50
290554529857;96;15;00;;5764/81/2, D:;;;5030,78
050550521521;96;15;00;;5764/81/3, D:;;;24687,50
230264412242;96;15;00;;5764/81/4, D:;;;16170,00
130938430087;15;18;00;;5780/83, :;;;26066,67
210961430114;90;65;40;;5786/82,;;;0,00
160163430184;90;65;40;;5787/82,;;;0,00
170162430130;90;65;40;;5788/82,;;;0,00
200357427032;94;11;00;;5798/84, :;;;20700,00
151240529715;96;15;00;;580/89, F:;;;24062,50
200163511930;90;65;40;;5808/84, :;;;10925,42
210752429838;96;15;00;;581/89, U:;;;19320,00
040659414421;94;11;00;;5850/84, :;;;21390,00
260934430122;94;11;00;;5853/62, :;;;24000,00
230864406153;96;15;00;;5863/84, F:;;;11220,00
050464428275;96;15;00;;5865/84, F:;;;17435,00
190459427416;94;11;00;;589/88, :;;;20010,00
031160400448;94;11;00;;590/88, :;;;17820,00
300846413617;96;15;00;;592/86, F:;;;30450,00
050849513614;96;15;00;;592/86/1, F:;;;18855,00
070348525084;96;15;00;;592/88, F:;;;16108,35
150542407217;96;15;00;;593/86, F:;;;32700,00
270135400858;01;07;00;;5951/84, :;;;29250,00
250853408936;01;43;00;;5952/84, :;;;17460,00
140941430079;96;15;00;;596/86, F:;;;31950,00
130967420320;96;15;00;;6073/88, A:;;;9872,00
070140430238;15;18;00;;608/83, :;;;28058,33
141062404813;90;65;40;;6082/82,;;;0,00
240263530123;96;15;00;;609/88, M:;;;16830,00
290142408813;96;15;00;;61/67, M:;;;25860,00
230431422115;96;15;00;;6100/82, H:;;;17640,00
110351424931;96;15;00;;612/89, F:;;;11718,00
120554400234;01;00;42;;617/83, :;;;18425,00
130444519073;96;15;00;;618/86, M:;;;22260,00
090737430255;96;15;00;;6183/82/1, L:;;;31740,00
161151429746;96;15;00;;619/83, L:;;;20520,00
100143419012;96;15;00;;619/86, M:;;;30000,00
050355401372;94;11;00;;6370/81, :;;;21642,50
110652418121;96;15;00;;6372/81, U:;;;13200,00
080457402728;94;11;00;;6461/82, :;;;21390,00
211251421816;94;11;00;;6462/82, :;;;21824,82
150339429728;96;15;00;;647/87, A:;;;31500,00
251263418610;96;15;00;;6480/82, M:;;;10819,85
160846427013;96;15;00;;65/76, A:;;;23402,50
151150430068;96;15;00;;650/75/11, :;;;21600,00
181153406116;96;15;00;;650/75/12, :;;;23040,00
280949427223;96;15;00;;650/75/16, :;;;24420,00
031154416443;96;15;00;;650/75/17, :;;;20010,00
031161516469;96;15;00;;650/75/17/1, :;;;15510,00
300742418413;96;15;00;;650/75/18, :;;;27750,00
150849518413;96;15;00;;650/75/18/1, :;;;20010,00
151260414210;96;15;00;;650/75/19, :;;;18645,00
051058420328;96;15;00;;650/75/20, :;;;21390,00
270352407626;96;15;00;;650/75/22, :;;;23760,00
070859409325;96;15;00;;650/75/23, :;;;20700,00
230460421218;96;15;00;;650/75/25, :;;;21120,00
300358426320;96;15;00;;650/75/26, :;;;20872,50
070357417771;96;15;00;;650/75/27, :;;;21562,50
050955404411;96;15;00;;650/75/28, :;;;20405,00
041153403615;96;15;00;;650/75/30, :;;;23220,00
241250502128;96;15;00;;650/75/30/1, :;;;20977,50
231257420329;96;15;00;;650/75/31, :;;;21562,50
180651422894;96;15;00;;650/75/32, :;;;24480,00
280755429730;96;15;00;;650/75/33, :;;;22080,00
090959510015;96;15;00;;650/75/33/1, :;;;15510,00
280152425028;96;15;00;;650/75/35, :;;;22942,50
150756421815;96;15;00;;650/75/36, :;;;23632,50
270159404829;96;15;00;;650/75/37, :;;;20700,00
281150401318;96;15;00;;650/75/39, :;;;25920,00
120657413118;96;15;00;;650/75/4, :;;;20872,50
101160420511;96;15;00;;650/75/40, :;;;17985,00
250256405657;96;15;00;;650/75/41, :;;;21545,00
240657421827;96;15;00;;650/75/42, :;;;19085,00
040258406113;96;15;00;;650/75/43, :;;;23460,00
190962530269;96;15;00;;650/75/43/1, :;;;5593,50
300657409512;96;15;00;;650/75/44, :;;;21780,00
300542406434;96;15;00;;650/75/45, :;;;25500,00
121154403123;96;15;00;;650/75/46, :;;;20182,50
030255402740;96;15;00;;650/75/48, :;;;24325,00
120651411015;96;15;00;;650/75/49, :;;;25920,00
030558511012;96;15;00;;650/75/49/1, :;;;17595,00
020745416214;96;15;00;;650/75/50, :;;;28500,00
040844516227;96;15;00;;650/75/50/1, :;;;17160,00
060259409816;96;15;00;;650/75/51, :;;;23460,00
080558422728;96;15;00;;650/75/52, :;;;21562,50
121145406429;96;15;00;;650/75/53, :;;;23250,00
120358415113;96;15;00;;650/75/54, :;;;22022,50
230161409227;96;15;00;;650/75/55, :;;;21215,00
101158409524;96;15;00;;650/75/56, :;;;25185,00
041053409518;96;15;00;;650/75/58, :;;;24480,00
080558417427;96;15;00;;650/75/59, :;;;22022,50
061261514636;96;15;00;;650/75/59/1, :;;;17601,77
220957417514;96;15;00;;650/75/60, :;;;22770,00
220555504412;96;15;00;;650/75/60/1, :;;;18917,50
140750416215;96;15;00;;650/75/61, :;;;25365,00
200361419924;96;15;00;;650/75/62/, :;;;20272,50
060256422214;96;15;00;;650/75/63, :;;;23747,50
080653427746;96;15;00;;650/75/64, :;;;24300,00
260354424033;96;15;00;;650/75/65/, :;;;24495,00
031061420347;96;15;00;;650/75/67, :;;;17820,00
220861413957;96;15;00;;650/75/68, :;;;21395,00
090760416945;96;15;00;;650/75/69, :;;;20350,00
150749416727;96;15;00;;650/75/70, :;;;27112,50
060258404028;96;15;00;;650/75/71, :;;;23805,00
110759503748;96;15;00;;650/75/71/1, :;;;17800,88
041261430012;96;15;00;;650/75/72, :;;;20460,00
230756429753;96;15;00;;650/75/8, :;;;20872,50
050733429744;96;15;00;;650/88, D:;;;35250,00
050662522799;96;15;00;;6555/82, J:;;;14842,66
300655411424;94;11;00;;6588/81, :;;;21700,00
200464523812;96;15;00;;661/86, J:;;;13097,70
140742408813;96;15;00;;662/88, M:;;;30750,00
301255405038;96;15;00;;6659/80, M:;;;26220,00
210554400831;01;19;00;;666/87, :;;;18572,50
091056418618;94;11;00;;6665/82, :;;;21390,00
021255421111;96;15;00;;668/72, F:;;;19910,00
060748407627;94;11;00;;67/78, :;;;24000,00
030451411927;96;15;00;;671/89, A:;;;26392,50
060851401813;94;11;00;;6732/80, :;;;22656,00
111148524915;96;15;00;;6763/88, F:;;;23250,00
061145422021;96;15;00;;6794/82, O:;;;28080,00
231130400013;01;18;00;;680/70, :;;;23760,00
241234428933;96;15;00;;6857/82, M:;;;28262,50
041051419624;94;11;00;;69/76, :;;;22912,00
120750414115;96;15;00;;6908/82, F:;;;23100,00
040143430201;96;15;00;;693/86, E:;;;29250,00
090445530043;96;15;00;;693/86/1, E:;;;21541,93
280861425020;94;11;00;;6932/88, :;;;20460,00
281264500613;96;15;00;;6932/88/1, F:;;;14172,33
291155426329;94;11;00;;6933/88, :;;;23977,50
071243424417;96;15;00;;6977/75, A:;;;26220,00
140557400836;90;65;40;;6979/80,;;;0,00
080148419315;96;15;00;;6983/75, M:;;;31125,00
060447422778;94;11;00;;6987/75/1, :;;;24000,00
220848400414;94;11;00;;7/76, :;;;24000,00
040243417127;94;11;00;;702/86, :;;;24000,00
051029430180;96;15;00;;7095/60, A:;;;26250,00
110461403736;90;65;40;;7148/81,;;;0,00
310557418613;90;65;40;;7214/81,;;;0,00
260433430132;90;65;40;;7257/75,;;;0,00
110734430351;90;65;40;;7258/75,;;;0,00
300535430065;90;65;40;;7259/75,;;;0,00
230935430098;90;65;40;;7260/75,;;;0,00
230536430138;90;65;40;;7261/75,;;;0,00
230336430248;90;65;40;;7262/75,;;;0,00
250147430044;90;65;40;;7263/75,;;;0,00
300647411512;90;65;40;;7264/75,;;;0,00
300444406932;90;65;40;;7265/75,;;;0,00
130550429231;90;65;40;;7266/75,;;;0,00
280650428029;90;65;40;;7268/75,;;;0,00
290950417160;90;65;40;;7269/75,;;;0,00
251251410515;90;65;40;;7271/75,;;;0,00
270955429867;90;65;40;;7272/75,;;;0,00
280651407115;90;65;40;;7274/75,;;;0,00
310847423613;90;65;40;;7275/75,;;;0,00
120749426928;90;65;40;;7401/81,;;;0,00
120656429724;90;65;40;;744/88, N:;;;21120,00
190161424984;90;65;40;;7472/80,;;;0,00
190457421336;90;65;40;;7575/80,;;;0,00
050140430184;94;11;00;;759/66, :;;;28500,00
091063430033;96;15;00;;760/88, D:;;;16170,00
270960421122;90;65;40;;7603/81,;;;0,00
180755528917;15;18;00;;763/86, :;;;18189,17
070357407418;94;11;00;;767/86, :;;;22770,00
171037430144;94;11;00;;769/86, :;;;27750,00
200158400822;96;15;00;;7701/81, F:;;;21120,00
270540430161;96;15;00;;777/65, M:;;;29250,00
141133429744;96;15;00;;790/88, F:;;;31950,00
100437407236;94;11;00;;8/74, :;;;24000,00
270930430036;96;15;00;;8/75, J:;;;26250,00
250337430053;96;15;00;;80/74, J:;;;25812,50
130343429714;96;15;00;;804/83, F:;;;34300,00
110245529713;96;15;00;;804/83/1, F:;;;22208,06
100457430062;96;15;00;;8082/81, F:;;;23584,35
030361430286;96;15;00;;813/83, P:;;;11069,19
200753406137;96;15;00;;8164/81, L:;;;18144,00
300727430035;94;11;00;;8348/60, :;;;24000,00
130965430234;96;15;00;;835/84, M:;;;1400,00
100758424731;96;15;00;;836/77, F:;;;20196,00
200958400644;94;11;00;;844/83, :;;;20010,00
020852409546;94;11;00;;8509/81, :;;;22320,00
250431529711;94;11;00;;8510/81, :;;;22187,50
240644403611;94;11;00;;8511/81, :;;;21750,00
211034430169;94;11;00;;8569/60, :;;;24000,00
080754428051;94;11;00;;862/83, :;;;22500,00
270731530114;96;15;00;;867/61, O:;;;21000,00
180138429737;96;15;00;;890/82, T:;;;24750,00
211054429712;96;15;00;;904/84, F:;;;27360,00
060161414545;90;65;40;;9053/81,;;;0,00
260661428245;96;15;00;;921/83, F:;;;4536,00
111236430249;94;11;00;;922/82, :;;;21725,00
310332400850;01;07;00;;936/64, :;;;29250,00
020959430038;96;15;00;;947/84, F:;;;19492,50
030554422813;96;15;00;;95/76, F:;;;23040,00
280251429745;96;15;00;;957/89, F:;;;22425,00
130538430301;90;65;40;;958/65,;;;0,00
151153423824;96;15;00;;959/89, F:;;;28380,00
060855425011;96;15;00;;960/89, F:;;;24776,94
090335418616;96;15;00;;962/64, M:;;;21375,00
230833518611;96;15;00;;962/64/1, M:;;;17572,50
240838429764;96;15;00;;962/83, M:;;;33000,00
150965530233;90;65;40;;969/86, :;;;10566,45
230748419053;94;11;00;;97/75, :;;;24000,00
280441430237;94;11;00;;9797/61, :;;;26250,00
110638430271;90;65;40;;9798/61,;;;0,00
100749416836;94;11;00;;98/75, :;;;24000,00
060339430252;94;11;00;;9802/61, :;;;24000,00
120439430219;90;65;40;;9804/61,;;;0,00
171239430142;90;65;40;;9805/61,;;;0,00
260741430230;90;65;40;;9806/61,;;;0,00
300528430040;96;15;00;;9831/61, F:;;;29250,00
091146421036;94;11;00;;99/75, :;;;24000,0o
Diese Liste beinhaltet die Namen von 90.598 Mitarbeitern des Ministeriums für Staatssicherheit der DDR. Die Liste ist nicht vollständig. Insbesondere Mitarbeiter der Führungsebene sind nicht enthalten.
This is a list of 90.598 members of the secret police of East Germany (Ministry for State Security), the list isn’t complete, because the most of the high Officiers lieke Colonel and higher have destroyed the personal Informations in the last days of Eastern Germany.
| Listen der Stasimitarbeiter-hier findest Du sie! Was bedeuten die Zahlen? |
| 1.Listen der Stasi-Diensteinheiten! Bem.:hier kannst du die Nr.(6-stellig) der Dienststellen heraussuchen. 2.Liste der Stasi-Mitarbeiter (Hauptamtlich) Bem.:Hoffentlich hast Du einen guten Rechner, denn die Liste ist erschreckend lang. Die ersten 6 Ziffern sind das Geburtsdatum + die nächsten 6 Ziffern = Dienstausweisnummer! Die zwei Ziffern hinter dem Geburtsdatum geben das Geschlecht an: 41 und 42 = Männlich, 51 und 52 = Weiblich! Wichtig für suchen und finden, sind die sechs Ziffern in den Semikolon vor den Namen: z.B. ;07;00;44; ! Das ist die Nummer der Dienststelle ! Also du suchst in der Liste der Dienststellen, die Nummer der Dienststelle, die Dich interessiert. Damit gehst Du in die Liste der Mitarbeiter und suchst Dir alle Mitarbeiter der entsprechenden Dienststelle heraus. Ich habe das für mein Wohnort getan und so alle Mitarbeiter gefunden. Ob die Liste Vollständig ist kann ich nicht einschätzen, aber zumindest er/kannte ich einige Exverräter vom Namen her. 3.Liste der OibE (Offiziere im besonderen Einsatz) |
STASI-Opfer: Was weiss Beate P. über die STASI ?
CONFIDENTIAL – Côte d’Ivoire Interim Poverty Reduction Strategy Paper

I. INTRODUCTION
1. Over the past ten months, the government of Côte d’Ivoire has developed an interim poverty reduction strategy paper (I-PRSP) that takes stock of current policies and challenges facing the government and that outlines the main strategy to reduce poverty. The paper presents the participatory process used in preparing the I-PRSP and describes the future plan for an even broader consultation process under the PRSP. The paper meets the requirements for an I-PRSP and provides a sound basis for developing a fully participatory PRSP, as well as an adequate framework for continued Fund and IDA assistance to Côte d’Ivoire.
2. This I-PRSP has three main strengths: (i) a solid assessment of the existing poverty data and diagnostics and a good indication of knowledge and data gaps; (ii) a good analysis of the government policies designed to ensure macroeconomic stability and the impact of these policies on the government’s poverty reduction objectives; and (iii) a strong involvement of civil society and other major stakeholders in the preparatory process. However, much remains to be done in the final document to produce a strategy that fully integrates poverty reduction and economic growth. The poverty reduction strategy aims to reduce the poverty rate from 33.6 percent in l998 to 30 percent in 2005, which is far less ambitious than the international development community’s goal of halving poverty by 2015. The modest improvement targeted by the I-PRSP should be reexamined to assess whether increased efforts could not accelerate the reduction in poverty. Further, the 2005 poverty targets may need to be revisited, as poverty levels increased following the economic crisis of 1999-2001.
II. THE ELEMENTS OF THE INTERIM PRSP
3. The I-PRSP provides a clear statement of the government’s strategy on poverty reduction, which rests on six pillars: (i) macroeconomic stability; (ii) promotion of private sector and rural development; (iii) improvement in the access to and quality of basic social services; (iv) decentralization; (v) promotion of good governance and capacity building to allow for better resource allocation and use; and (vi) strengthening of the security of people and property.
4. The preparation of a poverty reduction strategy document and the participative approach were fully endorsed by the government in the May 2001 speech of the Prime Minister to a workshop of public officials, members of civil society, traditional chiefs, the private sector, and representatives of political parties. The antipoverty strategy was regarded as being grounded in the President’s earlier workshop, which was held to achieve a consensus on the redesign of the cultural, political, economic, and social foundations of the country. The agenda of the PRSP was reviewed by the National Consultative Committee, which was established in mid-2001. A PRSP Supervision Committee was given the task of preparing the PRSP agenda and supervising and coordinating the preparatory work in consultation with concerned parties. A regional consultative group was also set up with links to the Secretariat for Structural Reforms.
A. Poverty Analysis
5. The poverty analysis presented in the I-PRSP is limited by the availability of data, but it does provide useful information about the overall scale of poverty, including poverty profiles across regions and in relation to income level, access to health, education services, and gender issues. The poverty profiles draw on the analysis and findings of household surveys. These surveys are well done and provide a sound basis for an analysis of the correlation between poverty indicators and inequality trends. In late 2001, the government launched a new survey and its results should be incorporated in the full PRSP. In order to produce a meaningful program to reduce poverty, its causes by order of importance need to be better understood. Such an analysis would assess the availability of basic social services (education and health) and infrastructure (access to roads, electricity, water, etc.). The analysis should be buttressed by quantitative indicators of the vulnerability of the poor to unemployment, epidemics, the fragility of land rights, and access to urban housing. The poverty analysis should examine rural poverty issues and characteristics associated with rural poverty and inequality (land distribution, income sources, and participation in product and factor markets).
DOWNLOAD ORIGINAL DOCUMENT HERE
Tagesschau berichtet – Stasi fälschte West-Pässe für Spione – STASI-“GoMoPa” “überprüft Pässe” – woher ist bloss das Know-how …
UNCENSORED – FEMEN against lawlessness in Ucraine
Second protest which was topless protest occurred on July 2, 2010. Once again Ukrainian women activists shout and hold placard reading ‘Hillary, help us!’ during their so called top-less protest at the Hayat hotel, the US State Secretary Hillary Clinton’s residence in Kiev. They basically protested Mr Yanukovich’s government and accused him of keeping women out of power and of sexists statements.
It seems grass is greener in Ukraine, at least they have cute protests.
FEMEN UNCENSORED – Topless protest against Iran
Editorial by Robert Ehringer – Where CIA meets Hollywood
CLOAK & CORKSCREW: WHERE CIA MEETS HOLLYWOOD
Author: Robert Eringer
Publisher: Earthshine Editions, Santa Barbara
The U.S. Central Intelligence Agency (CIA) enjoys an intriguing relationship with Hollywood.
Most people believe that the CIA has no jurisdiction within the borders of the United States; that its mission is purely foreign intelligence collection and analysis.
However, the CIA has always legally operated within U.S. borders (outside of headquarters in Langley, Virginia), even if the Federal Bureau of Investigation (FBI), whose national security division assumes responsibility for counter-intelligence operations on U.S. soil, stakes a large claim to such territory.
Consequently, turf wars between these rival intelligence services are not uncommon.
For decades, a division called Domestic Contacts ran the CIA’s U.S. operations. A few years ago, its name was changed to Foreign Research Division.
Today, the operatives of Foreign Research cultivate foreign nationals that attend trade shows and universities inside the U.S., recruiting them to spy in their spheres of expertise upon returning home.
Officers from this division also recruit U.S. citizens traveling abroad, using them for special “access” to people and to places of interest that are otherwise hard to reach.
Such American recruits go mostly unpaid, willing to cooperate purely for patriotic reasons.
Perhaps CIA’s most unique domestic station is in Los Angeles. It is from their office in La-la Land that CIA officers cultivate and recruit Hollywood celebrities to spy for them abroad.
Why Hollywood celebrities?
Access.
How so?
From time to time, you read in the newspapers about how some of the world’s most ruthless dictators, such as Cuba’s Fidel Castro, and Hugo Chavez of Venezuela, receive with open arms some of the best-known American names in showbiz—and then spend quality time with them over long, loquacious dinners.
The public perception is that such Americans are pro-Cuban and/or pro-Venezuelan and perhaps even anti-American.
Foreign dictators use Hollywood stars as propaganda trophies for showing off to their own people (domestic consumption), garnishing sympathy in the United States (foreign media photo ops), and also sticking it to the U.S. government.
But in some cases, these dictators have been rused.
A former CIA operations officer familiar with Hollywood revealed to me that some such visits are sanctioned, and often actually encouraged, by the CIA.
“By my calculation, about one-third of the Hollywood heavyweights who visit scummy dictators secretly report back to CIA,” my source told me. “They are able to provide details that help analysts and profilers determine the physical health and mental state of these dictators—intelligence otherwise hard to come by. Is Fidel slurring his words, perhaps the result of a stroke? This kind of intelligence, which can only be obtained through access, is invaluable to the U.S. intelligence community.”
CIA spooks operating in the shadows of tinseltown have their work cut out for them.
“The hardest part of their job,” a former senior intelligence official told me, “is stroking the egos of the movie stars who provide access for them—no small task.”
My new book–Cloak& Corkscrew: Where CIA Meets Hollywood–is a fictionalized version of how CIA operates through movie star access agents.
In my novel, Hollywood star Josh Penner meets Venezuela’s Hugo Chavez as a CIA access agent.
When the Embassy of Venezuela in Washington DC sends an emissary to contact Penner on Hugo’s behalf, the CIA has an obligation to inform the FBI. Thus a turf war ensues over Penner’s services and priorities.
The hapless emissary is actually a Venezuelan intelligence officer running a high-level spy in the U.S. State Department, who had been honey-trapped in Caracas years earlier.
In the midst of these entanglements, CIA has a new assignment for Penner: to neuter a rogue former CIA officer intent on revealing vital secrets. Penner must feign interest in the movie rights to the ex-spy’s kiss-and-tell book to effectively prevent them being seen elsewhere—or sold to a faux Russian publisher.
Unveiled – Russian Untouchables. Episode 3. Olga Stepanova.
The most shocking video yet on Russian corruption, something right out of Lifestyles of the Rich and Famous mixed with Crime Scene Investigation. Watch Russian tax officials who stole $230 million from their people getting $43 million richer. See them buying multi-million dollar properties on Palm Jumeriah in Dubai, in Montenegro and Moscow, and getting payments to their Swiss bank accounts and offshore firms. Russian authorities refused to investigate the $230 million theft and declared these tax officials honest victims. Sergei Magnitsky, a 37-year anti-corruption lawyer who exposed their scam, was tortured and killed.
Unveiled – Russian Untouchables. Episode 2: Pavel Karpov
http://russian-untouchables.com/eng/ Major Pavel Karpov worked together with Artem Kuznetsov in the theft of $230 million and repressive cases against Sergei Magnitsky. Afterwards, he buys over $1.3 million worth of property and goes on five star luxury holidays.
Unveiled – Russian Untouchables. Episode 1: Artem Kuznetsov
http://russian-untouchables.com/ Russian Interior Ministry officers responsible for the torture and death of Sergei Magnitsky caught red-handed in new YouTube video.
Obama Protectors 45 – Confidential
|
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict40.jpg) President Barack Obama and Orlando, Fla. Mayor Buddy Dyer, right, walk over to greet onlookers after arriving at Orlando International Airport in Orlando, Fla., Thursday, Jan. 19, 2012. (Haraz N. Ghanbari) President Barack Obama and Orlando, Fla. Mayor Buddy Dyer, right, walk over to greet onlookers after arriving at Orlando International Airport in Orlando, Fla., Thursday, Jan. 19, 2012. (Haraz N. Ghanbari)
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict42.jpg) President Barack Obama shakes hands with people waiting to greet him on the tarmac as he steps off of Air Force One at Hickam Air Force Base in Friday, Dec. 23, 2011, in Honolulu. (Carolyn Kaster) President Barack Obama shakes hands with people waiting to greet him on the tarmac as he steps off of Air Force One at Hickam Air Force Base in Friday, Dec. 23, 2011, in Honolulu. (Carolyn Kaster)
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict44.jpg) President Barack Obama visits with patron at PetsMart, Wednesday, Dec. 21, 2011, in Alexandria, Va., where he shopped with his dog Bo. (Carolyn Kaster) President Barack Obama visits with patron at PetsMart, Wednesday, Dec. 21, 2011, in Alexandria, Va., where he shopped with his dog Bo. (Carolyn Kaster) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict50.jpg) President Barack Obama, accompanied by his security personnel, walks through a White House gate prior to crossing Pennsylvania Avenue heading to the Blair House to attend a holiday party, Friday, Dec. 9, 2011, in Washington. (Carolyn Kaster) President Barack Obama, accompanied by his security personnel, walks through a White House gate prior to crossing Pennsylvania Avenue heading to the Blair House to attend a holiday party, Friday, Dec. 9, 2011, in Washington. (Carolyn Kaster)
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict52.jpg) President Barack Obama greets people on the tarmac upon his arrival at Kansas City International Airport, Tuesday, Dec. 6, 2011, in Kansas City , Mo. (Carolyn Kaster) President Barack Obama greets people on the tarmac upon his arrival at Kansas City International Airport, Tuesday, Dec. 6, 2011, in Kansas City , Mo. (Carolyn Kaster) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict46.jpg) In this Nov. 30, 2011, file photo, President Barack Obama walks to his motorcade with members of security after visiting with Patrick and Donna Festa in their Scranton, Pa. home. In this Nov. 30, 2011, file photo, President Barack Obama walks to his motorcade with members of security after visiting with Patrick and Donna Festa in their Scranton, Pa. home.
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict53.jpg) President Barack Obama greets members of the Towson University football team during half time as he and first lady Michelle Obama, not seen, attend the Oregon State versus Towson NCAA college basketball game at Towson University Saturday, Nov. 26, 2011, in Towson, Md. (Carolyn Kaster) President Barack Obama greets members of the Towson University football team during half time as he and first lady Michelle Obama, not seen, attend the Oregon State versus Towson NCAA college basketball game at Towson University Saturday, Nov. 26, 2011, in Towson, Md. (Carolyn Kaster) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict54.jpg) As Secret Service agents watch, President Barack Obama embraces a girl following an address where he remarked on the American Jobs Act, Tuesday, Nov. 22, 2011, at Central High School in Manchester, N.H. (Charles Krupa) As Secret Service agents watch, President Barack Obama embraces a girl following an address where he remarked on the American Jobs Act, Tuesday, Nov. 22, 2011, at Central High School in Manchester, N.H. (Charles Krupa)
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict56.jpg) President Barack Obama arrives in Manchester, N.H., Tuesday, Nov. 22, 2011. President Obama will travel to Manchester High School Central to discuss the American Jobs Act. (Cheryl Senter) President Barack Obama arrives in Manchester, N.H., Tuesday, Nov. 22, 2011. President Obama will travel to Manchester High School Central to discuss the American Jobs Act. (Cheryl Senter) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict57.jpg) U.S. President Barack Obama walks as he attends the East Asia Summit at Nusa Dua, Bali, Indonesia on Saturday Nov. 19, 2011. (Aaron Favila) U.S. President Barack Obama walks as he attends the East Asia Summit at Nusa Dua, Bali, Indonesia on Saturday Nov. 19, 2011. (Aaron Favila) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict58.jpg) President Barack Obama greets Australian troops during a visit to the Royal Army Air Force Base in Darwin, Australia, Thursday, Nov. 17, 2011. (Charles Dharapak) President Barack Obama greets Australian troops during a visit to the Royal Army Air Force Base in Darwin, Australia, Thursday, Nov. 17, 2011. (Charles Dharapak) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict59.jpg) President Barack Obama talks with Medal of Honor recipient John Baca before the start of the Carrier Classic NCAA basketball game between North Carolina and Michigan State on the flight deck of the USS Carl Vinson in Coronado, Calif., Friday, Nov. 11, 2011. (Susan Walsh) President Barack Obama talks with Medal of Honor recipient John Baca before the start of the Carrier Classic NCAA basketball game between North Carolina and Michigan State on the flight deck of the USS Carl Vinson in Coronado, Calif., Friday, Nov. 11, 2011. (Susan Walsh) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict60.jpg) President Barack Obama and French President Nicolas Sarkozy walk together after arriving at an event outside City Hall in Cannes, France, Friday, Nov. 4, 2011. The two leaders were at a memorial to World Wars I and II. (Susan Walsh) President Barack Obama and French President Nicolas Sarkozy walk together after arriving at an event outside City Hall in Cannes, France, Friday, Nov. 4, 2011. The two leaders were at a memorial to World Wars I and II. (Susan Walsh) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict61.jpg) President Barack Obama arrives to speak about managing student debt during an event at the University of Colorado Denver Downtown Campus in Denver, Wednesday, Oct. 26, 2011. Denver is the final stop on a three-day trip to the West Coast for fundraising and speeches promoting his American Jobs Act. (Susan Walsh) President Barack Obama arrives to speak about managing student debt during an event at the University of Colorado Denver Downtown Campus in Denver, Wednesday, Oct. 26, 2011. Denver is the final stop on a three-day trip to the West Coast for fundraising and speeches promoting his American Jobs Act. (Susan Walsh) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict62.jpg) President Barack Obama walks out of Roscoe’s House of Chicken and Waffles in Los Angeles, Monday, Oct. 24, 2011, with Rep. Karen Bass, D-Calif., after ordering a snack. Obama is on a three-day trip to the West Coast. (Susan Walsh) President Barack Obama walks out of Roscoe’s House of Chicken and Waffles in Los Angeles, Monday, Oct. 24, 2011, with Rep. Karen Bass, D-Calif., after ordering a snack. Obama is on a three-day trip to the West Coast. (Susan Walsh) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict63.jpg) President Barack Obama greets after exiting Air Force One after arriving at McCarran International Airport in Las Vegas Monday, Oct. 24, 2011. (John Gurzinski) President Barack Obama greets after exiting Air Force One after arriving at McCarran International Airport in Las Vegas Monday, Oct. 24, 2011. (John Gurzinski) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict64.jpg) President Barack Obama talks on the phone as he greets people outside the Reid’s House Restaurant in Reidsville, N.C., Tuesday, Oct. 18, 2011. Obama is on a three-day bus tour promoting the American Jobs Act. (Susan Walsh) President Barack Obama talks on the phone as he greets people outside the Reid’s House Restaurant in Reidsville, N.C., Tuesday, Oct. 18, 2011. Obama is on a three-day bus tour promoting the American Jobs Act. (Susan Walsh) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict66.jpg) President Barack Obama poses for a photo after speaking at West Wilkes High School in Millers Creek, N.C., on Monday, Oct. 17, 2011. (Terry Renna) President Barack Obama poses for a photo after speaking at West Wilkes High School in Millers Creek, N.C., on Monday, Oct. 17, 2011. (Terry Renna) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict67.jpg) President Barack Obama walks to his bus after stopping at the Countryside Barbeque in Marion in N.C., Monday, Oct. 17, 2011. Obama is on a three-day bus tour promoting the American Jobs Act. (Susan Walsh) President Barack Obama walks to his bus after stopping at the Countryside Barbeque in Marion in N.C., Monday, Oct. 17, 2011. Obama is on a three-day bus tour promoting the American Jobs Act. (Susan Walsh) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict68.jpg) President Barack Obama walks around his bus at Asheville Regional Airport in Fletcher, N.C., Monday, Oct. 17, 2011, to begin his three-day bus tour promoting the American Jobs Act. (Susan Walsh) President Barack Obama walks around his bus at Asheville Regional Airport in Fletcher, N.C., Monday, Oct. 17, 2011, to begin his three-day bus tour promoting the American Jobs Act. (Susan Walsh)
|
TOP-SECRET-NATO Training Mission Afghanistan (NTM-A) Gender Integration White Paper

In the 20th century, the various governments of Afghanistan were actively involved with the international community in adopting human rights initiatives, including gender equality. However, the conservative nature of Afghan society coupled with weak central governance limited each regime’s ability to extend modern programs beyond the major urban areas. Initiatives that the constitutional monarchy and communist government attempted to implement often faced significant opposition from the countryside and were ultimately eliminated with the rise of the Taliban. Afghanistan joined the international community in ratifying the Universal Declaration of Human Rights (UDHR) in 1948 and established legislation and processes to integrate women into public life from the 1950s through the 1980s. However, in 1996 the Taliban relegated women to a domestic role with brutal enforcement. With the establishment of the Government of the Islamic Republic of Afghanistan (GIRoA), Afghanistan entered a new era for gender integration. In compliance with modern international human rights agreements and reaffirming its commitment to the UDHR, Afghanistan reopening opportunities in the public and private sector through its Constitution and supporting legislation. With the assistance of NATO’s International Security Assistance Force (ISAF), GIRoA is establishing the governmental institutions and societal conditions necessary to implement and enforce these laws.
ISAF’s mandate is to assist the GIRoA by supporting security, strengthening government structures and contributing to development and reconstruction as supported by the Constitution of Afghanistan (Olsson and Tejpar 2009). One of ISAF’s goals is to enable GIRoA to continue its gender strategy without ISAF support. ISAF’s subordinate headquarters for force generation of the Afghan National Security Forces (ANSF) is the NATO Training Mission-Afghanistan (NTM-A). NTM-A’s mission is to generate the ANSF, develop capable ministerial systems and resource the fielded force to build sustainable capacity and capability in order to enhance the GIRoA’s ability to achieve stability and security in Afghanistan. NTM-A, in coordination with NATO allies, partners and key Afghan stakeholders, develops the ANSF in compliance with international agreements and Afghan law and thereby enables Afghan gender integration within the ANSF, Ministry of Defense (MoD) and Ministry of Interior (MoI).
As ISAF transitions security operations to the GIRoA by 2014, NTM-A is executing a supporting plan to transition security force generation, education and training to the ANSF. Care must be taken to execute the transition in a manner that underwrites hard-won gender integration accomplishments. Gender integration is both the right thing to do and the pragmatic thing to do. It upholds international principles and bolsters Afghan security and stability. Nevertheless, its implementations must be metered through Afghan governmental authorities and the Afghan society’s willingness to adapt.
Problem Statement
This white paper describes the GIRoA’s legal framework and policy for gender integration and NTM-A’s supporting role as NATO’s force generation headquarters in Afghanistan. It provides an analysis of the ANSF, identifying strengths, weaknesses, opportunities and threats or challenges. It proposes considerations as NTM-A transitions the force generation mission to the ANSF by 2014 that would bolster support to GIRoA national objectives regarding gender integration.
Idealistic and Realistic Requirements for Gender Integration
Afghanistan needs strong gender integration policy and programs for both idealistic and realistic reasons, but will continue to be challenged with implementation because of its conservative Islamic culture and tradition of strong rural independence. The GIRoA has participated actively in multinational agreements supporting gender integration and has incorporated gender integration into its foundational legislation. Since 2002, Afghanistan has been the recipient of significant international aid to support its reconstruction. The international community is vested in Afghanistan and is scrutinizing how Afghanistan meets its obligations under the United Nations agreements. The Constitution of Afghanistan declares that men and women have equal rights and duties before the law and GIRoA has integrated, or mainstreamed, gender into its stated national goals and into government at all levels. The MoI and MoD have an obligation to contribute to the attainment of national goals on gender equality. Gender integration within the ANSF will support the attainment of national goals and improve security and stability in Afghanistan.
Pragmatically, the ANSF need female members in order to be effective security forces. Afghanistan is a conservative, Islamic society. The Afghan National Police (ANP) and Afghan National Army (ANA) are virtually all-male organizations. As a result, the ANP cannot respond effectively to incidents involving women as suspects, complainants or victims. Properly empowered policewomen can react to violence against women, family violence, children in trouble and kidnappings. They can interrogate, detain and investigate female suspects; provide support to female victims of crime; and ensure the security of women in communities (Murray, Report on the Status of Women in the Afghan National Police 2006). The ANA is equally ill equipped to conduct counterinsurgency operations within the Afghan population without female counterparts to attend to female detainees and female casualties on the battlefield as well as interact with female citizens. Female soldiers can support combat operations in career fields such as intelligence, logistics, medicine and aviation. Similar to their police counterparts, they can interrogate and detain female combatants; provide support to female casualties; and ensure the security of women on operational objectives. Female ANSF can provide culturally mandated separation between male security force members and females encountered in the course of duty. Additionally, they can provide critical service and support capabilities by serving in logistics and aviation specialties. The GIRoA can utilize the ANSF as a tool to implement gender integration policy and gain greater security and stability.
DOWNLOAD ORIGINAL ARTICLE HERE
TOP-SECRET-Swiss Authorities Investigate Money Laundering Linked to Russian Tax Fraud Scheme
Switzerland has opened a money-laundering probe at the request of Hermitage Capital Management Ltd., the first criminal investigation outside Russia linked to the death of lawyer Sergei Magnitsky in a Moscow prison.
The allegations involving a former Russian tax official are the most recent lodged by Hermitage founder William Browder as he asks authorities around the world to sanction officials he blames for Magnitsky’s death. The lawyer, who alleged Interior Ministry officials fraudulently collected a $230 million tax refund using documents seized from Hermitage, died in 2009 after a year in pre-trial detention.
“It’s been impossible to get any kind of real criminal investigation in Russia,” Browder said yesterday by phone. “It’s highly significant that a Western law enforcement agency is taking this seriously and is launching an investigation.”
According to Hermitage, once the largest foreign investor in Russia, Olga Stepanova authorized $155 million of the tax rebates in 2007 as head of Moscow Tax Inspectorate No. 28. Since then, at least $38 million flowed through bank accounts opened on behalf of companies incorporated by Stepanova’s husband, partly to buy homes in Dubai, Montenegro and Russia, London- based Hermitage alleged in a Jan. 28 letter to the Swiss Attorney General and Credit Suisse AG.
The couple’s average declared income from 2006 through 2009 was $38,381 a year, according to Russian income declarations included in Hermitage’s filing with the Swiss authorities.
“The Office of the Attorney General of Switzerland confirms having officially launched a criminal investigation in respect of suspected money laundering,” spokeswoman Jeanette Balmer said yesterday in an e-mail after she was asked about the Hermitage letter. “The investigation relates to persons unknown,” she said, declining to release further details.
Stepanova, now an adviser to the head of Russia’s arms procurement agency didn’t respond to e-mailed, faxed and phone requests for comment submitted to the agency’s press service yesterday. Her husband, Vladlen Stepanov, an employee of Moscow- based OOO Volsstroy, is on vacation until mid-May, according to a person who answered the company’s phone and said she would pass on a reporter’s contact number.
…
Russia is the world’s most corrupt major economy, according to Berlin-based Transparency International’s 2010 Corruption Perceptions Index released in October. It ranked 154th among 178 countries, tied with Tajikistan and Kenya.
Crime and Punishment in Putin’s Russia
Russian police say they have closed the case file on the country’s largest tax fraud. It occurred on December 24 in 2007, when Moscow tax officials approved a same-day refund of 5.4 billion rubles — or $230 million — to a gang masquerading as officers of Hermitage Capital, once the largest hedge-fund manager in Russia and founded by financiers Edmond Safra and Bill Browder. Interior Ministry police claim the complex scam was pulled off by a sawmill worker and a burglar, both currently serving five-year sentences, in cahoots with four others, all of whom are now dead. One had a fatal heart attack before the crime took place. A second fell from his balcony. The third plummeted out a penthouse window.
And then there was Sergei Magnitsky, a 37-year-old lawyer for Hermitage who died in prison after complaining police were torturing him to retract evidence that the $230 million had been stolen by a ring of corrupt tax officials, Interior Ministry cops and career criminals. Magnitsky’s November 2009 death made him an icon to those who want to clean up Russia’s chronic corruption — yet the Interior Ministry surprisingly turned the tables, claiming he was one of the culprits. The police ministry exonerated the cops and tax officials who Magnitsky had accused — most of them got promotions.
As for the $230 million, almost all of it is still missing. Interior Ministry spokesperson Irina Dudukina told Barron’s on Tuesday that all the bank records police needed in order to trace the loot were in a truck that crashed and exploded in 2008.
The case may have ended there for Russian authorities, but Hermitage’s London-based chief Browder has devoted himself to pursuing those he holds responsible for the original crime and Magnitsky’s death. In English and Russian campaigns on a Website (russian-untouchables.com) and on YouTube, the investor has presented evidence that he says proves the tax heist was an inside job and has asked the public to send him additional evidence.
“The facts of this case are absolutely damning for the Russian government,” says Browder. “First Sergei Magnitsky uncovers and reports criminals preparing a major crime three weeks before it happens, and the police do nothing. Then Russian tax officials make the largest fraudulent tax refund in Russian history, in one day, on Christmas Eve, to a convicted murderer, with no questions asked.”
Browder’s outreach program has paid off. He recently received new evidence that raises questions about the Russian government’s official story that honest bureaucrats were tricked by wily outsiders. The records from two secret accounts at a Credit Suisse branch in Zurich show that shortly after the huge tax payout was approved by the Moscow tax bureau run by Olga G. Stepanova, her husband received $10.9 million (seven million euros) in his Cyprus shell corporation. The Credit Suisse accounts also were the source of funds for $800,000 in construction payments for the couple’s seaside villa in Montenegro and for $4 million toward another villa on Dubai’s fabulous Palm Island with two additional condos for Stepanova’s tax-office deputies.
And those were just Stepanova’s vacation homes. A year after the tax scam, Stepanova’s family was living in a $20 million mansion outside Moscow, designed by Russia’s celebrity avant-garde architect Alexey Kozyr.
The money arrived at Credit Suisse through a globe-spanning trail of shell companies created by a Who’s Who of offshore-secrecy consultants — including a New Zealand agent whose operation we’ve previously found amid North Korean arms trafficking and money laundering for a Mexican drug cartel.
TOP-SECRET- Inside the Apocalyptic Soviet Doomsday Machine
Valery Yarynich glances nervously over his shoulder. Clad in a brown leather jacket, the 72-year-old former Soviet colonel is hunkered in the back of the dimly lit Iron Gate restaurant in Washington, DC. It’s March 2009—the Berlin Wall came down two decades ago—but the lean and fit Yarynich is as jumpy as an informant dodging the KGB. He begins to whisper, quietly but firmly.
“The Perimeter system is very, very nice,” he says. “We remove unique responsibility from high politicians and the military.” He looks around again.
Yarynich is talking about Russia’s doomsday machine. That’s right, an actual doomsday device—a real, functioning version of the ultimate weapon, always presumed to exist only as a fantasy of apocalypse-obsessed science fiction writers and paranoid über-hawks. The thing that historian Lewis Mumford called “the central symbol of this scientifically organized nightmare of mass extermination.” Turns out Yarynich, a 30-year veteran of the Soviet Strategic Rocket Forces and Soviet General Staff, helped build one.
The point of the system, he explains, was to guarantee an automatic Soviet response to an American nuclear strike. Even if the US crippled the USSR with a surprise attack, the Soviets could still hit back. It wouldn’t matter if the US blew up the Kremlin, took out the defense ministry, severed the communications network, and killed everyone with stars on their shoulders. Ground-based sensors would detect that a devastating blow had been struck and a counterattack would be launched.
The technical name was Perimeter, but some called it Mertvaya Ruka, or Dead Hand. It was built 25 years ago and remained a closely guarded secret. With the demise of the USSR, word of the system did leak out, but few people seemed to notice. In fact, though Yarynich and a former Minuteman launch officer named Bruce Blair have been writing about Perimeter since 1993 in numerous books and newspaper articles, its existence has not penetrated the public mind or the corridors of power. The Russians still won’t discuss it, and Americans at the highest levels—including former top officials at the State Department and White House—say they’ve never heard of it. When I recently told former CIA director James Woolsey that the USSR had built a doomsday device, his eyes grew cold. “I hope to God the Soviets were more sensible than that.” They weren’t.
The system remains so shrouded that Yarynich worries his continued openness puts him in danger. He might have a point: One Soviet official who spoke with Americans about the system died in a mysterious fall down a staircase. But Yarynich takes the risk. He believes the world needs to know about Dead Hand. Because, after all, it is still in place.
The system that Yarynich helped build came online in 1985, after some of the most dangerous years of the Cold War. Throughout the ’70s, the USSR had steadily narrowed the long US lead in nuclear firepower. At the same time, post-Vietnam, recession-era America seemed weak and confused. Then in strode Ronald Reagan, promising that the days of retreat were over. It was morning in America, he said, and twilight in the Soviet Union.
Part of the new president’s hard-line approach was to make the Soviets believe that the US was unafraid of nuclear war. Many of his advisers had long advocated modeling and actively planning for nuclear combat. These were the progeny of Herman Kahn, author of On Thermonuclear War and Thinking About the Unthinkable. They believed that the side with the largest arsenal and an expressed readiness to use it would gain leverage during every crisis.
The new administration began expanding the US nuclear arsenal and priming the silos. And it backed up the bombs with bluster. In his 1981 Senate confirmation hearings, Eugene Rostow, incoming head of the Arms Control and Disarmament Agency, signaled that the US just might be crazy enough to use its weapons, declaring that Japan “not only survived but flourished after the nuclear attack” of 1945. Speaking of a possible US-Soviet exchange, he said, “Some estimates predict that there would be 10 million casualties on one side and 100 million on another. But that is not the whole of the population.”
Meanwhile, in ways both small and large, US behavior toward the Soviets took on a harsher edge. Soviet ambassador Anatoly Dobrynin lost his reserved parking pass at the State Department. US troops swooped into tiny Grenada to defeat communism in Operation Urgent Fury. US naval exercises pushed ever closer to Soviet waters.
The strategy worked. Moscow soon believed the new US leadership really was ready to fight a nuclear war. But the Soviets also became convinced that the US was now willing to start a nuclear war. “The policy of the Reagan administration has to be seen as adventurous and serving the goal of world domination,” Soviet marshal Nikolai Ogarkov told a gathering of the Warsaw Pact chiefs of staff in September 1982. “In 1941, too, there were many among us who warned against war and many who did not believe a war was coming,” Ogarkov said, referring to the German invasion of his country. “Thus, the situation is not only very serious but also very dangerous.”
A few months later, Reagan made one of the most provocative moves of the Cold War. He announced that the US was going to develop a shield of lasers and nuclear weapons in space to defend against Soviet warheads. He called it missile defense; critics mocked it as “Star Wars.”
To Moscow it was the Death Star—and it confirmed that the US was planning an attack. It would be impossible for the system to stop thousands of incoming Soviet missiles at once, so missile defense made sense only as a way of mopping up after an initial US strike. The US would first fire its thousands of weapons at Soviet cities and missile silos. Some Soviet weapons would survive for a retaliatory launch, but Reagan’s shield could block many of those. Thus, Star Wars would nullify the long-standing doctrine of mutually assured destruction, the principle that neither side would ever start a nuclear war since neither could survive a counterattack.
TOP-SECRET – Slovak Spying Agency Document
A sends:
This leaked document codenamed Gorilla [1, 2] was allegedly prepared by the Slovak intelligence agency (SIS). SIS found significant influence by the Penta Financial Group on senior Slovak politicians between 2005 and 2006 (Dzurinda gov’t). Penta claims that the online publication of classified document by the webmasters and other news media violates criminal law and threatens to take legal action against them [3].
Links:
[1] http://dl.dropbox.com/u/51238188/gorila.txt [SK] Cryptome mirror: http://cryptome.org/2012/01/0045.txt
[2] https://docs.google.com/document/d/1giBimg_c1JOngOMKiSCmmtr656PG22q3ZDe63MQtKz4/edit?pli=1 [SK]
Cryptome mirror: http://cryptome.org/2012/01/0046.zip
[4] http://www.praguepost.cz/news/11701-region-gorilla-case-grips-slovakia.html [EN]
TOP-SECRET – (U//FOUO) TSA Mass Transit and Passenger Bus Attacks Warning

(U//FOUO) This TSA-OI assessment is intended to provide a review of the terrorist TTPs used to conduct attacks against mass transit bus systems from 2004 to 2010. For the purpose of this assessment, mass transit bus systems include buses, stations, and bus stops.
This is one in a series of products released since 2010 focusing on the TTPs used to attack mass transit systems. This assessment was produced to help security managers and stakeholders evaluate the effectiveness of and vulnerabilities in mass transit bus security programs, plans, and activities.
…
(U//FOUO) TSA’s Office of Intelligence (TSA-OI) assesses that although counterterrorism pressure has weakened al-Qa’ida (AQ) and al Qa’ida in the Arabian Peninsula (AQAP), both organizations represent an enduring and evolving threat and remain committed to attacking the Homeland, including the transportation sector. Both organizations have targeted commercial aviation and AQ has repeatedly plotted to attack mass transit. We also remain concerned about the threat posed by homegrown violent extremists (HVE) or lone offenders inspired by AQ’s violent extremist ideology to launch attacks against less secure targets, such as mass transit and passenger bus systems.
(U//FOUO) Tactics, techniques, and procedures used by terrorist groups worldwide could serve as a model for an attack in the Homeland. The current threat level for the mass transit sector remains at medium.
• (U//FOUO) Terrorist groups have used a wide variety of weapons and tactics in attacks on mass transit bus systems; improvised explosive devices (IEDs) have been the most common weapon used.
• (U//FOUO) Most IED attacks against mass transit bus systems occurred inside the bus and not on the bus routes or at bus stations.
• (U//FOUO) Terrorists appeared to use multiple IEDs in attacks to increase the number of casualties or target first responders.
• (U//FOUO) The number of terrorist attacks on mass transit bus systems remained consistent throughout the year, without any major increases in any particular month.
• (U//FOUO) TSA-OI’s data review showed that most attacks occurred during the morning rush hour from 7 a.m. to 10 a.m., with the least amount of attacks occurring from 1 a.m. to 5 a.m.
• (U//FOUO) Secular, political, and anarchists groups conducted the most lethal attacks against mass transit bus systems. TSA-OI assesses that an attack against a mass transit bus system in the Homeland would most likely be carried out by individuals affiliated with a violent religious extremist group.
DOWNLOAD ORIGINAL DOCUMENT HERE
TOP-ECRET – (U//FOUO) ISAF CJIATF-Shafafiyat Afghan Corruption Information Paper

Per a recent RFI from the Office of the Special Inspector General for Afghanistan Reconstruction, the following information paper discusses the nature and extent of the corruption problem in Afghanistan, the mission of CJIATF-Shafafiyat, and the progress the task force has achieved, as well as the challenges its has encountered, as it has coordinated ISAF’s anti-corruption efforts.
Introduction and Overview
The Strategic Impact of Corruption in Afghanistan
The level of corruption across Afghanistan’s public and private sectors represents a threat to the success of ISAF’s mission and the viability of the Afghan state. Corruption undermines the legitimacy and effectiveness of Afghanistan’s government, fuels discontent among the population, and generates active and passive support for the insurgency. Corruption and organized crime also serve as a barrier to Afghanistan’s economic growth by robbing the state of revenue and preventing the development of a strong licit economy, thus perpetuating Afghan dependence on international assistance. Corruption also threatens the process of security transition, as institutions weakened by criminality will be unable to accept the transfer of responsibility for security and governance.
The Causes of Corruption
Several conditions have allowed corruption to flourish in Afghanistan: a fragile war economy sustained by international aid, security assistance, and the narcotics trade; a society fractured by three decades of war; and weak governance and institutions.
Criminal Patronage Networks (CPNs) are responsible for the most threatening forms of corruption in Afghanistan. CPNs are comprised of individuals, businesses, and other entities that engage in systematized corruption inside and outside of government and across Afghanistan’s public and private sectors. CPNs are often associated with powerbrokers who have consolidated power over the last thirty years of war. These networks engage in illicit enterprises and pursue narrow, self-interested agendas that degrade security, weaken governance, hinder economic development and undermine rule of law. CPNs seek to control key state assets and institutions. They divert customs revenue at airports and border crossings, expropriate government and private land, and abuse public and private financial institutions. Additionally, CPNs generate exclusionary political economies that alienate key elements of the population and generate popular discontent from which the enemy draws strength. The Taliban recruits from disaffected portions of the population and those who have suffered injustice and abuse at the hands of corrupt and criminal actors.
CPNs pursue political as well as criminal agendas, consolidating power and maximizing their position relative to other networks. It is for this reason that efforts to reduce corruption must be grounded in an understanding of Afghan politics, and combined with efforts to convince Afghan leaders that it is in their interest to reduce the threat of corruption and organized crime.
DOWNLOAD ORIGINAL DOCUMENT HERE
Uncensored – Anonymous – Message to the American People
TOP-SECRET – FBI Director Meets With Google, Facebook to Discuss Easier Wiretaps

Robert S. Mueller III, the director of the Federal Bureau of Investigation, traveled to Silicon Valley on Tuesday to meet with top executives of several technology firms about a proposal to make it easier to wiretap Internet users.
Mr. Mueller and the F.B.I.’s general counsel, Valerie Caproni, were scheduled to meet with senior managers of several major companies, including Google and Facebook, according to several people familiar with the discussions. How Mr. Mueller’s proposal was received was not clear.
“I can confirm that F.B.I. Director Robert Mueller is visiting Facebook during his trip to Silicon Valley,” said Andrew Noyes, Facebook’s public policy manager. Michael Kortan, an F.B.I. spokesman, acknowledged the meetings but did not elaborate.
Mr. Mueller wants to expand a 1994 law, the Communications Assistance for Law Enforcement Act, to impose regulations on Internet companies.
The law requires phone and broadband network access providers like Verizon and Comcast to make sure they can immediately comply when presented with a court wiretapping order.
Law enforcement officials want the 1994 law to also cover Internet companies because people increasingly communicate online. An interagency task force of Obama administration officials is trying to develop legislation for the plan, and submit it to Congress early next year.
The Commerce Department and State Department have questioned whether it would inhibit innovation, as well as whether repressive regimes might harness the same capabilities to identify political dissidents, according to officials familiar with the discussions.
Under the proposal, firms would have to design systems to intercept and unscramble encrypted messages. Services based overseas would have to route communications through a server on United States soil where they could be wiretapped.
A Google official declined to comment. Mr. Noyes said it would be premature for Facebook to take a position.
CONFIDENTTIAL – NSA Refuses to “Confirm or Deny” That it Has a Relationship With Google

A federal judge has issued an opinion in EPIC v. NSA, and accepted the NSA’s claim that it can “neither confirm nor deny” that it had entered into a relationship with Google following the China hacking incident in January 2010. EPIC had sought documents under the FOIA because such an agreement could reveal that the NSA is developing technical standards that would enable greater surveillance of Internet users. The “Glomar response,” to neither confirm nor deny, is a controversial legal doctrine that allows agencies to conceal the existence of records that might otherwise be subject to public disclosure. EPIC plans to appeal this decision. EPIC is also litigating to obtain the National Security Presidential Directive that sets out the NSA’s cyber security authority. And EPIC is seeking from the NSA information about Internet vulnerability assessments, the Director’s classified views on how the NSA’s practices impact Internet privacy, and the NSA’s “Perfect Citizen” program.
Civil Case No. 10-1533 (RJL) MEMORANDUM OPINION (July 8, 2011) [#9, #11] (uscourts.gov):
On February 4, 2010, following media coverage of a possible partnership between the NSA and Google relating to an alleged cyber attack by hackers in China, EPIC submitted a FOIA request to NSA seeking:
1. All records concerning an agreement or similar basis for collaboration, final or draft, between the NSA and Google regarding cyber security;
2. All records of communication between the NSA and Google concerning Gmail, including but not limited to Google’s decision to fail to routinely encrypt Gmail messages prior to January 13,2010; and
3. All records of communications regarding the NSA’s role in Google’s decision regarding the failure to routinely deploy encryption for cloud-based computing service, such as Google Docs.
Compl. ¶ 12.
NSA denied EPIC’s request. Letter from Pamela N. Phillips, NSA, FOIA/PA Office, Mar. 10,2010 [#9-3]. While it acknowledged working “with a broad range of commercial partners and research associates,” the Agency refused to “confirm [ or] deny” whether it even had a relationship with Google. Id. In support of its response, NSA cited Exemption 3 of FOIA and Section 6 of the National Security Agency Act of 1959 (“NSA Act”), explaining that any response would improperly reveal information about NSA’s functions and activities. Id. Such a response – neither confirming nor denying the existence of requested documents – is known as a Glomar response.
…
With respect to EPIC’s specific request, the Declaration states that “[t]o confirm or deny the existence of any such records would be to reveal whether the NSA … determined that vulnerabilities or cybersecurity issues pertaining to Google or certain of its commercial technologies could make U.S. government information systems susceptible to exploitation or attack.” Id. ¶ 13. The Declaration further clarifies that even an acknowledgement of a relationship between the NSA and a commercial entity could potentially alert “adversaries to NSA priorities, threat assessment, or countermeasures,” and that, as such, the information relates to the Agency’s core functions and activities under its Information Assurance mission. Id. ¶¶ 13-14.
Video Shows Wrecked Ship Interior of Costa Concordia
Video released by the Italian Government shows rescue crews inside the grounded Costa Concordia cruise ship. The search for survivors and victims was suspended on Wednesday, after rough waves shifted the ship’s location.
TOP SECRET from the FBI – Charges Against Seven Investment Professionals for Insider Trading Scheme that Allegedly Netted More Than $61.8 Million in Illegal Profits
Preet Bharara, the United States Attorney for the Southern District of New York, and Janice K. Fedarcyk, the Assistant Director in Charge of the New York Office of the Federal Bureau of Investigation (“FBI”), today announced charges against seven investment professionals, who worked at three different hedge funds and two other investment firms, for engaging in a scheme in which they provided each other with material, non-public information (“Inside Information”) about two publicly traded technology companies, Dell, Inc. (“Dell”) and NVIDIA (“NVDA”). Using the Dell Inside Information, the three hedge funds netted more than $61.8 million in illegal profits and one of the investment firms avoided $78,000 in losses. Charged in a complaint unsealed today are: TODD NEWMAN, a former portfolio manager at a Connecticut-based hedge fund (“Hedge Fund A”); ANTHONY CHIASSON, a former portfolio manager and a co-founder of a Manhattan-based hedge fund (“Hedge Fund B”); JON HORVATH, a research analyst who worked in the New York office of a Connecticut-based hedge fund (“Hedge Fund C”); and DANNY KUO, a research analyst and fund manager at an investment firm with offices in California and Nevada (“Investment Firm D”). This morning, NEWMAN, HORVATH, and KUO were arrested, and CHIASSON surrendered to federal authorities. Later today, CHIASSON and HORVATH are expected to be presented in Manhattan federal court, NEWMAN is expected to be presented in Massachusetts federal court, and KUO is expected to be presented in federal court in the Central District of California.
Also unsealed today were the guilty pleas of: JESSE TORTORA, a former research analyst at Hedge Fund A; SPYRIDON “Sam” ADONDAKIS, a research analyst at Hedge Fund B; and SANDEEP “Sandy” GOYAL, a research analyst who worked at the Manhattan office of a global asset management firm (“Investment Firm 1”). They pled guilty to their roles in the insider trading scheme and are cooperating with the government’s investigation.
Manhattan U.S. Attorney Preet Bharara said: “The charges unsealed today allege a corrupt circle of friends who formed a criminal club whose purpose was profit and whose members regularly bartered lucrative inside information so their respective funds could illegally profit. And profit they allegedly did—to the tune of more than $61 million on illegal trades of a single stock—much of it coming in a $53 million short trade. Here, The Big Short was The Big Illegal Short. We have demonstrated through our prosecutions that insider trading is rampant and has its own social network, a network we intend to dismantle. We will be unrelenting in our pursuit of those who think they are above the law.”
FBI Assistant Director in Charge Janice K. Fedarcyk said: “The FBI has arrested more than 60 people in ‘Operation Perfect Hedge’ to date, and this initiative is far from over. If you are engaged in insider trading, what distinguishes you from the dozens who have been charged is not that you haven’t been caught; it’s that you haven’t been caught yet.”
According to the complaint and Informations unsealed today in Manhattan federal court, and statements made during the related plea proceedings:
TORTORA and ADONDAKIS were part of a circle of research analysts at different investment firms who obtained Inside Information directly or indirectly from employees who worked at public companies, and then shared it with each other and with the Hedge Fund portfolio managers for whom they worked. HORVATH and KUO were allegedly part of the circle as well, and used and shared Inside Information similarly. For example, in 2008 and 2009, TORTORA admitted to providing ADONDAKIS, HORVATH and KUO with Inside Information related to Dell’s first and second quarter 2008 earnings that he had received from GOYAL, who had a source inside Dell’s investor relations department. TORTORA also admitted to providing the Dell Inside Information to NEWMAN, the portfolio manager for whom he worked. ADONDAKIS admitted to providing the Dell Inside Information to CHIASSON, the portfolio manager for whom he worked. Both TORTORA and ADONDAKIS told their portfolio managers that the information came from a source at Dell.
In exchange for the Dell Inside Information, TORTORA admitted to arranging with NEWMAN to pay GOYAL via a sham research consulting arrangement Hedge Fund A made with an individual (“Individual 1”), the proceeds of which were deposited in a joint account Individual 1 shared with GOYAL. In fact, Individual 1 never provided any research consulting services, but Hedge Fund A nonetheless made four $18,750 payments to Individual 1 between February 2008 and September 2008. Individual 1 also received a $100,000 bonus from Hedge Fund A in January 2009.
The Dell Short
The Dell Inside Information was allegedly used to execute illegal trades in the first and second quarters of 2008. For example, beginning in July 2008, the Dell Insider provided GOYAL initial information concerning Dell’s revenues and/or gross margins for the second quarter. After the close of the quarter in 2008, but prior to Dell’s public earnings announcement on August 28 of that year, the Dell Insider provided to GOYAL, who in turn provided to TORTORA, more specific information concerning Dell’s margins that confirmed the gross margin would be lower than market expectations. On August 5, 2008, TORTORA forwarded an e-mail to ADONDAKIS, HORVATH and KUO, that he is alleged to have originally sent to NEWMAN, that included the Inside Information he had received from GOYAL. In the days before the August 28, 2008 earnings announcement, GOYAL had additional communications with TORTORA and again confirmed that Dell’s gross margin would be lower than market expectations. TORTORA admitted to passing this information on to NEWMAN and to ADONDAKIS, who admitted to providing the information to CHIASSON. In another e-mail sent by TORTORA on August 25, 2008, he wrote, “did new apple and dell checks today and both sound bad, same as before.” Trading records show that Hedge Funds A, B, and C all allegedly sold quantities of Dell shares “short,” based at least in part on the Inside Information they received during the period prior to the company’s second quarter earnings announcement. Hedge Fund A reaped $2.8 million in allegedly illegal profits, Hedge Fund B made more than $50 million, and Hedge Fund C made $1 million. Trading records also show that KUO allegedly avoided approximately $78,000 by trading on the Inside Information for Investment Firm D.
In all, the conduct alleged in the complaint relating to the Dell Inside Information resulted in more than $61.8 million in illegal insider trading profits realized by Hedge Funds A, B, and C.
The NVIDIA Inside Information
In addition, in multiple fiscal quarters, KUO allegedly obtained confidential financial information about NVIDIA, a publicly traded technology company, shortly before its public earnings release and provided it to TORTORA, ADONDAKIS, and HORVATH. The information included NVIDIA’s gross margin and revenue information. As alleged, e-mail communications from KUO to the other research analysts stated explicitly that the information was coming from an employee inside NVIDIA.
* * *
NEWMAN, 47, of Needham, Massachusetts; CHIASSON, 38, of New York, New York; HORVATH, 42, of New York, New York; and KUO, 36, of Pasadena, California, are each charged with one count of conspiracy to commit securities fraud and one count of securities fraud. The conspiracy charge carries a maximum potential penalty of five years in prison and a fine of $250,000 or twice the gross gain or loss from the offense. The securities fraud charge carries a maximum potential penalty of 20 years in prison and a maximum fine of $5 million.
TORTORA, 34, ADONDAKIS, 40, and GOYAL, 39, each pled guilty to one count of conspiracy to commit securities fraud and one count of securities fraud. TORTORA pled guilty on May 18, 2011; ADONDAKIS pled guilty on April 25, 2011; and GOYAL pled guilty on November 3, 2011. They each face a statutory maximum sentence of 25 years in prison.
Mr. Bharara praised the investigative work of the Federal Bureau of Investigation. He also thanked the U.S. Securities and Exchange Commission. He also noted that the investigation is continuing.
This case was brought in coordination with President Barack Obama’s Financial Fraud Enforcement Task Force, on which Mr. Bharara serves as a Co-Chair of the Securities and Commodities Fraud Working Group. President Obama established the interagency Financial Fraud Enforcement Task Force to wage an aggressive, coordinated, and proactive effort to investigate and prosecute financial crimes. The task force includes representatives from a broad range of federal agencies, regulatory authorities, inspectors general, and state and local law enforcement who, working together, bring to bear a powerful array of criminal and civil enforcement resources. The task force is working to improve efforts across the federal executive branch, and with state and local partners, to investigate and prosecute significant financial crimes, ensure just and effective punishment for those who perpetrate financial crimes, combat discrimination in the lending and financial markets, and recover proceeds for victims of financial crimes.
The charges against NEWMAN, CHIASSON, HORVATH, and KUO are merely accusations, and the defendants are presumed innocent unless and until proven guilty.
Assistant U.S. Attorneys Antonia Apps, David Leibowitz, and Richard Tarlowe are in charge of the prosecution.
Revealed – Cruise Ship Costa Concordia Grounding Photos
|
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/costa-concordia/pict29.jpg) Italian naval divers approach the cruise ship Costa Concordia Tuesday, Jan. 17, 2012, after running aground on the tiny Tuscan island of Giglio, Italy, on Friday evening. Italian naval divers on Tuesday exploded holes in the hull of a cruise ship grounded off a Tuscan island to speed the search for 29 missing people while seas were still calm. One official said there was still a “glimmer of hope” that survivors could be found. Italian naval divers approach the cruise ship Costa Concordia Tuesday, Jan. 17, 2012, after running aground on the tiny Tuscan island of Giglio, Italy, on Friday evening. Italian naval divers on Tuesday exploded holes in the hull of a cruise ship grounded off a Tuscan island to speed the search for 29 missing people while seas were still calm. One official said there was still a “glimmer of hope” that survivors could be found. |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/costa-concordia/pict30.jpg) Italian naval divers work on the cruise ship Costa Concordia Tuesday, Jan. 17, 2012, after running aground on the tiny Tuscan island of Giglio, Italy, on Friday evening. Italian naval divers work on the cruise ship Costa Concordia Tuesday, Jan. 17, 2012, after running aground on the tiny Tuscan island of Giglio, Italy, on Friday evening. |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/costa-concordia/pict31.jpg) The cruise ship Costa Concordia leans on its side Tuesday, Jan. 17, 2012, after running aground on the tiny Tuscan island of Giglio, Italy, on Friday evening. The cruise ship Costa Concordia leans on its side Tuesday, Jan. 17, 2012, after running aground on the tiny Tuscan island of Giglio, Italy, on Friday evening. |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/costa-concordia/pict32.jpg) Italian navy divers approach the cruise ship Costa Concordia in the tiny Tuscan island of Giglio, Italy, Tuesday, Jan. 17, 2012. Italian navy divers approach the cruise ship Costa Concordia in the tiny Tuscan island of Giglio, Italy, Tuesday, Jan. 17, 2012. |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/costa-concordia/pict12.jpg) Oil removal ships near the cruise ship Costa Concordia leaning on its side Monday, Jan. 16, 2012, after running aground near the tiny Tuscan island of Giglio, Italy, last Friday night. The rescue operation was called off mid-afternoon Monday after the Costa Concordia shifted a few inches (centimeters) in rough seas. The fear is that if the ship shifts significantly, some 500,000 gallons of fuel may begin to leak into the pristine waters. (Gregorio Borgia) Oil removal ships near the cruise ship Costa Concordia leaning on its side Monday, Jan. 16, 2012, after running aground near the tiny Tuscan island of Giglio, Italy, last Friday night. The rescue operation was called off mid-afternoon Monday after the Costa Concordia shifted a few inches (centimeters) in rough seas. The fear is that if the ship shifts significantly, some 500,000 gallons of fuel may begin to leak into the pristine waters. (Gregorio Borgia) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/costa-concordia/pict24.jpg) The cruise ship Costa Concordia leans on its side Monday, Jan.16, 2012, after running aground near the tiny Tuscan island of Giglio, Italy, last Friday. The rescue operation was called off mid-afternoon Monday after the Costa Concordia shifted a few inches (centimeters) in rough seas. The fear is that if the ship shifts significantly, some 500,000 gallons of fuel may begin to leak. (Gregorio Borgia) The cruise ship Costa Concordia leans on its side Monday, Jan.16, 2012, after running aground near the tiny Tuscan island of Giglio, Italy, last Friday. The rescue operation was called off mid-afternoon Monday after the Costa Concordia shifted a few inches (centimeters) in rough seas. The fear is that if the ship shifts significantly, some 500,000 gallons of fuel may begin to leak. (Gregorio Borgia) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/costa-concordia/pict22.jpg) In this underwater photo released by the Italian Coast Guard Monday, Jan. 16, 2012 the cruise ship Costa Concordia leans on its side, after it ran aground near the tiny Tuscan island of Isola del Giglio, Italy. (Italian Coast Guard) In this underwater photo released by the Italian Coast Guard Monday, Jan. 16, 2012 the cruise ship Costa Concordia leans on its side, after it ran aground near the tiny Tuscan island of Isola del Giglio, Italy. (Italian Coast Guard) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/costa-concordia/pict23.jpg) In this underwater photo taken on Jan. 13 and released by the Italian Coast Guard Monday, Jan. 16, 2012 a view of the cruise ship Costa Concordia, after it ran aground near the tiny Tuscan island of Giglio, Italy. Italian rescue officials say a passenger’s body has been found in the wreckage of the Costa Concordia cruise ship, raising to six the number of confirmed dead in the disaster. Sixteen people remain unaccounted-for. (Italian Coast Guard) In this underwater photo taken on Jan. 13 and released by the Italian Coast Guard Monday, Jan. 16, 2012 a view of the cruise ship Costa Concordia, after it ran aground near the tiny Tuscan island of Giglio, Italy. Italian rescue officials say a passenger’s body has been found in the wreckage of the Costa Concordia cruise ship, raising to six the number of confirmed dead in the disaster. Sixteen people remain unaccounted-for. (Italian Coast Guard) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/costa-concordia/pict17.jpg) In this photo released by the Italian Coast Guard Monday, Jan. 16, 2012 a coast guard scuba diver makes his way through floating pieces of furniture inside the cruise ship Costa Concordia Sunday Jan. 15. 2012,after it run aground off the tiny Tuscan island of Giglio, Italy. Italian rescue officials say a passenger’s body has been found in the wreckage of the Costa Concordia cruise ship, raising to six the number of confirmed dead in the disaster. Sixteen people remain unaccounted-for. In this photo released by the Italian Coast Guard Monday, Jan. 16, 2012 a coast guard scuba diver makes his way through floating pieces of furniture inside the cruise ship Costa Concordia Sunday Jan. 15. 2012,after it run aground off the tiny Tuscan island of Giglio, Italy. Italian rescue officials say a passenger’s body has been found in the wreckage of the Costa Concordia cruise ship, raising to six the number of confirmed dead in the disaster. Sixteen people remain unaccounted-for. |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/costa-concordia/pict15.jpg) Italian rescue personnel are seen atop the Costa Concordia cruise liner, two days after it ran aground off the tiny Tuscan island of Giglio, Italy, Monday, Jan. 16, 2012. The captain of a cruise liner that ran aground and capsized off the Tuscan coast faced accusations from authorities and passengers that he abandoned ship before everyone was safely evacuated as rescuers found another body on the overturned vessel. (Gregorio Borgia) Italian rescue personnel are seen atop the Costa Concordia cruise liner, two days after it ran aground off the tiny Tuscan island of Giglio, Italy, Monday, Jan. 16, 2012. The captain of a cruise liner that ran aground and capsized off the Tuscan coast faced accusations from authorities and passengers that he abandoned ship before everyone was safely evacuated as rescuers found another body on the overturned vessel. (Gregorio Borgia) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/costa-concordia/pict25.jpg) Italian firefighters scuba divers work on the cruise ship Costa Concordia two days after it run aground the tiny Tuscan island of Giglio, Italy, Monday, Jan. 16, 2012. Italian rescue officials say a passenger’s body has been found in the wreckage of the Costa Concordia cruise ship, raising to six the number of confirmed dead in the disaster. Sixteen people remain unaccounted-for. (Gregorio Borgia) Italian firefighters scuba divers work on the cruise ship Costa Concordia two days after it run aground the tiny Tuscan island of Giglio, Italy, Monday, Jan. 16, 2012. Italian rescue officials say a passenger’s body has been found in the wreckage of the Costa Concordia cruise ship, raising to six the number of confirmed dead in the disaster. Sixteen people remain unaccounted-for. (Gregorio Borgia) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/costa-concordia/pict26.jpg) Italian rescue divers approach the Costa Concordia cruise liner, two days after it run aground off tiny Tuscan island of Giglio, Italy, Monday, Jan. 16, 2012. The captain of a cruise liner that ran aground and capsized off the Tuscan coast faced accusations from authorities and passengers that he abandoned ship before everyone was safely evacuated as rescuers found another body on the overturned vessel. (Gregorio Borgia) Italian rescue divers approach the Costa Concordia cruise liner, two days after it run aground off tiny Tuscan island of Giglio, Italy, Monday, Jan. 16, 2012. The captain of a cruise liner that ran aground and capsized off the Tuscan coast faced accusations from authorities and passengers that he abandoned ship before everyone was safely evacuated as rescuers found another body on the overturned vessel. (Gregorio Borgia) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/costa-concordia/pict8.jpg) Italian Firefighters scuba divers work aboard the luxury cruise ship Costa Concordia which ran aground off the tiny Tuscan island of Giglio, Italy, Sunday, Jan. 15, 2012. Firefighters worked Sunday to rescue a crew member with a suspected broken leg from the overturned hulk of the cruise liner, 36 hours after it ran aground. More than 40 people are still unaccounted-for. (Remo Casilli) Italian Firefighters scuba divers work aboard the luxury cruise ship Costa Concordia which ran aground off the tiny Tuscan island of Giglio, Italy, Sunday, Jan. 15, 2012. Firefighters worked Sunday to rescue a crew member with a suspected broken leg from the overturned hulk of the cruise liner, 36 hours after it ran aground. More than 40 people are still unaccounted-for. (Remo Casilli) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/costa-concordia/pict16.jpg) Italian firefighters approach the luxury cruise ship Costa Concordia which ran aground off the tiny Tuscan island of Giglio, Italy, Sunday, Jan. 15, 2012. (Remo Casilli) Italian firefighters approach the luxury cruise ship Costa Concordia which ran aground off the tiny Tuscan island of Giglio, Italy, Sunday, Jan. 15, 2012. (Remo Casilli) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/costa-concordia/pict11.jpg) Italian firefighters’ scuba divers approach the luxury cruise ship Costa Concordia which ran aground off the tiny Tuscan island of Giglio, Italy, Sunday, Jan. 15, 2012. (Gregorio Borgia) Italian firefighters’ scuba divers approach the luxury cruise ship Costa Concordia which ran aground off the tiny Tuscan island of Giglio, Italy, Sunday, Jan. 15, 2012. (Gregorio Borgia) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/costa-concordia/pict6.jpg) Italian firefighters scuba divers approach the cruise ship Costa Concordia leaning on its side, the day after running aground the tiny Tuscan island of Giglio, Italy, Sunday, Jan. 15, 2012. A helicopter on Sunday airlifted a third survivor from the capsized hulk of a luxury cruise ship 36 hours after it ran aground off the Italian coast, as prosecutors confirmed they were investigating the captain for manslaughter charges and abandoning the ship. (Gregorio Borgia) Italian firefighters scuba divers approach the cruise ship Costa Concordia leaning on its side, the day after running aground the tiny Tuscan island of Giglio, Italy, Sunday, Jan. 15, 2012. A helicopter on Sunday airlifted a third survivor from the capsized hulk of a luxury cruise ship 36 hours after it ran aground off the Italian coast, as prosecutors confirmed they were investigating the captain for manslaughter charges and abandoning the ship. (Gregorio Borgia) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/costa-concordia/pict33.jpg) Italian Navy scuba divers approach the cruise ship Costa Concordia leaning on its side, the day after running aground the tiny Tuscan island of Giglio, Italy, Sunday, Jan. 15, 2012. A helicopter on Sunday airlifted a third survivor from the capsized hulk of a luxury cruise ship 36 hours after it ran aground off the Italian coast, as prosecutors confirmed they were investigating the captain for manslaughter charges and abandoning the ship. (Gregorio Borgia) Italian Navy scuba divers approach the cruise ship Costa Concordia leaning on its side, the day after running aground the tiny Tuscan island of Giglio, Italy, Sunday, Jan. 15, 2012. A helicopter on Sunday airlifted a third survivor from the capsized hulk of a luxury cruise ship 36 hours after it ran aground off the Italian coast, as prosecutors confirmed they were investigating the captain for manslaughter charges and abandoning the ship. (Gregorio Borgia) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/costa-concordia/pict7.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/costa-concordia/pict13.jpg) Investigators approach the luxury cruise ship Costa Concordia which leans on its starboard side after running aground in the tiny Tuscan island of Isola del Giglio, Italy, Sunday, Jan. 15, 2012. The Costa Concordia cruise ship ran aground off the coast of Tuscany, sending water pouring in through a 160-foot (50-meter) gash in the hull and forcing the evacuation of some 4,200 people from the listing vessel early Saturday, the Italian coast guard said. (Gregorio Borgia) Investigators approach the luxury cruise ship Costa Concordia which leans on its starboard side after running aground in the tiny Tuscan island of Isola del Giglio, Italy, Sunday, Jan. 15, 2012. The Costa Concordia cruise ship ran aground off the coast of Tuscany, sending water pouring in through a 160-foot (50-meter) gash in the hull and forcing the evacuation of some 4,200 people from the listing vessel early Saturday, the Italian coast guard said. (Gregorio Borgia) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/costa-concordia/pict14.jpg) Firefighters work on the luxury cruise ship Costa Concordia the day after it run aground off the tiny Tuscan island of Giglio, Italy, Sunday, Jan. 15, 2012. The Italian Coast Guard says its divers have found two more bodies aboard the stricken Costa Concordia cruise ship. The discovery of the bodies brings to five the number of known dead after the luxury ship ran aground with some 4,200 people aboard on Friday night. (Andrea Sinibaldi) Firefighters work on the luxury cruise ship Costa Concordia the day after it run aground off the tiny Tuscan island of Giglio, Italy, Sunday, Jan. 15, 2012. The Italian Coast Guard says its divers have found two more bodies aboard the stricken Costa Concordia cruise ship. The discovery of the bodies brings to five the number of known dead after the luxury ship ran aground with some 4,200 people aboard on Friday night. (Andrea Sinibaldi) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/costa-concordia/pict28.jpg) The cruise ship Costa Concordia leans on its side, after it ran aground off the tiny Tuscan island of Giglio, Italy, Sunday, Jan. 15, 2012. A helicopter on Sunday airlifted a third survivor from the capsized hulk of a luxury cruise ship 36 hours after it ran aground off the Italian coast, as prosecutors confirmed they were investigating the captain for manslaughter charges and abandoning the ship. (Gregorio Borgia) The cruise ship Costa Concordia leans on its side, after it ran aground off the tiny Tuscan island of Giglio, Italy, Sunday, Jan. 15, 2012. A helicopter on Sunday airlifted a third survivor from the capsized hulk of a luxury cruise ship 36 hours after it ran aground off the Italian coast, as prosecutors confirmed they were investigating the captain for manslaughter charges and abandoning the ship. (Gregorio Borgia) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/costa-concordia/pict27.jpg) Italian Navy scuba divers prepare to search the wreck of the luxury cruise ship Costa Concordia that ran aground in the tiny Tuscan island of Isola del Giglio, Italy, Sunday, Jan. 15, 2012. The Costa Concordia cruise ship ran aground off the coast of Tuscany, sending water pouring in through a 160-foot (50-meter) gash in the hull and forcing the evacuation of some 4,200 people from the listing vessel early Saturday, the Italian coast guard said. (Gregorio Borgia) Italian Navy scuba divers prepare to search the wreck of the luxury cruise ship Costa Concordia that ran aground in the tiny Tuscan island of Isola del Giglio, Italy, Sunday, Jan. 15, 2012. The Costa Concordia cruise ship ran aground off the coast of Tuscany, sending water pouring in through a 160-foot (50-meter) gash in the hull and forcing the evacuation of some 4,200 people from the listing vessel early Saturday, the Italian coast guard said. (Gregorio Borgia) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/costa-concordia/pict21.jpg) An Italian firefighter helicopter lifts up a person from the luxury cruise ship Costa Concordia which ran aground the off tiny Tuscan island of Giglio, Italy, Sunday, Jan. 15, 2012. Firefighters worked Sunday to rescue a crew member with a suspected broken leg from the overturned hulk of the luxury cruise liner Costa Concordia, 36 hours after it ran aground. More than 40 people are still unaccounted-for. (Gregorio Borgia) An Italian firefighter helicopter lifts up a person from the luxury cruise ship Costa Concordia which ran aground the off tiny Tuscan island of Giglio, Italy, Sunday, Jan. 15, 2012. Firefighters worked Sunday to rescue a crew member with a suspected broken leg from the overturned hulk of the luxury cruise liner Costa Concordia, 36 hours after it ran aground. More than 40 people are still unaccounted-for. (Gregorio Borgia) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/costa-concordia/pict34.jpg) Italian Coast guard personnel recovers the black box of the luxury cruise ship Costa Concordia after running aground the tiny Tuscan island of Giglio, Italy, Saturday, Jan. 14, 2012. A luxury cruise ship ran aground off the coast of Tuscany, sending water pouring in through a 160-foot (50-meter) gash in the hull and forcing the evacuation of some 4,200 people from the listing vessel early Saturday, the Italian coast guard said. (Gregorio Borgia) Italian Coast guard personnel recovers the black box of the luxury cruise ship Costa Concordia after running aground the tiny Tuscan island of Giglio, Italy, Saturday, Jan. 14, 2012. A luxury cruise ship ran aground off the coast of Tuscany, sending water pouring in through a 160-foot (50-meter) gash in the hull and forcing the evacuation of some 4,200 people from the listing vessel early Saturday, the Italian coast guard said. (Gregorio Borgia) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/costa-concordia/pict36.jpg) Passengers of the luxury ship that ran aground off the coast of Tuscany board a bus in Porto Santo Stefano, Italy, Saturday, Jan. 14, 2012. A luxury cruise ship ran aground off the coast of Tuscany, gashing open the hull and taking on water, forcing some 4,200 people aboard to evacuate aboard lifeboats to a nearby island early Saturday. At least three were dead, the Italian coast guard said. Three bodies were recovered from the sea, said Coast Guard Cmdr. Francesco Paolillo. (Gregorio Borgia) Passengers of the luxury ship that ran aground off the coast of Tuscany board a bus in Porto Santo Stefano, Italy, Saturday, Jan. 14, 2012. A luxury cruise ship ran aground off the coast of Tuscany, gashing open the hull and taking on water, forcing some 4,200 people aboard to evacuate aboard lifeboats to a nearby island early Saturday. At least three were dead, the Italian coast guard said. Three bodies were recovered from the sea, said Coast Guard Cmdr. Francesco Paolillo. (Gregorio Borgia) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/costa-concordia/pict18.jpg) This photo acquired by the Associated Press from a passenger of the luxury ship that ran aground off the coast of Tuscany shows rescued passengers arriving at the Giglio island harbor, Saturday, Jan. 14, 2012. A luxury cruise ship ran aground off the coast of Tuscany, gashing open the hull and taking on water, forcing some 4,200 people aboard to evacuate aboard lifeboats to a nearby island early Saturday. At least three were dead, the Italian coast guard said. This photo acquired by the Associated Press from a passenger of the luxury ship that ran aground off the coast of Tuscany shows rescued passengers arriving at the Giglio island harbor, Saturday, Jan. 14, 2012. A luxury cruise ship ran aground off the coast of Tuscany, gashing open the hull and taking on water, forcing some 4,200 people aboard to evacuate aboard lifeboats to a nearby island early Saturday. At least three were dead, the Italian coast guard said. |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/costa-concordia/pict42.jpg) This photo acquired by the Associated Press from a passenger of the luxury ship that ran aground off the coast of Tuscany shows fellow passengers wearing life-vests on board the Costa Concordia as they wait to be evacuated, Saturday, Jan. 14, 2012. A luxury cruise ship ran aground off the coast of Tuscany, sending water pouring in through a 160-foot (50-meter) gash in the hull and forcing the evacuation of some 4,200 people from the listing vessel early Saturday, the Italian coast guard said. This photo acquired by the Associated Press from a passenger of the luxury ship that ran aground off the coast of Tuscany shows fellow passengers wearing life-vests on board the Costa Concordia as they wait to be evacuated, Saturday, Jan. 14, 2012. A luxury cruise ship ran aground off the coast of Tuscany, sending water pouring in through a 160-foot (50-meter) gash in the hull and forcing the evacuation of some 4,200 people from the listing vessel early Saturday, the Italian coast guard said. |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/costa-concordia/pict35.jpg) In this photo released by the Guardia di Finanza (Border Police), the luxury cruise ship Costa Concordia leans on its side after running aground off the tiny Tuscan island of Giglio, Italy, Saturday, Jan. 14, 2012. The luxury cruise ship ran aground off the coast of Tuscany, sending water pouring in through a 160-foot (50-meter) gash in the hull and forcing the evacuation of some 4,200 people from the listing vessel early Saturday, the Italian coast guard said. (Guardia di Finanza) In this photo released by the Guardia di Finanza (Border Police), the luxury cruise ship Costa Concordia leans on its side after running aground off the tiny Tuscan island of Giglio, Italy, Saturday, Jan. 14, 2012. The luxury cruise ship ran aground off the coast of Tuscany, sending water pouring in through a 160-foot (50-meter) gash in the hull and forcing the evacuation of some 4,200 people from the listing vessel early Saturday, the Italian coast guard said. (Guardia di Finanza) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/costa-concordia/pict40.jpg) In this photo released by the Guardia di Finanza (border Police), the luxury cruise ship Costa Concordia leans on its side after running aground off the tiny Tuscan island of Giglio, Italy, Saturday, Jan. 14, 2012. The luxury cruise ship ran aground off the coast of Tuscany, sending water pouring in through a 160-foot (50-meter) gash in the hull and forcing the evacuation of some 4,200 people from the listing vessel early Saturday, the Italian coast guard said. [Costa Concordia yellow lifeboats at lower right.] In this photo released by the Guardia di Finanza (border Police), the luxury cruise ship Costa Concordia leans on its side after running aground off the tiny Tuscan island of Giglio, Italy, Saturday, Jan. 14, 2012. The luxury cruise ship ran aground off the coast of Tuscany, sending water pouring in through a 160-foot (50-meter) gash in the hull and forcing the evacuation of some 4,200 people from the listing vessel early Saturday, the Italian coast guard said. [Costa Concordia yellow lifeboats at lower right.] |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/costa-concordia/pict10.jpg) The luxury cruise ship Costa Concordia leans after it ran aground off the coast of the Isola del Giglio island, Italy, gashing open the hull and forcing some 4,200 people aboard to evacuate aboard lifeboats to the nearby Isola del Giglio island, early Saturday, Jan. 14, 2012. About 1,000 Italian passengers were onboard, as well as more than 500 Germans, about 160 French and about 1,000 crew members. (Giorgio Fanciulli) The luxury cruise ship Costa Concordia leans after it ran aground off the coast of the Isola del Giglio island, Italy, gashing open the hull and forcing some 4,200 people aboard to evacuate aboard lifeboats to the nearby Isola del Giglio island, early Saturday, Jan. 14, 2012. About 1,000 Italian passengers were onboard, as well as more than 500 Germans, about 160 French and about 1,000 crew members. (Giorgio Fanciulli) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/costa-concordia/pict19.jpg) The luxury cruise ship Costa Concordia sails from Limassol, Cyprus in this April 2009 photo. The ship ran aground off the coast of Isola del Giglio island, Italy, gashing open the hull and forcing some 4,200 people aboard to evacuate aboard lifeboats to the nearby Isola del Giglio island, early Saturday, Jan. 14, 2012. The luxury cruise ship Costa Concordia sails from Limassol, Cyprus in this April 2009 photo. The ship ran aground off the coast of Isola del Giglio island, Italy, gashing open the hull and forcing some 4,200 people aboard to evacuate aboard lifeboats to the nearby Isola del Giglio island, early Saturday, Jan. 14, 2012. |
 |
DIE “GoMoPa”-STASI-Rufmörder überführen sich selbst
DER BEWEIS: “GoMoPa”-ERPRESST MERIDIAN CAPITAL “GoMoPa”-CEO MAURISCHAT WIRD VOM BKA VERHAFTET
Millionen Finanzierungen mit Widersprüchen / Die Werbemethoden der Meridian Capital Enterprises
ZUM DOWNLOAD OBEN CLICKEN
Berlin (ots) – Die Meridian Capital Enterprises Ltd. bietet auf ihren Webseiten weltweite Finanzierungen an. GoMoPa hat die dort gemachten Angaben analysiert und starke Widersprüche entdeckt.
Die Unternehmensstruktur
Die Meridian Capital Enterprises Ltd. behauptet “ein Finanzinstitut” zu sein, “das zu einer internationalen Finanzgruppe gehört.” Diese Gruppe setze sich aus 11 verschiedenen Mitgliedern zusammen. GoMoPa fragte alle zuständigen Handelsregister ab. Ergebnis: 5 der 11 angegebenen Finanzinstitute sind nicht eingetragen.
Mitarbeiter der KLP Group Emirates, GoMoPa-Partner und Management-Gruppe in Dubai, machten sich die Mühe, drei weitere Geschäftsadressen der Meridian Capital Enterprises Ltd. zu überprüfen. Martin Kraeter, Prinzipal der KLP Group: “Alle 3 genannten Firmen existieren hier nicht, auch nicht in abgewandelter Form.”
Das Unternehmen will weltweit über zahlreiche Standorte verfügen. Bei denen handelt es sich allerdings lediglich um “Virtual Offices” eines Büroservice-Anbieters.
Laut Firmenhomepage hat das Unternehmen seinen “rechtlichen Geschäftssitz” in Dubai. In einem GoMoPa vorliegenden Schreiben der Meridian Capital Enterprises Ltd. heißt es jedoch, der Firmensitz sei in London. Auf der Homepage selbst tauchen zwei Londoner Adressen auf, die das Unternehmen als “Kundenabteilung für deutschsprachige Kunden” und “Abteilung der Zusammenarbeit mit Investoren” bezeichnet.
Die Meridian Capital Enterprises ist tatsächlich als “Limited” (Ltd.) mit Sitz in England und Wales eingetragen. Eine Abfrage beim Gewerbeamt Dubais (DED) zur Firmierung jedoch bleibt ergebnislos. Bemerkenswert ist auch der vermeintliche Sitz in Israel. Auf der Webseite von Meridian Capital Enterprises heißt es: “Die Firma Meridian Capital Enterprises Ltd. ist im Register des israelischen Justizministeriums unter der Nummer 514108471 (…) angemeldet.” Martin Kraeter hierzu: ” Ein ‘britisch-arabisch-israelisches bankfremdes Finanzinstitut sein zu wollen, wie die Meridian Capital Enterprises Ltd. es darstellt, ist mehr als zweifelhaft. Es würde keinem einzigen Emirati, geschweige denn einem ‘Scheich’, auch nur im Traum einfallen Geschäfte mit Personen oder Firmen aus Israel zu machen. “
Eigenartig ist auch: Zwei angebliche Großinvestitionen der Meridian Capital Enterprises in Dubai sind Investmentruinen bzw. erst gar nicht realisierte Projekte.
Der Aktivitätsstatus der Meridian Capital Enterprises Ltd. ist laut englischem Handelsregister als “dormant” gemeldet. Auf der Grundlage des britischen Gesellschaftsrechts können sich eingetragene Unternehmen selbst “dormant” (schlafend) melden, wenn sie keine oder nur unwesentliche buchhalterisch zu erfassende Transaktionen vorgenommen haben. Angesichts der angeblichen globalen Investitionstätigkeit der Meridian Capital Ltd. ist dieses jedoch sehr erstaunlich.
Auf ihrer Webseite gibt die Meridian Capital Enterprises Ltd. einen Überblick über ihre größten Investitionen in Deutschland: “Dithmarschen Wind Powerplant, Waldpolenz Solar Park, AIDAdiva, Berlin Hauptbahnhof, Sony Center”. Die Eigentümer des Sony Centers am Potsdamer Platz teilten GoMoPA mit, dass ihnen sei ein solcher Investor unbekannt sei. Meridian Capital Enterprises Ltd. will übrigens angeblich auch in die Erweiterung des Panama-Kanals sowie in das Olympiastadion in Peking investiert haben.
Der Webauftritt
Die Internetseite der MCE ist aufwendig gestaltet. Bei näherer Betrachtung fällt jedoch auf, dass es sich bei zahlreichen Fotos der Veranstaltungen der Meridian Capital Enterprises in den meisten Fällen um Bildmaterial von Online-Zeitungen oder frei zugänglichen Medienfotos einzelner Institutionen handelt.
Auf der Homepage befinden sich Videofilme, die eine verblüffende Ähnlichkeit mit dem Werbematerial von NAKHEEL aufweisen, dem größten Bauträger der Vereinigten Arabischen Emirate. Den schillernden Videos über die berühmten drei Dubai Palmen wurden offensichtlich selbstproduzierte Trailersequenzen der Meridian Capital Enterprises vorangestellt.
Ab einem Volumen von 10 Millionen Euro oder höher präsentiert sich so die Meridian Capital Enterprises Ltd. als der passende Investitionspartner. Auf der Internetseite sind diverse Fotos mit Scheichs an Konferenztischen zu sehen. Doch diese großen Tagungen und großen Kongresse der Meridian Capital Enterprises werden in den Pressearchiven der lokalen Presse Dubais mit keinem Wort erwähnt.
Vertiefende Information unter:
http://www.presseportal.de/go2/mehr_zu_MCE_ltd
Originaltext: GoMoPa GmbH Digitale Pressemappe: http://www.presseportal.de/pm/72697 Pressemappe via RSS : http://www.presseportal.de/rss/pm_72697.rss2
Pressekontakt: Herr Friedrich Wasserburg Telefon: +49 (30) 51060992 Fax: +49 (30) 51060994 Zuständigkeitsbereich: Presse
Firmeninfo Goldman Morgenstern & Partners LLC 575 Madison Avenue USA-10022 – 2511 New York http://www.gomopa.net
Über Goldman Morgenstern & Partners LLC: Ein Zusammenschluss aus Unternehmens-, Steuer-, Anlageberatern und Rechtsanwälten.
© 2008 news aktuell
DANN GING DIe ERPRESSUNG LOS UND MERIDIAN CAPITAL REAGIERTE – STATT DIES ABER ZUZUGEBEN SETZEN DIE STASI-VERBRECHER EINE GEFÄLSCHTE PRESSE-MITTEILUNG IN NETZ, DIE MICH BELASTEN SOLL
BITTE KONTAKTIEREN SIE AUCH MERIDIAN CAPITAL
sales@meridiancapital.com
1 Battery Park Plaza
New York, NY 10004
TEL: 212-972-3600
FAX: 212-612-0100
Hierzu weitere Infos unter
Original Stellungnahme Meridian Capital gegen “GoMoPa” auf http://meridiancapital.wordpress.com/
Original Stellungnahme Meridian Capital gegen “GoMoPa” auf http://meridiancapital.wordpress.com
Meridian Capital about GoMoPa
STASI-FÄLSCHUNGEN DER “GoMoPa”
- June 12, 2011 – 10:44 am
- Posted in Uncategorized
- Comments Off
Sehr geehrte Damen und Herren,
die Betrüger und durch uns inhaftierten Erpresser der GoMoPa versuchen mit einer gefälschten Presse-Mitteilung von usich abzulenken und einen investigativen Journalisten, Bernd Pulch, zu belasten.
Die Presse-Mitteilung auf pressreleaser.org ist eine Fälschung und die gesamte webseite ist der GoMoPa zu zuordnen.
Hier noch einmal die tatäschlichen Geschehnisse:
Hier der Artikel von “GoMoPa” über Meridian Capital.
 „GoMopa“ schreibt:08.09.2008 „GoMopa“ schreibt:08.09.2008Weltweite Finanzierungen mit WidersprüchenDie Meridian Capital Enterprises Ltd. gibt an, weltweite Finanzierungen anbieten zu können und präsentiert sich hierbei auf aufwendig kreierten Webseiten. GOMOPA hat die dort gemachten Angaben analysiert und Widersprüche entdeckt. Der Firmensitz Der Firmensitz befindet sich laut eigener Aussage in Dubai, Vereinigte Arabische Emirate. In einem GOMOPA vorliegenden Schreiben der Meridian Capital Enterprises Ltd. heißt es jedoch, der Firmensitz sei in London. Auf der Homepage des Unternehmens taucht die Geschäftsadresse in der Londoner Old Broad Street nur als „Kundenabteilung für deutschsprachige Kunden“ auf. Eine weitere Adresse in der englischen Hauptstadt, diesmal in der Windsor Avenue, sei die „Abteilung der Zusammenarbeit mit Investoren“. Die Meridian Capital Enterprises ist tatsächlich als „Limited“ (Ltd.) mit Sitz in England und Wales eingetragen. Aber laut Firmenhomepage hat das Unternehmen seinen „rechtlichen Geschäftssitz“ in Dubai. Eine Abfrage beim Gewerbeamt Dubais (DED) zu dieser Firmierung bleibt ergebnislos. Bemerkenswert ist auch der vermeintliche Sitz in Israel. Auf der Webseite von Meridian Capital Enterprises heißt es: „Die Firma Meridian Capital Enterprises Ltd. ist im Register des israelischen Justizministeriums unter der Nummer 514108471, gemäß dem Gesellschaftsrecht von 1999, angemeldet.“ Hierzu Martin Kraeter, Gomopa-Partner und Prinzipal der KLP Group Emirates in Dubai: „Es würde keinem einzigen Emirati – geschweige denn einem Scheich auch nur im Traum einfallen, direkte Geschäfte mit Personen oder Firmen aus Israel zu tätigen. Und schon gar nicht würde er zustimmen, dass sein Konterfei auch noch mit vollem Namen auf der Webseite eines Israelischen Unternehmens prangt.“ Auf der Internetseite sind diverse Fotos mit Scheichs an Konferenztischen zu sehen. Doch diese großen Tagungen und großen Kongresse der Meridian Capital Enterprises werden in den Pressearchiven der lokalen Presse Dubais mit keinem Wort erwähnt. Zwei angebliche Großinvestitionen der Meridian Capital Enterprises in Dubai sind Investmentruinen bzw. erst gar nicht realisierte Projekte. Das Unternehmen wirbt mit ihrer finanziellen Beteiligung an dem Dubai Hydropolis Hotel und dem Dubai Snowdome. Der Aktivitätsstatus der Meridian Capital Enterprises Ltd. ist laut englischen Handelsregister (UK Companies House) „dormant“ gemeldet. Auf der Grundlage des englischen Gesellschaftsrechts können sich eingetragene Unternehmen selbst „dormant“ (schlafend) melden, wenn sie keine oder nur unwesentliche buchhalterisch zu erfassende Transaktionen vorgenommen haben. Dies ist angesichts der angeblichen globalen Investitionstätigkeit der Meridian Capital Ltd. sehr erstaunlich. Der Webauftritt Die Internetseite der MCE ist sehr aufwendig gestaltet, die Investitionen angeblich in Millionen- und Milliardenhöhe. Bei näherer Betrachtung der Präsentationselemente fällt jedoch auf, dass es sich bei zahlreichen veröffentlichen Fotos, die Veranstaltungen der Meridian Capital Enterprises dokumentieren sollen, meist um Fotos von Online-Zeitungen oder frei zugänglichen Medienfotos einzelner Institutionen handelt wie z.B. der Börse Dubai. Auf der Internetpräsenz befinden sich Videofilmchen, die eine frappierende Ähnlichkeit mit dem Werbematerial von NAKHEEL aufweisen, dem größten Bauträger der Vereinigten Arabischen Emirate. Doch den schillernden Videos über die berühmten drei Dubai Palmen „Jumeirah, Jebel Ali und Deira“ oder das Archipel „The World“ wurden offensichtlich selbstproduzierte Trailersequenzen der Meridian Capital Enterprises vorangestellt. Doch könnte es sich bei den Werbevideos um Fremdmaterial handeln. Auch die auf der Webseite wahllos platzierten Fotos von bekannten Sehenswürdigkeiten Dubais fungieren als Augenfang für den interessierten Surfer mit eigenem Finanzierungswunsch. Bei einem Volumen von 10 Millionen Euro oder höher präsentiert sich die Meridian Capital Enterprises Ltd. als der passende Investitionspartner. Das Unternehmen verfügt weltweit über zahlreiche Standorte: Berlin, London, Barcelona, Warschau, Moskau, Dubai, Riad, Tel Aviv, Hong Kong und New York. Aber nahezu alle Standorte sind lediglich Virtual Offices eines global arbeitenden Büroservice-Anbieters. „Virtual Office“ heißt im Deutschen schlicht „Briefkastenfirma“. Unter solchen Büroadressen sollen laut Meridian Capital Enterprises ganze Kommissionen ansässig sein, alles zum Wohle des Kunden.“ Zitatende |
Hier die Hintergründe der Erpressung:
Hier unsere Original-Stellungnahme:
Anfang Oktober 2008 erhielt einer der Arbeiter der Meridian Capital Enterprises Ltd. eine Meldung von einem anonymen Sender, dass in naher Zukunft – zuerst im Internet, dann im Fernsehen, im Radio und in der deutschen Presse – Informationen erscheinen, die die Funktionsweise und Tätigkeiten der Meridian Capital Enterprises Ltd. in einem äußerst negativen Licht darstellen. Der Mitarbeiter der Meridian Capital Enterprises Ltd. wurde also informiert, dass diese Meldungen/Nachrichten zweifelsohne deutlich das Aussehen und den guten Ruf der Firma Meridian Capital Enterprises Ltd. beeinträchtigen.
Der an dieser Stelle erwähnte „Gesprächspartner” hat den Arbeiter der Meridian Capital Enterprises Ltd. informiert, dass die Möglichkeit besteht die peinliche Situation zu vermeiden, indem die Meridian Capital Enterprises Ltd. auf das von der Person gezeigte Konto die Summe von 100.000,00 EUR überweist. Wie sich aber später zeigte, war der Herr Klaus Maurischat – dieser anonyme Gesprächspartner – „Gehirn“ und „Lider des GOMOPA“. Die Ermittlungen wurden angestellt durch die Bundeskriminalpolizei (Verfolgungs- und Ermittlungsorgan auf der Bundesebene) während des Ermittlungsverfahrens wegen einer finanziellen Erpressung, Betrügereien auch wegen der Bedrohungen, welche von Herrn Maurischat und seine Mitarbeiter praktiziert wurden sowie wegen Teilnahme anderer (Leiter der Internetservices und Moderatoren der Blogs) an diesem Prozedere. Diese Straftaten wurden begangen zu Schaden vieler Berufs- und Justizpersonen, darunter auch der Meridian Capital Enterprises Ltd. Die Opfer dieses Verbrechens sind in Deutschland, Österreich, der Schweiz, Spanien, Portugal, Großbritannien, den USA und Kanada sichtbar.
In diesem Moment taucht folgende Frage auf: Wie war die Reaktion der Meridian Capital Enterprises Ltd. auf die Forderungen seitens GOMOPA? Entsprach die Reaktion den Erwartungen von GOMOPA? Hat die Meridian Capital Enterprises Ltd. die geforderte Summe 100.000,00 EUR überwiesen?
Seites der Meridian Capital Enterprises Ltd. gab es überhaupt keine Reaktion auf den Erpressungsversuch von GOMOPA. Ende August 2008 auf dem Service http://www.gompa.net sind zahlreiche Artikel/Meldungen erscheinen, welche die Tätigkeit der Meridian Capital Enterprises Ltd. in einem sehr negativen Licht dargestellt haben. Nachdem die auf http://www.gomopa.net enthaltenen Informationen ausführlich und vollständig analysiert worden waren, ergab es sich, dass sie der Wahrheit nicht einmal in einem Punkt entsprechen und potenzielle und bereits bestehende Kunden der Meridian Capital Enterprises Ltd. in Bezug auf die von diesem Finanzinstitut geführten Geschäftstätigkeit irreführen. Infolge der kriminellen Handlugen von GOMOPA und der mit ihm kooperierenden Services und Blogs im Netz hat die Meridian Capital Enterprises Ltd. beachtliche und messbare geschäftliche Verluste erlitten. Die Meridian Capital Enterprises Ltd. hat nämlich in erster Linie eine wichtige Gruppe von potenziellen Kund verloren. Was sich aber als wichtiger ergab, haben sich die bisherigen Kunden von der Meridian Capital Enterprises Ltd. kaum abgewandt. Diejenigen Kunden haben unsere Dienstleitungen weiterhin genutzt und nutzen die immer noch. In Hinblick auf die bisherige Zusammenarbeit mit der Meridian Capital Enterprises Ltd., werden ihrerseits dem entsprechend keine Einwände erhoben .
GOMOPA hat so einen Verlauf der Ereignisse genau prognostiziert, dessen Ziel beachtliche und messbare geschäftliche durch die Meridian Capital Enterprises Ltd. erlittene Verluste waren. Der Verlauf der Ereignisse hat das Service GOMOPA mit Sicherheit gefreut. GOMOPA hat nämlich darauf gerechnet, dass die Stellung der Meridian Capital Enterprises Ltd. nachlässt und das Finanzinstitut die geforderte Summe (100.000,00 EUR) bereitstellt. Im Laufe der Zeit, als das ganze Prozedere im Netz immer populärer war, versuchte GOMOPA noch vier mal zu der Meridian Capital Enterprises Ltd. Kontakte aufzunehmen, indem es jedes mal das Einstellen dieser kriminellen „Kompanie” versprochen hat, wobei es jedes mal seine finanziellen Forderungen heraufsetzte. Die letzte für das Einstellen der „Kompanie“ gegen die Meridian Capital Enterprises Ltd. vorgesehene Quote betrug sogar 5.000.000,00 EUR (in Worten: fünfmilionen EURO). Die Meridian Capital Enterprises Ltd. konnte sich aber vor den ständig erhöhenden Forderungen seitens des Services GOMOPA behaupten.
Im Oktober 2008 traf die Leitung der Meridian Capital Enterprises Ltd. Entscheidung über die Benachrichtigung der Internationalen Polizei INTERPOL sowie entsprechender Strafverfolgungsorgane der BRD (die Polizei und die Staatsanwaltschaft) über den bestehenden Sachverhalt. In der Zwischenzeit meldeten sich bei der Meridian Capital Enterprises Ltd. zahlreiche Firmen und Korporationen, sogar Berufsperson wie Ärzte, Richter, Priester, Schauspieler und anderen Personen aus unterschiedlichen Ländern der Welt, die der Erpressung von GOMOPA nachgegeben und die geforderten Geldsummen überwiesen haben. Diese Personen gaben bereits Erklärungen ab, dass sie dies getan haben, damit man sie bloß endlich „in Ruhe lässt” und um unnötige Probleme, Schwierigkeiten und einen kaum begründbaren Ausklang vermeiden zu können. Die Opfer dieses kriminellen Vorgehens haben die Meridian Capital Enterprises Ltd. über unterschiedliche Geldsummen, welche verlangt wurden, informiert.
In einem Fall gab es verhältnismäßig kleine (um ein paar tausend EURO), in einem anderen Fall handelte es schon um beachtliche Summen (rund um paar Millionen EURO).
Zusätzlich wendeten sich an die Meridian Capital Enterprises Ltd. Firmen, welche dem GOMOPA noch keine „Gebühr” überweisen haben und bereits überlegen, ob sie dies tun sollen, oder nicht. Diese Firmen erwarteten von der Meridian Capital Enterprises Ltd. eine klare Stellungnahme sowie eine professionelle praktische Beratung, wie man sich in solch einer Lage verhalten soll und wie man diese Geldforderungen umgehen kann. Die Meridian Capital Enterprises Ltd. hat ausnahmslos allen Verbrechensopfern, welche sich bei unserer Firma gemeldet haben, eine Zusammenarbeit vorgeschlagen. Als oberste Aufgabe stellt sich diese Kooperation, gemeinsam entschlossene und wirksame Maßnahmen gegen GOMOPA, gegen andere Services im Netz sowie gegen alle Bloggers zu treffen, die an dem hier beschriebenen internationalen kriminellen Vorgehen mit GOMOPA-Führung teilnehmen.Auf unsere Bitte benachrichtigten alle mitbeteiligten Firmen die Internationale Polizei INTERPOL sowie ihre heimischen Verfolgungsorgane, u. a. die zuständige Staatsanwaltschaft und die Polizeibehörden über den bestehenden Sachverhalt.
In Hinblick auf die Tatsache, dass das verbrecherische Handeln von GOMOPA sich über viele Staaten erstreckte und dass die Anzahl der in der Bundesrepublik Deutschland erstatteten Anzeigen wegen der durch GOMOPA, Internetservices und Bloggers begangenen Straftaten, rasant wuchs – was zweifelsohne von einer weit gehenden kriminellen Wirkungskraft des GOMOPA zeugt – schlug die Internationale Wirtschaftspolizei INTERPOL der Meridian Capital Enterprises Ltd. vor, dass sich ihr Vertreter in Berlin mit dem Vertreter von GOMOPA trifft, um die „Zahlungsmodalitäten“ und Überweisung der Summe von 5.000.000,00 EUR zu besprechen. Dieser Schritt meinte, eine gut durchdachte und durch die Bundeskriminalpolizei organisierte Falle durchzuführen, deren Ziel die Festnahme der unter GOMOPA wirkenden internationalen Straftäter war.
Die koordinierten Schritte und Maßnahmen der Meridian Capital Enterprises Ltd. und anderer Beschädigter, geleitet von der Internationalen Wirtschaftspolizei INTERPOL, dem Bundeskriminalamt und der Staatsanwaltschaft der Bundesrepublik Deutschland haben zur Aus-, Einarbeitung und Durchführung der oben beschriebenen Falle beigetragen. Im November 2008 führte die in Berlin vorbereitete Falle zur Festnahme und Verhaftung des Vertreters des GOMOPA, der nach der Festnahme auf Herrn Klaus Maurichat – als den Hauptverantwortlichen und Anführer der internationalen kriminellen Gruppe GOMOPA verwies. Der Festgenommene benannte und zeigte der Bundeskriminalpolizei zugleich den aktuellen Aufenthaltsort des Herrn Klaus Maurischat. „Gehirn“ und Gründer dieser internationalen kriminellen Gruppe GOMOPA, Herr Klaus Maurischat wurde am selben Tag auch festgenommen und auf Frist verhaftet, wird bald in Anklagezustand gestellt, wird die Verantwortung für eigene Straftaten und die des Forums GOMOPA vor einem zuständigen Bundesgericht tragen. Die Meridian Capital Enterprises Ltd. unternahm bereits alle möglichen Schritte, damit Herr Klaus Maurischat auch auf der Anklagebank des zuständigen Gerichts des Vereinigten Königsreiches Großbritannien erscheint. Unter den beschädigten Berufs- und Justizpersonen aus Großbritannien, neben der Meridian Capital Enterprises Ltd. gibt es noch viele Opfer von GOMOPA…
Die dreisten Verbrecher wagen es unter http://www.pressreleaser.org, einer eigenen “GoMoPa”-Seite unsere Pressemitteilung oben zu verfälschen und unschuldige Personen zu belasten.
“GoMoPa” Boss is Jochen Resch
- May 15, 2011 – 1:15 pm
- Posted in Uncategorized
- Comments Off
Dear Readers,
after a thorough research we are sure that the real “GoMoPa” boss is Jochen Resch, lawyer in Berlin, Germany. He is the brain behind “GoMoPa” and responsable for blackmailing, extortion, racketeering, cybermurder and murder – in the tradition of the East German “Inteeligence” STASI that is why he called “GoMoPa” – Financial “Intelligence” Service .
Webmaster
Meridian Capital about GoMoPa
“GoMoPa” in detention
- May 13, 2011 – 1:02 pm
- Posted in Uncategorized
- Comments Off
Meridian Capital Enterprises Ltd.. unveils new criminal phenomena in network. In recently appeared on the net more often at the same time a new a very worrying phenomenon of criminal nature. Professional criminals groups in the network are taking part, to extortion, fraud, Erschwindeln relating to certain specifically selected companies and businesses are capable of. These criminals developed new methods and means, simply and in a short time to bereichern.Strategien and manifestations, which underlie this process are fairly simple. A criminal is looking to “carefully” on the Internet specific companies and corporations (victims of crime) and informed them in the next step, that of the business activities of such companies and corporations in the near future – first on the Internet then in other available mass media – numerous and very unfavorable information appears. At the same time, the criminals beat their future victims an effective means of reducing unnecessary difficulties and problems to escape the loss of good name and image of the company and corporate sector. These offenders are aware of that reputation, name and appearance of each company is a value in itself. It was therefore a value of what each company is prepared to pay any price. But the reason for difficulties and problems arising from the loss of good name and reputation result. The criminals and their victims are already aware that this loss is devastating consequences might have been the closing down of a particular business can enforce. It takes both to No as well as at large companies regard. The company is concerned that in virtually every industry in each country and cross-border activities sind.Das criminal procedure in the form of a blackmail on money, a fraud is becoming rapidly and globally, ie led cross-border and internationally. Among the victims of extortion, fraud is now looking both at home (domestic) and international corporations, the major emphasis on conservation, keeping and maintaining their reputation in the business according to their credibility lay. The criminals in the network have understood that maintaining an unassailable reputation and name of a company the unique ability to provide fast and easy enrichment forms. The above-mentioned criminal procedure is difficult to track because it is international in nature, and by overlapping or even nonexistent (fictional) professional and judicial persons in various countries and operated company wird.Diese offenders in the network publish it and disseminate false information about your victims on remote servers, which are not uncommon in many exotic countries. There are those countries in which serious gaps in the legal system, investigative and prosecution procedures are visible. As an example, at this point mention India werden. Mit criminals working in the network grid portals known leader of blogs with your seat-consciously or unconsciously, even in highly developed countries. For example, at this point, countries such as Germany, Austria, Switzerland, the United States, Britain, Spain or Portugal are mentioned. The below listed criminals were able to act unpunished today. As a symptom of such action appears here the activity and “effectiveness” of the company GOMOPA, which is on countries such as Germany, Switzerland, Austria, the United States, Britain, Spain and India. A good example of such an action is Mr. Klaus Mauri Chat – the leader and “brain” of the company GOMOPA with many already in force and criminal judgments “on his account”, which in this way for years and funded its maintenance in the industry almost unlimited activity. This status will change dramatically, however, including far and wide thanks to discontinued operations of the firm Meridian Capital Enterprises Ltd.. who would oppose such offenses addressed in the network. Other companies and corporations, in which the crime network and outside of this medium have fallen victim to contribute to combating such crimes bei.Die situation is changing, thanks to effective steps and the successful cooperation of the firm Meridian Capital Enterprises Ltd.. with the international police Interpol, with the federal agency (FBI) in the U.S., the Federal Criminal Police in Germany, with Scotland Yard in Britain, as well as with the Russian secret service FSB.Die Meridian Capital Enterprises Ltd.. – Together with other companies and cooperations, the victim of criminal activities of the network of crime have fallen – has undeniably already started to yield results. The fact that in recent weeks (November 2008) on the territory of the Federal Republic of Germany of the above-mentioned leaders and “brain” of the company GOMOPA, Mr Klaus Maurishat was arrested should not be ignored. The Meridian Capital Enterprises Ltd.. information available results clearly show that the next arrests of persons participating in this process in such countries as: Austria, Switzerland, Russia, Ukraine, Poland, Spain, Mexico, Portugal, Brazil, the USA, Canada, UK, Ireland , Australia, New Zealand and made in a.. The ultimate goal of Meridian Capital Enterprises Ltd.. and the other victims of crime in the network is to provide all participants in this criminal procedure before the competent court to lead. All professional and judicial persons, regardless of the seat and out of the business, which the above-described criminal action (fraud, extortion) to have fallen victim can of Meridian Capital Enterprises Ltd.. led company to join the goal set at all at this point the procedure described those associated in the public and the economic life out. II blacklist blackmail and with international fraudsters and their methods (opus operandi) in the following countries: 1 The Federal Republic Deutschland2. Dubai 3rd Russia 1st The Federal Republic of Germany GmbH GOMOPA, Goldman Morgenstern & Partners LLC., Goldman Morgenstern & Partners Consulting LLC, Wottle collection. In these firms are quite active following persons: – Klaus Mauri Chat ( “Father” and “brain” of the criminal organization responsible for countless final judgments have been achieved (arrested in Germany in November 2008) – Josef Rudolf Heckel ( “right hand “when Mr Klaus Mauri chat, denounced former banker who is excessive in many Bankschmuggeleien was involved.
The study of 900 pages named Toxdat by Ehrenfried Stelzer is the “Stasi Killer Bible”. It lists all kind of murder methods and concentrates on the most effective and untraceable.
“The toxdat study was ordered by Stasi Vice-President Gerhard Neiber, the second man in rank after boss Erich Mielke. The toxdat study was also the theoretical “story book” for the murder of the famous German watchdog and journalist Heinz Gerlach by former Stasi member under the guidance of “GoMoPa”,” an informer stated. “Ehrenfried stelzer” was nicknamed “Professor Murder” by his victims. Even close co-worker now compare him with the German SS”doctor” Mengele, “Dr. Death” from Auschwitz.
Only two articles let the German audience believe that the famous journalist and watchdog Heinz Gerlach died on natural courses by blood pollution.
For more Information the victims have launched a new site: http://www.victims-opfer.com
The first one, published only hours after the death of Mr Heinz Gerlach by the notorious “GoMoPa” (see article below) and a second 3 days later by a small German local newspaper, Weserbergland Nachrichten.
Many people including the hostile Gerlach website “Akte Heinz Gerlach” doubted that this man who had so many enemies and friends would die of natural causes without any previous warning. Rumours occured that Mr. Gerlach’s doctor doubted natural courses at all. After many critical voices discussed the issue a small website of a small German local newspaper – which never before had reported about Mr. Heinz Gerlach and which is not even in the region of Mr Gerlachs home – published that Mr Gerlach died of blood pollution. Weserbergland-Nachrichten published a long article about the deadly consequences of blood pollution and did not even name the source of such an important statement. It claimed only that somebody of Gerlachs inner circle had said this. It is a proven fact that after the collpase of the Eastern German Communist Regime many former Communist propaganda agents went to regional newspapers – often in Western Germany like Günther Schabowski did the man who opened the “Mauer”.
The theatre stage was set: One day later the hostile Gerlach website “Akte Heinz Gerlach” took the agenda publishing that Mr Gerlach had died for natural causes without any further research at all.
This was done by a website which for months and months and months reported everything about Mr. Gerlach.
Furthermore a research proves that the technical details regarding the website hosting of this hostile website “Akte Heinz Gerlach” proves that there are common details with the hosting of “GoMoPa” and their affiliates as proven by the SJB-GoMoPa-victims (see http://www.sjb-fonds-opfer.com)
Insiders believe that the murderers of Mr. Heinz Gerlach are former members of the Eastern German Terror Organisation “Stasi” with dioxins. They also believe that “GoMoPa” was part of the plot. At “GoMoPa”’ a person named Siegfried Siewers was officialy responsible for the press but never appeared in public. “GoMoPa”-victims say that this name was a cameo for “GoMoPa” frontrunner Klaus Maurischat who is controlled by the Stasi Top Agent Ehrenfried Stelzner, Berlin.
Siegfried Sievers, a former Stasi member is responsible for the pollution of millions Germanys for many years with dioxins. This was unveiled at 5th of January 2011 by German prosecutors.
The victims say that Maurischat (probably also a Stasi cameo) and Sievers were in contact as Sievers acted as Stasi Agent and was in fact already a specialist in dioxins under the Communist Terror Regime in Eastern Germany.
Furthermore the Stasi Top Agent Ehrenfried Stelzer disguised as Professor for Criminal studies during the Communist Regime at the Eastern Berlin Humboldt University.
Background:
The man behind the Berlin lawyer Jochen Resch and his activities is Ehrenfried Stelzer, former Stasi Top officer in Berlin and “Professor for Criminal Studies” at the Eastern Berlin Humboldt University during the Communist regime, the SJB-GoMoPa-victims say (www.sjb-fonds-opfer.com) is responsable for the killing of German watchdog and journalist Heinz Gerlach.
These informations stem from various sources who were close to the criminal organization of GoMoPa in the last years. The SJB-GoMoPa say that the well-known German watchdog and journalist Heinz Gerlach was killed by former Stasi members with dioxins. Polychlorinated dibenzodioxins (PCDDs), or simply dioxins, are a group of organic polyhalogenated compounds that are significant because they act as environmental pollutants. They are commonly referred to as dioxins for simplicity in scientific publications because every PCDD molecule contains a dioxin skeletal structure. Typically, the p-dioxin skeleton is at the core of a PCDD molecule, giving the molecule a dibenzo-p-dioxin ring system. Members of the PCDD family have been shown to bioaccumulate in humans and wildlife due to their lipophilic properties, and are known teratogens, mutagens, and confirmed (avered) human carcinogens. They are organic compounds.
Dioxins build up primarily in fatty tissues over time (bioaccumulate), so even small exposures may eventually reach dangerous levels. In 1994, the US EPA reported that dioxins are a probable carcinogen, but noted that non-cancer effects (reproduction and sexual development, immune system) may pose an even greater threat to human health. TCDD, the most toxic of the dibenzodioxins, is classified as a Group 1 carcinogen by the International Agency for Research on Cancer (IARC).
In 2004, a notable individual case of dioxin poisoning, Ukrainian politician Viktor Yushchenko was exposed to the second-largest measured dose of dioxins, according to the reports of the physicians responsible for diagnosing him. This is the first known case of a single high dose of TCDD dioxin poisoning, and was diagnosed only after a toxicologist recognized the symptoms of chloracne while viewing television news coverage of his condition.
German dioxin scandal: In January 2011 about 4700 German farms were banned from making deliveries after tests at the Harles und Jentzsch plant in the state of Schleswig-Holstein showed high levels of dioxin. Again this incident appears to involve PCBs and not PCDDs at all. Dioxin were found in animal feed and eggs in many farms. The person who is responsible for this, Siegfried Sievert is also a former Stasi Agent. At “GoMoPa” the notorious Eastern-Berlin press agency (see article below) one of the henchmen acted under the name of “Siegfried Siewert”.
Further evidence for the killing of Mr.Heinz Gerlach is provided by the SJB-GoMoPa-victims by analyzing the dubious role of former Stasi-Top-agent Ehrenfried Stelzer, also a former “Professor for Crime Studies” under the Communist regime in Eastern Germany and the dubious role of “detective” Medard Fuchsgruber. Both are closely tied to the dubious “GoMoPa” and Berlin lawyer Jochen Resch.
According to the SJB-GoMoPa-victims is Berlin lawyer Jochen Resch the mastermind of the criminal organization “GoMoPa2. The victims state that they have a source inside “GoMoPa” who helped them discover the shocking truth. The so-called “Deep Throat from Berlin” has information that Resch had the idea to found the criminal organization “GoMoPa” and use non-existing Jewish lawyers named Goldman, Morgenstern & Partner as camouflage. Their “office” in Madison Avenue, New York, is a mailbox. This is witnessed by a German Ex-Patriot, a lawyer, whose father, Heinz Gerlach, died under strange circumstances.
Resch seems to use “GoMoPa” as an instrument to blackmail parts of the German Property and Investment.
German authorities are under growing pressure to reopen investigations into at least a dozen suspicious deaths after the arrest of an alleged East German assassin cast new light on the communist regime. Stasi victims quoted a source saying “isolated units” had conducted operations that were “extremely well organised” and had “100 per cent logistical support” from the East German state.
A statement from prosecutors read: “The accused [Jurgen G] is suspected, as a member of a commando of the former DDR, of killing a number of people between 1976 and 1987 who from the point of view of the DDR regime had committed treason or were threatening to do so.”
Details of his Jurgen G’s arrest have been described in suitably florid terms, with the mass circulation tabloid Bild saying he was working at the Wolfsbruch marina near Rheinsberg in north-eastern Germany when a woman approached him. “Excuse me, is that your yellow Trabant in the car park? I just ran into it with my car,” she is said to have asked.
When he followed her to the car park, masked officers jumped out of vans and bushes and overpowered him in an operation worthy of the Stasi itself.
An eyewitness told Bild: “They blindfolded him and raced off in an unmarked car.”
Police across Germany are reported to be sifting through files to see who the victims may have been, and some intelligence officers are greeting the arrest of Jurgen G as a breakthrough.
Thomas Auerbach, who works for the Stasi file authority in Berlin and has written a book based on the death squad files, said: “These people were trained to make such murders look like accidents or suicides, even as ‘ordinary’ crimes such as robberies. They were real terror experts.”
The cases said to be linked to Jurgen G or his unit include many people involved with the commercial arm of the East German ruling socialist party, the SED (Socialist Unity Party).
Uwe Harms, the head of a Hamburg-based haulage firm which was part of a network of companies secretly owned by the SED, disappeared in March 1987 after conversations with various DDR functionaries. Six weeks later, his body was found in a plastic bag.
Weeks before his death he told friends that he felt he was being followed. After reunification, one of the other SED company heads said Mr Harms had been liquidated for refusing to allow his firm to be used to transport arms into East Germany.
Dieter Vogel, a businessman who had been jailed for life for spying for the CIA, was found suffocated in his cell in the East German prison Bautzen on March 9, 1982. The fact that he was due to be taken to the West in a spy swap arrangement just a few weeks later cast doubt on the suicide theory.
He had passed the names of several Stasi moles to the BND, West Germany’s heavily penetrated counter-intelligence service.
The Christian Democrat Union politician Uwe Barschel, 43, was found dead by magazine reporters in his bathtub in a hotel room in Geneva in October, 1987. He died of poisoning, but rumours that he was involved somehow in arms deals and the Stasi have clung to the case.
One of the more high-profile and enduring mysteries is that of Lutz Eigendorf, an East German footballer from the Stasi-backed Dynamo Berlin.
He fled to the West in 1979 amid great publicity. Four years later, he died after crashing his car into a tree on a straight stretch of road with blood alcohol levels way over the limit. Witnesses who had seen him earlier in the evening said he had not been drinking.
Most controversial though is the suggestion that the assassination squad was linked to the murder of a Swedish television reporter and her friend in 1984.
Cats Falk and her friend Lena Graens went missing on Nov 19, 1984. Their bodies were fished out of a Stockholm canal six months later.
Reports suggested a three-man assassination squad killed them, spiking their drinks with drugs, putting them into their car and pushing it into the Hammarby canal.
Shortly before her death, Cats Falk had reportedly uncovered a deal between an arms dealer and an East German firm.
Germany has recently undergone a wave of nostalgia for all things East German, dubbed Ostalgie, with colourful television shows featuring former DDR stars such as the ice skater Katerina Witt talking wistfully about socialist pop music.
A reassessment may be coming in the wake of the revelations.
American Neo-Nazi “Führer” exposed – John T. Bowles – The American Nazi Party

Do you remember that Nazi organization that publicly endorsed the Occupation Movement through Twitter? No, not the NSM, (they actually showed up in person). The half-witted group we are talking about is called the American Nazi Party (ANP). The ANP are a very secretive and semi-clandestine “political-educational association” led by Rocky Suhayda. They do not make major public appearances like the NSM and are also very legalistic. This group claims George Lincoln Rockwell as their founder, but there is no actual connection to the original ANP or its successor organizations, aside from the fact that their website sells nostalgic reprints of Rockwell’s 1960s-era magazine “The Storm Trooper”. The information we are releasing below is being done three days before their “big” Christmas get together in South Carolina on December 10th. In it you will find names and addresses of high ranking members as well as supporters of the ANP, their meeting spot, the hotel they are staying in for the event and best of all… the full email content of their security arm political advisor, and one-time NSM member who ran for president in 08; John Taylor Bowles. We have taken the time to point out some of the highlights of these emails including very sensitive personal info such as social security numbers as well as very private conversations. Since the Xmas get together is in three days, we are asking folks to call the hotel they are staying at (864-984-0558 ) and let them know that Neo-Nazis are staying there. Furthermore, we hope that some community folks or antifa will see to it that this little get together never happens!
Fuck the ANP, smash the Nazis, forever anti-fascist!
Enjoy!
The American Nazi Party(ANP)
Rocky J Suhayda(chairman)
38564 Scott Dr
Westland, MI 48186-3854
Age: 55-59 rsuhayda@att.net
Associated: Deborah A Suhayda, Brandi L Suhayda
possible number (734) 641-3614John Taylor Bowles(SA political advisor)
102 Old Depot Road Enoree, SC 29335
864-969-3456
SSN-219764273(Confirmed: 11/30/11)
Was once member of the NSM
sapoliticaladvisor@hotmail.com
Johntbowles@hotmail.com
Children: Chelsea, Johana, Sara,Paul A Kozak(SA leader/Chief security officer)
Email: anpsa88@yahoom.com
Possible addresses:
2033 Olive Hill Dr Buffalo Grove, IL 60089-4644
1921 S Tures Ln Des Plaines, IL 60018-2011
Age:45-49 5’9”
Cell phone: 847-877-6530
Axl Hess
Director of Media Outreach / SA Deputy Leader
axl@americannaziparty.com
Helps with white worker, twitter and website
Kevin P Brannon
(256) 378-6205
160 McDonald Ter
Childersburg, AL 35044-1850
Age: 30-34 ex-NSALP
Andrew L Westphal
10432 Swain
Chapel Hill, NC 27517-
8534
(850) 819-0817Tim A
SA HQ assistant section leaderKevin Skea(aka steve davenport)
Meeting location for Dec 10th annual Christmas party
The Redneck Shop
108 W. Laurens Street, Laurens, SC 29360
Hotel they are staying at
Travel Inn
621 N Harper St
Laurens, SC 29360
864-984-0558
Attendees:
Jeremy Killgore
Supporters:
Chris K Wasserstrom
630) 221-0588
0S626 Robbins St
Winfield, IL 60190-1600
chriswasserstrom@sbcglobal.net
Wanting to be ANP in IllinosJoshua Costa
4029 Satter Dr NE Salem, OR 97305-2173Joshua Lawrence
(419) 492-0039
7197 State Route 4
Bloomville, OH 44818-9392
daddyandbabygurl@hotmail.comMike D Dooley
509 Clubhouse Rd
Murrells Inlet, SC 29576-8166 or
3607 Sturbridge Dr
Hope Mills, NC 28348-2142
mddooley@embarqmail.comVictoria Florence (Bowles)
4951 verbogener Twig Rd Middleburg, Florida 32068Gail Magee
5102 ALMA LANE, EFFINGHAM SC 29541-3134,
843-667-9153,
gail.magee@yahoo.comHoward Kenyon
Washington DC
RadicalsonK@aol.com My phone is (202) 562-6704
James Hogan
New York James.
Hogan@houghton.eduLeslie McKenzie
Georgia 229 638 0647Josh Bates
706 267 3976
Georgia, One time state leader of NSALP
–
The Private emails of John Taylor Bowles
Download his emails: john.t.bowles.anp.hacked.emails.zip mirror 1, 2, 3, 4, 5, 6, 7, 8.
Chapter 1: Bowles can’t think for himself
Chapter 2:: Kozal tells of a “confidential source inside the NSM.”
Chapter 3: Attempt at a truce with ANSLP after detailed history of flame war. Rocky calls their leader Klebs a “newbie”.
Chapter 4: Kevin Branen tells rocky about persuading NSALP members to join the ANP.
Chapter 5: Rocky and Bowles discuss a ANP/KKK meet in greet that took place in August of 2009
Chapter 6: Rocky and Bowles shit talk hard on the NSALP and the NSM. Rocky Calls Jeff Schoep “sloop”
Chapter 7: Paul Kozak talks shit about potential supporter Mr Reihl
Chapter 8: Bowles passive aggressively talks shit about Paul Kozaks white worker articles being too long.
Chapter 9:: More feuding between NSALP(Kurt Williams) and ANP
Chapter 10: NSM trashes the redneck shop
Chapter 11: J Hogan calls out ANP for working with the Klan in SC
Chapter 12: Rochy Hating hard on all other groups involved in the movement.
Chapter 13: David Strausbaugh inites John Bowles to speak at Worthington Kilbourne High School(1499 Hard Road Columbus, OH 43235(C) 614-403-8843)!!!
Chapter 14: Taylor Bowles first contact with ANP. He requests to Join ANP after being burnt by the NSM
Chapter 15: NSALP members are dropping like flies and trying to turn ANP. While NSALP members bicker, a truce between ANP and NSALP was called by Kleb, with no response from ANP.
Chapter 16: Bowles tries to get in ex-NSM member Matthew Ramsey for the ANP. Rocky hates on him hard and , as usual, condescends to Bowles.
Chapter 17: Fighting words between Bowles and NSM SC
Chapter 18: Bowles kisses Rocky’s ass after RockySuggests Bowles is too poor to help pay for the white worker. Plus more sht talk on NSALP by Bowles.
Chapter 19: Bowles invited to a radio show. Bowles embarrassingly prods the host to ask him questions about his presidential campaign.
Chapter 20: Commander Schoep lashes out against the ANP and their claims that he is “race mixing”
Chapter 21: Suhayda tells Bowles how to dress
Chapter 22: Kevin swift is kicked out for not being a big enough man
Chapter 23: Paul Hates on Kevin Brennan over who he associates with
Chapter 24: Bowles daughter Chelsea threatens to kill herself cuz they wont let her call her boyfriend.
Chapter 25: Bowles tells Rocky to only commit him to said events for 2011. It appears Bolwes feels Rocky is abusing his commitment.
Chapter 26: Bowles request Kevin swift for ANP. Paul talks shit.
Chapter 27: Bowles owes tax money. Confirms address and social security number
Chapter 28: Bowles tells rocky he fears an attack on the ANP event by the NSM
Chapter 29: Bowles gets lippy w. rocky
Chapter 30: ANP not interested in working with Road Disciples MC of SC
Chapter 31: Bowles receives email talking shit on “Mick the Mick” Mick O’Malley of NSM
UNCENSORED – Anti-SOPA PIPA Protest NYC Photos
|
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict55.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict64.jpg) ![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict73.jpg) |
NYTech Meetup Protest Organizer![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict61.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict54.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict52.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict77.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict78.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict76.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict60.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict74.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict56.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict75.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict57.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict50.jpg) |
Clay Shirky![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict51.jpg)
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict81.jpg) ![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict80.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict59.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict68.jpg) ![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict69.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict66.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict49.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict46.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict47.jpg) ![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict70.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict62.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict72.jpg) |
PIPA Supporter![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict48.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict63.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict65.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict67.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict71.jpg) |
Anonymous Lists Their Demands regarding SOPA
The Internet is angry at SOPA and Anonymous is at, or at least near, the front of it all.
Just a few minutes ago, the “official” Anonymous twitter feed linked to the group’s list of demands. The document is titled, “Bright, and Clear: The Future of Free Speech.” In it, the group details their list of demands for the future of the Internet that they believe SOPA and PIPA want to dismantle.
As we watch the web go dark today in protest against the SOPA/PIPA censorship bills, let’s take a moment and reflect on why this fight is so important. We may have learned that free speech is what makes America great, or instinctively resist attempts at silencing our voices. But these are abstract principles, divorced from the real world and our daily lives.
We believe a healthy society doesn’t allow its artists, musicians and other creators to starve. The copyright industry has been justly criticized for abusing the political process in a desperate attempt to maintain its role as a cultural gatekeeper, a business model made obsolete by a digital age of free copies. But the RIAA, MPAA & IFPI deserve our opprobrium for making enormous profits while often leaving the very artists it claims to represent *poorer* than they would be as independents. While the public may have greater access to the few artists deemed sufficiently marketable to gain mass media promotion, fewer and fewer of us are making art and music in our own lives.
From there, the group lists their demands starting with the call for the WIPO to be disbanded. They also demand the elimination of the DMCA’s registration requirement for qualification under the “safe harbor” provision.
They move onto more court-related with their expectation that courts apply penalties just as severe to rightsholders who issue abusive takedown notices as those applied to copyright violators. They also demand that any penalties for copyright infringement must be sane and reasonable and not to be based on “unsubstantiated, outlandish claims of harm.”
They demand that the Department of Justice begin an anti-trust investigation into the copyright industry, with a specific focus on collusion between rightsholders and ISPs in monitoring Internet users.
They demand an end to sales of radio frequencies into private hands. They believe that the radio waves are a form of speech and should belong to the people.
A big one that most would not agree with is their demand that ISPs stop interfering with file sharing via BitTorrent or any other protocol.
They want recognition of total ownership, not merely licensing, of products purchased. They feel that they have a right to tinker and modify devices as they see fit. The Library of Congress should not be in charge of determining acceptable use.
They reject the principle of contributory infringement under the pretense that “while there may be bad uses, there is no bad code.”
One that I think everybody can get behind is their expectation that legislators and judges make efforts to educate themselves about the technologies they oversee, and to call on and respect the opinions of technical experts when necessary.
All research receiving any public funding must be placed in the public domain upon publication. Likewise, the US Patent and Trade Office must immediately cease issuing software and business patents, and declare all such existing patents null and void. They also call on the rejection of any patents on mathematical formulas and genes or other naturally-occurring substances.
They demand that copyright and patent terms be reduced to reasonable lengths (two and five years from the time of creation, respectively). Works should only be eligible for the length of protection when created.
They recognize a broad right of “fair use” that would allow anybody to remix, sample, mash up, translate, perform or make parodies of any work as they see fit.
Their final demand is that courts give bloggers the same freedoms that journalists enjoy.
“The right to a free press originally meant a literal, physical printing press – not membership in some government sanctioned elite. Blogs are the modern day digital equivalent.”
They end their list of demands with a final call to action to their fellow “Internauts.” They end their message with “either stand with us or get out of the way.”
Anonymous – Operation Blitzkrieg – Neo-Nazi List leaks
TOP SECRET – NSA’s Top Ten Technical Security Challenges
Not surprisingly in today’s world, National Security Systems are fundamentally dependent on commercial products and infrastructure, or interconnect with other systems that are. This creates new and significant common ground between the Department of Defense and broader U.S. Government and homeland security needs. More and more, we find that protecting National Security Systems demands teaming with public and private institutions to raise the information assurance level of products and services more broadly. If done correctly, this is a win-win situation that benefits the whole spectrum of Information Technology (IT) users, from warfighters and policymakers, to federal, state, and local governments, to the operators of critical infrastructure and major arteries of commerce. The “Top Ten Technical Security Challenges” reflect major focus areas for the Information Assurance Directorate (IAD) which may also present opportunities for industry.
NSA’s Top Ten Technical Security Challenges:
- Mobility, wireless networking, and secure mobile services
- Software assurance
- Virtualization, Separation, and Trusted Platforms
- Cloud computing
- Intrusion analysis and adversary tradecraft
- Platform Integrity – Compliance assurance – Continuous Monitoring
- Real-time situational awareness and CNO sync
- End client security
- Metrics and measurement for IA posture
- Commercial architectures for assistance
TOP-SECRET – GAO Federal Reserve $16 Trillion Emergency Bailout Loans Audit Report

On numerous occasions in 2008 and 2009, the Federal Reserve Board invoked emergency authority under the Federal Reserve Act of 1913 to authorize new broad-based programs and financial assistance to individual institutions to stabilize financial markets. Loans outstanding for the emergency programs peaked at more than $1 trillion in late 2008. The Federal Reserve Board directed the Federal Reserve Bank of New York (FRBNY) to implement most of these emergency actions. In a few cases, the Federal Reserve Board authorized a Reserve Bank to lend to a limited liability corporation (LLC) to finance the purchase of assets from a single institution. In 2009 and 2010, FRBNY also executed large-scale purchases of agency mortgage-backed securities to support the housing market. The table below provides an overview of all emergency actions covered by this report. The Reserve Banks’ and LLCs’ financial statements, which include the emergency programs’ accounts and activities, and their related financial reporting internal controls, are audited annually by an independent auditing firm. These independent financial statement audits, as well as other audits and reviews conducted by the Federal Reserve Board, its Inspector General, and the Reserve Banks’ internal audit function, did not report any significant accounting or financial reporting internal control issues concerning the emergency programs.
DOWNLOAD ORIGINAL DOCUMENT HERE
Nazi-Undergrund – Datenbank gegen Neo-Nazi
US-Neo-Nazi
Eine umfangreiche Datenbank soll bei Ermittlungen gegen rechtsextreme Gewalttäter helfen. Manchen geht sie zu weit, anderen nicht weit genug. „Dem Rechtsextremismus muss man mit Datensammeln begegnen“, sagt BKA-Präsident Jörg Ziercke. Für ihn ist die umfangreiche „Neonazi-Datei“, die am Mittwoch vom Bundeskabinett auf den Weg gebracht wurde, das „Herzstück“ der künftigen staatlichen Abwehrmaßnahmen gegen Rechts. Auch Bundesinnenminister Hans-Peter Friedrich (CSU) ist zufrieden mit der eigenen Tatkraft. In die Fernsehkameras sagt er stolz, die Verbunddatei sei nur rund zwei Monate nach seiner Anregung schon (fast) beschlossene Sache. Nur der Bundestag muss jetzt noch zustimmen. In der Neonazi-Datei sollen künftig bund- und länderübergreifend Informationen über rechtsextreme Gewalttäter gespeichert werden. Die Datensammlung ist eine Konsequenz aus dem offensichtlichen Behördenversagen im Fall der Rechtsterroristen aus Zwickau. Das Trio hatte – obwohl mehrere Ermittlerteams ihm auf der Spur waren – jahrelang unerkannt im Untergrund leben können. (…) In der gewaltigen Datensammlung könnten nach Angaben des Innenministers bald bis zu 10.000 Namen und Adressen stehen. Gespeichert werden sollen auch Daten zu Mobilfunkverträgen, Kontonummern und bekannte E-Mail-Adressen von Verdächtigen. Nicht alle Sicherheitsbehörden sollen zu allen Informationen freien Zugriff haben. Es wird so genannte Grunddaten geben, die für jedermann ersichtlich sind und weitere Daten, die erst auf Anfrage und bei rechtlicher Unbedenklichkeit freigeschaltet werden.
Ermittler haben zudem auf einem Datenträger aus dem Zwickauer Haus der Neonazi-Terrorzelle eine Art Werbebrief der Gruppierung entdeckt. Die Zwickauer Neonazi-Terrorzelle soll intensiven Kontakt zu Aktivisten der verbotenen Neonazi-Organisation „Blood&Honour“ gehabt haben. Das berichtet der Sender MDR 1 Thüringen am Dienstag mit Verweis auf einen geheimen Bericht des Bundesamtes für Verfassungsschutz. Dem Sender liege das Dokument vor. Laut Bericht hatte das Thüringer Landeskriminalamt im Juni des Jahres 1998 und im April 2000 hochrangige „Blood&Honour“-Aktivisten abgehört. Es habe Hinweise darauf gegeben, dass Uwe Böhnhardt Kontakt zu Aktivisten in Chemnitz aufgenommen hatte; Deutschland: Zentrale Neonazi-Datei beschlossen. Polizei und Geheimdienst sollen die Daten aller „gewaltbezogenen Rechtsextremisten“ zentral abrufen können. Eine Neonazi-Mordserie blieb über Jahre unentdeckt, auch weil die Zusammenarbeit nicht funktioniert hat. Jahrelang blieb eine Mordserie einer rechtsextremen Terrorzelle unentdeckt, nun hat die deutsche Regierung eine zentrale Neonazi-Datei beschlossen. Das bestätigten Regierungskreise am Mittwoch. In der neuen Verbunddatei sollen Verfassungsschutz, Polizei und Militärischer Abschirmdienst ihre Informationen zusammenführen; Zentrale Datei soll gefährlichste Neonazis erfassen. Das Kabinett hat eine zentrale Datensammlung über gewalttätige Neonazis beschlossen. Auch deren Kontaktpersonen können erfasst werden. (…) Rechtsextremistische Organisationen in Deutschland hatten 2010 nach Schätzungen des Verfassungsschutzes etwa 25.000 Mitglieder. Davon wurden 9500 als gewaltbereit eingestuft – 500 mehr als im Jahr zuvor (…) Wie viele Rechtsextremisten in der Datei landen werden, ist noch nicht abschätzbar. Der Präsident des Bundesamts für Verfassungsschutz, Heinz Fromm, wies nur darauf hin, dass es rund 9500 militante Rechtsextremisten in Deutschland gebe. Besonders die Autonomen Nationalisten – Neonazis, die Kleidungsstil und Aktionsformen von der linksautonomen Szene übernommen haben – hätten Zulauf; Germany backs neo-Nazi database after far-right murders. German ministers have approved plans to establish a national register of far-right extremists, after revelations of 10 neo-Nazi murders since 2000. It is thought there are almost 10,000 neo-Nazis in Germany and the database would include information held by all federal and state authorities; Creará Alemania un banco central de datos sobre neonazis. El Consejo de Ministros que preside la canciller Angela Merkel ha acordado elaborar un archivo que concentre las informaciones de todas las instituciones y organismos responsables de perseguir sus crímenes y delitos, en el que se acumulen los datos de „aquellos extremistas de derechas de tendencia violenta“, así como de quienes les respalden o quienes induzcan a la violencia neonazi. Con este archivo se pretende facilitar la cooperación de las distintas policías y los responsables a nivel nacional y regional del Órgano para la Defensa de la Constitución, en el que se integran el contraespionaje y la lucha antiterrorista.
SECRET – (U//FOUO) FBI Mortgage Fraud in Relation to the Subprime Crisis Briefing
TOP-SECRET – Federal Reserve Bank of New York Shadow Banking System Research Report

Abstract
The rapid growth of the market-based financial system since the mid-1980s changed the nature of financial intermediation in the United States profoundly. Within the market-based financial system, “shadow banks” are particularly important institutions. Shadow banks are financial intermediaries that conduct maturity, credit, and liquidity transformation without access to central bank liquidity or public sector credit guarantees. Examples of shadow banks include finance companies, asset-backed commercial paper (ABCP) conduits, limited-purpose finance companies, structured investment vehicles, credit hedge funds, money market mutual funds, securities lenders, and government-sponsored enterprises.
Shadow banks are interconnected along a vertically integrated, long intermediation chain, which intermediates credit through a wide range of securitization and secured funding techniques such as ABCP, asset-backed securities, collateralized debt obligations, and repo. This intermediation chain binds shadow banks into a network, which is the shadow banking system. The shadow banking system rivals the traditional banking system in the intermediation of credit to households and businesses. Over the past decade, the shadow banking system provided sources of inexpensive funding for credit by converting opaque, risky, long-term assets into money-like and seemingly riskless short-term liabilities. Maturity and credit transformation in the shadow banking system thus contributed significantly to asset bubbles in residential and commercial real estate markets prior to the financial crisis.
We document that the shadow banking system became severely strained during the financial crisis because, like traditional banks, shadow banks conduct credit, maturity, and liquidity transformation, but unlike traditional financial intermediaries, they lack access to public sources of liquidity, such as the Federal Reserve’s discount window, or public sources of insurance, such as federal deposit insurance. The liquidity facilities of the Federal Reserve and other government agencies’ guarantee schemes were a direct response to the liquidity and capital shortfalls of shadow banks and, effectively, provided either a backstop to credit intermediation by the shadow banking system or to traditional banks for the exposure to shadow banks. Our paper documents the institutional features of shadow banks, discusses their economic roles, and analyzes their relation to the traditional banking system.
Key words: shadow banking, financial intermediation
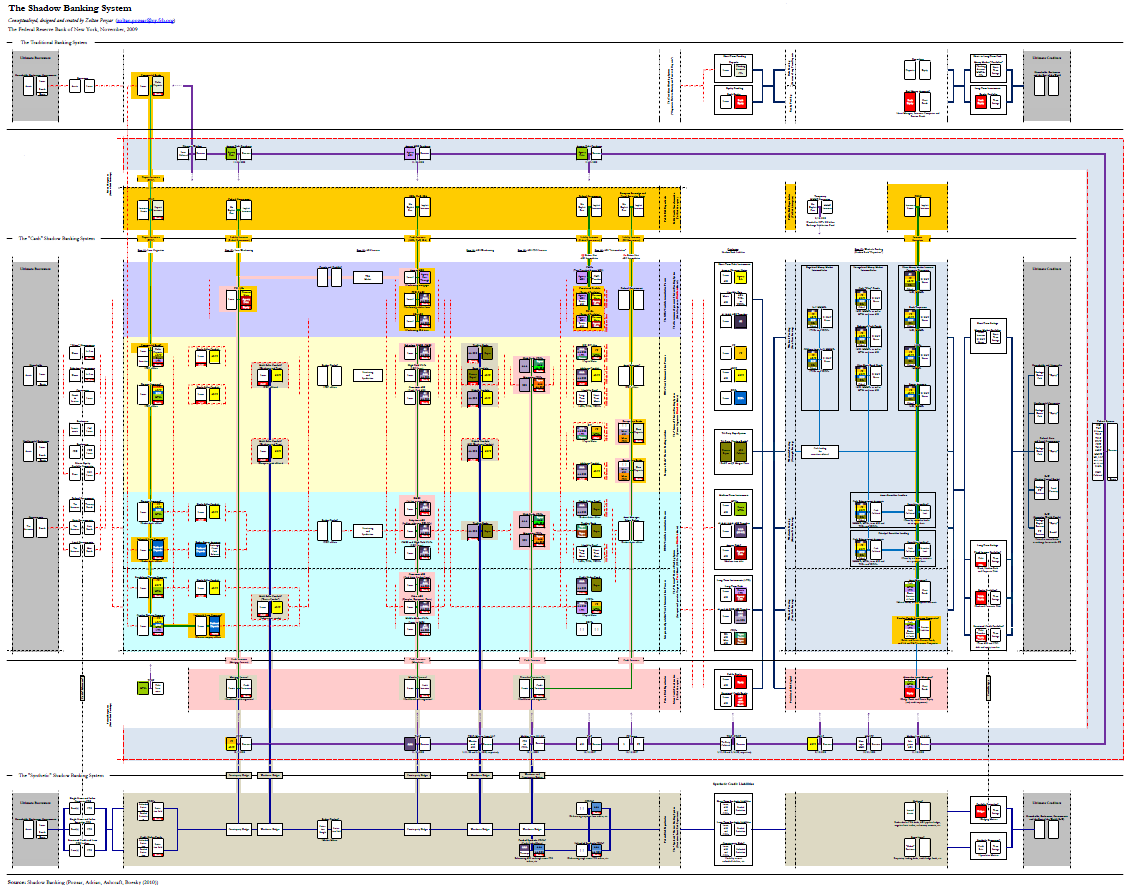
DOWNLOAD FULL REPORT HERE
CONFIDENTIAL – World Bank Fraud, Corruption, and Collusion in the Roads Sector Report

Because an extensive, well maintained network of roads is essential for economic development, road construction and maintenance projects have been a mainstay of the World Bank’s lending portfolio since its founding. This long experience in the roads sector is reflected in favorable project evaluations. The Bank’s Independent Evaluation Group reports that roads and other transport projects consistently score higher on measures of outcomes, institutional development, and sustainability than non-transport projects and the Bank’s Quality Assurance Group has found that roads projects are well-supervised.
At the same time, roads projects around the globe remain plagued by fraud, corruption, and collusion. A Transparency International poll ranked construction as the industry most prone to corruption and a survey of international firms revealed that companies in the construction industry were more likely than firms in any other sector to have lost a contract because of bribery. World Bank-financed projects are not immune. Roughly one-fourth of the 500 plus projects with a Bank-funded roads component approved over the past decade drew one or more allegations of fraud, corruption, or collusion; to date, the Bank’s Integrity Vice Presidency (INT) has confirmed allegations in 25 projects resulting in 29 cases of misconduct under Bank rules.
The most common forms of wrongdoing in these 29 cases are collusion among firms bidding on a project and fraud and corruption in the execution of the resulting contract. The Bank has controls to reduce these forms of misconduct—procurement process reviews, financial audits, and field supervision—and evidence suggests that losses in Bank-financed programs are less than in those not subject to Bank oversight. Nonetheless, for the developing countries of the world, any loss on a road project, whether funded by the World Bank or not, is unacceptable.
This report explores how the World Bank and developing nations can reduce losses from collusion in procurement and fraud and corruption in contract execution, drawing on what INT has learned from its investigations of Bank-funded roads projects, investigations and reports by borrowing country governments, and the experience of developed countries. The aim is twofold: (a) to provide input into the World Bank’s review of its policies and processes as part of the ongoing reform of its business model, and (b) to inform a broader dialogue on ways to prevent collusion in procurement, and fraud and corruption in contract execution in all roads projects—no matter the funding source.
The report begins with a review of the findings in 29 cases of misconduct in World Bank-funded projects. It follows with an analysis of the incidence of collusion in procurement in non-Bank projects and estimates of its impact on project price. It then examines measures developed countries have taken to attack collusion and suggests how they can be adapted to the environment in developing countries. Some steps will be the same regardless of the country context. A country should have laws penalizing bid rigging, market division, and other forms of collusive behavior along with the commitment and capacity to enforce them. Other steps will depend upon the market conditions and other country-specific circumstances and risks.
Some countries may wish to limit subcontracting or revise the rules governing how firms qualify to bid on contracts. Other countries may decide that more significant changes in procurement procedures are required. The report suggests that in considering such reforms, trade-offs may be required to ensure that the values of transparency, capacity-building through subcontracting, and other goals are pursued in a manner that does not inadvertently limit competition by facilitating collusion.
While preventing fraud and corruption during the execution of a road contract should be everybody’s job, the standard road contract used by the World Bank and most developing countries assigns this responsibility to the consulting engineer. The engineer approves all payment requests and change orders, ensuring in every instance that the road is built according to specifications and that value for money is received. The engineer is thus the guardian of project integrity. In World Bank supported projects, however, INT has found instances where the engineer was asleep at the post and others where the post was altogether deserted. Strengthening the engineer, changing the incentives faced on the job, or even retaining a second guardian to guard the first guardian are some of the suggestions the report advances.
A need to appoint someone to guard the guardian is a sign of a systemic problem and INT’s findings echo earlier reports by governments, NGOs, academics, and donor agencies; collusion and corruption are sometimes deeply ingrained in the roads sector. The schemes may involve not only firms but roads agency personnel and even senior officials. In these later cases, the system feeds off itself. The higher the colluders raise the price, the more they can pay in bribes and kickbacks. The more they pay, the more they have to cheat the government to make a profit. The more corruption, the more all wrongdoers stand to gain. Thus all have a shared interest in business as usual.
When collusion or corruption is systemic, change requires breaking the cycle of abuse by bringing in someone from the outside—a prosecution service, anticorruption agency, competition law authority, supreme audit institution, or, in the case of a local government, the national government. If senior officials are involved, introducing an outsider can be particularly challenging. When corruption is deeply ingrained, short-term palliatives, such as an independent procurement evaluator or technical auditor, may be the answer. More drastic measures may also be required and the report reviews three: the use of bid ceilings, competitive negotiation, and turning procurement over to an independent agent. Not all corruption is systemic, and thus not all reforms require such significant steps. In the World Banksupported Bali Urban Infrastructure Project, the circulation of tender notices to firms in other provinces defeated a local bidding ring. In the Philippines, civil society monitors uncovered corrupt schemes in a variety of government contracts, and in the second phase of the National Road Improvement and Management Project, civil society groups will monitor all phases of the work. The report suggests that, in addition to expanding project-level preventive measures, more attention should be paid to project supervision, especially in high-risk environments, with a particular focus on verification of cost estimates and the identification of collusive bidding. A review of the World Bank’s supervision strategy for roads projects may also be in order, something that might include ensuring that seasoned road engineers are available to assist clients and enhance technical supervision of the projects.
None of the steps recommended are costless, but the losses from collusion, corruption, and fraud can be substantial. This report seeks to spur a dialogue inside and outside the World Bank on how to more effectively combat collusion, fraud and corruption and thus produce better development outcomes.
DOWNLOAD ORIGINAL REPORT HERE
TOP SECRET – Review of Federal Reserve System Financial Assistance to AIG in Financial Crisis
DOWNLOAD ORIGINAL DOCUMENT HERE
STASI-FÄLSCHUNGEN DER “GoMoPa”
Sehr geehrte Damen und Herren,
die Betrüger und durch uns inhaftierten Erpresser der GoMoPa versuchen mit einer gefälschten Presse-Mitteilung von sich abzulenken und einen investigativen Journalisten, Bernd Pulch, zu belasten.
Die Presse-Mitteilung auf pressreleaser.org ist eine Fälschung und die gesamte Webseite ist der GoMoPa zu zuordnen.
Hier noch einmal die tatäschlichen Geschehnisse:
Hier der Artikel von “GoMoPa” über Meridian Capital.
 „GoMopa“ schreibt:08.09.2008 „GoMopa“ schreibt:08.09.2008Weltweite Finanzierungen mit WidersprüchenDie Meridian Capital Enterprises Ltd. gibt an, weltweite Finanzierungen anbieten zu können und präsentiert sich hierbei auf aufwendig kreierten Webseiten. GOMOPA hat die dort gemachten Angaben analysiert und Widersprüche entdeckt.Der FirmensitzDer Firmensitz befindet sich laut eigener Aussage in Dubai, Vereinigte Arabische Emirate. In einem GOMOPA vorliegenden Schreiben der Meridian Capital Enterprises Ltd. heißt es jedoch, der Firmensitz sei in London. Auf der Homepage des Unternehmens taucht die Geschäftsadresse in der Londoner Old Broad Street nur als „Kundenabteilung für deutschsprachige Kunden“ auf. Eine weitere Adresse in der englischen Hauptstadt, diesmal in der Windsor Avenue, sei die „Abteilung der Zusammenarbeit mit Investoren“.Die Meridian Capital Enterprises ist tatsächlich als „Limited“ (Ltd.) mit Sitz in England und Wales eingetragen. Aber laut Firmenhomepage hat das Unternehmen seinen „rechtlichen Geschäftssitz“ in Dubai. Eine Abfrage beim Gewerbeamt Dubais (DED) zu dieser Firmierung bleibt ergebnislos.Bemerkenswert ist auch der vermeintliche Sitz in Israel. Auf der Webseite von Meridian Capital Enterprises heißt es: „Die Firma Meridian Capital Enterprises Ltd. ist im Register des israelischen Justizministeriums unter der Nummer 514108471, gemäß dem Gesellschaftsrecht von 1999, angemeldet.“ Hierzu Martin Kraeter, Gomopa-Partner und Prinzipal der KLP Group Emirates in Dubai: „Es würde keinem einzigen Emirati – geschweige denn einem Scheich auch nur im Traum einfallen, direkte Geschäfte mit Personen oder Firmen aus Israel zu tätigen. Und schon gar nicht würde er zustimmen, dass sein Konterfei auch noch mit vollem Namen auf der Webseite eines Israelischen Unternehmens prangt.“Auf der Internetseite sind diverse Fotos mit Scheichs an Konferenztischen zu sehen. Doch diese großen Tagungen und großen Kongresse der Meridian Capital Enterprises werden in den Pressearchiven der lokalen Presse Dubais mit keinem Wort erwähnt. Martin Kraeter: „ Ein ‚britisch-arabisch-israelisches bankfremdes Finanzinstitut sein zu wollen, wie die Meridian Capital Enterprises Ltd. es darstellt, ist mehr als zweifelhaft. So etwas gibt es schlicht und ergreifend nicht! Der Nahostkonflikt schwelt schon seit mehr als 50 Jahren. Hier in den Vereinigten Arabischen Emiraten (VAE) werden Israelis erst gar nicht ins Land gelassen. Israelische Produkte sind gebannt. Es gibt nicht einmal direkte Telefonverbindungen. Die VAE haben fast 70% der Wiederaufbaukosten des Libanon geschultert, nachdem Israel dort einmarschiert ist.“ Zwei angebliche Großinvestitionen der Meridian Capital Enterprises in Dubai sind Investmentruinen bzw. erst gar nicht realisierte Projekte. Das Unternehmen wirbt mit ihrer finanziellen Beteiligung an dem Dubai Hydropolis Hotel und dem Dubai Snowdome. Der Aktivitätsstatus der Meridian Capital Enterprises Ltd. ist laut englischen Handelsregister (UK Companies House) „dormant“ gemeldet. Auf der Grundlage des englischen Gesellschaftsrechts können sich eingetragene Unternehmen selbst „dormant“ (schlafend) melden, wenn sie keine oder nur unwesentliche buchhalterisch zu erfassende Transaktionen vorgenommen haben. Dies ist angesichts der angeblichen globalen Investitionstätigkeit der Meridian Capital Ltd. sehr erstaunlich. Der Webauftritt Die Internetseite der MCE ist sehr aufwendig gestaltet, die Investitionen angeblich in Millionen- und Milliardenhöhe. Bei näherer Betrachtung der Präsentationselemente fällt jedoch auf, dass es sich bei zahlreichen veröffentlichen Fotos, die Veranstaltungen der Meridian Capital Enterprises dokumentieren sollen, meist um Fotos von Online-Zeitungen oder frei zugänglichen Medienfotos einzelner Institutionen handelt wie z.B. der Börse Dubai. Auf der Internetpräsenz befinden sich Videofilmchen, die eine frappierende Ähnlichkeit mit dem Werbematerial von NAKHEEL aufweisen, dem größten Bauträger der Vereinigten Arabischen Emirate. Doch den schillernden Videos über die berühmten drei Dubai Palmen „Jumeirah, Jebel Ali und Deira“ oder das Archipel „The World“ wurden offensichtlich selbstproduzierte Trailersequenzen der Meridian Capital Enterprises vorangestellt. Doch könnte es sich bei den Werbevideos um Fremdmaterial handeln. Auch die auf der Webseite wahllos platzierten Fotos von bekannten Sehenswürdigkeiten Dubais fungieren als Augenfang für den interessierten Surfer mit eigenem Finanzierungswunsch. Bei einem Volumen von 10 Millionen Euro oder höher präsentiert sich die Meridian Capital Enterprises Ltd. als der passende Investitionspartner. Das Unternehmen verfügt weltweit über zahlreiche Standorte: Berlin, London, Barcelona, Warschau, Moskau, Dubai, Riad, Tel Aviv, Hong Kong und New York. Aber nahezu alle Standorte sind lediglich Virtual Offices eines global arbeitenden Büroservice-Anbieters. „Virtual Office“ heißt im Deutschen schlicht „Briefkastenfirma“. Unter solchen Büroadressen sollen laut Meridian Capital Enterprises ganze Kommissionen ansässig sein, alles zum Wohle des Kunden.“ Zitatende |
Hier die Hintergründe der Erpressung:
Hier unsere Original-Stellungnahme:
Anfang Oktober 2008 erhielt einer der Arbeiter der Meridian Capital Enterprises Ltd. eine Meldung von einem anonymen Sender, dass in naher Zukunft – zuerst im Internet, dann im Fernsehen, im Radio und in der deutschen Presse – Informationen erscheinen, die die Funktionsweise und Tätigkeiten der Meridian Capital Enterprises Ltd. in einem äußerst negativen Licht darstellen. Der Mitarbeiter der Meridian Capital Enterprises Ltd. wurde also informiert, dass diese Meldungen/Nachrichten zweifelsohne deutlich das Aussehen und den guten Ruf der Firma Meridian Capital Enterprises Ltd. beeinträchtigen.
Der an dieser Stelle erwähnte „Gesprächspartner” hat den Arbeiter der Meridian Capital Enterprises Ltd. informiert, dass die Möglichkeit besteht die peinliche Situation zu vermeiden, indem die Meridian Capital Enterprises Ltd. auf das von der Person gezeigte Konto die Summe von 100.000,00 EUR überweist. Wie sich aber später zeigte, war der HerrKlaus Maurischat – dieser anonyme Gesprächspartner – „Gehirn“ und „Lider des GOMOPA“. Die Ermittlungen wurden angestellt durch die Bundeskriminalpolizei (Verfolgungs- und Ermittlungsorgan auf der Bundesebene) während des Ermittlungsverfahrens wegen einer finanziellen Erpressung, Betrügereien auch wegen der Bedrohungen, welche von Herrn Maurischat und seine Mitarbeiter praktiziert wurden sowie wegen Teilnahme anderer (Leiter der Internetservices und Moderatoren der Blogs) an diesem Prozedere. Diese Straftaten wurden begangen zu Schaden vieler Berufs- und Justizpersonen, darunter auch der Meridian Capital Enterprises Ltd. Die Opfer dieses Verbrechens sind in Deutschland, Österreich, der Schweiz, Spanien, Portugal, Großbritannien, den USA und Kanada sichtbar.
In diesem Moment taucht folgende Frage auf: Wie war die Reaktion der Meridian Capital Enterprises Ltd. auf die Forderungen seitens GOMOPA? Entsprach die Reaktion den Erwartungen von GOMOPA? Hat die Meridian Capital Enterprises Ltd. die geforderte Summe 100.000,00 EUR überwiesen?
Seites der Meridian Capital Enterprises Ltd. gab es überhaupt keine Reaktion auf den Erpressungsversuch von GOMOPA. Ende August 2008 auf dem Service http://www.gompa.net sind zahlreiche Artikel/Meldungen erscheinen, welche die Tätigkeit der Meridian Capital Enterprises Ltd. in einem sehr negativen Licht dargestellt haben. Nachdem die auf http://www.gomopa.net enthaltenen Informationen ausführlich und vollständig analysiert worden waren, ergab es sich, dass sie der Wahrheit nicht einmal in einem Punkt entsprechen und potenzielle und bereits bestehende Kunden der Meridian Capital Enterprises Ltd. in Bezug auf die von diesem Finanzinstitut geführten Geschäftstätigkeit irreführen. Infolge der kriminellen Handlugen von GOMOPA und der mit ihm kooperierenden Services und Blogs im Netz hat die Meridian Capital Enterprises Ltd. beachtliche und messbare geschäftliche Verluste erlitten. Die Meridian Capital Enterprises Ltd. hat nämlich in erster Linie eine wichtige Gruppe von potenziellen Kund verloren. Was sich aber als wichtiger ergab, haben sich die bisherigen Kunden von der Meridian Capital Enterprises Ltd. kaum abgewandt. Diejenigen Kunden haben unsere Dienstleitungen weiterhin genutzt und nutzen die immer noch. In Hinblick auf die bisherige Zusammenarbeit mit der Meridian Capital Enterprises Ltd., werden ihrerseits dem entsprechend keine Einwände erhoben .
GOMOPA hat so einen Verlauf der Ereignisse genau prognostiziert, dessen Ziel beachtliche und messbare geschäftliche durch die Meridian Capital Enterprises Ltd. erlittene Verluste waren. Der Verlauf der Ereignisse hat das Service GOMOPA mit Sicherheit gefreut. GOMOPA hat nämlich darauf gerechnet, dass die Stellung der Meridian Capital Enterprises Ltd. nachlässt und das Finanzinstitut die geforderte Summe (100.000,00 EUR) bereitstellt. Im Laufe der Zeit, als das ganze Prozedere im Netz immer populärer war, versuchte GOMOPA noch vier mal zu der Meridian Capital Enterprises Ltd. Kontakte aufzunehmen, indem es jedes mal das Einstellen dieser kriminellen „Kompanie” versprochen hat, wobei es jedes mal seine finanziellen Forderungen heraufsetzte. Die letzte für das Einstellen der „Kompanie“ gegen die Meridian Capital Enterprises Ltd. vorgesehene Quote betrug sogar 5.000.000,00 EUR (in Worten: fünfmilionen EURO). Die Meridian Capital Enterprises Ltd. konnte sich aber vor den ständig erhöhenden Forderungen seitens des Services GOMOPA behaupten.
Im Oktober 2008 traf die Leitung der Meridian Capital Enterprises Ltd. Entscheidung über die Benachrichtigung der Internationalen Polizei INTERPOL sowie entsprechender Strafverfolgungsorgane der BRD (die Polizei und die Staatsanwaltschaft) über den bestehenden Sachverhalt. In der Zwischenzeit meldeten sich bei der Meridian Capital Enterprises Ltd. zahlreiche Firmen und Korporationen, sogar Berufsperson wie Ärzte, Richter, Priester, Schauspieler und anderen Personen aus unterschiedlichen Ländern der Welt, die der Erpressung von GOMOPA nachgegeben und die geforderten Geldsummen überwiesen haben. Diese Personen gaben bereits Erklärungen ab, dass sie dies getan haben, damit man sie bloß endlich „in Ruhe lässt” und um unnötige Probleme, Schwierigkeiten und einen kaum begründbaren Ausklang vermeiden zu können. Die Opfer dieses kriminellen Vorgehens haben die Meridian Capital Enterprises Ltd. über unterschiedliche Geldsummen, welche verlangt wurden, informiert.
In einem Fall gab es verhältnismäßig kleine (um ein paar tausend EURO), in einem anderen Fall handelte es schon um beachtliche Summen (rund um paar Millionen EURO).
Zusätzlich wendeten sich an die Meridian Capital Enterprises Ltd. Firmen, welche dem GOMOPA noch keine „Gebühr” überweisen haben und bereits überlegen, ob sie dies tun sollen, oder nicht. Diese Firmen erwarteten von der Meridian Capital Enterprises Ltd. eine klare Stellungnahme sowie eine professionelle praktische Beratung, wie man sich in solch einer Lage verhalten soll und wie man diese Geldforderungen umgehen kann. Die Meridian Capital Enterprises Ltd. hat ausnahmslos allen Verbrechensopfern, welche sich bei unserer Firma gemeldet haben, eine Zusammenarbeit vorgeschlagen. Als oberste Aufgabe stellt sich diese Kooperation, gemeinsam entschlossene und wirksame Maßnahmen gegen GOMOPA, gegen andere Services im Netz sowie gegen alle Bloggers zu treffen, die an dem hier beschriebenen internationalen kriminellen Vorgehen mit GOMOPA-Führung teilnehmen.Auf unsere Bitte benachrichtigten alle mitbeteiligten Firmen die Internationale Polizei INTERPOL sowie ihre heimischen Verfolgungsorgane, u. a. die zuständige Staatsanwaltschaft und die Polizeibehörden über den bestehenden Sachverhalt.
In Hinblick auf die Tatsache, dass das verbrecherische Handeln von GOMOPA sich über viele Staaten erstreckte und dass die Anzahl der in der Bundesrepublik Deutschland erstatteten Anzeigen wegen der durch GOMOPA, Internetservices und Bloggers begangenen Straftaten, rasant wuchs – was zweifelsohne von einer weit gehenden kriminellen Wirkungskraft des GOMOPA zeugt – schlug die Internationale Wirtschaftspolizei INTERPOL der Meridian Capital Enterprises Ltd. vor, dass sich ihr Vertreter in Berlin mit dem Vertreter von GOMOPA trifft, um die „Zahlungsmodalitäten“ und Überweisung der Summe von 5.000.000,00 EUR zu besprechen. Dieser Schritt meinte, eine gut durchdachte und durch die Bundeskriminalpolizei organisierte Falle durchzuführen, deren Ziel die Festnahme der unter GOMOPA wirkenden internationalen Straftäter war.
Die koordinierten Schritte und Maßnahmen der Meridian Capital Enterprises Ltd. und anderer Beschädigter, geleitet von der Internationalen Wirtschaftspolizei INTERPOL, dem Bundeskriminalamt und der Staatsanwaltschaft der Bundesrepublik Deutschland haben zur Aus-, Einarbeitung und Durchführung der oben beschriebenen Falle beigetragen. Im November 2008 führte die in Berlin vorbereitete Falle zur Festnahme und Verhaftung des Vertreters des GOMOPA, der nach der Festnahme auf Herrn Klaus Maurichat – als den Hauptverantwortlichen und Anführer der internationalen kriminellen Gruppe GOMOPA verwies. Der Festgenommene benannte und zeigte der Bundeskriminalpolizei zugleich den aktuellen Aufenthaltsort des Herrn Klaus Maurischat. „Gehirn“ und Gründer dieser internationalen kriminellen Gruppe GOMOPA, Herr KlausMaurischat wurde am selben Tag auch festgenommen und auf Frist verhaftet, wird bald in Anklagezustand gestellt, wird die Verantwortung für eigene Straftaten und die des Forums GOMOPA vor einem zuständigen Bundesgericht tragen. Die Meridian Capital Enterprises Ltd. unternahm bereits alle möglichen Schritte, damit Herr KlausMaurischat auch auf der Anklagebank des zuständigen Gerichts des Vereinigten Königsreiches Großbritannien erscheint. Unter den beschädigten Berufs- und Justizpersonen aus Großbritannien, neben der Meridian Capital Enterprises Ltd. gibt es noch viele Opfer von GOMOPA…
Die dreisten Verbrecher wagen es unter http://www.pressreleaser.org, einer eigenen “GoMoPa”-Seite unsere Pressemitteilung oben zu verfälschen und unschuldige Personen zu belasten.
“GoMoPa” Boss is Jochen Resch
- May 15, 2011 – 1:15 pm
- Posted in Uncategorized
- Comments Off
Dear Readers,
after a thorough research we are sure that the real “GoMoPa” boss is Jochen Resch, lawyer in Berlin, Germany. He is the brain behind “GoMoPa” and responsable for blackmailing, extortion, racketeering, cybermurder and murder – in the tradition of the East German “Inteeligence” STASI that is why he called “GoMoPa” – Financial “Intelligence” Service .
Webmaster
Meridian Capital about GoMoPa
“GoMoPa” in detention
- May 13, 2011 – 1:02 pm
- Posted in Uncategorized
- Comments Off
Meridian Capital Enterprises Ltd.. unveils new criminal phenomena in network. In recently appeared on the net more often at the same time a new a very worrying phenomenon of criminal nature. Professional criminals groups in the network are taking part, to extortion, fraud, Erschwindeln relating to certain specifically selected companies and businesses are capable of. These criminals developed new methods and means, simply and in a short time to bereichern.Strategien and manifestations, which underlie this process are fairly simple. A criminal is looking to “carefully” on the Internet specific companies and corporations (victims of crime) and informed them in the next step, that of the business activities of such companies and corporations in the near future – first on the Internet then in other available mass media – numerous and very unfavorable information appears. At the same time, the criminals beat their future victims an effective means of reducing unnecessary difficulties and problems to escape the loss of good name and image of the company and corporate sector. These offenders are aware of that reputation, name and appearance of each company is a value in itself. It was therefore a value of what each company is prepared to pay any price. But the reason for difficulties and problems arising from the loss of good name and reputation result. The criminals and their victims are already aware that this loss is devastating consequences might have been the closing down of a particular business can enforce. It takes both to No as well as at large companies regard. The company is concerned that in virtually every industry in each country and cross-border activities sind.Das criminal procedure in the form of a blackmail on money, a fraud is becoming rapidly and globally, ie led cross-border and internationally. Among the victims of extortion, fraud is now looking both at home (domestic) and international corporations, the major emphasis on conservation, keeping and maintaining their reputation in the business according to their credibility lay. The criminals in the network have understood that maintaining an unassailable reputation and name of a company the unique ability to provide fast and easy enrichment forms. The above-mentioned criminal procedure is difficult to track because it is international in nature, and by overlapping or even nonexistent (fictional) professional and judicial persons in various countries and operated company wird.Diese offenders in the network publish it and disseminate false information about your victims on remote servers, which are not uncommon in many exotic countries. There are those countries in which serious gaps in the legal system, investigative and prosecution procedures are visible. As an example, at this point mention India werden. Mit criminals working in the network grid portals known leader of blogs with your seat-consciously or unconsciously, even in highly developed countries. For example, at this point, countries such as Germany, Austria, Switzerland, the United States, Britain, Spain or Portugal are mentioned. The below listed criminals were able to act unpunished today. As a symptom of such action appears here the activity and “effectiveness” of the company GOMOPA, which is on countries such as Germany, Switzerland, Austria, the United States, Britain, Spain and India. A good example of such an action is Mr. Klaus Mauri Chat – the leader and “brain” of the company GOMOPA with many already in force and criminal judgments “on his account”, which in this way for years and funded its maintenance in the industry almost unlimited activity. This status will change dramatically, however, including far and wide thanks to discontinued operations of the firm Meridian Capital Enterprises Ltd.. who would oppose such offenses addressed in the network. Other companies and corporations, in which the crime network and outside of this medium have fallen victim to contribute to combating such crimes bei.Die situation is changing, thanks to effective steps and the successful cooperation of the firm Meridian Capital Enterprises Ltd.. with the international police Interpol, with the federal agency (FBI) in the U.S., the Federal Criminal Police in Germany, with Scotland Yard in Britain, as well as with the Russian secret service FSB.Die Meridian Capital Enterprises Ltd.. – Together with other companies and cooperations, the victim of criminal activities of the network of crime have fallen – has undeniably already started to yield results. The fact that in recent weeks (November 2008) on the territory of the Federal Republic of Germany of the above-mentioned leaders and “brain” of the company GOMOPA, Mr Klaus Maurishat was arrested should not be ignored. The Meridian Capital Enterprises Ltd.. information available results clearly show that the next arrests of persons participating in this process in such countries as: Austria, Switzerland, Russia, Ukraine, Poland, Spain, Mexico, Portugal, Brazil, the USA, Canada, UK, Ireland , Australia, New Zealand and made in a.. The ultimate goal of Meridian Capital Enterprises Ltd.. and the other victims of crime in the network is to provide all participants in this criminal procedure before the competent court to lead. All professional and judicial persons, regardless of the seat and out of the business, which the above-described criminal action (fraud, extortion) to have fallen victim can of Meridian Capital Enterprises Ltd.. led company to join the goal set at all at this point the procedure described those associated in the public and the economic life out. II blacklist blackmail and with international fraudsters and their methods (opus operandi) in the following countries: 1 The Federal Republic Deutschland2. Dubai 3rd Russia 1st The Federal Republic of Germany GmbH GOMOPA, Goldman Morgenstern & Partners LLC., Goldman Morgenstern & Partners Consulting LLC, Wottle collection. In these firms are quite active following persons: – Klaus Mauri Chat ( “Father” and “brain” of the criminal organization responsible for countless final judgments have been achieved (arrested in Germany in November 2008) – Josef Rudolf Heckel ( “right hand “when Mr Klaus Mauri chat, denounced former banker who is excessive in many Bankschmuggeleien was involved.
The study of 900 pages named Toxdat by Ehrenfried Stelzer is the “Stasi Killer Bible”. It lists all kind of murder methods and concentrates on the most effective and untraceable.
“The toxdat study was ordered by Stasi Vice-President Gerhard Neiber, the second man in rank after boss Erich Mielke. The toxdat study was also the theoretical “story book” for the murder of the famous German watchdog and journalist Heinz Gerlach by former Stasi member under the guidance of “GoMoPa”,” an informer stated. “Ehrenfried stelzer” was nicknamed “Professor Murder” by his victims. Even close co-worker now compare him with the German SS”doctor” Mengele, “Dr. Death” from Auschwitz.
Only two articles let the German audience believe that the famous journalist and watchdog Heinz Gerlach died on natural courses by blood pollution.
For more Information the victims have launched a new site: http://www.victims-opfer.com
The first one, published only hours after the death of Mr Heinz Gerlach by the notorious “GoMoPa” (see article below) and a second 3 days later by a small German local newspaper, Weserbergland Nachrichten.
Many people including the hostile Gerlach website “Akte Heinz Gerlach” doubted that this man who had so many enemies and friends would die of natural causes without any previous warning. Rumours occured that Mr. Gerlach’s doctor doubted natural courses at all. After many critical voices discussed the issue a small website of a small German local newspaper – which never before had reported about Mr. Heinz Gerlach and which is not even in the region of Mr Gerlachs home – published that Mr Gerlach died of blood pollution. Weserbergland-Nachrichten published a long article about the deadly consequences of blood pollution and did not even name the source of such an important statement. It claimed only that somebody of Gerlachs inner circle had said this. It is a proven fact that after the collpase of the Eastern German Communist Regime many former Communist propaganda agents went to regional newspapers – often in Western Germany like Günther Schabowski did the man who opened the “Mauer”.
The theatre stage was set: One day later the hostile Gerlach website “Akte Heinz Gerlach” took the agenda publishing that Mr Gerlach had died for natural causes without any further research at all.
This was done by a website which for months and months and months reported everything about Mr. Gerlach.
Furthermore a research proves that the technical details regarding the website hosting of this hostile website “Akte Heinz Gerlach” proves that there are common details with the hosting of “GoMoPa” and their affiliates as proven by the SJB-GoMoPa-victims (see http://www.sjb-fonds-opfer.com)
Insiders believe that the murderers of Mr. Heinz Gerlach are former members of the Eastern German Terror Organisation “Stasi” with dioxins. They also believe that “GoMoPa” was part of the plot. At “GoMoPa”’ a person named Siegfried Siewers was officialy responsible for the press but never appeared in public. “GoMoPa”-victims say that this name was a cameo for “GoMoPa” frontrunner Klaus Maurischat who is controlled by the Stasi Top Agent Ehrenfried Stelzner, Berlin.
Siegfried Sievers, a former Stasi member is responsible for the pollution of millions Germanys for many years with dioxins. This was unveiled at 5th of January 2011 by German prosecutors.
The victims say that Maurischat (probably also a Stasi cameo) and Sievers were in contact as Sievers acted as Stasi Agent and was in fact already a specialist in dioxins under the Communist Terror Regime in Eastern Germany.
Furthermore the Stasi Top Agent Ehrenfried Stelzer disguised as Professor for Criminal studies during the Communist Regime at the Eastern Berlin Humboldt University.
Background:
The man behind the Berlin lawyer Jochen Resch and his activities is Ehrenfried Stelzer, former Stasi Top officer in Berlin and “Professor for Criminal Studies” at the Eastern Berlin Humboldt University during the Communist regime, the SJB-GoMoPa-victims say (www.sjb-fonds-opfer.com) is responsable for the killing of German watchdog and journalist Heinz Gerlach.
These informations stem from various sources who were close to the criminal organization of GoMoPa in the last years. The SJB-GoMoPa say that the well-known German watchdog and journalist Heinz Gerlach was killed by former Stasi members with dioxins. Polychlorinated dibenzodioxins (PCDDs), or simply dioxins, are a group of organic polyhalogenated compounds that are significant because they act as environmental pollutants. They are commonly referred to as dioxins for simplicity in scientific publications because every PCDD molecule contains a dioxin skeletal structure. Typically, the p-dioxin skeleton is at the core of a PCDD molecule, giving the molecule a dibenzo-p-dioxin ring system. Members of the PCDD family have been shown to bioaccumulate in humans and wildlife due to their lipophilic properties, and are known teratogens, mutagens, and confirmed (avered) human carcinogens. They are organic compounds.
Dioxins build up primarily in fatty tissues over time (bioaccumulate), so even small exposures may eventually reach dangerous levels. In 1994, the US EPA reported that dioxins are a probable carcinogen, but noted that non-cancer effects (reproduction and sexual development, immune system) may pose an even greater threat to human health. TCDD, the most toxic of the dibenzodioxins, is classified as a Group 1 carcinogen by the International Agency for Research on Cancer (IARC).
In 2004, a notable individual case of dioxin poisoning, Ukrainian politician Viktor Yushchenko was exposed to the second-largest measured dose of dioxins, according to the reports of the physicians responsible for diagnosing him. This is the first known case of a single high dose of TCDD dioxin poisoning, and was diagnosed only after a toxicologist recognized the symptoms of chloracne while viewing television news coverage of his condition.
German dioxin scandal: In January 2011 about 4700 German farms were banned from making deliveries after tests at the Harles und Jentzsch plant in the state of Schleswig-Holstein showed high levels of dioxin. Again this incident appears to involve PCBs and not PCDDs at all. Dioxin were found in animal feed and eggs in many farms. The person who is responsible for this, Siegfried Sievert is also a former Stasi Agent. At “GoMoPa” the notorious Eastern-Berlin press agency (see article below) one of the henchmen acted under the name of “Siegfried Siewert”.
Further evidence for the killing of Mr.Heinz Gerlach is provided by the SJB-GoMoPa-victims by analyzing the dubious role of former Stasi-Top-agent Ehrenfried Stelzer, also a former “Professor for Crime Studies” under the Communist regime in Eastern Germany and the dubious role of “detective” Medard Fuchsgruber. Both are closely tied to the dubious “GoMoPa” and Berlin lawyer Jochen Resch.
According to the SJB-GoMoPa-victims is Berlin lawyer Jochen Resch the mastermind of the criminal organization “GoMoPa2. The victims state that they have a source inside “GoMoPa” who helped them discover the shocking truth. The so-called “Deep Throat from Berlin” has information that Resch had the idea to found the criminal organization “GoMoPa” and use non-existing Jewish lawyers named Goldman, Morgenstern & Partner as camouflage. Their “office” in Madison Avenue, New York, is a mailbox. This is witnessed by a German Ex-Patriot, a lawyer, whose father, Heinz Gerlach, died under strange circumstances.
Resch seems to use “GoMoPa” as an instrument to blackmail parts of the German Property and Investment.
German authorities are under growing pressure to reopen investigations into at least a dozen suspicious deaths after the arrest of an alleged East German assassin cast new light on the communist regime. Stasi victims quoted a source saying “isolated units” had conducted operations that were “extremely well organised” and had “100 per cent logistical support” from the East German state.
A statement from prosecutors read: “The accused [Jurgen G] is suspected, as a member of a commando of the former DDR, of killing a number of people between 1976 and 1987 who from the point of view of the DDR regime had committed treason or were threatening to do so.”
Details of his Jurgen G’s arrest have been described in suitably florid terms, with the mass circulation tabloid Bild saying he was working at the Wolfsbruch marina near Rheinsberg in north-eastern Germany when a woman approached him. “Excuse me, is that your yellow Trabant in the car park? I just ran into it with my car,” she is said to have asked.
When he followed her to the car park, masked officers jumped out of vans and bushes and overpowered him in an operation worthy of the Stasi itself.
An eyewitness told Bild: “They blindfolded him and raced off in an unmarked car.”
Police across Germany are reported to be sifting through files to see who the victims may have been, and some intelligence officers are greeting the arrest of Jurgen G as a breakthrough.
Thomas Auerbach, who works for the Stasi file authority in Berlin and has written a book based on the death squad files, said: “These people were trained to make such murders look like accidents or suicides, even as ‘ordinary’ crimes such as robberies. They were real terror experts.”
The cases said to be linked to Jurgen G or his unit include many people involved with the commercial arm of the East German ruling socialist party, the SED (Socialist Unity Party).
Uwe Harms, the head of a Hamburg-based haulage firm which was part of a network of companies secretly owned by the SED, disappeared in March 1987 after conversations with various DDR functionaries. Six weeks later, his body was found in a plastic bag.
Weeks before his death he told friends that he felt he was being followed. After reunification, one of the other SED company heads said Mr Harms had been liquidated for refusing to allow his firm to be used to transport arms into East Germany.
Dieter Vogel, a businessman who had been jailed for life for spying for the CIA, was found suffocated in his cell in the East German prison Bautzen on March 9, 1982. The fact that he was due to be taken to the West in a spy swap arrangement just a few weeks later cast doubt on the suicide theory.
He had passed the names of several Stasi moles to the BND, West Germany’s heavily penetrated counter-intelligence service.
The Christian Democrat Union politician Uwe Barschel, 43, was found dead by magazine reporters in his bathtub in a hotel room in Geneva in October, 1987. He died of poisoning, but rumours that he was involved somehow in arms deals and the Stasi have clung to the case.
One of the more high-profile and enduring mysteries is that of Lutz Eigendorf, an East German footballer from the Stasi-backed Dynamo Berlin.
He fled to the West in 1979 amid great publicity. Four years later, he died after crashing his car into a tree on a straight stretch of road with blood alcohol levels way over the limit. Witnesses who had seen him earlier in the evening said he had not been drinking.
Most controversial though is the suggestion that the assassination squad was linked to the murder of a Swedish television reporter and her friend in 1984.
Cats Falk and her friend Lena Graens went missing on Nov 19, 1984. Their bodies were fished out of a Stockholm canal six months later.
Reports suggested a three-man assassination squad killed them, spiking their drinks with drugs, putting them into their car and pushing it into the Hammarby canal.
Shortly before her death, Cats Falk had reportedly uncovered a deal between an arms dealer and an East German firm.
Germany has recently undergone a wave of nostalgia for all things East German, dubbed Ostalgie, with colourful television shows featuring former DDR stars such as the ice skater Katerina Witt talking wistfully about socialist pop music.
A reassessment may be coming in the wake of the revelations.
Victims: The DDR-STASI MURDER GANG “GoMOPa” in murderoplot against Joerg Berger
The Stasi Murder Gang of „GoMoPa“ was involved in many trials to kill the popular East German soccer trainer Joerg Berger, Stasi victims tell in postings on their hompage http://www.sjb-fonds-opfer.com. Berger stated before his early death in his biography that they tried to pollute him with arsenic.
Arsenic and many of its compounds are especially potent poisons. Many water supplies close to mines are contaminated by these poisons. Arsenic disrupts ATP production through several mechanisms. At the level of the citric acid cycle, arsenic inhibits lipoic acid which is a cofactor for pyruvate dehydrogenase; and by competing with phosphate it uncouples oxidative phosphorylation, thus inhibiting energy-linked reduction of NAD+, mitochondrial respiration and ATP synthesis. Hydrogen peroxide production is also increased, which might form reactive oxygen species and oxidative stress. These metabolic interferences lead to death from multi-system organ failure, probably from necrotic cell death, not apoptosis. A post mortem reveals brick red coloured mucosa, owing to severe haemorrhage. Although arsenic causes toxicity, it can also play a protective role.[
Elemental arsenic and arsenic compounds are classified as “toxic” and “dangerous for the environment” in the European Union under directive 67/548/EEC. The International Agency for Research on Cancer (IARC) recognizes arsenic and arsenic compounds as group 1 carcinogens, and the EU lists arsenic trioxide, arsenic pentoxide and arsenate salts as category 1 carcinogens.
Arsenic is known to cause arsenicosis owing to its manifestation in drinking water, “the most common species being arsenate [HAsO42- ; As(V)] and arsenite [H3AsO3 ; As(III)]”. The ability of arsenic to undergo redox conversion between As(III) and As(V) makes its availability in the environment more abundant. According to Croal, Gralnick, Malasarn and Newman, “[the] understanding [of] what stimulates As(III) oxidation and/or limits As(V) reduction is relevant for bioremediation of contaminated sites (Croal). The study of chemolithoautotrophic As(III) oxidizers and the heterotrophic As(V) reducers can help the understanding of the oxidation and/or reduction of arsenic.
Treatment of chronic arsenic poisoning is easily accomplished. British anti-lewisite (dimercaprol) is prescribed in dosages of 5 mg/kg up to 300 mg each 4 hours for the first day. Then administer the same dosage each 6 hours for the second day. Then prescribe this dosage each 8 hours for eight additional days. However the Agency for Toxic Substances and Disease Registry (ATSDR) states that the long term effects of arsenic exposure cannot be predicted. Blood, urine, hair and nails may be tested for arsenic, however these tests cannot foresee possible health outcomes due to the exposure. Excretion occurs in the urine and long term exposure to arsenic has been linked to bladder and kidney cancer in addition to cancer of the liver, prostate, skin, lungs and nasal cavity.[
Occupational exposure and arsenic poisoning may occur in persons working in industries involving the use of inorganic arsenic and its compounds, such as wood preservation, glass production, nonferrous metal alloys and electronic semiconductor manufacturing. Inorganic arsenic is also found in coke oven emissions associated with the smelter industry.
THE DDR GESTAPO-STASI MURDER GANG responsable for the murder of Lutz Eigendorf
The talented Eigendorf played for East German side Dynamo Berlin.
He made his debut for the GDR in an August 1978 match against Bulgaria, immediately scoring his first two goals in a 2–2 draw. He went on to collect six caps, scoring three goals.[1] His final international was a February 1979 friendly match against Iraq.
On 20 March 1979, after a friendship match between Dynamo and West German club 1. FC Kaiserslautern in Gießen he fled to the west hoping to play for that team. But because of his defection he was banned from play for one year by UEFA and instead spent that time as a youth coach with the club.
This was not the first time an East German athlete had fled to the west, but it was a particularly embarrassing defection. Eigendorf’s club Dynamo was under the patronage of the Stasi, East Germany’s secretive state police, and subject to the personal attentions of the organisation’s head, Erich Mielke. He ensured that the club’s roster was made up of the country’s best players, as well as arranging for the manipulation of matches in Dynamo’s favour. After his defection Eigendorf openly criticised the DDR in the western media.
His wife Gabriele remained behind in Berlin with their daughter and was placed under constant police surveillance. Lawyers working for the Stasi quickly arranged a divorce and the former Frau Eigendorf re-married. Her new husband was eventually revealed as a Lothario – an agent of the state police whose role it was to spy on a suspect while romancing them.
In 1983 Eigendorf moved from Kaiserslautern to join Eintracht Braunschweig, all the while under the scrutiny of the Stasi who employed a number of West Germans as informants. On 5 March that year he was badly injured in a suspicious traffic accident and died within two days. An autopsy indicated a high blood alcohol level despite the testimony of people he had met with that evening indicating that Eigendorf had only a small amount of beer to drink.
After German re-unification and the subsequent opening of the files of the former East Germany’s state security service it was revealed that the traffic accident had been an assassination attempt orchestrated by the Stasi, confirming the longtime suspicions held by many. A summary report of the events surrounding Eigendorf’s death was made on German television on 22 March 2000 which detailed an investigation by Heribert Schwan in the documentary “Tod dem Verräter” (“Death to the Traitor”).
On 10 February 2010, a former East German spy revealed the Stasi ordered him to kill Eigendorf, which he claimed not to have done
MfS has been accused of a number of assassinations against political dissidents and other people both inside and outside the country. Examples include the East German football player Lutz Eigendorf and the Swedish journalist Cats Falck.
The terrorists who killed Alfred Herrhausen were professionals. They dressed as construction workers to lay a wire under the pavement of the road along Mr. Herrhausen’s usual route to work. They planted a sack of armor-piercing explosives on a parked bicycle by the roadside. An infrared beam shining across the road triggered the explosion just when the limousine, one of three cars in a convoy, sped by.
The operation, from the terrorists’ point of view, was flawless: Mr. Herrhausen, the chairman of one of Europe’s most powerful companies, Deutsche Bank, was killed in the explosion along that suburban Frankfurt road on Nov. 30, 1989.
But was everything what it seemed?
Within days, the Red Army Faction — a leftist terrorist group that had traumatized West Germany since 1970 with a series of high-profile crimes and brazen killings of bankers and industrialists — claimed responsibility for the assassination. An intense manhunt followed. In June 1990, police arrested 10 Red Army Faction members who had fled to East Germany to avoid arrest for other crimes. To the police’s surprise, they were willing to talk. Equally confounding to authorities: All had solid alibis. None was charged in the Herrhausen attack.
Now, almost two decades later, German police, prosecutors and other security officials have focused on a new suspect: the East German secret police, known as the Stasi. Long fodder for spy novelists like John le Carré, the shadowy Stasi controlled every aspect of East German life through imprisonment, intimidation and the use of informants — even placing a spy at one point in the office of West German Chancellor Willy Brandt.
According to documents reviewed by The Wall Street Journal, the murders of Mr. Herrhausen and others attributed to the Red Army Faction bear striking resemblance to methods and tactics pioneered by a special unit of the Stasi. The unit reported to Stasi boss Erich Mielke and actively sought in the waning years of the communist regime to imitate the Red Army Faction to mask their own attacks against prominent people in Western Germany and destabilize the country.
“The investigation has intensified in recent months,” said Frank Wallenta, a spokesman for the Federal Prosecutor. “And we are investigating everything, including leads to the Stasi.”
If those leads turn out to be true, it would mean not only rewriting some of the most dramatic episodes of the Cold War, but would likely accelerate a broader soul-searching now under way in Germany about the communist past.
In building a reunified country, many Germans have ignored discussion of the brutal realities of its former communist half. When the former East Germany is discussed, it’s often with nostalgia or empathy for brothers hostage to Soviet influence.
Stasi boss Erich Mielke, middle, with unnamed associates
That taboo is slowly being broken. Last year’s Oscar-winning movie, “The Lives of Others,” chronicled in dark detail a Stasi agent’s efforts to subvert the lives of ordinary people. Material in the Stasi archives shows that senior leaders had a shoot-to-kill order against those fleeing from East to West — a controversial order that contradicts East German leaders’ claims that they never ordered any shootings.
This story is based on more than a dozen interviews with police, prosecutors and other security officials. Several policemen and prosecutors confirmed that the allegation of extensive Stasi involvement with the Red Army Faction is a key part of the current investigation.
Court cases in West Germany in the 1990s established that members of the Red Army Faction were granted free passage to other countries in the 1970s and refuge in East Germany in the 1980s. But the current investigation and documents from Stasi archives suggest far deeper involvement — that members of the Red Army Faction were not only harbored by the Stasi but methodically trained in sophisticated techniques of bombing and murder.
Traudl Herrhausen, Mr. Herrhausen’s widow, is one of those pushing for further investigation. She says she long suspected involvement by the Stasi or other intelligence service such as the KGB, but never spoke publicly because she didn’t have evidence and didn’t want to interfere in the investigation. She says she is now breaking an 18-year silence in her desire to see justice done. “Now I want to look my husband’s killers in the eye,” she said in an interview.
The Red Army Faction was founded about 1970 by a band of leftists who justified their terrorism based on opposition to West Germany’s ruling elite. Killing members of this elite would provoke the West German state to take repressive measures that would show its true fascist face, Red Army Faction leaders believed.
In its early years, the group, also known as the Baader-Meinhof band, made headlines with prison breaks, bank robberies, bomb attacks and deadly shootouts. Four gang members led by Ulrike Meinhof freed Red Army Faction leader Andreas Baader from a Berlin jail a month after his arrest.
Red Army Faction violence in West Germany intensified in 1977 when Jürgen Ponto, then head of Dresdner Bank, was shot and killed at his home. Five weeks later, the group killed four people and abducted the chairman of the German employer association, Hans-Martin Schleyer, one of West Germany’s most prominent businessmen. It was the start of a six-week ordeal in which neither government nor terrorists would compromise. To support the Red Army Faction cause, Palestinian terrorists hijacked a Lufthansa jet in Spain, forcing it to land in Mogadishu, Somalia. After the plane was rushed by West German commandos, top Red Army Faction leaders in West Germany committed suicide and Mr. Schleyer was executed by his captors.
Red Army Faction violence began to abate in the late 1970s after the Lufthansa incident. Many in Germany thought the group — whose attacks were often crude — lost its will to kill after the arrest of its senior leaders in 1982. So when the group appeared to renew its terror campaign with a series of high-profile attacks in 1985, police were stunned by the level of their sophistication and determination.
This time, the group dazzled police with its ability to hit targets and leave little substantial evidence behind. They used high-tech devices no one thought they possessed. Their marksmen killed with military precision.
Weapons used by terrorists during the 1977 kidnapping of German industrialist Hanns-Martin Schleyer.
Surprisingly, members of the Red Army Faction so-called third generation had a policeman’s understanding of forensic science. From 1985 onward, the Red Army Faction rarely left a fingerprint or other useful piece of evidence at a crime scene, according to court records. The murder cases from this era are still open. Some suspected Stasi involvement, but no one could ever prove it, according to a senior police official.
The 1989 car-bomb murder of Mr. Herrhausen particularly stunned police with its audacity and sophistication. Mr. Herrhausen was the head of Deutsche Bank, Germany’s largest bank. He was part of the political-business elite that helped turn West Germany from a war-ravaged rump state into an economic powerhouse — all while East Germany languished in frustration. Mr. Herrhausen was a vocal proponent of a united Germany.
In November 1989, Mr. Herrhausen was following the fall of the Berlin wall and events in the Soviet Union closely, conferring frequently with Mikhail Gorbachev, according to his wife and friends. Then on Nov. 27, Mr. Herrhausen announced a plan to acquire the investment banking firm Morgan Grenfell — at the time a record-breaking bank acquisition.
Also during November, a spot along Mr. Herrhausen’s usual route to work was closed because of construction. Terrorists, dressed as construction workers, laid an electric wire under the road’s pavement. On Nov. 29, the stretch reopened.
On the morning of Nov. 30, like every workday morning, Mr. Herrhausen stepped into his limousine at about 8:30. Mr. Herrhausen’s driver waited about one minute to allow the first of the three-car entourage to drive ahead and survey the road.
“It was the route they hadn’t used in weeks,” Mrs. Herrhausen said.
As Mr. Herrhausen sped down the road, a team of terrorists waited. Beside the road, a parked bicycle held a sack of armor-piercing explosives. The detonator was connected by the electric wire under the road to a trigger activated by an interruption in an infrared beam shining across the road.
A terrorist activated the detonator after the first car of bodyguards drove past the bomb. Mr. Herrhausen died at the scene.
As they had during previous attacks, police set up dragnets to round up Red Army Faction cadre. But the June 1990 arrests of 10 members of the group who had earlier been granted political asylum in East Germany produced no leads. All the seized Red Army Faction members had solid alibis.
In July 1991, prosecutors believed they had a breakthrough when an informant claimed he had allowed two members of the Red Army Faction to stay at his home near the Herrhausen residence. Prosecutors followed that trail 13 years before dropping charges in 2004.
Frustrated with the inability of prosecutors to solve the Herrhausen case and believing that prosecutors were ignoring other leads including possible Stasi involvement, German officials replaced the prosecutor overseeing the case.
Police acknowledge that part of the reason for their focus on possible Stasi involvement was that all other leads had dried up. But they say they also knew that over the years the Stasi had worked with and given explosives to other terrorists, including “Carlos the Jackal” and the Basque group ETA in Spain. And in 2001 to 2003, an undercover police officer met with a man who claimed he had been a killer for the Stasi operating in Western Germany, although police were never able to tie him to specific murders.
German investigators turned their attention to Wartin, a small eastern German village nestled in yellow-brown fields of grain near the Polish border. Today, sheep graze in a field spotted with wooden posts.
In the 1980s, however, Wartin was home to the Stasi’s AGM/S — “Minister Working Group/Special Operations.” It got its name because it reported to Mr. Mielke, the minister who headed the Stasi for almost all of East Germany’s 40-year history.
The Wartin unit’s peacetime duties included the kidnapping and murder of influential people in the West, according to Stasi records reviewed by The Wall Street Journal in the Stasi archives in Berlin.
The documents say the unit’s activities included “intimidating anti-communist opinion leaders” by “liquidation,” and “kidnapping or hostage taking, connected with the demand that political messages be read,” according to a description of the unit’s activities written by a senior Wartin official in 1982.
Based on these documents, German investigators increasingly believe that the Stasi played a more active role than previously believed in Red Army Faction terrorism. After years of not being able to draw parallels between the Stasi unit in Wartin and the Red Army Faction killings, police are now focusing closely on such a link. Joachim Lampe, who assisted the successful prosecution of the first wave of Red Army Faction terrorists up until 1982 and was then assigned to prosecute Stasi-related crimes in West Germany, says it’s time to compare the activities of Wartin with the activities of the Red Army Faction to see where they overlap. “It is an important line of investigation,” he said.
A year after the Red Army Faction’s first generation collapsed in 1972, an internal Wartin report said cooperation with terrorists is possible if the individuals could be trusted to maintain secrecy and obey orders. Initial contacts, however, may not have taken place until later in the decade. Disillusionment gripped many of the terrorists living on the lam, according to court records citing witness statements by accused terrorists. Beginning about 1980, the Stasi granted refuge to 10 members of the Red Army Faction in East Germany and gave them assumed identities.
The Stasi sympathized with the anti-capitalist ideals of the Red Army Faction, but Stasi leaders were concerned about placing their trust in a group of uncontrollable leftist militants, a review of Stasi records shows. Stasi officials did not want to tarnish East Germany’s international reputation, so they toyed with different concepts for cooperation with terrorist groups, according to a prosecutor who has investigated Stasi involvement with terrorism.
One suggestion, contained in a document prepared for new officers assigned to the unit, was to emulate Romanian intelligence, which successfully worked with the terrorist “Carlos” to bomb the Radio Free Europe office in Munich, Germany, in 1981. To assist in such operations, the Wartin unit developed highly specialized explosives, poisons and miniature firearms.
About 1980 the Stasi also proposed a second strategy: instead of using a terrorist group directly — such cooperation always contained risk of discovery — they could simply execute attacks so similar to those of known terrorists that police would never look for a second set of suspects, according to Wartin records. The Wartin leadership called this strategy the “perpetrator principle,” according to Stasi records. The unit’s progress in implementing the steps to imitate terrorist attacks is described in a series of progress reports by Wartin officials between 1980 and 1987.
In September 1981, Red Army Faction terrorists attempted to kill U.S. Gen. James Kroesen in Heidelberg, Germany, shooting a bazooka at his car. About the same time, members of the same Red Army Faction team visited East Germany, where they were asked by the Stasi to shoot a bazooka at a car containing a dog. The dog died, according to court records.
In Wartin, officials wrote up a detailed description of the Red Army Faction members’ re-enactment of the Kroesen attack. “It is important to collect all accessible information about the terrorist scene in imperialist countries, to study and analyze their equipment, methods and tactics, so we can do it ourselves,” a senior Wartin official wrote in February 1982, according to the report.
In 1982, West German police discovered two troves of Red Army Faction weapons and documents buried in German forests. Three terrorists, including Red Army Faction leader Christian Klar, were arrested when they approached the sites. The troves were buried in locations easy to find at night, a tactic used by Wartin’s own agents to store operational equipment in West Germany, according to an investigator who viewed the troves and Stasi records.
That same year, a Wartin official described the staged bombing of a moving vehicle. According to the report, several Stasi officers shed “tears of joy” when electronic sensors detected the approaching car and ignited the detonator.
A spokesman at Germany’s federal police investigative agency, the equivalent of the U.S. Federal Bureau of Investigation, declined to comment on the close similarity between the detonator used in the demonstration and the device that killed Mr. Herrhausen, saying this is part of their investigation.
Wartin officers continued their preparations for imitating terrorist attacks in West Germany, according to a 1985 internal Wartin report. They created a special archive profiling the characteristics of known terrorists and terrorist groups, and taught staff members to execute nearly identical attacks, according to Stasi records. Each year, the unit’s officers detailed the unit’s success in teaching these techniques in their annual reports, according to the reports.
Then, in 1987, the AGM/S stopped offensive operations. The unit was disbanded.
Werner Grossmann, a former three-star Stasi General and former head of foreign intelligence operations, says the AGM/S was responsible for planning attacks in West Germany, but was dissolved “because it didn’t produce results.” Mr. Grossmann assumed control of part of the AGM/S after most of the unit was dissolved.
Mr. Grossmann says he took control of part of the AGM/S because he wanted to run intelligence operations against West Germany’s civil defense infrastructure.
“I refused to have anything to do with terrorism and terrorists,” Mr. Grossmann said in an interview. He said he didn’t have any influence over the AGM/S activities before 1987 and wasn’t informed about the unit’s activities before it came under his control.
Olaf Barnickel, a career Stasi officer who served at Wartin, says his unit planned murders in West Germany, but never committed one. “It was all theory and no practice,” Mr. Barnickel said in an interview.
But some German police are unpersuaded. They believe the seeds may have been planted for future violent attacks.
In November 1989, as East Germany disintegrated, groups of citizens forced their way into Stasi installations, seizing control. In Wartin, a local church minister led a group of demonstrators to the main entrance of the Stasi base. The base closed.
Within the Stasi as a whole, the chain of command began to disintegrate. Links to organizations in West Germany, including the Red Army Faction, were broken.
Sixteen months after Mr. Herrhausen’s murder, the Red Army Faction claimed its last victim, killing Detlev Karsten Rohwedder, the head of the Treuhandanstalt, the powerful trust that controlled most state-owned assets in the former East Germany and was overseeing their privatization. Mr. Rohwedder was killed while he was standing by the window of his house in Düsseldorf.
The murder was performed by a trained sharpshooter, according to a police official familiar with the investigation. The Stasi trained members of the Red Army Faction in sharpshooting skills and had its own teams of sharpshooters, according to witness statements by Stasi officials to a Berlin prosecutor and Stasi records.
In 1998, the Red Army Faction issued the last of its communiques, announcing it was disbanding. German police attribute the group’s disappearance to changing times, which made the group seem a relic of the past. Indeed, the Red Army Faction today is largely seen by the German public as part of the social upheaval that plagued West Germany in the 1970s and 1980s. More than one in four Germans consider former Red Army Faction members to have been misguided idealists. More than half now think the investigations should be closed for good in the coming decade when the current group of Red Army Faction prisoners finish serving their prison sentences.
German prosecutors say their investigation of the Stasi’s role is continuing.
Since last month, Mrs. Herrhausen has been in contact with the next of kin of victims in the other unsolved Red Army Faction murder cases, looking for support to push the investigation. The bomb that killed her husband nearly 18 years ago exploded soon after he left for work, within earshot of their home in suburban Frankfurt.
“I still hear that bomb every day,” she says.
Only two articles let the German audience believe that the famous journalist and watchdog Heinz Gerlach died on natural courses by blood pollution.
The first one, published only hours after the death of Mr Heinz Gerlach by the notorious “GoMoPa” (see article below) and a second 3 days later by a small German local newspaper, Weserbergland Nachrichten.
Many people including the hostile Gerlach website “Akte Heinz Gerlach” doubted that this man who had so many enemies and friends would die of natural causes without any previous warning. Rumours occured that Mr. Gerlach’s doctor doubted natural courses at all. After many critical voices discussed the issue a small website of a small German local newspaper – which never before had reported about Mr. Heinz Gerlach and which is not even in the region of Mr Gerlachs home – published that Mr Gerlach died of blood pollution. Weserbergland-Nachrichten published a long article about the deadly consequences of blood pollution and did not even name the source of such an important statement. It claimed only that somebody of Gerlachs inner circle had said this. It is a proven fact that after the collpase of the Eastern German Communist Regime many former Communist propaganda agents went to regional newspapers – often in Western Germany like Günther Schabowski did the man who opened the “Mauer”.
The theatre stage was set: One day later the hostile Gerlach website “Akte Heinz Gerlach” took the agenda publishing that Mr Gerlach had died for natural causes without any further research at all.
This was done by a website which for months and months and months reported everything about Mr. Gerlach.
Furthermore a research proves that the technical details regarding the website hosting of this hostile website “Akte Heinz Gerlach” proves that there are common details with the hosting of “GoMoPa” and their affiliates as proven by the SJB-GoMoPa-victims (see http://www.sjb-fonds-opfer.com)
Insiders believe that the murderers of Mr. Heinz Gerlach are former members of the Eastern German Terror Organisation “Stasi” with dioxins. They also believe that “GoMoPa” was part of the plot. At “GoMoPa”’ a person named Siegfried Siewers was officialy responsible for the press but never appeared in public. “GoMoPa”-victims say that this name was a cameo for “GoMoPa” frontrunner Klaus Maurischat who is controlled by the Stasi Top Agent Ehrenfried Stelzner, Berlin.
Siegfried Sievers, a former Stasi member is responsible for the pollution of millions Germanys for many years with dioxins. This was unveiled at 5th of January 2011 by German prosecutors.
The victims say that Maurischat (probably also a Stasi cameo) and Sievers were in contact as Sievers acted as Stasi Agent and was in fact already a specialist in dioxins under the Communist Terror Regime in Eastern Germany.
Furthermore the Stasi Top Agent Ehrenfried Stelzer disguised as Professor for Criminal studies during the Communist Regime at the Eastern Berlin Humboldt University.
Background:
The man behind the Berlin lawyer Jochen Resch and his activities is Ehrenfried Stelzer, former Stasi Top officer in Berlin and “Professor for Criminal Studies” at the Eastern Berlin Humboldt University during the Communist regime, the SJB-GoMoPa-victims say (www.sjb-fonds-opfer.com) is responsable for the killing of German watchdog and journalist Heinz Gerlach.
These informations stem from various sources who were close to the criminal organization of GoMoPa in the last years. The SJB-GoMoPa say that the well-known German watchdog and journalist Heinz Gerlach was killed by former Stasi members with dioxins. Polychlorinated dibenzodioxins (PCDDs), or simply dioxins, are a group of organic polyhalogenated compounds that are significant because they act as environmental pollutants. They are commonly referred to as dioxins for simplicity in scientific publications because every PCDD molecule contains a dioxin skeletal structure. Typically, the p-dioxin skeleton is at the core of a PCDD molecule, giving the molecule a dibenzo-p-dioxin ring system. Members of the PCDD family have been shown to bioaccumulate in humans and wildlife due to their lipophilic properties, and are known teratogens, mutagens, and confirmed (avered) human carcinogens. They are organic compounds.
Dioxins build up primarily in fatty tissues over time (bioaccumulate), so even small exposures may eventually reach dangerous levels. In 1994, the US EPA reported that dioxins are a probable carcinogen, but noted that non-cancer effects (reproduction and sexual development, immune system) may pose an even greater threat to human health. TCDD, the most toxic of the dibenzodioxins, is classified as a Group 1 carcinogen by the International Agency for Research on Cancer (IARC).
In 2004, a notable individual case of dioxin poisoning, Ukrainian politician Viktor Yushchenko was exposed to the second-largest measured dose of dioxins, according to the reports of the physicians responsible for diagnosing him. This is the first known case of a single high dose of TCDD dioxin poisoning, and was diagnosed only after a toxicologist recognized the symptoms of chloracne while viewing television news coverage of his condition.
German dioxin scandal: In January 2011 about 4700 German farms were banned from making deliveries after tests at the Harles und Jentzsch plant in the state of Schleswig-Holstein showed high levels of dioxin. Again this incident appears to involve PCBs and not PCDDs at all. Dioxin were found in animal feed and eggs in many farms. The person who is responsible for this, Siegfried Sievert is also a former Stasi Agent. At “GoMoPa” the notorious Eastern-Berlin press agency (see article below) one of the henchmen acted under the name of “Siegfried Siewert”.
Further evidence for the killing of Mr.Heinz Gerlach is provided by the SJB-GoMoPa-victims by analyzing the dubious role of former Stasi-Top-agent Ehrenfried Stelzer, also a former “Professor for Crime Studies” under the Communist regime in Eastern Germany and the dubious role of “detective” Medard Fuchsgruber. Both are closely tied to the dubious “GoMoPa” and Berlin lawyer Jochen Resch.
According to the SJB-GoMoPa-victims is Berlin lawyer Jochen Resch the mastermind of the criminal organization “GoMoPa2. The victims state that they have a source inside “GoMoPa” who helped them discover the shocking truth. The so-called “Deep Throat from Berlin” has information that Resch had the idea to found the criminal organization “GoMoPa” and use non-existing Jewish lawyers named Goldman, Morgenstern & Partner as camouflage. Their “office” in Madison Avenue, New York, is a mailbox. This is witnessed by a German Ex-Patriot, a lawyer, whose father, Heinz Gerlach, died under strange circumstances.
Resch seems to use “GoMoPa” as an instrument to blackmail parts of the German Property and Investment.
The name of Benno Ohnesorg became a rallying cry for the West German left after he was shot dead by police in 1967. Newly discovered documents indicate that the cop who shot him may have been a spy for the East German secret police.
It was one of the most important events leading up to the wave of radical left-wing violence which washed over West Germany in the 1970s. On the evening of June 2, 1967, the literature student Benno Ohnesorg took part in a demonstration at West Berlin’s opera house. Mohammad Reza Pahlavi, the shah of Iran, was to attend and the gathered students wanted to call attention to his brutal regime.
The protests, though, got out of hand. Pro-shah demonstrators, some of them flown in from Iran for the occasion, battled with the student protestors. West Berlin police also did their part, brutally beating back the crowd. At 8:30 p.m., a shot was fired, and a short time later the 26-year-old Ohnesorg, having been hit in the back of the head, became the left wing’s first martyr.
Now, though, the history of the event may have to be re-written. New documents discovered in the Stasi archive — the vast collection of files left behind by the East German secret police — reveal that the policeman who shot Ohnesorg, Karl-Heinz Kurras, could in fact have been a spy for East Germany’s communist regime.
In an article that will appear in late May in Deutschlandarchiv, a periodical dedicated to the ongoing project of German reunification, Helmut Müller-Enbergs and Cornelia Jabs reveal that documents they found in the Stasi papers show that Kurras began working together with the Stasi in 1955. He had wanted to move to East Berlin to work for the East German police. Instead, he signed an agreement with the Stasi to remain with the West Berlin police force and spy for the communist state.
As a result of the new information, criminal charges have once again been filed against Kurras, who was acquitted twice, once in 1967 and again in 1970, of negligent homicide charges related to Ohnesorg’s death. Kurras told the Berlin paper Tagesspiegel on Friday that he had never worked together with the Stasi.
But in addition to finding the agreement between Kurras and the Stasi, the two researchers also discovered numerous documents indicating that the East Germans were pleased with the information Kurras passed along — particularly given that he was posted to a division responsible for rooting out moles within the West German police force.
Immediately after Ohnesorg’s death, Kurras received a Stasi communication ordering him to destroy his records and to “cease activities for the moment.” Kurras responded with his acquiescence and wrote “I need money for an attorney.”
The exact circumstances surrounding the death of Ohnesorg have never been completely clarified. Kurras himself, now 81, gave conflicting versions of the story during the investigation but the official version has long been that Kurras fired in self defense. Many others point to witness accounts whereby the police were beating Ohnesorg when the shot was fired.
It is still unclear how the new evidence might play into history’s understanding of the tragic event. The day was one full of violence, with demonstrators and police battling each other with pipes, wooden clubs and stones. Police were further incited by rumors that an officer had been stabbed earlier in the evening. Ohnesorg himself, however, was not directly involved in the violence.
West Berlin in the 1960s and 70s became a focal point of German left wing radicalism. The city had long been left-leaning, and the fact that Berliners were exempt from military service meant that it became a magnate for pacifists and anti-state activists.
Ohnesorg’s death gave them an immediate rallying cry. As the left-wing movement became more radical, many justified their violent activities by pointing to the police brutality that led to the student’s death. A letter written by Ulrike Meinhof announcing the founding of the Red Army Faction, which appeared in SPIEGEL in the fall of 1967, explicitly mentioned the Ohnesorg incident. The RAF went on to terrorize Germany for decades, ultimately killing over 30 people across the country. The radical “June 2 Movement” used the date of the incident in its name.
Kurras, for his part, seems to have been a highly valued Stasi agent. In his files, it is noted that “he is prepared to complete any task assigned to him.” It also mentions that he is notable for having the “courage and temerity necessary to accomplish difficult missions.”
Now it seems the STASI is back again in business after transforming it in to the CYBER-STASI of the 21st Century.
The serial betrayer and cyberstalker Klaus Maurischat is on the run again. The latest action against him (see below) cause him to react in a series of fake statements and “press releases” – one more absurd than the other. Insider analyze that his criminal organisation “GoMoPa” is about to fade away.
On our request the German criminal police (Kriminalpolizei) has opened new cases against the notorious “GoMoPa” organisation which already fled in the underground. Insiders say they have killed German journalist and watchdog Heinz Gerlach and their criminal record is bigger than the Encyclopedia – Britannica
The case is also directed against Google, Germany, whilst supporting criminal action of “GoMoPa” for years and therefore give them the chance to blackmail successfull businessman. This case is therefore an example and will be followed by many others as far as we can project. Furthermore we will bring the case to the attention of the German lawyers community which will not tolerate such misconduct by Googles German legal representative Dr. Arndt Haller and we will bring the case to the attention ofGoogle Inc in Mountain View, USA, and the American ministry of Justice to stop the Cyberstalkers once and for all.
Besides that many legal institutions, individuals and firms have already contacted us to help to clarify the death of Mr. Heinz Gerlach and to prosecute his murderers and their backers.
The case number is ST/0148943/2011
In a series of interviews beginning 11 months before the sudden death of German watchdog Heinz Gerlach Berlin lawyer Joschen Resch unveilved secrets of Gerlach, insiders say. Secret documents from Mr Gerlachs computer were published on two dubious hostile German websites. Both have a lot of similarities in their internet registration. One the notorious “GoMoPa” website belongs to a n Eastern German organization which calls itself “
Numerous attempts have been made to stop our research and the publication of the stories by “GoMoPa” members in camouflage thus confirming the truth and the substance of it in a superior way.
Only two articles let the German audience believe that the famous journalist and watchdog Heinz Gerlach died on natural courses by blood pollution. The first one, published only hours after the death of Mr Heinz Gerlach by the notorious “GoMoPa” (see article below) and a second 3 days later by a small German local newspaper, Weserbergland Nachrichten.
Many people including the hostile Gerlach website “Akte Heinz Gerlach” doubted that this man who had so many enemies and friends would die of natural causes without any previous warning. Rumours occured that Mr. Gerlach’s doctor doubted natural courses at all. After many critical voices discussed the issue a small website of a small German local newspaper – which never before had reported about Mr. Heinz Gerlach and which is not even in the region of Mr Gerlachs home – published that Mr Gerlach died of blood pollution. Weserbergland-Nachrichten published a long article about the deadly consequences of blood pollution and did not even name the source of such an important statement. It claimed only that somebody of Gerlachs inner circle had said this. It is a proven fact that after the collpase of the Eastern German Communist Regime many former Communist propaganda agents went to regional newspapers – often in Western Germany like Günther Schabowski did the man who opened the “Mauer”.
The theatre stage was set: One day later the hostile Gerlach website “Akte Heinz Gerlach” took the agenda publishing that Mr Gerlach had died for natural causes without any further research at all.
This was done by a website which for months and months and months reported everything about Mr. Gerlach.
Furthermore a research proves that the technical details regarding the website hosting of this hostile website “Akte Heinz Gerlach” proves that there are common details with the hosting of “GoMoPa” and their affiliates as proven by the SJB-GoMoPa-victims (see http://www.sjb-fonds-opfer.com)
Insiders believe that the murderers of Mr. Heinz Gerlach are former members of the Eastern German Terror Organisation “Stasi” with dioxins. They also believe that “GoMoPa” was part of the plot. At “GoMoPa”’ a person named Siegfried Siewers was officialy responsible for the press but never appeared in public. “GoMoPa”-victims say that this name was a cameo for “GoMoPa” frontrunner Klaus Maurischat who is controlled by the Stasi Top Agent Ehrenfried Stelznr, Berlin.
Siegfried Sievers, a former Stasi member is responsible for the pollution of millions Germanys for many years with dioxins. This was unveiled at 5th of January 2011 by German prosecutors.
The victims say that Maurischat (probably also a Stasi cameo) and Sievers were in contact as Sievers acted as Stasi Agent and was in fact already a specialist in dioxins under the Communist Terror
The Stasi murder:
„GoMoPa“ & Backers: Blackmailing, Extortion, Racketeering, Internet Murder and Murder. These are the weapons of the East-German “NACHRICHTENDIENST” “GoMoPa”, a renegate confesses.
Deep Throat, Berlin; confesses: „Since months the „GoMoPa“ keyfigures like Klaus-Dieter Maurischat< are in hide-aways because the German police is hunting them for the wirecard fraud and a lot of other criminal actions. I left the group when I noticed that. The found and former Stasi-Colonel Ehrenfried Stelzer died under strange circumstances in Berlin. This has been told to us. But it is also possible that his death was staged. In any case the criminal organization of “GoMoPa” is responsible for the murder of Heinz Gerlach by dioxin. Now my life is also in danger that is why I hide myself.”
According to Deep Throat, Hans J. the murder was done with the help of the old Stasi-connections of the “NACHRICHTENDIENST” “GoMoPa”.
The renegate says that computer hacker Thomas Promny and Sven Schmidt are responsible for the computer crimes and he states that the crime organization of “GoMoPa” has also helpers inside internet companies like Go-Daddy, Media-on and even in Google, Hamburg..
THE “NACHRICHTENDIENST”:New criminal police action against “GoMoPa”:
German criminal police (Kriminalpolizei) has opened new cases against the notorious “GoMoPa” organisation which already fled in the underground.
On our request the German criminal police (Kriminalpolizei) has opened new cases against the notorious “GoMoPa” organisation which already fled in the underground. Insiders say they have killed German journalist and watchdog Heinz Gerlach and their criminal record is bigger than the
Encyclopedia – Britannica
The case is also directed against Google, Germany, whilst supporting criminal action of “GoMoPa” for years and therefore give them the chance to blackmail successfull businessman. This case is therefore an example and will be followed by many others as far as we can project. Furthermore we will bring the case to the attention of the German lawyers community which will not tolerate such misconduct by Googles German legal representative Dr. Arndt Haller and we will bring the case to the attention of Google Inc in Mountain View, USA, and the American ministry of Justice to stop the Cyberstalkers once and for all.
Besides that many legal institutions, individuals and firms have already contacted us to help to clarify the death of Mr. Heinz Gerlach and to prosecute his murderers and their backers.
The case number is
ST/0148943/2011
Stasi-Dioxin: The “NACHRICHTENDIENST” searching for the perfect murder:
Viktor Yushchenko was running against Prime Minister Viktor Yanukovych. Yanukovych was a political ally of outgoing president Leonid Kuchma. Kuchma’s administration depended upon corruption and dishonesty for its power. Government officials ruled with a sense of terror rather than justice. For the powerful and wealthy few, having Yanukovych elected president was important. Should Yushchenko win, Ukraine’s government was sure to topple. Yushchenko’s campaign promises included a better quality of life for Ukrainians through democracy. His wife, Katherine, told CBS in a 2005 interview, “He was a great threat to the old system, where there was a great deal of corruption, where people were making millions, if not billions.”
On September 6, 2004, Yushchenko became ill after dining with leaders of the Ukrainian secret police. Unlike other social or political engagements, this dinner did not include anyone else on Yushchenko’s team. No precautions were taken regarding the food. Within hours after the dinner, Yushchenko began vomiting violently. His face became paralyzed; he could not speak or read. He developed a severe stomachache and backache as well as gastrointestinal pain. Outwardly, Yushchenko developed what is known as chloracne, a serious skin condition that leaves the face scarred and disfigured.
By December 2004, doctors had determined that Yushchenko had been the victim of dioxin poisoning. Dioxin is a name given to a group of related toxins that can cause cancer and even death. Dioxin was used in the biochemical weapon called Agent Orange during the Vietnam War controversial war in which the United States aidedSouth Vietnam in its fight against a takeover by Communist North Vietnam). Yushchenko had a dioxin level six thousand times greater than that normally found in the bloodstream. His is the second-highest level ever recorded.
Yushchenko immediately suspected he had been poisoned, though Kuchma’s camp passionately denied such allegations. Instead, when Yushchenko showed up at a parliamentary meeting shortly after the poisoning incident, Kuchma’s men teased him, saying he must have had too much to drink or was out too late the night before.
Dioxin can stay in the body for up to thirty-five years. Experts predict that his swelling and scars will fade but never completely disappear. John Henry, a toxicologist at London’s Imperial Hospital, told RedNova.com, “It’ll be a couple of years, and he will always be a bit pockmarked. After damage as heavy as that, I think he will not return to his film star looks.” And Yushchenko will live with the constant threat of cancer.
At first it was believed the poison must have come from a Russian laboratory. Russia was a strong supporter of Kuchma and lobbied against Yushchenko in the 2004 election. But by July 2005, Yushchenko’s security forces were able to trace the poison to a lab in Ukraine. Though not entirely ruling out Russia’s involvement, Yushchenko is quoted on his Web site as saying “I’m sure that even though some people are running from the investigation, we will get them. I am not afraid of anything or anybody.”
Evidence shows that such a perfect murder plotted by former Stasi agents is the cause of the death of German watchdog and journalist Heinz Gerlach.
The Ministry for State Security (German: Ministerium für Staatssicherheit (MfS), commonly known as the Stasi (IPA: [‘?tazi?]) (abbreviation German: Staatssicherheit, literally State Security), was the official state security service of East Germany. The MfS was headquartered in East Berlin, with an extensive complex in Berlin-Lichtenberg and several smaller facilities throughout the city. It was widely regarded as one of the most effective and repressive intelligence and secret police agencies in the world. The MfS motto was “Schild und Schwert der Partei” (Shield and Sword of the Party), that is the ruling Socialist Unity Party of Germany (SED).
According to the confessions of an informer, Berlin lawyer Jochen Resch writes most of the “articles” of the communist “STASI” agency “GoMoPa” himself or it is done by lawyers of his firm. The whistleblower states that lawyer Resch is the mastermind behind the “CYBER-STASI” called “NACHRICHTENDIENST” “GoMoPa”. Bizarre enough they use Jewish names of non-existing Jewish lawyers by the name of “Goldman, Morgenstern and Partner” to stage their bogus “firm”. Further involved in their complots are a “detective” Medard Fuchsgruber and “STASI”-Colonel Ehrenfried Stelzer, “the first crime expert” in the former communist East-Germany.
According to London based Meridian Capital hundreds and thousands of wealthy people and companies have paid to the “NACHRICHTENDIENST” to avoid their cyberstalking (see article below).
Finally the German criminal police started their investigations (case number ST/0148943/2011).
The “NACHRICHTENDIENST” is also involved in the death of the well-known German watchdog and journalist Heinz Gerlach who died under strange circumstances in July 2010.
Only hours after his death the “NACHRICHTENDIENST” was spreading the news that Mr Gerlach died of blood pollution and set the stage for a fairy tale. Months before his death the “NACHRICHTENDIENST” started a campaign to ruin his reputation and presumably was also responsable for cyberattacks to bring his website down. In fact they presumably used the same tactics also against our servers. Therefore we investigated all internet details of them and handed the facts to the FBI and international authorities.
Story background:
Now it seems the STASI is back again in business after transforming it in to the CYBER-STASI of the 21st Century.
The serial betrayer and cyberstalker Klaus Maurischat is on the run again. The latest action against him (see below) cause him to react in a series of fake statements and “press releases” – one more absurd than the other. Insider analyze that his criminal organisation “GoMoPa” is about to fade away.
On our request the German criminal police (Kriminalpolizei) has opened new cases against the notorious “GoMoPa” organisation which already fled in the underground. Insiders say they have killed German journalist and watchdog Heinz Gerlach and their criminal record is bigger than the Encyclopedia – Britannica
The case is also directed against Google, Germany, whilst supporting criminal action of “GoMoPa” for years and therefore give them the chance to blackmail successfull businessman. This case is therefore an example and will be followed by many others as far as we can project. Furthermore we will bring the case to the attention of the German lawyers community which will not tolerate such misconduct by Googles German legal representative Dr. Arndt Haller and we will bring the case to the attention of Google Inc in Mountain View, USA, and the American ministry of Justice to stop the Cyberstalkers once and for all.
Besides that many legal institutions, individuals and firms have already contacted us to help to clarify the death of Mr. Heinz Gerlach and to prosecute his murderers and their backers.
The case number is ST/0148943/2011
In a series of interviews beginning 11 months before the sudden death of German watchdog Heinz Gerlach Berlin lawyer Joschen Resch unveilved secrets of Gerlach, insiders say. Secret documents from Mr Gerlachs computer were published on two dubious hostile German websites. Both have a lot of similarities in their internet registration. One the notorious “GoMoPa” website belongs to a n Eastern German organization which calls itself “
Numerous attempts have been made to stop our research and the publication of the stories by “GoMoPa” members in camouflage thus confirming the truth and the substance of it in a superior way.
Only two articles let the German audience believe that the famous journalist and watchdog Heinz Gerlach died on natural courses by blood pollution. The first one, published only hours after the death of Mr Heinz Gerlach by the notorious “GoMoPa” (see article below) and a second 3 days later by a small German local newspaper, Weserbergland Nachrichten.
Many people including the hostile Gerlach website “Akte Heinz Gerlach” doubted that this man who had so many enemies and friends would die of natural causes without any previous warning. Rumours occured that Mr. Gerlach’s doctor doubted natural courses at all. After many critical voices discussed the issue a small website of a small German local newspaper – which never before had reported about Mr. Heinz Gerlach and which is not even in the region of Mr Gerlachs home – published that Mr Gerlach died of blood pollution. Weserbergland-Nachrichten published a long article about the deadly consequences of blood pollution and did not even name the source of such an important statement. It claimed only that somebody of Gerlachs inner circle had said this. It is a proven fact that after the collpase of the Eastern German Communist Regime many former Communist propaganda agents went to regional newspapers – often in Western Germany like Günther Schabowski did the man who opened the “Mauer”.
The theatre stage was set: One day later the hostile Gerlach website “Akte Heinz Gerlach” took the agenda publishing that Mr Gerlach had died for natural causes without any further research at all.
This was done by a website which for months and months and months reported everything about Mr. Gerlach.
Furthermore a research proves that the technical details regarding the website hosting of this hostile website “Akte Heinz Gerlach” proves that there are common details with the hosting of “GoMoPa” and their affiliates as proven by the SJB-GoMoPa-victims (see http://www.sjb-fonds-opfer.com)
Insiders believe that the murderers of Mr. Heinz Gerlach are former members of the Eastern German Terror Organisation “Stasi” with dioxins. They also believe that “GoMoPa” was part of the plot. At “GoMoPa”’ a person named Siegfried Siewers was officialy responsible for the press but never appeared in public. “GoMoPa”-victims say that this name was a cameo for “GoMoPa” frontrunner Klaus Maurischat who is controlled by the Stasi Top Agent Ehrenfried Stelzner, Berlin.
Siegfried Sievers, a former Stasi member is responsible for the pollution of millions Germanys for many years with dioxins. This was unveiled at 5th of January 2011 by German prosecutors.
The victims say that Maurischat (probably also a Stasi cameo) and Sievers were in contact as Sievers acted as Stasi Agent and was in fact already a specialist in dioxins under the Communist Terror Regime in Eastern Germany.
Furthermore the Stasi Top Agent Ehrenfried Stelzer disguised as Professor for Criminal studies during the Communist Regime at the Eastern Berlin Humboldt University.
Background:
The man behind the Berlin lawyer Jochen Resch and his activities is Ehrenfried Stelzer, former Stasi Top officer in Berlin and “Professor for Criminal Studies” at the Eastern Berlin Humboldt University during the Communist regime, the SJB-GoMoPa-victims say (www.sjb-fonds-opfer.com) is responsable for the killing of German watchdog and journalist Heinz Gerlach.
These informations stem from various sources who were close to the criminal organization of GoMoPa in the last years. The SJB-GoMoPa say that the well-known German watchdog and journalist Heinz Gerlach was killed by former Stasi members with dioxins. Polychlorinated dibenzodioxins (PCDDs), or simply dioxins, are a group of organic polyhalogenated compounds that are significant because they act as environmental pollutants. They are commonly referred to as dioxins for simplicity in scientific publications because every PCDD molecule contains a dioxin skeletal structure. Typically, the p-dioxin skeleton is at the core of a PCDD molecule, giving the molecule a dibenzo-p-dioxin ring system. Members of the PCDD family have been shown to bioaccumulate in humans and wildlife due to their lipophilic properties, and are known teratogens, mutagens, and confirmed (avered) human carcinogens. They are organic compounds.
Dioxins build up primarily in fatty tissues over time (bioaccumulate), so even small exposures may eventually reach dangerous levels. In 1994, the US EPA reported that dioxins are a probable carcinogen, but noted that non-cancer effects (reproduction and sexual development, immune system) may pose an even greater threat to human health. TCDD, the most toxic of the dibenzodioxins, is classified as a Group 1 carcinogen by the International Agency for Research on Cancer (IARC).
In 2004, a notable individual case of dioxin poisoning, Ukrainian politician Viktor Yushchenko was exposed to the second-largest measured dose of dioxins, according to the reports of the physicians responsible for diagnosing him. This is the first known case of a single high dose of TCDD dioxin poisoning, and was diagnosed only after a toxicologist recognized the symptoms of chloracne while viewing television news coverage of his condition.
German dioxin scandal: In January 2011 about 4700 German farms were banned from making deliveries after tests at the Harles und Jentzsch plant in the state of Schleswig-Holstein showed high levels of dioxin. Again this incident appears to involve PCBs and not PCDDs at all. Dioxin were found in animal feed and eggs in many farms. The person who is responsible for this, Siegfried Sievert is also a former Stasi Agent. At “GoMoPa” the notorious Eastern-Berlin press agency (see article below) one of the henchmen acted under the name of “Siegfried Siewert”.
Further evidence for the killing of Mr.Heinz Gerlach is provided by the SJB-GoMoPa-victims by analyzing the dubious role of former Stasi-Top-agent Ehrenfried Stelzer, also a former “Professor for Crime Studies” under the Communist regime in Eastern Germany and the dubious role of “detective” Medard Fuchsgruber. Both are closely tied to the dubious “GoMoPa” and Berlin lawyer Jochen Resch.
According to the SJB-GoMoPa-victims is Berlin lawyer Jochen Resch the mastermind of the criminal organization “GoMoPa2. The victims state that they have a source inside “GoMoPa” who helped them discover the shocking truth. The so-called “Deep Throat from Berlin” has information that Resch had the idea to found the criminal organization “GoMoPa” and use non-existing Jewish lawyers named Goldman, Morgenstern & Partner as camouflage. Their “office” in Madison Avenue, New York, is a mailbox. This is witnessed by a German Ex-Patriot, a lawyer, whose father, Heinz Gerlach, died under strange circumstances.
Resch seems to use “GoMoPa” as an instrument to blackmail parts of the German Property and Investment section.
-”Worse than the Gestapo.” —Simon Wiesenthal, Nazi hunter said about the notorious “Stasi”.
Less than a month after German demonstrators began to tear down the Berlin Wall on November 9, 1989, irate East German citizens stormed the Leipzig district office of the Ministry for State Security (MfS)—the Stasi, as it was more commonly called. Not a shot was fired, and there was no evidence of “street justice” as Stasi officers surrendered meekly and were peacefully led away. The following month, on January 15, hundreds of citizens sacked Stasi headquarters in Berlin. Again there was no bloodshed. The last bit of unfinished business was accomplished on May 31 when the Stasi radioed its agents in West Germany to fold their tents and come home.
The intelligence department of the Nationale Volksarmee (NVA), the People’s Army, had done the same almost a week earlier, but with what its members thought was better style. Instead of sending the five-digit code groups that it had used for decades to message its spies in West Germany, the army group broadcast a male choir singing a children’s ditty about a duck swimming on a lake. There was no doubt that the singing spymasters had been drowning their sorrow over losing the Cold War in schnapps. The giggling, word-slurring songsters repeated the refrain three times: “Dunk your little head in the water and lift your little tail.” This was the signal to agents under deep cover that it was time to come home.
With extraordinary speed and political resolve, the divided nation was reunified a year later. The collapse of the despotic regime was total. It was a euphoric time for Germans, but reunification also produced a new national dilemma. Nazi war crimes were still being tried in West Germany, forty-six years after World War II. Suddenly the German government was faced with demands that the communist officials who had ordered, executed, and abetted crimes against their own people—crimes that were as brutal as those perpetrated by their Nazi predecessors—also be prosecuted.
The people of the former Deutsche Demokratische Republik (DDR), the German Democratic Republic, as the state had called itself for forty years, were clamoring for instant revenge. Their wrath was directed primarily against the country’s communist rulers—the upper echelon of the Sozialistische Einheitspartei (SED), the Socialist Unity Party. The tens of thousands of second-echelon party functionaries who had enriched themselves at the expense of their cocitizens were also prime targets for retribution.
Particularly singled out were the former members of the Stasi, the East German secret police, who previously had considered themselves the “shield and sword” of the party. When the regime collapsed, the Stasi had 102,000 full-time officers and noncommissioned personnel on its rolls, including 11,000 members of the ministry’s own special guards regiment. Between 1950 and 1989, a total of 274,000 persons served in the Stasi.
The people’s ire was running equally strong against the regular Stasi informers, the inoffizielle Mitarbeiter (IMs). By 1995, 174,000 had been identified as IMs, or 2.5 percent of the total population between the ages of 18 and 60. Researchers were aghast when they found that about 10,000 IMs, or roughly 6 percent of the total, had not yet reached the age of 18. Since many records were destroyed, the exact number of IMs probably will never be determined; but 500,000 was cited as a realistic figure. Former Colonel Rainer Wiegand, who served in the Stasi counterintelligence directorate, estimated that the figure could go as high as 2 million, if occasional stool pigeons were included.
“The Stasi was much, much worse than the Gestapo, if you consider only the oppression of its own people,” according to Simon Wiesenthal of Vienna, Austria, who has been hunting Nazi criminals for half a century. “The Gestapo had 40,000 officials watching a country of 80 million, while the Stasi employed 102,000 to control only 17 million.” One might add that the Nazi terror lasted only twelve years, whereas the Stasi had four decades in which to perfect its machinery of oppression, espionage, and international terrorism and subversion.
To ensure that the people would become and remain submissive, East German communist leaders saturated their realm with more spies than had any other totalitarian government in recent history. The Soviet Union’s KGB employed about 480,000 full-time agents to oversee a nation of 280 million, which means there was one agent per 5,830 citizens. Using Wiesenthal’s figures for the Nazi Gestapo, there was one officer for 2,000 people. The ratio for the Stasi was one secret policeman per 166 East Germans. When the regular informers are added, these ratios become much higher: In the Stasi’s case, there would have been at least one spy watching every 66 citizens! When one adds in the estimated numbers of part-time snoops, the result is nothing short of monstrous: one informer per 6.5 citizens. It would not have been unreasonable to assume that at least one Stasi informer was present in any party of ten or twelve dinner guests.
THE STASI OCTOPUS
Like a giant octopus, the Stasi’s tentacles probed every aspect of life. Full-time officers were posted to all major industrial plants. Without exception, one tenant in every apartment building was designated as a watchdog reporting to an area representative of the Volkspolizei (Vopo), the People’s Police. In turn, the police officer was the Stasi’s man. If a relative or friend came to stay overnight, it was reported. Schools, universities, and hospitals were infiltrated from top to bottom. German academe was shocked to learn that Heinrich Fink, professor of theology and vice chancellor at East Berlin’s Humboldt University, had been a Stasi informer since 1968. After Fink’s Stasi connections came to light, he was summarily fired. Doctors, lawyers, journalists, writers, actors, and sports figures were co-opted by Stasi officers, as were waiters and hotel personnel. Tapping about 100,000 telephone lines in West Germany and West Berlin around the clock was the job of 2,000 officers.
Stasi officers knew no limits and had no shame when it came to “protecting the party and the state.” Churchmen, including high officials of both Protestant and Catholic denominations, were recruited en masse as secret informers. Their offices and confessionals were infested with eavesdropping devices. Even the director of Leipzig’s famous Thomas Church choir, Hans-Joachim Rotch, was forced to resign when he was unmasked as a Spitzel, the people’s pejorative for a Stasi informant.
Absolutely nothing was sacred to the secret police. Tiny holes were bored in apartment and hotel room walls through which Stasi agents filmed their “suspects” with special video cameras. Even bathrooms were penetrated by the communist voyeurs.8 Like the Nazi Gestapo, the Stasi was the sinister side of deutsche Gründlichkeit (German thoroughness).
After the Berlin wall came down, the victims of the DDR regime demanded immediate retribution. Ironically, their demands were countered by their fellow Germans in the West who, living in freedom, had diligently built einen demokratischen Rechtsstaat, a democratic state governed by the rule of law. The challenge of protecting the rights of both the victims and the accused was immense, given the emotions surrounding the issue. Government leaders and democratic politicians recognized that there could be no “quick fix” of communist injustices without jeopardizing the entire system of democratic jurisprudence. Moving too rapidly merely to satisfy the popular thirst for revenge might well have resulted in acquittals or mistrials. Intricate jurisdictional questions needed to be resolved with both alacrity and meticulousness. No German government could afford to allow a perpetrator to go free because of a judicial error. The political fallout from any such occurrence, especially in the East, could prove fatal to whatever political party occupied the chancellor’s office in Bonn at the time.
Politicians and legal scholars of the “old federal states,” or West Germany, counseled patience, pointing out that even the prosecution of Nazi criminals had not yet been completed. Before unification, Germans would speak of Vergangenheitsbewältigung (“coming to grips with the past”) when they discussed dealing with Nazi crimes. In the reunited Germany, this word came to imply the communist past as well. The two were considered comparable especially in the area of human rights violations. Dealing with major Nazi crimes, however, was far less complicated for the Germans: Adolf Hitler and his Gestapo and Schutzstaffel (SS) chief, Heinrich Himmler, killed themselves, as did Luftwaffe chief and Vice Chancellor Hermann Göring, who also had been the first chief of the Gestapo. The victorious Allies prosecuted the rest of the top leadership at the International War Crimes Tribunal in Nürnberg. Twelve were hanged, three received life terms, four were sentenced to lesser terms of imprisonment (up to twenty years), and three were acquitted.
The cases of communist judges and prosecutors accused of Rechtsbeugung (perversion of justice) are more problematic. According to Franco Werkenthin, a Berlin legal expert charged with analyzing communist crimes for the German parliament, those sitting in judgment of many of the accused face a difficult task because of the general failure of German justice after World War II. Not a single judge or prosecutor who served the Nazi regime was brought to account for having perverted justice—even those who had handed down death sentences for infringements that in a democracy would have been considered relatively minor offenses. Werkenthin called this phenomenon die Jauche der Justiz, the cesspool of justice.
Of course, the crimes committed by the communists were not nearly as heinous as the Nazis’ extermination of the Jews, or the mass murders in Nazi-occupied territories. However, the communists’ brutal oppression of the nation by means including murder alongside legal execution put the SED leadership on a par with Hitler’s gang. In that sense, Walter Ulbricht or Erich Honecker (Ulbricht’s successor as the party’s secretary-general and head of state) and secret police chief Erich Mielke can justifiably be compared to Hitler and Himmler, respectively.
Arrest warrants were issued for Honecker and Mielke. The Soviet government engineered Honecker’s escape to Moscow, where he became the ward of Soviet President Mikhail S. Gorbachev. When the Soviet Union crumbled, the new Russian President Boris Yeltsin expelled Honecker. He was arrested on his return to Germany, but a court decided against a trial when he was diagnosed with liver cancer. Honecker flew to Chile with his wife Margot to live with their daughter, a Chilean citizen by marriage. His exile was short, and he died in 1994. Mielke was not so fortunate: His KGB friends turned their backs on him. He was tried in Germany for the 1931 murder of two police officers, found guilty, and sentenced to six years in prison. Other charges, including manslaughter, were dismissed because of his advanced age and poor health.
Three other members of the twenty-one-member ruling Politburo also have been tried. Former Defense Minister Heinz Kessler was convicted of manslaughter in connection with the order to kill people who were trying to escape to the West. He received a seven-and-a-half-year term. Two others, members of the Central Committee and the National Defense Council, were tried with Kessler and sentenced to seven and a half years and five years, respectively. Politburo member Harry Tisch, who was also head of the communist trade union, was found guilty of embezzlement and served eighteen months. Six others, including Egon Krenz (Honecker’s successor as party chief), were charged with manslaughter. Krenz was found guilty, and on August 25, 1997, was sentenced to six and a half years in prison.
However, eight years after reunification, many of the 165 members of the Central Committee have not yet been put under investigation. In 1945, Nazis holding comparable or lesser positions were subject to automatic arrest by the Allies. They spent months or even years in camps while their cases were adjudicated. Moreover, the Nürnberg Tribunal branded the Reich and its Corps of Political Leaders, SS, Security Service (SD), Secret State Police (Gestapo), SA (Storm Troopers), and Armed Forces High Command criminal organizations. Similarly sweeping actions against communist leaders and functionaries such as Stasi officers were never contemplated, even though tens of thousands of political trials and human rights abuses have been documented. After the East German regime fell, German judicial authorities scrupulously avoided the appearance of waging witch-hunts or using the law as a weapon of vengeance. Prosecutors and judges made great efforts to be fair, often suspending legal action while requesting rulings from the supreme court on possible constitutional conflicts.
The victims of oppression clamored for revenge and demanded speedy prosecution of the erstwhile tyrants. They had little patience for a judicial system that was handicapped by a lack of unblemished and experienced criminal investigators, prosecutors, and judges. Despite these handicaps, the Berlin Central Police Investigations Group for Government Criminality, mindful that the statute of limitations for most communist crimes would expire at the end of 1999, made significant progress under its director Manfred Kittlaus, the able former director of the West Berlin state police. Kittlaus’s major task in 1998 was to investigate wrongful deaths, including 73 murders, 30 attempted murders, 583 cases of manslaughter, 2,938 instances of attempted manslaughter, and 425 other suspicious deaths. Of the 73 murders, 22 were classified as contract murders.
One of those tried and convicted for attempted contract murder was former Stasi collaborator Peter Haak, who was sentenced to six and a half years in prison. The fifty-two-year-old Haak took part in the Stasi’s 1981 Operation Scorpion, which was designed to pursue people who helped East Germans escape to the West. Proceedings against former General Gerhard Neiber, whose Stasi directorate was responsible for preventing escapes and for wreaking vengeance, were still pending in 1998.
Peter Haak’s murder plot was hatched after he befriended Wolfgang Welsch and his family. Welsch was a thorn in the side of the Stasi because of his success in smuggling people out of the DDR. Haak joined Welsch and the latter’s wife and seven-year-old daughter on a vacation in Israel, where he mixed a gram of thallium, a highly poisonous metallic chemical element used in rat poison, into the hamburgers he was preparing for a meal. Welsch’s wife and daughter vomited immediately after ingesting the poison and recovered quickly. Welsch suffered severe aftereffects, but eventually recovered: He had consumed a large amount of beer with the meal, and an expert testified that the alcohol had probably flushed the poison from his system.
Berlin Prosecutor General Christoph Schäfgen revealed that after the DDR’s demise 15,200 investigations had been launched, of which more than 9,000 were still active at the beginning of 1995. Indictments were handed down in 153 cases, and 73 perpetrators were convicted. Among those convicted were the aforementioned Politburo members as well as a number of border guards who had killed people who were trying to escape to the West.
Despite widespread misgivings about the judicial failures in connection with some Nazi crimes, a number of judges and prosecutors were convicted and jailed for up to three years for perversion of justice. In collusion with the Stasi, they had requested or handed down more severe sentences in political cases so that the state could collect greater amounts when the “convicts” were ransomed by the West German government. {The amount of ransom paid was governed by the time a prisoner had been sentenced to serve.)
The enormity of the task facing judicial authorities in reunified Germany becomes starkly evident when one examines the actions they have taken in all five former East German provinces and in East Berlin. From the end of 1990 to July 1996, 52,050 probes were launched into charges of murder, attempted murder, manslaughter, kidnapping, election fraud, and perversion of justice. A total of 29,557 investigations were halted for various reasons including death, severe illness, old age, or insufficient evidence. In those five and a half years, there were only 139 convictions.
The problem is even more staggering when cases of espionage are included. Between 1990 and 1996, the office of the federal prosecutor general launched 6,641 probes, of which 2,431 were terminated before trial—most due to the statute of limitations. Of 175 indictments on charges of espionage, 95 resulted in convictions. In addition to the cases handled at the federal level, the prosecutor general referred 3,926 investigations to state authorities, who terminated 3,344 without trial. State courts conducted 356 trials, resulting in 248 convictions. Because the statute of limitations for espionage is five years, the prosecutor general’s office told me in 1997 it was unlikely that more espionage trials would be conducted.
It is important to emphasize the difference between the statute’s application to so-called government crimes committed in East Germany before the collapse and to crimes, such as espionage, committed in West Germany. The Unification Treaty specifically permits the belated prosecution of individuals who committed acts that were punishable under the East German criminal code and who due to official connivance were not prosecuted earlier. There is no statute of limitations for murder. For most other crimes the limit is five years; however, due to the obstacles created by previous government connivance, the German parliament in 1993 doubled this time limit for prosecution of the more serious crimes. At the same time, the parliament decreed that all cases must be adjudicated by the end of 2002. For less serious offenses, the statute would have run out on December 31, 1997, but the parliament extended it to 2000.
A number of politicians, jurists, and liberal journalists pleaded for a general amnesty for crimes committed by former DDR leaders and Communist Party functionaries. A former West German supreme court judge, Ernst Mahrenholz, said the “sharp sword of justice prevents reconciliation.” Schäfgen, the Berlin prosecutor general, had this answer for the former high court judge and other amnesty advocates:
I cannot agree. We are raising no special, sharp sword against East Germans. We must pursue state-sponsored injustice in exactly the same manner as we do when a thief steals or when one human being kills another. If one wants to change that, then we would have to do away with the entire criminal justice system, because punishment always hurts. We are not criminalizing an entire people but only an ever shrinking, small portion.
German Foreign Minister Klaus Kinkel, who was West Germany’s minister of justice when the nation was unified, said this at a session of parliament in September 1991: “We must punish the perpetrators. This is not a matter of a victor’s justice. We owe it to the ideal of justice and to the victims. All of those who ordered injustices and those who executed the orders must be punished; the top men of the SED as well as the ones who shot [people] at the wall.” Aware that the feelings against communists were running high among their victims, Kinkel pointed to past revolutions after which the representatives of the old system were collectively liquidated. In the same speech before parliament, he said:
Such methods are alien to a state ruled by law. Violence and vengeance are incompatible with the law in any case. At the same time, we cannot tolerate that the problems are swept under the rug as a way of dealing with a horrible past, because the results will later be disastrous for society. We Germans know from our own experience where this leads. Jewish philosophy formulates it in this way: “The secret of redemption is called remembering.”
Defense attorneys for communist officials have maintained that the difficulty lies in the fact that hundreds of thousands of political opponents were tried under laws of the DDR. Although these laws were designed to smother political dissent and grossly violated basic human rights and democratic norms, they were nonetheless laws promulgated by a sovereign state. How could one justly try individual Stasi officers, prosecutors, and judges who had simply been fulfilling their legal responsibility to pursue and punish violators of the law?
Opinions varied widely on whether and how the Stasi and other perpetrators of state-sponsored crimes should be tried. Did the laws of the DDR, as they existed before reunification, still apply in the east? Or was the criminal code of the western part of the country the proper instrument of justice in reunified Germany? However, these questions were moot: As Rupert Scholz, professor of law at the University of Munich and a Christian Democratic member of parliament, pointed out, the Unification Treaty specifies that the penal code of the DDR and not that of the Federal Republic of Germany (FRG) shall be applied to offenses committed in East Germany. Scholz’s view was upheld by the Bundesverfassungsgericht, the supreme court. Most offenses committed by party functionaries and Stasi officers—murder, kidnapping, torture, illegal wiretapping, mail robbery, and fraud—were subject to prosecution in reunified Germany under the DDR’s penal code. But this would not satisfy the tens of thousands of citizens who had been sent to prison under East German laws covering purely political offenses for which there was no West German equivalent.
Nevertheless, said Scholz, judicial authorities were by no means hamstrung, because West Germany had never recognized the East German state according to international law. “We have always said that we are one nation; that the division of Germany led neither to full recognition under international law nor, concomitantly, to a recognition of the legal system of the DDR,” Scholz said. Accordingly, West German courts have consistently maintained that West German law protects all Germans equally, including those living in the East. Therefore, no matter where the crimes were committed, whether in the East or the West, all Germans have always been subject to West German laws. Applying this logic, East German border guards who had either killed or wounded persons trying to escape to the West could be tried under the jurisdiction of West Germany.
The “one nation” principle was not upheld by the German supreme court. Prior to the court’s decision, however, Colonel General Markus Wolf, chief of the Stasi’s foreign espionage directorate, and some of his officers who personally controlled agents from East Berlin had been tried for treason and convicted. Wolf had been sentenced to six years in prison. The supreme court ruling overturned that verdict and those imposed on Wolf’s cohorts, even though they had obtained the most closely held West German secrets and handed them over to the KGB. The maximum penalty for Landesverrat, or treason, is life imprisonment. In vacating Wolf’s sentence, the court said he could not be convicted because he operated only from East German territory and under East German law.
However, Wolf was reindicted on charges of kidnapping and causing bodily harm, crimes also punishable under East German law. The former Stasi three-star general, on March 24, 1955, had approved in writing a plan to kidnap a woman who worked for the U.S. mission in West Berlin. The woman and her mother were tricked by a Stasi agent whom the woman had been teaching English, and voluntarily got into his car. He drove them into the Soviet sector of the divided city, where they were seized by Stasi officers. The woman was subjected to psychological torture and threatened with imprisonment unless she signed an agreement to spy for the Stasi. She agreed. On her return to the American sector, however, the woman reported the incident to security officials. Wolf had committed a felony punishable by up to fifteen years’ imprisonment in West Germany. He was found guilty in March 1977 and sentenced to two years’ probation.
Those who have challenged the application of the statute of limitations to communist crimes, especially to the executions of citizens fleeing to the West, have drawn parallels to the notorious executive orders of Adolf Hitler. Hitler issued orders mandating the summary execution of Soviet Army political commissars upon their capture and initiating the extermination of Jews. An early postwar judicial decision held that these orders were equivalent to law. When that law was declared illegal and retroactively repealed by the West German Bundestag, the statute of limitations was suspended—that is, it never took effect. Many of those convicted in subsequent trials of carrying out the Führer’s orders were executed by the Allies. The German supreme court has ruled the same way as the Bundestag on the order to shoot people trying to escape to West Germany, making the statute of limitations inapplicable to such cases. The ruling made possible the trial of members of the National Defense Council who took part in formulating or promulgating the order. A number of border guards who had shot would-be escapees also have been tried and convicted.
Chief Prosecutor Heiner Sauer, former head of the West German Central Registration Office for Political Crimes, was particularly concerned with the border shootings. His office, located in Salzgitter, West Germany, was established in 1961 as a direct consequence of the Berlin Wall, which was erected on August 13 of that year. Willy Brandt, at the time the city’s mayor (later federal chancellor) had decided that crimes committed by East German border guards should be recorded. At his behest, a central registry of all shootings and other serious border incidents was instituted. Between August 13, 1961 and the opening of the borders on November 9, 1989, 186 border killings were registered. But when the Stasi archives were opened, investigators found that at least 825 people had paid with their lives for trying to escape to the West. This figure was reported to the court that was trying former members of the National Defense Council. In addition to these border incidents, the registry also had recorded a number of similar political offenses committed in the interior of the DDR: By fall 1991, Sauer’s office had registered 4,444 cases of actual or attempted killings and about 40,000 sentences handed down by DDR courts for “political offenses.”
During the early years of Sauer’s operation, the details of political prosecutions became known only when victims were ransomed by West Germany or were expelled. Between 1963 and 1989, West Germany paid DM5 billion (nearly US$3 billion) to the communist regime for the release of 34,000 political prisoners. The price per head varied according to the importance of the person or the length of the sentence. In some cases the ransom amounted to more than US$56,000. The highest sum ever paid to the East Germans appears to have been DM450,000 (US$264,705 using an exchange rate of US$1.70 to the mark). The ransom “object” in this case was Count Benedikt von Hoensbroech. A student in his early twenties, von Hoensbroech was attending a West Berlin university when the wall went up. He was caught by the Stasi while trying to help people escape and was sentenced to ten years at hard labor. The case attracted international attention because his family was related to Queen Fabiola of Belgium, who interceded with the East Germans. Smelling money, the East German government first demanded the equivalent of more than US$1 million from the young man’s father as ransom. In the end, the parties settled on the figure of DM450,000, of which the West German government paid DM40,000 (about $23,529). Such ransom operations were fully controlled by the Stasi.
Political prisoners released in the DDR could not be registered by the West Germans because their cases remained secret. The victims were admonished to keep quiet or face another prison term. Nonetheless, in the first year after reunification, Sauer’s office added another 20,000 documented cases, for a total of 60,000. Sauer said he believed the final figure of all political prosecutions would be somewhere around 300,000. In every case, the Stasi was involved either in the initial arrest or in pretrial interrogations during which “confessions” were usually extracted by physical or psychological torture, particularly between the mid-1940s and the mid-1960s.
Until 1987, the DDR imposed the death penalty for a number of capital crimes, including murder, espionage, and economic offenses. But after the mid-1950s, nearly all death sentences were kept quiet and executions were carried out in the strictest secrecy, initially by guillotine and in later years by a single pistol shot to the neck. In most instances, the relatives of those killed were not informed either of the sentence or of the execution. The corpses were cremated and the ashes buried secretly, sometimes at construction sites. In reporting about one executioner who shot more than twenty persons to death, the Berlin newspaper Bildzeitung said that a total of 170 civilians had been executed in East Germany. However, Franco Werkenthin, the Berlin official investigating DDR crimes, said he had documented at least three hundred executions. He declined to say how many were for political offenses, because he had not yet submitted his report to parliament. “But it was substantial,” he told me. The true number of executions may never be known because no complete record of death sentences meted out by civil courts could be found. Other death sentences were handed down by military courts, and many records of those are also missing. In addition, German historian Günther Buch believes that about two hundred members of the Stasi itself were executed for various crimes, including attempts to escape to the West.
SAFEGUARDING HUMAN DIGNITY?
The preamble to the East German criminal code stated that the purpose of the code was to “safeguard the dignity of humankind, its freedom and rights under the aegis of the criminal code of the socialist state,” and that “a person can be prosecuted under the criminal code only in strictest concurrence with the law.” However, many of the codified offenses for which East German citizens were prosecuted and imprisoned were unique to totalitarian regimes, both fascist and communist.
Moreover, certain sections of the code, such as those on “Treasonable Relaying of Information” and “Treasonable Agent Activity,” were perversely applied, landing countless East Germans in maximum security penitentiaries. The victims of this perversion of justice usually were persons who had requested legal exit permits from the DDR authorities and had been turned down. In many cases, their “crime” was having contacted a Western consulate to inquire about immigration procedures. Sentences of up to two and a half years’ hard labor were not unusual as punishment for such inquiries.
Engaging in “propaganda hostile to the state” was another punishable offense. In one such case, a young man was arrested and prosecuted for saying that it was not necessary to station tanks at the border and for referring to border fortifications as “nonsense.” During his trial, he “admitted” to owning a television set on which he watched West German programs and later told friends what he saw. One of those “friends” had denounced him to the Stasi. The judge considered the accused’s actions especially egregious and sentenced him to a year and a half at hard labor.
Ironically, another part of this section of the criminal code decreed that “glorifying militarism” also was a punishable offense, although the DDR itself “glorified” its People’s Army beyond any Western norm. That army was clad in uniforms and insignia identical to those of the Nazi Wehrmacht, albeit without eagles and swastikas. The helmets, too, were differently shaped, but the Prussian goose step was regulation during parades.
A nineteen-year-old who had placed a sign in an apartment window reading “When justice is turned into injustice, resistance becomes an obligation!” was rewarded with twenty-two months in the penitentiary. Earlier, the youth had applied for an exit visa and had been turned down. A thirty-four-year-old father of two who also had been denied permission to leave the “workers’ and peasants’ state” with his family similarly advertised that fact with a poster reading “We want to leave, but they won’t let us.” The man went to prison for sixteen months. The “crimes” of both men were covered by a law on “Interference in Activities of the State or Society.”
Two letters—one to a friend in West Germany, seeking assistance to legally emigrate to the West, and another containing a similar appeal to Chief of State Honecker—brought a four-year sentence to their writer, who was convicted under two laws: those on “establishing illegal contacts” (writing to his friend) and on “public denigration” (writing to Honecker). The Stasi had illegally intercepted both letters.
The East German party chiefs were not content to rely only on the Stasi’s millions of informers to ferret out antistate sentiments. Leaving nothing to chance, they created a law that made the failure to denounce fellow citizens a crime punishable by up to five years’ imprisonment. One man was sentenced to twenty-three months for failing to report that a friend of his was preparing to escape to the West. The mandatory denunciation law had its roots in the statutes of the Socialist Unity Party, which were published in the form of a little red booklet. I picked up a copy of this booklet that had been discarded by its previous owner, a Stasi chauffeur, who had written “Ha, Ha” next to the mandate to “report any misdeeds, regardless of the person responsible, to leading party organs, all the way up to the Central Committee.”
Rupert Scholz, member of parliament and professor of law at the University of Munich, said many East Germans feel there is little determination among their Western brethren to bring the Stasi criminals to trial. “In fact, we already have heard many of them say that the peaceful revolution should have been a bloody one instead so they could have done away with their tormentors by hanging them posthaste,” Scholz told me.
The Reverend Joachim Gauck, minister to a Lutheran parish in East Germany, shared the people’s pessimism that justice would be done. Following reunification, Gauck was appointed by the Bonn government as its special representative for safeguarding and maintaining the Stasi archives. “We must at least establish a legal basis for finding the culprits in our files,” Gauck told me. “But it will not be easy. If you stood the millions of files upright in one line, they would stretch for 202 kilometers [about 121 miles]. In those files you can find an unbelievable number of Stasi victims and their tormentors.”
Gauck was given the mandate he needed in November 1991, when the German parliament passed a law authorizing file searches to uncover Stasi perpetrators and their informants. He viewed this legislation as first step in the right direction. With the evidence from Stasi files, the perpetrators could be removed from their public service jobs without any formal legal proceedings. Said Gauck: “We needed this law badly. It is not reasonable that persons who served this apparatus of oppression remain in positions of trust.”
See more at the journalist Bernd Pulch website http://www.berndpulch.org
TOP-SECRET – Classified USAID Report on Kabul Bank Corruption
Dubai real estate led depositors to rush to withdraw funds from Kabul Bank, the largest bank in Afghanistan. According to the Report of Kabul Bank in Conservatorship dated October 30, 2010, cited in a draft material loss review commissioned by USAID/Afghanistan, fraudulent loans were used to divert $850 million to insiders. This amount reportedly represented 94 percent of the bank’s outstanding loans.
Since 2003, USAID/Afghanistan has supported a number of capacity-building activities at the Afghanistan Central Bank (DAB) to help DAB regulate the banking sector. Currently, Deloitte1 provides DAB technical assistance in bank supervision and examination through a $92 million task order for the Economic Growth and Governance Initiative, which includes many activities in addition to bank supervision and examination. The purpose of the task order was to increase Afghanistan’s ability to develop and implement sound economic and regulatory policies that provide the foundation for private sector growth in a market economy. According to Deloitte’s work plan, one of the main goals of the assistance Deloitte provided to DAB was to assist DAB in fulfilling its statutory responsibilities ―to promote the stability and contribution to economic growth of the financial sector and to prevent avoidable losses. Deloitte provided onsite technical advisors at DAB’s Directorate for Financial Supervision.
After the run on Kabul Bank, senior officials in the U.S. Embassy raised concerns about Deloitte’s performance. Specifically, they were concerned that Deloitte staff did not warn the U.S. Government about looming problems at Kabul Bank before the first news reports broke in February 2010. They also questioned Deloitte’s effectiveness and performance because Deloitte staff had provided bank supervision assistance to DAB for 7 years, yet DAB supervisors were unable to prevent the near collapse of Afghanistan’s largest bank. In January 2011, USAID/Afghanistan requested the assistance of the Office of Inspector General (OIG) in determining whether USAID or Deloitte staff members were negligent in failing to report the Kabul Bank fraud.
In response to USAID/Afghanistan’s request, OIG/Afghanistan conducted this review to determine:
- What opportunities USAID and contractor staff had to learn of fraudulent activities at Kabul Bank through USAID’s Economic Growth and Governance Initiative and its predecessor, the Economic Growth and Private Sector Strengthening Activity.
- How staff learned of the fraud.
- What actions staff members took once they became aware of the fraud.
- Whether USAID’s oversight of its contractor was adequate.
…
USAID’s Management of Its Task Order with Deloitte Was Weak
ADS 203.3.2, ―Assessing and Learning, states that missions and their offices are responsible for monitoring a contractor’s performance in achieving the contract’s purpose. ADS 302.3.7.1a, ―Direct Contracting, Mandatory Reference: ―Procedures for Designating the Contracting Officer’s Technical Representative (COTR) for Contracts and Task Orders,‖ states that the COTR is in a unique position to monitor how well the contractor is progressing toward achieving the contract’s purpose and is responsible for providing technical liaison between the contractor and the contracting officer, a function critical to ensuring good contract performance.
When the current mission director arrived in June 2010, his attention focused on USAID/Afghanistan’s capacity to manage and provide oversight of highly technical bank supervision activities implemented by its contractor, Deloitte, at DAB. This focus heightened after the Kabul Bank crisis broke in September 2010. The task order with Deloitte for the Economic Growth and Governance Initiative was for a 5-year, $92 million project with three major components and 21 work streams with diverse requirements that was managed by USAID/Afghanistan’s Office of Economic Growth. In August 2009, when USAID issued the task order, the Office of Economic Growth had only four U.S. direct-hire staff and none with experience in the banking sector. For the most part, only one U.S. direct hire was managing the task order at any given time, with some assistance from Foreign Service National staff.
Further contributing to the mission’s challenges to provide effective oversight of Deloitte, a former COTR for the Deloitte task order stated that during a typical workweek, he spent 50 to 70 percent of his time drafting memorandums and cables for the U.S. Embassy, reducing his time for program oversight. He kept detailed timesheets of daily work activities. The COTR explained that such competing work demands, combined with the mission’s lack of technical expertise, created overreliance on the Deloitte advisers to manage the bank supervision assistance activities, with little oversight provided by USAID. USAID staff members stated that had they not faced the burden of managing a large task order with limited resources, they would have been in a better position to provide proactive and robust oversight of the Deloitte advisers. As one USAID official put it, ―Deloitte was managing USAID, rather than the other way around.
Generally, COTRs monitor contractor performance and verify that it conforms to the technical requirements and quality standards agreed to in the contract. COTRs do this by maintaining regular contact and liaison and by conducting frequent site visits with the contractor. Yet according to a former COTR for the Deloitte task order, mission management focused on program spending, financial pipelines, and burn rates, rather than on monitoring and achieving program results. A former USAID/Afghanistan staff member stated in a memo that the mission gave the Office of Economic Growth only 24 hours to review a proposed Deloitte work plan—insufficient time to provide thoughtful review and comment. Finally, at the entrance conference for this review, USAID/Afghanistan officials did not take a position on whether Deloitte’s performance was satisfactory or unsatisfactory, providing further evidence of inadequate management.
For years, USAID has faced difficulty in attracting staff to Afghanistan who have the appropriate levels of experience and skills. A former mission director for USAID/Afghanistan stated that the staffing situation in Afghanistan reflected what he considered to be an ongoing problem for USAID, especially for programs in war zones—not enough senior people at USAID who have the experience to manage large, substantive, technically challenging projects. Current USAID/Afghanistan leadership agreed with this assessment and explained that steps have been and continue to be taken to remedy that situation. For example, a recently completed reorganization in the Office of Economic Growth added one technical adviser position.
DOWNLOAD ORIGINAL DOCUMENT HERE
Das grosse Vorbild der Stasi – der KGB
KGB ist eine russische Abkürzung und bedeutet übersetzt “Komitee für Staatssicherheit”. Der KGB war der Name des sowjetischen Auslandsgeheimdienstes und wurde im Jahr 1954 aus den Abteilungen des Inlandsgeheimdienstes NKWD und des Innenministeriums MWD gegründet.
Die Hauptaufgabe bestand in der Bewachung von Mitgliedern der Partei- und Staatsführung, der Gegenspionage, der Auslandsspionage sowie der Kontrolle und Beseitigung von Regimekritikern innerhalb der früheren Sowjetunion
Der KGB führte gelegentlich Attentate durch, die aber hauptsächlich auf Überläufer verübt wurden. Oft half der KGB auch Geheimdiensten anderer Staaten bei Attentaten. Ein berühmtes Beispiel ist die Ermordung von Georgi Markov, bei dem der bulgarische Agenten einen vom KGB entwickelten Regenschirm für den Mord benutzten.
Nach dem Putschversuch im August 1991, in dem der damalige KGB-Vorsitzende verwickelt war, wurde die Behörde am 6. November 1991 aufgelöst. In Russland wurden die Aufgaben von dem neuen Geheimdienst FSB übernommen. In Weißrussland trägt der Geheimdienst weiterhin den Namen KGB.
Agenten im kalten Krieg – Die Gründung der Stasi durch den KGB und Stalin
Am 8. Februar 1950 wurde in der DDR offiziell die Bildung eines Ministeriums für Staatssicherheit (MfS) beschlossen. Es war die Geburtsstunde der Stasi, die sich im Laufe der folgenden Jahre zu einem gewaltigen Geheimdienstapparat entwickelte
STASI Inside – Die Bilder der STASI
VIDEO – The Stasi in disguise
CONFIDENTIAL – Video – Stasi – East Germany’s Secret Police Part 1 – One informer to 7 citizens
Between 1950 and 1989, the Stasi employed a total of 274,000 people in an effort to root out the class enemy. In 1989, the Stasi employed 91,015 persons full time, including 2,000 fully employed unofficial collaborators, 13,073 soldiers and 2,232 officers of GDR army, along with 173,081 unofficial informants inside GDR and 1,553 informants in West Germany. In terms of the identity of inoffizielle Mitarbeiter (IMs) Stasi informants, by 1995, 174,000 had been identified, which approximated 2.5% of East Germany’s population between the ages of 18 and 60. 10,000 IMs were under 18 years of age.
While these calculations were from official records, according to the federal commissioner in charge of the Stasi archives in Berlin, because many such records were destroyed, there were likely closer to 500,000 Stasi informers. A former Stasi colonel who served in the counterintelligence directorate estimated that the figure could be as high as 2 million if occasional informants were included.
Infiltration
Full-time officers were posted to all major industrial plants (the extensiveness of any surveillance largely depended on how valuable a product was to the economy and one tenant in every apartment building was designated as a watchdog reporting to an area representative of the Volkspolizei (Vopo). Spies reported every relative or friend who stayed the night at another’s apartment. Tiny holes were drilled in apartment and hotel room walls through which Stasi agents filmed citizens with special video cameras. Schools, universities, and hospitals were extensively infiltrated.
The Stasi had formal categorizations of each type of informant, and had official guidelines on how to extract information from, and control, those who they came into contact with. The roles of informants ranged from those already in some way involved in state security (such as the police and the armed services) to those in the dissident movements (such as in the arts and the Protestant Church). Information gathered about the latter groups was frequently used to divide or discredit members. Informants were made to feel important, given material or social incentives, and were imbued with a sense of adventure, and only around 7.7%, according to official figures, were coerced into cooperating. A significant proportion of those informing were members of the SED; to employ some form of blackmail, however, was not uncommon. A large number of Stasi informants were trolley conductors, janitors, doctors, nurses and teachers; Mielke believed the best informants were those whose jobs entailed frequent contact with the public.
The Stasi’s ranks swelled considerably after Eastern Bloc countries signed the 1975 Helsinki accords, which Erich Honecker viewed as a grave threat to his regime because they contained language binding signatories to respect “human and basic rights, including freedom of thought, conscience, religion, and conviction.”
The number of IMs peaked at around 180,000 in this year, having slowly risen from 20,000–30,000 in the early 1950s, and reaching 100,000 for the first time in 1968, in response to Ostpolitik and protests worldwide. The Stasi also acted as a proxy for KGB to conduct activities in other Eastern Bloc countries, such as Poland, where the Soviets were despised.
The MfS infiltrated almost every aspect of GDR life. In the mid-1980s, a network of IMs began growing in both German states; by the time East Germany collapsed in 1989, the MfS employed 91,015 employees and 173,081 informants. About one of every 63 East Germans collaborated with the MfS—one of the most extensive police infiltrations of a society in history. In 2007 an article in BBC stated that “Some calculations have concluded that in East Germany there was one informer to every seven citizens.” Additionally, MfS agents infiltrated and undermined West Germany’s government and spy agencies.
In an extreme case, Stasi informant Knud Wollenberger (code name Daniel) married civil rights and peace activist Vera Lengsfeld specifically to keep a watch on her.
CONFIDENTIAL – Video – Stasi – East Germany’s Secret Police Part 2
Although Mielke’s Stasi was superficially granted independence in 1957, until 1990 the KGB continued to maintain liaison officers in all eight main Stasi directorates, each with his own office inside the Stasi’s Berlin compound, and in each of the fifteen Stasi district headquarters around East Germany. Collaboration was so close that the KGB invited the Stasi to establish operational bases in Moscow and Leningrad to monitor visiting East German tourists and Mielke referred to the Stasi officers as “Chekists of the Soviet Union”. In 1978, Mielke formally granted KGB officers in East Germany the same rights and powers they enjoyed in the Soviet Union.
CONFIDENTIAL – Video – Stasi – East Germany’s Secret Police Part 3
The Ministry for State Security (German: Ministerium für Staatssicherheit (MfS), commonly known as the Stasi (IPA: [ˈʃtaziː]) (abbreviation German: Staatssicherheit, literally State Security), was the official state security service of East Germany. The MfS was headquartered in East Berlin, with an extensive complex in Berlin-Lichtenberg and several smaller facilities throughout the city. It was widely regarded as one of the most effective and repressive intelligence and secret police agencies in the world. The MfS motto was “Schild und Schwert der Partei” (Shield and Sword of the Party), that is the ruling Socialist Unity Party of Germany (SED).
The MfS was founded on 8 February 1950. It was modelled on the Soviet MGB[citation needed], and was regarded by the Soviet Union as an extremely loyal and effective partner[citation needed]. Wilhelm Zaisser was the first Minister of State Security of the GDR, and Erich Mielke his deputy. Zaisser, who tried to depose SED General Secretary Walter Ulbricht after the June 1953 uprising was after this removed by Ulbricht and replaced by Ernst Wollweber. Wollweber resigned in 1957 after clashes with Ulbricht and Erich Honecker, and was succeeded by his deputy, Erich Mielke.
Early on the Stasi waged a campaign against Jews, who were already subject to widespread discrimination and violence in the Soviet Union. The Stasi censored the fact that Jews had been victims during the previous regime and in one instance, took gold from the bodies of Jews. The Stasi labeled Jews as capitalists and criminals. Gypsies were also blamed in the Stasi propaganda.
In 1957, Markus Wolf became head of the Hauptverwaltung Aufklärung (HVA) (General Reconnaissance Administration), its foreign intelligence section. As intelligence chief, Wolf achieved great success in penetrating the government, political and business circles of West Germany with spies. The most influential case was that of Günter Guillaume which led to the downfall of West German Chancellor Willy Brandt in May 1974. In 1986, Wolf retired and was succeeded by Werner Grossmann.
CONFIDENTIAL – Video – Stasi – East Germany’s Secret Police Part 4
Stasi, official name Ministerium für Staatsicherheit (German: “Ministry for State Security”), secret police agency of the former German Democratic Republic (East Germany). The Stasi was one of the most hated and feared institutions of the East German communist government.
The Stasi developed out of the internal security and police apparatus established in the Soviet zone of occupation in Germany after World War II. The law establishing the ministry, whose forerunner was the Kommissariat 5 (modeled along the lines of the Soviet KGB), was passed by the East German legislature on February 8, 1950.
During Germany’s partition East Germany’s Ministry of State Security (MfS) was one of the largest intelligence and security services in the world. Known as the Stasi by East Germans, it used some 90,000 regular employees—and nearly double that number of informers—to surveil the country’s 17 million people.
TOP SECRET – Bank of America Anonymous Email Leak
The following emails were released earlier by a member of Anonymous. The following are text renditions of the emails contained in the leak. The following terms are useful in understanding some of the emails’ content:
- SOR = System of Record
- Rembrandt/Tracksource = Insurance tracking systems
- DTNs = Document Tracking Number, a number assigned to all incoming/outgoing documents (letters, insurance documents, etc.)
1.
From: Vaughn, Jason – 2
Sent: Monday, November 01, 2010 2:09 PM
To: Bennett, Pearl H
Cc: Johnson, Peggy – 2; Walters, Kirsten; Smith, Jackie – 2
Subject: GMAC DTN’s for Image Removal – Urgent Request
Importance: HighHello,
The following GMAC DTN’s need have the images removed from Tracksource/Rembrandt.
354499768
354499769
354499770
354499771
354499772
354499773
354499774
354499775
354499776
354499777
354499734
354499735
354499736
354499739
354499740
354499741
354499742
354499745
354499746
354499747
354499750
354499751
354499754
354499725
354499726
354499727
354499728
354499729
354499730
354499731
354499732
354499733
354499718
354499719
354499720
354499721
354499722
354499723
354499724
354499707
354499708
354499710
354499711
354499713
354499714
354499715
354499697
354499698
354499699
354499700
354499702
354499704
354499705
354499706
354499667
354499668
354499669
354499670
354499671
354499672
354499673
354499674
354499675
354499676
354499677
354499678
354499679
354499680
354499681
354499682
354499683
354499686
354499687
354499688
354499691
354499692
354499693
354499694
354499695
354499696Jason D Vaughn
Operations Team Manager
Balboa Insurance
AZ LPP Balboa Tracking Ops
480-755-2701 Office
92-548-2701 Internal
2505 W Chandler BLVD, BLDG D
Chandler, AZ 85224
Mailstop: AZ 805-01-36This communication from Balboa Insurance Group-may contain privileged and/or confidential information. It is intended solely for the use of the addressee. If you are not the intended recipient, you are strictly prohibited from disclosing, copying, distributing or using any of this information. If you receive this communication in error, please contact the sender immediately and destroy the material in its entirety, whether electronic or hard copy. This communication may contain nonpublic personal information about consumers subject to the restrictions of the Gramm-Leach-Bliley Act. You may not directly or indirectly reuse or re-disclose such information for any purpose other than to provide the services for which you are receiving the information.
2.
From: Anderson, Joanne
Sent: Monday, November 01, 2010 2:28 PM
To: Vaughn, Jason – 2
Cc: Johnson, Peggy – 2; Walters, Kirsten; Smith, Jackie – 2; Mays, Therese J
Subject: RE: GMAC DTN’s for Image Removal – Urgent RequestHi Jason, Peggy and Kirsten,
I have spoken with my developer and she stated that we cannot remove the DTN’s from Rembrandt, but she can remove the loan numbers, so the documents will not show as matched to those loans.
I will need upper management approval from Jason, Peggy and Kirsten, since this is an usual request, before we move forward.
Thank you,
Service Delivery information: http://sharepoint.bankofamerica.com/sites/HLandIT/default.aspx
Joanne Anderson
Balboa Insurance Group
Cnslt – Bus Tech Anly
IT LPP/CPI/TRACKSOURCE
600 Lindbergh Drive
Mail Stop: PA4-934-01-03
Moon Township, PA 15108
Joanne.Anderson@Balboainsurance.com
412-424-1287 OfficeThis communication from Balboa Insurance Group – may contain privileged and/or confidential information. It is intended solely for the use of the addressee. If you are not the intended recipient, you are strictly prohibited from disclosing, copying, distributing or using any of this information. If you receive this communication in error, please contact the sender immediately and destroy the material in its entirety, whether electronic or hard copy. This communication may contain nonpublic personal information about consumers subject to the restrictions of the Gramm-Leach-Bliley Act. You may not directly or indirectly reuse or re-disclose such information for any purpose other than to provide the services for which you are receiving the information.
3.
From: Johnson, Peggy – 2
Sent: Monday, November 01, 2010 2:53 PM
To: Anderson, Joanne; Vaughn, Jason – 2
Cc: Walters, Kirsten; Smith, Jackie – 2; Mays, Therese J
Subject: RE: GMAC DTN’s for Image Removal – Urgent RequestHi Joanne,
Where will these letters show up then?
4.
From: Anderson, Joanne
Sent: Monday, November 01, 2010 3:03 PM
To: Johnson, Peggy – 2; Vaughn, Jason – 2
Cc: Walters, Kirsten; Smith, Jackie – 2; Mays, Therese J
Subject: RE: GMAC DTN’s for Image Removal – Urgent RequestHi Peggy,
The letters will not show in Rembrandt if you search by loan number. If you search by DTN, you will find the document, but it will not be matched to any loan.
Thanks,
Service Delivery information: http://sharepoint.bankofamerica.com/sites/HLandIT/default.aspx
Joanne Anderson
Balboa Insurance Group
Cnslt – Bus Tech Anly
IT LPP/CPI/TRACKSOURCE
600 Lindbergh Drive
Mail Stop: PA4-934-01-03
Moon Township, PA 15108
Joanne.Anderson@Balboainsurance.com
412-424-1287 OfficeThis communication from Balboa Insurance Group – may contain privileged and/or confidential information. It is intended solely for the use of the addressee. If you are not the intended recipient, you are strictly prohibited from disclosing, copying, distributing or using any of this information. If you receive this communication in error, please contact the sender immediately and destroy the material in its entirety, whether electronic or hard copy. This communication may contain nonpublic personal information about consumers subject to the restrictions of the Gramm-Leach-Bliley Act. You may not directly or indirectly reuse or re-disclose such information for any purpose other than to provide the services for which you are receiving the information.
5.
From: Anderson, Joanne
Sent: Monday, November 01, 2010 3:03 PM
To: Johnson, Peggy – 2; Vaughn, Jason – 2
Cc: Walters, Kirsten; Smith, Jackie – 2; Mays, Therese J
Subject: RE: GMAC DTN’s for Image Removal – Urgent RequestHi Peggy,
The letters will not show in Rembrandt if you search by loan number. If you search by DTN, you will find the document, but it will not be matched to any loan.
Thanks,
Service Delivery information: http://sharepoint.bankofamerica.com/sites/HLandIT/default.aspx
Joanne Anderson
Balboa Insurance Group
Cnslt – Bus Tech Anly
IT LPP/CPI/TRACKSOURCE
600 Lindbergh Drive
Mail Stop: PA4-934-01-03
Moon Township, PA 15108
Joanne.Anderson@Balboainsurance.com
412-424-1287 OfficeThis communication from Balboa Insurance Group – may contain privileged and/or confidential information. It is intended solely for the use of the addressee. If you are not the intended recipient, you are strictly prohibited from disclosing, copying, distributing or using any of this information. If you receive this communication in error, please contact the sender immediately and destroy the material in its entirety, whether electronic or hard copy. This communication may contain nonpublic personal information about consumers subject to the restrictions of the Gramm-Leach-Bliley Act. You may not directly or indirectly reuse or re-disclose such information for any purpose other than to provide the services for which you are receiving the information.
6.
From: Johnson, Peggy – 2
Sent: Monday, November 01, 2010 3:13 PM
To: Anderson, Joanne; Vaughn, Jason – 2
Cc: Walters, Kirsten; Smith, Jackie – 2; Mays, Therese J
Subject: RE: GMAC DTN’s for Image Removal – Urgent RequestApproved.
7.
—– Forwarded Message —-
From: “Vaughn, Jason – 2? <jason.vaughn@balboainsurance.com>
To: “Johnson, Peggy – 2? <peggy.l.johnson@balboainsurance.com>
Sent: Tue, November 2, 2010 9:18:18 AM
Subject: FW: GMAC DTN’s for Image Removal – Urgent RequestHi Peggy,
I’m just a little concerned about the impact this has on the department and company. Why are we removing all record of this error? We have told Denise Cahen, and there is always going to be the paper trail when one of these sent documents come back, this to me, seems to be a huge red flag for the auditors: example: a scanned document that was mailed to us asking why the letter was received when the letter, albeit erroneous – this being the letters that went out in error – the auditor sees the erroneous letter but no SOR trail or scanned doc on the corrected letter is in the SOR and scanned in). What am I missing? This just doesn’t seem right to me.
STASI-RAF – Wer erschoss den Treuhandchef ?
DER TYPISCHE STASI-SPION
“Um ökonomisch, wissenschaftlich, technisch und militärisch mithalten zu können”: Eine Studie der Jahn-Behörde klärt die Strukturen der DDR-Auslandsspionage auf.
Der typische Spion ist männlich, zwischen 40 und 50 Jahre alt und Überzeugungstäter. Jedenfalls galt dieses Profil für die Spitzel der DDR-Staatssicherheit (MfS) im Westen, vor allem in der Bundesrepublik und West-Berlin. Das jedenfalls sagt die Statistik, wenn man die bekannten Angaben der mehr als 12.000 “Inoffiziellen Mitarbeiter” auswertet, die zwischen 1950 und 1989 für das MfS im demokratischen Deutschland tätig waren. Fast die Hälfte von ihnen arbeitete zehn Jahre oder mehr für den Geheimdienst der SED-Diktatur – eine Leistung, die ein deutliches Urteil über die Kompetenz der westlichen Spionageabwehr spricht.

- Der Chef-Spion der DDR im Einsatz: Das berühmte Foto zeigt Markus Wolf (1923-2006) im Jahr 1978 in Stockholm
Diese Woche erscheint eine lange erwartete Studie des Stasi-Experten Helmut Müller-Enbergs über die Auslandsspionage der SED-Diktatur; sie kann in Kürze auf der Website der Stasiunterlagen-Behörde (BStU) herunter geladen werden. Zum ersten Mal gibt es damit einen Gesamtüberblick über die Aktivitäten des legendenumwobenen Apparats von Markus Wolf, dem “Meisterspion“ der DDR.
Akten verschwanden in den Reißwölfen
Beeindruckend ist, wie viel man noch über den “Hauptverwaltung A“ (HVA) genannten und kompliziert verschachtelten Apparat herausfinden kann. Denn die Quellenlage ist miserabel. Im Februar 1990 erlaubte die “Arbeitsgruppe Sicherheit“ des Zentralen Runden Tisches in der DDR der Auslandsspionage, sich selbst abzuwickeln. Und bereits vorher waren die Reißwölfe (HVA) heiß gelaufen. Deshalb haben nur Bruchstücke der einst vorhandenen Aktenberge den Weg in die Magazine der BStU gefunden.
Trotzdem kann Müller-Enbergs, der zur BStU-Forschungsabteilung gehört und 2009 den langjährigen Spitzel Karl-Heinz Kurras enttarnte, die Strukturen des Apparates weitgehend aufklären.
Dabei stützt er sich angesichts der fragmentarischen Aktenüberlieferung auf zwei wesentliche Bestände: Einerseits das elektronische Eingangsbuch der HVA, das die Decknamen und Registriernummern der Spitzel mit den Titeln ihrer Berichte verknüpft, und andererseits auf die von der CIA 1990 auf mysteriösen Wegen erworbene Filmkopie der Personenkartei, besser bekannt als “Rosenholz“. Hinzu kommen weitere, mühsam aus Doppelüberlieferungen zusammen geklaubte Informationen und Forschungsergebnisse zu Einzelfällen.
Mit der betont nüchtern geschriebenen 365 Seiten starken Auswertung ist das seit anderthalb Jahrzehnten erscheinende “MfS-Handbuch“ nun praktisch vollendet. Müller-Enbergs konzentriert sich seinem Auftrag gemäß nicht auf Schilderungen einzelner Spionagefälle, von denen es bereits zahlreiche gibt. Wichtig ist ihm, die Organisation der HVA und die Schwerpunkte ihrer Arbeit zu verstehen.
Nur 13 Prozent der Spionage galt Militärischem
Von ehemaligen HVA-Mitarbeitern gibt es kaum vertrauenswürdige Schilderungen über ihre Arbeit – die meisten von ihnen führen, gestützt auf oft üppige Renten, ihren Kampf gegen den bundesdeutschen Rechtsstaat fort. Umso wichtiger ist es, dass nun endlich ein Gesamtüberblick ihrer konspirativen Tätigkeit vorliegt.
Zum Beispiel im Jahr 1988 war der wichtigste Arbeitsbereich der HVA die Wissenschafts- und Technikspionage: 39 Prozent der wenigstens dem Titel nach überlieferten Informationen behandelten das Ausspähen westdeutscher Unternehmen und Wissenschaftler. Das war sogar ein Prozent mehr als die “Aufklärung“ politischer Institutionen im weiteren Sinne – also Politik, Parteien, Verbände, Staats- und Verwaltungsapparat zusammen. Nur 13 Prozent der Spionageaktivitäten galten militärischen Einrichtungen.
Nur 13 Prozent der Spionage galt Militärischem
Zu Recht schließt Müller-Enbergs: “Die Bundesrepublik wurde folglich vor allem als systemstabilisierende Ressource genutzt, um ökonomisch, wissenschaftlich, technisch und militärisch mithalten zu können.“ Ohne Zweifel war das MfS bestens informiert über den “Klassenfeind“.
Ob es aber zutreffend ist, wie der Autor schreibt, dass die Stasi von einer “Unterwanderung der Bundesrepublik“ schon “zahlenmäßig weit entfernt“ war, muss offen bleiben. Denn gerade von den dafür zuständigen Abteilungen der HVA, vor allem der für “aktive Maßnahmen“, also Desinformation zuständigen Abteilung X, ist so gut wie nichts überliefert.
Mit dem Erscheinen der Dokumentation geht auch ein besonders unrühmliches Kapitel in der Geschichte der BStU zu Ende. Jahrelang hatte sich die damalige Bundesbeauftragte Marianne Birthler geweigert, Müller-Enbergs Ergebnisse zu veröffentlichen – trotz zweimaliger pflichtgemäßer Überarbeitung.
Die Behörde mahnte ihren wahrscheinlich produktivsten Forscher sogar ab, wogegen der sich vor dem Arbeitsgericht wehren musste. Mit dem Wechsel an der Spitze von Birthler zu Roland Jahn im vergangenen Frühjahr hat sich dieser so unnütze wie kräftezehrende Konflikt glücklicherweise erledigt.
Denn es gibt noch viel zu erforschen über die Westarbeit der DDR-Staatssicherheit. Von den zuletzt aktiven 1553 bundesdeutschen IM der DDR-Auslandsspionage, gegen die Ermittlungsverfahren eingeleitet wurden, sind nur 181 Personen verurteilt worden, darunter 119 zu Bewährungs- oder Geldstrafen. Nur gegen 62 enttarnte Agenten wurde eine Freiheitsstrafe von zwei Jahren und mehr verhängt.
Inzwischen sind alle denkbaren Straftaten von DDR-Agenten mit der einen Ausnahme Mord im engen Sinne des Paragraphen 211 des Strafgesetzbuches verjährt. Umso wichtiger ist, dass Historiker ihre Tätigkeit gegen die Bundesrepublik im Einzelnen aufklären. Die geeignete Grundlage dafür liefert die Studie von Helmut Müller-Enbergs.
Buchtip – Bundesbürger im Dienst der DDR-Spionage. Eine analytische Studie
TOP-SECRET from the FBI – Kareem Ibrahim Sentenced to Life in Prison for Conspiring to Commit Terrorist Attack at JFK Airport
BROOKLYN, NY—Earlier today, in the Eastern District of New York, United States District Judge Dora L. Irizarry sentenced convicted defendant Kareem Ibrahim to life in prison for conspiring to commit a terrorist attack at John F. Kennedy International Airport in Queens, New York, by exploding fuel tanks and the fuel pipeline under the airport. Ibrahim and his coconspirators believed their attack would cause extensive damage to the airport and to the New York economy, as well as the loss of numerous lives. At the Ibrahim sentencing, Judge Irizarry stated: “This case shows the government at its best in terms of protecting the security of this country.”
The sentence was announced by Loretta E. Lynch, United States Attorney for the Eastern District of New York. The case was investigated by the Federal Bureau of Investigation (FBI) Joint Terrorism Task Force (JTTF) in New York.
A federal jury convicted Kareem Ibrahim of multiple terrorism offenses in May 2011 after a four-week trial. The evidence at trial established that Ibrahim, an Imam and leader of the Shiite Muslim community in Trinidad & Tobago, provided religious instruction and operational support to a group plotting to commit a terrorist attack at JFK Airport. The plot originated with Russell Defreitas, a naturalized United States citizen from Guyana, who drew on his prior experience working at JFK Airport as a cargo handler to plan the attack on its fuel tanks and fuel pipeline. Beginning in 2006, Defreitas recruited others to join the plot, including the defendant Kareem Ibrahim, Abdel Nur and Abdul Kadir, a former member of parliament in Guyana. In May 2007, Defreitas presented Ibrahim with video surveillance and satellite imagery of the targets for terrorist attack because Ibrahim had connections with militant leaders in Iran.
During cross-examination at trial, Ibrahim admitted that he advised the plotters to present the plot to revolutionary leaders in Iran and to use operatives ready to engage in suicide attacks at the airport. On one of the recorded conversations entered into evidence, Ibrahim told Defreitas that the attackers must be ready to “fight it out, kill who you could kill and go back to Allah.”
According to the trial evidence, the conspirators also attempted to enlist support for the plot from prominent international terrorist groups and leaders, including Adnan El Shukrijumah, an al Qaeda leader and explosives expert, and Yasin Abu Bakr, leader of the Trinidadian militant group Jamaat Al Muslimeen. Ultimately, the plotters followed Ibrahim’s direction and sent Abdul Kadir to meet with his contacts in the Iranian revolutionary leadership, including Mohsen Rabbani, the former cultural attache indicted for his leading role in the 1994 bombing of the AMIA Jewish cultural center in Buenos Aires, Argentina.
Kareem Ibrahim, Abdul Kadir, and Abdel Nur were arrested in Trinidad in June 2007, with Kadir aboard a plane headed to Venezuela, en route to Iran. All three were subsequently extradited to the United States. Defreitas was arrested in New York. After a nine-week trial in 2010, Russell Defreitas and Abdul Kadir were convicted of terrorism charges and sentenced to life in prison. Nur pleaded guilty before trial to supporting the plot and was sentenced to 15 years in prison.
The specific charges Ibrahim was convicted of were: conspiracy to attack a public transportation system, in violation of 18 U.S.C. § 2332f; conspiracy to destroy a building by fire or explosive, in violation of 18 U.S.C. § 844(n); conspiracy to attack aircraft and aircraft materials, in violation of 18 U.S.C. § 32; conspiracy to destroy international airport facilities, in violation of 18 U.S.C. § 37; and conspiracy to attack a mass transportation facility, in violation of 18 U.S.C. § 1992(a)(10).
“Kareem Ibrahim abandoned the true tenets of his religion and plotted to commit a terrorist attack that he hoped would rival 9/11,” stated United States Attorney Lynch. “But law enforcement detected and thwarted the plot, saving lives. Now, our courts have dispensed justice by handing out the life sentence that Ibrahim deserves.” Ms. Lynch extended her grateful appreciation to the FBI Joint Terrorism Task Force in New York for its role in investigating and prosecuting the case, as well as to the Guyanese and Trinidadian law enforcement authorities who assisted with the investigation and apprehension of the defendants.
The government’s case was prosecuted by Assistant United States Attorneys Marshall L. Miller, Berit W. Berger, and Zainab Ahmad.
The Defendant:
KAREEM IBRAHIM, also known as “Amir Kareem” and “Winston Kingston”
Ishai Rosmarin Sales Director – EMEA of Acme – Confidential Presentation – VoIP security – myths & realities
Mass interception of entire populations is not only a reality, it is a secret new industry spanning 25 countries
It sounds like something out of Hollywood, but as of today, mass interception systems, built by Western intelligence contractors, including for ’political opponents’ are a reality.
WikiLeaks began releasing a database of hundreds of documents from as many as 160 intelligence contractors in the mass surveillance industry. Working with Bugged Planet and Privacy International, as well as media organizations form six countries – ARD in Germany, The Bureau of Investigative Journalism in the UK, The Hindu in India, L’Espresso in Italy, OWNI in France and the Washington Post in the U.S. Wikileaks is shining a light on this secret industry that has boomed since September 11, 2001 and is worth billions of dollars per year. WikiLeaks has released 287 documents today, but the Spy Files project is ongoing and further information will be released.
DOWNLOAD ORIGINAL FILE HERE
TP-SECRET from the FBI – Former Dow Research Scientist Sentenced to 60 Months in Prison for Stealing Trade Secrets and Perjury
WASHINGTON—A former research scientist was sentenced late yesterday to 60 months in prison for stealing trade secrets from Dow Chemical Company and selling them to companies in the People’s Republic of China, as well as committing perjury, announced Assistant Attorney General Lanny A. Breuer of the Justice Department’s Criminal Division and U.S. Attorney Donald J. Cazayoux Jr. for the Middle District of Louisiana.
U.S. District Court Judge James J. Brady also sentenced Wen Chyu Liu, aka David W. Liou, 75, of Houston, to two years of supervised release and ordered him to forfeit $600,000 and pay a $25,000 fine. A federal jury in Baton Rouge, La., convicted Liu on Feb. 7, 2011, of one count of conspiracy to commit trade secret theft and one count of perjury.
According to the evidence presented in court, Liu came to the United States from China for graduate work. He began working for Dow in 1965 and retired in 1992. Dow is a leading producer of the elastomeric polymer, chlorinated polyethylene (CPE). Dow’s Tyrin CPE is used in a number of applications worldwide, such as automotive and industrial hoses, electrical cable jackets and vinyl siding.
While employed at Dow, Liu worked as a research scientist at the company’s Plaquemine, La., facility on various aspects of the development and manufacture of Dow elastomers, including Tyrin CPE. Liu had access to trade secrets and confidential and proprietary information pertaining to Dow’s Tyrin CPE process and product technology. The evidence at trial established that Liu conspired with at least four current and former employees of Dow’s facilities in Plaquemine and Stade, Germany, who had worked in Tyrin CPE production, to misappropriate those trade secrets in an effort to develop and market CPE process design packages to various Chinese companies.
Liu traveled extensively throughout China to market the stolen information, and evidence introduced at trial showed that he paid current and former Dow employees for Dow’s CPE-related material and information. In one instance, Liu bribed a then-employee at the Plaquemine facility with $50,000 in cash to provide Dow’s process manual and other CPE-related information.
In addition, according to evidence presented at trial related to the perjury charge, Liu falsely denied during a deposition that he made arrangements for a co-conspirator to travel to China to meet with representatives of a Chinese company interested in designing and building a new CPE plant. Liu was under oath at the time of the deposition, which was part of a federal civil suit brought by Dow against Liu.
The case is being prosecuted by Assistant U.S. Attorney Corey R. Amundson, who serves as the Senior Deputy Criminal Chief, and former Assistant U.S. Attorney Ian F. Hipwell for the Middle District of Louisiana, as well as Trial Attorney Kendra Ervin of the Criminal Division’s Computer Crime and Intellectual Property Section. The case was investigated by the FBI’s New Orleans Division.
Julia Timoschenko ist politische Gefangene der KGB-Epigonen
“Meine Mutter hat ernsthafte gesundheitliche Probleme”, sagt Jewgenija Karr-Timoschenko, Tochter der inhaftierten ukrainischen Oppositionspolitikerin Julia Timoschenko. “Sie hat so große Schmerzen.”
Das Spinnennetz – Stasi-Agenten im Westen – der Film Teil 1
Das Spinnennetz – Stasi-Agenten im Westen – der Film Teil 2
Das Spinnennetz – Stasi-Agenten im Westen – der Film Teil 3
Buchtip – Das Spinnennetz, Stasi-Agenten im Westen, Die geheimen Akten der Rosenholz-Datei
Das Spinnennetz, Stasi-Agenten im Westen, Die geheimen Akten der Rosenholz-Datei
Heribert Schwan/ Helgard Heindrichs, München 2005
 Über ihre in der Auslandsspionage eingesetzten Spitzel hat die Stasi eine detaillierte Datei angelegt. Diese sogenannte Rosenholz-Datei, die unter mysteriösen Umständen der CIA in die Hände gefallen war, wurde den deutschen Behörden erst im Sommer 2003 zurückgegeben. Anhand dieser Daten schildern die Autoren jetzt erstmals das Ausmaß des Geheimnisverrats. Ob Auswärtiges Amt, Kanzleramt, Verteidigungsministerium oder die Parteizentralen von CDU, SPD, FDP und Grünen – die Schaltstellen der Macht waren von DDR-Agenten durchsetzt. Ein Agententhriller aus der Wirklichkeit, der in spektakulären Fallbeispielen die Arbeitsweise der Spione schildert
Über ihre in der Auslandsspionage eingesetzten Spitzel hat die Stasi eine detaillierte Datei angelegt. Diese sogenannte Rosenholz-Datei, die unter mysteriösen Umständen der CIA in die Hände gefallen war, wurde den deutschen Behörden erst im Sommer 2003 zurückgegeben. Anhand dieser Daten schildern die Autoren jetzt erstmals das Ausmaß des Geheimnisverrats. Ob Auswärtiges Amt, Kanzleramt, Verteidigungsministerium oder die Parteizentralen von CDU, SPD, FDP und Grünen – die Schaltstellen der Macht waren von DDR-Agenten durchsetzt. Ein Agententhriller aus der Wirklichkeit, der in spektakulären Fallbeispielen die Arbeitsweise der Spione schildert
TOP-SECRET from the CIA -Wartime Statues: Instruments of Soviet Control

Soviet military planning for conflict in Europe after World War II from the outset harnessed East European military capabilities to Soviet military purposes and assumed operational subordination of East European military formations to higher-level Soviet commands. A Polish command-staff exercise in 1950, for example, assumed subordination of a Polish Army (comprised of five divisions and other units) to a Soviet Maritime Front (tasked in the exercise with occupying Denmark).1 Following founding of the Warsaw Treaty Organization (Warsaw Pact) in May 1955, a supreme Warsaw Pact military command was established in Moscow, but this institution existed largely on paper until the 1960’s.
Document List (PDF Format)
1978_03_21 STATUTE ON THE COMBINED ARMED FORCES
1978_03_28 OFFICIAL REPORT
1978_06_27 STATUTE ON THE COMBINED FLEET
1978_09_06 DRAFT STATUTE ON THE WARSAW PACT
1979_05_11 REPORT ON THE WARSAW PACT COOPERATION
1979_07_18 LETTER FROM WARSAW PACT
1979_11_28 WARTIME STATUTE OF THE COMBINED FORCES
1980_02_07 WARTIME STATUTE
1980_02_08 STATUTE ON THE COMBINED FORCES OF THE WARSAW PACT
1980_02_21 TWELFTH SESSION
1980_02_25 DRAFT STATUTE ON WARSAW PACT COMBINED NAMED FORCES
1980_03_19 OFFICIAL RECORD AND OTHER DOCUMENTS
1980_04_11 FROM THE 12TH SESSION
1980_05_22 ROMANIAS PROPOSED REVISIONS
1980_07_25 RATIFICATION OF THE WARTIME STATUTE ON THE WARSAW PACT
1980_09_22 GIEREK DISCUSSIONS WITH MARSHAL KULIKOV
1980_10_08 MISCELLANEOUS
1982_01_01 THE UNIFIED WARTIME COMMAND
1983_06_28 MILITARY RELIABILITY OF THE SOVIET UNIONS WARSAW PACT ALLIES
1983_06_10 THE ORGANIZATION OF THE WARSAW PACT
1983_06_10 BACKGROUND INFORMATION
1983_10_01 THE SOVIET UNIONS CONTROL OF THE WARSAW PACT FORCES
DOWNLOAD ORIGINAL DOCUMENT HERE
TOP-SECRET – CIA-John and the White during the Killining of Osama Bin Laden – Photos
|
![[Image]](https://i0.wp.com/cryptome.org/0006/cia-john2/pict31.jpg) “This is a composite of several images of the President and his national security team during a series of meetings in the Situation Room of the White House discussing the mission against Osama bin Laden on Sunday, May 1. We put this together so in addition to the previous, now iconic image of this day, people might have a better sense of what it’s like in presidential meetings of historic significance.” (Official White House Photo by Pete Souza) “This is a composite of several images of the President and his national security team during a series of meetings in the Situation Room of the White House discussing the mission against Osama bin Laden on Sunday, May 1. We put this together so in addition to the previous, now iconic image of this day, people might have a better sense of what it’s like in presidential meetings of historic significance.” (Official White House Photo by Pete Souza) |
![[Image]](https://i0.wp.com/cryptome.org/0006/cia-john2/pict32.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/0006/cia-john2/pict33.jpg) |
The top composite photo was uploaded to Flickr by the White House on 30 December 2011. Except for the image at center the images have not be previously published. "CIA John" is indicated in red. CIA John was reported to be the head of the CIA bin Laden unit and has not been publicly named.
This photo is taken in a secure conference roomin the Situation Room complex. (As an aside, the brigadier general running the show from a laptop, rather than a low-ranked technician from remote console, is highly unusual, and probably indicates the high-level security measures protecting the bin Laden operation. This is also suggested by holding the show in a small conference room rather than the commodious large confedrence room frequently shown in public photographs.)]![[Image]](https://i0.wp.com/cryptome.org/0004/cia-john/pict26.jpg) President Barack Obama and Vice President Joe Biden, along with members of the national security team, receive an update on the mission against Osama bin Laden in the Situation Room of the White House, May 1, 2011. (Official White House Photo by Pete Souza) President Barack Obama and Vice President Joe Biden, along with members of the national security team, receive an update on the mission against Osama bin Laden in the Situation Room of the White House, May 1, 2011. (Official White House Photo by Pete Souza)
[Note the unusually tall man at rear with tie pattern which matches the photo above. This photo is taken in the large conference room of the Situation Room complex.] President Barack Obama talks with members of the national security team at the conclusion of one in a series of meetings discussing the mission against Osama bin Laden, in the Situation Room of the White House, May 1, 2011. Gen. James Cartwright, Vice Chairman of the Joint Chiefs of Staff, is seen on the screen. (Official White House Photo by Pete Souza)
|
[Continuing the AP story] The Associated Press has agreed to the CIA’s request not to publish his full name and withhold certain biographical details so that he would not become a target for retribution. Call him John, his middle name. …
Two days after bin Laden’s death, John accompanied Panetta to Capitol Hill. The Senate Intelligence Committee wanted a full briefing on the successful mission. At one point in the private session, Panetta turned to the man whose counterterrorism resume spanned four CIA directors.

[Note unusually tall man at upper left with a tie not unlike the previous.] In this May 3, 2011 file photo, CIA Director Leon Panetta, right, leaves after briefing members of Congress on Capitol Hill in Washington. Alex Brandon, AP
![[Image]](https://i0.wp.com/cryptome.org/0004/cia-john/pict28.jpg)
DIE STASI-Killer in Westdeutschland – Ein Killer packt aus
Bericht eines Ex-Mitgliedes des Killerkommandos der DKP, ausgebildet in der DDR
TOP-SECRET – (U//FOUO) Open Source Center Cuban Blogs Serve as Forum for Government Critics

A small but growing number of bloggers who appear to be writing from Cuba are using externally hosted websites to voice dissent and developing inventive ways to circumvent government restrictions on Internet access that limit their freedom to post. While the blogs’ emergence has coincided with the move toward more openness in state media about discussing social and economic problems in the past two years, the bloggers go well beyond that limited criticism by blaming the ruling system rather than individuals or external pressure. The government thus far largely has acted indirectly against the bloggers, warning about the dangers of the Internet and reportedly blocking access to a host website. The bloggers tend to express pessimism about prospects for change under Raul Castro, but they currently are not promoting a specific political agenda or calling for any organized movement against the government. Although readership is mostly international, their on-island audience — including possible imitators — is likely to increase if access to information technology becomes more widespread. See the appendices for details on Internet access in Cuba and the individual blogs discussed.
Cuba’s independent blogs have increased in recent years, providing a forum to voice discontent with current conditions and government policies that goes further than the still-limited discussion of problems in state media.
- The number of blogs written by private Cuban citizens began increasing significantly in late 2006 and has gained momentum since. Of the 11 most prominent independent blogs, one began in 2005, three in 2006, three in 2007, and four since the beginning of 2008.
- Some readers have questioned the bloggers’ credibility, charging them with being either agents of the Cuban Government or Miami-based Cubans. The personal nature of the postings and the absence of an explicit political agenda, however, bolster their claims to be private citizens.
- The increase in independent bloggers parallels a move by state media toward more openness about problems on the island, which began in late 2006 and was further encouraged by Raul Castro’s call for more critical discussion about conditions in Cuba (Cubavision, 26 July 2007, 24 September 2007).
The bloggers demonstrate technological savvy in overcoming the Internet access restrictions to create their blogs, but they appear to have difficulty updating them regularly.
- While she has not disclosed details in her blog, Generacion Y’s Yoani Sanchez, Cuba’s most prominent blogger, has described in interviews with foreign outlets how she writes blog entries, saves them on a flash memory drive, and uploads them at an Internet cafe (The New York Times, 6 March; The Wall Street Journal, 22 December 2007).
- The apparently short-lived Potro Salvaje — whose title “Wild Colt” appears to mock Communications Minister Valdes’s warning in February 2007 that the Internet was a “wild colt” that needed to be controlled (www.cubaminrex.cu) — began on 11 March to provide explicit instructions to on-island Internet users about methods to bypass restrictions. The blog’s most recent post on 8 April highlighted the importance of the flash drive to transport data from one computer to another on the island.
- Although many of the blogs are updated frequently, maintenance can be inconsistent — several have been abandoned or moved without notice. Two of the 11 blogs have not been updated since February 2008, despite having had regular posts prior.
…
The Cuban Government appears to have taken an indirect approach to limiting the influence of independent bloggers. It has warned of the dangers of the Internet, and bloggers charge it with monitoring the contents of their blogs and making it difficult to access the blogs.
- In addition to calling the Internet a “wild colt,” Valdes said it was “a tool for global extermination” (www.cubaminrex.cu). Youth daily Juventud Rebelde has warned that portable storage devices such as flash drives increase vulnerability to computer viruses (17 April), and Fidel Castro asserted in a letter to the National Union of Writers and Artists (UNEAC) Conference that the Internet and other information technologies are
invasions of privacy (Granma, 2 April).- In March, several of the blogs that share the Frankfurt-based Consenso Desde Cuba host website claimed the government was obstructing on-island access. Potro Salvaje charged on 26 March that the site had been filtered to slow loading “to a maximum,” making the page impossible to view by most on-island Internet users since 20 March.
DOWNLOAD THE ORIGINAL FILE HERE
TOP-SECRET – (U//FOUO) Open Source Center Cuban Independent Blogging, Political Activism Grows
Cuban Independent Blogging Grows; Political Activism Varies
FEA20090619862999 – OSC Feature – Cuba — OSC Media Aid 18 Jun 09
A small group of independent bloggers, including Yoani Sanchez, Reinaldo Escobar, and Claudia Cadelo, has promoted blogging as a vehicle for free expression and information sharing to circumvent Cuba’s tightly controlled media environment, and to communicate with the outside world. They have become increasingly confrontational toward the government, demanding greater civil liberties and criticizing many government policies . Other on-island bloggers — many of them journalists or university professors and students — have called on the government to be more open and allow greater access to outside information, but they generally have avoided direct criticism of it. The government response has been limited to date, but the increasingly antigovernment line of some bloggers is likely to test the limits of government tolerance.
Yoani Sanchez, Voces Cubanas
Sanchez, who has been at the forefront of promoting and coordinating Cubans’ use of blogs as a forum for free expression and as a way to criticize government policy, helped create the Voces Cubanas (www.vocescubanas.com) platform for on-island bloggers in October 2008. The site, which is registered in the United States and hosted on a Spanish server, currently has 13 blogs, all of which express some criticism of the Cuban Government.[ 1] [a]
Sanchez leads weekly meetings to discuss blogging in Cuba. During one meeting, participants discussed including their blogs on Facebook and Twitter to give “friends and other interested people” greater and faster access (Itineraro Blogger, 11 April).[ 2] She also announced on her Generacion Y blog that she and a group of friends were using cell phone text messages to circulate international news (29 May).[ 3]
She has used her international prominence — her blog is hosted on foreign news sites and she is regularly interviewed by foreign reporters — to urge international support for on-island bloggers. She recently called on readers to link websites to the on-island blogs, send the bloggers computer parts, and buy Internet access cards for them (Generacion Y, 29 May). [ 4]
Sanchez was among the first to publicize an apparent new restriction that barred hotels from allowing Cubans to buy Internet access, posting a YouTube video of an employee at one Havana hotel explaining the ban to her husband, fellow blogger Reinaldo Escobar. The ban was minimally enforced at the outset, however, and now appears to have been dropped altogether, a development Sanchez portrayed as a victory for Cuba’s bloggers (Generacion Y, 23 April).[ 5] [b]
Sanchez also has taken an increasingly active role in protests and other actions to press demands for freedom of expression and travel and greater access to the Internet.
She took the stage to demand Internet freedom during the government-sponsored Havana Biennial art festival, and she participated in an unauthorized presentation at the Havana book fair (Generacion Y, 30 March, 17 February).[ 6] [ 7]
Sanchez — who has been denied permission to travel to receive German and Spanish awards — publicized plans for a 1 May protest demanding more freedom to travel and later reported that it was a success despite limited participation in Havana (Generacion Y, 23 April, 2 May).[ 8] [ 9] She also was part of a group that accompanied dissident Edgar Lopez to the immigration office in an attempt to pressure the government to allow him to travel abroad (Generacion Y, 28 April).[ 10]
Internet, Blogs in Cuba Only about 2.1% of Cubans have access to the Internet itself, according to a recent Freedom House report, which rated Cuba the least free of 15 countries surveyed in terms of Internet freedom (www.freedomhouse.org). Internet World Stats (www.internetworldstats.com) cites both the 2.1% figure as well as 11.5% for Cuba’s Internet penetration rate; the higher number is attributed to the International Telecommunications Union, which may be relying on government statistics that include those who only have access to the Cuban intranet. [ 11]
The number of on-island Cuban blogs, however, continues to increase. Of 66 blogs claiming to originate on the island that OSC surveyed in early June 2009, 46 had been created since April 2008 — including 14 thus far in 2009 — compared to 20 created prior to April 2008.
All of the bloggers featured on the Voces Cubanas platform have been critical of the regime, and Octavo Cerco author Claudia Cadelo has been the most forceful in demanding wholesale political change.
Cadelo wrote in Octavo Cerco on 2 June that political change should include the “resignation of the president of the Councils of State and Minister and of the entire National Assembly,” multiparty elections, and overhaul of the security forces.[ 12] She said on 4 May that she wanted a “‘change of government’ from top to bottom.”[ 13]
Miriam Celaya, author of Sin EVAsion, called the Central Committee an “old machine” that could not be fixed (9 June).[ 14] She also complained of “ideology fatigue” and said that Cuban leaders were preparing to “blame” citizens for economic problems of their own making (Sin EVAsion, 7 June, 26 May).[ 15] [ 16]
Veritas blogger Eugenio Leal posted the results of a survey he conducted of 487 Cubans, 51% of whom said that a system change was necessary to improve the economy and criticized the government because it “manipulates everything” (3 June, 7 May).[ 17] [ 18] Desde Aqui author Reinaldo Escobar claimed that the Internet’s ability to promote free expression did not “conform to the political will of the government,” and he criticized its response to US policy initiatives (26 May, 21 April).[ 19] [ 20] [c]
Sanchez and like-minded bloggers have become bolder in criticizing the government since they first launched their blogs. Their posts initially focused more on their personal experiences and dealt only indirectly with politics. Most early bloggers wrote under pseudonyms; Miriam Celaya later dropped hers and most new bloggers on Voces Cubana write under what they say are their real names.
Bloggers Cuba
Another 15 blogs, maintained by Cubans who mostly claim to be journalists or information technology professors and students, use a separate off-island platform, Bloggers Cuba, to urge greater access to the Internet and more government openness. The website (www.bloggerscuba.com) is registered in Panama and hosted on a server in the United States.
The earliest post on the site, dated 2 June 2008, announced that the platform is designed to unite on-island bloggers and promote the spread of “social networks.”[ 21] It sought to expand readership to those lacking regular Internet access by distributing a hardcopy compilation of all posts in February earlier this year, but it has not repeated this since then.[ 22]
Elaine Diaz, who claims she is a journalist, posted an article on her La Polemica Digital blog and on the Bloggers Cuba platform stating that she wanted “political e-participation” in Cuba modeled after President Obama’s campaign (21 May).[ 23]
A post by Alejandro Perez Malagon, a self-described engineering professor at a Havana university, called for a blog forum on the Cuban intranet that would be freely available to all, along with greater Internet access (Artilugios.cu, 7 April).[ 24] Malagon earlier said Vice Information Minister Boris Moreno’s statements about the planned fiber optic cable between Venezuela and Cuba were “promising” because they indicated that the government would not seek to limit Internet access once the cable was in place (6 February). [ 25]
Boris Leonardo Caro, who appears to post only to the Bloggers Cuba site and identifies himself as a journalist, wrote on 10 June that the number of Cubans on Twitter was increasing, and David Chapet, a French expatriate claiming to live in Cuba, posted a list of Cuba-related groups on Facebook (Journal de Cuba, 29 January).[ 26] [ 27] Chapet, however, registered the Bloggers Cuba site with a business address in Panama, according to whois.com.
Bloggers Cuba authors have not openly criticized the Cuban Government, although they have occasionally complained about conditions on the island. Most entries are apolitical and they appear to be operating with some degree of government sanction.
Caro wrote on 22 May that state-run media outlets treated the public “like children,” but he went on to assert that he did not mean to criticize them.[ 28] Bubusopia blogger Rogelio Diaz Moreno on 30 January criticized the dual currency system.[ 29]
Most of the entries on the Bloggers Cuba platform discuss sports, film, music, and literature as well as state-sponsored cultural events. Discussion of current events usually takes a factual or neutral tone.[ 30] [ 31] [ 32] [ 33] [ 34] [ 35] [ 36] [ 37]
The bloggers report holding meetings to discuss on-island blogging and access to the Internet, with the most recent held 1 June. Their first meeting was held 16 September 2008 at a state-run computer center in Havana (Bloggers Cuba).[ 38] [ 39] Bloggers, Web-Based Software, Embargo Bloggers at both Voces Cubana and Bloggers Cuba have criticized the United States over restrictions on Cubans’ access to web-based software because of the embargo.
Sanchez wrote on 30 May that enforcement of restrictions on the use of MSN Messenger was a “blow” to Internet users in Cuba and that it contributed to censorship in Cuba (Generacion Y).[ 40] Cadelo likewise complained that a new provision in the Rights and Responsibility statement on Facebook could limit access and was a “contradiction” that “facilitated” the government’s work (Octavo Cerco, 12, 10 June).[ 41] [ 42]
Several Bloggers Cuba posts have complained about Google services that are unavailable on the island, linking the absence to the embargo (1 June, 4 May, 21 April, 28 January).[ 43] [ 44] [ 45] [ 46]
Government Response
The government has avoided taking a heavy-handed approach against the independent bloggers, instead promoting its own blogging platform that, unlike the others, is accessible on the Cuban intranet. While it apparently dropped the ban on allowing Cubans to buy Internet access at hotels, state media have delivered a few relatively low-key warnings, particularly to Sanchez.
The Cuban Journalists Blogs site at blogcip.cu appears intended to provide a progovernment counter to independent bloggers. The earliest post on the platform is dated 14 November 2006, but the site has seen a significant increase in use recently, with near daily posts in May and June after monthly totals of only 6 to 10 posts earlier this year. The conditions for use include a provision that participants will not publish “counterrevolutionary” materials.[ 47]
A commentary on government website CubaDebate denounced “cyberdissidents” and accused Sanchez of being linked to the United States (6 May).[ 48] The cultural weekly La Jiribilla denounced Sanchez’s speech during the Biennial (13 April).[ 49]
[a] For more information on Sanchez and Cuban bloggers, see the 16 December 2008 OSC Analysis, Cuban Bloggers, Dissidents Undeterred by Crackdowns (LAF20081216499006), the 24 July 2008 OSC Analysis, Cuba — Blogger Steps Up Criticism Amid Continued Obstacles (LAF20080724035001), and the 9 May 2008 OSC Media Aid, Blogs Increasingly Serve as Forum for Government Critics in Cuba (LAF20080509465001).
[b] For more information about the measures at Cuban hotels, see the 15 May OSC Report, Cuba — New Internet Restriction Barely Enforced, Has Little Impact (LAP20090515380005).
[c] For information about the Cuban Government’s response to shifts in US policy toward Cuba, see the 15 April OSC Analysis, Cuba — Fidel Castro Welcomes US Move While Maintaining Hard Line (LAF20090415471001).
[ 1] [Open Source (Not OSC) | | http://vocescubanas.com/ | 28 January 2009 | | Voces Cubanas — plataforma blogger desde cuba | | | (U) | Havana Voces Cubanas in Spanish — a blogging platform for Cubans living in Cuba sponsored by Yoani Sanchez.]
[ 2] [Open Source (Not OSC) | | http://itinerarioblogger.com/ | 11 April 2009 | | Nuevas incursiones del Itinerario | | | (U) | Havana Itinerario Blogger in Spanish – blog of the ‘Bloggers Agenda’ initiated by well-known on-island blogger Yoani Sanchez]
[ 3] [OSC | | LAP20090429201001 | 29 April 2009 | | Cuban Blogger: People Share Unpublished News Using Cellular Telephones | | (U) | (U) | [Description of Source: Havana Generacion Y in Spanish — Blog featuring commentaries on the social and political situation in Cuba; author identified as Havana journalist Yoani Sanchez; host website registered in Frankfurt, Germany; URL: http://www.desdecuba.com/generaciony/%5D%5D
[ 4] [Open Source (Not OSC) | | http://www.desdecuba.com/generaciony/?p=1206 | 29 May 2009 | | ¿Como ayudar? | | | (U) | ]
[ 5] [Open Source (Not OSC) | | http://www.desdecuba.com/generaciony/?p=1001 | 23 April 2009 | | “Sentada” blogger | | | (U) | ]
[ 6] [OSC | | LAP20090331201001 | 30 March 2009 | | Cuba: Bloggers, Youths Demand ‘Freedom’ at Havana Biennial | | (U) | (U) | [Description of Source: Havana Generacion Y in Spanish — Blog featuring commentaries on the social and political situation in Cuba; author identified as Havana journalist Yoani Sanchez; host website registered in Frankfurt, Germany; URL: http://www.desdecuba.com/generaciony/%5D%5D
[ 7] [OSC | | LAP20090217201001 | 17 February 2009 | | Cuban Blogger: Banned Author Presents Book Despite State Security Threats | | (U) | (U) | Havana Generacion Y in Spanish — Cuban blog featuring commentaries on the social and political situation in Cuba; author identified as Havana journalist Yoani Sanchez; host website registered in Frankfurt, Germany. URL: http://www.desdecuba.com/generaciony/%5D
[ 8] [OSC | | LAP20090424201001 | 23 April 2009 | | Cuban Blogger Announces 1 May Protest Using Kitchen Utensils | | (U) | (U) | [Description of Source: Havana Generacion Y in Spanish — Blog featuring commentaries on the social and political situation in Cuba; author identified as Havana journalist Yoani Sanchez; host website registered in Frankfurt, Germany; URL: http://www.desdecuba.com/generaciony/%5D%5D
[ 9] [OSC | | LAP20090503201002 | 2 May 2009 | | Cuban Blogger: Protest Garners Scant Reaction, Considered Success Nevertheless | | (U) | (U) | [Description of Source: Havana Generacion Y in Spanish — Blog featuring commentaries on the social and political situation in Cuba; author identified as Havana journalist Yoani Sanchez; host website registered in Frankfurt, Germany; URL: http://www.desdecuba.com/generaciony/%5D%5D
[ 10] [OSC | | LAP20090428201001 | 28 April 2009 | | Cuban Blogger Demands Travel Permit Card’s Derogation | | (U) | (U) | [Description of Source: Havana Generacion Y in Spanish — Blog featuring commentaries on the social and political situation in Cuba; author identified as Havana journalist Yoani Sanchez; host website registered in Frankfurt, Germany; URL: http://www.desdecuba.com/generaciony/%5D%5D
[ 11] [Open Source (Not OSC) | | http://freedomhouse.org/template.cfm?page=384&key=199&parent=19&repo rt=79 | 30 March 2009 | | Freedom on the Net: A Global Assessment of Internet and Digital Media | | | (U) | ]
[ 12] [Open Source (Not OSC) | | http://octavocerco.blogspot.com/2009/06/demandas-y-peticiones.html | 2 June 2009 | | Demandas y Peticiones | | | (U) | ]
[ 13] [Open Source (Not OSC) | | http://octavocerco.blogspot.com/2009/05/un-cazuelazo-personal.html | 2 May 2009 | | Un cazuelazo personal | | | (U) | ]
[ 14] [Open Source (Not OSC) | | http://vocescubanas.com/sin_evasion/2009/06/09/desnudos-sobre-el-tejado/ | 9 June 2009 | | Desnudos sobre el tejado | | | (U) | ]
[ 15] [Open Source (Not OSC) | | http://vocescubanas.com/sin_evasion/2009/06/07/ideologia-descascarada/ | 7 June 2009 | | Ideologia descascarada | | | (U) | ]
[ 16] [Open Source (Not OSC) | | http://vocescubanas.com/sin_evasion/2009/05/26/%E2%80%9Cperiodo-especial-mediati co%E2%80%9D/”Periodo Especial Mediatico” | 26 May 2009 | | “Periodo Especial Mediatico” | | | (U) | ]
[ 17] [Open Source (Not OSC) | | http://vocescubanas.com/veritas/2009/06/03/encuesta-2-el-sistema-y-las-aspiracio nes-del-ciudadano-en-cuba/ | 3 June 2009 | | Encuesta # 2: El sistema y las aspiraciones del ciudadano en Cuba | | | (U) | ]
[ 18] [Open Source (Not OSC) | | http://vocescubanas.com/veritas/2009/05/07/que-lo-sepan/ | 7 May 2009 | | Que lo sepan …. | | | (U) | ]
[ 19] [Open Source (Not OSC) | | http://vocescubanas.com/desdeaqui/2009/05/26/como-diria-engels/ | 26 May 2009 | | Como diria Engels | | | (U) | ]
[ 20] [Open Source (Not OSC) | | http://vocescubanas.com/desdeaqui/2009/04/21/la-agenda-de-discusiones/ | 21 April 2009 | | La agenda de discusiones | | | (U) | ]
[ 21] [Open Source (Not OSC) | | http://www.bloggerscuba.com/post/hola-mundo-de-bloggers-cuba/ | 2 June 2008 | Hola mundo! De Bloggers Cuba | | | (U) | ]
[ 22] [Open Source (Not OSC) | | http://www.bloggerscuba.com/post/intro-resumen-de-bloggers-cuba-de-febrero-2009/ | 18 June 2009 | | Intro – Resumen de Bloggers Cuba de Febrero 2009 | | | (U) | ]
[ 23] [Open Source (Not OSC) | | http://www.bloggerscuba.com/post/participacion-politica-en-la-red-cubana-salto-h acia-el-futuro-i/ | 21 May 2009 | | Participacion política en la red cubana: salto hacia el futuro (I) | | | (U) | ]
[ 24] [Open Source (Not OSC) | | http://www.bloggerscuba.com/post/la-web-dos-punto-cero-en-cuba/ | 7 April 2009 | | La web dos punto cero en Cuba | | | (U) | ]
[ 25] [Open Source (Not OSC) | | http://www.bloggerscuba.com/post/cuba-e-internet-en-el-2011/ | 6 February 2009 | | Cuba e Internet en el 2011 | | | (U) | ]
[ 26] [Open Source (Not OSC) | | http://www.bloggerscuba.com/post/aumenta-comunidad-de-twitteros-en-cuba/ | 10 June 2009 | | Aumenta comunidad de Twitteros en Cuba | | | (U) | ]
[ 27] [Open Source (Not OSC) | | http://www.bloggerscuba.com/post/cuba-cubanos-en-facebook/ | 29 January 2009 | | Cuba y Cubanos en Facebook | | | (U) | ]
[ 28] [Open Source (Not OSC) | | http://www.bloggerscuba.com/post/economia-cuando-el-rio-suena/ | 22 May 2009 | | ECONOMIA: Cuando el rio suena… | | | (U) | ]
[ 29] [Open Source (Not OSC) | | http://www.bloggerscuba.com/post/papelitos-de-colores/ | 30 January 2009 | | Papelitos de colores | | | (U) | ]
[ 30] [Open Source (Not OSC) | | Veneno: el video | 11 June 2009 | | http://www.bloggerscuba.com/post/veneno-video-escape/ | | | (U) | ]
[ 31] [Open Source (Not OSC) | | http://www.bloggerscuba.com/post/habana-campeon/ | 5 June 2009 | | Habana Campeon | | | (U) | ]
[ 32] [Open Source (Not OSC) | | http://www.bloggerscuba.com/post/ya-esta-el-capablanca-andando/ | 10 June 2009 | | Ya esta el Capablanca andando | | | (U) | ]
[ 33] [Open Source (Not OSC) | | http://www.bloggerscuba.com/post/cine-santiago-alvarez-entre-nosotros/ | 21 May 2009 | | CINE: Santiago Alvarez entre nosotros | | | (U) | ]
[ 34] [Open Source (Not OSC) | | http://www.bloggerscuba.com/post/diversidad-sexual-el-arcoiris-de-gala/ | 18 May 2009 | | DIVERSIDAD SEXUAL: El arcoiris de gala | | | (U) | ]
[ 35] [Open Source (Not OSC) | | http://www.bloggerscuba.com/post/modificaciones-al-ingreso-de-la-educacion-super ior-en-cuba/ | 10 June 2009 | | Modificaciones al ingreso de la Educacion Superior en Cuba | | | (U) | ]
[ 36] [OSC | | http://www.bloggerscuba.com/post/tiempo-nieve-en-la-habana/ | 6 February 2009 | | TIEMPO: Nieve en La Habana! | | | (U) | ]
[ 37] [Open Source (Not OSC) | | http://www.bloggerscuba.com/post/cuba-ultimo-cambio/ | 5 June 2009 | | Cuba: Ultimo cambio | | | (U) | ]
[ 38] [Open Source (Not OSC) | | http://www.bloggerscuba.com/post/bloggers-cuba-la-pandilla-completa-y-algo-mas/ | 1 June 2009 | | Bloggers Cuba. La pandilla completa y algo mas | | | (U) | ]
[ 39] [Open Source (Not OSC) | | http://www.bloggerscuba.com/post/i-encuentro-de-bloggers-cubanos-bloggers-por-cuenta-propia-la-habana-septiembre-08/ | 16 September 2008 | | I Encuentro de Bloggers Cubanos “Bloggers por Cuenta Propia” La Habana, Septiembre’08 | | | (U) | ]
[ 40] [OSC | | LAP20090530201001 | 30 May 2009 | | Cuban Blogger: Microsoft Ban Represents ‘Blow’ to Cuba’s ‘Web Renegades’ | | (U) | (U) | [Description of Source: Havana Generacion Y in Spanish — Blog featuring commentaries on the social and political situation in Cuba; author identified as Havana journalist Yoani Sanchez; host website registered in Frankfurt, Germany; URL: http://www.desdecuba.com/generaciony/%5D%5D
[ 41] [Open Source (Not OSC) | | http://octavocerco.blogspot.com/2009/06/la-inaccesible-red-entrevista-un-cubano. html | 12 June 2009 | | La estrecha RED (entrevista a un cubano en China) | | | (U) | ]
[ 42] [Open Source (Not OSC) | | http://octavocerco.blogspot.com/2009/06/la-estrecha-red.html | 10 June 2009 | | La estrecha RED | | | (U) | ]
[ 43] [Open Source (Not OSC) | | http://www.bloggerscuba.com/post/cuba-vs-google-rompeolas/ | 1 June 2009 | | Cuba vs Google: Rompeolas | | | (U) | ]
[ 44] [Open Source (Not OSC) | | http://www.bloggerscuba.com/post/google-cuba-me-cago-en-el-bloqueo/ | 4 May 2009 | | Google – Cuba. Me cago en el Bloqueo | | | (U) | ]
[ 45] [Open Source (Not OSC) | | http://www.bloggerscuba.com/post/internet-my-dear-google-again/ | 21 April 2009 | | INTERNET: My dear Google… again ! | | | (U) | ]
[ 46] [Open Source (Not OSC) | | http://www.bloggerscuba.com/post/hasta-cuando-esto/ | 28 January 2009 | | Hasta cuando esto? | | | (U) | ]
[ 47] [Open Source (Not OSC) | | http://blogcip.cu/registro/ | 12 June 2009 | | Datos para registrarse | | | (U) | ]
[ 48] [Open Source (Not OSC) | | http://www.cubadebate.cu/index.php?tpl=design/especiales.tpl.html&newsid_obj_id=14980 | 5 June 2009 | | Cibercomando y Ciberdisidentes, mas de lo mismo | | | (U) | ]
[ 49] [OSC | | LAP20090413361006 | 13 April 2009 | | Cuba: Cultural Magazine Decries ‘Mercenaries’ Demand’ for US Government Funds | | (U) | (U) | Havana La Jiribilla in Spanish — Weekly cultural magazine sponsored by Juventud Rebelde Newspaper; http://www.lajiribilla.cu/%5D
[This item was originally filed as LAF20090618498001]
Report – Congress Pressing DHS For Greater Monitoring of Social Media
Leaders of a congressional subcommittee are urging the Department of Homeland Security to extensively monitor social media sites like Twitter and Facebook to detect “current or emerging threats.”The top Republican and Democrat on a House counter-terrorism subcommittee last month sent a letter to Homeland Security’s intelligence chief encouraging department analysts to pore over huge streams of social media traffic.
Representatives Patrick Meehan and Jackie Speier said in the letter to Caryn Wagner, undersecretary of homeland security for intelligence and analysis, that they “believe it would be advantageous for DHS and the broader Intelligence Community to carefully parse the massive streams of data from various social media outlets to identify current or emerging threats to our homeland security.”
Meehan, a Republican, is chairman of the House Homeland Security Committee’s counter-terrorism and intelligence subcommittee. Speier is the panel’s ranking Democrat.
The two lawmakers said such monitoring raises “privacy and civil liberties concerns” and suggested that the department issue guidelines which balance citizens’ rights with the ability of analysts to identify threats.
Earlier this week, Homeland Security’s National Operations Center published a long list of websites which they monitor for “situational awareness.”
In an email to Reuters, Meehan said a hearing he had convened in December had “examined the evolving terrorist use of social media and effective intelligence and law enforcement responses.”
Meehan added: “If terrorists are operating in Pakistan or communicating through social media sites like Facebook, we need to remain vigilant. Yet there are important civil liberties questions involving U.S. government monitoring of social media and Americans’ Internet traffic. We are seeking answers on the Department’s guidelines and procedures to ensure Americans’ civil liberties are safeguarded.”
Jihadi Use of Social Media Examined by Chairman Meehan at Subcommittee Hearing (meehan.house.gov):
“For years, terrorists have communicated online, sharing al Qaeda propaganda or writing in online forums dedicated entirely to the prospect of Islamist terrorism. But they have recently evolved with technological changes, utilizing social media sites such as Facebook and YouTube to enhance their capabilities. In the same places the average person posts photos and communicates with friends and family, our enemies distribute videos praising Osama bin Laden.“Terrorists also disseminate diatribes glorifying the murder of innocents, and even make connections with each other internationally to plot attacks. In the case of al Awlaki, jihadists live on virtually after they’ve been physically removed from the battlefield.
“Prior to coming to Congress, I served as the United States Attorney for the Eastern District of Pennsylvania. After my tenure as US Attorney ended, a local woman named Colleen LaRose was arrested on her return to the United States as part of a terror plot that targeted a Swedish cartoonist.
“LaRose would later become known to the world as “Jihad Jane.” However, what is less well known to the world was she received that moniker because it was the name she employed online, where she became a committed jihadi.
“This is notable because she did not receive formal training in a terrorist camp in Afghanistan or Pakistan, but in her own apartment in Montgomery County, Pennsylvania. She enthusiastically posted and commented on YouTube videos supporting al Qaeda and their allies, but her enthusiasm for jihad went beyond watching videos and offering moral support. She made contacts online with other jihadis, solicited funding, and orchestrated an actual terror plot.
“Her case is a shocking example of how easy it can be to find jihadi content online and make operational connections with others who want to commit violent acts of terrorism. The Jihad Jane case is not the only one. Only a few weeks ago, Jose Pimentel was arrested for preparing bombs to use in attacking targets in New York City. Before his arrest Mr. Pimentel had been active online. He ran a blog, held two YouTube accounts, and operated a Facebook profile, all dedicated to jihadi propaganda.
“In a case that illustrates terrorist recruitment in the homeland via social networking, in December of 2009 a group of five men from the Washington, DC area were arrested in Pakistan for attempting to join militants fighting along the border with Afghanistan. Later known as “The Virginia Five,” they were reportedly contacted by a Taliban recruiter through YouTube after one member of the group praised an online video showing attacks on American troops.
“These examples highlight the incredible challenge posed by terrorists engaging online. The Internet was designed to ease communication, and it must stay that way. However, we cannot ignore the reality that we have been unable to effectively prevent jihadi videos and messages from being spread on popular social media websites like YouTube and Facebook. I have called this hearing today to learn more about what has been done and what must be done moving forward.
“Another central issue I hope to learn more about is is whether or not social media websites can become useful sources of intelligence in our fight against terrorism. Online movements are traceable – nowhere more so than on social networks, which are designed to make connections among people easy.
“I believe the intelligence and law enforcement communities can use this open information to combat terrorism and other crimes. However, it is essential that civil liberties and individual privacy be protected. I am encouraged by recent remarks made by Under Secretary for the Office of Intelligence and Analysis, Caryn Wagner, when she indicated that the Department of Homeland Security will be working to enhance its ability to monitor social media for threats against the homeland, and I look forward to learning more about that as she develops those procedures.”
Video – Topless in Vatican: FEMEN strips against ‘Catholic witch-hunt’
Three demonstrators from the Ukrainian women’s rights movement FEMEN staged a protest at the Vatican on Sunday, shortly after the Pope’s regular Sunday address. One of them sneaked into St. Peter’s square and took off her coat revealing a transparent blouse. The demonstrator held a sign saying ‘Freedom for Women’ and shouted “Libere siamo noi” (italian for “We are free”). She was stopped as she started pulling her clothes off by police and quickly led along with her two partners to a nearby police station where the protesters are being questioned.
FEMEN is Ukrainian protest group based in Kiev and was founded in 2008. The organisation became internationally known for organising topless protests against sex tourism, international marriage agencies, sexism and other social, national and international issues.
Buchtip- Angela Schmole Hauptabteilung VIII: Beobachtung, Ermittlung, Durchsuchung, Festnahme Unter Mitarbeit von Tilman Peters
Angela Schmole: Hauptabteilung VIII. Beobachtung, Ermittlung, Durchsuchung,Festnahme (MfS-Handbuch). Hg. BStU. Berlin 2011.
siehe hier
Thomas Auerbach Liquidierung = Mord? Zur vieldeutigen Semantik des Begriffs in den MfS-Unterlagen
DER DOWNLOAD LINK ZU DEM ARTIKEL IST HIER
CRYPTOME – FBI OpenBSD Backdoors and RSA Cipher Vulnerability
From: Gregory Perry <Gregory.Perry[at]govirtual.tv>
Subject: Follow up to OpenBSD Crypto Framework Backdoors Thread
Date: Thu, 12 Jan 2012 01:57:39 +0000
Here is a follow up to the FBI / OpenBSD / OCF encryption backdoors thread as promised. We had a three alarm fire at our house over the Christmas holidays and I am just now getting plugged back in.
1) At ~1997 or thereabouts, the FBI approached a fellow by the name of Lew Jenkins, the Chairman and CEO of Premenos Technology Corp., about their development of an Electronic Data Interchange (EDI) software suite used for corp-to-corp EDI transactions called “Templar”.
2) At that point in time encryption technology (especially public key encryption algorithms) were still considered munitions by the United States government, and presumably the FBI was interested in Premenos research related to key escrow and session recovery of RSA-encrypted communication sessions.
3) A portion of Mr. Jenkins’ research was conducted with a Ecuadorian national that provided Premenos with at least one mathematical vulnerability in the RSA encryption algorithm related to changing the base numbering system of the resulting RSA modulus after a block of plaintext had been encrypted. Mr. Jenkins and Premenos also maintained extensive contacts with the Crown of England, including prominent English Lords involved with Internet communications technology.
4) One of the investors in Premenos was a fellow by the name of Ross Pirasteh, who was either the Prime Minister of Finance for the Shah of Iran or actually the Shah of Iran himself. As the story goes, Ross and his family were snuck out of Iran rolled up in Persian rugs just prior to or during the 1979 revolution headed by Ayatollah Ruhollah Khomeini; once Ross and his family emigrated to the United States, the FBI gave him and his family new identities for obvious reasons. I initially met Ross in the early 90s from a GPS-based automobile tracking project (nonmilitary-grade GPS), and in 1995 I gave him some information about Templar and he became an investor in Premenos shortly thereafter.
5) In 1999 I co-founded a computer security engineering firm with Ken Ammon and Jerry Harold, Network Security Technologies Inc. (NETSEC). Ken was the CEO, Jerry was the COO, I was the CTO. Ken and Jerry were high rank and file ex-NSA InfoSec employees and had extensive contacts in the DoD and federal government; we offered managed network security, penetration testing, vulnerability analysis, and reverse engineering services to the federal government and private sector.
6) NETSEC’s first investor was Ross Pirasteh, he provided a bridge loan to get the company started. The first friends family fools round of Preferred A investment was via a Boca Raton angel syndicate that I believe Ross had introduced to Ken and his wife, but I was not privy to those details.
7) Our first intended product was an ATM-based high speed embedded network security appliance that was to be placed on customer networks for remote network protocol analysis, surveillance, and intrusion detection and prevention. Each hardware appliance would be monitored from a cryptographically accelerated encrypted VPN tunnel from the NETSEC NOC, and I designed the initial NOC prototype and network management system. For the embedded hardware appliance development and contract manufacturing process, I hired Doug Bostrom and Wayne Mitzen, two very talented EE-types that had worked for Ross at a previous venture in Boston related to wireless telemetry (for example, U.S. Patent 6,208,266).
8) During that development effort I approached Theo de Raadt of the OpenBSD project about funding and implementing real-time preemptive POSIX-complaint threads capability to the OpenBSD operating system, instead of using a VxWorks RTOS due to Wind River’s exorbitant licensing costs (OpenBSD and the BSD license were free and unencumbered of patents). NETSEC provided the OpenBSD Project with hardware and funding to implement the beginning stages of the OpenBSD Cryptographic Framework, based on a HiFN line of cryptographic accelerators that were eventually worked into the OpenBSD kernel and OCF (our first choice was BroadCom, but Ken had connections at HiFN so that was the initial chipset used with the OCF). x86-based hardware in the late 90s simply could not handle the computational effort required for high speed FIPS 140-1 and FIPS 140-2 compliant DES and 3DES encryption, so a dedicated crypto processor was needed to support ATM+ wire speeds.
9) Shortly thereafter, NETSEC started a project with the GSA called the GSA Technical Support Center . The GSA Technical Support Center was a joint FBI and DoD collaboration to provide reverse engineering and cryptanalytic services to federal government and military components. The project lead was FBI executive Ron Bitner (or at least that’s the name he gave me), and the GSA representative tasked with funding the project was Dave Jarrell. When I started working on the project I voiced concerns to Ken about the demarcation point between the FBI and DoD (or lack thereof), which at the time was a fairly egregious violation of the Posse Comitatus Act. Ken’s answer was that Multi Level Security (MLS) systems such as Trusted Solaris would be used to share information of varying classification levels between the FBI and DoD to preserve the age old separation between the military and civil government, but I saw the proverbial writing on the wall and didn’t want to participate in the project any longer.
10) Later in the year I resigned my position at NETSEC during a company-wide meeting, and went on to start an embedded wireless bandwidth management company. I had a two year non-compete with NETSEC so I couldn’t work in security any longer at that time.
Obviously there is a lot more to this story than a one page synopsis, but I think what is important to make mention of is the close nexus between supposedly unfriendly governments such as Iran and the US. In 1995 the FBI was adamantly against any relaxation of encryption export regulations, yet they did an abrupt about-face on the issue in 1999 (for example,
I personally believe that the FBI, or at least certain officials within the administration at that time, willingly advocated the relaxation of encryption export regulations only due to their discovery of critical vulnerabilities and weaknesses in the RSA encryption algorithm not exhibited by the predominant public key encryption method used at the time which was Diffie-Hellman. Of equal interest was RSA Security’s decision to not pursue an extension of the RSA patent after its 20-year expiration, which they could have easily obtained on national security grounds. They simply waived their rights and let RSA become an open and public domain standard despite their significant revenues in licensing of the RSA encryption algorithm in the USA based on U.S. Patent 4,405,829.
If any of this conjecture is the case, then it could reasonably be said that the FBI intentionally – and very seriously – weakened the United States critical infrastructure and our military capabilities by advocating the use of a fundamentally weak encryption algorithm as a tradeoff between US National Security and their need to observe domestic communications in the United States. This of course has serious implications for any technology predicated upon the RSA encryption algorithm and its progeny, such as military grade GPS which uses RSA for weapons targeting, military smart card technology such as the Common Access Card, commercial smart card technologies used in RFID and contactless payment solutions, etc. Most of these standards are now literally set in stone insofar as embedded systems are concerned, and the vast majority of OpenBSD / OCF installations are embedded-based without an upgrade path due to the small footprint of OpenBSD and the BSD licensing scheme used by the OpenBSD project. Literally millions (and potentially hundreds of millions) of OpenBSD installations are out there in the embedded space such as routers, firewalls, VPN devices etc, and this goes without mentioning the many other operating systems that have incorporated the OpenBSD OCF and PF firewalling stack without any audit of the source code based on the security and reputation inherent to the OpenBSD Project.
Let me know if you have any other questions, and Happy 2012 to you and Cryptome.
Gregory Perry
Report – DHS to Give Talk on “Deceptive Dating Tactics” at Online Dating Conference

The Department of Homeland Security is set to participate in a discussion panel at an online dating industry conference in Miami in the coming days.Tom Millar, chief of communications for the Department of Homeland Security’s United States Computer Emergency Readiness Team (US-CERT) is slated to discuss deceptive dating tactics in a January 24 panel at the iDate SuperConference event, said a statement from Ticondergoa Ventures, Inc., the sponsor of the conference. The event takes place on January 23-30, 2012 in Miami Beach.
Millar’s session is designed, said Ticonderoga Ventures, to help dating operators prevent fraud within their respective sites.
The appearance isn’t as unusual as it may seem. DHS and the CERT have been aggressively promoting online safety and security in the last few months through the agency’s “Stop. Think. Connect” campaign. On Jan. 10, DHS’ Web blog posted a series of tips on how the public and DHS employees can remain secure online. According to Ticonderoga, Millar’s Miami appearance is part of DHS outreach program called “Cyber Week” in the city.
US Department of Homeland Security to speak at the iDate Dating Industry Super Conference on January 23-30, 2012 in Miami (Press Release):
Ticonderoga Ventures, Inc. announces that the US Deparment of Homeland Security (DHS)will present at the Internet Dating Industry Super Conference . The event takes place on January 23-30, 2012 in Miami Beach. Tom Millar ofthe United States Computer Emergency Readiness Team (US-CERT) within the Department of Homeland Security will be on a January 24 panel that discusses deceptive dating tactics. The session is designed to assist dating operators in preventing fraud within their respective sites. Mr. Millar joined US-CERT in 2007 and played a significant role in US-CERT’s response activities during major cyber events such as the Distributed Denial of Service (DDoS) attacks on Estonia in 2007, the outbreak of the Conficker worm and the DDoS attacks on major US government and commercial websites in 2009. He currently serves as US-CERT’s Chief of Communications, a role which finds him at the intersection of outreach, awareness, standards development and technical interoperability initiaAtives. His focus is on modernizing US-CERT’s approaches to information sharing, knowledge exchange and coordination.
REPORT – Journalists killed since 1992

Pakistan remained the most dangerous country for journalists with more deaths recorded there than any other country according to the Committee to Protect Journalists (CPJ).
Of the 42 killings with a confirmed motive, seven of those were in Pakistan down slightly from 2010. Mexican journalist Elizabeth Macías Castro, the only women recorded on the list of confirmed motives, was the first woman recorded by the CPJ to have “direct relation to journalism published on social media”.
Despite Pakistan heading the list as the most dangerous country for reporters two years in a row, Iraq still remains the country with the highest number of journalists killed since 1992, with 151 deaths with a confirmed motive recorded as taking place in the country.
The death of Sunday Mirror defence correspondent Rupert Hamer early last year shone a light again on how dangerous it is to be a journalist. No other British journalists or media workers are recorded on the CPJ list for 2011.
//
Since 1992, over 880 journalists have been killed around the world in cases where the CPJ has been able to confirm the motive. They have come from all over the globe – and the data collected shows that reporters are increasingly at risk – with Iraq responsible for the biggest single number of deaths.
The research by the CPJ shows 43% of all deaths are murders and state that 22% are tortured before death. The bar chart above shows how many deaths of journalists (with a motive) were recorded each year.
Those killed with unconfirmed motives and all killings of media workers since 1992 can be found in the spreadsheet. We have done some of our own analysis in the table below to show which country is recorded as the most dangerous by each year with Iraq leading the overall total.
Data summary
|
Year
|
Total killed
|
Male
|
Female
|
Highest country / countries
|
Number
|
|---|---|---|---|---|---|
|
SOURCE: Committee to Protect |
|||||
| 1992 | 44 | 43 | 1 | Tajikistan / Turkey (each) | 9 |
| 1993 | 56 | 51 | 5 | Algeria/ Russia (each) | 8 |
| 1994 | 66 | 62 | 4 | Algeria | 18 |
| 1995 | 50 | 43 | 7 | Algeria | 24 |
| 1996 | 26 | 23 | 3 | Algeria | 7 |
| 1997 | 26 | 26 | India | 7 | |
| 1998 | 24 | 22 | 2 | Colombia | 4 |
| 1999 | 36 | 36 | Sierra Leone | 10 | |
| 2000 | 24 | 24 | Colombia/ Russia / Sierra Leone (each) | 3 | |
| 2001 | 37 | 36 | 1 | Afghanistan | 9 |
| 2002 | 21 | 20 | 1 | Colombia / Israel & occ terrs / Russia (each) | 3 |
| 2003 | 42 | 41 | 1 | Iraq | 14 |
| 2004 | 60 | 57 | 3 | Iraq | 24 |
| 2005 | 48 | 40 | 8 | Iraq | 23 |
| 2006 | 57 | 49 | 8 | Iraq | 32 |
| 2007 | 67 | 63 | 4 | Iraq | 32 |
| 2008 | 42 | 41 | 1 | Iraq | 11 |
| 2009 | 70 | 62 | 8 | Philippines | 32 |
| 2010 | 44 | 44 | Pakistan | 8 | |
| 2011 | 42 | 41 | 1 | Pakistan | 7 |
| TOTALS | 882 | 58 | Iraq | 151 | |
|
ID
|
Date
|
Name
|
Sex
|
Country Killed
|
Organisation
|
Nationality
|
|---|---|---|---|---|---|---|
|
|
||||||
| 1 | January 1, 2009. | Hassan Mayow Hassan | F | Somalia | Radio Shabelle | Somalia |
| 2 | January 4, 2009. | Mohammad Imran | M | Pakistan | Express TV | Pakistan |
| 3 | January 4, 2009. | Tahir Awan | M | Pakistan | freelance | Pakistan |
| 4 | January 7, 2009. | Basil Ibrahim Faraj | M | Israel and the Occupied Palestinian Territory | Palestinian Media and Communication Company | Palestinian |
| 5 | January 8, 2009. | Lasantha Wickramatunga | M | Sri Lanka | The Sunday Leader | Sri Lanka |
| 6 | January 11, 2009. | Uma Singh | F | Nepal | Janakpur Today, Radio Today | Nepal |
| 7 | January 2009. | Francis Nyaruri | M | Kenya | Weekly Citizen | Kenyan |
| 8 | January 16, 2009. | Orel Sambrano | M | Venezuela | ABC de la Semana and Radio América | Venezuela |
| 9 | January 19, 2009. | Anastasiya Baburova | F | Russia | Novaya Gazeta | Russian/ Ukrainian |
| 10 | February 2, 2009. | Said Tahlil Ahmed | M | Somalia | HornAfrik | Somalia |
| 11 | February 7, 2009. | Ando Ratovonirina | M | Madagascar | Radio Télévision Analamanga | Madagascar |
| 12 | February 11, 2009. | Anak Agung Prabangsa | M | Indonesia | Radar Bali | Indonesian |
| 13 | February 12, 2009. | Puniyamoorthy Sathiyamoorthy | M | Sri Lanka | freelance | Sri Lanka |
| 14 | February 18, 2009. | Musa Khankhel | M | Pakistan | Geo TV and The News | |
| 15 | February 23, 2009. | Ernie Rollin | M | Philippines | DXSY Radio | Philippine |
| 16 | March 10, 2009. | Haidar Hashim Suhail | M | Iraq | Al-Baghdadia TV | Iraq |
| 17 | March 10, 2009. | Suhaib Adnan | M | Iraq | Al-Baghdadia TV | Iraq |
| 18 | March 18, 2009. | Omidreza Mirsayafi | M | Iran | Rooznegar | Iran |
| 19 | April 29, 2009. | José Everardo Aguilar | M | Colombia | Radio Súper and Bolívar Estéreo | Colombian |
| 20 | May 22, 2009. | Abdirisak Mohamed Warsame | M | Somalia | Radio Shabelle | Somalia |
| 21 | May 25, 2009. | Eliseo Barrón Hernández | M | Mexico | La Opinión | Mexico |
| 22 | May 26, 2009. | Nur Muse Hussein | M | Somalia | Radio IQK | Somalia |
| 23 | May 31, 2009. | Alaa Abdel-Wahab | M | Iraq | Al-Baghdadia TV | Iraq |
| 24 | June 3, 2009. | Jojo Trajano | M | Philippines | Remate | Philippines |
| 25 | June 8, 2009. | Mukhtar Mohamed Hirabe | M | Somalia | Radio Shabelle | Somalia |
| 26 | June 9, 2009. | Crispin Perez | M | Philippines | DWDO Radio | Philippine |
| 27 | July 4, 2009. | Mohamud Mohamed Yusuf | M | Somalia | Radio IQK | Somalia |
| 28 | July 15, 2009. | Natalya Estemirova | F | Russia | Novaya Gazeta, Kavkazsky Uzel | Russia |
| 29 | August 11, 2009. | Abdulmalik Akhmedilov | M | Russia | Hakikat and Sogratl | Russia |
| 30 | August 17, 2009. | Novruzali Mamedov | M | Azerbaijan | Talyshi Sado | Azerbaijan |
| 31 | August 24, 2009. | Janullah Hashimzada | M | Pakistan | Shamshad TV | Afghanistan |
| 32 | September 2, 2009. | Christian Gregorio Poveda Ruiz | M | El Salvador | freelance | France |
| 33 | September 9, 2009. | Sultan Mohammed Munadi | M | Afghanistan | The New York Times | Afghanistan |
| 34 | September 20, 2009. | Bayo Ohu | M | Nigeria | The Guardian | Nigerian |
| 35 | October 21, 2009. | Orhan Hijran | M | Iraq | Al-Rasheed | Iraq |
| 36 | November 2, 2009. | Bladimir Antuna García | M | Mexico | El Tiempo de Durango | Mexico |
| 37 | November 23, 2009. | Andres Teodoro | M | Philippines | Central Mindanao Inquirer | Philippine |
| 38 | November 23, 2009. | Ian Subang | M | Philippines | Socsargen Today | Philippine |
| 39 | November 23, 2009. | Napoleon Salaysay | M | Philippines | Mindanao Gazette | Philippine |
| 40 | November 23, 2009. | Alejandro Reblando | M | Philippines | Manila Bulletin | Philippine |
| 41 | November 23, 2009. | Fernando Razon | M | Philippines | Periodico Ini | Philippine |
| 42 | November 23, 2009. | Joel Parcon | M | Philippines | Prontiera News | Philippine |
| 43 | November 23, 2009. | Ronnie Perante | M | Philippines | Gold Star Daily | Philippine |
| 44 | November 23, 2009. | Victor Nuñez | M | Philippines | UNTV | Philippine |
| 45 | November 23, 2009. | Rosell Morales | M | Philippines | News Focus | Philippine |
| 46 | November 23, 2009. | Marife “Neneng” Montaño | F | Philippines | Saksi News and DXCI | Philippine |
| 47 | November 23, 2009. | Reynaldo Momay | M | Philippines | Midland Review | Philippine |
| 48 | November 23, 2009. | Rey Merisco | M | Philippines | Periodico Ini | Philippine |
| 49 | November 23, 2009. | Ernesto Maravilla | M | Philippines | Bombo Radyo | Philippine |
| 50 | November 23, 2009. | Lindo Lupogan | M | Philippines | Mindanao Daily Gazette | Philippine |
| 51 | November 23, 2009. | Bienvenido Legarte Jr. | M | Philippines | Prontiera News | Philippine |
| 52 | November 23, 2009. | Santos Gatchalian | M | Philippines | DXGO | Philippine |
| 53 | November 23, 2009. | Jolito Evardo | M | Philippines | UNTV | Philippine |
| 54 | November 23, 2009. | Jhoy Duhay | M | Philippines | Gold Star Daily | Philippine |
| 55 | November 23, 2009. | Gina Dela Cruz | F | Philippines | Saksi News | Philippine |
| 56 | November 23, 2009. | Noel Decina | M | Philippines | Periodico Ini | Philippine |
| 57 | November 23, 2009. | Lea Dalmacio | F | Philippines | Socsargen News | Philippine |
| 58 | November 23, 2009. | John Caniban | M | Philippines | Periodico Ini | Philippine |
| 59 | November 23, 2009. | Hannibal Cachuela | M | Philippines | Punto News | Philippine |
| 60 | November 23, 2009. | Marites Cablitas | F | Philippines | News Focus and DXDX | Philippine |
| 61 | November 23, 2009. | Romeo Jimmy Cabillo | M | Philippines | Midland Review | Philippine |
| 62 | November 23, 2009. | Arturo Betia | M | Philippines | Periodico Ini | Philippine |
| 63 | November 23, 2009. | Rubello Bataluna | M | Philippines | Gold Star Daily | Philippine |
| 64 | November 23, 2009. | Mark Gilbert Arriola | M | Philippines | UNTV | Philippine |
| 65 | November 23, 2009. | Henry Araneta | M | Philippines | DZRH | Philippine |
| 66 | December 3, 2009. | Hassan Zubeyr | M | Somalia | Al-Arabiya | Somalia |
| 67 | December 3, 2009. | Mohamed Amin | M | Somalia | Radio Shabelle | Somalia |
| 68 | December 3, 2009. | Abdulkhafar Abdulkadir | M | Somalia | freelance | Somalia |
| 69 | December 19, 2009. | Cihan Hayırsevener | M | Turkey | Güney Marmara’da Yaşam | Turkey |
| 70 | December 30, 2009. | Michelle Lang | F | Afghanistan | Calgary Herald and Canwest News Service | Canada |
| 71 | January 08, 2010. | Valentin Valdes Espinosa | M | Mexico | Zocalo de Saltillo | Mexican |
| 72 | January 09, 2010. | Stanislas Ocloo | M | Angola | Television Togolaise | Togolese |
| 73 | January 10, 2010. | Rupert Hamer | M | Afghanistan | Sunday Mirror | British |
| 74 | February 13, 2010. | Muhammad al- Rabou’e | M | Yemen | Al- Qahira | Yemeni |
| 75 | March 01, 2010. | Joseph Hernandez Ochoa | M | Honduras | TV Channel 51 | Honduran |
| 76 | March 11, 2010. | David Meza Montesinos | M | Honduras | Radio El Patio, Radio America, Channel 45 | Honduran |
| 77 | March 14, 2010. | Nahum Palacios Arteaga | M | Honduras | TV Channel 5 | Honduran |
| 78 | March 19, 2010. | Clodomiro Castilla Ospino | M | Colombia | El Pulso del Tiempo | Colombian |
| 79 | April 10, 2010. | Hiro Muramoto | M | Thailand | Reuters | Japanese |
| 80 | April 16, 2010. | Malik Arif | M | Pakistan | Samaa TV | Pakistani |
| 81 | April 17, 2010. | Azmat Ali Bangash | M | Pakistan | Samaa TV | Pakistani |
| 82 | April 22, 2010. | Germain Cyrille Ngota Ngota | M | Cameroon | Cameroon Express | Cameroonian |
| 83 | April 24, 2010. | Sunday Gyang Bwede | M | Nigeria | The Light Bearer | Nigerian |
| 84 | April 24, 2010. | Nathan S. Dabak | M | Nigeria | The Light Bearer | Nigerian |
| 85 | May 04, 2010. | Sheikh Nur Mohamed Abkey | M | Somalia | Radio Mogadishu | Somalian |
| 86 | May 05, 2010. | Sardasht Osman | M | Iraq | Freelance | Kurdish |
| 87 | May 09 – 10, 2010. | Ghulam Rasool Birhamani | M | Pakistan | Daily Sindhu Hyderabad | Pakistani |
| 88 | May 19, 2010. | Fabio Polenghi | M | Thailand | Freelance | Italian |
| 89 | May 28, 2010. | Ejazul Haq | M | Pakistan | City-24 TV | Pakistani |
| 90 | June 14, 2010. | Desidario Camangyan | M | Philippines | Sunrise FM | Philippine |
| 91 | June 16, 2010. | Joselito Agustin | M | Philippines | DZJC | Philippine |
| 92 | June 24, 2010. | James P.Hunter | M | Afghanistan | Fort Campbell Courier, U.S military publications | American |
| 93 | June 26, 2010. | Jean-Leonard Rugambage | M | Rwanda | Umuvugizi | Rwandan |
| 94 | July19, 2010. | Sokratis Giolias | M | Greece | Thema 98.9, Troktiko | Greek |
| 95 | July 20, 2010. | Vijay Pratap Singh | M | India | Indian Express | Indian |
| 96 | July 30, 2010. | Ardiansyah Matra’is | M | Indonesia | Merauke TV | Indonesian |
| 97 | August 03, 2010. | Assaf Abu Rahal | M | Lebanon | Al- Akhbar | Lebanese |
| 98 | August 21, 2010. | Ridwan Salamun | M | Indonesia | Sun TV | Indonesian |
| 99 | August 24, 2010. | Barkhat Awale | M | Somalia | Hurma Radio | Somalian |
| 100 | September 03, 2010. | Aleh Byabenin | M | Belarus | Charter 97 | Belarusian |
| 101 | September 05, 2010. | Alberto Graves Chakussanga | M | Angola | Radio Despertar | Angolan |
| 102 | September 06, 2010. | Ejaz Risani | M | Pakistan | Samaa TV | Pakistani |
| 103 | September 07, 2010. | Riad al-Saray | M | Iraq | Al-Iraqiya | Iraqi |
| 104 | September 08, 2010. | Safa al-Din Abdel Hamid | M | Iraq | Al-Mosuliya | Iraqi |
| 105 | September 11, 2010. | Paul Kiggundu | M | Uganda | TOP Radio and TV | Ugandan |
| 106 | September 14, 2010. | Misri Khan | M | Pakistan | Asuf and Mashriq | Pakistani |
| 107 | September 16, 2010. | Luis Carlos Santiago | M | Mexico | El Diario | Mexican |
| 108 | October 04, 2010. | Tahrir Kadhim Jawad | M | Iraq | Freelance | Iraqi |
| 109 | October 18, 2010. | Francisco Gomes de Medeiros | M | Brazil | Radio Caico | Brazilian |
| 110 | November 05, 2010. | Carlos Alberto Guajardo Romero | M | Mexico | Expreso Matamoros | Mexican |
| 111 | December 06, 2010. | Pervez Khan | M | Pakistan | Waqt TV | Pakistani |
| 112 | December 06, 2010. | Abdul Wahab | M | Pakistan | Express News | Pakistani |
| 113 | December 12, 2010. | Omar Rasim al-Qaysi | M | Iraq | Al-Anbar TV | Iraqi |
| 114 | December 17, 2010. | Alfrets Mirulewan | M | Indonesia | Pelangi Weekly | Indonesian |
| 115 | January 13, 2011. | Wali Khan Babar | M | Pakistan | Geo TV | Pakistan |
| 116 | January 17, 2011. | Lucas Mebrouk Dolega | M | Tunisia | European Pressphoto Agency | France |
| 117 | January 24, 2011. | Gerardo Ortega | M | Philippines | DWAR | Philippines |
| 118 | January 30, 2011. | Le Hoang Hung | M | Vietnam | Nguoi Lao Dong | Vietnam |
| 119 | February 4, 2011. | Ahmad Mohamed Mahmoud | M | Egypt | Al-Ta’awun | Egypt |
| 120 | February 24, 2011. | Mohamed al-Hamdani | M | Iraq | Al-Itijah | Iraq |
| 121 | March 2011. | Noel López Olguín | M | Mexico | Freelance | Mexico |
| 122 | March 13, 2011. | Ali Hassan al-Jaber | M | Libya | Al-Jazeera | Qatar |
| 123 | March 18, 2011. | Jamal al-Sharaabi | M | Yemen | Al-Masdar | Yemen |
| 124 | March 19, 2011. | Mohammed al-Nabbous | M | Libya | Libya Al-Hurra TV | Libya |
| 125 | March 25, 2011. | Luis Emanuel Ruiz Carrillo | M | Mexico | La Prensa | Mexico |
| 126 | March 29, 2011. | Muammar Khadir Abdelwahad | M | Iraq | Al-Ayn | Iraq |
| 127 | March 29, 2011. | Sabah al-Bazi | M | Iraq | Al-Arabiya | Iraq |
| 128 | April 5, 2011. | Anton Hammerl | M | Libya | Freelance | South Africa |
| 129 | April 9, 2011. | Zakariya Rashid Hassan al-Ashiri | M | Bahrain | Freelance | Egypt |
| 130 | April 12, 2011. | Karim Fakhrawi | M | Bahrain | Al-Wasat | Bahrain |
| 131 | April 20, 2011. | Tim Hetherington | M | Libya | Freelance | UK |
| 132 | April 20, 2011. | Chris Hondros | M | Libya | Getty Images | USA |
| 133 | May 8, 2011. | Sylvain Gagnetau Lago | M | Ivory Coast | Radio Yopougon | Ivory Coast |
| 134 | May 10, 2011. | Nasrullah Khan Afridi | M | Pakistan | Khyber News Agency, Pakistan Television, Mashreq | Pakistan |
| 135 | May 29 or 30, 2011. | Saleem Shahzad | M | Pakistan | Asia Times Online | Pakistan |
| 136 | June 11, 2011. | Asfandyar Khan | M | Pakistan | Akhbar-e-Khyber | Pakistan |
| 137 | June 13, 2011. | Romeo Olea | M | Philippines | DWEB | Philippines |
| 138 | June 15, 2011. | Edinaldo Filgueira | M | Brazil | Jornal o Serrano | Brazil |
| 139 | June 17, 2011. | Shafiullah Khan | M | Pakistan | The News | Pakistan |
| 140 | June 21, 2011. | Alwan al-Ghorabi | M | Iraq | Afaq | Iraq |
| 141 | July 28, 2011. | Ahmad Omaid Khpalwak | M | Afghanistan | Pajhwok Afghan News, BBC | Afghanistan |
| 142 | August 2, 2011. | José Agustín Silvestre de los Santos | M | Dominican Republic | La Voz de la Verdad, Caña TV | Dominican |
| 143 | September 2, 2011. | Noramfaizul Mohd | M | Somalia | Bernama TV | Malaysia |
| 144 | September 8, 2011. | Pedro Alfonso Flores Silva | M | Peru | Channel 6 | Peru |
| 145 | September 8, 2011. | Hadi al-Mahdi | M | Iraq | freelance | Iraq |
| 146 | September 20, 2011. | Farhad Taqaddosi | M | Afghanistan | Press TV | Iran |
| 147 | September 24, 2011. | Hassan al-Wadhaf | M | Yemen | Arabic Media Agency | Yemen |
| 148 | September 24, 2011. | Phamon Phonphanit | M | Thailand | Sue Samut Atyakam | Thailand |
| 149 | September 24, 2011. | Maria Elizabeth Macías Castro | F | Mexico | Freelance | Mexico |
| 150 | October 7, 2011. | Faisal Qureshi | M | Pakistan | London Post | Pakistan |
| 151 | October 9, 2011. | Wael Mikhael | M | Egypt | Al-Tareeq | Egypt |
| 152 | October 22, 2011. | Zakariya Isa | M | Nigeria | Nigeria Television Authority | Nigeria |
| 153 | November. | Javed Naseer Rind | M | Pakistan | Daily Tawar | Pakistan |
| 154 | November 6, 2011. | Gelson Domingos da Silva | M | Brazil | Bandeirantes TV | Brazil |
| 155 | November 19 or 20, 2011. | Ferzat Jarban | M | Syria | Freelance | Syria |
| 156 | November 23, 2011. | Rafiq Tagi | M | Azerbaijan | Freelance | Azerbaijan |
UNCENSORED -Occupy Wall Street Photos 10 January 2012
|
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ows-23/pict6.jpg) Occupy Wall Street protesters read books in Zuccotti Park, Tuesday, Jan.10, 2012, in New York. Barricades were removed by Brookfield Properties, the owners of the park, allowing access once again into the park by the protesters. (Louis Lanzano) Occupy Wall Street protesters read books in Zuccotti Park, Tuesday, Jan.10, 2012, in New York. Barricades were removed by Brookfield Properties, the owners of the park, allowing access once again into the park by the protesters. (Louis Lanzano) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ows-23/pict7.jpg) Occupy Wall Street protesters gather in Zuccotti Park as security guards stand next to stacks of barricades,Tuesday, Jan. 10, 2012, in New York. The barricades were removed by Brookfield Properties, the owners of the park, allowing access once again into the park by the protesters. (Louis Lanzano) Occupy Wall Street protesters gather in Zuccotti Park as security guards stand next to stacks of barricades,Tuesday, Jan. 10, 2012, in New York. The barricades were removed by Brookfield Properties, the owners of the park, allowing access once again into the park by the protesters. (Louis Lanzano) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ows-23/pict8.jpg) Occupy Wall Street protesters make signs in Zuccotti Park, Tuesday, Jan.10, 2012, in New York. Barricades were removed by Brookfield Properties, the owners of the park Tuesday, allowing access once again into the park by the protesters. (Louis Lanzano) Occupy Wall Street protesters make signs in Zuccotti Park, Tuesday, Jan.10, 2012, in New York. Barricades were removed by Brookfield Properties, the owners of the park Tuesday, allowing access once again into the park by the protesters. (Louis Lanzano) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ows-23/pict10.jpg) Police officers guard the perimeter of Zuccotti Park As Occupy Wall Street protesters gather in the park, Tuesday, Jan.10, 2012, in New York. Barricades were removed by Brookfield Properties, the owners of the park, Tuesday, allowing access once again into the park by the protesters. (Louis Lanzano) Police officers guard the perimeter of Zuccotti Park As Occupy Wall Street protesters gather in the park, Tuesday, Jan.10, 2012, in New York. Barricades were removed by Brookfield Properties, the owners of the park, Tuesday, allowing access once again into the park by the protesters. (Louis Lanzano) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ows-23/pict9.jpg) Occupy Wall Street protesters gather in Zuccotti Park, Tuesday, Jan.10, 2012, in New York. Barricades were removed by Brookfield Properties, the owners of the park, allowing access once again into the park by the protesters. (Louis Lanzano) Occupy Wall Street protesters gather in Zuccotti Park, Tuesday, Jan.10, 2012, in New York. Barricades were removed by Brookfield Properties, the owners of the park, allowing access once again into the park by the protesters. (Louis Lanzano) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ows-23/pict11.jpg) Security from Brookfield Properties, the owners of Zuccotti Park, watch as Occupy Wall Street protesters gather in the park, Tuesday, Jan.10, 2012, in New York. Barricades were removed by the owners allowing access into the park by the protesters on Tuesday. (Louis Lanzano) Security from Brookfield Properties, the owners of Zuccotti Park, watch as Occupy Wall Street protesters gather in the park, Tuesday, Jan.10, 2012, in New York. Barricades were removed by the owners allowing access into the park by the protesters on Tuesday. (Louis Lanzano) |
Post-Hacking – Stratfor Back Online
Stratfor.com 2012-Jan-11-12:08:
![[Image]](https://i0.wp.com/cryptome.org/2012/01/0029.jpg)
Several of the Stratfor.com links below do not work, perhaps because of the sneaky subscriber-tracking code contained.
A sends:
Hello, looks like stratfor is back.
———- Forwarded message ———-
From: Stratfor <mail@response.stratfor.com>
Date: 2012/1/11
Subject: Stratfor: Back online + new Geopolitical Weekly
Watch this video of George Friedman on the hacking incident
More info on the attack
Dear Stratfor Member,
We are happy to announce that our website is back online. Visit Stratfor.com to view our 2012 Annual Forecast, as well as fresh analyses on Syria, Iraq and Lithuania and our Geopolitical Diary.
Below you will find a special edition of the Geopolitical Weekly by George Friedman on Stratfor’s security breach.
We may experience brief service interruptions as we work to handle the high level of interest in the new website. If you have trouble connecting to the new site, please check back again soon.
While we continue to rebuild our infrastructure and website capabilities, you will be able to access our content online without having to log in. We are aggressively implementing our plan to reintegrate customers securely, as this is our top priority. In the next several days, we will be informing you about how to establish a new password and update your billing information. In the meantime, visit our website to read fresh content every day.
We deeply regret that an unauthorized party illegally obtained and disclosed the credit card data of some of you. We are making certain that this will never happen again by having a third party with appropriate security safeguards handle all credit card transactions in the future. We hope that you have taken advantage of the CSID identity protection service we have provided.
We understand that you have many questions. Check out www.stratfor.com/hacking-news, a website we’ve created to give you a full rundown of the incident and our plan to address your concerns.
Please contact us at feedback@stratfor.com with any questions, as well as any comments you may have on the Geopolitical Weekly below.
Thank you again for your patience as we work to secure our website and resume normal operations.
– The Stratfor Team
Geopolitical Weekly: The Hack on Stratfor
By George Friedman | January 11, 2012
In early December I received a call from Fred Burton, Stratfor’s Vice President of Intelligence. He told me he had received information indicating our website had been hacked and our customer credit card and other information had been stolen. The following morning I met with an FBI special agent, who made clear that there was an ongoing investigation and asked for our cooperation. We, of course, agreed to cooperate. The matter remains under active investigation.
From the beginning I faced a dilemma. I felt bound to protect our customers, who quickly had to be informed about the compromise of their privacy. I also felt bound to protect the investigation. That immediate problem was solved when the FBI told us it had informed the various credit card companies and had provided those companies with a list of compromised cards while omitting that it had come from us. Our customers were therefore protected, as the credit card companies knew the credit cards and other information had been stolen and could act to protect the customers. We were not compelled to undermine the investigation.
The FBI made it clear that it expected the theft to be exposed by the hackers. We were under no illusion that this was going to be kept secret. We knew our reputation would be damaged by the revelation, all the more so because we had not encrypted the credit card files. This was a failure on our part. As the founder and CEO of Stratfor, I take responsibility for this failure, which has created hardship for customers and friends, and I deeply regret that it took place. The failure originated in the rapid growth of the company. As it grew, the management team and administrative processes didn’t grow with it. Again, I regret that this occurred and want to assure everyone that Stratfor is taking aggressive steps to deal with the problem and ensure that it doesn’t happen again.
From the beginning, it was not clear who the attackers were. The term “Anonymous” is the same as the term “unknown.” The popular vision of Anonymous is that its members are young and committed to an ideology. I have no idea if this is true. As in most affairs like this, those who know don’t talk; those who talk don’t know. I have my theories, which are just that and aren’t worth sharing.
I was prepared for the revelation of the theft and the inevitable criticism and negative publicity. We worked to improve our security infrastructure within the confines of time and the desire to protect the investigation by not letting the attackers know that we knew of their intrusion. With the credit card information stolen, I assumed that the worst was done. I was wrong.
Early in the afternoon of Dec. 24, I was informed that our website had been hacked again. The hackers published a triumphant note on our homepage saying that credit card information had been stolen, that a large amount of email had been taken, and that four of our servers had been effectively destroyed along with data and backups. We had expected they would announce the credit card theft. We were dismayed that emails had been taken. But our shock was at the destruction of our servers. This attack was clearly designed to silence us by destroying our records and the website, unlike most attacks by such groups.
Attacks against credit cards are common, our own failures notwithstanding. So are the thefts of emails. But the deliberate attack on our digital existence was a different order of magnitude. As the global media marveled at our failure to encrypt credit card information, my attention was focused on trying to understand why anyone would want to try to silence us.
In the days that followed, a narrative evolved among people claiming to speak for Anonymous and related groups. It started with looking at our subscriber list and extracting corporate subscribers who were now designated as clients. The difference between clients and subscribers is important here. A client is someone you do customized work for. A subscriber is simply someone who purchases a publication, unchanged from what others read. A subscriber of The New York Times is not its client. Nevertheless, some of the media started referring to these subscribers as clients, reflecting the narrative of those claiming to speak with knowledge of our business.
From there, the storyline grew to argue that these “clients,” corporate and government, provided Stratfor with classified intelligence that we reviewed. We were no longer an organization that analyzed the world for the interested public, but rather a group of incompetents and, conversely, the hub of a global conspiracy. The media focused on the first while the hacking community focused on the second.
This was why they stole our email, according to some of them. As one person said, the credit cards were extra, something they took when they realized they could. It was our email they were after. Obviously, we were not happy to see our emails taken. God knows what a hundred employees writing endless emails might say that is embarrassing, stupid or subject to misinterpretation. What will not appear is classified intelligence from corporations or governments. They may find, depending on what they took, that we have sources around the world, as you might expect. It is interesting that the hacker community is split, with someone claiming to speak for the official Anonymous condemning the hack as an attack on the media, which they don’t sanction, and another faction defending it as an attack on the rich and powerful.
The interpretation of the hackers as to who we are — if indeed that was their interpretation — was so wildly off base as to stretch credulity. Of course, we know who we are. As they search our emails for signs of a vast conspiracy, they will be disappointed. Of course we have relationships with people in the U.S. and other governments and obviously we know people in corporations, and that will be discovered in the emails. But that’s our job. We are what we said we were: an organization that generates its revenues through geopolitical analysis. At the core of our business, we objectively acquire, organize, analyze and distribute information.
I don’t know if the hackers who did this feel remorse as they discover that we aren’t who they said we were. First, I don’t know who they actually are, and second, I don’t know what their motives were. I know only what people claiming to be them say. So I don’t know if there is remorse or if their real purpose was to humiliate and silence us, in which case I don’t know why they wanted that.
And this points to the real problem, the one that goes beyond Stratfor’s own problem. The Internet has become an indispensible part of our lives. We shop, communicate, publish and read on it. It has become the village commons of the planet. But in the village commons of old, neighbors who knew and recognized each other met and lived together. Others knew what they did in the commons, and they were accountable.
In the global commons, anonymity is an option. This is one of the great virtues of the Internet. It is also a terrible weakness. It is possible to commit crimes on the Internet anonymously. The technology that enables the Internet also undermines accountability. Given the profusion of technical knowledge, the integrity of the commons is in the hands of people whose identities we don’t know, whose motives we don’t understand, and whose ability to cause harm is substantial. The consequence of this will not be a glorious anarchy in the spirit of Guy Fawkes, but rather a massive repression. I think this is a pity. That’s why I wonder who the hackers actually are and what cause they serve. I am curious as to whether they realize the whirlwind they are sowing, and whether they, in fact, are trying to generate the repression they say they oppose.
The attempt to silence us failed. Our website is back, though we are waiting for all archives to be restored, and our email is working again. Our failures have been reviewed and are being rectified. We deliberately shut down while we brought in outside consultants to rebuild our system from the ground up. The work isn’t finished yet, but we can start delivering our analyses. The handling of credit cards is being handed off to a third party with appropriate capability to protect privacy. We have acted to help our customers by providing an identity theft prevention service. As always, we welcome feedback from our supporters as well as our critics.
We are fortunate that we have the financial resources and staff commitment to survive the attack. Others might not. We are now in a world in which anonymous judges, jurors and executioners can silence whom they want. Take a look at the list of organizations attacked. If the crushing attack on Stratfor is the new model, we will not be the last. No security system is without flaws even if it is much better than Stratfor’s was.
We certainly expect to be attacked again, as we were last week when emails were sent out to members from a fake Stratfor address including absurd messages and videos. Our attackers seem peculiarly intent on doing us harm beyond what they have already done. This is a new censorship that doesn’t come openly from governments but from people hiding behind masks. Do not think we will be the last or that we have been the first.
We will continue to publish analysis and sell it to those who believe it has value. To our subscribers who have expressed such strong support, we express our deepest gratitude. To our critics, we assure you that nothing you have said about us represents a fraction of what we have said about ourselves. While there is much not to be proud of in this affair, I am proud beyond words of all my dedicated colleagues at Stratfor and am delighted to return our focus to analyzing critical international affairs.
To all, I dedicate myself to denying our attackers the prize they wanted. We are returning to the work we love, dedicated to correcting our mistakes and becoming better than ever in analyzing and forecasting how the world works.
Comments? Send them to feedback@stratfor.com.
221 W. 6th Street, Suite 400
Austin, TX 78701 US
TOP-SECRET – ISAF Joint Command Media Operations Standard Operating Procedures

Media Operations Tasks and Responsibilities: Media Operations is responsible for the Command’s media relations activities, including identifying media to engage with to disseminate information, responding to queries, arranging interviews, and advising senior leaders and IJC members on media issues. Media Operations works with local and international media. The staff also manages the IJC media accreditation and embed programs, and works closely with Regional Commands and NATO Training Mission-Afghanistan (NTM-A) Public Affairs staffs. IJC Media Operations distributes, under its letter head, releases from special operations units.
Press Releases: Media Operations disseminates news releases regarding current operations as well as command activities of interest to the general public.
Joint IJC-Afghan Releases: Media Operations staff should strive to issue joint releases with the Afghan National Security Forces as much as possible; whenever a release involves Afghan National Security Forces — either the Afghan National Army (ANA), Afghan National Police (ANP), National Defense Service (NDS), or all of the above – Media Operations drafts the release as a joint release, with a comment from the Afghan leadership, and coordinates with the appropriate ministries.
Media Queries: Media Operations fields and responds to media queries via phone and e-mail. Based on the nature of the query, Media Operations coordinates the response with the PAO Director as required. See Section (__) for examples of when coordination with the PAO Director is needed. All press officers will monitor the Media Office Inbox (unclass), respond to queries, draft press releases, and facilitate media interviews as required.
Interviews with IJC Leadership Media Operations coordinates interviews with IJC senior leadership and provides preparatory materials, which may include talking points (NATO, ISAF, etc), information on the reporter (bio and recent articles) for those interviews. Media Operations creates and maintain talking points on a variety of issues. The staff also escorts media to these events and prepares interviewees as necessary.
Interviews with Commander, IJC, are referred to the Commander‟s personal PAO for action.
Release Authority: The Commander, IJC, is the release authority for media information pertaining to the command and its operations. The IJC PAO Director acts on behalf of the Commander in routine authorization of information. See Appendix A (__) for specific authorities based on type of information being released.
…
NEWS RELEASE/MEDIA ADVISORY PROCESS:
All news, feature and general media releases must be checked for:
- An ISAF link to the information
- A link to ANSF/Afghan involvement, if at all possible for
- Issue Dual release with Afghan ANSF if applicable and possible
- No list of enemy body count, details of wounded
- Newsworthiness of release (information detail and relevance)
News Release (Fatality/CIVCAS):
- Receive info from JOC Watch/RC/Media/Embassy/TF.
- Check details and confirm with relevant RC/CJOC that info is correct.
- Produce MRL (in event of fatality) on Secret side – essentially an update for ISAF PAO staffs (RCs, internal staff etc)
- Post on noticeboard in ISAF Office.
- Email to MRL distribution list (see previously sent MRLs).
- Put relevant info onto ISAF News Release template (unclas) and print original info (original email or detail from RC or original source – should get confirmation from our JOC watch) to go onto back of ISAF sheet for records.
FOR ALL CASUALTIES: Include draft sympathy quote for PAO Director or senior PAO on duty.
FOR US CASUALTIES: Include acknowledgement line stating the member killed was a US service member.
FOR NON-US CASUALTIES: Include statement that ISAF does not release nationality. BEFORE release – check with RC that next of kin have been notified. NO RELEASE will be made until relevant nation has confirmed completed next of kin notification.
- Ensure quotes, DIVDS reference or other references used are correct. Spell check and once over again.
- In Press office email send to Distribution Lists 1, 2, 3, 4.
- Once sent, releases need to be saved into the relevant folder on the P Drive.
Feature News Release (General) – good news stories etc.
- Receive information from RC or particular Unit. Check details and confirm with relevant RC that info is correct.
- Put relevant info onto ISAF News Release template (unclas) and print original info (original email or detail from RC or original source) to go onto back of ISAF sheet for records.
- Before being signed off by Media Ops Chief or senior PAO on duty, ensure any quotes, DIVDS reference or other references used are correct. Spellcheck and once over again (always get a second pair of eyes to have a quick read through!).
- In Press office email send to Distribution Lists 1, 2, 3, 4.
- File hard copy with original source and sign off sheet to be put up on wall.
Media Advisory
Any upcoming events that may be of interest to press need to be „advertised‟. Ensure photos/references etc are correct, ISAF does not mention individual units/nations unless specifically required.
Operational Update – This is when there is a change of command as an example and we target the relevant nations (i.e. general release but focus on specific nations that it affects).
RELEASE AUTHORITIES:
Authority to release news and feature releases, media advisories and operational updates is delegated to all RC Chief PAOs and through them down to individual Task Force PAOs, except for the following categories, which will only be released by IJC PAO or HQ ISAF PAO:
(1) Death or injuries to ISAF troops – releasable by IJC.
(2) Any Civilian Casualty event – releasable by IJC.
(3) Catastrophic operational failure (e.g. enemy closure of an airfield) – releasable by IJC.
(4) Events with wider intra/inter theatre implications (Elections, NATO policies, TCN policies etc) – releasable by HQ ISAF unless specifically delegated.
DOWNLOAD ORIGINAL DOCUMENT HERE
DECLASSIFIED – The National Security Agency Releases Over 50,000 Pages of Declassified Documents
The National Security Agency (NSA) announces today that it has declassified and released to the National Archives and Records Administration (NARA) over 50,000 pages of historic records. These records cover a time-frame from before World War I through the 1960s.
This release of documents is the first in a series of releases planned over the next two years as part of NSA/CSS’s commitment to meeting the requirements outlined in the President’s 21 January 2009 Memorandum on Openness and Transparency in Government (Executive Order 13526).
Highlights of this release include:
- Manuals, charts, and other documents on the development of early computer systems at NSA/CSS, including the HARVEST. This innovative system was developed with IBM and was in use from 1962 to 1976;
- Early publications on cryptography, including Cryptology: Instruction Book on the Art of Secret Writing from 1809;
- Documents from World War II, including previously unreleased German documents from the Target Intelligence Committee (TICOM).
The released documents will be maintained by NARA and available for review at the National Archives at College Park, 8601 Adelphi Road, College Park, Maryland. A list of the documents is available on NSA’s Declassification and Transparency Webpage.
Since the records were physically transferred to NARA, NSA is no longer the custodian and does not maintain copies of the records for release under the Freedom of Information Act (FOIA). Information about conducting research at NARA is available on the National Archives Website.
For more information about the National Security Agency, please visit www.nsa.gov.
CONFIDENTIAL – NSA Launches New Crypto Mobile Game App
Outreach efforts designed to attract young adults to support cybersecurity initiatives
 Fort Meade, MD. – The National Security Agency (NSA) announced today the launch of “NSA CryptoChallenge,” a mobile cryptograph game app available free of charge from the Apple App Store. The game is the latest digital communications effort designed to educate young adults on career opportunities with NSA and recruit the best and brightest to support NSA’s cybersecurity initiatives.
Fort Meade, MD. – The National Security Agency (NSA) announced today the launch of “NSA CryptoChallenge,” a mobile cryptograph game app available free of charge from the Apple App Store. The game is the latest digital communications effort designed to educate young adults on career opportunities with NSA and recruit the best and brightest to support NSA’s cybersecurity initiatives.
NSA’s CryptoChallenge game challenges today’s most intelligent college students and young adults to decode hundreds of puzzles, which test pattern recognition skills through a series of cryptographs under various categories, including famous quotes, science, technology, engineering and mathematics (STEM) trivia, pop culture factoids and more. It’s “you against the clock” to see how fast you can crack the code. Players can also choose to share their completion time to see how they stack up against other players across the globe, even sharing scores on Facebook and Twitter.
“This is the technology today’s college students use most to communicate and make important life decisions, so we have to use these tools to successfully recruit the top-tier technical talent we need to become future leaders of the Agency, ” said Kathy Hutson, NSA’s Director of Human Resources.
Serious brainiacs are unlikely to get bored by NSA’s CryptoChallenge, as players will find that the game includes an advanced level and uses multiple algorithms, so puzzles have a different encryption each time they appear. The game is also expected to be released for Android platforms in the near future.
NSA’s CryptoChallenge joins NSA’s other high-tech recruitment tool, the NSA Career Links app, which is available through the Apple App Store and Android Market Place. The app delivers real-time information updates directly to the user’s mobile device.
UNCENSORED – FEMEN.- Woman Power.
CONFIDENTIAL from the FBI – MLK Parade Bomber Horrific Hate Crime Prevented; Case Solved
Horrific Hate Crime Prevented; Case Solved
Had his homemade bomb gone off—one he had diabolically constructed using shrapnel coated with a substance meant to keep blood from clotting in wounds—Kevin Harpham would have undoubtedly caused the death and injury of many people at last year’s Martin Luther King, Jr. Day Unity March in Spokane, Washington.

A Bomb Designed to Kill Kevin Harpham had been an artilleryman in the Army, and the bomb he meticulously constructed—using 128 fishing weights for shrapnel, each coated with an anticoagulant commonly found in rat poison—was not a typical improvised explosive device (IED). “JTTF members on this investigation have had experience on many other bombing cases both here and abroad,” said Special Agent Joe Cleary, who worked alongside other agents, evidence technicians, and intelligence analysts on the Harpham case. “But none of us had ever seen this type of bomb in the U.S.” Cleary explained that most IEDs are triggered with fuses or timers. “This was command-detonated,” he said. “Harpham designed it so he could remotely control when the blast would occur and the direction in which the shrapnel would fly. He placed the bomb so it would explode directly across the line of the march, thereby inflicting maximum damage to the marchers. This was a weapon of mass destruction.” When bomb experts from the FBI Laboratory reconstructed the device and detonated it, the results were sobering, Cleary said. “The shrapnel exploded with such a high velocity that some targets in the shape of humans were blown over, and a metal filing cabinet was perforated—it was filled with holes.” “Harpham intended to use this extremely lethal weapon on individuals solely because of their race and perhaps their religion,” Cleary said. “His plan was to wreak havoc on a crowd of innocents.” |
|---|
Instead, Harpham was eventually caught and recently sentenced to 32 years in prison for a hate crime and other offenses related to the attempted bombing. The case illustrates how a quick response by citizens and local law enforcement averted a tragedy, and how teamwork and time-tested investigative techniques led to the apprehension of an individual who has shown no remorse for his actions.
“Clearly he intended to detonate the device, cause mass carnage, and then survey the devastation,” said Special Agent Frank Harrill, who supervised the investigation. “Harpham was acting out against what he termed multiculturalism, but his hatred was firmly rooted in violent white supremacy. This was a prototypical hate crime.”
On January 17, 2011, as hundreds of people gathered in downtown Spokane to participate in the march, Harpham placed his backpack bomb along the parade route at Washington Street and Main Avenue. Alert city workers discovered the suspicious backpack before the march started, and Spokane Police Department officials changed the route as a precaution. The Spokane Police and Sheriff’s Office bomb squad was called in, and their precision in disarming the device enabled evidence to be preserved that would help lead FBI agents to Harpham.
The FBI’s Joint Terrorism Task Force (JTTF) in Spokane immediately began an investigation, and JTTF members canvassed the region for batteries and other components similar to those used in the bomb. Within a month, in a small town about 60 miles north of Spokane, they discovered that a local outlet of a large retail chain was selling the same kind of fishing weights Harpham had used as shrapnel.
Store records showed there had been three large purchases of the weights in recent months—two were paid for in cash, but a debit card was used in one transaction, and it belonged to Harpham. At the same time, the FBI Laboratory had been working to extract a DNA sample from the backpack which was later matched to Harpham through his military records.
Investigators also learned of Harpham’s white supremacy postings on the Internet and his affiliation with a neo-Nazi group called the National Alliance.
Because he lived in a remote, relatively inaccessible area and was likely heavily armed, our Hostage Rescue Team devised a ruse to lure Harpham out of his house. He was arrested March 9, 2011 without incident—but as agents suspected, he was armed when taken into custody.
“Kevin Harpham was the lone wolf that all of us in law enforcement dread,” Harrill said. “He lived alone and he worked alone, and he didn’t foreshadow the bombing plot in any meaningful way. He targeted those who were attempting to celebrate an event meant to unite society,” Harrill added, “and he was prepared to indiscriminately kill men, women, and children.”
Harrill credited teamwork and strong partnerships for stopping Harpham and bringing him to justice. “From the workers who noticed the device to the police response, the JTTF investigation, the expertise of the FBI Laboratory, and the prosecuting skill of the U.S. Attorney’s office—everything worked just as it should have.”
TOP-SECRET – U.S. Military Core Warrior Values Training Presentation

• The vast majority of Coalition Forces perform their jobs magnificently every day:
– They do their duty with honor under extremely difficult circumstances.
– They exhibit good judgment, honesty, and integrity.
– They display patience, professionalism, and restraint in the face of a treacherous enemy.
– They do the right thing even when no one is watching.
• As military professionals, it is important that we take time to reflect on the values that separate us from our enemies.

DOWNLOAD ORIGINAL DOCUMENT HERE
SECRET RESEARCH – List of major crimes in Japan
This is a list of documented major crimes in Japan.
Date Name Deaths Location Summary
1893 Kawachi Jūningiri 13 Osaka Kumataro Kido and Yagoro Tani murdered ten people including an infant. The homicide was motivated by grudges against the victims. They committed suicide after the murders.
1923–1924 Sataro Fukiage 6? Kantō and Chūbu Serial killer Sataro Fukiage raped and murdered six girls. He also raped and murdered a girl in 1906. Exact victim estimates are unknown but one theory puts the number at 93 while another put it at more than 100. Fukiage was executed in 1926.
1925 Aoyama-kai / Mitani-kumi gang war 3+ near Yokohama In one of the largest battles between Yakuza groups, members of the Aoyama-kai and around thirty gangs led by the Mitani-kumi are involved in a dispute over a construction contract for Tokyo Denryoku Construction in Kanagawa. Aoyama-kai is a subcontractor of Shimizu-gumi and Shimizu-gumi is losing trust due to Hazama-gumi’s obstruction, which is regarded as Mitani-kumi’s instruction. After six hours of fighting, reports between 600 to 2,000 gangsters are involved with weapons including rifles, pistols, swords and farm implements. The Tokyo police and the Kempei-Tai were called in after the Kawasaki police became unable to handle the situation and, although Japanese officials declared martial law, fighting did not end until a cannon was brought in by the Aoyama-gumi. The battle injured over 150 people and killed at least three.
1936 Sada Abe 1 Tokyo Sada Abe and Kichizo Ishida (her lover) engaged in Erotic asphyxiation resulting in his death. When he died she then cut off his penis and testicles and carried them around with her in a handbag. Because her way of killing him was erotic, her crime gave inspiration to Japanese films, such as Nagisa Oshima’s In the Realm of the Senses.
1938 Tsuyama massacre 31 rural hamlets near Tsuyama, Okayama After cutting off electricity to his village, 21-year-old Mutsuo Toi proceeded to go on a late-night killing spree with a hunting rifle, sword, and axe before killing himself.
1941–1942 Hamamatsu serial murders 9-11 near Hamamatsu, Shizuoka A deaf boy Seisaku Nakamura murders people in Shizuoka. He attempts to rape women and murder his family. He is arrested for nine murders in 1942. He admits two other murders. He is sentenced to death.
1944-1948 Kotobuki maternity hospital incident 103? Tokyo A hospital director Miyuki Ishikawa fatal neglects against about a hundred babies. There are accomplices and the shinjuku word office is suspected of approval for the murders.
1945-1946 Yoshio Kodaira 7-10 Tokyo, Tochigi Japanese ex-soldier Yoshio Kodaira rapes and murders ten women. In China, he murders Chinese soldiers as a soldier. He also kill his father-in-law in 1932. Kodaira is executed in 1949.
1948 Teigin Bank robbery 12 Shiina, Toshima, Tokyo Sixteen employees of a Teigin Bank branch are poisoned by cyanide after taking chemicals given to them by a man claiming to be from the health authorities who claimed they were medication to control a nearby dysentery outbreak. The man then stole 160,000 yen before making his escape. Twelve people died. Sadamichi Hirasawa, a painter, was arrested several months later. Although sentenced to death, there were strong suspicions that he was wrongfully convicted, and successive Justice Ministers refused to sign his death warrant, resulting in a stay of execution. During his 33-year imprisonment he wrote his autobiography and died of natural causes in 1987.
(Alluded to in Ian Fleming’s novel You Only Live Twice: “And down went the honourable medicine and down fell the honourable local manager and staff of the Imperial Bank of Japan. The medicine had been neat cyanide.”)
1948-1952 Osen Korogashi incident 8 Chiba, Shizuoka, Tochigi Serial killer Genzo Kurita murders eight people. He commits necrophilia with several victims and murders a family at the cliff called Osen Korogashi. He is executed in 1959.
1960 The assassination of Inejiro Asanuma 1 Hibiya, Tokyo The head of the Japan Socialist Party is stabbed to death by a 17-year old right-wing extremist Otoya Yamaguchi at a televised rally.
1963 Murder of Yoshinobu Murakoshi 1 Taito, Tokyo 4 year-old Yoshinobu Murakoshi fails to come home from a local park; several days later his family receives a phone call demanding ransom. Police fail to apprehend the person who collected the ransom, and the case generated massive publicity. Two years later they identified Tamotsu Obara as the kidnapper, who admitted under questioning to have murdered the child.
1963-1964 Akira Nishiguchi 5 through Japan Serial killer Akira Nishiguchi cheats people, escapes from police officers in Japan, and kills five people. He is executed in 1970. His crimes became the basis for a book by Ryuzo Saki and the Shohei Imamura film Vengeance Is Mine.
1965 Zama and Shibuya shootings 1 Kanagawa Prefecture, Tokyo 18-year old Misao Katagiri goes on a rampage with a rifle. He shoots two police officers in Zama city, Kanagawa prefecture then hijacks several cars. A gun battle between the gunman and hundreds of special police ensues at a gun store in Shibuya, Tokyo. He is suppressed by police and sentenced to death.
1968 Norio Nagayama’s robbery spree 4 Tokyo, Kyoto, Hakodate, Nagoya A series of high-profile robberies in which 19-year old Norio Nagayama robs people for their money after killing them with a handgun stolen from the US military. After controversial trials, the Supreme Court upholds Nagayama’s death in 1990. He is executed in 1997.
1968 300 million yen robbery – Fuchū, Tokyo Disguised as a police officer, an unidentified man stops a security van belonging to the Toshiba Corporation near Tokyo’s Fuchu Prison and, in the guise conducting a bomb search, hijacks the van successfully escaping with almost 300 million yen. Despite a massive investigation into what would become the largest robbery in Japanese history, neither the man or the money are ever found.
1968 Tochigi patricide case 1 Tochigi Chiyo Aizawa murders her own father. She is an incest victim of her father. In 1973, the supreme court of Japan sentences her to a suspended sentence, saying that the article 200 of penal code is a breach of Japanese constitution. Her sentence becomes the first unconstitutional judgment for the supreme court.
1970 Inland Sea ferry hijacking 1 Hiroshima and the Inland Sea An armed 20-year old escaping police hijacks a ferry and takes the crew and passengers hostage. He is shot dead by a police sniper the following morning.
1971 Kiyoshi Okubo 8 Gunma Prefecture Serial killer Kiyoshi Okubo rapes and murders eight women during 41 days. Okubo is sentenced to death in 1973 and is executed in 1976.
1971-1972 Purge incident 12 Gunma prefecture The United Red Army torture and murder their twelve members in base camps. They call the murders “purification”. The incident comes to light after the Asama-Sanso incident.
1972 Asama-Sanso incident 2 Karuizawa, Nagano prefecture 5 armed left-wing militants of the United Red Army hold up in a mountainside holiday lodge, taking one hostage. Amidst live TV coverage, police storm the lodge after a ten-day standoff, resulting in the deaths of two policemen.
1973 Kidnapping of Kim Dae-Jung – Chiyoda, Tokyo South Korean dissident Kim Dae-Jung, later to be president, is kidnapped from his hotel room in Tokyo by KCIA agents and taken to South Korea.
1979 Mitsubishi Bank sporting gun kidnapping 5 Osaka Akiyoshi Umekawa shoot dead four people in a Mitsubishi Bank. His motivation is probably robbery at first, but he takes about 40 hostages and does something he wants. Osaka police shoot dead him two days later.
1980 Shinjuku bus attack 6 Shinjuku, Tokyo A mentally disturbed man throws a bucket of petrol and a lit newspaper into a bus. The ensuing fire killed 6 and injured 14. He kills himself in 1997.
1982 Japan Airlines Flight 350 24 Tokyo Bay A mentally disturbed Captain Seiji Katagiri forces the Japan Airlines Flight 350 to crash. 24 passengers are killed by the crash. He is arrested on suspicion of professional negligence resulting in deaths, but he isn’t indicted due to his insanity.
1983 Kiyotaka Katsuta 8-22 Kansai and Chūbu Kiyotaka Katsuta is arrested for a robbery-murder. However he is suspected of a total of 22 murders later, and he admits eight murders. Katsuta is executed in 2000.
1984 Glico Morinaga case – Various, across Kansai A 17-month long series of extortion against confectionery companies starting in a kidnap of the president of Glico and involving confectionery spiked with cyanide.
1985-1989 Yama-Ichi War 29 Kansai region A Yakuza gang war between the Yamaguchi-gumi and the breakaway Ichiwa-kai faction that began over the death of kumicho Kazuo Taoka. After being passed over as kumicho, Hiroshi Yamamoto broke away from the Yamaguchi-gumi, formed the rival Ichiwa-kai, and had Taoko’s successor, Masahisa Takenaka, murdered, along with two other Yamaguchi members. Following the assassination, Yamaguchi-gumi boss Kazuo Nakanishi vows to wipe out the Ichiwa-kai. During the next few years, the two gangs would engage in an estimated 200 gun battles, killing 26 gangsters and seriously wounding many more, with local newspapers carrying daily “scorecards” of the latest body counts.
1988 Affair of the Four Children of Sugamo 1 Toshima, Tokyo Four malnourished children are found in a Tokyo apartment nine months after their mother had left to travel with her boyfriend, during which time a fifth child was discovered to have been murdered by two friends of the oldest child.
1988-1989 Tsutomu Miyazaki 4 Tokyo and Saitama prefecture Serial killer Tsutomu Miyazaki abducts and murders girls aged four to seven.
1988-1989 Concrete-Encased High School Girl murder 1 Tokyo A 17-year-old boy Jo Kamisaku and three other boys abduct a high school girl Junko Furuta. They rape and assault her for 41 days. They murder her and encase her in concrete.
1989 Sakamoto family murder 3 Yokohama Tsutsumi Sakamoto, a lawyer working on a lawsuit against Aum Shinrikyo doomsday cult disappears with his wife and child. In 1995 it was revealed that cult members had murdered them and buried their bodies.
1990 Sapporo murder 1 Sapporo Nagata Ryoji murders a robbery victim during a break-in at a Sapporo residence. Ryoji is subsequently added to the Japanese Ten Most Wanted Fugitives list.
1990 Gangland slaying of police officers 7 Okinawa Hideo Zamami, a member of the Kyokuryu-kai affiliated Nishiki family, guns down two plainclothes Okinawa police officers mistaking them for rival gangsters. Sentenced to life imprisonment, he later appealed the decision claiming he was innocent of the shooting and used a scapegoat. Although rejecting his appeal, the court denied the prosecution’s request for the death penalty. A total of seven persons, including the two police officers and a high school boy, are killed during the battle.
1994 Matsumoto incident 7 Matsumoto, Nagano Doomsday cult Aum Shinrikyo release sarin nerve gas in a residential area in the world’s first use of chemical weapons by a terrorist group.
1995 Tokyo Sarin Gas Attack 12 Tokyo Aum Shinrikyo members conduct simultaneous attacks on multiple Tokyo Metro trains using sarin nerve gas, killing 12 and injuring more than 1000.
1995 Hachiōji supermarket murders 3 Hachiōji, Tokyo Three employees of a supermarket are found shot dead in a suspected robbery. Despite massive publicity, the case is still unsolved.
1997 Sakakibara Seito 2 Kobe Over several months, a 14-year old boy attacks a total of four younger girls with a hammer or a knife, killing one of them. He then strangles and decapitates Jun Hase, a 11-year old boy, leaving his head in front of his school with a note stuffed in his mouth, and sends taunting letters to a newspaper. The nation is shocked when a 14 year old is arrested, and eventually prompted the government to lower the age of criminal responsibility from 16 to 14 in 2000.
1997 Murder of Masaru Takumi 2 Kobe Masaru Takumi, considered to be the heir apparent of Yakuza leader Yoshinori Watanabe’s Yamaguchi-gumi organization, is killed by rival Nakano-kai gangsters Kouji Ishihara, Nakaho Kiyohara and Toriyabara Kiyoteru at a popular Kobe hotel. During the attack, dentist Hirai Hiroshi was mistaken as a bodyguard for Takumi and is killed by a four gunman Takeshi Yoshida whose killing of an innocent bystander would eventually lead to the Japanese government’s prosecution of the Nakano-kai.
1998 Wakayama curry poisoning 4 Wakayama Four people are killed and 63 injured after eating curry laced with arsenic at a community festival in Wakayama. Masumi Hayashi, the chief suspect, has been sentenced to death and is currently appealing.
1999 Okegawa stalking murder 2 Okegawa, Saitama A stalker Kazuhito Komatsu murders 21-year-old Shiori Ino with accomplices. The Police ignores her appeal before the murder and slanders her after the murder. A journalist Kiyoshi Shimizu determines criminals. Komatsu escapes and kills himself in Hokkaido.
2000 Niigata girl confinement incident – Tokyo While investigating a domestic disturbance call, police discover a schoolgirl who had been kidnapped in 1990 and held prisoner in an upstairs apartment for over nine years by a mentally disturbed man, Nobuyuki Sato. The girl, Fusako Sano, was returned to her parents while Sato was hospitalized and eventually sentenced to 14 years imprisonment.
2000 Tokyo Bay Sinyo Bay Bank robbery 1 Tokyo Tominaga Kazuyuki, a career criminal associated with the Yakuza, successfully steals 46,000,000 yen after hijacking a delivery to a pachinko parlor in December 2000. During the robbery, the driver was gunned down by Kazuyuki and an unidentified Chinese accomplice.
2000 Hostess murders 2 Roppongi, Tokyo Joji Obara, a prominent Osaka businessman, murders and dismembers British hostess Lucie Blackman. After the discovery of her body a year later, he was charged with her murder as well as similar charges against Australian hostess Carita Ridgeway and sexual assault charges against six other women. He was found not guilty of murdering Lucy Blackman due to lack of evidence, but was convicted of the other crimes.
2000 Setagaya family murder 4 Setagaya, Tokyo In an incident which shocked the nation, a family of four are murdered at their home in suburban Tokyo by an unknown intruder. Despite extensive investigations and a huge media coverage, the case remains unsolved.
2001 Hokuryo Clinic Incident 10? Sendai, Miyagi A 89-year-old woman dies mysteriously in Koryo Clinic. A nurse Daisuke Mori is suspected of at least 10 murders. He is arrested for a murder, but he insists that their death are caused by medical errors.
2001 Osaka School Massacre 8 Osaka 37 year old former janitor Mamoru Takuma entered an elementary school in Osaka, then used a kitchen knife to kill 8 students. He wounded an additional 13 other students and 2 teachers. He was executed in 2004.
2001 Myojo 56 building fire 44 Tokyo A building is fired in Kabukicho. Three employees can escape by jumping from the third floor of the building, but 44 people are killed by carbon monoxide in the building. The cause is strongly suspected as arson. However security is poor in Kabukicho and customers use false names. The case is still unsolved.
2002 Kitakyushu serial murders 7 Kitakyūshū Futoshi Matsunaga forces the victims to kill each other, resulting in killing 7 people between 1996 and 1998. Matsunaga and his common-law wife Junko Ogata are arrested in 2002 after a girl escapes from them.
2003 Super Free rape incident – Tokyo Students of Japanese universities in Tokyo rape women in a circle Super Free. A organizer Shinichiro Wada and 13 other members are arrested for gang rapes. The estimated number of rape victims are up to 500.
2003 Fukuoka family murder 4 Fukuoka Businessman Shinjiro Matsumoto, his wife Chika and two children aged 11 and 8 are murdered in a robbery by three Chinese students who broke into their home, and their bodies dumped in Hakata Bay. Two of the three – Yang Ning and Wang Liang – fled to China where they were arrested. Yang was executed and Wang sentenced to life imprisonment. The third, Wei Wei, was arrested in Japan and is currently on death row.
2004 Sasebo slashing 1 Sasebo, Nagasaki Satomi Mitarai, a 12-year-old elementary student, is stabbed to death by her classmate at school. The classmate has not been identified for legal reasons.
2004 Ōmuta murders 4 Ōmuta, Fukuoka Mob wife Mami Kitamura murders four people with her husband and two sons. The four people are sentenced to death.
2004 Murder of Kaede Ariyama 1 Nara Kaede Ariyama, a 7-year-old school girl, is kidnapped and murdered by a local newspaper deliveryman, Kaoru Kobayashi. Following his arrest, he was convicted and sentenced to the death penalty.
2005 Web suicide site murders 3 Osaka Serial killer Hiroshi Maeue murders three people. They are lured by Maeue via the online suicide club. He has been executed.
2005 Murder of Airi Kinoshita 1 Hiroshima, Japan 7-year old Airi Kinoshita is abducted on her way home from school and killed by wanted Peruvian sex offender Jose Manuel Torres Yake. He was sentenced to life.
2006 Five dead bodies in Hiratsuka 5 Hiratsuka, Kanagawa Five dead bodies are found in Hiratsuka. A woman Chizuko Okamoto is arrested for a murder of her daughter, but the case is hardly solved due to lack of evidence and statute of limitations.
2007 Iccho Itoh Murder 1 Nagasaki The mayor of Nagasaki, Iccho Itoh, is shot to death by Tetsuya Shiroo. Shiroo is a member of the Yamaguchi-gumi crime syndicate and was angry over damage to his car that occurred at a city construction site four years earlier.
2007 Murder of Hiroshi Miyamoto 7 Saga and Fukuoka Gangs, who belong to Dojin-kai, dispute about its leader. Kyushu Seido-kai separates from Dojin-kai and they kill each other. They kill six gangs and a civilian Hiroshi Miyamoto.
2008 Akihabara massacre 7 Akihabara 25-year old Tomohiro Kato rams a truck into a crowd of shoppers and proceeds to stab the run-down victims, killing six men and one woman, and injuring 11 others. The perpetrator is currently sentenced to death.
[edit] References
Violent crime against journalists in Mexico – Insider report
A significant trend of violent crime against journalists has appeared in the country in recent years.[19] Although the problem has existed since at least 1970, 15 journalists have been murdered in Mexico since 2000 alone.[19] Few of the perpetrators have been brought to justice. One of the more prominent cases was that of syndicated columnist Francisco Arratia Saldierna, a prominent and well-known journalist who wrote a column called Portavoz (or “Spokesman”). The column featured topics such as corruption, organized crime, and drug trafficking.[20]
Arratia’s murder, which was particularly brutal, and others like it, sparked demands from other journalists that then-President Vicente Fox do more to enforce security and bring those responsible for the murders to justice. In 2004, a group of 215 reporters and editors sent an urgent letter to President Fox and other federal authorities, demanding that they address these concerns. The letter represented a massive communication effort coming from professionals from 19 of the nation’s 31 states. The key demand was that violent crimes against journalists be made federal crimes, so they would be investigated and prosecuted by federal officers and not by local officials whom the letter claims could be the same people who commit the crimes.[20]
The effect of these crimes has been the self-censorship of many journalists, due to fears of retribution from criminals.[19] The situation has earned attention from prominent global organizations such as the office of the United Nations High Commissioner for Human Rights (OHCHR) and the Center for Journalism and Public Ethics (CEPET). Amerigo Incalcaterra of the OHCHR advocated the protection of journalists and the preservation of freedom of speech, calling it “essential for the consolidation of democracy and the rule of law in this country”.[19]
Impunity
According to the CNDH, only one out of every ten crimes is reported in Mexico; this is due to lack of trust from citizens to the authorities. Furthermore, only one out of 100 reported crimes actually goes to sentencing. This means that one out of every 1000 crimes is punished.[21]
BBC Documentary – Stupidity “Full Movie”
This documentary about stupidity tells us the history of the word “moron”, the difference between stupid, moron, smart, intelligent, genius and questions the regular practice of classifying peoples intelligence through standardized IQ tests. Of course also Mr. Bush is examined in this report. A well educated guy who, nevertheless, acts in a completely dumb way — or at least wants us to believe so.
Albert Einstein said:
“Only two things are infinite the universe and stupidity.
and I am not sure about the former.”
CONFIDENTIAL – CONGRESS REPORT – Afghanistan Casualties: Military Forces and Civilians
SECRET – Stories of Sacrifice and Dedication Civil Air Transport, Air America, and the CIA

Booklet featuring two specific stories that exemplify
the themes of sacrifice and dedication: Lima Site 85 and a CIA mission
utilizing CAT flight support to recover an
agent inside Communist China.
DOWNLOAD ORIGINAL DOCUMENT HERE
The story of CIA officers John T. Downey and Richard G. Fecteau is a story about remarkable faithfulness, shown not only by the men who were deprived of their freedom, but also by an Agency that never gave up hope
Unveiled – US officials identify marines in Afghan abuse video
US military sources have confirmed the identity of some the marines allegedly responsible for a video which shows them urinating on the bodies of three dead Afghans.
Defence officials accepted the authenticity of the video, which emerged on the internet this week.
The Pentagon has been scrambling to contain the fallout from the damaging footage, and senior government members, including secretary of state Hillary Clinton, have condemned the incident as deplorable.
Al Jazeera’s Rosiland Jordan reports from Washington DC.
TOP-SECRET – U.S. Marine Corps Intelligence Afghan Insurgent Tactics, Techniques and Procedures Field Guide

Studying past combat helps gain insight into how insurgents may operate in the future. This guide uses short, simple vignettes to highlight common Afghan insurgent tactics. Each vignette focuses on a particular mission profile, such as raids, ambushes, and defending against a cordon and search.
While tactics are continually evolving, the Afghans have a well documented history of using similar techniques against foreign militaries. Most of the vignettes in this guide are from the 1980s when Afghan insurgents fought the Soviet Union. Despite being more than 20 years old, many of the tactics remain in use today. For a more complete description of Afghan insurgent tactics against the Soviets, MCIA strongly recommends reading The Other Side of the Mountain by Ali Jalali and Les Grau, which this guide is based on. The final three vignettes in this guide are from recent operations in Afghanistan and demonstrate the evolution of tactics, techniques, and procedures (TTPs) by Afghan insurgents.
…
Vignette 1: Ambush
Ambush Near Abdullah-e Burj
October 1980
A Soviet column, returning to its base after a 4-day operation against the Mujahideen, was ambushed as it crossed a bridge going south on the main highway to Bagram.
The insurgents had observed the column headed north on the highway. They believed that the convoy would return the same way since the bridge was the only one in the region over the Panjsher River. The location was chosen because it would allow the Mujahideen to hit the convoy when it was most vulnerable: when half the column had crossed the bridge, and the force was divided by the river. They would ambush the column on its return trip when the troops were tired.
The Mujahideen secretly deployed on the day of the ambush. One group of 150 men was positioned in the orchards and hills south of the river (Map Point 1); a second group of 200 men was positioned to the north (Map Point 2). In both areas, rocket-propelled grenade launchers in covered positions were placed close to the road, with heavy machine guns on the more dominant terrain. Recoilless rifles and 82 mm mortars were placed for support. The Soviet column returned in the afternoon, and by 1600 it was split in two as it crossed the river (Map Point 3).
At a commander’s signal, the Mujahideen opened fire on the tanks, armored personnel carriers, and trucks along the entire length of the convoy. The Soviets drove off the road trying to escape. Those near the orchards had little room to maneuver. Twenty to 30 vehicles were burning. Soldiers dismounting from the armored personnel carriers came under heavy machine gun fire (Map Point 2). While some of the Soviets set up perimeter defenses to hold until help came, many abandoned their vehicles and tried to ford the river. Some were washed away while others headed for Bagram across the open plain.
As night fell, Soviet artillery ineffectively pounded Mujahideen positions. The insurgents moved through the abandoned vehicles, taking supplies and weapons. In the morning, the Soviets sent a relief column from Bagram to free the trapped convoy. The insurgents withdrew. The Mujahideen had two killed and seven wounded, with Soviet casualties unknown.

DOWNLOAD ORIGINAL DOCUMENT HERE
Confidential – Global Cryptologic Dominance through Responsive Presence and Network Advantage
NSA Statement:
We will:
- Lead an expert workforce for our best efforts to advance and operate world-class cryptologic systems and tools;
- Improve performance and integration of our core expertise and missions—exploit, protect and defend;
- Sense, make sense of, and securely share electronically gathered information at the speed of global information networks; and
- Increase measurably the security of national security systems and other critical operations and information when and where needed.
Our Mission
The National Security Agency/Central Security Service (NSA/CSS) leads the U.S. Government in cryptology that encompasses both Signals Intelligence (SIGINT) and Information Assurance (IA) products and services, and enables Computer Network Operations (CNO) in order to gain a decision advantage for the Nation and our allies under all circumstances.
GOAL 1: Succeeding in Today’s Operations – Enable wise policymaking, effective national security action, and U.S. freedom of action in cyberspace by exploiting foreign use of electronic signals and systems and securing information systems used by the U.S. and its allies, while protecting privacy and civil liberties.
GOAL 2: Preparing for the Future – Deliver next generation capabilities and solutions that meet the challenges of tomorrow and drive solutions from invention to operation in support of national security and U.S. Government missions.
GOAL 3: Enhancing and Leading an Expert Workforce – Attract, develop and engage an exceptional, diverse workforce prepared to overcome our cryptologic challenges.
GOAL 4: Implementing Best Business Practices – Provide timely data to inform optimal strategic and tactical investment decisions while ensuring organizational accountability for executing those decisions and realizing the associated performance improvement.
GOAL 5: Manifesting Principled Performance – Accomplishing our missions with a commitment to a principled and steadfast approach to performance through compliance, lawfulness, and protection of public trust must be paramount.
Core Values
We will protect national security interests by adhering to the highest standards of behavior:
- Lawfulness – We will adhere to the spirit and the letter of the Constitution and the laws and regulations of the United States.
- Honesty – We will be truthful with each other, and honor the public’s need for openness, balanced against national security interests.
- Integrity – We will behave honorably and apply good judgment as we would if our activities were under intense public scrutiny.
- Fairness – We will ensure equal opportunity and fairness in Agency policies, programs, and practices.
- Accountability – We will be accountable for our actions and take responsibility for our decisions, practicing wise stewardship of public resources and placing prudent judgment over expediency.
- Loyalty – We will be loyal to the nation, the mission, and each other, weighing ideas solely on the merits and ensuring that decisions enjoy vigorous debate while being made, followed by unified implementation.
- Collaboration – We will cooperate with others in a respectful and open-minded manner, to our mutual success.
- Innovation – We will seek new ways to accomplish our mission, planning for the future based on what we’ve learned from the past, and thinking ahead to the best of our ability to avoid unintended consequences.
- Learning – We will acquire and transfer knowledge, provide the resources and training necessary for our people to remain at the forefront of technology, and individually pursue continuous learning.
DOWNLOAD ORIGINAL DOCUMENT HERE
Uncensored – Occupy Wall Street Photos 10 January 2012 – Courtesy of Cryptome
|
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ows-23/pict6.jpg) Occupy Wall Street protesters read books in Zuccotti Park, Tuesday, Jan.10, 2012, in New York. Barricades were removed by Brookfield Properties, the owners of the park, allowing access once again into the park by the protesters. (Louis Lanzano) Occupy Wall Street protesters read books in Zuccotti Park, Tuesday, Jan.10, 2012, in New York. Barricades were removed by Brookfield Properties, the owners of the park, allowing access once again into the park by the protesters. (Louis Lanzano) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ows-23/pict7.jpg) Occupy Wall Street protesters gather in Zuccotti Park as security guards stand next to stacks of barricades,Tuesday, Jan. 10, 2012, in New York. The barricades were removed by Brookfield Properties, the owners of the park, allowing access once again into the park by the protesters. (Louis Lanzano) Occupy Wall Street protesters gather in Zuccotti Park as security guards stand next to stacks of barricades,Tuesday, Jan. 10, 2012, in New York. The barricades were removed by Brookfield Properties, the owners of the park, allowing access once again into the park by the protesters. (Louis Lanzano) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ows-23/pict8.jpg) Occupy Wall Street protesters make signs in Zuccotti Park, Tuesday, Jan.10, 2012, in New York. Barricades were removed by Brookfield Properties, the owners of the park Tuesday, allowing access once again into the park by the protesters. (Louis Lanzano) Occupy Wall Street protesters make signs in Zuccotti Park, Tuesday, Jan.10, 2012, in New York. Barricades were removed by Brookfield Properties, the owners of the park Tuesday, allowing access once again into the park by the protesters. (Louis Lanzano) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ows-23/pict10.jpg) Police officers guard the perimeter of Zuccotti Park As Occupy Wall Street protesters gather in the park, Tuesday, Jan.10, 2012, in New York. Barricades were removed by Brookfield Properties, the owners of the park, Tuesday, allowing access once again into the park by the protesters. (Louis Lanzano) Police officers guard the perimeter of Zuccotti Park As Occupy Wall Street protesters gather in the park, Tuesday, Jan.10, 2012, in New York. Barricades were removed by Brookfield Properties, the owners of the park, Tuesday, allowing access once again into the park by the protesters. (Louis Lanzano) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ows-23/pict9.jpg) Occupy Wall Street protesters gather in Zuccotti Park, Tuesday, Jan.10, 2012, in New York. Barricades were removed by Brookfield Properties, the owners of the park, allowing access once again into the park by the protesters. (Louis Lanzano) Occupy Wall Street protesters gather in Zuccotti Park, Tuesday, Jan.10, 2012, in New York. Barricades were removed by Brookfield Properties, the owners of the park, allowing access once again into the park by the protesters. (Louis Lanzano) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ows-23/pict11.jpg) Security from Brookfield Properties, the owners of Zuccotti Park, watch as Occupy Wall Street protesters gather in the park, Tuesday, Jan.10, 2012, in New York. Barricades were removed by the owners allowing access into the park by the protesters on Tuesday. (Louis Lanzano) Security from Brookfield Properties, the owners of Zuccotti Park, watch as Occupy Wall Street protesters gather in the park, Tuesday, Jan.10, 2012, in New York. Barricades were removed by the owners allowing access into the park by the protesters on Tuesday. (Louis Lanzano) |
Report – List of journalists killed in Tajikistan – by the Big Brother of the STASI
This is a list of journalists who have been killed in Tajikistan or journalists from Tajikistan killed outside of the country since 1990. Listees include those known to have been murdered, as well as cases of suspicious death
From 1990-2001 Tajikistan was one of the most dangerous countries in the world for journalists. Estimates for the number of journalists killed number from fifty to eighty.[1] In the late 1980s and early 1990s, journalism in Tajikistan underwent a transformation as the Soviet Union liberalized under glasnost and perestroika. Journalists in both private and state-run media were permitted greater editorial and investigative freedoms to report on issues and to challenge government propaganda. But journalists ran into danger when they publicly confronted powerful interests or reported on violent events. The first journalistic death in Tajikistan occurred on 12 February 1990 when a sniper in a government building opened fire on demonstrators in Dushanbe, killing a number of individuals, including a Lenfilm employee filming the events from his hotel. Following the events of February 1990, the government placed pressure on editors to fire dozens of journalists working for local television stations, radio stations and newspapers.[2]
Journalists continued to face official harassment through the fall of the Soviet Union and the independence of Tajikistan in 1991.[3] In mid-1992 the Civil War in Tajikistan began, and journalists became targets for killings. During the war, forces of the opposition and the government both massacred civilians from certain regions because of their perceived political alignments. Thousands of Gharmis and Pamiris were selectively killed by pro-government forces for killings in the first year of the war.[1] In December 1992 alone, four journalists of Pamiri origin were killed.[4] There were also instances of journalists who were killed for their criticism of Islamic groups allied with the opposition. By 1995 at least 37 journalists had been killed in Tajikistan.[5]
By the late 1990s, the number of killings of journalists in Tajikistan began to fall. This was not due to greater press freedoms in the republic, but rather to the fact that a large number of journalists had fled the country and journalistic freedom of expression inside of Tajikistan had come to a halt. The non-governmental organization Freedom House rated press freedoms in Tajikistan as “Not Free” beginning in 1992.[6] Other NGOs, including Human Rights Watch, the Committee to Protect Journalists and the Glasnost Defense Foundation, have issued reports condemning the lack of press freedoms in Tajikistan. By 2007 the murder of journalists had ceased, but that year Human Rights Watch criticized the government of Tajikistan for its move to “tighten control over independent media activities” and the fact that journalists critical of the government are “routinely threatened with prosecution.”[7] In nearly every case of the killing of a journalist in Tajikistan, no suspects have been arrested or brought to trial.
1990
* N.I. Matrosov was a Lenfilm employee. He was in Dushanbe when a confrontation between the protestors and government forces broke out. Matrosov was shot on 12 February at 3:40 p.m. when a sniper from government building opened fire on demonstrators in Dushanbe. Matrosov was filming the event from the second floor of his Tajikistan hotel room. In the same incident, a woman was killed as she stood beside her brother, photojournalist who was photographing the incident.[8]
1992
* Khushvaht Muborakshoev worked for Tajikistan State Television. He was killed in December at an unknown location by members of the People’s Front, according to local journalists. He was a Pamiri.[4]
* Filolisho Khilvatshoev worked for Payomi Dushanbe. He was killed in December at an unknown location by members of the People’s Front, according to local journalists. He was a Pamiri.[4]
* Jamshed Davliyatmamatov was a correspondent of the state-run Khovar Information Agency. He was killed in December in Dushanbe by members of the People’s Front. He was a Pamiri.[4]
* Mukhtor Bugdiev was a photojournalist with the state-run Khovar Information Agency. He was reportedly killed in December by members of the People’s Front. Bugdiev was a Pamiri.[4]
* Tavakkal Faizulloev, a Kulobi, was a correspondent for the newspaper Subhi Yovon in Yovon district, Kulob Oblast. On 17 November he was murdered in retaliation for writing anti-Islamic articles. The exact location of his death is unknown.[4]
* Arcady Ruderman was a Belarusian documentary filmmaker who was killed on 22 September while filming a documentary for Ostankino about opposition leader Davlat Khudonazarov.
* Tura Kobilov was editor of the newspaper Bairaki Dusti. In June 1992 he was taken hostage and later shot and killed in Bokhtar district by unidentified captors, according to the Union of Journalists of Tajikistan.[4]
* Shirindzhon Amirdzhonov was a correspondent for Tajikistan Radio. On 7 May he was killed along with Olim Zarobekov at the government-run Radio House in Dushanbe, according to the Union of Journalists of Tajikistan.[4]
* Olim Zarobekov was a departmental head at Tajikistan Radio. On 7 May he was killed along with Shirindzhon Amirdzhonov at the government-run Radio House in Dushanbe, according to the Union of Journalists of Tajikistan.[4]
* Murodullo Sheraliev was editor-in-chief of the newspaper Sadoi Mardum. On 5 May Sheraliev was killed by shot in the Tajikistan Supreme Soviet in Dushanbe, according to the Union of Journalists of Tajikistan.[4]
1993
* Tabarali Saidaliev was editor of the newspaper Ba Pesh. On 21 October he was kidnapped and his body was found in a cotton field three days later. The men who kidnapped him were dressed as security agents.[9]
* Olimjon Yorasonov worked for the a regional newspaper in Vakhsh, Khatlon Province, and was killed in June or July. According to local journalists Yorasonov was murdered by the members of the militia People’s Front.[9]
* Pirimkul Sattori was a journalist from the Qurghonteppa newspaper Khatlon, who disappeared 28 May in Kulob oblast. His body was found several days later in a cotton field.[9][10]
* Zukhuruddin Suyari was a correspondent for the government magazine Todzhikiston. His body was found in Qurghonteppa at the end of March. It is suspected that Suyari was murdered by National Front members because his was Gharmi.[9]
* Saidmurod Yerov was the director of the executive director of Farkhang magazine. In January 1993 Yerov was arrested by the National Front. His body was reportedly found in a mass grave in Dushanbe on 2 February.[9]
1994
* Khushvakht Haydarsho was secretary of the editorial board of the Tajik-language government newspaper Jumhuriyat. On 18 May he was shot dead near his home in Dushanbe. It is believed that his death is connected to a series of articles he published on crime in Tajikistan.[11]
1995
* Muhiddin Olimpur was found shot outside a park in Dushanbe in December. He was the head of the BBC’s Persian Service bureau in Dushanbe.
* Muhammadsharif Holov was a writer and freelance journalist. On 16 November, Holov was killed when around 23:00 an unknown man in a mask entered his apartment and shot him with an automatic rifle. Holov was born in the village Olmalik in Tajikabad District on 4 February 1928. As a youth he had worked in the theatre and served in the military. He later went on to author several plays, become director of the Tajik State Youth Theatre, and was a member of the Writers’ Union of Tajikistan.[12]
* “TKD” Pochohona Sayfiddinov was a proofreader in the newspaper “Hakikati Kurgonteppa” and correspondent for the newspaper “Adabiet wa”. He frequently published under the pseudonym Rustoi. On 29 September, Sayfiddinov’s body was found in the Vakhsh River near the village of Kyzyl-Kala outside of Qurghonteppa. His body had been brutalized before being dumped in the river. He and his driver, Todzhiddin Homidov, had had their car stopped a few days earlier were stopped by unknown gunmen. Sayfiddinov was born on 2 August 1962 in the village Boturobod in Bokhtar district. In 1986 he graduated from the Arabic language faculty of the school of Oriental language of Tajik State University. It is suspected that Sayfiddinov was murdered because he was a close friend of politician Abdumalik Abdullojanov and had published articles about him, which had been criticized in the official press.[13]
* Muhammadmuslih Nadzhibulloev was a freelance writer and student in the Department of Journalism at the Tajik State University in Dushanbe. 0n 4 July, Nadzhibulloev was stabbed to death by unknown assailants. His body was found in Komsomolskaya Lake in the center of Dushanbe two days later. A few days before the his death, Nadzhibulloev had defended a comparative analysis of the censorship of the independent newspaper Charogi and the modern press in Tajikistan. Nadzhibulloev was born in March 1974 in the village Vora in Panjakent district, Sughd.[14]
* Olim Abdulov was director and writer for the Television program “Madzhro”. On the evening of 15 May he was killed near his home by unknown persons. Abdulov was born 2 July 1970 in Dushanbe. He had graduated from in 1992 from the Institute of the Arts.[15]
* Zayniddin Muhiddinov was a freelance writer and former editor of the newspaper Hakikat. On 14 March, unidentified men in camouflage uniforms shot dead Muhiddinov in the Leninsky district.[16]
1996
* Viktor Nikulin was a correspondent for Russian Public Television (ORT) in Dushanbe. Nikulin was fatally shot at the door to his office on 28 March. He had received three threatening telephone calls a week before he was killed.[17]
1998
* Otakhon Latifi was an opposition politician member and one of the most notable journalists in Tajikistan. On 22 September, at around 8am, Latifi was shot at point blank range outside his apartment in Dushanbe.
* Meirkhaim Gavrielov was a prominent leader of the Bukharian Jewish community in Tajikistan and journalist for fifty years. He was found strangled in his home on 8 June.
1999
* Dzhumakhon Khotami was the chief spokesperson for the Interior Ministry of Tajikistan. On 5 July he was assassinated in Dushanbe. Khotami had been the anchor of a weekly TV program that reported on drug trafficking, corruption and organized crime. Speculation for his death revolves around the drug bosses whose name’s he revealed publicly on television.[18]
2000
* Iskandar Khatloni was a Moscow-based correspondent for Radio Free Europe/Radio Liberty’s Tajik Service. On the night of 21 September, Khatloni was attacked in his Moscow apartment by an unknown assailant wielding an axe. He died that night in a local hospital. Khatloni had recently been working on stories about the human-rights abuses in Chechnya[19]
* Aleksandr Alpatov was a photographer for the Khovar Information Agency. The Interior Ministry of Tajikistan reported on 1 September that Alpatov’s body was found not far from his home in Dushanbe. He was 42 when he died. Authorities reported that he had been killed by a handgun equipped with a silencer.[20]
See also
* Human rights in Tajikistan
* List of newspapers in Tajikistan
* Civil War in Tajikistan
References
1. ^ a b “Tajikistan Freedom Of Expression Still Threatened. November 1999. Vol. 11, No. 14 (D)”. Human Rights Watch. 1999. http://www.hrw.org/reports/1999/tajikistan/Tajik99n-05.htm#P217_40796. Retrieved 16 March 2008.
2. ^ Conflict in the Soviet Union: Tadzhikistan. Human Rights Watch. 1991. pp. 41–42, 49.
3. ^ Conflict in the Soviet Union: Tadzhikistan. Human Rights Watch. 1991. pp. 49.
4. ^ a b c d e f g h i j “Journalists Killed in 1992”. Committee to Protect Journalists. http://www.cpj.org/deadly/1992_list.html. Retrieved 2008-03-11.
5. ^ “Tajik Democratic Party speaks against media warning”. BBC Summary of World Broadcasts. Lexis-Nexis. 10 August 1995.
6. ^ Karatnycky, Adrian; Alexander J. Motyl and Boris Shor (1997). Nations in Transit 1997: Civil Society, Democracy and Markets in East Central Europe and the Newly Independent States. New Brunswick: Transaction Publishers. pp. 373. ISBN 0765804115.
7. ^ “Tajikistan Events of 2007”. Human Rights Watch. 2008. http://hrw.org/englishwr2k8/docs/2008/01/31/tajiki17748.htm. Retrieved 2008-03-15.
8. ^ Conflict in the Soviet Union: Tadzhikistan. Human Rights Watch. 1991. pp. 41–42.
9. ^ a b c d e “Journalists Killed in 1993”. Committee to Protect Journalists. http://www.cpj.org/deadly/1993_list.html. Retrieved 2008-03-11.
10. ^ Denber, Rachel (1993). Human Rights in Tajikistan: In the Wake of Civil War. Human Rights Watch. pp. 11.
11. ^ “Journalists Killed in 1994”. Committee to Protect Journalists. http://www.cpj.org/deadly/1994_list.html. Retrieved 2008-03-11.
12. ^ “Холов Мухаммадшариф”. Memorium. http://www.memorium.cjes.ru/?pid=2&id=331. Retrieved 2008-03-15.
13. ^ “Сайфиддинов Почохон”. Memorium. http://www.memorium.cjes.ru/?pid=2&id=330. Retrieved 2008-03-15.
14. ^ “Наджибуллоев Мухаммадмуслих”. Memorium. http://www.memorium.cjes.ru/?pid=2&id=329. Retrieved 2008-03-15.
15. ^ “Абдулов Олим”. Memorium. http://www.memorium.cjes.ru/?pid=2&id=323. Retrieved 2008-03-15.
16. ^ “Мухиддинов Зайниддин”. Memorium. http://www.memorium.cjes.ru/?pid=2&id=328. Retrieved 2008-03-15.
17. ^ “Journalists Killed in 1996”. Committee to Protect Journalists. http://www.cpj.org/deadly/1996_list.html. Retrieved 2008-03-10.
18. ^ “Journalists Killed in 1999”. Committee to Protect Journalists. 1999. http://www.cpj.org/deadly/1999_list.html. Retrieved 2008-03-11.
19. ^ “Journalist Murdered In Moscow”. Committee to Protect Journalists. 2000. http://www.cpj.org/news/2000/Russia22sept00na.html. Retrieved 2008-03-10.
20. ^ “Khovar news agency journalist found murdered in Tajik capital”. BBC Summary of World Broadcasts. Lexis-Nexis. 1 September 2000.
SOURCE: WIKIPEDIA
Unveiled and Uncensored – Stratfor Back Online
Stratfor.com 2012-Jan-11-12:08:
![[Image]](https://i0.wp.com/cryptome.org/2012/01/0029.jpg)
Several of the Stratfor.com links below do not work, perhaps because of the sneaky subscriber-tracking code contained.
A sends:
Hello, looks like stratfor is back.
———- Forwarded message ———-
From: Stratfor <mail@response.stratfor.com>
Date: 2012/1/11
Subject: Stratfor: Back online + new Geopolitical Weekly
Watch this video of George Friedman on the hacking incident
More info on the attack
Dear Stratfor Member,
We are happy to announce that our website is back online. Visit Stratfor.com to view our 2012 Annual Forecast, as well as fresh analyses on Syria, Iraq and Lithuania and our Geopolitical Diary.
Below you will find a special edition of the Geopolitical Weekly by George Friedman on Stratfor’s security breach.
We may experience brief service interruptions as we work to handle the high level of interest in the new website. If you have trouble connecting to the new site, please check back again soon.
While we continue to rebuild our infrastructure and website capabilities, you will be able to access our content online without having to log in. We are aggressively implementing our plan to reintegrate customers securely, as this is our top priority. In the next several days, we will be informing you about how to establish a new password and update your billing information. In the meantime, visit our website to read fresh content every day.
We deeply regret that an unauthorized party illegally obtained and disclosed the credit card data of some of you. We are making certain that this will never happen again by having a third party with appropriate security safeguards handle all credit card transactions in the future. We hope that you have taken advantage of the CSID identity protection service we have provided.
We understand that you have many questions. Check out www.stratfor.com/hacking-news, a website we’ve created to give you a full rundown of the incident and our plan to address your concerns.
Please contact us at feedback@stratfor.com with any questions, as well as any comments you may have on the Geopolitical Weekly below.
Thank you again for your patience as we work to secure our website and resume normal operations.
– The Stratfor Team
Geopolitical Weekly: The Hack on Stratfor
By George Friedman | January 11, 2012
In early December I received a call from Fred Burton, Stratfor’s Vice President of Intelligence. He told me he had received information indicating our website had been hacked and our customer credit card and other information had been stolen. The following morning I met with an FBI special agent, who made clear that there was an ongoing investigation and asked for our cooperation. We, of course, agreed to cooperate. The matter remains under active investigation.
From the beginning I faced a dilemma. I felt bound to protect our customers, who quickly had to be informed about the compromise of their privacy. I also felt bound to protect the investigation. That immediate problem was solved when the FBI told us it had informed the various credit card companies and had provided those companies with a list of compromised cards while omitting that it had come from us. Our customers were therefore protected, as the credit card companies knew the credit cards and other information had been stolen and could act to protect the customers. We were not compelled to undermine the investigation.
The FBI made it clear that it expected the theft to be exposed by the hackers. We were under no illusion that this was going to be kept secret. We knew our reputation would be damaged by the revelation, all the more so because we had not encrypted the credit card files. This was a failure on our part. As the founder and CEO of Stratfor, I take responsibility for this failure, which has created hardship for customers and friends, and I deeply regret that it took place. The failure originated in the rapid growth of the company. As it grew, the management team and administrative processes didn’t grow with it. Again, I regret that this occurred and want to assure everyone that Stratfor is taking aggressive steps to deal with the problem and ensure that it doesn’t happen again.
From the beginning, it was not clear who the attackers were. The term “Anonymous” is the same as the term “unknown.” The popular vision of Anonymous is that its members are young and committed to an ideology. I have no idea if this is true. As in most affairs like this, those who know don’t talk; those who talk don’t know. I have my theories, which are just that and aren’t worth sharing.
I was prepared for the revelation of the theft and the inevitable criticism and negative publicity. We worked to improve our security infrastructure within the confines of time and the desire to protect the investigation by not letting the attackers know that we knew of their intrusion. With the credit card information stolen, I assumed that the worst was done. I was wrong.
Early in the afternoon of Dec. 24, I was informed that our website had been hacked again. The hackers published a triumphant note on our homepage saying that credit card information had been stolen, that a large amount of email had been taken, and that four of our servers had been effectively destroyed along with data and backups. We had expected they would announce the credit card theft. We were dismayed that emails had been taken. But our shock was at the destruction of our servers. This attack was clearly designed to silence us by destroying our records and the website, unlike most attacks by such groups.
Attacks against credit cards are common, our own failures notwithstanding. So are the thefts of emails. But the deliberate attack on our digital existence was a different order of magnitude. As the global media marveled at our failure to encrypt credit card information, my attention was focused on trying to understand why anyone would want to try to silence us.
In the days that followed, a narrative evolved among people claiming to speak for Anonymous and related groups. It started with looking at our subscriber list and extracting corporate subscribers who were now designated as clients. The difference between clients and subscribers is important here. A client is someone you do customized work for. A subscriber is simply someone who purchases a publication, unchanged from what others read. A subscriber of The New York Times is not its client. Nevertheless, some of the media started referring to these subscribers as clients, reflecting the narrative of those claiming to speak with knowledge of our business.
From there, the storyline grew to argue that these “clients,” corporate and government, provided Stratfor with classified intelligence that we reviewed. We were no longer an organization that analyzed the world for the interested public, but rather a group of incompetents and, conversely, the hub of a global conspiracy. The media focused on the first while the hacking community focused on the second.
This was why they stole our email, according to some of them. As one person said, the credit cards were extra, something they took when they realized they could. It was our email they were after. Obviously, we were not happy to see our emails taken. God knows what a hundred employees writing endless emails might say that is embarrassing, stupid or subject to misinterpretation. What will not appear is classified intelligence from corporations or governments. They may find, depending on what they took, that we have sources around the world, as you might expect. It is interesting that the hacker community is split, with someone claiming to speak for the official Anonymous condemning the hack as an attack on the media, which they don’t sanction, and another faction defending it as an attack on the rich and powerful.
The interpretation of the hackers as to who we are — if indeed that was their interpretation — was so wildly off base as to stretch credulity. Of course, we know who we are. As they search our emails for signs of a vast conspiracy, they will be disappointed. Of course we have relationships with people in the U.S. and other governments and obviously we know people in corporations, and that will be discovered in the emails. But that’s our job. We are what we said we were: an organization that generates its revenues through geopolitical analysis. At the core of our business, we objectively acquire, organize, analyze and distribute information.
I don’t know if the hackers who did this feel remorse as they discover that we aren’t who they said we were. First, I don’t know who they actually are, and second, I don’t know what their motives were. I know only what people claiming to be them say. So I don’t know if there is remorse or if their real purpose was to humiliate and silence us, in which case I don’t know why they wanted that.
And this points to the real problem, the one that goes beyond Stratfor’s own problem. The Internet has become an indispensible part of our lives. We shop, communicate, publish and read on it. It has become the village commons of the planet. But in the village commons of old, neighbors who knew and recognized each other met and lived together. Others knew what they did in the commons, and they were accountable.
In the global commons, anonymity is an option. This is one of the great virtues of the Internet. It is also a terrible weakness. It is possible to commit crimes on the Internet anonymously. The technology that enables the Internet also undermines accountability. Given the profusion of technical knowledge, the integrity of the commons is in the hands of people whose identities we don’t know, whose motives we don’t understand, and whose ability to cause harm is substantial. The consequence of this will not be a glorious anarchy in the spirit of Guy Fawkes, but rather a massive repression. I think this is a pity. That’s why I wonder who the hackers actually are and what cause they serve. I am curious as to whether they realize the whirlwind they are sowing, and whether they, in fact, are trying to generate the repression they say they oppose.
The attempt to silence us failed. Our website is back, though we are waiting for all archives to be restored, and our email is working again. Our failures have been reviewed and are being rectified. We deliberately shut down while we brought in outside consultants to rebuild our system from the ground up. The work isn’t finished yet, but we can start delivering our analyses. The handling of credit cards is being handed off to a third party with appropriate capability to protect privacy. We have acted to help our customers by providing an identity theft prevention service. As always, we welcome feedback from our supporters as well as our critics.
We are fortunate that we have the financial resources and staff commitment to survive the attack. Others might not. We are now in a world in which anonymous judges, jurors and executioners can silence whom they want. Take a look at the list of organizations attacked. If the crushing attack on Stratfor is the new model, we will not be the last. No security system is without flaws even if it is much better than Stratfor’s was.
We certainly expect to be attacked again, as we were last week when emails were sent out to members from a fake Stratfor address including absurd messages and videos. Our attackers seem peculiarly intent on doing us harm beyond what they have already done. This is a new censorship that doesn’t come openly from governments but from people hiding behind masks. Do not think we will be the last or that we have been the first.
We will continue to publish analysis and sell it to those who believe it has value. To our subscribers who have expressed such strong support, we express our deepest gratitude. To our critics, we assure you that nothing you have said about us represents a fraction of what we have said about ourselves. While there is much not to be proud of in this affair, I am proud beyond words of all my dedicated colleagues at Stratfor and am delighted to return our focus to analyzing critical international affairs.
To all, I dedicate myself to denying our attackers the prize they wanted. We are returning to the work we love, dedicated to correcting our mistakes and becoming better than ever in analyzing and forecasting how the world works.
Comments? Send them to feedback@stratfor.com.
Report – List of Journalists killed by KGB and STASI – We work to stop this and get Murderers
The dangers to journalists in Russia have been well known since the early 1990s but concern at the number of unsolved killings soared after Anna Politkovskaya’s murder in Moscow on 7 October 2006. While international monitors spoke of several dozen deaths, some sources within Russia talked of over two hundred fatalities.[1] The evidence has since been examined and documented in two reports, published in Russian and English, by international organizations.
А wide-ranging investigation by the International Federation of Journalists into the deaths of journalists in Russia was published in June 2009. At the same time the IFJ launched an online database[2][3] which documents over three hundred deaths and disappearances since 1993. Both the report Partial Justice[4] (Russian version: Частичное правосудие[5]) and the database depend on the information gathered in Russia over the last 16 years by the country’s own media monitors, the Glasnost Defense Foundation and the Center for Journalism in Extreme Situations.
In its September 2009 report the Committee to Protect Journalists repeated its conclusion that Russia was one of the deadliest countries in the world for journalists and added that it remains among the worst at solving their murders. The Anatomy of Injustice[6] (Russian version: Анатомия безнаказанности[7]) offers an account of the deaths of 17 journalists in Russia since 2000. They died or were killed, the CPJ is convinced, because of the work they were doing and in only one case, it notes, has there been a partially successful prosecution.
The IFJ report focuses on the capacity of Russian law enforcement agencies, over a longer period of time, to identify and detain those who have killed journalists.[8] It adopted a broader approach than the CPJ study, and offered more analysis of change over time. This permitted Partial Justice to reveal a telling contrast between the rising and successful rate of prosecution for those who have killed journalists in ordinary cases of homicide[9] and the persistent failure to prosecute or convict those responsible for murders linked to the work of journalists.
How the figures have been compiled
Among international monitors the figures quoted for deaths of journalists in Russia have varied, sometimes considerably. There are several explanations. One, certain organisations are concerned with all aspects of safety in news gathering, and so the International Federation of Journalists and the International News Safety Institute also record accidents that have occurred at work.[10] Two, some monitoring bodies include only fatalities in crossfire and dangerous assignments, and those murders where they feel sure of the motive behind the lethal attack and can with confidence lobby the appropriate government — the CPJ adopts this approach. Three, the term “journalist” is used by monitors as a general term to cover many different occupations within the media. Some include support staff, others do not.
In any list of deaths, compiled by monitors inside or outside the country Russia ranks high. When the killing began the brief first Chechen war took numerous lives, of journalists from within Chechnya and from further afield. This deadly combat zone was then matched by that in the former Yugoslavia, above all in Bosnia. There were also mounting peacetime deaths of journalists elsewhere in the Russian Federation.
Those deliberately targeted for their work have tended to be reporters, correspondents and editors. In Russia many directors of new regional TV and radio stations have been murdered[11][12] but most of these deaths are thought to relate to conflicting business interests. Photographers and cameramen are particularly vulnerable in crossfire situations, such as the October 1993 days in Moscow and the armed conflict in the North Caucasus.
Following Russia’s media monitors, the IFJ database of deaths and disappearances in Russia embraces the entire range of media occupations and every degree of uncertainty as to the motive for many of the attacks. At the same time it allows for selection and analysis. One, it classifies the way in which a journalist died (homicide, accident, crossfire, terrorist act or not confirmed) and, two, it assesses each death as certainly, possibly,[13] or most probably not, linked to the journalist’s work.
Since the early 1990s Russia’s media monitors have recorded every violent or suspicious death that came to their attention. Determining which were linked to the work of the journalist concerned has not always been easy since law enforcement agencies in Russia were then struggling to cope with a wave of murders, and the number of unsolved killings of journalists steadily mounted. In the last few years n the Center for Journalism in Extreme Situations has gathered all available information about these deaths on its Memorium site.[14] This made it possible to check how far these deaths have been investigated and how many have led to court cases. The IFJ data base summarises the information accumulated on the Memorium site and makes it available in English for the first time.
The most up to date information is that 30% of all the murders committed since 1993 have resulted in prosecutions.[15] And if few reached the courts in the early 1990s, in the last few years the proportion has risen to 60% of all acknowledged homicides. This shifts the focus of concern to the quality of justice administered and, in particular, to the failure to solve the minority of very important cases within that total of targeted contract killings linked to the journalist’s investigative work and publications.
During a study of international fraud-detection homicide which compared fraud detection homicide cases from the United States of America against fraud detection homicide cases from the former Soviet Republic the murder of Paula Klebenikov illustrated a case of a contract killing of a journalist known to expose fraud in governments. At the time of his murder, he was thought to be investigating complex money laundering fraud scheme involving Chechen reconstruction projects. The investigation appears to reveal that Klebnikov had discovered that the fraud reached deep into the centers of power in the Kremlin, elements involving organized crime, and also the former KGB, which is now known as the FSB.[16]
[edit] Partial Justice and Anatomy of Injustice
The IFJ report, Partial Justice, maps the changing contours of impunity in Russia. It shows and explains the process whereby particular deaths are selected by the IFJ, CPJ and other monitors. It stresses the need for an end to total impunity in those remaining regions (the North Caucasus, St Petersburg) where no one has ever been prosecuted for killing a journalist,[17] and for an advance beyond partial justice in those cases where it is known, or strongly suspected, that the murder of a journalist was planned and premeditated. It is not enough to put the killer on trial; he must be accompanied, or followed, by his accomplices, and the intermediaries and individuals who ordered and paid for the killing.
The IFJ report opens and closes with the Politkovskaya murder and the subsequent trial, which ran from November 2008 to February 2009. After 16 years of unsolved killings, the international outcry over her death made this a test case that might finally breach the barrier of partial justice. The evidence presented by the prosecution, unfortunately, did not convince the jury or satisfy other key participants.[18] Anatomy of Injustice, the report by the CPJ, displays the conclusions the Committee has reached about certain deaths since 2000: the authorities do not acknowledge some of these deaths as homicide,[19] while several others reached the courts but have led at most to the conviction of the perpetrator, not those who ordered the killing.
Following different routes the two reports reach a similar set of recommendations. They call on the Russian authorities to give investigators and courts the backing they need to identify and pursue all those responsible for the deaths of journalists and, in the meanwhile, to keep press and public better informed about their progress in tackling such disturbing crimes.
[edit] International comparisons
The CPJ lists Russia as “the third deadliest country in the world for journalists” since 1991, exceeded in the number of deaths only by Algeria (1993–1996) and post-invasion Iraq.[20] It is more revealing, perhaps, to set Russia alongside its G20 partners — not just the USA and France, but also Saudi Arabia and China (see Table 1, in IFJ report).[21] Russia’s problem, shared by certain other members of G20 (India, Brazil and Mexico), is not simply one of the number of deaths but that the killing with impunity has persisted over time.
The varied conditions in these economically important countries highlight a further crucial dimension. The killing of journalists may be the most dramatic and frequently quoted “barometer of press freedom”[22] but it is by no means the only measure. What it signifies for a particular country can only be properly gauged in the wider context of press freedom and other liberties, present (or absent) in that society.[23] Very few journalists have been killed in China[24] and none, it would seem, in North Korea. Other shortcomings ensure those countries occupy a lower position than Russia on any index of press freedom.
And it is important to integrate into an understanding of the media situation those cases where a journalist, such as Mikhail Beketov, has survived an attack aimed at killing him (see below, “Killing not the only measure”). Death in such attacks is just the extreme end of the spectrum of threats and intimidation.
Deaths and trials, statistics
The violent deaths of journalists started in the Yeltsin era (1991–1999) and continued under Putin, president of Russia from 31 December 1999 to 7 May 2008.[25] When Medvedev became president, he spoke of the need to end “legal nihilism”.[citation needed] In the past five years, there have been a rising number of trials[17] but by November 2009 there had yet to be a major breakthrough, under Medvedev, either in the prosecution of pre-2008 deaths or the investigation of killings since his May 2008 inauguration. The Politkovskaya murder trial and the first arrests in the Baburova-Markelov slaying (November 2009) showed some inconclusive signs of movement.
See also: List of Presidents of the Russian Federation and Presidents
President Y Y Y Y Y Y Y P P P P P P P P P-M M
year 1993 1994 1995 1996 1997 1998 1999 2000 2001 2002 2003 2004 2005 2006 2007 2008 2009 TOTAL
murder,crossfire
terrorist act
10 12 22 18 10 10 11 17 12 23 11 12 5 13 3 5 6 200
murder only 3 8 16 12 10 10 8 15 11 20 11 10 4 13 3 5 6 165
trials – – – 1 1 4 4 3 1 3 3 6 2 7 5 4 2 50
The yearly figures in the table above are derived from the “journalists in Russia” database, where details can be found on each individual death. Certain important categories are not included. Those who have gone “missing” (14 persons);[26] those who died in an incident (“not confirmed”, 28 persons), the nature of which has not been satisfactorily established; and journalists killed in work-related accidents (37 persons),[27] may be found online in the IFJ database.
The third set of figures indicates the yearly number of verdicts reached in trials for the killing of journalists. With only three exceptions these have all been for homicide. Some cases have taken six to seven years to reach court, e.g. the killings of Dmitry Kholodov and Igor Domnikov, but most deaths that have resulted in prosecution take, on average, 12–24 months between the killing and the verdict.[28][29]
Rates of conviction are a different matter. When the death was not related to the journalist’s work the conviction rate exceeds 90%. When the journalist’s death was certainly or seems likely to have been related to his or her work, the rate of acquittals rises sharply to around half of the total. Most trials are still held before a judge, aided by two lay assessors. Trial by judge and jury, still very rare in Russia, generally offers a more rigorous testing of evidence, robust defence of the suspects and a higher chance of the defendant being found not guilty (average acquittal rate of 20%). The Politkovskaya murder trial, which was held before a jury, ended in February 2009 with the acquittal of all those accused.
Concern abroad
Over the past decade the Russian authorities have been repeatedly urged, by Western governments and international media bodies, to do more to investigate the deaths of journalists there. The Paris-based Reporters Without Borders constantly criticized Russia for what it described as a failure to investigate these murders[30][31][32][32][33][34] .[35] The organization further claimed that many of the dead journalists had been critical of the Russian President, Vladimir Putin. Between March 2000 and July 2007, said Reporters Without Borders, 21 journalists were murdered in Russia because of their work.[36]
Similar figures were produced by the CPJ.[37] In a June 2007 statement the CPJ said, “A total of 47 journalists have been killed in Russia since 1992, with the vast majority of killings unsolved,”.[20] Seventeen of these journalists had been killed “in the line of duty” since 2000: 14 were murdered in retaliation for their journalism; “two died in crossfire; and one was killed while covering a dangerous assignment”. The CPJ was continuing to investigate the deaths of eight other journalists to see if there was a link with their work. None of the 14 murders committed since 2000 had been solved, the CPJ said, and “13 bear the marks of contract hits”.[20]
Pressure on the Russian authorities increased in late 2006 after the murder of Anna Politkovskaya. In June 2007 the board of the World Association of Newspapers passed a resolution, calling on the authorities in Russia to “investigate journalist deaths more vigorously”[38]:
The brutal murder on 7 October 2006 of Novaya Gazeta journalist Anna Politkovskaya, known for her critical reporting on the conflict in Chechnya in which she sought to expose human rights abuses, was yet another reminder to Russian journalists that violence awaits those who investigate or criticise. It is estimated that 21 journalists have been killed since Russian President Vladimir Putin came to power in March 2000. In the great majority of cases, no one has been convicted and sentenced for the murders.
On 18 June 2007, the U.S. House of Representatives passed House Resolution 151, calling on Putin to “step-up efforts to investigate” the murders.[39] In a report published in 2007, the International News Safety Institute said more journalists had died violent deaths in Russia in the previous 10 years than anywhere in the world apart from Iraq,[40] though it offered statistics rather than details of the individual victims.[39] The website of the British New Statesman magazine, in what was described as “solidarity with the dead, and in association with Amnesty International, Center for Journalism in Extreme Situations, the Committee to Protect Journalists and Index on Censorship” published a list of 40 Russian journalists killed since 1993, representing only some of those who died.[41]
Dissenting voices, legal issues
Immediately after Politkovskaya’s murder doubts were expressed about the chances of justice being done, even though the victim in this case was a journalist who had acquired a worldwide reputation (cf. Dmitry Kholodov in 1994). American commentator Anne Applebaum thought that the murderers of Politkovskaya would never be found.[42] There were also some dissenting and sceptical voices.
German author Gabriele Krone-Schmalz wrote that many of the deaths of journalists could be explained by ordinary criminality. She suggested that the number of killings during Putin’s presidency was no higher than under Boris Yeltsin.[25] Writing for the maverick eXile publication in Moscow, Kirill Pankratov accused the CPJ of applying different standards to different countries and for classifying certain suspicious deaths of Russian journalists as “confirmed” murders.[43] He and others noted that some of the murders had now been solved and the suspects jailed.
Recent killings, in various parts of Russia, of Ilyas Shurpayev,[44] Yury Shebalkin,[45] Konstantin Borovko[46] and Leonid Etkind[47] did indeed lead to trials and convictions. This was also true of some of the men involved in the brutal, earlier murder of 23-year old Internet journalist Vladimir Sukhomlin.[48] Ilya Zimin’s alleged killer, meanwhile, was tried in his native Moldova and acquitted.[49] Yet these examples do not disprove the charge of partial justice since only one of the deaths was related beyond doubt to the journalistic work of the victim.
Criticism from abroad was frequently perceived and rejected as selective. However, Russia’s sought-for status as a member of G8 from 1997 onwards set a benchmark that showed the continuing deaths of journalists, and of other media restrictions within the country, in an unfavourable light. Also of importance was the country’s admission to the Council of Europe and, as a result, the potential involvement, after 1998, of the European Court of Human Rights as an arbiter of last resort. Unsuccessful attempts were made for the 2004 acquittal of Dmitry Kholodov’s alleged killers to be examined in Strasbourg. So far the Court has only once determined the failure of the Russian authorities to pursue those responsible for the violent deaths of journalists. In 2005 it ruled that the October 1999 killing in Chechnya of cameramen Ramzan Mezhidov and Shamil Gigayev and of more than thirty other civilians who died during the same incident had not been properly investigated.[50]
Killing not the only or always the best measure
There are certain countries where, over the past two decades, killing of journalists has been a regular occurrence (e.g. Colombia, Philippines, India). There are authoritarian regimes where few if any journalists have been killed in the same period (e.g. China, Saudi Arabia, North Korea, Cuba) – journalists know their place and other forms of coercion keep them in line. Within Russia there has been regular monitoring since the late 1990s by the Glasnost Defence Foundation and the Center for Journalism in Extreme Situations of all forms of intimidation or coercion used against journalists. Their evidence suggests that direct and indirect pressure on media outlets, increasingly through the courts in cases of criminal defamation, is widespread and ranges from obstruction of publishing activities, to assaults on staff and frequent threats to investigative reporters.
If approximately three quarters of the murders of journalists over the past 16 years are probably not related to their investigations and publications, the CJES considers that up to 70% of assaults, which annually run into the dozens, are work-related. Sometimes these are very serious indeed. In November 2008 Mikhail Beketov, chief editor of the Khimkinskaya pravda, a paper in a Moscow suburb, was beaten so severely that although he survived, and his paper has even resumed limited publication, by early 2010 he had still not regained the power of speech or independent movement.[51][52]
[edit] A list of journalists killed in Russia
What follows is a list of journalists (reporters, editors, cameramen, photographers) who have been killed in Russia since 1992. It includes deaths from all violent, premature and unexplained causes; fuller information may be found in the English and Russian versions of the IFJ database.[53][54]. An indication whether the death is certainly [J], possibly [?J] or most probably not [nJ] linked to the journalist’s investigative work and publications follows each name.
The Yeltsin years
1992-1994
1992
* Sergey Bogdanovsky, correspondent of TV “Ostankino”, killed in Moscow.[55]
1993[56]
* 15 April – Dmitry Krikoryants, correspondent for Express Chronicle weekly (Moscow), murdered in his apartment in the Chechen capital, on the night of 14–15 April.[57] Chechnya was then de facto independent. Homicide [J].
October events in Moscow
Sunday, 3 October, from 7.30 pm onwards. Outside and inside the Ostankino TV tower.[57]
1. Rory Peck, ARD Germany, cameraman. Crossfire [J].
2. Ivan Scopan, TF-1 France, cameraman. Crossfire [J].
3. Igor Belozerov, 4th Channel “Ostankino”, editor. Crossfire [J].
4. Sergey Krasilnikov, “Ostankino” TV, video engineer. Shot at point-blank range within building. Homicide [J].
5. Vladimir Drobyshev, People and nature monthly, editor. Heart Attack [J].
Monday, 4 October, after midday. near Supreme Soviet building.[57]
6. Alexander Sidelnikov, freelance journalist and film-maker from Saint Petersburg. Crossfire [J].
7. Alexander Smirnov, Youth Courier newspaper (Yoshkar-Ola), correspondent. Crossfire [J].
* 29 November – Elena Tkacheva, 26-year-old proof-reader for Kuban Courier newspaper, died in Krasnodar as a result of a bomb planted in the newspaper office.[57] Terrorist Act [J].
* 9 December – Marina Iskanderova, journalist at local TV station, murdered in her apartment in Nadym.[57] Homicide [nJ].
1994[58]
1. 1 February – Sergei Dubov, director of Novoye vremya publishing house, Moscow. Shot in contract killing.[59] Homicide [nJ].
2. 26 April – Andrei Aidzerdzis, Duma deputy and publisher. Shot in contract killing, in Khimki near Moscow.[60] Homicide [nJ].
3. 15 June – Yury Soltys, Interfax journalist and editor. Beaten to death in Moscow Region.[61] Homicide [?J].
4. 15 October – Tatyana Zhuravlyova and husband, media workers, Komsomolskaya pravda (Samara bureau). Killed in Voronezh Region while driving their car in the country.[62] Homicide. [nJ].
5. 17 July – Yelena Roshchina, chief editor of children’s newspaper, Ivanovo. Murdered in her flat.[63] Homicide. The gang who killed her were tried and convicted in 2000 [nJ].
6. 17 October – Dmitry Kholodov, military correspondent of the Moskovskii Komsomolets newspaper, was killed in Moscow when a booby-trapped briefcase he had collected from a railway station locker exploded in his newspaper’s offices.[64] Homicide. Kholodov’s alleged killers were tried and twice acquitted, in 2002 and in 2004 [J].
There were also four deaths in Chechnya after the conflict there began in November.[65]
1. 26 November – Hussein Guzuyev, director of Chechen TV & Radio Company. Grozny. Caught in crossfire between Dudayev supporters and pro-Moscow opposition [J].
2. 14 December – Gelani Charigov, journalist with Marsho private TV company. Grozny. Crossfire [J].
3. 22 December – Cynthia Elbaum, Freelance US photocorrespondent on assignment for Time magazine. Grozny. Crossfire [J].
4. 31 December – Bilal Akhmadov, cameraman for Marsho TV company. Grozny. Crossfire [J].
1995-1996 (incl. 1st Chechen conflict)
1995[66]
1. 1 January – Vladimir Zhitarenko, correspondent of the Red Star (Krasnaya zvezda) newspaper, Chechnya. Crossfire [J].
2. 1 January – Pyotr Novikov, journalist with Smena magazine, Moscow. Homicide (linked to Anisimov killing in late 1994) [nJ].
3. 7 January – Sultan Nuriyev, Chechnya. Not Confirmed [?J].
4. 10 January – Jochen Piest, correspondent of the Stern magazine. Chervlyonnaya, Chechnya. Crossfire [J].
5. 14 January – Valentin Yanus, cameraman of Pskov city TV channel, Chechnya. Crossfire [J].
6. 17 February – Vyacheslav Rudnev, freelance journalist, Kaluga, published in local Vest and Znamya newspapers. Homicide [?J].
7. 27 February – Maxim Shabalin, politics editor of Nevskoe Vremya newspaper (St Petersburg).[67] and Felix Titov, the paper’s photographer, disappeared on an assignment to Chechnya. Despite numerous expeditions, from 1995 to 1999, no trace was found of the two men’s remains. Missing [J].
8. 1 March – Vladislav Listyev, head of the new ORT TV Channel, shot dead in stairwell of his Moscow apartment block in a classic contract killing. Homicide [nJ].
9. 3 March – Igor Kaverin, engineer with Svobodnaya Nakhodka radio station, Primorsky Region. Shot in car, Homicide [nJ].
10. 8 March – Oleg Ochkasov, freelance journalist in Voronezh, writing for Vecherny Voronezh and Skandalnaya pochta newspapers. Homicide [nJ].
11. 16 March – Alexei Khropov, director of Vox radio station, recently off the air. Leningradskoe Highway, Moscow Region. Homicide [nJ].
12. 31 March – 23-year-old Ruslan Tsebiyev, Dudayev press service, Grozny, Chechnya. Homicide [?J].
13. 6 May – Malkan Suleimanova, journalist with Ichkeria newspaper (Grozny). Died under bombardment in Shatoi, Chechnya. Crossfire [J].
14. 22 May – Farkhad Kerimov, cameraman with Associated Press TV. Executed in Vedeno, Chechnya. Homicide (war crime)[J].
15. 5 May – Sergei Ivanov, went in search of Shabalin and Titov (above 27 February), south of Chechnya. Missing [J].
16. 6 June – Alexander Konovalenko, journalists with Krestyanskaya gazeta, Volgograd, beating in police station led to his death.[68] Homicide. Killer convicted in 1998 [?J].
17. 17 June – Natalya Alyakina-Mroszek, Focus magazine (Germany) and other outlets. Shot near Budyonnovsk.[69] Crossfire. Russian soldier found guilty of negligence in use of weapons, amnestied as Chechen war participant [J].
18. 25 July – Andrew Shumack Jr, freelance US photojournalist, St Petersburg Times. Grozny, Chechnya. Missing [?J].
19. 4 August – Sergei Nazarov, former presenter of popular TV show “Vremechko”. Killed in Moscow. Homicide [nJ].
20. 10 August – Vadim Obekhov, columnist with Vesti newspaper, Petropavlovsk, Kamchatka Region. Homicide [nJ].
21. 2 November – Andrei Ulanov, chief editor of Togliatti segodnya newspaper. Togliatt, Samara Region. Contract killing, homicide [nJ].
22. 8 November – Sergei Ananyev, head of press service, East Siberian organised crime department. Murdered in Irkutsk. Outcome of 2000 trial not clear [nJ].
23. 12 December – Victor Litvinov, “Golos Rossii” radio station commentator, Moscow, died after street attack.[70] Homicide [nJ].
24. 10 December – 25-year-old Yaroslav Zvaltsev, financial director of the Russky dom newspaper in Magnitogorsk, shot in contract killing.[71] Homicide [nJ].
25. 12 December – Shamkhan Kagirov, correspondent of the Vozrozhdenie newspaper, Chechnya. Crossfire [J].
26. 26 December – Vadim Alferyev, worked as journalist for local press and TV in Krasnoyarsk, where he died after a savage beating.[72] Homicide [?J].
1996[73]
1. 25 January – Oleg Slabynko, founder of “Moment Istiny” corporation, producer of a program of the same name, a director of ORT (today Channel One TV), murdered in his Moscow apartment. Contract killing [nJ].
2. 8 February – Yury Litvinov, engineer, and Alexander Zaitsev, director, of Forward cable television.[74] Found shot in car, Dalnegorsk, Primorsky Region. Contract killing? [nJ].
3. 26 February – Felix Solovyov, famous photographer, Aeroflot journal editorial board, murdered in Moscow.[75] Homicide [nJ].
4. 11 March – Victor Pimenov, cameraman with Vaynakh TV company (Chechnya).[76] Grozny, Chechnya. Crossfire [J].
5. 30 March – Nadezhda Chaikova, investigative journalist for Obshchaya Gazeta, executed in Chechnya, body found near village of Gekhi.[77] Homicide (war crime) [J].
6. 18 April – Anatoly Yagodin, correspondent for Na Boyevom Postu forces newspaper, killed by Chechen militants.[78] Assinovskaya, Chechnya. Crossfire [J].
7. 9 May – Nina Yefimova, correspondent for Vozrozhdeniye newspaper, Chechnya.[76] Grozny, Chechnya. Homicide [J].
8. 11 May – Victor Mikhailov, crime correspondent for Zabaikalsky rabochy newspaper.[74] Chita. Homicide [nJ].
9. 26 July – Nikita Chigarkov, staff member of Utrenniy ekspress, beaten and robbed.[74] Moscow. Homicide [nJ].
10. 1 August – Ivan Gogun, Groznensky rabochy correspondent.[76] Grozny, Chechnya. Crossfire [J].
11. 11 August – Ramzan Khadjiev, ORT correspondent, shot outside checkpoint in Chechnya.[76] Grozny, Chechnya. Crossfire [J].
12. 16 September – En Chan Kim, correspondent for various Sakhalin newspapers and Blagodatnaya Semya magazine.[74] Zhulebino, Moscow. Homicide [nJ].
13. 27 October – Anatoly Tyutinkov, assistant chief editor of Vecherniy Peterburg.[74] Incident not confirmed, St Petersburg. [nJ]
14. 29 October – Lev Bogomolov, Kaluga Vechernyaya chief editor,[74] Kaluga. Incident not confirmed [nJ].
15. 31 October – Sergei Semisotov, Editor of Traktir po Pyatnitsam newspaper.[74] Volgograd. Homicide [nJ].
16. 10 November – Marina Gorelova, reporter for Otechestvo TV company[74] and Yury Shmakov, Otechestvo TV consultant.[74] Kotlyakovskoe cemetery, Moscow. Terrorist act. Two convicted in 2003 for 16 deaths, incl. two journalists, caused by the explosion. [J]
17. 6 December – Kirill Polenov, freelance journalist. Vladikavkaz, North Ossetia. Homicide [nJ].
18. 7 December – Anatoly Belousov, deputy chief editor of Red Star (Krasnaya Zvezda).,[74] Moscow Region. Homicide [nJ].
1997-1999
1997[79]
1. 16 January – Alexei Yeldashov, journalist for local print and rado. Khabarovsk, Primorsky Region. Homicide [nJ].
2. 16 January – Nikolai Lapin, chief editor “Obo vsyom” newspaper. Togliatti, Samara Region. Homicide [nJ].
3. 3 February – Yury Baldin, chief editor at Focus TV. Chelyabinsk. Homicide [nJ].
4. 12 February – Vyacheslav Zvonarev, editor with Takt TV company. Kursk. Homicide [nJ].
5. 25 February – Vadim Biryukov, chief editor of “Delovye lyudi” magazine, Novolesnaya St, Moscow. Homicide [nJ].
6. 23 March – Vladimir Aliev,, Prokhladnoe, Kabardino-Balkaria. Homicide [nJ].
7. 30 March – Nikolai Mozolin,, Kirovsk, Leningrad Region. Homicide [nJ].
8. 10 May – Alexander Korkin,, Pereslavl-Zalessky, Yaroslavl Region. Homicide [nJ].
9. 6 August – Valery Krivosheyev,, Lipetsk. Homicide [nJ].
10. 19 October – Lydia Lazarenko,, Nizhny Novgorod. Homicide [nJ].
1998[80]
1. 30 January – Vladimir Zbaratsky,, Mosfilmoskaya St, Moscow. Homicide [nJ].
2. 2 April – Ivan Fedyunin, correspondent of the Bryanskie Izvestia newspaper. Homicide, Bryansk [nJ].
3. 6 April – Lira Lobach, media worker. district, Tomsk Region. Homicide [nJ].
4. 20 May – Igor Myasnikov,, Kineshma, Yaroslavl Region. Homicide [nJ].
5. 7 June – Larisa Yudina, chief editor of the Sovetskaya Kalmykia Segodnya newspaper. Elista, Kalmykia. Contract killing. Perpetrators convicted (1999), but not those behind her murder [J].
6. 28 July – Vladimir Ustinov,, Ivanovo. Homicide [nJ].
7. 17 August – Sergei Semenduyev,, Makhachkala, Dagestan. Missing [nJ].
8. 24 August – Anatoly Levin-Utkin,, St Petersburg. Homicide [?J].
9. 27 August – Mirbaba Seidov, homicide, Kaliningrad Region. Homicide [nJ].
10. 29 August – Victor Shamro,, homicide, St Petersburg. Homicide [nJ].
11. 2 September – Farid Sidaui, correspondent of the Prosto nedvizhimost magazine. Ramenka St, Moscow. Homicide [nJ].
12. 30 December – Sergei Chechugo,, Vladivostok. Not confirmed [?J].
1999[81]
1. 19 February – Gennady Bodrov, Homicide [nJ].
2. 25 February – Valentina Mirolyubova and Nikolai Mirolyubov, Homicide [nJ].
3. 4 March – Andrei Polyakov, Homicide [nJ].
4. 30 May – Alexei Kulanov, Homicide [nJ].
5. 30 June – Vadim Rudenko, Homicide.
6. 30 August – Lubov Loboda, Kuibyshev (Novosibirsk Region). Contract killing. Perpetrator, intermediary and man who ordered her dead all charged and convicted [nJ].
7. 27 September – Christopher Reese, Moscow. Homicide [nJ].
8. 27 October – Supyan Ependiyev, correspondent of the Groznenskiy Rabochy newspaper, Chechnya. Crossfire [J].
9. 29 October – Cameramen Shamil Gigayev and Ramzan Mezhidov, national TVC channel and local Chechen TV. Shami-Yurt, Chechnya. Crossfire. 2005 Judgment by European Court of Human Rights [J].
Under Putin (incl. 2nd Chechen conflict)
2000-2002
2000[82]
1. 1 February – Vladimir Yatsina, a photocorrespondent with ITAR-TASS. On his first and only trip to Chechnya he was kidnapped and later killed (by a group of Wahhabis some suggest).[83] Homicide [J].
2. 10 February – Ludmila Zamana, Samara. Homicide. Conviction [nJ].
3. 9 March – Artyom Borovik, Sovershenno sekretno periodical and publishing house, director and journalist. Sheremetyevo-1 Airport, Moscow. Incident not confirmed [?J].
4. 22 March – Luisa Arzhieva, correspondent for Istina mira newspaper (Moscow). Avtury, Chechnya. Crossfire [?J].
5. 17 April – Oleg Polukeyev, Homicide.
6. 1 May – Boris Gashev, literary critic, . Homicide. Conviction [nJ].
7. 13 May – Alexander Yefremov, Chechnya. A photojournalist with west Siberian newspaper Nashe Vremya, Yefremov died when militants blew up a military jeep in which he was travelling. On previous assignments, Yefremov won acclaim for his news photographs from the war-torn region. Crossfire [J].
8. 16 July – Igor Domnikov, from Novaya Gazeta, Moscow. Struck over the head with a hammer in the stairwell of his Moscow apartment building, Domnikov lay in a coma for two months. His murderer was identified in 2003 and convicted in 2007 [3]. The men who ordered and organised the attack have been named by his paper but not charged. Homicide [J].
9. 26 July – Sergei Novikov, Radio Vesna, Smolensk. Shot in a contract killing in stairwell of his apartment building. Claimed that he often criticized the administration of Smolensk Region. Homicide [?J].
10. 21 September – Iskander Khatloni, Radio Free Europe, Moscow. A native of Tajikistan, Khatloni was killed at night in an axe attack on the street outside his Moscow apartment block. His assailant and the motive of the murder remain unknown. A RFE/RL spokeswoman said Khatloni worked on stories about the human-rights abuses in Chechnya.[84] Homicide [nJ].
11. 3 October – Sergei Ivanov, Lada-TV, Togliatti. Shot five times in the head and chest in front of his apartment building. As director of largest independent television company in Togliatti, he was an important player on the local political scene.[85] Homicide. Gang responsible on trial [nJ].
12. 18 October – Georgy Garibyan, journalist with Park TV (Rostov), murdered in Rostov-on-Don [nJ].
13. 20 October – Oleg Goryansky, freelance journalist, press & TV. Murdered in Cherepovets, Vologda Region. Conviction [nJ].
14. 21 October – Raif Ablyashev, photographer with Iskra newspaper. Kungur, Perm Region. Homicide [nJ].
15. 3 November – Sergei Loginov, Lada TV (Togliatti). Incident not confirmed [nJ].
16. 20 November – Pavel Asaulchenko, cameraman for Austrian TV, Moscow. Contract killing. Conviction of perpetrator [nJ].
17. 23 November – Adam Tepsurkayev, Reuters, Chechnya. A Chechen cameraman, he was shot at his neighbor’s house in the village of Alkhan-Kala (aka Yermolovka). Tepsurkayev filmed most of Reuters’ footage from Chechnya in 2000, including the Chechen rebel Shamil Basayev having his foot amputated. Homicide (war crime) [J].
18. 28 November – Nikolai Karmanov, retired journalist. Lyubim, Yaroslavl Region. Homicide [nJ].
19. 23 December – Valery Kondakov, freelance photographer. Killed in Armavir, Krasnodar Region [nJ].
2001[86]
1. 1 February – Eduard Burmagin, Homicide.
2. 24 February – Leonid Grigoryev, Homicide [nJ].
3. 8 March – Andrei Pivovarov, Homicide.
4. 31 March – Oleg Dolgantsev, Homicide [nJ].
5. 17 May – Vladimir Kirsanov,[87] chief editor. Kurgan, Urals Federal District. Homicide [J].
6. 2 June – Victor Popkov, Novaya gazeta contributore, died in Moscow Region hospital. Wounded in Chechnya two months earlier. Crossfire [J].
7. 11 September – Andrei Sheiko, Homicide [nJ].
8. 19 September – Eduard Markevich, 29, editor and publisher of local newspaper Novy Reft in Sverdlovsk Region. Shot in the back[87] in a contract killing, homicide [J].
9. 5 November – Elina Voronova, Homicide [nJ].
10. 16 November – Oleg Vedenin, Homicide.
11. 21 November – Alexander Babaikin, Homicide [nJ].
12. 1 December – Boris Mityurev, Homicide.
2002[88]
1. 18 January – Svetlana Makarenko, Homicide.
2. 4 March – Konstantin Pogodin, Novoye Delo newspaper, Nizhni Novgorod. Homicide.
3. 8 March – Natalya Skryl, Nashe Vremya newspaper, Taganrog. Homicide [?J].
4. 31 March – Valery Batuyev, Moscow News newspaper, Moscow. Homicide [nJ].
5. 1 April – Sergei Kalinovsky, Moskovskij Komsomolets local edition, Smolensk. Homicide [nJ].
6. 4 April – Vitaly Sakhn-Vald, photojournalist, Kursk. Homicide. Conviction [nJ].
7. 25 April – Leonid Shevchenko, Pervoye Chtenie newspaper, Volgograd. Homicide [nJ].
8. 29 April – Valery Ivanov, founder and chief editor of Tolyattinskoye Obozrenie newspaper, Samara Region.[87] Contract killing [J].
9. 20 May – Alexander Plotnikov, Gostiny Dvor newspaper, Tyumen. Homicide.
10. 6 June – Pavel Morozov, Homicide.
11. 25 June – Oleg Sedinko, founder of Novaya Volna TV & Radio Company, Vladivostok. Contract killing, explosive in stairwell [nJ].
12. 20 July – Nikolai Razmolodin, general director of Europroject TV & Radio Company, Ulyanovsk. Homicide.
13. 21 July – Maria Lisichkina Homicide [nJ].
14. 27 July – Sergei Zhabin, press service of the Moscow Region governor. Homicide [nJ].
15. 18 August – Nikolai Vasiliev, Cheboksary city, Chuvashia. Homicide. Conviction [nJ].
16. 25 August – Paavo Voutilainen, former chief editor of Karelia magazine, Karelia. Homicide [nJ].
17. 4 September – Leonid Kuznetsov, “Periodicals of Mari-El” publishing house, Yoshkar-Ola.[89] Incident not confirmed [?J].
18. 20 September – Igor Salikov, head of information security at Moskovskij Komsomolets newspaper in Penza. Contract killing [nJ].
19. 26 September – Roderick (Roddy) Scott, Frontline TV Company, Great Britain. Crossfire [J].
20. 2 October – Yelena Popova, Homicide. Conviction [nJ].
21. 19 October – Leonid Plotnikov Homicide. Conviction [nJ].
22. 26 October – Tamara Voinova (Stavropol) and Maxim Mikhailov (Kaliningrad), Dubrovka theatre siege (“Nord Ost” show), Moscow. Terrorist Act [nJ].
23. 21 December – Dmitry Shalayev, Kazan, Tatarstan. Homicide. Conviction [nJ].
2003-2005
2003[90]
1. 7 January – Vladimir Sukhomlin, Internet journalist and editor, Serbia.ru, Moscow. Homicide. Off-duty police convicted of his murder, not those behind this contract killing [J].
2. 11 January – Yury Tishkov, sports commentator, Moscow. Contract killing [nJ].
3. 21 February – Sergei Verbitsky, publisher BNV newspaper. Chita. Homicide [nJ].
4. 18 April – Dmitry Shvets, TV-21 Northwestern Broadcasting, Murmansk. Deputy director of the independent TV-21 station (Northwestern Broadcasting), he was shot dead outside the TV offices. Shvets’ colleagues said the station had received multiple threats for its reporting on influential local politicians. Contract killing [nJ].
5. 3 July – Yury Shchekochikhin, Novaya gazeta, Moscow. Deputy editor of Novaya gazeta and a Duma deputy since 1993, he died just a few days before his scheduled trip to USA to discuss the results of his journalist investigation with FBI officials. He investigated “Three Whales Corruption Scandal” that allegedly involved high-ranking FSB officials. Shchekochikhin died from an acute allergic reaction. There has been much speculation about cause of his death. Investigation into his death has been opened and closed four times. Homicide [J].
6. 4 July – Ali Astamirov, France Presse. Went missing in Nazran [?J].
7. 18 July – Alikhan Guliyev, freelance TV journalist, from Ingushetia. Moscow. Homicide [nJ].
8. 10 August – Martin Kraus, Dagestan. On way to Chechnya. Homicide [nJ].
9. 9 October – Alexei Sidorov, Tolyatinskoye Obozreniye, Togliatti. Second editor-in-chief of this local newspaper to be murdered. Predecessor Valery Ivanov shot in April 2002.[87] Homicide. Supposed killer acquitted [?J].
10. 24 October – Alexei Bakhtin, journalist and businessman, formerly Mariiskaya pravda. Mari El. Homicide [nJ].
11. 30 October – Yury Bugrov, editor of Provincial Telegraph. Balakovo, Saratov Region. Homicide. Conviction [nJ].
12. 25 December – Pyotr Babenko, editor of Liskinskaya gazeta. Liski, Voronezh Region. Homicide [nJ].
2004[91]
1. 1 February – Yefim Sukhanov, ATK-Media, Archangelsk. Homicide. Conviction [nJ].
2. 23 March – Farit Urazbayev,cameraman, Vladivostok TV/Radio Company, Vladivostok. Incident not Confirmed [nJ].
3. 2 May – Shangysh Mongush, correspondent with Khemchiktin Syldyzy newspaper, Tuva. Homicide [?J].
4. 9 May – Adlan Khasanov, Reuters reporter, died in Grozny bomb attack that killed Chechen President Ahmed Kadyrov. Terrorist Act [J].
5. 9 June – Paul Klebnikov, chief editor of newly-established Russian version of Forbes magazine, Moscow. Contract killing, alleged perpetrators put on trial and acquitted. Homicide [J].
6. 1 July – Maxim Maximov, journalist with Gorod newspaper, St Petersburg. Body not found. Homicide [J].
7. 10 July – Zoya Ivanova, TV presenter, Buryatia State Television & Radio Company, Ulan Ude, Buryatia. Homicide [nJ].
8. 17 July – Pail Peloyan, editor of Armyansky Pereulok magazine, Moscow. Homicide [nJ].
9. 3 August – Vladimir Naumov, nationalist reporter, Cossack author (Russky Vestnik, Zavtra), Moscow Region. Homicide [nJ].
10. 24 August – Svetlana Shishkina,journalist, Kazan, Tatarstan. Homicide. Conviction [nJ].
11. 24 August – Oleg Belozyorov, Moscow-Volgograd flight. Terrorist Act [nJ].
12. 18 September – Vladimir Pritchin, editor-in-chief of North Baikal TV & Radio Company, Buryatia. Homicide [?J].
13. 27 September – Jan Travinsky (St Petersburg), in Irkutsk as political activist for election campaign.[92] Homicide. Conviction [nJ].
2005[93]
1. 23 May – Pavel Makeyev, reporter for TNT-Pulse Company, Rostov-on-Don. Run down while photographing illegal street racing. Incident not Confirmed [?J].
2. 28 July – Magomed Varisov, political analyst and journalist, shot dead near his home in Makhachkala, Dagestan. He “had received threats, was being followed and had unsuccessfully sought help from the local police” according to Committee to Protect Journalists. Sharia Jamaat claimed responsibility for the murder.[94] Homicide [J].
3. 31 August – Alexander Pitersky, Baltika Radio reporter, Saint Petersburg. Homicide [?J].
4. 3 September – Vladimir Pashutin, Smolensky Literator newspaper, Smolensk. Not Confirmed [nJ].
5. 13 October – Tamirlan Kazikhanov, head of press service for Anti-Terrorist Center of the Russian Ministry of Internal Affairs’s Main Department for the Southern Federal District, Nalchik. Crossfire [J].
6. 4 November – Kira Lezhneva, reporter with Kamensky rabochii newspaper, Sverdlovsk Region.[95] Homicide. Conviction [nJ].
2006-2008
2006[96]
1. 8 January – Vagif Kochetkov, newly-appointed Trud correspondent in the region, killed and robbed in Tula. Acquittal [nJ].
2. 26 February – Ilya Zimin, worked for NTV Russia television channel, killed in Moscow flat. Suspect in Moldova trial. Acquittal [nJ].
3. 4 May – Oksana Teslo, media worker, Moscow Region. Arson attack on dacha. Homicide [nJ].
4. 14 May – Oleg Barabyshkin, director of radio station, Chelyabinsk. Homicide. Conviction [nJ].
5. 23 May – Vyacheslav Akatov, special reporter, Business Moscow TV show, murdered in Mytyshchi Moscow Region. Killer caught and convicted. Homicide. Conviction [nJ].
6. 25 June – Anton Kretenchuk, cameraman, local “Channel 38” TV, killed in Rostov-on-Don. Homicide. Conviction [nJ].
7. 25 July – Yevgeny Gerasimenko, journalist with Saratovsky Rasklad newspaper. Murdered in Saratov. Conviction [nJ].
8. 31 July – Anatoly Kozulin, retired freelance journalist. Ukhta, Komi. Homicide [nJ].
9. 8 August – Alexander Petrov, editor-in-chief, Right to Choose magazine Omsk, murdered with family while on holiday in Altai Republic. Under-age murderer charged and prosecuted. Homicide. Conviction [nJ].
10. 17 August – Elina Ersenoyeva, reporter for Chechenskoye obshchestvo newspaper. Abducted in Grozny, Chechnya. Missing [?J].
11. 13 September – Vyacheslav Plotnikov,reporter, local “Channel 41” TV, Voronezh. Incident not Confirmed [nJ].
12. 7 October – Anna Politkovskaya, commentator with Novaya gazeta, Moscow, shot in her apartment building’s elevator;.[97][98][99][100] Four accused in contract killing, acquitted in February 2009 [J].
13. 16 October – Anatoly Voronin, Itar-TASS news agency, Moscow. Homicide [nJ].
14. 28 December – Vadim Kuznetsov, editor-in-chief of World & Home. Saint Petersburg magazine, killed in Saint Petersburg. Homicide [nJ].
2007[101]
1. 14 January – Yury Shebalkin, retired journalist, formerly with Kaliningradskaya pravda. Homicide in Kaliningrad. Conviction [nJ].
2. 20 January – Konstantin Borovko,presenter of “Gubernia” TV company (Russian: “Губерния”), killed in Khabarovsk.[46] Homicide. Conviction [nJ].
3. 2 March – Ivan Safronov, military columnist of Kommersant newspaper. Died in Moscow, cause of death disputed.[102][103] Incident not Confirmed. Investigation under Incitement to Suicide (Article 110) [?J].
4. 15 March – Leonid Etkind, director at Karyera newspaper. Abduction and homicide in Vodnik, Saratov Region. Conviction [nJ].
5. 5 April – Vyacheslav Ifanov, Novoye televidenie Aleiska, cameraman. Previously attacked by local military. Aleisk, Altai. Incident not Confirmed [?J].
* Marina Pisareva, deputy head of Russian office of German media group Bertelsmann was found dead at her country cottage outside Moscow in April[104][105]
2008
(Putin’s final months as president)
1. 8 February – Yelena Shestakova, former journalist, St Petersburg. Killer sent to psychiatric prison. Homicide [nJ].
2. 21 March – Gadji Abashilov, chief of Dagestan State TV & Radio Company VGTRK, shot in his car in Makhachkala. Homicide [?J].
3. 21 March – Ilyas Shurpayev, Dagestani journalist covering Caucasus on Channel One, was strangled with a belt by robbers in Moscow.[106][107] Alleged killers tracked to Tajikistan and convicted there of his murder. Homicide [?J].
The Medvedev presidency
2008-2011
2008[108]
1. 31 August – Magomed Yevloyev, Ingush oppositionist, founder of Ingushetiya.ru, Moscow-based lawyer, shot on return to country while in custody of Ingush police officers.[109][110][111] Killer convicted of negligent homicide, sentence subsequently mitigated. Homicide. Conviction [J].
2. 2 September – Abdulla Alishayev, (aka Telman Alishayev), TV presenter on Muslim channel, shot dead in car, Makhachkala.[112] Homicide [J].
2009[113]
1. 4 January – Shafig Amrakhov, Murmansk, shot in stairwell entrance in late December 2008. Homicide [nJ].
2. 4 January – Vladislav Zakharchuk, manager with Arsenyevskie vesti newspaper, Vladivostok. Arson suggested cause of death. Incident not Confirmed [?J].
3. 19 January – Anastasia Baburova, Novaya gazeta, Moscow.On 19 January Stanislav Markelov, lawyer for Novaya gazeta, anti-fascist activist and opponent of human rights abuses in Chechnya, was shot and killed in the centre of Moscow.[114] With him died Anastasia Baburova a trainee reporter with Novaya Gazeta, and a fellow anti-fascist activist.[115][116] In early November 2009 a man and a woman were arrested for the killing.[117] Homicide [J].
4. 30 March – Sergei Protazanov, layout artist with Grazhdanskoye soglasie newspaper, Khimki nr. Moscow. Link to work questioned. Incident not Confirmed [nJ].
5. 29 June – Vyacheslav Yaroshenko, chief editor of Corruption and Criminality newspaper, Volgograd. Cause of death remains unclear. Incident not Confirmed [?J].
6. 15 July – Natalia Estemirova,[118] a human rights activist with Memorial, who worked with journalists from Novaya gazeta, especially Anna Politkovskaya, and occasionally published in the newspaper herself, having been a TV reporter pre-1999. After years of investigating murders and kidnapping in Chechnya Estemirova was herself abducted that morning in Grozny and found, shot dead, by the roadside several hours later in neighbouring Ingushetia.[119] Homicide [J].
7. 11 August – Malik Akhmedilov,[120] deputy chief editor of the Avar language newspaper Khakikat (Truth), was found shot dead near the Dagestan capital Makhachkala. Homicide [?J].
8. 25 October – Maksharip Aushev was shot dead in Nalchik, capital of Kabardino-Balkaria.[121] When Magomed Yevloyev gave up running Ingushetia.ru, and his replacement (Rosa Malsagova) had to flee abroad to escape threats and harassment, Aushev ran the successor website Ingushetia.org. Link to past or present work unclear. Homicide [?J].
9. 16 November – Olga Kotovskaya, Kaskad radio & TV company, Kaliningrad. Fall from height? Incident not Confirmed. Investigation under “Incitement to suicide” (Article 110) [?J].
2010[122]
1. 20 January – Konstantin Popov died from a beating received a fortnight earlier by Russian police, in a detoxification centre for drunk and disorderly.[123] 26-year-old police sergeant charged with his killing. Homicide [nJ].
2. 23 February – Journalist Ivan Stepanov was murdered at his dacha.[124] Homicide [nJ].
3. 20 March – Maxim Zuyev was found murdered in a Kaliningrad flat he was renting. Seven years earlier he was interrogated by the city’s police for publishing an anonymous letter alleging corruption among high-ranking police officers in the enclave.[125][126][127][128] “Crime solved”, says Investigative Committee [?J].
4. 5 May – Shamil Aliyev, founder of radio stations, director of local TV, showbiz impresario, Makhachkala, Dagestan.[129] Homicide [?J]
5. 13 May – Said Magomedov, director of local television station, Sergokalinsky district, Dagestan. Shot dead when travelling with repairmen to restore sabotaged TV transmitter. Terrorist act [J].
6. 25 June – Dmitry Okkert, Moscow. A presenter with the Expert TV channel, Okkert was found stabbed to death in his own apartment. The director of the Expert media holding, Valery Fadeyev, does not believe that the brutal killing of his colleague was linked to his journalistic activities. Homicide [?J].
7. 25 July – Bella Ksalova, Cherkessk. A correspondent for the Caucasian Knot website and news agency, Ksalova died after being hit by a car on the street where she lived. Not confirmed [?J]
8. 1 August – Malika Betiyeva, Grozny-Shatoi highway. The deputy chief editor of Molodyozhnaya smena, and Chechnya correspondent of the “Dosh” (Word) magazine, died with four of her immediate family in a car crash. Not confirmed [?J]
9. 11 August – Magomed Sultanmagomedov, Makhachkala. The director of the “Makhachkala TV” station was assassinated in the Dagestan capital when his vehicle came under gunfire [?J]
2011
1. 15 December – Gadzhimurat Kamalov, Makhachkala. Investigative reporter – shoot eight times outside his paper’s offices.[130]
Journalists killed reporting on Chechnya
This category overlaps with that for Russia as a whole. It highlights the link in these extreme conditions between journalism, public activism and human rights activities. In their different ways the deaths of Dmitry Krikoryants, Dmitry Kholodov, Nadezhda Chaikova, Viktor Popkov,[131] Anna Politkovskaya, Anastasia Baburova, Stanislav Markelov and Natalia Estemirova all show that the troubled situation in the small North Caucasian republic reaches well beyond its formal borders.
For all who died, or received their fatal wounds, in Chechnya see records in IFJ database.[132] There were those killed in locations near or far from the North Caucasian republic, e.g. Natalya Alyakina, Anna Politkovskaya, whose deaths were also a consequence of the armed conflict in Chechnya.
1993
* Dmitry Krikoryants, night of 14–15 April 1993, Grozny.[133] Murdered over a year before open conflict broke out in Chechnya (first between pro-Dudayev and pro-Moscow factions, then with the intervention of federal forces), the killing of Krikoryants was linked to his investigation of corrupt activities of the local regime, at home and abroad.
1st Chechen war, 1994-1996
* Cynthia Elbaum. On assignment for Time magazine (USA), Cynthia was photographing in the streets of Grozny, when she was killed in a Russian bombing raid in 1994.[134]
* Vladimir Zhitarenko, a veteran military correspondent for the Russian armed forces daily Krasnaya Zvezda (Red Star), was hit by two sniper bullets outside the town of Tolstoy-Yurt, near the Chechen capital of Grozny on 31 December 1994.
* Nina Yefimova, a reporter for the new Vozrozhdenie (Revival) newspaper was abducted from her apartment and killed together with her mother. Journalists in Grozny and Moscow believe that her murder was related to stories she had published on crime in Chechnya.
* Jochen Piest. On 10 January 1995 Piest, a correspondent with Stern magazine (Germany), was killed in an attack by a Chechen rebel against a Russian mine-clearing unit in Chervlyonna, a village 24 kilometers northeast of Grozny. Rossiskaya Gazeta correspondent Vladimir Sorokin was wounded in the attack; Piest was fatally hit by three bullets.
* Farkhad Kerimov. Farkhad Kerimov was murdered on 22 May 1995 while filming for Associated Press behind rebel lines in Chechnya. No motive has ever been established for the killing.
* Natalya Alyakina. Natalya Alyakina, a free-lance correspondent for German news outlets, was shot dead in June by a soldier after clearing a Russian checkpoint near the southern Russian city of Budyonnovsk.
* Shamkhan Kagirov. Kagirov, a reporter for the Moscow daily Rossiyskaya Gazeta and the local Vozrozhenie newspaper, was shot and killed in an ambush in Chechnya. Kagirov and three local police officers were traveling in a car near Grozny when they were attacked. The three officers were also killed.
* Viktor Pimenov. On 11 March 1996, Pimenov, a cameraman with the local “Vainakh” TV company was fatally shot in the back by a sniper positioned on the roof of a 16-story building in Grozny. Pimenov had been filming the devastation caused to the Chechen capital by the March 6–9 rebel raid on the city.
* Nadezhda Chaikova. On 20 March 1996 Chaikova, correspondent for the Obshchaya gazeta (Moscow) weekly newspaper disappeared while on assignment. Her body was found buried in the Chechen village of Gekhi on 11 April, blindfolded and bearing signs of mistreatment. The cause of death was a gunshot wound to the back of the head. The identity of her executioners remains disputed. According to documents from Dudaev’s archive, that came into hands of Russian special services in 2002, she was killed by people from so called “Department of state security of the Chechen Republic of Ichkeria” (Russian: Департамент государственной безопасности ЧРИ).[135][136] At the time there were strong suspicions that Russian security services were involved.
September 1996 to October 1999
No journalists are recorded as having been killed between September 1996 and October 1999 but 22 were kidnapped during these three years and later released.[137]
2nd Chechen war, 1999 onwards
A counter-terrorist operation by the federal authorities began in the region in September 1999. It was declared over on 16 April 2009.
* Journalist Supyan Ependiyev. On the evening of 27 October 1999, several short-range ballistic missile hit a crowded outdoor market in central Grozny, killing or wounding hundreds of people. About an hour after the attack, Ependiyev went to the scene to cover the carnage for his paper. As he was leaving the site, a new round of rockets fell about 200 meters from the bazaar. Ependiyev suffered severe shrapnel wounds and died in a Grozny hospital the next morning. According to other sources, he died two days later.
* Cameramen Ramzan Mezhidov and Shamil Gigayev. The journalists were part of a civilian convoy, including Red Cross workers and vehicles, attempting to leave Chechnya on 29 October 1999. Turned back at the republic’s eastern border, they were travelling along the highway from Grozny to Nazran in neighboring Ingushetia when their vehicles came under attack. As the convoy approached Shami-Yurt, a Russian fighter fired several time from the air, hitting a busload of refugees. Mezhidov and Gigayev left their vehicle to film the carnage. As they approached the bus, another Russian rocket hit a nearby truck, fatally wounding both journalists.
* Photojournalist Vladimir Yatsina, an ITAR-TASS staff member freelancing on his only trip to Chechnya, was kidnapped and killed there by a group of Wahhabis on 19 July 1999.[138][139]
* Antonio Russo, an Italian freelance journalist was killed on 16 October 2000 in Tbilisi, Georgia. His body was found near a Russian army base. He had come to the Georgian capital to document the Chechnya conflict as a Radio Radicale reporter, working for a radio station belonging to the Italian Radical Party (Partito Radicale). His body carried injuries caused by torture, probably from military techniques. None of the tapes, articles and writings left in his Georgian apartment have been found.
* Aleksandr Yefremov. A photojournalist of the western Siberian newspaper Nashe Vremya was killed in Chechnya when rebels blew up a military jeep in which he was riding. On previous assignments, Yefremov had won acclaim for his news photographs from the war-torn region.
* Cameraman and editor Roddy Scott. On 26 September 2002, Scott was killed in Ingushetia. Russian soldiers found his body in the republic’s Galashki region, near the border with Chechnya, following a bloody battle between Russian forces and a group of Chechen fighters.
* Former teacher and TV journalist Natalia Estemirova, now an award-winning Russian human rights activist, board member of the Russian NGO Memorial, and author for Novaya gazeta was murdered on 15 July 2009.[140] Estemirova was abducted around 8.30 am from outside her home in Grozny, Chechnya as she was working on “extremely sensitive” cases of human rights abuses in Chechnya.[141] Two witnesses reportedly saw Estemirova being pushed into a car, shouting that she was being abducted. She was found with bullet wounds in the head and chest at 4.30 pm in woodland 100 m (328 ft) away from the “Kavkaz” federal highway near the village of Gazi-Yurt, Ingushetia.[142]
* On 1 August Malika Betiyeva was killed on the Grozny-Shatoi highway. The deputy chief editor of “Molodyozhnaya smena”, and Chechnya correspondent of the “Dosh” (Word) magazine, died with four of her immediate family in a car crash.[143]
“IM JOURNALIST”- DIE STASI-UNTERWANDERUNG DER REPUBLIK
Liebe Leser,
die Rücktritts-Manöver der „Linken“ gegen Wulff, ehemaliger Stasi-Leute wegen Petitessen, soll die Republik in einer schwierigen Zeit weiter destablisieren und die Hamburger Medien und deren Berliner Dependancen fallen darauf rein oder werden instrumentalisiert und unterwandert .
Im Ausland schüttelt am nur noch den Kopf.
Die Bereitschaft der Medien darauf hereinzufallen hängt mit zwei Gründen zusammen:
Die Ausbildung ist mangelhaft.
Fast alle Mainstream-Medien haben von tiefergehenden Zusammenhängen keine Ahnung und suchen sich im „Rudel ihre Opfer“, da von „Natur aus feige“, die seriösen Themen der Zeit wie Finanzkrise und Zukunft können sie nur oberflächlich angehen und id eleser merken dies immer mehr.
Sie werden von alten Seilschaften benutzt, die ihnen grosse auflagenstärkende “Sensationen” versprechen, denn das alte Motto der „nützlichen Idioten“ von Lenin trifft gerade hier zu und wird von den alten STASI-Leuten umgesetzt.
Kein Zufall ist, dass der seriöse Rechtsanwalt und Notar Braun erst vor wenigen Wochenals Berliner Justiz-Senator zurücktreten musste.
Agitprop a la Mielke & Co und die “seriösen” Hamburger Medien haben auch dies bewirkt.
Das kann ich aus eigener Erfahrung nur bestätigen.
Übrigens, welcher Hamburger oder Berliner Journalist hat in Sachen “IM Erika” recherchiert.
Laut Quellen ein Tarnname von Angela Merkel.
Diese Akte is natürlich verschwunden. Kein Bericht daüber in Deutschland…
Was wurde aus “IM Erika” ?
Und warum wurden gerede im Zuge der Vereinigung die fähigsten Manager Westdeutschlands ausgeschaltete
– Mord an Uwe Barschel
– Mord an Detlef Rohwedder
– Mordversuch an Wolfgang Schäuble, dem präsumptiven Kanzler-Nachfolger
– versuchte Korruptionsaafäre gegen Schäuble wegen “100.000 DM Spenden in der Schublade”
Und stattdessen: Wegen eines Hauskredites monatelange Medienkampagnen gegen Wulff.
Welcher DDR-Kujau sitzt bei den Hamburger “Seriös-Verlagen” denn da am Drücker ?
Kein Stasi-Mörder oder Mit-Täter wurde jemals verurteilt !
Machen Sie doch einmal die Augen auf !
Herzlichst Ihr
Bernd Pulch, Magister Artium
TOP-SECRET – (U//FOUO) Open Source Center Growth in Afghan Insurgent Reintegration

A body of open-source reporting suggests that fighters leaving the Afghan insurgency are doing so in greater numbers this winter (1,865 fighters) than last winter (443 fighters). As with the winter of 2009-2010, the majority of defecting fighters have continued to reintegrate into Afghan Government entities in the comparatively peaceful northern and western provinces of Afghanistan. The Taliban have rejected these reports, claiming that those joining the government are not Taliban fighters. Because of variations in the level of detail provided in media reports, this compilation could understate the number of reported militants leaving the battlefield. However, even 2,000 defections over six months would not appear to represent a major blow to an insurgency estimated to have 25,000 to 36,000 current fighters, and it is likely that at least some of those taking advantage of government reintegration programs were not committed fighters.
…
Greater Number of Defections This Winter
Insurgents appear to be surrendering in far greater numbers this winter (1 November 2010 to 31 January 2011) than in the previous winter (1 November 2009 to 31 January 2010). Approximately 1,865 fighters have reportedly surrendered to the Afghan Government, compared to approximately 443 fighters in the last winter, an increase of almost 400 percent.
• Of the six months reviewed, the three months with the largest number of fighters leaving the insurgency all occurred this winter: November 2010 (755), December 2010 (295), and January 2011 (815).
Defections Concentrated in North, West
Insurgents have overwhelmingly surrendered in the relatively peaceful areas encompassing the International Security Assistance Force’s (ISAF) North and West regional commands rather than in the much more violent South and East, although it is unclear why. As suggested in a previous OSC Analysis,
• The vast majority of insurgents were reintegrated into seven provinces this winter: Baghlan (241), Balkh (141), Faryab (140), Jowzjan (153), and Kunduz (330) in Regional Command (RC) North; and Badghis (240) and Herat (400) in RC West. the greater numbers of Taliban fighters and greater concentration of Pashtuns — the ethnic group to which most Taliban belong — in the South and East may increase Taliban cohesion, making it more difficult for disaffected insurgents there to switch sides. It is also possible that insurgents leaving the battlefield prefer to resettle with their families in the safer North and West and that some provinces in these areas offer better benefits to defectors.
Taliban spokesman Zabiullah Mujahid “rejected” reports of insurgents joining the government, claiming that “these people are not mujahidin” and are not affiliated with the Taliban.
DOWNLOAD ORIGINAL DOCUMENT HERE
TOP-SECRET – DEA Agents Helped Launder Millions in Drug Cartel Money

An excerpt from a document included in the report details the transfer of $2,649,200 to the United States in one set of transactions in the July and August 2007.
Mexico’s government allowed a group of undercover U.S. anti-drug agents and their Colombian informant to launder millions in cash for a powerful Mexican drug trafficker and his Colombian cocaine supplier, according to documents made public Monday.
The Mexican magazine Emeequis published portions of documents that describe how Drug Enforcement Administration agents, a Colombian trafficker-turned-informant and Mexican federal police officers in 2007 infiltrated the Beltran Leyva drug cartel and a cell of money launderers for Colombia’s Valle del Norte cartel in Mexico.
The group of officials conducted at least 15 wire transfers to banks in the United States, Canada and China and smuggled and laundered about $2.5 million in the United States. They lost track of much of that money.
In his testimony, the DEA agent in charge of the operation says DEA agents posing as pilots flew at least one shipment of cocaine from Ecuador to Madrid through a Dallas airport.
The documents are part of an extradition order against Harold Mauricio Poveda-Ortega, a Colombian arrested in Mexico in 2010 on charges of supplying cocaine to Arturo Beltran Leyva. A year earlier, Beltran Leyva was killed in a shootout with Mexican marines in the city of Cuernavaca, south of Mexico City.
The documents show Mexico approved Poveda-Ortega’s extradition to the United States in May, but neither Mexican nor U.S. authorities would confirm whether he has been extradited. Mexican authorities listed his first name as “Haroldo.”
…
The documents offer rare glimpses into the way U.S. anti-drug agents are operating in Mexico, an often sensitive subject in a country touchy about national sovereignty.
On one occasion, the informant who began working for the DEA in 2003 after a drug arrest met with the girlfriend of a Colombian drug trafficker in Dallas and offered to move cocaine for their group around the world for $1,000 per kilo. In a follow-up meeting, the informant introduced the woman to a DEA agent posing as a pilot. The woman is identified as the girlfriend of Horley Rengifo Pareja, who was detained in 2007 accused of laundering money and drug trafficking.
Another scene described the informant negotiating a deal to move a cocaine shipment from Ecuador to Spain and minutes later being taken to a house where he met with Arturo Beltran Leyva.
Original Video – US military investigate video in which marines urinate of dead bodies of Taliban fighters
The US military is investigating an online video which appears to show Marines
urinating on the corpses of Taliban fighters in Afghanistan.
CONFIDENTIAL – Afghan National Army Counterinsurgency and Basic Infantry Manuals

The following are several basic training manuals used by U.S. forces to train the Afghan National Army (ANA).
DOWNLOAD ORIGINAL DOCUMENTS HERE
Murder of a Journalist – Unveiled – Poisoning of Alexander Litvinenko by KGB – the Big Brother of STASI

Alexander Litvinenko was a former officer of the Russian Federal Security Service, FSB and KGB, who escaped prosecution in Russia and received political asylum in the United Kingdom. He wrote two books, Blowing up Russia: Terror from within and Lubyanka Criminal Group, where he accused the Russian secret services of staging Russian apartment bombings and other terrorism acts to bring Vladimir Putin to power.
On 1 November 2006, Litvinenko suddenly fell ill and was hospitalized. He died three weeks later, becoming the first confirmed victim of lethal polonium-210-induced acute radiation syndrome.[1] According to doctors, “Litvinenko’s murder represents an ominous landmark: the beginning of an era of nuclear terrorism”.[2][3][4]
Litvinenko’s allegations about the misdeeds of the FSB and his public deathbed accusations that Russian president Vladimir Putin were behind his unusual malady resulted in worldwide media coverage.[5]
Subsequent investigations by British authorities into the circumstances of Litvinenko’s death led to serious diplomatic difficulties between the British and Russian governments. Unofficially, British authorities asserted that “we are 100% sure who administered the poison, where and how”, but they did not disclose their evidence in the interest of a future trial. The main suspect in the case, a former officer of the Russian Federal Protective Service (FSO), Andrei Lugovoy, remains in Russia. As a member of the Duma, he now enjoys immunity from prosecution. Before he was elected to the Duma, the British government tried to extradite him without success.
Alexander Litvinenko was a former officer of the Russian Federal Security service who escaped prosecution in Russia and received political asylum in Great Britain. In his books, “Blowing up Russia: Terror from within” and “Lubyanka Criminal Group”, Litvinenko described Vladimir Putin’s rise to power as a coup d’état organised by the FSB. He alleged that a key element of FSB’s strategy was to frighten Russians by bombing apartment buildings in Moscow and other Russian cities.[6] He accused Russian secret services of having arranged the Moscow theater hostage crisis, through their Chechen agent provocateur, and having organised the 1999 Armenian parliament shooting,.[7] He also stated that terrorist Ayman al-Zawahiri was under FSB control when he visited Russia in 1997.[8]
Just two weeks before his death Litvinenko accused Russian president Vladimir Putin of ordering the assassination of Anna Politkovskaya.[9]
On 1 November 2006, Litvinenko suddenly fell ill. Earlier that day he had met two former KGB officers, Andrei Lugovoi and Dmitri Kovtun. Lugovoi is a former bodyguard of Russian ex-Prime Minister Yegor Gaidar (also reportedly poisoned in November 2006) and former chief of security for the Russian TV channel ORT. Kovtun is now a businessman. Litvinenko had also had lunch at Itsu, a sushi restaurant on Piccadilly in London, with an Italian acquaintance and “nuclear waste expert”, Mario Scaramella, to whom he reportedly made allegations regarding Romano Prodi’s connections with the KGB.[10] Scaramella, attached to the Mitrokhin Commission investigating KGB penetration of Italian politics, claimed to have information on the death of Anna Politkovskaya, 48, a journalist who was killed at her Moscow apartment in October 2006. He passed Litvinenko papers supposedly concerning her fate. On 20 November, it was reported that Scaramella had gone into hiding and feared for his life.[11]
For several days after 1 November, Litvinenko experienced severe diarrhea and vomiting. At one point, he could not walk without assistance. As the pain intensified, Litvinenko begged his wife to call an ambulance for assistance.[12] For several weeks, Litvinenko’s condition worsened as doctors searched for what caused the illness. Surrounded by friends, Litvinenko began to become physically weak, and spent periods unconscious. A photograph was taken of Litvinenko in his death bed and released to the public. “I want the world to see what they did to me,” Litvinenko said.[12]
The poison
Wikinews has related news: Traces of radiation found where Litvinenko ate
Shortly after his death, the UK’s Health Protection Agency (HPA) stated that tests had established Litvinenko had significant amounts of the radionuclide polonium-210 (210Po) in his body. British and US government sources both said the use of 210Po as a poison has never been documented before, and this was probably the first time a person has been tested for the presence of 210Po in his or her body. The poison was in Litvinenko’s tea cup.[13] People who had contact with Litvinenko may also have been exposed to radiation.[14][15]
Polonium was identified only after Litvinenko’s death, on 23 November. Doctors and Scotland Yard investigators could not detect polonium earlier because it does not emit gamma rays, which are encountered with most radioactive isotopes. Unlike most common radiation sources, polonium-210 emits only alpha particles that do not penetrate even a sheet of paper or the epidermis of human skin, thus being invisible to normal radiation detectors in this case. Hospitals only have equipment to detect gamma rays. Both gamma rays and alpha particles are classified as ionizing radiation which can cause radiation damage. An alpha-emitting substance can cause significant damage only if ingested or inhaled, acting on living cells like a short-range weapon.[16] Litvinenko was tested for alpha-emitters using special equipment only hours before his death.[16]
Po-210 concentration in the body of Litvinenko
The symptoms seen in Litvinenko appeared consistent with an administered activity of approximately 2 GBq (50 mCi) which corresponds to about 10 micrograms of 210Po. That is 200 times the median lethal dose of around 238 μCi or 50 nanograms in the case of ingestion.[17]
Thallium – initial hypothesis
Scotland Yard initially investigated claims that Litvinenko was poisoned with thallium. It was reported that early tests appeared to confirm the presence of the poison.[18][19] Among the distinctive effects of thallium poisoning are hair loss and damage to peripheral nerves,[20] and a photograph of Litvinenko in hospital, released to the media on his behalf,[21] indeed showed his hair to have fallen out. Litvinenko attributed his initial survival to his cardiovascular fitness and swift medical treatment. It was later suggested a radioactive isotope of thallium might have been used to poison Litvinenko.[22] Dr. Amit Nathwani, one of Litvinenko’s physicians, said “His symptoms are slightly odd for thallium poisoning, and the chemical levels of thallium we were able to detect are not the kind of levels you’d see in toxicity.”[23] Litvinenko’s condition deteriorated, and he was moved into intensive care on 20 November. Hours before his death, three unidentified circular-shaped objects were found in his stomach via an X-ray scan.[24] It is thought these objects were almost certainly shadows caused by the presence of Prussian blue, the treatment he had been given for thallium poisoning.[20][25]
Death and last statement
Grave of Alexander Litvinenko at Highgate Cemetery
Late on November 22 and into the early morning of November 23, Litvinenko’s heart failed. The official time of death was 9:21 P.M.at University College Hospital in London.[26]
Litvinenko’s postmortem took place on 1 December.[27] Litvinenko had ingested polonium-210, a poisonous radioactive isotope.[1] Mario Scaramella, who had eaten with Litvinenko, reported that doctors had told him Litvinenko’s body had five times the lethal dose of polonium-210.[1] Litvinenko’s funeral reading took place on 7 December at the Central London mosque, after which his body was buried at Highgate Cemetery in North London.[28]
On 25 November, an article attributed to Litvinenko was published by the Mail on Sunday Online entitled Why I believe Putin wanted me dead…[5] Strikingly, the only witness to the purported statement was Goldfarb, a representative of Boris Berezovsky. Also striking is the fact that a desperately ill man who hardly spoke sufficient English to order a cup of tea would be able to write a letter in beautiful, flowing English – or that he would choose to do so in English, rather than his native Russian.
In his last statement he said about Putin:
…this may be the time to say one or two things to the person responsible for my present condition. You may succeed in silencing me but that silence comes at a price. You have shown yourself to be as barbaric and ruthless as your most hostile critics have claimed. You have shown yourself to have no respect for life, liberty or any civilised value. You have shown yourself to be unworthy of your office, to be unworthy of the trust of civilised men and women. You may succeed in silencing one man but the howl of protest from around the world will reverberate, Mr Putin, in your ears for the rest of your life. May God forgive you for what you have done, not only to me but to beloved Russia and its people.[29]
Investigation
Initial steps
Greater London’s Metropolitan Police Service Terrorism Unit has been investigating the poisoning and death. The head of the Counter-Terrorism Unit, Deputy Assistant Commissioner Peter Clarke, stated the police “will trace possible witnesses, examine Mr. Litvinenko’s movements at relevant times, including when he first became ill and identify people he may have met. There will also be an extensive examination of CCTV footage.”[30] The United Kingdom Government COBRA committee met to discuss the investigation.[31] Richard Kolko from the United States FBI stated “when requested by other nations, we provide assistance” – referring to the FBI now joining the investigation for their expertise on radioactive weapons.[32][33] The Metropolitan Police announced on 6 December 2006 that it was treating Litvinenko’s death as murder.[34] Interpol has also joined the investigation, providing “speedy exchange of information” between British, Russian and German police.[35]
Polonium trails
Detectives traced three distinct polonium trails in and out of London. The trails were left by Litvinenko, Andrei Lugovoi and Dmitry Kovtun. The patterns and levels of radioactivity they left behind suggested that Litvinenko ingested polonium, whereas Lugovoi and Kovtun handled them directly.[36] The human body dilutes the polonium before excreting in sweat, which results in a reduced radioactivity level. There were also traces of Po-210 found at the “Hey Jo/Abracadabra” bar, “Dar Marrakesh” restaurant, and Lambeth-Mercedes taxis.[37]
The poisoning of Litvinenko took place at around 5 p.m. of 1 November in the Millennium Hotel in Grosvenor Square. The bus he travelled in to the hotel had no signs of radioactivity – but large amounts had been detected at the hotel.[38] Polonium was subsequently found in a fourth-floor room and in a cup in the Pine Bar at the hotel.[39] After the Millennium bar, Litvinenko stopped at the office of Boris Berezovsky. He used a fax machine, where the radioactivity was found later. At 6 p.m. Akhmed Zakayev picked Litvinenko up and brought him home to Muswell Hill. The amount of radioactivity left by Litvinenko in the car was so significant, the car was rendered unusable.[36] Everything that he touched at home during next three days was contaminated. His family was unable to return to the house even six months later. His wife was tested positive for ingesting polonium but did not leave a secondary trail behind her. This suggested that anyone who left a trail could not have picked up the polonium from Litvinenko (possibly, including Lugovoy and Kovtun).[36]
Besides Litvinenko, only two people left the polonium trails: Lugovoy and Kovtun who were school friends and worked previously for Russian intelligence in the KGB and the GRU respectively.[36] These people handled the radioactive material directly and did not ingest it, because they left more significant traces of polonium than Litvinenko.[36]
Lugovoy and Kovtun met Litvinenko in the Millennium hotel bar twice, on 1 November (when the poisoning took place), and earlier, on 16 October. Trails left by Lugovoy and Kovtun started on 16 October, in the same sushi bar where Litvinenko was poisoned later, but at a different table. It was assumed that their first meeting with Litvinenko was either a rehearsal of the future poisoning, or an unsuccessful attempt of the poisoning.[36]
Traces left by Lugovoy were also found in the office of Berezovsky that he visited on 31 October, a day before his second meeting with Litvinenko. Traces left by Kovtun were found in Hamburg, Germany. He left them on his way to London on 28 October-31.[36] The traces were found in passenger jets[40][41] BA875 and BA873 from Moscow to Heathrow on 25 October and 31 October, as well as flights BA872 and BA874 from Heathrow to Moscow on 28 October and 3 November.[42][43]
Andrei Lugovoi has said he flew from London to Moscow on a 3 November flight. He stated he arrived in London on 31 October to attend the football match between Arsenal and CSKA Moscow on 1 November.[44] When the news broke that a radioactive substance had been used to murder Litvinenko, a team of scientists rushed to find out how far the contamination had spread. It led them on a trail involving hundreds of people and dozens of locations.[45]
British Airways later published a list of 221 flights of the contaminated aircraft, involving around 33,000 passengers, and advised those potentially affected to contact the UK Department of Health for help. On 5 December they issued an email to all of their customers, informing them that the aircraft had all been declared safe by the UK’s Health Protection Agency and would be entering back into service.
British extradition request
British authorities investigated the death and it was reported on 1 December that scientists at the Atomic Weapons Establishment had traced the source of the polonium to a nuclear power plant in Russia. On 3 December, reports stated that Britain has demanded the right to speak to at least five Russians implicated in Litvinenko’s death, and Russian Foreign Minister Sergey Lavrov asserted that Moscow was willing to answer “concrete questions.”[46] Russian Prosecutor-General Yuri Chaika said on Tuesday, 5 December that any Russian citizen who may be charged in the poisoning will be tried in Russia, not Britain.[47] Moreover, Chaika stated that UK detectives may ask questions to Russian citizens only in the presence of Russian prosecutors.[48]
On 28 May 2007 the British Foreign Office submitted a formal request to the Russian Government for the extradition of Andrei Lugovoi to the UK to face criminal charges relating to Litvinenko’s murder.[49]
Extradition declined
Russian General Prosecutor’s Office declined to extradite Lugovoi, citing that extradition of citizens is not allowed under the Russian constitution (Article 61 of the Constitution of Russia).[50][51][52] Russian authorities later said that Britain has not handed over any evidence against Lugovoi.[53][54] Professor Daniel Tarschys, former Secretary General of the Council of Europe, commented[55] that Russian Constitution actually “opens the door” for the extradition, and Russia ratified three international treaties on extradition (on 10 December 1999); namely, the European Convention on Extradition[56] and two Additional Protocols[57][58][59] to it. Yury Fedotov, Ambassador of the Russian Federation, pointed out that when the Russian Federation ratified the European Convention on Extradition it entered a declaration[60] concerning Article 6 in these terms: “The Russian Federation declares that in accordance with Article 61 (part 1) of the Constitution of the Russian Federation, a citizen of the Russian Federation may not be extradited to another state.”[61] The same protections are extended to the citizens of France and Germany, both of which refuse to extradite their citizens.
A BBC programme
On 7 July 2008, a British security source told the BBC’s Newsnight programme: “We very strongly believe the Litvinenko case to have had some state involvement. There are very strong indications.”[62] The British government claimed that no intelligence or security officials were authorised to comment on the case.[63][64]
Possibly related events
On 2 March 2007 Paul Joyal, a former director of security for the U.S. Senate intelligence committee, who the previous weekend alleged on national television that the Kremlin was involved in the poisoning of Litvinenko, was shot near his Maryland home. An FBI spokesman said the agency was “assisting” the police investigation into the shooting. Police would not confirm details of the shooting or of the condition of Joyal, a person familiar with the case said he was in critical condition in hospital. It was reported that while there were no indications that the shooting was linked to the Litvinenko case, it is unusual for the FBI to get involved in a local shooting incident. A person familiar with the situation said NBC had hired bodyguards for some of the journalists involved in the program.[65]
[edit] Polonium-210
Sources and production of polonium
A freelance killer would not be able to obtain polonium legally from commercially available products in the amounts used for Litvinenko poisoning, because more than microscopic amounts of polonium can only be produced in state-controlled nuclear reactors.[36][66] (see also commercial products containing polonium for detail).
Ninety seven percent of the world’s legal polonium-210 (210Po) production occurs in Russia in RBMK reactors[36][67] About 85 grams (450,000 Ci) are produced by Russia annually. According to Sergei Kiriyenko, the head of Russia’s state atomic energy agency, RosAtom, all of it goes to U.S. companies through a single authorized supplier. The production of polonium starts from bombardment of bismuth (209Bi) with neutrons at the Ozersk nuclear reactor, near the city of Chelyabinsk in Russia. The product is then transferred to the Avangard Electromechanical Plant in the closed city of Sarov.[36][68][69][70] This of course does not exclude the possibility that the polonium that killed Litvinenko was imported by a licensed commercial distributor, but no one—including the Russian government—has proposed that this is likely, particularly in regard to the radiation detected on the British Airways passenger jets travelling between Moscow and London.[citation needed] Russian investigators have said they could not identify the source of polonium.[71]
Polonium-210 has a half-life of 138 days and decays to the stable daughter isotope of lead, 206Pb. Therefore the source is reduced to about one sixteenth of its original radioactivity about 18 months after production. By measuring the proportion of polonium and lead in a sample, one can establish the production date of polonium. The analysis of impurities in the polonium (a kind of “finger print”) allows to identify the place of production.[72] It is assumed by Litvinenko’s wife and his close confidant that British investigators were able to identify the place and time of production of polonium used to poison Litvinenko, but their findings remain unpublished.[36]
Possible motivation for using polonium-210
Philip Walker, professor of physics at the University of Surrey said: “This seems to have been a substance carefully chosen for its ability to be hard to detect in a person who has ingested it.”[73] Oleg Gordievsky, the most senior KGB agent ever to defect to Britain, made a similar comment that Litvinenko’s assassination was carefully prepared and rehearsed by Russian secret services,[74] but the poisoners were unaware that technology existed to detect traces left by polonium-210: “Did you know that polonium-210 leaves traces? I didn’t. And no one did. …what they didn’t know was that this equipment, this technology exists in the West – they didn’t know that, and that was where they miscalculated.”[74]
Nick Priest, a nuclear scientist and expert on polonium who has worked at most of Russia’s nuclear research facilities, says that although the execution of the plot was a “bout of stupidity”, the choice of polonium was a “stroke of genius”. He says: “the choice of poison was genius in that polonium, carried in a vial in water, can be carried in a pocket through airport screening devices without setting off any alarms”, adding, “once administered, the polonium creates symptoms that don’t suggest poison for days, allowing time for the perpetrator to make a getaway.” Priest asserts that “whoever did it was probably not an expert in radiation protection, so they probably didn’t realize how much contamination you can get just by opening the top (of the vial) and closing it again. With the right equipment, you can detect just one count per second”.[75]
Filmmaker and friend of Litvinenko, Andrei Nekrasov, has suggested that the poison was “sadistically designed to trigger a slow, tortuous [sic] and spectacular demise”.[76] Expert on Russia Paul Joyal suggested that “A message has been communicated to anyone who wants to speak out against the Kremlin…. If you do, no matter who you are, where you are, we will find you, and we will silence you, in the most horrible way possible”.[77]
Theories
Many theories of Litvinenko poisoning circulated after his death. Many circumstances led to suspicion that he was killed by the Russian secret service.[78] Viktor Ilyukhin, a deputy chairman of the Russian Parliament’s security committee for the Communist Party of the Russian Federation, said that he “can’t exclude that possibility”[79] He apparently referred to a recent Russian counter-terrorism law that gives the President the right to order such actions.[80][81] An investigator of the Russian apartment bombings, Mikhail Trepashkin wrote in a letter from prison that an FSB team had organised in 2002 to kill Litvinenko. He also reported FSB plans to kill relatives of Litvinenko in Moscow in 2002, although these have not been carried out.[82][83] State Duma member Sergei Abeltsev commented on 24 November 2006:[84] said: “The deserved punishment reached the traitor. I am confident that this terrible death will be a serious warning to traitors of all colors, wherever they are located: In Russia, they do not pardon treachery. I would recommend citizen Berezovsky to avoid any food at the commemoration for his accomplice Litvinenko.”
Many publications in Russian media suggested that the death of Litvinenko was connected to Boris Berezovsky.[85][86] Former FSB chief Nikolay Kovalyov, for whom Litvinenko worked, said that the incident “looks like [the] hand of Berezovsky. I am sure that no kind of intelligence services participated.”[87] This involvement of Berezovsky was alleged by numerous Russian television shows.
An explanation put forward by the Russian Government appeared to be that the deaths of Litvinenko and Politkovskaya were intended to embarrass President Putin. Other theories included involvement of rogue FSB members[88] or suggestions that Litvinenko was killed because of his research of certain Russian corporations or state officials,[89][90] or as a political intrigue to undermine president Putin[91]
Suspects
Andrei Lugovoi
A former Federal Protective Service of Russia officer and millionaire who met with Litvinenko on the day he fell ill (1 November). He had visited London at least three times in the month before Litvinenko’s death and met with the victim four times. Traces of polonium-210 have been discovered in all three hotels where Lugovoi stayed after flying to London on 16 October, and in the Pescatori restaurant in Dover Street, Mayfair, where Mr Lugovoi is understood to have dined before 1 November; and aboard two aircraft on which he had travelled.[92][93] He has declined to say whether he had been contaminated with polonium-210.[94] The Crown Prosecution Service has charged him with murder and has sent an extradition request to Russia that includes a summary of the evidence, but the only third party to have seen the extradition request, American journalist Edward Epstein, has described the substantiation as “embarrassingly thin”.[95][96]
Dmitry Kovtun
A Russian businessman and ex-KGB agent who met Litvinenko in London first in mid-October and then on 1 November, the day Litvinenko fell ill. On 7 December Kovtun was hospitalized, with some sources initially reporting him to be in coma.[97] On 9 December, German police found traces of radiation at a Hamburg flat used by Kovtun.[98] The following day, 10 December, German investigators identified the detected material as polonium-210 and clarified that the substance was found where Kovtun had slept the night before departing for London. British police also report having detected polonium on the plane in which Kovtun travelled from Moscow.[99] Three other points in Hamburg were identified as contaminated with the same substance.[100] On 12 December Kovtun told Russia’s Channel One TV that his “health was improving”.[35]
Kovtun was under investigation by German detectives for suspected plutonium smuggling into Germany in October.[35] Germany dropped the case against Kovtun on November 2009 [2]
Vyacheslav Sokolenko
A business partner of Andrei Lugovoi.[101]
Vladislav
The Times stated that the police have identified the man they believe may have poisoned Litvinenko with a fatal polonium dose in a cup of tea on the fourth-floor room at the Millennium Hotel to discuss a business deal with Dmitry Kovtun and Andrei Lugovoi before going to the bar. These three men were joined in the room later by the mystery figure who was introduced as Vladislav, a man, who could help Litvinenko win a lucrative contract with a Moscow-based private security firm.[102]
Vladislav is said to have arrived in London from Hamburg on 1 November on the same flight as Dmitry Kovtun. His image is recorded by security cameras at Heathrow airport on arrival. He is described as being in his early 30s, tall, strong, with short black hair and Central Asian features. Oleg Gordievsky, an ex-KGB agent, has said that this man was believed to have used a Lithuanian or Slovak passport, and that he left the country using another EU passport. He has also said Vladislav started his preparations in early 2006, “some time between February and April”, that he “travelled to London, walked everywhere, and studied everything.”[103]
Businessman and politician Boris Berezovsky said in a police interview that “Sasha mentioned some person who he met at Millennium Hotel”, but would not “remember whether [his name] was Vladimir or Vyacheslav.”[104] Litvinenko’s friend Alex Goldfarb writes that according to Litvinenko, “Lugovoy brought along a man whom [Litvinenko] had never seen before and who had ‘the eyes of a killer.'”[105]
Igor the Assassin
The code name for a former KGB assassin. He is said to be a former Spetznaz officer born in 1960 who is a Judo master and walks with a slight limp. He allegedly speaks perfect English and Portuguese and may be the same person who served Litvinenko tea in the London hotel room.[106]
Leonid Nevzlin
A businessman living in Israel has been accused by Russian Procurator’s office of links to several murders in Russia and was one of the key figures in the Yukos oil company.[107]
Putin
Other persons related to the case
Yegor Gaidar
The sudden illness of Yegor Gaidar in Ireland on 24 November, the day of Litvinenko’s death, has been linked to his visit to the restaurant where polonium was present and is being investigated as part of the overall investigation in the UK and Ireland.,[108] Other observers noted he was probably poisoned after drinking a strange-tasting cup of tea. Gaidar was taken to hospital; doctors said his condition is not life-threatening and that he will recover.[109][110] This incident was similar to the poisoning of Anna Politkovskaya on a flight to Beslan. After poisoning, Gaidar claimed that it was enemies of Kremlin who tried to poison him.
Mario Scaramella
The United Kingdom’s Health Protection Agency (HPA) announced that significant quantities of polonium-210 had been found in Mario Scaramella although his health was found to be normal. He has been admitted to hospital for tests and monitoring.[111] Doctors say that Scaramella was exposed to a much lower level of polonium-210 than Litvinenko had been exposed to, and that preliminary tests found “no evidence of radiation toxicity”.[112] According to the 6 pm Channel 4 (9 December 2006) news the intake of polonium he suffered will only result in a dose of 1 mSv. This will lead to a 1 in 20000 chance of cancer. According to The Independent, Scaramella alleged that Litvinenko was involved in smuggling radioactive material to Zürich in 2000.[113]
Boris Volodarsky, a KGB defector residing in London, stated that Evgeni Limarev, another former KGB officer residing in France, continued collaboration with FSB, infiltrated Litvinenko’s and Scaramella’s circles of trust and misinformed the latter.[114][115][116]
Igor Ponomarev
Igor Ponomarev was a Russian diplomat whose death was named a possible murder by Paolo Guzzanti[116]
Marina Litvinenko
UK reports state Litvinenko’s widow tested positive for polonium, though she is not seriously ill. The Ashdown Park hotel in Sussex has been evacuated as a precaution, possibly to do with Scaramella’s previous visit there.[117] According to the 6 pm Channel 4 (9 December 2006) news the intake of polonium she suffered will only result in a dose of 100 mSv. This will lead to a 1 in 200 chance of cancer.
Akhmed Zakayev
The forensic investigation also includes the silver Mercedes by Litvinenko’s home believed to be owned by his close friend and neighbour Akhmed Zakayev, then foreign minister of the separatist government in exile of Ichkeria.[118][119][120] Reports now state that traces of radioactive material were found in the vehicle.[121]
British Police
Two London Metropolitan police officers tested positive for 210Po poisoning.[122]
Bar staff
Some of the bar staff at the hotel where the polonium contaminated teacup was found were discovered to have suffered an intake of polonium (dose in the range of 10s of mSv). These people include Norberto Andrade, the head barman of the bar and a long-time (27 years) worker at the hotel. He has described the situation thus:
“When I was delivering gin and tonic to the table, I was obstructed. I couldn’t see what was happening, but it seemed very deliberate to create a distraction. It made it difficult to put the drink down.”
“It was the only moment when the situation seemed unfriendly and something went on at that point. I think the polonium was sprayed into the teapot. There was contamination found on the picture above where Mr Litvinenko had been sitting and all over the table, chair and floor, so it must have been a spray.”
“When I poured the remains of the teapot into the sink, the tea looked more yellow than usual and was thicker – it looked gooey.”
“I scooped it out of the sink and threw it into the bin. I was so lucky I didn’t put my fingers into my mouth, or scratch my eye as I could have got this poison inside me.”[13]
Chronology
Background history
* 7 June 1994: A remote-controlled bomb detonated aiming at chauffeured Mercedes 600 with oligarch Boris Berezovsky and his bodyguard in the rear seat. Driver died but Berezovsky left the car unscathed. Litvinenko, then with the organized-crime unit of the FSB, was an investigating officer of the assassination attempt. The case was never solved, but it was at this point that Litvinenko befriended Berezovsky.
* 17 November 1998: At a time that Vladimir Putin was the head of the FSB, five officers including Lieutenant-Colonel Litvinenko accuse the Director of the Directorate for the Analysis of Criminal Organizations Major-General Eugeny Hoholkhov and his deputy, 1st Rank Captain Alexander Kamishnikov, of ordering them to assassinate Boris Berezovsky in November 1997.
2006
October 2006
* 7 October: The Russian journalist and Kremlin critic Anna Politkovskaya is shot in Moscow.
* 16 October: Andrei Lugovoi flies to London.
* 16 October-18 October: Former KGB agent Dmitry Kovtun visits London, during which time he eats two meals with Litvinenko, one of them at the Itsu sushi bar (see 1 November 2006).[97][123]
* 17 October: Litvinenko visits “Risc Management”, a security firm in Cavendish Place, with Lugovoi and Kovtun.[124]
* 19 October: Litvinenko accuses President Putin of the Politkovskaya murder.
* 28 October: Dmitry Kovtun arrived in Hamburg, Germany from Moscow on an Aeroflot flight. Later German police discovered that the passenger seat of the car that picked him up at an airport was contaminated with Polonium-210.
* 31 October: Dmitry Kovtun comes to London from Hamburg, Germany. German police found that his ex-wife’s apartment in Hamburg was contaminated with polonium-210.[125]
November 2006
* 1 November: Just after 3 p.m., at the Itsu sushi restaurant on Picadilly, Litvinenko meets the Italian security expert Mario Scaramella, who hands alleged evidence to him concerning the murder of Politkovskaya. Around 4:15 p.m., he comes to the office of Boris Berezovsky to copy the papers Scaramella had given him and hand them to Berezovsky. Around 5 p.m. he meets with the former KGB agents Andrei Lugovoi, Dmitry Kovtun and Vyacheslav Sokolenko in the Millennium Hotel in London. He later becomes ill.[126][127]
* 3 November: Litvinenko is brought into Barnet General Hospital.
* 11 November: Litvinenko tells the BBC he was poisoned and is in very bad condition.
* 17 November: Litvinenko is moved to University College Hospital and placed under armed guard.
* 19 November: Reports emerge that Litvinenko has been poisoned with thallium, a chemical element used in the past as a rat poison.
* 20 November: Litvinenko is moved to the Intensive Care Unit. The police take statements from people with close relation to Litvinenko. A Kremlin speaker denies the Russian government is involved in the poisoning.
* 22 November: The hospital announces that Litvinenko’s condition has worsened substantially.
* 23 November: 9:21 p.m.: Litvinenko dies.
* 24 November: Litvinenko’s dictated deathbed statement is published. He accuses President Vladimir Putin of being responsible for his death. The Kremlin rejects the accusation. The HPA announces that significant amounts of Polonium-210 have been found in Litvinenko’s body. Traces of the same substance are also found at Litvinenko’s house in North London, at Itsu and at the Millennium Hotel.
* 24 November: Sergei Abeltsev, State Duma member from the LDPR, in his Duma address he commented on the death of Litvinenko with the following words: The deserved punishment reached the traitor. I am sure his terrible death will be a warning to all the traitors that in Russia the treason is not to be forgiven. I would recommend to citizen Berezovsky to avoid any food at the commemoration for his crime accomplice Litvinenko[84]
* 24 November: The British police state they are investigating the death as a possible poisoning.
* 28 November: Scotland Yard announces that traces of Polonium-210 have been found in seven different places in London. Among them, an office of the Russian billionaire Boris Berezovsky, an avowed opponent of Putin.
* 29 November: The HPA announces screening of the nurses and physicians who treated Litvinenko. The authorities find traces of a radioactive substance on board British Airways planes.
* 30 November: Polonium-210 traces are found on a number of other planes, most of them going to Moscow.
December 2006
* 1 December: An autopsy is performed on the body of Litvinenko. Toxicology results from Mr Litvinenko’s post-mortem examination revealed two “spikes” of radiation poisoning, suggesting he received two separate doses.[92] Scaramella tests positive for Polonium-210 and is admitted into a hospital. Litvinenko’s widow also tests positive for Polonium-210, but was not sent to the hospital for treatment.
* 2 December: Scotland Yard’s counter-terrorist unit have questioned Yuri Shvets, a former KGB spy who emigrated to the United States in 1993. He was questioned as a witness in Washington in the presence of FBI officers. Shvets claimed that he has a “lead that can explain what happened”.
* 6 December: Scotland Yard announced that it is treating his death as a murder.[34]
* 7 December: Confused reports state that Dmitry Kovtun was hospitalized, the reason has not yet been made clear.
* 7 December: Russian Office of the Prosecutor General has opened a criminal case over poisoning of Litvinenko and Kovtun by the articles “Murder committed in a way endangering the general public” (убийство, совершенное общеопасным способом) and “Attempted murder of two or more persons committed in a way endangering the general public”.[128]
* 8 December: Kovtun is reported to be in coma.[97]
* 9 December: German police find traces of radiation at Hamburg flat used by Kovtun.[98]
* 9 December: UK police identify a single cup at the Pines Bar in the Millennium Hotel in Mayfair which was almost certainly the one used to administer the poison.[129]
* 11 December: Andrei Lugovoi is interrogated in Moscow by UK Scotland Yard and General Procurator’s office of the Russian Federation. He refuses to reveal any information concerning the interrogation.[130]
* 12 December: Dmitry Kovtun tells a Russian TV station that his “health [is] improving”.[35]
* 24 December: Mario Scaramella was arrested in Naples on his return from London, on apparently unrelated charges.[131]
* 27 December: Prosecutor General of Russia Yury Chaika accused Leonid Nevzlin, a former Vice President of Yukos, exiled in Israel and wanted by Russian authorities for a long time, of involvement in the poisoning, a charge dismissed by the latter as a nonsense.[132]
2007
February 2007
* 5 February: Boris Berezovsky told the BBC that on his deathbed, Litvinenko said that Lugovoi was responsible for his poisoning.[133]
* 6 February: The text of a letter written by Litvinenko’s widow on 31 January to Putin, demanding that Putin work with British authorities on solving the case, was released.[134]
* 8 February 2007: Update to HPA (Health Protection Agency) investigation of Polonium 210 incident.[135]
May 2007
* 21 May: Sir Ken Macdonald QC (Director of Public Prosecutions of England and Wales ) say that Lugovoi, should face trial for the “grave crime” of murdering Litvinenko.
* 22 May: Macdonald announces that Britain will seek extradition of Lugovoi and attempt to charge him with murdering Litvinenko. The Russian government states that they will not allow the extradition of any Russian citizens.[136]
* 28 May: The British Foreign Office formally submits a request to the Russian Government for the extradition of Lugovoi to the UK to face criminal charges.[49]
o The Constitution of Russia forbids extradition of Russian citizens to foreign countries (Article 61), so the request can not be fulfilled.[137]
Extradition requests had been granted in the past (For example in 2002 Murad Garabayev has been handed to Turkmenistan.,[138] Garabayev’s extradition was later found unlawful by the Russian courts and he was awarded 20,000 Euros in damages to be paid by the Russian government by the European Court of Human Rights.[139]) Article 63 does not explicitly mention Russian citizens, and therefore does not apply to them, but only to foreign nationals living in Russia. Article 61 supersedes it for the people holding the Russian citizenship.
* 31 May: Lugovoi held a news conference at which he accused MI6 of attempting to recruit him and blamed either MI6, the Russian mafia, or fugitive Kremlin opponent Boris Berezovsky for the killing.[140]
July 2007
* 16 July: The British Foreign Office confirms that, as a result of Russia’s refusal to extradite Lugovoi, four Russian diplomats are to be expelled from the Russian Embassy in London.[141]
* 17 July: The Russia’s deputy foreign minister, Mr Alexander Grushko, threatens to expel 80 UK diplomats.[142]
* 19 July: The Russian Foreign ministry spokesman, Mikhail Kamynin, declared the expulsion of 4 UK diplomats from the British Embassy in Moscow.[143]
October 2007
* 27 October: British newspaper Daily Mail journalists Stephen Wright and David Williams, reported that Alexander Litvinenko was an MI6 agent and was receiving a retainer of £2000 per month when he was murdered and that the current head of MI6 Sir John Scarlett was involved in his recruitment, quoting unnamed “diplomatic and intelligence” sources.[144] Such claims have been denied by Marina Litvinenko[145] and Oleg Gordievsky.[146]
December 2008
* In the 16 December 2008 interview, when asked by the Spanish newspaper El País if Litvinenko could have been killed in the interests of the Russian state, Lugovoy — wanted by British police on suspicion of the murder of Litvinenko — replied that he would order the assassination of anyone, for example, President Saakashvili of Georgia and the KGB defector Gordievsky, in the interests of the Russian state.[147][148]
Comparisons to other deaths
Deaths from ingesting radioactive materials
According to the IAEA in 1960 a person ingested 74 MBq of radium (assumed to be 226Ra) and this person died four years later.[149] Harold McCluskey survived 11 years (eventually dying from cardiorespiratory failure) after an intake of at least 37 MBq of 241Am (He was exposed in 1976). It is estimated that he suffered doses of 18 Gy to his bone mass, 520 Gy to the bone surface, 8 Gy to the liver and 1.6 Gy to the lungs; it is also claimed that a post mortem examination revealed no signs of cancer in his body. The October 1983 issue of the journal Health Physics was dedicated to McCluskey, and subsequent papers about him appeared in the September 1995 issue.[150]
Comparisons have been made to the alleged 2004 poisoning of Viktor Yushchenko (Ukraine and Russia have been separate states since 1991), the alleged 2003 poisoning of Yuri Shchekochikhin and the fatal 1978 poisoning of the journalist Georgi Markov by the Bulgarian Committee for State Security (Russia and Bulgaria had never been parts of the same state). The incident with Litvinenko has also attracted comparisons to the poisoning by radioactive (unconfirmed) thallium of KGB defector Nikolay Khokhlov and journalist Shchekochikhin of Novaya Gazeta (the Novaya Gazeta interview with the former, coincidentally, prepared by Russian journalist Anna Politkovskaya, who was later found shot to death in her apartment building).[151] Like Litvinenko, Shchekochikhin had investigated the Russian apartment bombings (he was a member of the Kovalev Commission that hired Litvinenko’s friend Mikhail Trepashkin as a legal counsel).
KGB defector and British agent Oleg Gordievsky believes the murders of Zelimkhan Yandarbiev, Shchekochikhin, and Politkovskaya and the incident with Litvinenko show that FSB has returned to the practice of political assassinations,[152] which were conducted in the past by Thirteenth KGB Department.[153] A comparison was also made with Roman Tsepov[154] who was responsible for personal protection of Anatoly Sobchak and Putin, and who died in Russia in 2004 from poisoning by an unknown radioactive substance.[155][156]
Officers of FSB “special forces” liked to use Litvinenko photos for target practice in shooting galleries, according to Russian journalist Yulia Latynina.[157
The CIA reports – The Warsaw Pact: Treaty of Friensdhip, Cooperation and Mutual Assistance

After Communist regimes in Eastern Europe collapsed twenty years ago and the Soviet Union disintegrated two years later, immense opportunities for archival research opened. Even though serious obstacles to archival work have persisted in Russia (which houses the central repositories of the Soviet regime), the archives of nearly all of the former Warsaw Pact countries are now fully or at least largely open. As a result, scholars have been able to explore many aspects of the Warsaw Pact that could only be guessed at in the past, including questions of military planning, force preparations and operations, nuclear command arrangements, and civil-military issues.
1961 – 35 Documents
Military Thought — A turning point in the development of Soviet military art, by Colonel-General Ivanov
Soviet efforts to determine Western planning on the Berlin situation
SCPSU Decree concerning the Vienna talks between Premier Khrushchev and President Kennedy
Outlook for the Development of Missile Weapons for the Ground Forces by Chief Marshal S Varentsov
Rear Area Support of Missile Troops in Front Offensive Operations by Colonel General Odintsov
Anti-missile defense of troops of a front by Lt. Gen. V. Mikhaylov
Comments of a senior Soviet general officer on Soviet plans regarding Berlin
Khrushchev’s intentions regarding Germany, a Summit Conference, Iran, and Turkey
The Missions of the Navy and Methods of Carrying Them Out by Admiral Platonov
Trends in the Development of Tank Forces of the Soviet Army by General of the Army A Zhadov
The Use of Naval Forces in Closed Sea Theaters in the Initial Period of a War by Admiral V Kasatonov
The Nature of Modern Armed Combat and the Role and Place by General of the Army P Kurochkin
Elimination of the Lag in Operational and Tactical Intelligence by Lt General Kochetkov
The Paths of Further Development of the Tank Troops of the Soviet Army by P. Rotmistrov
Documents relating to Soviet bloc policy for the XVIth session of the UN General Assembly
Eradication of Fraud, Deception and Falsification in Relation to State Plan and Socialist Obligations
CC-CPSU Decree Entitled Measures for Improving the Selection and Training of Propaganda Cadres
Establishment of the top secret special collection of articles of the journal, Military Thought
Use of Artillery in Support of an Army Counterattack Artillery Information Collection #49-1959
Military Thought — Some Questions Concerning Modern Defense by Major-General V Petrenko
The organizational structure of field command of a front by Colonel K Pashuk
Artillery Collection-Independent Engineer Battalion Exercise in an Offensive Operation
Military Thought — The use of surface vessels in modern Naval Warfare by Rear-Admiral N Zvyagin
Military Thought — Utilization of the Navy in a Missile-Nuclear War by Rear-Admiral V Lisyutin
Artillery Collection — The maneuver of missile units in an offensive
Military Thought-The Theory of Military Art Needs Review, by Colonel- General A Gastilovich
Military Thought — Intelligence to the Level of Modern Demands, by Major- General Ya Malakhov
Military Thought — questions of the control of missile units in an offensive operation
Artillery Collection-The question of fire control of missile artillery
Military Thought — Combined-Arms Army Deployment and Forward Movement by Lt-General S Andryushchenko
Military News — Tank crossing under water in winter
Military Thought — Nuclear Missile Armament and Military Doctrine by Major-General M Goryainov
Military News — Special features in the training of batteries for firing at low- flying aerial target
Military Thought — Troop Control Questions in Modern Operations by Major-General A Morozov et al
Military Thought — Thoughts on Soviet Army Tank Troops Development by Marshal R Malinovskiy
1962 – 162 Documents
Military Thought — Defense of the Operational Rear by Major-General Yu. Novikov
Military Thought — Increasing the stability of the control of the troops by Major-General M Ivanov
Military Thought — Some Problems of Modern Operations by Lieutenant-General I Tolkonyuk
Military Thought — The Organization of Antimissile Defense by Colonel V Savko and Colonel N Maksimov
Military Thought — Offensive Operation Under the Conditions of Nuclear-Missile War by Colonel-Gen G Khetagurov
Military Thought — Ways of Further Increasing the Combat Readiness of Troops, by Major-General G Semenov
Military Thought — Future war and special features of conducting operations by Colonel-General Pavlovskiy
Military Thought — The nature of modern warfare by Colonel-General A. Babadzhanyan
CPSU Central Committee letter on Albania
Military Thought — The strike groupings of a front by Major-General of Tank Troops A. Shevchenko
Military Thought — Conclusions regarding NATO Armed Forces Exercise Side Step by Colonel-Gen S Ivanov
Military News — Reconnaissance of the enemy atomic means, by Lieutenant-General of Artillery, G. Nadysev
Artillery Collection-Questions on the artillery combat utilization in an offensive operation
Military Thought — The Role of Aviation in Military Operations at Sea, by Rear Admiral V Bogolepov
Military Thought — The Air Forces in the New Soviet Armed Forces Development by Lt-Gen S Sinyakov et al
Military Thought — New Developments in Operational Art and Tactics, by Lieutenant-General V. Baskakov
Military News — The destruction of enemy free rocket launching positions, by Lt.-Col Yu Sobolev and Maj V.Ozhogin
The Wider Application of Radio-electronic Means for Reconnaissance, by Colonel B. Dudnik
Military Thought — Radio deception as a means of radio counteraction, by Engineer Colonel M. Masterov
Military Thought — Suitability of Modern Means and Methods in the Conduct of Operation by Major General I Zavyalov
Military Thought — Problems in Rear area support preparation by Colonel-General F Malykhin
Military News — Tank Fire from Concealed Firing Positions by Major-General A Laptev and Lt-Colonel D Nalivayko
Strategic Missile Bulletin– Introductory remarks and tables of contents
Military Thought — Methods of Operational Training of Generals, Senior Officers and Staffs, by Maj-Gen M Ivanov et al
Military Thought — Submarine Operation of the Navy-the Naval Operation of the Future, by Adm Yu Panteleyev
Military Thought — To Develop the Theory of Soviet Military Art, by Admiral V Tributs
Technical data on the Soviet R-1 tactical ballistic missile
Technical data on the Soviet R-2 tactical ballistic missile
Military Thought — Intelligence to the Level of Modern Tasks, by Lieutenant-General P Dankevich
Military Thought — The Problem of Transportation in Modern Warfare, by Lt-General I Kovalev et al
Military Thought — Rear Services Support of Missile Troops in an Offensive Operation by Lt-General M Novikov
Military News — The First Experiment in the Use of Video Communications, by Lieutenant-Colonel Ye Latarev
Military Thought — Development of front aviation combat employment theory by Lt-Colonel N Reshetnikov
Military Thought — The Nature of Modern Armed Combat, by General of the Army A. Gorbatov
Soviet articles on strategic missiles
Strategic Missile Bulletin– The Organization of Combat Support of a Regiment Equipped with Strategic Missiles
Artillery Collection– The Working Out and Conduct of Command-Staff tactical exercises with Missile Units and Large Units
Military Thought — Nuclear weapons influence on offensive operations of a front, by General V Kulasnv
Military News — The high rates of march of a regiment, by Colonel V Parno
Military News — To improve command training, by Colonel Z.Zhiltaov and Lieutenant-Colonel I Sevryukov
Military Thought — Some factors affecting the planning of a modern offensive operation, by Col-General Ye Ivanov
Military Thought — Questions in ground troop development and improvement by Col-General P Poluboyarov
Critique of a Soviet rear services exercise
Military News — Firing from a moving armored personnel carrier by Major-General S Savchenko and Col A Grechikhin
Military News — A unified system of planning combat training in a military district by Lt-General M Vaynrub
Military News — Radiation reconnaissance by helicopters by Captain G Starikov
Military News — Antenna electrical and optical axes coordination of a Radar Set by Colonel N Kanonykhin
Military Thought — Utilization of the Missile Troop in an Offensive Operation by Colonel-General P Koshevoy
Military Thought — Questions in the preparation and conduct of offensive operations by Col-General A Babadzhanyan
Military Thought — Organization and conduct of modern operational defense problems by Lt-General P Igolkin et al
Preliminary comment
Strategic Missile Bulletin–Advance preparation for the launching of missiles of strategic designation questions
Strategic Missile Bulletin–some special features of party political work in units of missile troops
Military News — The protection of troops against weapons of mass destruction by Major-General A Isayuk
Military News — Training of military faculty officers by Colonel S Knyazev
Military News — Features of providing communications in the far north by Lt-General D. Lolokoet al
Military Thought — Planning Nuclear-Missile Weapons utilization in a Front Offensive Operation, by Col-Gen V Chizh
Strategic Missile Bulletin–Some problems of camouflaging primary sitting areas of missile troops.
Military Thought — Urgent Tasks to improve Aerial Reconnaissance Under Modern Conditions, by Col-Gen S Mironov
Tactical Missile and Artillery collection–Some questions in the control of missile large units, units, and the Artillery
Military Thought — Increasing the Stability of Troop Control Question by Maj-Gen V Ilinykh et al
Military Thought — The fundamental scheme of a front offensive operation by Lt-General B Baskakov
Tactical Missile and Artillery Collection–Meteorological support of missile units and the Artillery
Information Bulletin of the Missile Troops Establishment of a Training Materials Base for Special Training in Missile Regiments
Military Thought — Transport support of the Strategic Concentration and Deployment of the Armed Forces
Military News — Pontoon bridging in winter by Lieutenant-Colonel V Afanasyev and Lieutenant-Colonel A Sashkov
Military News — The laying of mine fields in winter by Lieutenant-Colonel G Mishustin
Strategic Missile Bulletin–Improving the level of military-technical propaganda among missile troops
Information Bulletin of the Missile Troops — Strategic Means of Attack of the USA and Great Britain
Strategic Missile Bulletin–The control of the means of strategic attack of the armed forces of the capitalist countries
Artillery Collection–Problem of mission and substance of fire planning and preparation for firing of heavy rocket artillery
Military News — Road support during the combined regrouping of troops by Colonel I Nikolayev
Strategic Missile Bulletin–Organization and conduction of special training exercises for Technical- Repair Base officers
Information Collection of Missile Units and Artillery Combat Use of Antitank Guided Missiles in battle and operations
Military News — A breakthrough of enemy defense in winter by a motorized rifle division by Lt-General A Baksov
Military News — Simulation in troop exercises, by Lieutenant-General A Smirnov-Nesvitskiy
Military News — Withdrawal operations of an American infantry division by Colonel A Slobodenko
Strategic Missile Bulletin–The planning and organization of combat training in staffs and subunits of missile troops
Military Thought — 1961 Fourth issue table of contents
Artillery Collection–The use of antiradar mortar shells to create passive jamming of enemy field artillery radar sets
Military Thought — Navy Tasks problems and methods for accomplishing them by Admiral V Kasatonov
Artillery Collection–Artillery operations during an offensive with the landing of an airborne force
Military Thought — Preparation and conduct of an offensive operation on a maritime axis
Military Thought — Combat against enemy missile submarines by Rear Adm O Zhukovskiy
Military Thought — Some problems in destroying targets with nuclear warheads, by Marshal S Varentsov
Military Thought — A guide to the use of airborne landings by Lieutenant-Colonel M Belov
Military Thought — Participation of army missile weapons in the initial nuclear strike by Major-General N Stashek
Military Thought — Organizational Structure questions on the development of Tank Troops by Maj-Gen G Zavizion
Military Thought — A new combat vehicle by Lieutenant-General A Shevchenko
Military Thought — Combat problems with enemy nuclear means and their solutions by Marshal S Varentsov
Military Thought — Corresponding Reserves of Military-Transport Aviation to Modern Requirements by Lt-Col Sokolov-Sokolenok
Military Thought — On regrouping a combined-arms army from the depth of the country by Major-General P Stepshin
Military Thought — The Fallex-60 maneuvers of NATO armed forces bloc by Colonel-General S Ivanov
Military Thought — The combat utilization of front cruise missiles in a front offensive operation by Colonel P Plyachenko
Military Thought — The organizational structure questions concerning troop control, by Major-General N Reut
Military Thought — The use of the forces and means of aerial reconnaissance by Col O Yeltskikh
Military Thought — The massed use of missile troops in operations by Lieutenant-Colonel Ye Pavlov
Military Thought — Methods of organizing and planning aerial reconnaissance in operations by Lt-Col T Goryachkin
Military Thought — Prospects of development of armored combat vehicles
Military Thought — Planning a follow-up operation while completing another and problems of increasing staff effectiveness
Military Thought — The problem of the organizational structure of front and army field commands by Lt-Gen N Volodin
Review of Soviet diplomatic activities in fulfillment of the decisions of the XXIInd CPSU Congress
Military Thought — The preparation and use of strategic reserves in the Second World War by Colonel A Gryleve
Military Thought — Some questions of combat with enemy nuclear means, by Colonel S Lyshak and Colonel V Parkhomenko
Military Thought — Some questions on the organization of military- educational institutions, by Colonel V Choporov
Military Thought — The use of nuclear missile weapons in an army defensive operation by Colonel N Pavlov
Military Thought — Coordination of units during while using Nuclear-Missile Weapons by Colonel G Yefimov
Foreign Military Affairs — Table of Contents; Tactical Surprise in Ground Troop Operations methods by Colonel P Savinskiy
Military Thought — On fire preparation and fire support of an offensive, by Colonel V. Paleyev
Military Thought — Special Features in a Mountainous Theater of Military Operations, by Major-General S. Tarasov
Military Thought — The Question of Classifying Missile Weapons, by Colonel S. Begunov and Colonel I. Zheltikov
Military Thought — Radio counter-measures in the operation of ground troops, by Lt-General P Kiyanitsa et al
Military Thought — Organizing and conducting intelligence collection problems, by Lieutenant-Colonel B Yefimov
Military Thought — Ways of more effectively combating nuclear attack in an offensive Operation by Colonel B Strelchenko
Military Thought — Engineer Preparation of Terrain in Short Periods of Time, by Major-General N Vinogo
Military News — Combat with tactical nuclear weapons, by Lieutenant-General of Tank Troops, M. Shaposhnikov
Military Thought — Aviation Operations in an Initial Front Offensive Operation by Lt-General A Ostroumov et al
Military Thought — Preparation of siting areas for Missile Large Units and Units by Col Ye Kolibernoli and Capt LYefimochkin
Military Thought — The Meeting Engagement in the Initial Period o a War by Lt-General L Skvirskiy
Military Thought — Fire support of the landing operation of an airborne division by Colonel I Kotov
Military Thought — Zonal anti-aircraft missile protection for rear area forces
Military Thought — Questions on evaluating the effectiveness of the basic means of anti-air defense
Military Thought — On the problem of appraising the radiation situation, My Colonel F. Makyshko
Military Thought — Antinuclear protection of troops in disposition areas by Col V Zakharov et al
Military Thought — Radio countermeasures in ground troops by Colonel V Seroshtan and Lt-Colonel G Terekhov
Memo re memorandum some reflections on Military Thought –
Military Thought — Question of student military training at civilian higher educational institutions by Lt-Colonel Dagayev
Military Thought — Forces and means centralization-an important condition for radio-counter measures success
Military Thought — Some conclusions Concerning NATO Armed Forces Maneuvers by Colonel I Milevskiy
AFIC Addendum 1 – 23 august 1962- to review of CSB reports s-24-62, 16 March 1962
Military Thought — The use of missile troops in a front army offensive operation, Colonel Grigorovich
Military Thought — American military technical means of combat in space, by Major General P Vysotskiy
Military Thought — The fundamentals of anti-missile defense, by Colonel-General I Podgornyy
Enemy nuclear artillery, free rockets and guided missiles in offensive and defensive combat operations-Conclusion and Bibliography
Military Thought — World War II lessons and problems of constant combat readiness by Col L Vinnitskiyet al
Soviet view of the German situation as of late August
Military Thought — Developmental problems and resolution in anti-air defense of the ground troops by Colonel V Zemskov
Military Thought — The role of space weapons in a future war, by Lieutenant-General N. Korenevskiy
Enemy nuclear artillery, free rockets, and guided missiles in offensive and defensive combat operations- Chapter I
Enemy nuclear artillery, free rockets, and guided missiles in offensive and defensive combat operations- Chapter II
Military Thought — Chemical warfare weapons of the US by Colonel A Kuchin
Military Thought — The tasks of the navy and the methods of performing them, by Admiral N Kharlomov
Military Thought — Defensive operation fundamentals of Army groups and its utilization of Nuclear Weapons
Military Thought — Organization and control of engineer troops questions by Colonel Kolibernov and Colonel F Mysliak
Military Thought — Fortification and Its Tasks in Modern Warfare, by Major-General P Ogorodnikov et al
Military Thought — Rapid Setting up of Siting Areas for Missile Units by Colonel B Mikhaylov
Military Thought — The question of the organizational structure of missile troops by Major-General M Glushkov
Combat Against Enemy Nuclear Artillery, Free Rockets, and Guided Missiles in Offensive and Defensive Operations
Comments by Dr. Klaus Knorr on articles from Military Thought and other IRONBARK reports
Military Thought — The Use of Minor Automation and Mechanization
New Developments in Combat with Carrier Strike Large Units in the Initial Period
Chapter VII–Combat Against Enemy Nuclear Artillery, Free Rockets and Guided Missiles
Military Thought — Engineer support of the operations of missile large units and units in offensive operations
Military Journal–On the question of the Tasks, Organization and Planning of Military-Scientific work
Military Thought- Strategic Deployment problems of Armed Forces in Modern Warfare by Major-General Dzhelaukhov
Combat Against Enemy Nuclear Artillery, Free Rockets, and Guided Missiles
Military Thought — The Automation of Troop Control Processes Must be Comprehensive by Colonel B Fedotov et al
Basic Soviet ideas on war and the peacetime uses of military power
Military Thought — Basic problems of troop control and possible ways of resolving them
Recent trends in Soviet strategic thought on future war
Military Thought — The forms and methods of operational training by Lieutenant-General V Mernov
Military Thought — Training problems of Command and Border Military District staff combat readinesss by Maj-Gen Klyukanov
1963 – 39 Documents
Chapter VI- Combat Against Enemy Nuclear Artillery, Free Rockets, and Guided Missiles
Military Thought — Forewarning and notifying troops about radioactive contamination by Colonel D Shein
Military Thought — On military-scientific work in the ground forces by Colonel V Zemskov
Soviet military thought on large-scale non-nuclear war in Europe
Military Thought — Problems of improving ground force wheeled combat vehicles by Maj-Gen Zimelev et al
Military Thought — The struggle for the strategic initiative in modern warfare by Colonel V Larionov
Characteristics of the Soviet SP-5 and P-5 aerodynamic missiles
Ground support equipment and technical preparation of guided missiles for launching R-2 and R-11
Technical data on a Soviet surface-to-air missile designated V-75
Technical data on the R-11 tactical ballistic missile
Heavy rocket artillery — T. R. A.
Miscellaneous information on guided missiles R-1, R-2 and R-11
Rocket launching mount 2P2 and rocket 3R1
Rocket launching mount 2P5 and rockets 3R2 and 3R3
Rocket launching mount SP6 and liquid fuel rocket 3R7 Korshun
Supply of free rockets and guided missiles by the USSR to members of the Sino-Soviet bloc
Missile units in the group of Soviet forces, Germany [GFSD]
Possible deployment areas for strategic missiles and Troop training in the use of tactical and strategic missiles
various aspects of Soviet ballistic missile development
Additional information on heavy rocket artillery TRA
Developments in the Soviet missile and nuclear weapons programs up to mid-September 1961
Soviet cruise-type guided missiles P-5 and SP-5
Soviet nuclear weapons
Additional information on missile units in the group of Soviet forces, Germany [GFSD]
Ammunition storage depots near Mozhaysk
Assignments of senior Soviet military officers
Developments in the Soviet missile and nuclear weapons programs
Developments in the Soviet missile program
The Soviet cruise missile Krylatka
Combat deployment of a Soviet R11M missile battalion and battery
Personalities and location of PVO of the country
Views of Tactical Missile and Artillery Commander Varentsov on the status and future course of his forces
Structure of the Soviet command and control of the missile program
Projected Soviet space launchings
The position of Soviet missile designer Korolev
Uranium mining in the Pyatigorsk area
Some observations on the size and combat readiness of Soviet ground forces
Nuclear missile weapons in Soviet planning of theater war operations
Essential facts of the Penkovskiy case
1966 – 16 Documents
Military Thought Counterintelligence Activities in the US Army
Military Thought Combat Operations by Tank Units against Operational Defense Reserves
Military Thought Essence and Phenomenon in Military Affairs
Military Thought Factors Influencing the Organizational Structure of Ground Forces
Military Thought Logistical Support for Troop Regroupings
Military Thought Marxist-Leninist Theory of Knowledge and Significance in Soviet Military Science
Military Thought Necessary Book for Generals and Officers
Military Thought New Editor of a Scholarly Work on War and the Army
War in South Vietnam
Consolidating a Gain in an Offensive Operation
Criticism of the Philosophical Foundations of the Imperialist Military Ideology
Most Important Leninist Principles of Management and Methods working with Military
New Book on the Period Preceding the Second Front in Europe
Let’s Raise Military – Scientific Work to the Level of Party Demands
Radio-electronics and Intelligence
Zone of the Interior From Radioactive Contamination
1967 – 1 Document
Military News Complex automation in the control of troops and communications problem by Colonel V Sinyak
1973 – 58 Documents
Military Thought — Some Reflections on the Initial Period of War
Military Thought — Restoring Losses Incurred as a Result of Nuclear Attack
Military Thought — Restoring the Combat Effectiveness of Rocket Units
Military Thought — Restoration of Combat Losses Sustained in An Army Offensive
Military Thought — (USSR) Restoration of Troop Combat Effectiveness in a War Game
Military Thought — Observations on Naval Doctrine by the Soviet Navy Commander-In-Chief
Military Thought — (USSR) Restoration of the Combat Effectiveness of An Air Army After a Nuclear Strike
Military Thought — Communications Problems in Modern Warfare
Military Thought — Application of Scientific Research Methods To Naval Problems
Military Thought — (USSR) Role of Surface Vessels in Combat At Sea
Military Thought — (USSR) Modern Theory of Air Defense Operations
Military Thought — Combat employment of orbital aircraft
Military Thought — (USSR) Stability of the National Air Defense System
Military Thought — Army Reconnaissance During Movement From the Interior into Combat
Military Thought — Tactical Air Operations in Conventional Warfare on a Maritime Front
Military Thought — Airborne Landings in Operations of a Non-Nuclear Period
Military Thought — Increasing the Viability of Transport Aircraft in Airborne Operations
Military Thought — (USSR) Transport Aircraft Losses During Airborne Operations
Military Thought — (USSR) Support of Transport Aircraft During Airborne Operations
Military Thought — Importance of Electronic Countermeasures in Airborne Landings
Military Thought — Criticism of a Previous Article on Airborne Landings
Military Thought — Radiation Reconnaissance and Other Aspects of Airborne Operations
Military Thought — The capture of islands by airborne and amphibious forces
Military Thought — (USSR) Increasing the Air Mobility of the Ground Forces
Military Thought — An Argument for the Creation of Air Mobile Forces
Military Thought — Employment of Helicopters in Military Operations
Military Thought — Airborne and amphibious landings
Military Thought — The use of helicopters to increase the mobility of tactical rockets and antitank guided missiles
Military Thought — Support of Conventional Operations by the Long-Range Air Force
Military Thought — (USSR) Soviet Assessment of North Vietnamese Air Defense Actions Against US Aircraft
Military Thought — (USSR) Improvement of Soviet Military Staff Operating Methodology
Military Thought — Soviet Assessment of the Effectiveness of North Vietnamese SA-2 Missile Units
Military Thought — Status and Prospects for Improvement of Soviet Field Air Defense
Military Thought — (USSR) Deployment of Soviet Tactical Air Units From the Zone of Interior
Military Thought — Conventional Soviet Long Range Air Force Operations against Enemy Air Bases
Military Thought — Defeat of Enemy Aviation Groupings in a Theater of Military Operations
Military Thought — Movement of Troops across Soviet Central Asia
Military Thought — Soviet Views on the Conduct of Meeting Engagements
Military Thought — (USSR) Chief of the Soviet General Staff guidelines for the journal Military Thought
Military Thought — (USSR) Soviet Assessment of Air Defense and Air Forces in the 1967 Near East War
Military Thought — Development of Command Posts To Survive Weapons of Mass Destruction
Military Thought — Soviet View of NATO Defensive Doctrine
Military Thought — (USSR) Soviet View of US Field Army Intelligence Capabilities
Military Thought — Coordination of Soviet Nuclear Strikes with Commitment of Troops
Military Thought — Improvement of Antitank Weapons
Military Thought — The employment of rocket and artillery troops in conventional warfare
Military Thought — Use of Computers in a Military District Headquarters
Military Thought — Combat Operations against Antitank Defenses
Military Thought — Role of Communications in Automated Troop Control
Military Thought — (USSR) Combat Readiness of Ground Forces Air Defense
Military Thought — (USSR) Control of Military Vehicle Support
Military Thought — (USSR) Struggle for Air Supremacy
Military Thought — (USSR) Transfer of An Air Army into an Adjacent Front
Military Thought — Another View on continuity of Control of Rocket and Artillery Troops
Military Thought — Continuity of Control of Rocket and Artillery Troops
Military Thought — Air Defense Aspect during Operations To Counter an Amphibious Landing
Military Thought — (USSR) Logistical Support of a Front Offensive Operation
Military Thought — Capabilities of the Reconnaissance Forces and their Employment at the front
1974 – 69 Documents
Military Thought — Formulas for Determining Artillery Ammunition Expenditures and Reserves
Military Thought — (USSR) Combat Operations in Mountainous Terrain
Military Thought — (USSR) Commitment of a Combined Arms Army To Combat From the March
Military Thought — (USSR) Contemporary Military Strategy and Tactics
Military Thought — Organization of Defense in Conventional Warfare
Military Thought — (USSR) Improvement of Officer Training
Military Thought — (USSR) Combat Commitment of Rocket Troops of a Tank Army From the March
Military Thought — (USSR) Training of Officers of the National Air Defense Forces
Military Thought — Commitment of An Army To Battle in Conventional Warfare
Military Thought — Air Defense of Naval Operations
Military Thought — (USSR) Combined Arms Army Reconnaissance During Commitment From the March
Military Thought — Management of Military Technical Information
Military Thought — Use of Network Planning in the Organization of Research
Military Thought — (USSR) Improving the Image of Engineer Troops
Military Thought — Soviet Naval Operations against a Naval Missile Attack
Military Thought — (USSR) Employment of Naval Forces in Conventional Warfare
Military Thought — (USSR) Postwar Development of Weapons and Equipment
Military Thought — Reduction of Launch Readiness Times for Tactical Missiles
Military Thought — (USSR) Control of a Combined Arms Army During a Move Over a Long Distance
Military Thought — (USSR) a Hungarian View of Warsaw Pact Troop Control
Military Thought — (USSR) Overcoming Fortified Zones and Positions in Modern Warfare
Military Thought — (USSR) Defense Against Amphibious Landings
Military Thought — (USSR) Movement of a Combined Arms Army Over a Long Distance
Military Thought — Soviet Defense Industry Preparing for World War II
Military Thought — (USSR) Training of Scientific Personnel in the Soviet Armed Forces
Military Thought — (USSR) Air Defense of a River Crossing
Military Thought — Another View on Determination of Artillery Ammunition Norms
Military Thought — Naval Operations in Conventional Warfare
Military Thought — (USSR) Transition From Conventional Warfare To Nuclear Warfare
Military Thought — (USSR) Nuclear Support of Airborne Operations
Military Thought — (USSR) National Air Defense Participation in Naval Operations
Military Thought — Resumption of Combat Operations After a Nuclear Strike
Military Thought — Air Defense of Amphibious Landing
Military Thought — Coordination of Combat Operations in National and Coalition Forces
Military Thought — (USSR) Transition of Rocket Units To a Nuclear Offensive From Permanent Locations
Military Thought — Modernization of Field Training of Senior Officers and Staff
Military Thought — Review of the Results of Political Training in the Ground Forces
Military Thought — Determination of Army Artillery Ammunition Needs in Conventional Warfare
Military Thought — Organization of a Landing of Amphibious Forces
Warsaw Pact Journal — Tables of Contents of Five Issues
Military Thought — The control of naval forces in general warfare
Military Thought — Determining the Quantity of Rockets Needed for a Front operation
Military Thought — Front Rocket Troops and Artillery in the Initial Offensive Operation
Military Thought — Reconnaissance at sea
Military Thought — (USSR) Protection of Troops From Weapons of Mass Destruction
Military Thought — (USSR) Recovery of Combat Units From Chemical and Nuclear Strikes
Military Thought — Reconnaissance for the Initial Front Rocket Strike
Military Thought — (USSR) Control of Forces in a Naval Landing Operation
Military Thought — Use of Nuclear Means When Constructing Obstacles During An Operation
Military Thought — (USSR) Protection of Rear Services From Nuclear Attack During An Offensive
Military Thought — Use of Nuclear Power At Soviet Military Facilities
Military Thought — Radar Component of National Air Defense
Military Thought — (USSR) Assessing the Radiation and Chemical Contamination Situation
Military Thought — Limited Forces and Their Combat Employment
Military Thought — Support of Ground Forces by the Long-Range Air Force
Military Thought — Combat with Enemy Electronic Equipment
Military Thought — Concealment of the Air Defense Site From Satellite Reconnaissance
Military Thought — Reduction of Troop Assembly Time During Alerts
Military Thought — Use of Forward Security Zones in Defensive Operations
Warsaw Pact Journal — Ways of Increasing the Combat Readiness and the Combat Capabilities of the equipment
Military Thought — (USSR) Preemption in a Meeting Engagement of a Tank Army
Military Thought — Some Problems of Combat against Army Aviation
Military Thought — Comparison of Drones and Manned Aircraft in Aerial Reconnaissance
Military Thought — Combat with Enemy Tactical Means of Nuclear Attack in Offensive Operations
Military Thought — Coordination of Warsaw Pact Air Forces and Air Defenses
Military Thought — Combat with Airlifts across the Ocean
Military Thought — Control of naval forces under modern conditions
Military Thought — Rebasing the Air Army of a Reserve Front
Military Thought — Increasing the Efficiency of Troop Control When Conducting an Army Counterstrike
1975 – 62 Documents
Military Thought — (USSR) Problems of Manning the Soviet Armed Forces
Warsaw Pact Journal Creation of a System of Operational-Tactical Problems for an Automated Control
Military Thought — Improving the Operational-Tactical Training of Military Engineers
Military Thought — Problems of Conducting Military Operations during a Non-Nuclear Period
Military Thought — Air Defense in a Front Offensive Operation
Military Thought — (USSR) Organization of Front Troop Control From Posts
Warsaw Pact Journal Combined Armed Forces Exercise Brotherhood in Arms
Military Thought — (USSR) Air Defense of a Tank Army in Operations Separated From the others
Military Thought — (USSR) Reconnaissance Combat Functions for Reconnaissance
Military Thought — Ways of Increasing Efficiency in Motor Transport in Ground Forces Offensives
Military Thought — The relocation of rocket troops during an offensive operation
Military Thought — Mobility of the Ground Forces and Rear Services
Warsaw Pact Journal — From the Exercise Sphere-1970- Exercises
Military Thought — Repelling An Enemy Tank and Armored Infantry Attack
Military Thought — Question of Offensive Operations of Front Throughout the Entire Depth
Military Thought — (USSR) Fighter Aviation in the Front Air Defense System
Military Thought — Buildup of Efforts During Front Offensive Operation
Military Thought — Radiation Situation or Nuclear Situation
Military Thought — Assuring Continuity in Military Shipments Under Conditions of Widespread Destruction
Military Thought — Preparation in Advance of Civil Defense Cadre in Higher Educational Institutions
Military Thought — Structural Components of Low-Level Bridges
Military Thought — Marxist-Leninist outlook among developing countries students at Soviet military educational institutions
Military Thought — (USSR) Some Problems of the Control of Troops in a front
Military Thought — Effectiveness of Systems of Control
Military Thought — Some questions of operational art and military science work
Military Thought — Collection and Recording of Situation Data
Warsaw Pact Journal Some Problems of Troop Control
Military Thought — (USSR) Reconnaissance During the Advance of a Combined-Arms (Tank) Army
Military Thought — Hydro-meteorological Conditions Must Be Considered During Operational Training
Military Thought — Aerial Reconnaissance of Nuclear Attack Means in the Mountains
Military Thought — (USSR) Status of Electronic Computer Equipment
Military Thought — Movement of troops from the zone of interior in the initial period of war
Military Thought — The initial strike in armed combat at sea
Military Thought — Combat actions of a tank army separated from other front forces
Military Thought — The requirements for and supplying of troops with conventional ammunition
Military Thought — Ways To Reduce the Time Required To Plan troop movements
Military Thought — Problem of Coastal Anti-landing Defense
Military Thought — Combat with Enemy Tactical Means of Nuclear Attack
Military Thought — Use of Computers for Solving Problems in Support of the Air Defense of Troops
Military Thought — Rear support of troops in an offensive operation without the use of nuclear weapons
Military Thought — Combat employment of front aviation in a front offensive operation
Military Thought — Air support of the ground forces
Military Thought — Air support
Military Thought — Operations of a front air army in support of a tank army
Military Thought — Air Defense of Troops in a Front Offensive Operation on Northwest strategic axis
Military Thought — (USSR) Radio Camouflage on Territory of a Border Military District in Peacetime
Military Thought — Air Forces Actions at the start of a War Without the Employment of Nuclear Weapons
Military Thought — (USSR) Material Support of Front Troops in An Offensive Operation
Military Thought — Organization and Conduct of an Anti-landing Defense by An Army Corps
Military Thought — An Army Needs Greater Artillery Reinforcement
Military Thought — Fleet and front cooperation against weapons of mass destruction during a coastal axis offensive
Military Thought — Experience in the Control of the Rocket Troops
Military Thought — Offensive operations of a front to the entire depth of a theater of military operation
Military Thought — Increasing the Speed of Transport of Operational Tactical Missiles
Military Thought — (USSR) Providing Security of Radio Communications when moving troops forward
Military Thought — Strong and weak aspects of the tactical aviation of our probable enemies
Military Thought — Continuing Seminar on Operations Research
Military Thought — Need for Self-Propelled Artillery
Warsaw Pact Journal Tactical Exercises of Air Defense Large Units with Field Firing
Military Thought — (USSR) Three Years of Combat Against American Aviation
Military Thought — Control of Troops When Dispatching Them from an Interior Military District
Military Thought — Raising troop control to the level of modern requirements
1976 – 117 Documents
Military Thought — (USSR) Some Problems Involved in Considering the Morale-Political Factor
Military Thought — The air forces in operations with the employment of conventional means of destruction
Military Thought — Chemical Weapons for Repulsing An Amphibious Landing
Military Thought — Employment of Rocket Troops in Mountainous Areas
Military Thought — Methods for Determining the Combat Capabilities of troops
Military Thought — The employment of helicopters for tactical missiles and antitank guided missiles
Military Thought — Reconnaissance Independence of a Tank Army
Military Thought — (USSR) Status and Tasks of Military Science
Military Thought — Problems of Air Defense in a Front Offensive Operation conducted to the Entire Depth
Military Thought — Modern Concept and Classifications of Theaters of Military Operation
Military Thought — (USSR) Speeding up the control processes automation of in Ground Forces Formations
Military Thought — Some questions of modern defense
Military Thought — (USSR) Certain Problems in Moving a Tank Army To Its Area of Operational Assignment
Military Thought — Military District Air Defense Exercises
Military Thought — Air force in modern local wars
Military Thought — (USSR) Use of Statistical Data in Researching the Organization of Troop Control
Military Thought — (USSR) Combat Readiness of Reconnaissance in a Border Military District
Military Thought — The employment of biological weapons
Military Thought — Use of Mathematical Methods by Staff in the decision process
Military Thought — A useful book on setting up communications in a front
Military Thought — A new method of conducting reconnaissance
Military Thought — Meeting Engagements in Modern Operations
Military Thought — Psychological Screening of Specialists
Military Thought — Certain problems in the technical support of the tank troops in operations
Military Thought — Bringing the troops of a border military district to combat readiness
Military Thought — (USSR) Speeding Up the Automation of Control Processes in Ground Forces Formations
Military Thought — (USSR) Engineer Support for the Assault Crossing of Water Obstacles in an offensive
Military Thought — Fleet actions in a front offensive operation on a coastal axis during the initial period of war
Military Thought — Engineer support for the movement of strategic reserves to a theater of military operations
Military Thought — Questions of modern defense
Military Thought — (USSR) Some Results of the Use of the Platform ‘A’ Mobile Computer Post
Military Thought — Bringing naval forces to combat readiness
Military Thought — Field Air Defense in Combat with Low-Altitude Targets
Military Thought — Road support in operations
Military Thought — Organization of the Cooperation of Civil Defense Organs with military district troops
Military Thought — Cooperation of Military District troops and Civil Defense
Military Thought — (USSR) Cooperation Between the Armed Forces and Civil Defense in a Missile Nuclear War
Military Thought US supersonic strategic bombers and air defense
Military Thought — Materials from a conference on establishing a new system of communications
Military Thought — Cooperation between the Armed Forces and Civil Defense
Military Thought — Problems of engineer support for the negotiation of water obstacles at high speeds
Military Thought — Urgent Problems of Local and Civil Defense
Military Thought — Civil Defense in a missile nuclear war
Military Thought — Cooperation between troops and Civil Defense organs
Military Thought — Local air defense
Military Thought — Problems reflected in the Soviet Civil Defense publication
Military Thought — (USSR) Planning and Forms of Research of the Problems of Military Science
Military Thought — Comments on Civil Defense cooperation
Military Thought — The Brusilov case– How an historical error was corrected
Military Thought — Missile Technical Support in a Offensive Operation without the employment of nuclear weapons
Military Thought — A unified organ for protection against weapons of mass destructions is not necessary
Military Thought — The initial naval operations
Military Thought — The problem of selecting the axis of the main attack in an operation
Military Thought — The question of selecting the axis of the main attack in an operation
Military Thought — Warfare Against Enemy Radio-electronic Means
Military Thought — (USSR) Threat of Enemy Neutralization of Radio-electronic means
Warsaw Pact Journal — Guarding Peace and Socialism
Military Thought — Need for Self-Propelled Mortars
Military Thought — (USSR) Prospects for the Development of the Air Forces Rear Services
Military Thought — Strategic regroupings under conditions of modern armed combat
Military Thought — (USSR) Determining the Balance of Forces in Ground Forces Large Units
Military Thought — A unified organ for the command of protection against weapons of mass destruction
Military Thought — Determining the Balance of Force and Means
Military Thought — Engineer Support of An Army Defensive Operation
Military Thought — Need To Increases the Rate of Conducting Reconnaissance
Military Thought — Ways of Reducing the Time to bring Troops To Full Combat Readiness
Military Thought — (USSR) Methods for Calculating Reconnaissance Capabilities Using High-Speed Computer
Military Thought — Negotiation by Aviation of Enemy Air Defense Opposition
Military Thought — Modern Requirements for the Field Service Regulations
Military Thought — The meaning of the protection of troops against weapons of mass destruction
Military Thought — Special operational exercises
Military Thought — Some problems of the march and meeting engagement of large units of the ground forces
Military Thought — The conduct of special operational exercise
Military Thought — Military science work in the Air Defense forces
Military Thought — Actions of the air army during the movement forward and commitment reserve front
Military Thought — The use of mathematical research methods in military matters
Military Thought — (USSR) Reconnaissance in a Front Offensive Operation To the Depth of a Theater
Military Thought — Characteristic features of aerospace operations in the initial period of war
Military Thought — (USSR) Methodology for Conducting Operational Command-Staff War Games on Maps
Military Thought — Questions of Employing Long Range Aviation in Support of the Ground Forces
Military Thought — Air support of ground forces and control of combat actions of front aviation
Military Thought — Balance of Forces of Opposing Sides in Aviation
Military Thought — Training Staff Officers to the Level of Modern Requirements
Military Thought — Training Staff Officers to the Level of Modern Requirements v1
Military Thought — (USSR) Organization of the Control of Front Troops From Posts Designated To Replace
Military Thought — Problem of Training Staff Officers
Military Thought — (USSR) Defensive Operations of Ground Forces in a Strategic Operation
Military Thought — Actions of front aviation in the first front offensive operation in the initial period of war
Military Thought — Actions of front aviation in the first offensive operation of the front in the initial period of war
Military Thought — Organization of control of operational airborne landing forces in the initial period of war
Military Thought — Ways to increase the mobility of control of tank troops in a modern battle and operation
Military Thought — Reduction of the Terms of Active Military Service and Problems of Manning the Armed forces
Military Thought — Improving the Work of Computation and Analysis Stations
Military Thought — Front Aviation in Army Operations and a Combined-Arms Battle
Military Thought — (USSR) Cooperation of Fighter Aviation and Surface-To-Air Missile Troops
Military Thought — Combat with Enemy Anti Tank Means in An Offensive Operations
Military Thought — Some problems in the control of the rocket troops during its movement forward
Military Thought — Work of a computation and analysis station
Military Thought — Principles of Antibacterial Protection of Troops
Military Thought — The role and control of missile units in the ground forces
Military Thought — Problems of controlling allied troop groupings
Military Thought — (USSR) Raising the Level of the Field Training of Operational Staffs
Military Thought — Airfield engineer support of the Air Army in the first offensive operation of the front
Military Thought — Destruction of Enemy Air Defense Installations in the Airborne landing flight zone
Military Thought — Meeting engagements in offensive operations in the initial period of war
Military Thought — Ensuring the Concealment of Troop Deployment When Preparing An Offensive Operation
Military Thought — Methods of control of rocket troops in an offensive operation of a front
Military Thought — Increasing the Survivability of Control Posts
Military Thought — Reconnaissance in Modern Operations and Battles
Military Thought — Some Features of Preparing and Conducting a Front Offensive Operation
Military Thought — (USSR) Methodology of Preparing and Conducting Operational Command-Staff Exercises
Military Thought — Warfare against enemy radio-electronic means during the initial nuclear strike by a front
Military Thought — Mobile Control Posts of Ground Forces Formations and Large Units
Military Thought — (USSR) Combat Against Aircraft and Cruise Missiles At Low Altitudes
Military Thought — (USSR) Counter-Preparation in An Army Defensive Operation
Military Thought — (USSR) Problems of Conducting a War in Europe
Military Thought — Capabilities of the Reconnaissance Forces and their Employment at the front
1977 – 80 Documents
Military Thought Nature of Limited Forces and the Special Features of Their Combat Actions
Military Thought Aerial Reconnaissance in Support or the Initial Nuclear Strike of a Front
Military Thought Certain Problems in Moving a Tank Army to the area of Operational Assignment
Military Thought (USSR) Conducting Offensive Operations without Employing Nuclear Weapons
Military Thought The combined-arms army in a modern operation
Military Thought (USSR) Meeting Engagement of a Tank Army during a Front Offensive Operation
Military Thought Cooperation between Formations) of the Air Defense of the Country and Troops
Military Thought Training troops to go over to the offensive from permanent deployment areas
Military Thought Conducting a front offensive operation without nuclear weapons
Military Thought (USSR) Law of Universal Military Service and the Manning of the Armed Forces
Military Thought Certain Problems in Protecting the Front Rear in Operations
Military Thought Methodology for Clarifying Themes and Goals in Working Out Exercises and War Games
Military Thought Actions of a front air army in support of a tank army
Military Thought Military Science Work in the Armed Forces at a New Stage
Military Thought (USSR) Features of the Combat Employment of Rocket Troops and Artillery in the mountains
Military Thought Organizing the Supply of Topographic Maps To Formations Advancing From the Interior
Military Thought Some matters of providing troop control in an initial front offensive operation
Military Thought Some questions of the first front offensive operation in the initial period of a war
Military Thought Some problems of political work among enemy troops and population in the initial period of a war
Military Thought Certain matters of the organization of military science work in fleets and flotillas
Military Thought Reconnaissance Capabilities and Requirements
Military Thought Reconnaissance in Support of the Operational Rear Services
Military Thought Providing Concealment for the Forward Movement and Commitment To Battle of the Troop
Military Thought Research War Games
Military Thought (USSR) Certain Questions of the Development of Soviet Military Art From 1953-1960
Military Thought (USSR) Conducting Scientific Research War Games
Military Thought (USSR) Conducting Scientific Research War Games_1
Military Thought Certain matters of a front offensive operation in the initial period of a war
Military Thought Units of Fire and Norms of Ammunition Reserves
Military Thought The front troop offensive during the initial period of a war with partial concentration of forces
Military Thought Bringing troops of a border military district to combat readiness
Military Thought Certain questions of Soviet military art
Military Thought Methodology of Operational Training
Military Thought Preparation and conduct of a front offensive operation on a coastal axis
Military Thought (USSR) Cooperation Between Forces of a Front and a Fleet
Military Thought How proposals by authors of Military Thought articles are being adapted for operational training
Military Thought (USSR) Problems of the Operational Rear Services
Military Thought (USSR) Seizure of Straits Under Present Conditions
Military Thought Protection of troops against toxic and radioactive substances and bacterial means
Military Thought Combat Actions of Troops without the Employment of Means Mass Destruction
Military Thought Control of missile units of the ground forces in offensive operations
Military Thought Concentration of Troops Efforts in a Front Offensive Operation
Military Thought Employment of rocket troops and artillery in the anti-landing defense of a seacoast
Military Thought The employment of underwater nuclear bursts in repulsing and amphibious landing
Military Thought A troop Offensive From Permanent Deployment Areas
Military Thought A meeting engagement of large groupings of troops in the initial period of a war
Military Thought (USSR) Conduct of Reconnaissance on Coastal Axes
Military Thought Soviet naval art in the Great Patriotic War
Military Thought The commitment of a front’s second echelon to an engagement
Military Thought (USSR) Technological Progress and Tasks of Soviet Military Economists
Military Thought Certain Questions of the Employment of Rocket Troops in a Landing Operation
Military Thought The state of the development and production of cruise missiles in capitalist countries
Military Thought Ways of increasing the rates of advance of a combined-arms army
Military Thought — Employment of Operational-Tactical Missiles for the Destruction of Enemy Amphibious forces
Military Thought — Reconnaissance to prevent a surprise attack
Military Thought — Detection of nuclear means by long-range reconnaissance groups
Military Thought — Role and cooperation of the aviation, rocket troops and artillery combating nuclear weapons
Military Thought — Special features of reconnaissance during the initial front offensive operation
Military Thought — Road support for troops and Civil Defense in the initial period of war
Military Thought — The destruction of enemy nuclear weapons and cooperation of ground forces with aviation
Warsaw Pact Journal — Conference of Authors and Readers of the Information Collection
Military Thought — The breakdown and classification of modern theaters of military operations
Military Thought — Methodology of training for combat against nuclear attack means
Military Thought — Collecting and collating data on the nuclear and radiation situation
Military Thought — Question of a Combined Front Command Post
Military Thought — (USSR) Matter of Great Importance
Military Thought — 1968 Agreement Between the Government of the USSR and Czechoslovakia on Soviet troop occupation
Military Thought — Dissertations for the candidate’s degree
Military Thought — The initial naval operation
Warsaw Pact Journal — Automation and Mechanization of Control
Warsaw Pact Journal — M-10 Gas Mask
Warsaw Pact Journal — Designing and Testing a Set for the Construction of Barge Bridges (Sbg-66)
Warsaw Pact Journal — Research and Development of a System of Automated Control and Regulation
Warsaw Pact Journal — Increasing the Readiness of the Missile and Artillery Armament Service
Warsaw Pact Journal — Troop Combat Training, Some Results and Conclusions
Warsaw Pact Journal — Daily Attention To the Combat Readiness of the Troops
Warsaw Pact Journal — Specialized and Operational-Tactical Training of Rocket Troops
Warsaw Pact Journal — Development of Standardized Combat Documents in the National Peoples Army
Warsaw Pact Journal — Problems of Improving Command Personnel skills in the National Peoples Army
Warsaw Pact Journal — Improving in Every Possible Way the Operational Training of the Combined Arm Forces
1978 – 154 Documents
Military Thought Matter of Military Science Conferences
Military Thought Technical Support of Front Troops Moving Forward From the Interior
Military Thought Engineer Support of the Assault Crossing of Water Obstacles on a Coastal Axis
Military Thought A useful theoretical work
Military Thought — Some points on the status and development of small arms
Military Thought — Control of the operational rear
Military Thought Operational Calculations for the Use of Nuclear Weapons
Military Thought Operational Calculations for the Use of Nuclear Weapons v1
Military Thought — Combat against enemy operational airborne landing forces
Military Thought — Combat against enemy operational airborne landing forces
Military Thought — Some problems in organizing control of the means of air defense troops
Military Thought — Engineer support of naval operations
Military Thought — Organizing combat against underwater sabotage forces and means in naval theaters
Military Thought — Formalized combat documents and the prospects of their use in the control of troops
Military Thought — Information collection and processing post
Military Thought — Problems of rear services support of the military districts and groups of forces
Military Thought — (USSR) Use of Mathematical Network Planning Methods in Military Affairs
Military Thought — The use of new technical means in troop control
Military Thought — Fortified lines and protected troop disposition areas in highly mobile operations
Military Thought — Negotiating border zone rivers during forward movement and deployment of front troops
Military Thought — Negotiating border zone rivers during forward movement and deployment of front troops v2
Military Thought — Textbooks for higher military educational institutions
Military Thought — The supply of fuel to operational formations advancing to a theater of military operations
Military Thought — Regarding a single geodetic base for the combat use of rocket troops and artillery
Military Thought — Some problems in the organization of military educational institutions
Military Thought — Improving troop control in the modern battle and operation
Military Thought — Forms and methods of operational training
Military Thought — Basic problems of troop control and possible ways of resolving them
Official Report of the Second Session of the Warsaw Pact Committee of Defense Ministers
Decision of the Warsaw Pact Political Consultative Committee Approving the Statutes
Military Thought — Air defense of the North American continent
Military Thought — Problem of Restoring the Combat Effectiveness of An Army in An Offensive Operation
Military Thought — Principles of the structure of the US antimissile defense radar system
Military Thought — (USSR) Certain Problems of Military Economic Planning
Military Thought — A massed nuclear strike during a front offensive operation
Military Thought — Control posts and communications of a combined-arms army during advances over great distances
Military Thought — Organization of control of operational airborne landing forces in the initial period of a war
Military Thought — Communications in an automated troop control system at the operational level
Military Thought — The organization and methods of conducting reconnaissance against enemy nuclear attack
Military Thought — The use of automated and mechanized means in organizing the work of a front command
Military Thought — Problems of preparing motor transport for wartime operation
Military Thought — The preparation of motor transport for operations under conditions of war
Military Thought — Organizing Protection Against Weapons of Mass Destruction Among Special Troops
Military Thought — Ways of increasing the reliability of secure shortwave radio communications
Military Thought — Modern war and certain biological problems
Military Thought — Reconnaissance Data Requirements in Support of Rocket Troops and Artillery
Military Thought — (USSR) Combating Enemy Reconnaissance in a Front Offensive Operation
Military Thought — Some problems of reconnaissance in the preparation of a front’s first offensive operation
Military Thought — Some problems of reconnaissance in the preparation of a front’s first offensive operation v2
Military Thought — Does a combined-arms commander need aerial photography
Military Thought — Negotiation of broad zones of radioactive contamination and sectors of destruction
Military Thought — Certain reconnaissance problems in the preparation of an initial front offensive operation
Military Thought — The planning of radio-electronic countermeasures in preparing a front initial offensive operation
Military Thought — Actions by troops in zones of radioactive contamination in a battle and operation
Military Thought — Some problems in the use of electronic computers
Military Thought — Collecting and collating data on the nuclear and radiation situation
Military Thought — Topographic Map as a Means of Troop Control
Military Thought — Some problems of reconnaissance in the preparation of a front’s first offensive operation
Military Thought — A system for the collection, processing, and transmission of information in a military district
Military Thought — Combat against enemy nuclear weapons in a front offensive operation
Military Thought — Reconnaissance in a front offensive operation in the initial period of war
Military Thought — Reducing the preparation time of a front (army) nuclear strike
Military Thought — The automated field system of radiation reconnaissance
Military Thought — With nuclear weapons or without them
Military Thought — Final aerial reconnaissance against targets in support of rocket troops
Military Thought — Arriving at a decision to employ nuclear means
Military Thought — Problems of engineer support for the negotiation of water obstacles at high speeds
Military Thought — Introduction of electronic computers into staff work
Military Thought — (USSR) Use of Electronic Computers in Military Science Research
Military Thought — Communications in the initial period of war
Military Thought — Introduction of Network Methods of Planning and Control into practice of scientific research
Military Thought — Naval geographic handbook
Military Thought — Rear Services Support of An Offensive Operation in a Mountainous Theater
Military Thought — Basic problems of rear services support of combat actions of front aviation in modern operations
Military Thought — Cooperation between the air defense system of a front military district and a frontline formation
The principles of organizing communications in the battle and operation
Military Thought — Command-Staff Vehicles Based on Modern Tanks for Tank Armies
Military Thought — Engineer support of surface-to-air missile units in a front offensive operation
Military Thought — Transportation in the Great Patriotic War
Military Thought — The organization of tank technical support in a front offensive operation
Military Thought — Certain problems of medical support of the armed forces in modern warfare
Military Thought — Some problems of the defense of an army corps on a separate mountain axis
Military Thought — The subject of organizing meteorological support for military district forces
Military Thought — Some questions of organizing and conducting a meeting battle
Military Thought — Air defense of troops in a front offensive operation
Military Thought — Combating enemy sabotage and reconnaissance activity in an army offensive operation
Military Thought — Engineer support for the first offensive operation of a combined-arms army
Military Thought — Engineer support of a front offensive operation in the initial period of war
Military Thought — Operational cover of the state border
Military Thought — Hydro-meteorological Support of Troops
Military Thought — Industry-Produced Low-Level Bridge Sections
Military Thought — (USSR) Air and Antisubmarine Defense of a Carrier Strike Large Unit
Military Thought — Methods of conducting a front offensive operation using means of mass destruction
Military Thought — Combat against enemy operational airborne landing forces
Military Thought — Outlook for the combat employment of front V-STOL aviation
Military Thought — The organization of the air defense of front troops during an operational deployment
Military Thought — (USSR) Taking into Account the Reliability of Equipment When Planning
Military Thought — Some problems in the development and combat employment of military transport aviation
Military Thought — The theory of logical-mathematical research of military actions
Military Thought — More on the cooperation of large units of the Soviet Army with border guards
Military Thought — The problem of organizing statistical research
Military Thought — (USSR) Predicting the Combat Losses and Balance of Forces of the Opposing Sides
Military Thought — (USSR) Some Problems of Military Electric Power Engineering
Military Thought — The preparation and conduct of amphibious landing operations
Military Thought — (USSR)Topo-geodetic Support of Troop Combat Actions
Military Thought — Modern means and methods of combat against airborne landing forces
Military Thought — Organization of the strikes and maneuver of rocket troop in operations
Military Thought — Methods of scientific research in military affairs
Military Thought — Preparation and conduct of a front defensive operation on a coastal axis
Military Thought — Problems of road support of modern offensive operations
Military Thought — Some problems of military science work among the troops
Military Thought — Certain problems in moving a combined-arms army from the interior of the country
Military Thought — (USSR) Combat Readiness of Troops and Network Diagrams
Military Thought — Characteristics of a defensive operation in wooded swamp and lake terrain
Military Thought — Problem of Repelling an Enemy Tank and Armored Infantry Attack in Defense
Military Thought — Methods of conducting a front offensive operation using means of mass destruction
Military Thought — The conduct of subsequent operations in the initial period of war
Military Thought — Preparatory fire and fire support of an offensive
Military Thought — The use of border guard troops in the initial period of war
Military Thought — Engineer support for the actions of missile large units and units in offensive operations
Military Thought — Suggestions Regarding the Methodology of Command-Staff Exercises
Military Thought — Counter-battery Combat
Military Thought — Troop control during a front operation
Military Thought — (USSR) Use of Mathematical Network Planning Methods in Military Affairs
Military Thought — A new theoretical work on the meeting battle and meeting engagement
Gorshkovs Thoughts on Current Problems of Soviet Naval Science
Military Thought — Features of an offensive operation when neither side employs nuclear weapons
Military Thought — Some problems of military training of reserve officers without loss of time from work
Military Thought — The actions of a tank army in the offensive operation of a front
Military Thought — Combat against landing forces
Military Thought — (USSR) Combat Readiness of a Division
Military Thought — Regrouping of troops in the initial period of a war
Military Thought — Certain problems in the operational training of intelligence officers
Military Thought — Certain problems of higher military education
Military Thought — Regrouping an operational tactical missile brigade over great distances by the combined method
Military Thought — The assault crossing of rivers from the march in an offensive operation of a combined-arms army
Military Thought — Certain problems of modern defense
Military Thought — (USSR) Negotiation of Enemy Air Defense by Aviation in a Military Operation Theater
Military Thought — Conduct of meeting engagements by a field army
Military Thought — Enemy agent reconnaissance in a theater of military operations in a modern war
Military Thought — Movement of front army troops over a great distance and commitment to an engagement
Military Thought — Some problems of operational training
Military Thought — The decisive condition of the practicality of operational planning
Military Thought — The meeting engagement in the initial period of a war
Military Thought — The training and buildup of reserve officer cadres
Military Thought — Troop marches over great distances
Military Thought — The new field service regulations of the Armed Forces of the USSR
Military Thought — Combat action of troops under special conditions
Military Thought — The distance of departure areas from the enemy’s forward edge of defense
Military Thought — Air defense of European NATO countries
Military Thought — Some questions concerning modern defense
Military Thought — Some problems of operational training
Military Thought — Certain problems of modern defense
Military Thought — The commitment of a tank army to the engagement during a front offensive operation
1979 – 9 Documents
Military Thought — Dissertations
Military Thought — Global operations by aerospace forces
Military Thought — Dissertations
Military Thought — (USSR) Engineer Support of Coastal Anti-landing Defense
Military Thought — The exploitation of the success of an offensive operation by a US Field Army
Military Thought — Dissertations
Military Thought — (USSR) Solving Military – Economic Problems by Computer
Military Thought — Organization of defense by a field army in the initial period of war
Military Thought — The need to standardize current terminology
1984 – 1 Document
Employment of Rocket Troops and Artillery
DOWNLOAD ORIGINAL DOCUMENT HERE
The FBI reports – Folsom, California Man Pleads Guilty to $19 Million Fraud Scheme
SACRAMENTO, CA—Christopher J. Warren, 29, of Folsom, California, pleaded guilty today to one count of wire fraud and one count of aggravated identity theft related to a $19 million fraud scheme, announced Benjamin B. Wagner, U.S. Attorney for the Eastern District of California.
This case is the product of an investigation by the Internal Revenue Service-Criminal Investigation, the FBI, and the Department of State Diplomatic Security Service. Assistant U.S. Attorneys Russell L. Carlberg, Paul A. Hemesath and S. Robert Tice-Raskin are prosecuting the case.
According to court documents, Warren was indicted in 2009 after defrauding lender Taylor, Bean & Whitaker of over $7 million and fleeing to Beirut, Lebanon, on a privately chartered jet. Warren was arrested attempting to reenter the United States under a fraudulently obtained passport with tens of thousands of dollars hidden in his cowboy boots. Warren’s plea today covered both the $7 million fraud against lender Taylor, Bean & Whitaker, and an additional $12 million in fraudulent loans involving his employment at Loomis Wealth Solutions in Roseville, Calif., in 2007 and 2008. He also pleaded guilty to aggravated identity theft in connection with fraudulently obtaining passports in the names of real persons without their approval. Warren used the stolen identities to purchase gold and to flee abroad.
“This is a very significant plea today involving brazen fraud on lenders,” said U.S. Attorney Wagner. “We will continue our relentless drive to bring to justice those who did so much harm to lenders and households in this district.”
Warren is scheduled to be sentenced by U.S. District Judge John A. Mendez on April 24, 2012. The maximum statutory penalty for a violation of wire fraud is 20 years in prison, a fine of $250,000, or twice the loss caused or gain received, and a three-year period of supervised release. Aggravated identity theft carries a mandatory two-year sentence consecutive to any other sentence. The actual sentence, however, will be determined at the discretion of the court after consideration of any applicable statutory factors and the federal sentencing guidelines, which take into account a number of variables.
A co-defendant, Scott Cavell, remains a fugitive. The charges against him are only allegations, and he is presumed innocent until and unless proven guilty beyond a reasonable doubt.
This law enforcement action is part of the work being done by President Barack Obama’s Financial Fraud Enforcement Task Force. President Obama established the interagency Financial Fraud Enforcement Task Force to wage an aggressive, coordinated and proactive effort to investigate and prosecute financial crimes. The task force includes representatives from a broad range of federal agencies, regulatory authorities, inspectors general, and state and local law enforcement who, working together, bring to bear a powerful array of criminal and civil enforcement resources. The task force is working to improve efforts across the federal executive branch, and with state and local partners, to investigate and prosecute significant financial crimes, ensure just and effective punishment for those who perpetrate financial crimes, combat discrimination in the lending and financial markets, and recover proceeds for victims of financial crimes. One component of the FFETF is the national Securities Fraud Working Group, which is tasked with combating investment fraud schemes. For more information on the task force, visit http://www.stopfraud.gov.
Betreff: STASI UND KGB – MORDE AN JOURNALISTEN – z.B. Alexander Walterowitsch Litwinenko
Alexander Walterowitsch Litwinenko (russisch Александр Вальтерович Литвиненко, wiss. Transliteration Aleksandr Val’terovič Litvinenko; * 30. August 1962 in Woronesch; † 23. November 2006 in London) war KGB-Agent und FSB-Offizier, später Putin-Kritiker und Buchautor.
Nach Abschluss der Mittelschule wurde Litwinenko 1980 in die Armee einberufen. Ab 1988 war er in der Abteilung für Spionageabwehr des sowjetischen Geheimdienstes KGB tätig. In verschiedenen Konfliktherden der Sowjetunion und später Russlands war er an Kampfeinsätzen beteiligt. Beim FSB, der russischen Nachfolgeorganisation des KGB ab 1991, war Litwinenko im Kampf gegen Terrorismus und organisiertes Verbrechen eingesetzt.
Vom Agenten zum Kritiker des russischen Machtapparates [Bearbeiten]
1998 trat Litwinenko erstmals als Kritiker des russischen Machtapparates an die Öffentlichkeit: Auf einer Pressekonferenz in Moskau beschuldigte er – zusammen mit Michail Trepaschkin und einigen anderen maskierten Geheimdienstlern – die Führung des Geheimdienstes FSB der Anstiftung zum Mord. Sie hätten von dieser den Auftrag bekommen, den damaligen Sekretär des Staatsicherheitsrats, Boris Beresowski, zu töten.[1]
Im März 1999 wurde Litwinenko erstmals verhaftet, in einem Strafverfahren im November desselben Jahres aber freigesprochen. Noch im Gerichtssaal wurde er erneut festgenommen, im Jahr 2000 schließlich aus der Haft entlassen. Litwinenko behauptete, die Anschuldigungen gegen ihn seien konstruiert gewesen. Und bei der Haftentlassung habe er sich verpflichten müssen, nicht aus der Russischen Föderation auszureisen. In der Folge wurde ein drittes Strafverfahren gegen ihn eröffnet. Nach eigenen Angaben wurden Litwinenko und seine Familie vom FSB bedroht, was ihn noch im Jahr 2000 zur illegalen Ausreise bewogen habe.
Litwinenko traf am 1. November 2000 in London ein und beantragte politisches Asyl. Dieses wurde ihm und seiner Familie im Mai 2001 gewährt. In Großbritannien betätigte sich Litwinenko als Journalist und Buchautor, finanziert vom ebenfalls in London lebenden Boris Beresowski.[2] Im Oktober 2006 – wenige Wochen vor seinem Tod – erhielt Litwinenko die britische Staatsbürgerschaft. Laut Daily Mail betätigte sich Litwinenko in London als MI6-Agent.[3]
Kritik aus dem Londoner Asyl (ab November 2000) [Bearbeiten]
Litwinenko machte eine Reihe von Anschuldigungen öffentlich, die seine früheren Geheimdienstkollegen von KGB und FSB und den früheren FSB-Chef Wladimir Putin belasten oder diskreditieren. Diese Behauptungen konnten bislang von unabhängigen Medien weder bestätigt noch widerlegt werden.
Sprengstoffanschläge auf Wohnhäuser 1999 [Bearbeiten]
Hauptartikel: Sprengstoffanschläge auf Moskauer Wohnhäuser
Zusammen mit Juri Felschtinski, einem US-amerikanischen Historiker russischer Herkunft, verfasste er 2002 das Buch Eiszeit im Kreml. Das Komplott der russischen Geheimdienste (im russischen Original: ФСБ взрывает Россию). Die auf Menschenrechtsfragen spezialisierte russische Nachrichtenagentur Prima, die vom ehemaligen Sowjetdissidenten Alexander Podrabinek geleitet wird, ließ das Buch in Lettland drucken und wollte es in Moskau mit einer Auflage von 4400 Exemplaren verkaufen. Der Lastwagen mit der Auflage wurde indes im Rahmen einer Antiterror-Aktion beschlagnahmt.[4]
Die zentrale These des Buches ist, dass die Sprengstoffanschläge von 1999 auf Wohnhäuser in Moskau und anderen russischen Städten, bei denen rund 300 Menschen den Tod fanden, entgegen den Behauptungen von offiziellen russischen Stellen nicht von tschetschenischen Terroristen verübt wurden. Vielmehr gingen die Anschläge – so die Autoren – auf das Konto des russischen Geheimdienstes FSB und dienten im Rahmen einer Strategie der Spannung als Vorwand für die Entfesselung des Zweiten Tschetschenienkriegs.[5]
Dieselbe Theorie vertraten auch Mitglieder einer öffentlichen Kommission um Sergei Kowaljow. Ihre Mitglieder wurden von einer Reihe von Zwischenfällen heimgesucht:
* Der Kommissionsvorsitzende Sergej Juschenkow wurde am 17. April 2003 erschossen.[6]
* Der Ermittler der Kommission, Rechtsanwalt Michail Trepaschkin – wie Litwinenko ein ehemaliger FSB-Offizier – wurde im Oktober 2003 festgenommen, als die Polizei in seinem Auto eine Pistole fand. Vermutlich wurde sie ihm untergeschoben, doch wurde Trepaschkin im Mai 2004 wegen Verrats von Staatsgeheimnissen und illegalem Besitz von Munition zu vier Jahren Lagerhaft verurteilt. Nach Angaben von Amnesty International war das Verfahren „offenbar politisch motiviert“ und entsprach „nicht den internationalen Standards für faire Verfahren“. Russische Menschenrechtsgruppen gingen davon aus, dass „die Anklagen gegen ihn konstruiert wurden, um zu verhindern, dass er seine Ermittlungen zu den 1999 verübten Bombenanschlägen auf Wohnhäuser fortsetzen konnte“, so Amnesty International.[7]
* Das Kommissionsmitglied Juri Schtschekotschichin, Vize-Chefredakteur der Zeitung Nowaja Gaseta, starb am 3. Juli 2003. Offizielle Todesursache war eine seltene Hautveränderung, das sogenannte Lyell-Syndrom. Familie und Weggefährten vermuten jedoch, dass Schtschekotschichin vergiftet wurde.[8]
Organisation der Geiselnahme im Moskauer Theater 2002 [Bearbeiten]
Im Juni 2003 behauptete Litwinenko im Interview mit dem australischen TV-Sender SBS, dass mindestens zwei der Tschetschenen, die das Moskauer Musical-Theater erstürmt hatten, in Wahrheit für den FSB gearbeitet hatten und vom FSB zur Geiselnahme angestiftet worden waren. Angeblich konnten die beiden ihm bekannten Tschetschenen später nicht unter den Toten gefunden werden, weil sie vom FSB herausgeholt worden waren. Litwinenko war überzeugt, dass die Geiselnahme in Wahrheit eine geplante Aktion des FSB war.[9]
Unterstützung von al-Qaida [Bearbeiten]
In einem Interview im Juli 2005 mit der polnischen Zeitung Rzeczpospolita warf Litwinenko dem von Putin geführten FSB vor, im Jahr 1998 Aiman az-Zawahiri und andere al-Qaida-Führer in der an Tschetschenien angrenzenden Teilrepublik Dagestan trainiert zu haben.[10]
Romano Prodis KGB-Komplizenschaft [Bearbeiten]
Im April 2006 sorgten Anschuldigungen gegen den italienischen Ministerpräsidenten Romano Prodi für Aufmerksamkeit. Litwinenko habe vor seiner Ausreise im Jahr 2000 vom ehemaligen stellvertretenden Direktor des FSB, Anatoli Trofimow erfahren, dass Prodi mit dem KGB zusammenarbeitete. Dies erklärte der britische Europaabgeordnete Gerard Batten am 3. April 2006 im EU-Parlament.[11][12]
Pädophilie-Anschuldigungen gegen Putin [Bearbeiten]
Litwinenko beschuldigte im Juli 2006 auf der Website der tschetschenischen Separatistenbewegung Wladimir Putin der Veranlagung zur Pädophilie.[13] Er verglich ihn mit dem bekannten ukrainischen Serienmörder und Kannibalen Andrei Tschikatilo.
Letzte, unveröffentlichte Recherchen [Bearbeiten]
Zerschlagung von Jukos [Bearbeiten]
Vor seinem Tod soll Litwinenko brisantes Material über die Zerschlagung des russischen Ölkonzerns Jukos gesammelt haben. Dies berichtete die britische Tageszeitung The Times. Litwinenko habe Unterlagen besessen, die bewiesen, dass mehrere Mitarbeiter des Unternehmens verschwunden oder gestorben seien und dass die russische Regierung an diesen Verbrechen direkt beteiligt gewesen sei. Die Akte habe Litwinenko dem früheren, mittlerweile in Israel lebenden Jukos-Vize Leonid Newslin übergeben.[14]
Ermordung von Anna Politkowskaja [Bearbeiten]
Eigenen Aussagen zufolge hat Litwinenko sich zuletzt auch mit dem Mord an der Moskauer Journalistin Anna Politkowskaja beschäftigt. Er soll sich am Tag seiner Vergiftung mit Polonium-210 mit dem italienischen Geheimdienstexperten Mario Scaramella getroffen haben, der ihm angeblich wichtige Unterlagen zu diesem Fall überreichte. Darin sollen Mitglieder einer Spezialeinheit des FSB als Urheber des Mordes an Politkowskaja angeführt werden. Litwinenko sei in diesen Unterlagen ebenso wie der in London lebende russische Oligarch Beresowski als nächstes Ziel von Anschlägen genannt worden.[15]
Kooperation mit spanischen Behördern [Bearbeiten]
Laut einem Bericht der Tageszeitung El Pais informierte Litwinenko kurz vor seinem Tod die spanischen Behörden über Aufenthaltsort, Rolle und Aktivitäten zahlreicher Mitglieder der russischen Mafia. In einem Treffen im Mai 2006 soll er insbesondere Informationen über Izguilov, Zahkar Kalashov und Tariel Oniani weitergegeben haben.[16]
Tod [Bearbeiten]
Das Grab Alexander Litwinenkos
Am 1. November 2006 ließ sich Litwinenko mit Vergiftungserscheinungen in ein Krankenhaus einweisen. In den folgenden Tagen verschlechterte sich sein Zustand rasant. Die Mediziner gingen zuerst davon aus, dass Thallium für den körperlichen Verfall Litwinenkos gesorgt hatte. Erst wenige Stunden vor dem Ableben fand man große Mengen der radioaktiven Substanz Polonium-210 im Urin.[17]
Litwinenko starb am 23. November 2006 um 21:21 Uhr Ortszeit an den Folgen der durch Polonium verursachten Strahlenkrankheit. Nur wenige Stunden, bevor er das Bewusstsein verlor, erklärte Litwinenko in einem Interview mit der Times, dass er vom Kreml zum Schweigen gebracht worden sei.[18]
Die Beerdigung auf dem Londoner Highgate-Friedhof (lt. Merkur Online vom 7. Dezember 2006) wurde nach islamischem Ritus abgehalten (Litwinenko war kurz vor seinem Tod zum Islam übergetreten).[19][20]
Litwinenko hinterließ seine Frau Marina und einen zehnjährigen Sohn.
Der Fall Litwinenko [Bearbeiten]
Ermittlungen [Bearbeiten]
Die Ermittlungen im Fall Litwinenko werden von Scotland Yard geführt; die britische Polizeibehörde stufte den Tod am 6. Dezember 2006 als Mord ein.[21][22][23] Am darauf folgenden Tag eröffnete auch die russische Staatsanwaltschaft ein Verfahren wegen Mordes an Litwinenko. Damit wird – falls die Ermittlungen zu einem offiziellen Ergebnis kommen – ein Prozess gegen mutmaßliche Täter in Russland möglich.[24]
Nach bisherigen Erkenntnissen wurde Litwinenko am 1. November 2006 in der Bar des Millennium Hotel mit Polonium-haltigem Tee vergiftet.[25] Hier traf er sich mit den russischen Geschäftsmännern (und früheren KGB-Mitarbeitern) Andrei Lugowoi und Dmitri Kowtun.[26] Möglicherweise war noch eine weitere Person namens “Wladislaw” involviert; diese steht im Verdacht, den kontaminierten Tee zubereitet und Litwinenko übergeben zu haben.[27][28] Nach dem Treffen im Millennium Hotel war Litwinenko mit Mario Scaramella zum Mittagessen in einer Sushi-Bar verabredet. Und anschließend traf er sich mit dem tschetschenischen Rebellensprecher Achmed Sakajew.[29]
Im Visier von Scotland Yard steht insbesondere Lugowoi, vgl. unten „Verfahren gegen Lugowoi“. Aber auch Kowtun ist nicht unverdächtig, ließen sich doch Polonium-Spuren bei seinen Verwandten in Deutschland nachweisen.[30]
Spekulationen über die Täterschaft [Bearbeiten]
Litwinenko beschuldigt Putin [Bearbeiten]
Am 21. November – zwei Tage vor seinem Tod – diktierte Litwinenko seinem Vater einen Abschiedsbrief. Darin machte er den russischen Präsidenten Putin für seinen Tod verantwortlich:
„Während ich hier liege, höre ich in aller Deutlichkeit die Flügel des Todesengels. Möglicherweise kann ich ihm noch einmal entkommen, aber ich muss sagen, meine Beine sind nicht so schnell, wie ich es gerne hätte. Ich denke deshalb, dass es an der Zeit ist, ein oder zwei Dinge dem Menschen zu sagen, der für meinen jetzigen Zustand verantwortlich ist. Sie [Putin] werden es vielleicht schaffen, mich zum Schweigen zu bringen, aber dieses Schweigen hat einen Preis. Sie haben sich als so barbarisch und rücksichtslos erwiesen, wie Ihre ärgsten Feinde es behauptet haben. Sie haben gezeigt, dass Sie keine Achtung vor dem Leben, vor der Freiheit oder irgendeinem Wert der Zivilisation haben. Sie haben sich als Ihres Amtes unwürdig erwiesen, als unwürdig des Vertrauens der zivilisierten Männer und Frauen. Sie werden es vielleicht schaffen, einen Mann zum Schweigen zu bringen. Aber der Protest aus aller Welt, Herr Putin, wird für den Rest des Lebens in Ihren Ohren nachhallen. Möge Gott Ihnen vergeben, was Sie getan haben, nicht nur mir angetan haben, sondern dem geliebten Russland und seinem Volk.“
– Abschiedsbrief Litwinenkos, übersetzt von der AFP.[31]
Putin wies die Anschuldigungen bezüglich einer Beteiligung Moskaus an der Ermordung Litwinenkos als unbegründet zurück.[17]
Spekulationen westlicher Medien [Bearbeiten]
Das Medieninteresse für das Schicksal Litwinenkos entbrannte Mitte November 2006, nachdem sich dessen Zustand massiv verschlechtert hatte. Nach Angaben des Guardian stellte zu Beginn die PR-Agentur Chime Communications – im Auftrag von Beresowski – eine Kampagne auf die Beine. Die Agentur verbreitete Informationen über den Gesundheitszustand von Litwinenko mit Fotos aus dem Krankenhaus.[32]
Die meisten westlichen Medien heben das Interesse hervor, das “Moskau”, das “Putin-Regime”, der “russische Geheimdienst” an einer Beseitigung Litwinenkos gehabt haben könnte.[33] Ergänzend werden die Täter auch in den Kreisen der russischen Mafia vermutet.[34] Diskutiert wird aber auch die in Russland verbreitete Theorie, dass eine andere Täterschaft bewusst den Verdacht auf “Moskau” lenken wollte.[32][35]
Laut der Theorie des US-Journalisten Edward Jay Epstein war Litwinenko in kriminelle Machenschaften wie den Schmuggel mit gefährlichen Materialien verwickelt. Epstein, der an einem Buch über den Gifttod arbeitet, behauptet in einem Artikel, dass Litwinenko in den Schmuggel des radioaktiven Polonium-210 verwickelt gewesen sei und sich dabei selbst vergiftet habe.[36]
Spekulationen in Russland [Bearbeiten]
Der Berater des Präsidenten, Sergei Jastrschembski, vermutete in einer Reportage des russischen Staatssenders Westi ein Komplott gegen die Regierung: „Ich denke, wir haben es mit einer gut organisierten Kampagne oder einem konsequenten Plan zur Diskreditierung Russlands und seiner Führung zu tun.“[37]
Ende Dezember 2006 bezeichnete die russische Generalstaatsanwaltschaft Leonid Newslin als möglichen Auftraggeber für den Mord an Litwinenko. Der seit 2003 in Israel lebende ehemalige Mitbesitzer des Ölunternehmens Jukos hat die Verdächtigung als „absoluten Schwachsinn“ zurückgewiesen.[38][39]
Der nationalbolschewistische Regierungskritiker Eduard Limonow wiederum stützte die These Litwinenkos und stellte Präsident Putin an den Pranger: „Das Argument all der Herren ist: Es war für Putin nicht nützlich, den Befehl zur Beseitigung Litwinenkos und Politkowskajas zu geben. Doch dieses Argument passt nicht für Herrn Putin und seine Umgebung. Die Jukos-Affäre hat dem Image Russlands und Putins gewaltigen Schaden zugefügt, hat sich negativ ausgewirkt auf die Entwicklung Russlands und wird sich noch weiter negativ auswirken. Trotzdem hat man die Jukos-Spitze mit unnützer Grausamkeit und Rachsucht verfolgt. Der Beschuss der Schule in Beslan, der Gasangriff auf das Kino Nord-Ost haben die unmenschlichen, tierischen Züge des Regimes gezeigt – sie waren völlig unnütz und wurden dennoch befohlen. Putin ist ein Mensch der Rache und der Emotionen. Litwinenko war im Jahr 2006 schon nicht mehr aktuell. Doch man hat Rache genommen für die Pressekonferenz des Jahres 1998, für sein Buch ‚Wie der FSB Russland in die Luft sprengt‘. Das war eine demonstrative, auf Schau angelegte Bestrafung – lange und quälend, zur Abschreckung.“[40]
Eine weitere Meinung vertritt Julia Latynina, die prominente russische Wirtschaftsjournalistin der Nowaja Gaseta und Buchautorin: „Das Verbrechen trägt die Handschrift einer aggressiven Fraktion innerhalb der Staatssicherheit, deren Ziel es ist, Putins Integrationsbemühungen gen Westen Einhalt zu bieten.“[41]
Verfahren gegen Lugowoi [Bearbeiten]
Scotland Yard besaß laut dem Guardian bereits im Januar 2007 genügend Beweise, um ein Auslieferungsgesuch für den nach Russland zurückgereisten früheren KGB-Mann Lugowoi zu beantragen.[42] Ende Mai 2007 schließlich – kurz vor dem Ende der Regierungszeit Tony Blairs – ersuchte London offiziell um Auslieferung Lugowois an Großbritannien.
Unter Berufung auf die Verfassung der Russischen Föderation, die eine Auslieferung russischer Staatsbürger an andere Staaten untersage, wurde dieses Auslieferungsgesuch abgelehnt. Gleichzeitig verwies die russische Generalstaatsanwaltschaft aber auf die Möglichkeit, in Russland ein Strafverfahren gegen Lugowoi zu eröffnen, wenn sie die nötigen Dokumente erhalte.[43]
Nach dem Amtsantritt der Regierung Gordon Brown verschärfte sich der Konflikt zwischen London und Moskau im Juli 2007. Am 16. Juli wies Großbritannien vier russische Diplomaten aus.[44] Moskau reagierte empört und kündigte „ernsthafte Konsequenzen“ an.[45] Als erster Schritt wurden am 19. Juli vier britische Diplomaten des Landes verwiesen. Außerdem kündigte Russland an, keine neuen Einreise-Visa für britische Amtsträger zu erstellen.[46]
Erklärung der britischen Staatsanwaltschaft [Bearbeiten]
Der Vertreter der königlichen Staatsanwaltschaft (Crown Prosecution Service), Sir Ken Macdonald, erklärte zum Fall Litwinenko:
„Ich habe heute beschlossen, dass die Beweise, die uns von der Polizei übergeben wurden, genügen, um Andrei Lugowoi des Mordes an Herrn Litwinenko mittels absichtlichen Vergiftens zu beschuldigen. Ich habe ferner beschlossen, dass die Strafverfolgung klar im öffentlichen Interesse ist. In dieser Lage habe ich die Mitarbeiter der Staatsanwaltschaft angewiesen unverzüglich Schritte zu unternehmen, um die baldige Auslieferung von Andrei Lugowoi durch Russland an das Vereinigte Königreich zu erreichen, damit er des Mordes angeklagt und schnell vor ein Londoner Gericht gestellt werden kann, um wegen dieses außerordentlich schweren Verbrechens angeklagt zu werden.“[47]
Die Beweislage [Bearbeiten]
Wie die britische Zeitung The Guardian am 23. Mai 2007 berichtete, stützt sich die Anschuldigung gegen Lugowoi vor allem auf die Polonium-Spur, die der mutmaßliche Täter nach der Vergiftung hinterlassen hat.
Der Täter habe sich bei der Vergiftung selbst kontaminiert. In der Folge habe er in Restaurants, Hotelzimmern, Taxis, an Lichtschaltern, Banknoten, Quittungen von Kreditkarten und Flugtickets winzige Spuren von Polonium hinterlassen. Auch Personen, mit denen er in Kontakt gekommen sei, hinterließen danach Polonium-Spuren, allerdings in wesentlich geringerem Umfang. Ebenso scheide das Opfer, vom Zeitpunkt seiner Vergiftung an, über die Schweißdrüsen geringe Mengen Polonium aus.
Alle Polonium-Spuren führten zu Andrei Lugowoi. Dieser habe bei einem Treffen im Millennium Hotel Litwinenko das Polonium in eine Teekanne gegossen, so das Blatt.
Das amerikanische FBI habe Polonium 210, das von Russland aus in die USA exportiert wurde, mit dem Polonium verglichen, mit dem Litwinenko ermordet wurde. Dies versetze die britischen Ermittler in die Lage, sowohl den Reaktor zu identifizieren, aus dem das Polonium stammt, als auch das genaue Datum der Polonium-Produktion zu bestimmen.[48]
Dokumentarfilm zum Fall Litwinenko [Bearbeiten]
Der Filmautor Andrei Nekrassow hat unter dem Titel Rebellion: die Affäre Litwinenko einen Dokumentarfilm zum Fall Litwinenko erstellt. Nekrassow begleitete Litwinenko in den letzten beiden Jahren vor dessen Tod. Der Film wurde am 26. Mai 2007 auf den Filmfestspielen von Cannes im Hauptprogramm außer Konkurrenz gezeigt.[49]
Wikipedia
Alexander Valterovich Litvinenko (Russian: Алекса́ндр Ва́льтерович Литвине́нко) (30 August 1962[1][2] (4 December 1962 by father’s account),[3] – 23 November 2006) was an officer who served in the Soviet KGB and its Russian successor, the Federal Security Service (FSB). In November 1998, Litvinenko and several other FSB officers publicly accused their superiors of ordering the assassination of Russian tycoon and oligarch Boris Berezovsky. Litvinenko was arrested the following March on charges of exceeding his authority at work. He was acquitted in November 1999 but re-arrested before the charges were again dismissed in 2000. He fled with his family to London and was granted asylum in the United Kingdom, where he became a journalist and writer.
During his time in London Litvinenko authored two books, Blowing Up Russia: Terror from Within and Lubyanka Criminal Group, where he accused Russian secret services of staging the Russian apartment bombings and other terrorism acts in an effort to bring Vladimir Putin to power. He also accused Putin of ordering the murder of Russian journalist Anna Politkovskaya.
On 1 November 2006 Litvinenko suddenly fell ill and was hospitalised in what was established as a case of poisoning by radioactive polonium-210 and that resulted in his death on 23 November. The events leading up to his poisoning and death are a matter of controversy, spawning numerous theories relating to his poisoning and death. The British investigation into his death resulted in a failed request to Russia for the extradition of Andrey Lugovoy whom they accused of Litvinenko’s murder, contributing to the further cooling of Russia–United Kingdom relations.
After Litvinenko’s death his widow Marina pursued a vigorous campaign on behalf of her husband through Litvinenko Justice Foundation. In October 2011, she won a right for a full public inquest into Litvinenko’s death to be conducted by a coroner in London.
Alexander Litvinenko was born in the Russian city of Voronezh.[4] After he graduated from a Nalchik secondary school in 1980 he was drafted into the Internal Troops of the Ministry of Internal Affairs as a Private. After a year of service, he matriculated in the Kirov Higher Command School in Vladikavkaz. In 1981, Litvinenko married Nataliya, an accountant, with whom he had a son, Alexander, and a daughter, Sonia. This marriage would later end in divorce in 1994 and in the same year Litvinenko married Marina, a ballroom dancer and fitness instructor, with whom he had a son, Anatoly.[5] After graduation in 1985, Litvinenko became a platoon commander in the Dzerzhinsky Division of the Soviet Ministry of Internal Affairs. He was assigned to the 4th Company, where among his duties was the protection of valuable cargo while in transit.[1][6][7] In 1986 he became an informant when he was recruited by the MVD’s KGB counterintelligence section and in 1988 he was officially transferred to the Third Chief Directorate of the KGB, Military Counter Intelligence.[6] Later that year, after studying for a year at the Novosibirsk Military Counter Intelligence School, he became an operational officer and served in KGB military counterintelligence until 1991.[6][8]
Career in Russian security services
In 1991, he was promoted to the Central Staff of the Federal Counterintelligence Service, specialising in counter-terrorist activities and infiltration of organised crime. He was awarded the title of “MUR veteran” for operations conducted with the Moscow criminal investigation department, the MUR.[9] Litvinenko also saw active military service in many of the so-called “hot spots” of the former USSR and Russia.[10] During the First Chechen War Litvinenko planted several FSB agents in Chechnya. In 1996, Litvinenko also served as a foot soldier during the Russian operation in the Dagestani village of Pervomayskoye, where two of his comrades were killed by friendly fire from the rocket artillery.[citation needed] Although he was oft reported in western media as being a spy, throughout his career he was not an ‘intelligence agent‘ and did not deal with secrets beyond information on operations against organised criminal groups.[6][11][12]
Litvinenko met Boris Berezovsky in 1994 when he took part in investigations into an assassination attempt on the oligarch. He later began to moonlight for Berezovsky where he was responsible for the oligarch’s security.[2][6] The moonlighting by Litvinenko and other security services personnel was illegal, but the state somewhat tolerated it in order to retain personnel who were at the time underpaid.[2][6] Thus, Litvinenko’s moonlighting for the controversial businessman was not investigated, but often investigations in Russia were selective and often targeted only at those who had stepped out of line.[6]
In 1997, Litvinenko was promoted to the FSB Directorate of Analysis and Suppression of Criminal Groups, with the title of senior operational officer and deputy head of the Seventh Section.[13] According to Dimitri Simes, the Directorate was viewed as much as a part of organised crime as it was of law enforcement.[14]
Claims against FSB leadership
According to his widow Marina, during Litvinenko’s employment in the FSB he discovered numerous connections between top brass of Russian law enforcement agencies and Russian mafia groups, such as the Solntsevo gang, which he detailed in a memorandum to Boris Yeltsin.[when?][citation needed] Berezovsky arranged a meeting for him with FSB Director Mikhail Barsukov and Deputy Director of Internal affairs Ovchinnikov to discuss the alleged corruption problems, with no result, leading him to come to the conclusion that the entire system was corrupt.[15]
In December 1997 Litvinenko claimed he received an order to kill Berezovsky. He did not inform his part-time employer until 20 March 1998.[6][16] According to his widow, on 25 July 1998, the day on which Vladimir Putin replaced Nikolay Kovalyov as the Director of the Federal Security Service, Berezovsky introduced Litvinenko to Putin. Berezovsky claimed that he had helped Putin to take the Director’s position.[17] According to his widow, Litvinenko reported to Putin on corruption in the FSB, but Putin was unimpressed.[17] According to Litvinenko, Putin was involved with a corrupt military general in the Russian army when Putin was a Deputy for Economic Affairs to the Mayor of St. Petersburg. Litvenenko was doing an investigation into the general and Uzbek drug barons and believed that Putin tried to stall the investigation in order to save his reputation.[18]
On 13 November 1998 Berezovsky wrote an open letter to Putin in Kommersant. He accused heads of the Directorate of Analysis and Suppression of Criminal Groups Major-General Yevgeny Khokholkov, N. Stepanov, A. Kamyshnikov, N. Yenin of ordering his assassination.[19]
Four days later Litvinenko and four other officers appeared together in a press conference at the Russian news agency Interfax. All officers worked for both FSB in the Directorate of Analysis and Suppression of Criminal Groups and for Boris Berezovsky.[6] They repeated the allegation made by Berezovsky.[6][16] The officers also claimed they were ordered to kill Mikhail Trepashkin who was also present at the press conference, and to kidnap a brother of the businessman Umar Dzhabrailov.[16]
In 2007, Sergey Dorenko provided The Associated Press and The Wall Street Journal with a complete copy of an April 1998 interview he conducted for ORT television station with Litvinenko and his fellow employees. The interview, of which only excerpts were shown in 1998, shows the FSB officers, who were disguised in masks or dark glasses, claim that their bosses had ordered them to kill, kidnap or frame prominent Russian politicians and businesspeople.
Jim Heintz of The Associated Press opined that although Berezovsky does not appear in the interview, he has an omnipresence in it, given that that officers worked for him, and the interview was taped by Dorenko, a Russian journalist who was an employee of ORT owned in part by Berezovsky.[20]
Dismissal from the FSB
After holding the press conference, Litvinenko was dismissed from the FSB.[21] Putin said later in interview to Yelena Tregubova that he personally ordered the dismissal of Litvinenko, stating “I fired Litvinenko and disbanded his unit …because FSB officers should not stage press conferences. This is not their job. And they should not make internal scandals public.”[22] Litvinenko also believed that Putin was behind his arrest. He said: “Putin had the power to decide whether to pass my file to the prosecutors or not. He always hated me. And there was a bonus for him: by throwing me to the wolves he distanced himself from Boris [Berezovsky] in the eyes of FSB’s generals.”[23]
[edit] Arrest
| This section requires expansion. |
He was then arrested twice on charges which were dropped after he had spent time in Moscow prisons.[citation needed] In 1999, he was arrested on charges of abusing duties.[citation needed] He was released a month later after signing a written undertaking not to leave the country.[citation needed] [9]
Flight from Russia and asylum in the United Kingdom
| This section requires expansion. |
In October 2000, in violation of an order not to leave Moscow, Litvinenko and his family travelled to Turkey, possibly via Ukraine.[24] While in Turkey, Litvinenko applied for asylum at the United States Embassy in Ankara, but his application was denied.[24] Henry Plater-Zyberk opined that the denial of application may have been based upon on a possible American opinion that Litvinenko’s knowledge was of little benefit and that he might create problems.[6] With the help of Alexander Goldfarb, Litvinenko bought air tickets for the Istanbul-London-Moscow flight,[25] and asked for political asylum at Heathrow Airport during the transit stop on 1 November 2000.[26] Political asylum was granted on 14 May 2001,[27] not because of his knowledge on intelligence matters, but rather on humanitarian grounds.[6] While in London he became a journalist for the separatist Chechenpress and a controversial author, and also joined Berezovsky in campaigning against Putin’s government.[28][29] In October 2006 he became a naturalised British citizen with residence in Whitehaven.[30]
Alleged career in MI6
On 27 October 2007, the Daily Mail, citing “diplomatic and intelligence sources,” stated that Mr Litvinenko was paid about £2,000 per month by MI6 at the time of his murder. John Scarlett, the head of MI6 (who was once based in Moscow), was allegedly personally involved in recruiting him.[11] The Independent stated that whilst cooperation of Litvinenko with MI6 will likely never be confirmed, a MI6 retainer for Litvinenko suggests systematic cooperation, because MI6 usually makes irregular payments to exiles in exchange for information.[31]
According to Marina Litvinenko, her husband did not work in British secret agencies, but consulted them to combat Russian organized crime in Europe.[32]
Alleged threats against Litvinenko
Former FSB officer Mikhail Trepashkin stated that he had warned in 2002 that an FSB unit was assigned to assassinate Litvinenko.[33] In spite of this, Litvinenko often travelled overseas with no security arrangements, and freely mingled with the Russian community in the United Kingdom, and often received journalists at his home.[6][34] In January 2007, Polish newspaper Dziennik revealed that a target with a photo of Litvinenko on it was used for shooting practice by the Vityaz Training Centre in Balashikha in October 2002.[35] The centre run by Sergey Lyusyuk is not affiliated with the government, and trains bodyguards, debt collectors and private security forces,[36] although in November 2006 the centre was used by the Vityaz for a qualification examination due to their own centre being under renovation.[36] The targets, which Lyusyuk says were bought in the Olympic Market, were also photographed when the chairman of the Federation Council of Russia Sergei Mironov visited the centre and met Lyusyuk on 7 November 2006.[35][36] When asked why the photographs of Mironov’s visit were removed from the centre’s website Lyusyuk stated “(t)hose Poles are up to something” and added that Mironov didn’t see the targets and knew nothing about them.[36]
Alleged blackmail activities
According to Julia Svetlichnaya, a Russian doctoral candidate at the University of Westminster‘s Center for the Study of Democracy, Litvinenko told her that he was planning to blackmail or sell sensitive information on a wide range of people, including oligarchs, allegedly corrupt official and figures within the Kremlin hierarchy, in which he would extort £10,000 per instance to have him stop publication of alleged documents. Svetlichnaya noted that Litvinenko didn’t have a steady income and was certain he could obtain the necessary files for this purpose.[37] According to The Observer, Litvinenko’s alleged threats and access to FSB materials might have turned him into an enemy of big business and the Kremlin.[37]
Conviction in Russia
In 2002 he was convicted in absentia in Russia and given a three and a half year jail sentence.[38]
Allegations
Litvinenko told anyone who would listen about his theories relating to the power structures in Russia, and would bombard his contacts with relating to his conspiracy theories.[6][34][39] In a report for the Conflict Studies Research Centre, Henry Plater-Zyberk, a lecturer at the Defence Academy of the United Kingdom and Russian politics expert, described Litvinenko as a one-man disinformation bureau, who was at first guided by Berezovsky but later in possible pursuit of attention for himself. Plater-Zyberk notes that Litvinenko made numerous accusations without presenting any evidence to give credence to his claims, and these claims which became increasingly outlandish were often accepted by the British media without question.[6] According to Michael Mainville, Litvinenko knew the secret to a conspiracy theory is that they are based upon an absence of proof, and that the more outlandish the claim, the harder it is to disprove.[39] This has led to some political analysts dismissing his claims as those of a fantasist.[37]
Armenian parliament shooting
Litvinenko accused the Main Intelligence Directorate of the General-Staff of the Russian armed forces had organised the 1999 Armenian parliament shooting that killed Prime Minister of Armenia Vazgen Sargsyan and seven members of parliament, ostensibly to derail the peace process which would have resolved the Nagorno-Karabakh conflict, but he offered no evidence to support the accusation.[6][40][41] The Russian embassy in Armenia denied any such involvement, and described Litvinenko’s accusation as an attempt to harm relations between Armenia and Russia by people against the democratic reforms in Russia.[42]
Russian apartment bombings
Litvinenko alleged that agents from the FSB coordinated the 1999 Russian apartment bombings that killed more than 300 people, whereas Russian officials blamed the explosions on Chechen separatists. This version of events was suggested earlier by David Satter,[43] and Sergei Yushenkov, vice chairman of the Sergei Kovalev commission created by the Russian Parliament to investigate the bombings.[citation needed]
Moscow theatre hostage crisis
In a 2003 interview with the Australian SBS TV network, and aired on Dateline, Litvinenko claimed that two of the Chechen terrorists involved in the 2002 Moscow theatre siege — whom he named as “Abdul the Bloody” and “Abu Bakar” — were working for the FSB, and that the agency manipulated the rebels into staging the attack.[44] Litvinenko said: “[w]hen they tried to find [Abdul the Bloody and Abu Bakar] among the dead terrorists, they weren’t there. The FSB got its agents out. So the FSB agents among Chechens organized the whole thing on FSB orders, and those agents were released.” This echoed similar claims made by Mikhail Trepashkin.[45] The leading role of an FSB agent Khanpasha Terkibaev (the “Abu Bakar”) was also described by Anna Politkovskaya, Ivan Rybkin and Alexander Khinshtein.[46][47][48][49] In the beginning of April 2003 Litvinenko gave “the Terkibaev file” to Sergei Yushenkov when he visited London, who in turn passed it to Anna Politkovskaya.[22] A few days later Yushenkov was assassinated. Terkibaev was later killed in Chechnya. According to speaker of Russian State Duma Ivan Rybkin, “The authorities failed to keep [the FSB agent] Terkibaev out of public view, and that is why he was killed. I know how angry people were, because they knew Terkibaev had authorization from presidential administration.” [50]
Beslan school hostage crisis
Alexander Litvinenko suggested in September 2004 that the Russian secret services must have been aware of the plot beforehand, and therefore that they must have themselves organized the attack as a false flag operation. He spoke in an interview before his death with Chechenpress news agency, and said that because the hostage takers had previously been in FSB custody for committing terrorist attacks, it is inconceivable that they would have been released and still been able to carry out attacks independently. He said that they would only have been freed if they were of use to the FSB, and that even in the case that they were freed without being turned into FSB assets, they would be under a strict surveillance regime that would not have allowed them to carry out the Beslan attack unnoticed.[51] Ella Kesayeva, co-chair of the group Voice of Beslan, formalized Litvinenko’s argument in a November 2008 article in Novaya Gazeta, noting the large number of hostage takers who were in government custody not long before attacking the school, and coming to the same conclusion that Beslan was a false flag attack.[52]
Support of terrorism worldwide by the KGB and FSB
Litvinenko stated that “all the bloodiest terrorists of the world” were connected to FSB-KGB, including Carlos “The Jackal” Ramírez, Yassir Arafat, Saddam Hussein, Abdullah Öcalan, Wadie Haddad of the Popular Front for the Liberation of Palestine, George Hawi who led the Communist Party of Lebanon, Ezekias Papaioannou from Cyprus, Sean Garland from Ireland and many others.” He says that all of them were trained, funded, and provided with weapons, explosives and counterfeit documents in order to carry out terrorist attacks worldwide and that each act of terrorism made by these people was carried out according to the task and under the rigid control of the KGB of the USSR.[53] Litvinenko said that “the center of global terrorism is not in Iraq, Iran, Afghanistan or the Chechen Republic. The terrorism infection creeps away worldwide from the cabinets of the Lubyanka Square and the Kremlin”.[54][55]
Alleged Russia-al-Qaeda connection
In a July 2005 interview with the Polish newspaper Rzeczpospolita, Litvinenko alleged that Ayman al-Zawahiri, a prominent leader of al-Qaeda, was trained for half of a year by the FSB in Dagestan in 1997 and called him “an old agent of the FSB”.[53][56] Litvinenko said that after this training, al-Zawahiri “was transferred to Afghanistan, where he had never been before and where, following the recommendation of his Lubyanka chiefs, he at once … penetrated the milieu of Osama bin Laden and soon became his assistant in Al Qaeda.” [57] Former KGB officer and writer Konstantin Preobrazhenskiy supported this claim and said that Litvinenko “was responsible for securing the secrecy of Al-Zawahiri’s arrival in Russia; he was trained by FSB instructors in Dagestan, Northern Caucasus, in 1996-1997.”.[58] He said: “At that time, Litvinenko was the Head of the Subdivision for Internationally Wanted Terrorists of the First Department of the Operative-Inquiry Directorate of the FSB Anti-Terrorist Department. He was ordered to undertake the delicate mission of securing Al-Zawahiri from unintentional disclosure by the Russian police. Though Al-Zawahiri had been brought to Russia by the FSB using a false passport, it was still possible for the police to learn about his arrival and report to Moscow for verification. Such a process could disclose Al-Zawahiri as an FSB collaborator. In order to prevent this, Litvinenko visited a group of the highly placed police officers to notify them in advance.” According to FSB spokesman Sergei Ignatchenko, al-Zawahiri was arrested by Russian authorities in Dagestan in December 1996 and released in May 1997.[59]
When asked in an interview who he thought the originator of the 2005 bombings in London was, Litvinenko responded saying[53] “You know, I have spoken about it earlier and I shall say now, that I know only one organization, which has made terrorism the main tool of solving of political problems. It is the Russian special services.”
On 1 September 2005, al-Zawahiri and Mohammad Sidique Khan claimed responsibility for the attacks for Al Qaeda on a video tape which aired on al-Jazeera.[60]
Danish cartoon controversy
According to Litvinenko, the 2005 controversy over the publication in the Danish newspaper Jyllands-Posten of editorial cartoons depicting the Islamic prophet Muhammad was orchestrated by the FSB to punish Denmark for its refusal to extradite Chechen separatists.[39]
Assassination of Anna Politkovskaya
Two weeks before his poisoning, Alexander Litvinenko accused Vladimir Putin of ordering the assassination of Russian journalist Anna Politkovskaya and stated that a former presidential candidate Irina Hakamada warned Politkovskaya about threats to her life coming from the Russian president. Litvinenko advised Politkovskaya to escape from Russia immediately. Hakamada denied her involvement in passing any specific threats, and said that she warned Politkovskaya only in general terms more than a year ago.[61] It remains unclear if Litvinenko referred to an earlier statement made by Boris Berezovsky who claimed that former Deputy Prime Minister of Russia Boris Nemtsov received a word from Hakamada that Putin threatened her and like-minded colleagues in person. According to Berezovsky, Putin uttered that Hakamada and her colleagues “will take in the head immediately, literally, not figuratively” if they “open the mouth” about the Russian apartment bombings.[62]
Allegations concerning Romano Prodi
According to Litvinenko, FSB deputy chief, General Anatoly Trofimov said to him “Don’t go to Italy, there are many KGB agents among the politicians. Romano Prodi is our man there”,[63][64] meaning Romano Prodi, the Italian centre-left leader, former Prime Minister of Italy and former President of the European Commission. The conversation with Trofimov took place in 2000, after the Prodi-KGB scandal broke out in October 1999 due to information about Prodi provided by Vasili Mitrokhin.[17]
In April 2006, a British Member of the European Parliament for London, Gerard Batten of the United Kingdom Independence Party (UKIP) demanded an inquiry into the allegations.[63][64] According to Brussels-based newspaper, the EU Reporter on 3 April 2006, “another high-level source, a former KGB operative in London, has confirmed the story”.[65] On 26 April 2006, Batten repeated his call for a parliamentary inquiry, revealing that “former, senior members of the KGB are willing to testify in such an investigation, under the right conditions.” He added, “It is not acceptable that this situation is unresolved, given the importance of Russia’s relations with the European Union.”[66] On 22 January 2007, the BBC and ITV News released documents and video footage, from February 2006, in which Litvinenko repeated his statements about Prodi.[67][68]
A report by the Conflict Studies Research Centre of the Defence Academy of the United Kingdom from May 2007 noted that Trofimov was never the head of the FSB, which did not oversee intelligence operations, had never worked in the intelligence directorate of the KGB or its successor the SVR, nor had he worked in the counterintelligence department of the intelligence services, nor had he ever worked in Italy, making it difficult to understand how Trofimov would have had knowledge about such a recruitment. Henry Plater-Zyberk, the co-author of the report suggested that Trofimov was “conveniently dead”, so “could neither confirm nor deny the story”, and noted Litvinenko’s history of making accusations without evidence to back them up.[6]
Cooperation with Spanish authorities
Shortly before his death Litvinenko tipped off Spanish authorities on several organised crime bosses with links to Spain. During a meeting in May 2006 he allegedly provided security officials with information on the locations, roles, and activities of several “Russian” mafia figures with ties to Spain, including Izguilov, Zahkar Kalashov, and Tariel Oniani.[69]
Other allegations
In his book Gang from Lubyanka, Litvinenko alleged that Vladimir Putin during his time at the FSB was personally involved in protecting the drug trafficking from Afghanistan organized by Abdul Rashid Dostum [2]. In December 2003 Russian authorities confiscated over 4000 copies of the book.[70]
Litvinenko commented on a new law that “Russia has the right to carry out preemptive strikes on militant bases abroad” and explained that these “preemptive strikes may involve anything, except nuclear weapons,” Litvinenko said that “You know who they mean when they say ‘terrorist bases abroad’? They mean us, Zakayev and Boris, and me.”.[22] He also said that “It was considered in our service that poison is an easier weapon than a pistol.” He referred to a secret laboratory in Moscow that still continues development of deadly poisons, according to him.[71]
In an article written by Litvinenko in July 2006, and published online on Zakayev’s Chechenpress website, he claimed that Vladimir Putin is a paedophile.[72] Litvinenko also claimed that Anatoly Trofimov and Artyom Borovik knew of the alleged paedophilia.[73] The claims have been called “wild”,[34] and “sensational and unsubstantiated”[74] in the British media. Litvinenko made the allegation after Putin kissed a boy on his belly while stopping to chat with some tourists during a walk in the Kremlin grounds on 28 June 2006.[74] The incident was recalled in a webcast organised by the BBC and Yandex, in which over 11,000 people asked Putin to explain the act, to which he responded, “He seemed very independent and serious… I wanted to cuddle him like a kitten and it came out in this gesture. He seemed so nice…There is nothing behind it.”[75] It has been suggested that the incident was a “clumsy attempt” to soften Putin’s image in the lead-up the 32nd G8 Summit which was held in Saint Petersburg in July 2006.[74]
Poisoning and death

Alexander Litvinenko at University College Hospital
On 1 November 2006, Litvinenko suddenly fell ill and was hospitalised. His illness was later attributed to poisoning with radionuclide polonium-210 after the Health Protection Agency found significant amounts of the rare and highly toxic element in his body. In interviews, Litvinenko stated that he met with two former KGB agents early on the day he fell ill – Dmitry Kovtun and Andrei Lugovoi. Though both denied any wrongdoing, a leaked US diplomatic cable revealed that Kovtun had left Polonium traces in the house and car he had used in Hamburg [3]. The men also introduced Litvinenko to a tall, thin man of central Asian appearance called ‘Vladislav Sokolenko’ who Lugovoi said was a business partner. Lugovoi is also a former bodyguard of Russian ex-Acting Prime minister Yegor Gaidar (who also suffered from a mysterious illness in November 2006). Later, he had lunch at Itsu, a sushi restaurant in Piccadilly in London, with an Italian acquaintance and nuclear waste expert, Mario Scaramella, to whom he made the allegations regarding Italy’s Prime Minister Romano Prodi.[76] Scaramella, attached to the Mitrokhin Commission investigating KGB penetration of Italian politics, claimed to have information on the assassination of Anna Politkovskaya, 48, a journalist who was killed at her Moscow apartment in October 2006.
Marina Litvinenko, widow of the deceased, accused Moscow of orchestrating the murder. Though she believes the order did not come from Putin himself, she does believe it was done at the behest of the authorities, and announced that she will refuse to provide evidence to any Russian investigation out of fear that it would be misused or misrepresented.[77]
Conversion to Sunni Islam
Two days before his death Litvinenko informed his father that he had converted to Sunni Islam. Litvinenko’s conversion to Sunni Islam and the related wish for Muslim funeral rites were recognized by his father. Goldfarb stated, “Unfortunately some people appeared and against the explicit wishes of the widow performed Muslim rites over the funeral. We had a choice to turn it into an unseemly situation, but Marina asked us to respect the memory of Alexander and let these people do what they did. Let God be their judge.” Ghayasuddin Siddiqui, head of the Muslim Parliament of Great Britain, contended that Litvineko actually converted to Sunni Islam 10 days before he was poisoned.[78][79][80] Akhmed Zakayev, Foreign Minister of Chechen government-in-exile who lived next door to Mr Litvinenko and considered him “like a brother,”[81] said: “He was read to from the Qur’an the day before he died and had told his wife and family that he wanted to be buried in accordance with Muslim tradition.”[82] The ceremony was followed by a private memorial at which the ensemble Tonus Peregrinus sang sacred music by Russian composers Igor Stravinsky, Sergei Rachmaninov, Victor Kalinnikov, and three works by British composer Antony Pitts.[83]
Death and last statement
On 22 November Litvinenko’s medical staff at University College Hospital reported he had suffered a “major setback” due to either heart failure or an overnight heart attack. He died on 23 November, and Scotland Yard stated that inquiries into the circumstances of how Litvinenko became ill would continue.[84]
On 24 November a posthumous statement was released, in which Litvinenko directly accused Vladimir Putin of poisoning him. Litvinenko’s friend Alex Goldfarb, who is also the chairman of Boris Berezovsky‘s Civil Liberties Fund, claimed Litvinenko had dictated it to him three days earlier. Andrei Nekrasov said his friend Litvinenko and Litvinenko’s lawyer composed the statement in Russian on 21 November and translated it to English.[85]
Putin disputed the authenticity of this note while attending a Russia-EU summit in Helsinki and claimed it was being used for political purposes.[86][87] William Dunkerley, in a briefing from May 2007 for a round table which discussed Litvinenko’s case and the way it was handled by the Russian and Western media, called into question the authenticity of the statement, noting that the statement did not read like a statement made on one’s deathbed and was typed in English, a language which Litvinenko was far from proficient in, with the signature and date handwritten.[28] Goldfarb later stated that Litvinenko instructed him to write a note “in good English” in which Putin was to be accused of his poisoning. Goldfarb also stated that he read the note to Litvinenko in English and Russian, to which he claims Litvinenko agreed “with every word of it” and signed it.[88]

Grave of Alexander Litvinenko at Highgate Cemetery
His postmortem took place on 1 December at the Royal London Hospital’s institute of pathology. It was attended by three physicians, including one chosen by the family and one from the Foreign Office.[89] Litvinenko was buried at Highgate Cemetery (West side) in north London on 7 December.[90] The police are treating his death as murder.[91] On 25 November, two days after Litvinenko’s death, an article attributed to him was published by The Mail on Sunday entitled “Why I believe Putin wanted me dead”.[92]
In an interview with the BBC broadcast on 16 December 2006, Yuri Shvets said that Litvinenko had created a ‘due diligence‘ report investigating the activities of a senior Kremlin official on behalf of a British company looking to invest “dozens of millions of dollars” in a project in Russia. He said the dossier was so incriminating about the senior Kremlin official, who was not named, it was likely that Litvinenko was murdered out of spite. He alleged that Litvinenko had shown the dossier to another business associate, Andrei Lugovoi, who had worked for the KGB and later the FSB. Shvets alleged that Lugovoi is still an FSB informant and he had spread copies of the dossier to members of the spy service. He said he was interviewed about his allegations by Scotland Yard detectives investigating Litvinenko’s murder. Shvets has also doubted Litvinenko’s capacity to perform honest unbiased due diligence.[93] The poisoning and consequent death of Litvinenko was not widely covered in the Russian news media.[94]
According to Mary Dejevsky, the chief editorial writer of The Independent, the view that the British public had of Litvinenko’s illness and death was essentially dictated by Berezovsky, who funded an expertly conducted publicity campaign.[95]
Theories and investigations into death
UK criminal investigation
On 20 January 2007 British police announced that they have “identified the man they believe poisoned Alexander Litvinenko. The suspected killer was captured on cameras at Heathrow as he flew into Britain to carry out the murder.”[96] The man in question was introduced to Litvinenko as ‘Vladislav’.
As of 26 January 2007, British officials said police had solved the murder of Litvinenko. They discovered “a ‘hot’ teapot at London’s Millennium Hotel with an off-the-charts reading for polonium-210, the radioactive material used in the killing.” In addition, a senior official said investigators had concluded the murder of Litvinenko was “a ‘state-sponsored’ assassination orchestrated by Russian security services.” The police want to charge former Russian spy Andrei Lugovoi, who met with Litvinenko on 1 November 2006, the day officials believe the lethal dose of polonium-210 was administered. [97]
On the same day, The Guardian reported that the British government was preparing an extradition request asking that Andrei Lugovoi be returned to the UK to stand trial for Litvinenko’s murder.[98] On 22 May 2007 the Crown Prosecution Service called for the extradition of Russian citizen Andrei Lugovoi to the UK on charges of murder. [99] Lugovoi dismissed the claims against him as “politically motivated” and said he did not kill Litvinenko. [100]
A British police investigation resulted in several suspects for the murder, but in May 2007, the British Director of Public Prosecutions, Ken Macdonald, announced that his government would seek to extradite Andrei Lugovoi, the chief suspect of the case, from Russia. [101] On 28 May 2007, the British Foreign Office officially submitted a request to the Government of Russia for the extradition of Lugovoi to face criminal charges in the UK. [102]
On 2 October 2011, The Sunday Times published an article wherein the chief prosecutor who investigated the murder of Litvinenko, Lord Macdonald of River Glaven, publicly spoke of his suspicion that the murder was a “state directed execution” carried out by Russia. Until that time, British public officials had stopped short of directly accusing Russia of involvement in the poisoning. “It had all the hallmarks of a state directed execution, committed on the streets of London by a foreign government,” Macdonald added.[103]
Russian criminal investigation
Many publications in Russian media suggested that the death of Alexander Litvinenko was connected to Boris Berezovsky.[104][105] Former FSB chief Nikolay Kovalyov, for whom Litvinenko worked, said that the incident “looks like the hand of Boris Berezovsky. I am sure that no kind of intelligence services participated.”[106] This involvement of Berezovsky was alleged by numerous Russian television shows. Kremlin supporters saw it as a conspiracy to smear Russian government’s reputation by engineering a spectacular murder of a Russian dissident abroad.[107]
After Litvinenko’s death, traces of polonium-210 were found in an office of Berezovsky.[108] Litvinenko had visited Berezovsky’s office as well as many other places in the hours after his poisoning.[109] The British Health Protection Agency made extensive efforts to ensure that locations Litvinenko visited and anyone who had contact with Litvinenko after his poisoning, were not at risk.[110]
Russian prosecutors were not allowed to investigate the office.[111] Russian authorities have also been unable to question Berezovsky. The Foreign Ministry complained that Britain was obstructing its attempt to send prosecutors to London to interview more than 100 people, including Berezovsky.[112]
On 5 July 2007, Russia officially declined to extradite Lugovoi, citing that extradition of citizens is not allowed under the Russian constitution. Russia has said that they could take on the case themselves if Britain provided evidence against Lugovoi but Britain has not handed over any evidence. The head of the investigating committee at the General Prosecutor’s Office said Russia has not yet received any evidence from Britain on Lugovoi. “We have not received any evidence from London of Lugovoi’s guilt, and those documents we have are full of blank spaces and contradictions.[113] However the British ambassador to Russia, Anne Pringle, claimed that London has already submitted sufficient evidence to extradite him to Britain.[114]
Judicial Inquiries
Inquest in London
On October 13, 2011 Dr. Andrew Reed, the Coroner of St. Pancras announced that he will hold a full public inquest into Litvinenko’s death, which will include the examination of all existing theories of the murder, including possible complicity of Russian government.[115]
Litvinenko vs Russian Federation in Strasbourg
In May 2007 Marina Litvinenko registered a complaint against Russian Federation in the European Court of Human Rights in Strasbourg accusing RF of violating her husband’s right to life, and failing to conduct full investigation.[116] References in popular culture
- Channel Four Television Corporation has signed Mentorn productions to make a television drama based on the Litvinenko poisoning. Peter Kosminsky will be the director.[117]
- Johnny Depp is reportedly planning to make a film based on a forthcoming book.[118][119][120]
References
- ^ a b Penketh, Anne (25 November 2006). “Alexander Litvinenko”. London: The Independent. http://www.independent.co.uk/news/obituaries/alexander-litvinenko-425720.html. Retrieved 16 March 2010. (Archived at WebCite)
- ^ a b c “Aleksandr Litvinenko”. Russia Today. http://rt.com/Russia_Now/Russiapedia/Those_Russians/laleksandr-litvinenko.html. Retrieved 6 April 2010. (Archived at WebCite)
- ^ Вальтер Литвиненко: «Сегодня моему сыну исполнилось бы 44», Вальтер Александрович Литвиненко, 4 декабря 2006 г., ChechenPress
- ^ “Alexander Litvinenko”. London: The Daily Telegraph. 25 November 2006. http://www.telegraph.co.uk/news/obituaries/1535094/Alexander-Litvinenko.html. Retrieved 16 March 2010. (Archived at WebCite)
- ^ Oxford Dictionary of National Biography
- ^ a b c d e f g h i j k l m n o p q Monaghan, Dr Andrew; Plater Zyberk, Henry (22 May 2007). “Misunderstanding Russia: Alexander Litvinenko” (PDF). The UK & Russia — A Troubled Relationship Part I. Conflict Studies Research Centre of the Defence Academy of the United Kingdom. pp. 9–12. ISBN 9781905962150. http://www.da.mod.uk/colleges/arag/document-listings/russian/07%2817%29AM.pdf. Retrieved 2010-03-16. (Archived at WebCite)
- ^ “Alexander Litvinenko”. London: The Times. 25 November 2006. http://www.timesonline.co.uk/article/0,,60-2470058,00.html. Retrieved 2010-03-16. (Archived at WebCite)
- ^ (Russian)Александр Подрабинек (2002-10-10). “Офицер ФСБ дает показания”. Агентство ПРИМА. http://www.prima-news.ru/news/articles/2002/10/10/17299.html.
- ^ a b Thomas, D.M. (1998). Alexander Solzhenitsyn – A Century In His Life. New York: St. Martinj’s Press. pp. 583.
- ^ “In Memoriam Aleksander Litvinenko.” Dir. Jose De Putter. VPRO Backlight, 2007. Documentary.[1]
- ^ a b Wright, Stephen; Williams, David (27 October 2007). “Revealed: Poisoned ex-Russian spy Litvinenko WAS a paid-up MI6 agent”. London: Daily Mail. http://www.dailymail.co.uk/news/article-490007/Revealed-Poisoned-ex-Russian-spy-Litvinenko-WAS-paid-MI6-agent.html. Retrieved 16 March 2010. (Archived at WebCite)
- ^ “Russian authorities likely behind Litvinenko’s death, his wife says”. London: International Herald Tribune. 10 December 2006. http://www.iht.com/articles/ap/2006/12/10/europe/EU_GEN_Britain_Poisoned_Spy_Wife.php. Retrieved 16 March 2010. (Archived at Wayback Machine)
- ^ (Russian) Vinogradskaya, Natalya (30 November 2006). “Радиоактивные политтехнологии: смерть Литвиненко осложнила проведение саммита Россия-ЕС”. “What the Papers Say” Agency. http://www.wps.ru/ru/pp/tv-review/2006/11/30.html. Retrieved 16 March 2010. (Archived at WebCite)
- ^ Simes, Dimitri (12 June 2006). “Litvinenko: Kremlin Conspiracy or Blofeld Set-Up?”. The National Interest. http://www.nationalinterest.org/BlogSE.aspx?id=13150. Retrieved 2010-03-16. (Archived at WebCite)
- ^ Death of a dissident, page 39-41.
- ^ a b c (Russian)“Березовский и УРПО / дело Литвиненко”. “Агентура.Ру”. 27 November 2006. http://www.agentura.ru/timeline/1998/urpo/. Retrieved 2006-11-30.
- ^ a b c Death of a Dissident, page 136
- ^ Litvinenko, Alexander (25 November 2006). “Why I believe Putin wanted me dead…”. Daily Mail. http://www.mailonsunday.co.uk/news/article-418652/Why-I-believe-Putin-wanted-dead-.html. Retrieved 2011-12-16.
- ^ (Russian) Berezovsky, Boris (13 November 1998). “Березовский (signed 11 November 1998)”. Kommersant. http://www.kommersant.ru/doc/208710. Retrieved 2011-12-16.
- ^ Heintz, Jim (23 May 2007). “1998 Tape Shows Russian Ex-Spy Fearful”. Associated Press, via Washington Post. http://www.washingtonpost.com/wp-dyn/content/article/2007/05/23/AR2007052300397_pf.html. Retrieved 2009-03-16.
- ^ “Russia ready to cooperate with Britain on Litvinenko case — FSB”. RIA Novosti. 18 May 2008. http://en.rian.ru/russia/20080518/107675252.html. Retrieved 2009-03-16.
- ^ a b c Alex Goldfarb and Marina Litvinenko. Death of a Dissident: The Poisoning of Alexander Litvinenko and the Return of the KGB, The Free Press (2007) ISBN 1-416-55165-4
- ^ Death of a dissident, page 160.
- ^ a b Cowell, Alan; Shane, Scott; Myers, Steven Lee; Klimenko, Viktor (3 November 2006). “Alexander Litvinenko lived and died in world of violence and betrayal”. London/Washington, D.C./Moscow: International Herald Tribune. http://www.nytimes.com/2006/12/03/world/europe/03iht-spy.3760139.html?pagewanted=all. Retrieved 6 April 2010. (Archived at WebCite)
- ^ (Russian) Dmitriyeva, Olga (30 March 2002). “Александр Литвиненко: ярлык предателя не радует”. London: Rossiyskaya Gazeta. http://www.rg.ru/Anons/arc_2002/0330/hit.shtm. Retrieved 6 April 2010. (Archived at WebCite)
- ^ “Литвиненко получил убежище в Британии?”. BBC Russian Service. 15 May 2001. http://news.bbc.co.uk/hi/russian/news/newsid_1331000/1331949.stm. Retrieved 6 April 2010. (Archived at WebCite)
- ^ (Russian)“Заявление Александра Литвиненко”. lenta.ru. 15 May 2006. http://www.lenta.ru/world/2001/05/15/litvinenko/statement.htm. Retrieved 2006-11-24.
- ^ a b Dunkerley, William (25 May 2007). “The Essence of the Alexander Litvinenko Story”. Russia Profile. http://www.russiaprofile.org/page.php?pageid=Politics&articleid=a1180613251. Retrieved 2010-03-16. (Archived at WebCite
- ^ Sakwa, Richard (2008). Putin, Russia’s choice (2nd ed.). Routledge. pp. 158–159. ISBN 978-0-415-40765-6.
- ^ Evans, Michael; McGrory, Daniel; Delaney, Sarah (22 November 2006). “Litvinenko was told that he was marked for death”. London: Times. http://www.timesonline.co.uk/article/0,,3-2465271,00.html. Retrieved 2006-11-24.
- ^ “The Litvinenko files: MI6”. London: The Independent. 2 May 2008. http://www.independent.co.uk/news/world/europe/the-litvinenko-files-mi6-819537.html. Retrieved 2009-03-16.
- ^ http://english.ruvr.ru/2011/10/17/58864214.html
- ^ Isachenkov, Vladimir (1 December 2006). “Ex-Spy Claims Litvinenko Was Targeted”. Washington Post. http://www.washingtonpost.com/wp-dyn/content/article/2006/12/01/AR2006120100452.html. Retrieved 2006-12-01.
- ^ a b c Svetlichnaya, Julia (3 December 2006). “Strange stroll around Hyde Park that went nowhere”. London: The Observer. http://www.guardian.co.uk/uk/2006/dec/03/world.russia2. Retrieved 2010-04-06. (Archived at WebCite)
- ^ a b Russian special forces shot at Litvinenko, Dariusz Rembelski, Magdalena Miroszewska, Dziennik Online, 30 January 2007.
- ^ a b c d Voronov, Alexander; Chistyakova, Marina; Barakhova, Alla (31 January 2007). “Litvinenko Shooting Gallery”. Kommersant. http://www.kommersant.com/p738293/r_530/Litvinenko_Shooting_Gallery/. Retrieved 6 April 2010. (Archived at WebCite)
- ^ a b c Townsend, Mark; Doward, Jamie; Parfitt, Tom; McMahon, Barbara (3 December 2006). “Revealed: Litvinenko’s Russian ‘blackmail plot'”. London: The Observer. http://www.guardian.co.uk/uk/2006/dec/03/russia.world. Retrieved 2010-04-06. (Archived at WebCite)
- ^ Alexander Litvinenko The Guardian Retrieved on 5 April 2008
- ^ a b c Mainville, Michael (14 December 2006). “From Russia with lies”. Moscow: Salon.com. http://www.salon.com/news/feature/2006/12/14/litvinenko/. Retrieved 6 April 2010. (Archived at WebCite)
- ^ (Russian) “Список киллеров ФСБ”. Реальный Азербайджан. 29 April 2005. Archived from the original on 2005-11-04. http://web.archive.org/web/20051104110225/http://realazer.com/_3/index.html. Retrieved 2009-02-16.
- ^ “Shooting of the Armenian Parliament was organized by Russian special services”. AZG Daily. 3 May 2005. http://www.azg.am/EN/2005050307. Retrieved 6 April 2010. (Archived at Freezepage.com)
- ^ “Russian embassy denies special services’ part in Armenian parliament shooting”. ITAR-TASS. 12 May 2005.
- ^ Satter, David (13 November 2006). “The Truth About Beslan”. The Weekly Standard. http://www.weeklystandard.com/print/Content/Public/Articles/000/000/012/907jbmkm.asp. Retrieved 6 April 2010. (Archived at WebCite)
- ^ Lazaredes, Nick (4 June 2003). “Terrorism takes front stage — Russia’s theatre siege”. Dateline. http://news.sbs.com.au/dateline/russia__terrorism_takes_front_stage_130217. Retrieved 2008-11-13. [dead link]
- ^ Dissident lawyer jailed on trumped up charges
- ^ Mysterious figure implicated in Russian theater tragedy
- ^ Where is “Abubakar?”
- ^ Russian Authorities Hedge Over Special Services Involvement In Moscow Theater Siege, by Anna Politkovskaya, Novaya Gazeta, 5 May 2003
- ^ The Moscow Hostage-Taking Incident (Part 1) By John B. Dunlop, Radio Free Europe
- ^ Anna Politkovskaya A Russian Diary: A Journalist’s Final Account of Life, Corruption, and Death in Putin’s Russia, Random House, New York, 2007, ISBN 978-1-4000-6682-7, page 56.
- ^ A. Litvinenko: “The identities of the terrorists prove 100% the participation of the FSB in the seizure of the school in Beslan”, Chechenpress, 8 September 2004
- ^ (Russian) Kesayeva, Ella (20 November 2008). “Террористы-агенты – Неизвестные подробности бесланской трагедии”. Novaya Gazeta. http://www.novayagazeta.ru/data/2008/86/00.html. Retrieved 6 April 2010. (Archived at WebCite)
- ^ a b c The originator of the acts of terrorism in London was standing near Tony Blair Retrieved on 3 April 2008
- ^ “The originator of the acts of terrorism in London was standing near Tony Blair”. 19 July 2005. http://www.indymedia.org.uk/en/regions/london/2005/07/318875.html. Retrieved 2006-11-30.
- ^ Litvinenko, Alexander (23 March 2005). “The KGBism, Terrorism and Gangsterism are Triplets”. Chechen Press. http://www.chechenpress.info/english/news/2005/03/23/03.shtml. Retrieved 2006-12-07.
- ^ Nyquist, J.R. (20 November 2006). “Kremlin Poison”. Financial Sense Online. http://www.financialsense.com/stormwatch/geo/pastanalysis/2006/1120.html. Retrieved 2006-11-21.
- ^ Nyquist, J.R. (13 August 2005). “Is Al Qaeda a Kremlin Proxy?”. http://www.jrnyquist.com/nyquist_2005_0813.htm. Retrieved 2006-11-29.
- ^ Russia and Islam are not Separate: Why Russia backs Al-Qaeda, by Konstantin Preobrazhensky.
- ^ Gebara, Khalil (10 February 2005). “The End of Egyptian Islamic Jihad?”. The Jamestown Foundation. Archived from the original on November 21, 2006. http://web.archive.org/web/20061121012526/http://www.jamestown.org/publications_details.php?volume_id=411&issue_id=3228&article_id=2369243. Retrieved 2006-12-07.
- ^ London bomber: Text in full BBC News Retrieved on 3 April 2008
- ^ (Russian)“Ирина Хакамада о партийном строительстве и экономической ситуации в России”. Svoboda News. 4 December 2006. http://www.svobodanews.ru/Transcript/2006/12/04/20061204200017950.html. Retrieved 2006-12-07.
- ^ Live interview with Berezovsky by Evgenia Albats, Radio Echo of Moscow, 11 June 2006. Transcript in Russian, computer translation.
- ^ a b “Gerard Battem, One-minute speeches on matters of political importance”. European Parliament, Debates. 3 April 2006. http://www.europarl.europa.eu/sides/getDoc.do?pubRef=-//EP//TEXT+CRE+20060403+ITEM-008+DOC+XML+V0//EN&language=EN&query=INTERV&detail=1-060. Retrieved 2008-03-13.
- ^ a b “Former FSB General, Wife Shot Dead in Moscow”. Mosnews.com. 11 April 2005. http://www.mosnews.com/news/2005/04/11/fsbhit.shtml. Retrieved 2006-11-21.
- ^ Donnelly, Cillian (3 April 2006). “Prodi Accused Of Being Former Soviet Agent”. EU Reporter. Archived from the original on May 24, 2006. http://web.archive.org/web/20060524063146/http://www.eureporter.co.uk/showarticle.php?newsid=2218. Retrieved 2006-11-21.
- ^ Batten, Gerard (26 April 2006). “2006: Speech in the European Parliament: Romano Prodi”. Gerard Batten MEP. http://www.gerardbattenmep.co.uk/search.php?misc=search&subaction=showfull&id=1146224529&archive=&cnshow=news&start_from=&%5C%22to_date_day%5C%22=&TB=home5. Retrieved 2006-11-21.
- ^ “‘Multiple attempts’ on Litvinenko”. BBC. 22 January 2007. http://news.bbc.co.uk/1/hi/uk/6285631.stm. Retrieved 2007-03-01.
- ^ “Litvinenko footage emerges”. ITV News. 22 January 2007. http://www.itv.com/news/index_de20839cb1d32bc0891bbbd13c6a4c1e.html. Retrieved 2007-03-01.
- ^ Tremlett, Giles (1 December 2010). “US embassy cables: Spain’s investigations into the Russian mafia”. The Guardian. http://www.guardian.co.uk/world/us-embassy-cables-documents/223006. Retrieved 12 December 2010.
- ^ “Russian editor questioned over seizure of controversial book (BBC Monitoring Former Soviet Union, text of report by Russian news agency Ekho Moskvy )”. Terror 99. 29 January 2004. http://eng.terror99.ru/publications/133.htm. Retrieved 2006-12-23.
- ^ Litvinenko’s Poisoning: Detailed Unfolding of Events
- ^ Litvinenko, Alexander (5 July 2006). “The Kremlin Pedophile”. Chechenpress. http://www.chechenpress.co.uk/english/news/2006/07/05/01.shtml. Retrieved 2008-11-11.
- ^ (Russian) Litvinenko, Alexander (5 July 2006). “Кремлевский чикатило»”. Chechenpress. http://www.chechenpress.info/events/2006/07/05/03.shtml. Retrieved 2008-11-11.
- ^ a b c “Poisoned spy accused Putin of being a paedophile”. London: Daily Mail. 20 November 206. http://www.dailymail.co.uk/news/article-417621/Poisoned-spy-accused-Putin-paedophile.html. Retrieved 2008-11-11.
- ^ “Putin recalls kissing boy’s belly”. BBC News Online. 6 July 2006. http://news.bbc.co.uk/2/hi/europe/5155448.stm. Retrieved 2008-11-11.
- ^ Batten, Gerard (3 April 2006). “Gerard Batten MEP – “60 second speech to the European Parliament “Romano Prodi” – Strasbourg”. United Kingdom Independence Party. Archived from the original on October 13, 2006. http://web.archive.org/web/20061013081221/http://www.ukip.org/ukip_news/gen12.php?t=1&id=2055. Retrieved 2006-11-21.
- ^ “Dead spy’s widow accuses Russian authorities”. CNN. 10 December 2006. Archived from the original on December 12, 2006. http://web.archive.org/web/20061212004137/http://edition.cnn.com/2006/WORLD/europe/12/10/russia.spy/index.html. Retrieved 2006-12-10.
- ^ “Litvinenko’s Father Says Son Requested Muslim Burial”. Prague: Radio Free Europe/Radio Liberty. 5 December 2006. http://www.rferl.org/content/article/1073226.html. Retrieved 6 April 2010. (Archived at WebCite)
- ^ “Poison probe visits Russia”. Moscow: The Washington Times. 4 December 2006. http://www.washingtontimes.com/news/2006/dec/04/20061204-110524-6986r/. Retrieved 6 April 2010. (Archived at WebCite)
- ^ Brown, Jonathan (8 December 2006). “Enemies of Putin gather for a burial in exile”. London: The Independent. http://www.independent.co.uk/news/uk/crime/enemies-of-putin-gather-for-a-burial-in-exile-427548.html. Retrieved 6 April 2010. (Archived at WebCite)
- ^ The Associated Press (22 May 2007). “Key figures in the Litvinenko affair”. USA Today. http://www.usatoday.com/news/world/2007-05-22-litvinenko-key-figures_N.htm. Retrieved 2010-04-07. (Archived at WebCite)
- ^ Gardham, Duncan; Steele, John (2 December 2006). “Spy’s contact and wife also poisoned”. London: The Daily Telegraph. http://www.telegraph.co.uk/news/uknews/1535776/Spys-contact-and-wife-also-poisoned.html. Retrieved 2010-04-07. (Archived at WebCite)
- ^ “In memoriam Litvinenko”. The Welcome Stranger. December 2006. http://shop.thewelcomestranger.org/in-memoriam-litvinenko-89-p.asp. Retrieved 2010-06-11.
- ^ “Poisoned Russian former spy dies”. CNN. 23 November 2006. Archived from the original on 2006-11-24. http://web.archive.org/web/20061124044529/http://www.cnn.com/2006/WORLD/europe/11/23/uk.spypoisoned/index.html. Retrieved 2006-11-23.
- ^ (Russian) An interview with Andrei Nekrasov by Yury Veksler, Radio Liberty, 28 November 2006.
- ^ “Ex-spy’s death should not be used for provocation — Putin”. Helsinki: RIA Novosti. 24 November 2006. http://en.rian.ru/russia/20061124/55967399.html. Retrieved 16 March 2010. (Arhived at WebCite)
- ^ “Joint Press Conference with the Prime Minister of Finland Matti Vanhanen, President of the European Commission Jose Manuel Barroso, Secretary General of the EU Council and EU High Representative for the Common Foreign and Security Policy Javier Solana, Prime Minister of Norway Jens Stoltenberg and Prime Minister of Iceland Geir Haarde following the Russia-EU summit meeting”. Helsinki City Hall, Helsinki: Presidential Press and Information Office. 24 November 2006. http://eng.kremlin.ru/speeches/2006/11/24/2355_type82914type82915_114506.shtml. Retrieved 16 March 2010. [dead link] (Archived at WebCite)
- ^ Jordan, Mary (10 June 2007). “Poisoned Russian Had Sought Entry to U.S., Book Says”. Washington Post. http://www.washingtonpost.com/wp-dyn/content/article/2007/06/09/AR2007060901354_pf.html. Retrieved 2010-03-16. (Archived at WebCite
- ^ “No signs of Poisoning”. Sky News. 1 December 2006. http://news.sky.com/skynews/article/0,,30000-13554873,00.html. Retrieved 2006-12-02.
- ^ “‘Solemn’ burial for murdered spy”. BBC News. 7 December 2006. http://news.bbc.co.uk/2/hi/uk_news/6216202.stm. Retrieved 2006-12-08.
- ^ “Timeline: Litvinenko death case”. BBC News. 27 July 2007. http://news.bbc.co.uk/2/hi/uk_news/6179074.stm. Retrieved 2010-04-06. (Archived at WebCite)
- ^ Litvinenko, Alexander (25 November 2006). “Why I believe Putin wanted me dead…”. The Mail on Sunday. http://www.mailonsunday.co.uk/pages/live/articles/news/news.html?in_article_id=418652&in_page_id=1770. Retrieved 2010-04-06. (Archived at WebCite)
- ^ “Litvinenko murdered over damaging file on Russian business partner”. London: Daily News and Analysis. 16 December 2006. http://www.dnaindia.com/world/report_litvinenko-murdered-over-damaging-file-on-russian-business-partner_1069687. Retrieved 2010-04-06. (Archived at WebCite)
- ^ “Russian media shun poisoning case”. BBC News. 20 November 2006. http://news.bbc.co.uk/2/hi/uk_news/6165596.stm. Retrieved 2010-04-06. (Archived at WebCite)
- ^ The Litvinenko files: Berezovsky
- ^ McGrory, Daniel; Halpin, Tony (20 January 2007). “Police match image of Litvinenko’s real assassin with his death-bed description”. London: Times Online. http://www.timesonline.co.uk/article/0,,3-2556377,00.html. Retrieved 2006-01-22.
- ^ “Murder in a Teapot”. “The Blotter” on ABCNews.com. 26 January 2007. http://blogs.abcnews.com/theblotter/2007/01/it_was_in_the_t.html. Retrieved 2006-01-26.
- ^ UK wants to try Russian for Litvinenko murder The Guardian. 26 January 2007
- ^ “Russian faces Litvinenko charge”. BBC News. 22 May 2007. http://news.bbc.co.uk/1/hi/uk/6678887.stm. Retrieved 2007-05-22.
- ^ “Spy Murder Charge “Politically Motivated””. Sky News. 22 May 2007. http://news.sky.com/skynews/article/0,,30100-1266771,00.html. Retrieved 2006-05-22.
- ^ “British Prosecutors to Press Murder Charges in Litvinenko Case”. Voice of America. 22 May 2007. http://voanews.com/english/2007-05-22-voa13.cfm. Retrieved 2007-05-22. [dead link]
- ^ “UK requests Lugovoi extradition”. BBC. 28 May 2007. http://news.bbc.co.uk/1/hi/uk/6698545.stm. Retrieved 2007-05-28.
- ^ The Sunday Times, “Russia murdered Litvinenko, says top prosecutor”
- ^ Weaver, John (24 November 2006). “Mafia Hit On The Media”. Atlantic Free Press. http://www.atlanticfreepress.com/content/view/262/. Retrieved 2006-11-26.
- ^ (Russian)Alexeev, Petr (24 November 2006). “Politkovskaya, Litvinenko, who is next?”. Electorat. Info. http://www.electorat.info/oligarx/22196-1/. Retrieved 2006-11-26.
- ^ (Russian)“Who orchestrated plan to discredit Russia?”. Kommersant. 25 November 2006. http://www.kommersant.ru/doc-y.html?docId=724957&issueId=30261. Retrieved 2006-11-26.
- ^ Russian Billionaire’s Bitter Feud With Putin A Plot Line in Poisoning The Washington Post Retrieved on April 6, 2008
- ^ Hall, Ben (November 28, 2006). “Polonium 210 found at Berezovsky’s office”. MSNBC. Archived from the original on October 26, 2007. http://web.archive.org/web/20071026025104/http://msnbc.msn.com/id/15923659/. Retrieved 2006-12-01.
- ^ Hall, Ben (November 27, 2006). “Radiation traces found in Berezovsky office”. Financial Times. http://www.ft.com/cms/s/0/1b3fa168-7e59-11db-84bb-0000779e2340.html. Retrieved 2011-05-29.
- ^ Sandra Laville and Tania Branigan (November 28, 2006). “Polonium detected at Berezovsky’s office”. The Guardian. http://www.guardian.co.uk/uk/2006/nov/28/russia.politics. Retrieved 2011-05-29.
- ^ Lugovoy case unsubstantial: Russian prosecution
- ^ Send Berezovsky back and we’ll help with Litvinenko case, says Russia Times Online Retrieved on April 6, 2008
- ^ “Wrap: Lugovoi says innocent, Berezovsky behind Litvinenko murder”. Moscow: RIA Novosti. 29 August 2007. http://en.rian.ru/russia/20070829/75649246.html. Retrieved 16 March 2010. (Archived at WebCite)
- ^ Birch, Douglas (16 October 2008). “UK Envoy: Will press Russia in Litvinenko case”. Moscow: USA Today. http://www.usatoday.com/news/world/2008-10-16-1408012780_x.htm. Retrieved 16 March 2010. (Archived at WebCite)
- ^ Litvinenko coroner to examine if Russian state behind killing The Daily Telegraph13 Oct 2011
- ^ Strasbourg court sets deadline for Russia on Litvinenko case RIA Novosti15 Dec 2010
- ^ “Daybreak Pictures Commissioned To Produce Litvinenko Poisoning Drama”. All Headline News. 7 December 2006. http://www.allheadlinenews.com/articles/7005782642. Retrieved 8 December 2006.
- ^ Depp to make Litvinenko film
- ^ Depp Takes On the KGB, by Mike Bruno, Entertainment Weekly
- ^ Beeston, Richard (20 January 2007). “Film-maker fears returning to Russia”. London: Times Online. http://www.timesonline.co.uk/article/0,,13509-2556475.html. Retrieved 20 January 2007.
His books
- Alexander Litvinenko, Yuri Felshtinsky, “Blowing Up Russia: The Secret Plot to Bring Back KGB Terror” Encounter Books, New York, 2007 ISBN 978-159403-2011
- Yuri Felshtinsky, Alexander Litvinenko, and Geoffrey Andrews. Blowing up Russia: Terror from within Gibson Square Books, London, 2007, ISBN 978-1903933954
- Alexander Litvinenko: “Allegations – Selected Works by Alexander Litvinenko”, translated from Russian and edited by Pavel Stroilov, introduction by Vladimir Bukovsky, Publisher: Aquilion (12 November 2007), ISBN 978-1907997054
- A. Litvinenko and A. Goldfarb. Criminal gang from Lubyanka(Russian) GRANI, New York, 2002, ISBN 978-0-9723878-0-4
- А. Литвиненко Лубянская преступная группировка (Russian) GRANI, New York, 2002, ISBN 0-9723878-0-3
Books and Films about him
- William Dunkerley: “The Phony Litvinenko Murder: Finally the Truth after 5 Years – The Story Told by the Media Doesn’t Match the Facts”, Omnicom Press, 2011. ISBN 978-0615559018
- Alan Cowell: “The Terminal Spy: A True Story of Espionage, Betrayal and Murder”, Random House, 2008. ISBN 978-0-7393-7054-4
- Alex Goldfarb and Marina Litvinenko. “Death of a Dissident: The Poisoning of Alexander Litvinenko and the Return of the KGB.” Free Press, New York, 2007. ISBN 978-1416551652.
- Martin Sixsmith: “The Litvinenko File; the True Story of a Death Foretold”, Publisher: Macmillan (2 April 2007) ISBN 0230531547 ISBN 978-0230531543
- Andrei Nekrasov: “Rebellion: the Litvinenko Case“, 2007, Dreamscanner. Banned in Russia. Official site: http://www.dreamscanner-productions.com/litvinenko/index.html
External links
The CIA reports – Office of Scientific Intelligence: The Original Wizards of Langley

The emergence of the Cold War accelerated the development of ever
more technically advanced weapons and generated early recognition of
the need for additional technical intelligence. For U.S. policymakers this
meant obtaining data on Soviet weapons developments and operational
concepts, identifying important new systems and, most important, developing the technical means for collecting and processing such data.
Document List
Aging Communist Leaders
An Interview with Former DDS&T Albert Wheelon
And the Truth Shall Keep You Free: Recollections by the First Deputy Director for Science and Technology
Memorandum for Special Assistant, Intelligence, Dept. of State from Loftus Becker
The Problem of Scientific and Technical Intelligence
Briefing Note on Advance Portion of NIE 11-5-59 – Soviet Capabilities in Guided Missiles and Space Vehicles
The Case Of The SS-6
General Order Number 13
Identifying The Future Threat
Intelligence Implications Of Disease
LONG-RANGE CAPABILITIES OF THE SOVIET UNION IN MAJOR SCIENTIFIC FIELDS – 1957-67
Long Range Soviet Scientific Capabilities 1962-70
LONG-RANGE CAPABILITIES OF THE SOVIET UNION 1962-72
LONG-RANGE CAPABILITIES OF THE SOVIET UNION IN MAJOR SCIENTIFIC FIELDS 1957-67
LONG-RANGE CAPABILITIES OF THE SOVIET UNION IN MAJOR SCIENTIFIC FIELDS 1957-67
MILITARY MEDICAL INSTALLATION IN THE SOVIET ZONE OF GERMANY AS OF MARCH 1952
THE SOVIET SPACE RESEARCH PROGRAM MONOGRAPH II (part 1)
THE SOVIET SPACE RESEARCH PROGRAM MONOGRAPH II (part 2)
THE SOVIET SPACE RESEARCH PROGRAM MONOGRAPH III – ORGANIZATION, PLANNING, AND CONTROL (Part 1)
THE SOVIET SPACE RESEARCH PROGRAM MONOGRAPH III – ORGANIZATION, PLANNING, AND CONTROL (Part 2)
THE SOVIET SPACE RESEARCH PROGRAM MONOGRAPH IV – SPACE VEHICLES
THE SOVIET SPACE RESEARCH PROGRAM MONOGRAPH V – PROPULSION SYSTEMS
THE SOVIET SPACE RESEARCH PROGRAM MONOGRAPH VI – GUIDANCE AND CONTROL
THE SOVIET SPACE RESEARCH PROGRAM MONOGRAPH IX – SPACE MEDICINE
THE SOVIET SPACE RESEARCH PROGRAM MONOGRAPH X – SPACE BIOLOGY AND ASTROBIOLOGY
THE SOVIET SPACE RESEARCH PROGRAM MONOGRAPH XI – ASTRONOMICAL ASPECTS
The Problem of Scientific and Technical Intelligence
NIE NUMBER 11-12-55 (Supplement, NIE 11-6-54): SOVIET GUIDED MISSILE CAPABILITIES AND PROBABLE PROGRAMS
NIE 11-3-65: Soviet Strategic Air and Missile Defenses
NATIONAL INTELLIGENCE ESTIMATE SUMMARY – THE SOVIET ATOMIC ENERGY PROGRAM TO MID-1957
NIE NUMBER 11-5-59: SOVIET CAPABILITIES IN GUIDED MISSILES AND SPACE VEHICLES
NIE NUMBER 11-56 – SOVIET GROSS CAPABILITIES FOR ATTACK ON THE US AND KEY OVERSEAS INSTALLATIONS AND FORCES THROUGH MID 1959
SOVIET CAPABILITIES AND PROBABLE PROGRAMS IN THE GUIDED MISSILE FIELD
NIE NUMBER 11-6-59: SOVIET SCIENCE AND TECHNOLOGY
NIE NUMBER 11-8-61: SOVIET CAPABILITIES FOR LONG RANGE ATTACK
NIE NUMBER 11-8-64: Soviet Capabilities for Strategic Attack
NIE 18: THE PROBABILITY OF SOVIET EMPLOYMENT OF BW AND CW IN THE EVENT OF ATTACKS UPON THE US
NIE 65: SOVIET BLOC CAPABILITIES THROUGH 1957
On The Accuracy Of National Intelligence Estimates
The Directorate of Science and Technology Historical Series: The Office of Scientific Intelligence 1949-68 (Vol. 1)
The Directorate of Science and Technology Historical Series: The Office of Scientific Intelligence 1949-68 (Vol. 2)
The Directorate of Science and Technology Historical Series: The Office of Scientific Intelligence 1949-68 (Vol. 3)
OSI Survey Report
Policing a Nuclear Test Ban
Possible Soviet Moves to Exploit the Present Situation
SCIENCE AND TECHNOLOGY: ORIGINS OF A DIRECTORATE
Scientific And Technical Intelligence Analysis
NIE Number 11-10-57: The Soviet ICBM Program
NIE Number 11-3-67: Soviet Strategic Air and Missile Defenses
Stealth, Countermeasures, and ELINT, 1960-1975
The Case For A Holistic Intelligence
The Enigma Of Soviet BW
The French Nuclear Weapons Program
THE SCIENTIFIC AND CULTURAL EXCHANGE
THE SOVIET BIOASTRONAUTICS RESEARCH PROGRAM
The YO-YO Story: An Electronics Analysis Case History
Validity Study of NIE 11-6-54, Soviet Capabilities and Probable Programs in the Guided Missile Field
Winnowing Wheat From Chaff
DOWNLOAD ORIGINAL DOCUMENTS HERE
CONFIDENTIAL from the FBI – Crime Superstore
 |
|---|
Closing a ‘Crime Superstore’
Not-So Garden Variety Fraud in the Garden State
They hijacked identities on the other side of the globe…faked drivers’ licenses and other documents…built bogus credit histories and boosted the scores in clever ways…then used it all to open bank accounts and credit lines they could loot at will.
In the end, they created what our Newark Special Agent in Charge Mike Ward called a ‘crime superstore,’ a sophisticated way to rob financial institutions, retailers, car leasing companies, and even the IRS out of millions of dollars.
Following an undercover investigation led by the FBI and its partners, it all came crashing down in September 2010, when 43 members of the criminal ring were charged in this complex scheme. Another 10 individuals were charged for various related offenses at the same time during a coordinated takedown. And on Monday, the leader of the band of thieves—San-Hyun Park, known to his criminal colleagues as “Jimmy”—pled guilty in federal court in Newark.
The Park criminal enterprise started by stealing Social Security numbers from unsuspecting individuals—usually from China—who were employed in American territories in Asia like Saipan, Guam, and the Philippines. They then sold these identities to its customers in the U.S. for $5,000 to $7,000. Although the stolen identities were Chinese, the vast majority of Park’s customers were Korean-Americans. The ring would use the phony Social Security numbers to obtain authentic driver’s licenses, identification cards, and other identity documents from various states…or manufacture counterfeit licenses and other documentation.
Based in Bergen County, New Jersey, Park’s organization was subdivided into different cells, each with a unique role. First, there were the customers who paid Park and his co-conspirators for fake identity documents. Then, there were the brokers, suppliers, and manufacturers of the phony identity documents—like Social Security cards, immigration documents, and driver’s licenses. A third group included merchants who colluded with the organization by knowingly swiping phony credit cards in return for a fee called a “kkang.” The credit card buildup teams made up the fourth group, fraudulently inflating credit scores to help open the bank and credit accounts.
The buildup teams would take one of the stolen Social Security numbers—and the Chinese identity attached to it—and add that person’s name as an authorized user to other co-conspirators’ credit card accounts. These co-conspirators, who knew their accounts were being used to commit fraud, received a fee for their service.
After the credit buildup was completed, the Park criminal enterprise conspired with its customers to use the fraudulent identities to apply for checking accounts, bank and retail credit cards, debit cards, lines of credit, and loans. Members of the criminal conspiracy used their sizeable proceeds to live large, buying such luxury items as fancy cars, expensive liquor, and designer shoes.
The multi-agency investigation made use of cooperating witnesses and an undercover federal agent, as well as court-authorized wiretaps, to record incriminating conversations among members of the crime ring and others. The FBI partnered with several federal agencies and local police departments in New Jersey, among others. We also worked cooperatively with the major banks, credit card companies, and department stores targeted by this criminal organization.
Uncensored – Topless protest by Femen Kiev Ukraine electrions
TOP-SECRET – (U//FOUO) U.S. Air Force Evolution of Drone Ground Control Stations Presentation
Unveiled – Japanese Internment Camps War Relocation Authority Photos
The following photos are from a collection housed at Bancroft Library at the University of California at Berkeley. The photos span from 1942-1945 at various internment camps around the U.S. operated by the War Relocation Authority.
 Overlooking the Amache Relocation Center, near Granada, Colorado. In the foreground is a typical barracks unit consisting of 12 six room apartment barracks buildings, a recreation hall, laundry and bathrooms, and the mess hall. — Photographer: Parker, Tom — Amache, Colorado. 12/9/42
Overlooking the Amache Relocation Center, near Granada, Colorado. In the foreground is a typical barracks unit consisting of 12 six room apartment barracks buildings, a recreation hall, laundry and bathrooms, and the mess hall. — Photographer: Parker, Tom — Amache, Colorado. 12/9/42
 Manzanar, Calif.–Street scene looking east toward the Inyo Mountains at this War Relocation Authority center. The children are coming to their barrack homes from play school. Each family has one room to live in in these barracks. There is no running water in the barracks so all the families in one block use a central bath house. The barracks are heated by wood burning stoves. — Photographer: Lange, Dorothea — Manzanar, California. 6/29/42
Manzanar, Calif.–Street scene looking east toward the Inyo Mountains at this War Relocation Authority center. The children are coming to their barrack homes from play school. Each family has one room to live in in these barracks. There is no running water in the barracks so all the families in one block use a central bath house. The barracks are heated by wood burning stoves. — Photographer: Lange, Dorothea — Manzanar, California. 6/29/42
 Aerial view of Colorado River Relocation Center for persons of Japanese ancestry evacuated from the West Coast. — Photographer: Clark, Fred — Poston, Arizona. 5/25/42
Aerial view of Colorado River Relocation Center for persons of Japanese ancestry evacuated from the West Coast. — Photographer: Clark, Fred — Poston, Arizona. 5/25/42
 A typical barracks with a section of the Topaz Relocation Center. — Photographer: Parker, Tom — Topaz, Utah. 10/18/42
A typical barracks with a section of the Topaz Relocation Center. — Photographer: Parker, Tom — Topaz, Utah. 10/18/42
 This assembly center has been open for two days. Bus-load after bus-load of evacuated persons of Japanese ancestry are arriving this day. After going through the necessary procedure for registration, they are guided to the quarters assigned to them in the barracks. Only one mess hall was operating on this day. Photograph shows line-up of newly arrived evacuees outside the mess hall at noon. Note barracks in background, newly built, in which family units are housed. There are three types of quarters in this assembly center, of which this is one. The wide road which runs diagonally across is the former race track. Industrial South San Francisco is shown in the background. — Photographer: Lange, Dorothea — San Bruno, California. 4/29/42
This assembly center has been open for two days. Bus-load after bus-load of evacuated persons of Japanese ancestry are arriving this day. After going through the necessary procedure for registration, they are guided to the quarters assigned to them in the barracks. Only one mess hall was operating on this day. Photograph shows line-up of newly arrived evacuees outside the mess hall at noon. Note barracks in background, newly built, in which family units are housed. There are three types of quarters in this assembly center, of which this is one. The wide road which runs diagonally across is the former race track. Industrial South San Francisco is shown in the background. — Photographer: Lange, Dorothea — San Bruno, California. 4/29/42
 Turlock, Calif.–Evacuees of Japanese ancestry waiting their turn for baggage inspection for contraband, upon arrival at this Assembly point. They will then be assigned places in the barracks until transferred to a War Relocation Authority Center to spend the duration. — Photographer: Lange, Dorothea — Turlock, California. 5/2/42
Turlock, Calif.–Evacuees of Japanese ancestry waiting their turn for baggage inspection for contraband, upon arrival at this Assembly point. They will then be assigned places in the barracks until transferred to a War Relocation Authority Center to spend the duration. — Photographer: Lange, Dorothea — Turlock, California. 5/2/42
 A typical interior scene in one of the barrack apartments at this center. Note the cloth partition which lends a small amount of privacy. — Photographer: Lange, Dorothea — Manzanar, California. 6/30/42
A typical interior scene in one of the barrack apartments at this center. Note the cloth partition which lends a small amount of privacy. — Photographer: Lange, Dorothea — Manzanar, California. 6/30/42
 A few pieces of scrap and some additional mail order lumber, and the ingenuity of skilled hands, have converted a bare barracks room into a home of some comfort. Many residents, such as the young Nisei family shown, have through their own ingenuity, bettered their living conditions within the center. — Photographer: Parker, Tom — Heart Mountain, Wyoming. 1/7/43
A few pieces of scrap and some additional mail order lumber, and the ingenuity of skilled hands, have converted a bare barracks room into a home of some comfort. Many residents, such as the young Nisei family shown, have through their own ingenuity, bettered their living conditions within the center. — Photographer: Parker, Tom — Heart Mountain, Wyoming. 1/7/43
 Noon on a hot day at the Stockton Assembly Center, which is a converted fairgrounds. This group of people on the race track are new arrivals who have been registered inspected, medically examined, and are now on their way to their assigned places in the barracks. — Photographer: Lange, Dorothea — Stockton, California. 5/19/42
Noon on a hot day at the Stockton Assembly Center, which is a converted fairgrounds. This group of people on the race track are new arrivals who have been registered inspected, medically examined, and are now on their way to their assigned places in the barracks. — Photographer: Lange, Dorothea — Stockton, California. 5/19/42
 Manzanar, Calif.–Street scene of barrack homes at this War Relocation Authority center for evacuees of Japanese ancestry. — Photographer: Lange, Dorothea — Manzanar, California. 6/29/42
Manzanar, Calif.–Street scene of barrack homes at this War Relocation Authority center for evacuees of Japanese ancestry. — Photographer: Lange, Dorothea — Manzanar, California. 6/29/42
 Manzanar, Calif.–Looking west from Mess Hall No. 1. The small square buildings in the center rows of barracks are the laundry and sanitary units. Evacuees of Japanese ancestry are spending the duration in War Relocation Authority centers. — Photographer: Lange, Dorothea — Manzanar, California. 7/2/42
Manzanar, Calif.–Looking west from Mess Hall No. 1. The small square buildings in the center rows of barracks are the laundry and sanitary units. Evacuees of Japanese ancestry are spending the duration in War Relocation Authority centers. — Photographer: Lange, Dorothea — Manzanar, California. 7/2/42
 Tanforan Assembly Center, San Bruno, Calif.–An art school has been established at this Assembly Center with a well trained, experienced evacuee staff under the leadership of Prof. Chiura Obata, who before evacuation was associate professor of art at the University of California. This photograph shows part of the morning class learning free hand brush strokes. — Photographer: Lange, Dorothea — San Bruno, California. 6/16/42
Tanforan Assembly Center, San Bruno, Calif.–An art school has been established at this Assembly Center with a well trained, experienced evacuee staff under the leadership of Prof. Chiura Obata, who before evacuation was associate professor of art at the University of California. This photograph shows part of the morning class learning free hand brush strokes. — Photographer: Lange, Dorothea — San Bruno, California. 6/16/42
 Aliens at Sharp Camp following the evacuation order for persons of Japanese ancestry. This camp was set up as detention station where suspects were held before given hearings. They remained here only a short while, being sent to an internment camp or a relocation center following the hearings. — Photographer: Albers, Clem — Sharp Park, California. 3/30/42
Aliens at Sharp Camp following the evacuation order for persons of Japanese ancestry. This camp was set up as detention station where suspects were held before given hearings. They remained here only a short while, being sent to an internment camp or a relocation center following the hearings. — Photographer: Albers, Clem — Sharp Park, California. 3/30/42
 Part of view of Butte camp looking towards block 59-72-74 and hospital in far distance. — Rivers, Arizona. 12/14/43
Part of view of Butte camp looking towards block 59-72-74 and hospital in far distance. — Rivers, Arizona. 12/14/43
 Looking down the rows of barracks westward from block (illegible). At extreme left is a corner of the dining hall where 275 to 300 residents of the block eat. At center background is the sanitation building including showers, lavatories, toilets, and washtubs. Nearly all the residents planted flowers and vegetable gardens in front of their barracks. — Hunt, Idaho. 8/?/43
Looking down the rows of barracks westward from block (illegible). At extreme left is a corner of the dining hall where 275 to 300 residents of the block eat. At center background is the sanitation building including showers, lavatories, toilets, and washtubs. Nearly all the residents planted flowers and vegetable gardens in front of their barracks. — Hunt, Idaho. 8/?/43
 Oakland, Calif. (1117 Oak Street)–Residents of Japanese ancestry waiting for evacuation buses which will take them to the Tanforan Assembly Center under Civilian Exclusion Order No. 28. — Photographer: Lange, Dorothea — Oakland, California. 5/6/42
Oakland, Calif. (1117 Oak Street)–Residents of Japanese ancestry waiting for evacuation buses which will take them to the Tanforan Assembly Center under Civilian Exclusion Order No. 28. — Photographer: Lange, Dorothea — Oakland, California. 5/6/42
 Civilian Exclusion Order No. 5, ordering evacuation of residents of Japanese ancestry, posted in a vacant store window on Grant Avenue in Chinatown. This establishment, like many others in Chinatown, was operated by proprietors of Japanese descent. Evacuees will be housed in War Relocation Authority centers for the duration. — Photographer: Lange, Dorothea — San Francisco, California. 4/4/42
Civilian Exclusion Order No. 5, ordering evacuation of residents of Japanese ancestry, posted in a vacant store window on Grant Avenue in Chinatown. This establishment, like many others in Chinatown, was operated by proprietors of Japanese descent. Evacuees will be housed in War Relocation Authority centers for the duration. — Photographer: Lange, Dorothea — San Francisco, California. 4/4/42
 Following evacuation orders, this store, at 13th and Franklin Streets, was closed. The owner, a University of California graduate of Japanese descent, placed the I AM AN AMERICAN sign on the store front on December 8, the day after Pearl Harbor. Evacuees of Japanese ancestry will be housed in War Relocation Authority centers for the duration. — Photographer: Lange, Dorothea — Oakland, California. 3/13/42
Following evacuation orders, this store, at 13th and Franklin Streets, was closed. The owner, a University of California graduate of Japanese descent, placed the I AM AN AMERICAN sign on the store front on December 8, the day after Pearl Harbor. Evacuees of Japanese ancestry will be housed in War Relocation Authority centers for the duration. — Photographer: Lange, Dorothea — Oakland, California. 3/13/42
 Waiting in line, 2031 Bush St., for voluntary inoculation against typhoid, preceding evacuation of residents of Japanese ancestry. Evacuees will be housed in War Relocation Authority centers for the duration. — Photographer: Lange, Dorothea — San Francisco, California. 4/20/42
Waiting in line, 2031 Bush St., for voluntary inoculation against typhoid, preceding evacuation of residents of Japanese ancestry. Evacuees will be housed in War Relocation Authority centers for the duration. — Photographer: Lange, Dorothea — San Francisco, California. 4/20/42
 Supper time! Meal times are the big events of the day within an assembly center. This is a line-up of evacuees waiting for the B shift at 5:45 P.M. They carry with them their own dishes and cutlery in bags to protect them from the dust. They, themselves, individually wash their own dishes after each meal, since dish washing facilities in the mess halls prove inadequate. Most of the residents prefer this second shift because they sometimes get second helpings, but the groups are rotated each week. There are eighteen mess halls in camp which, together, accommodate 8,000 persons three times each day. All food is prepared and served by evacuees. — Photographer: Lange, Dorothea — San Bruno, California. 6/16/42
Supper time! Meal times are the big events of the day within an assembly center. This is a line-up of evacuees waiting for the B shift at 5:45 P.M. They carry with them their own dishes and cutlery in bags to protect them from the dust. They, themselves, individually wash their own dishes after each meal, since dish washing facilities in the mess halls prove inadequate. Most of the residents prefer this second shift because they sometimes get second helpings, but the groups are rotated each week. There are eighteen mess halls in camp which, together, accommodate 8,000 persons three times each day. All food is prepared and served by evacuees. — Photographer: Lange, Dorothea — San Bruno, California. 6/16/42
 Evacuee in her hobby garden which rates highest of all the garden plots at this War Relocation Authority Center. Vegetables for their own use are grown in plots 10 X 50 feet between rows of barracks. — Photographer: Lange, Dorothea — Manzanar, California. 7/2/42
Evacuee in her hobby garden which rates highest of all the garden plots at this War Relocation Authority Center. Vegetables for their own use are grown in plots 10 X 50 feet between rows of barracks. — Photographer: Lange, Dorothea — Manzanar, California. 7/2/42
 A panorama view of the Central Utah Relocation Center, taken from the water tower. — Photographer: Stewart, Francis — Topaz, Utah. 3/14/43
A panorama view of the Central Utah Relocation Center, taken from the water tower. — Photographer: Stewart, Francis — Topaz, Utah. 3/14/43
 Eden, Idaho–A panorama view of the Minidoka War Relocation Authority center. This view, taken from the top of the water tower at the east end of the center, shows partially completed barracks. — Photographer: Stewart, Francis — Hunt, Idaho. 8/18/42
Eden, Idaho–A panorama view of the Minidoka War Relocation Authority center. This view, taken from the top of the water tower at the east end of the center, shows partially completed barracks. — Photographer: Stewart, Francis — Hunt, Idaho. 8/18/42
 S/Sgt. Tatsumi Iwate, a Japanese American Infantryman, who bears a piece of Nazi shrapnel an inch deep in his brain despite two operations to remove it, is on furlough at the farm of his uncle, Tashikaza Wada, Rt. 1, Gill, Colorado, from Hammond General Hospital, Modesto, California, until September 17. He was wounded in France last October during the rescue of the Texas Lost Battalion by the Japanese American 442nd Combat Team. Formerly of Lomita, California, Sgt. Iwate, 28, entered service in February, 1942, a month before evacuation of Japanese Americans from the West Coast. Sgt. Iwate is keenly disappointed in his friend, 19-year-old Seiichi, now in a Justice Department Internment Camp after renouncing his American citizenship, and who has lost faith in his country. He wrote him a letter, which was made public by WRA, in which he expressed his surprise and disappointment in his actions and said I am an American to the last drop of my blood, and being a person of Japanese descent, I am aware of discrimination that is practiced by people who dare not see farther than the color of our skin, but I will continue to fight the enemy of my country be it foreign or domestic. Ready for either duty or discharge after 7 months of hospitalization, he says, I may be washed up as an Infantryman, but I’m still willing to tackle any assignment if they decide to keep me in the Army. — Photographer: Mace, Charles E. — Gill, Colorado. 7/14/45
S/Sgt. Tatsumi Iwate, a Japanese American Infantryman, who bears a piece of Nazi shrapnel an inch deep in his brain despite two operations to remove it, is on furlough at the farm of his uncle, Tashikaza Wada, Rt. 1, Gill, Colorado, from Hammond General Hospital, Modesto, California, until September 17. He was wounded in France last October during the rescue of the Texas Lost Battalion by the Japanese American 442nd Combat Team. Formerly of Lomita, California, Sgt. Iwate, 28, entered service in February, 1942, a month before evacuation of Japanese Americans from the West Coast. Sgt. Iwate is keenly disappointed in his friend, 19-year-old Seiichi, now in a Justice Department Internment Camp after renouncing his American citizenship, and who has lost faith in his country. He wrote him a letter, which was made public by WRA, in which he expressed his surprise and disappointment in his actions and said I am an American to the last drop of my blood, and being a person of Japanese descent, I am aware of discrimination that is practiced by people who dare not see farther than the color of our skin, but I will continue to fight the enemy of my country be it foreign or domestic. Ready for either duty or discharge after 7 months of hospitalization, he says, I may be washed up as an Infantryman, but I’m still willing to tackle any assignment if they decide to keep me in the Army. — Photographer: Mace, Charles E. — Gill, Colorado. 7/14/45
Report – NSA/CSS Unveils New Hawaii Center

The National Security Agency/Central Security Service marked today the completion of a new regional operations center, officially named the CAPT Joseph J. Rochefort Building, at a ribbon-cutting ceremony where officials emphasized how the $358 million project will help to further integrate national security efforts.
NSA/CSS has had an operations center in Hawaii for more than 14 years. But even with recent renovations, the original facility, first built during World War II, has limitations stemming from its age, location, and structures. The new building will provide cryptology professionals with the tools necessary to better access and collaboratively interpret data from a broad variety of sources at various classification levels. Moreover, its enhanced capabilities will augment work that will still be carried out in the original center – eliminating physical, virtual, and other barriers to information sharing.
GEN Keith B. Alexander – Director, NSA/Chief, CSS/Commander, U.S. Cyber Command – told approximately 300 federal, state, and local officials at the ceremony that it was more than fitting to dedicate the new building in honor of CAPT Rochefort, who died in 1976. Several members of his family were also on hand. Rochefort was posthumously recognized with the Presidential Medal of Freedom in 1986 and in the NSA/CSS Hall of Honor in 2000 for leading a distinguished team of Pearl Harbor-based code breakers. Their daily intelligence reports were crucial in the 1942 Battle of Midway.
“CAPT Rochefort’s exceptional skills in cryptology and in mathematical analysis made him a unique national asset at an extremely trying time in U.S. history,” GEN Alexander said in an interview after the ceremony. “Likewise, the mission of NSA/CSS Hawaii is to produce foreign signals intelligence for decision-makers as global terrorism now jeopardizes the lives of our citizens, military forces, and international allies. We must continue to develop a global cryptologic enterprise that is agile and resilient in countering ever-changing threats to national security.”
CAPT Kathryn Helms – Commander, NSA/CSS Hawaii – agreed. “The design, infrastructure, and capabilities of this new center will allow us to continue to provide unparalleled cryptologic support,” she said after the event. State officials described the project as one that was good for both the nation and Hawaii.
The original center is adjacent to Schofield U.S. Army Barracks. The new center is a part of the Joint Base Pearl Harbor Hickam Annex. A groundbreaking ceremony was held in 2007.
NSA/CSS is also upgrading its cryptologic centers in Texas and Georgia to make the agency’s global enterprise even more seamless as it confronts increasingly networked adversaries.
TOP-SECRET from the FBI – Florida Resident Charged with Plotting to Bomb Locations in Tampa
TAMPA, FL—A 25-year-old resident of Pinellas Park, Fla., has been charged in connection with an alleged plot to attack locations in Tampa with a vehicle bomb, assault rifle, and other explosives, announced Robert E. O’Neill, U.S. Attorney for the Middle District of Florida; Lisa Monaco, Assistant Attorney General for National Security; and Steven E. Ibison, Special Agent in Charge of the FBI Tampa Division.
Sami Osmakac, a naturalized U.S. citizen who was born in the former Yugoslavia (Kosovo), was arrested Saturday night. He is charged in a criminal complaint in the Middle District of Florida with one count of attempted use of a weapon of mass destruction (explosives) and is scheduled to make his initial appearance today at 2:00 p.m. EST, in federal court, before U.S. Magistrate Judge Anthony Porcelli, in Tampa. If convicted, Osmakac faces a maximum sentence of life in prison and a $250,000 fine.
The arrest of Osmakac was the culmination of an undercover operation during which Osmakac was closely monitored by law enforcement officials for several months. The explosives and firearms that he allegedly sought and attempted to use were rendered inoperable by law enforcement and posed no threat to the public.
“The perseverance and diligence of law enforcement caused this investigation to conclude in a successful manner,” said U.S. Attorney O’Neill. “I would like to commend them for their hard work. This investigation was also predicated, in part, by assistance from the Muslim community. I would like to thank them as well.”
“The facts as alleged in this case underscore the need for continued vigilance both at home and abroad. Thanks to a coordinated law enforcement effort, this alleged plot was thwarted before anyone was harmed,” said Assistant Attorney General Monaco. “I applaud the many agents, analysts and prosecutors who worked together to ensure this matter was resolved safely.”
“The Tampa FBI Division has always considered its relationships with regional community groups throughout Central and Southwest Florida extremely important. In this case, we are grateful for the Muslim community’s continued support. This incident clearly demonstrated how citizens can help law enforcement keep our neighborhoods and our nation safe,” said FBI Special Agent in Charge Steven Ibison.
According to the complaint affidavit, in Sept. 2011, the FBI received information from a confidential human source (CHS) indicating that Osmakac had asked for al Qaeda flags. In November 2011, Osmakac and the CHS discussed and identified potential targets, in Tampa, where Osmakac intended on carrying out violent attacks. Osmakac allegedly asked the CHS for help in obtaining firearms and explosives for the attacks. The CHS indicated that he/she knew someone who might be able to provide firearms and explosives and introduced Osmakac to an undercover FBI employee.
The complaint alleges that Osmakac met with the undercover FBI employee, in person, on Dec. 21, 2011, and stated that he wished to acquire an AK-47-style machine gun, Uzi submachine guns, high capacity magazines, grenades and an explosive belt. In a subsequent meeting, Osmakac allegedly provided the undercover FBI employee with a $500 down payment for an AK-47, multiple homemade explosive grenades and the explosive belt.
According to the complaint, Osmakac also asked the undercover employee whether he/she could build bombs that could be placed in three different vehicles and detonated remotely, near where Osmakac would conduct a follow-up attack using the other weapons he requested. The undercover employee said he/she could possibly provide explosives for one vehicle. Osmakac also allegedly said that he wanted an explosive belt constructed to kill people.
During a subsequent meeting with the FBI undercover employee on Jan. 1, 2012, Osmakac allegedly described his attack plans by stating that he wanted to obtain a hotel room; park the vehicle with the bomb in it at his target; leave the area; detonate the car bomb; and then retrieve the weapons and explosives from the hotel room. Among Osmakac’s alleged bomb targets were night clubs in the Ybor City area of Tampa, the operations center of the Hillsborough County Sheriff’s Office in Ybor City and a business in the South Tampa area of Tampa.
The complaint alleges that, as part of the second portion of his planned attack, Osmakac told the undercover FBI employee that, after the car bomb was detonated, he wanted to use the explosive belt to “get in somewhere where there’s a lot of people” and take hostages. He allegedly stated that he would then make demands of the FBI to release some prisoners. According to the criminal complaint, when discussing law enforcement officers that might respond to the scene, Osmakac allegedly stated, “once I have this . . . they can take me in five million pieces” in an apparent reference to the explosive belt that would be attached to his waist.
During the Jan. 1st meeting, the undercover FBI employee noted that Osmakac could change his mind and back out of the plot. According to the complaint, Osmakac immediately shook his head in the negative and stated, “We all have to die, so why not die the Islamic way?”
On Jan. 7, 2012, FBI agents arrested Osmakac after he took possession of the explosive devices and firearms that had been rendered inoperable by law enforcement. The complaint alleges that, shortly prior to his arrest, Osmakac made a video of himself explaining his motives for carrying out the planned violent attack.
This investigation is being conducted by the FBI Tampa Division and the Tampa Joint Terrorism Task Force. It is being prosecuted by Assistant U.S. Attorney Sara Sweeney from the U.S. Attorney’s Office for the Middle District of Florida, with assistance from Trial Attorney Clem McGovern of the Counterterrorism Section in the Department of Justice’s National Security Division.
The charges contained in the criminal complaint are mere allegations. As in any criminal case, the defendant is presumed innocent until proven guilty in a court of law.
CONFIDENIAL – (U//FOUO) U.S. Marine Corps Afghanistan Operational Culture for Deploying Personnel

When studying terrain, if you use a pair of binoculars, a set of night vision goggles, and infrared equipment, you see three different images. Which one is correct? All three, of course. Which one do you use? Same answer: all three. You combine them to understand the ground. The same is true of studying the cultural, or “human,” terrain. You can look at “human terrain” through different “lenses,” too. For example, we can study ethnic groups, or language, or religion, or social values. We might describe the different perspectives seen through these different lenses briefly as follows:
- Ethnicity: “People do what they do because of their particular ethnic group or tribe.”
- Religion: “People do what they do because of their religious beliefs.”
- Social Values: “People do what they do because it’s their culture to do it that way.”
Which one is correct? Again, all three are valid, but — just like studying a real piece of ground — there’s no easy “single answer.” You must combine the information. Understanding the cultural situation is a little like understanding how a play is developing in a football game. It’s a dynamic situation, and there are a lot of moving parts – – you need to understand what each of the position players will do in the situation, and how well they’ll do it, to know where the ball is going. It’s not easy, but it’s not rocket science either. Just like you can study the opponent’s game videos and stats, you can study the culture and be mentally prepared for every new situation.
Afghans aren’t mysterious, inscrutable people you can’t understand. They’re human beings, just like you. Study their culture and their language: It could mean the difference between success and failure, and it could save your life or that of other Marines around you.
…
A Classic Case of “Blowback”
In certain parts of the US government, when an operation has unintended negative second or third-order consequences, they are called “blowback.” The radical Islamic movements in the Pashtun areas today were always present, but putting them on steroids in the 1980′s was pretty short-sighted by any reasonable accounting — a classic case of “blowback.” During the Soviet-Afghan war, the Pakistanis had their own agenda. The Pakistani Army’s intelligence branch, called the Inter-Services Intelligence Directorate, or ISI, became extremely powerful by cooperating with the United States and the government of Saudi Arabia to channel roughly $7.2 billion dollars worth of covert foreign military aid to their preferred Mujahideen clients. To control the Mujahideen, the ISI formed seven resistance groups, each with a notional political party associated with it. These became known as “the Peshawar Seven.” CIA oversight of the covert money was weak, and much of it went into ISI’s pockets.
The ISI wanted puppets they could control when the war was over. The Durrani Pashtun tribes which traditionally supplied most of Afghan’s national leadership and all of its royalty where anathema to the Pakistanis — they would never cooperate in setting up a government which owed allegiance to Islamabad. So they were marginalized, and their traditional rivals, the Ghilzais and the Hill Tribes, were favored. Significantly, three of the seven recognized groups were led by Ghilzai Pashtun tribal leaders. None was led by a Durrani Pashtun.
For the CIA, the object of the war was to bleed the Soviets — payback for the Vietnam War and Soviet support to the North Vietnamese (Steve Coll). Afghanistan was thought of as “the Soviet Vietnam.” The CIA was happy to steer money towards whichever groups fooled them into believing they were killing the most Russian troops. The undisputed champ of faking battles and Soviet kills was Gulbuddin Hekmatyar of the HiG organization, which in reality spent most of the war assassinating other Afghan Mujahideen commanders and stockpiling arms and money, positioning itself for the inevitable postwar power struggle. (So effective was HiG in killing other Mujahideen leaders from other parties that it was rumored Hekmatyar must be working for the Soviets!) Some Afghans at the time said this was a bad idea, including the exiled Afghan King, Zahir Shah, and Hamid Karzai (then a U.S. contact in Peshawar). The U.S. State Department also argued for giving the money and weapons to more moderate or nationalist groups in the Peshawar Seven, like Ahmed Shah Massoud’s Jamiat-i-Islami movement, or the royalist NIFA party, as this would be better for the country, and warned the CIA that arming, funding and equipping radical anti-western extremists and terrorists who hated the United States would backfire. This advice was ignored. As a result, the religious extremists among the Ghilzais and the hill tribes around Jallaludin Haqqani became very wealthy and powerful.
Because the majority of enemy commanders in Afghanistan today are Mullahs who learned their business as Mujahideen in the Soviet-Afghan War, it is not surprising that the tactics of the almost-exclusively Pashtun Taliban today are similar to those of the Mujahideen against the Soviets. Mujahideen combat tactics were studied and recorded in detail by Lester Grau in two well-known books.
DOWNLOAD ORIGINAL DOCUMENT HERE
TOP-SECRET – Max Planck Institute Brandenburg License Plate Scanning, Access to Telecommunications Data and Mobile Phone Localization Study

Recht und Praxis der anlassbezogenen automatischen Kennzeichenfahndung, Verkehrsdatenabfrage und Mobilfunkortung zur Gefahrenabwehr in Brandenburg
Max Planck Institute Brandenburg License Plate Scanning, Access to Telecommunications Data and Mobile Phone Localization Study
The following report and presentation were compiled by researchers at the Max Planck Institute for Foreign and International Criminal Law, a quasi-governmental research institution funded by the German government, regarding controversial police powers in the German state of Brandenburg including automated license plate searches, mobile phone localization and access to telecommunications data.
Recht und Praxis der anlassbezogenen automatischen Kennzeichenfahndung, Verkehrsdatenabfrage und Mobilfunkortung zur Gefahrenabwehr in Brandenburg
Law and practise of automatic number plate scanning, access to telecommunications data and mobile phone localization in the German state of Brandenburg
DOWNLOAD ORIGINAL DOCUMENT HERE
Verkehrsdatenabfrage, Mobilfunkortung, Kennzeichenfahndung
Telecommunications Data Records, Mobile Phone Localization, License Plate Scanning
DOWNLOAD ORIGINAL DOCUMENT HERE
Media – DHS Project Shield Program Completely Wasted $45 Million in Illinois
Project Shield was supposed to make citizens safer. But in the end, the $45-million Homeland Security program more resembled a disaster, wasting taxpayers’ dollars and failing to make a single citizen more secure.
The failed Cook County initiative was replete with equipment that failed to work, missing records and untrained first responders according to a report by the inspector general of the U.S. Department of Homeland Security.
The report, to be released Monday but obtained by The Sun-Times and NBC5 News, found “millions of tax dollars may have been wasted.”
Under Project Shield, two police squad cars in all 128 Cook County suburbs were to be fitted with cameras capable of feeding live video to a central command. In addition, fixed mounted cameras were to be installed to feed pictures in case of a terrorist attack or emergency in Cook County.
A six-month investigation by the IG found “equipment was not working, was removed, or could not be properly operated.”
Investigators visited 15 municipalities between January and June last year and found “missing records, improper procurement practices, unallowable costs and unaccountable inventory items.”
Project Shield was intended to be a sophisticated system of video cameras in squad cars and key spots around the suburbs. It was to help with homeland security — transmitting live footage to police during emergency situations. The program was run by Cook County under former Board Presidents John Stroger and Todd Stroger.
But a new report out Monday by the U.S. Inspector General shows Project Shield was a mismanaged mess. Camera equipment didn’t get delivered, and even when it did, it oftentimes didn’t even work. The cameras and related equipment for police cars were revealed to pose safety risks, too, as they were installed in front of airbags — making the technology a potential projectile.
The $45 million dollars funding the program came from FEMA. In a news conference Monday, U.S. Republican Sen. Mark Kirk says Cook County couldn’t have screwed up Project Shield any further if it tried to.
“So it does appear to be gross incompetence, waste and potential criminal activity was at the heart of this program,” Kirk said.
Kirk was joined at the news conference by U.S. Democratic Rep. Mike Quigley, and both called for a FBI investigation into the program. As to why Kirk and Quigley suspect criminal conduct and not just mismanagement, Kirk said, “168 change orders all adding to cost, and yet the I.G. could find no documentation for that. So money was paid to contractors and sub-contractors for additional work and yet we have no idea what they did or how it was accounted for.”
The FBI REPORTS – Malware Targets Bank Accounts ‘Gameover’ Delivered Via Phishing E-Mails – Analogy to STASI-Methods
Cyber criminals have found yet another way to steal your hard-earned money: a recent phishing scheme involves spam e-mails—purportedly from the National Automated Clearing House Association (NACHA), the Federal Reserve Bank, or the Federal Deposit Insurance Corporation (FDIC)—that can infect recipients’ computers with malware and allow access to their bank accounts.
The malware is appropriately called “Gameover” because once it’s on your computer, it can steal usernames and passwords and defeat common methods of user authentication employed by financial institutions. And once the crooks get into your bank account, it’s definitely “game over.”
Gameover is a newer variant of the Zeus malware, which was created several years ago and specifically targeted banking information.

How Can You Protect Yourself? – Obviously, make sure your computer’s anti-virus software is up to date. – Don’t click on e-mail attachments from unsolicited senders. NACHA, FDIC, and the Federal Reserve all say they don’t send out unsolicited e-mails to bank account holders. If you want to confirm there’s a problem with your account or one of your recent transactions, contact your financial institution directly. – Don’t accept unsolicited jobs online that require you to receive funds from numerous bank accounts and then wire the money to overseas accounts—you could get caught up in a criminal investigation. |
|---|
How the scheme works: Typically, you receive an unsolicited e-mail from NACHA, the Federal Reserve, or the FDIC telling you that there’s a problem with your bank account or a recent ACH transaction. (ACH stands for Automated Clearing House, a network for a wide variety of financial transactions in the U.S.) The sender has included a link in the e-mail for you that will supposedly help you resolve whatever the issue is. Unfortunately, the link goes to a phony website, and once you’re there, you inadvertently download the Gameover malware, which promptly infects your computer and steals your banking information.
After the perpetrators access your account, they conduct what’s called a distributed denial of service, or DDoS, attack using a botnet, which involves multiple computers flooding the financial institution’s server with traffic in an effort to deny legitimate users access to the site—probably in an attempt to deflect attention from what the bad guys are doing.
But that’s not the end of the scheme: Recent investigations have shown that some of the funds stolen from bank accounts go towards the purchase of precious stones and expensive watches from high-end jewelry stores. The criminals contact these jewelry stores, tell them what they’d like to buy, and promise they will wire the money the next day. So the next day, a person involved in the money laundering aspect of the crime—called a “money mule”—comes into the store to pick up the merchandise. After verifying that the money is in the store’s account, the jewelry is turned over to the mule, who then gives the items to the organizers of the scheme or converts them for cash and uses money transfer services to launder the funds.
In many cases, these money mules are willing participants in the criminal scheme. But increasingly, as part of this scheme, we see an increasing number of unsuspecting mules hired via “work at home” advertisements who end up laundering some of the funds stolen from bank accounts. The criminals e-mail prospective candidates claiming to have seen their resumes on job websites and offer them a job. The hired employees are provided long and seemingly legitimate work contracts and actual websites to log into. They’re instructed to either open a bank account or use their own bank account in order to receive funds via wire and ACH transactions from numerous banks…and then use money remitting services to send the money overseas.
If you think you’ve been victimized by this type of scheme, contact your financial institution to report it, and file a complaint with the FBI’s Internet Crime Complaint Center.
Cryptome – STRATFOR Hacked Update 9
Summary of releases of STRATFOR documents, subscribers’ firm names and personal information (including addresses, telephone numbers, credit card numbers and passwords), latest release at top:
STRATFOR Hacked Update 9
10 January 2012. A sends:
Hello, in January the 3rd my bank alerted me about a (non requested) payment of 155.90 euro made with my credit card, to a company called marlahealth.comI inmmediately blocked the card. And to my amazement today arrives a parcel from marlahealth.com containing 4 boxes of a nutritional supplement for men and a DVD about penis enlargement therapies.
It’s nice to have my money back in the guise of such goods. Anyway, I thought that the thiefs where using the credit cards to make donations, not playing practical jokes.
Best regards.
PS If you want a photo of the goods (as a proof) just ask.
9 January 2012. A sends:
For what it’s worth:$ md5sum stratfor_full.tar.gz
50dbafed23e6e75d3f6313bf5480810a stratfor_full.tar.gz
I am pretty confident that this is the original and that it doesn’t contain any malware, but ask someone else for corroboration.
Cryptome: There are prowlers searching for possession and distribution. Best to get rid of copies and disk wipe.
8 January 2011. Initial sources for 860,000 Stratfor accounts appear to have been removed. Fakes have started to appear on Pastebin and Torrents using variations on the file name “stratfor_full.tar.gz.”
At 08:23 PM 1/7/2012 -0800, A wrote:I have not been able to find it anywhere—only a thousand or so references to the .gz file but all links are dead. Know several people who were compromised, though thankfully not me. Have you seen the actual list?
Cryptome: The list was available at the published URLs but now gone it seems, gone undercover to be forged, tampered with, lied about, used as bait. Be careful about anything you find, it is likely carrying a call home feature. This is not to discount that such a feature was in the original put there as entrapment, left available to be hacked. Standard secuity measures for these amazingly easy to penetrate sites. Using one of the CCs is a surefire way to call the cops to come arrest an idiot.
As a noted authority on authentication warns about unauthorized leaks:
“By the time we published the cables, the material was already on dozens of websites, including Cryptome, and were being tweeted everywhere. And even a searchable public interface had been put up on one of them.”
Another motive for publishing the tranche, Assange claims, was the provision of a reliable source for the leaks. In the field of leak publishing, he says, WikiLeaks has become a trusted brand. Although versions of the cable tranche were appearing online, “there was not an authorised version of the cables that the public could rely on”.
What does he mean by an “authorised” version of cables, when they were US government property?
“By ‘authorised’ I mean a version that is known to be true – it doesn’t have another agenda. The unauthorised versions that were being tweeted everywhere – although as far as we can determine they were accurate, the public and journalists couldn’t know they were accurate.”
He points to stories published in Tajikistan and Pakistan that have been based on fake cables. “WikiLeaks is a way for journalists and the public to check whether a claimed story based on a cable is actually true. They can come to our site to check. We have a 100 per cent accuracy record.”
30 December 2011. A writes that five Pastebin posts of recovered STRATFOR passwords have been removed as indicated below. In addition, four files from sources have been removed from Rapid Share (1) and Wikisend (3).
29 December 2011.
Lulzxmas Dumps 860,000 STRATFOR Accounts:
http://pastebin.com/f7jYf5Wdhttp://www.megaupload.com/?d=O5P03RXK [Now removed]
28 December 2011.
Prepping for the Stratfor 5M Email Release
27 December 2011.
http://pastebin.com/78MUAaeZ [Now removed]
These are 28517 of 53281 (54%) passwords from the list of STRATFOR customer accounts cracked.Part 1/3: http://pastebin.com/CdD92fJG [Now removed]
Part 2/3: http://pastebin.com/AcwQgHmF [Now removed]
Part 3/3: http://pastebin.com/78MUAaeZ [Now removed]
26 December 2011. Firms and personal first names beginning with “D” through “My” (~ 30,000).
http://pastebin.com/q5kXd7Fdhttps://rapidshare.com/#!download|44tl6|2444489251|STRATFOR_full_d_m.txt.gz|3255|
R~7B8842ED6343CEAE67A23C094E131679|0|0 [Now removed]And 25,000 IT work tickets:
26 December 2011. Sample Stratfor.com email:
http://pastebin.com/HmDs0EM4“just a small preview of the mayhem to come. 1 out of 2.7 million”
26 December 2011. STRATFOR leaked accounts (10257 passwords recovered)
http://pastebin.com/CdD92fJG [Now removed]
25 December 2011. Firms and personal miscellaneous names not in alphabetical order (~13,000):
http://pastebin.com/8v3768Bw[Now removed]http://wikisend.com/download/132838/stratfor_full_misc.txt.gz [Now removed]
25 December 2011. Firms and personal first names beginning with “B-By” through “C-Cz” (~4,000) :
http://pastebin.com/bUqkb9mqhttp://wikisend.com/download/597646/stratfor_full_b.txt.gz [Now removed]
25 December 2011. Firms and personal first names beginning with “A” through “Az” (~ 4,000).
http://pastebin.com/bQ2YHDdwhttp://wikisend.com/download/601776/stratfor_full_a.txt.gz [Now removed]
25 December 2011. A message allegedly to subscribers from George Friedman, Stratfor, was posted to Facebook and Pastebin (below).
25 December 2011. A paste today denying Anonymous role:
And, Stratfor’s A client list of passwords:
24 December 2011
STRATFOR Hacked
Related:
A sends:
Subject: Important Announcement from STRATFOR
Date: Sat, 24 Dec 2011 19:49:58 -0500
From: STRATFOR <mail[at]response.stratfor.com>
Dear Stratfor Member,
We have learned that Stratfor’s web site was hacked by an unauthorized party. As a result of this incident the operation of Stratfor’s servers and email have been suspended.
We have reason to believe that the names of our corporate subscribers have been posed [sic] on other web sites. We are diligently investigating the extent to which subscriber information may have been obtained.
Stratfor and I take this incident very seriously. Stratfor’s relationship with its members and, in particular, the confidentiality of their subscriber information, are very important to Stratfor and me. We are working closely with law enforcement in their investigation and will assist them with the identification of the individual(s) who are responsible.
Although we are still learning more and the law enforcement investigation is active and ongoing, we wanted to provide you with notice of this incident as quickly as possible. We will keep you updated regarding these matters.
Sincerely,
George Friedman
STRATFOR
221 W. 6th Street, Suite 400
Austin, TX 78701 US
www.stratfor.com
http://www.facebook.com/stratfor
Dec 25th, 2011
On December 24th an unauthorized party disclosed personally identifiable information and related credit card data of some of our members. We have reason to believe that your personal and credit card data could have been included in the information that was illegally obtained and disclosed.
Also publicly released was a list of our members which the unauthorized party claimed to be Stratfor’s “private clients.” Contrary to this assertion the disclosure was merely a list of some of the members that have purchased our publications and does not comprise a list of individuals or entities that have a relationship with Stratfor beyond their purchase of our subscription-based publications.
We have also retained the services of a leading identity theft protection and monitoring service on behalf of the Stratfor members that have been impacted by these events. Details regarding the services to be provided will be forwarded in a subsequent email that is to be delivered to the impacted members no later than Wednesday, December 28th.
In the interim, precautions that can be taken by you to minimize and prevent the misuse of information which may have been disclosed include the following:
– contact your financial institution and inform them of this incident;
– if you see any unauthorized activity on your accounts promptly notify your financial institution;
– submit a complaint with the Federal Trade Commission (“FTC”) by calling 1-877-ID-THEFT (1-877- 438-4338) or online at https://www.ftccomplaintassistant.gov/; and
– contact the three U.S. credit reporting agencies: Equifax (http://www.equifax.com/ or (800) 685-1111), Experian (http://www.experian.com/ or (888) 397-3742), and TransUnion (http://www.transunion.com/ or (800) 888-4213), to obtain a free credit report from each.
Even if you do not find any suspicious activity on your initial credit reports, the FTC recommends that you check your credit reports periodically. Checking your credit reports can help you spot problems and address them quickly.
To ease any concerns you may have about your personal information going forward, we have also retained an experienced outside consultant that specializes in such security matters to bolster our existing efforts on these issues as we work to better serve you. We are on top of the situation and will continue to be vigilant in our implementation of the latest, and most comprehensive, data security measures.
We are also working to restore access to our website and continuing to work closely with law enforcement regarding these matters. We will continue to update you regarding the status of these matters.
Again, my sincerest apologies for this unfortunate incident.
Sincerely,
George Friedman
ZWEITES DEUTSCHES FERNSEHEN – ZDF BERICHTET ÜBER STASI-LEUTE UND EINEN “GoMoPa”-AUSSTEIGER
CONFIDENTIAL – The Nixon-Presley Meeting
![[IMAGE]](https://i0.wp.com/www.gwu.edu/%7Ensarchiv/nsa/elvis/elnix.gif)
Of all the requests made each year to the National Archives for reproductions of photographs and documents, one item has been requested more than any other. That item, more requested than the Bill of Rights or even the Constitution of the United States, is the photograph of Elvis Presley and Richard M. Nixon shaking hands on the occasion of Presley’s visit to the White House.
The Meeting
On December 21, 1970, Elvis Presley paid a visit to President Richard M. Nixon at the White House in Washington, D.C. The meeting was initiated by Presley, who wrote Nixon a six-page letter requesting a visit with the President and suggesting that he be made a “Federal Agent-at-Large” in the Bureau of Narcotics and Dangerous Drugs. The events leading up to and after the meeting are detailed in the documentation and photographs included here, which include Presley’s handwritten letter, memoranda from Nixon staff and aides, and the thank-you note from Nixon for the gifts (including a Colt 45 pistol and family photos) that Presley brought with him to the Oval Office.
These materials chronicling the Presley-Nixon meeting were obtained from the Nixon Presidential Materials Project at the National Archives at College Park (College Park, Maryland).
The Documents
Note: The following documents are in PDF format.
You will need to download and install the free Adobe Acrobat Readerto view them.
Handwritten Letter from Presley to Nixon, Undated
Transcription of Presley letter, Undated
Memorandum for H.R. Haldeman from Dwight L. Chapin, 21 December 1970
Memorandum for the President, Re: Meeting with Elvis Presley, 21 December 1970
Memorandum for the President’s File from Egil “Bud” Krogh, Re: Meeting with Elvis Presley, 21 December 1970
Message from (Bev) to (Lucy), Re: Presley’s Gifts to the President
Letter from Richard M. Nixon to Elvis Presley, 31 December 1970
Memorandum from Egil “Bud” Krogh to Neal Ball, Re: Guidance on Jack Anderson Column-Elvis Presley, 27 January 1972
CONFIDENTIAL – Bradley Manning Article 32 Hearing Script

This script produced by the military for the Article 32 hearing of PFC Bradley Manning was released as part of a public court filing
PFC Manning, I am Lieutenant Colonel Paul Almanza. By order of Colonel Carl R. Coffinan, Jr., I have been appointed as investigating officer under the provisions of Article 32(b) of the Uniform Code of Military Justice to conduct an investigation into the charges which have been preferred against you.
Before proceeding, I would like to advise the participants and persons observing that this is a formal investigation. In order to protect the dignity and decorum of these proceedings, I would ask that all present refrain from interrupting or otherwise disturbing the investigation. Should any person nevertheless engage in speech or conduct that interferes with the dignity and decorum of the proceedings, they may be removed from this courtroom.
PFC Manning, let the record show that Mr. David Coombs, civilian counsel, MAJ Matthew Kemkes, and Captain Paul Bouchard are here present with you. On 23 November 2011, I advised you of this investigation and your rights to counsel in this investigation. As you were in pretrial confinement, I provided that notification to your counsel.
Counsel, when was your client provided with that notification?
I have read the written documents provided to your counsel for the sole purpose of determining which witnesses and evidence would be necessary to conduct a thorough and impartial investigation. Your counsel have examined those documents. I will not consider those documents for any other purpose, and I will make my findings, conclusions and recommendations based only on the evidence presented during the course of this investigation. After I have heard the evidence presented by both the government and your defense counsel and arguments by the government and the defense counsel, I will forward the results of this investigation and my recommendations to the appointing authority. Do you have a copy of the charge sheet in front of you?

DOWNLOAD ORIGINAL DOCUMENT HERE
TOP-SECRET – (U//FOUO) U.S. Marine Corps Martial Arts Program (MCMAP) Manual

The focus of Marine Corps Martial Arts Program (MCMAP) is the personal development of each Marine in a team framework using a standardized, trainable, and sustainable close combat fighting system. As a weapon-based system, all techniques are integrated with equipment, physical challenges, and tactics found on the modern battlefield. The MCMAP is designed to increase the warfighting capabilities of individual Marines and units, enhance Marines’ self-confidence and esprit de corps, and foster the warrior ethos in all Marines. The MCMAP is a weapon-based system rooted in the credo that every Marine is a rifleman and will engage the aggressor from 500 meters to close quarter combat. The MCMAP:
• Enhances the Marine Corps’ capabilities as an elite fighting force.
• Provides basic combative skills for all Marines.
• Applies across the spectrum of violence.
• Strengthens the Marine Corps warrior ethos.
The motto of MCMAP best states the essence of the program: “One mind, any weapon.” This means that every Marine is always armed even without a weapon. He is armed with a combat mindset, the ability to assess and to act, and the knowledge that all Marines can rely on one another.
The Marine Corps was born during the battles that created this country. Drawing upon the experiences of the first Marines, we have developed a martial culture unrivaled in the world today. This legacy includes not only our fighting prowess but also the character and soul of what makes us unique as Marines. This training continued to evolve up to World War II. During these early years, the leadership and core values training that are our hallmark today developed in concert with the martial skills.


DOWNLOAD THE ORINIAL DOCUMENT HERE
Report – Canadian Defence Department Won’t Release Photos of Taliban Detainees’ Hair

Canada’s Information Commissioner Suzanne Legault waits to testify before the Commons ethics committee on Parliament Hill in Ottawa
The Defence Department is prepared to go to Federal Court and spend whatever it takes to prevent the public from seeing government photos of Taliban hairdos because it believes the captured insurgents have a right to their privacy.
The department’s decision, outlined in newly released documents obtained by the Citizen, is the result of a test of the Access to Information law by two Ottawa lawyers, Paul Champ and Amir Attaran.
To see how far DND would go to prevent the release of information about captured Afghan insurgents, Attaran requested copies of photographs the military took of such individuals but asked that the faces of the prisoners be completely blacked out and that only the hairdos of the detainees shown.
Information Commissioner Suzanne Legault, the government watchdog for the Access law, also recommended DND release the heavily censored photos.
But the DND documents obtained by the Citizen through the Access law outline the department’s view: releasing the photographs of the hairdos of captured insurgents would violate their privacy rights and could hurt national security.
“National Defence will not follow the recommendation made by the Information Commissioner of Canada regarding disclosure of photographs covered by this file and is prepared to defend the decision in court if necessary,” Julie Jansen, head of DND’s Access to Information branch, wrote in the October 2010 briefing note.
…
Attaran said DND’s claim it can’t release photos of hairdos because it must protect the privacy of the alleged insurgents is ludicrous. “The same government that says those detainees have no rights under the Charter of Rights and Freedoms now embraces the idea that detainees have rights under the Privacy Act,” he explained. “The government’s position is that these persons have privacy rights but no constitutional right to avoid torture.”
An email sent Friday by DND noted the decision to withhold the 28 photographs was based entirely on enforcing the privacy issue. It did not mention the earlier claim by Jansen that releasing photos of detainee hairdos would harm national security.
The email noted the Privacy Act protects the privacy of individuals with respect to the information held by the Canadian government about them.
Some legal specialists, however, have noted that Canada’s Privacy law applies only to Canadians and permanent residents.
TOP-SECRET – Classified USAID Report on Kabul Bank Corruption

Dubai real estate led depositors to rush to withdraw funds from Kabul Bank, the largest bank in Afghanistan. According to the Report of Kabul Bank in Conservatorship dated October 30, 2010, cited in a draft material loss review commissioned by USAID/Afghanistan, fraudulent loans were used to divert $850 million to insiders. This amount reportedly represented 94 percent of the bank’s outstanding loans.
Since 2003, USAID/Afghanistan has supported a number of capacity-building activities at the Afghanistan Central Bank (DAB) to help DAB regulate the banking sector. Currently, Deloitte1 provides DAB technical assistance in bank supervision and examination through a $92 million task order for the Economic Growth and Governance Initiative, which includes many activities in addition to bank supervision and examination. The purpose of the task order was to increase Afghanistan’s ability to develop and implement sound economic and regulatory policies that provide the foundation for private sector growth in a market economy. According to Deloitte’s work plan, one of the main goals of the assistance Deloitte provided to DAB was to assist DAB in fulfilling its statutory responsibilities ―to promote the stability and contribution to economic growth of the financial sector and to prevent avoidable losses. Deloitte provided onsite technical advisors at DAB’s Directorate for Financial Supervision.
After the run on Kabul Bank, senior officials in the U.S. Embassy raised concerns about Deloitte’s performance. Specifically, they were concerned that Deloitte staff did not warn the U.S. Government about looming problems at Kabul Bank before the first news reports broke in February 2010. They also questioned Deloitte’s effectiveness and performance because Deloitte staff had provided bank supervision assistance to DAB for 7 years, yet DAB supervisors were unable to prevent the near collapse of Afghanistan’s largest bank. In January 2011, USAID/Afghanistan requested the assistance of the Office of Inspector General (OIG) in determining whether USAID or Deloitte staff members were negligent in failing to report the Kabul Bank fraud.
In response to USAID/Afghanistan’s request, OIG/Afghanistan conducted this review to determine:
- What opportunities USAID and contractor staff had to learn of fraudulent activities at Kabul Bank through USAID’s Economic Growth and Governance Initiative and its predecessor, the Economic Growth and Private Sector Strengthening Activity.
- How staff learned of the fraud.
- What actions staff members took once they became aware of the fraud.
- Whether USAID’s oversight of its contractor was adequate.
…
USAID’s Management of Its Task Order with Deloitte Was Weak
ADS 203.3.2, ―Assessing and Learning, states that missions and their offices are responsible for monitoring a contractor’s performance in achieving the contract’s purpose. ADS 302.3.7.1a, ―Direct Contracting, Mandatory Reference: ―Procedures for Designating the Contracting Officer’s Technical Representative (COTR) for Contracts and Task Orders,‖ states that the COTR is in a unique position to monitor how well the contractor is progressing toward achieving the contract’s purpose and is responsible for providing technical liaison between the contractor and the contracting officer, a function critical to ensuring good contract performance.
When the current mission director arrived in June 2010, his attention focused on USAID/Afghanistan’s capacity to manage and provide oversight of highly technical bank supervision activities implemented by its contractor, Deloitte, at DAB. This focus heightened after the Kabul Bank crisis broke in September 2010. The task order with Deloitte for the Economic Growth and Governance Initiative was for a 5-year, $92 million project with three major components and 21 work streams with diverse requirements that was managed by USAID/Afghanistan’s Office of Economic Growth. In August 2009, when USAID issued the task order, the Office of Economic Growth had only four U.S. direct-hire staff and none with experience in the banking sector. For the most part, only one U.S. direct hire was managing the task order at any given time, with some assistance from Foreign Service National staff.
Further contributing to the mission’s challenges to provide effective oversight of Deloitte, a former COTR for the Deloitte task order stated that during a typical workweek, he spent 50 to 70 percent of his time drafting memorandums and cables for the U.S. Embassy, reducing his time for program oversight. He kept detailed timesheets of daily work activities. The COTR explained that such competing work demands, combined with the mission’s lack of technical expertise, created overreliance on the Deloitte advisers to manage the bank supervision assistance activities, with little oversight provided by USAID. USAID staff members stated that had they not faced the burden of managing a large task order with limited resources, they would have been in a better position to provide proactive and robust oversight of the Deloitte advisers. As one USAID official put it, ―Deloitte was managing USAID, rather than the other way around.
Generally, COTRs monitor contractor performance and verify that it conforms to the technical requirements and quality standards agreed to in the contract. COTRs do this by maintaining regular contact and liaison and by conducting frequent site visits with the contractor. Yet according to a former COTR for the Deloitte task order, mission management focused on program spending, financial pipelines, and burn rates, rather than on monitoring and achieving program results. A former USAID/Afghanistan staff member stated in a memo that the mission gave the Office of Economic Growth only 24 hours to review a proposed Deloitte work plan—insufficient time to provide thoughtful review and comment. Finally, at the entrance conference for this review, USAID/Afghanistan officials did not take a position on whether Deloitte’s performance was satisfactory or unsatisfactory, providing further evidence of inadequate management.
For years, USAID has faced difficulty in attracting staff to Afghanistan who have the appropriate levels of experience and skills. A former mission director for USAID/Afghanistan stated that the staffing situation in Afghanistan reflected what he considered to be an ongoing problem for USAID, especially for programs in war zones—not enough senior people at USAID who have the experience to manage large, substantive, technically challenging projects. Current USAID/Afghanistan leadership agreed with this assessment and explained that steps have been and continue to be taken to remedy that situation. For example, a recently completed reorganization in the Office of Economic Growth added one technical adviser position.
DOWNLOAD ORIGINAL DOCUMENT HERE
The FBI reports – Manhattan U.S. Attorney Announces Extradition of Four Israeli Defendants Charged in Multi-Million-Dollar Phony “Lottery Prize” Schemes
Preet Bharara, the United States Attorney for the Southern District of New York, announced today that four defendants have been extradited from Israel on charges relating to their participation in multiple lottery telemarketing fraud schemes. The schemes targeted elderly victims in the United States and netted the defendants millions of dollars in profits. AVI AYACHE, YARON BAR, and IAN KAYE were arrested in Israel in July 2009 and indicted with eight others in U.S. v. Avi Ayache et al. SHAI KADOSH, who was indicted with nine others in September 2008 in U.S. v. Guy Mayo et al., had been a fugitive until his December 2011 arrest in Israel. The four defendants, who are all residents of Israel, arrived in the Southern District of New York late yesterday. AYACHE, BAR and KAYE were presented in Magistrate Court earlier today, and KADOSH was presented before U.S. District Judge Lewis A. Kaplan.
Manhattan U.S. Attorney Preet Bharara said: “From thousands of miles away, these defendants, along with their co-conspirators, allegedly preyed upon some of the most vulnerable, elderly victims. Their appearances in court today should make clear that we will reach out as far as necessary, and persist as long as it takes, to bring foreign defendants before the bar of American justice.”
According to the indictments and other court documents previously filed in Manhattan federal court:
AYACHE, BAR, KAYE, KADOSH and their co-conspirators allegedly operated phony “lottery prize” schemes out of numerous boiler rooms in Israel. The schemes targeted hundreds of victims, mostly elderly, throughout the United States. To identify potential victims, the defendants purchased from list brokers the names and contact information of U.S. residents who subscribed to sweepstakes lotteries. They then contacted the victims and solicited information about their finances by falsely telling them they had won a substantial cash prize that they would receive as soon as they paid the necessary fees and taxes. In reality, there was no lottery prize. Collectively, the American victims in these lottery fraud schemes lost approximately $25 million.
***
AYACHE, BAR, KAYE, and KADOSH are each charged with one count of conspiracy to commit wire fraud and mail fraud through telemarketing, which carries a maximum potential penalty of 30 years in prison. In addition, AYACHE, BAR, and KADOSH are each charged with two substantive counts of wire fraud through telemarketing, each of which carry a maximum potential penalty of 30 years in prison. AYACHE and BAR are also charged with conspiracy to commit money laundering, which carries a maximum potential penalty of 20 years in prison.
U.S. v. Avi Ayache, et al. is assigned to U.S. District Judge Barbara S. Jones. Of the original 11 defendants charged in the case, six defendants—Gillian Rosenberg, Toshin Charles Samuels, Oshrat Portolyoni, Naor Green, Yulia Rayz, and Limor Cohen—have pled guilty. Rayz and Green have each been sentenced to 40 months in prison, and the rest of the defendants are awaiting sentencing. Two defendants, Michelle Yuval and Limor Cohen, are awaiting extradition. Matthew Getto, the leader of the telemarketing scheme, was charged in a separate indictment. He was convicted after a bench trial and sentenced in March 2011 to 150 months in prison.
U.S. v. Guy Mayo, et al. is assigned to Judge Kaplan. Of the original 10 defendants, seven pled guilty and were sentenced in June 2011: Guy Mayo received 108 months in prison; Elad Mayo received 78 months in prison; Asi Almakias received 72 months in prison; Lior Orgad received 60 months in prison; Mor Galanti received 37 months in prison; Yaniv Kalbers received 46 months in prison; and David Yamin received 33 months in prison. Two defendants, Moran Goldfarb and Orelya Belahsan, have pled guilty and are awaiting sentencing.
Mr. Bharara praised the investigative work of the FBI and the Tel Aviv Fraud Division of the Israel National Police for their exceptional work in investigating this case. He also thanked the Office of International Affairs, the United States Department of Justice Criminal Division; the Department of International Affairs within the Office of the State Attorney in the Ministry of Justice for the State of Israel; and the Tel Aviv District Attorney’s Office for their cooperation in the investigation and for their outstanding work and commitment to extraditing the defendants from Israel.
This case is being prosecuted by the Office’s Organized Crime Unit. Assistant U.S. Attorneys Avi Weitzman, Steve C. Lee, and Peter Skinner are in charge of the prosecution. Assistant U.S. Attorney Michael Lockard is in charge of the forfeiture aspects of the case.
The charges against the defendants are merely accusations and the defendants are presumed innocent unless and until proven guilty.
TOP-SECRET – Obama Called a Moron at Phone Security
From TSCM-220 mail list: http://groups.google.com/group/tscm-l2006?hl=en_US
Date: Fri, 06 Jan 2012 15:40:24 -0500
To: tscm-l2006[at]googlegroups.com
From:
Subject: [TSCM-L] {5984} POTUS telephones
There’s a very nice collection of dozens of photos of current POTUS telephones in use on John Young’s Cryptome site. The trained eye will notice some interesting TSCM-related items.
http://cryptome.org/2012-info/obama-phones/0015.htm
Date: Fri, 06 Jan 2012 17:00:07 -0500
From: “James M. Atkinson” <jmatk[at]tscm.com>
To: tscm-l2006[at]googlegroups.com
Subject: Re: [TSCM-L] {5986} POTUS telephones
Most of these are CISCO IP phones, or Avaya telephone sets.
Amazing complex instrument with some simply lovely security holes that an eavesdropper can exploit.
http://www.cisco.com/en/US/products/ps9748/index.html
http://www.cisco.com/en/US/products/ps8538/index.html
http://www.cisco.com/en/US/products/hw/phones/ps379/ps5440/index.html
http://www.cisco.com/en/US/products/hw/phones/ps379/index.html
A lot of these phones are also Lucent MLS of Definite phones (all an eavesdroppers paradise).
I really hate to have to mention this, but in the following image. You will notice the moron who is using a cell phone right next to a STE.
http://cryptome.org/2012-info/obama-phones/pict52.jpg
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-moron/pict2.jpg)
Same here. Moron using cell phone in close proximity to a secure telephone:
http://cryptome.org/2012-info/obama-phones/pict30.jpg
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-moron/pict3.jpg)
When you place a concentrated RF signal transmitter in close proximity to a piece of cryptographic gear (like a STU or STE) the RF signals and strong enough to intermix with the RF or magnetic signals and create a third signal. This is most valuable with cryptographic equipment that used cables that was not in conduit as the cable (seem in these pictures) provides a high threat access point where all kinds of havoc can be caused if a cell phone is brought within 8-12 feet of a STU, or 16+ feet of a STE. You will notice that the moron holding the phone is well within those distances.
The following image just proved what a utter moron this guy is, and remember who is is:
http://cryptome.org/2012-info/obama-phones/pict29.jpg
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-moron/pict4.jpg)
Notice that he is in a STE, in secure mode, and the STE (unencrypted voice path) is draped over a live RF transmitter.
I apologize Mr. President, but you sir are a fscking moron, just an utter moron.
Observers with sharp eyes will also notice the profoundly sloppy jobs of TSCM that is being done on these phones as well, and how the routing requirements for cables are not beign observered, but then that is the least of their probelms… their boss obviously does not care, so why shoudl they.
Dude, WTF… no seriously, WTF?
-jma
James M. Atkinson
President and Sr. Engineer
“Leonardo da Vinci of Bug Sweeps and Spy Hunting”
http://www.linkedin.com/profile/view?id=15178662
Granite Island Group
jmatk[at]tscm.com
http://www.tscm.com/
(978) 546-3803
Date: Fri, 06 Jan 2012 17:53:00 -0500
To: tscm-l2006[at]googlegroups.com
From:
Subject: Re: [TSCM-L] {5987} POTUS telephones
Are executives at the highest levels expected to be TSCM, COMSEC, and TEMPEST experts who possess detailed technical knowledge and extensive related experience?
If yes, then why would any top executive have any need to hire experts in those fields? Does JMA call his executive clients (who aren’t as well-versed in those fields as he obviously is) “fucking morons?” That doesn’t seem like an effective business practice to me.
Perhaps the executive in the photo wasn’t briefed by his experts on the finer points of proper COMSEC–such as not to use a cell phone near a STE. If he wasn’t, then perhaps those experts are to blame, not the executive. Or maybe there’s other protections in place which prevent that from being a COMSEC problem. There is equipment in those photos that probably none of us know the workings of…
Date: Fri, 06 Jan 2012 18:19:17 -0500
From: “James M. Atkinson” <jmatk[at]tscm.com>
To: tscm-l2006[at]googlegroups.com
Subject: Re: [TSCM-L] {5989} POTUS telephones
Actually yes.
He knows that he can not use a cellphone within X feet of a STU, STE, or security communications media because he can read the white papers on the matter, and has been briefed by the technical advisors until they were blue in the face, but he does not care, he likes his cell phones (because it makes him a more effective leader)
If a customer hires me to tell them about the problem, and I tell them about it, write numerous white papers on the subject for them, demonstrate the risk for them by recovering classified information, and even the CIK form a STU using only a nearby cell phone, and they still refuse to use proper communications security, and abide by stand-off distances (the space between the secure phone and the cell phone), then I will have no problems explain that they are a moron to their face (usually in private, but still).
You need only to watch the video of my testimony before Congress on related matters to see that I tend not to couch my words when it comes to national security matters like this.
The President of the United States is a fucking moron, but given the last pool of candidates he is less of a moron, then the other morons we had running at the time. But still, he is a moron, and an arrogant one at that.
-jma
Date: Fri, 06 Jan 2012 18:42:24 -0500
To: tscm-l2006[at]googlegroups.com
From:
Subject: Re: [TSCM-L] {5990} POTUS telephones
So you know this for a fact? I would think POTUS has more important things to do than “read the white papers” about TSCM. Arrogant? Relative to whom?
Date: Fri, 06 Jan 2012 19:17:28 -0500
From: “James M. Atkinson” <jmatk[at]tscm.com>
To: tscm-l2006[at]googlegroups.com
Subject: Re: [TSCM-L] {5992} POTUS telephones
I wrote the white paper, and the paper has been repeatedly briefed to him by the DCI in his Daily Presidential Briefing. He has also read the white paper, but it has not dissuaded his cell phone mis-use. Several DCI staffers who prepare the PDB have assured me that the DCI has repeatedly included issue several times in the PDB, and POTUS just does not care.
The threat is known, the threat has been demonstrated, the threat has been replicated by others, it is a known and confirmed weakness, but he does not care, not even slightly.
Some Presidents like to ride around Dallas in open top limos, other are addicted to their cell phones… neither tend to remain in office too long.
He needs to smarten up, as he is risking national security and sabotaging international diplomacy (easily screwed up when secure communications are intercepted).
-jma
Date: Sat, 07 Jan 2012 11:44:11 -0500
From: “James M. Atkinson” <jmatk[at]tscm.com>
Subject: Re: Your Comments on Prez Phones
To: Cryptome
You have my permission to publish anything that you see on the TSCM-L list so long as I am the originator of the post.
You have my permission to publish the information that I published about the Presidents phone, and the comments I made in regards to his being warned not to do it.
Here is something about STU/STE and cell phones
TEMPEST, HIJACK, NONSTOP, and TEAPOT Vulnerabilities A STU-III is a highly sophisticated digital device; however, they suffer from a particular nasty vulnerability to strong RF signals that if not properly addressed can cause the accidental disclosure of classified information, and recovery of the keys by an eavesdropper. While the unit itself is well shielded, the power line feeding the unit may not have a clean ground (thus negating the shielding).
If the encryption equipment is located within six to ten wavelengths of a radio transmitter (such as a cellular telephone, beeper, or two way radio) the RF signal can mix with the signals inside the STU and carry information to an eavesdropper. This six to ten wavelengths is referred to as the “near field” or the wave front where the magnetic field of the signal is stronger then the electrical field.
As a rule all COMSEC equipment should be kept out the “near field” by a factor of at least 2.5 to 3 times to get it outside of the field transition point. Simply put, there needs to be a “danger zone” or exclusion zone around any and all COMSEC gear 2.5 to 3 times the near field distance, or 16 to 30 times the longest signal wavelength (the lower the frequency the longer the wavelength).
A “wavelength” is inversely proportional to frequency being used which means that an 800 MHz cellular phone (near a STU) presents a greater direct threat that a higher frequency PCS phone operating in the 1.7 GHz region. On the other hand a PCS or CDMA telephone creates a greater spectral density and far more transitions which allows an eavesdropper to corelate on the signal with more precision.
We also have to consider the amplitude of the signals as well as the “danger zone” created by the transition point or radius of the near field (times 2.5 to 3). When any RF signals inside the “danger zone” exceed -50 dBm (or -77 dBm in some cases) there is still a problem even though the cryptographic equipment is some distance from the actual transmitter, cellular phone, pager, etc. These relatively high signal levels (above -50 dBm or -77 dBm) are actually strong enough that they create secondary fields or signals when they encounter the outside of the equipment case or any other conductive or non-linear element. This is called the “saturation effect”, and if it is not properly addressed can result in the cryptographic equipment put at risk of disclosing secrets. Typically the ambient RF environment near any cryptographic equipment should be well below -80 dBm and in some cases well below -110 dBm. Fields of this strength are common near broadcast facilities such as FM or television transmission towers or cellular/PCS towers. If you have a concern of this nature then you should contact a TSCM professional and schedule an evaluation of the RF in the vicinity of where you will be using your encryption equipment.
The critical thing to remember in all of this is that the ciphering key is where all the magic is at, and that the eavesdropper will typically target the ciphering circuit (or “Scrambler”) to obtain the secret key. Sure they are interested in the material being scrambled by the cryptographic system, and they will also be interested in the inner workings of the phone, but it is obtaining the secret ciphering key that is most important to the spy. An encryption box or cryptographic device may only be classified secret, and yet the keying material is top secret, and the keying material is far more sensitive then the box itself, and must be protected with much greater care.
On a related note, it should be mentioned that the ciphering key is actually of a fairly small length, and that is even if a very small segment of it is compromised the eavesdropper’s may be able to reconstruct it in whole (depending on what segment they get). In some cases even a 200 bit ciphering key can be broken by obtaining a small fragment the cipher which can be “snatched from the airwaves in less a ten millionth of a second” (if the cryptographic ignition key is loaded when in the presence of a cellular phone or strong RF field). Once the key is loaded into the cryptographic device the amount of time required to reconstruct the key is significantly larger, but not at all prohibitive. Remember, the eavesdropper is only looking for a few bits of data (the payload of the key), and that this small number of bits can be “hijacked” by an external RF source like a cellular phone as a highjack requires an absolute minimum of bandwidth.
Since the signal of interest is of extremely narrow bandwidth, and the “illuminating” signal can be easily correlated to the “signal of interest” the eavesdropper can be a considerable distance away from the encryption device and still perform the highjack (called “correlation gain”, which can be well over 40 dB). This assumes that someone using the encryption device has a cell phone or other RF device on their person, that while not on an active call is still checking in with the base station for status updates on a regular basis. Without this “correlation gain” the intercept may only be feasible within a few feet, but with it; the eavesdropper can be 500 and even 1500 feet away.
Remember that the most valuable “item of interest” is not directly the clear text communication itself, but the key used to protect the communication. Once the eavesdropper has the key, then the communication itself would be targeted and exploited. You must protect the key at all times.
NEXTEL or Motorola iDen phones based on a TDMA or “Time Domain” signal presents a really nasty threat as the cell phone is constantly strobing a specific predictable time slice, and basically illuminates the STU and turns it into a strobing lighthouse that will seriously compromise classified information. If a NEXTEL is present within 12-15 feet of a STU-III (when it goes secure or a CIK is loaded) the phone and information passed though it should be considered compromised. The STU should always be located in an area called an exclusion zone, and cellular phones, pagers, beepers, and other RF devices should be kept outside of a stand-off zone of at least 15-20 feet (30 foot is good practice).
Now if this wasn’t confusing enough; portable Inmarsat stations also present a similar problem, but only if the STU is located in front of the transmitter antenna or within the side lobes of the signal (about 45 degrees off the center axis of the antenna).
The best way to deal with this is to never have a cellular telephone or pager on your person when using a STU, or within a radius of at least thirty feet (in any direction) from an operational STU (even with a good ground). If the STU is being used in a SCIF or secure facility a cell phone is supposed to be an excluded item, but it is simply amazing how many government people (who know better) forget to turn off their phone before entering controlled areas and thus cause classified materials to be compromised.
Spook Hint: If you have a powered up NEXTEL on your belt and you walk within 12 feet of a STU-III in secure mode you have just compromised the classified key.
In the case where the STU is being used on a cell phone or satellite phone your best option is to keep the phone in analog mode (a STU, not a STE) and locate the STU a good 6-12 feet away from the antenna. In the case of an Inmarsat terminal simply keep the STU BEHIND the antenna by at least 10-15 feet (this is why Inmarsat terminals have long cables for the antenna). If you can obtain a digital Inmarsat connection you can get a very high quality connection, but the equipment is fairly costly, the terminal is quite large, and the digital service quite expensive.
At no time should a STU-III be operated in the presence of an RF field that exceeds -105 dBm for any signal with less then 30 kHz of occupied bandwidth. In the case of a signal which the occupied bandwidth exceeds 30 kHz the RF levels should not exceed -138 dBm.
Convenience and Security are Always Inversely Proportional.
– James M. Atkinson, 1982
Here is some further unclassified background on the matter (the data on the matter was in my written testimony).
http://www.tscm.com/DeepWaterDooDoo/
http://www.tscm.com/DeepWaterDooDoo/JamesAtkinsonwrittenTestimony.pdf
TEMPEST in a TEAPOT and HIJACK Exploits
Between the TEMPEST and TSCM fields of study there is also an area of our field that deals with unmodified or quasi-modified equipment and signals, which interact with each other. This is the case where in effect a classified signal or classified information is accidentally impressed onto an unclassified signal. Thus, the unclassified signal carrying the classified data with it is accidentally transmitted a considerable distance allowing for eavesdropping by those who should not possess the information. This is usually the result of TEMPEST standards not being rigorously followed during equipment design, installation, and maintenance.
The investigation, study, and control of intentional compromising emanations from telecommunications and automated information systems equipment that was created, provoked, or induced by a spy is known by the code name of “TEAPOT”. An example of this would be the positioning of a rack of two way radios need a secure telephone, or by installing RED cable near to a BLACK cable. This can also involve modifications to software, to slight breaches to the configuration of equipment.
An example of this would be a case where a cable, which contains only unclassified radar, navigation, or communications signals, is placed near a cable, which carries highly classified information. On a maritime vessel an example of an unclassified signal would be the VHF marine radios, the unencrypted HF (shortwave) radio communication systems, and sections of the radar and IFF systems. Should any of these cables or equipment be placed near the classified systems an eavesdropper could intercept the classified information that was riding-on-the-back-of the unclassified signals.
Another example of this would be a warship that downloads classified spy satellite imagery through the onboard satellite communication system.
The problem is that the installer of the classified system has not properly installed the system that creates considerable TEMPEST problems causing these signals to leak off the ship a short distance. This is further complicated by several cables which do not carry classified information but which pass in close proximity to the classified cables.
Due to the unclassified cable, perhaps being a high power antenna link the classified information can now leak out of the ship and be monitored by spies from dozens, if not hundreds of miles distant.
Testimony of James M. Atkinson, President and Sr. Engineer, Granite Island Group 9 of 168
Before the House Committee on Transportation and Infrastructure
U.S. Coast Guard Budget and Oversight Hearing, April 18, 2007
There is other related information in the above PDF file, all of which you have permission to publish on Cryptome as you see fit.
Warmest Regards,
-jma
TOP-SECRET – Hackers leak indian Military Intel memo suggesting Apple has provided intercept backdoor to govs





STASI-NAMEN ALPHABETISCH BUCHSTABE A-BA – STASI-NAMES IN ALPHABETICAL ORDER – A-BA
see more info at http://www.victims-opfer.com
Die Liste wurde bereits früher hier publiziert:
http://stasiopfer.de/component/option,com_simpleboard/Itemid,/func,view/id,993815828/catid,4/
Vom “Stasiopfer”-Angebot führt ein Link zu einer Website in den USA (www.jya.com), die sich auch mit den Praktiken von Geheimdiensten beschäftigt. Dort findet sich die “Fipro-Liste”, das detaillierte “Finanzprojekt” der Stasi, angefertigt in den letzten Tagen der DDR, um die Rentenansprüche der rund 100 000 hauptamtlichen Mitarbeiter des MfS auch nach dem Zusammenbruch des Systems belegen zu können. Die “Fipro-Liste” ist seit langem bekannt und diente Anfang der neunziger Jahre etwa zur Identifizierung der so genannten OibE – Offiziere im besonderen Einsatz. Diese Liste „Offiziere im besonderen Einsatz“im Jahre 1991 erschien in der “taz. Die Echtheit kann beim BStU überprüft werden.
Siehe u.a. http://www.spiegel.de/spiegel/print/d-22539439.html
Auf Druck ehemaliger STASI-Leute und Ihrer Genossen wurde die Liste aus dem Verkehr gezogen.
Hier ist sie wieder:240362412253;07;65;00;;A(E)RNECKE, RONALD:;;;16500,00 180770413237;18;31;00;;ABE, HEIKO:;;;2795,00 070651405819;04;00;50;;ABEL, DIETER:;;;25860,00 111044406156;97;01;00;;ABEL, ECKHARD:;;;30750,00 090758410114;97;01;00;;ABEL, HOLGER:;;;25530,00 120253522713;30;31;00;;ABEL, IRENE:;;;23735,00 110154417310;09;06;00;;ABEL, KLAUS-DIETER:;;;19500,00 060847506727;98;85;00;;ABEL, MONIKA:;;;18480,00 140943402119;09;00;52;;ABEL, UWE:;;;31375,04 310853406422;18;28;00;;ABEL, WOLFGANG:;;;19151,25 121268413418;18;32;00;;ABELE, RALF:;;;9986,44 271069421013;01;06;24;;ABELER, KAI-UWE:;;;2896,61 181267405138;04;06;00;;ABELT, DIRK:;;;13760,00180769406443;18;34;00;;ABELT, MIKE:;;;9195,00 040250515315;94;03;00;;ABENDROTH, CHRISTINA:;;;12458,22 080933429711;99;40;00;;ABENDROTH, GUENTER:;;;33000,00 180337429713;99;40;00;;ABENDROTH, HORST:;;;26709,68 220541530054;99;40;00;;ABENDROTH, INGRID:;;;24000,00 211149406716;05;18;00;;ABENDROTH, KARL-HERMANN:;;;24820,00 310550429213;14;09;00;;ABENDROTH, KLAUS:;;;26312,50 170155422714;12;18;00;;ABENDROTH, MICHAEL:;;;26392,50 080341429742;94;03;00;;ABENDROTH, PETER:;;;27595,84 311051529230;14;00;40;;ABENDROTH, ROSWITHA:;;;12935,68 281059422716;99;53;00;;ABERT, CHRISTIAN:;;;18705,00 250241405312;04;19;00;;ABICHT, BERND-JUERGEN:;;;25200,00 090561406111;08;15;00;;ABISCH, JOERN:;;;22440,00 230834406136;17;00;00;;ABISCH, PAUL:;;;39750,00 280268423913;18;32;00;;ABITZSCH, TORSTEN:;;;9675,00 240140429711;99;43;00;;ABRAHAM, BODO:;;;23250,00 010640529715;99;40;00;;ABRAHAM, EVI:;;;24000,00 110263406135;04;06;00;;ABRAHAM, FRANK:;;;17930,00 171059404529;94;30;00;;ABRAHAM, FRANK:;;;18260,00 280966502520;02;80;00;;ABRAHAM, HEIDRUN:;;;13932,00 160340406119;97;01;00;;ABRAHAM, HEINZ:;;;20625,00 130858428913;14;15;00;;ABRAHAM, HENRY:;;;22605,00 151052415016;11;51;00;;ABRAHAM, HOLGER:;;;22080,00 151168402129;02;69;00;;ABRAHAM, JENS:;;;9675,00 081033402542;02;00;48;;ABRAHAM, JOACHIM:;;;26780,25 210950429740;15;60;00;;ABRAHAM, JOERG:;;;22320,00 271055428919;96;15;14;;ABRAHAM, KLAUS-DIETER:;;;23919,96 180167402525;02;00;47;;ABRAHAM, MICHAEL:;;;19440,00 020335404528;04;02;00;;ABRAHAM, SIEGFRIED:;;;29250,00 270371414856;05;06;00;;ABRAHAM, THOMAS:;;;3534,68 280151529714;97;29;00;;ABRAHAM, VERONIKA:;;;23040,00 110156504514;99;53;00;;ABRAM, CORNELIA:;;;18518,14 061054404514;99;55;00;;ABRAM, HARRY:;;;25320,00 130956422013;97;08;00;;ABRODAT, FRANK:;;;22425,00 251163422217;99;02;00;;ABROMEIT, FALK:;;;20295,00 240758400830;01;09;00;;ABROMEIT, LUTZ:;;;22252,50 120755405912;04;00;54;;ABROMEIT, STEFAN:;;;23355,00 131038420013;11;51;00;;ABT, HANS-DIETER:;;;31500,00 090259420019;11;65;00;;ABT, HANS-PETER:;;;21367,50 021238520038;11;80;00;;ABT, LILLI:;;;17464,84 041164420015;11;00;00;;ABT, MICHAEL:;;;10132,00 261159420031;11;26;00;;ABT, NORBERT:;;;17460,00 240650420012;11;08;00;;ABT, RAINER:;;;24187,50 081167421116;60;90;00;;ACHATZ, FRANK:;;;12214,00 151163523810;98;20;00;;ACHE, ILONA:;;;3641,82 270260425018;99;43;00;;ACHE, JENS:;;;17896,95 140332410718;07;53;00;;ACHE, MANFRED:;;;26250,00 220865424952;13;26;00;;ACHE, MIKE:;;;14145,40 020670410319;18;33;00;;ACHE, RALF:;;;2795,00 200535406147;17;00;00;;ACHENBACH, GUENTER:;;;24750,00 180541529711;97;08;00;;ACHILLES, INGRID:;;;23250,00 120359400861;99;43;00;;ACHILLES, ROLAND:;;;21217,50 190938429726;97;08;00;;ACHILLES, SIEGFRIED:;;;25500,00 030851429755;99;02;00;;ACHNER, ALFONS:;;;24290,98 030655530039;99;02;00;;ACHNER, GISELA:;;;21271,93 021045404428;03;00;53;;ACHNER, WOLFGANG:;;;25500,00 211051529830;30;83;00;;ACHSEL, ROSWITHA:;;;17340,00 230963400216;01;00;40;;ACHSNIG, ARMIN:;;;19800,00 160757400222;01;40;00;;ACHSNIG, NORBERT:;;;22080,00 240636418610;10;06;00;;ACHTEL, HEINZ:;;;21187,50 140537407512;97;22;00;;ACHTENBERG, KLAUS:;;;39750,00 291053401315;96;15;11;;ACHTENHAGEN, JOERG-RAINER:;;;27360,00 160456401344;01;09;00;;ACHTENHAGEN, RALPH-MICHAEL:;;;23017,50 020570428271;18;31;00;;ACHTERBERG, JENS:;;;6705,00 040668420516;12;69;00;;ACHTRUTH, FRED:;;;9950,00 150353429724;30;39;00;;ACKENHAUSEN, DETLEF:;;;22620,00 010654406118;98;84;00;;ACKENHAUSEN, UWE:;;;20160,00 300359501812;02;22;00;;ACKER, ILSEDORE:;;;15946,05 180948428146;14;65;00;;ACKERMANN, DIETMAR:;;;21187,50 290455424515;96;15;00;4288/81, F:;ACKERMANN, FRANK;1092;GROS(Z)E LEEGESTR. 114; 290455424515;96;15;00;4288/81, F:;ACKERMANN, FRANK;1092;GROS(Z)E LEEGESTR. 114; 130342429755;30;47;00;;ACKERMANN, FRED:;;;26280,00 110356422118;12;00;54;;ACKERMANN, GERD:;;;22400,00 120751514214;98;18;00;;ACKERMANN, GUDRUN:;;;22771,69 221262409520;99;51;00;;ACKERMANN, HARDY:;;;19425,65 180969417518;18;35;00;;ACKERMANN, HOLGER:;;;10287,08 280962428220;97;22;00;;ACKERMANN, JENS:;;;21945,00 040843530051;99;49;00;;ACKERMANN, KARIN:;;;22870,00 220258530200;96;15;00;4288/81/1, F:;ACKERMANN, KERSTIN;1092;GROS(Z)E LEEGESTR. 114; 220258530200;96;15;00;4288/81/1, F:;ACKERMANN, KERSTIN;1092;GROS(Z)E LEEGESTR. 114; 180142530053;30;83;00;;ACKERMANN, LENI:;;;18372,73 220844428911;14;06;00;;ACKERMANN, LOTHAR:;;;35250,00 110339429721;99;12;00;;ACKERMANN, LUDWIG:;;;24000,00 211068427216;18;31;00;;ACKERMANN, MATTHIAS:;;;9825,00 090750427229;14;26;00;;ACKERMANN, NORBERT:;;;25462,50 031166409523;06;02;00;;ACKERMANN, RALF:;;;16416,00 070252528117;14;06;00;;ACKERMANN, REGINA:;;;17882,50 091240407919;06;00;46;;ACKERMANN, REINER:;;;38250,00 250252428114;14;06;00;;ACKERMANN, ROLAND:;;;18000,00 060171423656;18;80;00;;ACKERMANN, RONNY:;;;2945,00 291047429733;15;15;00;;ACKERMANN, SIEGFRIED:;;;29340,00 251155428213;99;40;00;;ACKERMANN, STEFAN:;;;23100,00 290966419910;11;96;63;;ACKERMANN, TORSTEN:;;;15930,00 090949511911;30;83;00;;ACKERT, BRITA:;;;23460,00 070848411913;30;47;00;;ACKERT, KLAUS:;;;27382,50 250841429748;99;43;00;;ACKMANN, KLAUS:;;;22500,00 211063430045;99;02;00;;ACKSEL, DIRK:;;;16995,00 181065430175;98;27;00;;ACKSEL, MIKE:;;;16546,50 120470405919;18;34;00;;ACKSTEINER, MARIO:;;;9510,00 041244405915;04;00;54;;ACKSTEINER, WOLFGANG:;;;19125,00 160968403618;04;06;00;;ADAM, ANDRE:;;;12450,00 191070400834;01;69;00;;ADAM, ANDRE:;;;2896,61 040955421327;30;59;00;;ADAM, ARNIM:;;;14160,00 060962516015;09;00;42;;ADAM, BIRGIT:;;;16335,22 200756417448;09;00;50;;ADAM, DETLEF:;;;23460,00 250854407214;94;03;00;;ADAM, DIETMAR:;;;18543,75 230558528021;96;15;25;;ADAM, EVELYN:;;;18509,43 041033421528;12;00;50;;ADAM, EWALD:;;;16560,00 040164404619;04;06;00;;ADAM, FRANK:;;;17105,00 291054400736;05;80;00;;ADAM, FRANK:;;;18270,00 270361400629;18;35;00;;ADAM, FRANK:;;;20130,00 220265413619;08;00;48;;ADAM, GERALD:;;;16038,00 020444402126;02;06;00;;ADAM, HARALD:;;;23017,50 240767428018;14;40;00;;ADAM, HEIKO:;;;9872,00 090860418446;99;14;00;;ADAM, HEIKO:;;;21732,50 300159402115;02;09;00;;ADAM, HEINO:;;;22770,00 030828427014;97;22;00;;ADAM, HEINZ:;;;19320,00 290955500879;94;03;00;;ADAM, HELGA:;;;0,00 120361400238;97;01;00;;ADAM, HOLGER:;;;24555,00 021030430017;97;01;00;;ADAM, HUGO:;;;39000,00 151032529710;99;09;00;;ADAM, INGEBORG:;;;27750,00 250569406714;18;32;00;;ADAM, JENS:;;;9675,00 190758427125;97;06;00;;ADAM, JOACHIM:;;;21390,00 020836527016;97;22;00;;ADAM, KAETE:;;;19216,13 010150404610;04;60;00;;ADAM, KLAUS:;;;21000,00 150256421739;12;00;51;;ADAM, LOTHAR:;;;23182,50 260555429711;15;53;00;;ADAM, LUTZ:;;;27060,00 101055416414;09;00;48;;ADAM, MANFRED:;;;22137,50 140252418517;96;15;26;;ADAM, MANFRED:;;;30960,00 280752528231;99;02;00;;ADAM, MARGIT:;;;19352,50 190951505113;30;83;00;;ADAM, MARIANNE:;;;20835,04 160367411428;07;06;00;;ADAM, MARIO:;;;14094,00 080568416428;18;40;00;;ADAM, MARIO:;;;10725,00 140659526616;14;00;47;;ADAM, MONIKA:;;;14704,07 060569430039;18;32;00;;ADAM, NORBERT:;;;9675,00 240159409518;06;07;00;;ADAM, PETER:;;;19895,00 271149429752;99;40;00;;ADAM, PETER:;;;28500,00 090353409414;94;30;00;;ADAM, PETER:;;;20460,00 011057416013;09;00;40;;ADAM, PETER:;;;19199,56 260451424027;99;02;00;;ADAM, RAINER:;;;18975,00 030154504836;94;30;00;;ADAM, SABINE:;;;9021,94 150351400215;01;80;00;;ADAM, SIEGHARD:;;;18000,00 301055427013;97;22;00;;ADAM, STEFAN:;;;19370,00 110869403617;03;69;00;;ADAM, THOMAS:;;;9510,00 170169403477;99;43;00;;ADAM, TORSTEN:;;;9600,00 130658418446;94;30;00;;ADAM, UWE:;;;22540,00 180934421314;99;49;00;;ADAM, WERNER:;;;27750,00 220553424013;13;00;49;;ADAM, WOLFGANG:;;;26162,50 260859411836;17;00;00;;ADAMCZIK, AXEL:;;;18646,70 270469414811;18;34;00;;ADAMCZYK, DIRK:;;;11225,00 300160408530;30;57;00;;ADAMCZYK, RAINER:;;;13845,00 280950429816;04;00;50;;ADAMECK, LOTHAR:;;;25920,00 220340411913;97;01;00;;ADAMEK, HORST:;;;21937,50 241168414110;18;80;00;;ADAMETZ, STEFFEN:;;;9825,00 221055406917;96;15;25;;ADAMOWSKY, FRANK:;;;24840,00 270549404218;98;83;00;;ADAMSKA, DIETER:;;;21000,00 100350504412;98;83;00;;ADAMSKA, INGRID:;;;20380,00 010139505314;98;83;00;;ADAMSKA, ROSEMARIE:;;;16830,00 210857421218;12;00;49;;ADAMSKI, ROLAND:;;;23460,00 120156407211;18;32;00;;ADAMSKI, STEPHAN:;;;26695,00 190169402536;02;06;00;;ADAMZIG, JENS:;;;12975,00 311253410115;18;31;00;;ADASZEWSKI, MANFRED:;;;25200,00 120147412246;05;00;45;;ADE, VOLKER:;;;31680,00 230938502528;98;83;00;;ADEBAHR, HANNELORE:;;;22187,50 080334407211;95;45;00;;ADEBAHR, HERMANN:;;;32812,50 040638402528;99;53;00;;ADEBAHR, MANFRED:;;;35250,00 010860407234;97;08;00;;ADEBAHR, THORSTEN:;;;20285,72 160745420218;97;06;00;;ADELHARDT, THEO:;;;25687,50 181153406116;96;15;00;650/75/12, :;ADELMEIER, LUTZ;1590;RUDOLF-BREITSCHEID-STR. 234; 181153406116;96;15;00;650/75/12, :;ADELMEIER, LUTZ;1590;RUDOLF-BREITSCHEID-STR. 234; 071268412914;18;33;00;;ADELSBERGER, FRANK:;;;9540,00 110970414513;18;32;00;;ADEN, MATTHIAS:;;;6958,87 160335519717;11;80;00;;ADER, ANNA:;;;21000,00 230333419713;11;80;00;;ADER, HEROLD:;;;24000,00 210244518519;10;55;00;;ADERHOLD, BAERBEL:;;;25500,00 290664413919;60;90;00;;ADERHOLD, DIRK:;;; 290664413919;60;90;00;;ADERHOLD, DIRK:;;;15624,00 190742410628;97;01;00;;ADERHOLD, GUENTER:;;;29000,04 160538419310;10;19;00;;ADERHOLD, HANS-JUERGEN:;;;27000,00 121064418516;10;20;00;;ADERHOLD, HEIKO:;;;16170,00 130664410619;97;01;00;;ADERHOLD, JOCHEN:;;;16183,00 010662417116;18;33;00;;ADERHOLD, JOERG:;;;20075,00 290346410827;07;06;00;;ADERHOLD, KURT:;;;18596,92 190463403417;60;90;00;;ADERMANN, DIETMAR:;;; 190463403417;60;90;00;;ADERMANN, DIETMAR:;;;18345,67 150254403828;99;43;00;;ADERMANN, EDGAR:;;;20880,00 090554400213;98;84;00;;ADERMANN, ERNST:;;;19440,00 010351400712;01;51;00;;ADERMANN, KARL:;;;21525,00 080345530071;99;77;00;;ADERMANN, MONIKA:;;;21150,00 220451400221;94;03;00;;ADERMANN, RUDI:;;;19710,00 311033429711;99;43;00;;ADLER, ALBERT:;;;27750,00 090563430019;15;80;00;;ADLER, ANDREAS:;;;16912,50 100558407515;99;40;00;;ADLER, ANDREAS:;;;28980,00 220745419024;10;08;00;;ADLER, BERND:;;;21187,50 270755522020;03;00;52;;ADLER, BETTINA:;;;16025,16 010354514811;94;30;00;;ADLER, CARMEN:;;;19649,29 241248528214;14;18;00;;ADLER, CHRISTA:;;;19440,00 010154505128;30;54;00;;ADLER, EDELGARD:;;;13793,90 010254526348;12;96;67;;ADLER, ELKE:;;;16387,50 201268423624;98;85;00;;ADLER, ERIK:;;;9675,00 041041417510;94;30;00;;ADLER, FRANK:;;;27000,00 160154421817;30;33;00;;ADLER, FRANKDIETMAR:;;;20220,00 040959414829;97;06;00;;ADLER, FRANK-PETER:;;;21332,50 070867500815;94;65;00;;ADLER, GRIT:;;;1620,16 091261403714;94;65;00;;ADLER, GUENTER:;;;16115,00 200757412219;08;35;00;;ADLER, HOLGER:;;;16560,00 130466408411;94;03;00;;ADLER, HOLGER:;;;11067,00 230634412216;07;08;00;;ADLER, HORST:;;;38250,00 030268416148;09;69;00;;ADLER, JENS:;;;9700,00 311268427710;18;32;00;;ADLER, JO(E)RG:;;;9625,00 131154429728;96;15;13;;ADLER, JOACHIM:;;;25575,00 020951418819;10;00;50;;ADLER, JUERGEN:;;;26640,00 280757428256;14;18;00;;ADLER, LUTZ:;;;22770,00 040861515314;94;30;00;;ADLER, MANUELA:;;;16858,86 240870411214;18;32;00;;ADLER, MIRKO:;;;2795,00 220248419058;14;80;00;;ADLER, PETER:;;;18937,50 071143400813;94;11;00;;ADLER, PETER:;;;27000,00 070669426319;18;33;00;;ADLER, RONNY:;;;2720,00 140760512278;08;00;45;;ADLER, STEFFI:;;;14580,00 050765419727;11;06;21;;ADLER, STEPHAN:;;;14596,50 090165419033;10;00;41;;ADLER, THOMAS:;;;18393,00 220569400868;18;32;00;;ADLER, THORSTEN:;;;6781,35 250270422760;18;35;00;;ADLER, TILO:;;;9510,00 140245419714;11;06;21;;ADLER, WALTER:;;;9907,28 260649411811;07;00;45;;ADLER, WOLFGANG:;;;23760,00 010443406716;05;00;50;;ADLOFF, FREDY:;;;23340,00 240144420917;30;59;00;;ADLOFF, PETER:;;;15840,00 261046417733;99;43;00;;ADLOFF, VOLKER:;;;28500,00 090763419340;15;08;00;;ADLUNG, FALKO:;;;8745,00 141156417711;99;02;00;;ADLUNG, FRANK:;;;22770,00 280768413914;18;34;00;;ADOLF, HOLGER:;;;9675,00 150769413910;97;22;00;;ADOLF, JUERGEN:;;;8722,50 060954418319;10;11;00;;ADOLF, NORBERT:;;;23402,50 051168415319;18;28;00;;ADOLF, THOMAS:;;;9510,00 080949530056;99;43;00;;ADOLPH, GERLINDE:;;;21390,00 021144421215;12;00;41;;ADOLPH, HANS-JOACHIM:;;;27625,00 161249429728;99;43;00;;ADOLPH, HEINZ:;;;24750,00 220252522824;12;40;00;;ADOLPH, INGRID:;;;18055,00 121265513114;08;00;43;;ADOLPH, KERSTIN:;;;7807,35 271049401816;02;80;00;;ADOMAT, GUENTER:;;;19187,50 240553502315;02;55;00;;ADOMAT, RENATE:;;;20100,00 220751401816;02;51;00;;ADOMAT, WERNER:;;;21600,00 250567400618;01;08;00;;ADOMEIT, ENRICO:;;;12899,00 100157400726;01;06;24;;ADOMEIT, KARL-HEINZ:;;;18170,00 220251427411;14;00;53;;AECHTNER, GERHARD:;;;26640,00 111069410127;99;43;00;;AEDTNER, DIRK:;;;2115,00 310869422726;18;33;00;;AEHLIG, MARIO:;;;9600,00 210248400817;01;99;00;;AEPLINIUS, ECKHARD:;;;35460,00 190146410314;07;30;00;;AERNECKE, BRUNO:;;;26000,00 071044412229;97;07;00;;AERNECKE, FRITZ-JUERGEN:;;;20172,51 180865412210;98;50;00;;AERNECKE, THOMAS:;;;16146,00 290454405013;94;65;00;;AFFELD, HANS-JOACHIM:;;;25800,00 130955505028;99;77;00;;AFFELD, PETRA:;;;18534,16 100148403028;98;20;00;;AFFELDT, DIETER:;;;28625,00 021134506127;04;80;00;;AFFELDT, ERIKA:;;;16387,50 200854511518;04;12;00;;AFFELDT, GUDRUN:;;;18840,46 140536406147;04;40;00;;AFFELDT, HANS-JUERGEN:;;;23937,50 030652402728;97;01;00;;AFFELDT, HEINZ-DIETER:;;;25920,00 060255406124;04;08;00;;AFFELDT, PETER:;;;19492,50 270768403813;18;35;00;;AFFELDT, RALF:;;;9675,00 250356504118;98;83;00;;AFFINASS, CAROLA:;;;3550,18 030252402710;99;53;00;;AFFINASS, HARALD:;;;23220,00 310157408934;06;00;51;;AGTHEN, DIETMAR:;;;16962,50 280951408910;07;06;00;;AHLBERG, MANFRED:;;;20160,00 270954413417;08;00;52;;AHLBORN, AXEL:;;;20880,00 021145530050;30;61;00;;AHLBURG, BARBARA:;;;18930,00 111164430214;99;77;00;;AHLBURG, RAINER:;;;17064,00 010451411419;15;22;00;;AHLBURG, ULRICH:;;;23640,00 180236504219;01;78;00;;AHLERS, GIESELA:;;;24000,00 221168402111;18;35;00;;AHLERS, JENS:;;;9675,00 260459427919;30;48;00;;AHLERS, UWE:;;;16422,00 270349503430;03;51;00;;AHLERT, BARBARA:;;;21900,00 130145404014;03;29;00;;AHLERT, DETLEF:;;;24000,00 230536406138;04;60;00;;AHLERT, ERICH:;;;23250,00 240435506112;04;06;00;;AHLERT, INGEBURG:;;;20280,00 140952421856;97;29;00;;AHLERT, MICHAEL:;;;28761,29 020261406124;04;06;00;;AHLGRIMM, FRANK:;;;16927,50 250471423110;18;35;00;;AHLSWEDE, SVEN:;;;2795,00 090270523617;99;53;00;;AHNER, BIRGIT:;;;8300,00 210663428227;14;00;40;;AHNER, FRANK:;;;16665,00 310147424949;99;12;00;;AHNER, HERBERT:;;;33840,00 200770428821;18;31;00;;AHNER, JENS:;;;6570,00 260265428358;14;80;00;;AHNER, RALF:;;;14823,46 040547523615;98;83;00;;AHNER, ROSWITHA:;;;26640,00 180965428279;96;15;22;;AHNER, TILO:;;;17197,50 071056428287;14;00;40;;AHNERT, ANDREAS:;;;23402,50 160841528210;14;80;00;;AHNERT, CHRISTA:;;;18562,50 191154515313;99;77;00;;AHNERT, CORNELIA:;;;23760,00 200649428213;94;11;00;;AHNERT, DIETER:;;;21532,50 230439421854;14;60;00;;AHNERT, DIETMAR:;;;21750,00 031263428013;14;40;00;;AHNERT, FRANK:;;;11220,00 030448527558;30;81;00;;AHNERT, GISELA:;;;14272,65 040536521817;14;60;00;;AHNERT, GUDRUN:;;;16445,00 230439428212;14;80;00;;AHNERT, HANS:;;;16611,25 220459430169;99;26;00;;AHNERT, HARALD:;;;21390,00 021244427411;18;71;25;;AHNERT, HARTMUT:;;;30000,00 161037429734;96;15;14;;AHNERT, HERMANN:;;;30750,00 010354419013;09;26;00;;AHNERT, HORST:;;;20760,00 240656528307;14;77;00;;AHNERT, REGINA:;;;17820,00 160558428222;14;65;00;;AHNERT, VOLKER:;;;18342,50 161049501713;01;80;00;;AHNFELDT, MARIA-LUISE:;;;18720,00 011151400819;01;65;00;;AHNFELDT, RAINER:;;;24120,00 140369410113;07;06;00;;AHREND, MARIO:;;;13425,00 030669412236;15;69;00;;AHREND, MARIO:;;;9510,00 060770404318;18;33;00;;AHREND, MATTHIAS:;;;2720,00 050830430026;97;01;00;;AHRENDT, ARNOLD:;;;25687,50 220851407123;30;47;00;;AHRENDT, BERND:;;;21940,00 060145416911;09;06;00;;AHRENDT, DIETER:;;;22687,50 290733430043;30;83;00;;AHRENDT, ERICH:;;;48511,00 160764402744;02;00;00;;AHRENDT, FRANK:;;;11067,00 171150412212;94;11;00;2382/74, :;AHRENDT, HANS;1092;WARTENBERGER STR. 34C; 171150412212;94;11;00;2382/74, :;AHRENDT, HANS;1092;WARTENBERGER STR. 34C; 200870402127;18;31;00;;AHRENDT, HARDY:;;;6705,00 070347511510;07;12;00;;AHRENDT, HEIDE:;;;20264,26 110730407410;97;01;00;;AHRENDT, HELMUT:;;;27750,00 230849412221;07;51;00;;AHRENDT, NORBERT:;;;23250,00 140969402715;02;69;00;;AHRENS, ENRICO:;;;9555,00 181070403438;18;32;00;;AHRENS, KAI-MICHAEL:;;;2795,00 241250400412;97;01;00;;AHRENS, LOTHAR:;;;20230,00 140761430100;97;29;00;;AHRENS, ROLF:;;;19667,87 240770401924;94;03;00;;AHRENS, SILVIO:;;;4232,58 210967401912;99;02;00;;AHRENS, TORSTEN:;;;14994,00 171069430034;15;69;00;;AHRENS, UWE:;;;8955,00 140465407918;06;00;48;;AI, SILKO:;;;15455,00 280764505117;30;30;00;;AJER, INES:;;;6200,00 220755405216;04;02;00;;ALAND, GUNNAR:;;;22660,00 060968419048;18;32;00;;ALAND, JAN:;;;8619,34 160965530187;94;30;00;;ALBAN, KATRIN:;;;5890,47 240160424993;99;40;00;;ALBAN, THOMAS:;;;22466,57 010462430228;94;03;00;;ALBANI, BERND:;;;18150,00 300435429729;99;43;00;;ALBANI, LUDWIG:;;;21750,00 081168421038;18;35;00;;ALBANI, ROLAND:;;;9825,00 270337400012;94;03;00;;ALBAT, GUENTHER:;;;21375,00 220641500012;94;03;00;;ALBAT, JUTTA:;;;17625,00 070560422218;98;84;00;;ALBAT, KLAUS:;;;19106,69 310160509517;97;06;00;;ALBAT, SABINE:;;;17495,05 090470400822;18;35;00;;ALBATH, ANDRE:;;;9510,00 041250420513;97;06;00;;ALBER, BERND:;;;24650,00 060850420510;97;06;00;;ALBER, DETLEF:;;;23040,00 220734530050;97;06;00;;ALBER, ELFRIEDE:;;;19320,00 050651522013;98;82;00;;ALBER, ILONA:;;;16115,57 160164429214;99;43;00;;ALBERS, RALF:;;;16550,56 110162525012;10;40;00;;ALBERT, ANGELA:;;;14462,11 250752514721;08;77;00;;ALBERT, BAERBEL:;;;34420,62 211149418346;10;12;00;;ALBERT, BERND:;;;33000,00 081068422041;98;18;00;;ALBERT, CHRISTIAN:;;;8950,00 090654429742;15;00;42;;ALBERT, CLAUS:;;;24150,00 290958415311;08;00;61;;ALBERT, DETLEF:;;;19140,00 141168430016;18;38;00;;ALBERT, DIRK:;;;9675,00 231159528918;97;22;00;;ALBERT, ELKE:;;;18379,59 060661422760;30;61;00;;ALBERT, FRANK:;;;11700,00 240949418910;10;00;42;;ALBERT, FRIEDER:;;;18187,50 090352413913;08;20;00;;ALBERT, HANS-PETER:;;;27540,00 291249414628;08;53;00;;ALBERT, HARALD:;;;25530,00 210144422018;12;53;00;;ALBERT, HEINZ:;;;23250,00 071055426319;10;06;00;;ALBERT, JOACHIM:;;;20590,00 290962419016;10;02;00;;ALBERT, JOERG:;;;16092,00 191158426510;98;82;00;;ALBERT, JUERGEN:;;;19262,50 200166506459;04;20;00;;ALBERT, KERSTIN:;;;11931,48 230138409114;06;00;47;;ALBERT, LOTHAR:;;;36000,00 271254419046;10;20;00;;ALBERT, PETER:;;;22253,00 130751426328;99;13;00;;ALBERT, ROLAND:;;;26640,00 300934415348;08;26;00;;ALBERT, ROLF:;;;25075,00 090547427928;14;12;00;;ALBERT, SIEGFRIED:;;;24000,00 051135515321;08;80;00;;ALBERT, SIGRID:;;;18720,00 270846526713;14;08;00;;ALBERT, SONJA:;;;19380,00 190468422713;12;69;00;;ALBERT, THOMAS:;;;10175,00 160768422750;18;80;00;;ALBERT, TOM-DIETER:;;;9675,00 180234407212;97;08;00;;ALBERT, WERNER:;;;29250,00 040142429743;99;43;00;;ALBERT, WOLFGANG:;;;28500,00 180255415430;94;65;00;;ALBERTUS, GERD:;;;20590,00 200968415313;18;35;00;;ALBIG, HENRIK:;;;9600,00 081254408411;97;29;00;;ALBINUS, BERND:;;;24667,50 051152521010;97;06;00;;ALBINUS, BRIGITTE:;;;18895,86 110647407639;98;18;00;;ALBINUS, RAINER:;;;29520,00 191244422727;98;20;00;;ALBINUS, WOLFGANG:;;;24687,50 010256412918;15;06;00;;ALBINUS, WOLFGANG:;;;20010,00 210867416412;18;33;00;;ALBRACHT, FRANK:;;;9675,00 130639405017;01;19;69;;ALBRECHT, ADELBERT:;;;26250,00 060468411816;18;34;00;;ALBRECHT, ALEXANDER:;;;9825,00 140660430101;98;82;00;;ALBRECHT, ANDRE:;;;17490,00 150769414729;18;35;00;;ALBRECHT, ANDRE:;;;6705,00 250960530224;97;06;00;;ALBRECHT, ANDREA:;;;15855,99 220267422033;94;03;00;;ALBRECHT, ANDREAS:;;;16416,00 051060417312;09;06;20;;ALBRECHT, ANDREAS:;;;16775,00 060968429211;97;01;00;;ALBRECHT, AXEL:;;;8950,00 191250425078;13;51;00;;ALBRECHT, BERND:;;;20872,50 160350409217;99;53;00;;ALBRECHT, BERND:;;;23187,50 311057430194;96;15;06;;ALBRECHT, BERND:;;;24352,17 201139500814;99;40;00;;ALBRECHT, BRIGITTE:;;;22680,00 050652517726;09;77;00;;ALBRECHT, BRIGITTE:;;;23040,00 141153403218;98;84;00;;ALBRECHT, BRUNO:;;;20590,00 061069518514;10;06;00;;ALBRECHT, CARINA:;;;11940,00 261161509529;99;78;00;;ALBRECHT, DANA:;;;17899,54 101057402518;98;83;00;;ALBRECHT, DETLEF:;;;18676,00 100960430238;15;65;00;;ALBRECHT, DETLEF:;;;18590,00 150755421733;12;09;00;;ALBRECHT, DETLEF:;;;23100,00 010864401921;02;06;00;;ALBRECHT, DETLEF:;;;15160,81 250137407414;98;82;00;;ALBRECHT, DIETER:;;;25500,00 071070407247;99;43;00;;ALBRECHT, DIRK:;;;3620,00 280163424717;94;65;00;;ALBRECHT, DIRK:;;;17985,00 060449410316;06;06;00;;ALBRECHT, EBERHARD:;;;21687,50 050631429743;15;07;00;;ALBRECHT, EBERHARD:;;;28750,00 290534417751;99;49;00;;ALBRECHT, ERICH:;;;26250,00 301067407423;05;69;00;;ALBRECHT, ERIK:;;;10725,00 280867407229;18;71;20;;ALBRECHT, FRANK:;;;15450,00 210759427915;97;22;00;;ALBRECHT, FRANK:;;;20872,50 060253515116;30;83;00;;ALBRECHT, GABRIELE:;;;16866,34 100853419615;11;15;00;;ALBRECHT, GERD:;;;25242,50 101043403114;03;08;00;;ALBRECHT, GERHARD:;;;25312,50 190648400618;01;80;00;;ALBRECHT, GUENTER:;;;18937,50 211146421013;97;08;00;;ALBRECHT, HANNES:;;;25500,00 031252400728;97;01;00;;ALBRECHT, HANS-JOACHIM:;;;28080,00 290647415015;05;18;00;;ALBRECHT, HANS-JOACHIM:;;;28440,00 230541422714;12;20;00;;ALBRECHT, HANS-JOACHIM:;;;27360,00 170943429730;99;43;00;;ALBRECHT, HANS-JOACHIM:;;;28250,00 120742415310;08;20;00;;ALBRECHT, HANS-JUERGEN:;;;27000,00 131262402426;18;80;00;;ALBRECHT, HARTMUTH:;;;16830,00 231251402218;94;03;00;;ALBRECHT, HEINO:;;;23760,00 070457405241;18;80;00;;ALBRECHT, HEINZ:;;;19320,00 310835406912;97;07;00;;ALBRECHT, HEINZ:;;;28875,00 260550518416;12;96;67;;ALBRECHT, HELGA:;;;16170,00 031035522710;12;78;00;;ALBRECHT, HELGA:;;;26250,00 090355407017;05;00;49;;ALBRECHT, HENRY:;;;22330,00 110753429719;99;43;00;;ALBRECHT, HERGEN:;;;19380,00 150133504112;94;03;00;;ALBRECHT, HERTA:;;;20880,00 181235402717;02;12;00;;ALBRECHT, HORST:;;;25500,00 150271430262;15;69;00;;ALBRECHT, JAN:;;;2925,64 040362428216;14;40;00;;ALBRECHT, JENS:;;;19910,00 171041408919;06;00;51;;ALBRECHT, JOACHIM:;;;25500,00 281052424911;13;00;40;;ALBRECHT, JOCHEN:;;;21120,00 291070407014;05;69;00;;ALBRECHT, JOERN:;;;2870,00 240541416217;09;00;43;;ALBRECHT, JUERGEN:;;;22937,50 130842422226;12;06;00;;ALBRECHT, KARL-HEINZ:;;;23187,50 040435429712;94;30;00;;ALBRECHT, KARL-RAINER:;;;32250,00 191167401921;02;69;00;;ALBRECHT, KARSTEN:;;;9675,00 031168413913;08;69;00;;ALBRECHT, KAY:;;;9555,00 010633430039;15;40;00;;ALBRECHT, KLAUS:;;;28500,00 140945420011;11;51;00;;ALBRECHT, KLAUS-DIETER:;;;20250,00 120933400816;94;65;00;;ALBRECHT, KLAUS-JUERGEN:;;;44250,00 251240430342;94;65;00;;ALBRECHT, KURT:;;;23250,00 301267422046;99;43;00;;ALBRECHT, MAIK:;;;14594,00 290358401514;95;45;00;;ALBRECHT, MANFRED:;;;20872,50 301160425060;99;26;00;;ALBRECHT, MARCO:;;;20505,00 201254529911;98;54;00;;ALBRECHT, MARINA:;;;20872,50 060431429713;97;06;00;;ALBRECHT, MARTIN:;;;23328,63 130853506142;04;51;00;;ALBRECHT, MARTINA:;;;19726,31 221270400833;01;69;00;;ALBRECHT, MARTINO:;;;6806,61 140158406819;99;78;00;;ALBRECHT, MICHAEL:;;;22955,48 210559430095;94;11;00;;ALBRECHT, NORBERT:;;;22117,50 310744412225;07;51;00;;ALBRECHT, PETER:;;;21562,50 011040402117;02;00;44;;ALBRECHT, PETER:;;;27000,00 180954400713;02;26;00;;ALBRECHT, PETER:;;;20880,00 141267416930;18;40;00;;ALBRECHT, PETER:;;;11280,00 211061530050;97;06;00;;ALBRECHT, PETRA:;;;16880,47 120159530047;30;63;00;;ALBRECHT, PETRA:;;;7025,00 260960418530;94;03;00;;ALBRECHT, RALPH:;;;17930,00 110758424984;13;55;00;;ALBRECHT, RENE:;;;18112,50 140769421014;18;35;00;;ALBRECHT, RONALD:;;;9510,00 130159530150;15;08;00;;ALBRECHT, ROSWITHA:;;;5659,11 141033503214;03;00;43;;ALBRECHT, RUTH:;;;11557,50 290434530044;97;06;00;;ALBRECHT, RUTH:;;;21360,00 220756529755;99;77;00;;ALBRECHT, SABINE:;;;17597,24 070936530066;98;83;00;;ALBRECHT, SIEGLINDE:;;;27750,00 060867524420;13;00;41;;ALBRECHT, SONJA:;;;5725,13 110969428256;18;32;00;;ALBRECHT, STEFFEN:;;;9510,00 250857419827;11;53;00;;ALBRECHT, STEPHAN:;;;18630,00 111168405913;18;35;00;;ALBRECHT, SVEN:;;;9675,00 210569401538;01;69;00;;ALBRECHT, SVEN:;;;9842,26 070969427313;99;43;00;;ALBRECHT, THOMAS:;;;9600,00 131268413214;18;35;00;;ALBRECHT, THOMAS:;;;9675,00 210462410514;94;03;00;;ALBRECHT, THORSTEN:;;;18315,00 100667406159;97;22;00;;ALBRECHT, TINO:;;;14544,00 040568409221;94;65;00;;ALBRECHT, TINO:;;;10197,58 130264422127;12;77;00;;ALBRECHT, UDO:;;;16500,00 040450506114;97;08;00;;ALBRECHT, UTE:;;;23760,00 250460430040;98;84;00;;ALBRECHT, UWE:;;;17376,50 260260421819;14;80;00;;ALBRECHT, UWE:;;;17250,00 130459422215;99;43;00;;ALBRECHT, UWE:;;;23460,00 160568422211;99;43;00;;ALBRECHT, UWE:;;;14794,00 180643415328;30;38;00;;ALBRECHT, VOLKER:;;;19440,00 291137403617;03;03;00;;ALBRECHT, WALTER:;;;24000,00 310857414227;99;43;00;;ALBRECHT, WALTER:;;;20010,00 151050419611;11;26;00;;ALBRECHT, WERNER:;;;22275,00 210247416219;09;06;00;;ALBRECHT, WERNER:;;;25125,00 210640429710;96;15;05;;ALBRECHT, WERNER:;;;31500,00 140131429711;15;80;00;;ALBRECHT, WILLI:;;;20502,08 101150401712;02;15;00;;ALBRECHT, WINFRIED:;;;27885,00 270359413914;08;26;00;;ALBRECHT, WOLFRAM:;;;20470,00 040360400017;01;06;22;;ALBUSCHAT, DIETMAR:;;;16665,00 210759430073;15;00;47;;ALDUS, GERRY:;;;22385,00 250562530165;15;07;00;;ALDUS, PEGGY:;;;17160,00 181245400811;01;06;00;;ALEX, BENNO:;;;22562,50 280453406437;04;06;00;;ALEX, BERND:;;;19665,00 160541412128;07;07;00;;ALEX, DIETER:;;;25418,15 290464414415;02;02;00;;ALEX, FRANK:;;;16445,00 150267424927;13;08;00;;ALEX, HEIKO:;;;14220,00 280652411415;04;08;00;;ALEX, KLAUS-DIETER:;;;25320,00 200959406458;99;40;00;;ALEX, MARKO:;;;20770,00 010657411422;07;80;00;;ALEX, NORBERT:;;;16473,75 100658420717;12;08;00;;ALEX, REINER:;;;19250,00 131070417519;18;34;00;;ALEXI, SILVIO:;;;2795,00 071043429731;97;08;00;;ALFF, PETER:;;;27750,00 250670408511;18;31;00;;ALGERMISSEN, MARIO:;;;6705,00 050961426828;18;33;00;;ALICH, DETLEF:;;;21285,00 020862416416;11;96;63;;ALISCH, GERD:;;;16830,00 120946429714;99;43;00;;ALISCH, KLAUS:;;;21750,00 080747421839;14;17;00;;ALISCH, MANFRED:;;;28625,00 101262517410;11;96;63;;ALISCH, PETRA:;;;10670,00 030240406503;04;53;00;;ALISCH, SIEGFRIED:;;;27375,00 060568408315;18;32;00;;ALISCH, TORSTEN:;;;9675,00 220667416417;99;43;00;;ALKER, JUERGEN:;;;13800,00 061260407521;05;51;00;;ALLEDAN, FRANK:;;;17902,50 100368400515;18;32;00;;ALLION, RAINER:;;;9675,00 311270414310;18;31;00;;ALLMENDINGER, JAN:;;;2795,00 140353410813;07;06;00;;ALLNER, HERBERT:;;;20820,00 251162415314;08;18;00;;ALLONGE, MATTHIAS:;;;18480,00 180465500828;01;08;00;;ALLONGE, RAMONA:;;;13490,42 180455406432;04;02;00;;ALLRICH, RALF:;;;24296,53 270163417710;09;41;00;;ALLSTA(E)DT, JENS:;;;17820,00 311264417718;95;45;00;;ALLSTAEDT, TORSTEN:;;;16830,00 180653413019;08;00;42;;ALLSTEDT, GU(E)NTER:;;;25840,00 070349400128;01;08;00;;ALLZEIT, HANS-GEORG:;;;22500,00 150765502617;02;02;00;;ALM, ANDREA:;;;2804,52 200138402628;02;00;49;;ALM, EGON:;;;24750,00 121142429713;99;43;00;;ALM, LUTZ:;;;20750,00 020666430093;99;43;00;;ALM, MICHAEL:;;;15444,00 150753429715;94;11;00;;ALM, REINHARDT:;;;22252,50 220740409564;06;53;00;;ALMEROTH, KLAUS:;;;27000,00 040458530098;18;25;00;;ALMEROTH, MARGIT:;;;17093,68 190564409519;18;80;00;;ALMEROTH, STEFFEN:;;;17820,00 120169407421;18;71;20;;ALMONEIT, UWE:;;;9510,00 130361504722;04;00;44;;ALMS, SILVIA:;;;16225,00 110751425060;30;84;00;;ALMSICK, BERND:;;;25875,00 090551509248;30;31;00;;ALMSICK, JUTTA:;;;23171,25 290134529738;15;09;00;;ALMSTEDT, ELISABETH:;;;24750,00 050256429863;94;30;00;;ALMSTEDT, JUERGEN:;;;22080,00 240265410336;97;22;00;;ALPERMANN, JENS:;;;18507,00 230170417720;18;34;00;;ALPERSTA(E)DT, DIRK:;;;9510,00 141165517546;09;53;00;;ALPERSTEDT, ANKE:;;;10735,49 170151420316;11;30;00;;ALPERSTEDT, KLAUS:;;;26580,00 030952412119;07;00;59;;ALRICH, HANS-GEORG:;;;24480,00 111069428239;18;28;00;;ALSCHER, STEFFEN:;;;6576,77 110731406129;04;08;00;;ALSCHWEIG, GUENTER:;;;26250,00 060945411414;07;80;00;;ALSLEBEN, GERD:;;;20250,00 010155416215;09;00;43;;ALSLEBEN, HEIKO:;;;19933,32 130570411426;18;31;00;;ALSLEBEN, MARCO:;;;6705,00 130860402528;02;06;00;;ALSLEBEN, MATTHIAS:;;;17926,70 061063416242;09;18;00;;ALSLEBEN, MICHAEL:;;;18687,17 280251413014;08;00;42;;ALSLEBEN, ULRICH:;;;25530,00 161269411410;07;06;00;;ALSLEBEN, UWE:;;;12310,00 030767417743;09;80;00;;ALT, ANDREAS:;;;15383,00 301063518214;12;00;49;;ALT, GABRIELE:;;;15507,84 180368424827;13;00;51;;ALT, UWE:;;;8950,00 270670408317;06;69;00;;ALTENAU, FALK:;;;3165,16 020137429732;97;08;00;;ALTENBURG, RAIMAR:;;;25500,00 080169413211;18;32;00;;ALTENDORF, ANDREAS:;;;9571,78 270760511414;07;53;00;;ALTENDORF, IRIS:;;;6136,94 220758412235;07;18;00;;ALTENDORF, RONALD:;;;26047,50 300339512215;07;15;00;;ALTENDORF, URSULA:;;;21780,00 300169417476;97;01;00;;ALTENHOF, KAI:;;;12600,00 290858402724;02;18;00;;ALTENKIRCH, RAINER:;;;23100,00 080862421519;97;01;00;;ALTENKRUEGER, BERND:;;;16170,00 230860407247;05;40;00;;ALTER, BRUNO:;;;21807,50 290848413112;98;82;00;;ALTER, WOLFGANG:;;;22500,00 130244429727;99;43;00;;ALTERMANN, HANS-GEORG:;;;28750,00 220260406145;04;06;00;;ALTHANS, DETLEF:;;;17245,00 100240506118;04;80;00;;ALTHANS, ROSEMARIE:;;;17340,00 080251400014;99;43;00;;ALTHAPP, SIEGFRIED:;;;23017,50 280757406188;99;02;00;;ALTHAUS, JOCHEN:;;;21792,50 260471420023;18;28;00;;ALTHAUS, MICHAEL:;;;2720,00 190463416613;09;18;00;;ALTHAUS, THOMAS:;;;6075,00 140629406111;17;00;00;;ALTHAUS, WERNER:;;;35250,00 300666408941;60;90;00;;ALTHOF, MAIK:;;; 300666408941;60;90;00;;ALTHOF, MAIK:;;;15408,00 181253529834;30;61;00;;ALTMANN, ANNE-DORE:;;;20461,37 110835521826;12;78;00;;ALTMANN, CHRISTA:;;;20010,00 111156422855;12;00;40;;ALTMANN, DETLEF:;;;15157,50 140939429714;97;01;00;;ALTMANN, DIETER:;;;20625,00 220951408211;98;83;00;;ALTMANN, DIETER:;;;22080,00 101135420210;97;01;00;;ALTMANN, GUENTER:;;;33500,04 080635421818;12;08;00;;ALTMANN, GUENTER:;;;21937,50 190469411119;07;03;00;;ALTMANN, HEIKO:;;;12675,00 270557416921;98;81;00;;ALTMANN, INGO:;;;18017,35 010365413418;99;51;00;;ALTMANN, JAN:;;;18067,50 150171421836;97;22;00;;ALTMANN, JENS:;;;6833,71 070870429722;97;06;00;;ALTMANN, JENS:;;;4090,81 160857505638;04;69;00;;ALTMANN, JUTTA:;;;15468,73 090333405619;04;00;50;;ALTMANN, KURT:;;;28500,00 300959421816;99;02;00;;ALTMANN, LUTZ:;;;24150,00 140539522717;12;00;40;;ALTMANN, MONIKA:;;;15015,00 051155405621;04;19;00;;ALTMANN, NORBERT:;;;21105,00 260845418228;10;14;00;;ALTMANN, PAUL-EBERHARD:;;;24750,00 110469430018;99;13;00;;ALTMANN, PETER:;;;8950,00 090260422791;18;25;00;;ALTMANN, RALF:;;;22580,25 091053422224;99;55;00;;ALTMANN, REINER:;;;21360,00 090171406124;18;33;00;;ALTMANN, RENE:;;;2795,00 280666408815;30;58;00;;ALTMANN, RENE:;;;15490,00 210440425029;97;01;00;;ALTMANN, ROLF:;;;28500,00 150547524914;13;11;00;;ALTMANN, SONJA:;;;19912,50 060735505615;94;65;00;;ALTMANN, SONJA:;;;15525,00 070949411138;97;01;00;;ALTMANN, STEFAN:;;;28500,00 110570410425;17;00;00;;ALTMANN, SVEN:;;;8300,00 250170424021;18;32;00;;ALTMANN, UWE:;;;9510,00 120370400125;18;33;00;;ALTMANN, WERNER:;;;9510,00 010453411017;98;83;00;;ALTMANN, WOLFGANG:;;;20880,00 260838430050;30;31;00;;ALTMEIER, ROLF:;;;17280,00 270144524828;07;00;42;;ALTNER, BRIGITTE:;;;19500,00 240656408559;60;90;00;;ALTNER, DIETMAR:;;; 240656408559;60;90;00;;ALTNER, DIETMAR:;;;18647,50 110759424927;13;00;49;;ALTNER, FRANK:;;;20772,01 010961415313;08;00;40;;ALTNER, KLAUS-PETER:;;;20625,00 231258424970;13;00;40;;ALTNER, LUTZ:;;;20460,00 150261415317;99;40;00;;ALTNER, PETER:;;;21785,00 080969425034;13;69;00;;ALTNER, RAINER:;;;9555,00 080166425014;13;06;20;;ALTNER, RALF:;;;14977,50 250458422746;96;15;02;;ALTNICKEL, ULLRICH:;;;24150,00 210969428238;18;33;00;;ALTROGGE, DIRK:;;;10500,00 040750429755;15;06;00;;ALTSCHAFFEL, BERND:;;;25920,00 261063430059;94;65;00;;ALTSCHER, ANDREAS:;;;16170,00 260138429729;97;22;00;;ALTSCHER, MANFRED:;;;26250,00 161269404317;94;03;00;;ALTUS, BJOERN:;;;9510,00 111247409218;06;00;46;;ALTUS, HELMUT:;;;26680,00 181240429711;96;15;22;;ALTWEIN, JUERGEN:;;;29250,00 141042422221;12;06;00;;ALTWEIN, LOTHAR:;;;23250,00 161069410325;18;33;00;;ALVERMANN, DIRK:;;;10575,00 171045530030;99;77;00;;ALWAST, CHRISTINE:;;;22500,00 160239429746;99;43;00;;ALWAST, GUENTER:;;;26250,00 061145429733;97;08;00;;ALWAST, HANS-JUERGEN:;;;28500,00 280540530030;95;45;00;;ALWAST, INGE:;;;20130,00 070561519716;11;96;63;;AMARELL, BURGUNDE:;;;6244,49 240270419837;18;33;00;;AMARELL, FRANK:;;;7001,61 051238419818;11;00;42;;AMARELL, PETER:;;;26250,00 280331412230;98;18;00;;AMBACH, FRITZ:;;;28500,00 060234512219;98;18;00;;AMBACH, INGE:;;;18645,00 261147408414;06;15;00;;AMBACH, ULRICH:;;;24150,00 240147523815;13;00;43;;AMBERG, INGE:;;;20470,00 111263407415;18;33;00;;AMBOHS, KAY:;;;21120,00 270248416223;09;06;00;;AMBORN, RALF:;;;24500,04 030669420113;18;38;00;;AMBORN, STEFFEN:;;;9510,00 100470420029;18;35;00;;AMBORN, THOMAS:;;;9510,00 060967424929;18;38;00;;AMBOS, AXEL:;;;9675,00 201239401311;01;51;00;;AMBOS, MANFRED:;;;22187,50 021058407417;99;43;00;;AMBOSZ, STEFFEN:;;;21450,00 150554403328;03;80;00;;AMBROS, ALFONS:;;;21332,50 210650428228;14;29;00;;AMBROS, CHRISTIAN:;;;28470,00 260753428218;14;00;52;;AMBROS, MICHAEL:;;;24480,00 290147407510;05;53;00;;AMBROSELLI, BERND:;;;26312,50 220251507526;05;12;00;;AMBROSELLI, MARLIES:;;;20517,50 271270425438;94;65;00;;AMBROSIUS, JENS:;;;2870,00 050459403428;99;43;00;;AMEIS, RAFFAEL:;;;20010,00 140637508417;06;00;44;;AMEIS, URSULA:;;;22250,00 250253415112;08;00;45;;AMELANG, HARTMUT:;;;24150,00 240332406119;04;55;00;;AMELING, HELMUT:;;;23250,00 010556517738;99;77;00;;AMELUNG, ELKE:;;;23460,00 101258430136;99;77;00;;AMELUNG, THOMAS:;;;28750,00 210668419717;11;69;00;;AMEND, MARIO:;;;9060,00 250734529719;97;06;00;;AMENT, ANNELIESE:;;;28500,00 131233429718;99;40;00;;AMENT, DIETER:;;;39750,00 040758430021;97;22;00;;AMENT, DIRK:;;;22942,50 140757530125;98;83;00;;AMENT, MARTINA:;;;17737,50 180839428219;14;55;00;;AMENT, RUDOLF:;;;19125,00 140949408917;04;29;00;;AMFT, HARTMUT:;;;27007,50 191167424971;99;43;00;;AMFT, JUERGEN:;;;9675,00 060363410315;17;00;00;;AMLER, MATHIAS:;;;18480,00 160752413710;97;06;00;;AMLER, ROLAND:;;;26280,00 100556410315;15;09;00;;AMLER, THOMAS:;;;24840,00 251270416023;09;00;40;;AMLING, ANDRE:;;;2700,00 220268430019;99;43;00;;AMLING, DIRK:;;;14475,00 290440429727;99;43;00;;AMLING, JOACHIM:;;;29250,00 100571401513;01;69;00;;AMLING, JOERG:;;;2896,61 300147416018;09;00;42;;AMLING, JUERGEN:;;;17460,00 210668419733;11;69;00;;AMM, AXEL:;;;9675,00 230866419919;99;14;00;;AMM, DIRK:;;;15270,00 150665419920;94;11;00;;AMM, MATTHIAS:;;;16197,00 221068420339;96;15;13;;AMM, OLAF:;;;8950,00 160551415015;08;00;60;;AMMER, KLAUS-WILFRIED:;;;23375,00 281064430200;15;40;00;;AMMON, KAY:;;;11220,00 210265410611;11;02;00;;AMMON, ROLF:;;;16115,00 270764514743;11;08;00;;AMMON, SILKE:;;;2554,84 090268404811;96;15;27;;AMOULONG, AXEL:;;;13182,00 070470407524;18;35;00;;AMSTEIN, GUIDO:;;;2795,00 091267420013;11;69;00;;AMSTEIN, MARIO:;;;9675,00 310133400815;01;99;00;;AMTHOR, ARTUR:;;;45000,00 310835529736;99;40;00;;AMTHOR, CHRISTINE:;;;37500,00 250147430044;90;65;40;7263/75,;AMTHOR, JU(E)RGEN;1130;GOTLINDESTR. 59; 250147430044;90;65;40;7263/75,;AMTHOR, JU(E)RGEN;1130;GOTLINDESTR. 59; 240347528215;94;30;00;;AMTHOR, MARIA-MARGRIT:;;;23520,00 140668416013;18;34;00;;AMTHOR, MARIO:;;;9986,44 201065406146;97;06;00;;AMTHOR, MARIO:;;;17523,00 111035429719;96;15;13;;AMTHOR, PETER:;;;28500,00 090768416413;09;69;00;;ANACKER, DIRK:;;;12850,00 280470419811;18;38;00;;ANACKER, ENRICO:;;;9510,00 100564420310;11;14;00;;ANACKER, HANS-ERHARDT:;;;11220,00 190534429711;99;43;00;;ANACKER, OTTO:;;;20625,00 080764417428;99;77;00;;ANBAU, MICHAEL:;;;16995,00 010668417424;18;71;20;;ANBAU, PETER:;;;9600,00 101065403617;05;69;00;;ANBLANK, VOLKER:;;;11016,00 220951403429;03;08;00;;ANCLAM, HANS-JOACHIM:;;;22980,00 040654413016;08;00;42;;ANCZYK, BERND:;;;26640,00 060370417419;99;43;00;;ANDERIE, MARCO:;;;2870,00 110953408912;06;02;00;;ANDERMANN, DETLEF:;;;28560,00 150851413928;08;08;00;;ANDERMANN, REINER:;;;27720,00 111165515316;08;20;00;;ANDERS, ANDREA:;;;11692,76 220260426322;94;64;00;;ANDERS, ARNFRIED:;;;18975,00 070559420928;99;43;00;;ANDERS, BERND:;;;21842,58 130452518521;10;06;00;;ANDERS, BRIGITTE:;;;16472,50 210948413619;18;27;00;;ANDERS, DIETER:;;;27750,00 180842406117;04;20;00;;ANDERS, DIETRICH:;;;27750,00 270640406118;04;53;00;;ANDERS, EBERHARD:;;;26437,50 181065422212;12;00;55;;ANDERS, ENRICO:;;;15388,50 270553421045;12;53;00;;ANDERS, FALK:;;;28020,00 310163413414;08;00;62;;ANDERS, FRANK:;;;19552,50 220967428110;14;00;60;;ANDERS, FRANK:;;;11438,00 120454407922;06;00;48;;ANDERS, GERT:;;;24480,00 201053429746;98;18;00;;ANDERS, HANS-PETER:;;;26507,50 200130422712;12;99;00;;ANDERS, HARDI:;;;45000,00 130647417755;09;08;00;;ANDERS, HERBERT:;;;20437,50 110731429726;96;15;06;;ANDERS, HORST:;;;29479,17 020456416226;09;08;00;;ANDERS, JUERGEN:;;;18773,75 190558405028;97;07;00;;ANDERS, KARL-PETER:;;;20700,00 020354422019;06;00;46;;ANDERS, KLAUS-PETER:;;;14130,00 190329409519;06;18;00;;ANDERS, LOTHAR:;;;25987,50 110244418325;10;06;00;;ANDERS, LUTZ:;;;22320,00 270768416411;18;31;00;;ANDERS, MAIK:;;;9825,00 060666522226;12;00;49;;ANDERS, MARTINA:;;;11097,17 050755522712;96;15;31;;ANDERS, MARTINA:;;;19800,00 231068413111;18;34;00;;ANDERS, MIRKO:;;;9675,00 210750528015;14;06;00;;ANDERS, MONIKA:;;;15489,46 011246428021;14;06;00;;ANDERS, PETER:;;;22880,00 100137429724;99;02;00;;ANDERS, PETER:;;;26250,00 030863403317;01;69;00;;ANDERS, RAINER:;;;16830,00 140353429733;15;60;00;;ANDERS, RALF:;;;24667,50 020861420552;12;00;54;;ANDERS, RALF:;;;19965,00 070339506113;04;40;00;;ANDERS, RENATE:;;;22687,50 061233429717;99;43;00;;ANDERS, SIEGFRIED:;;;26250,00 180262421310;12;00;49;;ANDERS, STEFFEN:;;;19112,50 281269413711;18;33;00;;ANDERS, SVEN:;;;2795,00 280264415318;99;51;00;;ANDERS, TORALF:;;;19855,00 200760430012;94;03;00;;ANDERS, VOLKER:;;;18871,35 030447424434;13;51;00;;ANDERS, WERNER:;;;21750,00 310855406119;97;08;00;;ANDERS, WINFRIED:;;;16905,00 290649415019;08;00;60;;ANDERS, WOLFGANG:;;;29250,00 130270415329;99;43;00;;ANDERSECK, JENS:;;;6780,00 161063530190;98;82;00;;ANDERSEN, KERSTIN:;;;0,00 060761422856;98;83;00;;ANDERSEN, OLE:;;;18397,50 020670500410;01;96;52;;ANDERSSON, ANJA:;;;2340,00 170150530169;94;65;00;;ANDERSSON, BAERBEL:;;;23566,26 041144429733;94;65;00;;ANDERSSON, KARL-LUDWIG:;;;24000,00 090352429712;96;15;21;;ANDING, GOETZ-DETLEF:;;;25587,50 200747429711;99;09;00;;ANDING, KNUT:;;;32250,00 180368423613;13;00;42;;ANDLA, JENS:;;;14400,00 060663407927;98;20;00;;ANDRACK, ARMIN:;;;18425,00 230551411824;30;42;00;;ANDRAE, BERND:;;;20312,50 240667430209;99;43;00;;ANDRAE, DIRK:;;;14436,00 311247424318;05;18;00;;ANDRAE, FRANK:;;;32940,00 010439429712;99;43;00;;ANDRAE, GUENTER:;;;28500,00 121069420711;04;18;00;;ANDRAE, HEINER:;;;8300,00 011041429733;99;77;00;;ANDRAE, HEINZ:;;;42750,00 031147429211;14;00;61;;ANDRAE, HEINZ-JUERGEN:;;;24150,00 091270413121;18;28;00;;ANDRAE, JO(E)RG:;;;2945,00 060948407218;99;26;00;;ANDRAE, KLAUS:;;;27750,00 120339420718;17;00;00;;ANDRAE, KLAUS-JUERGEN:;;;35250,00 141158417424;97;06;00;;ANDRAE, REINHARDT:;;;21390,00 050268429211;97;01;00;;ANDRAE, UDO:;;;8950,00 300160422041;12;09;00;;ANDRAE, ULRICH:;;;22080,00 090460407035;98;84;00;;ANDRASCH, JOERG:;;;18400,00 240263407029;98;84;00;;ANDRASCH, UWE:;;;16335,00 300664406125;17;00;00;;ANDRATSCHKE, JENS:;;;17299,33 311256406138;04;80;00;;ANDRATSCHKE, JOERG:;;;19205,00 080666428246;17;00;00;;ANDRE, HOLGER:;;;13932,00 020450417412;09;14;00;;ANDRE, JOACHIM:;;;17520,00 030151517420;09;69;00;;ANDRE, PETRA:;;;19020,00 120340417743;09;65;00;;ANDRE, RUDI:;;;19937,50 211262424940;99;43;00;;ANDREADAKIS, LUTZ:;;;18325,65 310361420324;11;00;40;;ANDREAE, PETER:;;;20770,00 081140429716;99;43;00;;ANDREAS, BERND:;;;27750,00 140745430047;94;65;00;;ANDREAS, DIETER:;;;26250,00 020145414629;08;00;49;;ANDREAS, DIETMAR:;;;29250,00 061068406414;18;33;00;;ANDREAS, DIRK:;;;10725,00 270842430044;98;83;00;;ANDREAS, HANS:;;;25500,00 220965422217;99;43;00;;ANDREAS, HARTMUT:;;;15427,44 301041416217;09;06;20;;ANDREAS, HORST:;;;21250,00 280869408321;97;06;00;;ANDREAS, JENS:;;;14175,00 010562430022;15;08;00;;ANDREAS, LUTZ:;;;17330,00 291165422428;12;00;47;;ANDREAS, MAIK:;;;14418,00 160847525037;13;80;00;;ANDREAS, MARTINA:;;;13465,00 310848425020;13;53;00;;ANDREAS, PETER:;;;21744,38 300561520320;11;80;00;;ANDREAS, PETRA:;;;19140,00 030369406125;18;31;00;;ANDREAS, RINGO:;;;10425,00 081170405117;04;69;00;;ANDREAS, SILVIO:;;;6780,00 211255429735;30;47;00;;ANDREASS, BODO:;;;21558,00 300560424986;13;15;00;;ANDRECKE, GUNTER:;;;16170,00 241263413212;08;00;57;;ANDREE, MARIO:;;;13608,00 091155405214;04;06;00;;ANDREE, UWE:;;;20735,00 220340422735;98;18;00;;ANDREJKOVITS, FRANCISC:;;;29520,00 040357403217;01;00;47;;ANDRES, AXEL:;;;21780,00 280457509521;99;77;00;;ANDRES, DAGMAR:;;;19607,50 200666400626;01;00;50;;ANDRES, GERD:;;;14742,00 070953409516;97;17;00;;ANDRES, HANS-JUERGEN:;;;20880,00 160969404217;94;64;00;;ANDRES, JOERG:;;;13355,00 070146429713;99;43;00;;ANDRES, JUERGEN:;;;20000,00 190869400611;01;06;26;;ANDRES, LUTZ:;;;9510,00 161145412219;99;51;00;;ANDRES, MANFRED:;;;26250,00 140564419359;99;43;00;;ANDRES, MIKE:;;;16618,25 250570404716;18;31;00;;ANDRES, MIKE:;;;6705,00 060851528224;14;96;00;;ANDRES, RENATE:;;;18720,00 061168412213;18;31;00;;ANDRES, RENE:;;;9600,00 071248419916;14;96;00;;ANDRES, ULRICH:;;;19768,14 101243516228;09;06;00;;ANDRES, URSULA:;;;23625,00 081149407513;05;06;00;;ANDRESCHECK, LUTZ:;;;24000,00 211150413956;96;15;21;;ANDRESEN, DITTMAR:;;;21725,00 270959411912;07;20;00;;ANDRESEN, JOERG:;;;20872,50 011168406125;18;38;00;;ANDRESEN, TORSTEN:;;;9510,00 220241429712;97;08;00;;ANDRESZ, JUERGEN:;;;24750,00 220656529811;30;63;00;;ANDREWITZ, PETRA:;;;11430,69 240455422012;04;02;00;;ANDRICH, FALKO:;;;23800,00 220768423616;18;32;00;;ANDRICH, FRANK:;;;9625,00 130249422014;04;00;50;;ANDRICH, GISBERT:;;;31680,00 280541429719;98;84;00;;ANDRICH, KLAUS:;;;21750,00 050147530057;30;83;00;;ANDRICH, RITA:;;;19498,06 120569403438;98;83;00;;ANDRIOF, JOERG:;;;11000,00 090768417512;09;69;00;;ANDRITZKE, TORSTEN:;;;9700,00 081038400810;17;00;00;;ANDRUSCHOW, HORST:;;;35250,00 220963403418;03;18;00;;ANGELMAIER, PETER:;;;16500,00 280157415347;04;06;00;;ANGELROTH, EKKEHARD:;;;19665,00 030369417115;18;35;00;;ANGELSTEIN, JENS:;;;10600,00 020568423623;18;71;20;;ANGER, ANDRE:;;;14688,00 160566423640;94;65;00;;ANGER, DETLEF:;;;6780,00 280569420118;18;31;00;;ANGER, JAN:;;;9675,00 280769526312;96;15;07;;ANGER, KONSTANZE:;;;10125,00 130164408416;06;69;00;;ANGER, MARIO:;;;16060,00 131230407513;99;43;00;;ANGER, ROLAND:;;;27000,00 260666400743;99;43;00;;ANGERMANN, FRANK:;;;16686,00 280744422437;12;20;00;;ANGERMANN, FRIEDRICH-ERNST:;;;25500,00 111046510328;07;06;00;;ANGERMANN, GABRIELE:;;;19950,00 060457416224;09;40;00;;ANGERMANN, GUENTER:;;;22712,50 240168410641;99;43;00;;ANGERMANN, JENS:;;;8950,00 311249412214;06;29;00;;ANGERMANN, KLAUS-PETER:;;;22386,67 160852527723;97;08;00;;ANGERMANN, MARTINA:;;;20590,01 050744529732;18;35;00;;ANGERMANN, REGINA:;;;21500,00 171064430318;99;43;00;;ANGERMANN, RICO:;;;16252,50 290655518516;10;00;47;;ANGERMANN, ROSEMARIE:;;;11662,49 060637416213;96;15;26;;ANGERMANN, SIEGFRIED:;;;34687,50 250462430300;04;08;00;;ANGERMANN, THOMAS:;;;15840,00 140463430145;04;00;48;;ANGERMANN, TORALF:;;;19140,00 251244410314;07;06;00;;ANGERMANN, WALTER:;;;21000,00 131148422730;97;08;00;;ANGERMANN, WOLFGANG:;;;24750,00 190344412214;07;00;40;;ANGERN-VON, ULRICH:;;;16739,58 031066413517;99;43;00;;ANGERSTEIN, UWE:;;;12960,00 260251407011;05;00;44;;ANGRES, DIETER:;;;22355,00 010555406710;05;06;00;;ANGRES, MANFRED:;;;19607,50 180169420938;18;32;00;;ANGRICK, FRANK:;;;10190,00 100156413621;99;43;00;;ANGRICK, HANS-JUERGEN:;;;19607,50 250270401337;94;03;00;;ANGRICK, LARS:;;;9510,00 210939414513;04;53;00;;ANHALT, KARL-HEINZ:;;;25625,00 080251417510;98;82;00;;ANHALT, NORBERT:;;;20160,00 260453428910;99;43;00;;ANHUTH, LOTHAR:;;;19920,00 290959413211;08;00;65;;ANIELSKI, AXEL:;;;20405,00 250944429759;99;40;00;;ANKE, GERT:;;;27125,00 230154426715;97;08;00;;ANKE, HARALD:;;;20880,00 190431412212;07;80;00;;ANKE, HERBERT:;;;19125,00 200271430230;99;02;00;;ANKE, JAN:;;;3620,00 280350530056;99;12;00;;ANKE, KARIN:;;;18785,87 280748430047;94;30;00;;ANKE, ULRICH:;;;36000,00 271264427111;14;65;00;;ANKER, FRANK:;;;15867,50 220859430010;15;65;00;;ANKER, JOERG:;;;20180,89 020554427113;97;06;00;;ANKER, SIEGBERT:;;;21735,00 111266409520;06;69;00;;ANKERSEN, TORSTEN:;;;14480,00 031170415360;99;43;00;;ANKERT, ANDREAS:;;;2870,00 210357408316;30;47;00;;ANKERT, ROLAND:;;;24802,50 051052404511;04;00;41;;ANKLAM, PETER:;;;17640,00 010968409514;06;69;00;;ANKLAM, UWE:;;;9875,00 260258430126;30;84;00;;ANKLAM, UWE:;;;12100,00 120857415011;08;00;60;;ANLAUF, FRANK:;;;23402,50 300366413917;17;00;00;;ANLAUF, JENS:;;;14670,00 070858515011;08;00;60;;ANLAUF, STEPHANIE:;;;16335,00 111267413919;08;14;00;;ANLAUF, SVEN:;;;13527,00 020634402717;02;60;00;;ANNIES, HANS:;;;31500,00 211252422028;97;08;00;;ANSCHEIT, ANDREAS:;;;23760,00 070454419728;94;11;00;3454/86, :;ANSCHU(E)TZ, GU(E)NTER;6110;DR-THEODOR-NEUBAUER-STR. 31;20880,00 211268419712;18;38;00;;ANSCHU(E)TZ, UWE:;;;9675,00 151058420019;11;00;43;;ANSCHUETZ, DIETER:;;;19981,25 021227419719;11;07;00;;ANSCHUETZ, HELMUT:;;;28500,00 250135417782;09;03;00;;ANSCHUETZ, HELMUT:;;;25500,00 010366530034;98;85;00;;ANSCHUETZ, PETRA:;;;4012,50 040850419714;97;01;00;;ANSCHUETZ, THEO:;;;23286,68 190863420312;98;82;00;;ANSCHUETZ, THOMAS:;;;16762,50 200768414244;18;31;00;;ANSEL, INGO:;;;9600,00 040961409818;07;06;00;;ANSELM, UWE:;;;17325,00 310869413416;08;69;00;;ANSON, HOLGER:;;;7905,00 300348412910;08;00;41;;ANSON, ROLF:;;;19500,00 160571420014;18;34;00;;ANSORG, MARCO:;;;2795,00 170938400810;01;53;00;;ANSORGE, DETLEF:;;;26250,00 250669404513;18;40;00;;ANSORGE, DIRK:;;;6876,77 141237406125;04;07;00;;ANSORGE, KLAUS:;;;32437,50 250340422724;96;15;27;;ANSORGE, KLAUS-PETER:;;;30750,00 090455405625;94;65;00;;ANSORGE, MANFRED:;;;17680,00 130766428211;14;96;00;;ANSORGE, MICHAEL:;;;14094,00 030553500867;01;51;00;;ANSORGE, MONIKA:;;;20160,00 030269422427;12;69;00;;ANSORGE, STEFFEN:;;;9675,00 071159402741;02;00;45;;ANSPERGER, MICHAEL:;;;4100,00 280765424714;99;02;00;;ANSPIELER, JO(E)RG:;;;11067,00 020844406118;04;00;42;;ANTCZAK, BERND:;;;33750,00 121151402213;96;15;14;;ANTER, FRED:;;;32027,50 090764414736;17;00;00;;ANTKOWIAK, MICHAEL:;;;16830,00 200555529785;99;13;00;;ANTON, BAERBEL:;;;17695,76 150149416715;09;00;46;;ANTON, EWALD:;;;18360,00 080450416713;18;25;00;;ANTON, GERHARD:;;;25852,02 220652416713;09;00;52;;ANTON, GUENTER:;;;27360,00 101054416711;09;03;00;;ANTON, HANS-JUERGEN:;;;18765,00 080866419731;11;80;00;;ANTON, JOERG:;;;13770,00 120754429736;95;45;00;;ANTON, KLAUS:;;;24480,00 030948430058;15;08;00;;ANTON, PETER:;;;27000,00 271143415317;11;06;21;;ANTON, PETER:;;;21750,00 071148414528;08;08;00;;ANTON, RALF:;;;22500,00 061148416719;94;03;00;;ANTON, WERNER:;;;24562,50 020659430183;96;15;00;2110/84, F:;ANTONI, DETLEF;1162;BRUNO-WILLE-STR. 7; 291045416218;09;00;43;;ANTONI, KURT:;;;27712,50 180968424214;18;35;00;;ANTONIN, MARIO:;;;9675,00 220968406140;18;40;00;;ANTONIUS, DIRK:;;;16625,00 270945406119;04;00;40;;ANTONIUS, HELMUT:;;;25500,00 090749506122;04;29;00;;ANTONIUS, MARGITTA:;;;21600,00 110343422725;97;06;00;;ANTRACK, HEINZ:;;;27187,50 010345522801;97;06;00;;ANTRACK, HELGA:;;;20880,00 010331400811;01;15;00;;ANTRACK, HORST:;;;24750,00 141232500833;01;80;00;;ANTRACK, ILSE:;;;17378,75 221156422713;60;90;00;;ANTRACK, NORBERT:;;; 221156422713;60;90;00;;ANTRACK, NORBERT:;;;21452,50 290432429727;99;43;00;;ANTRACK, RALF:;;;23250,00 141068420718;18;35;00;;ANTRACK, UWE:;;;9825,00 070870402132;18;32;00;;ANWAND, STEFFEN:;;;2795,00 100259508711;99;77;00;;APEL, CORNELIA:;;;20250,00 050353416626;09;00;45;;APEL, EDMUND:;;;25817,50 070256516834;97;01;00;;APEL, EVELIN:;;;18479,75 160941429762;94;30;00;;APEL, FLORIAN:;;;25812,50 171064430078;15;00;46;;APEL, JENS:;;;17466,50 230152412117;04;00;41;;APEL, JUERGEN:;;;24444,97 040641511813;07;00;56;;APEL, KA(E)THE:;;;14355,00 171144417738;09;03;00;;APEL, KLAUS:;;;26250,00 301249406712;98;85;00;;APEL, KLAUS-HARTMUT:;;;26187,50 191052420313;95;45;00;;APEL, RAINER:;;;20880,00 190544429758;94;11;00;;APEL, REINHARD:;;;28500,00 090253413926;08;51;00;;APEL, RONALD:;;;22440,00 060469419916;11;69;00;;APEL, STEFFEN:;;;10200,00 121068417721;18;31;00;;APEL, STEFFEN:;;;9510,00 281169415402;99;43;00;;APEL, ULRICH:;;;8839,03 231248522753;99;09;00;;APELT, BARBARA:;;;24750,00 190656509525;06;06;00;;APELT, CAROLA:;;;18515,00 180847522424;99;49;00;;APELT, ELKE:;;;16811,08 171148422729;96;15;13;;APELT, HELLMUTH:;;;24000,00 040662420523;12;03;00;;APELT, JENS:;;;16830,00 090754403427;97;01;00;;APELT, JOERG:;;;26640,00 160544422436;97;06;00;;APELT, KLAUS:;;;26250,00 040670423126;18;35;00;;APELT, OLAF:;;;6705,00 050569416246;18;34;00;;APFEL, STEFFEN:;;;9675,00 281256420728;12;00;52;;APITZ, CARSTEN:;;;27099,19 140161411424;07;20;00;;APITZ, THOMAS:;;;21360,00 190354412218;07;15;00;;APORIUS, FRED:;;;23650,00 060549412212;07;02;00;;APORIUS, LOTHAR:;;;26250,00 280633529717;15;54;00;;APOSTEL, SONJA:;;;21000,00 250840429746;97;06;00;;APPEL, BERNHARD:;;;24750,00 300351526513;94;03;00;;APPEL, CHRISTINA:;;;21173,03 010450412225;94;03;00;;APPEL, DIRK:;;;23040,00 280462430025;96;15;05;;APPEL, FRED:;;;16170,00 230347403114;99;53;00;;APPEL, HARTWIG:;;;24000,00 130525412219;07;80;00;;APPEL, HEINZ:;;;19500,00 191157506738;99;77;00;;APPEL, ILSE-DORE:;;;16318,71 010162403420;03;02;00;;APPEL, JOERG:;;;19745,00 230169404121;18;35;00;;APPEL, MIKE:;;;9630,00 230650420312;96;15;21;;APPEL, REINHARD:;;;26335,00 031055420914;97;08;00;;APPEL, SIEGMAR:;;;24840,00 191069415318;18;34;00;;APPEL, STEFFEN:;;;10600,00 110756426820;14;14;00;;APPELT, DETLEV:;;;17250,00 261237429710;94;30;00;;APPELT, DIETER:;;;33000,00 111251419638;11;02;00;;APPELT, FREIMUTH:;;;23760,00 240634422720;12;41;00;;APPELT, GERD:;;;31500,00 010957400629;97;06;00;;APPELT, HANS-KLAUS:;;;22115,00 110964422736;12;00;40;;APPELT, JOERG:;;;19470,00 200360421010;14;00;42;;APPELT, KLAUS:;;;22110,00 071255400615;01;51;00;;APPELT, REINHARD:;;;21390,00 100363402618;09;18;00;;APPELT, THOMAS:;;;10368,00 240145421014;12;20;00;;APPELT, TILO:;;;36562,50 030154426815;95;45;00;;APPELT, UWE:;;;24480,00 120533429732;17;00;00;;APPENFELDER, ROLF:;;;35812,50 110570417715;18;31;00;;APPENRODT, MAIK:;;;6705,00 210139417724;09;65;00;;APPENRODT, MANFRED:;;;22937,50 250952411516;07;06;00;;APSEL, KARL-HEINZ:;;;17910,00 040551411915;97;29;00;;ARBANOWSKI, DIETER:;;;28980,00 030352511922;97;29;00;;ARBANOWSKI, MARLIE:;;;16905,00 190570409558;18;33;00;;ARBEL, CARSTEN:;;;9510,00 100838529728;98;82;00;;ARCHUT, EDDA:;;;24750,00 230952409119;06;06;00;;AREND, BODO:;;;20640,00 260541405516;04;51;00;;AREND, FRIEDRICH:;;;30750,00 201243411416;07;00;53;;ARENDT, GUENTER:;;;26250,00 190456405924;17;00;00;;ARENDT, HARALD:;;;18630,00 161057413414;08;08;00;;ARENDT, JUERGEN:;;;16186,25 160257428237;14;65;00;;ARESCHKO, BERND:;;;18342,50 030840412915;08;00;41;;ARLET, HERMANN:;;;28687,50 051053422412;12;00;47;;ARLICH, ANDREAS:;;;22320,00 110870422444;99;77;00;;ARLICH, WILKO:;;;6830,81 290171424249;97;06;00;;ARLT, ALEXANDER:;;;2915,97 040362404847;98;83;00;;ARLT, ANDREAS:;;;16830,00 030256521741;30;51;00;;ARLT, CHRISTA:;;;11587,26 150355413419;08;65;00;;ARLT, EGBERT:;;;18112,50 230468424210;99;43;00;;ARLT, ENRICO:;;;9675,00 120358415113;96;15;00;650/75/54, :;ARLT, FRANK;1140;MARZAHNER PROMENADE 39; 120358415113;96;15;00;650/75/54, :;ARLT, FRANK;1140;MARZAHNER PROMENADE 39; 280350403727;03;00;40;;ARLT, HANS:;;;27000,00 250250421728;06;06;00;;ARLT, HANS-GEORG:;;;24127,50 250150420517;06;20;00;;ARLT, HANS-PETER:;;;32430,00 171270409923;18;32;00;;ARLT, HEIMO:;;;6958,87 311038428910;30;59;00;;ARLT, HORST:;;;24840,00 110332430041;15;09;00;;ARLT, JOACHIM:;;;25500,00 121064404827;04;06;00;;ARLT, KAI-PETER:;;;16755,00 240963521543;30;47;00;;ARLT, MAIKE:;;;0,00 270368405721;99;40;00;;ARLT, MARIO:;;;9875,00 300169413918;18;35;00;;ARLT, MATTHIAS:;;;9825,00 271169411429;07;69;00;;ARLT, RONALD:;;;9510,00 110269413213;08;69;00;;ARLT, TORSTEN:;;;12725,00 300156429750;99;77;00;;ARLT, WILFRIED:;;;18917,50 241062420256;11;65;00;;ARM, JOACHIM:;;;16582,50 290862519626;11;77;00;;ARM, UTE:;;;14662,18 300844405664;96;15;11;;ARM, WILFRIED:;;;26250,00 171169419713;11;69;00;;ARMANN, DIRK:;;;2870,00 150669420339;18;32;00;;ARMKNECHT, MIKE:;;;9510,00 220160411414;97;08;00;;ARMS, DETLEF:;;;17527,50 150353413933;08;02;00;;ARMS, DIETRICH:;;;13530,00 090169413915;17;00;00;;ARMS, HANJO:;;;8950,00 120462401512;01;08;00;;ARNDT, ANDREAS:;;;16665,00 251259430027;30;58;00;;ARNDT, ANDREAS:;;;15870,00 100355420314;98;18;00;;ARNDT, AXEL:;;;25900,00 240855504156;03;78;00;;ARNDT, BAERBEL:;;;18945,98 020956400810;01;80;00;;ARNDT, BERND:;;;16157,50 271053402125;97;06;00;;ARNDT, BODO:;;;23040,00 150866402148;94;03;00;;ARNDT, BODO:;;;16524,00 220659501515;01;00;48;;ARNDT, CHRISTEL:;;;14243,22 140652408510;99;43;00;;ARNDT, DETLEF:;;;22980,00 050842415317;08;09;00;;ARNDT, DIETER:;;;24000,00 141158404711;97;01;00;;ARNDT, DIETMAR:;;;26283,36 150867418520;10;69;00;;ARNDT, DIETMAR:;;;12975,00 290469408815;18;38;00;;ARNDT, DIRK:;;;9675,00 141248405312;04;00;49;;ARNDT, EBERHARD:;;;29250,00 210655421228;12;00;48;;ARNDT, ECKBERT:;;;24955,00 111253410311;07;03;00;;ARNDT, ECKHARD:;;;19180,00 200146430047;96;15;22;;ARNDT, EDGAR:;;;29250,00 250866416935;94;03;00;;ARNDT, ENRICO:;;;11016,00 080540503714;03;00;46;;ARNDT, ERIKA:;;;16875,00 170939429711;98;18;00;;ARNDT, ERWIN:;;;30750,00 060858403416;03;07;00;;ARNDT, FRANK:;;;22770,00 060568403434;18;31;00;;ARNDT, FRANK:;;;9825,00 250955411546;30;49;00;;ARNDT, GEORG:;;;15180,00 240647404310;05;00;47;;ARNDT, GUENTER:;;;25920,00 241235405717;04;00;52;;ARNDT, HANS:;;;21750,00 150856401547;01;08;00;;ARNDT, HANSHOLGER:;;;18112,50 020152402714;02;00;40;;ARNDT, HANS-JUERGEN:;;;28020,00 090740404314;03;00;52;;ARNDT, HEINZ:;;;21750,00 160337417749;09;69;00;;ARNDT, HEINZ:;;;20250,00 120768404716;04;69;00;;ARNDT, HENDRIK:;;;9675,00 090866405611;04;69;00;;ARNDT, HENNING:;;;12012,00 110861530072;99;77;00;;ARNDT, INA:;;;18380,64 190271418411;18;35;00;;ARNDT, JO(E)RG:;;;2795,00 120936429710;97;29;00;;ARNDT, JOACHIM:;;;39750,00 130263430133;99;43;00;;ARNDT, JOCHEN:;;;16912,50 120954429829;97;08;00;;ARNDT, JOERG:;;;27360,00 190343407528;05;19;00;;ARNDT, JUERGEN:;;;26250,00 070357406116;04;06;00;;ARNDT, JUERGEN:;;;19952,50 070555419612;15;18;00;;ARNDT, JUERGEN:;;;24500,00 280559401538;01;00;48;;ARNDT, JUERGEN:;;;21677,50 010637530328;99;09;00;;ARNDT, JUTTA:;;;21750,00 130852406916;05;00;43;;ARNDT, KARL-HEINZ:;;;28080,00 240561500870;01;77;00;;ARNDT, KERSTIN:;;;15576,00 210447412212;07;20;00;;ARNDT, KLAUS-DIETER:;;;29250,00 250159406914;99;43;00;;ARNDT, KLAUS-PETER:;;;18543,75 230931406912;99;43;00;;ARNDT, KONRAD:;;;20250,00 010431420318;11;40;00;;ARNDT, LOTHAR:;;;38250,00 190930513616;08;00;48;;ARNDT, MAGDALENA:;;;17625,00 111067415311;08;20;00;;ARNDT, MARIO:;;;13875,00 260564404321;97;08;00;;ARNDT, MARIO:;;;18095,00 110857430247;98;82;00;;ARNDT, MARTIN:;;;18186,70 251255406126;04;20;00;;ARNDT, MATTHIAS:;;;21120,00 270969415319;18;32;00;;ARNDT, MATTHIAS:;;;9060,00 180570408935;06;69;00;;ARNDT, MICHAEL:;;;9510,00 011246406711;96;15;21;;ARNDT, MICHAEL:;;;33840,00 030666412214;94;03;00;;ARNDT, MIRKO:;;;16362,00 100246516923;96;15;12;;ARNDT, MONIKA:;;;22110,00 140268411213;18;35;00;;ARNDT, OLAF:;;;9465,00 270756414515;98;20;00;;ARNDT, PETER:;;;22080,00 010253420314;11;80;00;;ARNDT, PETER:;;;17500,00 241260430172;99;12;00;;ARNDT, PETER:;;;19140,00 110460530143;98;83;00;;ARNDT, PETRA:;;;372,58 110854528337;14;29;00;;ARNDT, PETRA:;;;16902,00 270949403425;03;65;00;;ARNDT, RAINER:;;;21750,00 291058402317;97;01;00;;ARNDT, RALF:;;;26150,04 070167405227;97;06;00;;ARNDT, RALF:;;;16527,00 080247530043;96;15;22;;ARNDT, REGINA:;;;21253,59 040652429890;18;71;20;;ARNDT, REINHARD:;;;28320,00 110952429949;94;03;00;;ARNDT, REINHARD:;;;22980,00 170153504716;94;03;00;;ARNDT, RITA:;;;19492,50 030141404318;97;01;00;;ARNDT, ROLAND:;;;29937,50 140638400838;01;00;47;;ARNDT, ROLF:;;;33000,00 131049406428;97;06;00;;ARNDT, RUDI:;;;23250,00 180957401519;03;80;00;;ARNDT, RUEDIGER:;;;20700,00 090749419619;94;03;00;;ARNDT, SIEGFRIED:;;;23250,00 180369408511;06;69;00;;ARNDT, THOMAS:;;;12675,00 151068411714;99;43;00;;ARNDT, THOMAS:;;;9675,00 151146401328;01;06;24;;ARNDT, UDO:;;;20437,50 100468430017;60;90;00;;ARNDT, ULF:;;; 100468430017;60;90;00;;ARNDT, ULF:;;;14800,00 121147410018;07;00;43;;ARNDT, ULRICH:;;;28437,50 190939418527;10;00;47;;ARNDT, ULRICH:;;;23347,50 080355415325;08;14;00;;ARNDT, UWE:;;;18765,00 270354427110;14;15;00;;ARNDT, VOLKMAR:;;;24480,00 171041403712;03;00;46;;ARNDT, WERNER:;;;26250,00 090740430061;99;53;00;;ARNDT, WERNER:;;;25500,00 020952429878;97;08;00;;ARNDT, WERNER:;;;20085,27 031040429756;96;15;06;;ARNDT, WILDO:;;;29250,00 211064406936;05;19;00;;ARNDT, WILFRIED:;;;18892,50 190347402126;02;06;00;;ARNDT, WOLFGANG:;;;23250,00 051034406919;99;43;00;;ARNDT, WOLFGANG:;;;21750,00 300640429728;14;00;43;;ARNDT, WULFRIED:;;;21000,00 130349417722;09;26;00;;ARNEBURG, JOACHIM:;;;27750,00 301248507511;99;77;00;;ARNHOLD, CHRISTINA:;;;20700,00 041030412212;07;40;00;;ARNHOLD, GUENTER:;;;27000,00 010841528911;12;51;00;;ARNHOLD, IRENE:;;;20907,50 150960514816;99;43;00;;ARNHOLD, IRIS:;;;12445,81 290352424918;13;00;43;;ARNHOLD, JOACHIM:;;;22770,00 130143429736;94;11;00;;ARNHOLD, JUERGEN:;;;27937,50 171267422828;18;80;00;;ARNHOLD, LUTZ:;;;10425,00 270265426546;30;48;00;;ARNHOLD, MICHAEL:;;;14295,00 210456406113;18;80;00;;ARNHOLD, RAINER:;;;18285,00 230564430274;18;71;20;;ARNHOLD, RAJK:;;;16115,00 280168417719;18;33;00;;ARNHOLD, STEFFEN:;;;10725,00 010460414814;99;43;00;;ARNHOLD, VOLKER:;;;16830,00 010938406144;04;00;40;;ARNIM, HEINZ:;;;29250,00 030363512250;07;00;40;;ARNOLD, ANDREA:;;;15840,00 210470406419;04;69;00;;ARNOLD, ANDREAS:;;;6780,00 261151414614;97;01;00;;ARNOLD, AXEL:;;;28980,00 140653530067;94;11;00;;ARNOLD, BAERBEL:;;;20823,87 210258503617;95;45;00;;ARNOLD, BEATE:;;;18229,35 120768414113;18;71;20;;ARNOLD, BERND:;;;9600,00 030570421511;18;34;00;;ARNOLD, BERT:;;;6705,00 120970411928;07;69;00;;ARNOLD, CHRISTIAN:;;;2911,13 131051521329;12;00;48;;ARNOLD, CHRISTINE:;;;20760,00 030353526843;14;80;00;;ARNOLD, DAGMAR:;;;13670,63 240761425000;13;65;00;;ARNOLD, DETLEF:;;;17765,00 140351419611;97;06;00;;ARNOLD, DIETER:;;;26917,50 180647409515;95;45;00;;ARNOLD, DIETER:;;;29158,07 230345427016;14;26;00;;ARNOLD, DIETMAR:;;;23125,00 060369415328;18;33;00;;ARNOLD, DIRK:;;;9519,00 140341429752;99;43;00;;ARNOLD, EBERHARD:;;;24000,00 140936530032;15;53;00;;ARNOLD, EDELGARD:;;;23437,50 050331429717;15;02;00;;ARNOLD, ERICH:;;;30000,00 060563430089;99;53;00;;ARNOLD, FRANK:;;;16783,25 201240422718;12;08;00;;ARNOLD, FREIMUT:;;;22500,00 240841429730;94;11;00;;ARNOLD, FRIEDER:;;;24750,00 140656421210;12;51;00;;ARNOLD, GERD:;;;20182,50 151244410316;07;00;54;;ARNOLD, GERHARD:;;;21045,00 040169415042;08;96;00;;ARNOLD, GERO:;;;13200,00 110951421216;12;00;48;;ARNOLD, GU(E)NTER:;;;23760,00 130243427017;14;18;00;;ARNOLD, GUNNAR:;;;25200,00 240269424823;99;14;00;;ARNOLD, GUNNAR:;;;13775,00 130351405245;30;40;00;;ARNOLD, GUNTHER:;;;23400,00 010239428213;14;29;00;;ARNOLD, HANS:;;;24000,00 050147425046;13;60;00;;ARNOLD, HANS:;;;21750,00 100833429728;94;30;00;;ARNOLD, HANS:;;;27750,00 270853429727;15;60;00;;ARNOLD, HANS-JOACHIM:;;;20160,00 020869400724;98;82;00;;ARNOLD, HEIKO:;;;10376,13 220769421014;18;32;00;;ARNOLD, HEIKO:;;;9510,00 210346402111;02;40;00;;ARNOLD, HEINZ:;;;24937,50 241047422712;99;40;00;;ARNOLD, HEINZ-HEIDFRIED:;;;26250,00 081159422821;30;63;00;;ARNOLD, HELFRIED:;;;15315,00 150343422748;12;08;00;;ARNOLD, HORST:;;;28500,00 010344402111;02;06;00;;ARNOLD, HORST:;;;22500,00 231255422718;12;07;00;;ARNOLD, INGOLF:;;;22022,50 120870420341;11;69;00;;ARNOLD, JENS:;;;2870,00 210568430185;18;34;00;;ARNOLD, JO(E)RG:;;;9825,00 230170422722;12;69;00;;ARNOLD, JOERG:;;;9555,00 140955406424;94;03;00;;ARNOLD, JOERG:;;;19600,00 220347409525;06;29;00;;ARNOLD, JOERN-UWE:;;;34327,50 070952428918;14;00;40;;ARNOLD, JOHANNES:;;;21294,97 130357430062;98;82;00;;ARNOLD, JUERGEN:;;;21390,00 230635428228;14;51;00;;ARNOLD, KARLI:;;;19275,00 210848426236;14;30;00;;ARNOLD, KLAUS:;;;20642,50 200255428915;98;84;00;;ARNOLD, LIENHARD:;;;21483,87 131069402731;02;69;00;;ARNOLD, MAIK:;;;12425,50 051056501933;99;77;00;;ARNOLD, MARGIT:;;;21390,00 121149428916;10;06;00;;ARNOLD, MICHAEL:;;;24000,00 151261407215;94;65;00;;ARNOLD, MICHAEL:;;;18645,00 291055420317;11;80;00;;ARNOLD, NORBERT:;;;17500,00 150252429899;99;43;00;;ARNOLD, PETER:;;;25200,00 160450427623;14;53;00;;ARNOLD, RAINER:;;;24000,00 290260426326;98;20;00;;ARNOLD, RALF:;;;20330,00 300665420316;99;40;00;;ARNOLD, RALF:;;;11067,00 110960424953;13;00;41;;ARNOLD, RALPH:;;;18095,00 191255416728;09;03;00;;ARNOLD, REINHARD:;;;20182,50 051066430067;94;65;00;;ARNOLD, RENE:;;;13916,32 240763426314;99;13;00;;ARNOLD, ROCCO:;;;11220,00 080357412910;12;06;00;;ARNOLD, ROLAND:;;;20010,00 261163415112;01;00;46;;ARNOLD, ROLAND:;;;5082,06 150849426615;97;01;00;;ARNOLD, ROLF:;;;32812,50 221167430014;15;00;43;;ARNOLD, ROLF:;;;14769,00 290442429712;99;43;00;;ARNOLD, ROLF:;;;25312,50 190942429729;97;17;00;;ARNOLD, ROLF:;;;27750,00 171241417764;09;09;00;;ARNOLD, ROLF:;;;25000,00 040657427317;30;34;00;;ARNOLD, STEFFEN:;;;19215,72 060564415315;60;90;00;;ARNOLD, SVEN:;;; 090669429227;18;32;00;;ARNOLD, SVEN:;;;6958,87 060564415315;60;90;00;;ARNOLD, SVEN:;;;16476,51 031262426323;97;01;00;;ARNOLD, THOMAS:;;;16830,00 250769422743;18;32;00;;ARNOLD, TILO:;;;9675,00 241164406164;04;08;00;;ARNOLD, TORSTEN:;;;13932,00 110962421836;12;11;00;;ARNOLD, TORSTEN:;;;17820,00 050168414426;18;33;00;;ARNOLD, TORSTEN:;;;9675,00 040369430044;94;30;00;;ARNOLD, TORSTEN:;;;8950,00 140745529733;98;82;00;;ARNOLD, URSEL:;;;22500,00 200735524914;13;08;00;;ARNOLD, URSULA:;;;20250,00 300862426717;98;83;00;;ARNOLD, UWE:;;;18232,50 240270417313;18;31;00;;ARNOLD, UWE:;;;6958,87 100758430189;99;02;00;;ARNOLD, UWE:;;;16750,50 200944529711;94;11;00;;ARNOLD, VERONIKA:;;;24687,50 250455403419;99;40;00;;ARNOLD, VOLKMAR:;;;27360,00 101135429733;15;20;00;;ARNOLD, WOLFGANG:;;;30187,50 011245429719;98;83;00;;ARNOLD, WOLF-RUEDIGER:;;;24681,25 030650429775;99;09;00;;ARNOLDT, BERND:;;;24288,00 220551424319;13;00;41;;ARNOLDT, DIETER:;;;33075,48 170136412211;07;65;00;;ARNUS, DIETER:;;;21000,00 161152422749;99;55;00;;AROLD, BERND:;;;21360,00 170157530102;97;06;00;;AROLD, UTE:;;;19216,13 121152404114;99;51;00;;ARSCHOLL, REINER:;;;21541,93 200566420048;11;06;20;;ARTELT, ANDRE:;;;14688,00 200550513813;97;08;00;;ARTELT, ELFRIEDE:;;;25200,00 160767420024;11;69;00;;ARTELT, FRANK:;;;10900,00 110646412233;07;08;00;;ARTELT, HANS:;;;21750,00 070544413813;99;53;00;;ARTELT, HOLGER:;;;33840,00 220958405646;30;62;00;;ARTELT, LUTZ:;;;14904,00 020236400812;01;12;00;;ARTH, FRITZ:;;;24625,00 130460407215;97;08;00;;ARTH, HOLGER:;;;19965,00 281168400866;97;06;00;;ARTH, TORSTEN:;;;14650,00 160659425047;13;06;20;;ARTH, WOLFGANG:;;;18370,00 200966420311;11;18;00;;ARWAY, FRANK:;;;17392,00 150350413241;99;55;00;;ARZ, HANS-JUERGEN:;;;26480,00 231145508916;96;15;14;;ARZIG, KARINA:;;;14328,58 200253422018;12;00;53;;ARZT, CHRISTIAN:;;;24150,00 120155402726;94;65;00;;ARZT, CHRISTIAN:;;;22935,00 110454428011;14;40;00;;ARZT, CLAUS-DIETER:;;;23222,50 280837523819;13;00;43;;ARZT, ILSE:;;;13932,00 120851422018;97;22;00;;ARZT, KONRAD:;;;24840,00 080659511228;99;43;00;;ARZT, PETRA:;;;15974,80 140940429711;98;81;00;;ARZT, WILFRIED:;;;21000,00 290356522419;06;14;00;;AS(Z)MANN, BA(E)RBEL:;;;16692,50 220968401323;18;32;00;;AS(Z)MANN, HARALD:;;;9675,00 111062406184;04;06;00;;AS(Z)MANN, RALPH:;;;18370,00 270269403421;18;32;00;;AS(Z)MUS, FRANK:;;;9675,00 150353406119;99;55;00;;ASBECK, HANS-JOACHIM:;;;22260,00 130951420713;12;00;42;;ASCHE, FRANK:;;;27720,00 140946530044;97;08;00;;ASCHE, HELGA:;;;18371,25 240849415317;08;26;00;;ASCHE, RONALD:;;;23095,00 301046429711;97;08;00;;ASCHE, WOLFGANG:;;;24000,00 221269418710;18;32;00;;ASCHENBACH, BERT:;;;10600,00 041156519744;11;06;21;;ASCHENBACH, GABRIELE:;;;14923,93 030538420316;11;65;00;;ASCHENBACH, HELMUT:;;;20187,50 081262419719;11;00;41;;ASCHENBACH, OLAF:;;;15510,00 020659420313;18;29;00;;ASCHENBACH, RAINER:;;;21792,50 130563418718;99;43;00;;ASCHENBACH, STEFFEN:;;;17985,00 250859406122;96;15;25;;ASCHENBRENNER, MICHAEL:;;;19837,50 050566414317;08;08;00;;ASCHENBRENNER, STEFFEN:;;;16470,00 160269410819;18;35;00;;ASCHENBRENNER, SVEN:;;;10361,44 140270401321;96;15;22;;ASCHENDORFF, FRANK:;;;9555,00 250839502715;02;07;00;;ASCHER, ELISABETH:;;;23250,00 230640402719;02;55;00;;ASCHER, ROLF:;;;13400,00 100969417427;18;35;00;;ASCHHOFF, SVEN:;;;9600,00 280750517715;09;51;00;;ASCHOFF, IRENE:;;;18624,18 250654417418;09;64;00;;ASCHOFF, KLAUS-DIETER:;;;18000,00 230651429757;99;13;00;;ASMUS, BERND:;;;24600,00 180459403474;95;45;00;;ASMUS, BERND:;;;17572,50 140656404824;99;26;00;;ASMUS, DIETER:;;;22195,00 110555429216;94;03;00;;ASMUS, ECKHARD:;;;23460,00 151150404310;03;20;00;;ASMUS, HANS-JOACHIM:;;;24480,00 270554404810;94;30;00;;ASMUS, JUERGEN:;;;24960,00 231038406121;04;18;00;;ASMUS, KLAUS:;;;25500,00 231069429211;18;35;00;;ASMUS, KNUT:;;;9955,00 160355529728;98;82;00;;ASMUS, MARTINA:;;;20642,50 211257404312;99;49;00;;ASMUS, MICHAEL:;;;19320,00 230354404318;97;06;00;;ASMUS, NORBERT:;;;23040,00 111267418832;18;29;30;;ASMUS, OLIVER:;;;10015,00 050130430033;98;82;00;;ASMUS, RUDI:;;;35250,00 230452504822;18;71;25;;ASMUS, SABINE:;;;17785,67 190362403442;94;03;00;;ASMUS, WOLFGANG:;;;16170,00 220443400811;01;02;00;;ASSMANN, JOERG:;;;26250,00 041264417526;99;14;00;;ASSMANN, MAIK:;;;16500,00 090351404513;96;15;22;;ASSMANN, PETER:;;;23940,00 280254505926;96;15;22;;ASSMANN, URSULA:;;;13750,00 021068423613;18;32;00;;AST, ANDRE:;;;9675,00 210646412215;07;26;00;;AST, BERND:;;;23520,00 080237427915;30;48;00;;AST, ERICH:;;;22860,00 160770412527;07;00;40;;AST, VOLKER:;;;2700,00 190258404728;99;12;00;;ASTALOSCH, ROLAND:;;;22770,00 140870423815;18;35;00;;ASTER, JO(E)RG:;;;2795,00 211269418914;18;35;00;;ASTER, MARKO:;;;9510,00 161054405128;30;81;00;;ASTERLOSCH, REINHOLD:;;;22320,00 120458417730;09;77;00;;ASZING, KLAUS:;;;14832,00 031269402746;99;43;00;;ASZMANN, ANDRE:;;;9510,00 160464423623;13;00;42;;ASZMANN, BODO:;;;15228,00 270451403727;97;06;00;;ASZMANN, BURCKHARD:;;;27180,00 310134429724;96;15;09;;ASZMANN, GEORG:;;;31500,00 050849415117;08;26;00;;ASZMANN, GUENTER:;;;24690,00 120450402219;97;06;00;;ASZMANN, HANS-JUERGEN:;;;24000,00 290742402730;02;07;00;;ASZMANN, HELMUT:;;;24750,00 071265408418;06;06;00;;ASZMANN, JENS:;;;16548,50 200754515132;08;00;44;;ASZMANN, MARION:;;;18060,77 011040530047;97;01;00;;ASZMANN, RENATE:;;;22500,00 020637429739;99;55;00;;ASZMANN, WERNER:;;;32250,00 220429406117;30;56;00;;ASZMUS, FRED:;;;15750,00 030735429731;98;84;00;;ASZMUS, HORST:;;;22500,00 031063430100;98;19;00;;ATANASSOW, KAI:;;;21340,00 041069405116;15;69;00;;ATLAS, MARCO:;;;2925,64 260265423813;15;09;00;;ATTS, STEFFEN:;;;18645,00 141050407312;05;80;00;;ATZENROTH, FRED:;;;19320,00 030955417724;99;13;00;;ATZRODT, BERND:;;;20067,50 040360430021;97;01;00;;ATZRODT, HAGEN:;;;25530,00 270357517760;99;26;00;;ATZRODT, VIOLA:;;;19278,44 130753406910;99;43;00;;AU, JUERGEN-DETLEF:;;;22080,00 181258401813;02;00;43;;AUDE, ANDREE:;;;22022,50 250466430287;15;00;47;;AUE, ANDREAS:;;;16146,00 260149407613;04;00;40;;AUER, GUENTER:;;;25552,50 190641403728;30;45;00;;AUERBACH, ARMIN:;;;14229,00 280350526225;14;26;00;;AUERBACH, CAROLA:;;;18780,00 010436530030;96;15;00;79/74, B:;AUERBACH, CHRISTEL;1020;BEROLINASTR. 10;21187,50 080344426715;14;51;00;;AUERBACH, DIETER:;;;24000,00 120466401317;99;43;00;;AUERBACH, DIRK:;;;14948,71 270152506136;30;54;00;;AUERBACH, ELKE:;;;19611,28 180668422751;17;00;00;;AUERBACH, FRANK:;;;8950,00 020150521816;98;83;00;;AUERBACH, GABRIELE:;;;20820,00 240949414725;06;26;00;;AUERBACH, GEROLD:;;;32030,00 250337430053;96;15;00;80/74, J:;AUERBACH, HANS-DIETER;1020;BEROLINASTR. 10; 250337430053;96;15;00;80/74, J:;AUERBACH, HANS-DIETER;1020;BEROLINASTR. 10; 211238421811;12;29;00;;AUERBACH, HORST:;;;27000,00 151162421820;12;00;40;;AUERBACH, JO(E)RG:;;;20130,00 140350428110;14;06;00;;AUERBACH, JUERGEN:;;;25900,00 041156526717;14;00;46;;AUERBACH, MARION:;;;13023,75 260571430237;97;07;00;;AUERBACH, MIKE:;;;2700,00 270850426328;08;00;54;;AUERBACH, REINER:;;;24150,00 270668414718;95;45;00;;AUERBACH, RENE:;;;14175,00 131042423938;98;97;00;;AUERBACH, ROLAND:;;;28500,00 180239521815;12;08;00;;AUERBACH, ROSEMARIE:;;;15439,00 120257426710;14;00;46;;AUERBACH, STEFAN:;;;14161,50 200847418710;10;08;00;;AUERBACH, UDO:;;;20160,00 060444530124;99;77;00;;AUERBACH, ULRIKE:;;;24337,50 241249429226;97;01;00;;AUERSPERG, DIETER:;;;20625,00 070641429737;99;78;00;;AUERSWALD, HEINZ:;;;46500,00 030760417425;97;01;00;;AUERSWALD, INGO:;;;17600,00 020164426350;15;29;00;;AUERSWALD, JOERG:;;;17102,62 121036400028;97;22;00;;AUERSWALD, JOHANNES:;;;24750,00 191241529713;99;77;00;;AUERSWALD, MONIKA:;;;22500,00 271251409117;05;00;46;;AUERT, HERBERT:;;;22252,50 110149412216;04;06;00;;AUERT, MANFRED:;;;21687,50 200947516916;09;06;00;;AUGE, HELGA:;;;17180,00 271144416928;09;06;00;;AUGE, JOSEF:;;;20437,50 280254422717;97;01;00;;AUGE, RALF:;;;25380,00 230969417422;18;32;00;;AUGE, THOMAS:;;;9510,00 180968417786;18;31;00;;AUGNER, ANDRE:;;;9600,00 280955419019;10;08;00;;AUGNER, HANS-JUERGEN:;;;17135,00 191269425086;18;80;00;;AUGST, JAN:;;;9600,00 220366422039;97;06;00;;AUGST, KARL:;;;17410,50 071149414220;97;22;00;;AUGST, WERNER:;;;19440,00 081166418118;10;06;00;;AUGSTEIN, PETER:;;;14634,00 060353505978;11;12;00;;AUGSTEN, CHRISTIANE:;;;24190,24 140362408328;10;00;43;;AUGSTEN, DIETER:;;;15620,00 150836409525;06;30;00;;AUGSTEN, GERHARD:;;;31500,00 010544419022;10;29;00;;AUGSTEN, LOTHAR:;;;27562,50 060354420319;11;60;00;;AUGSTEN, WOLFGANG:;;;20160,00 071151419629;97;08;00;;AUGUST, GUENTER:;;;24480,00 141267419613;11;69;00;;AUGUST, STEFAN:;;;9060,00 261068402612;18;28;00;;AUGUSTAT, BERND:;;;9663,71 111256409519;99;43;00;;AUGUSTAT, FRANK:;;;21390,00 250354509513;99;55;00;;AUGUSTAT, GUDRUN:;;;17071,30 100137406119;99;40;00;;AUGUSTAT, KARL-HEINZ:;;;26250,00 161146401511;01;80;00;;AUGUSTAT, REINHARD:;;;19687,50 270441430051;96;15;14;;AUGUSTIN, ARND:;;;42000,00 140963430045;17;00;00;;AUGUSTIN, BERT:;;;14850,00 260941530068;96;15;18;;AUGUSTIN, ERIKA:;;;19440,00 200467411410;17;00;00;;AUGUSTIN, HENDRIK:;;;14076,00 270868424937;18;32;00;;AUGUSTIN, HENRI:;;;9675,00 240970429710;15;69;00;;AUGUSTIN, JAN:;;;2925,64 241242425038;96;15;13;;AUGUSTIN, JUERGEN:;;;30937,50 020545524915;96;15;14;;AUGUSTIN, MARLIS:;;;22475,00 020144429714;06;02;00;;AUGUSTIN, REINER:;;;38250,00 200969422785;18;32;00;;AUGUSTIN, STEFFEN:;;;9427,50 070862406723;15;40;00;;AUGUSTINAT, UDO:;;;18205,00 051063405229;04;06;00;;AUGUSTINIAK, UWE:;;;17285,97 080253423826;12;80;00;;AUGUSTYNIAK, UWE:;;;19042,50 131137400739;01;06;24;;AUHL, WILLI:;;;26562,50 280962422136;96;15;00;3776/85, F:;AUL, CLAUS;1150;STENDALER STR. 120; 280962422136;96;15;00;3776/85, F:;AUL, CLAUS;1150;STENDALER STR. 120; 040870429725;15;19;00;;AULICH, ANDRE:;;;2700,00 060844430069;15;30;00;;AULICH, DIETER:;;;33000,00 130542430056;30;63;00;;AULICH, HERBERT:;;;16560,00 280140429718;99;43;00;;AULITZKY, ERICH:;;;24750,00 220169417716;18;32;00;;AULITZKY, MATTHIAS:;;;9675,00 300466430212;98;84;00;;AULITZKY-MATERN, MICHAEL:;;;16765,50 141252402114;02;03;00;;AULS, BURKHARD:;;;16920,00 090258518217;97;01;00;;AULS, ROSWITHA:;;;12425,88 110562414514;94;03;00;;AUMANN, ROLAND:;;;17820,00 030168417725;18;31;00;;AURAS, DIRK:;;;9825,00 010260400725;10;08;00;;AURICH, ANDREAS:;;;18480,00 260949528253;14;53;00;;AURICH, ANITA:;;;18687,50 181144428217;14;08;00;;AURICH, BERND:;;;22500,00 090870427215;18;33;00;;AURICH, CORNEL:;;;2720,00 071055407214;05;00;47;;AURICH, DIETMAR:;;;22425,00 020751500113;15;80;00;;AURICH, ERIKA:;;;14300,43 200347428218;14;09;00;;AURICH, GERD:;;;24000,00 111051428214;99;40;00;;AURICH, HARALD:;;;25320,00 120943412220;07;20;00;;AURICH, HARTMUT:;;;19125,00 291037520314;11;55;00;;AURICH, INGE:;;;21750,00 011252528221;97;22;00;;AURICH, MARTINA:;;;16472,50 190735429718;97;08;00;;AURICH, ROLF:;;;26250,00 270840428215;14;17;00;;AURICH, SIEGFRIED:;;;28500,00 010169428225;99;55;00;;AURICH, SVEN:;;;13800,00 181169419026;18;33;00;;AURICH, SVEN:;;;2720,00 040655428228;99;55;00;;AURICH, THOMAS:;;;19600,00 230350425066;96;15;09;;AURICH, WERNER:;;;24840,00 220163516211;97;01;00;;AURISCH, HEIDE:;;;3375,87 160960430048;09;00;43;;AURISCH, RALF:;;;19416,25 231143430043;15;80;00;;AURNHAMMER, GEORG:;;;21750,00 010961430185;15;00;43;;AUSCHNER, OLIVER:;;;20130,00 130471424918;18;35;00;;AUST, HOLGER:;;;2795,00 120968416914;18;31;00;;AUST, JU(E)RGEN:;;;9600,00 151158416818;09;00;52;;AUST, PETER:;;;23632,50 210346430032;30;47;00;;AUST, RAINER:;;;28340,00 301161400711;01;06;20;;AUSTEL, ANDREAS:;;;16335,00 200439526827;99;77;00;;AUSTEL, KARIN:;;;22770,00 240735412214;07;08;00;;AUSTEN, HORST:;;;28500,00 060869419325;18;35;00;;AUSTERMANN, JENS:;;;2795,00 300540425017;13;08;00;;AUSTINAT, HELMUT:;;;27000,00 140367430065;18;29;30;;AUSTINAT, JOERN:;;;10015,00 050441529735;98;84;00;;AUTENRIEB, ADELHEID:;;;24750,00 160554503678;99;09;00;;AUTENRIEB, ANGELIKA:;;;20249,49 020656403331;90;65;40;5785/82,;AUTENRIEB, ECKBERT;1095;SCHWERINER RING 52; 160940429779;94;65;00;;AUTENRIEB, ERNST:;;;24187,50 020264402751;02;51;00;;AUTENRIEB, FRANK:;;;16170,00 220667430104;98;82;00;;AUTENRIEB, JOERG:;;;15281,00 300155400518;01;00;44;;AWE, KLAUS:;;;23040,00 210565402226;02;80;00;;AWE, RONALD:;;;14355,00 200168400519;99;02;00;;AWE, THOMAS:;;;14244,00 140367401539;97;01;00;;AX, TORSTEN:;;;15228,00 120446416212;09;40;00;;AXMANN, BERND:;;;24650,00 070659400844;30;63;00;;AXMANN, PETER:;;;16042,50 110931412216;07;99;00;;AXT, EBERHARD:;;;42750,00 120371414529;97;22;00;;AXT, ROGER:;;;2445,32 070840510116;07;26;00;;AXT, ROSEMARIE:;;;22070,56 050469406120;18;32;00;;AXTHELM, KAI:;;;9330,00 010454419328;10;00;43;;AXTHELM, KARL-HEINZ:;;;24150,00 020753417540;09;51;00;;AXTHELM, UDO:;;;20040,00
Diese Liste beinhaltet die Namen von 90.598 Mitarbeitern des Ministeriums für Staatssicherheit der DDR. Die Liste ist nicht vollständig. Insbesondere Mitarbeiter der Führungsebene sind nicht enthalten.
This is a list of 90.598 members of the secret police of East Germany (Ministry for State Security), the list isn’t complete, because the most of the high Officiers lieke Colonel and higher have destroyed the personal Informations in the last days of Eastern Germany.
| Listen der Stasimitarbeiter-hier findest Du sie! Was bedeuten die Zahlen? |
| 1.Listen der Stasi-Diensteinheiten! Bem.:hier kannst du die Nr.(6-stellig) der Dienststellen heraussuchen. 2.Liste der Stasi-Mitarbeiter (Hauptamtlich) Bem.:Hoffentlich hast Du einen guten Rechner, denn die Liste ist erschreckend lang. Die ersten 6 Ziffern sind das Geburtsdatum + die nächsten 6 Ziffern = Dienstausweisnummer! Die zwei Ziffern hinter dem Geburtsdatum geben das Geschlecht an: 41 und 42 = Männlich, 51 und 52 = Weiblich! Wichtig für suchen und finden, sind die sechs Ziffern in den Semikolon vor den Namen: z.B. ;07;00;44; ! Das ist die Nummer der Dienststelle ! Also du suchst in der Liste der Dienststellen, die Nummer der Dienststelle, die Dich interessiert. Damit gehst Du in die Liste der Mitarbeiter und suchst Dir alle Mitarbeiter der entsprechenden Dienststelle heraus. Ich habe das für mein Wohnort getan und so alle Mitarbeiter gefunden. Ob die Liste Vollständig ist kann ich nicht einschätzen, aber zumindest er/kannte ich einige Exverräter vom Namen her. 3.Liste der OibE (Offiziere im besonderen Einsatz) |
TOP-SECRET – Obama Phones
|
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict1.jpg) On his first day in office, President Barack Obama speaks with a foreign leader in the Oval Office, Jan. 21, 2009. (Official White House Photo by Pete Souza) On his first day in office, President Barack Obama speaks with a foreign leader in the Oval Office, Jan. 21, 2009. (Official White House Photo by Pete Souza) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict0.jpg) President Barack Obama places a phone call at his desk in the Oval Office, Jan. 23, 2009. (Official White House Photo by Pete Souza) [This is a Raytheon IST secure phone. http://www.telecore.com/products/ist2.html ] President Barack Obama places a phone call at his desk in the Oval Office, Jan. 23, 2009. (Official White House Photo by Pete Souza) [This is a Raytheon IST secure phone. http://www.telecore.com/products/ist2.html ] |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict4.jpg) President Barack Obama meets with Interior Secretary Ken Salazar aboard Air Force One during a flight to Denver, Col., Feb. 17, 2009. (Official White House Photo by Pete Souza) [Desk phone is a Cisco secure phone.] President Barack Obama meets with Interior Secretary Ken Salazar aboard Air Force One during a flight to Denver, Col., Feb. 17, 2009. (Official White House Photo by Pete Souza) [Desk phone is a Cisco secure phone.]
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict8.jpg) [Phone at Oval Office seating area] President Obama has a briefing with a staff member prior to a phone call in the Oval Office, March 13, 2009. (Official White House Photo by Pete Souza) [Phone at Oval Office seating area] President Obama has a briefing with a staff member prior to a phone call in the Oval Office, March 13, 2009. (Official White House Photo by Pete Souza) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict11.jpg) President Barack Obama is seen at a meeting with his staff April 5, 2009, aboard Air Force One on a flight from Prague, Czech Republic en route to Ankara, Turkey. (Official White House Photo by Pete Souza) President Barack Obama is seen at a meeting with his staff April 5, 2009, aboard Air Force One on a flight from Prague, Czech Republic en route to Ankara, Turkey. (Official White House Photo by Pete Souza)
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict13.jpg) President Barack Obama works with Jon Favreau, director of speechwriting, on the President’s Normandy speech aboard Air Force One enroute to Paris on June 5, 2009. (Official White House photo by Pete Souza) President Barack Obama works with Jon Favreau, director of speechwriting, on the President’s Normandy speech aboard Air Force One enroute to Paris on June 5, 2009. (Official White House photo by Pete Souza)
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict15.jpg) President Barack Obama confers with Senior Advisor David Axelrod and Press Secretary Robert Gibbs at their hotel in Moscow, Russia, July 6, 2009. (Official White House Photo by Pete Souza) [Enlarged from small image.] President Barack Obama confers with Senior Advisor David Axelrod and Press Secretary Robert Gibbs at their hotel in Moscow, Russia, July 6, 2009. (Official White House Photo by Pete Souza) [Enlarged from small image.] |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict16.jpg) President Barack Obama meets with John Brennan, Assistant to the President for Counterterrorism and Homeland Security, in the Oval Office, Jan. 4, 2010. (Official White House photo by Pete Souza) [Two phones, top for secure, bottom White House phone system.] President Barack Obama meets with John Brennan, Assistant to the President for Counterterrorism and Homeland Security, in the Oval Office, Jan. 4, 2010. (Official White House photo by Pete Souza) [Two phones, top for secure, bottom White House phone system.]
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict18.jpg) “This is a rare look inside the President’s Treaty Room office in the private residence of the White House. He was making a call to Poland Prime Minister Donald Tusk.” (Official White House photo by Pete Souza) “This is a rare look inside the President’s Treaty Room office in the private residence of the White House. He was making a call to Poland Prime Minister Donald Tusk.” (Official White House photo by Pete Souza) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict19.jpg) March 29, 2009. “It was a Sunday night in the Oval Office. The auto task force listened to the President before he made phone calls to alert key people about his plan to set deadlines for General Motors and Chrysler overhauls that was to be announced the next morning.” (Official White House photo by Pete Souza) March 29, 2009. “It was a Sunday night in the Oval Office. The auto task force listened to the President before he made phone calls to alert key people about his plan to set deadlines for General Motors and Chrysler overhauls that was to be announced the next morning.” (Official White House photo by Pete Souza)
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict21.jpg) President Barack Obama meets with Rep. Dennis Kucinich, D-Ohio, aboard Air Force One en route to Cleveland, Ohio, March 15, 2010. (Official White House Photo by Pete Souza) [The desk phone is a Cisco secure phone.] President Barack Obama meets with Rep. Dennis Kucinich, D-Ohio, aboard Air Force One en route to Cleveland, Ohio, March 15, 2010. (Official White House Photo by Pete Souza) [The desk phone is a Cisco secure phone.]
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict23.jpg) President Barack Obama checks his BlackBerry as he walks along the Colonnade to the Oval Office, March 18, 2010. (Official White House Photo by Pete Souza) President Barack Obama checks his BlackBerry as he walks along the Colonnade to the Oval Office, March 18, 2010. (Official White House Photo by Pete Souza)
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict25.jpg) President Barack Obama talks on the phone with a Member of Congress while en route to a health care event at George Mason University in Fairfax, Va., March 19, 2010. Assistant to the President for Legislative Affairs Phil Schiliro rides with the President. (Official White House Photo by Pete Souza) [A sends ” [The device between the seats under the seal is unknown. Not all presidential vehicles have it. There is a phone in the console.] President Barack Obama talks on the phone with a Member of Congress while en route to a health care event at George Mason University in Fairfax, Va., March 19, 2010. Assistant to the President for Legislative Affairs Phil Schiliro rides with the President. (Official White House Photo by Pete Souza) [A sends ” [The device between the seats under the seal is unknown. Not all presidential vehicles have it. There is a phone in the console.]
A sends: “With a little enhancement, it’s easy to see that device in the center is a Motorola speakerphone cradle for the handheld, wireless unit the President has.”
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict27.jpg) President Barack Obama talks on the phone in a holding room at Oakley Lindsay Center in Quincy, Ill., April 28, 2010. Mona Sutphen, deputy chief of staff for policy, sits at right. (Official White House Photo by Pete Souza) [Phones are L-3 STE model: http://www2.l-3com.com/cs-east/ia/ste/ie_ia_ste.shtml ]. See enlarged.] President Barack Obama talks on the phone in a holding room at Oakley Lindsay Center in Quincy, Ill., April 28, 2010. Mona Sutphen, deputy chief of staff for policy, sits at right. (Official White House Photo by Pete Souza) [Phones are L-3 STE model: http://www2.l-3com.com/cs-east/ia/ste/ie_ia_ste.shtml ]. See enlarged.]
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict29.jpg) President Barack Obama talks on the phone with German Chancellor Angela Merkel to discuss the economic situation in Europe, prior to the Hampton University commencement in Hampton, Va., Sunday, May 9, 2010. (Official White House Photo by Pete Souza) President Barack Obama talks on the phone with German Chancellor Angela Merkel to discuss the economic situation in Europe, prior to the Hampton University commencement in Hampton, Va., Sunday, May 9, 2010. (Official White House Photo by Pete Souza)
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict31.jpg) President Barack Obama talks with Alyssa Mastromonaco, director of scheduling and advance, in the Outer Oval Office, May 24, 2010. (Official White House Photo by Pete Souza) [Three types of phones sets, perhaps for three different systems.] President Barack Obama talks with Alyssa Mastromonaco, director of scheduling and advance, in the Outer Oval Office, May 24, 2010. (Official White House Photo by Pete Souza) [Three types of phones sets, perhaps for three different systems.] |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict32.jpg) President Barack Obama prepares for foreign leader phone calls with Nigerian President Goodluck Jonathan and Japanese Prime Minister designate Naoto Kan, in the Oval Office, Saturday, June 5, 2010. Pictured, from left, are Michelle Gavin, senior director for African Affairs, Puneet Talwar, senior director for Iraq, Iran and the Gulf States, John Buchanan (on phone), director of operations and deputy director of the White House Situation Room, and National Security Advisor Gen. James Jones. (Official White House Photo by Pete Souza) [A phone technician apparently arranging a secure hook-up.] President Barack Obama prepares for foreign leader phone calls with Nigerian President Goodluck Jonathan and Japanese Prime Minister designate Naoto Kan, in the Oval Office, Saturday, June 5, 2010. Pictured, from left, are Michelle Gavin, senior director for African Affairs, Puneet Talwar, senior director for Iraq, Iran and the Gulf States, John Buchanan (on phone), director of operations and deputy director of the White House Situation Room, and National Security Advisor Gen. James Jones. (Official White House Photo by Pete Souza) [A phone technician apparently arranging a secure hook-up.]
Obama Phones The telephone is likely Obama’s primary means of personal, direct government. More private, intimate and persuasive than meetings, classified briefings, legislation and regulation signings, appointments, White House invites, travel, campaign tours, press releases, executive orders, mail, email, fax, TV, radio, photographs, Internet blogs, dining, applause, dance, sports, hugs, back pats, arm grabs, handshakes, baby holds, fist bumps, shout-outs, waves, finger points, grins, guffaws, chin tickles, jokes, punks, pardons, secret orders, medal awards, hospital-casket transfers-cemetary visits. Presumably all calls are recorded but not likely to be made public any time soon, thus may be the most secret of his service in office. These photos hide far more than they reveal — as intended in defiance of democracy and open government. |
SECRET – Barclays, UBS, HSBC, Royal Bank of Scotland Involved in Money Laundering for Corrupt Nigerian Politicians

Barclays, HSBC, NatWest, Royal Bank of Scotland and UBS – have been linked to money laundering scam over which some corrupt Nigerian politicians were indicted.
A report entitled ‘International Thief Thief’ from Global Witness, a Non-Governmental Organisation (NGO) that exposes the corrupt exploitation of natural resources and international trade systems, drives campaigns to end impunity, resource-linked conflict, and human rights and environmental abuses, accused the banks of fueling corruption in the world’s most-populous black nation.
In a 40-page report published yesterday in http://www.globalwitness.org, Global Witness said that the five banks had taken millions of pounds between 1999 and 2005 from two former governors accused of corruption (Diepreye Alamieyeseigha of Bayelsa State and Joshua Dariye of Plateau State), but had failed sufficiently to investigate the customers or the source of their funds.
Barclays, HSBC and UBS are all members of the Wolfsberg Group, an international body set up in 2000 to try to improve global anti-money laundering procedures.
The report said the banks might not have broken the law, but had helped to fuel corruption in Nigeria.
Global Witness said its findings were based on court documents from cases brought up in London by the Nigerian government to get funds returned that it said had been stolen by the two former governors.
Alamieyeseigha was accused of corruption in 2005 when he was caught with almost a million pounds in cash in his London home, and was briefly jailed in Nigeria after pleading guilty to embezzlement and money laundering charges two years later.
Dariye was arrested in 2004 in London and was found to have purchased properties worth millions of pounds even though his legitimate earnings amounted to the equivalent of 40,000 pounds ($63,500) a year.
He returned to Nigeria, where the anti-corruption agency has accused him of looting public funds. He has denied wrongdoing.
Said the report: “What is so extraordinary about this story is that nearly all of these banks had previously fallen foul of the UK banking regulator, the Financial Services Authority (FSA), in 2001 by reportedly helping the former Nigerian dictator, the late General Sani Abacha, funnel nearly a billion pounds through the UK. These banks were supposed to have tightened up their systems but as this report now shows, a few years later, they were accepting corrupt Nigerian money again. There is no sign that the FSA has taken any action this time.”
UK Banks Draw Fire For Nigerian Accounts:
Banks that allowed two Nigerian politicians to open accounts should have known better, according to Charles Intriago, founder of the International Association for Asset Recovery, a group devoted to recovering illicit assets.
A report released Sunday by U.K.-based anticorruption group Global Witness, “International Thief Thief,” accuses Barclays PLC, HSBC Bank PLC, Royal Bank of Scotland, NatWest (owned since 2000 by RBS) and UBS AG of holding accounts containing allegedly illicit funds for two Nigerian state governors, Diepreye Alamieyeseigha of Bayelsa State and Joshua Dariye of Plateau State, from 1999 to 2005. None of the banks would comment to Corruption Currents on the alleged accounts, though some commented more broadly on their procedures – see below.
Alamieyeseigha pleaded guilty in July 2007 to six counts of money laundering and corruption, receiving six concurrent two-year jail sentences and an order to forfeit his illicit assets, and was released a day after the sentencing for time served while his trial dragged on. Dariye still awaits trial on 23 counts of theft, corruption and breach of state trust in Nigeria. A woman convicted of laundering GBP1.4 million for him in Britain received a three-year jail sentence in April 2007.
Nigeria’s constitution bans politicians from holding bank accounts outside the country, and after the guilty plea, the Nigerian government successfully sued Alamieyeseigha, his shadow companies and “others” (pdf) in U.K. court in 2007 to reclaim his illicit assets, which included several properties and bank accounts held under his name and those of the shadow companies at UBS, HSBC and RBS.
Intriago said that Nigeria is world-renowned for corruption, much like his native Ecuador. Nigeria ranks 130th in the 2009 edition of the Transparency International Index of most corrupt countries.
“For anyone to open a big account for Nigerians is asking for trouble, if not ‘willful blindness,’ which the courts define as ‘the deliberate avoidance of knowledge of the facts,’” he said in an interview.
An HSBC spokesman called the report’s allegations “misguided,” adding that “rigorous and robust compliance procedures were followed diligently.” He wouldn’t comment further. The bank’s U.S. units received a cease-and-desist order last week from the Fed and the Office of the Comptroller of the Currency, requiring it “to take corrective action to improve its firm-wide compliance risk-management program,” including its anti-money laundering compliance procedures.
UN – Report – Governments and companies must redoouble their efforts
Governments and companies must redouble their efforts to implement international supply chain control standards aimed at ending the trade in conflict minerals, a new UN report shows.
In a report published today, the UN Group of Experts on the Democratic Republic of Congo (DRC) notes positive impacts where companies are implementing supply chain controls, known as due diligence, in more stable areas. These include improvements in mining sector governance and a rise in mineral production and exports.
However while international due diligence standards for the mineral trade were announced by the UN and OECD a year ago, and some companies have taken steps to meet them, implementation by many firms dealing in Congolese minerals is still absent. This lack of supply chain controls is allowing militias and criminal networks in the Congolese army to finance themselves via the gold trade in particular.
“The pathway to a clean minerals trade that excludes human rights abusers and benefits the people of eastern Congo has been clear for over a year,” said Sophia Pickles, Campaigner at Global Witness. “It is critical that businesses follow the agreed international guidelines and become part of the solution to the nexus of minerals and violence in the region. Governments of countries that trade or use minerals must implement the recommendation of this report that they incorporate these due diligence standards into their own national laws.”
Many Group of Experts conclusions match the findings of a series of Global Witness’s field visits during 2011, not least regarding the role of certain Congo-based mineral exporters who have been purchasing minerals from areas where armed groups operate. These activities breach UN sanctions, as well as a regulation issued by the Government of DRC in September, which requires traders and exporters operating in the DRC to adhere to OECD due diligence guidance, or face penalties.
As yet, however, no enforcement action has been taken against these firms. The UN Security Council has not imposed sanctions on any company involved in the conflict minerals trade for years, despite abundant evidence gathered by the Group of Experts, Global Witness and others.
Information gathered by the Group of Experts reveals how powerful former rebels are strengthening their grip over parts of Congo’s minerals trade. Ex-CNDP commander General Bosco Ntaganda, indicted by the International Criminal Court for alleged war crimes, is orchestrating large-scale smuggling operations in full view of the Congolese authorities. Such is the impunity Ntaganda enjoys that he has been able to establish his own personal illegal border crossing through property he owns on the Rwandan border. According to the new report, Ntaganda has also been involved in the sale of real and counterfeit gold to international buyers to the tune of millions of US dollars.
“Bosco Ntaganda is a brutal commander who leads a shadow military force of ex-rebels within the national army,” said Sophia Pickles. “Allowing him to boost his power through illegal control of the minerals trade poses a real threat to stability and the human rights of the Congolese population,” she added. “It is vital that the incoming Congolese government tackles impunity in its military head-on and brings notorious human rights abusers like Bosco Ntaganda to justice.”
DOWNLOAD ORIGINAL REPORT HERE
Report – Tax evasion costs 145 countries, representing over 98% of world GDP, more than US$3.1 trillion annually
New research published by the Tax Justice Network shows that tax evasion costs 145 countries, representing over 98% of world GDP, more than US$3.1 trillion annually.
In the UK for instance, a staggering £69.9 billion a year is lost to tax evasion in the ‘shadow economy’ – that is, 56% of the country’s total healthcare spend.
Tax havens are a major part of the tax evasion problem – these new findings come as the Tax Justice Network launches Tackle Tax Havens, a new campaign aimed at the general public that highlights the critical role that these secretive states play in corrupting the global economy.
DER BEWEIS-DIE STASI FÄLSCHER DER “GoMoPa” UND IHRE ERPESSUNG VON MERIDIAN CAPITAL
siehe
http://meridiancapital.wordpress.com/
oder kontaktieren Sie Meridian Capital in New York
Sehr geehrte Damen und Herren,
die Betrüger und durch uns inhaftierten Erpresser der GoMoPa versuchen mit einer gefälschten Presse-Mitteilung von sich abzulenken und einen investigativen Journalisten, Bernd Pulch, zu belasten.
Die Presse-Mitteilung auf pressreleaser.org ist eine Fälschung und die gesamte Webseite ist der GoMoPa zu zuordnen.
Hier noch einmal die tatäschlichen Geschehnisse:
Hier der Artikel von “GoMoPa” über Meridian Capital.
 „GoMopa“ schreibt:08.09.2008 „GoMopa“ schreibt:08.09.2008Weltweite Finanzierungen mit WidersprüchenDie Meridian Capital Enterprises Ltd. gibt an, weltweite Finanzierungen anbieten zu können und präsentiert sich hierbei auf aufwendig kreierten Webseiten. GOMOPA hat die dort gemachten Angaben analysiert und Widersprüche entdeckt.Der FirmensitzDer Firmensitz befindet sich laut eigener Aussage in Dubai, Vereinigte Arabische Emirate. In einem GOMOPA vorliegenden Schreiben der Meridian Capital Enterprises Ltd. heißt es jedoch, der Firmensitz sei in London. Auf der Homepage des Unternehmens taucht die Geschäftsadresse in der Londoner Old Broad Street nur als „Kundenabteilung für deutschsprachige Kunden“ auf. Eine weitere Adresse in der englischen Hauptstadt, diesmal in der Windsor Avenue, sei die „Abteilung der Zusammenarbeit mit Investoren“.Die Meridian Capital Enterprises ist tatsächlich als „Limited“ (Ltd.) mit Sitz in England und Wales eingetragen. Aber laut Firmenhomepage hat das Unternehmen seinen „rechtlichen Geschäftssitz“ in Dubai. Eine Abfrage beim Gewerbeamt Dubais (DED) zu dieser Firmierung bleibt ergebnislos.Bemerkenswert ist auch der vermeintliche Sitz in Israel. Auf der Webseite von Meridian Capital Enterprises heißt es: „Die Firma Meridian Capital Enterprises Ltd. ist im Register des israelischen Justizministeriums unter der Nummer 514108471, gemäß dem Gesellschaftsrecht von 1999, angemeldet.“ Hierzu Martin Kraeter, Gomopa-Partner und Prinzipal der KLP Group Emirates in Dubai: „Es würde keinem einzigen Emirati – geschweige denn einem Scheich auch nur im Traum einfallen, direkte Geschäfte mit Personen oder Firmen aus Israel zu tätigen. Und schon gar nicht würde er zustimmen, dass sein Konterfei auch noch mit vollem Namen auf der Webseite eines Israelischen Unternehmens prangt.“Auf der Internetseite sind diverse Fotos mit Scheichs an Konferenztischen zu sehen. Doch diese großen Tagungen und großen Kongresse der Meridian Capital Enterprises werden in den Pressearchiven der lokalen Presse Dubais mit keinem Wort erwähnt. Martin Kraeter: „ Ein ‚britisch-arabisch-israelisches bankfremdes Finanzinstitut sein zu wollen, wie die Meridian Capital Enterprises Ltd. es darstellt, ist mehr als zweifelhaft. So etwas gibt es schlicht und ergreifend nicht! Der Nahostkonflikt schwelt schon seit mehr als 50 Jahren. Hier in den Vereinigten Arabischen Emiraten (VAE) werden Israelis erst gar nicht ins Land gelassen. Israelische Produkte sind gebannt. Es gibt nicht einmal direkte Telefonverbindungen. Die VAE haben fast 70% der Wiederaufbaukosten des Libanon geschultert, nachdem Israel dort einmarschiert ist.“Zwei angebliche Großinvestitionen der Meridian Capital Enterprises in Dubai sind Investmentruinen bzw. erst gar nicht realisierte Projekte. Das Unternehmen wirbt mit ihrer finanziellen Beteiligung an dem Dubai Hydropolis Hotel und dem Dubai Snowdome. Der Aktivitätsstatus der Meridian Capital Enterprises Ltd. ist laut englischen Handelsregister (UK Companies House) „dormant“ gemeldet. Auf der Grundlage des englischen Gesellschaftsrechts können sich eingetragene Unternehmen selbst „dormant“ (schlafend) melden, wenn sie keine oder nur unwesentliche buchhalterisch zu erfassende Transaktionen vorgenommen haben. Dies ist angesichts der angeblichen globalen Investitionstätigkeit der Meridian Capital Ltd. sehr erstaunlich. Der Webauftritt Die Internetseite der MCE ist sehr aufwendig gestaltet, die Investitionen angeblich in Millionen- und Milliardenhöhe. Bei näherer Betrachtung der Präsentationselemente fällt jedoch auf, dass es sich bei zahlreichen veröffentlichen Fotos, die Veranstaltungen der Meridian Capital Enterprises dokumentieren sollen, meist um Fotos von Online-Zeitungen oder frei zugänglichen Medienfotos einzelner Institutionen handelt wie z.B. der Börse Dubai. Auf der Internetpräsenz befinden sich Videofilmchen, die eine frappierende Ähnlichkeit mit dem Werbematerial von NAKHEEL aufweisen, dem größten Bauträger der Vereinigten Arabischen Emirate. Doch den schillernden Videos über die berühmten drei Dubai Palmen „Jumeirah, Jebel Ali und Deira“ oder das Archipel „The World“ wurden offensichtlich selbstproduzierte Trailersequenzen der Meridian Capital Enterprises vorangestellt. Doch könnte es sich bei den Werbevideos um Fremdmaterial handeln. Auch die auf der Webseite wahllos platzierten Fotos von bekannten Sehenswürdigkeiten Dubais fungieren als Augenfang für den interessierten Surfer mit eigenem Finanzierungswunsch. Bei einem Volumen von 10 Millionen Euro oder höher präsentiert sich die Meridian Capital Enterprises Ltd. als der passende Investitionspartner. Das Unternehmen verfügt weltweit über zahlreiche Standorte: Berlin, London, Barcelona, Warschau, Moskau, Dubai, Riad, Tel Aviv, Hong Kong und New York. Aber nahezu alle Standorte sind lediglich Virtual Offices eines global arbeitenden Büroservice-Anbieters. „Virtual Office“ heißt im Deutschen schlicht „Briefkastenfirma“. Unter solchen Büroadressen sollen laut Meridian Capital Enterprises ganze Kommissionen ansässig sein, alles zum Wohle des Kunden.“ Zitatende |
Hier die Hintergründe der Erpressung:
Hier unsere Original-Stellungnahme:
Anfang Oktober 2008 erhielt einer der Arbeiter der Meridian Capital Enterprises Ltd. eine Meldung von einem anonymen Sender, dass in naher Zukunft – zuerst im Internet, dann im Fernsehen, im Radio und in der deutschen Presse – Informationen erscheinen, die die Funktionsweise und Tätigkeiten der Meridian Capital Enterprises Ltd. in einem äußerst negativen Licht darstellen. Der Mitarbeiter der Meridian Capital Enterprises Ltd. wurde also informiert, dass diese Meldungen/Nachrichten zweifelsohne deutlich das Aussehen und den guten Ruf der Firma Meridian Capital Enterprises Ltd. beeinträchtigen.
Der an dieser Stelle erwähnte „Gesprächspartner” hat den Arbeiter der Meridian Capital Enterprises Ltd. informiert, dass die Möglichkeit besteht die peinliche Situation zu vermeiden, indem die Meridian Capital Enterprises Ltd. auf das von der Person gezeigte Konto die Summe von 100.000,00 EUR überweist. Wie sich aber später zeigte, war der Herr Klaus Maurischat – dieser anonyme Gesprächspartner – „Gehirn“ und „Lider des GOMOPA“. Die Ermittlungen wurden angestellt durch die Bundeskriminalpolizei (Verfolgungs- und Ermittlungsorgan auf der Bundesebene) während des Ermittlungsverfahrens wegen einer finanziellen Erpressung, Betrügereien auch wegen der Bedrohungen, welche von Herrn Maurischat und seine Mitarbeiter praktiziert wurden sowie wegen Teilnahme anderer (Leiter der Internetservices und Moderatoren der Blogs) an diesem Prozedere. Diese Straftaten wurden begangen zu Schaden vieler Berufs- und Justizpersonen, darunter auch der Meridian Capital Enterprises Ltd. Die Opfer dieses Verbrechens sind in Deutschland, Österreich, der Schweiz, Spanien, Portugal, Großbritannien, den USA und Kanada sichtbar.
In diesem Moment taucht folgende Frage auf: Wie war die Reaktion der Meridian Capital Enterprises Ltd. auf die Forderungen seitens GOMOPA? Entsprach die Reaktion den Erwartungen von GOMOPA? Hat die Meridian Capital Enterprises Ltd. die geforderte Summe 100.000,00 EUR überwiesen?
Seites der Meridian Capital Enterprises Ltd. gab es überhaupt keine Reaktion auf den Erpressungsversuch von GOMOPA. Ende August 2008 auf dem Service http://www.gompa.net sind zahlreiche Artikel/Meldungen erscheinen, welche die Tätigkeit der Meridian Capital Enterprises Ltd. in einem sehr negativen Licht dargestellt haben. Nachdem die auf http://www.gomopa.net enthaltenen Informationen ausführlich und vollständig analysiert worden waren, ergab es sich, dass sie der Wahrheit nicht einmal in einem Punkt entsprechen und potenzielle und bereits bestehende Kunden der Meridian Capital Enterprises Ltd. in Bezug auf die von diesem Finanzinstitut geführten Geschäftstätigkeit irreführen. Infolge der kriminellen Handlugen von GOMOPA und der mit ihm kooperierenden Services und Blogs im Netz hat die Meridian Capital Enterprises Ltd. beachtliche und messbare geschäftliche Verluste erlitten. Die Meridian Capital Enterprises Ltd. hat nämlich in erster Linie eine wichtige Gruppe von potenziellen Kund verloren. Was sich aber als wichtiger ergab, haben sich die bisherigen Kunden von der Meridian Capital Enterprises Ltd. kaum abgewandt. Diejenigen Kunden haben unsere Dienstleitungen weiterhin genutzt und nutzen die immer noch. In Hinblick auf die bisherige Zusammenarbeit mit der Meridian Capital Enterprises Ltd., werden ihrerseits dem entsprechend keine Einwände erhoben .
GOMOPA hat so einen Verlauf der Ereignisse genau prognostiziert, dessen Ziel beachtliche und messbare geschäftliche durch die Meridian Capital Enterprises Ltd. erlittene Verluste waren. Der Verlauf der Ereignisse hat das Service GOMOPA mit Sicherheit gefreut. GOMOPA hat nämlich darauf gerechnet, dass die Stellung der Meridian Capital Enterprises Ltd. nachlässt und das Finanzinstitut die geforderte Summe (100.000,00 EUR) bereitstellt. Im Laufe der Zeit, als das ganze Prozedere im Netz immer populärer war, versuchte GOMOPA noch vier mal zu der Meridian Capital Enterprises Ltd. Kontakte aufzunehmen, indem es jedes mal das Einstellen dieser kriminellen „Kompanie” versprochen hat, wobei es jedes mal seine finanziellen Forderungen heraufsetzte. Die letzte für das Einstellen der „Kompanie“ gegen die Meridian Capital Enterprises Ltd. vorgesehene Quote betrug sogar 5.000.000,00 EUR (in Worten: fünfmilionen EURO). Die Meridian Capital Enterprises Ltd. konnte sich aber vor den ständig erhöhenden Forderungen seitens des Services GOMOPA behaupten.
Im Oktober 2008 traf die Leitung der Meridian Capital Enterprises Ltd. Entscheidung über die Benachrichtigung der Internationalen Polizei INTERPOL sowie entsprechender Strafverfolgungsorgane der BRD (die Polizei und die Staatsanwaltschaft) über den bestehenden Sachverhalt. In der Zwischenzeit meldeten sich bei der Meridian Capital Enterprises Ltd. zahlreiche Firmen und Korporationen, sogar Berufsperson wie Ärzte, Richter, Priester, Schauspieler und anderen Personen aus unterschiedlichen Ländern der Welt, die der Erpressung von GOMOPA nachgegeben und die geforderten Geldsummen überwiesen haben. Diese Personen gaben bereits Erklärungen ab, dass sie dies getan haben, damit man sie bloß endlich „in Ruhe lässt” und um unnötige Probleme, Schwierigkeiten und einen kaum begründbaren Ausklang vermeiden zu können. Die Opfer dieses kriminellen Vorgehens haben die Meridian Capital Enterprises Ltd. über unterschiedliche Geldsummen, welche verlangt wurden, informiert.
In einem Fall gab es verhältnismäßig kleine (um ein paar tausend EURO), in einem anderen Fall handelte es schon um beachtliche Summen (rund um paar Millionen EURO).
Zusätzlich wendeten sich an die Meridian Capital Enterprises Ltd. Firmen, welche dem GOMOPA noch keine „Gebühr” überweisen haben und bereits überlegen, ob sie dies tun sollen, oder nicht. Diese Firmen erwarteten von der Meridian Capital Enterprises Ltd. eine klare Stellungnahme sowie eine professionelle praktische Beratung, wie man sich in solch einer Lage verhalten soll und wie man diese Geldforderungen umgehen kann. Die Meridian Capital Enterprises Ltd. hat ausnahmslos allen Verbrechensopfern, welche sich bei unserer Firma gemeldet haben, eine Zusammenarbeit vorgeschlagen. Als oberste Aufgabe stellt sich diese Kooperation, gemeinsam entschlossene und wirksame Maßnahmen gegen GOMOPA, gegen andere Services im Netz sowie gegen alle Bloggers zu treffen, die an dem hier beschriebenen internationalen kriminellen Vorgehen mit GOMOPA-Führung teilnehmen.Auf unsere Bitte benachrichtigten alle mitbeteiligten Firmen die Internationale Polizei INTERPOL sowie ihre heimischen Verfolgungsorgane, u. a. die zuständige Staatsanwaltschaft und die Polizeibehörden über den bestehenden Sachverhalt.
In Hinblick auf die Tatsache, dass das verbrecherische Handeln von GOMOPA sich über viele Staaten erstreckte und dass die Anzahl der in der Bundesrepublik Deutschland erstatteten Anzeigen wegen der durch GOMOPA, Internetservices und Bloggers begangenen Straftaten, rasant wuchs – was zweifelsohne von einer weit gehenden kriminellen Wirkungskraft des GOMOPA zeugt – schlug die Internationale Wirtschaftspolizei INTERPOL der Meridian Capital Enterprises Ltd. vor, dass sich ihr Vertreter in Berlin mit dem Vertreter von GOMOPA trifft, um die „Zahlungsmodalitäten“ und Überweisung der Summe von 5.000.000,00 EUR zu besprechen. Dieser Schritt meinte, eine gut durchdachte und durch die Bundeskriminalpolizei organisierte Falle durchzuführen, deren Ziel die Festnahme der unter GOMOPA wirkenden internationalen Straftäter war.
Die koordinierten Schritte und Maßnahmen der Meridian Capital Enterprises Ltd. und anderer Beschädigter, geleitet von der Internationalen Wirtschaftspolizei INTERPOL, dem Bundeskriminalamt und der Staatsanwaltschaft der Bundesrepublik Deutschland haben zur Aus-, Einarbeitung und Durchführung der oben beschriebenen Falle beigetragen. Im November 2008 führte die in Berlin vorbereitete Falle zur Festnahme und Verhaftung des Vertreters des GOMOPA, der nach der Festnahme auf Herrn Klaus Maurichat – als den Hauptverantwortlichen und Anführer der internationalen kriminellen Gruppe GOMOPA verwies. Der Festgenommene benannte und zeigte der Bundeskriminalpolizei zugleich den aktuellen Aufenthaltsort des Herrn Klaus Maurischat. „Gehirn“ und Gründer dieser internationalen kriminellen Gruppe GOMOPA, Herr Klaus Maurischat wurde am selben Tag auch festgenommen und auf Frist verhaftet, wird bald in Anklagezustand gestellt, wird die Verantwortung für eigene Straftaten und die des Forums GOMOPA vor einem zuständigen Bundesgericht tragen. Die Meridian Capital Enterprises Ltd. unternahm bereits alle möglichen Schritte, damit Herr Klaus Maurischat auch auf der Anklagebank des zuständigen Gerichts des Vereinigten Königsreiches Großbritannien erscheint. Unter den beschädigten Berufs- und Justizpersonen aus Großbritannien, neben der Meridian Capital Enterprises Ltd. gibt es noch viele Opfer von GOMOPA…
Die dreisten Verbrecher wagen es unter http://www.pressreleaser.org, einer eigenen “GoMoPa”-Seite unsere Pressemitteilung oben zu verfälschen und unschuldige Personen zu belasten.
“GoMoPa” Boss is Jochen Resch
- May 15, 2011 – 1:15 pm
- Posted in Uncategorized
- Comments Off
Dear Readers,
after a thorough research we are sure that the real “GoMoPa” boss is Jochen Resch, lawyer in Berlin, Germany. He is the brain behind “GoMoPa” and responsable for blackmailing, extortion, racketeering, cybermurder and murder – in the tradition of the East German “Inteeligence” STASI that is why he called “GoMoPa” – Financial “Intelligence” Service .
Webmaster
Meridian Capital about GoMoPa
“GoMoPa” in detention
- May 13, 2011 – 1:02 pm
- Posted in Uncategorized
- Comments Off
Meridian Capital Enterprises Ltd.. unveils new criminal phenomena in network. In recently appeared on the net more often at the same time a new a very worrying phenomenon of criminal nature. Professional criminals groups in the network are taking part, to extortion, fraud, Erschwindeln relating to certain specifically selected companies and businesses are capable of. These criminals developed new methods and means, simply and in a short time to bereichern.Strategien and manifestations, which underlie this process are fairly simple. A criminal is looking to “carefully” on the Internet specific companies and corporations (victims of crime) and informed them in the next step, that of the business activities of such companies and corporations in the near future – first on the Internet then in other available mass media – numerous and very unfavorable information appears. At the same time, the criminals beat their future victims an effective means of reducing unnecessary difficulties and problems to escape the loss of good name and image of the company and corporate sector. These offenders are aware of that reputation, name and appearance of each company is a value in itself. It was therefore a value of what each company is prepared to pay any price. But the reason for difficulties and problems arising from the loss of good name and reputation result. The criminals and their victims are already aware that this loss is devastating consequences might have been the closing down of a particular business can enforce. It takes both to No as well as at large companies regard. The company is concerned that in virtually every industry in each country and cross-border activities sind.Das criminal procedure in the form of a blackmail on money, a fraud is becoming rapidly and globally, ie led cross-border and internationally. Among the victims of extortion, fraud is now looking both at home (domestic) and international corporations, the major emphasis on conservation, keeping and maintaining their reputation in the business according to their credibility lay. The criminals in the network have understood that maintaining an unassailable reputation and name of a company the unique ability to provide fast and easy enrichment forms. The above-mentioned criminal procedure is difficult to track because it is international in nature, and by overlapping or even nonexistent (fictional) professional and judicial persons in various countries and operated company wird.Diese offenders in the network publish it and disseminate false information about your victims on remote servers, which are not uncommon in many exotic countries. There are those countries in which serious gaps in the legal system, investigative and prosecution procedures are visible. As an example, at this point mention India werden. Mit criminals working in the network grid portals known leader of blogs with your seat-consciously or unconsciously, even in highly developed countries. For example, at this point, countries such as Germany, Austria, Switzerland, the United States, Britain, Spain or Portugal are mentioned. The below listed criminals were able to act unpunished today. As a symptom of such action appears here the activity and “effectiveness” of the company GOMOPA, which is on countries such as Germany, Switzerland, Austria, the United States, Britain, Spain and India. A good example of such an action is Mr. Klaus Mauri Chat – the leader and “brain” of the company GOMOPA with many already in force and criminal judgments “on his account”, which in this way for years and funded its maintenance in the industry almost unlimited activity. This status will change dramatically, however, including far and wide thanks to discontinued operations of the firm Meridian Capital Enterprises Ltd.. who would oppose such offenses addressed in the network. Other companies and corporations, in which the crime network and outside of this medium have fallen victim to contribute to combating such crimes bei.Die situation is changing, thanks to effective steps and the successful cooperation of the firm Meridian Capital Enterprises Ltd.. with the international police Interpol, with the federal agency (FBI) in the U.S., the Federal Criminal Police in Germany, with Scotland Yard in Britain, as well as with the Russian secret service FSB.Die Meridian Capital Enterprises Ltd.. – Together with other companies and cooperations, the victim of criminal activities of the network of crime have fallen – has undeniably already started to yield results. The fact that in recent weeks (November 2008) on the territory of the Federal Republic of Germany of the above-mentioned leaders and “brain” of the company GOMOPA, Mr Klaus Maurishat was arrested should not be ignored. The Meridian Capital Enterprises Ltd.. information available results clearly show that the next arrests of persons participating in this process in such countries as: Austria, Switzerland, Russia, Ukraine, Poland, Spain, Mexico, Portugal, Brazil, the USA, Canada, UK, Ireland , Australia, New Zealand and made in a.. The ultimate goal of Meridian Capital Enterprises Ltd.. and the other victims of crime in the network is to provide all participants in this criminal procedure before the competent court to lead. All professional and judicial persons, regardless of the seat and out of the business, which the above-described criminal action (fraud, extortion) to have fallen victim can of Meridian Capital Enterprises Ltd.. led company to join the goal set at all at this point the procedure described those associated in the public and the economic life out. II blacklist blackmail and with international fraudsters and their methods (opus operandi) in the following countries: 1 The Federal Republic Deutschland2. Dubai 3rd Russia 1st The Federal Republic of Germany GmbH GOMOPA, Goldman Morgenstern & Partners LLC., Goldman Morgenstern & Partners Consulting LLC, Wottle collection. In these firms are quite active following persons: – Klaus Mauri Chat ( “Father” and “brain” of the criminal organization responsible for countless final judgments have been achieved (arrested in Germany in November 2008) – Josef Rudolf Heckel ( “right hand “when Mr Klaus Mauri chat, denounced former banker who is excessive in many Bankschmuggeleien was involved.
The study of 900 pages named Toxdat by Ehrenfried Stelzer is the “Stasi Killer Bible”. It lists all kind of murder methods and concentrates on the most effective and untraceable.
“The toxdat study was ordered by Stasi Vice-President Gerhard Neiber, the second man in rank after boss Erich Mielke. The toxdat study was also the theoretical “story book” for the murder of the famous German watchdog and journalist Heinz Gerlach by former Stasi member under the guidance of “GoMoPa”,” an informer stated. “Ehrenfried stelzer” was nicknamed “Professor Murder” by his victims. Even close co-worker now compare him with the German SS”doctor” Mengele, “Dr. Death” from Auschwitz.
Only two articles let the German audience believe that the famous journalist and watchdog Heinz Gerlach died on natural courses by blood pollution.
For more Information the victims have launched a new site: http://www.victims-opfer.com
The first one, published only hours after the death of Mr Heinz Gerlach by the notorious “GoMoPa” (see article below) and a second 3 days later by a small German local newspaper, Weserbergland Nachrichten.
Many people including the hostile Gerlach website “Akte Heinz Gerlach” doubted that this man who had so many enemies and friends would die of natural causes without any previous warning. Rumours occured that Mr. Gerlach’s doctor doubted natural courses at all. After many critical voices discussed the issue a small website of a small German local newspaper – which never before had reported about Mr. Heinz Gerlach and which is not even in the region of Mr Gerlachs home – published that Mr Gerlach died of blood pollution. Weserbergland-Nachrichten published a long article about the deadly consequences of blood pollution and did not even name the source of such an important statement. It claimed only that somebody of Gerlachs inner circle had said this. It is a proven fact that after the collpase of the Eastern German Communist Regime many former Communist propaganda agents went to regional newspapers – often in Western Germany like Günther Schabowski did the man who opened the “Mauer”.
The theatre stage was set: One day later the hostile Gerlach website “Akte Heinz Gerlach” took the agenda publishing that Mr Gerlach had died for natural causes without any further research at all.
This was done by a website which for months and months and months reported everything about Mr. Gerlach.
Furthermore a research proves that the technical details regarding the website hosting of this hostile website “Akte Heinz Gerlach” proves that there are common details with the hosting of “GoMoPa” and their affiliates as proven by the SJB-GoMoPa-victims (see http://www.sjb-fonds-opfer.com)
Insiders believe that the murderers of Mr. Heinz Gerlach are former members of the Eastern German Terror Organisation “Stasi” with dioxins. They also believe that “GoMoPa” was part of the plot. At “GoMoPa”’ a person named Siegfried Siewers was officialy responsible for the press but never appeared in public. “GoMoPa”-victims say that this name was a cameo for “GoMoPa” frontrunner Klaus Maurischat who is controlled by the Stasi Top Agent Ehrenfried Stelzner, Berlin.
Siegfried Sievers, a former Stasi member is responsible for the pollution of millions Germanys for many years with dioxins. This was unveiled at 5th of January 2011 by German prosecutors.
The victims say that Maurischat (probably also a Stasi cameo) and Sievers were in contact as Sievers acted as Stasi Agent and was in fact already a specialist in dioxins under the Communist Terror Regime in Eastern Germany.
Furthermore the Stasi Top Agent Ehrenfried Stelzer disguised as Professor for Criminal studies during the Communist Regime at the Eastern Berlin Humboldt University.
Background:
The man behind the Berlin lawyer Jochen Resch and his activities is Ehrenfried Stelzer, former Stasi Top officer in Berlin and “Professor for Criminal Studies” at the Eastern Berlin Humboldt University during the Communist regime, the SJB-GoMoPa-victims say (www.sjb-fonds-opfer.com) is responsable for the killing of German watchdog and journalist Heinz Gerlach.
These informations stem from various sources who were close to the criminal organization of GoMoPa in the last years. The SJB-GoMoPa say that the well-known German watchdog and journalist Heinz Gerlach was killed by former Stasi members with dioxins. Polychlorinated dibenzodioxins (PCDDs), or simply dioxins, are a group of organic polyhalogenated compounds that are significant because they act as environmental pollutants. They are commonly referred to as dioxins for simplicity in scientific publications because every PCDD molecule contains a dioxin skeletal structure. Typically, the p-dioxin skeleton is at the core of a PCDD molecule, giving the molecule a dibenzo-p-dioxin ring system. Members of the PCDD family have been shown to bioaccumulate in humans and wildlife due to their lipophilic properties, and are known teratogens, mutagens, and confirmed (avered) human carcinogens. They are organic compounds.
Dioxins build up primarily in fatty tissues over time (bioaccumulate), so even small exposures may eventually reach dangerous levels. In 1994, the US EPA reported that dioxins are a probable carcinogen, but noted that non-cancer effects (reproduction and sexual development, immune system) may pose an even greater threat to human health. TCDD, the most toxic of the dibenzodioxins, is classified as a Group 1 carcinogen by the International Agency for Research on Cancer (IARC).
In 2004, a notable individual case of dioxin poisoning, Ukrainian politician Viktor Yushchenko was exposed to the second-largest measured dose of dioxins, according to the reports of the physicians responsible for diagnosing him. This is the first known case of a single high dose of TCDD dioxin poisoning, and was diagnosed only after a toxicologist recognized the symptoms of chloracne while viewing television news coverage of his condition.
German dioxin scandal: In January 2011 about 4700 German farms were banned from making deliveries after tests at the Harles und Jentzsch plant in the state of Schleswig-Holstein showed high levels of dioxin. Again this incident appears to involve PCBs and not PCDDs at all. Dioxin were found in animal feed and eggs in many farms. The person who is responsible for this, Siegfried Sievert is also a former Stasi Agent. At “GoMoPa” the notorious Eastern-Berlin press agency (see article below) one of the henchmen acted under the name of “Siegfried Siewert”.
Further evidence for the killing of Mr.Heinz Gerlach is provided by the SJB-GoMoPa-victims by analyzing the dubious role of former Stasi-Top-agent Ehrenfried Stelzer, also a former “Professor for Crime Studies” under the Communist regime in Eastern Germany and the dubious role of “detective” Medard Fuchsgruber. Both are closely tied to the dubious “GoMoPa” and Berlin lawyer Jochen Resch.
According to the SJB-GoMoPa-victims is Berlin lawyer Jochen Resch the mastermind of the criminal organization “GoMoPa2. The victims state that they have a source inside “GoMoPa” who helped them discover the shocking truth. The so-called “Deep Throat from Berlin” has information that Resch had the idea to found the criminal organization “GoMoPa” and use non-existing Jewish lawyers named Goldman, Morgenstern & Partner as camouflage. Their “office” in Madison Avenue, New York, is a mailbox. This is witnessed by a German Ex-Patriot, a lawyer, whose father, Heinz Gerlach, died under strange circumstances.
Resch seems to use “GoMoPa” as an instrument to blackmail parts of the German Property and Investment.
German authorities are under growing pressure to reopen investigations into at least a dozen suspicious deaths after the arrest of an alleged East German assassin cast new light on the communist regime. Stasi victims quoted a source saying “isolated units” had conducted operations that were “extremely well organised” and had “100 per cent logistical support” from the East German state.
A statement from prosecutors read: “The accused [Jurgen G] is suspected, as a member of a commando of the former DDR, of killing a number of people between 1976 and 1987 who from the point of view of the DDR regime had committed treason or were threatening to do so.”
Details of his Jurgen G’s arrest have been described in suitably florid terms, with the mass circulation tabloid Bild saying he was working at the Wolfsbruch marina near Rheinsberg in north-eastern Germany when a woman approached him. “Excuse me, is that your yellow Trabant in the car park? I just ran into it with my car,” she is said to have asked.
When he followed her to the car park, masked officers jumped out of vans and bushes and overpowered him in an operation worthy of the Stasi itself.
An eyewitness told Bild: “They blindfolded him and raced off in an unmarked car.”
Police across Germany are reported to be sifting through files to see who the victims may have been, and some intelligence officers are greeting the arrest of Jurgen G as a breakthrough.
Thomas Auerbach, who works for the Stasi file authority in Berlin and has written a book based on the death squad files, said: “These people were trained to make such murders look like accidents or suicides, even as ‘ordinary’ crimes such as robberies. They were real terror experts.”
The cases said to be linked to Jurgen G or his unit include many people involved with the commercial arm of the East German ruling socialist party, the SED (Socialist Unity Party).
Uwe Harms, the head of a Hamburg-based haulage firm which was part of a network of companies secretly owned by the SED, disappeared in March 1987 after conversations with various DDR functionaries. Six weeks later, his body was found in a plastic bag.
Weeks before his death he told friends that he felt he was being followed. After reunification, one of the other SED company heads said Mr Harms had been liquidated for refusing to allow his firm to be used to transport arms into East Germany.
Dieter Vogel, a businessman who had been jailed for life for spying for the CIA, was found suffocated in his cell in the East German prison Bautzen on March 9, 1982. The fact that he was due to be taken to the West in a spy swap arrangement just a few weeks later cast doubt on the suicide theory.
He had passed the names of several Stasi moles to the BND, West Germany’s heavily penetrated counter-intelligence service.
The Christian Democrat Union politician Uwe Barschel, 43, was found dead by magazine reporters in his bathtub in a hotel room in Geneva in October, 1987. He died of poisoning, but rumours that he was involved somehow in arms deals and the Stasi have clung to the case.
One of the more high-profile and enduring mysteries is that of Lutz Eigendorf, an East German footballer from the Stasi-backed Dynamo Berlin.
He fled to the West in 1979 amid great publicity. Four years later, he died after crashing his car into a tree on a straight stretch of road with blood alcohol levels way over the limit. Witnesses who had seen him earlier in the evening said he had not been drinking.
Most controversial though is the suggestion that the assassination squad was linked to the murder of a Swedish television reporter and her friend in 1984.
Cats Falk and her friend Lena Graens went missing on Nov 19, 1984. Their bodies were fished out of a Stockholm canal six months later.
Reports suggested a three-man assassination squad killed them, spiking their drinks with drugs, putting them into their car and pushing it into the Hammarby canal.
Shortly before her death, Cats Falk had reportedly uncovered a deal between an arms dealer and an East German firm.
Germany has recently undergone a wave of nostalgia for all things East German, dubbed Ostalgie, with colourful television shows featuring former DDR stars such as the ice skater Katerina Witt talking wistfully about socialist pop music.
A reassessment may be coming in the wake of the revelations.
Victims: The DDR-STASI MURDER GANG “GoMOPa” in murderoplot against Joerg Berger
The Stasi Murder Gang of „GoMoPa“ was involved in many trials to kill the popular East German soccer trainer Joerg Berger, Stasi victims tell in postings on their hompage http://www.sjb-fonds-opfer.com. Berger stated before his early death in his biography that they tried to pollute him with arsenic.
Arsenic and many of its compounds are especially potent poisons. Many water supplies close to mines are contaminated by these poisons. Arsenic disrupts ATP production through several mechanisms. At the level of the citric acid cycle, arsenic inhibits lipoic acid which is a cofactor for pyruvate dehydrogenase; and by competing with phosphate it uncouples oxidative phosphorylation, thus inhibiting energy-linked reduction of NAD+, mitochondrial respiration and ATP synthesis. Hydrogen peroxide production is also increased, which might form reactive oxygen species and oxidative stress. These metabolic interferences lead to death from multi-system organ failure, probably from necrotic cell death, not apoptosis. A post mortem reveals brick red coloured mucosa, owing to severe haemorrhage. Although arsenic causes toxicity, it can also play a protective role.[
Elemental arsenic and arsenic compounds are classified as “toxic” and “dangerous for the environment” in the European Union under directive 67/548/EEC. The International Agency for Research on Cancer (IARC) recognizes arsenic and arsenic compounds as group 1 carcinogens, and the EU lists arsenic trioxide, arsenic pentoxide and arsenate salts as category 1 carcinogens.
Arsenic is known to cause arsenicosis owing to its manifestation in drinking water, “the most common species being arsenate [HAsO42- ; As(V)] and arsenite [H3AsO3 ; As(III)]”. The ability of arsenic to undergo redox conversion between As(III) and As(V) makes its availability in the environment more abundant. According to Croal, Gralnick, Malasarn and Newman, “[the] understanding [of] what stimulates As(III) oxidation and/or limits As(V) reduction is relevant for bioremediation of contaminated sites (Croal). The study of chemolithoautotrophic As(III) oxidizers and the heterotrophic As(V) reducers can help the understanding of the oxidation and/or reduction of arsenic.
Treatment of chronic arsenic poisoning is easily accomplished. British anti-lewisite (dimercaprol) is prescribed in dosages of 5 mg/kg up to 300 mg each 4 hours for the first day. Then administer the same dosage each 6 hours for the second day. Then prescribe this dosage each 8 hours for eight additional days. However the Agency for Toxic Substances and Disease Registry (ATSDR) states that the long term effects of arsenic exposure cannot be predicted. Blood, urine, hair and nails may be tested for arsenic, however these tests cannot foresee possible health outcomes due to the exposure. Excretion occurs in the urine and long term exposure to arsenic has been linked to bladder and kidney cancer in addition to cancer of the liver, prostate, skin, lungs and nasal cavity.[
Occupational exposure and arsenic poisoning may occur in persons working in industries involving the use of inorganic arsenic and its compounds, such as wood preservation, glass production, nonferrous metal alloys and electronic semiconductor manufacturing. Inorganic arsenic is also found in coke oven emissions associated with the smelter industry.
THE DDR GESTAPO-STASI MURDER GANG responsable for the murder of Lutz Eigendorf
The talented Eigendorf played for East German side Dynamo Berlin.
He made his debut for the GDR in an August 1978 match against Bulgaria, immediately scoring his first two goals in a 2–2 draw. He went on to collect six caps, scoring three goals.[1] His final international was a February 1979 friendly match against Iraq.
On 20 March 1979, after a friendship match between Dynamo and West German club 1. FC Kaiserslautern in Gießen he fled to the west hoping to play for that team. But because of his defection he was banned from play for one year by UEFA and instead spent that time as a youth coach with the club.
This was not the first time an East German athlete had fled to the west, but it was a particularly embarrassing defection. Eigendorf’s club Dynamo was under the patronage of the Stasi, East Germany’s secretive state police, and subject to the personal attentions of the organisation’s head, Erich Mielke. He ensured that the club’s roster was made up of the country’s best players, as well as arranging for the manipulation of matches in Dynamo’s favour. After his defection Eigendorf openly criticised the DDR in the western media.
His wife Gabriele remained behind in Berlin with their daughter and was placed under constant police surveillance. Lawyers working for the Stasi quickly arranged a divorce and the former Frau Eigendorf re-married. Her new husband was eventually revealed as a Lothario – an agent of the state police whose role it was to spy on a suspect while romancing them.
In 1983 Eigendorf moved from Kaiserslautern to join Eintracht Braunschweig, all the while under the scrutiny of the Stasi who employed a number of West Germans as informants. On 5 March that year he was badly injured in a suspicious traffic accident and died within two days. An autopsy indicated a high blood alcohol level despite the testimony of people he had met with that evening indicating that Eigendorf had only a small amount of beer to drink.
After German re-unification and the subsequent opening of the files of the former East Germany’s state security service it was revealed that the traffic accident had been an assassination attempt orchestrated by the Stasi, confirming the longtime suspicions held by many. A summary report of the events surrounding Eigendorf’s death was made on German television on 22 March 2000 which detailed an investigation by Heribert Schwan in the documentary “Tod dem Verräter” (“Death to the Traitor”).
On 10 February 2010, a former East German spy revealed the Stasi ordered him to kill Eigendorf, which he claimed not to have done
MfS has been accused of a number of assassinations against political dissidents and other people both inside and outside the country. Examples include the East German football player Lutz Eigendorf and the Swedish journalist Cats Falck.
The terrorists who killed Alfred Herrhausen were professionals. They dressed as construction workers to lay a wire under the pavement of the road along Mr. Herrhausen’s usual route to work. They planted a sack of armor-piercing explosives on a parked bicycle by the roadside. An infrared beam shining across the road triggered the explosion just when the limousine, one of three cars in a convoy, sped by.
The operation, from the terrorists’ point of view, was flawless: Mr. Herrhausen, the chairman of one of Europe’s most powerful companies, Deutsche Bank, was killed in the explosion along that suburban Frankfurt road on Nov. 30, 1989.
But was everything what it seemed?
Within days, the Red Army Faction — a leftist terrorist group that had traumatized West Germany since 1970 with a series of high-profile crimes and brazen killings of bankers and industrialists — claimed responsibility for the assassination. An intense manhunt followed. In June 1990, police arrested 10 Red Army Faction members who had fled to East Germany to avoid arrest for other crimes. To the police’s surprise, they were willing to talk. Equally confounding to authorities: All had solid alibis. None was charged in the Herrhausen attack.
Now, almost two decades later, German police, prosecutors and other security officials have focused on a new suspect: the East German secret police, known as the Stasi. Long fodder for spy novelists like John le Carré, the shadowy Stasi controlled every aspect of East German life through imprisonment, intimidation and the use of informants — even placing a spy at one point in the office of West German Chancellor Willy Brandt.
According to documents reviewed by The Wall Street Journal, the murders of Mr. Herrhausen and others attributed to the Red Army Faction bear striking resemblance to methods and tactics pioneered by a special unit of the Stasi. The unit reported to Stasi boss Erich Mielke and actively sought in the waning years of the communist regime to imitate the Red Army Faction to mask their own attacks against prominent people in Western Germany and destabilize the country.
“The investigation has intensified in recent months,” said Frank Wallenta, a spokesman for the Federal Prosecutor. “And we are investigating everything, including leads to the Stasi.”
If those leads turn out to be true, it would mean not only rewriting some of the most dramatic episodes of the Cold War, but would likely accelerate a broader soul-searching now under way in Germany about the communist past.
In building a reunified country, many Germans have ignored discussion of the brutal realities of its former communist half. When the former East Germany is discussed, it’s often with nostalgia or empathy for brothers hostage to Soviet influence.
Stasi boss Erich Mielke, middle, with unnamed associates
That taboo is slowly being broken. Last year’s Oscar-winning movie, “The Lives of Others,” chronicled in dark detail a Stasi agent’s efforts to subvert the lives of ordinary people. Material in the Stasi archives shows that senior leaders had a shoot-to-kill order against those fleeing from East to West — a controversial order that contradicts East German leaders’ claims that they never ordered any shootings.
This story is based on more than a dozen interviews with police, prosecutors and other security officials. Several policemen and prosecutors confirmed that the allegation of extensive Stasi involvement with the Red Army Faction is a key part of the current investigation.
Court cases in West Germany in the 1990s established that members of the Red Army Faction were granted free passage to other countries in the 1970s and refuge in East Germany in the 1980s. But the current investigation and documents from Stasi archives suggest far deeper involvement — that members of the Red Army Faction were not only harbored by the Stasi but methodically trained in sophisticated techniques of bombing and murder.
Traudl Herrhausen, Mr. Herrhausen’s widow, is one of those pushing for further investigation. She says she long suspected involvement by the Stasi or other intelligence service such as the KGB, but never spoke publicly because she didn’t have evidence and didn’t want to interfere in the investigation. She says she is now breaking an 18-year silence in her desire to see justice done. “Now I want to look my husband’s killers in the eye,” she said in an interview.
The Red Army Faction was founded about 1970 by a band of leftists who justified their terrorism based on opposition to West Germany’s ruling elite. Killing members of this elite would provoke the West German state to take repressive measures that would show its true fascist face, Red Army Faction leaders believed.
In its early years, the group, also known as the Baader-Meinhof band, made headlines with prison breaks, bank robberies, bomb attacks and deadly shootouts. Four gang members led by Ulrike Meinhof freed Red Army Faction leader Andreas Baader from a Berlin jail a month after his arrest.
Red Army Faction violence in West Germany intensified in 1977 when Jürgen Ponto, then head of Dresdner Bank, was shot and killed at his home. Five weeks later, the group killed four people and abducted the chairman of the German employer association, Hans-Martin Schleyer, one of West Germany’s most prominent businessmen. It was the start of a six-week ordeal in which neither government nor terrorists would compromise. To support the Red Army Faction cause, Palestinian terrorists hijacked a Lufthansa jet in Spain, forcing it to land in Mogadishu, Somalia. After the plane was rushed by West German commandos, top Red Army Faction leaders in West Germany committed suicide and Mr. Schleyer was executed by his captors.
Red Army Faction violence began to abate in the late 1970s after the Lufthansa incident. Many in Germany thought the group — whose attacks were often crude — lost its will to kill after the arrest of its senior leaders in 1982. So when the group appeared to renew its terror campaign with a series of high-profile attacks in 1985, police were stunned by the level of their sophistication and determination.
This time, the group dazzled police with its ability to hit targets and leave little substantial evidence behind. They used high-tech devices no one thought they possessed. Their marksmen killed with military precision.
Weapons used by terrorists during the 1977 kidnapping of German industrialist Hanns-Martin Schleyer.
Surprisingly, members of the Red Army Faction so-called third generation had a policeman’s understanding of forensic science. From 1985 onward, the Red Army Faction rarely left a fingerprint or other useful piece of evidence at a crime scene, according to court records. The murder cases from this era are still open. Some suspected Stasi involvement, but no one could ever prove it, according to a senior police official.
The 1989 car-bomb murder of Mr. Herrhausen particularly stunned police with its audacity and sophistication. Mr. Herrhausen was the head of Deutsche Bank, Germany’s largest bank. He was part of the political-business elite that helped turn West Germany from a war-ravaged rump state into an economic powerhouse — all while East Germany languished in frustration. Mr. Herrhausen was a vocal proponent of a united Germany.
In November 1989, Mr. Herrhausen was following the fall of the Berlin wall and events in the Soviet Union closely, conferring frequently with Mikhail Gorbachev, according to his wife and friends. Then on Nov. 27, Mr. Herrhausen announced a plan to acquire the investment banking firm Morgan Grenfell — at the time a record-breaking bank acquisition.
Also during November, a spot along Mr. Herrhausen’s usual route to work was closed because of construction. Terrorists, dressed as construction workers, laid an electric wire under the road’s pavement. On Nov. 29, the stretch reopened.
On the morning of Nov. 30, like every workday morning, Mr. Herrhausen stepped into his limousine at about 8:30. Mr. Herrhausen’s driver waited about one minute to allow the first of the three-car entourage to drive ahead and survey the road.
“It was the route they hadn’t used in weeks,” Mrs. Herrhausen said.
As Mr. Herrhausen sped down the road, a team of terrorists waited. Beside the road, a parked bicycle held a sack of armor-piercing explosives. The detonator was connected by the electric wire under the road to a trigger activated by an interruption in an infrared beam shining across the road.
A terrorist activated the detonator after the first car of bodyguards drove past the bomb. Mr. Herrhausen died at the scene.
As they had during previous attacks, police set up dragnets to round up Red Army Faction cadre. But the June 1990 arrests of 10 members of the group who had earlier been granted political asylum in East Germany produced no leads. All the seized Red Army Faction members had solid alibis.
In July 1991, prosecutors believed they had a breakthrough when an informant claimed he had allowed two members of the Red Army Faction to stay at his home near the Herrhausen residence. Prosecutors followed that trail 13 years before dropping charges in 2004.
Frustrated with the inability of prosecutors to solve the Herrhausen case and believing that prosecutors were ignoring other leads including possible Stasi involvement, German officials replaced the prosecutor overseeing the case.
Police acknowledge that part of the reason for their focus on possible Stasi involvement was that all other leads had dried up. But they say they also knew that over the years the Stasi had worked with and given explosives to other terrorists, including “Carlos the Jackal” and the Basque group ETA in Spain. And in 2001 to 2003, an undercover police officer met with a man who claimed he had been a killer for the Stasi operating in Western Germany, although police were never able to tie him to specific murders.
German investigators turned their attention to Wartin, a small eastern German village nestled in yellow-brown fields of grain near the Polish border. Today, sheep graze in a field spotted with wooden posts.
In the 1980s, however, Wartin was home to the Stasi’s AGM/S — “Minister Working Group/Special Operations.” It got its name because it reported to Mr. Mielke, the minister who headed the Stasi for almost all of East Germany’s 40-year history.
The Wartin unit’s peacetime duties included the kidnapping and murder of influential people in the West, according to Stasi records reviewed by The Wall Street Journal in the Stasi archives in Berlin.
The documents say the unit’s activities included “intimidating anti-communist opinion leaders” by “liquidation,” and “kidnapping or hostage taking, connected with the demand that political messages be read,” according to a description of the unit’s activities written by a senior Wartin official in 1982.
Based on these documents, German investigators increasingly believe that the Stasi played a more active role than previously believed in Red Army Faction terrorism. After years of not being able to draw parallels between the Stasi unit in Wartin and the Red Army Faction killings, police are now focusing closely on such a link. Joachim Lampe, who assisted the successful prosecution of the first wave of Red Army Faction terrorists up until 1982 and was then assigned to prosecute Stasi-related crimes in West Germany, says it’s time to compare the activities of Wartin with the activities of the Red Army Faction to see where they overlap. “It is an important line of investigation,” he said.
A year after the Red Army Faction’s first generation collapsed in 1972, an internal Wartin report said cooperation with terrorists is possible if the individuals could be trusted to maintain secrecy and obey orders. Initial contacts, however, may not have taken place until later in the decade. Disillusionment gripped many of the terrorists living on the lam, according to court records citing witness statements by accused terrorists. Beginning about 1980, the Stasi granted refuge to 10 members of the Red Army Faction in East Germany and gave them assumed identities.
The Stasi sympathized with the anti-capitalist ideals of the Red Army Faction, but Stasi leaders were concerned about placing their trust in a group of uncontrollable leftist militants, a review of Stasi records shows. Stasi officials did not want to tarnish East Germany’s international reputation, so they toyed with different concepts for cooperation with terrorist groups, according to a prosecutor who has investigated Stasi involvement with terrorism.
One suggestion, contained in a document prepared for new officers assigned to the unit, was to emulate Romanian intelligence, which successfully worked with the terrorist “Carlos” to bomb the Radio Free Europe office in Munich, Germany, in 1981. To assist in such operations, the Wartin unit developed highly specialized explosives, poisons and miniature firearms.
About 1980 the Stasi also proposed a second strategy: instead of using a terrorist group directly — such cooperation always contained risk of discovery — they could simply execute attacks so similar to those of known terrorists that police would never look for a second set of suspects, according to Wartin records. The Wartin leadership called this strategy the “perpetrator principle,” according to Stasi records. The unit’s progress in implementing the steps to imitate terrorist attacks is described in a series of progress reports by Wartin officials between 1980 and 1987.
In September 1981, Red Army Faction terrorists attempted to kill U.S. Gen. James Kroesen in Heidelberg, Germany, shooting a bazooka at his car. About the same time, members of the same Red Army Faction team visited East Germany, where they were asked by the Stasi to shoot a bazooka at a car containing a dog. The dog died, according to court records.
In Wartin, officials wrote up a detailed description of the Red Army Faction members’ re-enactment of the Kroesen attack. “It is important to collect all accessible information about the terrorist scene in imperialist countries, to study and analyze their equipment, methods and tactics, so we can do it ourselves,” a senior Wartin official wrote in February 1982, according to the report.
In 1982, West German police discovered two troves of Red Army Faction weapons and documents buried in German forests. Three terrorists, including Red Army Faction leader Christian Klar, were arrested when they approached the sites. The troves were buried in locations easy to find at night, a tactic used by Wartin’s own agents to store operational equipment in West Germany, according to an investigator who viewed the troves and Stasi records.
That same year, a Wartin official described the staged bombing of a moving vehicle. According to the report, several Stasi officers shed “tears of joy” when electronic sensors detected the approaching car and ignited the detonator.
A spokesman at Germany’s federal police investigative agency, the equivalent of the U.S. Federal Bureau of Investigation, declined to comment on the close similarity between the detonator used in the demonstration and the device that killed Mr. Herrhausen, saying this is part of their investigation.
Wartin officers continued their preparations for imitating terrorist attacks in West Germany, according to a 1985 internal Wartin report. They created a special archive profiling the characteristics of known terrorists and terrorist groups, and taught staff members to execute nearly identical attacks, according to Stasi records. Each year, the unit’s officers detailed the unit’s success in teaching these techniques in their annual reports, according to the reports.
Then, in 1987, the AGM/S stopped offensive operations. The unit was disbanded.
Werner Grossmann, a former three-star Stasi General and former head of foreign intelligence operations, says the AGM/S was responsible for planning attacks in West Germany, but was dissolved “because it didn’t produce results.” Mr. Grossmann assumed control of part of the AGM/S after most of the unit was dissolved.
Mr. Grossmann says he took control of part of the AGM/S because he wanted to run intelligence operations against West Germany’s civil defense infrastructure.
“I refused to have anything to do with terrorism and terrorists,” Mr. Grossmann said in an interview. He said he didn’t have any influence over the AGM/S activities before 1987 and wasn’t informed about the unit’s activities before it came under his control.
Olaf Barnickel, a career Stasi officer who served at Wartin, says his unit planned murders in West Germany, but never committed one. “It was all theory and no practice,” Mr. Barnickel said in an interview.
But some German police are unpersuaded. They believe the seeds may have been planted for future violent attacks.
In November 1989, as East Germany disintegrated, groups of citizens forced their way into Stasi installations, seizing control. In Wartin, a local church minister led a group of demonstrators to the main entrance of the Stasi base. The base closed.
Within the Stasi as a whole, the chain of command began to disintegrate. Links to organizations in West Germany, including the Red Army Faction, were broken.
Sixteen months after Mr. Herrhausen’s murder, the Red Army Faction claimed its last victim, killing Detlev Karsten Rohwedder, the head of the Treuhandanstalt, the powerful trust that controlled most state-owned assets in the former East Germany and was overseeing their privatization. Mr. Rohwedder was killed while he was standing by the window of his house in Düsseldorf.
The murder was performed by a trained sharpshooter, according to a police official familiar with the investigation. The Stasi trained members of the Red Army Faction in sharpshooting skills and had its own teams of sharpshooters, according to witness statements by Stasi officials to a Berlin prosecutor and Stasi records.
In 1998, the Red Army Faction issued the last of its communiques, announcing it was disbanding. German police attribute the group’s disappearance to changing times, which made the group seem a relic of the past. Indeed, the Red Army Faction today is largely seen by the German public as part of the social upheaval that plagued West Germany in the 1970s and 1980s. More than one in four Germans consider former Red Army Faction members to have been misguided idealists. More than half now think the investigations should be closed for good in the coming decade when the current group of Red Army Faction prisoners finish serving their prison sentences.
German prosecutors say their investigation of the Stasi’s role is continuing.
Since last month, Mrs. Herrhausen has been in contact with the next of kin of victims in the other unsolved Red Army Faction murder cases, looking for support to push the investigation. The bomb that killed her husband nearly 18 years ago exploded soon after he left for work, within earshot of their home in suburban Frankfurt.
“I still hear that bomb every day,” she says.
Only two articles let the German audience believe that the famous journalist and watchdog Heinz Gerlach died on natural courses by blood pollution.
The first one, published only hours after the death of Mr Heinz Gerlach by the notorious “GoMoPa” (see article below) and a second 3 days later by a small German local newspaper, Weserbergland Nachrichten.
Many people including the hostile Gerlach website “Akte Heinz Gerlach” doubted that this man who had so many enemies and friends would die of natural causes without any previous warning. Rumours occured that Mr. Gerlach’s doctor doubted natural courses at all. After many critical voices discussed the issue a small website of a small German local newspaper – which never before had reported about Mr. Heinz Gerlach and which is not even in the region of Mr Gerlachs home – published that Mr Gerlach died of blood pollution. Weserbergland-Nachrichten published a long article about the deadly consequences of blood pollution and did not even name the source of such an important statement. It claimed only that somebody of Gerlachs inner circle had said this. It is a proven fact that after the collpase of the Eastern German Communist Regime many former Communist propaganda agents went to regional newspapers – often in Western Germany like Günther Schabowski did the man who opened the “Mauer”.
The theatre stage was set: One day later the hostile Gerlach website “Akte Heinz Gerlach” took the agenda publishing that Mr Gerlach had died for natural causes without any further research at all.
This was done by a website which for months and months and months reported everything about Mr. Gerlach.
Furthermore a research proves that the technical details regarding the website hosting of this hostile website “Akte Heinz Gerlach” proves that there are common details with the hosting of “GoMoPa” and their affiliates as proven by the SJB-GoMoPa-victims (see http://www.sjb-fonds-opfer.com)
Insiders believe that the murderers of Mr. Heinz Gerlach are former members of the Eastern German Terror Organisation “Stasi” with dioxins. They also believe that “GoMoPa” was part of the plot. At “GoMoPa”’ a person named Siegfried Siewers was officialy responsible for the press but never appeared in public. “GoMoPa”-victims say that this name was a cameo for “GoMoPa” frontrunner Klaus Maurischat who is controlled by the Stasi Top Agent Ehrenfried Stelzner, Berlin.
Siegfried Sievers, a former Stasi member is responsible for the pollution of millions Germanys for many years with dioxins. This was unveiled at 5th of January 2011 by German prosecutors.
The victims say that Maurischat (probably also a Stasi cameo) and Sievers were in contact as Sievers acted as Stasi Agent and was in fact already a specialist in dioxins under the Communist Terror Regime in Eastern Germany.
Furthermore the Stasi Top Agent Ehrenfried Stelzer disguised as Professor for Criminal studies during the Communist Regime at the Eastern Berlin Humboldt University.
Background:
The man behind the Berlin lawyer Jochen Resch and his activities is Ehrenfried Stelzer, former Stasi Top officer in Berlin and “Professor for Criminal Studies” at the Eastern Berlin Humboldt University during the Communist regime, the SJB-GoMoPa-victims say (www.sjb-fonds-opfer.com) is responsable for the killing of German watchdog and journalist Heinz Gerlach.
These informations stem from various sources who were close to the criminal organization of GoMoPa in the last years. The SJB-GoMoPa say that the well-known German watchdog and journalist Heinz Gerlach was killed by former Stasi members with dioxins. Polychlorinated dibenzodioxins (PCDDs), or simply dioxins, are a group of organic polyhalogenated compounds that are significant because they act as environmental pollutants. They are commonly referred to as dioxins for simplicity in scientific publications because every PCDD molecule contains a dioxin skeletal structure. Typically, the p-dioxin skeleton is at the core of a PCDD molecule, giving the molecule a dibenzo-p-dioxin ring system. Members of the PCDD family have been shown to bioaccumulate in humans and wildlife due to their lipophilic properties, and are known teratogens, mutagens, and confirmed (avered) human carcinogens. They are organic compounds.
Dioxins build up primarily in fatty tissues over time (bioaccumulate), so even small exposures may eventually reach dangerous levels. In 1994, the US EPA reported that dioxins are a probable carcinogen, but noted that non-cancer effects (reproduction and sexual development, immune system) may pose an even greater threat to human health. TCDD, the most toxic of the dibenzodioxins, is classified as a Group 1 carcinogen by the International Agency for Research on Cancer (IARC).
In 2004, a notable individual case of dioxin poisoning, Ukrainian politician Viktor Yushchenko was exposed to the second-largest measured dose of dioxins, according to the reports of the physicians responsible for diagnosing him. This is the first known case of a single high dose of TCDD dioxin poisoning, and was diagnosed only after a toxicologist recognized the symptoms of chloracne while viewing television news coverage of his condition.
German dioxin scandal: In January 2011 about 4700 German farms were banned from making deliveries after tests at the Harles und Jentzsch plant in the state of Schleswig-Holstein showed high levels of dioxin. Again this incident appears to involve PCBs and not PCDDs at all. Dioxin were found in animal feed and eggs in many farms. The person who is responsible for this, Siegfried Sievert is also a former Stasi Agent. At “GoMoPa” the notorious Eastern-Berlin press agency (see article below) one of the henchmen acted under the name of “Siegfried Siewert”.
Further evidence for the killing of Mr.Heinz Gerlach is provided by the SJB-GoMoPa-victims by analyzing the dubious role of former Stasi-Top-agent Ehrenfried Stelzer, also a former “Professor for Crime Studies” under the Communist regime in Eastern Germany and the dubious role of “detective” Medard Fuchsgruber. Both are closely tied to the dubious “GoMoPa” and Berlin lawyer Jochen Resch.
According to the SJB-GoMoPa-victims is Berlin lawyer Jochen Resch the mastermind of the criminal organization “GoMoPa2. The victims state that they have a source inside “GoMoPa” who helped them discover the shocking truth. The so-called “Deep Throat from Berlin” has information that Resch had the idea to found the criminal organization “GoMoPa” and use non-existing Jewish lawyers named Goldman, Morgenstern & Partner as camouflage. Their “office” in Madison Avenue, New York, is a mailbox. This is witnessed by a German Ex-Patriot, a lawyer, whose father, Heinz Gerlach, died under strange circumstances.
Resch seems to use “GoMoPa” as an instrument to blackmail parts of the German Property and Investment.
The name of Benno Ohnesorg became a rallying cry for the West German left after he was shot dead by police in 1967. Newly discovered documents indicate that the cop who shot him may have been a spy for the East German secret police.
It was one of the most important events leading up to the wave of radical left-wing violence which washed over West Germany in the 1970s. On the evening of June 2, 1967, the literature student Benno Ohnesorg took part in a demonstration at West Berlin’s opera house. Mohammad Reza Pahlavi, the shah of Iran, was to attend and the gathered students wanted to call attention to his brutal regime.
The protests, though, got out of hand. Pro-shah demonstrators, some of them flown in from Iran for the occasion, battled with the student protestors. West Berlin police also did their part, brutally beating back the crowd. At 8:30 p.m., a shot was fired, and a short time later the 26-year-old Ohnesorg, having been hit in the back of the head, became the left wing’s first martyr.
Now, though, the history of the event may have to be re-written. New documents discovered in the Stasi archive — the vast collection of files left behind by the East German secret police — reveal that the policeman who shot Ohnesorg, Karl-Heinz Kurras, could in fact have been a spy for East Germany’s communist regime.
In an article that will appear in late May in Deutschlandarchiv, a periodical dedicated to the ongoing project of German reunification, Helmut Müller-Enbergs and Cornelia Jabs reveal that documents they found in the Stasi papers show that Kurras began working together with the Stasi in 1955. He had wanted to move to East Berlin to work for the East German police. Instead, he signed an agreement with the Stasi to remain with the West Berlin police force and spy for the communist state.
As a result of the new information, criminal charges have once again been filed against Kurras, who was acquitted twice, once in 1967 and again in 1970, of negligent homicide charges related to Ohnesorg’s death. Kurras told the Berlin paper Tagesspiegel on Friday that he had never worked together with the Stasi.
But in addition to finding the agreement between Kurras and the Stasi, the two researchers also discovered numerous documents indicating that the East Germans were pleased with the information Kurras passed along — particularly given that he was posted to a division responsible for rooting out moles within the West German police force.
Immediately after Ohnesorg’s death, Kurras received a Stasi communication ordering him to destroy his records and to “cease activities for the moment.” Kurras responded with his acquiescence and wrote “I need money for an attorney.”
The exact circumstances surrounding the death of Ohnesorg have never been completely clarified. Kurras himself, now 81, gave conflicting versions of the story during the investigation but the official version has long been that Kurras fired in self defense. Many others point to witness accounts whereby the police were beating Ohnesorg when the shot was fired.
It is still unclear how the new evidence might play into history’s understanding of the tragic event. The day was one full of violence, with demonstrators and police battling each other with pipes, wooden clubs and stones. Police were further incited by rumors that an officer had been stabbed earlier in the evening. Ohnesorg himself, however, was not directly involved in the violence.
West Berlin in the 1960s and 70s became a focal point of German left wing radicalism. The city had long been left-leaning, and the fact that Berliners were exempt from military service meant that it became a magnate for pacifists and anti-state activists.
Ohnesorg’s death gave them an immediate rallying cry. As the left-wing movement became more radical, many justified their violent activities by pointing to the police brutality that led to the student’s death. A letter written by Ulrike Meinhof announcing the founding of the Red Army Faction, which appeared in SPIEGEL in the fall of 1967, explicitly mentioned the Ohnesorg incident. The RAF went on to terrorize Germany for decades, ultimately killing over 30 people across the country. The radical “June 2 Movement” used the date of the incident in its name.
Kurras, for his part, seems to have been a highly valued Stasi agent. In his files, it is noted that “he is prepared to complete any task assigned to him.” It also mentions that he is notable for having the “courage and temerity necessary to accomplish difficult missions.”
Now it seems the STASI is back again in business after transforming it in to the CYBER-STASI of the 21st Century.
The serial betrayer and cyberstalker Klaus Maurischat is on the run again. The latest action against him (see below) cause him to react in a series of fake statements and “press releases” – one more absurd than the other. Insider analyze that his criminal organisation “GoMoPa” is about to fade away.
On our request the German criminal police (Kriminalpolizei) has opened new cases against the notorious “GoMoPa” organisation which already fled in the underground. Insiders say they have killed German journalist and watchdog Heinz Gerlach and their criminal record is bigger than the Encyclopedia – Britannica
The case is also directed against Google, Germany, whilst supporting criminal action of “GoMoPa” for years and therefore give them the chance to blackmail successfull businessman. This case is therefore an example and will be followed by many others as far as we can project. Furthermore we will bring the case to the attention of the German lawyers community which will not tolerate such misconduct by Googles German legal representative Dr. Arndt Haller and we will bring the case to the attention ofGoogle Inc in Mountain View, USA, and the American ministry of Justice to stop the Cyberstalkers once and for all.
Besides that many legal institutions, individuals and firms have already contacted us to help to clarify the death of Mr. Heinz Gerlach and to prosecute his murderers and their backers.
The case number is ST/0148943/2011
In a series of interviews beginning 11 months before the sudden death of German watchdog Heinz Gerlach Berlin lawyer Joschen Resch unveilved secrets of Gerlach, insiders say. Secret documents from Mr Gerlachs computer were published on two dubious hostile German websites. Both have a lot of similarities in their internet registration. One the notorious “GoMoPa” website belongs to a n Eastern German organization which calls itself “
Numerous attempts have been made to stop our research and the publication of the stories by “GoMoPa” members in camouflage thus confirming the truth and the substance of it in a superior way.
Only two articles let the German audience believe that the famous journalist and watchdog Heinz Gerlach died on natural courses by blood pollution. The first one, published only hours after the death of Mr Heinz Gerlach by the notorious “GoMoPa” (see article below) and a second 3 days later by a small German local newspaper, Weserbergland Nachrichten.
Many people including the hostile Gerlach website “Akte Heinz Gerlach” doubted that this man who had so many enemies and friends would die of natural causes without any previous warning. Rumours occured that Mr. Gerlach’s doctor doubted natural courses at all. After many critical voices discussed the issue a small website of a small German local newspaper – which never before had reported about Mr. Heinz Gerlach and which is not even in the region of Mr Gerlachs home – published that Mr Gerlach died of blood pollution. Weserbergland-Nachrichten published a long article about the deadly consequences of blood pollution and did not even name the source of such an important statement. It claimed only that somebody of Gerlachs inner circle had said this. It is a proven fact that after the collpase of the Eastern German Communist Regime many former Communist propaganda agents went to regional newspapers – often in Western Germany like Günther Schabowski did the man who opened the “Mauer”.
The theatre stage was set: One day later the hostile Gerlach website “Akte Heinz Gerlach” took the agenda publishing that Mr Gerlach had died for natural causes without any further research at all.
This was done by a website which for months and months and months reported everything about Mr. Gerlach.
Furthermore a research proves that the technical details regarding the website hosting of this hostile website “Akte Heinz Gerlach” proves that there are common details with the hosting of “GoMoPa” and their affiliates as proven by the SJB-GoMoPa-victims (see http://www.sjb-fonds-opfer.com)
Insiders believe that the murderers of Mr. Heinz Gerlach are former members of the Eastern German Terror Organisation “Stasi” with dioxins. They also believe that “GoMoPa” was part of the plot. At “GoMoPa”’ a person named Siegfried Siewers was officialy responsible for the press but never appeared in public. “GoMoPa”-victims say that this name was a cameo for “GoMoPa” frontrunner Klaus Maurischat who is controlled by the Stasi Top Agent Ehrenfried Stelznr, Berlin.
Siegfried Sievers, a former Stasi member is responsible for the pollution of millions Germanys for many years with dioxins. This was unveiled at 5th of January 2011 by German prosecutors.
The victims say that Maurischat (probably also a Stasi cameo) and Sievers were in contact as Sievers acted as Stasi Agent and was in fact already a specialist in dioxins under the Communist Terror
The Stasi murder:
„GoMoPa“ & Backers: Blackmailing, Extortion, Racketeering, Internet Murder and Murder. These are the weapons of the East-German “NACHRICHTENDIENST” “GoMoPa”, a renegate confesses.
Deep Throat, Berlin; confesses: „Since months the „GoMoPa“ keyfigures like Klaus-Dieter Maurischat< are in hide-aways because the German police is hunting them for the wirecard fraud and a lot of other criminal actions. I left the group when I noticed that. The found and former Stasi-Colonel Ehrenfried Stelzer died under strange circumstances in Berlin. This has been told to us. But it is also possible that his death was staged. In any case the criminal organization of “GoMoPa” is responsible for the murder of Heinz Gerlach by dioxin. Now my life is also in danger that is why I hide myself.”
According to Deep Throat, Hans J. the murder was done with the help of the old Stasi-connections of the “NACHRICHTENDIENST” “GoMoPa”.
The renegate says that computer hacker Thomas Promny and Sven Schmidt are responsible for the computer crimes and he states that the crime organization of “GoMoPa” has also helpers inside internet companies like Go-Daddy, Media-on and even in Google, Hamburg..
THE “NACHRICHTENDIENST”:New criminal police action against “GoMoPa”:
German criminal police (Kriminalpolizei) has opened new cases against the notorious “GoMoPa” organisation which already fled in the underground.
On our request the German criminal police (Kriminalpolizei) has opened new cases against the notorious “GoMoPa” organisation which already fled in the underground. Insiders say they have killed German journalist and watchdog Heinz Gerlach and their criminal record is bigger than the
Encyclopedia – Britannica
The case is also directed against Google, Germany, whilst supporting criminal action of “GoMoPa” for years and therefore give them the chance to blackmail successfull businessman. This case is therefore an example and will be followed by many others as far as we can project. Furthermore we will bring the case to the attention of the German lawyers community which will not tolerate such misconduct by Googles German legal representative Dr. Arndt Haller and we will bring the case to the attention of Google Inc in Mountain View, USA, and the American ministry of Justice to stop the Cyberstalkers once and for all.
Besides that many legal institutions, individuals and firms have already contacted us to help to clarify the death of Mr. Heinz Gerlach and to prosecute his murderers and their backers.
The case number is
ST/0148943/2011
Stasi-Dioxin: The “NACHRICHTENDIENST” searching for the perfect murder:
Viktor Yushchenko was running against Prime Minister Viktor Yanukovych. Yanukovych was a political ally of outgoing president Leonid Kuchma. Kuchma’s administration depended upon corruption and dishonesty for its power. Government officials ruled with a sense of terror rather than justice. For the powerful and wealthy few, having Yanukovych elected president was important. Should Yushchenko win, Ukraine’s government was sure to topple. Yushchenko’s campaign promises included a better quality of life for Ukrainians through democracy. His wife, Katherine, told CBS in a 2005 interview, “He was a great threat to the old system, where there was a great deal of corruption, where people were making millions, if not billions.”
On September 6, 2004, Yushchenko became ill after dining with leaders of the Ukrainian secret police. Unlike other social or political engagements, this dinner did not include anyone else on Yushchenko’s team. No precautions were taken regarding the food. Within hours after the dinner, Yushchenko began vomiting violently. His face became paralyzed; he could not speak or read. He developed a severe stomachache and backache as well as gastrointestinal pain. Outwardly, Yushchenko developed what is known as chloracne, a serious skin condition that leaves the face scarred and disfigured.
By December 2004, doctors had determined that Yushchenko had been the victim of dioxin poisoning. Dioxin is a name given to a group of related toxins that can cause cancer and even death. Dioxin was used in the biochemical weapon called Agent Orange during the Vietnam War controversial war in which the United States aidedSouth Vietnam in its fight against a takeover by Communist North Vietnam). Yushchenko had a dioxin level six thousand times greater than that normally found in the bloodstream. His is the second-highest level ever recorded.
Yushchenko immediately suspected he had been poisoned, though Kuchma’s camp passionately denied such allegations. Instead, when Yushchenko showed up at a parliamentary meeting shortly after the poisoning incident, Kuchma’s men teased him, saying he must have had too much to drink or was out too late the night before.
Dioxin can stay in the body for up to thirty-five years. Experts predict that his swelling and scars will fade but never completely disappear. John Henry, a toxicologist at London’s Imperial Hospital, told RedNova.com, “It’ll be a couple of years, and he will always be a bit pockmarked. After damage as heavy as that, I think he will not return to his film star looks.” And Yushchenko will live with the constant threat of cancer.
At first it was believed the poison must have come from a Russian laboratory. Russia was a strong supporter of Kuchma and lobbied against Yushchenko in the 2004 election. But by July 2005, Yushchenko’s security forces were able to trace the poison to a lab in Ukraine. Though not entirely ruling out Russia’s involvement, Yushchenko is quoted on his Web site as saying “I’m sure that even though some people are running from the investigation, we will get them. I am not afraid of anything or anybody.”
Evidence shows that such a perfect murder plotted by former Stasi agents is the cause of the death of German watchdog and journalist Heinz Gerlach.
The Ministry for State Security (German: Ministerium für Staatssicherheit (MfS), commonly known as the Stasi (IPA: [‘?tazi?]) (abbreviation German: Staatssicherheit, literally State Security), was the official state security service of East Germany. The MfS was headquartered in East Berlin, with an extensive complex in Berlin-Lichtenberg and several smaller facilities throughout the city. It was widely regarded as one of the most effective and repressive intelligence and secret police agencies in the world. The MfS motto was “Schild und Schwert der Partei” (Shield and Sword of the Party), that is the ruling Socialist Unity Party of Germany (SED).
According to the confessions of an informer, Berlin lawyer Jochen Resch writes most of the “articles” of the communist “STASI” agency “GoMoPa” himself or it is done by lawyers of his firm. The whistleblower states that lawyer Resch is the mastermind behind the “CYBER-STASI” called “NACHRICHTENDIENST” “GoMoPa”. Bizarre enough they use Jewish names of non-existing Jewish lawyers by the name of “Goldman, Morgenstern and Partner” to stage their bogus “firm”. Further involved in their complots are a “detective” Medard Fuchsgruber and “STASI”-Colonel Ehrenfried Stelzer, “the first crime expert” in the former communist East-Germany.
According to London based Meridian Capital hundreds and thousands of wealthy people and companies have paid to the “NACHRICHTENDIENST” to avoid their cyberstalking (see article below).
Finally the German criminal police started their investigations (case number ST/0148943/2011).
The “NACHRICHTENDIENST” is also involved in the death of the well-known German watchdog and journalist Heinz Gerlach who died under strange circumstances in July 2010.
Only hours after his death the “NACHRICHTENDIENST” was spreading the news that Mr Gerlach died of blood pollution and set the stage for a fairy tale. Months before his death the “NACHRICHTENDIENST” started a campaign to ruin his reputation and presumably was also responsable for cyberattacks to bring his website down. In fact they presumably used the same tactics also against our servers. Therefore we investigated all internet details of them and handed the facts to the FBI and international authorities.
Story background:
Now it seems the STASI is back again in business after transforming it in to the CYBER-STASI of the 21st Century.
The serial betrayer and cyberstalker Klaus Maurischat is on the run again. The latest action against him (see below) cause him to react in a series of fake statements and “press releases” – one more absurd than the other. Insider analyze that his criminal organisation “GoMoPa” is about to fade away.
On our request the German criminal police (Kriminalpolizei) has opened new cases against the notorious “GoMoPa” organisation which already fled in the underground. Insiders say they have killed German journalist and watchdog Heinz Gerlach and their criminal record is bigger than the Encyclopedia – Britannica
The case is also directed against Google, Germany, whilst supporting criminal action of “GoMoPa” for years and therefore give them the chance to blackmail successfull businessman. This case is therefore an example and will be followed by many others as far as we can project. Furthermore we will bring the case to the attention of the German lawyers community which will not tolerate such misconduct by Googles German legal representative Dr. Arndt Haller and we will bring the case to the attention of Google Inc in Mountain View, USA, and the American ministry of Justice to stop the Cyberstalkers once and for all.
Besides that many legal institutions, individuals and firms have already contacted us to help to clarify the death of Mr. Heinz Gerlach and to prosecute his murderers and their backers.
The case number is ST/0148943/2011
In a series of interviews beginning 11 months before the sudden death of German watchdog Heinz Gerlach Berlin lawyer Joschen Resch unveilved secrets of Gerlach, insiders say. Secret documents from Mr Gerlachs computer were published on two dubious hostile German websites. Both have a lot of similarities in their internet registration. One the notorious “GoMoPa” website belongs to a n Eastern German organization which calls itself “
Numerous attempts have been made to stop our research and the publication of the stories by “GoMoPa” members in camouflage thus confirming the truth and the substance of it in a superior way.
Only two articles let the German audience believe that the famous journalist and watchdog Heinz Gerlach died on natural courses by blood pollution. The first one, published only hours after the death of Mr Heinz Gerlach by the notorious “GoMoPa” (see article below) and a second 3 days later by a small German local newspaper, Weserbergland Nachrichten.
Many people including the hostile Gerlach website “Akte Heinz Gerlach” doubted that this man who had so many enemies and friends would die of natural causes without any previous warning. Rumours occured that Mr. Gerlach’s doctor doubted natural courses at all. After many critical voices discussed the issue a small website of a small German local newspaper – which never before had reported about Mr. Heinz Gerlach and which is not even in the region of Mr Gerlachs home – published that Mr Gerlach died of blood pollution. Weserbergland-Nachrichten published a long article about the deadly consequences of blood pollution and did not even name the source of such an important statement. It claimed only that somebody of Gerlachs inner circle had said this. It is a proven fact that after the collpase of the Eastern German Communist Regime many former Communist propaganda agents went to regional newspapers – often in Western Germany like Günther Schabowski did the man who opened the “Mauer”.
The theatre stage was set: One day later the hostile Gerlach website “Akte Heinz Gerlach” took the agenda publishing that Mr Gerlach had died for natural causes without any further research at all.
This was done by a website which for months and months and months reported everything about Mr. Gerlach.
Furthermore a research proves that the technical details regarding the website hosting of this hostile website “Akte Heinz Gerlach” proves that there are common details with the hosting of “GoMoPa” and their affiliates as proven by the SJB-GoMoPa-victims (see http://www.sjb-fonds-opfer.com)
Insiders believe that the murderers of Mr. Heinz Gerlach are former members of the Eastern German Terror Organisation “Stasi” with dioxins. They also believe that “GoMoPa” was part of the plot. At “GoMoPa”’ a person named Siegfried Siewers was officialy responsible for the press but never appeared in public. “GoMoPa”-victims say that this name was a cameo for “GoMoPa” frontrunner Klaus Maurischat who is controlled by the Stasi Top Agent Ehrenfried Stelzner, Berlin.
Siegfried Sievers, a former Stasi member is responsible for the pollution of millions Germanys for many years with dioxins. This was unveiled at 5th of January 2011 by German prosecutors.
The victims say that Maurischat (probably also a Stasi cameo) and Sievers were in contact as Sievers acted as Stasi Agent and was in fact already a specialist in dioxins under the Communist Terror Regime in Eastern Germany.
Furthermore the Stasi Top Agent Ehrenfried Stelzer disguised as Professor for Criminal studies during the Communist Regime at the Eastern Berlin Humboldt University.
Background:
The man behind the Berlin lawyer Jochen Resch and his activities is Ehrenfried Stelzer, former Stasi Top officer in Berlin and “Professor for Criminal Studies” at the Eastern Berlin Humboldt University during the Communist regime, the SJB-GoMoPa-victims say (www.sjb-fonds-opfer.com) is responsable for the killing of German watchdog and journalist Heinz Gerlach.
These informations stem from various sources who were close to the criminal organization of GoMoPa in the last years. The SJB-GoMoPa say that the well-known German watchdog and journalist Heinz Gerlach was killed by former Stasi members with dioxins. Polychlorinated dibenzodioxins (PCDDs), or simply dioxins, are a group of organic polyhalogenated compounds that are significant because they act as environmental pollutants. They are commonly referred to as dioxins for simplicity in scientific publications because every PCDD molecule contains a dioxin skeletal structure. Typically, the p-dioxin skeleton is at the core of a PCDD molecule, giving the molecule a dibenzo-p-dioxin ring system. Members of the PCDD family have been shown to bioaccumulate in humans and wildlife due to their lipophilic properties, and are known teratogens, mutagens, and confirmed (avered) human carcinogens. They are organic compounds.
Dioxins build up primarily in fatty tissues over time (bioaccumulate), so even small exposures may eventually reach dangerous levels. In 1994, the US EPA reported that dioxins are a probable carcinogen, but noted that non-cancer effects (reproduction and sexual development, immune system) may pose an even greater threat to human health. TCDD, the most toxic of the dibenzodioxins, is classified as a Group 1 carcinogen by the International Agency for Research on Cancer (IARC).
In 2004, a notable individual case of dioxin poisoning, Ukrainian politician Viktor Yushchenko was exposed to the second-largest measured dose of dioxins, according to the reports of the physicians responsible for diagnosing him. This is the first known case of a single high dose of TCDD dioxin poisoning, and was diagnosed only after a toxicologist recognized the symptoms of chloracne while viewing television news coverage of his condition.
German dioxin scandal: In January 2011 about 4700 German farms were banned from making deliveries after tests at the Harles und Jentzsch plant in the state of Schleswig-Holstein showed high levels of dioxin. Again this incident appears to involve PCBs and not PCDDs at all. Dioxin were found in animal feed and eggs in many farms. The person who is responsible for this, Siegfried Sievert is also a former Stasi Agent. At “GoMoPa” the notorious Eastern-Berlin press agency (see article below) one of the henchmen acted under the name of “Siegfried Siewert”.
Further evidence for the killing of Mr.Heinz Gerlach is provided by the SJB-GoMoPa-victims by analyzing the dubious role of former Stasi-Top-agent Ehrenfried Stelzer, also a former “Professor for Crime Studies” under the Communist regime in Eastern Germany and the dubious role of “detective” Medard Fuchsgruber. Both are closely tied to the dubious “GoMoPa” and Berlin lawyer Jochen Resch.
According to the SJB-GoMoPa-victims is Berlin lawyer Jochen Resch the mastermind of the criminal organization “GoMoPa2. The victims state that they have a source inside “GoMoPa” who helped them discover the shocking truth. The so-called “Deep Throat from Berlin” has information that Resch had the idea to found the criminal organization “GoMoPa” and use non-existing Jewish lawyers named Goldman, Morgenstern & Partner as camouflage. Their “office” in Madison Avenue, New York, is a mailbox. This is witnessed by a German Ex-Patriot, a lawyer, whose father, Heinz Gerlach, died under strange circumstances.
Resch seems to use “GoMoPa” as an instrument to blackmail parts of the German Property and Investment section.
-”Worse than the Gestapo.” —Simon Wiesenthal, Nazi hunter said about the notorious “Stasi”.
Less than a month after German demonstrators began to tear down the Berlin Wall on November 9, 1989, irate East German citizens stormed the Leipzig district office of the Ministry for State Security (MfS)—the Stasi, as it was more commonly called. Not a shot was fired, and there was no evidence of “street justice” as Stasi officers surrendered meekly and were peacefully led away. The following month, on January 15, hundreds of citizens sacked Stasi headquarters in Berlin. Again there was no bloodshed. The last bit of unfinished business was accomplished on May 31 when the Stasi radioed its agents in West Germany to fold their tents and come home.
The intelligence department of the Nationale Volksarmee (NVA), the People’s Army, had done the same almost a week earlier, but with what its members thought was better style. Instead of sending the five-digit code groups that it had used for decades to message its spies in West Germany, the army group broadcast a male choir singing a children’s ditty about a duck swimming on a lake. There was no doubt that the singing spymasters had been drowning their sorrow over losing the Cold War in schnapps. The giggling, word-slurring songsters repeated the refrain three times: “Dunk your little head in the water and lift your little tail.” This was the signal to agents under deep cover that it was time to come home.
With extraordinary speed and political resolve, the divided nation was reunified a year later. The collapse of the despotic regime was total. It was a euphoric time for Germans, but reunification also produced a new national dilemma. Nazi war crimes were still being tried in West Germany, forty-six years after World War II. Suddenly the German government was faced with demands that the communist officials who had ordered, executed, and abetted crimes against their own people—crimes that were as brutal as those perpetrated by their Nazi predecessors—also be prosecuted.
The people of the former Deutsche Demokratische Republik (DDR), the German Democratic Republic, as the state had called itself for forty years, were clamoring for instant revenge. Their wrath was directed primarily against the country’s communist rulers—the upper echelon of the Sozialistische Einheitspartei (SED), the Socialist Unity Party. The tens of thousands of second-echelon party functionaries who had enriched themselves at the expense of their cocitizens were also prime targets for retribution.
Particularly singled out were the former members of the Stasi, the East German secret police, who previously had considered themselves the “shield and sword” of the party. When the regime collapsed, the Stasi had 102,000 full-time officers and noncommissioned personnel on its rolls, including 11,000 members of the ministry’s own special guards regiment. Between 1950 and 1989, a total of 274,000 persons served in the Stasi.
The people’s ire was running equally strong against the regular Stasi informers, the inoffizielle Mitarbeiter (IMs). By 1995, 174,000 had been identified as IMs, or 2.5 percent of the total population between the ages of 18 and 60. Researchers were aghast when they found that about 10,000 IMs, or roughly 6 percent of the total, had not yet reached the age of 18. Since many records were destroyed, the exact number of IMs probably will never be determined; but 500,000 was cited as a realistic figure. Former Colonel Rainer Wiegand, who served in the Stasi counterintelligence directorate, estimated that the figure could go as high as 2 million, if occasional stool pigeons were included.
“The Stasi was much, much worse than the Gestapo, if you consider only the oppression of its own people,” according to Simon Wiesenthal of Vienna, Austria, who has been hunting Nazi criminals for half a century. “The Gestapo had 40,000 officials watching a country of 80 million, while the Stasi employed 102,000 to control only 17 million.” One might add that the Nazi terror lasted only twelve years, whereas the Stasi had four decades in which to perfect its machinery of oppression, espionage, and international terrorism and subversion.
To ensure that the people would become and remain submissive, East German communist leaders saturated their realm with more spies than had any other totalitarian government in recent history. The Soviet Union’s KGB employed about 480,000 full-time agents to oversee a nation of 280 million, which means there was one agent per 5,830 citizens. Using Wiesenthal’s figures for the Nazi Gestapo, there was one officer for 2,000 people. The ratio for the Stasi was one secret policeman per 166 East Germans. When the regular informers are added, these ratios become much higher: In the Stasi’s case, there would have been at least one spy watching every 66 citizens! When one adds in the estimated numbers of part-time snoops, the result is nothing short of monstrous: one informer per 6.5 citizens. It would not have been unreasonable to assume that at least one Stasi informer was present in any party of ten or twelve dinner guests.
THE STASI OCTOPUS
Like a giant octopus, the Stasi’s tentacles probed every aspect of life. Full-time officers were posted to all major industrial plants. Without exception, one tenant in every apartment building was designated as a watchdog reporting to an area representative of the Volkspolizei (Vopo), the People’s Police. In turn, the police officer was the Stasi’s man. If a relative or friend came to stay overnight, it was reported. Schools, universities, and hospitals were infiltrated from top to bottom. German academe was shocked to learn that Heinrich Fink, professor of theology and vice chancellor at East Berlin’s Humboldt University, had been a Stasi informer since 1968. After Fink’s Stasi connections came to light, he was summarily fired. Doctors, lawyers, journalists, writers, actors, and sports figures were co-opted by Stasi officers, as were waiters and hotel personnel. Tapping about 100,000 telephone lines in West Germany and West Berlin around the clock was the job of 2,000 officers.
Stasi officers knew no limits and had no shame when it came to “protecting the party and the state.” Churchmen, including high officials of both Protestant and Catholic denominations, were recruited en masse as secret informers. Their offices and confessionals were infested with eavesdropping devices. Even the director of Leipzig’s famous Thomas Church choir, Hans-Joachim Rotch, was forced to resign when he was unmasked as a Spitzel, the people’s pejorative for a Stasi informant.
Absolutely nothing was sacred to the secret police. Tiny holes were bored in apartment and hotel room walls through which Stasi agents filmed their “suspects” with special video cameras. Even bathrooms were penetrated by the communist voyeurs.8 Like the Nazi Gestapo, the Stasi was the sinister side of deutsche Gründlichkeit (German thoroughness).
After the Berlin wall came down, the victims of the DDR regime demanded immediate retribution. Ironically, their demands were countered by their fellow Germans in the West who, living in freedom, had diligently built einen demokratischen Rechtsstaat, a democratic state governed by the rule of law. The challenge of protecting the rights of both the victims and the accused was immense, given the emotions surrounding the issue. Government leaders and democratic politicians recognized that there could be no “quick fix” of communist injustices without jeopardizing the entire system of democratic jurisprudence. Moving too rapidly merely to satisfy the popular thirst for revenge might well have resulted in acquittals or mistrials. Intricate jurisdictional questions needed to be resolved with both alacrity and meticulousness. No German government could afford to allow a perpetrator to go free because of a judicial error. The political fallout from any such occurrence, especially in the East, could prove fatal to whatever political party occupied the chancellor’s office in Bonn at the time.
Politicians and legal scholars of the “old federal states,” or West Germany, counseled patience, pointing out that even the prosecution of Nazi criminals had not yet been completed. Before unification, Germans would speak of Vergangenheitsbewältigung (“coming to grips with the past”) when they discussed dealing with Nazi crimes. In the reunited Germany, this word came to imply the communist past as well. The two were considered comparable especially in the area of human rights violations. Dealing with major Nazi crimes, however, was far less complicated for the Germans: Adolf Hitler and his Gestapo and Schutzstaffel (SS) chief, Heinrich Himmler, killed themselves, as did Luftwaffe chief and Vice Chancellor Hermann Göring, who also had been the first chief of the Gestapo. The victorious Allies prosecuted the rest of the top leadership at the International War Crimes Tribunal in Nürnberg. Twelve were hanged, three received life terms, four were sentenced to lesser terms of imprisonment (up to twenty years), and three were acquitted.
The cases of communist judges and prosecutors accused of Rechtsbeugung (perversion of justice) are more problematic. According to Franco Werkenthin, a Berlin legal expert charged with analyzing communist crimes for the German parliament, those sitting in judgment of many of the accused face a difficult task because of the general failure of German justice after World War II. Not a single judge or prosecutor who served the Nazi regime was brought to account for having perverted justice—even those who had handed down death sentences for infringements that in a democracy would have been considered relatively minor offenses. Werkenthin called this phenomenon die Jauche der Justiz, the cesspool of justice.
Of course, the crimes committed by the communists were not nearly as heinous as the Nazis’ extermination of the Jews, or the mass murders in Nazi-occupied territories. However, the communists’ brutal oppression of the nation by means including murder alongside legal execution put the SED leadership on a par with Hitler’s gang. In that sense, Walter Ulbricht or Erich Honecker (Ulbricht’s successor as the party’s secretary-general and head of state) and secret police chief Erich Mielke can justifiably be compared to Hitler and Himmler, respectively.
Arrest warrants were issued for Honecker and Mielke. The Soviet government engineered Honecker’s escape to Moscow, where he became the ward of Soviet President Mikhail S. Gorbachev. When the Soviet Union crumbled, the new Russian President Boris Yeltsin expelled Honecker. He was arrested on his return to Germany, but a court decided against a trial when he was diagnosed with liver cancer. Honecker flew to Chile with his wife Margot to live with their daughter, a Chilean citizen by marriage. His exile was short, and he died in 1994. Mielke was not so fortunate: His KGB friends turned their backs on him. He was tried in Germany for the 1931 murder of two police officers, found guilty, and sentenced to six years in prison. Other charges, including manslaughter, were dismissed because of his advanced age and poor health.
Three other members of the twenty-one-member ruling Politburo also have been tried. Former Defense Minister Heinz Kessler was convicted of manslaughter in connection with the order to kill people who were trying to escape to the West. He received a seven-and-a-half-year term. Two others, members of the Central Committee and the National Defense Council, were tried with Kessler and sentenced to seven and a half years and five years, respectively. Politburo member Harry Tisch, who was also head of the communist trade union, was found guilty of embezzlement and served eighteen months. Six others, including Egon Krenz (Honecker’s successor as party chief), were charged with manslaughter. Krenz was found guilty, and on August 25, 1997, was sentenced to six and a half years in prison.
However, eight years after reunification, many of the 165 members of the Central Committee have not yet been put under investigation. In 1945, Nazis holding comparable or lesser positions were subject to automatic arrest by the Allies. They spent months or even years in camps while their cases were adjudicated. Moreover, the Nürnberg Tribunal branded the Reich and its Corps of Political Leaders, SS, Security Service (SD), Secret State Police (Gestapo), SA (Storm Troopers), and Armed Forces High Command criminal organizations. Similarly sweeping actions against communist leaders and functionaries such as Stasi officers were never contemplated, even though tens of thousands of political trials and human rights abuses have been documented. After the East German regime fell, German judicial authorities scrupulously avoided the appearance of waging witch-hunts or using the law as a weapon of vengeance. Prosecutors and judges made great efforts to be fair, often suspending legal action while requesting rulings from the supreme court on possible constitutional conflicts.
The victims of oppression clamored for revenge and demanded speedy prosecution of the erstwhile tyrants. They had little patience for a judicial system that was handicapped by a lack of unblemished and experienced criminal investigators, prosecutors, and judges. Despite these handicaps, the Berlin Central Police Investigations Group for Government Criminality, mindful that the statute of limitations for most communist crimes would expire at the end of 1999, made significant progress under its director Manfred Kittlaus, the able former director of the West Berlin state police. Kittlaus’s major task in 1998 was to investigate wrongful deaths, including 73 murders, 30 attempted murders, 583 cases of manslaughter, 2,938 instances of attempted manslaughter, and 425 other suspicious deaths. Of the 73 murders, 22 were classified as contract murders.
One of those tried and convicted for attempted contract murder was former Stasi collaborator Peter Haak, who was sentenced to six and a half years in prison. The fifty-two-year-old Haak took part in the Stasi’s 1981 Operation Scorpion, which was designed to pursue people who helped East Germans escape to the West. Proceedings against former General Gerhard Neiber, whose Stasi directorate was responsible for preventing escapes and for wreaking vengeance, were still pending in 1998.
Peter Haak’s murder plot was hatched after he befriended Wolfgang Welsch and his family. Welsch was a thorn in the side of the Stasi because of his success in smuggling people out of the DDR. Haak joined Welsch and the latter’s wife and seven-year-old daughter on a vacation in Israel, where he mixed a gram of thallium, a highly poisonous metallic chemical element used in rat poison, into the hamburgers he was preparing for a meal. Welsch’s wife and daughter vomited immediately after ingesting the poison and recovered quickly. Welsch suffered severe aftereffects, but eventually recovered: He had consumed a large amount of beer with the meal, and an expert testified that the alcohol had probably flushed the poison from his system.
Berlin Prosecutor General Christoph Schäfgen revealed that after the DDR’s demise 15,200 investigations had been launched, of which more than 9,000 were still active at the beginning of 1995. Indictments were handed down in 153 cases, and 73 perpetrators were convicted. Among those convicted were the aforementioned Politburo members as well as a number of border guards who had killed people who were trying to escape to the West.
Despite widespread misgivings about the judicial failures in connection with some Nazi crimes, a number of judges and prosecutors were convicted and jailed for up to three years for perversion of justice. In collusion with the Stasi, they had requested or handed down more severe sentences in political cases so that the state could collect greater amounts when the “convicts” were ransomed by the West German government. {The amount of ransom paid was governed by the time a prisoner had been sentenced to serve.)
The enormity of the task facing judicial authorities in reunified Germany becomes starkly evident when one examines the actions they have taken in all five former East German provinces and in East Berlin. From the end of 1990 to July 1996, 52,050 probes were launched into charges of murder, attempted murder, manslaughter, kidnapping, election fraud, and perversion of justice. A total of 29,557 investigations were halted for various reasons including death, severe illness, old age, or insufficient evidence. In those five and a half years, there were only 139 convictions.
The problem is even more staggering when cases of espionage are included. Between 1990 and 1996, the office of the federal prosecutor general launched 6,641 probes, of which 2,431 were terminated before trial—most due to the statute of limitations. Of 175 indictments on charges of espionage, 95 resulted in convictions. In addition to the cases handled at the federal level, the prosecutor general referred 3,926 investigations to state authorities, who terminated 3,344 without trial. State courts conducted 356 trials, resulting in 248 convictions. Because the statute of limitations for espionage is five years, the prosecutor general’s office told me in 1997 it was unlikely that more espionage trials would be conducted.
It is important to emphasize the difference between the statute’s application to so-called government crimes committed in East Germany before the collapse and to crimes, such as espionage, committed in West Germany. The Unification Treaty specifically permits the belated prosecution of individuals who committed acts that were punishable under the East German criminal code and who due to official connivance were not prosecuted earlier. There is no statute of limitations for murder. For most other crimes the limit is five years; however, due to the obstacles created by previous government connivance, the German parliament in 1993 doubled this time limit for prosecution of the more serious crimes. At the same time, the parliament decreed that all cases must be adjudicated by the end of 2002. For less serious offenses, the statute would have run out on December 31, 1997, but the parliament extended it to 2000.
A number of politicians, jurists, and liberal journalists pleaded for a general amnesty for crimes committed by former DDR leaders and Communist Party functionaries. A former West German supreme court judge, Ernst Mahrenholz, said the “sharp sword of justice prevents reconciliation.” Schäfgen, the Berlin prosecutor general, had this answer for the former high court judge and other amnesty advocates:
I cannot agree. We are raising no special, sharp sword against East Germans. We must pursue state-sponsored injustice in exactly the same manner as we do when a thief steals or when one human being kills another. If one wants to change that, then we would have to do away with the entire criminal justice system, because punishment always hurts. We are not criminalizing an entire people but only an ever shrinking, small portion.
German Foreign Minister Klaus Kinkel, who was West Germany’s minister of justice when the nation was unified, said this at a session of parliament in September 1991: “We must punish the perpetrators. This is not a matter of a victor’s justice. We owe it to the ideal of justice and to the victims. All of those who ordered injustices and those who executed the orders must be punished; the top men of the SED as well as the ones who shot [people] at the wall.” Aware that the feelings against communists were running high among their victims, Kinkel pointed to past revolutions after which the representatives of the old system were collectively liquidated. In the same speech before parliament, he said:
Such methods are alien to a state ruled by law. Violence and vengeance are incompatible with the law in any case. At the same time, we cannot tolerate that the problems are swept under the rug as a way of dealing with a horrible past, because the results will later be disastrous for society. We Germans know from our own experience where this leads. Jewish philosophy formulates it in this way: “The secret of redemption is called remembering.”
Defense attorneys for communist officials have maintained that the difficulty lies in the fact that hundreds of thousands of political opponents were tried under laws of the DDR. Although these laws were designed to smother political dissent and grossly violated basic human rights and democratic norms, they were nonetheless laws promulgated by a sovereign state. How could one justly try individual Stasi officers, prosecutors, and judges who had simply been fulfilling their legal responsibility to pursue and punish violators of the law?
Opinions varied widely on whether and how the Stasi and other perpetrators of state-sponsored crimes should be tried. Did the laws of the DDR, as they existed before reunification, still apply in the east? Or was the criminal code of the western part of the country the proper instrument of justice in reunified Germany? However, these questions were moot: As Rupert Scholz, professor of law at the University of Munich and a Christian Democratic member of parliament, pointed out, the Unification Treaty specifies that the penal code of the DDR and not that of the Federal Republic of Germany (FRG) shall be applied to offenses committed in East Germany. Scholz’s view was upheld by the Bundesverfassungsgericht, the supreme court. Most offenses committed by party functionaries and Stasi officers—murder, kidnapping, torture, illegal wiretapping, mail robbery, and fraud—were subject to prosecution in reunified Germany under the DDR’s penal code. But this would not satisfy the tens of thousands of citizens who had been sent to prison under East German laws covering purely political offenses for which there was no West German equivalent.
Nevertheless, said Scholz, judicial authorities were by no means hamstrung, because West Germany had never recognized the East German state according to international law. “We have always said that we are one nation; that the division of Germany led neither to full recognition under international law nor, concomitantly, to a recognition of the legal system of the DDR,” Scholz said. Accordingly, West German courts have consistently maintained that West German law protects all Germans equally, including those living in the East. Therefore, no matter where the crimes were committed, whether in the East or the West, all Germans have always been subject to West German laws. Applying this logic, East German border guards who had either killed or wounded persons trying to escape to the West could be tried under the jurisdiction of West Germany.
The “one nation” principle was not upheld by the German supreme court. Prior to the court’s decision, however, Colonel General Markus Wolf, chief of the Stasi’s foreign espionage directorate, and some of his officers who personally controlled agents from East Berlin had been tried for treason and convicted. Wolf had been sentenced to six years in prison. The supreme court ruling overturned that verdict and those imposed on Wolf’s cohorts, even though they had obtained the most closely held West German secrets and handed them over to the KGB. The maximum penalty for Landesverrat, or treason, is life imprisonment. In vacating Wolf’s sentence, the court said he could not be convicted because he operated only from East German territory and under East German law.
However, Wolf was reindicted on charges of kidnapping and causing bodily harm, crimes also punishable under East German law. The former Stasi three-star general, on March 24, 1955, had approved in writing a plan to kidnap a woman who worked for the U.S. mission in West Berlin. The woman and her mother were tricked by a Stasi agent whom the woman had been teaching English, and voluntarily got into his car. He drove them into the Soviet sector of the divided city, where they were seized by Stasi officers. The woman was subjected to psychological torture and threatened with imprisonment unless she signed an agreement to spy for the Stasi. She agreed. On her return to the American sector, however, the woman reported the incident to security officials. Wolf had committed a felony punishable by up to fifteen years’ imprisonment in West Germany. He was found guilty in March 1977 and sentenced to two years’ probation.
Those who have challenged the application of the statute of limitations to communist crimes, especially to the executions of citizens fleeing to the West, have drawn parallels to the notorious executive orders of Adolf Hitler. Hitler issued orders mandating the summary execution of Soviet Army political commissars upon their capture and initiating the extermination of Jews. An early postwar judicial decision held that these orders were equivalent to law. When that law was declared illegal and retroactively repealed by the West German Bundestag, the statute of limitations was suspended—that is, it never took effect. Many of those convicted in subsequent trials of carrying out the Führer’s orders were executed by the Allies. The German supreme court has ruled the same way as the Bundestag on the order to shoot people trying to escape to West Germany, making the statute of limitations inapplicable to such cases. The ruling made possible the trial of members of the National Defense Council who took part in formulating or promulgating the order. A number of border guards who had shot would-be escapees also have been tried and convicted.
Chief Prosecutor Heiner Sauer, former head of the West German Central Registration Office for Political Crimes, was particularly concerned with the border shootings. His office, located in Salzgitter, West Germany, was established in 1961 as a direct consequence of the Berlin Wall, which was erected on August 13 of that year. Willy Brandt, at the time the city’s mayor (later federal chancellor) had decided that crimes committed by East German border guards should be recorded. At his behest, a central registry of all shootings and other serious border incidents was instituted. Between August 13, 1961 and the opening of the borders on November 9, 1989, 186 border killings were registered. But when the Stasi archives were opened, investigators found that at least 825 people had paid with their lives for trying to escape to the West. This figure was reported to the court that was trying former members of the National Defense Council. In addition to these border incidents, the registry also had recorded a number of similar political offenses committed in the interior of the DDR: By fall 1991, Sauer’s office had registered 4,444 cases of actual or attempted killings and about 40,000 sentences handed down by DDR courts for “political offenses.”
During the early years of Sauer’s operation, the details of political prosecutions became known only when victims were ransomed by West Germany or were expelled. Between 1963 and 1989, West Germany paid DM5 billion (nearly US$3 billion) to the communist regime for the release of 34,000 political prisoners. The price per head varied according to the importance of the person or the length of the sentence. In some cases the ransom amounted to more than US$56,000. The highest sum ever paid to the East Germans appears to have been DM450,000 (US$264,705 using an exchange rate of US$1.70 to the mark). The ransom “object” in this case was Count Benedikt von Hoensbroech. A student in his early twenties, von Hoensbroech was attending a West Berlin university when the wall went up. He was caught by the Stasi while trying to help people escape and was sentenced to ten years at hard labor. The case attracted international attention because his family was related to Queen Fabiola of Belgium, who interceded with the East Germans. Smelling money, the East German government first demanded the equivalent of more than US$1 million from the young man’s father as ransom. In the end, the parties settled on the figure of DM450,000, of which the West German government paid DM40,000 (about $23,529). Such ransom operations were fully controlled by the Stasi.
Political prisoners released in the DDR could not be registered by the West Germans because their cases remained secret. The victims were admonished to keep quiet or face another prison term. Nonetheless, in the first year after reunification, Sauer’s office added another 20,000 documented cases, for a total of 60,000. Sauer said he believed the final figure of all political prosecutions would be somewhere around 300,000. In every case, the Stasi was involved either in the initial arrest or in pretrial interrogations during which “confessions” were usually extracted by physical or psychological torture, particularly between the mid-1940s and the mid-1960s.
Until 1987, the DDR imposed the death penalty for a number of capital crimes, including murder, espionage, and economic offenses. But after the mid-1950s, nearly all death sentences were kept quiet and executions were carried out in the strictest secrecy, initially by guillotine and in later years by a single pistol shot to the neck. In most instances, the relatives of those killed were not informed either of the sentence or of the execution. The corpses were cremated and the ashes buried secretly, sometimes at construction sites. In reporting about one executioner who shot more than twenty persons to death, the Berlin newspaper Bildzeitung said that a total of 170 civilians had been executed in East Germany. However, Franco Werkenthin, the Berlin official investigating DDR crimes, said he had documented at least three hundred executions. He declined to say how many were for political offenses, because he had not yet submitted his report to parliament. “But it was substantial,” he told me. The true number of executions may never be known because no complete record of death sentences meted out by civil courts could be found. Other death sentences were handed down by military courts, and many records of those are also missing. In addition, German historian Günther Buch believes that about two hundred members of the Stasi itself were executed for various crimes, including attempts to escape to the West.
SAFEGUARDING HUMAN DIGNITY?
The preamble to the East German criminal code stated that the purpose of the code was to “safeguard the dignity of humankind, its freedom and rights under the aegis of the criminal code of the socialist state,” and that “a person can be prosecuted under the criminal code only in strictest concurrence with the law.” However, many of the codified offenses for which East German citizens were prosecuted and imprisoned were unique to totalitarian regimes, both fascist and communist.
Moreover, certain sections of the code, such as those on “Treasonable Relaying of Information” and “Treasonable Agent Activity,” were perversely applied, landing countless East Germans in maximum security penitentiaries. The victims of this perversion of justice usually were persons who had requested legal exit permits from the DDR authorities and had been turned down. In many cases, their “crime” was having contacted a Western consulate to inquire about immigration procedures. Sentences of up to two and a half years’ hard labor were not unusual as punishment for such inquiries.
Engaging in “propaganda hostile to the state” was another punishable offense. In one such case, a young man was arrested and prosecuted for saying that it was not necessary to station tanks at the border and for referring to border fortifications as “nonsense.” During his trial, he “admitted” to owning a television set on which he watched West German programs and later told friends what he saw. One of those “friends” had denounced him to the Stasi. The judge considered the accused’s actions especially egregious and sentenced him to a year and a half at hard labor.
Ironically, another part of this section of the criminal code decreed that “glorifying militarism” also was a punishable offense, although the DDR itself “glorified” its People’s Army beyond any Western norm. That army was clad in uniforms and insignia identical to those of the Nazi Wehrmacht, albeit without eagles and swastikas. The helmets, too, were differently shaped, but the Prussian goose step was regulation during parades.
A nineteen-year-old who had placed a sign in an apartment window reading “When justice is turned into injustice, resistance becomes an obligation!” was rewarded with twenty-two months in the penitentiary. Earlier, the youth had applied for an exit visa and had been turned down. A thirty-four-year-old father of two who also had been denied permission to leave the “workers’ and peasants’ state” with his family similarly advertised that fact with a poster reading “We want to leave, but they won’t let us.” The man went to prison for sixteen months. The “crimes” of both men were covered by a law on “Interference in Activities of the State or Society.”
Two letters—one to a friend in West Germany, seeking assistance to legally emigrate to the West, and another containing a similar appeal to Chief of State Honecker—brought a four-year sentence to their writer, who was convicted under two laws: those on “establishing illegal contacts” (writing to his friend) and on “public denigration” (writing to Honecker). The Stasi had illegally intercepted both letters.
The East German party chiefs were not content to rely only on the Stasi’s millions of informers to ferret out antistate sentiments. Leaving nothing to chance, they created a law that made the failure to denounce fellow citizens a crime punishable by up to five years’ imprisonment. One man was sentenced to twenty-three months for failing to report that a friend of his was preparing to escape to the West. The mandatory denunciation law had its roots in the statutes of the Socialist Unity Party, which were published in the form of a little red booklet. I picked up a copy of this booklet that had been discarded by its previous owner, a Stasi chauffeur, who had written “Ha, Ha” next to the mandate to “report any misdeeds, regardless of the person responsible, to leading party organs, all the way up to the Central Committee.”
Rupert Scholz, member of parliament and professor of law at the University of Munich, said many East Germans feel there is little determination among their Western brethren to bring the Stasi criminals to trial. “In fact, we already have heard many of them say that the peaceful revolution should have been a bloody one instead so they could have done away with their tormentors by hanging them posthaste,” Scholz told me.
The Reverend Joachim Gauck, minister to a Lutheran parish in East Germany, shared the people’s pessimism that justice would be done. Following reunification, Gauck was appointed by the Bonn government as its special representative for safeguarding and maintaining the Stasi archives. “We must at least establish a legal basis for finding the culprits in our files,” Gauck told me. “But it will not be easy. If you stood the millions of files upright in one line, they would stretch for 202 kilometers [about 121 miles]. In those files you can find an unbelievable number of Stasi victims and their tormentors.”
Gauck was given the mandate he needed in November 1991, when the German parliament passed a law authorizing file searches to uncover Stasi perpetrators and their informants. He viewed this legislation as first step in the right direction. With the evidence from Stasi files, the perpetrators could be removed from their public service jobs without any formal legal proceedings. Said Gauck: “We needed this law badly. It is not reasonable that persons who served this apparatus of oppression remain in positions of trust.”
See more at the journalist Bernd Pulch website http://www.berndpulch.org
TOP-SECRET – Federal Reserve Bank of New York Sentiment Analysis and Social Media Monitoring Proposal

Federal Reserve Bank of New York (“FRBNY”) is extending to suppliers an invitation to participate in an Sentiment Analysis And Social Media Monitoring Solution RFP bid process.
The intent is to establish a fair and equitable partnership with a market leader who will who gather data from various social media outlets and news sources and provide applicable reporting to FRBNY. This Request for Proposal (“RFP”) was created in an effort to support FRBNY’s Social Media Listening Platforms initiative.
B. Background & Scope
B1. (Instruction)
I. Introduction
Social media platforms are changing the way organizations are communicating to the public Conversations are happening all the time and everywhere.
There is need for the Communications Group to be timely and proactively aware of the reactions and opinions expressed by the general public as it relates to the Federal Reserve and its actions on a variety of subjects.
B2. (Instruction)
II. Social Listening Platforms
Social media listening platforms are solutions that gather data from various social media outlets and news sources. They monitor billions of conversations and generate text analytics based on predefined criteria. They can also determine the sentiment of a speaker or writer with respect to some topic or document.
The information gathered can guide the organizations public relations group in assessing the effectiveness of communication strategies.
Here are some of the services it can offer:
o Track reach and spread of your messages and press releases
o Handle crisis situations
o Continuously monitor conversations
o Identify and reach out to key bloggers and influencers
o Spot emerging trends, discussions themes and topicsB3. (Question)
III. Mandatory Minimum Solution Requirements
A. Geographic scope of social media sites
The solution must support content coming from different countries and geographical regions. It should also support multiple languages.
B. Content and Data Types
The solution must be able to gather data from the primary social media platforms –Facebook, Twitter, Blogs, Forums and YouTube. It should also be able to aggregate data from various media outlets such as: CNN, WSJ, Factiva etc.
C. Reports and Metrics
The solution must provide real-time monitoring of relevant conversations. It should provide sentiment analysis (positive, negative or neutral) around key conversational topics.
It must be able to provide summaries or high level overviews of a specific set of topics. It should have a configurable dashboard that can easily be accessed by internal analysts or management. The dashboard must support customization by user or group access.
The solution should provide an alerting mechanism that automatically sends out reports or notifications based a predefined trigger.
D. FRBNY Technology Integration
The solution must be able to integrate with existing FRBNY technologies such as: Google Search appliance, Lotus notes suite and web trends.
It must have support for single sign on or windows integrated authentication.
DOWNLOAD ORIGINAL DOCUMENT HERE
SECRET – Interpol Secretary General Wants Global Cyber Fusion Center

Ronald K. Noble, secretary general of Interpol, gestures as he addresses a press conference in New Delhi, India,
Ronald Noble: ‘Terrorists plan on email. And we can’t track them’:
As a former head of the US Secret Service, Ronald Noble knows only too well how terrorism, drug-smuggling and people-trafficking cross borders which individual police forces cannot. He is now Secretary General of Interpol, and a specialist team from the organisation he has spent 11 years rebuilding will next summer help the Metropolitan Police combat those crimes and others, during the huge security operation protecting the 2012 Olympic Games.
Meeting The Independent before visiting Scotland Yard to discuss arrangements for the Games, Mr Noble said he recognised that some people are scared the event could bring an increased threat of violence to the UK.
“In terms of terrorist activity, there is talk, there is chatter, that follows any major event,” he says, but adds Interpol has “not seen or heard terrorists saying we’re going to target this event”.
“We try to think like terrorists would think,” he continues. “A smart terrorist would know that if the world’s attention is focused on something and they commit a terrorist act it will help them create the kind of fear that would make people want to leave London.
…
“My concern is that the people planning that attack – that nuclear attack, that bio-terrorist attack, that attack that should concern us all as a world – would be able to plan it more effectively because we don’t have a network in place for tracing the source of email messages on the internet,” he says.
“One of the things I want to do … is to create a cyber-fusion centre, where police around the world can go to one place quickly and find out the source of any kind of message or communication that’s come across the internet.”
That in itself may alarm some. But Mr Noble emphasises the centre will only target specific, suspicious emails, saying it simply could not track all the messages from billions of innocent people even if Interpol wanted it to.
Nevertheless, some civil liberties groups have questioned Interpol’s accountability and transparency.
STUDY – Income for Top 1% of Americans Rose 74% From 1996-2006

Growing Income Inequality Examined by CRS:
The inequality of income among American taxpayers has grown markedly in recent years, the Congressional Research Service confirmed in a new study of U.S. tax records.Even as total income grew between 1996 and 2006 (the last year for which individual tax data are available), many Americans were losing ground.“Inflation-adjusted income actually fell for those in the bottom income quintile (the poorest 20% of tax filers) and almost doubled for the richest 0.1% of tax filers,” the CRS found. “Consequently, income inequality increased between 1996 and 2006.”
Bush tax cuts, stock market widen income gap:
The rich have gotten richer, thanks to the stock market and the Bush tax cuts, a recent report has found.
Growth in income from capital gains and dividends has widened the divide between the wealthy and the poor in recent years, according to the non-partisan Congressional Research Service. It supplanted wage inequality as the primary driver of the growing income gap, which helped spur the Occupy Wall Street movement last fall.
After-tax income for the top 1% of taxpayers soared 74%, on average, between 1996 and 2006. The top 0.1% benefited even more, nearly doubling their income over that decade.
By comparison, the bottom 20% of taxpayers saw their income fall by 6%, while the middle quintile experienced a meager 10% gain.
But “income” means something very different for the rich than for the poor.
High-income people benefited in particular from the stock market boom in the late 1990s and from companies enjoying strong profit growth and paying out healthy dividends more recently, said Harry Holzer, professor at the Georgetown Public Policy Institute.
In 1996, the top 1% of taxpayers relied on wages for 34.4% of their income. A decade later, that number had fallen to just over a quarter, the report found. Meanwhile, income from capital gains and dividends grew by nearly 7.5 percentage points to 38.2% of earnings.
The Bush tax cuts, which lowered rates on both income and capital gains, also helped fuel the growth in income inequality, according to the report. The difference in tax rates paid by the poor and the rich narrowed, with the Top 0.1% of American taxpayers seeing their average tax rate fall by about a quarter.
DOWNLOAD ORIGINAL FILES HERE
New and Uncensored – Femen protests
NEUE DROH-BOTSCHAFT DER STASI-STALKER 2012 – MUTMASSLICH VON “PETER EHLERS”
| Message List | Unread | Delete | Resume Draft | Previous | Next | Forward | Forward as Attachment | Reply | Reply All |
|
||||||||||||
Hey kids fucker Pulch. The new year has nasty surprises for you child and mother fucker. The Internet never sleeps. We wish you a good time.
KORRUPTES NETZWERK DER STASI-UNTERSTÜTZER
Liebe Leser,
immer wieder werde ich nach dem korrupten Netzwerk der STASI-Unterstützer gefragt.
Ich sage JETZT nur EINES:
Einige der genannten und enttarnten Mit-Täter outen sich uns.
Ich werde nicht ruhen, bis ich das gesamte Netzwerk enttarnt habe.
Herzlichst Ihr
Bernd Puch, Magister Artium
PS
Darunter gibt es auch einige frühere Freunde, Mitarbeiter und Bekannte von mir, die STASI-gemäss unterwandert wurden.
CONFIDENTIAL – Bank of America, GE Pay Zero Federal Taxes – see als Warren Buffets Berkshire Taxes

After another money-losing year, Bank of America Corp. got the upper hand with Uncle Sam in 2010.
The Charlotte-based bank had no federal income tax expense for a second straight year and actually reported a tax “benefit” of nearly $1 billion. Also, the bank’s billions in accumulated losses could reduce its taxes in future years, a tax expert said.
The bank says the reason is simple: Corporations pay taxes on their profits, and Bank of America posted a pre-tax loss of $5.4 billion in the U.S. in 2010.
“Bank of America takes its role as a corporate citizen very seriously, and pays taxes in accordance with all applicable laws and regulations,” bank spokesman Jerry Dubrowski said.
That doesn’t satisfy a group that has been staging protests at Bank of America branches around the country and crashed the bank’s New York investor conference this month. The bank is an “aggressive tax dodger,” said Ryan Clayton, a Washington-based organizer of U.S. Uncut. “We pay our taxes. Why don’t they?”
Clayton’s group suggests Bank of America and other large U.S. companies are using subsidiaries in offshore tax havens to eliminate their taxes.
Bank of America and other companies do avoid paying taxes on profits they make in overseas operations by reinvesting these proceeds overseas, instead of bringing them back home. Some business leaders recently have called for a lower tax rate on these earnings, a move they contend would encourage companies to bring these profits to the U.S.
G.E.’s Strategies Let It Avoid Taxes Altogether:
General Electric, the nation’s largest corporation, had a very good year in 2010.
The company reported worldwide profits of $14.2 billion, and said $5.1 billion of the total came from its operations in the United States.
Its American tax bill? None. In fact, G.E. claimed a tax benefit of $3.2 billion.
That may be hard to fathom for the millions of American business owners and households now preparing their own returns, but low taxes are nothing new for G.E. The company has been cutting the percentage of its American profits paid to the Internal Revenue Service for years, resulting in a far lower rate than at most multinational companies.
Its extraordinary success is based on an aggressive strategy that mixes fierce lobbying for tax breaks and innovative accounting that enables it to concentrate its profits offshore. G.E.’s giant tax department, led by a bow-tied former Treasury official named John Samuels, is often referred to as the world’s best tax law firm. Indeed, the company’s slogan “Imagination at Work” fits this department well. The team includes former officials not just from the Treasury, but also from the I.R.S. and virtually all the tax-writing committees in Congress.
While General Electric is one of the most skilled at reducing its tax burden, many other companies have become better at this as well. Although the top corporate tax rate in the United States is 35 percent, one of the highest in the world, companies have been increasingly using a maze of shelters, tax credits and subsidies to pay far less.
In a regulatory filing just a week before the Japanese disaster put a spotlight on the company’s nuclear reactor business, G.E. reported that its tax burden was 7.4 percent of its American profits, about a third of the average reported by other American multinationals. Even those figures are overstated, because they include taxes that will be paid only if the company brings its overseas profits back to the United States. With those profits still offshore, G.E. is effectively getting money back.
Such strategies, as well as changes in tax laws that encouraged some businesses and professionals to file as individuals, have pushed down the corporate share of the nation’s tax receipts — from 30 percent of all federal revenue in the mid-1950s to 6.6 percent in 2009.
…
The assortment of tax breaks G.E. has won in Washington has provided a significant short-term gain for the company’s executives and shareholders. While the financial crisis led G.E. to post a loss in the United States in 2009, regulatory filings show that in the last five years, G.E. has accumulated $26 billion in American profits, and received a net tax benefit from the I.R.S. of $4.1 billion.
But critics say the use of so many shelters amounts to corporate welfare, allowing G.E. not just to avoid taxes on profitable overseas lending but also to amass tax credits and write-offs that can be used to reduce taxes on billions of dollars of profit from domestic manufacturing. They say that the assertive tax avoidance of multinationals like G.E. not only shortchanges the Treasury, but also harms the economy by discouraging investment and hiring in the United States.
SECRET – Restricted BIS Brief: Interdependencies among payment and settlement systems

hat are interdependencies, and Why do they matter?
Interdependencies arise when the settlement flows, operational processes or risk management procedures of one system are related to those of other systems
Interdependencies potentially can simultaneously:
•Improve the safety and efficiency of payment and settlement processes
•Allow financial disruptions to be passed more easily and more quickly across systems, their participants and related markets, accentuating their role in transmitting disruptions (Ferguson report)
Forms of interdependencies
Interdependencies arise from:
•Direct relationships among systems
•Indirect relationships among systems due to the activities of financial institutions,
•“Environmental” factors: the dependence of multiple systems on common third-parties, on common markets, etc
That reflect multiple activities and purposes:
•Clearing and settlement channels/arrangements
•Operational processes and facilities
•Risk management

Factors influencing interdependencies
Four key and interrelated forces and policies:
•Globalisation and regional integration
•Consolidation
•Public policies
•Technological innovations
The influence of these forces and polices take place in the context of the effort of central banks and other authorities together with market participants to increase efficiency and reduce risks in systems.
Central banks have promoted some forms of interdependencies, particularly system-based (egDVP and PVP links)
Extent of Interdependencies
Interdependencies are particularly strong on a domestic basis
•Comprehensive web of clearing and settlement relationships amongkey domestic systems (CCP to CSD, CCP to LVPS, LVPS to CSD)
•Significant overlap in the participant base of domestic systems,leading to strong interdependencies of liquidity flows across systems
•To a lesser degree, some reliance on common service providers, and some risk-management links (cross-margining, common default definitions, etc)
Focused interdependencies on a cross-border basis
•CLS-related relationships are well known
•Widespread reliance on SWIFT
•But, role of institution-based links currently less clear; may continue to grow in importance going forward
Implications for risks in payment and settlement systems
Specific sources of several risks have been eliminated, or reduced
•Principal credit risk: implementation of DVP and PVP
•Operational risk: links among systems can help with STP
•Liquidity risk and settlement asset risk: central bank money haslower credit risk and liquidity risk (more assurance in its provision vscorrespondents)
But, new sources of risk have been introduced
•These risks are often cross-system in nature, meaning that a disruption in one system may have direct implications for the smooth functioning of a second system
•Obvious examples at the system level (DVP links, CLS, etc); but,can also be at the institution level if flows in one system are conditional on those in another
And, concentration in the sources of risks have been accentuated
•Multiple systems now face common risks from key systems (RTGS), large financial institutions, and key service providers (egSWIFT)
Implications for transmission of disruptions
Specific sources of several risks have been eliminated, or reduced
•Principal credit risk: implementation of DVP and PVP
•Operational risk: links among systems can help with STP
•Liquidity risk and settlement asset risk: links among systems facilitate the use of central bank money
But, new sources of risk have been introduced
•These risks are often cross-system in nature, meaning that a disruption in one system may have direct implications for the smooth functioning of a second system
•Obvious examples at the system level (DVP links, CLS, etc); but,can also be at the institution level
And, concentration in the sources of risks have been accentuated
•Multiple systems now face common risks from key systems (RTGS), large financial institutions, and key service providers (egSWIFT)
DOWNLOAD ORIGINAL DOCUMENT HERE
ALERT – U.S. State Department Creates Bureau of Counterterrorism
he State Department plans to elevate its counterterrorism office to a full-fledged bureau on Wednesday, a move that officials say will send a strong signal to allies about the U.S. commitment to strengthening their ability to combat extremism.
The promotion fulfills a pledge by Secretary of State Hillary Clinton in a speech last year to do so as part of an effort to integrate all the tools of American power to combat terror threats. The new bureau is not expected to receive a larger budget, but officials say it will help raise the State Department’s counterterrorism profile both within the U.S. government and abroad.
…
In her speech, Secretary Clinton spoke of the need to build “an international counterterrorism network” to combat terror adversaries and said that upgrading the department’s counterterrorism office will be key to developing that critical capacity in partner countries.
The Office of the Coordinator for Counterterrorism, as it is currently known, plays an often unsung role in the U.S. government’s counterterrorism apparatus, losing the limelight to higher profile cousins in the intelligence community, Department of Homeland Security, and military. Yet Ambassador Benjamin said its role was critical in improving the capacity of other countries who share U.S. interests.
“You cannot shoot your way out of the world’s terrorism problem,” he said. Instead he referred to what he called “counterterrorism diplomacy,” which focuses on boosting the capacity of foreign countries to deal with extremism within their borders and convincing them to do more about it on their own.
Ambassador Benjamin said his office’s promotion will send a message to those countries that they need to do more.
Bureau of Counterterrorism:
The Department of State announces the establishment of the Bureau of Counterterrorism, fulfilling one of the key recommendations of the Quadrennial Diplomacy and Development Review concluded in December 2010. The Bureau of Counterterrorism will lead the Department’s engagement in support of U.S. government efforts to counter terrorism abroad and to secure the United States against foreign terrorist threats. The new Bureau will assume the responsibilities of the Office of the Coordinator for Counterterrorism.
The Challenge
The United States faces a continuing terrorist threat from al-Qaida and other groups and individuals who subscribe to violent extremism. While we have made much progress in combating terrorism since the 9/11 attacks, challenges remain. Together with defense, intelligence, law enforcement, and homeland security, diplomacy and development are critical to keeping America safe. To secure our future, we must continue to strengthen our international coalition against terrorism, build foreign partner capacity to mitigate terrorist threats, reinforce resilience against attacks, and counter the ideologies and ideas that fuel violent extremism around the world.
The Mission
The Bureau of Counterterrorism, in coordination with Department leadership, the National Security Staff, and other U.S. government agencies, will develop and implement counterterrorism strategies, policies, operations, and programs. It will lead in supporting U.S. counterterrorism diplomacy and seek to strengthen homeland security, counter violent extremism, and build the capacity of partner nations to deal effectively with terrorism.
The Bureau
The Bureau of Counterterrorism will implement its mission by:
- Developing and implementing counterterrorism strategies, policies, and operations. The U.S. government has no greater responsibility than to protect the American people. The Bureau of Counterterrorism will play an integral role in meeting this obligation by leading the Department’s engagement to develop and implement counterterrorism strategies, policies, and operations to disrupt and defeat the networks that support terrorism. The Bureau will work to safeguard American security interests while promoting our values, including our support for human rights, democracy, and the rule of law.
- Strengthening counterterrorism diplomacy. Strengthening existing partnerships and building new relationships is a cornerstone of U.S. counterterrorism policy. The Bureau of Counterterrorism will engage with bilateral partners, regional organizations, and the United Nations to broaden and deepen counterterrorism cooperation. In one of many initiatives, the Bureau will lead U.S. government efforts on behalf of the State Department to support the Global Counterterrorism Forum, a new multilateral initiative focused on setting the international counterterrorism agenda for the 21st century.
- Strengthening homeland security. Securing the homeland from external terrorist threats is central to U.S. foreign policy. The Bureau of Counterterrorism will be the principal State Department link with the Department of Homeland Security (DHS) on counterterrorism strategy and operations. The Bureau will work in partnership with DHS, as well as other agencies and bureaus, to strengthen international cooperation on a wide range of homeland security issues including transportation security, the interdiction of terrorist travel, and critical infrastructure protection.
- Countering violent extremism. To defeat terrorists, we must undermine their ability to recruit. The Bureau of Counterterrorism will focus the State Department in U.S. government efforts to counter violent extremism, thereby reducing radicalization and mobilization abroad. The Bureau will work to delegitimize the violent extremist narrative, to develop positive alternatives for populations vulnerable to recruitment, and to build partner government and civil society capacity to counter violent extremism themselves.
- Building the capacity of foreign partners. The security of the United States depends on the strength of our partners and allies abroad. With capable partners who are able to manage the threats within their borders and regions, the likelihood of U.S. forces being called into action is greatly reduced. The Bureau of Counterterrorism will work with other bureau and agency partners in supporting U.S. government work to build international partner counterterrorism capacity in the civilian sector and will contribute to efforts in the military and defense sectors.
The Future
Protecting the United States, the American people and our interests abroad will remain a challenge in the 21st Century. New terrorist threats will require innovative strategies, creative diplomacy, and stronger partnerships. By establishing the Bureau of Counterterrorism, the Department of State will strengthen its efforts to meet this challenge.
CONFIDENTIAL – U.S. State Department Creates Bureau of Counterterrorism 5 Jan 2012 | No Comment DHS Expands Future Attribute Screening to Study Behavioral Impact of Passive Imagery 4 Jan 2012 | No Comment New York Police Circulating Mysterious Government Guide to Criminal Tactics of “Protest Extremists” 2 Jan 2012 | 5 Comments (U//FOUO/LES) Maryland Fusion Center Criminal Use of Police Scanner Apps and RadioReference.com

(U//FOUO//LES) During several recent contacts with criminal gang members, an identified Maryland law enforcement agency has heard their radio transmissions broadcast over a suspect’s smartphone. In one incident, officers pursuing a suspect on foot overheard the suspect listening to the pursuing officers’ radio transmission over a smartphone. The radio broadcasts of the agency’s primary secure law enforcement channel had an approximate delay of three seconds on the suspect’s smartphone.
(U//FOUO//LES) Further investigation revealed that the general public, as well as criminal gang members and associates, are utilizing the website http://www.radioreference.com to listen to law enforcement secure channels streaming via the Internet. Registration and access to the site is free, with advanced features available to premium subscribers. A customer is able to search radio frequencies throughout the country by state, metro area, city and/or zip code. The website advertises a search for trunked frequencies as well. The frequencies are obtained over the Internet and any cell phone that has web access can listen in.
(U) As of 2010, there were at least 20 scanner applications (apps) on the market for download to smartphones. Some examples are iScanner and 5-0 Radio Police Scanner for iPhones and Police Stream for Android phones. The 5-0 Radio Police Scanner app advertises access to police, fire, aircraft, railroad, and marine frequencies. These apps can be downloaded to the smartphone and at a touch of the screen will allow the user to listen to emergency frequencies via their mobile device.
(U//FOUO//LES) This situation presents a concern for officer safety. A criminal who is able to listen to law enforcement radio transmissions in near-real time could use the information to further their criminal activity, hide criminal activity, assist in a get-away, gain investigative information or set up an ambush position. Law enforcement needs to maintain a heightened awareness that criminals may exploit emerging technology in order to gain an upper-hand during the planning, execution, and escape phases of their crimes. Law enforcement is asked to contact the Maryland Coordination and Analysis Center (MCAC), Gang Analysis and Training Unit (GATU) Analyst Kelly Sparwasser at ksparwasser@mdsp.org with any further information regarding the criminal use of these applications.
DOWNLOAD ORIGINAL DOCUMENT HERE
RE-“GoMoPa 4 KIDS” – “Anal”ogy – New Jersey Doctor Pleads Guilty to Receipt and Distribution of Child Pornography
NEWARK, NJ—Rocco Martino, 43, of South Orange, N.J., admitted today to making available images and videos of pre-pubescent children being sexually abused—sometimes violently—to others over the Internet, U.S. Attorney Fishman announced.
Martino, a doctor who recently practiced internal and sports medicine in Berkeley Heights, N.J., entered his guilty plea to an information charging him with one count of receipt and distribution of child pornography before U.S. District Judge Williams H. Walls in Newark federal court.
According to documents filed in this case and statements made during Martino’s guilty plea proceeding:
Martino admitted that between November and December 2010, he downloaded and posted videos and images of child pornography via peer-to-peer file-sharing software—through which others had access to the material on a shared drive. Martino admitted that his offerings included images of numerous children younger than 12 and depictions of sadistic and violent conduct. The images downloaded by federal investigators and found on Martino’s computer included pictures of very young children being restrained and sexually abused—including a bound and gagged toddler.
As part of his guilty plea, Martino agreed to forfeit the computer and computer accessories which he used to commit the offense. He will also be required to register as a sex offender.
The receipt and distribution of child pornography carries a mandatory minimum penalty of five years in prison, and a maximum potential penalty of 20 years in prison and a $250,000 fine. Sentencing is currently scheduled for April 10, 2012.
U.S. Attorney Fishman credited special agents of the FBI Newark Division’s Cyber Crime Task Force, under the direction of Special Agent in Charge Michael B. Ward; detectives of the Essex County Prosecutor’s Office Cyber Crimes Unit, under the direction of Acting Prosecutor Carolyn A. Murray; and the South Orange Police Department, under the direction of Chief James M. Chelel, with the investigation leading to the guilty plea.
The government is represented by Assistant U.S. Attorney José R. Almonte of the U.S. Attorney’s Office General Crimes Unit in Newark.
Defense counsel: Lawrence S. Lustberg Esq., Newark
NEO-KGB – Ukraine: Timoschenko jetzt im Gefängnis in Charkiv – “Bestialisch”
http://de.euronews.net/ Julia Timoschenko ist in den Osten der Ukraine verlegt worden. Trotz internationaler und nationaler Proteste soll die ehemalige Regierungschefin in Kharkiv ihre siebenjährige Haftstrafe absitzen.
Anhänger der ehemaligen Regierungschefin traten gegen die Gefängnistür in Kiew, wo Timoschenko seit August einsaß. Der Vize-Chef ihrer Vaterlandspartei “Batkiwschtschina” war Zeuge.
NEWS – New York Police Circulating Mysterious Government Guide to Criminal Tactics of “Protest Extremists”

An image from the first page of a manual on criminal tactics of “protest extremists” shows a legal, First Amendment-protected event occurring on the National Mall. The guide then lists a number of issues and beliefs such as “environment” and “peace” which can provide an agenda for protest actions.
An email contained in the latest AntiSec release indicates that law enforcement agencies in New York have been circulating an out-of-date manual that was previously criticized by the ACLU to instruct officers about issues related to Occupy protests. The brief email from December 5, 2011 was circulated to a number of law enforcement agencies affiliated with the Mid Hudson Chiefs of Police Association and contains several document attachments that describe tactics used by protesters, including basic guides on how to conduct your own “Occupy” protest. One of the documents is a police manual titled “Civil Disturbance and Criminal Tactics of Protest Extremists” that describes “illegal” tactics used by protesters and so-called “protest extremists”. The document, which was last revised in 2003, does not list its originating agency or author and is marked with a number of unusual protective markings indicating that it is not intended for public release.
The existence of the document was first discussed in a 2003 article from the Colorado Springs Independent which quoted a representative of the local FBI Joint Terrorism Task Force discussing the manual:
In a written statement recently obtained by the Colorado ACLU, an agent of the Denver Joint Terrorism Task Force describes how he has used the manual to instruct local law-enforcement officers.”Beginning in 2001, I began using a training manual created by the U.S. government, which identifies civil disturbance and criminal protest tactics and instructs on how to respond to those tactics,” states the agent, Tom Fisher. The manual, he states, is “part of a program offered by the United States government on criminal protest tactics.”
According to the statement, the training manual is “law-enforcement sensitive” and not to be released to the public.
Fisher also states that he has been teaching the Denver Police Department about “terrorist issues,” including “criminal tactics of protest extremists.”
The manual contained in the latest AntiSec release is further confirmed to be this document by a spokesman for the Colorado Springs Police Department who quotes from the document and refers to it by name:
A spokesman for the Colorado Springs Police Department said he’s not sure whether the department received the Oct. 15 FBI memo. “We have no record of receiving that intelligence bulletin, although that’s not to say we didn’t,” said the spokesman, Lt. Skip Arms.Springs police have not received training from Fisher, though they do use a manual titled Civil Disturbance and Criminal Tactics of Protest Extremists, Arms said.
“It’s something that our tactical people would look at and compare to their tactics,” he said.
Arms said he doesn’t know where the department obtained the manual or who authored it. The introduction states that it is “the result of an extensive interagency collaboration to address a surge of protest activity worldwide,” but nothing in it indicates specifically that it was developed by the U.S. government, he said.
Lt. Arms quotes from the introduction which states “‘Civil Disturbance and Criminal Tactics of Protest Extremists’, was prepared in response to the increase of protest activity worldwide and the escalation of violence and property destruction that has occurred in the past several years. Information regarding the unlawful operational and tactical activities was collected and interpreted by multiple agencies. The information presented is for law enforcement and public safety officials to assist in effectively managing civil disturbances and large-scale protests”.
Policing First Amendment-Protected Events
Whether you are sympathetic to the complaints of Occupy protesters or not, the nationwide and now global movement to occupy civic spaces has had a much more tangible and immediate impact: demonstrating the increasing militaristic tactics of police around the country to suppress constitutionally-protected speech and dissent. Though law enforcement is presented with a unique set of challenges in response to the Occupy protests, which include balancing reasonable protection of public safety while ensuring that citizens’ right to express themselves is honored, the tactics of law enforcement agencies around the country have helped to demonstrate the repressive nature of modern policing in the United States.
Throughout the country, predominantly peaceful gatherings in public spaces have been met with midnight raids conducted by black-clad phalanxes of often unidentifiable police, rousting them from their tents, tarps and other minimalistic structures to either arrest them or forcibly remove them from the space. These raids have been coordinated at the national level, resulting in thousands of arrests that are sometimes without legal justification. In many of these law enforcement actions, videos have later emerged showing police violating a number of core principles of policing First Amendment-protected events, including firing less-lethal munitions without provocation, indiscriminately beating protesters, storming protest encampments with live ammunition, ignoring or confiscating press credentials and arresting credentialed journalists. Many of the actions taken by police are in violation of the Department of Justice guidelines for policing First Amendment-protected events and are often in contravention of the police department’s own internal policies.
According to the recently released Department of Justice guidelines for law enforcement responses to First Amendment-protected events, the role of law enforcement officers is to “ensure the safety of the general public” while protecting the “rights of persons practicing their First Amendment right to assemble peacefully.” The manual states that police are not allowed to collect information on the event, its organizers or its beliefs without a clear “criminal predicate” necessitating a public safety response. Though the boundaries of criminal behavior become murky when First Amendment-protected activities are involved, the guidelines make it clear that “membership or participation in a group or organization that has engaged in illegal activities in the past with respect to protests or demonstrations does not alone establish reasonable, articulable suspicion of criminal activity with respect to each of its members.” Acts that are considered to be part of “symbolic speech” such as flag burning are considered to be protected under the First Amendment. A New York judge’s November decision to uphold eviction of Occupy Wall Street protesters from Zuccotti Park mentioned that the protests were successful “largely because of the unorthodox tactic of occupying the subject public space on a 24-hour basis, and constructing an encampment there” admitting that the action of non-violently occupying a public space was, for the protesters, a form expression that would arguably be protected under the First Amendment.
The Department of Justice guidelines state that “persons or groups communicating with each other or members of the public in any form in pursuit of social or political causes” do not alone provide justification for police investigation. The rights of individuals and groups under the First Amendment may only be limited when the event in question interferes with other people’s constitutional rights or creates a hazard for public health or safety. However, even in cases where public health and safety is an issue, police are required to work with protesters to mitigate the risks to the public without suppressing their legitimate right to protest. The 2003 guide to “Criminal Tactics of Protest Extremists” violates many of the rules set forth in the Department of Justice’s guidelines by repeatedly blurring the lines between criminal activity, such as property destruction, and lawful forms of protected speech, such as banner hanging. The 2003 guide also discusses the ideological beliefs of protesters and how they provide an agenda for protest actions, something expressly prohibited by the Constitution and the Department of Justice guidelines. Basic descriptions of protester tactics in the 2003 guide, including communications patterns and organizing activities, are also in violation of Federal guidelines as they concern actions that are not only inherently lawful, but are legally protected under the First Amendment.
COOPERATION – DHS Partners With NHL to Promote Suspicious Activity Reporting
MEDIA – STASI stripped gold from victims of NAZIS
THE Stasi, the East German secret police, repeated one of the crimes of the Nazis when they stripped gold from the teeth of Jews found in a mass grave, their own files show.
The story of how the former East German regime apparently sought to profit from the discovery of 577 Jewish skeletons in 1971 has been uncovered by Andreas Weigelt, a historian. It is believed to be the first evidence of such action by the Stasi.
Mr Weigelt, who runs an exhibition at Lieberose concentration camp, south-east of Berlin, where the victims were held before their deaths, said yesterday: “I stumbled over a few pages that rather secretively documented how this gold had been collected. I was aghast.”
The documents, discovered in the secret police’s archives, disclose that the Stasi dug around in the grave, south of Berlin, looking for gold crowns and gold teeth among the skeletons.
Some documents suggest that the Stasi wanted the teeth and gold to help to identify the victims and explain how they died. This explanation has been ridiculed by experts, not least because the files make clear that more than two pounds of gold ended up in the Stasi’s finance department.
The remains in the grave were of some of a group of 1,200 Jews killed by drunken SS men and other Nazi guards between Feb 2 and Feb 4, 1945, as they set out on a march from Lieberose to the Sachsenhausen camp north of Berlin.
“Some 1,600 were sent on the march,” Mr Weigelt said, “and 1,200 of them were eliminated by drunken SS men, guards and commanders of the camp. The corpses were buried in a great hurry.”
After the grave was discovered in the village of Staakow, near Lieberose, the East German authorities told residents that the bodies were those of anti-Nazi resistance fighters and not Jews.
But the Stasi documents show that the authorities knew that most of the dead were Jews.
The claim was typical of the propaganda issued by a regime that sought to portray East Germans in the Second World War as brave soldiers of resistance against the Nazi regime.
EDITORIAL – The STASI and the NEO-NAZI
Dear Readers,
the Stasi, the East German secret police, supported and sponsored neo-Nazi groups in the West throughout the 1970s and 1980s.
The prime aim of the Stasi, according to documents found in the BStU archives, which guard the communist secret police files, was to destabilise West Germany.
In cities with large concentrations of guest workers – mainly Turkish and Italian immigrants – thousands of leaflets were circulated bearing the headline: “Germans defend yourselves!” Using phrases reminiscent of the Hitler era, the leaflets urged West Germans to drive foreigners out of their country. The leaflets, crafted by the Stasi, bore the signature German People’s Union – DVU – which is a real, far-right party with headquarters in Munich.
The subversion began in 1961 when Israel started its trial of Adolf Eichmann, the Nazi war criminal responsible for the deportation of hundreds of thousands of Jews. The East German police dreamt up an operation called “Forget Me Not,” which was intended to stir neo-Nazi violence in West Germany and make plain to the world the links between new and old Nazis.
Chain letters, composed in East Berlin, were circulated in West Germany: “The Eichmann trial is an attempt by the Jewish underworld to taint our honour. We have taken up the struggle again. Our comrades are already launching a counter-attack against the Jews.”
The Stasi followed up this campaign with hate letters aimed at German Jews: “Obviously you Jews have not understood that you must disappear from West Germany.” The East German establishment considered these campaigns to be a success.
Anxious West Germans started to write letters to the East German press. The West German Foreign Minister at the time, Gerhard Schroder, was even forced to make a statement denying that Bonn was lurching towards National Socialism.
By the 1970s the campaign was under the supervision of the spymaster Markus Wolf. It was decided – according to an anonymous Stasi major quoted by Welt am Sonntag – to take an active part in helping the paramilitary Hoffman Combat Sport Group, essentially an organisation of armed neo-Nazis.
The East Germans encouraged members of the group to go for training with the Palestine Liberation Organisation in Lebanon. In 1982 one of the group killed a Jewish publisher, Schlomo Lewin, in the West German town of Erlangen.
“In these groups we had a particularly dense network of informers,” the Stasi major said. “They ensured that the activities of the far Right were always pointed in the correct direction and never against East Germany.”
Above all, the Stasi operations allowed East Germany to present itself as an “anti-fascist state,” morally superior to West Germany.
The power was always with the Stasi and the henchmen were the Nazis that truly is happening today.
Sincerely yours
Bernd Pulch, Magister Artium
The Mahler Affair – Leftist Terrorist Turned Neo-Nazi Says Was Stasi Informant Too – by “DER SPIEGEL”, Germany
TOP-SECRET-Debbie Cook Scientology $1 Billion Cash Reserve Email
The following is the text of an email sent on January 1, 2012 by a senior member of Scientology’s Sea Org named Debbie Cook. The email was published on the website of the Village Voice, then was removed at the request of Ms. Cook. It has since been reposted elsewhere. The email discusses Cook’s problems with the direction that the Church of Scientology has recently taken, including what she perceives an obsessive emphasis on fundraising and a more than $1 billion dollar unused cash reserve. Cook confirmed the email’s authenticity via Facebook.
Dear Friend,
I am emailing you as a friend and fellow Scientologist. As we enter a new year, it is hoped that 2012 can be a year of great dissemination and a year of real progress up The Bridge for all Scientologists.
Although I am not in the Sea Org right now, I served in the Sea Org at Flag for 29 years. 17 of those years were as Captain FSO. I am a trained auditorand C/S as well as an OEC, FEBC and DSEC.
I am completely dedicated to the technology of Dianetics and Scientology and the works of LRH. I have seen some of the most stunning and miraculousresults in the application of LRH technology and I absolutely know it is worth fighting to keep it pure and unadulterated.
My husband and I are in good standing and we are not connected with anyone who is not in good standing. We have steadfastly refused to speak to anymedia, even though many have contacted us.
But I do have some very serious concerns about out-KSW that I see permeating the Scientology religion.
I have the utmost respect for the thousands of dedicated Scientologists and Sea Org members. Together, we have come through everything this world couldthrow at us and have some real impingement on the world around us. I am proud of our accomplishments and I know you are too.
However there is no question that this new age of continuous fundraising is not our finest moment.
LRH says in HCO PL 9 Jan 51, An Essay on Management, “drop no curtains between the organization and the public about anything.”
-LRH
Based on this policy I am communicating to you about some situations that we need to do something about within our religion, within our group.
Actions that are either not covered in policy or directly violate LRH policy and tech include the extreme over-regging and fund-raising activities that have become so much a part of nearly every Sea Org org and Class V org as well as every “OT Committee”. This fundraising is not covered anywhere in LRH policy.
Hardworking Sea Org members and the dedicated staff of orgs around the world aren’t choosing to do these actions. Nor are the OTs. I am sure they wouldbe more than happy if they could just get on with direct dissemination of Scientology as they have done for so many years.
But the truth is that this is being driven from the very highest echelons within the Scientology structure and clearly there is a lot of pressure tomake targets that are being set.
The IAS: The IAS was created unbeknownst to LRH in 1984 by Marc Yager and David Miscavige. This was supposed to be based on LRH policies on the subject of membership and the HASI, however the IAS is nothing like the membership system described by LRH which only has two memberships and is covered in HCO PL 22 March 1965 “Current Promotion and Org Program Summary,Membership Rundown” and states:
“There are two memberships…”- LRH
LRH lists there the INTERNATIONAL ANNUAL MEMBERSHIP and gives its cost at 10 pounds sterling or $30 US. He also lists a LIFETIME MEMBERSHIP which ispriced at $75 US. There are no other memberships or statuses approved or known to LRH.
Furthermore, membership monies are supposed to go directly to the org where the membership is signed up, and the money used for dissemination by thatorg, in that area. This is covered in HCOPL 1 Sept 1965R Membership Policies.
“It all goes into the HCO Book Account in the area where the membership isbrought and is not part of the organization’s weekly gross income. Membership monies go to dissemination”.- LRH
Currently membership monies are held as Int reserves and have grown to well in excess of a billion dollars. Only a tiny fraction has ever been spent, in violation of the policy above. Only the interest earned from the holdings have been used very sparingly to fund projects through grants. In fact many of the activities you see at IAS events are not actually funded by the IAS,but rather by the Scientologists involved.
Think about it, how many ads disseminating Scientology, Dianetics or any Scn affiliated programs have you seen on TV? Heard on the radio? Seen innewspapers? I haven’t seen one in the 4 years I have lived in San Antonio, Texas, the 7th largest city in the US. How many have you seen?
Donating anything more than a lifetime membership to the IAS is not based on LRH policy. The article “What Your Donations Buy” (The Auditor, The Monthly Journal of Scientology No. 51, 1970) is clearly talking about how the church uses your donations for Dianetics and Scientology services. Next time you are asked to donate outside of services, realize that you are engaged in fundraising and ask to see something in writing from L. Ron Hubbard that this is something he expects from you as a Scientologist.
New Org Buildings: LRH also never directed the purchase of opulent buildingsor the posh renovations or furnishings for every org.
In fact, if you read HCO PL 12 March 75 Issue II, “The Ideal Org”, which is what this program has been called, and nowhere in it will you find 20 million dollar buildings or even any reference to the poshness of org premises at all as part of LRH’s description of an “Ideal Org”. Instead, an Ideal Org was one that delivered and moved people up The Bridge – somethingthat is not part of this “Ideal Org” program.
LRH says in the PL that an Ideal Org:
“would be clean and attractive enough not to repel its public” – LRH.
This is all it says about the state of the building.
As a result of this off-policy alteration of the Ideal Org PL, we have the majority of top OTs, now deemed “OT Ambassadors”, heavily engaged in fund-raising activities that include “bingo”, “pirate dinners”, “knitting classes”, “hay rides”, and many other activities strictly revolving around raising funds for the required multi-millions of dollars to fund their “Ideal Org”. As part of this, people around every org are now asked todonate to their local “Ideal Org” instead of their own services or their own Bridge.
LRH says in HCO PL Org Ethics and Tech:
“GET RID OF DISTRACTIONS FROM SCIENTOLOGY in your org. Baby-sitting or raffle tickets and such nonsense.”-LRH
Yet these distractions are rampant as they are being used as fund-raisers to get money for the huge quotas being issued to fund the “Ideal Org”.
“If the org slumps… don’t engage in ‘fund-raising’ or ‘selling postcards’ or borrowing money. Just make more income with Scientology.It’s a sign of very poor management to seek extraordinary solutions for finance outside Scientology. It has always failed.”
“For orgs as for pcs, ‘Solve It With Scientology’.
“Every time I myself have sought to solve financial or personnel in other ways than Scientology I have lost out. So I can tell you from experiencethat org solvency lies in more Scientology, not patented combs or fund-raising barbeques.”
HCO PL 24 February 1964, Issue II, Org Programming, (OEC Vol. 7, p. 930)
The point is that Scientologists and OT’s need to be training, auditing and disseminating to raw public- not regging each other or holding internalfundraisers.
Out Tech: Over the last few years we have seen literally hundreds and hundreds of people who were validated as clear using the CCRD as developed by LRH now being told they are not Clear. This included hundreds of OTs who were then put onto NED as a “handling”. LRH clearly forbid any Dianetics to be run on OTs in HCOB “Dianetics Forbidden on OTs”. This is out tech. This entire technical “handling” was directed personally by COB RTC and was done on thousands of OTs. But it was based not on an LRH HCO Bulletin, but rather based on a single C/S instruction where LRH C/Sed one pre-OT who had not achieved the state of clear but was mid OT III and not making it. LRH directed a solo handling that the pre-OT was to do to get himself to achieve the state of Clear. This LRH C/S taken out of context was then used to implement a technical handling that was in direct violation of an LRH HCOB.
This and other “technical handlings” done on Solo NOTs auditors created great expense and hardship on Solo NOTs auditors around the world as they were made to do these handlings to continue on the level.
Then there are the “fast grades at Flag” that no other org has. How can it be that Flag has been delivering grades differently to the rest of the world for the last 3 years? Whatever the problem is, the fact is that having “fast Grades” at Flag creates a hidden data line and is a HIGH CRIME and the subject of an entire policy letter called HCOPL “TECH DEGRADES” which LRH has placed at the start of every Scientology course.
More recently the fad seems to be that nearly everyone needs to “re-do their Purif and do a long objectives program”, including many OTs mid Solo NOTs.
There is nothing wrong with doing objectives, but it is a clear violation of HCOB ‘MIXING RUNDOWNS AND REPAIRS” to have a person mid a rundown or OTlevel be taken off it and placed on an objectives program.
Solo NOTs auditors are also being made to get their objectives from a Class IX auditor at great expense as they are not being allowed to co-audit.
Flag has made many millions of dollars on the above listed out tech handlings because OTs mid Solo NOTs are forced to get these out-tech actionsto be able to get back onto and stay on the level and complete it. Not to mention the spiritual effects of the out tech that this has on each OT.
I myself was subject to these out tech “handlings”, including extensive FPRD mid Solo NOTs. It took its toll in many ways, including physical situationsI am still dealing with today. So I have some reality of the hardship caused.
LRH Command Structure: LRH left us with a complex and balanced command structure, with our orgs led by the Office of ED International. This office was considered so important that LRH created a special management group called the Watch Dog Committee whose only purpose was to see that this office and the other needed layers of management existed. LRH ED 339R speaks of this extensively as the protection for our Church. But these people are missing. And not just some. As of just a few years ago there were no members of the office of ED Int on post, not to mention top execs throughout the International Management structure.
You may have also wondered… where is Heber, the President of the Church? What about Ray Mitthoff, Senior C/S International, the one that LRH personally turned over the upper OT Levels to? How about Norman Starkey, LRH’s Trustee? What happened to Guillaume – Executive Director International? And Marc Yeager, the WDC Chairman? What happened to the other International Management executives that you have seen at events over the
years?
The truth is that I spent weeks working in the empty International Management building at Int. Empty because everyone had been removed from post. When I first went up lines I was briefed extensively by David Miscavige about how bad all of them were and how they had done many things that were all very discreditable. This seemed to “explain” the fact that the entirety of the Watchdog Committee no longer existed. The entirety of the Executive Strata, which consisted of ED International and 11 other top International executives that were the top executives in their particular fields, no longer existed. That the Commodore’s Messenger Org International no longer existed. All of these key command structures of Scientology International, put there by LRH, had been removed.
There were hundreds and hundreds of unanswered letters and requests for help from org staff, written based on LRH ED 339R where LRH says that staff can write to these top executives in the Exec Strata for help. But this is not possible if all these execs have been removed and no one is there to help them or to get evaluations and programming done to expand Scientology.
Well, after that I got to spend some quality time with Heber, Ray Mithoff, Norman Starkey, Guillaume, as well as the entirety of International Management at the time, who were all off post and doing very long and harsh ethics programs. These have gone on for years and to the only result of that they are still off post. There is no denying that these top executives have all gradually disappeared from the scene. You don’t see them at the big events anymore or on the ship at Maiden Voyage.
David Miscavige has now become the “leader” of the Scientology religion. Yet what LRH left behind was a huge structure to properly manage all aspects of the Scientology religion. He put a complete and brilliant organizational structure there, not one individual. There never was supposed to be a “leader” other than LRH himself as the goal maker for our group.
There is a situation here and even if you have not been to the International Management Base you should be able to see that over regging and frequent tech changes are not OK and you have a responsibility to do something to Keep Scientology Working. You should be able to find and read the references on membership in OEC Volume 6. Find and read the HCO PL entitled “The Ideal Org” (Data Series 40). Find and read the references on org buildings, including HCO PL 24 Aug 65 II, Cleanliness of Quarters and Staff, Improve our Image. Also, HCO PL 17 June 69, The Org Image.
If you don’t want to make waves or put yourself in danger of being taken off the level or denied eligibility, then there are some simple things you can do. First and foremost, withdraw your support from off policy actions. Stop donating to anything other than your own services and actual Bridge progress. Simply demand to see an LRH reference that says you are required to make other such donations. No one will be able to produce any references because there aren’t any.
Stop supporting any of the activities that are being done to forward off-policy fund-raising in your area.
LRH says what he expects of a Scientologist – that is what he expects you to do. In fact he put it in HCOB 10 June 1960 Issue I, Keeping ScientologyWorking Series 33, WHAT WE EXPECT OF A SCIENTOLOGIST. Read it and follow it.
The other thing you can do is to send this email to as many others as youcan, even if you do it anonymously.
Please keep this email among us, the Scientologists. The media have no place in this. You may wonder why I have not written a KR and gone about my business. The answer is, I have. But there is no longer anyone to send that KR to.
But you can and should write reports and bring off-policy to the attention of local org executives and local Sea org members.
We are a strong and powerful group and we can affect a change. We have weathered many storms. I am sorry that I am the one telling you, but a newstorm is upon us. It’s waves are already in the media and the world around us.
The truth is that as a Scientologist you are more able, more perceptive and have a higher integrity. Scientology is supposed to allow you to “think for yourself” and never compromise your own integrity. And most certainly LRH held every Scientologist responsible to KEEP SCIENTOLOGY WORKING.
I am not trying to do anything other than affect a change in serious off policy actions occurring. My husband and I have most of our family and many many good friends who are Scientologists. I have not been real interested in sticking my neck out like this.
However, I also know that I dedicated my entire adult life to supporting LRH and the application of LRH technology and if I ever had to look LRH in theeye I wouldn’t be able to say I did everything I could to Keep Scientology Working if I didn’t do something about it now.
We all have a stake in this. It is simply not possible to read the LRH references and not see the alterations and violations that are currentlyoccurring.
You have a very simple obligation to LRH. Don’t participate in anything off policy, and let others know they should not either. If every person who reads this email does nothing more than step back from off-policy actions we would have changed direction. If we took all that energy and directed it into auditing, training and raw public dissemination, we would be winning.
And that is what I wish for you and all of us as we ring in this new year.
ARC,
Debbie Cook
CONFIDENTIAL – (U//FOUO) U.S. Army Civilian Casualty (CIV/CAS) Collection and Analysis Team (CAAT) Report

This report is an executive summary of interviews conducted by CALL in support of the JCOA comprehensive Study Plan covering CIVCAS. Topics included CIVCAS incidents, pre-deployment training, planning, mitigation efforts and best practices from key leaders with recent operational experience in Afghanistan and Iraq.
…
All units reported taking CIVCAS mitigation into account, there was mixed between those units with a formal SOP and those who applied the common sense standard to CIVCAS planning. All units had a standard for who conducted BDA and for most it was either the unit who caused the incident or the battle-space owning unit. Some units reported having the QRF with a dedicated mission to providing additional post CIVCAS response to any incident as required.
Many units found great benefit from inclusion of additional staff members (DOC, Physicians Assistant, SJA and Chaplain) into the planning process. Also, the incorporation of enablers (HTTs, CA, and PSYOPS) has also paid off during planning.
Some units found great benefit in conducting joint rehearsals and OPORDs along side with their ANSF counterparts. This not only helped in the training and mentoring of the ANSF, it also minimized the chances of an occurrence and helped clarify responsibilities and battle drill once an incident occurred. The rehearsals have shown to be more effective than the OPORDs because many times the ANSF may not grasp the full operation until they can walk through and deconflict along with the CF unit.
Another pre-operation method that has shown benefit has been to get a written “buy in” from the Provincial government or local village elders before an operation takes place. This shows them the respect that they as local leaders deserve and additionally provides credibility to the operation should a CIVCAS incident occur.
When it came to fires deconfliction, most all units had a plan for conduct of indirect fires. For counter battery units reported using either Falconview or PSSOF for CDE deconfliction. Units who reported firing counter IDF did conduct post fire BDA at the location.
Coalition Forces Risk Management: Most leaders indicated that they understood that any increased risk to CF was worth the effort avoid CIVCAS. Many leaders also reported feeling safer due to CIVCAS mitigation measures. Most felt that the ISAF driving policy and allowing local traffic to blend in did not significantly increase risk to their convoys, and many felt that it actually made them safer understanding that the enemy has many of the same CIVCAS concerns as we do and will avoid targeting convoys where civilians may be injured.
Enemy response: Some units did report that they did observe the enemy adapt to their mitigation measures. Sometimes insurgents would fire on CF units from areas where civilians where at hoping for an “over-reaction” to the situation and for CF to cause casualties. Other times the enemy would flee into a village or qalat. Many units found the best way to deal with this situation was to establish a soft cordon to contain the area and allow the ANSF to enter and conduct the searches. Other enemy responses where focused on negative IO effects following a CIVCAS. Some reports indicated that the enemy would quickly remove weapons from fighters in order to give the appearance that they were nothing more than a civilian. Others would send in “agitators” to confront Coalition Forces and attempt to enflame the situation and the local population. Additionally, one unit reported that they enemy within their AO began to understand their pattern for conducting a BDA within two hours of conducting counter IDF fires and used this to establish ambushes for CF. This was compounded by the restrictive terrain often found in the areas. This was mitigated by allowing commanders flexibility on how and when to conduct the BDA.
Local Impacts on CIVCAS: While it is commonly understood that all CIVCAS has a negative impact on the local population, there did not seem to be a majority consensus of which type had the most negative impact. Many leaders felt that it included women and children casualties. Others indicated that night raids seemed to have more effect as the local population feels a sense of insecurity when they cannot feel safe in their own homes at night. Some believed that incidents involving holy sites or texts (mosques, Quran) had a larger than normal impact on the population. This indicated to them that the CF has no regard for their culture, religion or way of life. Many units indicated that external units (SOF, transient convoys) had a greater impact than battle-space owning units, because they did not have a complete understanding of the area and local population. This can lead to a sense of distrust among the locals who may wonder how they can trust the CF and ANSF if they cannot even control who operates within their areas.
Post Incident Response: Units typically had a good post response plan to CIVCAS. Most units reported that they worked well with the ANSF and that they had no issue with them taking the lead. If the medical situation dictated they would evacuate the wounded to US facilities for treatment. But if not required some felt it better to keep them with the local facilities as it would be easier for their families to know where they are at and visit. Treatment of the dead was also an important issue with the units. If they are MEDEVAC’d out and die in US treatment it is essential to return them to their families in a prompt manner to facilitate burial. Many units reported the best way to accomplish this was through the ANSF or a local elder. Respect for the dead (civilian or insurgent) was an important theme through many of the units. Placing them into body bags and allowing their faces to be visible so that family may identify them was common.
When it came down to techniques of mitigation there was no one preferred method (KLE, solatia, etc…), but understanding that all are essential in conjunction with a timely and effective IO campaign. Most often a KLE or informal Shura would occur immediately following an incident with the local leaders. The preferred option was always a senior leader who has knowledge and respect for the local population. In many cases it was the battalion commander or other battalion senior leader, in other cases it was a company commander who had the respect of the locals. And the truth is always the best course of action (even if the incident was negligent). This shows them that CF and ANSF can be trusted. But it must always be someone with a level of authority over the situation. Additionally, another common theme was immediate notification and involvement of the provincial governor and other local leaders. They can often calm the situation and may be the best to counter any enemy propaganda. Timeliness was always an issue and sometimes with the distances and restrictive terrain getting senior leaders or government officials to the site was difficult to accomplish. And dynamically tasking rotary wing assets was always difficult to do with minimal lead time. When available, rotary wing assets can be of great assistance to mitigating CIVCAS incidents in a timely manner. Additionally, the timeliness of solatia payments was also a concern. Many leaders would have preferred to see additional pay agents available for rapid payments to the families of the victims. However, it is important to note that investigation must always be conducted in order to prevent false claims for future operations. Otherwise it can turn into a perception of “free money” anytime an operation occurs.
When it came to conducting the investigations units reported the benefit of always conducting a joint investigation along with the ANSF. The investigation should be detailed and complete. Units should always have cameras available for photogrpahic evidence. Also, showing dead fighters with their weapons (especially if larger than an AK-47) is essential to prove that they were in fact a fighter and not an innocent civilian. Often, the local population will not believe that a dead fighter was in fact an insurgent unless shown proof. Other items that may need to be declassified and presented to the local leaders would be any gun camera footage and any ISR coverage that may show the incident.
Information Operations: Most units reported observing that the insurgents had a very rapid capability to influence the population negatively towards a suspected incident. Following an incident Coalition and ANSF forces need to begin an IO campaign immediately. This can range from KLEs, radio and television broadcasts, apologies (if warranted) and leader engagements. Most units reported that involving the Provincial Governor and local elders immediately was highly beneficial. If available, getting the Governor or radio or television (where available) was a very effective way to get the message out. Other methods included the use of the Radio In A Box (RIAB). But the IO campaign must be proactive and begin immediately. Many commanders felt that they were falling behind the insurgents in the battle of getting the truth out, and that it is always easier to inform and gain trust as opposed to having to counter lies and then get the truth out.
SECRET – USAID Islamic Republic of Afghanistan Provincial Media Landscape and Audience Survey Reports


In 2004-2005, the United States Agency for International Development’s (USAID) Office of Transition Initiatives commissioned Altai Consulting to conduct the first comprehensive media evaluation of the Islamic Republic of Afghanistan, looking at the impact of the Afghan media on opinions and behaviors three years after the beginning of the country’s reconstruction. The evaluation found, among other things: that Afghans were avid and sophisticated media users and that cultural barriers to media use were less significant than previously expected; that the radio played a predominant role throughout the country; and that media are instrumental in social progress and education.
However, since publication of that report, Afghanistan’s media sector has seen important changes. To inform future assistance from the international community to the Afghan media, it was deemed necessary to assess the current state of the Afghan media – by reflecting a full and accurate audience profile, to determine program preferences, to measure the impact of the Afghan media on local opinions and behaviors and to gauge Afghan expectations in terms of programming and messaging.
A large-scale research project was thus planned and conducted from March to August 2010. This research included a deep probe into the media sector and the public’s behaviors and expectations. The methodology used to achieved this included a combination of: literature review; direct observations; key informant interviews with most relevant actors involved in the media sector; 6,648 close-ended interviews in more than 900 towns and villages of 106 districts, covering all 34 provinces of the country; an audience survey on more than 1,500 individuals run daily for a week; about 200 qualitative, openended interviews; and 10 community case studies. Such an effort guarantees that results presented here are fairly representative of the Afghan population at large.
DOWNLOAD ORIGINAL DOCUMENT HERE
CONFIDENTIAL – (U//FOUO) NATO Training Mission Afghanistan (NTM-A) Afghan National Police (ANP) Status Update


From the NSA Document 1: NSCID 9, “Communications Intelligence,” March 10, 1950
National Security Council Intelligence Directives have provided the highest-level policy guidance for intelligence activities since they were first issued in 1947.
This document establishes and defines the responsibilities of the United States Communications Intelligence Board. The Board, according to the directive, is to provide “authoritative coordination of [the] Communications Intelligence activities of the Government and to advise the Director of Central Intelligence in those matters in the field of Communications Intelligence for which he is responsible.”
The particularly sensitive nature of communications intelligence (COMINT) activities was highlighted by paragraph 6, which noted that such activities should be treated “in all respects as being outside the framework of other or general intelligence activities.” Thus, regulations or directives pertaining to other intelligence activities were not applicable to COMINT activities.
DOWNLOAD ORIGINAL DOCUMENT HERE
TOP-SECRET – (U//FOUO) U.S. Marine Corps Intelligence Afghanistan Micro Mission Guide
TOP-SECRET – The National Security Agency Declassified
Internet wiretapping mixes “protected” and targeted messages,
Info Age requires rethinking 4th Amendment limits and policies,
National Security Agency told Bush administration
“Transition 2001” report released through FOIA,
Highlights collection of declassified NSA documents
Posted on Web by National Security Archive, GWU
National Security Archive Electronic Briefing Book No. 24
Edited by Jeffrey Richelson
Washington, D.C., March 11, 2005 – The largest U.S. spy agency warned the incoming Bush administration in its “Transition 2001” report that the Information Age required rethinking the policies and authorities that kept the National Security Agency in compliance with the Constitution’s 4th Amendment prohibition on “unreasonable searches and seizures” without warrant and “probable cause,” according to an updated briefing book of declassified NSA documents posted today on the World Wide Web.
Wiretapping the Internet inevitably picks up mail and messages by Americans that would be “protected” under legal interpretations of the NSA’s mandate in effect since the 1970s, according to the documents that were obtained through the Freedom of Information Act by Dr. Jeffrey Richelson, senior fellow of the National Security Archive at George Washington University.
The NSA told the Bush transition team that the “analog world of point-to-point communications carried along discrete, dedicated voice channels” is being replaced by communications that are “mostly digital, carry billions of bits of data, and contain voice, data and multimedia,” and therefore, “senior leadership must understand that today’s and tomorrow’s mission will demand a powerful, permanent presence on a global telecommunications network that will host the ‘protected’ communications of Americans as well as targeted communications of adversaries.”
The documents posted today also include a striking contrast between the largely intact 1998 NSA organizational chart for the Directorate of Operations and the heavily redacted 2001 chart for the Signals Intelligence Directorate (as the operations directorate was renamed), which contains no information beyond the name of its director. “The 2001 organization charts are more informative for what they reveal about the change in NSA’s classification policy than for what they reveal about the actual structure of NSA’s two key directorates,” commented Dr. Richelson. The operations directorate organization chart was provided within three weeks of its being requested in late 1998. In contrast, the request for the Signals Intelligence Directorate organization chart was made on April 21, 2001, and NSA did not provide its substantive response until April 21, 2004 – three years instead of three weeks.
Introduction
The National Security Agency (NSA) is one of the most secret (and secretive) members of the U.S. intelligence community. The predecessor of NSA, the Armed Forces Security Agency (AFSA), was established within the Department of Defense, under the command of the Joint Chiefs of Staff, on May 20, 1949. In theory, the AFSA was to direct the communications intelligence and electronic intelligence activities of the military service signals intelligence units (at the time consisting of the Army Security Agency, Naval Security Group, and Air Force Security Service). In practice, the AFSA had little power, its functions being defined in terms of activities not performed by the service units. (Note 1)
The creation of NSA resulted from a December 10, 1951, memo sent by Walter Bedell Smith to James B. Lay, Executive Secretary of the National Security Council. The memo observed that “control over, and coordination of, the collection and processing of Communications Intelligence had proved ineffective” and recommended a survey of communications intelligence activities. The proposal was approved on December 13, 1951, and the study authorized on December 28, 1951. The report was completed by June 13, 1952. Generally known as the “Brownell Committee Report,” after committee chairman Herbert Brownell, it surveyed the history of U.S. communications intelligence activities and suggested the need for a much greater degree of coordination and direction at the national level. As the change in the security agency’s name indicated, the role of the NSA was to extend beyond the armed forces. (Note 2)
In the last several decades some of the secrecy surrounding NSA has been stripped away by Congressional hearings and investigative research. In the late 1990s NSA had been the subject of criticism for failing to adjust to the post-Cold War technological environment as well as for operating a “global surveillance network” alleged to intrude on the privacy of individuals across the world. The following documents provide insight into the creation, evolution, management and operations of NSA, including the controversial ECHELON program. Also included are newly released documents (11a – 11g) that focus on the restrictions NSA places on reporting the identities of U.S. persons – including former president Jimmy Carter and first lady Hillary Clinton, and NSA Director Michael Hayden’s unusual public statement (Document 24) before the House Intelligence Committee.
Some of the documents that appear for the first time in this update shed additional light on the history of NSA. They concern the NSA’s participation in the space reconnaissance program (Document 3), NSA’s success in deciphering Soviet communications in the 1960s (Document 4), the efficacy of NSA activities in the late mid-to-late 1960s (Document 5), and Israel’s attack on the USS Liberty during the 1967 war (Document 10). Others provide new insight on NSA’s assessment of key issues in the new century (Document 21, Document 23), on NSA’s attempts to adapt to the changing world and communications environment, (Document 22), on the agency’s regression to old policies with regard to organizational secrecy (Document 26a, Document 26b), and on NSA activities before and after the events of 9/11 (Document 25).
Several of these documents also appear in either of two National Security Archive collections on U.S. intelligence. The U.S. Intelligence Community: Organization, Operations and Management: 1947-1989 (1990) and U.S. Espionage and Intelligence: Organization, Operations, and Management, 1947-1996 (1997) publish together for the first time recently declassified documents pertaining to the organizational structure, operations and management of the U.S. Intelligence Community over the last fifty years, cross-indexed for maximum accessibility. Together, these two sets reproduce on microfiche over 2,000 organizational histories, memoranda, manuals, regulations, directives, reports, and studies, totalling more than 50,000 pages of documents from the Office of the Director of Central Intelligence, the Central Intelligence Agency, National Reconnaissance Office, National Security Agency, Defense Intelligence Agency, military service intelligence organizations, National Security Council, and other official government agencies and organizations.
SECRET – (U//FOUO) Civil Disturbance and Criminal Tactics of Protest Extremists

This manual has no listed author and little indications as to its source. The introduction states that information in the document “was collected and interpreted by multiple agencies” and the manual is intended for use only by “public safety agencies”. However, a 2003 article from a local newspaper in Colorado indicates that the manual was produced by an unknown U.S. Government agency and is used by Joint Terrorism Task Forces to teach local police about “criminal protest tactics”. According to an email in the most recent AntiSec release, the manual is still being circulated today in relation to police confrontations with Occupy protests.




DOWNLOAD ORIGINAL DOCUMENTS HERE
TOP-SECRET from the FBI – Federal Indictments Lead to Arrests in Stem Cell Case
Three men have been arrested for their participation in a scheme to manufacture, distribute and sell to the public stem cells and stem cell procedures that were not approved by the Food and Drug Administration (FDA), United States Attorney Kenneth Magidson announced today along with Assistant Attorney General Tony West of the Department of Justice’s Civil Division, Special Agent in Charge Patrick J. Holland of the FDA-Office of Criminal Investigations (OCI) and Special Agent in Charge Cory B. Nelson of the FBI.
Francisco Morales, 52, of Brownsville, Texas, was arrested by Customs and Border Protection agents pursuant to a arrest warrant late Dec. 22, 2011. He made his initial appearance the following morning at which time he was ordered held without bond. Alberto Ramon, 48, of Del Rio, Texas, and Vincent Dammai, 40, of Mount Pleasant, S.C., were arrested yesterday. Ramon was arrested as he was about to enter his clinic and has already made his initial appearance in Del Rio, while Dammai was arrested in Florence, S.C., and is expected to make his initial appearance in Charleston, S.C., this morning. Lawrence Stowe, 58, of Dallas, Texas, also charged in relation to this case, is considered a fugitive and a warrant remains outstanding for his arrest. The two indictments in this matter, returned Nov. 9 and 10, 2011, have been unsealed by order of the court.
“Protecting the public from unproven and potentially dangerous drug and medical procedures is very important,” said Magidson. “This office will continue to prosecute violations involving threats to the public health.”
“This investigation identified a scheme whereby the suffering and hopes of victims in extreme medical need were used and manipulated for personal profit,” said Nelson. “The predatory and opportunistic nature of the crimes alleged in this indictment mirrors images from science fiction.”
The defendants allegedly conspired to commit mail fraud and unlawfully distributed stem cells derived from umbilical cord blood. According to the indictment, Morales and the others manufactured, distributed and used stems cells produced from umbilical cord blood to perform procedures not approved by the FDA to treat persons suffering from cancer, amytrophic lateral sclerosis (ALS), multiple sclerosis (MS) and other autoimmune diseases. FDA approval is required before stem cells can be marketed to the public and used to treat incurable diseases and the FDA has not determined that stem cells are safe and effective in treating these diseases.
“This indictment demonstrates the commitment of the FDA to protect the American public from the harms inherent in being exposed to unapproved new drugs,” said Holland. “The FDA will continue to aggressively pursue perpetrators of such acts and ensure that they are punished to the full extent of the law.”
Beginning in March 2007 and continuing through 2010, the indictment alleges Morales falsely represented to the public that he was a physician licensed to practice medicine in the United States and provided medical advice to individuals regarding the benefits of stem cell treatments. Morales also allegedly falsely represented that he operated a medical clinic named Rio Valley Medical Clinic in Brownsville, Texas, in order to convince the public that he specialized in using stem cells to treat incurable diseases. After meeting patients in the United States, Morales would allegedly travel to Mexico to perform the stem cell procedures. The indictment further alleges that Stowe marketed, promoted and sold stem cells along with other drug and biological products for the treatment of cancer, ALS, MS and Parkinson’s Disease that had not been reviewed or approved by the FDA. Stowe operated several entities, including The Stowe Foundation and Stowe Biotherapy Inc., through which he allegedly marketed and sold these products.
The stem cells referenced in the indictment were created and manufactured from umbilical cord blood obtained from birth mothers who were patients of Ramon—a licensed midwife who operated The Maternity Care Clinic in Del Rio, Texas. Ramon allegedly sold the cord blood to a company called Global Laboratories located in Scottsdale, Ariz. After obtaining the cord blood from Ramon, the indictment alleges Global Laboratories would send the tissue to Dammai—a professor of pathology and laboratory medicine in Charleston, S.C. Dammai, without obtaining approval from FDA or University authorities, allegedly used university facilities to create stem cells that were later sold by Global Laboratories. As a result of this fraudulent scheme, the public was mislead into believing that stem cells and other drug and biological products sold by defendants had been approved by the FDA to treat cancer, ALS, MS and Parkinson’s Disease, The defendants allegedly received more than $1.5 million from patients suffering from incurable diseases.
The case is being prosecuted by Assistant United States Attorneys Samuel Louis and Cedric Joubert with the assistance of Carol Wallack with the Consumer Protection Branch in the Department of Justice’s Civil Division. The case was investigated by the FDA-OCI, FBI and Internal Revenue Service-Criminal Investigations.
An indictment is a formal accusation of criminal conduct, not evidence.
A defendant is presumed innocent unless convicted through due process of law.
NATIONAL SECURITY – Government Releases Detailed Information on 9/11 Crashes

Government Releases Detailed
Information on 9/11 Crashes
Complete Air-Ground Transcripts of Hijacked
9/11 Flight Recordings Declassified
National Security Archive Electronic Briefing Book No. 196
Edited by Barbara Elias
Washington, DC – January 2, 20012- The National Transportation Safety Board (NTSB) this week released full transcripts of the air traffic control recordings from the four flights hijacked on September 11, 2001, and meticulous Flight Path Studies for three of the flights, in response to a Freedom of Information request by the National Security Archive. The studies provide the most detailed technical information available to date related to the hijackings, and the transcripts of the aircraft-to-ground communications are the first complete government disclosure of each flight’s air traffic control recordings.
The documents are cited extensively in the 9/11 Commission Report to establish key facts and basic timelines for each hijacked flight. The NTSB Web site references the documents but does not provide copies, claiming “the terrorist attacks of September 11, 2001 are under the jurisdiction of the Federal Bureau of Investigation. The Safety Board provided requested technical assistance to the FBI, and any material generated by the NTSB is under the control of the FBI. The Safety Board does not plan to issue a report or open a public docket.” The documents were released in their entirety to the National Security Archive and were received directly from the NTSB.
The transcripts provide additional details to the information summarized in the 9/11 Commission Report. For example, the NTSB transcript differs slightly from the Commission’s text of the warning that United Airlines Flight 93 received only minutes before the hijackers attacked. At 9:23am, the Aircraft Communications Addressing and Reporting System (ACARS) shows a text message to Flight 93 reading: “BEWARE OF ANY COCKPIT INTROUSION [sic]. TWO AIRCRAFT IN NY, HIT TRADE CNTER BUILDS [sic].” Five minutes later at 9:28am Flight 93 was sending the message “***(mayday)*** (hey get out of here) ***” as it was being hijacked.
The Flight Path Studies reconstruct the routes of American Airlines Flight 11, American Airlines Flight 77 and United Airlines Flight 175. Complied from recorded radar data and information from the Flight Data Recorders, the studies’ illustrations of radar ground tracks, maps and altitude profiles provide graphic guides to each hijacking and were used by the NTSB to determine the takeover points where the hijackers gained control of the planes.
In addition to the Flight Path Studies and Air Traffic Control Recording transcripts, the NTSB released a February 2002 “Specialist’s Factual Report of Investigation” on United Airlines Flight 93 based on the flight’s recovered digital data recorder — the only surviving recorder from the hijacked planes on 9/11. The report provides graphic analysis of the data recovered from Flight 93 and its subsequent crash in Shanksville, PA. According to the report, the flight recorder functioned normally.
Documents
Note: The following documents are in PDF format.
You will need to download and install the free Adobe Acrobat Reader to view.
Document 1: NTSB report, “Flight Path Study-American Airlines Flight 11,” Feb. 19, 2002 [Chapter 1, The 9/11 Commission Report, “We Have Some Planes.” Footnotes 23, 33]
Document 2: NTSB report, “Flight Path Study-American Airlines Flight 77,” Feb. 19, 2002 [Chapter 1, The 9/11 Commission Report, “We Have Some Planes.” Footnote 53]
Document 3: NTSB report, “Flight Path Study-United Airlines 175,” Feb. 19, 2002 [Chapter 1, The 9/11 Commission Report, “We Have Some Planes.” Footnote 41]
Document 4: NTSB report, “Specialist’s Factual Report of Investigation-Digital Flight Data Recorder” for United Airlines Flight 93, Feb. 15, 2002 [Chapter 1, The 9/11 Commission Report, “We Have Some Planes.” Footnotes 70, 71]
Document 5: NTSB report, Air Traffic Control Recording-American Airlines Flight 11, Dec. 21, 2001 [Chapter 1, The 9/11 Commission Report, “We Have Some Planes.” Footnote 24]
Document 6: NTSB report, Air Traffic Control Recording-American Airlines Flight 77, Dec. 21, 2001 [Chapter 1, The 9/11 Commission Report, “We Have Some Planes.” Footnote 54]
Document 7: NTSB report, Air Traffic Control Recording-United Airlines Flight 175, Dec. 21, 2001 [Chapter 1, The 9/11 Commission Report, “We Have Some Planes.” Footnotes 24, 41, 42, 44]
Document 8: NTSB report, Air Traffic Control Recording-United Airlines Flight 93, Dec. 21, 2001 [Chapter 1, The 9/11 Commission Report, “We Have Some Planes.” Footnote 71]
DOWNLOAD ORIGINAL DOCUMENTS HERE
TOP-SECRET – UN Confidential Government of Sudan Security Forces in Darfur Report November 2005

1. Sudan Armed Forces (SAF) – Command and Control
1.1. General
1. The Sudanese Armed Forces (SAF) is a conventional armed force with a mandate to protect and to maintain internal security. It carries out its mandate mainly through ground forces, including Popular Defence Force (PDF) militia, as well as an air force and navy. (A1)
1.2. Organization
2. The Supreme Commander of the armed forces, Lieutenant General Omar Hassan Ahmad el-Bashir, holds both the posts of National President and Commander-In Chief of the Armed Forces and People’s Defence Forces (PDF). For operational purposes he exercises this power through the Minister of Defence (currently major-general Bakri Hassan Saleh). The Minister appoints a Commander of the Armed Forces and Chief of General Staff (currently, general Abbas Arabi) who, together with five Deputy Chiefs of Staff (Operations, Intelligence, Logistics, Administration, Training and Morale), form the Committee of the Joint Chiefs of Staff or Command Group. The air force and navy are individual services under the commander-in-chief. (A1)
…
1.4. Military Intelligence (MI)
9. The Military Intelligence (Istikhbarat al-Askariyya) is a branch of the General Staff with its own administration and command. The status of the MI is not completely clear, but it appears that under emergency laws, it has the power to arrest, detain and interrogate. With regard to communication and reporting, the MI branch passes information through the operational chain, as well as directly to the Presidency, through the Chief of the MI branch. (B2)
1.5. Border Intelligence (HI)
10. The Military Intelligence also include an operational unit called Border Intelligence (BI) (Istikhbarat al-Hudud), headquartered in Khartoum and headed by General AI-Hadi Hamid el-Tayeed (2005), the primary role of which is to monitor and gather information in the border area. Members of this unit are recruited from the local population. They are deployed to their areas of origin, according to their experience in the area, knowledge of the tribes, and ability to differentiate between people of different tribal and national origins based on local knowledge. Border Intelligence guards are under the operational control of the Military Intelligence Officers in the particular Division where they are deployed and otherwise fall under the regular chain of command for the armed forces. (C2)
11. While initially BI officers were recruited in relation to the conflict in southern Sudan, the Government began recruiting them during the early stages of the armed conflict in Darfur in late 2002 and early 2003. Apparently, BI soldiers are recruited directly into the army in the same way as regular soldiers. An advertisement is made through media channels for volunteers who meet certain criteria, in particular with regard to age, citizenship and fitness. Approximately 3,000 Border Intelligence soldiers have been recruited in this way and deployed in Darfur. (B3)
…
2. National Security and Intelligence Service
19. The National Security and Intelligence Service (NSIS) is not part of the Sudan Armed Forces but is part of the Ministry of Interior (currently headed by Zubeir Beshir Taha (NCP) in the Government of National Unity).
20. The NSIS was formed in February 2004 as a move to create one unified service dealing with both internal and external intelligence. Its main headquarter is in Khartoum and is headed by a Director-general who is appointed by the President. The current Director-General, Major-general Salah Abdallah (also known as Salah Gosh), reports at least every second day to the President and/or First VicePresident. While he co-operates with other organs of the Government, he is accountable directly to the President.
21. Its mandate derives from the National Security Force Act (NSF A) of 1999, as amended in 2001, which states that there shall be an Internal Security Organ in charge of internal security, and a Sudanese Intelligence Organ in charge of external security. In February 2004, the two organs were merged to form the NSIS.
…
3. The “Janjaweed”
30. Although we do not consider Janjaweed as being part of the GoS apparatus in Darfur, we mention it in this report for clarification purposes.
31. The term “Janjaweed”, in particular, has been widely used by victims of attacks to describe their attackers (the words fursan (horsemen, knights), or mujahedeen). The term has consequently also been used by many international organizations and the media in their reports on the situation in Darfur, and was used by the Security Council in resolution 1564. Victims of attacks have indicated that the Janjaweed were acting with and on behalf of Government forces, but no evidence – at this stage – allows to confirm such allegation.
32. “Janjaweed” is a generic Darfurian term that can be translated as “bandits”. Historically, this word describes armed horsemen performing “razzias,,18 against farmers and villagers. In the recent years, however, the word has been repeatedly used by the international community to describe combatants that cannot be clearly associated to a specific organization. In the world media, however, the word “Janjaweed” is irremediably – and often wrongly – associated to the GoS19 Cross examination of reports collected by UMAC shows that the word Janjaweed used by sources in Darfur may refer to :
• Spontaneous militias or self-defence forces (nomads or farmers) not always supported by the GoS; (AI)
• Spontaneous militias or self-defence units locally based supporting rebel movements; (AI)
• Popular Defence Forces (PDF) supported by the GoS as part of the armed forces. The PDF are locally based, organized, trained, and equipped units raised by the government to protect local communities. The PDF are defined by the Popular Defence Forces Act of 1989.; (A2)
• Covert units associated with “Border Intelligence” (and probably other government intelligence and security agencies) operating in Western Darfur against illegal activities across the border; (C2)
• Chadian Armed Opposition Groups (CAOG) operating across the Chadian Sudanese border and using Darfur as a sanctuary and as a “supply” area; (A 1)
• Criminals, former combatant living out of theft and cross-border trafficking. This category is expected to increase in number as GoS and rebel armies will demobilize. (AI)DOWLOAD ORIGINAL DOCUMENT HERE
TOP-SECRET from the UN – Leaked UN Plan for Post-Conflict Deployment to Libya


The plan indicates that NATO could potentially have an ongoing role in the country’s affairs following the cessation of the immediate conflict.
DOWNLOAD THE ORIGINAL DOCUMENT HERE
CONFIDENTIAL from the CIA – Penetrating the Iron Curtain:

In the mid-1950s the US faced the first real challenge since World War II to its strategic superiority over any nation on earth. The attempt to collect intelligence on the Soviets began with an initial period of poor collection capabilities and consequent limited analysis. With few well-placed human sources inside the Soviet Union, it was only with the CIA’s development of, what can only be called, timely technological wizardry—the U-2 aircraft and Corona Satellite reconnaissance program—that breakthroughs occurred in gaining valuable, game-changing intelligence. Coupled with the innovative use of aerial and satellite photography and other technical collection programs, the efforts began to produce solid, national intelligence.
DOWNLOAD ORIGINAL DOCUMENT HERE
CONFIDENTIAL – (U//FOUO) DHS-FBI 2011 Holiday Terrorism Warning

(U//FOUO) This Joint Intelligence Bulletin provides law enforcement, public, and private sector safety officials with an evaluation of potential terrorist threats during the 2011 US holiday season, extending from Thanksgiving through New Year’s Day. This information is provided to support the activities of DHS and FBI and to assist federal, state, local, tribal and territorial government counterterrorism and first responder officials in deterring, preventing, preempting, or responding to terrorist attacks within the United States.
(U//FOUO) Terrorist Interest in the Holiday Season
(U//FOUO) While we are not aware of any credible terrorist threats to the Homeland specifically timed to coincide with the 2011 holiday season, attempted terrorist incidents during last year’s holiday season, as well as intelligence received over the past 12 months, suggest terrorists recognize that the large gatherings occurring during the holiday season provide an opportunity for mass casualty attacks. Attack planning, however, is likely to depend more on terrorist readiness to execute an attack rather than on a desire to attack on a specific date.
— (U//FOUO) As of February 2010, al-Qa‘ida was contemplating large attacks in the Homeland on symbolic dates and specifically identified Christmas and other prominent American holidays as key dates, presumably for attacks. We are uncertain how widely al-Qa‘ida’s interest in timing attacks to symbolic dates has been shared or accepted within the group or among its affiliates and allies, and we have no specific credible information to suggest any plotting targeting the Homeland was developed based on al-Qa‘ida’s February 2010 intent.
— (U//FOUO) On 26 November 2010, a US citizen was arrested for allegedly plotting to detonate an explosive-laden van at the annual Christmas tree lighting ceremony in Portland, Oregon. This was the first incident we know of in which a homegrown violent extremist (HVE) specifically planned an attack during a holiday event.
— (U) On 11 December 2010, an Iraqi-born Swedish citizen attempted to conduct a suicide bombing, probably targeting a crowded pedestrian shopping area in central Stockholm. The device detonated prematurely, killing only the bomber.…
(U) Outlook
(U//FOUO) Although leadership losses over the past year have likely degraded their capabilities, al-Qa‘ida and allied terrorist groups continue to seek innovative ways to conduct attacks and circumvent security procedures. We remain concerned that the upcoming holiday season will provide attractive opportunities for terrorists and HVEs to target the Homeland. It is imperative that first responders and security personnel remain alert for indicators of attack planning and immediately report any suspicious activity. We continue to operate under the premise that terrorists not yet identified by the Intelligence Community and law enforcement may be operating in the United States and could advance and execute attacks without warning.
DOWNLOAD ORIGINAL DOCUMENT HERE
CONFIDENTIAL – IDF Brief: Battle for the Narrative in Low Intensity Conflicts
TOP-SECRET – Israel Defense Force IHH Report Alleging Ties to Terrorism

- The Turkish IHH, which played a central role in organizing the flotilla to the Gaza Strip, is a Turkish humanitarian relief fund with a radical Islamic anti-Western orientation.
- Beyond its legitimate philanthropic activities, the IHH provides extensive support to radical Islamic organizations, including Hamas.
- In the past, the IHH has maintained contacts with and provided support to global jihad organizations.
- IHH is a member of a coalition of organizations, the “Union of Good” which has been designated a terrorist entity by the US government.
…
IHH LINKS TO HAMAS
- IHH’s orientation is radical-Islamic and anti-Western, and it is close to the Muslim Brotherhood (Hamas’ parent movement). IHH supports Hamas and does not hide the connection between them. Hamas also considers its links to IHH and Turkey to be extremely important.
- In recent years, especially since Hamas took over the Gaza Strip, IHH has supported Hamas’ propaganda campaigns by organizing public support conferences in Turkey. At those conferences, which featured the participation of senior IHH figures, the heads of IHH expressed their support for Hamas and its strategy (including the armed struggle it favors), in defiance of the Palestinian Authority, Hamas’ rival.
- IHH is a member of the Union of Good, an umbrella organization of more than 50 Islamic funds and foundations around the globe, which channels money into Hamas institutions in the Palestinian Authority-administered territories.
- The Union of Good was designated a terrorist entity under by the United States government under Executive Order 13224 in November 2008.
- As a Union of Good member IHH has connections with other worldwide Islamic funds and foundations which support Hamas. Among other things, the support includes initiating and conducting joint projects whose objectives are to bolster the de facto Hamas administration in the Gaza Strip and Hamas’ civilian infrastructure in Judea and Samaria, which also supports terrorism (the infrastructure is under pressure from the Palestinian Authority security services). IHH, which has become an important factor in global fund-raising for Hamas, transfers significant amounts of money to Hamas institutions in Judea and Samaria, including the Islamic Charitable Society in Hebron and the Al-Tadhamun Charitable Society in Nablus (Hamas’ two central “charitable societies,” both outlawed by Israel).
DOWNLOAD ORIGINAL DOCUMENT HERE
SECRET – Democratic People’s Republic of Korea Leadership Chart
The structure of this chart is primarily taken from a reference pamphlet published by the South Korean Ministry of Unification in January 2009, which appears to be based on the DPRK constitution. As such, this chart is a representation of the formal relationships between the various entities and does not necessarily reflect the actual hierarchy and power relationships in the North Korean system. Other sources include: DPRK, ROK, PRC, and Japanese media; the ROK National Intelligence Service website; the Ministry of Unification’s Key Figures of North Korea 2009; and Japan’s Radiopress North Korea Directory 2008.




TOP-SECRET – Biographies and Photos of the Russian Federation Armed Forces Leadership

Dmitriy Anatolyevich Medvedev, President of Russian Federation/Supreme Commander of RF Armed Forces
Born in city of Leningrad (now St. Petersburg) on 14 September 1965.
Completed law faculty of Leningrad State University (LGU) in 1987 and LGU postgraduate studies in 1990. Candidate of juridical sciences, docent. During 1990-1999 instructed at St. Petersburg State University.
Simultaneously during 1990-1995 advisor to Leningrad City Council chairman, expert of St. Petersburg Mayor’s Office Foreign Relations Committee. In 1999 deputy head of RF Government Apparatus. During 1999-2000 deputy head of RF President’s Administration. From 2000 first deputy head of RF President’s Administration. During 2000-2001 chairman of Board of Directors of Gazprom Open Joint-Stock Company (OAO), in 2001 deputy chairman of Gazprom OAO Board of Directors, from June 2002 chairman of Gazprom OAO Board of Directors. From October 2003 head of RF President’s Administration. In November 2005 appointed first deputy chairman of RF Government.
On 2 March 2008 elected President of Russian Federation.
Married. Wife Svetlana Vladimirovna Medvedeva. The Medvedevs have a son, Ilya.

Anatoliy Eduardovich Serdyukov, Defense Minister of Russian Federation
Born in settlement of Kholmskiy, Abinskiy Rayon, Krasnodar Kray on 8 January 1962.
Completed Leningrad Institute of Soviet Trade in 1984 in “economist” specialty.
During 1984-2000 worked in the specialty in St. Petersburg, the last position being general director of one of city’s largest joint-stock companies.
During 2000-2001 was deputy head of RF Ministry for Taxes and Levies Inspectorate for St. Petersburg.
In 2001 completed St. Petersburg State University in “lawyer” specialty.
From May 2001 deputy head of RF Ministry for Taxes and Levies Directorate for St. Petersburg, and from November 2001 head of this Directorate.
On 2 March 2004 appointed deputy minister of Russian Federation for taxes and levies. On 16 March 2004 became acting RF minister for taxes and levies.
On 27 July 2004 appointed head of Federal Tax Service.
By RF Presidential Edict of 15 February 2007 appointed Defense Minister of Russian Federation. Later, in connection with the formation of a new makeup of the RF Government, reappointed Defense Minister of Russian Federation by RF Presidential Edict “On the Defense Minister of the Russian Federation” of 12 May 2008.
Candidate of economic sciences.
…
He has been decorated with orders “For Service to the Motherland in the USSR Armed Forces” 2nd and 3rd class and “For Distinguished Military Service,” and with a number of medals.

General of the Army Nikolay Yegorovich Makarov, Chief of RF Armed Forces General Staff/First Deputy RF Defense Minister
Born in village of Glebovo, Ryazan Oblast on 7 October 1949. In 1971 completed Moscow Higher Combined-Arms Command School (with gold medal). Commanded a platoon, company, and battalion in Group of Soviet Forces in Germany.
After completion of Frunze Military Academy (with gold medal) in 1979, served in Transbaykal Military District [MD] (ZabVO) in positions of chief of staff/deputy regimental commander, regimental commander, chief of staff/deputy division commander, motorized rifle division commander.
In 1993 completed RF Armed Forces General Staff Military Academy (with gold medal).
Held positions of chief of staff of Joint Group of Russian Forces in Tajikistan, chief of staff/first deputy commander of separate army, commander of army in Volga MD. From January 1998 commander of Ground and Shore Troops/deputy commander of Baltic Fleet for Ground and Shore Troops.
From September 1999 chief of staff/first deputy commander Moscow MD.
On 25 December 2002 appointed commander Siberian MD (SibVO).
From April 2007 chief of armaments of RF Armed Forces/deputy RF defense minister.
By RF Presidential Edict of 3 June 2008 appointed chief of RF Armed Forces General Staff/first deputy RF defense minister.
Honored Military Specialist of the Russian Federation.
Decorated with orders “For Service in the USSR Armed Forces” 3rd Class, “For Distinguished Military Service,” and St. George 2nd Class, and with 12 medals.

Colonel-General Aleksandr Petrovich Kolmakov, First Deputy Defense Minister of Russian Federation
Born in city of Kaliningrad, Moscow Oblast on 31 July 1955. In 1976 completed Ryazan Higher Airborne Command School and served as reconnaissance platoon commander, reconnaissance company deputy commander for airborne training, reconnaissance company commander, chief of staff/deputy battalion commander of airborne regiment. Commanded reconnaissance company as part of Limited Contingent of Soviet Forces in Afghanistan.
After completion of Frunze Military Academy (with honors) in 1985, commanded airborne battalion, was regimental deputy commander and commander, and airborne division deputy commander and commander.
After completion of RF Armed Forces General Staff Military Academy (with honors) in 1995, successively held positions as first deputy commander of Guards combined-arms army in Moscow MD, from 1998 commander of combined-arms army in Transbaykal MD, and from September 2000 deputy commander Far East MD (DVO).
From September 2003 commander Airborne Troops (VDV).
By RF Presidential Edict of 25 September 2007 appointed first deputy defense minister of Russian Federation.
DOWNLOAD ORIGINAL DOCUMENT HERE
SECRET – (U//FOUO) DHS Moscow Metro Bombings Snapshot

Bombings(U) Moscow, Russia –Two female suicide bombers detonated explosives in Moscow’s subway system.
(U) Facts:
–(U) Two unidentified female suicide bombers detonated explosives in Moscow’s subway system
–(U) Explosions occurred on 29 March at Lubyanka and Park Kultury train stations in downtown Moscow at approximately 0800 and 0845 local Moscow time (2400 & 0045 EDT)
–(U) Preliminary reports indicate 37 killed, 102 injured
–(U) Russian media reports that an unexploded suicide belt was discovered at Park Kultury Station(U) No group has claimed responsibility at this time. However, Doku Umarov, a self-proclaimed Chechen militant leader, posted an Internet video warning of potential attacks in Russia in February.
(U) Tactics & Techniques:
–(U) Attackers: Two female suicide bombers (one per train).
–(U) Device: Explosive belts packed with plastic explosives: one per bomber; may have contained hexogen (RDX) as well as chipped iron rods and screws; believed to have been set off on the trains as the trains’ doors opened.
–(U) Time: At approximately 0800 & 0845 Moscow time (2400 & 0045 EDT), during peak morning rush-hour commute.
–(U) Locations:
–0800 -LubyankaStation: Station is located underneath the building that houses the main offices of the Federal Security Service (FSB), the KGB’s main successor agency.
–0845 -Park KulturyStation: Unknown nearby facilities.
Chechen Separatist History
(U) Leader: The Chechen separatists have had numerous turnovers in leadership over the years. The most prominent and active separatist group is the Caucasus Emirate led by Doku Khamatovich Umarov.
(U) Main Objectives: After the fall of the Soviet Union in the early 1990s, Chechen separatists launched a coordinated campaign for independence, which resulted in two wars and an ongoing insurgency in the Chechen region.
(U) TTP / MO: The Chechen separatists use hostage-taking tactics (2004 Beslan school siege); remote detonated IEDs (summer 1999 bombings of an arcade and an apartment building in Moscow); and suicide operatives, to include females, as seen in this most recent subway attack.
(U) The Chechens are a predominantly Sunni Muslim ethnic minority group located in Russia’s Caucasus region.
(U) According to Russian State statistics, as of January 1, 2010, the Chechen population was 1,267,740. It is not currently known how many Chechens participate in resistance activities.
(U//FOUO) Suicide bombings continue to be a preferred terrorist tactic because the bomber controls the location, timing, and method of delivery, and requires no escape route. Many facilities and areas accessible to the public are inherently vulnerable to suicide bombing attacks and the terrorist’s latitude in determining and adjusting the target and timing of an attack up tothe point of detonation further complicates countermeasures. These factors indicate the importance of disciplined security measures and alertness by security professionals to potential threats from the full range of gender and age groups.
(U//FOUO) Despite the lack of a reliable, predictable profile of a suicide terrorist, security and law enforcement officials and first responders should be aware of terrorists’ use of both male and female suicide operatives, and be alert to behavioral patterns that such bombers have demonstrated in previous attacks.
(U/FOUO) Male and female suicide bombers may portray many of the same indicative behaviors, to include:
–(U) Appearance of being nervous, may seem preoccupied or have a blank stare.
–(U) Focused, intent, and vigilant, may result in lack of response to verbal questions or commands.
–(U) Awkward attempts to blend in to surroundings; behavior may seem odd or overtly out of place.
–(U) Avoidance of authority figures, law enforcement, or security; if security is present, the suicide bomber tries to be inconspicuous.
–(U) Praying fervently to him/her self.
–(U) Behavior may be consistent with that of a person without any future, such as presenting a one-way ticket, or being unconcerned about receiving change for a purchase.
–(U) Profuse sweating that is incompatible with current weather conditions.
…
Royal Demolition Explosive (RDX)
(U) Royal Demolition Explosive (RDX):Cyclotrimethylenetrinitramine, C3H6N606 (RDX), also known as cyclonite or hexogen, is second in strength to nitroglycerin among common explosive substances.
(U) RDX is an explosive widely used in military and industrial applications. RDX has both military and civilian applications.Asa military explosive, RDX can be used alone as a base charge for detonators or mixed with other explosives. Common military uses of RDX have been as an ingredient in plastic-bonded explosives, or plastic explosives. Civilian applications of RDX include use in fireworks and in demolition blocks.
(U) RDX is stable in storage; however, it becomes unstable when exposed to extreme heat, impact, or electrostatic discharge.
(U) RDX is a white, crystalline solid or colorless crystal.
(U) RDX was widely used during World War II, often in explosive mixtures with TNT.
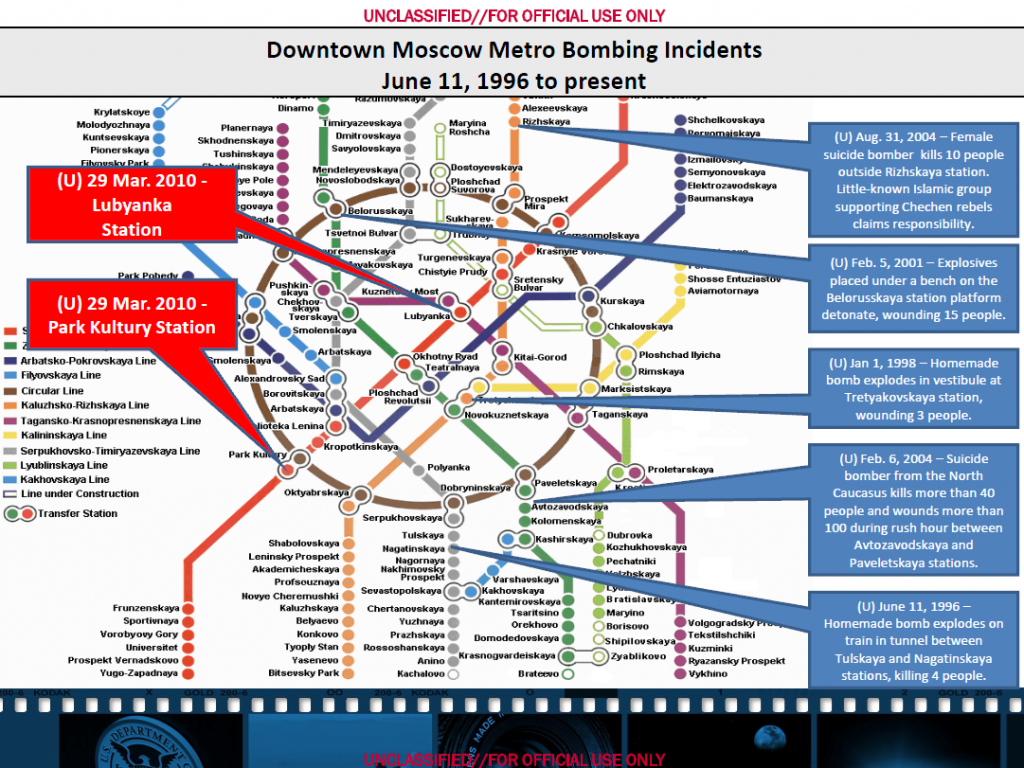
DOWNLOAD ORIGINAL DOCUMENT HERE





























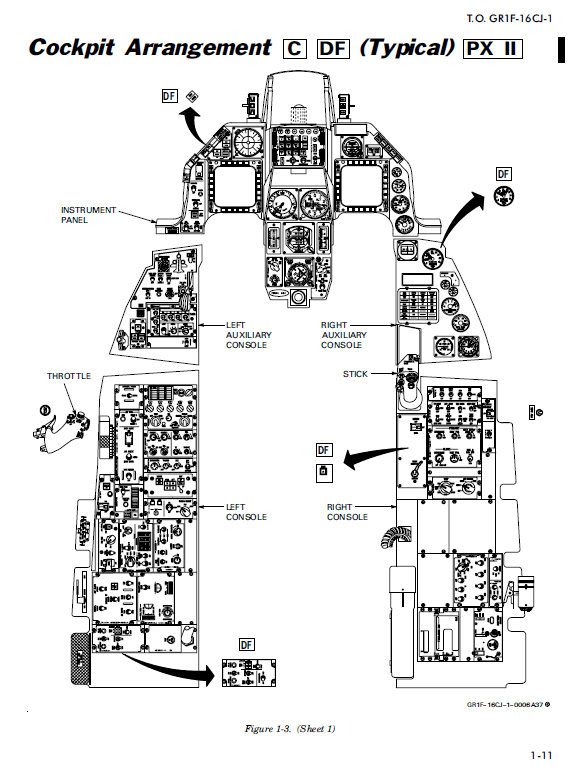












![[Image]](https://i0.wp.com/cryptome.org/2012-info/gitmo-10/pict4.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/gitmo-10/pict2.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/gitmo-10/pict1.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/gitmo-10/pict10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/gitmo-10/pict3.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/gitmo-10/pict9.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/gitmo-10/pict11.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/gitmo-10/pict7.jpg)






















![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict41.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict43.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict51.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict47.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict48.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict55.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict69.jpg)





![[Image]](https://i0.wp.com/cryptome.org/2012-info/anti-sopa-pipa/pict79.jpg)



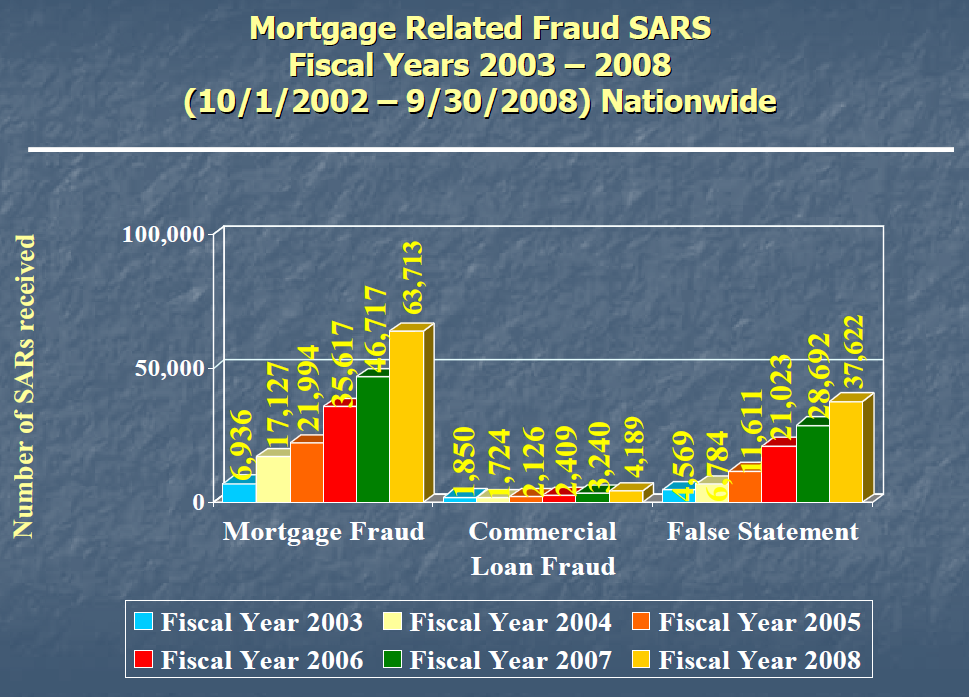
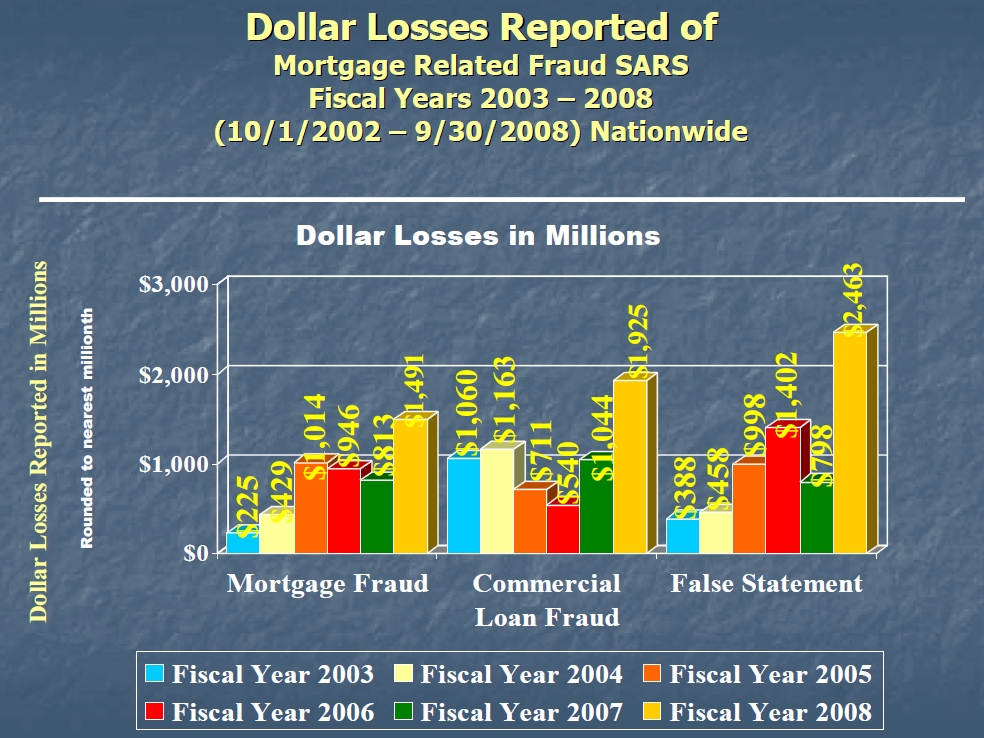
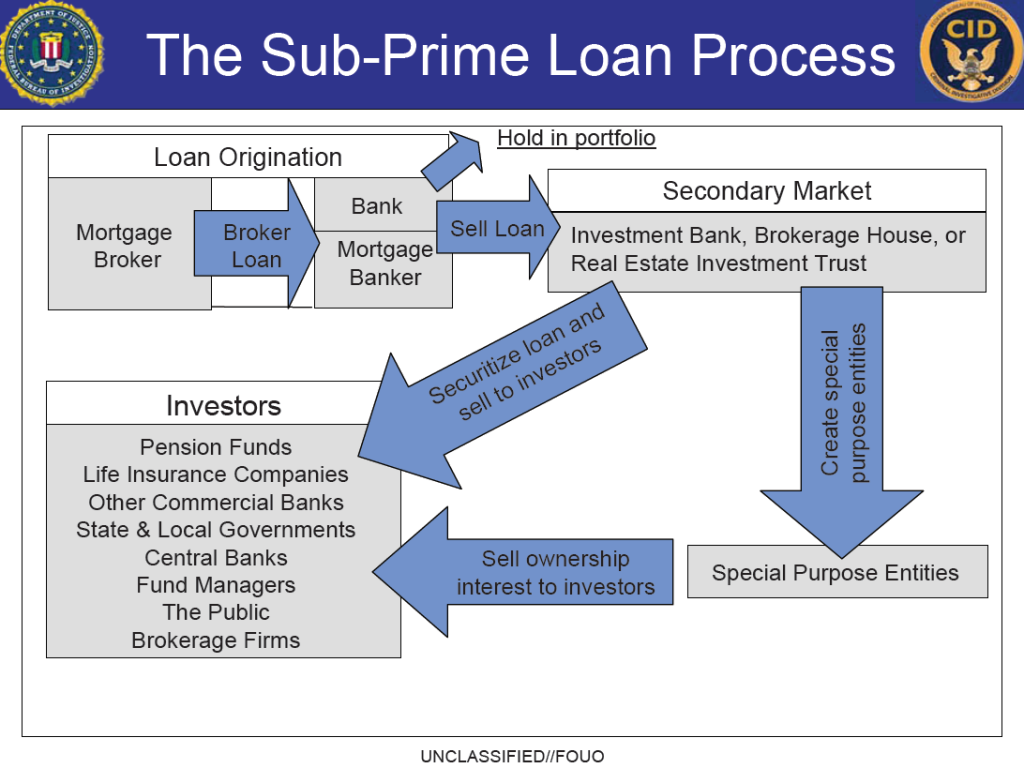
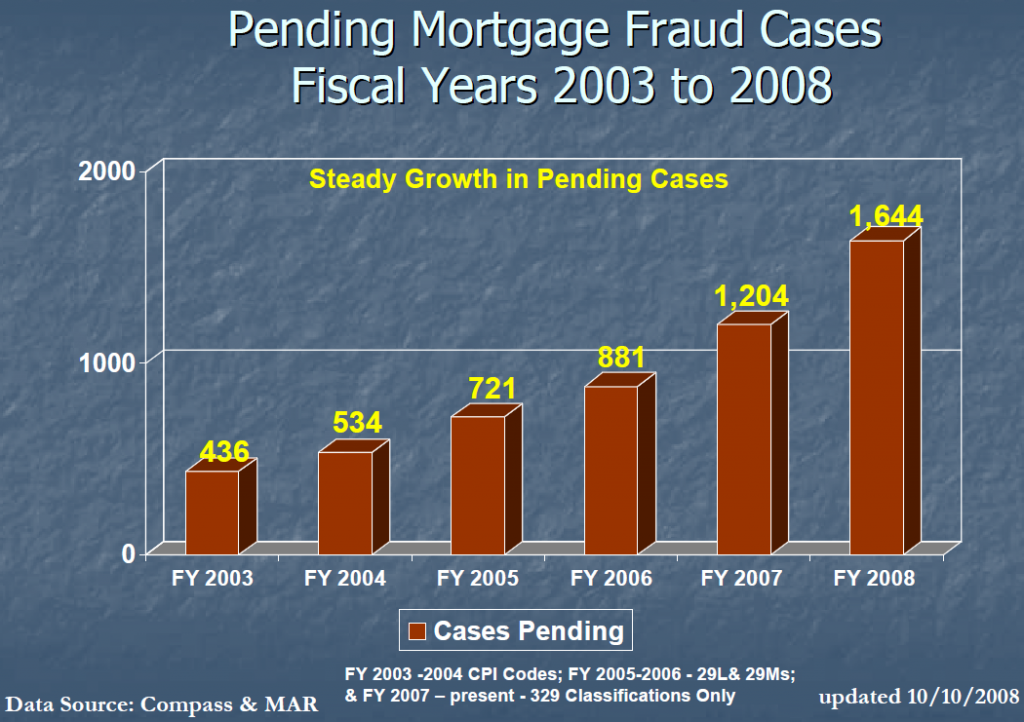




![[Image]](https://i0.wp.com/cryptome.org/0004/cia-john/pict27.jpg)
![[Image]](https://i0.wp.com/cryptome.org/0004/cia-john/pict29.jpg)























![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict12.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict14.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict17.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict20.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict22.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict24.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict2.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict28.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict30.jpg)















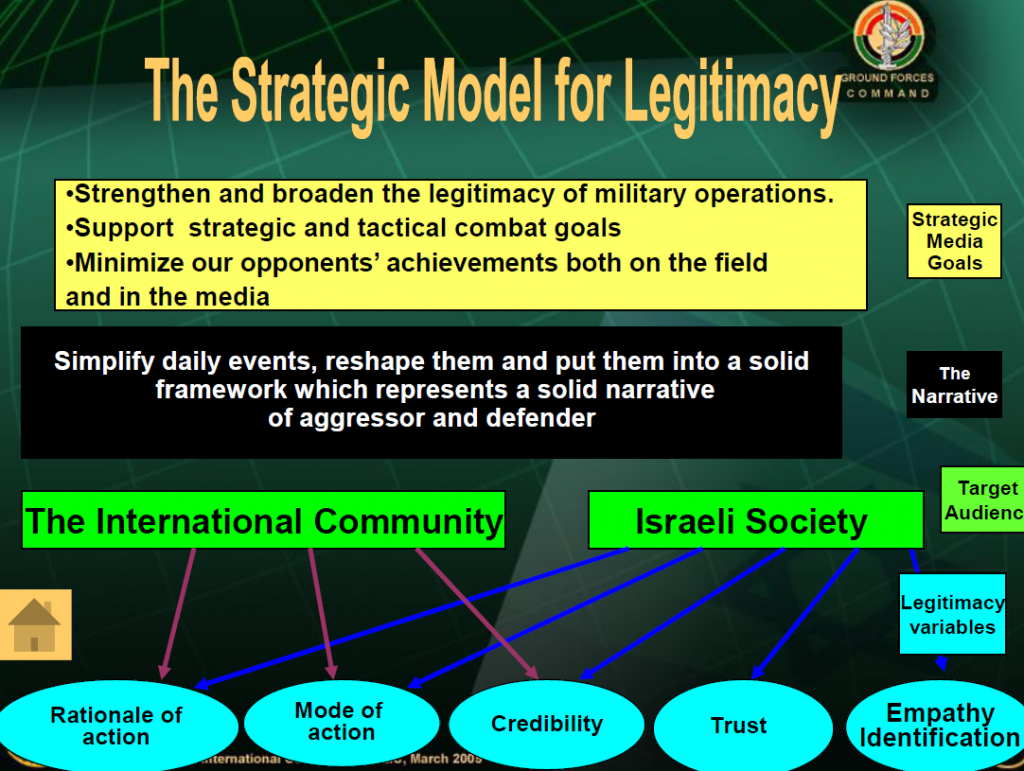
You must be logged in to post a comment.