Become a Patron!
True Information is the most valuable resource and we ask you to give back.

SMA White Paper: Maneuver and Engagement in the Narrative Space
Page Count: 44 pages
Date: January 2016
Restriction: None
Originating Organization: Joint Staff J39 in support of Special Operations Command Central
File Type: pdf
File Size: 2,765,122 bytes
File Hash (SHA-256):8A91FA06FBC9FEADA017FC4FCACEADDE33C5D1E728C5E07710E80885092C9E06
Download File
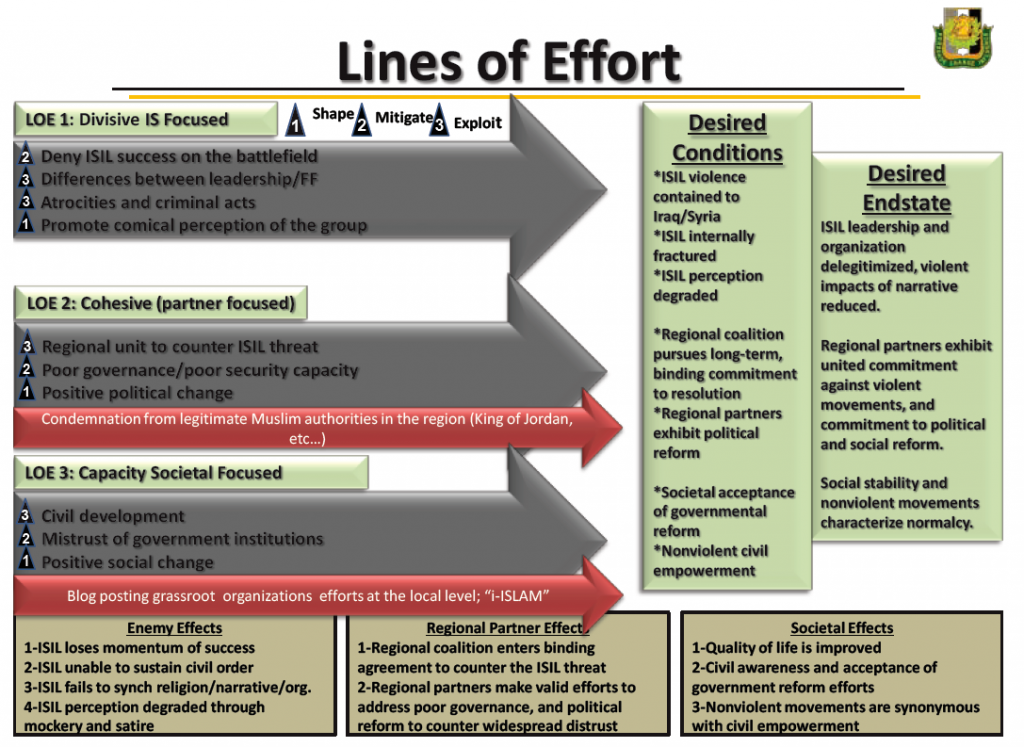
This paper was produced in support of the Strategic Multi-layer Assessment (SMA) of the Islamic State of Iraq and the Levant (ISIL) led by Joint Staff J39 in support of the Special Operations Command Central (SOCCENT). The paper leverages and melds the latest thinking of academic and operational subject matter experts in fields of organizational and social dynamics, network analysis, psychology, information operations and narrative development, social media analysis, and doctrine development related to aspects of maneuver and engagement in the narrative space.
The authors emphasize the concept of countering ISIL in the narrative space in synchronization with combat operations. While maneuver and engagement in the narrative space could be conducted independently of combat operations, conducting maneuver and engagement in the narrative space in support of combat operations is more likely to achieve lasting effects in the human domain. These ideas reflect a new view of what is required to succeed in future conflict because of the growing realization that decisive effects are often achieved in the narrative space.
…
Warfare is ultimately a human endeavor. When planning to deal with any adversary or potential adversary, it is essential to understand who they are, how they function, their strengths and vulnerabilities, and why they oppose us. Events over the course of the last year and a half highlight the importance of those factors as they relate to the Islamic State of Iraq and the Levant (ISIL). One of ISIL’s obvious strengths is their ability to propagate tailored narratives that resonate with target audiences. If the US and our allies are to counter ISIL effectively, we must attack this center of gravity. A recent white paper endorsed by General Votel, Commanding General of US Special Operations Command (USSOCOM), states,
Thousands of airstrikes helped to check their [ISIL’s] rapid expansion, but the decisive effort against them will require discrediting their narrative and connecting the people to legitimate governing structures – areas where Department of Defense should not have primacy.
Discrediting ISIL’s narrative will require a long-term effort by a team of experts. It will require: (1) developing an in-depth understanding of ISIL’s narratives and why they resonate with target audiences, (2) building a whole of government team that can effectively counter and replace ISIL narratives with a strategic communications plan that directly supports our desired end states, (3) globally employing counter-narratives and replacement narratives, (5) gathering and collecting data to assess the effects of narratives (theirs and ours), and (6) continually refining the content and employment of our narratives based on an assessment of their effectiveness.
An effective, whole of government, Strategic Communications plan requires close coordination and synchronization across all lines of effort. The US Department of State should lead the US effort with support from the other Departments/Agencies on behalf of the US government. To be successful, our approach must also include our friends and allies. Specific multinational partners can help us understand why some ISIL narratives resonate and how they can be countered and/or replaced. In fact, truly effective influence operations require a combination of art and science. The best approach will most likely require contributions from neuroscientists, sociologists, psychological operations specialists, intelligence analysts, civil affairs planners, law enforcement professionals, and others. The melding of these diverse inputs into a comprehensive strategy demands skill, patience, close coordination and an inherent understanding of the ultimate end states. Ultimately, discrediting ISIL’s narrative will most likely take years and will require significant resources. However, the execution of our strategic communication game plan, from initial analysis to our measure of effectiveness, must be conducted with the speed and agility necessary to not only replace ISIL’s narrative but to drive and shape their perceptions and subsequent actions. Simply put, to achieve victory we must outmaneuver and outpace ISIL in the narrative space. Currently, the opposite is occurring and is a trend that must be reversed.
Joint Staff J7, Joint Staff Suffolk, Joint Staff J5, Joint Staff J6, Joint Staff College, Joint Staff J8, Joint Staff Badge, Joint Staff Directorates, Joint Staff Organization, Joint Staff J4, Joint Staff Alcohol And Substance Abuse Prevention, Joint Staff Annual Ethics Training, Joint Staff Address, Joint Staff Action Processing, Joint Staff Ataaps, Joint Staff Action Processing System, Joint Staff Awards, Joint Staff Action Officer Of The Year, Joint Staff Badge, Joint Staff Badge Wear Air Force, Joint Staff Biographies, Joint Staff Badge Wear Army, Joint Staff Badge Wear Navy, Joint Staff Badge Wear, Joint Staff Briefing Format, Joint Staff Breach, Joint Staff Battlespace Awareness, Joint Staff Briefing, Joint Staff College, Joint Staff Composite Risk Management Operations Course, Joint Staff Complex Suffolk Va, Joint Staff Counterintelligence Awareness And Reporting, Joint Staff Codes, Joint Staff Commendation Medal, Joint Staff Correspondence Preparation, Joint Staff Counterintelligence Awareness And Reporting Answers, Joint Staff Composite Risk Management, Joint Staff Comptroller, Joint Staff Directorates, Joint Staff Dod, Joint Staff Doctrine, Joint Staff Dictionary, Joint Staff Dom, Joint Staff Department, Joint Staff Definitions, Joint Staff Designations, Joint Staff Directives, Joint Staff Deputy J8, Joint Staff Email Owa, Joint Staff Equal Opportunity Pre Test, Joint Staff Email, Joint Staff Emblem, Joint Staff Enterprise Portal, Joint Staff Electronic Library, Joint Staff Ebas, Joint Staff Email Outage, Joint Staff Estimates, Joint Staff Email Address, Joint Staff Flickr, Joint Staff Functions, Joint Staff Facebook, Joint Staff Flag Room Pentagon, Joint Staff Focal Point Program, Joint Staff Form 136, Joint Staff Functional Capability Boards, Joint Staff Forms, Joint Staff Forces College, Joint Staff Form 31, Joint Staff Guide 5711, Joint Staff Guide 5260, Joint Staff Global Force Management, Joint Staff Gatekeeper, Joint Staff General Officers, Joint Staff Gfm, Joint Staff Gomo, Joint General Staff, Joint Staff Officer’s Guide, Joint Staff Surgeon General, Joint Staff Hampton Roads, Joint Staff Headquarters, Joint Staff Headquarters Chaklala Address, Joint Staff Headquarters Chaklala, Joint Staff Hack, Joint Staff Handbook, Joint Staff Homepage, Joint Staff Has Oversight Of Interoperability Requirements, Joint Staff History Office, Joint Staff Historian, Joint Staff Identification Badge, Joint Staff Integrated Vulnerability Assessment, Joint Staff Intelligence, Joint Staff Industry Day, Joint Staff Instructions, Joint Staff Industry Conference, Joint Staff Innovation Group, Joint Staff Insignia, Joint Staff Ig, Joint Staff Information Paper Format, Joint Staff J7, Joint Staff J5, Joint Staff J6, Joint Staff J8, Joint Staff J4, Joint Staff J3, Joint Staff J39, Joint Staff J2, Joint Staff J1, Joint Staff J33, Joint Staff Key Terrain Methodology, Joint Staff Knowledge Management, Joint Staff Knowledge Online, Joint Chiefs Of Staff Kennedy Administration, Joint Chiefs Of Staff Korea, Joint Chiefs Of Staff Korean War, Joint Chiefs Of Staff Kennedy, Joint Chiefs Of Staff, Kmds Joint Staff, Staph Infection In Knee Joint, Joint Staff Law Of War Pretest, Joint Staff Leadership, Joint Staff Logo, Joint Staff Library, Joint Staff Letterhead Template, Joint Staff Law Of War, Joint Staff Letterhead, Joint Staff Lessons Learned, Joint Staff Legislative Affairs, Joint Staff Logistics Directorate J4, Joint Staff Manual, Joint Staff Mission Statement, Joint Staff Members, Joint Staff Manual 5100.01, Joint Staff Mailing Address, Joint Staff Military Security Force, Joint Staff Memorandum Format, Joint Staff Military And Civilian Awards Programs, Joint Staff Montessori School Chaklala, Joint Staff Memo, Joint Staff Norfolk, Joint Staff Numbering System, Joint Staff Network, Joint Staff Numbers, Joint Staff National Guard Bureau, Joint Staff News, Joint Staff Nco Pme, Joint Staff No Fear Act Training, Joint Staff New Norm Exord, Joint Staff Network Down, Joint Staff Organization, Joint Staff Officer, Joint Staff Officer’s Guide, Joint Staff Officer Handbook, Joint Staff Organization Chart, Joint Staff Operations Security, Joint Staff Owa, Joint Staff Owa Access, Joint Staff Operations Directorate, Joint Staff Org Chart, Joint Staff Pentagon, Joint Staff Portal, Joint Staff Publications, Joint Staff Pme, Joint Staff Positions, Joint Staff Public Affairs Office, Joint Staff Pentagon Mailing Address, Joint Staff Pension Fund, Joint Staff Public School Rawalpindi, Joint Staff Public School And College Chaklala, Joint Staff Officer Qualification, Joint Commission Staff Questions, Joint Chiefs Of Staff Quizlet, Joint Staff J7 Joint Qualification Report, Joint Forces Staff College Quarterdeck, Joint Staff Law Of War Quizlet, Joint Staff Report, Joint Staff Records Management, Joint Staff Responsibilities, Joint Staff Remote Access, Joint Staff Requirements, Joint Staff Reading List, Joint Staff Robotic And Autonomous Systems Team, Joint Staff Report On The Corporate Practice Of Dentistry, Joint Staff Roles, Joint Staff Risk Assessment, Joint Staff Suffolk, Joint Staff Surgeon, Joint Staff Structure, Joint Staff Support Center, Joint Staff South, Joint Staff Security Office, Joint Staff Sections, Joint Staff Strategic Multilayer Assessment, Joint Staff Sharepoint Portal, Joint Staff School Rawalpindi, Joint Staff Training Course, Joint Staff T2c2, Joint Staff Targeting, Joint Staff Training Program, Joint Staff Tank, Joint Staff Training Course Northcom, Joint Staff Telephone Directory, Joint Staff The Pentagon, Joint Staff Top 5, Joint Targeting Staff Course Dam Neck, Joint Staff Us, Joint Staff Uic, Joint Staff Uniform Policy, Joint Staff Uk, Joint Staff Unit Award, Joint Staff University, Joint Staff Ujtl, Joint Un Staff Pension Fund, Joint Staff Is Under Exclusive Authority, Joint Staff Report Us Treasury Market, Joint Staff Vice Chairman, Joint Staff Vice Director, Joint Staff Vdi, Joint Venture Staff, Joint Staff Suffolk Va, Joint Staff Suffolk Va Address, Joint Staff Integrated Vulnerability Assessment, Joint Staff Norfolk Va, Joint Staff Integrated Vulnerability Assessment Program, Joint Staff College Virginia, Joint Staff Writing Guide, Joint Staff Webmail, Joint Staff Wiki, Joint Staff Working Document, Joint Staff Website, Joint Staff Working Document Eastern Partnership, Joint Staff War College, Joint Staff Wire Diagram, Joint Staff When, Joint Staff Badge Wear Navy, Joint Staff Young Minds Program, Joint Chiefs Of Staff Youtube, Joint Staff Zip Code, Strategic Assessment Model, Strategic Assessment Template, Strategic Assessment Example, Strategic Assessment Journal, Strategic Assessment Plan, Strategic Assessment Definition, Strategic Assessment In War, Strategic Assessment Process, Strategic Assessment In Spm, Strategic Assessment Framework, Strategic Assessment And Technical Assessment, Strategic Assessment Approach, Strategic Assessment A, Strategic Aptitude Assessment, Strategic Alignment Assessment, Strategic Assessment Perth And Peel, Strategic Environmental Assessment Australia, Strategic Environmental Assessment And Land Use Planning, Strategic Risk Assessment And Management For Agribusiness Firms, Strategic Environmental Assessment And Climate Change, Strategic Business Assessment, Strategic Brand Assessment, Strategic Business Assessment Definition, Strategic Assessment Great Barrier Reef, Strategic Environmental Assessment Benefits, Strategic Environmental Assessment Better Practice Guide, Strategic Environmental Assessment Books, Strategic Assessment Of Building Adaptive Reuse Opportunities, Strategic Environmental Assessment Best Practice, Strategic Environmental Assessment Belgium, Strategic Assessment Crime, Strategic Assessment Community Safety, Strategic Assessment Cma, Strategic Assessment Center, Strategic Assessment Course, Strategic Assessment Capability, Strategic Conflict Assessment, Strategic Corporate Assessment Systems Inc, Strategic Conflict Assessment Dfid, Strategic Conflict Assessment Nigeria, Strategic Assessment Definition, Strategic Assessment Dtf, Strategic Assessment Der, Strategic Deterrence Assessment Lab, Strategic Environmental Assessment Directive, Strategic Environmental Assessment Definition, Strategic Needs Assessment Definition, Strategic Assessment Of Development Of The Arctic, Strategic Impact Assessment Definition, Strategic Conflict Assessment Dfid, Strategic Assessment Example, Strategic Assessment Epbc Act, Strategic Assessment Environmental, Strategic Environmental Assessment Directive, Strategic Environmental Assessment Ppt, Strategic Environmental Assessment Pdf, Strategic Environmental Assessment Regulations, Strategic Environmental Assessment Principles, Strategic Environmental Assessment Canada, Strategic Environmental Assessment Uk, Strategic Assessment Framework, Strategic Assessment For Perth And Peel, Strategic Assessment Format, Strategic Assessment For, Strategic Fit Assessment, Strategic Fit Assessment Matrix, Strategic Assessment Guidelines For Planning Scheme Amendments, Strategic Questioning Assessment For Learning, Strategic Environmental Assessment Framework, Strategic Environmental Assessment For Transport Plans And Programmes, Strategic Assessment Guidelines For Planning Scheme Amendments, Strategic Assessment Great Barrier Reef, Strategic Assessment Guidelines Checklist, Strategic Assessment Gbrmpa, Strategic Assessment Group, Strategic Growth Assessment, Strategic Goals Assessment, Strategic Gender Assessment, Strategic Environmental Assessment Guidelines, Strategic Environmental Assessment Guidance, Strategic Housing Assessment, Nca Strategic Assessment Human Trafficking, Strategic Environmental Assessment Hs2, Strategic Environmental Assessment Hk, Strategic Environmental Assessment History, Strategic Environmental Assessment Highways, Strategic Market Housing Assessment, Joint Strategic Needs Assessment Hertfordshire, Marine Corps Strategic Health Assessment, Strategic Environmental Assessment Of Hydropower On The Mekong Mainstream, Strategic Assessment In War, Strategic Assessment In Spm, Strategic Assessment In Software Project Management, Strategic Assessment In Project Evaluation, Strategic Assessment In Project Evaluation Ppt, Strategic Assessment Inss, Strategic Impact Assessment, Strategic Intelligence Assessment, Strategic Impact Assessment Report, Strategic Impact Assessment Directive, Strategic Assessment Journal, Strategic Environmental Assessment Jobs, Strategic Environmental Assessment Journal, Joint Strategic Assessment Wiltshire, Joint Strategic Assessment, Joint Strategic Assessment Team Iraq, Strategic Environmental Assessment In Japan, Strategic Environmental Assessment Kenya, Strategic Flood Risk Assessment Kensington And Chelsea, Strategic Flood Risk Assessment Kent, Strategic Housing Market Assessment Kirklees, Strategic Flood Risk Assessment Kingston, Joint Strategic Needs Assessment Kent, Joint Strategic Needs Assessment Kirklees, Strategic Environmental Assessment Tool Kit, Joint Strategic Needs Assessment Kensington And Chelsea, Joint Strategic Needs Assessment Kingston Upon Thames, Strategic Leadership Assessment, Strategic Learning Assessment Map, Strategic Land Assessment, Strategic Level Assessment, Strategic Leadership Assessment Tool, Strategic Environmental Assessment Limitations, Strategic Environmental Assessment Local Plan, Strategic Environmental Assessment Legislation, Strategic Environmental Assessment Landscape, Strategic Environmental Assessment Lecture Notes, Strategic Assessment Model, Strategic Assessment Meaning, Strategic Assessment Melbourne, Strategic Assessment Matrix, Strategic Assessment Methodology, Strategic Assessment Military, Strategic Assessment Management, Strategic Multilayer Assessment, Strategic Market Assessment, Strategic Multilayer Assessment Office, Strategic Assessment Nim, Strategic Needs Assessment, Strategic Needs Assessment Definition, Strategic Needs Assessment Template, Strategic Net Assessment, Strategic Needs Assessment Scotland, Strategic Needs Assessment Uk, Strategic Environmental Assessment Neighbourhood Plan, Strategic Siting Assessment Nuclear, Strategic Environmental Assessment Northern Ireland, Strategic Assessment Of The Perth And Peel Regions, Strategic Assessment Of Service Requirement, Strategic Assessment Of The Ethiopian Mineral Sector, Strategic Assessment Of Implementing Bi, Strategic Assessment Of A Company, Strategic Assessment Of Risk And Risk Tolerance, Strategic Assessment Of The Great Barrier Reef, Strategic Assessment Of Readiness For Training, Strategic Environmental Assessment, Strategic Assessment Of Crime, Strategic Assessment Plan, Strategic Assessment Process, Strategic Assessment Police, Strategic Assessment Perth Peel, Strategic Assessment Paper, Strategic Assessment Ppt, Strategic Assessment Pdf, Strategic Assessment Project Evaluation Ppt, Strategic Planning Assessment Tools, Strategic Planning Assessment Questions, Strategic Assessment Questions, Strategic Assessment Questionnaire, Strategic Questioning Assessment For Learning, Strategic Risk Assessment Questionnaire, Strategic Risk Assessment Questions, Strategic Environmental Assessment Quality, Strategic Environmental Assessment Qatar, Strategic Management Assessment Questionnaire, Strategic Planning Process Self-assessment Questionnaire For Businesses, Strategic Environmental Assessment Quebec, Strategic Assessment Report, Strategic Assessment Report Example, Strategic Assessment Report Template, Strategic Assessment Report Nopsema, Strategic Assessment Rms, Strategic Risk Assessment, Strategic Risk Assessment Template, Strategic Risk Assessment Questionnaire, Strategic Risk Assessment Process, Strategic Risk Assessment And Management For Agribusiness Firms, Strategic Assessment Software Project Management, Strategic Siting Assessment Nuclear, Strategic Service Assessment, Strategic Siting Assessment, Strategic Sourcing Assessment, Strategic Sustainability Assessment, Strategic Environmental Assessment Scotland, Strategic Assessment In Spm, Strategic Environmental Assessment (Sea), Strategic Environmental Assessment South Africa, Strategic Assessment Template, Strategic Assessment Tools, Strategic Assessment Tool Sight Words, Strategic Assessment Terms Of Reference, Strategic Thinking Assessment, Strategic Threat Assessment, Strategic Technology Assessment, Strategic Technology Assessment Review, Strategic Talent Assessment, Strategic Thinking Assessment Accenture, Strategic Assessment Uk, Strategic Assessment Urban Planning, Strategic Assessment Un, Strategic Environmental Assessment Uk, Strategic Environmental Assessment Uganda, Strategic Environmental Assessment Usa, Strategic Environmental Assessment Urban Planning, Strategic Environmental Assessment Unep, Strategic Needs Assessment Uk, Strategic Environmental Assessment Uranium Mining, Strategic Value Assessment, Strategic Value Assessment Model, Strategic Vulnerability Assessment, Strategic Environmental Assessment Vietnam, Strategic Environmental Assessment Vacancy, Strategic Assessment And Technical Assessment, Solidworks Strategic Value Assessment, Adobe Strategic Value Assessment, Strategic Assessment Wa, Strategic Workforce Assessment Program, Strategic Environmental Assessment Wales, Strategic Environmental Assessment World Bank, Strategic Environmental Assessment Wiki, Strategic Assessment In War, Joint Strategic Assessment Wiltshire, Strategic Risk Assessment Workshop, Strategic Environmental Assessment Wa, Strategic Environmental Assessment Wind Energy, Strategic Flood Risk Assessment York, Joint Strategic Needs Assessment York, Strategic Environmental Assessment Zambia, Strategic Environmental Assessment Zero Alternative, Strategic Environmental Assessment New Zealand, Strategic Environmental Assessment Coastal Zone















You must be logged in to post a comment.