Gambling addicts may want to take note of who Kim Kardashian picked to win the Super Bowl… because Lord knows this chick knows how to make a buck!
Month: January 2013
TOP-SECRET – FBI Bomb Data Center Bulletin: The Bomb Threat Challenge

FBI Bomb Data Center General Information Bulletin 2012-1
- 13 pages
- September 2012
As we enter an era in which the administration of law enforcement becomes more complicated, greater challenges are thrust not only upon police officials, but also upon the community at large. The bomb threat is one such challenge. The bomber has a distinct advantage over other criminals because he can pick his time and place from afar, and use the bomb threat as a weapon to achieve his criminal objectives. This bulletin has been prepared in order to provide law enforcement and public safety agencies with a working base from which to establish their own bomb threat response capability; and to enable these same agencies, when called upon by potential bomb or bomb threat targets in the business community, to offer assistance in developing guidelines for a bomb threat response plan.
In developing a bomb threat response plan, there are four general areas of consideration: (1) Planning and Preparation, (2) Receiving a Threat, (3) Evacuation, and (4) Search. Information presented under each of these four topics will assist in the preparation of an effective bomb threat plan. Suggested methods described in this bulletin will apply in most cases; however, specific requirements will be unique for each facility and will need to be worked out on an individual basis. Once the function of the organization, size of the facility, number of personnel, location and relation to other establishments, and available resources are evaluated; a comprehensive bomb threat plan can be formulated.
Words used in conjunction with this phase include organization, liaison, coordination, and control. Only with a properly organized plan will those affected by a bomb threat know how, when, and in what order to proceed.
Liaison should be maintained between appropriate public safety agencies and facilities likely to be subject to bomb threats or bombings; and also between public safety agencies and military Explosive Ordnance Disposal (EOD) teams charged with responding to bombing incidents.Through such contact, it will be possible to determine what technical and training services might be needed by potential bomb threat targets. Note that while some public safety agencies may provide considerable aid in bomb threat situations, most public and private facilities must plan and carryout the major portion of the plan, including internal control and decision making. Both liaison and coordination are factors which a bomb threat plan must take into consideration, especially when neighboring establishments or businesses may share the same building. Proper coordination will assure smooth handling of the bomb threat with the least amount of inconvenience to all concerned. Control is especially important during evacuation and search efforts, and effective security will lessen the risk of an actual explosive device ever being planted.
…
RECEIVING A THREAT
In preparation for the eventuality of a telephone bomb threat, all personnel who handle incoming calls to a potential target facility should be supplied with a bomb threat checklist as shown in Figure 1. When a bomb threat is received, it may be advisable for the person receiving the call to give a prearranged signal. For instance, the signal can be as simple as holding up a red card. This would allow monitoring of the call by more than one person, and it would enable someone else to attempt to record and/or trace the telephone call.
Tape recording the call can reduce the chance or error in recording information provided in the bomb threat. It may serve as evidence valuable to the investigation and assist in evaluating the authenticity of the bomb threat.
Since local jurisdictions may have statutes restricting this sort of recording, the proper officials should be contacted prior to installation and use of such equipment. If a continuous recording setup is not deemed economically practical, a system which could be activated upon receipt of a threat call might be considered feasible. A local telephone company representative can provide information regarding specific services available. Regardless of whether the bomb threat call is to be recorded and/or monitored, the person handling it should remain calm and concentrate on the exact wording of the message, and any other details which could prove valuable in evaluating the threat.In those instances when a bomb threat has been electronically recorded, voice identification techniques may be employed. While the courts and the scientific community are divided over the reliability of “voice printing” as evidence, it can serve as an investigative tool. Upon request, the FBI will perform audio examinations, for the purpose of investigative leads only, for any law enforcement agency. Departments interested in this service may contact their local FBI Field Office for further assistance.
Although comprising a smaller percentage of bomb threats, the written threat must be evaluated as carefully as one received over the telephone or the Internet. Written bomb threats often provide excellent document-type evidence. Once a written threat is recognized, further handling should be avoided in order to preserve fingerprints, handwriting, typewriting, postmarks, and other markings for appropriate forensic examination. This may be accomplished by immediately placing each item (i.e., threat documents, mail envelope, etc.) in separate protective see through covers, allowing further review of the pertinent information without needless handling. In order to effectively trace such a bomb threat and identify its writer, it is imperative to save all evidentiary items connected with the threat.
Regardless of how the bomb threat is received (e.g., e-mail, telephone, written), the subsequent investigation is potentially an involved and complex one requiring a substantial degree of investigative competency in order to bring the case to a successful conclusion. Cognizant of this, and of the fact that useful evidence regarding the threat seldom proceeds past the bomb threat stage, the efficient accumulation and preservation of evidence cannot be over stressed.
After a bomb threat has been received, the next step is to immediately notify the people responsible for carrying out the bomb threat response plan. During the planning phase, it is important to prepare a list setting forth those individuals and agencies to be notified in the event of a bomb threat. In addition to those people mentioned previously, the police department, fire department, FBI and other Federal public assistance agencies, medical facilities, neighboring businesses, employee union representatives, and local utility companies are among those whose emergency contact information should be included on such a list.
The bomb threat must now be evaluated for its potential authenticity. Factors involved in such an evaluation are formidable, and any subsequent decision is often based on little reliable information. During this decision making process, until proven otherwise, each threat should be treated as though it involved an actual explosive device; even though bomb threats in which an IED is present comprise a small percentage.
Monty Python Live Hollywood Bowl – Pope and Michaelangelo
Monty Python Live Hollywood Bowl
http://www.amazon.com/Complete-Monty-Pythons-Flying-Circus/dp/B001E77XNA/ref=…
Video – Confirmed – Ukraine ex-policeman jailed for murder of journalist Gongadze
http://www.euronews.com/ A former Ukrainian police officer has been jailed for life for the murder of a campaigning journalist Georgiy Gongadze in 2000.
General Oleksiy Pukach implied in court that others, including ex-President Leonid Kuchma, were equally guilty.
A case against the former leader was dismissed two years ago.
Gongadze wrote about political corruption and crime.
The discovery of the 31-year-old’s headless body sparked a wave of public anger which eventually led to the “Orange Revolution”.
His widow’s lawyer said she intended to appeal, arguing that the court has failed to determine the motives for the killing.
Find us on:
Youtube http://bit.ly/zr3upY
Facebook http://www.facebook.com/euronews.fans
Twitter http://twitter.com/euronews
SECRET – Iranian Hackers Target US-UK Joint Operations
Iranian Hackers Target US-UK Joint Operations
A sends:
Source : http://www.rce.ir/viewtopic.php?f=8&t=245#p860
An observer we trust has let us know that in an underground Iranian hacker and reverse engineering forum, one article shows some guys have been up to no good against US-UK Joint Operations and hacked into the Waves as well as the C4I system.
Ironically, there is a link and quote from cryptome.us [link added by Cryptome] regarding IRGC’s drones flying over US carriers and put both conclusions together in a way that reader, indirectly, understands that military SATCOMS and JTRS terrestrial (say military VHF) are not safe for US-UK and to our understanding they could easily use these capabilities to grab scores from catastrophic events. The fact Iran is still talking to 5+1 in addition to these efforts, to the best of our analysis, are Iranian Deterrence.
TMZ – Hulk Hogan: Brooke Hogan’s SEXY Legs!
Hulk Hogan is catching some heat for tweeting a picture of his daughter’s sexy legs in a short skirt. Is Hulk just being a proud parent or just REALLY, SUPER CREEPY?
PI-Restricted U.S. Army Training for Reconnaissance Troop and Below in Urban Operations

TC 90-5 Training for Reconnaissance Troop and Below in Urban Operations
- 116 pages
- Distribution authorized to U.S. government agencies and their contractors only to protect technical or operational information that is for official government use.
- February 2010
- 5.09 MB
Because the operational environment (OE) requires Army forces to operate in urban areas, commanders must have accurate information on the complex human elements, infrastructure, and physical terrain that make up the urban environment. The limits on imagery and electronic reconnaissance and surveillance (R&S) capabilities place a premium on human-based visual reconnaissance. Reconnaissance troops and platoons must be trained to gather and analyze the necessary information and provide it to their commanders and higher headquarters. This chapter discusses definitions, training strategy, prerequisite training, individual task training, and collective task training designed to prepare reconnaissance units at troop level and below for operations in urban terrain.
…
URBAN-SPECIFIC TASKS FOR STABILITY OPERATIONS AND CIVIL SUPPORT OPERATIONS
1-25. The following sample tasks are listed in TC 7-98-1:
- Conduct cordon and search operations, including site exploitation (SE).
- Conduct roadblock/checkpoint operations.
- Conduct civil disturbance operations.
- Secure civilians during operations.
- Process detainees and enemy prisoners of war (EPW).
1-26. See FM 3-06.11 for a review of additional tasks related to stability operations and civil support operations. These include, but are not limited to, the following:
- Conduct area security, including presence patrols.
- Conduct convoy escort.
- Conduct route clearance operations.
…
SECTION IX – CONTROL CIVILIAN MOVEMENT/DISTURBANCE
3-60. The likelihood of civil disturbances during urban operations is high. Handled poorly, the reaction to a civil disturbance can quickly escalate out of control, with potential long-term negative effects for mission accomplishment. Conversely, a well-handled situation will lead to an enhanced view of the reconnaissance platoon’s discipline and professionalism and potentially could result in fewer such incidents in the future.
SUPPORTING TASKS
3-61. Table 3-9 lists the supporting tasks that must be accomplished as part of controlling civilian movement and disturbances.
OPERATIONAL CONSIDERATIONS
3-62. A possible TTP description for this task is covered by procedures known by the acronym of IDAM:
- Isolate.
- Dominate.
- Maintain common situational awareness (SA).
- Employ multidimensional/multiecheloned actions.
3-63. The first step entails isolating, in time and space, the trouble spot from outside influence or interaction. Unit tactical operation centers in the theater must develop TTP that “isolate” riots or demonstrations to keep them from becoming larger and potentially more violent. The idea is to close access into and out of the demonstration location (Figure 3-13). Once access is closed, rioters tend to tire within hours, and the demonstration dies down, eventually resulting in a peaceful conclusion. Figure 3-14 provides a technique for positioning several tiers of checkpoints and tactical control points, given the mission to isolate a riot. Controlling major road networks into and out of the demonstration area also serves to enhance trafficability if the riot escalates.
3-64. Units dominate the situation through force presence and control of information resources. They can demonstrate an overwhelming show of force at command posts (CP) and dispatch helicopters to conduct overflights above demonstrations and massing civilian mobs. In addition, use of appropriate air assets can give commanders a bird’s-eye view of events, providing real-time updates on the situation and ensuring that units know the “ground truth” at all times. This knowledge gives commanders a decisive advantage both in negotiations with potentially hostile elements and in tactical maneuvers.
3-65. The following factors apply for the platoon in attempting to dominate the situation:
- Although units can dominate a civil disturbance using nonlethal munitions, it is important to consider force protection issues. In addition, if aviation assets are available, reconnaissance or utility helicopters can provide a show of force. Attack helicopters should be used in anoverwatch or reserve position.
- Forces may need to detain group leaders or instigators to dominate a civil disturbance. An instigator is identified as a person who is “prodding” others to commit disruptive acts or who is orchestrating the group. Often, an instigator carries a bullhorn or hand-held radio.
- The smallest unit that can employ the “snatch-and-grab” technique is a platoon. Before a platoon deploys to quell a riot, identify a four-person snatch-and-grab team, two to secure the individual and two to provide security. It is imperative that each member of the snatch-and-grab team wears the Kevlar helmet with face shield and flak vest, but the team should not bring weapons or load-bearing equipment with them into the crowd. See Figure 3-15 for an illustration of the snatch-and-grab team.
- In accordance with Executive Order 11850, the President of the United States must approve the use of the riot control agency (RCA). The U.S. policy is to employ RCAs in limited circumstances, though never as a method of warfare. Commanders should be conscious that use of RCAs might pose a risk of escalation or public panic if it creates the erroneous perception that a chemical weapon is being used.
- Another element that is crucial for successful civil disturbance operations is the use of combat camera personnel. Document events to hold personnel, factions, and gangs or groups accountable. To ensure that the right message is being presented, control the information environment through the synchronized efforts of information engagement assets, with support from the staff judge advocate (SJA) and civil affairs (CA) offices.
3-66. Commanders and leaders maintain SA through timely, accurate, and complete multisource reporting. They can receive reports from a broad spectrum of sources. Unit CPs, air assets, and close liaison with HN police, NGOs, PVOs, and other civilian agencies all contribute to an accurate assessment of any situation. In addition, UAS, such as the Predator and Pioneer, are effective in observing large sectors of an AO. Analyze the reports produced and relay them to each unit involved in the operation.
3-67. As part of the IDAM procedures, multidimensional/multiechelon actions may entail the following considerations:
- Policy and legal considerations.
- ROE.
- Standards of conduct.
- High visibility of civil disturbance operations with the media, including leaders who must interact with the media.
- Crowd dynamics.
- Communication skills for leaders who must manage aggressive and violent behavior of individuals and crowds.
- Use of electronic warfare to monitor and control belligerent communications.
- Tactics.
- Lethal overwatch.
- Search and seizure techniques.
- Apprehension and detention.
- Neutralization of special threats.
- Recovery team tactics.
- Cordon operations to isolate potential areas of disturbance.
…
PSYCHOLOGICAL OPERATIONS
5-33. The smallest organizational PSYOP element is the tactical PSYOP team (TPT), consisting of three Soldiers. In high-intensity conflict, the TPT normally provides PSYOP support to a squadron. During counterinsurgency (COIN) and stability operations, planning and execution are primarily conducted at the troop level because the troop is the element that most often directly engages the local government, populace, and adversary groups. Operating in the troop AO allows TPTs to develop rapport with the target audience. This rapport is critical to the accomplishment of the troop’s mission. The TPT chief, usually a SSG or SGT, is the PSYOP planner for the troop commander. He also coordinates with the tactical PSYOP detachment (TPD) at the squadron level for additional support to meet the troop commander’s requirements. PSYOP planning considerations include the following:
- The most effective methods for increasing acceptance of friendly forces in occupied territory.
- The most effective methods of undermining the will of the threat to resist.
- The impact of PSYOP on the civilian population, friendly government, and law enforcement agencies in the area.
- Clearly identified, specific PSYOP target group(s).
- Undermining the credibility of threat leadership and whether or not it will bring about the desired behavioral change.
Monty Python – Holy Grail – Black Knight
Monty Python – Holy Grail – Black Knight
Monty Python Holy Grail
http://www.amazon.com/Monty-Python-Trinity-Pythons-Meaning/dp/B001E12ZAM/ref=…
TMZ – Hilary Duff — Rich Girl Hair
Hilary Duff is definitely stinkin’ rich and has very nice hair… and one (male) member of the TMZ newsroom just so happens to be her exact hair doppelganger!
TOP-SECRET-U.S. Northern Command Title 10 Dual Status Commander Standard Operating Procedures

USNORTHCOM PUBLICATION 3-20 TITLE 10 SUPPORT TO DUAL STATUS COMMANDER LED JOINT TASK FORCE STANDARD OPERATING PROCEDURES
- 194 pages
- January 31, 2012
The Council of Governors and the President of the United States have identified the need for Dual Status Commanders (DSC) to unify the response efforts within the 54 Territories and States of the United States of America. United States Northern Command (USNORTHCOM) has identified Title 10 Deputy Commanders (O-6 in grade) to lead a Joint Support Force Staff Element (JSF-SE) that will integrate with the State-Level DSC staff in order to provide unity of effort to the response of both Title 32/State Active Duty (SAD) and Title 10 forces. This Standard Operating Procedures document outlines the USNORTHCOM Staff support to the DSC Program, a template for a T10 Deputy Commander Handbook and the methods, procedures and best practices for the JSF-SE.
…
This chapter provides an overview and background of the Dual Status Commander (DSC) program, and it provides an introduction to the Title 10 Support to Dual-Status Commander Led Joint Task Force Standard Operating Procedures which details the roles, responsibilities and processes/procedures for USNORTHCOM Staff, components, subordinates, and assigned/attached forces in supporting the DSC program.
1.1 Purpose
1.1.1. This standard operating procedure (SOP) outlines the Title 10 (T10) staff roles, responsibilities, and processes/procedures for support to a DSC during Defense Support of Civil Authorities (DSCA) operations (events/incidents requiring a Federal response).
1.1.2. This SOP consists of five chapters which provide: an overview of the DSC program (Chapter One); an outline of the roles, responsibilities, and processes/procedures for United States Northern Command (USNORTHCOM) Staff Support to DSC led Joint Task Forces (JTFs) (Chapter Two); T10 Deputy Commander (Chapter Three); the Joint Support Force Staff Element (JSF-SE) SOP (Chapter Four); and a recommended JSF-SE training curriculum (Chapter Five).
1.1.3. This SOP assumes that USNORTHCOM will provide a baseline JSF-SE that will integrate with the State JTF staff to support the T10 requirements. The JSF-SE will leverage support from the State JTF staff to meet the T10 requirements (e.g., reporting of JTF Situation Report (SITREP)/Storyboard, joint personnel status reports (JPERSTATs), logistical status reports (LOGSTATs), etc). While DSC led JTFs can organize with parallel and separate staff structures under a DSC, the best practice referenced within this SOP is the integrated staff model, where T10 staff are fully integrated with the State Active Duty/Title 32 (SAD/T32) staff.
1.1.4. All references to State within this SOP are used to refer to States, Territories, Commonwealths and the District of Columbia.
1.2 Background
1.2.1. In January 2009, the Secretary of Defense (SecDef) directed the development of options and protocols that allow Federal military forces supporting the Primary Agency to assist State emergency response personnel in a coordinated response to domestic disasters and emergency operations, while preserving the President’s authority as Commander in Chief.
1.2.2. In February 2010, during the first Council of Governors meeting, the SecDef acknowledged mutually exclusive sovereign responsibilities of Governors and the President, and urged all participants to focus on common ground and build a consensus approach to coordinate disaster response.
1.2.3. In August 2010, the Commander, United States Northern Command (CDRUSNORTHCOM) hosted an orientation visit for the initial State DSC candidates (i.e., Florida, California, and Texas).
1.2.4. In December 2010, a Joint Action Plan for DSC was approved by the Council of Governors, Department of Defense (DOD), Department of Homeland Security (DHS), and Federal Emergency Management Agency (FEMA), stating that the appointment of a DSC is the “usual and customary command and control arrangement” when State and Federal military forces are employed simultaneously
in support of civil authorities in the United States.1.2.5. In May 2011, CDRUSNORTHCOM assigned USNORTHCOM/J36 Domestic Operations (NC/J36) as office of primary responsibility (OPR) for DSC. NC/J36 will coordinate with NORADUSNORTHCOM (N-NC) J5 and N-NC/J7 on doctrine and training, respectively.
1.2.6. This SOP is one of many documents which address the DSC integrated response to a DSCA event.
1.2.7. Figure 1-2 provides a hierarchy of DOD’s DSCA-related documents. Links to these references can be found in Annex A.
1.2.7.1. DOD Directive 3025.18 outlines the DOD roles in providing DSCA.
1.2.7.2. DOD Directive 5105.83 National Guard Joint Force Headquarters – State (NG JFHQs-State) establishes policy for and defines the organization and management, responsibilities and functions, relationships, and authorities of the NG JFHQs-State.
1.2.7.3. The Chairman, Joint Chiefs of Staff (CJCS) DSCA Standing Execution Order (EXORD) directs DSCA operations in support of the National Response Framework (NRF) and identified primary agencies in the USNORTHCOM and United States Pacific Command (USPACOM) domestic geographic areas of responsibility (AOR).
1.2.7.4. The CDRUSNORTHCOM Standing EXORD for DSCA operations outlines how USNORTHCOM will employ DOD forces in support of other federal agencies in the USNORTHCOM Operational Area (OA).
1.2.7.5. USNORTHCOM concept plan (CONPLAN) for DSCA is the Geographic Combatant Command (GCC) plan to support the employment of T10 forces providing DSCA in accordance with (IAW) the NRF, applicable federal laws, DOD Directives, and other policy guidance including those hazards defined by the National Planning Scenarios that are not addressed by other Joint Strategic Capabilities Plan tasked plans.
1.2.7.6. USNORTHCOM operations order (OPORD) 01-11/01-12 provides direction on the conduct of military operations within the USNORTHCOM AOR. USNORTHCOM produces an OPORD annually to address planned/forecasted military operations in support of the USNORTHCOM Theater Campaign Plan.
1.2.7.6.1. Subsequent Fragmentary Orders (FRAGOs) provide specific guidance (or changes to previous guidance) on unique events to address unforecasted military support operations.
1.2.7.7. The DSC Concept of Operations (CONOPS) describes the terms, responsibilities, and procedures governing the qualification, certification, appointment, and employment of a DSC for designated planned events, or in response to an emergency or major disaster within the United States, or its territories, possessions, and protectorates.
1.2.7.8. The USNORTHCOM Initial Entry Concept of Execution (CONEX) provides USNORTHCOM doctrine and procedures for establishing Joint initial command and control (C2) and support capability for its Civil Support (CS), Homeland Defense (HD) and Department of State (DOS) support operations.
1.2.7.9. The JTF Commander Training Course (JCTC) Handbook serves as a working reference and training tool for individuals who will command and employ JTFs for HD and CS at the federal and/or state level.
Monty Python – Holy Grail – Witch Village
Monty Python – Holy Grail – Witch Village
Monty Python Holy Grail
http://www.amazon.com/Monty-Python-Trinity-Pythons-Meaning/dp/B001E12ZAM/ref=…
Cryptome unveils – ATT Greenstar Secretly Spied Millions of Calls
ATT Project Greenstar Secretly Spied Millions of Calls
Greenstar prefigures current ATT’s once-secret participation in intercepting vast telecommunications data for the National Security Agency. More: https://www.eff.org/nsa-spying/faq
EXPLODING THE PHONE
The Untold Story of the Teenagers and Outlaws Who Hacked Ma Bell
PHIL LAPSLEY
Grove Press New York
[pp. 92-97]
If there were no billing records for fraudulent calls, there was no way to know how many fraudulent calls there were or how long they lasted. And that meant AT&T was gazing into the abyss. Say the phone company catches some college students with electronic boxes. Fantastic! But elation is soon replaced by worry. Is that all of them? Or is that just the tip of the iceberg? Are there another ten college students doing it? A hundred? Are there a thousand fraudulent calls a year or are there a million?
Engineers hate stuff like this.
Bell Labs, filled to the brim with engineers, proposed a crash program to build an electronic toll fraud surveillance system and deploy it throughout the network. It would keep a watchful eye over the traffic flowing from coast to coast, ever vigilant for suspicious calls — not every call, mind you, but a random sampling of a subset of them, enough to gather statistics. For the first time Bell Labs — and AT&T’s senior management — would have useful data about the extent of the electronic toll fraud problem. Then they’d be in a position to make billion-dollar decisions.
The project was approved; indeed, AT&T gave Bell Labs a blank check and told them to get right to work. Tippy-top secret, the program had the coolest of code names: Project Greenstar. Within Bell Labs Greenstar documents were stamped with a star outlined in green ink to highlight their importance and sensitivity. Perhaps as a joke, the project lead was given a military dress uniform hat with a green general’s star on it, an artifact that was passed on from one team lead to the next over the years.
Greenstar development began in 1962 and the first operational unit was installed at the end of 1964. Bill Caming, AT&T’s corporate attorney for privacy and fraud matters, became intimately familiar with the program. “We devised six experimental units which we placed at representative cities,” Caming said. “Two were placed in Los Angeles because of not only activity in that area, but also different signaling arrangements, and one was placed in Miami, two were originally placed in New York, one shortly thereafter moving to Newark, NJ, and one was placed in Detroit, and then about January 1967 moved to St. Louis.”
Ken Hopper, a longtime Bell Labs engineer involved in network security and fraud detection, recalls that the Greenstar units were big, bulky machines. “I heard the name ‘yellow submarine’ applied to one of them,” he says. They lived in locked rooms or behind fenced-in enclosures in telephone company switching buildings. A single Greenstar unit would be connected to a hundred outgoing long-distance trunk lines and could simultaneously monitor five of them for fraud. The particular long-distance trunk lines being monitored were selected at random as calls went out over them. At its core, Greenstar looked for the presence of 2,600 Hz on a trunk line when it shouldn’t be there. It could detect both black box and blue box fraud, since both cases were flagged by unusual 2,600 Hz signaling.
As Caming described it, “there were in each of these locations a hundred trunks selected out of a large number, and the [ … ] logic equipment would select a call. There were five temporary scanners which would pick up a call and look at it with this logic equipment and determine whether or not it had the proper [ … ] supervisory signals, whether, for example, there was return answer supervision. When we have a call, we have a supervisory signal that goes to and activates the billing equipment which usually we call return answer supervision. That starts the billing process and legitimizes the call, and if you find voice conversation without any return answer signal, and that is what it was looking for, it is an indication, a strong indication, of a possible black box that the caller called in; and if, for example, you heard the tell-tale blue box tone [ … ] this was a very strong indication of illegality because that tone has no normal presence upon our network at that point.”
When Greenstar detected something unusual, it took an audacious next step: it recorded the telephone call. With no warrant and with no warning to the people on the line, suspicious calls were silently preserved on spinning multitrack reel-to-reel magnetic tapes. If Greenstar judged it had found a black box call it recorded for sixty to ninety seconds; if it stumbled upon a blue box it recorded the entire telephone call. Separate tracks recorded the voice, supervisory signals, and time stamps.
When the tapes filled up they were removed by two plant supervisors. “They were the only two who had access from the local [telephone] company,” Caming says. Then they were sent via registered mail to New York City. There, at the Greenstar analysis bureau, specially trained operators — “long-term chief operators who had great loyalty to the system [who] were screened for being people of great trust,” Ken Hopper says — would listen to the tapes, their ears alert for indications of fraud. The operators would determine whether a particular call was illegal or was merely the result of an equipment malfunction or “talk off” — somebody whose voice just happened to hit 2,600 Hz and had caused a false alarm. When these operators were finished listening, the tapes would be bulk erased and sent back for reuse.
“The greatest caution was exercised,” Bill Caming recalls. “I was very concerned about it. The equipment itself was fenced in within the central office so that no one could get to it surreptitiously and extract anything of what we were doing. We took every pain to preserve the sanctity of the recordings.”
Project Greenstar went on for more than five and a half years. Between the end of 1964 and May 1970, Greenstar randomly monitored some 33 million U.S. long-distance phone calls, a number that was at once staggeringly large and yet still an infinitesimally tiny fraction of the total number of long-distance calls placed during those years. Of these 33 million calls, between 1.5 and 1.8 million were recorded and shipped to New York to be listened to by human ears. “We had to have statistics,” said Caming. Statistics they got: they found “at least 25,000 cases of known illegality” and projected that in 1966 they had “on the order of 350,000 [fraudulent] calls nationwide.”
“Boy, did it perk up some ears at 195 Broadway,” says Hopper. It wasn’t even that 350,000 fraudulent calls was that big a number. Rather, it was the fact that there was really nothing that could be . done about it, at least not at once. “It was immediately recognized that if such fraud could be committed with impunity, losses of staggering proportions would ensue,” Caming said. ”At that time we recognized — and we can say this more confidently in public in retrospect — that we had no immediate defense. This was a breakthrough almost equivalent to the advent of gunpowder, where the hordes of Genghis Khan faced problems of a new sort, or the advent of the cannon.”
The initial plan with Greenstar was simple: Wait. Watch. Listen. Gather statistics. Tell no one. Most important, don’t do anything that would give it away. “There was no prosecution during those first couple of years,” Hopper says. “It was so the bad guys would not be aware of the fact that they’re being measured.” It was only later, Hopper says. that AT&T decided to switch from measurement to prosecution. Even then! Hopper said, “The presence of Greenstar would not be divulged and that evidence gathered to support toll fraud prosecutions would be gathered by other means.” Instead, Hopper relates, Greenstar would be used to alert Bell security agents to possible fraud. The security agents would then use other means, such as taps and recordings, to get the evidence needed to convict. “Greenstar bird-dogging it would not be brought out,” says Hopper. “It was just simply a toll fraud investigation brought about by unusual signaling and you would not talk about the fact that there was a Greenstar device. That was the ground rule as I understood it. Any court testimony that I ever gave, I never talked about any of that.” As another telephone company official put it, “If it ever were necessary to reveal the existence of this equipment in order to prosecute a toll fraud case, [AT&T] would simply decline to prosecute.”
Bill Caming became AT&T’s attorney for privacy and fraud matters in September 1965. Greenstar had been in operation for about a year when he was briefed on it. His reaction was immediate: “Change the name. I don’t even know what it is, but it just sounds illegal. Change the name.” More innocent-sounding code names like “Dewdrop” and “Ducky” were apparently unavailable, so AT&T and Bell Labs opted for something utilitarian and unlikely to attract attention: Greenstar was rechristened “Toll Test Unit.”
As the new legal guy at AT&T headquarters, Caming faced questions that were both important and sensitive. Forget how it sounded, was Greenstar actually illegal? And if it was, what should be done about it? Before joining AT&T Caming had been a prosecutor at the Nuremberg war crimes trials after World War II. He was highly regarded, considered by many to be a model of legal rectitude. Was there any way he could see that the AT&T program was legit?
There was. He later stated under oath that there was “no question” Greenstar was in fact legal under laws of the day — a surprising conclusion for what at first blush appears to be an astonishing overreach on the part of the telephone company. There were two parts to Caming’s reasoning. The first had to do with the odd wording of the wiretap laws of the early 1960s; using this wording Caming was able to thread a line of legal logic through the eye of a very specific needle to conclude that the program was legal under the law prior to 1968. The second part had to do with his position at American Telephone and Telegraph. In 1968, when Congress was considering new wiretapping legislation, Caming was in a position to help lawmakers draft the new law. He made very sure that the new wiretap act didn’t conflict with AT&T’s surveillance program.
Caming even informed the attorneys at the Justice Department’s Criminal Division about Greenstar in 1966 and 1967, in connection with some prosecutions. “Now, that does not say that they cleared it or gave me their imprimatur,” he allowed. But then, he added, “we did not feel we needed it.”
Years later, the Congressional Research Service agreed with Caming regarding the legality of the program — to a degree. While not going so far as to say there was “no question” that Greenstar was legal, it was concluded that “It is not certain that the telephone company violated any federal laws by the random monitoring of telephone conversations during the period from 1964 to 1970. This uncertainty exists because the Congressional intent [in the law] is not clear, and case law has not clearly explained the permissible scope of monitoring by the company.”
This whole mess formed a challenging business conundrum for AT&T executives, the sort of thing that would make for a good business school case study. Put yourself in their shoes. You have made an incredibly expensive investment in a product — the telephone network — that turns out to have some gaping security holes in it. You have, as Bill Caming said, no immediate defense against the problem. You finally have some statistics about how bad the problem is. It’s bad, but it’s not terrible, unless it spreads, in which case it’s catastrophic. Replacing the network will take years and cost a billion dollars or so. The Justice Department isn’t sure there are any federal laws on the books that actually apply. And every time you prosecute the fraudsters under state laws, not only do you look bad in the newspapers — witness the Milwaukee Journal’s 1963 front-page headline “Lonely Boy Devises Way of Placing Free Long Distance Calls” — but the resulting publicity makes the problem worse.
AT&T played the best game it could with a bad hand. For now it would quietly monitor the network, keeping a weather eye on the problem. When the company found college kids playing with the network, investigators would give them a stern talking — to and confiscate their colored boxes. Execs would start thinking about a slow, long-term upgrade to the network to eliminate the underlying problem. And if opportunity knocked and they could help out the feds with an organized crime prosecution — and in the process set a clear precedent for the applicability of the federal Fraud by Wire law — well, that would be lovely.
That opportunity came knocking in 1965. As it turned out used a sledgehammer.
[pp. 115-16]
On May 5, 1969, the Supreme Court declined to hear their case. More than three years after the FBI took a sledgehammer to Ken Hanna’s door, the issue was finally settled. If you were making illegal calls you had no right to privacy. The phone company could tap your line and turn the recordings over to law enforcement.
For the phone company, the victory was about much more than convicting Hanna or Dubis. AT&T now had a case that had gone all the way to the Supreme Court, one that proved, definitively, that 18 USC 1343 — the Fraud by Wire law that the Justice Department had believed wasn’t relevant — did apply to blue boxes. Thanks to Hanna’s failed appeal, the matter was now settled. AT&T finally had an arrow in its quiver to use against the fraudsters.
Throughout all of this legal drama one mystery remains: how had the telephone company found out about Hanna’s or Dubis’s blue box calls in the first place?
In the Hanna case, Miami telephone company security agent Jerry Doyle received a telephone call from the Internal Audit and Security Group at AT&T headquarters in New York asking him to investigate Hanna’s telephone line for a possible blue box. How did investigators in New York know that somebody in Miami was making illegal calls? Hanna’s attorneys asked Doyle this very question but Doyle said he didn’t know.
There was a one-word answer that nobody was giving: Greenstar. Hanna had been caught up in AT&T’s toll fraud surveillance network. Imagine what would have happened if this had come out during Hanna’s trial. After all, the Hanna case took almost four years to resolve and went to the Supreme Court based on tape recordings of each of his illegal calls. Think of the legal circus that would have ensued if Hanna’s defense attorneys had learned that the telephone company had been randomly monitoring millions of telephone calls nationwide and recording hundreds of thousands of them.
This added considerably to the stress of prosecuting Greenstar cases. AT&T attorney Caming recalls, “That was the problem in the Hanna case! Fortunately, defense counsel never probed too far as to what our original sources of information were.” With blue box prosecutions, he adds, “We were always on pins and needles as to what might spill over into the public press.”
Fortunately for AT&T in the Hanna and Bubis cases their luck held. And although Caming wasn’t a gambler or a bookmaker, he knew a thing or two about luck. In particular, he knew it didn’t last forever.
[p. 144]
At that point, the phone company billing records show something anomalous: here’s a call to a number, 555-1212, that should never look like it answered and yet it does. The phone company doesn’t like anomalies in its network, not so much because they think somebody might be messing with them, but just because anomalies probably mean that something is broken somewhere and needs repair.
“I knew that was an irregularity,” Acker says. “My fear was, you know, if this registers on your tape” — Acker knew the phone company in those days used paper tape for billing records — “they’ll be able to tell that [the call] answered, and they know it’s not supposed to.” Acker’s fears were right on the money. The phone company was indeed using computer-generated reports of supervision irregularities to spot blue boxes. Along with Greenstar, these reports were a primary tool the Bell System used to detect such fraud and, due to Greenstar’s secrecy, were among the most effective for prosecution.
Acker’s surprise caller was a security agent from his telephone company, New York Telephone. The agent had already talked to Acker’s friend John, likely because of 555-1212 supervision anomalies. But the reason the agent wanted to talk to Acker was more concrete. John had ratted out Acker to the security agent.
“He spilled his guts,” Acker says. “That was just an inconceivable no-no to me. That pretty much trashed our friendship. Forever and ever.” Forty years later you can still hear the intensity in Acker’s voice. “When you get in trouble, you don’t squeal on anybody.”
[p. 182]
Charlie Schulz and Ken Hopper, members of the technical staff of the Telephone Crime Lab at Bell Laboratories.
Hopper’s path to the Telephone Crime Lab was a circuitous one. In 1971 he was a distinguished-looking forty-five-year-old electrical engineer, a bit on the heavy side, with blue eyes, short brown hair, and glasses. Hopper had joined the Bell System some twenty-five years earlier, shortly after the end of World War II. Within a few years he had found himself at Bell Laboratories’ Special Systems Group working on government electronics projects. The stereotype of government work is that it’s boring, but Hopper was a lightning rod for geek adventure: wherever he went to do technical things physical danger never seemed far behind. There was the time he had to shoot a polar bear that had broken into his cabin while he was stationed up in the Arctic working on the then secret Distant Early Warning Line, the 1950s-era radar system that would provide advance warning of a Soviet bomber attack. Or the time he almost died in a cornfield in Iowa while building a giant radio antenna for a 55-kilowatt transmitter to “heat up the ionosphere” for another secret project. Then there’s the stuff he still can’t really talk about in detail, involving submarines and special tape recorders and undersea wiretaps of Soviet communications cables.
The Special Systems Group was a natural to help AT&T with the Greenstar toll-fraud surveillance network in the 1960s, Hopper says, and that work led to involvement with other telephone security matters. But the Telephone Crime Lab also owes its existence to the FBI. Hopper recalls, “In the mid-1960s the FBI laboratory came to our upper management and said they were getting electronic-involved crimes. They had no people in their laboratory that could examine evidence in these cases, especially related to communication systems, and they asked for Bell Labs’ assistance. Upper management of Bell Labs agreed that this was in the public interest and that we would do that. The work was assigned to my organization, Charlie Schulz being the supervisor. We had just a few people, never more than two or three, working on this stuff.
[pp. 304-05]
The Ashley-Gravitt affair was much in the newspapers that fall and attracted the attention of Louis Rose, an investigative reporter at the St. Louis Post-Dispatch, Missouri’s preeminent newspaper. Rose had written a series of articles examining the apparently cozy relationship between Southwestern Bell and the Missouri Public Service Commission, its regulator in that state. “I had been looking at all the expenditures and all of the salaries and donations by Southwestern Bell,” Rose recalls. James Ashley, he says, “found a convenient thing in me, because I was already looking up these ties.”
In January 1975 the Texas scandal spread to North Carolina when a former Southern Bell vice president — another who had been forced out of the telephone company, as it happened — admitted during an interview that he had run a $12,000-a-year political kickback fund for the Bell System. The telephone company soon found itself being investigated by an assortment of agencies: the Securities and Exchange Commission, the Department of Justice, the Federal Wiretap Commission, the FCC, and the Texas attorney general.
The next shoe to drop in the scandal was, in a way, predictable, so predictable, in fact, that Bill Caming, AT&T’s patrician attorney for privacy and fraud matters, had predicted it ten years earlier. Caming couldn’t say exactly when it would happen, or exactly how it would happen, but he was sure it would happen. Ever since I965, when he had first learned about AT&T’s Greenstar toll-fraud surveillance system, with its tape recordings of millions of long-distance calls and its racks of monitoring equipment kept behind locked cages in telephone company central offices, Caming had maintained it was a matter of when — and not if — the news of Greenstar would eventually leak.
The “when” turned out to be February 2, 1975. The “how” was a front-page headline in the St. Louis Post-Dispatch: “Bell Secretly Monitored Millions of Toll Calls.” The article, by Louis Rose, quoted an anonymous source within the phone company and was chock-full of details: a list of the cities where Greenstar had been installed, the specifics of its operation, the stunning news that the phone company had monitored 30 million calls and tape-recorded some 1.5 million of them. Someone — someone high up, it seemed — had spilled the beans. By the next day the story had been picked up by the newswires and the New York Times.
Caming didn’t need a crystal ball to predict what happened next: a phone call from the chair of the House Subcommittee on Courts, Civil Liberties, and the Administration of Justice. “He said. ‘I think we’re going to have to have one of your guys come down and explain all this to us,” Caming knew, as he had known for ten years now, that he would be the guy.
Less than three weeks later Caming found himself before the U.S. Congress. swearing to tell the truth, the whole truth, and nothing but the truth. Seated with Caming were Earl Conners, chief of security for Chesapeake and Potomac Telephone Company, and John Mack, a Bell Labs engineer who was intimately familiar with the technical details of Greenstar. True to his reputation for loquaciousness (or maybe it was his legal training) Caming made sure his colleagues never got to speak more than two dozen words over the course of the three-hour hearing. Caming explained AT&T’s motivations for launching the surveillance system, how it operated, and, most important, why it was legal — indeed, not just legal, but in fact the only option AT&T had to combat blue box and black box fraud at the time. Never once did he refer to it as “Greenstar,” the name that ten years earlier he said “just sounds illegal.” Perhaps it was Caming’s legal reasoning, perhaps it was his appearance — competent, prepared, confident, yet self-effacing — or perhaps it was 195 Broadway’s deft handling of the press on the matter, but AT&T managed to weather the Greenstar storm without much damage. Despite some alarming headlines there was little fallout and no criminal investigation. The Greenstar matter quickly faded away.
[pp. 358-59]
Notes
95 “decline to prosecute”: Rose, “Bell Secretly Monitored Millions of Toll Calls.”
96 “Change the name”: During my interviews with Bill Caming I often used the term Greenstar in our discussions. Ever the AT&T attorney, he would periodically correct me: “No, that’s not its name. That was an internal code name that we stopped using.” Sometime later I visited the AT&T Archives in Warren, New Jersey, which maintains a computerized index of old Bell System files. I typed in “Greenstar” and watched the display light up like a Christmas tree as it found relevant documents. When I mentioned this to Caming a few days later, he gave a rueful laugh and responded, “Well, I guess you can’t keep a good name down.”
96 two parts to Caming’s reasoning: Before 1968, the federal wiretapping law was Section 605 of Title 18 of the United States Code. It was a strangely written law. As discussed in the next chapter, section 605 did not make wiretapping (“interception”) itself illegal. Rather, to commit a crime under 605 you had to both intercept a communication and then disclose the contents of the communication to someone else. Clearly when Greenstar recorded a call and a human listened to it, there was an interception, but because the trained operator listening to the tapes never discussed the contents of the communication (just the signaling of the call itself), there was no disclosure, and thus, AT&T asserted, no crime. In 1968 the Omnibus Crime Control and Safe Streets Act became the new law that governed wiretapping — but that law had specific carve outs for random monitoring and interception of communications by telephone company personnel attempting to protect the assets of the telephone company.
96 “imprimatur”: Caming, “Surveillance,” pp. 243-44.
96 Congressional Research Service: Ibid., p. 234.
97 “Lonely Boy”: “Lonely Boy Devises Way of Placing Free Long Distance Calls.”
TMZ – Is ‘American Idol’ Racist!?
Nine black former contestants on “American Idol” are threatening to sue the show for being racist… and it led Harvey to go on one of his all-time CLASSIC rants about who he would fire in the TMZ newsroom!
SECRET – U.S. Northern Command-NORAD Battle Staff Standard Operating Procedures

NORAD AND USNORTHCOM PUBLICATION 1-01 BATTLE STAFF STANDARD OPERATING PROCEDURES
- 171 pages
- March 11, 2011
1.1.1 NORAD and USNORTHCOM Publication Series
The North American Aerospace Defense Command (NORAD) and U.S. Northern Command (USNORTHCOM) Publication Series is the authoritative reference defining the Commands’ missions and structure, force employment objectives, mission area planning considerations and operational processes from the strategic to the tactical level. The NORAD and USNORTHCOM Publication Series also defines the Commands’ doctrine, as well as their operational tactics, techniques, and procedures (TTP). The NORAD and USNORTHCOM Publication Series is authoritative because it defines the actions and methods implementing joint doctrine and describes how assigned and attached military forces will be employed in the Commands’ joint and combined operations. The NORAD and USNORTHCOM Publication Series consists of:
• Capstone publication: USNORTHCOM Publication (NCP) 1, Capstone Guidance
• Keystone publications:
− NCP 0-1, Homeland Defense Concept of Employment (HD CONEMP)
− NCP 0-2, Civil Support Concept of Employment (CS CONEMP)
− NORAD and USNORTHCOM Publication (N-NCP) 1-01, Battle Staff Standard Operating Procedures (BSOP)
• Supporting publications: Supporting publications provide execution-level operational and tactical guidance, force employment direction and TTP. Supporting publications are called concepts of Execution (CONEX). These supporting publications can be functionally aligned (e.g., NCP 3-05 Joint Task Force Concept of Execution) or created by a subordinate unit (e.g., NCP 10-01, Joint Task Force North Concept of Execution), assigned component command headquarters (e.g., NCP 10-05, Army Forces North Concept of Execution) or supporting commander (e.g., NCP 10-08, United States Fleet Forces Command Concept of Execution in Support of USNORTHCOM)NORAD and USNORTHCOM Instruction (N-NCI) 10-154, NORAD and USNORTHCOM Publication Series provides further background on the Publication series policy and purpose.
1.1.2 NORAD and USNORTHCOM Battle Staff
The NORAD and USNORTHCOM Battle Staff is activated during contingencies and crises to facilitate the Commander’s timely strategy and operational decision making. The NORAD and USNORTHCOM Battle Staff task organizes using an adaptive joint headquarters construct, integrating J-code staff, special staff and agency liaisons into various Battle Staff nodes. This cross-functional Battle Staff organization ensures processes critical to the NORAD and USNORTHCOM missions are reliable, repeatable and efficient, and minimizes functional stove piping. The adaptive joint headquarters construct evolves beyond the traditional J-code staff organization thereby creating a Battle Staff organization optimized to execute cross-functional, joint war fighting processes to improve collaboration and increase understanding of the operational environment.
Though NORAD and USNORTHCOM are separate commands with different establishing authorities, they have complimentary missions. The two Commands share common values, understanding the urgency and significance of their duties in light of very real and present dangers. Operations and incidents could occur within the NORAD area of operations (AO) and USNORTHCOM area of responsibility (AOR) that would involve responses by both Commands. Canada and the United States also share a common border and have mutual defense and civil support and civil assistance interests. The NORAD and USNORTHCOM Battle Staff organization and processes defined in this BSOP are intended to ensure the two Commands’ missions are accomplished effectively, efficiently and in close cooperation.
…
1.3 NORAD and USNORTHCOM Battle Staff Organization
Headquarters NORAD and Headquarters USNORTHCOM accomplishes its routine operations within the traditional J-code staff organizational structure and transitions to the NORAD and USNORTHCOM Battle Staff construct in response to preplanned events or contingencies as directed by the Commander. For preplanned events (contingency planning), the NORAD and USNORTHCOM Chief of Staff (N-NC/CS) will designate an OPR to stand up a joint planning team (JPT) or operations planning team (OPT). These teams can be led by any directorate, but are typically led by the Directorate of Strategy, Policy and Plans (N-NC/J5), NORAD Directorate of Operations (N/J3) or USNORTHCOM Directorate of Operations (NC/J3). The work of the JPT or OPT is conducted outside of the Battle Staff organization and processes, but may be transitioned to the Battle Staff’s crisis action planning (CAP) responsibility as the preplanned event approaches. The Battle Staff is designed to provide cross-functional expertise and leverage information technology to improve collaboration and decision superiority in CAP. The NORAD and USNORTHCOM Battle Staff’s primary role is to support the Commander’s operational decision-making process during CAP and execution. The Battle Staff coordinates and collaborates with higher, adjacent, supporting, supported commands and agencies internal and external to the Department of Defense (DOD). This BSOP generally assumes Battle Staff activation will be required for a period between 12 hours and 30 days. However, such activation (Chapter 2) is scalable based on the nature and magnitude of the crisis or contingency.
The NORAD and USNORTHCOM Battle Staff is a three-tiered organization:
• The Command Executive Group (CEG), led by the Battle Staff Executive Director (N-NC/CS)
• Battle Staff Core Centers
− NORAD and USNORTHCOM Command Center (N2C2)
− NORAD Future Operations Center (N/FOC)
− USNORTHCOM Future Operations Center (NC/FOC)
− NORAD and USNORTHCOM Future Plans Center (FPC)
• Battle Staff supporting nodes (i.e., Centers, Cells, Boards and working groups [WG], as required)…
Monty Python – Holy Grail – Killer Rabbit
Monty Python – Holy Grail – Killer Rabbit
TMZ – Meet the ‘Plastic Wives!’
Hollywood’s so-called “Plastic Wives” aren’t just married to plastic surgeons… they’re also very proud (and VERY OBVIOUS) clients as well!
SECRET – NSA Technology Directorate Manual: Cable Installation at NSA Facilities

Cable Installation at NSAW Facilities
- Document Number: X312-061-1006
- Version 1.4
- 25 pages
- For Official Use Only
- September 25, 2008
(U//FOUO) This document provides detailed instructions for the implementation and installation of premise wire infrastructure in support of unclassified and classified networks within NSAW, Build-out Facilities, domestic facilities where NSA controls the plenum, domestic facilities where NSA does not control the plenum and all OCONUS field sites. This document provides instructions for implementations and installations of premise wiring in communications facilities, office spaces and machine rooms by ITD Internal Service Providers (ISP), External Service providers (ESP), field personnel stationed at the respective facilities or authorized NSA agents.
(U//FOUO) This document applies to all new voice, video, and data cabling including TS/SCI, Secret and Unclassified networks for all NSA facilities identified in the previous paragraph. This includes any construction, restoration, and modernization projects. This document is not intended to justify wholesale replacement and upgrade of existing premise wiring or cable infrastructure unless security violations are found.
(U//FOUO) It is presumed that any facility in which these instructions pertain is protected by approved means of anti-terrorist force protection (ATFP), owned or leased by the NSA/CSS and perimeters monitored by security cameras, intrusion alarms or other means approved and implemented by the Office of Physical Security, Countermeasures/Headquarters Security and Program Protection or Field Security. Where these do not apply, additional Security and TEMPEST counter measures are required. Details are provided in the respective sections of this document.
(U//FOUO) Prior to the installation of any Red communications or network infrastructure, all facilities will have Sensitive Compartmented Information Facility (SCIF) accreditation in accordance with NSA/CSS Manual 130-1, Annex P and NSA/CSS Policy 6-3, Operational Information Systems Security Policy. All installation personnel must be legal U.S. citizens in accordance with NSA/CSS Policy 5-23, Physical Security Requirements for Controlled Areas.
(U//FOUO) Failure to adhere to the Standards outlined in this document will result in delays in activation and possibly denial of services until the facility is certified to be in compliance. Additional site surveys will be conducted by the Office of Technical Security Countermeasures as part of the automated Annex P process detailing appropriate Countermeasures for the respective facility.
…
Monty Python Holy Grail – French Taunter
Monty Python Holy Grail – French Taunter
Monty Python Holy Grail
http://www.amazon.com/Monty-Python-Trinity-Pythons-Meaning/dp/B001E12ZAM/ref=…
TMZ – Steven Tyler’s Speedo-Clad Bongo Bash!
Steven Tyler didn’t just rage his face off at a wild bongo bash on the beach in Hawaii… he did it while wearing a tiny mankini!
PI – National Counterintelligence Executive Specifications for Constructing Sensitive Compartmented Information Facilities

TECHNICAL SPECIFICATIONS FOR CONSTRUCTION AND MANAGEMENT OF SENSITIVE COMPARTMENTED INFORMATION FACILITIES
- IC Tech Spec‐for ICD/ICS 705
- 166 pages
- April 23, 2012
This Intelligence Community (IC) Technical Specification sets forth the physical and technical security specifications and best practices for meeting standards of Intelligence Community Standard (ICS) 705-1 (Physical and Technical Standards for Sensitive Compartmented Information Facilities). When the technical specifications herein are applied to new construction and renovations of Sensitive Compartmented Information Facilities (SCIFs), they shall satisfy the standards outlined in ICS 705-1 to enable uniform and reciprocal use across all IC elements and to assure information sharing to the greatest extent possible. This document is the implementing specification for Intelligence Community Directive (ICD) 705, Physical and Technical Security Standards for Sensitive Compartmented Information Facilities (ICS-705-1) and Standards for Accreditation and Reciprocal Use of Sensitive Compartmented Information Facilities (ICS-705-2) and supersedes Director of Central Intelligence Directive (DCID) 6/9.
The specifications contained herein will facilitate the protection of Sensitive Compartmented Information (SCI) against compromising emanations, inadvertent observation and disclosure by unauthorized persons, and the detection of unauthorized entry.
…
A. Analytical Risk Management Process
1. The Accrediting Official (AO) and the Site Security Manager (SSM) should evaluate each proposed SCIF for threats, vulnerabilities, and assets to determine the most efficient countermeasures required for physical and technical security. In some cases, based upon that risk assessment, it may be determined that it is more practical or efficient to mitigate a standard. In other cases, it may be determined that additional security measures should be employed due to a significant risk factor.
2. Security begins when the initial requirement for a SCIF is known. To ensure the integrity of the construction and final accreditation, security plans should be coordinated with the AO before construction plans are designed, materials ordered, or contracts let.
a) Security standards shall apply to all proposed SCI facilities and shall be coordinated with the AO for guidance and approval. Location of facility construction and or fabrication does not exclude a facility from security standards and or review and approval by the AO. SCI facilities include but are not limited to fixed facilities, mobile platforms, prefabricated structures, containers, modular applications or other new or emerging applications and technologies that may meet performance standards for use in SCI facility construction.
b) Mitigations are verifiable, non-standard methods that shall be approved by the AO to effectively meet the physical/technical security protection level(s) of the standard. While most standards may be effectively mitigated via non-standard construction, additional security countermeasures and/or procedures, some standards are based upon tested and verified equipment (e.g., a combination lock meeting Federal Specification FF-L 2740A) chosen because of special attributes and could not be mitigated with non-tested equipment. The AO’s approval is documented to confirm that the mitigation is at least equal to the physical/technical security level of the standard.
c) Exceeding a standard, even when based upon risk, requires that a waiver be processed and approved in accordance with ICD 705.
3. The risk management process includes a critical evaluation of threats, vulnerability, and assets to determine the need and value of countermeasures. The process may include the following:
a) Threat Analysis. Assess the capabilities, intentions, and opportunity of an adversary to exploit or damage assets or information. Reference the threat information provided in the National Threat Identification and Prioritization Assessment (NTIPA) produced by the National Counterintelligence Executive (NCIX) for inside the U.S. and/or the Overseas Security Policy Board (OSPB), Security Environment Threat List (SETL) for outside the U.S. to determine technical threat to a location. When evaluating for TEMPEST, the Certified TEMPEST Technical Authorities (CTTA) shall use the National Security Agency Information Assurance (NSA IA) list as an additional resource for specific technical threat information. It is critical to identify other occupants of common and adjacent buildings. (However, do not attempt to collect information against U.S. persons in violation of Executive Order (EO) 12333.) In areas where there is a diplomatic presence of high and critical threat countries, additional countermeasures may be necessary.
b) Vulnerability Analysis. Assess the inherent susceptibility to attack of a procedure, facility, information system, equipment, or policy.
c) Probability Analysis. Assess the probability of an adverse action, incident, or attack occurring.
d) Consequence Analysis. Assess the consequences of such an action (expressed as a measure of loss, such as cost in dollars, resources, programmatic effect/mission impact, etc.).
Monty Python – Always Look On The Bright Side of Life – Filmclip
SECRECY NEWS – FORMER CIA OFFICER KIRIAKOU SENTENCED FOR LEAK
|
Monty Python – Hermit – Life of Brian
SI Swimsuit: Jessica Gomes – Body Painting Video
Jessica Gomes tells you about experience being a human canvas for the SI Swimsuit 2008 body painting shoot.
For more photos and videos visit http://www.si.com/swimsuit
SI Swimsuit: Jessica Gomes – Body Painting Video
NSA – ALAN GROSS CASE SPOTLIGHTS U.S. DEMOCRACY PROGRAMS IN CUBA

ALAN GROSS CASE SPOTLIGHTS U.S. DEMOCRACY PROGRAMS IN CUBALAWSUIT FILED BY FAMILY YIELDS DOCUMENTATION ON “OPERATIONAL” NATURE OF USAID EFFORTCONTRACTOR INTRODUCES CONFIDENTIAL RECORDS IN COURT ARGUMENTSNational Security Archive Electronic Briefing Book No. 411Posted – January 24, 2013 Edited by Peter Kornbluh For more information contact: |
Related PostingsAmerican jailed in Cuba wants US to sign ‘non-belligerency pact’ to speed release Secrecy, politics at heart of Cuba project Cuba Proposes Exchange Deal for Imprisoned American, Alan Gross
|
Washington, D.C., January 18, 2013 – The U.S. government has “between five to seven different transition plans” for Cuba, and the USAID-sponsored “Democracy” program aimed at the Castro government is “an operational activity” that demands “continuous discretion,” according to documents filed in court this week, and posted today by the National Security Archive. The records were filed by Development Alternatives Inc (DAI), one of USAID’s largest contractors, in response to a lawsuit filed by the family of Alan Gross, who was arrested in Cuba in December 2009 for attempting to set up satellite communications networks on the island, as part of the USAID program.
In an August 2008 meeting toward the end of the George W. Bush administration, according to a confidential memorandum of conversation attached to DAI’s filing, officials from the “Cuba Democracy and Contingency Planning Program,” as the Democracy effort is officially known, told DAI representatives that “USAID is not telling Cubans how or why they need a democratic transition, but rather, the Agency wants to provide the technology and means for communicating the spark which could benefit the population.” The program, the officials stated, intended to “provide a base from which Cubans can ‘develop alternative visions of the future.'” Gross has spent three years of a 15-year sentence in prison in Cuba, charged and convicted of “acts against the integrity of the state” for attempting to supply members of Cuba’s Jewish community with Broadband Global Area Network (BGAN) satellite communications consoles and establish independent internet networks on the island. Last year, he and his wife, Judy, sued both DAI and USAID for failing to adequately prepare, train and supervise him given the dangerous nature of the democracy program activities. During a four-hour meeting last November 28, 2012, with Archive analyst Peter Kornbluh at the military hospital where he is incarcerated, Gross insisted that “my goals were not the same as the program that sent me.” He called on the Obama administration to meet Cuba at the negotiating table and resolve his case, among other bilateral issues between the two nations. The exhibits attached to DAI’s court filing included USAID’s original “Request for Proposals” for stepped up efforts to bring about political transition to Cuba, USAID communications with DAI, and Gross’s own proposals for bringing computers, cell phones, routers and BGAN systems-“Telco in a Bag,” as he called it-into Cuba. According to Kornbluh, DAI’s filing is “a form of ‘graymail'”–an alert to the U.S. government that unless the Obama administration steps up its efforts to get Gross released, the suit would yield unwelcome details of ongoing U.S. intervention in Cuba. In its effort to dismiss the suit, DAI’s filing stated that it was “deeply concerned that the development of the record in this case over the course of litigation [through discovery] could create significant risks to the U.S. government’s national security, foreign policy, and human rights interests.”
READ THE DOCUMENTSDocument l: USAID “Competitive Task Order Solicitation in Support of Cuba Democracy and Contingency Planning Program (CDCPP), May 8, 2008. Document 2: Memoranda of Conversation between USAID AND DAI officials, “Meeting Notes from USAID CDCPP Meeting, August 26, 2008. Document 3: Alan Gross, “Para La Isla,” Proposed Expansion of Scope of Work in Cuba Proposal, September 2009. Document 4: Declaration of John Henry McCarthy, DAI Global Practice Leader Document 5: Defendant Development Alternatives, Inc.’s Memorandum of Points and Authorities in Support of Its Motion to Dismiss for Lack of Subject-Matter Jurisdiction and Failure to State a Claim, January 15, 2013. Document 6: Cuban Court Ruling Against Alan Gross, March 11, 2011, certified English translation. |
TMZ – Steven Tyler — I’ll Play the Bongo … You Watch My Dongo
See if you can watch this video of a mankini-sportin’ Steven Tyler bangin’ away in a drum circle in Maui … and NOT stare at his drumstick.
SECRET – National Counterintelligence Executive Specifications

TECHNICAL SPECIFICATIONS FOR CONSTRUCTION AND MANAGEMENT OF SENSITIVE COMPARTMENTED INFORMATION FACILITIES
- IC Tech Spec‐for ICD/ICS 705
- 166 pages
- April 23, 2012
This Intelligence Community (IC) Technical Specification sets forth the physical and technical security specifications and best practices for meeting standards of Intelligence Community Standard (ICS) 705-1 (Physical and Technical Standards for Sensitive Compartmented Information Facilities). When the technical specifications herein are applied to new construction and renovations of Sensitive Compartmented Information Facilities (SCIFs), they shall satisfy the standards outlined in ICS 705-1 to enable uniform and reciprocal use across all IC elements and to assure information sharing to the greatest extent possible. This document is the implementing specification for Intelligence Community Directive (ICD) 705, Physical and Technical Security Standards for Sensitive Compartmented Information Facilities (ICS-705-1) and Standards for Accreditation and Reciprocal Use of Sensitive Compartmented Information Facilities (ICS-705-2) and supersedes Director of Central Intelligence Directive (DCID) 6/9.
The specifications contained herein will facilitate the protection of Sensitive Compartmented Information (SCI) against compromising emanations, inadvertent observation and disclosure by unauthorized persons, and the detection of unauthorized entry.
…
A. Analytical Risk Management Process
1. The Accrediting Official (AO) and the Site Security Manager (SSM) should evaluate each proposed SCIF for threats, vulnerabilities, and assets to determine the most efficient countermeasures required for physical and technical security. In some cases, based upon that risk assessment, it may be determined that it is more practical or efficient to mitigate a standard. In other cases, it may be determined that additional security measures should be employed due to a significant risk factor.
2. Security begins when the initial requirement for a SCIF is known. To ensure the integrity of the construction and final accreditation, security plans should be coordinated with the AO before construction plans are designed, materials ordered, or contracts let.
a) Security standards shall apply to all proposed SCI facilities and shall be coordinated with the AO for guidance and approval. Location of facility construction and or fabrication does not exclude a facility from security standards and or review and approval by the AO. SCI facilities include but are not limited to fixed facilities, mobile platforms, prefabricated structures, containers, modular applications or other new or emerging applications and technologies that may meet performance standards for use in SCI facility construction.
b) Mitigations are verifiable, non-standard methods that shall be approved by the AO to effectively meet the physical/technical security protection level(s) of the standard. While most standards may be effectively mitigated via non-standard construction, additional security countermeasures and/or procedures, some standards are based upon tested and verified equipment (e.g., a combination lock meeting Federal Specification FF-L 2740A) chosen because of special attributes and could not be mitigated with non-tested equipment. The AO’s approval is documented to confirm that the mitigation is at least equal to the physical/technical security level of the standard.
c) Exceeding a standard, even when based upon risk, requires that a waiver be processed and approved in accordance with ICD 705.
3. The risk management process includes a critical evaluation of threats, vulnerability, and assets to determine the need and value of countermeasures. The process may include the following:
a) Threat Analysis. Assess the capabilities, intentions, and opportunity of an adversary to exploit or damage assets or information. Reference the threat information provided in the National Threat Identification and Prioritization Assessment (NTIPA) produced by the National Counterintelligence Executive (NCIX) for inside the U.S. and/or the Overseas Security Policy Board (OSPB), Security Environment Threat List (SETL) for outside the U.S. to determine technical threat to a location. When evaluating for TEMPEST, the Certified TEMPEST Technical Authorities (CTTA) shall use the National Security Agency Information Assurance (NSA IA) list as an additional resource for specific technical threat information. It is critical to identify other occupants of common and adjacent buildings. (However, do not attempt to collect information against U.S. persons in violation of Executive Order (EO) 12333.) In areas where there is a diplomatic presence of high and critical threat countries, additional countermeasures may be necessary.
b) Vulnerability Analysis. Assess the inherent susceptibility to attack of a procedure, facility, information system, equipment, or policy.
c) Probability Analysis. Assess the probability of an adverse action, incident, or attack occurring.
d) Consequence Analysis. Assess the consequences of such an action (expressed as a measure of loss, such as cost in dollars, resources, programmatic effect/mission impact, etc.).
Monty Python – Biggus Dickus – Film – Life of Brian
Monty Python – Biggus Dickus – Film – Life of Brian
SI Swimsuit Video: Tori Praver Body Painting
Tori Praver tells you all about what it feels to become a human canvas in this SI Swimsuit 2008 bodypainting video.
For more SI Swimsuit photos and videos visit http://www.si.com/swimsuit.
The FBI – Former Chief Financial Officer of Stanford Group Entities Sentenced to Federal Prison
HOUSTON—James M. Davis, 64, formerly of Baldwyn, Mississippi, the former chief financial officer of Stanford International Bank (SIB) and Houston-based Stanford Financial Group, was sentenced today to five years in prison for his role in helping Robert Allen Stanford perpetrate a fraud scheme involving SIB and for conspiring to obstruct a U.S. Securities and Exchange Commission (SEC) investigation into SIB.
Today’s sentence was announced by U.S. Attorney Kenneth Magidson of the Southern District of Texas; Assistant Attorney General Lanny A. Breuer of the Justice Department’s Criminal Division; FBI Assistant Director Ronald T. Hosko of the Criminal Investigative Division; Assistant Secretary of Labor for the Employee Benefits Security Administration (DOL EBSA) Phyllis C. Borzi; Chief Postal Inspector Guy J. Cottrell of the U.S. Postal Inspection Service (USPIS); and Chief Richard Weber, of Internal Revenue Service-Criminal Investigation (IRS-CI).
The prison sentence was imposed by U.S. District Judge David Hittner of the Southern District of Texas, who also sentenced Davis to serve three years of supervised release. As part of Davis’ sentence, the court also imposed a personal money judgment of $1 billion, which is an ongoing obligation for Davis to pay back criminal proceeds.
During the sentencing proceeding, Judge Hittner noted that Davis began cooperating with the government in early 2009, shortly after SIB’s collapse. Judge Hittner also noted that over the following three years, Davis provided substantial assistance to the authorities in the investigation and prosecution of others, including testifying at Stanford’s trial; testifying during the trial of Gilbert T. Lopez, Jr. and Mark J. Kuhrt, Stanford’s former chief accounting officer and global controller, respectively; and preparing to testify against Laura Pendergest-Holt, Stanford’s chief investment officer. Holt eventually pleaded guilty; Stanford, Lopez, and Kuhrt were convicted at trial. Stanford and Holt are currently serving 110 years and three years in prison, respectively. Lopez and Kuhrt are in federal custody and await sentencing, scheduled for February 14, 2013.
As part of his 2009 guilty plea, Davis admitted that he was aware of Stanford’s misuse of SIB’s assets, kept the misuse hidden from the public and from almost all of Stanford’s other employees, and worked to prevent the misuse from being discovered. In addition, Davis acknowledged that in January 2009, when the SEC sought testimony and documents related to SIB’s entire investment portfolio, he conspired with others in an effort to impede the SEC’s investigation and help SIB continue operating.
The investigation was conducted by the FBI, USPIS, IRS-CI, and DOL EBSA. The case against Davis is being prosecuted by Assistant U.S. Attorney Jason Varnado of the Southern District of Texas, Deputy Chief Jeffrey Goldberg, Deputy Chief William Stellmach, and Trial Attorney Andrew Warren of the Justice Department Criminal Division’s Fraud Section. The Justice Department also thanks the SEC for their assistance and cooperation in this matter.
Cryptome unveils – New York City Pistol Permit Holders
New York City Pistol Permit Holders:
http://gawker.com/5974190/here-is-a-list-of-all-the-assholes-who-own-guns-in-new-york-city
312,462 New York State Pistol Permit Holders in April 2010:
http://cryptome.org/ny-packing-master.zip (7.8MB) (This has been on Cryptome since June 2010)Below, a link to a work-in-progress wooly Google fusion map of selected NY State holders. Note lack of NYC holders in the NY State list — one dot for each of the five boroughs! — apparently due to NYC.gov omitting addresses in data sent to the state as redacted from the Gawker list. Addresses are also omitted for most officials.
Geocoding the New York city/state data the Google program produced dots all over the world, perhaps erroneously using names of permit holders as location — a fix badly needed for the bloke pegged to be in Antartica. It also failed to plot two addresses in the CSV data for Robert DeNiro in NYC, and based on the scarcity of dots inside the state, what appears to be the bulk of the CSV data:
Trivia: Cryptome owns a couple of NYC-registered legacy long-guns, never-used, unloaded, locked and stashed under Grant’s Tomb, or was it the east abutment of GW Bridge.
NY Pistol Permit Owners
-
This goes out to the New York State Rifle and Pistol Association, the National Rifle Association, Christopher Fountain (you shameless scumbag), and everyone else who has threatened the Journal News and Gawker reporters and employees.
-
The internet doesn’t forget.
-
Free information. Ban ammunition.
TMZ – Katherine Webb Goes Hollywood… in a Bikini!
Alabama QB AJ McCarron’s girlfriend, Katherine Webb, has totally gone Hollywood… but good news folks — she’s doing so while wearing a skimpy bathing suit! ROLL TIDE!!!
SECRET – U.S. Army Doctrine Publication: Defense Support of Civil Authorities

ADP 3-28 Defense Support of Civil Authorities
- 26 pages
- July 26, 2012
- 7.09 MB
ARMY SUPPORT OF CIVIL AUTHORITIES
6. Army forces support civil authorities by performing defense support of civil authorities tasks. Defense support of civil authorities is defined as support provided by United States Federal military forces, DoD [Department of Defense] civilians, DoD contract personnel, DoD component assets, and National Guard forces (when the Secretary of Defense, in coordination with the Governors of the States, elects and requests to use those forces in title 32, United States Code, status) in response to requests for assistance from civil authorities for domestic emergencies, law enforcement support, and other domestic activities, or from qualifying entities for special events. Also known as civil support (DODD 3025.18).
7. Military forces provide civil support at federal and state levels. Federal military forces are active Army, Marine Corps, Navy, and Air Force; mobilized Army, Marine Corps, Navy, and Air Force Reserve; and National Guard mobilized for federal service under title 10, United States Code (USC). State National Guard forces under state control perform DSCA tasks when serving under title 32, USC.
READINESS
8. Numerous features of DSCA are distinct from the other tasks of decisive action—offense, defense, and stability. DSCA tasks stress the employment of nondestructive means to save lives, alleviate suffering, and protect property. Domestic operations are operations in the homeland: The physical region that includes the continental United States, Alaska, Hawaii, United States possessions and territories, and surrounding territorial waters and airspace (JP 3-28). Domestic operations are constrained by various laws to a greater degree, in comparison to the Law of Land Warfare and The Hague and Geneva Conventions. It is accurate to say that most tasks performed in domestic support are common to overseas operations; however, Soldiers conduct them under very different conditions.
9. Commanders gauge unit readiness for DSCA missions by assessing proficiency in three warfighting functions: mission command, sustainment, and protection. The requirement to deploy into a domestic operational environment—often with little warning—and to operate with joint and interagency partners requires mission command that can adapt systems and procedures for a noncombat, civilian-led structure.
10. The majority of DSCA missions will stress the sustainment warfighting function. Mission success depends on units’ ability to deliver personnel, medical support, supplies, and equipment, while maintaining their equipment and Soldiers. This is challenging because forces often provide support in areas devastated by a disaster and lacking potable water, electrical power, and sanitation. When needed, a federal installation identified as a base support installation will serve as a base for federal military forces throughout the mission.
11. The protection warfighting function is the third area for readiness assessment. It is imperative that commanders understand their protection capabilities. They must understand which of those capabilities may be exercised legally in domestic environments so they can be properly integrated into the overall scheme of protection.
MILITARY CAPABILITY
12. Soldiers are trained to exercise initiative in combat and training. They must understand which military capabilities may be exercised during domestic operations, including consideration for duty status (title 10, title 32, or state active duty). With this understanding, they will be able to maximize their initiative and efforts. Commanders maintain a balance between the willingness of their subordinates to engage any mission against the capability to accomplish it. Military capability comprises—
- The ability to perform a task effectively and efficiently.
- The ability to perform a task safely.
- The legal authority to perform a task.
PRIMARY PURPOSES FOR ARMY SUPPORT
13. While there are many potential missions for Soldiers as part of DSCA, the overarching purposes of all DSCA missions are, in the following order, to—
- Save lives.
- Alleviate suffering.
- Protect property.
Some DSCA missions may accomplish these purposes directly. An aircraft crew participating in a search and rescue operation is there to save lives. Soldiers fighting fires in a national forest are guarding public property, as are the National Guard Soldiers patrolling streets in the aftermath of a tornado. Some DSCA missions accomplish these purposes indirectly. Soldiers and civilians helping load medical supplies for shipment from an installation to a municipal shelter will not meet the people housed there, but their actions will help reduce the distress of their fellow citizens. In the absence of orders, or in uncertain and chaotic situations, each Soldier governs his or her actions based on these three purposes.
PRIMARY CHARACTERISTICS OF ARMY SUPPORT
14. Army forces operating within the United States encounter very different operational environments than they face outside the Nation’s boundaries. Although many of the small-unit tasks remain the same, there are important differences in the conditions associated with them. Principally, the roles of civilian organizations and the relationship of military forces to federal, state, tribal, and local agencies are different. The differences are pronounced enough to define a different task set than offense, defense, or stability. The support provided by Army forces depends on specific circumstances dictated by law. Soldiers and Army civilians need to understand domestic environments so they can employ the Army’s capabilities efficiently, effectively, and legally.
15. While every domestic support mission is unique, four defining characteristics shape the actions of commanders and leaders in any mission. These characteristics are that—
- State and federal laws define how military forces support civil authorities.
- Civil authorities are in charge, and military forces support them.
- Military forces depart when civil authorities are able continue without military support.
- Military forces must document costs of all direct and indirect support provided.
…
PROVIDE SUPPORT FOR DOMESTIC CIVILIAN LAW ENFORCEMENT
43. Providing support for domestic civilian law enforcement applies to the restricted use of military assets to support civilian law enforcement personnel within the United States and its territories. These operations are significantly different from operations outside the United States. Army forces support domestic civilian law enforcement agencies under constitutional and statutory restrictions, as prescribed by corresponding directives and regulations.
44. Except as expressly authorized by the Constitution of the United States or by another act of Congress, the Posse Comitatus Act prohibits the use of the Active Army, Air Force, and—through DODD 5525.5—the Marine Corps and Navy as enforcement officials to execute state or federal law and perform direct law enforcement functions. However, the Posse Comitatus Act does not apply to state National Guard forces in state active duty status and title 32 status. Nor does the Posse Comitatus Act restrict the Coast Guard, even when under the operational control of the Navy, since the Coast Guard has inherent law enforcement powers under title 14, USC. Intelligence activities during DSCA should be coordinated through higher headquarters for approval, in addition to consultation from a staff judge advocate. Additionally, Executive Order 12333 provides guidelines for the use of military intelligence, including permitted and prohibited activities during DSCA operations.
45. Law enforcement support falls into two broad categories: direct and indirect support. Direct support involves enforcing the law and engaging in physical contact with offenders. Indirect support consists of aid to law enforcement agencies but not enforcement of the law or direct contact with offenders. Federal laws, presidential directives, and Department of Defense policy restrict the use of federal military forces from enforcing laws and providing security except on military installations. These laws, policies, and directives carefully specify exceptions to the restrictions. When authorized by the Secretary of Defense, federal military forces may provide indirect support to law enforcement agencies, but support is limited to logistical, transportation, and training assistance except when emergency authority applies. State and territorial governors can use state National Guard forces for direct support of civilian law enforcement; however, such use is a temporary expedient and must be in accordance with state laws.
…
Monty Python – Stoning – Life of Brian Movie
“Warning
Don’t say Jehovah, Or This Will Happen To You..”
Life of Brian
http://www.amazon.com/Monty-Python-Trinity-Pythons-Meaning/dp/B001E12ZAM/ref=…
SI Swimsuit: Marisa Miller Body Painting Video
Marisa Miller’s body become a canvas in this SI Swimsuit 2008 Body Painting video.
For more SI Swimsuit photos and videos go to http://www.si.com/swimsuit
SECRET -White House National Strategy for Information Sharing and Safeguarding

National Strategy for Information Sharing and Safeguarding
- 24 pages
- December 2012
Our national security depends on our ability to share the right information, with the right people, at the right time. This information sharing mandate requires sustained and responsible collaboration between Federal, state, local, tribal, territorial, private sector, and foreign partners. Over the last few years, we have successfully streamlined policies and processes, overcome cultural barriers, and better integrated information systems to enable information sharing. Today’s dynamic operating environment, however, challenges us to continue improving information sharing and safeguarding processes and capabilities. While innovation has enhanced our ability to share, increased sharing has created the potential for vulnerabilities requiring strengthened safeguarding practices. The 2012 National Strategy for Information Sharing and Safeguarding provides guidance for effective development, integration, and implementation of policies, processes, standards, and technologies to promote secure and responsible information sharing.
Our responses to these challenges must be strategic and grounded in three core principles. First, in treating Information as a National Asset, we recognize departments and agencies have achieved an unprecedented ability to gather, store, and use information consistent with their missions and applicable legal authorities; correspondingly they have an obligation to make that information available to support national security missions. Second, our approach recognizes Information Sharing and Safeguarding Requires Shared Risk Management. In order to build and sustain the trust required to share with one another, we must work together to identify and collectively reduce risk, rather than avoiding information loss by not sharing at all. Third, the core premise Information Informs Decisionmaking underlies all our actions and reminds us better decisionmaking is the purpose of sharing information in the first place. The Strategy focuses on achieving five goals:
1. Drive Collective Action through Collaboration and Accountability. We can best reach our shared vision when working together, using governance models that enable mission achievement, adopting common processes where possible to build trust, simplifying the information sharing agreement development process, and supporting efforts through performance management, training, and incentives.
2. Improve Information Discovery and Access through Common Standards. Improving discovery and access involves developing clear policies for making information available to approved individuals. Secure discovery and access relies on identity, authentication, and authorization controls, data tagging, enterprise-wide data correlation, common information sharing standards, and a rigorous process to certify and validate their use.
3. Optimize Mission Effectiveness through Shared Services and Interoperability. Efforts to optimize mission effectiveness include shared services, data and network interoperability, and increased efficiency in acquisition.
4. Strengthen Information Safeguarding through Structural Reform, Policy, and Technical Solutions. To foster trust and safeguard our information, policies and coordinating bodies must focus on identifying, preventing, and mitigating insider threats and external intrusions, while departments and agencies work to enhance capabilities for data-level controls, automated monitoring, and cross-classification solutions.
5. Protect Privacy, Civil Rights, and Civil Liberties through Consistency and Compliance. Integral to maintaining the public trust is increasing the consistency by which we apply privacy, civil rights, and civil liberties protections across the government, building corresponding safeguards into the development of information sharing operations, and promoting accountability and compliance mechanisms.
As we execute the Strategy together, we will harness our collective resolve to treat information as a national asset, make it discoverable and retrievable by all authorized users, and arm those charged with preserving the security of our Nation. Only as we work together, hold ourselves accountable, and take concerted ownership of advancing our goals, will we achieve the safety and success our country rightfully demands and fully deserves.
…
Priority Objectives
Top FiveThe following objectives capture the highest five priorities of the Administration in achieving the information sharing and safeguarding goals of this Strategy.
1. Align information sharing and safeguarding governance to foster better decisionmaking, performance, accountability, and implementation of the Strategy’s goals.
2. Develop guidelines for information sharing and safeguarding agreements to address common requirements, including privacy, civil rights, and civil liberties, while still allowing flexibility to meet mission needs.
3. Adopt metadata standards to facilitate federated discovery, access, correlation, and monitoring across Federal networks and security domains.
4. Extend and implement the FICAM Roadmap across all security domains.
5. Implement removable media policies, processes and controls; provide timely audit capabilities of assets, vulnerabilities, and threats; establish programs, processes and techniques to deter, detect and disrupt insider threats; and share the management of risks, to enhance unclassified and classified information safeguarding efforts.
Additional Priority Objectives
The remaining objectives represent additional priority activities for departments, agencies, and other stakeholders to advance the goals of this Strategy.
6. Define and adopt baseline capabilities and common requirements to enable data, service, and network interoperability.
7. Provide information sharing, safeguarding, and handling training to appropriate stakeholders using a common curriculum tailored to promote consistent, yet flexible, and trusted processes.
8. Define and implement common processes and standards to support automated policy-based discovery and access decisions.
9. Establish information sharing processes and sector specific protocols, with private sector partners, to improve information quality and timeliness and secure the nation’s infrastructure.
10. Develop a reference architecture to support a consistent approach to data discovery and correlation across disparate datasets.
11. Implement the recommendations and activities of the Federal IT Shared Services Strategy among appropriate stakeholders to facilitate adoption of shared services.
12. Refine standards certification and conformance processes enabling standards-based acquisition among departments and agencies, standards bodies, and vendors to promote interoperable products and services.
13. Promote adherence to existing interagency processes to coordinate information sharing initiatives with foreign partners, as well as adopt and apply necessary guidelines, consistent with statutory authorities and Presidential policy to ensure consistency when sharing and safeguarding information.
14. Create a common process across all levels of government for Requests for Information, Alerts, Warnings, and Notifications to enable timely receipt and dissemination of information and appropriate response.
15. Complete the implementation of the NSI programs in the National Network of Fusion Centers and Federal entities while expanding training and outreach beyond law enforcement to the rest of the public safety community.
16. Achieve the four Critical Operational Capabilities, four Enabling Capabilities, and other prioritized objectives, across the National Network of Fusion Centers to enable effective and lawful execution of their role as a focal point within the state and local environment for the receipt, analysis, gathering and sharing of threat-related information.
National security stakeholders across the government, guided by our shared Principles, can now act in concert to accomplish these priority objectives and build implementation plans to realize the goals of this Strategy. As we execute the Strategy together, we will harness our collective resolve to treat information as a national asset, make it discoverable and retrievable by all authorized users, and arm those charged with preserving the security of our nation with all information available to drive decisions that protect our country and its people. Only as we work together, hold ourselves accountable, and take concerted ownership of advancing our goals, will we achieve the success our country rightfully demands and fully deserves.
Kim Kardashian’s Airport Escort! – TMZ
Kim Kardashian is accustomed to being the center of attention at the airport… but a ridiculous Segue-riding cop escorting her while blasting his siren DEFINITELY wasn’t helping matters.
Bild unveils – Dirty STASI-Money, the media and Eurojust after 1989
SECRECY NEWS – PROSECUTORIAL DISCRETION IN IMMIGRATION CASES
"Under the Federal criminal justice system, the prosecutor has wide
latitude in determining when, whom, how, and even whether to prosecute for
apparent violations of Federal criminal law," says the U.S. Attorneys'
Manual. "The prosecutor's broad discretion in such areas as initiating or
foregoing prosecutions, selecting or recommending specific charges, and
terminating prosecutions by accepting guilty pleas has been recognized on
numerous occasions by the courts." (Chapter 9-27).
Although prosecutors enjoy broad discretion concerning whether and whom to
prosecute, there are limits, the Manual says, and consequences for
prosecutorial overreaching: "Serious, unjustified departures from the
principles set forth herein are [to be] followed by such remedial action,
including the imposition of disciplinary sanctions, when warranted, as are
deemed appropriate."
(After the execution of Socrates, remorseful Athenians rose up against his
three prosecutors, according to the uncorroborated account of Diogenes
Laertius. Meletus was stoned to death, while Anytus and Lycon were
banished.)
The exercise of prosecutorial discretion is discussed in a new report from
the Congressional Research Service, which focuses particularly on
immigration cases.
The report "addresses the constitutional and other foundations for the
doctrine of prosecutorial discretion, as well as the potential ways in
which prosecutorial discretion may be exercised in the immigration
context." It also considers "potential constitutional, statutory, and
administrative constraints upon the exercise of prosecutorial discretion."
See "Prosecutorial Discretion in Immigration Enforcement: Legal Issues,"
January 17, 2013:
http://www.fas.org/sgp/crs/misc/R42924.pdf
Some other new and updated CRS products that Congress has not authorized
CRS to release to the public include these:
Chemical Facility Security: Issues and Options for the 113th Congress,
January 14, 2013:
http://www.fas.org/sgp/crs/homesec/R42918.pdf
Nonstrategic Nuclear Weapons, December 19, 2012:
http://www.fas.org/sgp/crs/nuke/RL32572.pdf
The Protection of Classified Information: The Legal Framework, January 10,
2013:
http://www.fas.org/sgp/crs/secrecy/RS21900.pdf
Crisis in Mali, January 14, 2013:
http://www.fas.org/sgp/crs/row/R42664.pdf
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
Monty Python Live Hollywood Bowl – Pope and Michaelangelo
Monty Python Live Hollywood Bowl – Pope and Michaelangelo
Monty Python Live Hollywood Bowl
http://www.amazon.com/Complete-Monty-Pythons-Flying-Circus/dp/B001E77XNA/ref=…
TOP-SECRET by Cryptome – Thales e-Security Supports Bank Security Critique
Thales e-Security Supports Bank Security Critique
DMCA notice: http://cryptome.org/2013/01/thales-dmca.htm
From: Dave Harrop <Dave.Harrop[at]thales-esecurity.com>
To: “cryptome[at]earthlink.net” <cryptome[at]earthlink.net>
Date: Wed, 16 Jan 2013 12:59:03 +0000
Subject: Re: Cryptome Copyright Infringement – DMCA Takedown Notice
Dear Mr Young
Further to my letter to you dated 11 January 2013 in connection with (a) the Zaxus Host Security Module RG7000, Operations and Installations Manual, 1270A513 Issue 3; and (b) the Zaxus Host Security Module RG7000, Programmer’s Manual, 1270A514 Issue 3 both of which are published on the cryptome.org website.
Thales is in no way trying to censor information that would benefit banking security research.
The information concerned, as has been noted, has been available since 2003 and is in fact obsolete. It also does not reflect the current Thales payment hardware security module.
It is not unusual for Thales to suggest that out-of-date information is removed from web sites so that it doesn’t cause confusion or mislead our customers. This would normally be handled with a polite request to the web site owner; on this occasion, unfortunately, we were over-zealous in initiating a takedown notice.
Thales fully appreciates the benefits of openly sharing information relating to our security products and fully supports legitimate academic research in this area. The most up-to-date and accurate information can be obtained directly from Thales.
Thales e-Security actively participates in key technical forums such as ASC X9, Global Platform, NACHA, PCI SSC, Smart Card Alliance and OASIS, which contribute heavily to banking security research and future requirements around security for the payment industry. Thales has always respected and continues to support external forums to further security within the banking industry.
I therefore wish to withdraw my earlier request for you to remove or disable access to the material in question and apologise for any distress it may have caused.
Yours faithfully,
Dave Harrop
Head of Contracts (EMEA & APAC)
Thales E-Security
Jupiter House, Station Road, Cambridge, CB1 2JD
t: +44 7802 555148
e: dave.harrop[at]thales-esecurity.com
[Attached letter]
http://cryptome.org/2013/01/thales-dmca-letter-02.pdf
TMZ – French Reality Star: Check Out My Beach Thong! — Nabilla Benattia
Want to see a hot French reality show star hit the beach in a thong bikini? Of course you do!
TOP-SECRET – U.K. Crown Prosecution Service Guidelines for Prosecuting Social Media Communications

Interim guidelines on prosecuting cases involving communications sent via social media
- 25 pages
- December 19, 2012
These guidelines set out the approach that prosecutors should take when making decisions in relation to cases where it is alleged that criminal offences have been committed by the sending of a communication via social media. The guidelines are designed to give clear advice to prosecutors who have been asked either for a charging decision or for early advice to the police, as well as in reviewing those cases which have been charged by the police. Adherence to these guidelines will ensure that there is a consistency of approach across the CPS.
The guidelines cover the offences that are likely to be most commonly committed by the sending of communications via social media. These guidelines equally apply to the resending (or retweeting) of communications and whenever they refer to the sending of a communication, the guidelines should also be read as applying to the resending of a communication. However, for the reasons set out below, the context in which any communication is sent will be highly material.
These guidelines are primarily concerned with offences that may be committed by reason of the nature or content of a communication sent via social media. Where social media is simply used to facilitate some other substantive offence, prosecutors should proceed under the substantive offence in question.
These guidelines are interim guidelines and they have immediate effect. At the end of the public consultation period, they will be reviewed in light of the responses received. Thereafter final guidelines will be published.
…
Initial assessment
12. Communications sent via social media are capable of amounting to criminal offences and prosecutors should make an initial assessment of the content of the communication and the course of conduct in question so as to distinguish between:
(1) Communications which may constitute credible threats of violence to the person or damage to property.
(2) Communications which specifically target an individual or individuals and which may constitute harassment or stalking within the meaning of the Protection from Harassment Act 1997 or which may constitute other offences, such as blackmail.
(3) Communications which may amount to a breach of a court order. This can include offences under the Contempt of Court Act 1981 or section 5 of the Sexual Offences (Amendment) Act 1992. All such cases should be referred to the Attorney General, and via the Principal Legal Advisor’s team where necessary.
(4) Communications which do not fall into any of the categories above and fall to be considered separately (see below): i.e. those which may be considered grossly offensive, indecent, obscene or false.
13. As a general approach, cases falling within paragraphs 12 (1), (2) or (3) should be prosecuted robustly where they satisfy the test set out in the Code for Crown Prosecutors. Whereas cases which fall within paragraph 12(4) will be subject to a high threshold and in many cases a prosecution is unlikely to be in the public interest.
Monty Python – Four Yorkshiremen – Film Clip
Monty Python Live Hollywood Bowl
http://www.amazon.com/Complete-Monty-Pythons-Flying-Circus/dp/B001E77XNA/ref=…
TMZ – Adam Levine & Behati Prinsloo — He’s a Supermodel Connoisseur
Maroon 5 front man Adam Levine is dating yet ANOTHER Victoria’s Secret supermodel, Behati Prinsloo. Seriously, does this dude just flip through the catalog to find his girlfriends?
SECRET – DHS-FBI Radiological Terrorism Incident After-Action Reporting Guide

Radiological Terrorism: A Reference Aid on After-Action Reporting for State and Local Incident Management Officials
- 10 pages
- For Official Use Only
- April 12, 2012
(U//FOUO) This Reference Aid was jointly produced by DHS and the FBI to assist in the acquisition of detailed information in the aftermath of a successful or attempted radiological terrorism incident that would be of interest to the national law enforcement and emergency response communities. It is intended to help state, local, tribal, and territorial agencies and private sector entities deter, prevent, preempt, or respond to terrorist attacks against the United States.
(U//FOUO) Incident response to a radiological terrorist attack would involve, but not necessarily be limited to, police, fire, hazardous materials, public health, and radiological and nuclear detection emergency management teams and offices. Incident response also would require establishing an incident command system, such as a unified command structure based on the National Incident Management System.
(U//FOUO) This Reference Aid focuses narrowly on those responders who complete after-action reports following incidents described in this Reference Aid. The information collected may provide broader situational awareness after an incident has occurred, support threat analysis of potential follow-on incidents, assist in identifying perpetrators, and facilitate the allocation of consequence-management resources.
(U//FOUO) Warning: Radiological dispersal devices (RDDs) or radiological exposure devices (REDs) may be hazardous, even at a distance. Individuals should not endanger themselves by approaching a dangerously radioactive source or device in an attempt to collect this information. State, local, tribal, territorial, and private sector medical officials will normally be involved in safety evaluations following such incidents.
…
(U) Incident Description and Details
(U//FOUO) For any incident suspected or confirmed of being a malicious attempt to expose or contaminate persons, property, infrastructure, or natural resources with radioactive materials, information of interest includes:
— (U//FOUO) Time and place of the incident—include street address and geographic coordinates, such as latitude and longitude or military grid reference system, if available.
— (U//FOUO) Types of buildings, activities, and infrastructure at the site. Describe what was occurring at the incident site immediately prior to the incident, including any special events taking place. Estimate how many people were present at the start of the incident.
— (U//FOUO) Information about persons fleeing the scene immediately prior to the incident.
— (U//FOUO) Details regarding how radioactive materials were dispersed or intended to be dispersed, to include explosive, manual, or other means of dispersal.
— (U//FOUO) Indications or evidence that other or secondary devices exist.
— (U//FOUO) Evidence of coordination or pre-planning between multiple persons.
— (U//FOUO) Indications or evidence that perpetrators were aware of or tried to circumvent security measures.
— (U//FOUO) Indications or evidence that the perpetrators took measures to confine people in proximity to the radiological device.
— (U//FOUO) Distractions, diversions, or other tactics used to transport or place a device at the incident scene.
— (U//FOUO) Unusual odors, airborne particles, smoke, powders, liquids, or vapors.
— (U//FOUO) Proximity, if known, of the incident site to intense radiation sources, such as those that might be found at hospitals, universities, or industrial sites using radiation devices.
— (U//FOUO) Status of the climate control system, windows, and doors—for incidents that occurred inside a building or vehicle—before and during the incident, to include any evidence of tampering or sabotage.
— (U//FOUO) Proximity of the incident site to critical infrastructure, including potentially symbolic targets or high-population areas.
— (U//FOUO) If the incident involved an attempt to create an RDD or RED by damaging a piece of equipment containing radiological material at its place of installation:
– (U//FOUO) Name, location, and function of the host facility.
– (U//FOUO) Type, purpose, and location of the equipment housing the radiological source within the facility.
– (U//FOUO) Type, quantity, and activity level of the radiological source used in the equipment.
– (U//FOUO) Any information about how the perpetrators might have gained access to the equipment.— (U//FOUO) If the incident involved an attempt to create an RDD or RED by breaching the packaging and containment measures of radiological material being transported in a vehicle:
– (U//FOUO) Origin, route, and final and intended destination of the vehicle (including all intermediate stops).
– (U//FOUO) Type, quantity, and activity level of the radiological source or sources being transported.
– (U//FOUO) Tactics and tools used by the perpetrators in both the attempt to interdict the shipment or release the radioactive material.
– (U//FOUO) Timeline of events that notes where on the vehicle’s route the radioactive release occurred.— (U//FOUO) Photos or video of the incident site before, during, and after the incident.
— (U//FOUO) For incidents occurring outdoors, weather conditions leading up to and during the incident—to include any micro-weather conditions peculiar to the incident site, such as unusual wind conditions (or lack thereof) caused by urban canyons, humidity, or whether the incident site was in full sunlight or shade.
— (U//FOUO) Aircraft, model aircraft, or balloons overflying the scene before, during, or after the incident, particularly if the activity was unusual or could be linked to reconnaissance of the incident site or dispersal of radiological materials. Describe the overflight activity and any suspicions it may have raised.
— (U//FOUO) Prior suspicious incidents at the same location, particularly descriptions of possible preoperational activity such as reconnaissance, surveillance, recent theft of radiological materials, or unusual photographing of infrastructure, facilities, or personnel.
Monty Python – Live Hollywood Bowl – Lumberjack Song
Monty Python – Live Hollywood Bowl – Lumberjack Song
Monty Python Live Hollywood Bowl
http://www.amazon.com/Complete-Monty-Pythons-Flying-Circus/dp/B001E77XNA/ref=…
TMZ – Miss Universe’s Underage BOOZE Party!
Despite not even being 21 yet, Miss Universe Olivia Culpo knows how to booze like a champ!
SECRET DHS-FBI Bulletin: Indicators of Suspicious Chemical, Biological, and Radiological Activity

ROLL CALL RELEASE
- 1 page
- For Official Use Only
- December 27, 2010
(U//FOUO) Law enforcement and first responders may encounter chemical, biological, or radiological (CBR) related material or equipment at private residences, businesses, or other sites not normally associated with such activities. There are legitimate reasons for possessing such material or equipment, but in some cases their presence can indicate intent or capability to build CBR weapons, particularly when other suspicious circumstances exist.
(U//FOUO) Potential Indicators of Suspicious Activity: A single indicator of CBR activity may not be conclusive, but combinations of indicators, including those associated with other suspicious activity, warrant thorough and careful investigation. Law enforcement and first responders should be vigilant for suspicious activities and report them to a Joint Terrorism Task Force via a Suspicious Activity Report, or contact the nearest state and major urban area fusion center.
— (U//FOUO) Unusual or unpleasant odors, chemical fires, brightly colored stains, or corroded or rusted metal fixtures in apartments, hotel or motel rooms, self-storage units, or garages.
— (U//FOUO) Unexplained presence of equipment, containers, or material that could be used for radiation shielding or protection, such as lead, concrete, or steel.
— (U//FOUO) Unexplained presence of radiation detection or identification equipment.
— (U//FOUO) Damage to clothing, evidence of serious illness, or injuries such as burns, skin lesions, infections, or missing hands or fingers.
— (U//FOUO) Presence of potential precursors for biological agent production, such as castor beans or bacterial growth materials.
— (U//FOUO) Laboratory equipment such as Bunsen burners, microscopes, and scientific glassware; personal protective equipment such as masks, goggles, and gloves; household items such as plant seeds, strainers, coffee grinders, and filters; and common household chemicals such as acetone located together in places that are unusual, hidden, or disguised.
— (U//FOUO) An individual’s reluctance or inability to explain the presence of toxic chemicals, radioactive materials, biological organisms, or related equipment.
— (U//FOUO) Presence of CBR training manuals, such as The Mujahideen Poisons Handbook or The Anarchist Cookbook.
— (U//FOUO) Chemical containers discarded in dumpsters.
— (U//FOUO) Evidence of unexplained animal deaths.
— (U//FOUO) Security measures that appear inappropriate for the location they protect.
Monty Python – Silly Olympics
Silly Olympics
Monty Python Live Hollywood Bowl
http://www.amazon.com/Complete-Monty-Pythons-Flying-Circus/dp/B001E77XNA/ref=…
SECRET – U.S. Army Operation Enduring Freedom Battle Command in Counterinsurgency

OEF ROAD TO WAR: BATTLE COMMAND IN COIN
- 90 pages
- For Official Use Only
- June 2010
- 13.5 MB
This newsletter was produced in conjunction with the Counterinsurgency (COIN) Training Center–Afghanistan (CTC–A) to provide current and relevant information for brigade combat team (BCT), battalion, and company commanders and staffs concerning current U.S. and coalition best practices in support of Operation Enduring Freedom. As a “living document,” it will be updated continuously in order to capture, analyze, and disseminate critical information in support of operations across all lines of effort. It will disseminate key observations, insights, and lessons (OIL) from theater to give commanders a better understanding of the operational environment into which they are preparing to deploy. The information is from your peers—commanders, staff officers, and small unit leaders —who served or who are currently serving in Afghanistan.
This newsletter provides “a way” to better understand and apply counterinsurgency and stability operation fundamentals in preparation for deployment. Key concepts include:
• Synchronizing the combined efforts of the Afghan government, Afghan Security Forces, combat advisors, BCTs, provincial reconstruction teams (PRTs), agricultural development teams, other governmental agencies, and enablers to achieve the commander’s goals. • Assisting commanders in the development of predeployment training plans, focusing both on combat skills and nonlethal aspects of operations.
• Enhancing the development of host nation security forces through best practices and OIL.
• Developing a long-term plan that integrates operations against all lines of effort.
• Integrating information operations into all plans and orders.
• Achieving better cultural understanding in the operational environment.
• Integrating PRTs with unit plans and operations to attain heightened situational understanding and unity of effort.…
Engaging Key Leaders
The ability to target key tribal, village, and district leaders is essential to building a bond between the Government of the Islamic Republic of Afghanistan (GIROA), ANA, Afghan National Police (ANP), and the ISAF. Engaging leaders over security alone will not separate the insurgents from the population or gain support for the GIROA. True concern for the needs of a tribe, village, and district with honest commitments is just as important. One needs to support the population, which is gained by applying the appropriate influence. If you can shape the operational environment by nonlethal means, the population becomes more flexible in its support of the lethal targeting of insurgents. However, without the ability to provide security, no amount of improvements in the standard of living will convince local leaders and their tribes to support the GIROA. Once the GIROA has established security in the isolated villages so insurgents cannot mass against them, then conditions can be set for effective reconstruction.
The use of the ANA or ANP, human terrain teams, provincial reconstruction teams, embedded training teams, and civil affairs using ASCOPE (area, structures, capabilities, organizations, people, and events) or PMESII (political, military, economic, social, infrastructure, and information) to assess villages and districts and their leaders leads to more focused key leader engagements (KLEs). Using ANA, ANP, or IROA representatives provides access to those who can influence the reduction of insurgent activities, reduce village support to insurgents, and boost support to the GIROA.
The KLE is about the individual, his cultural norms, his tribe, and his need to maintain control of his environment. Depending on the area, a key leader’s ethical decisions are not necessarily based upon a rigid moral compass but upon moral imperatives. Ethics are based on self-interest and self-preservation. Using one’s family, clan, village, or tribe is expected. Why else would a public official hold office?
Tribal Engagement
Tribal engagement is an important aspect of the COIN effort in Afghanistan. The tribal system in Afghanistan is a strong facet of day-to-day life. The system of government establishing itself in Afghanistan has sub-governors in each district, a governor for the province, and a parliament and president for the country. The elders represent their villages and tribes; the government must have the support of the elders if it is to survive. The majority of the population still views the elders as the decision-makers as opposed to the government representatives. This is evidenced when the elders ask for a prisoner release after a person is arrested by either the ANA or coalition forces. The elders will ask for release because they collectively “vouch” for the prisoner’s innocence and still believe the tribal system is a much more appropriate method for dealing with criminals. Efforts are constantly made to convince the elders that the person was arrested based on evidence collected according to the new Afghan law system outlined in the new Afghan constitution.
Tribal elders are reluctant to submit to the proposed system of government for a number of reasons. According to the proposed system of law, power is taken away from the tribal elder and given to an elected official. The tribal elder has been the cornerstone of Afghan governance for thousands of years, and elders are not willing to relinquish this power to someone who may be from a different tribe. Elders assume that their tribe or sub-tribe will not be represented appropriately, and they often are correct in this assumption. Tribal loyalty, in many cases, is more important than loyalty to the country of Afghanistan. Elders are not willing to place a united Afghanistan over advancement of their particular tribe.
ANA operations and tribal engagements are the keys to convincing the population and elders of Afghan government efforts and the importance of a united Afghanistan.
ANA is tasked with securing the country. Progress in governance can be made only when security is established. Only after security is established will the elders and the general population see the GIROA as a legitimate force for stabilizing the country. Integral to the stabilization of Afghanistan is allowing the tribes to retain their individual identities while conceding some power to the new system of governance. This can be accomplished only through the engagement of tribal elders by Afghanistan National Security Forces (ANSF) and GIROA representatives.
Tribal elders in close vicinity to ANA or coalition firebases and outposts are much more likely to support the GIROA government. Enemy groups and facilitators constantly engage local villagers, but most of the time they get little or no support because of constant ANA and coalition presence. The Afghan people understand power, and they will support the element that, in their eyes, has the power—either the ANSF or the enemy. The elders know the enemy can affect them more in remote areas, so they will harbor enemy facilitators more readily than elders who are near coalition firebases. The elders near a coalition or ANA presence understand the power of the ANA to arrest any facilitators that harbor enemy elements.
Monty Python – Ministry of Silly Walks – Film
Monty Python – Ministry of Silly Walks – Film
Monty Python’s Flying Circus
http://www.amazon.com/Complete-Monty-Pythons-Flying-Circus/dp/B001E77XNA/ref=…
Full Movie – The Last Of The Mohicans – Daniel Day-Lewis & Madeleine Stow
SECRECY NEWS – SANDIA SCIENTISTS MODEL DYNAMICS OF SOCIAL PROTEST
Researchers at Sandia National Laboratories have been studying the ways
that information, ideas and behaviors propagate through social networks in
order to gain advance warning of cyber attacks or other threatening
behavior.
The initial problem is how to explain the disparate consequences of
seemingly similar triggering events. Thus, in 2005, the Danish newspaper
Jyllands-Posten published cartoons featuring the Muslim Prophet Muhammad,
prompting widespread protests. In 2006, by contrast, the Pope gave a
lecture in which he made comments about Islam that were considered
derogatory by some, but the ensuing controversy quickly faded away.
"While each event appeared at the outset to have the potential to trigger
significant protests, the 'Danish cartoons' incident ultimately led to
substantial Muslim mobilization, including massive protests and
considerable violence, while outrage triggered by the pope lecture quickly
subsided with essentially no violence," wrote Sandia authors Richard
Colbaugh and Kristin Glass. "It would obviously be very useful to have the
capability to distinguish these two types of reaction as early in the event
lifecycle as possible."
What accounts for the difference in these outcomes? The intrinsic
qualities of the events are not sufficient to explain why one had
disruptive consequences and the other did not. Rather, the authors say, one
must factor in the mechanisms of influence by which individual responses
are shaped and spread.
By way of analogy, it has been shown that "it is likely to be impossible
to predict movie revenues, even very roughly, based on the intrinsic
information available concerning the movie" such as cast or genre, but that
"it *is* possible to identify early indicators of movie success, such as
temporal patterns in pre-release 'buzz', and to use these indicators to
accurately predict ultimate box office revenues."
The Sandia authors developed a methodology that reflects the "topological
properties" of social and information networks -- including the density and
hierarchy of connections among network members -- and modeled the dynamics
of "social diffusion events" in which individuals exercise influence on one
another.
They report that their model lends itself, among other things, to
"distinguishing successful mobilization and protest events, that is,
mobilizations that become large and self-sustaining, from unsuccessful ones
early in their lifecycle."
They tested the model to predict the spread of textual memes, to
distinguish between events that generated significant protest (a May 2005
Quran desecration) and those that did not (the knighting of Salman Rushdie
in 2007), and to provide early warning of cyber attacks.
The authors' research was sponsored by the Department of Defense and the
Department of Homeland Security, among others. See "Early warning analysis
for social diffusion events" by Richard Colbaugh and Kristin Glass,
originally published in Security Informatics, Vol. 1, 2012, SAND
2010-5334C.
http://www.fas.org/irp/eprint/diffusion.pdf
STRATEGY LACKING FOR DISPOSAL OF NUCLEAR WEAPONS COMPONENTS
There is a "large inventory" of classified nuclear weapons components
"scattered across" the nation's nuclear weapons complex and awaiting
disposal, according to an internal Department of Energy contractor report
last year.
But "there is no complex-wide cost-effective classified weapon disposition
strategy." And as a result, "Only a small portion of the inventory has been
dispositioned and it has not always been in a cost-effective manner."
See "Acceptance of Classified Excess Components for Disposal at Area 5,"
presented at the Spring 2012 Waste Generator Workshop, April 24, 2012.
http://www.fas.org/sgp/othergov/doe/excess.pdf
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
Videoclip – SI Swimsuit: Marisa Miller Body Painting
Marisa Miller’s body become a canvas in this SI Swimsuit 2008 Body Painting video.
For more SI Swimsuit photos and videos go to http://www.si.com/swimsuit
Cryptome – Assange’s International Subversive Vol 1
Assange International Subversive
A sends:
Here is “International Subversive” Vol#1, the Hacking E-zine produced / edited by the Australian ‘hacker’ Mendax in 1991 (reference: Dreyfus, “Underground: Tales of hacking, madness and obsession on the electronic frontier” Ch.8
http://suelette.home.xs4all.nl/underground/justin/chapter_8.html ) aka Assange
The document came to me in several pieces – I’ve made no changes to the content other than to stick them together in order and add in some formatting (spaces) that tidy up some of the headings, so all spelling mistakes etc are originals (there are two section “2.4” & two section “2.7”, the later of each should be sections “2.5” & “2.8” respectively I guess according to the contents section). Best viewed with a fixed-width font.
The E-zine lists its editor as ‘The Chthonic Hvee’, presumably Mendax wielded his electronic editorial pen to publish under a different alias (in the same way he was able to change is alias from ‘proff’ to ‘Mendax’ being a research contributor to the Dreyfus book. Interesting.).
I can’t confirm the original source of the document or the accuracy of its content so it comes to you with all appropriate disclaimers – perhaps some of Cryptomes readers will be familiar with the incidents , etc., discussed within and can comment further, if you decide to publish this.
http://cryptome.org/2013/01/International_Subversive__Volume1.txt.gz
TMZ – Britney Spears’s $100 MILLION Vegas Deal
Britney Spears is definitely not hurting for cash… but Brit may be on the brink of signing a deal that could make her an additional $100 million dollars… A YEAR!
TOP-SECRET – Restricted U.S. Army Access Control Handbook

TC 19-210 Access Control Handbook
- 137 pages
- Distribution is authorized to US Government agencies only to protect technical or operational information from automatic dissemination under the International Exchange Program or by other means.
- October 2004
This handbook provides installation commanders with the basic information necessary for effective access control to their installations. It does not discuss the technical issues involved with standards and designs. Information regarding standards and designs is evolving and will be resolved by the Headquarters (HQ) Department of the Army (DA) PS Review Board (DAPSRB) and the PS integrated concept teams. This handbook provides commanders with the legal and jurisdictional issues associated with the inspection procedures at an ACP. Additionally, this handbook equips operators (which includes military police [MP], DA police, and sentinels of augmenting units) of an ACP with the various vehicle inspection criteria and measures necessary to conduct an effective ACP.
The openness of the United States (US) society provides an opportunity for our enemies to operate with more freedom than they would have in more restrictive venues. Also exacerbating the threats is the global proliferation of cheap weapons of mass destruction (WMD) and the means to disseminate knowledge about such weapons. Few US cities are fully prepared to deal with incidents involving WMD. Critical infrastructure and the US economy are becoming increasingly more reliant on information and computer-based technologies that are vulnerable to covert attacks. Many military installations and facilities are key force projection platforms and are susceptible to attacks from terrorists using WMD, from unconventional special forces formed from elements infiltrated into the United States, or from indigenous hostile elements.
As a result of recent events, Army installations have increased their force protection (FP) readiness through increased access control operations. Access control is a major implied security mission that supports the installation FP program. The FPCON determines the level of operation at an ACP, and thus, the ACP must be able to quickly and easily enhance security under an increased FPCON. ACPs serve as the access point for all personnel, vehicles, and deliveries to an installation. The ACP becomes the first chance for forces to inspect incoming personnel, vehicles, and cargo in order to detect, assess, and deter an incident.
Installation commanders must establish installation access control procedures that comply with Department of Defense (DOD) and DA policies. In addition to these policies, installation commanders must consider—
- Manpower availability.
- FPCON.
- ACP layout.
- Other factors, all of which will influence a commander’s manning level for an access control operation.
When considering installation access control, commanders must reflect on its purpose, the impact on the surrounding community, and the end state. The purpose of access control is to identify, reduce, or eliminate installation and in-transit vulnerabilities to threats and to enhance the overall FP posture while minimizing the impact on normal operations. The end state is to protect the forces through a myriad of measures that are addressed in the installation access control plan. FPCON levels and access control measures are established in a graduated scale based on the intelligence provided by a threat fusion cell.
Monty Python – Job Interview
Monty Python’s Flying Circus
http://www.amazon.com/Complete-Monty-Pythons-Flying-Circus/dp/B001E77XNA/ref=…
CEO – Defrauding Gold Coin Investors of More Than $2.4 Million
DENVER—James P. Burg, age 61, formerly of Fairplay, Colorado, faces fraud charges related to a scheme to defraud gold coin investors, the U.S. Attorney’s Office, the FBI, the IRS-CI, and the U.S. Postal Inspection Service announced. Burg was indicted by a federal grand jury in Denver on November 6, 2012, for charges of wire fraud, mail fraud, money laundering, and failure to file tax returns. The indictment remained sealed until his arrest in California on November 29, 2012. Burg then appeared in U.S. District Court for the Southern District of California. In court there, Burg was ordered to be detained and transferred by U.S. Marshals from California to Colorado. Burg’s first Colorado court appearance occurred on January 2, 2013, where he was advised of his rights and the charges pending against him. He appeared in court on January 7, 2013, and again on January 14, 2013, for the purpose of a detention hearing. On January 14, 2013, U.S. Magistrate Judge Michael E. Hegarty ordered that Burg could be released prior to trial on a $50,000 secured property or cash bond. Once released on that pre-trial bond, Magistrate Judge Hegarty ordered Burg to a halfway house (once bed space is available), pending the resolution of the criminal case.
According to the indictment, beginning on or about October 1, 2007, and continuing through and including on or about January 12, 2012, in Colorado and elsewhere, James P. Burg devised and intended to devise a scheme to defraud customers that ordered coins from a business known as Superior Discount Coins and Gold Run Investments and for obtaining money from those customers by means of materially false and fraudulent pretenses, representations, and promises. Burg took and received $2,464,099 from customers that ordered coins, and he failed to deliver the coins as promised.
As part of the scheme, Burg represented that he was the chief executive officer of a company known as Superior Discount Coins (SDC) and that SDC was in the business of selling coins. Burg also conducted business using a company known as Gold Run Investments (GRI) and represented that GRI was in the business of selling coins. At times, Burg operated GRI using the alias “Tim Burke.” Burg advertised and solicited customers through radio advertisements and over the Internet using websites he controlled, including; http://www.superiordiscountcoins.com, http://www.yourcoinbroker.com, and http://www.goldruninvestments.net.
Burg misrepresented and promised customers that if they ordered coins from SDC or GRI and paid him for those coins, he would deliver the coins to them or to accounts designated by them. He sent and caused to be sent to customers that ordered coins from SDC or GRI invoices stating amounts of money owed for the coins and, in some cases, providing information about a bank account to which the customers should transfer their money to purchase the coins.
The money Burg received from customers was not used to purchase coins for such customers, but instead he converted the money to his own use and benefit. Burg refused to refund money to customers in several instances where the customers requested a return of their money after he failed to deliver coins as originally promised. To prevent the scheme’s detection, Burg sometimes filled customers’ orders for coins only after such customers threatened to take legal action or report him to law enforcement authorities. Burg used one customer’s payment for coins to refund funds to another customer.
For calendar years 2006, 2007, 2008, and 2009, Burg failed to file income tax returns with the Internal Revenue Service as required by law. These returns were required to be filed with the IRS on April 15 following the subsequent above mentioned years.
“A core mission of the U.S. Attorney’s Office is to protect victims from scam artists who try to trick them out of their hard earned money,” said U.S. Attorney John Walsh.
“The FBI has made protecting innocent investors a priority,” said FBI Special Agent in Charge James Yacone. “As such, we will vigorously investigate those who engage in schemes to swindle and defraud.”
“The U.S. Postal Inspection Service has no shortage of investment investigations and this is another example of greed overcoming honest business practices,” said Adam Behnen, Inspector in Charge, with the U.S. Postal Inspection Service. “These criminal charges illustrate the commitment of the U.S. Postal Inspection Service to protect the American public by investigating individuals who use the U.S. mail to further their schemes.”
“Fraud schemes are often described as a house of cards and will eventually fall apart exposing the individuals responsible,” said Stephen Boyd, Special Agent in Charge, IRS-Criminal Investigation, Denver Field Office. “This is a great example of federal agencies working together.”
Burg was charged with six counts of wire fraud, nine counts of mail fraud, four counts of money laundering, and four counts of willful failure to file tax returns. If convicted of the wire fraud and mail fraud counts, he faces not more than 20 years in federal prison, and a fine of up to $250,000 per count. If convicted of the money laundering counts, he faces not more than 10 years in federal prison and a fine of up to $250,000 per count. If convicted of failing to file tax returns, he faces not more than one year in federal prison and a fine of up to $25,000 per count.
This case was investigated by special agents with the Federal Bureau of Investigation (FBI), the IRS-Criminal Investigation, and the U.S. Postal Inspection Service.
Burg is being prosecuted by Assistant U.S. Attorney Timothy Neff.
The charges contained in the indictment are allegations, and the defendant is presumed innocent unless and until proven guilty.
Apocalypo – Full Movie by Mel Gibson
Cryptome unveils MIT Closet Allegedly Used by Aaron Swartz
MIT Closet Allegedly Used by Aaron Swartz
Closet in MIT Building 16 from Which Aaron Swartz Allegedly Downloaded JSTOR Docs (USG photos from court filing)
![[Image]](https://i0.wp.com/cryptome.org/2013/01/swartz/mit-closet-swartz-01.jpg)
Box Allegedly Used by Aaron Swartz to Hide Downloading Laptop
![[Image]](https://i0.wp.com/cryptome.org/2013/01/swartz/mit-closet-swartz-02.jpg)
Alleged Download Equipment of Aaron Swartz
![[Image]](https://i0.wp.com/cryptome.org/2013/01/swartz/mit-closet-swartz-03.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013/01/swartz/mit-closet-swartz-04.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013/01/swartz/mit-closet-swartz-05.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013/01/swartz/mit-closet-swartz-06.jpg)
Download Equipment Allegedly Stored in Separate Building W20
![[Image]](https://i0.wp.com/cryptome.org/2013/01/swartz/mit-closet-swartz-07.jpg)
SI Swimsuit: Quiana Bodypainting – Video
Quiana Grant’s Swimsuit 2008 bodypainting video
TMZ – Kobe Bryant vs. Bill Clinton — Who BANGED More Chicks?
It’s arguably the greatest question posed in the last century or so… who has taken down more chicks: Kobe Bryant or former President Bill Clinton?
TOP-SECRET – DHS-FBI Suspicious Activity Reporting Bulletin: Theft/Loss/Diversion

ROLL CALL RELEASE
- 1 page
- For Official Use Only
- November 15, 2012
(U//FOUO) Terrorists may attempt to steal or divert precursor materials, uniforms, identification, blueprints, documents, access cards, facility vehicles, or other items–possibly with the help of knowledgeable insiders–for use in pre-operational planning or attacks. Emilio Suarez Trashorras, a Spanish national convicted for his role in the 2004 Madrid train bombings, stole the explosives used in the attack and the vehicles used to transport the explosives from a mining company where he worked.
(U//FOUO) The following SAR incidents from the NSI shared space demonstrate types of behavior terrorists might exhibit during pre-operational stages for attacks. While none were ultimately linked to terrorist activity, they are cited as relevant examples for awareness and training purposes:
– (U) An individual approached a transit authority security officer on a rail platform to report a fight in progress. No fight was found, but the individual continued to engage the security officer with questions, then seized a set of transit keys from the officer’s pocket and fled. Efforts to apprehend the suspect were unsuccessful.
– (U) A powder company that supplies explosives to the mining and construction industries reported in 2011 that the locks to an explosives magazine were cut overnight, and numerous items were stolen, including three 50-lb bags of ammonium nitrate fuel oil, one case of emulsion explosive, two cases of cast boosters, and three 1,000-foot rolls of detonation cord.
(U) Possible Indicators of Pre-Operational Theft/Loss/Diversion
(U//FOUO) The following activities can indicate efforts to illegally obtain materials for use in terrorist pre-operational planning or attacks. Theft is a common criminal occurrence that is not necessarily associated with terrorism. Care should be taken to distinguish crimes of opportunity from those that may indicate a terrorist motive. Depending upon the context, theft, loss, or diversion incidents should be reported to the appropriate authorities, particularly if a terrorism link is suspected.
– (U//FOUO) Theft of chemicals, hazardous substances, weapons, pre-cursor materials, or items that could compromise facility security, such as uniforms, identification, blueprints, vehicles (or components), technology, or access keys or cards.
– (U//FOUO) Receipt, transfer, or delivery of any of the above without legitimate reason, necessary identification, or authorization.
– (U//FOUO) A pattern of losses or irregularities in facility inventory indicating sensitive materials may have been misdirected or are missing.
– (U//FOUO) Employees who frequently requisition extra uniforms, equipment, or other proprietary or sensitive materials, and/or who remove them from the facility without authorization.
(U//FOUO) First Ammendment-protected activities should not be reported in a SAR or ISE-SAR absent articulable facts and circumstances that support the source agency’s suspicion that the behavior observed is not innocent, but rather reasonably indicative of criminal activity associated with terrorism, including evidence of pre-operational planning related to terrorism. Race, ethnicity, national origin, or religious affiliation should not be considered as factors that create suspicion (although these factors may be used in specific subject descriptions).
Monty Phyton – Bicycle Repairman
Monty Python’s Flying Circus
http://www.amazon.com/Complete-Monty-Pythons-Flying-Circus/dp/B001E77XNA/ref=…
Unveiled by Crpytome – Plutonium-238 Production for NASA Radioisotope Power Systems
|
TMZ – Jodie Foster’s CRAZY Golden Globes Speech!
There were a lot of highlights from this year’s Golden Globe Awards… but none more shocking than Jodie Foster’s crazy, all over-the-place acceptance speech!
TOP-SECRET – Senate Permanent Subcommittee on Investigations HSBC Money Laundering Case History

U.S. Vulnerabilities to Money Laundering, Drugs, and Terrorist Financing: HSBC Case History
- 340 pages
- July 17, 2012
HSBC Case Study. To examine the current money laundering and terrorist financing threats associated with correspondent banking, the Subcommittee selected HSBC as a case study. HSBC is one of the largest financial institutions in the world, with over $2.5 trillion in assets, 89 million customers, 300,000 employees, and 2011 profits of nearly $22 billion. HSBC, whose initials originally stood for Hong Kong Shanghai Banking Corporation, now has operations in over 80 countries, with hundreds of affiliates spanning the globe. Its parent corporation, HSBC Holdings plc, called “HSBC Group,” is headquartered in London, and its Chief Executive Officer is located in Hong Kong.
Its key U.S. affiliate is HSBC Bank USA N.A. (HBUS). HBUS operates more than 470 bank branches throughout the United States, manages assets totaling about $200 billion, and serves around 3.8 million customers. It holds a national bank charter, and its primary regulator is the U.S. Office of the Comptroller of the Currency (OCC), which is part of the U.S. Treasury Department. HBUS is headquartered in McLean, Virginia, but has its principal office in New York City. HSBC acquired its U.S. presence by purchasing several U.S. financial institutions, including Marine Midland Bank and Republic National Bank of New York. A senior HSBC executive told the Subcommittee that HSBC acquired its U.S. affiliate, not just to compete with other U.S. banks for U.S. clients, but primarily to provide a U.S. platform to its non-U.S. clients and to use its U.S. platform as a selling point to attract still more non-U.S. clients. HSBC operates in many jurisdictions with weak AML controls, high risk clients, and high risk financial activities including Asia, Middle East, and Africa. Over the past ten years, HSBC has also acquired affiliates throughout Latin America. In many of these countries, the HSBC affiliate provides correspondent accounts to foreign financial institutions that, among other services, are interested in acquiring access to U.S. dollar wire transfers, foreign exchange, and other services. As a consequence, HSBC’s U.S. affiliate, HBUS, is required to interact with other HSBC affiliates and foreign financial institutions that face substantial AML challenges, often operate under weaker AML requirements, and may not be as familiar with, or respectful of, the tighter AML controls in the United States. HBUS’ correspondent services, thus, provide policymakers with a window into the vast array of money laundering and terrorist financing risks confronting the U.S. affiliates of global banks.
…
Disregarding Links to Terrorism. For decades, HSBC has been one of the most active global banks in the Middle East, Asia, and Africa, despite being aware of the terrorist financing risks in those regions. In particular, HSBC has been active in Saudi Arabia, conducting substantial banking activities through affiliates as well as doing business with Saudi Arabia’s largest private financial institution, Al Rajhi Bank. After the 9-11 terrorist attack in 2001, evidence began to emerge that Al Rajhi Bank and some of its owners had links to financing organizations associated with terrorism, including evidence that the bank’s key founder was an early financial benefactor of al Qaeda. In 2005, HSBC announced internally that its affiliates should sever ties with Al Rajhi Bank, but then reversed itself four months later, leaving the decision up to each affiliate. HSBC Middle East, among other HSBC affiliates, continued to do business with the bank.
Due to terrorist financing concerns, HBUS closed the correspondent banking and banknotes accounts it had provided to Al Rajhi Bank. For nearly two years, HBUS Compliance personnel resisted pressure from HSBC personnel in the Middle East and United States to resume business ties with Al Rajhi Bank. In December 2006, however, after Al Rajhi Bank threatened to pull all of its business from HSBC unless it regained access to HBUS’ U.S. banknotes program, HBUS agreed to resume supplying Al Rajhi Bank with shipments of U.S. dollars. Despite ongoing troubling information, HBUS provided nearly $1 billion in U.S. dollars to Al Rajhi Bank until 2010, when HSBC decided, on a global basis, to exit the U.S. banknotes business. HBUS also supplied U.S. dollars to two other banks, Islami Bank Bangladesh Ltd. and Social Islami Bank, despite evidence of links to terrorist financing. Each of these specific cases shows how a global bank can pressure its U.S. affiliate to provide banks in countries at high risk of terrorist financing with access to U.S. dollars and the U.S. financial system.
…
A. Findings
This Report makes the following findings of fact.
(1) Longstanding Severe AML Deficiencies. HBUS operated its correspondent accounts for foreign financial institutions with longstanding, severe AML deficiencies, including a dysfunctional AML monitoring system for account and wire transfer activity, an unacceptable backlog of 17,000 unreviewed alerts, insufficient staffing, inappropriate country and client risk assessments, and late or missing Suspicious Activity Reports, exposing the United States. to money laundering, drug trafficking, and terrorist financing risks.
(2) Taking on High Risk Affiliates. HBUS failed to assess the AML risks associated with HSBC affiliates before opening correspondent accounts for them, failed to identify high risk affiliates, and failed for years to treat HBMX as a high risk accountholder.
(3) Circumventing OFAC Prohibitions. For years in connection with Iranian U-turn transactions, HSBC allowed two non-U.S. affiliates to engage in conduct to avoid triggering the OFAC filter and individualized transaction reviews. While HBUS insisted, when asked, that HSBC affiliates provide fully transparent transaction information, when it obtained evidence that some affiliates were acting to circumvent the OFAC filter, HBUS failed to take decisive action to confront those affiliates and put an end to conduct which even some within the bank viewed as deceptive.
(4) Disregarding Terrorist Links. HBUS provided U.S. correspondent accounts to some foreign banks despite evidence of links to terrorist financing.
(5) Clearing Suspicious Bulk Travelers Cheques. In less than four years, HBUS cleared over $290 million in sequentially numbered, illegibly signed, bulk U.S. dollar travelers cheques for Hokuriku Bank, which could not explain why its clients were regularly depositing up to $500,000 or more per day in U.S. dollar travelers cheques obtained in Russia into Japanese accounts, supposedly for selling used cars; even after learning of Hokuriku’s poor AML controls, HBUS continued to do business with the bank.
(6) Offering Bearer Share Accounts. Over the course of a decade, HBUS opened over 2,000 high risk bearer share corporate accounts with inadequate AML controls.
(7) Allowing AML Problems to Fester. The OCC allowed HBUS’ AML deficiencies to fester for years, in part due to treating HBUS’ AML problems as consumer compliance matters rather than safety and soundness problems, failing to make timely use of formal and informal enforcement actions to compel AML reforms at the bank, and focusing on AML issues in specific HBUS banking units without also viewing them on an institution-wide basis.
Monty Phyton – Argument Clinic – Video
Sports Illustrated Swimsuit: Jarah Model Diary – Video
The Cia – CIA Analysis of the Warsaw Pact Forces
CIA Analysis of the Warsaw Pact Forces: The Importance Of Clandestine Reporting [PDF 17.2 MB*]
This study examines the role of clandestine reporting in CIA’s analysis of the Warsaw Pact from 1955 to 1985. The Soviet Union established itself as a threat to the West at the end of World War II by its military occupation of eastern European countries and the attempts of its armed proxies to capture Greece and South Korea. The West countered with the formation of NATO. While the West welcomed West Germany into NATO, the Soviets established a military bloc of Communist nations with the Warsaw Treaty of May 1955. This study continues CIA’s efforts to provide a detailed record of the intelligence derived from clandestine human and technical sources from that period. This intelligence was provided to US policymakers and used to assess the political and military balances and confrontations in Central Europe between the Warsaw Pact and NATO during the Cold War.
View this study’s photos and maps on the CIA Flickr stream [external link disclaimer]
View the videos from this publication on the CIA’sYouTube Channel.**
Download Catalogue of Documents and Summaries: Finished Intelligence, Clandestine Reporting, and Other Sources [PDF 1.1MB*]
Cryptome – Stephen John Nicgorski, CIA OBL Spy, Drone Tout
|
TMZ – What Happened to Kate Middleton’s Face!?
The Royal Family just released Kate Middleton’s official portrait… and let’s just say it’s ABSOLUTELY FRIGGIN’ HORRENDOUS!
PI – U.S. Army Tactical Questioning Pocket Reference Card
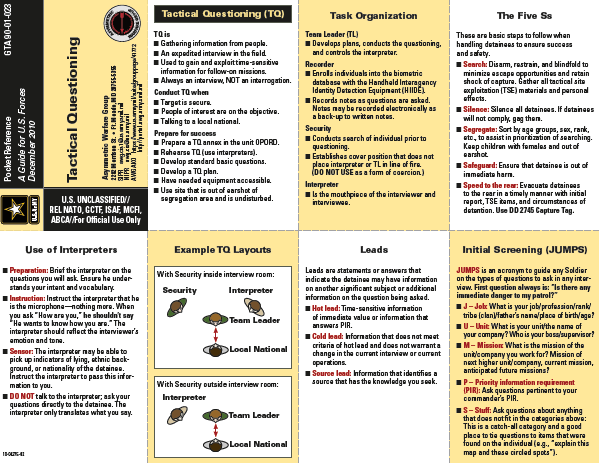
Asymmetric Warfare Group
- 2 pages
- For Official Use Only
- December 2010
Tactical Questioning (TQ)
TQ is
■Gathering information from people.
■An expedited interview in the field.
■Used to gain and exploit time-sensitive information for follow-on missions.
■Always an interview, NOT an interrogation.Conduct TQ when
■Target is secure.
■People of interest are on the objective.
■Talking to a local national.Prepare for success
■Prepare a TQ annex in the unit OPORD.
■Rehearse TQ (use interpreters).
■Develop standard basic questions.
■Develop a TQ plan.
■Have needed equipment accessible.
■Use site that is out of earshot of segregation area and is undisturbed.…
Leads are statements or answers that indicate the detainee may have information on another significant subject or additional information on the question being asked.
■Hot lead: Time-sensitive information of immediate value or information that answers PIR.
■Cold lead: Information that does not meet criteria of hot lead and does not warrant a change in the current interview or current operations.
■Source lead: Information that identifies a source that has the knowledge you seek.Initial Screening (JUMPS)
JUMPS is an acronym to guide any Soldier on the types of questions to ask in any interview. First question always is: “Is there any immediate danger to my patrol?”
■J – Job: What is your job/profession/rank/tribe (clan)/father’s name/place of birth/age?
■U – Unit: What is your unit/the name of your company? Who is your boss/supervisor?
■M – Mission: What is the mission of the unit/company you work for? Mission of next higher unit/company, current mission, anticipated future missions?
■P – Priority information requirement (PIR): Ask questions pertinent to your commander’s PIR.
■S – Stuff: Ask questions about anything that does not fit in the categories above: This is a catch-all category and a good place to tie questions to items that were found on the individual (e.g., “explain this map and these circled spots”).…
Types of Questions
Direct: (Only authorized technique)
■An efficient method of asking precise questions toward a specific objective. Normally, who, what, when, where, why, and how begin the question.
■DON’T FORGET “ELSE”! (Who else, why else, where else, etc.)Tips
■ “War game” your techniques in rehearsals.
■ Do not depend on lists or cheat sheets (you may lose eye contact and miss an indicator of deception).
■ Have a focused approach (erratic questions all over the map will confuse both you and the detainee).
■ Be specific and focused with questions (if you want to know what the person’s profession is, ask “What is your profession?” not “What do you do?”).
■ Ask questions that cannot be answered with yes or no.
■ If you are doing most of the talking, he is winning!Do Not Use:
Vague:
■Questions that are not specific. These may lead to answers that are misinterpreted by the interviewer or elicit broad answers that are of no use.
Compound:
■Multiple questions contained within a single question: “When did you stage and conduct the attack?”
Negative:
■Phrasing that prompts the interviewee to make a negative response, whether true or not: “You didn’t see any CF while on your recon, did you?”
Leading:
■Questions that prompt the interviewee to give the answer he believes you want.
Monty Phyton – Galaxy Song
Galaxy Song
TMZ – Is Paris Hilton STILL Richer than Kim Kardashian?
Kim Kardashian is arguably one of the biggest celebrities in Hollywood… but it turns out Paris Hilton is getting the last laugh in the end!
PI – FBI Analysis Finds That Only 4% of Active Shooter Incidents Since 2002 Were Perpetrated by Women
A training exercise for police academy recruits involves active shooter scenarios at an area elementary school.
A segment from KETV News in Omaha, Nebraska discusses active shooter training exercises held at a local elementary school. Similar training exercises have been held around the country following recent mass shootings.
Public Intelligence
An FBI analysis of active shooter incidents since 2002 found that 96% of the attacks were perpetrated by males, most of which acted alone. The statistic is found in a joint intelligence bulletin released at the end of December by the Department of Homeland Security and FBI titled “Recent Active Shooter Incidents Highlight Need for Continued Vigilance“. The bulletin provides brief advice on crisis response and long-term protective measures as well as statistics related to past active shooter incidents, which are defined as situations where one or more individuals participates in a “random or systematic killing spree demonstrating their intent to harm others with a firearm.” Active shooters are distinguished from other “traditional criminal acts, such as robbery or hostage-taking” by their intention to commit “mass murder”. The FBI analyzed 154 active shooter events in the United States between 2002 and 2012 that included three or more individuals being shot. This analysis found that:
- 96% of the shooters were males
- 51% of the shooters were deceased following the attack (43% committed suicide and 8% were shot and killed by responders)
- 96% of the attacks involved shooters acting alone
- 37% of the attacks occurred in workplaces and 17% occurred in an academic setting
- 40% of the attacks were unable to be linked to a clear motivation
- 21% of the attacks were motivated by workplace retaliation and 14% were motivated by domestic disputes
- Academic retaliation by a current or former student only accounted for 7% of the attacks
The FBI’s analysis found that active shooters were often described as “social isolates” who “harbored feelings of hate and anger” and had some contact with mental health professionals. Though mental illness is a common factor among many active shooters, its functional role in causing the massacre is indeterminate according to FBI analysis. Very few of the shooters in cases analyzed by the FBI had previous arrests for violent crimes, though many had encountered a significant emotional hardship prior to the attack such as “loss of significant relationships, changes in financial status, loss of a job, changes in living arrangements, major adverse changes to life circumstances, and/or feelings of humiliation or rejection on the part of the shooter.”
To help protect against active shooter situations, the DHS-FBI joint bulletin recommends that public facilities update their emergency and crisis management plans and conduct exercises to ensure a rapid response to a large-scale crisis. Long-term security plans for public facilities should “emphasize physical safeguards, including building enhancements that present a more robust deterrent and provide a more survivable environment.” Building enhancement can take the form of physical modification, such as the installation of “window and external door protection with quick-release capability”, as well as the establishment of “safe areas within the facility for assembly and refuge during crises.”
Monty Phyton Film – Every Sperm is Sacred
Every Sperm is Sacred
TMZ – Beyonce’s GQ Cover — HOLY CRAP SHE’S HOT!
Beyonce is on the cover of GQ… and HOLY MOTHER OF GOD SHE LOOKS SO HOT! This woman seriously just had a baby!?
SECRET – DHS, Fusion Centers Struggle to Respond to Mass Shootings
Public Intelligence
Four days after the mass shooting last July in Aurora, Colorado, a project of the Houston Office of Public Safety and Homeland Security called Ready Houston released a training video to help educate members the public about how to survive a mass shooting. The six-minute video, which was produced with $200,000 from the Department of Homeland Security’s Urban Area Security Initiative, includes a dramatic recreation of a man dressed entirely in black walking into an office building and beginning to shoot people at random with a shotgun that he pulls from a small satchel. Variously described as “outlandish“, “surreal” and “over-the-top“, the video has met with mixed responses since it was re-released by several fusion centers and local agencies, including most recently the Alabama Department of Homeland Security.
The response to the video and other instructional items produced by DHS, fusion centers and law enforcement agencies in response to recent mass shootings demonstrates the difficulty in responding to tragedies where often little can be done to save innocent lives. After the mass shooting last December at Sandy Hook Elementary School in Newtown, Connecticut, fusion centers around the country rushed to issue bulletins discussing everything from tactics for countering mass shooters to suggestions for dealing with children in response to the shooting. Some of the bulletins present useful facts regarding procedures for dealing with active shooter situations, the law enforcement term for incidents where an individual is attempting to kill people in a confined area, and links to resources for emergency planners and school officials. The Delaware Valley Intelligence Center issued a bulletin the day of the shooting to “provide some basic information on active shooter situations and immediate actions that should be taken in the event an active shooter incident were to occur.” The bulletin contains a three-point plan for reacting to an active shooter:
1. EVACUATE (if possible)
• Have an escape route and plan in mind.
• Leave your belongings behind.
• Keep your hands visible and open palms facing forward.
• Follow instructions of police officers.
• Have a designated meeting point and knowledge of everyone who is present.2. HIDE OUT
• If you are in an office, stay there.
• If you are in a hallway, lobby etc. get into a room.
• Lock and barricade the door with large items (i.e., desks, file cabinets). If the door can not be locked or barricaded, lay on your back with your feet up against the door to use your body weight as a barricade.
• Get as low as possible, lay on the floor.
• Silence all electronic devices.
• Remain quiet. Remain calm.
• Dial 911, if possible, to alert police of location, physical description, and type weapon(s) used by the shooter(s).
• If you cannot speak, leave the line open and allow the dispatcher to listen.3. TAKE ACTION
• As a last resort and only when your life is in imminent danger, attempt to take the active shooter down. When the shooter is at close range and you cannot flee, your chance of survival is much greater if you try to incapacitate him/her. Act with physical aggression, and throw items at the active shooter.
Another bulletin from the Colorado Information Analysis Center (CIAC) called “Helping Your Community Feel Safe” describes techniques for helping children cope with the most recent mass shooting. Given that the “magnitude of death and destruction in traumatic events require special attention and communication with children”, the bulletin recommends providing “structured time to discuss the event” and limiting “exposure to television and other sources of information about the disaster and its victims, especially for children.” The bulletin also recommends that parents and teachers be “alert to changes in a child’s usual behavior — drop in grades, loss of interest, not doing homework, increased sleepiness or distraction, isolating themselves and weight changes.” Teachers are particularly encouraged to increase their “students’ sense of control and mastery at school” by letting them plan a “special activity”.
Issues with providing practical responses to school attacks and mass shootings have also affected other agencies. Past bulletins from the Federal Bureau of Investigation’s National Center for the Analysis of Violent Crime have stated that “school shooters” often “engaged in repetitive viewing of violent media and were often fascinated with previous school shootings.” The bulletin warns of “repeated viewing of movies depicting school shootings, such as ‘Zero Day’ and ‘Elephant’,” which “may indicate a fascination with campus attacks.” A 2006 guide from the Regional Organized Crime Information Center (ROCIC), one of six Regional Information Sharing Systems funded by the Department of Justice’s Bureau of Justice Assistance, recommends identifying school shooters before they strike by their interests and school work. The guide lists interest in “Satanist cults, Nazism” and “violent media” as potential indicators of a school shooter, recommending that teachers look out for “dark themes present in school work, personal writing, humor, drawings, or doodles” that may indicate a predisposition towards violent behavior.
Film – Penis Song by Monty Phyton
Film – Penis Song by Monty Phyton
from
Monty Python’s Meaning of Life
Sports Illustrated Swimsuit: Melissa Haro Model Diary – Video
Melissa Haro gets personal during her SI Swimsuit 2008 shoot.
For more photos and videos go to http://www.si com/swimsuit.
SECRET by PI – Washington Fusion Center Newsletters
An image from the Washington State Fusion Center’s Fusion Liaison Officer newsletter encouraging readers to report suspicious behavior.
Public Intelligence
What kind of “suspicious” behaviors might put you in the sights of your local fusion center? A collection of Fusion Liaison Officer (FLO) reports from the Washington State Fusion Center (WSFC) obtained by police accountability activist Andrew Charles Hendricks via a public records request provide insight into the mechanics of suspicious activity reporting at the local level. More than a dozen reports, which are minimally redacted, detail monthly reporting by the WSFC to its “statewide network of agency-selected law enforcement, fire-fighting and critical infrastructure agency representatives” that ensure “vital disciplines are incorporated into the fusion process by serving as the conduit through which homeland security and crime related information flows to the WSFC for assessment and analysis through the state homeland security Regional Intelligence Groups.” According to the State of Washington, the “end state” of the FLO program “is to have FLOs throughout the state in all aspects of law enforcement, fire service and critical infrastructure” to facilitate the flow of information both to and from the state fusion center.
Though some of the reports contain information that seems to warrant further investigation, many of the reports often concern mundane activities such as photography or the discovery of abandoned items. Here are some examples of “tips and leads” derived from suspicious activity reports sent to the fusion center that are provided in the WSFC FLO Newsletter:
August 1, 2012 Volume 2, Issue 14:
(U//FOUO) On 17 July 2012 at approximately 1140 hours, a man in a gold colored vehicle was taking photos just outside the fence line of a prominent energy sector facility. The subject appeared to be taking photos of all inbound and outbound traffic to the facility. When the man was asked what he was doing, he put the camera in the car and left the area. WSFC Tracking No. TL_2012-07-18T11:38:29 Status: Closed (U//FOUO) On 26 July 2012 at 1059 hours, caller reported vandalism that occurred on a barge. Caller stated one of the door hatches was open and four padlocks were cutoff the door. An investigation was conducted on the barge, which was moored to a pier during the incident, and nothing was found missing. WSFC Tracking No. TL_2012-07-26T15:02:53 Status: Open (U//FOUO) On 13 July 2012 at 1942 hours, a white male with dark hair parked along the east side of 2nd Avenue near Madison Street in Seattle, exited a black BMW sedan with WA license plates. The subject took pictures of the federal building lobby/courtyard and surrounding property. The subject then took pictures, of what appeared to be, an almost 360 degree panoramic view of the skyline.While taking the pictures, the subject and a Security Officer (SO) took notice of each other. When the subject noticed the SO, he immediately stopped taking pictures. He then loitered along the sidewalk for a short time before departing the area on foot at approximately 1950 hours. He then headed southbound on the east side of 2nd Avenue. He returned from the south on the east side of 2nd Avenue by foot at approximately 2140 hours, at which time he entered the vehicle and drove away southbound on 2nd Avenue. WSFC Tracking No. TL_2012-07-19T16:41:09 Status: Open
July 5, 2012 Volume 2, Issue 13:
(U//FOUO) [Region 1] On 11 June 2012 at 0200 hours, adjacent to a refinery regulated area, a security officer observed a vehicle, with two people inside, stopping to pick up two white males that appeared from a nearby ditch. A search of the area around the ditch was conducted and nothing was found. WSFC Tracking No. TL_2012-06-13T13:42:58 Status: Closed (U//FOUO) [Region 6] On 26 June 2012 at approximately 1605 hours, an employee of the Puget Sound Naval Shipyard and Intermediate Maintenance Facility was approached at the Bremerton Gate turnstiles by two males, both clean shaven, “dressed nicely,” and with thick foreign accents. The employee stated that one of the males asked if visitors were allowed inside the shipyard, and after she replied no, the two males then asked if she would let them come in with her, where she replied absolutely not. WSFC Tracking No. TL_2012-06-27T14:57:30 Status: Open (U//FOUO) [Region 7] On 25 June 2012 at approximately 1145 hours, Chelan County PUD employees observed a male taking video of the Rocky Reach Hydro Project. His behavior did not appear to be consistent with usual tourist activity, as he was taking extensive video of the Project without visiting the museum, fish-viewing, park attractions, cafeteria, etc. On-duty security guards were unable to contact the male before he departed the visitor area. WSFC Tracking No. TL_2012-06-26T14:07:40 Status Closed
June 5, 2012 Volume 2, Issue 12:
(U//FOUO) [Region 4] On 22 May 2012 at approximately 0012 hours, an employee of a gasoline station, located in Vancouver, WA called 911 to report a suspicious device. Clark County Sheriff’s Deputies responded to find a small suspicious device located inside the store on the counter. Members of the Metro Bomb squad were called to investigate the device. As a precaution, the store was closed and the pumps were turned off. The device, determined to be a cell phone that had been damaged and pieced back together, was retrieved by the Metro Bomb squad and determined not to be explosive or hazardous. WSFC Tracking No. TL_2012-05-22T14:12:42 Status: Closed (U//FOUO) [Region 5] On 30 May 2012 at 0909 hours, a vehicle was observed by Port of Tacoma Security, with an identified male taking photos of the Port of Tacoma Road overpass. The subject was contacted, where he claimed he was taking pictures for his blog. With the subjects permission, photos on the camera were viewed by security and three photos out of many were of the port. The subject was cooperative during contact and said he understood that taking pictures around the port might seem suspicious. WSFC Tracking No. TL_2012-05-30T13:31:37 Status: Closed
May 16, 2012 Volume 2, Issue 11:
(U//FOUO) [Region 6] On 3 May 2012 at 1330 hours, an abandoned case of luggage was discovered at the Washington State Ferries Colman Dock outside a phone booth in front of a restaurant. The Washington State Patrol was called and the case was searched. Contents included female items and a female Air Force uniform. WSFC Tracking No. TL_2012-05-14T10:41:19 Status Closed (U//FOUO) [Region 1] On 15 May 2012, a refinery received a phone call from an identified individual who complained that he had ships anchoring off his property that were headed to the refinery. He also asked questions about ship traffic in the area. WSFC Tracking No. TL_2012-05-16T10:30:03 Status: Open
April 25, 2012 Volume 2, Issue 10:
(U//FOUO) [Region 6] On 21 April 2012 at 1520 hrs, a crew member on a dormant tug vessel discovered what appeared to be a pipe bomb (2 pipes taped together) in the Captain’s stateroom. The bomb squad responded and rendered the device safe exposing its contents as sand and not incendiary. WSFC Tracking No. TL_2012-04-22T11:13:45 Status: Closed (U//FOUO) [Region 4] On 12 April 2012, at one of Pierce Transit’s major transit centers, an individual was seen by transit security officers taking pictures and asking police and security related questions (patrol times, locations of police and security personnel, etc…). He was observed taking photographs of a police officer while the officer was not aware. The subject was also walking up to transit security and asking to take photographs of them. Tacoma Police was notified and questioned the subject. The subject stated that his interest in public safety was for an online class project. The subject was asked to leave since he was on transit property and he complied. WSFC Tracking No. TL_2012-04-13T12:38:42 Status: Closed
April 11, 2012 Volume 2, Issue 9:
(U//FOUO) [Region 6] On 25 March 2012 at approximately 0835 hours, an unidentified subject was observed taking photos of the new Amtrak Equipment Maintenance building. The person observing the subject felt the activity was suspicious due to the length of time the subject spent in the area and his continual pacing while taking the photos. The officer also felt the incident suspicious due to the clothing worn by the subject and the apparent high dollar value of the camera used. WSFC Tracking No. TL_2012-04-02T14:06:04 Status: Open
March 20, 2012 Volume 2, Issue 8:
(U//FOUO) [Region 6] On 14 March 2012 at approximately 0130 hours, Seattle Police officers observed a subject running around the blocks containing the U.S. Courthouse, and the Seattle Police Department West Precinct, taking photos of the buildings. When stopped, the subject stated he was in Seattle attending a conference and was a citizen of the Slovak Republic. The subject claimed to be staying at a hotel approximately seven blocks from the buildings he was photographing, and could give no explanation as to why he was taking photos of the buildings. SFC Tracking No. TL_2012-03-15T14:05:02 Status: Open
TMZ – Paris Hilton on Kim Kardashian Pregnancy — ‘I’m Really Happy For Her’
They ain’t exactly friends anymore … in fact, they’re more like fierce rivals … but Paris Hilton tells TMZ she’s actually happy that her ex-BFF Kim Kardashian is knocked up with Kanye’s baby.
CONFIDENTIAL – Scottsdale Inventions Electric Shock Handcuffs for Detainees Patent
APPARATUS AND SYSTEM FOR AUGMENTED DETAINEE RESTRAINT
- 43 pages
- November 29, 2012
There is provided a device and system for restraining detainees through devices attached to the detainees and configured to administer electrical shocks when certain predetermined conditions occur. Restraining devices may be activated by internal control systems or by external controllers that transmit activation signals to the restraining device. External controllers may be actuated by an external controlling entity such as a detention guard or other person or system, or may be controlled by an enabling signal sent by wired or wireless connections to the controller. There is also provided a system for detainee restraint where multiple detainees may be restrained collectively or individually in a controlled environment such as a detention facility, a jail, or a detainee transport vehicle.
…
SUMMARY OF THE INVENTION
[0016] There is provided a device and system for restraining detainees through devices attached to the detainees and configured to administer electrical shocks when certain predetermined conditions occur. Restraining devices may be activated by internal control systems or by external controllers that transmit activation signals to the restraining device. External controllers may be actuated by an external controlling entity such as a detention guard or other person or system, or may be controlled by an enabling signal sent by wired or wireless connections to the controller. There is also provided a system for detainee restraint where multiple detainees may be restrained collectively or individually in a controlled environment such as a detention facility, a jail, or a detainee transport vehicle.
[0017] Embodiments of the restraining device of the present invention includes a restraint for physically constraining movement of at least a portion of a detainee’s body; an electric shock component coupled to the restraint; and a control system coupled to the electric shock component, the control system configured to cause the electric shock component to deliver a shock to the detainee when a predetermined condition occurs. The restraining device may be any device capable ofbeing attached to a detainee and restraining at least a portion of the detainee’s body, and in various implementations may include at least one of: a handcuff; an ankle cuff; a restraining belt; a straightjacket; a harness; a facial restraint; a helmet; and a neck collar; and combinations thereof. The restraint further includes one or more electrodes coupled to the electric shock component, and one of the one or more electrodes are configured to contact the skin of the detainee to deliver a shock when a predetermined condition occurs. Warnings in various forms may be provided to the detainee by the restraining device prior to administration of shock, and may be managed selectively by the control system coupled to the restraining device. Examples of warnings may include one or more of: an audio warning; a tactile warning such as a vibration or low-intensity shock; a visual warning such as a flashing light or text indicating a shock may be administered; and combinations thereof. The warnings may be varied in intensity to attempt to modify behavior of the detainee prior to administration of a shock, and the output of the administered shock may be tailored to a predetermined or variable amount based upon conditions perceived by an external controlling entity.
[0018] In various embodiments, the shock output of the restraining device may be varied to achieve any desired result. For example, the control system may be configured to cause the electric shock component to vary at least one of: a magnitude of the electric shock; a frequency of a signal generating the electric shock; and duration of the electric shock.
[0019] Embodiments of the restraining device may further include one or more sensors in communication with the control system. A sensor may be configured to detect whether the detainee engages in an unauthorized activity, and when such condition occurs the control system may be configured to deliver a shock to the detainee. The unauthorized activity may be defined to include any condition such as the detainee entering an unauthorized location; the detainee approaching a restricted area within a predetermined distance; the detainee approaching a keep-out zone broadcasting a keep-out signal, wherein a signal power level of the keep-out signal received by the device exceeds a predetermined threshold; the detainee attempting to tamper with the restraining device; or the detainee exiting an authorized location. Additionally, unauthorized activities may include the detainee making a threatening movement, where the restraining device measures through its sensors that the detainee is making movements of an aggressive nature or is modifying posture to a posture of potential aggression, such as drawing back a fist to swing, raising an arm suddenly, yanking against the restraining device, or rising suddenly from a prone or seated posture. Also, sensors on the restraining device may determine an unauthorized activity has occurred when the detainee makes an utterance that exceeds a predetermined volume measured by sensors coupled to the restraining device (such as a microphone); such a situation may be desirable to prevent the detainee from interfering in court proceedings, for example. In another embodiment, an unauthorized activity may include use of an unauthorized system such as any structure, device, or system to which use or access by the detainee can be controlled, including: a door to a building, ignition to a police car, computer system, or a weapon. In one embodiment, if a weapon is equipped with an RFID or other identification device, sensors in the restraining device may transmit a signal and receive a response signal indicating that a weapon is in a predetermined the proximity, and if the detainee does not move away from the weapon to cause the response signal to fall below a predetermined threshold, a shock will be administered. In yet another embodiment, an unauthorized activity occurs when the detainee fails to provide a predetermined verbal acknowledgement. Various combinations of these states may lead to additional unauthorized activities being detected.
Monty Python’s Flying Circus – Party Political Broadcast
Monty Python’s Flying Circus S4E06: Party Political Broadcast
Video – Sports Illustrated Swimsuit: Tori Praver Model Diary
TMZ – Does Brent Musburger Want to BANG AJ McCarron’s Girlfriend Katherin
ESPN announcer Brent Musburger noticed Alabama QB AJ McCarron’s beauty queen girlfriend in the crowd during the National Championship… and let’s just say the old dude didn’t hold back his feelings towards the striking brunette!
TOP-SECRET – National Counterterrorism Center Special Report

Worldwide: IED Targeting of First Response Personnel—Tactics and Indicators
- 8 pages
- For Official Use Only
- August 7, 2012
(U) Key Findings
(U//FOUO) Although most terrorist IED attacks outside war zones target civilians or symbols of authority and usually involve a single device, some are designed specifically to target emergency response personnel. The most common tactics involve using secondary or tertiary devices in tiered or sequential attacks intended to kill or maim response personnel after they arrive on the scene of an initial IED incident.
• The extent of government control in the intended target zone is a critical variable in operational planning for attacks against first responders. Whether attackers have sufficient access to the target area to gain familiarity with the landscape, the presence of police or other security forces, and even possibly their emergency response procedures are significant factors in attack preparation.
• Terrorists who are well-versed in the render-safe procedures used by explosive ordnance disposal (EOD) teams are the most likely to construct secondary devices capable of defeating techniques to defuse or destroy them.
(U//FOUO) There is widespread concern about the availability of information in online manuals, videos, and extremist discussion forums on IED design and tactics that can be used by plotters in Western countries—including the US.
• Only one Homeland attack plot by homegrown violent extremists (HVEs)a in recent years was intended to specifically target first responders, but a successful Homeland attack may be imitated once it is publicized in the media. • Growing awareness of the tactics and techniques used by terrorists elsewhere in the world— particularly in East Africa, South Asia, and Yemen —could motivate HVEs and other Homeland adversaries to deliberately plot attacks that target first responders.
• The targeting of EOD personnel during execution of render-safe and exploitation procedures represents a higher level of adversary tactical sophistication that could provide an early indication of the need to reassess the Homeland IED threat environment.
…
(U//FOUO) Targeting Responders Depends on Context
(U//FOUO) All incidents involving IEDs, including those that fail or are a hoax, draw emergency responders to handle any casualties, secure the area, deactivate or dispose of other potential explosive devices, and begin the process of investigative forensics. Although most terrorist IED attacks target civilians or symbols of authority and usually involve a single device, some devices encountered outside war zones are designed specifically to target emergency response personnel. Motivations for targeting first responders are highly dependent on context.
• In countries coping with insurgencies or political unrest that result in a sustained level of violence, responders may be deliberately targeted to counter their capabilities to deal with attacks by the armed opposition. Insurgents in the Iraq and Afghanistan war zones primarily target first responders—military police and explosive ordnance disposal (EOD) personnel—to degrade their ability to counter the insurgent’s primary weapon of choice, the IED. Insurgents in countries like Thailand—where the primary focus is to counter government rule or occupation—most likely attack first responders because they represent the ruling government.
• Criminal organizations under law enforcement or military pressure—such as drug-trafficking organizations (DTOs) in countries like Mexico and Colombia—may attack first responders to deter or inhibit disruption operations against them.
• Terrorist groups or individual extremists with ideological agendas may target responders deliberately to enhance the magnitude of their terror attack, creating increased fear and media attention by demonstrating that even would-be rescuers are vulnerable to attack.
(U//FOUO) The extent of government control in the intended target zone is a critical variable in operational planning for attacks against first responders. Whether attackers have sufficient access to the target area to gain familiarity with the landscape, the presence of police or other security forces, and even possibly their emergency response procedures are significant factors in attack preparation. Freedom of access also allows time to set up the attack, which is particularly important if multiple devices are to be employed. Attacks against responders have been particularly successful where an adaptive adversary is able to control the response environment and rely on support from local populations, either through cooperation or coercion. A pervasive security presence or particular vigilance by local citizens or police forces may not prevent conducting a single attack targeting civilians but could make it much more difficult to specifically target response personnel.
…
(U//FOUO) Unconstrained Diffusion of Tactics and Techniques Proliferates Knowledge
(U//FOUO) Information on IED design and tactics has become available to plotters in Western countries—including the US—who might then employ options, such as tiered attacks targeting emergency responders, they otherwise might not have considered. Explosives training manuals, extremist literature such as Inspire magazine, and Internet videos and chat rooms are widely disseminated. Violent extremists making available knowledge of EOD procedures and countermeasures could facilitate and significantly enhance the capability of terrorists to lure responders into IED ambushes and construct devices that would detonate as authorities tried to contain or deactivate them. A successful attack against responders may be imitated once publicized in the media.
• The diffusion of IED design information and tactics is not bound by geographic or motivational constraints. A review of bombmaking publications available on the Internet or in printed form dating back to the 1960s illustrates that an extremist can readily access a wide variety of manuals detailing EOD procedures and information on how to build victim-operated IEDs.
• Manuals, videos, and forum discussions are not complete substitutes for practical experience in IED emplacement, however; evidence of handson training and IED testing by terrorists in Western countries could give security services and law enforcement indicators of possible attack plotting.
(U//FOUO) Terrorists interested in conducting complex IED attacks, including deliberately targeting emergency personnel responding to an initial IED attack, can also learn from the examples of groups that have such experience in high-threat Western environments, some of whom are willing to provide expert training or instruction. Provisional Irish Republican Army (PIRA) bombmakers in the UK in the early 1990s created and employed a wide array of IED switches intended to reduce the effectiveness of security forces by targeting British and Irish EOD and response personnel, according to military reporting.
Monty Python’s Flying Circus – A Book at Bedtime – Full Movie
Monty Python’s Flying Circus S3E12: A Book at Bedtime
SECRECY NEWS – HOMELAND SECURITY HAS TOO MANY DEFINITIONS, SAYS CRS
The existence of multiple, overlapping and inconsistent definitions of the
term "homeland security" reflects and reinforces confusion in the homeland
security mission, according to a newly updated report from the
Congressional Research Service.
"Ten years after the September 11, 2001, terrorist attacks, the U.S.
government does not have a single definition for 'homeland security.'
[Instead,] different strategic documents and mission statements offer
varying missions that are derived from different homeland security
definitions."
Most official definitions of homeland security include terrorism
prevention. Many but not all encompass disaster response. Most do not
include border security, or maritime security, or immigration matters, or
general resilience, though some do.
"An absence of consensus about the inclusion of these policy areas may
result in unintended consequences for national homeland security
operations," the CRS report said. "For example, not including maritime
security in the homeland security definition may result in policymakers,
Congress, and stakeholders not adequately addressing maritime homeland
security threats, or more specifically being able to prioritize federal
investments in border versus intelligence activities."
"The competing and varied definitions in these documents may indicate that
there is no succinct homeland security concept. Without a succinct homeland
security concept, policymakers and entities with homeland security
responsibilities may not successfully coordinate or focus on the highest
prioritized or most necessary activities."
"At the national level, there does not appear to be an attempt to align
definitions and missions among disparate federal entities," CRS said.
Without a uniform definition, a coherent strategy cannot be formulated and
homeland security policy is rudderless. "Potentially, funding is driving
priorities rather than priorities driving the funding."
Speaking of funding, there are thirty federal departments, agencies, and
entities receiving annual homeland security funding excluding the
Department of Homeland Security, the CRS report said. In fact,
approximately 50% of homeland security funding is appropriated for agencies
other than the Department of Homeland Security.
See "Defining Homeland Security: Analysis and Congressional
Considerations," January 8, 2013:
http://www.fas.org/sgp/crs/homesec/R42462.pdf
DESALINATION, DNA TESTING, AND MORE FROM CRS
New and updated reports from the Congressional Research Service that have
not been made available to the public include the following.
Desalination and Membrane Technologies: Federal Research and Adoption
Issues, January 8, 2013:
http://www.fas.org/sgp/crs/misc/R40477.pdf
The Corporation for Public Broadcasting: Federal Funding and Issues,
January 8, 2013:
http://www.fas.org/sgp/crs/misc/RS22168.pdf
DNA Testing in Criminal Justice: Background, Current Law, Grants, and
Issues, December 6, 2012:
http://www.fas.org/sgp/crs/misc/R41800.pdf
Environmental Considerations in Federal Procurement: An Overview of the
Legal Authorities and Their Implementation, January 7, 2013:
http://www.fas.org/sgp/crs/misc/R41297.pdf
Responsibility Determinations Under the Federal Acquisition Regulation:
Legal Standards and Procedures, January 4, 2013:
http://www.fas.org/sgp/crs/misc/R40633.pdf
Social Security: The Windfall Elimination Provision (WEP), January 8,
2013:
http://www.fas.org/sgp/crs/misc/98-35.pdf
Social Security: The Government Pension Offset (GPO), January 8, 2013:
http://www.fas.org/sgp/crs/misc/RL32453.pdf
Economic Growth and the Unemployment Rate, January 7, 2013:
http://www.fas.org/sgp/crs/misc/R42063.pdf
Overview and Issues for Implementation of the Federal Cloud Computing
Initiative: Implications for Federal Information Technology Reform
Management, January 4, 2013:
http://www.fas.org/sgp/crs/misc/R42887.pdf
The National Telecommunications and Information Administration (NTIA):
Issues for the 113th Congress, January 3, 2013:
http://www.fas.org/sgp/crs/misc/R42886.pdf
Military Medical Care: Questions and Answers, January 7, 2013:
http://www.fas.org/sgp/crs/misc/RL33537.pdf
Israel: 2013 Elections Preview, January 8, 2013:
http://www.fas.org/sgp/crs/mideast/R42888.pdf
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
TMZ – Kim Kardashian — She’s Showing a Baby Bump!
Kim Kardashian is finally showing signs of a baby bump! Brace yourself folks, we have a long road of Kim Kardashian pregnancy updates in the coming months. So prepare accordingly.
TOP-SECRET – National Intelligence Council Global Trends 2030: Alternative Worlds

Global Trends 2030: Alternative Worlds
- 160 pages
- December 2012
- 20.5 MB
This report is intended to stimulate thinking about the rapid and vast geopolitical changes characterizing the world today and possible global trajectories during the next 15-20 years. As with the NIC’s previous Global Trends reports, we do not seek to predict the future—which would be an impossible feat—but instead provide a framework for thinking about possible futures and their implications.
The world of 2030 will be radically transformed from our world today. By 2030, no country—whether the US, China, or any other large country—will be a hegemonic power. The empowerment of individuals and diffusion of power among states and from states to informal networks will have a dramatic impact, largely reversing the historic rise of the West since 1750, restoring Asia’s weight in the global economy, and ushering in a new era of “democratization” at the international and domestic level. In addition to individual empowerment and the diffusion of state power, we believe that two other megatrends will shape our world out to 2030: demographic patterns, especially rapid aging; and growing resource demands which, in the cases of food and water, might lead to scarcities. These trends, which are virtually certain, exist today, but during the next 15-20 years they will gain much greater momentum. Underpinning the megatrends are tectonic shifts—critical changes to key features of our global environment that will affect how the world “works” (see table on page v).
Extrapolations of the megatrends would alone point to a changed world by 2030—but the world could be transformed in radically different ways. We believe that six key game-changers—questions regarding the global economy, governance, conflict, regional instability, technology, and the role of the United States—will largely determine what kind of transformed world we will inhabit in 2030. Several potential Black Swans—discrete events—would cause large-scale disruption (see page xi). All but two of these—the possibility of a democratic China or a reformed Iran—would have negative repercussions. Based upon what we know about the megatrends and the possible interactions between the megatrends and the game-changers, we have delineated four archetypal futures that represent distinct pathways for the world out to 2030. None of these alternative worlds is inevitable. In reality, the future probably will consist of elements from all the scenarios.
Megatrends and Related Tectonic Shifts
Megatrend 1: Individual Empowerment
Individual empowerment will accelerate substantially during the next 15-20 years owing to poverty reduction and a huge growth of the global middle class, greater educational attainment, and better health care. The growth of the global middle class constitutes a tectonic shift: for the first time, a majority of the world’s population will not be impoverished, and the middle classes will be the most important social and economic sector in the vast majority of countries around the world. Individual empowerment is the most important megatrend because it is both a cause and effect of most other trends—including the expanding global economy, rapid growth of the developing countries, and widespread exploitation of new communications and manufacturing technologies. On the one hand, we see the potential for greater individual initiative as key to solving the mounting global challenges over the next 15-20 years. On the other hand, in a tectonic shift, individuals and small groups will have greater access to lethal and disruptive technologies (particularly precision-strike capabilities, cyber instruments, and bioterror weaponry), enabling them to perpetrate large-scale violence—a capability formerly the monopoly of states.
Megatrend 2: Diffusion of Power
The diffusion of power among countries will have a dramatic impact by 2030. Asia will have surpassed North America and Europe combined in terms of global power, based upon GDP, population size, military spending, and technological investment. China alone will probably have the largest economy, surpassing that of the United States a few years before 2030. In a tectonic shift, the health of the global economy increasingly will be linked to how well the developing world does—more so than the traditional West. In addition to China, India, and Brazil, regional players such as Colombia, Indonesia, Nigeria, South Africa, and Turkey will become especially important to the global economy. Meanwhile, the economies of Europe, Japan, and Russia are likely to continue their slow relative declines.
The shift in national power may be overshadowed by an even more fundamental shift in the nature of power. Enabled by communications technologies, power will shift toward multifaceted and amorphous networks that will form to influence state and global actions. Those countries with some of the strongest fundamentals—GDP, population size, etc.—will not be able to punch their weight unless they also learn to operate in networks and coalitions in a multipolar world.
Megatrend 3: Demographic Patterns
We believe that in the world of 2030—a world in which a growing global population will have reached somewhere close to 8.3 billion people (up from 7.1 billion in 2012)—four demographic trends will fundamentally shape, although not necessarily determine, most countries’ economic and political conditions and relations among countries. These trends are: aging—a tectonic shift for both for the West and increasingly most developing countries; a still-significant but shrinking number of youthful societies and states; migration, which will increasingly be a cross-border issue; and growing urbanization—another tectonic shift, which will spur economic growth but could put new strains on food and water resources. Aging countries will face an uphill battle in maintaining their living standards. Demand for both skilled and unskilled labor will spur global migration. Owing to rapid urbanization in the developing world, the volume of urban construction for housing, office space, and transport services over the next 40 years could roughly equal the entire volume of such construction to date in world history.
Megatrend 4: Growing Food, Water, and Energy Nexus
Demand for food, water, and energy will grow by approximately 35, 40, and 50 percent respectively owing to an increase in the global population and the consumption patterns of an expanding middle class. Climate change will worsen the outlook for the availability of these critical resources. Climate change analysis suggests that the severity of existing weather patterns will intensify, with wet areas getting wetter and dry and arid areas becoming more so. Much of the decline in precipitation will occur in the Middle East and northern Africa as well as western Central Asia, southern Europe, southern Africa, and the US Southwest.
We are not necessarily headed into a world of scarcities, but policymakers and their private sector partners will need to be proactive to avoid such a future. Many countries probably won’t have the wherewithal to avoid food and water shortages without massive help from outside. Tackling problems pertaining to one commodity won’t be possible without affecting supply and demand for the others. Agriculture is highly dependent on accessibility to adequate sources of water as well as on energy-rich fertilizers. Hydropower is a significant source of energy for some regions while new sources of energy—such as biofuels—threaten to exacerbate the potential for food shortages. There is as much scope for negative tradeoffs as there is the potential for positive synergies. Agricultural productivity in Africa, particularly, will require a sea change to avoid shortages. Unlike Asia and South America, which have achieved significant improvements in agricultural production per capita, Africa has only recently returned to 1970s’ levels.
…
Monty Python’s Flying Circus – Dennis Moore – Full Film
Monty Python’s Flying Circus S3E11: Dennis Moore
SI Swimsuit Video – Jessica
Travel to Israel with Jessica for her SI Swimsuit 2008 shoot. For more SI Swimsuit photos and videos visit http://www.si.com/swimsuit
SECRECY NEWS –
|
TMZ – Jessica Alba — Back on All Fours!
Jessica Alba hit the beach in Mexico and assumed the position that she made famous almost 8 years ago… and it’s STILL just as hot as it was then!
TOP-SECRET – Senator Coburn DHS Urban Areas Security Initiative Waste Report

Safety at Any Price: Assessing the Impact of Department of Homeland Security Spending in U.S. Cities
- 55 pages
- December 2012
- 4.46 MB
This report examines the UASI grant program, including a detailed review of 15 cities that have received funding through the program. It is intended to assess whether spending on DHS antiterrorism grants like UASI have made us safer, and whether the taxpayer dollars that have been spent on these programs have yielded an adequate return on investment in terms of improved security.
The results of the investigation find that taxpayer money spent on homeland security grant programs has not always been spent in ways obviously linked to terrorism or preparedness. Importantly, this does not mean money was spent outside the bounds of what was allowed. The decision by officials in Michigan to purchase 13 sno-cone machines and the $45 million that was spent by officials in Cook County, Illinois on a failed video surveillance network have already garnered national attention as examples of dubious spending. Both were defended or promoted by DHS.
Other examples have not received as much attention. Columbus, Ohio recently used a $98,000 UASI grant to purchase an “underwater robot.” Local officials explained that it would be used to assist in underwater rescues.
Keene, New Hampshire, with a population just over 23,000 and a police force of 40, set aside UASI funds to buy a BearCat armored vehicle. Despite reporting only a single homicide in the prior two years, the City of Keene told DHS the vehicle was needed to patrol events like its annual pumpkin festival. Tulsa, Oklahoma used UASI funding to harden a county jail and purchase a color printer.
In 2009, Pittsburgh, Pennsylvania purchased for $88,000 several “long-range acoustic device,” or LRAD, which is mounted on a truck and emits an ear-splitting sound. Local officials used it to disperse G-20 protestors, giving one bystander permanent hearing loss, but which they called “a kinder and gentler way to get people to leave.”
Peoria, Arizona spent $90,000 to install bollards and surveillance cameras at the Peoria Sports Complex, which is used for spring training by the San Diego Padres and Seattle Mariners. The Oxnard-Thousand Oaks UASI used $75,000 to also purchase surveillance equipment, alarms and closed-circuit television, which it installed in its Civic Arts Plaza, a local theater and cultural center.
UASI funds were also used for mundane expenses, such as paying the overtime costs of police and firefighters or purchasing new computers for the local emergency planning office. Some urban areas used their awards for local outreach, holding conferences, creating websites and posting videos on how citizens can spot signs of terror in their own neighborhoods. A video sponsored by the Jacksonville UASI alerted its residents to red flags such as people with “average or above average intelligence” or who displayed “increased frequency of prayer or religious behavior.”
When asked, FEMA could not explain precisely how the UASI program has closed security gaps or prepared the nation in the event of another attack. In part, FEMA has done very little oversight of the program, allowing cities to spend the money on almost anything they want, as long as it has broad ties to terror prevention. In fact, according to a June 2012 report by the Department of Homeland Security Inspector General, “FEMA did not have a system in place to determine the extent that Homeland Security Grant Program funds enhanced the states’ capabilities to prevent, deter, response to, and recover from terrorist attacks, major disasters and other emergencies before awarding more funds to the states.” Moreover, the agency failed to issue preparedness goals, intended to shape the use of UASI funds, until last year—nine years after the program was created. Because of this, it is difficult to measure the gains with any specificity.
…
Monty Python’s Flying Circus – Mr. Neutron – Full Movie
Monty Python’s Flying Circus S4E05: Mr. Neutron
SI Swimsuit Video: Julie in Israel
TOP SECRET – Thomas Donahue Fletcher
Thomas Donahue Fletcher
Thomas Donahue Fletcher is an undercover CIA officer identified to journalist Matthew Cole by former CIA officer John Kiriakou which has led to Kiriakou’s prosecution and guilty plea — to be sentenced to prison shortly. Fletcher is reported to be the officer heading the CIA’s waterboarding enhanced interrogation program.
NY Times front page story on Kiriakou, 6 January 2012:
NY Times does not print Fletcher’s name but he was identified on several web sites in October 2012. Cryptocomb reported then Fletcher was based at CIA headquarters and lived in Vienna, VA.
Joining infamously with Fletcher, but not yet publicly named, “CIA John” is reported to be the prinicipal proponent of the CIA drone assassination program.
http://cryptome.org/2012/12/cia-john-drone.htm
Photographs of CIA John:
http://cryptome.org/0004/cia-john/cia-john.htm
Photos of Fletcher and identity of CIA John invited: cryptome[at]earthlink.net
|
| http://www.city-data.com/fairfax-county/H/Huntrace-Way-2.html10413 Huntrace Way Vienna, VA Owner: THOMAS D FLETCHER Land value: $257,000 Land area: 21,534 square feet Exterior wall: Half Aluminum/Half Brick Additions: Addition type: Lower: Frame/brick Read more: http://www.city-data.com/fairfax-county/H/Huntrace-Way-2.html#ixzz2HClu2kh9 |
Google Maps![[Image]](https://i0.wp.com/cryptome.org/2013-info/01/pict8.jpg) |
Google Street View![[Image]](https://i0.wp.com/cryptome.org/2013-info/01/pict7.jpg) |
Bing Maps Birdseye![[Image]](https://i0.wp.com/cryptome.org/2013-info/01/pict5.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2013-info/01/pict2.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2013-info/01/pict1.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2013-info/01/pict4.jpg) |
| Intellius report on Fletcher — addresses, relatives, neighbors:http://cryptome.org/2013-info/01/fletcher-intellius.pdf |
TMZ – From the Vault: Paris Hilton Goes Postal — Caught on Tape
In 2008, a skeleton-hoodied Paris Hilton walked into this Toronto porn shop after spying a cardboard cutout of herself — hawking her sex tape!
Confidential – FBI Cyber Alert

Vulnerabilities in Tridium Niagara Framework Result in Unauthorized Access to a New Jersey Company’s Industrial Control System
- 5 pages
- For Official Use Only
- July 23, 2012
(U//FOUO) In February and March 2012, unauthorized IP addresses accessed the Industrial Control System (ICS) network of a New Jersey air conditioning company, US Business 1. The intruders were able to access a backdoor into the ICS system that allowed access to the main control mechanism for the company’s internal heating, ventilation, and air conditioning (HVAC) units. US Business 1 was using the Tridium Niagara ICS system, which has been widely reported in the media to contain multiple vulnerabilities that could allow an attacker to remotely control the system.
(U//FOUO) On 21 and 23 January 2012, an unknown subject posted comments on a known US website, titled “#US #SCADA #IDIOTS” and “#US #SCADA #IDIOTS part-II”. The postings were linked to the moniker “@ntisec”, and indicated that hackers were targeting SCADA systems this year, and something had to be done to address SCADA vulnerabilities.
(U) The user of the “@ntisec” moniker searched Google, and the website http://www.shodanhq.com, for the term “:(unknown character) slot:/” and “#TRIDIUM / #NIAGARA vector”. The posting by “@ntisec” included a list of URLs, one of which was an IP address that resolved to US Business 1, and was assigned to its office building’s HVAC control system.
(U//FOUO) The main control box for the HVAC system of US Business 1 was a Tridium brand, Niagara model controller. US Business 1 actively used this system in-house, but also installed the control system for customers, which included banking institutions and other commercial entities. An IT contractor of US Business 1 confirmed the Niagara control box was directly connected to the Internet with no interposing firewall.
(U//FOUO) US Business 1 had a controller for the system that was password protected, but was set up for remote/Internet access. By using the link posted by the hacktivist, the published backdoor URL provided the same level of access to the company’s control system as the password-protected administrator login. The backdoor required no password and allowed direct access to the control system.
(U//FOUO) Logs from the controller at US Business 1 dated back to 3 February 2012, and access to the controller was found from multiple unauthorized international and US-based IP addresses.
(U//FOUO) The URL that linked to the control system of US Business 1 provided access to a Graphical User Interface (GUI), which provided a floor plan layout of the office, with control fields and feedback for each office and shop area. All areas of the office were clearly labeled with employee names or area names.
(U) On 13 July 2012, the Department of Homeland Security released ICS-CERT ALERT entitled, “Tridium Niagara Directory Traversal and Weak Credential Storage Vulnerability”, which detailed vulnerabilities within the Niagara AX ICS that are exploitable by downloading and decrypting the file containing the user credential from the server.
(U) According to the Tridium website, over 300,000 instances of Niagara AX Framework are installed worldwide in applications that include energy management, building automation, telecommunications, security automation and lighting control.
Monty Python’s Flying Circus – Michael Ellis – Full Film
Monty Python’s Flying Circus S4E02: Michael Ellis
TMZ – Chris Brown — Rihanna Returns to the Scene of the Crime
Rihanna was photographed in the passenger seat of Chris Brown’s car… the same place where she was viciously beaten by Brown almost four years ago!
TOP-SECRET – DHS-FBI Suspicious Activity Reporting Bulletin: Observation/Surveillance

ROLL CALL RELEASE
- 1 page
- For Official Use Only
- October 15, 2012
(U//FOUO) Terrorists often conduct physical surveillance to identify suitable targets, determine vulnerabilities, plan attack methods, or assess the target’s security posture. In March 2010, David Coleman Headley pled guilty for his role in the November 2008 terrorist attacks in Mumbai, India by conducting video and photographic surveillance of potential targets, as well as later surveilling Danish newspaper offices–the target of another attack plot.
(U//FOUO) The following SAR incidents from the NSI shared space demonstrate types of behavior terrorists might exhibit during planning or actual attacks. Although none were linked to terrorist activity, we consider the examples relevant for situational awareness and training:
– (U//FOUO) A city utility company reported suspicious surveillance activity at a hydroelectric plant. On six occasions within a three-day period, two vehicles of the same color, make, and model (but with different license plate numbers) were observed traveling slowly on the road adjacent to the plant, stopping at specific posts on the property, turning around, and slowly returning in the other direction.
– (U//FOUO) A prominent hotel in a major metropolitan area reported a male and a female photographing the hotel entrances from a vehicle with Canadian license plates. Security camera footage showed the vehicle moved at lease twice to different locations around the hotel while the passenger took photos of the hotel and surrounding restaurants and the driver on a clipboard. No additional information regarding this incident is available.(U) Possible Indicators of Observation/Surveillance
(U//FOUO) The following may indicate suspicious observation/surveillance activity and should be reported to appropriate authorities, but context (time, location, personal behaviors, and other indicators) should be carefully considered to rule out legitimate, non-suspicious activities:
– (U//FOUO) Unusual, repeated, or prolonged observation of infrastructure (for example, with binoculars or video cameras);
– (U//FOUO) Taking notes or measurements, counting places, sketching floor plans, maps, or diagrams;
– (U//FOUO) Scrutinizing security personnel, shift changes, or facility activities; or
– (U//FOUO) Extended loitering without explanation, particularly in concealed locations with optimal visibility or potential targets.(U//FOUO) First Ammendment-protected activities should not be reported in a SAR or ISE-SAR absent articulable facts and circumstances that support the source agency’s suspicion that the behavior observed is not innocent, but rather reasonably indicative of criminal activity associated with terrorism, including evidence of pre-operational planning related to terrorism. Race, ethnicity, national origin, or religious affiliation should not be considered as factors that create suspicion (although these factors may be used in specific subject descriptions).
Monty Python’s Flying Circus: The Nude Organist – Full Movie
Monty Python’s Flying Circus S3E09: The Nude Organist
Revealed – Former C.I.A. Officer Is the First to Face Prison for a Classified Leak
The first C.I.A. officer to be convicted of disclosing classified information to a reporter in more than six decades is scheduled to be sentenced to 30 months in prison on Jan. 25. John Kiriakou is to be sentenced as part of a plea deal in which he admitted e-mailing the name of a covert officer to a reporter.His prosecution, as well as five others, has been lauded on Capitol Hill as a long-overdue response to a rash of dangerous disclosures and defended by both President Obama and Attorney General Eric H. Holder Jr.Mr. Kiriakou is remorseful, up to a point. “I should never have provided the name,” he said.Supporters say Mr. Kiriakou neither intended to damage national security nor did so. Some see a dark paradox in the impending imprisonment of Mr. Kiriakou, who in a 2007 appearance on ABC News defended the C.I.A.’s use of desperate measures to get information but also said that he had come to believe that waterboarding was torture and should no longer be used.
TMZ – Tamala Jones: Here’s What Kim Kardashian Should Name Her Baby…
“Castle” star Tamala Jones offered some free advice as to what Kim Kardashian should name her baby… and her suggestions are ABSOLUTELY FANTASTIC!
SECRET – Verizon Patent: DVR That Watches Users to Target Advertising
METHODS AND SYSTEMS FOR PRESENTING AN ADVERTISEMENT ASSOCIATED WITH AN AMBIENT ACTION OF A USER
- 14 pages
- November 29, 2012
Exemplary targeted advertising systems and methods are disclosed herein. An exemplary method includes a media content presentation system presenting a media content program comprising an advertisement break, detecting an ambient action performed by a user during the presentation of the media content program, selecting an advertisement associated with the detected ambient action, and presenting the selected advertisement during the advertisement break. Corresponding methods and systems are also disclosed.
…
[0001] The advent of set-top box devices and other media content access devices (“access devices”) has provided users with access to a large number and variety of media content choices. For example, a user may choose to experience a variety of broadcast television programs, pay-per-view services, video-on-demand programming, Internet services, and audio programming via a set-top box device. Such access devices have also provided service providers (e.g., television service providers) with an ability to present advertising to users. For example, designated advertisement channels may be used to deliver various advertisements to an access device for presentation to one or more users. In some examples, advertising may be targeted to a specific user or group of users of an access device.
[0002] However, traditional targeted advertising systems and methods may base targeted advertising solely on user profile information associated with a media content access device and/or user interactions directly with the media content access device. Accordingly, traditional targeted advertising systems and methods fail to account for one or more ambient actions of a user while the user is experiencing media content using a media content access device. For example, if a user is watching a television program, a traditional targeted advertising system fails to account for what the user is doing (e.g., eating, interacting with another user, sleeping, etc.) while the user is watching the television program. This limits the effectiveness, personalization, and/or adaptability of the targeted advertising.
…
[0015] Detection facility 104 may be configured to detect an ambient action performed by a user during the presentation of a media content program (e.g., by presentation facility 102). As used herein, the term “ambient action” may refer to any action performed by a user that is independent of and/or not directed at a media content access device presenting media content. For example, an ambient action may include any suitable action of a user during a presentation of a media content program by a media content access device, whether the user is actively experiencing (e.g., actively viewing) or passively experiencing (e.g., passively viewing and/or listening while the user is doing something else) the media content being presented.
[0016] To illustrate, an exemplary ambient action may include the user eating, exercising, laughing, reading, sleeping, talking, singing, humming, cleaning, playing a musical instrument, performing any other suitable action, and/or engaging in any other physical activity during the presentation of the media content. In certain examples, the ambient action may include an interaction by the user with another user (e.g., another user physically located in the same room as the user). To illustrate, the ambient action may include the user talking to, cuddling with, fighting with, wrestling with, playing a game with, competing with, and/or otherwise interacting with the other user. In further examples, the ambient action may include the user interacting with a separate media content access device (e.g., a media content access device separate from the media content access device presenting the media content). For example, the ambient action may include the user interacting with a mobile device (e.g., a mobile phone device, a tablet computer, a laptop computer, etc.) during the presentation of a media content program by a set-top box (“STB”) device.
Monty Python and the Holy Grail (1975) HD – Full Movie
Sports Illustrated Swimsuit Video : Daniella
Watch Brazilian super-model Daniella Sarahyba in Cayman Islands for her SI Swimsuit 2008 shoot. For more SI Swimsuit photos and videos visit http://www.si.com/swimsuit
SECRECY NEWS – AN OPEN SOURCE LOOK AT IRAN’S INTELLIGENCE MINISTRY
Iran's Ministry of Intelligence and Security is believed to employ more
than 30,000 intelligence officers and support personnel, making it "one of
the largest and most active intelligence agencies in the Middle East,"
according to a new report from the Federal Research Division of the Library
of Congress.
"The Ministry of Intelligence and Security (MOIS) uses all means at its
disposal to protect the Islamic Revolution of Iran, utilizing such methods
as infiltrating internal opposition groups, monitoring domestic threats and
expatriate dissent, arresting alleged spies and dissidents, exposing
conspiracies deemed threatening, and maintaining liaison with other foreign
intelligence agencies as well as with organizations that protect the
Islamic Republic's interests around the world," the report states.
See "Iran's Ministry of Intelligence and Security: A Profile," December
2012.
http://www.fas.org/irp/world/iran/mois-loc.pdf
The report was first obtained and reported by Bill Gertz in "Iran Spy
Network 30,000 Strong," Washington Free Beacon, January 3, 2013.
http://freebeacon.com/iran-spy-network-30000-strong/
The new report provides an informative account of the Ministry's history,
organizational structure, and recruitment practices, as far as these can be
discerned from published sources.
"The information in this report was collected mainly from Farsi and
English journals, online news Web sites, and Iranian blogs," the Preface
states. (Some older information from the FAS web site is cited at a couple
of points.)
"Needless to say, the Ministry of Intelligence and Security does not
publish information about its activities on Iranian Web sites.
Consequently, in the absence of official government information, this
report occasionally relies on social media, in particular blogs, as a
source of information more than might ordinarily be warranted. The
reliability of blog-based information may be questionable at times, but it
seems prudent to evaluate and present it in the absence of alternatives."
"Every minister of intelligence must hold a degree in ijtihad (the ability
to interpret Islamic sources such as the Quran and the words of the Prophet
and imams) from a religious school, abstain from membership in any
political party or group, have a reputation for personal integrity, and
possess a strong political and management background," the report says.
A newly disclosed U.S. Army intelligence document explains how to
determine whether weapons that were captured in Iraq were manufactured in
Iran.
Iranian weapons systems "have several distinctive visual identification
markings that identify their source" which are described in the Army
publication. The document was partially declassified last month and was
obtained under the Freedom of Information Act by Matthew Schroeder of the
FAS Arms Sales Monitoring Project.
See "Identifying Small Arms and RPGs Produced in Iran," U.S. Army National
Ground Intelligence Center, 2004.
http://www.fas.org/irp/world/iran/smallarms.pdf
ARMY DRAWDOWN, SPECIAL OPERATIONS FORCES, MORE FROM CRS
New and updated reports from the Congressional Research Service that
Congress has not made available to the public include the following.
Army Drawdown and Restructuring: Background and Issues for Congress,
January 3, 2013:
http://www.fas.org/sgp/crs/natsec/R42493.pdf
U.S. Special Operations Forces (SOF): Background and Issues for Congress,
January 3, 2013:
http://www.fas.org/sgp/crs/natsec/RS21048.pdf
The Unified Command Plan and Combatant Commands: Background and Issues for
Congress, January 3, 2013:
http://www.fas.org/sgp/crs/natsec/R42077.pdf
Internet Domain Names: Background and Policy Issues, January 3, 2013:
http://www.fas.org/sgp/crs/misc/97-868.pdf
Internet Governance and the Domain Name System: Issues for Congress,
January 2, 2013:
http://www.fas.org/sgp/crs/misc/R42351.pdf
Federal Regulation of Chemicals in Commerce: An Overview of Issues for the
113th Congress, January 3, 2013:
http://www.fas.org/sgp/crs/misc/R42879.pdf
Physician Practices: Background, Organization, and Market Consolidation,
January 2, 2013:
http://www.fas.org/sgp/crs/misc/R42880.pdf
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
TMZ – Kim Kardashian Getting Pregnant Sparks SEX TAPE Boom!
So how is everyone celebrating the wonderful news that Kim Kardashian is pregnant? By watching her sex tape!!! Yeah, there are A LOT of weirdos out there, folks…
TOP-SECRET – DHS-FBI Suspicious Activity Reporting Bulletin: Photography

ROLL CALL RELEASE
- 1 page
- For Official Use Only
- November 13, 2012
(U//FOUO) Terrorists and criminals may use photos or videos of potential targets to gain insight into security operations and details of facility operations, including traffic flow through and around facilities, opening times, and access requirements. In late 2000 and early 2001, convicted al-Oa’ida operative Dhiren Barot took extensive video footage and numerous photographs of sites in downtown New York City and Washington, DC in preparation for planned attacks. Photographs and video useful in planning an attack may include facility security devices (surveillance cameras, security locks, metal detectors, jersey walls and planters); security personnel; facility entrances and exits; and other features such as lighting, access routes, gates, roads, walkways, and bridges.
(U//FOUO) The following SAR incidents reported to the Nationwide SAR Initiative (NSI) shared space demonstrate types of suspicious photography and videography consistent with pre-operational activity and attack planning. Although none were ultimately linked to terrorist activity, they are cited as examples for awareness and training purposes:
(U//FOUO) An individual took photographs of several buildings, a control tower, and lighting system poles associated with an elevated runway approach at an aviation facility.
(U//FOUO) An individual was encountered videotaping in a well-known retail complex while in the garage. The individual had video of the building’s ventilating system. The individual was
arrested when he returned to the area after; having been directed to leave.(U//FOUO) An individual took photos and video in a mall while holding the phone close to his body at waist level. The photographs and video footage included the mall storefronts, upper mall structures, bridges, exit doors, and closed-circuit television cameras.
(U//FOUO) Indicators of Potentially Suspicious Photography
(U//FOUO) The following activities are consistent with suspicious photography. Although a single indicator may not be suspicious, one or more in combination may signify suspicious activity:
– (U//FOUO) Photography or videography focused on security features, including cameras, security personnel, gates, and barriers.
– (U//FOUO) Repeated visits by the same individual(s) taking photographs or video of vulnerable features, or security features of critical infrastructure.
– (U//FOUO) Individuals encountered with photographs of critical infrastructure, iconic buildings, or other sites not of tourist interest.(U//FOUO) First Ammendment-protected activities should not be reported in a SAR or ISE-SAR absent articulable facts and circumstances that support the source agency’s suspicion that the behavior observed is not innocent, but rather reasonably indicative of criminal activity associated with terrorism, including evidence of pre-operational planning related to terrorism. Race, ethnicity, national origin, or religious affiliation should not be considered as factors that create suspicion (although these factors may be used in specific subject descriptions).
Monty Python’s Flying Circus – Mr. and Mrs. Norris’ Ford Popular
Monty Python’s Flying Circus S3E02: Mr. and Mrs. Norris’ Ford Popular
The Chambers Brothers – Time Has Come Today (long version) – Video
(Rare live, extended version)
The FBI – Former Bank Employees Admit Embezzlement
Richard S. Hartunian, United States Attorney for the Northern District of New York, and George L. Piro, Acting Special Agent in Charge, Albany Division-Federal Bureau of Investigation, make the following announcement:
Megan Horton, 54, of Owego, Tioga County, New York; and Gwenn Gooding, 43, also of Owego, Tioga County, New York, pled guilty today in United States District Court to the felony crime of bank embezzlement. Shannon Moore, 38, of Athens, Bradford County, Pennsylvania, previously pled guilty on December 21, 2012, in United States District Court to a similar felony crime of bank embezzlement. Horton, Gooding, and Moore were former employees of Chemung Canal Trust Company Bank (CCTC), located at 203 Main Street, Owego, New York.
In their pleas before Senior United States District Court Judge Thomas J. McAvoy, Horton, former branch manager; Gooding, former head teller; and Moore, a former teller, admitted that, between December 2004, and September 2011, they embezzled large sums of money from CCTC. Horton admitted stealing more than $200,000; Gooding admitted stealing more than $100,000; and Moore admitted stealing more than $25,000. The embezzlement was uncovered as a result of an audit of the CCTC bank branch following the Southern Tier flooding in September 2011.
Horton, Gooding, and Moore each face a maximum sentence of 30 years’ imprisonment and a maximum fine of $1 million. Moore is scheduled to be sentenced on April 23, 2013; Gooding is scheduled to be sentenced on May 4, 2013; and Horton is scheduled to be sentenced on May 7, 2013.
The case was investigated by the Federal Bureau of Investigation, Albany Field Division, and is being prosecuted by Assistant United States Attorney Thomas P. Walsh. Further inquiries may be directed to the United States Attorney’s Office, Binghamton branch office, at (607) 773-2887.
SI Swimsuit Video: Irina
Watch super model Irina in Russia for her SI Swimsuit 2008 shoot. For more photos and videos visit http://www.si.com/swimsuit.
Transocean to Pay Record $1 Billion in Civil Penalties and $400 Million in Criminal Fines
WASHINGTON—Transocean Deepwater Inc. has agreed to plead guilty to violating the Clean Water Act (CWA) and to pay a total of $1.4 billion in civil and criminal fines and penalties for its conduct in relation to the Deepwater Horizon disaster, the Department of Justice announced today. The criminal information and a proposed partial civil consent decree to resolve the U.S. government’s civil penalty claims against Transocean Deepwater Inc. and related entities were filed today in U.S. District Court in the Eastern District of Louisiana.
Transocean Deepwater Inc. has signed a cooperation and guilty plea agreement with the government, also filed today, admitting its criminal conduct. As part of the plea agreement, Transocean Deepwater Inc. has agreed, subject to the court’s approval, to pay $400 million in criminal fines and penalties and to continue its ongoing cooperation in the government’s criminal investigation. In addition, pursuant to the terms of a proposed partial civil consent decree also lodged with the court today, Transocean Ocean Holdings LLC, Transocean Offshore Deepwater Drilling Inc., Transocean Deepwater Inc., and Triton Asset Leasing GMBH have agreed to pay an additional $1 billion to resolve federal Clean Water Act civil penalty claims for the massive, three-month-long oil spill at the Macondo Well and the Transocean drilling rig Deepwater Horizon. Under the civil settlement, the Transocean defendants also must implement court-enforceable measures to improve the operational safety and emergency response capabilities at all their drilling rigs working in waters of the United States.
“This resolution of criminal allegations and civil claims against Transocean brings us one significant step closer to justice for the human, environmental, and economic devastation wrought by the Deepwater Horizon disaster,” said Attorney General Eric Holder. “This agreement holds Transocean criminally accountable for its conduct and provides nearly a billion dollars in criminal and civil penalties for the benefit of the Gulf states. I am particularly grateful today to the many Justice Department personnel and federal investigative agency partners for the hard work that led to today’s resolution and their continuing pursuit of justice for the people of the Gulf.”
“Today’s announced settlement will aid the Gulf region’s recovery from the Deepwater Horizon oil spill and require Transocean to take important steps that will help guard against such incidents happening in the future,” said Acting Associate Attorney General Tony West. “This resolution is the culmination of the tremendous efforts of many attorneys and staff in the Justice Department’s Criminal, Civil, and Environment and Natural Resources Divisions—dedicated public servants whose hard work continues on behalf of the American people.”
“Transocean’s rig crew accepted the direction of BP well site leaders to proceed in the face of clear danger signs—at a tragic cost to many of them,” said Lanny A. Breuer, Assistant Attorney General for the Justice Department’s Criminal Division. “Transocean’s agreement to plead guilty to a federal crime and to pay a total of $1.4 billion in criminal and civil penalties, appropriately reflects its role in the Deepwater Horizon disaster.”
“The development and exploration of a domestic source of energy is vitally important, and it can and must be done in a responsible and sound manner. This unprecedented settlement under the Clean Water Act demonstrates that companies will be held fully accountable for their conduct and share responsibility for compliance with the laws that protect the public and the environment from harm,” said Ignacia S. Moreno, Assistant Attorney General for the Justice Department’s Environment and Natural Resources Division. “This settlement will provide immediate relief and benefits to the people of the five Gulf states and requires Transocean to implement significant safety measures, as well as stringent auditing and monitoring to reduce the risk of any future disasters.”
“Today’s settlement and plea agreement is an important step toward holding Transocean and those responsible for the Deepwater Horizon disaster accountable,” said Cynthia Giles, Assistant Administrator for the U.S. Environmental Protection Agency’s (EPA) Office of Enforcement and Compliance Assurance. “EPA will continue to work with DOJ and its federal partners to vigorously pursue the government’s claims against all responsible parties and ensure that we are taking every possible step to restore and protect the Gulf Coast ecosystem.”
According to court documents, on April 20, 2010, while stationed at the Macondo well site in the Gulf of Mexico, the Deepwater Horizon rig experienced an uncontrolled blowout and related explosions and fire, which resulted in the deaths of 11 rig workers and the largest oil spill in U.S. history. In agreeing to plead guilty, Transocean Deepwater Inc. has admitted that members of its crew onboard the Deepwater Horizon, acting at the direction of BP’s “Well Site Leaders” or “company men,” were negligent in failing fully to investigate clear indications that the Macondo well was not secure and that oil and gas were flowing into the well.
The criminal resolution is structured to directly benefit the Gulf region. Under the order presented to the court, $150 million of the $400 million criminal recovery is dedicated to acquiring, restoring, preserving, and conserving—in consultation with appropriate state and other resource managers—the marine and coastal environments, ecosystems, and bird and wildlife habitat in the Gulf of Mexico and bordering states harmed by the Deepwater Horizon oil spill. This portion of the criminal recovery will also be directed to significant barrier island restoration and/or river diversion off the coast of Louisiana to further benefit and improve coastal wetlands affected by the oil spill. An additional $150 million will be used to fund improved oil spill prevention and response efforts in the Gulf through research, development, education, and training.
The civil settlement secures $1 billion in civil penalties for violations of the CWA, a record amount that significantly exceeds last year’s $70 million civil penalty paid by MOEX Offshore 2007 LLC, a 10 percent partner with BP in the Macondo well venture. The unprecedented $1 billion civil penalty is subject to the Resources and Ecosystems Sustainability, Tourist Opportunities, and Revived Economies of the Gulf Coast States Act of 2012 (Restore Act), which provides that 80 percent of the penalty will be to be used to fund projects in and for the Gulf states for the environmental and economic benefit of the region. This civil resolution reserves claims for natural resource damages and clean-up costs.
Under the civil settlement, the Transocean defendants must also observe various court-enforceable strictures in its drilling operations, aimed at reducing the chances of another blowout and discharge of oil and at improving emergency response capabilities. Examples of these requirements include certifications of maintenance and repair of blowout preventers before each new drilling job, consideration of process safety risks, and personnel training related to oil spills and responses to other emergencies. These measures apply to all rigs operated or owned by the Transocean defendants in all U.S. waters and will be in place for at least five years.
The guilty plea agreement and criminal charge announced today are part of the ongoing criminal investigation by the Deepwater Horizon Task Force into matters related to the April 2010 Gulf oil spill. The Deepwater Horizon Task Force, based in New Orleans, is supervised by Assistant Attorney General Breuer and led by Deputy Assistant Attorney General John D. Buretta, who serves as the director of the task force. The task force includes prosecutors from the Criminal Division and the Environment and Natural Resources Division of the Department of Justice; the U.S. Attorney’s Office for the Eastern District of Louisiana, as well as other U.S. Attorneys’ Offices; and investigating agents from the FBI, EPA, Department of the Interior, National Oceanic and Atmospheric Administration Office of Law Enforcement, U.S. Coast Guard, U.S. Fish and Wildlife Service, and the Louisiana Department of Environmental Quality.
The civil resolution announced today is part of the ongoing litigation against defendants BP Exploration and Production Inc., the Transocean defendants, and Anadarko Petroleum Corporation (among others) for civil penalties, injunctive relief, and a declaration of unlimited liability for removal costs and damages under the Oil Pollution Act. The civil enforcement effort is supervised by Assistant Attorney General Moreno for the Environment and Natural Resources Division and Deputy Assistant Attorney General Brian Hauck of the Civil Division. Numerous federal agencies have contributed immeasurably to these enforcement and settlement efforts, including the EPA, the U.S. Coast Guard, the National Oceanic and Atmospheric Administration, the Department of the Interior and the Department of Agriculture.
The criminal case against Transocean is being prosecuted by Deepwater Horizon Task Force Deputy Directors Derek A. Cohen and Avi Gesser and task force prosecutors Richard R. Pickens, II, Scott M. Cullen, Colin Black, and Rohan Virginkar. Numerous Environment Division and Civil Division lawyers are pursuing the civil enforcement action, led by Steve O’Rourke and R. Michael Underhill.
An information is merely a charge, and a defendant is presumed innocent unless and until proven guilty beyond a reasonable doubt.
The proposed civil settlement is subject to a public comment period and final court approval. Information on submitting comment will be available at http://www.justice.gov/enrd/Consent_Decrees.html.
TMZ – Why Jessica Simpson Should HATE Kim Kardashian’s Baby!
Kanye West is beyond excited that Kim Kardashian is having his baby… but you know who shouldn’t be happy in the slightest? Jessica friggin’ Simpson — that’s who!
SECRET-DHS-FBI Suspicious Activity Reporting Bulletin: Materials Acquisition/Storage

ROLL CALL RELEASE
- 1 page
- For Official Use Only
- August 7, 2012
(U//FOUO) Terrorists overseas and in domestic attack plots have used various methods to acquire and store materials necessary to construct explosives. Najibullah Zazi, who pled guilty in 2010 to plotting to attack the New York subway system, made multiple, large-quantity purchases of chemical components needed to assemble the homemade explosive Triacetone Triperoxide (TATP)—6 bottles on one day and 12 bottles on a separate day—at beauty supply stores throughout the summer of 2009. Law enforcement and first responders should be aware that the possession, storage, or attempt to acquire unusual quantities of laboratory equipment, personal protective equipment, chemicals, and flammable accelerants—although legal to purchase and own—could provide indicators of preoperational attack planning.
(U//FOUO) The following SAR incidents reported to the NSI shared space demonstrate types of suspicious material acquisition and storage that could be indicative of preoperational activity and attack planning. While none were ultimately linked to terrorist activity, they are cited as examples for awareness and training purposes:
— (U//FOUO) A tip prompted police to search a residential property where they discovered TATP; bomb components such as fuses and pipes; laboratory equipment such as coolers and beakers; and precursor chemicals including hydrogen peroxide, acetone, hydrochloric acid, black/smokeless powder, glycerin, and aluminum powders.
— (U//FOUO) An individual contacted a home improvement store requesting to purchase 15 gallons of 35 percent food-grade hydrogen peroxide, a substance that can be used in making homemade explosives such as TATP and Hexamethylene Triperoxide Diamine.(U) Possible Indicators of Suspicious Materials Acquisition and Storage
(U//FOUO) The following activities can indicate storage or efforts to acquire materials for potentially illicit purposes. Depending on the context—type and quantity of materials, reason for possession, personal behaviors, and other indicators— suspicious activities associated with acquisition or storage of materials should be reported to appropriate authorities.
— (U//FOUO) Individuals with signs of chemical exposure, including inhalation and skin burns.
— (U//FOUO) Non-agricultural chemical impact on foliage in close proximity of a residence or a business.
— (U//FOUO) Possession or attempts by individuals to acquire unusual quantities of materials used to produce explosives inconsistent with their stated purpose, business, or purchase history.
— (U//FOUO) Presence of precursor materials and protective/specialized handling equipment in residential dwellings or chemical containers and laboratory equipment discarded in residential neighborhoods.
— (U//FOUO) Presence of metal or plastic drums for storing chemicals, foul odors or caustic fumes coming from room or building, large industrial fans in windows at odd times of year.(U//FOUO) Additionally, attempts to acquire official or fabricated uniforms, badges, access cards, or identification credentials or officially marked vehicles should be reported.
Monty Python’s Flying Circus – Spam – Full Show Movie
Monty Python’s Flying Circus S2E12 Spam
SECRERCY NEWS – INTELLIGENCE OVERSIGHT STEPS BACK FROM PUBLIC ACCOUNTABILITY
The move by Congress to renew the FISA Amendments Act for five more years
without amendments came as a bitter disappointment to civil libertarians
who believe that the Act emphasizes government surveillance authority at
the expense of constitutional protections. Amendments that were offered to
provide more public information about the impacts of government
surveillance on the privacy of American communications were rejected by the
Senate on December 27 and 28.
http://www.fas.org/irp/congress/2012_cr/faa-amend.html
http://www.fas.org/irp/congress/2012_cr/faa-reauth.html
Beyond the specifics of the surveillance law, the congressional action
appears to reflect a reorientation of intelligence oversight away from
public accountability. The congressional intelligence committees once
presented themselves as champions of disclosure. They no longer do so.
The first annual report of the Senate Select Committee on Intelligence,
chaired by the late Sen. Daniel K. Inouye, stated in 1977 that "While most
of the work of the Committee is, of necessity, conducted in secrecy, we
believe that even secret activities must be as accountable to the public as
possible."
http://www.intelligence.senate.gov/pubactivities.html
Of course, the question of how much accountability is "possible" has
always been debatable. But the basic principle of maximum possible
disclosure was endorsed by subsequent Committee leaders including Sen.
Barry Goldwater and Sen. Daniel P. Moynihan, who also wrote in 1981 that
"intelligence activities should be as accountable as possible to the
public."
In 1999, Senators Richard Shelby and Bob Kerrey affirmed on behalf of the
Intelligence Committee that "as much information as possible about
intelligence activities should be made available to the public."
But in recent years the Committee's periodic statement of principles has
changed in a subtle but significant way. In its most recent report in
2011, the Committee said it seeks "to provide as much information as
possible about its intelligence oversight activities to the American public
consistent with national security concerns." Instead of disclosure and
public accountability for intelligence activities, the Committee would
promise only to reveal as much as possible about its oversight activities.
What makes this rhetorical shift noteworthy is that it seems to correspond
in broad strokes to a shift in the character and activity of the Committee
away from public accountability for intelligence. Past Committees did not
always press for public accountability (and were not often successful when
they did), and the current Committee has not been completely indifferent to
it, but there does seem to be a perceptible trend.
The Senate Intelligence Committee used to be at the forefront of debates
over public disclosure of intelligence. Demands for declassification --
often for intelligence budget information -- were a normal feature of
annual intelligence legislation in the 1990s. Public hearings, including
hearings with non-governmental witnesses, were commonplace. To varying
degrees, Senators like Daniel Moynihan, Howard Metzenbaum, Arlen Specter,
Bob Kerrey, and others were thorns in the side of U.S. intelligence
agencies in support of public disclosure.
Over the past decade, however, the Committee's priorities appear to have
changed, to the detriment of public accountability. In fact, despite the
Committee's assurance in its annual reports, public disclosure even of the
Committee's own oversight activities has decreased.
In 2012, the Committee held only one public hearing, despite the
prevalence of intelligence-related public controversies. That is the
smallest number of public hearings the Committee has held in at least 25
years and possibly ever. A non-governmental witness has not been invited
to testify at an open Committee hearing since 2007.
(A congressional official countered that in recent years confirmation
hearings had provided the occasion for most public hearings by the
Intelligence Committee, and that in 2012 there were simply no nominees
requiring hearings. Meanwhile, the official noted, the Committee did
include a provision to reauthorize the Public Interest Declassification
Board in its markup of the 2013 intelligence bill. And the Committee is
engaged with agency Inspectors General that are reviewing classification
practices in the intelligence community and elsewhere. The Committee's own
web site has also been usefully supplemented with hearing records and
reports dating back to the 1970s.)
When annual disclosure of the intelligence budget total did finally become
a routine occurrence in 2007, it was principally through the legislative
efforts of Senators Joe Lieberman and Susan Collins of the Senate Homeland
Security Committee, not the Intelligence Committee. Similarly, efforts to
strengthen oversight of intelligence by the Government Accountability
Office were led by Senator Daniel Akaka, again from outside the
Intelligence Committee.
(The Intelligence Committee did, however, legislate a requirement in 2010
for disclosure of the budget request for the National Intelligence Program.
And it was cautiously supportive of an expanded role for GAO in
intelligence oversight.)
Most recently, the Intelligence Committee conducted a multi-year
investigation of the CIA's post-9/11 detention and interrogation program.
It is, said Senator Dianne Feinstein, the Intelligence Committee chair, "by
far the most important oversight activity ever conducted by this
committee." But the resulting report "will remain classified and is not
being released in whole or in part at this time," she said December 13.
Its importance is evidently independent of any public impact it might have.
http://www.fas.org/irp/news/2012/12/df121312.html
(A congressional official said there is an intent to make portions of the
report public over the coming months.)
Even in view of the contrary indications (noted above), and some others,
the dominant trend as we perceive it is that public accountability in
intelligence has been deemphasized.
Senator Feinstein made the point another way, when she said of the
Committee that "We are the public."
"I mean, we are the public check on the Executive Branch," Sen. Feinstein
said during the FISA reauthorization debate on December 27, explaining why
she believed greater disclosure of information concerning government
surveillance activities was unnecessary. "We are not of the intelligence
community. We are the public, and it is our oversight, it is our due
diligence to go in and read the classified material."
Intelligence Committee Vice Chair Sen. Saxby Chambliss also said that the
Committees themselves provided public oversight by serving as proxies for
the public: "In matters concerning the FISA Court, the congressional
Intelligence and Judiciary Committees serve as the eyes and ears of the
American people. Through this oversight, which includes being given all
significant decisions, orders, and opinions of the court, we can ensure
that the laws are being applied and implemented as Congress intended."
By these lights, public accountability is more or less superfluous.
Senator Chambliss said that a report on the privacy impact of government
surveillance advocated by Sen. Ron Wyden was unnecessary, because "If we do
our job, there is absolutely no reason for this amendment--and we do our
job."
Members of the House Judiciary Committee last month expressed their own
confidence in non-public intelligence oversight. They rejected a
resolution introduced by Rep. Dennis Kucinich to require the Attorney
General to produce legal justifications for the use of drones "relating to
the practice of targeted killing of United States citizens and targets
abroad," a subject of recurring public controversy.
In a December 18 report, the Committee said the Kucinich resolution was
unwarranted because "the House and Senate Intelligence Committees continue
to conduct robust oversight into the drone program that targets terrorists
and their associates." Public controversy is beside the point.
http://www.fas.org/irp/congress/2012_rpt/adverse.html
How should one understand the apparent diminished interest in public
accountability? It is hard to say. There is a strain of political
commentary that characteristically invokes official bad faith as the
sovereign explanation for all disfavored policy outcomes: Officials act
the way they do -- instead of the way I wanted them to -- because they are
power-hungry or compromised by financial interest, social affiliation, or
personal ambition. This is usually a lazy and self-serving explanation (if
my opponents are scoundrels, I must be okay) even if it is not always and
altogether wrong.
Another possibility is that intelligence collection is much more fragile
than is generally recognized. A senior intelligence agency official said
recently that if the specific surveillance methods authorized by the FISA
Amendments Act were to become public knowledge, those methods could be
circumvented or defeated "without much difficulty." The official did not
elaborate.
Even if that were true, however, it would not explain the broader trends
-- the declining number of public hearings on intelligence, the diminished
focus on declassification, the abandoned (or muted) commitment to
disclosure of "as much information as possible about intelligence
activities."
Nor does it fully explain the Senate's categorical rejection last month of
all of the proposed amendments to the FISA Amendments Act, which were about
as undemanding as they could be. (The intelligence community said that one
amendment to require preparation of an estimate of the number of American
communications collected was not feasible or would entail privacy
violations of its own). Most of the amendments would not have imposed any
change in policy or any compulsory disclosure, but only certain reporting
obligations, and even those had waivers for national security concerns. As
far as oversight and accountability are concerned, these proposals were
practically de minimis, of homeopathic proportions, and yet they were
rejected by the Senate.
(Although Sen. Jeff Merkley's amendment to promote declassification of
opinions of the Foreign Intelligence Surveillance Court was among the
rejected proposals, Sen. Feinstein said that she would work together with
Sen. Merkley to help achieve that end.)
"What it comes down to is what we define robust congressional oversight in
a program such as this to be," said Sen. Ron Wyden of his amendment to the
FISA Amendments Act, which was voted down on December 28.
"Plain and simple--we need more information," said Sen. Mark Udall. "How
else can we evaluate this policy? The American public has a right to know.
And needs to know. How many Americans are affected by FISA? Are existing
privacy protections working? Are they too weak? Do they need to be
strengthened? These are vital questions. They need to be answered. And so
far they have not been."
Now, for the foreseeable future, they will not be answered, at least not
to anyone outside of the intelligence committees.
NEW CRS REPORTS ON TAX POLICY
New and updated reports from the Congressional Research Service that
Congress has not made available to the public include the following items
on tax policy.
International Corporate Tax Rate Comparisons and Policy Implications,
December 28, 2012:
http://www.fas.org/sgp/crs/misc/R41743.pdf
Reform of U.S. International Taxation: Alternatives, December 27, 2012:
http://www.fas.org/sgp/crs/misc/RL34115.pdf
Distributional Effects of Taxes on Corporate Profits, Investment Income,
and Estates, December 27, 2012:
http://www.fas.org/sgp/crs/misc/RL32517.pdf
Tax Deductions for Individuals: A Summary, December 20, 2012:
http://www.fas.org/sgp/crs/misc/R42872.pdf
Funding and Financing Highways and Public Transportation, December 26,
2012:
http://www.fas.org/sgp/crs/misc/R42877.pdf
The Debt Limit: History and Recent Increases, December 27, 2012:
http://www.fas.org/sgp/crs/misc/RL31967.pdf
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
Video – Sports Illustrated Swimsuit : Brooklyn Decker
Travel to Israel with super model Brooklyn Decker for her SI Swimsuit 2008 shoot
The FBI – Sovereign Citizen Extremists Targeting Law Enforcement

Recent Sovereign Citizen Extremist Targeting of Law Enforcement Highlights Potential for Violence during Traffic Stops
- 5 pages
- Law Enforcement Sensitive
- June 1, 2012
(U//LES) The FBI assesses with medium confidence, based on reliable source reporting and reports from other law enforcement agencies, some sovereign citizen extremistsb are making more specific plans to interfere with state and local law enforcement officers during traffic stops and, in some cases, intentionally initiating contact with law enforcement. The FBI assesses with medium confidence that a shift from reacting to law enforcement scrutiny1,2 to targeting police officers indicates an increased interest in harassing and intimidating police and may lead to potentially hostile confrontations.
…
(U) Targeting Law Enforcement
(U//LES) Some sovereign citizen extremists have recently initiated contact with police officers, which the FBI assesses are attempts to harass officers. This assessment is based on sovereign citizen extremists’ past attempts to intimidate law enforcement and ideologically based distrust of government officials. If correct, this suggests a heightened interest among extremists in attempting to harass and intimidate law enforcement.
• (U) In April 2012, Arkansas law enforcement officers pulled over a self-proclaimed sovereign citizen. According to a news report, the man’s wife drove to the scene, told officers they had no right to arrest her husband, and said officers were committing “treason.” A struggle began and an officer used a Taser to subdue the man.
• (U//LES) In March 2012, self-described sovereign citizens in California demanded that law enforcement officers fill out a “Public Servant’s Questionnaire” during a traffic stop, with space for officers’ personal information. According to an officer of another law enforcement agency, sovereign citizens used the questionnaire to buy time and call others to the scene, who recorded the incident and made unreasonable demands.
• (U//LES) During a February 2012 traffic stop in Oregon involving a Republic for the united States of America (RuSA) [sic] member, the driver of a second vehicle traveled backward on a highway, parked, and became confrontational with the officers conducting the traffic stop, according to an officer of another law enforcement agency. The man, also a RuSA member, continued to approach even after officers ordered him to stop, but the incident ended peacefully.
• (U//LES) In December 2011, a self-described sovereign citizen followed an Arkansas state trooper and made a series of violations to deliberately initiate a traffic stop. The individual was hostile, and used a Bluetooth headset to speak to an unknown person during the stop. An unidentified driver of a second vehicle arrived at the scene, but the driver did not interact with the officer conducting the traffic stop.
(U) Plans to Target Law Enforcement Officers or Provide Armed Response to “Emergencies”
(U//LES) Some sovereign citizen extremist groups aspire to implement Ranger programs and other plans to respond to perceived law enforcement abuses. Given limited assets, the FBI assesses with high confidence complete implementation is unlikely. But the nature of these plans and beliefs that sovereign citizen extremists are legitimate law enforcement officers suggests even small or poorly funded versions of these plans have the potential for violence.
• (U) In March and April 2012, the RuSA released an American Ranger Plan to stand up full-time, armed Rangers authorized to use deadly force during official duty. Part of the plan details scenarios in which Rangers are authorized to act. Scenarios included negotiating with law enforcement for release of incarcerated RuSA members and using “all force necessary” to extract members from jail if negotiations fail, and responding to traffic stops, evictions, and “roadside piracy.” RuSA members determined these “scenarios” would not be released to the public, according to a source who has reported reliably in the past.
• (U//LES) As of late 2011, sovereign citizen extremists bought out-of-service police vehicles and trained to target police, according to officers of another law enforcement agency.
• (U//FOUO) Over the past several years, sovereign citizen extremist groups in Montana and Alaska sought to establish the Liberty Bell Network, a communications system designed to summon numerous armed group members to “emergencies,” according to reliable sources. In February 2012, a RuSA member in Arizona recommended the group implement a similar system because it worked well in Alaska.
TOP-SECRET- U.S. Army Responsible Drawdown and Reset Special Study

CENTER FOR ARMY LESSONS LEARNED
- 162 pages
- For Official Use Only
- September 2011
In 2008, in preparation for the eventual drawdown of United States military forces from Iraq, Army Materiel Command (AMC) began the search for lessons learned concerning the drawdown of forces that occurred after Operation Desert Storm. This search produced over ten thousand pages of documents that were fragmented in nature and contained no clear path to the end-state objectives of the current operational force. Thus, as Operation Iraqi Freedom (OIF) transitioned to Operation New Dawn (OND), the plan for the responsible drawdown of forces from Iraq had to be built from a new foundation, with no historical lessons learned to create an architecture in which planners could operate.
The purpose of this special study is to provide commanders, leaders, and planners at the tactical, operational, and strategic levels a guide that synchronizes strategic-level requirements and outcomes with operational- and tactical-level objectives, therefore providing synergy of effort that will support the Army Force Generation cycle and reset planning timelines. It is our hope that this information will be useful to both sustainment and maneuver commanders, that it will constitute a historical survey of recent drawdown operations, and that it will offer tactics, techniques, and procedures that can be used today and in the future to assist cornmanders at all levels with the planning and execution of the responsible drawdown of forces.
…
The responsible drawdown of forces (RDOF) process in Iraq remains one of the most complex undertakings by the U.S. Army in history. After nearly a decade in Iraq, the strategic relief in place/transfer of authority (RIP/TOA) between the Department of Defense (DOD) and the Department of State (DOS) requires all of the following events to occur within a seamless transition period: reduce U.S. and coalition forces, transition responsibility for security, assign key locations, and allocate necessary equipment to the DOS and/or the host nation. The RDOF process presents challenges at the tactical, operational, and strategic levels that are complex and multifaceted.
This special study has been written for the operational planner to discuss a wide range of strategic planning considerations during the RDOF process. The lessons captured in this document are largely derived from the Iraq perspective. These considerations will equally apply to a successful redeployment in Afghanistan or any other theater where a deliberate RDOF process will be undertaken with transition to another authority, whether it is government, host nation, or a coalition partner.
Consequently, this special study will describe a number of lessons learned along with considerations for RDOF at the strategic level. The chapters will describe important time frames and key strategic considerations, discuss transition to another authority, and explore contracting challenges and equipment disposition considerations.
Monty Python’s Flying Circus – Whicker’s World – Full Film
Monty Python’s Flying Circus S3E01: Whicker’s World
SI Swimsuit Video: Ana Beatriz
Watch super model Ana Beatriz in Nicaragua for her SI Swimsuit 2008 shoot.
Cryptome – Military Cyber Influence Operations Theory
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
TMZ – Kim Kardashian Pregnant with Kanye West’s Baby
We just got the full version of Kanye’s baby announcement… and it’s awesome. Check it out — when was the last time you saw Kanye look so happy? The answer is never.
SECRET-U.S. Army – Marine Corps Unmanned Ground Systems Presentation
Army-Marine Corps Board (AMCB) Unmanned Ground Vehicles (UGV)
- 34 pages
- For Official Use Only
- September 12, 2011
Unmanned Ground Systems consist of a powered physical system with no human operator on aboard the principal platform, which can act, either operated remotely or with some degree of autonomy, to accomplish assigned tasks. Unmanned Ground Systems may be mobile or stationary, can be smart learning, self-adaptive, and includes all associated supporting components such as Operator Control Units (OCU).
Subcategories of Unmanned Ground Systems include unmanned ground vehicles (UGV), and unattended munitions and sensors.
…
Monty Python’s Flying Circus – The Golden Age of Ballooning – Full Movie
Monty Python’s Flying Circus S4E01: The Golden Age of Ballooning

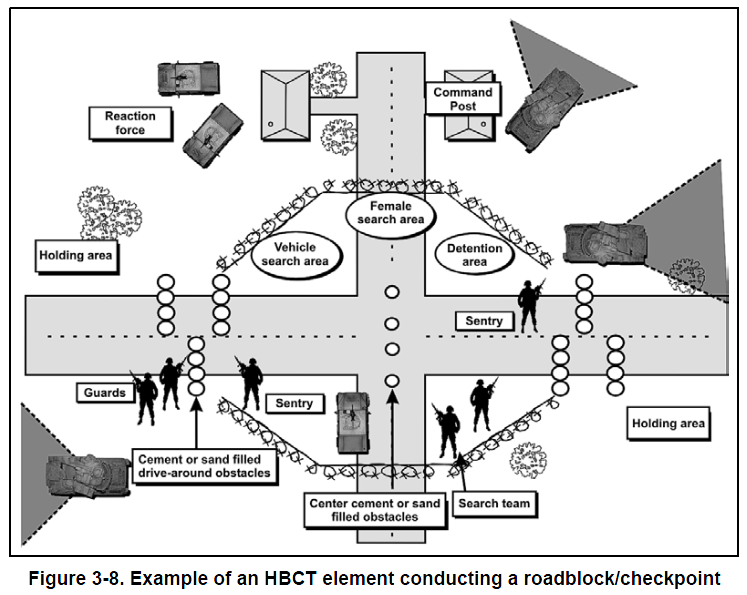
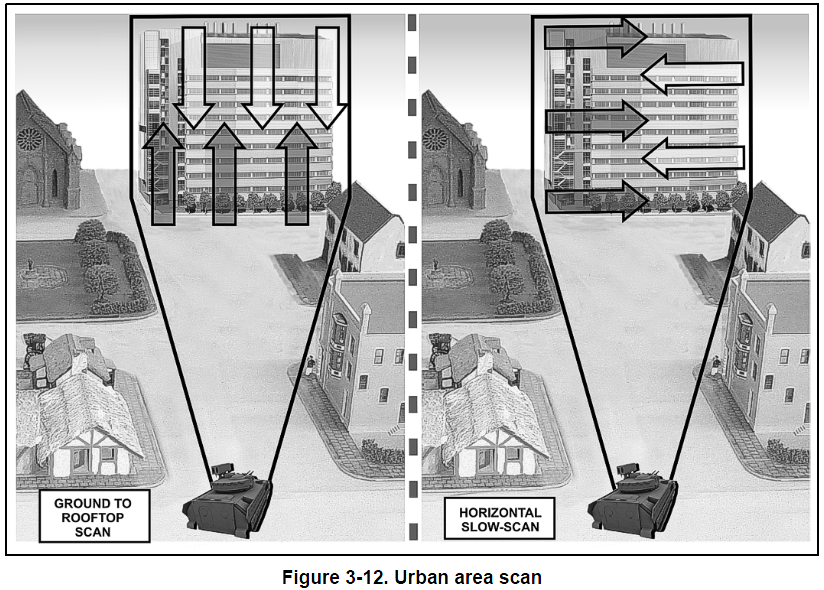
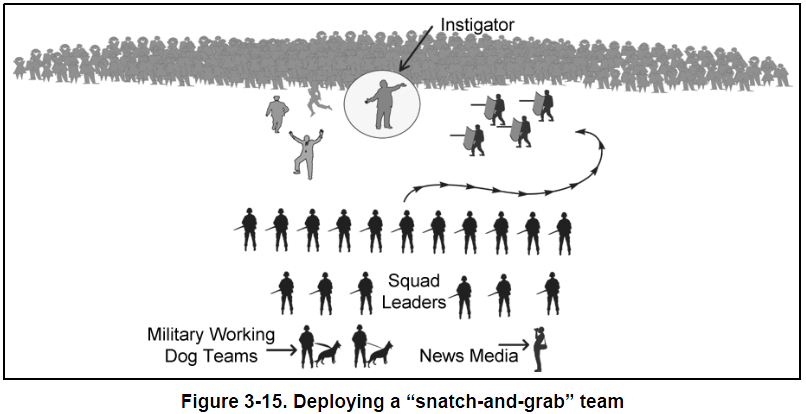
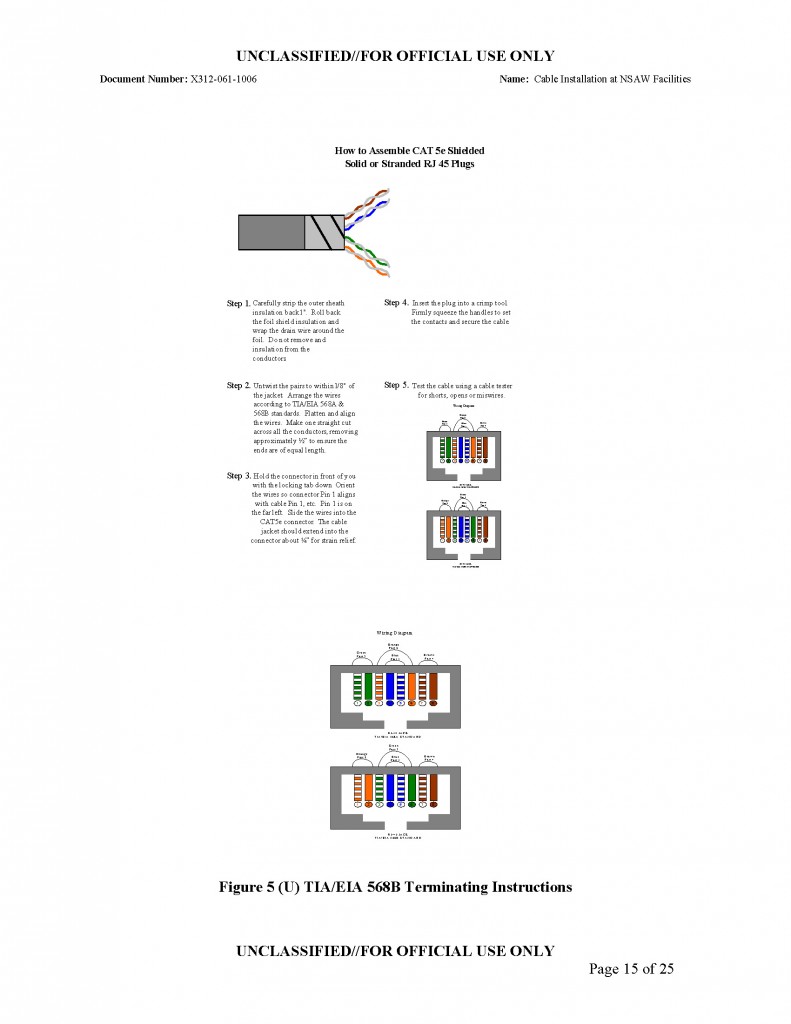


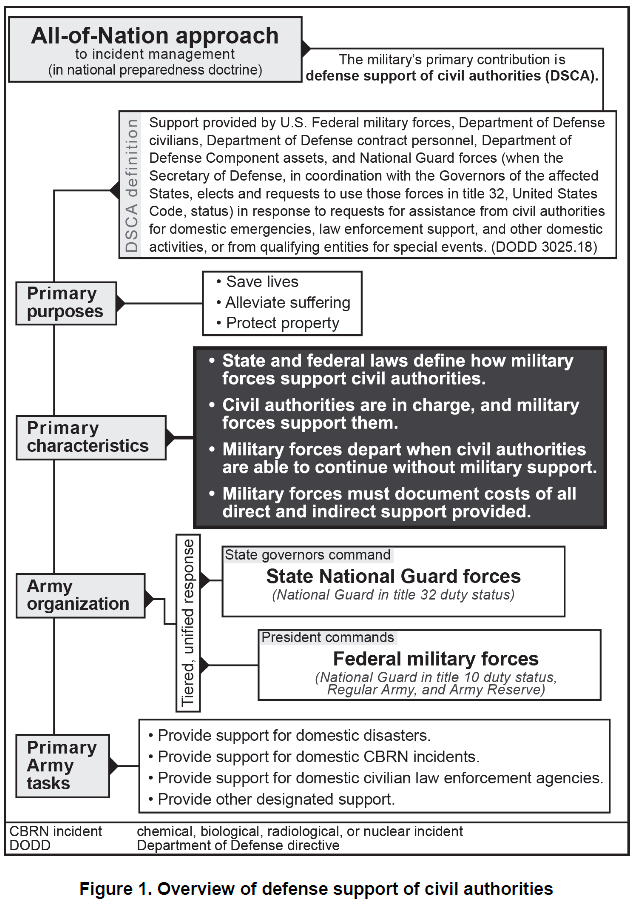


![[Image]](https://i0.wp.com/cryptome.org/2013/01/nicgorski/pict10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013/01/nicgorski/pict7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013/01/nicgorski/pict9.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013/01/nicgorski/pict8.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013/01/nicgorski/nicgorski-cia-john1.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013/01/nicgorski/pict27.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013/01/nicgorski/pict12.jpg)