Become a Patron!
True Information is the most valuable resource and we ask you to give back.

Date: Thu, 26 Mar 2015 12:19:23 +0100
From: “Dr Les Sachs” <l.sachs[at]inbox.lt>
Subject: Swiss gov letter: No Snowden asylum, he’s a CIA fraud
To: info[at]pandodaily.com
Here is the letter at the Swiss government agencies which terminated the plan to re-locate Snowden into Switzerland, with a link to the larger intelligence agency dossier at EU governments on how the US agencies have run this hoax.
Fine to publish the letter with my e-mail address as well, just please not the phone number
Cheers
Les
Dr Les (Leszek – Leslie) Sachs
tel. xxxxx
* * *
His Excellency Bénédict de Cerjat, Embassy of the Swiss Confederation to the Kingdom of Belgium Mr Roberto Balzaretti, Chief of Mission of the Swiss Confederation to the European Union Schweizer Nachrichtendienst des Bundes – Service de renseignement de la Confédération Suisse Schweizer Bundesamt für Polizei – Office fédéral de la police suisse
Re: Intelligence dossier on active CIA agent & fraud ‘Edward Snowden’, threats to Switzerland
Your Excellency, Chief of Mission, and Swiss Confederation Intel & Police Authorities,
Since the previous year – in case you did not know – the governments and intelligence agencies of Germany, France, the United Kingdom, Russia, and Belgium, have all known that the man in Russia ‘Edward Snowden’ publicly requesting Swiss asylum, is a liar and fraud, an active CIA agent hoaxing and defrauding European citizens, a man who may have already helped murder innocent people via the CIA ‘Operation Fake Dissident Snowden’.
There is a substantial intelligence agency file on ‘Snowden’ in the possession of the above countries, describing in detail the comprehensive CIA connections and evil purposes of this grand hoax, by which the US regime is attempting to humiliate Switzerland, the USA not being content with the billions already extorted from Swiss banks and institutions by the corrupt USA judicial apparatus. The ‘Snowden’ intel file is attached in e-mails to you, and can also be viewed online here:
Report to FSB SVR ‘Snowden, Greenwald are CIA frauds’
http://homment.com/3K3xdsYD7a
The Swiss Federal Intelligence Service will understand this report quickly, if not holding it already, and may find amusement confronting Mr Snowden himself, his lying CIA-backed ‘Snowden’ journalists, and the CIA and US regime over this ‘Snowden’ fraud, which was clear from the beginning, when Snowden was promoted by the same CIA media, Guardian & NY Times – who have criminal charge complaints registered against them in Europe for spreading criminal lies about a genuine exiled USA dissident. No real victim receives ‘Snowden’-type promotion by CIA media. And Snowden proved himself to be a fraud via his own words, not even interested in the corruption of the US judges who would put him on trial.
Everyone around Snowden is CIA – his lawyers, his journalists, etc. ‘Operation Snowden’ is a CIA ‘limited hang-out’, i.e., speaking some truths, to sell lies that defraud and murder. Among the purposes of ‘Snowden’ – who never ‘stole’ any documents – is to increase the sense of terrorism and blackmail among governments; to promote CIA-tied media, their lies and frauds; and very likely to entrap genuine USA dissidents, who may have already been silenced or killed after contacting ‘Team Snowden’.
The fraud ‘Snowden’ is now a subject for quiet USA-Russia negotiation. The USA would like to move this liar Snowden to Switzerland, where he can meet more easily with CIA colleagues and continue his criminal activity … the US prefers this option to bringing Snowden back to the USA for a fake ‘trial’ and an fake staged ‘imprisonment’ of a few years while Snowden would be hidden at a CIA site.
Edward Snowden has no hesitation about fraud, murder, deception, or even the violation of children. He has perhaps already defrauded Swiss citizens into donating ‘Snowden defence’ funds to what is already known in several nations as a proven CIA programme. The good Swiss citizens deserve your protection from ‘Operation Fake Dissident Snowden’; the file above will lead you to all that you need.
Very sincerely yours,
Dr Les (Leszek – Leslie) Sachs, contributor to ‘Snowden CIA fraud’ report, Harvard classmate of top US leaders, expert on USA judicial corruption and media control crimes, reporting to & informing EU governments; and genuine targeted political victim of the USA
tel. xxxxx
———- End of forwarded message ———-
Edward Snowden Wife, Edward Snowden Movie, Edward Snowden Twitter, Edward Snowden Dead, Edward Snowden Quotes, Edward Snowden Interview, Edward Snowden Wiki, Edward Snowden Russia, Edward Snowden Net Worth, Edward Snowden 2017, Edward Snowden Age, Edward Snowden Antarctica, Edward Snowden Articles, Edward Snowden Actor, Edward Snowden And Trump, Edward Snowden And Julian Assange, Edward Snowden And Wikileaks, Edward Snowden Apush, Edward Snowden Ama, Edward Snowden And Lindsay Mills, Edward Snowden Biography, Edward Snowden Book, Edward Snowden Bin Laden, Edward Snowden Booz Allen, Edward Snowden Birthday, Edward Snowden Bbc, Edward Snowden Blog, Edward Snowden Birth Chart, Edward Snowden Bernie Sanders, Edward Snowden Bitcoin, Edward Snowden Cia, Edward Snowden Cnn, Edward Snowden Cast, Edward Snowden Chelsea Manning, Edward Snowden Current News, Edward Snowden Citizen 4, Edward Snowden Conservative, Edward Snowden China, Edward Snowden Chemtrails, Edward Snowden Contact, Edward Snowden Dead, Edward Snowden Documentary, Edward Snowden Definition, Edward Snowden Documentary Netflix, Edward Snowden Doc, Edward Snowden Donald Trump, Edward Snowden Dell, Edward Snowden Documentary Hbo, Edward Snowden Date, Edward Snowden David Hoffman, Edward Snowden Essay, Edward Snowden Email, Edward Snowden Ethics, Edward Snowden Ethics Essay, Edward Snowden Early Life, Edward Snowden Effect, Edward Snowden Ecuador, Edward Snowden Education, Edward Snowden Everything About Donald Trump, Edward Snowden Event, Edward Snowden Facts, Edward Snowden Family, Edward Snowden Film, Edward Snowden First Interview, Edward Snowden Facebook, Edward Snowden Father, Edward Snowden Full Movie, Edward Snowden Flat Earth, Edward Snowden First Tweet, Edward Snowden Fox News, Edward Snowden Guardian, Edward Snowden Glenn Greenwald, Edward Snowden Glasses, Edward Snowden Global Warming, Edward Snowden Gif, Edward Snowden Google, Edward Snowden Girlfriend Movie, Edward Snowden Good, Edward Snowden Grandfather, Edward Snowden Genius, Edward Snowden Hero, Edward Snowden Height, Edward Snowden House, Edward Snowden Hawaii, Edward Snowden High School, Edward Snowden Hong Kong, Edward Snowden History, Edward Snowden Heartbeat, Edward Snowden Haarp, Edward Snowden Hbo, Edward Snowden Interview, Edward Snowden Iq, Edward Snowden Instagram, Edward Snowden Interview 2013, Edward Snowden Imdb, Edward Snowden Interview 2017, Edward Snowden Images, Edward Snowden Interview 2016, Edward Snowden Income, Edward Snowden Iphone, Edward Snowden Job, Edward Snowden Journalist, Edward Snowden Japan, Edward Snowden Julian Assange Bradley Manning, Edward Snowden Java, Edward Snowden Journalism, Edward Snowden Joseph Gordon-levitt, Edward Snowden Julian Assange, Edward Snowden John Oliver Passwords, Edward Snowden Jean Michel Jarre, Edward Snowden Kunia, Edward Snowden Kimdir, Edward Snowden Katie Couric Interview, Edward Snowden Katie Couric, Edward Snowden Kaskus, Edward Snowden Kim, Edward Snowden Kasus, Edward Snowden Kfc, Edward Snowden Kim Jest, Edward Snowden Koenig, Edward Snowden Location, Edward Snowden Lindsay Mills Moscow, Edward Snowden Laptop, Edward Snowden Lindsay Mills, Edward Snowden Living, Edward Snowden Lawyer, Edward Snowden Life, Edward Snowden Latest News, Edward Snowden Latest, Edward Snowden Live Stream, Edward Snowden Movie, Edward Snowden Movie Netflix, Edward Snowden Movie Cast, Edward Snowden Military, Edward Snowden Movie Online, Edward Snowden Memes, Edward Snowden Middlebury College, Edward Snowden Married, Edward Snowden Moscow, Edward Snowden Medical Condition, Edward Snowden Net Worth, Edward Snowden Now, Edward Snowden News, Edward Snowden New York Times, Edward Snowden Netflix, Edward Snowden Natal Chart, Edward Snowden Nobel Prize, Edward Snowden Nsa Salary, Edward Snowden Npr, Edward Snowden Nationality, Edward Snowden On Trump, Edward Snowden Osama Bin Laden, Edward Snowden Obama, Edward Snowden Oscar, Edward Snowden On Movie, Edward Snowden On Twitter, Edward Snowden Openstack, Edward Snowden On Antarctica, Edward Snowden Os, Edward Snowden Original Interview, Edward Snowden Parents, Edward Snowden Political Views, Edward Snowden Privacy Tips, Edward Snowden Political Party, Edward Snowden Patriot Act, Edward Snowden Pictures, Edward Snowden Podcast, Edward Snowden Phone Case, Edward Snowden Poll, Edward Snowden Putin, Edward Snowden Quotes, Edward Snowden Quizlet, Edward Snowden Questions, Edward Snowden Quien Es, Edward Snowden Quote About Privacy, Edward Snowden Quotes Citizenfour, Edward Snowden Quick Facts, Edward Snowden Qualifications, Edward Snowden Russia, Edward Snowden Reddit, Edward Snowden Research Paper, Edward Snowden Real Name, Edward Snowden Residence, Edward Snowden Resume, Edward Snowden Robot, Edward Snowden Recommended Apps, Edward Snowden Reporter, Edward Snowden Russian, Edward Snowden Story, Edward Snowden Salary, Edward Snowden Status, Edward Snowden Signal, Edward Snowden Speech, Edward Snowden Security Tips, Edward Snowden Shirt, Edward Snowden Siblings, Edward Snowden Special Forces, Edward Snowden Still Alive, Edward Snowden Twitter, Edward Snowden Today, Edward Snowden Trump, Edward Snowden Timeline, Edward Snowden Ted Talk, Edward Snowden The Guardian, Edward Snowden Trailer, Edward Snowden The Movie, Edward Snowden T Shirt, Edward Snowden Tor, Edward Snowden Update, Edward Snowden Ufo, Edward Snowden Us Army, Edward Snowden University Of Michigan, Edward Snowden Used Tails, Edward Snowden Umich, Edward Snowden University Of Maryland, Edward Snowden Ufo Wikileaks, Edward Snowden Ufo Video, Edward Snowden Urban Dictionary, Edward Snowden Video, Edward Snowden Vpn, Edward Snowden Vice, Edward Snowden And Julian Assange, Edward Snowden Voice, Edward Snowden And Bradley Manning, Edward Snowden Vault 7, Edward Snowden Visa, Edward Snowden And Wikileaks, Edward Snowden Vanity Fair, Edward Snowden Wife, Edward Snowden Wiki, Edward Snowden Wired, Edward Snowden William And Mary, Edward Snowden Washington Post, Edward Snowden Who Is He, Edward Snowden Website, Edward Snowden Worth, Edward Snowden Wikileak, Edward Snowden Washington Post 2013, Edward Snowden Youtube, Edward Snowden Young, Edward Snowden Yahoo Answers, Edward Snowden Youtube Channel, Edward Snowden Youtube Documentary, Edward Snowden Yokota, Edward Snowden And Lindsay Mills, Edward Snowden Yify, Edward Snowden Zodiac Sign, Edward Snowden Zcash, Edward Snowden Zuckerberg, Edward Snowden Zoho, Edward Snowden Zizek, Edward Snowden Zimbabwe, Edward Snowden Zitate, Edward Snowden Zusammenfassung, Edward Snowden Zivilisation, Edward Snowden Zvi\u017eda\u010d, Cia World Factbook, Cia Jobs, Cia Director, Cia Definition, Cia Headquarters, Cia Careers, Cia Salary, Cia Agent, Cia Agent Salary, Cia Internship, Cia Agent, Cia Agent Salary, Cia Analyst, Cia Application, Cia Airport, Cia Apush, Cia Address, Cia Auctions, Cia Alexa, Cia Assassinations, Cia Badge, Cia Black Sites, Cia Budget, Cia Bounce, Cia Building, Cia Black Ops, Ciao Bella, Cia Berg, Cia Books, Cia Brennan, Cia Careers, Cia Certification, Cia Cold War, Cia Culinary, Cia Copia, Cia Chief, Cia Crack, Cia Contractor, Cia Created Isis, Cia Cold War Definition, Cia Director, Cia Definition, Cia Director Salary, Cia Declassified Documents, Cia Definition Cold War, Cia Drug Trafficking, Cia Database, Cia Documentary, Cia Declassified, Cia During The Cold War, Cia Exam, Cia Employment, Cia Experiments, Cia Established, Cia Emblem, Cia Email, Cia Employees, Cia El Salvador, Cia Enhanced Interrogation Techniques, Cia Exam Fees, Cia Factbook, Cia Factbook Us, Cia Field Agent, Cia Factbook China, Cia Files, Cia Farm, Cia Factbook Russia, Cia Factbook North Korea, Cia Files 3ds, Cia Factbook India, Cia Gov, Cia Grs, Cia Greystone, Cia Ground Branch, Cia Glassdoor, Cia Guy, Cia Guatemala, Cia Games, Cia General Counsel, Cia Germany, Cia Headquarters, Cia Hyde Park, Cia Hacking Tools, Cia Hacking, Cia History, Cia Hyrule Warriors, Cia Heart Attack Gun, Cia Head, Cia Hacking Notepad++, Cia Headquarters Address, Cia Internship, Cia Insurance, Cia Iran, Cia Intelligence Analyst, Cia In Guatemala, Cia Intelligence, Cia Interview Questions, Cia Isis, Cia Interrogation, Cia India, Cia Jobs, Cia Jfk, Cia Job Openings, Cia Jfk Assassination, Cia Job Description, Cia Jurisdiction, Cia Japan, Cia Job Application, Cia Jobs Nyc, Cia Job Requirements, Cia Killed Jfk, Cia Kevin Hart, Cia Kryptos, Cia K9, Cia Kenya, Cia Kill List, Cia Kennedy Assassination, Cia Knife, Cia Killed Mlk, Cia Korea, Cia Logo, Cia Leaks, Cia Langley, Cia Login, Cia Library, Cia Locations, Cia Leader, Cia License, Cia Leadership, Cia Los Angeles, Cia Meaning, Cia Movies, Cia Most Wanted, Cia Meme, Cia Main Menu, Cia Museum, Cia Mind Control, Cia Malayalam Movie, Cia Music, Cia Maritima, Cia Napa, Cia New York, Cia News, Cia North Korea, Cia Number, Cia Noc, Cia Notepad++, Cia North Hollywood, Cia Nicaragua, Cia Napa Copia, Cia Operative, Cia Operations Officer, Cia Officer, Cia Officer Salary, Cia Office Locations, Cia Org Chart, Cia Operation Mockingbird, Cia Or Fbi, Cia Osama Bin Laden, Cia Origins, Cia Phone Number, Cia Police, Cia Paramilitary, Cia Protective Agent, Cia Purpose, Cia Pay Scale, Cia Positions, Cia Polygraph, Cia Programs, Cia Pompeo, Cia Quizlet, Cia Qualifications, Cia Quotes, Cia Quiz, Cia Questions, Cia Qr Codes, Cia Qatar, Cia Question Alexa, Cia Quantico Va, Cia Quizlet Apush, Cia Requirements, Cia Restaurants, Cia Recruitment, Cia Russia, Cia Reading List, Cia Ranks, Cia Remote Viewing, Cia Released Documents, Cia Responsibilities, Cia Report, Cia Salary, Cia Sad, Cia Stands For, Cia Services, Cia Spy, Cia Special Agent, Cia Scholarship, Cia Secrets, Cia San Antonio, Cia School, Cia Triad, Cia Training, Cia Trump, Cia Twitter, Cia Torture, Cia The World Factbook, Cia To 3ds Converter, Cia The Farm, Cia Tv Shows, Cia Torture Report, Cia University, Cia Ufo Files, Cia Uniform, Cia Usa, Cia Umbrage, Cia Ultra, Cia Undercover, Cia Ukraine, Cis Utah, Cia Uganda, Cia Vs Fbi, Cia Vault 7, Cia Vs Nsa, Cia Volleyball, Cia Vs Kgb, Cia Venezuela, Cia Vietnam, Cia Vault, Cia Virginia, Cia Video, Cia World Factbook, Cia Website, Cia World Factbook Us, Cia Wikileaks, Cia Wiki, Cia World Factbook China, Cia World Factbook India, Cia World Factbook Japan, Cia World Factbook Mexico, Cia World Factbook Russia, Cia X Link, Cia X Files, Cia X Link Lemon, Cia X Link Fanfic, Cia X Link Fanfiction, Cia Xbox, Cia X Male Reader, Xia Xia, Cia X Zelda, Cia X Bane, Cia Youtube, Cia Yuma Az, Cia Yemen, Cia Yearly Salary, Cia Year Founded, Cia Yearly Budget, Cia York Pa, Cia Year Established, Cia Youth Leadership Program, Cia Year Zero, Cia Zimbabwe, Cia Zip Code, Cia Zero Day Exploits, Cia Zambia, Cia Zero Day, Cia Zack Dela Rocha, Cia Zero Dark Thirty, Cia Zombie Apocalypse, Cia Zippo Lighter, Cia Zero, Fraud Definition, Fraud Alert, Fraud Triangle, Fraud Lyrics, Fraud Protection, Fraud Analyst, Fraud Investigator, Fraud Meaning, Fraud In The Inducement, Fraud Lawyers, Fraud Alert, Fraud Analyst, Fraud Alert Equifax, Fraud Attorney, Fraud Analyst Salary, Fraud Alert Credit, Fraud And Abuse, Fraud Analyst Jobs, Fraud Awareness Program, Fraud Affidavit, Fraud By Deception, Fraud By Omission, Fraud Bureau, Fraud By Concealment, Fraud Buster, Fraud Book, Fraud Business, Fraud Bankruptcy, Fraud Bank Account, Fraud By Wire, Fraud Charges, Fraud Cases, Fraud Check, Fraud Chase, Fraud Calls, Fraud Certification, Fraud Credit Card, Fraud Conference, Fraud Complaint, Fraud Calls From Irs, Fraud Definition, Fraud Department, Fraud Detection, Fraud Definition Law, Fraud Define, Fraud Diamond, Fraud Department Us Bank, Fraud Detection Software, Fraud Detection Machine Learning, Fraud Division, Fraud Examiner, Fraud Elements, Fraud Exposure Rectangle, Fraud Examiner Jobs, Fraud Enforcement And Recovery Act, Fraud Elements Illinois, Fraud Examiner Salary, Fraud Examination 5th Edition, Fraud Email, Fraud Examples, Fraud Fighter, Fraud Felony, Fraud Fox, Fraud For Property, Fraud For Profit, Fraud Film, Fraud For Housing, Fraud Fighter Pen, Fraud Famine And Fascism, Fraud Filter, Fraudguard, Fraud Gif, Fraud Go Fund Me, Fraud Government, Fraudguard Report, Fraud Gov, Fraud Games, Fraud Genius, Fraud German, Fraud Google Wallet, Fraud Hotline, Fraud Help, Fraud Healthcare, Fraud Hotline Services, Fraud Hat, Fraud Hotline Service Providers, Fraud Helpline, Fraud Hotline Poster, Fraud Helpline Number, Fraud Hypothesis, Fraud Investigator, Fraud In The Inducement, Fraud Investigator Jobs, Fraud Investigator Salary, Fraud In Spanish, Fraud Ilcs, Fraud In The Factum, Fraud Investigator Jobs Chicago, Fraud In The Execution, Fraud Illinois, Fraud Jobs Chicago, Fraud Jail Time, Fraud Jobs, Fraud Jobs Illinois, Fraud Jokes, Fraud Jobs Indeed, Fraud Jobs Near Me, Fraud Judgement, Fraud Jobs Raleigh Nc, Fraud Job Interview Questions, Fraud Kiting, Fraud Keywords, Fraud Keyword List, Fraud Kickstarter, Fraud Kpis, Fraud Kickbacks, Fraud Kill Chain, Fraud Key Risk Indicators, Fraud Keybank, Fraud Kenya, Fraud Lyrics, Fraud Lawyers, Fraud Legal Definition, Fraud Lawyer Chicago, Fraud Laws, Fraud Lawsuit, Fraud Liability, Fraud Line, Fraud Law Definition, Fraud List, Fraud Meaning, Fraud Movie, Fraud Meme, Fraud Magazine, Fraud Marriage, Fraud Medicaid, Fraud Management, Fraud Monitoring, Fraud Misrepresentation, Fraud Money, Fraud News, Fraud Number, Fraud News Articles, Fraud Net, Fraud Number For Bank Of America, Fraud News Cnn, Fraud News Network, Fraud Navy Federal, Fraud Number Lookup, Fraud Network, Fraud On The Market Theory, Fraud On The Court, Fraud Or Abuse, Fraud On Craigslist, Fraud On A Financial Institution Indiana, Fraud On A Financial Institution, Fraud On Credit Report, Fraud On Amazon, Fraud On Ebay, Fraud On Debit Card, Fraud Protection, Fraud Prevention, Fraud Prevention Services, Fraud Punishment, Fraud Phone Calls, Fraud Phone Numbers, Fraud Paypal, Fraud Prevention Jobs, Fraud Prevention And Detection, Fraud Prevention Exchange, Fraud Quotes, Fraud Quizlet, Fraud Questionnaire, Fraud Questions, Fraud Quiz, Fraud Questions To Ask, Fraud Question Persona 5, Fraud Quotes Images, Fraud Queen, Fraud Qualifications, Fraud Report, Fraud Risk Analyst Salary, Fraud Risk Assessment, Fraud Risk, Fraud Ring, Fraud Risk Management, Fraud Red Flags, Fraud Risk Definition, Fraud Risk Management Guide, Fraud Rsmo, Fraud Synonym, Fraud Statute Of Limitations Illinois, Fraud Statute Of Limitations, Fraud Specialist Chase, Fraud Stoppers, Fraud Syndrome, Fraud Sentence, Fraud Schemes, Fraud Specialist, Fraud Statistics, Fraud Triangle, Fraud Thesaurus, Fraud Tree, Fraud Theory, Fraud Transaction, Fraud Tort, Fraud Training, Fraud Triangle Theory, Fraud Trailer, Fraud Trends, Fraud Upon The Court, Fraud Unit, Fraud Us Bank, Fraud Upon Meaning, Fraud Usaa, Fraud Ucmj, Fraud Unemployment, Fraud Uber, Fraud Use Of Personal Id, Fraud University, Fraud Vs Abuse, Fraud Video, Fraud Verb, Fraud Victim, Fraud Vs Misrepresentation, Fraud Vs Negligence, Fraud Verizon, Fraud Vs Identity Theft, Fraud And Defraud, Fraud Vitiates Everything, Fraud Waste And Abuse, Fraud Waste And Abuse Training, Fraud Wells Fargo, Fraud Watch, Fraud Website, Fraud Waste And Abuse Hotline, Fraud Waste And Abuse In Healthcare, Fraud Waste And Abuse Policy, Fraud Waiver, Fraud Waste And Abuse Training 2017, Fraud Youtube, Fraud Years In Jail, Fraud Yahoo, Fraud Yorkshire Bank, Fraud Yorkville, Fraud Yac, Fraud Yellow Pages, Fraud Yahoo Answers, Fraud York University, Fraud Y-axis, Fraud Znaczenie, Fraud Zimlii, Fraud Znacenje, Fraud Zimbabwe, Fraud Zalando, Fraud Za, Fraud Zzzz Best, Fraud Zero Tolerance, Fraud Z-score Model, Fraud Zhongwen, Asylum Definition, Asylum Of Darkness, Asylum Movie, Asylum From New York, Asylum Seekers, Asylum Book, Asylum Skatepark, Asylum Cigars, Asylum Near Me, Asylum Demon, Asylum Application, Asylum Ahs, Asylum Anime, Asylum Arma 3, Asylum American Horror Story Cast, Asylum Application Form, Asylum Ale, Asylum Artwork, Asylum Access, Asylum Attorney Chicago, Asylum Book, Asylum Book Series, Asylum Blackout, Asylum Bay, Asylum Bay Oshkosh, Asylum Band, Asylum Beer, Asylum Brewery Madison, Asylum Book Wiki, Asylum Building, Asylum Cigars, Asylum Chicago, Asylum Cast, Asylum C Photography, Asylum Case, Asylum Challenge Sims 4, Asylum Characters, Asylum Canada, Asylum Choir, Asylum Comics, Asylum Definition, Asylum Demon, Asylum Destiny, Asylum Disturbed, Asylum Darkness, Asylum Documentary, Asylum Disturbed Lyrics, Asylum Denied, Asylum Demon Dark Souls 3, Asylum Demon Hammer, Asylum Entertainment, Asylum Extreme, Asylum Escape, Asylum Eligibility, Asylum Ead Renewal, Asylum Escape Room, Asylum Ead, Asylum Entertainment Games, Asylum Escape Chapter 5, Asylum Evolution Razor, Asylum From New York, Asylum Flower, Asylum Films, Asylum Form, Asylum Forums, Asylum File, Asylum Fallout 4, Asylum Ffxiv, Asylum For The Criminally Insane, Asylum Fibers, Asylum Gym, Asylum Game, Asylum Green Card, Asylum Gym Rockford Il, Asylum Granted, Asylum Ghost, Asylum Game Chapter 5, Asylum Ghost Location, Asylum Gatekeeper, Asylum Gaming Arma 3, Asylum Horror Movies, Asylum History, Asylum Hill, Asylum Horror Game, Asylum Haunted, Asylum Home Entertainment, Asylum Hank, Asylum Hospitals, Asylum House, Asylum Hearing, Asylum In Canada, Asylum In Usa, Asylum In Spanish, Asylum In Illinois, Asylum Interview Chicago, Asylum Interview, Asylum In Chicago, Asylum In Russia, Asylum Indiana, Asylum In The Us, Asylum Jacket, Asylum Jobs, Asylum Jerome Az, Asylum Jam, Asylum Jokes, Asylum Jurisdiction, Asylum Jerome Mcdonough, Asylum Judge, Asylum John Harwood, Asylum Jamaica, Asylum Kodi, Asylum Kentucky, Asylum Kiss, Asylum Knockoff, Asylum Kickstarter, Asylum Key, Asylum Kit, Asylum Kalamazoo, Asylum Kodi Addons, Asylum Ky, Asylum Law, Asylum Lyrics, Asylum Lake Bluff, Asylum Life, Asylum Loves Park Il, Asylum Lawyers, Asylum Life Forums, Asylum Lake, Asylum Locations, Asylum Lobotomy, Asylum Meaning, Asylum Movie, Asylum Madeleine Roux, Asylum Movie 2017, Asylum Mods, Asylum Milwaukee, Asylum Match, Asylum Movement, Asylum Movie 2008, Asylum Movie 2016, Asylum Near Me, Asylum News, Asylum Night Shift, Asylum Names, Asylum Novel, Asylum Number, Asylum Nyctophilia, Asylum Night Shift 2, Asylum Novellas, Asylum Netflix, Asylum Of Darkness, Asylum Office Chicago, Asylum Of The Daleks, Asylum Of Darkness Trailer, Asylum Of Darkness Review, Asylum Officer, Asylum Office Locator, Asylum Officer Basic Training Course, Asylum Of Darkness Wiki, Asylum Out Of The Shadows, Asylum Pictures, Asylum Patients, Asylum Plant, Asylum Point, Asylum Process, Asylum Party, Asylum Point Park, Asylum Photography, Asylum Popcorn, Asylum Photos, Asylum Quotes, Asylum Questions, Asylum Questionnaire, Asylum Questionnaire In Spanish, Asylum Quiz, Asylum Quizlet, Asylum Quartet, Asylum Questions In Spanish, Asylum Quotev, Asylum Questions And Answers, Asylum Records, Asylum Rockford Il, Asylum Research, Asylum Room, Asylum Requirements, Asylum Reform, Asylum Refugee, Asylum Roux, Asylum Restaurant, Asylum Ring, Asylum Seekers, Asylum Skatepark, Asylum Street Spankers, Asylum Series, Asylum Synonym, Asylum Seeker Definition, Asylum Schedule, Asylum Surgeon Ring, Asylum Sans, Asylum Stories, Asylumtale, Asylum Timeline, Asylum Tattoo, Asylum Tv Show, Asylum Tours, Asylum Trailer, Asylum The Movie, Asylum The Book, Asylum Treatments, Asylum Teamspeak, Asylum Usa, Asylum United States, Asylum Uk, Asylum Uniform, Asylum Used In A Sentence, Asylum Uscis Form, Asylum Upper Elite, Asylum Uscis Bulletin, Asylum Unaccompanied Minors, Asylum Ulmerton, Asylum Visitor, Asylum Visa, Asylum Video Game, Asylum Volume 2, Asylum Videos, Asylum Venezuela, Asylum Vertical Plyo, Asylum Visitor Price, Asylum Volume 1, Asylum Virginia, Asylum Workout, Asylum Work Permit, Asylum Weaponry Gatekeeper, Asylum Wiki, Asylum Winchester Indiana, Asylum Walkthrough, Asylum Work Authorization, Asylum Weaver, Asylum Walkthrough Chapter 6, Asylum Website, Asylum X Trainer, Asylum Xbox One, Asylum Extreme, Asylum X Reader, Asylum Experiments, Asylum Example, Asylum Exposed, Asylum Expedite Request, Asylum Extortion, Asylum Exercise, Asylum Youtube, Asylum Years, Asylum Yarn, Asylum Ya Book, Asylum Youku, Asylum Yard Dublin, Asylum Yamu, Asylum You’re Right To Worry, Asylum Years Tom Waits, Asylum Years Vinyl, Asylum Zin, Asylum Zombie Map, Asylum Zone, Asylum Zombie Soda, Asylum Z Nation, Asylum Zombie Movies, Asylum Zombie Apocalypse, Asylum Z, Asylum Z Walkthrough, Asylum Znaczenie, Switzerland Flag, Switzerland Map, Switzerland Language, Switzerland Currency, Switzerland Capital, Switzerland Population, Switzerland Weather, Switzerland Cities, Switzerland Country Code, Switzerland Gun Laws, Switzerland Abbreviation, Switzerland Airport, Switzerland Alps, Switzerland Attractions, Switzerland Army, Switzerland Activities, Switzerland Address Format, Switzerland Area Code, Switzerland Adapter, Switzerland Area, Switzerland Bern, Switzerland Banks, Switzerland Basel, Switzerland Beaches, Switzerland By Train, Switzerland Basic Income, Switzerland Borders, Switzerland Beer, Switzerland Biomes, Switzerland Begonia, Switzerland Currency, Switzerland Capital, Switzerland Cities, Switzerland Country Code, Switzerland County Indiana, Switzerland Chocolate, Switzerland Climate, Switzerland Culture, Switzerland Consulate Chicago, Switzerland Crime Rate, Switzerland Drinking Age, Switzerland Demographics, Switzerland Desserts, Switzerland Drug Laws, Switzerland Direct Democracy, Switzerland Debt, Switzerland Democracy, Switzerland Drinks, Switzerland Dress Code, Switzerland Dishes, Switzerland Economy, Switzerland Eu, Switzerland Education, Switzerland Embassy Chicago, Switzerland Embassy, Switzerland Education System, Switzerland Exports, Switzerland Euro, Switzerland Environment, Switzerland Economic System, Switzerland Flag, Switzerland Food, Switzerland Facts, Switzerland Flights, Switzerland Flag Emoji, Switzerland Fun Facts, Switzerland Florida, Switzerland Flag Joke, Switzerland Form Of Government, Switzerland Fashion, Switzerland Gun Laws, Switzerland Government, Switzerland Gdp, Switzerland Gdp Per Capita, Switzerland Geography, Switzerland Germany, Switzerland Gross Domestic Product, Switzerland Gay Marriage, Switzerland Girls, Switzerland Glacier Express, Switzerland Health Care, Switzerland History, Switzerland Hotels, Switzerland Hetalia, Switzerland Holidays, Switzerland Honeymoon, Switzerland Hiking, Switzerland Houses, Switzerland Homes For Sale, Switzerland Homes, Switzerland In Spanish, Switzerland Itinerary, Switzerland Immigration, Switzerland In Ww2, Switzerland Inn, Switzerland In German, Switzerland Indiana, Switzerland In French, Switzerland In September, Switzerland In October, Switzerland Jobs, Switzerland Jokes, Switzerland Jazz Festival, Switzerland Jail, Switzerland June Weather, Switzerland Jersey, Switzerland July Weather, Switzerland Jungfraujoch, Switzerland July, Switzerland Joins Un, Switzerland Kandersteg, Switzerland Known For, Switzerland King, Switzerland Knife, Switzerland Knife Laws, Switzerland Keychain, Switzerland Kayaking, Switzerland Keyboard, Switzerland Keuka Lake Ny, Switzerland Klingon, Switzerland Language, Switzerland Location, Switzerland Local Time, Switzerland Lucerne, Switzerland Landmarks, Switzerland Landscape, Switzerland Literacy Rate, Switzerland Life Expectancy, Switzerland Language Map, Switzerland Leader, Switzerland Map, Switzerland Money, Switzerland Mountains, Switzerland Minimum Wage, Switzerland Military, Switzerland Mountain Coaster, Switzerland Music, Switzerland Meme, Switzerland Main Language, Switzerland Major Cities, Switzerland Neutral, Switzerland News, Switzerland National Team, Switzerland National Language, Switzerland National Animal, Switzerland National Anthem, Switzerland Natural Resources, Switzerland Names, Switzerland National Flower, Switzerland Nazi Gold, Switzerland Official Language, Switzerland On Map, Switzerland Of America, Switzerland Outlet, Switzerland On World Map, Switzerland Outlet Type, Switzerland Official Website, Switzerland Olympics, Switzerland On Europe Map, Switzerland Outline, Switzerland Population, Switzerland People, Switzerland President, Switzerland Pictures, Switzerland Power Adapter, Switzerland Places To Visit, Switzerland Puns, Switzerland Per Capita Income, Switzerland Postal Code, Switzerland Power Outlet, Switzerland Quotes, Switzerland Quality Of Life, Switzerland Queen, Switzerland Quiz, Switzerland Quora, Switzerland Quality Of Life Ranking, Switzerland Questions, Switzerland Quick Facts, Switzerland Quran, Switzerland Quantitative Easing, Switzerland Religion, Switzerland Real Estate, Switzerland Rivers, Switzerland Refugees, Switzerland Rail Pass, Switzerland Resorts, Switzerland Racial Demographics, Switzerland Rail Map, Switzerland Recipes, Switzerland Rail, Switzerland Soccer, Switzerland Size, Switzerland Skiing, Switzerland Ski Resorts, Switzerland Slide, Switzerland Sports, Switzerland Schengen, Switzerland Socialist, Switzerland Scenery, Switzerland States, Switzerland Time, Switzerland Time Now, Switzerland Travel, Switzerland Tours, Switzerland Train, Switzerland Tourism, Switzerland Tax Rate, Switzerland Travel Guide, Switzerland Things To Do, Switzerland Trip, Switzerland Unemployment Rate, Switzerland Universities, Switzerland Us Embassy, Switzerland Universal Basic Income, Switzerland Un, Switzerland Universal Income, Switzerland Uber, Switzerland Usa, Switzerland Unemployment, Switzerland Unitary Or Federal, Switzerland Vacation, Switzerland Visa, Switzerland Visa Chicago, Switzerland Visa Usa, Switzerland Vs Sweden, Switzerland Vs France, Switzerland Voltage, Switzerland Village, Switzerland Vs Usa, Switzerland Visit, Switzerland Weather, Switzerland Ww2, Switzerland Watches, Switzerland Weather In July, Switzerland Wiki, Switzerland Weather In June, Switzerland World Map, Switzerland Weather In May, Switzerland Wars, Switzerland Wallpaper, Switzerland X Reader, Switzerland X Reader Lemon, Switzerland X Liechtenstein, Switzerland X Male Reader, Switzerland X Reader Fluff, Switzerland X Reader X Austria, Switzerland Xenophobia, Switzerland X Abused Reader, Switzerland X Shy Reader, Switzerland X Chubby Reader, Switzerland Yodeling, Switzerland Youtube, Switzerland Yellow Fields, Switzerland Year Round Weather, Switzerland Yellow Pages, Switzerland Youth Unemployment Rate, Switzerland Youth Hostel, Switzerland Yogurt, Switzerland Ywam, Switzerland Yoga Retreat, Switzerland Zurich, Switzerland Zip Code, Switzerland Zermatt, Switzerland Zug, Switzerland Zurich Airport, Switzerland Zoo, Switzerland Zip Line, Switzerland Zurich Weather, Switzerland Zurich Things To Do, Switzerland Zurich Hotels,











































































































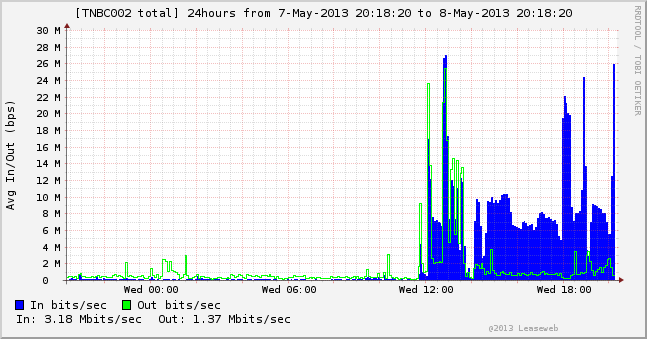


















![[Image]](https://i0.wp.com/cryptome.org/2013/03/iran-cyber-offense-01.jpg)
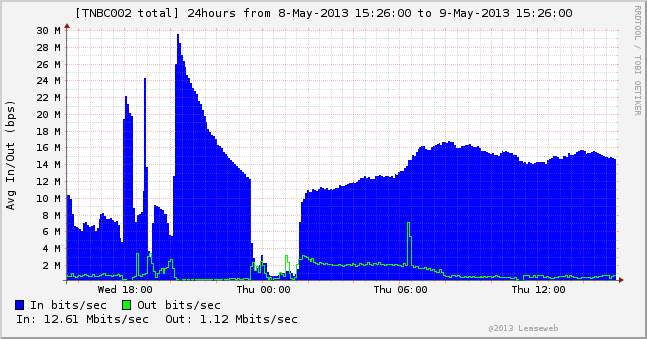
![[Image]](https://i0.wp.com/cryptome.org/2013/03/iran-cyber-offense-02.jpg)








4 comments:
Anonymous said…
Anonymous said…
see here said…
cyberzon said…
Post a Comment