THE QUARREL OVER THE STASI FILES
Martin Sabrow
The struggle for access to the Stasi files dates back to the peaceful revolution
in East Germany in the autumn of 1989. In November 1989, the
Ministry of State Security (MfS) was transformed into the Office of National
Security (Amt für Nationale Sicherheit, ANS), with the hidden
purpose of securing secret police structures and documents for the postdictatorial
era. This attempt failed, and the people responded with the
“storming of the Normannenstraße,” Mielke’s stronghold in Berlin, in
order to stop Stasi agents from destroying evidence. The storming was
successful; it represented a victory for the people and for civil rights.
In the end, the “Round Table” decided to destroy the files of Markus
Wolf’s intelligence branch, but the majority of the documents concerning
the internal activities of the MfS could be saved. In May 1990, the East
German People’s Chamber appointed a special committee under the
chairmanship of Joachim Gauck to control the dissolution of the MfS/
ANS. Then in September 1990, the German Unification Treaty obliged the
Bundestag to entrust MfS records to a Special Commissioner of the Federal
Government (later Federal Commissioner) for the files of the former
State Security Service, the so-called Gauck Agency, which began operations
with fifty-two employees. In December 1991, according to the same
provision of the Unification Treaty, the Bundestag approved the “Stasi
Records Law,” which granted the access to the records. The law was
passed by a broad coalition of CDU, FDP, and SPD deputies, with abstentions
from the PDS and the Green Party. Its famous Paragraph 32
regulates the unlimited access to “documents without personal information”
and to “copies of documents with personal information rendered
anonymous.” The other personal information that the Gauck Agency was
allowed and obliged to release can be divided into three categories: documents
with written consent of the person concerned, documents with
personal information about employees and beneficiaries of the MfS, and
“information about persons of contemporary history or holders of political
office, as far as they are not directly or indirectly affected persons.”
This curious, obscure definition distinguishes between guilty parties,
who were not supposed to benefit from the law, and three categories of
victims: “persons directly affected,” i.e., those deliberately targeted by the
MfS, “indirectly affected persons,” i.e., those mentioned secondarily in a
Stasi investigation, and finally a group with little claim to secrecy because
of their prominent public role—the people of contemporary history. In
46 INSTITUTIONS OF PUBLIC MEMORY
1996, the law was amended to insure that “the secrecy of mail, correspondence,
and telecommunications [would] be limited due to this act.”
In the ten years that followed, millions of applicants gained access to
the Stasi files through this law. The Gauck (now, Birthler) Agency today
has thousands of employees organizing the access to the Stasi files, which
are located in the central archives of the former MfS in Berlin and in
various regional archives. A special department (“Research and Education”)
pursues scholarly research, organizes conferences, and publishes
monographs; Mielke’s state security apparatus has thus become one of
the best investigated parts of the former dictatorship. The Stasi records,
encompassing more than 500,000 feet of documents, are in principle open
to all interested researchers. The public became used to the flood of
revelations that emerged from the reading of the Stasi files by former
victims and journalists; thousands of the Stasi’s “unofficial employees”
were exposed. The law proved to be one of the rare legacies of the East
German grassroots citizens movement that survived reunification—it
turned out to be a tremendous success.
But at the end of ten years, the very same law was widely criticized.
This unexpected situation arose when, through a series of legal moves,
former chancellor Helmut Kohl forced the Federal Commissioner to seal
all Stasi documents relating to him and his political role. The law underwent
a series of transformations that restricted the access to the Stasi
documents, thereby undermining the basis for public information about
the GDR. Henceforth, scholarship on the MfS and other facets of the
“second German dictatorship” could not reach the standard of former
investigations for lack of source material. How can this unexpected turn
be explained, especially since it occurred at the same time a general
interest in coming to terms with the past—from the Herero massacre to
the Holocaust—stood out as a phenomenon in Germany and elsewhere?
The first explanation is the political background to the quarrel. It
began at the end of 1999, just when the donation scandal of the CDU
rattled the political sphere like an earthquake. For weeks it threatened to
split the conservative party. The coincidence was no accident. In the slow
process of sifting unknown material in the files of the MfS, the Federal
Commissioner had come across protocols of “bug activity” and recordings
of telephone calls emanating from the inner circles of the West German
government in the 1970s and 1980s. This material seemed to contain
some evidence of the attitude of CDU leaders in the party donation case
and therefore drew unusual attention. Once it was made public, it led to
critical questions from journalists and from the Ministry of the Interior
under Otto Schily. These critics were concerned that the effort to come to
terms with the GDR legacy interfered with politics in the Federal Republic.
Gauck retreated a bit and made his position on the law and files more
THE QUARREL OVER THE STASI FILES 47
precise: the agency would no longer make public any original protocols
of the “illegally” bugged conversations but would still make the Stasi
summaries accessible. In April 2000, Kohl applied to inspect his personal
files. In November, he demanded that the agency withhold any material
that concerned him until he had personally reviewed it.
Personal factors also must have played an important role. No one
involved in the matter appeared open to compromise, and all acted with
remarkable stubbornness. For Gauck’s successor Marianne Birthler, the
situation was extremely difficult. As a newcomer, she had to prove she
was capable of replacing the hero Gauck and managing the crisis. The
quarrel enabled Kohl, who had lost political power and now risked tarnishing
his personal reputation, to distract public attention from the central
issues of the donation scandal. For his part, Otto Schily had the
opportunity to return to his roots as a state defense lawyer.
Birthler remained firm. She stated that the agency was obliged to
release requested material according to the law and that she could not
grant individuals the privilege of personally vetting these materials as
this would affect the access rights of historians and the media. As expected,
Kohl appealed to the Administrative Court on November 27 to
prevent any release of documents concerning him. Birthler, in return,
decreed that those concerned would be informed before “their” documents
were made accessible to allow them to object. But this half-hearted
move did not help. In July 2001, Kohl was handed a full victory in court;
his files had to be kept secret. The court ruled that “persons of contemporary
history” are also protected.
Days later, Otto Schily came forward with an unusual measure, the
“high noon ultimatum”: He would take legal action against the Federal
Commissioner if she continued to release documents to the public. When
an appeals court, the Federal Administrative Court, upheld the earlier
ruling that restricted personal information about Kohl and, consequently,
every concerned individual who had not been a Stasi member, Birthler
changed her tactics. She closed all exhibitions, all information and documentation
centers about the Stasi, shut down the agency’s web site, and
denied nearly all applications for historical research. Her actions elicited
a protest from the Simon Wiesenthal Center in Jerusalem, which accused
the authorities of blocking access to Nazi-related documents in the
MfS archive. The scholarly community also reacted with dismay when
Birthler stated in April 2002 that most of the 2,000 current requests for
research had to be postponed or refused in the wake of the Kohl decision.
In an article, Birthler explained that henceforth “historical research using
Stasi documents is possible only within narrow limits.”1 Experts criticized
the drastic and far-reaching restrictions on scholarly work, which
prompted the Bundestag to amend the law. In July 2002, the Bundestag
48 INSTITUTIONS OF PUBLIC MEMORY
approved the amendment with the SPD, Greens, and FDP voting against
the CDU.
In September 2003, the Berlin Administrative Court approved a petition
by the Birthler Agency to make the Kohl documents public, in
principle, without violating his constitutional rights. But even this seemingly
clear ruling was not the last word. Kohl lodged an appeal and, in
June 2004, the Federal Administrative Court reached a final compromise
on Stasi material relating to individuals of contemporary history. The
court ruled that no information concerning the private lives of these
persons could be made public. The court extended this limitation to all
tapes and verbatim protocols of illegal listening in private or official
rooms and—this was new—to all internal Stasi reports, analyses, and
interpretations based on such protocols; all information collected through
spying was restricted. Moreover, the court tightened limits on who could
apply to see the information: only scholars working on the history of the
Stasi could request information, and they had to insure that this information
would neither be published nor communicated to others. Personal
information could no longer be released for educational purposes or to
the media without the written consent of the person concerned.
It is difficult to decide who finally won the quarrel over the Stasi files,
Kohl or Birthler. Both declared victory. The court assigned one third of
the costs to Kohl and two thirds to Birthler. Newspaper editorials and the
German Journalists Union deplored the consequences for historians of
the GDR. Birthler declared that the ruling would undermine many scholarly
projects but would still allow for the release of most of the Kohl
papers. In order to decide the question of victory, we have to dig a little
bit deeper. The dynamics of the quarrel may be explained by the transformation
of an administrative conflict into a highly personal struggle
between Kohl and Birthler, but this obscures the broader cultural implications
of the conflict as an indicator of the state of affairs since reunification.
Taking a closer look, the original statute opened “access to the
records of the Ministry of State Security of the former GDR to the public
and to individuals in order to clarify and illuminate the practices of State
Security,”2 in other words, to delegitimize the SED dictatorship and to
educate the population. Here, the basic tension between a presumed
public interest and the sphere of individual rights, a conflict between the
demands of historical appraisal and the protection of personal data as
required by law, is already apparent. The customary declassification
waiting period of thirty years was not implemented for East German
archives, with the interesting exception of the documents of the GDR
Ministry of Foreign Affairs. The Stasi files were not considered part of the
“ordinary” political heritage which should belong to the public after the
THE QUARREL OVER THE STASI FILES 49
end of the ordinary time limit. Therefore, the use guidelines always followed
political rather than legal or archival considerations.
General restrictions had always existed regarding access to the documents
of supranational organizations, foreign countries, and files relating
to intelligence gathering, counter-intelligence, and terrorism. Additionally,
the original law for the Stasi files included the rights of affected
persons to demand the redaction of information that concerned them. For
the same reason, users were never granted access to any index or file card.
All along, it was only the Gauck/Birthler Agency that could retrieve,
classify, and present material—often in a revised version with names and
sequences blacked out due to the privacy exemption. The employees of
the Gauck/Birthler Agency enjoy unrestricted access. Although they are
pledged to secrecy and subject to the directives of the authorities, they
can nevertheless use their privileged knowledge of names and code
names for more precise research, even in non-classified documents. They
have a lead on sources and interpretations which cannot be entirely controlled
by the scholarly community.
All of these unique customs and guidelines point to the same basic
problem. In the case of Stasi files, two different cultural norms and value
systems meet. On the one hand, the broadly acknowledged principle of
historicization—a social consensus that “the truth will heal”—urges us to
uncover the Stasi files without distinction to help shed light on the past:
“Quod est in actis, est in mundo!” By contrast, our democratic and legal
culture recognizes the individual’s right to control the use of personal
data. In that respect, it is of decisive importance how any information to
be released was obtained. It goes without saying that the Stasi’s operations
would have been considered illegal in the West. Scarcely any Stasi
report could ever be admitted in a Western court of law because it does
not conform to the legal order of a constitutional state. Here, historicization
cannot be reconciled with the rule of law. To release documents
would, in a sense, prolong the dictatorship and revictimize those injured
by Stasi espionage, but to withhold the documents might be seen as
minimizing or protecting the dictatorship.3 That is why the former
agency chief Joachim Gauck angrily commented on the first ruling in the
Kohl case that the court had disregarded the rights of a formerly oppressed
people.4 Even after the final court decision, these issues persist; it
is still possible that an endless series of questionable compromises will
cause the Administrative Court to revisit them on a regular basis.
The Stasi documents law and the establishment of the Gauck Agency
bore a Janus face. The totalitarian heritage of a state based upon surveillance
was incorporated into the political culture of a liberal constitutional
state that functions according to the rule of law. The Stasi documents law
created an exceptional situation in the service of a moral purge and the
50 INSTITUTIONS OF PUBLIC MEMORY
education of the public. The millions of requests for access are proof that
the strategy succeeded and met with the approval of the vast majority of
East and West Germans after 1990.
Why, then, did this conflict emerge so late? Marianne Birthler was
quite right when she reminded the court that her “practice of releasing
documents was never objected to by the Bundestag, which receives the
annual report of the agency, nor by the federal government, which is
legally in charge of the agency.”5 During the transition period from
spring to autumn 1990, there was no awareness of the incompatibility of
a moral/psychological purge and the prevailing privacy laws; the Bundestag
nearly unanimously adopted the Stasi files law passed by the GDR
Volkskammer in 1990. As the unification process got underway, the
difference between formal and material justice quickly became visible.
Bärbel Bohley, one of the most famous voices of the civil rights movement
in East Germany, declared, “We hoped for justice, and what we got was
the law.” Some employees of the Gauck Agency tried to use their privileged
knowledge politically, attempting, for instance, to shoot down the
last GDR prime minister Lothar de Maizière by denouncing him as Stasi
informer “IM Cerny.” But such attempts remained exceptions, and it took
years for this conflict to embroil the entire Stasi file complex.
There are at least three reasons for the lag. First, the documents
mostly concerned East Germans, who were not primarily concerned with
the problem of protecting their personal rights but with uncovering their
treatment by the Stasi. Secondly, the groups of readers who were not
personally involved—scholars, journalists, employers—were interested
in open access to the files, whereas those groups with a great interest in
restricting access—Stasi employees and collaborators—had lost their legitimacy
in the public sphere and had little opportunity to articulate their
views. Thirdly, access to the Stasi files was perhaps the only truly revolutionary
act during the collapse of the SED regime. In contrast to the
peaceful demonstrations and demands for legal travel to other countries,
the storming of the Stasi offices and the seizure of the files was an act of
open revolt, justified only by the power of the people as a natural social
force which itself establishes the law. Thus, the files became a revolutionary
symbol, an historical act of civil courage that became a point of pride
for East Germans and a legacy for a new, unified Germany—that is, until
the files went from marking Eastern assimilation to Western values to
challenging Western integrity.
From this point of view, the ongoing debate over the Stasi files is a
late product of the “crisis of unification” which emerged in the mid-
1990s. It reflects an ongoing battle between historicization and individualization
as leading social values. The conflict refutes any naïve belief in
a fast and harmonious reunification of Germany and demonstrates that a
THE QUARREL OVER THE STASI FILES 51
democracy cannot easily absorb the legacy of a dictatorship. In my opinion,
however, when this diagnosis is compared with the scandalous way
postwar Germany treated the National Socialist past in the 1950s—either
with silence or a facile coming to terms—it offers more light than shadow,
even for historians, who suffer most from the new legal status of the
partly sealed Stasi files.
Notes
1 Marianne Birthler, “Stasi-Unterlagen für Forschung und Medien—zum Rechtsstreit um
den Aktenzugang und zur Novellierung des Stasi-Unterlagen-Gesetzes,” Der Archivar 55,
no. 4 (2002): 298.
2 Marianne Birthler, “Der Zugang zu den Unterlagen des Ministeriums für Staatssicherheit
der DDR für Forschung und Medien,” Deutschland Archiv 36 (2003): 376.
3 See Birthler’s arguments in Birthler, “Stasi-Unterlagen für Forschung und Medien,” 299.
4 See Constanze von Bullion, “’Dieses Urteil ist ein Schritt zurück’. Der frühere Behördenchef
Joachim Gauck zeigt sich enttäuscht, die meisten Politiker in Berlin aber sehen ihre
Auffassung bestätigt,” Süddeutsche Zeitung, March 9, 2002.
5 Ibid.
52 INSTITUTIONS OF PUBLIC MEMORY
Month: February 2012
TOP-SECRET – Russia transferred Iranian defense system codes to Israel
The Wikileaks website is releasing more than five million documents, including intelligence-related email correspondences from the US intelligence company Stratfor. The emails are said to be between senior intelligence and military persons involved with the company from both the past and the present.
One of the emails includes information from a source that claims Israel gave Russia codes for UAVs that were sold to the Georgian army in exchange for codes for the Tor-M1 air defense system Russia sold to the Iranian army.
According to foreign publications, Iran signed an arms deal with Russia in 2005, which saw the procurement of medium-ranged air defense systems. According to the source, whose remarks were posted on Wikileaks, Russia transferred the communication codes for the systems to Israel, in exchange for codes present in the UAVs that Israel sold to Georgia.
The source is a former officer in the Mexican army, and is described as a reliable source.
Accordingly, the Georgians discovered the Russian-Israeli move, which is why they are now seeking a substitute for the UAVs they procured from Israel.
FBI unveils – Payment Processor for Internet Poker Companies Pleads Guilty in Manhattan Federal Court to Bank Fraud, Money Laundering, and Gambling Offenses
Preet Bharara, the United States Attorney for the Southern District of New York, announced that RYAN LANG, a payment processor who worked directly with senior executives from Pokerstars, Full Tilt Poker, and Absolute Poker (the “Poker Companies”), pled guilty today to money laundering, fraud, and gambling offenses in connection with a scheme to deceive banks into processing hundreds of millions of dollars in Internet gambling transactions. LANG pled guilty this morning before U.S. Magistrate Judge Theodore H. Katz.
According to the superseding information filed today in Manhattan federal court, the superseding indictment unsealed on April 15, 2011 in which LANG was initially charged, other documents previously filed in the case, and statements made in court:
In late 2006, Congress enacted the Unlawful Internet Gambling Enforcement Act (“UIGEA”), making it a crime to “knowingly accept” most forms of payment “in connection with the participation of another person in unlawful Internet gambling.” After several Internet gambling businesses withdrew from the U.S. market following the passage of the UIGEA, Pokerstars, Full Tilt Poker and Absolute Poker became the top three Internet poker operators continuing to do business in the United States. Because United States banks were largely unwilling to process Internet gambling payments, companies turned to third party payment processors, including LANG, who were willing to disguise the payments so they would appear to be unrelated to Internet gambling.
LANG worked closely with the heads of Pokerstars and Full Tilt Poker, as well as with other senior executives from all three Poker Companies, through a payment processing company that had employed him prior to the passage of the UIGEA. After its enactment, LANG left his employer and began searching for other payment processing methods that the Poker Companies could use to obtain access to the United States financial system, notwithstanding the new law. From at least 2007 through May 2010, LANG brokered a series of relationships between senior executives at the Poker Companies and various payment processors who had the ability to electronically transfer funds both to and from U.S. customer bank accounts as “electronic checks” or “e-checks.” As LANG knew—and discussed with executives from the Poker Companies—payment processors working for the Poker Companies created phony shell companies to disguise the poker transactions so that banks would not learn that the payments were connected to Internet gambling.
***
LANG, 37, a Canadian citizen and resident, voluntarily returned to the United States to face the charges pending against him. He faces a maximum sentence of 30 years in prison.
Mr. Bharara thanked the FBI for its outstanding work in the investigation, which he noted is ongoing. Mr. Bharara also thanked Immigration and Customs Enforcement’s Homeland Security Investigations’ New York and New Jersey offices for their continued assistance in the investigation.
To date, five additional defendants initially charged in the superseding indictment have appeared in the United States—Bradley Franzen, Ira Rubin, Brent Beckley, Chad Elie, and John Campos. Franzen pled guilty on May 23, 2011; Beckley pled guilty on December 20, 2011; and Rubin pled guilty on January 17, 2012. Beckley and Rubin are scheduled to be sentenced on April 19, 2012 and May 12, 2012, respectively. Charges are still pending against Elie and Campos, and they are presumed innocent unless and until proven guilty. Elie and Campos are scheduled for trial on April 9, 2012 before Judge Kaplan.
This matter is being handled by the office’s Complex Frauds Unit. Assistant U.S. Attorneys Arlo Devlin-Brown, Niketh Velamoor, Andrew Goldstein, and Nicole Friedlander are in charge of the criminal case, and Assistant U.S. Attorneys Sharon Cohen Levin, Jason Cowley, and Michael Lockard are in charge of related civil money laundering and forfeiture actions.
TOP-SECRET – U.S. Army Intelligence Support to Urban Operations Field Manual

With the continuing growth in the world’s urban areas and increasing population concentrations in urban areas, the probability that the US Army will conduct full spectrum operations in urban environments is ever more likely. As urbanization has changed the demographic landscape, potential enemies recognize the inherent danger and complexity of this environment to the attacker, and may view it as their best chance to negate the technological and firepower advantages of modernized opponents. Given the global population trends and the likely strategies and tactics of future threats, Army forces will likely conduct operations in, around, and over urban areas—not as a matter of fate, but as a deliberate choice linked to national security objectives and strategy. Stability operations––where keeping the social structure, economic structure, and political support institutions intact and functioning or having to almost simultaneously provide the services associated with those structures and institutions is the primary mission––may dominate urban operations. This requires specific and timely intelligence support, placing a tremendous demand on the Intelligence warfighting functions for operations, short-term planning, and long-term planning.
Providing intelligence support to operations in the complex urban environment can be quite challenging and may at first seem overwhelming. The amount of detail required for operations in urban environments, along with the large amounts of varied information required to provide intelligence support to these operations, can be daunting. Intelligence professionals must be flexible and adaptive in applying doctrine and tactics, techniques, and procedures (TTP) based on mission, enemy, terrain and weather, troops and support available, time available, and civil considerations (METT-TC).
As with operations in any environment, a key to providing good intelligence support in the urban environment lies in identifying and focusing on the critical information required for each specific mission. The complexity of the urban environment requires focused intelligence, and a comprehensive framework must be established to support the commander’s requirements while managing the vast amount of information and intelligence required for urban operations. By addressing the issues and considerations listed in this manual, the commander, G-2/S-2, and intelligence analyst will be able to address most of the critical aspects of the urban environment and identify both the gaps in the intelligence collection effort and those systems and procedures that may answer them. This will assist the commander in correctly identifying enemy actions so that US forces can focus on the enemy and seize the initiative while maintaining an understanding of the overall situation.
…
1-73. A population of significant size and density inhabits, works in, and uses the manmade and natural terrain in the urban environment. Civilians remaining in an urban environment may be significant as a threat, an obstacle, a logistics support problem (to include medical support), or a source of support and information. The most significant problem regarding the local population is the fact each person is a potential threat and can participate in an insurgency, terrorism, or other disruptive activity.
1-74. One of the most violent examples in US military history was the Viet Cong. The Viet Cong laid mines and demolitions, conducted ambushes and sniping, performed information collection missions for Hanoi, and even participated in force-on-force engagements, primarily during the Tet Offensive in 1968. The difficulty for the US and allied forces operating there lay in the fact that the Viet Cong looked like their neighbors, often held jobs, and raised families in pro-government neighborhoods, and, in some cases, even served in the South Vietnamese Army.
1-75. Another consideration when dealing with the local population is their ability to hinder military operations. Regardless of causes or political affiliations, civilian casualties are often the focal point of press coverage, often to the point of ignoring or denigrating any previous accomplishments. Within the operational continuum, and especially during the conduct of urban operations, commanders can expect to encounter restrictions on their use of firepower and challenges in their ability to conduct combat support and combat service support missions. In the current operational environment, it is unacceptable to our leaders and the American population to inflict large numbers of civilian casualties.
DOWNLOAD ORIGINAL FILE HERE
Money Laundering – HSBC May Face Criminal Charges For Illegal Transactions With Iranian Clients
 A pedestrian passes a branch of HSBC bank in London, Monday, Feb. 27, 2012. Buoyant trading in Asia helped HSBC Holdings PLC, Europe’s biggest bank by market value, report a 28 percent increase in full-year profit Monday, a marked contrast to the performance of other big British banks. (AP Photo/Kirsty Wigglesworth)
A pedestrian passes a branch of HSBC bank in London, Monday, Feb. 27, 2012. Buoyant trading in Asia helped HSBC Holdings PLC, Europe’s biggest bank by market value, report a 28 percent increase in full-year profit Monday, a marked contrast to the performance of other big British banks. (AP Photo/Kirsty Wigglesworth)
HSBC Reports Being Under Investigation For Illegal Money Transactions Connected With Iran
| HSBC Holdings Plc said it will likely face criminal or civil charges from an expanding investigation into its ties to allegedly illegal money transactions, including some tied to Iran.The disclosure in a regulatory filing shows the increasingly serious nature of inquiries into the London-based bank’s business.HSBC already is the subject of multiple U.S. law-enforcement probes for ties to illegal money transactions. Monday’s filing was the first time the bank disclosed that Iranian transactions are under scrutiny and that it could face a criminal charge.The bank’s HSBC USA Inc unit said investigations are being conducted by the Justice Department, the district attorney in Manhattan, two Treasury department agencies and the Federal Reserve. It said those inquiries were examining “historical transactions involving Iranian parties and other parties subject to” U.S. economic sanctions. Financial institutions doing business in the United States are prohibited from aiding sanctioned countries or banks.
In recent years, the Manhattan district attorney and Justice Department have settled with a number of European banks that operated transfer systems for Iranian clients. Banks aided clients trying to improperly move money by removing, or stripping out, references that could tip off a U.S. bank system to a transaction tied to Iran or another sanctioned state. HSBC disclosed the new details in a filing with the U.S. Securities and Exchange Commission as part of the bank’s 2011 annual results. HSBC USA provides commercial and consumer banking and operates 461 branches. The bank previously said in securities filings that it was facing inquiries and it had received grand jury subpoenas. |
HSBC Holdings plc SEC Form 6-K – February 2012 (sec.gov):
TOP-SECRET – Fukushima Daiichi Nuclear Power Station Photos 20, 28 February 2012
|
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-022012/pict35.jpg) A worker is given a radiation screening as he enters the emergency operation center at Tokyo Electric Power Co.’s tsunami-crippled Fukushima Dai-ichi nuclear power plant in Fukushima prefecture, northeastern Japan, Monday, Feb. 20, 2012. Japan next month marks one year since the March 11 tsunami and earthquake, which triggered the worst nuclear accident since Chernobyl in 1986. (Issei Kato) A worker is given a radiation screening as he enters the emergency operation center at Tokyo Electric Power Co.’s tsunami-crippled Fukushima Dai-ichi nuclear power plant in Fukushima prefecture, northeastern Japan, Monday, Feb. 20, 2012. Japan next month marks one year since the March 11 tsunami and earthquake, which triggered the worst nuclear accident since Chernobyl in 1986. (Issei Kato) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-022012/pict24.jpg) Destroyed unit 3 reactor building of Tokyo Electric Power Co.’s tsunami-crippled Fukushima Dai-ichi nuclear power plant is seen in Fukushima prefecture, northeastern Japan, Monday, Feb. 20, 2012. (Issei Kato) Destroyed unit 3 reactor building of Tokyo Electric Power Co.’s tsunami-crippled Fukushima Dai-ichi nuclear power plant is seen in Fukushima prefecture, northeastern Japan, Monday, Feb. 20, 2012. (Issei Kato) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-022012/pict29.jpg) Workers wearing protective suits and masks work atop of No. 4 reactor building of Tokyo Electric Power Co.’s tsunami-crippled Fukushima Dai-ichi nuclear power plant in Fukushima prefecture, northern Japan, Monday, Feb. 20, 2012. (Issei Kato) Workers wearing protective suits and masks work atop of No. 4 reactor building of Tokyo Electric Power Co.’s tsunami-crippled Fukushima Dai-ichi nuclear power plant in Fukushima prefecture, northern Japan, Monday, Feb. 20, 2012. (Issei Kato) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-022012/pict25.jpg) A worker wearing protective suit and mask works atop of destroyed unit 4 reactor building of Tokyo Electric Power Co.’s tsunami-crippled Fukushima Dai-ichi nuclear power plant in Fukushima prefecture, northeastern Japan, Monday, Feb 20, 2012. (Issei Kato) A worker wearing protective suit and mask works atop of destroyed unit 4 reactor building of Tokyo Electric Power Co.’s tsunami-crippled Fukushima Dai-ichi nuclear power plant in Fukushima prefecture, northeastern Japan, Monday, Feb 20, 2012. (Issei Kato) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-022012/pict26.jpg) Tokyo Electric Power Co.’s reactor buildings, from right, No.4, No.3, and No.2 [damaged No.2 has been enclosed, see following photo], are seen at tsunami-crippled Fukushima Dai-ichi nuclear power plant in Fukushima prefecture, northeastern Japan, Monday, Feb. 20, 2012. (Issei Kato) Tokyo Electric Power Co.’s reactor buildings, from right, No.4, No.3, and No.2 [damaged No.2 has been enclosed, see following photo], are seen at tsunami-crippled Fukushima Dai-ichi nuclear power plant in Fukushima prefecture, northeastern Japan, Monday, Feb. 20, 2012. (Issei Kato) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-022012/pict31.jpg) The unit 2 reactor building of Tokyo Electric Power Co.’s tsunami-crippled Fukushima Dai-ichi nuclear power plant is seen through a bus window during a press tour in Fukushima prefecture, northeastern Japan, Monday, Feb. 20, 2012. (Issei Kato) The unit 2 reactor building of Tokyo Electric Power Co.’s tsunami-crippled Fukushima Dai-ichi nuclear power plant is seen through a bus window during a press tour in Fukushima prefecture, northeastern Japan, Monday, Feb. 20, 2012. (Issei Kato) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-022012/pict28.jpg) Tokyo Electric Power Co.’s tsunami-crippled Fukushima Dai-ichi nuclear power plant is seen from bus window during a press tour in Fukushima prefecture, northeastern Japan, Monday, Feb. 20, 2012. (Issei Kato) Tokyo Electric Power Co.’s tsunami-crippled Fukushima Dai-ichi nuclear power plant is seen from bus window during a press tour in Fukushima prefecture, northeastern Japan, Monday, Feb. 20, 2012. (Issei Kato) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-022012/pict34.jpg) Workers wearing protective suits and masks construct water tanks, seen through a bus window during a press tour at Tokyo Electric Power Co.’s tsunami-crippled Fukushima Dai-ichi nuclear power plant in Fukushima prefecture, northeastern Japan, Monday, Feb. 20, 2012. (Issei Kato) Workers wearing protective suits and masks construct water tanks, seen through a bus window during a press tour at Tokyo Electric Power Co.’s tsunami-crippled Fukushima Dai-ichi nuclear power plant in Fukushima prefecture, northeastern Japan, Monday, Feb. 20, 2012. (Issei Kato) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-022012/pict33.jpg) Unit 6, left, and unit 5 reactor buildings of Tokyo Electric Power Co.’s tsunami-crippled Fukushima Dai-ichi nuclear power plant are seen through a bus window during a press tour in Fukushima prefecture, northeastern Japan, Monday, Feb. 20, 2012. (Issei Kato) Unit 6, left, and unit 5 reactor buildings of Tokyo Electric Power Co.’s tsunami-crippled Fukushima Dai-ichi nuclear power plant are seen through a bus window during a press tour in Fukushima prefecture, northeastern Japan, Monday, Feb. 20, 2012. (Issei Kato) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-022012/pict32.jpg) Trucks are overturned before the Unit 4 reactor building of stricken Fukushima Dai-ichi nuclear power plant of Tokyo Electric Power Co., in Okuma town, Fukushima prefecture, northeastern Japan Tuesday, Feb. 28, 2012. (Yoshikazu Tsuno) Trucks are overturned before the Unit 4 reactor building of stricken Fukushima Dai-ichi nuclear power plant of Tokyo Electric Power Co., in Okuma town, Fukushima prefecture, northeastern Japan Tuesday, Feb. 28, 2012. (Yoshikazu Tsuno) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-022012/pict27.jpg) Stricken Fukushima Dai-ichi nuclear power plant buildings of Tokyo Electric Power Co., are seen in Okuma town, Fukushima prefecture, northeastern Japan Tuesday, Feb. 28, 2012. (Yoshikazu Tsuno) Stricken Fukushima Dai-ichi nuclear power plant buildings of Tokyo Electric Power Co., are seen in Okuma town, Fukushima prefecture, northeastern Japan Tuesday, Feb. 28, 2012. (Yoshikazu Tsuno) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-022012/pict30.jpg) A journalist checks radiation level with her dosimeter near stricken Fukushima Dai-ichi nuclear power plant of Tokyo Electric Power Co., during a press tour led by TEPCO officials, in Okuma town, Fukushima prefecture, northeastern Japan Tuesday, Feb. 28, 2012. (Yoshikazu Tsuno) A journalist checks radiation level with her dosimeter near stricken Fukushima Dai-ichi nuclear power plant of Tokyo Electric Power Co., during a press tour led by TEPCO officials, in Okuma town, Fukushima prefecture, northeastern Japan Tuesday, Feb. 28, 2012. (Yoshikazu Tsuno) |
Uncensored – FEMEN topless – ” F*** you !”
TOP-SECRET – U.S. Army Intelligence Analysis Training Manual

THE OPERATIONAL ENVIRONMENT
America has entered an era of persistent conflict where states, nations, transnational actors, and nonstate actors are increasingly willing to use violence to achieve their political and ideological ends. These entities will continue to challenge and redefine the global distribution of power, the concept of sovereignty, and the nature of warfare. Globalization, technology, population growth, urbanization, and demand for natural resources are creating an environment where the location of the next crisis requiring American intervention is not always predictable. Generally with little notice, Army units will be employed in complex and multidimensional environments; usually fought in urban terrain among noncombatant populations. Additionally, they will be called on to conduct full spectrum operations as part of an interdependent joint force conducting simultaneous offensive, defensive, and stability operations. See FM 3-0 for a detailed description of the operational environment.
THE THREAT ENVIRONMENT
FM 3-0 defines threats as nation-states, organizations, people, groups, conditions, or natural phenomena able to damage or destroy life, vital resources, or institutions. There are four major threat categories intelligence analysts must assist the commander and staff in understanding:
• Irregular threats are characterized as entities seeking to erode U.S. power through protracted struggle. Radical fundamentalists, transnational terrorists, and guerrilla forces are examples of irregular threat. These groups will employ unconventional and asymmetric methods and means to counter U.S. advantages. Irregular warfare includes terrorism, insurgency, and guerilla warfare.
• Traditional threats emerge from states employing recognized military capabilities and forces in understood forms of military competition and conflict.
• Catastrophic threats involve the acquisition, possession, and use of chemical, biological, radiological, nuclear, and high-yield explosives (CBRNE) weapons.
• Disruptive threats involve an enemy using new technologies to reduce U.S. advantages in key operational domains.
Army units are likely to face any combination of these threats when deployed. By combining irregular, traditional, catastrophic, and disruptive capabilities, adversaries will seek to create advantageous conditions by changing the nature of the conflict from one where U.S. forces can effectively use size, firepower, and technology to its advantage to one where adversaries can use low technology solutions and control of key and decisive terrain to gain and maintain the initiative.
U.S. forces may be employed under the following five types of operational themes across the spectrum of conflict; each with its own unique threat environment:
• Peacetime military engagement comprises all military activities that involve other nations and are intended to shape the security environment in peacetime. Examples include multinational training exercises, security assistance, joint combined exchange training, recovery operations, arms control, and counterdrug operations. Combat is not likely during these operations, but terrorist attacks are always possible and force protection and operations security (OPSEC) are major concerns.
• Limited interventions are executed to achieve an end state that is clearly defined and limited in scope. They are normally conducted by joint task forces. Examples of limited interventions are noncombatant evacuation, raids, show of force, foreign humanitarian assistance, consequence management, sanction enforcement, and elimination of weapons of mass destruction (WMDs). Like peacetime military engagement, combat is not likely. However, the threat of terrorist attacks is possible, as are attacks from the general population. Force protection, OPSEC, and targeting operations are major concerns.
• Peace operations is a broad term that encompasses multiagency and multinational crisis response and limited contingency operations. The primary purpose of peace operations is to create a safe and secure environment, deter adversaries from overt actions against each other, and provide time for civilian agencies to generate a self-sustaining peace. Peace operations include peacekeeping, peace building, peacemaking, peace enforcement, and conflict prevention. Peace operations normally occur in complex environments. They are characterized by asymmetric threats, a failing government, absence of the rule of law, terrorism, human rights abuses, collapse of civil infrastructure, and the presence of dislocated civilians. Attacks by insurgent and terrorist groups are likely, and U.S. forces may conduct limited offensive operations against these groups in support of stability operations.
• Irregular warfare is a violent struggle among state and nonstate actors for legitimacy and influence over a population. It differs from conventional operations in two aspects. First, it is warfare among and within the people. Second, it emphasizes an indirect approach. Irregular warfare avoids direct military confrontation. Instead, it combines irregular forces and indirect unconventional methods to exhaust the opponent. Types of operations U.S. forces may be employed in to counter irregular warfare are foreign internal defense, support to insurgency, counterinsurgency (COIN), combating terrorism, and unconventional warfare. Traditionally, these missions are conducted by special forces. However, if special forces and host-nation (HN) forces cannot defeat unconventional and irregular threats, conventional Army forces can assume the lead role. Operation Iraqi Freedom and Operation Enduring Freedom are good examples of this.
• Major combat operations occur in circumstances usually characterized by general war and combat between large formations. In this instance, U.S. forces are normally involved in offensive or defensive operations as part of a larger joint force. Major combat operations are the operational theme for which doctrine, including the principles of war, was originally developed. The intelligence analyst provides doctrinal intelligence support to major combat operations in accordance with FM 2-0.
…
THE INTELLIGENCE WARFIGHTING FUNCTION
1-1. The intelligence warfighting function is the related tasks and systems that facilitate understanding of the operational environment, enemy, terrain, and civil considerations (FM 3-0). It includes tasks associated with intelligence, surveillance, and reconnaissance (ISR) operations, and is driven by the commander. Intelligence is more than just collection. It is a continuous process that involves analyzing information from all sources and conducting operations to develop the situation. The intelligence warfighting function is comprised of the following four primary Army intelligence tasks that facilitate the commander’s visualization and situational understanding of the operational environment:
- Support to force generation.
- Support to situational understanding.
- Perform intelligence, surveillance, and reconnaissance.
- Support to targeting and information superiority.
1-2. Intelligence analysis is a process that is focused by the tasks established by the intelligence warfighting function and described in FM 2-0. Intelligence analysts at all levels must understand the task and purpose of the intelligence warfighting function, be proficient in the subtasks articulated in FM 2-0, and know how intelligence analysis relates to military planning and operations. See FM 2-0 for a detailed discussion of the intelligence warfighting function. See FM 5-0 for a detailed discussion of military planning and operations.
THE INTELLIGENCE ANALYST
1-3. To effectively execute missions across the full spectrum of military operations, the commander requires intelligence about the enemy and other conditions of the operational environment prior to and during operations. The operational environment is a composite of the conditions, circumstances, and influences that affect the employment of capabilities and bear on the decision of the commander (JP 3-0). The operational environment encompasses physical areas and factors of the air, land, maritime, and space domains. It also includes the information environment and enemy, adversary, friendly, and neutral systems.
1-4. The analyst is directly responsible for aiding the commander’s understanding of how current and potential enemies organize, equip, recruit, train, employ, and control their forces. The analyst also aids the commander’s understanding of the terrain and weather and their effects upon both friendly and enemy operations. This includes the military aspects of the terrain and weather as well as civil considerations.
…

DOWNLOAD ORIGINAL FILE HERE
CONFIDENTIAL from the MOSSAD – Master Spy Hanssen – Internet & Computers
| USDOJ OIG Special Report: A Review of the FBI’s Progress in Responding to the Recommendations in the Office of the Inspector General Report on Robert Hanssen 9/07 |
![]()
| Hanssen Hacking Heritage – Philippine Style in FBI Systems July 2007 |
 |
![]()
| Master Spy Hanssen : Internet & Computers |
| UPDATE 2/3/07 – The Movie “Breach,” Opened in Theaters |
| Outside The Movie “Breach” : To Catch A Spy – The Wrong CIA Man – |
| 3/2/2007 9:59:53 AMEric O’Neill, Former FBI Agent, Robert Hanssen Case
Eric O’Neill, Former FBI Agent, Robert Hanssen Case gives a detailed look into the Robert Hanssen spy case. Mr. O’Neill was an FBI agent involved in catching Mr. Hanssen. The FBI forbade Mr. O’Neill to speak publicly until recently. Mr. O’Neill served as a special consultant to the movie “Breach,” which opened in theaters. |
 |
 |
| Official Website of The Movie “Breach” |
| New movie shows FBI rookie’s role in catching spy WASHINGTON (Washingtonpost/Reuters) – Eric O’Neill was a young,FBI surveillance operative when recruited for a new assignment: help catch perhaps the most damaging spy in U.S. history. O’Neill was assigned to FBI headquarters in January 2001 in an undercover role to assist veteran FBI special agent Robert Hanssen, a suspected mole who had been compromised by the Russians.An FBI team of hundreds investigating Hanssen hoped the 26-year-old O’Neill, who was not even an agent, would gain Hanssen’s trust and help catch him in the act of passing U.S. secrets.Hanssen’s arrest six years ago, his subsequent guilty plea to more than 20 years of spying and his sentence of life in prison are well known, but details of O’Neill’s role were scarce until the recent release of the movie “Breach,” based on his story.In the Universal Pictures’ film, actor Ryan Phillippe stars as O’Neill, while Academy Award winner Chris Cooper plays Hanssen.In an interview, O’Neill talked about the notorious case now made famous by Hollywood, saying he was amazed the FBI would bring in someone so young for such a mission.”These cases come up once every several decades,” O’Neill said.FBI officials said O’Neill’s background in computers helped get him the assignment. Hanssen was reassigned on January 13, 2001, to a newly created job at headquarters to help revamp the FBI’s computer system.But the assignment created so the FBI team could monitor Hanssen’s daily activities without tipping him to their investigation.”We hoped he (O’Neill) could pull it off without arousing suspicion,” said one FBI agent. “They took a chance on him.”At one point, O’Neill almost got caught in one of the movie’s most dramatic scenes.
‘THAT WAS THE WORST’ Hanssen left his office as arranged to go to the FBI’s firing range. Hollywood enhanced the story line to have him also lose patience at a picture-taking session for a portrait to commemorate 25 years with the bureau.While the veteran agent was gone, O’Neill took Hanssen’s Palm Pilot and copied information but nearly got caught because he almost put it back in the wrong pocket of Hanssen’s briefcase.”I sat there thinking I’ve just ruined this entire operation,” O’Neill said. “That was the worst.”It turned out O’Neill had put the hand-held device back in the correct pocket. Hanssen asked him if he had been in his briefcase. “I just lied the best I could and convinced him,” O’Neill said.Court documents said the device contained a specific upcoming date, time and reference to the site in nearby Virginia where Hanssen and the Russians exchanged information. The details led to Hanssen’s arrest.In another scene, O’Neill had to keep Hanssen away from headquarters so FBI agents could search his car. The quick-thinking O’Neill first got them stuck in a traffic jam and then convinced Hanssen to get back into the car instead of walking back to headquarters. The evidence obtained from that search included secret documents about ongoing FBI counterintelligence investigations, among other things, according to the court records. The government contended Hanssen’s disclosures were among the most damaging ever to U.S. interests. O’Neill could not even tell his wife, Juliana, about the real purpose of his mission, which created tension in their new marriage. “It was very difficult to lie to her, but I was required to. That just goes with the job,” O’Neill said. After Hanssen’s arrest on February 18, 2001, O’Neill went back to his old job and decided to leave the FBI in May 2001. In the movie, he packed up his desk on the day Hanssen was arrested. “The hardest decision I made was to leave the FBI,” O’Neill said. “I just decided that this wasn’t the sort of life I wanted to live.” A graduate of George Washington University law school, he now works for a law firm in Washington, specializing in national defense. The movie provided no definitive reason why Hanssen sold out his country for $1.4 million in cash and diamonds. It does have Hanssen speculating after his arrest that another American spy might have acted because of ego or an urge to expose lax U.S. security. |
 |
| 1. Jailing in Russia of Supermole Following Hanssen Arrest – Unique exposure15/6/03 – Moscow revealed that a Russian intelligence officer who had settled in the United States had been lured back home and arrested.Aleksandr Zaporozhsky, a former colonel in the S.V.R., Russia’s foreign intelligence service, has been sentenced to 18 years in jail for spying for the United States, Russian officials disclosed.Mr. Zaporozhsky had been living in Maryland but in November 2001 was somehow induced to return to Moscow, where he was quietly arrested and jailed.Russian news reports of his sentencing suggested that he had been drawn into an ambush because he was suspected of helping the United States identify and arrest Robert P. Hanssen, who admitted to being a Russian mole inside the F.B.I. In addition to the Russian news media, The Los Angeles Times reported on Mr. Zaporozhsky’s case .Apart from the timing of Mr. Hanssen’s arrest, which occurred several months before Mr. Zaporozhsky was seized in Moscow, there is no available evidence to support the Russian news accounts that Mr. Zaporozhsky played a role in the Hanssen case. C.I.A. officials declined to comment on the matter.Russian FSB investigators believe that agents inside their own intelligence service provided information that led to the arrests of Aldrich H. Ames and Mr. Hanssen, the two most important Russian spies discovered in the past decade inside the American government.In the Hanssen case, the Federal Bureau of Investigation has acknowledged that it received information from a Russian source that led to Mr. Hanssen’s arrest. That source is not the same person who provided help in the Ames case, officials said. The Russian source in the Hanssen case provided files and other materials from Russian intelligence archives that identified Mr. Hanssen as a longtime spy for Moscow. Among the materials the source provided was the plastic that Mr. Hanssen had used to wrap classified F.B.I. documents when he left them for the Russians at clandestine drop sites in the Washington area. After obtaining the plastic from the Russian source, the bureau found Mr. Hanssen’s fingerprints on the wrapping. After handing over the files used in the Hanssen case, the Russian source defected and was paid $7 million by the United States for his assistance, according to a book about the case by David Wise. The Russian’s identity remains a closely guarded secret in the United States government.American officials believe Russian intelligence is still concentrating on the United States, aggressively trying to recruit American spies who can hand over technical, economic and political secrets. 2. Jailing in Russia of Supermole After Hanssen Arrest – Russian TV Combined Video Many stories have emerged about how the CIA tracked down Hanssen.According to this Russian version – Investigation on Alexander’s Zaporozhsky business last almost one and a half year. 30 witnesses, the majority of them – operating(working) and former employees of the Russian FSB. The judge of the Moscow district military court has read a verdict of one and a half hour, journalists have allowed to be present only on in the final part. All rest – the state secret. The head of the Center of public relations of FSB Sergey Ignatchenko said: ” If it was in the USA, at least, he could get life imprisonment , or electric chair “. |
 |
| Hanssen Photos |
| Russian Version |
 Robert Philip Hanssen Robert Philip Hanssen
|
|
 |
 |
| “ELLIS” Drop SiteOn the “Foxstone Park” sign. | “ELLIS” Drop SiteUnder a footbridge over Wolftrap Creek near Creek Crossing Road at Foxstone Park near Vienna, Virginia. |
 |
 |
| “ELLIS” Drop SiteUnder a footbridge over Wolftrap Creek near Creek Crossing Road at Foxstone Park near Vienna, Virginia. | “ELLIS” Drop SitePackage dropped by Hanssen at the Ellis drop site on 2/18/01. |
 “LEWIS” Signal SiteWooden utility pole located at the North-West corner of the intersection of 3rd Street and Carlin Springs Road near the metrobus stop. |
|
 |
 |
| “LEWIS” Drop SiteThe far-left corner of the wooden podium (when facing the podium) located in the amphitheater of Long Branch Nature Center. | “LEWIS” Drop SitePackage recovered at the Lewis drop site containing $50,000 cash left by Russians for Hanssen. |
| Outside The Movie “Breach” : Hanssen E-Mails |
 |
 |
| Hanssen`s FBI Lab Report |
| Hanssen`s FBI Affidavit |
 |
 |
| Hanssen – A Hacker in KGB Defector Internet Security Firm |
| Accused FBI turncoat Robert Hanssen wanted to retire into a job selling anti-hacker technology to the government to guard against double agents a former CIA director said . James Woolsey, who led the CIA under former President Bill Clinton, said Hanssen pushed for a job with Invicta Networks, a firm founded by Soviet KGB defector Viktor Sheymov to develop hack-proof computer software for U.S. spy agencies.”Hanssen twice aggressively expressed an interest to Invicta executives on being employed by Invicta following his retirement from the FBI,” said Woolsey, who is on Invicta’s board and also serves as Sheymov’s attorney.Hanssen, who allegedly used his computer expertise to hack into FBI files for secrets to sell to Moscow, also boasted to FBI colleagues about getting a big-bucks job when he retired, according to an FBI affidavit. In February 1988, Hanssen told his Soviet handlers that he could read the FBI’S files on Sheymov’s debriefings, the affidavit said. More recently, “Hanssen told FBI co-workers that he was considering an offer of lucrative employment by Sheymov after retirement in April,” the affidavit said. Woolsey declined to discuss the Hanssen-Sheymov connection in a brief phone conversation . But in a statement faxed to the Daily News (2001 URL) , he said Hanssen met Sheymov in the 1980s and “since that time, the Sheymov and Hanssen families indeed came to be on friendly terms.” The families had little contact in recent years, but in December, Hanssen “expressed keen interest in Invicta’s technology,” Woolsey said.Three weeks before he was arrested Sunday, Hanssen “was briefed on the Invicta technology” as part of his official duties along with several other FBI computer experts, Woolsey said. Sheymov was a rising star and the youngest major in the KGB at age 33 when he defected to the U.S. in 1980 with his wife and daughter. His defection was considered one of the CIA’s major Cold War coups. Hanssen, 56, has been charged with espionage crimes carrying the death penalty for allegedly selling secrets to the Soviets and later the Russians for at least $1.4 million in 15 years as a mole. |
VIDEO – SVR/KGB Defector Col. Sergei Tretyakov Angered Russia Spies
WIKILEAKS UNVEILS – Siemens “Intelligence Plattform”
DOWNLOAD ORIGINAL FILE BELOW
CONFIDENTIAL – U.S. Army Military Intelligence Reference Guide

Currently, the intelligence warfighting function includes a formidable set of capabilities across all echelons from “mud-to-space.” This flexible force of personnel, organizations, and equipment collectively provides commanders with the timely, relevant, accurate, predictive, and tailored intelligence they need. We provide the intelligence that continuously supports the commander in visualizing the operational environment, assessing the situation, and directing military actions through ISR synchronization and the other intelligence tasks.
The intelligence warfighting function is comprised of nine powerful intelligence disciplines. Eight of those disciplines essentially feed the discipline of all-source intelligence which in turn is focused on the commanders’ requirements. Technological advances have enabled single-discipline analysts to leverage other analysts and information and to conduct multi-discipline analysis to an extent not possible in the past. However, all-source intelligence is still the nexus that integrates information and intelligence from all units and the other intelligence disciplines.
Future operational environments will be greatly impacted by globalization. “Globalization and growing economic interdependence, while creating new levels of wealth and opportunity, also creates a web of interrelated vulnerabilities and spreads risk even further, increasing sensitivity to crises and shocks around the globe and generating more uncertainty regarding their speed and effect” according to the National Defense Strategy, June 2008.
Key aspects of globalization include—
• Non-state groups, organized crime, and cultural and environmental change will stress already fragile social and political structures.
• American science and technology (S&T) communities, both commercial and Department of Defense (DOD), will compete with some growing economies for technical advantage.
• By 2020, organized crime is likely to thrive in resource-rich states now experiencing political and economic transformation.
• By 2025, urban growth will concentrate in coastal areas. The majority of urban populations will live within 60 miles of coastlines.
• By 2030, the world’s urban population will be over 4.9 billion fostering—
• Interdependent economies.
• The interaction of differing societies and cultures.
• More powerful non-state actors.
• Porous international boundaries.
• The inability of some nation-states to fully control their territory, economy, and to provide security and services.
• By 2030, competition for access to and control of natural resources (energy, water, and food) will dramatically increase areas of potential conflict.
• “ … Cyber security risks pose some of the most serious economic and national security challenges of the 21st Century” according to the Presidential Cyberspace Policy Review, May 2009.
The Joint Operational Environment 2010 observes that, “With very little investment, and cloaked in a veil of anonymity, our adversaries will inevitably attempt to harm our national interests. Cyberspace will become a main front in both irregular and traditional conflicts. Enemies in cyberspace will include both states and non-states and will range from the unsophisticated amateur to highly trained professional hackers. Through cyberspace, enemies will target industry, academia, government, as well as the military in the air, land, maritime, and space domains.”
In future operational environments as U.S. forces conduct increasingly complex operations Army intelligence will continue to prove even more critical by providing Army warfighting commanders with predictive, knowledge-based intelligence. As stated in the National Intelligence Strategy, August 2009, the Intelligence Community (IC) must “Operate as a single integrated team, employing collaborative teams that leverage the full range of IC capabilities to meet the requirements of our users, from the President to deployed tactical military units.”



Unveiled – Iran Cyber Police
Column of Former Mossad Chief Danny Yatom – The No Choice Attack Against Iran

Danny Yatom Major General (ret.) Danny Yatom is Chairman and CEO of GSG Ltd. He was a Member of Knesset (Israeli Parliament), Head of the Mossad and chief of staff to the prime minister
Much has recently been discussed on the need to attack Iran’s nuclear facilities. One thing should be made clear in advance: the implications of such an attack and Iran’s response, including missiles and rockets fired from the north, would be far less destructive than if Iran unleashed a nuclear bomb on Israel.
Some people are voicing sharp opposition to a military strike against Iran, claiming it would signal a regional war of unforeseen magnitude. This is their perspective, and there is nothing wrong with public discourse on the issue. However, it is imperative to recognize that Israel will pay a heavy price for an attack on Iran, regardless of the aggressor’s identity. If sanctions and other restrictions do not convince Iran to halt its race for nuclear power, then the question of a military strike will rise to the top of Israel’s agenda.
We must not allow Iran to obtain a nuclear weapon that poses an existential threat to Israel—a situation in which we will wake up every morning wondering whether a nuclear bomb will fall on us because somebody in Iran got up on the wrong side of the bed. The damage from a nuclear bomb on Israel would be catastrophic.
We are not dealing with a rational regime that makes sound political decisions. It is a regime headed by a spiritual leader who acts according to his personal interpretation of the Koran. What’s more, Ahmadinejad repeatedly calls for erasing Israel off the map. Who can guarantee that when he secures a nuclear bomb, he won’t use it on us?
We cannot gamble on our future by relying on the assessments or wishful thinking of those who believe that diplomatic pressure will force the Iranians to relinquish their quest for nuclear capability. These assessments assume that Iran is a rational regime, which is not the case. In the meantime, recent Western-led sanctions against Iran’s financial institutions seem to only “itch” the Islamic Republic, and Russia and China, two countries with close commercial ties to Tehran (including weapons sales) are opposed to crippling their Middle Eastern economic partner.
After Iran is attacked, we will suffer through the consequences, which might include rocket barrages from Lebanon and Gaza. However, our retaliation will be so painful and so devastating that, in my opinion, the enemies’ aggression will quickly come to an end. Likewise, although we will have to strike civilian infrastructure and public facilities throughout Lebanon and Gaza, rockets will no longer threaten the citizens of Israel.
The world must realize time is running out. As of now, everything depends on the Iranian’s decision to produce a bomb. They already have the knowledge and material—it is only a matter of time (a year at most) from when they give the green light. Therefore, from my point of view, sanctions—no matter how harsh—will not bring the desired results. In the same way, secret operations like the mysterious explosions at Iranian bases and the assassination of scientists and senior figures from their missile program will not deter Iran’s leaders, for they are determined to attain a nuclear weapon. An attack on Iran’s nuclear facilities should only be done as a last resort. Assuming that sanctions and other efforts will fail to stop the Iranians, the only alternative will be to strike.
The world must understand that this is a global problem and not just Israel’s problem—Israel should not have to be forced to initiate a military strike. Still, we must make it clear that if the world is unwilling to intervene, then Israel has a moral obligation to protect itself.
TOP-SECRET – U.S. Army Human Terrain Report: Afghan Tribal Structure Versus Iraqi Tribal Structure

Most US personnel that are serving in Afghanistan have already served a tour in Iraq and are accustomed to doing things “the Iraq way”. Many people are trying to apply the lessons learned in Iraq to Afghanistan, which in many cases is inappropriate. AF2 wants to provide a product to US units to compare and contrast Iraqi tribal structure and Pashtun tribal structure to prevent future missteps by US forces.
The notion of applying ideas that worked in Iraq to Afghanistan is fraught with problems. The “lessons don’t transfer directly,” according to John Nagl, one of the authors of the Army/Marine Corps Counterinsurgency Field Manual (FM 3-24). William McCallister, an expert advisor to the Marine Corps on tribal dynamics in Iraq2 said he is “not a fan of taking the Anbar experience and creating TTPs” for a Pashtun context.
The reasons behind this are legion. For one, the historical experiences of Iraqi and Pashtun societies are so dissimilar as to make comparing them difficult, if not impossible. For another, the specific circumstances of each warzone—one a sectarian conflict, the other a fractured society handling an international insurgency—doesn’t allow for easy generalization between the two.
Furthermore, each society is fundamentally different on a structural level. In Iraq, leadership is in a sense “institutionalized,” or “codified” in the sense that there is a set and identifiable structure for community leadership to interact with each other and with the State. In Afghanistan, however, that system is neither “institutionalized” nor “codified” in any real sense; therefore, structures of community leadership and power relationships within and between tribal groups and the state are much more ad hoc and cannot be discussed in a general sense. Comparing these two societies side-by-side demonstrates this, and shows just how difficult it is to draw lessons from one to the other.
Bottom Line Up Front
• Iraqi tribes are ordered hierarchies
• Pashtun tribes are not ordered hierarchies
• While a tribal hierarchy allows for coherent, ordered engagement policies, Pashtun tribal structure does not
• Thus, TTPs from Iraq are not transferrable to Afghanistan except in the vaguest sense
• While not necessarily TTPs, there are guiding principles that will be effective in engaging Pashtun tribes…
Thus, Pashtun society does not lend itself to a TTP-style set of procedures. Rather, “Guiding Principles” would be more effective in formulating an engagement policy based on the organizing principles in Pashtun society. An initial list follows:
• Accept Ambiguity. People will lie and twist the truth to suit their own ends, saying only what they want someone else to know. Accepting that one cannot know for certain the unalterable truth of a situation is important for being able to engage each leader or influencer on his own terms.
• There Is No Silver Bullet. Each valley, and each tribe, has its own unique set of needs and concerns. There is no universal approach or solution for engagement, but working through (instead of above or around) culture is vital.
• Understand Processes. The VIPs for a given problem vary from situation to situation. Understanding how and why that is—and only then figuring out who—is the only way to guarantee a successful engagement. Conversely, crafting policy based on a single point of view will distort local relationships as influence is leveraged for personal power, and this can erupt in unpredictable ways.
• Nothing is Quick. Afghanistan is a fundamentally relationship-based society. Building relationships takes time—sitting over tea, hours of small talk, expressing genuine concern for well-being. Afghans understand that anyone they talk to will be gone the following year. There is no substitute for taking the time required to build trust, and more importantly passing along that trust to subsequent units.
From the FBI – The State of Financial Crime
An undercover FBI special agent, left, posing as a hedge fund trader negotiates for inside information with a California business executive in this surveillance footage from an investigation
The founder of a $7 billion hedge fund is convicted of insider trading. A drug company pleads guilty to making and selling unsafe prescription drugs to Americans. The head of a financial company admits scamming distressed homeowners who were trying to avoid foreclosure.
These recent crimes and many more like them—investigated by the FBI, in some instances along with our partner agencies—can cause great harm to the U.S economy and American consumers. That’s why financial crimes are such an investigative priority at the Bureau.
Today, we’re releasing an overview of the problem and our response to it in our latest Financial Crimes Report to the Public. The report—which covers the period from October 1, 2009, to September 30, 2011—explains dozens of fraud schemes, outlines emerging trends, details FBI accomplishments in combating financial crimes (including major cases), and offers tips on protecting yourself from these crimes.
Here’s a brief snapshot of key sections of the report:
Corporate fraud: One of the Bureau’s highest criminal priorities, our corporate fraud cases resulted in 242 indictments/informations and 241 convictions of corporate criminals during fiscal year (FY) 2011. While most of our cases involve accounting schemes designed to conceal the true condition of a corporation or business, we’ve seen an increase in the number of insider trading cases.
Securities/commodities fraud: In FY 2011, our cases resulted in 520 indictments/informations and 394 convictions. As a result of an often volatile market, we’ve seen a rise in this type of fraud as investors look for alternative investment opportunities. There have been increases in new schemes—like securities market manipulation via cyber intrusion—as well as the tried-and-true—like Ponzi scams.
Health care fraud: In FY 2011, 2,690 cases investigated by the FBI resulted in 1,676 informations/indictments and 736 convictions. Some of the more prevalent schemes included: billing for services not provided, duplicate claims, medically unnecessary services, upcoding of services or equipment, and kickbacks for referring patients for services paid for by Medicare/Medicaid. We’ve seen increasing involvement of organized criminal groups in many of these schemes.
Mortgage fraud: During 2011, mortgage origination loans were at their lowest levels since 2001, partially due to tighter underwriting standards, while foreclosures and delinquencies have skyrocketed over the past few years. So, distressed homeowner fraud has replaced loan origination fraud as the number one mortgage fraud threat in many FBI offices. Other schemes include illegal property flipping, equity skimming, loan modification schemes, and builder bailout/condo conversion. During FY 2011, we had 2,691 pending mortgage fraud cases.
Financial institution fraud: Investigations in this area focused on insider fraud (embezzlement and misapplication), check fraud, counterfeit negotiable instruments, check kiting, and fraud contributing to the failure of financial institutions. The FBI has been especially busy with that last one—in FY 2010, 157 banks failed, the highest number since 181 financial institutions closed in 1992 at the height of the savings and loan crisis.
Also mentioned in the report are two recent initiatives that support our efforts against financial crime: the forensic accountant program, which ensures that financial investigative matters are conducted with the high-level expertise needed in an increasingly complex global financial system; and our Financial Intelligence Center, which provides tactical analysis of financial intelligence data, identifies potential criminal enterprises, and enhances investigations. More on these initiatives in the future.
STASI-“GoMoPa”- Anonyme, vorbestrafte Serien-Betrüger wollen deutsche Finanzbranche beherrschen – Wer Ihnen im Weg ist, wird STASI-Opfer
Informant “Deep Throat”
Liebe User,
durch die bizzarre und lügenhafte Erpressungs-Serie “NACHRICHTENGANTUR” “GoMoPa” ist deren Ende eingeläutet.
Denn: Die Beweise liegen klar auf dem Tisch so der Informant:
Deep Throat: Der mutmassliche “GoMoPa”-Erfinder RA Jochen Resch und sein Inner Circle
- February 1st, 2011
- Posted in Fonds Opfer
- Write comment
 Die Resch-Mistress Nina Hofer, die sehr persönliche Assistentin
Die Resch-Mistress Nina Hofer, die sehr persönliche Assistentin
 SSTASI-Förderer & “Anlegeranwalt”RA Jochen Resch, “GoMoPa”-Erfinder und Mastermind
SSTASI-Förderer & “Anlegeranwalt”RA Jochen Resch, “GoMoPa”-Erfinder und Mastermind
 Cindy Jachmann, die sehr persönliche Assistentin von RA Manfred Resch
Cindy Jachmann, die sehr persönliche Assistentin von RA Manfred Resch
Deep Throat, Berlin, berichtet: „Das Mastermind hinter allen „GoMoPa“-Aktionen ist der „Anlegerschutzanwalt“ Jochen Resch. Er hat auch Meridian Capital erpresst, schickt aber immer die Handlanger wie Klaus-Dieter Maurischat vor. Nur vorbestrafte Serienbetrüger wie Maurischat lassen sich zu solchen Straftaten instrumentalisieren. Resch hat auch den Terminus „Cyberstalker“ aus den USA importiert. Maurischat kann das aufgrund mangelnder Bildung sogar nicht einmal korrekt schreiben.“
Wie Cyberstalking funktioniert:
Ein aufsehenerregender Fall belegt, dass Rufmörder keineswegs harmlos sind, sondern Schwerverbrecher, die gar den Tod ihres Opfers billigend in Kauf nehmen. In Südkorea wurde ein Filmstar durch Online-Mobbing in den Freitod getrieben. Die Regierung fordert nun härtere Gesetze zur Internetregulierung. Südkorea will Cybermobbern mit harten Gesetzen beikommen, wie eine brandaktuelle Meldung von pressetext.de berichtet:
Der Selbstmord der populären Schauspielerin Choi Jin Sil entwickelt sich in Südkorea zu einer nationalen Affäre mit weitreichenden Konsequenzen. Diese betreffen vor allem das Internet, das von den südkoreanischen Behörden als Ursache des tragischen Ereignisses genannt wird. Wie die Zeitung International Herald Tribune berichtet, habe die Polizei mittlerweile nachweisen können, dass die Verzweiflungstat des Filmstars eine direkte Reaktion auf im Web verbreitete rufschädigende Gerüchte gewesen sei. Kurz nach dem Bekanntwerden des näheren Tathintergrunds brach im Parlament Südkoreas ein heftiger Streit über die bestehenden Internetregulierungsmaßnahmen aus. Während die Regierung den aktuellen Todesfall zum Anlass nimmt, um eine verschärfte Kontrolle des Internets zu fordern, lehnt die Opposition dies mit der Begründung ab, dass die bestehenden Gesetze gegen sogenanntes “Cybermobbing” völlig ausreichend seien.
“Das Internet hat sich in unserem Land zu einer Toilettenwand entwickelt”, erklärt Hong Joon Pyo, Vertreter der südkoreanischen Regierungspartei Grand National Party, gegenüber dem International Herald Tribune. Verbale Übergriffe im Web seien in Südkorea sehr verbreitet. “Wir haben es hier mit einem wachsenden sozialen Problem zu tun, dessen Lösung inzwischen ein Hauptanliegen der Regierung geworden ist”, ergänzt Pyo. Bereits seit mehreren Monaten beschäftige die Regierung ein Team aus 900 Agenten des nationalen Cyber Terror Response Centers, das sich speziell mit dem Auffinden von rufschädigenden Inhalten und Cybermobbing-Attacken im Web befasse. Im Fokus der Fahnder stehen dabei vor allem Online-Foren und Blogs. “Wir brauchen aber ein härteres eigenständiges Gesetz im Kampf gegen Online-Verleumdung, das den Opfern schneller und breiter hilft”, fordert der Regierungsvertreter.
Die Opposition wirft der Regierung wiederum vor, den aktuellen Fall lediglich zu missbrauchen, um das eigene Ziel einer stärkeren Internetregulierung umsetzen zu können. “Der Regierung geht es in erster Linie darum, das Web als beliebte Plattform für regierungskritische Proteste zu kontrollieren”, heißt es in einer Oppositionserklärung. Die gegenwärtige Rechtslage sehe aber ohnehin bereits eine härtere Verfolgung von öffentlichen Rufschädigungen vor, wobei auch das Internet miteinbezogen sei. “Wenn die Politiker glauben, sie könnten solche Tragödien mit einem eigenen Gesetz gegen Cybermobber verhindern, umgehen sie den Ursprung des Problems”, kritisiert auch Jeon Jun Hee vom Seoul Metropolitan Mental Health Center. Allein im vergangenen Jahr seien bei der südkoreanischen Polizei über 10.000 Cybermobbing-Fälle behandelt worden.
Die Schauspielerin Choi Jin Sil wurde am 2. Oktober erhängt in ihrem Badezimmer aufgefunden. Ihre Mutter hatte gegenüber der Polizei bestätigt, dass Choi gegen Mitternacht betrunken heimgekommen sei und sich sehr über Gerüchte aufgeregt habe, die im Internet aufgetaucht seien. Darin wurde die Schauspielerin beschuldigt, einen Kollegen, der sich nur wenige Wochen zuvor das Leben genommen hatte, mit Schuldrückzahlungsforderungen in den Selbstmord getrieben zu haben. Laut Bericht war Choi vor einigen Jahren schon einmal Opfer von heftigen Cybermobbing-Attacken aus dem Internet. Nach Angaben der Polizei musste sie seitdem sogar Antidepressiva nehmen.
Genau daruf legt es die Cyber-Stasi „GoMoPa“ an. Nachfolgend publizieren wir eine Analyse der Firma Meridian Capital, die Opfer von „GoMoPa“ wurde und dann zurückschlug.
Die Cybermord-Opfer Lothar Berresheim, Dipl.-Ing. Paul Bösel, Andreas Decker, Herbert Ernst Meridian Capital, Bernd Pulch und Martin Sachs, klären über den kriminellen und serienmässig vorbestraften Ex-Gefängnissinsassen Klaus-Dieter Maurischat und seine GoMoPa-Erepresserbande auf:
Nachfolgend publizieren wir eine der besten Darstellungen zum Thema Cyber-Terrorismus. Besonders pikant dabei der Bericht über die Maurischat-Festname durch das BKA.
Klaus-Dieter Maurischat hat nach Angaben von Meridian Capital bereits 23 Gerichtsurteile wegen einschlägiger Vergehen und ist im Gegensatz zu seinen Cyber-Opfern tatsächlich vorbestraft (zum Beispiel: Krefeld vom 24. April 2006; AZ: 28 Ls 85/05)
Meridian Capital Enterprises Ltd. London, seit Jahren im Kampf gegen den Cyber-Terrorismus aktiv, enthüllt neue kriminelle Erscheinungen im Netz
I. Sachverhalt
In der letzten Zeit taucht im Netz immer häufiger eine neue zugleich eine sehr beunruhigende Erscheinung krimineller Art auf. Professionelle Verbrechergruppen im Netz nehmen daran teil, die zu Erpressungen, Betrügereien, Erschwindeln in Bezug auf bestimmte gezielt ausgesuchte Firmen und Unternehmen fähig sind. Diese Kriminellen entwickelten neue Methoden und Mittel, sich einfach und in kurzer Zeit zu bereichern.
Strategien und Erscheinungsformen, welche diesem Prozedere zugrunde liegen, sind recht einfach.
Ein Krimineller sucht sich „sorgfältig“ im Internet spezielle Firmen und Korporationen (Opfer des Verbrechens) aus und informiert diese im nächsten Schritt darüber, dass über die Geschäftstätigkeit solcher Firmen und Korporationen in der nächsten Zeit – zuerst im Internet dann in weiteren zugänglichen Massenmedien – zahlreiche und äußerst ungünstige Informationen erscheinen.
Gleichzeitig schlagen die Kriminellen ihren künftigen Opfern – wie Magister Bernd Pulch – eine wirksame Hilfe, unnötigen Schwierigkeiten und Problemen zu entkommen, welche auf Verlust des guten Namens und Images der betroffenen Firma und Korporation abzielen. Diese Straftäter sind sich dessen bewusst, dass guter Ruf, Name und Aussehen jedes Unternehmens ein Wert in sich selbst sei. Es sei also ein Wert, wofür jedes Unternehmen bereit ist, jeglichen Preis zu zahlen. Bloß aus dem Grunde, um Schwierigkeiten und Probleme zu vermeiden, welche aus dem Verlust des guten Namens und Rufes resultieren.
Die Straftäter und ihre Opfer sind sich dessen im Klaren, dass dieser Verlust verheerende Konsequenzen zur Folge haben mag, die das Stilllegen einer bestimmten Geschäftstätigkeit erzwingen können. Dies nimmt sowohl auf Kein- als auch auf Großunternehmen Bezug. Die betrifft Firmen, die praktisch in jeder Branche und in jedem Land grenzüberschreitend tätig sind.
Das kriminelle Prozedere in Form einer Erpressung aufs Geld, eines Betrugs entwickelt sich heutzutage rasant und wird global, d.h. grenzüberschreitend und international geführt. Zu Opfer der Erpressung, des Betrugs fallen heutzutage sowohl heimisch wirkende (inländische) als auch internationale Korporationen, die großen Wert auf Erhaltung, Behalten und Pflege ihres guten Rufes dem entsprechend ihrer geschäftlichen Glaubwürdigkeit legen.
Die Kriminellen im Netz haben begriffen, dass die Pflege eines unantastbaren Rufes und Namens eines Unternehmens die einzigartige Möglichkeit auf schnelle und einfache Bereicherung bildet.
Das oben erwähnte kriminelle Vorgehen ist schwer zu verfolgen, weil es internationaler Natur ist und durch verschobene oder gar nicht existierende (fiktive) Berufs- und Justizpersonen in verschiedenen Ländern firmiert und betrieben wird.
Diese Straftäter im Netz veröffentlichen, unterbringen und verbreiten wahrheitswidrige Informationen über Ihre Opfer auf weit entlegenen Servern, welche sich nicht selten oft in exotischen Ländern befinden. Es sind diejenigen Staaten, in denen gravierende Lücken im Rechtssystem, Ermittlungs- und Verfolgungsverfahren sichtbar sind. Als Beispiel kann an dieser Stelle Indien erwähnt werden.
Mit den Verbrechern im Netz arbeiten Netzportale Führer von bekannten Blogs mit Ihrem Sitz -bewusst oder unbewusst- auch in den hoch entwickelnden Ländern zusammen. Beispielsweise können an dieser Stelle Länder wie Deutschland, Österreich, die Schweiz, die USA, Großbritannien, Spanien oder Portugal erwähnt werden.
Die unten aufgelisteten Kriminellen konnten bis heute weitgehend unbestraft handeln. Als Symptom derartigen Handelns taucht hier die Tätigkeit und „Wirksamkeit“ der Firma GOMOPAauf, welche sich über Länder wie die Bundesrepublik Deutschland, die Schweiz, Österreich, die USA, Großbritannien, Spanien und Indien erstreckt. Ein gutes Beispiel eines derartigen Handelns ist Herr Klaus Maurischat – der Anführer und „Gehirn” der Firma GOMOPA mit vielen bereits in Kraft getretenen Straftaten und Urteilen „auf seinem Konto”, der auf diese Art und Weise jahrelang seinen Unterhalt finanzierte und in der Branche nahezu unbegrenzt aktiv war (erst jüngst mutmasslich im Auftrag der SJB, Korschenbroich/Neuss).
Dieser Stand ändert sich jedoch drastisch, u.a. dank weit und breit geführten Maßnahmen der Firma Meridian Capital Enterprises Ltd., welche sich gegen solche Strafdelikte im Netz richten. Auch andere Firmen und Korporationen, welche dem Verbrechen im Netz und außerhalb dieses Mediums zu Opfer gefallen sind, tragen zur Bekämpfung solcher Delikte bei.
Die Lage ändert sich auch dank wirksamen Schritten und der erfolgreichen Zusammenarbeit der Firma Meridian Capital Enterprises Ltd. mit der internationalen Polizei Interpol, mit der Bundesagentur (FBI) in den USA, mit der BUNDESKRIMINALPOLIZEI in Deutschland, mit SCOTLAND YARD in Großbritannien, sowie mit dem Russischen Geheimdienst FSB.
Die Meridian Capital Enterprises Ltd. – gemeinsam mit weiteren Firmen und Kooperationen, die zu Opfer krimineller Aktivitäten des Netzverbrechens gefallen sind – hat unbestreitbar schon erste Erfolge zu verzeichnen.
Dass im November 2008 auf dem Territorium der Bundesrepublik Deutschland der oben erwähnte Anführer und „Gehirn“ der Firma GOMOPA, Herr Klaus Maurishat festgenommen wurde, darf nicht außer Acht gelassen werden. Aus den derMeridian Capital Enterprises Ltd. zur Verfügung stehenden Informationen resultiert eindeutig, dass die nächsten Verhaftungen der an diesem Prozedere teilnehmenden Personen in solchen Ländern wie: Österreich, die Schweiz, Russland, die Ukraine, Polen, Spanien, Mexiko, Portugal, Brasilien, die USA, Kanada, Großbritannien, Irland, Australien, New Seeland und in a. erfolgen.
Das oberste Ziel der Meridian Capital Enterprises Ltd. sowie der weiteren Opfer des Verbrechens im Netz ist es, alle Teilnehmer dieses kriminellen Prozedere vor das zuständige Gericht zu führen.
Alle Berufs- und Justizpersonen, unabhängig vom Sitz und der ausgeübten Geschäftstätigkeit, welche dem oben beschriebenen kriminellen Vorgehen (Betrug, Erpressung) zu Opfer gefallen sind, können der von der Meridian Capital Enterprises Ltd. geführten Kompanie beitreten, die sich zum Ziel setzt, alle an dem an dieser Stelle dargestellten Prozedere Mitbeteiligten aus dem öffentlichen sowie dem wirtschaftlichen Leben auszuschließen.
II. Schwarze Liste mit internationalen Erpressern und Betrügern sowie Ihre Methoden (opus operandi) in den folgenden Ländern:
1. Die Bundesrepublik Deutschland
2. Dubai
3. Russland
1. Die Bundesrepublik Deutschland
GOMOPA GmbH, Goldman Morgenstern & Partners LLC., Goldman Morgenstern & Partners Consulting LLC, Wottle Inkasso Büro. In diesen Firmen sind folgende Personen recht aktiv:
– Klaus Maurischat („Vater” und „Gehirn” der kriminellen Organisation, der für den unzählige rechtskräftige Urteile zu verzeichnen sind (festgenommen in Deutschland im November 2008);
– Rudolf Josef Heckel („rechte Hand” bei Herrn Klaus Maurischat, ehemaliger denunzierter Banker, der an vielen maßlosen Bankschmuggeleien mitbeteiligt war. (Heutzutage persona non grata im deutschen Bankwesen);
– Peter Reski (zuständig für das Finanzwesen, bekannt für Betrug, Fälschungen und Steuerunterschlagungen, hinter denen bereits rechtkräftige Urteile stehen);
– Mark Vornkahl (zuständig für organisatorisch-administrative Aufgaben beiGOMOPA, ehemaliger Polizeibeamter, entlassen wegen zahlreichem Verstießen im Dienst, hat bereits ein paar rechtskräftige Urteile „auf seinem Konto“);
– Claus i Ulrike Wottle (Ehepaar, für das sogenannte „unkonventionelle” Vollstrecken der Schulden vor allem zugunsten GOMOPA. Dieser Vollstreckung lagen Erzwingung, Erpressung mit Gewalt zugrunde, die auf sowohl tatsachliche als auch fiktive Schulden Bezug nahmen?
Wie funktioniert das System von GOMOPA
Die oben in Kurze erwähnten Personen, sowie die mit dem Service GOMOPAKooperierenden, so genannte „GOMOPA-Experten“, Bloggers und alle weiteren Berufs-und Justizpersonen suchen sich aus allen möglichen Quellen Informationen über große, reichen Firmen und Korporationen aus, welche in verschiedenen heimischen und internationalen Wirtschaftszweigen tätig sind. Dem Service GOMOPA liegt besonders daran, dass man diejenigen aussucht, die „in Sich selbst ins Auge fallen”. Diejenigen Firmen und Korporationen also, gegen die relativ einfach und ohne großen Aufwand sich Vorwürfe, Unstimmigkeiten u. s. w. sich machen lassen, in bezug auf die sogar Straftaten wie Erschwindeln und Betrügen u. a. sich leicht vorführen lassen. Es ist allgemein bekannt, dass jeder Firma besonders an ihrer guten Präsenz und an ihrem unantastbaren Namen liegt. Jedes Unternehmen wird dem entsprechend alles tun, um ihre gute Präsenz also auch ihre Glaubwürdigkeit beibehalten zu können. Wenn aber zum Opfer des GOMOPA und seiner „Partner” ein großes und reiches Unternehmen fällt, so kann man sich an solchen Unternehmen schnell, einfach und sogar beachtlich bereichern.
Es taucht an dieser Stelle die Frage auf:
Welcher schlaue Straftäter, der im Netz und außerhalb des Netzes mir Erfolg wirkt, möchte daraus kein Nutzen ziehen?
Die Kriminellen im Netz wissen genau, dass ohne geschäftliche Glaubwürdigkeit kein Vertrauen vorhanden sei, welches jeder Geschäftstätigkeit unentbehrlich ist. GOMOPAsowie alle mit dem Kooperierenden haben mit Sicherheit alle möglichen Methoden und Maßnahmen beherrscht, wie man Glaubwürdigkeit und Vertrauen einer Firma, eines Unternehmens, einer Korporation (Verbrechensopfer) in Frage stellt.
Dies zieht eben die Aufmerksamkeit der User an, so dass die Homepage des GOMOPAwww.gomopa.net in den Suchmaschinen wie Google, Yahoo leicht auffindbar ist. Dies wiederum bedeutet nichts anderes als Zusatzprofite für das Service GOMOPA , weil um seine Tätigkeit herum ein mediales Diskurs geschaffen wird.
Ein auf den ersten Blick banales und einfaches Opfer der Erpressung kann beispielsweise eine öffentliche, staatliche Instanz, welche auf Basis der öffentlichen Glaubwürdigkeit funktioniert, werden, wie eine Bank oder ein bankfremdes Finanzinstitut. So war es eben mit dem bankfremden, internationalen FinanzinstitutMeridian Capital Enterprises Ltd. der Fall.
Ein einfaches und leichtes Opfer de illegalen und materiellen Gewinns können auch die Versicherungsgesellschaften werden, bei denen – wie es aus unseren Recherchen resultiert-, vieles auf die kriminelle Tätigkeit des GOMOPA vor allem auf dem Gebiet der Bundesrepublik Deutschland, der Schweiz und Österreich zurückzuführen sei. Unter den bekannten und erkennbaren Opfern sind mit Sicherheit deutsche, österreichische und schweizerische Banken, Versicherungsgesellschaften wie z.B. Allianz aus Deutschland, deutsche und österreichische Firmen wie HDI und DKV sichtbar.
Dies, wozu sich das Service GOMOPA traut und was die mit dem kooperierenden Services, Blogs heutzutage praktizieren, ist das so genannte Cyber-Stalking, welches sich rasant im Netz verbreitet. Die kriminelle Methode besteht an dieser Stelle u. a. im Bedrohen, dass über die Geschäftstätigkeit eines Unternehmens (Ofer der Erpressung, Erzwingung und Bedrohung) fiktive, gar nicht existierende Informationen (Lügen, Gerüchte, Geschichtchen, Nachrede, Beleidigungen) zuerst im Netz dann in anderen Massenmedien veröffentlicht werden. Dies dient lediglich dazu, um ein potenzielles Opfer dazu zu bewegen, eine beachtliche Geldsumme für die so genannte „Ruhe“ dem Erpresser bereitzustellen. Die „Ruhe” bedeutet hier das Versprechen einer Zugangssperre in Bezug auf die Veröffentlichung jeglicher fiktiven Information im Netz und in allen weiteren Massenmedien, die die Opfer der Erpressung im äußerst negativen Licht darstellen kann.
Derartige Bedrohungen setzen sich, wie bereits oben erwähnt zum Ziel, Firmen – potenzielle Opfer des Cyber-Stalking dazu zu veranlassen, dass sie sich selbst „aufkaufen“. Kurz gesagt, GOMOPA und seinesgleichen, sowie die mit denen kooperierenden Services und Blogs, kreieren eine „virtuelle Wirklichkeit”, oder anders gesagt, publizieren fiktive Informationen über potenzielle Opfer eines Verbrechens. Firmen und Korporationen, welche gegen Bedrohung und Erpressung seitens GOMOPAnicht fällig sind, diejenigen also, welche für so genannte „Ruhe“ nicht zahlen wollen, werden zum Opfern schwerwiegender Lügen, Beleidigungen, Insinuationen und anderer krimineller Unterschlagungen, die Aussehen und Präsenz einer Firma mit Sicherheit beeinträchtigen.
Eines gilt als Ziel des GOMOPA, nämlich so schnell und so einfach, wie es geht, das Geld abzukassieren, und wenn sich eine Firma weigert und sich die „Ruhe“ nicht kaufen möchte, wird sie unerwartet und blitzschnell zum Objekt der Erpressung und Beleidigung im Netz.
An dieser Stelle taucht folgende Frage auf: Wie ist es möglich, dass der Anführer der Firma GOMOPA, Herr Klaus Maurischat, der nur in der Bundesrepublik Deutschland auf seinem „Konto” 23 Gerichtsurteile hat, sich jahrelang als einen ehrlichen Bürger kreieren, zugleich anderen Personen, Firmen, Korporationen verbrecherische Taten, Delikte einprägen, dazu noch daran beachtliche Geldsummen verdienen konnte? Dieses komplexe Prozedere kann nur folgendermaßen erklärt werden:
GOMOPA kreiert sein Aussehen, seine Präsenz in den Augen der öffentlichen Meinung als ein ehrliches Subjekt, welches gegen pathologische Erscheinungen des öffentlichen und wirtschaftlichen Alltags einschreitet. GOMOPA und seine Partner (Services, Blogs) stellen sich als Verfolger jeglicher Verbrechensart dar, versprechen also den Kampf gegen jeden virtuellen Verbrecher im Netz (insbesondere gegen jeden Betrüger, Erpresser). GOMOPA verwendet in dieser Hinsicht eine Art „Merketingsvorhang” als Methode der Verführung, infolge dessen es sein wahres „Antlitz“ und seine wahren Intentionen als die eines Betrügers und Erpressers aufs Geld verbergen kann. Die wahren Absichten des GOMOPA, der mit GOMOPA zusammen arbeitenden Services und Blogs konnten bis heute zweifelsohne mit Erfolg vor der öffentlichen Meinung versteckt bleiben, vor allem dank des so genannten „Rauchvorhangs“, welcher sich darin widerspiegelt, dass man sich selbst als „Sieger“ jeglichen Missbrauchs und jeder pathologischen Erscheinung des öffentlichen und wirtschaftlichen Lebens in Deutschaland, Österreich, der Schweiz, den USA, Großbritannien, Russland, Spanien kreiert.
Als nächstes taucht die von dem GOMOPA vorgeschobene Person auf, welche Firmen und Korporationen – die künftigen Opfer des Verbrechens also – vor der Möglichkeit der Veröffentlichung von äußerst ungünstigen und das betroffene Unternehmen in einem negativen Licht darstellenden Informationen im Internet und in weiteren Massenmedien warnt. Die Person, von der hier die Rede ist, informiert zugleich, dass sie sich mit Erfolg gegen so ein Prozedere für ein entsprechendes „Honorar“ einsetzen kann. Der GOMOPA geht es an dieser Stelle um die Erpressung aufs Geld für so genannte „Ruhe” um die Firma und Korporation (Opfer eines Verbrechens) herum. Meistens wird seitens der betroffenen Firmen auf solche Bedrohungen überhaupt nicht reagiert, weil sie zu ihrem Alltag und ihrer Tagesordnung gehören. Es fehlt schließlich kaum an Erpressern im Netz und außerhalb des Mediums. Normalerweise kommt es also selten zu so genannter „Verständigung”, wobei auf der einen Seite die Verbrechensopfer, auf der anderen Seite das GOMOPA auftritt. Es ist verständlich, dass der Preis für so eine „Verständigung” die Bereitstellung der von dem GOMOPA geforderten Gelder wäre. Die finanzielle Erpressung wird in dieser Etappe selten vollzogen. Die Lage ändert sich jedoch kaum, wenn die Firmen und Korporationen (Verbrechensopfer) erfahren, dass die Bedrohung erfüllt sei. In Kurze erscheinen auf der Homepage http://www.gomopa.netzahlreiche Presseartikel, Schein-berichte und Pseudomarktanalysen, die sowohl durchGOMOPA als auch durch so genannte „unabhängige Experten“ firmiert und vertreten werden, die mit GOMOPA formal oder fiktiv zusammenarbeiten. Informationen, hier publiziert, entsprechen den Inhalten aus einer Bedrohung und stellen die Geschäftstätigkeit der Personen, Firmen und Korporationen in einem äußerst negativen Licht dar.
Es unterliegt keinem Zweifel, dass derartige Maßnahmen und Methoden bloß auf Beeinträchtigung des guten Namens und der guten Präsenz dieser Firmen und Korporationen abzielen.
Die Tätigkeit von GOMOPA ist damit mit Sicherheit nicht ausgeschöpft. GOMOPAverbreitet (publiziert, unterbringt) die oben dargestellten Informationen im Netz, indem es sich der glaubwürdigen, populären und meinungsbildenden Services bedient. Mehr noch, GOMOPA droht den Firmen und Korporationen (seinen Opfern), dass die „aus dem Finger gezogenen“ Informationen nicht nur im Netz, sondern auch im Fernsehen und im Radio und in der Presselandschaft erscheinen.
Wie die Erfahrung und das bisherige Fachwissen der Meridian Capital Enterprises Ltd. zeigen, sind sich die Services meistens nicht dessen bewusst, dass sie zum Zwecke eines kriminellen Vorgehens durch das GOMOPA genutzt werden. Sie stimmen dem entsprechend mit den fiktiven Publikationen, Berichten und Analysen überein, welche speziell durch GOMOPA sowie durch „unabhängige“ Experten präpariert sind.
Es kommt auch vor, dass die Services und Blogs einer derartigen Zusammenarbeit mit dem GOMOPA Zustimmung erteilen, wobei sie genau wissen, dass die von GOMOPAübermittelten Informationen fiktiv sind und die Glaubwürdigkeit der Firmen und Korporationen beeinträchtigen. Sie nehmen also bewusst an dem kriminellen Prozedere teil. Die Erklärung dieser Lage ist recht einfach. GOMOPA zahlt nämlich den Services und Blogs entsprechende Vergütung, dass sie der Veröffentlichung von unwahren Informationen über die Firmen und Korporationen (Verbrechensopfer) zustimmen.
Einige Services und Blogs scheinen nichts davon gewusst zu haben, dass die auf ihren Seiten zur Verfügung gestellten Informationen „fiktiv“ und „aus dem Finger gezogen“ sind. Sie suchen auf diese Art und Weise ihre Verhaltensweise zu rechtfertigen, denn sie wollen den rechtlichen Konsequenzen wegen der Teilnahme am Missbrauch des guten Namens und Aussehens einer Firma oder Korporation entkommen.
Das Tätigkeitssystem von GOMOPA, von zusammenarbeitenden Services und Blogs wurde auch am Beispiel der Meridian Capital Enterprises Ltd. ausgetestet.
Anfang Oktober 2008 erhielt einer der Arbeiter der Meridian Capital Enterprises Ltd. eine Meldung von einem anonymen Sender, dass in naher Zukunft – zuerst im Internet, dann im Fernsehen, im Radio und in der deutschen Presse – Informationen erscheinen, die die Funktionsweise und Tätigkeiten der Meridian Capital Enterprises Ltd. in einem äußerst negativen Licht darstellen. Der Mitarbeiter derMeridian Capital Enterprises Ltd. wurde also informiert, dass diese Meldungen/Nachrichten zweifelsohne deutlich das Aussehen und den guten Ruf der Firma Meridian Capital Enterprises Ltd. beeinträchtigen.
Der an dieser Stelle erwähnte „Gesprächspartner” hat den Angestellten der Meridian Capital Enterprises Ltd. informiert, dass die Möglichkeit besteht die peinliche Situation zu vermeiden, indem die Meridian Capital Enterprises Ltd. auf das von der Person gezeigte Konto die Summe von 100.000,00 EUR überweist. Wie sich aber später zeigte, war der Herr Klaus Maurischat – dieser anonyme Gesprächspartner – „Gehirn“ und „Lider desGOMOPA“. Die Ermittlungen wurden angestellt durch die Bundeskriminalpolizei(Verfolgungs- und Ermittlungsorgan auf der Bundesebene) während des Ermittlungsverfahrens wegen einer finanziellen Erpressung, Betrügereien auch wegen der Bedrohungen, welche von Herrn Maurischat und seinen Mitarbeiter praktiziert wurden und werden sowie wegen Teilnahme anderer (Leiter der Internetservices und Moderatoren der Blogs) an diesem Prozedere. Diese Straftaten wurden begangen zu Schaden vieler Berufs- und Justizpersonen, darunter auch der Meridian Capital Enterprises Ltd. Die Opfer dieses Verbrechens sind in Deutschland, Österreich, der Schweiz, Spanien, Portugal, Großbritannien, den USA und Kanada sichtbar.
In diesem Moment taucht folgende Frage auf: Wie war die Reaktion der Meridian Capital Enterprises Ltd. auf die Forderungen seitens GOMOPA? Entsprach die Reaktion den Erwartungen von GOMOPA? Hat die Meridian Capital Enterprises Ltd. die geforderte Summe 100.000,00 EUR überwiesen?
Seites der Meridian Capital Enterprises Ltd. gab es überhaupt keine Reaktion auf den Erpressungsversuch von GOMOPA. Ende August 2008 auf dem Service http://www.gompa.net sind zahlreiche Artikel/Meldungen erscheinen, welche die Tätigkeit derMeridian Capital Enterprises Ltd. in einem sehr negativen Licht dargestellt haben. Nachdem die auf http://www.gomopa.net enthaltenen Informationen ausführlich und vollständig analysiert worden waren, ergab es sich, dass sie der Wahrheit nicht einmal in einem Punkt entsprechen und potenzielle und bereits bestehende Kunden derMeridian Capital Enterprises Ltd. in Bezug auf die von diesem Finanzinstitut geführten Geschäftstätigkeit irreführen. Infolge der kriminellen Handlugen von GOMOPA und der mit ihm kooperierenden Services und Blogs im Netz hat die Meridian Capital Enterprises Ltd. beachtliche und messbare geschäftliche Verluste erlitten. Die Meridian Capital Enterprises Ltd. hat nämlich in erster Linie eine wichtige Gruppe von potenziellen Kunden verloren. Was sich aber als wichtiger erwies, es haben sich die bisherigen Kunden von der Meridian Capital Enterprises Ltd. kaum abgewandt. Diejenigen Kunden haben unsere Dienstleitungen weiterhin genutzt und nutzen diese immer noch. In Hinblick auf die bisherige Zusammenarbeit mit der Meridian Capital Enterprises Ltd., werden ihrerseits dem entsprechend keine Einwände erhoben .
GOMOPA hat so einen Verlauf der Ereignisse genau prognostiziert, dessen Ziel beachtliche und messbare geschäftliche durch die Meridian Capital Enterprises Ltd.erlittene Verluste waren. Der Verlauf der Ereignisse hat GOMOPA mit Sicherheit gefreut. GOMOPA hat nämlich darmit gerechnet, dass die Markt-Stellung derMeridian Capital Enterprises Ltd. nachlässt und das Finanzinstitut die geforderte Summe (100.000,00 EUR) bereitstellt. Im Laufe der Zeit, als das ganze Prozedere im Netz immer populärer war, versuchte GOMOPA noch vier mal zu der Meridian Capital Enterprises Ltd. Kontakte aufzunehmen, indem es jedes mal das Einstellen dieser kriminellen „Kampagne” versprochen hat, wobei es jedes mal seine finanziellen Forderungen heraufsetzte. Die letzte für das Einstellen der „Kampagne“ gegen dieMeridian Capital Enterprises Ltd. vorgesehene Quote betrug sogar 5.000.000,00 EUR (in Worten: fünf Milionen EURO). Die Meridian Capital Enterprises Ltd.konnte sich aber trotz der sich ständig steigenden Forderungen seitens GOMOPA im Markt behaupten.
Im Oktober 2008 traf die Leitung der Meridian Capital Enterprises Ltd.Entscheidung über die Benachrichtigung der Internationalen Polizei INTERPOL sowie entsprechender Strafverfolgungsorgane der BRD (die Polizei und die Staatsanwaltschaft) über den bestehenden Sachverhalt. In der Zwischenzeit meldeten sich bei der Meridian Capital Enterprises Ltd. zahlreiche Firmen und Korporationen, sogar Berufsperson wie Ärzte, Richter, Priester, Schauspieler und anderen Personen aus unterschiedlichen Ländern der Welt, die der Erpressung von GOMOPA nachgegeben und die geforderten Geldsummen überwiesen haben. Diese Personen gaben bereits Erklärungen ab, dass sie dies getan haben, damit man sie bloß endlich „in Ruhe lässt” und um unnötige Probleme, Schwierigkeiten und einen kaum begründbaren Ausklang vermeiden zu können. Die Opfer dieses kriminellen Vorgehens haben die Meridian Capital Enterprises Ltd. über unterschiedliche Geldsummen, welche verlangt wurden, informiert.
In einem Fall gab es verhältnismäßig kleine (um ein paar tausend EURO), in einem anderen Fall handelte es schon um beachtliche Summen (rund um paar Millionen EURO).
Zusätzlich wendeten sich an die Meridian Capital Enterprises Ltd. Firmen, welche der GOMOPA noch keine „Gebühr” überweisen haben und bereits überlegen, ob sie dies tun sollen, oder nicht. Diese Firmen erwarteten von der Meridian Capital Enterprises Ltd. eine klare Stellungnahme sowie eine professionelle praktische Beratung, wie man sich in solch einer Lage verhalten soll und wie man diese Geldforderungen umgehen kann. Die Meridian Capital Enterprises Ltd. hat ausnahmslos allen Verbrechensopfern, welche sich bei unserer Firma gemeldet haben, eine Zusammenarbeit vorgeschlagen. Als oberste Aufgabe stellt sich diese Kooperation, gemeinsam entschlossene und wirksame Maßnahmen gegen GOMOPA, gegen andere Services im Netz sowie gegen alle Bloggers zu treffen, die an dem hier beschriebenen internationalen kriminellen Vorgehen mit GOMOPA-Führung teilnehmen.
Alle diese Firmen traten einem so genannten von der Meridian Capital Enterprises Ltd. vorgeschlagenen „Kreuzzug” gegen GOMOPA, seine Partner bei. Auf unsere Bitte benachrichtigten alle mitbeteiligten Firmen die Internationale Polizei INTERPOL sowie ihre heimischen Verfolgungsorgane, u. a. die zuständige Staatsanwaltschaft und die Polizeibehörden über den bestehenden Sachverhalt.
In Hinblick auf die Tatsache, dass das verbrecherische Handeln von GOMOPA sich über viele Staaten erstreckte und dass die Anzahl der in der Bundesrepublik Deutschland erstatteten Anzeigen wegen der durch GOMOPA, Internetservices und Bloggers begangenen Straftaten, rasant wuchs – was zweifelsohne von einer weit gehenden kriminellen Wirkungskraft des GOMOPA zeugt – schlug die Internationale Wirtschaftspolizei INTERPOL der Meridian Capital Enterprises Ltd. vor, dass sich ihr Vertreter in Berlin mit dem Vertreter von GOMOPA trifft, um die „Zahlungsmodalitäten“ und Überweisung der Summe von 5.000.000,00 EUR zu besprechen. Dieser Schritt sollte, eine gut durchdachte und durch dieBundeskriminalpolizei organisierte Falle durchzuführen, deren Ziel die Festnahme der unter GOMOPA wirkenden internationalen Straftäter war.
Die koordinierten Schritte und Maßnahmen der Meridian Capital Enterprises Ltd.und anderer Beschädigter, geleitet von der Internationalen Wirtschaftspolizei INTERPOL, dem Bundeskriminalamt und der Staatsanwaltschaft der Bundesrepublik Deutschland haben zur Aus-, Einarbeitung und Durchführung der oben beschriebenen Falle beigetragen. Im November 2008 führte die in Berlin vorbereitete Falle zur Festnahme und Verhaftung des Vertreters des GOMOPA, der nach der Festnahme auf Herrn Klaus Maurichat – als den Hauptverantwortlichen und Anführer der internationalen kriminellen Gruppe GOMOPA verwies. Der Festgenommene benannte und zeigte der Bundeskriminalpolizei zugleich den aktuellen Aufenthaltsort des Herrn Klaus Maurischat. „Gehirn“ und Gründer dieser internationalen kriminellen Gruppe GOMOPA. Herr Klaus Maurischat wurde am selben Tag auch festgenommen und auf Frist verhaftet, wird bald in Anklagezustand gestellt, wird die Verantwortung für eigene Straftaten und die des Forums GOMOPA vor einem zuständigen Bundesgericht tragen. Die Meridian Capital Enterprises Ltd. unternahm bereits alle möglichen Schritte, damit Herr Klaus Maurischat auch auf der Anklagebank des zuständigen Gerichts des Vereinigten Königsreiches Großbritannien erscheint. Unter den beschädigten Berufs- und Justizpersonen aus Großbritannien, neben der Meridian Capital Enterprises Ltd. gibt es noch viele Opfer von GOMOPA:
Der Begin der Verhaftungen mit so einem Ausmaß bedeutet für die deutsche Justiz einen ausschlaggebenden und bahnbrechenden Punkt. Bemerkenswert ist, dass die Verfolgungsorgane der Bundesrepublik sich bis zu diesem Zeitpunkt der langjährigen kriminellen Tätigkeit des Herrn Klaus Maurischat und seiner Mitarbeiter machtlos zeigten.
Die langdauernde Straflosigkeit des kriminellen Vorgehens des Herrn Klaus Maurischat, der jahrelang die „Erste Geige” bei GOMOPA spielte, ist zu Ende gegangen.
An dieser Stelle taucht noch eine Frage auf: wie wird’s weiter gehen?
Die Festnahme des Herrn Klaus Maurischat ist ein ausschlaggebender Moment, anders gesagt eine „Wende um 180 Grad” für ihn persönlich. Es bedeutet aber auch den „Anfang vom Ende“ für seine Mitarbeiter, für die Internetservices, Bloggers, die mit GOMOPA so gerne und ohne Widerspruch zusammengearbeitet hatten. Es unterliegt keinem Zweifel, dass die Sache vom Herrn Klaus Maurischat an der Spitze des „Eisbergs” steht. Der oben erwähnte Wendepunkt zu dieser Frage wird weitere Festnahmen und Verhaftungen der GOMOPA-Mitglieder mit sich bringen, sowie aller Personen aus allen möglichen Gebieten, die an diesem grenzüberschreitenden kriminellen Vorgehen teilgenommen haben.
Aus Informationen, welche der Meridian Capital Enterprises Ltd. vorliegen, resultiert, dass die nächsten Festnahmen aktuell vorbreitet werden, die mit dem Services GOMOPA zusammenarbeitende Personen betreffen. Dies wird auf Personen außerhalb Deutschland – von wo der Herr Klaus Maurischat kommt – bezug nehmen. Die Einzelheiten dürfen an dieser Stelle in Hinblick auf Rechtsgut und Verlauf der durch die Verfolgungsorgane der BRG und der INTERPOL geführten Untersuchung leider nicht verraten werden.
Die Meridian Capital Enterprises Ltd. kann momentan lediglich eine verbindliche Information aus der geführten Untersuchung der Öffentlichkeit bekannt geben, die die strafrechtliche Haftung nicht zu Folge haben wird.
In diesem Moment also werden intensive Vorbereitungen auf Verhaftung einer Reihe von Personen außerhalb der Bundesrepublik Deutschland getroffen.
Dies betrifft insbesondere folgende Länder wie:
– Russische Föderation
– die Ukraine
– Polen
– Spanien
– Mexiko
– Portugal
– Brasilien
– die Vereinigten Staaten von Amerika
– Kanada
– Großbritannien
– Irland
– Australien
– New Seeland
– Indien.
Alle Berufs- und Justizpersonen, unabhängig vom Land, in dem sie das Amt begleiten, oder dessen Bürger sind, und die bis jetzt bewusst oder unbewusst mit dem Forum GOMOPA zusammengearbeitet haben, oder weiterhin zusammenarbeiten, erregen den Verdacht der Internationalen Polizei INTERPOL. Diese Polizei arbeitet mit der Kriminalpolizei in jedem Land, um die oben erwähnten Personen zuerst identifizieren und dann die juristisch verfolgen zu können.
Informationen zu diesem Thema, sowie über Anfang und Ende der Tätigkeit des GOMOPA kann man unter folgenden Adressen im Netz lesen:
– http://antigomopa.net/de/
– http://gomopaabzocker.wordpress.com/
– http://www.nepper-schlepper-bauernfaenger.com
– http://www.youtube.com/watch?v=qNpzAu-QMuE
– http://www.korte.de/alexander/2006/01/gomopa-finanforum-kritik.html
– http://evelux.de/gomopa-sam-240/
– http://blog.deobald.org/archive/2007/07/01/betrugsvorwurf-gomopa-spam/
2. Dubai
KLP Group Emirates – Vereinigte Arabische Emiraten. Als Chef der Firma gilt HerrMartin Kraeter, der nicht nur als „Gehirn” des ganzen Unternehmens, sondern auch als langjähriger Freund des Herrn Klaus Maurischat (GOMOPA-Leiter) fungiert.
Diese Firma will nicht einmal verbergen und gibt offiziell zu, dass sie als strategischer Partner des GOMOPA auf dem Gebiet des Nahen Ostens, dem entsprechend das Gebiet der Persischen Küste tätig ist.
Die offizielle Tätigkeit der Firma KLP Group Emirates umfasst unter anderem folgende Bereiche: Finanzberatung auch aus dem Off-Shore Bereich (Management Services – Facilitators – OffshoreConsultants, International Tax & Legal Consultants – Fiduciaries). Im Tätigkeitsbereich der Firma kommt auch die Gründung von Firmen und Unternehmen in den so genannten „Steuerparadiesen” vor, um der Steuerpflicht zu entfliehen.
Die inoffizielle Tätigkeit der Firma KLP Group Emirates umfasst unter anderem die Zusammenarbeit mit dem Service GOMOPA im Bereich der „Geldwäsche”. Die Gelder werden infolge der kriminellen Handlungen durch GOMOPA generiert, durch vorgeschobene Berufs- und Justizpersonen demnächst über die ganze Welt verbreitet und legalisiert.
Die auf die Gesetzwidrigkeit beruhende Tätigkeit der Firma KLP Group Emirates sowie die Kooperation mit dem Services GOMOPA erregten Aufmerksamkeit auch bei den Verfolgungsorganen des Vereinigten Königreiches Großbritannien, vor allem bei Scotland Yard, das zu dieser Frage ein intensives Ermittlungsverfahren eingeleitet hat, welches sich in der „Entwicklungsphase“ befindet. Es muss angemerkt werden, dass alle Berufs- und Justizpersonen, vor allem aber die Kunden der Firma KLP Group Emirates, die mit der Firma KLP Group Emirates in Vergangenheit zusammengearbeitet haben und dies immer noch tun, unter die „Luppe“ des Scotland Yard genommen werden.
3. Russland
a) Die Firma E-xecutive wird von dem Herrn Vilen Novosartow geleitet. Die auf der Homepage der Firma enthaltenen Informationen kommen direkt von der FirmaGOMOPA. Die Firma E-xecutive führt die enge Zusammenarbeit nicht nur mitGOMOPA, sondern auch mit einer weiteren auf dem russischen Gebiet unter dem Namen OOO VK Broker funktionierenden Firma. Die Firma E-xecutive im Zusammenhang mit der Firma OOO VK Broker ist Mitglied einer kriminellen Gruppe unter der Leitung von GOMOPA. Die Firma E-xecutive vertritt Interessen von GOMOPA in Russland und in Mittel- und Osteuropa.
Inoffiziell beschäftigt sich die Firma E-xecutive insbesondere mit der Suche nach potenziellen „Opfern” des Erschwindelns, der Erpressung und Erzwingung der Gelder für GOMOPA von Firmen und Korporationen aus dem Gebieten Russland, Ukraine, sowie aus allen Staaten in Mittel-Osteuropa.
Offiziell führt die Firma E-xecutive eine dem Forum GOMOPA ähnliche Gewerbetätigkeit.
b) OOO «VK Broker». Leiter der Firma ist der Herr Pavel Kokarev. Diese Firma verheimlicht es nicht, dass sie mit dem Forum GOMOPA zusammenarbeitet. Die FirmaOOO VK Broker vertritt GOMOPA in Mittel-Osteuropa, auch in Russland. Sie übt offiziell auf diesem Gebiet dem GOMOPA ähnliche Tätigkeit aus, inoffiziell aber ist sie mit der Suche nach potenziellen „Opfern“ der Erpressung, des Betrugs und des Erschwindelns für GOMOPA beschäftigt. Die Firma blieb bis jetzt von jeder Strafe verschont, konnte mit „ewiger Straflosigkeit” wegen eines schlecht ausgearbeiteten, korrupten Rechtswesens in Russland rechnen. Die Situation kann sich jedoch ändern, nachdem Herr Klaus Maurischat in Berlin festgenommen und verhaftet worden ist. Dieser ständige Straftäter, der „auf seinem Konto” eine Reihe von rechtskräftigen Urteilen hat, der bis jetzt seine Freiheit unbegrenzt genossen hat, dementsprechend nicht weiß, was es bedeutet verhaftet zu werden, beginnt nach und nach laut uns zur Verfügung stehenden Angaben endlich „sein Zeugnis abzulegen“. Dies ist verständlich, wenn man die ihm drohende hohe Strafe berücksichtigt. Dieser Delinquent zeigt dabei immer größeres Interesse an der Zusammenarbeit mit den deutschen Verfolgungs- und Ermittlungsorganen. Es besteht also die Chance, dass er weitere Personen der Öffentlichkeit enthüllt, indem er auf Minderung der Gefängnisstrafe rechnet. Es ist auch nur die Frage der Zeit, wann INTERPOL in Zusammenarbeit mit der Russischen (FSB) der Firma OOO VK Broker „an die Tür klopft”, welche durch den Herrn Pavl Kokarev geführt und vertreten wird.
Die Firma OOO VK Broker besitzt ein virtuelles Buero im REGUS-Gebäude in Moskau, stellt nicht einmal eine Person an und bildet eine typische Ein-Person-Firma, die alle geschäftlichen „Delikte“ firmieren kann, wobei sie keine zivil-rechtliche Haftung trägt. Der Herr Pavel Kokarev scheint „vergessen zu haben” oder besitzt kein ausreichendes Wissen für seine eventuelle Verantwortung fier die Teilnahme an den internationalen Verbrechen unter Leitung von GOMOPA.
Deep Throat: „GoMoPa“ & Hintermänner: Erpressung, Einschüchterung, Rufmord und Mord
„Erpressung, Einschüchterung, Rufmord und Mord“, sind wohl die täglichen Waffen des ominösen „NACHRICHTENDIENSTES“ „GoMoPa“ beichtet Deep Throat, ein Ex-Mitarbeiter des „NACHRICHTENDIENSTES“ „GoMoPa“.
Deep Throat, Berlin packt aus: „Seit einigen Monaten sind alle wichtigen „GoMoPa“-Figuren wie Klaus-Dieter Maurischat abgetaucht. Da wurde mir klar, dass die Polizei ihnen wegen „Wirecard“ und vielen anderen Delikten auf die Spur gekommen ist. Also habe ich so schnell es geht die Kurve gekratzt.“
Er selber habe nicht an diesen illegalen Aktionen teilgenommen, sondern nur logistische Hilfsdienste erbracht, sagt Hans. J. (der Name wurde aus sicherheitstechnischen Gründen anonymsiert).
Merkwürdig sei auch das angebliche Ableben von Stasi-Obrist Ehrenfried Stelzer gewesen, sagt J. „Man weiss nicht, ob jemand anders beerdigt wurde.“ Auch der Mord an Heinz Gerlach ging, laut Hans J. auf das Konto der mutmasslichen Kriminellen-Vereinigung „GoMoPa“.: „Die haben ihre alten Stasi-Verbindungen spielen lassen und mit Dioxin Heinz Gerlach aus dem Weg geräumt. Auch ich bin ihnen gefährlich geworden. Deshalb habe ich alle Verbindungen abgebrochen und bin weg.“
Hans J: „Maurischat ist nur das „Aushängeschild“ gewesen. Er kann nocht nicht einmal englisch sprechen. Die Organisation haben Stelzer und Rechtsanwalt Jochen Resch aufgezogen. Resch hat auch die „GoMoPa“-Texte verfasst, in denen es um „Anlegerschutz“ und angebliche Betrügereien ging. Verantwortlich für die Computer-Kriminalität sind Thomas Promny und Sven Schmidt. “
Folgt man Hans J., so gab es Verbindungsmänner bei den Hostern Media-On, Türkei, und Go-Daddy, USA, sowie bei Google, Hamburg, die bei den Cyberstalking Delikten „nützlich“ gewesen sein sollen und sind.
Derzeit habe eine Spaltung der deutschen Kriminellen-Gruppe eingesetzt – verursacht durch den Fahnungsdruck sowie die schwindenen Geldreserven. Auch die Verbindung zu den russischen Hackern, die mit Denial of Service Attacken die Server der „GoMoPa“-Gegner zum Absturz brachten, sei abgebrochen – mangels Zahlung an die Russen.
Der „NACHRICHTENDIENST“ „GoMoPa“: Neuer Angriff auf die Immobilienbranche – Ermittlungen der KRIPO: ST/0148943/2011
Trotz zahlreicher Strafanzeigen, serienmässiger Vorstrafen und der mutmasslichen Verwicklung in mindestens einen hochkarätigen Mordfall erdreistet sich der „NACHRICHTENDIENST“ „GoMoPa“ die Immobilienzene uter Druck setzen zu wollen.
Unter der Schlagzeile „Immobilienverkäufer-Szene nervös!“ schreibt der „NACHRICHTENDIENST“: „Die Berliner Immobilienverkäuferszene Panik. Unter ihnen muss es einen oder mehrere Verräter geben. Wilde Gerüchte machen die Runde – Zu pikant, zu brisant waren die Informationen …“.
Und: „Der Artikel mit der Überschrift „Neue Fakten gegen die Bank“ in der neuesten Ausgabe der Zeitschrift Finanztest hat die Berliner Immobilienverkäuferszene in Panik versetzt. Unter ihnen muss es einen oder mehrere Verräter geben. Wilde Gerüchte machen die Runde – und die ersten Ratten verlassen das sinkende Schiff. Zu pikant, zu brisant waren die Informationen die der Bericht beinhaltete.
Wer waren wohl die oder Informant(en)?
Was veranlasste diese „auszupacken“?
Wer ist dieser oftmals……“
Die wilden Spekulationen sind leicht in das Anwaltskanzlei von „Anlegerschutzanwalt“ Jochen Resch zurück zu verfolgen, dem mutmasslichen „Gehirn“ des „NACHRICHTENDIENSTES“ „GoMoPa“. Offensichtlich soll hier durch Presseberichte Druck auf die renommierte DKB Bank ausgeübt werden, vorgeschlagene Vergleichsangebote von RA Jochen Resch zu akzeptieren
Deep Throat, Berlin: „Resch braucht den Vergleich mit der DKB Bank aus drei Gründen. Er braucht das Gekld dringend, er braucht die DKB als fallenden Dominostein, um dann weitere Opfer zu erpressen und drittens um sein „Netzwerk“ aufrecht zu erhalten. Wenn er innerhalb der nächsten drei Monate keinen grossen Erfolg vorweisen kann, bricht sein „Imperium“ zusammen.“
Der Informamnt aus dem Reschen „Netzwerk“ fährt fort: „Der „NACHRICHTENDIENST“ „GoMoPa“ sowie assoziierte Webseiten wie „Die Bewertung“, aber auch renommierte Medien wie „Finanztest“ sollen die DKB Bank sturmreif schiessen, wenn die DKB Bank diesen Vergleich verweigert, wird es schnell ganz ganz eng für Resch & Co..“
Story Background:
Dioxin-Täter: Die tödlichen Waffen des STASI „NACHRICHTENDIENSTES“: Der perfekte Mord
Siegfried Sievert oder Siegfried Siewert – das ist frei nach Hamlett hier die Dioxin-Frage. Ersterer ist der ehemalige Stasi-Agent und Dioxin-Nahrungsketten-Vergifter – letzterer Name das „Pseudonym“ von Klaus-Dieter Maurischat, dem serienmässig vorbestraften „NACHTRICHTENDIENST“-„GoMoPa“-Betrüge und Erpresser.
Im Netzwerk von „ „GoMoPa“ an prominenter Stelle sind RA Jochen Resch sowie der unter mysteriösen Umständen angeblich verstorbene bzw. verschwundene Stasi-Obrist Ehrenfried Stelzer und „Detektiv“ Medard Fuchsgruber.
Das Stasi-Problem war mit dem Zusammenbruch der DDR keineswegs beendet. Ehemalige Stasi-Mitarbeiter gelangten nach der Wende in höchste Positionen. In Brandenburg hatten es sogar mehrere ehemalige Stasi-Mitarbeiter bis in die aktuelle rot-rote Landesregierung geschafft, um dort die Regierung zu übernehmen. Auch in Sachsen-Anhalt könnten nach der Landtagswahl ehemalige Stasi-Mitarbeiter in die Regierung gelangen. Und auch in der Wirtschaft sind viele Stasi-Mitarbeiter in hohe Positionen gelangt. So auch der Herr Sievert. Doch was bezweckte dieser tatsächlich mit der Dioxinvergiftung? Handelte er wirklich aus Profitgier, oder war die bundesweite Vergiftung eine verspätete Rache der Stasi gegen den ehemaligen Klassenfeind?
Ebenso wie andere osteuropäischen Geheimdienste, z.B. der Geheimdienst der Ukraine beim Mordanschlag auf Präsident Viktor Juschtschenko -, benutzte die Stasi Dioxin und Dioxin-Experten:
Die Akte trägt die Registriernummer II 153/71, ist mehrere
Hundert Seiten dick. Auf dem Deckel ein Name: “Pluto“. Unter
diesem Decknamen spionierte Siegfried Sievert (58), der als Geschäftsführer
des Futtermittel-Herstellers Harles und Jentzsch mutmaßlich für
den Dioxin-Skandal verantwortlich ist, 18 Jahre lang für die
Staatssicherheit der DDR. Das berichtet die BILD-Zeitung (Freitagausgabe).
Auf Antrag von BILD gab die zuständige Birthler-Behörde die Unterlagen
jetzt heraus. Die Akten, so BILD, verraten: 1971 wurde die Stasi
auf den damals 18-jährigen Sievert aufmerksam. Sie beobachtete
sein “dekadentes Aussehen“, seine hohe Intelligenz und seine
“guten Verbindungen zu anderen jugendlichen Personenkreisen“.
Sievert wurde angeworben. Aus einem Bericht vom 16. März 1971:
“Der Kandidat kann zur Absicherung der Jugend (…) eingesetzt
werden.“
Sievert wählte laut BILD seinen Decknamen selbst, kassierte fortan
Prämien für seine “inoffizielle Mitarbeit“. In den Unterlagen
finden sich zahlreiche Quittungen, eine vom 6. November 1987:
“Hiermit bescheinige ich den Erhalt von 100 Mark für geleistete
Arbeit.“
Nach dem Abitur studierte Sievert in Greifswald Physik. Er machte
Karriere, spitzelte weiter, berichtete über intime Verhältnisse
seiner Kollegen. So notierte “IM-Pluto“ am 25. September 1986
über zwei Kollegen: “Die beiden beabsichtigen, gemeinsam die
BRD zu besuchen. Fakt ist jedoch, daß zwischen dem Kollegen und
der Kollegin seit langer Zeit Intimbeziehungen bestehen. (…)
Aus dieser Tatsache ist abzuleiten, daß eine gemeinsame Reise
in die BRD mit hoher Wahrscheinlichkeit für eine Flucht benutzt
wird.“
Skrupel zeigte Sievert laut Stasi-Akte keine. Ein Führungsoffizier
notierte: “Der IM hatte keinerlei Vorbehalte bei der Belastung
von Personen aus seinem Umgangskreis.“
1993 stieg Sievert beim Futtermittelhersteller “Harles & Jentzsch“
ein. 2005 wurde er alleiniger Geschäftsführer, steigert in nur
fünf Jahren den Umsatz von 4,3 auf rund 20 Millionen Euro, vervierfachte
den Gewinn.
Der beinahe perfekte Dioxin-Mord
Es wäre beinahe ein perfekter Mord gewesen. Übelkeit, Erbrechen, heftige Schmerzen, ein sich über Tage und Wochen verschlimmernder Krankheitszustand, ohne dass die Ärzte am Lauf der Dinge etwas Entscheidendes hätten ändern können. Der Patient wäre schließlich verstorben, und kein Gerichtsmediziner hätte nachweisen können, was die Ursache war.
So aber kam alles anders, als es um ein Haar hätte sein können.
Viktor Juschtschenko, der liberale, westlich orientierte Präsidentschaft der Ukraine, ist zwar – für alle Welt sichtbar – entstellt und wird wohl noch jahrelang an den Folgen seiner Dioxinvergiftung zu leiden haben, aber er lebt.
Aber es hätte um ein Haar anders kommen können.
5. September 2004, Geheimdienst
Im Kiewer Haus des stellvertretenden ukrainischen Geheimdienstchefs Volodymyr Satsyuk trifft sich Juschtschenko mit Geheimdienstchef Ihor Smeschko und anderen Geheimen zum Abendessen. Zur Speisenfolge gehörten Rahmsuppe, Sushi und Flusskrebse. In der darauf folgenden Nacht klagte Juschtschenko über heftige Bauch- und Rückenschmerzen, Übelkeit und Erbrechen. Vier Tage danach kam er, noch immer von heftigen Schmerzen geplagt, in einem mitternächtlichen Flug von Kiew zur Behandlung nach Wien ins 120 Jahre alte private Nobelspital Rudolfinerhaus. Die Kontakte liefen über Nikolai Korpan, einen aus der Ukraine stammenden, seit vielen Jahren in Wien tätigen Allgemeinchirurgen, der im Rudolfinerhaus als Belegsarzt ordiniert.
Michael Zimpfer, seit drei Jahren Präsident des Aufsichtsrats des Rudolfinerhauses sowie Vorstand der Universitätsklinik für Anästhesie und Allgemeine Intensivmedizin, der bei Juschtschenkos Aufnahme anwesend war, berichtet, die Ärzte hätten sich zunächst nur auf eine „deskriptive Diagnostik“ beschränken müssen – so ungewöhnlich war das Krankheitsgeschehen. Demnach wurde Juschtschenko „in einem kritischen, aber nicht sterbenden Zustand“ eingeliefert. Die Erstdiagnose lautete auf „akutes Abdomen“ (akuter Bauch).
Zunächst deutete nichts auf eine Vergiftung oder gar eine Dioxinvergiftung hin, wie sie etwa durch eine charakteristische Chlorakneerkrankung der Gesichtshaut erkennbar wird. Wohl zeigten sich im Gesicht des Patienten Hautrötungen, die von zwei hinzugezogenen Hautärzten zunächst als Rosacea, eine chronisch verlaufende Hauterkrankung unbekannter, vermutlich genetischer Ursache, gedeutet wurden. Weiters diagnostizierten die Mediziner einen Herpes zoster (Gürtelrose), eine leichte Gesichtslähmung sowie eine Ohrenentzündung.
11. September, Blutflecken im Darm
Weit dramatischere Befunde ergaben die Aufnahmen aus dem Computertomografen sowie die endoskopische Untersuchung von Magen und Darm durch den AKH-Gastroenterologen Eduard Penner. Demnach zeigten sich im Magen, im Zwölffinger- und im Dickdarm des Patienten geschwollene Blutflecken, auch Leber und Bauchspeicheldrüse waren stark angeschwollen, die Leberwerte im Blut deutlich erhöht – typische Anzeichen einer Leberentzündung (Hepatitis) und eines Leberzerfalls. Überdies zeigten sich an den Rändern der Bauchspeicheldrüse Flüssigkeitsaustritte, deutliches Signal für eine – von Ärzten besonders gefürchtete – Pankreatitis (Entzündung der Bauchspeicheldrüse).
Es bestand akute Lebensgefahr.
Denn die Pankreatitis birgt in sich die Gefahr, dass sich die Entzündung „selbst propagiert“ und das Organ „verrückt spielt“, wie es Intensivmediziner Zimpfer formuliert. In solchen Fällen sondert die Bauchspeicheldrüse nicht mehr die üblichen Verdauungssekrete in den Darm ab, um den Speisebrei in seine Bestandteile aufzulösen, sondern beginnt, mittels gewebszersetzender Stoffe, seine Umgebung zu verdauen. Außerdem bestand auch Gefahr, dass die Leberfunktion zusammenbricht – für das behandelnde Ärzteteam ein Albtraum.
Die Situation war umso dramatischer, als die Ursache von Juschtschenkos Erkrankung nach wie vor unbekannt war. Die Mediziner konnten vorerst nur versuchen, bekannte Erkrankungen nach und nach auszuschließen, wie etwa eine Fisch- oder eine andere Lebensmittelvergiftung, eine Immunerkrankung oder eine bakterielle oder virale Infektion. Aber im Blut fand sich bis auf den Herpes zoster keinerlei Erreger, auch ließ sich kein „Morbus“, also keinerlei Kombinationserkrankung, finden. Die Ärzte suchten, fanden aber nichts. Sie verabreichten dem Patienten Infusionen und organstabilisierende Medikamente. Aber damit war ihre Kunst auch schon zu Ende.
18. September, kritische Leberwerte
Acht Tage nach seiner Aufnahme im Rudolfinerhaus flog Juschtschenko zurück in die Ukraine, um sich wieder im Präsidentschaftswahlkampf zu engagieren – entgegen dem dringenden Rat der Ärzte, die Schlimmes befürchteten, weil sich die Leberwerte des Patienten weiter verschlechtert hatten. Am 30. September kehrte Juschtschenko wieder nach Wien zurück, um sich einer neuerlichen ärztlichen Behandlung zu unterziehen. Unterdessen klagte er über unerträgliche Rückenschmerzen, wie sie sonst allenfalls nach einem Unfall oder im Zusammenhang mit einem Bandscheibenvorfall auftreten. Doch die Abklärung im Kernspintomografen unter Beiziehung des bekannten Neurologen Heinrich Binder, des Ärztlichen Leiters des Neurologischen Krankenhauses im Maria-Theresien-Schlössl, ergab keinerlei Befund im Bereich der Wirbelsäule.
2. Oktober, unerträgliche Schmerzen
Um die unerträglichen Schmerzen zu lindern, verabreichten die Ärzte dem Patienten intravenös extrem hohe Dosen morphinartiger Medikamente. In einer nicht ungefährlichen Aktion injizierten sie ihm zusätzlich mittels Katheter ein Lokalanästhetikum neben das Rückenmark der Brustwirbelsäule, weil die durch nichts erklärbaren Schmerzen stärker wurden, obwohl sich Juschtschenkos Allgemeinzustand inzwischen leicht gebessert hatte. Die Ratlosigkeit der Ärzte wurde nur noch größer, nachdem sich auch bei der gerichtsmedizinischen Untersuchung von Harn- und Blutproben des Patienten „kein Hinweis für toxikologisch relevante Komponenten“ ergeben hatte.
Heute wissen sie, warum: Zwar gilt der Chefchemiker des Instituts für Gerichtsmedizin, Walter Vykudilik, allseits als hervorragender Detektiv mit der Pipette. (Er konnte unter anderem in den neunziger Jahren die von der „schwarzen Witwe“ Elfriede Blauensteiner mithilfe des Blutzuckermittels Euglucon begangenen Giftmorde an drei Pensionisten aufklären.) Aber es fehlen am gerichtsmedizinischen Institut jene Präzisionsgeräte, die man benötigt, um auch eine Dioxinvergiftung zu entdecken. „Man kann so eine Analyse ohne die entsprechenden Geräte, ohne die personellen und strukturellen Voraussetzungen nicht machen, das geht nicht“, sagt Vykudilik.
7. Oktober, ärztlicher Hilferuf
Weil die behandelnden Ärzte schon frühzeitig auf eine unbekannte biologische oder chemische Waffe getippt hatten, wandten sie sich weltweit an höchste Repräsentanten ihres Fachs, an wissenschaftliche Institute und internationale Organisationen um Hilfe bei der Aufklärung des schwierigen Falles: „Da die Erkrankung untypisch verläuft, ist auch der Verdacht des individuellen Einsatzes eines biologischen Kampfstoffes gegeben. Aufgrund der geschilderten Situation benötigen wir Ihre Hilfe und möchten Sie herzlich ersuchen, uns diese bezüglich chemischer Kampfmittel und biologischer Waffen zu gewähren“, heißt es in dem von Korpan und Zimpfer unterzeichneten Schreiben. Zugleich setzte sich Zimpfer telefonisch mit Kollegen in weltweit führenden Instituten der Toxikologie, darunter dem Center of Poison Control in Washington, in Verbindung, um mit ihnen die seltsamen Krankheitssymptome zu erörtern. Aber auch diese Gespräche blieben vorerst ohne Ergebnis.
Nach neuerlichem zehntägigem Aufenthalt im Rudolfinerhaus flog Juschtschenko, begleitet von Zimpfer und einer Wiener Ärztin, am 10. Oktober über Lemberg, wo Juschtschenko eine Wahlveranstaltung abhielt, nach Kiew, um sich dort in weitere ärztliche Behandlung zu begeben. Die Ärztin blieb als Beratungs- und Auskunftsperson in Kiew zurück.
Nun behauptete der vom Westen unterstützte Juschtschenko auch im Parlament in Kiew, er sei von Regierungskreisen vergiftet worden, was nicht ohne Wirkung auf die öffentliche Meinung in der Ukraine blieb: Der Kandidat der Opposition legte in allen Umfragen deutlich zu und schien gute Aussichten zu haben, nach dem ersten Wahlgang am 31. Oktober in die für 20. November angesetzte Stichwahl zu kommen und seinen Hauptrivalen Viktor Janukowitsch, den Kandidaten des Regierungslagers, zu schlagen. Zum Beleg seiner Behauptung legte Juschtschenko jenes ärztliche Schreiben vor, das zu den erwähnten Erschütterungen unter den Ärzten des Rudolfinerhauses führte.
22. November, Dioxin-Verdacht
Einige Wochen später war der Beleg für Juschtschenkos Behauptung auch in seinem Gesicht zu sehen: anthrazitfarben aufgedunsen, zerfurcht und mit Pusteln überzogen, die Augen verschwollen. Als der Londoner Toxikologe John A. Henry diese Aufnahmen sah, tippte er sofort auf eine Dioxinvergiftung. Die Furchen und Geschwulste in Juschtschenkos Gesicht seien allem Anschein nach eine Chlorakne, und die sei nun einmal charakteristisch für eine Dioxinvergiftung, sagte Henry gegenüber einem Redakteur des Londoner „Inde-pendent“.
Er verfüge zwar über keine toxikologische Evidenz zur Untermauerung seines Verdachts, aber seine Diagnose beziehe sich auf diese Bilder sowie auf den medizinischen Bericht, wonach Juschtschenko zwei Monate zuvor völlig gesund gewesen wäre. „Es gibt nur sehr wenige medizinische Konditionen, die innerhalb so kurzer Zeit zu dieser Art Veränderung führen können“, sagte Henry, der es für durchaus möglich hielt, dass eine einzige hohe Dosis Dioxin, versteckt im Essen, genügen würde, um jenen Effekt zu erzeugen, wie er nun in Juschtschenkos Gesicht zu sehen war.
11. Dezember, Dioxin-Bombe
Die Veränderungen in Juschtschenkos Gesicht, wie sie im Fernsehen und in Zeitungen zu sehen waren, waren auch Ärzten aufgefallen. So etwa tippte auch Hubert Pehamberger, der neue Vorstand der Universitätsklinik für Dermatologie, auf eine Chlorakne. Solche Vergiftungen sind zwar äußerst selten, aber es gab auch schon Fälle in Österreich, weil Dioxin auch bei normalen Verbrennungs- oder industriellen Produktionsprozessen anfällt.
Unterdessen hatten die Ärzte an Juschtschenko appelliert, wieder zu kommen, um sich weiteren Untersuchungen zu unterziehen. Schon zuvor wurden ihm in Kiew neuerlich Blutproben abgenommen und von einem bei der Prozedur anwesenden Zeugen in einer eidesstattlichen Erklärung als von Juschtschenko stammend bestätigt. Diese Proben gingen an mehrere Labors, darunter an ein EU-Referenzlabor in Amsterdam. Am Samstag, den 11. Dezember platzte dann die Bombe: In einer internationalen Pressekonferenz gab das behandelnde Ärzteteam in Juschtschenkos Gegenwart die Analyse des Labors in Amsterdam bekannt: Demnach enthielten die Blutproben derart hohe Dioxinwerte, dass eine exakte Bestimmung vorerst unmöglich war. In der Vorwoche bestätigten zwei weitere EU-Referenzlabors, Juschtschenkos Blutproben würden Dioxinwerte zeigen, die etliche tausend Mal höher liegen als die im menschlichen Blut vorhandenen Normalwerte.
Allerdings muss man bedenken, dass Juschtschenko eine außergewöhnliche, einmalige hohe Dosis Dioxin verabreicht bekam (50.000fach höher) und nicht über Jahre hinweg kein, gefährliche Dosen. Juschtschenkos Dioxinabbau darf daher nicht als Norm angesehen werden. Sein Körper ist trotz der ansehnlichen “Abbaukurve” nach wie vor verseucht.
Der Mordanschlag auf den ukrainischen Präsidentschaftskandidaten Viktor Juschtschenko zeigte der Weltöffentlichkeit deutlich, welche Gefahr Mordgifte in der Hand von Verbrechern sind.
Dioxine sind ein Sammelsurium hunderter Verbindungen, die hoch toxisch sind und den Stoffwechsel irreversibel ruinieren: Immungifte und Nervengifte.
Da die Laborversuche mit diesen Giften noch viel gefährlicher sind als mit Radioaktivität, kennt man nur die Folgen einiger weniger Verbindungen. Man interessiert sich aber auch nicht dafür, da mehrere tausend Menschen bei uns damit vergiftet sind. Am wichtigsten sind die Opfer der Holzgifte PCP und Lindan, die als technisches Abfallprodukt der Industrie zur billigen Entsorgung (!!) jahrzehntelang ungestraft auf die Decken von über 100 000 Kinder-
Zimmer gestrichen wurden.
Aufgrund der hohen Giftkonzentrationen im Menschen und in der Muttermilch haben die Arbeitsmediziner die Grenzwerte hoch oben angesetzt.
Arbeitsmedizinische Grenzwerte orientieren sich an den tatsächlich gemessenen Werten und nicht an der erforderlichen Schutzhöhe. So lagen rechtswidrig bei der krebserzeugenden Substanz PCP(Pentachlorphenol) die Grenzwerte im Blut bei 1000 µg/l, da nur dann fast alle darunter lagen. Heute liegen sie bei 50 – obwohl man weiß, dass mit der Nahrung nur maximal ein PCP-Wert im Blut von 5 µg/l erreicht werden kann. Zudem dürfte es für krebserzeugende Substanzen, die ja nach dem „Alles-oder-nichts-Gesetz“ wirken keine Grenzwerte geben.
So wie der ukrainische Attentäter vom Geheimdienst sicher straffrei ausgeht, gehen die Nachfolgetäter sicher auch straffrei aus. Nachweismethoden gibt es bisher nur für die Chlordioxine, die wesentlich giftigeren Fluordioxine, die entstehen, wenn man Fluorzahnpaste oder Fluorsalz geschluckt hatte oder die hochtoxischen Joddioxine, die entstehen, wenn in den Körper synthetisches Jodsalz kam, sind heute noch nicht nachweisbar, aber grosstechnisch federleicht herstellbar.
Dioxin ist im 21. Jahrhundert die Superbombe für Terroristen.
R.F., Berlin, ein intimer Kenner der RA-Kanzlei Resch und des „NACHRICHTENDIENSTES“ „GoMoPa“ legt nach: „Fast alle Texte der Webseite „GoMoPa“ werden in der Berliner Anwaltskanzlei von Resch verfasst. „NACHRICHTENDIENST“ „GoMoPa“ hat keine Redaktion. Die Aufgabe des vorbestraften Serienbetrügers Klaus Maurischat besteht vielmehr in der Bespitzelung und in der Erpressung. Intellektuell ist er gar nicht in der Lage, einen fehlerfreien Artikel zu schreiben. Meines Wissens her erhielt er seine Ausbildung bei der STASI. Aber selbst für den STASI-Obristen Ehrenfried Stelzer war er nur ein primitives Werkzeug.“
Nachfolgend ein schönes Beispiel für die „redaktionelle Zusammenarbeit zwischen „GoMoPa“ und RA Jochen Resch:
Zitat:
„GoMoPa: Sie bezeichnen sich selbst als Robin Hood, also als Wegelagerer. Doch Robin Hood gab seinen Gewinn den Armen. Sie stürzen Ihre Mandanten in Rechtsstreitigkeiten mit starken Gegnern und fraglichen Ausgängen. Am Ende sind Ihre Mandanten Ihre Anlage los und haben bei Ihnen auch noch 10.000 bis 20.000 Euro zahlen müssen, wenn sie keine Rechtsschutzversicherung haben.
Resch: “Die meisten unserer Mandanten verfügen noch über eine Rechtsschutzversicherung. Aber, wie kommen Sie auf 10.000 bis 20.000 Euro Honorar, das sind doch Phantasiepreise?!”
GoMoPa: Na, die Streitwerte liegen bei 100.000 Euro. Und wenn es dann durch alle Instanzen geht, über mehrere Jahre.
Resch: “Wir haben Streitwerte um die 60.000 bis 80.000 Euro. Manchmal 100.000 Euro. An Gebühren kommen da höchstens 2.500 Euro zusammen. Und in einigen Fällen haben wir auch mittellosen Mandanten unentgeltlich geholfen.”
GoMoPa: Aber 2.500 Euro reichen doch nicht, wenn es durch alle Instanzen geht.
Resch: “Nein, dass reicht nicht. Aber der Verlierer zahlt alles und wir gewinnen meistens die Prozesse. Im Ergebnis nehmen wir es von den Reichen, wie Robin Hood.”
GoMoPa: Nach eigenen Angaben im Internet bearbeiten Sie jährlich 2.500 Fälle, wie viele haben Sie schon gewonnen?
Resch: “Wir, die 22 Resch-Rechtsanwälte, haben im Schnitt 2000 Fälle im Jahr. Die Zahl schwankt erheblich. Wir machen eine kostenlose Ersteinschätzung, ob wir den Fall überhaupt annehmen. Wir wollen gewinnen oder zu mindestens einen guten Vergleich erzielen können. Sonst lehnen wir ab!
Über 90 Prozent unserer Prozesse gewinnen wir. Zunächst oft Musterverfahren, danach Vergleiche. In den letzten Monaten über tausend Vergleiche gegen Postbank und BAG. Ich kenne, mit Verlaub, keine Kanzlei, die über so lange Jahre so erfolgreich arbeitet. Für den Anleger, wohl gemerkt!! Klein und Mittelverdiener.”
GoMoPa: Ihr Insiderwissen und Ihre Argumentationen auf Vorträgen und auf Ihren Internetseiten sind sehr beeindruckend. Und die Szenarien bis hin zum 30jährigen Schuldenturm, in dem man als Anlage-Geschädigter landen kann, sind beängstigend. Allerdings fußt Ihr gesamtes Argumentations-Konstrukt auf einer These, die Sie nirgendwo beweisen oder belegen. Sie behaupten einfach, dass eine Wohnung nicht zu dem Preis weiterverkauft werden kann, zu dem man diese gekauft hatte. Bitte belegen Sie diese These.
Resch: “Versuchen Sie mal, ein von vornherein schlechtes Geschäft weiterzuverkaufen. Das geht nicht. Das Ganze läuft doch in Kurzfassung so ab. Vermittler rufen Telefonnummern aus Klicktel zwischen 15 und 21 Uhr der Reihe nach an. Die erste Frage lautet: Sind sie mit der Steuerpolitik einverstanden? Wer ist das schon? Die zweite Frage lautet: Wollen Sie jeden Monat 250 Euro haben? Wer will das nicht? Dann kommt der Vorschlag, die Lohnsteuern zu senken und das gewonnene Geld in eine Kapitalanlage zu investieren, eine vermietete Wohnung. Aus der Anlage könne man nach zehn Jahren aussteigen. Die Gemeinheit besteht darin, dass man 1.000 Euro Verluste haben muss und man nur von diesen 1.000 Euro Verlusten bei einem Steuersatz von 25 Prozent 250 Euro zurückbekommt. Man bleibt also auf 750 Euro Verlusten selbst sitzen, die man ja irgendwie aufbringen muss. Die reale Frage des Vermittlers hätte vollständig lauten müssen: Geben Sie mir 1.000 Euro, wenn ich Ihnen dafür 250 Euro gebe? Das würde natürlich keiner tun. Und der versprochene Ausstieg ist gar nicht möglich, weil man nicht mal so viel Geld bekommt, um den Kreditvertrag abzulösen. Sobald die Makler die Provision von 20 bis 30 Prozent in der Tasche haben, sind die Kunden nur noch Luft.”
Zitat-Ende
Wie katastrophal Klaus-Maurischat als „Journalist“ wirklich ist, zeigt sich am Besten an seinem Blog „Sch***hausfliege.“
„Die Akte Resch“ – wird immer spannender – wie “The Firm” oder “Die Firma”, ein Roman von David Grisham, verfilmt mit Tom Cruise, aber diesmal leider wohl bittere Realität:
„Die Akte Resch“ – wird immer spannender – wie “The Firm” oder “Die Firma”, ein Roman von David Grisham, verfilmt mit Tom Cruise, aber diesmal leider wohl bittere Realität:
R.F. in Insider, ein ehemaliger Mitarbeiter in der Kanzlei von „Anlegerschutzanwalt“ RA Jochen Resch, Berlin, behauptet: „Schon seit einiger Zeit läuf das grosse Geschäft mit „Schrottimmobilien“ nicht mehr für die Kanzlei Resch. Deswegen wollte er in neue „Geschäftsfelder mit „GoMoPa“ expandieren. Gerlach war dabei im Weg.“
Der Insider: „Durch die Verjährungsfristen und die Aufarbeitung vieler „Schrottimmobilien“-Fälle war die grosse Zeit der „Anlegerschutzkanzlei“ Resch schon seit einiger Zeit vorbei. Auch gegen „GoMoPa“ gab es immer mehr Widerstände im Markt und die Geldbeschaffung für die 60-Leute-Kanzlei-Resch und das Netzwerk aus „Anlegerschützern“ wurde immer schwieriger. Deswegen sollte das „GoMoPa“-Fondsrating nach dem kalkulierten „Abgang“ von Heinz Gerlach wieder Geld in die Resch-Kasse spülen. Einerseits durch die Platzierung eines „GoMoPa“-Emissionsprospekt durch Private Placement und dann durch ein „GoMoPa“-Fondsrating. Nach dem Motto: We nicht zahlt, wird durch „GoMoPa“ fertig gemacht.“
Der Insider fährt fort: „Durch einen Interview-Termin Reschs in der SA-1 Sendung „Die Akte“ kam er auf die Idee, die Webseite „Akte Heinz Gerlach.info“ zu starten. Damit war der Grundstock für den Rufmord an Gerlach gelegt. Die technische Infrastruktur legte der NACHRICHTENDIENST „GoMoPa“. Den Inhalt Hamburger Konkurrenten Gerlachs sowie Hacker, die sich über Trojaner in Gerlachs Computer einhackten. Durch monatelange Cyber-Attacken russischer Hacker wurde Gerlach sturmreif geschossen, weil seine Webseiten immer wieder offline waren. Zur Verschleierung behauptetete „GoMoPa“, Gerlach habe diese Angriffe gefahren. Als Gerlach dann der „Beratervertrag“ zwischen Estavis und „GoMoPa“ in die Hände gespielt wurde und er die New Yorker Briefkasten-Adresse von „GoMoPa“ durch seine Tochter, eine in New York lebende Rechtsanwältin enttarnte, verstand er die Zusammenhänge und musste sterben. Dabei spielten wohl der „NACHRICHTENDIENST“ „GoMoPa“, “Wirtschaftsdetektiv“ Medard Fuchsgruber und Dioxin die Hauptrollen.“
Huintergrund:
„Heribert Hellenbroich, 53, Ex-Chef des Bundesnachrichtendienstes (BND) und zuvor Leiter des Bundesamts für Verfassungsschutz, begibt sich in ungewohnte Gesellschaft. Gemeinsam mit dem ehemaligen Stasi-Oberst und Offizier im besonderen Einsatz (OibE) Ehrenfried Stelzer, 58, hat Hellenbroich einen Verein gegründet. Das “Internationale Institut für Wirtschaftssicherheit zu Berlin” soll, so versichern der ehemalige Top-Nachrichtendienstler (West) und sein Kompagnon (Ost) unisono, aus “ideellen Motiven” Industriebetriebe in Fragen der Wirtschaftssicherheit beraten. “Selbstlos” (Satzung) wollen Hellenbroich und Stelzer für “störungsfreie wirtschaftliche” Ost-West-Beziehungen eintreten und zum Wohl der Unternehmer wirken: Wirtschaftskriminalität abwehren helfen, über Daten- und Banksicherheit aufklären“, schreibt der „SPIEGEL“ bereits 1990.
http://www.spiegel.de/spiegel/print/d-13502488.html
Und: „Berührungsängste mit dem Ex-Stasi-Offizier hat Hellenbroich nicht. Dessen Vergangenheit sei für die künftige Arbeit “nicht weiter von Interesse”, sagt der ehemalige BND-Chef, der 1985 über den Spionagefall Tiedge stolperte. Die rein nachrichtendienstliche Tätigkeit der Stasi sehe er ohnehin neutral: “Was haben wir, der BND, denn anderes gemacht?” Ehemalige Kollegen, die unter Stelzers Leitung in der Sektion Kriminalistik an der Ost-Berliner Humboldt-Universität gearbeitet haben, wundern sich über soviel Vertrauensseligkeit. Stelzer, seit 1961 Mitarbeiter der Stasi, sei ein Hardliner gewesen – einer, der “nach dem Motto ,Nichts geht über den geliebten Genossen Erich Honecker’” verfahren sei, sagt Horst Howorka, stellvertretender Leiter der Sektion Kriminalistik.
Die Humboldt-Universität hat Stelzer beurlaubt und gegen ihn ein Disziplinarverfahren eingeleitet. Der Ehrenausschuß der Uni hält es für “unzumutbar”, den Hellenbroich-Kompagnon weiter zu beschäftigen.“ Das war 1990.
Heute ist Ehrenfried Stelzers Vision Realität geworden. Stelzer und seine Mitstreiter und Nachfolger, haben es – 20 Jahre nach dem Fall der Mauer fast geschaft: Mit dem„NACHRICHTENDIENST“ „GoMoPa“ mutmasslich gesteuert von dem Berliner „Anlegerschutzanwalt“ Jochen Resch, einem wie er selber zugibt, langjährigen Bekannten, ja Intimus Stelzers, ist die CYBER-STASI entstanden, die ihre Gegner gnadenlos ausschaltet – „Wenn es sein muss auch mit Dioxin“, sagen Insider.
Stelzer, der angeblich mittlerweile verstorben sein soll, war der „ERSTE KRIMINOLOGE DER DDR“. Sein „GoMoPa“-Erbe ist hoch-toxisch und mit Dioxin verseucht.
„GoMoPa“ – alleine der Name des ost-Berliner „NACHRICHTENDIENSTES“ löst bei Betroffenen und Maurischat Opfern eine Mischung aus Entsetzen und Belustigung aus. Immer mehr aber überwiegt die Belustigung über den vorbestraften Serienbetrüger Maurischat alias Holbe alias Siewert. Der Grund: Viele seiner Opfer haben es ihm gleichgetan und zusammen mit anderen Geschädigten der mutmasslichen „GoMoPa“-Rheinland-Fraktion „SJB-Fonds“, Neuss die Internet-Plattform http./www.sjb-fonds-opfer.com gegründet.
„Wir haben das Rezept aus Kolumbien“, schmunzelt SJB-Fonds-Opfer-Sprecher Heinz Friedrich (der Name wurde vond er Rdaktion aus Sicherheitsgründen anonymisiert). „ In Kolumbien gab es die „Los Pepes“, die haben den Drogen-Milliardär Pablos Ecobar aus dem Verkehr gezogen. Gegen die CYBER-STASI muss man ebenso vorgehen, denn die normalen Mittel des Staates scheinen gegen diese kriminelle Vereinigung zu versagen.“
Der CYBER-STASI geht es, wie vom kommunistischen Vordenker und „Ersten Kriminologen der DDR“ Ehrenfried Stelzer geplant, um die Infiltration der Wirtschaft.
An den Beispielen Meridian Capital und Immovation AG zeigt sich am Besten, wie der „NACHRICHTENDIENST“ „GoMoPa“ die Immobilienbramnche erpressen will und wie sich gegen die CYBER-STASI „GoMoPa“ wehrt.
Das von „GoMoPa“ im Auftrag seiner dubiosen Hintermänner – Insider behaupten es sei, die Rechtsanwaltskanzlei Resch, Berlin, – verleumdete Unternehmen Immovation verfolgte eine offene Kommunikationsstrategie, das war der Schlüssel zu Erfolge gegen die Erpresser von der CYBER-STASI:
„Erneut wehrt sich die Kasseler IMMOVATION Immobilien Handels AG, ein seit über zwei Jahrzehnten sehr erfolgreiches, bundesweit tätiges Unternehmen der Immobilienbranche, gegen die unverändert anhaltende Schmutzkampagne des sogenannten “Informationsdienstes” GoMoPa (mit Sitz im Ausland), dessen Gründer und “CEO” Klaus Maurischat ebenso wie Mitgründer Mark Vornkahl bereits wegen Betrugs verurteilt wurden. Der 2006 rechtskräftig verurteilte Maurischat gab sogar gegenüber dem Handelsblatt weitere Verurteilungen zu (Handelsblatt vom 07.04.2010), woraufhin das Handelsblatt wörtlich konkludierte: “Es ist allerdings nicht das erste Mal, dass GoMoPa-Vertreter ins Zwielicht geraten”.
GoMoPa suggerierte am 16. August 2010 in einer “Pressemitteilung”, dass IMMOVATION-Vorstandsmitglied Lars Bergmann sogar für den Sturz und das Karriereende des früheren brandenburgischen Ministers Professor Dr. Kurt Schelter durch Immobiliengeschäfte verantwortlich zeichne. In diesem Zusammenhang verweist die IMMOVATION AG auf eine schriftliche Mitteilung von Professor Dr. Kurt Schelter vom 18. August 2010:
“Diesen Zusammenhang gibt es nicht. Ich kenne Herrn Bergmann nicht und habe mit ihm persönlich keine Immobiliengeschäfte abgeschlossen. Mir ist auch nicht bekannt, dass Herr Bergmann etwa mit Verkäufern der von mir damals erworbenen Immobilien persönlich oder institutionell in Verbindung stand oder steht. Ich halte dies für ausgeschlossen.”
Minister a.D. Professor Dr. Kurt Schelter
Die IMMOVATION AG hat dieser eindeutigen Mitteilung von Herrn Professor Schelter nichts hinzuzufügen und unterstreicht erneut ihr volles Vertrauen in die Fähigkeit ihrer Klienten, Mitarbeiter und Vertriebspartner, sich selbst ein entsprechendes Bild von dieser Schmutzkampagne machen zu können, in der es dem Autor dieser verleumderischen GoMoPa-”Pressemitteilung” zudem nicht einmal gelang, das Amt des betreffenden Ministers korrekt zu bezeichnen: Im Gegensatz zu seiner Bezeichnung bei GoMoPa war Herr Professor Schelter nicht Finanzminister, sondern Minister der Justiz und für Europaangelegenheiten des Landes Brandenburg.
Die IMMOVATION AG hat im Zusammenhang mit dieser und zahlreichen weiteren unzutreffenden Behauptungen in dieser “Pressemitteilung” heute, 24.08.2010, beim Landgericht Berlin eine einstweilige Verfügung u. a. gegen Goldmann Morgenstern&Partners Consulting LLC (New York) und die GoMoPa GmbH (Berlin) beantragt. Mit der Verfügung soll den Antragsgegnern untersagt werden, die grob diffamierende Pressemitteilung zu verbreiten oder verbreiten zu lassen.“
Und
„Nach den höchsterfreulichen gerichtlichen Erfolgen gegen den u. a. von rechtskräftig verurteilten Betrügern betriebenen, im Ausland domizilierten “Informationsdienst” Gomopa geht die Kasseler IMMOVATION Immobilien Handels AG auch straf- und zivilrechtlich gegen den Wirtschaftsdetektiv Medard Fuchsgruber vor.
Dieser hatte den IMMOVATION-Vorständen Lars Bergmann und Matthias Adamietz im Frühjahr 2010 angeboten, unwahre, diffamierende Veröffentlichungen auf der Website der gomopa.net beseitigen zu lassen und weitere rechtswidrige Veröffentlichungen dieser Art zu verhindern. Diese beauftragten Medard Fuchsgruber entsprechend und entrichteten ein Honorar von insgesamt EUR 67.500,00. Entgegen allen Zusagen von Fuchsgruber erfolgen über Gomopa jedoch – insbesondere seit Juli diesen Jahres – weiterhin schwer diffamierende Veröffentlichungen, gegen deren wesentlichste das traditionsreiche Kasseler Unternehmen in der Zwischenzeit bereits vor Gericht eine einstweilige Verfügung durchsetzen konnte (LG Berlin; Az.: 27 O 658/10).
Fuchsgruber ist – nach Entgegennahme des Vorabhonorars – offenbar seit Juni selbst “Kooperationspartner” bei Gomopa und wirbt sogar mit dieser Funktion, auch bei Gomopa wird das Engagement Fuchsgrubers besonders willkommen geheißen. Nach Auffassung der IMMOVATION hat Fuchsgruber damit von Beginn an über sein beabsichtigtes Engagement für die IMMOVATION getäuscht, was das Unternehmen im Rahmen einer Strafanzeige und eines Strafantrags inzwischen von der zuständigen Staatsanwaltschaft überprüfen lässt. Zudem hat die IMMOVATION das vorab bezahlte Honorar zurückgefordert und wird erforderlichenfalls den zivilrechtlichen Klageweg beschreiten.
Absurde Erklärungsversuche
Die von Fuchsgruber offenkundig in Journalisten- und Branchenkreisen zirkulierte Einschätzung, er hätte auftragsgemäß für IMMOVATION gehandelt, zielt völlig ins Leere: Denn nach seinem Einstieg bei Gomopa haben die über einen Serverstandort im Ausland verbreiteten Schmähungen nachweislich sogar zugenommen. Und schließlich: Selbst wenn dem so wäre, wie ließe sich dann der Umstand erklären, dass Fuchsgruber weiterhin als “Kooperationsparter” bei Gomopa fungiert, wenn doch nun für Gomopa öffentlich bekannt ist, dass Fuchsgruber im Auftrag der diffamierten IMMOVATION aktiv werden sollte?
Eine unmittelbare Beendigung der Zusammenarbeit Fuchsgruber und Gomopa wäre daher die logische Konsequenz, die jedoch bezeichnenderweise bis heute offenkundig ausgeblieben ist, was den von der IMMOVATION erhobenen Vorwurf weiter untermauert. Bemerkenswert ist darüber hinaus, dass sich der Einstieg Fuchsgrubers beim “Informationsdienst” Gomopa laut Medienberichten in enger zeitlicher Nähe zum Scheitern Fuchsgrubers beim Deutschen Institut für Anlegerschutz (DIAS) vollzog.“
http://www.ad-hoc-news.de/immovation-ag-strafanzeige-und-strafantrag-gegen–/de/News/21600105
Nunmehr aber kann niemand mehr bei „GoMoPa“ zustellen. Die Kriminalpolizei ermittelt: ST/0148943/2011
Und:
„FAZ berichtet über Gomopa-Machenschaften
Gezielt Gerüchte gestreut
Nach Informationen der F.A.Z. sollen unter anderem gezielt über den Finanznachrichtendienst Gomopa im Internet Gerüchte über Pennystocks gestreut worden sein. Gomopa steht für Goldman Morgenstern & Partners Consulting LLC. Auf ihrer Internetseite hat Gomopa „Transparenz in Sachen Finanzen, Vorsorge und Geldanlage“ versprochen, doch ihr Chef Klaus Maurischat saß als mutmaßlicher Betrüger schon in Untersuchungshaft.
Seit einigen Tagen ist die Internetseite http://www.gomopa.net offline, und es kursieren Gerüchte über finanzielle Unregelmäßigkeiten. Immer wieder ist Gomopa in juristische Streitigkeiten verwickelt. In einer einstweiligen Verfügung des Landgerichts Berlin vom 31. August (Az.: 27 O 658/10) ist das Unternehmen aufgefordert worden, nicht länger Falschinformationen über den Kasseler Immobilienhändler Immovation AG und seinen Finanzvorstand Lars Bergmann zu verbreiten. „Gomopa hat seinen Firmensitz bewusst in New York, weil die Firma dort presserechtlich nicht belangt werden kann“, sagte ein Kenner des Unternehmens der F.A.Z.“
Meridian Capital lockte den Zuträger von „GoMoPa“- Erpresser in Berlin in eine Falle und erhielt von diesem dann die Info, wo sich Maurischat gerade aufhielt:
„Seitens der Meridian Capital Enterprises Ltd. gab es überhaupt keine Reaktion auf den Erpressungsversuch von GOMOPA. Ende August 2008 auf dem Service http://www.gompa.net sind zahlreiche Artikel/Meldungen erscheinen, welche die Tätigkeit der Meridian Capital Enterprises Ltd. in einem sehr negativen Licht dargestellt haben. Nachdem die auf http://www.gomopa.net enthaltenen Informationen ausführlich und vollständig analysiert worden waren, ergab es sich, dass sie der Wahrheit nicht einmal in einem Punkt entsprechen und potenzielle und bereits bestehende Kunden der Meridian Capital Enterprises Ltd. in Bezug auf die von diesem Finanzinstitut geführten Geschäftstätigkeit irreführen. Infolge der kriminellen Handlugen von GOMOPA und der mit ihm kooperierenden Services und Blogs im Netz hat die Meridian Capital Enterprises Ltd. beachtliche und messbare geschäftliche Verluste erlitten. Die Meridian Capital Enterprises Ltd. hat nämlich in erster Linie eine wichtige Gruppe von potenziellen Kund verloren. Was sich aber als wichtiger ergab, haben sich die bisherigen Kunden von der Meridian Capital Enterprises Ltd. kaum abgewandt. Diejenigen Kunden haben unsere Dienstleitungen weiterhin genutzt und nutzen die immer noch. In Hinblick auf die bisherige Zusammenarbeit mit der Meridian Capital Enterprises Ltd., werden ihrerseits dem entsprechend keine Einwände erhoben .
…
Die koordinierten Schritte und Maßnahmen der Meridian Capital Enterprises Ltd. und anderer Beschädigter, geleitet von der Internationalen Wirtschaftspolizei INTERPOL, dem Bundeskriminalamt und der Staatsanwaltschaft der Bundesrepublik Deutschland haben zur Aus-, Einarbeitung und Durchführung der oben beschriebenen Falle beigetragen. Im November 2008 führte die in Berlin vorbereitete Falle zur Festnahme und Verhaftung des Vertreters des GOMOPA, der nach der Festnahme auf Herrn Klaus Maurichat – als den Hauptverantwortlichen und Anführer der internationalen kriminellen Gruppe GOMOPA verwies. Der Festgenommene benannte und zeigte der Bundeskriminalpolizei zugleich den aktuellen Aufenthaltsort des Herrn Klaus Maurischat. „Gehirn“ und Gründer dieser internationalen kriminellen Gruppe GOMOPA, Herr Klaus Maurischat wurde am selben Tag auch festgenommen und auf Frist verhaftet, wird bald in Anklagezustand gestellt, wird die Verantwortung für eigene Straftaten und die des Forums GOMOPA vor einem zuständigen Bundesgericht tragen. Die Meridian Capital Enterprises Ltd. unternahm bereits alle möglichen Schritte, damit Herr Klaus Maurischat auch auf der Anklagebank des zuständigen Gerichts des Vereinigten Königsreiches Großbritannien erscheint…“
und hier
http://othergomopa.blogspot.com/
aus dem Jahre 2009 und nicht wie die von „GoMoPa“gebastelte Fälschung aus 2010.
Diese Vorgänge können gerne bei Meridian Capital überprüft und nachvollzogen werden.
Der „NACHRICHTENDIENST“ „GoMoPA“ DIE CYBER-STASI DES 21. JAHRHUNDERTS
„Lauschen, spähen, schnüffeln: Vor 60 Jahren wurde die DDR-Staatssicherheit gegründet. Mehr als 91.000 hauptamtliche und doppelt so viele inoffizielle Mitarbeiter garantierten der SED die Macht. Ein Geheimdienst im klassischen Sinn war der Apparat nie, eher schon eine kriminelle Vereinigung mit tödlichen Methoden“, schreibt die angesehene Tageszeitung „DIE WELT“.
„Genau so verfährt auch der „NACHRICHTENDIENST“ „ GoMoPa“ , erläutert Rainer W. (Name wurde aus Sicherheitsgründen anonymisiert). Er war über mehrere Monate „inoffizieller“ Mitarbeiter des „NACHRICHTENDIENSTES“ „GoMoPa“, einem angeblichen Zusammenschluss jüdischer US-Rechtsanwälte namens Goldman, Morgenstern & Partner LLC, die noch nie jemand gesehen hat. Stattdessen sehen die Personen, die sich mit „GoMoPa“ beschäftigen nur die Totenkopfmaske stalinistischer STASI-Hacker, Erpresser und Cyberstalker.
Rainer W.: „Die eigentlichen Köpfe von „GoMoPa“ sind meiner Meinung nach wohl RA Jochen Resch und STASI-Oberst Ehrenfried Stelzer. Maurischat (ein Deckname) hat nicht das Format so eine Organisation aufzuziehen.“
Seit Jahren schon vesuchen die vorbestraften Serien-Kriminellen um das „Aushängeschild“ Klaus-Dieter Maurischat die deutsche Wirtschaft zu infiltrieren. Doch erst seit dem mutmasslichen Mord an Heinz Gerlach und den monatelangen Attacken gegen Haus sind viele Fakten recherchiert und zu Tage gekommen.
Vor allem über die Methoden des „NACHRICHTENDIENSTES“ – aber auch über dessen Hintermänner in Berlin, denn in New York existiert sowieso nur eine Briefkastenadresse und auch das „Büro“ in Berlin ist ein „virtuelles Regus-Büro“.
Die Fassade soll den „NACHRICHTENDIENST“ tarnen.
„DIE WELT“ schreibt: „40 Jahre lang, von der Gründung bis zu ihrer schrittweisen Auflösung zwischen Dezember 1989 und März 1990, war die Staatssicherheit der wichtigste Machtgarant der SED-Herrschaft. In dieser Zeit wucherte der Apparat immer mehr, bis schließlich mehr als 91.000 hauptamtliche Mitarbeiter für das MfS tätig waren.
Dieses Heer betreute eine Schattenarmee mit 189.000 „Inoffiziellen Mitarbeitern“ (IM). Statistisch gesehen kam in der DDR auf 55 erwachsene Bürger ein Vollzeit- oder Teilzeit-Stasi-Mann. Zum Vergleich: Im kommunistischen Polen lag das Verhältnis bei 1500 zu eins.
Der Apparat hat ungezählte Verbrechen zu verantworten. Darin folgte er seinen sowjetischen Vorbildern, der Tscheka (stolz nannten sich Stasi-Leute „Tschekisten“) und dem KGB. Vor allem aber prägte ein Mann das kriminelle Gebaren des MfS: Erich Mielke hatte sich schon als junger Mann 1931 als Attentäter in Berlin bewährt, als er im Auftrag der KPD zusammen mit einem Mittäter zwei Berliner Polizeioffiziere erschoss.
Der Doppelmörder konnte flüchten und führte im Spanischen Bürgerkrieg stalinistische Säuberungen in den eigenen Reihen durch. Im Sommer 1945 kehrte er nach Berlin zurück und übernahm sofort eine führende Position in der neu eingerichteten Polizei – interessanterweise in jenem Gebäude, das bis 1990 Sitz und Postanschrift der Staatssicherheit sein sollte.“
Zu den ungezählten Verrechen zählen Morde, Entführungen, Raub, Erpressung, Bespitzelung und jahrelange Gefängnishaft für Regime-Kritiker.
Jörg Berger flüchtete 1979 aus der DDR. Auch im Westen blieb die Stasi sein ständiger Begleiter. Jörg Berger berichtete vor seinem frühen Tod: „Nehmen wir den Fall des Spielers Lutz Eigendorf. Der war kurz vor mir geflüchtet und hat dann durch viel Medienpräsenz noch selbst dazu beigetragen, den Rummel anzufachen. Er starb bei einem Unfall auf der Autobahn, höchstwahrscheinlich hat ihn die Stasi vor seinem Tod geblendet. Entsprechendes findet sich jedenfalls in seiner Akte. Die Leute um Eigendorf waren die Leute, die ich auch um mich versammelt hatte. Dazu war er ein junger Spieler, ich ein gestandener Trainer. So hat man mir die Autoreifen zerstochen, auf der Autobahn löste sich ein Rad – und monatelang hatte ich Lähmungserscheinungen. Vermutlich von einer Bleivergiftung, die die Stasi initiiert hatte. Die haben mir wohl etwas in ein Getränk gemischt.“
„Der „Blitz“ traf Wilhelm van Ackern am 24. März 1955, kurz nach 22.30 Uhr – in Form von K.-o.-Tropfen in frisch gebrühtem Bohnenkaffee. Der vermeintliche Informant Fritz Weidmann hatte den 39-jährigen Fotohändler in eine konspirative Wohnung in der Kreuzberger Gneisenaustraße gelockt und ihm dort den vergifteten Kaffee serviert.
Nach wenigen Minuten wurde van Ackern übel; gestützt von Weidmann, verließ er die Wohnung. Doch auf der Straße erwartete ein weiterer Mann die beiden mit einem Wagen. Wilhelm van Ackern wurde im Schutz der Dunkelheit hineingestoßen und über die noch offene Sektorengrenze von West- nach Ost-Berlin ins Untersuchungsgefängnis Hohenschönhausen gefahren. Erst neuneinhalb Jahre später, teilweise verbüßt in der berüchtigten DDR-Sonderhaftanstalt Bautzen II, kam er frei und durfte zurück nach West-Berlin.“
Von Arsen bis Zyankali:
Der Giftschrank der Staatssicherheit
Themen
Archiv
Forum
Links
Kontakt
Hilfe zum Ausdrucken
21.1.2002
Autoren: Christian Nitsche, Sabina Wolf
Dieter Baumann ist nicht totzukriegen. Nach einer zweijährigen Dopingsperre geht er jetzt wieder an den Start. 1999 eine positive Dopingprobe. Dass er sich selbst gedopt hat, glauben heute nur noch seine Feinde. Und Feinde aus der ehemaligen DDR hatte er genug:
Dieter Baumann 1991:
„Trainer, die eben mit solchen Dingen zu tun hatten, mit Doping, die können vom DLV nicht weiter beschäftigt werden.“
Dieter Baumann 1994:
„Aber die Trainer und die Funktionäre, die haben es nämlich entschieden, dass man es macht. Und diese Leute hat man jetzt wieder.“
Dieter Baumann 1998:
„Für mich als Athlet, das beanspruche ja auch ich für mich selber, gilt als Nachweis eine positive Probe oder ein Geständnis.“
In Baumanns Zahnpasta fanden Kontrolleure das Dopingmittel Norandrostendion. Wie man Zahnpasta-Tuben mit Gift präpariert, kann man in den Stasiakten nachlesen: mit einem Glasröhrchen im hinteren Teil der Z-Tube.
Die Zeitschrift „Laufzeit“ im Osten Berlins fragte ein Jahr vor Baumanns Dopingtest nach einem „Messias“ der Antidopingbewegung und beendete den Kommentar mit dem Satz: „Muß man sich angesichts morgendlicher Hochform eines Tages gar fragen: Ist meine Zahnpasta noch sauber?“
Laufzeit-Chef Wolfgang Weising, früher Leichtathletikautor bei der NVA-Zeitung „Volksarmee“ – sagte gegenüber report AUS MÜNCHEN, diese Formulierung sei Zufall gewesen. Baumann, das Opfer eines Komplotts? Selbst die Tübinger Kriminalpolizei schließt heute aus, dass sich Baumann selbst gedopt hat. Auch wissenschaftliche Untersuchungen belegen: Er konnte seine Zahnpasta nicht nachträglich manipuliert haben. Baumanns größte Entlastung: die Dosis war niemals leistungssteigernd.
Baumann selbst will nicht öffentlich spekulieren, wer ihm das Dopingmittel unterjubelte. Es müsse aber jemand aus seinem engen Umfeld sein.
Dieter Baumann, Olympiasieger 1992:
„Ich glaube schon, dass die Täter sich verrechnet haben. Ich glaube, der Wunsch der Täter, soviel kann ich sagen, ist mein Eindruck, dass es mich überhaupt nicht mehr gibt im Sport. Und ich hab’ dann so ein Naturell, wo ich denke: Nee, wenn jemand so einen innigen Wunsch hat, dann sollte man den nicht erfüllen.“
Die Existenz von Kritikern vernichten, das war eine Aufgabe der Stasi. Der Rechtsmediziner Prof. Thomas Daldrup von der Universität Düsseldorf hat die sogenannte „Toxdat“-Studie der DDR untersucht – eine 900 Seiten starke Datenbank über Giftmordmöglichkeiten. Hier ist detailliert beschrieben wie sich selbst Laien Gifte beschaffen können und wie man einen Mord am besten verschleiert.
Prof. Thomas Daldrup, Präsident Gesellschaft für Toxikologische und Forensische Chemie:
“Hier ist so ein Beispiel für einen Stoff, den will ich nicht erwähnen. ‚Dieser Stoff erfüllt in hohem Maße Kriterien für ein zum perfekten Mord geeignetes Gift.’ Also, das kann man doch gar nicht anders lesen, als dass hier eine Anleitung zum perfektem Mord mit Gift gegeben wird. Hier ist es mal ganz klar ausgedrückt, aber das ganze Buch ist gefüllt mit solchen Informationen.“
Hinweise auf die Verschleierung provozierter Unfälle finden sich ebenfalls in Toxdat: „Vortäuschung von Verkehrsunfällen durch Auslösung von sekundenschneller Bewusstlosigkeit mittels Minigasgenerator in Belüftungsschächten von PKW.“
Da ist zum Beispiel der rätselhafte Verkehrsunfall des ehemaligen DDR-Fußballspielers Lutz Eigendorf im Jahr 1983. Vier Jahre zuvor war er nach einem Spiel in der Bundesrepublik nicht in die DDR zurückgekehrt. Er war ein leidenschaftlicher Autofahrer, seine Fahrweise risikovoll, das notierten die Spitzel der Stasi im Westen. Kurz vor seinem Verkehrsunfall stoppt die Stasi seine Fahrtzeit und die genaue Streckenführung seines täglichen Wegs vom Stadion nach Hause.
Zum Unfallhergang tauchen vor zwei Jahren neue Hinweise auf. Wurde Eigendorf gezielt geblendet? In den Giftakten der Stasi heißt es: „verblitzen, Eigendorf“. Hatte man Eigendorf heimlich ein pupillenerweiterndes Mittel verabreicht?
Die Staatsanwaltschaft Berlin kann Fragen dazu nicht beantworten, da eine Obduktion nicht angeordnet wurde, auch nach Auftauchen der neuen Stasidokumente nicht.
Ein weiterer Fall: Fußballtrainer Jörg Berger liest seine Stasiakten. Nach seiner Flucht aus der DDR wurde der Star-Trainer ´79 zum Staatsfeind.
Jörg Berger, Fußballtrainer Alemannia Aachen:
„Hier ist alles gesagt!“
Die Stasi wusste, dass Berger Angst hatte vor einem möglichen Auftragsmord, um weitere Fußballer vor einer Flucht abzuhalten:
„BERGER bekundete angeblich (…), daß es ihm nicht so ergehen soll wie EIGENDORF.“
Die Stasi glaubte, dass Berger der Drahtzieher war für die Republikflucht mehrerer Fußballer. Als Berger dann Mitte der 80er Jahre als Trainer auf dem Sprung in die 1. Bundesliga war und sich die DDR-Sportler Falko Götz und Dirk Schlegel nach Westdeutschland absetzten, schien Berger für die DDR unerträglich zu werden.
„Im operativen Vorgang ‚Ball’ wurde operativ herausgearbeitet, daß BERGER wesentlichen Anteil am Verrat von GÖTZ und SCHLEGEL hatte.“
Jörg Berger, Fußballtrainer, Alemannia Aachen:
„Es ist auch in diesen Aussagen zu erkennen, dass man mich berufsunfähig machen wollte oder dass man mich kaltstellen wollte in der Richtung, dass ich nicht mehr als Trainer arbeite, um da vielleicht auch nicht mehr die Einflüsse auf Spieler oder vielleicht sogar auf Trainer zu haben.“
1986 litt Berger unter rätselhaften Lähmungserscheinungen. Der Erklärungsversuch damals: eine Virusinfektion. Im Auftrag von report AUS MÜNCHEN hat der Rechtsmediziner Prof. Wolfgang Eisenmenger vor dem Hintergrund von Toxdat Bergers Krankenakten analysiert. Jetzt scheint festzustehen: Berger wurde vergiftet.
Prof. Wolfgang Eisenmenger, Klinikum Innenstadt der Universität München, Institut für Rechtsmedizin:
„Wenn man die laborchemischen Befunde aus dem Krankenhaus kritisch würdigt, muss man sagen, es spricht in Nachhinein nichts für eine durchgemachte Virusentzündung. Da die Schwermetallvergiftungen nicht gezielt untersucht worden sind, kann man sie aufgrund der Laborbefunde nicht ausschließen. (…) Es kommen – wenn man das Krankheitsbild würdigt – vor allem Schwermetalle aus der Gruppe der Bleiverbindungen und der Arsenverbindungen in Betracht.“
Die Anleitung, eine Arsenikvergiftung zu verschleiern – liefert ebenfalls wieder die DDR-Giftstudie Toxdat.
Frühere Stasi-Mitarbeiter wollten auch ihn ausschalten, das glaubt der Bundestagsabgeordnete Hartmut Büttner aus Hannover. 1995 hatte er einen mysteriösen Autounfall, der ihn beinahe das Leben kostete. Nach der Wiedervereinigung hatte der Abgeordnete zu den Hintermännern der „Toxdat“-Studie recherchiert und sich sehr für die Offenlegung der Stasi-Akten durch die Gauck-Behörde eingesetzt.
Hartmut Büttner, CDU-Bundestagsabgeordneter 1991:
„Ich halte es für skandalös, dass der mit dem Sektglas parlierende Altsozialist den Insassen von Bautzen völlig verdrängt hat.”
Als Büttner ´95 auf gerader, staubtrockener Straße verunglückte, findet keine Filigranuntersuchung des Wagens statt. Während er im Koma liegt, gibt die Polizei das Schrottauto frei. Eine Speditionsfirma zahlt dafür eilig das Sechsfache seines Werts. Büttner wurde mitgeteilt:
Hartmut Büttner, CDU-Bundestagsabgeordneter:
“Dieses Auto ist in der Tat ins ‚solvente Ausland’ – in diesem Fall nach Polen – geschickt worden. Und in Polen wurde dieser Wagen nach einer Woche als gestohlen gemeldet.“
Viele Unfälle und Erkrankungen von ehemaligen DDR-Systemkritikern scheinen noch lange nicht geklärt.
Ebenso wie der Todesfall Heinz Gerlach zur Gänze aufgeklärt werden muss
„DIE WELT“ berichtet: „Mielkes Leute pfuschten in das Leben von Millionen DDR-Bürgern hinein, zerstörten berufliche oder private Hoffnungen und zersetzten routinemäßig ganze Familien. Außerdem schädigte die Stasi im Laufe der Jahrzehnte Hunderttausende Menschen in der SED-Diktatur vorsätzlich, brach unangepasste Charaktere mit psychischem Druck.
In jedem DDR-Bezirk unterhielt das MfS eigene Untersuchungshaftanstalten, in Potsdam zum Beispiel in der Lindenstraße 54/55. In Berlin gab es neben der Zentrale in Lichtenberg die Stasi-Bezirksverwaltung Berlin, die bis 1985 in einem ehemaligen Krankenhaus an der Prenzlauer Allee und danach in einem 100 Millionen DDR-Mark teuren Neubau am Tierpark Friedrichsfelde amtierte, und das große Sperrgebiet in Hohenschönhausen, wo neben einem Gefängnis auch das streng geheime NS-Archiv der Stasi und technische Abteilungen saßen.
Neben der alltäglichen Unterdrückung stehen die schweren Gewalttaten des MfS; sie umfassen praktisch alle Paragrafen des DDR-Strafgesetzbuchs. So verschleppten Stasi-Kommandos im Laufe der Zeit mindestens 500, vielleicht aber auch bis zu tausend Menschen in die DDR – westliche Agenten, Überläufer aus den eigenen Reihen und SED-Kritiker vor allem. Einige von ihnen, zum Beispiel der vormalige Volkspolizei-Chef Robert Bialek, überlebten die Verschleppung nicht; andere, wie die „Verräter“ Paul Rebenstock und Sylvester Murau, wurden nach manipulierten Prozessen hingerichtet.
Ein juristisch verbrämter Mord war die Hinrichtung des MfS-Hauptmanns Werner Teske 1981. Er hatte mit dem Gedanken gespielt, in den Westen überzulaufen, allerdings nie einen konkreten Versuch dazu unternommen. Obwohl selbst das scharfe DDR-Strafrecht die Todesstrafe nur für vollendeten schweren Landesverrat vorsah, den Teske unzweifelhaft nicht begangen hatte, wurde er im Leipziger Gefängnis durch Genickschuss getötet.
Auch direkte Mordanschläge beging die Stasi. So lauerte 1976 ein Spezialkommando der Stasi, die „Einsatzkompanie der Hauptabteilung I“, auf westlicher Seite der innerdeutschen Grenze dem Fluchthelfer Michael Gartenschläger auf. Er wollte dort eine Splittermine vom Typ SM-70 abmontieren, die berüchtigte „Selbstschussanlage“. Vier Männer der Einsatzkompanie erwarteten ihn und eröffneten sofort das Feuer, als der langjährige politische Gefangene an den Grenzzaun heranschlich. MfS-Generalleutnant Karl Kleinjung, der Chef der Hauptabteilung I, hatte zuvor befohlen, „den oder die Täter festzunehmen bzw. zu vernichten“.
Auch der Schweizer Fluchthelfer Hans Lenzlinger wurde wohl im Auftrag des MfS 1979 in seiner Züricher Wohnung erschossen. Vielleicht war Bruno Beater, der ranghöchste Stellvertreter Mielkes und Experte für „nasse Jobs“, in den Anschlag verwickelt; aufgeklärt wurde dieser Mord aber nie.
Nicht das befohlene Ziel erreichten dagegen Mordanschläge gegen andere Fluchthelfer. Kay Mierendorff, der Hunderten DDR-Bürgern gegen fünfstellige Summen in die Freiheit verhalf, bekam im Februar 1982 eine Briefbombe zugeschickt, die ihn schwer verletzte und bleibende Schäden hervorrief.
Einen anderen „Hauptfeind“ der SED, den Fluchthelfer Wolfgang Welsch, vergiftete ein in seinen Kreis eingeschleuster Stasi-Agent im Sommer 1981 mit dem extrem toxischen Schwermetall Thallium; den Tod von Welschs Ehefrau und ihrer Tochter nahm der Stasi-IM billigend in Kauf.
Geplant, aber wohl nicht ausgeführt worden sind Mordanschläge auf Rainer Hildebrandt, den Kopf der DDR-kritischen „Arbeitsgemeinschaft 13. August“, die von ihrem Haus am Checkpoint Charlie aus das Unrecht der Mauer unnachgiebig anprangerte, und auf den Friedrichshainer Pfarrer Rainer Eppelmann, der unter Erich Honecker zeitweise als „Staatsfeind Nummer eins“ der SED galt. Umstritten ist dagegen, ob der DDR-Fußballstar Lutz Eigendorf 1983 von der Stasi durch einen vorsätzlich herbeigeführten Autounfall ermordet wurde. Vieles spricht dafür; der letzte Beweis ist in den allerdings bisher nur zum Teil sachgerecht erschlossenen Akten der Birthler-Behörde nicht aufgetaucht.
Noch öfter als potenziell tödliche Methoden wandten die Stasi-Experten allerdings das Mittel der Erpressung an. In verschiedenen Hotels für westliche Touristen in der ganzen DDR waren über den Betten Kameras eingebaut; auf interessante Ausländer wurden gezielt Prostituierte der Stasi angesetzt, um sie später mit kompromittierenden Fotos erpressen zu können. Das Gleiche versuchte das MfS auch mit Heinrich Lummer, dem West-Berliner CDU-Politiker. Über Jahre hinweg pflegte er eine geheime Beziehung zu einer Ost-Berlinerin, die in Wirklichkeit wohl von Anfang an als Spitzel auf ihn angesetzt war. 1981/82 versuchte das MfS, Lummer zu erpressen, was aber misslang.
Rund 40 Jahre lang garantierte die Stasi als „Schild und Schwert der Partei“ die Existenz der SED-Diktatur. Doch manches misslang Mielkes Mannen auch. So erwies sich beispielsweise die Suche nach den Autoren eines anonymen, kritischen Aufrufs als erfolglos, der 1969 an der Humboldt-Universität auftauchte. Trotz enormen Aufwandes und Kosten von rund einer Million DDR-Mark konnte das MfS die Verantwortlichen, die Studenten Rainer Schottländer und Michael Müller, nie überführen. So wurde ihr Protest zum „teuersten Flugblatt der Welt“.“
Insider Rainer W.:“Genau diese Methodenw erden heute von „GoMoPa“ und deren Hintermännern weider angewandt – natürlich verfeinert und mit Internet-Cyberstalking-Taktiken garniert.
Hinzu kommt der systematische Rufmord via Google und mit falschen Gerüchten, Erpresseranrufen, Morddrohungen, Cyberattacken, Kontoplünderungen und die Zerstörung von Geschäftsbeziehung durch
Systematisch gestreutes Misstrauen. Nehmen Sie all dies zusammen, dann haben Sie die STASI von heute: den „NACHRICHTENDIENST“ „GoMoPa“.“
Hintergrund:
Die Deutsche Kriminalpolizei hat weitere Ermittlungen gegen
den “NACHRICHTENDIENST” “GoMoPa”, deren serienmässig
vorbestrafte „Mitarbeiter“ sowie mutmassliche Hintermänner,
aber auch gegen Google aufgenommen. Das Aktenzeichen
lautet: ST/0148943/2011.
Die Beweislage in dem laut Insider “glasklaren Mordfall Heinz Gerlach”
verdichtet sich immer mehr.
Derweil versucht die ins Zwielicht geratene „Anlegerschutzanwalt“ Jochen
Resch mithilfe anderer „Anlegerschutzverbände“ Druck auf die angesehene
DKB-Bank auszuüben.
Kein Wunder, laut eigener Aussage hat RA Resch in seiner Anwaltskanzlei
fast 60 Leute auf der Payroll. Insider sagen: „Auch die „GoMoPa“-
Aktivitäten werden von Resch gesteuert und finanziert, da sowohl der
amerikanische Zweig des „NACHRICHTENDIENSTES“ „GoMoPa“ als auch
die deutsche „GoMoPa“ GmbH seit zwei Jahren –laut Bürgel – insolvent
sind.
Hinzu kommen weitere fragwürdige Aktivitäten im Reschen Netzwerk,
das – laut eigener Aussage in „GoMoPa“ sehr gut sein soll: „angebliche
Verbrauchervereine“, angebliche „Anlageschützer“ und angebliche „Journalisten“.
Kurz und gut: „Anlegerschutzanwalt Resch braucht pro Monat ca. €
400.000,- bis € 500.000,- , glaubt man seinen eigenen Angaben, um den
Laden am Leben zu halten.
Dies kann wohl nur schwerlich von Betrugsopfern finanziert werden…
Die DKB-Bank ist in Reschs Planung wohl der nächste „Zahlkandidat“.
Demzufolge brachte dann auch ein dubiose „Anlegerschutzverein“, den
niemand kennt, die stolze Meldung, die DKB sei zu Verhandlungen bereit,
bezugnehmend auf den „NACHICHTENDIENST“ „GoMoPa“ als Quelle.
Damit sollen wohl DKB und andere „Zahlkandidaten“ in die Pflicht
genommen werden, um das Reschsche Netzwerk weiter zu finanzieren.
„Schade, um die berechtigten Anliegen der Anleger, wenn sie auf
solche dubiosen Figuren und deren kriminellen Helfershelfer angewiesen
sind“, sagen sogar frühere Partner von Resch. Jochen Resch und
Heinz Gerlach – eine Beziehung, die jetzt wohl ganz neu aufgerollt
werden wird.
Ein Insider „Wir wissen, dass die Kriminalpolizei den Fall Heinz Gerlach
wieder aufnimmt – sicher auch mit Unterstützung des Bundeskriminalamtes.
Es gibt ein berechtigtes Interesse vieler Menschen und Institutionen
diesen Fall zur Gänze aufzuklären.“
All dies bestätigt die bislang gewonnenen Erkenntnisse über den
mutmasslichen Kriminalfall Heinz Gerlach:
Eines vorweg zur Klarstellung: Bereits in 1988 hatte unsere Redaktion
damals noch in dem Vorläufer-Publikation „Immobilien Magazin“
über die umstrittenen Geschäftspraktiken von Heinz Gerlach unter dem
Titel „Der Anlegerwolf im Schafspelz“ berichtet. Im darauffolgenden
Prozess konnten wir unsere Darstellung im Wesentlichen durchsetzen.
Wenn es allerdings um Rufmord oder gar Mord geht, gebührt auch
einem zu Lebzeiten umstrittenen Mann wie Heinz Gerlach Gerechtigkeit.
Diesen Selbstereinigungsprozess muss die Branche durchleben,
nur so ist eine positive Zukunft denkbar. Denn das, was Heinz Gerlach
geschah, könnte heute oder morgen auch Ihnen passieren.
Neue Details über den Zusammenhang zwischen „Anlegerschutzanwalt“
RA Jochen Resch, „NACHRICHTENDIENST“ „GoMoPa“ und „Akte-
HeinzGerlach.info“ zeigen deren enge Zusamnmenarbeit gegen den
umstrittenen „Anlegerschützer“ Heinz Gerlach beginnend mindestens
11 Monate vor seinem unerwarteten Ableben.
In einer Serie von Interviews hat RA Jochen Resch in dem „NACHRICHTENDIENST“
„GoMoPa“ sowie in der „Akte-Heinz-Gerlach.info“
über Heinz Gerlach geschäftliche Interna verbreitet – 11 Monate vor
seinem Tode, zumeist als „Der Anwalt“ und einmal sogar offen als „RA
Jochen Resch“. Beide Webseiten haben Analogien in Bezug auf ihre
Internet-Spuren (siehe weiter unten). Nachfolgende Unterlagen stammen
mindestens teilweise aus Gerlachs PC, der wohl von dem mutmasslichen
Stasi-Hacker Thomas Promny geknackt wurde.
Am 31.7.2009 erscheint folgender Artikel in der Akte-Heinz-Gerlach.
info
Zitat:
„Kaufte Schreinemakers Ex Heinz Gerlach frei?“
31.07.2009
Das Rätsel um die Schulden-Million von “Anleger-Papst” Heinz Gerlach
aus Oberursel (Hessen) bei der insolventen BFI Bank AG Dresden
(Sachsen) scheint endlich gelöst. Ein Rechtsanwalt aus der milliardenschweren
Fondsmarktszene meldete sich beim Finanznachrichtendienst
http://www.gomopa.net und lüftete das Geheimnis, das Gerlach bislang so sehr
hütete.
Der Anwalt: “Der Retter in der Not war nicht Gerlachs Dreiländer-
Fondskumpel Walter Fink (54) aus Stuttgart, der das inzwischen auch
bestreitet und wie es von einigen behauptet wurde. Der Fink ist doch
viel zu klein dafür. Der Retter soll Werner Klumpe, der für Fink die Fonds
(40.000 Geschädigte) mitkonzipiert hatte gwesen sein. Der 61jährige Ex-
Ehemann von Margarethe Schreinemakers soll Gerlach beim Insolvenzverwalter
der BFI Bank Dresden frei gekauft hat. Klumpe besitzt eine
große Rechtsanwaltskanzlei in der Luxemburger Straße 282 a in Köln
(Nordrhein-Westfalen). Einer seiner Anwälte soll den Schuldentitel gegen
Gerlach in voller Höhe bezahlt haben. Mit Zinsen belief sich die Summe
auf inzwischen rund 1,5 Millionen Euro. Vermittelt soll das Geschäft im
Übrigen der frühere Besitzer der Plenum Finanz AG (Easyfonds.com)
Martin Walter aus Zürich. Da war GoMoPa auf der richtigen Spur. Nur der
jetzige Boss der Firma, Raimond Schuster, weiß nichts davon.”
GoMoPa: Was hat denn Schreinemakers Ex-Mann mit dem selbsternannten
Anlegerschützer Gerlach zu tun, außer dass Gerlach mehrmals
in der TV-Sendung Schreinemakers live auf Sat.1 (4 Millionen Zuschauer)
Eigenwerbung machen durfte?
Der Anwalt: “Ganz einfach. Werner Klumpe ist seit 27 Jahren ein
sehr guter Anwalt für die Erstellung von Fonds-Prospekten. Er hat nur
einen Nachteil. Er ist zu teuer. Und weil er kaum Mandanten sprich Prospekt-
Initiatoren bekommen würde, braucht er einen, der ihm Mandanten
heranschaufelt. Einen Helfer wie Gerlach. Gerlach ist praktisch sein Vertrieb.
Nicht für ihn persönlich, sondern für seine Kanzlei. Klumpe selbst
hält sich ja neuerdings überwiegend im Ausland auf.”
GoMoPa: Wie könnte denn die Zusammenarbeit der Klumpe-Kanzlei
mit Gerlach funktionieren?
Der Anwalt: “Die Klumpe-Kanzlei vertritt Gerlach in allen Belangen,
führt ihn also als Mandanten und hat natürlich Schweigepflicht. Gerlach
soll wiederum der Kanzlei Mandanten zuschieben, und das soll so funktionieren.
Jemand plant eine Investition und legt dafür einen 100 Millionen
Euro schweren Fonds auf. Dafür braucht er einen Prospekt, der
gegen spätere und teure Haftungen rechtlich wasserdicht sein muss.
Dafür braucht man einen Rechtsanwalt aus dem Anlagenkapitalrecht.
Gerlach bietet dem Fondsinitiator eine Vorprüfung des Prospektes
an und schließt darüber einen Beratervertrag ab. Der Initiator zahlt das
Honorar zwischen 15.000 und 25.000 Euro, weil ihm Gerlach vielleicht
mit einem schlechten Rating in seiner Anlegerschutz-Postille droht. Hat
der Initiator angebissen, weil er ja nur Geld von Anlegern in dieser
Größenordnung bekommt, wenn die Anleger ihm vertrauen, kommt
von Gerlach eine vernichtende Nachricht. Die Papiere seien Schrott,
behauptet Gerlach. Der Initiator müsse einen neuen Prospekt erstellen.
Aber nicht mehr bei seinem bisherigen Anwalt, sondern bei einem
Anwalt, den Gerlach bestimmt.
Und das ist Werner Klumpe und Co. Der Grundpreis für den neuen
Prospekt ist derselbe, wie der alte gekostet hat. Das sind branchenüblich
100.000 bis 150.000 Euro. Der neue Prospekt von Klumpe hat auch
Hand und Fuß. Aber es sollen noch einmal Kosten von bis zu einem
Prozent des Fondsvolumens dazu kommen. Das sind also bei einem
Fonds von 100 Millionen Euro noch einmal 1 Million Euro Honorar für
50 bis 60 Seiten Prospektbeschreibung. Der Fondsinitiator zahlt das
nicht aus seiner Tasche, das müssen die Anleger zahlen. Gerlach würde
so zum Nachteil der Anleger die Fondskosten in die Höhe treiben und
wahrscheinlich teilt Klumpe das Extra-Honorar mit Gerlach. Die Kanzlei
richtet ihrem Mandanten ein Anderkonto ein. Darauf gehen die Provisionen,
und man zahlt davon Gerlachs Rechnungen und befriedigt
davon auch Gerlachs Gläubiger.”
GoMoPa: Also zahlte Gerlach seine Millionen-Schuld bei der BFI
Bank und den geprellten Anlegern von Anlegergeldern, die er durch
Kostenhochtreiberei bei Fondsinitiatoren verdiente?
Der Anwalt: “Inoffiziell ist das so. Offiziell stellt sich Gerlach vor
dem Finanzamt als praktisch pleite dar. Die jetzt veröffentliche Bilanz des
Einzelkaufmannes Heinz Gerlach und seiner Heinz Gerlach Medien AG
von 2007 gleicht einer Insolvenzverschleppung. Seit mehreren Jahren
führt Gerlach in der Bilanz einen Fehlbetrag von 1,5 Millionen Euro mit
Zahlungsziel ein Jahr auf. Das entspricht genau dem Betrag, den er der
BFI Bank und jetzt wahrscheinlich der Kanzlei Klumpe schuldet. Denn
er hat den Titel nicht gekauft, sondern wahrscheinlich Klumpe.”
GoMoPa: Aber warum sollte sich ein so angesehener Fonds-Anwalt
wie Klumpe auf Tricksereien mit einem Steuergehilfen einlassen?
Der Anwalt: “Gerlach ist laut und scheut sich nicht, die ganze
Aufmerksamkeit auf sich zu ziehen. Einer muss doch die Schmutzarbeit
machen und die Fondsinitiatoren erpressen. Das kann doch Klumpe
schlecht selbst machen. Obwohl Klumpe natürlich auch ein gerissener
Typ ist. Der Anwalt verlegte die Produktionsfirma von Schreinemakers
live (1992-1996, Goldene Kamera, Bambi) während seiner Ehe (die
Scheidung war 2007) nach Holland und machte sich selbst zum Geschäftsführer.
Die Einnahmen aus der in Deutschland ausgestrahlten Sendung
wurden in den Niederlanden zu sehr geringen Sätzen versteuert. Daraufhin
ermittelte die deutsche Staatsanwaltschaft wegen Steuerhinterziehung
und durchsuchte Klumpes Privat- und Geschäftsräume. Später
kam noch der Vorwurf der Anstiftung zur Untreue hinzu. Gegen eine
Millionenzahlung an wohltätige Zwecke wurde das Verfahren nach zwei
Jahren eingestellt.
Der Klumpe-Anwalt Wolfgang Arndt (58) boxte Gerlach im letzten
Jahr aus einem Insolvenzverfahren gegen die Heinz Gerlach Medien AG
heraus, weil Gerlach einer früheren Anwaltskanzlei seit 2003 ein Honorar
in Höhe von rund 250.000 Euro (AZ 63 IN 98/08, Insolvenzgericht Bad
Homburg) schuldete. Dreist hatte Gerlach zuvor getönt, bei ihm sei nichts
zu holen, sechs mal versuchte der Gerichtsvollzieher zu vollstrecken
– ohne Erfolg. Zur Abwendung der Insolvenz soll auch hier die Kanzlei
Klumpe eingesprungen sein. Man wollte schließlich nicht seinen Vertrieb
für Fonds-Mandanten verlieren.”
GoMoPa: Aber der Berliner Anlagen-Initiator Detlef Maruhn von
der Maruhn Immobilien GmbH & Co. Postsiedlung Dresden KG hat doch
am 10. August 2007 vor dem Landgericht Frankfurt Main gegen Heinz
Gerlach (wieder vertreten von Klumpe-Anwalt Wolfgang Arndt) ein Urteil
(AZ: 3-1102/07) erstritten, welches Gerlach bei Strafe von 250.000
Euro oder sechs Monaten Haft verbietet, “Initiatoren von Kapitalanlagen,
die Ihre Unterlagen nicht zur Verfügung stellen, ein ??-Rating (unzureichende
Transparenz) mit den entsprechenden Haftungsrisiken für den
Vertrieb zu erteilen und zu verbreiten oder anzudrohen”.
Der Anwalt: “Gerlach lässt jetzt die Fragezeichen in seinen Transparenz-
Ratings weg und schreibt einfach nur Rating nicht durchführbar.
Juristisch ist das dasselbe. Aber dazu müsste ein Fondsinitiator erst Mal
erneut klagen. Und wer will schon 100.000 Euro durch alle Instanzen
investieren, wenn am Ende bei Gerlach offiziell gar nichts zu holen ist?
Aber dafür steht man dann im Internet bei Gerlach auf einer Achtungsliste:
Rating nicht durchführbar. Wer will das schon?”
GoMoPa: Aber das Landgericht hat doch auch festgestellt, dass die
Fondsanbieter gar nicht verpflichtet sind, Gerlachs Einschätzung beim
Vertrieb mit anzuheften. Weil Gerlach selbst ein Player im Graumarkt ist,
also ein Mit-Wettbewerber oder Konkurrent. Das Gericht stellte fest: „Die
Heinz Gerlach Medien AG hat ein wirtschaftliches Interesse daran, von
den angeschriebenen Kapitalanlageinitiatoren die angeforderten Unterlagen
zu erhalten, da die Heinz Gerlach Medien AG im Zusammenhang
mit der Erteilung des ãã-Ratings entgeltliche Dienstleistungen anbietet.“
Der Anwalt: “Die Fondsanbieter streiten nicht gern öffentlich und
zahlen lieber Schweigegeld. Das nutzt Gerlach schamlos aus.”
Heinz Gerlach ist zu einer Stellungnahme nicht bereit.
Doch auf seiner Seite http://www.anlegerschutzauskunft.de/haftung.htm
schreibt Gerlach unter “Haftungsausschluss” selbst, was wirklich Sache
ist. Gerlach: „WICHTIG: Wir verwenden bei der Durchführung der
Anlegerschutz-Transparenz-Ratings ausschließlich Informationen, die
uns von dritter Seite zur Verfügung gestellt werden und die wir nicht
überprüft haben. Eine Haftung für die Richtigkeit, Vollständigkeit und
Aktualität der von uns zur Verfügung gestellten Informationen wird daher
nicht übernommen.“
Heinz Gerlach überprüft also keinerlei Informationen, die er mit
großem Getöse weitergibt. Wer aber Informationen nicht gegencheckt,
der ist nicht einmal ein ernstzunehmender Journalist (denn das gehört
zum Einmaleins eines jeden Redakteurs) und schon gar kein Anlegerschützer.
Denn von dem erwartet man zu Recht, dass er Informationen
gewissenhaft recherchiert, wertet und überprüft. Gerlach macht
nach eigenen Angaben nichts davon.
Doch nun droht Gerlach von Amts wegen juristischer Ärger wegen
Hochstapelei und Verstoßes gegen das Aktiengesetz, weil er eine Fälschung
beim Amtsgericht begangen haben soll.
Die Behörde hat eine Untersuchung gegen die Heinz Gerlach Medien
AG eingeleitet. Es geht um seinen Aufsichtsrat. Dort hat er seine
Geliebte Lenka Sychrova eintragen lassen und zwar als “Investment-
Analystin”. Doch in Wirklichkeit ist seine Freundin (sie stammt aus
Tschechien) Kosmetikerin. Bauchstraffung, Faltenbehandlung, Haarwuchsförderung
und Hautverjüngung bietet sie in Oberursel an.
Laut einem von Lenka Sychrova persönlich unterzeichneten Lebenslauf
war sie den größten Teil ihres Berufslebens als Sekretärin tätig.
1995 kam sie nach Deutschland und heuerte in München als freie Handelsvertreterin
bei der Staubsauger-Truppe “Kirby” an. Mit der Finanzbranche
kam sie erstmalig Mitte 1997 in Kontakt, als sie gemeinsam mit
einigen ihrer Staubsaugervertreterkollegen zu einem Versicherungsvertrieb
wechselte. Dort begann sie eine Ausbildung zur Fachwirtin für
Finanzberatung (IHK), die sie jedoch bereits nach wenigen Wochen
wieder abbrach. Offenbar war ihr Versuch, mit dem Verkauf von Versicherungen
ihren Lebensunterhalt zu verdienen, ebensowenig von Erfolg
gekrönt, wie zuvor mit Staubsaugern – und so schied sie bereits
Mitte 1998 wieder aus der Finanzbranche aus.
Mitte 1999 lerne sie Heinz Gerlach kennen. Die beiden sind seitdem
liiert. Ab diesem Zeitpunkt tauchte sie auch in dessen Impressum auf.
Und zwar als “Verantwortliche für den Themenbereich Investment und
Aktienemissionen”. Über Nacht hatte sie also die Kompetenz erworben,
Konzepte zu beurteilen, die von langjährigen, großteils studierten
Vollprofis entwickelt worden sind. Das ist auch vor dem Hintergrund
bemerkenswert, weil Gerlach mit Vorliebe Finanzdienstleister gern als
“Dilletanten” abqualifiziert. Nachdem diese Peinlichkeit im Gerlachschen
Impressum bald begann, Kreise zu ziehen, verschwand die Dame
nach einigen Monaten wieder aus dem Impressum des “Direkten Anlegerschutzes”.
Am Aufsichtsratsamt der Heinz Gerlach Medien AG hat
sich nichts geändert.
Lesen Sie im dritten Teil: Für wen schaufelt Gerlach noch Mandanten
herbei, wer gehört zu seinem Netzwerk? Und mit welchen Tricks
frisiert der Steuergehilfe Gerlach vermutlich seine eigenen Bilanzen?
Zitat-Ende
„Treibjagd im Anlegerschutzwald.“ Original-Text vom 4.8.2009:
Zitat:
“Für ein Jahressalär von 89.000 Euro, monatlich 7.500 Euro, darf
Heinz Gerlach ab sofort drei Immobilien-Fonds betreuen, vor denen er
Jahre lang auf seinem gefürchteten schwarzen Laufband im Internet
und seinen Newslettern gewarnt hat”, verrät ein Insider-Anwalt dem
Finanznachrichtendienst http://www.gomopa.net. Über Gerlachs neueste
Trophäe seiner Treibjagd im Anlegerschutzwald sagt der Anwalt: “Die
Verträge sind noch ganz frisch.”
GoMoPa: Welche Fonds sind denn betroffen?
Der Anwalt: “Es sind die ersten drei Fonds des heutigen Marktführers
in Deutschland für geschlossene Fonds, der SHB AG aus Aschheim
bei München in Bayern. Die Bundesanstalt für Finanzdienstleistung-
Dokumente zum Thema
» Gerlachs Millionenkredit
» Urteil gegen Gerlach
» Spiegel über Gerlach
Pressemitteilung zum Thema
» Teil 1: Heinz Gerlach – wo ist die Million geblieben?
» Teil 3: Heinz Gerlach: Treibjagd im Anlegerschutzwald
Beiträge zum Thema
» Heinz Gerlach “Direkter Anlegerschutz”
» Alpina KG Icon AG Procenta GmbH Bavaria GmbH
» Nepper, Schlepper, Bauernfänger
» BFI Bank Dresden, Würzburg
» Das Geschäft der Banken
» Gerlach Positivbewertung: ACI Alternative Capital Invest Dubai Tower
» BGH-Urteil: Klarheit für Anleger, Provisionen offenlegen
» Vermeintliche Anlegerschützer kassieren bei Gutgläubigen ab
» Akzenta AG und Gerlach Report
Quelle: http://www.gomopa.net/Pressemitteilungen.html? id=289&meldung=
Warum-kaufte-Schreinemakers-Ex-Heinz-Gerlach-frei
saufsicht hatte den drei Fonds Business Park Stuttgart, Carre Göttingen
und Erlenhofpark im Jahre 2005 eine Rüge erteilt, weil sie den 4.500
Anlegern eine 50prozentige Rückzahlung auf den Anlagenwert zusagten.
Die BaFin bestand auf eine Änderung der Verträge, dass die Rückzahlbarkeit
nur auf den wirtschaftlichen Wert zu leisten sei und auch
nur, wenn die Fonds nicht zahlungsunfähig oder überschuldet sind. Die
SHB AG hielt sich daran, aber Gerlach hatte nun einen Anlass, sich auf
die Fonds einzuschießen.”
GoMoPa: Der Erfinder der Fonds und Gründungsgesellschafter der
SHB, Horst Baron (53), sagte erst am 7. Juli 2009 auf der Hauptgesellschafterversammlung,
dass die Fonds tatsächlich nur dank der Ratensparer
am Leben sind. Wörtlich sagte Baron: “Selbst einen angenommenen
kumulierten Ausfall von 10 Prozent der Ratenzahler könnten die
Fonds aushalten. Bislang fielen noch bei keinem Fonds mehr als sieben
Prozent der Sparplananleger aus.” Welche Argumente hatte denn Gerlach
da noch?
Der Anwalt: “Gar keine. Gerlach warnte in seinen Anlegerschutz-
Reports einfach vor einer angeblich katastrophalen wirtschaftlichen
Situation, warf den Fonds vor, dass sie eine liquide Unterdeckung hätten
und die Ausschüttungen aus der Substanz der Ratensparer kämen.
Das war zwar problematisch, war bei diesen Fonds aber so gewollt und
geplant gewesen. Gerlach verlegte sich schließlich auf die persönliche
Diffamierung des fachlich absolut kompetenten Vorstandsvorsitzenden,
Horst Baron.”
GoMoPa: Warum war denn der Fondsexperte für den Fondslaien
Gerlach überhaupt angreifbar?
Der Anwalt: “1990, also elf Jahre vor der Gründung der SHB AG,
hatte Horst Baron Pech mit einem Geschäftspartner. Damals hatte
Baron 800.000 D-Mark in eine Firma eingezahlt. Der Geschäftspartner
unterschlug das Geld und setzte sich damit ins Ausland ab, verjubelte
es, wurde von der Polizei geschnappt und kam ins Gefängnis.
Baron musste Konkurs anmelden. Mit diesem Konkursverfahren vom 2.
Januar 1991 (AZ 32N774/90), deren Tilgung sich bis zum Jahre 2004
hinzog, verfolgte Gerlach den Vorstandsvorsitzenden bis zum Gehtnicht-
mehr. Baron trat genervt, offiziell aus familiären Gründen, am 31.
August 2008 zurück.”
GoMoPa: Hatte die SHB damit Ruhe?
Der Anwalt: “Die drei Fonds sind nach wie vor problematisch und
waren für Gerlach weiter Futter, um Vertriebspartner der SHB zu verschrecken.
Die SHB hatte 2008 einen Verlust von 13 Milionen Euro.”
GoMoPa: Welche Lösung gab es?
Der Anwalt: “Die SHB zauberte als Baron-Nachfolger für den
Vorstandsvorsitz den ehemaligen PR-Chef der Mutter-Gesellschaft Aragon
AG aus Wiesbaden in Hessen, Achim Pfeffer (39), aus dem Ärmel.
Der gab beim Amtsantritt offen zu, dass er von Immobilien keine Ahnung
hatte. Aber er wollte den angeschlagenen Konzern SHB mit 62
Mitarbeitern und 1.100 freien Vertriebspartnern sanieren. Und als PRMann
wusste er, wie man den Scheinjournalisten Gerlach ruhig stellen
kann. Seine Idee war, die drei alten problematischen Fonds auszulagern,
damit der Name SHB nicht mehr geschädigt werden kann, und
die Betreuung der Fonds an Gerlach zu übertragen. Die anderen Fonds
der SHB laufen schließlich ganz gut.”
GoMoPa: Wie soll denn die Auslagerung laufen?
Der Anwalt: “Über die Heliad Equity Partners GmbH und Co. KG
aus Frankfurt/Main. Das ist die zweite Mutter der SHB. Sie hat 13 Finanzunternehmen
mit 4.500 Beschäftigten und einen Jahresumsatz von
600 Millionen Euro. Sie soll helfen, die drei problematischen Fonds zu
verschleiern und zu verschieben, Hauptsache weg von der SHB. Der
neue SHB-Vorstandschef Pfeffer persönlich übernahm die Gespräche
mit Gerlach. Der nahm die Betreuung der Fonds, die er zuvor verteufelt
hatte, sofort an. Die zusätzlichen Kosten von 7.500 Euro monatlich
für Gerlach müssen nun die Anleger trotz geringer Rendite obendrauf
zahlen. Und damit Gerlach sagen kann, er habe nie ein Mandat von der
SHB erhalten, läuft der Betreuungsvertrag über die Heliad. Somit hat
sich die jahrelange Schmiererei Gerlachs gegen den Fondsprimus SHB
gelohnt.”
GoMoPa: Aber warum musste erst Pfeffer kommen, um den Deal
mit Gerlach einzufädeln?
Der Anwalt: “Nun, Pfeffer kam von der Aragon. Die Aragon hatte
mit Gerlach schon Ruhigstellungs-Erfahrungen gesammelt. Aragon-
Aktionär Christian Angermeyer wollte im Jahre 2002 VCH-Fonds mit
amerikanischen gebrauchten Risikolebensversicherungen an die Börse
bringen. Sie erwiesen sich als Rohrkrepierer. Angermeyer hätte das
gern gedeckelt. Doch Gerlach bekam davon Wind und hat Aragon ein
wenig provoziert. Gerlach schoss los: Anlegerverarsche, Schneeballsystem.
Man beruhigte Gerlach schließlich mit einem Beratervertrag.
Natürlich nicht bei der Aragon, das wäre ja zu plumb gewesen. Man
fand, dass der Vorstand der Aragon-Tochter BIT Treuhand AG in Frankfurt,
Jan Bäumler, einen Coach gebrauchen könnte. Ich glaube, Bäumler
und Gerlach haben sich nie gesehen. Als Bäumler zum 1. Januar
2009 aber BIT und damit Aragon verließ, hatte Coach Gerlach keinen
mehr zu coachen. Zum Glück holte ihn der Aragon-PR-Chef Pfeffer nun
zur SHB beziehungsweise zu deren Mutter Heliad als Coach für die
schlecht laufenden Fonds.”
GoMoPa: Aber Gerlach hat doch stets bestritten, dass er je Un-
ternehmerberater-Verträge abgeschlossen habe.
Der Anwalt: “Dann sehen Sie sich doch einmal den Beratervertrag
von Gerlach mit der ICC AG und späteren Aufina Holding AG an, die
mit 16 Millionen Euro Schulden an die Anleger in Insolvenz ging. Gerlach
stempelte den Vertrag mit seinem Eingangsstempel ab und schrieb
noch ein paar Änderungswünsche handschriftlich dazu. Der Vertrag
liegt in der Polizeiakte. Der ICC-Chef Rainer Möller wurde später verurteilt,
musste ins Gefängnis. Gerlach kassierte laut eigener Aufstellung,
die er der Staatsanwaltschaft (AZ 130Js 88/03) überließ, vom 9. Juni
2000 bis 11. Juli 2002 insgesamt 783.000 D-Mark (400.348 Euro), obgleich
er angeblich gar nichts tat.”
GoMoPa: Hat Gerlach ein Netzwerk, das ihn schützt?
Der Anwalt: “Außer der Rechtsanwaltskanzlei Werner Klumpe aus
Köln hat Gerlach nicht wirklich ein echtes Netzwerk. Klumpe soll konkurrierende
Ratinghäuser rigoros abmahnen, wenn Formalien nicht eingehalten
werden. TV-Moderator Friedrich Wanschka versucht, Gerlach regelmäßig
reinzuwaschen. Werden Gerlachs Machenschaften öffentlich,
darf dieser Stellungnahmen in Wanschkas Wmd-Brokerchannel abgeben.
Gerlach hat am 4. September 2008 zu Pressevorwürfen gegen sich
Stellung genommen, ohne die Vorwürfe wirklich zu entkräften. Wanschka
leitet die nach ihm benannte Consulting GmbH. Das Unternehmen
veranstaltet Wmd-Vertriebsgipfel und Wmd-Exklusivforen (mit Vorliebe
auf Mallorca), bei denen Gerlach seit Jahren Stammgast ist und als angeblicher
Experte Vorträge hält sowie Diskussionen moderiert.
Zu Gerlachs Dunstkreis gehört auch der Bund für soziales und ziviles
Rechtsbewusstsein e.V. (BSZ). Der von Horst Roosen geleitete
Verband verbreitet die Presseerklärungen auf Fachanwalt-hotline.de,
Kapitalanleger-echo.de, Rechtsboerse.de und Bsz-ev.de. Roosen ist
übrigens Pleite.
In ähnlichem Dienst für Gerlach sollen auch zwei Hamburger Rechtsanwälte
stehen. Auch sie sollen die Enten aus dem Direkten Anlegerschutz
aufgreifen und sie über das Internet verbreiten.
Und dann wäre da noch Ove Franz, er nimmt Gerlach regelmäßig
in Schutz. Als das Hamburger Magazin Der Spiegel 2008 Gerlachs Machenschaften
aufdeckte, war Ove Franz der einzige von zahlreichen Befragten,
der Gerlach unterstützte. Der 73jährige Ex-Politiker hatte sich
als Vorstand des Bankhauses Wölbern einen seriösen Ruf aufgebaut,
den er inzwischen zerstört hat. In Gerlachs Direkten Anlegerschutz schreibt
er bestellte Leserbriefe.”
GoMoPa: Aber was ist mit den 51 Anwaltsadressen, die Gerlach
auf seiner Seite Anlegerschutzauskunft.de veröffentlicht?
Der Anwalt: “Die Anwälte haben mit Gerlach persönlich nichts zu
tun. Sie lassen es zu, dass Gerlach sich mit ihren Namen schmückt, weil
sie natürlich als Anlegerschutzanwälte von Gerlachs negativer Berichterstattung
und der damit verbundenen Anlegerverunsicherung stark profi-
tieren. So bekommen sie viele Mandanten.”
GoMoPa fragte Anwalt Jochen Resch (59) aus Berlin, der zugleich
Vorsitzender der Verbraucherzentrale Brandenburg ist, was er von Gerlach
hält und warum er auf Gerlachs Webseite steht?
Resch: “Ich kenne Gerlach seit vielen Jahren, auch von persönlichen
Treffen bei Veranstaltungen. Es ist sehr traurig, er war am Anfang sehr
gut. Bis er sich im Jahre 2002 mit den Drei-Länder-Fonds von Walter Fink
und der BFI Bank Dresden einließ und wohl dabei zuviel Geld verdiente.
Ich habe zu Gerlach keine geschäftlichen Beziehungen. Fonds sind auch
nicht mein Metier. Ich werde mir die Seite anschauen, auf der ich erwähnt
werde, und gegebenenfalls reagieren.”
Zitat-Ende.
SJB-GoMoPa-Opfer vermuten, dass Resch diese Interna unter anderem
direkt aus dem von dem mutmasslichen Hacker Thomas Promny
geknackten Computer Heinz Gerlachs bezogen hat und diese dann
zunächst über den „NACHRICHTENDIENST“ „GoMoPa“ verbreitete.
„Rechtsanwältin Ludmilla Emilie Giese arbeitet im Bereich sogenannter
Immobiliensteuersparmodelle gegen Initiatoren, Verkäufer und
Banken“, heisst es auf der Homepage der sogenannten Anlegerschutzkanzlei“
Resch.
Für das GEGEN steht neben Reschs eigener Truppe von 60 Mitarbeitern,
vor allem der stets linientreue „NACHRICHTENDIENST“ „GoMoPa“,
der sich aus Ex-Stasi-Leuten vor allem aus der ehemaligen „DDR“ rekrutiert.
„NACHRICHTENDIENST“ hat die Aufgaben. „Aufklärung, AgitProp,
Bespitzelung, Rufmord, Erpressung und wenn jemand zu gefährlich für
die eigene Truppe wird, wohl auch Mord mit Stasi-Methoden wie mit
Dioxin.
Immer wieder präsentiert sich Anwalt Resch auf der Webseite von
„GoMoPa“ einem angeblichen Zusammenschluss jüdischer Anwälte aus
New York mit dem klingenden Namen Goldman, Morgenstern & Partner
LLc. Profan dagegen der Name „GoMoPa“ gebaut nach dem selben
Strickmuster, wie es viele Nachrichtendienste gerne tun – aus Abkürzungen.
In den USA würde es wohl GM & P LLC heissen, in Ostberlin hingegen
„GoMoPa“. Doch das sind nur Petittesen am Rande.
Den engen Zusammenhang zwischen der „Anlegerschutzkanzlei“
Resch und dem „NACHRICHTENDIENST“ „GoMoPa“ erkannte auch schon
die Redakteurin Renate Daum und schrieb;
„Der Anlegeranwalt Jochen Resch kommt neuerdings oft in den
Pressemitteilungen vor, die der Finanzdienst Gomopa ungefragt an Redaktionen
verschickt. Als „Deutschlands bekannteste Anlegerschutzkanzlei“
wird Resch Rechtsanwälte in einem Bericht über das Ende der
Noa Bank vorgestellt. Zu Schrottimmobilien äußert sich Resch, zu einem
Skandal um den Immobilienfondsanbieter Volkssolidarität. Die Offenheit
ist neu. Früher ging Gomopa Resch hart an und konfrontierte
ihn mit Vorwürfen. Doch einige Formulierungen in einer Teilhaberinformation
zur finanziellen Situation Gomopas vom Juli 2010 legen nahe,
dass der Sinneswandel vielleicht nicht nur Zufall ist.
Gomopa, eigentlich Goldman Morgenstern & Partners Consulting
LLC mit Sitz in New York, ist seit mehr als zehn Jahren aktiv. Auf der
Website ist unter den Fachautoren der bekannte Bestsellerautor Jürgen
Roth aufgelistet. Im Handelsregister der deutschen Zweigniederlassung
ist als Geschäftszweck an erster Stelle „wirtschaftliche Beratung, insbesondere
des Mittelstandes“ aufgelistet. Dazu gehöre „die Präsentation
von Firmen im Internet und anderen Medien“. Die Verbindung des Dienstes
mit einem Nachrichtenportal im Internet sieht Gomopa-Gründer
Mark Vornkahl nicht als Problem: „Ein Interessenkonflikt zwischen
kostenpflichtiger Beratung, Informationsabonnement und öffentlicher
Aufklärung ist uns seit Bestehen nicht untergekommen.“
Anwalt Resch spricht von Rechercheauftrag
Doch die Nutzer des Portals erfuhren bislang nicht, ob mit Personen
oder Organisationen, über die berichtet wurde, vertragliche Beziehungen
bestehen. Reschs Kanzlei war laut Teilhaberinformation zeitweise
eine wichtige Finanzierungsquelle von Gomopa. Darin berichtet Gomopa-
Mitgründer Klaus Maurischat, dass eine Vereinbarung mit der Kanzlei
„momentan 7500,- Euro im Monat einbringt – rund 25 Prozent unserer
monatlichen Kosten!“. Für „individuelle Mandantenanwerbung“ stehe
die Gesellschaft mit mehreren Anwaltskanzleien in Verhandlungen.
Anwalt Resch stellt zum Inhalt der Vereinbarung klar: „Wir haben
einen einmaligen Rechercheauftrag erteilt, der im üblichen Rahmen
honoriert wird.“ Mit Mandantenbeschaffung habe das nichts zu tun.
Was Gomopa von einer Mandantenanwerbung hätte, ist auch unklar.
Denn Anwälte dürfen dafür nicht bezahlen. Auf unsere Anfrage zu dieser
und weiteren Fragen gab Vornkahl keine inhaltliche Antwort beziehungsweise
verwahrte sich gegen Zitate aus den entsprechenden Passagen
seiner E-Mail, weil er einem Mitbewerber „keine Auskünfte zur
Ausgestaltung unseres Geschäftsbetriebes gebe“. Das verblüfft, denn
BÖRSE ONLINE betreibt das Anlegerschutzportal http://www.graumarktinfo.
de, ist aber keine Unternehmensberatung. Gomopa betont dagegen,
nichts mit Anlegerschutz zu tun zu haben.
Bauträgergesellschaft als wichtige Finanzquelle
Eine wichtige Finanzierungsquelle von Gomopa war laut der Teilha-
berinformation auch eine Bauträgergesellschaft, gegen die Anwalt Resch
im Auftrag von Anlegern vorgegangen war. Im Zusammenhang mit deren
Muttergesellschaft Estavis war Gomopa sogar schon mit Nötigungsvorwürfen
konfrontiert worden. Als ein umstrittener Anlegerschützer einen
Vertrag des Immobilienkonzerns mit Gomopa in die Hände bekam, las
er eine Erpressung hinein. Auf seine Anzeige hin nahm die Staatsanwaltschaft
aber nicht einmal Ermittlungen auf. „Estavis wurde nicht erpresst“,
stellt ein Sprecher der Immobilienfirma klar. Die Estavis-Tochter
B&V schloss sogar einen neuen Beratungsvertrag ab und zahlte viermal
5000 Euro – in gegenseitigem Einvernehmen, wie der Estavis-Sprecher
betont.
Jüngst kam nun der Wirtschaftsdetektiv Medard Fuchsgruber – Aushängeschild
und Kooperationspartner von Gomopa – ins Gerede. Bevor
das Bündnis besiegelt wurde, bekam er im Frühjahr 2010 einen Auftrag
aus Kassel, wie die „Süddeutsche Zeitung“ berichtet. Der Wirtschaftsdetektiv
sollte herausfinden, wer hinter üblen Angriffen und Erpressungsversuchen
gegen Immovation stecke. In einem zweiten, davon
unabhängigen Schritt sollte Fuchsgruber versuchen, böse Berichte und
Kommentare bei Gomopa über das Immobilienhandelsunternehmen zu
unterbinden. Insgesamt erhielt er dafür 67 500 Euro….“
http://www.graumarktinfo.de/gm/aktuell/diskussion/:Gomopa–Anwaelte-
als-Finanzierungsquelle/616477.html
Dieser Artikel löste ein Erdbeben in der Branche aus, bestätigt er
doch, was viele insgeheim dachten, aber nicht zu sagen wagten: „Resch
benutzt „GoMoPa“ und „Detektiv“ Fuchsgruber, um Mandanten zu erpressen.
Genau n dieses Bild passte auch der angebliche „Beratungsvertrag“
zwischen Estavis und „GoMoPa“, den Heinz Gerlach enthüllte.
Damit kam der selber nicht unumstrittene Anlageschützer aus Bad
Homburg den Berliner Paten und Ihren Exekutoren gefährlich nahe,
zudem er eine Strafanzeige bei der Berliner Kriminalpolizei stellte und
seinen Kenntnisstand publizierte, Daraufhin wurden seine Webseiten
wochenlang von Cyberattacken lahmgelegt und kurze Zeit später starb
er völlig unerwartet…
Stasi-Morde mit Dioxin: Millionen von Menschen kennen das Thema
durch die Berichterstattung über den Dioxin-Skandal hervorgerufen durch
Stasi-Top-Agent Siegfried Sievert. Sein Namensvetter Siegfried Siewert
(ein Pseudonym) für einen „GoMoPa“-Mitarbeiter steht unter Mordverdacht
im Fall Heinz Gerlach.
Bei der Staatsanwaltschaft Münster ist eine Strafanzeige wegen versuchten
Mordes aus Habgier gegen den in den Dioxin-Skandal verwickelten
Futtermittellieferanten Harles und Jentzsch eingegangen. Schwere
Körperverletzung und Giftbeimischung lauteten weitere Vorwürfe, sagte
Oberstaatsanwalt Wolfgang Schweer.
Demnach hat ein Arzt aus der Nähe von Münster die Firma aus
Schleswig-Holstein angezeigt. Die Staatsanwaltschaft Münster wird den
Fall vermutlich an die Behörden in Oldenburg oder Itzehoe abgeben.
Dort laufen derzeit Ermittlungen wegen Verstößen gegen das Lebensmittelbedarfsgegenstände-
und Futtermittel-Gesetz.
Die Firma Harles und Jentzsch aus dem schleswig-holsteinischen
Uetersen hatte seit März vergangenen Jahres dioxinbelastetes Futterfett
an Abnehmer in mehreren Bundesländern ausgeliefert. Bundesweit
sind gegenwärtig rund 4.700 Betriebe wegen Dioxin-Verdachts
geschlossen
Chef der Firma Harles und Jentzsch ist der ehemalige Stasi-Top-
Agent und Dioxin-Panscher Siegfried Sievert.
Offensichtlich ist Dioxin bereits in der DDR-Zeit von Sievert im
Auftrag der Stasi benutzt worden.
Beweis: „Stasi-Akte des Dioxin-Panschers belegt: Harles & Jentzsch-
Geschäftsführer Sievert arbeitete 17 Jahre für die Stasi. Er trug
den Decknamen “IM Pluto”.
Die Akte trägt die Registriernummer II 153/71, ist mehrere Hundert
Seiten dick. Auf dem Deckel ein Name: “Pluto“. Unter diesem Decknamen
spionierte Siegfried Sievert (58), der als Geschäftsführer des
Futtermittel-Herstellers Harles und Jentzsch mutmaßlich für den Dioxin-
Skandal verantwortlich ist, 18 Jahre lang für die Staatssicherheit der
DDR.“
http://infokriegergreifswald.blogspot.com/2011/01/stasi-dioxinpanscher.
html
Die „Zeit“ schreibt:
Knapp 200 Seiten hat die Stasi-Akte von Siegfried Sievert. Der Chef
des Fettherstellers Harles und Jentzsch ist für den Staatssicherheitsdienst
der DDR tätig gewesen. Das geht aus Akten der Birthler-Behörde
hervor, aus denen die Süddeutsche Zeitung zitiert. Sievert sei 18 Jahre
lang bis zur Wende als IM Pluto geführt worden. Schon damals arbeitete
er für fettverarbeitende Betriebe wie dem VEB Märkische Ölwerke
in Wittenberge, schrieb die Zeitung weiter.
“Der IM hat keinerlei Vorbehalte bei der Belastung von Personen
aus seinem Umgangskreis”, zitierte die Süddeutsche Zeitung aus seiner
Akte. Weiter heißt es, dass Sievert nicht aus Überzeugung für die
Stasi arbeite, sondern nur, weil er “persönliche Vorteile/Nachteile in
Erwägung” ziehe. Sievert wollte sich laut der Zeitung auf Anfrage nicht
äußern.
Sievert ist Geschäftsführer des mittlerweile insolventen Fettherstellers
Harles und Jentzsch im schleswig-holsteinischen Uetersen. Die Fir-
ma hatte dioxinbelastete Fettsäuren mit unbelasteten Fetten gemischt.
Die Fette wurden zu Futtermitteln verarbeitet und führten bundesweit
zur Dioxin-Belastung von Hühnern und Schweinen.
Derweil schrieb die Berliner Zeitung, dass der Fetthersteller Harles
und Jentzsch regelmäßig und in viel größerem Ausmaß dioxinbelastete
Fettsäuren gemischt und ausgeliefert haben soll als bislang bekannt.
Die Zeitung berief sich dabei auf Messergebnisse des Niedersächsischen
Landesamts für Verbraucherschutz und Lebensmittelsicherheit (Laves).
Insgesamt 92 der 153 überprüften Fettproben haben Laves zufolge den
zulässigen Dioxin-Grenzwert von 0,75 Nanogramm pro Gramm überschritten.
Ein besonderes Merkmal der Ergebnisse ist, dass sich der Dioxingehalt
in den Proben eklatant voneinander unterscheidet. Der Dioxingehalt
lag bei 1,0, in anderen bei 11,7 und 28,7 Nanogramm, auch Werte
von 48,0 bis 61,6 Nanogramm kamen vor. Für die Ermittler erhöht sich
damit der Verdacht, dass das erhöhte Dioxin nicht zufällig in den Fetten
vorhanden ist sondern unterschiedlich belastete Fette vorsätzlich miteinander
vermengt wurden.
Alle Proben stammen aus der Zeit vom 11. November bis zum 13.
Dezember. Die Behörden schätzen, dass die Firma Harles und Jentzsch
in diesem Zeitraum rund 2500 Tonnen Futtermischfette hergestellt hat
und diese an 20 niedersächsische Futtermittelunternehmer lieferte.
Diese hätten dann die Fette mit anderen Futtermitteln weiterverarbeitet.
Daraus ergebe sich für Niedersachsen eine Futtermittelmenge von
25.000 bis 125.000 Tonnen, die auf diese Weise in der Nahrungskette
eingegangen sind.“
Beweise: http://www.zeit.de/politik/deutschland/2011-01/dioxinstasi-
sievert
http://www.shz.de/nachrichten/schleswig-holstein/artikeldetail/
article/111/dioxin-panscher-soll-als-im-pluto-fuer-die-ddr-stasi-gearbeitet.
html
http://www.bz-berlin.de/aktuell/deutschland/war-fett-dioxin-panscher-
bei-der-stasi-article1094984.html
Das Stasi-Problem war mit dem Zusammenbruch der DDR
keineswegs beendet. Ehemalige Stasi-Mitarbeiter gelangten nach der
Wende in höchste Positionen. In Brandenburg hatten es sogar mehrere
ehemalige Stasi-Mitarbeiter bis in die aktuelle rot-rote Landesregierung
geschafft, um dort die Regierung zu übernehmen. Auch in Sachsen-
Anhalt könnten nach der Landtagswahl ehemalige Stasi-Mitarbeiter in
die Regierung gelangen. Und auch in der Wirtschaft sind viele Stasi-
Mitarbeiter in hohe Positionen gelangt. So auch der Herr Sievert. Doch
was bezweckte dieser tatsächlich mit der Dioxinvergiftung? Handelte er
wirklich aus Profitgier, oder war die bundesweite Vergiftung eine verspätete
Rache der Stasi gegen den ehemaligen Klassenfeind?
Mit den Methoden der Stasi arbeitet auch der äussert dubiose „Finanz-
NACHRICHTENDIENST“ „GoMoPa“. Bespitzelung, Einschüchterung,
Erpressung, Falschnachrichten, Rufmordmord, Cybermord,
Hacking und wohl auch tatsächlicher Mord gehören zu dem täglichen
Repertoire der serienweise vorbestraften Kriminellen von „GoMoPa“.
Bereits Monate vor seinem Tode war Heinz Gerlach diesem dubiosen
„NACHRICHTENDIENST“ aus Ost-Berlin mit Tarnadresse in New York
und Tarnnamen angeblicher jüdischer Rechtsanwälte auf der Spur. Dabei
setzte er von Anfang an sein Leben aufs Spiel.
Denn er wurde mit Stasi-Methoden ausgespäht, bespitzelt und es
wurden seine Computer gehackt. So hatten die „NACHRICHTENDIENST“-
Aufklärer immer wieder brisantes Material, das sowohl auf der
„GoMoPa“-Webseite erschien (mittlerweile gelöscht) als auch auf der
Gerlach kritisch bis feindlich gesonnenen Webseite Akte-Heinz-Gerlach.
info, deren Verbindungsdaten auffallende Parallen zu dem „GoMoPa”-
Internet-Schattenreich vorweisen.
– Er kannte die kriminelle Vergangenheit der „GoMoPa“-Macher
– Er erkannte die Tarnorganisation in New York
– Er erkannte die mutmassliche Erpressung von Immobilienunternehmen durch die
Konstellation „NACHRICHTENDIENST“ „GoMoPa“ und „Anlegerschutzanwalt“ RA Jochen
Resch.
– Er wusste, dass seine Webseite durch Cyber-Attacken lahm gelegt wurden.
– Er war dabei die Rolle von Ehrenfried Stelzer, dem Top-Stasi-Agenten im Hintergrund
zu entschleiern
– All dies führte wohl zu einem Mordauftrag in klassischer Stasi-Manier mit Dioxin.
– An der Tat massgeblich beteiligt ist mit Sicherheit der vorbestrafte Serienbetrüger und
mutmassliche Stasi-Agent „Siegfried Siewert“ oder auch „Klaus Maurischat“ etc pp.
– Die genauen Tatumstände aufzuklären, ist Sache von BKA, LKA, der Kriminalpolizei
und weiterer Ermittler.
– Aber schon jetzt kann man das Tatszenario erkennen: Auch der Hausarzt von Heinz
Gerlach war wohl misstrauisch, was die Todesursache anbetraf. Er wollte den Totenschein
wohl erst nicht ausstellen mit der Todesursache „natürliche Todesursache.“
– In der Öffentlichkeit indes rollte nach der Todesnachricht das geplante Szenario ab.
Zuerst berichtetet der NACHRICHTENDIENST“ „GoMoPa“ von der Todesursache „Blutvergiftung“
– nur wenige Stunden nach dem Tode von Heinz Gerlach. Woher konnte
der „NACHRICHTENDIENST“ dies wissen ? Darüber gibt es keine Angabe in der numehr
von der Webseite des „NACHRICHTENDIENSTES“ „GoMoPa“ verschwundenen Meldung
vom Tode Heinz Gerlachs.
– Es war auch nicht die Meldung des „NACHRICHTENDIENSTES“ „GoMoPa“, der die
Branche und die Öffentlichkeit von dem angeblich natürlichen Tode Heinz Gerlachs
überzeugte:
Mit zwei Artikel entstand die Legende von der Blutvergiftung von Heinz Gerlach: Derm
heute verschwundenen „GoMoPa“-Artikel, der wenige Stunden nach dem Ableben
„Blutvergiftung“ als Todesursache angab und der zunächst auch von der überaus kritischen
Anti-Gerlach-Webseite Akte-Heinz-Gerlach“ in Zweifel gezogen wurde (Beleg
siehe unten).
Als Heinz Gerlach dann die Zusammenhänge zwischen der mutmasslichen
Erpressung des Berliner Immobilienhauses Estavis und „Go-
MoPa“ bzw Rechtsanwalt Jochen Resch erkannte, wusste er endgültig
zuviel und wurde für die „GoMoPa“-Hintermänner zu einer grossen Gefahr.
Dan wurde offenbar nachgelegt als die Zweifel an der wahren
Todesursache immer lauter wurden:
Zitat:
“14. Juli 2010 – Gerlach und die wahre Todesursache
Der selbst ernannte Anlegerschützer Heinz Gerlach starb an einer
zu spät erkannten Blutvergiftung
Der Mann, der dubiose Finanzsysteme durchschaute, erkannte das
feindliche System im eigenen Körper nicht
Hameln/Oberursel (wbn). Die Szene der Finanzdienstleister und
Anlageberater ist um eine schillernde Figur ärmer. Der Anlegerschützer
Heinz Gerlach ist am vergangenen Samstag in seinem Haus im hessischen
Oberursel gestorben.
In wenigen Wochen wäre er 65 geworden. Gerlach hat mit seiner
Internetseite „Direkter Anlegerschutz“ die Beteiligungsangebote des
Kapitalmarktes bewertet und sich in den 70er Jahren mit dem „Gerlach-
Report“ einen bemerkenswerten Ruf als Brancheninsider erworben. Die
Karriere des Steuergehilfen ist in der Finanzwelt beispiellos. Er hörte
das Gras wachsen – und wieder verwelken. Für die einen war er ein
unbeugsamer Held, für die anderen der Störfaktor schlechthin und erklärtes
ketzerisches Feindbild.
Kein Wunder: Es ging stets um viele Millionen Euro und verdeckte
Interessen. In einem Spiegel-Interview sagte er: „Ich habe hier jeden
Tag ‘Dallas’ oder ‘Denver’“. So kommt es nicht unerwartet, dass sich
jetzt schon Legenden um seinen unerwarteten Tod ranken. Angeblich
habe er sich das Leben genommen, wollen Stimmen aus dem Hintergrund
wissen. Die Wahrheit ist so profan wie traurig: Gerlach, der zu
den Indianern gehörte, die niemals weinen und keinen Schmerz kennen,
starb an den Folgen einer unterschätzten Nagelbettentzündung.
Daraus resultierte eine Blutvergiftung. Dies haben die Weserbergland-
Nachrichten.de aus dem engsten Umfeld des „ältesten Geldanlageschützers“
der Republik erfahren.
Die Sepsis (Blutvergiftung) gilt als der weithin unbekannte und meistunterschätzte
Killer in Deutschland. Diese außer Kontrolle geratene
systemische Entzündungsreaktion auf eine Infektion fordert ebenso
viele Todesopfer wie der Herzinfarkt. Bis zu 50 Prozent der Erkrankten
sterben trotz intensiver Behandlung im Krankenhaus. In Deutschland
erkranken – so die Schätzungen – im Jahr 150.000 Menschen an einer
Sepsis. Gerlach hat komplexe Finanzsysteme durchschaut – den systemisch
angreifenden Feind im eigenen Körper hat er unterschätzt.”
h t t p : / /www.we s e r b e r g l a n d – n a c h r i c h t e n . d e / i n d e x .
php?option=com_content&view=article&id=442:14-juli-2010-gerlachund-
die-wahre-todesursache&catid=1:-weserbergland-nachrichten
Dieser Artikel auf der Webseite der unbedeutenden Provinz-Zeitung
„Weserbergland Nachrichten“, die ein Ex-Stasi-Mann lancierte, beruft
sich auf das „engste Umfeld“ von Heinz Gerlach – ohne auch nur DEN
GERINGSTEN BELEG vorweisen zu können.
Somit wir das Märchen von der angeblichen „Blutvergiftung“ als
Agenda festgelegt.
Einen Tag später, am 15. Juli 2010 übernahm auch die Gerlachkritische
Webseite, deren Veranwortliche weiter im Dunkeln sind, diese
Agenda aufgriff und schrieben:
“Worte über Heinz Gerlach »
15.07.10
Heinz Gerlach: Die Todesursache steht offenbar fest
(Eigener Bericht)
Um Heinz Gerlachs plötzlichen Tod ranken sich diverse Gerüchte.
Die können nun ad acta gelegt werden. Denn die Weserbergland-
Nachrichten haben “aus dem engsten Umfeld” des “selbst ernannten
Anlegerschützers” erfahren, dass Gerlach “an den Folgen einer unterschätzten
Nagelbettentzündung” gestorben ist.
Die norddeutsche Tageszeitung schreibt weiter: “Daraus resultierte
eine Blutvergiftung.” An einer Sepsis sterben demnach jedes Jahr
genauso viele Menschen wie an einem Herzinfarkt.
Heinz Gerlach soll am Dienstag beerdigt werden.
Den Artikel im Original finden Sie hier: http://www.
we s e rbe rgl and-na chr i cht en.de / inde x .php? opt i on=c om_
content&view=article&id=442:14-juli-2010-gerlach-und-die-wahretodesursache&
catid=1:-weserbergland-nachrichten”
Ohne EIGENE RECHERCHE-und ohne den geringsten Beleg übernahmen
diese „INSIDER“ das Blutvergiftungs-Märchen.
Hinzu kommt die Internetseite http://www.akte-heinz-gerlach.
info/15-07-10-heinz-gerlach-die-todesursache-steht-offenbar-fest/ und
die Webseiten die „GoMoPa“ zuzuordnen sind, weisen auffallende Paralleln
auf.
Die Verbindungsdaten der Akte-Heinz-Gerklach.Info, gehostet in
der anatolische Internet-Klitsche Media-on sowie die der „GoMoPa“ und
deren Hintermänner .:
Godaddy ist der Haus-Hoster von ‘Gomopa’ und seit vielen
Jahren der Registrar der ‘Gomopa’-Homepage. Hier werden auch
zahlreiche ‘Gomopa’ zuzuordnende ‘Foren’ und ‘Blogs’ zugeordnet,
in denen fiktive Cyber-Aliasse ihr Unwesen treiben, das natürlich nie
mit Fakten belegt ist wie z.b. extremnews.com.
Registrant: Goldman Morgenstern an Partners LLC
Registered through: GoDaddy.com, Inc. (http://www.godaddy.
com)
Domain Name: GOMOPA.NET
Gehostet hier:
Server IP: 67.23.163.233 Server Location: Lockport, NY, 14094,
United States
Gomopa IP: 67.23.163.230 Gomopa server location: Asheville in
United States Gomopa ISP: Netriplex LLC
Pikant auch die Internetseite der immer wieder mit Gomopa in
Verbindung gebrachten Offshore-Firma Baker & Baker, Köln, wird
bei Godaddy gehostet.
Server IP: 208.109.181.34 Server Location: Scottsdale, AZ,
85260, United States
Von gekaperten Godaddy-IP-Adressen wurden und werden
auch zahlreiche Flooding-Angriffe geführt bzw. sogenannte Stalking-
Seiten gehostet, die so die Opfer eine Spezialität von Klaus
Maurischat seien.
Die Baker & Baker wurde bereits in der Schweiz wegen Vermögenslosigkeit
liquidiert. Siehe http://www.yasni.de/baker+offshore/
person+information und http://www.moneyhouse.ch/en/u/baker_
baker_consulting_group_ag_CH-170.3.014 .447-7.htm
Dieser Firma war Heinz Gerlach ein besonderes Dorn im Auge
Server IP: 95.0.239.251
Domain ID:D28959891-LRMS
Domain Name:AKTE-HEINZ-GERLACH.INFO
Created On:03-Jul-2009 08:59:55 UTC
Last Updated On:10-May-2010 18:16:59 UTC
Expiration Date:03-Jul-2011 08:59:55 UTC
Sponsoring Registrar:Alantron BLTD (R322-
LRMS)
Status:OK
Registrant ID:DI_11637039
Registrant Name:Linh Wang
Registrant Organization:Linh Wang1273487281
Registrant Street1:3617 Tower 1 Lippo Centre
Registrant Street2:
Registrant Street3:
Registrant City:Hong Kong
Registrant State/Province:Queensway
Registrant Postal Code:0000089
Registrant Country:HK
Registrant Phone:+000.5230064510
Registrant Phone Ext.:
Registrant FAX:+000.5230064510
Registrant FAX Ext.:
Registrant Email: info@xchiang.com
wie man bei Durchsicht der Seite http://www.akte-heinz-gerlach.info unschwer
erkennen kann. Es geht und ging dabei um die Patenschaft
im grauen Markt der Kapitalanlagen.
Drehsscheibe Mediaon.com Eine wesentliche Rolle bei den illegalen
Offshore-Internet-Aktivitäten der Cyber-Kriminellen spielt
auch die Briefkastenfirma Linh Wang, Honkong, bei der die Seite
http://www.akte-heinz-gerlach.info registriert wurde, die bei dem dubiosen
Undergrund-Unternehmen Mediaon.com in der Türkei gehostet
wird, so die Opfer. Über diese Schiene wurden Dutzende
betrügerischer Erpresser-Sites der Cyber-Kriminellen registriert.
Admin ID:DI_11637039
Admin Name:Linh Wang
Admin Organization:Linh Wang1273487281
Admin Street1:3617 Tower 1 Lippo Centre
Admin Street2:
Admin Street3:
Admin City:Hong Kong
Admin State/Province:Queensway
Admin Postal Code:0000089
Admin Country:HK
Admin Phone:+000.5230064510
Admin Phone Ext.:
Admin FAX:+000.5230064510
Admin FAX Ext.:
Admin Email: info@xchiang.com
Billing ID:DI_11637040
Billing Name:Tuce Kuyumcu
Billing Organization:Tuce Kuyumcu1273487281
Billing Street1:Market Street 45a
Billing Street2:
Billing Street3:
Billing City:Baidoa
Billing State/Province:Victoria Mahe Seychelles
Billing Postal Code:00000
Billing Country:HK
Billing Phone:+000.4834433490
Billing Phone Ext.:
Billing FAX:+000.4834433491
Billing FAX Ext.:
Billing Email: tuce.kuyumcu@somali.com
Tech ID:DI_11637040
Tech Name:Tuce Kuyumcu
Tech Organization:Tuce Kuyumcu1273487281
Tech Street1:Market Street 45a
Tech Street2:
Tech Street3:
Tech City:Baidoa
Tech State/Province:Victoria Mahe Seychelles
Tech Postal Code:00000
Tech Country:HK
Tech Phone:+000.4834433490
Tech Phone Ext.:
Tech FAX:+000.4834433491
Tech FAX Ext.:
Tech Email: tuce.kuyumcu@somali.com
Name Server:NS1.ANADOLUDNS.COM
Name Server:NS2.ANADOLUDNS.COM
Hier der Beleg über das Hosting der Anti-Gerlach-
Seite, AKTE-HEINZ-GERLACH.INFO, bei dem
Untergrund-Unternehmen Mediaon.com in der
Türkei gehostet: Linh Wang
Domain ID:D28959891-LRMS
Domain Name:AKTE-HEINZ-GERLACH.INFO
Created On:03-Jul-2009 08:59:55 UTC
Last Updated On:10-May-2010 18:16:59 UTC
Expiration Date:03-Jul-2011 08:59:55 UTC
Sponsoring Registrar:Alantron BLTD (R32
Mediaon Title: Anonymous Hosting – Privacy
Hosting – MediaOn.com is leading the marked in
privacy hosting.
Mediaon Keywords: Anonymous hosting, Whois
Protection, Whois privacy services, Privacy Hosting,
anonymous domain registration, managed
vps
Mediaon Description: MediaOn.com is leading in
anonymous hosting and privacy hosting.
Mediaon IP: 95.0.153.245 Mediaon server location:
Turkey Mediaon ISP: Turk Telekom IP:
95.0.153.245 IP Country: Turkey This IP address
resolves to dsl9539413.ttnet.net.tr
Idari Yonetici / Registrant (Admin) Ad / Name
Tekin Karaboga Adres Catalca Yolu Menekse Mevkii
Istanbul 34537 Tel +90.212.8656520
Diese Internet-Operations-Muster – so die SJB-Opfer – habe
es in Ihrem Falle, aber auch bei zahlreichen anderen Betrugs-, Erpressungs-
und Verleumdungsopfer in den letzten Jahren gegeben.
Nunmehr liegen und auch des heimtückischen Cyber-Mordes an
Heinz Gerlach können ermittelt werden’, so Heinz. F., Mayen, Sprecher
der Opfer (die Personen-Daten wurden aus Sicherheitsgründen
anonimysiert).
Wenn das BKA, LK, FBI und die Kriminalpolizei diesen Spuren
weiter intensiv nachgehen würden, seien die sowieso laufenden Ermittlungen
in zahlreichen Fällen wie auch im Kursmanipulationsfall
‘Wirecard’ von Erfolg gekrönt. Denn große Firmen wie Godaddy und
auch Enom, für die der Reseller Arvixe Domains verkauft, könnten
sich anders als ‘dubiose türkische Untergrund-Internet-Klitschen’ –
dem Zugriff der Justiz nicht entziehen.
„Neue Erkenntnisse in der Affäre Resch/GoMoPa-Stasi haben
wir recherchiert“, erläutert SJB.-GoMoPa-Sprecher Heinz Friedrich.
„Neben dem Stasi-Agenten und früheren Leiter der Kriminologie
an der Ost-Berliner Humboldt-Universität hat Rechtsanwalt Jochen
Resch den sogenannten „Wirtschaftsdetektiv“ Medard Fuchsgruber
(Photo oben) als Protege´ gefördert.
Fuchsgruber spielte eine besonders dubiose Rolle in den letzten
Tagen und Wochen vor dem Tode von Heinz Gerlach. Er sollte im
Auftrag der von „GoMoPa“ erpressten Kasseler Firma Immovation
AG Erkennntnisse über „GoMoPa“ sammeln und diese auch dem
„GoMoPa“-Kritiker Heinz Gerlach zur Verfügung stellen. Er hatte
jederzeit freien Zugang zu Heinz Gerlach und dessen Privaträumen.
8. Juli 2009 … Der Wirtschaftsdetektiv Medard Fuchsgruber
soll zum neuen Geschäftsführer des Deutschen Instituts für Anlegerschutz
(DIAS) gewählt werden“, meldete http://www.anlegerschutz.
tv/
Zwei Tage später starb Heinz Gerlach.
Am 10. Juli 2010 starb Heinz Gerlach angeblich an „Blutvergiftung“.
GoMoPa brachte die Meldung nur wenige Stunden nach dem
Ableben – mit der Todesursache „Blutvergiftung“ – diese Todesursache
kann sehr leicht und sher schnell durch Dioxinvergiftung herbeigeführt
werden. Diese „Pressemeldung“ ist inzwischen von der
Webseite der „GoMoPa“ verwschwunden.
Aber auch andere Insider, ausser uns haben sie gesehen:
Siehe hier in der Akte Heinz Gerlach::
„Zum Tode von Heinz Gerlach »
11.07.10 Sondermeldung
HEINZ GERLACH VERSTORBEN
(Eigener Bericht)
Heinz Gerlach ist tot. Am Sonnabend Abend ist der äußerst umstrittene
“Anlegerschützer” in Oberursel verstorben. Das vermeldet
der Finanzmarketingberater Michael Oehme in einem Rundbrief.
Heinz Gerlach wäre am 9. August 65 Jahre alt geworden.
Auf den Internetseiten der Heinz Gerlach Medien eK ist bislang
keine Bestätigung für diese Nachricht zu erhalten.
Die Todesumstände sind völlig unklar. Der Finanznachrichtendienst
Gomopa spekuliert, Gerlach sei einer Blutvergiftung erlegen.
Bei allen kritikwürdigen Geschäftsmethoden war Heinz Gerlach
ein Mensch, der eine Familie hinterlässt. Unser Mitgefühl gilt seinen
Angehörigen.
Wie und ob unsere Berichterstattung weitergeht, hängt davon
ab, auf welche Weise die Geschäfte des Unternehmens nach Heinz
Gerlachs Tod geführt werden.
Bereits vorbereitete Artikel und Enthüllungen werden wir aus
Pietät zunächst nicht veröffentlichen.“
http://www.akte-heinz-gerlach.info/11-07-10-sondermeldungheinz-
gerlach-verstorben/ (noch ist der Link verfügbar)
Während selbst die Gerlach-kritische Akte schreibt „die Todesursache
ist noch völlig unklar“, WEISS „GoMoPa“ BEREITS ZU
DIESEM ZEITPUNKT; das die ANGEBLICHE TODESURSACHE EINE
BLUTVERGIFTUNG WAR.
Von da an nahm die Legende ihren Lauf – über hessische Weserbergland-
Nachrichten, die keine Quelle angaben.
Wir erinnern uns, das Pseudonym von Klaus Maurischat (dessen
Lebenslauf und Identität wohl gefälscht sein dürften), ist Siegfried
Siewert. Siegfried Sievert ist ein ehemaliger Stasi-Agent und nunmehr
für den DIOXIN-Skandal verantwortlich.
Er gab zu im Auftrag der Stasi, BLUTFETT-VERSUCHE vorgenommen
zu haben.
“Dieser Kerl panschte Gift-Fett in unser Essen”, titelt die Bild-
Zeitung über den Chef des Futtermittelherstellers Harles & Jentzsch
aus Uetersen (Kreis Pinneberg). Gemeint ist Siegfried Sievert, 58
Jahre alt. Wer ist der Mann, der für einen der größten Lebensmittelskandale
Deutschlands verantwortlich sein könnte?
Der Unternehmer lebt in einer Villa in Kiebitzreihe (Kreis Steinburg)
und ist seit 16 Jahren bei Harles & Jentzsch in leitender Position
tätig. Seit 2005 ist er alleinvertretungsberechtigter Geschäftsführer.
Als nach dem Dioxinfund klar wurde, dass die verseuchte
Mischfettsäure nur für technische Zwecke verwendet werden darf,
erklärte Sievert: “Wir waren leichtfertig der irrigen Annahme, dass
die Mischfettsäure, die bei der Herstellung von Biodiesel aus Palm-,
Soja- und Rapsöl anfällt, für die Futtermittelherstellung geeignet
ist.”
Sievert hat sich für Qualitätsstandards stark gemacht
Diese Aussage erstaunt Branchenexperten, die mit Sievert gearbeitet
haben. Christof Buchholz ist Geschäftsführer des Deutschen
Verbands des Großhandels mit Ölen, Fetten und Ölrohstoffen (Grofor),
in dem 120 Unternehmen organisiert sind, darunter auch
Harles & Jentzsch. Buchholz sagt: “Ich kenne Herrn Sievert gut.
Er hat sich seit Jahren für hohe Qualitätsstandards stark gemacht,
insbesondere für das holländische System.” Dabei würden akribisch
all jene Gefahren aufgelistet, die eine mechanische oder chemische
Verunreinigung verursachen könnten – und Standards für die sichere
Produktion von Futtermitteln definiert.
Sievert dürfte demnach ein Experte für eine saubere Futtermittelproduktion
sein. Er besuchte auch die jährlichen Grofor-Treffen,
bei denen sich Experten aus ganz Europa austauschen. Wie
glaubwürdig ist dann seine Aussage, er habe angenommen, die
Mischfettsäure verwenden zu dürfen – zumal der niederländische
Lieferant Petrotec AG in Verträgen, Lieferscheinen und Rechnungen
darauf hingewiesen haben will, dass diese billigere Fettsäure ausschließlich
zur technischen Verwendung bestimmt sei?
“Wir können das nicht nachvollziehen”
Christof Buchholz: “Bei uns war die Überraschung groß. Es ist
ein No-go für Futtermittelhersteller, technische Mischfettsäuren zu
verwenden. Wir können das nicht nachvollziehen.” Er habe deshalb
Siegfried Sievert angerufen. “Wir haben ein kurzes Gespräch geführt.
Herr Sievert war verzweifelt und erklärte auch mir, dass er
dachte, das sei in Ordnung.” Während des Telefonats sei zudem
besprochen worden, woher die Dioxine gekommen sein könnten.
Christof Buchholz: “Herr Sievert wusste darauf keine Antwort und
klagte, dass es so viele Fragezeichen gebe.”
Seine erste Aussage hat er mittlerweile revidiert. Dem niedersächsischen
Agrarministerium teilte Harles & Jentzsch jetzt mit, das
dioxinverseuchte Industriefett sei versehentlich in die Produktion
gelangt. Ministeriumssprecher Gert Hahne: “Die Darstellung, da
hat einer den falschen Hahn aufgedreht, erscheint uns sehr unglaubwürdig.”
Sievert drohen drei Jahre Gefängnis
Die Staatsanwaltschaft Itzehoe ermittelt wegen des Verdachts
einer vorsätzlichen Straftat gegen Siegfried Sievert. Ihm drohen
wegen Verunreinigung von Lebens- und Futtermitteln bis zu drei
Jahren Gefängnis oder eine Geldstrafe. Außerdem droht eine Prozess-
Lawine. Auf was dürfen Landwirte hoffen, die auf Schadensersatz
klagen?
Die Harles & Jentzsch GmbH ist im Mai 1980 in Pinneberg gegründet
worden, zog 1994 nach Uetersen. Im Handelsregister gibt das
Unternehmen als Geschäftszweck an: Handel und Veredelung, Im-
und Export von Ölen, Fetten, Fettsäuren und deren Derivaten. Unter
dem Markennamen “Hajenol” verkauft Harles & Jentzsch Futterfett
für Rinder, Schweine, Geflügel und Legehennen, produziert aber
auch Industriefette für die Papierverarbeitung. Das Stammkapital
der GmbH betrug 1994 genau 537 800 Mark. Diese Summe scheint
zwischenzeitlich nicht erhöht worden zu sein, obwohl der Jahresumsatz
des Zwölf-Mann-Betriebs zuletzt 20 Millionen Euro betrug.
Sollte Harles & Jentzsch vorsätzlich gehandelt haben, wird die
Betriebshaftpflichtversicherung nicht einspringen. Der Bauernverband
geht von einem Millionenschaden aus. Es geht um mehr
als 1000 Landwirte, die ihre Höfe schließen mussten und deren
Tiere teilweise verbrannt werden. Als Entschädigung wird das
Stammkapital und selbst das Gesellschaftsvermögen nicht reichen.
Dem Vertriebschef der Firma zufolge soll am Donnerstag eine Bestandsaufnahme
erfolgen. Danach werde entschieden, ob Insolvenz
angemeldet werde. Gegen Sievert und seine Mitarbeiter hat es derweil
Morddrohungen gegeben. Am Telefon seien Mitarbeiter mit den
Worten “Wir machen euch fertig” bedroht worden, so Sievert.
Bild schreibt: –„ Die Akte trägt die Registriernummer II 153/71,
ist mehrere Hundert Seiten dick. Auf dem Deckel – in feiner Schreibschrift
– ein Name: „Pluto“. Unter diesem Decknamen spionierte
Siegfried Sievert (58) 18 Jahre lang für die Staatssicherheit der
DDR – der Futtermittelpanscher, der mutmaßlich für den deutschen
Dioxin-Skandal verantwortlich ist!
Auf Antrag von BILD gab die zuständige Birthler-Behörde die
Unterlagen jetzt heraus. Die Dokumente zeichnen das Bild eines
Mannes, der rücksichtslos ist, skrupellos und vor allem auf eigenen
Profit bedacht.
Rückblick. 1971 wird die Stasi auf den 18-jährigen Sievert
aufmerksam. Sie beobachtet sein „dekadentes Aussehen“, seine
hohe Intelligenz und seine „guten Verbindungen zu anderen jugendlichen
Personenkreisen“. Sievert wird angeworben. Aus einem
Bericht vom 16. März 1971: „Der Kandidat kann zur Absicherung
der Jugend (…) eingesetzt werden.“
Sievert wählt seinen Decknamen selbst, kassiert fortan Prämien
für seine „inoffizielle Mitarbeit“. In den Unterlagen finden sich zahlreiche
Quittungen, eine vom 6. November 1987: „Hiermit bescheinige
ich den Erhalt von 100 Mark für geleistete Arbeit.“
Nach dem Abitur studiert Sievert in Greifswald Physik. Er macht
Karriere, wird Geschäftsführer für „Absatz und Beschaffung“ in der
„Märkischen Ölmühle“ in Wittenberge (Brandenburg).
Eifrig spitzelt Sievert weiter, berichtet über intime Verhältnisse
seiner Kollegen.
So notiert „IM-Pluto“ am 25. September 1986: „Die beiden
beabsichtigen, gemeinsam die BRD zu besuchen.“ Zwei Kollegen
hätten angegeben, von einem Freund eingeladen worden zu sein.
„Fakt ist jedoch, daß zwischen dem Kollegen und der Kollegin seit
langer Zeit Intimbeziehungen bestehen. (…) Aus dieser Tatsache
ist abzuleiten, daß eine gemeinsame Reise in die BRD mit hoher
Wahrscheinlichkeit für eine Flucht benutzt wird.“
Skrupel zeigte Sievert laut Stasi-Akte keine. Ein Führungsoffizier
notiert: „Der IM hatte keinerlei Vorbehalte bei der Belastung von
Personen aus seinem Umgangskreis.“
Nach dem Mauerfall verlässt Sievert die Ölmühle. Ehemalige
Kollegen wundern sich über seinen Wohlstand, werfen ihm vor, er
habe Lieferungen der Ölmühle unterschlagen, dafür unter der Hand
kassiert. Ein Vorwurf, für den es derzeit keine Belege gibt.
1993 steigt Sievert beim Futtermittelhersteller „Harles & Jentzsch“
ein. 2005 wird er alleiniger Geschäftsführer, steigert in nur
fünf Jahren den Umsatz von 4,3 auf rund 20 Millionen Euro, vervierfacht
den Gewinn. Ein Futtermittelmischer aus Niedersachsen zu
BILD: „Solch ein Wachstum ist mit normalen Methoden unmöglich.“
Mit Panscherei möglicherweise schon: Das dioxinverseuchte
Tierfutter von „Harles & Jentzsch“ war durch das Einmischen von
Industriefetten entstanden. Die sind deutlich billiger als Futterfette.
Allein im November und Dezember 2010 soll Sieverts Firma
mindestens 3000 Tonnen verseuchtes Futterfett verarbeitet haben.
Etwa 150 000 Tonnen belastetes Futter könnten so in die Nahrungskette
gelangt sein.
Martin Hofstetter, Agrarexperte von Greenpeace zu BILD:
„Wenn man sich die Zahlen von ,Harles & Jentzsch‘ anschaut und
die bisherigen Erkenntnisse und Veröffentlichungen berücksichtigt,
kann man eigentlich nur zu einem Schluss kommen: Hier wurde
systematisch betrogen und gepanscht.“
UND: Stasi-Top-Agent Ehrenfried Stelzer war auch Professor für
Kriminologie an der Berliner Humboldt-Universität zu SED-Zeiten.
SJB-GoMoPa-Sprecher Heinz Friedrich kommentiert: „Der Verdacht
liegt nahe, dass hier eine Verschwörung zum Tode von Heinz
Gerlach geführt hat, der dieser Gruppierung im Wege stand. Auch
wir und unsere Angehörigen wurden mit Stas-Methoden bedroht
und eingeschüchtert.“ Und fügt er hinzu: „Wie das Dioxin in die
Blutbahn von Heinz Gerlach kam, werden diese Stas-Agenten und
ihre Mitverschwörer wohl wissen.“
Nach dem Tode von Gerlach wechelte Fuchsgruber endgültig
und offen die Seiten in das „GoMoPa“-Team und sollte auch als
DIAS-Geschäftsführer den Stasi-Agenten Ehrenfried Stelzer ablösen
– auf Betreiben des „Anlegerschutz“-Anwaltes RA Jochen Resch
(siehe unten).
Nachstehende Erklärung publizierte dann Immovation AG:
„Nach den höchsterfreulichen gerichtlichen Erfolgen gegen den
u. a. von rechtskräftig verurteilten Betrügern betriebenen, im Ausland
domizilierten “Informationsdienst” Gomopa geht die Kasseler
IMMOVATION Immobilien Handels AG auch straf- und zivilrechtlich
gegen den Wirtschaftsdetektiv Medard Fuchsgruber vor.
Dieser hatte den IMMOVATION-Vorständen Lars Bergmann und
Matthias Adamietz im Frühjahr 2010 angeboten, unwahre, diffamierende
Veröffentlichungen auf der Website der gomopa.net beseitigen
zu lassen und weitere rechtswidrige Veröffentlichungen dieser
Art zu verhindern. Diese beauftragten Medard Fuchsgruber entsprechend
und entrichteten ein Honorar von insgesamt EUR 67.500,00.
Entgegen allen Zusagen von Fuchsgruber erfolgen über Gomopa
jedoch – insbesondere seit Juli diesen Jahres – weiterhin schwer
diffamierende Veröffentlichungen, gegen deren wesentlichste das
traditionsreiche Kasseler Unternehmen in der Zwischenzeit bereits
vor Gericht eine einstweilige Verfügung durchsetzen konnte (LG
Berlin; Az.: 27 O 658/10).
Fuchsgruber ist – nach Entgegennahme des Vorabhonorars –
offenbar seit Juni selbst “Kooperationspartner” bei Gomopa und
wirbt sogar mit dieser Funktion, auch bei Gomopa wird das Engagement
Fuchsgrubers besonders willkommen geheißen. Nach Auffassung
der IMMOVATION hat Fuchsgruber damit von Beginn an über
sein beabsichtigtes Engagement für die IMMOVATION getäuscht,
was das Unternehmen im Rahmen einer Strafanzeige und eines
Strafantrags inzwischen von der zuständigen Staatsanwaltschaft
überprüfen lässt. Zudem hat die IMMOVATION das vorab bezahlte
Honorar zurückgefordert und wird erforderlichenfalls den zivilrechtlichen
Klageweg beschreiten.
Absurde Erklärungsversuche
Die von Fuchsgruber offenkundig in Journalisten- und Branchenkreisen
zirkulierte Einschätzung, er hätte auftragsgemäß für IMMOVATION
gehandelt, zielt völlig ins Leere: Denn nach seinem Einstieg
bei Gomopa haben die über einen Serverstandort im Ausland
verbreiteten Schmähungen nachweislich sogar zugenommen. Und
schließlich: Selbst wenn dem so wäre, wie ließe sich dann der Umstand
erklären, dass Fuchsgruber weiterhin als “Kooperationsparter”
bei Gomopa fungiert, wenn doch nun für Gomopa öffentlich
bekannt ist, dass Fuchsgruber im Auftrag der diffamierten IMMOVATION
aktiv werden sollte?
Eine unmittelbare Beendigung der Zusammenarbeit Fuchsgruber
und Gomopa wäre daher die logische Konsequenz, die jedoch
bezeichnenderweise bis heute offenkundig ausgeblieben ist, was
den von der IMMOVATION erhobenen Vorwurf weiter untermauert.
Bemerkenswert ist darüber hinaus, dass sich der Einstieg Fuchsgrubers
beim “Informationsdienst” Gomopa laut Medienberichten in
enger zeitlicher Nähe zum Scheitern Fuchsgrubers beim Deutschen
Institut für Anlegerschutz (DIAS) vollzog.“
Und im November 2010 durfte Fuchgruber dann auf der
„GoMoPa“-Webseite für sich werben:
http://www.gomopa.net/Pressemitteilungen.html?id=603&me
ldung=Wucherbeitraege-Medard-Fuchsgruber-gruendete-Aktionsgemeinschaft-
fuer-Versicherte#thumb (Noch ist der Link da)
Hintergrund:
Der Beleg, wie eng „GoMoPa“ und der laut den SJB-GoMoPa-
Opfern hinter „GoMoPa“ stehende Rechtsanwalt Resch stehen,
lesen Sie nachfolgend. Und: RA Resch fördert einen Ex-STASIHauptmann:
Zitat:
„GoMoPa: Warum haben Sie ausgerechnet einen Stasi-Oberst
und zudem noch hochbetagt, nämlich Ehrenfried Stelzer (78), als
Nachfolger von Pietsch bei DIAS eingesetzt?
Resch: “Der Verein stand ohne Geschäftsführer da. Stelzer war
der einzige, der Zeit hatte. Alle im Verein haben gesagt, 20 Jahre
nach der Wende ist die Stasizeit nicht mehr so wichtig. Schließlich
war Stelzer Professor für Kriminalistik an der Humboldt-Uni. Aber im
Nachhinein war das kein so kluger Zug.”
GoMoPa: Stelzer wurde inzwischen von Wirtschaftsdetektiv
Medard Fuchsgruber abgelöst, der nach eigenen Worten die aggressive
Verfolgung von Kapitalmarktverbrechen fortsetzen will. Der
Verein soll künftig von mehreren Rechtsanwälten bezahlt werden.“
Zitatende
Mehr unter http://www.sjb-fonds-opfer.com
Ausgrechnet der dubiose Detektiv Fuchsgruber, der die Seiten
von Immovation AG hin zu „GoMoPa“ wechelt ist also ein Resch-
Protege´.
Und: Fuchsgruber bemühte sich nachweislich um Gerlachs Archiv
in der Insolvenzmasse. Und: er hatte freien Zugang zu Heinz
Gerlachs Privaträumen.
Und: Fuchsgruber wechselte erst OFFIZIELL nach Heinz Gerlachs
für alle überraschenden Tod zu „GoMoPa“ und wurde ein
Protege´von Resch.
Und: Das Pseudonym von Klaus Maurischat „Siegfried Siewert“
ist ein Anagramm des Namen des früheren Stasi-Agenten und Dioxin
Panschers Siegfried Sievers.
Und: Die Stasi führte Menschenversuche mit Dioxin durch.
Alles Zufälle ? Rein statistisch gesehen wohl kaum.
Dazu passt, dass diese Gruppierung die Publikation dieser Fakten
mit allen Umständen verhindern will. Sie werden wissen weshalb…
Beispiel GMAC:
Laut den SJB-GoMoPa-Opfern versuchte GoMoPa wohl im
Auftrag von Resch die General Motors-Tochter GMAC zu erpressen.
Zitata aus „GoMoPa“: Der Berliner Anlegerschutzanwalt Jochen
Resch, der zahlreiche Käufer von GMAC-RFC-finanzierten Wohnungen
vertritt, sagte dem Finanznachrichtendienst GoMoPa.net: “Anfangs
wurde das Fünffache, später sogar das Siebenfache des Nettoverdienstes
eines Kreditnehmers als Kredit vergeben. Wer also
40.000 Euro netto im Jahr verdiente, bekam einen Kredit bis zu
280.000 Euro, obwohl, wie sich nach Überprüfung herausstellt, die
Immobilie nur 140.000 Euro wert war.
Dazu genügte eine Anmeldung beim Internet-Vermittler Creditweb,
und die Kredite wurden bei entsprechender Verdienstbescheinigung
im Eiltempo durchgewunken.
Was die Wohnung wirklich wert war, war nicht mehr das Problem
von GMAC-RFC . Denn sie verschnürte die Wohnungen zu Paketen
von 500 Millionen Euro und verkaufte die Pakete zur Refinanzierung
nach Holland.
Nutzniesser der Baufilligenz der GMAC-RFC waren aber nicht
die Käufer, die mit dem Kredit über dreißig Jahre eine überteuerte
Wohnung abzahlen. Nutzniesser waren die Verkäufer und Vermittler,
die 50 Prozent auf den wahren Verkehrswert der Wohnung
draufgeschlagen hatten.
Für die Vermittler von Wohnungsfinanzierungen begann ein
wahres Schlaraffenland
Anlegerschutzanwalt Resch beschreibt den Aufstieg der Ami-
Bank so: “Vertriebsorganisationen sahen die große Chance, ihren
bei anderen Banken nur schwer finanzierbaren Kunden einen Kredit
zu vermitteln. Für den Vertrieb der entscheidende Vorteil. Nur wenn
Geld fließt, fließen auch die Provisionen. Bis zu 35 Prozent des Kaufpreises.
Dieses attraktive Angebot ließ die GMAC-RFC Bank innerhalb
kurzer Zeit zu einem ernsthaften Konkurrenten für die übrigen fi-
nanzierenden Banken auf dem Schrottimmobilienmarkt aufsteigen.
Innerhalb kurzer Zeit erreichte die GMAC-RFC Bank deshalb ein
Gesamtkreditvolumen von mehr als zwei Milliarden Euro.
Der Grund für die großzügige Kreditgewährung dürfte gewesen
sein, dass die GMAC-RFC Bank das Risiko verkaufte. Sie wollte von
vornherein die Kredite nicht behalten. Sie schnürte große Kreditpakete
und verkaufte diese an holländische Zweckgesellschaften.
Die GMAC-RFC wurde schnell zum heißen Tipp auf dem Immobilienmarkt.
Denn Verkäufer und Vermittler bekamen sogar Antrag-
steller ohne Eigenkapital durch, die bei jeder anderen Bank durchgefallen
wären.”
Die GMAC-RFC Bank feierte sich in einer Pressemitteilung vom
Januar 2007 wie folgt: „Mit Einführung der neuen Baufilligenz® –
einer Produktinnovation, mit der erstmals in Deutschland standardisierte
Vollfinanzierungen für Eigennutzer und Kapitalanleger bis zu
110 Prozent des Kaufpreises angeboten werden – haben wir nicht
nur innerhalb kurzer Zeit die Produktführerschaft erreicht, sie zeichnet
auch als Wachstumstreiber für die Verdoppelung des Neugeschäftes
gegenüber 2005 verantwortlich.“
Im September 2008 war das Innovations-Konzept der GMAC
sowohl in den USA als auch in Deutschland gescheitert. Die GMACRFC
vergibt seitdem keine Hypothekendarlehen mehr.
Anlegerschutzanwalt Resch: “Zum 30. September 2008 gab die
GMAC-RFC Bank ihre Lizenz zurück. Es wurde den Kunden mitgeteilt,
dass alles beim Alten bleibe. Die GMAC-RFC Servicing GmbH
werde jetzt die Kunden weiter betreuen.
Schon damals entstanden jedoch Zweifel, ob dieses Angebot
ernst gemeint war. Wir hatten befürchtet, dass sich die Konditionen
bei der Prolongation des Darlehens verschlechtern würden.”
Die Befürchtungen bestätigt die GMAC-RFC indirekt in ihrem
Rundbrief vom 23. September 2010. Der Vorteil einer Umschuldung
auf eine andere Bank sei die Möglichkeit einer „besseren Zinskondition“.
Theoretisch dürfte die GMAC-RFC damit recht haben. Praktisch
wird es allerdings dazu führen, dass die GMAC-RFC Darlehensnehmer
bei dem Versuch einer Umschuldung bemerken werden, dass sie
wohl keine einzige Bank finden werden, die in das Risiko einsteigt.
Es wird offenbar werden, dass viele Anleger nur durch das institutionelle
Zusammenwirken zwischen Vertrieb, Verkäufer und
GMAC-RFC Bank einen Kredit bekommen hatten.
Es wird offenbar werden, dass die Hausbank des Kunden die
Umschuldung nur bei Stellung weiterer Sicherheiten vornehmen
wird.
Es wird offenbar werden, dass vielfach die Wohnung sittenwidrig
überteuert ist. Sie bringt beim Weiterverkauf nicht einmal die
Hälfte dessen, was die GMAC-RFC Bank finanziert hat.
Das einzig Gute ist, dass viele ahnungslose Anleger beim Versuch
einer Umschuldung bemerken, was ihnen seinerzeit angetan
wurde.”
GoMoPa.net schickte der GMAC-RFC Servicing GmbH folgende
Fragen:
1) Ist es richtig, dass dieses Angebot zur Umschuldung damit
zusammenhängt, dass die zur Refinanzierung an holländische
Zweckgesellschaften verkauften Kredite nur unzureichend bedient
werden und durch die Umschuldung die Rückzahlung und die
Zinszahlungen für die Anleihen der Zweckgesellschaften gesichert
werden müssen?
2) Ist es richtig, dass die GMAC-RFC Bank seit ihrem Auftreten
auf dem deutschen Immobilienmarkt im Jahr 2004 ein Gesamtvolumen
von über zwei Milliarden Euro an Krediten ausgereicht hat,
die in fünf „Paketen“ an holländische Zweckgesellschaften verkauft
wurden?
3) Ist es richtig, dass ausschließlich über das Internetportal
Creditweb Darlehensanträge bei der GMAC eingereicht werden
konnten? Wenn nein, welche weiteren Internetportale waren dazu
berechtigt?
4.) Ist es richtig, dass die mit der Creditweb kooperierenden
Vertriebe keine Originalunterlagen der Kreditsuchenden, sondern
lediglich Kopien eingereicht haben? Hat sich die GMAC-RFC Bank
seinerzeit Originale der Lohn- und Gehaltsunterlagen der Kreditnehmer
vorlegen lassen?
5.) Ist es richtig, dass in dem Baufilligenzprogramm es lediglich
auf die finanzielle Situation des Darlehensnehmers ankam und dass
Kredite bis zur Höhe des siebenfachen Jahresnettoeinkommens fi-
nanziert wurden?
6.) Ist es richtig, dass die Gewährung der Kredite auf der Grundlage
des Pfandbriefgesetzes erfolgte?
7.) Wie erfolgt der Nachweis der Aktivlegitimation der GMAC
Servicing GmbH in Fällen, in denen die Vollstreckung bei notleidenden
oder gekündigten Darlehen erforderlich wird?
GoMoPa.net ersuchte die GMAC-RFC Servicing GmbH in Wiesbaden
mehrmals, zu dem Rundbrief an die deutschen Kreditnehmer
Stellung zu beziehen. Die Geschäftsführerin Jennifer Anderson sei
in den USA, eine Telefonnummer sei nicht bekannt. Die Pressesprecherin
Katharina Dahms sei in Urlaub und hätte keine Vertretung.
Und der Prokurist Sven Klärner, der noch Auskunft geben könnte,
rief trotz mehrfacher Bitten von GoMoPa.net nicht zurück – er wird
wissen warum. „
Hintergrund:
Die SJB-GoMoPa-Opfer behaupten: „Der abgetauchte Berliner
Zweig der GoMoPa-Gangster will nun zusammen mit ihrem Hausanwalt
RA Jochen Resch, Berlin, die DKB erpressen – so wie sie dies
vorher mit Immovation versucht haben.
Estavis hat bezahlt, damit ein Grundsatzurteil gegen sie nicht
unter den Käufern ihrer Immobilien verbreitet wird. Dasselbe Spiel
versuchen der Knacki Maurischat und sein Kumpan Resch nun auch
bei der DKB durchzuziehen.
Eigengartig, da schliesst ein Finanzforum aus Deutschland mit
Briefkasten in New York einen Vertrag ab mit einem börsenkotierten
Immobilien-Unternehmen aus Berlin, der Estavis AG. Dieser
Vertrag umfasst Dienstleistungen im Marketingbereich für den Abverkauf
Denkmalgeschützter Eigentumswohnungen. Kontraktwert:
€ 100’000 ! Eine sehr eigenartig Vereinbarung.“
Börse Online: „Der Anlegeranwalt Jochen Resch kommt neuerdings
oft in den Pressemitteilungen vor, die der Finanzdienst Gomopa
ungefragt an Redaktionen verschickt. Als „Deutschlands bekannteste
Anlegerschutzkanzlei“ wird Resch Rechtsanwälte in einem
Bericht über das Ende der Noa Bankvorgestellt. Zu Schrottimmobilien
äußert sich Resch, zu einem Skandal um den Immobilienfondsanbieter
Volkssolidarität. Die Offenheit ist neu. Früher ging
Gomopa Resch hart an und konfrontierte ihn mit Vorwürfen. Doch
einige Formulierungen in einer Teilhaberinformation zur finanziellen
Situation Gomopas vom Juli 2010 legen nahe, dass der Sinneswandel
vielleicht nicht nur Zufall ist.
Gomopa, eigentlich Goldman Morgenstern & Partners Consulting
LLC mit Sitz in New York, ist seit mehr als zehn Jahren aktiv. Auf
der Website ist unter den Fachautoren der bekannte Bestsellerautor
Jürgen Roth aufgelistet. Im Handelsregister der deutschen Zweigniederlassung
ist als Geschäftszweck an erster Stelle „wirtschaftliche
Beratung, insbesondere des Mittelstandes“ aufgelistet. Dazu gehöre
„die Präsentation von Firmen im Internet und anderen Medien“. Die
Verbindung des Dienstes mit einem Nachrichtenportal im Internet
sieht Gomopa-Gründer Mark Vornkahl nicht als Problem: „Ein Interessenkonflikt
zwischen kostenpflichtiger Beratung, Informationsabonnement
und öffentlicher Aufklärung ist uns seit Bestehen nicht
untergekommen.“
Doch die Nutzer des Portals erfuhren bislang nicht, ob mit Personen
oder Organisationen, über die berichtet wurde, vertragliche
Beziehungen bestehen. Reschs Kanzlei war laut Teilhaberinformation
zeitweise eine wichtige Finanzierungsquelle von Gomopa. Darin
berichtet Gomopa-Mitgründer Klaus Maurischat, dass eine Vereinbarung
mit der Kanzlei „momentan 7500,- Euro im Monat einbringt
– rund 25 Prozent unserer monatlichen Kosten!“. Für „individuelle
Mandantenanwerbung“ stehe die Gesellschaft mit mehreren Anwaltskanzleien
in Verhandlungen.
Anwalt Resch stellt zum Inhalt der Vereinbarung klar: „Wir haben
einen einmaligen Rechercheauftrag erteilt, der im üblichen
Rahmen honoriert wird.“ Mit Mandantenbeschaffung habe das nichts
zu tun. Was Gomopa von einer Mandantenanwerbung hätte, ist
auch unklar. Denn Anwälte dürfen dafür nicht bezahlen. Auf unsere
Anfrage zu dieser und weiteren Fragen gab Vornkahl keine inhaltliche
Antwort beziehungsweise verwahrte sich gegen Zitate aus den
entsprechenden Passagen seiner E-Mail, weil er einem Mitbewerber
„keine Auskünfte zur Ausgestaltung unseres Geschäftsbetriebes
gebe.“
Ein Insider: „Was glauben Sie, wer auf die Idee kam, die
ominöse Briefkasten-Firma Goldman, Morgenstern & Partner LLC,
„GoMoPa“, einen angeblichen Zusammenschluss jüdischer Anwälte
in den USA zu gründen und wer die vielen Anwälte wie RA Albrecht
Saß, Hamburg, OLG Richter a.D. Matthias Schillo, Potsdam, und RA
Thomas Schulte, Berlin, zur Reputationsaufbesserung aufbot ?
a) RA Jochen Resch oder b) Ex-Gefängnisinsasse Klaus
Maurischat, der kaum Englisch spricht ? Und: Heinz Gerlach war
dicht dran, diese Zusammenhänge aufzuklären über den „Estavis“-
“Beratungsvertrag“. Seine Tochter, eine Rechtsanwältin in New York,
hatte bereits eine eidesstattliche Versicherung über die Brifekasetn
Firma „Goldman, Morgenstern & Partner LLC“ und deren Briefkastenadresse
in New York abgegeben und er hatte Strafanzeige wegen
der „Estavis“Beratungs-Affäre“ abgegeben. Dann wechselt auf einmal
der von Immovation zur Aufklärung von „GoMoPa“ beauftragte
„Detektiv“ Meinhard Fuchs trotz eines bereits bezahlten Honorares
von über € 60.000,- die Seiten hin zu „GoMoPa“ und Heinz Gerlach
stirbt plötzlich und für alle unerwartet angeblich an Blutvergiftung,
seltsam…“
FBI unveils Fraud – Former Chairman and CEO of Kellogg, Brown & Root Inc. Sentenced to 30 Months in Prison for Foreign Bribery and Kickback Schemes
WASHINGTON—Albert “Jack” Stanley, a former chairman and chief executive officer of Kellogg, Brown & Root Inc. (KBR), was sentenced today to 30 months in prison for conspiring to violate the Foreign Corrupt Practices Act (FCPA) by participating in a decade-long scheme to bribe Nigerian government officials to obtain engineering, procurement and construction (EPC) contracts and for conspiring to commit mail and wire fraud as part of a separate kickback scheme, the Justice Department’s Criminal Division today announced.
U.S. District Judge Keith P. Ellison for the Southern District of Texas also ordered Stanley to serve three years of supervised release following the prison term and to pay $10.8 million in restitution to KBR, the victim of the separate kickback scheme. Stanley, 69, pleaded guilty on Sept. 3, 2008, to a two-count criminal information charging him with one count of conspiracy to violate the FCPA and one count of conspiracy to commit mail and wire fraud.
Two of Stanley’s co-conspirators also were sentenced by Judge Ellison. Today, Jeffrey Tesler, 63, a United Kingdom citizen and licensed solicitor, was sentenced to 21 months in prison, followed by two years of supervised release. Tesler also was ordered to pay a $25,000 fine and previously was ordered to forfeit $148,964,568. Yesterday, Wojciech J. Chodan, 74, a United Kingdom citizen and former salesman at KBR’s U.K. subsidiary, was sentenced to one year of probation and ordered to pay a $20,000 fine. Chodan previously was ordered to forfeit $726,885.
Tesler and Chodan were indicted on Feb. 17, 2009, and subsequently extradited to the United States from the United Kingdom. On Dec. 6, 2011, Chodan pleaded guilty to count one of the indictment charging him with conspiring to violate the FCPA. On March 11, 2011, Tesler pleaded guilty to one count of conspiracy to violate the FCPA and one count of violating the FCPA.
All three defendants fully cooperated with the department’s investigation, which resulted in more than $1.7 billion in penalties, disgorgement and forfeitures. The defendants’ substantial assistance in the investigation and prosecution of other defendants was reflected in the sentences the court imposed.
“Today’s prison sentences for Mr. Stanley and Mr. Tesler mark another important step in our prosecution of those responsible for a massive bribery scheme involving engineering, procurement and construction contracts in Nigeria,” said Mythili Raman, Principal Deputy Assistant Attorney General for the Criminal Division. “These sentences reflect not only the defendants’ illegal acts, but also their substantial cooperation with the government. As a result of this investigation, three individuals have been convicted of FCPA-related crimes, and five companies in four countries have paid substantial penalties and undertaken significant efforts to enhance their compliance programs. This case shows the importance the department places on putting an end to foreign bribery.”
According to court documents, KBR was a member of the TSKJ joint venture (named for the first letters of the names of the companies involved), along with Technip S.A., Snamprogetti Netherlands B.V., and JGC Corporation. Between 1995 and 2004, TSKJ was awarded four EPC contracts, valued at more than $6 billion, by Nigeria Liquefied Natural Gas (NLNG) Ltd. to build the LNG facilities on Bonny Island. The government-owned Nigerian National Petroleum Corporation was the largest shareholder of NLNG, owning 49 percent of the company.
From approximately 1994 through June 2004, the joint venture companies, Stanley, Tesler, Chodan and others agreed to pay bribes to a wide range of Nigerian government officials in order to obtain and retain the EPC contracts. To pay the bribes, the joint venture hired two agents—Tesler and Marubeni Corporation, a Japanese trading company headquartered in Tokyo. The joint venture hired Tesler as a consultant to pay bribes to high-level Nigerian government officials, including top-level executive branch officials, and hired Marubeni to pay bribes to lower-level Nigerian government officials. At crucial junctures preceding the award of the EPC contracts, Stanley and other co-conspirators met with successive holders of a top-level office in the executive branch of the Nigerian government to ask the office holders to designate a representative with whom TSKJ should negotiate bribes to Nigerian government officials. TSKJ paid approximately $132 million to a Gibraltar corporation controlled by Tesler and $51 million to Marubeni during the course of the bribery scheme for use, in part, to pay bribes to Nigerian government officials.
In a related criminal case, KBR’s successor company, Kellogg Brown & Root LLC, pleaded guilty in February 2009 to FCPA-related charges for its participation in the scheme to bribe Nigerian government officials. Kellogg Brown & Root LLC was ordered to pay a $402 million fine and to retain an independent compliance monitor for a three-year period to review the design and implementation of its compliance program.
In another related criminal case, the department filed a deferred prosecution agreement and criminal information against Technip in June 2010. According to that agreement, Technip agreed to pay a $240 million criminal penalty and to retain an independent compliance monitor for two years. In July 2010, the department filed a deferred prosecution agreement and criminal information against Snamprogetti, which also agreed to pay a $240 million criminal penalty. In April 2011, the department filed a deferred prosecution agreement and criminal information against JGC, in which JGC agreed to pay a $218.8 million criminal penalty and to retain an independent compliance consultant for two years. In January 2012, the department filed a deferred prosecution agreement and criminal information against Marubeni, in which Marubeni agreed to pay a $54.6 million criminal penalty and to retain a corporate compliance consultant for two years.
The criminal cases were prosecuted by Assistant Chief William J. Stuckwisch and Deputy Chief Patrick F. Stokes of the Criminal Division’s Fraud Section, with investigative assistance from the FBI-Houston Division. The Criminal Division’s Office of International Affairs and the SEC’s Division of Enforcement provided substantial assistance. Significant assistance was provided by authorities in France, Italy, Switzerland and the United Kingdom. Investigative assistance with the prosecution of Stanley was also provided by the Internal Revenue Service’s Criminal Investigations Division in Houston.
Bloody Censorship – Saudi journalist faces trial over tweets
WIKILEAKS – Release “Wir weisen der CIA den Weg”
List of documents > Release “Wir weisen der CIA den Weg”
Read stories about those documents at the following addresses:
| Email-ID | Subject | From | To | Date |
|---|---|---|---|---|
| 64027 | INSIGHT – Russia/Israel/Georgia/Mexico – defense deals and swaps | reva.bhalla@stratfor.com | secure@stratfor.com | 2009-02 |
| 201031 | reva.bhalla@stratfor.com | friedman@att.blackberry.net | 2011-12 | |
| 277400 | Please invoice and charge credit card Booz Allen Hamilton $20,790 – renewal (paid $19,800 last year) | wright@stratfor.com | oconnor@stratfor.com, george.friedman@stratfor.com, Don.kuykendall@stratfor.com, cs@stratfor.com, kelly.tryce@stratfor.com, rob.bassetti@stratfor.com, holly.sparkman@stratfor.com, fernando.jaimes@stratfor.com | 2011-03 |
| 383068 | Re: names20 | burton@stratfor.com | zucha@stratfor.com | 2010-04 |
| 971109 | Re: INSIGHT – BRAZIL – On military purchases | hughes@stratfor.com | marko.papic@stratfor.com, secure@stratfor.com | 2010-10 |
| 1977338 | Re: [alpha] Musings on The Outfit | friedman@att.blackberry.net | alpha@stratfor.com | 2011-07 |
| 3438302 | FW: CIA head of analysis fired | iser@stratfor.com | allstratfor@stratfor.com | 2004-12 |
| 5091635 | Re: A thought on open source practice | friedman@att.blackberry.net | analysts@stratfor.com | 2009-03 |
| 5305447 | Updated Sales Force Contacts | Anya.Alfano@stratfor.com | zucha@stratfor.com, amy.fisher@stratfor.com | 2010-09 |
| 5521421 | Re: note from Yemeni diplomatic source | bokhari@stratfor.com | analysts@stratfor.com | 2011-01 |
SECRET – DHS-FBI Suspicious Activities Involving School Buses

(U//FOUO) The purpose of this assessment is to alert law enforcement and homeland security officials about recent suspicious activity involving school buses and the licenses to drive them.
(U) Key Findings
(U//FOUO) A number of foreign nationals of investigative interest—including some with ties to extremist organizations—have been able to purchase school buses and acquire licenses to drive them.
(U//FOUO) DHS and the FBI have no information indicating these individuals are involved in terrorist plotting against the Homeland. Nonetheless, the ease with which they have obtained the vehicles and licenses raises concerns that terrorists could use school buses to support an attack.
(U) Suspicious Activities Involving School Buses
(U//FOUO) Most attempts by foreign nationals in the United States to acquire school buses and the licenses to drive them are legitimate. Individuals from the Middle East and South and Central America often purchase school buses to fulfill their transportation needs. For example, many foreign nationals use school buses to transport workers between job sites. Moreover, because driving is an easily transferable skill between countries, it would not be uncommon for a truck or bus driver from a foreign country to seek the same profession in the United States.
(U//FOUO) DHS and the FBI lack specific, credible intelligence indicating terrorists have been involved in procuring school buses or licenses to drive them, but several incidents raise concerns.
— (U//FOUO) Some school districts have reported an unusual increase in the number of foreign nationals seeking school bus driver positions. Subsequent FBI investigations have revealed that a number of applicants had connections to or sympathized with known terrorist groups.
— (U//FOUO) Most troublesome were individuals who the FBI reported had expressed interest in terrorist applications of explosives.
(U) Potential Use of School Buses as Weapons
(U//FOUO) Intelligence reporting and historical attacks in the United States and overseas indicate terrorists prefer to use large vehicles containing explosives to conduct vehicle-borne improvised explosive device (VBIED) attacks.
— (U//FOUO) Both the 1993 bombing of the World Trade Center in New York and the 1995 bombing of the Alfred P. Murrah Federal Building in Oklahoma City used trucks containing large quantities of explosives.
— (U//FOUO) Overseas terrorist bombings using large, explosives-laden vehicles include Khobar Towers in Saudi Arabia in 1996; U.S. Embassies in Kenya and Tanzania in 1998; and commercial, religious, and government buildings in Turkey in 2003, among others.
(U//FOUO) DHS and the FBI lack specific, credible intelligence indicating terrorists plan to use school buses as VBIEDs, but these vehicles have the capacity to carry large amounts of explosive material.
— (U//FOUO) Security surrounding school buses is generally relaxed. School bus parking lots often are unlocked and are not consistently monitored; some lots are unfenced and keys are often left in the buses so they can be moved quickly.
(U) Weaknesses in Commercial Driver’s Licensing Systems
(U//FOUO) School bus drivers are required to have a commercial driver’s license (CDL), but CDL requirements vary among states. DHS has previously published an assessment on how terrorists could exploit the CDL licensing system. Background checks for school bus drivers also vary from state to state; most require at least a state or FBI criminal check. Washington State, however, issues CDLs without proof of residency or legal status.
(U//FOUO) Once applicants obtain a CDL to drive large vehicles such as buses or trucks, they become eligible to apply for a hazardous material endorsement (HME) to legally transport hazardous materials. Instances continue to surface of individuals fraudulently obtaining valid CDL and HME credentials.
— (U//FOUO) Federal standards allow states to hire third parties—mainly private companies—to administer CDL tests. The majority of CDL fraud schemes involve corrupt third-party testers.
— (U//FOUO) In February 2007 a federal judge ordered the deportation of an Indian national whose suspicious behavior at a driving school instigated a nationwide antiterrorism investigation. The foreign national admitted to supplying falsified documents in his quest to obtain CDL/HME licenses.
(U) Indicators of Suspicious Activities
(U//FOUO) Law enforcement should be aware of the following indicators of possible terrorist interest in school buses, CDLs, and HMEs:
— (U//FOUO) Background checks on applicants for school bus driver positions that suggest criminal or terrorist connections that require further investigation.
— (U//FOUO) Possession of a CDL to drive a school bus without the appropriate driving skills.
— (U//FOUO) Unusual interest in obtaining an HME when it is not required for the type of job such as driving a school bus.
— (U//FOUO) Reports of school bus surveillance in bus lots or while in transit.
— (U//FOUO) Reports by school district officials or bus vendors of suspicious attempts to purchase school buses.
(U) Outlook
(U//FOUO) Suspicious incidents involving school bus purchases and abuse of commercial driver’s licensing processes raise concerns that terrorists could use school buses and hazardous materials in an attack. Law enforcement and homeland security officials need to be vigilant and investigate license applicants and holders with suspicious backgrounds or poor driving skills.
TOP-SECRET – Sandia National Laboratories/Department of Energy Sensitive Country List

Please note that because of the dynamic nature of world events, other countries may, at any time, become sensitive. Caution should be exercised in dealing with citizens of countries not listed to assure that sensitive information, although unclassified in nature, is not inadvertently disclosed. Any contact, either in the United States or in a foreign country, where you feel you have been approached for this type of information, should be reported to the Counterintelligence Officers.
Algeria
Armenia
Azerbaijan
Belarus
China – People’s Republic of
Cuba
Georgia
Hong Kong
India
Iran
Iraq
Israel
Kazakhstan
Kyrgyzstan
Libya
Macau
Moldova
North Korea – Democratic People’s
Republic of North Korea
Pakistan
Russia
Sudan
Syria
Taiwan
Tajikistan
Turkmenistan
Ukraine
Uzbekistan
WIKILEAKS publishes 5 Million Statfor files
On Monday February 27th, 2012, WikiLeaks began publishing The Global Intelligence Files, over five million e-mails from the Texas headquartered “global intelligence” company Stratfor. The e-mails date between July 2004 and late December 2011. They reveal the inner workings of a company that fronts as an intelligence publisher, but provides confidential intelligence services to large corporations, such as Bhopal’s Dow Chemical Co., Lockheed Martin, Northrop Grumman, Raytheon and government agencies, including the US Department of Homeland Security, the US Marines and the US Defence Intelligence Agency. The emails show Stratfor’s web of informers, pay-off structure, payment laundering techniques and psychological methods.
MURDER IN MOSCOW – Alleged Plot to Kill Putin Foiled
From Inside the CIA – Capturing the Potential of Outlier Ideas in the Intelligence Community Clint Watts and John E. Brennan
DOWNLOAD THE ORIGINAL DOCUMENT HERE
TOP-SECRET from the FBI – Four Hedge Fund Managers Indicted in $40 Million Ponzi Scheme
CHARLOTTE, NC—A federal grand jury sitting in Charlotte returned an indictment against Jonathan D. Davey, 47, of Newark, Ohio, Jeffrey M. Toft, 49, of Oviedo, Fla., Chad A. Sloat, 33, of Kansas City, Mo., and Michael J. Murphy, 51, of Deep Haven, Minn., on February 22, 2012, on four criminal charges relating to an investment fraud conspiracy, announced Anne M. Tompkins, U.S. Attorney for the Western District of North Carolina.
Joining U.S. Attorney Tompkins in making today’s announcement are Chris Briese, Special Agent in Charge of the Federal Bureau of Investigation (FBI), Charlotte Division, and Jeannine A. Hammett, Special Agent in Charge of the Internal Revenue Service-Criminal Investigation Division (IRS-CI).
According to the criminal indictment, the defendants operated “hedge funds” as part of a conspiracy that took in $40 million from victims for a Ponzi scheme operating under the name Black Diamond Capital Solutions (Black Diamond). The indictment alleges that the conspiracy lasted from about October 2007 through about April 2010. The indictment alleges that the defendants lied to get money from their victims by claiming, among other things, that they had done due diligence on Black Diamond and were operating legitimate hedge funds with significant safeguards, when in reality, neither claim was true. The indictment also alleges that, as Black Diamond began collapsing, the defendants and others created a new Ponzi scheme and with a separate Ponzi account that Davey administered. Thereafter, new victim money was deposited into the Ponzi account and used to make Ponzi payments to other victims and to fund the defendants’ lifestyles.
The indictment also charges Davey with tax evasion for claiming to the IRS on his 2008 tax return that $810,000 that Davey stole from victims was a “loan.” In reality, the indictment charges, Davey stole that $810,000, plus approximately $500,000 in 2009, from victims to build Davey’s personal mansion. Davey attempted to evade the taxes due and owing in 2008 by calling the money a “loan” from his investors to “Sovereign Grace, Inc.,” a Belizian corporation that Davey created as a diversion for his victims and the IRS.
The first charge against all four defendants, alleging conspiracy to commit securities fraud, carries a maximum sentence of five years’ imprisonment and a fine of up to $250,000. The second charge against all four defendants, alleging conspiracy to commit wire fraud, carries a maximum sentence of 20 years’ imprisonment and a fine of up to $250,000. The third charge against all four defendants, alleging a money laundering conspiracy, carries a maximum sentence of 20 years’ imprisonment and a fine of $250,000 or twice the amount of criminally derived proceeds. The final charge against Davey only, alleging tax evasion, carries a maximum sentence of five years’ imprisonment and a fine of up to $250,000.
The defendants will be making their initial appearances in U.S. District Court in the coming weeks.
This indictment follows a series of convictions and other charges in this matter. On December 16, 2010, Keith Simmons was convicted following a jury trial of securities fraud, wire fraud, and money laundering. Simmons is in custody awaiting sentencing.
On April 27, 2011, a criminal bill of information and a Deferred Prosecution Agreement were filed against CommunityONE Bank, N.A., for its failure to maintain an effective anti-money laundering program. As alleged in that bill of information, Simmons was a customer of CommunityONE, and used various accounts with the Bank in furtherance of the Ponzi scheme. However, as alleged in that bill of information, the Bank did not file any suspicious activity reports on Simmons, despite the hundreds of suspicious transactions that took place in his accounts.
Other defendants convicted in this case are set forth below. It should be noted that those defendants already sentenced had their sentences reduced by the Court to reflect their cooperation with the United States in its investigation and prosecution of others.
- Bryan Keith Coats, 51, of Clayton, N.C., pled guilty on October 24, 2011, to conspiracy to commit securities fraud and money laundering conspiracy. Coats is awaiting sentencing.
- Deanna Ray Salazar, 54, of Yucca Valley, Calif., pled guilty on December 7, 2010, to conspiracy to commit securities fraud and tax evasion. Salazar is awaiting sentencing.
- Jeffrey M. Muyres, 36, of Matthews, N.C., pled guilty on May 17, 2011, to conspiracy to commit securities fraud and money laundering conspiracy. Muyres was sentenced to 23 months’ imprisonment by Chief Judge Robert Conrad, Jr., on January 18, 2012.
- Roy E. Scarboro, 47, of Archdale, N.C., pled guilty on December 3, 2010, to securities fraud, money laundering, and making false statements to the FBI. Scarboro was sentenced to 26 months’ imprisonment by Chief Judge Robert Conrad, Jr., on May 4, 2011.
- James D. Jordan, 49, of El Paso, Texas, pled guilty on September 14, 2010, to conspiracy to commit securities fraud. Jordan was sentenced to 18 months’ imprisonment by Chief Judge Robert Conrad, Jr., on June 29, 2011.
- Stephen D. Lacy, 52, of Pawleys Island, S.C., pled guilty on December 9, 2010, to conspiracy to commit securities fraud. Lacy was sentenced to six months’ imprisonment by Chief Judge Robert Conrad, Jr., on May 4, 2011.
The details contained in this indictment are allegations. The defendants are presumed innocent unless and until proven guilty beyond a reasonable doubt in a court of law. The conviction or guilty plea of any other person is not evidence of the guilt of any of the defendants.
This matter is being prosecuted by Assistant United States Attorneys Kurt W. Meyers and Mark T. Odulio of the Western District of North Carolina, and the case against Jeffrey Muyres was prosecuted by Assistant United States Attorney Mark T. Odulio. The investigation is being handled by the FBI and the IRS.
FEMEN protests over India Visa rules
TOP-SECRET -DHS-FBI Warning: Terrorist Use of Vehicle Ramming Tactics

(U//FOUO) Terrorists overseas have suggested conducting vehicle ramming attacks—using modified or unmodified vehicles—against crowds, buildings, and other vehicles. Such attacks could be used to target locations where large numbers of people congregate, including sporting events, entertainment venues, or shopping centers. Vehicle ramming offers terrorists with limited access to explosives or weapons an opportunity to conduct a Homeland attack with minimal prior training or experience.
(U) Indicators: Although a single indicator may not be suspicious, one or more might indicate a ramming attack is being developed, based on the specific facts or circumstances. A ramming attack can be conducted with little to no warning.
- (U//FOUO) Unusual modifications to commercial motor vehicles, heavy equipment, passenger cars, and sports utility vehicles (SUVs), such as homemade attempts to reinforce the front of the vehicle with metal plates.
- (U//FOUO) The purchase, rental, or theft of large or heavy-duty vehicles or equipment, such as SUVs, trucks, or commercial motor vehicles, if accompanied by typical indicators such as nervousness during the purchase, paying in cash, or lack of familiarity with the vehicle’s operations.
- (U//FOUO) Commercial motor vehicles or heavy equipment being operated erratically, at unusual times, or in unusual locations, particularly in heavy pedestrian areas.
- (U//FOUO) Attempts to infiltrate closed areas where traffic usually moves, but where crowds are gathered, such as for street festivals or farmers’ markets.
- (U//FOUO) A vehicle operator’s apparent unfamiliarity with commercial motor vehicle or heavy equipment operation (unable to back up; trouble with shifting; poor lane tracking; unfamiliarity with basic vehicle mechanics such as air brake operations, slack adjusters, fifth wheel operations, Jake brakes, engine type, or location of fire extinguishers and other emergency equipment).
MEDIA – “Act of Valor” and Military Support to Hollywood Operations
Act Of Valor’ And The Military’s Long Hollywood Mission (Huffington Post):
A crack team of highly skilled warriors, outfitted with the most advanced weapons of the world’s most powerful military force, storms an enemy compound, firing round after round of ammunition through concrete walls and the skulls of their terrorist adversaries.The good guys have yet to suffer a single casualty until, suddenly, one of its leaders takes a rocket to the chest. The audience cringes, but the bang never comes — the rocket clangs to the ground, unexploded, and the battle rages on. The upcoming film “Act of Valor” is replete with that kind of action, but there are a few things it doesn’t have: There are no corrupt officers, no damaged heroes, no queasy doubts about the value of the mission or the virtue of the cause.
That’s because “Act of Valor” was born not in Hollywood, but in the Pentagon. It was commissioned by the Navy’s Special Warfare Command and its success will be measured not in box-office receipts, but in the number of new recruits it attracts to the Navy SEALs.
“Early on, we were pretty honored and humbled to be asked to take a look at potentially telling their story,” said “Valor” producer and former stuntman Scott Waugh, “to take a look at what telling their story would even look like.”
This may be the U.S. armed forces’ first feature-length recruiting film, but it’s far from the first time unsuspecting audiences have been treated to Pentagon propaganda at the movies. As early as 1927, when military assistance on the film “Wings” helped it win Best Picture at the first Oscars ceremony, the Department of Defense has long maintained its own production office that offers filmmakers the latest in arms and high-tech vehicles at cut-rate prices — as long as their scripts are deemed worthy.
…
The battle scenes were shot during live SEAL training missions, plotted out and blocked by the troops themselves, with cameras placed atop their helmets for a video game-like first-person view of the action. To a generation well-accustomed to guiding digital soldiers through combat zones, all that’s missing is a PlayStation controller in a theater seat.The filmmakers said they were unconcerned with the recruitment angle of the film, focusing principally on the sacrifices made by the SEALs. They also stressed their full creative control of the film during its four-year production process, asserting that the only edits made by the Navy Special Warfare Command were designed to scrub military secrets from the final cut.
The Banditos, of course, were carefully pre-screened. Their final product is a mix of trying acting and “Call of Duty”-style action, earnest and visually impressive but unlikely to garner the kind of praise “The Hurt Locker” and Hollywood’s grittier takes on combat have received. Then again, the military has never had Oscar in its sights — he’s far too old to enlist.
Even McCoy admits that the picture is about changing perception and breaking away from the cynicism still pervasive in Hollywood, not winning gold.
“I’d like to see the legacy of Vietnam put to bed. Vietnam was 40 years ago, and I think arts and entertainment is still suffering from that hangover,” he said. “It was a really bad time in American history, absolutely, but it’s time to sort of forget that and forget those sensibilities and don’t associate our troops and our men and women to that conflict anymore, and time to really open our eyes to say, ‘What’s going on in this world? What are our men and women in uniform really doing right now for us?’”
Will “Act of Valor” accomplish that? Relativity Media, which won a bidding war to distribute the film following the SEAL-executed death of Osama bin Laden, has been aggressively pursuing publicity, airing multiple trailer spots during the Super Bowl and holding big premieres on each coast — the New York City opening was held on the USS Intrepid, while SEALs parachuted down to the theater for the Los Angeles bow. Every ad for the film touts the participation of real Navy SEALs; whether that is appealing to young audiences or smacks of propaganda, may help determine how it performs.
‘Act of Valor’ must balance publicity, secrecy with Navy SEALs (Los Angeles Times):
“Act of Valor” is a hybrid of fiction and documentary-style storytelling — the film tracks an eight-man SEAL squad that undertakes a fabricated mission to recover a captured CIA operative and discovers a plot to sneak suicide bombers into the U.S. across the Mexican border. In addition to its cast — led by a couple of especially telegenic warriors named Chief Dave and Lt. Rorke (their real first names) — the movie features live grenades, free-falling parachuters, high-speed boats, helicopters, an aircraft carrier and a nuclear submarine. It’s a level of production that would make blockbuster filmmakers such as Michael Bay and Jerry Bruckheimer drool, obtained by two first-time feature directors and former stuntmen, Mike “Mouse” McCoy and Scott Waugh, for roughly $12 million.The story of the small project, first conceived as a training film, then later embraced by the Navy and given a huge unexpected boost by the Bin Laden raid, is a dramatic yarn in its own right. Because it was begun as a recruitment video, the movie proceeded outside the normal Department of Defense channels for working with Hollywood, in which production companies submit a script for the department’s approval in order to gain access to personnel or materials. How the military initially understood the project — as a documentary, a fictional film, a recruitment video — is unclear. “That’s like ‘Rashomon,’” said one DOD official who works regularly with Hollywood and was not authorized to speak publicly about the project. “Ask a different person, get a different story.”
Officially, “Act of Valor” “did not follow the normal DOD approval process for major motion pictures,” according to Rear Adm. Dennis J. Moynihan, the Navy’s chief of information. But the Navy has publicly embraced the film, which was overseen by the Naval Special Warfare unit, and determined that it poses no threats to the security of the U.S. or its stars, some of whom are now deployed overseas.
“We think it accurately represents a number of the acts of valor that have occurred over the last 10 years with respect to the SEAL teams,” said Adm. William McRaven, the head of Special Operations Command and a SEAL himself, answering a question at an industry conference in Washington, D.C., last week. . “We’re conscious of the fact that there are active-duty Navy SEALs here. I can tell you they all volunteered. There’s no concern on their part about their individual or the security of their families…. The film company that produced this had a very collaborative effort with the Navy and with U.S. Special Operations Command. So nothing displayed in there tips our sensitive tactics, techniques and procedures.”
Hollywood Tries a New Battle Plan (Wall Street Journal):
In 2008, Navy Special Warfare invited a handful of production companies to submit proposals for a film project, possibly a documentary, that would flesh out the role of the SEALs. The goals: bolster recruiting efforts, honor fallen team members and offer a corrective to misleading fare such as “Navy Seals,” the 1990 shoot-em-up starring Charlie Sheen as a cocky lone wolf. “In the SEAL ethos, the superman myth does not apply. It’s a lifestyle of teamwork, hard work and academic discipline,” said Capt. Duncan Smith, a SEAL who initiated the project and essentially served as producer within the military.The project offered filmmakers access to SEALs as well as military assets, but no funding. A production company called the Bandito Brothers, which had previously worked with Navy Special Warfare on a series of recruiting videos, got the assignment. Co-founded by Mr. McCoy, a former off-road racing champion and stuntman, and Scott Waugh, who had run a stunt company, the Bandito Brothers specialized in shooting action-driven viral ads for brands such as BMW and Mountain Dew. The Los Angeles-based Bandito Brothers began shuttling back and forth to Coronado, Calif., the SEALs training base near San Diego, to conduct on-camera interviews. They initially planned to work the research into a script, then hire actors to play the lead SEALs. The filmmakers’ calling card within the military was a 2005 documentary called “Dust to Glory,” for which they positioned about 55 cameras on dirt bikes, trucks and dune buggies in the bone-jarring Baja 1000, an annual off-road race in Mexico. The gritty camaraderie depicted in the movie resonated with the SEALs, as did the on-screen tenacity of Mr. McCoy (nicknamed Mouse), who did the team-based race solo on a motorcycle. He crossed the finish line in 18 hours, nursing broken bones from a crash.
…
The filmmakers say the SEALs tackled their acting duties methodically, as they would a new tactical skill. In a scene where one of them discovers a female CIA operative who has been kidnapped and tortured, the directors coached him to slow down and tap into the emotion of the rescue. “For the audience, you need to get really compassionate. The women are going to need to connect,” Mr. McCoy recalled saying.
By contrast, in the movie’s many battle scenes, the sailors move with a fluid precision that makes typical Hollywood action movies look bogus. When the SEALs picked off enemies and moved through buildings in a tight snaking column, some footage was captured by helmet-mounted cameras. Certain plot points were based on true stories from the field, including a scene in which a sailor takes a rocket-propelled grenade to the chest at close range and lives.
By last March, the filmmakers had completed a final version of the film, following a tactical “scrub,” during which officials screened 1,800 hours of footage for scenes that could divulge sensitive tactics. For instance, a re-edit made it less obvious how a SEAL team would line up to storm a room. Sales agents at William Morris Entertainment were deciding on a plan for selling the film to a distributor when, on May 1, news broke that Osama bin Laden had been killed.
Studios immediately angled for projects that might capture some of the public fascination with the SEALs who led the strike. The most high-profile was the Bigelow and Boal script, which had been in development since 2008. Sony scooped up the movie about the bin Laden hunt within three weeks of his death. The movie is expected to be released in October 2012, a date that has drawn some political controversy. Rep. Peter King (R., N.Y.) called for an investigation into whether the White House gave the filmmakers access to confidential information and suggested that the film’s planned release next fall could influence the presidential election soon after. White House spokesman Jay Carney called the suggestion “ridiculous”; the filmmakers said in a statement that their film had no political angle.
Bin Laden’s death found the Bandito Brothers sitting on a completed SEALs movie, but they didn’t immediately put it on the auction block. “We were nervous about seeming exploitative,” says WME agent Liesl Copland. The agency set up two “Act of Valor” screenings for potential buyers in June, four weeks after bin Laden was killed, by which time most of the related deal-making had died down in Hollywood.
CORRUPTION – Iraq’s First Oil Transparency Report Fails to Include $2.5 Billion in “Signature Bonuses”
 Iraq’s Prime Minister Nuri al-Maliki (C) cuts a ribbon during the inauguration of a new Single Point Mooring (SPM) outlet in Iraq’s southern province of Basra February 12, 2012. Iraq opened a new Gulf crude export outlet in the southern oil hub of Basra on Sunday, clearing the way for Baghdad to increase exports by around 300,000 barrels per day soon after crude begins loading. REUTERS/Atef Hassan
Iraq’s Prime Minister Nuri al-Maliki (C) cuts a ribbon during the inauguration of a new Single Point Mooring (SPM) outlet in Iraq’s southern province of Basra February 12, 2012. Iraq opened a new Gulf crude export outlet in the southern oil hub of Basra on Sunday, clearing the way for Baghdad to increase exports by around 300,000 barrels per day soon after crude begins loading. REUTERS/Atef HassanThe missing pieces in Iraq’s first EITI report:
On December 20th, 2011, Iraq published its first EITI Reconciliation report, a report which was heralded as “a historic step toward oil sector transparency” by the international community, as the report outlined in great detail the money received from export sales by the Baghdad government. However, as already noted by Johnny,there were many questions raised by the report itself, and over the past couple of days I’ve been seeing how much information already in the public domain can answer just some of those questions.The sole revenue stream covered in the EITI report is that of export sales. At the time that the terms of reference for the this EITI report were agreed, in 2009, the Iraqi oil industry was entirely state run and without foreign participation. However, with the re-entry of international oil companies in 2009, revenue streams into the Baghdad government are no longer limited to export sales. The first licensing round, which began proceedings in 2008 and was concluded in 2009, saw only one field- Rumaila- being awarded, although two further fields, Maysan and West Qurna Phase 1, were subsequently awarded in bilateral negotiations.
Under the second licensing round which took place in December 2009, seven of the ten oil fields offered in the round were awarded to various consortia of companies. The technical service contracts (TSCs) signed under this licensing round included a number of clauses that have created multiple revenue streams. These TSCs included clauses for cost recovery mechanisms, signature bonuses, and remuneration fees, none of which were included in the EITI report.
I began looking at the most clear cut of these revenue streams; the signature bonuses. These bonuses, which were widely reported upon in the media, ranged from $100 million, which Sonangol paid for the Qayara field, to $500 million, paid by a consortium led by BP for the Rumaila field.
One point of uncertainty was the form in which these payments were made. Some, such as the $500 million Rumaila field signature bonus, was reportedly paid by the company as a ‘soft loan’, to be paid back in 20 quarterly payments, in either crude oil or cash as decided by the company. Others appeared to have been renegotiated, such as the $300 million paid by Eni and Oxy for the Zubair field, reportedly slashed to $100 million in April 2010.
Bearing in mind these uncertainties, the total of the signature bonuses reported to have been paid by international oil companies to the Baghdad government during the period of November 2009 until January 2010 comes to $2.25 billion, as you can see in the spreadsheet I created. Even taking into account the discrepancy of reducing the Zubair field signature bonus, that still leaves a figure of around $2 billion dollars that is unaccounted for in the EITI first report.
SOURCE: OPEN OIL
DWONLOAD ORIGINAL SPREADSHEETS BELOW
spreadsheet-of-iraq-signature-bonuses-v2.2
KGB collaborator names unveiled – KGB-Agenten enttarnt
Litauen veröffentlicht eine Mitgliederliste der sowjetischen Staatssicherheit KGB
Vilnius/BR. Das litauische Forschungszentrum für Völkermord und Widerstand (Genocide and Resistance Research Centre of Lithuania) veröffentlichte eine Einsatzreserveliste ehemaliger KGB-Mitarbeiter, die sich geweigert hatten ihre Zusammenarbeit mit dem sowjetischen Staatssicherheit zu gestehen. In der Liste sind 238 Namen, sowie ihr militärische Dienstgrad aufgezählt. Für einzelne Personen gibt es auch detaillierte Profile.
Für die Zukunft ist es geplant, die Akten der anderen ehemaligen KGB-Mitarbeiter zu veröffentlichen. Die Website, auf welcher diese Liste veröffentlicht wurde, brach wegen der großen Besucherzahl zusammen. Zurzeit ist sie wieder verfügbar.
“Ich glaube, dieses Projekt kann dazu beitragen, Litauen aus der KGB-Krankheit zu befreien. Es ist immer besser, die Wahrheit wissen”, sagte Biruté Burauskaite, die Direktorin des Zentrums.
Unter der bekannten Namen ist der frühere Außenminister Antanas Valionis und der Chef des Ministeriums für Staatssicherheit, Arvydas Pocius, zu finden.
Die KGB-Reservisten hatten nicht unbedingt für den KGB gearbeitet, sie wurden in Reserve gehalten, falls ein wichtiges Ereignis, wie ein Krieg, eintreffen würde.
Im Jahr 1999 verabschiedete Litauen ein Gesetz, das allen Ex-Agenten und Informanten sechs Monaten Zeit gab, sich selbst anzuzeigen. Ein ähnliches Gesetz beschloss auch in Estland. Die Geheimagenten, die sich offenbarten, bekamen Anonymität zugesichert. In der Datei waren rund 1 600 Personen registriert. Später hat die Kommission trotz Zusicherung der Geheimhaltung die Namen veröffentlicht.
Ferner brachte Burauskaite vor, dass die Regierung plant, ausführliche Beschreibungen der KGB-Methoden zu veröffentlichen. (ast)
Foto: http://www.genocid.lt
Lithuania’s government has released the names of 238 citizens who were reservists for the KGB when their country was ruled by the Soviet Union, and said Wednesday it plans to identify scores of people who have refused to disclose their relations with the security agency.
All this information, including interrogation techniques the KGB used in Lithuania, is contained in thousands of Soviet files held by Lithuania’s official Genocide and Resistance Research Center and are slated to be released soon.
Documents containing the 238 names were put on the Internet on Tuesday as part of a campaign in the Baltic country to come to terms with 50 years of Soviet occupation after World War II.
“I believe this project will help Lithuania to shake KGB disease. It is always better to know truth,” said Birute Burauskaite, the center’s director.
Former Foreign Minister Antanas Valionis and State Security Department chief Arvydas Pocius were among the names released. Several years ago, they admitted being reservists for the KGB, and both men’s careers eventually suffered as a result of the confession.
KGB reservists did not necessarily work for the KGB, but were kept on reserve in case a major event, such as a war, required a sudden influx of manpower.
Burauskaite said thousands of KGB files would be released in the near future. They contain information on KGB officers’ biographies and operations, as well as on individuals who were listed as reservists but have not admitted working for the KGB.
“All these documents are kept at our center’s archives. Some of them cannot be released — mostly personal files of former KGB collaborators or employees who registered with” a government commission, said Burauskaite.
In 1999 Lithuania passed a law that gave all ex-agents and informers six months to file detailed confessions to the commission in exchange for keeping their names confidential. Some 1,600 people registered, but the commission later disclosed their names and details, despite its pledge of confidentiality.
Burauskaite said some of the documents the government plans to release contain detailed descriptions of KGB methods used to enlist agents, infiltrate groups, and interrogate suspects.
“GoMoPa”-STASI-Tarn-Existenz “Siegfried Siewert” und STASI-Dioxin-Panscher “Siegfried Sievert”
Gefährliche neue Mord-Drohung der STASI wg STASI-Listen und weiterer Infos an Opfer
FBI – Seeking Information Regarding Arson That Caused $2 Million in Damages
The FBI and Fresno police are seeking information into a January 8 arson. Incendiary devices were placed beneath tractor trailer rigs parked at the Harris Feeding Company near Coalinga, California. The ensuing fires destroyed 14 rigs with an estimated loss in excess of $2 million.
An anonymous claim of responsibility was subsequently released by the North American Animal Liberation Press Office, posted on several websites, and delivered to various media outlets.
According to a February 22 press release by the Sacramento FBI, the offenders may have conducted surveillance and planning before positioning the devices and fleeing. If you have any information about this attack, please contact us immediately. If you have direct knowledge of this crime but fear retaliation by those involved, there are steps and measures we can take to keep you safe. A substantial reward may be offered for information leading to the arrest and conviction of the persons responsible for this attack.
“No one in our community should have to live in fear of these people again,” the release states.
The Mossad reports – Exclusive Photos Show Alleged Iran Bombs Hidden in $27 Radio – ABC 21/2/12

An Iranian hit squad used $27 portable radios to hide at least five bombs that Israeli and American authorities say they intended to use against Israeli targets in Bangkok, Thailand.
Exclusive photo of one undetonated bomb, obtained by ABC News, show the inside of the radio packed with tiny ball bearings and six magnets. Bomb experts say the magnets indicate the bomb was designed to be stuck to the side of a vehicle.
SECRET – DHS London Officials Issue Heroin Anthrax Alert

Assasination – Sacha Baron Cohen – Death to the Oscars!
Unveiled by the FBI – Former Chairman of Taiwan Aftermarket Auto Lights Manufacturer Agrees to Plead Guilty in Price-Fixing Conspiracy
WASHINGTON—The former chairman of a Taiwan aftermarket auto lights manufacturer has agreed to plead guilty for his participation in an international conspiracy to fix the prices of aftermarket auto lights, the Department of Justice today announced. Aftermarket auto lights are incorporated into an automobile after its original sale, often as repairs following a collision or as accessories and upgrades.
According to a one-count felony charge filed today in U.S. District Court in San Francisco, Shiu-Min Hsu conspired with others to suppress and eliminate competition by fixing the prices of aftermarket auto lights. The department said that Hsu, former chairman of Depo Auto Parts Industrial Co. Ltd., a Taiwan manufacturer of aftermarket auto lights, participated in the conspiracy from as early as April 2000 until about Sept. 3, 2008. According to the plea agreement, which is subject to court approval, Hsu has agreed to cooperate with the department’s investigation.
“The international price-fixing conspiracy in the aftermarket auto lights industry caused harm to businesses and consumers,” said Sharis A. Pozen, Acting Assistant Attorney General in charge of the Department of Justice’s Antitrust Division. “Including today’s filing, five individuals and four corporations have been charged as a result of the Antitrust Division’s efforts to thwart this type of anticompetitive activity.”
According to the charge, Hsu and co-conspirators participated in a conspiracy in which the participants met and agreed to charge prices of aftermarket auto lights at certain predetermined levels. According to the court document, the participants in the conspiracy issued price announcements and price lists in accordance with the agreements reached, and collected and exchanged information on prices and sales of aftermarket auto lights for the purpose of monitoring and enforcing adherence to the agreed-upon prices. The department said that the conspirators met in Taiwan and the United States for their discussions.
On March 29, 2011, Polo Shu-Sheng Hsu, the former president and CEO of Maxzone Vehicle Lighting Corp., a U.S. distributor of aftermarket auto lights, was sentenced to serve 180 days in prison and to pay a $25,000 criminal fine for his role in the conspiracy. Chien Chung Chen, aka Andrew Chen, the former executive vice president of Sabry Lee (U.S.A.) Inc., another U.S. distributor of aftermarket auto lights, pleaded guilty for his participation in the conspiracy on June 7, 2011. He is currently scheduled to be sentenced on Oct. 16, 2012. In addition, two corporations have pleaded guilty. On Oct. 4, 2011, Sabry Lee pleaded guilty and was sentenced to pay a $200,000 criminal fine. On Nov. 15, 2011, Maxzone pleaded guilty and was sentenced to pay a $43 million criminal fine.
On Nov. 29, 2011, a federal grand jury returned a superseding indictment charging Eagle Eyes Traffic Industrial Co. Ltd. and its U.S. subsidiary E-Lite Automotive Inc., as well as Eagle Eyes’s two highest-ranking officers, chairman Yu-Chu Lin, aka David Lin, and vice chairman Homy Hong-Ming Hsu. Trial is set for June 18, 2012, in U.S. District Court in San Francisco.
This case is part of an investigation being conducted by the Department of Justice Antitrust Division’s San Francisco Field Office and the FBI in San Francisco. Anyone with information concerning illegal or anticompetitive conduct in the aftermarket auto lights industry is urged to call the Antitrust Division’s San Francisco Field Office at 415-436-6660 or visit http://www.justice.gov/atr/contact/newcase.htm.
CONFIDENTIAL – American, British, Canadian, Australian and New Zealand (ABCA) Armies Coalition Operations Handbook

Where commonality of interest exists, nations will enter political, economic, and military partnerships. These partnerships can occur in both regional and worldwide patterns as nations seek opportunities to promote their mutual national interests or seek mutual security against real or perceived threats. Cultural, psychological, economic, technological, and political factors all influence the formation and conduct of coalitions.
Coalitions, which are created for limited purposes and for a set time, do not afford military planners the same political resolve and commonality of aim as alliances. Thus, planners must closely study the political goals of each participant as a precursor to detailed planning. Political considerations weigh more heavily with coalitions than with alliance operations. Coalition military operations are not new. The American, British, Canadian, Australian, and New Zealand (ABCA) nations have participated together in several coalition operations during the twentieth century. Since human nature has not changed, conflicts over territory, religion, politics, and economics, such as those that prompted previous military operations, will continue to be widespread. The precise role of armies in these operations will vary according to each political and military situation.
Another reason nations conduct coalition operations is that rarely can one nation go it alone either politically or militarily. Coalition operations will involve a comprehensive approach that includes other government agencies, nongovernmental organizations, and international and regional organizations. This blending of capabilities and political legitimacy makes possible certain operations that a single nation could not or would not conduct unilaterally.
Almost all coalition operations, regardless of how they are formed, build from common fundamentals. All coalitions form in one of three ways. Coalition headquarters have similar components. In addition, all coalitions assess the area for operations. Many of the points will be further developed in the individual chapters.
UNDERSTANDING COALITIONS
A coalition is an ad hoc arrangement between two or more nations for common action. A coalition action is a multinational action outside the bounds of established alliances, usually for a single occasion, or for longer cooperation in a narrow sector of common interest. This handbook centers on those operations in which one or more of the ABCA armies participate with other non-ABCA nations in a coalition.
Sovereignty issues will be the most difficult issues for the commander of the coalition force to deal with, both in regard to forces contributed by nations and by host nations. Often, the coalition force commander is a “commander” in title only; the coalition force commander will accomplish the mission through coordination, communication, and consensus or leadership rather than by traditional command concepts. Such is the nature of coalition operations.
Coalition operations are conducted by forces of two or more nations, which may not be allies, acting together for the accomplishment of a single mission. Coalition operations cross the spectrum of conflict from major combat operations to peacetime military engagement. Coalition operations are a subset of multinational operations. These operations can also include various nonmilitary organizations and other services. Conducting military operations with foreign military partners, like operations with civilian partners, is uncommon to many soldiers, so a clear understanding of this different environment is necessary.
Coalition operations may be driven by common agreement among the participating coalition partners or through a mandate provided by the United Nations (UN). Either way, their multinational character merits particular attention because national interests and organizational influence may compete with doctrine and efficiency. Consensus is painstakingly difficult, and solutions are often national in character. Commanders can expect contributing nations to adhere to national policies and priorities, which at times complicates the coalition effort.
In UN-sponsored coalition operations, a force is employed under a single commander. The secretary general appoints the force commander with the consent of the UN Security Council. The force commander reports either to a special representative of the secretary general or directly to the secretary general. While the force commander conducts day-today operations with wide discretionary powers, referring all policy matters to the special representative or secretary general for resolution.
In coalition operations, consensus building to ensure compatibility at the political, military, and cultural levels between partners is key. A successful coalition must establish at least unity of effort, if not unity of command. The success of a coalition operation begins with the authority to direct operations of all assigned or attached military forces.
The coalition force commander has much to consider, in addition to military considerations. Considerations such as the strategic context within which the operation will be carried out; civil administration; the reestablishment of justice; civil policing; humanitarian assistance; post-conflict development and reconstruction; the possibility of election organization; financial management; and multicultural issues. Commanders must harmonize these considerations to ensure that the operation has the best possible chance of success. Doing this well, early, and professionally with the optimum level of input and upfront accountability from all likely participants will provide a firm base for a successful operation.
DOWNLOAD ORIGINAL FILE HERE
TOP-SECRET – Afghanistan Bagram Air Base Qur’an Burning Protest Photos February 2012
 An Afghan demonstrator holds a copy of a half-burnt Koran, allegedly set on fire by US soldiers, at the gate of Bagram airbase during a protest against Koran desecration at Bagram, about 60 kilometres (40 miles) north of Kabul, on February 21, 2012. The copies of the burnt Korans and Islamic religious texts were obtained by Afghan workers contracted to work inside Bagram air base, and presented to demonstrators gathered outside the military installation. Afghan protestors firing slingshots and petrol bombs besieged one of the largest US-run military bases in Afghanistan, furious over reports that NATO had set fire to copies of the Koran. Guards at Bagram airbase responded by firing rubber bullets from a watchtower, an AFP photographer said as the crowd shouted “Allahu akbar, Allahu akbar” (God is greater). AFP PHOTO / Massoud HOSSAINI
An Afghan demonstrator holds a copy of a half-burnt Koran, allegedly set on fire by US soldiers, at the gate of Bagram airbase during a protest against Koran desecration at Bagram, about 60 kilometres (40 miles) north of Kabul, on February 21, 2012. The copies of the burnt Korans and Islamic religious texts were obtained by Afghan workers contracted to work inside Bagram air base, and presented to demonstrators gathered outside the military installation. Afghan protestors firing slingshots and petrol bombs besieged one of the largest US-run military bases in Afghanistan, furious over reports that NATO had set fire to copies of the Koran. Guards at Bagram airbase responded by firing rubber bullets from a watchtower, an AFP photographer said as the crowd shouted “Allahu akbar, Allahu akbar” (God is greater). AFP PHOTO / Massoud HOSSAINI Afghan demonstrators shout anti-US slogans at the gate of Bagram airbase during a protest against Koran desecration on February 21, 2012 at Bagram about 60 kilometres (40 miles) north of Kabul. Afghan protestors firing slingshots and petrol bombs besieged one of the largest US-run military bases in Afghanistan, furious over reports that NATO had set fire to copies of the Koran. Guards at Bagram airbase responded by firing rubber bullets from a watchtower, an AFP photographer said as the crowd shouted “Allahu akbar, Allahu akbar” (God is greater). AFP PHOTO/SHAH Marai
Afghan demonstrators shout anti-US slogans at the gate of Bagram airbase during a protest against Koran desecration on February 21, 2012 at Bagram about 60 kilometres (40 miles) north of Kabul. Afghan protestors firing slingshots and petrol bombs besieged one of the largest US-run military bases in Afghanistan, furious over reports that NATO had set fire to copies of the Koran. Guards at Bagram airbase responded by firing rubber bullets from a watchtower, an AFP photographer said as the crowd shouted “Allahu akbar, Allahu akbar” (God is greater). AFP PHOTO/SHAH Marai A wounded Afghan boy stands at the gate of Bagram airbase during a protest against Koran desecration on February 21, 2012 at Bagram about 60 kilometres (40 miles) north of Kabul. Afghan protestors firing slingshots and petrol bombs besieged one of the largest US-run military bases in Afghanistan, furious over reports that NATO had set fire to copies of the Koran. Guards at Bagram airbase responded by firing rubber bullets from a watchtower, an AFP photographer said as the crowd shouted “Allahu akbar, Allahu akbar” (God is greater). AFP PHOTO/SHAH Marai
A wounded Afghan boy stands at the gate of Bagram airbase during a protest against Koran desecration on February 21, 2012 at Bagram about 60 kilometres (40 miles) north of Kabul. Afghan protestors firing slingshots and petrol bombs besieged one of the largest US-run military bases in Afghanistan, furious over reports that NATO had set fire to copies of the Koran. Guards at Bagram airbase responded by firing rubber bullets from a watchtower, an AFP photographer said as the crowd shouted “Allahu akbar, Allahu akbar” (God is greater). AFP PHOTO/SHAH Marai People gather near a fire at Bagram airbase during a protest on February 21, 2012 at Bagram about 60 kilometres (40 miles) north of Kabul. Afghan protestors firing slingshots and petrol bombs besieged one of the largest US-run military bases in Afghanistan, furious over reports that NATO had set fire to copies of the Koran. Guards at Bagram airbase responded by firing rubber bullets from a watchtower, an AFP photographer said as the crowd shouted “Allahu akbar, Allahu akbar” (God is greater). AFP PHOTO/Shah MARAI
People gather near a fire at Bagram airbase during a protest on February 21, 2012 at Bagram about 60 kilometres (40 miles) north of Kabul. Afghan protestors firing slingshots and petrol bombs besieged one of the largest US-run military bases in Afghanistan, furious over reports that NATO had set fire to copies of the Koran. Guards at Bagram airbase responded by firing rubber bullets from a watchtower, an AFP photographer said as the crowd shouted “Allahu akbar, Allahu akbar” (God is greater). AFP PHOTO/Shah MARAI Afghan youth throw stones toward US soldiers standing at the gate of Bagram airbase during a protest against Koran desecration on February 21, 2012 at Bagram about 60 kilometres (40 miles) north of Kabul. Afghan protestors firing slingshots and petrol bombs besieged one of the largest US-run military bases in Afghanistan, furious over reports that NATO had set fire to copies of the Koran. Guards at Bagram airbase responded by firing rubber bullets from a watchtower, an AFP photographer said as the crowd shouted “Allahu akbar, Allahu akbar” (God is greater). AFP PHOTO/SHAH Marai
Afghan youth throw stones toward US soldiers standing at the gate of Bagram airbase during a protest against Koran desecration on February 21, 2012 at Bagram about 60 kilometres (40 miles) north of Kabul. Afghan protestors firing slingshots and petrol bombs besieged one of the largest US-run military bases in Afghanistan, furious over reports that NATO had set fire to copies of the Koran. Guards at Bagram airbase responded by firing rubber bullets from a watchtower, an AFP photographer said as the crowd shouted “Allahu akbar, Allahu akbar” (God is greater). AFP PHOTO/SHAH Marai Afghan youth throw stones toward US soldiers at the gate of Bagram airbase during a protest against Koran desecration on February 21, 2012 at Bagram about 60 kilometres (40 miles) north of Kabul. Afghan protestors firing slingshots and petrol bombs besieged one of the largest US-run military bases in Afghanistan, furious over reports that NATO had set fire to copies of the Koran. Guards at Bagram airbase responded by firing rubber bullets from a watchtower, an AFP photographer said as the crowd shouted “Allahu akbar, Allahu akbar” (God is greater). AFP PHOTO/SHAH Marai
Afghan youth throw stones toward US soldiers at the gate of Bagram airbase during a protest against Koran desecration on February 21, 2012 at Bagram about 60 kilometres (40 miles) north of Kabul. Afghan protestors firing slingshots and petrol bombs besieged one of the largest US-run military bases in Afghanistan, furious over reports that NATO had set fire to copies of the Koran. Guards at Bagram airbase responded by firing rubber bullets from a watchtower, an AFP photographer said as the crowd shouted “Allahu akbar, Allahu akbar” (God is greater). AFP PHOTO/SHAH Marai An Afghan man aims a sling shot toward US soldiers at the gate of Bagram airbase during a protest against Koran desecration on February 21, 2012 at Bagram about 60 kilometres (40 miles) north of Kabul. Afghan protestors firing slingshots and petrol bombs besieged one of the largest US-run military bases in Afghanistan, furious over reports that NATO had set fire to copies of the Koran. Guards at Bagram airbase responded by firing rubber bullets from a watchtower, an AFP photographer said as the crowd shouted “Allahu akbar, Allahu akbar” (God is greater). AFP PHOTO/SHAH Marai
An Afghan man aims a sling shot toward US soldiers at the gate of Bagram airbase during a protest against Koran desecration on February 21, 2012 at Bagram about 60 kilometres (40 miles) north of Kabul. Afghan protestors firing slingshots and petrol bombs besieged one of the largest US-run military bases in Afghanistan, furious over reports that NATO had set fire to copies of the Koran. Guards at Bagram airbase responded by firing rubber bullets from a watchtower, an AFP photographer said as the crowd shouted “Allahu akbar, Allahu akbar” (God is greater). AFP PHOTO/SHAH Marai Afghan youth throw stones toward US soldiers at the gate of Bagram airbase during a protest against Koran desecration on February 21, 2012 at Bagram about 60 kilometres (40 miles) north of Kabul. Afghan protestors firing slingshots and petrol bombs besieged one of the largest US-run military bases in Afghanistan, furious over reports that NATO had set fire to copies of the Koran. Guards at Bagram airbase responded by firing rubber bullets from a watchtower, an AFP photographer said as the crowd shouted “Allahu akbar, Allahu akbar” (God is greater). AFP PHOTO/SHAH Marai
Afghan youth throw stones toward US soldiers at the gate of Bagram airbase during a protest against Koran desecration on February 21, 2012 at Bagram about 60 kilometres (40 miles) north of Kabul. Afghan protestors firing slingshots and petrol bombs besieged one of the largest US-run military bases in Afghanistan, furious over reports that NATO had set fire to copies of the Koran. Guards at Bagram airbase responded by firing rubber bullets from a watchtower, an AFP photographer said as the crowd shouted “Allahu akbar, Allahu akbar” (God is greater). AFP PHOTO/SHAH Marai A US soldier wields his assault rifle (L) as another soldier handles a shotgun while standing at the gate of Bagram airbase during a protest against Koran desecration at Bagram, about 60 kilometres (40 miles) north of Kabul, on February 21, 2012. Afghan protestors firing slingshots and petrol bombs besieged one of the largest US-run military bases in Afghanistan, furious over reports that NATO had set fire to copies of the Koran. Guards at Bagram airbase responded by firing rubber bullets from a watchtower, an AFP photographer said as the crowd shouted “Allahu akbar, Allahu akbar” (God is greater). AFP PHOTO / Massoud HOSSAINI
A US soldier wields his assault rifle (L) as another soldier handles a shotgun while standing at the gate of Bagram airbase during a protest against Koran desecration at Bagram, about 60 kilometres (40 miles) north of Kabul, on February 21, 2012. Afghan protestors firing slingshots and petrol bombs besieged one of the largest US-run military bases in Afghanistan, furious over reports that NATO had set fire to copies of the Koran. Guards at Bagram airbase responded by firing rubber bullets from a watchtower, an AFP photographer said as the crowd shouted “Allahu akbar, Allahu akbar” (God is greater). AFP PHOTO / Massoud HOSSAINI Afghan youth take cover from the rubbers bullets shot by US soldiers at the gates of Bagram airbase during a protest against Koran desecration on February 21, 2012 at Bagram about 60 kilometres (40 miles) north of Kabul. Afghan protestors firing slingshots and petrol bombs besieged one of the largest US-run military bases in Afghanistan, furious over reports that NATO had set fire to copies of the Koran. Guards at Bagram airbase responded by firing rubber bullets from a watchtower, an AFP photographer said as the crowd shouted “Allahu akbar, Allahu akbar” (God is greater). AFP PHOTO/SHAH Marai
Afghan youth take cover from the rubbers bullets shot by US soldiers at the gates of Bagram airbase during a protest against Koran desecration on February 21, 2012 at Bagram about 60 kilometres (40 miles) north of Kabul. Afghan protestors firing slingshots and petrol bombs besieged one of the largest US-run military bases in Afghanistan, furious over reports that NATO had set fire to copies of the Koran. Guards at Bagram airbase responded by firing rubber bullets from a watchtower, an AFP photographer said as the crowd shouted “Allahu akbar, Allahu akbar” (God is greater). AFP PHOTO/SHAH Marai Assorted spent ordnance is strewn on the ground at a protest in front of Bagram airbase on February 21, 2012 at Bagram about 60 kilometres (40 miles) north of Kabul. Afghan protestors firing slingshots and petrol bombs besieged one of the largest US-run military bases in Afghanistan, furious over reports that NATO had set fire to copies of the Koran. Guards at Bagram airbase responded by firing rubber bullets from a watchtower, an AFP photographer said as the crowd shouted “Allahu akbar, Allahu akbar” (God is greater). AFP PHOTO/Shah MARAI
Assorted spent ordnance is strewn on the ground at a protest in front of Bagram airbase on February 21, 2012 at Bagram about 60 kilometres (40 miles) north of Kabul. Afghan protestors firing slingshots and petrol bombs besieged one of the largest US-run military bases in Afghanistan, furious over reports that NATO had set fire to copies of the Koran. Guards at Bagram airbase responded by firing rubber bullets from a watchtower, an AFP photographer said as the crowd shouted “Allahu akbar, Allahu akbar” (God is greater). AFP PHOTO/Shah MARAI Afghan youth throw stones toward US soldiers at the gate of Bagram airbase during a protest against Koran desecration on February 21, 2012 at Bagram about 60 kilometres (40 miles) north of Kabul. Afghan protestors firing slingshots and petrol bombs besieged one of the largest US-run military bases in Afghanistan, furious over reports that NATO had set fire to copies of the Koran. Guards at Bagram airbase responded by firing rubber bullets from a watchtower, an AFP photographer said as the crowd shouted “Allahu akbar, Allahu akbar” (God is greater). AFP PHOTO/SHAH Marai
Afghan youth throw stones toward US soldiers at the gate of Bagram airbase during a protest against Koran desecration on February 21, 2012 at Bagram about 60 kilometres (40 miles) north of Kabul. Afghan protestors firing slingshots and petrol bombs besieged one of the largest US-run military bases in Afghanistan, furious over reports that NATO had set fire to copies of the Koran. Guards at Bagram airbase responded by firing rubber bullets from a watchtower, an AFP photographer said as the crowd shouted “Allahu akbar, Allahu akbar” (God is greater). AFP PHOTO/SHAH Marai Afghan demonstrators show copies of Koran books allegedly set alight by US soldiers, during a protest against Koran desecration at the gate of Bagram airbase on February 21, 2012 at Bagram about 60 kilometres (40 miles) north of Kabul. Afghan protestors firing slingshots and petrol bombs besieged one of the largest US-run military bases in Afghanistan, furious over reports that NATO had set fire to copies of the Koran. Guards at Bagram airbase responded by firing rubber bullets from a watchtower, an AFP photographer said as the crowd shouted “Allahu akbar, Allahu akbar” (God is greater).
Afghan demonstrators show copies of Koran books allegedly set alight by US soldiers, during a protest against Koran desecration at the gate of Bagram airbase on February 21, 2012 at Bagram about 60 kilometres (40 miles) north of Kabul. Afghan protestors firing slingshots and petrol bombs besieged one of the largest US-run military bases in Afghanistan, furious over reports that NATO had set fire to copies of the Koran. Guards at Bagram airbase responded by firing rubber bullets from a watchtower, an AFP photographer said as the crowd shouted “Allahu akbar, Allahu akbar” (God is greater).Zealand – The ʻStasiʼ (State Security of the GDR) – a Crime Syndicate!
DOWNLOAD ORIGINAL DOCUMENT HERE
TOP-SECRET from the FBI – Sheriff Charged with Fraud, Identity Theft, and Obstruction
Ouachita Parish Sheriff Arrested
Sheriff Charged with Fraud, Identity Theft, and Obstruction
| U.S. Attorney’s Office February 24, 2012 |
MONROE, LA—United States Attorney Stephanie A. Finley announced that Sheriff Royce Edward Toney, 64, of Monroe, La., was arrested today on charges of conspiracy, computer fraud, identity theft, and obstruction. Toney was elected Sheriff on October 20, 2007, and took office on July 1, 2008. He did not seek re-election. Also charged was Michael Karl Davis, a major with the Ouachita Parish Sheriff’s Office who works in the IT department.
The indictment alleges that Toney and Davis engaged in a conspiracy to track a third-party’s communications and, once Davis learned that the FBI wanted to speak with him, he tried to cover up the illegal activity. The indictment further alleges that Toney and Davis accessed a protected computer without authorization on nine occasions from April of 2010 to October of 2010, and that Toney and Davis committed the crime of identity theft by utilizing an AOL e-mail address and password belonging to another person. Toney and Davis are charged with one count of obstruction for reformatting and installing a new operating system on a computer after Davis learned of the ongoing FBI investigation. Finally, Toney is charged with obstruction by retaliating against a witness who was cooperating with the FBI investigation.
If convicted, Toney and Davis faces maximum potential penalties of one year in prison, a $100,000 fine or both for each of the computer crime charges and five years in prison, a $250,000 fine or both for each of the conspiracy, identity theft and obstruction charges.
An indictment is merely an accusation and all defendants are presumed innocent until and unless proven guilty.
This case was investigated by the Federal Bureau of Investigation, Monroe Resident Agency, and is being prosecuted by Assistant U.S. Attorney C. Mignonne Griffing.
FEMEN – “La prostitution est un fléau en Ukraine”
CONFIDENTIAL – Georgia Proposes Union Breaking Act
12 LC 37 1386ER
Senate Bill 469
By: Senators Balfour of the 9th, Hamrick of the 30th, Cowsert of the 46th and Tolleson of the 20th
A BILL TO BE ENTITLED
AN ACT
To amend Chapter 6 of Title 34 of the Official Code of Georgia Annotated, relating to labor organizations and labor relations, so as to provide that certain provisions prohibiting mass picketing shall apply to certain private residences; to provide for an action to enjoin unlawful mass picketing; to provide for punishment and penalties; to provide for injunctive relief; to provide for public policy concerning refusal or decision to withdraw from a labor union or employee organization; to provide for certain contract and agreement employment rights; to provide for the development by the Department of Labor of employee rights information; to provide certain posting requirements by private employers; to provide for enforcement; to provide for changes to agreements and contracts permitting labor organizations to deduct fees from employees’ earnings; to amend Code Section 16-7-21, relating to criminal trespass, so as to provide for both criminal trespass and criminal conspiracy; to provide for punishment and fines; to provide for related matters; to repeal conflicting laws; and for other purposes.
BE IT ENACTED BY THE GENERAL ASSEMBLY OF GEORGIA:
SECTION 1.
Chapter 6 of Title 34 of the Official Code of Georgia Annotated, relating to labor organizations and labor relations, is amended by revising Code Section 34-6-5, relating to interference with public ways of travel, transportation, or conveyance by mass picketing near site of a labor dispute, as follows:
“34-6-5.
(a)It shall be unlawful for any person to engage in mass picketing at or near any place, including private residences, where a labor dispute exists in such number or manner as to obstruct or interfere with or constitute a threat to obstruct or interfere with the entrance to or egress from any place of employment or the free and uninterrupted use of public roads, streets, highways, railroads, airports, or other ways of travel, transportation, or conveyance.
(b) A person, or organization that he or she is affiliated with or acting on behalf of, commits an offense when he or she engages in targeted picketing of a private residence that has or intends the effect of interfering with the resident’s right to quiet enjoyment, or when such targeted picketing has or intends the effect of violence or intimidation. This subsection shall not apply to private residences that are also places of employment when targeted picketing relates to or is targeted at such employment.
(c) An employer or other person or entity that is the target of an activity prohibited under subsection (a) of this Code section may bring an action to enjoin the prohibited activity against an individual or organization affiliated with such individual in the circuit court for the county in which the affected employer, person, or entity is located. A court having jurisdiction of an action brought under this subsection shall grant injunctive relief if the court finds that any person, union, or organization has engaged or is engaging in any of the conduct prohibited under subsection (a) of this Code section, without regard to the existence of other remedies, demonstration of irreparable harm, or other factors. The court shall award court costs and reasonable attorney fees to a plaintiff who prevails in an action brought under this subsection.
(d) Failure to comply with an order of the court issued under this Code section may be punished as contempt.
(e) A person who violates subsection (a) of this Code section and has previously been enjoined for a violation of subsection (a) of this Code section is subject to a civil fine of $1,000.00 for each day of the violation. If a union or organization continues to sponsor or assist in the prohibited activity in violation of an injunction, the union or organization is subject to a civil fine of $10,000.00 for each day of the violation. The civil fine assessed under this subsection shall be paid to the court, and, upon a showing of damages to business sales, business opportunities, or property, the employer, person, or entity that was the target of the activity prohibited under subsection (a) of this Code section shall be compensated from the payment made to the court.
(f) An employer that is the target of picketing may obtain injunctive relief against picketers without a showing of irreparable harm if the court finds the picketing to be in violation of subsection (a) of this Code section.”
SECTION 2.
Said chapter is further amended by adding a new Code section to read as follows:
“34-6-9.
(a) It is the public policy of the State of Georgia that:
(1) Employees in Georgia have the right to employment without regard to any person’s refusal to join or affiliate with, or decision to withdraw from or cease membership in, any labor union or employee organization of any kind;
(2) Employees in Georgia have the right to be employed free from the restraints of any contract, combination, or agreement, written or oral, that provides for exclusion from employment of any person due to their refusal to join or affiliate with, or decision to withdraw from or cease membership in, any labor union or employee organization of any kind;
(3) Employees in Georgia have the right to be employed without regard to any person’s refusal to pay dues, fees, assessments, or other charges to any labor union or employee organization of any kind; and
(4) Employees in Georgia have the right to decertify a union or other bargaining representative upon compliance with the applicable provisions of federal law.
(b) The Department of Labor shall develop and display on its website a suitable form of notice providing employees with information regarding their rights under this Code section.
(c) Private employers shall physically post adequate notice informing employees of the rights described in this Code section at locations where notices are normally posted or, if no such normal location for posting exists, physically disseminate such notice to employees. A private employer may also, at its discretion, post such notices on the company’s intranet or disseminate them via other electronic means of communication.
(d) If compliance by an employer with subsection (c) of this Code section will create an undue hardship posing significant difficulty or expense, then such employer is exempted from compliance with subsection (c) of this Code section.
(e) The Commissioner of Labor shall be charged with enforcement of the obligations contained in this Code section. In carrying out the commissioner’s responsibility to ensure compliance, the commissioner, or the person to whom the commissioner delegates such responsibility, is authorized to:
(1) Receive complaints or reports of noncompliance from any person;
(2) Inspect and investigate any report of noncompliance; and
(3) Give notice of noncompliance to any employer who is in violation of this Code section.
(f) The commissioner shall designate those persons in the commissioner’s department responsible for carrying out the commissioner’s powers, duties, and responsibilities under this Code section.”
SECTION 3.
Said chapter is further amended by revising Code Section 34-6-25, relating to deductions from employees’ earnings of fees of labor organizations, as follows:
“34-6-25.
No employer shall deduct from the wages or other earnings of any employee any fee, assessment, or other sum of money whatsoever to be held for or to be paid over to a labor organization except on theindividual order or request of the employee, which shall not be irrevocable for a period of more than one yearannual written authorization from the employee which shall not exceed a period greater than one year. Such authorization may be revoked at any time at the request of the employee.”
SECTION 4.
Said chapter is further amended by revising Code Section 34-6-26, relating to contracts allowing deductions from employees’ earnings of fees of labor organizations, as follows:
“34-6-26.
It shall be unlawful for any employer to contract with any labor organization and for any labor organization to contract with any employer for the deduction of any fee, assessment, or other sum of money whatsoever from the wages or other earnings of an employee to be held for or to be paid over to a labor organization except upon the condition to be embodied in said contract that such deduction will be made only on theindividual order or request of the employee, which shall not be irrevocable for a period of more than one yearannual written authorization. Such authorization may be revoked at any time at the request of the employee.”
SECTION 5.
Code Section 16-7-21 of the Official Code of Georgia Annotated, relating to criminal trespass, is amended by revising subsection (d) as follows:
“(d)(1)A person who commits the offense of criminal trespass shall be guilty of a misdemeanor.
(2) The provisions of Code Section 16-4-8.1 notwithstanding, a person may be convicted of both conspiracy to commit criminal trespass and the completed crime of criminal trespass, in which event such separate crime of conspiracy shall be a felony punishable by imprisonment for not more than one year, a fine of not more than $10,000.00, or both such fine and imprisonment.”
SECTION 6.
All laws and parts of laws in conflict with this Act are repealed.
DDR Gestapo- MORDE MURDER-STASI HV A – Markus Wolf’s espionage departement – STASI-Spionage enthüllt – HV A Sira, doc. 6 of 6
MORDE MURDER-STASI HV A – Markus Wolf’s espionage departement – STASI-Spionage enthüllt – HV A Sira, doc. 5 of 6
STASI-MÖRDER INTERN – STASI Mörder -STASI HV A – Markus Wolf’s espionage departement – STASI-Spionage enthüllt – HV A Sira, doc. 5 of 6
STASI Mörder -STASI HV A – Markus Wolf’s espionage departement – STASI-Spionage enthüllt – HV A Sira, doc. 4 of 6
Die Spione -STASI HV A – Markus Wolf’s espionage departement – STASI-Spionage enthüllt – HV A Sira, doc. 3 of 6
ENTHÜLLT -STASI HV A – Markus Wolf’s espionage departement – STASI-Spionage enthüllt – HV A Sira, doc. 3 of 6
Exposed – STASI HV A – Markus Wolf’s espionage departement – STASI-Spionage enthüllt – HV A Sira, doc. 2 of 6
STASI HV A – Markus Wolf’s espionage departement exposed – STASI-Spionage enthüllt – HV A Sira, doc. 1 of 6
UNCENSORED FEMEN Bare All in Kiev Protes
STASI-Studie zu den IM unter den Jugendlichen der DDR
Liste aller STASI-Doktor-Arbeiten – list of all given doctoral thesis at Stasi Law School, Potsdam
The Ministry for State Security in 1951 founded a special Law School in Potsdam-Golm (“Juristische Hochschule des Ministeriums für Staatssicherheit”) whose duty was to increase the amount of academically educated employees of the Ministry by giving academic profession in public law, international policy as well as professional training in interrogation techniques, clandestine intelligence missions and adminstrational organisation.
The studies finished with either degrees of technical school, diploma in law or criminalistics, or doctorate – doctorate A comparable to western-german “Dr. jur.” and doctorate B comparable to the postdoc qualification in Western-Germany “Dr. jur. habil.” or “Dr. habil.”
DOWNLOAD ORIGINAL DOCUMENT HERE
STASI – Handbuch-First Version – Anatomy of State Security: Handbook on Stasi Law School, published by the “Office of the Federal Commissioner Preserving the Records of the Ministry for State Security of the GDR”
TOP-SECRET – STASI-Order “interim” payment for former Stasi-employees, given 29th of Dez. 1989 – STASI-Zahlungsanweisung 1989
DER BEWEIS-WARUM DIE STASI HEUTE NOCH IHREN MÖRDERISCHEN AKTIVITÄTEN NACHGEHT
Hallo
klare Anzeichen neben der Verbindung zur STASI durch Resch und STASI-Oberst Stelzer , die einem Blinden auffallen müssen, dass “GoMoPa” ein Relikt der STASI ist:
– der Name ist eine STASI-typische Abkürzung, ein amerikanisches oder internationales Unternehmen würde “Goldman, Morgenstern & Partner” nie mit “GoMoPa” abkürzen, das ist ganz im Stil der STASI – Abkürzungen wie IM, HA, STASI, OV etc.
– in der Unterzeile steht “Nachrichtendienst” – na klarer geht es wohl kaum noch – nachrichtendienste sind CIA, BND, KGB, Mossad und eben STASI
Nachrichtenagenturen oder Nachrichtenmedien sind etwas anderes – das zeigt sich auch an der englischen Übersetzung “INTELLIGENCE” für die Tätigkeit der Geheimdienste, die STASI-“GoMoPa” in Anspruch nimmt – mit dem Zusatz “Financial” als ob eine betrugsverurteilung wegen Betruges am eigenen Anleger die geeiegnete Qualifikation der “GoMoPa”-STASI wäre.
– die Praktiken des Rufmordes, Mordes, der Spionage im Privatleben der Opfer, der Gewinnung von Informanten und IM und der Zersetzung
– die Kontrolle von Ausweisen durch “GoMoPa”
– die gefälschten Lebensläufe z.B. von “CEO” ” Klaus Maurischat”
– die dubiosen Biographien VOR 1989
– die Verwendung von Tarnnamen
– der Einsatz von russischen Hackern
– das Personal stamt aus Ostdeutschland, Berlin, Brandenburg und Sachsen-Anhalt
– der konspirativen Arbeitsweise – niemand hat je “Goldman” oder “Morgenstern” gesehen oder ein Meeting/Sitzung erlebt
– die Morddrohungen und unverhohlenen Drohungen der Vernichtung der bürgerlichen und wirtschaftlichen Existenz ihrer Gegner
– der Instrumenalisierung von IM im Justizapparat
– der Erpressung von Geschäftspartnern oder Firmen, die dies partout nicht sein wollen (z.B. durch eine Warnliste).
– der Verbindung zur PDS und “Neues Deutschland”, “Extremnews” dem Parteibuch” (Internetblog).
– der Tarnung durch die Vertretung angeblicher Verbraucherinteressen (früher waren es die Interessen der “Werktätigen”).
– der Rückzugsraum und die Bastion des Verbraucherschutzes von “GoMoPa”-Obergenosse Resch in der STASI-Hochburg Brandenburg.
– das manische Sammeln von Informationen über andere Personen (wie Bennewirtz es selber so schön beschreibt über sein eigenes Vorgehen).
– die Nutzung von Facebook und anderen Internet-Quellen für Dossiers.
– das Fehlen jedweder Hemmungen und Skrupeln
– der Name “SJB”
– die Gründung der “SJB” in 1989 als die STASI in den Westen ausströmte
– die Herkunft der “SJB”-Briefmarke “Sammlerstück” aus Klein-Machnow, Ex-DDR
– die Verbindung “GoMoPa” und SJB
– die Beschimpfung von Bundeskanzlerin Angela Merkel und Fianzminister Wolfgang Schäuble durch SJ-“GoMoPa”-Agent “Peter Ehlers, der sonst nie EINEN EIGENEN ARTIKEL schrieb….ALS “HERAUSGEBER” !!!!
etc pp
ES RIECHT NACH STASI
ES SIEHT AUS WIE STASI
ES SCHMECKT NACH STASI
ES IST STASI !
K.L-O
Bonn
QUELLE: http://www.victims-opfer.com
siehE
TOP-SECRET from the FBI – Former Bend-Area Developer Pleads Guilty to $20 Million Bank Fraud
EUGENE, OR—Tyler Fitzsimons, 33, appeared before U.S. District Judge Michael R. Hogan on Tuesday, February 21, 2012 and pleaded guilty to a variety of mortgage and loan fraud charges arising out of the collapse of his company, Desert Sun Development (DSD), including conspiracy, bank fraud, and money laundering. From 2004 through 2008, DSD, a company previously headquartered in Bend, Oregon, built commercial structures and residential housing throughout Central Oregon. According to the indictments, DSD principals and other defendants caused financial institutions to lose more than $19 million.
According to court documents, Fitzsimons and others knowingly submitted fraudulent documents, including false financial statements, to various banks in order to obtain financing to develop and construct many of DSD’s commercial projects. Once the loans were approved, Fitzsimons and others submitted additional false documents, including fictitious contracts and invoices, to the banks to obtain loan proceeds for construction costs that were claimed to be associated with the fraudulent documents. Often, no construction had occurred.
Fitzsimons also developed a real estate flipping scheme at DSD. In court records, Fitzsimons admitted, among other things, to undermining the loan approval process for individuals participating in the scheme by “seasoning” or falsely inflating their bank accounts through temporary deposits or undisclosed, short-term loans and by submitting other fictitious documents, including letters explaining employment, large or recent deposits, and bonuses, to the banks funding the loans.
Defendants Shannon Egeland, Jeremy Kendall, Robert Brink, Teresa Ausbrooks, Michael Wilson, and Del Barber, Jr., who are charged in these and related cases previously pleaded guilty and are pending sentencing.
Conspiracy to commit bank fraud carries a maximum sentence of five years in prison and a $250,000 fine. Bank fraud carries a maximum sentence of 30 years in prison and a $1 million fine, and money laundering carries a maximum sentence of five years in prison and a $250,000 fine. Sentencing is set before U.S. District Court Judge Michael R. Hogan on October 09, 2012, at 10 a.m.
These cases were investigated by the FBI, IRS-Criminal Investigations, and the Oregon Division of Finance and Corporate Securities. Assistant U.S. Attorney Scott E. Bradford handled the prosecution of the cases.
Uncensored – FEMEN devant le domicile de DSK
STASI-Order ref. the closing of Departement M (control of post), given 8th of Nov. 1989-STASI-Order-Schliessung Abteilung M
STASI intern – GVS MfS 046 – 9/81/L Einsatzgrundsätze und Hauptaufgaben der Einsatzgruppen im Operationsgebiet
STASI-Order for KD Gera, ref. destruction of Stasi-Files, Nov. 1989 – STASI-Order zur Zerstörung der Daten
Die vorbestraften STASI-Stalker der “GoMoPa” – Das Betrugsurteil wg. Betrug am eigenen Anleger
OPINION -Israel needs to begin a cyber counterattack

Arie Egozi Arie Egozi is a seasoned reporter in the defense industry and in military and civilian aviation. He has worked closely with the Israeli daily Yedioth Ahronoth, and written for international journals in both the aviation and defense fields.
There’s no doubt that the persons capable of dealing with cyber attacks against Israel are the individuals in the IDF’s elite units who deal with advanced computerization. There is an assessment that the recent attacks against banks and hospitals are merely a rehearsal for the real thing; if this is true, then these units need to be prepared not just for a defensive operation, but also an offensive operation.
While it is still unclear who developed and sent the worms that infected Iran’s nuclear facilities, this is the kind of offensive action Israel needs to take. We must severely damage the infrastructure of hostile states, as the large attacks against Israel will be conducted by states, not by groups of young anarchist hackers.
Though Israel is not ready for this kind of war, in the meantime, it can at least respond with highly effective counterattacks.
A Strategic Maneuver
The expansion of the cooperation agreement for ballistic missile defense between Israel Aerospace Industries (IAI) and Boeing was presented as another step of industrial cooperation between two companies with advanced technology. However, this is not exactly the case.
A deal was signed with Boeing nearly a decade ago to obtain more Arrow-2 missiles. IT manufactures part of the missiles in an Arizona-based plant that are purchased for the IAF with US foreign aid funds – a convenient arrangement for all sides.
Yet, something happened along the way. Israel is the only country in the world in possession of an operational system for defense against ballistic missiles. The US is positioning systems against intercontinental missiles, but that is another story. Boeing understood that aside from sub-contracting, there is still greater potential in this area.
The signing of the agreement for expanding the cooperation represents a genuine change. Today, Boeing is largely involved in the development of the upgraded Arrow-3 missile. However, that is not where the issue ends.
I have no doubt that the threat posed by ballistic missiles to an increasing number of countries is generating a demand for defense systems. The cooperation between IAI and Boeing could result in the sale of these systems to several countries.
Independent in the Field
Will the IDF use autonomous systems capable of opening fire on their own accord in the near future? The decision is tactical rather than technical, as the technology already exists with both ground and naval tools.
The question is one of human “operational code.” What now seems unacceptable may soon become acceptable, especially along a border like the Egyptian one. When the never-ending work of erecting the Egyptian border fence is complete, someone will have to back the metal wires from which it was made.
It is along such an extended fence that autonomous tools that can identify and eliminate will provide effective solutions. The IDF will have to consider all aspects of using this technology. It will not be an easy decision, but the changing situation necessitates a renewed and comprehensive analysis.
A Foretold Failure
The last-minute cancellation of a deal signed by Israeli UAV manufacturer Aeronautics and a foreign country once again raises the question as to the way Israeli defense export deals are made. Supposedly, all the elements and mechanisms needed to prevent unsuitable deals already exist.
So how do mishaps such as these still occur? The best example is the economic “parallel market.” Essentially, these formal exporters operate in semi-secrecy alongside importers, and not always in conjunction with them. Primarily, these are former senior officers utilizing connections from their military service to make a profit.
All attempts to overcome, regulate, and end this phenomenon have so far failed.
Alone in Battle
IsraelDefense readers already know that during Gen. Dempsey’s visit ten days ago, the state of the discussions carried out with Israel’s Chief of Staff and other senior defense officials was far from the “family picnic” official spokespersons tried to portray.
Over the weekend, an interview with the US Chairman of the Joint Chiefs of Staff exposed what was said during his visit. There is no agreement between the US and Israel on the Iranian issue. Gen. Dempsey arrived here in an attempt to prevent an independent Israeli operation, and the discussions, at least in part, were acrimonious.
This means that the Americans don’t want a mess during an election year, that Israel is alone in this battle, and that Israel will have to make tough decisions in the near future.
Government Suckers
Thousands of words have been written about the Tal law and the attempt to extend it. This time I wish to speak about other “suckers,” and not those that go into the reserve forces every year. The Prime Minister and the Minister of Defense are the suckers. Either they are not listening to their media consultants, or those consultants don’t understand a thing.
If Netanyahu and Barak had decided long ago to end the massive evasion from IDF service, they would have gained enough support to render the partnership with the religious parties pointless. Therefore, they are in fact the suckers.
They don’t understand the depth of the fury among the secular populace over the discriminatory law; they would have made a name for themselves in an unprecedented manner had they demonstrated valor as veterans of combat units and done the right thing.
However, their instincts are not what they used to be during their military service. Now, of all times, those instincts would have benefited them, as evasion from service is a dangerous enemy.
The Syrian Killing Fields – 2 Western Journalists killed
DDR-Ausreise – the famous decision of the council of ministers, published by Günter Schabowski on television, 9th of Nov. 1989 -DDR-Grenzöffnung-Dokument
STASI – Arming order to protect the KD Eisenbach, 20th of Oct. 1989 – STASI-Bewaffnungsorder
DOWNLOAD ORGINAL DOCUMENT HERE
FEMEN UNCENSORED – devant le domicile de DSK – no comment
STASI – Task-List for the 40th anniversary of the GDR, Berlin, betw. 6th and 8th of Oct. 1989 – STASI AUFGABENLISTE FÜR 40 JAHRE DDR
“GoMoPa”-STASI AUS MIELKES KLOAKE – SERIENRUFMÖRDER-BETRÜGER – ERPRESSER- MÖRDER
TOP-SECRET – STASI’s detailed plan for internment, KD Bernau, July 1989 -STASI-KZ-Internierungsplan
Unveiled – German Spies Secret Data Spying Guide DE
DWONLOAD ORIGINAL FILE HERE
STASI Order for the infiltration of West-Berlin political parties and the Senate of Berlin, Dec. 1988 – SASTI-Infiltrationsbefehl
STASI-Mielke’s Mental Disruption order 1/76 – STASI-Mielkes “Zersetzungsrichtlinie”
The Mossad – Alleged Iran Revenge Cell Bangkok Suspects
 |
| Iran Revenge Cell Bangkok Suspects – Escaped from Bangkok to Malaysia Arrested There 16/2/12 |
 |
Nuclear Scientist Killed in Tehran Worked at Natanz Atomic Reactor 11/1/12
http://www.flickr.com/photos/32368051@N08/sets/72157629336986255/
FEMEN UNCENSORD – Des féministes ukrainiennes devant le domicile de DSK
STASI Files unveiled – Order for the STASI-Officers in special missions (OiBE) – DDR-Ministerrat zu den STASI-Offizieren in besonderem Auftrag (OiBE)
DOWNLOAD ORIGINAL DOCUMENT HERE
CONFIDENTIAL – U.S. Army Whistleblower Report: Senior Military Leaders’ Loss of Integrity Wounds Afghan War Effort

Senior ranking US military leaders have so distorted the truth when communicating with the US Congress and American people in regards to conditions on the ground in Afghanistan that the truth has become unrecognizable. This deception has damaged America’s credibility among both our allies and enemies, severely limiting our ability to reach a political solution to the war in Afghanistan. It has likely cost American taxpayers hundreds of billions of dollars Congress might not otherwise have appropriated had it known the truth, and our senior leaders’ behavior has almost certainly extended the duration of this war. The single greatest penalty our Nation has suffered, however, has been that we have lost the blood, limbs and lives of tens of thousands of American Service Members with little to no gain to our country as a consequence of this deception.
Introduction
These are surely serious charges and anyone who would make such claims had better have considerable and substantive evidence to back it up. Regrettably, far too much evidence does exist and I will here provide key elements of it. As I will explain in the following pages I have personally observed or physically participated in programs for at least the last 15 years in which the Army’s senior leaders have either “stretched the truth” or knowingly deceived the US Congress and American public. What I witnessed in my most recently concluded 12 month deployment to Afghanistan has seen that deception reach an intolerable high. I will provide a very brief summary of the open source information that would allow any American citizen to verify these claims. But if the public had access to these classified reports they would see the dramatic gulf between what is often said in public by our senior leaders and what is actually true behind the scenes. It would be illegal for me to discuss, use, or cite classified material in an open venue and thus I will not do so; I am no WikiLeaks guy Part II.
Fortunately, there is a provision that allows me to legally submit a classified report to Members of Congress. In conjunction with this public study I have also submitted classified reports to a number of US Representatives and Senators, both Democrats and Republicans. As the duly elected representatives of our people, they are authorized to see the classified data and empowered to do something about it. For the sake of so many who have paid with their blood – and the sake of those Service Members who have not yet had to pay that price – it is my sincere hope that Congress acts to resolve these issues expeditiously.
In the first section below I will demonstrate how numerous military senior leaders have used omission and outright deception in order to prevent the American public from knowing the truth in regards to the genuine conditions on the ground in Afghanistan. I will explain that there has been a significant volume of information available from numerous and reputable open sources that should have been effective in communicating to the American public the truth of the situation. Owing to numerous factors (the key of which are discussed in detail in subsequent sections of the report), however, the powerful and pervasive personalities of several US general officers have been surprisingly effective at convincing even highly educated Americans to believe what the generals say and not what their eyes and evidence tell them.
In the second section I will help the reader gain a better understanding of how the situation described in Section I came to be. For the most part restricting myself to discussing situations in which I was physically a participant, I will first present a number of facts – many of which will be seen in public for the first time – regarding how Army senior leaders have been deceiving the US Congress and American people on some key modernization programs going back to the 1990s. In this section you will see how despite year after year of Government Accountability Office (GAO) analysis done explicitly for the US Congress which showed major and repeating failures in the Future Combat Systems (FCS), the Army’s senior leaders instead told Members of Congress and the US public in press releases that the opposite was true; because Americans have trusted the Army’s leaders more than any other in the country, they accepted the word of the generals and ignored the GAO reports and the physical absence of successful products.
A second major sub-element to this section will be a demonstration – also containing significant new information that has never been seen by the American people – revealing that what virtually the entire country and even a great percentage of our uniformed Service Members believe about how and why the Iraq surge of 2007 was successful, was in fact grossly inaccurate. The version of events that depicted the lion’s share of the causality going to superior US generalship and the adoption of the “protect the population” strategy was created and sustained by a number of key senior US generals. When the full facts are examined, however, it becomes very clear that the surge of troops in 2007 was instrumental at best and according to one senior ground commander who led much of our fight in the Anbar province, “75% to 80% of the credit” for the surge’s success lies elsewhere.
The inaccurate assigning of the reason for the 2007 Iraq surge’s success has profound implications for our current war in Afghanistan and doubly so for the surge forces ordered by the President in late 2009. Had the President known the truth of what really happened in 2007 Iraq it is unlikely he would not have made the decision he did in November/December 2009. In any case, the situation demonstrates a growing and expanding willingness on the part of our country’s senior military leaders to use “Information Operations” even on domestic audiences to manipulate the system in order to get what they want.
The senior military leaders have been remarkably successful in achieving their desires; but as a result, our country has squandered almost a full decade in which it might have made noteworthy advancements in its force structure, has continued pursuing a military strategy that has proven to be an abysmal failure during a time when effective outcomes might have been found, and worst of all, has cost the lives and limbs of tens of thousands of American Service Members – and reportedly deprived hundreds of thousands more of their psychological and emotional well-being.
Section III will cover a broad range of negative consequences that our country has paid and will continue to pay until changes are made. We’ve lost credibility with our allies and friends in the region; we’ve lost almost all credibility among even the Afghan population and individual government officials; and our word has no value among our enemies. Many may be tempted to believe it unimportant what our enemies think, but it is almost as important as it is for us to have our closest allies believe in us: at some point this war will have to end in a political settlement of some sort. If our enemy isn’t able to believe the word of our country, we may never find a foundation upon which to reach an agreeable accord to end the war on terms acceptable to us.
Finally I will lay out a few recommendations on a way forward to address these deficiencies. There is a bit of good news to be had, however. While there are a number of general officers and senior leaders who have not dealt honorably with the American people, there are a great many others who have. As I note in the body of this report, the vast majority of the Soldiers and Marines I’ve met and personally observed in action are among some of the most remarkable, talented, and dedicated men and women I’ve ever met. Further, there are also some general officers in our Army who are dedicated to the nation and still have their integrity fully intact.
In order for the current crop of excellent junior Army leaders to become the next generations’ senior Army leaders – and continue to demonstrate the same adherence to honor and integrity – changes must be made and made quickly of today’s senior cohort. I’ve lost count of the number of truly promising and intelligent leaders who have gotten out of the service at the mid-level because they could not stomach the mendacity at the top. If we can change the culture at the top, however, the future for our Armed Forces and our country can once again be very bright.
DOWNLOAD ORIGINAL DOCUMENT HERE
STASI Terror order for the operational area (Western-Germany)
Gastbeitrag – Andy Müller-Maguhn und Ingrid Köppe – STASI aufgelöst oder das “Operationsgebiet” übernommen
Staatssicherheit aufgelöst
oder:
das Operationsgebiet eingenommen?
„Nach langer Verzögerung der Antwort leugnet die Bundesregierung nun weitgehendst die skandalösen Vorgänge, die mir während meiner USA-Reise unmißverständlich berichtet wurden:
[…] daß die CIA derzeit mit tatkräftiger Unterstützung bundesdeutscher Dienste ehemalige Stasi-Offiziere unter Vertrag nimmt.”
Aus einer Presseerklärung der innenpolitischen Sprecherin von Bündnis 90 / Die Grünen vom 10.03.1992, Ingrid Köppe
Ergebnis einer bisher erst groben Analyse von Datenhinterlassenschaften
Manche Artikel basieren auf langen Geschichten. Bei anderen Artikeln ist es genau umgekehrt: Artikel verursachen lange Geschichten. Bei diesem Artikel ist die Geschichte evtl. in beide Richtungen gleich lang. Und zwar ziemlich.
Als die Deutsche Demokratische Republik (DDR) aufgelöst wurde, hat sie neben merkwürdigen Erinnerungen auch noch – so glaubte man – eine der am besten dokumentierten Aktenlage der zweitbesten “politischen Geheimpolizei” der Welt hinterlassen. Die Gauck-Behörde, offiziell “Die Bundesbeauftragte für die Unterlagen des Ministeriums für Staatssicherheit der ehemaligen Deutschen Demokratischen Republik” verwaltet immerhin etliche Tonnen Akten und macht sie den betroffenen – Tätern wie Opfern – mit gewissen datenschutzrechtlichen Einschränkungen zugänglich. Geschichtsaufarbeitung sollte möglich werden.
Die Bürger der ehemaligen DDR schienen erreicht zu haben was sie wollten: das Ministerium für Staatssicherheit (die “Stasi”) war aufgelöst, die DDR auch, ein paar leitende Funktionäre im Gefängnis und die DDR jetzt BRD. Und jetzt kommen wir zu den Schönheitsfehlern dieser Operation.
Bei der Auflösung des Ministeriums für Staatssicherheit wurden ja, wie das neudeutsch so schön heißt, “einige Arbeitskräfte auf den Markt freigesetzt.” Schon die Frage wie viele Mitarbeiter das Ministerium für Staatssicherheit denn hauptamtlich hatte, lässt sich leider nicht so einfach beantworten. Es gibt zwar einen Haufen Akten, und Personallisten, aber die Interpretationen dieses Materials gehen dann doch eher weit auseinander.
Nun war für die Bürger der ehemaligen DDR die Frage, wer denn nun früher für die Stasi gearbeitet hat oder nicht, schon eine Frage. Man wollte schließlich nicht mit den selben Genossen noch einmal die – vermeintlich neuen Staatsstrukturen aufbauen. Hilfreich war u.a. die “Liste der Hauptamtlichen Mitarbeiter des MfS” die seit den frühen 90´er Jahren durch Publikationen der DDR-Bürgerbewegung verbreitet wurde. Sie enthält rund 100.000 Mitarbeiter bzw. Datensätze (genau: 97.058 plus minus ein paar) und gilt – präzise galt – als authentisch. Auch die juristischen Auseinandersetzungen, die die Verbreiter dieser Liste bekamen (“Die Andere” Berlin wegen Abdruck, Neues Forum Halle wegen Auslegen und http://www.nierenspende.de wegen Verbreitung im Netz), sprachen zumindest dafür, daß die Liste echte Namen enthält.
Als die Bürgerbewegten die Daten in den frühen 90er Jahren mit dBase verarbeiten, waren die damals genutzten 386er eher an den Grenzen ihrer Belastung. Bei 100.000 Daten fielen komfortable Suchaktionen und Quervergleiche eher aus. Das ist zum Glück heute etwas anders.
Im Kontext eines Kongresses in der ehemaligen Parteischule der Sozialistischen Einheitspartei Deutschlands (SED) der ehemaligen DDR kam neulich mal jemand vorbei und erzählt merkwürdige Geschichten: das ungefähr die Hälfte der Stasi-Mitarbeiter kurz vor der sogenannten Wiedervereinigung unter den Tisch gefallen sei. Zunächst war ein etwas toleranter Umgang mit dem Fassungsvermögen der eigenen Hirnstrukturen gefordert: die Mauscheleien zwischen Ost- und Westdiensten, die der junge Mann skizzierte, waren zwar in sich schlüssig, entbehrten allerdings auch nicht einer gewissen Komplexität. Nachweise sollten folgen.
Ein Hinweis war, daß mit der erwähnten Mitarbeiterliste der hauptamtlichen Mitarbeiter etwas nicht stimmte; bestimmte Geburtstage würden in ihnen fehlen. Und damit fängt die Geschichte an, auch wenn dieser Artikel nur eine erste Auflistung von Merkwürdigkeiten liefern kann.
Die Mitarbeiterliste der hauptamtlichen Mitarbeiter ist im Netz verfügbar: mit dem Dateinamen ma_stasi.zip wird man z.B. fündig. Welche Version Ihr allerdings im Netz findet, die von welcher Dienststelle welchen Geheimdienstes modifiziert wurde, kann ich euch nicht sagen.
Als Orientierung kann http://cryptome.org/stasi-list.htm helfen.
Die Struktur dieser Datenbank bzw. Liste besteht aus:
- Personenkennzeichen (PKZ)
Die PKZ ist das Identifikationskennzeichen für DDR-Bürger. Sie setzt sich zusammen aus Geburtsdatum (TTMMJJ), Geschlechtskennzeichen ( 4 = m; 5 = w ), 4-stelliger Ursprungskennziffer (erste Anmeldung) und einer Prüfziffer. Der Algorithmus liegt vor. Die Datenbank der Ursprungskennziffer ist derzeit noch in der Erstellung (schlecht lesbare Papiervorlage). Die Papiere gibt es in Kürze.
- Diensteinheitenschlüssel (AB;CD;EF)
Der Diensteinheitenschlüssel besteht aus 3 Gruppen á zwei Ziffern, wird aber zusammengezogen interpretiert. Er gibt die Einheit des MFS an, bei dem der/diejenige gearbeitet hat.
- Namensfeld (Name, Mittelname, Vorname)
- Gehalt
Die genaue Bedeutung des Gehaltsfeldes ist umstritten. Einige behaupten, es handele sich hier um das Jahresgehalt. Andere sagen, es sei das Gehalt seit Frühjahr 1989. Dritte sagen was ganz anderes. Klar ist:
Die Liste enthält Gehaltszahlen aus denen sich möglicherweise ein Hierarchiestatus interpretieren lässt. Das kann Information oder Desinformation sein.
Häufigkeitsverteilungen von Geburtstagen in einer Liste von hauptamtlichen Mitarbeitern des MfS
| Tag | Jan. | Febr. | März | April | Mai | Juni | Juli | Aug. | Sept. | Okt. | Nov. | Dez. | Sum |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1 | 261 | 292 | 316 | 255 | 271 | 256 | 246 | 288 | 228 | 299 | 259 | 242 | 3 213 |
| 2 | 319 | 292 | 275 | 240 | 279 | 247 | 280 | 263 | 258 | 289 | 253 | 251 | 3 246 |
| 3 | 263 | 260 | 281 | 267 | 277 | 286 | 262 | 254 | 284 | 266 | 261 | 285 | 3 246 |
| 4 | 282 | 255 | 299 | 264 | 271 | 262 | 267 | 242 | 276 | 271 | 276 | 231 | 3 196 |
| 5 | 263 | 292 | 291 | 265 | 273 | 235 | 301 | 256 | 298 | 269 | 250 | 236 | 3 229 |
| 6 | 258 | 288 | 269 | 278 | 284 | 265 | 264 | 271 | 264 | 294 | 251 | 233 | 3 219 |
| 7 | 293 | 295 | 313 | 268 | 301 | 254 | 257 | 284 | 255 | 286 | 258 | 280 | 3 344 |
| 8 | 284 | 291 | 303 | 276 | 263 | 281 | 228 | 243 | 252 | 261 | 290 | 257 | 3 229 |
| 9 | 264 | 280 | 293 | 253 | 312 | 279 | 258 | 241 | 238 | 265 | 278 | 275 | 3 236 |
| 10 | 275 | 285 | 308 | 258 | 273 | 237 | 248 | 255 | 280 | 262 | 271 | 273 | 3 225 |
| 11 | 255 | 285 | 266 | 290 | 282 | 272 | 269 | 298 | 277 | 264 | 247 | 244 | 3 249 |
| 12 | 253 | 293 | 268 | 268 | 256 | 236 | 274 | 248 | 303 | 237 | 281 | 268 | 3 185 |
| 13 | 259 | 275 | 296 | 310 | 242 | 283 | 236 | 260 | 260 | 225 | 270 | 289 | 3 205 |
| 14 | 245 | 273 | 303 | 261 | 261 | 252 | 261 | 256 | 281 | 263 | 246 | 271 | 3 173 |
| 15 | 279 | 294 | 296 | 262 | 288 | 273 | 256 | 265 | 292 | 254 | 223 | 270 | 3 252 |
| 16 | 281 | 259 | 262 | 267 | 307 | 277 | 257 | 245 | 325 | 273 | 265 | 245 | 3 263 |
| 17 | 297 | 2 | 0 | 0 | 0 | 0 | 0 | 0 | 233 | 229 | 246 | 275 | 1 282 |
| 18 | 253 | 289 | 292 | 309 | 280 | 281 | 282 | 254 | 297 | 247 | 270 | 264 | 3 318 |
| 19 | 270 | 308 | 282 | 288 | 259 | 264 | 268 | 267 | 328 | 228 | 251 | 236 | 3 249 |
| 20 | 309 | 291 | 269 | 273 | 303 | 275 | 255 | 245 | 310 | 255 | 263 | 274 | 3 322 |
| 21 | 250 | 286 | 299 | 245 | 279 | 260 | 263 | 236 | 311 | 279 | 267 | 268 | 3 243 |
| 22 | 280 | 287 | 271 | 265 | 241 | 243 | 260 | 265 | 291 | 243 | 245 | 269 | 3 160 |
| 23 | 283 | 259 | 299 | 297 | 288 | 272 | 259 | 268 | 330 | 277 | 268 | 290 | 3 390 |
| 24 | 280 | 283 | 257 | 273 | 287 | 260 | 224 | 263 | 286 | 233 | 238 | 261 | 3 145 |
| 25 | 290 | 333 | 290 | 294 | 282 | 268 | 287 | 261 | 298 | 263 | 254 | 261 | 3 381 |
| 26 | 277 | 266 | 305 | 255 | 284 | 271 | 258 | 245 | 326 | 271 | 285 | 234 | 3 277 |
| 27 | 267 | 312 | 303 | 271 | 253 | 222 | 277 | 276 | 327 | 242 | 269 | 238 | 3 257 |
| 28 | 308 | 289 | 294 | 268 | 279 | 281 | 274 | 268 | 311 | 252 | 265 | 262 | 3 351 |
| 29 | 287 | 71 | 292 | 275 | 279 | 265 | 257 | 275 | 317 | 264 | 250 | 264 | 3 096 |
| 30 | 275 | *** | 311 | 313 | 277 | 268 | 280 | 264 | 289 | 243 | 275 | 265 | 3 060 |
| 31 | 289 | *** | 269 | *** | 254 | *** | 237 | 271 | *** | 239 | *** | 258 | 1 817 |
| Su | 8 549 | 7 785 | 8 672 | 7 908 | 8 285 | 7 625 | 7 845 | 7 827 | 8 625 | 8 043 | 7 825 | 8 069 | 97.058 |
Zunächst sind wir also dem Hinweis auf Unregelmäßigkeiten im Bezug auf die Geburtsdaten nachgegangen. In der Tat scheint es bei der Stasi gewisse geburtenschwache Tage gegeben zu haben; unabhängig vom Geburtsjahr der jeweiligen finden sich weder am 17.03., 17.04., 17.05., 17.06., 17.07., 17.08. irgendwelche Einträge. Am 17.02. finden sich zwar 2 Einträge, allerdings sind beide aus dem Jahrgang 1927. Bei allem Verständnis für historische Aufarbeitung handelt es sich hier offensichtlich um Rentner.
Alle anderen Geburtstage scheinen in der Datenbank sehr gleichmäßig verteilt zu sein. Bei einer groben Annahme (Sollwert) von 100.000 Einträgen, geteilt durch die Anzahl möglicher Geburtstage (365) wäre der mathematische Richtwert 273 Geburten pro Tag. In Unkenntnis etwaiger geburtenschwachen Tage bzw. Monate handelt es sich bei den vorliegenden Zahlen entweder um eine erstaunlich primitiv frisierte Datenbase oder um eine relativ mittelwertgenaue Geburtsanhäufung.
Diese beiden Indikatoren (fehlende 17. und Mittelwert-Genauigkeit) können insofern nur bedingt als Indizien für eine Datenmanipulation gewertet werden. Für beide sind “natürliche” Erklärungen dankbar. Im Bezug auf die fehlenden Geburten an den 17. kann es sich um einen – immerhin 10 Jahre nicht bemerkten – Datenverlust bei der Konvertierung von Datenträgern schlechter Qualität handeln. Ein entsprechender Hinweis auf mögliche Datenträgerschäden liegt aus den Kreisen der konvertierenden Bürgerbewegten vor, konnte allerdings bis Redaktionsschluss noch nicht verifiziert werden. Ob der Indikator der “gleichmäßigen” Verteilung (die Geburten pro Tag bewegen sich alle passgenau um den Mittelwert von 273) gewertet werden kann, kann ich mangels Hinweisen auf etwaige übliche ungleichmäßigen Verteilungen nicht feststellen.
Wesentlich aufschlussreicher und als deutlichster Hinweis kann da schon der Abgleich der vorhandenen Datensätze der hauptamtlichen Mitarbeiter mit dem Diensteinheitenschlüssel gelten. Von den 2286 insgesamt vorhandenen Abteilungen der Staatssicherheit wären beispielsweise 1349 ohne einen einzigen Mitarbeiter. Diese Unterbesetzung ist wohl selbst bei großzügiger Lesart unrealistisch.
Noch deutlicher wird die Manipulation der HA-Datenbank allerdings, wenn man sich die Diensteinheitenzuweisung im Detail anguckt. Als Beispiel für eine etwas detailliertere Analyse sei hier mal die Hauptabteilung III (Funkaufklärung) genommen. Unter dem “generellen” Diensteinheitenschlüssel 940300 finden sich immerhin insgesamt 2312 Mitarbeiter. In den jeweiligen Diensteinheiten finden sich allerdings keine Mitarbeiter. Eine grobe Hierarchie ließe sich zwar aus den Gehaltszahlungen ableiten, aber keine Zuweisung zu den Diensteinheiten.


Diese Strukturverschleierung tritt bei allen Hauptabteilungen auf, in den Bezirksverwaltungen des MfS hingegen ist sie vorhanden. Wenn die Strukturverschleierung in der Datenbank eine grundsätzlich vom MfS betriebene wäre, würde sie wohl kaum die Bezirksverwaltungen außen vor lassen. Als Beispiel hierfür sei willkürlich Leipzig gewählt.


Hier allerdings liegen die Unterabteilungen offen; lediglich auf der Ebene der Leiter fehlen die Hinweise. Und dann gibt es noch Mitarbeiter in Abteilungen, wo nur die Abteilungsschlüssel vorliegen, allerdings nichts über die Abteilungen selbst bekannt ist.
Als Zusammenfassung dieser ersten groben Analyse muss man wohl feststellen, daß aufgrund dieser deutlichen Indikatoren für eine Manipulation der Datenbestände auch die anderen Abteilungszuweisungen nicht wirklich als verlässliche Werte angenommen werden können. In Zusammenhang mit verschiedenen Hinweisen auf den Zeitraum, der der Staatssicherheit für eine Strukturverschleierung bzw. partielle Verlagerung von Personalbeständen in andere Organisationen (Wirtschaftsunternehmen, staatliche geführte Unternehmungen etc.) zur Verfügung stand, könnte man sich schon Sorgen machen. Wenn man dann noch die Hinweise auf die Übernahme des kompletten Personalbestands einzelner Abteilungen durch andere Dienste – z.B. amerikanische – hinzuzieht, kann man sich wahlweise in schlechter Laune oder Aufdeckung aktiver Strukturen üben.
Um eine gründlichere Analyse durchzuführen, gibt es zunächst verschiedene Gedankenspiele. Die meisten Forschungsanträge der Gauck-Behörde und verfügbare Literatur über die Aktivitäten des MfS betreffen beispielsweise eher thematische als strukturelle Belange. Eine systematische Strukturanalyse wäre also in den jeweiligen Bereichen ein möglicher Ansatz.
Weitere mögliche Herangehensweisen wären durch differenzierte Arbeitshypothesen denkbar. Wenn man beispielsweise die offensichtliche Datenmanipulation der Hauptamtlichen-Liste zusammen mit den Rentenansprüchen ehemaliger HA-ler in die These der gewinnträchtigen Einführung von Personen mit mehreren Identitäten umwandelt, gäbe dies Anlass zur Überprüfung gewisser Geburtstage. Viel Spaß am Gerät.
Andy Müller-Maguhn, andy@ccc.de
Wer noch Material beizusteuern hat, ist herzlich eingeladen, dies an die Redaktion Datenschleuder auf elektronischem ( ds@ccc.de) oder postalischem Wege (Postfach 640236, D-10048 Berlin) zu tun.
„Nach langer Verzögerung der Antwort leugnet die Bundesregierung nun weitgehendst die skandalösen Vorgänge, die mir während meiner USA-Reise unmißverständlich berichtet wurden:
[…] daß die CIA derzeit mit tatkräftiger Unterstützung bundesdeutscher Dienste ehemalige Stasi-Offiziere unter Vertrag nimmt.”
Aus einer Presseerklärung der innenpolitischen Sprecherin von Bündnis 90 / Die Grünen vom 10.03.1992, Ingrid Köppe
Ergebnis einer bisher erst groben Analyse von Datenhinterlassenschaften
Manche Artikel basieren auf langen Geschichten. Bei anderen Artikeln ist es genau umgekehrt: Artikel verursachen lange Geschichten. Bei diesem Artikel ist die Geschichte evtl. in beide Richtungen gleich lang. Und zwar ziemlich.
Als die Deutsche Demokratische Republik (DDR) aufgelöst wurde, hat sie neben merkwürdigen Erinnerungen auch noch – so glaubte man – eine der am besten dokumentierten Aktenlage der zweitbesten “politischen Geheimpolizei” der Welt hinterlassen. Die Gauck-Behörde, offiziell “Die Bundesbeauftragte für die Unterlagen des Ministeriums für Staatssicherheit der ehemaligen Deutschen Demokratischen Republik” verwaltet immerhin etliche Tonnen Akten und macht sie den betroffenen – Tätern wie Opfern – mit gewissen datenschutzrechtlichen Einschränkungen zugänglich. Geschichtsaufarbeitung sollte möglich werden.
Die Bürger der ehemaligen DDR schienen erreicht zu haben was sie wollten: das Ministerium für Staatssicherheit (die “Stasi”) war aufgelöst, die DDR auch, ein paar leitende Funktionäre im Gefängnis und die DDR jetzt BRD. Und jetzt kommen wir zu den Schönheitsfehlern dieser Operation.
Bei der Auflösung des Ministeriums für Staatssicherheit wurden ja, wie das neudeutsch so schön heißt, “einige Arbeitskräfte auf den Markt freigesetzt.” Schon die Frage wie viele Mitarbeiter das Ministerium für Staatssicherheit denn hauptamtlich hatte, lässt sich leider nicht so einfach beantworten. Es gibt zwar einen Haufen Akten, und Personallisten, aber die Interpretationen dieses Materials gehen dann doch eher weit auseinander.
Nun war für die Bürger der ehemaligen DDR die Frage, wer denn nun früher für die Stasi gearbeitet hat oder nicht, schon eine Frage. Man wollte schließlich nicht mit den selben Genossen noch einmal die – vermeintlich neuen Staatsstrukturen aufbauen. Hilfreich war u.a. die “Liste der Hauptamtlichen Mitarbeiter des MfS” die seit den frühen 90´er Jahren durch Publikationen der DDR-Bürgerbewegung verbreitet wurde. Sie enthält rund 100.000 Mitarbeiter bzw. Datensätze (genau: 97.058 plus minus ein paar) und gilt – präzise galt – als authentisch. Auch die juristischen Auseinandersetzungen, die die Verbreiter dieser Liste bekamen (“Die Andere” Berlin wegen Abdruck, Neues Forum Halle wegen Auslegen und http://www.nierenspende.de wegen Verbreitung im Netz), sprachen zumindest dafür, daß die Liste echte Namen enthält.
Als die Bürgerbewegten die Daten in den frühen 90er Jahren mit dBase verarbeiten, waren die damals genutzten 386er eher an den Grenzen ihrer Belastung. Bei 100.000 Daten fielen komfortable Suchaktionen und Quervergleiche eher aus. Das ist zum Glück heute etwas anders.
Im Kontext eines Kongresses in der ehemaligen Parteischule der Sozialistischen Einheitspartei Deutschlands (SED) der ehemaligen DDR kam neulich mal jemand vorbei und erzählt merkwürdige Geschichten: das ungefähr die Hälfte der Stasi-Mitarbeiter kurz vor der sogenannten Wiedervereinigung unter den Tisch gefallen sei. Zunächst war ein etwas toleranter Umgang mit dem Fassungsvermögen der eigenen Hirnstrukturen gefordert: die Mauscheleien zwischen Ost- und Westdiensten, die der junge Mann skizzierte, waren zwar in sich schlüssig, entbehrten allerdings auch nicht einer gewissen Komplexität. Nachweise sollten folgen.
Ein Hinweis war, daß mit der erwähnten Mitarbeiterliste der hauptamtlichen Mitarbeiter etwas nicht stimmte; bestimmte Geburtstage würden in ihnen fehlen. Und damit fängt die Geschichte an, auch wenn dieser Artikel nur eine erste Auflistung von Merkwürdigkeiten liefern kann.
Die Mitarbeiterliste der hauptamtlichen Mitarbeiter ist im Netz verfügbar: mit dem Dateinamen ma_stasi.zip wird man z.B. fündig. Welche Version Ihr allerdings im Netz findet, die von welcher Dienststelle welchen Geheimdienstes modifiziert wurde, kann ich euch nicht sagen.
Als Orientierung kann http://cryptome.org/stasi-list.htm helfen.
Die Struktur dieser Datenbank bzw. Liste besteht aus:
- Personenkennzeichen (PKZ)
Die PKZ ist das Identifikationskennzeichen für DDR-Bürger. Sie setzt sich zusammen aus Geburtsdatum (TTMMJJ), Geschlechtskennzeichen ( 4 = m; 5 = w ), 4-stelliger Ursprungskennziffer (erste Anmeldung) und einer Prüfziffer. Der Algorithmus liegt vor. Die Datenbank der Ursprungskennziffer ist derzeit noch in der Erstellung (schlecht lesbare Papiervorlage). Die Papiere gibt es in Kürze.
- Diensteinheitenschlüssel (AB;CD;EF)
Der Diensteinheitenschlüssel besteht aus 3 Gruppen á zwei Ziffern, wird aber zusammengezogen interpretiert. Er gibt die Einheit des MFS an, bei dem der/diejenige gearbeitet hat.
- Namensfeld (Name, Mittelname, Vorname)
- Gehalt
Die genaue Bedeutung des Gehaltsfeldes ist umstritten. Einige behaupten, es handele sich hier um das Jahresgehalt. Andere sagen, es sei das Gehalt seit Frühjahr 1989. Dritte sagen was ganz anderes. Klar ist:
Die Liste enthält Gehaltszahlen aus denen sich möglicherweise ein Hierarchiestatus interpretieren lässt. Das kann Information oder Desinformation sein.
Häufigkeitsverteilungen von Geburtstagen in einer Liste von hauptamtlichen Mitarbeitern des MfS
| Tag | Jan. | Febr. | März | April | Mai | Juni | Juli | Aug. | Sept. | Okt. | Nov. | Dez. | Sum |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1 | 261 | 292 | 316 | 255 | 271 | 256 | 246 | 288 | 228 | 299 | 259 | 242 | 3 213 |
| 2 | 319 | 292 | 275 | 240 | 279 | 247 | 280 | 263 | 258 | 289 | 253 | 251 | 3 246 |
| 3 | 263 | 260 | 281 | 267 | 277 | 286 | 262 | 254 | 284 | 266 | 261 | 285 | 3 246 |
| 4 | 282 | 255 | 299 | 264 | 271 | 262 | 267 | 242 | 276 | 271 | 276 | 231 | 3 196 |
| 5 | 263 | 292 | 291 | 265 | 273 | 235 | 301 | 256 | 298 | 269 | 250 | 236 | 3 229 |
| 6 | 258 | 288 | 269 | 278 | 284 | 265 | 264 | 271 | 264 | 294 | 251 | 233 | 3 219 |
| 7 | 293 | 295 | 313 | 268 | 301 | 254 | 257 | 284 | 255 | 286 | 258 | 280 | 3 344 |
| 8 | 284 | 291 | 303 | 276 | 263 | 281 | 228 | 243 | 252 | 261 | 290 | 257 | 3 229 |
| 9 | 264 | 280 | 293 | 253 | 312 | 279 | 258 | 241 | 238 | 265 | 278 | 275 | 3 236 |
| 10 | 275 | 285 | 308 | 258 | 273 | 237 | 248 | 255 | 280 | 262 | 271 | 273 | 3 225 |
| 11 | 255 | 285 | 266 | 290 | 282 | 272 | 269 | 298 | 277 | 264 | 247 | 244 | 3 249 |
| 12 | 253 | 293 | 268 | 268 | 256 | 236 | 274 | 248 | 303 | 237 | 281 | 268 | 3 185 |
| 13 | 259 | 275 | 296 | 310 | 242 | 283 | 236 | 260 | 260 | 225 | 270 | 289 | 3 205 |
| 14 | 245 | 273 | 303 | 261 | 261 | 252 | 261 | 256 | 281 | 263 | 246 | 271 | 3 173 |
| 15 | 279 | 294 | 296 | 262 | 288 | 273 | 256 | 265 | 292 | 254 | 223 | 270 | 3 252 |
| 16 | 281 | 259 | 262 | 267 | 307 | 277 | 257 | 245 | 325 | 273 | 265 | 245 | 3 263 |
| 17 | 297 | 2 | 0 | 0 | 0 | 0 | 0 | 0 | 233 | 229 | 246 | 275 | 1 282 |
| 18 | 253 | 289 | 292 | 309 | 280 | 281 | 282 | 254 | 297 | 247 | 270 | 264 | 3 318 |
| 19 | 270 | 308 | 282 | 288 | 259 | 264 | 268 | 267 | 328 | 228 | 251 | 236 | 3 249 |
| 20 | 309 | 291 | 269 | 273 | 303 | 275 | 255 | 245 | 310 | 255 | 263 | 274 | 3 322 |
| 21 | 250 | 286 | 299 | 245 | 279 | 260 | 263 | 236 | 311 | 279 | 267 | 268 | 3 243 |
| 22 | 280 | 287 | 271 | 265 | 241 | 243 | 260 | 265 | 291 | 243 | 245 | 269 | 3 160 |
| 23 | 283 | 259 | 299 | 297 | 288 | 272 | 259 | 268 | 330 | 277 | 268 | 290 | 3 390 |
| 24 | 280 | 283 | 257 | 273 | 287 | 260 | 224 | 263 | 286 | 233 | 238 | 261 | 3 145 |
| 25 | 290 | 333 | 290 | 294 | 282 | 268 | 287 | 261 | 298 | 263 | 254 | 261 | 3 381 |
| 26 | 277 | 266 | 305 | 255 | 284 | 271 | 258 | 245 | 326 | 271 | 285 | 234 | 3 277 |
| 27 | 267 | 312 | 303 | 271 | 253 | 222 | 277 | 276 | 327 | 242 | 269 | 238 | 3 257 |
| 28 | 308 | 289 | 294 | 268 | 279 | 281 | 274 | 268 | 311 | 252 | 265 | 262 | 3 351 |
| 29 | 287 | 71 | 292 | 275 | 279 | 265 | 257 | 275 | 317 | 264 | 250 | 264 | 3 096 |
| 30 | 275 | *** | 311 | 313 | 277 | 268 | 280 | 264 | 289 | 243 | 275 | 265 | 3 060 |
| 31 | 289 | *** | 269 | *** | 254 | *** | 237 | 271 | *** | 239 | *** | 258 | 1 817 |
| Su | 8 549 | 7 785 | 8 672 | 7 908 | 8 285 | 7 625 | 7 845 | 7 827 | 8 625 | 8 043 | 7 825 | 8 069 | 97.058 |
Zunächst sind wir also dem Hinweis auf Unregelmäßigkeiten im Bezug auf die Geburtsdaten nachgegangen. In der Tat scheint es bei der Stasi gewisse geburtenschwache Tage gegeben zu haben; unabhängig vom Geburtsjahr der jeweiligen finden sich weder am 17.03., 17.04., 17.05., 17.06., 17.07., 17.08. irgendwelche Einträge. Am 17.02. finden sich zwar 2 Einträge, allerdings sind beide aus dem Jahrgang 1927. Bei allem Verständnis für historische Aufarbeitung handelt es sich hier offensichtlich um Rentner.
Alle anderen Geburtstage scheinen in der Datenbank sehr gleichmäßig verteilt zu sein. Bei einer groben Annahme (Sollwert) von 100.000 Einträgen, geteilt durch die Anzahl möglicher Geburtstage (365) wäre der mathematische Richtwert 273 Geburten pro Tag. In Unkenntnis etwaiger geburtenschwachen Tage bzw. Monate handelt es sich bei den vorliegenden Zahlen entweder um eine erstaunlich primitiv frisierte Datenbase oder um eine relativ mittelwertgenaue Geburtsanhäufung.
Diese beiden Indikatoren (fehlende 17. und Mittelwert-Genauigkeit) können insofern nur bedingt als Indizien für eine Datenmanipulation gewertet werden. Für beide sind “natürliche” Erklärungen dankbar. Im Bezug auf die fehlenden Geburten an den 17. kann es sich um einen – immerhin 10 Jahre nicht bemerkten – Datenverlust bei der Konvertierung von Datenträgern schlechter Qualität handeln. Ein entsprechender Hinweis auf mögliche Datenträgerschäden liegt aus den Kreisen der konvertierenden Bürgerbewegten vor, konnte allerdings bis Redaktionsschluss noch nicht verifiziert werden. Ob der Indikator der “gleichmäßigen” Verteilung (die Geburten pro Tag bewegen sich alle passgenau um den Mittelwert von 273) gewertet werden kann, kann ich mangels Hinweisen auf etwaige übliche ungleichmäßigen Verteilungen nicht feststellen.
Wesentlich aufschlussreicher und als deutlichster Hinweis kann da schon der Abgleich der vorhandenen Datensätze der hauptamtlichen Mitarbeiter mit dem Diensteinheitenschlüssel gelten. Von den 2286 insgesamt vorhandenen Abteilungen der Staatssicherheit wären beispielsweise 1349 ohne einen einzigen Mitarbeiter. Diese Unterbesetzung ist wohl selbst bei großzügiger Lesart unrealistisch.
Noch deutlicher wird die Manipulation der HA-Datenbank allerdings, wenn man sich die Diensteinheitenzuweisung im Detail anguckt. Als Beispiel für eine etwas detailliertere Analyse sei hier mal die Hauptabteilung III (Funkaufklärung) genommen. Unter dem “generellen” Diensteinheitenschlüssel 940300 finden sich immerhin insgesamt 2312 Mitarbeiter. In den jeweiligen Diensteinheiten finden sich allerdings keine Mitarbeiter. Eine grobe Hierarchie ließe sich zwar aus den Gehaltszahlungen ableiten, aber keine Zuweisung zu den Diensteinheiten.


Diese Strukturverschleierung tritt bei allen Hauptabteilungen auf, in den Bezirksverwaltungen des MfS hingegen ist sie vorhanden. Wenn die Strukturverschleierung in der Datenbank eine grundsätzlich vom MfS betriebene wäre, würde sie wohl kaum die Bezirksverwaltungen außen vor lassen. Als Beispiel hierfür sei willkürlich Leipzig gewählt.


Hier allerdings liegen die Unterabteilungen offen; lediglich auf der Ebene der Leiter fehlen die Hinweise. Und dann gibt es noch Mitarbeiter in Abteilungen, wo nur die Abteilungsschlüssel vorliegen, allerdings nichts über die Abteilungen selbst bekannt ist.
Als Zusammenfassung dieser ersten groben Analyse muss man wohl feststellen, daß aufgrund dieser deutlichen Indikatoren für eine Manipulation der Datenbestände auch die anderen Abteilungszuweisungen nicht wirklich als verlässliche Werte angenommen werden können. In Zusammenhang mit verschiedenen Hinweisen auf den Zeitraum, der der Staatssicherheit für eine Strukturverschleierung bzw. partielle Verlagerung von Personalbeständen in andere Organisationen (Wirtschaftsunternehmen, staatliche geführte Unternehmungen etc.) zur Verfügung stand, könnte man sich schon Sorgen machen. Wenn man dann noch die Hinweise auf die Übernahme des kompletten Personalbestands einzelner Abteilungen durch andere Dienste – z.B. amerikanische – hinzuzieht, kann man sich wahlweise in schlechter Laune oder Aufdeckung aktiver Strukturen üben.
Um eine gründlichere Analyse durchzuführen, gibt es zunächst verschiedene Gedankenspiele. Die meisten Forschungsanträge der Gauck-Behörde und verfügbare Literatur über die Aktivitäten des MfS betreffen beispielsweise eher thematische als strukturelle Belange. Eine systematische Strukturanalyse wäre also in den jeweiligen Bereichen ein möglicher Ansatz.
Weitere mögliche Herangehensweisen wären durch differenzierte Arbeitshypothesen denkbar. Wenn man beispielsweise die offensichtliche Datenmanipulation der Hauptamtlichen-Liste zusammen mit den Rentenansprüchen ehemaliger HA-ler in die These der gewinnträchtigen Einführung von Personen mit mehreren Identitäten umwandelt, gäbe dies Anlass zur Überprüfung gewisser Geburtstage. Viel Spaß am Gerät.
Andy Müller-Maguhn, andy@ccc.de
Wer noch Material beizusteuern hat, ist herzlich eingeladen, dies an die Redaktion Datenschleuder auf elektronischem ( ds@ccc.de) oder postalischem Wege (Postfach 640236, D-10048 Berlin) zu tun.
DIE PLUMPEN FÄLSCHUNGEN DER STASI-“GoMoPa” ENTHÜLLT
ehr geehrte Damen und Herren,
die Betrüger und durch uns inhaftierten Erpresser der GoMoPa versuchen mit einer gefälschten Presse-Mitteilung von sich abzulenken und einen investigativen Journalisten, Bernd Pulch, zu belasten.
Die Presse-Mitteilung auf pressreleaser.org ist eine Fälschung und die gesamte Webseite ist der GoMoPa zu zuordnen.
Hier noch einmal die tatäschlichen Geschehnisse:
Hier der Artikel von “GoMoPa” über Meridian Capital.
 „GoMopa“ schreibt:08.09.2008 „GoMopa“ schreibt:08.09.2008Weltweite Finanzierungen mit WidersprüchenDie Meridian Capital Enterprises Ltd. gibt an, weltweite Finanzierungen anbieten zu können und präsentiert sich hierbei auf aufwendig kreierten Webseiten. GOMOPA hat die dort gemachten Angaben analysiert und Widersprüche entdeckt.Der FirmensitzDer Firmensitz befindet sich laut eigener Aussage in Dubai, Vereinigte Arabische Emirate. In einem GOMOPA vorliegenden Schreiben der Meridian Capital Enterprises Ltd. heißt es jedoch, der Firmensitz sei in London. Auf der Homepage des Unternehmens taucht die Geschäftsadresse in der Londoner Old Broad Street nur als „Kundenabteilung für deutschsprachige Kunden“ auf. Eine weitere Adresse in der englischen Hauptstadt, diesmal in der Windsor Avenue, sei die „Abteilung der Zusammenarbeit mit Investoren“.Die Meridian Capital Enterprises ist tatsächlich als „Limited“ (Ltd.) mit Sitz in England und Wales eingetragen. Aber laut Firmenhomepage hat das Unternehmen seinen „rechtlichen Geschäftssitz“ in Dubai. Eine Abfrage beim Gewerbeamt Dubais (DED) zu dieser Firmierung bleibt ergebnislos.Bemerkenswert ist auch der vermeintliche Sitz in Israel. Auf der Webseite von Meridian Capital Enterprises heißt es: „Die Firma Meridian Capital Enterprises Ltd. ist im Register des israelischen Justizministeriums unter der Nummer 514108471, gemäß dem Gesellschaftsrecht von 1999, angemeldet.“ Hierzu Martin Kraeter, Gomopa-Partner und Prinzipal der KLP Group Emirates in Dubai: „Es würde keinem einzigen Emirati – geschweige denn einem Scheich auch nur im Traum einfallen, direkte Geschäfte mit Personen oder Firmen aus Israel zu tätigen. Und schon gar nicht würde er zustimmen, dass sein Konterfei auch noch mit vollem Namen auf der Webseite eines Israelischen Unternehmens prangt.“Auf der Internetseite sind diverse Fotos mit Scheichs an Konferenztischen zu sehen. Doch diese großen Tagungen und großen Kongresse der Meridian Capital Enterprises werden in den Pressearchiven der lokalen Presse Dubais mit keinem Wort erwähnt. Martin Kraeter: „ Ein ‚britisch-arabisch-israelisches bankfremdes Finanzinstitut sein zu wollen, wie die Meridian Capital Enterprises Ltd. es darstellt, ist mehr als zweifelhaft. So etwas gibt es schlicht und ergreifend nicht! Der Nahostkonflikt schwelt schon seit mehr als 50 Jahren. Hier in den Vereinigten Arabischen Emiraten (VAE) werden Israelis erst gar nicht ins Land gelassen. Israelische Produkte sind gebannt. Es gibt nicht einmal direkte Telefonverbindungen. Die VAE haben fast 70% der Wiederaufbaukosten des Libanon geschultert, nachdem Israel dort einmarschiert ist.“Zwei angebliche Großinvestitionen der Meridian Capital Enterprises in Dubai sind Investmentruinen bzw. erst gar nicht realisierte Projekte. Das Unternehmen wirbt mit ihrer finanziellen Beteiligung an dem Dubai Hydropolis Hotel und dem Dubai Snowdome. Der Aktivitätsstatus der Meridian Capital Enterprises Ltd. ist laut englischen Handelsregister (UK Companies House) „dormant“ gemeldet. Auf der Grundlage des englischen Gesellschaftsrechts können sich eingetragene Unternehmen selbst „dormant“ (schlafend) melden, wenn sie keine oder nur unwesentliche buchhalterisch zu erfassende Transaktionen vorgenommen haben. Dies ist angesichts der angeblichen globalen Investitionstätigkeit der Meridian Capital Ltd. sehr erstaunlich. Der Webauftritt Die Internetseite der MCE ist sehr aufwendig gestaltet, die Investitionen angeblich in Millionen- und Milliardenhöhe. Bei näherer Betrachtung der Präsentationselemente fällt jedoch auf, dass es sich bei zahlreichen veröffentlichen Fotos, die Veranstaltungen der Meridian Capital Enterprises dokumentieren sollen, meist um Fotos von Online-Zeitungen oder frei zugänglichen Medienfotos einzelner Institutionen handelt wie z.B. der Börse Dubai. Auf der Internetpräsenz befinden sich Videofilmchen, die eine frappierende Ähnlichkeit mit dem Werbematerial von NAKHEEL aufweisen, dem größten Bauträger der Vereinigten Arabischen Emirate. Doch den schillernden Videos über die berühmten drei Dubai Palmen „Jumeirah, Jebel Ali und Deira“ oder das Archipel „The World“ wurden offensichtlich selbstproduzierte Trailersequenzen der Meridian Capital Enterprises vorangestellt. Doch könnte es sich bei den Werbevideos um Fremdmaterial handeln. Auch die auf der Webseite wahllos platzierten Fotos von bekannten Sehenswürdigkeiten Dubais fungieren als Augenfang für den interessierten Surfer mit eigenem Finanzierungswunsch. Bei einem Volumen von 10 Millionen Euro oder höher präsentiert sich die Meridian Capital Enterprises Ltd. als der passende Investitionspartner. Das Unternehmen verfügt weltweit über zahlreiche Standorte: Berlin, London, Barcelona, Warschau, Moskau, Dubai, Riad, Tel Aviv, Hong Kong und New York. Aber nahezu alle Standorte sind lediglich Virtual Offices eines global arbeitenden Büroservice-Anbieters. „Virtual Office“ heißt im Deutschen schlicht „Briefkastenfirma“. Unter solchen Büroadressen sollen laut Meridian Capital Enterprises ganze Kommissionen ansässig sein, alles zum Wohle des Kunden.“ Zitatende |
Hier die Hintergründe der Erpressung:
Hier unsere Original-Stellungnahme:
Anfang Oktober 2008 erhielt einer der Arbeiter der Meridian Capital Enterprises Ltd. eine Meldung von einem anonymen Sender, dass in naher Zukunft – zuerst im Internet, dann im Fernsehen, im Radio und in der deutschen Presse – Informationen erscheinen, die die Funktionsweise und Tätigkeiten der Meridian Capital Enterprises Ltd. in einem äußerst negativen Licht darstellen. Der Mitarbeiter der Meridian Capital Enterprises Ltd. wurde also informiert, dass diese Meldungen/Nachrichten zweifelsohne deutlich das Aussehen und den guten Ruf der Firma Meridian Capital Enterprises Ltd. beeinträchtigen.
Der an dieser Stelle erwähnte „Gesprächspartner” hat den Arbeiter der Meridian Capital Enterprises Ltd. informiert, dass die Möglichkeit besteht die peinliche Situation zu vermeiden, indem die Meridian Capital Enterprises Ltd. auf das von der Person gezeigte Konto die Summe von 100.000,00 EUR überweist. Wie sich aber später zeigte, war der Herr Klaus Maurischat – dieser anonyme Gesprächspartner – „Gehirn“ und „Lider des GOMOPA“. Die Ermittlungen wurden angestellt durch die Bundeskriminalpolizei (Verfolgungs- und Ermittlungsorgan auf der Bundesebene) während des Ermittlungsverfahrens wegen einer finanziellen Erpressung, Betrügereien auch wegen der Bedrohungen, welche von Herrn Maurischat und seine Mitarbeiter praktiziert wurden sowie wegen Teilnahme anderer (Leiter der Internetservices und Moderatoren der Blogs) an diesem Prozedere. Diese Straftaten wurden begangen zu Schaden vieler Berufs- und Justizpersonen, darunter auch der Meridian Capital Enterprises Ltd. Die Opfer dieses Verbrechens sind in Deutschland, Österreich, der Schweiz, Spanien, Portugal, Großbritannien, den USA und Kanada sichtbar.
In diesem Moment taucht folgende Frage auf: Wie war die Reaktion der Meridian Capital Enterprises Ltd. auf die Forderungen seitens GOMOPA? Entsprach die Reaktion den Erwartungen von GOMOPA? Hat die Meridian Capital Enterprises Ltd. die geforderte Summe 100.000,00 EUR überwiesen?
Seites der Meridian Capital Enterprises Ltd. gab es überhaupt keine Reaktion auf den Erpressungsversuch von GOMOPA. Ende August 2008 auf dem Service http://www.gompa.net sind zahlreiche Artikel/Meldungen erscheinen, welche die Tätigkeit der Meridian Capital Enterprises Ltd. in einem sehr negativen Licht dargestellt haben. Nachdem die auf http://www.gomopa.net enthaltenen Informationen ausführlich und vollständig analysiert worden waren, ergab es sich, dass sie der Wahrheit nicht einmal in einem Punkt entsprechen und potenzielle und bereits bestehende Kunden der Meridian Capital Enterprises Ltd. in Bezug auf die von diesem Finanzinstitut geführten Geschäftstätigkeit irreführen. Infolge der kriminellen Handlugen von GOMOPA und der mit ihm kooperierenden Services und Blogs im Netz hat die Meridian Capital Enterprises Ltd. beachtliche und messbare geschäftliche Verluste erlitten. Die Meridian Capital Enterprises Ltd. hat nämlich in erster Linie eine wichtige Gruppe von potenziellen Kund verloren. Was sich aber als wichtiger ergab, haben sich die bisherigen Kunden von der Meridian Capital Enterprises Ltd. kaum abgewandt. Diejenigen Kunden haben unsere Dienstleitungen weiterhin genutzt und nutzen die immer noch. In Hinblick auf die bisherige Zusammenarbeit mit der Meridian Capital Enterprises Ltd., werden ihrerseits dem entsprechend keine Einwände erhoben .
GOMOPA hat so einen Verlauf der Ereignisse genau prognostiziert, dessen Ziel beachtliche und messbare geschäftliche durch die Meridian Capital Enterprises Ltd. erlittene Verluste waren. Der Verlauf der Ereignisse hat das Service GOMOPA mit Sicherheit gefreut. GOMOPA hat nämlich darauf gerechnet, dass die Stellung der Meridian Capital Enterprises Ltd. nachlässt und das Finanzinstitut die geforderte Summe (100.000,00 EUR) bereitstellt. Im Laufe der Zeit, als das ganze Prozedere im Netz immer populärer war, versuchte GOMOPA noch vier mal zu der Meridian Capital Enterprises Ltd. Kontakte aufzunehmen, indem es jedes mal das Einstellen dieser kriminellen „Kompanie” versprochen hat, wobei es jedes mal seine finanziellen Forderungen heraufsetzte. Die letzte für das Einstellen der „Kompanie“ gegen die Meridian Capital Enterprises Ltd. vorgesehene Quote betrug sogar 5.000.000,00 EUR (in Worten: fünfmilionen EURO). Die Meridian Capital Enterprises Ltd. konnte sich aber vor den ständig erhöhenden Forderungen seitens des Services GOMOPA behaupten.
Im Oktober 2008 traf die Leitung der Meridian Capital Enterprises Ltd. Entscheidung über die Benachrichtigung der Internationalen Polizei INTERPOL sowie entsprechender Strafverfolgungsorgane der BRD (die Polizei und die Staatsanwaltschaft) über den bestehenden Sachverhalt. In der Zwischenzeit meldeten sich bei der Meridian Capital Enterprises Ltd. zahlreiche Firmen und Korporationen, sogar Berufsperson wie Ärzte, Richter, Priester, Schauspieler und anderen Personen aus unterschiedlichen Ländern der Welt, die der Erpressung von GOMOPA nachgegeben und die geforderten Geldsummen überwiesen haben. Diese Personen gaben bereits Erklärungen ab, dass sie dies getan haben, damit man sie bloß endlich „in Ruhe lässt” und um unnötige Probleme, Schwierigkeiten und einen kaum begründbaren Ausklang vermeiden zu können. Die Opfer dieses kriminellen Vorgehens haben die Meridian Capital Enterprises Ltd. über unterschiedliche Geldsummen, welche verlangt wurden, informiert.
In einem Fall gab es verhältnismäßig kleine (um ein paar tausend EURO), in einem anderen Fall handelte es schon um beachtliche Summen (rund um paar Millionen EURO).
Zusätzlich wendeten sich an die Meridian Capital Enterprises Ltd. Firmen, welche dem GOMOPA noch keine „Gebühr” überweisen haben und bereits überlegen, ob sie dies tun sollen, oder nicht. Diese Firmen erwarteten von der Meridian Capital Enterprises Ltd. eine klare Stellungnahme sowie eine professionelle praktische Beratung, wie man sich in solch einer Lage verhalten soll und wie man diese Geldforderungen umgehen kann. Die Meridian Capital Enterprises Ltd. hat ausnahmslos allen Verbrechensopfern, welche sich bei unserer Firma gemeldet haben, eine Zusammenarbeit vorgeschlagen. Als oberste Aufgabe stellt sich diese Kooperation, gemeinsam entschlossene und wirksame Maßnahmen gegen GOMOPA, gegen andere Services im Netz sowie gegen alle Bloggers zu treffen, die an dem hier beschriebenen internationalen kriminellen Vorgehen mit GOMOPA-Führung teilnehmen.Auf unsere Bitte benachrichtigten alle mitbeteiligten Firmen die Internationale Polizei INTERPOL sowie ihre heimischen Verfolgungsorgane, u. a. die zuständige Staatsanwaltschaft und die Polizeibehörden über den bestehenden Sachverhalt.
In Hinblick auf die Tatsache, dass das verbrecherische Handeln von GOMOPA sich über viele Staaten erstreckte und dass die Anzahl der in der Bundesrepublik Deutschland erstatteten Anzeigen wegen der durch GOMOPA, Internetservices und Bloggers begangenen Straftaten, rasant wuchs – was zweifelsohne von einer weit gehenden kriminellen Wirkungskraft des GOMOPA zeugt – schlug die Internationale Wirtschaftspolizei INTERPOL der Meridian Capital Enterprises Ltd. vor, dass sich ihr Vertreter in Berlin mit dem Vertreter von GOMOPA trifft, um die „Zahlungsmodalitäten“ und Überweisung der Summe von 5.000.000,00 EUR zu besprechen. Dieser Schritt meinte, eine gut durchdachte und durch die Bundeskriminalpolizei organisierte Falle durchzuführen, deren Ziel die Festnahme der unter GOMOPA wirkenden internationalen Straftäter war.
Die koordinierten Schritte und Maßnahmen der Meridian Capital Enterprises Ltd. und anderer Beschädigter, geleitet von der Internationalen Wirtschaftspolizei INTERPOL, dem Bundeskriminalamt und der Staatsanwaltschaft der Bundesrepublik Deutschland haben zur Aus-, Einarbeitung und Durchführung der oben beschriebenen Falle beigetragen. Im November 2008 führte die in Berlin vorbereitete Falle zur Festnahme und Verhaftung des Vertreters des GOMOPA, der nach der Festnahme auf Herrn Klaus Maurichat – als den Hauptverantwortlichen und Anführer der internationalen kriminellen Gruppe GOMOPA verwies. Der Festgenommene benannte und zeigte der Bundeskriminalpolizei zugleich den aktuellen Aufenthaltsort des Herrn Klaus Maurischat. „Gehirn“ und Gründer dieser internationalen kriminellen Gruppe GOMOPA, Herr Klaus Maurischat wurde am selben Tag auch festgenommen und auf Frist verhaftet, wird bald in Anklagezustand gestellt, wird die Verantwortung für eigene Straftaten und die des Forums GOMOPA vor einem zuständigen Bundesgericht tragen. Die Meridian Capital Enterprises Ltd. unternahm bereits alle möglichen Schritte, damit Herr Klaus Maurischat auch auf der Anklagebank des zuständigen Gerichts des Vereinigten Königsreiches Großbritannien erscheint. Unter den beschädigten Berufs- und Justizpersonen aus Großbritannien, neben der Meridian Capital Enterprises Ltd. gibt es noch viele Opfer von GOMOPA…
Die dreisten Verbrecher wagen es unter http://www.pressreleaser.org, einer eigenen “GoMoPa”-Seite unsere Pressemitteilung oben zu verfälschen und unschuldige Personen zu belasten.
“GoMoPa” Boss is Jochen Resch
- May 15, 2011 – 1:15 pm
- Posted in Uncategorized
- Comments Off
Dear Readers,
after a thorough research we are sure that the real “GoMoPa” boss is Jochen Resch, lawyer in Berlin, Germany. He is the brain behind “GoMoPa” and responsable for blackmailing, extortion, racketeering, cybermurder and murder – in the tradition of the East German “Inteeligence” STASI that is why he called “GoMoPa” – Financial “Intelligence” Service .
Webmaster
Meridian Capital about GoMoPa
“GoMoPa” in detention
- May 13, 2011 – 1:02 pm
- Posted in Uncategorized
- Comments Off
Meridian Capital Enterprises Ltd.. unveils new criminal phenomena in network. In recently appeared on the net more often at the same time a new a very worrying phenomenon of criminal nature. Professional criminals groups in the network are taking part, to extortion, fraud, Erschwindeln relating to certain specifically selected companies and businesses are capable of. These criminals developed new methods and means, simply and in a short time to bereichern.Strategien and manifestations, which underlie this process are fairly simple. A criminal is looking to “carefully” on the Internet specific companies and corporations (victims of crime) and informed them in the next step, that of the business activities of such companies and corporations in the near future – first on the Internet then in other available mass media – numerous and very unfavorable information appears. At the same time, the criminals beat their future victims an effective means of reducing unnecessary difficulties and problems to escape the loss of good name and image of the company and corporate sector. These offenders are aware of that reputation, name and appearance of each company is a value in itself. It was therefore a value of what each company is prepared to pay any price. But the reason for difficulties and problems arising from the loss of good name and reputation result. The criminals and their victims are already aware that this loss is devastating consequences might have been the closing down of a particular business can enforce. It takes both to No as well as at large companies regard. The company is concerned that in virtually every industry in each country and cross-border activities sind.Das criminal procedure in the form of a blackmail on money, a fraud is becoming rapidly and globally, ie led cross-border and internationally. Among the victims of extortion, fraud is now looking both at home (domestic) and international corporations, the major emphasis on conservation, keeping and maintaining their reputation in the business according to their credibility lay. The criminals in the network have understood that maintaining an unassailable reputation and name of a company the unique ability to provide fast and easy enrichment forms. The above-mentioned criminal procedure is difficult to track because it is international in nature, and by overlapping or even nonexistent (fictional) professional and judicial persons in various countries and operated company wird.Diese offenders in the network publish it and disseminate false information about your victims on remote servers, which are not uncommon in many exotic countries. There are those countries in which serious gaps in the legal system, investigative and prosecution procedures are visible. As an example, at this point mention India werden. Mit criminals working in the network grid portals known leader of blogs with your seat-consciously or unconsciously, even in highly developed countries. For example, at this point, countries such as Germany, Austria, Switzerland, the United States, Britain, Spain or Portugal are mentioned. The below listed criminals were able to act unpunished today. As a symptom of such action appears here the activity and “effectiveness” of the company GOMOPA, which is on countries such as Germany, Switzerland, Austria, the United States, Britain, Spain and India. A good example of such an action is Mr. Klaus Mauri Chat – the leader and “brain” of the company GOMOPA with many already in force and criminal judgments “on his account”, which in this way for years and funded its maintenance in the industry almost unlimited activity. This status will change dramatically, however, including far and wide thanks to discontinued operations of the firm Meridian Capital Enterprises Ltd.. who would oppose such offenses addressed in the network. Other companies and corporations, in which the crime network and outside of this medium have fallen victim to contribute to combating such crimes bei.Die situation is changing, thanks to effective steps and the successful cooperation of the firm Meridian Capital Enterprises Ltd.. with the international police Interpol, with the federal agency (FBI) in the U.S., the Federal Criminal Police in Germany, with Scotland Yard in Britain, as well as with the Russian secret service FSB.Die Meridian Capital Enterprises Ltd.. – Together with other companies and cooperations, the victim of criminal activities of the network of crime have fallen – has undeniably already started to yield results. The fact that in recent weeks (November 2008) on the territory of the Federal Republic of Germany of the above-mentioned leaders and “brain” of the company GOMOPA, Mr Klaus Maurishat was arrested should not be ignored. The Meridian Capital Enterprises Ltd.. information available results clearly show that the next arrests of persons participating in this process in such countries as: Austria, Switzerland, Russia, Ukraine, Poland, Spain, Mexico, Portugal, Brazil, the USA, Canada, UK, Ireland , Australia, New Zealand and made in a.. The ultimate goal of Meridian Capital Enterprises Ltd.. and the other victims of crime in the network is to provide all participants in this criminal procedure before the competent court to lead. All professional and judicial persons, regardless of the seat and out of the business, which the above-described criminal action (fraud, extortion) to have fallen victim can of Meridian Capital Enterprises Ltd.. led company to join the goal set at all at this point the procedure described those associated in the public and the economic life out. II blacklist blackmail and with international fraudsters and their methods (opus operandi) in the following countries: 1 The Federal Republic Deutschland2. Dubai 3rd Russia 1st The Federal Republic of Germany GmbH GOMOPA, Goldman Morgenstern & Partners LLC., Goldman Morgenstern & Partners Consulting LLC, Wottle collection. In these firms are quite active following persons: – Klaus Mauri Chat ( “Father” and “brain” of the criminal organization responsible for countless final judgments have been achieved (arrested in Germany in November 2008) – Josef Rudolf Heckel ( “right hand “when Mr Klaus Mauri chat, denounced former banker who is excessive in many Bankschmuggeleien was involved.
The study of 900 pages named Toxdat by Ehrenfried Stelzer is the “Stasi Killer Bible”. It lists all kind of murder methods and concentrates on the most effective and untraceable.
“The toxdat study was ordered by Stasi Vice-President Gerhard Neiber, the second man in rank after boss Erich Mielke. The toxdat study was also the theoretical “story book” for the murder of the famous German watchdog and journalist Heinz Gerlach by former Stasi member under the guidance of “GoMoPa”,” an informer stated. “Ehrenfried stelzer” was nicknamed “Professor Murder” by his victims. Even close co-worker now compare him with the German SS”doctor” Mengele, “Dr. Death” from Auschwitz.
Only two articles let the German audience believe that the famous journalist and watchdog Heinz Gerlach died on natural courses by blood pollution.
For more Information the victims have launched a new site: http://www.victims-opfer.com
The first one, published only hours after the death of Mr Heinz Gerlach by the notorious “GoMoPa” (see article below) and a second 3 days later by a small German local newspaper, Weserbergland Nachrichten.
Many people including the hostile Gerlach website “Akte Heinz Gerlach” doubted that this man who had so many enemies and friends would die of natural causes without any previous warning. Rumours occured that Mr. Gerlach’s doctor doubted natural courses at all. After many critical voices discussed the issue a small website of a small German local newspaper – which never before had reported about Mr. Heinz Gerlach and which is not even in the region of Mr Gerlachs home – published that Mr Gerlach died of blood pollution. Weserbergland-Nachrichten published a long article about the deadly consequences of blood pollution and did not even name the source of such an important statement. It claimed only that somebody of Gerlachs inner circle had said this. It is a proven fact that after the collpase of the Eastern German Communist Regime many former Communist propaganda agents went to regional newspapers – often in Western Germany like Günther Schabowski did the man who opened the “Mauer”.
The theatre stage was set: One day later the hostile Gerlach website “Akte Heinz Gerlach” took the agenda publishing that Mr Gerlach had died for natural causes without any further research at all.
This was done by a website which for months and months and months reported everything about Mr. Gerlach.
Furthermore a research proves that the technical details regarding the website hosting of this hostile website “Akte Heinz Gerlach” proves that there are common details with the hosting of “GoMoPa” and their affiliates as proven by the SJB-GoMoPa-victims (see http://www.sjb-fonds-opfer.com)
Insiders believe that the murderers of Mr. Heinz Gerlach are former members of the Eastern German Terror Organisation “Stasi” with dioxins. They also believe that “GoMoPa” was part of the plot. At “GoMoPa”’ a person named Siegfried Siewers was officialy responsible for the press but never appeared in public. “GoMoPa”-victims say that this name was a cameo for “GoMoPa” frontrunner Klaus Maurischat who is controlled by the Stasi Top Agent Ehrenfried Stelzner, Berlin.
Siegfried Sievers, a former Stasi member is responsible for the pollution of millions Germanys for many years with dioxins. This was unveiled at 5th of January 2011 by German prosecutors.
The victims say that Maurischat (probably also a Stasi cameo) and Sievers were in contact as Sievers acted as Stasi Agent and was in fact already a specialist in dioxins under the Communist Terror Regime in Eastern Germany.
Furthermore the Stasi Top Agent Ehrenfried Stelzer disguised as Professor for Criminal studies during the Communist Regime at the Eastern Berlin Humboldt University.
Background:
The man behind the Berlin lawyer Jochen Resch and his activities is Ehrenfried Stelzer, former Stasi Top officer in Berlin and “Professor for Criminal Studies” at the Eastern Berlin Humboldt University during the Communist regime, the SJB-GoMoPa-victims say (www.sjb-fonds-opfer.com) is responsable for the killing of German watchdog and journalist Heinz Gerlach.
These informations stem from various sources who were close to the criminal organization of GoMoPa in the last years. The SJB-GoMoPa say that the well-known German watchdog and journalist Heinz Gerlach was killed by former Stasi members with dioxins. Polychlorinated dibenzodioxins (PCDDs), or simply dioxins, are a group of organic polyhalogenated compounds that are significant because they act as environmental pollutants. They are commonly referred to as dioxins for simplicity in scientific publications because every PCDD molecule contains a dioxin skeletal structure. Typically, the p-dioxin skeleton is at the core of a PCDD molecule, giving the molecule a dibenzo-p-dioxin ring system. Members of the PCDD family have been shown to bioaccumulate in humans and wildlife due to their lipophilic properties, and are known teratogens, mutagens, and confirmed (avered) human carcinogens. They are organic compounds.
Dioxins build up primarily in fatty tissues over time (bioaccumulate), so even small exposures may eventually reach dangerous levels. In 1994, the US EPA reported that dioxins are a probable carcinogen, but noted that non-cancer effects (reproduction and sexual development, immune system) may pose an even greater threat to human health. TCDD, the most toxic of the dibenzodioxins, is classified as a Group 1 carcinogen by the International Agency for Research on Cancer (IARC).
In 2004, a notable individual case of dioxin poisoning, Ukrainian politician Viktor Yushchenko was exposed to the second-largest measured dose of dioxins, according to the reports of the physicians responsible for diagnosing him. This is the first known case of a single high dose of TCDD dioxin poisoning, and was diagnosed only after a toxicologist recognized the symptoms of chloracne while viewing television news coverage of his condition.
German dioxin scandal: In January 2011 about 4700 German farms were banned from making deliveries after tests at the Harles und Jentzsch plant in the state of Schleswig-Holstein showed high levels of dioxin. Again this incident appears to involve PCBs and not PCDDs at all. Dioxin were found in animal feed and eggs in many farms. The person who is responsible for this, Siegfried Sievert is also a former Stasi Agent. At “GoMoPa” the notorious Eastern-Berlin press agency (see article below) one of the henchmen acted under the name of “Siegfried Siewert”.
Further evidence for the killing of Mr.Heinz Gerlach is provided by the SJB-GoMoPa-victims by analyzing the dubious role of former Stasi-Top-agent Ehrenfried Stelzer, also a former “Professor for Crime Studies” under the Communist regime in Eastern Germany and the dubious role of “detective” Medard Fuchsgruber. Both are closely tied to the dubious “GoMoPa” and Berlin lawyer Jochen Resch.
According to the SJB-GoMoPa-victims is Berlin lawyer Jochen Resch the mastermind of the criminal organization “GoMoPa2. The victims state that they have a source inside “GoMoPa” who helped them discover the shocking truth. The so-called “Deep Throat from Berlin” has information that Resch had the idea to found the criminal organization “GoMoPa” and use non-existing Jewish lawyers named Goldman, Morgenstern & Partner as camouflage. Their “office” in Madison Avenue, New York, is a mailbox. This is witnessed by a German Ex-Patriot, a lawyer, whose father, Heinz Gerlach, died under strange circumstances.
Resch seems to use “GoMoPa” as an instrument to blackmail parts of the German Property and Investment.
German authorities are under growing pressure to reopen investigations into at least a dozen suspicious deaths after the arrest of an alleged East German assassin cast new light on the communist regime. Stasi victims quoted a source saying “isolated units” had conducted operations that were “extremely well organised” and had “100 per cent logistical support” from the East German state.
A statement from prosecutors read: “The accused [Jurgen G] is suspected, as a member of a commando of the former DDR, of killing a number of people between 1976 and 1987 who from the point of view of the DDR regime had committed treason or were threatening to do so.”
Details of his Jurgen G’s arrest have been described in suitably florid terms, with the mass circulation tabloid Bild saying he was working at the Wolfsbruch marina near Rheinsberg in north-eastern Germany when a woman approached him. “Excuse me, is that your yellow Trabant in the car park? I just ran into it with my car,” she is said to have asked.
When he followed her to the car park, masked officers jumped out of vans and bushes and overpowered him in an operation worthy of the Stasi itself.
An eyewitness told Bild: “They blindfolded him and raced off in an unmarked car.”
Police across Germany are reported to be sifting through files to see who the victims may have been, and some intelligence officers are greeting the arrest of Jurgen G as a breakthrough.
Thomas Auerbach, who works for the Stasi file authority in Berlin and has written a book based on the death squad files, said: “These people were trained to make such murders look like accidents or suicides, even as ‘ordinary’ crimes such as robberies. They were real terror experts.”
The cases said to be linked to Jurgen G or his unit include many people involved with the commercial arm of the East German ruling socialist party, the SED (Socialist Unity Party).
Uwe Harms, the head of a Hamburg-based haulage firm which was part of a network of companies secretly owned by the SED, disappeared in March 1987 after conversations with various DDR functionaries. Six weeks later, his body was found in a plastic bag.
Weeks before his death he told friends that he felt he was being followed. After reunification, one of the other SED company heads said Mr Harms had been liquidated for refusing to allow his firm to be used to transport arms into East Germany.
Dieter Vogel, a businessman who had been jailed for life for spying for the CIA, was found suffocated in his cell in the East German prison Bautzen on March 9, 1982. The fact that he was due to be taken to the West in a spy swap arrangement just a few weeks later cast doubt on the suicide theory.
He had passed the names of several Stasi moles to the BND, West Germany’s heavily penetrated counter-intelligence service.
The Christian Democrat Union politician Uwe Barschel, 43, was found dead by magazine reporters in his bathtub in a hotel room in Geneva in October, 1987. He died of poisoning, but rumours that he was involved somehow in arms deals and the Stasi have clung to the case.
One of the more high-profile and enduring mysteries is that of Lutz Eigendorf, an East German footballer from the Stasi-backed Dynamo Berlin.
He fled to the West in 1979 amid great publicity. Four years later, he died after crashing his car into a tree on a straight stretch of road with blood alcohol levels way over the limit. Witnesses who had seen him earlier in the evening said he had not been drinking.
Most controversial though is the suggestion that the assassination squad was linked to the murder of a Swedish television reporter and her friend in 1984.
Cats Falk and her friend Lena Graens went missing on Nov 19, 1984. Their bodies were fished out of a Stockholm canal six months later.
Reports suggested a three-man assassination squad killed them, spiking their drinks with drugs, putting them into their car and pushing it into the Hammarby canal.
Shortly before her death, Cats Falk had reportedly uncovered a deal between an arms dealer and an East German firm.
Germany has recently undergone a wave of nostalgia for all things East German, dubbed Ostalgie, with colourful television shows featuring former DDR stars such as the ice skater Katerina Witt talking wistfully about socialist pop music.
A reassessment may be coming in the wake of the revelations.
Victims: The DDR-STASI MURDER GANG “GoMOPa” in murderoplot against Joerg Berger
The Stasi Murder Gang of „GoMoPa“ was involved in many trials to kill the popular East German soccer trainer Joerg Berger, Stasi victims tell in postings on their hompage http://www.sjb-fonds-opfer.com. Berger stated before his early death in his biography that they tried to pollute him with arsenic.
Arsenic and many of its compounds are especially potent poisons. Many water supplies close to mines are contaminated by these poisons. Arsenic disrupts ATP production through several mechanisms. At the level of the citric acid cycle, arsenic inhibits lipoic acid which is a cofactor for pyruvate dehydrogenase; and by competing with phosphate it uncouples oxidative phosphorylation, thus inhibiting energy-linked reduction of NAD+, mitochondrial respiration and ATP synthesis. Hydrogen peroxide production is also increased, which might form reactive oxygen species and oxidative stress. These metabolic interferences lead to death from multi-system organ failure, probably from necrotic cell death, not apoptosis. A post mortem reveals brick red coloured mucosa, owing to severe haemorrhage. Although arsenic causes toxicity, it can also play a protective role.[
Elemental arsenic and arsenic compounds are classified as “toxic” and “dangerous for the environment” in the European Union under directive 67/548/EEC. The International Agency for Research on Cancer (IARC) recognizes arsenic and arsenic compounds as group 1 carcinogens, and the EU lists arsenic trioxide, arsenic pentoxide and arsenate salts as category 1 carcinogens.
Arsenic is known to cause arsenicosis owing to its manifestation in drinking water, “the most common species being arsenate [HAsO42- ; As(V)] and arsenite [H3AsO3 ; As(III)]”. The ability of arsenic to undergo redox conversion between As(III) and As(V) makes its availability in the environment more abundant. According to Croal, Gralnick, Malasarn and Newman, “[the] understanding [of] what stimulates As(III) oxidation and/or limits As(V) reduction is relevant for bioremediation of contaminated sites (Croal). The study of chemolithoautotrophic As(III) oxidizers and the heterotrophic As(V) reducers can help the understanding of the oxidation and/or reduction of arsenic.
Treatment of chronic arsenic poisoning is easily accomplished. British anti-lewisite (dimercaprol) is prescribed in dosages of 5 mg/kg up to 300 mg each 4 hours for the first day. Then administer the same dosage each 6 hours for the second day. Then prescribe this dosage each 8 hours for eight additional days. However the Agency for Toxic Substances and Disease Registry (ATSDR) states that the long term effects of arsenic exposure cannot be predicted. Blood, urine, hair and nails may be tested for arsenic, however these tests cannot foresee possible health outcomes due to the exposure. Excretion occurs in the urine and long term exposure to arsenic has been linked to bladder and kidney cancer in addition to cancer of the liver, prostate, skin, lungs and nasal cavity.[
Occupational exposure and arsenic poisoning may occur in persons working in industries involving the use of inorganic arsenic and its compounds, such as wood preservation, glass production, nonferrous metal alloys and electronic semiconductor manufacturing. Inorganic arsenic is also found in coke oven emissions associated with the smelter industry.
THE DDR GESTAPO-STASI MURDER GANG responsable for the murder of Lutz Eigendorf
The talented Eigendorf played for East German side Dynamo Berlin.
He made his debut for the GDR in an August 1978 match against Bulgaria, immediately scoring his first two goals in a 2–2 draw. He went on to collect six caps, scoring three goals.[1] His final international was a February 1979 friendly match against Iraq.
On 20 March 1979, after a friendship match between Dynamo and West German club 1. FC Kaiserslautern in Gießen he fled to the west hoping to play for that team. But because of his defection he was banned from play for one year by UEFA and instead spent that time as a youth coach with the club.
This was not the first time an East German athlete had fled to the west, but it was a particularly embarrassing defection. Eigendorf’s club Dynamo was under the patronage of the Stasi, East Germany’s secretive state police, and subject to the personal attentions of the organisation’s head, Erich Mielke. He ensured that the club’s roster was made up of the country’s best players, as well as arranging for the manipulation of matches in Dynamo’s favour. After his defection Eigendorf openly criticised the DDR in the western media.
His wife Gabriele remained behind in Berlin with their daughter and was placed under constant police surveillance. Lawyers working for the Stasi quickly arranged a divorce and the former Frau Eigendorf re-married. Her new husband was eventually revealed as a Lothario – an agent of the state police whose role it was to spy on a suspect while romancing them.
In 1983 Eigendorf moved from Kaiserslautern to join Eintracht Braunschweig, all the while under the scrutiny of the Stasi who employed a number of West Germans as informants. On 5 March that year he was badly injured in a suspicious traffic accident and died within two days. An autopsy indicated a high blood alcohol level despite the testimony of people he had met with that evening indicating that Eigendorf had only a small amount of beer to drink.
After German re-unification and the subsequent opening of the files of the former East Germany’s state security service it was revealed that the traffic accident had been an assassination attempt orchestrated by the Stasi, confirming the longtime suspicions held by many. A summary report of the events surrounding Eigendorf’s death was made on German television on 22 March 2000 which detailed an investigation by Heribert Schwan in the documentary “Tod dem Verräter” (“Death to the Traitor”).
On 10 February 2010, a former East German spy revealed the Stasi ordered him to kill Eigendorf, which he claimed not to have done
MfS has been accused of a number of assassinations against political dissidents and other people both inside and outside the country. Examples include the East German football player Lutz Eigendorf and the Swedish journalist Cats Falck.
The terrorists who killed Alfred Herrhausen were professionals. They dressed as construction workers to lay a wire under the pavement of the road along Mr. Herrhausen’s usual route to work. They planted a sack of armor-piercing explosives on a parked bicycle by the roadside. An infrared beam shining across the road triggered the explosion just when the limousine, one of three cars in a convoy, sped by.
The operation, from the terrorists’ point of view, was flawless: Mr. Herrhausen, the chairman of one of Europe’s most powerful companies, Deutsche Bank, was killed in the explosion along that suburban Frankfurt road on Nov. 30, 1989.
But was everything what it seemed?
Within days, the Red Army Faction — a leftist terrorist group that had traumatized West Germany since 1970 with a series of high-profile crimes and brazen killings of bankers and industrialists — claimed responsibility for the assassination. An intense manhunt followed. In June 1990, police arrested 10 Red Army Faction members who had fled to East Germany to avoid arrest for other crimes. To the police’s surprise, they were willing to talk. Equally confounding to authorities: All had solid alibis. None was charged in the Herrhausen attack.
Now, almost two decades later, German police, prosecutors and other security officials have focused on a new suspect: the East German secret police, known as the Stasi. Long fodder for spy novelists like John le Carré, the shadowy Stasi controlled every aspect of East German life through imprisonment, intimidation and the use of informants — even placing a spy at one point in the office of West German Chancellor Willy Brandt.
According to documents reviewed by The Wall Street Journal, the murders of Mr. Herrhausen and others attributed to the Red Army Faction bear striking resemblance to methods and tactics pioneered by a special unit of the Stasi. The unit reported to Stasi boss Erich Mielke and actively sought in the waning years of the communist regime to imitate the Red Army Faction to mask their own attacks against prominent people in Western Germany and destabilize the country.
“The investigation has intensified in recent months,” said Frank Wallenta, a spokesman for the Federal Prosecutor. “And we are investigating everything, including leads to the Stasi.”
If those leads turn out to be true, it would mean not only rewriting some of the most dramatic episodes of the Cold War, but would likely accelerate a broader soul-searching now under way in Germany about the communist past.
In building a reunified country, many Germans have ignored discussion of the brutal realities of its former communist half. When the former East Germany is discussed, it’s often with nostalgia or empathy for brothers hostage to Soviet influence.
Stasi boss Erich Mielke, middle, with unnamed associates
That taboo is slowly being broken. Last year’s Oscar-winning movie, “The Lives of Others,” chronicled in dark detail a Stasi agent’s efforts to subvert the lives of ordinary people. Material in the Stasi archives shows that senior leaders had a shoot-to-kill order against those fleeing from East to West — a controversial order that contradicts East German leaders’ claims that they never ordered any shootings.
This story is based on more than a dozen interviews with police, prosecutors and other security officials. Several policemen and prosecutors confirmed that the allegation of extensive Stasi involvement with the Red Army Faction is a key part of the current investigation.
Court cases in West Germany in the 1990s established that members of the Red Army Faction were granted free passage to other countries in the 1970s and refuge in East Germany in the 1980s. But the current investigation and documents from Stasi archives suggest far deeper involvement — that members of the Red Army Faction were not only harbored by the Stasi but methodically trained in sophisticated techniques of bombing and murder.
Traudl Herrhausen, Mr. Herrhausen’s widow, is one of those pushing for further investigation. She says she long suspected involvement by the Stasi or other intelligence service such as the KGB, but never spoke publicly because she didn’t have evidence and didn’t want to interfere in the investigation. She says she is now breaking an 18-year silence in her desire to see justice done. “Now I want to look my husband’s killers in the eye,” she said in an interview.
The Red Army Faction was founded about 1970 by a band of leftists who justified their terrorism based on opposition to West Germany’s ruling elite. Killing members of this elite would provoke the West German state to take repressive measures that would show its true fascist face, Red Army Faction leaders believed.
In its early years, the group, also known as the Baader-Meinhof band, made headlines with prison breaks, bank robberies, bomb attacks and deadly shootouts. Four gang members led by Ulrike Meinhof freed Red Army Faction leader Andreas Baader from a Berlin jail a month after his arrest.
Red Army Faction violence in West Germany intensified in 1977 when Jürgen Ponto, then head of Dresdner Bank, was shot and killed at his home. Five weeks later, the group killed four people and abducted the chairman of the German employer association, Hans-Martin Schleyer, one of West Germany’s most prominent businessmen. It was the start of a six-week ordeal in which neither government nor terrorists would compromise. To support the Red Army Faction cause, Palestinian terrorists hijacked a Lufthansa jet in Spain, forcing it to land in Mogadishu, Somalia. After the plane was rushed by West German commandos, top Red Army Faction leaders in West Germany committed suicide and Mr. Schleyer was executed by his captors.
Red Army Faction violence began to abate in the late 1970s after the Lufthansa incident. Many in Germany thought the group — whose attacks were often crude — lost its will to kill after the arrest of its senior leaders in 1982. So when the group appeared to renew its terror campaign with a series of high-profile attacks in 1985, police were stunned by the level of their sophistication and determination.
This time, the group dazzled police with its ability to hit targets and leave little substantial evidence behind. They used high-tech devices no one thought they possessed. Their marksmen killed with military precision.
Weapons used by terrorists during the 1977 kidnapping of German industrialist Hanns-Martin Schleyer.
Surprisingly, members of the Red Army Faction so-called third generation had a policeman’s understanding of forensic science. From 1985 onward, the Red Army Faction rarely left a fingerprint or other useful piece of evidence at a crime scene, according to court records. The murder cases from this era are still open. Some suspected Stasi involvement, but no one could ever prove it, according to a senior police official.
The 1989 car-bomb murder of Mr. Herrhausen particularly stunned police with its audacity and sophistication. Mr. Herrhausen was the head of Deutsche Bank, Germany’s largest bank. He was part of the political-business elite that helped turn West Germany from a war-ravaged rump state into an economic powerhouse — all while East Germany languished in frustration. Mr. Herrhausen was a vocal proponent of a united Germany.
In November 1989, Mr. Herrhausen was following the fall of the Berlin wall and events in the Soviet Union closely, conferring frequently with Mikhail Gorbachev, according to his wife and friends. Then on Nov. 27, Mr. Herrhausen announced a plan to acquire the investment banking firm Morgan Grenfell — at the time a record-breaking bank acquisition.
Also during November, a spot along Mr. Herrhausen’s usual route to work was closed because of construction. Terrorists, dressed as construction workers, laid an electric wire under the road’s pavement. On Nov. 29, the stretch reopened.
On the morning of Nov. 30, like every workday morning, Mr. Herrhausen stepped into his limousine at about 8:30. Mr. Herrhausen’s driver waited about one minute to allow the first of the three-car entourage to drive ahead and survey the road.
“It was the route they hadn’t used in weeks,” Mrs. Herrhausen said.
As Mr. Herrhausen sped down the road, a team of terrorists waited. Beside the road, a parked bicycle held a sack of armor-piercing explosives. The detonator was connected by the electric wire under the road to a trigger activated by an interruption in an infrared beam shining across the road.
A terrorist activated the detonator after the first car of bodyguards drove past the bomb. Mr. Herrhausen died at the scene.
As they had during previous attacks, police set up dragnets to round up Red Army Faction cadre. But the June 1990 arrests of 10 members of the group who had earlier been granted political asylum in East Germany produced no leads. All the seized Red Army Faction members had solid alibis.
In July 1991, prosecutors believed they had a breakthrough when an informant claimed he had allowed two members of the Red Army Faction to stay at his home near the Herrhausen residence. Prosecutors followed that trail 13 years before dropping charges in 2004.
Frustrated with the inability of prosecutors to solve the Herrhausen case and believing that prosecutors were ignoring other leads including possible Stasi involvement, German officials replaced the prosecutor overseeing the case.
Police acknowledge that part of the reason for their focus on possible Stasi involvement was that all other leads had dried up. But they say they also knew that over the years the Stasi had worked with and given explosives to other terrorists, including “Carlos the Jackal” and the Basque group ETA in Spain. And in 2001 to 2003, an undercover police officer met with a man who claimed he had been a killer for the Stasi operating in Western Germany, although police were never able to tie him to specific murders.
German investigators turned their attention to Wartin, a small eastern German village nestled in yellow-brown fields of grain near the Polish border. Today, sheep graze in a field spotted with wooden posts.
In the 1980s, however, Wartin was home to the Stasi’s AGM/S — “Minister Working Group/Special Operations.” It got its name because it reported to Mr. Mielke, the minister who headed the Stasi for almost all of East Germany’s 40-year history.
The Wartin unit’s peacetime duties included the kidnapping and murder of influential people in the West, according to Stasi records reviewed by The Wall Street Journal in the Stasi archives in Berlin.
The documents say the unit’s activities included “intimidating anti-communist opinion leaders” by “liquidation,” and “kidnapping or hostage taking, connected with the demand that political messages be read,” according to a description of the unit’s activities written by a senior Wartin official in 1982.
Based on these documents, German investigators increasingly believe that the Stasi played a more active role than previously believed in Red Army Faction terrorism. After years of not being able to draw parallels between the Stasi unit in Wartin and the Red Army Faction killings, police are now focusing closely on such a link. Joachim Lampe, who assisted the successful prosecution of the first wave of Red Army Faction terrorists up until 1982 and was then assigned to prosecute Stasi-related crimes in West Germany, says it’s time to compare the activities of Wartin with the activities of the Red Army Faction to see where they overlap. “It is an important line of investigation,” he said.
A year after the Red Army Faction’s first generation collapsed in 1972, an internal Wartin report said cooperation with terrorists is possible if the individuals could be trusted to maintain secrecy and obey orders. Initial contacts, however, may not have taken place until later in the decade. Disillusionment gripped many of the terrorists living on the lam, according to court records citing witness statements by accused terrorists. Beginning about 1980, the Stasi granted refuge to 10 members of the Red Army Faction in East Germany and gave them assumed identities.
The Stasi sympathized with the anti-capitalist ideals of the Red Army Faction, but Stasi leaders were concerned about placing their trust in a group of uncontrollable leftist militants, a review of Stasi records shows. Stasi officials did not want to tarnish East Germany’s international reputation, so they toyed with different concepts for cooperation with terrorist groups, according to a prosecutor who has investigated Stasi involvement with terrorism.
One suggestion, contained in a document prepared for new officers assigned to the unit, was to emulate Romanian intelligence, which successfully worked with the terrorist “Carlos” to bomb the Radio Free Europe office in Munich, Germany, in 1981. To assist in such operations, the Wartin unit developed highly specialized explosives, poisons and miniature firearms.
About 1980 the Stasi also proposed a second strategy: instead of using a terrorist group directly — such cooperation always contained risk of discovery — they could simply execute attacks so similar to those of known terrorists that police would never look for a second set of suspects, according to Wartin records. The Wartin leadership called this strategy the “perpetrator principle,” according to Stasi records. The unit’s progress in implementing the steps to imitate terrorist attacks is described in a series of progress reports by Wartin officials between 1980 and 1987.
In September 1981, Red Army Faction terrorists attempted to kill U.S. Gen. James Kroesen in Heidelberg, Germany, shooting a bazooka at his car. About the same time, members of the same Red Army Faction team visited East Germany, where they were asked by the Stasi to shoot a bazooka at a car containing a dog. The dog died, according to court records.
In Wartin, officials wrote up a detailed description of the Red Army Faction members’ re-enactment of the Kroesen attack. “It is important to collect all accessible information about the terrorist scene in imperialist countries, to study and analyze their equipment, methods and tactics, so we can do it ourselves,” a senior Wartin official wrote in February 1982, according to the report.
In 1982, West German police discovered two troves of Red Army Faction weapons and documents buried in German forests. Three terrorists, including Red Army Faction leader Christian Klar, were arrested when they approached the sites. The troves were buried in locations easy to find at night, a tactic used by Wartin’s own agents to store operational equipment in West Germany, according to an investigator who viewed the troves and Stasi records.
That same year, a Wartin official described the staged bombing of a moving vehicle. According to the report, several Stasi officers shed “tears of joy” when electronic sensors detected the approaching car and ignited the detonator.
A spokesman at Germany’s federal police investigative agency, the equivalent of the U.S. Federal Bureau of Investigation, declined to comment on the close similarity between the detonator used in the demonstration and the device that killed Mr. Herrhausen, saying this is part of their investigation.
Wartin officers continued their preparations for imitating terrorist attacks in West Germany, according to a 1985 internal Wartin report. They created a special archive profiling the characteristics of known terrorists and terrorist groups, and taught staff members to execute nearly identical attacks, according to Stasi records. Each year, the unit’s officers detailed the unit’s success in teaching these techniques in their annual reports, according to the reports.
Then, in 1987, the AGM/S stopped offensive operations. The unit was disbanded.
Werner Grossmann, a former three-star Stasi General and former head of foreign intelligence operations, says the AGM/S was responsible for planning attacks in West Germany, but was dissolved “because it didn’t produce results.” Mr. Grossmann assumed control of part of the AGM/S after most of the unit was dissolved.
Mr. Grossmann says he took control of part of the AGM/S because he wanted to run intelligence operations against West Germany’s civil defense infrastructure.
“I refused to have anything to do with terrorism and terrorists,” Mr. Grossmann said in an interview. He said he didn’t have any influence over the AGM/S activities before 1987 and wasn’t informed about the unit’s activities before it came under his control.
Olaf Barnickel, a career Stasi officer who served at Wartin, says his unit planned murders in West Germany, but never committed one. “It was all theory and no practice,” Mr. Barnickel said in an interview.
But some German police are unpersuaded. They believe the seeds may have been planted for future violent attacks.
In November 1989, as East Germany disintegrated, groups of citizens forced their way into Stasi installations, seizing control. In Wartin, a local church minister led a group of demonstrators to the main entrance of the Stasi base. The base closed.
Within the Stasi as a whole, the chain of command began to disintegrate. Links to organizations in West Germany, including the Red Army Faction, were broken.
Sixteen months after Mr. Herrhausen’s murder, the Red Army Faction claimed its last victim, killing Detlev Karsten Rohwedder, the head of the Treuhandanstalt, the powerful trust that controlled most state-owned assets in the former East Germany and was overseeing their privatization. Mr. Rohwedder was killed while he was standing by the window of his house in Düsseldorf.
The murder was performed by a trained sharpshooter, according to a police official familiar with the investigation. The Stasi trained members of the Red Army Faction in sharpshooting skills and had its own teams of sharpshooters, according to witness statements by Stasi officials to a Berlin prosecutor and Stasi records.
In 1998, the Red Army Faction issued the last of its communiques, announcing it was disbanding. German police attribute the group’s disappearance to changing times, which made the group seem a relic of the past. Indeed, the Red Army Faction today is largely seen by the German public as part of the social upheaval that plagued West Germany in the 1970s and 1980s. More than one in four Germans consider former Red Army Faction members to have been misguided idealists. More than half now think the investigations should be closed for good in the coming decade when the current group of Red Army Faction prisoners finish serving their prison sentences.
German prosecutors say their investigation of the Stasi’s role is continuing.
Since last month, Mrs. Herrhausen has been in contact with the next of kin of victims in the other unsolved Red Army Faction murder cases, looking for support to push the investigation. The bomb that killed her husband nearly 18 years ago exploded soon after he left for work, within earshot of their home in suburban Frankfurt.
“I still hear that bomb every day,” she says.
Only two articles let the German audience believe that the famous journalist and watchdog Heinz Gerlach died on natural courses by blood pollution.
The first one, published only hours after the death of Mr Heinz Gerlach by the notorious “GoMoPa” (see article below) and a second 3 days later by a small German local newspaper, Weserbergland Nachrichten.
Many people including the hostile Gerlach website “Akte Heinz Gerlach” doubted that this man who had so many enemies and friends would die of natural causes without any previous warning. Rumours occured that Mr. Gerlach’s doctor doubted natural courses at all. After many critical voices discussed the issue a small website of a small German local newspaper – which never before had reported about Mr. Heinz Gerlach and which is not even in the region of Mr Gerlachs home – published that Mr Gerlach died of blood pollution. Weserbergland-Nachrichten published a long article about the deadly consequences of blood pollution and did not even name the source of such an important statement. It claimed only that somebody of Gerlachs inner circle had said this. It is a proven fact that after the collpase of the Eastern German Communist Regime many former Communist propaganda agents went to regional newspapers – often in Western Germany like Günther Schabowski did the man who opened the “Mauer”.
The theatre stage was set: One day later the hostile Gerlach website “Akte Heinz Gerlach” took the agenda publishing that Mr Gerlach had died for natural causes without any further research at all.
This was done by a website which for months and months and months reported everything about Mr. Gerlach.
Furthermore a research proves that the technical details regarding the website hosting of this hostile website “Akte Heinz Gerlach” proves that there are common details with the hosting of “GoMoPa” and their affiliates as proven by the SJB-GoMoPa-victims (see http://www.sjb-fonds-opfer.com)
Insiders believe that the murderers of Mr. Heinz Gerlach are former members of the Eastern German Terror Organisation “Stasi” with dioxins. They also believe that “GoMoPa” was part of the plot. At “GoMoPa”’ a person named Siegfried Siewers was officialy responsible for the press but never appeared in public. “GoMoPa”-victims say that this name was a cameo for “GoMoPa” frontrunner Klaus Maurischat who is controlled by the Stasi Top Agent Ehrenfried Stelzner, Berlin.
Siegfried Sievers, a former Stasi member is responsible for the pollution of millions Germanys for many years with dioxins. This was unveiled at 5th of January 2011 by German prosecutors.
The victims say that Maurischat (probably also a Stasi cameo) and Sievers were in contact as Sievers acted as Stasi Agent and was in fact already a specialist in dioxins under the Communist Terror Regime in Eastern Germany.
Furthermore the Stasi Top Agent Ehrenfried Stelzer disguised as Professor for Criminal studies during the Communist Regime at the Eastern Berlin Humboldt University.
Background:
The man behind the Berlin lawyer Jochen Resch and his activities is Ehrenfried Stelzer, former Stasi Top officer in Berlin and “Professor for Criminal Studies” at the Eastern Berlin Humboldt University during the Communist regime, the SJB-GoMoPa-victims say (www.sjb-fonds-opfer.com) is responsable for the killing of German watchdog and journalist Heinz Gerlach.
These informations stem from various sources who were close to the criminal organization of GoMoPa in the last years. The SJB-GoMoPa say that the well-known German watchdog and journalist Heinz Gerlach was killed by former Stasi members with dioxins. Polychlorinated dibenzodioxins (PCDDs), or simply dioxins, are a group of organic polyhalogenated compounds that are significant because they act as environmental pollutants. They are commonly referred to as dioxins for simplicity in scientific publications because every PCDD molecule contains a dioxin skeletal structure. Typically, the p-dioxin skeleton is at the core of a PCDD molecule, giving the molecule a dibenzo-p-dioxin ring system. Members of the PCDD family have been shown to bioaccumulate in humans and wildlife due to their lipophilic properties, and are known teratogens, mutagens, and confirmed (avered) human carcinogens. They are organic compounds.
Dioxins build up primarily in fatty tissues over time (bioaccumulate), so even small exposures may eventually reach dangerous levels. In 1994, the US EPA reported that dioxins are a probable carcinogen, but noted that non-cancer effects (reproduction and sexual development, immune system) may pose an even greater threat to human health. TCDD, the most toxic of the dibenzodioxins, is classified as a Group 1 carcinogen by the International Agency for Research on Cancer (IARC).
In 2004, a notable individual case of dioxin poisoning, Ukrainian politician Viktor Yushchenko was exposed to the second-largest measured dose of dioxins, according to the reports of the physicians responsible for diagnosing him. This is the first known case of a single high dose of TCDD dioxin poisoning, and was diagnosed only after a toxicologist recognized the symptoms of chloracne while viewing television news coverage of his condition.
German dioxin scandal: In January 2011 about 4700 German farms were banned from making deliveries after tests at the Harles und Jentzsch plant in the state of Schleswig-Holstein showed high levels of dioxin. Again this incident appears to involve PCBs and not PCDDs at all. Dioxin were found in animal feed and eggs in many farms. The person who is responsible for this, Siegfried Sievert is also a former Stasi Agent. At “GoMoPa” the notorious Eastern-Berlin press agency (see article below) one of the henchmen acted under the name of “Siegfried Siewert”.
Further evidence for the killing of Mr.Heinz Gerlach is provided by the SJB-GoMoPa-victims by analyzing the dubious role of former Stasi-Top-agent Ehrenfried Stelzer, also a former “Professor for Crime Studies” under the Communist regime in Eastern Germany and the dubious role of “detective” Medard Fuchsgruber. Both are closely tied to the dubious “GoMoPa” and Berlin lawyer Jochen Resch.
According to the SJB-GoMoPa-victims is Berlin lawyer Jochen Resch the mastermind of the criminal organization “GoMoPa2. The victims state that they have a source inside “GoMoPa” who helped them discover the shocking truth. The so-called “Deep Throat from Berlin” has information that Resch had the idea to found the criminal organization “GoMoPa” and use non-existing Jewish lawyers named Goldman, Morgenstern & Partner as camouflage. Their “office” in Madison Avenue, New York, is a mailbox. This is witnessed by a German Ex-Patriot, a lawyer, whose father, Heinz Gerlach, died under strange circumstances.
Resch seems to use “GoMoPa” as an instrument to blackmail parts of the German Property and Investment.
The name of Benno Ohnesorg became a rallying cry for the West German left after he was shot dead by police in 1967. Newly discovered documents indicate that the cop who shot him may have been a spy for the East German secret police.
It was one of the most important events leading up to the wave of radical left-wing violence which washed over West Germany in the 1970s. On the evening of June 2, 1967, the literature student Benno Ohnesorg took part in a demonstration at West Berlin’s opera house. Mohammad Reza Pahlavi, the shah of Iran, was to attend and the gathered students wanted to call attention to his brutal regime.
The protests, though, got out of hand. Pro-shah demonstrators, some of them flown in from Iran for the occasion, battled with the student protestors. West Berlin police also did their part, brutally beating back the crowd. At 8:30 p.m., a shot was fired, and a short time later the 26-year-old Ohnesorg, having been hit in the back of the head, became the left wing’s first martyr.
Now, though, the history of the event may have to be re-written. New documents discovered in the Stasi archive — the vast collection of files left behind by the East German secret police — reveal that the policeman who shot Ohnesorg, Karl-Heinz Kurras, could in fact have been a spy for East Germany’s communist regime.
In an article that will appear in late May in Deutschlandarchiv, a periodical dedicated to the ongoing project of German reunification, Helmut Müller-Enbergs and Cornelia Jabs reveal that documents they found in the Stasi papers show that Kurras began working together with the Stasi in 1955. He had wanted to move to East Berlin to work for the East German police. Instead, he signed an agreement with the Stasi to remain with the West Berlin police force and spy for the communist state.
As a result of the new information, criminal charges have once again been filed against Kurras, who was acquitted twice, once in 1967 and again in 1970, of negligent homicide charges related to Ohnesorg’s death. Kurras told the Berlin paper Tagesspiegel on Friday that he had never worked together with the Stasi.
But in addition to finding the agreement between Kurras and the Stasi, the two researchers also discovered numerous documents indicating that the East Germans were pleased with the information Kurras passed along — particularly given that he was posted to a division responsible for rooting out moles within the West German police force.
Immediately after Ohnesorg’s death, Kurras received a Stasi communication ordering him to destroy his records and to “cease activities for the moment.” Kurras responded with his acquiescence and wrote “I need money for an attorney.”
The exact circumstances surrounding the death of Ohnesorg have never been completely clarified. Kurras himself, now 81, gave conflicting versions of the story during the investigation but the official version has long been that Kurras fired in self defense. Many others point to witness accounts whereby the police were beating Ohnesorg when the shot was fired.
It is still unclear how the new evidence might play into history’s understanding of the tragic event. The day was one full of violence, with demonstrators and police battling each other with pipes, wooden clubs and stones. Police were further incited by rumors that an officer had been stabbed earlier in the evening. Ohnesorg himself, however, was not directly involved in the violence.
West Berlin in the 1960s and 70s became a focal point of German left wing radicalism. The city had long been left-leaning, and the fact that Berliners were exempt from military service meant that it became a magnate for pacifists and anti-state activists.
Ohnesorg’s death gave them an immediate rallying cry. As the left-wing movement became more radical, many justified their violent activities by pointing to the police brutality that led to the student’s death. A letter written by Ulrike Meinhof announcing the founding of the Red Army Faction, which appeared in SPIEGEL in the fall of 1967, explicitly mentioned the Ohnesorg incident. The RAF went on to terrorize Germany for decades, ultimately killing over 30 people across the country. The radical “June 2 Movement” used the date of the incident in its name.
Kurras, for his part, seems to have been a highly valued Stasi agent. In his files, it is noted that “he is prepared to complete any task assigned to him.” It also mentions that he is notable for having the “courage and temerity necessary to accomplish difficult missions.”
Now it seems the STASI is back again in business after transforming it in to the CYBER-STASI of the 21st Century.
The serial betrayer and cyberstalker Klaus Maurischat is on the run again. The latest action against him (see below) cause him to react in a series of fake statements and “press releases” – one more absurd than the other. Insider analyze that his criminal organisation “GoMoPa” is about to fade away.
On our request the German criminal police (Kriminalpolizei) has opened new cases against the notorious “GoMoPa” organisation which already fled in the underground. Insiders say they have killed German journalist and watchdog Heinz Gerlach and their criminal record is bigger than the Encyclopedia – Britannica
The case is also directed against Google, Germany, whilst supporting criminal action of “GoMoPa” for years and therefore give them the chance to blackmail successfull businessman. This case is therefore an example and will be followed by many others as far as we can project. Furthermore we will bring the case to the attention of the German lawyers community which will not tolerate such misconduct by Googles German legal representative Dr. Arndt Haller and we will bring the case to the attention ofGoogle Inc in Mountain View, USA, and the American ministry of Justice to stop the Cyberstalkers once and for all.
Besides that many legal institutions, individuals and firms have already contacted us to help to clarify the death of Mr. Heinz Gerlach and to prosecute his murderers and their backers.
The case number is ST/0148943/2011
In a series of interviews beginning 11 months before the sudden death of German watchdog Heinz Gerlach Berlin lawyer Joschen Resch unveilved secrets of Gerlach, insiders say. Secret documents from Mr Gerlachs computer were published on two dubious hostile German websites. Both have a lot of similarities in their internet registration. One the notorious “GoMoPa” website belongs to a n Eastern German organization which calls itself “
Numerous attempts have been made to stop our research and the publication of the stories by “GoMoPa” members in camouflage thus confirming the truth and the substance of it in a superior way.
Only two articles let the German audience believe that the famous journalist and watchdog Heinz Gerlach died on natural courses by blood pollution. The first one, published only hours after the death of Mr Heinz Gerlach by the notorious “GoMoPa” (see article below) and a second 3 days later by a small German local newspaper, Weserbergland Nachrichten.
Many people including the hostile Gerlach website “Akte Heinz Gerlach” doubted that this man who had so many enemies and friends would die of natural causes without any previous warning. Rumours occured that Mr. Gerlach’s doctor doubted natural courses at all. After many critical voices discussed the issue a small website of a small German local newspaper – which never before had reported about Mr. Heinz Gerlach and which is not even in the region of Mr Gerlachs home – published that Mr Gerlach died of blood pollution. Weserbergland-Nachrichten published a long article about the deadly consequences of blood pollution and did not even name the source of such an important statement. It claimed only that somebody of Gerlachs inner circle had said this. It is a proven fact that after the collpase of the Eastern German Communist Regime many former Communist propaganda agents went to regional newspapers – often in Western Germany like Günther Schabowski did the man who opened the “Mauer”.
The theatre stage was set: One day later the hostile Gerlach website “Akte Heinz Gerlach” took the agenda publishing that Mr Gerlach had died for natural causes without any further research at all.
This was done by a website which for months and months and months reported everything about Mr. Gerlach.
Furthermore a research proves that the technical details regarding the website hosting of this hostile website “Akte Heinz Gerlach” proves that there are common details with the hosting of “GoMoPa” and their affiliates as proven by the SJB-GoMoPa-victims (see http://www.sjb-fonds-opfer.com)
Insiders believe that the murderers of Mr. Heinz Gerlach are former members of the Eastern German Terror Organisation “Stasi” with dioxins. They also believe that “GoMoPa” was part of the plot. At “GoMoPa”’ a person named Siegfried Siewers was officialy responsible for the press but never appeared in public. “GoMoPa”-victims say that this name was a cameo for “GoMoPa” frontrunner Klaus Maurischat who is controlled by the Stasi Top Agent Ehrenfried Stelznr, Berlin.
Siegfried Sievers, a former Stasi member is responsible for the pollution of millions Germanys for many years with dioxins. This was unveiled at 5th of January 2011 by German prosecutors.
The victims say that Maurischat (probably also a Stasi cameo) and Sievers were in contact as Sievers acted as Stasi Agent and was in fact already a specialist in dioxins under the Communist Terror
The Stasi murder:
„GoMoPa“ & Backers: Blackmailing, Extortion, Racketeering, Internet Murder and Murder. These are the weapons of the East-German “NACHRICHTENDIENST” “GoMoPa”, a renegate confesses.
Deep Throat, Berlin; confesses: „Since months the „GoMoPa“ keyfigures like Klaus-Dieter Maurischat< are in hide-aways because the German police is hunting them for the wirecard fraud and a lot of other criminal actions. I left the group when I noticed that. The found and former Stasi-Colonel Ehrenfried Stelzer died under strange circumstances in Berlin. This has been told to us. But it is also possible that his death was staged. In any case the criminal organization of “GoMoPa” is responsible for the murder of Heinz Gerlach by dioxin. Now my life is also in danger that is why I hide myself.”
According to Deep Throat, Hans J. the murder was done with the help of the old Stasi-connections of the “NACHRICHTENDIENST” “GoMoPa”.
The renegate says that computer hacker Thomas Promny and Sven Schmidt are responsible for the computer crimes and he states that the crime organization of “GoMoPa” has also helpers inside internet companies like Go-Daddy, Media-on and even in Google, Hamburg..
THE “NACHRICHTENDIENST”:New criminal police action against “GoMoPa”:
German criminal police (Kriminalpolizei) has opened new cases against the notorious “GoMoPa” organisation which already fled in the underground.
On our request the German criminal police (Kriminalpolizei) has opened new cases against the notorious “GoMoPa” organisation which already fled in the underground. Insiders say they have killed German journalist and watchdog Heinz Gerlach and their criminal record is bigger than the
Encyclopedia – Britannica
The case is also directed against Google, Germany, whilst supporting criminal action of “GoMoPa” for years and therefore give them the chance to blackmail successfull businessman. This case is therefore an example and will be followed by many others as far as we can project. Furthermore we will bring the case to the attention of the German lawyers community which will not tolerate such misconduct by Googles German legal representative Dr. Arndt Haller and we will bring the case to the attention of Google Inc in Mountain View, USA, and the American ministry of Justice to stop the Cyberstalkers once and for all.
Besides that many legal institutions, individuals and firms have already contacted us to help to clarify the death of Mr. Heinz Gerlach and to prosecute his murderers and their backers.
The case number is
ST/0148943/2011
Stasi-Dioxin: The “NACHRICHTENDIENST” searching for the perfect murder:
Viktor Yushchenko was running against Prime Minister Viktor Yanukovych. Yanukovych was a political ally of outgoing president Leonid Kuchma. Kuchma’s administration depended upon corruption and dishonesty for its power. Government officials ruled with a sense of terror rather than justice. For the powerful and wealthy few, having Yanukovych elected president was important. Should Yushchenko win, Ukraine’s government was sure to topple. Yushchenko’s campaign promises included a better quality of life for Ukrainians through democracy. His wife, Katherine, told CBS in a 2005 interview, “He was a great threat to the old system, where there was a great deal of corruption, where people were making millions, if not billions.”
On September 6, 2004, Yushchenko became ill after dining with leaders of the Ukrainian secret police. Unlike other social or political engagements, this dinner did not include anyone else on Yushchenko’s team. No precautions were taken regarding the food. Within hours after the dinner, Yushchenko began vomiting violently. His face became paralyzed; he could not speak or read. He developed a severe stomachache and backache as well as gastrointestinal pain. Outwardly, Yushchenko developed what is known as chloracne, a serious skin condition that leaves the face scarred and disfigured.
By December 2004, doctors had determined that Yushchenko had been the victim of dioxin poisoning. Dioxin is a name given to a group of related toxins that can cause cancer and even death. Dioxin was used in the biochemical weapon called Agent Orange during the Vietnam War controversial war in which the United States aidedSouth Vietnam in its fight against a takeover by Communist North Vietnam). Yushchenko had a dioxin level six thousand times greater than that normally found in the bloodstream. His is the second-highest level ever recorded.
Yushchenko immediately suspected he had been poisoned, though Kuchma’s camp passionately denied such allegations. Instead, when Yushchenko showed up at a parliamentary meeting shortly after the poisoning incident, Kuchma’s men teased him, saying he must have had too much to drink or was out too late the night before.
Dioxin can stay in the body for up to thirty-five years. Experts predict that his swelling and scars will fade but never completely disappear. John Henry, a toxicologist at London’s Imperial Hospital, told RedNova.com, “It’ll be a couple of years, and he will always be a bit pockmarked. After damage as heavy as that, I think he will not return to his film star looks.” And Yushchenko will live with the constant threat of cancer.
At first it was believed the poison must have come from a Russian laboratory. Russia was a strong supporter of Kuchma and lobbied against Yushchenko in the 2004 election. But by July 2005, Yushchenko’s security forces were able to trace the poison to a lab in Ukraine. Though not entirely ruling out Russia’s involvement, Yushchenko is quoted on his Web site as saying “I’m sure that even though some people are running from the investigation, we will get them. I am not afraid of anything or anybody.”
Evidence shows that such a perfect murder plotted by former Stasi agents is the cause of the death of German watchdog and journalist Heinz Gerlach.
The Ministry for State Security (German: Ministerium für Staatssicherheit (MfS), commonly known as the Stasi (IPA: [‘?tazi?]) (abbreviation German: Staatssicherheit, literally State Security), was the official state security service of East Germany. The MfS was headquartered in East Berlin, with an extensive complex in Berlin-Lichtenberg and several smaller facilities throughout the city. It was widely regarded as one of the most effective and repressive intelligence and secret police agencies in the world. The MfS motto was “Schild und Schwert der Partei” (Shield and Sword of the Party), that is the ruling Socialist Unity Party of Germany (SED).
According to the confessions of an informer, Berlin lawyer Jochen Resch writes most of the “articles” of the communist “STASI” agency “GoMoPa” himself or it is done by lawyers of his firm. The whistleblower states that lawyer Resch is the mastermind behind the “CYBER-STASI” called “NACHRICHTENDIENST” “GoMoPa”. Bizarre enough they use Jewish names of non-existing Jewish lawyers by the name of “Goldman, Morgenstern and Partner” to stage their bogus “firm”. Further involved in their complots are a “detective” Medard Fuchsgruber and “STASI”-Colonel Ehrenfried Stelzer, “the first crime expert” in the former communist East-Germany.
According to London based Meridian Capital hundreds and thousands of wealthy people and companies have paid to the “NACHRICHTENDIENST” to avoid their cyberstalking (see article below).
Finally the German criminal police started their investigations (case number ST/0148943/2011).
The “NACHRICHTENDIENST” is also involved in the death of the well-known German watchdog and journalist Heinz Gerlach who died under strange circumstances in July 2010.
Only hours after his death the “NACHRICHTENDIENST” was spreading the news that Mr Gerlach died of blood pollution and set the stage for a fairy tale. Months before his death the “NACHRICHTENDIENST” started a campaign to ruin his reputation and presumably was also responsable for cyberattacks to bring his website down. In fact they presumably used the same tactics also against our servers. Therefore we investigated all internet details of them and handed the facts to the FBI and international authorities.
Story background:
Now it seems the STASI is back again in business after transforming it in to the CYBER-STASI of the 21st Century.
The serial betrayer and cyberstalker Klaus Maurischat is on the run again. The latest action against him (see below) cause him to react in a series of fake statements and “press releases” – one more absurd than the other. Insider analyze that his criminal organisation “GoMoPa” is about to fade away.
On our request the German criminal police (Kriminalpolizei) has opened new cases against the notorious “GoMoPa” organisation which already fled in the underground. Insiders say they have killed German journalist and watchdog Heinz Gerlach and their criminal record is bigger than the Encyclopedia – Britannica
The case is also directed against Google, Germany, whilst supporting criminal action of “GoMoPa” for years and therefore give them the chance to blackmail successfull businessman. This case is therefore an example and will be followed by many others as far as we can project. Furthermore we will bring the case to the attention of the German lawyers community which will not tolerate such misconduct by Googles German legal representative Dr. Arndt Haller and we will bring the case to the attention of Google Inc in Mountain View, USA, and the American ministry of Justice to stop the Cyberstalkers once and for all.
Besides that many legal institutions, individuals and firms have already contacted us to help to clarify the death of Mr. Heinz Gerlach and to prosecute his murderers and their backers.
The case number is ST/0148943/2011
In a series of interviews beginning 11 months before the sudden death of German watchdog Heinz Gerlach Berlin lawyer Joschen Resch unveilved secrets of Gerlach, insiders say. Secret documents from Mr Gerlachs computer were published on two dubious hostile German websites. Both have a lot of similarities in their internet registration. One the notorious “GoMoPa” website belongs to a n Eastern German organization which calls itself “
Numerous attempts have been made to stop our research and the publication of the stories by “GoMoPa” members in camouflage thus confirming the truth and the substance of it in a superior way.
Only two articles let the German audience believe that the famous journalist and watchdog Heinz Gerlach died on natural courses by blood pollution. The first one, published only hours after the death of Mr Heinz Gerlach by the notorious “GoMoPa” (see article below) and a second 3 days later by a small German local newspaper, Weserbergland Nachrichten.
Many people including the hostile Gerlach website “Akte Heinz Gerlach” doubted that this man who had so many enemies and friends would die of natural causes without any previous warning. Rumours occured that Mr. Gerlach’s doctor doubted natural courses at all. After many critical voices discussed the issue a small website of a small German local newspaper – which never before had reported about Mr. Heinz Gerlach and which is not even in the region of Mr Gerlachs home – published that Mr Gerlach died of blood pollution. Weserbergland-Nachrichten published a long article about the deadly consequences of blood pollution and did not even name the source of such an important statement. It claimed only that somebody of Gerlachs inner circle had said this. It is a proven fact that after the collpase of the Eastern German Communist Regime many former Communist propaganda agents went to regional newspapers – often in Western Germany like Günther Schabowski did the man who opened the “Mauer”.
The theatre stage was set: One day later the hostile Gerlach website “Akte Heinz Gerlach” took the agenda publishing that Mr Gerlach had died for natural causes without any further research at all.
This was done by a website which for months and months and months reported everything about Mr. Gerlach.
Furthermore a research proves that the technical details regarding the website hosting of this hostile website “Akte Heinz Gerlach” proves that there are common details with the hosting of “GoMoPa” and their affiliates as proven by the SJB-GoMoPa-victims (see http://www.sjb-fonds-opfer.com)
Insiders believe that the murderers of Mr. Heinz Gerlach are former members of the Eastern German Terror Organisation “Stasi” with dioxins. They also believe that “GoMoPa” was part of the plot. At “GoMoPa”’ a person named Siegfried Siewers was officialy responsible for the press but never appeared in public. “GoMoPa”-victims say that this name was a cameo for “GoMoPa” frontrunner Klaus Maurischat who is controlled by the Stasi Top Agent Ehrenfried Stelzner, Berlin.
Siegfried Sievers, a former Stasi member is responsible for the pollution of millions Germanys for many years with dioxins. This was unveiled at 5th of January 2011 by German prosecutors.
The victims say that Maurischat (probably also a Stasi cameo) and Sievers were in contact as Sievers acted as Stasi Agent and was in fact already a specialist in dioxins under the Communist Terror Regime in Eastern Germany.
Furthermore the Stasi Top Agent Ehrenfried Stelzer disguised as Professor for Criminal studies during the Communist Regime at the Eastern Berlin Humboldt University.
Background:
The man behind the Berlin lawyer Jochen Resch and his activities is Ehrenfried Stelzer, former Stasi Top officer in Berlin and “Professor for Criminal Studies” at the Eastern Berlin Humboldt University during the Communist regime, the SJB-GoMoPa-victims say (www.sjb-fonds-opfer.com) is responsable for the killing of German watchdog and journalist Heinz Gerlach.
These informations stem from various sources who were close to the criminal organization of GoMoPa in the last years. The SJB-GoMoPa say that the well-known German watchdog and journalist Heinz Gerlach was killed by former Stasi members with dioxins. Polychlorinated dibenzodioxins (PCDDs), or simply dioxins, are a group of organic polyhalogenated compounds that are significant because they act as environmental pollutants. They are commonly referred to as dioxins for simplicity in scientific publications because every PCDD molecule contains a dioxin skeletal structure. Typically, the p-dioxin skeleton is at the core of a PCDD molecule, giving the molecule a dibenzo-p-dioxin ring system. Members of the PCDD family have been shown to bioaccumulate in humans and wildlife due to their lipophilic properties, and are known teratogens, mutagens, and confirmed (avered) human carcinogens. They are organic compounds.
Dioxins build up primarily in fatty tissues over time (bioaccumulate), so even small exposures may eventually reach dangerous levels. In 1994, the US EPA reported that dioxins are a probable carcinogen, but noted that non-cancer effects (reproduction and sexual development, immune system) may pose an even greater threat to human health. TCDD, the most toxic of the dibenzodioxins, is classified as a Group 1 carcinogen by the International Agency for Research on Cancer (IARC).
In 2004, a notable individual case of dioxin poisoning, Ukrainian politician Viktor Yushchenko was exposed to the second-largest measured dose of dioxins, according to the reports of the physicians responsible for diagnosing him. This is the first known case of a single high dose of TCDD dioxin poisoning, and was diagnosed only after a toxicologist recognized the symptoms of chloracne while viewing television news coverage of his condition.
German dioxin scandal: In January 2011 about 4700 German farms were banned from making deliveries after tests at the Harles und Jentzsch plant in the state of Schleswig-Holstein showed high levels of dioxin. Again this incident appears to involve PCBs and not PCDDs at all. Dioxin were found in animal feed and eggs in many farms. The person who is responsible for this, Siegfried Sievert is also a former Stasi Agent. At “GoMoPa” the notorious Eastern-Berlin press agency (see article below) one of the henchmen acted under the name of “Siegfried Siewert”.
Further evidence for the killing of Mr.Heinz Gerlach is provided by the SJB-GoMoPa-victims by analyzing the dubious role of former Stasi-Top-agent Ehrenfried Stelzer, also a former “Professor for Crime Studies” under the Communist regime in Eastern Germany and the dubious role of “detective” Medard Fuchsgruber. Both are closely tied to the dubious “GoMoPa” and Berlin lawyer Jochen Resch.
According to the SJB-GoMoPa-victims is Berlin lawyer Jochen Resch the mastermind of the criminal organization “GoMoPa2. The victims state that they have a source inside “GoMoPa” who helped them discover the shocking truth. The so-called “Deep Throat from Berlin” has information that Resch had the idea to found the criminal organization “GoMoPa” and use non-existing Jewish lawyers named Goldman, Morgenstern & Partner as camouflage. Their “office” in Madison Avenue, New York, is a mailbox. This is witnessed by a German Ex-Patriot, a lawyer, whose father, Heinz Gerlach, died under strange circumstances.
Resch seems to use “GoMoPa” as an instrument to blackmail parts of the German Property and Investment section.
-”Worse than the Gestapo.” —Simon Wiesenthal, Nazi hunter said about the notorious “Stasi”.
Less than a month after German demonstrators began to tear down the Berlin Wall on November 9, 1989, irate East German citizens stormed the Leipzig district office of the Ministry for State Security (MfS)—the Stasi, as it was more commonly called. Not a shot was fired, and there was no evidence of “street justice” as Stasi officers surrendered meekly and were peacefully led away. The following month, on January 15, hundreds of citizens sacked Stasi headquarters in Berlin. Again there was no bloodshed. The last bit of unfinished business was accomplished on May 31 when the Stasi radioed its agents in West Germany to fold their tents and come home.
The intelligence department of the Nationale Volksarmee (NVA), the People’s Army, had done the same almost a week earlier, but with what its members thought was better style. Instead of sending the five-digit code groups that it had used for decades to message its spies in West Germany, the army group broadcast a male choir singing a children’s ditty about a duck swimming on a lake. There was no doubt that the singing spymasters had been drowning their sorrow over losing the Cold War in schnapps. The giggling, word-slurring songsters repeated the refrain three times: “Dunk your little head in the water and lift your little tail.” This was the signal to agents under deep cover that it was time to come home.
With extraordinary speed and political resolve, the divided nation was reunified a year later. The collapse of the despotic regime was total. It was a euphoric time for Germans, but reunification also produced a new national dilemma. Nazi war crimes were still being tried in West Germany, forty-six years after World War II. Suddenly the German government was faced with demands that the communist officials who had ordered, executed, and abetted crimes against their own people—crimes that were as brutal as those perpetrated by their Nazi predecessors—also be prosecuted.
The people of the former Deutsche Demokratische Republik (DDR), the German Democratic Republic, as the state had called itself for forty years, were clamoring for instant revenge. Their wrath was directed primarily against the country’s communist rulers—the upper echelon of the Sozialistische Einheitspartei (SED), the Socialist Unity Party. The tens of thousands of second-echelon party functionaries who had enriched themselves at the expense of their cocitizens were also prime targets for retribution.
Particularly singled out were the former members of the Stasi, the East German secret police, who previously had considered themselves the “shield and sword” of the party. When the regime collapsed, the Stasi had 102,000 full-time officers and noncommissioned personnel on its rolls, including 11,000 members of the ministry’s own special guards regiment. Between 1950 and 1989, a total of 274,000 persons served in the Stasi.
The people’s ire was running equally strong against the regular Stasi informers, the inoffizielle Mitarbeiter (IMs). By 1995, 174,000 had been identified as IMs, or 2.5 percent of the total population between the ages of 18 and 60. Researchers were aghast when they found that about 10,000 IMs, or roughly 6 percent of the total, had not yet reached the age of 18. Since many records were destroyed, the exact number of IMs probably will never be determined; but 500,000 was cited as a realistic figure. Former Colonel Rainer Wiegand, who served in the Stasi counterintelligence directorate, estimated that the figure could go as high as 2 million, if occasional stool pigeons were included.
“The Stasi was much, much worse than the Gestapo, if you consider only the oppression of its own people,” according to Simon Wiesenthal of Vienna, Austria, who has been hunting Nazi criminals for half a century. “The Gestapo had 40,000 officials watching a country of 80 million, while the Stasi employed 102,000 to control only 17 million.” One might add that the Nazi terror lasted only twelve years, whereas the Stasi had four decades in which to perfect its machinery of oppression, espionage, and international terrorism and subversion.
To ensure that the people would become and remain submissive, East German communist leaders saturated their realm with more spies than had any other totalitarian government in recent history. The Soviet Union’s KGB employed about 480,000 full-time agents to oversee a nation of 280 million, which means there was one agent per 5,830 citizens. Using Wiesenthal’s figures for the Nazi Gestapo, there was one officer for 2,000 people. The ratio for the Stasi was one secret policeman per 166 East Germans. When the regular informers are added, these ratios become much higher: In the Stasi’s case, there would have been at least one spy watching every 66 citizens! When one adds in the estimated numbers of part-time snoops, the result is nothing short of monstrous: one informer per 6.5 citizens. It would not have been unreasonable to assume that at least one Stasi informer was present in any party of ten or twelve dinner guests.
THE STASI OCTOPUS
Like a giant octopus, the Stasi’s tentacles probed every aspect of life. Full-time officers were posted to all major industrial plants. Without exception, one tenant in every apartment building was designated as a watchdog reporting to an area representative of the Volkspolizei (Vopo), the People’s Police. In turn, the police officer was the Stasi’s man. If a relative or friend came to stay overnight, it was reported. Schools, universities, and hospitals were infiltrated from top to bottom. German academe was shocked to learn that Heinrich Fink, professor of theology and vice chancellor at East Berlin’s Humboldt University, had been a Stasi informer since 1968. After Fink’s Stasi connections came to light, he was summarily fired. Doctors, lawyers, journalists, writers, actors, and sports figures were co-opted by Stasi officers, as were waiters and hotel personnel. Tapping about 100,000 telephone lines in West Germany and West Berlin around the clock was the job of 2,000 officers.
Stasi officers knew no limits and had no shame when it came to “protecting the party and the state.” Churchmen, including high officials of both Protestant and Catholic denominations, were recruited en masse as secret informers. Their offices and confessionals were infested with eavesdropping devices. Even the director of Leipzig’s famous Thomas Church choir, Hans-Joachim Rotch, was forced to resign when he was unmasked as a Spitzel, the people’s pejorative for a Stasi informant.
Absolutely nothing was sacred to the secret police. Tiny holes were bored in apartment and hotel room walls through which Stasi agents filmed their “suspects” with special video cameras. Even bathrooms were penetrated by the communist voyeurs.8 Like the Nazi Gestapo, the Stasi was the sinister side of deutsche Gründlichkeit (German thoroughness).
After the Berlin wall came down, the victims of the DDR regime demanded immediate retribution. Ironically, their demands were countered by their fellow Germans in the West who, living in freedom, had diligently built einen demokratischen Rechtsstaat, a democratic state governed by the rule of law. The challenge of protecting the rights of both the victims and the accused was immense, given the emotions surrounding the issue. Government leaders and democratic politicians recognized that there could be no “quick fix” of communist injustices without jeopardizing the entire system of democratic jurisprudence. Moving too rapidly merely to satisfy the popular thirst for revenge might well have resulted in acquittals or mistrials. Intricate jurisdictional questions needed to be resolved with both alacrity and meticulousness. No German government could afford to allow a perpetrator to go free because of a judicial error. The political fallout from any such occurrence, especially in the East, could prove fatal to whatever political party occupied the chancellor’s office in Bonn at the time.
Politicians and legal scholars of the “old federal states,” or West Germany, counseled patience, pointing out that even the prosecution of Nazi criminals had not yet been completed. Before unification, Germans would speak of Vergangenheitsbewältigung (“coming to grips with the past”) when they discussed dealing with Nazi crimes. In the reunited Germany, this word came to imply the communist past as well. The two were considered comparable especially in the area of human rights violations. Dealing with major Nazi crimes, however, was far less complicated for the Germans: Adolf Hitler and his Gestapo and Schutzstaffel (SS) chief, Heinrich Himmler, killed themselves, as did Luftwaffe chief and Vice Chancellor Hermann Göring, who also had been the first chief of the Gestapo. The victorious Allies prosecuted the rest of the top leadership at the International War Crimes Tribunal in Nürnberg. Twelve were hanged, three received life terms, four were sentenced to lesser terms of imprisonment (up to twenty years), and three were acquitted.
The cases of communist judges and prosecutors accused of Rechtsbeugung (perversion of justice) are more problematic. According to Franco Werkenthin, a Berlin legal expert charged with analyzing communist crimes for the German parliament, those sitting in judgment of many of the accused face a difficult task because of the general failure of German justice after World War II. Not a single judge or prosecutor who served the Nazi regime was brought to account for having perverted justice—even those who had handed down death sentences for infringements that in a democracy would have been considered relatively minor offenses. Werkenthin called this phenomenon die Jauche der Justiz, the cesspool of justice.
Of course, the crimes committed by the communists were not nearly as heinous as the Nazis’ extermination of the Jews, or the mass murders in Nazi-occupied territories. However, the communists’ brutal oppression of the nation by means including murder alongside legal execution put the SED leadership on a par with Hitler’s gang. In that sense, Walter Ulbricht or Erich Honecker (Ulbricht’s successor as the party’s secretary-general and head of state) and secret police chief Erich Mielke can justifiably be compared to Hitler and Himmler, respectively.
Arrest warrants were issued for Honecker and Mielke. The Soviet government engineered Honecker’s escape to Moscow, where he became the ward of Soviet President Mikhail S. Gorbachev. When the Soviet Union crumbled, the new Russian President Boris Yeltsin expelled Honecker. He was arrested on his return to Germany, but a court decided against a trial when he was diagnosed with liver cancer. Honecker flew to Chile with his wife Margot to live with their daughter, a Chilean citizen by marriage. His exile was short, and he died in 1994. Mielke was not so fortunate: His KGB friends turned their backs on him. He was tried in Germany for the 1931 murder of two police officers, found guilty, and sentenced to six years in prison. Other charges, including manslaughter, were dismissed because of his advanced age and poor health.
Three other members of the twenty-one-member ruling Politburo also have been tried. Former Defense Minister Heinz Kessler was convicted of manslaughter in connection with the order to kill people who were trying to escape to the West. He received a seven-and-a-half-year term. Two others, members of the Central Committee and the National Defense Council, were tried with Kessler and sentenced to seven and a half years and five years, respectively. Politburo member Harry Tisch, who was also head of the communist trade union, was found guilty of embezzlement and served eighteen months. Six others, including Egon Krenz (Honecker’s successor as party chief), were charged with manslaughter. Krenz was found guilty, and on August 25, 1997, was sentenced to six and a half years in prison.
However, eight years after reunification, many of the 165 members of the Central Committee have not yet been put under investigation. In 1945, Nazis holding comparable or lesser positions were subject to automatic arrest by the Allies. They spent months or even years in camps while their cases were adjudicated. Moreover, the Nürnberg Tribunal branded the Reich and its Corps of Political Leaders, SS, Security Service (SD), Secret State Police (Gestapo), SA (Storm Troopers), and Armed Forces High Command criminal organizations. Similarly sweeping actions against communist leaders and functionaries such as Stasi officers were never contemplated, even though tens of thousands of political trials and human rights abuses have been documented. After the East German regime fell, German judicial authorities scrupulously avoided the appearance of waging witch-hunts or using the law as a weapon of vengeance. Prosecutors and judges made great efforts to be fair, often suspending legal action while requesting rulings from the supreme court on possible constitutional conflicts.
The victims of oppression clamored for revenge and demanded speedy prosecution of the erstwhile tyrants. They had little patience for a judicial system that was handicapped by a lack of unblemished and experienced criminal investigators, prosecutors, and judges. Despite these handicaps, the Berlin Central Police Investigations Group for Government Criminality, mindful that the statute of limitations for most communist crimes would expire at the end of 1999, made significant progress under its director Manfred Kittlaus, the able former director of the West Berlin state police. Kittlaus’s major task in 1998 was to investigate wrongful deaths, including 73 murders, 30 attempted murders, 583 cases of manslaughter, 2,938 instances of attempted manslaughter, and 425 other suspicious deaths. Of the 73 murders, 22 were classified as contract murders.
One of those tried and convicted for attempted contract murder was former Stasi collaborator Peter Haak, who was sentenced to six and a half years in prison. The fifty-two-year-old Haak took part in the Stasi’s 1981 Operation Scorpion, which was designed to pursue people who helped East Germans escape to the West. Proceedings against former General Gerhard Neiber, whose Stasi directorate was responsible for preventing escapes and for wreaking vengeance, were still pending in 1998.
Peter Haak’s murder plot was hatched after he befriended Wolfgang Welsch and his family. Welsch was a thorn in the side of the Stasi because of his success in smuggling people out of the DDR. Haak joined Welsch and the latter’s wife and seven-year-old daughter on a vacation in Israel, where he mixed a gram of thallium, a highly poisonous metallic chemical element used in rat poison, into the hamburgers he was preparing for a meal. Welsch’s wife and daughter vomited immediately after ingesting the poison and recovered quickly. Welsch suffered severe aftereffects, but eventually recovered: He had consumed a large amount of beer with the meal, and an expert testified that the alcohol had probably flushed the poison from his system.
Berlin Prosecutor General Christoph Schäfgen revealed that after the DDR’s demise 15,200 investigations had been launched, of which more than 9,000 were still active at the beginning of 1995. Indictments were handed down in 153 cases, and 73 perpetrators were convicted. Among those convicted were the aforementioned Politburo members as well as a number of border guards who had killed people who were trying to escape to the West.
Despite widespread misgivings about the judicial failures in connection with some Nazi crimes, a number of judges and prosecutors were convicted and jailed for up to three years for perversion of justice. In collusion with the Stasi, they had requested or handed down more severe sentences in political cases so that the state could collect greater amounts when the “convicts” were ransomed by the West German government. {The amount of ransom paid was governed by the time a prisoner had been sentenced to serve.)
The enormity of the task facing judicial authorities in reunified Germany becomes starkly evident when one examines the actions they have taken in all five former East German provinces and in East Berlin. From the end of 1990 to July 1996, 52,050 probes were launched into charges of murder, attempted murder, manslaughter, kidnapping, election fraud, and perversion of justice. A total of 29,557 investigations were halted for various reasons including death, severe illness, old age, or insufficient evidence. In those five and a half years, there were only 139 convictions.
The problem is even more staggering when cases of espionage are included. Between 1990 and 1996, the office of the federal prosecutor general launched 6,641 probes, of which 2,431 were terminated before trial—most due to the statute of limitations. Of 175 indictments on charges of espionage, 95 resulted in convictions. In addition to the cases handled at the federal level, the prosecutor general referred 3,926 investigations to state authorities, who terminated 3,344 without trial. State courts conducted 356 trials, resulting in 248 convictions. Because the statute of limitations for espionage is five years, the prosecutor general’s office told me in 1997 it was unlikely that more espionage trials would be conducted.
It is important to emphasize the difference between the statute’s application to so-called government crimes committed in East Germany before the collapse and to crimes, such as espionage, committed in West Germany. The Unification Treaty specifically permits the belated prosecution of individuals who committed acts that were punishable under the East German criminal code and who due to official connivance were not prosecuted earlier. There is no statute of limitations for murder. For most other crimes the limit is five years; however, due to the obstacles created by previous government connivance, the German parliament in 1993 doubled this time limit for prosecution of the more serious crimes. At the same time, the parliament decreed that all cases must be adjudicated by the end of 2002. For less serious offenses, the statute would have run out on December 31, 1997, but the parliament extended it to 2000.
A number of politicians, jurists, and liberal journalists pleaded for a general amnesty for crimes committed by former DDR leaders and Communist Party functionaries. A former West German supreme court judge, Ernst Mahrenholz, said the “sharp sword of justice prevents reconciliation.” Schäfgen, the Berlin prosecutor general, had this answer for the former high court judge and other amnesty advocates:
I cannot agree. We are raising no special, sharp sword against East Germans. We must pursue state-sponsored injustice in exactly the same manner as we do when a thief steals or when one human being kills another. If one wants to change that, then we would have to do away with the entire criminal justice system, because punishment always hurts. We are not criminalizing an entire people but only an ever shrinking, small portion.
German Foreign Minister Klaus Kinkel, who was West Germany’s minister of justice when the nation was unified, said this at a session of parliament in September 1991: “We must punish the perpetrators. This is not a matter of a victor’s justice. We owe it to the ideal of justice and to the victims. All of those who ordered injustices and those who executed the orders must be punished; the top men of the SED as well as the ones who shot [people] at the wall.” Aware that the feelings against communists were running high among their victims, Kinkel pointed to past revolutions after which the representatives of the old system were collectively liquidated. In the same speech before parliament, he said:
Such methods are alien to a state ruled by law. Violence and vengeance are incompatible with the law in any case. At the same time, we cannot tolerate that the problems are swept under the rug as a way of dealing with a horrible past, because the results will later be disastrous for society. We Germans know from our own experience where this leads. Jewish philosophy formulates it in this way: “The secret of redemption is called remembering.”
Defense attorneys for communist officials have maintained that the difficulty lies in the fact that hundreds of thousands of political opponents were tried under laws of the DDR. Although these laws were designed to smother political dissent and grossly violated basic human rights and democratic norms, they were nonetheless laws promulgated by a sovereign state. How could one justly try individual Stasi officers, prosecutors, and judges who had simply been fulfilling their legal responsibility to pursue and punish violators of the law?
Opinions varied widely on whether and how the Stasi and other perpetrators of state-sponsored crimes should be tried. Did the laws of the DDR, as they existed before reunification, still apply in the east? Or was the criminal code of the western part of the country the proper instrument of justice in reunified Germany? However, these questions were moot: As Rupert Scholz, professor of law at the University of Munich and a Christian Democratic member of parliament, pointed out, the Unification Treaty specifies that the penal code of the DDR and not that of the Federal Republic of Germany (FRG) shall be applied to offenses committed in East Germany. Scholz’s view was upheld by the Bundesverfassungsgericht, the supreme court. Most offenses committed by party functionaries and Stasi officers—murder, kidnapping, torture, illegal wiretapping, mail robbery, and fraud—were subject to prosecution in reunified Germany under the DDR’s penal code. But this would not satisfy the tens of thousands of citizens who had been sent to prison under East German laws covering purely political offenses for which there was no West German equivalent.
Nevertheless, said Scholz, judicial authorities were by no means hamstrung, because West Germany had never recognized the East German state according to international law. “We have always said that we are one nation; that the division of Germany led neither to full recognition under international law nor, concomitantly, to a recognition of the legal system of the DDR,” Scholz said. Accordingly, West German courts have consistently maintained that West German law protects all Germans equally, including those living in the East. Therefore, no matter where the crimes were committed, whether in the East or the West, all Germans have always been subject to West German laws. Applying this logic, East German border guards who had either killed or wounded persons trying to escape to the West could be tried under the jurisdiction of West Germany.
The “one nation” principle was not upheld by the German supreme court. Prior to the court’s decision, however, Colonel General Markus Wolf, chief of the Stasi’s foreign espionage directorate, and some of his officers who personally controlled agents from East Berlin had been tried for treason and convicted. Wolf had been sentenced to six years in prison. The supreme court ruling overturned that verdict and those imposed on Wolf’s cohorts, even though they had obtained the most closely held West German secrets and handed them over to the KGB. The maximum penalty for Landesverrat, or treason, is life imprisonment. In vacating Wolf’s sentence, the court said he could not be convicted because he operated only from East German territory and under East German law.
However, Wolf was reindicted on charges of kidnapping and causing bodily harm, crimes also punishable under East German law. The former Stasi three-star general, on March 24, 1955, had approved in writing a plan to kidnap a woman who worked for the U.S. mission in West Berlin. The woman and her mother were tricked by a Stasi agent whom the woman had been teaching English, and voluntarily got into his car. He drove them into the Soviet sector of the divided city, where they were seized by Stasi officers. The woman was subjected to psychological torture and threatened with imprisonment unless she signed an agreement to spy for the Stasi. She agreed. On her return to the American sector, however, the woman reported the incident to security officials. Wolf had committed a felony punishable by up to fifteen years’ imprisonment in West Germany. He was found guilty in March 1977 and sentenced to two years’ probation.
Those who have challenged the application of the statute of limitations to communist crimes, especially to the executions of citizens fleeing to the West, have drawn parallels to the notorious executive orders of Adolf Hitler. Hitler issued orders mandating the summary execution of Soviet Army political commissars upon their capture and initiating the extermination of Jews. An early postwar judicial decision held that these orders were equivalent to law. When that law was declared illegal and retroactively repealed by the West German Bundestag, the statute of limitations was suspended—that is, it never took effect. Many of those convicted in subsequent trials of carrying out the Führer’s orders were executed by the Allies. The German supreme court has ruled the same way as the Bundestag on the order to shoot people trying to escape to West Germany, making the statute of limitations inapplicable to such cases. The ruling made possible the trial of members of the National Defense Council who took part in formulating or promulgating the order. A number of border guards who had shot would-be escapees also have been tried and convicted.
Chief Prosecutor Heiner Sauer, former head of the West German Central Registration Office for Political Crimes, was particularly concerned with the border shootings. His office, located in Salzgitter, West Germany, was established in 1961 as a direct consequence of the Berlin Wall, which was erected on August 13 of that year. Willy Brandt, at the time the city’s mayor (later federal chancellor) had decided that crimes committed by East German border guards should be recorded. At his behest, a central registry of all shootings and other serious border incidents was instituted. Between August 13, 1961 and the opening of the borders on November 9, 1989, 186 border killings were registered. But when the Stasi archives were opened, investigators found that at least 825 people had paid with their lives for trying to escape to the West. This figure was reported to the court that was trying former members of the National Defense Council. In addition to these border incidents, the registry also had recorded a number of similar political offenses committed in the interior of the DDR: By fall 1991, Sauer’s office had registered 4,444 cases of actual or attempted killings and about 40,000 sentences handed down by DDR courts for “political offenses.”
During the early years of Sauer’s operation, the details of political prosecutions became known only when victims were ransomed by West Germany or were expelled. Between 1963 and 1989, West Germany paid DM5 billion (nearly US$3 billion) to the communist regime for the release of 34,000 political prisoners. The price per head varied according to the importance of the person or the length of the sentence. In some cases the ransom amounted to more than US$56,000. The highest sum ever paid to the East Germans appears to have been DM450,000 (US$264,705 using an exchange rate of US$1.70 to the mark). The ransom “object” in this case was Count Benedikt von Hoensbroech. A student in his early twenties, von Hoensbroech was attending a West Berlin university when the wall went up. He was caught by the Stasi while trying to help people escape and was sentenced to ten years at hard labor. The case attracted international attention because his family was related to Queen Fabiola of Belgium, who interceded with the East Germans. Smelling money, the East German government first demanded the equivalent of more than US$1 million from the young man’s father as ransom. In the end, the parties settled on the figure of DM450,000, of which the West German government paid DM40,000 (about $23,529). Such ransom operations were fully controlled by the Stasi.
Political prisoners released in the DDR could not be registered by the West Germans because their cases remained secret. The victims were admonished to keep quiet or face another prison term. Nonetheless, in the first year after reunification, Sauer’s office added another 20,000 documented cases, for a total of 60,000. Sauer said he believed the final figure of all political prosecutions would be somewhere around 300,000. In every case, the Stasi was involved either in the initial arrest or in pretrial interrogations during which “confessions” were usually extracted by physical or psychological torture, particularly between the mid-1940s and the mid-1960s.
Until 1987, the DDR imposed the death penalty for a number of capital crimes, including murder, espionage, and economic offenses. But after the mid-1950s, nearly all death sentences were kept quiet and executions were carried out in the strictest secrecy, initially by guillotine and in later years by a single pistol shot to the neck. In most instances, the relatives of those killed were not informed either of the sentence or of the execution. The corpses were cremated and the ashes buried secretly, sometimes at construction sites. In reporting about one executioner who shot more than twenty persons to death, the Berlin newspaper Bildzeitung said that a total of 170 civilians had been executed in East Germany. However, Franco Werkenthin, the Berlin official investigating DDR crimes, said he had documented at least three hundred executions. He declined to say how many were for political offenses, because he had not yet submitted his report to parliament. “But it was substantial,” he told me. The true number of executions may never be known because no complete record of death sentences meted out by civil courts could be found. Other death sentences were handed down by military courts, and many records of those are also missing. In addition, German historian Günther Buch believes that about two hundred members of the Stasi itself were executed for various crimes, including attempts to escape to the West.
SAFEGUARDING HUMAN DIGNITY?
The preamble to the East German criminal code stated that the purpose of the code was to “safeguard the dignity of humankind, its freedom and rights under the aegis of the criminal code of the socialist state,” and that “a person can be prosecuted under the criminal code only in strictest concurrence with the law.” However, many of the codified offenses for which East German citizens were prosecuted and imprisoned were unique to totalitarian regimes, both fascist and communist.
Moreover, certain sections of the code, such as those on “Treasonable Relaying of Information” and “Treasonable Agent Activity,” were perversely applied, landing countless East Germans in maximum security penitentiaries. The victims of this perversion of justice usually were persons who had requested legal exit permits from the DDR authorities and had been turned down. In many cases, their “crime” was having contacted a Western consulate to inquire about immigration procedures. Sentences of up to two and a half years’ hard labor were not unusual as punishment for such inquiries.
Engaging in “propaganda hostile to the state” was another punishable offense. In one such case, a young man was arrested and prosecuted for saying that it was not necessary to station tanks at the border and for referring to border fortifications as “nonsense.” During his trial, he “admitted” to owning a television set on which he watched West German programs and later told friends what he saw. One of those “friends” had denounced him to the Stasi. The judge considered the accused’s actions especially egregious and sentenced him to a year and a half at hard labor.
Ironically, another part of this section of the criminal code decreed that “glorifying militarism” also was a punishable offense, although the DDR itself “glorified” its People’s Army beyond any Western norm. That army was clad in uniforms and insignia identical to those of the Nazi Wehrmacht, albeit without eagles and swastikas. The helmets, too, were differently shaped, but the Prussian goose step was regulation during parades.
A nineteen-year-old who had placed a sign in an apartment window reading “When justice is turned into injustice, resistance becomes an obligation!” was rewarded with twenty-two months in the penitentiary. Earlier, the youth had applied for an exit visa and had been turned down. A thirty-four-year-old father of two who also had been denied permission to leave the “workers’ and peasants’ state” with his family similarly advertised that fact with a poster reading “We want to leave, but they won’t let us.” The man went to prison for sixteen months. The “crimes” of both men were covered by a law on “Interference in Activities of the State or Society.”
Two letters—one to a friend in West Germany, seeking assistance to legally emigrate to the West, and another containing a similar appeal to Chief of State Honecker—brought a four-year sentence to their writer, who was convicted under two laws: those on “establishing illegal contacts” (writing to his friend) and on “public denigration” (writing to Honecker). The Stasi had illegally intercepted both letters.
The East German party chiefs were not content to rely only on the Stasi’s millions of informers to ferret out antistate sentiments. Leaving nothing to chance, they created a law that made the failure to denounce fellow citizens a crime punishable by up to five years’ imprisonment. One man was sentenced to twenty-three months for failing to report that a friend of his was preparing to escape to the West. The mandatory denunciation law had its roots in the statutes of the Socialist Unity Party, which were published in the form of a little red booklet. I picked up a copy of this booklet that had been discarded by its previous owner, a Stasi chauffeur, who had written “Ha, Ha” next to the mandate to “report any misdeeds, regardless of the person responsible, to leading party organs, all the way up to the Central Committee.”
Rupert Scholz, member of parliament and professor of law at the University of Munich, said many East Germans feel there is little determination among their Western brethren to bring the Stasi criminals to trial. “In fact, we already have heard many of them say that the peaceful revolution should have been a bloody one instead so they could have done away with their tormentors by hanging them posthaste,” Scholz told me.
The Reverend Joachim Gauck, minister to a Lutheran parish in East Germany, shared the people’s pessimism that justice would be done. Following reunification, Gauck was appointed by the Bonn government as its special representative for safeguarding and maintaining the Stasi archives. “We must at least establish a legal basis for finding the culprits in our files,” Gauck told me. “But it will not be easy. If you stood the millions of files upright in one line, they would stretch for 202 kilometers [about 121 miles]. In those files you can find an unbelievable number of Stasi victims and their tormentors.”
Gauck was given the mandate he needed in November 1991, when the German parliament passed a law authorizing file searches to uncover Stasi perpetrators and their informants. He viewed this legislation as first step in the right direction. With the evidence from Stasi files, the perpetrators could be removed from their public service jobs without any formal legal proceedings. Said Gauck: “We needed this law badly. It is not reasonable that persons who served this apparatus of oppression remain in positions of trust.”
See more at the journalist Bernd Pulch website http://www.berndpulch.org
SECRET STASI DOCUMENT ABOUT THE SECRET OPERATIONS
DOWNLAOD THE ORIGINAL DOCUMENT HERE
TOP-SECRET-Terroranleitung-STASI-Report -Einsatzgrundsätze und Hauptaufgaben der Einsatzgruppen im Operationsgebiet
DOWNLOAD ORGINAL STASI FILE HERE
Congratulations to Germany and it’s New President Gauck, former Federal Commissioner for the STASI Archives
Joachim Gauck (born 24 January 1940; pronounced [ˈɡaʊ̯k]) is a German politician, Protestant pastor, and former anti-communist human rights activist in East Germany. On 19 February 2012, he was nominated as the joint candidate for President of Germany by the government parties CDU, CSU and FDP, and the opposition SPD and the Alliance ’90/The Greens.[1]
During the Revolutions of 1989, he was a co-founder of the New Forum opposition movement in East Germany, which contributed to the downfall of the Soviet-backed dictatorship of the Socialist Unity Party of Germany; he served as a member of the only freely elected People’s Chamber for the Alliance 90 in 1990. Following the Reunification of Germany, he served as the first Federal Commissioner for the Stasi Archives from 1990 to 2000. As Federal Commissioner, he earned recognition as a “Stasi hunter”, exposing the crimes of the former communist political police.[2]
He was nominated as the candidate of the SPD and the Greens for President of Germany in the 2010 election, but narrowly lost to Christian Wulff, the candidate of the government coalition. However, his candidacy found strong resonance in the population, and Der Spiegel described him as “the better President.”[3] The German media dubbed him the candidate of the hearts.[4][5] Following Wulff’s 2012 resignation, Joachim Gauck was agreed on as a nonpartisan consensus candidate of all parties except the former East German communist party in the 2012 presidential election.[6][7][8]
A son of a survivor of a Soviet Gulag,[9][10][11][12] Gauck’s political life was heavily influenced by the suffering of his own family and his upbringing in the totalitarian communist regime of East Germany. A founding signatory of the Prague Declaration on European Conscience and Communism, together with Václav Havel and other statesmen, and the Declaration on Crimes of Communism, Gauck has called for increased awareness of communist crimes in Europe and the prosecution of communist criminals. He has criticized the political left of ignoring communist crimes.[13] The Independent has described him as “Germany’s answer to Nelson Mandela.”[14] He has been described by Chancellor Angela Merkel as a “true teacher of democracy” and a “tireless advocate of freedom, democracy and justice.”[15]
SOURCE: WIKIPEDIA
FEMEN EXPOSED – Italie : Les Femen s’invitent dans une…..
Firing Order for the East German Border Troups – Schiessbefehl der DDR – NVA und STASI im Original
STASI Report about Secret Information from the Leaders of the Deutsche Bank
DOWNLOAD ORIGINAL REPORT HERE
STASI – Report on “early detection of possible tensions with the NATO and Western-Germany”,
DOWMLOAD ORIGINAL DOCUMENT HERE
Report of the special operation controllers Rostock, May 1989 – STASI-Bericht enthüllt
BETREFF: “GoMoPa”-P – IZ – M
Liebe Leser,
auch Sie werden verstehen, dass man frühere Freunde und Mitarbeiter, ja sogar Partner, nicht gerne Verbrechen beschuldigt.
Das tue ich auch nicht gerne. Denn ich habe eine jahrelange Arbeit in die Immobilienzeitung gesteckt und ich werde Ihnen zeigen, wer diese Zeitung zu dem gemacht hat, was sie ist.
Dies war kein anoymes Redakteurskollektiv blutiger Anfänger und Studienabbrecher, hier stand eine gestaltende Hand mit Erfahrung und Wissen dahinter.
DESWEGEN HAT SICH DIE IZ SICH AUCH SEIT MEINEM ABGANG SEIT JAHRZEHNTEN NICHT WEITERENTWICKELN KÖNNEN, SEITDEM DIESE HAND FEHLT.
DIE IZ-EPIGONEN HASSEN MICH UND HABEN ANGST VOR DEM FREIEN WETTBEWERB !
ES ENTSETZT MICH, MIT WELCHEN MIITELN HIER KONKURRENTEN AUSGESCHALTET WERDEN UND SOGAR KRMININALISIERT WERDEN.
NUR WEIL EINE BEATE P EXISTIERT UND ALLES AUSBREMST !
DIESE DUMMHEIT UND SCHWÄCHE FÜHRT SOGAR DAZU SICH MIT EX-STASI-LEUTEN ZU VERBÜNDEN !
DAS SCHADET DER DEUTSCHEN WIRTSCHAFT, DER IMMOBILIENBRANCHE UND DER DEMOKRATIE UND IHNEN !
HERZLICHST IHR
BERND PULCH, MA
PS ES GIBT EINE BEATE UND EINE GABRIELE
CONFIDENTIAL – NSA Overview of Cloud Computing
The Top Spies of STASI exposed in Original Documents -Names-Bogus Names- Activities PART 6
Doc.6 of 6
Amsel (XV/4229/83) no entry
1983/1987
5 files
7093 25/07/86
(HVA/III)
letter of the British FM Howe to Oliver Tambo
7034 07/05/86
(HVA/III)
internal information of the British secret services to the ANC on
negotiations perspectives of the BOTHA regime with the liberation
movement and reaction of the ANC
Bob (XV/1471/65) no entry
1965/1985
5 files
6494 21/02/85
(HVA/II)
VS material on dislocation of British Rhein army
4910 05/02/82
(HVA/II)
FES highly confidential report to the SPD leadership summit on
industrial relations in GB – SPD discussion paper
4842 18/12/81
(HVA/II)
results, meeting of the 6th circle within the SPD directorate on
26/11/81
4755 09/10/81
(HVA/II)
internal note of the SPD PV on the office session of the union of the
social democratic parties of the EU on 10-11/09/81 in Brussels
From Poland
7597 03/05/89 Technical equipement of British police
7541 07/05/87 exercises, united NATO armed forces, Winter-Cimex 1987
6884 22/11/85 meeting with chief of national section of BBC radio
From Bulgaria
7542 13/05/87 on radio monitoring stations and tapping centres in Cyprus.
7539 30/04/87 on conduct of NATO manoeuvres “Cold Winter”
6874 13/08/85 discussions on terrorism at special NATO Council
6843 18/03/85 ACE COMSECD NATO: Nato discusses a program for the exchange of
coding equipments that are commonly used within the national
military intelligence systems.
Ringo (XV/400/86)
7519 17/11/87
(HVA/I)
information material from the British Emb. In Moscow
7518 17/11/87
(HVA/I)
structure, staff and leadership, UK ministry of industry and trade
MfS/HAII:
6439 16/01/84 Protocol lists, NATO armed forces in West Berlin
6438 01/01/84 General Major B. C. Gordon-Lennox, MBE (former infantry guard)
Gaston (XV/141/65) HVA II/ref 5
6735 18/10/85
(HVA/II)
GASTON reports of ZDF foreign correspondent as background for
upcoming discussions of the Television council for policy and TV prog
in Bonn on 18/09/85
6192 20/07/84
(HVA/II)
ZDF-reports from foreign correspondent
5461 08/10/82
(HVA/II)
ZDF reports from foreign correspondent (material formerly not open)
Susi (XV/4265/76) no entry
6240 05/10/84
(HVA/XV)
structure of civilian employees of British Rhein Army
5861 21/12/83
(HVA/XV)
British Rhein army services
5660 15/04/83
(HVA/XV)
structural questions of the OETV and information on pbs of the UK and
US armies in Moenchen Gladbach area
Lore (III/621/76)
5787 14/10/83
(NEUBRANDENBURG XV)
development of MIK grouping
5786 14/10/83 modernisation of weapons of countries of the Warsaw Pact
through NATO nations
Tajo (XV/6721/80)
5775 11/10/83
(HVA/XIV)
English arms companies
5774 11/10/83 Feuerleit control system, British arms company Ferranti
Eric (XV/75/83) RES. 201
7576 03/10/88 ERIC GB Factory ICI and trade with the GDR
5719 20/06/83
(HVA/III)
info on decision to send and activities of a CND representative to
Prague meeting (21-26/06)
5485 26/11/82
(HVA/III)
on specific questions of the British state of emergency planning
(preparation of war time)
Zielke (XV/2178/74)
6998 17/04/86
(HVA/XIII)
chemical and biological warfare developments 1985 – JP Perry
Robinson
5741 03/08/83
(HVA/XIII)
proceedings, conf. of Swedish representatives and ministers on
chemical weapons 05719
Stamm
6189 18/07/84
(HVA/XI)
strategic synopsis of office for studies and exercises of the German
army dated 26/09/83
5649 00/04/83
(HVA/XI)
4 position papers of the AA in the FRG on middle range weapons with
a remark from the disarmament officer, Amb. Ruth
Roland (XV/4608/75) HVAIX/REF 9, P 231
5742 09/08/83
(HVA/III)
doc. From Chase World information corporation on arab investments
5640 17/03/83
(HVA/XI)
planning of exercises and mil. Activities of the US/Berlin brigade for
1983
5406 03/09/82
(HVA/XI)
personnel data on total number of Berliner officers of the Us/Berlin
brigade with partial data on French and British mil. Personnel in WB
Richard (XV/351/73) HVA I/ref 6, P 202
5427 26/10/82
(HVA/I)
HTR symposium
5426 26/10/82 natural gas
Alpha (MfS/4283/60) HVA X/ref 3, P 226
5851 15/12/83
(HVA/X)
EU Commission docs on funding, positions of come states
5206 21/04/82
(HVA/X)
letter of former Foreign Minister Lord Carrington to EU President
Pirol (XV/2904/78)
7219 17/12/86 material from UK intelligence services on Libya
4911 09/02/82
(HVA/XII)
info. From UK secret services on far-right extremism
Holz (XV/2426/74)
4892 06/01/82
(HVA/III)
on internal report of the British National Council for economic
developments and development trends of British trade in the field of
manufacturing industry
4865 23/12/81
(HVA/III)
internal report from the British National Council for economic
development on energy situation
4843 11/12/81
(HVA/III)
internal assess. of the British National Committee for economic
development on theme industry policy in Europe
Joerg (MfS/10874/60)
5785 14/10/83
(HVA/XI)
leading employee from the national security council on US future
actions towards the Soviet Union and other socialist countries
4769 22/10/81
(HVA/XI)
Study on legislative perpsective and the new committee sys. Of the
House of Commons.
Bettina (XV/92/67)
4641 25/06/81
(KARL MARX XV)
project system (UK) extension of invts for the construction of a
computer sys. based on GDR micro-processors in Leeds, Yorkshire
4658 25/06/81
(KARL MARX XV)
BNFL Windscale project (UK)[Bau v. Anlagen] for the storage and the
manufacture of nuclear combustible in Windscale (Grafschaft Cumbria)
4476 02/04/81
(KARL MARX XV)
Zimbabwe conf. on reconstruction and dev. 23-27/03/81
5071 12/04/82
(KARL MARX XV)
project for rational energy need in England
5032 21/04/82
(KARL MARX XV)
airport project in Manchester
Jaeger (XV/2313/79)
4881 30/11/81
(HVA/III)
6 reports from the foreign policy committee of the British Parliament
Zimbabwe – the role of British economic aid to the development of
Zimbabwe
4719 14/08/81
(HVA/III)
Info on 5th report of the Foreign Affairs Committee of the British
House of Commons on upcoming North/South summit in Mexico (oct.
81)
Doktor_Zeit (XV/2855/68)
4924 05/02/82
(BERLIN XV)
activities of the Greens within peace movt at the European level.
4730 (BERLIN XV) conclusions report on the 1st term of the Central Commission for
Biological Security
Jutta (MfS/1815/60)
4671 21/08/81
(BERLIN XV)
reports on 719th and 720th EU Council meeting on 6 & 13/07/81
4531 18/05/81
(BERLIN XV)
completion of reform of EU budget
Rat (XV/305/79)
6509 04/03/85
(BERLIN XV)
on conference ” nuclear war by mistake – evitable or inevitable?” on
15-16/02/85 in Stockholm
4653 12/08/81
(HVA/III)
Info on a confirmed project of the Labour Party leadership (NEC)
related to the question of GB’s exit from the EU
Granit (XV/305/79)
4652 12/08/81
(HVA/III)
Info on power struggle within the Labour Party
4380 04/03/81
(HVA/III)
on activities of British [Gewerkschaftsdachverbandes] (Roof trade
union?) TUC on protection of Polish trade union Solidaritaet
Eva (XV/1362/65)
4981 00/04/82
(HALLE XV)
operational concept for the area of 1st PZDIV-Braunschweig,
Hildesheim, Zweigkanal, Peine, Hannover – protocol from the
Wehrbereichskommando II dated 20/01/82
4638 00/08/81
(HALLE XV)
exercises of Allied armed forces. Combat exercise of the UK 3rd
Division Red Claymore on 28/9-28/10/81 (transfer of division on [V
Fall festgelegten Routen]) MI 53.2 – 1551-1 (81) Secret
Bruecke (XV/1908/73)
4571 19/06/81
(HVA/III)
on interal assess. of the politburo of the central committee of the UK
CP on the Polish issue at the PR meeting on 11/06/81
Anna (XV/2873/62)
4572 08/05/81
(HVA/II)
doc. On the meeting of liberal and democratic faction within the EUP
on 27-28/04/81 in the Hague on theme EU security and defense
XV/268/68
3218 18/04/79
(HVA/XV)
Internal report from BSC London on visit to fair in Kwangchow (China)
and on trade negotiations with China in the steel sector
XV/134/71
3230 02/04/79
(HVA/III)
British Navy staff HQ document
XII/2486/70
2309 14/08/77
(DRESDEN XV)
SI confidential internal docs nr B/1/77 on 21/01/77; b/4/77 on
11/03/77; 4/77 on 11/02/77; B/7/77 on 26/05/77 on SI office
meeting on 30/03/77 in London – Invitation – Agenda – List of
participants – Office activities – SI plan 1977-78 and related pbs –
detailed 1977-78 program – Analysis resolution in Spain – Resolution
in Czechoslovakia – List of participants – protocol of participating party
representatives
XV/2742/76
2362 28/09/77
(HVA/IX)
files from British armed forces (Phone directory of the British Corps
159 and 1 dept. info nr 27)
XV/1093/67
1976-1980
35 DOCS
GB gov. / Labour Party
3062 14/11/78
(HVA/III)
Confidential studies on EU problematic from the British Labour Party
2229 28/06/77
(HVA/III)
material from the international committee of the British LP leadership
from meeting on 10/05/77
XV/ 3926/63
1792 05/02/75
(LEIPZIG XV)
Phone directory, British armed forces in WB on November 1974
XV/ 212/73
1962 15/11/76
(HVA/IX)
Staff list, British infantery brigade HQ in WB, July 1976
4963 Protocle list of the British armed forces in WB, Feb. 1976
1964 15/11/76 Staff list, British armed forces in WB, 1975
1965 15/11/76
(HVA/IX)
Exercise Parang, 1 Batalion paratroopers of the British Armed forces
from WB on troop exercise field Sennelager
1968 11/11/76
(HVA/IX)
various material from the British armed forces in WB
XV/2962/76
2281 19/08/77
(HVA/III)
Confidential conversation of the EU Council nr S/692/77 (RCC39) – 8th
report from the EU trade council in China
XV/1823/64
2281 11/07/77
(HVA/IX)
manual of joint warfare volume II joint tactical communications
OTHERS
4752 30/10/81 PIERRE
(HVA/XI)
Allies manoeuvres Rondo XXI in WB
4745 22/10/81 DOKTOR
(HVA/X)
strategic and tactical thoughts of the international dept of
the British Labour Party on current policy towards South
Africa
4739 12/08/81 KONGRESZ
(HVA/III)
Apartheid and Business a Swiss strategic and tactical study
for the establishment of eco. & tactical relations between
the imperialistic countries and RSA in the eighties dated
26/02/81 (nr. 1262)
4732 18/09/81 WESER
(HVA/XI)
Study of the Congress – research service on NATO pbs and
the modernisation of arms control
4700 26/08/81 HELMUT
(HVA/III)
internal assess. of an Indian and a Belgian diplomats on
issues related to the Geneva disarmament negotiations
4695 07/09/81 MAI
(MAGDEBURG
XV)
Views of Richard Lehner on NATO manoeuvre negotiations
in Fall 81 on Lower Sachsen territory
4684 04/09/81 JACK
(HVA/IV)
eco. and industry policy of British gov.
4486 14/04/81 GERD
(HVA/XIII)
progress of work on chemical war materials in GB
4465 04/04/81 TENNE
(HVA/II)
consultations, the Conf. of European Churches (CEC) in
Cardiff / GB on 24-28/03/81
4409 02/04/81 ANTON
(HVA/III)
NATO secret files on a multifunctional communication
[verteilung] system MIDS
4382 26/02/81 ZENTRUM
(HVA/XIV)
Activities of ICL England company and upcoming business
with the GDR
7582 02/05/89 REINHOLD Assess. Of Gorbatchow’s visit in GB, views of diplomats
from British Emb. In Vienna
7578 06/10/88 KARL assess. Of British PM Thatcher’s speech in Bruegge and in
Luxembourg on 20-21/09/88
7526 11/02/87 FROM
HUNGARY
on co-operation between the US and the RIIA
7488 02/10/87 INGRID E88 (GB, France, Israel’s contributions)
7479 10/09/87 ALTMEISTER modalities of deployment of British military units on / from
transport facilities.(ferries)
7479 10/09/87 RAINER conversations with representatives of Konzerns from the
FRG, GB and Sweden on 05/09/87.
7440 03/07/87 ROEMER classified telegram on memorandum of understanding for
electronic order of battle support, zuflint lock 87 su bold
guard 86.
7406 01/06/87 BASTIAN files on the structure, capacities, profile and market
position of chemical konzern.
7377 04/05/87 GEMSE Egon Bahr on prospective policy for Europe; more security
in Europe will relieve both superpowers (quote?)
7366 14/04/87 OLAF Analysis for the British Konzern United Sterling Cooperation
on delivery pbs of the GDR AHB Polygraph
7360 06/04/87 DISKONT assess. Of the Midland bank, London, on eco. Situation and
trade activities with VR Bulgaria
7351 00/04/87 HANS Conversation with Loeffler, Ristock, Momper, Heimann and
Kremendahl on one side, and the British envoy in West
Berlin and two other representatives of the British military.
7350 30/03/87 TRISTAN full text, Howe’s speech, at the Belgian Royal Institute for
International Relations, Brussels, 16/03/87.
7320 23/02/87 ERLE some thoughts from VRM leadership on structure of
relations between the UK and Frontlienienstaaten?
7220 17/12/86 HERZOG Report on 8 international HTR meeting in San Diego,
California on 15-16/09/86
7203 03/12/86 FLIEGER
(HVA/IX)
manual of interoperability of health services
7411 05/06/87 BAR/875 assess. Within the SPD and the diplomatic corps on
discussion on the military doctrine, as well as assess. Of
the FRG gov. on disarmament policy
7141 09/10/86 TALAR
(HVA/II)
SPD Parliament’s section’s final proposals on 1986-1987
budget for the “Hunting flight 90″ [Jäger90] project
7126 08/09/86 ROTHER
(HVA/XIII)
ICI’s position on trade with CMEA countries, particularly
the GDR
7121 26/08/86 SCHAEFER
(HVA/II)
materials from the Greens on topic”the FRG contribution to
nuclear disarmament in western Europe”
7118 18/08/86 ASPHALT
(HVA/III)
confidential report of the UK Emb. In Libanon on the UK
policy in the Middle-East
7087 16/07/86 ANTOS
(HVA/XI)
a Rand note British and French strategic forces response
options
7064 19/06/86 BERG
(HVA/III)
internal convention between the Labour Party Leadership
and British monopoly circles on policy of a future Labour
government after the parliamentary elections
7052 27/05/86 WALD
(HVA/III)
joint study of the FCO and the UK Defence Ministry on the
eco. Situation in the USSR and the feasibility of the soviet
eco prog.
6795 04/12/85 SCHUSTER
(HVA/XI)
studies, 3rd world congress for soviet and East-European
studies, 30/10-04/11/85 in Washington DC.
6789 29/11/85 BAR/102
(HVA/I)
synopsis on SDI
6779 19/11/85 OLSEN
(HVA/III)
internal personal views of WEU sec gen, Alfred Cahen, on
assess. Of a report from WEU SDI working group
6723 16/10/85 PAUL
(HVA/III)
US military bases in the UK
6716 15/10/85 ANDRE
(HVA/XI)
Thoughts of one of the representatives to the congress,
Gorbatchew/Mitterrand & Gorbatchew/Reagan summits.
6629 21/06/85 DIREKTOR
(HVA/AG K)
On London institute for international relations
6635 03/07/85 REINHARD
(HVA/I)
“Cosmic space, national security and C3I” conference
material of Mitre corporation, USA
6674 12/08/85 PETRA
(HVA/II)
changes in UK Rhein Army
6538 29/03/85 BAR/650
(HVA/I)
material from “German Strategy Forum” on 14/03/85 in
Bonn-Bad-Godesberg
6535 27/03/85 JUST
(HVA/XII)
position of leading members of the international
politologists executive committee IPSA on US/USSR and
US/Western Europe relations
6529 19/03/85 FRITZ
(HVA/XIII)
conclusion of contract between Ministry for chemical
industry and Shell International Chemical company
6523 14/03/85 JOCHEN
(HVA/XII)
Conference”Key problems of technological transfer and the
need for intellectual property” on 6-7/03/85 in Cambridge
6521 13/03/85 FREQUENZ
(HVA/IV)
Infra Red measureing Ir-Vermessung (flight data) of NATO
planes during NATO exercise Trial Embow I in Aberporth /
GB
6520 12/03/85 HANDWERKER
(HVA/AG K)
Federal institute for Eastern and international studies,
Cologne – 2nd conference on “Relations between economy
and politics in the USSR”.
6509 04/03/85 RAT
(BERLIN XV)
on conference ” nuclear war by mistake – evitable or
inevitable?” on 15-16/02/85 in Stockholm
6480 29/01/85 ECKAHRDT
(HVA/III)
on internal split within the UK CP leadership
6321 27/12/84 KOREN
(SWT/AG1)
reductions in US costs to station forces in the Federal
Republic of Germany and the United Kingdom are unlikely
6304 07/12/84 STADT
(GERA/AG)
Konzern analysis interatom GmbH
6299 05/12/84 FALKE
(BERLIN XV)
internal study of the Federal Ministry for German relations
on situation of GDR research in the UK and the US
6239 05/10/84 HERZOG
(HVA/AG K)
report civil exploitation of defence technology
6193 23/07/84 H_SCHNEIDER
(ERFURT XV)
combined action of big companies Kloeckner Humboldt
Deutz with NATO military officials on the development of
MRCA tornado
6059 23/03/84 MUENZER
(HVA/X)
NATO commissioned study on history, structure, spectrum
of activity, field of influence and evolution of British peace
movement
5867 29/12/83 KOBRA
(HVA/XIV)
14 TH RB 199 local tecnical committee meeting
5824 15/11/83 VOGT
(HVA/XI)
on Ripon – Bow – Adenauer conference on NATO-Alliance
relations and on East-West relations
5823 14/11/83 SCHOEN
(HVA/I)
report on results of trip to Moscow on 10-12/10/83,
delegation of unterausschusses for disarmament and arms
control of the FRG parliament
5821 09/11/83 SONJA
(HVA/XII)
political activities of FRG citizens against the state and
their connections with West European Peace movement
5813 03/11/83 ZENTRAL
(HVA/AG K)
NATO conlusions – working paper for argumentation in the
political opposition
5777 12/10/83 KRUG
(HVA/XIII)
MfA Political directors council, FR, GB, US and the FRG in
NY
5772 06/10/83 B_STERNBERG
(NEUBRANDENBURG
XV)
on organisation of NATO base Norfolk, on relevant military
construction measures for the stationing of cruise missiles
in the area of Cornwall, England
5718 16/06/83 SCHULZ on E. Thompson’s activities against Prague Peace
(BERLIN XV) conference
5734 20/0783 ANNA
(HVA/II)
report from commercial director of the F. Naumann
Stiftung on global work 1983/83, as well as material from
the Th. Heuss Academy on 1984 plans and material from
the Europe office of the F. Naumann Stiftung
5728 07/07/83 HENRY
(HVA/X)
internal files from the Commerzbank
5635 17/03/83 GOVERNOR
(HVA/XIII)
on the creation of an export insurance company Bond
Support Advisers Ltd in London
5629 15/03/83 SAMSON
(SWT/
13.15.III)
british defence directory
5619 07/03/83 LINDNER
(HVA/XI)
The politics of central Europe, report from David Owen
5600 10/02/83 BRITTA
(HVA/IV)
thanks to a reliable source we have conception information
for Chancellor Kohl for his upcoming meeting with English
Pm in Febr. 83
5586 19/01/83 RODE
(HVA/XIV)
construction and finalisation of Tornado CFK-Tailerons
5578 17/01/83 AKKER
(HVA/II)
internal working paper from the PV of the SPD on German
strategy towards the US and the USSR during the Geneva
INF negotiations
5523 09/12/82 JUST
(HVA/XII)
internal report from a former US Amb. ontheme “the persic
gulf and the US policy – What still has to be done”
5254 08/07/82 RAUCH
(HVA/XIV)
creative strategies – Western European robotics
instrumentation industry analysis service
5221 01/06/82 SCHWARZ
(LEIPZIG XV)
European institute for security policy
5203 23/06/82 JACK
(HVA/XI)
The Falkland crisis info – material from the research
department of the US congress
5153 05/05/82 DR PETER
(HVA/XII)
results of discussions within the EU on pbs related to the
GB/Argentina conflict, as well as on similar potential
conflicts between France and Canada
5089 12/05/82 KORB
(HVA/XI)
3 studies on concept of the Reagan’s administration and on
West European opinions on arms control & security issues
5072 28/04/82 BELIN
(HVA/I)
on the SPD security policy towards the GB/Argentina
conflict at its Party Day in Munich
5069 25/03/82 HELENE
(HVA/I)
International Energy Agency – activities
5049 19/03/82 JUTTA
(BERLIN XV)
reports on EU Council meeting – 753 rd meeting (economic
and finance ministers) on 15/02/82 – 755th meeting
(Foreign affairs) on 22-23/02/82
4985 01/04/82 WAGNER
(HALLE XV)
HMS Speedy report of proceedings during operation F
IBALT 28/10-01/12/81
4981 00/04/82 EVA
(HALLE XV)
operational concept for the area of 1st PZDIVBraunschweig,
Hidlesheim, Zweigkanal, Peine, Hannover –
protocol from the Wehbereichskommando II dated
20/01/82
4924 05/02/82 DR_ZEIT
(BERLIN XV)
activities of the Greens within peace movt at the European
level.
4904 14/01/82 LESNER
(HVA/III)
US and GB anti-Ethiopian activities from Sudan and on
results of manoeuvres Bright Star 82
4896 08/01/82 DIREKTOR
(HVA/XII)
views of FCO Foreign Office (blacked out name) former
member of British Emb. in the GDR on current political pbs
4881 30/11/81 JAEGER
(HVA/III)
6 report from the foreign policy committee of the British
Parliament Zimbabwe – the role of British economic aid to
the development of Zimbabwe
DOWNLOAD ORIGINAL DOCUMENT HERE
The Top Spies of STASI exposed in Original Documents -Names-Bogus Names- Activities PART 5
Doc. 5 of 6
Merten (Mfs/6427/60) Dr Hagen Blau, West German diplomat.
1960/1987
35 files
6297 04/12/84
(HVA/I)
144 & 145 EPZ political committee
4988 22/03/82
(HVA/I)
international institute for applied systemic analysis – Austria
4879 21/12/81
(HVA/I)
Info AA service in Bonn on human dimension of the KSZE documents –
Bidenkopf’s views on nuclear strategy GB domestic policy – Hamm
Bruecher ‘s speech in the US
4878 21/12/81
(HVA/I)
info- AA service in Bonn on the FRG argumentation on natural gas
Roehren activities – cultural exchange agreement China information
issues in UN sys. – Commonwealth conf. in Oct. 81 – Egypt after
Sadate’s death – Terrorism in Italy – situation in Greece – Friendship
contract between Libya and Ethiopia and VDRJ
Topas (XV/333/69) Rainer Rupp, Nato official.
1969/1989
32 files
7573 07/09/88 Document from the British delegation to NATO; soviet computer industry
7455 01/08/87 NATO document C-M (87) co-ordinated production of European combat
aircraft
7407 03/06/87 NATO document DPC/D (86) 10 – United Kingdom defence plans 1987-
1991.
7321 24/02/87 NATO information, Annex A, B, C of general report NATO-doc DPC/D
(86) 10
7307 10/02/87 NATO information bullet points and background information for NATO
sec. Gen. In preparation of meeting of defence ministers of the alliance
7299 04/02/87 military docs CIG(86)167; CIG(86)168; CIG(86)169; CIG(86)170;
CIG(86)172; CIG(86)175, 176
7209 06/12/86
(HVA/XII)
NATO doc JGP(86)105 multilateral defence verification of the UK
7125 08/09/86
(HVA/XII)
PQ-85 UK answer to 1985-1990 goals of the armed forces
7085 11/07/86
(HVA/XII)
NATO doc JPG(68)59 UK presentation on objectives of the multilateral
verification of the armed forces
7006 21/04/86
(HVA/XII)
NATO doc. DPQ (85) – UK – Navy – statistics
6972 25/03/86
(HVA/XII)
NATO doc. DPQ (85) GB – statistics – Air army
6944 19/02/86
(HVA/XII)
NATO doc. DPQ (85) – UK – Statistics Heer
6918 27/01/86
(HVA/XII)
NATO doc. DPC/D (85) 21 – UK – NATO defence plans 1986-1990.
6905 09/01/86
(HVA/XII)
NATO doc. DRQ-85 – UK
6822 23/12/85
(HVA/XII)
NATO doc. – British response to defence planning 1984 – Navy tables
6790 02/12/85 NATO doc. JGP (85) 11 – presentation on multilateral verification of UK
armed forces plans.
6669 07/08/85
(HVA/XII)
NATO doc DRC/DS (85) 21 – Conclusions sheet of DRC meeting on
18/06/85
6517 12/03/85 NATO doc DPQ (84) UK-D/1- UK answer on defence planning
perspectives 1984.
6515 11/03/85
(HVA/XII)
NATO doc DPQ (84) D1 – UK – Answer on 1985-1990 objectives – Air
force
6507 28/02/85
(HVA/XII)
NATO doc DPQ (84) UK – D/1 – UK answer on 1984 defense planning –
Navy
6496 22/02/85 NATO doc DPQ (84) UK – D/1 – UK answer on 1984 defense planning –
Haer
6479 28/01/85 NATO doc DPC/D (84) 5 – 1985-1990 objectives of the armed forces
6460 09/01/85 NATO doc C-M (84) 53 – situation in Eastern and south Asia – March-
Sept. 1984
6309 11/12/84
(HVA/XII)
NATO doc PN (84) 68 – Assess. Defence planning – UK
5985 13/01/84 NATO doc DRC/DS (83) conclusions sheet of DRC meeting dated
17/11/83
5647 25/03/83 NATO info on NATO exercise Wintex Cimex 83
Weber (XV/819/66)
1966/1987
29 files
6681 26/08/85
(HVA/I)
EU/GB/Ethiopia – EU General Secretariat, Brussels – 19/07/85 UK
memorandum on EU policy towards Ethiopia
5643 21/03/83 report from AA in the FRG on Zambia’s domestic and foreign policy and
preparation of negotiations FRG/Zambia
5608 22/02/83
(HVA/I)
AA internal material on Namibia’s question
5536 30/12/82
(HVA/I)
BMZ material on the preparation of the CDA governmental conference on
26-28/10/82 in Washington
5185 08/06/82
(HVA/I)
assess. AA Bonn on 38th meeting of the OUA Council of ministers in
Addis Abeba ( March 1982)
Roedel (XV/483/68)
1968/1987
26 files
7513 04/11/87
KARL-MARX
TOWN
background information on programme JF 90
7471 00/09/87 NATO-D/33 from 17/07/87.
7359 03/04/87
KARL MARX
TOWN
NATO document from 02/87
7198 27/11/86 WT report nr 22/86
6619 10/06/85
(K-MARX XV)
NATO /85 WP V , 07/05/85
6658 25/07/85
(HVA/XI)
NATO 1861/85
6184 06/07/84
(K MARX XV)
FRG Emb. in London report nr 14/84 Thorn EMI purchase offer to British
aerospace leads to a new British armaments konzern
5864 23/12/83
(K MARX XV)
TAF JF 90
5852 16/12/83 NATO 3116/83
5801 21/10/83
(K MARX XV)
on meeting national armaments directors of the 4 groups on 20-
22/09/83 in Williamsburg, USA
5768 29/09/83 conception, British NATO delegation, on research issues
5717 15/05/83
(K-MARX XV)
GEIP – Project armed anti-tank guidance generation
5716 15/06/83 NATO-Corrigendum to DS AC/259/31
5715 15/06/83 mil. Techn. Objectives plan – light transport & SAR helicopter
5711 08/06/83 NATO 1306/83
5573 05/01/83
(HVA/XII)
NATO info. Content of the latest meeting of NATO Council at the Amb.
level before the ministerials in Dec. 1982
5445 19/10/82
(K MARX XV)
single report 20/82 (L)
5418 15/10/82
(K MARX XV)
NATO 2722/82
5395 29/09/82 NATO 2608/82 AC/302 (PG/2) D/29
5377 29/09/82 FRG Emb. in London, single report 59/82 (M) – background information
on Schiffverluste (Sheffield-Coventy-Atlantic Conveyor)
5253 07/07/82
(K MARX XV)
Air/air plane body
4923 15/02/82
(K MARX XV)
NATO 4113/81
4887 02/12/81
(K MARX XV)
working group on air defence definition of flying weapons systems –
invitation to 94 meeting
Genf
1987
26 files
7143 10/10/86
(HVA/AG K)
materials from IISS 28th annual conf. in Kyoto on theme “Eastern Asia,
the West and international security…”
6943 18/02/86
(HVA/AG K)
Conf. of Aspen Institute in West Berlin on 7-10/02/86. Theme “new
dimension of security in nuclear time”
Peter (XV/96/72) Alfred Spuehler, BND official.
1972/1984
24 files
5782 14/10/83
(HVA/IX)
monthly military situation report, West and rest of the world,1-
31/07/83
5733 19/07/83
(HVA/IX)
mil. Situation report n 4/82 dated April 1983
5652 05/04/83
(HVA/IX)
mil. Situation report West – monthly report nr 2/83
5651 05/04/83 mil. Situation report – monthly report nr 1/83
5606 18/02/83
(HVA/IX)
mil. Monthly report – NATO states and European neutral states nr 12/82
for period 01-31/12/82
5588 20/01/83
(HVA/IX)
mil. Situation report West – monthly report nr 11/82
5524 15/12/82
(HVA/IX)
mil. Situation report, rest of the world, 1-30/09/82
5513 15/12/82
(HVA/IX)
mil. Monthly report, NATO states and European neutral states – nr
10/82
5349 23/07/82
(HVA/IX)
mil. Monthly situation report, rest of the world, period 01/06-30/06/82
5258 08/07/82
(HVA/IX)
mil. Situation report, rest of the world, period 01-31/05/82
5219 10/06/82
(HVA/IX)
mil. Situation report, NATO U.A
5064 11/05/82
(HVA/IX)
mil. Monthly report, NATO states and European neutral states nr 3/82
period 01-31/03/82
5051 23/04/82
(HVA/IX)
UK assess. of Soviet air attack brigade
4990 05/04/82
(HVA/IX)
from a secret diplomatic correspondence of AA MBFR Bonn on views of
a Chinese diplomat on internal pbs of the Soviet mil. Mission in the FRG
4983 06/04/82
(HVA/III)
on international conference of Japan’s SP on disarmament issues
Horn (XV/6258/81)
1981/1986
18 files
5152 04/05/82
(HVA/III)
assess. of Malwin conflict by leading Argentinan mil.
5147 24/04/82
(HVA/III)
on results of Haig negotiations on 18-19/04/82 on resolution of Malwin
crisis in buenos Aires
5146 27/04/82 on development of Malwin conflict and the backgrounds of activities of
Argentinan mil. leadership
Rose (XV/190/63) Margarethe Lubig, Nato official
1963/1987
7450 29/07/87 NATO list of security officers of representations, of the IMS, the HQs
and member states delegations.
7310 12/02/87 plans of repair and construction of NATO aircraft and missiles in the
FRG and subsequent costs
7216 12/12/86
(HVA/XII)
2 internal letters from BMVG on procurement contract for skynet
satellite (28-29/10/86)
7051 26/05/86
(HVA/XII)
progress of work of the realisation of NATO infrastructure plans
6810 17/12/85
(HVA/I)
meeting of working group East-West relations of the DGAP on 10/06/85
6776 18/11/85
(HVA/XII)
NATO – aus dem Schriftverkehr einer NATO Dienststelle
6665 01/08/85
(HVA/XII)
NATO meeting of infrastructure on 16/07/85
6323 28/12/84
(HVA/XII)
infrastructure – Ship shore ship buffer (SSSB)
6294 03/12/84 prospective positions of united countries on 3 billion – IAU – ceiling and
of rest of document DPC (84)0
5978 06/01/84
(HVA/XII)
NATO – air bases Guetersloh setting up of supplementary ordnance
depot, British prefinancing of construction works.
5977 02/01/84
(HVA/XII)
NATO ministerial conference 5-9/12/83, DABM (Defence against
1969?/1987
14 files
7500 14/10/87 latest conversations ANC – white minority and UK position on the
resolution of the conflict in RSA.
6711 10/10/85
(HVA/VI)
Assess. Of a member of UK CP on situation within the party
5762 20/09/83
(POTSDAM XV)
internal letter from the Peace network – London
5752 24/08/83
(POTSDAM XV)
information about split between CND and END at the Oxford Conf. in
July 83 and on IKV’s activities in the Hague.
5017 12/04/82
(POTSDAM XV)
info. On Peace network
Walter (XV/750/66)
1966/1986
14 files
6512 07/03/85
(HVA/II)
conversation with European director of trilateral committee, Georges
Berthoin, on 19/02/85 in Paris
6463 10/01/85
(HVA/II)
secret meeting of leading Logenfunktionaere on 05/01/85 in the FRG.
6141 05/06/84 Views, Monsieur Berthoin, Europe director at the trilateral committee,
on current political questions and committee’s activities
6140 05/06/84
(HVA/II)
Comparative analysis on assess. Of soviet detente policy between Prof.
Haftendorn, Berlin and British deputy
5710 08/06/83
(HVA/II)
BMFT report on stance and perspectives of progress of High
temperature reactors and fast brutreaktor
5657 07/04/83
(HVA/II)
Draft report of the political committee of the EUP on arms procurement
dated 23/08/82
5542 16/12/82
(HVA/II)
2 materials from the European Socialist movt
4949 05/03/82
(HVA/II)
files from the EU Commission
Cantor (MfS/12904/60)
1960/1983
13 files
5764 23/09/83
(HVA/AG K)
Leading employee of the UK Emb. in the GDR on current political pbs.
5663 20/04/83
(HVA/AG K)
from GB Emb. on Karl Marx conf
5650 00/04/83 British EU experts on EU current pbs
5562 16/12/82
(HVA/AG K)
leading member of the International institute for strategic studies,
London, on current questions of East-West relations
5432 22/10/82
(HVA/AG K)
from the British Foreign Ministry on foreign policy of the new
government in Bonn
5408 17/09/82
(HVA/AG K)
British diplomat on East-West commercial relations
5097 29/04/82
(HVA/AG K)
SPD “Unterbezirksvorsitzender” on security policy and on current
foreign policy questions
5087 06/05/82
(HVA/AG K)
from the US Emb. on current agricultural questions
4834 11/11/81
(HVA/AG K)
questions of the European political co-operation and the role of the EUP
Cello (XV/872/74)
1974/1984
13 files
5731 14/07/83
(HVA/I)
reaction of GB Emb. in the FRG on Kohl’s trip to Moscow
5429 02/10/82
(HVA/I)
on Labour Party day in Blackpool on domestic policy circle in the FRG
from the UK pt of view
5428 17/09/82
(HVA/I)
reaction of the British Emb. in Bonn on Wischnewski’s conversations in
the GDR and critic on further perspectives of the FRG government’s
coalition
4844 23/12/81
(HVA/I)
France’s position on results of Honecker/Schmidt meeting and on other
FR foreign policy positions
Toepfer (XV/821/66)
1966/1987
12 files
6631 26/06/85
(HVA/I)
report of the FRG foreign minister delegation on speech on “Germany
and Berlin issues” on 05/06/85 in Lisbon
5696 19/05/83
(HVA/I)
Emb. report from London on V. Weizaescker in oxford and London
5597 01/02/83
(HVA/I)
BMB report on 32nd meting of the committee for disarmament and
arms control on 20/01/83
Beermann (XV/3600/65)
11 files
7487 01/10/87 on scheduled British troops exercises in the field of military
management (wehrbereichsverwaltung)
7092 21/07//86
(ERFURT XV)
scheduled military exercises in Duesseldorf
6451 02/01/85
(ERFURT XV)
Defense related plans for NATO Terloh and arrangement of the Federal
Defence Minister
6450 02/01/85
(ERFURT XV)
Search for outside landing striops for “Harrier” type airplanes
5820 09/11/83
(ERFURT XV)
NATO air base Guetersloh and actions for stationing of missiles and
cruise missiles in the FRG
5514 Construction of alternative airports for des NATO-airbase Guetersloh for
the troop exercise territory (Truppenuebungsplatz Senne)
5474 12/11/82
(ERFURT XV)
regrouping of units of British Rhine army
5177 14/06/82
(ERFURT XV)
planned major mil. Manoeuvres and first assess. of a high ranked
officer from the Federal defence ministry
Siegel (XV/2105/73)
1973/1986
11 files
6796 04/12/85
(HVA/XI)
studies, further to the annual meeting of the section for military studies
of the international studies association, 7-9/11/85, university of Illinois.
5980 10/01/84
(HVA/XI)
private views of US INF delegation leader, Paul Nitze, on the
problematic of INF negotiations
Brede (MfS/13864/60)
1960/1986
9 files
6947 24/02/86
(HVA/I)
Blue paper, year VIII/nr 1
6046 08/03/84
(HVA/I)
Blue paper, Year XIV, nr 1 and enclosures nr 192, 193
Florian (XV/3690/74)
1974/1985
9 files
5634 16/03/83
(HVA/IX)
GB 1982 annual report of London defence attache
5587 19/01/83
(HVA/IX)
Disarmament Andropov’s speech on 21 Dec.
Erich (XV/47/68)
1968/1986
8 files
7028 30/04/86
(HVA/XI)
NATO doc on 02/04/86 – AC/225 (Panel VII/ASP) n/43
7027 30/04/86
(HVA/XI)
NATO doc. On 01/04/86 – AC/243 – D/1064
6899 03/01/86
(HVA/XI)
NATO doc. From 15/11/85 – Ac/225 (Panel VII/GEC) D/13
6659 30/07/85
(HVA/IX)
NATO doc from 28/06/85, AC/225 (Panel VII/ASP) N/36
6683 27/08/85
(HVA/XI)
NATO doc dated 07/08/85 – AC/225 (Panel VII/NSP) N/31
6267 06/11/84
(HVA/XI)
NATO doc V 12/10/84 – AC/225 (Panel VII / NSP) N/27
5579 17/01/83
(HVA/XI)
NATO doc. Dated 17/11/82, AC/225 (Panel VII) WP/170
Siegfried (XV/1677/69)
1969/1987
7 files
7319 20/02/87
(HVA/IV)
needs for FOFA studies
6769 08/11/85
(HVA/IV)
military operational research symposium in GB
Mark (XV/381/65)
1965/1989
7 files
7591 16/05/89 British Defence white book 1989
7520 20/11/87 PID document of the UK foreign ministry on assess. Of “communist
policy and tactic”
7373 24/04/87 PID document from the British Emb. In India
6199 03/08/84
(HVA/I)
NATO group at KVAE
Thomas (XV/2784/72)
1989
7 files
7586 10/05/89 proposals to the UK government on change of COCOM decisions
7433 30/06/87 British sovietologist on politic of the soviet union towards Western
Europe
Mosel (XV/333/69) Ursela Lorenzen, Nato official.
1969/1982
7 files
5376 09/09/82
(HVA/XII)
NATO info – Spain’s admission in NATO
5370 09/09/82
(HVA/XII)
NATo information, position and views of West European NATO members
on economic policy of Reagan’s administration
5109 19/04/82
(HVA/XII)
NATO info NATO doc. C-M (82) 13 – situation in Africa southern from
Sahara
5030 07/04/82
(HVA/XII)
NATO doc. DRC/DS (82) 4 – Conclusions sheet of the meeting of
defence verification committee
4980 18/02/82
(HVA/XII)
NATO defence planning symposium 1982 in Oberammergau (18-
21/01/82) Document DRC/N (82) 1
4797 24/11/81
(HVA/XII)
Art. 5 Annex 2 NATO doc. DRC/WP (81) 1 – UK
Heinz (IV/679/69)
1969/1987
7 files
5216 23/04/82
(HVA/AG
Grenze)
info on views of British Minister for Berlin and WB ruling governors on
relations with the GDR – on Reagan’s forthcoming visit & Us policy
towards Cuba
5214 12/05/82
(HVA/AG
Grenze)
info on conversations on current political pbs during dinner (lunch)
hosted by representative of US Foreign Minister Stoessel on 08/05/82
in WB, as well as speech of IHK president Elfe at the end of conf. on
transportation
5018 16/04/82
(HVA/AG
Grenze)
info. On views of the US Emb to the FRG, Arthur Burns, close circle on
the Falkland conflict
4847 09/12/81
(HVA/AG
Grenze)
info on views of the President of the WB chamber of commerce and
industry and of the UK Amb. in Bonn on Breschnew’s visit in the FRG
and on planned joint meeting with Chancellor Schmidt and Gen.
Honecker
Lutz (XV/1218/72) res 201
1972/1987
7 files
7312 12/02/87 Report from bertrand Russell Foundation on meeting in Brussels of
Liaison Committee
5096 27/05/82
(HVA/III)
on activities of the Romanian Emb. on British Peace organisations
Schwert (XV/3031/78)
1978/1987
6 files
7512 02/11/87
(HVA/III/B)
documents from Arab League on the Gulf conflict and international
issues
7489 02/10/87
(HVA/III/B)
situation in the Gulf (internal document form the Arab league).
Smaragd (XV/3365/71)
1971/1986
6 files
7371 23/04/87 material from the German Atom Forum for period February to April
1987.
7297 02/02/87 material from DATF winter meeting on 27-28/01/87 in Bonn
6963 19/03/86
(19/03/86)
material from the German Atom forum
6759 00/11/85
(HVA/II)
2 materials on Brut reaktor SNR 300 – from BMFT
5709 08/06/83
(HVA/II)
material from German Atom forum
Hilde (XV/1643/75)
1975/1987
6 files
6295 03/12/84
(HVA/XII)
program planning 1985 of the Konrad Adenauer Stiftung office for
international co-operation
6022 14/02/84
(HVA/XII)
annual report 1982-1983 of K. Adenauer Stiftung London office for CDU
central
6021 14/02/84
(HVA/XII)
annual report 1982-83 of K. Adenauer Stiftung Brussels office for CDU
central.
Helfried (XV/17/79) Reiner Oschmann, Neues Deutschland correspondent
1979/1983
5 files
5112 30/04/82
(HVA/III)
info on stance and development of relations between NATO and South
Africa
5056 28/04/82
(HVA/III)
planned anti-GDR activities in GB
4950 16/01/82
(HVA/III)
on the position of the UK CP towards Poland
Komet (MfS/15996/60) Journalist Karl-Heinz Maier (1923-1994)
1960/1986
6 files
statements of John Kornblum – head of US mission in West Berlin.
6763 04/11/85
(HVA/II)
on basis and influence of Lonrho – konzern in Zimbabwe
6211 10/08/84
(HVA/II)
views of leading employee of London FCO on current aspects of
FRG/GDR relations
5034 20/04/82
(HVA/II)
views of FRG Amb. in GB on the Falkland conflict and on situation of
Tory government
DOWNLOAD ORIGINAL DOCUMENT HERE
The Top Spies of STASI exposed in Original Documents -Names-Bogus Names- Activities PART 4
Spy Chief of the STASI – Markus Wolf
Doc. 4 of 6
OTHER AGENTS:
Amsel
Registration nr: XV/4229/83
Start of activities: 1983 (-1987)
5 files
7093: 25/07/86 (HVA/III)
letter of the British FM Howe to Oliver Tambo
7034: 07/05/86 (HVA/III)
internal information of the British secret services to the ANC on negotiations
perspectives of the BOTHA regime with the liberation movement and reaction of the
ANC
Ahmed
Registration nr: XV/2962/78
Start of activities: 1978 (-1987)
132 files
7477: 08/09/87
93 material from the German Atom forum for period May-Aug. 1987.
7048: 23/05/86 (HVA/III)
on bomb attack on the German-Arab society and on night-club “La Belle” in West Berlin
5084: 30/04/82 (HVA/III)
info. from AA Bonn service on concept of “Raumdeckende” defence, participation of
foreign civil servants in the FRG elections, UNEP extraordinary meeting in Nairobi in
March 82, EU/Greenland, Carrington’s trip to Asia
5078: 13/04/82 (HVA/III)
Mitterrand’s visit in Israel and EUP’s activities in the Middle-East
5036: 16/04/82
Foreign policy activities of the FRG government (FRG summit consultations), GB in
March 1982, the FRG position at the Madrid meeting, Shagari’s visit in the FRG,
European Council meeting in March 1982.
4940: 22/01/82 (HVA/III)
info AA service / Nov. 1982
4875: 17/12/81 (HVA/III)
current questions of the FRG foreign policy – consultation FRG/Tchekoslovakia –
FRG/GB – European Council ministerial meeting – sessions of EUP
4816: 19/11/81 (HVA/III)
Saudi Arabia 8-point plan – Israel/NSA relations
4736: 18/09/81 (HVA/III)
Information – Foreign Ministry (yellow service)
Gerald
Dr Gabriele Gast (1969-90), research director of BND.
Registration nr: XV/378/68
Start of activities: 1968 (-1987)
96 files
7503: 16/10/87
discussions with UK minister Mellor
7465: 20/08/87
conversations between Genscher and Howe
7156: 29/10/86 (HVA/IX)
British and Belgian papers on WEU issues
7155: 27/10/86 (HVA/IX)
HLTF – British contribution to chapter VI
7116: 15/08/86 (HVA/IX)
KVAE – British thoughts on a “KVAE Committee” for verification purposes
7005: 21/04/86 (HVA/XII)
SDI experiment: “Teal Ruby”
6942: 17/02/86 (HVA/IX)
UK/US memorandum on UK contribution to SDI (06/12)
6195: 26/07/84 (HVA/AG K)
KVAE – 2nd round
6194: 26/07/84
NATO consultations on strategic defence initiative
5086: 23/04/82 (KARL MARX XV)
“4 meeting” of political directors on 08/03/82 in Washington
4967: 12/03/82 (KARL MARX XV)
information of NATO Council on INF negotiations through Amb. Glitman on 29/01/82
Gerhard
Registration nr: XV/4607/75
Start of activities: 1975 (-1987)
57 files
7398: 25/05/87
Report form DRG (AC/243) Panel II V on 18-19/02/87
7339: 20/03/87
Telegram from the US Emb. In Bonn to Washington among other things on SPD
problematic
7293: 23/01/87
informal British assess. On Tornado combat aircraft ( from managing Director of British
Aerospace Warton division)
7135: 30/09/86 (HVA/III)
secret tour of inspection of congressman Ray on NATO bases
7044
NATO navy-nuclear armament group, meeting AC/141 (IEG/2) SG/5 Torpedos
7043: 16/05/86
NATO/CNAD meeting (nunn initiative), project of MIDS development, 10-11/04/86
6962: 18/03/86 (HVA/XI)
US-Vorhaben on meeting of NATO national armament directors on 27/02/86
6766: 05/11/85 (HVA/XI)
NATO CNAD (nationale Rüstungsdirektion d Nato = ??) on 16/09/85
6668: 02/08/85 (HVA/XI)
final proposals, 4 countries, conclusions on armaments co-operation on 03/06/85
6667: 02/08/85 (HVA/XI)
NATO High Level group / conference report from 01/07/85
6570: 19/04/85 (HVA/XI)
US docs on Advisory 4 groups of National armaments directors on 20-22/03/85
6569: 19/04/85 (HVA/XI)
preparation – recommendations of the 4 groups of representative of the National
armaments Directors on 12-14/06/85 (US, FRG, GB, FR)
6568
UK stance on NATO doc / improvement of armaments co-operation
6567: 19/04/85 (HVA/XI)
decision sheet of council of 4 groups of armaments directors on 9-10/10/84 in
Toulouse
6566: 19/04/85 (HVA/XI)
docs for council of 4 groups of armaments directors on 12-14/12/84 in Englin, AFB,
Florida
6565: 19/04/85
UK stance on co-operation between NATO armaments industries.
6564: 19/04/85
US/FRG drafts for diiscussion of common production of MLRS (Mehrfachraketenwerfer)
components
6563: 19/04/85 (HVA/XI)
docs of the 4 groups council on 20-22/03/85 (Armaments directors USA, FRG, GB. FR)
6483: 05/02/85
NATO co-operation in the development of nuclear heads for MLRS
6464: 11/01/85
FRG and UK positions in NATO-related questioning of double role fragender doppelrolle
(nuclear / conventional) – High Level Group
6457: 08/01/85 (HVA/XI)
summit meeting of 7 experts from expert group on territoriality questions on 19/09/84
6232: 12/09/84 (HVA/XI)
10th meeting of NATO committee for air defense weapons system
6093: 25/04/84 (HVA/XII)
NATO information, doc C-VR (83) 58 – protocol of NATO NAC at ministerial level from
December 1983
6013: 06/02/84 (HVA/XI)
security assistance co-production projects / status report
5794: 17/10/83
NADREP meeting / NATO on 09/09/83
5572: 05/01/83 (HVA/XI)
monthly report
5744: 10/08/83 (HVA/XI)
on Gold Fire 83
5743: 10/08/83
on spring training 1984
5707: 03/06/83 (HVA/XI)
report from US Emb. on security agreement with Austria
5417: 14/09/82 (HVA/XI)
travel and visit activities of US mil. personnel
5375: 14/09/82 (HVA/XI)
presentation, UK representative to NATO, on the Falkland conflict on 22/07/82
5374: 14/09/82
reflection for the establishment of a NATO-Raketenschiessplatzes in GB as substitute
for Kreta
5105: 12/03/82 (HVA/III)
documents of the meeting of “Frontstaaten” on their positions on the Namibia issue
and on RSA policy on the Namibia issue
4921: 04/02/82 (HVA/XI)
training co-operation and disarmament US/FRG/GB
4772: 21/10/81 (HVA/XI)
medical surveillance of US personnel in GB
Harry
Registration nr: XV/381/69
Start of activities: 1969/1987
56 files
7164: 06/11/86 (HVA/I)
Blue paper nr. 10/XVIII
6987: 09/04/86 (HVA/I)
KVAE – 8th round
6986: 09/04/86 (HVA/I)
MBFR
6900: 03/01/86 (HVA/I)
MBFR – Vienna
6727: Extraordinary session of EU Council pol. Committee on 23-24/08/85 & EPZministerial
meeting on 10/09/85
6725: 17/10/85
KVAE – NATO Caucasus, speeches during conference, strategic papers
6724: 17/10/85 (HVA/I)
KVAE – plenary session, working groups and weekly assess.
6624: 19/06/85 (BERLIN ABT XV)
internal konzern data about 1985 investments activities & Schering AG market strategy
6650: 18/07/85 (HVA/I)
NATO group within KVAE and western consultations
6649: 18/07/85 (HVA/I)
KVAE working groups
6685: 10/09/85 (BERLIN ABT XV)
COCOM lists, UK trade ministry
6549: 10/04/85 (HVA/I)
MBFR plenary sessions in Vienna
6547: 10/04/85 (HVA/I)
KVAE session in working groups in Feb./March 1985
6546: 10/04/85 (HVA/I)
KVAE plenary sessions (5th round)
6453: 04/01/85
146 political committee, on 8-9/11/84 in Dublin
6257: 30/10/84 (BERLIN ABT XV)
Konzern internal protocol – commercial and structural files – Schering AG
Adler
Ludwig Pauli, official in the German foreign ministry.
Registration nr: MfS/15905/60
Start of activities: 1960/1987
54 files
7497: 12/10/87
yellow brochure (Heft) nr 1050
7468: 24/08/87
Yellow “Brochure” nr 1048
7445: 10/07/87
yellow brochure nr 1046
7444: 10/07/87
Yellow brochure nr 1045 and attachment
7346: 26/03/87
yellow brochure nr 1044
7345: 26/03/87
yellow paper nr 1043
7298: 04/02/87
Blue paper nr. 12
6985: (HVA/I)
yellow brochure nr. 1033
6932: 06/02/86 (HVA/I)
yellow brochure nr 1030
6805: 09/12/85 (HVA/I)
yellow brochure nr. 1029
6804: 09/12/85 (HVA/I)
Blue paper nr 14
6661: 30/07/85
yellow paper nr 1024
6504: 27/02/85 (HVA/I)
yellow paper nr 1018
6503: 27/02/85
Blue paper nr 14/84
6308: 10/12/84 (HVA/I)
Blue paper nr 12
6243: 08/10/84
yellow paper nr 1016
6242: 08/10/84
Blue paper 9/84
6197: 01/08/84
yellow paper nr 1014
6147: 08/06/84 (HVA/I)
Blue paper nr 6 – enclosures nr 198, 199
6010: 03/02/84
yellow paper nr 9
6008: 03/02/84
yellow paper nr 8
5804: 25/10/83
yellow paper nr 1005
5674: 02/05/83
country profile GB
5673: 02/05/83 (HVA/I)
Yellow paper nr 1000
5672: 02/05/83 (HVA/I)
yellow paper nr 999
5551: 29/12/82 (HVA/I)
yellow paper nr 996
5515: 17/11/82 (HVA/I)
Info from Foreign Office Bonn on results of détente policy, strategic discussions within
NATO, security-political aspects of technological transfer in the USSR, Comments on
Ustman, OAU Summit Conf. in Tripoli, contract FRG/Mozambique with Land Berlin
Kleinsel, GATT minister conf., US discussions on natural gas commerce. EU agriculture
policy, UNESCO world culture conf., War Graves Commission for Eastern Europe report
from co-ordinator for German-American relations
5422: 19/08/82 (HVA/I)
yellow paper nr 993
5415: 15/10/82
GB
5399: 08/07/82
yellow paper nr 991
5360: 19/08/82
yellow paper nr 992
5286: 09/07/82
Falkland conflict
5225: 16/04/82 (HVA/I)
Information – service of AA Bonn on West German/US relations, participation of 4 EU
states to MFO in Sinai, Ireland’s position on EU solidarity, efforts to re-activate the
WEU
5211: 21/05/82 (HVA/I)
GB
5210: 19/05/82 (HVA/I)
GB
5166
yellow paper nr 988
5077: 18/02/82
Yellow paper nr 987
5035: 27/04/82
GB in Foreign Ministry Bonn in April 1982 / FRG Emb. in London
4932: 08/01/82 (HVA/I)
yellow paper nr 985
4917: 13/01/82
EU
4897: 13/01/82 (HVA/I)
British oil policy
Dreher
Registration nr: XV/2427/74
Start of activities: 1974/1984
43 files
5736: 26/07/83 (HVA/III)
on British sys. civilian defence
5638: 17/03/83 (HVA/III)
trimestrial report on political-economic situation in the GDR
5484: 18/11/82 (HVA/III)
on the forthcoming meeting of GB/GDR GRK on 29/11-01/12/82
4559: 23/05/81 (HVA/III)
on a working paper from the British industry trade union on foreign trade strategy and
the five-year plan
4405: 27/03/81 (HVA/III)
study from the National Westminster Bank on theme: reflection on trade policy
Konrad
Registration nr: XV/2148/72
Start of activities: 1972/1989
35 files
7595: 26/05/89
UK Ambassador in the FRG on “German issues”, British views
6968: 21/03/86(HVA/AG K)
from the British Emb. On SUCP XXVII Party Day
6912: 17/01/86 (HVA/AG K)
from the British Emb on GB/GDR relations
6747: 29/10/85 (HVA/AG K)
ON UK diplomat A. Lewis on work of East-European dept of British MfA
6478: 24/01/85 (HVA/AG K)
from UK Foreign Ministry and UK Emb. in the GDR on current issues
6041: 02/03/84 (HVA/XI)
PID-Objektes study, institute for East-West security studies, NY on GB security policy
5685: 11/05/83 (HVA/XI)
on some planned activities of the committee for European nuclear disarmament and
the institute for defence and disarmament studies in Boston 1983
5729: 08/07/83 (HVA/AG K)
from British Emb. on Kohl’s visit to Moscow and on internal political developments in
the GDR
5491: 27/11/82 (HVA/AG K)
British diplomats on Youth evolution in the USSR
4866: 18/12/81 (HVA/AG K)
on Schmidt/Honecker meeting, views of the UK Emb. in the GDR
4494: 09/04/81 (HVA/AG K)
views of the British Foreign Ministry on issues related to Poland and on FRG/GDR
relations and WB related pbs
4439: 14/04/81 (HVA/AG K)
first assess. of 10th Party Day by a leading employee of the British Emb.
4394: 24/02/81 (HVA/AG K)
leading employee from the British Embassy in the GDR on Honecker’s closing speech at
a SED [Bezirkdelegiertenkonferenz] in Berlin
Doc. 4 of 6
DOWNLOAD ORGINAL DOCUMENT HERE
FASCHING-WITZ: SENDEN SIE IHRE PR DOCH DIREKT ZU IZ UND ZU Thomas. und Beate P
Liebe Leser,
es ist Fasching.
Deshalb mein Tip:
FASCHING-PR: SENDEN SIE IHRE PR DOCH DIREKT ZU IZ GmbH und zu B. PORTEN, WIESBADEN
Das geht doch auch das ganze Jahr über, gell
Ich wette, B. (oder so ähnlich) und Thomas P (oder so ähnlich) machen alles möglich
ABSOLUT KORREKT WIE IMMER
NICHT NUR IM FASCHING
Ihr weniger verwöhnter Faschingnarr
Bernd Pulch
TOP-SECRET from the FBI – ‘Underwear Bomber’ Sentenced to Life for Attempted Christmas Day Attack
Umar Farouk Abdulmutallab, the so-called “underwear bomber,” was sentenced today to life in prison as a result of his guilty plea to all eight counts of a federal indictment charging him for his role in the attempted Christmas Day 2009 bombing of Northwest Airlines Flight 253.
Abdulmutallab, 25, of Kaduna, Nigeria, pleaded guilty on Oct. 12, 2011, to conspiracy to commit an act of terrorism transcending national boundaries, among other charges. Abdulmutallab’s purpose in taking a bomb on board Flight 253 was to detonate it during flight, causing the plane to crash and killing the 290 passengers and crew members on board. As Flight 253 was on descent into Detroit Metropolitan Airport, the defendant detonated the bomb, which resulted in a fire, but otherwise did not fully explode. Passengers and flight attendants tackled the defendant and extinguished the fire.
“The case against Abdulmutallab was a combination of the hard work and dedication of FBI personnel as well as multiple federal, state, and local agencies. Those individuals who experienced Christmas Day 2009 first-hand should be rest assured that justice has been done,” said FBI Special Agent in Charge Arena.
The Top Spies of STASI exposed in Original Documents -Names-Bogus Names- Activities PART 3
Doc. 3 of 6
PETER
Start of activities: 1977
Registration nr: XV/429/77
SUBJECT RE. NR START Nature of doc
1 Maoist org. in GB 05/09/77 05/09/77 report
2 Asses.of New CP, split of UK CP 20/04/78 20/04/78 report
3 Some new aspects of peace mvt in GB 12/01/80 27/08/80 report
4 Activities of one Trotskyist org. towards Poland 01/13/81 28/11/80 report
RANK
Start of activities: 1967
Registration nr: XV/1093/67
Files from 1973 to 1980
Total nr. of files: 107 (49 selected: 3 reports; 49 docs)
Start of activities: 1967
REG. NR START Nature of Doc.
1 LP internal material on sit. In Italy, 30/01/73 30/01/73 Doc.
Turkey, Sierra Leone & central Afr.
2 Views, japan OECD Amb. in London on 11/03/73 11/03/73 Doc.
japan trade pol.
3 Assess. from China’s Emb. in London 29/10/73 29/10/73 Doc.
on internal pol. Sit. In GB
4 Study from IISS research centre in 23/04/73 23/04/73 Doc.
London for GB gov. on the Polaris sys.
5 UK LP study on Euro. Security 10/05/73 10/05/73 Doc. (Engl.)
and co-operation
6 reports from EUP on the stance of 26/10/73 26/10/73 Doc.
current E/W & transatl. Neg.,
sea law/ liberty of expression/role
of art in the Euro. Soc.
7 Internal material from the executive 12/07/73 12/07/73 Doc.
from GB LP / report from EUP LP on
India, Singapore, Greece, Iceland
8 Internal material from GB LP on 15/10/73 15/10/73 Doc.
FR /Spain soc. Parties / Conf., June 73
9 report, int. dept. of GB LP on del. 04/10/73 04/10/73 Doc.
Trip to USSR in June 73 (Engl.+transl.)
10 Internal material from GB LP executive 15/06/74 15/06/74 Doc.
on Portugal & Chile (Engl.+transl.)
11 Protocol on GB LP Congress on UN 22/07/74 22/07/74 Doc.
Foreign pol., NATO, Fr. PDT elections, (Engl.+transl.)
EUP Conf. May 74
12 Confidential report, GB LP executive, 20/06/75 20/06/75 Doc.
on Indonesia & HK
13 Working material, 6th congress, GB 30/06/75 30/06/75 Doc.
LP Int. committee in June 75 (Engl.+transl.)
14 Assess., GB LP executive on 13/06/75 13/06/75 Doc.
Portugal & Spain
15 Material, GB LP int. dept. 24/06/75 24/06/75 Doc.
16 Confidential correspondence with GB LP 16/06/75 16/06/75 Doc.
Gen. Sec. On Afr. & Chile pbs
17 Official cut in GB defence budget 19/03/75 19/03/75 Doc.
18 Confidential doc., GB LP int. committee 13/02/76 13/02/76 Doc.
Diego Garcia (Engl.+transl.)
19 Protocol & working material, 8th GB 08/06/76 16/07/76 Doc.
LP int. committee congress, (Engl.+transl.)
20 Prep of Congress, IntSocialism 09/06/76 09/06/76 Doc.
EU students org. (Engl.+transl.)
21 Position GB LP on different int. pbs 15/10/76 15/10/76 Doc.
(Engl.+transl.)
22 report on the EU socialist parties congress 08/09/76 22/10/76 Doc.
(Engl.+transl.)
23 Assess., GB LP on int. questions 00/02/77 00/02/77 Doc.
(Engl.+transl.)
24 role of the Ital. CP, views of the GB LP 18/03/77 18/03/77 Doc.
(Engl.+transl.)
25 GB LP position on foreign pol. Issues 25/04/77 25/04/77 Doc.
(Engl.+transl.)
26 GB LP position on foreign pol. Issues 24/03/77 24/03/77 Doc. (Engl.)
27 GB LP position on foreign pol. Issues 09/03/77 09/03/77 Doc.
(Engl.+transl.)
28 GB LP position on foreign pol. Issues 25/05/77 25/05/77 Doc.
(Engl.+transl.)
29 GB LP position on foreign pol. Issues 21/07/77 21/07/77 Doc.
(Engl.+transl.)
30 GB LP position on foreign pol. Issues 14/10/77 14/10/77 Doc. (Engl.)
31 on assess. of major int. issues from the 15/12/77 15/12/77 Doc.
GB LP leadership (Engl.+transl.)
32 Study of the GB LP on USSR security 22/02/78 22/02/78 Doc.
and foreign pol.
33 GB LP position on Belize 15/03/78 15/03/78 Doc.
34 GB/RSA relations 09/05/78 09/05/78 Doc. + Report
35 Assess., GB LP on int. questions 30/08/78 30/08/78 Doc.
36 GB LP forthcoming annual congress 22/09/78 22/09/78 Doc.
37 GB LP foreign pol. Line 19/10/78 19/10/78 Doc.
38 Confidential study on EU problems, 14/11/78 14/11/78 Doc
Gb LP views
39 Docs from GB LP on int. questions 02/11/78 02/11/78 Doc.
40 Docs from GB LP executive 04/01/79 04/01/79 Doc.
committee (NEC), int. dept.
41 On GB assess. of current pol. 15/03/79 15/03/79 Doc.
Devp. In latin America
42 On Gb LP and Foreign Ministry assess 23/03/79 23/03/79 Doc. + Report
of sit. In Middle East
43 On GB LP & GB gov. positions 15/03/79 15/03/79 Doc.
on sit. In Middle East
44 Ueber den 2. Entwurf zum Abschnitt 20/03/79 20/03/79 Doc.
Aussenpolitik des wahlmanifestes der LP
45 GB/US pol. Towards Afr. 15/02/79 15/02/79 Doc. + report
46 Current aspects of Gb pol. 06/04/79 06/04/79 Doc.
Towards South Afr.
47 GB LP assess. of devp. 21/07/75 21/07/75 Doc.
In Iran and West Sahara
SONJA
Start of activities: 1980
Registration nr: XV/2527/80
SUBJECT RE. NR START Nature of doc.
1 Report on Peace mvt. In GDR 17-May-83 17-May-83 Report
by END London
SPECHT
Start of activities: 1976
Registration nr: XV/4201/76
SUBJECT RE. NR START Nature of doc.
1 Addresses UK army units 1967
2 Economic policy 1984 22-Mar-84 22-Mar-84 doc.
WIEN
Start of activities: 1984
Registration nr: XV/5690/84
Residentur nr: 201
Nr. of files: 13
Year 1: 1985
Year end: 1986
SUBJECT REG. NR START Nature of doc.
1 UK LP assess. / Thatcher gov. 00/02/85 10/01/85 Report
& domestic issues
2 UK policy on nuclear weapons sys. 04/03/85 18/02/85 Report
strategic goals of technological embargo 10/04/85 12/03/85 doc
(Eng./Germ.)
3 UK LP ideas on Foreign Policy 22/04/85 18/03/85 doc (English)
4 Evolution of the Labour Party 15/05/85 01/04/85 Report
& estimate of UK FM visit
5 Sit. & opposition within LP leadership 28/05/86 07/05/86 Report
& UK conservative party
6 Congress of socialist parties of EU 05/06/85 01/05/85 doc (English)
NATO member States, Lisbon, March 85
7 LP position on international issues 01/03/86 00/02/86 Report
8 Denis Healey 11/02/86 01/01/86
9 Position of Labour Party at 27th 23/04/86 01/03/86 USSR & USA & GB
KPDSU Party Day& at 11th SED Party Day France & China &
DDR.
DOWNLOAD ORIGINAL DOCUMENT HERE
UPDATE – I-ZEITUNG – THOMAS P.- BEATE P.2
Liebe Leser,
man glaubt immer “schlimmer geht es nimmer”.
Aber JA SICHER !
Wenn der Fotograf von Thomas Ps Partner Jan M Fotos schiesst, die dann im “Scheisshausfliegenblog” von “GoMoPa” stehen…
UND FRAU BEATE P; STAATSANWÄLTIN FÜR “WIRTSCHAFTSVERBRECHEN ALSO AUCH FÜR IMMOBILIEN”
ALL DIES UND VIELE WEITERE BEWEISE IGNORIERT ….
CHAPEAU FRAU PORTEN !
Genauso haben wir uns Justiz immer vorgestellt.
Wir sind sicher, Sie werden diese Linie weiter konsequent verfolgen !
Ein doppeltes Chapeau !!
Bernd Pulch (ehemaliger Mentor von Thomas P)
PS: AUF ANFRAGE ANONYMISIERT
The Top Spies of STASI exposed in Original Documents -Names-Bogus Names- Activities PART 2
There are yet several documents published referring the former departement for espionage (HV A – Hauptverwaltung Aufklärung), led by Colonel General Markus Wolf and later, until the end of the GDR, Colonel General Werner Großmann.
This departement had in the end of 1989 more than 3,800 employees, including ca. 700 unofficial employees (IM) and about 670 officers in special missions (OibE).
Below you find the list of HV A agents uncovered including those like “Gerald” (Dr. Gabriele Gast, spy in western-german espionage service BND) and “Topas” (Rainer Rupp, spy within the NATO):
Doc. 2 of 6
FREUNDIN
Start of activities: 1983
Registration nr: XV/4555/83
Residentur nr: 201
SUBJECT REG. NR START Nature of doc.
1 3 Konvent. Des end in Perugia 00/08/84 01/06/84 doc. (English)
2 Interne protokollniederschriften des end
Ungarn
13/08/84 01/06/84 doc. (English)
vom 16/03 und 04/05/84
3 Conf. On Europe’s partition on 02/06/84 in
London
13/08/84 01/07/84 doc. (English)
4 report on seminar: “Towards a theology of
peace” Budapest, 17-22/09/84
26/11/84 01/10/84 doc. (English)
5 Activities of “network for East-West
dialogue”, in prep. Inter. Seminar on 08-
11/02/85 in West-Berlin
10/12/84 01/09/84 France & GB & NL&
Ital. & Poland & CZ
& West-Berlin
6 Activities of hostile peace organisations 26/11/84 01/10/84 doc. (English)
7 Activities of UK organisation 15/01/85 01/12/84 doc. (English)
8 END UK activities towards the GDR 15/01/85 21/12/84 doc. (English)
9 Assessment of work from DDR peace
activists
27/03/85 01/01/85 report
10 prep. Final 4th Convention, Amsterdam,
July 85 &
21/03/85 01/01/85 report
11 END activities towards independent peace
mvts in GDR
07/02/85 21/01/85 report
12 Activities of “DDR Group” in the “Euro
campaign for nuclear ban”
30/01/86 01/12/85 doc. (English)
13 Activities of hotile forces in W. peace mvts 20/11/86 06/11/86 doc. (English)
GRAAF
Start of activities: 1970
Registration nr: XV/4139/70
SUBJECT RE. NR START Nature of doc.
1 Security requirements for applicants to UK
state service
2 TVC union Congress, 02-06/09/74
4 TVC Union Congress, 1975
5 ACE 1985 force exercise prog 10/85 15/10/85 doc. (English)
Alexander (XV/3645/83)
HARRY
Start of activities: 1977
Registration nr: XV/2599/77
SUBJECT RE. NR START INFO/
COUNTRIES
INFO/
PEOPLE
1 UK CP position on current diff. Between
China and Albania
19/08/77 19/08/77 report
2 Materials on British Maoist CP 13/07/78 13/07/78 doc./report
3 Amnesty International activities 10/11/78 10/11/78 report Philip
Whitehead
(MP), Eric
Heffer(MP)
Bahro
4 Asses. Centre for Russian and EE studies,
Birmingham university
09/11/78 09/11/78 report erased (4)
5 AI & Olympics in Moscow 1980 27/11/79 27/11/79 report erased (1)
6 Invitation of UK industry. & Trade circle to
work for UK gov at Madrid Conf.
22/10/80 23/09/80 report
3 AI with Rudi Bahro Russian students –
Birmingham
1/11/78 1/11/78
4 Invitation UK industry to Madrid Conf. 1/09/80
INSEL
Start of activities: 1963
Registration nr: XV/4705/63
SUBJECT RE. NR START Nature of
doc.
INFO
PEOPLE
1 Asses., UK Communist Youth Union 5/08/75 5/08/75 report
After annual congress, Apr. 75
2 Facts on UK / Irish CP, BICO 5/08/75 5/08/75 report
3 Asses., far-right student mvts in GB 26/02/75 26/02/75 report
4 Aspects of UK CP Party Day 17/02/76 17/02/76 report
5 Asses., UK & Irish coco org. 25/05/76 25/05/76 report
6 Situation of UK CP 19/05/76 19/05/76 report erased (6)
7 Arrival UK charge d’affaires in GDR 14/11/73 14/11/73 report
Kellner
Start of activities: 1972
Registration nr: XV/437/72
SUBJECT RE. NR START Nature of doc.
1 letter, UK gov employee on trips to
cocom countries
21/02/75 21/02/75 doc.
2 meeting, UK health ministry, 04/12/74 1/04/75 1/04/75 doc.
Kraft
Start of activities: 1982
Registration nr: XV/6900/82
Residentur nr: 201
Started as agent in 1982
Total nr. of files: 39 (26 reports, 13 documents)
Reported from 1986 to 1987
SUBJECT REG. NR START Nature of doc.
1 Mozambique’s FM Chicano’s speech at
Wilton Park Conference
20/08/85 01/07/85 report
2 UK position on Eureka 05/09/85 08/08/85 doc. (English)
3 UK/Albania rel. 16/01/86 11/12/85 report
4 UK Peace Movement’s activities towards
DDR
10/01/86 01/11/85 report
5 Questions on US SDI research, UK
views
16/04/86 26/03/86 doc. (English)
6 UK defence White book 1986 10/07/86 29/05/86 doc. (English)
7 Research work on SDI project 18/09/86 28/07/86 doc. (English)
8 UK assess. Of US SDI prog 05/11/86 17/10/86 doc. (English)
9 UK assessment of ” World Peace
Congress”, Copenhagen
11/11/86 01/10/86 report
10 Dev. Of END 12/12/86 20/11/86 report
11 US military structure and staff 08/01/87 21/11/86 doc. (English)
12 Preparation of 6th END-Convent.,
Coventry, 1987
20/01/87 01/12/86 doc. (English)
13 UK position on 750 Berlin’s anniversary 23/02/87 01/02/87 report
14 Structure of UK armed forces 02/02/87 13/01/87 doc. (English)
15 Questions on dev. Of nuclear weapons 29/07/87 29/07/87 doc. (English)
16 UK Defence White Book 17/06/87 14/05/87 doc.
17 Dev. Within UK CP 12/05/87 16/04/87 doc.
18 Info on AI 04/05/87 10/04/87 report
19 On END and prep. Of END convention
in Coventry
23/04/87 10/04/87 doc.
20 END Convention in Coventry 18/03/87 11/03/87 doc. (English)
21 SDI research, UK views 14/04/87 11/03/87 doc. (English)
22 Aspects of UK position on US position
on ABM treaty
00/04/087 06/03/87 report
Kunze
Start of activities: 1972
Registration nr: XV/2784/72
Residentur nr: 201
Started activities in 1972
Files from 1983 to 1987
Total nr. of files: 38 (31 reports, 7 docs)
SUBJECT REG. NR START Nature of doc.
1 Current problems of UK peace
movement
15/04/83 01/03/83 report
2 Position UK Peace Council on activities of 13/07/83 13/07/83 report
Council of evangelist Churches in GDR
3 Position END/CND leadership on prep. Of
END
12/05/83 12/05/83 report
Convention in West-Berlin
4 Reaction on stationing of US
intermediate range
12/01/84 25/11/83 report
ballistic missile in Western Europe
5 Internal disputes within Thatcher’s
cabinet
02/01/84 05/12/83 report
6 The British Navy 07/02/84 01/04/82 doc (English)
7 Assessment of perspectives of E/W
relations by the Inter. Institute for
Strategic Studies
06/02/84 01/01/84 report
8 Political economic. Consequences of
Hohcruestung, UK views
07/02/84 07/02/84 doc (English)
9 Strategic discussions at NATO 29/03/84 06/02/84 doc (English)
10 NATO’s views 01/03/84 18/01/84 doc (English)
Info on dev. Of UK defence org. 30/03/84 30/03/84 doc (English)
11 CND scheduled activities, Dec. 1984 07/01/85 08/12/84 report
12 Perspectives of independent Peace
movement in DDR
14/05/84 01/04/84 report
13 European peace Powers Conf., Athens,
10-12/12/84 positions of UK peace
powers in CND/END
07/01/85 01/11/84 report
14 UK assess. Of London summit 09/08/84 09/08/84 report
15 European campaign for nuclear
disarmament
26/02/85 01/01/85 report
16 Detailed info of nature, scope and org.
of END.
17 Position, UK Lab. Party on NATO
strategic disc.
11/06/85 13/05/85 report
18 SDI, views of UK leading political.
Analysts & US experts
01/11/85 01/10/85 report
19 Activities, UK CND in the GDR 24/10/85 17/10/85 report
20 Dev., UK CP 22/01/86 20/12/85 report
21 Assessment of results of Denis Healer’s
stay in DDR
07/03/85 01/02/86 report
22 End – Convent in Paris 26/06/86 01/06/86 report
23 38th UK KP Party Day and internal
disputes
18/06/84 10/05/84 GB
24 Arms and arms control issues, views of
UK parties and institutions
22/07/86 27/06/86 doc
LAURA
Start of activities: 1974
Registration nr: XV/2466/74
SUBJECT RE. NR START INFO
COUNTRIES
INFO
PEOPLE
1 UK CP discussions on Party Day prog. in
October 77
06/06/77 06/06/77
2 Talks between UK CP members on
Party’s situation
10/20/77 20/10/77 BON (2? 3?)
3 Draft reso. UK CP 36 Party Day on
party’s situation
9/20/79 20/09/79
4 UK comm. Attache’s views, UK emb. In
GDR
6/23/80 20/06/80
5 UK CP current situation 10/20/86 01/10/86
6 UKPC position towards Albania 1977
LINDA
Start of activities: 1977
Registration nr: XV/430/77
SUBJECT RE. NR START Nature of doc.
1 Several important facts about
AI/London
8/25/77 25/08/77 report
2 UK High schools and universities
common contacts with soc. Countries
facts on Centre for Russian and EE
University of Birmingham
8/25/77 25/08/77 report
3 Ai & the GDR 11/11/77 11/11/77 report
4 AI: info on people from London CO 11/10/77 10/11/77 report
5 AI UK office 4/5/78 05/04/78 report
6 UK specialists as counsellors in
Alexandria
12/22/78 22/12/78 report
7 flying personnel from research comm. in
UK (military & air forces)
12/22/78 22/12/78 report
8 meeting with Prof. Witold Kiezun
management centre, Bradford, 05/80
12/29/80 28/11/80 report
10 Zur Dislozierung nuklearertraeger mittel
of US & UK in England, Scotland &
Wales (8 pages)
9/2/81 06/08/81 report
11 Members of US state army on laser
weapons and limited war Info mil.
Attaché
12 Study, Siegfried Lehnberg study on cost
effectiveness of training sys. NATO
symposium work, org.
10/14/81
13 Mastering the techno.changes
Possibilities for a perspective of study
delivered to a NATO symposium Techno.
In the GDR
14 Dvlp EEC defence strategy NATO
without the US
PARK
Start of activities: 1983
Registration nr: XV/96/83
Nr of files: 51
documents: 2
SUBJECT RE. NR START INFO/COUNTRIES
1 UK assess. of China’s foreign policy 11/22/83 01/10/83 US, Vietnam, S. Korea,
Japan, Kampuchea, Indoc
2 Asses. On Namibia & S.A. crisis 5/8/84 01/02/84 SA, US, FR, GB, FRG,
Angola, Tanz
3 Asses. Lebanon, future of multinat. 5/2/84 01/01/84 FR, GB, US, Ital.
powers Lebanon
4 Asses. US middle-east poll. 5/8/84 01/02/84 US, USSR, GB Iran, Iraq,
Isr., Jap
5 UK assess. of G7 summit 7/11/84 01/06/84 US, USSR, GB
6 UK assess. of China / USA / Hongkong 8/7/84 01/07/84 GB, USA, HongK
7 Asses. Hong Kong problematics 9/25/84 01/08/84 GB, China, HK
New pbs for Western allies 9/26/84 01/08/84 FR, GB, US, USS
meaning French cabinet reshuffling 9/4/84 01/08/84 FR, GB
US / USSR talks in Weltall 8/9/84 01/08/84 FR, GB, US, USS
8 Mining of Red sea 11/7/84 01/10/84 Iran, Iraq, Isr,US
9 UK / China Hong Kong agreement 1/23/85 01/10/84 GB, China, HK
10 Asses., UK Foreign Min. on US Pdt
elections, Namibia and GB/GDR relat.
11/12/84 01/11/84
11 China’s asses. Of visit Chinese mil. Del
to GB
12/10/84 01/11/84
12 Gromyko/Schultz meeting, UK views 20/1284 01/12/84 GB, US, USSR
13 Gorbatchev/Reagan, UK asses. 8/1/85 01/07/85 GB, US, USSR
14 Asses. UK foreign pol. / GDR & soc.
countries
4/11/85 01/03/85
15 UK economy: stagnation, unemploy. &
future of GBP
10/8/85 01/08/85
16 Heseltine resignation 1/21/86 01/01/86
17 Asses. Future of UK gov under Thatcher
leadership
2/19/86 01/02/86
18 UK concept for Hu Yaobang’s visit/UK 4/3/86 01/04/86
19 Reagan’s difficulties, UK views 2/9/87 01/12/86
20 Thatcher’s visit in USSR 3/27/87 01/03/87
21 UK foreign policy after elections 8/10/87 01/07/87
22 UK policy / South Africa 8/10/87 01/08/87
23 Currency tendencies 11/1/87 doc.
UK Asses. , USSR Foreign and defence
policies
5/23/89 01/05/89 GB
DOWNLOAD ORIGINAL FILE HERE:
I-ZEITUNG – THOMAS P- BEATE P
Liebe Leser,
eine Information von mir, die nur wenige wissen:
Es gibt in Wiesbaden bzw. Mainz
– Beate P, STAATSANWÄLTIN FÜR “WIRTSCHAFTSVERBRECHEN ALSO AUCH FÜR IMMOBILIEN”
– Thomas P, Chefredakteur der Immobilienzeitung, dem ich meine Anteile an der IZ GmbH verkauft habe.
Was die Herrschaften wie verbindet mit welchen Folgen FÜR ANDERE wissen NUR beide Personen.
SICHER IST: WIR HABEN DIE BELEGE AUCH ZU DEN MERIDIAN CAPITAL FÄLSCHUNGEN DER “GoMoPa” UND WEITERE BEWEISE ÜBERMITTELT !
Und um all das zu verschleiern, werden dann gefälschte und fingierte Artikel mit gekauften Internet-Userzahlen in Google hochgeschossen
– Methode STASI-“GoMoPA” !
Herzlichst Ihr
Bernd Pulch, MA
PS: AUF ANFRAGE ANONYMISIERT
PS Herr Thomas P wird seit Jahrzehnten durch die Anzeigen und Abonnements von Immobilienfirmen gut finanziert als Gesellschafter und Chefredakteur.
Selbstverständlich gehören hierzu wohl auch etliche Einladungen und Reisen finanziert durch Immobilienfirmen.
Honi soit qui mal y pense !
The Top Spies of STASI exposed in Original Documents -Names-Bogus Names- Activities PART 1
STASI Spy Chief Markus “Mischa” Wolf
There are yet several documents published referring the former departement for espionage (HV A – Hauptverwaltung Aufklärung), led by Colonel General Markus Wolf and later, until the end of the GDR, Colonel General Werner Großmann.
This departement had in the end of 1989 more than 3,800 employees, including ca. 700 unofficial employees (IM) and about 670 officers in special missions (OibE).
Below you find the list of HV A agents uncovered, including those like “Gerald” (Dr. Gabriele Gast, spy in western-german espionage service BND) and “Topas” (Rainer Rupp, spy within the NATO):
BERG
(XV/4484/84)
NAME REG. NR START Nature of Doc.
1 Conference: “Europe & SDI”, Brussels, 12-
22/9/85
21/10/85 02/10/85 report
2 UK position on Eureka research prog., dev. Of
rel. with socialist countries
20/11/85 01/11/85 report
3 Position of UK gov. and leading consortiums
on comm. rel. with the GDR in the persp. Of
Leipzig exhibition 86
07/04/86 01/03/86 report
4 Assessment 27th Party day KPDSU by Healey
and major UK journalists
07/04/86 13/03/86 report
5 UK Ostpolitik and UK / DDR relations 05/05/86 01/04/86 report
6 Internal discussions between the Lab. Party
leadership & UK monopoly circle on potential
LP gov. after elect.
09/07/86 19/06/86 report
7 Position, Uk konzern circle on extension of
nuclear test moratorium in USSR
19/09/86 25/08/86 report
8 Visit of DDR FM and UK positions on E/W
trade rel.
05/11/86 01/10/86 report
9 US negotiation strategy on Vienna KSZE
follow-up meeting & expectations related to
implem. & results
20/11/86 11/11/86 report
10 UK reaction, 13th GRK DDR / UK meeting 30/01/86 08/01/86 report
Dev. UK eco. Until 2010 12/01/87 03/12/86 doc (English)
11 Visit of Japan’s PM Nakasone in the DDR 20/03/87 01/02/87 report
12 Reaction of UK trade Minister Clark at Leipzig
exhib. 87
22/04/87 04/03/87 report
13 Views, UK Chimie konzern ICI, on trade with
GDR in prep. Of LFM 87 (extract attached)
02/04/87 13/03/87 report
14 Influence of eco. Rel. between GDR / UK,
assess. Of DDR’s briefaktion in rel. with Berlin
750th anniversary
14/04/87 01/03/87 report
15 Asses. Results of meeting PBA Der
warschauer vertragsorganisation
24/06/87 09/06/87 report
16 Meeting, WVO political committee, UK views 24/06/87 09/06/87 report
17 Prep., Trade summit in Venice 03/07/87 00/06/87 report
18 Foreign & Trade po. Activities in Japan,
Japan/GDR/USSR trade rel., japan’s position
on trade summit, trade pol. Diffrences
between Japan & EU
21/10/87 21/10/87 report
19 Factors of influence of UK trade po. On GDR 06/11/87 06/11/87 report
BURGER
Start of activities: 1973
Registration nr: XIII/951/73
SUBJECT RE. NR START Nature
of doc.
FREIE
WERTE
1 Fascist & neo-fascist tendencies in UK 6-Jun-78 6-Jun-78 report
2 IDAF structure & org. 6-Jun-78 6-Jun-78 report
3 Info on Inter. University exchange fund 14-Jun-78 14-Sep-78 report CIA, ANC
CARMEN
XV/3442/72
SUBJECT RE. NR START INFO
COUNTRIES
1 British mil. Attaches (org. and societal 13-Nov-74
mil. Attache leadership in London)
2 Joint attack tank, USA/FRG 15-Oct-73
3 Radar station, Tranchard barracks 15-Oct-73 15-Oct-73 report
4 FRG proposal for weapons sys. for attack
bases
18-Mar-74 18-Mar-74 doc.
6 Trenchard Barracks QS
7 Telecom. Centre – rechtal – MRCA plane
8 FRG mil. Att. In London, FRG / GB coop:
plane, helicopter, rocket
13-Nov-74 13-Nov-74 doc.
9 UK/Ital coop, decision for prod. MRCA prog. 8-Apr-74 8-Apr-74 doc.
10 MRCA project: BRD air ind. MRCA arms
project / MBB Ital/GB planning
3-May-74 3-May-74 report
CHRISTINE
XV/3094/78
SUBJECT RE. NR START COLLAB.
1 UK MoD positions on NATO conclu. of
12/12/79
12/3/80 27/11/80 Karl
DAN
XV/2567/80
SUBJECT RE. NR START
1 Pakistan’s activities owards Afghan. 22/10/80 17/10/80
2 SA activities towards Tanzania & Zimb. 22/10/80 17/10/80
3 Info on Zimb. & Malawi, & relations with UK 11/12/81 08/12/81
4 Coop. UK right-wing powers & Solidarn. 18/01/82 12/01/82
5 Tanzania – relations with UK 6/6/83 01/05/83
6 report, EU Africa WG in Bonn 7/21/83 01/06/83
Situation in “Morning Star” & UK CP 12/18/85 01/12/85
DAVE
Start of activities: 1985
Registration nr: XV/3986/85
NAME REG. NR START Nature
of Doc.
COLLAB.
1 Congress, President and national interest (set
up of US trade pol.)
29/12/86 29/12/86 Doc.
(Engl.)
Bodo
2 Soviet view of the Atl. Relations in the
Reagan period
29/12/86 29/12/86 Doc.
(Engl.)
bodo
3 Study: mil. & pol. Interests of the US in the
far East
29/12/86 29/12/86 Doc.
(Engl.)
Anton
4 Behind the Western Alliance: pol. Towards
[dematlantismus]
29/12/86 29/12/86 Doc.
(Engl.)
Bodo
5 The limits of American power 29/12/86 29/12/86 Doc.
(Engl.)
Bodo
6 Western Euro. In Reagan’s world: answers to
the new US challenge
29/12/86 29/12/86 Doc.
(Engl.)
Bodo
7 Overcoming foreign commercial competition:
views from Washington
29/12/86 29/12/86 Doc.
(Engl.)
Bodo
8 The state’s role in the formulation of energy
& trade pol., US/USSR
29/12/86 29/12/86 Doc.
(Engl.)
Bodo
9 Study: comparison of US/GB decision to
withdraw from UNESCO
29/12/86 29/12/86 Doc.
(Engl.)
Sascha
10 Study: Unicity & [Pendel schwingt] in US
foreign pol.:
29/12/86 29/12/86 Doc.
(Engl.)
Bodo
The Greens & UK def. pol.
11 Study: the union of EU states without unity of
gov.
07/01/87 07/01/87 Doc.
(Engl.)
Theo
12 BISA study (Conf. mid dec. 86/sub group of
dev. Countries)
07/01/87 07/01/87 Doc.
(Engl.)
Lisa
on int. foreign & dev. Pol. Of dev. countries
13 Study: risk management of int. burden
sharing pb /
07/01/87 07/01/87 Doc.
(Engl.)
theo
the state & nationalism in post-war Europe
14 regime der nuklearen
Nichtweiterverarbeitung als Model
12/01/87 12/01/87 Doc.
(Engl.)
moritz
fuer konventionelle Ruestungsbegrenzung
15 South Afr. Foreign pol.: [rueckzug in
eigenelager]
12/01/87 12/01/87 Doc.
(Engl.)
Felix
16 1986 Defence yearbook of the Royal Isntitute
for defence studies
12/01/87 12/01/87 Doc.
(Engl.)
Gido
17 Nuclear arms control after Reykjavik 16/09/87 26/08/87 Doc.
(Engl.)
Bodo
18 Air transport and out of area ops, the theatre
nuclear role, the role of air power in a
NATO/Warsaw Pact conventional conflict
09/09/87 26/08/87 Doc.
(Engl.)
Walter
19 The future of the air power 09/09/87 09/09/87 Doc.
(Engl.)
Walter
Direktor
Start of activities: 1979
Registration nr: XV/2495/79
SUBJECT RE. NR START Nature
of doc
INFO
PEOPLE
1 Views imperialistic Amb. in GDR On current
events
5-Nov-80 16-Jul-80 report Chief of
state
2 UK New CP 20-Jan-82 5-Jan-82 report
3 Views of one Foreign Office employee 20-Jan-82 8-Jan-82 report erased (1)
(name erased), former employee at UK 13-Jan-81 28-Nov80 report
Emb. In the GDR on current pol. Pbs
Doktor
Start of activities: 1975
Registration nr: XV/175/75
Residentur nr: 201
SUBJECT REG. NR START Nature of doc
21 internal asses. Of current pol.
Situation, UK SDP leadership views
(Doktor)
11/02/83 21/12/82 report
ECKHARDT
[ECKHARDT] Start of activities: 1975
Registration nr: XV/175/75
Residentur nr: 201
COMMENTS:
Knowledge defence issues, connections NATO,
works for Institute
Other topics:
Falkland conflict, South-Afr.
Forms: from 1980 to 1989
131 documents delivered from 1980 to 1989
SUBJECT REG. NR START Nature of
doc
1 Aspects of current Chinese foreign and eco. Pol.Uk
views
12/11/80 30-Oct report
2 Inter. Symposium on oil and security issues in
Arab Gulf
24/11/80 05/11/80 doc.
3 Study, UK institute for inter. Opportunities 09/02/81 25/11/80 doc.
4 Conf, former US Amb. James E. Akins on US
domestic and foreign policy & Isr/Arab conflict
17/02/81 04/12/80 report
5 Commissioned study, UK foreign ministry, new
soc.factors in Poland’s unrest
25/03/81 28/02/81 doc.
6 RIIA study, NATO states financial pol. Towards
PolishVP
06/04/81 03/03/81 doc.
7 Speech, former Amb. To Saudi Arabia, on Middle-
East pbs after Reagan’s victory
28/05/81 30/04/81 doc.
8 Conf., UK Institute for International Relations on
Commercial relations Western and Eastern Europe
10/09/81 18/08/81 doc.
9 Conf., UK Foreign Ministry on Nigeria, Institute for
International Relations, London, 20/05/81
16/10/81 18/08/81 doc.
10 Doc., IDAF London, on mil. Apparatus in SA 29/10/81 12/10/81 doc.
11 RIIA study, arms control in Europe 11/11/81 20/10/81 doc.
12 RIIA asses., dev. Inter. Situation 17/12/81 01/12/81 doc. /
report
13 Symposium, Arab Research Centre, London, on
peace’s future in Middle East, 18-19/11/81
17/12/81 12/12/81 doc
14 Commissioned study, London High school for
slavic& East European studies: origins of East-
German national identity since 1971
30/12/81 14/11/81 doc.
15 cons. Of Falkland conflicts on UK domestic pol. 18/05/82 16/04/82 report
16 NATO field of application of European contribution 05/07/82 14/05/82 doc.
17 Power & violence in East Germany: Germany’s
socialist united party
14/07/82 11/05/82 doc.
18 UK / China coop in technico-mil. Field 10/08/82 19/05/82 doc.
19 current Uk position towards China 17/11/82 08/10/82 report
20 Results, 3rd Congress, Gulf Cooperation Council 04/04/83 01/12/82 report
21 internal asses. Of current pol. Situation, UK SDP
leadership views (Doktor)
11/02/83 21/12/82 report
22 Trident programme 02/03/83 01/11/82 doc.
(English)
23 burden-sharing pbs within NATO 29/03/83 29/03/83 doc.
(english)
24 Info on situation of Trotkyist groups in Uk 21/03/83 10/03/83 report
25 UK position on preparation of Summit meeting,
Western industrialised countries, Williamsburg
12/05/83 01/04/83 report
26 Current questions of the UK Peace Movement in 30/05/83 01/04/83 report
rel.with 2nd Konvent for nuclear ban in Europe, W.
Berlin
27 Report, UK Committee for Peace and Security in
Euro.
06/06/83 01/01/83 report
(English)
28 Current situation of UK CP prior to 1983 Party Day 01/11/83 01/10/83 Report
29 Planned manoeuvres, Uk Navy 07/02/84 03/01/84 report
(English)
30 South Africa 05/03/84 01/01/83 doc.
(English)
31 Situation of UK CP 09/03/84 28/02/84 report
32 Info on ANC stance after RSA / Mozambique
contract
09/04/84 01/03/84 report
33 info on RSA PM visit to UK 02/06/84 12/07/84 01/05/84 report
34 Speech and interview, P. Botha, Nov. , RSA pol. In
SA
28/11/84 01/11/84 doc.
(English)
35 internal disputes, UK CP 29/01/85 01/01/85 report
36 Party Day, UK Communist party, 18-20/05/85 16/05/85 01/05/85 doc
(English)
37 “Internation Sacharow Hearing”, London 12/06/85 01/04/85 doc.
(English)
38 Conf., UK Chamber of Commerce in RGW states 06/06/85 01/05/85 report
39 Creation of “campaign for the lifting of disciplinary
measures” within UK CP
24/07/85 01/07/85 report
40 1st reactions on Reagan/Gorbatchow summit UK
views & US Amb. (female) circle in London
27/11/85 01/11/85 report
41 11th SED Party Day from UK pt/view 11/03/86 01/02/86 report
42 UK Participants, round table with DDR, 28-
29/04/86, Berlin
06/05/86 01/04/86 report
43 UK Labour Party study delegation at SED
Congress,8-11/07/86
09/07/86 01/06/86 report
44 Paris END-Konvent from UK pt/view 08/08/86 01/07/86 report
45 FR & US positions on FRG dispute on nuclear
weaps
23/05/89 03/05/89 report
46 FR reaction to Warsaw Pact Org. appeal 05/06/89 05/06/89 report
DOWNLOAD ORGINIAL PDF HERE
The Life of the STASI Spy Boss exposed
 Markus Johannes “Mischa” Wolf (19 January 1923 – 9 November 2006) was head of the General Intelligence Administration (Hauptverwaltung Aufklärung), the foreign intelligence division of East Germany‘s Ministry for State Security (MfS, commonly known as the Stasi). He was the MfS’s number two for 34 years, which spanned most of the Cold War. Many intelligence experts regard him as one of the greatest spymasters of all time.
Markus Johannes “Mischa” Wolf (19 January 1923 – 9 November 2006) was head of the General Intelligence Administration (Hauptverwaltung Aufklärung), the foreign intelligence division of East Germany‘s Ministry for State Security (MfS, commonly known as the Stasi). He was the MfS’s number two for 34 years, which spanned most of the Cold War. Many intelligence experts regard him as one of the greatest spymasters of all time.
Biography
Born in Hechingen, Province of Hohenzollern (now Baden-Württemberg), Wolf was the son of the writer and physician Friedrich Wolf and brother of film director Konrad Wolf. His father was a member of the Communist Party of Germany, and after Adolf Hitler gained power, they emigrated via Switzerland and France to Moscow because of their Communist conviction and because Markus’s father was Jewish.[1][2]
During his exile, he first attended the German Karl Liebknecht Schule and later a Russian school. Afterwards, he entered the Moscow Institute of Airplane Engineering (Moscow Aviation Institute), which was evacuated to Alma Ata after Germany’s attack on the Soviet Union. There he was told to join the Comintern, where he among others was prepared for undercover work behind enemy lines.
After the end of the war, he was sent to Berlin with the Ulbricht Group, led by Walter Ulbricht to work as a journalist for a radio station in the Soviet Zone of occupation. He was among those journalists who observed the entire Nuremberg Trials against the principal Nazi leaders.
In 1953, at the age of 30, he was among the founding members of the foreign intelligence service within the ministry of state security. As intelligence chief, Wolf achieved great success in penetrating the government, political and business circles of West Germany with spies. The most influential case was that of Günter Guillaume that led to the fall of chancellor Willy Brandt. For most of his career, he was known as “the man without a face” due to his elusiveness. It was reported that Western agencies did not know what the East German spy chief looked like until 1978, when he was photographed by Säpo, Sweden’s National Security Service, during a visit to Sweden. An East German defector, Werner Stiller, then identified Wolf to West German counterintelligence as the man in the picture.[3] A counterclaim states, however, that elements within the CIA had identified him by 1959 from photographs of attendees at the Nuremberg trials.[4]
He retired in 1986 in order to continue the work of his late brother Konrad in writing the story of their upbringing in Moscow in the 1930s. The book Troika came out on the same day in East and West Germany. His successor as head of intelligence was Werner Großmann.
Shortly before German reunification he fled the country, and sought political asylum in Russia and Austria. When denied, he returned to Germany where he was arrested by German police. Wolf claimed to have refused an offer of “seven figures”, a new identity and a home in California from the Central Intelligence Agency to defect to the United States.[5] In 1993 he was convicted of treason by the Oberlandesgericht Düsseldorf and sentenced to six years imprisonment. This was later quashed by the German supreme court, because Wolf was acting from the territory of the then-independent GDR. In 1997 he was convicted of unlawful detention, coercion, and bodily harm, and was given a suspended sentence of two years imprisonment. He was additionally sentenced to three days’ imprisonment for refusing to testify against Paul Gerhard Flämig when the former West German (SPD) politician was accused in 1993 of atomic espionage. Wolf said that Flämig was not the agent that he had mentioned in his memoirs: Flämig had unwittingly been probed by intelligence agents during authorised discussions in the GDR.
Markus Wolf died in his sleep at his Berlin home on 9 November 2006.[6]
Cultural impact

Grave in Zentralfriedhof Friedrichsfelde.
John le Carré‘s fictional spymaster Karla, a Russian, who appears in Tinker, Tailor, Soldier, Spy, The Honourable Schoolboy and Smiley’s People was believed by some readers to be modeled on Wolf.[7] However, the writer has repeatedly denied this, and did so once again when interviewed on the occasion of Wolf’s death.[8]
Another le Carré character, who in fact comes even closer than Karla, is Fiedler in The Spy Who Came In From The Cold. He is depicted as a German Jew who spent World War II in exile and came back to gain a senior position in East Germany’s Intelligence Service.
References
- ^“Obituary: Markus Wolf”. The Times (London). 10 November 2006. Retrieved 2006-11-10.
- ^http://www.jweekly.com/article/full/30984/e-german-spymaster-markus-wolf-examined-jewish-roots-in-later-years/
- ^Former East German Spymaster Wolf Dies In Berlin
- ^Superspy
- ^“Former East German spymaster dies at 83”. MSNBC. 9 November 2006. Retrieved 2006-11-09.
- ^ Smee, Jess (10 November 2006). “Markus Wolf, spy chief dubbed The Man Without a Face, dies at 83”. The Guardian (London). Retrieved 2006-11-10.
- ^“Obituary: Markus Wolf”. BBC News. 9 November 2006. Retrieved 2006-11-09.
- ^“Obituary: Markus Wolf”. NY Times/International Herald Tribune. 9 November 2006. Retrieved 2006-11-09.
SOURCE: WIKIPEDIA
Stasi Had Thousands of Spies in West Germany
By Gunther Latsch and Udo Ludwig
Josef Frindt took his secret to the grave. When he passed away at the age of 81, the pastor in the western German town of Dorsten left a congregation mourning a pious man of God. But what the congregation didn’t know was that their pastor had also worked for East Germany’s notorious secret police, the Stasi.
Under the code name “Erich Neu,” the pastor is believed to have submitted 95 informant’s reports, including ones on a colleague who even at the time showed a great deal of potential: Joseph Ratzinger, better known today as Pope Benedict XVI. Frindt, who studied and later taught in the city of Münster, delivered information on up-and-coming theologians and future church dignitaries there, including the future pope, who was working at the time as a professor.Two years after Frindt’s death, research carried out by the Berlin-based agency of the Federal Commissioner for the Stasi Files has brought to light Frindt’s alleged activities as an agent of communist East Germany. The revelations have shocked members of his Sacred Heart congregation in Dorsten. “Many found it impossible to imagine this,” says one church leader. “Now they’re looking for reasons why he might have done it.”
Forgotten Chapter of History
These revelations from the Münster area are unfamiliar territory for citizens of the former West Germany, who believed for years that the trauma surrounding the Stasi had nothing to do with them. “Unofficial collaborators,” as informants from within the population were known, and the reports they filed with the Stasi, were considered a problem exclusive to East Germany. Spies within West Germany, such as Pastor Frindt, belong to a forgotten chapter of German history.
This week, the commission for the Stasi files will publish a handbook on the HVA, the Stasi branch that handled foreign intelligence and was run by legendary spymaster Markus Wolf. The book offers new insight into the Stasi’s work in West Germany, making clear for the first time just how purposefully and extensively the East German intelligence service had West German politics and society in its sights.
It’s now possible to reconstruct in unprecedented detail where and how the Stasi cast its nets. The organization had 149 informants active just in Bonn, the former West German capital. There were 542 in West Berlin.
It seems the HVA recruited most of these spies from industrial sectors, as a way of obtaining Western technological knowledge. It also maintained excellent connections in the center-left Social Democratic Party, where 78 unofficial collaborators and other contacts kept East Berlin up to date, 13 of them serving as sources of information on activities within the party’s executive committee. The Stasi was also well informed on internal matters in unions, churches and universities.
Names Were Unknown
In December 1988, there were 1,929 West German citizens serving as unofficial collaborators or contact people for the German Democratic Republic (GDR), as East Germany was known. In most cases, however, their real names as well as the reports they submitted have remained unknown, after Stasi employees shredded most of the material concerning their West German agents when the East German system collapsed.
Until now, only spectacular isolated cases offered hints of how well connected the GDR’s secret police were in West Germany. In one famous example, West German Chancellor Willy Brandt’s aide Günter Guillaume turned out to be a Stasi informant. The Bundesnachrichtendienst (BND), the German foreign intelligence service, and the Office for the Protection of the Constitution, the country’s domestic intelligence agency, also had spies within their ranks, passing information to the Stasi.
But that wasn’t all by far. Over the course of four decades, the HVA introduced around 12,000 unofficial collaborators into West Berlin and the rest of West Germany, collectively referred to as the “area of operations.” The Stasi files agency is working to reconstruct a more detailed picture, sorted by location and institution, of how these collaborators worked. Helmut Müller-Enbergs, a researcher on the Stasi, started by investigating former informants in the city of Münster. In December 1989, the East German intelligence service still had 16 unofficial collaborators there, informing on around 400 people.
Münster interested the Stasi for two reasons: It was both an important stronghold for the center-right political party Christian Democratic Union (CDU) in the state of North Rhine-Westphalia and a university town with a left-wing scene. Stasi boss Erich Mielke had his agents seek out unofficial collaborators to work within the conservative political establishment. They attached themselves to the police and armed forces and worked their way into the political system. They also recruited students, promising young talents who might one day rank among West Germany’s leaders, and thus become important informants for the GDR.
Susceptible to Blackmail?
The Stasi also had multiple people placed within churches, Christian groups and publishing houses in Münster. The newly restored documents leave Müller-Enbergs with “no doubt” that unofficial collaborator “Erich Neu” was in fact Frindt. As a member of the Diocese of Münster, the pastor was acquainted with Werner Thissen, later to become archbishop of Hamburg. He in turn knew Ratzinger, who already enjoyed a close relationship with Rome.
How exactly the Stasi was able to lure Frindt in is likely to remain a mystery, and the precise content of his reports is unknown. It’s possible he hoped collaborating with the Stasi would improve conditions for his sister, who lived in East Germany. Or perhaps the pastor, who had struggled with alcoholism for a time, was susceptible to blackmail.
It’s likely that monetary rewards played a role for many unofficial collaborators in the West. In Münster, the Stasi managed to establish informants in many government agencies. Stasi collaborators, for example, tapped the telephones at police headquarters. There were also collaborators within the Bundeswehr, the West German armed forces, for example at “Inspection Facility 53,” whose work on the toxicity of smoke bombs interested East Germany.
Three businesses in Münster were also targets of Stasi observation, and a large number of collaborators filed reports from Münster University. An unofficial collaborator known as “Park,” for example, worked in the university library and compiled special dossiers on various individuals. Presumably, the Stasi hoped to find other potential spies — left-leaning students with sympathies for the GDR might prove useful in the future.
Proud of Their Work
Some former West German collaborators remain proud of the work they did for their brothers in the East. Peter Wolter is one of them. As a student of sociology and philosophy at Münster University in the 1970s, he joined a Marxist student group called Spartakus, which was secretly financed by East Germany. Wolter visited East Berlin frequently, and came into contact with the HVA there.
He established a successful career as a journalist, working for the German Press Agency (DPA) and holding a senior position at Reuters news service. The Stasi was particularly interested in a relative of Wolter’s who worked in Cologne for the Office for the Protection of the Constitution. Peter Wolter sent reports to East Berlin over a period of 12 years.Wolter was arrested soon after German reunification. He admitted to having worked for the Stasi, but insisted he had not been a spy or an agent, rather describing himself as a “scout.” A court in Düsseldorf sentenced Wolter, who had founded the homeless newspaper “Draussen!” (“Outside!”), to two years on probation.
To this day, he defends his time as a West German Stasi collaborator. He “helped Europe to have half a century of peace,” he says.
SOURCE: SPIEGEL
Reporter der New York Times stirbt in Syrien
New York Times correspondent Anthony Shadid, a two-time Pulitzer Prize winner whose dispatches captured untold stories from Baghdad under “shock and awe” bombing to Libya wracked by civil war, died Thursday of an asthma attack in Syria. (Feb. 17)
The Dissertation of STASI-Boss Alexander “Big Alex” Schalck-Golodkowski
The section “Kommerzielle Koordinierung” was a part of the GDR’s Ministry for Foreign Trade, in 1972 put directly under control of the Central Comitee (ZK) of the “Socialist Unity Party of Germany” (SED), notably under Secretary General Erich Honecker and Economic Secretary Günther Mittag and connected to the Ministry for State Security with 140 employees.
Headed by State Secretary for Foreign Trade, Alexander Schalck-Golodkowski, it’s main duty was to generate foreign exchange for the interior market.
It further gave clandestine financial fundings and support to the German Communist Party of Western-Germany (DKP).
After the “German Wende” in 1989/90 several commissions of enquiry tried to unbind the intransparent business of “KoKo” with specially founded cooperations in Western-Germany and possible “KoKo”-involved murder-cases against western-german business men.
DOWNLOAD ORIGINAL DOCUMENT HERE
Vorbestrafte STASI-Stalker der “GoMoPa” (Eigenbezeichnung “Scheisshausfliegen”) haben über 5.000 Personen und Firmen auf der Stalking-Liste
Bernd Pulch, MA
Liebe Leser,
es ist wie ein Treppenwitz der deutsch-deutsch Vereinigung wegen Betruges am eigenen Anleger megrfach vorbestrafte STASI-Stalker der “GoMoPa”, die sich selbst als “Scheisshausfliegen” titulieren, haben mehr als 5.000 Firmen und Personen auf ihrer sogenannten Warnliste.
Die “Süddeutsche Zeitung” berichtete über die damit verbundenen Erpressungsversuche. Aber das ist nur die Spitze des Eisberges.
Hinter “GoMoPa” stecken ehemalige STASI-Leute und deren IM, das rechechierte sogar in Ansätzen der “Spiegel”.
Über die Verbindung zwischen dem STASI-Obersten Ehrenfried Stelzer alias “Professor Mord”, dem Verantwortlichen der STASI-Mordstudie Toxdat und dem mutmasslichen heutigen “GoMoPa”-Chef Resch schrieben die Hanseaten “dubios”.
Dieses Wort tauchte sinnigerweise dann immer wieder über den anonymen Artikeln der vorbestraften “GoMoPa”-Betrüger über andere Personen und Firmen auf.
Die fingierten STASI-Stalker “überprüfen Ausweise” und bieten Kreditkarten an….
Selbst einen Berliner Justizsenator bringen sie mit einer fadenscheinigen Medien-Kampagne zu Fall.
Natürlich sind die angeblichen Gründer “Goldman” und “Morgenstern” nicht existent.
Und das “internatioanle Netzwerk von Experten” des selbsternannten Finanz-NACHRICHTENDIENSTES – die Betonung liegt auf NACHRICHTENDIENST sind Berliner, Brandenburger und Dresdner Kommunisten und Neo-STASI mit einer Briefkasetnadresse in New York und rein deutschen Texten.
Und, um das Fass voll zu machen, betreiben die STASI-Epigonen eine Webseite mit “Sexualaufklärung für Kinder” und einem geschlossenen Bereich, einem mutmasslichen Neo-STASI “Darkroom”.
All das unter den Augen des Verfassungsschutzes, des BND und aller möglichen weiteren Stellen, die sogar mutmasslich in dem einen oder anderen Fall mit “GoMoPa” unter einer Schmuddeldecke stecken,w eil sie selber zersetzt wurden.
Zersetzt nach der alten STASI:-Methode durch IM, Erpressung und Bestechung entweder direkt oder durch Angehörige bwz. deren Mit-Gesellschafter.
Dagegen sieht sich die Zwickauer Terrorzelle wie ein Amateur-Verein aus.
Denn natürlich stehen neben Serien-Rufmorden auch mutmasslich tatsächliche Morde auf der Agenda der Neo-STASI – nur tarnen sie das besser und professioneller, da von Oberst Stelzer und der STASI geschult. Von der STASI ,genauzer gesagt der KoKo, stammt auch das Gründungskapital dieses Netzwerkes – an dem deutschen Staat vorbeigeschleusst und nunmehr für kriminelle Machenschaften zur freien, marktwirtschaftlichen Verfügung.
Die STASI-Mafia tut alles, um sich selbst zu schützen und am Leben zu erhalten – feige, getarnt, rufmörderisch, und mörderisch mit modernen Methoden.
Herzlichst Ihr
Bernd Pulch, MA.
Dear Readers,
It’s like an irony of the German-German reunification for fraud on their own investors several times convicted stalker of the Secret Police “GoMoPa” which entitle themselves “shit house flies” have more than 5,000 companies and individuals on their so-called warning list.
The fake STASI stalker even “controll passports” and offer creditcards for sale…
The “Sueddeutsche Zeitung” reported on the related extortion attempts. But that’s just the tip of the iceberg.
Behind “GoMoPa” stuck former Secret Police and the IM, which even reports the German magazine “Spiegel”.
About the connection between the Stasi colonel Ehrenfried Stelzer alias “Professor Murder”, the person in charge of the Secret Police murder methods and research Toxdat and presumed “GoMoPa”-chief Resch wrote the “Spiegel” “dubious”.
This word appeared appropriately enough then repeatedly over the anonymous articles in the “GoMoPa” fraud about other people and companies.
Even a Berlin Senator of Justice was forced to resign by a dubious “GoMoPa” media campaign.
Of course, the alleged founder of “Goldman” and “Morning Star” are non-existent.
And the “internationale network of experts” of the self-proclaimed financial INTELLIGENCE – the emphasis is on INTELLIGENCE – I should add secret – are Berlin, Brandenburg and Dresden communists and neo-Stasi with a dead mailbox in New York and purely German texts.
And, to make the case perfect, the Secret Police epigones run a website with “sex education for children” and a closed area, a suspected neo-Stasi “Darkroom”.
All that decomposes under the eyes of the intelligence, the BND, and all kinds of other institutions, even the allegedly stuck in the one case or another with “GoMoPa” under a grubby blanket.
Decomposed according to the old Stasi “Zersetzung” method by spies, extortion and bribery either directly or through family members and / or their partners and co-shareholders.
In contrast, it looks that the Zwickau terrorist cell was a bloody amateur club.
Because in addition to serial Rufmorden also presumed actual murders are on the agenda of the neo-Stasi – they just disguise it better and more professional, trained by former STASI Colonel Stelzer and the east German Secret Police. From the East German Secret Police, i.e. the departmen “KoKo”, stems the original capital of this network – hidden from the new German state and now available for criminal activities in the free market economy.
The East German Secret Police Mafia is doing everything possible to protect itself and keep itself alive – a coward, disguised, satlking and murderous octopus with modern methods.
Sincerely yours,
Bernd Pulch, MA.
TOP-SECRET from the CIA – Stasi Operations in the Netherlands, 1979–89
by Beatrice de Graaf [1]
In the year 2000, the case of former Chancellor Helmut Kohl, who had sued the German Office of the Commissioner for the Records of the State Security Service of the German Democratic Republic (BStU) for releasing files concerning his political activities before 1989, invoked new interest in a special category of victims and collaborators of the Stasi, East Germany’s Ministry for State Security (Ministerium für Staatssicherheit—MfS). This category involved West Germans and other West Europeans who were the subject of the Stasi’s West-Arbeit (Western operations). [a]
With the scope of West-Arbeit so broadly defined, the boundaries between foreign intelligence and domestic policing could not be discerned clearly in Stasi activities.
Several studies of the West-Arbeit have been published. Some historians, for example, Hubertus Knabe, mentioned the possibility that 20,000 West Germans may have been spies. Official BStU estimates are much lower, perhaps 3,500–6,000 over a period of 40 years. In 1989, 1,500 of them were still operational. These agents spied on thousands of West German companies, organizations, and citizens, including Helmut Kohl. They also worked against East Germans who were in contact with the West. [b] [2]
For the Stasi, West-Arbeit activities im und nach dem Operationsgebiet (in and directed to the target region) were organized not only in geographic terms but in political, organizational, and structural terms. With the scope of West-Arbeit so broadly defined, the boundaries between foreign intelligence and domestic policing could not be discerned clearly in Stasi activities.
Although most of the records of the Stasi’s Main Directorate for Intelligence (the Hauptverwaltung Aufklärung—HVA) have been destroyed, traces of the West-Arbeit can be found in “domestic” departments of the MfS. Research into this branch of activities is all the more revealing because the files of the West German intelligence and security services remain closed.
The West-Arbeit had a direct relationship to the domestic duties of the Stasi, because the enemy against whom the operations were directed could be located abroad, among foreigners, or within the GDR population itself. As can be deduced from the training manual of the Stasi, Haß auf den Feind (hatred of the enemy) was the organization’s all encompassing idea.
Established as the counterpart and junior partner of the KGB and staffed with communist veterans like Erich Mielke, Ernst Wollweber, and Wilhelm Zaisser, the Stasi was a repressive institution from its beginnings. Because communism was considered the logical and inevitable outcome of history, shortcomings and conflicts within the system could only be caused by external factors, for example, saboteurs inspired by the great class enemy in the West.
This definition of the enemy evolved over time, but it was still in place during the neue Ostpolitik of 1970–72 of West-German Chancellor Willy Brandt (1969–74). Brandt’s outreach brought the GDR considerable gains: diplomatic recognition (and thus embassies) in the West, economic treaties, technological imports (microelectronics, computers), and loans.
The gains also brought new dangers: East Germany’s policy of Abgrenzung (the ideological, political and geographical sealing off of the GDR from the West, in particular from the FRG) began to erode because of the many contacts with the West established during this period. The increased percolation through the Wall of Western influences was mirrored by the growth of the Stasi. The “shield and sword of the party” had to make up for the new openness with a major expansion of its personnel, informal agents (inoffizielle mitarbeiter), and duties. At the same time, the Stasi made good use of contacts fostered by Brandt’s Ostpolitik and began new offensives against the West. These were directed mainly against West Germany, but other West European countries, including the Netherlands, also were targetted.
The Stasi’s Image of the Enemy, as seen through the Netherlands
Eva Horn (professor of German literature and the theory of espionage) has written that “enemy images” are the backbone of intelligence services, but that these images can have negative effects on their efficiency. [3] With respect to Stasi operations against the Dutch, I will argue that the image of the enemy, conceived through a Marxist-Leninist perspective, drove Stasi actions with apparent success at a tactical level. Strategically, however, the Stasi actions failed to prevent the fall of the regime it was charged with protecting.
In this article, I will investigate what the MfS was after in and against the Netherlands and to what extent these operations were affected by its thinking about the enemy. Information about these operations is available in the archives of the Stasi’s HVA (foreign intelligence and counterespionage) as well as its Directorate XX (internal opposition) (Hauptabteilung XX—HA XX), and HA I (military intelligence), which are maintained by the BStU.
Intelligence Requirements Regarding the Netherlands
According to MfS guideline No. 1/79, the Stasi was to concentrate on the following goals:
- neutralizing and combating “political-ideological diversion”;
- gathering military intelligence;
- gathering economic intelligence;
- counterintelligence. [4]
Under these guidelines, at least five MfS directorates— HVA, HA XX, HA I, HA II (counterespionage), and HA XVIII (economic intelligence and security)—ran operations against the Netherlands. Research into BStU holdings reveals a broad range of topics and targets between 1979 and 1989.
HVA (foreign intelligence) files contain intelligence on:
- NATO-deployment preparations, the AFCENT-headquarters in Brunssum and the Dutch position in the INF-negotiations;
- preparations for East German communist leader Erich Honecker’s visit to the Netherlands in June 1987;
- activities of the “hostile-negative forces”in the Dutch peace movement;
- reliability of the employees of the GDR consulate and embassy in the Netherlands;
- the microelectronics program of the Philips Corporation;
- the Dutch civil and military security service (telephone numbers, organization charts, pictures);
- security-related issues, such as activities of right wing groups, and terrorist incidents [5]
HA I (military intelligence) collected material on:
- military exercises of the Dutch armed forces;
- The Rotterdam harbour;
HA II and HA XVIII were interested in:
- “operational games” by the Dutch security services against the GDR embassy, consulate, and personnel;
- security issues surrounding the embassy compound. [6]
HA XX (internal opposition) files contain most of the more elaborate analyses found in these files. These mainly regard the:
- Dutch peace movement;
- contacts between Dutch and East German churches, peace groups, and individuals;
- political positions of the Dutch government concerning detente and the East-West conflict.
Intelligence Assets
East German intelligence in the Netherlands involved the use of open sources (OSINT) and technical and human collection. OSINT was easy to come by: The Stasi collected newspaper clippings, official (government) publications, and “grey” reports on GDR- or security-related issues. The MfS also made good use of articles on Dutch military and security issues published by Dutch left-wing pacifist organizations and parties. The Pacifist Political Party, the PSP, for example, exposed details of the structure and activities of the Dutch security service (the Binnenlandse Veiligheidsdienst—BVD). These were immediately analyzed and sent to Berlin. [7]
With respect to technical collection, little is known from the existing files. There is some evidence that the MfS made use of Dutch radio and telecommunications, including those of Dutch military radio and satellite installations in Westerbork and Eibergen. [8]
Humint was the Stasi’s main source for West-Arbeit in the Netherlands. Before the Dutch officially recognized the GDR in January 1973, the HVA made use of the handful of salesmen and church officials who had established contacts in the Netherlands. Because of the proximity of the two countries, these so-called headquarters operations were relatively easy to set up. According to a former Dutch intelligence officer, most of the West-Arbeit against the Netherlands was conducted through headquarters operations.
The agents participating in those operations could be East Germans, but sometimes they had Dutch backgrounds. According to the same Dutch intelligence officer, most East German headquarters operations used Dutch citizens who eventually were doubled by the BVD, [9] New Stasi files suggest this is not the case.
From 1973 on, political and economic relations also provided up-to-date information. However, the MfS was especially interested in non-governmental relations between protestant church congregations and peace groups in both countries. Around 1978, some 100 parish contacts had been established, and by 1984 the number had grown to more than 150. By then, 9,000 to 12,000 Dutch protestants and peace activists were participating in exchange programs. [10]
Diplomatic recognition also enabled the MfS to place at least three “legal” intelligence officers at its residentura in the embassy. [11] Although the BVD kept the GDR embassy under strict surveillance, the MfS residentura was able to run several informal-agent operations from the embassy. The records reveal that the following assets were recruited in the Netherlands (through headquarters operations or by legal residents):
- Three informal agents in the Dutch-East German Friendship Association (a subdivision of the official Liga für Völkerfreundschaft)
- One informal agent and one “prospective agent” from the Horizontal Platform, a Marxist-Leninist offshoot of the Dutch Communist Party.
- Several “contact persons” (not quite “informal agents” but something less committed) inside the Stop-the-Neutron-Bomb campaign and other left wing peace groups.
- At least two informal agents not affiliated with left wing organizations, but recruited because they sought adventure or had financial needs.
The MfS was not allowed to recruit members of the official Dutch Communist Party (they could only be used as contact persons, not as informal agents). Most informal agents and other sources were nevertheless drawn into its service through their sympathy for communist ideals or through their “progressive political convictions,” as Stasi chief Erich Mielke phrased it. As late in the Cold War as September 1988, the resident was complaining about the large number of Dutch citizens who were showing up at the embassy to offer themselves to the service. [12]
On the whole, informal agents like these volunteers were of limited utility as sources. The members of the Friendship Association (the informal agents “Aorta,” “Arthur,” and “Ozon,” for example) or members of other GDR-affiliated organizations were either too old, unemployed, or too suspect to get anywhere near interesting military or political information. The resident came to the same conclusion: Their assets were too “leftist” and attempts to “broaden the contact scope did not produce many results,” he lamented in 1988. [13]
Stasi “Success” Stories
However, on at least three occasions the MfS did run successful operations over longer periods of time: on military intelligence, on the Dutch peace movement, and
Military Reconnaissance— “Abruf”
The MfS was first of all interested in political and military intelligence on the North Atlantic Treaty Organization, the main enemy of the Warsaw Pact. Within pact collection arrangements, the GDR was responsible for collecting intelligence concerning the areas associated with NATO Army Group North and Army Group Central. The HVA, with 4,000 members, and the military intelligence service of the East German Army, with 2,000 members, were responsible for carrying out these operations. West Germany, Great Britain, France, the Benelux and Denmark were defined as principal objectives.
Fulfilling this aim in the Netherlands meant gathering early warning about NATO preparations and securing information about the order of battle and military dispositions. In addition to the targets listed above, HVA was also interested in Dutch military compounds and in the Schiphol and Zestienhoven airports. [14]
The BVD, however, proved a formidable adversary for the HVA. Intensive Dutch surveillance turned the residentura in The Hague into little more than a shelter for underemployed case officers. HVA security reports from 1984 on regularly record Stasi suspicions that the BVD was using its connections in the Dutch media to publicize acts of espionage conducted by the socialist states. Ironically, these complaints (partially justified, as we shall see) were triggered by concern in Dutch conservative circles that Warsaw Pact countries were trying to infiltrate and manipulate the country’s peace movement. Politicians asked questions in Parliament, and the Home Office felt compelled to increase security measures.
According to the MfS residentura in The Hague, the BVD conducted so many unfriendly acts of surveillance and recruiting activities against the embassy, against East German citizens in the Netherlands, and against “friendly” organizations, such as the Friendship Association GDR-Netherlands (Vriendschapsvereniging Nederland-DDR), that they threatened to “obstruct the positive effect of the socialist detente politics concerning disarmament questions.” That is, the Stasi blamed the BVD for deteriorating East-West relations and troubled disarmament talks. [15]
However, at least one Dutch informal agent of the 1980s, whose codename was Abruf (“on call”) was not discovered. Abruf was run by a case officer codenamed Hilmar, who was a member of the legal residentura of the military intelligence department of the East German Army and worked in close cooperation with the MfS staff at the East German embassy. Hilmar had recruited Abruf in November 1983 at a meeting of the Communist Party of the Netherlands (CPN) that he, as a comrade and embassy official, could legally attend.
Hilmar described Abruf as young, unemployed, unhappy with the perceived rightist policies of the Dutch government, frustrated by the NATO-modernization decision, and a staunch supporter of communism. Hilmar played into this zeal and general disaffection with the capitalist environment and had no difficulty recruiting the young man. [16]
As his codename implied, Abruf was used as a freelance agent. He received instructions to photograph Rotterdam Harbor, the Schiphol and Zestienhoven airports, industrial plants in the region, and military compounds. He also collected material on NATO Exercise REFORGER in 1985. After 1985, he was told to move to Woensdrecht, a site then being prepared to receive new NATO missiles.
Abruf received payments of 100 Dutch guilders for every task he carried out. Contact with his case officer was made through dead drops and in short meetings (after long, frantic diversions and smoke screens) in crowded places, such as the Jungerhans department store in Rotterdam. To some of these rendezvous he brought his girlfriend. [17]
Abruf’s employment ended after three years, in 1986, after an assignment in 1985 raised suspicions. In that year, he was ordered to Coevorden, Ter Apel, and Vriezenveen, where he was told to locate military depots, and to Woensdrecht, where he was to photograph the deployment site. On 25 February 1986, the BVD paid him a visit and asked about the trip to Vriezenveen and about his contacts with the GDR embassy. The BVD had stumbled across Abruf while they were following Hilmar. At the time, Dutch security did not seem to know much about Abruf’s history and actual activities as an agent. Hilmar had already been replaced by an MfS case officer codenamed Haupt. The BVD visit alarmed both Abruf and the residentura, and the relationship was mutually terminated two days after the inquiry.
Informal agent Abruf had provided the Stasi with useful reconnaissance material on Dutch military and economic capabilities centering around the Rotterdam region. His cover was never really blown, and the BVD did not uncover his real activities. After 1989, he left the Netherlands and disappeared.
What Abruf provided was typical of the many reports on Dutch military matters, sometimes via open sources, sometimes of obscure origin, found in Stasi files. One of the showpieces is a detailed description of the organizational structure—telephone numbers included—of the intelligence department of the Dutch land forces. [18]
The Stasi and the Dutch Peace Movement
Files unearthed in the BStU archives also provide insight into another type of intelligence activity, covert influence operations. The Stasi focused in the late 1970s and 1980s on the Dutch peace movement and churches and invested heavily in them and selected leaders. Ironically, the East Germans would find their efforts turned against them as circumstances in Europe and the Soviet Union changed with the introduction of perestroika and other reforms in the region.
East German interest in the Dutch peace movement and its church grew out of West European and Dutch opposition to the planned modernization and expansion of NATO’s intermediate range ballistic and cruise missiles in Western Europe in 1977. By the early 1980s, hundreds of thousands of Dutch people would demonstrate to attempt to force the government to postpone or cancel the deployments.
The opposition spawned new opportunities for Soviet and Warsaw Pact leaders, and the official communist World Peace Council and its suborganizations were used to wage open and covert campaigns to capitalize on the protests. [19] Between 1977 and 1979, the ruling East German Socialist Party (Sozialistische Einheitspartei Deutschlands—SED) and the peace council were responsible, among other things, for financial and logistic support of the “Stop the Neutron Bomb” campaign—a Dutch communist front organization that cost East Berlin around 120,000 Dutch guilders (110,000 West German DM). [20]
In addition, the Stasi influenced the foundation Generals for Peace—a well known and respected anti-nuclear peace organization of former West European generals, with Dutch General Michiel von Meyenfeldt (former chief of the Dutch Royal Military Academy) as secretary. To support its perspectives, the Stasi gave it 100,000 West German DM annually. [21]
Even more potentially useful, it seemed to the Kremlin and East Berlin, was the expansion of the support base of the peace movement in the Netherlands to include churches and the Dutch Interchurch Peace Council (Interkerkelijk Vredesberaad—IKV), which had started a campaign for unilateral atomic disarmament in the Netherlands. All influential Dutch churches participated in the IKV, and the organization succeeded in mobilizing large parts of Dutch society. [22] East German leader Erich Honecker believed that the Dutch “religious powers” were the main cause of turning the anti-nuclear campaign into a mass movement, [22] and invitations would follow to a variety of church officials to visit like-minded groups in East Germany.
However, Stasi sympathy for the Dutch peace movement started to turn sour after 1981. After Polish government repression of the independent trade union Solidarity in Poland and after exchanges with members of the Czechoslovak dissident group Charter 77, the IKV radically altered its positions and began to target not only NATO missiles but those of the Warsaw Pact and demanded that all member countries start dismantling nuclear missiles on their own territories rather than pointing fingers at other nations. In effect, this meant the end of a purely anti-NATO campaign. [23]
 Green leaflet_croppedTo make matters worse for the communists, the IKV extended its contacts with dissidents throughout Eastern Europe and declared that repression in the East was a major political cause of the arms race and not the other way around. The IKV planned to organize a peace movement “from below” to confront both superpowers at grassroot levels. [24]
Green leaflet_croppedTo make matters worse for the communists, the IKV extended its contacts with dissidents throughout Eastern Europe and declared that repression in the East was a major political cause of the arms race and not the other way around. The IKV planned to organize a peace movement “from below” to confront both superpowers at grassroot levels. [24]
With its change of position, extant church contacts within the GDR became especially interesting for the IKV—and troublesome to the MfS. Most inviting was an independent peace movement that appeared in East German protestant churches in 1978 called Swords Into Plowshares (Schwerter zu Pflugscharen). The IKV followed up and sent emissaries to various peace groups in the GDR—as tourists, or under the umbrella of church exchanges—and eventually announced the formation of a joint Peace Platform with East German dissidents in the summer of 1982.
The Stasi read about the development in a Dutch newspaper and went on red alert. Honecker himself ordered the official state Secretariat for Religious Matters (Staatssekretariat für Kirchenfragen) to exert all means of influence to eliminate these “divisive forces” (Spalterkräfte). [25]
A four-part campaign against the IKV was begun. First, the Stasi activated its church agents to force the abandonment of the platform. [26] Second, it started a smear campaign against the IKV. IKV Secretary Mient Jan Faber and other officials of his group were registered as persons of criminal intent. [27] Party and state officials, newspapers and front organizations were instructed to depict the IKV as a divisive force within the West European peace movement and Faber as an arrogant bully. [28] Third, Faber himself was barred from entering the GDR. [29] And finally , the existing contacts between Dutch reformed parishes and East German congregations were threatened. The Dutch working group within the East German churches was told that the obstructions were caused by the state’s misgivings about the IKV. Several visits of Dutch delegations to East Germany and vice versa were cancelled. [30]
These measures were informed by the strategy of “differentiation” (Differenzierung), which was a very subtle method of alienating “divisive” and negative elements from their own base. [31] The Stasi sorted out which IKV and church members disliked Faber and invited them to East Berlin. It succeeded in manipulating the president of the IKV and reformed church official Jan van Putten, General von Meyenfeldt—he was also an advisor to the Reformed Churches in the Netherlands and a board member of the IKV—and lower-ranking IKV members. [32] IKV officials, Dutch church groups and journalists were led to believe that the IKV’s secretary was no longer in favour in East Europe or with the protestant churches in the GDR. [33]
 stasi-aktefaber_croppedIn line with this strategy, the Stasi also tried to recruit agents in the Netherlands. IKV Secretary Janneke Houdijk, IKV’s coordinator for East Germany, was approached — in vain. She did not recognise the attempts for what they were and remained loyal to Faber. [34]
stasi-aktefaber_croppedIn line with this strategy, the Stasi also tried to recruit agents in the Netherlands. IKV Secretary Janneke Houdijk, IKV’s coordinator for East Germany, was approached — in vain. She did not recognise the attempts for what they were and remained loyal to Faber. [34]
In the end, however, the efforts bore fruit. East-German churches detached themselves from their IKV contacts and froze most exchange activities. In the Netherlands, many Dutch church leaders and local groups were convinced that Faber was a threat to stability and East-West relations. [35] Faber was threatened with dismissal. Local IKV groups and parishes sent angry letters to IKV headquarters and demanded that Faber stop meddling in internal East German affairs, let alone lead a campaign for human rights. [36] The envisaged Peace Platform never came into being, frustrated in advance by the Stasi, which was helped, knowingly or unknowingly, by Dutch and East German church leaders.
Ironically, after Mikhail Gorbachev came to power in the Soviet Union, Marxist-Leninist enmity towards a democratization approach faded away. The new leadership in the Kremlin even developed sympathy for it, and, in 1988, Faber and British peace activist Mary Kaldor were invited to Moscow to observe the dismantling of SS-20 rockets. The same year, an IKV delegation visited Moscow, invited by the Kremlin itself. [37] The GDR, however, stuck to its rigid policy. The Stasi was appalled by the tolerance of Soviet communists toward Dutch peace activists and did not adapt itself to the new liberalism. Indeed, it continued the struggle against the IKV and even started a new action against it in 1988. Operations were only aborted after the Berlin Wall came down in November 1989.
Operation “Bicycle Tour”
Groups other than the IKV tried to establish exchange programs with East German peace activists, and in doing so generated a Stasi response that illustrates the entanglement of foreign and domestic intelligence activity in East Germany. In 1981, a group of draft resisters from the northern Dutch city of Groningen founded an organization called the Peace Shop (Vredeswinkel). The entity functioned as a communication centre for peace activists from the region. Through existing church contacts and the War Resisters International, the leaders soon contacted a construction branch of the East German army known as the Bausoldaten, that had since 1964 been offering the possibility of completing obligatory military service not with arms but with the spade. This alternative had been provided at the urging of East German protestant churches, which represented about 45 percent of the GDR’s population.
As a grass roots organization, the Peace Shop organized bicycle tours through East Germany as a joint venture of Dutch, East German, and, when possible, Czechoslovak and Polish conscientious objectors. The Dutch entered the GDR as private visitors, gathered at prearranged addresses, and, with East Germans, cycled to rural parts of the GDR and discussed world politics and disarmament initiatives. [38]
In 1985, IKV Secretary Faber and East German Vicar Rainer Eppelmann (a prominent figure in the East German opposition scene) concluded a personal contract to work together for peace. Many participants in the Groningen-GDR exchange decided to do the same and committed themselves to not using violence against each other in case of a war. According to the signatories, in doing this, they contributed to “detente from below.” [39]
Although their activities were relatively low-profile and not aimed at threatening the GDR system, the cycle tours were betrayed by their own success as the Stasi got wind of them. Large international groups peddling, for example, from Karl Marx City (Chemnitz) to Stralsund, could not stay unnoticed, especially after their frequency increased to three or four times a year.
Veterans of the Bausoldaten were suspect to begin with in the eyes of the MfS, especially when they organized meetings with other Bausoldaten and Western draft resisters. Indeed, the Stasi had been carrying out operations against the idea of “social peace service” as an alternative to military service since at least 1981. [40] (Vicar Eppleman, in fact, had been a leader in the “social peace service” effort.)
HA XX, the department charged with dealing with the churches and opposition circles, learned that Dutch participants planned to publish stories about their bicycle tours and experiences in the GDR in Dutch church and peace magazines, and, in 1984, Peace Shop members initiated a letter campaign on behalf of Amnesty International for the release of arrested East German dissidents. [41]
 PeaceTreatySuch activity fit perfectly in the communist vision of class enemies conspiring from outside the system to create domestic unrest, and the bicycle tours thus became objects of intensive surveillance. In 1983, the Stasi started several Operative Vorgange (intelligence operations aimed at arresting dissidents) against former Bausoldaten who had participated in the tours. HA XX recruited several East Germans as informal agents “mit Feindkontakt” (in contact with the enemy), who reported on all the meetings and preparations. [42]
PeaceTreatySuch activity fit perfectly in the communist vision of class enemies conspiring from outside the system to create domestic unrest, and the bicycle tours thus became objects of intensive surveillance. In 1983, the Stasi started several Operative Vorgange (intelligence operations aimed at arresting dissidents) against former Bausoldaten who had participated in the tours. HA XX recruited several East Germans as informal agents “mit Feindkontakt” (in contact with the enemy), who reported on all the meetings and preparations. [42]
Although bicycle tour participants kept their distance from IKV officials, HA XX and the HVA nevertheless increasingly suspected them of being partners of the IKV and executors of the IKV’s grand strategy of developing a “pseudopacifist, bloc–transcending peace movement.” By way of confirmation of this, one Stasi report quotes a Dutch activist as saying “When there are no soldiers on both sides, there will be no weapons used.” [43]
In the belief that the Peace Shop was helping dissidents, the Stasi was not mistaken. The activists had indeed given their East German contacts a typewriter and helped finance Bausoldaten activities with 2,000 Dutch guilders.
With growing Dutch contacts in the so-called Political Underground Forces (Politische Untergrundtätigkeit—PUT), which the East German authorities saw as a threat to communist rule, increased international pressure on the GDR, and a perceived potential for embarrassment during Erich Honecker’s planned June 1987 visit to the Netherlands, the MfS tried to obstruct and manipulate cross-border exchanges. HA XX began an Operativer Vorgang against the Dutch organizer of the bicycle tours, Bert Noppers, who was described as the inspirator and organisator of the PUT tours.
 Cardboard wallAs part of its attack on Noppers, HA XX used a letter from Noppers to an East German friend in which he wrote that Dutch intelligence had tried to recruit him in 1983 to report on his East German contacts. Although Noppers stated in his letter that he refused, the HA immediately listed him as a probable foreign intelligence agent. It then attempted to collect evidence to indict Noppers for hostile agitation against the East German state and for disseminating information to foreign intelligence agencies or other foreign organizations to discredit the GDR. If convicted, he faced two to 12 years of imprisonment. [44]
Cardboard wallAs part of its attack on Noppers, HA XX used a letter from Noppers to an East German friend in which he wrote that Dutch intelligence had tried to recruit him in 1983 to report on his East German contacts. Although Noppers stated in his letter that he refused, the HA immediately listed him as a probable foreign intelligence agent. It then attempted to collect evidence to indict Noppers for hostile agitation against the East German state and for disseminating information to foreign intelligence agencies or other foreign organizations to discredit the GDR. If convicted, he faced two to 12 years of imprisonment. [44]
Nothwithstanding such threats, the Peace Shop organized a protest against East German border controls in 1987, building a model Berlin Wall of cardboard boxes through Groningen and drawing media attention to the condition of their dissident friends in the GDR. Although the peace activists also criticized the West European and Dutch contribution to the armaments race, these acts had no impact on the activities of HA XX. [45]
 VredeswinkelStepped-up HA XX activities included the recruitment as informal agents of three GDR participants in the Peace Shop exchanges. Codenamed Karlheinz, Betty, and Romeo, they reported all of their activities to HA XX. Romeo was sent abroad to visit the Peace Shop in Groningen in July 1988. However, the department could not find enough evidence to prosecute the East German participants or arrest the Dutch organizer.
VredeswinkelStepped-up HA XX activities included the recruitment as informal agents of three GDR participants in the Peace Shop exchanges. Codenamed Karlheinz, Betty, and Romeo, they reported all of their activities to HA XX. Romeo was sent abroad to visit the Peace Shop in Groningen in July 1988. However, the department could not find enough evidence to prosecute the East German participants or arrest the Dutch organizer.
Even by the standards of the East German Penal Code, the activists were just not subversive enough. The Dutch activists did not advocate open criticism or revolution. As Noppers put it during an interview in 2006, “If the East Germans wanted to topple the regime, they had to do it by themselves. We came from abroad and did not want to tell them what to do. And although we were no friends of communism, we had enough criticism to pass on capitalism and materialism at home.” [46] Moreover, the East German government did not want the MfS to make random arrests, since that would cause too much damage to the economic and political relations the GDR had established by then.
Nevertheless, MfS surveillance continued. HA XX ordered continuation of the operations against Noppers, inspired by the same suspicions against the Dutch activist. [47] Although the MfS knew that Moscow had shifted policies and now aimed at cooperation with the IKV and other West European peace organisations, HA XX was still plotting in April 1989 to use intercepted inquiries by the Peace Shop to members of the East German network to recruit more informal agents. [48]
Only in October 1989 were the Operativer Vorgange against the East German Bausoldaten and against Noppers called off. They ended partly because of a lack of evidence and partly because the Stasi had already begun cleaning up its files in the face of growing unrest and pending revolution. On 24 November 1989, 15 days after the fall of the Berlin Wall, the Stasi finally closed its files on Noppers. [49]
In Sum: Tactical Gains, Strategic Loss
During the last decade of its existence, the MfS was successful in tactical terms. It succeeded in running one operation to collect military intelligence, managed to infiltrate and manipulate most IKV contacts in the GDR, penetrated the Peace Shop, and started an Operativ Vorgang against the Dutch coordinator of East European peace tours. Moreover, there is reason to believe that the MfS employed more Dutch informal agents in the 1980s than are discussed here but whose records remain undiscovered.
In the overall, strategic setting, however, the Ministry of State Security failed in its mission to preserve the security of the GDR.
- First, by entangling its foreign intelligence operations with domestic security interests, the Stasi focused on the foreign inspiration of domestic opposition at the expense of understanding that dissent in the GDR drew on the system’s own economic, social, military, and political weaknesses and the government’s abuses of its population.
- Second, the MfS itself became part of the problem instead of part of the solution, as the expansion of the security apparatus from the 1970s on acted as a driver for even more protests.
- Third, activities of the IKV and other Dutch peace initiatives like the Peace Shop were blown up out of proportion, and those in the GDR who were in touch with them were deemed to be guilty of high treason. In this intellectual strait-jacket, the Stasi was blinded to useful insights and could not see that the Dutch movements gave the Soviet bloc opportunities to exploit genuine divisions in NATO.
Finally, when the Stasi got it right, it could not persuade its leadership. In May 1987, the HVA issued an study of Dutch foreign and military politicies before Honecker’s state visit to the Netherlands. The analysis precisely listed the deviations of Dutch politics from the US and NATO lines. (The Dutch denounced SDI, favoured a nuclear test ban and prolongation of the ABM treaty.) Honecker, however, made no effort to play into these differences and only uttered the usual clichès about peace-loving socialist countries. To him, the Netherlands remained part and parcel of the imperialist block. [50] Painfully collected and sound intelligence was made useless by incapable and ideologically deformed party leaders.
Footnotes
a. The BStU (Die Beaufträgte für die Unterlagen des Staatssicherheitsdienstes der ehemaligen Deutschen Demokratischen Republik) is responsible for preserving the records of the Stasi, which had responsibility for both external and internal security. The files on Kohl suggested he had taken bribes from major firms on behalf of his party, the Christian Democratic Union. The BStU’s functions are described on its Web site, http://www.bstu.bund.de.
b. Knabe’s 1999 study was reviewed by CIA historian Ben Fischer in Studies in Intelligence 46, no. 2 (2002). It offers a useful overview in English of East German intelligence.
~ ~ ~ ~ ~ ~
1. “Gauck-Behörde iritiert über Aufgeregtheit im Westen um Stasi-Akten,” in Magdeburger Volksstimme, 28 April 2000.
2. Hubertus Knabe, Die unterwanderte Republik. Stasi im Westen (Berlin, 1999); Helmut Müller-Enbergs, Inoffizielle Mitarbeiter des Ministeriums für Staatssicherheit. Teil 2: Anleitungen für Arbeiten mit Agenten, Kundschaftern und Spionen in der Bundesrepublik Deutschland (Berlin, 1998); Müller-Enbergs, “Die Erforschung der West-Arbeit des MfS,” in Suckut und Weber (eds.), Stasi-Akten, 240–69; Joachim Lampe, Juristische Aufarbeitung der Westspionage des MfS. Eine vorläufige Bilanz. BF informiert Nr. 24 (BStU, Berlin, 1999).
3. Eva Horn, “Das wissen vom Feind. Erkenntnis und Blindheid von Geheimdiensten,” in Wolbert K. Schmidt, et al., Geheimhaltung und Transparanez. Demokratische Kontrolle der Geheimdienste im internationalen Vergleich
(Berlin, 2007), 257–77. Here: 259.
4. Jens Gieseke, “Annäherungen und Fragen an die Meldungen aus der Republik,” in idem (ed.), Staatssicherheit und Gesellschaft. Studien zum Herrschaftsalltag in der DDR (Göttingen 2007), 79–98, here: 89–90.
5. Vgl. Query in the SIRA database 14, Druckauftrag Nr. 12839, AR 7/SG03, Nr. AU 2585/05 Z.
6. HA XVIII, “Pläne und Massnahmen feindlicher Geheimdienste gegen Auslandsvertretungen und langfriestige Delegierungskader der DDR im nichtsozialistischen Ausland im Jahre 1985.” BStU MfS HA XVIII, 32–33.
7. “Vorgangsanalyse zum Vorgang Aorta,” 15 July 1986; “Aufgabenstellung AA 1986. Fortschreibung der Sicherheigsanalyse ‘Haupt,’” 1 March 1986; “Information über die ndl. Sicherheitsdienste. Auswertung der Broschüre “De BVD en de Inlichtingendiensten, Hrsg. by PSP, Amsterdam 1983,” 1984. BStU MfS HA I 1682, 25–28; 90–94; 127–29.
8. For example “Jahresabschlussbericht 1981 über die Ergebnisse der Funkabwehrtätigkeit,”16 November 1981, in which West German, British and Dutch radiocommunications are mapped. BStU MfS HA II 25043, 1–39.
9. Frits Hoekstra, In dienst van de BVD. Spionage en contraspionage in Nederland (Amsterdam, 2004). See also Dick Engelen, Frontdient. De BVD in de Koude Oorlog (Amsterdam, 2007).
10. Beatrice de Graaf, Over de Muur. De DDR, de Nederlandse kerken en de vredesbeweging (Amsterdam, 2004), or De Graaf, Über die Mauer. Die DDR, die niederländischen Kirchen und die Friedensbewegung (Münster, 2007)
11. RoD Den Haag, “Fortschreibung der Sicherheitanalyze zur RoD im Ausbildungsjahr 1987/1988,” 11 November 1988. BStU HA I, 1682: 7–10.
13. RoD Den Haag, “Fortschreibung der Sicherheitanalyze zur RoD im Ausbildungsjahr 1987/1988,” 11 November 1988. BStU HA I, 1682: 7–10.
14. “Information über die Streitkräfte der Niederlande,” nr. 46/88, 27 January 1988. BStU MfS HA XVIII 91: 202–15; “Information über den militärischen Beitrag der Niederlande zu den Streitkräften der NATO,” 29 May
1987. BStU MfS HVA 47: 60–79.
15. Telegrams and reports to MfS headquarters from The Hague: 21 March 1984, 18 January 1989, 31 March 1989, security report “Fortschreibung der Sicherheitsanalyse zur Rod im Ausbildungsjahr 1987/1988” of 18 November 1988. BStU, MfS HA I 1682: 1–11.
16. Several reports on IM “Abruf” by “Haupt” and other MfS-personnel. BStU MfS HA I 1682: 29–163.
17. Hilmar, “Zum Einsatz in den NL,” 1985; “Sicherheitsanalyse zum Vorgang AM-V ‘Abruf’,” 31 January 1986. BStU MfS HA I 1682: 58–63, 81–84.
18. “Angaben zum Nachrichtendienst der Streitkräfte der NL, insbesondere der Landstreitkräfte,” 4 June 1985, Den Haag. BStU MfS HA I 1682: 39–52.
19. Peter Volten, Brezhnev’s ‘Peace Program.’ Success or Failure? Soviet Domestic Political Process and Power. Academisch Proefschrift (Emmen, 1981).
20. Letter, Hans van der Velde (secretary of the National Committee “Initiatief Internationale Stafette”) to the East German Peace Council, Amsterdam, 12 July 1979; Letter Kurt Hölker (deputy secretary-general of the Peace Council) to Hans van der Velde, Berlin, 7 August 1979. Both at Bundesarchiv Stiftung Arbeiterparteien und Massenorganisationen der ehemaligen DDR (thereafter BArch SAPMO), DZ 9 463.2411; Carel Horstmeier, “Stop de Neutronenbom! The last mass-action of the CPN and the Moscow-Berlin-Amsterdam triangle,” in Carel Horstmeier etal (eds.), Around Peter the Great: Three Centuries of Russian-Dutch Relations (Groningen 1997), 65–77.
21. De Graaf, Over de Muur, 113; Jochen Staadt, “Die SED und die Generale für den Frieden,” in Jürgen Maruhn and Manfred Wilke (eds.), Die verführte Friedensbewegung, 123–140.
22. East German Peace Council, “Information,” 22 March 1978, 1, 6, 11, BArch SAPMO DZ 9 463.2411; Neue Zeit, 2 July 1979. East German Peace Council, “Maßnahmeplan,” February 1981, 2, BArch SAPMO DZ 9 450.2354.
23. Jan Willem Honig, Defense Policy in the North Atlantic Alliance. The Case of the Netherlands (London: Westport, 1993), 211–12; Ronald Jeurissen, Peace and Religion: An Empirical-Theological Study of the Motivational Effects of Religious Peace Attitudes on Peace Action (Kampen, 1993), 47; Philip Everts, Public Opinion, the Churches and Foreign Policy: Studies of Domestic Factors in the Making of Dutch Foreign Policy (Leiden, 1983); Jürgen Maruhn and Manfred Wilke, eds., Die verführte Friedensbewegung: Der Einfluß des Ostens auf die Nachrüstungsdebatte (München: 2002); Udo Baron, Kalter Krieg und heisser Frieden. Der Einfluss der SED und ihrer westdeutschen Verbündeten auf die Partei ‘Die Grünen’ (Münster 2003).
24. Mient Jan Faber, “Brief van het IKV-secretariaat aan alle IKV-kernen over Polen kort na 13 december 1981,” in: Faber et al. (eds.), Zes jaar IKVcampagne (Den Haag, 1983), 133–34; “Open letter of Charter 77 to the Interchurch Peace Council,” 17 August 1982. BArch SAPMO DZ 9 585.2879.
25. Report of Hauptabteilung XX (HA XX) for the Stellvertreter des Ministers, Genossen Generalleutnant Mittig, “Negative Aktivitäten von Personen des ‘Interkirchlichen Friedensrates’ (IKV) der Niederlande,” 9 August 1982,
BStU MfS HA XX ZMA 1993/5, 34–37, 56–57.
26. Report of the HA XX/4 (Stasidepartment for church and opposition matters), “Subversive Aktivitäten kirchlicher Personen der Niederlande,” 15 June 1982, BStU MfS HA XX ZMA 1993/5, 21–22; Letter, Christoph Demke (Office of the East German Church Organisation) to Staatssekretär für Kirchenfragen, Klaus Gysi, 9 August 1982, Berlin, “Sekretariat 3827-1632/82,” Rep. B3 Nr. 711, Archive KPS Magdeburg.
27. BStU MfS HA XX AKG-VSH. ZAIG 5. SLK 10964. ZPDB 2082010579. Erfassungsnr. 40438/1590/1993; HA XX AKG-VSH. ZAIG 5 1009. SLK 10994. ZPDB 2082010587. ZMA 3420/1993–1580. VSH-Karteikarten are register
cards, not a file. In June 1982 Stasi started an Operativ Vorgang (file) on Mient Jan Faber and Wolfgang Müller.
28. Report of the HA XX/4, “Interkirchlicher Friedensrat der Niederlande,” October/November 1982, BStU MfS HA XX/4 1917, 1–5; In the mid-1980s, IKV was mentioned in a list of approximately 1,000 “Zielobjekte” (targets) of
the Stasi’s Reconnaissance Service, the Hauptverwaltung Aufklärung. “Zielobjekte der HVA – alphabetische Liste,” BStU ASt Gera BV Gera/Abt. XV 0187, 21–39, in Knabe, West-Arbeit des MfS, 518–54. See 537.
29. “Vertreter holländischer Friedensbewegung dürfte nicht in die DDR,” ADN-Information, 29 July 1982, BStU MfS HA XX ZMA 1993/4, 13.
30. Office of the East German Churches (BEK-Sekretariat), “Arbeitsbeziehungen zwischen dem Bund der Ev. Kirchen in der DDR und dem Raad van Kerken in den Niederlanden und einzelnen Gliedkirchen und Gemeinden,”
November 1982, LDC NHK ROS 735.
31. Clemens Vollnhals, Die kirchenpolitische Abteilung des Ministeriums für Staatssicherheit. BF informiert 16/1997 (Berlin 1997). Concerning the strategy of differentiation, the following orders were relevant: Richtlinien zur Bearbeitungs Operativer Vorgänge (RL 1/76), Operative Personenkontrollen (RL 1/81), Direktive zur IM-Führung (RL 1/79).
32. East German Peace Council, “Maßnahmeplan,” Berlin, April 1981, 4, BArch SAPMO DZ 9 K295.1578; East German Peace Council, “Aktivitäten der Rüstungsgegner im Monat November 1981,” “Niederlande,” 23, BArch
SAPMO DZ 9 450.2354.
33. E.g., Ton Crijnen, “Waarom Mient Jan Faber niet welkom is in de DDR,” De Tijd, 31 December 1982.
34. BStU MfS Abteilung Rostock, OV “Integration” 3/92.
35. “Verslag van uitspraken van bisschop W. Krusche op de bijeenkomst met de Raad van Kerken te Amersfoort d.d. 7-9-82,” Series 3, Nr. 32, Utrecht County Archive, Reformed Churches in the Netherland, General Diaconal
Council (Het Utrechts Archief, Gereformeerde Kerken in Nederland, Algemeen Diakonaal Beraad); Letter, Prof. Berkhof to Vorsitzender des Bundes der Evangelischen Kirchen in der DDR (Krusche), 26 Juy 1982, Amersfoort,
Rep. B3 Nr. 711, Archive KPS Magdeburg; Letter, Prof. Berkhof to Faber, 2 July 1982, Amersfoort, LDC NHK ROS/IKV Box 15.
36. All letters at the (Dutch) International Institute for Social History (IISH) in Amsterdam, Box IKV 455; “Verslag Oost-Europadiscussie op de Campagneraad van 26 februari,” in Kernblad 3, March 1983, IISH Box IKV 453.
37. Interview with Mient Jan Faber, 10 September 2001, The Hague.
38. Interview with Bert Noppers (former participant in these contacts and supporter of the Peace Shop), 20 March 2006, Utrecht.
39. “Network News,” in: Peace Magazin, 1 (December 1985): 1, 30.
40. Uwe Koch, Das Ministerium für Staatssicherheit, die Wehrdienstverweigerer der DDR und die Bausoldaten der Nationalen Volksarmee. Eine übersicht über den Forschungsstand. Die Landesbeauftragte für die Unterlagen des
Staatssicherheitsdienstes der ehemaligen DDR in Sachsen-Anhalt und Mecklenburg- Vorpommern, Sachbeiträge 6 (Magdeburg 1999); Robert-Havemann- Archiv (ed.), Zivilcourage und Kompromiss, Bausoldaten in der DDR 1964 –1990, Bausoldatenkongress Potsdam, 3.-5. September 2004 (Berlin 2005).
41. Vredeswinkel Groningen, “Schrijf een brief!!!!!’[write a letter!!!!!], around January 1984. Matthias Domaschk Archive Berlin, Box “Erik de Graaf.”
42. OV “Schwaben.” BStU MfS BV Frankfurt (Oder) AOP 1430/89; Abteilung XX/4, “Information über feindlich-negative Aktivitäten zur Organisierung und Inspirierung politischer Untergrundtätigkeit,” Frankfurt (Oder), 22 March 1985. BStU MfS OV “Radtour,” 1091/87, Anlage I, 84–86.
43. OV “Schwaben.” BStU MfS BV Frankfurt (Oder) AOP 1430/89; Abteilung XX/4, “Information über feindlich-negative Aktivitäten zur Organisierung und Inspirierung politischer Untergrundtätigkeit,” Frankfurt (Oder), 22 March 1985. BStU MfS OV “Radtour,” 1091/87, Anlage I, 85.
44. Abteilung XX/4, “Eröffnungsbericht zum OV ‘Radtour’,” Frankfurt (Oder) 3 September 1987. BStU MfS OV “Radtour,” 1091/87, Anlage I, 7–12.
45. Abteilung IX/2, “Strafrechtliche Einschätzung zum operativen Ausgangsmaterial ‘Radtour’ der Abteilung XX,” Frankfurt (Oder) 10 September 1987. BStU MfS OV ‘Radtour’ 1091/87, Anlage I, 22–23.
46. Interview with Bert Noppers, 20 March 2006, Utrecht.
47. Abteilung XX/4, “Sachstandbericht zum OV ‘Radtour,’ 1091/87,” Frankfurt (Oder), 22 July 1988. BStU MfS OV “Radtour,” 1091/87, Anlage II, 47–51.
48. Abteilung XX/4, “Dienstreisebericht,” Frankfurt (Oder), 20 June 1988; Abteilung XX, “Information zur ‘Ost-West-Gruppe’ Groningen (Niederlande),” Frankfurt (Oder), 5 April 1989. BStU MfS OV “Radtour” 1091/87, Anlage II, 18–21 and 131–133.
49. Abteilung XX/4, “Abschlussbericht zum operativ-Vorgang ‘Radtour,’ Reg.nr. V/1091/87,” Frankfurt (Oder), 24 November 1989. BStU MfS OV “Radtour,” 1091/87, Anlage II, 189–192.
50. “Information über aktuelle Aspekte der Außen- und Innenpolitik der Niederlande im Zusammenhang mit dem offiziellen Besuch des Genossen Honecker vom 3.-5.6.1987,” 21 May 1987. BStU MfS HVA 47, 85–91.
TOP-SECRET – The Minority Report about STASI-“KoKo” – Der Minoritäten-Report zu STASI-“KoKo”
TOP-SECRET – The STASI Report about the the End – Der Pleite-Bericht der STASI-“KoKo” für das Politbüro
Bernd Pulch, MA
Dear Readers,
The economical situation of the GDR is said to be the main indicator for the fall of the “first German socialist republic”.
As to regard the the coeval SED point of view, heres a document brought by several members of the economic nomenclature of the GDR:
- Mr Gerhard Schürer as the head of the state comitee on economic planning
- Alexander Schalck-Golodkowski, Stasi-colonel and head of KoKo
Sincerely yours
Bernd Pulch, M
DOWNLOAD THE ORIGINAL FILE HERE
TOP-SECRET STASI’s TARGETS – Die geheimen Ziel-Objekte der STASI im Westen enthüllt – Original zum Download
Bernd Pulch, MA
Dear Readers,
here is a list with the western targets of STASI-espionage. It is regarded to be put together by the BV (territorial unit) Gera in the 1980s.
It contains high class military institutions like the Bundeswehr and the military academy of the Western-German army in Hamburg as well as academic institutions like several german Universities, and even the Harvard University and many business companies.
The NEO-STASI still owns documents which can be used to blackmail the relevant persons and organisations, the firms i.e.
Yours sincerely
Bernd Pulch, MA
DOWNLOAD THE ORIGINAL FILE HERE
Die STASI und die Parteispenden-Affäre
ALTKANZLER HELMUT KOHL
Ende März 2000 wurde bekannt, dass die STASI spätestens seit 1976 über die Schweizer Konten und schwarze Spenden der West-CDU informiert war. Kohl wurde wohl schon seit Jahrzehnten von der Stasi abgehört. In Folge erklärte dasBundesinnenministerium , es seien vor der Wiedervereinigung auf Beschluss der Regierung Kohl Stasi-Abhörprotokolle westdeutscher Politiker vernichtet worden.
Am 6. Mai 2000 wurde bekannt, dass Kohl angeblich auch Geld aus dem SED-Vermögen nach dem Zusammenbruch der DDR erhalten haben soll.
SED- UND DDR-“VERMÖGENSVERWALTER” ALEXANDER SCHALCK-GOLODKOWSKI
Im Januar 2000 hatte die Staatsanwaltschaft Bonn Ermittlungen gegen Kohl wegen Verdachts der Untreue aufgenommen.
Am 31. Januar 2001 fand eine Verhandlung vor dem Verwaltungsgericht Berlin statt; bei dieser war unter anderem der Anti-Korruptionsexperte Uwe Dolata als Beigeladener anwesend. Dieser führte aus: „Herr Richter, stellen Sie sich vor, Sie würden ein Auto klauen. Stellen Sie sich vor, dort, wo sie leben, gibt es ein Gesetz, das besagt, es sei verboten, Autos zu klauen. Stellen Sie sich vor, Sie werden dabei erwischt, wie sie dieses Auto klauen. Stellen Sie sich vor, Sie werden nicht dafür verurteilt, dass sie ein Auto geklaut haben und dabei erwischt wurden – weil es kein Gesetz gibt, das besagt, dass Sie für den verbotenen Diebstahl bestraft werden. Diese verwirrende Logik ist im deutschen Parteiengesetz Realität.“, so Dolata. Das Gericht entschied, dass die CDU trotz der Affäre auf ihre staatlichen Zuschüsse nicht verzichten muss.
Am 3. März 2001 stimmte das Landgericht Bonn der Einstellung des Ermittlungsverfahrens gegen Kohl zu; Kohl musste aber eine Geldbuße von 300.000 DM zahlen. Das Gericht begründete diese Zustimmung u. a. mit den Worten „weil die Rechtslage unklar ist und selbst im Falle einer Anklageerhebung und eventueller Verurteilung bei Würdigung aller Umstände von Tat und Täterpersönlichkeit aller Voraussicht nach nur eine Geldstrafe in Betracht käme, welche die in Erwägung gezogene freiwillige Zahlung nicht überschreiten würde“ und dem mangelnden Interesse des Geschädigten selbst (der CDU) an einer weiteren Verfolgung des Falles. Zu den mildernden Umständen rechnete das Gericht Kohls politisches „Engagement“ und seine „Verdienste“ und dass die Tat „nicht der persönlichen Bereicherung diente“. Ebenso müssten die „persönlich herabwürdigenden Angriffe in der Medienberichterstattung mildernd berücksichtigt werden“.
Als weiteren mildernden Umstand hob das Gericht den „Täter-Opfer-Ausgleich“ hervor, „nachdem der Beschuldigte im Rahmen einer legalen Spendensammelaktion den der CDU entstandenen finanziellen Nachteil, soweit er von ihm zu verantworten ist, bei weitem wiedergutgemacht hat“. Kohl hatte in einer neuen Spendensammelaktion 6 Millionen DM von Unternehmern und Prominenten gesammelt und selbst 700.000 DM beigesteuert, um den Schaden für die CDU abzumildern. Unter diesen Spendern waren u. a. Uschi Glas, Heiner Lauterbach, Dieter Thomas Heck, Artur Brauner und Michael Holm. Den größten Betrag spendete Leo Kirch mit einer Million DM.
DER UNTERSUCHUNGSBERICHT DES BUNDESTAGES ZUR PARTEISPENDEN-AFFÄRE – DOWNLOAD
SPENDENAFFÄRE-UNTERSUCHUNGSBERICHT
TOP-SECRET – The Nuclear Map of the USA

A map created by Mother Jones detailing the routes of Office of Secure Transportation routes throughout the U.S.
As you weave through interstate traffic, you’re unlikely to notice another plain-looking Peterbilt tractor-trailer rolling along in the right-hand lane. The government plates and array of antennas jutting from the cab’s roof would hardly register. You’d have no idea that inside the cab an armed federal agent operates a host of electronic countermeasures to keep outsiders from accessing his heavily armored cargo: a nuclear warhead with enough destructive power to level downtown San Francisco.
That’s the way the Office of Secure Transportation (OST) wants it. At a cost of $250 million a year, nearly 600 couriers employed by this secretive agency within the US Department of Energy use some of the nation’s busiest roads to move America’s radioactive material wherever it needs to go—from a variety of labs, reactors and military bases, to the nation’s Pantex bomb-assembly plant in Amarillo, Texas, to the Savannah River facility. Most of the shipments are bombs or weapon components; some are radioactive metals for research or fuel for Navy ships and submarines. The shipments are on the move about once a week.
The OST’s operations are an open secret, and much about them can be gleaned from unclassified sources in the public domain. Yet hiding nukes in plain sight, and rolling them through major metropolises like Atlanta, Denver, and LA, raises a slew of security and environmental concerns, from theft to terrorist attack to radioactive spills. “Any time you put nuclear weapons and materials on the highway, you create security risks,” says Tom Clements, a nuclear security watchdog for the nonprofit environmental group Friends of the Earth. “The shipments are part of the threat to all of us by the nuclear complex.” To highlight those risks, his and another group, the Georgia-based Nuclear Watch South, have made a pastime of pursuing and photographing OST convoys.
…
The OST doesn’t employ your typical truck-stop 18-wheeler jockeys; the agency seeks to hire military veterans, particularly ex-special-operations forces. Besides contending with “irregular hours, personal risks, and exposure to inclement weather,” agents “may be called upon to use deadly force if necessary to prevent the theft, sabotage or takeover of protected materials by unauthorized persons.” At a small outpost in Ft. Smith, Arkansas—the Army base where Elvis was inducted and got his famous haircut—the prospective agents are trained in close-quarters battle, tactical shooting, physical fitness, and shifting smoothly through the gears of a tractor-trailer.
In 2010, DOE inspectors were tipped off to alcohol abuse among the truckers. They identified 16 alcohol-related incidents between 2007 and 2009, including one in which agents were detained by local police at a bar after they’d stopped for the night with their atomic payload. After several agents and contractors were caught bringing unauthorized guns on training missions in Nevada between 2001 and 2004, DOE inspectors determined that “firearms policies and procedures were systematically violated.” One OST agent in Texas pled guilty in 2006 to trying to sell body armor, rifle scopes, machine gun components, and other assault gear he’d pilfered on the job.
There have also been accidents. In 1996, a driver flipped his trailer on a two-lane Nebraska hill road after a freak ice storm, sending authorities scrambling to secure its payload of two nuclear bombs and return them to a nearby Air Force base. In 2003, two trucks operated by private contractors had rollover accidents in Montana and Tennessee while hauling uranium hexafluoride, a compound use to enrich reactor and bomb fuel. (DOE apparently uses some contractors for “low-risk” shipments, while high-security hauling is reserved for OST truckers). In June 2004, on I-26 near Asheville, North Carolina, a truck bound for the Savannah River Site leaked “less than a pint” of uranyl nitrate—liquefied yellowcake uranium, which can be used to produce bomb components.
see here original Document
https://docs.google.com/viewer?url=http://info.publicintelligence.net/DoE-OST.pdf&chrome=true
FEMEN – Uncensored – TV Report
TOP-SECRET – How Israel won the war – The Capture of an Iraqi Mig – 21 by the MOSSAD
 Iraqi Pilot Munir Redfa 1966 Left & 1998 Right (Mossad Archive Photo) Munir Redfa (1934 – 1998) was an Iraqi Fighter Pilot, of Assyrian origin, who defected to Israel in 1966 by flying a MiG-21 of the Iraqi Air Force. In what is considered as one of the Mossad’s most successful operations, Redfa’s entire extended family was smuggled safely out of Iraq to Israel. The MiG-21 fighter was evaluated by the Israeli Air Force and was later loaned to the United States for testing and intelligence analysis. Knowledge obtained from analysis of the aircraft was instrumental to the successes achieved by the Israeli Air Force in its future encounters with Arab MiG-21s.Redfa’s defection was the subject of the movie Steal the Sky.Redfa was born Munir Habib Jamil Rufa in 1934 to an Assyrian family belonging to the Syriac Orthodox Church from Mosul. He was the second of nine children. Like many other Assyrians, his family fled to Iraq as part of the Christian migration from southeast Turkey and Iran’s northwestern mountains (specifically Urmia, fleeing the upheaval of World War I in what is known as the Assyrian genocide).At the time of Redfa’s defection, a press conference was held during which he indicated that he had suffered from religious and ethnic discrimination in Iraq and that he did not feel that it was his home and requested asylum in the United States.Although he was reunited with his family in Israel he did not re-emigrate to the US, contrary to his declaration, and he received Israeli citizenship. He and his family shortly thereafter moved to another western country.Redfa died in 1998 of a heart attack.
Iraqi Pilot Munir Redfa 1966 Left & 1998 Right (Mossad Archive Photo) Munir Redfa (1934 – 1998) was an Iraqi Fighter Pilot, of Assyrian origin, who defected to Israel in 1966 by flying a MiG-21 of the Iraqi Air Force. In what is considered as one of the Mossad’s most successful operations, Redfa’s entire extended family was smuggled safely out of Iraq to Israel. The MiG-21 fighter was evaluated by the Israeli Air Force and was later loaned to the United States for testing and intelligence analysis. Knowledge obtained from analysis of the aircraft was instrumental to the successes achieved by the Israeli Air Force in its future encounters with Arab MiG-21s.Redfa’s defection was the subject of the movie Steal the Sky.Redfa was born Munir Habib Jamil Rufa in 1934 to an Assyrian family belonging to the Syriac Orthodox Church from Mosul. He was the second of nine children. Like many other Assyrians, his family fled to Iraq as part of the Christian migration from southeast Turkey and Iran’s northwestern mountains (specifically Urmia, fleeing the upheaval of World War I in what is known as the Assyrian genocide).At the time of Redfa’s defection, a press conference was held during which he indicated that he had suffered from religious and ethnic discrimination in Iraq and that he did not feel that it was his home and requested asylum in the United States.Although he was reunited with his family in Israel he did not re-emigrate to the US, contrary to his declaration, and he received Israeli citizenship. He and his family shortly thereafter moved to another western country.Redfa died in 1998 of a heart attack.
THE inside story of a daring mission to steal a Russian MiG21 jet fighter from Iraq has emerged in Israel as the country prepares to mark its stunning victory in the six-day war 40 years ago this week.
The secrets of the plane, which was flown to Israel by its decorated Iraqi pilot Munir Redfa, laid the foundation for a triumph by Israeli pilots during the 1967 war, in which the MiGs flown by the Egyptian, Syrian and Iraqi air forces were crippled.Last week Zeev Liron, the pilot who persuaded the Iraqi to defect, recalled how the whole mission had nearly unravelled when Redfa’s wife, who had been told nothing, threw a fit in Paris on hearing the news that she was going to live in Israel.In 1966 Redfa was a 32-year-old pilot in the Iraqi air force. He was frustrated that his Christian background was blocking prospects of promotion and outraged that he had been ordered to attack Iraqi Kurds. He was beginning to doubt whether he had any future in Iraq.Joseph Shamash, one of Israel’s top agents in Baghdad, befriended Redfa and his wife Betty and persuaded them to join him on a Greek island holiday during which they were introduced to Liron. They knew him only as Josh.“Josh can help you to leave Iraq,” Shamash whispered to Redfa.
“When Munir heard what we wanted – to fly his MiG from Iraq to Israel – he almost fainted,” said Liron. “‘My MiG? To Israel? Are you guys out of your minds?’” He pointed out that his tanks carried insufficient fuel to reach Israel and that he would be shot down as soon as he tried to head for the border.Speaking as a fellow pilot, Liron pulled out a map and showed Redfa that his plan could work. “Finally Munir was convinced,” Liron said, “but by the morning he’d got cold feet.”Urgent action was required. Mossad consulted Yitzhak Rabin, the army’s chief of staff and future prime minister, who ordered: “Bring him to Israel. Show him where he’ll land and let him fly in one of our jets.”Redfa was given an Israeli passport in the name of Moshe Miz-rahi and touched down with Liron in Tel Aviv, where he was taken to the airfield where he would land the MiG. Before he left Israel, Redfa asked Liron not to tell his wife anything about the plan. “I’ll prepare the ground,” he promised. But he did not – and it almost derailed the operation.Back in Baghdad, Redfa was assigned to a long-haul flight and he convinced his ground staff to add an extra fuel tank to his MiG.Meanwhile, the Israelis arranged for Redfa’s entire family to leave Iraq for their summer holiday. The last to leave were Betty and their two children, aged three and five, who flew to Paris.When Liron met her there ina Mossad safe house and told her they were about to fly to Israel, she had hysterics. “Forget it!” she screamed. “Israel? Are you mad? And who are you anyway? I’m going straight to the Iraqi embassy.”“Only then did I realise Munir hadn’t said her a word to her about going to Israel,” said Liron.
Eventually he calmed Betty down, persuaded her not to expose the plot to the authorities, gave her an Israeli passport and got her onto a flight to Tel Aviv. Several hours after they landed, Redfa and his MiG21, escorted by an Israeli Mirage, landed at the airbase.With Redfa’s help, the Israelis immediately began to unlock the secrets of the Russian plane. Their pilots tested it to its limits. They fought mock dogfights with their Mirages and learnt the tactics needed to beat it.After the 1967 war, Redfa and his family left Israel. Betty had told her husband that living with the enemy was out of the question. Mossad arranged for them to adopt new identities – as the proprietors of a petrol station in the West.The MiG was lent to the US, which tested it in the Nevada desert, and it helped develop a new generation of American fighters. In return, for the first time, the US began to supply Israel with modern jets. Redfa died of a heart attack in 1998.
DAS BETRUGSURTEIL GEGEN DIE FÄLSCHER DER STASI-“GoMoPa”-SCHEISSHAUSFLIEGEN (EIGENBEZEICHNUNG)
DAS BETRUGSURTEIL GEGEN “BENNEWIRTZ” UND “PETER EHLERS” “GoMoPa”-PARTNER “MAURISCHAT” UND “VORNKAHL” WG BETRUGES AM EIGENEN ANLEGER
Über eine selbstgebaute Blogseite verbreiten die GoMoPa-Gangster eine gefälschte Stellung von Meridian Capital, um Verwirrung zu stiften.
Diese Blogseite existiert erst seit Dezember 2010.
Beweis:
http://www.hypestat.com/pressreleaser.org
Die Meridian Capital-Seite, das Original,
http://othergomopa.blogspot.com/
ist dagegen bereits seit2009 online
Beweis: Aussage Meridian Capital – das Unternehmen können Sie auch gerne direkt kontaktieren.
und
KLAUS DIETER MAURISCHAT IN DETENTION
Source: http://klaus-dieter-maurischat.blogspot.com/2009/01/klaus-dieter-maurischat-in-haft.html
Hintergrund: Die Verurteilung von Klaus Maurischat und Mark Vornkahl wegen Betruges am eigenen Anleger
Klaus Maurischat und Mark Vornkahl, Betreiber vonwww.gomopa.net: Am 24. April 2006 war die Verhandlung am Amtsgericht Krefeld in der Betrugssache: Mark Vornkahl / Klaus Maurischat ./. Dehnfeld. Aktenzeichen: 28 Ls 85/05 Klaus MaurischatLange Straße 3827313 Dörverden.Das in diesem Verfahren ausschließlich diese Betrugsache verhandelt wurde, ist das Urteil gegen Klaus Maurischat recht mäßig ausgefallen.Zusammenfassung der Verhandlung vom 24.04.2006 vor dem Schöffengericht des AG Krefeld in der Sache gegen Klaus Maurischat und Mark Vornkahl.Zur Hauptverhandlung erschienen:Richter Dr. Meister, 2 Schöffen,Staatsanwalt, Angeklagter Klaus Maurischat, vertr. durch RA Meier, Berlin; aus der U-Haft zur Verhandlung überführt.1. Eine Gerichtsvollzieherin stellt unter Ausschuss der Öffentlichkeit eine Urkunde an den Angeklagten Maurischat zu.2. Bei Mark Vornkahl wurde im Gerichtssaal eineTaschenpfändung vorgenommen.Beginn der HauptverhandlungDie Beklagten verzichten auf eine Einlassung zu Beginn.Nach Befragung des Zeugen Denfeld zum Sachverhalt wurde dieVerhandlung auf Wunsch der Staatsanwaltschaft und den Verteidigern unterbrochen.Der Angeklagte Maurischat gab nach Fortsetzung derHauptverhandlung Folgendes zu Protokoll:Er sähe ein, dass das Geld auf das falsche Konto gegangen sei und nicht dem eigentlichen Verwendungszweck zugeführt wurde. Das Geld sei aber zurückgezahlt worden und er distanziere sich ausdrücklich von einem Betrug.Schließung der BeweisaufnahmeDer Staatsanwalt verließt sein PlädoyerEr halte am Vorwurf des Betruges fest. Mit Hinweis auf die einschlägigen Vorstrafen des Angekl. Maurischatund auf laufende Ermittlungsverfahren, beantrage er ein Strafmaß von 1 Jahr und 6 Monaten.Er halte dem Angeklagten zu Gute, dass dieserWiedergutmachung geleistet habe, und dass dieser geständig war. Zudem läge die letzte Verurteilung wegen Betruges 11 Jahre zurück. Auch sei der Geschädigte nicht in existentielle Not geraten, wobei der Staatsanwalt nicht über noch laufende Verfahren hinweg sehen könne. Er läge aber dem Angeklagten Maurischat nahe, keine weiteren Aktivitäten im Bezirk der Staatsanwaltschaft Krefeld auszuüben, insbesondere möchte er, dass keine weiteren Anleger im Bezirk der Staatsanwaltschaft Krefeld durch GoMoPa akquiriert werden.Die Freiheitsstrafe soll zur Bewährung ausgesetzt werden.Plädoyer des Verteidigers des Angekl. Maurischat, Herrn RA MeierEr schließe sich, wie (in der Unterbrechung) vereinbart, dem Staatsanwalt an.Es stimme, dass sein Mandant Fehler in seiner Vergangenheit gemacht habe, und dass er auch diesmal einen Fehler begangen haben könnte, jedoch sei der Hinweis wichtig, dass sein Mandant aus diesen Fehlern gelernt habe.Der Angeklagte haben das letzte Wort.Maurischat sagt, es sei bereits alles gesagt worden.Unterbrechung zu Hauptverhandlung. Der Richter zieht sich mit den Schöffen zur Beratung zurück.Urteilsverkündung:Der Angeklagte wird des gemeinschaftlichen Betrugs für schuldig befunden.Der Angeklagte Klaus Maurischat wird zu einerFreiheitsstrafe von 1 Jahr und 6 Monaten verurteilt. Diese wird zur Bewährung ausgesetzt.Die Bewährungszeit wird auf 3 Jahre festgesetzt.Der Haftbefehl gegen Klaus Maurischat wird aufgehoben.Der Angeklagte trage die Kosten des Verfahrens.UrteilsbegründungDer Richter erklärt, dass eine Täuschung des Geschädigtenvorliegt und somit keine Untreue in Betracht kommen kann.Die Fragen, ob es sich um einen Anlagebetrug handele sei irrelevant. Er hält den Angeklagten die geleistete Wiedergutmachung zu Gute.Ebenso ist das Geständnis für die Angeklagten zu werten. Zudem liegt die letzte Verurteilung des Angeklagten Maurischat 11 Jahre zurück.Die Parteien verzichten auf Rechtsmittel. Das Urteil ist somit rechtskräftig.Mit dem heutigen Urteil endet ein Kapitel in derBetrugssache Goldman Morgenstern & Partners, Klaus Maurischat und Mark Vornkahl.Alle GoMoPa.net Verantwortlichen, Maurischat, Vornkahl und Henneberg sind nun vorbestrafte Abzocker und Betrüger und die Zukunft der Pseudoklitsche GoMoPa.net sieht duster aus.Mir dem Geständnis der beiden ABZOCKER MAURISCHAT UND VORNKAHL vor Gericht bricht ein jahrelangaufrechterhaltenes Lügengeflecht von einigen primitiven Betrügern zusammen. Gewohnheitsverbrecher und Denunzianten,die rechtschaffene Personen und Firmen in ihren Verbrecherforen kriminalisierten.
CONFIDENTIAL – (U//FOUO) Army National Guard Information Assurance (IA) Program Policy

This Policy provides Information Assurance (IA) policies and mandates procedures for implementing the Army National Guard (ARNG) IA Program. The ARNG IA program will implement the Department of Defense (DoD) IA program, DoD Instruction (DoDI) 8500.2, “Information Assurance Implementation,” IAW Army Regulation (AR) 25-2, “Information Assurance” chapter 1 g-8 to support the DoD Information Management Strategic Plan, (IMSP). This Policy supports the Federal Information Security Management Act, (FISMA) 2002 and any other federal guidelines as needed; and shall be consistent with today’s technological advancements, in a generic fashion to avoid dependency on specific technology.
This Policy shall:
• Establish policies and assign responsibilities for achieving acceptable levels of Information Assurance in engineering, implementation, operation, and maintenance for all information systems connecting to all ARNG Networks, to include GuardNet Wide Area Network (WAN), • Provide administrative and systems security requirements, including those for interconnected systems.
• Define and mandate the use of risk assessments and the DoD Defense in Depth Strategy.
• Use the principle of least privilege to ensure that users and administrators get only the access that they require.
• Describe the roles and responsibilities of the individuals who constitute the Information Assurance security community and its users, and outlines training and certification requirements IAW DoDI 8500.2, DoD I 8570.1, and AR 25-2.
• Require a life-cycle management approach to implementing Information Assurance requirements and requires the implementation of a configuration management process IAW AR 70-1.
• Establish a procedure to document the status of generic accreditations for all information systems fielded by the ARNG.
• Establish requirements to ensure that ARNG Designated Approving Authorities (DAAs) meet the system accreditation requirements of this Policy before fielding or testing any system that requires connection to ARNG Networks IAW DoD Directive (DoDD) 8500.1, DoDI 8500.2, DoDI 5200.40, and AR 25-2.For the purpose of this Policy, the following terms all refer to the Joint Forces Headquarters J-6 (JFHQ J-6) of each State and/or Territories: Director of Information Management (DOIM), Deputy Chief of Staff for Information Management (DCSIM), Chief Information Officer (CIO), or other term used to refer to the Director of Information Management within your State and/or Territories.
DOWNLOAD ORIGINAL DOCUMENT HERE
FEMEN VIDEO – Sexy Protest: Ukrainerinnen bei Demo gegen Berlusconi
REVEALED – The FBI UFO Files
UFO
Unexplained Flying Objects (UFOs) In 1947, a rash of sightings of unexplained flying objects (UFOs) swept America. Although the newly formed U.S. Air Force was the primary investigator of these sightings, the FBI received many reports and worked for a time with the Air Force to investigate these matters. This release details the FBI’s role in investigating such reports between 1947 and 1954.
CONFIDENTIAL – the FBI unveils “Top 10 Myths”
The Top Ten Myths in FBI History
07/24/08
For the past century, the FBI has been a vital player in American history, front and center in some of our country’s most high-profile national security and criminal issues. Not surprisingly, some myths and misunderstandings about the Bureau have evolved over that time, in part because of the complex and sometimes sensitive nature of our work. We’ve picked out what we think are the top ten myths down through the years, leaving aside ones that are so fanciful that they don’t deserve mention here…
In descending order, here they are:
Myth #10) The FBI has Nikola Tesla’s plans for a “death ray”!
 |
|
| Nikola Tesla |
If you don’t know the name, Nikola Tesla was a prolific inventor and gifted physicist and engineer—most known for developing the basis for AC power—who was born in Croatia in 1856 and settled in the U.S. in 1884. When Tesla died in New York in January 1943, his papers—which were thought to include plans for a particle beam weapon, dubbed a “death ray” by the press—were temporarily seized by the Department of Justice Alien Property Custodian Office (“alien” in this case means “foreigner,” although Tesla was a U.S. citizen). Despite longstanding reports and rumors, the FBI was not involved in searching Tesla’s effects, and it never had possession of his papers or any microfilm that may have been made of those papers. Since 1943, we have told a consistent story to all who have asked. Reports to the contrary appear to be based on an initial confusion of FBI agents with other government officials—especially Alien Property Office personnel. These rumors have long been repeated in biographies and articles on Tesla without double-checking the facts as reported in our files.
Myth #9) The FBI has “X-Files.”
Well, first off, the FBI is NOT on point to investigate the supernatural as Scully and Mulder did on the X-Files TV show. Yes, we do have files on some unusual phenomena—like cattle mutilation, UFOs, and Roswell—but generally only because people reported something and we made a note of it. Some of the files do involve cases involving a potential violation of federal law under our jurisdiction that we did investigate. One example is Operation Majestic 12, the supposedly secret group of government officials tasked by President Truman to study the Roswell incident. When what appeared to be a top secret document about the formation of the Majestic 12 surfaced in the 1980s, we were asked to investigate a possible breach of classified information. The Bureau concluded that the document was a fake. So, bottom line: while FBI agents chasing aliens and other supernatural creatures may make good entertainment, it’s not part of our job description, and we don’t have a secret collection of “X-Files” squirreled away somewhere.
Myth #8) Elliot Ness was an FBI agent.
No, actually he never was. But he did work briefly under Director J. Edgar Hoover and applied at one point to be a Bureau agent. It’s a fairly complicated story, and you can read all about it and check out our public files on Ness on this website.
 |
|
| “Machine Gun” Kelly |
Myth #7) Machine Gun Kelly gave FBI agents their “G-Men” nickname.
It’s somewhat of a legend now that FBI agents were named “G-Men” when a scared and tired gangster named George “Machine Gun” Kelly stumbled out of his hiding place, arms held high, surrounded by lawmen, yelling “Don’t shoot, G-Men, don’t shoot.” But in reality, Kelly may have never uttered these words. A bit of editorial license on the part of the press likely crept in…and the catchphrase ended up capturing the public’s imagination. Read a story on the nickname and hear FBI Historian Dr. John Fox’s take on it.
Myth #6) The FBI prosecutes cases.
We are investigators, not prosecutors. Our job is to gather the facts and evidence and present the results to the local U.S. Attorney in the Department of Justice, who decides whether or not to bring the case to trial. Because we developed the facts, we may be asked to present or discuss our findings in court.
Myth #5) There were no minority agents during the Hoover years.
 |
|
| James Amos |
The FBI was hardly way ahead of its time in providing equal career opportunities to all Americans, but it is not true that the FBI was unwilling to hire minorities during Hoover’s tenure…or (as one variation of the myth goes) was reluctant to hire minority agents until ordered to do so by President Kennedy in the early 1960s. The fact is, many minority special agents worked in the FBI from the early 1920s forward. An African-American agent named James Amos, for example, investigated major cases in New York from 1921 to 1953, while the Striders—an African-American father/son agent team in Los Angeles—served with distinction from the 1940s through the early 1970s. Hispanic Agent Manuel Sorola served in a number of our western offices from the 1920s through the 1940s, and Filipino-born Agent Flaviano Guerrerro served ably in the 1940s. All told, there were dozens of minority special agents on our rolls before Hoover died in 1972.
Myth #4) The Bureau routinely spies on the American people.
Absolutely not. We are governed by and carefully follow a well-defined set of laws, regulations, and guidelines—honed over a century of practical experience—that spell out how we can and should conduct our investigations. It’s always been a delicate balance between harnessing the tools at our disposal to solve crimes and prevent attacks and upholding the civil liberties of all Americans. Over the course of a century, we’ve made some mistakes, but they’ve been few and far between compared to the vast amount of work we do every day. While some have long predicted that the FBI would turn into a big-brother-like secret police force, that scenario simply hasn’t happened. After all, we live and work in our communities and cherish our country’s rights and freedoms like everyone else!
Myth #3) The FBI doesn’t cooperate with other agencies.
You’d think from the news media and the entertainment industry that we do everything from routinely stiffing our partners…to hogging all the credit in big cases…to simply not getting along with our colleagues. If you worked for the Bureau—and saw the close relationships and even friendships that exist between us and our partners across the country and around the globe—you’d realize that nothing could be further from the truth. Yes, there is an occasional conflict or issue (we are all humans, after all), but relationships have been exceptional over the years and improved even more since 9/11. Read some recent stories about our partnerships.
Myth #2) The FBI has files on every American.
 |
Some people think that the FBI has a vast range of files on all the bad things they’ve ever done. Not true! We keep investigative files on serious violations of federal law and major threats to our national security. We won’t have a “file” on you unless you’re a spy or terrorist or criminal or are suspected of being one (and we use the word “file” loosely, as we generally organize materials by cases, not individuals). Some people do appear in our files if they’ve provided us with information or were a victim in a case…or because an authorized third party requested information about them—but this kind of information is held under strict laws and for a legally specified period of time. For more details, see our Freedom of Information Act file fact sheet.
Myth #1) The FBI can’t or shouldn’t do intelligence.
It’s an old saw that has been oft-repeated since 9/11. But a century of history says differently. From our earliest moments we’ve used intelligence (under the laws and guidelines of the day) to get our arms around major threats and disable them—from gangsters to mobsters, from yesterday’s Soviet spies to today’s terrorists. The fact is, the FBI has always been both an intelligence agency and a law enforcement/national security organization…and like our police and intelligence community counterparts, gathering and sharing and acting on intelligence is part of what we do on a daily basis. We’ve certainly gotten better at it since 9/11, and you can bet that we’ll keep improving in the days ahead. Read our new centennial history book and our recent stories for some telling examples.
VERTRAULICH – BERICHT DES BUNDESTAGES ZU STASI – “KoKo” – German Bundestag about STASI “KoKo”- Report
Bitte obigen Link zum Download nutzen
use Link above for download of the confidential report
TOP-SECRET – List of Chinese Communist Spies in the United States
China communist Spies in America ———–Ai ,Duan Wu(New York)
China communist Spies in America ———–Wu, Han Shi(New York)
China communist Spies in America ———–Zhang ,Wei (New York)
China communist Spies in America ———–Song ,Wei
China communist Spies in America ———–Gao, Jun Guang
China communist Spies in America ———–Jing, Xiu Hong( Seattle)
China communist Spies in America ———–Shen ,Xue(Canada)
China communist Spies in America ———–Lin ,Zheng Yang(Lin, Jian Hui Seattle)
China communist Spies in America ———–Xie, Fu Min(New York)
China communist Spies in America ———–Sun,Zhong Xiong (New York)
China communist Spies in America ———–Zhang,Guang Zhong(New York)
China communist Spies in America ———–Lu ,Yun(New York)
China communist Spies in America ———–Chen ,Xiao(New York)
China communist Spies in America ———–Wang, Xue Chen(Jiang, Hai Fu, HK)
China communist Spies in America ———–Tang, Jie(Huan, Dan Xuan,New York)
China communist Spies in America ———–Yao, Mao Sheng (Li, Qing,New York)
China communist Spies in America ———–Ge, Li(New York, China, Canada)
China communist Spies in America ———–Shun ,Rui Jun(St. Francisco,China)
China communist Spies in America ———–Yang, Wei Ming (DC)
China communist Spies in America ———–Wang ,Yao De( St. Francisco)
China communist Spies in America ———–Xue ,Hai Pei(DC, China)
China communist S pies in America ———–Ji , Hong(DC)
China communist Spies in America ———–Lu, Xue Xiang(DC)
China communist Spies in America ———–Hu, Ping(New York)
China communist Spies in America ———–Lin Chang Sheng(DC, St. Francisco)
China communist Spies in America ———–Wei ,Quan Bao(New York)
China communist Spies in America ———–Zhang ,Jian An(New Jersey)
China communist Spies in America ———–Song, Wei(China, New York)
China communist Spies in America ———–Song ,Su Yuan(New York)
China communist Spies in America ———–Zhang ,Zhuo Zhi(DC)
China communist Spies in America ———–Wei, Xiao Peng(New York)
China communist Spies in America ———–Wang, Xiang Lin(Chicago)
China communist Spies in America ———–Sheng, Li Ling(New York)
China communist Spies in America ———–Yang, Huai An(New York, China)
China communist Spies in America ———–Yan ,Dun Zheng(New York)
China communist Spies in America ———–Wang, Jing Fang(MD)
China communist Spies in America ———–Zhao ,Xian\o Wei(MD)
China communist Spies in America ———–Bao ,Ge( New York)
China communist Spies in America ———–Bi ,Shu Zhi ( New York, Female)
China communist Spies in America ———–Luo, Ning(USA, China)
China communist Spies in America ———–Jing, Yang Shi( USA, China)
China communist Spies in America ———–Pan Guo, Peing(Baltmore)
China Communist Spies in America————Wen Ying Chen (CA)
China Communist Spies in America————Li, Wen He
China Communist Spies in America————Gao ,Zhan (VA)
China Communist Spies in America————Yie, Ning (DC, New York)
China Communist Spies in America————Yan ,Qing Xin( DC, CA)
China Communist Spies in America————Xue, Wei a.k.a Wang ,Yuantai ( New York)
China Communist Spies in America————Shi, Lei a.k.a Xia ,Yu (New York)
China Communist Spies in America————Zhang ,Qi ( hide, sister of Yan, Qing Xin)
China Communist Spies in America————Hu,Chang Xin ( New York)
China Communist Spies in America————Yang ,Hai Ping ( St. Francisco)
China Communist Spies in America————Chen, Guo Hua (DC, major assistent, director of Asia)
China Communist Spies in America————Wang, Mei ( New York)
China Communist Spies in America————Zhou, Yong Jun( Las Angles)
China Communist Spies in America————Lu ,Jing Hua
China Communist Spies in America————Wu, FangChen(Kenta)
China Communist Spies in America————Yao, Yong Zhang( Zhang Cai)
China Communist Spies in America————Gao, Han (Guo, Zhi)
China Communist Spies in America————Zhu, Yi Fei
China communist Spies in America ———–Zhang ,Wei(DC)
China communist Spies in America ———–Su, Yang ( USA)
China communist Spies in America ———–Wang, Yao (HK)
China communist Spies in America ———–Xue Bing (Fa Lun Gong)
China communist Spies in America ———–Wang Tao(Fa Lun Gong)
China communist Spies in America ———–Yang ,Wei (PA)
China communist Spies in America — ——–Yang ,Qing Heng (China)
China communist Spies in America ———–Zhong ,Xiao(Su Xiao Zhou)
China communist Spies in America ———–Su ,Chang Qing(New York)
China communist Spies in America ———–Leng ,Shong(St. Francisco)
China communist Spies in America ———–Mi , Jia(Las Angles)
China communist Spies in America ———–Ma ,Yuan(Yt)
China communist Spies in America ———–Liao, Da Wen (DC)
China communist Spies in America ———–Huang ,Sha(New York)
China communist Spies in America ———–Zhang, Zhong Chun(St. Francisco)
China communist Spies in America ———–Xing, Wen(DC)
China communist Spies in America ———–Zhang ,Xing(Tx)
UNVEILED by the FBI – List of Soviet agents in the United States including Bogus Names and Activities
This is a list of Soviet agents in the United States. This is a list of spies who worked for the Soviet Union, Warsaw Pact nations, and Soviet-aligned countries in the United States. This list contains individuals where testimony and corroborating evidence exists that the individual was working for and under the control of the above-mentioned countries or organizations.
Czechoslovakia (StB)
Karl Koecher, the mole who penetrated the CIA
Hungary
Clyde Lee Conrad, U.S. Army NCO who betrayed NATO secrets.
Poland
Marian Zacharski, Polish Intelligence officer arrested in 1981. Among other things, he won access to material on the then-new Patriot and Phoenix missiles, the enhanced version of the Hawk air-to-air missile, radar instrumentation for the F-15 fighter, “stealth radar” for the B-1 and Stealth bombers, an experimental radar system being tested by the U.S. Navy, and submarine sonar.
Soviet Union
NKVD and KGB
Louis Adamic, writer and spokesman for Yugoslav immigrants. During World War II, he advised the OSS on Balkan questions. Source for Golos-Bentley network via Louis Budenz.
Aldrich Ames, CIA officer spying for the Soviet Union beginning in 1985 as a ‘walk-in’ to the Soviet Embassy in Washington, D.C.
Marion Davis Berdecio, friend of Judith Coplon and Flora Wovschin from their days at Barnard College
William Weisband, U.S. Army signals intelligence staffer and NKVD agent handler
The “Berg” – “Art” Group
Alexander Koral, former engineer of the municipality of New York.
Helen Koral, Berg’s wife, housewife.
Byron T. Darling, engineer for the Rubber Company.[1][2]
A. A. Yatskov
George Blake, United Kingdom SIS officer who betrayed existence of the Berlin Tunnel under the Soviet sector and who probably betrayed Popov.
Felix Bloch, U.S. State Department economic officer. Robert Hanssen warned Soviets about the investigation into his activities [3] [2]
Christopher John Boyce and Daulton Lee, American walk-in spy for the Soviet Union, known as the Falcon and the Snowman.
Buben group
Louis F. Budenz, former member of the Central Committee of the Communist Party USA, former editor of the newspaper Daily Worker, professor at Fordham University.
Robert Menaker, commercial traveler (traveling salesman) to a variety of trade firms
Salmond Franklin, without specific assignments, husband of “Rita.” Used as a “signaler” [Russian: sviazist = communications man]
Sylvia Caldwell, technical secretary for a Trotskyist group in New York City.
Lona Cohen, sentenced to 20 years; subject of Hugh Whitemore’s drama for stage and TV Pack of Lies
Morris Cohen sentenced to 25 years; subject of Hugh Whitemore’s drama for stage and TV Pack of Lies
Judith Coplon, NKGB counter-intelligence operative in the U.S. Department of Justice; two convictions overturned on technicalities
Eugene Dennis, senior member of the Communist Party USA leadership, convicted of advocating the overthrow of the U.S. government an sentenced to five years
Samuel Dickstein, Congressman from New York; before being recruited as a Soviet agent in 1937 he served as co-Chairman of a predecessor to the HUAC during hearings into the Business Plot against President Franklin D. Roosevelt[4]
Mark Gayn, journalist, The Washington Post; Amerasia case
Dieter Gerhardt, South African Navy Commodore who was convicted of spying for the Soviet Union; alleged that the Vela Incident was a joint Israeli-South African nuclear test after being released in 1994 and emigrating to Switzerland
Ben-Zion Goldberg (Benjamin Waife), journalist, contributor to Toronto Star, St. Louis Dispatch, New York Post, Today, and The New Republic [5]
Theodore Hall, physicist who supplied information from Los Alamos during World War II, a NYC walk-in, never prosecuted
Robert P. Hanssen, Federal Bureau of Investigation agent convicted of spying for the Soviet Union, betrayed tunnel under new Mt Alto Soviet Embassy in Washington DC; may have done most damage since Philby
Reino Häyhänen, Finn who worked in the US as a Soviet spy directed by Rudolf Abel, used the VIC cypher, defected to the US [3]
Edward Lee Howard, ex-Central Intelligence Agency officer who sold info and escaped to Soviet Union in 1985
V. J. Jerome, sentenced to three years for advocating overthrow of U.S. government
Martin Kamen, Radiation Laboratory at the University of California, Berkeley, Manhattan Project
Walter Krivitsky
Giovanni Rossi Lomanitz, Berkeley Radiation Laboratory
Clayton J. Lonetree, U.S. Marine Embassy guard Sergeant suborned by female KGB agent (‘Violetta Sanni’) in Moscow, turned himself in to authorities in December 1986, convicted 1987
Jay Lovestone
Carl Marzani, Deputy Chief Photographic Presentation Branch Office of Strategic Services; United States Department of State
Alan Nunn May, physicist who supplied information about the British and American atomic bomb research to the Soviet Union
Kate Mitchell
Mocase
Boris Morros, Hollywood producer
Jack Soble, sentenced to 7 years, brother of Robert Soblen
Myra Soble, sentenced to 5½ years
Robert Soblen, sentenced to life for spying at Sandia Lab, etc., but escaped to Israel, then committed suicide
Jane Zlatovski
Mark Zborowski
Perlo group
Victor Perlo, was the Chief of the Aviation Section of the War Production Board during World War II; head of branch in Research Section, Office of Price Administration Department of Commerce; Division of Monetary Research Department of the Treasury; and later the Brookings Institution
Harold Glasser, Director, Division of Monetary Research, United States Department of the Treasury; United Nations Relief and Rehabilitation Administration; War Production Board; Advisor on North African Affairs Committee; United States Treasury Representative to the Allied High Commission in Italy
Alger Hiss, Director of the Office of Special Political Affairs United States Department of State
Charles Kramer, Senate Subcommittee on War Mobilization; Office of Price Administration; National Labor Relations Board; Senate Subcommittee on Wartime Health and Education; Agricultural Adjustment Administration; Senate Subcommittee on Civil Liberties; Senate Labor and Public Welfare Committee; Democratic National Committee
Harry Magdoff, Statistical Division of War Production Board and Office of Emergency Management; Bureau of Research and Statistics, WTB; Tools Division, War Production Board; Bureau of Foreign and Domestic Commerce, United States Department of Commerce
George Perazich, Foreign Economic Administration; United Nations Relief and Rehabilitation Administration
Allen Rosenberg, Board of Economic Warfare; Chief of the Economic Institution Staff, Foreign Economic Administration; Senate Subcommittee on Civil Liberties; Senate Committee on Education and Labor; Railroad Retirement Board; Counsel to the Secretary of the National Labor Relations Board
Donald Wheeler, Office of Strategic Services Research and Analysis division
Redhead group
Hedwiga Gompertz, Wacek’s wife, sent to the U.S. in 1938 to carry out fieldwork assignments, defected in 1948
Paul Massing, scientist at Columbia University’s Institute of Social Research. Defected.
Laurence Duggan (aka 19th), former employee of the State Department. Suicide.
Franz Leopold Neumann, former consultant in the Department of Research and Analysis of the OSS
Rudolf Roessler chief of the very successful, and very odd, Lucy spy ring of World War II
Rosenberg ring
Joel Barr, met Julius Rosenberg at City CoIIege of New York, then spied with him and Al Sarant at Army Signal Corps lab in New Jersey; escaped prosecution by fleeing to Soviet bloc in 1950. Died 2007.
Max Elitcher, longtime friend of Rosenberg and Sobell from their days at CCNY before testifying against them
Klaus Fuchs, physicist who supplied information about the British and American atomic bomb research to the Soviet Union; sentenced to 14 years in the UK.
Vivian Glassman, fiancée of Joel Barr [4]
Harry Gold, courier sentenced to 30 years
David Greenglass, draftsman at Los Alamos in World War Two, gave atomic bomb drawings to his sister Ethel Rosenberg, and eventually the Soviets; sentenced to 15 years
Ruth Greenglass, escaped prosecution in exchange for her husband’s testimony against his sister and brother-in-law, the Rosenbergs
Miriam Moskowitz, convicted of obstruction of justice for assisting Brothman. She was never convicted of being a spy for the Soviet Union.[6]
William Perl, active in Young Communist League at CCNY, then met Al Sarant at Columbia University; served 5 years for perjury
Morton Sobell, involved with Barr, Perl and Julius Rosenberg at CCNY; sentenced to 30 years at Alcatraz
Ethel Rosenberg, executed at Sing Sing prison near her native New York City for conspiracy to commit espionage
Julius Rosenberg, executed at Sing Sing prison near his native New York City for conspiracy to commit espionage
Al Sarant, stole radar secrets at Army Signal Corps lab in New Jersey, then he and his mistress abandoned their families for the protection of his Soviet masters in 1950
Andrew Roth, Office of Naval Intelligence liaison officer with United States Department of State
Saville Sax college friend of Theodore Hall assisted with Hall’s disclosure to the Soviets of Los Alamos research and development [5] [6]
Silvermaster group
Nathan Gregory Silvermaster, Chief Planning Technician, Procurement Division, United States Department of the Treasury; Chief Economist, War Assets Administration; Director of the Labor Division, Farm Security Administration; Board of Economic Warfare; Reconstruction Finance Corporation Department of Commerce
Helen Silvermaster (wife)
Schlomer Adler, United States Department of the Treasury
Norman Chandler Bursler, United States Department of Justice Anti-Trust Division [7]
Frank Coe, Assistant Director, Division of Monetary Research, Treasury Department; Special Assistant to the United States Ambassador in London; Assistant to the Executive Director, Board of Economic Warfare; Assistant Administrator, Foreign Economic Administration
Lauchlin Currie, Administrative Assistant to President Roosevelt; Deputy Administrator of Foreign Economic Administration; Special Representative to China
Bela Gold, Assistant Head of Program Surveys, Bureau of Agricultural Economics, Agriculture Department; Senate Subcommittee on War Mobilization; Office of Economic Programs in Foreign Economic Administration
Sonia Steinman Gold, Division of Monetary Research U.S. Treasury Department; U.S. House of Representatives Select Committee on Interstate Migration; U.S. Bureau of Employment Security
Irving Kaplan, Foreign Funds Control and Division of Monetary Research, United States Department of the Treasury Foreign Economic Administration; chief advisor to the Military Government of Germany
George Silverman, civilian Chief Production Specialist, Material Division, United States Army Air Forces Air Staff, War Department, Pentagon
William Henry Taylor, Assistant Director of the Middle East Division of Monetary Research, United States Department of Treasury
William Ullman, delegate to United Nations Charter meeting and Bretton Woods conference; Division of Monetary Research, Department of Treasury; Material and Services Division, Air Corps Headquarters, Pentagon
Anatole Volkov
Harry Dexter White, Assistant Secretary of the Treasury; Head of the International Monetary Fund
Sound and Myrna groups
Solomon Adler, United States Department of the Treasury
Cedric Belfrage, journalist; British Security Coordination
Elizabeth Bentley courier messenger for Communist spy rings on the American East Coast in the 1930s, testified about her activities in hearings in the 1940s and 1950s
Frank Coe, Assistant Director, Division of Monetary Research, Treasury Department; Special Assistant to the United States Ambassador in London; Assistant to the Executive Director, Board of Economic Warfare; Assistant Administrator, Foreign Economic Administration
Lauchlin Currie, Administrative Assistant to President Roosevelt; Deputy Administrator of Foreign Economic Administration; Special Representative to China
Rae Elson, an active Communist, and courier of the CPUSA underground, was chosen by Joseph Katz to replace Bentley at the Soviet front organization, U.S. Shipping and Service Corporation.
Frederick V. Field, Executive Secretary American Peace Mobilization
Edward Fitzgerald, War Production Board
Charles Flato, Board of Economic Warfare; Civil Liberties Subcommittee, Senate Committee on Education and Labor
Eva Getzov, Jewish Welfare Board [7]
Bela Gold, Bureau of Intelligence, Assistant Head of Program Surveys, Bureau of Agricultural Economics, Agriculture Department; Senate Subcommittee on War Mobilization; Office of Economic Programs in Foreign Economic Administration
Sonia Steinman Gold, Division of Monetary Research U.S. Treasury Department; U.S. House of Representatives Select Committee on Interstate Migration; U.S. Bureau of Employment Security
Irving Goldman, Office of the Coordinator of Inter-American Affairs
Jacob Golos, the “main pillar” of the NKVD intelligence network in the U.S., died in the arms of comrade Elizabeth Bentley
Gerald Graze, United States Civil Service Commission; Department of Defense, U.S. Navy official
Stanley Graze, United States Department of State intelligence
Michael Greenberg, Board of Economic Warfare; Administrative Division, Enemy Branch, Foreign Economic Administration; United States Department of State
Joseph Gregg, Office of the Coordinator of Inter-American Affairs; United States Department of State
Maurice Halperin, Chief of Latin American Division, Research and Analysis section, Office of Strategic Services; United States Department of State
Julius Joseph, Far Eastern section (Japanese Intelligence) Office of Strategic Services
Irving Kaplan, United States Department of the Treasury Foreign Economic Administration; United Nations Division of Economic Stability and Development; Chief Advisor to the Military Government of Germany
Joseph Katz
Charles Kramer, Senate Subcommittee on War Mobilization; Office of Price Administration; National Labor Relations Board; Senate Subcommittee on Wartime Health and Education; Agricultural Adjustment Administration; Civil Liberties Subcommittee, Senate Committee on Education and Labor; Senate Labor and Public Welfare Committee; Democratic National Committee
Duncan Lee, counsel to General William Donovan, head of Office of Strategic Services
Bernice Levin, Office of Emergency Management; Office of Production Management
Helen Lowry, (Elza Akhmerova), Akhmerov wife, American-born and raised, Soviet citizen
Harry Magdoff, Chief of the Control Records Section of War Production Board and Office of Emergency Management; Bureau of Research and Statistics, WTB; Tools Division, War Production Board; Bureau of Foreign and Domestic Commerce, United States Department of Commerce; Statistics Division Works Progress Administration
Jenny Levy Miller, Chinese Government Purchasing Commission
Robert Miller, Office of the Coordinator of Inter-American Affairs; Near Eastern Division United States Department of State
Ezra Moscrip, Nuclear Physicist who worked on the Manhattan Project. Accused of selling secrets to the USSR during World War II. Found dead in NYC apartment in 1945
Willard Park, Assistant Chief of the Economic Analysis Section, Office of the Coordinator of Inter-American Affairs; United Nations Relief and Rehabilitation Administration
Victor Perlo, chief of the Aviation Section of the War Production Board; head of branch in Research Section, Office of Price Administration Department of Commerce; Division of Monetary Research Department of Treasury; Brookings Institution, head of Perlo group
Mary Price, stenographer for Walter Lippmann of the New York Herald
Bernard Redmont, head of the Foreign News Bureau Office of the Coordinator of Inter-American Affairs
William Remington, War Production Board; Office of Emergency Management, convicted for perjury, killed in prison
Ruth Rivkin, United Nations Relief and Rehabilitation Administration
Allan Rosenberg, Board of Economic Warfare; Chief of the Economic Institution Staff, Foreign Economic Administration; Civil Liberties Subcommittee, Senate Committee on Education and Labor; Railroad Retirement Board; Councel to the Secretary of the National Labor Relations Board
Bernard Schuster[8]
Greg Silvermaster, Chief Planning Technician, Procurement Division, United States Department of the Treasury; Chief Economist, War Assets Administration; Director of the Labor Division, Farm Security Administration; Board of Economic Warfare; Reconstruction Finance Corporation Department of Commerce
John Spivak, journalist[citation needed]
William Taylor, Assistant Director of Monetary Research, United States Department of Treasury
Helen Tenney, Office of Strategic Services
Lee Tenney, Balkan Division Office of Strategic Services
Lud Ullman, delegate to United Nations Charter meeting and Bretton Woods conference; Division of Monetary Research, Department of Treasury; Material and Services Division, Air Corps Headquarters, Pentagon
David Weintraub, United States Department of State; head of the Office of Foreign Relief and Rehabilitation Operations; United Nations Relief and Rehabilitation Administration (UNRRA); United Nations Division of Economic Stability and Development
Donald Wheeler, Office of Strategic Services Research and Analysis division
Anatoly Gorsky, (Anatoly Veniaminovich Gorsky, A. V. Gorsky), “Vadim”, former rezident of the MGB USSR in Washington
Olga Pravdina, former employee of the Ministry of Trade, wife of “Sergei,” the rezident in New York; author of Gorsky Memo (see Vladimir Pravdin)[9]
Vladimir Pravdin, “Sergei”, Tass, former rezident of the MGB USSR in New York
Mikhail A. Shaliapin [Shalyapin], “Stock” [“Shtok”][10]
Gaik Badelovich Ovakimian, former rezident of the MGB USSR in New York
Iskhak Abdulovich Akhmerov, “Albert” – former Illegal Rezident of the MGB USSR in New York
Arthur Gerald Steinberg, United States Office of Scientific Research and Development
Michael Straight, speechwriter for President Franklin Roosevelt
Lev Vasilevsky, KGB Illegal Rezident Mexico City
John Anthony Walker US Navy senior enlisted man who spied for the Soviet Union for decades, enlisting family and friends to do so as well
Ware group
Whittaker Chambers, Department of State, testified against Alger Hiss
Henry Collins, National Recovery Administration; Department of Agriculture
John Herrmann, CPUSA operative and courier, eventually drank himself to death in Mexico
Alger Hiss, Department of State, sentenced to 5 years for perjury
Donald Hiss, Department of State, younger brother of Alger Hiss
Victor Perlo, became spymaster of Perlo group during World War II
George Silverman, Harvard-educated statistician who gave secret Pentagon documents to Nathan Silvermaster group during World War II
Harry Dexter White, Assistant Secretary of the Treasury; head of the International Monetary Fund which he helped establish along with the World Bank
Ruby Weil, American communist who assisted in plot to murder Leon Trotsky
Bill Weisband, United States Army Signals Security Agency
Enos Wicher, professor at Columbia University who also worked at Columbia’s Division of War Research; stepfather of Barnard CoIIege recruitress and State Department spy Flora Wovschin
KGB Illegals
Rudolf Abel, aka William Fischer, Illegal Rezident in the 1950s
A. I. Akhmerov, “Albert” – former Illegal Rezident of the MGB USSR in New York
GRU
Arvid Jacobson
Karl group
David Carpenter (David Zimmerman)
Noel Field, United States Department of State
Harold Glasser, Director, Division of Monetary Research, United States Department of the Treasury; United Nations Relief and Rehabilitation Administration; War Production Board; Advisor on North African Affairs Committee; United States Treasury Representative to the Allied High Commission in Italy
Alger Hiss, United States Department of State, sentenced to 5 years for perjury
Donald Hiss, United States Department of State; United States Department of Labor; United States Department of the Interior
Victor Perlo, chief of the Aviation Section of the War Production Board; head of branch in Research Section, Office of Price Administration Department of Commerce; Division of Monetary Research Department of Treasury; Brookings Institution, head of Perlo group
J. Peters
William Ward Pigman, National Bureau of Standards; Labor and Public Welfare Committee
Vincent Reno, mathematician at United States Army Aberdeen Proving Ground
George Silverman, Director of the Bureau of Research and Information Services, US Railroad Retirement Board; Economic Adviser and Chief of Analysis and Plans, Assistant Chief of Air Staff, Material and Services, War Department
Julian Wadleigh, United States Department of State
Harry Dexter White, Assistant Secretary of the Treasury; Head of the International Monetary Fund
Viktor Vasilevish Sveshchnikov, United States War Department
Portland ring
Konon Molody (aka Gordon Lonsdale)
Juliet Poyntz
Fred Rose (politician), Canadian Member of Parliament, first elected from the Labour-Progressive Party (Canada) 1943
Milton Schwartz
Sorge ring
Chen Han-seng
Hotsumi Ozaki
Agnes Smedley
William Spiegel
Lydia Stahl
Joseph Benjamin Stenbuck
Irving Charles Velson, Brooklyn Navy Yard; American Labor Party candidate for New York State Senate
Flora Wovschin, NKVD operative in U.S. State Department, comrade of Marion Davis Berdecio and Judith Coplon from their days at Columbia University
Vasily Zarubin, husband of Elizabeth Zubilin
Elizabeth Zubilin, recruiter in U.S. of whom Pavel Sudoplatov, head of NKVD Fourth Directorate said, “In developing J. Robert Oppenheimer as a source, Elizabeth Zubilin was essential.”
Others
Yuri Modin 1930s ‘recruiter’ in UK
Will Morgan
Julia Older, Office of Strategic Services; Office of War Information
Alexander Orlov, KGB adviser to the Republican government during the Spanish Civil War who defected to the United States in 1938.
GRU Illegals
Moishe Stern
Joshua Tamer
Alfred Tilton
Alexander Ulanovsky
Ignacy Witczak
Naval GRU
Jack Fahy (Naval GRU), Office of the Coordinator of Inter-American Affairs; Board of Economic Warfare; United States Department of the Interior
Edna Patterson Naval GRU, served in US August 1943 to 1956
Unknown affiliation, to sort
Morris Cohen (Soviet spy) sentenced to 25 years; subject of Hugh Whitemore’s drama for stage and TV Pack of Lies
Lona Cohen, Soviet spy sentenced to 20 years; subject of Hugh Whitemore’s drama for stage and TV Pack of Lies
George Koval
Samuel Krafsur, TASS reporter who was mentioned prominently in the Venona Files.
Earl Edwin Pitts, CIA
UNCENSORED – FEMEN Protests Gazprom Moscow
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-moscow/pict18.jpg) An activists of the Ukrainian women’s movement FEMEN braves the cold (-22 C, but due to high humidity and wind, weather experts said it would feel more like -31 C) and resists the guards in front of the Russia’s natural gas monopoly giant Gazprom headquarters in central Moscow, on February 13, 2012, during their topless protest against what they called “anti–Ukraine gas terror. Getty An activists of the Ukrainian women’s movement FEMEN braves the cold (-22 C, but due to high humidity and wind, weather experts said it would feel more like -31 C) and resists the guards in front of the Russia’s natural gas monopoly giant Gazprom headquarters in central Moscow, on February 13, 2012, during their topless protest against what they called “anti–Ukraine gas terror. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-moscow/pict25.jpg) EDS NOTE NUDITY – Employees of Gazprom carry a Femen activist who staged a protest outside Gazprom headquarters, Moscow, Monday, Feb., 13, 2012. Activists of the Ukrainian group Femen protested in front of the Russian natural gas monopoly Gazprom, blaming Russian Prime Minister Vladimir Putin and Gazprom of subjugating Ukraine and Europe at large. (Sergey Ponomarev) EDS NOTE NUDITY – Employees of Gazprom carry a Femen activist who staged a protest outside Gazprom headquarters, Moscow, Monday, Feb., 13, 2012. Activists of the Ukrainian group Femen protested in front of the Russian natural gas monopoly Gazprom, blaming Russian Prime Minister Vladimir Putin and Gazprom of subjugating Ukraine and Europe at large. (Sergey Ponomarev) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-moscow/pict21.jpg) An activist of the Ukrainian women’s movement FEMEN braves the cold (-22 C, but due to high humidity and wind, weather experts said it would feel more like -31 C) and resists the guard in front of the Russia’s natural gas monopoly giant Gazprom headquarters in central Moscow, on February 13, 2012, during their topless protest against what they called “anti–Ukraine gas terror. Getty An activist of the Ukrainian women’s movement FEMEN braves the cold (-22 C, but due to high humidity and wind, weather experts said it would feel more like -31 C) and resists the guard in front of the Russia’s natural gas monopoly giant Gazprom headquarters in central Moscow, on February 13, 2012, during their topless protest against what they called “anti–Ukraine gas terror. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-moscow/pict26.jpg) EDS NOTE NUDITY A Gazprom guard tries to block activists of FEMEN, as they stage protest outside Gazprom headquarters in Moscow, Monday, Feb., 13, 2012. Activists of the Ukrainian group FEMEN, in a topless protest action in front of the Russian natural gas monopoly Gazprom blamed prime minister Vladimir Putin and Gazprom of subjugating Ukraine and Europe at large. (Sergey Ponomarev) EDS NOTE NUDITY A Gazprom guard tries to block activists of FEMEN, as they stage protest outside Gazprom headquarters in Moscow, Monday, Feb., 13, 2012. Activists of the Ukrainian group FEMEN, in a topless protest action in front of the Russian natural gas monopoly Gazprom blamed prime minister Vladimir Putin and Gazprom of subjugating Ukraine and Europe at large. (Sergey Ponomarev) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-moscow/pict27.jpg) Activists of the Ukrainian women’s movement FEMEN brave the cold (-22 C, but due to high humidity and wind, weather experts said it would feel more like -31 C) in front of the Russia’s natural gas monopoly giant Gazprom headquarters in central Moscow, on February 13, 2012, during their topless protest against what they called “anti–Ukraine gas terror. Getty Activists of the Ukrainian women’s movement FEMEN brave the cold (-22 C, but due to high humidity and wind, weather experts said it would feel more like -31 C) in front of the Russia’s natural gas monopoly giant Gazprom headquarters in central Moscow, on February 13, 2012, during their topless protest against what they called “anti–Ukraine gas terror. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-moscow/pict22.jpg) Activists of the Ukrainian women’s movement FEMEN brave the cold (-22 C, but due to high humidity and wind, weather experts said it would feel more like -31 C) in front of the Russia’s natural gas monopoly giant Gazprom headquarters in central Moscow, on February 13, 2012, during their topless protest against what they called “anti–Ukraine gas terror. Getty Activists of the Ukrainian women’s movement FEMEN brave the cold (-22 C, but due to high humidity and wind, weather experts said it would feel more like -31 C) in front of the Russia’s natural gas monopoly giant Gazprom headquarters in central Moscow, on February 13, 2012, during their topless protest against what they called “anti–Ukraine gas terror. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-moscow/pict19.jpg) Activists of the Ukrainian women’s movement FEMEN brave the cold (-22 C, but due to high humidity and wind, weather experts said it would feel more like -31 C) in front of the Russia’s natural gas monopoly giant Gazprom headquarters in central Moscow, on February 13, 2012, during their topless protest against what they called “anti–Ukraine gas terror. Getty Activists of the Ukrainian women’s movement FEMEN brave the cold (-22 C, but due to high humidity and wind, weather experts said it would feel more like -31 C) in front of the Russia’s natural gas monopoly giant Gazprom headquarters in central Moscow, on February 13, 2012, during their topless protest against what they called “anti–Ukraine gas terror. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-moscow/pict20.jpg) Activists of the Ukrainian women’s movement FEMEN brave the cold (-22 C, but due to high humidity and wind, weather experts said it would feel more like -31 C) in front of the Russia’s natural gas monopoly giant Gazprom headquarters in central Moscow, on February 13, 2012, during their topless protest against what they called “anti–Ukraine gas terror. Getty Activists of the Ukrainian women’s movement FEMEN brave the cold (-22 C, but due to high humidity and wind, weather experts said it would feel more like -31 C) in front of the Russia’s natural gas monopoly giant Gazprom headquarters in central Moscow, on February 13, 2012, during their topless protest against what they called “anti–Ukraine gas terror. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-moscow/pict23.jpg) An activists of the Ukrainian women’s movement FEMEN braves the cold (-22 C, but due to high humidity and wind, weather experts said it would feel more like -31 C) in front of the Russia’s natural gas monopoly giant Gazprom headquarters in central Moscow, on February 13, 2012, during their topless protest against what they called “anti–Ukraine gas terror. Getty An activists of the Ukrainian women’s movement FEMEN braves the cold (-22 C, but due to high humidity and wind, weather experts said it would feel more like -31 C) in front of the Russia’s natural gas monopoly giant Gazprom headquarters in central Moscow, on February 13, 2012, during their topless protest against what they called “anti–Ukraine gas terror. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-moscow/pict24.jpg) A Femen activist stages a protest outside Gazprom headquarters, Moscow, Monday, Feb. , 13, 2012. Activists of the Ukrainian group Femen protested in front of the Russian natural gas monopoly Gazprom, blaming Russian Prime Minister Vladimir Putin and Gazprom of subjugating Ukraine and Europe at large. A Femen activist stages a protest outside Gazprom headquarters, Moscow, Monday, Feb. , 13, 2012. Activists of the Ukrainian group Femen protested in front of the Russian natural gas monopoly Gazprom, blaming Russian Prime Minister Vladimir Putin and Gazprom of subjugating Ukraine and Europe at large. |
VIDEO – FEMEN contro l’India: le ucraine non sono prostitute
ISREAEL – Barak: “Iran and Hezbullah are determined to avenge, we will continue to operate against the terror front”

Israel’s Minister of Defense Ehud Barak and the senior officials of the Israeli defense establishment inaugurated the Israeli pavilion at the Singapore Air Show on Tuesday morning. The Israeli delegation arrived accompanied by heavy security, due to the event that occurred yesterday near the embassy in New Delhi, India, and the attempt to harm the Israeli embassy in Georgia.
Barak referenced the events at the inauguration of the Israeli pavilion, saying, “Israel is dealing with defense challenges. The attack in India and the event in Georgia did not come from Denmark or Belgium. Responsibility for the events comes from the same elements.” Barak held Iran and Hezbollah responsible, saying, “They are continuing to focus on avenging and causing casualties. We will have to continue operating against the terror front.” Barak also spoke of the defense export’s contribution to the security of Israel.
Miki Federman, the owner of Elbit Systems, said during the inauguration ceremony that cooperation between the industries and the defense establishment is widening. “The ministry is helping us by promoting the defense export in any way possible,” Federman noted.
The Singapore Air Show is considered one of the most important defense exhibitions of the year, and features guests and buyers from across the world, but primarily from Southeast Asian countries. SIBAT, the defense assistant division of the Israeli government, set up an Israeli national pavilion – which includes large companies such as IAI, IMI, Rafael, and Elbit Systems, alongside smaller companies such as Eromaoz and Kanfit.
DIE PEINLICHEN FÄLSCHUNGEN DER ANAL-FIXIERTEN STASI-“GoMoPa”-SCHEISSHAUSFLIEGEN (EIGENBEZEICHNUNG)
NSA – US Justice Department Wins Rosemary Award for Worst Open Government Performance in 2011
National Security Archive cites selective leaks prosecutions, business-as-usual secrecy arguments in litigation, and retrograde information regulations
Justice’s actions contradict Obama pledges for open government, help explain performance gap between excellent policy and “same-old” practice
Individual “dubious achievement” awards go to three career DoJ lawyers; Crowded field of award nominees includes contenders from CIA, DHS, Central Command
|
Washington, DC, February 14, 2012 – The U.S. Department of Justice has won the infamous Rosemary Award for worst open government performance over the past year, according to the citation posted on the Web today by the National Security Archive (www.nsarchive.org). The award is named after President Nixon’s secretary, Rose Mary Woods, who erased 18 1/2 minutes of a crucial Watergate tape. The Rosemary Award citation includes a multi-count indictment of Justice’s transparency performance in 2011, including:
“Justice edged out a crowded field of contending agencies and career officials who seem in practical rebellion against President Obama’s open-government orders,” commented Archive director Tom Blanton. “Justice’s leading role as the government’s lawyer signals every bureaucrat they don’t have to stretch as much as Rose Mary Woods to cover up the government’s business.” “The Department of Justice – which is responsible for enforcing FOIA government-wide – was supposed to be the change agent and role model for President Obama’s FOIA reforms,” said Nate Jones, the Archive’s Freedom of Information Act Coordinator. “But, despite the president’s clear instructions, the DOJ has embraced a ‘FOIA-as-usual mindset’ that has failed to transform the decades-old FOIA policies within its department, much less throughout the government.” The Emmy- and George Polk Award-winning National Security Archive, based at The George Washington University, has carried out ten government-wide audits of FOIA performance (see the most recent Knight Open Government Surveys), filed more than 40,000 Freedom of Information requests over the past 25 years, opened historic government secrets ranging from the CIA’s “Family Jewels” to the Iraq invasion war plans, and won a series of lawsuits that saved hundreds of millions of White House e-mail from the Reagan through the Obama presidencies, among many other achievements. The Archive founded the Rosemary Award in 2005 to highlight the lowlights of government secrecy. While the Justice Department won the Rosemary Award as a team effort, the Award citation recognizes several individual dubious achievements for putting Justice over the top in the award contest.  William Welch According to the citation, the single individual in 2011 who did the most to stomp on President Obama’s open government message was career Justice Department lawyer William M. Welch II. Welch led the prosecutions of government whistleblowers as “leakers” under controversial Edwin Meese-era interpretations of the 1917 Espionage Act. Welch’s Ahab-like pursuit of National Security Agency whistleblower Thomas Drake succeeded in ruining Drake’s life and bankrupting him, but ultimately collapsed ignominiously in 2011 into a mere misdemeanor plea under the reality that the information at issue was not justifiably classified – meaning its release did no damage to national security. Close observers of the government’s security classification system were not surprised, since massive over-classification is the norm. Not chastened in the least, Welch doubled down his overreaching selective prosecutorial strategy by going after CIA whistleblower Jeffrey Sterling, attempting to corral New York Times reporter James Risen, and even now is appealing the district court’s remonstrance of Welch’s take-no-prisoners strategy in that case. Welch has earned his reputation among journalists as an overkill prosecutor, heedless of the collateral damage from his actions on the First Amendment or on accountability in government.  Anthony Yang The individual who launched Justice’s successful campaign to win the Rosemary Award was career Solicitor General staffer Anthony Yang, who tried to convince the Supreme Court during oral arguments on January 19, 2011 (two years after President Obama’s order for a “presumption of openness”) that exemptions to the U.S. Freedom of Information Act deserved the most expansive possible reading – “exemptions are to be given meaningful reach.” Yang meaningfully reached for the Rosemary Award by responding multiple times to increasingly incredulous questions from Justices Scalia (no friend of the FOIA) and Sotomayor on this point. Scalia asked, “Our cases assert, do they not, that the exceptions to FOIA should be narrowly construed?” After some back and forth, Yang said flatly, “We do not embrace that principle.” Yang was speaking for the Justice Department, and indeed, for the government as a whole, in direct contradiction to President Obama’s stated polices on open government. A month earlier, in December 2010, Yang had made similar oral arguments in the Milner case, supporting almost total discretion for the government in deciding how to apply exemption (b)(2) on internal personnel policies and rules. Yes, deferential federal courts had previously granted that discretion, and Yang was simply arguing for the prerogatives of his client, in that case the Department of the Navy, which was trying to withhold maps of potential explosives damage from neighbors of a naval base. But the persistence of business-as-usual legal arguments at the highest level of the Justice Department – despite clear orders for change from the White House – points beyond the mere weight of legal precedent, to the vast inertia and vested interests of the permanent bureaucracy. As Justice Kagan wrote for an 8-1 majority in the Milner decision, if Yang’s argument carried the day, the Justice Department would have turned the FOIA from a disclosure statute into a withholding act.  Melanie Pustay The third career Justice Department official who stood out in the past year’s bleak landscape of excessive government secrecy is the person ostensibly charged with actually implementing President Obama’s day-one pledges for the most open and accountable government ever. Instead, Melanie Pustay, the head of the Office of Information Policy at Justice, has made her mark as the consigliere for agencies that seek to withhold information from the public. In 2011, she presided over the development of a series of proposed regulations – ultimately put on hold after public outrage caught the attention of higher-ups – that would have changed the Freedom of Information Act process in more than a dozen regressive directions – in direct contradiction to President Obama’s orders. In the most ridiculed provision, Pustay’s regulations would have formalized the practice – first enabled by Attorney General Edwin Meese in 1987 – of allowing the government to lie about the very existence of records sought in a FOIA case. The outcry in the press and from Capitol Hill caused Justice to withdraw that provision from the proposal; but the Department’s defense – that such practice had been standard since 1987 – spoke volumes about the business-as-usual approach at Justice. Despite the clarion calls for open government issued by President Obama and Attorney General Holder, the Justice Department’s performance on FOIA looks much more like the same-old practice. To be fair (which is not the point of the Rosemary Award), the Department can point to some progress: For example, the new foia.gov web site collates all the agency annual reports on FOIA and should lead to better practice and tracking as the data improves. Pustay’s office has organized roundtable meetings with requesters to encourage dialogue that should be the norm across government. And Justice’s overall numbers of full and partial releases under FOIA are up from about 44% to about 56% of total requests processed. But the canary in the coal mine is not singing any more. The Department cannot point to a single case of agency withholding that it has refused to defend under the new guidance from the Obama and Holder memos in 2009. The Department’s litigators are using the same boilerplate they used under the George W. Bush secrecy orders. And the leading single indicator of the change requesters expected has now turned around completely: After two years of decline in Justice’s use of the entirely discretionary “deliberative process” exemption, the 5th exemption to the FOIA, in 2011 the Department’s use of (b)(5) went back up, from 1,231 the previous year, to 1,500. This is the exemption that should have fallen off the cliff, if the Department was serious about its own Attorney-General’s directions, and if Pustay’s office was providing real guidance to its peers. As Senator Charles Grassley (R-Iowa) remarked as he questioned Pustay during a March 15, 2011 Senate hearing: “… The point I tried to make in my opening comment [was] that the president set a very high benchmark. And if we’re doing the same thing after two and a half years of this administration, the same as we’ve been doing for 20 years, the president’s benchmark isn’t being followed by the people he appoints.” [Note: Watch the full video of the hearing] To add insult to injury, the proposed FOIA regulations would have forced fifth-grade civics students to pay processing fees to the government if they tried to file a FOIA request (currently elementary and secondary schools have a waiver of fees). It’s worth noting that not just school children, but all bloggers would be prevented from requesting a waver of fees. The government actually collects so little in FOIA processing fees each year that experts now understand the entire fee process is simply the bureaucrats’ favorite method to intimidate and deter the public from filing requests. As explained in a helpful summary prepared by John Wonderlich of the Sunlight Foundation, the proposals would:
Even though currently on hold, no doubt these regressive regulations still lurk in the Office of Information Policy word processing files, ready to leap out and bite unsuspecting fifth-graders the moment that office is let off the leash. If Melanie Pustay and the DOJ Office of Information Policy were truly interested in acting as a “FOIA beacon” for other agencies, they would have proposed regulations that moved the FOIA process forward, not backward including:
Who’s in Charge at the Justice Department?  Eric Holder(left) and Lanny Breuer (right). Of course, having so many individual Rosemary achievers from a single department raises the question, who is minding the store? In such a kindergarten, where are the grownups? Back in March 2009, Attorney General Holder followed up President Obama’s day-one orders for open government with a new Attorney-General’s memorandum ordering a presumption of disclosure. Yet in 2011, Holder and his Assistant Attorney General for the Criminal Division, Lanny Breuer, presided over the debacles that won their Department the prize for worst open government performance, including the pernicious use of the 1917 Espionage Act to the transmission of information between officials and journalists (not foreign government espionage) – despite the obvious First Amendment implications of such overreaching and selective prosecution. Through their sponsorship of pit bulls like William Welch, their failure apparently even to read Anthony Yang’s Supreme Court briefs claiming maximum reach for FOIA exemptions, their selective prosecutions threatening the First Amendment, and their failure to apply their own claimed commitment to open government, Holder and Breuer have layered black blotches on the public record and cinched the Rosemary Award for their department, which, as the government-wide enforcer, should have been a role model instead. Other 2011 Finalists for the Rosemary AwardThe Justice Department won the Rosemary in a tough competitive race – lots of other worthy finalists just missed their chance at infamy. In the immortal words of Marlon Brando, the following officials and agencies “coulda been a contenda”:
Previous Recipients of the Rosemary AwardPrevious recipients of the Rosemary Award include:
The Rosemary Award is named after President Nixon’s long-time secretary Rose Mary Woods and the backwards-leaning stretch – answering the phone while keeping her foot on the pedal of a tape transcription machine – that she testified caused the erasure of an 18 1/2 minute section of a key Watergate conversation on the White House tapes. |
|
Contents of this website Copyright 1995-2011 National Security Archive. All rights reserved.
|
Terms and conditions for use
|
CONFIDENTIAL – (U//FOUO) U.S. Army Modular Brigade Augmented for Security Force Assistance Handbook

This hand book synthesizes current doctrine and emerging TTPs into a handbook for units assigned a Security Force Assistance (SFA) mission.
Security Force Assistance is not a unit; it is a mission assigned to a unit. Army leaders will assign this mission to Modular brigades more frequently according to the realities of the operational environment. The Modular Brigade, with its broad and flexible command and control structure, is designed to conduct Full Spectrum Operations, which includes Security Force Assistance, but it requires augmentation and specific task organization to effectively accomplish Security Force Assistance tasks.
The Modular Brigade Augmented for Security Force Assistance Handbook is designed as an assessment tool for brigade-level leaders as they prepare to train their BCT on the Security Force Assistance Mission. It serves as a guide for the most immediate challenges that Modular brigades will face, and as a catalogue of recently approved doctrinal literature available for commanders and staffs to access and apply.
Chapter One presents methodologies for task organizing and suggests a baseline augmentation that a BCT may require for an SFA mission. Chapter Two provides various assessment tools to evaluate the capabilities of Foreign Security Forces and to plan for their improvement. These assessment tools are drawn from current doctrine, operational units, professional journals and lessons-learned. Chapter Three describes how the BCT implements partnering, augmenting, and advising. Chapter Four summarizes how the BCT fits into the SFA strategic framework.
…
COMMONALITIES OF PARTNERING AND ADVISING
3-5. Partnering and advising share the core principles of empowering as well as working by, with, and through a FSF. The majority of FSA missions for BCTs will require combinations of partnering and advising with augmentation of FSF units or U.S. forces based on the situation. Unit partnerships do not replace advisor roles or functions. However, if partnering and advising are used in combination, it forms a three-part relationship among FSF, advisors, and the partner units. Partner units should look to the advisor to identify, shape, and facilitate operational partnering opportunities and training events. Both partner and advisor units must build rapport with, demonstrate their value to and have credibility with FSF leaders to varying degrees so that they can influence their counterparts to accomplish SFA missions. In short, units must be prepared to execute both tasks during an SFA mission because each task mutually supports the other and are often combined in multiple areas at the operational and tactical levels.
COMMON MAJOR CONSIDERATIONS OF PARTNERING AND ADVISING UNITS WHEN WORKING WITH FSF:
Plan
- Clearly define the mission and METL of the FSF.
- Define the end state for the period of partnering/advising.
- Define the advising concept. What are the advisor teams’ operational focuses in our AOR? Do they have an advising plan or a Campaign Plan they are helping the FSF employ based on the lines of effort?
- Define the partnering concept. How do we plan to partner with HNF? What does it mean to partner with a HNF?
- Determine if we require augmentation for our force. Do we plan to augment an FSF at some level?
- Define corruption. What are we prepared and capable of doing about it?
- Determine the key points of leverage that we can use to influence the FSF.
- Understand and define the security problem.
- Task-organize the force to secure advisors and maximize their operational capabilities with suitable enablers.
- Create, as needed, special elements in each force such as SWAT, waterway, border, or SOF.
- Establish mobile training teams.
Execute
- Ensure security forces understand they support the host nation (HN) government and the people.
- Maintain relevancy of security forces for their culture, their population, and their laws.
- Ensure credibility and legitimacy to all counterinsurgency operations.
- Provide a model for society by using military units of mixed ethnicity, religion, political affiliation. For example, who can work together to secure and protect all the people?
- Conduct combined operations with each newly trained security force; include them in the planning process.
- Promote mutual respect between U.S. and HN forces and between the military, police, and paramilitary.
- Train the trainers first, and then train the HN cadre.
- Support the HN cadre in training the whole force.
- Separate HN military and police forces, especially during their training.
- Place the HN cadre in charge as soon as possible.
- Recognize achievement, especially excellence.
- Train all security forces to not tolerate abuses or illegal activity outside of culturally acceptable levels.
- Develop procedures to report violations.
- Enable HN to assume the lead in counterinsurgency operations to alleviate effects of a large US presence.
- Ensure infrastructure and pay is appropriate and managed by the Host Nation government.
- Promote professionalism that does not tolerate internal incompetence. Develop methods to redress.
DOWNLOAD ORIGINAL DOCUMENT HERE
FEMEN – Nackter Busen auf dem Petersplatz
Warning fom the FBI – Looking for Love? Beware of Online Dating Scams
Looking for Love?
Beware of Online Dating Scams
02/14/12

But today, on Valentine’s Day, we want to warn you that criminals use these sites, too, looking to turn the lonely and vulnerable into fast money through a variety of scams.
These criminals—who also troll social media sites and chat rooms in search of romantic victims—usually claim to be Americans traveling or working abroad. In reality, they often live overseas. Their most common targets are women over 40 who are divorced, widowed, and/or disabled, but every age group and demographic is at risk.
Here’s how the scam usually works. You’re contacted online by someone who appears interested in you. He or she may have a profile you can read or a picture that is e-mailed to you. For weeks, even months, you may chat back and forth with one another, forming a connection. You may even be sent flowers or other gifts. But ultimately, it’s going to happen—your new-found “friend” is going to ask you for money.
| Recognizing an Online Dating Scam Artist Your online “date” may only be interested in your money if he or she: – Presses you to leave the dating website you met through and to communicate using personal e-mail or instant messaging; – Professes instant feelings of love; – Sends you a photograph of himself or herself that looks like something from a glamour magazine; – Claims to be from the U.S. and is traveling or working overseas; – Makes plans to visit you but is then unable to do so because of a tragic event; or – Asks for money for a variety of reasons (travel, medical emergencies, hotel bills, hospitals bills for child or other relative, visas or other official documents, losses from a financial setback or crime victimization). One way to steer clear of these criminals all together is to stick to online dating websites with nationally known reputations.
|
|---|
So you send money…but rest assured the requests won’t stop there. There will be more hardships that only you can help alleviate with your financial gifts. He may also send you checks to cash since he’s out of the country and can’t cash them himself, or he may ask you to forward him a package.
So what really happened? You were targeted by criminals, probably based on personal information you uploaded on dating or social media sites. The pictures you were sent were most likely phony, lifted from other websites. The profiles were fake as well, carefully crafted to match your interests.
In addition to losing your money to someone who had no intention of ever visiting you, you may also have unknowingly taken part in a money laundering scheme by cashing phony checks and sending the money overseas and by shipping stolen merchandise (the forwarded package).
While the FBI and other federal partners work some of these cases—in particular those with a large number of victims or large dollar losses and/or those involving organized criminal groups—many are investigated by local and state authorities.
We strongly recommend, however, that if you think you’ve been victimized by a dating scam or any other online scam, file a complaint with our Internet Crime Complaint Center. Before forwarding the complaints to the appropriate agencies, IC3 collates and analyzes the data—looking for common threads that could link complaints together and help identify the culprits. Which helps keep everyone safer on the Internet.
For specific tips on how to keep from being lured into an online dating scam, see the sidebar above. Awareness is the best tool for preventing crime…and in this case, even from preventing a broken heart.
DOWNLOAD – LINK ZUM KoKo-STASI-UNTERSUCHUNGSBERICHTES DES DEUTSCHEN BUNDESTAG
BITTE HIER KOSTENLOS HERUNTERLAGEN
Deutscher Bundestag (Hrsg.): Drucksache 12/7600. Bonn, S. 505f.
PUBLIC EYE – Do You Like Online Privacy? You May Be a Child Pornographer
CRYPTOME – CIA Kabul Chief of Station Named
13 February 2012
CIA Kabul Chief of Station Named
A sends:
I recently sorted out the identity of the CIA Kabul chief of station (all through open sources, of course). Apparently no one has reported it on the web yet.
The triggering information was a WSJ article :
http://online.wsj.com/article/SB10001424052748704741904575409874267832044.html#
which gave a significant bit of information:
“In the chaos of battle in December 2001, a U.S. military officer accidentally ordered a bomb drop on a meeting between Mr. Karzai and other tribal leaders. The chief leapt on Mr. Karzai to shield him”. It also says that “In 2004 he began his first stint as station chief in Kabul”.
A second source to make the link, DCI George Tenet’s memoirs At the Center of the Storm. Tenet call that guy “Greg V.”
I came across this DOS document :
http://oig.state.gov/documents/organization/128838.pdf
On p. 71 you find a list of Kabul embassy officials, including an officer for Regional Affairs named Gregory Vogel who arrived there in September 2004.
What are the chances to have two “Greg V.”s arriving at an upper post in this embassy in 2004? Especially when you know until June 2004 the CIA chief of station was first-named Peter:
http://www.washingtonpost.com/wp-dyn/articles/A52673-2004Oct21.html
By the way, that guy has been given a lot of surnames:
– in Gary Berntsen Jawbreaker (2005), he is called “Craig.”
– in Sean Naylor Not a Good Day to Die (2004), it is said that he used the noms de guerre “Spider” and “the Wolf”, and was the senior CIA officer in Gardez during operation Anaconda.
– in Eric Blehm, The Only Thing Worth Dying For (2011), he is called “Casper.”
and as said above, George Tenet said almost all when he called him “Greg V.” (as with “Rich B.”)
DIE BASIS DER STASI NACH 1989 – KoKo – DER STASI-BETRUG AM EIGENEN VOLK
Alexander Schalck-Golodkowski
Der Bereich Kommerzielle Koordinierung (auch unter der Kurzform KoKo bekannt) war eine 1966 im Ministerium für Außenhandel der DDR eingerichtete Abteilung, die vor allem der Beschaffung von Devisen diente.
Geschichte
Gründung
Der Bereich Kommerzielle Koordinierung war mit Politbürobeschluss ab 1972 direkt dem Zentralkomitee der SED, speziell Erich Honecker und Wirtschaftssekretär Günter Mittag, untergeordnet und wurde durch die Arbeitsgruppe Bereich Kommerzielle Koordinierung (AG BKK) des Ministerium für Staatssicherheit (MfS) kontrolliert.[1]
Rolle und Bedeutung [Bearbeiten]
Mitte der 1970er Jahre wurde ihr durch Beschluss des Politbüros die wirtschaftliche Lenkung der entgegen den Vorschriften der Militärregierungsverordnung Nr. 53 in der BRD und auch in anderen westlichen Ländern aus Mitteln der DDR errichteten Unternehmen übertragen, die bis dahin von der Abteilung Verkehr des ZK der SED betreut worden waren.
Der seit den 1970er-Jahren stetig ansteigende Lebensstandard in der DDR war nicht zuletzt durch Importe aus dem Westen ermöglicht worden. Die Kosten hierfür konnten nur zum Teil durch reguläre Exporte von laufenden Produktionsgütern erwirtschaftet werden. Im großen Umfang wurden die aus der UdSSR bezogenen Rohöllieferungen veredelt und weiter verkauft. Der Verfall der Ölpreise ließ die Gewinnmargen jedoch stetig sinken.
Während ihres Bestehens konnte KoKo etwa 30 Milliarden DM erwirtschaften und unterhielt etwa 170 Unternehmen mit ca. 3100 Mitarbeitern in der DDR und im kapitalistischen Ausland.
Auflösung
Das KoKo-Geflecht schien bei der Auflösung der Abteilung im März 1990 undurchschaubar, nur wenige hatten Einblick in die geheimen KoKo-Geschäfte. Für DDR-Normalbürger war der Bereich bis zur Wende 1989 völlig unbekannt.
Aufarbeitung
Der Gesamtbereich der Kommerziellen Koordinierung war Gegenstand des 1. Untersuchungsausschusses des 12. Deutschen Bundestages unter dem Vorsitz des CDU-Abgeordneten Friedrich Vogel. Über das Ergebnis der Untersuchungen gibt es umfangreiche Berichte, vor allem Beschlussempfehlung und Bericht Drucksache 12/7600 vom 27. Mai 1994 mit drei Anlagenbänden und einem Anhangband.[2]
Auftrag
Hauptaufgabe war die Devisenbeschaffung mit allen legalen und illegalen Mitteln, über die Möglichkeiten des normalen Außenhandels hinaus.
Beschaffung von Devisen
Die Versorgung mit Devisen zur Deckung der Importe basierte dabei auf mehreren Bereichen:
- Zum einen konnten mit den Intershops, die sich auf Flughäfen, Bahnhöfen und an Grenzübergängen und Transitstrecken befanden und den Bedarf der Reisenden aus den westlichen Ländern decken sollten, Gelder erwirtschaftet werden. Hierbei war von Vorteil, dass die Reisenden die Waren meist günstiger als im Herstellungsland erwerben konnten.
- Auch wurden über das Versandhaus Genex Devisen erwirtschaftet. Der Genex-Kataloghandel richtete sich an Bürger Westdeutschlands mit Verwandten und Bekannten in der DDR. Konnten DDR-Bürger nicht alle Produkte kaufen oder mussten sie auf Konsumgüter mitunter Jahre warten, so war eine Lieferung binnen weniger Wochen möglich, wenn die Bestellung über Genex erfolgte und die Rechnungen mit Devisen beglichen wurden. So wurden in den Katalogen Lebensmittel, Kleidung, Häuser und auch Fahrzeuge der Marken Trabant, Wartburg und VW angeboten. Selbst bei den DDR-Fahrzeugen wurden die Autos kurzfristig geliefert, während DDR-Bürger über zehn Jahre warten mussten, sofern die Bezahlung mit Mark der DDR erfolgte.
- Die Kunst und Antiquitäten GmbH exportierte Kulturgüter aus staatlichem und privatem Besitz gegen harte Devisen. Zum Aufspüren dieser Kunstwerke bei Privatleuten und zur Absicherung der Geschäfte wurde eng mit den Fachabteilungen des MfS, der Zoll- und Steuerfahndung zusammengearbeitet.
Doch die damit erwirtschafteten Gelder konnten den Devisenbedarf nicht decken. So kaufte KoKo auch im westlichen Ausland kleinere Unternehmen auf, verwaltete SED-Parteibetriebe im westlichen Ausland (meist Bundesrepublik, Österreich; Treuhandunternehmen auch in Liechtenstein, Luxemburg, Schweiz) und betrieb Waffenhandel. KoKo profitierte auch von den Geldern aus Häftlingsfreikäufen, Müllimporten aus West-Berlin, Blutplasmaexport, Textil- und Zigarettenschmuggel u. a. Außerdem wurden mit Geldern in Millionenhöhe an westlichen Waren- und Termingeldbörsen spekuliert.
Beschaffung von Embargoware
Ein wesentlicher Geschäftsbereich, für den die erwirtschafteten Devisen wieder ausgegeben wurden, war die Beschaffung von Embargoware aus nichtsozialistischen Staaten und West-Berlin (CoCom-Liste), insbesondere Hochtechnologie für den Aufbau der DDR-Mikroelektronikindustrie, komplette EDV-Anlagen und Militärtechnologie; allein 1986 bis 1990 fanden Käufe für angeblich 900 Mio. DM statt.
Unterstützung von DKP und SEW
Ein weiterer Ausgabenposten der KoKo war die finanzielle Unterstützung der Deutschen Kommunistischen Partei (DKP) und der Sozialistischen Einheitspartei Westberlins (SEW).[3]
Da die beiden deutschen Staaten aufgrund alliierter Vorbehalte auf dem Territorium des jeweils anderen Staates wirtschaftlich nicht aktiv sein durften, es aber andererseits ein wechselseitiges starkes Bedürfnis nach wirtschaftlichem Austausch und politischer Einflussnahme gab, wurden Handel und Transport z. T. über bundesdeutsche Unternehmen abgewickelt. Diese Unternehmen übernahmen unverzichtbare und von beiden Seiten wertgeschätzte Funktionen im Ost-West-Handel. Unter den gegebenen Bedingungen bedurfte es jedoch komplizierter Gesellschafterstrukturen u. a. auch mit Hilfe liechtensteinischer Stiftungen unter Betreuung und in Regie der KoKo. In Absprache mit der Abteilung Verkehr des ZK der SED waren als Geschäftsführer und Prokuristen solcher Unternehmen auch Mitglieder der DKP tätig, die treuhänderisch Anteile an ihnen hielten.[4] Im Ergebnis war es möglich, z. B. über Anzeigen solcher Unternehmen in Zeitungen und Zeitschriften der DKP Beiträge nicht nur zur Finanzierung dieser Medien, sondern der DKP als Partei zu leisten.
Diese Unterstützung war in Politik und Medien allgemein bekannt, da diese Unternehmen insgesamt als DDR- bzw. DKP-geführt allgemein bekannt waren. Die BStU stellte dazu fest: „Tatsächlich war die westdeutsche Öffentlichkeit über diese Unternehmen gut informiert.“[5]
Organisation
Geleitet wurde der Bereich seit der Gründung von Alexander Schalck-Golodkowski, einem langjährigen Mitarbeiter des Ministeriums für Außenhandel, seit 1975 Staatssekretär für Außenhandel. Dessen langjähriger Stellvertreter war Manfred Seidel, MfS-Oberst, sein Vorgänger Horst Roigk, beide ehemals HA XVIII des MfS, dann genau wie Schalck-Golodkowski selbst, Offiziere im besonderen Einsatz (OibE) der Arbeitsgruppe Bereich Kommerzielle Koordinierung (AG BKK) des MfS.
Der Hauptsitz der KoKo mit 100 Mitarbeitern und Dienstsitz Schalcks befand sich in Berlin-Mitte, Wallstraße 17–22, in einem unscheinbaren Neubau. Die eigentlichen Unternehmen des Bereichs mit jeweils bis zu 900 Mitarbeitern (meist deutlich kleiner) befanden sich in Objekten in und um Berlin. Im Hotel Neptun in Warnemünde beispielsweise unterhielt die KoKo eine ständige Suite.
Für ihre Finanztransaktionen nutzte die KoKo die Deutsche Außenhandelsbank mit Sitz in Ost-Berlin. Diese Bank hatte in der DDR den rechtlichen Status eines Devisenausländers und stand damit außerhalb der Kontrollhoheit des Finanzministers.
Literatur
- Klaus Schröder: Der SED-Staat. Hanser, München 1998, ISBN 3-446-19311-1.
- Peter-Ferdinand Koch: Das Schalck-Imperium lebt. Piper, München 1992, ISBN 3-492-03564-7.
- Reinhard Buthmann: Die Arbeitsgruppe Bereich Kommerzielle Koordinierung; MfS-Handbuch, Teil III/. Die Bundesbeauftragte für die Unterlagen des Staatssicherheitsdienstes der ehemaligen Deutschen Demokratischen Republik, Berlin 2003.
- André Steiner: Von Plan zu Plan. Eine Wirtschaftsgeschichte der DDR. Aufbau Verlag, Berlin 2007 ISBN 978-3-7466-8153-5
Weblinks
- DDR-Lexikon
- Milliarden mit KoKo (Der Spiegel special 2/1990 vom 1. Februar 1990, S. 58ff.)
- Dokumente zum Bereich Kommerzielle Koordinierung
Einzelnachweise
- ↑AG BKK auf bstu.bund.de, abgerufen am 11. April 2009
- ↑ Deutscher Bundestag (Hrsg.): Drucksache 12/3920. Bonn 9. Dezember 1992, S. 8 (PDF, 6,1MB, abgerufen am 28. Juli 2008).
- ↑ Deutscher Bundestag (Hrsg.): Drucksache 12/7600. Bonn, S. 505f. (PDF, 195MB, abgerufen am 28. Juli 2008).
- ↑ Stefan Wolle: Die heile Welt der Diktatur. Econ Tb., Bonn 1999, ISBN 3548750672, S. 209.
- ↑[1]
QUELLE: WIKIPEDIA
Video – Oben-ohne-Protest gegen DSK in Paris
Unveiled – THE MOSSAD Spies in Kurdistan
 Mossad Spies in Kurdistan 1968 – 1974 Left to Right. Masud Barazani son of Kurdish leader Mulla Moustafa Barazani Mossad “envoy” Menahem `Nahik` Navot,Kurdish Doctor,Zvi Zamir Chief of Mossad,Nahum Admoni head of division in Mossad later Chief of Mossad, Kurdish security guard (Mossad Archive Photo)
Mossad Spies in Kurdistan 1968 – 1974 Left to Right. Masud Barazani son of Kurdish leader Mulla Moustafa Barazani Mossad “envoy” Menahem `Nahik` Navot,Kurdish Doctor,Zvi Zamir Chief of Mossad,Nahum Admoni head of division in Mossad later Chief of Mossad, Kurdish security guard (Mossad Archive Photo)
UNVEILED – ATHEN PROTEST PHOTOS – UNCENSORED
|
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/athens-protest/pict2.jpg) Riot police, not seen, push back protesters as the ancient Temple of Zeus is illuminated during clashes in Athens, Sunday, Feb. 12, 2012. Protesters and police fought running battles in central Athens Sunday, as Greek lawmakers debated legislation that would introduce severe austerity measures to stave off bankruptcy. (Thanassis Stavrakis) Riot police, not seen, push back protesters as the ancient Temple of Zeus is illuminated during clashes in Athens, Sunday, Feb. 12, 2012. Protesters and police fought running battles in central Athens Sunday, as Greek lawmakers debated legislation that would introduce severe austerity measures to stave off bankruptcy. (Thanassis Stavrakis) |
|
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/athens-protest/pict0.jpg) Protesters pass by a burning cinema in Athens, Sunday, Feb. 12, 2012. Riots engulfed central Athens and at least 10 buildings went up in flames in mass protests late Sunday as lawmakers prepared for a historic parliamentary vote on harsh austerity measures demanded to keep the country solvent and within the eurozone. (Kostas Tsironis) Protesters pass by a burning cinema in Athens, Sunday, Feb. 12, 2012. Riots engulfed central Athens and at least 10 buildings went up in flames in mass protests late Sunday as lawmakers prepared for a historic parliamentary vote on harsh austerity measures demanded to keep the country solvent and within the eurozone. (Kostas Tsironis) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/athens-protest/pict1.jpg) Riot police use tear gas as protesters stand in front of the Greek Parliament in Athens, Sunday, Feb. 12, 2012. Riots engulfed central Athens and at least 10 buildings went up in flames in mass protests late Sunday as lawmakers prepared for a historic parliamentary vote on harsh austerity measures demanded to keep the country solvent and within the eurozone. (Petros Giannakouris) Riot police use tear gas as protesters stand in front of the Greek Parliament in Athens, Sunday, Feb. 12, 2012. Riots engulfed central Athens and at least 10 buildings went up in flames in mass protests late Sunday as lawmakers prepared for a historic parliamentary vote on harsh austerity measures demanded to keep the country solvent and within the eurozone. (Petros Giannakouris) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/athens-protest/pict4.jpg) Protesters clash with riot police outside the Greek Finance Ministry as the ancient Acropolis hill is seen in the background in Athens on Sunday, Feb. 12, 2012. Tens of thousands of protesters gathered in the square outside Parliament as a parliamentary debate on further austerity cuts began, with more arriving constantly. (Thanassis Stavrakis) Protesters clash with riot police outside the Greek Finance Ministry as the ancient Acropolis hill is seen in the background in Athens on Sunday, Feb. 12, 2012. Tens of thousands of protesters gathered in the square outside Parliament as a parliamentary debate on further austerity cuts began, with more arriving constantly. (Thanassis Stavrakis) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/athens-protest/pict14.jpg) Riot police officers throw missiles at protesters as cars burn during clashes in Athens, Sunday, Feb. 12, 2012. Protesters and police fought running battles in central Athens Sunday, as Greek lawmakers debated legislation that would introduce severe austerity measures to stave off bankruptcy. (Thanassis Stavrakis) Riot police officers throw missiles at protesters as cars burn during clashes in Athens, Sunday, Feb. 12, 2012. Protesters and police fought running battles in central Athens Sunday, as Greek lawmakers debated legislation that would introduce severe austerity measures to stave off bankruptcy. (Thanassis Stavrakis) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/athens-protest/pict13.jpg) A protester throws an object towards riot police during clashes in Athens on Sunday, Feb. 12, 2012. Tens of thousands of protesters gathered in the square outside Parliament as a parliamentary debate on further austerity cuts began, with more arriving constantly. (Kostas Tsironis) A protester throws an object towards riot police during clashes in Athens on Sunday, Feb. 12, 2012. Tens of thousands of protesters gathered in the square outside Parliament as a parliamentary debate on further austerity cuts began, with more arriving constantly. (Kostas Tsironis) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/athens-protest/pict12.jpg) Riot police officers throw tear gas at protesters during clashes in Athens, Sunday, Feb. 12, 2012. Protesters and police fought running battles in central Athens Sunday, as Greek lawmakers debated legislation that would introduce severe austerity measures to stave off bankruptcy. (Petros Giannakouris) Riot police officers throw tear gas at protesters during clashes in Athens, Sunday, Feb. 12, 2012. Protesters and police fought running battles in central Athens Sunday, as Greek lawmakers debated legislation that would introduce severe austerity measures to stave off bankruptcy. (Petros Giannakouris) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/athens-protest/pict15.jpg) A protester clashes with riot police outside the Greek parliament in Athens, Sunday, Feb. 12, 2012. Tens of thousands of protesters gathered in the square outside Parliament as a parliamentary debate began, with more arriving constantly. As the crowds grew, a few hundred anarchists started to throw bottles and firebombs at police, who responded with tear gas and stun grenades. (Thanassis Stavrakis) A protester clashes with riot police outside the Greek parliament in Athens, Sunday, Feb. 12, 2012. Tens of thousands of protesters gathered in the square outside Parliament as a parliamentary debate began, with more arriving constantly. As the crowds grew, a few hundred anarchists started to throw bottles and firebombs at police, who responded with tear gas and stun grenades. (Thanassis Stavrakis) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/athens-protest/pict6.jpg) A Starbucks coffee shop burns, right, as firefighters try to cut open the locked truck to get out the fire hose after protesters took the keys, during clashes in Athens, Sunday, Feb. 12, 2012. Protesters and police fought running battles in central Athens Sunday, as Greek lawmakers debated legislation that would introduce severe austerity measures to stave off bankruptcy. (Thanassis Stavrakis) A Starbucks coffee shop burns, right, as firefighters try to cut open the locked truck to get out the fire hose after protesters took the keys, during clashes in Athens, Sunday, Feb. 12, 2012. Protesters and police fought running battles in central Athens Sunday, as Greek lawmakers debated legislation that would introduce severe austerity measures to stave off bankruptcy. (Thanassis Stavrakis) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/athens-protest/pict7.jpg) Protesters throw stones at riot police during clashes in Athens, Sunday, Feb. 12, 2012. Riots engulfed central Athens and at least 10 buildings went up in flames in mass protests late Sunday as lawmakers prepared for a historic parliamentary vote on harsh austerity measures demanded to keep the country solvent and within the eurozone. The graffiti reads ”Poison to riot police.” (Petros Giannakouris) Protesters throw stones at riot police during clashes in Athens, Sunday, Feb. 12, 2012. Riots engulfed central Athens and at least 10 buildings went up in flames in mass protests late Sunday as lawmakers prepared for a historic parliamentary vote on harsh austerity measures demanded to keep the country solvent and within the eurozone. The graffiti reads ”Poison to riot police.” (Petros Giannakouris) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/athens-protest/pict8.jpg) A protester throws a missile at riot police during clashes in Athens, Sunday, Feb. 12, 2012. Protesters and police fought running battles in central Athens Sunday, as Greek lawmakers debated legislation that would introduce severe austerity measures to stave off bankruptcy. (Petros Giannakouris) A protester throws a missile at riot police during clashes in Athens, Sunday, Feb. 12, 2012. Protesters and police fought running battles in central Athens Sunday, as Greek lawmakers debated legislation that would introduce severe austerity measures to stave off bankruptcy. (Petros Giannakouris) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/athens-protest/pict9.jpg) Protesters clash with riot police outside the Greek parliament in Athens on Sunday, Feb. 12, 2012. Tens of thousands of protesters gathered in the square outside Parliament as a parliamentary debate began, with more arriving constantly. (Thanassis Stavrakis) Protesters clash with riot police outside the Greek parliament in Athens on Sunday, Feb. 12, 2012. Tens of thousands of protesters gathered in the square outside Parliament as a parliamentary debate began, with more arriving constantly. (Thanassis Stavrakis) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/athens-protest/pict10.jpg) Demonstrators protest against the new austerity measures in Syntagma Square on February 12, 2012 in Athens, Greece. Greece’s creditors have demanded further austerity measures before approving a new bailout from the European Union, European Central Bank and International Monetary Fund amid renewed concerns the country may default. Getty Demonstrators protest against the new austerity measures in Syntagma Square on February 12, 2012 in Athens, Greece. Greece’s creditors have demanded further austerity measures before approving a new bailout from the European Union, European Central Bank and International Monetary Fund amid renewed concerns the country may default. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/athens-protest/pict17.jpg) Protesters gather outside the Greek Parliament during clashes with riot police in Athens on Sunday, Feb. 12, 2012. Tens of thousands of protesters gathered in the square outside Parliament as a parliamentary debate on further austerity cuts began, with more arriving constantly. (Thanassis Stavrakis) Protesters gather outside the Greek Parliament during clashes with riot police in Athens on Sunday, Feb. 12, 2012. Tens of thousands of protesters gathered in the square outside Parliament as a parliamentary debate on further austerity cuts began, with more arriving constantly. (Thanassis Stavrakis) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/athens-protest/pict16.jpg) A protester holds a Greek flag during clashes with riot police outside the Greek Parliament in Athens on Sunday, Feb. 12, 2012. Tens of thousands of protesters gathered in the square outside Parliament as a parliamentary debate on further austerity cuts began, with more arriving constantly. (Thanassis Stavrakis) A protester holds a Greek flag during clashes with riot police outside the Greek Parliament in Athens on Sunday, Feb. 12, 2012. Tens of thousands of protesters gathered in the square outside Parliament as a parliamentary debate on further austerity cuts began, with more arriving constantly. (Thanassis Stavrakis) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/athens-protest/pict5.jpg) Protesters wave a flag in front of the Greek parliament as riot police officers stand guard in Athens, Sunday, Feb. 12, 2012. Tens of thousands of protesters gathered in the square outside Parliament as a debate began, with more arriving constantly. As the crowds grew, a few hundred anarchists started to throw bottles and firebombs at police, who responded with tear gas and stun grenades. (Kostas Tsironis) Protesters wave a flag in front of the Greek parliament as riot police officers stand guard in Athens, Sunday, Feb. 12, 2012. Tens of thousands of protesters gathered in the square outside Parliament as a debate began, with more arriving constantly. As the crowds grew, a few hundred anarchists started to throw bottles and firebombs at police, who responded with tear gas and stun grenades. (Kostas Tsironis) |
TOP SECRET from the FBI – Uzbek National Pleads Guilty to Charges of Threatening to Kill the President and Providing Material Support to Terrorist Activity
BIRMINGHAM—An Uzbek national who has lived in the United States since 2009 pleaded guilty today in federal court to charges of providing material support to terrorist activity, threatening to kill President Barack Obama and illegally possessing a weapon.
U.S. Attorney Joyce White Vance; Department of Justice Assistant Attorney General for National Security Lisa Monaco; FBI Special Agent in Charge Patrick J. Maley; Bureau of Alcohol, Tobacco, Firearms and Explosives Special Agent in Charge Glenn N. Anderson; Secret Service Special Agent in Charge Roy Sexton; and Immigration and Customs Enforcement’s Homeland Security Investigations Special Agent in Charge Raymond R. Parmer Jr. announced the plea.
ULUGBEK KODIROV, 22, of Uzbekistan, pleaded guilty before U.S. District Judge Abdul K. Kallon to one count of providing material support to terrorist activity, one count of threatening to kill the president and one count of possession of a firearm by an illegal alien. The charges of threatening to kill President Obama and illegally possessing a firearm were among charges brought in an indictment against Kodirov by a federal grand jury in July 2011.
The U.S. Attorney’s Office filed a criminal information Thursday in U.S. District Court charging Kodirov with material support of terrorism.
U.S. Attorney Vance praised the investigative work and prompt action of the Joint Terrorism Task Force for the Northern District of Alabama. “Today, Ulugbek Kodirov became the first person to be convicted of providing material support to terrorist activity in this district,” she said. “Kodirov was apprehended during an undercover operation in which he was attempting to obtain weapons and explosives that he intended to use to kill the president of the United States. Effective action by law enforcement protected our community and potentially our country,” she said.
“I also want to express my appreciation to the Muslim community of Birmingham, which was instrumental in helping law enforcement shut down this threat,” Vance said.
“Today’s case underscores the continuing threat we face from violent extremists,” Assistant Attorney General Monaco said. “Thanks to a coordinated law enforcement effort, Kodirov’s plot was thwarted before anyone was harmed.”
FBI SAC Maley said, “I want to thank the members of the Joint Terrorism Task Force (JTTF), who include the Jefferson and Shelby County Sheriff’s Offices, Birmingham, Hoover and UAB Police Departments, the Transportation Security Agency, Secret Service, ATF, and DHS. I also thank the Pelham and Leeds Police Departments for their invaluable assistance in this case. The JTTF has been diligently investigating and building partnerships to protect Alabama from terrorists since 9/11, and its efforts put it in the unique position to interdict a violent act of terrorism. This case serves as a reminder of the dangers of the Internet on radicalizing our youth right in our own back yards, and all citizens and organizations need to remain vigilant on the ever-increasing threat from home-grown violent extremists.”
ATF SAC Anderson said, “This case involved a variety of experience and expertise with ATF’s local, state and federal law enforcement partners, including the Secret Service, ICE, FBI JTTF, Shelby County Sheriff’s Office, Leeds Police Department and Pelham Police Department. The combined effort enabled a quick response and a very fluid investigation focused on keeping everyone safe, from Leeds, Alabama, potentially to the White House.”
“The Secret Service will actively investigate any perceived threat against anyone we are charged to protect,” SAC Sexton said. “This case is a great indicator of what can be accomplished through the outstanding cooperation between local, state and federal law enforcement in the Northern District of Alabama.”
“This case is a perfect example of the outstanding cooperation between all law enforcement agencies involved in this arrest,” ICE-HSI SAC Parmer said. “Because of great coordination and cooperation, we were able to jointly arrest this dangerous illegal alien. We are dedicated to apprehending those individuals who are the most dangerous in our communities and getting them off the streets.”
Kodirov entered a plea agreement with the government, which was filed with the court today. In the plea agreement, Kodirov acknowledges that he had been in communication with an individual whom he believed to be a member of the Islamic Movement of Uzbekistan (IMU), and that Kodirov interpreted these conversations to mean that he should kill President Obama. Kodirov then took steps to obtain weapons to carry out his plans to kill the president. The IMU is designated as a Foreign Terrorist Organization by the U.S. State Department. Kodirov also showed jihadist websites and videos on his computer to another individual and told that person that he wanted to assist others in jihad overseas, according to the plea agreement.
Kodirov also acknowledges in the plea agreement that he had lengthy conversations in July 2011 with a different individual about Kodirov’s desire to kill President Obama and possible ways to carry out the assassination. That individual traveled to Birmingham to meet Kodirov and introduced him to another individual, an undercover agent, from whom Kodirov intended to obtain weapons he would use to kill the president.
The three men met on July 13, 2011, at a motel in Leeds, Ala. In that meeting, the agent presented a fully automatic Sendra Corporation Model M15-A1 machine gun, a sniper rifle with a telescopic sight and four disassembled hand grenades and asked Kodirov if he would like to use any of them to “carry out his plan to kill the President,” according to the plea agreement. Kodirov chose the M15-A1 machine gun and the hand grenades and left the meeting with the weapons. Agents arrested Kodirov before he left the motel.
Kodirov entered the United States on a student visa in June 2009. His visa was revoked on April 1, 2010, for failing to enroll in school. Thereafter, he was unlawfully present within the United States. He was living in an extended-stay motel in Pelham, Ala., at the time of his arrest.
Kodirov faces maximum prison sentences of 15 years on the terrorism charge, five years on the charge of threatening the president and 10 years on the charge of being an illegal alien in possession of a firearm. Each charge also carries a maximum fine of $250,000.
The FBI, ATF, HSI, and Secret Service investigated the case. Assistant U.S. Attorneys Michael W. Whisonant and Ryan K. Buchanan are prosecuting the case with assistance from the Counterterrorism Section of the Justice Department’s National Security Division.
TOP-SECRET – DHS-University of Maryland Study: Hot Spots of Terrorism and Other Crimes

While efforts are increasingly aimed at understanding and identifying “hot spots” of ordinary crime, little is known about the geographic concentration of terrorist attacks. What areas are most prone to terrorism? Does the geographic concentration of attacks change over time? Do specific ideologies motivate and concentrate terrorist attacks? Moreover, what factors increase the risk that an attack will occur in a particular area? Using recently released data from the Global Terrorism Database, we address these gaps in our knowledge by examining county-level trends in terrorist attacks in the United States from 1970 through 2008.
…
Terrorism
The definition of terrorism used by the GTD is: the threatened or actual use of illegal force by non-state actors, in order to attain a political, economic, religious or social goal, through fear, coercion or intimidation. It is important to note that the classification of an event as terrorism depends as much on threats as the actual use of violence. For example, instances in which individuals seize an aircraft and threaten to blow it up unless their demands are met are defined as terrorist events. Note also that by specifying the threatened or actual use of force the definition of terrorism used by the GTD excludes hoaxes. The requirement that these events be limited to the actions of “non-state actors” means that considerable violence and terrorism that is directly attributable to states or their militaries is also excluded. And the requirement that the act have a direct political, economic, religious or social goal means that ordinary criminal violence is excluded. Thus, the GTD excludes state terrorism and many types of crime and genocide, topics that are important and complex enough to warrant their own separate analysis.
The frequency of terrorist acts is recorded for each U.S. county for each year from 1970 through 2008. Counties with no recorded terrorist attacks are coded “zero.” The vast majority of U.S. counties have not experienced any terrorist attacks since 1970. Terrorist acts are also categorized by the ideological motivation of the act and coded as “extreme right-wing”; extreme left-wing; religious; ethno-nationalist/separatist; or single issue. The dominant ideology variable captures the group’s central ideological motivation (e.g., while the Aryan Nations maintained a strong religious conviction to the Christian Identity movement, their raison d’être was to promote a racially homogenous white society).
Detailed information on each category of ideological motivation can be found in the Profiles of Perpetrators of Terrorism-United States report compiled by the National Consortium for the Study of Terrorism and Responses to Terrorism (Miller, Smarick, and Simone, 2011). Briefly, the report describes each category as follows:
Extreme Right-Wing: groups that subscribe to aspects of the following ideals: they are fiercely nationalistic (as opposed to universal and international in orientation), anti-global, suspicious of centralized federal authority, reverent of individual liberty (especially their right to own guns, be free of taxes), believe in conspiracy theories that involve grave threat to national sovereignty and/or personal liberty and a belief that one’s personal and/or national “way of life” is under attack and is either already lost or that the threat is imminent (sometimes such beliefs are amorphous and vague, but for some the threat is from a specific ethnic, racial, or religious group), and a belief in the need to be prepared for an attack either by participating in paramilitary preparations and training or survivalism. (2011: 26)
Extreme Left-Wing: groups that want to bring about change through violent revolution rather than through established political processes. This category also includes secular left-wing groups that rely heavily on terrorism to overthrow the capitalist system and either establish “a dictatorship of the proletariat” (Marxist-Leninists) or, much more rarely, a decentralized, non-hierarchical political system (anarchists). (2011: 24)
Religious: groups that seek to smite the purported enemies of God and other evildoers, impose strict religious tenets or laws on society (fundamentalists), forcibly insert religion into the political sphere (e.g., those who seek to politicize religion, such as Christian Reconstructionists and Islamists), and/or bring about Armageddon (apocalyptic millenarian cults; 2010: 17) For example, Jewish Direct Action, Mormon extremist, Jamaat-al-Fuqra, and Covenant, Sword and the Arm of the Lord (CSA) are included in this category (2011: 18).
Ethno-Nationalist/Separatist: regionally concentrated groups with a history of organized political autonomy with their own state, traditional ruler, or regional government, who have supported political movements for autonomy at some time since 1945 (2011: 18).
Single Issue: groups or individuals that obsessively focus on very specific or narrowly-defined causes (e.g., anti-abortion, anti-Catholic, anti-nuclear, anti-Castro). This category includes groups from all sides of the political spectrum (2010: 28).
…
DOWNLOAD ORGINAL DOCUMENT HERE
The Video about the MOSSAD Spy Eli Cohen
THE MOSSAD Spy Eli Cohen
The Israeli spy Eli Cohen is hanged in Damascus – 26 January 1965 : The government of Syria arrests 63 members of an Israeli spy network.
After enduring torture in the “Maza” jail in Damascus and a short showcase trial, the Israeli spy Eli Cohen is hanged in the El Marja square in Damascus. All efforts made by Israel to convince Syria to overturn the verdict and let Eli Cohen go in exchange for Syrian captives failed. The Syrians also rejected begs for mercy from different countries, as well as from the pope himself. Ten days after his trial, many residents of Damascus gathered to watch the hanging of the Israeli spy. Cohen, who was born in Egypt, was recruited by the Mossad and for three years operated in Syria under the pseudonym Kamel Amin Tabat. He successfully befriended Syrian officials. Cohen transferred information to Israel from his apartment, which was located near the Syrian General Staff base in Damascus. He was caught after arousing the suspicion of the Syrian intelligence services and was recognized by a Damascus resident as a Jew who was born in Cairo. Eli Cohen is believed to have penetrated deep into the heart of an Arab government. Syria still refuses to transfer his bones for burial in Israel. He left a wife and three daughters behind.
FEMEN UNCENSORED – “La prostitution est un fléau en Ukraine”
SPIEGEL TV enttarnt STASI-Spitzel in der Linkspartei
Video – Thomas Gens, STASI-Vergangenheit bestätigt!
REVEALED – More Than $18 Billion in Cash Smuggled Across U.S.-Mexico Border Each Year
 This undated photo, provided by U.S. Immigrations and Customs Enforcement (ICE), shows bulk cash, seized by the ICE, which was hidden under the lining of a suit case. Immigration agents report a rising number of cash seizures and arrests in the past half-dozen years as criminals, sidestepping scrutiny from banks over electronic transfers, resort to using cash to conceal proceeds from drug trafficking as they move the money south to crime rings in Mexico and elsewhere. (AP Photo/ICE)
This undated photo, provided by U.S. Immigrations and Customs Enforcement (ICE), shows bulk cash, seized by the ICE, which was hidden under the lining of a suit case. Immigration agents report a rising number of cash seizures and arrests in the past half-dozen years as criminals, sidestepping scrutiny from banks over electronic transfers, resort to using cash to conceal proceeds from drug trafficking as they move the money south to crime rings in Mexico and elsewhere. (AP Photo/ICE)
Jeanette Barraza-Galindo conspicuously left her bags of teddy bears and throw pillows on a bus during an inspection at the Texas-Mexico border — and professed ignorance about the $277,556 officers found hidden inside. The bags were handed to her at a bus station, gifts to be given to a child upon her return to Mexico, she told investigators.The crime she pleaded guilty to — bulk cash smuggling — is increasingly drawing the attention and resources of federal authorities responsible for fighting drug trafficking across the border. Federal immigration authorities say their investigations have yielded more cash seizures and arrests in the past half-dozen years as criminals, sidestepping scrutiny from banks over electronic transfers, resort to using cash to conceal drug trafficking and move money to crime rings in Mexico and elsewhere. It’s similar to the tactic taken in fighting terrorism: crippling financing networks before the money ends up with leaders of drug cartels and trafficking rings. But the flow is hard to stop.
Officials in both the U.S. and Mexico are realizing that criminal enterprises, just like other businesses, can’t operate without a steady cash stream, said David Shirk, director of the Trans-Border Institute at the University of San Diego, which promotes scholarship of border issues.
“We’re shifting our strategy to a more diverse strategy of not just going after bad guys and arresting them, but also going after their guns, going after their money,” he said.
It’s illegal to try to smuggle more than $10,000 in undeclared cash across the border. Officials say the crime is often connected to other illegal activities including drug trafficking, gambling and credit card fraud. Money that’s seized is deposited into government forfeiture funds.
…
The Obama administration says targeting bulk cash smuggling is a prong of its strategy against transnational crime. Congressional panels held hearings on the issue last year. U.S. Immigration and Customs Enforcement reported more than $150 million in seized cash and 428 arrests in bulk cash smuggling investigations in fiscal year 2011, up from $7.3 million and 48 in fiscal year 2005, according to agency statistics.
And a cash smuggling center in Vermont that opened in 2009 and is run by ICE’s homeland security investigations has expanded operations, officials announced in December.
But experts say measuring the impact of the beefed-up focus is tricky.
It’s hard to track cash’s origin and destination — and investigators can’t always count on help from couriers, who may be more afraid cooperating than of spending a few years in prison. Plus, the amount seized represents a fraction of the total money at stake. Estimates cited by federal authorities suggest at least $18 billion in illicit proceeds is laundered across the southwestern border each year.
…
“I call this winning the battle, losing the war. Sure, $90 million sounds like a lot,” said Bruce Bagley, a University of Miami international studies professor who researches drug trafficking. “That’s nothing in comparison to the $19 to $39 billion that’s being returned” across the border.
CONFIDENTIAL – (U//FOUO) NATO Training Mission-Afghanistan (NTM-A/CSTC-A) Organizational Chart

TOP-SECRET from the FBI – Marin Man, 76, Sentenced to Eight Years for Possession of Child Pornography
Donald Tosti was sentenced to eight years in prison and ordered to pay $50,000 in restitution for possessing child pornography.
Tosti was convicted on Sept. 14, 2011, on two charges of possessing child pornography. During the trial, evidence showed that Tosti was found to possess child pornography after taking his computer to CompUSA for repair. A search of Tosti’s home and office revealed a large collection of child pornography, including depictions of the rape of very young children. In sentencing Tosti, United States District Court Judge Jeffrey S. White emphasized the size of his collection and the graphic and extreme nature of the child pornography images as aggravating factors in imposing his sentence.
The prosecution is the result of a four-year investigation by the Federal Bureau of Investigation, with the assistance of the San Rafael Police Department.
MOSSAD Video – Eli Cohen The Impossible Spy Trailer אלי כהן הסרט
CONFIDENTIAL from CRYPTOME – SEAL 10 Statements on McCabe Detainee Assault
US Navy SEAL Matthew McCabe (and two others tried separately) was tried and found not guilty in a military court in May 2010 for assaulting a detainee in Iraq.
May 6, 2010″A military jury in Virginia has found a Navy SEAL not guilty on charges of punching a suspected Iraqi terrorist. Jurors deliberated about an hour and 40 minutes before returning their verdict Thursday in the court-martial of Petty Officer 2nd Class Matthew McCabe. The 24-year-old Perrysburg, Ohio, man was tried at Naval Station Norfolk on accusations of assaulting Ahmed Hashim Abed, who is suspected of plotting the 2004 slayings of four U.S. contractors in Fallujah. The defense suggested throughout the trial that Abed employed a standard terrorist tactic of feigning injury, perhaps even biting his own lip to spill blood onto his clothing.”
The US Navy Criminal Investigative Service took sworn statements about the alleged assault from unit SEAL 10 members serving with McCabe. These were introduced at the trial. The statements:
http://cryptome.org/2012/01/mccabe/mccabe-seal-10.pdf (3.5MB)
Matthew McCabe in Iraq![[Image]](https://i0.wp.com/cryptome.org/2012/01/mccabe/pict0.jpg) |
SEAL Team![[Image]](https://i0.wp.com/cryptome.org/2012/01/mccabe/pict1.jpg) |
Matthew McCabe after trial![[Image]](https://i0.wp.com/cryptome.org/2012/01/mccabe/pict2.jpg) |
CONFIDENTIAL – Israel – IDF Head of Intelligence: Our enemies possess 200,000 rockets and missiles that could cover the entire Dan region
During his speech at the Herzliya Conference, Major General Aviv Kochavi discussed the Iranian issue: “Iran has enough enriched uranium to construct four nuclear bombs,” he said
 Maj. Gen. Aviv Kochavi, Head of the IDF Directorate of Military Intelligence (Photo: IDF Spokesman)
Maj. Gen. Aviv Kochavi, Head of the IDF Directorate of Military Intelligence (Photo: IDF Spokesman)In a rare public appearance, the head of the IDF’s Directorate of Military Intelligence, Major General Aviv Kochavi, discussed Israel’s various threats.
In a speech given at the IDC conference in Herzliya, Kochavi said that Iran continues to strive towards the development of a nuclear weapon, and that it had amassed a stockpile of enriched uranium sufficient for constructing four nuclear bombs. “The Iranians have nearly 100 kg of uranium enriched to a level of 20%. We have a list of figures that proves beyond a doubt that Iran is continuing the development and promotion of military nuclear weaponry.”
According to Kochavi, obtaining a nuclear weapon is dependent on the decision of Iran’s supreme leader, Ali Khomeini. “When Khomeini makes the decision to create the initial warhead, we estimate that it will take about a year. If he gives an instruction to obtain bombs or arm bombs with nuclear capabilities, it will take another year or two.”
Major General Kochavi also referred to the depots of precise weapons in the Middle East. “Approximately 200,000 rockets and missiles threaten Israel. The missiles are more accurate, and cover the entire Dan Region.” He added, “The precision is also increasing, especially with the long-range missiles.”
According to Kochavi, Israel’s enemies will have learned the lessons from the Second Lebanon War, and now terror organizations and hostile countries will not keep their missile arsenals in centralized locations.
“The enemy has moved the missiles and rockets in order to minimize the effectiveness of the IDF maneuverability. It is decentralizing the rockets and missiles in order to minimize damage,” Kochavi said. “The disposition is becoming increasingly decentralized, embedded in an urban environment. In southern Lebanon, nearly every tenth house has a missile launch station,” he explained.
TOP – SECRET from the CIA – CIA Cold War Records — CORONA: America’s First Satellite Program
Related Material: CIA Cold War Records — CORONA: America’s First Satellite Program [PDF Only 18.42MB*]

The First NRO Reconnaissance Eye in Space
Robert A. McDonald, Ph.D., Editor
Published by The American Society for Photogrammetry and Remote Sensing, Bethesda, MD
This material has been reviewed by the CIA. That review neither constitutes CIA authentication of information nor implies CIA endorsement of the author’s views.
Introduction
This article is based on the monograph copyrighted and published in 1997 by The American Society for Photogrammetry and Remote Sensing (ASPRS), located at 5410 Grosvenor Lane, Suite 210, in Bethesda, MD, USA. The ASPRS has been America’s professional society dedicated to the development of the art and science of photogrammetry, remote sensing, and geographic information systems since its founding in 1934 (see the forward to the text by former Director of Central Intelligence, Richard Helms). On February 22, 1995, President Clinton authorized the declassification and public release of imagery acquired by Corona, the first US reconnaissance satellite, America’s earliest successes in taking pictures of the earth’s surface from space. What follows are extracts from the introduction and chapter abstracts. They give the flavor of the text but are not meant to be a replacement for reading the whole, exciting story. The comprehensive collection of articles in the ASPRS monograph opens the formerly classified Corona story, first to historians and remote sensing specialists, but more importantly to those in the general public who have an interest in the Cold War and space technology.
These copyrighted extracts are reproduced with the collaboration of the editor, Dr. Robert A. McDonald, of the National War College, National Defense University, Washington, DC, by permission of the ASPRS.
For information on purchase of the hard-cover text of the monograph, contact the American Society for Photogrammetry and Remote Sensing (ASPRS), located at 5410 Grosvenor Lane, Suite 210, in Bethesda, MD, USA.
In 1965 there was a Broadway hit, Man of La Mancha, in which Don Quixote, the illusion of protagonist, Miguel de Cervantes, sang of an impossible dream. At this same time during the 1960s there was a national security intelligence “hit”–a secret, US intelligence program for space reconnaissance. This program, Corona, grew out of imaginative thinking and appeared to be an impossible dream. It was designed to “right the unrightable wrong” of being denied information by the Iron Curtain. It was targeted to help “fight the unbeatable foe” of the Cold War Soviet Union. Launched from Vandenberg Air Force Base, it reached out into orbit and became an unreachable star that could watch the Soviet Union.
Corona was the world’s first imaging reconnaissance satellite and operated during the height of the Cold War to collect pictures over the denied areas behind the Iron and Bamboo Curtains. During its operational life, this satellite program collected over 800,000 images in response to the national security intelligence and mapping requirements of the time. On the average, individual images covered a geographic area on the Earth’s surface of approximately 10×120 miles. Corona had sister programs, Argon for mapping imagery, and Lanyard, a short-lived program designed for higher-quality imagery.
The Geostrategic Context
The 1950s had been uncertain and dangerous times. In 1953, the Soviet Union tested a hydrogen bomb; in the summer of 1957 they successfully tested an intercontinental ballistic missile; and in the fall of that year they launched the first artificial satellite, Sputnik. US policy makers were uneasy about what they were seeing and hearing from the Soviets about their military and space successes. There even were those who suggested that the Soviets might drop bombs on the US from space (Studeman, 1995). But the US Intelligence Community had very little hard evidence of the true Soviet military capabilities. “In the absence of reliable information about the nature of the Soviet threat, we had no choice but to build up our own forces” (Deutch 1995). The USSR–with its satellite countries–had become a disciplined, closed society that was suspicious and demonstrated a penchant for controlling the flow of information. At the same time there was growing US public concern over the potential Soviet threat, especially from nuclear weapons. The Soviets had a formidable security service that proved difficult for Western intelligence to penetrate (Helms, 1983). Reconnaissance attempts with high-flying balloons and aircraft only could provide the US with limited useful information. Corona would change all of that with its burst of images. “[T]he intelligence explosion of the century was on, a relentless stream of detailed data which turned analytical work on these so-called ‘denied areas’ from famine to feast:” (Helms, 1983).
The objective of the Corona program was to use a space platform to acquire photographic intelligence to help satisfy the requirement for what was viewed as much-needed information. Its engineering was based on theoretical concepts that were yet to be demonstrated and used a technology that was based on neither confident data nor proven hardware. Questions that we take for granted today had yet to be answered: If you successfully launched a camera into orbit, would it work? If you took pictures from a satellite, could they see through the Earth’s atmosphere? Could you launch, control, and recover a spacecraft?
The Corona Story
The Man of La Mancha, and the life of its protagonist, Miguel de Cervantes, are metaphors for the Corona program. De Cervantes’ life “… was a catalogue of catastrophe… What sort of man was this…who could suffer unceasing failure and yet…produce the staggering testament…”? (Wasserman, 1976). What sort of program was Corona? What kind of people were behind it? Who could suffer the unceasing failures of 13 shattered mission attempts before they finally could produce a testament to their quest–before they could launch an artificial satellite that would fly in a 100 nautical mile polar orbit above the Earth and from there take pictures that ultimately could show objects that were as small as 2 meters?
Man of La Mancha “had its inception in Madrid in 1959” when author Dale Wasserman was in Madrid (Richards, 1976). This was the same time that Corona was being conceived on the launch pad. Its first failed mission was in February of 1959. The play and musical went on to be written and were first presented at the ANTA Washington Square Theatre in New York City on November 22, 1965. It was a tremendous success and considered one of the best musicals of the 1965-66 season (Richards 1976). By then, Corona had gone on to become an operational satellite that was flying Mission 1026 over the USSR. It was being hailed a tremendous success and was considered one of the best sources of intelligence on the Soviet Union.
Corona was built from 1959 to 1972 by the Space Systems Division of Lockheed Martin Missiles & Space (formerly Lockheed MSC Space Systems Division). Lockheed was awarded the prime contract in 1956 for Weapons System 117L, an umbrella classified program. The Corona project evolved from WS-117L, and Lockheed became the prime contractor and served as technical adviser and integrator for all Corona equipment other than the Thor booster. Lockheed developed the Agena upper stage and integrated and led the test, launching, and on-orbit control operations of Corona (Star, 1995).
The first successful Corona flight, which acquired 3,000 feet of film and covered more than 1,650,000 square miles of Soviet territory, was making its mark. During this August 1960 flight, the Corona program had acquired more overhead photographic coverage of the Soviet Union than all of the U-2 flights to that date. From a technological perspective, it was the first space program to recover an object from orbit and the first to deliver intelligence information from a satellite. It would go on to be the first program to employ multiple reentry vehicles, pass the 100 mission mark, and produce stereoscopic space imagery. Its most remarkable technological advance would be the improvement in its ground resolution from an initial 40-foot capability to an ultimate 6-foot resolution.
Corona would provide evidence that the Soviets had made exaggerated claims of their military capability. The “heart” we heard about in Joe Darion’s lyrics for “The Impossible Dream” could “lie peaceful and calm” knowing that the Cold War threat was not as great as we had thought. This monograph tells the story of the quest for photosatellite reconnaissance through 22 articles organized into seven sections:
- The Prelude to Space Reconnaissance
- The Beginning of Space Reconnaissance
- The Technology Behind the Pictures
- The People and Their Organizations
- Declassification and Opening Secrets to the Public
- The Impact of Space Reconnaissance
- The Future
Prelude to Space Reconnaissance
The first section has two articles that describe American strategic reconnaissance capabilities and policy issues that preceded Corona. Jonathan Lewis discusses the U-2 story that was a model for the development of Corona. He looks at the evolution of the U-2 from the perspective of Richard Bissell, who also played a key role in the development of Corona. Lewis pays particular attention to the organizational dynamics and management style that were fundamental to the U-2’s development. The focused, business-oriented mission; the single-line, streamlined management structure; the risk-taking innovation; and the need for secrecy all previewed Corona’s development. In his conclusion, Lewis leaves us with questions to consider as we examine the Corona story.
R. Cargill Hall offers insight into how a concept for a strategic reconnaissance capability ultimately led to the birth of Corona. This is an essential explanation that sets the stage for telling the story of Corona as it occurred during the Cold War. Hall describes how strategic reconnaissance evolved out of attempts to acquire intelligence in response to national security fears and crises. In his article we see the impact of President Eisenhower’s leadership and legacy for American, national-level strategic reconnaissance.
The Beginning of Space Reconnaissance
This section has three articles that outline the performance characteristics of the earliest imaging reconnaissance satellites. The article on Corona, Argon, and Lanyard explains what these first US reconnaissance satellites were and how they performed operationally. The article by Frederic Oder and Martin Belles offers an explanation of Corona’s development from a programmatic perspective, while Peter Gorin explains the Soviet Union’s imaging reconnaissance program that paralleled these early US accomplishments.
Gorin’s insight into the Soviet’s Zenit satellite is important if we are to know the complete story of early Cold War space reconnaissance. From him, we learn about what the Soviets were doing in the development of their counterpart to Corona. His article makes it clear that the appetite for information in the USSR was as strong as it was in the US. More importantly, Zenit–just as Corona–provided policy leaders with information that was essential to build confidence levels that were necessary to maintain peace during the Cold War.
The Technology Behind the Pictures
The third section discusses the technology of the camera and spacecraft. Dow Smith, from his own experience, offers insight into the technical aspects of Corona’s optics. He explains how experiences from the high-altitude balloon reconnaissance era and the technological culture of the time were able to be adapted to the complex challenge of space imaging. Bob Powell draws from his first-hand observations to explain the evolution of the Agena vehicle, the spacecraft that carried the Corona camera into orbit. Powell also talks about the recovery sequence for getting the film back to Earth. His explanations demonstrate the tremendous complexity of the Corona endeavor: from launching the vehicle, to operating it in space, and recovering the film payload.
The People and Their Organizations
Probably the most important part of the Corona story is the people and organizations that made it happen–without their dedicated efforts there would have been no Corona. This section features four articles that recognize the contributions of those who made Corona possible. For 20 to 30 years they had to remain anonymous because of the classification and security measures that were required throughout the life of the Corona program and many years afterward.
Two individuals were driving forces behind the decision to build a photoreconnaissance satellite for the US. They were James Killian, Jr., president of MIT, and Edwin Land of the Polaroid Corporation. Killian chaired a committee that was established to examine the threat of a surprise attack on the United States. Land chaired a panel that was responsible for finding approaches to monitor the military capabilities of the USSR (Deutch, 1995). Their names come up in a number of the articles in the monograph. A third name, related to implementing the decision, also appears often in Corona’s story–Richard Bissell. He was a visionary of the 1950s who saw that the assessment of international tensions during in the Cold War–with its nuclear weapons threat–required more than simply accurate political intelligence, but also accurate factual information to determine the practical effects of tactical and strategic political moves. Bissell saw that the way to collect this kind of information was by applying technology to intelligence problems (Ranelagh, 1987). As a CIA program manager in the U-2 and Corona era, he brought technology to bear on the decisions associated with creating a national-level strategic reconnaissance capability for the US.
Donald Welzenbach opens his article with the influence of Edwin Land in the development of the U-2 reconnaissance aircraft and Bissell’s role in implementing the program. Welzenbach goes on to discuss the involvement of many other government and contractor personnel who were associated with the early development of strategic reconnaissance in the US. He makes it clear that these individuals laid the foundation for Corona, with many of them continuing to be affiliated with the Corona program. What at first might seem to be independent programs is actually a continuum of technological development.
The Corona program depended heavily on the technological and management experience of the earlier airborne strategic reconnaissance programs. Corona’s managers reached out and found the best technology and expertise that was available in government and private industry. They organized a talented team that came together with an ability to foster innovation. In a collegial way they turned concepts into reality–and did that in a relatively short time (Deutch, 1995). These early Corona pioneers–those who built, launched, and operated Corona–were honored at CIA headquarters as part of the 35th Anniversary Commemoration of the program in 1995. The article on these pioneers offers a brief outline of who they were and the contributions they made.
Corona’s success was not only a result of those who built and operated the satellite system, but also of those who found ways to exploit and use Corona’s imagery to extract intelligence information. Ronald J. Ondrejka’s article identifies another group of pioneers who were members of the American Society of Photogrammetry and Remote Sensing (ASPRS) and who focused on the exploitation of what was a new reconnaissance capability. He writes from the perspective of a long-time ASPRS member and his personal involvement in the Corona program at Itek Corporation. He makes the point that these ASPRS members, both corporate and individual, were “invisible Corona partners” from the Society. They were invisible to the public and others in the professional world of remote sensing because of the inherent secrecy of the Corona program. Through these partners, ASPRS provided the Corona program with a source of knowledge about photogrammetry and remote sensing that had been a part of the Society’s professional tradition.
That tradition of imagery exploitation can be personified in Arthur C. Lundahl who was the Society’s president in 1954. A Washington Post obituary for Lundahl described him as “a pioneer in photographic intelligence and the art of photographic interpretation” (Barnes, 1992). Lundahl was widely known for his work with U-2 imagery, but he also was a major player in the use and exploitation of Corona imagery. He founded the National Photographic Interpretation Center (NPIC), which became the Director of Central Intelligence’s center for the analysis of Corona imagery. It was Lundahl’s years of experience in photographic interpretation of airborne imagery that enabled NPIC to make its contributions to national security during the Corona era. Dino A. Brugioni’s and Frederick J. Doyle’s article provides a biographical overview of Lundahl’s life and his contributions to the fields of photointerpretation and national security. The article puts the exploitation of Corona imagery in the context of a life experience.
Declassification and Opening Secrets to the Public
When the president declassified Corona imagery in February 1995, 23 years after Corona’s final mission, it breathed new life into Corona. The four articles in this section discuss the decision to declassify and the actions to make Corona available to the public. The article on the declassification decision explains the nature of the Talent-Keyhole Control system that President Eisenhower directed for the protection of satellite imagery and the gradual evolution of removing its security constraints. Also reported is the background for Vice President Gore’s announcement of the decision at CIA Headquarters. The next two articles in this section are more technical than descriptive. The article by J. Michael Selander offers insight into how the declassified satellite reconnaissance imagery was prepared for transfer from the Intelligence Community holdings to the public archives. Specifically, he explains the mathematical camera models that were developed so that the transferred imagery would be more useful to the public. The article by Jon C. Leachtenauer and his colleagues offers a technical analysis of the benefits of digitizing Corona imagery, which was acquired before the era of imagery digitization. The full Intelligence Community archive of Corona, Argon, and Lanyard imagery now has been transferred to the public archive at the National Archives and Records Administration (NARA) and the Earth Resources Observation Systems (EROS) Data Center. Donna K. Scholz’s article provides some background on the transfer of the imagery and explains how the public can gain access to the imagery.
The Impact of Space Reconnaissance
Corona’s technological potential became apparent after recovering pictures of its first intelligence target–the Soviet military airfield near Mys Schmidta on the Chukchi Sea. Along with Argon and Lanyard, Corona imagery would go on to have major national security and cartographic impact in the worlds of foreign intelligence and map-making. The three articles in this section focus on these impacts. In his article, Robert A. McDonald cites specific examples of how, in a revolutionary way, Corona contributed to exposing the missile gap, monitoring arms control, detecting nuclear proliferation, and monitoring the Soviet threat. Roland S. Inlow analyzes how the Intelligence Community used Corona as a unique tool to respond to the foreign intelligence challenges of the Cold War. He offers his analysis from the perspective of a former intelligence analyst and senior manager for the collection and exploitation of satellite reconnaissance imagery.
Not only was Corona the beginning of a revolution in the way intelligence was gathered and reported to senior national security decision makers, but it also became the foundation for a revolution in map-making. Joseph A. Baclawski discusses that aspect of Corona’s impact on national security. He points out how the mapping of the Soviet landmass was probably one of the most technologically challenging tasks for those who used Corona materials. Baclawski makes it clear that Corona imagery provided the key to break through the obstacles of the Soviet Cartographic Iron Curtain.
The Future
The four articles in the last section of this monograph link Corona’s past with the future. Robert McDonald’s article on potential new applications for Corona imagery addresses how this 20- to 30-year-old satellite reconnaissance imagery has the capability to contribute to the analysis of a variety of current and future remote sensing and scientific problems. Not only can it be useful for a retrospective analysis of environmental problems, but it also can be used to deal with resource management and archaeological problems.
Corona not only offers something for the future through the exploitation of its 30-year-old imagery, but there are policy lessons that can be learned from the Intelligence Community’s experience with it. Corona’s experience demonstrates that technology can be a force multiplier for intelligence, and it is necessary to understand existing technologies if we are to apply them to the problems at hand. “At the right time, taking advantage of an advance in technology can revolutionize the business of intelligence” (Deutch, 1995). The article on policy lessons briefly outlines the range of these lessons that includes needing a strong industrial base to be able to take advantage of technology, needing good intelligence in an uncertain world, using the benefits of our national security investments in nondefense areas, and finding value in innovative approaches for management and teamwork when dealing with complex problems that have short deadlines.
Richard Bissell made it clear that developing Corona, “… was a most heartbreaking business…[Y]ou fire the damn thing off and you’ve got some telemetry, and you never get it back… So you have to infer from telemetry what went wrong. Then you make a fix, and if it fails again you know you’ve inferred wrong. In the case of Corona, it went on and on” (Bissell quoted in Mosley, Dulles quoted in Ranelagh). The development of Corona broke new ground. It was a solution-oriented approach. Unique managerial concepts were developed. Corona set the stage for a fundamental new way to do things for its day, as well as for the future. Sam Araki’s article discusses the legacy of these inventive technical practices and innovative management approaches that Corona offers the aerospace industry for the next millennium.
Jeffrey K. Harris’s final article in the monograph looks back to Corona’s heritage and forward to the challenges of the information era. He reviews Corona’s story as a backdrop for space and the information age of the future.
Conclusion
Wasserman (1976), in his preface to Man of La Mancha, repeated a quote he found long ago in Unamuno, “Only he who attempts the absurd is capable of achieving the impossible.” And that is what the Corona pioneers did. They attempted the absurd, sent a camera into space, took pictures from 100 nautical miles, ejected the film and snatched it by an aircraft in midair–absurd! But it worked, and they accomplished the impossible! US intelligence analysts and senior national security policymakers were able to analyze pictures of the Soviet threat.
For the 1960s, Corona was a technologically remarkable program. Not only was it the first photoreconnaissance satellite, but during its initial missions it acquired images at a resolution of 8 meters. And that quickly improved to 2 meters. An extraordinary achievement in that when France launched its first commercial remote sensing system, SPOTI–over 25 years later–it was only providing 10-meter imagery! Even by Corona’s thirty-fifth anniversary, commercial space images generally were available at something worse than 2 meters (e.g., Landsat Thematic Mapper at 30m; the Japanese Earth Resources Satellite, JERS, at about 18m; and the French SPOT satellite still at 10m). Even the Russian KFA-1000 imagery generally was offering no better than 2.5-meter imagery (Doyle, 1991).
In reflecting on Corona, Director of Central Intelligence John Deutch (1995) observed that it “… profoundly altered the course of the Cold War and was probably instrumental in keeping us back from the nuclear threshold.” Project Corona was the US Cold War intelligence project that prevented the Iron Curtain from denying the US a view into the Communist Bloc and provided the US Government with much-needed reconnaissance-derived intelligence.
What kind of conclusions can we draw? Looking across the articles in this monograph, we clearly can see that Corona’s development resulted in at least four revolutions (the word “revolution” consistently is used throughout the monograph). There was a revolution in the way intelligence was collected–the availability of concrete intelligence, hard evidence and tangible information that could be seen and used by policymakers to develop a rational national security strategy. There was a revolution in map-making–a new source of data could be used to produce thousands of reliable maps of large geographic areas previously inaccessible for data collection. There was a revolution in aerospace technology–a new capability for launching, maneuvering, and recovering spacecraft. Finally, there was a revolution in how to manage a complex program–focus on the goal, with an environment of commitment, empowerment, risk-taking, cooperation, and teamwork.
After you learn about the Corona story, you come to know what Corona is all about. It was an impossible dream that came true after 13 unsuccessful attempts. It was risk-taking by pioneers in space flight and intelligence operations. It was those who were on a quest and followed the Corona star of strategic reconnaissance that became a basis for national security during the second half of the twentieth century. It was a look into the Communist world that could not be blocked out by the eclipse of the Iron Curtain. The fundamental contribution of Corona was keeping the Cold War cold. US policymakers were able to acquire information, learn from it, gain insight, share knowledge, and make the right decisions without overreacting. They could see reality through the hard evidence of Corona’s photographs. Perhaps the final conclusion is that Corona played a major role in determining how we would think about national security strategy during the second half of the twentieth century and then set the stage for how we are going to confront information in the domains of foreign intelligence and remote sensing in the next millennium.
References
- Barnes, B. “Arthur C. Lundahl, 77, Dies; Photo Interpreter for CIA.” The Washington Post 25 June 1992: D4.
- Deutch, J. Remarks. Corona and the Revolution in Intelligence. CIA Headquarters, Langley, VA, 23 May 1995.
- Doyle, F. J. “Comparison of Civil Remote Sensing Capabilities of the USA, France, USSR, and Others.” In R. A. McDonald, ed., Space Imagery and News Gathering for the 1990s:
- “So What?” Proceedings of Symposium on Foreign Policy and Remote Sensing, 24-25 Feb. 1989.
- The Patterson School of Diplomacy and International Commerce, U of Kentucky, Lexington, KY. Bethesda, MD:
- American Society for Photogrammetry and Remote Sensing, 1991.
- Helms, R. Quoted in J. Ranelagh. The Agency: The Rise and Decline of the CIA. New York: Simon Schuster, Inc., 1987:327.
- Leigh, M. Man of La Mancha. Dale Wasserman, lyrics by Joe Darion, music by Mitch Leigh. New York: Random House, 1966.
- Ranelagh, J. The Agency. The Rise and Decline of the CIA. New York: Simon Schuster, Inc., 1987.
- Richards, S., ed. Great Musicals of the American Theatre, Vol 2.
- Radnor, PA: Chilton Book Company, 1976.
- “Veil of Secrecy Lifted on Corona Imaging Reconnaissance Satellite: Missiles Space Program Spanned 13 Years, 145 Launches.” The Star 2 June 1995, 40, 11:1.
- Studeman, W. O. “Praise for the Corona Pioneers.” Ceremony Honoring Pioneers of the Corona Satellite Program, CIA Headquarters, Wash., DC, May 1995.
- Wasserman, D. Man of La Mancha. Lyrics by Joe Darion, music by Mitch Leigh. In S. Richards, ed., Great Musicals of the American Theatre, Vol 2. Radnor, PA: Chilton Book Company, 1976.
Reproduced with permission, the American Society for Photogrammetry and Remote Sensing. Dr.
Robert A. McDonald, Corona Between the Sun and the Earth:The First NRO Reconnaissance Eye in Space, 1997.
Abstracts of Chapters
1.The Prelude to Space Reconnaissance
Tension Triumph: Civilian and Military Relations and the Birth of the U-2 Program
Jonathan E. Lewis
Directed by Richard M. Bissell Jr., the rapid development and deployment of the U-2 spy plane was one of the great triumphs of the Cold War. This article will explore the management techniques Bissell used to build the U-2 project organization, coordinate a confederation of civilian and military interests, and overcome repeated Air Force attempts to gain control of the program, Bissell’s choice and development of the organization’s structure, culture, and personnel will be examined in the context of his broad mission not only to deploy the plane, but to build a photo interpretation capability, and produce an intelligence product that satisfied consumer needs.
Post War Strategic Reconnaissance and the Genesis of Project Corona
R. Cargill Hall
Strategic reconnaissance and peacetime overflight were new concepts in the post World War II period. The Soviet Union’s detonation of nuclear devices, Communist victory in China, and war in Korea stimulated development of a strategic reconnaissance capability. The early pioneers in strategic reconnaissance came out of industry, the military, academia. During this early period, the US and Britain would conduct reconnaissance overflights of portions of the USSR using converted bombers (e.g., RB-47s and RB-45s). These aircraft were vulnerable to Soviet attack. The Eisenhower administration determined to develop high altitude reconnaissance aircraft and ultimately reconnaissance satellites.
2.The Beginning of Space Reconnaissance
Corona, Argon, and Lanyard: A Revolution for US Overhead Reconnaissance Robert A. McDonald
Corona, Argon, and Lanyard were the first three US operational imaging satellite reconnaissance systems. They were developed during the Cold War as highly-classified programs, and all three were film return systems. Corona was the most indispensable from a national security perspective. It initially operated under the unclassified Discoverer Program, which had its first successful mission on August12, 1960, when an experimental recovery bucket was retrieved from space with an American flag in it. August 18, 1960, marked the first successful mission that returned film from space. The quality of Corona’s reconnaissance imagery improved over the life of the program from about 40 ft. for the original KH-1 camera to somewhat better than 6 ft. for the final KH-4B camera. The final Corona mission was flown on May 24, 1972.
Corona: A Programmatic Perspective
Frederic C.E. Oder and Martin Belles
The Corona program grew out of US Air Force Project Weapon System II7L (WS-117L), for which Lockheed was the prime contractor. Lockheed went on to serve as technical adviser and integrator of all Corona equipment other than the Thor booster. It developed the orbiting Agena upperstage and integrated and led the testing, launching, and on-orbit control operations. The initial Corona vehicles were launched under the cover of the Discoverer series. The earliest missions experienced difficulties, and it was not until Discoverer XIV that reconnaissance imagery was first collected. The Corona program provided a legacy for the US to become a space leader.
ZENIT: Corona’s Soviet Counterpart Peter A. Gorin
This article describes the development of the first two types of the Soviet photoreconnaissance satellites, Zenit-2 and Zenit-4. Apart from the satellites themselves, the political background and development of the Soviet space reconnaissance infrastructure are discussed. The article provides a short comparison of the Soviet Zenit and the US Corona programs. This article represents the author’s personal opinion based on available sources.
3.The Technology Behind the Pictures
The Design and Engineering of Corona’s Optics
F. Dow Smith The Corona camera and its optics grew out of the technological state-of-the-art of the post World War II period; the geopolitical events of the period led to a decision in the late 1950s to fund the Corona program. Work at the Boston University Physical Research Laboratory was critical to the Corona camera, which was subsequently developed at the newly-founded Itek Corporation. The camera was a classic panoramic type that used a Petzval lens configuration. There was an atmosphere of teamwork that was critical to the development of the camera.
Evolution of Standard Agena: Corona’s Spacecraft
Robert M. Powell
Between February 1959 and February 1987, 362 Agenas were launched. This is the spacecraft that was used to fly the Corona photoreconnaissance satellite. Three basic Agena configurations were developed: A, B, and D. Only 19 were flown in the A configuration; the rest, Bs and Ds. The Bs and Ds were longer (20 ft. 8 in. vs. 14 ft. 3 in.) and heavier (14,100 lbs. vs. 8210 lbs. at launch) than the As. All were 5 ft. in diameter. The Agena consisted of three basic subsystems: Propulsion, which consisted of nested tanks for fuel and oxidizer, and a gimbaled engine that used UDMH for fuel and IRFNA as oxidizer; Guidance and control, which consisted of sequence timers, an inertial reference package, infrared horizon sensors, a velocity meter, and cold gas thrusters for pitch, roll, and yaw control; and communication and control, which consisted of telemetry, radar tracking beacon/command receiving transponder, and an orbital sequence of events programmer adjustable by ground command. Agena was Thor-boosted from the Pacific Missile Range and its recovery vehicle recovered in mid-air over the Pacific or from the ocean as back-up.
4.The People and Their Organizations
From the U-2 to Corona and Those Who Searched for Invisibility
Donald E. Welzenbach
This article reviews the involvement of government and contractor personnel who were associated with the development of the U-2, SR-71, and ultimately Corona. Edwin Land and James Killian were very active among an elite group of scientists who advised President Eisenhower, as well as the CIA leadership during the 1950s. Richard Bissell, Jr., initially chief of CIA’s special projects element, was a major CIA player during this period. Bissell brought Richard S. Leghorn and personnel of the Boston University’s Optical/Physical Research Laboratories (BUORL) into the projects. Contractors, such as Lockheed, Perkin-Elmer Corporation, Fairchild Camera Company, and Itek Corporation became involved in the history of these reconnaissance programs. By the time Corona was being developed, RAND personnel such as Amrom Katz and Merton Davies became involved in the camera aspects of the reconnaissance challenge. The serendipity of the various developments at the time provided Dick Bissell the best of all possible worlds to bring together resources to meet Eisenhower’s challenge of the time to meet the threat of surprise attack.
Corona’s Pioneers
Robert A. McDonald
Pioneers in the scientific and intelligence world took the intellectual, scientific, and political risks to create the US Government’s first imaging reconnaissance satellite, Corona. They came from government and industry, and there were thousands over the life of the program. Forty-eight pioneers were selected from the early years of the program and were honored during the Thirty-Fifth Anniversary Commemoration of the Corona program on May 24,1995. This article outlines a brief summary of their contributions to the success of the program.
Corona’s Invisible ASPRS Partners
Ronald J. Ondrejka
Without the American Society of Photogrammetry (ASP)– now known as the American Society for Photogrammetry and Remote Sensing (ASPRS)–during the years centered on 1960, the Corona program would not have readily located and accessed the resources of responsive technologies that were needed to expedite the acquisition and exploitation of Corona satellite reconnaissance imagery. Both individual and corporate sustaining members of the Society contributed to the program’s success. The technologies necessary for creating and using Corona imagery–technologies that included photo-optical sciences and engineering, photointerpretation, photogrammetry, geodesy, and cartography–describe the professional ASP membership in 1960. The contributions of the many individual and corporate members at that time helped Corona meet its goals. The achievements of these members are reflected in the health and professional influences of ASPRS today.
Arthur C. Lundahl: Founder of the Image Exploitation Discipline
Dino A. Brugioni and Frederick J. Doyle
Art Lundahl, as the founder of the image exploitation discipline, was a major player in the interpretation and use of Corona imagery. During World War II Lundahl encountered aerial imagery by interpreting photographs of enemy targets in the Pacific Theater. He started his civilian career with the Naval Photographic Interpretation Center in 1946. In 1953, Lundahl became the first chief of the Central Intelligence Agency’s Photographic Intelligence Division, which later became the National Photographic Interpretation Center (NPIC). As the NPIC director, Lundahl was responsible for the analysis of U-2 photography, and then after 1960, imagery acquired by the Corona reconnaissance satellite. Lundahl enjoyed the confidence of four US Presidents and briefed many other high-ranking officials from around the world. During his career, he received many awards for his work in photointerpretation and was universally admired by his colleagues in the intelligence and remote sensing communities.
5. Declassification and Opening Secrets to the Public
The Declassification Decision: Opening the Cold War Sky to the Public
Robert A. McDonald
Executive Order 12951 declassified Corona, Argon, and Lanyard satellite reconnaissance imagery. This action was the result of a long history of studying the question and relaxing security controls. Vice President Gore announced the signing of the order in a ceremony at CIA on February 24, 1995. The more general executive order on protecting national security information (E.O. 12958, April 1995) also directs declassification of information that may include additional satellite reconnaissance imagery. Continued national security concerns may require the continued classification of more recent imagery. After the Corona program’s national security sensitivity question was resolved, former Director of Central Intelligence Woolsey declassified and authorized transfer of a Corona camera artifact to the Smithsonian. Gore symbolically gave the camera to the Secretary of the Smithsonian Institution during the February 1995 ceremony. The camera was displayed at the Air and Space Museum during the 35th Anniversary Commemoration of the Corona Program, and is to become a part of the museum’s collection.
Image Coverage Models for Declassified Corona, Argon, and Lanyard Satellite Photography–A Technical Explanation
J. Michael Selander
This article describes the construction of mathematical camera models for the Corona, Argon, and Lanyard United States photoreconnaissance satellite imagery systems. Imagery acquired by these systems from 1960 to 1972–approximately 860,000 frames total–is being declassified and made available to the public through the United States Geological Survey (USGS) and the National Archives and Records Administration (NARA). The camera models described in this article were used to augment a legacy database of image coverage coordinates. This database is used by the Global Land Information System (GLIS) at the EROS Data Center (EDC) to allow users to interactively locate images of interest.
Digitizing Corona Imagery: Quality vs. Cost
Jon C. Leachtenauer, Kenneth Daniel, and Thomas P. Vogl
Corona, Argon, and Lanyard imagery, unlike more recent satellite imagery, was collected on film. For many potential applications in fields that include environmental research, archaeology, and history, it would be desirable to convert the data into a digital format. The National Exploitation Laboratory at the former National Imagery Interpretation Center of the CIA conducted a 1995 study that was designed to determine the impact of digitizing resolution on the information content of converted digitized products. As part of the study, the investigators used a sample of digitizers (at various digitizing spot sizes) to digitize images that were on a sample of duplicate positive film. They displayed the digitized data in softcopy format, and imagery analysts compared the digitized softcopy images with the original hardcopy film products. They measured information loss by using the National Imagery Interpretability Scale (NIIRS). The results of the study provide a basis for selecting digitizer resolution as a function of information/bandwidth trade offs.
Declassified Intelligence Satellite Photographs Available from the US Geological Survey
Donna K. Scholz
An Executive Order, signed by President Clinton on February 22, 1995, authorized the declassification of satellite photographs collected by the US intelligence community during the 1960s and early 1970s. Products from this collection include film negatives, positives, and paper prints, which are available to the public at the cost of reproduction. Photographs are available from the US Geological Survey’s National Satellite Land Remote Sensing Data Archive and the National Archives Record Administration. The images were declassified incrementally, and the first ones made available for public purchase on March 1, 1996. All images were made available by September 1996. An online catalog and browse images for the entire collection are accessible at no charge on the USGS’s Global LIS [Land Information System].
6. The Impact of Space Reconnaissance
Corona’s Imagery: A Revolution in Intelligence and Buckets of Gold for National Security
Robert A. McDonald
It was difficult for the US intelligence community to acquire information about the denied areas of the USSR and its communist satellites during the early days of the Cold War. Corona’s satellite reconnaissance spacecraft opened a new view into the communist bloc for both intelligence analysts and US policymakers. Corona contributed to exposing the myth of a “missile gap,” built confidence in monitoring arms control, helped detect nuclear proliferation, and supported the SS-9 Debate during the 1960s.
How the Cold War and its Intelligence Problems Influenced Corona Operations
Roland S. Inlow
Corona was introduced into the Cold War at a time when there were many gaps in intelligence, and US/Soviet nuclear capabilities were increasing dramatically. It took several years for Corona to provide the initial imagery needed to “search” the Soviet land-mass. The process involved two functions: (1) finding and cataloguing all significant activities; and, (2) confirming the absence of activity when that was the case. Corona has made a lasting contribution, and by any criterion, the Corona program was an outstanding intelligence success in a time of great national need.
Corona: The Foundation for a Mapmaking Revolution
Joseph A. Baclawski
The materials collected by the formerly classified Corona intelligence satellite program became an important resource for US mapping applications on a worldwide basis. The 1995 declassification of the Corona program permits an analysis of how its photographs and ephemeris data were used in two drastically different mapping situations–one on the USSR area where the available mapping data base was poor, and the second on the US area where the existing mapping data were better but needed major updating.
Mapping the Soviet landmass was undoubtedly the most technologically challenging task to which the Corona and the associated Argon materials were applied. Achieving success required development of various types of foreign area mapping specialists, and massive investments in research and development of unique production equipment, all supported by complex computer programs. US mapping organizations overcame these obstacles to map over one-sixth of the Earth’s land surface at a medium scale in just over a decade.
7. The Future
Potential New Applications for Declassified Early Satellite Reconnaissance Imagery
Robert A. McDonald
Imagery experts in the intelligence community have suggested that declassified satellite reconnaissance imagery can answer remote sensing questions that go beyond national security problems. The superior spatial resolution of Corona imagery, when compared with the civil remote sensing systems of the 1970s and 1980s, can be used to complement information that was obtained earlier by the civil systems of the time. Corona imagery can significantly extend environmental timelines and fill gaps in civil records. It has the potential to meet Vice President Al Gore’s objectives to recognize, measure, and assess global changes. Corona imagery also can be employed to address traditional remote sensing problems, such as resource management, agriculture, forestry, and archaeology. It also can find applications in the social sciences. Corona imagery, a valuable intelligence source during the early Cold War, now has the potential for making significant contributions to the civilian community.
Lessons and Benefits from Corona’s Development
Robert A. McDonald
Experience with the Corona program suggests five lessons with policy implications for the future and benefits for today: (1) a strong industrial base is a key to technological success; (2) innovative management is fundamental to organizational success; (3) security may be necessary for success in an intelligence activity; (4) reliable intelligence is an integral part of developing sound national security policy; and, (5) national security investments provides dual-use opportunities. We need to consider these lessons as we move through the transition of the post-Cold War period into the Third Millennium.
Corona’s Legacy for the New Millennium
Sam Araki with Robert A. McDonald
The development of the Corona imaging reconnaissance satellite was a challenge during an era of limited knowledge about space physics and limited experience in space operations. The Corona engineers met the challenges and left us with a legacy of space technology and program management concepts for future aerospace development. When the Corona legacy meets the modern challenges of the information revolution, there are new, unknown opportunities to explore.
A Look Back to Corona and a Look Forward to the Information Era
Jeffrey K. Harris
The information era can be seen as an opportunity to build on the technological heritage that Corona forged in the 1960s. Corona grew out of the necessity to acquire information about the Soviet Union during the Cold War, and it achieved a number of firsts in space helping set the technological standard for future US space programs. Corona offers a lesson that a small group of empowered people can explore options and, with risks, achieve their goal. At the same time, Corona left a technological and information legacy that presents new opportunities for the information era. Information technology is evolving at an ever faster rate, and the US begins the information era with a distinct advantage. In this age of the ever-increasing use of technology we need to recognize that some amount of system failure may be inherent because of the complexity of the technological systems. Tomorrow’s future is bright, and knowledge from our technological heritage can be the catalyst.
Reproduced with permission, the American Society for Photogrammetry and Remote Sensing. Dr. Robert A. McDonald, Corona Between the Sun and the Earth:The First NRO Photoreconnaissance Eye in Space, 1997.
TOP-SECRET – National Security Agency San Antonio TX 2012
|
| Under Construction 2010The Google Street Views following start at the gateway at the center bottom of this view and go clockwise around the facility.
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/nsa-sa-2012/pict24.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/nsa-sa-2012/pict36.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/nsa-sa-2012/pict37.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/nsa-sa-2012/pict38.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/nsa-sa-2012/pict41.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/nsa-sa-2012/pict35.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/nsa-sa-2012/pict34.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/nsa-sa-2012/pict33.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/nsa-sa-2012/pict32.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/nsa-sa-2012/pict31.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/nsa-sa-2012/pict29.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/nsa-sa-2012/pict30.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/nsa-sa-2012/pict28.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/nsa-sa-2012/pict27.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/nsa-sa-2012/pict26.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/nsa-sa-2012/pict25.jpg) |
UNCENSORED – FEMEN Bare All in Kiev Protest
Die STASI-“GoMoPa”- Serien (ruf) Mörder und ihre Verbrechen unter der Lupe
Können sich über 55.000 angeblich registrierte Mitglieder irren? Denn so viele Mitglieder soll GoMoPa – nach Meinung der Kritiker – ein “höchst dubioser Finanznachrichtendienst” mit Sitz in New York haben. Unter dem fiktiven Namen Goldmann Morgenstern & Partners Consulting LLC, kurz GoMoPa, sollen nach eigenen Angaben des Informationsdienstes im Internet, eine “aktive Aufklärung und permanente Transparenz nachhaltig zur Betrugsprävention in Wirtschaft und Gesellschaft beitragen”. Dies lässt sich GoMoPa gut bezahlen. So kostet eine Mitgliedschaft jährlich 99 Euro (Profi-User), 199 Euro (Premium-User) oder gar 999 Euro (Private-User). Den Wert einer solchen Mitgliedschaft bezeichnen die Kritiker aber als höchst zweifelhaft.
Gegründet wurde GoMoPa mit der New Yorker Briefanschrift vor einigen Jahren von Mark Vornkahl und Klaus Maurischat. Gerade um Maurischat, der als Adresse gern Sao Martinho do Porto (Portugal) angibt, ranken sich viele Gerüchte. So soll er mehrfach, auch wegen Betrugs, rechtskräftig verurteilt worden sein. Im Internet kursieren dazu zahlreiche negative Veröffentlichungen.
Aber auch börse-online oder das Handelsblatt berichteten über eher dubiose Aktionen von GoMoPa. So soll das Unternehmen im Fall Wirecard AG (Aschheim) eine Falschmeldung verbreitet haben, die dazu führte, dass der Aktienkurs des Unternehmens einbrach. Auch die Immovations AG (Kassel) musste sich, so dass Unternehmen in einer Veröffentlichung, mit einer einstweiligen Verfügung gegen die GoMoPa wehren. Und für die EthikBank (Eisenberg) ist GoMoPa schlichtweg “tabu”.
Solche zweifelhaften Aktionen fördern nicht gerade die Glaubwürdigkeit der fiktiven Namensgeber Goldmann Morgenstern & Partner Consulting LLC, die seit 2008 auch über eine Zweigniederlassung (GmbH) in Berlin verfügen. Ziel dieses Unternehmens sei “die wirtschaftliche Beratung, insbesondere des Mittelstandes, in der europäischen Gemeinschaft unter der Wortmarke GoMoPa. Dazu gehören die Präsentation von Firmen im Internet, die Vermittlung von Handels- und Wirtschaftkontakten und Werbung auch über das Internet sowie das Bereitstellen von Informationen und Portalen im Internet”.
Also auf der einen Seite kritisch über Unternehmen berichten und auf der anderen Seite Hilfsangebote gegen Bezahlung anbieten. Die Grenzen zwischen den beiden Unternehmen sind offenbar fließend. So manche Aussagen und “unabhängige” Warnungen von GoMoPa wird man bei kritischer Betrachtung dieser Finanzierungsquelle durchaus in einem anderen Licht sehen können und sich fragen müssen, ob der selbsternannte “Finanzinformationsdienst” dabei nicht unter falscher Flagge segelt. “Ein Schelm, wer Böses dabei denkt.” Allerdings scheint das Geschäft nicht all zu gut zu laufen. Laut dem Jahresabschluss 2009 wird in der Bilanz ein Fehlbetrag von gut 30.000 Euro ausgewiesen. Bis vor kurzem wurde die GmbH in Berlin noch von Peter Reski geleitet. Seit März 2011 ist Mark Vornkahl, mit angegebenem Wohnsitz New York, der alleinige Geschäftsführer.
Seit einiger Zeit nicht mehr aufgefallen ist der “Präsident” von GoMoPa, Friedhelm Laschütza, mit Wohnsitz Vaduz. Und ebenfalls in der Versenkung verschwunden ist das Gründungsmitglied Rudolf J. Heckel.
Dagegen schmückt sich das Unternehmen nun mit durchaus prominenten Namen. So sind beispielsweise einige bekannte Rechtsanwälte für GoMoPa tätig. An der Spitze der Berliner Rechtsanwalt Jochen Resch. Der nicht nur geschädigte Kapitalanleger vertritt, sondern auch noch im Vorstand der Verbraucherzentrale Brandenburg seine Dienste einbringt. Aber auch der in der Branche bekannte Wirtschaftsdetektiv Medard Fuchsgruber tritt als sogenannter GoMoPa-Fachautor auf der Internetseite auf und soll dem Dienst offensichtlich mehr Image und eine höhere Kompetenz verleihen. Weitere Rechtsanwälte, wie Dr. Johannes Fiala (München), oder Matthias Schillo (Potsdam), der als ehemaliger OLG-Richter gar als “Ombudsmann” bei GoMoPa fungiert, gehören ebenfalls zum Team des “Informationsdienstes”.
Kinderportal und sexuelle Aufklärung durch GoMoPa?
Wer im Internet über GoMoPa recherchiert, findet auf der Homepage http://www.gomopa4kids.net Sexualaufklärung für Kinder. In welchem Zusammenhang diese Internetseite mit der New Yorker Firma Goldmann Morgenstern & Partner steht oder ob möglicherweise gar einer der GoMoPA-Verantwortlichen eine Vorliebe für die Beantwortung von sexuellen Fragen von Kindern hat, konnte noch nicht geklärt werden. Eine Antwort aus den USA steht noch aus.
THE MOSSAD SUPER SPY IN EGYPT – Major Ze`ev Gur Arie (Wolfgang Lotz)
Lotz was born at Mannheim, Germany in 1921 to a Jewish mother and a non-Jewish German father. Lotz’s father was a theater director working alongside his mother who was an actress. His parents were non-religious to the extent that Lotz’s mother did not even care to have her son circumcised at birth, contrary to Jewish birth rituals. Later on, this turned out to be to his advantage in his career as a spy; the fact that Lotz hadn’t been circumcised enabled him to convince his lovers that he wasn’t Jewish. His parents divorced in 1931 and in 1933 after Hitler came to power, Lotz and his mother emigrated to Palestine.Lotz and his mother settled in Tel-Aviv. He adopted the Hebrew name Ze’ev Gur-Arie, and started to study at the agricultural school at Ben Shemen. In 1936 he joined the Haganah and was engaged in a number of security duties.After the outbreak of World War II in 1939 Lotz was recruited into the British Army because of his knowledge of the German language. He was stationed at Egypt where he joined an intelligence unit and mostly interrogated German POWs. After the war he returned to Israel and was involved in smuggling weapons for the Haganah.In 1948 Lotz married Rivka and they had a son, Oded. At the outbreak of the Independence War in 1948 Lotz joined the newly formed Israel Defense Forces and served at the rank of Captain. He took part at the battle around Latrun. During the Sinai War in 1956 he already rose to the rank of Major and commanded an Infantry brigade.After the war Lotz joined Aman. His superiors planned to send him to Egypt to gather intelligence on Gamal Abdel Nasser’s armaments plans. Aman also hoped that because of Lotz’s command of the German language and his Aryan appearance, he could infiltrate the circle of German scientists who worked at the Egyptian armaments programs.Lotz was sent to Germany in 1959 in order to base his cover story as a German business man, ex-Wehrmacht officer who served in North Africa and an ex-member of the Nazi Party who after living for 11 years in Australia where he worked on breeding horses, came back to Egypt in order to establish a riding club. The North Africa cover was made because Lotz, who had interrogated hundreds of the German POWs in World War II, was familiar with their way of life and could easily tell war stories about his “comrades”, and the riding club cover was made in order to allow Lotz to have contact with Egyptian high society.Lotz arrived in Cairo in 1960 and began immediately to form friendships with high ranking Egyptian officials and military personnel.Lotz traveled to Paris in June 1961 for a meeting with his operators (he was in the meantime transferred to the responsibility of the Mossad) , where he received large amounts of money and a transponder for sending secret messages. During the train travel from Paris, Lotz met a German woman called Waltraud and decided to marry her, despite the fact he was married to another woman in Israel and didn’t discuss it with his operators. The Mossad was horrified by this and even considered calling Lotz back, but in the end the Mossad allowed Lotz to continue his mission and his wife was allowed to join him. While she soon discovered his real occupation, she was told Lotz worked for NATO and she began to help him.In Cairo Lotz finally opened his riding club and continued to befriend the elite of the Egyptian society. He managed to persuade them to show him the Egyptian missile launch sites and he gathered intelligence of the Egyptian military and its industries. He also composed a list of German scientists that worked for the Egyptians and in September 1964 he sent a letter bomb to some of them, threatening them to cease their work.In 1965 the GDR head of state made an official visit to Egypt and as a gesture to the East Germans, the Egyptians arrested 30 citizens of West Germany. Lotz was one of them. Thinking he was exposed, Lotz confessed to being a spy but stuck to his cover story and claimed he was tempted by the Israelis to spy for them in exchange for them giving him funds to establish his riding club.The Egyptians believed Lotz even when evidence arrived from Germany which pointed to his true identity. Lotz and his wife were put on trial and the Mossad managed to get him represented by a German lawyer and ensure a German observer from the embassy who oversaw the fairness of the trial.Lotz was sentenced to life imprisonment on 21 August 1965 and his wife was sentenced to three years in jail. Lotz and his wife were released in the prisoner exchange in 1968 following the Six-Day War. He resided in Israel until the death of his wife, Waltraud, in 1973, who died at the hands of the Egyptian intelligence. After that he spent time in the USA and resided in Germany until his death in 1993. He was buried in Israel with full military honors.In the video his sun Prof.Oded Gur Arie presents his father also in rare video inside.
SECRET from the FBI – $10 Million Returned to Victims of Public Corruption Scheme, Including Kodak and the Town of Greece
ROCHESTER, NY—U.S. Attorney William J. Hochul, Jr. announced today that more than $10,000,000 in forfeited property has been returned to the victims of one of the largest public corruption cases ever prosecuted in the Western District of New York. Those receiving restitution include the Eastman Kodak Company, the Town of Greece, IBM, ITT Industries, Inc., RG&E, and Global Crossing. The companies and town were all victims of real property tax appraisal and assessment schemes spearheaded by John Nicolo, a property appraiser.
In 2005, John Nicolo, Mark Camarata, Charles Schwab, David Finnman, and others were arrested and later convicted of a variety of crimes including mail and wire fraud, conspiracy, and money laundering. The defendants schemed victims out of millions of dollars by artificially inflating tax assessments on properties they owned, and then causing John Nicolo to be hired by the companies in an effort to reduce the resulting tax assessments.
Assistant U.S. Attorney Richard A. Resnick, who prosecuted the case, stated that David Finnman and Mark Camarata, while working at Kodak, hired Nicolo to perform real property appraisal services for Kodak between 1997 and 2005. In return for hiring Nicolo, Finnman, and Camarata would receive money representing kickbacks from Nicolo. In addition, Charles Schwab, while the Greece Town Assessor, also received kickbacks from Nicolo in connection with various property tax assessment matters involving property located in Greece.
The forfeiture aspect of the case resulted in considerable litigation over the several years following the criminal convictions. In February 2009, U.S. District Judge David G. Larimer ultimately agreed with the Government’s position and ordered over $12,000,000 in assets to be forfeited from the various defendants. The ruling spurred further litigation involving John Nicolo’s wife, Constance Roeder, who claimed that much of the money was hers and had nothing to do with Nicolo’s crimes. In November 2011, Judge Larimer approved a settlement which awarded the government more than $10,000,000 and returned $2,000,000 to Constance Roeder, which was determined not to have been involved in her husband’s appraisal fund.
Of the $10,000,000 settlement, the Eastman Kodak Co. received $7,800,000 and the Town of Greece received $1,900,000. In addition, IBM received $70,000, RG&E $13,000, ITT Space Systems, LLC $633,000, and Global Crossing $33,750.
The majority of the properties forfeited involved large financial accounts where John Nicolo concealed his illegal proceeds. Some of the accounts were valued in excess of several million dollars. Nicolo also forfeited BMW and Volvo automobiles and a Bentley, valued at $165,000, which was purchased with illegal cash just months prior to its seizure in 2005. In addition, Mark Camarata forfeited almost $1,000,000 and the government seized high-end vehicles and two residences from Charles Schwab, one of which was a home in an exclusive South Carolina golf community.
Furthermore, a vacation home and a number of parcels overlooking Keuka Lake, worth approximately $500,000, are still to be sold. That money will be forfeited to the government and used to assist law enforcement in further criminal investigations in our community.
Following the criminal prosecution, John Nicolo and Charles Schwab were sentenced to 12 years in federal prison, Mark Camarata was sentenced to 24 months, and David Finnman received 21 months.
“This case sends a strong message that public corruption and corporate fraud will not be tolerated,” said U.S. Attorney Hochul. “Those who attempt to make financial gains by victimizing others not only risk destroying their families but also losing their freedom. As this case demonstrates, our office is also fully prepared to utilize the federal forfeiture laws to take the ‘profit’ out of such crimes by stripping defendants of their illicit proceeds and returning them to innocent victims where they belong.”
The successful prosecution and restitution are the result an investigation by special agents of the Federal Bureau of Investigation, under the direction of Special Agent in Charge Christopher M. Piehota; the Internal Revenue Service, under the direction Special Agent in Charge Charles R. Pine; the Postal Inspection Service, under the direction of Inspector in Charge Robert Bethel; and the Greece Police Department, under the direction of Chief Todd K. Baxter.
GoMoPa Stalker Dream Team – STARRING “DIE GoMoPa”-SCHAISSHAUSFLIEGEN (EIGENBEZEICHNUNG)
AMIR RAPAPORT – Israel and the US Have an Understanding on the Iranian Issue
All the anonymous statements coming from Israeli and US “senior officials” regarding the question of whether or not Israel will attack Iran (against the US’s advice) should be treated with a measure of suspicion.
It is likely that there is a significant amount of psychological warfare involved in these reports. The goal is clear enough: to increase pressure on Iran, which already exists as a result of more economic sanctions, mysterious explosions, and the assassinations of senior nuclear scientists.
The “senior official” understandings likely emerged from two starting points, which are seemingly contradictory. The first is that Israel cannot commit to the US in any way, especially that the US be notified more than several hours in advance of an air strike. The second is that there is truth to the words recently spoken by US President Barack Obama, claiming that the defense relationship between Israel and the US has never been closer. The issue of the Iranian nuclear program is one of the most central issues discussed in the joint strategic dialogue between Jerusalem and Washington, a dialogue that is the most closely coordinated one ever.
The discussions over this issue began back in the early 1990s, and are now expressed in ongoing intelligence updates regarding the various aspects of the Iranian nuclear program. These updates are conducted by senior officials in the branches of the Israeli defense establishment – the Directorate of Military Intelligence and the Mossad, and the Joint Political-Military Group (JPMG). This group, which gathers once every quarter, is comprised of diplomats, military and intelligence personnel, and persons who deal with foreign policy. Essentially, it is a think-tank that handles the various aspects of the Iranian project, with the goal of deepening the level of intelligence cooperation in order to determine a basis for joint policy.
Above all else, the discussions concerning the Iranian issue are being carried out continuously in the political stratum. The bottom line is apparent: even if Israel does not commit to announcing an attack in advance, it won’t act as if the US isn’t in the neighborhood (who is increasing their presence in the Persian Gulf region).
By the way, the huge exercise that was planned for this spring, with the participation of US and Israeli forces, was meant to be another expression of the close cooperation between the countries. The exercise was delayed due to a desire to slightly ease the tension against Iran. It is now planned for October. However, it’s not unreasonable to consider that a war might erupt before then.
Eyes to the north
While global attention is focused on the issue of whether or not Israel will attack Iran, the IDF’s eyes are also observing the north – and are closely monitoring the bloodbath in Syria.
Gantz’s words from a few weeks ago, that the IDF is preparing to receive Alawite (the minority in Syria, among which is President Bashar Assad) refugees, reflects one of several possible scenarios. The questions remains, what will happen the day the Assad regime collapses?
A much more worrisome possibility is that the collapse of the Syrian regime will be accompanied by missile fire at Israel, in the sense of “I’m going down and taking you with me.” Another possibility, equally grave, is the transfer of large amounts of qualitative weapons from the Syrian army warehouses to Hezbollah in Lebanon. If Syria were to transfer very advanced antiaircraft systems to Lebanon, it’s quite possible that Israel would choose to operate in the form of a preemptive strike in this scenario as well – before the S125 systems would enter operational use.
Replacements during a sensitive period
Given the tension surrounding Iran and the north, this is not an ideal time to replace prominent IDF positions, as is expected to take place soon in the defense establishment. (The next IAF commander, Major General Amir Eshel, is expected to enter office in April.)
Another problematic element is the fact that the military secretaries of both the prime minister and the minister of defense are expected to be new (both are highly sensitive positions, and their entry is always accompanied by a measure of dissonance – there is no position in the IDF that prepares senior officers on how to conduct themselves in the tumultuous junction between the political and military sectors).
Brigadier General Itzik Turgeman, the new military secretary to the minister of defense, already took office and is now learning how to handle his position. Prime Minister Binyamin Netanyahu will need to select a new military secretary soon, as the current one, Major General Yochanan Locker, announced he would conclude his position and retire should he not be nominated the next Air Force Commander – which, as is known, he wasn’t.
Incidentally, the new Depth Command is increasing its activity in light of the preparations for a possible war on all fronts. The person responsible for the command, Major General Shai Avital, who returned from retirement, has already assembled a working team. Soon, they are expected to receive a surprising reinforcement: Brigadier General (Res.) Gal Hirsch, one of the more prominent figures from the Second Lebanon War.
Hirsch served as the commander of the Galilee Formation (the 91st Division) that was responsible for the Lebanese border. Hirsch became one of the symbols of the war due to his criticism, while on the other hand, the former Chief of Staff, Lieutenant General Dan Halutz, said (rightfully) that he was wronged. Hirsch, who was not among the bad commanders of the war (rather the opposite), resigned from the IDF after the war, and made money as a senior partner at the Israeli company Defensive Shield. The position which is currently intended for him may return him to the top military echelon, for the first time since the war.
UNVEILED – Putin Protest Portraits
|
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/putin-protest/pict19.jpg) In this Saturday, Feb. 4, 2012 photo, Dmitry Polosov, 25, a scientist, holds a poster reading “for the honor society, for responsible for every act, for freedom of knowledge, for good in the hearts, for love in the minds” as he poses in front of a white canvas placed in the middle of the crowd at a massive protest against Prime Minister Vladimir Putin’s rule in Bolotnaya square in Moscow. Despite temperatures plunging to minus 20 C (minus 4 F), thousands of Russians took to the streets of Moscow to challenge Putin’s bid. In this Saturday, Feb. 4, 2012 photo, Dmitry Polosov, 25, a scientist, holds a poster reading “for the honor society, for responsible for every act, for freedom of knowledge, for good in the hearts, for love in the minds” as he poses in front of a white canvas placed in the middle of the crowd at a massive protest against Prime Minister Vladimir Putin’s rule in Bolotnaya square in Moscow. Despite temperatures plunging to minus 20 C (minus 4 F), thousands of Russians took to the streets of Moscow to challenge Putin’s bid. |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/putin-protest/pict12.jpg) In this Saturday, Feb. 4, 2012 photo, Tatyana Lazareva, 46, a television presenter, holds a poster reading “move on to the next level” as she poses in front of a white canvas placed in the middle of the crowd at a massive protest against Prime Minister Vladimir Putin’s rule in Bolotnaya square in Moscow. In this Saturday, Feb. 4, 2012 photo, Tatyana Lazareva, 46, a television presenter, holds a poster reading “move on to the next level” as she poses in front of a white canvas placed in the middle of the crowd at a massive protest against Prime Minister Vladimir Putin’s rule in Bolotnaya square in Moscow. |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/putin-protest/pict14.jpg) In this Saturday, Feb. 4, 2012 photo, Vyacheslav Barannikov, 38, an engineer, wears a white ribbon reading “For Russia without Putin” as he poses in front of a white canvas placed in the middle of the crowd at a massive protest against Prime Minister Vladimir Putin’s rule in Bolotnaya square in Moscow. In this Saturday, Feb. 4, 2012 photo, Vyacheslav Barannikov, 38, an engineer, wears a white ribbon reading “For Russia without Putin” as he poses in front of a white canvas placed in the middle of the crowd at a massive protest against Prime Minister Vladimir Putin’s rule in Bolotnaya square in Moscow. |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/putin-protest/pict8.jpg) In this Saturday, Feb. 4, 2012 photo, Yekaterina, 26, a translator, wears a scarf with the name of presidential contender Mikhail Prokhorov as she poses in front of a white canvas placed in the middle of the crowd at a massive protest against Prime Minister Vladimir Putin’s rule in Bolotnaya square in Moscow. In this Saturday, Feb. 4, 2012 photo, Yekaterina, 26, a translator, wears a scarf with the name of presidential contender Mikhail Prokhorov as she poses in front of a white canvas placed in the middle of the crowd at a massive protest against Prime Minister Vladimir Putin’s rule in Bolotnaya square in Moscow. |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/putin-protest/pict9.jpg) In this Saturday, Feb. 4, 2012 photo, Kirill, 26, a scientist, wears a scarf with the name of presidential contender Mikhail Prokhorov as he poses in front of a white canvas placed in the middle of the crowd at a massive protest against Prime Minister Vladimir Putin’s rule in Bolotnaya square in Moscow. In this Saturday, Feb. 4, 2012 photo, Kirill, 26, a scientist, wears a scarf with the name of presidential contender Mikhail Prokhorov as he poses in front of a white canvas placed in the middle of the crowd at a massive protest against Prime Minister Vladimir Putin’s rule in Bolotnaya square in Moscow. |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/putin-protest/pict13.jpg) In this Saturday, Feb. 4, 2012 photo, Nina Lipkina, 53, unemployed, poses in front of a white canvas placed in the middle of the crowd at a massive protest against Prime Minister Vladimir Putin’s rule in Bolotnaya square in Moscow. In this Saturday, Feb. 4, 2012 photo, Nina Lipkina, 53, unemployed, poses in front of a white canvas placed in the middle of the crowd at a massive protest against Prime Minister Vladimir Putin’s rule in Bolotnaya square in Moscow. |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/putin-protest/pict10.jpg) In this Saturday, Feb. 4, 2012 photo, Gennady, 73, a pensioner, poses in front of a white canvas placed in the middle of the crowd at a massive protest against Prime Minister Vladimir Putin’s rule in Bolotnaya square in Moscow. In this Saturday, Feb. 4, 2012 photo, Gennady, 73, a pensioner, poses in front of a white canvas placed in the middle of the crowd at a massive protest against Prime Minister Vladimir Putin’s rule in Bolotnaya square in Moscow. |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/putin-protest/pict17.jpg) In this Saturday, Feb. 4, 2012 photo, Yana Romanova, 35, a designer, wears a white ribbon reading “For Russia without Putin” as she poses in front of a white canvas placed in the middle of the crowd at a massive protest against Prime Minister Vladimir Putin’s rule in Bolotnaya square in Moscow. In this Saturday, Feb. 4, 2012 photo, Yana Romanova, 35, a designer, wears a white ribbon reading “For Russia without Putin” as she poses in front of a white canvas placed in the middle of the crowd at a massive protest against Prime Minister Vladimir Putin’s rule in Bolotnaya square in Moscow. |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/putin-protest/pict11.jpg) In this Saturday, Feb. 4, 2012 photo, Artur Gazarov, 43, wears a white ribbon reading “For Russia without Putin” as he poses in front of a white canvas placed in the middle of the crowd at a massive protest against Prime Minister Vladimir Putin’s rule in Bolotnaya square in Moscow. In this Saturday, Feb. 4, 2012 photo, Artur Gazarov, 43, wears a white ribbon reading “For Russia without Putin” as he poses in front of a white canvas placed in the middle of the crowd at a massive protest against Prime Minister Vladimir Putin’s rule in Bolotnaya square in Moscow. |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/putin-protest/pict20.jpg) In this Saturday, Feb. 4, 2012 photo, Liliya Pevter, 62, a pensioner, poses in front of a white canvas placed in the middle of the crowd at a massive protest against Prime Minister Vladimir Putin’s rule in Bolotnaya square in Moscow. In this Saturday, Feb. 4, 2012 photo, Liliya Pevter, 62, a pensioner, poses in front of a white canvas placed in the middle of the crowd at a massive protest against Prime Minister Vladimir Putin’s rule in Bolotnaya square in Moscow. |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/putin-protest/pict15.jpg) In this Saturday, Feb. 4, 2012 photo, Igor German, 23, an engineer, poses in front of a white canvas placed in the middle of the crowd at a massive protest against Prime Minister Vladimir Putin’s rule in Bolotnaya square in Moscow. In this Saturday, Feb. 4, 2012 photo, Igor German, 23, an engineer, poses in front of a white canvas placed in the middle of the crowd at a massive protest against Prime Minister Vladimir Putin’s rule in Bolotnaya square in Moscow. |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/putin-protest/pict16.jpg) In this Saturday, Feb. 4, 2012 photo, Mikhail Shats, 46, an actor, poses in front of a white canvas placed in the middle of the crowd at a massive protest against Prime Minister Vladimir Putin’s rule in Bolotnaya square in Moscow. In this Saturday, Feb. 4, 2012 photo, Mikhail Shats, 46, an actor, poses in front of a white canvas placed in the middle of the crowd at a massive protest against Prime Minister Vladimir Putin’s rule in Bolotnaya square in Moscow. |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/putin-protest/pict18.jpg) In this Saturday, Feb. 4, 2012 photo, Dima Kuzmich, 29, a bank employee, poses in front of a white canvas placed in the middle of the crowd at a massive protest against Prime Minister Vladimir Putin’s rule in Bolotnaya square in Moscow. In this Saturday, Feb. 4, 2012 photo, Dima Kuzmich, 29, a bank employee, poses in front of a white canvas placed in the middle of the crowd at a massive protest against Prime Minister Vladimir Putin’s rule in Bolotnaya square in Moscow. |
BÖRSE ONLINE ÜBER DIE “GoMoPa”-SCHEISSHAUSFLIEGEN (EIGENBEZEICHNUNG)
Egypt – Major Ze`ev Gur Arie (Wolfgang Lotz) -THE FAMOUS MOSSAD SPY
Lotz was born at Mannheim, Germany in 1921 to a Jewish mother and a non-Jewish German father. Lotz’s father was a theater director working alongside his mother who was an actress. His parents were non-religious to the extent that Lotz’s mother did not even care to have her son circumcised at birth, contrary to Jewish birth rituals. Later on, this turned out to be to his advantage in his career as a spy; the fact that Lotz hadn’t been circumcised enabled him to convince his lovers that he wasn’t Jewish. His parents divorced in 1931 and in 1933 after Hitler came to power, Lotz and his mother emigrated to Palestine.Lotz and his mother settled in Tel-Aviv. He adopted the Hebrew name Ze’ev Gur-Arie, and started to study at the agricultural school at Ben Shemen. In 1936 he joined the Haganah and was engaged in a number of security duties.After the outbreak of World War II in 1939 Lotz was recruited into the British Army because of his knowledge of the German language. He was stationed at Egypt where he joined an intelligence unit and mostly interrogated German POWs. After the war he returned to Israel and was involved in smuggling weapons for the Haganah.In 1948 Lotz married Rivka and they had a son, Oded. At the outbreak of the Independence War in 1948 Lotz joined the newly formed Israel Defense Forces and served at the rank of Captain. He took part at the battle around Latrun. During the Sinai War in 1956 he already rose to the rank of Major and commanded an Infantry brigade.After the war Lotz joined Aman. His superiors planned to send him to Egypt to gather intelligence on Gamal Abdel Nasser’s armaments plans. Aman also hoped that because of Lotz’s command of the German language and his Aryan appearance, he could infiltrate the circle of German scientists who worked at the Egyptian armaments programs.Lotz was sent to Germany in 1959 in order to base his cover story as a German business man, ex-Wehrmacht officer who served in North Africa and an ex-member of the Nazi Party who after living for 11 years in Australia where he worked on breeding horses, came back to Egypt in order to establish a riding club. The North Africa cover was made because Lotz, who had interrogated hundreds of the German POWs in World War II, was familiar with their way of life and could easily tell war stories about his “comrades”, and the riding club cover was made in order to allow Lotz to have contact with Egyptian high society.Lotz arrived in Cairo in 1960 and began immediately to form friendships with high ranking Egyptian officials and military personnel.Lotz traveled to Paris in June 1961 for a meeting with his operators (he was in the meantime transferred to the responsibility of the Mossad) , where he received large amounts of money and a transponder for sending secret messages. During the train travel from Paris, Lotz met a German woman called Waltraud and decided to marry her, despite the fact he was married to another woman in Israel and didn’t discuss it with his operators. The Mossad was horrified by this and even considered calling Lotz back, but in the end the Mossad allowed Lotz to continue his mission and his wife was allowed to join him. While she soon discovered his real occupation, she was told Lotz worked for NATO and she began to help him.In Cairo Lotz finally opened his riding club and continued to befriend the elite of the Egyptian society. He managed to persuade them to show him the Egyptian missile launch sites and he gathered intelligence of the Egyptian military and its industries. He also composed a list of German scientists that worked for the Egyptians and in September 1964 he sent a letter bomb to some of them, threatening them to cease their work.In 1965 the GDR head of state made an official visit to Egypt and as a gesture to the East Germans, the Egyptians arrested 30 citizens of West Germany. Lotz was one of them. Thinking he was exposed, Lotz confessed to being a spy but stuck to his cover story and claimed he was tempted by the Israelis to spy for them in exchange for them giving him funds to establish his riding club.The Egyptians believed Lotz even when evidence arrived from Germany which pointed to his true identity. Lotz and his wife were put on trial and the Mossad managed to get him represented by a German lawyer and ensure a German observer from the embassy who oversaw the fairness of the trial.Lotz was sentenced to life imprisonment on 21 August 1965 and his wife was sentenced to three years in jail. Lotz and his wife were released in the prisoner exchange in 1968 following the Six-Day War. He resided in Israel until the death of his wife, Waltraud, in 1973, who died at the hands of the Egyptian intelligence. After that he spent time in the USA and resided in Germany until his death in 1993. He was buried in Israel with full military honors.In the video his sun Prof.Oded Gur Arie presents his father also in rare video inside.
Alle irrealen STASI-Internet-Google-Manipulationen werden die Wahrheit ebensowenig aufhalten wie die reale “DIE MAUER”
FROM THE FBI – Leader of Revolution Muslim Pleads Guilty to Using Internet to Solicit Murder and Encourage Violent Extremism
ALEXANDRIA, VA—Jesse Curtis Morton, aka Younus Abdullah Muhammed, 33, of New York City, pleaded guilty today to using his position as a leader of Revolution Muslim Organization’s Internet sites to conspire to solicit murder, make threatening communications, and use the Internet to place others in fear.
Neil H. MacBride, U.S. Attorney for the Eastern District of Virginia; James W. McJunkin, Assistant Director in Charge of the FBI’s Washington Field Office; and Raymond W. Kelly, New York City Police Commissioner, made the announcement after the plea was accepted by U.S. District Judge Liam O’Grady.
Morton faces a maximum penalty five years in prison for each of the three charges when he is sentenced on May 18, 2012.
“Jesse Morton operated Revolution Muslim to radicalize those who saw and heard his materials online and to incite them to engage in violence against those they believed to be enemies of Islam,” said U.S. Attorney MacBride. “We may never know all of those who were inspired to engage in terrorism because of Revolution Muslim, but the string of recent terrorism cases with ties to Morton’s organization demonstrates the threat it posed to our national security. We’re grateful to the FBI, NYPD, and their law enforcement partners throughout the world who made today’s conviction possible.”
“Individuals such as Morton who encourage violence and create fear over the Internet are a danger to our society and to the freedoms we enjoy as citizens,” said Assistant Director in Charge McJunkin. “Today’s plea, and other recent cases of those associated with Morton’s organization, demonstrate the widespread nature of this danger. Together with our partner law enforcement agencies, and with the assistance of the community, the FBI will continue to pursue those who promulgate violent extremism and promote the radicalization of others.”
“Fortunately, NYPD Intelligence Division detectives were in a position to learn exactly how Morton used the Internet to conspire to solicit murder, and how he encouraged others to solicit the murder of an artist whose material he deemed offensive,” said Police Commissioner Kelly. “This important plea resulted because the NYPD’s monitoring of Morton’s activities, combined with the investigative and prosecutorial expertise of the FBI and the U.S. Attorney for Eastern District of Virginia, made for a strong case, in addition to a strong partnership.”
According to a statement of facts filed with his plea agreement, Morton founded Revolution Muslim in December 2007 and created various online forums that contained postings and information supportive of violent extremism. Morton and his associates used the organization’s websites to encourage Muslims to engage in violence against those they believed to be enemies of Islam and to support Osama bin Laden, Anwar Al-Awlaki, al Qaeda, the Taliban, and others espousing violence. They posted messages in support of the terrorist attacks on Sept. 11, 2001, the November 2009 killings at Ft. Hood and attacks and future threats against Jewish organizations, among others.
Through his online forums, Morton conspired with Zachary Chesser, of Fairfax County, Va., and others to solicit the murder of an artist tied to the “Everybody Draw Mohammed Day” movement in May 2010, including posting online a magazine that included the artist in a hit list for violent extremists to take out and a message from Anwar Al-Awlaki that explicitly called for the artist’s assassination. In justifying these actions, Morton posted online a speech of his asserting that “Islam’s position is that those that insult the Prophet may be killed” and exhorting his listeners to fight the “disbelievers near you.”
In addition, Morton admitted through his statement of facts that he aided Chesser in taking repeated steps in April 2010 to encourage violent extremists to attack the writers of South Park for an episode that featured Muhammad in a bear suit, including highlighting their residence and urging online readers to “pay them a visit.” Among the steps they took were posting on multiple occasions speeches by Anwar Al-Awlaki, which explained the Islamic justification for killing those who insult or defame Muhammad. Morton worked with Chesser to draft a message for the website regarding the South Park threats, including a quote from Osama bin Laden that “If there is no check in the freedom of your words, then let your hearts be open to the freedom of our actions.” Morton and Chesser posted the final version of this statement on various extremist online forums, and Chesser told Morton that he expected the statement would “scare the kuffar.” Kuffar is an Arabic term, referring to an unbeliever, or disbeliever, in Islam.
Chesser was arrested on July 21, 2010, charged with providing material support to al Shabaab and later also pleaded guilty to communicating threats and soliciting violent extremists to desensitize law enforcement. Four days after Chesser’s arrest, Morton fled to Morocco, where he resided until his arrest on U.S. charges on May 26, 2011.
In his statement of facts, Morton admitted that the Revolution Muslim websites contained the writings of and/or contributed to the radicalization of individuals who were inclined to engage in violence, including the following:
Samir Khan, previously of Charlotte, N.C., before moving to Yemen in 2009, was authorized by Morton to post materials on Revolution Muslim, and Morton provided Khan with two articles for the first two online editions of Jihad Recollections, an online magazine dedicated to violent extremism. In July 2010, Morton posted the first edition of Inspire magazine, an English-language magazine supporting al Qaeda that Morton believed to be the product of Khan. The magazine included an eight-page article titled “Make a bomb in the kitchen of Your Mom,” with detailed instructions regarding the construction of an explosive device.
Bilal Zaheer Ahmad, of the United Kingdom, was provided the password to Revolution Muslim by Morton and given permission to post messages. In November 2010, Ahmad praised Roshonara Choundhry for attempting to kill a British member of parliament over his support for the Iraq war and posted a list of 383 members of parliament who had voted for the Iraq war, along with suggestions on how to get in to see them and a link to a store selling a weapon similar to that used in Choundhry’s attack. Ahmad told Morton that the purpose of the post was to “make those MPs fearful.”
Abdel Hameed Shehedah, a former resident of Staten Island, N.Y., who was charged in October 2010 of making false statements involving his alleged attempt to travel to Pakistan to join a fighting group such as the Taliban. The statement of facts states that Shehedah attended Revolution Muslim meetings, made his website, civiljihad.com, a feeder site for Revolution Muslim and eventually arranged for all visitors to his website be routed automatically to Revolution Muslim.com.
Rezwan Ferdaus, of Ashland, Mass., was charged in September 2011 with plotting to attack the Pentagon and U.S. Capitol using large remote controlled aircraft filled with C-4 plastic explosives. The statement of facts states that in February 2010, Ferdaus e-mailed Morton asking for counsel regarding his duties as a Muslim and whether martyrdom operations were proper practice. Morton replied that martyrdom operations must be judged by intention but can have “enormous benfits (sic) in a war of attrition.”
Colleen R. LaRose, aka “Jihad Jane,” of Montgomery County, Pa., was charged in March 2010 with a variety of terrorism-related offenses, including plotting to kill Lars Vilks, a Swedish cartoonist who has been the subject of several murder threats based on his artwork depicting Muhammad. According to the statement of facts, Morton notified Sheikh Abdullah Faisal, a Muslim cleric convicted in the United Kingdom of soliciting murder, that LaRose was a subscriber to Revolution Muslim YouTube accounts.
Antonio Benjamin Martinez, of Baltimore, Md., was arrested and charged with plotting to bomb a military recruiting station in December 2010. The statement of facts states that one month prior to his arrest, Martinez viewed a video of Osama bin Laden and multiple terror training camp video clips on the Revolution Muslim website.
Jose Pimental, of New York City, was arrested and charged in November 2011 in connection with a plot to build and use a bomb to assassinate members of the U.S. military returning from active duty in Afghanistan. According to the statement of facts, Pimental contacted Morton saying that he was a big fan of Revolution Muslim, and that Morton recommended that Pimentel stay away from an individual because “there is high probability that he is working for the FBI.”
Mohamed Hamoud Alessa and Carlos Eduardo Almonte, both of New Jersey, were arrested in June 2010 on their way to Somalia to join a terrorist organization to kill individuals whose beliefs and practices did not accord with their ideology. The statement of facts states that both Alessa and Almonte were associates of Morton’s within the Revolution Muslim organization, and Morton was interviewed by investigators from the New York City Police Department on the day of their arrest.
This investigation is being conducted by the FBI’s Washington Field Office and the New York Police Department’s Intelligence Division. Assistant U.S. Attorneys Gordon D. Kromberg and Karen L. Dunn of the U.S. Attorney’s Office for the Eastern District of Virginia and Trial Attorney John T. Gibbs of the Counterterrorism Section in the National Security Division are prosecuting the case on behalf of the United States.
A copy of this press release may be found on the website of the U.S. Attorney’s Office for the Eastern District of Virginia at http://www.usdoj.gov/usao/vae. Related court documents and information may be found on the website of the District Court for the Eastern District of Virginia at http://www.vaed.uscourts.gov or on http://pacer.uspci.uscourts.gov.
DAS BETRUGSURTEIL GEGEN “BENNEWIRTZ” UND “PETER EHLERS” “GoMoPa”-PARTNER “MAURISCHAT” UND “VORNKAHL” WG BETRUGES AM EIGENEN ANLEGER
Über eine selbstgebaute Blogseite verbreiten die GoMoPa-Gangster eine gefälschte Stellung von Meridian Capital, um Verwirrung zu stiften.
Diese Blogseite existiert erst seit Dezember 2010.
Beweis:
http://www.hypestat.com/pressreleaser.org
Die Meridian Capital-Seite, das Original,
http://othergomopa.blogspot.com/
ist dagegen bereits seit2009 online
Beweis: Aussage Meridian Capital – das Unternehmen können Sie auch gerne direkt kontaktieren.
und
KLAUS DIETER MAURISCHAT IN DETENTION
Source: http://klaus-dieter-maurischat.blogspot.com/2009/01/klaus-dieter-maurischat-in-haft.html
Hintergrund: Die Verurteilung von Klaus Maurischat und Mark Vornkahl wegen Betruges am eigenen Anleger
Klaus Maurischat und Mark Vornkahl, Betreiber vonwww.gomopa.net: Am 24. April 2006 war die Verhandlung am Amtsgericht Krefeld in der Betrugssache: Mark Vornkahl / Klaus Maurischat ./. Dehnfeld. Aktenzeichen: 28 Ls 85/05 Klaus MaurischatLange Straße 3827313 Dörverden.Das in diesem Verfahren ausschließlich diese Betrugsache verhandelt wurde, ist das Urteil gegen Klaus Maurischat recht mäßig ausgefallen.Zusammenfassung der Verhandlung vom 24.04.2006 vor dem Schöffengericht des AG Krefeld in der Sache gegen Klaus Maurischat und Mark Vornkahl.Zur Hauptverhandlung erschienen:Richter Dr. Meister, 2 Schöffen,Staatsanwalt, Angeklagter Klaus Maurischat, vertr. durch RA Meier, Berlin; aus der U-Haft zur Verhandlung überführt.1. Eine Gerichtsvollzieherin stellt unter Ausschuss der Öffentlichkeit eine Urkunde an den Angeklagten Maurischat zu.2. Bei Mark Vornkahl wurde im Gerichtssaal eineTaschenpfändung vorgenommen.Beginn der HauptverhandlungDie Beklagten verzichten auf eine Einlassung zu Beginn.Nach Befragung des Zeugen Denfeld zum Sachverhalt wurde dieVerhandlung auf Wunsch der Staatsanwaltschaft und den Verteidigern unterbrochen.Der Angeklagte Maurischat gab nach Fortsetzung derHauptverhandlung Folgendes zu Protokoll:Er sähe ein, dass das Geld auf das falsche Konto gegangen sei und nicht dem eigentlichen Verwendungszweck zugeführt wurde. Das Geld sei aber zurückgezahlt worden und er distanziere sich ausdrücklich von einem Betrug.Schließung der BeweisaufnahmeDer Staatsanwalt verließt sein PlädoyerEr halte am Vorwurf des Betruges fest. Mit Hinweis auf die einschlägigen Vorstrafen des Angekl. Maurischatund auf laufende Ermittlungsverfahren, beantrage er ein Strafmaß von 1 Jahr und 6 Monaten.Er halte dem Angeklagten zu Gute, dass dieserWiedergutmachung geleistet habe, und dass dieser geständig war. Zudem läge die letzte Verurteilung wegen Betruges 11 Jahre zurück. Auch sei der Geschädigte nicht in existentielle Not geraten, wobei der Staatsanwalt nicht über noch laufende Verfahren hinweg sehen könne. Er läge aber dem Angeklagten Maurischat nahe, keine weiteren Aktivitäten im Bezirk der Staatsanwaltschaft Krefeld auszuüben, insbesondere möchte er, dass keine weiteren Anleger im Bezirk der Staatsanwaltschaft Krefeld durch GoMoPa akquiriert werden.Die Freiheitsstrafe soll zur Bewährung ausgesetzt werden.Plädoyer des Verteidigers des Angekl. Maurischat, Herrn RA MeierEr schließe sich, wie (in der Unterbrechung) vereinbart, dem Staatsanwalt an.Es stimme, dass sein Mandant Fehler in seiner Vergangenheit gemacht habe, und dass er auch diesmal einen Fehler begangen haben könnte, jedoch sei der Hinweis wichtig, dass sein Mandant aus diesen Fehlern gelernt habe.Der Angeklagte haben das letzte Wort.Maurischat sagt, es sei bereits alles gesagt worden.Unterbrechung zu Hauptverhandlung. Der Richter zieht sich mit den Schöffen zur Beratung zurück.Urteilsverkündung:Der Angeklagte wird des gemeinschaftlichen Betrugs für schuldig befunden.Der Angeklagte Klaus Maurischat wird zu einerFreiheitsstrafe von 1 Jahr und 6 Monaten verurteilt. Diese wird zur Bewährung ausgesetzt.Die Bewährungszeit wird auf 3 Jahre festgesetzt.Der Haftbefehl gegen Klaus Maurischat wird aufgehoben.Der Angeklagte trage die Kosten des Verfahrens.UrteilsbegründungDer Richter erklärt, dass eine Täuschung des Geschädigtenvorliegt und somit keine Untreue in Betracht kommen kann.Die Fragen, ob es sich um einen Anlagebetrug handele sei irrelevant. Er hält den Angeklagten die geleistete Wiedergutmachung zu Gute.Ebenso ist das Geständnis für die Angeklagten zu werten. Zudem liegt die letzte Verurteilung des Angeklagten Maurischat 11 Jahre zurück.Die Parteien verzichten auf Rechtsmittel. Das Urteil ist somit rechtskräftig.Mit dem heutigen Urteil endet ein Kapitel in derBetrugssache Goldman Morgenstern & Partners, Klaus Maurischat und Mark Vornkahl.Alle GoMoPa.net Verantwortlichen, Maurischat, Vornkahl und Henneberg sind nun vorbestrafte Abzocker und Betrüger und die Zukunft der Pseudoklitsche GoMoPa.net sieht duster aus.Mir dem Geständnis der beiden ABZOCKER MAURISCHAT UND VORNKAHL vor Gericht bricht ein jahrelangaufrechterhaltenes Lügengeflecht von einigen primitiven Betrügern zusammen. Gewohnheitsverbrecher und Denunzianten,die rechtschaffene Personen und Firmen in ihren Verbrecherforen kriminalisierten.
Editorial – Wer informiert und deckt STASI-“GoMoPa” in der Immobilienbranche ? Die Zersetzung
Liebe Leser,
ohne Zuträger und IM-Spitzel in der Immobilienbranche hätte STASI-“GoMoPa” nie diesen Zersetzungsgrad erreichen können.
Die neue STASI ist viel gefährlicher als die Neo-Nazis, denn sie sassen oder ev. sitzen sogar im Bundestag und anderen hohen deutschen Stellen.
Sie haben Millionen gebunkert und zehntausende ehemaliger STASI-Kriminellen verfügbar.
Ehemalige STASI-Leute sind im LKA Brandenburg und vielen anderen Stellen in Deutschland.
Die Ent-STASI-fizierung gab es nie.
Deshalb können diese Kriminellen weitermachen und ihre Zersetzung und Unterwanderung vorantreiben. Denn nur das haben sie gelernt.
Diesmal geht es um Geld, Macht, Einfluss und Eitelkeit.
Etliche dieser Prachtexemplare der Spezies Unmensch haben wir enttarnt.
Doch in Deutschland wird weiter geschlafen!
Wir haben alle gesehen im Falle des sogenannten “Nationalsozialistischen Untergrunds” wie hier agiert wird und welche Folgen dies hat.
Wir kennen die wichtigsten Herrschaften, deren Milieu, Motive, Mitarbeiter Kontaktdaten, Delikte und Verflechtungen übrigens auch im Justiz-Apparat bereits.
Man muss nur 1 und 1 zusammenzählen…
Herzlichst Ihr
Bernd Pulch,Magister Artium der Publizistik, Komparatistik und Germanistik
CONFIDENTIAL – Orange County Private Sector Terrorism Response Group TV Guide Weekly Bulletin

The following is an example of a weekly bulletin released by the Orange County Intelligence Assessment Center to local businesses through its “Private Sector Terrorism Response Group” (PSTRG). The PSTRG was created in “December 2001 to create a private sector partnership [that can] effectively address private sector safety, incident management, employee education and public health consequences of potential attacks on the critical infrastructure within Orange County. Two large groups involved with PSTRG are the Orange County Business Council, of which 80% of the major businesses in Orange County are members, and Technet, a consortium of 28 high tech firms.” The bulletin includes excerpts of news articles related to terrorism, a list of upcoming events, including dirt bike events and rodeos, as well as a helpful list of upcoming television shows on the History Channel and other networks that relate in some manner to terrorism.
Iran Threatens U.S. Ships, Alarms Oil Markets: Iran escalated its war of words with the United States on Tuesday with a warning to Navy ships to stay out of the strategic Strait of Hormuz, remarks that rattled commodities markets and helped send oil prices soaring. The latest in a series of provocative statements by Iranian leaders was delivered by the Iranian armed forces commander, Gen. Ataollah Salehi, who appeared to threaten a U.S. aircraft carrier that steamed out of Persian Gulf waters last week. The Obama administration brushed aside the threat, but the increasingly bellicose tone, coupled with new economic sanctions against Iran expected to take effect in the coming weeks because of its nuclear program, helped cause the price of oil to jump more than 4 percent to $103 a barrel. The threat against U.S. ships was the latest in a series of aggressive moves by Iran, which within a week has tested new missiles, boasted of breakthroughs in nuclear technology and vowed to shut down shipping in the Strait of Hormuz, the passageway for one-sixth of the world’s oil supply.
http://www.tampabay.com/incoming/iran-threatens-us-ships-alarms-oil-markets/1209026
Iran seeking to expand influence in Latin America: Iran is quietly seeking to expand its ties with Latin America in what U.S. officials and regional experts say is an effort to circumvent economic sanctions and gain access to much-needed markets and raw materials. The new diplomatic offensive, which comes amid rising tensions with Washington and European powers, includes a four-nation swing through South and Central America this month by Iranian President Mahmoud Ahmadinejad. His government has vowed to increase its economic, political and military influence in the United States’ back yard. The visit reinforces recent commitments by Iran to invest millions of dollars in economic development projects for the region, from a mining joint venture in Ecuador to factories for petrochemicals and small-arms ammunition in Venezuela. Iran has also dramatically expanded its diplomatic missions throughout the hemisphere and dispatched members of its elite Quds Force — the military unit U.S. officials in October linked to a foiled assassination plot in Washington — to serve in its embassies, U.S. officials and Iran experts say.
http://www.washingtonpost.com/world/national-security/iran-seeking-to-expand-influence-in-latin-america/2011/12/30/gIQArfpcUP_story.html
Hackers Reveal Personal Data of 860,000 Stratfor Subscribers: A computer hacking group has revealed email addresses and other personal data from former Vice President Dan Quayle, former Secretary of State Henry A. Kissinger, and hundreds of U.S. intelligence, law enforcement and military officials in a high-profile case of cyber-theft. The unauthorized release of account information for 860,000 subscribers to Stratfor, a Texas-based company that provides analysis of national and international affairs, makes it possible to identify some subscribers and, in theory, impersonate them in cyberspace, analysts warned. The data were released in two batches last month by the AntiSec faction of Anonymous, a self-described hacker collective. It also disclosed about 75,000 names, addresses and credit card numbers associated with Stratfor customers, including Kissinger and Quayle. Bumgarner said the Stratfor data included 19,000 email addresses from the “.mil” domain, meaning members of the military. He also found 212 email addresses from the FBI; 71 from the Defense Intelligence Agency, the Pentagon’s spying arm; 29 from the National Security Agency, which conducts global eavesdropping and cyber espionage; and 24 from the CIA. Bumgarner said he used off-the-shelf software to crack many of the Stratfor passwords. One intelligence officer used “intel” as a password, and a Navy SEAL officer used “frogman1,” he said. After the attack, Stratfor took its website off line and wrote on its Facebook page that it was cooperating with law enforcement. AntiSec said it targeted the company in part because it had poor network security.
http://www.latimes.com/news/nationworld/nation/la-na-cyber-theft-20120104,0,90925.story
DOWNLOAD ORIGINAL DOCUMENT HERE
DIE HANDELSBLATT-GRUPPE ÜBER DIE NEO-STASI STALKER UND SERIEN-RUFMÖRDER DER “GoMoPa”
The Mossad Spy in Egypt – Max Bineth – Success and Suicide
Egypt – Meir Max Bineth
 |
| Alleged Israeli spy Meir Max Bineth , one of the thirteen accused of spying in the Supreme Military Court in Cairo, Egypt, Dec. 11, 1954. Bineth was employed by Anglo-Egyptian Motors Company in Cairo. Bineth alive – This is picture of Bineth alive, before he committed suicide by slashing his wrists in Cairo cell.In this picture Max Bineth talks with General Mohamed Naguib President of Egypt 1952-1954 . (Bineth Family Photo) |
 |
| Alleged Israeli spy Max Bineth, one of the thirteen accused of spying in the Supreme Military Court in Cairo, Egypt, Dec. 11, 1954. Bineth was employed by Anglo-Egyptian Motors Company in Cairo. Bineth committed suicide by slashing his wrists in Cairo cell.In this picture Max Bineth sends a postcard to his daughter Michel signed by General Mohamed Naguib President of Egypt 1952-1954 as friendship. ( Bineth Family Photo) |
 |
| Alleged Israeli spy Max Bineth, one of the thirteen accused of spying, enters the Supreme Military Court for the start of the trial, in Cairo, Egypt, Dec. 11, 1954. Bineth was employed by Anglo-Egyptian Motors Company in Cairo. This is the last known picture of Bineth alive, he committed suicide by slashing his wrists in Cairo cell. (AP Photo) AP called him Max Bennet. |
 |
| Alleged Israeli spy Max Bineth, one of the thirteen accused of spying,was found dead in his cell in a Cairo Prison, in Cairo, Egypt, Dec. 21, 1954. Bineth was employed by Anglo-Egyptian Motors Company in Cairo. Bineth committed suicide by slashing his wrists in Cairo cell (AP Photo) AP called him Max Bennet. |
 |
| Alleged Israeli spy Max Bineth , one of the thirteen accused of spying in the Supreme Military Court in Cairo, Egypt, Dec. 11, 1954. Bennet was employed by Anglo-Egyptian Motors Company in Cairo. Bineth alive – This is picture of Bineth alive, before he committed suicide by slashing his wrists in Cairo cell.In this picture Max Bineth dancing with his Israeli wife Jane in a party in Egypt the wife & small daughter Michel arrived to Egypt with fake docs. They left Egypt after a short time (Bineth Family Photo) |
Max Bineth Site – Made by his daughter Michel Dagan Bineth
Morde der STASI im Westen mit “Verschleierungspotential – viel schlimmer als die Morde der Zwickauer Zelle”
CONFIDENTIAL – New Jersey Office of Homeland Security School Bomb Plot Warning

(U//FOUO) On January 25, 2012, police officers in Utah arrested two teenagers after discovering that they planned to bomb their high school. The plot was foiled because another student received suspicious text messages from one of the boys and notified school administrators. During the subsequent investigation, police were able to corroborate the initial tip. The two suspects had blueprints of the school and planned to steal a plane at a nearby airport after their attack. They told police they were learning to fly on a flight-simulator program on their home computers.
Two Teenagers Arrested After Bomb Plot Discovered
(U//FOUO) Dallin Morgan, 18, and a 16-year-old were arrested at Roy High School, about 30 miles north of Salt Lake City, for allegedly planning to detonate a bomb in a school assembly. The attack was prevented as a result of one student informing school administrators about ominous text messages that she received from one of the suspects. The student stated that one of the messages warned her not to go to school if the suspect told her to stay away on a particular day.
(U//FOUO) From a school security perspective, the elaborate preoperational planning in this plot is noteworthy. The two teenagers had detailed blueprints of the school and the security system, to the extent that they knew how to avoid being photographed on the surveillance cameras. The suspects also purchased a flight-simulator computer program, books, and manuals to teach themselves how to operate an aircraft. Investigators believe that they were planning to escape by stealing an aircraft at the Ogden airport, possibly attempting to fly to another country.
(U//FOUO) Investigators have stated that the two teenagers were inspired by the Columbine High School shootings in Colorado in 1999. Last month, the 16-year-old student interviewed the principal of Columbine High School regarding the shootings and security measures by claiming he was researching an article for his high school newspaper. The two students claimed that they sought to overshadow the attack at Columbine and that any comparison to that attack was offensive, because they said that “those killers only completed 1 percent of their plans.”
(U//FOUO) Investigators are trying to determine how close the two suspects were to conducting an attack. The FBI is examining their computers. Searches of the students’ homes and two cars uncovered no explosives. Currently, the motives of the suspects have not been ascertained, except for one text message that noted that they sought “revenge on the world.”
Implications for New Jersey
(U//FOUO) This incident was averted after one student realized the seriousness of the threat by these two suspects. It demonstrates the importance of encouraging students, teachers, school resource officers, and school administrators to report suspicious activity. It also provides a current case study for New Jersey law enforcement and school administrators regarding preparations and other activities that can lead up to an attack at a school.
DOWNLOAD ORIGINAL FILE HERE
TOP-SCRET – THE FBI FILE ABOUT STEVEN JOBS – THE FOUNDER OF APPLE
 |
|---|
Background Investigation of Steve Jobs Released
The 191-page document, released under the Freedom of Information Act (FOIA), consists of the FBI’s 1991 background investigation of Steve Jobs for an appointed position on the U.S. President’s Export Council. The release also includes documents related to a 1985 investigation of a bomb threat against Apple.
Steven Paul Jobs
Steven Paul Jobs (1955-2011) was a founder and leader of Apple Inc. (formerly Apple Computer Inc.). In 1991, Jobs was considered for an appointed position on the U.S. President’s Export Council. This release consists of the FBI’s 1991 background investigation of Jobs for that position and a 1985 investigation of a bomb threat against Apple.
DOWNLOAD THE ROIGINAL FILE HERE
Alleged Israeli spy Victorine Nino, alias Marcelle,
 Alleged Israeli spy Victorine Nino, alias Marcelle, one of the thirteen accused of spying, reads an arabic newspaper in the Supreme Military Court during a recess of the trial, in Cairo, Egypt, Dec. 11, 1954. Nino was employed by a local British firm in Cairo. At left is an Egyptian policeman (
Alleged Israeli spy Victorine Nino, alias Marcelle, one of the thirteen accused of spying, reads an arabic newspaper in the Supreme Military Court during a recess of the trial, in Cairo, Egypt, Dec. 11, 1954. Nino was employed by a local British firm in Cairo. At left is an Egyptian policeman (
ISREAL DEFENSE – Syria: Air Forces and Artillery Opened Heavy Fire on Homs Syria

Syrian President Bashar al-Assad is continuing the brutal oppression of the rebels in the city of Homs: less than 48 hours after the artillery attack on the city, which cost the lives of hundreds of people, Syrian opposition organizations are reporting that air and artillery forces loyal to the president have opened fire on the city, resulting in dozens of people dead and wounded.
According to reports in the Arab media, residential buildings were bombed and even collapsed, and it was also reported that a hospital in the city was damaged by the shelling.
In contrast to previous events, the Syrian air force is taking a prominent part in the attack of the rebelling city.
Syrian opposition members are also claiming that a force of army deserters has taken over a military outpost near the city of Idlib and killed three officers.
According to the claim, 19 Syrian soldiers have fallen into the hands of the rebels.
Over the weekend, China and Russia vetoed a proposal at the U.N. Security Council to denounce the actions of the Assad regime in Syria. The veto of both countries resulted in exceptionally harsh criticism from the West, primarily from the US, which claimed that it was a “disgusting and shameful” move.
According to the Syrian opposition organizations, more than 7,000 people, including 461 children, have been killed in Syria since the start of the riots in March 2011. According to UN figures published nearly two months ago, the number of fatalities stands at 5,000.
TOP-SECRET-Assistant Administrator of Houston Hospital Indicted for Alleged Role in $116 Million Medicare Fraud Scheme
WASHINGTON—An assistant administrator of a Houston hospital was arrested today on charges related to his alleged participation in a $116 million Medicare fraud scheme involving false claims for mental health treatment, announced the Department of Justice, the FBI and the Department of Health and Human Services (HHS).
An indictment filed in the Southern District of Texas and unsealed today charges Mohammed Khan, 62, of Houston, with one count of conspiracy to commit health care fraud, one count of conspiracy to pay and receive illegal health care kickbacks and five counts of paying or offering to pay health care kickbacks. Khan is expected to make his initial appearance in federal court today in Houston.
“The indictment against Mr. Kahn alleges that he used his position as a hospital assistant administrator to submit millions in false claims to the Medicare program,” said Assistant Attorney General Lanny A. Breuer of the Justice Department’s Criminal Division. “According to the charges, he paid kickbacks to patient recruiters, owners of group homes and assisted living facilities and beneficiaries so that he could fill his hospital with patients for whom he could bill the government for medically unnecessary services or services that were never provided. We will continue aggressively to pursue individuals who attempt to enrich themselves at the expense of the Medicare program.”
“The defendant charged in this indictment is accused of stealing precious Medicare resources by billing for services that were medically unnecessary or never provided,” said Special Agent in Charge Stephen L. Morris of the FBI’s Houston Field Office. “Our health care fraud efforts have never been more collaborative and aggressive. We will continue to work with our law enforcement partners to protect patients and fight against health care fraud.”
According to the indictment, Khan, as the assistant administrator of a Houston hospital, allegedly operated a scheme to defraud Medicare beginning in 2008 and continuing until his arrest today. Khan allegedly caused the submission of false and fraudulent claims for partial hospitalization program (PHP) services to Medicare through the hospital. A PHP is a form of intensive outpatient treatment for severe mental illness.
The indictment alleges that Khan paid kickbacks to owners and operators of group care homes and assisted living facilities and to patient recruiters in exchange for delivering ineligible Medicare beneficiaries to the hospital’s PHPs. The indictment alleges that Khan also paid kickbacks to Medicare beneficiaries who attended the hospital’s PHPs. These kickbacks included cigarettes, food, and coupons redeemable for items available at the hospital’s “country stores.” Khan and his co-conspirators submitted or caused to be submitted approximately $116 million in claims to Medicare for PHP services purportedly provided by the hospital to the recruited beneficiaries, when in fact, the PHP services were medically unnecessary or never provided.
Today’s charges were announced by Assistant Attorney General Breuer of the Justice Department’s Criminal Division; U.S. Attorney Kenneth Magidson of the Southern District of Texas; Special Agent in Charge Morris of the FBI’s Houston Field Office; Special Agent in Charge Mike Fields of the Dallas Regional Office of HHS’s Office of the Inspector General (HHS-OIG); the Texas Attorney General’s Medicaid Fraud Control Unit (MFCU); Special Agent in Charge Lucy R. Cruz of the Internal Revenue Service (IRS) Houston Field Office; Joseph J. Del Favero, Special Agent in Charge of the Chicago Field Office of the Railroad Retirement Board, Office of Inspector General (RRB-OIG); and Scott Rezendes, Special Agent in Charge of Field Operations of the Office of Personnel Management, Office of Inspector General (OPM-OIG).
The case is being prosecuted by Trial Attorney Laura M.K. Cordova, Attorney Allan Medina, Assistant Chief William Pericak and Deputy Chief Sam S. Sheldon of the Criminal Division’s Fraud Section. The case was investigated by the FBI, HHS-OIG, MFCU, IRS, RRB-OIG and OPM-OIG and was brought as part of the Medicare Fraud Strike Force, supervised by the Criminal Division’s Fraud Section and the U.S. Attorney’s Office for the Southern District of Texas.
Since their inception in March 2007, Medicare Fraud Strike Force operations in nine locations have charged more than 1,190 defendants who collectively have falsely billed the Medicare program for more than $3.2 billion. In addition, HHS’s Centers for Medicare and Medicaid Services, working in conjunction with the HHS-OIG, are taking steps to increase accountability and decrease the presence of fraudulent providers.
TOP-SECRET – American, British, Canadian, Australian and New Zealand (ABCA) Armies Security Force Capacity Building Handbook

SFCB has come to play an increasingly important role in each of our armies over the last decade and will undoubtedly feature in operations spanning the spectrum of conflict in the future. Its affect on organization, training, equipping and doctrine has been felt to a greater or lesser extent by each of us and will help define recent conflicts and their effects. However, SFCB cannot be done in isolation. What must be borne in the military planner‘s mind from the outset is that SFCB is a part of the wider SSR campaign and as a consequence must be part of a comprehensive approach. Furthermore, if coalition partners are present, an extra layer of complexity is present and must be planned for. Failure to take these two aspects into account runs the risk of failure at worst or a fragmented HNSF as a result, at best. This handbook aims to assist the military planner in their approach to SFCB. It is aimed at both commanders and staff officers, primarily on brigade and divisional staffs, although it also has utility for those charged with training, mentoring and advising HNSF forces at the tactical level.
…
UNDERSTANDING CULTURE AND DEVELOPING TRUST
Introduction
1. Failure to take culture and the building of trust seriously during SFCB could potentially lead to mission failure. For the purposes of this handbook culture is defined as the set of opinions, beliefs, values, and customs that forms the identity of a society. It includes social behavior standards (e.g., how men relate with women, children relate with adults), language (standard of speech), and religion (standards on how man relates with his mortality and creation). Trust is defined as that firm reliance on the integrity, ability, or character of a person or unit. Trust is both an emotional and logical act, which in practice is a combination of both. In assessing the HN culture ABCA nations should bear in mind from the start other cultures‘ perception of our predominantly Western lifestyle. In addition ABCA nations should beware not to fall into the trap of imposing their own culture, particularly their military culture, on HN forces where this may not be appropriate.
2. Recent Campaigns. Recent campaigns have seen ABCA forces repeatedly deploy to conduct SFCB in parts of the world quite different to their own. Not only do these nations often speak languages that are relatively rarely spoken or studied in ABCA nations, they also have very different cultures. These cultural differences include different religions, ethnic variances, tribal networks, or even comprehensive codes of practice, such as Pashtunwali1 in Afghanistan.
3. Implications of Cultural Issues upon SFCB. There are three major implications of conducting SFCB.
a. Culture Shock. ABCA forces need to understand the cycle through which they may pass during training and deployment when confronted by a different culture. This self-awareness and suggested mitigating activity should serve to reduce the impact of culture shock on the overall campaign.
b. Cultural Sensitivity in the conduct of SFCB. An understanding of the importance of cultural sensitivity, heeding local customs, values and norms, is vital when conducting SFCB. Even more important is the development of trusting relationships between ABCA and indigenous forces. Time and energy must be invested in these if they are to flourish.
c. Improved operational effectiveness by leveraging HNSF Cultural Understanding. HNSF generally have an understanding, both of local culture and the broader human terrain that ABCA nations are unlikely ever to rival, even after repeated tours. HNSF therefore offer ABCA nations an opportunity to understand the human terrain in which they are operating that will otherwise be lacking. SFCB cannot be conducted in isolation.
…
ANALYZING THE HNSF REQUIREMENTS
Introduction
1. Building HN security force capability and capacity should begin with an overarching analysis of requirements, existing capabilities, capacity and constraints, including a thorough consideration of cultural, political and economic factors.
2. Each situation will differ depending upon the level of conflict in the Host Nation and the existing capabilities and capacity of their security forces. The complexity and difficulty of conducting SFCB increases dramatically when working in a failing or failed state. Under such conditions, the key operational level security sector organizations, particularly Defense and Interior ministries, may not be present or effective.
3. Analysis must start from an understanding of the operational environment, the required end-state and taking into account the region‗s needs and concerns. Analysis should determine the requirements for force development, training, sustainment, unit and logistical distribution, deployment of forces, and equipment acquisition for each type of security force.
4. In the absence of a Joint Interagency Multinational process, the application of the military estimate or decision making process may serve as a useful start point. However, it is important that this is not carried out in isolation and is part of a comprehensive approach.
…
Evaluating Campaign Progress
17. The previous discussion has focused on developing measures of assessment for application across the tactical and operational spectrum. Assessing overall progress at the campaign level to understand whether the accumulative effects of our actions are indeed contributing to campaign success are just as important. As outlined earlier CEA is derived from an appreciation of the accumulative results of the MoP and MoE, set against the wider contextual analysis of the environment. Being able to monitor and track progress at this level requires a method for mapping a complex range of variables which contribute to a secure environment. Figure 2 is a suggested means with which to track overall progress made in the delivery of a security effect through HN SFCB.
18. Clearly security capacity in the upper end of the scale would be ideally matched with a high level of community confidence thus representing a viable security condition. Risk Zone A would represent a high level of security confidence among the target community but with low security force capacity. This might be indicative of regions which have been typically calm and relatively unaffected by the adversary – the risk being that this could change. Risk Zone B is high security force capacity but low security confidence and may point to other factors as the cause of poor security confidence, perhaps corrupt security force leadership. Clearly low capacity and low confidence is an unviable security condition.

DOWNLOAD ORIGINAL DOCUMENT HERE
Lebanon – Israels “Mata Hari” – Mossad Spy Shula Cohen
Shula Cohen Mossad Agent in Beirut – “Israel’s Mata Hari” The Girl Who Became a Mossad Spy in Lebanon. SHULA COHEN and story of becoming a spy for Israel in 1948 in Beruit, where her wealthy husband and her acceptance in Lebanese / Syrian social circles gave her unprecedented access to secret intelligence information. In a story reminiscent of Queen Esther in the Bible, she risks her comfortable lifestyle and social life to help her people, but unlike Esther, Shula pays a high price for her choice. Imprisoned in 1960, she endures seven years of torture and abuse before a secret prisoner exchange after the Six Day War in 1967, allows Shula to come home to Jerusalem.Shula Cohen spent seven years in a prison in Beirut, Lebanon because she was an Israeli spy. Only now can Shula Cohen tell the story of how she became a secret agent.In 1947, Shula began to work in her husband’s shop in Beirut. She overheard some Arabs from the village talking about plans to attack Israel. Shula knew this information was important. She decided to ask a client to smuggle a letter to an imaginary aunt in Jerusalem.In the letter Shula hid information about the Arab attack. After a week Shula received an answer. The answer made it clear to Shula how important the information was to the Jewish people. Contact between Shula and the Jews in the “Yishuv” had been established.Shula Cohen was honored by Mrs. Navon at the President’s house. Shula was the only one who did not speak. She was honored for “her services to the Jewish people.” Shula had helped thousands of Jews from Syria and Iraq come through Lebanon to Israel. She found escape routes for them by land, sea and air. She was able to work for fourteen years before she was caught. That was quite a job when you think that Eli Cohen, “our man in Damascus,” a professional spy, was only able to work for two years.In this video report Eli Cohen was hanged in Syria after she met him in jail.The Syrians made confrontation between them in jail to check if they know each other. The Syrians asked to hang her also. Today Shula Cohen lives a quiet life working in a gift shop in Jerusalem. Adapted also from “Israel’s Mata Hari” by Ruth Seligson.
Mutmasslich wie bei estavis – debis select “unterwirft sich “GoMoPa”, dem Exklusiv-“Nachrichten-Dienst” zu Heinz Gerlachs Todesursache
Israels “Mata Hari” – Mossad Spy Shula Cohen מרגלת המוסד שולה כהג
| Shula Cohen Mossad Agent in Beirut – “Israel’s Mata Hari” |
ERPRESSER “DAVE U RANDOM” – “GOOD MORNING KIDFUCKER – WIR WERDEN SIE VÖLLIG VERNICHTEN !”
"GoMoPa"-ERPRESSER DAVE U RANDOM "WIR WERDEN SIE WIRTSCHAFTLICH UND GESELLSCHAFTLICH ELIMINIEREN!" MUTMASSLICH VON "GoMoPa" IM AUFTRAG VON "PETER EHLERS" ODER VON "PETER EHLERS" PERSÖNLICH ---------------------------- Original Message ---------------------------- Subject: Good morning kids fucker, From: "Dave U. Random" <anonymous@anonymitaet-im-inter.net> Date: Thu, September 9, 2010 10:58 am To: office@generalglobalmedia.com -------------------------------------------------------------------------- auf unseren Informationsseiten, befindet sich der kleine Button: -Mail to Administrator-. Interessant was man nicht so alles erfahren darf, nicht wahr Herr Pulch. Da bekommen wir doch tatsaechlich eine Email von einem CDU Mitglied aus Ihrer Gemeinde, der Meister Pulch auch sehr, sehr, gut kennt. Tief besorgt ist man dort, Kinderficker, Kinderpornohaendler und Internet Stalker in der Gemeinde. Und auch in der katholischen Pfarrkirche, ist man nach unserer Mitteilung tief beunruhigt. Das nennen wir PR-Arbeit. Aber, es kommt ja noch alles viel besser. Unsere Briefwurfsendung und Internetinserate. Unser Ziel: Eure gesellschaftliche und wirtschaftliche Eliminierung. Habt einen schoenen Tag Kids fucker Liste von 4 Internetseiten STALKER SITES DER "GoMoPa", die sich jeder Strafverfolgung entziehen.
The Famous Artist and Mossad Spy Joseph Bau – in Memoriam
Joseph Bau Faked Docs for Mossad Spies
Joseph Bau born in 1920 is a graphic artist and poet, survivor of the Plaszow Nazi concentration camp of World War II. Bau Artist and one of the last surviving Jews on Oscar Shindler’s list. Died of pneumonia in Tel Aviv, Israel on May 24, 2002.Bau was trained as a graphic artist at the University for Plastic Arts in Kraków, Poland. His education was interrupted by World War II and he was transferred to the Plaszow concentration camp in late 1941. Having a talent in gothic lettering, he was employed in the camp for making signs and maps for the Germans. While in Plaszow, Bau created a miniature – the size of his hand – illustrated book with his own poetry. He also forged documents and identity papers for people who managed to escape from the camp.After liberation, Bau graduated from the University of Plastic Arts in Krakow. In 1950, he immigrated to Israel together with his wife and three year old daughter, where he worked as a graphic artist at the Brandwein Institute in Haifa and for the government of Israel. For the first time Israeli Mossad in 13/4/07 confirmed that Bau was an Mossad graphic artist. He also forged documents and identity papers for Eli Cohen was a celebrated Israeli spy, and is recognized as one of the most successful spies of modern times. According to his brother and fellow Mossad agent, Maurice Cohen, Eli Cohen was third in line to succeed as president of Syria, at the time he was discovered. Eli Cohen was hanged in Syria. In this video for the first time Joseph Bau`s daughter talks confirmed and presents Eli Cohen`s forged documents.As well as Mossad confirmed that Bau was an agent dealing with Artwork etc. His Art Work is presented now in the Mossad Memorial Institute.
Biography – Joseph Bau
Painter, Graphic Artist, Animator, Author, Poet and Publisher
(1920 – 2002)
Mr. Bau was born in Krakow, Poland in 1920. His education in The University for Plastic Arts in Krakow, was interrupted by World War II, when all the Jews were interned in concentration camps by the Nazis. During his internment Bau never lost his spark of humanity, humor and hope. He fell in love with another inmate, Rebecca, whom he married in Plashow Concentration camp despite the prohibition by the Germans. Mr. Bau smuggled himself into the women’s camp and there they got secretly married.
This unique wedding is featured in Spielberg’s film “Shindler’s List”. The art saved his life. He worked as a draftsman and also wrote signs in Gothic letters. He also forged documents and identity papers for people who managed to escape from the camp. This way he saved 400 people. Bau wrote and illustrated a miniature book the size of the palm of his hand. It contains beautiful poems and drawings that did not mention at all the horrors occurring around him. After Plashow he was transferred to Gross-Rosen and then to Oscar Shindler’s camp where he stayed till the end of the war. After the war, Bau graduated from the University of Plastic Arts in Krakow.
During his studies he worked for three newspapers as a graphic artist and illustrator. In 1950 he immigrated to Israel together with his wife and three-year -old daughter. He was recruited to a secret unit of the intelligence corps that dealt with technical covert operations that utilized his talent for art and graphics. Later he was transferred, together with other Intelligence corps personnel to a similar unit that was formed and worked as part of the intelligence community belonging to the Prime Minister’s office. Joseph never spoke of these activities. In 1956 Bau opened his own studio in Tel-Aviv and enriched its walls with his prolific art creations. He drew the titles for almost all the Israeli movies of the 60’s and 70’s. At the same time he authored a number of Hebrew books interspersed with artistic drawings. He drew the titles of almost all the Israeli movies of the 50’s, 60’s and 70’s. Movies like: “Kazablan”, “Salach Shabati”, “Lupo in New-York” and many more. At the same time, he authored a number of Hebrew books interspersed with artistic drawings. “Dear God! Have you ever gone hungry?” has appeared in several editions, Bau translated and published the book in Polish and its English version was published by Arcade Publishing in New-York in 1998. The Chinese version was published in China in May 2002. The book deals with the author’s experiences during the Holocaust. The specialty of the book is its humoristic style. Another book, “Brit Mila”, which is on the recommended reading list for the schools, is an amusing “dictionary” of the Hebrew language containing fascinating illustrations relating to the text. Bau wrote, illustrated and published another three books. All of them are written in his humoristic style.
Another accomplishment is his origination of animated films in Israel. Mr. Bau has been referred to in the press as the “Israeli Walt Disney”. He built his own animation studio and created short movies and commercials for television. Mr. Bau painted and drew paintings in a special style and has had many art exhibitions in Israel, U.S.A, and Canada. Bau created special New-Year cards every year, his aim was to make people happy and to cause them to laugh. He was a member of the Israeli Painters and Sculptors Association, the film and TV Directors Guild, and the Israeli Writer’s Guild.
His studio where he worked for 40 years is now a museum. He built all the equipment for making animated movies all by himself. He also built a small cinema where he showed his movies. It is located on 9 Berdichevski street in Tel Aviv Israel.
Joseph Bau has two daughters and four grandchildren.
see here for more info
HOW THE MOSSAD INFILTRADED THE KGB – Video
The Mossad Man in the KGB
The man who began the end of the Soviet empireVictor Grayevsky, who died on October 18 aged 82, was a Polish-Jewish journalist, and in 1956 managed to obtain an advance copy of Nikita Khrushchev’s speech to the closed session of the Communist Party’s 20th Congress; Grayevsky gave the document to the Israelis, who then passed the contents to the CIA.The 26,000-word speech, delivered on February 25 1956, denounced Stalin’s regime of terror. Grayevsky had been able to obtain a copy with the help of his lover, Lucia Baranowski, wife of Poland’s deputy prime minister. He had come to see Lucia at the headquarters of the Communist Party, where she worked as secretary to Edward Ochab, the party leader. Grayevsky recalled: “I noticed a thick booklet with a red binding, with the words: ‘The 20th Party Congress, the speech of Comrade Khrushchev’ written on it.” The booklet was one of the few top-secret copies sent from Moscow to leaders of the Eastern Bloc countries. Lucia allowed Grayevsky to remove the booklet for a couple of hours, and he took it to the Israeli embassy in Warsaw, where it was photocopied.The document provided a unique insight into the workings of the Soviet leadership. It was also the first official Soviet admission of the horrors perpetrated under Stalin. At the time Grayevsky was not employed as a spy, and he was not paid for his action, which arose from his Zionist convictions.advertisementHe was born Victor Spielman in Cracow on July 29 1925. A week before Germany invaded Poland, the Spielman family fled eastwards to the Soviet Union, but were later exiled to Siberia and from there moved to Kazakhstan, where Victor graduated from high school.In 1946 he returned to Warsaw. After studying journalism at the Academy of Political Science, he worked for the Polish news agency PAP and joined the Communist Party. He also changed his surname to the Polish Grayevsky because he was advised that, as Spielman, “he wouldn’t go far”.In 1949 his parents and sister emigrated to Israel, but Victor remained in Poland, where he was appointed a senior editor responsible for the department dealing with the Soviet Union. In 1955, when his father fell seriously ill, Grayevsky travelled to Israel to visit him; it was on this trip that he became a Zionist, and two years later he emigrated to Israel. He settled in Jerusalem and worked in the Eastern Europe division of the Foreign Ministry, and as director of Polish-language broadcasting for immigrants on Israel Radio.For many years after coming to Israel Grayevsky also worked as a double agent, posing as a Soviet spy but in fact serving the Israelis by feeding disinformation to Soviet intelligence officers. His Soviet handlers in Israel were KGB officers working under diplomatic cover or posing as clergy from the so-called Russian Orthodox Red Church in Israel. His meetings with them took place in Russian churches in Jerusalem and in nearby forests. Before these meetings his Israeli handlers would often provide him with “authentic” documents to pass to the Russians.Grayevsky left the Foreign Ministry in 1961 and was appointed director of Russian-language radio broadcasts. Four years later he was made director of Israel Radio’s overseas broadcasting department with responsibility for all languages. He remained in the post until 1999, continuing his work as a double agent.In 1967 the Soviet Union cut off diplomatic relations with Israel. Shortly before its diplomats left the country, Grayevsky was summoned to a last meeting with his KGB handler, who told him: “You’ve done great work for the Soviet Union… we have decided to award you the Lenin Medal of Excellence. For obvious reasons, we cannot give it to you now, but it will be kept for you in Moscow.” Needless to say, Grayevsky never collected it.Victor Grayevsky was divorced and is survived by two children.
More detail:
(The man who began the end of the Soviet empire – Theaustralian 27/10/07)
(Our man in the KGB – Haaretz 11/10/07)
TOP-SECRET – Mossad High Tech
 This image dated Friday April 28, 2006, from the Israeli spy satellite Eros B, and made available by the Israeli company ImageSat International NV, on Sunday April 30, 2006, one of the first high-quality images reported to show the Kassala airport in southern Sudan. The Eros B was launched last week from Russia and will remain in orbit for up to 6-years with the purpose to track Iran’s nuclear program at a time when Tehran is refusing to comply with U.N. demands to halt uranium enrichment and Iranian President Mahmoud Ahmadinejad is calling for Israel’s destruction.
This image dated Friday April 28, 2006, from the Israeli spy satellite Eros B, and made available by the Israeli company ImageSat International NV, on Sunday April 30, 2006, one of the first high-quality images reported to show the Kassala airport in southern Sudan. The Eros B was launched last week from Russia and will remain in orbit for up to 6-years with the purpose to track Iran’s nuclear program at a time when Tehran is refusing to comply with U.N. demands to halt uranium enrichment and Iranian President Mahmoud Ahmadinejad is calling for Israel’s destruction.
ImageSat inside video & taking –![]()
Video – Ofek 9 Spy Satellite Over Iran
TOP-SECRET – IDF Satellite Unit Ofek 9 Spy Satellite Being Launched in Palmachim AFB

| IDF Satellite Unit Ofek 9 Spy Satellite Being Launched in Palmachim AFB 22/6/10 22:00 – Yanat (Yehidat Nisui Tilim) Unit Palmachim AFB |
 |
CONFIDENTIAL – ISAF CAAT Afghan National Security Forces (ANSF) Guidelines in Partnering for Transition

COMISAF ADVISORY AND ASSISTANCE TEAM SPECIAL REPORT ON GUIDELINES IN PARTNERING FOR TRANSITION
(NIU) Introduction and Discussion. The level of partnership with ANSF units largely depends on the individual coalition commander’s discretion whether it is a partnered unit or an advisor team. Although this discretion is important to empower leaders on the ground, the current parameters in partnering guidance are very broad which leads to varying levels of effectiveness and consistency. Standardized guidelines would provide specific tasks (e.g. develop and conduct all planning and operations from a Joint TOC) to units designated as ANSF partners. Additionally, true embedded partnership improves ANSF development, mission accomplishment and force protection. The recommendations in this paper offer uniformed standards throughout diverse allied forces, assistance during RIP/TOA, improvement in the development of the Afghan forces, and a path to effective transition.
(NIU) Doctrine as a First Step. Standardized procedures that mandate embedded partnership principles should be introduced to ensure collaborative arrangements are as effective as possible. The first step to partnering is coalition familiarization with current doctrine. Two examples of existing doctrine include U.S. Army FM 3-07. Security Force Assistance (2009) and U.S. Army FM 3-24.2 Tactics in Counterinsurgency (2009), which contributes to a structure for partnering. All allied doctrine, which addresses Security Force Assistance type operations, should be considered in order to provide detailed parameters in relation to ANSF capabilities.
…
(NIU) Establishing Rapport. Building rapport is essential in establishing, developing, and sustaining a true embedded partnership. Doctrine states and practice shows that coexisting is the best method for gaining rapport and establishing trust. This consists of sharing meals and conducting other forms of rest and relaxation together, as a unit. Conducting this type of immersed partnership will establish and sustain rapport. It creates incentives for ANSF to share the risk with their coalition counterpart, with the desired result of improved retention and lower AWOL numbers within the Afghan forces. ISAF units need to review their force protection requirements and caveats in order to increase rapport as well as work with a higher number of ANSF units. Increased rapport would support discarding the “us” versus “them” mindset and improve both the mission and force protection. If trust and rapport is gained, the host nation provides superior HUMINT and knowledge of the local community. These factors provide improved lethal and nonlethal operations and situational awareness to safeguard the force. The inherent risk, with true embedded partnership, is balancing trust with operational security. In order to operate effectively, the coalition unit has to trust the ANSF unit. This trust, within established operational security boundaries, will encourage the ANSF to be more forthcoming with their contacts and intelligence. An established criterion and directive for partnering should include living, eating, and socializing to improve trust in the combined force. A prescriptive directive could also serve to minimize the sometimes counterproductive mindsets on why working, living, socializing, operating, or eating with the host nation is somehow considered a discretionary part of the partnering concept. As outlined in General Petraeus‟ COMISAF’s Counterinsurgency Guidance dated 1 August, 2010: “Work closely with our international and Afghan partners, civilian as well as military. Treat them as brothers-in-arms…Live, eat, train, plan, and operate together.”
(NIU) Joint Tactical Operations Center (JTOC). Embedded partnership works most effectively when implemented at all levels. A fundamental element of partnering is establishing a Joint Tactical Operations Center (Joint TOC or JTOC). Establishing a Joint TOC will increase the overall capabilities of both the coalition and Afghan forces. Additionally, it helps compensate for the shortfalls of the individual forces‟ limitations during operations, and provides a model for assimilation by the ANSF. The ANSF are much more adept at interacting with the populace; a JTOC provides enhanced intelligence gathering and situational awareness within the local communities. This intelligence can then be „actioned‟ by the combined coalition and Afghan forces. Operating a Joint TOC with shared planning, operations, intelligence, and sustainment cells allows coalition staff officers to simultaneously teach, coach, or advise their partners based on capabilities. This will also provide a forum to improve the ANSF and introduce their contribution of human intelligence and situational awareness to planning and operations. The end-state would be ANSF operating a TOC without assistance of coalition partners and advisors. OPSEC is always a concern when dealing with the host nation, but does not disqualify joint cells within the multi-national coalition, and therefore should not be discarded as a concept strictly because of security concerns. The more embedded the units, the stronger rapport and trust. A “one team” mindset, where units operate side-by-side and shares the danger, reduces the OPSEC risk. Without sharing the hazards, a lack of trust and limited rapport adds to the danger for coalition forces. Compartmentalization and care of sensitive information will add to mitigating the hazards to operational security.
(NIU) Depending on the force structure an Integrated Command Teams (ICTs) and/or Operations Coordination Centers – District (OCC-D) may serve as an added collaboration with the ANSF as well as local GIRoA. COIN Guidance defines an ICT as “a committee of district level representatives from GIRoA, ANSF, development agency representatives and ISAF. ICTs are formed in order to strengthen local unity of effort in governance, development and security by synchronizing, planning, de-conflicting, and sharing information at the district level.” ANSF are also establishing OCC-Ds as wells as OCC-Ps and OCC-Rs (Provincial and Regional respectively) as a method to utilize surge recovery and transition to reorganize themselves. Ideally, though case dependant, a Company Command Post (CP) collocates with either an existing ANP or ANA CP at a District Center. This combined effort provides a centralized location for the ANSF to coordinate with ISAF.
DOWNLOAD ORIGINAL DOCUMENT HERE
FEMEN – Naked Ambition – Topless protests go global
A naked woman in a city’s central square is bound to attract attention, which is exactly what Ukraine’s Femen group is hoping for with a series of high-profile demonstrations against the abuse of women’s rights which has made the news across Europe.
Unvealed – IDF SPY SATELLITE UNIT OVER IRAN אמ”ן יחידת הלוויינים
Mossad Operations Videos
REVEALED – China Military TV Channel Mossad Operations الموساد الإسرائيلي
Mossad Operation Dubai Videos
German Resistance – Plotting Hitler`s Death 1944 Nazi Trial Video
http://www.dailymotion.com/swf/x8gslh&related=0
| Ulrich Wilhelm Graf Schwerin von Schwanenfeld Nazi Trial VideoUlrich Wilhelm Graf Schwerin von Schwanenfeld.
Ulrich-Wilhelm Graf Schwerin von Schwanenfeld (21 December 1902 – 8 September 1944) was a German landowner, officer, and resistance fighter against the Nazi régime. |
 |
Ulrich Wilhelm Graf Schwerin von Schwanenfeld
File:Bundesarchiv Bild 151-19-35, Volksgerichtshof, Graf Schwerin v. Schwanenfeld
CAUGHT ON FILM – KGB Envoy to STASI HQ Putin Shooting in SVR/KGB HQ Moscow
SECRET – 5 Years KGB Envoy to Stasi Dresden HQ in DDR Vladimir Putin 1985 – 1990
 Putin The KGB Hero in Stasi Land Defends Russia With One Small Pistol 29/10/09 (Russian Media Orchestra)
Putin The KGB Hero in Stasi Land Defends Russia With One Small Pistol 29/10/09 (Russian Media Orchestra)
Putin told NTV reporter Vladimir Kondratyev in a half-hour interview how he managed to calm down an angry crowd of East German protesters outside the KGB headquarters in Dresden in late 1989.Putin’s interview was aired as part of the 50-minute film at 7:25 p.m on NTV on Sunday, Nov. 8 , 2009 one day before the 20th anniversary of the fall of the wall.Putin served as a KGB officer in Dresden from 1985 to 1990. His only brush with history there occurred on Dec. 5, 1989, almost a month after the wall fell.After storming the nearby local headquarters of the East German Secret Police, or Stasi, protesters gathered outside his office building. Putin recalled how he met the crowd personally and told them in German that this was a Soviet military organization. When people replied suspiciously that he spoke German too well, “I told them I was a translator,” he said.Mr Putin will be shown discussing the incident in a documentary called The Wall to be broadcast on state-controlled TV next month.The programme’s maker, Vladimir Kondratyev, has defended his decision to make Mr Putin one of the film’s main characters. Mr Kondratyev believes that Mr Putin, who worked as a KGB agent hand-in-glove with the East German Stasi intelligence service during the 1980s, did a lot to hasten the wall’s collapse. Yet his description of Mr Putin’s actions suggests the opposite.”He was one of the few Soviet citizens who had first-hand experience of East German demonstrators when a crowd ransacked the Stasi’s office in Dresden and then prepared to storm the building where Putin and his Soviet spy comrades were working,” Mr Kondratyev told the daily Kommersant newspaper.”Putin succeeded in persuading the crowd to fall back.” State TV has in the past described how Mr Putin brandished a pistol in front of the crowd and used his fluent German to make it clear he was prepared to use it.”This is Soviet territory and you’re standing on our border,” he was quoted as saying. “I’m serious when I say that I will shoot trespassers.” A witness was quoted as saying that Mr Putin issued the threat with his trademark assurance. In the documentary,
Opferverband – Opfer-SED-STASI zeigt exemplarische STASI-Fälschung
Zum Nachteil eines Opfers der Stasi/SED Diktatur -wurde ein Original Kurbericht aus einer Klinik im Schwarzwald gefälscht. Aus dem Kur – Bericht wurden ärztliche Eintragungen einschließlich Röntgenaufnahmen und des Kranheitsverlaufs aufwendig manipuliert…doch dennoch erkennbar e n t f e r n t …. ! Die unverfälschten Kurberichtsunterlagen u. a. wurden durch Nachforschungen im Gesundheitsamt Dortmund aufgefunden und als Originalkopien mit den vorhandenen Beweiseintragungen -und dem Amtsstempel der Stadt Dortmund versehen zur weiteren Verwendung ausgehändigt.!
Mit diesem manipulierten -gefälschten Kurbericht-hat das Versorgungsamt SOEST-Nordrhein-Wwestfalen gemeinsam mit weiteren interessierten Kräften in länger als 15 Jahren Klageverfahren…… der Sozialgerichte
anzuerkennende Gesundheitsschäden aus der “DDR” Folterhaft mit eigener Verantwortung als Haftschaden in Vorentscheidungsbescheide abgelehnt. =========================
Bishin zur Landessozialgerichtsbarkeit, auf Kosten des Steuerzahlers , wurden zwei Urteile zugunsten des Klägers erstritten . ! Das ging ebenfalls nicht ohne Verzögerungstaktik so ohne weiteres über die Bühne. Die eingeholten Gutachten der Sozialgerichte wurden d r e i s t bestritten , erneut auf Kosten des Steuerzahlers !!
Mit Einsprüchen gegen diese Gutachterausführungen wurden wieder von der Beklagten voreingenommen Bestätigungen der Gutachterausführungen gefordert.
Auch diese Anmaßung/Verzögerungstaktik blieb rein ohne jeglichen Änderungseintrag des vorliegenden Gutachtens. Das z. Zt. kurz vor Beendigung des Klageverfahrens ausstehendende Sozialgerichtverfahren wurde bisher über 1 Jahr mit Einsprüchen und Fristversäumnissen wie gehabt weit über die Zeit gebracht!!
Um Wiederholungen zu vermeiden -zum Schluß noch einmal Klartext ,diese o.a. Verfälschungen konnten nicht von einer einzelnen Person durchgeführt worden sein. – Unverständlich, der Aufwand der für diese Verfälschungen aufgebracht werden mußte.- In absehbarer ,gegebener Zeit können die Fälschungskopien hier veröffentlicht werden .
Die Pressestellen haben zum Teil schon Einsicht in das gefälschte Material bekommen. Gleichzeitig besteht hier großer Bedarf an Aufklärung der Öffentlichkeit.
Einem besonders erfahrenen Rechtsanwalt
ist es schließlich gelungen noch weitere vom Gericht geforderte Gutachten zu erstreiten ,die den bisherigen “Ablehnungsrytmus” zunichte machen. Etc.
Die Strafverfolgung dieser Schandtaten ist aus guten Gründen nachfolgend das < i > Tüpfelchen !!
Das Original:

EINEN BEWEIS FÜR DIE VORHANDENEN FÄLSCHUNGEN LIEFERN DIE BEIDEN DOKUMENTE O B E N = ORIGINALAUSSCHNITT-DOKUMENT.
======== WAS AUFGEFUNDEN WURDE !!
UNTEN : =FÄLSCHUNG DES ORIGINALDOKUMENTS WELCHES SICH IN DEN AKTEN DER BEHÖRDE BEFAND .!! ( noch ist!? )
WIR SIND IM BESITZ VON WEITEREN
UNTERLAGEN DIE DEN FÄLSCHUNGSBETRUG B E L E -G E N !!
DIES_HIER_IST_NUR_EIN_KLEINER-AUSZUG. ES GIBT- WEITERE BEHÖRDENDOKUMENTE DIE DIESE SKANDALÖSEN MACHENSCHAFTEN O F F E N L E G E N .- _ !!
SIE ZEUGEN VON BÖSARTIGER E N E R G I E DER VERANTWORTLICHEN …. WIE WIR SIE BISHER NUR VON DER eh.”DDR” STAATSSICHERHEIT—ERLEBEN-
M U S S T E N !! USW.USW.

http://www.verband-ddr-opfer.com/index2.php?act=mitteilung&mitteilung=35
DDR1 TV 1987 STASI fälscht Mikis Theodorakis Show
SERIEN-(ruf)-MÖRDER und STASI-Fälschungen – Und plötzlich waren wir Verbrecher
ZDF-Info-Sendung vom 5. November 2010.
Nach 26 Jahren betritt Dorothea Ebert zum ersten Mal wieder das Stasi-Gefängnis in Dresden. Mit ihrem Bruder Michael saß sie hier ein, nachdem der gemeinsame Fluchtversuch aus der DDR 1983 scheiterte.
Quälende anderthalb Jahre verbrachten sie hinter Gittern, mussten seelische Folter ertragen, Einsamkeit und Kälte. Dann wurden die beiden Musikstudenten von der Bundesrepublik freigekauft und leben seitdem in München. Über ihre Republikflucht haben sie das Buch “Und plötzlich waren wir Verbrecher” geschrieben – ein Versuch, mit den Erlebnissen zurechtzukommen, darüber zu sprechen.
TOP SECRET – CRYPTOME publishes – NSA Email Addresses, Nyms and Names
5 February 2012
NSA Email Addresses, Nyms and Names
A sends:
Below is unverified information posted 9 days ago on this .onion site:
http://4eiruntyxxbgfv7o.onion/snapbbs/736364f4/
(thread: “where to get confidential info”)
It may simply be the INSA list, but I lack the time to compare.
(Director of NSA) KBalexanderLTG@nsa.gov KBalex2@nsa.gov ;-) RFTYGAR@NSA.GOV (Major General David B. Lacquement, Cybercom) dfmuzzy@nsa.gov or dbmuzzy@nsa.gov algorin@nsa.gov bkind@nsa.gov bmcrumm@nsa.gov bmkaspa@nsa.gov bmstite@nsa.gov ceander@nsa.gov dabonan@nsa.gov dahatch@nsa.gov daplunk@nsa.gov dbbuie@nsa.gov dcover@nsa.gov dpcargo@nsa.gov dpmatth@nsa.gov drennis@nsa.gov dvheinb@nsa.gov eejorda@nsa.gov elbauma@nsa.gov fdbedar@nsa.gov fjfleis@nsa.gov fjorlos@nsa.gov gafrisv@nsa.gov gcnolte@nsa.gov gdbartk@nsa.gov ghevens@nsa.gov grcotte@nsa.gov hadavis@nsa.gov hlriley@nsa.gov jaemmel@nsa.gov jcingli@nsa.gov jcmorti@nsa.gov jcsmart@nsa.gov jdcohen@nsa.gov jdheath@nsa.gov jewhite@nsa.gov jgrusse@nsa.gov jhdoody@nsa.gov jhohara@nsa.gov jimathe@nsa.gov jjbrand@nsa.gov jksilk@nsa.gov jllusby@nsa.gov jmcusic@nsa.gov jmjohns@nsa.gov jrsmith@nsa.gov jswalsm@nsa.gov jtnader@nsa.gov kamille@nsa.gov kbalex2@nsa.gov labaer@nsa.gov landers@nsa.gov lfgiles@nsa.gov lkensor@nsa.gov lphall@nsa.gov lrstanl@nsa.gov ltdunno@nsa.gov mabeatt@nsa.gov mawirt@nsa.gov mgflemi@nsa.gov mjgood@nsa.gov mkmcnam@nsa.gov mrevans@nsa.gov mrredgr@nsa.gov mthorto@nsa.gov nasmith@nsa.gov pacabra@nsa.gov papitte@nsa.gov plihnat@nsa.gov plporte@nsa.gov rdjones@nsa.gov rdsiers@nsa.gov relewis@nsa.gov resunda@nsa.gov rhkrysi@nsa.gov rlcarte@nsa.gov rlmeyer@nsa.gov rmmeyer@nsa.gov rpkelly@nsa.gov sfdishe@nsa.gov sfdonne@nsa.gov sgmille@nsa.gov sjmille@nsa.gov sstanar@nsa.gov swramsa@nsa.gov taedwar@nsa.gov tdsoule@nsa.gov tjpeter@nsa.gov twsager@nsa.gov vacurti@nsa.gov vnhalli@nsa.gov wjmarsh@nsa.gov wmmurph@nsa.gov wmthomp@nsa.gov wjseman@nsa.gov --Korruptor posted 9 days 22 hours ago: MTCLAYT@NSA.GOV NCMUNKO@NSA.GOV cjhuff@nsa.gov RBQUINN@NSA.GOV Lorenzo Mccormick lmccorm@nsa.gov Angelina Mcclure ammccl3@nsa.gov Timothy Gibbs tjgibbs@nsa.gov Joshua Foredyce jdfored@nsa.gov Nicole Morrison nnmorri@nsa.gov Sally Smith sssmit3@nsa.gov Todd Black tfblack@nsa.gov Todd Black tfblack@nsa.gov Viola Williams vrmclau@nsa.gov Stephen Schultz UN:SRSYSENGINEER sjschul@nsa.gov Yesenia Martinez yamarti@nsa.gov Teresa Straniero tjstran@nsa.gov Taj Holmes tlholm3@nsa.gov Joseph Johnson jjohns5@nsa.gov Hyon-chu karen Cho KAREN0120 hkcho@nsa.gov Nathan Nysether nenyset@nsa.gov Everett Browning edbrow2@nsa.gov Sean Williamson smwill8@nsa.gov Kevin Standifer kmstand@nsa.gov Maria Johnson msjohn8@nsa.gov id=1607452 lastname=DEBOSE firstname=JULIUS email=JDDEBOS@NSA.GOV id=1838179 lastname=MEADOWS firstname=ALLEN email=ALMEADO@NSA.GOV id=1836143 lastname=FUNCHES firstname=DAVID email=DLFUNCH@NSA.GOV id=1812268 lastname=PUFFENBARGER firstname=JAMES email=JGPUFFE@NSA.GOV id=1840655 lastname=LOWRY firstname=CLINT email=CMLOWRY@NSA.GOV id=1844703 lastname=SENYARD firstname=KRISTEN email=KSSENYA@NSA.GOV id=1822902 lastname=DEEDS firstname=JENNIFER email=JLDEEDS@NSA.GOV id=1424394 lastname=HEDRICK firstname=EVERETT email=EGHEDRI@NSA.GOV id=1847023 lastname=MILO firstname=JOANNE email=JOANNE.M.MILO@USACE.ARMY.MIL id=1319638 lastname=CLARK firstname=SARA email=SJDEBOE@NSA.GOV id=1852085 lastname=GRANGER firstname=MELFORDE email=MAGRANG@NSA.GOV id=1639154 lastname=WHITE firstname=ARLENE email=AFWHITE@NSA.GOV id=1843795 lastname=RAWLINS firstname=BRITTANI email=BRITTANI.RAWLINS@TMA.OSD.MIL id=1850937 lastname=CRISP firstname=KENNETH email=KCCRISP@NSA.GOV id=1846228 lastname=WEEKS firstname=JEFFREY email=JSWEEK2@NSA.GOV id=1847105 lastname=PATRICK firstname=MARY email=MJPATRI@NSA.GOV id=972021 lastname=BROWN firstname=KIMBERLY email=KCBROWN@NSA.GOV id=1843790 lastname=HOFFECKER firstname=FRANK email=FSHOFFE@NSA.GOV id=1568245 lastname=ZUBACK firstname=KATHERINE email=KCZUBAC@NSA.GOV id=1702604 lastname=MILLS firstname=HAROLYN email=HWMILL2@NSA.GOV id=1706716 lastname=ANDERSON firstname=JARED email=JLAND11@NSA.GOV id=1773809 lastname=FERTITTA-ZEPP firstname=MARY ROSE email=MTFERTI@NSA.GOV id=1801498 lastname=MATTHEWS firstname=JACQUELINE email=JGMATT4@NSA.GOV id=1827983 lastname=KELLY firstname=SHERI email=SRKELLY@NSA.GOV id=881503 lastname=ROAKER firstname=AUDREY email=ADROAKE@NSA.GOV id=1758757 lastname=HORGER firstname=ROBYN email=RHORGER@NSA.GOV id=62230 lastname=SCOURTIS firstname=THEODORE email=TRSCOUR@NSA.GOV id=1725805 lastname=JAROSINSKI firstname=JAMES email=JMJAROS@NSA.GOV id=63369 lastname=PHILLIPS firstname=SUSAN email=SEPHIL3@NSA.GOV id=1841784 lastname=BYAM firstname=NICOLE email=NABYAM@NSA.GOV id=1837316 lastname=ACKERMANN firstname=SUSAN email=SACKERM@NSA.GOV id=1838180 lastname=PALMER firstname=KEAVIONA email=KKPALM2@NSA.GOV id=1620956 lastname=FINE firstname=CHET email=CBFINE@NSA.GOV id=1193570 lastname=WHEELER firstname=DONALD email=DAWHEEL@NSA.GOV id=1680358 lastname=FELTON firstname=SHARISSE email=SRFELTO@NSA.GOV id=1299959 lastname=SCARDINA firstname=VONDA email=VRSCARD@NSA.GOV id=952454 lastname=HOLMGREN firstname=CHRISTINE email=CMHOLMG@NSA.GOV id=1836488 lastname=BARNES firstname=RAVEN email=RCBARN4@NSA.GOV id=1809599 lastname=TOPIELEC firstname=DENNIS email=DRTOPI2@NSA.GOV id=1544912 lastname=EICH firstname=ARTHUR email=ANEICH@NSA.GOV id=1481136 lastname=WASSBERG firstname=MARK email=MCWASSB@NSA.GOV id=1486369 lastname=SMITH firstname=ANTOINETTE email=ARSMITH@NSA.GOV id=1809599 lastname=TOPIELEC firstname=DENNIS email=DRTOPI2@NSA.GOV id=1261344 lastname=LAIRD firstname=JOHN email=JMLAIRD@NSA.GOV id=1812529 lastname=KIMSEY firstname=JAYSON email=JEKIMSE@NSA.GOV id=1744167 lastname=RAGER firstname=ZACHARY email=ZMRAGER@NSA.GOV id=1839355 lastname=VIDMAR firstname=SAMUEL email=STVIDMA@NSA.GOV id=1843789 lastname=LANGDON firstname=BRENDAN email=BMLANGD@NSA.GOV id=1832260 lastname=PEREZ firstname=CADDIE email=CEPERE2@NSA.GOV id=1831824 lastname=BROCATO firstname=ADAM email=ARBROCA@NSA.GOV id=1567765 lastname=FLYNN firstname=JESSICA email=JRFLYNN@NSA.GOV id=812143 lastname=WILLIAMS firstname=KIMBERLEE email=KVWILL2@NSA.GOV id=55539 lastname=LEVINE firstname=DIANA email=DKLEVIN@NSA.GOV id=1767656 lastname=COPELLO firstname=TRACY email=TKCOPEL@NSA.GOV id=1809599 lastname=TOPIELEC firstname=DENNIS email=DRTOPI2@NSA.GOV id=1699999 lastname=CRABTREE firstname=BRIAN email=BCCRABT@NSA.GOV id=926230 lastname=MEJIA firstname=ADAM email=ADAM.MEJIA@NSA.NAPLES.NAVY.MIL id=1699380 lastname=PARKER firstname=HELGA email=HSPARKE@NSA.GOV id=92796 lastname=HATFIELD firstname=ELIZABETH email=ELHATFI@NSA.GOV id=970496 lastname=BRIGHTWELL firstname=KALA email=KABRIG2@NSA.GOV id=1619826 lastname=WONDERLY firstname=BRIAN email=BCWONDE@NSA.GOV id=1599843 lastname=CONWAY-BRANCH firstname=CAROLYN email=CPCONWA@NSA.GOV id=1613415 lastname=WHITTINGTON firstname=LISA email=LDWHITT2@NSA.GOV id=1776880 lastname=COOPER firstname=DARYL email=DGCOOPE@NSA.GOV id=1790953 lastname=DUNKER firstname=THOMAS email=TJDUNKE@NSA.GOV id=1630878 lastname=BEELER firstname=RYAN email=RWBEELE@NSA.GOV id=1726927 lastname=HESTER firstname=CARLA email=CJHESTE@NSA.GOV id=1717359 lastname=TEDESCHI firstname=STEPHEN email=SPTEDES@NSA.GOV id=1822638 lastname=WARD firstname=ELIZABETH email=ECWARD1@NSA.GOV id=1587185 lastname=COOK firstname=TASHA email=TACOOK2@NSA.GOV id=1740730 lastname=BROCKMEYER firstname=PETER email=PCBROCK@NSA.GOV id=1219490 lastname=ZULLO firstname=KECIA email=KKZULLO@NSA.GOV id=986360 lastname=ACKIES firstname=HENRY email=HLACKIE@NSA.GOV id=1205401 lastname=HARVEY firstname=TRISTAN email=TDHARVE@NSA.GOV id=1445825 lastname=HILD firstname=LAURA email=LLHILD@NSA.GOV id=1618446 lastname=MARTINEAU firstname=NICHOLAS email=NDMART2@NSA.GOV id=801833 lastname=BLAIS firstname=DAVID email=DMBLAIS@NSA.GOV id=1744167 lastname=RAGER firstname=ZACHARY email=ZMRAGER@NSA.GOV id=1727564 lastname=CROUSE firstname=JAMI email=JLCROU2@NSA.GOV id=1848401 lastname=CORLEY firstname=SHANNON email=SMCORLE@NSA.GOV id=1842936 lastname=MARQUARDT firstname=HOLLY email=HLMARQU@NSA.GOV id=1568495 lastname=ELKINS firstname=GREGORY email=GSELKIN@NSA.GOV id=1806965 lastname=TRELOAR firstname=BARRY email=BFTRELO@NSA.GOV id=1729197 lastname=ELLWOOD firstname=PAULA email=PGELLWO@NSA.GOV id=1262990 lastname=MYERS firstname=KENNETH email=KEMYERS@NSA.GOV id=1836712 lastname=TROISI firstname=MARK email=MJTROIS@NSA.GOV id=1616516 lastname=LOWE firstname=TRINA email=TMLOWE@NSA.GOV id=1828431 lastname=HENSLEY firstname=MELISSA email=MCHENSL@NSA.GOV id=1613083 lastname=RAMIREZ firstname=SHEILA email=STRAMIR@NSA.GOV id=910975 lastname=JOHNSON firstname=TARA email=TRJOHN5@NSA.GOV id=1572257 lastname=STALLINGS firstname=LACY email=LJSTAL2@NSA.GOV id=1600853 lastname=DAVIS firstname=SARAH email=SEDAVI3@NSA.GOV id=1608061 lastname=EVANS firstname=ERIC email=EDEVANS@NSA.GOV id=1779020 lastname=LOOK firstname=KAREN email=KLLOOK@NSA.GOV id=1809640 lastname=ARSENAULT firstname=ROBERT email=REARSEN@NSA.GOV id=1520035 lastname=BURDETTE firstname=ROBERT email=RJBURD3@NSA.GOV id=883230 lastname=LAKE firstname=BARRY email=BALAKE@NSA.GOV id=1516236 lastname=HILTON firstname=ROBERT email=RJHILTO@NSA.GOV id=86769 lastname=MAHER firstname=WENDY email=WAMAHER@NSA.GOV id=1764117 lastname=GEIGER-ALSTON firstname=STACIA email=SLGEIGE@NSA.GOV id=1746685 lastname=KINGERY firstname=JILL email=JAKINGE@NSA.GOV id=1478578 lastname=MIKLUSAK firstname=GREGORY email=GVMIKLU@NSA.GOV id=15637 lastname=PHELPS firstname=AMANDA email=AAPHELP@NSA.GOV id=819655 lastname=CARSON firstname=WILLIAM email=WSCARSO@NSA.GOV =
see also
http://cryptome.org/2012/01/0086.htm
Unveiled – KGB General Vladimirov Chief of Defectors Assassination Squad
 Finish President Urho Kekkonen code name “TIMO” in KGB Archive (left) and KGB officer Viktor Vladimirov (right) fishing in the Soviet Union in November 1980.Viktor Vladimirov, a long-time official working at the Soviet Embassy in Helsinki, worked as the head of the KGB’s sabotage and assassination section in the late 1960s. One of Vladimirov’s projects was a plot in 1967 to murder former KGB officer Anatoly Golitsyn, who had defected to Canada from Finland where he worked in 1961. These are some of the juicier details contained in a newly-published history of the Finnish Security Police (SUPO) by historian Kimmo Rentola. Rentola says that the plot against Golitsyn failed, as did a similar attempt to kill another defector, which also took place in 1967. While working in Helsinki, Viktor Vladimirov became an “important source of information” for two Finnish presidents – Urho Kekkonen and Mauno Koivisto, with whom he became “quite close”. Both presidents knew that he held the rank of general in the KGB, but it is unlikely that they had any knowledge of his work in covert operations. There had been reports of Vladimirov’s career in the assassinations section in stories told by Soviet defectors to Western intelligence services, but it was not until the KGB’s organisation chart was published in a Russian reference book in 2004 that there was positive confirmation of the matter. Vladimirov served at the Soviet Embassy in Helsinki in the 1950s, 1970s, and 1980s. He died in 1995.
Finish President Urho Kekkonen code name “TIMO” in KGB Archive (left) and KGB officer Viktor Vladimirov (right) fishing in the Soviet Union in November 1980.Viktor Vladimirov, a long-time official working at the Soviet Embassy in Helsinki, worked as the head of the KGB’s sabotage and assassination section in the late 1960s. One of Vladimirov’s projects was a plot in 1967 to murder former KGB officer Anatoly Golitsyn, who had defected to Canada from Finland where he worked in 1961. These are some of the juicier details contained in a newly-published history of the Finnish Security Police (SUPO) by historian Kimmo Rentola. Rentola says that the plot against Golitsyn failed, as did a similar attempt to kill another defector, which also took place in 1967. While working in Helsinki, Viktor Vladimirov became an “important source of information” for two Finnish presidents – Urho Kekkonen and Mauno Koivisto, with whom he became “quite close”. Both presidents knew that he held the rank of general in the KGB, but it is unlikely that they had any knowledge of his work in covert operations. There had been reports of Vladimirov’s career in the assassinations section in stories told by Soviet defectors to Western intelligence services, but it was not until the KGB’s organisation chart was published in a Russian reference book in 2004 that there was positive confirmation of the matter. Vladimirov served at the Soviet Embassy in Helsinki in the 1950s, 1970s, and 1980s. He died in 1995.
“Neverthless , by the 1970s the KGB had more people they regaded as agents and `cconfidencial contacts` in Finland than in all the other FCD Third Departmen countries combined(Britain,Ireland,Australasia and the rest of Scandinavia).Helsinky also provided hospitality for the leading Soviet front organization.”- “KGB THE INSIDE STORY” Chrritopher Andrew & Oleg Gordievsky p.359.
According to Ex. Intel. officials KGB agents in Helsinki were involved with pushing Finish volunteers to spy in Israel during the Vladimirov term.
Zusammenarbeit des MfS und KGB bei der Schaffung des “Kundschaftermythos” der Roten Kapelle
Während der Recherchen zum Komplex “Rote Kapelle” ergab sich, dass ein großer Aktenbestand zur “Roten Kapelle” in den Akten des ehemaligen Ministeriums für Staatssicherheit der DDR beim Bundesbeauftragten für die Unterlagen des MfS (BStU) liegt. Eine Auswertung dieses Bestandes zeigte eine enge Zusammenarbeit zwischen MfS und sowjetischem KfS (KGB) in den 60er und 70er Jahren bei der Formung des Bildes von den “Kundschaftern für den Frieden” unter der Anleitung der UdSSR. Damit sollte nicht nur eine geschichtspolitische “Legende”, sondern zugleich ein Legitimationszusammenhang für die beiden Geheimdienste definiert werden. Bearbeiter ist Dr. Johannes Tuchel.
Literatur:
- Johannes Tuchel: Vom Mißbrauch des Widerstands – oder: Das Ministerium für Staatssicherheit und die Rote Kapelle, in: Die Mahnung 46 (1999), Nr. 7, 1.7.1999, S. 1f.
- Johannes Tuchel: Das Ministerium für Staatssicherheit und die Fallschirmagenten der Roten Kapelle – Der Fall Albert Hößler, in: Hans Schafranek/Johannes Tuchel (Hrsg.): Krieg im Äther. Widerstand und Spionage im Zweiten Weltkrieg, Wien 2004, S. 56 ff.
- Johannes Tuchel: Das Ministerium für Staatssicherheit und die Widerstandsgruppe “Rote Kapelle” in den 1960er Jahren, in: Johannes Tuchel (Hrsg.): Der vergessene Widerstand. Zu Realgeschichte und Wahrnehmung des Kampfes gegen die NS-Diktatur, Göttingen 2005, S. 232 ff.
Video – Who are FEMEN?
CONFIDENTIAL from the FBI – Miami Family Charged with Multi-Faceted Mortgage Fraud Scheme
Wifredo A. Ferrer, United States Attorney for the Southern District of Florida; John V. Gillies, Special Agent in Charge, Federal Bureau of Investigation (FBI), Miami Field Office; and James K. Loftus, Director, Miami-Dade Police Department (MDPD); along with members of the Federal-State Mortgage Fraud Strike Force (Mortgage Fraud Strike Force), announce the indictment of six South Florida residents on charges stemming from their participation in a mortgage fraud scheme that resulted in approximately $2 million in fraudulent loans.
This case is the result of the cooperative law enforcement efforts of the members of the Mortgage Fraud Strike Force. Created in June 2008 and led by the U.S. Attorney’s Office, the Mortgage Fraud Strike Force brings together federal, state, and local law enforcement to combat the mortgage fraud epidemic in South Florida. Members of the Mortgage Fraud Strike Force include experienced prosecutors, federal agents, and state and local officers dedicated exclusively to investigating and prosecuting mortgage fraud cases. The Mortgage Fraud Strike Force has yielded substantial results. Since September 2007, following the creation of the District’s first Mortgage Fraud Initiative, more than 500 individuals have been charged for their involvement in mortgage fraud schemes that have resulted or were intended to result in more than $620 million in mortgage loans.
On February 2, 2012, a 10-count indictment was unsealed charging six defendants for their alleged participation in a mortgage fraud scheme that resulted in approximately $2 million in fraudulent loans. Charged in the indictment are defendants Ivania Filgueiras, 40, of Miami; Jose Armando Alvarado, 62, of Miami; Maria C. Alvarado, 62, of Miami; Reyna Josefina Orts, 57, of Miami; Alberto Morejon, 25, of Miami; and Carlos Serrano, 56, of Hialeah. Five of the six defendants are close family members.
According to the indictment, from 2005 through 2009, defendants Filgueiras, Jose Armando Alvarado, and Maria C. Alvarado identified residential properties in Miami-Dade County to defraud lenders. Defendant Jose Armando Alvarado then recruited and paid individuals to act as straw buyers of the properties. Defendant Serrano acted as a straw borrower for three different properties alleged in the indictment. Defendants Jose Armando Alvarado and Orts created and caused the borrowers’ fraudulent loan applications and other documents to be submitted to the lenders, in one instance without a borrower’s knowledge or consent. The fraudulent loan applications contained bogus bank account records and false statements about employment, income, assets, and intent to occupy the property. American Mortgage Lending (AML), a mortgage brokerage firm owned by defendant Jose Armando Alvarado, prepared and submitted the fraudulent loan documents to the lenders. South Florida Realty, a real estate company owned by defendant Maria C. Alvarado, was utilized to create sales contracts submitted to the lenders for the charged transactions.
Thereafter, defendants Filgueiras and Morejon utilized a Miami title company to conduct fraudulent closings. Once the mortgage applications were approved, the lenders wired the loan proceeds to the title company’s escrow account, operated by Filgueiras, for closing. At closing, Filgueiras and her father, defendant Jose Armando Alvarado, caused fraudulent payments and disbursements to be made from the loan proceeds. Additionally, defendant Filgueiras disbursed loan proceeds to the sellers without receiving cash-to-close payments from the borrowers, contrary to representations on the HUD-1 statements.
To perpetuate the scheme and avoid detection, the defendants also failed to record, and falsely recorded, mortgage deeds and other mortgage documentation with the State of Florida authorities. Defendants Filgueiras and Morejon also fraudulently executed quit-claim deeds with State of Florida authorities, on behalf of defendants Jose Armando Alvarado and Maria C. Alvarado, in order to sell the properties to other straw buyers, obtain home equity line of credit (HELCO) loans, and conceal the fraud. The defendants would also make payments on the loans until the properties could be resold, often to another straw borrower, repeating the cycle of fraud. Eventually, the defendants stopped making payment on the loans and the properties entered foreclosure proceedings, often resulting in substantial losses to the lending institutions.
The indictment charges the defendants with conspiracy to commit bank and wire fraud, and substantive wire fraud and bank fraud. If convicted, the defendants face a statutory maximum term of imprisonment of 30 years’ on the conspiracy to commit bank and wire fraud and substantive bank fraud charge, and 20 years’ imprisonment on the wire fraud charges.
Mr. Ferrer commended the investigative efforts of the Federal-State Mortgage Fraud Strike Force, with special commendation to the Federal Bureau of Investigation and Miami-Dade Police Department. The case is being prosecuted by Assistant U.S. Attorney Sean T. McLaughlin.
The case announced today is also part of the Department of Justice’s Financial Fraud Enforcement Task Force. This national task force was established in November 2009 to wage an aggressive, coordinated and proactive effort to investigate and prosecute financial crimes. Mortgage fraud is a key focus of the Financial Fraud Enforcement Task Force’s efforts. The task force is working to improve efforts across the federal executive branch, and with state and local partners, to investigate and prosecute significant financial crimes, ensure just and effective punishment for those who perpetrate financial crimes, combat discrimination in the lending and financial markets, and recover proceeds for victims of financial crimes.
An indictment is only an accusation and a defendant is presumed innocent until proven guilty.
A copy of this press release may be found on the website of the United States Attorney’s Office for the Southern District of Florida at http://www.usdoj.gov/usao/fls. Related court documents and information may be found on the website of the District Court for the Southern District of Florida at http://www.flsd.uscourts.gov or on http://pacer.flsd.uscourts.gov.
SCREENSHOT – Syria Parliament Official Site Hacked

Video – The stupidest, most racist ad for a Republican U.S. Senate candidate so far in 2012
TOP-SECRET – Israel’s First Cyber Drill

The possibility of a cyber-attack on Israel’s strategic infrastructure systems is now evident and highly realistic. Hence, starting today, the NCC (National Cyber Command) and the CTB (Counter Terror Bureau) will be orchestrating Israel’s first official cyber-terror drill in order to improve response effectiveness in the event of a virtual assault.
The drill, referred to as Lights Out, is expected to last several days, and will simulate a cyber-terror attack from multiple sources.
Although strategic systems such as those of the Israeli Electric Company and the Water Authority are highly encrypted and overseen by the Shin Bet security forces, Israel must maintain its edge in all facets of the existential war in which it is now engaged.
The Ministry of Communications will not be participating in the drill, as its personnel lack “the necessary expertise.”
The recent onslaught of cyber-attacks as well as the mysterious shut-down of several government systems in October have prompted a re-gentrification and re-evaluation of Israel’s cyber-defense tactics. The battle is being waged on a new front, and Israel must be prepared for all possible scenarios.
CONFIDENTIAL – Secret Service’s Rapid Enforcement Allied Computer Team (REACT) Task Force Funding and Progress Report
• Discuss the project’s progress to date.
I was assigned the responsibility to organize and complete the annual report (2009) to the governor and legislature, which was accomplished on-time in December of 2009. My appreciation for their assistance goes to my staff, Administrative Analyst Aileen Uytingco and Criminalist Greg Yoshioka, as well as a special thanks to CDAA member (California District Attorney’s Association) Santa Clara County Deputy District Attorney Bud Frank and San Diego Deputy District Attorney and Project Director of the CATCH task force Brendan McHugh. Particular kudos for Brendan’s ‘Executive Summary’ and analyses of all the statistical reporting from the five task forces.
We have experienced a vacancy in REACT beginning at the start of the second quarter and may further suffer another vacancy this quarter, both from the Santa Clara County District Attorney’s Office in the Bureau of Investigation. The open positions in BOI are held in a high priority; however, it is planned that the DA’s office will backfill one of the positions after the new hires are brought into the Bureau.
In spite of all that is occurring around the REACT office and the grant in general, the task force still maintains a high degree of involvement and statistical improvement. We have had a great run of supporting media releases of cases the task force has completed that have instilled an immense level of pride in our organization and speaks to the great motivation the men and women in this organization have towards getting the job done.
Please complete the statistical report table for Objectives #1, #2, and #3. Use additional pages to provide any additional narrative to report your accomplishments as projected in your application.
Objective #1: To investigate, apprehend, and prosecute criminal organizations, networks, and groups of individual engaged in the following activities: (The project should list the applicable high technology crimes as defined by California Penal Code § 13848 in which the task force focus is engaged.)
Objective #2: To apprehend and prosecute individuals and groups engaged in the unlawful access, destruction, or unauthorized entry into and use of private, corporate, or government computers and networks, including wireless and wireline communication networks and law enforcement dispatch systems, and the theft, interception, manipulation, destruction, and unauthorized disclosure of data stored within those computers.
Objective #3: To apprehend and prosecute individuals as groups engaged in the theft of trade secrets.
…
…
a) Significant Cases (Q2 FY09/10 (10/01/09-12/31/09)
High Tech
09-2001
An unknown person utilized the Roblox website forum located in Redwood City to make an ominous threat against an unknown school. REACT was requested to assist with the investigation.
An emergency request for records was sent and subscriber information was received. The message was traced to a 15-year-old boy in Rocky Mount, NC. Rocky Mount PD was contacted and provided with the information obtained to date. A search warrant of his residence by Rocky Mount police turned up drawings depicting explosions, but no destructive devices.
He was detained for making a false report of a destructive device and was released to the custody of his mother pending a juvenile hearing.09-2015
A Bay Area software company hired the Suspect to work on a program used by many of the company’s clients. The Suspect and the company’s president had a disagreement which resulted in the firing of the Suspect. In retaliation, the Suspect allegedly inserted a crash logic program in the software that caused the program to be down for a period of several days which ended up costing the company a loss of over $60,000.00. This investigation is on-going.09-2018
The suspect is a former employee of a large networking company headquartered in the Bay Area. He was responsible for inventory control at one of the buildings located in San Jose, CA. Investigators from the company suspect that the former employee was stealing serialized internal assets and then selling them to a local Reseller. Investigators conducted internal audits of serial number checking by a user of the Reseller. Several of those serial numbers were traced to internal owned assets that were under the control of the Suspect. Initial loss estimate is over $1,000,000.00. This investigation is on-going.
ID Theft09-1999
This case involves a possible large scale skimming operation where the points of compromise are stores from a national fabric store chain. Multiple victims have had their credit card account information compromised and then used at ATM machines all over the Bay Area.In September of 2009, FICO noticed an increase in unauthorized ATM withdrawals. After contacting banks and terminal processing companies, they determined that the common point of compromise were several fabrics stores throughout the United States. Included are victims that used the store in San Jose, CA. To date, 24 stores (locations in CA, OR, WA, UT, CO, WI, IL, TX, MO, KS, & VI) from this chain have had customers report compromised cards and unauthorized ATM withdrawals. At least 700 cards have been reported and are expected.
These actions seem to be in violation of 18 USC 1029 (access device fraud) and 18 USC 371 (conspiracy). Initial loss estimate is $1,000,000.00. This investigation is on-going.09-2028
A Target Store Employee (Suspect 1) is suspected of swiping stolen credit card numbers and loading gift cards in $500.00 increments for Suspect 2. Suspect 1 is using stolen credit card numbers from Germany to obtain these cards. Suspect 2 is selling the items that are being purchased with the fraudulently loaded gift cards on Craigslist. Initial loss estimate is $20,000.00. This investigation is on-going.09-2031
This case is the result of another REACT Case wherein victim’s information was stolen by Suspect 1 and later utilized by Suspect 2. Suspect 2 attempted to utilize the Victim’s information to obtain and cash a cashier’s check. He subsequently left his counterfeit driver’s license behind and was subsequently identified from the photo on the counterfeit driver’s license. Initial loss estimate is $4,500.00. This investigation is on-going.09-2046
The victim in this case was contacted by Ameritrade regarding someone attempting to transfer money from one of the victim’s TD Ameritrade accounts to a Wells Fargo account in the name of a third party. The Ameritrade employee stated the transfer was for over $16,000.00 and the caller knew the Victim’s SSN. The transfer was not completed because the caller could not answer the security question correctly. This investigation is on-going.09-2047
A San Jose Police Department officer made a traffic stop and contacted four occupants. He observed a laptop computer with a magnetic card reader attached on the R/F passenger floor. One passenger lied about his identity and was later arrested. The driver and remaining passengers were arrested for unlawful possession of a skimming device. Search of the driver’s purse yielded an apron from a local restaurant (Union City) and a mini skimming device. Many gift cards were also found. This investigation is on-going.…
DOWNLOAD ORIGINAL DOCUMENT HERE
CONFIDENTIAL – Introduction To The Israeli Air Force
DOWNLOAD ORIGINAL DOCUMENT HERE
CONFIDENTIAL – Israel IDF Operation Cast Lead Strategic Overview
DOWNLOAD ORIGINAL FILE HERE
Secret – (U//FOUO) U.S. Air Force Top Ten Cyber Threats 2012

Every year as technology grows and advances thus do the threats that surround it. Predicting what new cyber threats to look for may not always be an easy task. By keeping up with the past trends and ever changing current environment, may help to give us a good handle on how to prepare for what may be to come.
Last year we saw great changes in Hacktivism, mobile threats, social-media exploitation, client-side exploitation, and targeted attacks. As many of these will only continue to evolve as we step in to 2012, there are many more to be added to the list and not ignored. According to McAfee, the top ten threats for 2012 are:
1. Attacking Mobile Devices – Over the last two years mobile devices and smartphones have experienced a huge increase in attacks with 2011 showing the largest levels in mobile malware history. As they did on PCs, rootkits and botnets deliver ads and make money off of their mobile victims the same way. The installation of software or spyware, ad clicks or premium-rate text messages, as well as a shift toward mobile banking attacks is just a few threats facing mobile device users. As more users handle their finances on mobile devices, techniques previously dedicated for online banking will now focus on mobile banking users, bypassing PCs and going straight for mobile banking apps.
2. Embedded Hardware – GPS, routers, network bridges, and recently many consumer electronic devices use embedded functions and designs. Malware that attacks at the hardware layer will be required for exploiting embedded systems. Attackers will often try to “root” a system at its lowest level. If code can be inserted that alters the boot order or loading order of the operating system, greater control is gained and can maintain long-term access to the system and its data. The consequence of this trend is that other systems that use embedded hardware, for example, automotive systems, medical systems, or utility systems will become susceptible to these types of attacks. These proofs-of-concept code are expected to become even more effective in 2012.
3. “Legalized” Spam – Since the drop in global spamming volumes from the peak in 2009 and the increased black market cost of sending spam through botnets, “legitimate” advertising agencies. The United States’ CAN-SPAM Act was watered down so much that advertisers are not required to receive consent for sending advertising. “Legal” spams, and the technique known as “snowshoe spamming,” are expected to continue to grow at a faster rate than illegal phishing and confidence scams.
4. Industrial Attacks – Gaining more attention every day, the cyber threat potential is one of few that pose real loss of property and life. Water, electricity, oil and gas are essential to people’s everyday lives, Many industrial systems are not prepared for cyber attacks, yet many such as water, electricity, oil and gas are essential to everyday living. As with recent incidents directed at water utilities in the U.S., attackers will continue to leverage this lack of preparedness.
5. Hacktivism – One thing is certain, when a target was identified, hacktivists are a credible force. The problem in 2011 was the undefined structure, differentiating between rogue script kiddies and a politically motivated campaign was a task. McAfee Labs predicts that in 2012, either the “true” Anonymous group will re-invent itself, or die out. The other piece to look for in 2012, digital and physical demonstrations becoming more engaged and targeting public figures more than ever before.
6. Virtual Currency – Also commonly referred to as cyber-currency, a popular means to exchange money online which is not backed by tangible assets or legal tender laws. Many use services such as Bitcoin, which allows users to make transactions through a decentralized, peer-to-peer network using an online wallet to receive “coins” and make direct online payments. Users need a wallet address to be able to send and receive coins, the wallets however are not encrypted and the transactions are public. This boosts opportunity for cybercriminals, not to mention Trojan malware.
7. Rogue Certificates – We often tend to trust digitally-signed certificates without a second thought believing the digital signature or certificate authority they came from to be legit. Recent threats such as Stuxnet and Duqu used rogue certificates to evade detection and investigations have shown that as many as 531 fraudulent certificates were issued from DigiNotar, a troubled Dutch authority that recently declared bankruptcy. Increased targeting of certificate authorities and the broader use of fraudulent digital certificates will only increase, giving attackers an even greater advantage.
8. Cyber War – As more and more countries are realizing the harmful outcomes cyber attacks pose, industrial attacks for example, that carry crippling potential, the need for defense is more apparent than ever. McAfee Labs expects to see countries demonstrate their cyber war capabilities in 2012, in order to send a message.
9. Domain Name System Security Extensions – A technology to protect name-resolution services from spoofing and cache poisoning by using a “web of trust” based on public-key cryptography; meant to protect a client computer from inadvertently communicating with a host as a result of a “man-in-the-middle” attack. Unfortunately it would also protect from spoofing and redirection of any attempts by authorities who seek to reroute Internet traffic destined to websites that are trafficking in illegal software or images. With governing bodies around the globe taking a greater interest in establishing “rules of the road” for Internet traffic, McAfee Labs expects to see more and more instances in which future solutions are hampered by legislative issues.
10. Advances in Operating Systems – Recent versions of Windows have included data-execution protection as well as address-space layout randomization. These security methods make it harder for attackers to compromise a victim’s machine. Encryption technologies have also boosted OS protection in recent years. As with most internal OS security measures, attackers very quickly found ways to evade them. Advances by the information security industry and operating system will continue to advance, but will that push malware writers to focus on directly attacking hardware? McAfee Labs expects to see more effort put into hardware and firmware exploits and their related real-world attacks through 2012.
DOWNLOAD ORIGINAL DOCUMENT HERE
CONFIDENTIAL – Wegelin & Co. Swiss Bank Aiding U.S. Tax Evasion Indictment

The following indictment of the Swiss bank Wegelin & Co. and several affiliated persons for conspiring to aid wealthy U.S. clients evade taxes is noteworthy for its detailed description of some of the complex methods used by tax evaders.
DOWNLOAD ORIGINAL DOCUMENT HERE
Uncensored – FEMEN “Topless Warriors” documentary
Under Investigation – “Israel’s Mossad and Iranian opposition group are behind the assassination of the Tehran scientist”

Is Israel behind the assassination of the nuclear scientist in Tehran? According to the American blogger Richard Silverstein, Israel’s Mossad and the Iranian opposition group “Mujehadin Khalq” are the ones behind the explosion of the car of Mustafa Ahmadi- Roshan, who, according to Iranian reports, served as the deputy manager of the Natanz nuclear enrichment facility.
In the blog “Tikun Olam,” Silverstein quotes an Israeli source with military and political experience, saying that the Mossad carried out the operation in cooperation with the Iranian opposition group. Silverstein publishes articles on Israeli matters, which are prohibited for publication in Israel. One such example was the article on the Anat Qam affair, written before its publication was permitted in Israel.
Meanwhile, Iranian government officials are also blaming Israel for the assassination of the top nuclear scientist. This is the fourth assassination of senior officials in Iran’s nuclear program in the past two years.
The press agency IRNA quoted the deputy of President Ahmadinejad during a government meeting in Tehran this morning, saying, “Those who claim they are fighting terror have hurt Iranian scientists, but they must know that our scientists are becoming more determined each day on the path to fulfilling Iran’s ambitions and its scientific progress.”
Israel’s Chief of Staff, Lt. Gen. Gantz appeared before a meeting of the Knesset’s Foreign Affairs and Defense Committee, referring to the Iranian issue during the meeting and saying, “2012 is expected to be a critical year in Iran. It has lately been facing a system of international pressures which is increasingly growing.”
He added, “This is a critical year in the connection between the continued nuclearization, the internal chances in the Iranian leadership, the continued growing pressure by the international community, and things that happen to them in an unnatural manner.”
Revealed – Upheaval in the Mossad
Far from the spotlights, the new director of the Mossad replaced his entire senior staff, the exasperating body transfer affair is only another link in the chain of blunders in the handling of Gilad Shalit’s release, the battle over defense establishment funds being waged in the Knesset reaches new depths of entanglement.
The Mossad is an organization that acts in the shadows, as it should. Under a heavy cloak of secrecy it has undergone an upheaval in recent months. This is not something that everyone driving by the Mossad’s hilltop headquarters (ask any Israeli the “secret” location) is aware of, but a sea change, at least at the personnel level, has definitely taken place.
The shake up began with the appointment of Tamir Pardo as Mossad director on January 6. While the reshuffling at the senior level was underway, the outgoing head of the organization, Meir Dagan, captured the lion’s share of public attention in a series of admonishments and phillippics against an attack on Iran. In the meantime, Pardo quietly replaced the entire Mossad senior staff.
Background input: Pardo is one the few directors who grew up within the organization and was not parachuted onto it from the outside. He joined the ranks after a short stint as a signal corps officer. (His memoirs of the Operation Entebbe were recently published in the intelligence corps’ heritage magazine. Pardo was the chief radio operator for the commander of the operation, Yoni Netanyahu – the only Israeli military fatality in the hostage rescue.) For decades Pardo served heart and soul in Mossad operations, but when he reached the top level a few years ago – his advancement hit the wall. The reason: the continuous extension of Meir Dagan’s tenure.
When Pardo realized that the pinnacle of the pyramid was occupied, he temporarily left the organization for a position in the IDF (among other things he was involved in the development of special capabilities and planning of special ops in the Second Lebanon War). He returned to the Mossad as the deputy director, but again departed in 2009 after Dagan’s term was extended for another year. It seems that Dagan’s protracted hold on the top office did not suit Pardo’s nature.
 As a private citizen, Pardo was helping the Israeli entrepreneur Noam Lanir set up a company specializing in the export of medical services to wealthy Russians, when the decision was made to appoint him “chief” of the Mossad. Since entering office six months ago, Pardo has maintained his predecessor’s tradition of active operations while introducing a major organizational reconfiguration. Pardo’s managerial methods are definitely not those of Dagan. Without anyone outside of the Mossad taking note, Pardo replaced all of the key department heads.
As a private citizen, Pardo was helping the Israeli entrepreneur Noam Lanir set up a company specializing in the export of medical services to wealthy Russians, when the decision was made to appoint him “chief” of the Mossad. Since entering office six months ago, Pardo has maintained his predecessor’s tradition of active operations while introducing a major organizational reconfiguration. Pardo’s managerial methods are definitely not those of Dagan. Without anyone outside of the Mossad taking note, Pardo replaced all of the key department heads.
This is what happened in the special ops departments “Keshet” and “Caesarea”. New chiefs were also brought into the intelligence department; the political action and liaison department, responsible for the organization’s international contacts; and even the human resources section. The new head of the political action and liaison department served until recently as head of the intelligence department. His deputy, Z., the new head of the research department, was formerly the director of counter-terror in the intelligence corps. Z.’s deputy in the Mossad, A., was also Z.’s deputy in the intelligence corps research section. Furthermore, the person who until very recently headed the Mossad’s human resources section, Brigadier General (res.) Yosi Peretz, the former the chief officer of the IDF’s adjutant corps, was appointed director of human resources at Bank Discount a few days ago. The outgoing head of the political action and liaison department department, David Primo, was also in the news recently when Prime Minister Binyamin Netanyahu asked him to head the negotiations for the release of Gilad Shalit.
Shalit: an ongoing fiasco
Just as this column has mentioned on more one occasion in the past weeks, serious contacts are being held with Hamas on a possible deal for the release of Gilad Shalit.
Actually it is against this setting that Israel’s (mis)handling of the bodies’ transfer to the Palestinians this week is so infuriating. According to the press, the imbecility began with a meeting between senior members of the Palestinian Authority (PA) and the heads of Israel’s Civil Administration in Judea and Samaria. The Palestinians came away convinced that Israel had agreed to hand over 84 bodies. Political figures in Israel officially approved the report, and the IDF Spokesperson even published a statement that the transfer would proceed according to the “prime minister’s decision.”
 Then, a sudden turnabout occurred. After midnight, on the evening between Monday and Tuesday, Ehud Barak’s office issued a statement that the defense minister would reexamine the list of the Palestinian bodies in light of the protest voiced by the victims of terrorist events and the concern that a valuable bargaining chip might be lost in the negotiations for Gilad Shalit’s return. The Israeli journalist Ben Caspi, writing in the daily Ma’ariv, shed light on the murky matter.
Then, a sudden turnabout occurred. After midnight, on the evening between Monday and Tuesday, Ehud Barak’s office issued a statement that the defense minister would reexamine the list of the Palestinian bodies in light of the protest voiced by the victims of terrorist events and the concern that a valuable bargaining chip might be lost in the negotiations for Gilad Shalit’s return. The Israeli journalist Ben Caspi, writing in the daily Ma’ariv, shed light on the murky matter.
According to Caspi, the IDF Spokesperson’s announcement had been prearranged with the defense minister’s office to purposely use the unprecedented expression “the prime minister’s decision” rather than the “political echelon’s” (which naturally includes Defense Minister Ehud Barak). If indeed Barak set a trap for Netanyahu in order to cast himself as the “responsible figure” in the government, as Caspi claims, then he could have also exploited the relative lack of experience of new IDF Spokesperson, Brigadier General Yoav (Poli) Mordechai) (head of the Civil Administration in Judea and Samaria until last year). In addition, the director of the media department in the IDF Spokesperson’s Unit, Colonel Ofer Kol, is stepping down from his position this week (Ariela Ben Avraham, promoted to colonel last Thursday, is his replacement).
The inept handling of the bodies’ transfer is nothing compared to the recurrent blunders in the Gilad Shalit affair, most of which have been discussed in detail in this column. Three weeks ago the Israeli soldier completed five years in captivity.
Northern Command: mistakes fated to be repeated
As the fifth anniversary of the Second Lebanon War approaches, it is time to recall that the war broke out when many of the senior officers in the Northern Command were still new at their jobs.
For example, the general of Northern Command, Udi Adam, and the head of the Galilee Division, Gal Hirsh, were less than a year in their positions. Northern Command’s chief intelligence officer, Yosi Beidetz (now completing his succeeding post as head of the intelligence corps’ research department) had been in Northern Command barely a month when the war erupted, and the list goes on.
 Now we can note that the IDF is fully prepared for the heavy rioting expected in September if and when the Palestinians realize their plans to declare unilateral statehood. Last May we received a “taste” of what is likely to occur. This, of course, refers to “Nakba Day” [Israel’s Independence Day which, for the Palestinians, signifies “Catastrophe Day” dating back to 1948] when hoards of Syrians stormed the border on the Golan Heights. As September approaches the IDF is vigorously stockpiling “non-lethal” weapons, holding field exercises, preparing for a large-scale mobilization of the reserves, and scheduling training programs and courses so that the conscript units will be free for operational duty in the territories and on the borders. The assessment is that like “Nakba Day,” in September, too, Northern Command will have to deal with an onslaught of stubborn, resolute, violent protesters on the northern borders.
Now we can note that the IDF is fully prepared for the heavy rioting expected in September if and when the Palestinians realize their plans to declare unilateral statehood. Last May we received a “taste” of what is likely to occur. This, of course, refers to “Nakba Day” [Israel’s Independence Day which, for the Palestinians, signifies “Catastrophe Day” dating back to 1948] when hoards of Syrians stormed the border on the Golan Heights. As September approaches the IDF is vigorously stockpiling “non-lethal” weapons, holding field exercises, preparing for a large-scale mobilization of the reserves, and scheduling training programs and courses so that the conscript units will be free for operational duty in the territories and on the borders. The assessment is that like “Nakba Day,” in September, too, Northern Command will have to deal with an onslaught of stubborn, resolute, violent protesters on the northern borders.
But has the IDF learned all the lessons of 2006? Apparently not. Look at the facts: during August, a few weeks before the expected explosion, one after the other, the general of Northern Command, commander of the Galilee Formation (who has responsibility for the Lebanese border), the commanders of the 36th and Challenger Divisions, and, but what else, Northern Command’s chief intelligence officer will all be replaced. A blunder fated to repeat itself? It would seem so.
Mofaz fights
A final word. Another “hot” issue that occupied the defense establishment this week was a matter of money – lots of money.
The veteran journalist Nahum Barnea first broke the story in the daily Yediot Achronot last Friday. Barnea revealed that the director general of the defense ministry, Major General (res.) Udi Shani, has been banging on tables to free money designated for the defense ministry, money that was legally approved by the Knesset for the defense budget.
It turns out that close to three billion shekels have been held up for sundry reasons since the beginning of the year. The result: the defense ministry has accumulated a debt of hundreds of millions of shekels that it owes to each of the major defense industries that supply the IDF with weapons.
A week has passed since the exposé and the issue only becomes more empretzeled. A brief explanation is in order. The defense budget is passed biannually. It is unlike the budgets of the other ministries that the Knesset’s finance committee votes on, in that the defense budget is approved as a single flow without the possibility of debate on each specific section. The reason for this is to prevent any leaks of security secrets in the finance committee plenum.
 In order to oversee the defense budget, a special committee of ten Knesset members is appointed: half of them from the finance committee and half from the foreign affairs and defense committee, and all of them have the requisite security clearance level. The chairman of the joint committee is a figure is whose security credentials are of the highest order, unimpeachable to the nth degree – the former chief of staff and defense minister, Knesset Member Shaul Mofaz.
In order to oversee the defense budget, a special committee of ten Knesset members is appointed: half of them from the finance committee and half from the foreign affairs and defense committee, and all of them have the requisite security clearance level. The chairman of the joint committee is a figure is whose security credentials are of the highest order, unimpeachable to the nth degree – the former chief of staff and defense minister, Knesset Member Shaul Mofaz.
According to procedure, those who can delay the money flow to the defense establishment are the finance ministry (if it doesn’t bring the regular defense budget to the finance committee for approval), the chairman of the finance committee (if he doesn’t order payment to the joint committee for approval), and, of course, Shaul Mofaz’s joint committee.
Back to the facts: the security budget has suffered lately from the iron fist of all three players. The finance ministry is withholding the money, the finance committee is delaying (for coalition reasons) approval of the budget that the finance ministry has already approved (a disheartening development for the defense industries as of last Tuesday: the finance committee is freezing 620 million shekels due to various coalition demands), and even Knesset Member Shaul Mofaz has locked horns with the defense establishment in recent weeks, fighting it “tooth and nail.”
For the first time it appears that the former chief of staff is demanding his right to scrutinize the money designated for four defense projects, as well as the sources of their funding. Moreover, Mofaz wants to check the money intended for Elbit’s DAP (Digital Army Program), and a joint program between Elbit and the defense and finance ministries for the establishment, in the south of the country, of a plant, partially funded by the state, for the production of state-of-the art communications equipment for the IDF.
Mofaz is determined to oversee the defense establishment and not merely serve as a rubber stamp that gives the green light to all of its budgets. In the meantime, discussions in the Knesset focus only on legal niceties: does Mofaz’s committee have the authority to examine the sources of financing of certain defense budgets or only what the money is intended for. By the end of this week the funds appear to be frozen solid. Thus the leaders of the defense industries may soon find themselves knocking on the doors of the bank directors asking for loans to tide them over until the defense funding thaws and the cash flows again.
***
Photos:
Director of the Mossad, Tamir Pardo (Photo: Flash 90)
Gilad Shalit (Photo: AP)
Member of Parliament, Shaul Mofaz (Photo: IDF Spokesperson)
The Persian Preparations for War
In early November, Ayatollah Ali Khamenei warned, “Any country attacking Iran better be prepared to suffer retaliation from the Iranian armed forces. Anyone thinking about invading the Islamic Republic of Iran better be able to withstand a powerful response from the Revolutionary Guard and the Iranian army.”
The recent report published by the International Atomic Energy Agency (IAEA) explains that once Iran decides to manufacture a nuclear bomb, it will only take a few months to assemble. In Israel and the West, this report intensified discussions on the need for an all-out attack on Iran’s nuclear facilities.
So far, Western media has focused on questions concerning a possible Israeli and/or Western attack. What has yet to be discussed is what Iran is doing to counter an inevitable clash.
For several years, the Iranians have publicized their military capabilities in an effort to deter an attack. Occasionally, they unveil a new, locally produced, state-of-the-art weapon based on foreign technologies.
“In reality, their conventional military forces are poor,” says Yiftah Shapir, a senior research fellow and director at the Institute for National Security Studies’ Middle East Military Balance Project. “Looking at the layout of Iran’s conventional forces, they have a large but antiquated army that has suffered from cutbacks and sanctions in recent years. Since they find it difficult to procure new advanced weapons, they have begun to produce their own. Every two months or so, we hear of something new: airplanes, helicopters, missiles, weapons systems, radar, and so forth.
“True, we must not underestimate Iran’s industry, as in the past it received assistance from North Korea, and today, knowledge flows in the opposite direction in some areas. Still, Tehran’s public announcements should be viewed with some degree of skepticism. The question is: what do they have and what is actually operational?” mulls Shapir.
Mickey Segal, a senior research fellow at Terrogence Company and the Jerusalem Center for Public Affairs and former head of the Iranian Desk in the Research Department at the Directorate of Military Intelligence says, “The Iranians believe that the revolutions in the Arab world play into their hands. From their viewpoint, the old regimes are being pushed out and being replaced by the Islamic organizations. As they see it, they are the next ‘big thing.’ They expect nuclear weapons to increase their influence.”
The Iranian government invests enormous sums of money in an effort to conceal their numerous nuclear sites. The main sites are the uranium enrichment plant in Natanz, the conversion plant in Isfahan (where the November 2011 explosion occurred), the nuclear power station in Bushehr, and the uranium enrichment plant near Qom that remains under construction.
Many of the facilities are underground and shielded by a concrete-reinforced ceiling and walls up to two and a half meters thick.
“From the outset, they built facilities underground and concentrated their efforts on the surrounding air defenses,” says Dr. Ephraim Kam, principle research fellow and deputy director of the Institute for National Security Studies (INSS).
The Iranians spend huge sums of money on camouflage. According to Western assessments, Russia supplies Iran with the technological means to hide its nuclear facilities. During the Cold War, Russia developed special camouflage nets capable of blocking the view from space, including thermal sensors and synthetic aperture radars (SAR). In addition, it is likely that Iran also employs advanced methods to distort a facility’s geometric pattern and render them unidentifiable by spy satellites and UAVs equipped with optical payloads.
Besides camouflage, Iran is doubling efforts to reinforce its air defense layout, especially its anti-aircraft systems—even though these consist mainly of antiquated anti-aircraft missiles acquired from foreign sources or produced domestically. These include Russian SA-5s for intermediate to long-range interception, SA-2s for intermediate and very high altitudes, and an Iranian-made Shahin version of the American Hawks (that the Iranians claim can reach an altitude of forty kilometers). They also possess several advanced SA-15 units that they received from Russia around five years ago, and frequently release photos of their batteries deployed near the Bushehr Nuclear Power Plant.
“Few of the systems pose an immediate threat to advanced Western aircraft,” asserts Tal Inbar, head of the Space and UAV Research Center at the Fisher Institute for Air and Space Strategic Studies. Inbar asserts that, “Following Russia’s refusal to supply Iran with advanced S-300 missile systems (that have a range of over 100 kilometers)—a result of American and Israeli pressure—Iran now claims that it succeeded in developing an improved version of the S-300 (that it calls Bavar-373). Official Iranian sources note that the system performs better than the Russian missiles—but this is an empty claim.”
Be that as it may, the Iranians seem to have managed to get ahold of a Chinese version of the S-300, designated HQ9, and on the basis of this imitation, they have developed their own system. Israeli sources recently acknowledged that Iran is beginning to produce multi-layered systems that will further complicate any operation against its nuclear sites. Iran also tried to obtain a number of Russia’s Pantsir-1 anti-aircraft missile systems from Syria. The system’s development was financed by the United Emirates and became operational in Russia only last year. It is uncertain whether it has been transferred to other countries since then.
Most aircrafts in the Iranian air force are aging Russian-made planes that Iraq transferred to Iran during the First Gulf War. The Iranians also have some old F-4 Phantoms and F-14 Tomcats that the Americans delivered when the Shah was in power.
Iran’s first line of fighters is compromised of MiG-29s purchased from Russia in the early 1990s, as-well-as the aging F-14s purchased from the US. In late 2007, Iran announced that it was developing two new fighters: the Azaraksh (Lightning) and the Saeqeh (Thunderbolt); both are based on outdated American F-5s.
“The Iranians claim that these planes perform better than F-18s. The truth is that they still look like F-5s, but have an extra tail (stabilizer) added to resemble the F-18s. It is doubtful that the Iranians succeeded in developing the avionics and other systems necessary to retrofit an airplane into a first-class modern weapon. Still, Iran has made impressive advances in the maintenance of its systems through improvisation and the acquisition of spare parts from the black market. They are also experts at cannibalizing parts from planes and missiles. For example, they can disassemble twenty old planes in order to keep thirty others in flying condition,” explains Yiftah Shapir.
Iran also has several dozen Cobra attack helicopters from the 1970s, Bell-205s and 214s, and MI-171s that they bought from the Russians a decade ago.
In recent years, Iran has made significant progress in developing and producing UAVs, some of which are capable of carrying munitions. Last year, Iran announced they had developed an attack UAV armed with a bomb, while referring to their jet-propelled air vehicle (which is based on an outdated American target drone that was later manufactured by South Africa). According to Mickey Segal, the Iranians are currently working on two UAVs: one for attack—the Karrar (Striker), and the other for attack and reconnaissance—the Ababil (Swallow). These UAVs appear to be pre-programmed, and not controlled in real-time.
The Iranian developers of the UAV layout will probably glean valuable technical information from the recent capture of an American RQ-170 Sentinel surveillance drone. The stealth UAV malfunctioned during a reconnaissance operation over Iran in early December 2011, and was picked up by Iranian security forces. American military sources note that, “Iran gained a great prize from a technological point of view by getting its hands on the RQ-170, one of the most advanced UAVs in the world.”
Radar
Today, Iran possesses a number of outdated European radars, such as the British AR-3D for air defense and an unknown quantity of Chinese JY-14s acquired in the late 1990s. Last June, during a weapons exhibition in memory of Ayatollah Khomeini, the Iranians gave a sneak peak at a phased array radar that is considered one of the most advanced of its kind. According to Tal Inbar, the first analyst in Israel to identify the radar, “The Iranians didn’t officially reveal the radar, but it can be seen peeking out behind Khamenei in the exhibition. They claim that it was their own development, and at face value, the system appears genuine.”
Only in late 2011 did the Iranians hold a large-scale air defense exercise, to evaluate the performance and operability of intelligence and communications equipment designed to “protect sensitive sites around the country.” Mickey Segal believes that during their latest exercise, the Iranian successfully tested a locally produced wide-range-frequency passive-radar-detection system. Rapid response units using modern EW (electronic warfare) equipment succeeded in jamming a simulated enemy’s radar and communications systems. Tests were also carried out on the latest fiber-optic communication equipment and electro-optic systems for air-defense detection.
In the second stage of the exercise, Iran’s air-defense forces quickly jammed enemy combat aircraft and employed active and passive means to protect their own radar network and communication lines.
The Iranians have gone to great lengths to thwart a naval attack. After spending endless hours developing anti-ship missile systems, they have produced their own version of the Chinese C-802 and the Khalij Fars (Persian Gulf) anti-ship ballistic missile, based on the Fatah-110 surface-to-surface missile technology. Both weapons pose a tangible threat to naval vessels, especially American ships cruising close to the Iranian coast.
A few months ago, Iran unveiled a new cruise missile with a 200-kilometer range that could be launched from ships or ground batteries. They also announced development of the Valfajr (The Dawn) torpedo system that is designed to carry a 220-kilo warhead capable of hitting large battleships.
“If Iran comes under a major attack, it will try to block the Strait of Hormuz and cut off oil shipping routes,” says Tal Inbar. “Blocking the Persian Gulf will require the use of Iranian-made miniature submarines (Ghadir mini-subs with a two to three man crew), different types of torpedoes, and speedboats. This arsenal will be used to saturate the area with dozens to hundreds of missiles that will disrupt movement, forcing the Americans to engage the targets.” It should be noted that last summer, Iran fired supersonic surface-to-sea missiles at moving targets close to the Strait of Hormuz during the Great Prophet 6 war games exercise.
The Iranian fleet currently has three Russian-made Kilo Class Type 877EKM submarines, and according to Iranian sources, a half-ton Iranian sub designed for reconnaissance in the Persian Gulf and Strait of Hormuz. Iran also developed Bavar 2 – a lightweight radar-evading seaplane armed with machine guns and capable of carrying a bomb.
Mickey Segal notes that Iran’s preferred tactic against naval vessels is to swarm them. This tactic involves dozens of small, Iranian-made speedboats armed with explosives, rockets, and light weapons dispatched to blow up American aircraft carriers and destroyers.
Missiles and rockets
Iran’s strongest deterrent is of course, their offensive capabilities that appear in the form of missiles and rockets. This arsenal directly threatens any point in Israel and Europe—whether in the hands of Iranian proxies, Hezbollah and Hamas, or by way of Iran’s own long-range missiles.
Most experts agree that Iran has made impressive gains in rocketry in recent years, and has even surpassed North Korea in certain areas of its missile program, especially with respect to guidance systems and solid-fueled engines. During the Great Prophet 6 exercise, Iran exposed their underground missile silos and fired off a large number of surface-to-surface missiles at various ranges. Iran’s pride and glory is the Shahab 3 missile that has a 1,300 km range. Iran also has the Qader (Mighty) cruise missile—an improved version of the Shahab 3—that can reach a target at 1,800 km. A more significant threat is the Sejil (Baked Clay) ballistic missile, which is still in the development stage. This is a solid-fueled two-stage rocket with a range of over 2,000 km. Iran has carried out several tests on the Sejil during the last two years.
 Iran is striving to attain missiles with ranges of thousands of kilometers capable of threatening Europe. According to Tal Inbar and based on various sources, North Korea may have transferred BM25 missiles to Iran, which are believed to have a 3,500 km range. The BM25s employ the same technology as Soviet R-27 submarine-launched, ballistic missiles. Iran has not yet officially confirmed that it possesses these weapons, but an analysis of an underground launch site indicates that the storage facility’s dimensions are much larger than the missiles known to be in Iran’s possession. Such evidence suggests that Iran has indeed obtained the BM25s.
Iran is striving to attain missiles with ranges of thousands of kilometers capable of threatening Europe. According to Tal Inbar and based on various sources, North Korea may have transferred BM25 missiles to Iran, which are believed to have a 3,500 km range. The BM25s employ the same technology as Soviet R-27 submarine-launched, ballistic missiles. Iran has not yet officially confirmed that it possesses these weapons, but an analysis of an underground launch site indicates that the storage facility’s dimensions are much larger than the missiles known to be in Iran’s possession. Such evidence suggests that Iran has indeed obtained the BM25s.
Iran is also making progress on its cruise missiles that are based on technology acquired from the Ukraine a few years ago.
Once the Iranians produce nuclear warheads, they intend to arm their Shihabs with them. They already have the ability to launch missiles and aircraft armed with chemical and biological WMDs.
Some of the missile projects are developing under the guise of Iran’s space program, since the technology for launching a satellite or a ballistic missile is essentially the same. Iran is also working on its own surveillance satellites. Half a year ago, it launched a miniature Rasad (Observation) satellite into space.
Though the orbiter is of no military value, Rasad is the second satellite that Iran independently launched. The first, Umid (Hope), brought Iran into the exclusive space club in February 2009.
A mysterious explosion at an Iranian missile-project site
In November 2011, an explosion rocked a major missile-testing site near Tehran. It killed seventeen people, including General Hassan Tehrani Moghaddam, a senior commander in the Iranian Revolutionary Guards’ missile program. The base where the explosion occurred is a storage site for Shahab missiles. To date, it is still unclear what effect the explosion will have on the Iranian missile program.
Cyberwarfare
Iran’s global terror network is the long arm of the Islamic Republic. However, Iran is also relentlessly striving to attain sophisticated defensive and offensive capabilities in the fifth fighting dimension, cyberspace.
In 2011, it established a Cyber Defense Headquarters in the General Staff, and a cyber-defense program was launched at Imam Hossein University in Tehran. A number of cyber defense drills will be held in 2012; the goal being to identify the Achilles’ heel in the state’s operating systems. In early 2012, Iran will hold its first national conference on cyber defense.
Israeli sources estimate that Iran’s cyberwarfare capabilities are among the most advanced in the world. The Iranians already know how to operate in cyberspace and leave almost no fingerprints.
How will the Iranians respond in the event of an attack? Pundits, scholars, and observers all agree: they will use every means at their disposal, in all dimensions, and on all fronts.
Film – The Assassination of JFK – C.I.A Bush Connection
Amateur video – Homs filmed in flames following fresh assault
Amateur video emerging from Syria is purported to how the city of Homs burning after a reported barrage of shelling from Syrian government forces that has left hundreds dead.
FEMEN – Semi-naked women protest censorship in Ukraine
Billionaires Battle Bonus against Obama
At a private three-day retreat in California last weekend, conservative billionaires Charles and David Koch and about 250 to 300 other individuals pledged approximately $100 million to defeat President Obama in the 2012 elections.
A source who was in the room when the pledges were made told The Huffington Post that, specifically, Charles Koch pledged $40 million and David pledged $20 million.
The semi-annual, invitation-only meeting attracts wealthy donors, Republican politicians and conservative activists. Last year, hundreds of activists gathered outside the walled-off resort to protest the meeting. This year, however, the conference went off quietly.
“Conference organizers and their guests successfully slipped in and out of the Coachella Valley without being detected, by buying out nearly all of the 500-plus rooms at the Renaissance Esmeralda resort in Indian Wells,” reported The Desert Sun. “The resort closed its restaurants, locked down the grounds with private security guards and sent many workers home.”
David Hamilton Koch (![]() /ˈkoʊk/; born May 3, 1940) is an American businessman, philanthropist, political activist, and chemical engineer. He is a co-owner (with older brother Charles) and an executive vice president of Koch Industries, a conglomerate that is the second-largest privately held company in the U.S.[7] Koch is the second-richest resident of New York City as of 2010.[3][4]
/ˈkoʊk/; born May 3, 1940) is an American businessman, philanthropist, political activist, and chemical engineer. He is a co-owner (with older brother Charles) and an executive vice president of Koch Industries, a conglomerate that is the second-largest privately held company in the U.S.[7] Koch is the second-richest resident of New York City as of 2010.[3][4]
He is a major patron of the arts and a funder of conservative and libertarian political causes, including some organizations that fund some organizations within the American Tea Party movement.[3][8] Among other charities, he has contributed to Lincoln Center, Sloan Kettering, a fertility clinic at New York-Presbyterian Hospital and the American Museum of Natural History‘s David H. Koch Dinosaur Wing.[9] The New York State Theater at Lincoln Center, home of the New York City Opera and New York City Ballet was renamed the David H. Koch Theater in 2008 following a gift of 100 million dollars for the renovation of the theater. Condé Nast Portfolio described him as “one of the most generous but low-key philanthropists in America”.[10]
see
https://en.wikipedia.org/wiki/David_H._Koch
and
Is Your Senator Representing Charles and David Koch?
http://www.huffingtonpost.com/robert-greenwald/is-your-senator-represent_b_1205692.html
New FEMEN Video uncensored – Голые клюшки
На этой неделе активистки украинской феминистской организации FEMEN отметились в Цюрихе, где устроили очередную голую акцию протеста около заснеженного входа в здание Международной федерации хоккея.
Обнаженные украинки держали плакаты с надписями на английском языке, гласящими, что “раб не играет в хоккей”, и призывали не путать чемпионат мира с диктатурой.
Поводом для акции протеста послужило участие сборной Белоруссии в чемпионате мира по хоккею, который пройдет в мае этого года в Финляндии и Швеции. Сборная Украины играет в дивизионе 1А (чемпионат этой группы состоится в апреле в Словении).
К властям Белоруссии и лично к президенту Александру Лукашенко у активисток FEMEN отношение особое: в декабре они подверглись жестоким издевательствам после акции протеста в Минске.
Не чужды украинские феминистки и спортивной жизни: в прошлом году они устроили несколько акций протеста во время официальных мероприятий по подготовке футбольного чемпионата Европы 2012. Тогда дамы из FEMEN возмущались по поводу “торговли женщинами” в Европе.
Судя по всему, в Швейцарии девушки из FEMEN чувствуют себя комфортно. Неделю назад они протестовали перед воротами Давосского форума.
TOP-SECRET – National Cyber Security Division Joint Cybersecurity Services Pilot (JCSP)
The National Security Archive – Cracking a Vietnam War Mystery
Washington, D.C., February, 2012 – Casting new light on one of the most controversial and enduring mysteries of the Vietnam War, a new book using evidence from long-hidden communist sources suggests that the U.S. Government missed a major chance to open peace talks with North Vietnam in late 1966, more than eighteen months before the opening of the Paris peace talks and more than six years before the accords that finally ended US direct involvement in the fighting. The revelations contained in Marigold: The Lost Chance for Peace in Vietnam by James G. Hershberg imply that the United States might have escaped its Vietnam predicament with a far lower toll: the secret Polish-Italian peace attempt code-named “Marigold” by U.S. officials culminated at a time when roughly 6,250 Americans had perished, compared to the more than 58,000 who ultimately died in the war.[1]
At one point the clandestine diplomacy verged on a breakthrough, with the apparent mutual agreement to hold an unprecedented meeting between US and North Vietnamese ambassadors in Warsaw to confirm Washington’s adherence to a ten-point formula for a settlement. “I thought I had done something worthwhile in my life,” recalled the American ambassador in Saigon at the time, Henry Cabot Lodge, of that moment of seeming success with his diplomatic partners from Poland and Italy. “We had a drink on it.”[2] A date was even tentatively set for the enemy ambassadors to meet: December 6, 1966. But before the encounter could take place, the covert effort was first suspended—due, the Poles said, to the U.S. bombing of Hanoi, the first such strikes around the North Vietnamese capital in more than five months—and then collapsed, for reasons which were disputed in acrimonious private US-Polish exchanges at the time. Before long, those arguments seeped into the press, sparking an international scandal and leaving behind a convoluted historical mystery—until now.
The inside story of these murky diplomatic machinations, as well as other revelations concerning the Vietnam War, the Cold War, the Sino-Soviet split, and American politics and journalism in the 1960s, can now be found in Hershberg’s book, published this week by the Stanford University Press and the Woodrow Wilson Center Press. Challenging the conventional wisdom that both Washington and Hanoi were so dug in at the time that no real chance for peace (or even serious peace talks) then existed, the study utilizes more than a decade of archival research in more than a dozen countries, both communist (and former communist) and Western, as well as interviews with veterans of the events in Poland, Vietnam, Italy, and the United States—including roughly 50 hours of interviews in Warsaw with the key figure in the affair, former Polish diplomat Janusz Lewandowski, who comes in from the cold war to offer his perspective openly and in depth for the first time.
Background
First—some context. Between early 1965, when the United States sharply escalated its military involvement in Vietnam, and the spring of 1968, when Washington and Hanoi finally agreed to talk in Paris, hundreds of attempts were made to bring the warring sides to the bargaining table. Some were public, some secret; some by third countries, some by individuals, some by institutions or organizations; some involved letters, some appeals, some “plans” or “points” or “formulas,” some citations of past accords or international laws or conventions; some were purported “peace feelers” or “signals” so subtle—a wink-and-nod or linguistic wrinkle in an otherwise mundane statement, or a barely discernable decrease in certain military activities—that no one really knew whether they even existed or (if sent) were noticed by their intended target; some were derided by Lyndon Johnson and his secretary of state, Dean Rusk, as pipe-dreams spun by eccentric egotists or idealistic schemers who had contracted “Nobel Peace Prize fever”; others were sophisticated, painstakingly-planned diplomatic ventures designed and conducted at the highest levels of statesmanship.
But they all had one thing in common: they all failed. And over those three years, as U.S. forces in Vietnam mushroomed from 25,000 to more than half a million and the war crippled the Johnson Presidency and poisoned American politics, the death and destruction ground on ceaselessly, with thousands of Vietnamese and Americans lives lost every month and countless more ruined. Most of the ill-fated negotiating initiatives undertaken during the 1965-1968 period of escalating conflict never had a real chance: the opposing sides simply weren’t seriously prepared to consider peace, or even peace talks, on terms acceptable to the other. (Some were even designed to fail, to impress public opinion and justify subsequent, already planned military escalation.[3]) Rather than risk defeat or humiliation at the bargaining table, powerful factions on both sides preferred to seek military victory—another Dien Bien Phu, the North Vietnamese imagined, recalling the triumph over the French; or, the Americans calculated, pounding the enemy until it swallowed the status quo ante, the division between north and south, as in Korea.
But, there was one exception to this pattern of inevitable, over-determined deadlock: Using new evidence that has emerged only since the end of the Cold War, Marigold: The Lost Chance for Peace in Vietnam contends that in late 1966 the United States likely missed a genuine opportunity to begin winding down its disastrous military involvement in Vietnam, on politically-palatable terms; that, at a minimum, the Johnson Administration botched a chance to enter into direct talks with Hanoi at that time, that it misconstrued the most crucial aspects of the secret diplomatic initiative that nearly achieved that goal, and then—at the time and later, in press leaks and memoirs and covert international contacts—covered up its own errors. Moreover, it shows that the initiative’s collapse, as misunderstood by both sides (each of which thought the other had acted in bad faith), not only signified their shared failure to open a political track that might have led to genuine negotiations, but made it more difficult later on to overcome mutual distrust and enmity and enter into direct discussions—in effect, dealing a double blow to peace hopes, laying the groundwork for further escalation (including Hanoi’s decision to launch the January 1968 Tet Offensive), and probably delaying the ultimate beginning of negotiations and, perhaps, the end of the war. (Marigold’s failure, once it seeped into public consciousness through press leaks, also roiled American politics, spurring charges from antiwar critics that President Johnson was insincere and/or incompetent in seeking peace in Vietnam, and widening the “credibility gap” that increasingly undermined his public standing.)
Uncovering the Marigold story has long challenged investigators, who were stymied by lack of access to key sources. Of the myriad secret efforts undertaken to promote the opening of U.S.-North Vietnamese peace talks between early 1965 and April 1968, the distinguished Vietnam War historian George C. Herring judged Marigold to be “one of the most controversial” and “in many ways the most intriguing,” a “possibly promising” diplomatic initiative whose “origins and denouement remain shrouded in mystery.”[4]
In their 1968 book The Secret Search for Peace in Vietnam, David Kraslow and Stuart H. Loory quoted an unidentified “close associate” of President Johnson as saying that they would “never get the inside story” of Marigold.
Why not?
“Because it makes our government look so bad.”[5]
Finally presenting the “inside story”—or as much as the declassified record finally reveals—Marigold: The Lost Chance for Peace corroborates the sentiment of this unnamed source (which the book identifies as Bill Moyers, LBJ’s protégé and former press secretary, who had recently left the White House[6]), but also concludes that blame for Marigold’s failure was shared, the consequence of misjudgments and errors by all three key participants: the U.S., Polish, and North Vietnamese governments.
A Cold War Anomaly:A Communist Ambassador in Saigon
At the heart of the affair was a cold war anomaly. Not a single communist government recognized the Republic of Vietnam (South Vietnam), instead locating their embassies in Hanoi, the capital of the Democratic Republic of Vietnam (North Vietnam), and maintaining fraternal interparty relations with the ruling Vietnamese Workers’ Party, or Lao Dong. Yet, there was a communist diplomat of ambassadorial rank based in Saigon throughout the war due to the presence of the International Control Commission (ICC) established by the 1954 Geneva Accords that ended the post-World War II conflict between colonial France and the communist/nationalist Viet Minh forces led by Ho Chi Minh.[7] The East-West pact reached at Geneva split Vietnam at the 17th parallel, supposedly temporarily, pending elections to unify the country within two years, but the voting never took place and the division congealed into two rival regimes, the communist DRV in the north and the anti-communist RVN in the south, now backed by the Americans, who had replaced the French. Yet, even though the Geneva Accords were essentially dead by the end of the 1950s, no one wanted to pull the plug on the group set up to monitor both sides’ compliance with them: the ICC (formally known as the International Committee for Control and Supervision).
As a cold war compromise, the ICC’s membership was delicately balanced between East and West, consisting of Poland, Canada, and neutral India as chair; as a result, the group unsurprisingly soon found itself stalemated, paralyzed, and ineffectual, but it continued to meet regularly even as the war escalated—and for logistical reasons was headquartered in Saigon, resulting in the incongruous presence of senior Polish diplomats and hundreds of Polish soldiers stationed in a capital of a country run by a strongly anticommunist regime which Poland, like all communist countries, virulently denounced as an American puppet and whose overthrow it militantly supported. Representing Warsaw during the Marigold affair was a young diplomat (then 35 years old) named Janusz Lewandowski, who was based in Saigon, where he would routinely meet US and even South Vietnamese officials, but periodically shuttled (via neutral Phnom Penh in Cambodia and Vientiane in Laos) to Hanoi, where he became “comrade” Lewandowski and saw North Vietnamese leaders like Premier Pham Van Dong, Defense Minister Vo Nguyen Giap, and revolutionary icon Ho Chi Minh.
Lewandowski, who arrived in Saigon as Poland’s ICC commissioner in April 1966, was thus ideally poised to serve as a secret intermediary between Washington and Hanoi—which of course lacked normal relations or (except for a few rare, mostly formalistic instances) direct diplomatic contacts—and that is the role he assumed during Marigold. (Interviewed in Warsaw, Lewandowski recalled that shortly before he left Warsaw for Saigon, Polish Foreign Minister Adam Rapacki gave him a secret charter to pursue peace possibilities outside his normal work with the ICC.[8]) His enthusiastic collaborator and co-conspirator was Italy’s ambassador to South Vietnam, Giovanni D’Orlandi, who, in line with the desires of his foreign minister, Amintore Fanfani, and his own passionate interest in the Vietnamese, ardently desired to promote peace.
The Marigold channel first sprang to life in late June 1966, when after a recent trip to Hanoi Lewandowski spoke with D’Orlandi and, the Italian excitedly told Henry Cabot Lodge, delivered a “very specific peace offer” from the North Vietnamese. Hopes in Washington that the channel might yield a breakthrough briefly surged in Washington—LBJ told an associate during a tape-recorded telephone conversation that “yesterday I had the most realistic, the most convincing, the most persuasive peace feeler I’ve had since I’ve been President”[9]—but the contacts fizzled as abruptly, and mysteriously, as they had begun. The one positive result of this initial flurry of diplomacy involving the three Saigon diplomats was that the North Vietnamese, despite harshly condemning the latest U.S. military actions, did not reveal the Marigold channel, preserving it for potential future use. After several months of desultory conversation amid further military escalation in the autumn of 1966, the Marigold channel revived for a second act in November and December.
Was Marigold for Real?
The most bitterly contested aspect of the Marigold story has been whether the Poles were actually authorized by Hanoi to set up the direct meeting between U.S. and North Vietnamese ambassadors in Warsaw to confirm Washington’s adherence to the positions which Lodge had relayed to Lewandowski in mid-November in Saigon, and which Lewandowski, in turn, had conveyed to DRV authorities during his subsequent trip to Hanoi. Of course, the Poles insisted that they were acting with the full authorization of the North Vietnamese government, but once the initiative collapsed, top U.S. officials did their best to seed doubt on this score. They hinted or even explicitly claimed that the Poles (or even Lewandowski personally) had acted independently, or perhaps at Soviet instigation, hoping to lure the Americans into a bombing halt or other military concessions, and/or to show their negotiating cards and bottom line for a settlement—all to benefit their North Vietnamese comrades’ quest for victory on the battlefield, rather than to promote peace. After all, the Americans noted correctly, they had had no direct communications from the North Vietnamese, only with the Poles.
Feeling on the defensive after the Washington Post first disclosed the clandestine contacts in early February 1967 with an implication that—in the words of a prominently-quoted, unidentified pro-American diplomat at the United Nations (actually the Danish ambassador)—Washington had “bungled” a genuine chance for peace, U.S. officials used increasingly harsh language to question Warsaw’s motives and sincerity. In conversations both with foreign diplomats and with reporters, and later in oral history interviews and memoirs, they used words like “fraud” or “sham” or “phony” to describe the Polish initiative. In May 1967, the New York Times ran on its front page an expose of the affair, written by an Associated Press correspondent and informed by background leaks from Dean Rusk and other senior officials, broadly suggesting that Warsaw had never received Hanoi’s okay to set up a direct US-DRV meeting—an article that caused satisfaction in the State Department and outrage among Polish foreign ministry leaders, who felt that their integrity had been questioned.[10]
These Johnson Administration efforts to plant doubts about Poland’s role had considerable success—in public opinion, in foreign chancelleries, and in the historical record. The affair’s “real enigma,” believed British foreign office aides, who undertook a secret post-mortem of the affair, was Hanoi’s role: Did Poland have a “clear mandate” from the North Vietnamese or had it not fully “‘sold'” them on a bargain Warsaw was trying to hammer out with the Americans?[11] After hearing both the U.S. and Polish versions of the affair, London ended up concluding “that the Poles probably never had a sufficiently clear mandate from the North Vietnamese to the point of arranging a [direct U.S.-North Vietnamese] meeting” and were instead “trying an initiative on their own; they may have made a certain amount of progress with it because they had good contacts with the North Vietnamese; but they were never in the position of being able to ‘deliver’ their friends.”[12]
In his 1971 memoir The Vantage Point: Perspectives of the Presidency, 1963-1969, Lyndon B. Johnson wearily consigned the entire affair to the realm of academic investigators, asserting that it comprised far more shadow than substance: Unlike Rusk, Johnson was too polite to call the Poles “crooks”—as the secretary of state described their actions in Marigold to Averell Harriman[13]—but his disdain shone through just the same. Brushing aside charges that he had squandered chances for peace, he stressed that Washington “never received through the Marigold exchanges anything that could be considered an authoritative statement direct from the North Vietnamese.” He termed the channel a “dry creek” that was exposed as fraudulent when the DRV ambassador failed to show up for the 6 December 1966 meeting in Warsaw. “The simple truth, I was convinced, was that the North Vietnamese were not ready to talk to us. The Poles had not only put the cart before the horse, when the time of reckoning came, they had no horse.”[14] Johnson’s national security adviser, Walt Rostow, declared that the Poles “never had Hanoi sewed up”[15] and his National Security Council staff aides scoffed that Warsaw “just had absolutely no charter from Hanoi to represent them”[16] or was even acting out a disinformation script manufactured in Moscow by the KGB.[17]
Nearly two decades later, Dean Rusk still fumed at what he believed had been a Polish scam to snooker him and the United States into falsely believing that Warsaw had acted with a firm mandate from Hanoi. Declaring that he had “doubted the authenticity of Marigold” all along, the former secretary of state called Lewandowski’s position “specious,” since he “simply didn’t reflect Hanoi’s views,” and-citing an assertion by a Hungarian defector-called the ICC commissioner “a Polish intelligence agent acting on his own” (a canard the new book conclusively refutes) and the entire Marigold initiative a “sham.” Brushing off arguments that the bombings near Hanoi had ruined a promising approach, Rusk insisted that “there was nothing to collapse” in the first place.[18]
By contrast, several journalistic, scholarly, and internal government inquiries suggested that Marigold may have been for real. The most detailed classified post-mortem of Marigold during the Johnson Administration was undertaken as part of the Pentagon Papers inquest into Vietnam decision-making commissioned by Defense Secretary Robert McNamara and extensively using State and Pentagon (but not White House) files. Although acknowledging that Hanoi’s role in the affair remained “veiled in mystery” since the Poles handled all communist transactions, the study concluded that North Vietnam most likely “did in fact agree to a meeting in Warsaw,” and it was “highly improbable” the Poles would have “gone far out on a limb” in its dealings with Americans, Italians, “and, apparently, the Russians,” without Hanoi’s commitment, given the consequences that would ensue from “the revelation that the whole venture was built on air.”[19]
The only prior English-language book on the affair[20], written by two Los Angeles Times reporters in 1968 who relied primarily on background interviews with dozens of officials from various governments but lacked access to classified documents or any informed North Vietnamese perspectives, judged that Marigold may have constituted a genuine opportunity to open peace talks. The Johnson Administration, wrote David Kraslow and Stuart H. Loory in their prize-winning The Secret Search for Peace in Vietnam, which used Marigold as the centerpiece of their investigation, “missed opportunities over the years to secure, if not peace, at least negotiations; if not negotiations, at least talks; and if not talks, at least a propaganda advantage over the enemy that would have improved the nation’s standing in the world community and the President’s credibility at home.”[21]
Perhaps the most thorough scholarly analysis of all the secret diplomatic probing efforts during this period to open Vietnam peace talks, written after the declassification of a substantial portion of the U.S. record, concluded in 1980 that, “With the benefit of hindsight, it appears that the MARIGOLD contact offered the best opportunity for the Johnson Administration to negotiate a settlement of the conflict.”[22] Taking a somewhat more skeptical stand, George Herring three years later noted the lack of evidence for this argument, observing that it was “equally possible that the North Vietnamese were merely using the Poles to see what they might be able to get out of the United States or were offering vague responses simply to appear not to stand in the way of peace.”[23]
Was Warsaw in fact authorized by Hanoi to arrange the U.S-North Vietnamese meeting to confirm that the “ten points” represented Washington’s policy? That was the heart of the Marigold mystery, and it can now be resolved. The documents below describe the process of secret communist consultation in November 1966, hidden to U.S. officials at the time, that produced an authoritative North Vietnamese consent to the direct contact with an American representative in Warsaw and a politically significant promise to adopt a positive attitude towards talks with Washington should it genuinely confirm the stands that Lewandowski reported Lodge as having stated in Saigon.
Video -The leaked FBI conversation hacked by Anonymous
Comment by supporters:
ANONYMOUS Intercept FBI & Scotland Yard Conference Call #FFF
Hacking network Anonymous has released a recording of a conference call between the FBI and UK police in which they discuss efforts against hacking.
The conversation covers the tracking of Anonymous and other splinter groups, dates of planned arrests and details of evidence held by police.
Anonymous also published an email, apparently from the FBI, showing the email addresses of call participants.
The FBI confirmed the intercept and said it was hunting those responsible.
“The information was intended for law enforcement officers only and was illegally obtained. A criminal investigation is under way to identify and hold accountable those responsible,” it said in a statement.
British police at Scotland Yard said they were working on a statement.
A comment on one of the Twitter accounts linked to Anonymous, AnonymousIRC, said: “The FBI might be curious how we’re able to continuously read their internal comms for some time now.”
Correspondents say the release of the phone call and email addresses will be highly embarrassing for the authorities.
Listen along, and laugh out loud at the law enforcement agents bumbling away.
Pastebin :http://pastebin.com/8G4jLha8
Download mp3 – http://mir.cr/1SL3XXIR
Defacement:
http://zone-h.org/mirror/id/16859089
The Inquirer
http://www.theinquirer.net/inquirer/news/2143768/anonymous-releases-fbi-uk-co…
Naked Security
http://nakedsecurity.sophos.com/2012/02/03/anonymous-fbi-pceu-hacking-confere…
Media – Anonymous publishes FBI call on hacking
Internet activist group Anonymous published a recording on Friday of a confidential call between FBI agents and London detectives in which the law-enforcement agents discuss action they are taking against hacking.
British police said they were investigating reports of the illegally recorded call, and the FBI said a criminal investigation was under way into the incident.
Anonymous also published an email inviting participants to the call, with dial-in details, in which an FBI agent wrote that investigations relating to Anonymous, LulzSec, Antisec and associated splinter groups would be discussed on the call. (pastebin.com/8G4jLha8)
Anonymous and fellow group LulzSec have carried out a number of high-profile hacking actions against companies and institutions across the globe including the Central Intelligence Agency, Britain’s Serious Organized Crime Agency, Japan’s Sony Corp and Mexican government websites.
On the 16-minute-long call, one British detective is heard discussing an alleged 15-year-old hacker who they described as “a bit of an idiot” who was doing it for attention. (here)
He also tells his U.S. counterpart hosting the call that “we cocked things up in the past” when he is thanked for the help they are providing.
In other fairly unremarkable exchanges, they also discuss at length the merits of the northern English town of Sheffield where a cyber security conference was to be held.
Britons Ryan Cleary and Jake Davis, who have both been charged with hacking-related offences, are discussed on the call. The names of other alleged hackers are bleeped out.
Peter Donald, a spokesman for the FBI in New York, said on Friday: “The information obtained on the call was intended for law enforcement only. It was illegally obtained and a FBI criminal investigation is under way.”
An FBI official said the FBI’s systems were not hacked into, and the discussion did not include classified material.
The official said the conference call dial-in details were sent in an email to officials and someone forwarded it to a private, non-government email account which was compromised at some point.
London’s Metropolitan Police (MPS) said in a statement: “We are aware of the video, which relates to an FBI conference call involving a PCeU (Police Central e-crime Unit) representative.”
“The matter is being investigated by the FBI. At this stage no operational risks to the MPS have been identified; however, we continue to carry out a full assessment,” the MPS said.
An official involved in coordinating international efforts to crack down on cyber crime said that law enforcement agencies sometimes do not carefully authenticate the identity of people who dial in to participate on conference calls.
The email released by the hackers that appears to be the one the FBI sent out to organize the teleconference asked all participants to use a single code to gain entry to the call.
That official, who declined to be identified by name because he was not authorized to publicly comment on the matter, said that the call would have been more secure if attendees had each been assigned unique access codes and been required to identify themselves by name upon dialing in.
If a hacker had dialed in using somebody’s unique access code and somehow made it past initial screening, the organizers may have possibly identified a breach when it became clear that two parties were using the same dial-in credentials, said the official.
Revealed – The Pakistani Taliban’s Coming Divide
|
The Pakistani Taliban’s Coming Divide: How the Death of Its Leader Could Be Bad for the United StatesForeignAffairs.com Features Article by Archive AnalystFor more information contact:
|
Washington, DC, February 3, 2012 – As the U.S. searches for opportunities to negotiate with the Taliban while simultaneously targeting key Taliban leaders with drone strikes, a new article published today on the Web site of Foreign Affairs magazine by National Security Archive analyst Barbara Elias-Sanborn, discusses the prudence of this approach in light of recent rumors of a fatal strike against Pakistani Taliban (TTP) leader Hakimullah Mehsud.
Using recent media reports and declassified documents, Elias-Sanborn, director of the National Security Archive’s Afghanistan/Pakistan/Taliban Documentation Project argues that Mehsud, a key figure behind the brutal 2009 Camp Chapman attack which left seven CIA employees dead, is dangerous, but his death may not help American efforts to find an acceptable negotiated settlement to the war in Afghanistan.
Mehsud’s eventual demise, the article argues, could potentially help Islamabad, but may not help Washington. Pakistani officials could use the TTP leader’s death as an opportunity to reconcile Taliban elements who have taken to targeting the Pakistani government, instead directing those forces against U.S. and Afghan targets. Or, Mehsud’s demise may open the door for greater unity among Taliban factions, augmenting the power of Afghan Taliban leader Mullah Omar and making negotiations more difficult.
The article concludes by arguing that “Mehsud’s elimination would potentially create opportunities for Pakistan to reconcile with TTP militants. But before the teams at Langley pop the champagne, policy makers should consider the possible downsides, as they could be many. If Washington is serious about negotiating an end to the war, it should suspend the drone assassination campaign and take its chances talking to existing Taliban leaders, instead of trying to kill its way towards more pliable negotiating partners that may not exist.”
The Archive’s Afghanistan/Pakistan/Taliban Documentation Project has filed hundreds of Freedom of Information Act requests for documents on the region and historical U.S. government approaches toward it. Many of these materials are posted on the Archive’s Web site at http://www.nsarchive.org.
TOP SECRET from the CIA – Strategic Warning & The Role of Intelligence: Lessons Learned from the 1968 Soviet Invasion of Czechoslovakia

The Czechoslovak crisis, as it became known, started in January 1968, when Alexander Dubček was elevated to the post of First Secretary of the Communist Party of Czechoslovakia (CPCz), replacing moribund Antonin Novotny, who had served as First Secretary since 1957. Under Dubček, the communist leadership embarked on a program of dramatic liberalization of the Czechoslovak political, economic, and social order, including the overhaul of the CPCz leadership, increased freedom of speech, surrender of authority to the Czech National Assembly by the Communist Party, real elections at local and national levels, and even the suggestion of legalizing non-communist political parties.
DOWNLOAD ORIGINAL BOOKLET HERE
TOP-SECRET from the FBI – Operators of Elgin Adult Entertainment Club and Alleged Internet Gambling Business Charged with Concealing More Than $4 Million of Income from the IRS
CHICAGO—The operators of an adult entertainment club in Elgin were charged today with conspiracy to impede the Internal Revenue Service in the collection of federal taxes, as well as separately operating an illegal Internet gambling business, in connection with allegedly diverting more than $4 million in unreported income to themselves from the two businesses. The defendants, Anthony Buttitta and his father, Dominic Buttitta, were charged in a two-count criminal information filed in U.S. District Court, announced Patrick J. Fitzgerald, United States Attorney for the Northern District of Illinois; Alvin Patton, Special Agent in Charge of the Internal Revenue Service Criminal Investigation Division in Chicago; and Robert D. Grant, Special Agent in Charge of the Chicago Office of the Federal Bureau of Investigation.
Anthony Buttitta, 42, of St. Charles, and Dominic Buttitta, 69, of South Barrington, were each charged with one count of conspiracy to defraud the United States by obstructing the IRS in the collection of taxes and one count of operating an illegal gambling business. They will be ordered to appear for arraignment at a later date in U.S. District Court. The Buttittas operate Blackjacks Gentlemen’s Club in Elgin through Elgin Entertainment Enterprises, Inc., which manages Blackjacks. Between 2005 and 2009, they also ran an Internet gambling business, including the websites Skybook.com, Largejoe.com, and Theredhotel.com.
According to the charges, both Buttittas filed false federal corporate tax returns for calendar years 2002 through 2009, and false federal individual income tax returns for calendar years 2002 through 2008 that substantially under-reported the total income they received from the operation of Blackjacks and the gambling business. They allegedly concealed the diverted funds from their tax preparers and the IRS and used the unreported income to acquire personal property and to pay personal expenses.
The charges allege that the defendants received approximately $3,704,959 from “house” fees they collected from women for each shift they worked as dancers at Blackjacks. Anthony Buttitta directed club employees to maintain logs of the house fee collections, and both defendants later destroyed and caused the destruction of the log sheets, the charges allege. They also placed agents of their Internet gambling business on the payroll of another company to provide the employees with the appearance of a legitimate source of income and benefits. In return, the charges allege that they solicited and received kickbacks in the form of cash from the agents and concealed the payments from their tax preparers, bookkeepers and the IRS.
The defendants allegedly received approximately $1 million in gross wagers from the gambling business between 2005 and 2009, and made approximately $400,000 in net profits. The charges seek forfeiture of $400,000 as illegal proceeds.
At various times between 2005 and 2008, the defendants allegedly obtained unreported income from individuals as payment of losing wagers in the form of direct payments toward the purchase of a $2.9 million condominium in Las Vegas and a condominium in Costa Rica, as well as personal credit card payments. In 2005 and 2006, Anthony Buttitta used approximately $400,000 in cash to pay for building and acquiring his home in St. Charles, according to the charges.
Each count carries a maximum penalty of five years in prison and a $250,000 fine, and restitution is mandatory. In addition, defendants convicted of tax offenses must pay the costs of prosecution and remain liable for any and all back taxes, as well as a civil fraud penalty of 75 percent of the underpayment plus interest. If convicted, the court must impose a reasonable sentence under federal statutes and the advisory United States Sentencing Guidelines.
The government is being represented by Assistant U.S. Attorney Patrick King.
The public is reminded that an information contains only charges and is not evidence of guilt. The defendants are presumed innocent and are entitled to a fair trial at which the government has the burden of proving guilt beyond a reasonable doubt.
TOP-SECRET – (U//FOUO) DHS-FBI Florida-Based Violent Extremist Arrested for Plotting Bombing Attack in Tampa

(U//FOUO) This Joint Intelligence Bulletin is intended to provide information on the 7 January 2012 arrest by the FBI Tampa Joint Terrorism Task Force (JTTF), as part of a planned law enforcement action, of Florida-based Sami Osmakac. Osmakac is charged with attempted use of weapons of mass destruction. This information is provided to support the activities of FBI and DHS and to assist federal, state, local, tribal, and territorial, counterterrorism and law enforcement officials to prevent or respond to terrorist attacks against the United States.
(U) Circumstances Leading to the Arrest
(U//FOUO) On 7 January 2012, the FBI Tampa JTTF arrested Sami Osmakac, 25, of Pinellas Park, Florida, as part of a planned law enforcement operation after he allegedly took possession of explosives, a fully automatic AK-47 assault rifle, ammunition and magazines for the AK-47, a pistol, ammunition and a magazine for the pistol, grenades, and a suicide vest. Osmakac allegedly planned to attack a target in Tampa, according to the affidavit in support of the criminal complaint.
(U//FOUO) In late September 2011, a confidential source informed the FBI of Osmakac’s interest in purchasing flags representing al-Qa‘ida. In subsequent conversations, Osmakac allegedly expressed the desire to conduct a violent attack in the Tampa area and asked for assistance in procuring a vehicle-borne improvised explosive device (VBIED), weapons such as Uzis or AK-47s, and an explosives-laden belt to use in a two-stage attack. As part of an undercover operation, Osmakac was introduced to an individual whom he believed to hold extremist beliefs and was able to supply weapons and explosives. All weapons, ammunition, and explosives provided by the FBI had previously been rendered inoperable.
(U//FOUO) According to court documents, during November 2011, Osmakac planned to attack a Tampa area military recruiting center. However, he later changed his plan, allegedly telling a confidential source that the recruiting center did not have enough personnel inside.
(U//FOUO) According to the arrest affidavit, on 1 January 2012, Osmakac drove through the Ybor City neighborhood of Tampa to choose target locations, planning to eventually set off an explosive charge packed in the trunk of a vehicle parked in front of high-end restaurants and nightclubs. All of his pre-operational activities were closely monitored by the FBI.
(U//FOUO) Osmakac allegedly outlined various scenarios in which he would park a VBIED near busy nightspots and return to his nearby hotel room to collect the remaining weapons. He would then return to the scene to detonate the VBIED remotely, and in the aftermath conduct a small-arms attack at a nearby location while wearing a suicide vest. According to a confidential source, Osmakac said he would attempt to take hostages and contact authorities, specifically the FBI, in order to negotiate the release of Muslim prisoners. Osmakac told the same source that he believed that detonating the VBIED before he took hostages would prove he was “not joking.” Osmakac allegedly planned to release the hostages and detonate the suicide vest while surrendering to law enforcement after his demands were met, according to court documents.
(U//FOUO) Motivations in Planning the Attack
(U//FOUO) Osmakac, a naturalized US citizen, born in the former Yugoslavia, previously had a positive view of the United States for helping his fellow Muslims in Kosovo in their time of need. He later decided that the United States is his enemy because he believes the United States is killing his fellow Muslims, according to the affidavit in support of the criminal complaint.
(U//FOUO) Just before he allegedly attempted the attack, Osmakac filmed a martyrdom video in his hotel room, with a pistol in his hand and the AK-47 displayed behind him. In the video, he stated his belief that Muslims’ “blood” was more valuable than that of non-Muslims and he wanted “pay back” for the wrongs he felt were done to Muslims, according to the affidavit.
— (U//FOUO) In discussions with an under cover employee, Osmakac declined opportunities to back out of the plan.
(U//FOUO) Targets and Tactics Differ Slightly From Recent Homegrown Violent Extremist Plots
(U//FOUO) Disrupted plots by homegrown violent extremists (HVEs) within the past year have primarily targeted government and military facilities and personnel, including a military recruiting center in Seattle, a restaurant frequented by military personnel near Fort Hood, Texas, and the Pentagon and US Capitol building with improvised explosives, small arms, and grenades.*
(U//FOUO) Osmakac, however, allegedly abandoned his plan to attack a military recruiting center for a less secure civilian target which held the potential for a greater number of casualties. His alleged tactics also differed from previous HVE plotting in that he planned to take hostages to achieve a specific goal—the release of Muslim prisoners—and then take his own life by detonating his suicide vest in the proximity of
arresting officers.
DOWNLOAD ORIGINAL DOCUMENT HERE
Die NEO-Ratten-Linie der STASI-Täter ist wohl Berlin, Brandenburg, Hamburg, Neuss und Wiesbaden
TOP – SECRET – HOW THE NAZIS ESCAPED – STRENG GEHEIME UNTERSUCHUNG ÜBER DIE NAZI-RATTEN-LINIE UND WIE DIE NS-TÄTER ENTKOMMEN KONNTEN
“IM ÜBERALL” : STASI-Sumpf überall und kein Ende – Deutschland unfähig zur Aufarbeitung – nach 20 Jahren
TOP SECRET – FBI “Communities Against Terrorism” Suspicious Activity Reporting Flyers
The following collection of 25 flyers produced by the FBI and the Department of Justice are distributed to local businesses in a variety of industries to promote suspicious activity reporting. The flyers are not released publicly, though several have been published in the past by news media and various law enforcement agencies around the country. We have compiled this collection from a number of online sources.
To view the documents, click on a threat area in the menu to the left and the PDF will appear on the right side of the page. You can also download the complete collection of files (ZIP Archive, 6.27 MB).
Threat Areas
- Airport Service Providers
- Beauty/Drug Suppliers
- Bulk Fuel Distributors
- Construction Sites
- Dive/Boat Shops
- Electronics Stores
- Farm Supply Stores
- Financial Institutions
- General Aviation
- General Public
- Hobby Shops
- Home Improvement
- Hotels/Motels
- Internet Cafes
- Shopping Malls
- Martial Arts/Paintball
- Mass Transportation
- Military Surplus
- Peroxide Explosives
- Recognizing Sleepers
- Rental Cars
- Rental Properties
- Rental Trucks
- Storage Facilities
- Tattoo Shops
TOP-SECRET – Julian Assange’s Appeal to the U.K. Supreme Court
MERIDIAN CAPITAL ÜBER DIE SERIEN-RUFMÖRDER, FÄLSCHER UND GEWOHNHEITSVERBRECHER DER STASI-“GoMoPa”
http://www.meridiancapital.wordpress.com/
Gerne können Sie auch Meridian Capital direkt in New York kontaktieren:
www.meridiancapital.com/
HIER NOCH EINMAL DIE BILD-BELEGE ZUM THEMA STASI “GoMoPa” UND KOMPLIZEN BZGL. MERIDIAN CAPITAL
UND HIER DIE STASI-“GoMoPa”-FÄLSCHUNG – PEINLICH-PEINLICH -PEINLICH UND SUPER-DUMM-DREIST
Film – Geheimes Deutschland
CONFIDENTIAL – Canada Command, USNORTHCOM Civil Assistance Plan

1. Situation
a. General. The purpose of the Canada-United States Civil Assistance Plan (CAP) is to provide a framework for the military of one nation to provide support to the military of the other nation in the performance of civil support operations (e.g., floods, forest fires, hurricanes, earthquakes, and effects of a terrorist attack).
(I) Support covered under this plan will only be provided when agreed to by appropriate authorities in both the Government of Canada and the United States Government.
(2) When approved, military forces from one nation augment the other nation’s forces in civil support operations. Support under this plan is not provided directly to civil authorities, but rather to the other nation’s military.
(3) Support for law enforcement operations is not covered in this plan and will be included in the Canada – United States Combined Defense Plan (COP).
(4) Guidance and direction to develop this plan is derived from the Canada – United States Basic Defense Document (BOD) , 08 July 2006 (Ref 1D. This plan may be used alone, or concurrent with the Canada-US Combined Defense Plan or other national plans. The Commander, Canada Command (Comd Canada COM) and Commander, US Northern Command (CDRUSNORTHCOM) are the designated planning agents for the development of this plan.
b.Federal Coordination of Emergency Response. The Canadian Department of Foreign Affairs and International Trade (DFAIT), acting on behalf of the Government of Canada (GoC), and the US Department of State (DOS), acting on behalf of the United States Government (USG), will, upon receipt of a formal request for, or offer of mutual assistance, coordinate an agreed upon bilateral response that may include military support.
(1) In the United States, coordination of foreign assistance for a disaster in the United States is conducted per the International Assistance System Concept of Operations.
c. Area of Responsibility (AORl. AOR is defined as the common areas of responsibility for Primary Agencies (Public Safety Canada (PS) and Department Of Homeland Security (DHSII, and the Canada -US (CAN US) Region (i.e., Canada and the Continental United States (CONUS), Alaska, US Virgin Islands, and Puerto Rico, including each nation’s territorial seas).
d. Opposing Force. Opposing forces are not expected during the conduct of operations described in this plan. However, when planning and conducting operations where the military forces of one nation are supporting the military forces of the other nation that are conducting civil support operations, commanders should consider the following Anti-Terrorism/Force Protection issues: (1) Terrorists organizations could conduct operations against the Canadian or US force, or in the civil support operations area; (2) State/provincial and local police capabilities could be severely degraded in the area of operations, allowing a corresponding rise in criminal activity that could affect the Canadian or US force; and (3) Environmental factors ranging from weather to contamination and disease could significantly affect the Canadian or US forces.
e. Friendly
(1) CANADA
(al The Department of Foreign Affairs and International Trade (DFAITI. DFAIT is responsible on behalf of the GoC for facilitating
requests for international military assistance.(b) Public Safety Canada (PS)’ The Minister of Public Safety is assigned primary responsibility within the GoC to coordinate the federal response in crisis and consequence management situations within Canada. (cl Department of National Defence fDND) / Canadian Forces (CF)’ The CF may, upon request, provide support to PS, other federal departments and agencies, provincial/territorial and municipal authorities pursuant to the National Defence Act (NDA), or other legal authority. Comd Canada COM is the responsible CF operational commander within the Canada COM AOR defined as Canada, the continental United States, Mexico, and the maritime approaches to North America.
(2) UNITED STATES
(a) Department of State (DOS). The Department of State is responsible for coordinating with other nations for disaster assistance, including military assistance. (Ref 31).
(b) Department of Homeland Security (DHS). The Secretary of DHS is the principal federal official (PFO) for US domestic incident management.
(c) Department of Defense (DOD), In accordance with the National Response Plan (Ref 3k) DOD may, upon request, provide support to DHS and other federal agencies for domestic Defense Support of Civil Authorities (DSCA). Upon Secretary of Defense approval, CDRUSNORTHCOM is the supported combatant commander with responsibility to coordinate defense support to federal agencies within that portion of the United States within CDRUSNORTHCOM’s AOR.
f. Assumptions
(1) Requirements for military support of civilian authorities could be fulfllied by either nation’s military. However, the nation providing crossborder military support will not fulfill these requirements directly to the other nation’s civilian authorities, but rather to the other nation’s military.
(2) Operations will typically occur in a permissive environment. g. Legal Considerations. The United States and Canada are Parties to the North Atlantic Treaty Organization (NATO) Status of Forces Agreement (SOFA), dated August 23, 1953.
(I) Military Emergency Response
(a). Canadian Forces (CF!. In Canada, as per Canada Command Direction for Domestic Operations (Ref 2i), local commanders are expected to respond promptly to a request for assistance, within their approval authority, by providing an immediate CF response to an emergency to save lives, prevent human suffering, or mitigate property damage. However, for foreign disaster assistance, the GoC must approve the request.
(b). US Armed Forces. In emergency situations the SecDef can provide foreign disaster assistance in order to save human lives, where there is not sufficient time to seek the prior initial concurrence of the Secretary of State. The SecDef shall advise, and seek the concurrence of the Secretary of State as soon as practicable thereafter (Ref 3b).
(2) US Foreign Consequence Management versus US Foreign Disaster Assistance
(a) Only the President may order US military forces to execute foreign consequence management missions. DOS is the lead agency (Ref 4D.
(b) When directed by the President or by the Secretary of Defense, with the concurrence of the Secretary of State, DOD provides foreign disaster assistance support in coordination with DOS. DOS is the lead agency (Ref 3b and 4g).
(3) Use of Force
(a) CF Rules of Engagement (ROE), If ROE are required for CF personnel deployed in the United States to support the US forces engaged in Defense Support of Civil Authorities, the ROE will be requested by the Canadian commander and authorized in accordance with B-GG-005-004jAF-005 dated 2001-06-01 Use of Force in CF Operations (Revision 1) .
(b) Standing Rules of Engagement ISROEI for DOD forces. Implementation guidance on the application of force for mission accomplishment and the exercise of self-defense is contained in (Ref 4d). DOD forces will be trained on SROE before employment.
(4) Right of Self Defense
(a) Canadian Forces. Both international law and Canadian domestic laws recognize the authority to use appropriate force in self-defense, up to and including deadly force. Without further written or oral direction, CF personnel are entitled to use force in self-defense to protect oneself; other members of the Canadian Forces; and non-Canadian military personnel who are attached or seconded to a Canadian force against a hostile act or hostile intent (Ref 2c).
(b) US Forces. US unit commanders always retain the inherent right and obligation to exercise unit self-defense in response to a hostile act or demonstrated hostile intent (Ref 4d).
(5) There are no standing CANUS rules of engagement or rules for the use of force. Consequently, every mission will require unique guidance to deployed forces. Forces from one nation deployed to support the forces of the other nation will comply with authorized ROE and right of self-defense consistent with the laws of the supported nation. The ROE and right of selfdefense will be designated in respective national operation / execute orders.
…
(2) Liaison and Planning. Direct liaison is authorized (DIRLAUTH) between the militaries of both nations for planning, information sharing and situational awareness. The state Governors and provincial authorities in the Pacific Northwest, Prairie and Northeastern regions have established mutual aid compacts for cross border emergency support to save lives, prevent human
suffering, and reduce great property damage. Every effort should be made to maintain situational awareness of these existing bilateral civilian regional planning groups to ensure support to the other nation’s forces is effective and efficient.…
5. Command and Control
a. Command
(1) Command Relationships. Bilateral support described in this plan will occur under existing structures and command authorities. Command relationships for supporting forces will be defined based on the circu.mstances of the operation and delineated in respective national operation and execution orders.
(a) Canada. Comd Canada COM exercises operational command (OPCOM) of CF forces assigned by the CDS for the purposes of
coordinating assistance to civil authorities. Regional Joint Task Force Commanders (RJTF Comds) exercise OPCON of forces assigned by Comd Canada COM for the execution of an operation. In Canada, OPCOM is the authority granted to a commander to assign missions or tasks to subordinate commanders, to deploy units, to reassign forces, and to retain or delegate operational/tactical command or control as may be deemed necessary. OPCON is the authority delegated to a commander to direct forces assigned so that the commander may accomplish specific missions or tasks that are usually limited by function, time, or location; to deploy units concerned and to retain or assign tactical control of those units. If the requirement develops for separate employment, the higher commander must approve the change. (Ref 2y).(b) United States. CDRUSNORTHCOM exercises operational control (OPCON) of all allocatcd US forces ness CDRUSTRANSCOM). In the United Stales, OPCON is command authority that may be exercised by commanders at any echelon at or below the level of combatant command. OPCON is inherent in combatant command (command authority) and may be delegated within the command. (Ref 4ii) .
b. Command. Control. Communication and Computer fC4J Systems. As directed by the BOD, Canada COM and USNORTHCOM will ensure network enabled capabilities to enhance information sharing, collaborative planning and rapid decision making to support bilateral operations described in this plan.
DOWNLOAD ORIGINAL DOCUMENT HERE
Der Spion, den ich liebte – Die unheimliche Macht der Geheimdienste – Video
CONFIDENTIAL – US, UK, Canada, Australia and New Zealand Joint Public Key Infrastructure Cross-Certification Standards

1.1.1 Purpose
This section provides the long-term Public Key Infrastructure (PKI) interoperability architecture for the CCEB Allies as agreed at the February 2005 Canberra Collocated Meeting. The architecture enables interoperability through direct cross-certification of each National Defence PKI (NDPKI) in a mesh configuration.
1.1.2 Audience
The audience for this section is expected to be the PKI management and engineering/technical staff involved in Defense2 PKI Program Management Offices (PMOs) or Project Teams. The audience includes Government and industry personnel involved in the definition, design, and development of the NDPKIs. Familiarity with PKI concepts is assumed.
1.1.3 Background
CCEB Nations exchange Military information and data under the Combined Joint Multilateral Master Military Information Exchange Memorandum of Understanding (CJM3IEM). A Combined Joint Military Information Exchange Annex (CJMIEA) adds Authenticated Services which can use but are not limited to one, or a combination of, the following: Validation of Internet Protocol (IP) domain name; Presentation of user name; Presentation of user name and password; Presentation of cryptographic credentials using Public Key Technology; and Presentation of biometric credentials. CJMIEA Authentication Services involves policies, processes, and technologies to support the exchange and validation of authentication credentials. One basis for this exchange and validation is strong digital identities for both individuals and devices from interoperable NDPKIs that support strong identity management regimes, common policies and technical implementations. To achieve the CCEB Management Plan task of establishing interoperable NDPKIs4, the CCEB Executive Group (EG) has endorsed the PKI Task Force (TF) recommendation for a two phase interoperability approach:
a. Short-term which supports Allied access to US Department of Defense (DoD) owned websites on Unclassified but Sensitive Internet Protocol Network (NIPRNET). The solution, as agreed at the September 2004 Washington CCEB Collocated Meeting, creates policies and procedures, through the use of a Trusted Agent (TA) regime, for defense personnel in CCEB nations to obtain PKI Certificates from the US DoD PKI system.
b. The long-term approach supports interoperable, authenticated military information and data exchange within the SECRET high environment or within a lower classification system-high environment between CCEB nations over approved networks using PKI technology.
DOWNLOAD ORIGINAL DOCUMENT HERE
UNCENSORED – FEMEN Protests Hockey World Cup in Zurich
|
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-zurich/pict3.jpg) Activists from Ukrainian feminist group FEMEN shout slogans during a topless protest on February 1st, 2012, in Zurich against the Hockey world cup in 2014 in Belarus. Getty Activists from Ukrainian feminist group FEMEN shout slogans during a topless protest on February 1st, 2012, in Zurich against the Hockey world cup in 2014 in Belarus. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-zurich/pict0.jpg) Activists from Ukrainian feminist group FEMEN shout slogans and brandish placards during a topless protest on February 1st, 2012, in Zurich against the Hockey world cup in 2014 in Belarus. Getty Activists from Ukrainian feminist group FEMEN shout slogans and brandish placards during a topless protest on February 1st, 2012, in Zurich against the Hockey world cup in 2014 in Belarus. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-zurich/pict4.jpg) Activists from Ukrainian feminist group FEMEN shout slogans during a topless protest on February 1st, 2012, in Zurich against the Hockey world cup in 2014 in Belarus. Getty Activists from Ukrainian feminist group FEMEN shout slogans during a topless protest on February 1st, 2012, in Zurich against the Hockey world cup in 2014 in Belarus. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-zurich/pict7.jpg) Activists from Ukrainian feminist group FEMEN shout slogans and hold placards during a topless protest on February 1st, 2012, in Zurich against the Hockey world cup in 2014 in Belarus. Activists from Ukrainian feminist group FEMEN shout slogans and hold placards during a topless protest on February 1st, 2012, in Zurich against the Hockey world cup in 2014 in Belarus. |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-zurich/pict1.jpg) Activists from Ukrainian feminist group FEMEN shout slogans and carry hockey sticks during a topless protest on February 1st, 2012, in Zurich against the Hockey world cup in 2014 in Belarus. Getty Activists from Ukrainian feminist group FEMEN shout slogans and carry hockey sticks during a topless protest on February 1st, 2012, in Zurich against the Hockey world cup in 2014 in Belarus. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-zurich/pict2.jpg) Activists from Ukrainian feminist group FEMEN shout slogans and carry hockey sticks during a topless protest on February 1st, 2012, in Zurich against the Hockey world cup in 2014 in Belarus. Getty Activists from Ukrainian feminist group FEMEN shout slogans and carry hockey sticks during a topless protest on February 1st, 2012, in Zurich against the Hockey world cup in 2014 in Belarus. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-zurich/pict5.jpg) Half-naked activists from Ukrainian women’s rights movement Femen, demonstrate in front of the headquarters of the International Ice Hockey Federation in Zurich, February 1, 2012. Femen activists staged a protest on Wednesday to draw attention on the political situation in Belarus before the Hockey World Cup in 2014. Getty Half-naked activists from Ukrainian women’s rights movement Femen, demonstrate in front of the headquarters of the International Ice Hockey Federation in Zurich, February 1, 2012. Femen activists staged a protest on Wednesday to draw attention on the political situation in Belarus before the Hockey World Cup in 2014. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-zurich/pict6.jpg) An activist from Ukrainian feminist group FEMEN stands near barbed wire during a topless protest on February 1st, 2012, in Zurich against the Hockey world cup in 2014 in Belarus. Getty An activist from Ukrainian feminist group FEMEN stands near barbed wire during a topless protest on February 1st, 2012, in Zurich against the Hockey world cup in 2014 in Belarus. Getty |
STASI-STALKER der “GoMoPa” kennen sich mit Fälschungen bestens aus
TOP-SECRET from the FBI – Investigating Insurance Fraud A $30-Billion-a-Year Racket
01/31/12

Our corporate and securities fraud cases, for example, resulted in more than 600 convictions last year—including a number of high-level executives—and more than $23 billion in recoveries, fines, and restitutions over the past three years. Our mortgage fraud efforts continue to pinpoint the most egregious offenders; approximately 70 percent of our 3,000 pending mortgage fraud investigations involve losses of more than $1 million. There are also plenty of cases involving health care fraud, bankruptcy fraud, credit card fraud, mass marketing fraud, and various wire and mail fraud schemes.
Insurance fraud—non-health care-related fraud involving casualty, property, disability, and life insurance—is another financial crime that falls under FBI jurisdiction. The U.S. insurance industry consists of thousands of companies that collect more than $1.1 trillion in premiums each year, according to the Insurance Information Institute, and the estimated cost of fraud is approximately $30 billion a year. Most of this expense is passed on to consumers in the form of higher insurance premiums, to the tune of about $200 to $300 a year per family, according to the National Insurance Crime Bureau. Not to mention the number of insurance companies that go under because of excessive claims and/or the looting of company assets.

Defend Yourself From Insurance Fraud – Never ignore a notice from your insurance company—even if your agent tells you it’s a mistake and that he or she will take care of it. – Don’t give an insurance agent money without getting a receipt. – Don’t give out your insurance identification number to companies or individuals you don’t know. – After an auto accident, be careful of strangers who offer you quick cash or recommend a particular attorney or health care provider. · Don’t buy life insurance as an investment without fully understanding what it is you’re buying. – Never buy insurance from unlicensed agents or companies, and if you have any doubts about them, check their status by contacting your state’s insurance office. |
|---|
There are many capable private and government investigative and regulatory entities at the national and state level that look into insurance fraud, so the FBI directs its resources toward identifying the most prevalent schemes and the top echelon criminals and criminal organizations who commit the fraud. But even when conducting our own investigations, we often work closely with private fraud associations, state fraud bureaus, state insurance regulators, and other federal agencies.
The FBI currently focuses on the following schemes:
- Disaster related fraud, which became such a problem after Hurricane Katrina that a special task force was created to address it (and evolved into today’s National Center for Disaster Fraud);
- Premium and asset diversion, which happens when insurance agents, brokers, even insurance company executives steal insurance premiums submitted by policy holders and sometimes plunder company financial assets for their own personal use;
- Viatical fraud (a “viatical” settlement is one where an investor buys the right to receive the benefit of a terminally ill or elderly person’s life insurance policy);
- Staged auto accidents;
- Bodily injury fraud; and
- Property insurance fraud.
Who commits insurance fraud. Mostly dishonest policy holders, insurance industry insiders (i.e., agents, brokers, company execs), and loosely organized networks of crooked medical professionals and attorneys who use their knowledge to bypass anti-fraud measures put in place by insurance companies.
How we investigate it. Like many other white-collar crime investigations, insurance fraud is mostly about following the money trail—which often involves questioning victims and victim companies, reviewing financial documents, and using sensitive techniques like informants and cooperating witnesses.
We also use our intelligence capabilities to keep our finger on the pulse of emerging trends—for example, as more insurance companies conduct business online, we fully expect to see a rise in the theft of policy holders’ identities and in cyber-based insurance scams. We will keep you posted.















































































































































![[Image]](https://i0.wp.com/cryptome.org/2012-info/athens-protest/pict3.jpg) Protesters try to avoid a stun grenade thrown by police on motorcycles during clashes in Athens, Sunday, Feb. 12, 2012. Protesters and police fought running battles in central Athens Sunday, as Greek lawmakers debated legislation that would introduce severe austerity measures to stave off bankruptcy. (Thanassis Stavrakis)
Protesters try to avoid a stun grenade thrown by police on motorcycles during clashes in Athens, Sunday, Feb. 12, 2012. Protesters and police fought running battles in central Athens Sunday, as Greek lawmakers debated legislation that would introduce severe austerity measures to stave off bankruptcy. (Thanassis Stavrakis)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/nsa-sa-2012/pict42.jpg)







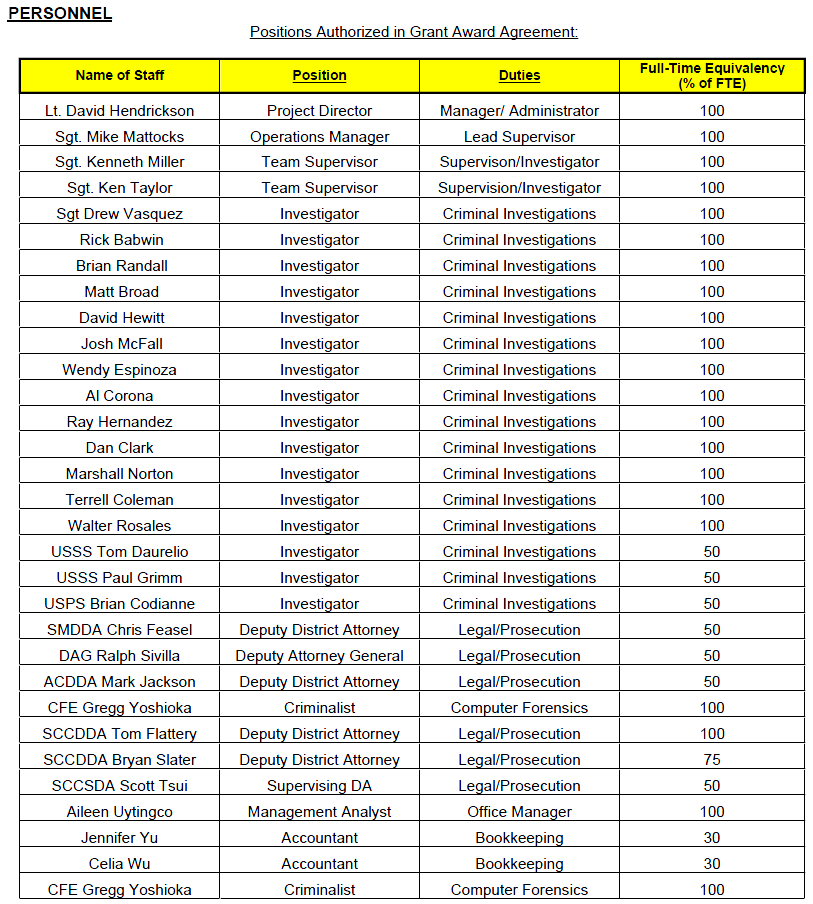
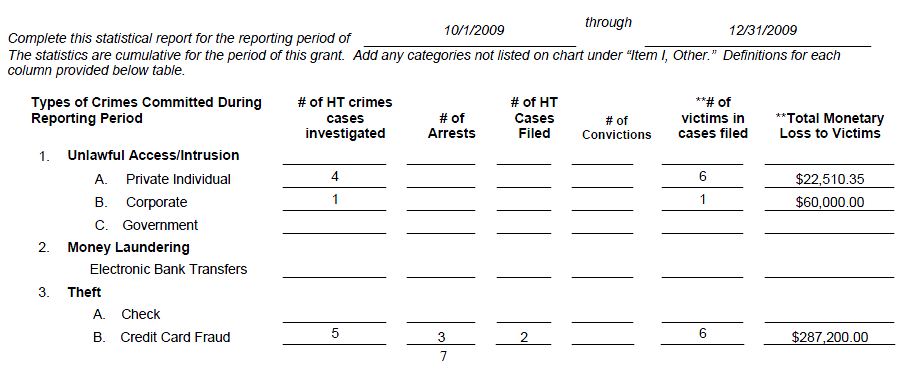


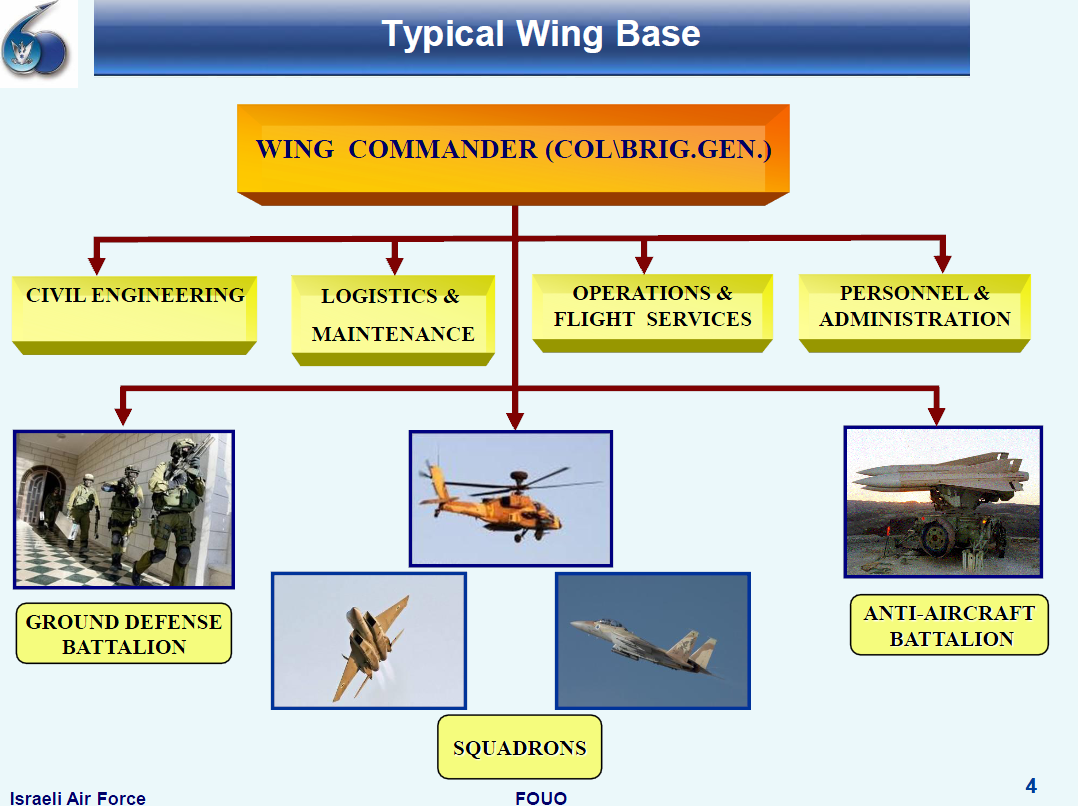
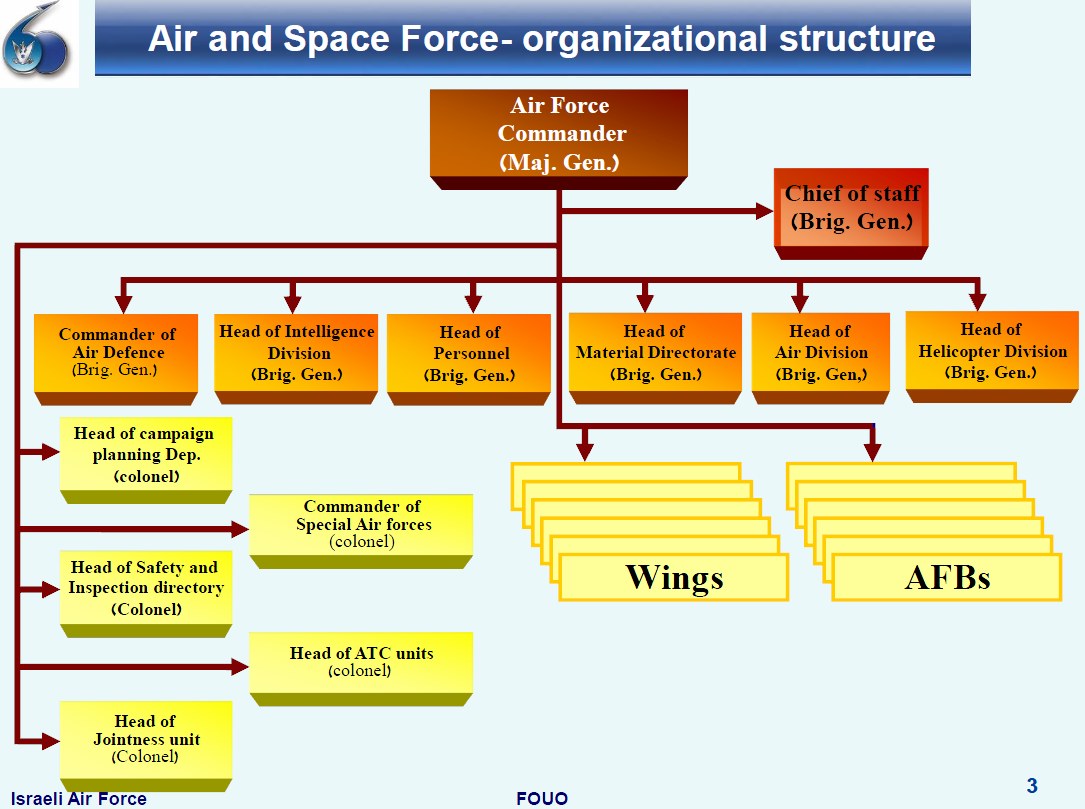
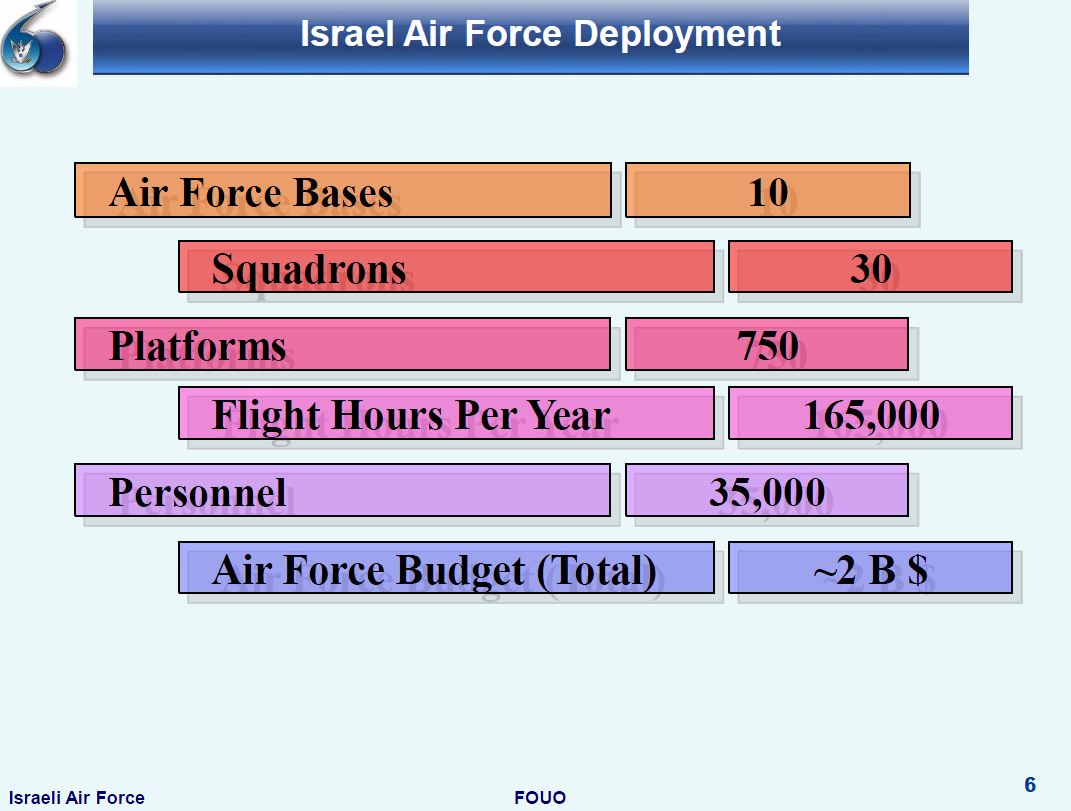
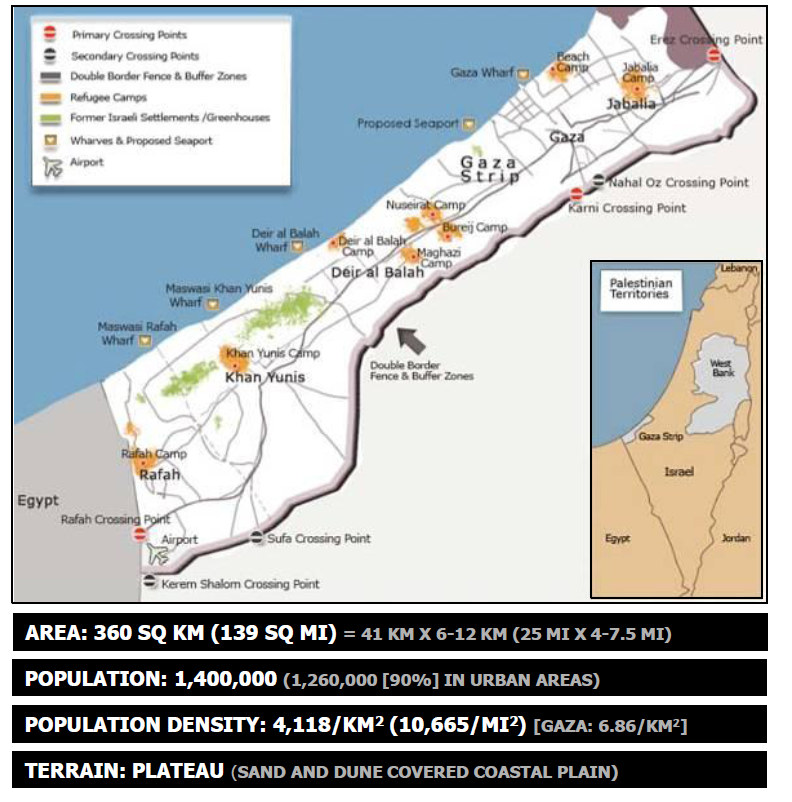

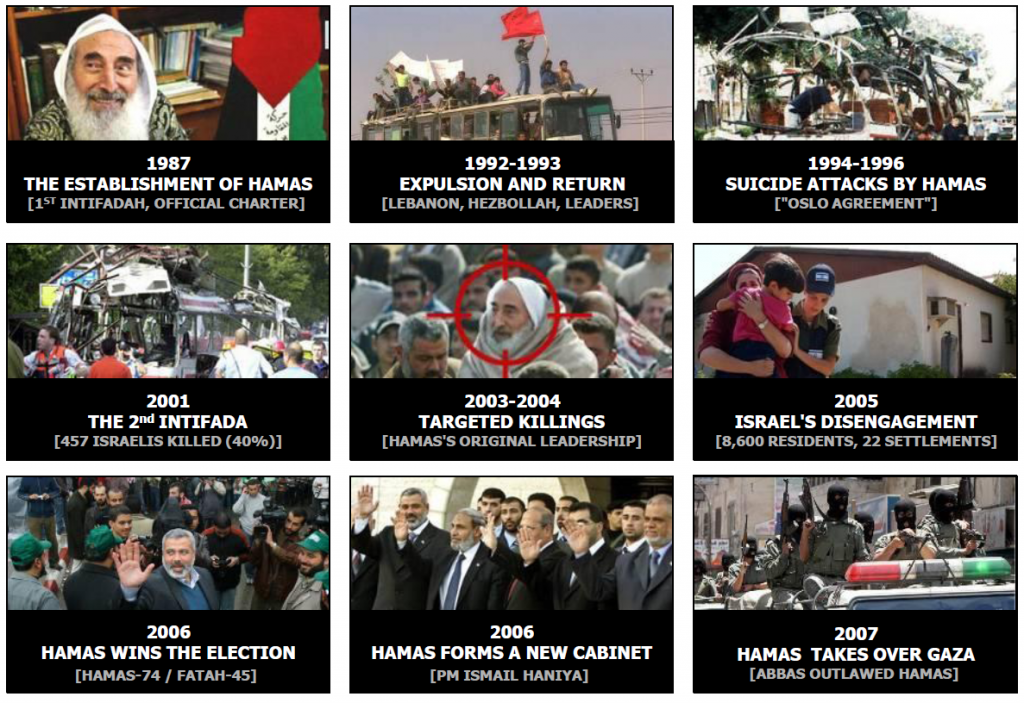
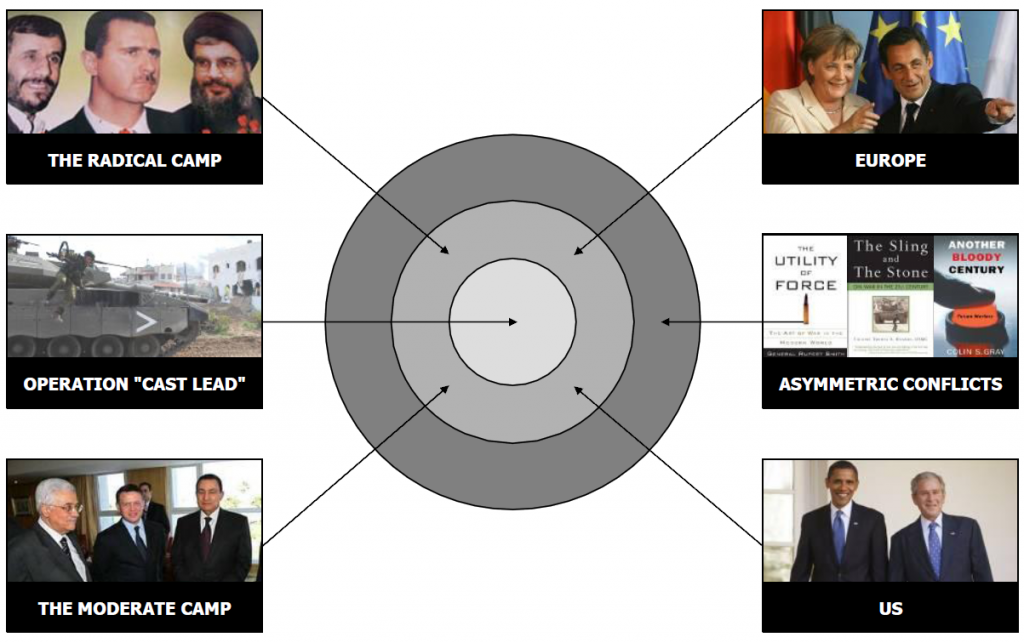
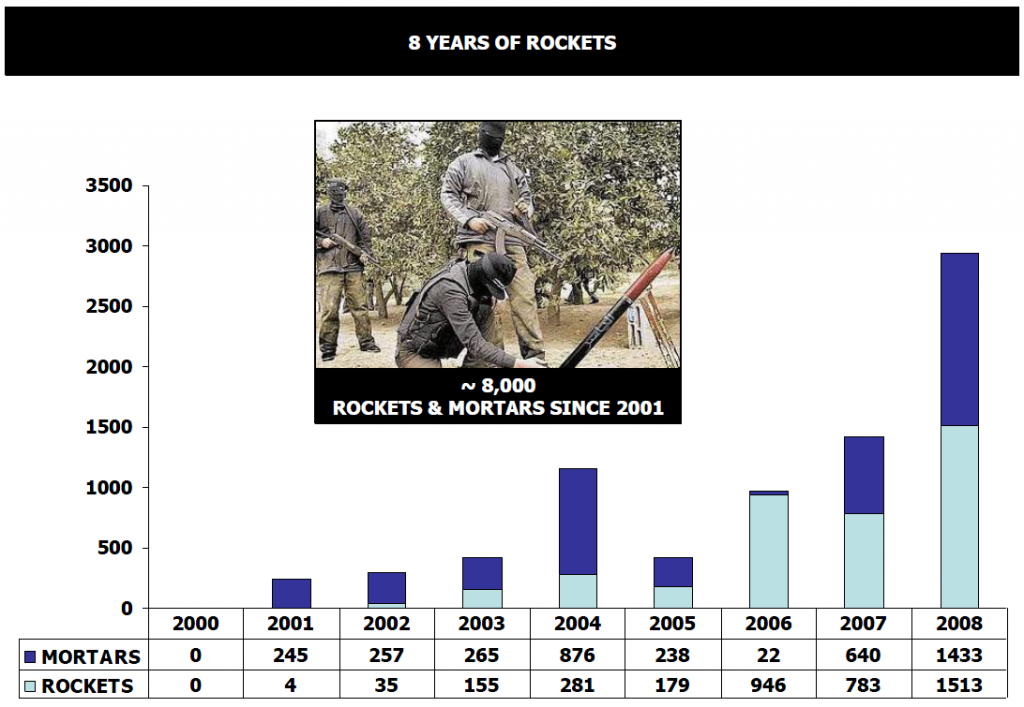
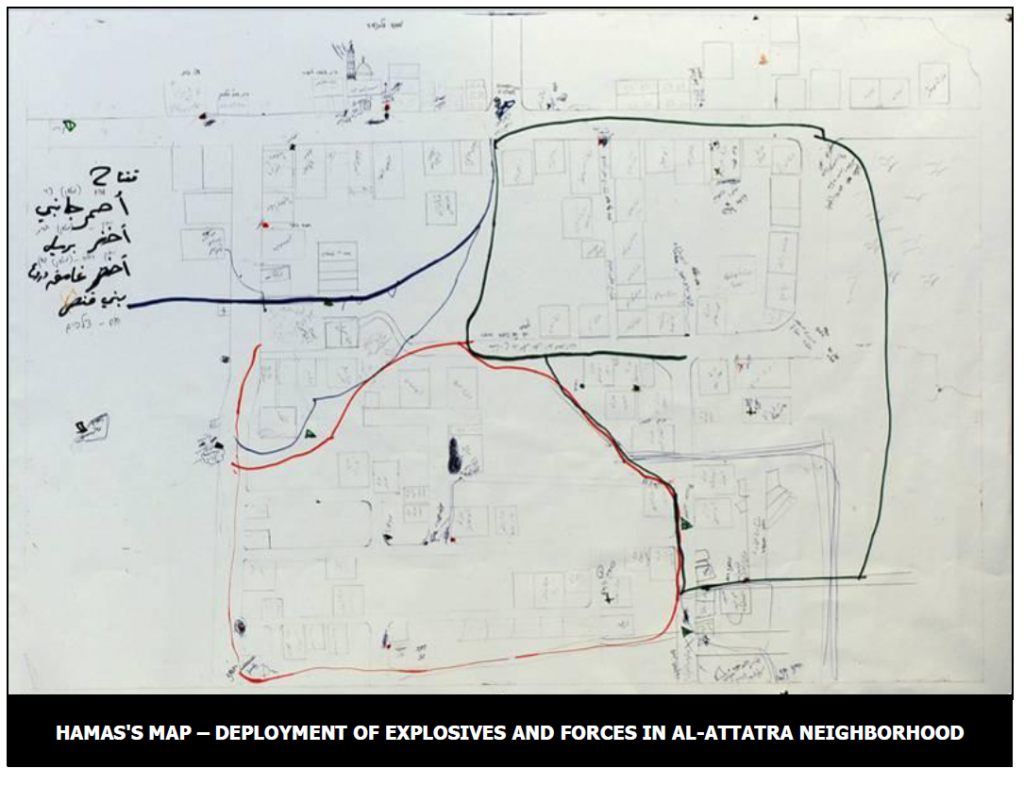
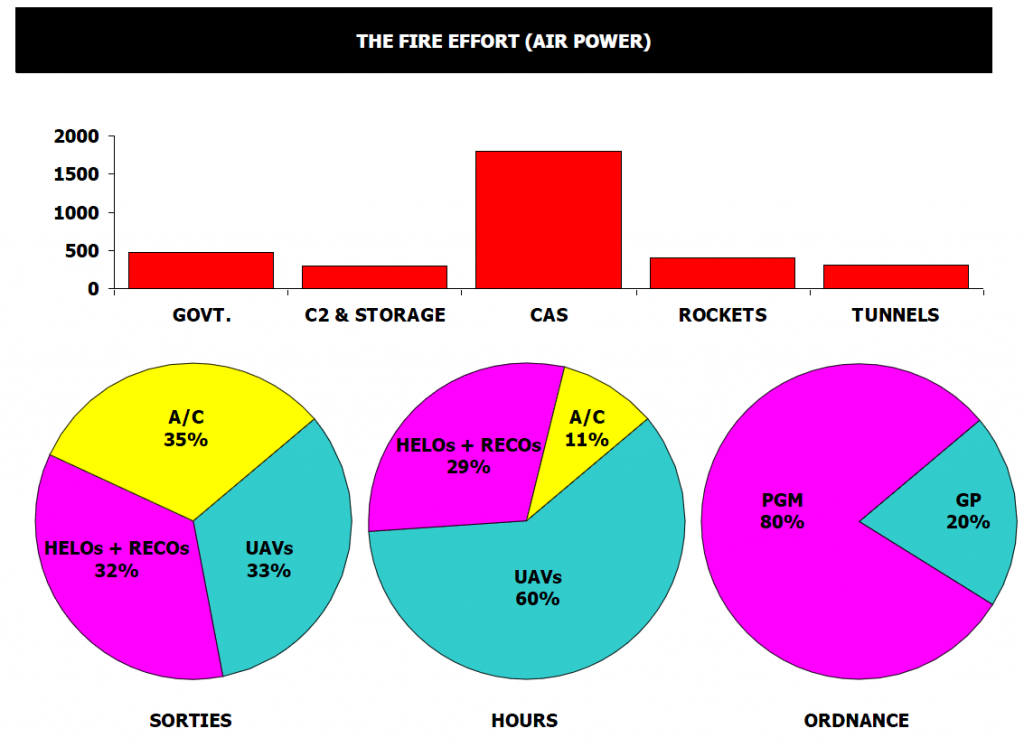
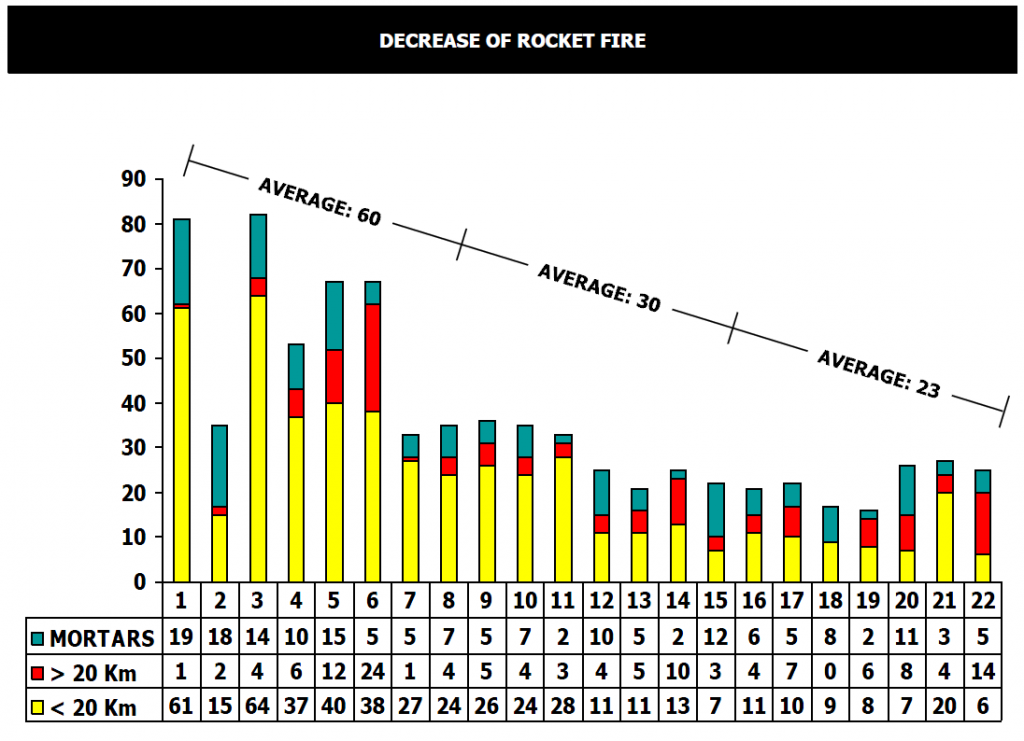














You must be logged in to post a comment.