A sends:
The Gentleperson’s Guide To Forum Spies (spooks, feds, etc.)
http://pastebin.com/irj4Fyd5
1. COINTELPRO Techniques for dilution, misdirection and control of a internet forum
2. Twenty-Five Rules of Disinformation
3. Eight Traits of the Disinformationalist
4. How to Spot a Spy (Cointelpro Agent)
5. Seventeen Techniques for Truth Suppression
______________________________________________________________________________________
COINTELPRO Techniques for dilution, misdirection and control of a internet forum..
There are several techniques for the control and manipulation of a internet forum no matter what, or who is on it. We will go over each technique and demonstrate that only a minimal number of operatives can be used to eventually and effectively gain a control of a ‘uncontrolled forum.’
Technique #1 – ‘FORUM SLIDING’
If a very sensitive posting of a critical nature has been posted on a forum – it can be quickly removed from public view by ‘forum sliding.’ In this technique a number of unrelated posts are quietly prepositioned on the forum and allowed to ‘age.’ Each of these misdirectional forum postings can then be called upon at will to trigger a ‘forum slide.’ The second requirement is that several fake accounts exist, which can be called upon, to ensure that this technique is not exposed to the public. To trigger a ‘forum slide’ and ‘flush’ the critical post out of public view it is simply a matter of logging into each account both real and fake and then ‘replying’ to prepositined postings with a simple 1 or 2 line comment. This brings the unrelated postings to the top of the forum list, and the critical posting ‘slides’ down the front page, and quickly out of public view. Although it is difficult or impossible to censor the posting it is now lost in a sea of unrelated and unuseful postings. By this means it becomes effective to keep the readers of the forum reading unrelated and non-issue items.
Technique #2 – ‘CONSENSUS CRACKING’
A second highly effective technique (which you can see in operation all the time at www.abovetopsecret.com) is ‘consensus cracking.’ To develop a consensus crack, the following technique is used. Under the guise of a fake account a posting is made which looks legitimate and is towards the truth is made – but the critical point is that it has a VERY WEAK PREMISE without substantive proof to back the posting. Once this is done then under alternative fake accounts a very strong position in your favour is slowly introduced over the life of the posting. It is IMPERATIVE that both sides are initially presented, so the uninformed reader cannot determine which side is the truth. As postings and replies are made the stronger ‘evidence’ or disinformation in your favour is slowly ‘seeded in.’ Thus the uninformed reader will most like develop the same position as you, and if their position is against you their opposition to your posting will be most likely dropped. However in some cases where the forum members are highly educated and can counter your disinformation with real facts and linked postings, you can then ‘abort’ the consensus cracking by initiating a ‘forum slide.’
Technique #3 – ‘TOPIC DILUTION’
Topic dilution is not only effective in forum sliding it is also very useful in keeping the forum readers on unrelated and non-productive issues. This is a critical and useful technique to cause a ‘RESOURCE BURN.’ By implementing continual and non-related postings that distract and disrupt (trolling ) the forum readers they are more effectively stopped from anything of any real productivity. If the intensity of gradual dilution is intense enough, the readers will effectively stop researching and simply slip into a ‘gossip mode.’ In this state they can be more easily misdirected away from facts towards uninformed conjecture and opinion. The less informed they are the more effective and easy it becomes to control the entire group in the direction that you would desire the group to go in. It must be stressed that a proper assessment of the psychological capabilities and levels of education is first determined of the group to determine at what level to ‘drive in the wedge.’ By being too far off topic too quickly it may trigger censorship by a forum moderator.
Technique #4 – ‘INFORMATION COLLECTION’
Information collection is also a very effective method to determine the psychological level of the forum members, and to gather intelligence that can be used against them. In this technique in a light and positive environment a ‘show you mine so me yours’ posting is initiated. From the number of replies and the answers that are provided much statistical information can be gathered. An example is to post your ‘favourite weapon’ and then encourage other members of the forum to showcase what they have. In this matter it can be determined by reverse proration what percentage of the forum community owns a firearm, and or a illegal weapon. This same method can be used by posing as one of the form members and posting your favourite ‘technique of operation.’ From the replies various methods that the group utilizes can be studied and effective methods developed to stop them from their activities.
Technique #5 – ‘ANGER TROLLING’
Statistically, there is always a percentage of the forum posters who are more inclined to violence. In order to determine who these individuals are, it is a requirement to present a image to the forum to deliberately incite a strong psychological reaction. From this the most violent in the group can be effectively singled out for reverse IP location and possibly local enforcement tracking. To accomplish this only requires posting a link to a video depicting a local police officer massively abusing his power against a very innocent individual. Statistically of the million or so police officers in America there is always one or two being caught abusing there powers and the taping of the activity can be then used for intelligence gathering purposes – without the requirement to ‘stage’ a fake abuse video. This method is extremely effective, and the more so the more abusive the video can be made to look. Sometimes it is useful to ‘lead’ the forum by replying to your own posting with your own statement of violent intent, and that you ‘do not care what the authorities think!!’ inflammation. By doing this and showing no fear it may be more effective in getting the more silent and self-disciplined violent intent members of the forum to slip and post their real intentions. This can be used later in a court of law during prosecution.
Technique #6 – ‘GAINING FULL CONTROL’
It is important to also be harvesting and continually maneuvering for a forum moderator position. Once this position is obtained, the forum can then be effectively and quietly controlled by deleting unfavourable postings – and one can eventually steer the forum into complete failure and lack of interest by the general public. This is the ‘ultimate victory’ as the forum is no longer participated with by the general public and no longer useful in maintaining their freedoms. Depending on the level of control you can obtain, you can deliberately steer a forum into defeat by censoring postings, deleting memberships, flooding, and or accidentally taking the forum offline. By this method the forum can be quickly killed. However it is not always in the interest to kill a forum as it can be converted into a ‘honey pot’ gathering center to collect and misdirect newcomers and from this point be completely used for your control for your agenda purposes.
CONCLUSION
Remember these techniques are only effective if the forum participants DO NOT KNOW ABOUT THEM. Once they are aware of these techniques the operation can completely fail, and the forum can become uncontrolled. At this point other avenues must be considered such as initiating a false legal precidence to simply have the forum shut down and taken offline. This is not desirable as it then leaves the enforcement agencies unable to track the percentage of those in the population who always resist attempts for control against them. Many other techniques can be utilized and developed by the individual and as you develop further techniques of infiltration and control it is imperative to share then with HQ.
______________________________________________________________________________________
Twenty-Five Rules of Disinformation
Note: The first rule and last five (or six, depending on situation) rules are generally not directly within the ability of the traditional disinfo artist to apply. These rules are generally used more directly by those at the leadership, key players, or planning level of the criminal conspiracy or conspiracy to cover up.
1. Hear no evil, see no evil, speak no evil. Regardless of what you know, don’t discuss it — especially if you are a public figure, news anchor, etc. If it’s not reported, it didn’t happen, and you never have to deal with the issues.
2. Become incredulous and indignant. Avoid discussing key issues and instead focus on side issues which can be used show the topic as being critical of some otherwise sacrosanct group or theme. This is also known as the ‘How dare you!’ gambit.
3. Create rumor mongers. Avoid discussing issues by describing all charges, regardless of venue or evidence, as mere rumors and wild accusations. Other derogatory terms mutually exclusive of truth may work as well. This method which works especially well with a silent press, because the only way the public can learn of the facts are through such ‘arguable rumors’. If you can associate the material with the Internet, use this fact to certify it a ‘wild rumor’ from a ‘bunch of kids on the Internet’ which can have no basis in fact.
4. Use a straw man. Find or create a seeming element of your opponent’s argument which you can easily knock down to make yourself look good and the opponent to look bad. Either make up an issue you may safely imply exists based on your interpretation of the opponent/opponent arguments/situation, or select the weakest aspect of the weakest charges. Amplify their significance and destroy them in a way which appears to debunk all the charges, real and fabricated alike, while actually avoiding discussion of the real issues.
5. Sidetrack opponents with name calling and ridicule. This is also known as the primary ‘attack the messenger’ ploy, though other methods qualify as variants of that approach. Associate opponents with unpopular titles such as ‘kooks’, ‘right-wing’, ‘liberal’, ‘left-wing’, ‘terrorists’, ‘conspiracy buffs’, ‘radicals’, ‘militia’, ‘racists’, ‘religious fanatics’, ‘sexual deviates’, and so forth. This makes others shrink from support out of fear of gaining the same label, and you avoid dealing with issues.
6. Hit and Run. In any public forum, make a brief attack of your opponent or the opponent position and then scamper off before an answer can be fielded, or simply ignore any answer. This works extremely well in Internet and letters-to-the-editor environments where a steady stream of new identities can be called upon without having to explain criticism, reasoning — simply make an accusation or other attack, never discussing issues, and never answering any subsequent response, for that would dignify the opponent’s viewpoint.
7. Question motives. Twist or amplify any fact which could be taken to imply that the opponent operates out of a hidden personal agenda or other bias. This avoids discussing issues and forces the accuser on the defensive.
8. Invoke authority. Claim for yourself or associate yourself with authority and present your argument with enough ‘jargon’ and ‘minutia’ to illustrate you are ‘one who knows’, and simply say it isn’t so without discussing issues or demonstrating concretely why or citing sources.
9. Play Dumb. No matter what evidence or logical argument is offered, avoid discussing issues except with denials they have any credibility, make any sense, provide any proof, contain or make a point, have logic, or support a conclusion. Mix well for maximum effect.
10. Associate opponent charges with old news. A derivative of the straw man — usually, in any large-scale matter of high visibility, someone will make charges early on which can be or were already easily dealt with – a kind of investment for the future should the matter not be so easily contained.) Where it can be foreseen, have your own side raise a straw man issue and have it dealt with early on as part of the initial contingency plans. Subsequent charges, regardless of validity or new ground uncovered, can usually then be associated with the original charge and dismissed as simply being a rehash without need to address current issues — so much the better where the opponent is or was involved with the original source.
11. Establish and rely upon fall-back positions. Using a minor matter or element of the facts, take the ‘high road’ and ‘confess’ with candor that some innocent mistake, in hindsight, was made — but that opponents have seized on the opportunity to blow it all out of proportion and imply greater criminalities which, ‘just isn’t so.’ Others can reinforce this on your behalf, later, and even publicly ‘call for an end to the nonsense’ because you have already ‘done the right thing.’ Done properly, this can garner sympathy and respect for ‘coming clean’ and ‘owning up’ to your mistakes without addressing more serious issues.
12. Enigmas have no solution. Drawing upon the overall umbrella of events surrounding the crime and the multitude of players and events, paint the entire affair as too complex to solve. This causes those otherwise following the matter to begin to lose interest more quickly without having to address the actual issues.
13. Alice in Wonderland Logic. Avoid discussion of the issues by reasoning backwards or with an apparent deductive logic which forbears any actual material fact.
14. Demand complete solutions. Avoid the issues by requiring opponents to solve the crime at hand completely, a ploy which works best with issues qualifying for rule 10.
15. Fit the facts to alternate conclusions. This requires creative thinking unless the crime was planned with contingency conclusions in place.
16. Vanish evidence and witnesses. If it does not exist, it is not fact, and you won’t have to address the issue.
17. Change the subject. Usually in connection with one of the other ploys listed here, find a way to side-track the discussion with abrasive or controversial comments in hopes of turning attention to a new, more manageable topic. This works especially well with companions who can ‘argue’ with you over the new topic and polarize the discussion arena in order to avoid discussing more key issues.
18. Emotionalize, Antagonize, and Goad Opponents. If you can’t do anything else, chide and taunt your opponents and draw them into emotional responses which will tend to make them look foolish and overly motivated, and generally render their material somewhat less coherent. Not only will you avoid discussing the issues in the first instance, but even if their emotional response addresses the issue, you can further avoid the issues by then focusing on how ‘sensitive they are to criticism.’
19. Ignore proof presented, demand impossible proofs. This is perhaps a variant of the ‘play dumb’ rule. Regardless of what material may be presented by an opponent in public forums, claim the material irrelevant and demand proof that is impossible for the opponent to come by (it may exist, but not be at his disposal, or it may be something which is known to be safely destroyed or withheld, such as a murder weapon.) In order to completely avoid discussing issues, it may be required that you to categorically deny and be critical of media or books as valid sources, deny that witnesses are acceptable, or even deny that statements made by government or other authorities have any meaning or relevance.
20. False evidence. Whenever possible, introduce new facts or clues designed and manufactured to conflict with opponent presentations — as useful tools to neutralize sensitive issues or impede resolution. This works best when the crime was designed with contingencies for the purpose, and the facts cannot be easily separated from the fabrications.
21. Call a Grand Jury, Special Prosecutor, or other empowered investigative body. Subvert the (process) to your benefit and effectively neutralize all sensitive issues without open discussion. Once convened, the evidence and testimony are required to be secret when properly handled. For instance, if you own the prosecuting attorney, it can insure a Grand Jury hears no useful evidence and that the evidence is sealed and unavailable to subsequent investigators. Once a favorable verdict is achieved, the matter can be considered officially closed. Usually, this technique is applied to find the guilty innocent, but it can also be used to obtain charges when seeking to frame a victim.
22. Manufacture a new truth. Create your own expert(s), group(s), author(s), leader(s) or influence existing ones willing to forge new ground via scientific, investigative, or social research or testimony which concludes favorably. In this way, if you must actually address issues, you can do so authoritatively.
23. Create bigger distractions. If the above does not seem to be working to distract from sensitive issues, or to prevent unwanted media coverage of unstoppable events such as trials, create bigger news stories (or treat them as such) to distract the multitudes.
24. Silence critics. If the above methods do not prevail, consider removing opponents from circulation by some definitive solution so that the need to address issues is removed entirely. This can be by their death, arrest and detention, blackmail or destruction of their character by release of blackmail information, or merely by destroying them financially, emotionally, or severely damaging their health.
25. Vanish. If you are a key holder of secrets or otherwise overly illuminated and you think the heat is getting too hot, to avoid the issues, vacate the kitchen.
______________________________________________________________________________________
Eight Traits of the Disinformationalist
1) Avoidance. They never actually discuss issues head-on or provide constructive input, generally avoiding citation of references or credentials. Rather, they merely imply this, that, and the other. Virtually everything about their presentation implies their authority and expert knowledge in the matter without any further justification for credibility.
2) Selectivity. They tend to pick and choose opponents carefully, either applying the hit-and-run approach against mere commentators supportive of opponents, or focusing heavier attacks on key opponents who are known to directly address issues. Should a commentator become argumentative with any success, the focus will shift to include the commentator as well.
3) Coincidental. They tend to surface suddenly and somewhat coincidentally with a new controversial topic with no clear prior record of participation in general discussions in the particular public arena involved. They likewise tend to vanish once the topic is no longer of general concern. They were likely directed or elected to be there for a reason, and vanish with the reason.
4) Teamwork. They tend to operate in self-congratulatory and complementary packs or teams. Of course, this can happen naturally in any public forum, but there will likely be an ongoing pattern of frequent exchanges of this sort where professionals are involved. Sometimes one of the players will infiltrate the opponent camp to become a source for straw man or other tactics designed to dilute opponent presentation strength.
5) Anti-conspiratorial. They almost always have disdain for ‘conspiracy theorists’ and, usually, for those who in any way believe JFK was not killed by LHO. Ask yourself why, if they hold such disdain for conspiracy theorists, do they focus on defending a single topic discussed in a NG focusing on conspiracies? One might think they would either be trying to make fools of everyone on every topic, or simply ignore the group they hold in such disdain.Or, one might more rightly conclude they have an ulterior motive for their actions in going out of their way to focus as they do.
6) Artificial Emotions. An odd kind of ‘artificial’ emotionalism and an unusually thick skin — an ability to persevere and persist even in the face of overwhelming criticism and unacceptance. This likely stems from intelligence community training that, no matter how condemning the evidence, deny everything, and never become emotionally involved or reactive. The net result for a disinfo artist is that emotions can seem artificial.
Most people, if responding in anger, for instance, will express their animosity throughout their rebuttal. But disinfo types usually have trouble maintaining the ‘image’ and are hot and cold with respect to pretended emotions and their usually more calm or unemotional communications style. It’s just a job, and they often seem unable to ‘act their role in character’ as well in a communications medium as they might be able in a real face-to-face conversation/confrontation. You might have outright rage and indignation one moment, ho-hum the next, and more anger later — an emotional yo-yo.
With respect to being thick-skinned, no amount of criticism will deter them from doing their job, and they will generally continue their old disinfo patterns without any adjustments to criticisms of how obvious it is that they play that game — where a more rational individual who truly cares what others think might seek to improve their communications style, substance, and so forth, or simply give up.
7) Inconsistent. There is also a tendency to make mistakes which betray their true self/motives. This may stem from not really knowing their topic, or it may be somewhat ‘freudian’, so to speak, in that perhaps they really root for the side of truth deep within.
I have noted that often, they will simply cite contradictory information which neutralizes itself and the author. For instance, one such player claimed to be a Navy pilot, but blamed his poor communicating skills (spelling, grammar, incoherent style) on having only a grade-school education. I’m not aware of too many Navy pilots who don’t have a college degree. Another claimed no knowledge of a particular topic/situation but later claimed first-hand knowledge of it.
8) Time Constant. Recently discovered, with respect to News Groups, is the response time factor. There are three ways this can be seen to work, especially when the government or other empowered player is involved in a cover up operation:
a) ANY NG posting by a targeted proponent for truth can result in an IMMEDIATE response. The government and other empowered players can afford to pay people to sit there and watch for an opportunity to do some damage. SINCE DISINFO IN A NG ONLY WORKS IF THE READER SEES IT – FAST RESPONSE IS CALLED FOR, or the visitor may be swayed towards truth.
b) When dealing in more direct ways with a disinformationalist, such as email, DELAY IS CALLED FOR – there will usually be a minimum of a 48-72 hour delay. This allows a sit-down team discussion on response strategy for best effect, and even enough time to ‘get permission’ or instruction from a formal chain of command.
c) In the NG example 1) above, it will often ALSO be seen that bigger guns are drawn and fired after the same 48-72 hours delay – the team approach in play. This is especially true when the targeted truth seeker or their comments are considered more important with respect to potential to reveal truth. Thus, a serious truth sayer will be attacked twice for the same sin.
______________________________________________________________________________________
How to Spot a Spy (Cointelpro Agent)
One way to neutralize a potential activist is to get them to be in a group that does all the wrong things. Why?
1) The message doesn’t get out.
2) A lot of time is wasted
3) The activist is frustrated and discouraged
4) Nothing good is accomplished.
FBI and Police Informers and Infiltrators will infest any group and they have phoney activist organizations established.
Their purpose is to prevent any real movement for justice or eco-peace from developing in this country.
Agents come in small, medium or large. They can be of any ethnic background. They can be male or female.
The actual size of the group or movement being infiltrated is irrelevant. It is the potential the movement has for becoming large which brings on the spies and saboteurs.
This booklet lists tactics agents use to slow things down, foul things up, destroy the movement and keep tabs on activists.
It is the agent’s job to keep the activist from quitting such a group, thus keeping him/her under control.
In some situations, to get control, the agent will tell the activist:
“You’re dividing the movement.”
[Here, I have added the psychological reasons as to WHY this maneuver works to control people]
This invites guilty feelings. Many people can be controlled by guilt. The agents begin relationships with activists behind a well-developed mask of “dedication to the cause.” Because of their often declared dedication, (and actions designed to prove this), when they criticize the activist, he or she – being truly dedicated to the movement – becomes convinced that somehow, any issues are THEIR fault. This is because a truly dedicated person tends to believe that everyone has a conscience and that nobody would dissimulate and lie like that “on purpose.” It’s amazing how far agents can go in manipulating an activist because the activist will constantly make excuses for the agent who regularly declares their dedication to the cause. Even if they do, occasionally, suspect the agent, they will pull the wool over their own eyes by rationalizing: “they did that unconsciously… they didn’t really mean it… I can help them by being forgiving and accepting ” and so on and so forth.
The agent will tell the activist:
“You’re a leader!”
This is designed to enhance the activist’s self-esteem. His or her narcissistic admiration of his/her own activist/altruistic intentions increase as he or she identifies with and consciously admires the altruistic declarations of the agent which are deliberately set up to mirror those of the activist.
This is “malignant pseudoidentification.” It is the process by which the agent consciously imitates or simulates a certain behavior to foster the activist’s identification with him/her, thus increasing the activist’s vulnerability to exploitation. The agent will simulate the more subtle self-concepts of the activist.
Activists and those who have altruistic self-concepts are most vulnerable to malignant pseudoidentification especially during work with the agent when the interaction includes matter relating to their competency, autonomy, or knowledge.
The goal of the agent is to increase the activist’s general empathy for the agent through pseudo-identification with the activist’s self-concepts.
The most common example of this is the agent who will compliment the activist for his competency or knowledge or value to the movement. On a more subtle level, the agent will simulate affects and mannerisms of the activist which promotes identification via mirroring and feelings of “twinship”. It is not unheard of for activists, enamored by the perceived helpfulness and competence of a good agent, to find themselves considering ethical violations and perhaps, even illegal behavior, in the service of their agent/handler.
The activist’s “felt quality of perfection” [self-concept] is enhanced, and a strong empathic bond is developed with the agent through his/her imitation and simulation of the victim’s own narcissistic investments. [self-concepts] That is, if the activist knows, deep inside, their own dedication to the cause, they will project that onto the agent who is “mirroring” them.
The activist will be deluded into thinking that the agent shares this feeling of identification and bonding. In an activist/social movement setting, the adversarial roles that activists naturally play vis a vis the establishment/government, fosters ongoing processes of intrapsychic splitting so that “twinship alliances” between activist and agent may render whole sectors or reality testing unavailable to the activist. They literally “lose touch with reality.”
Activists who deny their own narcissistic investments [do not have a good idea of their own self-concepts and that they ARE concepts] and consciously perceive themselves (accurately, as it were) to be “helpers” endowed with a special amount of altruism are exceedingly vulnerable to the affective (emotional) simulation of the accomplished agent.
Empathy is fostered in the activist through the expression of quite visible affects. The presentation of tearfulness, sadness, longing, fear, remorse, and guilt, may induce in the helper-oriented activist a strong sense of compassion, while unconsciously enhancing the activist’s narcissistic investment in self as the embodiment of goodness.
The agent’s expresssion of such simulated affects may be quite compelling to the observer and difficult to distinguish from deep emotion.
It can usually be identified by two events, however:
First, the activist who has analyzed his/her own narcissistic roots and is aware of his/her own potential for being “emotionally hooked,” will be able to remain cool and unaffected by such emotional outpourings by the agent.
As a result of this unaffected, cool, attitude, the Second event will occur: The agent will recompensate much too quickly following such an affective expression leaving the activist with the impression that “the play has ended, the curtain has fallen,” and the imposture, for the moment, has finished. The agent will then move quickly to another activist/victim.
The fact is, the movement doesn’t need leaders, it needs MOVERS. “Follow the leader” is a waste of time.
A good agent will want to meet as often as possible. He or she will talk a lot and say little. One can expect an onslaught of long, unresolved discussions.
Some agents take on a pushy, arrogant, or defensive manner:
1) To disrupt the agenda
2) To side-track the discussion
3) To interrupt repeatedly
4) To feign ignorance
5) To make an unfounded accusation against a person.
Calling someone a racist, for example. This tactic is used to discredit a person in the eyes of all other group members.
Saboteurs
Some saboteurs pretend to be activists. She or he will ….
1) Write encyclopedic flyers (in the present day, websites)
2) Print flyers in English only.
3) Have demonstrations in places where no one cares.
4) Solicit funding from rich people instead of grass roots support
5) Display banners with too many words that are confusing.
6) Confuse issues.
7) Make the wrong demands.
Cool Compromise the goal.
9) Have endless discussions that waste everyone’s time. The agent may accompany the endless discussions with drinking, pot smoking or other amusement to slow down the activist’s work.
Provocateurs
1) Want to establish “leaders” to set them up for a fall in order to stop the movement.
2) Suggest doing foolish, illegal things to get the activists in trouble.
3) Encourage militancy.
4) Want to taunt the authorities.
5) Attempt to make the activist compromise their values.
6) Attempt to instigate violence. Activisim ought to always be non-violent.
7) Attempt to provoke revolt among people who are ill-prepared to deal with the reaction of the authorities to such violence.
Informants
1) Want everyone to sign up and sing in and sign everything.
2) Ask a lot of questions (gathering data).
3) Want to know what events the activist is planning to attend.
4) Attempt to make the activist defend him or herself to identify his or her beliefs, goals, and level of committment.
Recruiting
Legitimate activists do not subject people to hours of persuasive dialog. Their actions, beliefs, and goals speak for themselves.
Groups that DO recruit are missionaries, military, and fake political parties or movements set up by agents.
Surveillance
ALWAYS assume that you are under surveillance.
At this point, if you are NOT under surveillance, you are not a very good activist!
Scare Tactics
They use them.
Such tactics include slander, defamation, threats, getting close to disaffected or minimally committed fellow activists to persuade them (via psychological tactics described above) to turn against the movement and give false testimony against their former compatriots. They will plant illegal substances on the activist and set up an arrest; they will plant false information and set up “exposure,” they will send incriminating letters [emails] in the name of the activist; and more; they will do whatever society will allow.
This booklet in no way covers all the ways agents use to sabotage the lives of sincere an dedicated activists.
If an agent is “exposed,” he or she will be transferred or replaced.
COINTELPRO is still in operation today under a different code name. It is no longer placed on paper where it can be discovered through the freedom of information act.
The FBI counterintelligence program’s stated purpose: To expose, disrupt, misdirect, discredit, and otherwise neutralize individuals who the FBI categorize as opposed to the National Interests. “National Security” means the FBI’s security from the people ever finding out the vicious things it does in violation of people’s civil liberties.
______________________________________________________________________________________
Seventeen Techniques for Truth Suppression
Strong, credible allegations of high-level criminal activity can bring down a government. When the government lacks an effective, fact-based defense, other techniques must be employed. The success of these techniques depends heavily upon a cooperative, compliant press and a mere token opposition party.
1. Dummy up. If it’s not reported, if it’s not news, it didn’t happen.
2. Wax indignant. This is also known as the “How dare you?” gambit.
3. Characterize the charges as “rumors” or, better yet, “wild rumors.” If, in spite of the news blackout, the public is still able to learn about the suspicious facts, it can only be through “rumors.” (If they tend to believe the “rumors” it must be because they are simply “paranoid” or “hysterical.”)
4. Knock down straw men. Deal only with the weakest aspects of the weakest charges. Even better, create your own straw men. Make up wild rumors (or plant false stories) and give them lead play when you appear to debunk all the charges, real and fanciful alike.
5. Call the skeptics names like “conspiracy theorist,” “nutcase,” “ranter,” “kook,” “crackpot,” and, of course, “rumor monger.” Be sure, too, to use heavily loaded verbs and adjectives when characterizing their charges and defending the “more reasonable” government and its defenders. You must then carefully avoid fair and open debate with any of the people you have thus maligned. For insurance, set up your own “skeptics” to shoot down.
6. Impugn motives. Attempt to marginalize the critics by suggesting strongly that they are not really interested in the truth but are simply pursuing a partisan political agenda or are out to make money (compared to over-compensated adherents to the government line who, presumably, are not).
7. Invoke authority. Here the controlled press and the sham opposition can be very useful.
8. Dismiss the charges as “old news.”
9. Come half-clean. This is also known as “confession and avoidance” or “taking the limited hangout route.” This way, you create the impression of candor and honesty while you admit only to relatively harmless, less-than-criminal “mistakes.” This stratagem often requires the embrace of a fall-back position quite different from the one originally taken. With effective damage control, the fall-back position need only be peddled by stooge skeptics to carefully limited markets.
10. Characterize the crimes as impossibly complex and the truth as ultimately unknowable.
11. Reason backward, using the deductive method with a vengeance. With thoroughly rigorous deduction, troublesome evidence is irrelevant. E.g. We have a completely free press. If evidence exists that the Vince Foster “suicide” note was forged, they would have reported it. They haven’t reported it so there is no such evidence. Another variation on this theme involves the likelihood of a conspiracy leaker and a press who would report the leak.
12. Require the skeptics to solve the crime completely. E.g. If Foster was murdered, who did it and why?
13. Change the subject. This technique includes creating and/or publicizing distractions.
14. Lightly report incriminating facts, and then make nothing of them. This is sometimes referred to as “bump and run” reporting.
15. Baldly and brazenly lie. A favorite way of doing this is to attribute the “facts” furnished the public to a plausible-sounding, but anonymous, source.
16. Expanding further on numbers 4 and 5, have your own stooges “expose” scandals and champion popular causes. Their job is to pre-empt real opponents and to play 99-yard football. A variation is to pay rich people for the job who will pretend to spend their own money.
17. Flood the Internet with agents. This is the answer to the question, “What could possibly motivate a person to spend hour upon hour on Internet news groups defending the government and/or the press and harassing genuine critics?” Don t the authorities have defenders enough in all the newspapers, magazines, radio, and television? One would think refusing to print critical letters and screening out serious callers or dumping them from radio talk shows would be control enough, but, obviously, it is not.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict99.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict82.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict83.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict92.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict87.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict84.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict85.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict86.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict88.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict91.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict89.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict90.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict98.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict93.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict96.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict97.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict94.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict101.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict100.jpg)







![[Image]](https://i0.wp.com/cryptome.org/2012-info/wh-obl-recycle/pict2.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/wh-obl-recycle/pict3.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/wh-obl-recycle/pict4.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/wh-obl-recycle/pict5.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/wh-obl-recycle/pict6.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/wh-obl-recycle/pict7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/wh-obl-recycle/pict8.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/wh-obl-recycle/pict9.jpg)












![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict26.jpg) A man wearing a mask of Spanish Prime Minister Mariano Rajoy protest during a demonstration organized by Unions on July 19, 2012 in Barcelona, against the government’s welfare cuts. In the latest measures to lower Spain’s deficit, conservative Prime Minister Mariano Rajoy announced 65 billion euros’ ($80 billion) worth of savings measures. Getty
A man wearing a mask of Spanish Prime Minister Mariano Rajoy protest during a demonstration organized by Unions on July 19, 2012 in Barcelona, against the government’s welfare cuts. In the latest measures to lower Spain’s deficit, conservative Prime Minister Mariano Rajoy announced 65 billion euros’ ($80 billion) worth of savings measures. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict46.jpg) A street performer dressed as an character from the science fiction film Avatar walks among the crowds near Mexico City’s main plaza, the Zocalo, Friday, July 13, 2012. Street performers, many dressed in costumes, gathered to protest in the historic downtown area where once they were allowed to perform but are now run off by police. AP
A street performer dressed as an character from the science fiction film Avatar walks among the crowds near Mexico City’s main plaza, the Zocalo, Friday, July 13, 2012. Street performers, many dressed in costumes, gathered to protest in the historic downtown area where once they were allowed to perform but are now run off by police. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict44.jpg) An anti-government demonstrator holds a molotov cocktail during clashes in the village of Sitra, south of Manama, Bahrain July 13, 2012. Dozens of demonstrators marched in an attempt to protest under the slogan ”Challenge Friday”, challenging the authorities after the government banned the protest. On Thursday, the Ministry of Interior issued a statement saying that the ministry is looking into venues where protests can be held. Reuters
An anti-government demonstrator holds a molotov cocktail during clashes in the village of Sitra, south of Manama, Bahrain July 13, 2012. Dozens of demonstrators marched in an attempt to protest under the slogan ”Challenge Friday”, challenging the authorities after the government banned the protest. On Thursday, the Ministry of Interior issued a statement saying that the ministry is looking into venues where protests can be held. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict51.jpg) An animal rights activist wearing an elephant-shaped headpiece arrives holding a placard for a protest in front of the Staples Center in Los Angeles, on July 11, 2012 in California, on the opening day of the Ringling Bros. and Barnum & Bailey Circus. Representatives of PETA, Animal Defenders International, In Defense of Animals, Last Chance for Animals, and the Animal Protection and Rescue League participated with a message for prospective circusgoers: Don’t go. Getty
An animal rights activist wearing an elephant-shaped headpiece arrives holding a placard for a protest in front of the Staples Center in Los Angeles, on July 11, 2012 in California, on the opening day of the Ringling Bros. and Barnum & Bailey Circus. Representatives of PETA, Animal Defenders International, In Defense of Animals, Last Chance for Animals, and the Animal Protection and Rescue League participated with a message for prospective circusgoers: Don’t go. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict40.jpg) A member of the Sikh community takes part in a protest against the Pakistani government in New Delhi on July 15, 2012. Sikh protesters demanded the immediate release of Indian national Sarabjit Singh who is currently held in a Pakistani prison. Sarabjit Singh is a high-profile prisoner who has spent two decades in solitary confinement on death row in Lahore after being convicted for his role in a string of bombings. Getty
A member of the Sikh community takes part in a protest against the Pakistani government in New Delhi on July 15, 2012. Sikh protesters demanded the immediate release of Indian national Sarabjit Singh who is currently held in a Pakistani prison. Sarabjit Singh is a high-profile prisoner who has spent two decades in solitary confinement on death row in Lahore after being convicted for his role in a string of bombings. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict42.jpg) An Israeli protester wearing a Guy Fawkes mask and Pharaoh headpiece chains his hand as he holds a slogan which reads in Hebrew ‘The justice is like Pharaoh’ during a demonstration in the Mediterranean coastal city of Tel Aviv on July 14, 2012 to mark the first anniversary of last summer’s social justice demonstrations that swept the country to protest the spiralling cost of living. Getty
An Israeli protester wearing a Guy Fawkes mask and Pharaoh headpiece chains his hand as he holds a slogan which reads in Hebrew ‘The justice is like Pharaoh’ during a demonstration in the Mediterranean coastal city of Tel Aviv on July 14, 2012 to mark the first anniversary of last summer’s social justice demonstrations that swept the country to protest the spiralling cost of living. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict11.jpg) Demonstrators march against student tuition hikes and Bill 78 in downtown Montreal, Quebec July 22, 2012. The mass demonstration, which is quickly becoming a monthly protest in Montreal since it started around six months ago, has drawn tens of thousands of people to protest in the city. Reuters
Demonstrators march against student tuition hikes and Bill 78 in downtown Montreal, Quebec July 22, 2012. The mass demonstration, which is quickly becoming a monthly protest in Montreal since it started around six months ago, has drawn tens of thousands of people to protest in the city. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict13.jpg) A woman wears an old police helmet during a protest by firefighters and police officers against government austerity measures in Valencia July 23, 2012. Reuters
A woman wears an old police helmet during a protest by firefighters and police officers against government austerity measures in Valencia July 23, 2012. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict12.jpg) A member of the movement ‘YoSoy#132’ takes part in a protest against the election results at Reforma avenue, in Mexico City, on July 22, 2012. The movement is protesting against Enrique Pena Nieto, candidate of the Institutional Revolutionary Party (PRI), who declared victory in the presidential election, after the first official results showed him with 38 percent of the vote. The candidate for the leftist coalition Progressive Movement of Mexico, Andres Manuel Lopez Obrador, the winner’s nearest rival, refused to concede the race to Pena Nieto until the official final results be released, claiming to have data showing different results. Getty
A member of the movement ‘YoSoy#132’ takes part in a protest against the election results at Reforma avenue, in Mexico City, on July 22, 2012. The movement is protesting against Enrique Pena Nieto, candidate of the Institutional Revolutionary Party (PRI), who declared victory in the presidential election, after the first official results showed him with 38 percent of the vote. The candidate for the leftist coalition Progressive Movement of Mexico, Andres Manuel Lopez Obrador, the winner’s nearest rival, refused to concede the race to Pena Nieto until the official final results be released, claiming to have data showing different results. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict14.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict15.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict16.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict17.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict18.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict19.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict20.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict22.jpg) Juan Antonio Torres, 42, a social worker and member of the Comisiones Obreras (CCOO), lies in a coffin while wearing a mask of Spain’s Prime Minister Mariano Rajoy during a protest march against austerity measures in Malaga, southern Spain, July 19, 2012. Hundreds of thousands of Spaniards marched against the centre-right government’s latest austerity measures on Thursday evening, following more than a week of demonstrations across the country. Reuters
Juan Antonio Torres, 42, a social worker and member of the Comisiones Obreras (CCOO), lies in a coffin while wearing a mask of Spain’s Prime Minister Mariano Rajoy during a protest march against austerity measures in Malaga, southern Spain, July 19, 2012. Hundreds of thousands of Spaniards marched against the centre-right government’s latest austerity measures on Thursday evening, following more than a week of demonstrations across the country. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict23.jpg) Firemen shouts slogans as they march during a protest against government austerity measures in Madrid July 19, 2012. A protest movement against the centre-right Spanish government’s latest austerity measures swelled on Thursday as public sector workers stepped up demonstrations in Madrid and around the country after more than a week of spontaneous action. The placard reads, “Our cut will be with a guillotine”. Reuters
Firemen shouts slogans as they march during a protest against government austerity measures in Madrid July 19, 2012. A protest movement against the centre-right Spanish government’s latest austerity measures swelled on Thursday as public sector workers stepped up demonstrations in Madrid and around the country after more than a week of spontaneous action. The placard reads, “Our cut will be with a guillotine”. Reuters
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict25.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict24.jpg) A demonstrator dresses as an skeleton during a protest against government austerity measures in Madrid July 19, 2012. A protest movement against the centre-right Spanish government’s latest austerity measures swelled on Thursday as public sector workers stepped up demonstrations in Madrid and around the country after more than a week of spontaneous action. The placard reads, “Market, money management thieves”. Reuters
A demonstrator dresses as an skeleton during a protest against government austerity measures in Madrid July 19, 2012. A protest movement against the centre-right Spanish government’s latest austerity measures swelled on Thursday as public sector workers stepped up demonstrations in Madrid and around the country after more than a week of spontaneous action. The placard reads, “Market, money management thieves”. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict27.jpg) A woman performs during a protest against the health care system in Bogota, Colombia, on July 19, 2012, requiring the dismantling of the Health Promotion Companies (EPS). Colombian President Juan Manuel Santos announced Thursday a package of drastic measures to save the health sector, threatened with bankruptcy because of debts incurred by the EPS. Getty
A woman performs during a protest against the health care system in Bogota, Colombia, on July 19, 2012, requiring the dismantling of the Health Promotion Companies (EPS). Colombian President Juan Manuel Santos announced Thursday a package of drastic measures to save the health sector, threatened with bankruptcy because of debts incurred by the EPS. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict28.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict29.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict31.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict30.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict32.jpg) A woman carries a gallows rope with the pictures Yahya Mohammed Abdullah Saleh (R), nephew of former Yemeni President Ali Abdullah Saleh, and Saleh’s son Ahmed Ali Abdullah Saleh, during a protest outside the home of Yemeni President Abd-Rabbu Mansour Hadi, to demand the dismissal of the rest of the Saleh’s family members, in Sanaa July 19, 2012. Reuters
A woman carries a gallows rope with the pictures Yahya Mohammed Abdullah Saleh (R), nephew of former Yemeni President Ali Abdullah Saleh, and Saleh’s son Ahmed Ali Abdullah Saleh, during a protest outside the home of Yemeni President Abd-Rabbu Mansour Hadi, to demand the dismissal of the rest of the Saleh’s family members, in Sanaa July 19, 2012. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict33.jpg) Hungarian rescue workers remove Greenpeace activists from the roof of a local petrol station in Budapest on July 19, 2012, during an action of Greenpeace’s Hungarian and foreign activists to protest against the Shell Oil Company’s plans to drill in the Arctic. Getty
Hungarian rescue workers remove Greenpeace activists from the roof of a local petrol station in Budapest on July 19, 2012, during an action of Greenpeace’s Hungarian and foreign activists to protest against the Shell Oil Company’s plans to drill in the Arctic. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict35.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict36.jpg) A Filipino woman protester gives vegetables to an activist wearing a mask of Uncle Sam while another with a mask of Philippine President Benigno Aquino III joins a symbolic protest outside the gates of the Malacanang Presidential Palace in Manila, Philippines on Tuesday, July 17, 2012. The protest aims to symbolize President Aquino and the U.S. of depriving and cheating Filipinos. AP
A Filipino woman protester gives vegetables to an activist wearing a mask of Uncle Sam while another with a mask of Philippine President Benigno Aquino III joins a symbolic protest outside the gates of the Malacanang Presidential Palace in Manila, Philippines on Tuesday, July 17, 2012. The protest aims to symbolize President Aquino and the U.S. of depriving and cheating Filipinos. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict37.jpg) Firefighters and other government employees take part in a demonstration against the Spanish government’s latest austerity measures, in front of the Spanish Parliament (Las Cortes) in Madrid, on July 16, 2012. Several hundreds government workers, including police officers, firefighters, and healthcare workers, joined the spontaneous protest after conservative Prime Minister Mariano Rajoy announced, on July 13, the latest measures to lower Spain’s deficit, a 65-billion-euro (80 billion USD) austerity package involving among other things an increase in the VAT (TVA) tax and cuts in unemployment benefits. Getty
Firefighters and other government employees take part in a demonstration against the Spanish government’s latest austerity measures, in front of the Spanish Parliament (Las Cortes) in Madrid, on July 16, 2012. Several hundreds government workers, including police officers, firefighters, and healthcare workers, joined the spontaneous protest after conservative Prime Minister Mariano Rajoy announced, on July 13, the latest measures to lower Spain’s deficit, a 65-billion-euro (80 billion USD) austerity package involving among other things an increase in the VAT (TVA) tax and cuts in unemployment benefits. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict38.jpg) A demonstrator holds up a sign during a protest in Tel Aviv July 15, 2012, against the economic policies of Israel’s conservative government and to show solidarity with Moshe Silman, who sustained serious burns after he poured flammable liquid on himself and lit it at another protest on Saturday. The sign reads in Hebrew “Bibi you burned me too”, referring to Israel’s Prime Minister Benjamin Netanyahu by his nickname. Reuters
A demonstrator holds up a sign during a protest in Tel Aviv July 15, 2012, against the economic policies of Israel’s conservative government and to show solidarity with Moshe Silman, who sustained serious burns after he poured flammable liquid on himself and lit it at another protest on Saturday. The sign reads in Hebrew “Bibi you burned me too”, referring to Israel’s Prime Minister Benjamin Netanyahu by his nickname. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict39.jpg) Israelis block a highway as they march through the streets to protest rising housing costs on July 15, 2012 in Tel Aviv, Israel. Growing discontent among Israelis over housing prices and other social inequalities have spurred marches, boycotts and labor strikes in the Jewish state. An Israeli man set himself on fire during the march for social justice protest yesterday. Getty
Israelis block a highway as they march through the streets to protest rising housing costs on July 15, 2012 in Tel Aviv, Israel. Growing discontent among Israelis over housing prices and other social inequalities have spurred marches, boycotts and labor strikes in the Jewish state. An Israeli man set himself on fire during the march for social justice protest yesterday. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict41.jpg) In this Sunday, July 15, 2012 photo, Lebanese women sit at a protest camp set up by Sheik Ahmad Assir, a harline Sunni cleric, in the southern port city of Sidon, Lebanon. Assir has set up the camp in the middle of a key road in Sidon, declaring it an uprising against Hezbollah’s weapons. Assir is taking aim at Hezbollah at a vulnerable time for the group when it faces the possible downfall of its crucial ally, President Bashar Assad in Syria. Assir may not be a direct threat to Hezbollah, but the willingness to publicly confront it underlines the dangers the group faces as it tries to retain the power and influence it has built up over the past 30 years in the face of the Syria crisis. AP
In this Sunday, July 15, 2012 photo, Lebanese women sit at a protest camp set up by Sheik Ahmad Assir, a harline Sunni cleric, in the southern port city of Sidon, Lebanon. Assir has set up the camp in the middle of a key road in Sidon, declaring it an uprising against Hezbollah’s weapons. Assir is taking aim at Hezbollah at a vulnerable time for the group when it faces the possible downfall of its crucial ally, President Bashar Assad in Syria. Assir may not be a direct threat to Hezbollah, but the willingness to publicly confront it underlines the dangers the group faces as it tries to retain the power and influence it has built up over the past 30 years in the face of the Syria crisis. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict43.jpg) A protester stands in front of Malaysia Islamic Party flag (PAS) during a protest march to the National Palace to to hand out a memorandum in protest of the listing of Malaysia’s Felda Global in Kuala Lumpur, Malaysia, Saturday, July 14, 2012. The Malaysian palm oil firm Felda Global surged 20 percent in its trading debut on June 28, as investors cheered on the world’s second largest Initial Public Offering (IPO) after Facebook. Felda’s listing plans were initially met with resistance from the farmers who partly owned the firm and feared the loss of control of an asset they had invested in for generations. AP
A protester stands in front of Malaysia Islamic Party flag (PAS) during a protest march to the National Palace to to hand out a memorandum in protest of the listing of Malaysia’s Felda Global in Kuala Lumpur, Malaysia, Saturday, July 14, 2012. The Malaysian palm oil firm Felda Global surged 20 percent in its trading debut on June 28, as investors cheered on the world’s second largest Initial Public Offering (IPO) after Facebook. Felda’s listing plans were initially met with resistance from the farmers who partly owned the firm and feared the loss of control of an asset they had invested in for generations. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict45.jpg) A street performer dressed as a Minotaur walks among the crowds near Mexico City’s main plaza, the Zocalo, Friday, July 13, 2012. Street performers, many dressed in costumes, gathered to protest in the historic downtown area where once they were allowed to perform but are now run off by police. AP
A street performer dressed as a Minotaur walks among the crowds near Mexico City’s main plaza, the Zocalo, Friday, July 13, 2012. Street performers, many dressed in costumes, gathered to protest in the historic downtown area where once they were allowed to perform but are now run off by police. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict47.jpg) A worker in a mask marches holding a sign which reads, “No to Conga, no to mine,” in solidarity with the anti-mining protest in Cajamarca, Lima July 12, 2012. More than 1,000 members of the General Confederation of Workers of Peru (CGTP), who marched in solidarity with the anti-mining protest, also protested against Peru’s President Ollanta Humala’s government and demanded better pay conditions. The Cajamarca region is still under state of emergency a week after five people died and 21 were injured in clashes between police and protesters against Newmont’s $5 billion gold mine project, known as Conga. Reuters
A worker in a mask marches holding a sign which reads, “No to Conga, no to mine,” in solidarity with the anti-mining protest in Cajamarca, Lima July 12, 2012. More than 1,000 members of the General Confederation of Workers of Peru (CGTP), who marched in solidarity with the anti-mining protest, also protested against Peru’s President Ollanta Humala’s government and demanded better pay conditions. The Cajamarca region is still under state of emergency a week after five people died and 21 were injured in clashes between police and protesters against Newmont’s $5 billion gold mine project, known as Conga. Reuters
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-02-05/pict10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-02-05/pict5.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-02-05/pict2.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-02-05/pict3.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-02-05/pict9.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-02-05/pict4.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-02-05/pict6.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-02-05/pict7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-02-05/pict8.jpg)










![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict41.jpg) U.S. President Barack Obama greets people gathered on the sidewalk after stopping for food at Skyline Chili in Cincinnati, July 16, 2012. Obama flew on Monday to Cincinnati for election campaign events. Reuters
U.S. President Barack Obama greets people gathered on the sidewalk after stopping for food at Skyline Chili in Cincinnati, July 16, 2012. Obama flew on Monday to Cincinnati for election campaign events. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict39.jpg) US President Barack Obama greets wellwishers upon arrival on Air Force One at Cincinnati Northern Kentucky International Airport in Boone, Kentucky, July 16, 2012, enroute to attend campaign events in Cincinnati, Ohio. Getty
US President Barack Obama greets wellwishers upon arrival on Air Force One at Cincinnati Northern Kentucky International Airport in Boone, Kentucky, July 16, 2012, enroute to attend campaign events in Cincinnati, Ohio. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict38.jpg) President Barack Obama passes his jacket to White House Trip Director Marvin Nicholson before heading over to greet people after arriving at Northern Kentucky International Airport in Boone, Ky. , Monday, July 16, 2012. Obama is spending the day campaigning in Cincinnati. AP
President Barack Obama passes his jacket to White House Trip Director Marvin Nicholson before heading over to greet people after arriving at Northern Kentucky International Airport in Boone, Ky. , Monday, July 16, 2012. Obama is spending the day campaigning in Cincinnati. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict40.jpg) U.S. Secret Service members use a golf cart while providing protection for President Barack Obama while he golfs at the Army installation’s course July 15, 2012 in Ft. Belvoir, Virginia. Obama also campaigned in Virginia, a state he won in 2008, on Saturday, holding events in Fairfax and Glen Allen. Getty
U.S. Secret Service members use a golf cart while providing protection for President Barack Obama while he golfs at the Army installation’s course July 15, 2012 in Ft. Belvoir, Virginia. Obama also campaigned in Virginia, a state he won in 2008, on Saturday, holding events in Fairfax and Glen Allen. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict31.jpg) US President Barack Obama greets supporters are he arrives at a campaign event on July 14, 2012 at Centreville High School in Clifton, Virginia. Getty
US President Barack Obama greets supporters are he arrives at a campaign event on July 14, 2012 at Centreville High School in Clifton, Virginia. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict32.jpg) U.S. President Barack Obama arrives at a campaign rally at Centreville High School in Clifton, Virginia, July 14, 2012. Obama travelled to Virginia on Saturday for campaign events. Reuters
U.S. President Barack Obama arrives at a campaign rally at Centreville High School in Clifton, Virginia, July 14, 2012. Obama travelled to Virginia on Saturday for campaign events. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict28.jpg) President Barack Obama walks up a set of stairs during a campaign rally at Centreville High School in Clifton, Va. , a Washington suburb, on Saturday, July 14, 2012. AP
President Barack Obama walks up a set of stairs during a campaign rally at Centreville High School in Clifton, Va. , a Washington suburb, on Saturday, July 14, 2012. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict35.jpg) People hold signs protesting against U.S. President Barack Obama along Obama’s motorcade route on his way to a campaign rally at Centreville High School in Clifton, Virginia, July 14, 2012. Obama travelled to Virginia on Saturday for campaign events. Reuters
People hold signs protesting against U.S. President Barack Obama along Obama’s motorcade route on his way to a campaign rally at Centreville High School in Clifton, Virginia, July 14, 2012. Obama travelled to Virginia on Saturday for campaign events. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict30.jpg) President Barack Obama laughs while campaigning under the pouring rain at the historic Walkerton Tavern & Gardens in Glen Allen, Va. , near Richmond Saturday, July 14, 2012. It is in the Congressional district represented by House Majority Leader Eric Cantor, R-Va. , a key county in a crucial swing state of the presidential election. AP
President Barack Obama laughs while campaigning under the pouring rain at the historic Walkerton Tavern & Gardens in Glen Allen, Va. , near Richmond Saturday, July 14, 2012. It is in the Congressional district represented by House Majority Leader Eric Cantor, R-Va. , a key county in a crucial swing state of the presidential election. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict26.jpg) U.S. President Barack Obama greets supporters at the end of his ”A Vision for Virginia’s Middle Class” campaign event July 14, 2012 at Walkerton Tavern in Glen Allen, Virginia. On the last day of his two-day campaign across Virginia, Obama continue to discuss his plan to restore middle class security and urged Congress to act on extending tax cuts to middle class families. Getty
U.S. President Barack Obama greets supporters at the end of his ”A Vision for Virginia’s Middle Class” campaign event July 14, 2012 at Walkerton Tavern in Glen Allen, Virginia. On the last day of his two-day campaign across Virginia, Obama continue to discuss his plan to restore middle class security and urged Congress to act on extending tax cuts to middle class families. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict27.jpg) President Barack Obama campaigns during the pouring rain at the historic Walkerton Tavern & Gardens in Glen Allen, Va. , near Richmond, Saturday, July 14, 2012. AP
President Barack Obama campaigns during the pouring rain at the historic Walkerton Tavern & Gardens in Glen Allen, Va. , near Richmond, Saturday, July 14, 2012. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict37.jpg) Protesters line an entrance route to a campaign event where President Barack Obama is scheduled to speak at the historic Walkerton Tavern & Gardens in Glen Allen, Va. , near Richmond Saturday, July 14, 2012. AP
Protesters line an entrance route to a campaign event where President Barack Obama is scheduled to speak at the historic Walkerton Tavern & Gardens in Glen Allen, Va. , near Richmond Saturday, July 14, 2012. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict36.jpg) Conservative local residents protest prior to U.S. President Barack Obama’s ”A Vision for Virginia’s Middle Class” campaign event July 14, 2012 at Walkerton Tavern in Glen Allen, Virginia. On the last day of his two-day campaign across Virginia, Obama continue to discuss his plan to restore middle class security and urged the Congress to act on extending tax cuts to middle class families. Getty
Conservative local residents protest prior to U.S. President Barack Obama’s ”A Vision for Virginia’s Middle Class” campaign event July 14, 2012 at Walkerton Tavern in Glen Allen, Virginia. On the last day of his two-day campaign across Virginia, Obama continue to discuss his plan to restore middle class security and urged the Congress to act on extending tax cuts to middle class families. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict29.jpg) President Barack Obama removes his jacket upon his arrival at Washington Dulles International Airport in Chantilly, Va. , Saturday, July 14, 2012, for a campaign event in the vicinity. AP
President Barack Obama removes his jacket upon his arrival at Washington Dulles International Airport in Chantilly, Va. , Saturday, July 14, 2012, for a campaign event in the vicinity. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict25.jpg) US President Barack Obama boards his limousine after greeting well-wishers upon arrival July 14, 2012 at Richmond International Airport in Richmond, Virginia. Obama is in Virginia to attend campaign events. Getty
US President Barack Obama boards his limousine after greeting well-wishers upon arrival July 14, 2012 at Richmond International Airport in Richmond, Virginia. Obama is in Virginia to attend campaign events. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict33.jpg) Secret Service members keep watch in front of Air Force One shortly before US President Barack Obama’s departure on July 14, 2012 at Richmond International Airport in Richmond, Virginia. Obama is in Virginia to attend campaign events. Getty
Secret Service members keep watch in front of Air Force One shortly before US President Barack Obama’s departure on July 14, 2012 at Richmond International Airport in Richmond, Virginia. Obama is in Virginia to attend campaign events. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict1.jpg) US President Barack Obama hold up a tomato during a stop at Berry’s Produce on July 14, 2012 in Mechanicsville, Virginia. Obama is campaigning in Virginia ahead of the November presidential election. Getty
US President Barack Obama hold up a tomato during a stop at Berry’s Produce on July 14, 2012 in Mechanicsville, Virginia. Obama is campaigning in Virginia ahead of the November presidential election. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict0.jpg) President Barack Obama shakes hands as he arrives at the Richmond International Airport in Richmond, Va. , Saturday, July 14, 2012. AP
President Barack Obama shakes hands as he arrives at the Richmond International Airport in Richmond, Va. , Saturday, July 14, 2012. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict14.jpg) President Barack Obama greets the crowd after a campaign stop at the historic Fire Station No.1, in downtown Roanoke, Virginia, Friday, July 13, 2012. Obama traveled to southwest Virginia to discuss choice in this election between two fundamentally different visions on how to grow the economy, create middle-class jobs and pay down the debt. AP
President Barack Obama greets the crowd after a campaign stop at the historic Fire Station No.1, in downtown Roanoke, Virginia, Friday, July 13, 2012. Obama traveled to southwest Virginia to discuss choice in this election between two fundamentally different visions on how to grow the economy, create middle-class jobs and pay down the debt. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict15.jpg) President Barack Obama greets the crowd during a campaign stop at the historic Fire Station No.1, in downtown Roanoke, Va. , Friday, July 13, 2012. Obama traveled to southwest Virginia to discuss choice in this election between two fundamentally different visions on how to grow the economy, create middle-class jobs and pay down the debt. AP
President Barack Obama greets the crowd during a campaign stop at the historic Fire Station No.1, in downtown Roanoke, Va. , Friday, July 13, 2012. Obama traveled to southwest Virginia to discuss choice in this election between two fundamentally different visions on how to grow the economy, create middle-class jobs and pay down the debt. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict16.jpg) President Barack Obama greets people after arriving at Roanoke Regional Airport in Roanoke, Va. , Friday, July 13, 2012. Obama is spending the day campaigning in Virginia. AP
President Barack Obama greets people after arriving at Roanoke Regional Airport in Roanoke, Va. , Friday, July 13, 2012. Obama is spending the day campaigning in Virginia. AP
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict20.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict18.jpg) President Barack Obama greets people after arriving at Roanoke Regional Airport in Roanoke, Va. , Friday, July 13, 2012. Obama is spending the day campaigning in Virginia. AP
President Barack Obama greets people after arriving at Roanoke Regional Airport in Roanoke, Va. , Friday, July 13, 2012. Obama is spending the day campaigning in Virginia. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict19.jpg) President Barack Obama arrives at the Roanoke Airport on Air Force One on the campaign trail, Friday, July 13, 2012 in Roanoke, Va. AP
President Barack Obama arrives at the Roanoke Airport on Air Force One on the campaign trail, Friday, July 13, 2012 in Roanoke, Va. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict17.jpg) President Barack Obama greets people after arriving at Roanoke Regional Airport in Roanoke, Va. , Friday, July 13, 2012. Obama is spending the day campaigning in Virginia. AP
President Barack Obama greets people after arriving at Roanoke Regional Airport in Roanoke, Va. , Friday, July 13, 2012. Obama is spending the day campaigning in Virginia. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict22.jpg) President Barack Obama greets the crowd after speaking at a campaign event at Phoebus High School in Hampton, Va. , Friday, July 13, 2012. Obama is spending the day in Virginia campaigning. AP
President Barack Obama greets the crowd after speaking at a campaign event at Phoebus High School in Hampton, Va. , Friday, July 13, 2012. Obama is spending the day in Virginia campaigning. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict21.jpg) President Barack Obama greets the crowd after speaking at a campaign event at Phoebus High School in Hampton, Va. , Friday, July 13, 2012. Obama is spending the day in Virginia campaigning. AP
President Barack Obama greets the crowd after speaking at a campaign event at Phoebus High School in Hampton, Va. , Friday, July 13, 2012. Obama is spending the day in Virginia campaigning. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict24.jpg) President Barack Obama arrives to speak at a campaign event at Phoebus High School in Hampton, Va. , Friday, July 13, 2012. Obama is spending the day in Virginia campaigning. AP
President Barack Obama arrives to speak at a campaign event at Phoebus High School in Hampton, Va. , Friday, July 13, 2012. Obama is spending the day in Virginia campaigning. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict12.jpg) U.S. President Barack Obama (C) greets supporters at the end of his ‘A Vision for Virginia’s Middle Class’ campaign event July 13, 2012 at Green Run High School in Virginia Beach, Virginia. Obama discussed his plan to restore middle class security and urged the Congress to act on extending tax cuts to middle class families. Getty
U.S. President Barack Obama (C) greets supporters at the end of his ‘A Vision for Virginia’s Middle Class’ campaign event July 13, 2012 at Green Run High School in Virginia Beach, Virginia. Obama discussed his plan to restore middle class security and urged the Congress to act on extending tax cuts to middle class families. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict13.jpg) U.S. President Barack Obama (R) greets supporters at the end of his ‘A Vision for Virginia’s Middle Class’ campaign event July 13, 2012 at Green Run High School in Virginia Beach, Virginia. Obama discussed his plan to restore middle class security and urged the Congress to act on extending tax cuts to middle class families. Getty [Two Secret Service in “hands ready” position.
U.S. President Barack Obama (R) greets supporters at the end of his ‘A Vision for Virginia’s Middle Class’ campaign event July 13, 2012 at Green Run High School in Virginia Beach, Virginia. Obama discussed his plan to restore middle class security and urged the Congress to act on extending tax cuts to middle class families. Getty [Two Secret Service in “hands ready” position.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict2.jpg) President Barack Obama reaches out to shake hands at a campaign event at Green Run High School in Virginia Beach, Va. , Friday, July 13, 2012. Obama is spending the day in Virginia campaigning. AP
President Barack Obama reaches out to shake hands at a campaign event at Green Run High School in Virginia Beach, Va. , Friday, July 13, 2012. Obama is spending the day in Virginia campaigning. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict3.jpg) President Barack Obama heads to his car after greeting people after arriving at Norfolk International Airport in Norfolk, Va. , Friday, July 13, 2012. AP
President Barack Obama heads to his car after greeting people after arriving at Norfolk International Airport in Norfolk, Va. , Friday, July 13, 2012. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict4.jpg) President Barack Obama is surrounded by secret service as he greets people after arriving at Norfolk International Airport in Norfolk, Va. , Friday, July 13, 2012. AP
President Barack Obama is surrounded by secret service as he greets people after arriving at Norfolk International Airport in Norfolk, Va. , Friday, July 13, 2012. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict6.jpg) President Barack Obama heads to his car after greeting people after arriving at Norfolk International Airport in Norfolk, Va. , Friday, July 13, 2012. AP
President Barack Obama heads to his car after greeting people after arriving at Norfolk International Airport in Norfolk, Va. , Friday, July 13, 2012. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict5.jpg) President Barack Obama meets with supporters after arriving aboard Air Force One at the Norfolk International Airport in Norfolk, Va. , Friday, July 13, 2012. AP
President Barack Obama meets with supporters after arriving aboard Air Force One at the Norfolk International Airport in Norfolk, Va. , Friday, July 13, 2012. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict7.jpg) President Barack Obama meets with supporters after arriving aboard Air Force One at the Norfolk International Airport in Norfolk, Va. , Friday, July 13, 2012. AP
President Barack Obama meets with supporters after arriving aboard Air Force One at the Norfolk International Airport in Norfolk, Va. , Friday, July 13, 2012. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict8.jpg) President Barack Obama walks to Air Force One at Andrews Air Force Base in Md. , Friday, July 13, 2012, enroute to Virginia for a series of campaign events. AP
President Barack Obama walks to Air Force One at Andrews Air Force Base in Md. , Friday, July 13, 2012, enroute to Virginia for a series of campaign events. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict9.jpg) Members of the media exit a house alongside US President Barack Obama’s SUV holding in the driveway as Obama meets with Jason McLaughlin, principal of Center Point-Urbana High School, his wife, Ali, an account manager for a document scanning company, and their 4-year-old son Cooper, on middle class tax cuts at their home in Cedar Rapids, Iowa, July 10, 2012. Getty
Members of the media exit a house alongside US President Barack Obama’s SUV holding in the driveway as Obama meets with Jason McLaughlin, principal of Center Point-Urbana High School, his wife, Ali, an account manager for a document scanning company, and their 4-year-old son Cooper, on middle class tax cuts at their home in Cedar Rapids, Iowa, July 10, 2012. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict34.jpg) Secret Service agents guard the door of the home of Jason and Ali McLaughlin while President Barack Obama visits with them in Cedar Rapids, Iowa, Tuesday, July 10, 2012. AP
Secret Service agents guard the door of the home of Jason and Ali McLaughlin while President Barack Obama visits with them in Cedar Rapids, Iowa, Tuesday, July 10, 2012. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict10.jpg) U.S. President Barack Obama arrives in Cedar Rapids, Iowa, July 10, 2012. Obama flew to Iowa for an event pushing for the extension of Bush-era tax cuts due to expire at the end of 2012. Reuters
U.S. President Barack Obama arrives in Cedar Rapids, Iowa, July 10, 2012. Obama flew to Iowa for an event pushing for the extension of Bush-era tax cuts due to expire at the end of 2012. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict11.jpg) President Barack Obama heads to his car after getting ice cream at Deb’s Ice Cream & Deli in Cedar Rapids, Iowa, Tuesday, July 10, 2012. AP
President Barack Obama heads to his car after getting ice cream at Deb’s Ice Cream & Deli in Cedar Rapids, Iowa, Tuesday, July 10, 2012. AP


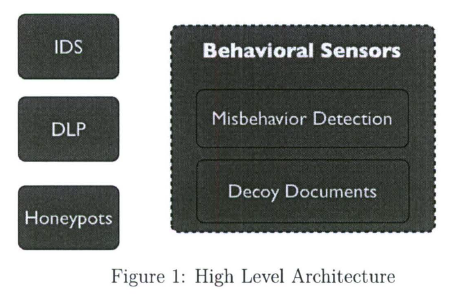
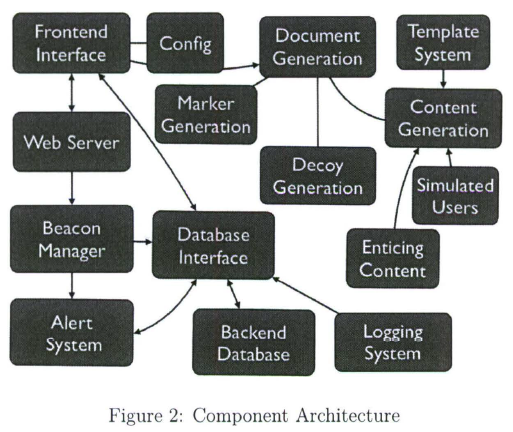




![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0711/pict8.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0711/pict0.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0711/pict1.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0711/pict2.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0711/pict3.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0711/pict6.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0711/pict5.jpg)





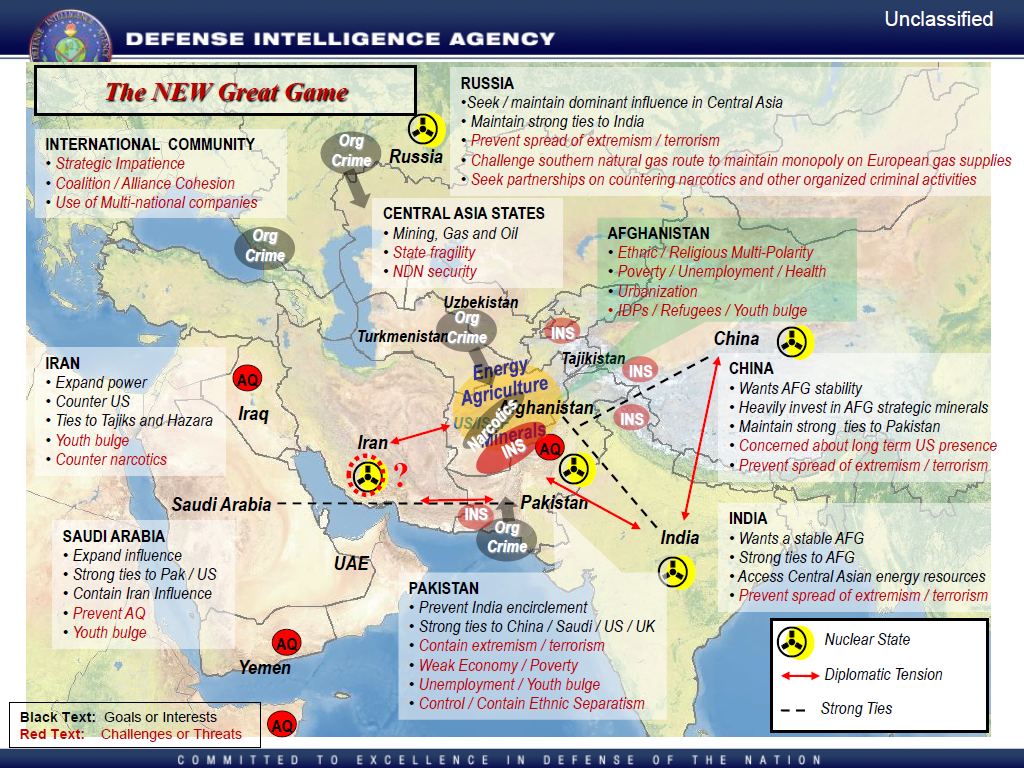
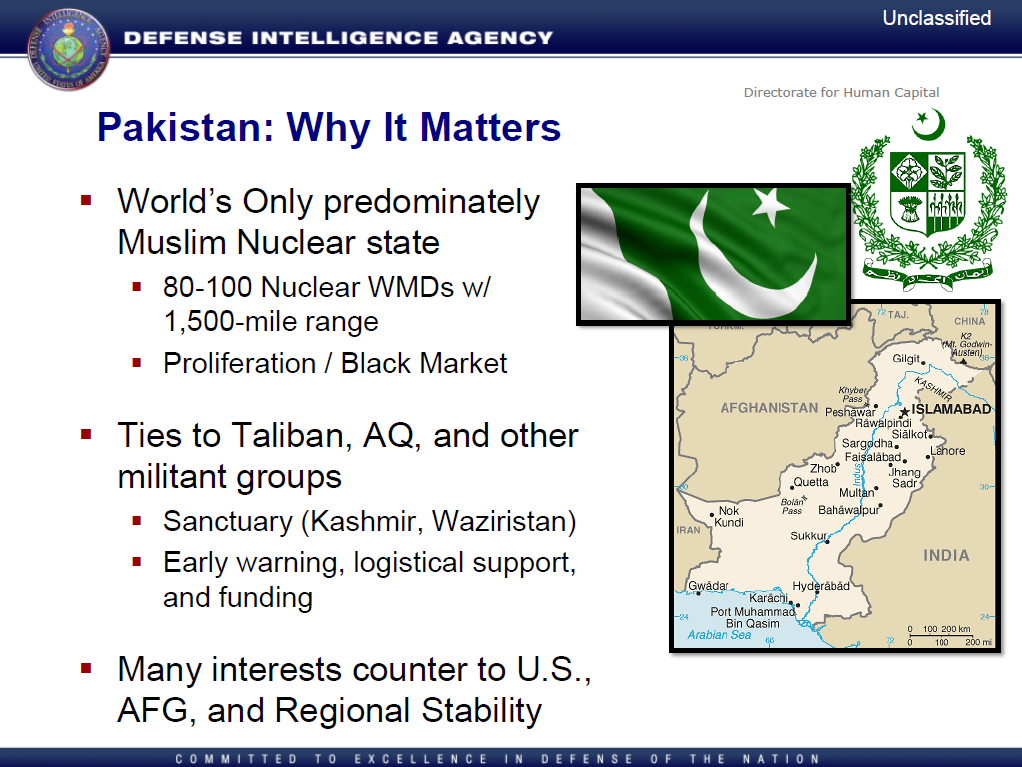

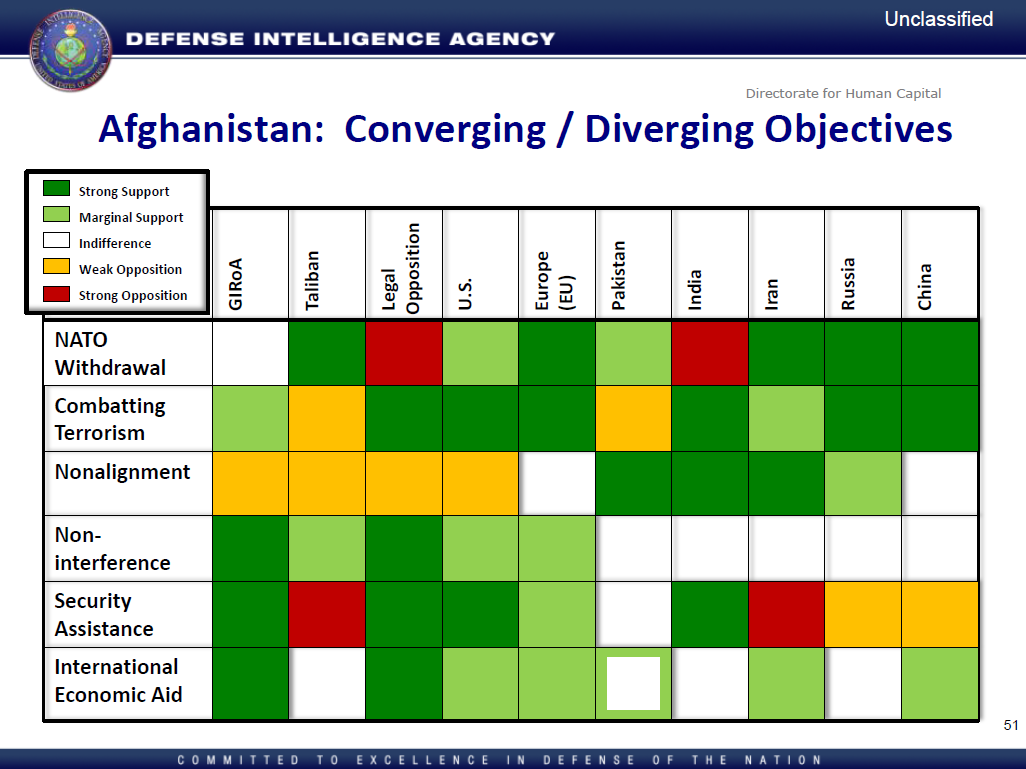



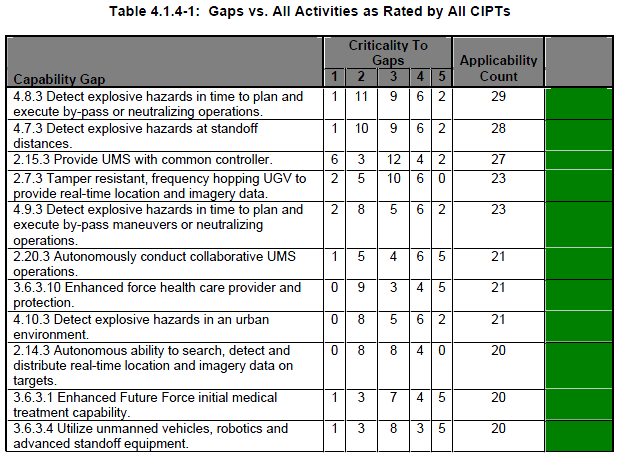
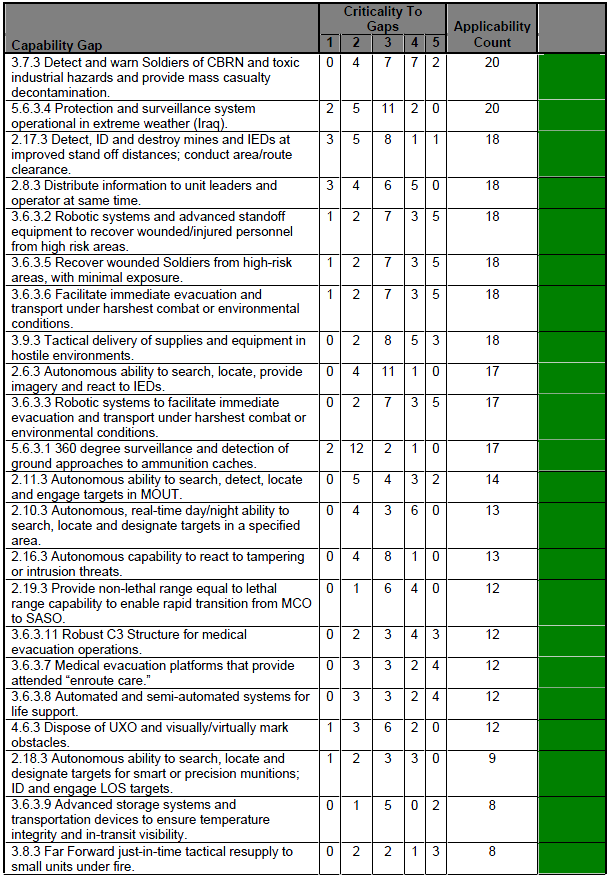
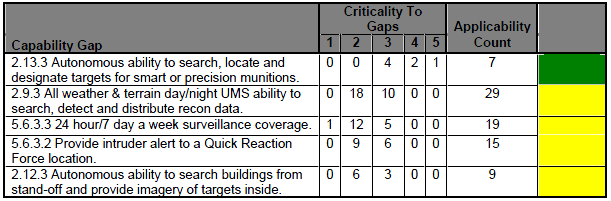







































You must be logged in to post a comment.