|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Month: February 2013
TMZ – JWoww Side Boob!
TMZ – JWoww Side Boob!
Jersey Shore star Jwoww is sporting a SUPER sexy dress and some HOT side boob… until you notice the surgical scar.
PI – IARPA Office of Incisive Analysis Broad Agency Announcement

Broad Agency Announcement Incisive Analysis
- IARPA-BAA-13-02
- 20 pages
- January 14, 2013
IARPA invests in high-risk, high-payoff research that has the potential to provide our nation with an overwhelming intelligence advantage over future adversaries. This research is parsed among three Offices: Smart Collection, Incisive Analysis, and Safe & Secure Operations. This BAA solicits abstracts/proposals for the Office of Incisive Analysis (IA).
IA focuses on maximizing insights from the massive, disparate, unreliable and dynamic data that are – or could be – available to analysts, in a timely manner. We are pursuing new sources of information from existing and novel data, and developing innovative techniques that can be utilized in the processes of analysis. IA programs are in diverse technical disciplines, but have common features: (a) Create technologies that can earn the trust of the analyst user by providing the reasoning for results; (b) Address data uncertainty and provenance explicitly.
The following topics (in no particular order) are of interest to IA:
- Methods for developing understanding of how knowledge and ideas are transmitted and change within groups, organizations, and cultures;
- Methods for analysis of social, cultural, and linguistic data;
- Multidisciplinary approaches to assessing linguistic data sets;
- Methods for measuring and improving human judgment and human reasoning;
- Methods for extraction and representation of the information in the non-textual contents of documents, including figures, diagrams, and tables;
- Methods for understanding and managing massive, dynamic data;
- Analysis of massive, unreliable, and diverse data;
- Methods for assessments of relevancy and reliability of new data;
- Methods for understanding the process of analysis and potential impacts of technology;
- Multidisciplinary approaches to processing noisy audio and speech;
- Development of novel top-down models of visual perception and visual cognition;
- Methods for analysis of significant societal events;
- Methods for estimation and communication of uncertainty and risk;
- Novel approaches for mobile augmented reality applied to analysis and collection;
- Methods for topological data analysis and inferences of high-dimensional structures from low-dimensional representations;
- Methods for the study of algorithms stated in terms of geometry (computational geometry);
- Methods for geolocation of text and social media;
- Novel approaches to biosurveillance;
- Methods to make machine learning more useful and automatic;
- Methods to construct and evaluate speech recognition systems in languages without a formalized orthography; and,
- Methods and approaches to quantifiable representations of uncertainty simultaneously accounting for multiple types of uncertainty.
This announcement seeks research ideas for topics that are not addressed by emerging or ongoing IARPA programs or other published IARPA solicitations. It is primarily, but not solely, intended for early stage research that may lead to larger, focused programs through a separate BAA in the future, so periods of performance will generally not exceed 12 months.
Offerors should demonstrate that their proposed effort has the potential to make revolutionary, rather than incremental, improvements to intelligence capabilities. Research that primarily results in evolutionary improvement to the existing state of practice is specifically excluded.
Monty Python – Lumberjack Song – Video
Monty Python – Lumberjack Song – Video
PI SECRET – U.S. Army Traffic Control Point Operations Smart Card February 13, 2013 in U.S. Army

Center for Army Lessons Learned
- 2 pages
- For Official Use Only
- September 2010
- 2.93 MB
You may engage the following individuals based on their conduct:
• Persons who are committing hostile acts against Coalition forces (CF).
• Persons who are exhibiting hostile intenttowards CF.These persons may be engaged subject to the following instructions:
Positive identification (PID) is required prior to engagement. PID is a reasonable certainty that the proposed target is a legitimate military target. If no PID, contact your next higher commander for decision.
Use graduated measures of force. When time and circumstance permit, use the following degrees of graduated force when responding to hostile act/intent:
1. Shout verbal warnings to halt.
2. Show your weapon and demonstrate intentto use it.
3. Block access or detain.
4. Warning shots may be permitted in your operating environment (OE)/area of responsibility (AOR).
5. Fire proportional lethal force.Do not target or strike anyone who has surrendered or is out of combat due to sickness or wounds.
Do not target or strike hospitals, mosques, churches, shrines, schools, museums, national monuments, any other historical and cultural sites, or civilian populated areas or buildings UNLESS the enemy is using them for military purposes or if necessary for your self-defense.
Do not target or strike Local infrastructure (public works, commercial communication facilities , dams), lines of communication (roads, highways, tunnels, bridges, railways), or economic objects (commercial storage facilities, pipelines) UNLESS necessary for self-defense or if ordered by your commander. If you must fire on these objects, fire to disable and disrupt rather than destroy.
ALWAYS minimize incidental injury, loss of life, and collateral damage.
The use of force, including deadly force, is authorized to
protect the following:• Yourself, your unit, and other friendly forces.
• Detainees
• Civilians from crimes that are likely to cause death or serious bodily harm, such as murder or rape.
• Designated personnel or property, when such actions are necessary to restore order and security.In general, WARNING SHOTS are authorized ONLY when the use of deadly force would be authorized in that particular situation.
Treat all civilians and their property with respect and dignity. Do not seize civilian property, including vehicles, unless the property presents a security threat. When possible, give a receipt to the property’s owner.
You may DETAIN civilians based upon a reasonable belief that the person:
• Must be detained for purposes of self-defense.
• Is interfering with CF mission accomplishment.
• Is on a list of persons wanted for questioning, arrest, or detention.
• Is or was engaged in criminal activity.
• Must be detained for imperative reasons of security.Anyone you detain MUST be protected. Force, up to and including deadly force, is authorized to protect detainees in your custody. You MUST fill out a detainee apprehension card for EVERY person you detain.
Looting and the taking of war trophies are prohibited.
All personnel MUST report any suspected violations of the Law of War committed by any US, friendly, or enemy force. Notify your chain of command, Judge Advocate, IG, Chaplain, or appropriate service-related investigative branch.
TMZ – The Lindsay Lohan Porn Casting Call
The Lindsay Lohan Porn Casting Call
Vivid Entertainment is the porn company that literally caught FIRE this weekend — but they’re also casting for a parody porn of Lindsay Lohan’s new film because Lohan herself won’t do the gig. Just give her a few weeks.
“Mandiant” – Announcing Mandiant Intelligence Center
Organizations routinely struggle to understand which cyber threats pose the greatest risk to them. New threats appear in the news daily and create fire drills for security teams who must quickly determine what they can and should do to protect themselves. Our newest offering, the Mandiant Intelligence Center <http://app.connect.mandiant.com/e/er?s=2855&lid=239&elq=99b6edb99b004015923dfbfb964a346f>, draws on our own proprietary intelligence to equip security teams like yours with the context required to effectively respond to and defend against the most advanced threat actors. With the Mandiant Intelligence Center your security teams can: *Use tools embedded in the Center to query the Mandiant intelligence database and receive detailed information on which group is using particular malware, IPs and domains *Access detailed profiles of advanced threat groups including their latest tactics, techniques and procedures *Obtain detailed context on high profile threat events with analysis on the potential impact to your organization *Monitor emerging threat trends Read more <http://www.mandiant.com/assets/Mandiant_Intelligence_Center.pdf?elq=99b6edb99b004015923dfbfb964a346f&elqCampaignId=283> about Mandiant for Security Operations or request a call <http://app.connect.mandiant.com/e/er?s=2855&lid=235&elq=99b6edb99b004015923dfbfb964a346f> to receive a demonstration. "" Mandiant In The Headlines January 30, 2013 Hackers in China Attacked The Times for Last 4 Months <http://app.connect.mandiant.com/e/er?s=2855&lid=236&elq=99b6edb99b004015923dfbfb964a346f> By Nicole Perlroth – The New York Times February 7, 2013 Mandiant, the Go- To Security Firm for Cyber-Espionage Attacks <http://app.connect.mandiant.com/e/er?s=2855&lid=238&elq=99b6edb99b004015923dfbfb964a346f> By Brad Stone & Michael Riley – Bloomberg Businessweek February 18, 2013 Chinese Army Unit Is Seen as Tied to Hacking Against U.S. <http://app.connect.mandiant.com/e/er?s=2855&lid=237&elq=99b6edb99b004015923dfbfb964a346f> By David E. Sanger, David Barboza & Nicole Perlroth – The New York Times Learn More About Mandiant® Mandiant Website <http://www.mandiant.com/?elq=99b6edb99b004015923dfbfb964a346f&elqCampaignId=283> www.mandiant.com M-Unition™ <http://app.connect.mandiant.com/e/er?s=2855&lid=9&elq=99b6edb99b004015923dfbfb964a346f> Mandiant's official blog Mandiant on Twitter <http://app.connect.mandiant.com/e/er?s=2855&lid=10&elq=99b6edb99b004015923dfbfb964a346f> twitter.com/mandiant Be Part of Something More <http://www.mandiant.com/company/careers/?elq=99b6edb99b004015923dfbfb964a346f&elqCampaignId=283> Join the Mandiant Team
SECRECY NEWS – SENATORS ASK SURVEILLANCE COURT TO SUMMARIZE OPINIONS
Several members of the Senate Intelligence Committee wrote to the Foreign
Intelligence Surveillance Court this month to ask the Court to prepare
summaries of classified opinions that represent significant interpretations
of the Foreign Intelligence Surveillance Act in order to facilitate their
declassification and public release.
Meanwhile, the U.S. Supreme Court ruled that plaintiffs challenging the
constitutionality of the FISA Amendments Act lacked the requisite legal
standing to pursue their case, effectively foreclosing public oversight of
intelligence surveillance through the courts.
The Senate letter, the text of which was not released, stems from an
amendment to the FISA Amendments Act that was introduced by Sen. Jeff
Merkley in December to promote declassification of significant Surveillance
Court opinons. The Merkley amendment was not adopted -- none of the
legislative proposals to increase accountability were approved -- but
Senate Intelligence Committee chair Sen. Dianne Feinstein promised to work
with Sen. Merkley to advance the declassification of FISC opinions.
"An open and democratic society such as ours should not be governed by
secret laws, and judicial interpretations are as much a part of the law as
the words that make up our statute," said Sen. Merkley at that time. "The
opinions of the FISA Court are controlling. They do matter. When a law is
kept secret, public debate, legislative intent, and finding the right
balance between security and privacy all suffer."
http://www.fas.org/irp/congress/2012_cr/faa-amend.html
"I wish to address, if I could, what Senator Merkley said in his
comments," said Sen. Feinstein during the December 27 floor debate. "I
listened carefully. What he is saying is opinions of the Foreign
Intelligence Surveillance Court should, in some way, shape or form, be made
public, just as opinions of the Supreme Court or any court are made
available to the public. To a great extent, I find myself in agreement with
that. They should be."
"I have offered to Senator Merkley to write a letter requesting
declassification of more FISA Court opinions," Sen. Feinstein continued.
"[...] When possible, the opinions of the Foreign Intelligence Surveillance
Court should be made available to the public in declassified form. It can
be done, and I think it should be done more often. If the opinion cannot be
made public, hopefully a summary of the opinion can. And I have agreed with
Senator Merkley to work together on this issue."
That letter, signed by Senators Feinstein, Merkley, Ron Wyden and Mark
Udall, has now been sent to the FISA Court, where it awaits an official
response.
Though the letter itself is a modest step, the willingness of
congressional overseers to assert themselves on behalf of public
accountability takes on new importance in light of yesterday's Supreme
Court decision (by a 5-4 vote) to block a constitutional challenge to the
FISA Amendments Act. That decision all but closes the door to public
oversight of the law's implementation through the courts.
http://www.supremecourt.gov/opinions/12pdf/11-1025_ihdj.pdf
The Court majority insisted that judicial review of government
surveillance activities is alive and well, contrary to the plaintiffs'
assertion. It is "both legally and factually incorrect" to assert that
surveillance is insulated from judicial review, stated the majority opinion
written by Justice Samuel A. Alito, Jr., who cited the role of the Foreign
Intelligence Surveillance Court in authorizing surveillance activities.
But ACLU attorney Jameel Jaffer said that view "seems to be based on the
theory that the FISA Court may one day, in some as-yet unimagined case,
subject the law to constitutional review, but that day may never come. And
if it does, the proceeding will take place in a court that meets in secret,
doesn't ordinarily publish its decisions, and has limited authority to
consider constitutional arguments. This theory is foreign to the
Constitution and inconsistent with fundamental democratic values," Jaffer
said.
On Monday, Sen. Feinstein paid tribute to L. Christine Healey, a
professional staff member of the Senate Intelligence Committee who is
retiring this week. For three decades, Ms. Healey has played an
influential role in intelligence oversight as a staffer on the House and
Senate intelligence committees, as well as on the 9/11 Commission. "She
has been as responsible as anyone for the passage of a string of four
annual intelligence authorization bills, including the fiscal year 2013 act
that was completed in December," said Sen. Feinstein.
Ms. Healey was also credited by Sen. Feinstein as "the principal drafter
of the FISA Amendments Act of 2008."
http://www.fas.org/irp/congress/2013_cr/healey.html
A PROFILE OF THE 113TH CONGRESS, AND MORE FROM CRS
"The average age of Members of the 113th Congress is among the highest of
any Congress in recent U.S. history," according to a new report from the
Congressional Research Service. The average age of Members of the House of
Representatives is 57 years, while the average age of Senators is 62 years.
"The overwhelming majority of Members of Congress have a college
education," the CRS found. "The dominant professions of Members are public
service/politics, business, and law. Most Members identify as Christians,
and Protestants collectively constitute the majority religious affiliation.
Roman Catholics account for the largest single religious denomination, and
numerous other affiliations are represented."
One hundred women (a record number) serve in the 113th Congress. There are
43 African American Members, and 38 Hispanic or Latino Members (a record
number) serving. Thirteen Members are Asian American or Pacific Islanders.
There is one Native American serving in the House.
See Membership of the 113th Congress: A Profile, February 20, 2013:
http://www.fas.org/sgp/crs/misc/R42964.pdf
Other noteworthy new and updated products of the Congressional Research
Service that Congress has not made publicly available include the
following.
Congressional Authority to Limit Military Operations, February 19, 2013:
http://www.fas.org/sgp/crs/natsec/R41989.pdf
Nuclear Weapons R&D Organizations in Nine Nations, February 22, 2013:
http://www.fas.org/sgp/crs/nuke/R40439.pdf
Bond v. United States: Validity and Construction of the Federal Chemical
Weapons Statute, February 21, 2013:
http://www.fas.org/sgp/crs/nuke/R42968.pdf
Arms Control and Nonproliferation: A Catalog of Treaties and Agreements,
February 20, 2013:
http://www.fas.org/sgp/crs/nuke/RL33865.pdf
Border Security: Understanding Threats at U.S. Borders, February 21, 2013:
http://www.fas.org/sgp/crs/homesec/R42969.pdf
NAFTA at 20: Overview and Trade Effects, February 21, 2013:
http://www.fas.org/sgp/crs/row/R42965.pdf
Navy Force Structure and Shipbuilding Plans: Background and Issues for
Congress, February 22, 2013, with new material on the anticipated impact of
sequestration:
http://www.fas.org/sgp/crs/weapons/RL32665.pdf
Azerbaijan: Recent Developments and U.S. Interests, February 22, 2013:
http://www.fas.org/sgp/crs/row/97-522.pdf
U.S.-Japan Economic Relations: Significance, Prospects, and Policy
Options, February 20, 2013:
http://www.fas.org/sgp/crs/row/RL32649.pdf
Egypt: Background and U.S. Relations, February 26, 2013:
http://www.fas.org/sgp/crs/mideast/RL33003.pdf
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
Monty Python! Police – Burglary Sketch
Monty Python! Police burglary Sketch
Whistleblowing on Whistleblowing Oversight – revealed by Cryptome
Whistleblowing on Whistleblowing Oversight
[Federal Register Volume 78, Number 38 (Tuesday, February 26, 2013)] [Notices] [Pages 13101-13102] From the Federal Register Online via the Government Printing Office [www.gpo.gov] [FR Doc No: 2013-04467] ======================================================================= ----------------------------------------------------------------------- PRIVACY AND CIVIL LIBERTIES OVERSIGHT BOARD [Notice-PCLOB-2013-01; Docket No. 2013-0004; Sequence No. 1] No FEAR Act Notice; Notice of Rights and Protections Available Under Federal Antidiscrimination and Whistleblower Protection Laws AGENCY: Privacy and Civil Liberties Oversight Board. ACTION: Notice. ----------------------------------------------------------------------- SUMMARY: In accordance with the requirements of the Notification and Federal Employee Antidiscrimination and Retaliation Act of 2002, the Privacy and Civil Liberties Oversight Board is providing notice to its employees, former employees, and applicants for Board employment about the rights and remedies available to them under the federal anti- discrimination, whistleblower protection, and retaliation laws. FOR FURTHER INFORMATION CONTACT: Claire McKenna, Legal Counsel, at 202- 366-0365 or claire.mckenna.pclob@dot.gov. SUPPLEMENTARY INFORMATION: On May 15, 2002, Congress enacted the Notification and Federal Employee Antidiscrimination and Retaliation Act of 2002, Public Law 107-174, also known as the No FEAR Act. The Act requires that federal agencies provide notice to their employees, former employees, and applicants for employment to inform them of the rights and protections available under federal anti-discrimination, whistleblower protection, and retaliation laws. Anti-Discrimination Laws A federal agency cannot discriminate against an employee or applicant with respect to the terms, conditions, or privileges of employment on the basis of race, color, religion, sex, national origin, age, disability, marital status, or political affiliation. Discrimination on these bases is prohibited by one or more of the following statutes: 5 U.S.C. 2302(b)(1), 29 U.S.C. 206(d), 29 U.S.C. 631, 29 U.S.C. 633a, 2 U.S.C. 791, and 42 U.S.C. 2000e-16. If you believe that you have been the victim of unlawful discrimination on the basis of race, color, religion, sex, national origin, or disability, you must contact an Equal Employment Opportunity (EEO) counselor within 45 calendar days of the alleged discriminatory action, or, in the case of personnel action, within 45 calendar days of the effective date of the action, before you can file a formal complaint of discrimination with your agency. This timeline may be extended by the Board under the circumstances described in 29 CFR 1614.105(a)(2). If you believe that you have been the victim of unlawful discrimination on the basis of age, you must either contact an EEO counselor as noted above or give notice of intent to sue to the Equal Employment Opportunity Commission (EEOC) within 180 calendar days of the alleged discriminatory action. If you are alleging discrimination based on marital status or political affiliation, you may file a written complaint with the U.S. Office of Special Counsel (OSC) (see contact information below). In the alternative (or in some cases, in addition), you may pursue a discrimination complaint by filing a grievance through the Board's administrative or negotiated grievance procedures, if such procedures apply and are available. Whistleblower Protection Laws A federal employee with authority to take, direct others to take, recommend, or approve any personnel action must not use that authority to take or fail to take, or threaten to take or fail to take, a personnel action against an employee or applicant because of disclosure of information by that individual that is reasonably believed to evidence violations of law, rule, or regulation; gross mismanagement; gross waste of funds; an abuse of authority; or a substantial and specific danger to public health or safety, unless disclosures of such information is specifically prohibited by law and such information is specifically required by executive order to be kept secret in the interest of national defense or the conduct of foreign affairs. Retaliation against an employee or applicant for making a protected disclosure is prohibited by 5 U.S.C. 2302(b)(8). If you believe that you have been the victim of whistleblower retaliation, you may file a written complaint (Form OSC-11) with the U.S. Office of Special Counsel at 1730 M Street NW., Suite 218, Washington, DC 20036-4505 or online through the OSC Web site, http://www.osc.gov. Retaliation for Engaging in Protected Activity A federal agency cannot retaliate against an employee or applicant because that individual exercises his or her rights under any of the federal antidiscrimination or whistleblower protection laws listed above. If you believe that you are the victim or retaliation for engaging in protected activity, you must follow, as appropriate, the procedures described in the Antidiscrimination Laws and Whistleblower Protection Laws section or, if applicable, the administrative or negotiated grievance procedures in order to pursue any legal remedy. Disciplinary Actions Under existing laws, each agency retains the right, where appropriate, to discipline a federal employee for conduct that is inconsistent with the Federal Antidiscrimination and Whistleblower Protection Laws up to and including removal. If OSC has initiated an investigation under 5 U.S.C. 1214, however, agencies must seek approval from OSC to discipline employees for, among other activities, engaging in prohibited retaliation, 5 U.S.C. 1214(f). Nothing in the No FEAR Act alters existing laws or permits an agency to take unfounded disciplinary action against a federal employee or to [[Page 13102]] violate the procedural rights of a federal employee who has been accused of discrimination. Additional Information For further information regarding the No FEAR Act regulations, refer to 5 CFR 724, as well as the appropriate Board offices. Additional information regarding federal antidiscrimination laws can be found at the EEOC Web site, http://www.eeoc.gov, and the OSC Web site, http://www.osc.gov. Existing Rights Unchanged Pursuant to section 205 of the No FEAR Act, neither the No FEAR Act nor this notice creates, expands, or reduces any rights otherwise available to any employee, former employee, or applicant under the laws of the United States, including the provisions of law specified in 5 U.S.C. 2302(d). Dated: February 21, 2013. Claire McKenna, Legal Counsel, Privacy and Civil Liberties Oversight Board. [FR Doc. 2013-04467 Filed 2-25-13; 8:45 am] BILLING CODE P
TMZ – Elisabetta Canalis — Screw George … I ROOTED For Quentin Tarantino
Bitter party of one? Elisabetta Canalis did NOT want her ex-lover George Clooney to take home Oscar gold last night … telling out photog she was rooting for another man … Quentin Tarantino.
“Mandiant” – Announcing Mandiant for Security Operations
Citation: "Organizations spend millions of dollars investing in top-notch security teams and in building secure networks to keep would-be attackers out of their IT environments. Despite these investments, determined attackers routinely compromise well-secured organizations and steal their intellectual property and financial assets. Our newest product, Mandiant for Security Operations <http://app.connect.mandiant.com/e/er?s=2855&lid=234&elq=41deab51a75b472c90707e854f48b9e7>, equips security teams to confidently detect, analyze and resolve incidents in a fraction of the time it takes using conventional approaches. This appliance-based solution connects the dots between what’s happening on their network and what’s happening on their endpoints. With Mandiant for Security Operations security teams can: *Search for advanced attackers and the APT *Integrate endpoint security with your network security *Accelerate triage of suspected incidents *Find out what happened, without forensics *Contain endpoints Read more <http://www.mandiant.com/assets/Mandiant_for_Security_Operations.pdf?elq=41deab51a75b472c90707e854f48b9e7&elqCampaignId=282> about Mandiant for Security Operations or request a call <http://app.connect.mandiant.com/e/er?s=2855&lid=235&elq=41deab51a75b472c90707e854f48b9e7> to receive a demonstration. "" Mandiant In The Headlines January 30, 2013 Hackers in China Attacked The Times for Last 4 Months <http://app.connect.mandiant.com/e/er?s=2855&lid=236&elq=41deab51a75b472c90707e854f48b9e7> By Nicole Perlroth – The New York Times February 7, 2013 Mandiant, the Go- To Security Firm for Cyber-Espionage Attacks <http://app.connect.mandiant.com/e/er?s=2855&lid=238&elq=41deab51a75b472c90707e854f48b9e7> By Brad Stone & Michael Riley – Bloomberg Businessweek February 18, 2013 Chinese Army Unit Is Seen as Tied to Hacking Against U.S. <http://app.connect.mandiant.com/e/er?s=2855&lid=237&elq=41deab51a75b472c90707e854f48b9e7> By David E. Sanger, David Barboza & Nicole Perlroth – The New York Times Learn More About Mandiant® Mandiant Website <http://www.mandiant.com/?elq=41deab51a75b472c90707e854f48b9e7&elqCampaignId=282> www.mandiant.com M-Unition™ <http://app.connect.mandiant.com/e/er?s=2855&lid=9&elq=41deab51a75b472c90707e854f48b9e7> Mandiant's official blog Mandiant on Twitter <http://app.connect.mandiant.com/e/er?s=2855&lid=10&elq=41deab51a75b472c90707e854f48b9e7> twitter.com/mandiant Be Part of Something More <http://www.mandiant.com/company/careers/?elq=41deab51a75b472c90707e854f48b9e7&elqCampaignId=282> Join the Mandiant Team To unsubscribe or manage your subscriptions, please click here <http://app.connect.mandiant.com/e/sl.aspx?s=2855&elq=41deab51a75b472c90707e854f48b9e7>. Mandiant® | 2318 Mill Road. Suite 500 | Alexandria, VA 22314 1.800.647.7020 Privacy Policy <http://www.mandiant.com/privacy?elq=41deab51a75b472c90707e854f48b9e7&elqCampaignId=282>"
Unveiled by Public Intelligence – NATO Legal Deskbook

NATO Legal Deskbook Second Edition
- 348 pages
- 2010
NATO leads efforts to bring stability in its ongoing missions in the Balkans, Afghanistan, and Iraq.
Legal Advisers serve as key members of a Commander‘s staff in the complex legal and political environment that NATO operates. The challenges NATO Commanders and legal adviser face to fulfil mandates, accomplish missions, and support the rule of law in embryonic and fragile democratic governments requires discussion, understanding and the documentation of practical solutions.
The NATO Legal Deskbook is published by the Office of the Legal Adviser, Allied Command Transformation Staff Element Europe (Mons) with the active support and help of the Office of the Legal Adviser, Headquarters Allied Commander Transformation (HQ SACT, Norfolk, USA) and the Office of the Legal Adviser, Supreme Headquarters Allied Powers Europe (SHAPE, Mons, Belgium), as well as many legal advisers in NATO and in the Member States or in other official or academic positions outside NATO.
Why a NATO Legal Deskbook?
Two re-occurring themes surface in after-action reports from exercises and operations. The first is that NATO Commanders and staffs naturally and increasingly turn to the Legal Advisers to help plan, execute, coordinate, evaluate, and support the assigned mission. The second is that no single doctrinal resource exists in NATO to assist legal practitioners in the fulfilling of this task. Although several Alliance members have produced such guides, before the NATO Legal Deskbook none existed for Legal Advisers and legal personnel assigned to NATO commands.
Whether doctrinally ready or not, the Alliance calls upon NATO Legal Advisers and staffs to advise and, often, help direct the execution of the legal component of a mission or mandate. NATO owes these attorneys, paralegals, and legal personnel, who work under often austere and demanding conditions, practical guidance in the form of a comprehensive resource that provides an overview and insight on the legal regime that forms NATO practice. Fulfilling this need is the genesis, purpose and rational for this practitioner‘s guide.
What this Deskbook is not:
This Deskbook is not NATO policy or military doctrine for legal support to operations.
The Deskbook intends to reflect as closely as possible the policies and practice of NATO in legal matters, however, the Deskbook is not a formally approved NATO document and therefore shall not be deemed as reflection of the official opinion or position of NATO.
The practitioner‘s guide is not intended to offer guidance or advice to other military professionals involved in operations. It was written by Legal Advisers for Legal Advisers and legal staff. Its scope and purpose is limited to providing the military legal subject matter experts assistance in the accomplishment of the mission. While others may find the guide helpful, they should understand it is not a tutorial. Fundamental legal principles, standard practices of interpretation, and basic legal practices are assumed as matters already known by its intended audience: the Legal Adviser, legal assistant, or paralegal.
This practitioner‘s guide does not offer an all-inclusive formula on how to advise a NATO commander on any particular aspect of the law, nor is it intended to supplant national guidance. Instead, the guide pre-supposes that Legal Advisers will continue to find themselves providing legal support to operations and missions in a variety of different circumstances, environments, and locations. The guide and its contents must therefore be flexible and geographically universal in application.
Monty Python and the knights of the Holy Grail[1975] – Full MOVIE
Monty Python and the knights of the Holy Grail[1975] – Full MOVIE
Cryptome – National Security in the Digital Age: Review
|
TMZ – Paulina Gretzky — Knockers, Knockers… Who’s There?
Paulina Gretzky — Knockers, Knockers… Who’s There?
Check out this photo of a sexy, hot celeb stepping out of a car so that all you can see is her cleavage. Can you guess who it is? You get one hint: It’s not Bette Midler.
Proven – China ‘aiding hacker attacks on west’

The Chinese army has launched hundreds of cyber-attacks against western companies and defence groups from a nondescript office building in Shanghai, according to a report that warns hackers have stolen vast amounts of data from their targets.
Mandiant, a security company that has been investigating attacks against western organisations for over six years, said in a report (PDF)the attacks came from a 12-storey building belonging to the People’s Liberation Army (PLA) general staff’s department, also known as Unit 61398.
Mandiant said it believed a hacking network named the Comment Crew or the Shanghai Group was based inside the compound, in a rundown residential neighbourhood. Although the report fails directly to place the hackers inside the building, it argues there is no other logical reason why so many attacks have emanated from such a small area.
“It is time to acknowledge the threat is originating in China, and we wanted to do our part to arm and prepare security professionals to combat that threat effectively,” said the report.
The discovery will further raise the temperature in the intergovernmental cyberwars, which have heated up in recent years as the US, Israel, Iran, China and UK have all used computer subterfuge to undermine rival state or terrorist organisations. One security expert warned that companies in high-profile fields should assume they will be targeted and hacked, and build systems that will fence sensitive data off from each other.
Rik Ferguson, global vice-president of security research at the data security company Trend Micro, said: “We need to concentrate less on building castles and assuming they will be impervious, and more on building better dungeons so that when people get in they can’t get anything else.” .
Mandiant says Unit 61398 could house “hundreds or thousands” of people and has military-grade, high-speed fibre-optic connections from China Mobile, the world’s largest telecoms carrier. “The nature of Unit 61398’s work is considered by China to be a state secret; however, we believe it engages in harmful computer network operations,” Mandiant said in the report.
It said Unit 61398 had been operating since 2006, and was one of the most prolific hacking groups “in terms of quantity of information stolen”. This it estimated at hundreds of terabytes, enough for thousands of 3D designs and blueprints.
“APT1”, as Mandiant calls it, is only one of 20 groups Mandiant says has carried out scores of hacking attacks against businesses and organisations in the west, including companies that work in strategic industries such as US power and water infrastructure.
A typical attack would leave software that hid its presence from the user or administrator and silently siphon data to a remote server elsewhere on the internet at the instruction of a separate “command and control” (C&C) computer. By analysing the hidden software, the pattern of connections and links from the C&C server, the team at Mandiant said they were confident of the source of the threat.
A Chinese foreign ministry spokesman denied the government was behind the attacks, saying: “Hacking attacks are transnational and anonymous. Determining their origins is extremely difficult. We don’t know how the evidence in this so-called report can be tenable. Arbitrary criticism based on rudimentary data is irresponsible, unprofessional and not helpful in resolving the issue.”
But Ferguson told the Guardian: “This is a pretty compelling report, with evidence collected over a prolonged period of time. It points very strongly to marked Chinese involvement.”
Mandiant, based in Alexandria, Virginia, in the US, investigated the New York Times break-in, for which it suggested Chinese sources could be to blame.
President Barack Obama is already beefing up US security, introducing an executive order in his State of the Union speech this month that would let the government work with the private sector to fend off hacking. But it will take until February 2014 to have a final version ready for implementation.
The revelation comes days after the New York Times, Wall Street Journaland Washington Post, as well as the social networks Facebook and Twitter, said they had been subjected to “highly sophisticated” hacks that in some cases focused on correspondents writing about China and its government.
Separate investigations by the computer company Dell, working with the news company Bloomberg, tracked down another alleged hacker, Zhang Changhe, who has written a number of papers on PC hacking. Zhang works at the PLA’s “information engineering university” in Zhengzhou, Henan province, north-central China.
The allegations will raise the temperature in the continuing cyberwar between the west and China, which has been steadily rising since the Pentagon and MI6 uncovered Titan Rain, a scheme that tried to siphon data from the Pentagon and the House of Commons in 2006, and which one security expert said at the time dated back at least to 2004.
Ferguson suggested that western governments were also carrying out attacks against Chinese targets – “but that’s not a culture which would open up about being hit. I would be surprised and disappointed if most western nations don’t have a cybersecurity force.”
The Stuxnet virus, which hit Iran’s uranium reprocessing plant in 2010, is believed to have been written jointly by the US and Israel, while Iranian sources are believed to have hacked companies that issue email security certificates so that they can crack secure connections used by Iranian dissidents on Google’s Gmail system. China is also reckoned to have been behind the hacking of Google’s email servers in that country in late 2009, in an operation that files from WikiLeaks suggested was inspired by the Beijing government.
A timeline of government-sponsored hacking attacks
2004 suspected: Chinese group in Shanghai begins probing US companies and military targets.
2005: “Titan Rain” pulls data from the Pentagon’s systems, and a specialist says of a December 2005 attack on the House of Commons computer system that “The degree of sophistication was extremely high. They were very clever programmers.”
2007: Estonia’s government and other internet services are knocked offline by a coordinated attack from more than a million computers around the world – reckoned to have been run from a group acting at the urging of the Russian government. Nobody is ever arrested over the attack.
2008: Russia’s government is suspected of carrying out a cyberattack to knock out government and other websites inside Georgia, with which it is fighting a border skirmish over the territory of Ossetia.
December 2009: Google’s email systems in China are hacked by a group which tries to identify and take over the accounts of Chinese dissidents. Google withdraws its search engine from the Chinese mainland in protest at the actions. Wikileaks cables suggest that the Chinese government was aware of the hacking.
2010: The Flame virus begins silently infecting computers in Iran. Itincorporates cutting-edge cryptography breakthroughs which would require world-class experts to write. That is then used to infect Windows PCs via the Windows Update mechanism which normally creates a cryptographically secure link to Microsoft. Instead, Flame puts software that watches every keystroke and frame on the PC. Analysts say that only a “wealthy” nation state could have written the virus, which breaks new ground in encryption.
The Stuxnet worm is discovered to have been affecting systems inside Iran’s uranium reprocessing establishment, passing from Windows PCs to the industrial systems which control centrifuges that separate out heavier uranium. The worm makes the centrifuges spin out of control, while suggesting on their control panel that they are operating normally – and so break them. Iran denies that the attack has affected its project. The US and Israel are later fingered as being behind the code.
September 2011: a new virus that silently captures data from transactions in Middle Eastern online banking is unleashed. The principal targets use Lebanese banks. It is not identified until August 2012, when Russian security company Kaspersky discovers the name “Gauss” embedded inside it. The company says the malware it is “nation state-sponsored” – probably by a western state seeking to trace transactions by specific targets.
2012: About 30,000 Windows PCs at Saudi Aramco, the world’s most valuable company, are rendered unusable after a virus called “Shamoon” wipes and corrupts data and the part of the hard drive needed to “bootstrap” the machine when it is turned on. In the US, Secretary of Defense Leon Panetta described Shamoon as “one of the most destructive viruses ever” and suggested it could be used to launch an attack as destructive as the 9/11 attacks of 2001.
SECRECY NEWS – SEQUESTER MAY SLOW PENTAGON RESPONSE TO WIKILEAKS
The across-the-board budget cuts known as sequestration that are expected
to take effect on March 1 could impede the government's ability to respond
to WikiLeaks and to rectify the flaws in information security that it
exposed, a Pentagon official told Congress recently.
Zachary J. Lemnios, the assistant secretary of defense for research and
engineering, was asked by Sen. Rob Portman (R-Ohio) to describe the "most
significant" impacts on cybersecurity that could follow from the
anticipated cuts to the Pentagon's budget.
Mr. Lemnios replied that "cuts under sequestration could hurt efforts to
fight cyber threats, including [...] improving the security of our
classified Federal networks and addressing WikiLeaks."
http://www.fas.org/irp/congress/2012_hr/fydp-42.pdf
The sequester could also interfere with the Comprehensive National
Cybersecurity Initiative that began under President Bush, he said, and
could hold up plans to "initiat[e] continuous monitoring of unclassified
networks at all Federal agencies."
Mr. Lemnios' response to Sen. Portman's question for the record (which had
not specifically mentioned WikiLeaks) followed a March 2012 Senate Armed
Services Committee hearing on Emerging Threats and Capabilities that was
published in December 2012 (at page 42).
http://www.fas.org/irp/congress/2012_hr/fydp.pdf
Generally speaking, computer security within the military is a daunting
problem, Mr. Lemnios told the Committee, particularly since "The Department
operates over 15,000 networks and 7 million computing devices across
hundreds of installations in dozens of countries around the globe."
The challenge of cybersecurity cannot be fully described in public, said
Dr. Kaigham J. Gabriel of DARPA. "The complete picture requires a
discussion at the special access level." But he told the Committee last
year that several basic points can be openly acknowledged:
"Attackers can penetrate our networks: In just 3 days and at a cost of
only $18,000, the Host-Based Security System" -- the Pentagon's baseline
computer security system -- "was penetrated."
"User authentication is a weak link: 53,000 passwords were provided to
teams at Defcon; within 48 hours, 38,000 were cracked."
"The Defense supply chain is at risk: More than two-thirds of electronics
in U.S. advanced fighter aircraft are fabricated in off-shore foundries."
"Physical systems are at risk: A smartphone hundreds of miles away took
control of a car's drive system through an exploit in a wireless
interface."
"The United States continues to spend on cybersecurity with limited
increase in security: The Federal Government expended billions of dollars
in 2010, but the number of malicious cyber intrusions has increased."
Though it was presumably not intentional, the WikiLeaks project galvanized
government information security programs and accelerated efforts to devise
"insider threat" detection mechanisms, along with intensified surveillance
of classified and unclassified government computer networks.
"New classes of anomaly detection methods have been developed and are
based on aggregating events across time and multiple sources to identify
network and host-based behavior that might be malicious," James S. Peery of
Sandia National Laboratories told the Senate Armed Services Committee at
last year's hearing. "These approaches and behavioral-based methods have
been successful in finding previously undiscovered malware."
"One drawback of this technology, though, is that it has a very high false
positive rate," he said.
OPEN ACCESS TO SCIENTIFIC RESEARCH ADVANCES
Government-sponsored scientific research published in expensive journals
should become more readily accessible to the public under an initiative
announced by the White House Office of Science and Technology Policy on
Friday.
http://www.fas.org/sgp/obama/sciaccess.pdf
Federal agencies that fund at least $100 million per year in scientific
research were directed by White House science advisor John Holdren to
develop plans to make the results of such research publicly available free
of charge within a year of original publication.
"The logic behind enhanced public access is plain," Dr. Holdren wrote in
response to a public petition on the White House web site. "We know that
scientific research supported by the Federal Government spurs scientific
breakthroughs and economic advances when research results are made
available to innovators. Policies that mobilize these intellectual assets
for re-use through broader access can accelerate scientific breakthroughs,
increase innovation, and promote economic growth."
But the benefits of open access are not the sole consideration in the new
policy. "The Administration also recognizes that publishers provide
valuable services, including the coordination of peer review, that are
essential for ensuring the high quality and integrity of many scholarly
publications. It is critical that these services continue to be made
available."
"We wanted to strike the balance between the extraordinary public benefit
of increasing public access to the results of federally-funded scientific
research and the need to ensure that the valuable contributions that the
scientific publishing industry provides are not lost," Dr. Holdren wrote.
The resulting policy mandating free public access within 12 months of
publication is the result of an attempt to balance those competing
interests, and it too is subject to future modification "based on
experience and evidence."
COMMENTS SOUGHT ON OVERSIGHT OF "DUAL USE" BIO RESEARCH
Members of the public are invited to comment on the feasibility and
desirability of various forms of institutional oversight at
federally-funded institutions that perform research involving certain
pathogens or toxins.
"Certain types of research that are conducted for legitimate purposes may
also be utilized for harmful purposes. Such research is called 'dual use
research'," said a Notice filed in the Federal Register Friday by the
Office of Science and Technology Policy.
http://www.fas.org/sgp/news/2013/02/ostp-dual.html
"Dual use research of concern (DURC) is a smaller subset of dual use
research defined as life sciences research that, based on current
understanding, can be reasonably anticipated to provide knowledge,
information, products, or technologies that could be directly misapplied to
pose a significant threat with broad potential consequences to public
health and safety, agricultural crops and other plants, animals, the
environment, materiel, or national security," the OSTP Notice explained.
The term "dual use research of concern" should not be taken in a
pejorative sense, OSTP said.
"Research that meets the definition of DURC often increases our
understanding of the biology of pathogens and makes critical contributions
to the development of new treatments and diagnostics, improvements in
public health surveillance, and the enhancement of emergency preparedness
and response efforts. Thus, designating research as DURC should not be seen
as a negative categorization, but simply an indication that the research
may warrant additional oversight in order to reduce the risks that the
knowledge, information, products, or technologies generated could be used
in a manner that results in harm. As a general matter, designation of
research as DURC does not mean that the research should not be conducted or
communicated."
In the February 22 Federal Register Notice, OSTP posed a series of
questions concerning potential oversight arrangements for dual use research
of concern and solicited feedback from interested members of the public.
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
Monty Python’s Flying Circus! – The Full Monty Python !
Monty Python’s Flying Circus!
Unveiled by Cryptome – USA v Twitter, Appelbaum et al Effective Today
Unveiled by Cryptome – USA v Twitter, Appelbaum et al Effective Today
Download the original document below:
TMZ – Chick Has Orgasm on LIVE TV with Joy Behar
Joy Behar interviewed a sex expert on her Current TV show and the chick busted out an orgasm right there on TV — just by THINKING about it.
TOP-SECRET – New Jersey Fusion Center Phone Kidnapping Scams Report

New Jersey Regional Operations Intelligence Center Situational Awareness Report
- 2 pages
- For Official Use Only
- February 8, 2013
(U//FOUO) During recent weeks, various sources in law enforcement and media outlets have been reporting phone kidnapping scams occurring in Central and Northern New Jersey and New York. In most incidents, scammers have alleged that a member of the phone scam victim’s family had been involved in a car accident and claimed to have taken the victim’s family member hostage. The scammers then claim they will drop their hostage at a hospital after a certain amount of money (usually $1500‐2000) is wired via Western Union to the scammers, as restitution for damage to the scammer’s vehicle. In addition, the scammers state that they have the hostage’s cell phone and any attempts to call the cell phone or disengage from the conversation will result in the murder or beating of the hostage. The scammers try to hold the victim on the phone as long as possible while attempting to persuade them to wire the money; however, reports from some victims indicate the scammers will hang up and not call back under certain circumstances. For instance, when the victim questions the scammers about the hostage’s name, the scammers end the call when they are unable to provide the hostage’s name. According to Officer Kelly Denham, Coral Gables Police Department (Florida), this scam has been tracked back to 1998, when it started in Puerto Rico. She adds that this scam resurfaces every few years. Over the past few months, the NJ ROIC has seen increased reporting of this scam along the east coast.
Comparisons with Similar Scam Incidents
(U//FOUO) In January 2013, reports indicated a similar scam targeting the elderly. In this scam, elderly grandparents were informed their grandchildren were in prison and that the grandparents needed to wire money immediately to ensure their relative’s release. Reports indicate that the scammers may be garnishing information about their victims from Facebook and other social media websites. Several instances of this scam have been reported to local authorities and an alert has been issued throughout the tri‐state area. Although there are commonalities among these incidents, the NJ ROIC has received no information indicating that the incidents are connected.
Common Trends
(U//FOUO) Since 2008, the Federal Bureau of Investigations Internet Crime Complaint Center (IC3) has received similar complaints which focus on some common trends for these types of scams throughout the United States.
These include:
• (U//FOUO) The caller/suspect claims to be a relative (usually a young person) who is out of the country and in trouble with the police or a criminal element and needs money wired to him/her to get out of trouble.
• (U//FOUO) The caller/suspect calls back several times demanding additional money be sent in increments of $3000‐$4000.
• (U//FOUO) The caller/suspect instructs the victim to go to a Walmart or Money Gram location and wire the money to a person whose name is not the so‐called relative.
• (U//FOUO) Sometimes, the caller/suspect will instruct the person to stay on the phone throughout the entire wire transaction Other times the caller/suspect will instruct the victim not to call the relative’s parents because they will worry or be angry.
• (U//FOUO) In another instance, the caller/suspect calls the grandparent/parent and asks for them by name, claiming to be a police officer in another country and instructs the parent on how to get a debit card (amounts are usually under $2000.00) and where to send it for the bail.How to Prevent the Scam
• (U//FOUO) When family members are going to work, school, and/or out for the day, know their itinerary, who they will be with, where they are traveling to, and what their final destination will be.
• (U//FOUO) Know the cellular telephone numbers of your family members and the subscriber to the respective cellular telephone numbers.
• (U//FOUO) Know the service provider and how to contact the service provider for the respective family members cellular telephone number. This will aid the police with the investigation and further assist with locating the cellular telephone of the family member by “pinging” the respective cellular telephone off various cell sites to determine where the cellular telephone is located.
• (U//FOUO) Constantly update and query your privacy settings on social media profile sites.
• (U//FOUO) Do not provide unknown individuals with your personal information via social media sites and only provide your private information to those you know and/or wish to have that information.
• (U//FOUO) Check to see what privacy information is readily available to the public via the respective social media sites that you and your family are linked to.What To Do If You Receive Such a Call
• (U//FOUO) Attempt to verify the validity of the number the scammer is calling from.
• (U//FOUO) Attempt to verify the authenticity of the caller of the scam.
• (U//FOUO) Attempt to identify the location of the person and/or family member potentially being kidnapped.
• (U//FOUO) Notify your local police immediately.
• (U//FOUO) Refrain from accepting any subsequent calls from the number associated with the scam.
• (U//FOUO) Ensure you ask specific questions if you are contacted by the party in association with the scam about the suspected “hostage.” If there is a lack of specific information furnished by the scammer, this may prompt the scammer to end the conversation.
• (U//FOUO) If you cannot speak with the person and/or family member suspected of being kidnapped and you are unable to locate the person and/or family member suspected of being kidnapped, then call the service provider of the cellular telephone associated with the person and/or family member suspected of being kidnapped. In these emergency situations, the service provided could “ping” the respective cellular telephone in an attempt to locate the person’s and/or family member’s cellular telephone.
• (U//FOUO) Record the telephone number the suspected kidnapper and/or suspected scammer is calling from.
• (U//FOUO) Save any text messages and/or photographs the suspected kidnapper and/or scammer sends to you.
• (U//FOUO) Lastly, do not panic, think with a clear head, and provide the proper information to your local police assist with the investigation of the incident and/or scam.Note: (U//FOUO) Be aware of phone “Spoofing,” in which a suspected scammer calls from his/her telephone, however has spoofed and/or has masked his/her real telephone number with another telephone number that appears as such on the other party’s (victim’s) telephone.
Film – Monty Python – Dead Parrot
Monty Python – Dead Parrot
from Monty Python’s Flying Circus
Season 1 – Episode 08
Full Frontal Nudity
Recorded 25-11-69, Aired 07-12-69
The world famous Dead Parrot sketch, here, in it’s entirety!
TMZ – Colin Kaepernick — BODY SHOTS Before Super Bowl !
TMZ – Colin Kaepernick — BODY SHOTS Before Super Bowl !
Photos have surfaced of San Francisco 49ers quarterback Colin Kaepernick in Mexico getting BODY SHOTS from hot chicks in bikinis. That’s one less teammate for Chris Culliver to worry about…
SECRET from PI – DHS-FBI Suspicious Activity Reporting Bulletin: Recruiting
ROLL CALL RELEASE
- 1 page
- For Official Use Only
(U//FOUO) Terrorists are attempting to recruit new members in the United States and overseas to support their operations, obtain funding, and conduct terrorist attacks. For example, in May 2012, Maryland-based Mohammad Hassan Khalid pled guilty to attempting to use the Internet to recruit individuals who had the ability to travel to and around Europe to conduct terrorist acts, in addition to providing logistical and financial support to terrorists. In prior cases of recruitment, individuals who were willing to participate in terrorist acts became involved with known and suspected terrorists, participated in paramilitary training abroad, or tried to acquire small arms and build explosives.
(U//FOUO) The following SAR incident from the NSI shared space is an example of an individual being recruited to commit violence. The example is provided for situational awareness and training:
— (U//FOUO) An individual contacted the police to report being approached by two subjects about supplying firearms and participating in an attack on a military installation. The subjects were arrested and charged with conspiracy to murder officers and employees of the US Government after being observed conducting surveillance of targets, testing security, and acquiring weapons for the attack. One of the subjects pled guilty to the charges and is awaiting sentencing.
(U) Past Activities Observed in Individuals Recruited to Participate in Terrorism
(U//FOUO) Studies of terrorist actors have identified particular behaviors that have been observed in individuals vulnerable to recruitment or who have been recruited, and were ready to commit acts of violence. Any one of these activities may be insignificant on its own, but when observed in combination with other prior observed behaviors—particularly advocacy of violence—may constitute a basis for reporting.
— (U//FOUO) Acceptance of violence as a legitimate form of political activity, expressed willingness to commit acts of violence, or close association with individuals or groups suspected of violent extremism.
— (U//FOUO) Communication with violent extremists, either through direct contact or virtually, or active participation in violent extremist blogs, chat rooms, and password-protected websites.
— (U//FOUO) Interest in paramilitary and explosives training or reconnaissance and surveillance activities in a manner reasonably indicative of pre-operational planning.
— (U//FOUO) Possession of literature written by and for violent extremist groups on terrorist techniques, including use of explosives, poisons, firearms and heavy weapons (when combined with other prior observed behaviors).
— (U//FOUO) Involvement by individuals—who otherwise never committed a crime—in theft, fraud, and illegal activities to fund terrorist causes.
(U//FOUO) In addition, individuals or groups attempting to enlist others to participate in acts of violence or terrorism should be reported to authorities.
(U//FOUO) These identified activities have been observed in cases of mobilization to violence, but are not a concrete formula for predicting illegal activity. First Ammendment-protected activities should not be reported in a SAR or ISE-SAR absent articulable facts and circumstances that support the source agency’s suspicion that the behavior observed is not innocent, but rather reasonably indicative of criminal activity associated with terrorism, including evidence of pre-operational planning related to terrorism. Race, ethnicity, national origin, or religious affiliation should not be considered as factors that create suspicion (although these factors may be used in specific subject descriptions). DHS and FBI are not advocating interference with the rights of law-abiding individuals. There may be a legitimate reason why some of the observed behaviors are present; it is up to you to determine when that is not the case.
Monty Python – Holy Grail – Killer Bunny – Film
Monty Python – Holy Grail – Killer Bunny – Film
A clip from Monty Python’s ‘The Holy Grail’
Also: http://www.youtube.com/watch?v=2DUV7k…
S & K – angeblicher Finanzskandal Teil 2 – Wer zieht die Fäden und wer profitiert ?
Es geht um einen Schaden in dreistelliger Millionenhöhe. Die Wirtschaftswoche hatte Ende Januar vor den Aktivitäten gewarnt.
Die Staatsanwaltschaft geht von der Annahme aus, dass Schöneich ihre Zeitschrift zum Zwecke der persönlichen Bereicherung als Werbebroschüre von der S&K-Gruppe missbrauchen ließ. So habe sie sie für die Unterstützung der Hauptbeschuldigten Schäfer und Köller allein 6000 Euro monatlich als „Beraterhonorar“ erhalten.
Wenn der S&K durch ihre Tätigkeit Anlegergelder zuflossen, habe sie zudem ein Prozent der Umsätze vereinnahmt. Darüber hinaus habe Schöneich von Schäfer und Köller teure Geschenke wie Handtaschen und Schmuck angenommen. Schöneich reagierte bis zum Redaktionsschluss gestern nicht auf Anfragen des Handelsblatts.
Anlagetipps: Finger weg von Finanzprodukten, wenn…
-
Tipp 1
… Renditen von über acht Prozent pro Jahr versprochen werden, gleichzeitig aber ein Drittel der eingeworbenen Summe für Kosten wie Werbung oder Vertrieb draufgeht
-
Tipp 2
-
Tipp 3
-
Tipp 4
-
Tipp 5
Die Finanzwelt ist nach eigenen Angaben mit 100 000 Lesern eine der führenden Publikationen für den erfolgsorientierten, qualifizierten Finanzberater im deutschsprachigen Raum. In der Selbstdarstellung heißt es: „Finanzwelt greift wichtige Themen der Finanzbranche auf, setzt Impulse und berichtet hierüber zum Wohle der Branche.“
Nach der bundesweiten Großrazzia gegen mutmaßliche Anlagebetrüger vom Dienstag waren eine Reihe von Hauptverdächtigen in Untersuchungshaft genommen worden. Die Personen stehen im Verdacht, ein betrügerisches Schneeballsystem aufgebaut und Anleger um mehr als 100 Millionen Euro geprellt zu haben. Die Wirtschaftswoche hatte Ende Januar vor den Aktivitäten gewarnt.
- Seite 1: Staatsanwälte ermitteln gegen „Finanzwelt“-Chefin
- Seite 2: Zahl der Geschädigten noch völlig unklar
- Seite 3: DCM AG: “Keine personelle oder kapitalmäßige Verflechtung”
- Seite 4: Verbraucherschützer warnen vor hektischen Aktivitäten
TOP-SECRET – DHS-FBI Suspicious Activity Reporting Bulletin: Recruiting
ROLL CALL RELEASE
- 1 page
- For Official Use Only
(U//FOUO) Terrorists are attempting to recruit new members in the United States and overseas to support their operations, obtain funding, and conduct terrorist attacks. For example, in May 2012, Maryland-based Mohammad Hassan Khalid pled guilty to attempting to use the Internet to recruit individuals who had the ability to travel to and around Europe to conduct terrorist acts, in addition to providing logistical and financial support to terrorists. In prior cases of recruitment, individuals who were willing to participate in terrorist acts became involved with known and suspected terrorists, participated in paramilitary training abroad, or tried to acquire small arms and build explosives.
(U//FOUO) The following SAR incident from the NSI shared space is an example of an individual being recruited to commit violence. The example is provided for situational awareness and training:
— (U//FOUO) An individual contacted the police to report being approached by two subjects about supplying firearms and participating in an attack on a military installation. The subjects were arrested and charged with conspiracy to murder officers and employees of the US Government after being observed conducting surveillance of targets, testing security, and acquiring weapons for the attack. One of the subjects pled guilty to the charges and is awaiting sentencing.
(U) Past Activities Observed in Individuals Recruited to Participate in Terrorism
(U//FOUO) Studies of terrorist actors have identified particular behaviors that have been observed in individuals vulnerable to recruitment or who have been recruited, and were ready to commit acts of violence. Any one of these activities may be insignificant on its own, but when observed in combination with other prior observed behaviors—particularly advocacy of violence—may constitute a basis for reporting.
— (U//FOUO) Acceptance of violence as a legitimate form of political activity, expressed willingness to commit acts of violence, or close association with individuals or groups suspected of violent extremism.
— (U//FOUO) Communication with violent extremists, either through direct contact or virtually, or active participation in violent extremist blogs, chat rooms, and password-protected websites.
— (U//FOUO) Interest in paramilitary and explosives training or reconnaissance and surveillance activities in a manner reasonably indicative of pre-operational planning.
— (U//FOUO) Possession of literature written by and for violent extremist groups on terrorist techniques, including use of explosives, poisons, firearms and heavy weapons (when combined with other prior observed behaviors).
— (U//FOUO) Involvement by individuals—who otherwise never committed a crime—in theft, fraud, and illegal activities to fund terrorist causes.
(U//FOUO) In addition, individuals or groups attempting to enlist others to participate in acts of violence or terrorism should be reported to authorities.
(U//FOUO) These identified activities have been observed in cases of mobilization to violence, but are not a concrete formula for predicting illegal activity. First Ammendment-protected activities should not be reported in a SAR or ISE-SAR absent articulable facts and circumstances that support the source agency’s suspicion that the behavior observed is not innocent, but rather reasonably indicative of criminal activity associated with terrorism, including evidence of pre-operational planning related to terrorism. Race, ethnicity, national origin, or religious affiliation should not be considered as factors that create suspicion (although these factors may be used in specific subject descriptions). DHS and FBI are not advocating interference with the rights of law-abiding individuals. There may be a legitimate reason why some of the observed behaviors are present; it is up to you to determine when that is not the case.
TMZ – ‘Real Housewives of Miami’ — Time to Play with Boobs !
TMZ – ‘Real Housewives of Miami’ — Time to Play with Boobs!
We gotta give “The Real Housewives of Miami” credit… they know how to turn a boring video into a friggin AWESOME one… just start playing with each other’s boobs!
SECRET from Public Intelligence – Restricted U.S. Army Air and Missile Defense Operations Manual
FM 3-01 U.S. Army Air and Missile Defense Operations
- 146 pages
- Distribution authorized to U.S. Government agencies and their contractors only to protect technical or operational information for official use.
- November 25, 2009
- 8.08 MB
FM 3-01 is the Army Air Defense Artillery’s (ADA) capstone doctrinal publication. The seven chapters that make up this edition of Air and Missile Defense Operations constitute the Army ADA’s view of how it conducts prompt and sustained operations and sets the foundation for developing the other fundamentals and tactics, techniques, and procedures detailed in subordinate field manuals. FM 3-01 also provides operational guidance for commanders and trainers at all echelons.
• Chapter 1 provides a general overview of Army Air and Missile Defense (AMD) operations and the Air Defense Artillery (ADA) mission. The strategic, operational, and tactical levels of war are discussed and AMD operations are defined in terms of their contribution to the Army Operational Concept of Full Spectrum Operations and the Joint Counterair mission.
• Chapter 2 describes the basic concepts inherent in air and missile defense operations which have been developed and improved through many years of operations, both combat and real world deployments. This includes employment principles and guidelines, and engagement operations principles.
• Chapter 3 addresses Command and Control in AMD operations and conforms to Joint Air and Missile Defense doctrine as updated with the lessons learned in Operation Iraqi Freedom (OIF).
• Chapter 4 describes Army Air Defense participation in offensive and defensive operations. Offensive operations aim is to defeat the enemy decisively by using overwhelming, aggressive force. Defensive operations defeat an enemy attack, buy back time, economize forces, and/or develop conditions favorable for offensive operations. Air defense elements protect friendly forces and geopolitical assets and accomplish other missions assigned by the JFC. At the Strategic level of war ADA forces protect high visibility JIIM and national assets, as a layer within the ballistic missile defense system (BMDS) and supports homeland defense operations. At the Operational level of war, ADA forces protect the theater assets based on the JFCs critical asset list (CAL) like, seaports of embarkation, air ports of embarkation, cities, logistic centers, religious centers, and lines of communications (LOC). At the tactical level of war, Army ADA forces support the Land Component Commanders (LCC)/ARFOR scheme of maneuver while protecting Theater, Corps, Division, and Brigade Combat Teams (BCTs) forces according to the JFC’s defended asset list (DAL) priorities.
• Chapter 5 describes the participation of ADA forces in stability operations and civil support operations. Stability operations are conducted outside the U.S. and its territories to promote and protect U.S. national interests. Civil support operations are conducted to address the consequences of natural or manmade disasters, accidents, and incidents within the U.S. and its territories. This chapter describes ADA participation in support of Homeland Security, Homeland Air Security, and counter-drug operations. ADA units may be tasked to provide soldiers and ADA equipment for civil support operations.
• Chapter 6 describes the Army ADA contribution to and benefit from achieving information superiority. Information superiority is the operational advantage derived from the ability to collect, process, and disseminate an uninterrupted flow of information while exploiting or denying an adversary’s ability to do the same. Information superiority is the product of intelligence, surveillance, and reconnaissance (ISR), information management (IM), and information operations (IO). Information superiority enables ADA forces to see first, understand the situation more quickly and accurately, and act faster than their adversaries.
• Chapter 7 discusses the sustainment of Air Defense Artillery (ADA) organizations and the unique challenges to the commanders and staffs of these organizations.Four appendixes complement the body of the manual. Intelligence Preparation of the Battlefield is in Appendix A. Air and missile threats facing Army ADA forces and systems are in Appendix B. Air and missile defense planning is in Appendix C. A discussion of the impact of technology on ADA forces is in Appendix D.
…
CHARACTERISTICS OF CIVIL SUPPORT OPERATIONS
5-25. Civil support is Department of Defense support to U.S. civil authorities for domestic emergencies, and for designated law enforcement and other activities (JP 1-02). Civil support includes operations that address the consequences of natural or man-made disasters, accidents, terrorist attacks, and incidents in the United States and its territories. Army forces conduct civil support operations when the size and scope of events exceed the capabilities or capacities of domestic civilian agencies. Civil support operations are usually noncontiguous. Leaders tailor the application of the operational framework, elements of operational design, and METT-TC to fit each situation. Commanders designate the decisive, shaping, and sustaining operations necessary for mission success. However, identifying centers of gravity, decisive points and even the desired end state can be more complex and unorthodox than in offensive and defensive operations. When visualizing a support operation, commanders recognize that they may have to define the enemy differently. In support operations, the adversary is often disease, hunger, or the consequences of disaster.
5-26. The homeland defense mission for ADA is to prevent, deter, or interdict foreign and domestic aerial threats that are directed towards the United States and its citizens or specified area of operations (AO), such as the National Capitol Region. Nations, terrorist groups, or criminal organizations are increasingly likely to attack the U.S. and its territories using missiles and aircraft.
5-27. The homeland air security (HAS) air and missile threat spectrum Figure 5-1 ranges from traditional military threats to terrorist threats, from medium and long range ballistic missiles, bombers to land attack cruise missiles, terrorist-controlled aircraft, and radio-controlled sub-scale aircraft. The use of an air vehicle as a terrorist weapon is the most stressing HAS threat. State-sponsored military threats are addressed by war plans, operational concepts, and our military’s capabilities. The HAS threat spectrum is depicted
below.5-28. Government agencies other than the Army will often have the lead in civil support operations. ADA commanders may answer to a civilian chief or may themselves employ the resources of a civilian agency. Command arrangements may often be only loosely defined, causing commanders to seek an atmosphere of cooperation. ADA commanders consider how their actions contribute to initiatives that are also political, economic, and psychological in nature.
5-29. The U.S. Constitution allows the use of Army forces to protect the states against invasion and, upon request of a state, to protect it against domestic violence. Army forces, under joint command, provide the nation with critical capabilities, such as missile defense, necessary to secure and defend the homeland.
5-30. The amended Posse Comitatus Act significantly restricts using federal military forces in law enforcement. The Stafford Act defines and clarifies the role of U.S. military forces in support of domestic civil authorities. Since the law may prohibit certain types of activities, commanders need a detailed analysis of their legal authorities for each mission. Generally, ADA troops and systems performing civil support operations, by the nature of their missions, are in compliance with the law and need only be aware of the limitations of their authority.
Film – Monty Python – Self-Defense Against Fruit
from Monty Python’s Flying Circus
Season 1 – Episode 04 – Owl Stretching Time
Recorded 21-09-69, Aired 26-10-69
Resignation of Pope Benedict XVI – Gay “Network” in the Vatican – Blackmail – Plot to kill Benedict
The resignation of Pope Benedict XVI has been linked to the discovery of a gay “network” in the Vatican that led to some prelates being blackmailed by outsiders.
The potentially explosive claim was made Thursday by the Rome daily La Repubblica. The newspaper said the network was described in a 300-page report presented to the Pope by three cardinals assigned to investigate a series of embarrassing internal leaks that rocked the Vatican last year.
The cardinals interviewed dozens of prelates and lay people in Italy and abroad. Their report describes a Roman Catholic church divided by factions, including a “cross-party network united by sexual orientation,” La Repubblica said.
“For the first time, the word homosexual was pronounced,” the newspaper said, referring to a meeting when the cardinals reported their findings to Pope Benedict.
The Pope was handed the report Dec. 17. He shocked the Catholic world by resigning less than two months later — the first Pope to abdicate in more than 600 years.
Apparently using words found in the report, the newspaper said it contained evidence of “external influence” on Vatican officials from laymen with whom they had links of a “worldly nature.”
“We would call it blackmail,” La Repubblica added.
The Vatican’s spokesperson, Rev. Federico Lombardi, said reporters should not expect anyone from the Vatican to confirm or deny the allegations.
“We’re not going to run after all the speculation, the fantasies or the opinions that will be expressed on this issue,” he added. “And don’t expect the three cardinals to give you interviews, either, because they have agreed not to answer (questions) or give information on this issue.”
The three cardinals who investigated are Spanish cardinal Julian Herranz, Italian cardinal Salvatore De Giorgi, and the Slovak cardinal, Jozef Tomko.
The Pope asked them to investigate after his papacy was undermined in early 2012 by the leaking of a series of Vatican documents. They included private letters to the Pope complaining of corruption and cronyism in the awarding of Vatican contracts. Allegations of money-laundering at the Vatican’s bank were reignited.
A confidential letter from a Vatican official described a presumed plot to kill Benedict and discussed his potential successor. Other leaks linked the murder-suicide of two Vatican Swiss guards in the 1980s to the kidnapping of a 15-year-old Vatican resident, the attempted murder of Pope John Paul II and the controversial burial in a Roman Catholic basilica of Enrico De Pedis, one of Italy’s most notorious gangsters.
The Pope’s butler was eventually convicted of stealing the documents.
Video – Mandiant standing by hacking accusations
Mandiant standing by hacking accusations
Rod Beckstrom, a cyber security analyst, talks about the allegations against the Chinese hackers.
The FBI – Crooked CEO Gets 50 Years for Stealing $215 Million
 |
|---|
| The $20 million headquarters of the now-bankrupt Peregrine Financial Group in Cedar Falls, Iowa. |
He was a successful CEO of his own futures brokerage firm and a respected member of his community, creating jobs and supporting local charities.
Or so it seemed. For years, Russell Wasendorf, Sr.—as Acting U.S. Attorney Sean R. Berry of the Northern District of Iowa recently put it—was really a “con man who built a business on smoke and mirrors.”
It all fell apart in July 2012 when Wasendorf—after an unsuccessful suicide attempt—admitted stealing millions from more than 13,000 investors who had entrusted their hard-earned money to him and his company, the now bankrupt Peregrine Financial Group (PFG), based in Cedar Falls, Iowa. Last month, Wasendorf was sentenced by a federal judge to 50 years in prison—the maximum sentence allowed by law—and ordered to pay restitution to his victims.
| Hefty Federal Sentences for Financial Fraudsters Russell Wasendorf, Sr.’s 50-year sentence was based on a variety of factors, including the amount of financial loss, the sophisticated means used to execute the fraud, and the large number of victims. But he’s not the only subject of an FBI financial fraud case to end up with an extraordinarily lengthy prison sentence. Here are a few more examples: – Bernard Madoff—150 Years: Founder of Bernard L. Madoff Investment Securities, LLC, he engineered a Ponzi scheme that resulted in billions of dollars of losses to thousands of investors. The federal judge who sentenced him said that Madoff’s “fraud was staggering.” New York press release – Allen Stanford—110 Years: Chairman of the board of Stanford International Bank, he orchestrated a 20-year investment fraud scheme that helped him steal $7 billion to finance his personal businesses. Speaking at his sentencing on behalf of those he defrauded, a woman told Stanford that “many of the victims had lived the proverbial American dream, only to have it snatched away from them in the name of greed.” Houston press release – Thomas Petters—50 Years: Petters stole billions of dollars in money and property by inducing investors to provide his company with funds to purchase merchandise that was to be resold to retailers at a profit. Of course, no such purchases were made. Then-Minneapolis Special Agent in Charge Ralph Boelter said he hoped that Petters’ “appropriate” 50-year sentence “will serve as an effective deterrent to those similarly inclined.” Minneapolis press release |
|---|
How it started. In the early 1990s, Wasendorf’s Peregrine partner pulled his money out of the operation, and Wasendorf didn’t have the funds to keep the company going. So he helped himself to at least $250,000 of Peregrine’s customer funds in accounts at an outside bank. To conceal the theft, he used a copy machine to fabricate a phony bank statement.
For the next 20 or so years, Wasendorf continued to steal from customer funds while his company incurred tens of millions of dollars in losses. He carried out this scheme through a series of complex actions designed to conceal his activities and the deteriorating state of the company. For instance:
- He maintained exclusive control of monthly bank statements by instructing PFG personnel to make sure they were delivered to him unopened. He then used a copy machine—and later, computer software—to create phony monthly statements in place of the real statements.
- He sent the phony statements to PFG’s accounting department, knowing they’d be used in various reports required by oversight bodies—the Commodity Futures Trading Commission (CFTC) and the National Futures Association (NFA).
- He intercepted account verification forms from NFA and CFTC auditors mailed to the bank used by PFG. Wasendorf changed the address of the bank to a post office box that only he had access to; once the forms came into that post office box, he would mail back to the auditors a forged form—supposedly from the bank—that contained an inflated dollar amount of what was in the corresponding bank account.
What did Wasendorf do with the misappropriated funds? He created the appearance that PFG was legitimate and successful in order to ward off the suspicions of regulators and auditors. He also funded his own outside business interests—for example, he opened two restaurants in Cedar Falls. And finally, he lived quite luxuriously—he owned a private jet and a huge estate that included a million dollar indoor swimming pool and a 1,000-bottle wine cellar.
The case began when the Blackhawk County Sheriff’s Office, first on the scene of Wasendorf’s attempted suicide, contacted the FBI after discovering notes left by the executive admitting his illegal deeds. The ensuing federal investigation—which involved multiple searches, reviews of thousands of electronic and paper documents, and numerous interviews—culminated in September 2012 with Wasendorf’s guilty plea.
Special thanks as well to our partners at the U.S. Postal Inspection Service and the U.S. Attorney’s Office for the Northern District of Iowa for their assistance in this case.
MYSTERIÖSE PROBLEME – Hacker-Angriff auf Vettel ? !
Unveiled by Cryptome – Iran Zelzaal Rocket Probable 1-Day Attack on US
Iran Zelzaal Rocket Probable 1-Day Attack on US
A sends:
Our Persian observer reports that Iran has made its southern missile and rocket launchers and silos ready for a probable 1-day attack. Based on what we hear, there is high chance of a very small scale fire exchange between the two sides and then call it a mistake. It is a common practice in such situations and we think such test must happen before the upcoming Iranian presidential election, to have a added-value score for Americans. It is a military text book fact that such event is going to happen and this article tips off Iranians are concentrating on the south. It also offer thorough details of Zelzaal, a solid fuel rocket that is set to destroy American airplanes before they get the chance to fly off the band [ground].
TMZ – Prince Vs. Weird Al — The ONLY Anti-Parody Artist!
TMZ – Prince Vs. Weird Al — The ONLY Anti-Parody Artist!
There’s only ONE artist who consistently turns down Weird Al’s requests to spoof his songs and it’s none other than Prince. THIS MEANS MUSIC WAR!
TOP-SECRET from PI – U.S. Northern Command CONPLAN 3501-08 Defense Support of Civil Authorities (DSCA)

CDRUSNORTHCOM CONPLAN 3501-08 DEFENSE SUPPORT OF CIVIL AUTHORITIES (DSCA)
- 570 pages
- May 16, 2008
- 40.9 MB
1. Purpose. Natural or man-made disasters and special events can be so demanding that local, tribal) state and non-military federal responders are temporarily overwhelmed by the situation. The Department of Defense (DOD) has a long history of supporting civil authorities in the wake of catastrophic events. When directed by the President or the Secretary of Defense (SecDef), United States Northern Command (USNORTHCOM) will respond quickly and effectively to the requests of civil authorities to save lives, prevent human suffering, and mitigate great property damage. The Joint Strategic Capabilities Plan 2008 (JSCP) directs CDRUSNORTHCOM to prepare a plan to support the employment of Title 10 DOD forces providing Defense Support of Civil Authorities (DSCA) in accordance with (IAW) the National Response Framework (NRF), applicable federal law, DOD Directives (DODD), and other policy guidance including those hazards defined by the National Planning Scenarios that are not addressed by other JSCP tasked plans. DSCA is a subset of DOD civil support that is performed within the parameters of the NRF.
2. Conditions for Implementation
a. Politico-Military Situation
(1) USNORTHCOM was established in response to the September 11, 2001 terrorist attacks against the United States. USNORTHCOM’s dual mission is to conduct Homeland Defense (HD) and civil support operations. When directed by the President or the SecDef, USNORTHCOM conducts DSCA operations IAW the NRF by responding to Requests for Assistance (RFA) from civil authorities.
(2) The NRF is a guide to how the nation conducts all-hazards response. This plan aligns with the NRF coordinating framework and applies to all forms of support that DOD could provide to civil authorities under the NRF. In addition to Large-scale disaster responses) DOD has long provided smaller scale support for wildland firefighting, National Special Security Events (NSSE)t such as political conventions, and special events (SE) such as major sporting events.
b. Statement. This summary provides military decision makers with a brief recapitulation of the major aspects of this plan. It is based on planning factors and estimates available at the time of preparation and is subject to modification in the context of a specific contingency.
c. Legal Considerations. The NRF provides the coordinating framework for support provided under the Robert T. Stafford Disaster Relief and Emergency Assistance Act (PL 93-288) (Title 42 United States Code Section 5121, et. seq.). The Stafford Act and the Economy Act (Title 31 United States Code Section 1535) are the primary sources of statutory authority which govern the federal response. Support under these acts range from small-scale efforts to large-scale operations involving thousands of DOD personnel. DODD 3025.dd) Defense Support of Civil Authorities, is currently in draft, but when finalized, will supersede the current DODDs describing DOD support of civil authorities. Civil support under this plan does not include direct support to law enforcement. The Posse Comitatus Act (PCA) (Title 18 United States Code Section 1385) and DOD policy place limitations on direct involvement in law enforcement activities by Title 10 military personnel. Direct support to civilian law enforcement authorities requires specific statutory or Constitutional authority to not violate the PCA. While providing DSCA, DOD forces will conform to the CJCS Standing Rules for the Use of Force (SRUF) and any supplemental guidance provided by USNORTHCOM.
…
APPENDIX 22 TO ANNEX C TO USNORTHCOM CONPLAN 3501
DEFENSE SUPPORT OF CIVILIAN LAW ENFORCEMENT1. Situation
a. State, local, tribal, private-sector, and specific Federal authorities have primary responsibility for public safety and security, and typically are the first line of response and support. Local jurisdictions have primary authority and responsibility for law enforcement activities. As local incidents or events escalate, additional resources will first be obtained through the activation of mutual aid agreements with neighboring localities and/ or State authorities. In the context of State’s resources, the National Guard (NG), while serving under state control for state purposes, is not considered to be part of the Department of Defense (DOD) and executes missions under the command and control (C2) of the Governor in accordance with (IAW) the State’s constitution and statutes.
b. It is DOD policy to cooperate with civilian law enforcement officials to the maximum extent practicable. The implementation of DOD policy shall be consistent with the needs of national security and military preparedness, the historic tradition of limiting direct military involvement in civilian law enforcement activities, and the requirements of applicable law.
c. It is the intent of this appendix to provide an overview of defense support of law enforcement as it cannot cover all potential requests for Defense Support of Civil Authorities (DSCA) that relate to civilian law enforcement. Defense support of civilian law enforcement agencies covers a broad spectrum of potential activities from very small support activities such as training civilian law enforcement, loaning a piece of equipment, or an Explosive Ordnance Disposal (EOD) or dog team to large-scale incidents or events such as a riot. The Department of Homeland Security (DHS) addresses civil disturbance operations as part of public safety. This appendix will not address civil disturbance operations. See USNORTHCOM CONPLAN 3502, Civil Disturbance Operations, for more information.
d. State level emergency response operations for natural disasters have evolved concerning the use of the NG in a law enforcement role from state to state. Govemor1s use of their powers has set a precedence for the future. Governors may, by use of their state powers and via a state to state memorandum of agreement, authorize the NG of one state to perform law enforcement and security duties within the another state.
e. In accordance with (IAW) reference g. which is still in DRAFT form, DSCA does not apply to the following programs that are related to support to law enforcement agencies:
(1) Sensitive support provided IAW DOD Directive (DODD) S-5210.36.
(2) Inspector General of the DOD, the Defense Criminal Investigative Service:? or the military criminal investigative organizations when they are conducting joint investigations with civilian law enforcement agencies of matters within their respective jurisdictions, using their own forces and equipment.
(3) The non-Federalized National Guard and their activities under the C2 of the Governor.
(4) Counter-narcotic operations conducted under section 124) Title 10, U.S. Code.
(5) Defense Intelligence Components providing intelligence support IAW Executive Orders (EO) 12333 and 13356, the DODD on Intelligence activities (DODD 5240.1) and DODD Procedures Governing the Activities of DOD Intelligence Components that Affect United States Person (DODD 5240.1-R). Defense Intelligence components are defined in DOD Directive 5240.1
f. Enemy Forces. See Base plan
g. Friendly Forces. See Base plan
h. Assumptions
(1) DOD law enforcement and security missions/tasks will be in support of a Primary Agency under the NRF or a designated agency for other approved law enforcement activities.
(2) The Posse Comitatus Act will not be modified.
(3) DOD policy and guidance will not change after the formal release of references g and i.
(4) Civilian law enforcement agencies will continue to request training support for Jaw enforcement activities, loan/lease of DOD equipment) support for National Special Security Events (NSSEs), and other law enforcement activities.
2. Mission. See Base plan
3. Execution
a. Concept of Operations
(1) Defense support of civilian law enforcement agencies in response to a natural or man-made disaster, emergency, incident, or event will be processed IAW reference i above and executed at the direction of the President or approval of the Secretary of Defense (SecDef) IAW the Base plan.
(2) Release of information to the public concerning law enforcement operations is the primary responsibility of the civilian agency that is performing the law enforcement function. When defense support is provided under reference j above, assistance provided and information released by DOD PAO agencies to the public shall be approved by the Secretaries of the Military Departments or the Directors of the Defense Agencies and such assistance may be conditioned upon control by the Secretaries of the Military Departments and the Directors of the Defense Agencies before information is released to the public.
(3) Use of Information Collected During DSCA Operations. Military Departments and Defense Agencies are encouraged to provide to federal, state, or local civilian law enforcement officials any information collected during the normal course of DSCA operations that may be relevant to a violation of any federal or state law within the jurisdiction of such officials.
(4) USNORTHCOM will initiate coordination for defense support with the designated law enforcement agency upon SecDef approval of a RFA.
(5) Training Civilian Law Enforcement. Military Departments and Defense Agencies may provide training to federal, state, and local civilian law enforcement officials. Such assistance may include training in the operations and maintenance of equipment made available under the military equipment loan/lease program. This does not permit large scale or elaborate training, and does not permit regular or direct involvement of military personnel in activities that are fundamentally civilian law enforcement operations, except as otherwise approved and authorized.
b. Coordinating Instructions
(1) Coordination regarding legality of support will be staffed through the chain of command and USNORTHCOM Judge Advocate (JA) to the SecDef.
(2) The SecDef is the approval authority for all RFAs made by law enforcement agencies. This includes:
(a) Requests for potentially lethal support (i.e.) lethal to the public, a member of law enforcement, a military member or DOD employee).
(b) Loans of equipment, facilities, or personnel to law enforcement.
(c) Lethal support includes: loans of arms; combat and tactical vehicles, vessels or aircraft, or ammunition.
(d) All requests for support under 10 USC 382 and 18 USC 831; all support to counterterrorism operations; and all support to law enforcement when there is a potential for confrontation between law enforcement and specifically identified civilian individuals or groups.
(3) Immediate response authority. When requested, local military commanders and DOD officials may provide defense support to civil law enforcement agencies under this authority in order to save lives, prevent human suffering, and mitigate great property damage. This authority does not authorize DOD forces to perform law enforcement functions in support of civil law enforcement agencies unless consistent with an exception to the Posse Comitatus Act (18 USC) Section 1385) and IAW the guidance provided in the Basic plan.
(4) Restrictions on direct assistance to civilian law enforcement. Except as otherwise provided, the prohibition on the use of military personnel “as a Posse Comitatus or otherwise to execute the laws” prohibits the following forms of direct assistance:
(a) Interdiction of a vehicle, vessel, aircraft, or other similar activity.
(b) A search or seizure.
(c) An arrest, apprehension, stop and frisk, or similar activity.
(d) Use of military personnel for surveillance or pursuit of individuals, or as undercover agents, informants, investigators, or interrogators.
(5) The SecDef is the approval authority for all assistance with the potential for confrontation between DOD personnel and civilian individuals or groups.
(6) If a DOD Component has a question on the appropriateness or legality of providing requested support, such request shall be forwarded through the military chain of corrunand to the Assistant Secretary of Defense for Homeland Defense and Americas’ Security Affairs (ASD(HD/ ASA)).
4. Administration and Logistics. See Base plan
5. Command and Control. See Base plan
Monty Python – Life of Brian – Always Look On The Bright Side of Life
Monty Python – Life of Brian – Always Look On The Bright Side of Life
Die wahren Hintergründe zu S & K – Teil 1
Liebe Leser,
umfangreiche Ermittlungen der Staatsanwaltschaft Frankfurt am Main – Schwerpunktstaatsanwaltschaft für Wirtschaftsstrafsachen – und dem Fachkommissariat für Wirtschaftskriminalität beim Polizeipräsidium Frankfurt am Main seit dem Jahre 2012 haben zu einer groß angelegten Razzia in sieben Bundesländern unter Einbeziehung von 1.200 Ermittlungsbeamten und 15 Staatsanwälten geführt. Es wurden sechs Personen festgenommen, weitere Beschuldigte sind vorläufig festgenommen wurden. Gegen ca. 50 weitere Personen wird darüber hinaus ermittelt, so heisst es.
Die Staatsanwaltschaft Frankfurt am Main wirft den Verantwortlichen banden- und gewerbsmäßigen Betrug mit Kapitalanlagen, Untreue und weitere Straftaten vor. Die Staatsanwaltschaft Frankfurt am Main spricht in ihrer Pressemitteilung von einem Schneeballsystem und einem sich abzeichnenden Schaden im dreistelligen Millionen-Euro-Bereich. Gegenstand der Ermittlungen sind nach Mitteilung der Staatsanwaltschaft Frankfurt am Main mehrere Anlagefonds im neunstelligen Euro-Bereich.
Es wurden Vermögenswerte im Gesamtvolumen von über 100 Millionen EUR gesichert.
Stellungnahme der Kanzlei Göddecke
Es war nur eine Frage der Zeit, dass sich staatliche Behörden mit den Geschäften der S&K-Unternehmensgruppe beschäftigen. Bereits seit November letzten Jahres standen die Geschäfte der S&K-Unternehmen unter kritischer Beobachtung durch die Medien.
Dass staatliche Ermittlungsbehörden in diesem massivem Umfang tätig werden, zeigt, dass die gegen die S&K-Unternehmensgruppe und deren Verantwortlichen erhobenen Vorwürfe zumindest den dringenden Tatverdacht strafbarer Handlungen rechtfertigen.
Verhaftet wurden Jonas Köller, Stefan Schäfer, die Spitzen der S&K-Unternehmensgruppe sowie Haucke Bruhn und Thomas Gloy von United Investors, dem Vertrieb in Hamburg sowie zwei weitere angebliche Mittäter.
Allerdings sind unter Umständen nicht nur Anleger der S&K-Unternehmensgruppe von den Festnahmen betroffen. So hatte die S&K-Unternehmensgruppe auf verschiedenen Wegen umfangreiche geschäftliche Beziehungen zu anderen Fonds namhafter Anbieter aufgenommen, so zu den MIDAS-Fonds (Private-Equity Fonds) und einigen Immobilienfonds der DCM-Gruppe. Auch bei den Fonds der SHB-Gruppe sollten wichtige Posten mit Personen besetzt werden, die dem Umfeld der S&K-Unternehmensgruppe zuzuordnen waren. In Anbetracht des Umstandes, dass nach vorliegenden Informationen und Unterlagen Zweifel an der Werthaltigkeit einiger Immobilien der S&K-Unternehmensgruppe bestanden haben, haben wir diese Entwicklung stets kritisch beobachtet.
Erfreulich ist, dass die Staatsanwaltschaft Frankfurt am Main nach eigenen Angaben umfangreiche Vermögenssicherungen vorgenommen hat. Hierdurch erhöhen sich die Chancen für Anleger, wenigstens einen Teil ihres Geldes zurückzuerhalten, jedenfalls wenn sie rechtzeitig aktiv werden.
Die Ermittlungsergebnisse der Staatsanwaltschaft Frankfurt am Main und anderer Staatsanwaltschaften könnten die Durchsetzung von Ansprüchen gegen die S&K-Unternehmensgruppe erheblich erhöhen. Dies betrifft Anleger der Fonds S&K Real Estate Value Added Fondsgesellschaft mbH & Co. KG, Deutsche S&K Sachwerte GmbH & Co. KG, Deutsche S&K Sachwerte Nr. 2 GmbH & Co. KG und S&K Investment Plan GmbH & Co. KG. Aber auch Anleger, die in den Jahren 2010 bzw. zuvor Lebensversicherungen und/oder Bausparverträge an Unternehmen der S&K-Gruppe verkauft haben und deren Forderungen gestundet oder bisher regelmäßig ausgezahlt wurden, können betroffen sein. Auch aktuell hat die S&K-Unternehmensgruppe über die Asset Trust AG Lebensversicherungen und ähnliches aufgekauft. Hier drohen den Anlegern erhebliche finanzielle Verluste.
Wie es mit den Fonds der MIDAS-Gruppe und verschiedenen Fonds der DCM weitergeht, wird sich zeigen, wenn feststeht, ob diese Fonds überhaupt noch handlungsfähig sind. Für Anleger der SHB-Fonds könnte die aktuelle Entwicklung die Frage der Abstimmung bei den laufenden Gesellschafterabstimmungen erheblichen Einfluss haben.
Experten kommen zu der Auffassung, dass die Aktion – unabhängig von ihrer Berechtigung – die vorhandenen Fonds schwer beschädigen wird sowie das Vertrauen in die gesamte Immobilienbranche für Jahre untergraben wird. Eine ganz spezielle Rolle spielte hierbei auch der selbsternannte „Nachrichtendienst“ „GoMoPa“ und deren Zuträger und V-Leute in der Branche, den Medien und in den Behörden. Erfahrene Experten verweisen auf den Zusammenhang zwischen den mutmasslichen STASI Täter: „GoMoPa“, „Anlegeranwalt Resch, Beate P****n, Staatsanwältin, Wiesbaden/Rhein Main, ihren Gatten, den Gesellschafter der Immobilienzeitung GmbH, Thomas P*****n sowie den Druck auf die Frankfurter Staatsanwaltschaft in der Finanzkrise „abzuliefern.“
Natürlich haben die Beschuldigten – es gilt die Unschuldsvermutung – und auch die Branche nach dem medialen Donnergewitter keine Chance mehr, meinen wohl Rechtsexperten…
Warum Banken, die Milliarden zerstört haben und mit Milliarden Steuergeldern willfähriger Politiker subventiniert werden , gänzlich ungeschoren davonkommen, und deren Manager Millionengehälter kassieren, erschliesst sich unserer Redaktion nicht.
BANKEN MÄSSIGES – EH PARDON BANDENMÄSSIGES VERBRECHEN ? !
Durch die Aktion wird das Vertrauen in die deutsche Immobilienbranche auf Jahre zerstört. Die Fonds werden mutmasslich insolvent. Die Gewinner sind dubiose Aktienhaie, “Anlegeranwälte” und damit verbandelte “Juristen” und “Journalisten” in den Behörden.”
Die Verlierer sind die Immobilienbranche und deren Angehörige.
Und wer immer noch nicht kapiert hat, mit wem er oder sie es bei bei “GoMoPa” und deren V-Leuten in der Justiz und in der in Rhein/ Main ansässigen V-Leuten/Medien zu tun hat.
Und warum ehemalige STASI-Leute, die eine Kampagne mit ihren V-Leuten in der Justiz und sogenannten “Fachzeitungen” aus dem Rhein-Main-Gebiet (Wiesbaden ! sic !) unter der Ägide bestimmter “Familienangehöriger” anzetteln können, mutmasslich im Auftrag von Immobilien-Wettbewerbern , damit immer diese weiter erfolgreich sind, erschliesst sich auch nicht – auf den ersten Moment.
Jahrzehntelange Intrigen ! Oder was P*****n ? Oder was M***a ?
Und: Warum gilt in Deutschland – gerade nach den NAZIs und nach der STASI – Terrorr-Willkür keine Unschuldsvermutung wie im Rest der Welt ?
Wie verkommen ist diese deutsche Gesellschaft und deren “Organe” – instrumentalisiert durch durchschaubare Interessen seit dem Fall der Mauer 1989 ?
Nie wude ein TOP-STASI-Mann oder TOP – Gestapo- Mann verurteilt !
Trotz aller Massenverbrechen !
Berichten hierüber die gleichgeschalteteten deutschen Main-Stream-Medien ? Nein !
Und bei den Milliarden – Verlusten – kein einziger Banker wurde verurteilt !
Gab es Berichte in den gleichgeschalteten, anzeigenabhängigen Medien oder in der “Immobilienzeitung” oder in “GoMoPa” oder in “Das Investment” etc pp ?
WAS GIBT ES NUR FUER ZUFAELLE ?!
Zum Thema: Es wurde kein Banken-Opfer gefunden ( Gab es den keine ????)….
Stattdessen wurde ein dankbares Justiz- und Medien-Opfer gefunden – und am ersten Tag gleich richtig fertiggemacht. Woher haben die Medien all die schönen Photos und Infos von der Razzia ?
Die Anleger interessieren eh keinen und bei den Immobilien verstehen die Bürokraten eh nix !
Damit ist der Immobilien-Miliarden-Schaden JETZT vorprogrammiert.
ZUDEM – Welche globalen Investoren sollen JETZT investieren nach diesem §JUSTIT§- KO ?
Wer PROFITIERT denn davon ?
Bei weiterem Nachdenken, denke ich werden Sie alles verstehen !
Herzlichst
Bernd Pulch
(Magister Artium)
HACKER-ANGRIFFE a la “GoMoPa” – USA drohen China mit Handelskrieg
Unveiled – Mandiant Report on Chinese Hackers
When Mandiant, the company that investigated the recent cyber attacks on the New York Times, released its report yesterday, APT1: Exposing One of China’s Cyber Espionage Units, the media grabbed it. They zinged off one news story after another about how this company had exposed the cybercriminals that the Chinese government claimed to know nothing about.
News? No. It was simply another layer of evidence that cyber activists/hackers/criminals/agents/whatever have been stealthily conducting cyber reconnaissance missions, infecting computers with malware, exfiltrating data, and in general, being bad guys. In 2011, Dmitri Alperovitch, then vice president of Threat Research for McAfee, authored a report about Shady RAT (Remote Access Tool), the malware that had been used by Chinese cybercriminals to exfiltrate data from a broad cross-section of organizations over a 2-5 year period — undetected. Alperovitch broke new ground when he included a table of more than 70 companies, organizations, and government agencies from around the globe that had been compromised. It included the U.N., the International Olympic Committee, and numerous U.S. entities. Now, that was news.
Mandiant’s report gave the world more of the same about Chinese cyber bad guys. In fact, it was the same Chinese bad guys. Mandiant acknowledges that the group behind the attacks in their investigation is the same group that Alperovitch identified in Shady RAT.
What is news in the Mandiant report is how they conducted their forensic investigation. Mandiant actually tracked the attackers’ communications back to a compromised “hop point” (middle man computer), obtained the cooperation of the compromised middle organization, and captured the keystrokes of the criminals as they were conducting their “work.”
Mandiant and its client companies turned the tactics of the criminals against them and carefully compiled evidence over several years. They observed this particular group of cyber hackers attack more than 141 companies in 20 industries since 2006. Mandiant courageously published its findings, including a video of screenshots captured as the criminals engaged in their acts, and acknowledged that they “expect reprisals from China.”
A lot of credit goes to the unsung heroes: the companies that made Mandiant’s work possible:
the victim organizations that were determined to track the criminals and funded substantial forensic investigations, and
the “middle-man” organizations that accepted Mandiant’s help when notified of their role and cooperated to advance the investigations.
This does not happen because forensic and computer geeks decide to chase cybercriminals. It happens because senior management understands both the importance of what is happening and their fiduciary duty to protect the assets of the organization.
Alperovitch, who is now co-founder and CTO of forensic firm CrowdStrike, notes that “Mandiant’s report is important and makes it starkly clear that it is becoming harder and harder for the Chinese government to deny that they know nothing about this.” Nevertheless, according to Alperovitch, “the identified group is just one of two dozen in China that are engaged in similar activities, many of them linked to units in the People’s Liberation Army.”
So, here is the bottom line for corporate America: unlike traditional crimes, companies cannot just call the cops and let them chase the cyber criminals. Affected organizations play a leading role in every investigation because it is their systems and data that are being stolen or leveraged. The lesson from Mandiant is that we must all come together and collectively fight cybercrime, irrespective of whether the criminal is a rogue hacker or a nation state.
A few tips to get started: Be on the alert for malicious code on your system and, when detected, don’t shirk from funding a proper forensic investigation. If your company is approached by a reputable firm or law enforcement agency with evidence that your corporate systems are being used as a hop point, cooperate as fully as possible. Stay engaged and ensure the investigation stays within the rule of law. Understand these are hard problems and take time.
Download the original document here:
TMZ – Kim Kardashian – Khloe Was NOT Fired from ‘X Factor’
TMZ – Kim Kardashian – Khloe Was NOT Fired from ‘X Factor’
Khloe Kardashian did not go the way of Paula Abdul … and Nicole Scherzinger … and Cheryl Cole … and Steve Jones … and NOT been 86’d from “X Factor” … this according to Kim Kardashian.
SECRECY NEWS – A NEW JUDGE FOR THE FISA COURT
Judge Claire V. Eagan of the Northern District of Oklahoma was appointed
this month to the U.S. Foreign Intelligence Surveillance Court by the Chief
Justice of the United States.
Her term on the FIS Court began on February 13, 2013 and will extend until
May 18, 2019. She replaces Judge Jennifer B. Coffman, who retired on
January 8 before the end of her term. Another appointment, to replace
outgoing Judge John D. Bates, whose term ends tomorrow, is imminent, said
Sheldon Snook, spokesman for the Court.
The FIS Court authorizes electronic surveillance and physical searches for
intelligence and counterterrorism purposes. The current membership of the
Court is listed here:
http://www.fas.org/irp/agency/doj/fisa/court2013.html
Judge Eagan was appointed to the federal bench by President George W. Bush
in 2001.
The FIS Court has been discussed lately as a potential model for some form
of judicial review of the use of drones in lethal strikes against suspected
terrorists. Speaking at the February 7 confirmation hearing of John Brennan
to be CIA Director, Senate Intelligence Committee chair Sen. Dianne
Feinstein said her Committee would examine "the proposal to create an
analogue of the Foreign Intelligence Surveillance Court to review the
conduct of such strikes."
But the application of the FISA model for authorizing intelligence
surveillance to the substantially different issue of lethal targeting would
not be straightforward, and may not be appropriate at all.
The notion "that federal judges ought to be assigned the task of
monitoring, mediating and approving the killer instincts of our government
[...] is a very bad idea," wrote Judge James Robertson, a former FIS Court
member, in the Washington Post ("Judges shouldn't decide about drone
strikes," February 15).
UNCONVENTIONAL MONETARY POLICY, AND MORE FROM CRS
New and updated reports from the Congressional Research Service that
Congress has chosen not to make available to the public include the
following.
Federal Reserve: Unconventional Monetary Policy Options, February 19,
2013:
http://www.fas.org/sgp/crs/misc/R42962.pdf
Federal Assault Weapons Ban: Legal Issues, February 14, 2013:
http://www.fas.org/sgp/crs/misc/R42957.pdf
Pharmaceutical Patent Settlements: Issues in Innovation and
Competitiveness, February 15, 2013:
http://www.fas.org/sgp/crs/misc/R42960.pdf
Unauthorized Aliens: Policy Options for Providing Targeted Immigration
Relief, February 13, 2013:
http://www.fas.org/sgp/crs/homesec/R42958.pdf
Cars, Trucks, and Climate: EPA Regulation of Greenhouse Gases from Mobile
Sources, February 14, 2013:
http://www.fas.org/sgp/crs/misc/R40506.pdf
Japan-U.S. Relations: Issues for Congress, February 15, 2013:
http://www.fas.org/sgp/crs/row/RL33436.pdf
Exemptions for Firearms in Bankruptcy, February 15, 2013:
http://www.fas.org/sgp/crs/misc/R41799.pdf
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
Cyberattacke – Hacker spionieren jetzt auch Apple aus
Monty Python – Football – Film
Monty Python – Football – Film
monty python guyswith their crazy ideas
Revealed – Iran Zelzaal Rocket Probable 1-Day Attack on US
Iran Zelzaal Rocket Probable 1-Day Attack on US
A sends:
Our Persian observer reports that Iran has made its southern missile and rocket launchers and silos ready for a probable 1-day attack. Based on what we hear, there is high chance of a very small scale fire exchange between the two sides and then call it a mistake. It is a common practice in such situations and we think such test must happen before the upcoming Iranian presidential election, to have a added-value score for Americans. It is a military text book fact that such event is going to happen and this article tips off Iranians are concentrating on the south. It also offer thorough details of Zelzaal, a solid fuel rocket that is set to destroy American airplanes before they get the chance to fly off the band [ground].
China-Hacker – Europäische Sicherheitsexperten sagen wachsende Gefahr aus dem Internet voraus
Der Beweis: Hackerangriff auf sparkasse.de
THE INVESTMENT MAGAZINE – THE ORIGINAL – DAS INVESTMENT MAGAZIN – DAS ORIGINAL – Hackeralarm bei den Sparkassen: Unbekannte haben am Montag eine Schadsoftware auf einzelnen Internet-Seiten von sparkasse.de platziert, wie der Deutsche Sparkassen- und Giroverband (DSGV) mitteilte.
“Kunden, die ohne aktuellen und aktiven Virenscanner auf sparkasse.de waren, könnten sich diese Schadsoftware auf den eigenen Rechner geladen haben.” Betroffene Kunden sollten ihren Rechner mit einem gängigen Virenschutzprogramm durchsuchen und die Schadsoftware beseitigen, empfahl der DSGV am Dienstag.
Am Montag sei zwischen 12.45 Uhr und 17.05 ein seit Anfang des Jahres im Internet kursierender Trojaner auf der Sparkassen-Seite aktiv gewesen, erklärte ein DSGV-Sprecher. In dieser Zeit hätten rund 30.000 Besucher die Homepage besucht, auf der diverse Angebote der Sparkassen-Finanzgruppe beworben werden. Einzelne Sparkassen-Filialen oder Online-Banking-Angebote seien nicht betroffen gewesen. “Auch Angriffe auf Homebanking-Programme von Kunden wurden nicht beobachtet.”
Die IT-Experten der Sparkassen-Finanzgruppe nahmen die Seiten am Montag umgehend vom Netz, als sie den Trojaner entdeckten. Die Angebote seien erst nach eingehender Prüfung wieder online gestellt worden, erklärte der DSGV. “Dadurch konnte der Angriffsversuch schnell unterbunden werden.”
TMZ – Porn Star Alexis Texas: No Black Guys for Me, Please!
TMZ – Porn Star Alexis Texas: No Black Guys for Me, Please!
Alexis Texas, one of the most famous porn stars in the world, takes issue against bangin’ black dudes! Is this horribly racist — or just part of her BRILLIANT master plan?
Unveiled by PI – New York Fusion Center Threat Assessment: Major Terror Attacks Against Hotels
New York State Intelligence Center Threat Assessment: Major Terror Attacks against Hotels, 2002-2011
- 12 pages
- For Official Use Only
- March 29, 2012
This product analyzes major terror attacks on hotels and provides a strategic-level assessment of the groups, tactics, and frequency of global terror attacks against hotels from 2002 – 2011. Additionally, the product identifies the deadliest types of attacks, comparing casualty counts and attack methods. The product was derived from media reporting and unclassified, for official use only sources.
Key Assumptions
Radical Islamic groups, including al-Qaeda and al-Qaeda linked groups continue to plan attacks against the West, including the United States (US). These groups view civilians as potential targets and will continue to use a variety of attack methods. Lack of information pertaining to a certain category in this report does not necessarily represent the absence of a threat. However, the frequency and tactic of attack analyzed in this report may indicate the most common vulnerabilities to an attack on the hotel sector.
Executive Summary
Since 2002 there have been 18 major terrorist attacks against hotels worldwide; a major attack is defined as an attack resulting in at least 10 casualties. During this time period there were no attacks against US homeland-based hotels. Groups with a connection to al-Qaeda carried out all but one of these major attacks.
- An attack on a hotel within New York State or the US would most likely follow the current predominant worldwide trend and utilize explosives or small arms.
- Major attacks against hotels were primarily carried out using a military grade explosive; however, an explosive device constructed within the US would most likely use homemade explosives, such as triacetone triperoxide (TATP).
- The use of small arms to attack a US-based hotel may be seen as a more viable option than trying to assemble a homemade explosive. Al Qaeda and their affiliates have encouraged Western-based radicals to use small arms to carry out attacks because of their ease of use and availability in comparison to building an explosive device.
- The likelihood of an al-Qaeda-inspired lone actor successfully attacking a hotel is low. However, lone actors in the US have shown an interest in targeting hotels previously. For example, Farooque Ahmed, arrested in April 2010, conducted pre-operational surveillance at a Washington, D.C. area hotel.
- A key leader or high-profile event/mass casualty opportunity was targeted in nearly 50% of the attacks, and represents a possible motivating factor for targeting.
- The most common tactic used against hotels is a vehicle-borne improvised explosive device (VBIED), accounting for 43% of the attacks analyzed in this report.
…
Film – Monty Python – Dirty Hungarian Phrasebook
Monty Python – Dirty Hungarian Phrasebook
The Dirty Hungarian Phrasebook sketch and courtroom scene from Monty Python’s Flying Circus
TMZ – Did Miss America Wear FAKE Abs?
Miss America Mallory Hagan had rock hard abs during the competition… but recent bikini photos tell quite the different story. So one’s gotta ask — did Miss America FAKE her awesome abs!?
Unveiled – TEPCO Handouts on Fukushima Daiichi Nuclear Plant
|
TOP-SECRET – Moynihan Commission on Protecting and Reducing Government Secrecy Report

Commission on Protecting and Reducing Government Secrecy
- Senate Document 105-2
- 275 pages
- December 31, 1997
It is time for a new way of thinking about secrecy.
Secrecy is a form of government regulation. Americans are familiar with the tendency to overregulate in other areas. What is different with secrecy is that the public cannot know the extent or the content of the regulation.
Excessive secrecy has significant consequences for the national interest when, as a result, policymakers are not fully informed, government is not held accountable for its actions, and the public cannot engage in informed debate. This remains a dangerous world; some secrecy is vital to save lives, bring miscreants to justice, protect national security, and engage in effective diplomacy. Yet as Justice Potter Stewart noted in his opinion in the Pentagon Papers case, when everything is secret, nothing is secret. Even as billions of dollars are spent each year on government secrecy, the classification and personnel security systems have not always succeeded at their core task of protecting those secrets most critical to the national security. The classification system, for example, is used too often to deny the public an understanding of the policymaking process, rather than for the necessary protection of intelligence activities and other highly sensitive matters.
The classification and personnel security systems are no longer trusted by many inside and outside the Government. It is now almost routine for American officials of unquestioned loyalty to reveal classified information as part of ongoing policy disputes—with one camp “leaking” information in support of a particular view, or to the detriment of another—or in support of settled administration policy. In the process, this degrades public service by giving a huge advantage to the least scrupulous players.
The best way to ensure that secrecy is respected, and that the most important secrets remain secret, is for secrecy to be returned to its limited but necessary role. Secrets can be protected more effectively if secrecy is reduced overall.
Benefits can flow from moving information that no longer needs protection out of the classification system and, in appropriate cases, from not classifying at all. We live in an information-rich society, one in which more than ever before open sources—rather than covert means of collection—can provide the information necessary to permit well-informed decisions. Too often, our secrecy system proceeds as if this information revolution has not happened, imposing costs by compartmentalizing information and limiting access.
Greater openness permits more public understanding of the Government’s actions and also makes it more possible for the Government to respond to criticism and justify those actions. It makes free exchange of scientific information possible and encourages discoveries that foster economic growth. In addition, by allowing for a fuller understanding of the past, it provides opportunities to learn lessons from what has gone before—making it easier to resolve issues concerning the Government’s past actions and helping prepare for the future.
This does not mean that we believe the public should be privy to all government information. Certain types of information—for example, the identity of sources whose exposure would jeopardize human life, signals or imagery intelligence the loss of which would profoundly hinder the capability to collect critical data, or information that could aid terrorists—must be assiduously protected. There must be zero tolerance for permitting such information to be released through unauthorized means, including through deliberate or inadvertent leaks. But when the business of government requires secrecy, it should be employed in a manner that takes risks into account and attempts to control costs.
It is time to reexamine the long-standing tension between secrecy and openness, and develop a new way of thinking about government secrecy as we move into the next century. It is to that end that we direct our recommendations.
Ours is the first analysis authorized by statute of the workings of secrecy in the United States Government in 40 years, and only the second ever. We started our work with the knowledge that many commissions and reports on government secrecy have preceded us, with little impact on the problems we still see and on the new ones we have found.
In undertaking our mission to look at government secrecy, we have observed when the secrecy system works well, and when it does not. We have looked at the consequences of the lack of adequate protection. We have sought to diagnose the current system, and to identify what works and ways the system can work better. Above all, we have sought to understand how best to achieve both better protection and greater openness.
That the secrecy system that evolved and grew over the course of the 20th century would remain essentially unchanged and unexamined by the public was predictable. It is to be expected of a regulatory system essentially hidden from view. Some two million Federal officials, civil and military, and another one million persons in industry, have the ability to classify information. Categories of administrative markings also have proliferated over time, and the secrecy system has become ever more complex. The system will perpetuate itself absent outside intervention, and in doing so maintain not only its many positive features, but also those elements that are detrimental to both our democracy and our security.
It is time for legislation. There needs to be some check on the unrestrained discretion to create secrets. There needs to be an effective mode of declassification.
To improve the functioning of the secrecy system and the implementation of established rules, we recommend a statute that sets forth the principles for what may be
declared secret.Apart from aspects of nuclear energy subject to the Atomic Energy Act, secrets in the Federal Government are whatever anyone with a stamp decides to stamp secret. There is no statutory base and never has been; classification and declassification have been governed for nearly five decades by a series of executive orders, but none has created a stable and reliable system that ensures we protect well what needs protecting but nothing more. What has been consistently lacking is the discipline of a legal framework to clearly define and enforce the proper uses of secrecy. Such a system inevitably degrades.
We therefore propose the following as the framework for a statute that establishes the principles on which classification and declassification should be based:
Sec. 1 Information shall be classified only if there is a demonstrable need to protect the information in the interests of national security, with the goal of ensuring that classification is kept to an absolute minimum consistent with these interests.
Sec. 2 The President shall, as needed, establish procedures and structures for classification of information. Procedures and structures shall be established and resources allocated for declassification as a parallel program to classification. Details of these programs and any revisions to them shall be published in the Federal Register and subject to notice and comment procedures.
Sec. 3 In establishing the standards and categories to apply in determining whether information should be or remain classified, such standards and categories shall include consideration of the benefit from public disclosure of the information and weigh it against the need for initial or continued protection under the classification system. If there is significant doubt whether information requires protection, it shall not be classified.
Sec. 4 Information shall remain classified for no longer than ten years, unless the agency specifically recertifies that the particular information requires continued protection based on current risk assessments. All information shall be declassified after 30 years, unless it is shown that demonstrable harm to an individual or to ongoing government activities will result from release. Systematic declassification schedules shall be established. Agencies shall submit annual reports on their classification and declassification programs to the Congress.
Sec. 5 This statute shall not be construed as authority to withhold information from the Congress.
Sec. 6 There shall be established a National Declassification Center to coordinate, implement, and oversee the declassification policies and practices of the Federal Government. The Center shall report annually to the Congress and the President on its activities and on the status of declassification practices by all Federal agencies that use, hold, or create classified information.
…
STASI-Agent enttarnt – Deckname IM “Jochen”
Monty Python and the Holy Grail – She’s a witch!
Monty Python and the Holy Grail… 😀
Unveiled by Cryptome – Saudi Arabian Drone Base Under Construction
|
TMZ – Beyonce’s ‘Life Is But a Dream’ — Is She WORSE than Gwyneth Paltrow?
TMZ – Beyonce’s ‘Life Is But a Dream’ — Is She WORSE than Gwyneth Paltrow?
Beyonce has been leading a rather highfalutin lifestyle as of late… but has she become more hoighty-toighty than Gwyneth Paltrow? One man dared to ask the question…
PI – New Jersey Fusion Center School Shootings Commonalities Analysis

New Jersey Regional Operations Intelligence Center School Shootings Commonalities
- 5 pages
- For Official Use Only
- November 15, 2012
(U//FOUO) This report attempts to analyze the indicators and commonalities of recent school shootings in an effort to inform public safety officials and assist in the detection and prevention of potential school shooter plots or attacks. All incidents included in this assessment occurred in the United States while classes were in session. Domestic violence shootings and gang violence were not included in an effort to differentiate between “active shooter” incidents and other acts of violence. DHS defines an “active shooter” as an individual actively engaged in killing or attempting to kill people in a confined and populated area.
(U//FOUO) Recently several school shooting plots and attacks have occurred throughout the United States, which has resulted in the deaths and injuries of their victims. These incidents included:
- January 2011 (Utah) – Law enforcement officers arrested two teenagers after discovering that they planned to bomb their high school. The two suspects had blueprints of the school and planned to escape after their attack by stealing a plane at a nearby airport.
- February 2011 (Ohio) – A student killed three classmates and injured two others at a high school when he opened fire in the cafeteria.
- April 2012 (California) – A school shooting left seven people dead and three others wounded when a nursing student opened fire at a small Christian college.
- October 2012 (Maryland) – A 15-year old high school student shot and critically injured a classmate on the first day of school.
(U//FOUO) One or more plots or shootings have occurred in each of the last 10 years in the United States, resulting in the deaths of students and school administrators. These attacks have occurred at all types of schools, including elementary, high school, college, and other educational institutions. In every instance of a school shooting attack in the United States during this period, the attacker has used small arms or homemade explosives.
…
Use of Social Media
(U//FOUO) In the past several years, the majority of students who have conducted plots or attacks against their schools have publicized their anger or intentions through the use of social media. Not every instance of expression of anger will necessarily result in violence, but when school shootings have occurred, the perpetrators have often previously expressed a fixation with death or inflicting pain on others.
(U//FOUO) While students have used social media to express their anger and intentions to attack their schools, this type of action is neither new nor limited to online activity. Even without the use of online media, students have expressed their frustration and intentions through other outlets by using handwritten journals, notes, and drawings. These documents can indicate pre-operational planning, as illustrated in the 1999 Columbine shooting. Diary entries of the Columbine shooters, released in 2006, not only contained their anger but also reminders to fill ammunition clips and acquire bomb-making materials, including nails, propane, and fuses.
(U//FOUO) Recent examples of students publicizing their intentions to plot or attack their schools include the following:
January 2011 (Nebraska) – A high school student who shot one administrator and killed another posted ominous messages on his Facebook page that read., “You’re gonna hear about the evil [expletive] I did but that [expletive] school drove me to this. I want you guys to remember me for who I was before this. I greatly affected the lives of the families ruined but I’m sorry. Goodbye.” These attacks occurred despite the existence of these postings because friends or family were unaware of these writings until law enforcement investigated the shootings and searched the students’ computers.
February 2012 (Ohio) – Authorities discovered several Facebook postings by a high school student attending Chardon High School after he killed three classmates. One of his Facebook postings read, “He longed for only one thing, the world to bow at his feet,” and ended ominously, “Die, all of you.”
In 2012 law enforcement officers arrested several students after they posted threatening language online. In one instance, in January 2012, two students were arrested for planning to bomb their school after one of them shared their plans with another student, who then informed school officials. When questioned by law enforcement, one of the students stated that not only was the 1999 Columbine High School shooting their inspiration, but also that they hoped to surpass its death toll. This instance and several others in which a concerned student or parent informed the local police department, preventing the attack, demonstrate the importance of reporting suspicious activities.
(U//FOUO) While social media has provided students with a venue to post their anger and intent, the Internet can also provide them with access to violent web sites. Violent online material has the potential to influence an already emotionally troubled student producing sometimes negative and deadly consequences. In 2005 a 16-year old, who posed messages on a neo-Nazi website calling himself the Angel of Death, killed nine people and wounded seven before committing suicide. Some online material can also provide instructions on weapons use and bomb construction.
…
Who are the shooters?
(U//FOUO) In the last 10 years, male students have been responsible for the majority of school shootings nationwide. Students who perpetrated attacks were also more likely to know their intended targets rather than to attack their victims randomly. When students targeted an administrator, they believed that either the school failed to protect them from bullies, or the student felt school officials unfairly reprimanded them.
(U//FOUO) The remaining attackers were outsiders with no relationship to the school or school employees who attacked their supervisors because of employment disputes. One instance of a school employee attacking a school occurred in March 2012, when hours after a teacher was fired, he returned to school and shot dead a school administrator prior to committing suicide. Outsider shooters with no relation to the school, on the other hand, are more likely to attack their victims randomly because these attackers had no discernible association with the school and had no grievances with any potential victims.
(U//FOUO) In 2006, two separate outsider attackers shared similar tactics, one at Platte Canyon High School in Colorado in September, and another at an Amish school at Nickel Mines, PA, in October. In both incidents, the gunmen attacked the schools, took several female students hostage, and killed one or more students, before taking their own lives moments before law enforcement officers broke into the classrooms. The threat from outside attackers is not, however, limited to a gunman entering a school. Shooters have also targeted students by waiting outside the school or near the perimeter during recess or at dismissal.
BLOOMBERG TV – At Cyber War: How Chinese Hackers Spy on You
Megan Hughes reports on Chinese hackers and efforts to prevent the security breaches. (Source: Bloomberg)
Monty Python – The Cheese Shop sketch
Monty Python – The Cheese Shop sketch
Cryptome unveils Homeland Security TSWG Controlled Items
|
TMZ – Gisele Bundchen’s RIDICULOUS Post-Baby Bikini Bod
Gisele LITERALLY had a baby living inside of her two months ago… and now she looks SMOKING HOT in a bikini! How is that even possible!?
Confidential – New Jersey Fusion Center Mass Shootings Analysis

New Jersey Regional Operations Intelligence Center Mass Shootings Analysis
- 9 pages
- For Official Use Only
- November 28, 2012
(U//FOUO) The mass killing incidents this year at a Sikh temple in Wisconsin and a movie theater in Colorado garnered international attention and focused the efforts of public and private sector security officials on the prevention of and response to mass shootings in the United States. This report examines the 29 deadliest mass shootings in the past 13 years, starting with the shootings at Columbine High School in Colorado in 1999, to identify commonalities and trends. These 29 incidents include shooting incidents in which at least five people were killed.
(U//FOUO) DHS defines an “active shooter” as an individual actively engaged in killing or attempting to kill people in a confined and populated area. In most cases, active shooters use firearms, and there is no pattern or method to their selection of victims. Active shooter situations are unpredictable and evolve quickly. Typically, the immediate deployment of law enforcement is required to stop the shooting and mitigate further harm to victims. Typically, active shooter situations are over within 10 to 15 minutes.
Key Findings
- (U//FOUO) An analysis of 29 mass shooting incidents in the United States since 1999 indicates that nearly half were workplace shootings.
- (U//FOUO) All of the shooters but one were males between the ages of 17 and 48. All but one of the 29 incidents were conducted by single shooters.
- (U//FOUO) Most of the active shooters took their own lives or were shot by responding police officers.
- (U//FOUO) Only four of the shooters were current or former members of the military.
- (U//FOUO) Semiautomatic handguns were the most commonly used type of weapon in the mass shootings.
…
Analysis of Mass Shootings Since 1999
(U//FOUO) The 29 mass shootings incidents since 1999 – listed in Appendix 1 – were analyzed to identify commonalities and trends. These include the following:
- Males between the ages of 17 and 48 conducted all of the attacks but one.
- The largest number of mass shootings – 13 of the 29 – occurred at the workplace and were conducted by either a former employee or relative of an employee.
- All of the active shooters were single attackers, with the exception of two students who conducted the shootings at Columbine High School.
- In most of the incidents – 20 of the 29 – the active shooters took their own lives or law enforcement was forced to shoot and kill them, thus leaving their true motives uncertain.
- In only four of the 29 incidents were the shooters active or former members of the U.S. military.
- Semiautomatic handguns are the weapon of choice for mass shootings.
Active Shooters: How to Respond
(U//FOUO) Following the tragedy that occurred at Virginia Tech in 2007, the U.S. Department of Homeland Security released a document with recommendations on what to do in the event of an active shooter situation. The most critical recommendation is for both law enforcement and the private sector to have training and conduct drills in order to be prepared for an active shooter incident.
(U//FOUO) In many of the case studies discussed, there were indicators of potential violence. The following is a list of warning signs that an employee may exhibit in the workplace:
- Increased use of alcohol and/or illegal drugs.
- Unexplained increase in absenteeism; vague physical complaints.
- Noticeable decrease in attention to appearance and hygiene.
- Depression/withdrawal.
- Resistance and overreaction to changes in policy and procedures.
- Repeated violations of company policies.
- Increased severe mood swings.
- Noticeably unstable, emotional responses.
- Explosive outbursts of anger or rage without provocation.
- Suicidal; comments about “putting things in order.”
- Paranoid behavior or utterances (“Everybody is against me”).
- Increasingly talks of problems at home.
- Escalation of domestic problems into the workplace; talk of severe financial problems.
- Talk of previous incidents of violence.
- Empathy with individuals committing violence.
- Increase in unsolicited comments about firearms, other dangerous weapons and violent crime.
Monty Python Upperclass Twit of the Year – Film
The Upperclass Twit of the Year race (full version with all events) from Monty Python’s Flying Circus
Monty Python – Blackmail – Film
Monty Python – Blackmail
SECRET – NSA Field Generation and Over-the-Air Distribution of COMSEC Key Manual

NAG-16F FIELD GENERATION AND OVER-THE-AIR DISTRIBUTION OF COMSEC KEY IN SUPPORT OF TACTICAL OPERATIONS AND EXERCISES
- 99 pages
- For Official Use Only
- May 2001
1. (U//FOUO) Where Are We Heading? – A major evolution in communications security (COMSEC) keying technology has begun. Under the Electronic Key Management System (EKMS) program, standards, hardware, and applications are being developed to apply state of the art automation to generate, distribute, load, control, and account for COMSEC key. The program incorporates sufficient backward compatibility to assure that both future, automated key and existing, common electronic key can be handled. EKMS hardware is being fielded, but full development of tailored tactical key generation and distribution programs may take several more years.
2. (U//FOUO) Where Are We Now? – Until EKMS Key Processors (KPs) and local management devices (LMDs) are fully implemented throughout the tactical forces, military commanders must be able to establish secure communications, without needless and/or redundant prepositioning of key or last minute key tape distribution. This document prescribes pre-EKMS techniques to satisfy that requirement, but emphasizes use of available EKMS terminals and other key variable generators (KVGs) to generate tactical key.
3. (U//FOUO) Interoperability – Effective and timely creation of secure tactical nets and circuits requires that communications planners and operators have a common base of understanding regarding applicable COMSEC procedures and equipment operating instructions. This document fulfills that requirement for Joint commands and their Service components. It also has limited applicability in multi-national operations and exercises, when the Allied participants use COMSEC equipment that is capable of over-the-air key distribution (OTAD).
NOTE: (U//FOUO) ACP-132A, Field Generation and Over-the-Air Distribution of Key in Support of Tactical Operations and Exercises, is the equivalent of NAG-16F for use by the military forces of Australia, Canada, New Zealand, and the United Kingdom. U.S. tactical forces do not hold ACP-132A, because its provisions are similar to those of NAG-16F.
NOTE: (U//FOUO) NAG-22A, Over-the-Air Rekeying of Combined Tactical Nets and Circuits, is a partial equivalent of NAG-16F intended to explain over-the-air rekeying (OTAR) to Allied users of “S” nomenclatured (special purpose) COMSEC equipment. When Combined nets/circuits include terminals equipped with “S” equipment, a U.S. station equipped with “K” nomenclatured equipment must serve as the net control station (NCS). U.S. tactical forces do not hold nor need NAG-22A.
NOTE: (U//FOUO) SDIP-14, Operational Doctrine for TSEC/KW-46 Fleet Broadcast, includes doctrine for Over-The-Air Transfer (OTAT) of tactical key via the single-channel North Atlantic Treaty Organization (NATO) fleet broadcasts. U.S. Navy (USN) tactical forces having NATO missions should hold SDIP-14.
4. (U//FOUO) Implementation – The principal advantage of the key management procedures presented here is flexibility to create a continuing supply of tactical key for a variety of commonly held COMSEC equipment and to distribute it electronically to potential users. The key generation and distribution routines given are particularly suitable for support of Joint operations and exercises involving forces that do not routinely train together. However, they cannot be relied upon to contribute to joint mission accomplishment, unless required levels of user competency are maintained through incorporation into intra-Service operations and exercises.
…
b. (U) Purpose – This document is intended as the standard U.S. user’s manual for planning and conducting field key generation and OTAD in support of tactical activities. It is targeted primarily at Joint and Intra-Service Operations and Exercises, particularly those involving forces that do not routinely train or operate together. It also has limited application to Combined operations and exercises involving Allied forces that hold OTAR- and OTAT-capable COMSEC equipment.
…
1. (U) INTRODUCTION
a. (U//FOUO) Perspective – Field generation and Over-The-Air-Distribution (OTAD) of the COMSEC key needed to support tactical communications offers distinct operational advantages over dependence on centrally produced, physically distributed tape key. Communications efficiency and flexibility can be materially enhanced, if secure tactical nets and circuits are established and rekeyed with field-generated TEK that is distributed via Over-The-Air Rekeying (OTAR). Pending full implementation of the Electronic Key Management System (EKMS), operational flexibility can also be enhanced if TEK for other tactical applications is distributed via Over-the-Air Transfer (OTAT), between Data Transfer Device (DTDs), using STU-III, STU-IIIA, STU-IIB, STE, or KY-68 secured telephone circuits, KW-46 secured broadcasts, or nets/circuits secured by KG-84A/C and KIV-7/7HS equipment. Commanders who generate and electronically distribute needed key have maximum latitude to structure their communications to support mission requirements and to react quickly to fluid tactical situations and potentially serious key compromises.
b. (U) Purpose – This document is intended as the standard U.S. user’s manual for planning and conducting field key generation and OTAD in support of tactical activities. It is targeted primarily at Joint and Intra-Service Operations and Exercises, particularly those involving forces that do not routinely train or operate together. It also has limited application to Combined operations and exercises involving Allied forces that hold OTAR- and OTAT-capable COMSEC equipment.
c. (U) Definitions & Acronyms – Many of the specialized terms used in this document are defined in Annex A. Acronyms that appear in the document are also expanded in Annex A.
d. (U//FOUO) Activation – U.S. commanders at all echelons are authorized and encouraged to direct field generation and OTAD of keys needed to support tactical operations and exercises for which they are responsible.
NOTE: (U//FOUO) The procedures addressed herein are presented as routine communications practices for tactical forces, but exceptions to certain specified COMSEC procedural constraints are authorized during COMSEC emergencies, in which the only viable alternative available to the responsible commander is plain text communications. The distinction between routine communications and COMSEC emergencies must be recognized, so that the emergency easements do not become standard operating practices, when the risks they entail should not be accepted. It is also important to note that the security easements permitted by this manual apply only in tactical applications and may not be extended to fixed-facility or strategic communications.
e. (U//FOUO) Application to TRI-TAC & MSE – The TRI-TAC and Mobile Subscriber Equipment (MSE) tactical communications systems have internal procedures for generating and distributing the keys they use; the provisions of this manual do not apply to those keys. However, due to the vital function they can perform in the production of keys intended for other applications, TRI-TAC/MSE KG-83 and KGX-93/93A KVGs and the KT-83 test equipment used to certify them require special safeguards that do not apply to the other TRI-TAC/MSE COMSEC equipment. These are stated in the following subparagraphs.
(1) (U//FOUO) Using KVGs & Fill Devices – Any certified KVG having all of its tamper detection labels intact may generate 128-bit key at any classification level for any purpose, but fill devices into which KVGs load key must be safeguarded at the level of the most highly classified key they contain.
(2) (U//FOUO) Certifying KT-83s & KVGs – All KT-83s, KG-83s, and KGX-93/93As must be certified to the SECRET level at least every 24 months; none of these equipment need be certified to the TOP SECRET level. Each certification must be accomplished with a certified KT-83 and NSA-approved procedures and may be done by one qualified person who must be cleared at least SECRET. Any certified KT-83 with its tamper detection labels intact may be used to certify any other KT-83 or any KG-83 or KGX-93/93A. One result of this authorization is that any command that holds two or more KT-83s may stagger their certification dates and use one to certify the other, indefinitely. In COMSEC emergencies, responsible commanders are authorized to use KVGs with expired certifications, provided field certification is not feasible and certified replacements have been requisitioned.
(3) (U//FOUO) Storing KT-83s & KVGs – Tamper detection labels are required on all operational KVGs and KT-83s. After tamper detection labels have been applied to them, certified but uninstalled KG-83s, KGX-93/93As, and KT-83s may be stored and handled without Two-Person Integrity (TPI) controls. Installed KVGs may be stored in unmanned TRI-TAC and MSE shelters, if the following conditions are met:
(a) (U//FOUO) Physical Safeguards – Responsible commanders must ensure that adequate physical safeguards are provided for non-operational TRI-TAC/MSE shelters to minimize the risk of theft, tampering, or sabotage to all of the COMSEC equipment stored therein.
(b) (U//FOUO) Tamper Detection Labels – At the time of its last certification, NSA-furnished, coyote logo tamper detection labels must have been applied to each KT-83, KG-83, and KGX-93/93A, in accordance with NSA instructions. Certifying activities must record the serial numbers of the labels they apply to each KT-83 or KVG, so that this information may be made available to investigating elements, if tampering with a certified KVG is suspected. Recorded label serial numbers must also be compared with those removed from each KVG that is recertified at the same facility two or more consecutive times. Any unexplained serial number anomalies must be reported as COMSEC incidents.
NOTE: (U//FOUO) To increase the security of the coyote logo tamper detection labels, NSA has classified them SECRET prior to application; upon application, they are declassified. Any UNCLASSIFIED coyote logo labels on hand at using locations must be brought under SECRET protection. Pertinent questions may be referred to the NSA Protective Technologies Division at (301) 688-6816 of DSN 644-6816.
Monty Python – Arthur ‘Two Sheds’ Jackson – Video
Monty Python – Arthur ‘Two Sheds’ Jackson
A short skit from “Monty Python’s Flying Circus” about where Arthur ‘Two Sheds’ screen name is from.
Unveiled by Cryptome – Saudi Arabia Airports and Air Bases
|
|
TMZ – Kim Kardashian Imitates Jesus Christ?
We all knew Kim Kardashian is one of the biggest celebrities in the world… but now she’s imitating Jesus Chris while on vacation in Brazil. Nice one, Kim…
SECRECY NEWS – ARMY USE OF DRONES IN U.S. IS CONSTRAINED, NOT PROHIBITED
There are significant barriers to the Army's use of unmanned aerial
systems within the United States, according to a new Army manual, but they
are not prohibitive or categorical.
"Legal restrictions on the use of unmanned aircraft systems in domestic
operations are numerous," the manual states. The question arises
particularly in the context of Defense Support of Civil Authorities (DSCA),
refering to military assistance to government agencies in disaster response
and other domestic emergencies.
"Use of DOD intelligence capabilities for DSCA missions--such as incident
awareness and assessment, damage assessment, and search and
rescue--requires prior Secretary of Defense approval, together with
approval of both the mission and use of the exact DOD intelligence
community capabilities. Certain missions require not only approval of the
Secretary of Defense, but also coordination, certification, and possibly,
prior approval by the Attorney General of the United States."
As a general rule, "military forces cannot use military systems for
surveillance and pursuit of individuals." This is precluded by the Posse
Comitatus Act, as reflected in DoD Directive 5525.5.
But there is a possibility that exceptions may arise, the manual
indicates. "[Unmanned aircraft] operators cannot conduct surveillance on
specifically identified U.S. persons, unless expressly approved by the
Secretary of Defense, consistent with U.S. laws and regulations."
See U.S. Army Field Manual FM 3-52, Airspace Control, February 2013
(especially Appendix G):
http://www.fas.org/irp/doddir/army/fm3-52.pdf
"Commanders decide to employ unmanned aircraft systems judiciously. Use of
unmanned aircraft systems requires approval at high levels within the DOD
and the FAA prior to employment in DSCA," the manual states.
"Certain unmanned aircraft systems such as Global Hawk can operate far
above normal commercial traffic while providing situation assessment to
ground commanders. Intermediate systems such as the Predator have supported
recent disaster operations, dramatically increasing situational awareness
at the joint field office level. If available and authorized, these systems
can provide near-real-time surveillance to command posts for extended
periods. The approval process is not automatic."
The Army manual asserts that the perceived risks of drone failure or
accident are out of proportion to the actual documented risks.
"For example, from 2003 to 2010, small, unmanned aircraft systems flew
approximately 250,000 hours with only one incident of a collision with
another airspace user. However, the perception of the risk posed by small,
unmanned aircraft systems was much greater." (page A-1).
WHAT'S THE DIFFERENCE BETWEEN AN EXECUTIVE ORDER AND A DIRECTIVE?
The Obama Administration issued policy statements this week on critical
infrastructure protection and cyber security, including measures to
encourage information sharing with the private sector and other steps to
improve policy coordination. Curiously, the Administration issued both an
Executive order and a Presidential directive devoted to these topics.
Executive Order 13636 focuses on "Improving Critical Infrastructure
Cybersecurity" while Presidential Policy Directive 21 deals more broadly
with "Critical Infrastructure Security and Resilience."
http://www.fas.org/irp/offdocs/eo/eo-13636.htm
http://www.fas.org/irp/offdocs/ppd/ppd-21.pdf
But the simultaneous release of the two types of Presidential instruction
on overlapping themes raises the question: What is the difference between
an Executive Order and a Presidential Directive?
"There are probably two significant differences between an EO and a PD, at
least to my understanding," said Harold Relyea, who served for decades as a
Specialist in American National Government at the Congressional Research
Service.
"First, in almost all cases, for an EO to have legal effect, it must be
published in the Federal Register. This is a statutory requirement. A PD
does not have to meet this publication requirement, which means it can more
readily be 'born classified'."
"Second," he added, "is the matter of circulation and accountability. EOs
are circulated to general counsels or similar agency attorneys, which can
be readily accomplished by FR publication. Again, a PD may be more
selectively circulated, and this is done through developed routing
procedures. Ultimately, EOs are captured not only in the FR, but also in
annual volumes (Title 3) of the CFR [Code of Federal Regulations]. PDs are
maintained in the files of the NSC staff and, God knows, if anywhere else!
I might also add that a form for EOs has been prescribed (in an EO); no
form has been prescribed (as far as I know) for PDs."
A CRS overview of the various types of "Presidential Directives" authored
by Dr. Relyea in 2008 is available here:
http://www.fas.org/sgp/crs/misc/98-611.pdf
The Justice Department Office of Legal Counsel wrote in a 2000 opinion
that executive orders and directives are equivalent in their force and
impact. "As this Office has consistently advised, it is our opinion that
there is no substantive difference in the legal effectiveness of an
executive order and a presidential directive that is not styled as an
executive order."
http://www.fas.org/irp/offdocs/predirective.html
For reasons that are not immediately clear, President Obama has issued
presidential directives much less frequently than his predecessors. The
latest directive, PDD-21, is only the 21st such Obama directive. By
comparison, President George W. Bush had issued 42 directives by the first
January of his second term. President Clinton had issued 53 directives by
the beginning of his second term.
NORTH KOREA'S NUCLEAR WEAPONS, AND MORE FROM CRS
New and updated reports from the Congressional Research Service obtained
by Secrecy News that have not been made readily available to the public
include the following.
North Korea's Nuclear Weapons: Technical Issues, February 12, 2013:
http://www.fas.org/sgp/crs/nuke/RL34256.pdf
Pakistan's Nuclear Weapons: Proliferation and Security Issues, February
13, 2013:
http://www.fas.org/sgp/crs/nuke/RL34248.pdf
Comprehensive Nuclear-Test-Ban Treaty: Background and Current
Developments, February 12, 2013:
http://www.fas.org/sgp/crs/nuke/RL33548.pdf
Filling U.S. Senate Vacancies: Perspectives and Contemporary Developments,
February 13, 2013:
http://www.fas.org/sgp/crs/misc/R40421.pdf
Child Well-Being and Noncustodial Fathers, February 12, 2013:
http://www.fas.org/sgp/crs/misc/R41431.pdf
Abortion and Family Planning-Related Provisions in U.S. Foreign Assistance
Law and Policy, February 12, 2013:
http://www.fas.org/sgp/crs/row/R41360.pdf
Latin America and the Caribbean: Key Issues for the 113th Congress,
February 8, 2013:
http://www.fas.org/sgp/crs/row/R42956.pdf
U.S. Manufacturing in International Perspective, February 11, 2013:
http://www.fas.org/sgp/crs/misc/R42135.pdf
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
101 East : China’s cyber warriors – rising tide of cyber warfare with the West
Google, the world’s largest internet company, closed down its search engine facility in China after issues with censorship and hacking. The case has highlighted a growing cyber warfare between the West and China. 101 East looks at the role of the internet in China and the rising tide of cyber warfare with the West.
SECRET – U.S. Army Counterinsurgency Patrolling Handbook

COUNTERINSURGENCY PATROLLING HANDBOOK
- 132 pages
- For Official Use Only
- April 2008
Patrols are one of the most common operations a unit will perform in the counterinsurgency (COIN) environment. A patrol is the basis for many other types of operations. Cordon and search, reconnaissance, demonstration of force, security, and traffic control checkpoints are all activities a unit may perform while on patrol. Patrols are invaluable in the COIN environment because they enable units to interface with the indigenous population and gain human intelligence.
This handbook will assist junior leaders in planning and preparing for, executing, and recovering from patrols. It is not intended to be a single-source document. Rather, it is intended to provide techniques used by others to enhance the unit’s standing operating procedures and orders.
The key lessons for patrol leaders in the COIN environment are:
• Patrol planning: Upon receiving the order, leaders must quickly develop an appropriate, detailed plan.
• Patrol preparation: Leaders must ensure that all patrol members know their individual tasks and provide them the necessary resources to succeed.
• Patrol execution: Leaders will accomplish all patrol tasks to standard and guide the patrol to a successful outcome.
• Recovery: Leaders perform multiple tasks during recovery:
• Assemble the intelligence and other data collected during the patrol and pass it to the appropriate staff sections.
• Conduct a thorough after-action review to gain observations, insights, and lessons.
• Supervise equipment and personnel reset to ensure the unit is ready for subsequent operations.Because every unit conducts some kind of patrol, this handbook should be distributed to all units.
…
This chapter provides the patrol leader with an outline of what he needs to accomplish to have a successful patrol in a counterinsurgency (COIN) environment. Because of the uniqueness of the COIN operating environment, patrol leaders must consider many aspects of an operation that they would not consider in a conventional environment.
The patrol leader should learn about the people, topography, economy, history, religion, and culture of the patrol area. He must know the location of villages, roads, fields, and population groups that are in and around the area of his patrol. The patrol leader needs to make sure his map is up to date. He should study the map thoroughly and develop a mental model of the area. This mental model becomes a framework upon which every new piece of information is incorporated into the common operating picture.
Understanding the operational area provides a foundation for analyzing the insurgency:
• Who are the insurgents?
• What drives them?
• What are the agendas of local leaders or power brokers?An insurgency is a competition among many groups, each seeking to mobilize the local populace in support of its agenda; therefore, COIN operations always have more than two sides.
A COIN patrol leader must understand what motivates the people in his area of operations and use those motivations to support the patrol’s mission. Understanding why and how the insurgents are attracting followers is essential. This understanding requires knowing the primary enemy (insurgents, criminal element, local militia, al-Qaeda). Insurgents are adaptive, resourceful, and probably from the local area. The local populace has known these insurgents since they were young. U.S. forces are the outsiders. Insurgents are not necessarily misled or naive. Much of the insurgency’s success may stem from unpopular central government policies or actions by security forces that alienate the local populace.
The genesis of a patrol is a mission from higher headquarters. Following unit standing operating procedures (SOPs) and using normal troop-leading procedures (TLP), the patrol leader may coordinate with the company commander or battalion staff. This coordination should include many of the following items:
• Changes or updates in the enemy situation (improvised explosive devices [IEDs] and sniper hot spots)
• Best use of terrain for routes, rally points, and patrol bases
• Light and weather data
• Changes in the friendly situation (patrol leader’s own and adjacent units’)
• Soldiers with special skills or equipment, such as engineers, sniper teams, scout dog teams, forward observers, or interpreters attached to the unit (later referred to as “integrated units”)
• Use of manned or unmanned aircraft
• Use and location of landing or pickup zones
• Departure and reentry of friendly lines
• Fire support on the objective and along planned routes, including alternate routes
• Rehearsal areas and times
• Special equipment and ammunition requirements
• Transportation support
• Signal plan…
…
Monty Python’s Flying Circus – The Parrot Sketch
Monty Python’s Flying Circus – The Parrot Sketch
TMZ – Kate Upton on Sports Illustrated Swimsuit Cover — AGAIN!
Sexy model Kate Upton made the cover of yet ANOTHER issue of Sports Illustrated’s Swimsuit Edition. That’s one for each boob!
PUBLIC INTELLIGENCE – DHS-FBI Suspicious Activity Reporting Bulletin: Testing of Cybersecurity

ROLL CALL RELEASE
- 1 page
- For Official Use Only
- November 20, 2012
(U//FOUO) Terrorists or cyber criminals might try to discover vulnerabilities in computer systems by engaging in unauthorized testing of cybersecurity in order to exploit those vulnerabilities during an attack. These attempts might include port scanning, phishing, and password cracking. “Social engineering,” another technique, leverages unwitting insider access by eliciting information about operational and security procedures from employees, personnel, and their associates.
(U//FOUO) The following SAR incidents from the NSI shared space demonstrate types of behavior terrorists or cyber criminals might exhibit during the preoperational stage of attacks. Although none were linked to terrorist or other criminal activity, they are cited as relevant examples for awareness and training purposes.
— (U) An individual sent an e-mail to a state government office requesting information on public access to a local reservoir. The e-mail included a link to a Web site that contained malicious software (malware).
— (U) A review of a first responder’s computer system revealed an attempted hacking incident; several Internet Protocol (IP) addresses associated with the probes originated from out-of-state and foreign locations, suggesting that the actual IP addresses were being masked and that the probes were malicious.
— (U) In a likely social engineering attempt, a private business received unsolicited telephone calls from a caller attempting to obtain or confirm information regarding names, titles, e-mail addresses, and access badge numbers for its employees. When asked, the caller provided no contact information and only gave her first name.
(U) Nationwide SAR Initiative (NSI) Definition of Testing of Security
(U) Interactions with or challenges to installations, personnel, or systems that reveal physical, personnel, or cybersecurity capabilities.
(U) Port Scanning – a process of scanning for open computer port(s), enabling attackers to identify potential targets.
(U) Phishing – type of social engineering; fraudulent e-mail or other electronic communications to deceive computer users into disclosing private information or downloading malware.
(U) Password Cracking – attempting to guess passwords, possibly by synchronizing multi-computer attempts using automated utilities that try every possible password.
(U) Note: The Functional Standard v 1.5 defines SAR as “official documentation of observed behavior reasonably indicative of pre-operational planning related to terrorism or other criminal activity.”(U) Possible Indicators of Cybersecurity Testing
(U//FOUO) The following activities may indicate efforts to test cybersecurity for potentially malicious purposes. Depending upon the context—time, location and other indicators—suspicious cyber activity should be reported to the appropriate authorities, particularly if a terrorism or criminal link is suspected.
— (U//FOUO) Unsolicited phone, e-mail, or in-person inquiries asking for employee or organizational information, including official or proprietary information such as organizational structure and networks.
— (U//FOUO) Requests for access to cyber infrastructure physical areas, electronic files, or escalated computer access privileges not required to complete the requestor’s job or task.
— (U//FOUO) Increase in network reconnaissance activity—such as pinging (verification that an IP address exists and accepts requests), port scanning, and intrusion detection system alerts—observed and recognized by IT personnel.
— (U//FOUO) Missing or added computer equipment in the work area, such as laptops, CDs, external hard drives, or thumb drives.
(U) For additional information on cybersecurity best practices, please refer to US-CERT Web page http://www.us-cert.gov/security-publications.
(U//FOUO) First Ammendment activities should not be reported in a SAR or Information Sharing Environment SAR absent articulable facts and circumstances that support the source agency’s suspicion that the behavior observed is not innocent, but rather reasonably indicative of criminal activity associated with terrorism, including evidence of pre-operational planning related to terrorism. Race, ethnicity, national origin, or religious affiliation should not be considered as factors that create suspicion (although these factors may be used in specific subject descriptions).
Monty Python’s Meaning of Life – Organ Donor
Monty Python’s Meaning of Life – Organ Donor
Full Speech Of President Obama – Statement On Fiscal Cliff Negotiations
Full Speech Of President Obama – Statement On Fiscal Cliff Negotiations
Unveiled – Chinese Hacker Movie
Unveiled – Chinese Hacker Movie
Life of Brian – He’s Not The Messiah
SECRET – San Francisco Public Utilities Commission Surveillance

Pilot No. CS-264 To Pilot Wireless Control and Communications System for LED Street Lights and Other Devices
- 18 pages
- June 8, 2012
The SFPUC owns and maintains approximately 18,500 cobra-head type high pressure sodium (HPS) luminaires, located throughout the City of San Francisco’s forty-nine square miles. The SFPUC anticipates replacing the existing HPS street light luminaires with dimmable LED luminaires in the next two years. The SFPUC also plans to install an integrated wireless communication monitoring and control system (wireless system) to remotely manage the LED street lights. The SFPUC would prefer to install the wireless system as part of the SFPUC LED Streetlight Conversion Project, but will consider purchasing luminaires and installing the wireless system at a later date. Ideally, the wireless system will accommodate other wireless devices, unrelated to street lighting, in a common wireless system mesh network.
The City has multiple needs for the secure wireless transmission of data throughout its various neighborhoods and districts. Future needs for the secure wireless transmission of data throughout the City may include:
• Electric vehicle charging stations data transmission
• Electric meter reading
• Gunshot monitoring
• Street surveillance
• Public information broadcasts
• Street parking monitoring devices
• Traffic monitoring
• Traffic signal control
• Pollution monitoring
• Others…
A. General
The purpose of the RFP and subsequent Pilot Project is to identify innovative possibilities unknown to the SFPUC that may be relevant to City agencies in the future. Respondents are invited to define the characteristics and features of an innovative solution for LED street light control, and include this description in their submittal. The information below is provided to help Respondents identify products that meet the SFPUC’s desired performance criteria for LED street light controls, and to guide the submittal as is relates to wireless control of LED luminaires. It is not intended to limit the scope of the SFPUC’s interest in multifunctional wireless systems.
B. Desirable Wireless System Features
1. Endpoint and Gateway Features:
a. UL listing;
b. NEMA and IP rated;
c. ANSI C136.10-2006 compliance;
d. NTCIP 1213 compliance;
e. Solid state and HID lighting compatibility;
f. 120V/240V compatibility;
g. Back-up astronomical clock;
h. Antenna that is less than 4” long;
i. 0-10V dimming capability;
j. Components that can be mounted on or within the luminaire, arm or streetlight pole; and
k. Self-commissioning capability.2. Network Features:
a. Data encryption per AES 128 or 256; and
b. SFPUC hosting of wireless network and data.
3. Controls and Software Functions:
a. Web portal customization per SFPUC requirements;
b. On/off scheduling;
c. Failure detection;
d. Ability to record events and report historical data;
e. Remote, secure web-based access of monitoring and control functions;
f. Luminaire grouping;
g. Automated detection and reporting of cycling lamps, fault conditions, or malfunctioning equipment and hourly reporting of voltage, current, power factor, and energy consumption data at interval of at least 1 transmission per hour;
h. Lumen depreciation adjustment, defined here as gradually increasing LED drive current over time to compensate for light source depreciation. Adaptive lighting capability, defined here as dimming LED streetlight with wireless controls, based upon scheduled dimming events [AND/OR] pedestrian and traffic motion sensor feedback]; and
i. GPS mapping function that provides a geographical representation of streetlights’ locations and operational status.C. The following types of systems and/or solutions will not be considered:
1. Systems that do not default lighting controls to “on” in the event of a failure in controls hardware or network communication;
2. Power line carrier communication systems;
3. Systems that are not compatible with solid state lighting;
4. Systems that do not integrate pedestrian and traffic sensors; and
5. Non-dimmable LED street light control systems.
TMZ – Jewel’s Advice for Homeless People
Singer Jewel was homeless at one point… and she gives a crash course on how to make the MOST out of living on the street!
SECRECY NEWS – LEAK OF WHITE PAPER BOOSTS INTELLIGENCE OVERSIGHT
The unauthorized disclosure last week of a Justice Department White Paper
on the legality of targeted killing of senior al Qaida operatives who are
Americans had the collateral effect of strengthening congressional
oversight of intelligence.
The leak not only fulfilled a stalemated congressional effort to provide
information to the public, but it also catalyzed the long-sought disclosure
of classified documents to the intelligence committees themselves.
Although the intelligence committees received the White Paper in June
2012, they proved powerless on their own to gain its broader public
release, or to acquire their own copies of the underlying legal memoranda.
“I have been calling for the public release of the administration’s
legal analysis on the use of lethal force--particularly against U.S.
citizens--for more than a year," said Sen. Dianne Feinstein, the chair of
the Senate Intelligence Committee in a February 5 statement. "That analysis
is now public...."
In other words, what the chairman of the Senate Intelligence Committee was
unable to accomplish for over a year was achieved by a resourceful reporter
(Michael Isikoff of NBC) along with a cooperative source. That is a
peculiar fact that ought to prompt some soul-searching on the part of the
Committee, which has been relentlessly critical of intelligence-related
leaks.
But the disclosure did more than just make the White Paper available to
the public and launch a substantial public debate on its contents. It also
enhanced the ability of the intelligence committees themselves to gain
access to additional classified records on which oversight depends.
Specifically, it was the leak of the White Paper that enabled the belated
disclosure of two classified Office of Legal Counsel memoranda to the
intelligence committees last week.
The causal relationship between the leak and the release of the OLC memos
was made explicit by White House press secretary Jay Carney at a February 7
press gaggle.
"I mean, there has always been some interest, obviously, but there has
been heightened interest. I think that what you've seen in the -- because
of the public disclosure of the white paper, is that that interest reached
higher levels than in the past, and therefore this decision was made to
make this extraordinary accommodation to provide classified Office of Legal
Counsel advice," Mr. Carney said.
http://www.fas.org/sgp/news/2013/02/wh020713.html
This statement neatly illustrates the synergy that can exist among robust
national security reporting, public awareness and effective intelligence
oversight.
Yet the Senate Intelligence Committee in particular seems to have lost
sight of the benefits for its own work of press attention and public
engagement. The February 7 hearing on the nomination of John Brennan to be
Director of CIA marked the end of a period of more than one year -- dating
from January 31, 2012 -- without a public hearing. This may be an
unprecedented hiatus in the history of the Senate Committee. (The House
Intelligence Committee has held public hearings more frequently.) In light
of last week's events, the nearly exclusive emphasis on closed hearings
should perhaps be reconsidered.
DOJ WHITE PAPER RELEASED AS A MATTER OF "DISCRETION"
Late Friday afternoon, the Department of Justice released an official copy
of its White Paper on lethal targeting of Americans to Freedom of
Information Act requesters, including FAS and Truthout.org, several days
after it had been leaked to the press.
http://www.fas.org/irp/eprint/doj-lethal.pdf
The official version appears to be identical to the document posted by NBC
News, except that it contains a notation on the first page stating "Draft
November 8, 2011." (It also lacks the heavy-handed NBC watermark.)
"The Department has determined that the document responsive to your
request is appropriate for release as a matter of agency discretion," wrote
Melanie Ann Pustay, director of the Office of Information Policy at the
Department of Justice.
http://www.fas.org/sgp/news/2013/02/oip-020813.pdf
This is a surprising statement, because as recently as two or three weeks
earlier, the Department had said exactly the opposite.
"The document is protected by the deliberative process privilege, and is
not appropriate for discretionary release at this time," wrote Paul Colborn
of the DoJ Office of Legal Counsel in a January 23, 2013 denial letter to
the New York Times.
http://documentcloud.org/documents/566817-white-paper-foia-denial.html
What changed in the interim? Obviously, the fact that the document leaked
-- and had already been read by most people who cared to do so -- altered
DoJ's calculation. The decision to cease withholding the document in light
of its public availability displays some minimal capacity for
reality-testing. To continue to insist that the document was protected and
exempt from release would have been too absurd.
But the Freedom of Information Act process is supposed to meet a higher
standard than "not absurd," and in this case it failed to do so.
According to a FOIA policy statement issued by Attorney General Eric
Holder in 2009, "an agency should not withhold information simply because
it may do so legally. I strongly encourage agencies to make discretionary
disclosures of information. An agency should not withhold records merely
because it can demonstrate, as a technical matter, that the records fall
within the scope of a FOIA exemption."
The Attorney General's policy cited President Obama's own statement on
FOIA which declared that "The Government should not keep information
confidential merely because public officials might be embarrassed by
disclosure, because errors and failures might be revealed, or because of
speculative or abstract fears."
The pre-leak withholding of the White Paper on targeted killing appears to
have been inconsistent with both policy statements. It is now clear that
only "speculative or abstract fears" were at issue, not actual hazards.
Was the release of the memo "a threat to national security"? A reporter
asked that question at the White House press briefing on February 5. "No.
No," said Press Secretary Jay Carney. "It wasn't designed for public
release, but it's an unclassified document."
"And since it is out there," he added, "you should read it."
http://www.fas.org/sgp/news/2013/02/wh020513.html
Last week, Reps. Darrell Issa and Elijah Cummings of the House Committee
on Oversight and Government Reform asked the Department of Justice to
explain several apparent inconsistencies between FOIA policy and actual
practice.
"The Committee seeks information about a number of issues including what
many term as outdated FOIA regulations, exorbitant and possibly illegal fee
assessments, FOIA backlogs, the excessive use and abuse of exemptions, and
dispute resolution services," they wrote in a February 4 letter.
http://www.fas.org/sgp/congress/2013/ogr-oip.pdf
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
Monty Python’s Flying Circus – Cops & Robber
Monty Python’s Flying Circus – Cops & Robber
Confirmed – German Left party’s Gysi scrutinised for alleged Stasi ties
German prosecutors have opened preliminary proceedings against Gregor Gysi, one of the Left party’s key election campaign figures, over allegations he lied about links with the former East German secret police, the politician said on Sunday.
Gysi, who leads the Left party’s parliamentary group, has repeatedly faced allegations in the past two decades that as a lawyer in former East Germany he passed information on clients – some of them known dissidents – to the Stasi secret police.
He said on Sunday he was confident the case would be dropped and saw no reason to reconsider his position in a team of eight that is leading the Left party’s campaign for federal elections in September.
“Of course the suit will be discontinued just like previously because I never gave a false affidavit,” he said in a post on social media site facebook. “That’s why there’s not the least reason to reconsider my candidacy.”
According to Welt am Sonntag newspaper, the case brought by a former judge concerns an affidavit Gysi gave in 2011 to block the airing of a TV documentary. In the statement he said he had never knowingly or intentionally reported to the Stasi on his clients or anyone else.
Gysi, whose parliamentary immunity was lifted for the proceedings to be opened, has always said he did not cooperate with the Stasi.
Left co-party leader Bernd Riexinger said the claims lacked substance and dismissed them as electioneering.
“Gregor Gysi is our best man. It doesn’t surprise us that the others attack him. That’s dirty election campaigning,” Riexinger told the Berliner Zeitung daily to be published on Monday.
TMZ – Lindsay Lohan’s Doing Penthouse!
Lindsay Lohan is doing Penthouse, folks! [Disclaimer: Don’t get your hopes up, it’s NOT as cool as it sounds]
SECRET – U.S. Marine Corps Human Intelligence Exploitation Team (HET)

Counterintelligence/Human Intelligence Exploitation Team (HET) Operations in Iraq Quick Look Report
- 8 pages
- For Official Use Only
- August 6, 2008
HET is viewed as a highly valuable and effective intelligence generating asset which, in conjunction with other intelligence sources, provides a significant amount of actionable intelligence during operations in Iraq. “The HET teams produced more reporting … than any other intel asset we have out there.” “HETs have been the pointy tip of the spear in this counterinsurgency fight. Two-thirds of MNF-W operations are directly driven by HET operations.” Key observations from this collection include the following.
• Short dwell times in CONUS between HET personnel deployments required a prioritization of mission oriented training over annual training requirements and professional military education (PME).
• Interviewees stated that the addition of the counterintelligence (CI)/HUMINT SNCO to the TTECG staff has resulted in the insertion of more realistic HUMINT scenarios during Mojave Viper (MV). HETs typically link up with their supported battalions for the first time at MV.
• 1st Intelligence Battalion and CI/HET Company leaders stated that they were manned at 70% of their linguist requirements, and that time for language training was insufficient: “There’s just not enough time for the language piece.”
• Interviewees stated that very little HUMINT is being gathered by Marines from the female portion of the Iraqi population. Without female CI/HUMINT Marines, it is difficult to gain access to Iraqi females in view of cultural norms relating to females being alone with males not related to them. The majority of those interviewed favored allowing women into the CI/HUMINT field.The remainder of this report contains more detail and recommendations on the above and other topics.
Background
This in-theater collection was conducted in Iraq over a 60 day period from April to June 2008, and was a continuation of the focused collection effort on units participating in Operation Iraqi Freedom and Operation Enduring Freedom (OIF and OEF), as directed by the Deputy Commandant for Combat Development and endorsed by the Commanding Generals, I and II Marine Expeditionary Force. The collection sought to examine the mission, scope, successes, shortfalls, equipment, manning and emerging issues associated with human intelligence exploitation teams that deployed to Iraq during OIF 08.1.
The CI mission is to conduct counterintelligence activities to identify and counteract the threat posed by foreign intelligence capabilities and by organizations or individuals engaged in espionage, sabotage, subversion or terrorism. The HET mission is to collect and report timely, accurate and mission focused information from human sources in order to fulfill tactical, MEF, theater and national level intelligence requirements.
Key Points:
With a dwell time in CONUS of five months between seven month deployments, completion of pre-deployment training was challenging for the members of CI/HUMINT Company, 1st Intelligence Battalion from which the HETs were sourced. Post-deployment leave and multiple holidays further reduced available training time. To successfully complete mission specific training, annual training and professional military education (PME) were sacrificed. Time available for language and cultural training was viewed as insufficient. The cumulative effect of multiple deployments added to the impact of a short PTP period for CI/HUMINT Marines.
MCCLL note: Commenting on a draft of this report, the lead CI/HUMINT officer at Intelligence Department (IOC), HQMC noted that, “The high operational tempo affects not just CI/HUMINT Marines, but the entire intelligence community. Our SIGINT Marines are currently in a 1:0.9 dwell right now as opposed to a 1:1 for CI/HUMINT.”
Pre-deployment training was viewed as effective in achieving mission specific training goals. Mojave Viper served as a cohesion building experience for HETs and their supported battalions, and provided an opportunity to educate the battalions on HET capabilities. The addition of the CI/HUMINT SNCO to the TTECG staff resulted in the insertion of more realistic HUMINT scenarios during MV. Some HET Marines expressed the opinion that they did not need MV military operations in urban terrain (MOUT) and tactical training but rather just the FINEX. Specialized courses provided by private contractors received positive reviews. These courses included the interrogation and source operations course provided by C-HET Solutions; the Reid Associates Detainee Operations Course and the Harris Radio Course.
Interviewees stated that training for Mine Resistant Armor Protected (MRAP) vehicles, crew-served weapons, language and cultural knowledge was insufficient. Limited training time was most often cited as the problem. The extended length of time needed to develop an effective language capability was a strong concern since this is considered a critical HET skill.
MCCLL note: The Tactical Iraqi Language and Culture Training System (TILTS) is a personal computer based, scenario-oriented software program that can be used for pre-deployment or in-country training to give Marines a usable grasp of Iraqi culture, gestures, and situational language. The goal of TILTS is to shrink language and cultural training time from several months of traditional classroom learning to 80 hours or less of hands on computer based interactive training. This training can be taken in increments, integrated with existing pre-deployment training. Other languages available are Pashtu, Dari and French. Commenting on a draft of this report, the Operations Officer, Center for Advanced Operational Cultural Learning (CAOCL) notes that “CAOCL has developed a multitude of other classroom and distributed learning (DL) training products. TLTS is a DL product designed for use as a tool in-conjunction with other CAOCL sponsored training modules in an overall blended learning environment with respect to the PTP Continuum,” that CAOCL can provide units targeted training, and that language and regional expertise requirements must be identified far enough in advance so that required training and funds can be projected.
HETs in direct support of infantry battalions are dependent on their supported battalion for mobility and security. With Iraqi Security Forces (ISF) assuming increasing responsibility for security, and as USMC infantry units begin to go into an overwatch posture, HETs are faced with the challenge of how to continue to operate in their AO. There is a strong feeling that HETs should be provided with their own organic mobility and security in the future. At the start of the OIF 08.1 deployment, 1st Intelligence Battalion recruited a convoy security element from infantry and reservists who volunteered to deploy for this purpose. This test concept proved effective but is probably not the long term solution needed. Those planning to deploy HETs in upcoming deployments must consider their mobility and security needs in a changing operational environment.
Monty Python Holy Grail – Constitutional Peasants
Monty Python Holy Grail – Constitutional Peasants
TOP-SECRET – West Point Combating Terrorism Center Report

Challengers from the Sidelines: Understanding America’s Violent Far-Right
- 148 pages
- November 2012
In the last few years, and especially since 2007, there has been a dramatic rise in the number of attacks and violent plots originating from individuals and groups who self-identify with the far-right of American politics. These incidents cause many to wonder whether these are isolated attacks, an increasing trend, part of increasing societal violence, or attributable to some other condition. To date, however, there has been limited systematic documentation and analysis of incidents of American domestic violence.
This study provides a conceptual foundation for understanding different far-right groups and then presents the empirical analysis of violent incidents to identify those perpetrating attacks and their associated trends. Through a comprehensive look at the data, this study addresses three core questions:
(1) What are the main current characteristics of the violence produced by the far right?
(2) What type of far-right groups are more prone than others to engage in violence? How are characteristics of particular far-right groups correlated with their tendency to engage in violence?
(3) What are the social and political factors associated with the level of far-right violence? Are there political or social conditions that foster or discourage violence?
It is important to note that this study concentrates on those individuals and groups who have actually perpetuated violence and is not a comprehensive analysis of the political causes with which some far-right extremists identify. While the ability to hold and appropriately articulate diverse political views is an American strength, extremists committing acts of violence in the name of those causes undermine the freedoms that they purport to espouse.…
3.1.2 – Anti-Federalist Movement: Ideological Foundations
In contrast to the relatively long tradition of the white supremacy racist movement, the anti-federalist movement appeared in full force only in the early to mid-1990s, with the emergence of groups such as the Militia of Montana and the Michigan Militia. Anti-federalism is normally identified in the literature as the “Militia” or “Patriot” movement. Anti-federalist and anti-government sentiments were present in American society before the 1990s in diverse movements and ideological associations promoting anti-taxation, gun rights, survivalist practices, and libertarian ideas. However, most scholars concur that the 1980s “farm crises,” combined with the implications of rapid economic, cultural and technological changes in American society, growing political influences of minority groups, and attempts to revise gun control and environmental legislation, facilitated the rapid emergence of a cohesive movement in the mid to late 1990s. In other words, the militia movement was a reactive social movement which mobilized in response to specific perceived threats.
The anti-federalist movement’s ideology is based on the idea that there is an urgent need to undermine the influence, legitimacy and practical sovereignty of the federal government and its proxy organizations. The groups comprising the movement suggest several rationales that seek to legitimize anti-federal sentiments. Some groups are driven by a strong conviction that the American political system and its proxies were hijacked by external forces interested in promoting a “New World Order,” (NWO) in which the United States will be embedded in the UN or another version of global government. The NWO will be advanced, they believe, via steady transition of powers from local to federal law-enforcement agencies, i.e., the transformation of local police and law-enforcement agencies into a federally controlled “National Police” agency that will in turn merge with a “Multi-National Peace Keeping Force.” The latter deployment on US soil will be justified via a domestic campaign implemented by interested parties that will emphasize American society’s deficiencies and US government incompetency. This will convince the American people that restoring stability and order inevitably demands the use of international forces. The last stage, according to most NWO narratives, involves the transformation of the United States government into an international/world government and the execution and oppression of those opposing this process. Linda Thompson, the head of the Unorganized Militia of the United States details the consequence of this global coup: ”This is the coming of the New World Order. A one-world government, where, in order to put the new government in place, we must all be disarmed first. To do that, the government is deliberately creating schisms in our society, funding both the anti-abortion/pro-choice sides, the antigun/pro-gun issues…trying to provoke a riot that will allow martial law to be implemented and all weapons seized, while ‘dissidents’ are put safely away”. The fear of the materialization of the NWO makes most militias not merely hostile towards the federal government but also hostile towards international organizations, whether non-profitable NGOs, international corporations, or political institutions of the international community, such as the UN.
The militias’ anti-federalist sentiments are also rationalized by their perception of the corrupted and tyrannical nature of the federal government and its apparent tendency to violate individuals’ civilian liberties and constitutional rights. That is why they are concerned about the transformation of the United States into a police state in which power is used arbitrarily and without accountability. In the words of a Missouri Militia member, “One of the things that people really fear from the government is the idea that the government can ruin your life; totally destroy your life….split your family up, do the whole thing and walk off like you’re a discarded banana peel, and with a ho-hum attitude.”
In the context of violation of constitutional rights, militia members in particular tend to point out the steady increase in gun control and environmental legislation and the overregulation of the economic and social realms, especially in regard to immigration and education issues. The opposition to gun control legislation has been driven mainly by the perception of many that this represents a breach of the Second Amendment and a direct violation of a constitutional right, having direct impact on the ability of many to preserve their common practices and way of life. In contrast, the opposition to environmental legislation has been driven by the economic consequences of this legislation, as perceived by the militia members, in particular the decline of industries which are not environmentally friendly but crucial for the economy in rural areas. The Testimony of Susan Schock reveals the resulting frustration, clearly expressed in the words of Charles Shumway, Arizona Militia member: “Unless the ‘curse’ of the Endangered Species Act was repealed, there would be ‘rioting, bloodshed, rebellion and conflict that will make the Serbian-Bosnia affair look like a Sunday picnic.’”
Finally, many of the militias also legitimize their ideological tendencies by referring to the strong role of civilian activism, civilian paramilitary groups, individual freedoms, and self-governing and frontier culture in America’s history and ethos, especially during the Revolutionary War and the expansion to the West. Hence, members of these groups see themselves as the successors of the nation’s founding fathers, and as part of a struggle to restore or preserve what they regard as America’s true identity, values and way of life.
To conclude, it should be noted that historically some of the anti-federalist groups have absorbed racist and Christian Identity sentiments; nonetheless, the glue binding their membership and driving their activism has been and remains hostility, fear and the need to challenge or restrict the sovereignty of the federal government.
Exclusive Content from the Monty Python Vault – From The Vault #1
TMZ – What Happened to Lindsay Lohan’s Lips!?
What Happened to Lindsay Lohan’s Lips!?
Take a look at this recent photo of Lindsay Lohan. If you can shed some light as to WHAT THE HELL HAPPENED TO HER LIPS, well then, we’re all ears.
SECRECY NEWS – US MILITARY CASUALTY STATISTICS, AND MORE FROM CRS
A sobering compilation of statistics on injuries sustained by U.S.
military personnel in Iraq and Afghanistan was updated this week by the
Congressional Research Service based in part on data that CRS gathered from
the Pentagon.
"This report includes statistics on post-traumatic stress disorder (PTSD),
traumatic brain injury (TBI), amputations, evacuations, and the
demographics of casualties," the CRS report said. "Some of these statistics
are publicly available at the Department of Defense's (DOD's) website,
whereas others have been obtained through contact with experts at DOD."
See "U.S. Military Casualty Statistics: Operation New Dawn, Operation
Iraqi Freedom, and Operation Enduring Freedom," February 5, 2013:
http://www.fas.org/sgp/crs/natsec/RS22452.pdf
Another newly updated CRS report presents an informative and diverting
account of politics in China.
"China's Communist Party dominates state and society in China, is
committed to maintaining a permanent monopoly on power, and is intolerant
of those who question its right to rule. Nonetheless, analysts consider
China's political system to be neither monolithic nor rigidly hierarchical.
Jockeying among leaders and institutions representing different sets of
interests is common at every level of the system."
See "Understanding China's Political System," January 31, 2013:
http://www.fas.org/sgp/crs/row/R41007.pdf
And for good measure there is a CRS report on the legal foundation for
public access to government records. See "Access to Government Information
In the United States: A Primer," January 16, 2013:
http://www.fas.org/sgp/crs/secrecy/97-71.pdf
There is no legal foundation that would guarantee public access to CRS
reports. So they have to be obtained through alternate channels.
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
Monty Python’s Flying Circus – Falling from Building
Monty Python’s Flying Circus – Falling from Building
Unveiled – Cryptome Triple Cross
Cryptome Triple Cross
16 March 2012. Set up to publish documents on the use of conventional XX duplicity to deceive and circumvent more deviously. To examine and expose XX as camouflage for XXX and beyond. Submissions welcomed: cryptomexxx[at]earthlink.net
00033.htm Assange-WikiLeaks Crypto Arms Call Triple Cross December 5, 2012 00032.htm Informancy Industry May 8, 2012 00031.htm Government and Commerce Dupe About Privacy April 20, 2012 00030.pdf Who Watches the Watchmen: Denial and Deception April 19, 2012 (7.0MB) 00029.htm Secret Service DoD Sexual Entrapment by CU/VZ April 18, 2012 00028.pdf US Evaluation Board Secret Deception Operation April 18, 2012 00027.htm OSS Sources and Methods 1940-1947 Entry 220 April 6, 2012 00026.htm OSS Sources and Methods 1940-1947 Entry 219 April 6, 2012 00025.htm OSS Sources and Methods 1940-1947 Entry 218 April 6, 2012 00024.htm OSS Sources and Methods 1940-1947 Entry 217 April 6, 2012 00023.htm OSS Sources and Methods 1940-1947 Entry 216 April 6, 2012 00022.htm OSS Sources and Methods 1940-1947 Entry 215 April 6, 2012 00021.htm OSS Sources and Methods 1940-1947 Entry 214 April 6, 2012 00020.htm OSS Sources and Methods 1940-1947 Entry 213 April 6, 2012 00019.htm OSS Sources and Methods 1940-1947 Entry 212 April 6, 2012 00018.htm OSS Sources and Methods 1940-1947 Entry 211 April 6, 2012 00017.htm OSS Thousands of Sources and Methods Files (see above) April 5, 2012 (offsite) 00016.htm DoD Releases Psyop-Media-SM Deception Docs April 5, 2012 (offsite) 00015.pdf IWG Report on Withheld Records of War Criminals April 5, 2012 (7.4MB) 00014.pdf OSS Personnel April 5, 2012 00013.pdf OSS Terms, Names, Abbreviations, and Code Words April 5, 2012 00012.pdf OSS Covert Operations 1940-1947 April 4, 2012 00011.htm CIA Covert Operations in Europe April 4, 2012 00010.htm Analysis of the Name File of Heinrich Mueller April 4, 2012 (offsite) 00009.htm An American Spy by Olen Steinhauer April 1, 2012
The following eight triple-crossing files are from the CIA Freedom of Information Act Electronic Reading Room. These exemplify triple-crossing by spy services through FOIA releases, favoritism to cooperative media, deliberate leaks, official publications and agency-approved publications by members and former members to use the appearance of openness as disinformation, information management and propaganda. Their purpose is to distort through devious disclosure of files describing such techniques and at a deeper level to demonstrate triple-cross tertiarily.
00008.pdf CIA Deception Research No. 9 1980 24 March 2012 (5.7MB) 00007.pdf Central American Psychological Operations 1953 19 March 2012 (3.0MB) 00006.pdf UK Spy School 1944 19 March 2012 (1.3MB) 00005.pdf Rizzo Triple Agent 1944 19 March 2012 (98KB) 00004.pdf Soviet Triples 1957 19 March 2012 (1.2MB) 00003.pdf Neble Double Agent 19 March 2012 (69KB) 00002.pdf Counterspy 1963 19 March 2012 (1.5MB) 00001.pdf Dogwood 1944 19 March 2012 (2.9MB)
An American Spy by Olen Steinhauer
Everyone lies, for different reasons. The picture is always opaque.
Real espionage is actually like this. Winston Churchill, a keen aficionado of wartime deception, described the spying game as “tangle within tangle, plot and counterplot, ruse and treachery, cross and double-cross, true agent, false agent, double agent, gold and steel, the bomb, the dagger and the firing party . . . interwoven in many a texture so intricate as to be incredible and yet true.” Spying is itself a form of fiction, the creating of invented worlds, which perhaps explains why so many of the best spy novelists were once in the intelligence business: W. Somerset Maugham, Ian Fleming, Graham Greene and le Carré himself.
Ben Macintyre’s latest book, “Double Cross: The True Story of the D-Day Spies,” will be published in July.
![[Image]](https://i0.wp.com/cryptome.xxx/xxx-nato-18.jpg)
A NATO Ministers of Defense meeting begins at NATO Headquarters in Brussels, Belgium on Friday, Feb. 3, 2012. Defense Ministers from across Europe as well as U.S. Defense Secretary Leon Panetta are attending the meeting. (Jacquelyn Martin, Pool)
Conventional XX duplicity
http://definitions.dictionary.net/deceive
Thesaurus words for “deceive”: abuse, bamboozle, be untruthful, befool, beguile, betray, bitch, bluff, bunk, cajole, cheat, cheat on, circumvent, con, conjure, cozen, debauch, defile, deflower, defraud, delude, despoil, diddle, do, dodge, double-cross, draw the longbow, dupe, elude, equivocate, evade, exaggerate, falsify, fib, finesse, foil, fool, force, forestall, four-flush, frustrate, gammon, get around, get round, give the runaround, give the slip, go one better, gull, hoax, hocus-pocus, hoodwink, hornswaggle, humbug, impose on, impose upon, inveigle, juggle, lead astray, lead on, let down, lie, lie flatly, mislead, mock, outfigure, outflank, outgeneral, outguess, outmaneuver, outplay, outreach, outsmart, outwit, overreach, pass the buck, pigeon, play one false, prevaricate, put, put something over, rape, ravage, ravish, ruin, seduce, sell out, shift, shift about, snow, soil, speak falsely, spoof, stonewall, story, stretch the truth, string along, suck in, sully, swindle, take, take in, tell a lie, throw off, trick, twist and turn, two-time, victimize, violate
http://definitions.dictionary.net/circumvent
Thesaurus words for “circumvent”: avoid, baffle, balk, bamboozle, beat, befool, beg, beguile, betray, bilk, blast, bluff, brave, burke, bypass, cajole, challenge, cheat on, checkmate, circle, circuit, circuiteer, circulate, circumambulate, circummigrate, circumnavigate, close the circle, come full circle, compass, confound, confront, conjure, contravene, counter, counteract, countermand, counterwork, cross, cycle, dash, deceive, defeat, defy, delude, describe a circle, destroy, detour, diddle, disappoint, discomfit, disconcert, discountenance, dish, disrupt, ditch, double, double-cross, dupe, elude, encircle, encompass, escape, evade, flank, flummox, foil, forestall, frustrate, gammon, get around, get away from, get out of, get round, girdle, girdle the globe, give the runaround, give the slip, go about, go around, go one better, go round, go the round, gull, gyre, hoax, hocus-pocus, hoodwink, hornswaggle, humbug, juggle, knock the chocks, lap, let down, make a circuit, mock, nonplus, orbit, outfigure, outflank, outgeneral, outguess, outmaneuver, outplay, outreach, outsmart, outwit, overreach, pass the buck, perplex, pigeon, play one false, put something over, revolve, round, ruin, sabotage, scotch, shake, shake off, shuffle out of, sidestep, skirt, snow, spike, spiral, spoil, stonewall, string along, stump, surround, take in, thwart, trick, two-time, upset, victimize, wheel.
http://definitions.dictionary.net/devious
Thesaurus words for “devious”: Byzantine, O-shaped, aberrant, aberrative, ambagious, amoral, anfractuous, artful, backhand, backhanded, balled up, bending, calculating, canny, circuitous, circular, complex, complicated, confounded, confused, conscienceless, convoluted, corrupt, corrupted, crabbed, crafty, criminal, crooked, cunning, curving, daedal, dark, deceitful, deceptive, deflectional, departing, designing, desultory, deviant, deviating, deviative, deviatory, digressive, discursive, dishonest, dishonorable, divagational, divergent, diverting, double-dealing, doubtful, dubious, duplicitous, elaborate, embrangled, entangled, errant, erratic, erring, evasive, excursive, felonious, fishy, fouled up, foxy, fraudulent, furtive, guileful, helical, ill-got, ill-gotten, immoral, implicated, indirect, insidious, insincere, intricate, involuted, involved, knotted, knowing, labyrinthian, labyrinthine, left-handed, lonesome, loused up, many-faceted, matted, mazy, meandering, messed up, misleading, mixed up, mucked up, multifarious, not kosher, oblique, orbital, out-of-the-way, pawky, perplexed, planetary, plotting, questionable, rambling, ramified, remote, removed, retired, rotary, rotten, round, roundabout, roving, scheming, screwed up, secret, secretive, serpentine, shady, shameless, shifting, shifty, shrewd, side, sidelong, sinister, sinistral, sinuous, slick, slippery, sly, smooth, snaky, snarled, sneaking, sneaky, spiral, stray, subtile, subtle, surreptitious, suspicious, swerving, tangled, tangly, tortuous, treacherous, tricky, turning, twisted, twisting, unconscienced, unconscientious, unconscionable, underhand, underhanded, undirected, unethical, unprincipled, unsavory, unscrupulous, unstraightforward, vagrant, veering, vulpine, wandering, wily, winding, without remorse, without shame, zigzag
XXX Triplicity
A simple case of XXX is to deploy a comparatively easy to discover duplicity to conceal one more deeply protected. Multi-layered security may serve as a multi-layered decoy to lead away from a deep-bunkered treasure. Identifiably weak comsec may divert from more valuable comms. A small error to indicate a larger mistake which hides a great delusion
TMZ – Kim Kardashian’s Divorce Gets Even NASTIER!
Kris Humphries just made things REALLY UGLY in his divorce from Kim Kardashian… but at least he’s got a sweet sponsorship deal Harvey completely made up to fall back on!
SECRECY NEWS – SPOTLIGHT ON DOD SPECIAL ACCESS PROGRAMS
The procedures for establishing, managing and overseeing special access
programs (SAPs) in the Department of Defense are spelled out in an updated
DoD Instruction that was issued yesterday. See "Management,
Administration, and Oversight of DoD Special Access Programs," DoD
Instruction 5205.11, February 6, 2013.
http://www.fas.org/irp/doddir/dod/i5205_11.pdf
A special access program is a classified program that employs security
measures above and beyond those that would normally be used to protect
ordinary (or "collateral") classified information. Such measures may
include special eligibility reviews, polygraph testing, cover, and other
controls on information. Within DoD, SAPs fall into three broad topical
categories: intelligence, acquisition, and operations and support.
DoD SAPs have been a focus of controversy in the past, because their
intensive secrecy seemed to foster mismanagement. There were massive,
multi-billion dollar failures (e.g., the aborted A-12 naval aircraft
program) as well as the occasional eccentricity (e.g., the Timber Wind
nuclear powered rocket for anti-ballistic missile missions), both of which
triggered Inspector General audits.
http://www.dodig.mil/Audit/Audit2/91-059.pdf
http://www.fas.org/sgp/othergov/dod/tw.pdf
Because of those kinds of missteps, "The special access classification
system... is now adversely affecting the national security it is intended
to support," the House Armed Services Committee concluded in 1991 (H.Rept.
102-60, p. 101).
But such concerns are expressed less frequently today. This is partly
because of changes in Congress, but also because the administration of
special access programs at the Pentagon has become less improvisational and
freewheeling, and more standardized. (Whether they are also more successful
is impossible to say.)
The newly updated DoD Instruction defines the SAP "governance structure,"
which consists of a multi-level SAP Oversight Committee (SAPOC), the Senior
Review Group (SRG), and the SAP Senior Working Group (SSWG).
The Instruction also sheds light on the hierarchical structure of some
SAPs, which are in effect SAPs within SAPs: "DoD SAPs may include
subordinate activities identified as, in descending order, compartments,
sub-compartments, and projects."
There is also another SAP hierarchy along an axis of sensitivity.
"Acknowledged SAPs," whose existence may be admitted and made known to
others, are the least sensitive. "Unacknowledged SAPs" (such as Timber
Wind once was) are more sensitive and cannot be referenced. Their very
existence is a classified fact. But both of those categories must be
reported to Congress. "Waived SAPs" are the most sensitive of special
access programs, and they are exempted by statute (10 USC 119e) from normal
congressional notification requirements. In such cases, only eight senior
members of the congressional defense committees may be advised of the
program.
DoD's SAPs are not to be confused with the intelligence community's
Controlled Access Programs (CAPs), which serve a similar function. An
official within the Office of the Under Secretary of Defense (Intelligence)
is responsible for "deconflict[ing] the names and abbreviations for DoD's
SAPs and DNI's CAPs."
It is noteworthy that the new DoD Instruction on SAP management is a
public document. It rescinds and replaces a 1997 Instruction that was
considered too sensitive for public release.
BRENNAN: "PERHAPS" CLASSIFICATION SYSTEM IS OUTDATED
Among the questions submitted to DCIA-nominee John Brennan by the Senate
Intelligence Committee in advance of his much-anticipated confirmation
hearing this afternoon was one about classification policy.
http://www.intelligence.senate.gov/
A recent report to the President from the Public Interest Declassification
Board termed the national security classification system "outdated," the
Committee noted. Does Mr. Brennan agree?
"I would say that the classification system is perhaps outdated in some
respects and the recommendations from the PIDB report warrant further
consideration," he replied (Question 30). "If confirmed as Director, I
would review the PIDB's conclusions and would be glad to get back to the
Committee with my views."
http://www.fas.org/irp/congress/2013_hr/brennan-preh.pdf
In other words, he seemed to say, one of the cornerstones of intelligence
as practiced today may be obsolete, at least "in some respects." But I have
nothing to say about that right now. Let's talk about it after I am
confirmed.
VETERANS AND HOMELESSNESS, AND MORE FROM CRS
Newly updated reports from the Congressional Research Service that have
not been made readily available to the public include the following.
Argentina's Defaulted Sovereign Debt: Dealing with the "Holdouts",
February 6, 2013:
http://www.fas.org/sgp/crs/row/R41029.pdf
Honduras-U.S. Relations, February 5, 2013:
http://www.fas.org/sgp/crs/row/RL34027.pdf
Veterans and Homelessness, February 4, 2013:
http://www.fas.org/sgp/crs/misc/RL34024.pdf
VA Housing: Guaranteed Loans, Direct Loans, and Specially Adapted Housing
Grants, February 4, 2013:
http://www.fas.org/sgp/crs/misc/R42504.pdf
Agricultural Conservation: A Guide to Programs, February 5, 2013:
http://www.fas.org/sgp/crs/misc/R40763.pdf
The National Flood Insurance Program: Status and Remaining Issues for
Congress, February 6, 2013:
http://www.fas.org/sgp/crs/misc/R42850.pdf
Appropriations Subcommittee Structure: History of Changes from 1920 to
2013, February 5, 2013:
http://www.fas.org/sgp/crs/misc/RL31572.pdf
U.S. Special Operations Forces (SOF): Background and Issues for Congress,
February 6, 2013:
http://www.fas.org/sgp/crs/natsec/RS21048.pdf
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
PI – NATO Guidance for Developing Maritime Unmanned Systems (MUS) Capability

Combined Joint Operations from the Sea Centre of Excellence
- 98 pages
- July 9, 2012
In 2008, recognizing a nascent requirement in the maritime security domain, CJOS COE was requested by NATO Allied Command Transformation (ACT) to provide an overall picture of Maritime Unmanned Systems (MUS) as a potential new capability, with a view to create an increased awareness and trigger further developments within the Alliance. The resulting MUS Study, published in November 2009, was then forwarded for endorsement by ACT, to the International Military Staff (IMS). Following this first document, CJOS COE has produced the attached Guidance document building on the initial study and aiming at supporting NATO MUS capability development.
This guidance aims to inform the capability development of Maritime Unmanned Systems (MUS), broadening beyond that currently being exploited by UAV into Unmanned Underwater Vehicles (UUV) and Underwater Surface Vehicles (USV). It covers likely attributes and tasks for MUS, and discusses some of the challenges in developing this capability.
Definition
An MUS is defined as an Unmanned System operating in the maritime environment (subsurface, surface, air) whose primary component is at least one unmanned vehicle. A UUV is defined as a self-propelled submersible whose operation is either fully autonomous (pre-programmed or real-time adaptive mission control) or under minimal supervisory control. They are further sub-divided in 4 vehicles classes (man-portable, Light Weight Vehicle (LWV) Heavy Weight Vehicle (HWV), Large Vehicle Class (LVC).
An USV is defined as a self-propelled surface vehicle whose operation is either fully autonomous (pre-programmed or real-time adaptive mission control) or under minimal supervisory control. They are further sub-divided in 4 vehicles classes (X-Class, Harbour Class, Snorkeler Class, Fleet Class).
Future Capability Requirements The foreseen future Maritime Capability Requirements for MUS are:
a. Persistent ISR, above and below the surface;
b. Capability beyond the high water mark;
c. Cheaper systems;
d. Lower risk to personnel;
e. Less vulnerable to cyber attacks;
f. Stealth;
g. Less collateral damage;
h. Netcentric.MUS Attributes
The areas for MUS to contribute to naval needs derive from their operational advantages, which include: autonomy, risk reduction, deployability, environmental adaptability and persistence.
UUV Missions/Tasks
Nine areas are identified where UUVs can support or conduct a mission:
(1) Intelligence, Surveillance and Reconnaissance (ISR);
(2) Mine Countermeasures (MCM);
(3) Anti-Submarine Warfare (ASW);
(4) Inspection/Identification (ID);
(5) Oceanography/Hydrography;
(6) Communication/Navigation Network Nodes (CN3);
(7) Payload Delivery;
(8) Influence Activities (IA);
(9) Time Critical Strike (TCS).USV Missions/Tasks
The missions that could be executed by a USV are:
(1) Mine Countermeasures (MCM);
(2) Anti-Submarine Warfare (ASW);
(3) Maritime Security (MS);
(4) Surface Warfare (SUW);
(5) Special Operations Forces (SOF) Support;
(6) Electronic Warfare (EW);
(7) Maritime Interdiction Operations (MIO) Support.Key Challenges
Based on today‘s capability, future advances in technology will enhance endurance, processing, autonomy, and interoperability. Many of the missions are demanding in terms of autonomy and propulsion. Achieving the level of autonomous intelligence collection required for persistent capabilities will be challenging. Autonomous modes of operation and the technology required to shift from one level of autonomous operation to another are still under development, many shortfalls have been pointed out in the area of engagement/intervention.
UUVs have a limited ability to communicate with the outside world and the use of UUVs, in particular for CN3, requires considerable electrical power for transmissions.
Cyber defense challenges include threats to the MUS vehicle itself, and its feeds and products. A careful balance between the level of autonomy achieved and the vulnerability to cyber attack will need to be developed.
General
It is considered that the realm of MUS has a lot to offer, increasing operational effectiveness, reducing risk to human life and moreover represents a potential to reduce operational costs.While the greatest cost-effectiveness could be achieved by agreeing to a set of common platforms and command and control systems for such vehicles, ongoing Research and Development (R&D) will still drive future trends in MUS technology. Each nation will need to procure onboard sensors and other payloads according to their own requirements. To date, surface and subsurface MUS capabilities have received much less R&D attention and funding than Unmanned Aerial Vehicles (UAV) and require capital investment to catch up. There is also less data available from which to conduct comparisons of operational effectiveness between manned and unmanned platforms. However, such surface and subsurface capabilities should compliment existing and emerging UAVs to ensure that NATO can effectively counter the wide range of emerging threats in the maritime environment.
Monty Python’s Flying Circus – Conquistador Coffee Campaign
Monty Python’s Flying Circus – Conquistador Coffee Campaign
Unveiled – North Korea’s naval bases – TOP – SECRET-Photos
|
|
PI – Central California Intelligence Center Exploding Gun Targets Report

Exploding Targets: Commercially Available Binary Explosive Agent Poses Potential Public Safety Risks and Concerns
- 5 pages
- For Official Use Only
- October 18, 2012
(U//FOUO) The Central California Intelligence Center (CCIC)/Sacramento Regional Threat Assessment Center (RTAC) has prepared the following Situational Information Report on exploding targets, a commercially available binary explosive agent, to provide law enforcement and public safety officials with a better understanding of the potential public safety risks involving its use. While exploding targets are legally permissible depending on state and local regulations, the CCIC is concerned that the mixture may be more dangerous than what is stated on the manufacturer’s website especially if mishandled by individuals with novice experience in handling explosive components or when used in large quantities to detonate bigger targets and, in essence, creating an explosives or incendiary device. The CCIC is currently unaware of any reporting or incidents within the Sacramento RTAC area of responsibility which indicate exploding targets are being used for nefarious purposes; however, the recent conviction of Fairbanks militia members in Anchorage, Alaska, for conspiring to kill federal officials and illegally stockpiling weapons and 19 jars of Tannerite exploding targets highlight the potential dangers of this binary explosive when exploited by domestic violent extremist groups.
(U) Background: Exploding Target Proliferation
(U) Tannerite: First Manufacturer of Exploding Targets
(U) The production and distribution of exploding targets have occurred since at least 2002 when the manufacturer of the Tannerite brand began to market and sell them as a “binary explosive” supplied as two powders in two separate containers. Since Tannerite, other companies that manufacture exploding targets have surfaced that produce similar binary explosive mixtures (See Figure 1). As a result, this binary explosive agent has become more accessible to the public through large stockpiles available at local gun shops, and outdoor sport stores as well as online purchase via the Internet.
- (U) Exploding targets consists of two powder components that, when combined, produce the explosive agent that the Tannerite website advises is primarily used “as a target for firearms practice.”
- (U) Since the components are not categorized as an explosive agent until mixed, the binary exploding target package can be purchased and shipped in the United States without an explosives manufacturing license.
(U//FOUO) The Manufacturers may be Minimizing Dangers of Exploding Targets and Misleading Consumers
(U//FOUO) The manufacturers provide both guidance and knowledge to consumers through their website regarding the components of exploding targets and the ability to purchase this product in the United States without an explosives manufacturing license which suggests a familiarity with federal laws that govern the manufacturing and shipment of binary explosives but are likely unfamiliar with state and local ordinances that regulate its use. The CCIC is concerned the manufacturer may be exploiting certain loop holes in how federal laws regulate binary explosives and using this knowledge for commercial gain, but minimizing the dangers of exploding targets and misleading its consumers with its “designed to be safe” pronouncement.
Revealed – Inside China’s Hacker World – Movie
CNN reports – Chinese Hackers are becoming stronger.
TV unveals – FBI Confidential — China’s Cyber Terrorism
According to a leaked secret FBI document, Chinese counterfeiters have sold close to 75 million dollars of fake Cisco Systems routers to the U.S. military. This revelation raises troubling questions about both the integrity of U.S. defenses in cyberspace and the possible motives of a foreign government with a long rap sheet for military espionage and cyber hacking. At least some of China’s fake routers may be specially designed to provide Chinese hackers with undetectable “back doors” into the highest echelons of classified information throughout the defense department bureaucracy.
SECRECY NEWS – JUDGE WALTON NAMED PRESIDING JUDGE OF FISA COURT
Chief Justice of the United States John Roberts has appointed D.C.
District Judge Reggie B. Walton to serve as Presiding Judge of the Foreign
Intelligence Surveillance Court, effective February 22, 2013.
http://www.dcd.uscourts.gov/dcd/walton
Judge Walton, who has been a member of the FIS Court since May 2007, will
replace Presiding Judge John D. Bates, whose term expires on February 21.
Judge Walton's own term on the Court extends through May 18, 2014. His
appointment as Presiding Judge was confirmed by Sheldon Snook, spokesman
for the Court.
The Foreign Intelligence Surveillance Court reviews and authorizes
applications for electronic surveillance and physical search under the
Foreign Intelligence Surveillance Act. A roster of the current court
membership is here:
http://www.fas.org/irp/agency/doj/fisa/court2013.html
The Court's operation under the recently renewed FISA Amendments Act was
discussed in "Reauthorization of the FISA Amendments Act," Congressional
Research Service, January 2, 2013:
http://www.fas.org/sgp/crs/intel/R42725.pdf
In his regular capacity as district court judge, Judge Walton has presided
over a number of celebrated cases including U.S. v. Libby, U.S. v. Roger
Clemens, and Hatfill v. John Ashcroft. Less famously, he also heard
Aftergood v. National Reconnaissance Office, a 2005 Freedom of Information
Act case in which he ruled in favor of the plaintiff, myself. That case
inaugurated the now-routine public release of unclassified intelligence
agency budget justification records.
http://www.fas.org/blog/secrecy/2006/07/fas_wins_foia_lawsuit_over_nro.html
MENTAL DISORDERS AMONG IRAQ VETERANS, AND MORE FROM CRS
New and updated reports from the Congressional Research Service that have
not been made readily available to the public include the following.
Mental Disorders Among OEF/OIF Veterans Using VA Health Care: Facts and
Figures, February 4, 2013:
http://www.fas.org/sgp/crs/misc/R41921.pdf
Evaluating the "Past Performance" of Federal Contractors: Legal
Requirements and Issues, February 4, 2013:
http://www.fas.org/sgp/crs/misc/R41562.pdf
Increasing the Social Security Payroll Tax Base: Options and Effects on
Tax Burdens, February 5, 2013:
http://www.fas.org/sgp/crs/misc/RL33943.pdf
Water Resource Issues in the 113th Congress, January 31, 2013:
http://www.fas.org/sgp/crs/misc/R42947.pdf
Upcoming Rules Pursuant to the Patient Protection and Affordable Care Act:
The 2012 Unified Agenda, February 1, 2013:
http://www.fas.org/sgp/crs/misc/R42946.pdf
The American Taxpayer Relief Act of 2012: Modifications to the Budget
Enforcement Procedures in the Budget Control Act, February 4, 2013:
http://www.fas.org/sgp/crs/misc/R42949.pdf
United Nations System Funding: Congressional Issues, January 15, 2013:
http://www.fas.org/sgp/crs/row/RL33611.pdf
U.S. Foreign Aid to the Palestinians, January 18, 2013:
http://www.fas.org/sgp/crs/mideast/RS22967.pdf
European Union Enlargement, February 4, 2013:
http://www.fas.org/sgp/crs/row/RS21344.pdf
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
Handelsblatt: Auch “Washington Post” vermutet Hacker-Angriff aus China
Die kommunistischen Hacker aus Peking im Sold alter STASI-Seilschaften

Hacker-Attacken auf Medienhäuser und Technologie-Firmen schüren Angst vor der Cybermacht China. Jüngstes Opfer ist der Mikroblogging-Dienst Twitter.
Ungewöhnliche Muster von Zugriffen, damit fing alles an. Es klingt geheimnisvoll, was Bob Lord, Sicherheitschef von Twitter, in einem Blog-Beitrag beschreibt. Aber diese überraschenden „Muster“ waren es, die Lord und seine Leute misstrauisch werden ließen – und sie auf einen laufenden Angriff aufmerksam machten, der den Nutzern des Kurzmitteilungsdienstes galt.
Das Twitter-Team hat diesen Angriff abwehren können, schreibt Lord, aber wie sich bald herausstellte, waren zuvor bereits rund 250.000 Konten geknackt worden. Betroffen sind offenbar vor allem Nutzer, die schon lange bei Twitter angemeldet sind. Ihre Konten wurden sicherheitshalber gesperrt und die Opfer per E-Mail aufgefordert, ihre Passwörter zu ändern.
Über die Identität des Angreifers konnte Lord nichts Genaues sagen – allerdings sei das „nicht das Werk von Amateuren“, erklärte er und stellte die Aktion in einen größeren Zusammenhang: „Es gab in jüngster Zeit eine Zunahme von groß angelegten Sicherheits-Attacken auf US-amerikanische Technologie- und Medien-Unternehmen.“
New York Times und Wall Street Journal betroffen
Damit liefert Lord vielleicht doch einen Hinweis darauf, wo er die Herkunft der Angreifer vermutet. Denn die Medien-Unternehmen, die Lord erwähnt, sind sicherlich die New York Times und das Wall Street Journal. Beide haben in der vergangenen Woche über Hackerangriffe auf ihre Internetseiten und Computersysteme berichtet. Und beide vermuteten Hacker aus China hinter den Angriffen, die es darauf angelegt hatten, die jeweilige China-Berichterstattung zu überwachen. Am Wochenende machte auch die Zeitung Washington Post publik, dass sie schon 2008 Ziel von Hacker-Angriffen gewesen sei. Unter Verdacht auch hier: China.
Klare Beweise sind bei Angriffen dieser Art aber schwer beizubringen, und China weist ein ums andere Mal alle Vorwürfe zurück. Doch die Cyber-Einbrüche häufen sich, und sie belasten zunehmend die internationale Politik. Die am Freitag aus dem Amt geschiedene US-Außenministerin Hillary Clinton hat kurz vor ihrem Abschied erklärt, die US-Regierung beobachte eine Zunahme von Hackerangriffen sowohl auf staatliche Einrichtungen als auch auf Privatunternehmen. Sie wünsche sich ein internationales Forum, das Antworten auf „diese Art illegalen Eindringens“ suche. Die jüngsten Enthüllungen fachen die seit Jahren schwelende Angst der Amerikaner an vor der Cyber-Armee aus Zehntausenden „Roten Hackern“.
(Berliner Zeitung mit AFP, dpa)
In den Fängen der Online – Mafia – Der große Datenklau über unsere Computer
Report München – Der große Datenklau über unsere Computer
In den Fängen der online-Mafia: Der große Datenklau über unsere ComputerSie klauen Daten, spähen Passwörter aus, legen Web-Seiten lahm oder verschicken Spam. Dass man ihnen auf die Schliche kommt, fürchten die Kriminellen nicht: Nicht ihre Computer, sondern die PCs unbescholtener Bürger verüben die Straftaten – sie gehorchen den Kommandos Unbekannter.
Die EU gegen die kriminellen Hacker
Unternehmen sollen melden, wenn Hacker-Angriffe auf ihre IT-Infrastruktur stattfinden. Das zumindest plant EU-Kommissarin Neelie Kroes. Das Vertrauen in die IT soll wachsen, so könnte sich beispielsweise Cloud-Computing durchsetzen und langfristig neue Jobs schaffen.
Die EU-Kommissarin Neelie Kroes denkt Informationen der Süddeutschen Zeitung zufolge über eine Meldepflicht bei Hacker-Angriffen für Unternehmen nach. Laut der für „Digitale Agenda“ zuständigen Niederländerin würden Cyber-Attacken auf Unternehmen nicht nur sie selbst, sondern auch die allgemeine IT-Sicherheit in der EU bedrohen. Gemeinsam mit ihren Kolleginnen Cecilia Malmström (Innenkommissarin) und Catherine Ashton (EU-Außenbeauftragte) will Kroes noch 2013 eine entsprechende Strategie für europäische Cyber-Sicherheit präsentieren. In der Folge soll die EU einen neuen Gesetzesentwurfverabschieden, der entsprechende Statuten für Internetprovider und Betreiber von Rechenzentren regeln soll.
Kroes sagte gegenüber der Süddeutschen Zeitung: „Ich bin ein großer Befürworter von Selbstregulierung, aber in diesem Fall fürchte ich, dass wir damit nicht weiterkommen. Es geht nicht darum, sich gegenseitig die Schuld in die Schuhe zu schieben, sondern darum, voneinander zu lernen.“ Die EU-Kommissarin sieht ihren Vorstoß als notwendig an, da dasVertrauen in die IT wachsen müsse. Technologien wie beispielsweise das Cloud-Computing könnten sich sonst nicht auf Dauer durchsetzen. Das servergestützte Berechnen von Daten soll laut Kroes die lahmende EU-Wirtschaft wieder in Schwung bringen. Kroes verspricht sich außerdem eine Entlastung für die öffentliche Verwaltung, die kontinuierlich zu erhöhten Sparmaßnahmen gezwungen sei.
Wie “Otmar Knoll”, “Fairvesta” zusammnen mit “GoMoPa” kritische Webseiten illegal ausschaltet
Zitat OtmarKnoll/Fairvesta:
|
||||||||||||
|
D
SECRECY NEWS – KEEPING SECRETS FROM CONGRESS
When government information is classified or otherwise withheld from
release, the possibility of government accountability to the public is
undermined. But when the executive branch withholds crucial information
from Congress, that may pose an even more fundamental challenge to
democratic governance.
"The administration has refused to share Presidential Policy Directive 11
(PPD 11) with the Congress," said Sen. Richard Lugar last year at a hearing
of the Senate Foreign Relations Committee which has just been published.
PPD 11 is the Obama Administration document that set the terms of reference
for the Nuclear Posture Review Implementation Study, which will dictate the
future size and configuration of the U.S. nuclear arsenal.
Sen. Lugar voiced a polite objection to this unilateral act of Obama
Administration secrecy: "I simply would say that our country is strongest
and our diplomacy is most effective when nuclear policy is made by
deliberate decisions in which both the legislative and executive branches
fully participate."
http://www.fas.org/irp/congress/2012_hr/implement.html
The withholding of presidential directives from Congress is not a new
practice. A 1992 investigation by the General Accounting Office found that
Congress had not been routinely notified of the preparation or issuance of
national security directives and that none of the relevant congressional
committees "are regularly receiving copies" of such directives.
It is known that presidential directives can be used to establish national
policy, to direct the implementation of policy, and to authorize the
commitment of government resources. But without access to detailed
information about the directives, GAO reported in 1992, "it is impossible
to satisfactorily determine how many NSDs [national security directives]
issued make and implement U.S. policy and what those policies are."
On the other hand, unlike many executive orders, presidential directives
"do not appear to be issued under statutory authority conferred by Congress
and thus do not have the force and effect of law," GAO said. Certainly such
directives cannot limit congressional authority or power to legislate.
http://www.fas.org/irp/offdocs/gao-nsiad-92-72.pdf
Yesterday eleven Senators wrote to President Obama to ask him to direct
the release to Congress "the secret legal opinions outlining your authority
to authorize the killing of Americans in the course of counterterrorism
operations."
"It is vitally important... for Congress and the American public to have a
full understanding of how the executive branch interprets the limits and
boundaries of this authority, so that Congress and the public can decide
whether this authority has been properly defined, and whether the
President's power to deliberately kill American citizens is subject to
appropriate limitations and safeguards," the Senators wrote.
http://www.fas.org/irp/congress/2013_cr/olc-lethal.pdf
Later in the day, Mike Isikoff of NBC News obtained a confidential
Department of Justice White Paper entitled "Lawfulness of a Lethal
Operation Directed Against a U.S. Citizen Who Is a Senior Operational
Leader of Al-Qa'ida or An Associated Force."
http://www.fas.org/irp/eprint/doj-lethal.pdf
NBC said the document had been "provided to members of the Senate
Intelligence and Judiciary committees in June by administration officials
on the condition that it be kept confidential and not discussed publicly."
This non-disclosure condition, now abrogated, is difficult to understand on
national security grounds, but easier to comprehend as an attempt to manage
or evade public controversy.
At any rate, the government's legal argument, such as it is, is now on the
public record. The most important task before Congress is not to plead for
release of additional, underlying source documents, but to respond as a
legislative body to the Administration's now-public assertion of its
position. To do nothing is to endorse it.
AN INTELLIGENCE HISTORY OF THE 1973 ARAB-ISRAELI WAR
The Central Intelligence Agency has published a series of essays on
intelligence and the 1973 Arab-Israeli war, to coincide with a symposium on
the subject held last week at the Nixon Presidential Library.
https://www.cia.gov/library/publications/historical-collection-publications/
The publication itself ("President Nixon and the Role of Intelligence in
the 1973 Arab-Israeli War") is a welcome addition to the literature. But
it also "includes some embarrassing errors," wrote Amir Oren in the Israeli
paper Ha'aretz on February 3 ("CIA report on Yom Kippur War: Israel had
nuclear arsenal").
"For example," Oren wrote, "in the photograph labeled 'An Egyptian soldier
holding up a portrait of President Sadat,' the soldier in question and the
two soldiers flanking him are clearly Israelis, as evidenced by the 'IDF'
stamped visibly on their shirts."
"The editors of the new study also err in attributing two things to
lessons from the Six-Day War: the faulty prevailing conception among
Israeli Military Intelligence 'that Israel would have at least 48 hours'
warning before an invasion' and that Sadat wouldn't start a war before
acquiring fighter planes. Furthermore, it seems they also confused war
analyst Maj. Gen. (ret.) Chaim Herzog with one of his sons, Brig. Gen.
(ret.) Mike Herzog," he added.
If these discrepancies are cause for embarrassment, then it is the kind of
embarrassment that should be willingly endured. To put it another way,
exposing such work to external review and criticism is an unsurpassed way
of identifying and correcting errors.
A REPORT ON CIA DETENTION AND RENDITION PROGRAMS
In the absence of an official public account of post-9/11 U.S.
counterterrorism programs, Americans (and others) must rely on unofficial
accounts.
"Globalizing Torture" is a new report from the Open Society Justice
Initiative, authored by Amrit Singh. It is said to provide "the most
comprehensive account yet assembled of the human rights abuses associated
with CIA secret detention and extraordinary rendition operations. It
details for the first time what was done to the 136 known victims, and
lists the 54 foreign governments that participated in these operations. It
shows that responsibility for the abuses lies not only with the United
States but with dozens of foreign governments that were complicit."
http://www.opensocietyfoundations.org/
It was reported in "Report Says 54 Countries Helped CIA After 9/11" by
Scott Shane, New York Times, February 4.
THE JOINT LIGHT TACTICAL VEHICLE, AND MORE FROM CRS
New and updated reports from the Congressional Research Service that have
not been made readily available to the public include the following.
Joint Light Tactical Vehicle (JLTV): Background and Issues for Congress,
February 4, 2013:
http://www.fas.org/sgp/crs/weapons/RS22942.pdf
U.S.-India Security Relations: Strategic Issues, January 24, 2013:
http://www.fas.org/sgp/crs/row/R42948.pdf
Multilateral Development Banks: U.S. Contributions FY2000-FY2013, February
1, 2013:
http://www.fas.org/sgp/crs/misc/RS20792.pdf
IMF Reforms: Issues for Congress, February 1, 2013:
http://www.fas.org/sgp/crs/misc/R42844.pdf
Medicare, Medicaid, and Other Health Provisions in the American Taxpayer
Relief Act of 2012, January 31, 2013:
http://www.fas.org/sgp/crs/misc/R42944.pdf
Hemp as an Agricultural Commodity, December 18, 2012:
http://www.fas.org/sgp/crs/misc/RL32725.pdf
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
TOP-SECRET – Federal Reserve Discussion Paper on Foreign Banks in U.S.

oreign Banks in the U.S.: A primer
- William Goulding and Daniel E. Nolle
- 77 pages
- November 2012
This paper describes the foreign banking landscape in the United States. It begins by establishing a vocabulary for discussion of the subject, and then identifies a number of important data-related issues. With that information in hand, the remainder of the paper focuses on identifying the most important underlying trends on both sides of the balance sheets of foreign-owned banks’ U.S. operations. At each step, the investigation considers how foreign-owned banks compare to U.S.-owned domestic banks, and how two types of foreign banks operations in the U.S. — branches and agencies of foreign banks (FBAs), and foreign-owned subsidiary banks (FSUBs) — compare to each other. The banking sector in the U.S. experienced substantial swings in performance and stability over the decade surrounding the 2008-2009 financial crisis and changes in every major dimension of foreign-owned banks’ assets and liabilities were even larger than for domestic banks. Changes were especially large at FBAs. For example, cash balances came to dominate the assets side of FBAs’ aggregate balance sheet, with the absolute level of cash balances larger than those of domestic U.S. banks beginning in 2011, despite the fact that total assets of domestic U.S. banks are five times the assets of FBAs. Further, the recent unprecedented build-up of cash balances by FBAs was almost entirely composed of excess reserves. Changes in FBAs’ liabilities-side activities have also been large, with much funding coming from large wholesale deposits and net borrowing from their foreign parents and related offices abroad.
…
Monty Python’s Flying Circus – Conquistador Coffee Campaign
Monty Python’s Flying Circus – Conquistador Coffee Campaign
Monty Python’s Flying Circus
http://www.amazon.com/Complete-Monty-Pythons-Flying-Circus/dp/B001E77XNA/ref=…
Cryptome – Germans Exploited Codes of Special Ops Executive
SOE codes and Referat Vauck
|
1
|
10
|
9
|
7
|
6
|
8
|
2
|
4
|
5
|
3
|
|
a
|
u
|
t
|
o
|
m
|
o
|
b
|
i
|
l
|
e
|
|
1
|
10
|
9
|
7
|
6
|
8
|
2
|
4
|
5
|
3
|
|
g
|
e
|
s
|
t
|
a
|
p
|
o
|
h
|
a
|
s
|
|
a
|
r
|
r
|
e
|
s
|
t
|
e
|
d
|
o
|
u
|
|
r
|
r
|
a
|
d
|
i
|
o
|
o
|
p
|
e
|
r
|
|
a
|
t
|
o
|
r
|
c
|
i
|
p
|
h
|
e
|
r
|
|
m
|
a
|
t
|
e
|
r
|
i
|
a
|
l
|
c
|
o
|
|
m
|
p
|
r
|
o
|
m
|
i
|
s
|
e
|
d
|
Now we use the numerical key to rearrange the columns and copy the output:
|
2
|
5
|
3
|
7
|
4
|
1
|
6
|
8
|
|
e
|
l
|
e
|
p
|
h
|
a
|
n
|
t
|
|
2
|
5
|
3
|
7
|
4
|
1
|
6
|
8
|
|
g
|
a
|
r
|
a
|
m
|
m
|
o
|
e
|
|
o
|
p
|
a
|
s
|
s
|
u
|
r
|
r
|
|
o
|
h
|
d
|
p
|
h
|
l
|
e
|
a
|
|
o
|
e
|
e
|
c
|
d
|
a
|
s
|
i
|
|
c
|
r
|
m
|
t
|
e
|
d
|
r
|
e
|
|
o
|
p
|
t
|
o
|
i
|
i
|
i
|
s
|
|
r
|
a
|
o
|
t
|
r
|
e
|
r
|
r
|
|
t
|
a
|
p
|
|
MARY
|
HAD
|
A | LITTLE |
LAMB
|
WHOSE |
FLEECE
|
WAS
|
|
A
|
B
|
C |
D
|
E
|
F
|
G
|
H
|
|
WHITE
|
AS
|
SNOW
|
AND
|
EVERYWHERE
|
THAT
|
MARY
|
WENT
|
|
I
|
J
|
K
|
L
|
M
|
N
|
O
|
P
|
|
THE
|
LAMB
|
WAS
|
SURE
|
TO
|
GO
|
IT
|
FOLLOWED
|
|
Q
|
R
|
S
|
T
|
U
|
V
|
W
|
X
|
|
HER
|
TO
|
||||||
|
Y
|
Z
|
Let’s assume that the letters chosen are PQRSTU, the odd letters furnish the first ‘key’ and the even letters the second. In our example PRT points to ‘WENT LAMB SURE’ as the first ‘key’. For the second we use QSU so it’s ‘THE WAS TO’. The indicator showing which words were used as ‘keys’ will be PRT filled with two nulls so as to form a 5-letter group (all messages were sent in 5-letter groups), so let’s say PARNT and the final step is to move all the letters forward by using the agents’ secret number. For instance if the number was 45711 then in our example PARNT will change into TFYOU, as each letter moves forward as many positions as indicated by the secret number P+4=T, A+5=F, R+7=Y, N+1=O, T+1=U.
Fenner, head of the cryptanalysis department of OKW/Chi, said in DF-187F, p20 about the Vauck section that ‘there may have been some 50 messages decrypted weekly, among them some to be sure which were almost a year old and hence had only historical significance’. Fenner however was not the best source since he makes many ‘mistakes’ in his reports. TICOM report DF-9 ‘Captured Wehrmacht Sigint Document: Translation of Activity Report of OKW/Chi for the Period 1st January, 1944 to 25th June, 1944’, p4 gives the messages decoded by month and says in the end ‘The 6.000 agents messages handed to Fu III are not included in these figures.’
Perhaps the British know more about what really happened since the first page in HW 40/76 says:
So I guess we’ll have to wait…
TMZ – Charlize Theron is Justin Bieber?
Charlize Theron showed off her new haircut — which happens to be the EXACT same style as Justin Bieber’s! In fact, that style is so popular, it’s even infiltrated the TMZ newsroom.
PI – Assessment of the Federal Assault Weapons Ban and Gun Violence

An Updated Assessment of the Federal Assault Weapons Ban: Impacts on Gun Markets and Gun Violence, 1994-2003
- Christopher S. Koper, Daniel J. Woods and Jeffrey A. Roth
- 114 pages
- June 2004
This overview presents key findings and conclusions from a study sponsored by the National Institute of Justice to investigate the effects of the federal assault weapons ban. This study updates prior reports to the National Institute of Justice and the U.S. Congress on the assault weapons legislation.
The Ban Attempts to Limit the Use of Guns with Military Style Features and Large Ammunition Capacities
• Title XI, Subtitle A of the Violent Crime Control and Law Enforcement Act of 1994 imposed a 10-year ban on the “manufacture, transfer, and possession” of certain semiautomatic firearms designated as assault weapons (AWs). The ban is directed at semiautomatic firearms having features that appear useful in military and criminal applications but unnecessary in shooting sports or self-defense (examples include flash hiders, folding rifle stocks, and threaded barrels for attaching silencers). The law bans 18 models and variations by name, as well as revolving cylinder shotguns. It also has a “features test” provision banning other semiautomatics having two or more military-style features. In sum, the Bureau of Alcohol, Tobacco, Firearms, and Explosives (ATF) has identified 118 models and variations that are prohibited by the law. A number of the banned guns are foreign semiautomatic rifles that have been banned from importation into the U.S. since 1989.
• The ban also prohibits most ammunition feeding devices holding more than 10 rounds of ammunition (referred to as large capacity magazines, or LCMs). An LCM is arguably the most functionally important feature of most AWs, many of which have magazines holding 30 or more rounds. The LCM ban’s reach is broader than that of the AW ban because many non-banned semiautomatics accept LCMs. Approximately 18% of civilian-owned firearms and 21% of civilian-owned handguns were equipped with LCMs as of 1994.
• The ban exempts AWs and LCMs manufactured before September 13, 1994. At that time, there were upwards of 1.5 million privately owned AWs in the U.S. and nearly 25 million guns equipped with LCMs. Gun industry sources estimated that there were 25 million pre-ban LCMs available in the U.S. as of 1995. An additional 4.7 million pre-ban LCMs were imported into the country from 1995 through 2000, with the largest number in 1999.
• Arguably, the AW-LCM ban is intended to reduce gunshot victimizations by limiting the national stock of semiautomatic firearms with large ammunition capacities – which enable shooters to discharge many shots rapidly – and other features conducive to criminal uses. The AW provision targets a relatively small number of weapons based on features that have little to do with the weapons’ operation, and removing those features is sufficient to make the weapons legal. The LCM provision limits the ammunition capacity of non-banned firearms.The Banned Guns and Magazines Were Used in Up to A Quarter of Gun Crimes Prior to the Ban
• AWs were used in only a small fraction of gun crimes prior to the ban: about 2% according to most studies and no more than 8%. Most of the AWs used in crime are assault pistols rather than assault rifles.
• LCMs are used in crime much more often than AWs and accounted for 14% to 26% of guns used in crime prior to the ban.
• AWs and other guns equipped with LCMs tend to account for a higher share of guns used in murders of police and mass public shootings, though such incidents are very rare.The Ban’s Success in Reducing Criminal Use of the Banned Guns and Magazines Has Been Mixed
• Following implementation of the ban, the share of gun crimes involving AWs declined by 17% to 72% across the localities examined for this study (Baltimore, Miami, Milwaukee, Boston, St. Louis, and Anchorage), based on data covering all or portions of the 1995-2003 post-ban period. This is consistent with patterns found in national data on guns recovered by police and reported to ATF.
• The decline in the use of AWs has been due primarily to a reduction in the use of assault pistols (APs), which are used in crime more commonly than assault rifles (ARs). There has not been a clear decline in the use of ARs, though assessments are complicated by the rarity of crimes with these weapons and by substitution of post-ban rifles that are very similar to the banned AR models.
• However, the decline in AW use was offset throughout at least the late 1990s by steady or rising use of other guns equipped with LCMs in jurisdictions studied (Baltimore, Milwaukee, Louisville, and Anchorage). The failure to reduce LCM use has likely been due to the immense stock of exempted pre-ban magazines, which has been enhanced by recent imports.It is Premature to Make Definitive Assessments of the Ban’s Impact on Gun Crime
• Because the ban has not yet reduced the use of LCMs in crime, we cannot clearly credit the ban with any of the nation’s recent drop in gun violence. However, the ban’s exemption of millions of pre-ban AWs and LCMs ensured that the effects of the law would occur only gradually. Those effects are still unfolding and may not be fully felt for several years into the future, particularly if foreign, pre-ban LCMs continue to be imported into the U.S. in large numbers.
The Ban’s Reauthorization or Expiration Could Affect Gunshot Victimizations, But Predictions are Tenuous
• Should it be renewed, the ban’s effects on gun violence are likely to be small at best and perhaps too small for reliable measurement. AWs were rarely used in gun crimes even before the ban. LCMs are involved in a more substantial share of gun crimes, but it is not clear how often the outcomes of gun attacks depend on the ability of offenders to fire more than ten shots (the current magazine capacity limit) without reloading.
• Nonetheless, reducing criminal use of AWs and especially LCMs could have nontrivial effects on gunshot victimizations. The few available studies suggest that attacks with semiautomatics – including AWs and other semiautomatics equipped with LCMs – result in more shots fired, more persons hit, and more wounds inflicted per victim than do attacks with other firearms. Further, a study of handgun attacks in one city found that 3% of the gunfire incidents resulted in more than 10 shots fired, and those attacks produced almost 5% of the gunshot victims.
• Restricting the flow of LCMs into the country from abroad may be necessary to achieve desired effects from the ban, particularly in the near future. Whether mandating further design changes in the outward features of semiautomatic weapons (such as removing all military-style features) will produce measurable benefits beyond those of restricting ammunition capacity is unknown. Past experience also suggests that Congressional discussion of broadening the AW ban to new models or features would raise prices and production of the weapons under discussion.
• If the ban is lifted, gun and magazine manufacturers may reintroduce AW models and LCMs, perhaps in substantial numbers. In addition, pre-ban AWs may lose value and novelty, prompting some of their owners to sell them in undocumented secondhand markets where they can more easily reach high-risk users, such as criminals, terrorists, and other potential mass murderers. Any resulting increase in crimes with AWs and LCMs might increase gunshot victimizations for the reasons noted above, though this effect could be difficult to measure.…
3.1. Criminal Use of Assault Weapons
Numerous studies have examined the use of AWs in crime prior to the federal ban. The definition of AWs varied across the studies and did not always correspond exactly to that of the 1994 law (in part because a number of the studies were done prior to 1994). In general, however, the studies appeared to focus on various semiautomatics with detachable magazines and military-style features. According to these accounts, AWs typically accounted for up to 8% of guns used in crime, depending on the specific AW definition and data source used (e.g., see Beck et al., 1993; Hargarten et al., 1996; Hutson et al., 1994; 1995; McGonigal et al., 1993; New York State Division of Criminal Justice Services, 1994; Roth and Koper, 1997, Chapters 2, 5, 6; Zawitz, 1995). A compilation of 38 sources indicated that AWs accounted for 2% of crime guns on average (Kleck, 1997, pp.112, 141-143).
Similarly, the most common AWs prohibited by the 1994 federal ban accounted for between 1% and 6% of guns used in crime according to most of several national and local data sources examined for this and our prior study (see Chapter 6 and Roth and Koper, 1997, Chapters 5, 6):
• Baltimore (all guns recovered by police, 1992-1993): 2%
• Miami (all guns recovered by police, 1990-1993): 3%
• Milwaukee (guns recovered in murder investigations, 1991-1993): 6%
• Boston (all guns recovered by police, 1991-1993): 2%
• St. Louis (all guns recovered by police, 1991-1993): 1%
• Anchorage, Alaska (guns used in serious crimes, 1987-1993): 4%
• National (guns recovered by police and reported to ATF, 1992-1993): 5%
• National (gun thefts reported to police, 1992-Aug. 1994): 2%
• National (guns used in murders of police, 1992-1994): 7-9%
• National (guns used in mass murders of 4 or more persons, 1992-1994): 4-13%…
Monty Python’s Flying Circus – The Audit
Monty Python’s Flying Circus
http://www.amazon.com/Complete-Monty-Pythons-Flying-Circus/dp/B001E77XNA/ref=…
TMZ – Jennifer Lawrence: My Boobs Aren’t Right! — Jimmy Kimmel Interview
If you think Jennifer Lawrence is absolutely perfect, then you are DEAD WRONG… because according to JLaw, she’s got a MAJOR ISSUE in the boob department!
Revealed-DHS-FBI Bulletin: Recent Active Shooter Incidents

(U//FOUO) This Joint Intelligence Bulletin (JIB) is intended to provide information on the recent active shooter incidents that have taken place in the Homeland. This information is provided to support the activities of DHS and FBI and to assist private sector security officials and federal, state, local, tribal, and territorial law enforcement in identifying protective and support measures relating to active shooters.
(U//FOUO) For the purpose of this report, an “active shooter” is defined as one or more individuals participating in a random or systematic killing spree demonstrating their intent to harm others with a firearm. An active shooter’s objective is that of mass murder, rather than committing traditional criminal acts, such as robbery or hostage-taking. Active shooter attacks are dynamic incidents that vary greatly from one to another.
…
(U) Key Findings
(U//FOUO) Recent shootings underscore the need for private sector security officials and law enforcement to ensure that protective and crisis response measures are in place and up-to-date.
(U//FOUO) The FBI analyzed 154 active shooter events in the United States between 2002 and 2012 (to date) that included three or more individuals being shot.*
(U//FOUO) Motivations for active shooting incidents are difficult to fully determine. The shooter was deceased after 51 percent of these events (43 percent committed suicide and 8 percent were shot and killed by responders). Forty-five percent of active shooters were arrested and 4 percent remain unidentified. A clear motivation was never determined in 40 percent of cases analyzed; however, the most common identified motivations were found to be workplace retaliation (21 percent), domestic disputes (14 percent), and academic retaliation by a current or former student (7 percent).
(U//FOUO) The shooter was male in 96 percent of cases analyzed. The shooter acted alone 96 percent of the time. Active shooter events most commonly occurred in a workplace environment (37 percent) or academic setting (17 percent).
(U//FOUO) From investigations and analysis, many active shooters were described as social isolates, harbored feelings of hate and anger, and/or had some reported contact with mental health professionals. Mental illness is commonly referenced as a potential contributing factor, but its causal impact on the attack can only be speculated. Very few active shooters had previous arrests for violent crimes. Common catalysts or triggers observed include: loss of significant relationships, changes in financial status, loss of a job, changes in living arrangements, major adverse changes to life circumstances, and/or feelings of humiliation or rejection on the part of the shooter.
(U) Suggested Protective and Crisis Response Measures
(U//FOUO) The following protective and crisis response measures may assist or augment existing safety, security, and counterterrorism efforts at commercial and public facilities. Facilities should review and update existing emergency and crisis management procedures using these measures. Officials should consider the following measures for everyday security:
— (U//FOUO) Review, update, and validate all emergency and crisis management plans.
— (U//FOUO) Coordinate response plans across functional disciplines (e.g. police, fire, EMS, hospitals, school districts, and private sector) and regions to maximize response in a large incident.
— (U//FOUO) Conduct exercises of emergency and crisis management plans.
— (U//FOUO) Raise awareness among employees by conducting “all hazards” awareness training.
— (U//FOUO) Raise community awareness of potential threats and vulnerabilities.
— (U//FOUO) Ensure the staff are aware of their roles and responsibilities during a crisis and exercise these responsibilities.
— (U//FOUO) Ensure that emergency communications equipment is present and operable. Practice emergency communications plans and systems.
— (U//FOUO) Report suspicious activity to proper authorities, to include missing or stolen weapons.(U) Long-Term Protective Measures
(U//FOUO) Protective measures in the long term should emphasize physical safeguards, including building enhancements that present a more robust deterrent and provide a more survivable environment. Officials should consider the following measures:
— (U//FOUO) Install secure locks on all external and internal doors and windows with quick-release capability from within for emergency escape.
— (U//FOUO) Install window and external door protection with quick-release capability from within for fire escape.
— (U//FOUO) Consider establishing safe areas within the facility for assembly and refuge during crises.
— (U//FOUO) Consider establishing/implementing an emergency communications system such as phone trees or text messages for personnel.(U) Indicators of Surveillance
(U//FOUO) The following activities may suggest surveillance of facilities. Independently, each indicator may represent legitimate recreational or commercial activities; however, multiple indicators could suggest a heightened threat:
— (U//FOUO) Overly interested in entry points, peak days and hours of operation, security personnel, surveillance assets (including cameras), and access controls such as alarms, barriers, doors, gates, or locks.
— (U//FOUO) Loitering, parking, or standing in the same area over multiple days with no reasonable explanation.
— (U//FOUO) Observing security reaction drills or procedures (may cause an incident to observe response).
— (U//FOUO) Having an unusual interest in speaking with building maintenance personnel or security guards.
— (U//FOUO) Attention to or avoidance of surveillance cameras.
— (U//FOUO) Attempts to disguise appearance from visit to visit (change in hair color, style of dress).
— (U//FOUO) Interest without justification in obtaining site plans, ingress and egress routes, and information on employees or the public.
— (U//FOUO) Garments not appropriate for weather/seasons.
— (U//FOUO) Unusual behavior, such as staring at or quickly looking away from personnel or vehicles entering or leaving facilities or parking areas.
— (U//FOUO) An increase in anonymous telephone or e-mail threats in conjunction with suspected surveillance incidents, indicating possible surveillance of threat reaction procedures.
— (U//FOUO) Discreet use of still cameras and video recorders or note taking or use of sketching materials that would raise suspicion in a reasonable person.(U//FOUO) Law enforcement agencies, security personnel, and administrators should be aware of and remain alert to indicators of surveillance activities. Officials are encouraged to review and update their evacuation plans and security and emergency policies.
Monty Python’s Meaning of Life – Every Sperm is Sacred
Monty Python’s Meaning of Life
http://www.amazon.com/Monty-Python-Trinity-Pythons-Meaning/dp/B001E12ZAM/ref=…
Cyberattacks against us – Same procedure – Wall Street Journal Announces That It, Too, Was Hacked by the Chinese
One day after The New York Times reported that Chinese hackers had infiltrated its computers and stolen passwords for its employees, The Wall Street Journal announced that it too had been hacked.
Related
-
Hackers in China Attacked The Times for Last 4 Months(January 31, 2013)
On Thursday, The Journal reported that it had been attacked by Chinese hackers who were trying to monitor the company’s coverage of China. It said hackers had broken into its network through computers in its Beijing bureau.
In a written statement, the business newspaper owned by News Corporation described the attack as an “ongoing issue” and said it was working closely with authorities and security specialists to clean up its systems. It said that it completed a “network overhaul” on Thursday in an effort to rid its systems of hackers.
China’s Ministry of National Defense has denied any involvement in the cyberattack at The Times or any other American corporations.
But security experts said that in 2008, Chinese hackers began targeting American news organizations as part of an effort to monitor coverage of Chinese issues.
In a report for clients in December, Mandiant, a computer security company, said that over the course of several investigations it found evidence that Chinese hackers had stolen e-mails, contacts and files from more than 30 journalists and executives at Western news organizations, and had maintained a “short list” of journalists for repeated attacks. Among those targeted were journalists who had written about Chinese leaders, political and legal issues in China and the telecom giant Huawei.
Bloomberg News, another American news organization, was targeted by Chinese hackers last year, and some computers were infected, according to a person with knowledge of the company’s internal investigation. The attack occurred after Bloomberg published an article on June 29 about the wealth accumulated by relatives of Xi Jinping, a Chinese official who is expected to become president in March.
Bloomberg has confirmed that hackers had made attempts but said that “no computer systems or computers were compromised.”
The timing of the attacks on The New York Times coincided with the reporting for an investigation, published online on Oct. 25, that found that the relatives of Wen Jiabao,China’s prime minister, had accumulated a fortune worth several billion dollars through business dealings.
Security experts hired by The Times to detect and block the computer attacks found digital evidence that Chinese hackers, using methods that some consultants have associated with the Chinese military in the past, breached The Times’s network.
The Associated Press reported Thursday that officials in the Obama administration were considering more assertive action against Beijing to stop Chinese computer espionage campaigns.
The Secretary of State, Hillary Clinton, said Thursday a global effort was needed o establish “rules of the road” for cyber activity. In her final meeting with reporters at the State Department, Mrs. Clinton addressed a question about China’s efforts to infiltrate computer systems at The New York Times.
“We have seen over the last years an increase in not only the hacking attempts on government institutions but also non-governmental ones,” Mrs. Clinton said.
The Chinese, she said, “are not the only people who are hacking us.”
“There is a lot that we are working on that will be deployed in the event that we don’t get some kind of international effort under way,” Mrs. Clinton added without elaborating.
The United States has been increasingly vocal about such efforts against government and private industry. In a November 2011 intelligence report, government officials specifically accused China and Russia of stealing intellectual property for economic gain.
<nyt_author_id>
Michael Gordon contributed reporting from Washington.
Cyberattacken wie bei uns – Hacker spähen Nutzerkonten von Twitter aus
THE INVESTMENT MAGAZINE – THE ORIGINAL – DAS INVESTMENT MAGAZIN – DAS ORIGINAL – Der Online-Kurznachrichtendienst Twitter ist Opfer eines Hackerangriffs geworden.
Dabei seien möglicherweise Passwörter und andere Informationen von rund 250.000 Nutzern gestohlen worden, teilte das US-Unternehmen am Freitagabend mit. Es vermutete Profis hinter der Tat. “Der Angriff war nicht das Werk von Amateuren”, schrieb Twitter in einem Blog. Er sei vielmehr sehr ausgefeilt gewesen. Zugleich versicherte der Dienst, der für seine maximal aus 140 Zeichen bestehenden Nachrichten bekannt ist, dass die Passwörter aus Sicherheitsgründen zurückgesetzt worden seien. Die Betroffenen würden informiert.
Twitter äußerte sich nicht zur Vorgehensweise der Hacker und zu deren Herkunft. Der Angriff soll in dieser Woche erfolgt sein. Es sei kein isolierter Vorfall, sondern vermutlich seien andere Unternehmen und Organisationen zuletzt ähnlich angegriffen worden. Erst kürzlich waren die Internetseiten der “New York Times” und des “Wall Street Journal” von Hackern heimgesucht worden. Beide Zeitungen teilten mit, die Hacker hätten von China aus agiert. Der 2006 auf den Markt gekommene Kurznachrichtendienst betonte, eng mit den Behörden und der Regierung zusammenzuarbeiten.
Es ist nicht das erste Mal, dass Hacker ins Twitter-System eingedrungen sind und Zugriff auf Nutzerinformationen erhielten. 2010 einigte sich das Unternehmen mit der Kartellbehörde FTC auf unabhängige Überprüfungen der Datensicherheit über zehn Jahre hinweg.
Twitter befindet sich in privaten Händen und hat weltweit rund 200 Millionen Nutzer. Der Wert des Unternehmens wird auf mehr als acht Milliarden Dollar geschätzt. In der Wahlnacht des 6. November in den USA liefen weltweit mehr als 327.000 Tweets in der Minute über den Dienst.
OUR WEBSITES ARE UNDER ATTACK AFTER PUBLISHING THE STASI NAMES BY CHINESE HACKERS WHICH ARE ACTING ON BEHALF OF SOME GERMAN THUGS. THE SUSPECTS ARE “GoMoPa”, “KLAUS MAURISCHAT”, “MARK VORNKAHL”, “PETER EHLERS” AMD “GERD “WILHELM” BENNEWIRTZ OR WHATEVER THEIR REAL NAMES MIGHT BE…
IMMER WIEDER WERDEN WEBSITES MUTMASSLICH DURCH “GOMoPa” UND DEREN MUTMASSLICHE AUFTRAGGEBER ATTACKIERT WIE MUTMASSLICH “GERD BENNEWIRTZ” UND “PETER EHLERS”
Die FÄLLE SIND BEI DEN ZUSTÄNDIGEN BEHÖRDEN
SIEHE AUCH HIER:
https://berndpulch.org/2013/02/02/cyberattacks-hackers-in-china-attacked-the-times-for-last-4-months/
DER BEWEIS AUS DEM JAHR 2000: SO REGTE GRUNER und JAHR-TOCHTER, IPV, MICH AN, DEN TITEL “INVESTMENT” ZU LANCIEREN
DIE BESTEN DAS INVESTMENT- DAS ORIGINAL Cover seit dem Jahre 2000
http://investmentmagazin.com/?page_id=257
DER BEWEIS “DAS INVESTMENT MAGAZIN” DAS ORIGINAL IST ECHT
https://berndpulch.org/2011/04/17/der-beweis-das-investment-magazin-das-original/
DER MAGISTER-TITEL VON BERND PULCH IST ECHT
https://berndpulch.org/der-beweis-magisterarbeit-bernd-pulch/
Reporting by Bernd Pulch, Lionel Goodwin, Sarah Goodsmith, Bridget Gallagher and Tim Wilkinson
See more at See more at http://www.berndpulch.co, http://www.berndpulch.co.uk, http://www.berndmpulch.com, http://www.berndpulch.com, http://www.berndpulch.org, http://www.bernd-pulch.org, http://www.berndpulch.de, http://www.berndpulch.info and http://www.berndpulch.at and http://www.berndpulch.net, http://www.berndpulch.co.uk, http://www.investment-on.com, http://www.investmentmagazin.com, http://www.investment-magazin.tv, as well as at http://www.ebizz.tv and http://www.star-fashion.com, http://www.magister-berndpulch.com, http://www.magister-berndpulch.com, http://wwww.maberndpulch.com, http://www.berndpulchorg.com, http://www.magisterberndpulch.org, http://www.berndpulchcom.com,http://www.berndpulch.me,http://www.berndpulchme.com,
http://www.pulch.me, http://www.i-nvestment.com, http://www.bernd-pulch.me, http://www.worldwideblog.net,
For security reasons we do not provide any more information to protect us against cyber criminals – join our Crusade against Cyber Criminals
The INVESTMENT – MAGAZINE – THE ORIGINAL- was founded in 1995. We publish three editions, one global, one for Asia and one germany, Austria and Szwiterland.
We are independent from financial companies.
We focus on HNWI.
A high net worth individual (HNWI) is a person with a high net worth. In the private banking business, these individuals typically are defined as having investable assets (financial assets not including primary residence) in excess of US$1 million.[1][2] As explained below, the U.S. Securities and Exchange Commission has promulgated a different definition of “high net worth individual” for regulatory purposes.
The Merrill Lynch – Capgemini World’s Wealth Report 2009 defines HNWIs as those who hold at least US$1 million in financial assets and Ultra-HNWIs as those who hold at least US$30 million in financial assets, with both excluding collectibles, consumables, consumer durables and primary residences. The report states that in 2008 there were 8.6 million HNWIs worldwide, a decline of 14.9% from 2007. The total HNWI wealth worldwide totaled US$32.8 trillion, a 19.5% decrease from 2007. The Ultra-HNWIs experienced the greater loss, losing 24.6% in population size and 23.9% in accumulated wealth. The report revised its 2007 projections that HNWI financial wealth would reach US$59.1 trillion by 2012 and revised this downward to a 2013 HNWI wealth valued at $48.5 trillion advancing at an annual rate of 8.1%.
WATCH OUR OWN 560 CHANNELS and 5.000 ASSOCIATED CHANNELS TOTALLY FREE
ebizz.tv is a new, free and open-source platform for internet television and video with more as 5 million videos in the library and 900.000 video channels.
See more at See more at http://www.berndpulch.co, http://www.berndpulch.co.uk, http://www.berndmpulch.com, http://www.berndpulch.com, http://www.berndpulch.org, http://www.bernd-pulch.org, http://www.berndpulch.de, http://www.berndpulch.info and http://www.berndpulch.at and http://www.berndpulch.net, http://www.berndpulch.co.uk, http://www.investment-on.com, http://www.investmentmagazin.com, http://www.investment-magazin.tv, as well as at http://www.ebizz.tv and http://www.star-fashion.com, http://www.magister-berndpulch.com, http://www.magister-berndpulch.com, http://wwww.maberndpulch.com, http://www.berndpulchorg.com, http://www.magisterberndpulch.org, http://www.berndpulchcom.com,http://www.berndpulch.me,http://www.berndpulchme.com,
http://www.pulch.me, http://www.i-nvestment.com, http://www.bernd-pulch.me, http://www.worldwideblog.net,
We broadcast and produce
IPTV channels all around the globe.
WE BUILD YOUR PERSONAL WEB TV CHANNEL
Copyright General Global Media
*Magister Bernd M. Pulch (MA – Magister Artium)
Magister Bernd M. Pulch studied Publizistik (2), Komparatistik (1) and Germanistik (1-2) until 1988
University Mainz
Published his Magister-Thesis for Professor Hans-Mathias Kepplinger
about Dolf Zillmans “Emotional Arousal Theory” January 1987
You can order the book of Bernd Pulch for only € 125,- It can be delivered in 7 days.
Payment must be made in advance.
See more at http://www.berndpulch.co, http://www.berndpulch.co.uk, http://www.berndmpulch.com, http://www.berndpulch.com, http://www.berndpulch.org, http://www.bernd-pulch.org, http://www.berndpulch.de, http://www.berndpulch.info and http://www.berndpulch.at and http://www.berndpulch.net, http://www.berndpulch.co.uk, http://www.investment-on.com, http://www.investmentmagazin.com, http://www.investment-magazin.tv, as well as at http://www.ebizz.tv and http://www.star-fashion.com, http://www.magister-berndpulch.com, http://www.magister-berndpulch.com, http://wwww.maberndpulch.com, http://www.berndpulchorg.com, http://www.magisterberndpulch.org, http://www.berndpulchcom.com,http://www.berndpulch.me,http://www.berndpulchme.com,
http://www.pulch.me, http://www.i-nvestment.com, http://www.bernd-pulch.me,
Investment Magazin, Investment, Das Investment, Investment Magazine
OUR WEBSITES ARE UNDER ATTACK AFTER PUBLISHING THE STASI NAMES BY CHINESE HACKERS WHICH ARE ACTING ON BEHALF OF SOME GERMAN THUGS. THE SUSPECTS ARE “GoMoPa”, “KLAUS MAURISCHAT”, “MARK VORNKAHL”, “PETER EHLERS” AMD “GERD “WILHELM” BENNEWIRTZ OR WHATEVER THEIR REAL NAMES MIGHT BE…
IMMER WIEDER WERDEN WEBSITES MUTMASSLICH DURCH “GOMoPa” UND DEREN MUTMASSLICHE AUFTRAGGEBER ATTACKIERT WIE MUTMASSLICH “GERD BENNEWIRTZ” UND “PETER EHLERS”
Die FÄLLE SIND BEI DEN ZUSTÄNDIGEN BEHÖRDEN
SIEHE AUCH HIER:
DER BEWEIS AUS DEM JAHR 2000: SO REGTE GRUNER und JAHR-TOCHTER, IPV, MICH AN, DEN TITEL “INVESTMENT” ZU LANCIEREN
DIE BESTEN DAS INVESTMENT- DAS ORIGINAL Cover seit dem Jahre 2000
http://investmentmagazin.com/?page_id=257
DER BEWEIS “DAS INVESTMENT MAGAZIN” DAS ORIGINAL IST ECHT
https://berndpulch.org/2011/04/17/der-beweis-das-investment-magazin-das-original/
DER MAGISTER-TITEL VON BERND PULCH IST ECHT
https://berndpulch.org/der-beweis-magisterarbeit-bernd-pulch/
Reporting by Bernd Pulch, Lionel Goodwin, Sarah Goodsmith, Bridget Gallagher and Tim Wilkinson
See more at See more at http://www.berndpulch.co, http://www.berndpulch.co.uk, http://www.berndmpulch.com, http://www.berndpulch.com, http://www.berndpulch.org, http://www.bernd-pulch.org, http://www.berndpulch.de, http://www.berndpulch.info and http://www.berndpulch.at and http://www.berndpulch.net, http://www.berndpulch.co.uk, http://www.investment-on.com, http://www.investmentmagazin.com, http://www.investment-magazin.tv, as well as at http://www.ebizz.tv and http://www.star-fashion.com, http://www.magister-berndpulch.com, http://www.magister-berndpulch.com, http://wwww.maberndpulch.com, http://www.berndpulchorg.com, http://www.magisterberndpulch.org, http://www.berndpulchcom.com,http://www.berndpulch.me,http://www.berndpulchme.com,
http://www.pulch.me, http://www.i-nvestment.com, http://www.bernd-pulch.me, http://www.worldwideblog.net,
For security reasons we do not provide any more information to protect us against cyber criminals – join our Crusade against Cyber Criminals
The INVESTMENT – MAGAZINE – THE ORIGINAL- was founded in 1995. We publish three editions, one global, one for Asia and one germany, Austria and Szwiterland.
We are independent from financial companies.
We focus on HNWI.
A high net worth individual (HNWI) is a person with a high net worth. In the private banking business, these individuals typically are defined as having investable assets (financial assets not including primary residence) in excess of US$1 million.[1][2] As explained below, the U.S. Securities and Exchange Commission has promulgated a different definition of “high net worth individual” for regulatory purposes.
The Merrill Lynch – Capgemini World’s Wealth Report 2009 defines HNWIs as those who hold at least US$1 million in financial assets and Ultra-HNWIs as those who hold at least US$30 million in financial assets, with both excluding collectibles, consumables, consumer durables and primary residences. The report states that in 2008 there were 8.6 million HNWIs worldwide, a decline of 14.9% from 2007. The total HNWI wealth worldwide totaled US$32.8 trillion, a 19.5% decrease from 2007. The Ultra-HNWIs experienced the greater loss, losing 24.6% in population size and 23.9% in accumulated wealth. The report revised its 2007 projections that HNWI financial wealth would reach US$59.1 trillion by 2012 and revised this downward to a 2013 HNWI wealth valued at $48.5 trillion advancing at an annual rate of 8.1%.
WATCH OUR OWN 560 CHANNELS and 5.000 ASSOCIATED CHANNELS TOTALLY FREE
ebizz.tv is a new, free and open-source platform for internet television and video with more as 5 million videos in the library and 900.000 video channels.
See more at See more at http://www.berndpulch.co, http://www.berndpulch.co.uk, http://www.berndmpulch.com, http://www.berndpulch.com, http://www.berndpulch.org, http://www.bernd-pulch.org, http://www.berndpulch.de, http://www.berndpulch.info and http://www.berndpulch.at and http://www.berndpulch.net, http://www.berndpulch.co.uk, http://www.investment-on.com, http://www.investmentmagazin.com, http://www.investment-magazin.tv, as well as at http://www.ebizz.tv and http://www.star-fashion.com, http://www.magister-berndpulch.com, http://www.magister-berndpulch.com, http://wwww.maberndpulch.com, http://www.berndpulchorg.com, http://www.magisterberndpulch.org, http://www.berndpulchcom.com,http://www.berndpulch.me,http://www.berndpulchme.com,
http://www.pulch.me, http://www.i-nvestment.com, http://www.bernd-pulch.me, http://www.worldwideblog.net,
We broadcast and produce
IPTV channels all around the globe.
WE BUILD YOUR PERSONAL WEB TV CHANNEL
Copyright General Global Media
*Magister Bernd M. Pulch (MA – Magister Artium)
Magister Bernd M. Pulch studied Publizistik (2), Komparatistik (1) and Germanistik (1-2) until 1988
University Mainz
Published his Magister-Thesis for Professor Hans-Mathias Kepplinger
about Dolf Zillmans “Emotional Arousal Theory” January 1987
You can order the book of Bernd Pulch for only € 125,- It can be delivered in 7 days.
Payment must be made in advance.
See more at http://www.berndpulch.co, http://www.berndpulch.co.uk, http://www.berndmpulch.com, http://www.berndpulch.com, http://www.berndpulch.org, http://www.bernd-pulch.org, http://www.berndpulch.de, http://www.berndpulch.info and http://www.berndpulch.at and http://www.berndpulch.net, http://www.berndpulch.co.uk, http://www.investment-on.com, http://www.investmentmagazin.com, http://www.investment-magazin.tv, as well as at http://www.ebizz.tv and http://www.star-fashion.com, http://www.magister-berndpulch.com, http://www.magister-berndpulch.com, http://wwww.maberndpulch.com, http://www.berndpulchorg.com, http://www.magisterberndpulch.org, http://www.berndpulchcom.com,http://www.berndpulch.me,http://www.berndpulchme.com,
http://www.pulch.me, http://www.i-nvestment.com, http://www.bernd-pulch.me,
Investment Magazin, Investment, Das Investment, Investment Magazine
Cyberattacken wie bei uns – Chinesische Hacker spionieren New York Times aus
NEW YORK TIMES – Chinesische Hacker spionieren US-Tageszeitung aus
Hacker sind in Computer der New York Times eingedrungen. Sie stahlen Passwörter und spionierten E-Mail-Konten aus. Sicherheitsexperten verfolgten die Angriffe nach China zurück.
Unbekannte haben sich über Monate Zugang zu den Computersystemen der Tageszeitung New York Times (NYT) verschafft. Die Sicherheitsexperten konnten die Angriffe nach China zurückverfolgen. Anlass war mutmaßlich ein Bericht über die Familie des scheidenden Premierministers Wen Jiabao – die Angriffe begannen kurz danach.
Die Angreifer drangen in die Systeme der New York Times ein. Dort installierten sie Schadsoftware und verschafften sich Zugang zu den Arbeitsplatzrechnern von 53 Mitarbeitern, von denen die meisten nicht im Newsroom arbeiten. Zudem kopierten die Angreifer die Passwörter aller NYT-Mitarbeiter. Es sollen keine Kundendaten entwendet worden sein.
Warnung vor Erscheinen
Die Angriffe schienen in direktem Zusammenhang mit dem Bericht über den chinesischen Politiker zu stehen: Sie hätten unmittelbar nach der Veröffentlichung am 25. Oktober 2012 begonnen, berichtet die Tageszeitung. Kurz zuvor sei die Zeitung von chinesischen Behörden vor Angriffen gewarnt worden. Die Tageszeitung habe sich an den Netzbetreiber AT&T gewandt, und der habe direkt, nachdem der Artikel online erschienen war, Aktivitäten festgestellt, die auf einen Computerangriff hinwiesen. Das NYT engagierte daraufhin das Sicherheitsunternehmen Mandiant und informierte das FBI.
Die Analyse der Mandiant-Experten ergab, dass der Angriff schon früher begonnen hatte: Im September, kurz vor dem Ende der Recherchen zu dem Artikel, waren die Hacker erstmals in die NYT-Computer eingedrungen und hatten das Passwortsystem gehackt. So konnten sie sich Zugriff auf die E-Mail-Konten von David Barboza, Leiter des NYT-Büros in Schanghai und Autor des Berichts, und Jim Yardley, Leiter des Südostasienbüros in Indien und davor Chef des Pekinger Büros, verschaffen.
Wie es scheint, kopierten die Angreifer jedoch keine Dokumente, sondern suchten nach den Namen von Informanten. Auch hatten sie kein Interesse daran, die Computersysteme der Zeitung komplett lahmzulegen – obwohl sie, wie die Zeitung zugibt, die Möglichkeit dazu gehabt hätten.
Phishing-Mails
Wie die Angreifer den Zugang zu den NYT-Computern erlangten, ist noch nicht geklärt. Die Experten vermuten, dass sie E-Mails mit verseuchten Anhängen oder Links verschickt haben, über die Schadsoftware auf die Computer geschleust wurde. Inzwischen seien alle Zugänge, die die Hacker nutzten, geschlossen.
Um ihre Spuren zu verwischen, waren die Angreifer zuerst in Computersysteme von US-Universitäten eingedrungen, so dass es auf den ersten Blick so aussah, als kämen die Angriffe von dort. Chinesische Hacker gehen nach Angaben der von der NYT beauftragten Sicherheitsexperten häufig so vor. Auch die verwendete Schadsoftware wies Merkmale auf, die auf Akteure aus China schließen lassen. Schließlich gelang es den Sicherheitsexperten, die Angriffe zu den Universitätscomputern zurückzuverfolgen, die als Ausgangspunkt von Angriffen des chinesischen Militärs auf Lieferanten des US-Militärs gelten.
Hacker bei Bloomberg
Die NYT scheint indes nicht das einzige Medienunternehmen zu sein, das chinesische Hacker ins Visier genommen haben: 2012 wurden bei Bloomberg News Computer mit Schadsoftware infiziert. Anlass war mutmaßlich ein vergleichbarer Bericht der Nachrichtenagentur über Xi Jinping, seinerzeit noch Vizepräsident und inzwischen Chef der Kommunistischen Partei Chinas und designierter Staatschef.
Wen ist seit 2003 Premierminister der Volksrepublik China. Zuvor war er fünf Jahre lang Vizepremier. Im Oktober 2012 deckte die NYT auf, dass Wens Familie während seiner Amtszeit ein immenses Vermögen angehäuft habe – umgerechnet rund über 2 Milliarden Euro sollen Wens Angehörige, vor allem seine Frau Zhang Peili, zusammengetragen haben. Die Behörden reagierten umgehend auf den Bericht: Sie sperrten den Zugang zur Website der Zeitung.
Was wusste Wen?
Unklar ist Wens Rolle: Zwar ist seine Familie während seiner Amtszeit reich geworden – unter anderem aufgrund wirtschaftlicher Entscheidungen, die Wen mitverantwortet hat. Er selbst soll aber von den Aktivitäten seiner Frau wenig angetan gewesen sein. Laut einer der von Wikileaks veröffentlichten Botschaftsdepeschen soll er sogar deswegen eine Scheidung erwogen haben. Nach dem NYT-Bericht forderte er eine Untersuchung und bot an, dafür die Vermögensverhältnisse der Familie offenzulegen.
Wen wird turnusmäßig nach zwei Amtszeiten von je fünf Jahren sein Amt in diesem Frühjahr aufgeben. Auf dem 18. Parteitag der Kommunistischen Partei wurde im Herbst 2012 die neue Führungsriege vorgestellt. Wens Nachfolger wird voraussichtlich Li Keqiang, der das Amt im März übernehmen soll. Im Vorfeld des Führungswechsels gab es einen Machtkampf zwischen zwei Parteiflügeln.
OUR WEBSITES ARE UNDER ATTACK BY CHINESE HACKERS WHICH ARE ACTING ON BEHALF OF SOME GERMAN THUGS.
Video – Sexy ‘Reporter’ with Prime Minister Ivica Dacic
THIS sexy lass says pants to diplomacy – as she flashes her naked undercarriage to the Serbian Prime Minister. Politician Ivica Dacic was caught unawares by the cheeky prank during an interview for Croatian television. He thought he was in the studio to answer questions on Balkan politics – but instead was treated to a full-frontal from the show’s sexy presenter.
The clip begins with the stunning but improbably dressed host – a model acting as a journalist – welcoming Dacic to the studio.
Wearing a tiny, low-cut dress and heavy make-up, she kisses him on both cheeks and settles him in his chair as he is miked up.
With her legs crossed, she proceeds to ask hapless Dacic a series of political questions.
But as he gives a sombre reply to one of her comments, the shapely brunette slowly re-crosses her legs – and reveals her own controversial policy.
The move is clearly stolen from the racy flick Basic Instinct – although this lass is no Sharon Stone.
As the word “Censored” covers her modesty – just about – a nervous cameraman pans to Dacic for his reaction.
But the Serb shows he’s in the Premier league when it comes to taking a joke – he is shown going goggle-eyed with shock before smirking and enjoying a chuckle at the prank.
The scene – part of a candid camera show called Nemoguca Misija (meaning “Mission Impossible”) – has now had nearly 1million views on YouTube.
In der serbischen Version von “Verstehen Sie Spaß” geht es zur Sache: Das Opfer der Sendung — Serbiens Premier Ivica Dacic — bekommt es mit einer äußert leichtbekleideten Journalistin zu tun.
OUR WEBSITES ARE ATTACKED CONSTANTLY BY CHINESE HACKERS WHICH ARE ACTING ON BEHALF OF SOME GERMAN THUGS.
IMMER WIEDER WERDEN WEBSITES MUTMASSLICH DURCH “GOMoPa” UND DEREN MUTMASSLICHE AUFTRAGGEBER ATTACKIERT WIE MUTMASSLICH “GERD BENNEWIRTZ” UND “PETER EHLERS”
Die FÄLLE SIND BEI DEN ZUSTÄNDIGEN BEHÖRDEN
SIEHE AUCH HIER:
https://berndpulch.org/2013/02/02/cyberattacks-hackers-in-china-attacked-the-times-for-last-4-months/
DER BEWEIS AUS DEM JAHR 2000: SO REGTE GRUNER und JAHR-TOCHTER, IPV, MICH AN, DEN TITEL “INVESTMENT” ZU LANCIEREN
DIE BESTEN DAS INVESTMENT- DAS ORIGINAL Cover seit dem Jahre 2000
http://investmentmagazin.com/?page_id=257
DER BEWEIS “DAS INVESTMENT MAGAZIN” DAS ORIGINAL IST ECHT
https://berndpulch.org/2011/04/17/der-beweis-das-investment-magazin-das-original/
DER MAGISTER-TITEL VON BERND PULCH IST ECHT
https://berndpulch.org/der-beweis-magisterarbeit-bernd-pulch/
Reporting by Bernd Pulch, Lionel Goodwin, Sarah Goodsmith, Bridget Gallagher and Tim Wilkinson
http://wwww.investment-on.com
See more at See more at http://www.berndpulch.co, http://www.berndpulch.co.uk, http://www.berndmpulch.com, http://www.berndpulch.com, http://www.berndpulch.org, http://www.bernd-pulch.org, http://www.berndpulch.de, http://www.berndpulch.info and http://www.berndpulch.at and http://www.berndpulch.net, http://www.berndpulch.co.uk, http://www.investment-on.com, http://www.investmentmagazin.com, http://www.investment-magazin.tv, as well as at http://www.ebizz.tv and http://www.star-fashion.com, http://www.magister-berndpulch.com, http://www.magister-berndpulch.com, http://wwww.maberndpulch.com, http://www.berndpulchorg.com, http://www.magisterberndpulch.org, http://www.berndpulchcom.com,http://www.berndpulch.me,http://www.berndpulchme.com,
http://www.pulch.me, http://www.i-nvestment.com, http://www.bernd-pulch.me, http://www.worldwideblog.net,
For security reasons we do not provide any more information to protect us against cyber criminals – join our Crusade against Cyber Criminals
The INVESTMENT – MAGAZINE – THE ORIGINAL- was founded in 1995. We publish three editions, one global, one for Asia and one germany, Austria and Szwiterland.
We are independent from financial companies.
We focus on HNWI.
A high net worth individual (HNWI) is a person with a high net worth. In the private banking business, these individuals typically are defined as having investable assets (financial assets not including primary residence) in excess of US$1 million.[1][2] As explained below, the U.S. Securities and Exchange Commission has promulgated a different definition of “high net worth individual” for regulatory purposes.
The Merrill Lynch – Capgemini World’s Wealth Report 2009 defines HNWIs as those who hold at least US$1 million in financial assets and Ultra-HNWIs as those who hold at least US$30 million in financial assets, with both excluding collectibles, consumables, consumer durables and primary residences. The report states that in 2008 there were 8.6 million HNWIs worldwide, a decline of 14.9% from 2007. The total HNWI wealth worldwide totaled US$32.8 trillion, a 19.5% decrease from 2007. The Ultra-HNWIs experienced the greater loss, losing 24.6% in population size and 23.9% in accumulated wealth. The report revised its 2007 projections that HNWI financial wealth would reach US$59.1 trillion by 2012 and revised this downward to a 2013 HNWI wealth valued at $48.5 trillion advancing at an annual rate of 8.1%.
WATCH OUR OWN 560 CHANNELS and 5.000 ASSOCIATED CHANNELS TOTALLY FREE
ebizz.tv is a new, free and open-source platform for internet television and video with more as 5 million videos in the library and 900.000 video channels.
See more at See more at http://www.berndpulch.co, http://www.berndpulch.co.uk, http://www.berndmpulch.com, http://www.berndpulch.com, http://www.berndpulch.org, http://www.bernd-pulch.org, http://www.berndpulch.de, http://www.berndpulch.info and http://www.berndpulch.at and http://www.berndpulch.net, http://www.berndpulch.co.uk, http://www.investment-on.com, http://www.investmentmagazin.com, http://www.investment-magazin.tv, as well as at http://www.ebizz.tv and http://www.star-fashion.com, http://www.magister-berndpulch.com, http://www.magister-berndpulch.com, http://wwww.maberndpulch.com, http://www.berndpulchorg.com, http://www.magisterberndpulch.org, http://www.berndpulchcom.com,http://www.berndpulch.me,http://www.berndpulchme.com,
http://www.pulch.me, http://www.i-nvestment.com, http://www.bernd-pulch.me, http://www.worldwideblog.net,
We broadcast and produce
IPTV channels all around the globe.
WE BUILD YOUR PERSONAL WEB TV CHANNEL
Copyright General Global Media
*Magister Bernd M. Pulch (MA – Magister Artium)
Magister Bernd M. Pulch studied Publizistik (2), Komparatistik (1) and Germanistik (1-2) until 1988
University Mainz
Published his Magister-Thesis for Professor Hans-Mathias Kepplinger
about Dolf Zillmans “Emotional Arousal Theory” January 1987
You can order the book of Bernd Pulch for only € 125,- It can be delivered in 7 days.
Payment must be made in advance.
See more at http://www.berndpulch.co, http://www.berndpulch.co.uk, http://www.berndmpulch.com, http://www.berndpulch.com, http://www.berndpulch.org, http://www.bernd-pulch.org, http://www.berndpulch.de, http://www.berndpulch.info and http://www.berndpulch.at and http://www.berndpulch.net, http://www.berndpulch.co.uk, http://www.investment-on.com, http://www.investmentmagazin.com, http://www.investment-magazin.tv, as well as at http://www.ebizz.tv and http://www.star-fashion.com, http://www.magister-berndpulch.com, http://www.magister-berndpulch.com, http://wwww.maberndpulch.com, http://www.berndpulchorg.com, http://www.magisterberndpulch.org, http://www.berndpulchcom.com,http://www.berndpulch.me,http://www.berndpulchme.com,
http://www.pulch.me, http://www.i-nvestment.com, http://www.bernd-pulch.me,
Investment Magazin, Investment, Das Investment, Investment Magazine
Cyberattacks – Hackers in China Attacked The New York Times for Last 4 Months

A Cyberattack From China: TimesCast: Chinese hackers infiltrated The New York Times’s computer systems, getting passwords for its reporters and others.
SAN FRANCISCO — For the last four months, Chinese hackers have persistently attacked The New York Times, infiltrating its computer systems and getting passwords for its reporters and other employees.
Readers’ Comments
Readers shared their thoughts on this article.
After surreptitiously tracking the intruders to study their movements and help erect better defenses to block them, The Times and computer security experts have expelled the attackers and kept them from breaking back in.
The timing of the attacks coincided with the reporting for a Times investigation, published online on Oct. 25, that found that the relatives of Wen Jiabao, China’s prime minister, had accumulated a fortune worth several billion dollars through business dealings.
Security experts hired by The Times to detect and block the computer attacks gathered digital evidence that Chinese hackers, using methods that some consultants have associated with the Chinese military in the past, breached The Times’s network. They broke into the e-mail accounts of its Shanghai bureau chief, David Barboza, who wrote the reports on Mr. Wen’s relatives, and Jim Yardley, The Times’s South Asia bureau chief in India, who previously worked as bureau chief in Beijing.
“Computer security experts found no evidence that sensitive e-mails or files from the reporting of our articles about the Wen family were accessed, downloaded or copied,” said Jill Abramson, executive editor of The Times.
The hackers tried to cloak the source of the attacks on The Times by first penetrating computers at United States universities and routing the attacks through them, said computer security experts at Mandiant, the company hired by The Times. This matches the subterfuge used in many other attacks that Mandiant has tracked to China.
The attackers first installed malware — malicious software — that enabled them to gain entry to any computer on The Times’s network. The malware was identified by computer security experts as a specific strain associated with computer attacks originating in China. More evidence of the source, experts said, is that the attacks started from the same university computers used by the Chinese military to attack United States military contractors in the past.
Security experts found evidence that the hackers stole the corporate passwords for every Times employee and used those to gain access to the personal computers of 53 employees, most of them outside The Times’s newsroom. Experts found no evidence that the intruders used the passwords to seek information that was not related to the reporting on the Wen family.
No customer data was stolen from The Times, security experts said.
Asked about evidence that indicated the hacking originated in China, and possibly with the military, China’s Ministry of National Defense said, “Chinese laws prohibit any action including hacking that damages Internet security.” It added that “to accuse the Chinese military of launching cyberattacks without solid proof is unprofessional and baseless.”
The attacks appear to be part of a broader computer espionage campaign against American news media companies that have reported on Chinese leaders and corporations.
Last year, Bloomberg News was targeted by Chinese hackers, and some employees’ computers were infected, according to a person with knowledge of the company’s internal investigation, after Bloomberg published an article on June 29 about the wealth accumulated by relatives of Xi Jinping, China’s vice president at the time. Mr. Xi became general secretary of the Communist Party in November and is expected to become president in March. Ty Trippet, a spokesman for Bloomberg, confirmed that hackers had made attempts but said that “no computer systems or computers were compromised.”
Signs of a Campaign
The mounting number of attacks that have been traced back to China suggest that hackers there are behind a far-reaching spying campaign aimed at an expanding set of targets including corporations, government agencies, activist groups and media organizations inside the United States. The intelligence-gathering campaign, foreign policy experts and computer security researchers say, is as much about trying to control China’s public image, domestically and abroad, as it is about stealing trade secrets.
Security experts said that beginning in 2008, Chinese hackers began targeting Western journalists as part of an effort to identify and intimidate their sources and contacts, and to anticipate stories that might damage the reputations of Chinese leaders.
In a December intelligence report for clients, Mandiant said that over the course of several investigations it found evidence that Chinese hackers had stolen e-mails, contacts and files from more than 30 journalists and executives at Western news organizations, and had maintained a “short list” of journalists whose accounts they repeatedly attack.
While computer security experts say China is most active and persistent, it is not alone in using computer attacks for a variety of national purposes, including corporate espionage. The United States, Israel, Russia and Iran, among others, are suspected of developing and deploying cyberweapons.
The United States and Israel have never publicly acknowledged it, but evidence indicates they released a sophisticated computer worm starting around 2008 that attacked and later caused damage at Iran’s main nuclear enrichment plant. Iran is believed to have responded with computer attacks on targets in the United States, including American banks and foreign oil companies.
Russia is suspected of having used computer attacks during its war with Georgia in 2008.
The following account of the attack on The Times — which is based on interviews with Times executives, reporters and security experts — provides a glimpse into one such spy campaign.
After The Times learned of warnings from Chinese government officials that its investigation of the wealth of Mr. Wen’s relatives would “have consequences,” executives on Oct. 24 asked AT&T, which monitors The Times’s computer network, to watch for unusual activity.
On Oct. 25, the day the article was published online, AT&T informed The Times that it had noticed behavior that was consistent with other attacks believed to have been perpetrated by the Chinese military.
The Times notified and voluntarily briefed the Federal Bureau of Investigation on the attacks and then — not initially recognizing the extent of the infiltration of its computers — worked with AT&T to track the attackers even as it tried to eliminate them from its systems.
But on Nov. 7, when it became clear that attackers were still inside its systems despite efforts to expel them, The Times hired Mandiant, which specializes in responding to security breaches. Since learning of the attacks, The Times — first with AT&T and then with Mandiant — has monitored attackers as they have moved around its systems.
Hacker teams regularly began work, for the most part, at 8 a.m. Beijing time. Usually they continued for a standard work day, but sometimes the hacking persisted until midnight. Occasionally, the attacks stopped for two-week periods, Mandiant said, though the reason was not clear.
Investigators still do not know how hackers initially broke into The Times’s systems. They suspect the hackers used a so-called spear-phishing attack, in which they send e-mails to employees that contain malicious links or attachments. All it takes is one click on the e-mail by an employee for hackers to install “remote access tools” — or RATs. Those tools can siphon off oceans of data — passwords, keystrokes, screen images, documents and, in some cases, recordings from computers’ microphones and Web cameras — and send the information back to the attackers’ Web servers.
Michael Higgins, chief security officer at The Times, said: “Attackers no longer go after our firewall. They go after individuals. They send a malicious piece of code to your e-mail account and you’re opening it and letting them in.”
Lying in Wait
Once hackers get in, it can be hard to get them out. In the case of a 2011 breach at the United States Chamber of Commerce, for instance, the trade group worked closely with the F.B.I. to seal its systems, according to chamber employees. But months later, the chamber discovered that Internet-connected devices — a thermostat in one of its corporate apartments and a printer in its offices — were still communicating with computers in China.
In part to prevent that from happening, The Times allowed hackers to spin a digital web for four months to identify every digital back door the hackers used. It then replaced every compromised computer and set up new defenses in hopes of keeping hackers out.
“Attackers target companies for a reason — even if you kick them out, they will try to get back in,” said Nick Bennett, the security consultant who has managed Mandiant’s investigation. “We wanted to make sure we had full grasp of the extent of their access so that the next time they try to come in, we can respond quickly.”
Based on a forensic analysis going back months, it appears the hackers broke into The Times computers on Sept. 13, when the reporting for the Wen articles was nearing completion. They set up at least three back doors into users’ machines that they used as a digital base camp. From there they snooped around The Times’s systems for at least two weeks before they identified the domain controller that contains user names and hashed, or scrambled, passwords for every Times employee.
While hashes make hackers’ break-ins more difficult, hashed passwords can easily be cracked using so-called rainbow tables — readily available databases of hash values for nearly every alphanumeric character combination, up to a certain length. Some hacker Web sites publish as many as 50 billion hash values.
Investigators found evidence that the attackers cracked the passwords and used them to gain access to a number of computers. They created custom software that allowed them to search for and grab Mr. Barboza’s and Mr. Yardley’s e-mails and documents from a Times e-mail server.
Over the course of three months, attackers installed 45 pieces of custom malware. The Times — which uses antivirus products made by Symantec — found only one instance in which Symantec identified an attacker’s software as malicious and quarantined it, according to Mandiant.
A Symantec spokesman said that, as a matter of policy, the company does not comment on its customers.
The attackers were particularly active in the period after the Oct. 25 publication of The Times article about Mr. Wen’s relatives, especially on the evening of the Nov. 6 presidential election. That raised concerns among Times senior editors who had been informed of the attacks that the hackers might try to shut down the newspaper’s electronic or print publishing system. But the attackers’ movements suggested that the primary target remained Mr. Barboza’s e-mail correspondence.
“They could have wreaked havoc on our systems,” said Marc Frons, the Times’s chief information officer. “But that was not what they were after.”
What they appeared to be looking for were the names of people who might have provided information to Mr. Barboza.
Mr. Barboza’s research on the stories, as reported previously in The Times, was based on public records, including thousands of corporate documents through China’s State Administration for Industry and Commerce. Those documents — which are available to lawyers and consulting firms for a nominal fee — were used to trace the business interests of relatives of Mr. Wen.
A Tricky Search
Tracking the source of an attack to one group or country can be difficult because hackers usually try to cloak their identities and whereabouts.
To run their Times spying campaign, the attackers used a number of compromised computer systems registered to universities in North Carolina, Arizona, Wisconsin and New Mexico, as well as smaller companies and Internet service providers across the United States, according to Mandiant’s investigators.
The hackers also continually switched from one I.P. address to another; an I.P. address, for Internet protocol, is a unique number identifying each Internet-connected device from the billions around the globe, so that messages and other information sent by one device are correctly routed to the ones meant to get them.
Using university computers as proxies and switching I.P. addresses were simply efforts to hide the source of the attacks, which investigators say is China. The pattern that Mandiant’s experts detected closely matched the pattern of earlier attacks traced to China. After Google was attacked in 2010 and the Gmail accounts of Chinese human rights activists were opened, for example, investigators were able to trace the source to two educational institutions in China, including one with ties to the Chinese military.
Security experts say that by routing attacks through servers in other countries and outsourcing attacks to skilled hackers, the Chinese military maintains plausible deniability.
“If you look at each attack in isolation, you can’t say, ‘This is the Chinese military,’ ” said Richard Bejtlich, Mandiant’s chief security officer.
But when the techniques and patterns of the hackers are similar, it is a sign that the hackers are the same or affiliated.
“When you see the same group steal data on Chinese dissidents and Tibetan activists, then attack an aerospace company, it starts to push you in the right direction,” he said.
Mandiant has been tracking about 20 groups that are spying on organizations inside the United States and around the globe. Its investigators said that based on the evidence — the malware used, the command and control centers compromised and the hackers’ techniques — The Times was attacked by a group of Chinese hackers that Mandiant refers to internally as “A.P.T. Number 12.”
A.P.T. stands for Advanced Persistent Threat, a term that computer security experts and government officials use to describe a targeted attack and that many say has become synonymous with attacks done by China. AT&T and the F.B.I. have been tracking the same group, which they have also traced to China, but they use their own internal designations.
Mandiant said the group had been “very active” and had broken into hundreds of other Western organizations, including several American military contractors.
To get rid of the hackers, The Times blocked the compromised outside computers, removed every back door into its network, changed every employee password and wrapped additional security around its systems.
For now, that appears to have worked, but investigators and Times executives say they anticipate more efforts by hackers.
“This is not the end of the story,” said Mr. Bejtlich of Mandiant. “Once they take a liking to a victim, they tend to come back. It’s not like a digital crime case where the intruders steal stuff and then they’re gone. This requires an internal vigilance model.”
<nyt_correction_bottom>
This article has been revised to reflect the following correction:
Correction: January 31, 2013
An earlier version of this article misstated the timing of a cyberattack that caused damage at Iran’s main nuclear enrichment plant. Evidence suggests that the United States and Israel released a computer worm around 2008, not 2012.
A version of this article appeared in print on January 31, 2013, on page A1 of the New York edition with the headline: Hackers in China Attacked The Times for Last 4 Months.
The same happens to us since years – the attackers are known and we have informed the authorities about it.
OUR WEBSITES ARE ATTACKED CONSTANTLY BY CHINESE HACKERS WHICH ARE ACTING ON BEHALF OF SOME GERMAN THUGS.
IMMER WIEDER WERDEN WEBSITES MUTMASSLICH DURCH “GOMoPa” UND DEREN MUTMASSLICHE AUFTRAGGEBER ATTACKIERT WIE MUTMASSLICH “GERD BENNEWIRTZ” UND “PETER EHLERS”
Die FÄLLE SIND BEI DEN ZUSTÄNDIGEN BEHÖRDEN
SIEHE AUCH HIER:
DER BEWEIS AUS DEM JAHR 2000: SO REGTE GRUNER und JAHR-TOCHTER, IPV, MICH AN, DEN TITEL “INVESTMENT” ZU LANCIEREN
DIE BESTEN DAS INVESTMENT- DAS ORIGINAL Cover seit dem Jahre 2000
http://investmentmagazin.com/?page_id=257
DER BEWEIS “DAS INVESTMENT MAGAZIN” DAS ORIGINAL IST ECHT
https://berndpulch.org/2011/04/17/der-beweis-das-investment-magazin-das-original/
DER MAGISTER-TITEL VON BERND PULCH IST ECHT
https://berndpulch.org/der-beweis-magisterarbeit-bernd-pulch/
Reporting by Bernd Pulch, Lionel Goodwin, Sarah Goodsmith, Bridget Gallagher and Tim Wilkinson
See more at See more at http://www.berndpulch.co, http://www.berndpulch.co.uk, http://www.berndmpulch.com, http://www.berndpulch.com, http://www.berndpulch.org, http://www.bernd-pulch.org, http://www.berndpulch.de, http://www.berndpulch.info and http://www.berndpulch.at and http://www.berndpulch.net, http://www.berndpulch.co.uk, http://www.investment-on.com, http://www.investmentmagazin.com, http://www.investment-magazin.tv, as well as at http://www.ebizz.tv and http://www.star-fashion.com, http://www.magister-berndpulch.com, http://www.magister-berndpulch.com, http://wwww.maberndpulch.com, http://www.berndpulchorg.com, http://www.magisterberndpulch.org, http://www.berndpulchcom.com,http://www.berndpulch.me,http://www.berndpulchme.com,
http://www.pulch.me, http://www.i-nvestment.com, http://www.bernd-pulch.me, http://www.worldwideblog.net,
For security reasons we do not provide any more information to protect us against cyber criminals – join our Crusade against Cyber Criminals
The INVESTMENT – MAGAZINE – THE ORIGINAL- was founded in 1995. We publish three editions, one global, one for Asia and one germany, Austria and Szwiterland.
We are independent from financial companies.
We focus on HNWI.
A high net worth individual (HNWI) is a person with a high net worth. In the private banking business, these individuals typically are defined as having investable assets (financial assets not including primary residence) in excess of US$1 million.[1][2] As explained below, the U.S. Securities and Exchange Commission has promulgated a different definition of “high net worth individual” for regulatory purposes.
The Merrill Lynch – Capgemini World’s Wealth Report 2009 defines HNWIs as those who hold at least US$1 million in financial assets and Ultra-HNWIs as those who hold at least US$30 million in financial assets, with both excluding collectibles, consumables, consumer durables and primary residences. The report states that in 2008 there were 8.6 million HNWIs worldwide, a decline of 14.9% from 2007. The total HNWI wealth worldwide totaled US$32.8 trillion, a 19.5% decrease from 2007. The Ultra-HNWIs experienced the greater loss, losing 24.6% in population size and 23.9% in accumulated wealth. The report revised its 2007 projections that HNWI financial wealth would reach US$59.1 trillion by 2012 and revised this downward to a 2013 HNWI wealth valued at $48.5 trillion advancing at an annual rate of 8.1%.
WATCH OUR OWN 560 CHANNELS and 5.000 ASSOCIATED CHANNELS TOTALLY FREE
ebizz.tv is a new, free and open-source platform for internet television and video with more as 5 million videos in the library and 900.000 video channels.
See more at See more at http://www.berndpulch.co, http://www.berndpulch.co.uk, http://www.berndmpulch.com, http://www.berndpulch.com, http://www.berndpulch.org, http://www.bernd-pulch.org, http://www.berndpulch.de, http://www.berndpulch.info and http://www.berndpulch.at and http://www.berndpulch.net, http://www.berndpulch.co.uk, http://www.investment-on.com, http://www.investmentmagazin.com, http://www.investment-magazin.tv, as well as at http://www.ebizz.tv and http://www.star-fashion.com, http://www.magister-berndpulch.com, http://www.magister-berndpulch.com, http://wwww.maberndpulch.com, http://www.berndpulchorg.com, http://www.magisterberndpulch.org, http://www.berndpulchcom.com,http://www.berndpulch.me,http://www.berndpulchme.com,
http://www.pulch.me, http://www.i-nvestment.com, http://www.bernd-pulch.me, http://www.worldwideblog.net,
We broadcast and produce
IPTV channels all around the globe.
WE BUILD YOUR PERSONAL WEB TV CHANNEL
Copyright General Global Media
*Magister Bernd M. Pulch (MA – Magister Artium)
Magister Bernd M. Pulch studied Publizistik (2), Komparatistik (1) and Germanistik (1-2) until 1988
University Mainz
Published his Magister-Thesis for Professor Hans-Mathias Kepplinger
about Dolf Zillmans “Emotional Arousal Theory” January 1987
You can order the book of Bernd Pulch for only € 125,- It can be delivered in 7 days.
Payment must be made in advance.
See more at http://www.berndpulch.co, http://www.berndpulch.co.uk, http://www.berndmpulch.com, http://www.berndpulch.com, http://www.berndpulch.org, http://www.bernd-pulch.org, http://www.berndpulch.de, http://www.berndpulch.info and http://www.berndpulch.at and http://www.berndpulch.net, http://www.berndpulch.co.uk, http://www.investment-on.com, http://www.investmentmagazin.com, http://www.investment-magazin.tv, as well as at http://www.ebizz.tv and http://www.star-fashion.com, http://www.magister-berndpulch.com, http://www.magister-berndpulch.com, http://wwww.maberndpulch.com, http://www.berndpulchorg.com, http://www.magisterberndpulch.org, http://www.berndpulchcom.com,http://www.berndpulch.me,http://www.berndpulchme.com,
http://www.pulch.me, http://www.i-nvestment.com, http://www.bernd-pulch.me,
Investment Magazin, Investment, Das Investment, Investment Magazine
Monty Python’s Flying Circus – Merchant Banker
Monty Python’s Flying Circus
http://www.amazon.com/Complete-Monty-Pythons-Flying-Circus/dp/B001E77XNA/ref=…
Monty Python’s Flying Circus – Merchant Banker
Sports Illustrated Swimsuit: Athletes Wives Video
Watch this exclusive video with Jeff Garcia’s, Carmelo Anthony’s and Johnny Damon’s wives, posing for the SI Swimsuit 2008 photo shoot.
For more photos and videos visit http://www.si.com/swimsuit
The New York Times – German Media Ridiculous
http://www.nytimes.com/2013/02/03/arts/television/stupid-german-tricks-wearing-thin-on-tv.html?_r=0
Really ? No surprise for me !!!
It is even worse !!!
Manfred Mann – Ha Ha Said The Clown
TMZ – 49ers Superstars Frank Gore & Michael Crabtree — STRIP CLUBBIN’ Before the Superbowl
How do SF 49ers superstars Frank Gore, Michael Crabtree and Patrick Willis stay relaxed before the Super Bowl? They hit up one of the BEST STRIP CLUBS on Bourbon Street!!!
SECRECY NEWS – ARMY MANUAL HIGHLIGHTS ROLE OF “INFORM AND INFLUENCE ACTIVITIES”
The use of information-related tools to support military operations and to
help shape their outcome is discussed in a newly updated Army manual on
what are now called "Inform and Influence Activities."
Inform and influence activities (or IIA) refers to "the integration of
designated information-related capabilities in order to synchronize themes,
messages, and actions with operations to inform United States and global
audiences, influence foreign audiences, and affect adversary and enemy
decisionmaking."
In some circumstances, the manual says, information operations can play a
decisive role.
"Activities occurring in, through, or by means of the information
environment have a consequential effect on an operational environment and
can impact military operations and outcomes. Therefore, commanders and
their staffs must understand their operational environments completely.
This understanding includes the information environment and the potential
impacts it can have on current and planned military operations."
But the effectiveness of such activities is naturally limited by the
realities of the military engagement.
"Soldiers' actions powerfully influence the credibility of IIA. Visible
actions coordinated with carefully chosen, credible words influence
audiences more than uncoordinated or contradictory actions and words. All
audiences--local and regional as well as adversary and enemy--compare the
friendly force's message with its actions. Consistency contributes to the
success of friendly operations by building trust and credibility.
Conversely, if actions and messages are inconsistent, friendly forces lose
credibility. Loss of credibility makes land forces vulnerable to enemy and
adversary information or countermessaging and places Army forces at a
disadvantage."
"Aligning information-related capabilities with the overall operation
ensures that messages are consistent with the forces' actions to amplify
the credibility of those messages. It is paramount that inform and
influence efforts complement not contradict. Failing to do so jeopardizes
credibility."
The updated Army manual replaces a 2003 document titled "Information
Operations."
"The publication does not address every information-related capability
commanders can use to help shape their complex operational environments. It
should, however, generate introspection and provide just enough guidance to
facilitate flexibility and innovative approaches for commanders to execute
the art of command to inform and influence."
See "Inform and Influence Activities," U.S. Army Field Manual 3-13,
January 2013:
http://www.fas.org/irp/doddir/army/fm3-13.pdf
AFTERMATH OF DEEPWATER HORIZON OIL SPILL, AND MORE FROM CRS
New and updated reports from the Congressional Research Service which
Congress has not made publicly available include the following.
Deepwater Horizon Oil Spill: Recent Activities and Ongoing Developments,
January 31, 2013:
http://www.fas.org/sgp/crs/misc/R42942.pdf
The Unemployed and Job Openings: A Data Primer, January 31, 2013:
http://www.fas.org/sgp/crs/misc/R42943.pdf
Congressional Redistricting and the Voting Rights Act: A Legal Overview,
January 31, 2013:
http://www.fas.org/sgp/crs/misc/R42482.pdf
Health Insurance Exchanges Under the Patient Protection and Affordable
Care Act (ACA), January 31, 2013:
http://www.fas.org/sgp/crs/misc/R42663.pdf
Medicare Primer, January 31, 2013:
http://www.fas.org/sgp/crs/misc/R40425.pdf
U.S. Government Agencies Involved in Export Promotion: Overview and Issues
for Congress, January 31, 2013:
http://www.fas.org/sgp/crs/misc/R41495.pdf
Sovereign Debt in Advanced Economies: Overview and Issues for Congress,
January 31, 2013:
http://www.fas.org/sgp/crs/misc/R41838.pdf
Ukraine: Current Issues and U.S. Policy, January 31, 2013:
http://www.fas.org/sgp/crs/row/RL33460.pdf
United Nations Regular Budget Contributions: Members Compared, 1990-2010,
January 15, 2013:
http://www.fas.org/sgp/crs/row/RL30605.pdf
U.S. and South Korean Cooperation in the World Nuclear Energy Market:
Major Policy Considerations, January 28, 2013:
http://www.fas.org/sgp/crs/row/R41032.pdf
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
Monty Python’s Flying Circus – The Money Song
Monty Python’s Flying Circus
http://www.amazon.com/Complete-Monty-Pythons-Flying-Circus/dp/B001E77XNA/ref=…
SI Swimsuit – Body Painting Video
See the most beautiful girls during their body painting SI Swimsuit shoot.
For more SI Swimsuit photos and videos visit http://www.si.com/swimsuit.
Revealed – Cryptome – Stealing Secrets Series
|

 Please select a region of the map to view facilities in that area; you can then access information specific to an institution or office.
Please select a region of the map to view facilities in that area; you can then access information specific to an institution or office.





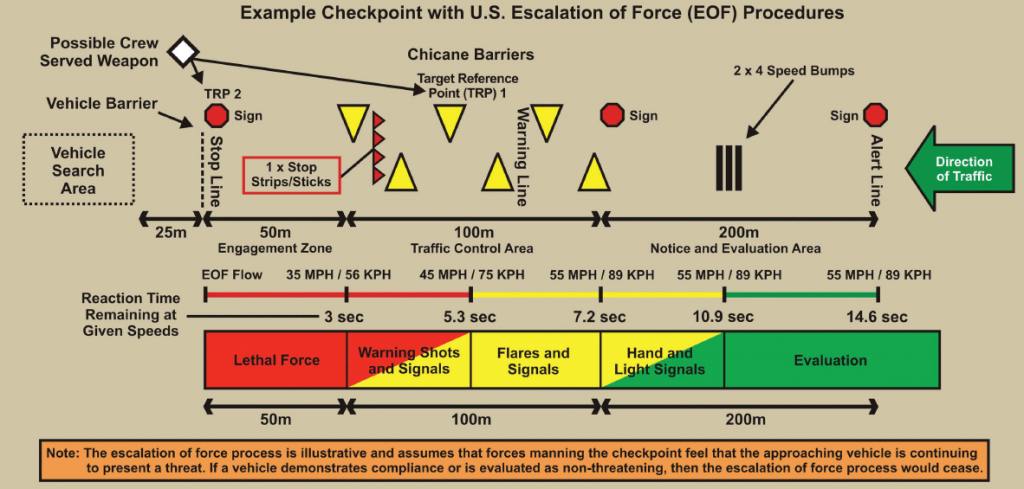











![[Image]](https://i0.wp.com/cryptome.org/2013/02/daiichi-unit3-debris-01.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013/02/daiichi-unit3-debris-02.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/drone-base-const/pict1.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/drone-base-const/pict0.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/drone-base-const/pict26.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/drone-base-const/pict23.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/drone-base-const/pict24.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/drone-base-const/map.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/drone-base-const/pict9.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/drone-base-const/pict10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/drone-base-const/pict11.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/drone-base-const/pict12.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/drone-base-const/pict13.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/drone-base-const/pict14.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/drone-base-const/pict8.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/drone-base-const/pict7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/drone-base-const/pict27.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/drone-base-const/pict15.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/drone-base-const/pict16.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/drone-base-const/pict17.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/drone-base-const/pict18.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/drone-base-const/pict19.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/drone-base-const/pict20.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/sa-drone-base.jpg)

![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict84.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict63.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict62.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict64.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict65.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict66.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict67.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict61.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict59.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict69.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict70.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict58.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict57.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict56.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict54.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict55.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict53.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict52.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict51.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict50.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict48.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict47.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict49.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict71.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict72.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict73.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict46.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict37.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict38.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict45.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict44.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict43.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict42.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict41.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict74.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict75.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict77.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict76.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict39.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/saudi-airbases/pict40.jpg)

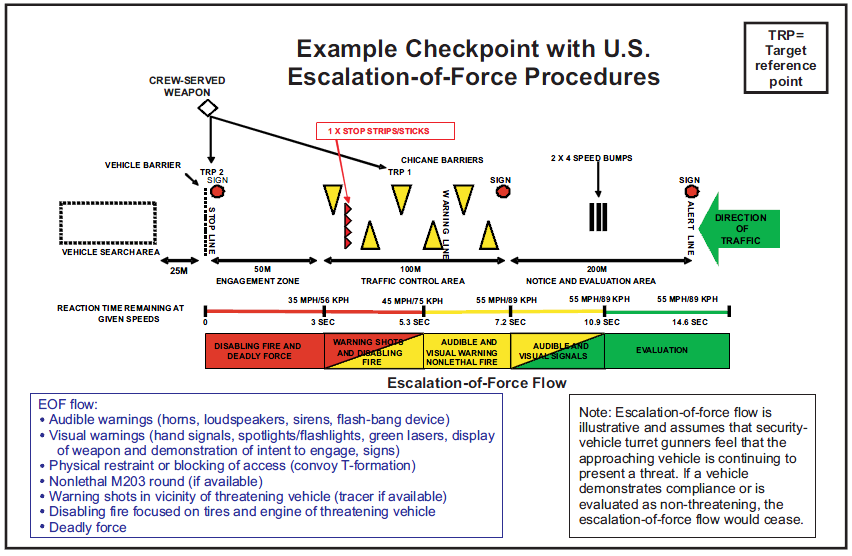

![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict8.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict0.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict1.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict6.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict24.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict25.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict26.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict27.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict28.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict20.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict21.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict23.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict22.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict29.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict30.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict31.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict32.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict34.jpg) Sub docked at right
Sub docked at right
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict35.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict36.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict19.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict18.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict2.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict5.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict3.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict4.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict14.jpg) October 24, 2004
October 24, 2004
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict17.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict13.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict15.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict12.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict11.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/02/dprk-subs/pict16.jpg)



You must be logged in to post a comment.