180554407529;05;06;00;;MUCHAJER, BERND:;;;19986,00
120768408813;04;69;00;;MUCHAN, STEFFEN:;;;10080,00
150569415372;08;69;00;;MUCHAU, MICHAEL:;;;9675,00
150850403832;15;19;00;;MUCHOW, ERHARD:;;;23980,00
160969405025;18;40;00;;MUCHOW, TORSTEN:;;;6615,00
010748427411;94;03;00;;MUCK, KARL-HEINZ:;;;23250,00
220770409522;06;69;00;;MUCK, RENE:;;;2870,00
070541406917;15;29;00;;MUCK, WERNER:;;;34312,50
031251516956;98;50;00;;MUCKE, CAROLA:;;;21480,00
060756506932;98;81;00;;MUCKE, CHRISTINE:;;;19707,74
080143429725;94;65;00;;MUCKE, GERD:;;;23250,00
240649529715;99;40;00;;MUCKE, HEIDEMARIE:;;;22002,08
181146413211;99;02;00;;MUCKE, JOACHIM:;;;25930,00
080162426810;12;00;40;;MUCKE, PETER:;;;21065,00
270442429722;99;77;00;;MUCKE, PETER:;;;40320,00
240264522854;12;08;00;;MUCKE, PETRA:;;;13201,33
281070420711;18;32;00;;MUCKE, THOMAS:;;;2795,00
091045406427;99;02;00;;MUCKE, WOLFGANG:;;;30750,00
210349424973;99;43;00;;MUCKER, ERHARD:;;;21750,00
290756518910;10;00;40;;MUCKISCH, MARION:;;;17792,50
240668404838;99;43;00;;MUCKWAR, UWE:;;;9675,00
050459430223;97;01;00;;MUECKE, BURKHARD:;;;25530,00
181036530054;97;06;00;;MUECKE, CHRISTA:;;;21750,00
201256421322;12;51;00;;MUECKE, HARALD:;;;17422,50
160447422119;99;43;00;;MUECKE, HEINZ:;;;21000,00
200330430231;96;15;05;;MUECKE, HUBERT:;;;24375,00
020532420543;12;03;00;;MUECKE, JOHANNES:;;;18000,00
260264412258;30;39;00;;MUECKE, UWE:;;;17160,00
210761421520;12;06;00;;MUECKEL, STEFFEN:;;;18425,00
291040400831;94;03;00;;MUECKENHEIM, MANFRED:;;;23687,50
210662406157;04;80;00;;MUEER, THOMAS:;;;14688,00
260656413014;30;47;00;;MUEGGE, KARLHEINZ:;;;18975,00
040632429738;98;84;00;;MUEGGE, MANFRED:;;;21000,00
270158530049;30;61;00;;MUEGGE, PETRA:;;;14013,25
130547400411;01;08;00;;MUEGGE, WERNER:;;;24937,50
020352400713;14;06;00;;MUEGGENBORG, KARLHEINZ:;;;13500,00
240546411028;02;40;00;;MUEGGENBURG, BERND:;;;25920,00
020854414314;18;80;00;;MUEGGENBURG, MANFRED:;;;18780,00
030168421839;12;69;00;;MUEHL, DETLEF:;;;9750,00
030168421847;12;69;00;;MUEHL, JOERG:;;;9750,00
031259427317;60;90;00;;MUEHL, PETER:;;;
031259427317;60;90;00;;MUEHL, PETER:;;;15624,00
111137427116;14;14;00;;MUEHL, ROLF:;;;22500,00
221065411218;18;29;30;;MUEHLAST, HAGEN:;;;14125,50
271153407118;97;22;00;;MUEHLBACH, DETLEF:;;;23700,00
081168415391;08;69;00;;MUEHLBACH, JENS-UWE:;;;13475,00
190554416715;09;06;00;;MUEHLBACH, LUTZ:;;;19105,15
220265415390;08;69;00;;MUEHLBACH, MICHAEL:;;;16252,50
150950428287;14;53;00;;MUEHLBACH, MICHAEL:;;;24265,00
221270421538;12;18;00;;MUEHLBAUER, DIRK:;;;2700,00
190250421531;12;19;00;;MUEHLBAUER, FRANK:;;;30284,52
300755410824;17;00;00;;MUEHLBAUER, HANS-ULRICH:;;;26070,00
260845506914;98;83;00;;MUEHLBAUER, HEIDRUN:;;;17150,00
231069407418;99;43;00;;MUEHLBAUER, JENS:;;;8955,00
311047406916;98;82;00;;MUEHLBAUER, PETER:;;;26187,50
020349421548;12;09;00;;MUEHLBAUER, REINHARD:;;;27000,00
290956424935;97;22;00;;MUEHLBERG, BERND:;;;18630,00
071068408515;06;69;00;;MUEHLBERG, JENS:;;;9510,00
310354422049;18;28;00;;MUEHLBERG, JUERGEN:;;;22320,00
211059406456;04;18;00;;MUEHLBERG, KARSTEN:;;;21615,00
061155529957;18;80;00;;MUEHLBERG, MARTINA:;;;16867,85
020339430045;99;44;00;;MUEHLBERGER, PETER:;;;35250,00
060449421218;06;00;46;;MUEHLE, EBERHARD:;;;22770,00
120245420514;94;03;00;;MUEHLE, HANS-JUERGEN:;;;24750,00
091230430015;99;40;00;;MUEHLE, HEINZ:;;;29250,00
101143420915;30;59;00;;MUEHLE, KLAUS:;;;14490,00
031051500810;94;03;00;;MUEHLE, MARIANNE:;;;22860,00
280256406948;96;15;13;;MUEHLE, MARIO:;;;18689,22
011135522779;12;51;00;;MUEHLE, RENATE:;;;23437,50
040670422756;99;43;00;;MUEHLE, RONALD:;;;6780,00
270864430010;99;09;00;;MUEHLE, THOMAS:;;;18480,00
080139406133;17;00;00;;MUEHLE, WERNER:;;;28616,94
260966400825;99;12;00;;MUEHLENBECK, RICCO:;;;14568,00
190662400825;01;20;00;;MUEHLENBECK, WOLFGANG:;;;19470,00
090458408434;99;40;00;;MUEHLENBERG, GERD-MICHAEL:;;;22425,00
190160403620;03;02;00;;MUEHLENBERG, GUNNAR:;;;23362,50
260965503726;03;53;00;;MUEHLENBERG, IRIS:;;;2430,00
081039408013;06;00;41;;MUEHLFRIEDEL, EBERHARD:;;;25500,00
200443530044;18;27;00;;MUEHLFRIEDEL, INGE:;;;24000,00
010347425001;13;26;00;;MUEHLHAHN, ROLF:;;;24480,00
181052413413;18;40;00;;MUEHLHAUSE, HORST:;;;20880,00
080154417746;09;18;00;;MUEHLHEIM, MANFRED:;;;19906,00
131246419025;02;00;43;;MUEHLIG, FRANK:;;;28750,00
200250427315;30;59;00;;MUEHLIG, RUEDIGER:;;;20160,00
030669424958;13;69;00;;MUEHLMANN, ALEXANDER:;;;9555,00
120349419032;14;53;00;;MUEHLMANN, GERD:;;;26250,00
130945429738;97;01;00;;MUEHLMANN, HANS-JOACHIM:;;;30500,04
211160410513;99;02;00;;MUEHLMANN, JENS:;;;20460,00
230466422748;94;03;00;;MUEHLMANN, KAI-UWE:;;;16848,00
310362424239;99;43;00;;MUEHLNER, HAGEN:;;;16417,50
251229430026;98;84;00;;MUEHLNER, HANS:;;;46500,00
161055429818;99;43;00;;MUEHLNER, RALF:;;;19035,00
210136528285;99;51;00;;MUEHLNER, URSULA:;;;24539,99
040547430160;94;30;00;;MUEHLPFORTE, REINHARD:;;;33840,00
011262414615;99;02;00;;MUEHLSTAEFF, JOERG:;;;17765,00
210635417803;09;65;00;;MUEHLSTEIN, KARL:;;;20937,50
010868428259;14;69;00;;MUEHLSTEIN, STEFFEN:;;;13475,00
130262422721;98;84;00;;MUEHMEL, PETER:;;;18232,50
080642402746;02;18;00;;MUEHMELT, DETLEF:;;;29250,00
050447500722;14;80;00;;MUEHSINGER, MARIANNE:;;;13406,00
180264408435;99;43;00;;MUELBREDT, LUTZ:;;;17132,50
180343429752;98;85;00;;MUELKE, ALF-HOLGER:;;;27937,50
261151517779;99;02;00;;MUELKE, ANGELIKA:;;;24150,00
201250416127;99;40;00;;MUELKE, KLAUS-HENDRIK:;;;31140,00
181155425038;97;06;00;;MUELLENHAUPT, GERD:;;;24150,00
240440414538;08;00;57;;MUELLER, ACHIM:;;;29250,00
150135420545;12;40;00;;MUELLER, ACHIM:;;;28500,00
011240426519;94;30;00;;MUELLER, ACHIM:;;;26562,50
030140420017;11;03;00;;MUELLER, ALBERT:;;;33687,50
301239406911;99;41;00;;MUELLER, ALBRECHT:;;;30000,00
090238405346;04;00;49;;MUELLER, ALFRED:;;;26250,00
220368430091;17;00;00;;MUELLER, ANDRE:;;;8950,00
071169423618;13;69;00;;MUELLER, ANDRE:;;;9555,00
260764420246;11;07;00;;MUELLER, ANDRE:;;;16657,00
190767430131;17;00;00;;MUELLER, ANDRE:;;;9872,00
290968418719;10;69;00;;MUELLER, ANDRE:;;;9555,00
161268427226;95;45;00;;MUELLER, ANDRE:;;;13392,74
240561530025;98;82;00;;MUELLER, ANDREA:;;;16475,59
230764517120;97;01;00;;MUELLER, ANDREA:;;;11769,33
261064412303;07;08;00;;MUELLER, ANDREAS:;;;16252,50
251061413918;08;03;00;;MUELLER, ANDREAS:;;;19305,00
091070406453;04;69;00;;MUELLER, ANDREAS:;;;2870,00
191169403816;05;69;00;;MUELLER, ANDREAS:;;;9817,26
291068407525;05;69;00;;MUELLER, ANDREAS:;;;2870,00
121143429723;15;00;40;;MUELLER, ANDREAS:;;;28500,00
280559427615;14;14;00;;MUELLER, ANDREAS:;;;18129,75
190862426317;14;18;00;;MUELLER, ANDREAS:;;;19745,00
120862426815;14;65;00;;MUELLER, ANDREAS:;;;17077,50
260364412917;12;07;00;;MUELLER, ANDREAS:;;;5720,00
140764422819;12;65;00;;MUELLER, ANDREAS:;;;17001,00
290664416829;99;43;00;;MUELLER, ANDREAS:;;;16886,77
101151425054;18;80;00;;MUELLER, ANDREAS:;;;23040,00
031064409522;18;80;00;;MUELLER, ANDREAS:;;;16912,50
040757418311;99;02;00;;MUELLER, ANDREAS:;;;21505,00
300964430071;94;65;00;;MUELLER, ANDREAS:;;;11220,00
150162428112;30;34;00;;MUELLER, ANDREAS:;;;18340,00
081164426536;60;90;00;;MUELLER, ANDREAS:;;;16430,00
080367405925;18;28;00;;MUELLER, ANDREAS:;;;15876,00
190566417336;09;00;00;;MUELLER, ANDREAS:;;;16038,00
070155429838;94;03;00;;MUELLER, ANDREAS:;;;22320,00
041054422124;94;03;00;;MUELLER, ANDREAS:;;;20220,00
190161422030;94;30;00;;MUELLER, ANDREE:;;;19217,50
021267408440;06;69;00;;MUELLER, ANDY:;;;11117,00
170960500228;01;96;43;;MUELLER, ANGELA:;;;15380,75
150354507528;30;42;00;;MUELLER, ANGELIKA:;;;9909,46
150250506117;96;15;14;;MUELLER, ANITA:;;;22437,50
110968519324;10;18;00;;MUELLER, ANJA:;;;11940,00
020569519934;11;08;00;;MUELLER, ANNE-KATHRIN:;;;13175,00
070550525045;30;80;00;;MUELLER, ANNELIE:;;;22061,52
120147504714;04;14;00;;MUELLER, ANNEROSE:;;;16847,50
250870522714;12;96;67;;MUELLER, ANNETT:;;;2190,00
121169506133;17;00;00;;MUELLER, ANTJE:;;;5580,00
210656406150;04;20;00;;MUELLER, ARIS:;;;22022,50
081048417122;09;51;00;;MUELLER, ARND:;;;21937,50
100359427214;14;99;00;;MUELLER, ARNDT:;;;22770,00
150464501530;01;96;52;;MUELLER, ASTRID:;;;12810,27
130159409537;07;00;57;;MUELLER, AXEL:;;;14960,00
260357422754;12;06;00;;MUELLER, AXEL:;;;20700,00
280154429807;99;26;00;;MUELLER, AXEL:;;;23160,00
141062514828;10;80;00;;MUELLER, BA(E)RBEL:;;;15345,00
160268506157;04;02;00;;MUELLER, BABETTE:;;;12600,00
280344507028;98;83;00;;MUELLER, BAERBEL:;;;19440,00
290649514412;15;00;41;;MUELLER, BAERBEL:;;;16224,00
070757511433;17;00;00;;MUELLER, BAERBEL:;;;14189,52
290937506417;30;56;00;;MUELLER, BARBARA:;;;26940,00
070248424825;98;83;00;;MUELLER, BERND:;;;25500,00
160850427120;97;01;00;;MUELLER, BERND:;;;20880,00
160755411227;07;06;00;;MUELLER, BERND:;;;19320,00
101070408316;06;69;00;;MUELLER, BERND:;;;2870,00
270454407432;05;06;00;;MUELLER, BERND:;;;25980,00
020463407248;05;00;47;;MUELLER, BERND:;;;15876,00
031146409518;06;60;00;;MUELLER, BERND:;;;23250,00
310861428111;14;00;60;;MUELLER, BERND:;;;21780,00
210155428220;14;26;00;;MUELLER, BERND:;;;19320,00
260947429227;14;65;00;;MUELLER, BERND:;;;22250,00
011054420519;12;06;00;;MUELLER, BERND:;;;23760,00
141242428230;02;80;00;;MUELLER, BERND:;;;21062,50
290855411211;99;43;00;;MUELLER, BERND:;;;19211,25
300555413617;99;43;00;;MUELLER, BERND:;;;20880,00
100144416235;99;43;00;;MUELLER, BERND:;;;24000,00
031044417146;99;40;00;;MUELLER, BERND:;;;27000,00
170142429749;94;65;00;;MUELLER, BERND:;;;23250,00
211043424967;94;65;00;;MUELLER, BERND:;;;21750,00
240470403119;94;65;00;;MUELLER, BERND:;;;9510,00
040352417118;09;00;48;;MUELLER, BERND:;;;24480,00
060346416918;09;00;47;;MUELLER, BERND:;;;28560,00
220942429731;94;65;00;;MUELLER, BERND-JOACHIM:;;;26250,00
010357415376;97;22;00;;MUELLER, BERND-MICHAEL:;;;21562,50
031251417755;09;08;00;;MUELLER, BERND-RUEDIGER:;;;28080,00
300739420918;30;53;00;;MUELLER, BERNDT:;;;19080,00
241153410029;07;00;43;;MUELLER, BERNHARD:;;;24480,00
300837400515;01;00;44;;MUELLER, BERNHARD:;;;24750,00
190142429720;94;03;00;;MUELLER, BERNHARD:;;;24000,00
110857503127;03;80;00;;MUELLER, BETTINA:;;;17250,01
190458507414;99;77;00;;MUELLER, BETTINA:;;;20010,00
140960504117;97;07;00;;MUELLER, BIRGIT:;;;16421,25
181156403324;03;80;00;;MUELLER, BODO:;;;18630,00
230153500717;01;06;24;;MUELLER, BRIGITTE:;;;16854,62
171151505138;99;77;00;;MUELLER, BRIGITTE:;;;21600,00
260533429710;97;06;00;;MUELLER, BRUNO:;;;27750,00
050749402722;02;14;00;;MUELLER, BURCKHART:;;;24750,00
191253403712;01;99;10;;MUELLER, BURKHARD:;;;23460,00
110866530135;98;82;00;;MUELLER, CAROLA:;;;1233,92
090370417117;99;43;00;;MUELLER, CARSTEN:;;;13285,00
050564417338;09;51;00;;MUELLER, CARSTEN:;;;16280,00
010857424316;96;15;11;;MUELLER, CARSTEN:;;;25012,50
310839530128;99;43;00;;MUELLER, CHRISTA:;;;18380,00
011241529712;99;12;00;;MUELLER, CHRISTA:;;;22920,00
220749529247;94;11;00;;MUELLER, CHRISTA:;;;20100,00
030858529257;94;03;00;;MUELLER, CHRISTEL:;;;15516,37
051146429234;97;06;00;;MUELLER, CHRISTIAN:;;;28500,00
090652426919;14;00;40;;MUELLER, CHRISTIAN:;;;21600,00
191067402214;02;06;00;;MUELLER, CHRISTIAN:;;;14746,00
280444426823;99;53;00;;MUELLER, CHRISTIAN:;;;25140,00
050270401533;01;69;00;;MUELLER, CHRISTIAN:;;;2896,61
260954512248;07;06;00;;MUELLER, CHRISTINE:;;;16046,91
250753512226;07;80;00;;MUELLER, CHRISTINE:;;;14827,65
270341507437;94;11;00;;MUELLER, CHRISTINE:;;;21447,50
110855509517;30;41;00;;MUELLER, CHRISTINE:;;;18024,00
140350429850;99;09;00;;MUELLER, CHRISTOPH:;;;29215,00
300662504717;04;80;00;;MUELLER, CORNELIA:;;;15331,25
050766407234;97;08;00;;MUELLER, DANILO:;;;11016,00
291248415397;08;80;00;;MUELLER, DETLEF:;;;23632,50
110562407410;94;03;00;;MUELLER, DETLEF:;;;17820,00
281236401810;02;00;42;;MUELLER, DETLOF:;;;18000,00
080843429718;98;82;00;;MUELLER, DIETER:;;;22500,00
040635429725;98;84;00;;MUELLER, DIETER:;;;21750,00
190361410819;07;06;00;;MUELLER, DIETER:;;;17820,00
030338412223;07;00;40;;MUELLER, DIETER:;;;33750,00
150148412210;07;19;00;;MUELLER, DIETER:;;;18732,58
130448400811;07;00;46;;MUELLER, DIETER:;;;23760,00
240242407310;05;80;00;;MUELLER, DIETER:;;;20625,00
080949426857;14;06;00;;MUELLER, DIETER:;;;21875,00
301250419019;14;65;00;;MUELLER, DIETER:;;;20440,00
071243414737;13;51;00;;MUELLER, DIETER:;;;23250,00
181038424917;13;99;01;;MUELLER, DIETER:;;;42750,00
240247418617;10;06;00;;MUELLER, DIETER:;;;22437,50
281249419358;10;06;00;;MUELLER, DIETER:;;;22320,00
090653418611;10;03;00;;MUELLER, DIETER:;;;18543,75
080540429737;99;43;00;;MUELLER, DIETER:;;;29250,00
300447423623;99;40;00;;MUELLER, DIETER:;;;33000,00
240142429715;97;08;00;;MUELLER, DIETER:;;;24750,00
200654403715;30;84;00;;MUELLER, DIETER:;;;17110,16
300450406736;30;47;00;;MUELLER, DIETER:;;;23580,00
100753406438;30;40;00;;MUELLER, DIETER:;;;20565,00
161251400879;01;80;00;;MUELLER, DIETER:;;;18000,00
100155429816;94;03;00;;MUELLER, DIETER:;;;25920,00
230448426817;14;00;52;;MUELLER, DIETMAR:;;;31500,00
261048429770;15;40;00;;MUELLER, DIETMAR:;;;23250,00
060550426830;14;06;00;;MUELLER, DIETMAR:;;;24030,00
310347429752;15;14;00;;MUELLER, DIETMAR:;;;22500,00
260150426328;10;00;46;;MUELLER, DIETMAR:;;;30750,00
130656420219;11;08;00;;MUELLER, DIETMAR:;;;19952,50
031247419635;99;77;00;;MUELLER, DIETMAR:;;;25500,00
031050422718;18;40;00;;MUELLER, DIETMAR:;;;27472,50
250356429824;99;02;00;;MUELLER, DIETMAR:;;;24680,00
070255417519;09;80;00;;MUELLER, DIETMAR:;;;17997,50
040939429732;94;03;00;;MUELLER, DIETMAR:;;;27750,00
050563424018;98;20;00;;MUELLER, DIRK:;;;17847,50
010959407613;05;02;00;;MUELLER, DIRK:;;;22252,50
030363407549;03;06;00;;MUELLER, DIRK:;;;17050,00
210965427326;14;14;00;;MUELLER, DIRK:;;;15351,00
261068429233;18;33;00;;MUELLER, DIRK:;;;9675,00
060463407324;99;02;00;;MUELLER, DIRK:;;;20130,00
150962422253;94;03;00;;MUELLER, DIRK:;;;18755,00
150170415354;01;69;00;;MUELLER, DIRK:;;;9315,67
080567413233;96;15;31;;MUELLER, DIRK:;;;11016,00
111162515361;18;33;00;;MUELLER, DORIS:;;;14722,66
231253513229;99;40;00;;MUELLER, DORIS:;;;21460,00
260352500135;94;03;00;;MUELLER, DORIS:;;;20010,00
200646504516;04;00;41;;MUELLER, DOROTHEA:;;;18360,00
071044415374;08;00;61;;MUELLER, EBERHARD:;;;24150,00
100137409520;06;00;40;;MUELLER, EBERHARD:;;;38250,00
160142406177;04;40;00;;MUELLER, EBERHARD:;;;24375,00
090546408418;12;80;00;;MUELLER, EBERHARD:;;;20100,00
090451418410;10;00;46;;MUELLER, EBERHARD:;;;27660,00
181044406918;99;43;00;;MUELLER, EBERHARD:;;;21562,50
261150400528;08;00;50;;MUELLER, EBERHARD:;;;27472,50
040451416938;94;03;00;;MUELLER, EBERHARD:;;;21600,00
080239429738;96;15;12;;MUELLER, EBERHARD:;;;27375,00
310361426224;14;09;00;;MUELLER, ECKHARD:;;;20045,00
200950503016;98;83;00;;MUELLER, EDELGARD:;;;20181,45
120547530110;98;83;00;;MUELLER, EDELTRAUD:;;;23250,00
190340415397;08;40;00;;MUELLER, EDGAR:;;;24000,00
041133522828;12;55;00;;MUELLER, EDITH:;;;25625,00
281238407239;94;03;00;;MUELLER, EGON:;;;29250,00
231151409826;96;15;18;;MUELLER, EGON:;;;20880,00
120448505948;04;80;00;;MUELLER, ELEONORE:;;;22260,00
010356506110;99;40;00;;MUELLER, ELEONORE:;;;17206,22
041249522459;98;85;00;;MUELLER, ELKE:;;;18227,50
310169419710;11;69;00;;MUELLER, ENRICO:;;;9600,00
301135430052;99;02;00;;MUELLER, ERICH:;;;22050,00
100245417747;97;01;00;;MUELLER, ERICH-PETER:;;;28500,00
201238529727;94;30;00;;MUELLER, ERIKA:;;;14098,79
080542429730;15;00;46;;MUELLER, ERNST:;;;24000,00
150152404811;97;08;00;;MUELLER, ERNST-DIETER:;;;14890,64
280654518216;04;08;00;;MUELLER, EVA-MARIA:;;;16920,00
100943528241;14;02;00;;MUELLER, EVELINE:;;;22687,50
151062419918;94;03;00;;MUELLER, FALK:;;;11220,00
041056430195;98;20;00;;MUELLER, FRANK:;;;22252,50
100160407427;98;18;00;;MUELLER, FRANK:;;;26162,50
250963410025;07;06;00;;MUELLER, FRANK:;;;16395,32
221160410336;07;06;22;;MUELLER, FRANK:;;;17056,00
110262412234;07;06;00;;MUELLER, FRANK:;;;14544,00
200559407611;05;06;00;;MUELLER, FRANK:;;;19262,50
091161430061;15;00;48;;MUELLER, FRANK:;;;19800,00
220270427214;14;69;00;;MUELLER, FRANK:;;;3220,00
100651425005;13;14;00;;MUELLER, FRANK:;;;21360,00
230862422117;12;00;54;;MUELLER, FRANK:;;;18630,00
011260422224;12;00;55;;MUELLER, FRANK:;;;20770,00
010667419719;11;00;41;;MUELLER, FRANK:;;;10700,00
190660402720;02;02;00;;MUELLER, FRANK:;;;21120,00
230969400217;01;06;24;;MUELLER, FRANK:;;;9510,00
260471402239;02;00;45;;MUELLER, FRANK:;;;2700,00
180856421828;99;51;00;;MUELLER, FRANK:;;;22540,00
220470423429;99;43;00;;MUELLER, FRANK:;;;6780,00
180661418215;99;51;00;;MUELLER, FRANK:;;;19195,00
080654413928;18;33;00;;MUELLER, FRANK:;;;20160,00
051069428923;18;31;00;;MUELLER, FRANK:;;;9510,00
070369421516;18;35;00;;MUELLER, FRANK:;;;9675,00
270170424417;18;35;00;;MUELLER, FRANK:;;;9600,00
150668428267;18;35;00;;MUELLER, FRANK:;;;9675,00
100860411910;99;09;00;;MUELLER, FRANK:;;;19965,00
230153424611;99;02;00;;MUELLER, FRANK:;;;21600,00
180450426848;97;08;00;;MUELLER, FRANK:;;;25191,53
160363417750;94;03;00;;MUELLER, FRANK:;;;18024,41
120660415376;18;29;00;;MUELLER, FRANK:;;;22522,50
070559419652;30;59;00;;MUELLER, FRANK:;;;13742,10
011259418412;10;80;00;;MUELLER, FRANK:;;;18572,50
080860422737;94;03;00;;MUELLER, FRANK:;;;19430,00
151257406439;94;03;00;;MUELLER, FRANK:;;;21780,00
160346429717;97;17;00;;MUELLER, FRED:;;;29250,00
200256407438;30;42;00;;MUELLER, FRED:;;;19332,50
250941428259;14;18;00;;MUELLER, FRIEDBERT:;;;24687,50
210948424414;08;00;62;;MUELLER, FRIEDRICH:;;;25920,00
290948402218;99;43;00;;MUELLER, FRIEDRICH:;;;24750,00
240743429729;99;26;00;;MUELLER, FRIEDWALD:;;;33000,00
091049413237;98;81;00;;MUELLER, FRITZ-GERHARD:;;;24750,00
110959414416;18;80;00;;MUELLER, GERALD:;;;18372,50
280642429734;97;06;00;;MUELLER, GERALD:;;;24750,00
280437429719;94;03;00;;MUELLER, GERALD:;;;28500,00
101135430056;98;82;00;;MUELLER, GERD:;;;35250,00
130646415352;98;82;00;;MUELLER, GERD:;;;27930,00
110952415344;98;83;00;;MUELLER, GERD:;;;23760,00
300745406119;04;60;00;;MUELLER, GERD:;;;33750,00
260454424911;13;69;00;;MUELLER, GERD:;;;18000,00
281041403410;02;12;00;;MUELLER, GERD:;;;25145,85
311046417779;99;02;00;;MUELLER, GERD:;;;22125,00
240954413225;08;00;45;;MUELLER, GERD:;;;23820,00
270963417313;09;80;00;;MUELLER, GERD:;;;15510,00
211142419012;96;15;06;;MUELLER, GERD:;;;41812,50
200831516420;09;00;44;;MUELLER, GERDA:;;;17625,00
120746418914;02;15;00;;MUELLER, GERD-WALTER:;;;34500,00
170134429714;98;20;00;;MUELLER, GERHARD:;;;27000,00
161143404813;98;83;00;;MUELLER, GERHARD:;;;27750,00
021251409318;06;60;00;;MUELLER, GERHARD:;;;20880,00
280952408218;06;09;00;;MUELLER, GERHARD:;;;25920,00
031134422037;12;00;41;;MUELLER, GERHARD:;;;33750,00
301239421556;12;00;50;;MUELLER, GERHARD:;;;21750,00
161050420224;11;08;00;;MUELLER, GERHARD:;;;21780,00
071048419823;11;55;00;;MUELLER, GERHARD:;;;20500,00
150450429849;99;43;00;;MUELLER, GERHARD:;;;22080,00
130242429715;97;06;00;;MUELLER, GERHARD:;;;24000,00
130830430018;94;30;00;;MUELLER, GERHARD:;;;44250,00
071144409510;06;00;40;;MUELLER, GERNOT:;;;23722,50
300736412226;07;08;00;;MUELLER, GEROLD:;;;28500,00
130138430169;94;03;00;;MUELLER, GERT:;;;23250,00
220937530181;94;30;00;;MUELLER, GIESELA:;;;26640,00
200461517724;99;40;00;;MUELLER, GINA:;;;12287,85
220652513943;08;02;00;;MUELLER, GISELA:;;;22140,00
230155529783;99;43;00;;MUELLER, GISELA:;;;23430,00
160843509558;94;30;00;;MUELLER, GISELA:;;;21792,50
140351500129;98;85;00;;MUELLER, GUDRUN:;;;21460,00
210653511916;07;96;00;;MUELLER, GUDRUN:;;;16387,50
280851504614;99;40;00;;MUELLER, GUDRUN:;;;21780,00
020944530167;96;15;31;;MUELLER, GUDRUN:;;;23760,00
060951408836;06;15;00;;MUELLER, GUENTER:;;;21390,00
011234406167;04;06;00;;MUELLER, GUENTER:;;;23250,00
050635405124;04;00;47;;MUELLER, GUENTER:;;;24000,00
031152407914;04;06;00;;MUELLER, GUENTER:;;;22320,00
171028428333;14;20;00;;MUELLER, GUENTER:;;;24150,00
030251429241;99;09;00;;MUELLER, GUENTER:;;;26487,50
230539422774;97;22;00;;MUELLER, GUENTER:;;;30750,00
120328400228;01;96;52;;MUELLER, GUENTER:;;;10209,67
020945426812;96;15;14;;MUELLER, GUENTER:;;;28900,00
280628430026;96;15;33;;MUELLER, GUENTER:;;;42000,00
151050406124;60;90;00;;MUELLER, GUENTHER:;;;
010951413947;08;53;00;;MUELLER, GUENTHER:;;;24840,00
151050406124;60;90;00;;MUELLER, GUENTHER:;;;23760,00
200970403127;01;69;00;;MUELLER, GUIDO:;;;2896,61
060150405336;04;65;00;;MUELLER, GUNTER:;;;20150,00
021258429231;13;65;00;;MUELLER, GUNTER:;;;17621,83
030956422816;12;01;00;;MUELLER, GUNTER:;;;24165,00
260662424959;99;02;00;;MUELLER, GUNTER:;;;20790,00
281158409218;94;03;00;;MUELLER, HAGEN:;;;21390,00
260950509527;06;00;40;;MUELLER, HANNELORE:;;;15243,07
020840529727;99;77;00;;MUELLER, HANNELORE:;;;27250,00
260349529711;30;83;00;;MUELLER, HANNELORE:;;;18000,00
040850505110;08;00;47;;MUELLER, HANNELORE:;;;15525,00
191044419013;98;18;00;;MUELLER, HANS:;;;28500,00
190339421351;98;50;00;;MUELLER, HANS:;;;37500,00
061134400417;06;06;00;;MUELLER, HANS:;;;23250,00
200834409524;06;80;00;;MUELLER, HANS:;;;19250,00
140227430012;15;60;00;;MUELLER, HANS:;;;27750,00
020446429744;97;08;00;;MUELLER, HANS:;;;24750,00
120837430150;30;47;00;;MUELLER, HANS:;;;20760,00
110346424996;18;27;30;;MUELLER, HANS:;;;25875,00
060544416732;09;40;00;;MUELLER, HANS:;;;28500,00
211052422218;12;00;55;;MUELLER, HANS-DIETER:;;;25200,00
231141402719;99;02;00;;MUELLER, HANS-DIETER:;;;35250,00
060751411811;07;06;00;;MUELLER, HANS-EBERHARD:;;;20160,00
090144415367;08;96;00;;MUELLER, HANS-GEORG:;;;26250,00
240552419827;97;06;00;;MUELLER, HANS-GEORG:;;;24060,00
210848417735;09;14;00;;MUELLER, HANSJOACHIM:;;;19312,50
310539429714;98;18;00;;MUELLER, HANS-JOACHIM:;;;27937,50
290849424323;98;83;00;;MUELLER, HANS-JOACHIM:;;;24480,00
180629422820;12;06;00;;MUELLER, HANS-JOACHIM:;;;29250,00
221151420217;11;20;00;;MUELLER, HANS-JOACHIM:;;;33840,00
240235403629;03;51;00;;MUELLER, HANS-JOACHIM:;;;21240,00
090651403619;03;80;00;;MUELLER, HANS-JOACHIM:;;;19440,00
130653412926;99;43;00;;MUELLER, HANS-JOACHIM:;;;23760,00
200556417427;98;84;00;;MUELLER, HANS-JUERGEN:;;;20070,00
290345410331;07;55;00;;MUELLER, HANS-JUERGEN:;;;17882,50
281055404326;03;00;52;;MUELLER, HANS-JUERGEN:;;;17825,00
270354401324;01;00;40;;MUELLER, HANS-JUERGEN:;;;25920,00
300440400410;01;00;43;;MUELLER, HANS-JUERGEN:;;;22437,50
030653419011;18;34;00;;MUELLER, HANS-JUERGEN:;;;25920,00
140154418417;97;07;00;;MUELLER, HANS-JUERGEN:;;;21060,00
021055416924;09;08;00;;MUELLER, HANS-JUERGEN:;;;21060,00
050754400617;96;15;22;;MUELLER, HANS-JUERGEN:;;;23042,50
160945422816;12;06;00;;MUELLER, HANS-KARL:;;;21187,50
080947409527;98;19;00;;MUELLER, HANS-MICHAEL:;;;26640,00
081258409817;07;00;41;;MUELLER, HANS-PETER:;;;22712,50
080442411920;07;03;00;;MUELLER, HANS-PETER:;;;19449,00
031037429720;99;09;00;;MUELLER, HANS-PETER:;;;30750,00
150947416226;09;00;48;;MUELLER, HANS-PETER:;;;26250,00
141254427526;94;03;00;;MUELLER, HANS-PETER:;;;23400,00
280755422790;96;15;12;;MUELLER, HANS-PETER:;;;23980,00
020448428227;99;02;00;;MUELLER, HANS-ULRICH:;;;27750,00
280851421026;12;06;00;;MUELLER, HARALD:;;;21540,00
120244400415;01;00;43;;MUELLER, HARALD:;;;27000,00
290361430092;94;03;00;;MUELLER, HARALD:;;;19430,00
170938404838;98;18;00;;MUELLER, HARRY:;;;27687,50
280360417743;99;43;00;;MUELLER, HARRY:;;;17975,00
240846409421;08;51;00;;MUELLER, HARTMUT:;;;24750,00
040951412220;07;78;00;;MUELLER, HARTMUT:;;;21000,00
231052427420;14;00;56;;MUELLER, HARTMUT:;;;25200,00
150352420218;11;08;00;;MUELLER, HARTMUT:;;;22112,90
190950420724;30;33;00;;MUELLER, HARTMUT:;;;22770,00
140255429887;98;84;00;;MUELLER, HARTWIG:;;;20880,00
230948518216;10;03;00;;MUELLER, HEIDEMARIE:;;;23937,50
280541530163;30;83;00;;MUELLER, HEIDEMARIE:;;;18094,00
140551515317;08;40;00;;MUELLER, HEIDI:;;;1852,26
220461519613;11;08;00;;MUELLER, HEIKE:;;;14749,11
090263415343;08;00;64;;MUELLER, HEIKO:;;;12567,50
040169422752;12;08;00;;MUELLER, HEIKO:;;;10050,00
310370428264;18;35;00;;MUELLER, HEIKO:;;;9600,00
110267401534;99;02;00;;MUELLER, HEIKO:;;;16038,00
140868415381;18;31;00;;MUELLER, HEIKO:;;;9825,00
310344403418;03;53;00;;MUELLER, HEINRICH:;;;25500,00
081047408232;97;06;00;;MUELLER, HEINRICH:;;;22500,00
070269404719;04;06;00;;MUELLER, HEINTJE:;;;13369,36
101036411423;07;06;00;;MUELLER, HEINZ:;;;21750,00
110454415018;08;14;00;;MUELLER, HEINZ:;;;24480,00
130550428239;11;06;20;;MUELLER, HEINZ:;;;21062,50
100135429712;97;08;00;;MUELLER, HEINZ:;;;24750,00
210235429733;94;65;00;;MUELLER, HEINZ:;;;28500,00
050350421542;96;15;09;;MUELLER, HEINZ-DETLEF:;;;28290,00
030443409579;06;19;00;;MUELLER, HEINZ-DIETER:;;;28187,50
120148424417;15;00;50;;MUELLER, HEINZ-GUENTHER:;;;31680,00
140154421827;94;11;00;;MUELLER, HEINZ-JOACHIM:;;;20040,00
081141530189;04;12;00;;MUELLER, HELGA:;;;20880,00
290440403631;98;82;00;;MUELLER, HELMUT:;;;30750,00
041054404225;98;84;00;;MUELLER, HELMUT:;;;21600,00
251029412210;07;06;00;;MUELLER, HELMUT:;;;21750,00
280635412221;07;00;43;;MUELLER, HELMUT:;;;31500,00
180754409123;06;00;52;;MUELLER, HELMUT:;;;14182,00
300644404712;04;53;00;;MUELLER, HELMUT:;;;26437,50
260146403211;03;00;43;;MUELLER, HELMUT:;;;23303,23
160931424511;13;00;49;;MUELLER, HELMUT:;;;32100,00
080931400210;01;06;27;;MUELLER, HELMUT:;;;27000,00
140155419016;10;26;00;;MUELLER, HELMUT:;;;16885,00
191260430049;98;84;00;;MUELLER, HENDRIK:;;;19575,00
240840415409;08;03;00;;MUELLER, HENRY:;;;33750,00
250552427121;14;00;49;;MUELLER, HENRY:;;;22500,00
030244409541;06;02;00;;MUELLER, HERBERT:;;;29250,00
300335404620;99;40;00;;MUELLER, HERBERT:;;;27750,00
031025427912;30;48;00;;MUELLER, HERBERT:;;;20880,00
120535529227;14;51;00;;MUELLER, HILDEGARD:;;;23250,00
240151427439;98;18;00;;MUELLER, HOLGER:;;;23632,50
010370418619;98;83;00;;MUELLER, HOLGER:;;;10658,63
140151400887;01;06;20;;MUELLER, HOLGER:;;;19400,00
210633429720;97;06;00;;MUELLER, HORST:;;;26250,00
120937424962;13;00;40;;MUELLER, HORST:;;;23250,00
300947420330;11;15;00;;MUELLER, HORST:;;;34560,00
220244402144;02;06;00;;MUELLER, HORST:;;;31500,00
251135400117;01;00;45;;MUELLER, HORST:;;;27000,00
130842415368;94;30;00;;MUELLER, HORST:;;;24500,00
180833422801;30;53;00;;MUELLER, HORST:;;;30600,00
241133429718;96;15;19;;MUELLER, HORST:;;;46500,00
140144406738;97;06;00;;MUELLER, HORST-WERNER:;;;28250,00
141130402124;02;40;00;;MUELLER, HUBERT:;;;27000,00
030255511218;07;06;00;;MUELLER, ILONA:;;;18850,85
280954510718;07;00;40;;MUELLER, ILONA:;;;17880,65
300563511815;97;01;00;;MUELLER, INES:;;;15746,14
300367530074;94;65;00;;MUELLER, INES:;;;11715,96
090152529823;98;83;00;;MUELLER, INGE:;;;21039,25
021032500218;01;96;52;;MUELLER, INGEBORG:;;;12540,45
191059510418;98;83;00;;MUELLER, INGETRAUT:;;;15499,44
070744424971;60;90;00;;MUELLER, INGO:;;;
260269409533;06;69;00;;MUELLER, INGO:;;;9600,00
030967405835;04;06;00;;MUELLER, INGO:;;;11158,00
210667420046;17;00;00;;MUELLER, INGO:;;;9872,00
310869423622;13;69;00;;MUELLER, INGO:;;;9555,00
051247401521;01;06;22;;MUELLER, INGO:;;;22500,00
200463401557;99;43;00;;MUELLER, INGO:;;;15531,09
190967424836;94;03;00;;MUELLER, INGO:;;;14382,00
070744424971;60;90;00;;MUELLER, INGO:;;;23760,00
110368400629;01;69;00;;MUELLER, INGO:;;;7481,61
220937530202;98;83;00;;MUELLER, INGRID:;;;21677,50
160546530078;15;29;00;;MUELLER, INGRID:;;;21540,00
230639522772;12;78;00;;MUELLER, INGRID:;;;31437,50
260253522814;96;15;20;;MUELLER, INGRID:;;;19350,00
210370522455;12;00;47;;MUELLER, IRENA:;;;8760,00
220570403417;98;20;00;;MUELLER, JAN:;;;8300,00
191168407620;05;69;00;;MUELLER, JAN:;;;9510,00
250266428924;14;03;00;;MUELLER, JAN:;;;15621,00
080870519014;97;07;00;;MUELLER, JANA:;;;5400,00
291269428912;99;43;00;;MUELLER, JANOS:;;;13225,00
171067419026;98;18;00;;MUELLER, JENS:;;;14382,00
230267430032;98;84;00;;MUELLER, JENS:;;;16038,00
061169420020;97;01;00;;MUELLER, JENS:;;;2700,00
250270409558;06;69;00;;MUELLER, JENS:;;;3070,16
030167409336;06;69;00;;MUELLER, JENS:;;;9875,00
210670409411;04;06;00;;MUELLER, JENS:;;;8235,00
100367428276;14;07;00;;MUELLER, JENS:;;;13682,03
260365428152;14;69;00;;MUELLER, JENS:;;;17820,00
010866402135;02;15;00;;MUELLER, JENS:;;;11537,52
051167414736;17;00;00;;MUELLER, JENS:;;;9872,00
040566430238;18;71;10;;MUELLER, JENS:;;;16524,00
010170410823;97;06;00;;MUELLER, JENS:;;;14100,00
030670401710;97;06;00;;MUELLER, JENS:;;;2700,00
220265404317;95;45;00;;MUELLER, JENS:;;;16381,12
011267420248;11;06;21;;MUELLER, JENS-UWE:;;;14095,00
240961415368;96;15;13;;MUELLER, JENS-UWE:;;;17738,39
211066426228;15;00;50;;MUELLER, JO(E)RG:;;;15228,00
220334425059;98;84;00;;MUELLER, JOACHIM:;;;21000,00
150354410144;07;03;00;;MUELLER, JOACHIM:;;;22884,00
090652429722;99;55;00;;MUELLER, JOACHIM:;;;22320,00
260849407913;99;13;00;;MUELLER, JOACHIM:;;;24000,00
050945423811;99;26;00;;MUELLER, JOACHIM:;;;24125,00
190449430064;97;06;00;;MUELLER, JOACHIM:;;;24000,00
161146405918;94;30;00;;MUELLER, JOACHIM:;;;25750,00
190557418214;30;53;00;;MUELLER, JOACHIM:;;;16215,00
100151407927;30;80;00;;MUELLER, JOACHIM:;;;21120,00
240750417734;09;80;00;;MUELLER, JOACHIM:;;;19800,00
071256416838;09;06;24;;MUELLER, JOACHIM:;;;17009,66
180543427436;14;00;53;;MUELLER, JOCHEN:;;;29250,00
071258411125;10;00;51;;MUELLER, JOERG:;;;19468,85
260266422775;12;19;00;;MUELLER, JOERG:;;;15984,00
160571423215;12;69;00;;MUELLER, JOERG:;;;3199,35
260256410316;99;49;00;;MUELLER, JOERG:;;;17077,50
011269403425;99;40;00;;MUELLER, JOERG:;;;3620,00
071163407414;94;65;00;;MUELLER, JOERG:;;;16500,00
050265419026;10;65;00;;MUELLER, JOERG:;;;15546,00
270465419068;10;14;00;;MUELLER, JOERG:;;;15812,00
291054429918;15;07;00;;MUELLER, JOERG-DIETRICH:;;;20155,00
080158420010;11;51;00;;MUELLER, JOSEF:;;;19952,50
290160403442;98;20;00;;MUELLER, JUERGEN:;;;22695,00
300848400115;98;85;00;;MUELLER, JUERGEN:;;;27750,00
160556429715;97;01;00;;MUELLER, JUERGEN:;;;25530,00
050741429744;15;18;00;;MUELLER, JUERGEN:;;;27750,00
140549421530;14;55;00;;MUELLER, JUERGEN:;;;21750,00
100668426928;14;69;00;;MUELLER, JUERGEN:;;;12675,00
060855428263;14;80;00;;MUELLER, JUERGEN:;;;17420,00
250467424815;13;00;43;;MUELLER, JUERGEN:;;;13308,39
260864419912;11;00;44;;MUELLER, JUERGEN:;;;14748,00
120352420042;11;80;00;;MUELLER, JUERGEN:;;;18953,23
290745402517;02;00;44;;MUELLER, JUERGEN:;;;28250,00
090757410411;99;02;00;;MUELLER, JUERGEN:;;;20297,50
161149408313;97;08;00;;MUELLER, JUERGEN:;;;24750,00
010340412224;97;08;00;;MUELLER, JUERGEN:;;;18285,00
160854415426;97;06;00;;MUELLER, JUERGEN:;;;24782,50
120957426324;94;03;00;;MUELLER, JUERGEN:;;;19320,00
160469419922;95;45;00;;MUELLER, JUERGER:;;;13875,00
010933529719;15;11;00;;MUELLER, KAETE:;;;26250,00
110664429258;99;77;00;;MUELLER, KAI-UWE:;;;14080,00
250448529232;97;06;00;;MUELLER, KARIN:;;;20125,00
110754506122;97;06;00;;MUELLER, KARIN:;;;17349,27
040645516216;09;06;00;;MUELLER, KARIN:;;;20837,50
301056516210;09;00;43;;MUELLER, KARIN:;;;15600,12
181243429717;98;19;00;;MUELLER, KARL:;;;21187,50
061039404524;04;08;00;;MUELLER, KARL:;;;25375,00
280438428240;14;80;00;;MUELLER, KARL:;;;20875,00
100951425015;18;32;00;;MUELLER, KARL-HEINZ:;;;25920,00
270453410138;09;00;51;;MUELLER, KARL-HEINZ:;;;18000,00
040452417721;09;80;00;;MUELLER, KARL-HEINZ:;;;19140,00
310144419044;96;15;12;;MUELLER, KARL-HERMANN:;;;27187,50
070957530225;97;08;00;;MUELLER, KAROLA:;;;15467,13
271165409110;12;19;00;;MUELLER, KARSTEN:;;;19111,50
280169416929;18;41;30;;MUELLER, KARSTEN:;;;12600,00
140369425067;99;14;00;;MUELLER, KARSTEN:;;;14450,00
210860420013;96;15;26;;MUELLER, KARSTEN:;;;18144,00
230663506115;04;08;00;;MUELLER, KATHRIN:;;;5316,26
110866510310;07;00;45;;MUELLER, KATRIN:;;;14526,00
211066515458;08;51;00;;MUELLER, KATRIN:;;;13651,20
150662500424;01;00;43;;MUELLER, KERSTIN:;;;12330,84
290162506218;99;43;00;;MUELLER, KERSTIN:;;;588,15
301167502428;97;08;00;;MUELLER, KERSTIN:;;;12715,33
240563530264;97;08;00;;MUELLER, KERSTIN:;;;17297,50
130564520917;30;53;00;;MUELLER, KERSTIN:;;;10049,83
290860430054;98;18;00;;MUELLER, KLAUS:;;;18760,00
020556428224;97;01;00;;MUELLER, KLAUS:;;;25290,00
021053414714;98;85;00;;MUELLER, KLAUS:;;;20160,00
191140417771;97;01;00;;MUELLER, KLAUS:;;;29250,00
031146405218;07;19;00;;MUELLER, KLAUS:;;;26250,00
200339409543;06;09;00;;MUELLER, KLAUS:;;;33187,50
110345428258;14;08;00;;MUELLER, KLAUS:;;;22500,00
220839425097;13;00;40;;MUELLER, KLAUS:;;;24000,00
271253422745;12;00;40;;MUELLER, KLAUS:;;;24840,00
120466419920;11;51;00;;MUELLER, KLAUS:;;;14580,00
101051429234;99;51;00;;MUELLER, KLAUS:;;;23760,00
250141429720;99;40;00;;MUELLER, KLAUS:;;;26250,00
300133429715;99;02;00;;MUELLER, KLAUS:;;;37500,00
310847429724;94;65;00;;MUELLER, KLAUS:;;;24000,00
260153422787;30;57;00;;MUELLER, KLAUS:;;;21720,00
200155419026;10;53;00;;MUELLER, KLAUS:;;;22252,50
200755429850;94;03;00;;MUELLER, KLAUS:;;;22770,00
060348422422;98;85;00;;MUELLER, KLAUS-DIETER:;;;25500,00
040354411211;07;08;00;;MUELLER, KLAUS-DIETER:;;;20820,00
260247412221;07;00;00;;MUELLER, KLAUS-DIETER:;;;24562,50
140447409522;06;65;00;;MUELLER, KLAUS-DIETER:;;;19215,72
020444429767;99;55;00;;MUELLER, KLAUS-DIETER:;;;26375,00
270554419019;10;07;00;;MUELLER, KLAUS-DIETER:;;;24912,00
190551413148;08;00;62;;MUELLER, KLAUS-JUERGEN:;;;26795,00
190954404510;04;06;00;;MUELLER, KLAUS-PETER:;;;22260,00
200560425008;13;41;00;;MUELLER, KLAUS-PETER:;;;22080,00
130655427726;30;49;00;;MUELLER, KLAUS-PETER:;;;18850,00
141249400855;30;43;00;;MUELLER, KLAUS-PETER:;;;18000,00
050752424965;94;03;00;;MUELLER, KLAUS-ULRICH:;;;23580,00
150370412238;07;69;00;;MUELLER, KNUT:;;;2911,13
160569409529;94;65;00;;MUELLER, KNUT:;;;13800,00
110341416129;96;15;19;;MUELLER, KONRAD:;;;21000,00
121033429714;98;50;00;;MUELLER, KURT:;;;30000,00
210640407511;05;53;00;;MUELLER, KURT:;;;26250,00
011033430136;18;80;00;;MUELLER, KURT:;;;30000,00
220538430116;30;83;00;;MUELLER, KURT:;;;21240,00
280133430075;18;28;00;;MUELLER, KURT:;;;27750,00
210446427025;96;15;17;;MUELLER, KURT-PETER:;;;28800,00
230536429719;97;07;00;;MUELLER, LEO:;;;30750,00
070730519910;11;00;44;;MUELLER, LILLY:;;;15870,00
240837506131;17;00;00;;MUELLER, LISELOTTE:;;;20880,00
301248419028;98;20;00;;MUELLER, LOTHAR:;;;28080,00
050359430197;98;83;00;;MUELLER, LOTHAR:;;;17464,37
300153412240;07;09;00;;MUELLER, LOTHAR:;;;24480,00
120348408411;06;18;00;;MUELLER, LOTHAR:;;;26910,00
130648426514;04;06;00;;MUELLER, LOTHAR:;;;23187,50
160350428266;14;18;00;;MUELLER, LOTHAR:;;;26250,00
230650425017;13;40;00;;MUELLER, LOTHAR:;;;24195,00
180337418213;10;06;00;;MUELLER, LOTHAR:;;;23937,50
060451420329;11;80;00;;MUELLER, LOTHAR:;;;20093,47
060542424990;99;51;00;;MUELLER, LOTHAR:;;;25000,00
110451428286;94;65;00;;MUELLER, LOTHAR:;;;25920,00
220839502718;30;44;00;;MUELLER, LOTTI:;;;13680,00
150851429241;14;00;61;;MUELLER, LUTZ:;;;24840,00
021057430017;15;15;00;;MUELLER, LUTZ:;;;22195,00
170970423246;99;43;00;;MUELLER, LUTZ:;;;8955,00
161057430089;99;43;00;;MUELLER, LUTZ:;;;18975,00
300957412254;99;09;00;;MUELLER, LUTZ:;;;22252,50
200659408953;97;06;00;;MUELLER, LUTZ:;;;20700,00
210742426828;96;15;22;;MUELLER, LUTZ:;;;23434,03
270769421220;18;35;00;;MUELLER, MAIK:;;;9510,00
220245416919;97;01;00;;MUELLER, MANFRED:;;;30750,00
260146429710;97;01;00;;MUELLER, MANFRED:;;;30750,00
210455412263;07;65;00;;MUELLER, MANFRED:;;;17750,00
080251409414;04;00;44;;MUELLER, MANFRED:;;;28275,00
220134428239;14;03;00;;MUELLER, MANFRED:;;;17733,34
201152423622;13;40;00;;MUELLER, MANFRED:;;;20700,00
070557419632;11;06;20;;MUELLER, MANFRED:;;;16732,50
300145418212;10;00;44;;MUELLER, MANFRED:;;;28625,00
110449422416;12;06;00;;MUELLER, MANFRED:;;;24000,00
280349422728;12;08;00;;MUELLER, MANFRED:;;;22320,00
150864430073;99;43;00;;MUELLER, MANFRED:;;;16912,50
080541429739;17;00;00;;MUELLER, MANFRED:;;;37500,00
050337430209;30;31;00;;MUELLER, MANFRED:;;;20160,00
220235429732;96;15;15;;MUELLER, MANFRED:;;;35250,00
090867501912;02;14;00;;MUELLER, MANUELA:;;;10440,92
090469427446;98;83;00;;MUELLER, MARCEL:;;;10200,00
171070402946;04;06;00;;MUELLER, MARCO:;;;3310,00
051052506438;04;08;00;;MUELLER, MARGARETE:;;;14687,87
230844519011;99;40;00;;MUELLER, MARGIT:;;;24750,00
090851500624;97;06;00;;MUELLER, MARGIT:;;;20764,01
210849506721;30;79;00;;MUELLER, MARGITTA:;;;22110,00
180652512111;08;00;56;;MUELLER, MARGRIT:;;;16757,75
140350524911;99;02;00;;MUELLER, MARIA:;;;564,19
270158506719;98;85;00;;MUELLER, MARIANNE:;;;17500,41
120649519625;99;77;00;;MUELLER, MARIANNE:;;;17628,75
260964402544;02;06;00;;MUELLER, MARIO:;;;12875,00
161263503314;99;09;00;;MUELLER, MARION:;;;6922,01
051048514611;99;13;00;;MUELLER, MARION:;;;23880,00
120463518712;99;77;00;;MUELLER, MARJANA:;;;18975,00
041039512244;97;08;00;;MUELLER, MARLIES:;;;17595,00
201044504118;30;74;00;;MUELLER, MARLIS:;;;19800,00
270360530202;99;77;00;;MUELLER, MARTINA:;;;19285,00
120357513010;94;03;00;;MUELLER, MARTINA:;;;17216,62
150857522033;09;08;00;;MUELLER, MARTINA:;;;17297,50
070150415349;08;80;00;;MUELLER, MATHIAS:;;;28290,00
100868411923;18;32;00;;MUELLER, MATHIAS:;;;9600,00
010166416210;60;90;00;;MUELLER, MATHIAS:;;;14706,00
121056427316;14;15;00;;MUELLER, MATTHIAS:;;;24150,00
170157418516;10;00;51;;MUELLER, MATTHIAS:;;;25012,50
040154426910;94;03;00;;MUELLER, MATTHIAS:;;;23040,00
140128415343;96;15;10;;MUELLER, MAX:;;;30750,00
110953416437;09;19;00;;MUELLER, MEINHARDT:;;;22080,00
190262430056;98;82;00;;MUELLER, MICHAEL:;;;17270,00
030856427919;97;01;00;;MUELLER, MICHAEL:;;;26150,04
060861425229;13;65;00;;MUELLER, MICHAEL:;;;17160,00
180161421573;12;77;00;;MUELLER, MICHAEL:;;;20898,00
160865420351;11;96;63;;MUELLER, MICHAEL:;;;15244,50
121257422781;12;06;00;;MUELLER, MICHAEL:;;;20642,50
240252403436;03;80;00;;MUELLER, MICHAEL:;;;22320,00
070756402729;02;65;00;;MUELLER, MICHAEL:;;;17882,50
221049424959;99;43;00;;MUELLER, MICHAEL:;;;26250,00
081260430228;99;43;00;;MUELLER, MICHAEL:;;;21157,50
221163407511;99;02;00;;MUELLER, MICHAEL:;;;18425,00
290762405656;97;08;00;;MUELLER, MICHAEL:;;;22385,00
130362430091;96;15;21;;MUELLER, MICHAEL:;;;20460,00
220369424929;05;69;00;;MUELLER, MIKE:;;;10500,00
150367429266;14;02;00;;MUELLER, MIKE:;;;15390,00
010761430228;15;00;42;;MUELLER, MIKE:;;;19772,50
010370418627;99;43;00;;MUELLER, MIKE:;;;6780,00
300467411929;94;03;00;;MUELLER, MIKE:;;;16200,00
051168409525;06;69;00;;MUELLER, MIRKO:;;;12392,50
270855513236;98;82;00;;MUELLER, MONIKA:;;;16783,25
220353530049;98;84;00;;MUELLER, MONIKA:;;;20880,00
281247512233;07;77;00;;MUELLER, MONIKA:;;;21060,00
280552526936;14;00;51;;MUELLER, MONIKA:;;;9280,45
020441510324;97;07;00;;MUELLER, MONIKA:;;;22022,50
171070530251;96;15;22;;MUELLER, MYRIAM:;;;9383,39
130464430156;05;06;00;;MUELLER, NILS:;;;16500,00
181254412224;07;65;00;;MUELLER, NORBERT:;;;16795,00
240961402719;02;08;00;;MUELLER, NORBERT:;;;10340,00
110248429718;97;08;00;;MUELLER, NORBERT:;;;27000,00
220250400217;97;22;00;;MUELLER, NORBERT:;;;24000,00
151252401372;94;03;00;;MUELLER, NORBERT:;;;23340,00
151259411514;97;01;00;;MUELLER, OLAF:;;;24150,00
261263430205;99;43;00;;MUELLER, OLAF:;;;16317,26
040465412233;99;51;00;;MUELLER, OLAF:;;;18810,00
100455410324;07;00;45;;MUELLER, OTTMAR:;;;22007,50
110336405919;04;51;00;;MUELLER, OTTO:;;;28500,00
250470420217;11;69;00;;MUELLER, PATRICK:;;;9555,00
220541412218;07;06;00;;MUELLER, PAUL:;;;21687,50
290346416225;09;06;00;;MUELLER, PAUL:;;;21250,00
090968409517;06;69;00;;MUELLER, PEER:;;;9510,00
090454429254;98;82;00;;MUELLER, PETER:;;;19095,00
140552414227;08;20;00;;MUELLER, PETER:;;;25320,00
020450411213;07;00;40;;MUELLER, PETER:;;;25500,00
181152412223;07;26;00;;MUELLER, PETER:;;;21780,00
200263409124;06;06;00;;MUELLER, PETER:;;;17160,00
150342406121;04;06;00;;MUELLER, PETER:;;;26250,00
081052406119;04;00;40;;MUELLER, PETER:;;;27000,00
071044429258;04;51;00;;MUELLER, PETER:;;;21390,00
040152428218;14;00;40;;MUELLER, PETER:;;;24495,00
030242428917;14;06;00;;MUELLER, PETER:;;;23250,00
260146423626;13;00;42;;MUELLER, PETER:;;;23250,00
250258426910;14;80;00;;MUELLER, PETER:;;;18687,50
210235402717;02;02;00;;MUELLER, PETER:;;;38250,00
220141420323;99;53;00;;MUELLER, PETER:;;;28500,00
161164406711;99;43;00;;MUELLER, PETER:;;;16030,72
151069400419;99;40;00;;MUELLER, PETER:;;;8955,00
151258430035;99;40;00;;MUELLER, PETER:;;;21390,00
050340429735;99;26;00;;MUELLER, PETER:;;;37500,00
120464420020;97;22;00;;MUELLER, PETER:;;;17490,00
260758430173;97;06;00;;MUELLER, PETER:;;;20010,00
100858409539;30;41;00;;MUELLER, PETER:;;;15555,00
221041402544;98;83;00;;MUELLER, PETER-BERND:;;;21620,97
141256414825;94;03;00;;MUELLER, PETER-MICHAEL:;;;20700,00
290759514114;08;00;52;;MUELLER, PETRA:;;;12000,00
120358530162;04;77;00;;MUELLER, PETRA:;;;16994,47
120259520217;11;12;00;;MUELLER, PETRA:;;;16541,44
241165530028;99;53;00;;MUELLER, PETRA:;;;13633,71
261259519928;99;77;00;;MUELLER, PETRA:;;;24305,22
310562414828;08;06;00;;MUELLER, RAIK:;;;17270,00
060868413247;18;32;00;;MUELLER, RAIK:;;;9105,00
140546413711;08;40;00;;MUELLER, RAINER:;;;24913,30
030847408214;04;53;00;;MUELLER, RAINER:;;;23220,00
240541428250;14;09;00;;MUELLER, RAINER:;;;33562,50
260750427324;14;60;00;;MUELLER, RAINER:;;;23760,00
211052409232;01;06;20;;MUELLER, RAINER:;;;23040,00
250965403734;03;19;00;;MUELLER, RAINER:;;;16362,00
050944424986;99;77;00;;MUELLER, RAINER:;;;24300,00
310559413111;99;02;00;;MUELLER, RAINER:;;;23450,00
230759419913;99;02;00;;MUELLER, RAINER:;;;23632,50
050852421315;94;65;00;;MUELLER, RAINER:;;;23040,00
270749411519;07;00;54;;MUELLER, RALF:;;;23760,00
040657407324;05;69;00;;MUELLER, RALF:;;;27772,50
120769414414;06;69;00;;MUELLER, RALF:;;;10695,00
300556408932;06;51;00;;MUELLER, RALF:;;;22540,00
021255407328;05;06;00;;MUELLER, RALF:;;;19419,12
060862430097;04;00;50;;MUELLER, RALF:;;;5390,00
030761405127;04;00;47;;MUELLER, RALF:;;;19305,00
190365424521;99;43;00;;MUELLER, RALF:;;;16649,03
180767413826;99;43;00;;MUELLER, RALF:;;;8950,00
230860416960;94;03;00;;MUELLER, RALF:;;;14345,00
201261416472;09;06;20;;MUELLER, RALF:;;;16775,00
060860405613;01;00;43;;MUELLER, RALPH:;;;18488,98
160552509136;06;00;52;;MUELLER, REGINA:;;;16042,50
081052526719;14;80;00;;MUELLER, REGINA:;;;18669,67
201050516211;09;55;00;;MUELLER, REGINA:;;;19722,50
210650506118;04;11;00;;MUELLER, REGINE:;;;20310,00
031058526343;99;13;00;;MUELLER, REGINE:;;;4950,00
110666402710;04;06;00;;MUELLER, REICO:;;;14904,00
100339428260;14;80;00;;MUELLER, REINER:;;;19823,40
070859409560;99;43;00;;MUELLER, REINER:;;;19430,00
270869430183;18;35;00;;MUELLER, REINER:;;;9510,00
210846410310;07;06;00;;MUELLER, REINHARD:;;;21375,00
220351421826;12;00;52;;MUELLER, REINHARD:;;;24480,00
160358402327;02;00;46;;MUELLER, REINHARD:;;;14770,16
080551409328;94;11;00;;MUELLER, REINHARD:;;;21300,00
101049419918;10;06;00;;MUELLER, REINHOLD:;;;22437,50
030852513262;10;01;00;;MUELLER, RENATE:;;;20160,00
190741529723;94;30;00;;MUELLER, RENATE:;;;21687,50
180669428258;14;69;00;;MUELLER, RENE:;;;3220,00
080271407010;99;43;00;;MUELLER, RENE:;;;6780,00
240569413923;18;35;00;;MUELLER, RENE:;;;9675,00
080170424022;96;15;22;;MUELLER, RENE:;;;9555,00
150962514414;97;08;00;;MUELLER, RIA:;;;16177,25
150259421013;98;20;00;;MUELLER, RICARDO:;;;22861,43
010966422790;12;06;00;;MUELLER, RICO:;;;15930,00
210666426227;95;45;00;;MUELLER, RICO:;;;11271,19
021149500836;94;03;00;;MUELLER, RITA:;;;16280,00
050855413935;08;09;00;;MUELLER, ROLAND:;;;22534,50
071043405713;04;06;00;;MUELLER, ROLAND:;;;23625,00
200760424990;13;64;00;;MUELLER, ROLAND:;;;18427,50
010241428212;14;65;00;;MUELLER, ROLAND:;;;19687,50
250239428267;14;80;00;;MUELLER, ROLAND:;;;21250,00
071050424517;11;06;20;;MUELLER, ROLAND:;;;20910,00
241047420012;11;12;00;;MUELLER, ROLAND:;;;21937,50
100538419068;10;01;00;;MUELLER, ROLAND:;;;30937,50
201037403415;03;64;00;;MUELLER, ROLAND:;;;20437,50
260552407939;99;49;00;;MUELLER, ROLAND:;;;22320,00
290848424647;18;35;00;;MUELLER, ROLAND:;;;24625,00
020653413446;97;08;00;;MUELLER, ROLAND:;;;23040,00
020233429740;96;15;05;;MUELLER, ROLAND:;;;23187,50
051041428024;14;00;59;;MUELLER, ROLF:;;;29250,00
201052427028;14;60;00;;MUELLER, ROLF:;;;23040,00
140350419919;11;80;00;;MUELLER, ROLF:;;;18900,00
051238429717;99;43;00;;MUELLER, ROLF:;;;21750,00
120562418610;94;03;00;;MUELLER, ROLF-PETER:;;;16830,00
260758508946;30;83;00;;MUELLER, ROMY:;;;15458,11
150857420221;98;82;00;;MUELLER, RONALD:;;;22080,00
190969400440;01;06;20;;MUELLER, RONALD:;;;7031,61
160156416448;09;80;00;;MUELLER, RONALD:;;;16905,00
140556417724;09;15;00;;MUELLER, RONALD:;;;22770,00
091169400860;01;69;00;;MUELLER, RONALD:;;;11642,26
130662530051;30;72;00;;MUELLER, ROSEMARIE:;;;11718,26
070151527422;14;77;00;;MUELLER, ROSWITHA:;;;17604,00
140949524811;14;78;00;;MUELLER, ROSWITHA:;;;19571,73
020158500016;99;02;00;;MUELLER, ROSWITHA:;;;17721,53
160469426217;99;43;00;;MUELLER, ROY:;;;13285,00
250534429721;98;84;00;;MUELLER, RUDOLF:;;;23250,00
210641404638;04;40;00;;MUELLER, RUDOLF:;;;26375,00
030927424919;13;51;00;;MUELLER, RUDOLF:;;;22500,00
041240429725;94;65;00;;MUELLER, RUDOLF:;;;24000,00
151254401333;01;00;47;;MUELLER, RUEDIGER:;;;18112,50
130650413413;09;06;00;;MUELLER, RUEDIGER:;;;20422,50
010369517126;98;18;00;;MUELLER, SABINE:;;;13500,00
031156500841;06;78;00;;MUELLER, SABINE:;;;17075,92
110355516921;09;00;47;;MUELLER, SABINE:;;;15923,79
150249513248;96;15;14;;MUELLER, SABINE:;;;19205,00
250669410315;07;69;00;;MUELLER, SANDRO:;;;9133,50
061143530168;98;18;00;;MUELLER, SIBYLLE:;;;20010,00
140356411432;97;01;00;;MUELLER, SIEGBERT:;;;19320,00
300931429728;97;06;00;;MUELLER, SIEGFRIED:;;;27750,00
130240407539;05;29;00;;MUELLER, SIEGFRIED:;;;29250,00
250655417444;15;99;00;;MUELLER, SIEGFRIED:;;;25740,00
061231429721;99;02;00;;MUELLER, SIEGFRIED:;;;30750,00
150236414216;30;61;00;;MUELLER, SIEGFRIED:;;;20385,00
031038419049;10;80;00;;MUELLER, SIEGFRIED:;;;19620,00
130752522223;05;02;00;;MUELLER, SIEGLINDE:;;;20820,00
221159400026;94;03;00;;MUELLER, SIEGMAR:;;;20642,50
020151529780;30;31;00;;MUELLER, SIGRID:;;;23940,00
300847507623;05;80;00;;MUELLER, SIGRIED:;;;23187,50
030767508223;06;00;42;;MUELLER, SILKE:;;;12800,00
161063522801;12;53;00;;MUELLER, SIMONE:;;;11971,19
130768530121;99;55;00;;MUELLER, SIMONE:;;;0,00
200835529712;99;43;00;;MUELLER, SONJA:;;;20625,00
101269430131;15;14;00;;MUELLER, STEFAN:;;;3620,00
210649428255;14;80;00;;MUELLER, STEFAN:;;;23222,50
131266430133;01;80;00;;MUELLER, STEFAN:;;;12852,00
040263430310;98;84;00;;MUELLER, STEFFEN:;;;18150,00
010766415377;08;11;00;;MUELLER, STEFFEN:;;;12460,00
060955427612;14;02;00;;MUELLER, STEFFEN:;;;24500,00
220369427724;14;69;00;;MUELLER, STEFFEN:;;;13311,60
180670420229;11;69;00;;MUELLER, STEFFEN:;;;2870,00
050670425454;99;43;00;;MUELLER, STEFFEN:;;;6780,00
230869424940;99;77;00;;MUELLER, STEFFEN:;;;9600,00
250367422775;99;12;00;;MUELLER, STEFFEN:;;;16902,00
160263407512;94;03;00;;MUELLER, STEFFEN:;;;18645,00
110363400814;30;61;00;;MUELLER, STEPHAN:;;;15180,00
230470404120;04;69;00;;MUELLER, SVEN:;;;2870,00
211068424963;13;00;40;;MUELLER, SVEN:;;;8950,00
260868428269;18;35;00;;MUELLER, SVEN:;;;9510,00
070568417747;09;51;00;;MUELLER, SVEN:;;;12900,00
210471409427;95;60;00;;MUELLER, SVEN:;;;3620,00
280564403618;95;60;24;;MUELLER, SVEN:;;;18480,00
271070420712;12;69;00;;MUELLER, SWEN:;;;6780,00
100138406110;17;00;00;;MUELLER, THEO:;;;28500,00
150468430098;98;27;00;;MUELLER, THOMAS:;;;14332,00
010154426921;97;01;00;;MUELLER, THOMAS:;;;27360,00
240567413647;08;07;00;;MUELLER, THOMAS:;;;14946,00
030869405129;04;69;00;;MUELLER, THOMAS:;;;9862,26
300369405234;04;69;00;;MUELLER, THOMAS:;;;9555,00
180867405217;04;06;00;;MUELLER, THOMAS:;;;15047,81
071069409587;15;69;00;;MUELLER, THOMAS:;;;2925,64
100968413969;17;00;00;;MUELLER, THOMAS:;;;7575,00
011254421532;12;53;00;;MUELLER, THOMAS:;;;25310,00
230860420310;11;31;00;;MUELLER, THOMAS:;;;20945,30
101167420135;11;55;00;;MUELLER, THOMAS:;;;13607,00
130658420116;11;06;20;;MUELLER, THOMAS:;;;18342,50
250458408944;12;18;00;;MUELLER, THOMAS:;;;11232,00
030456426319;99;43;00;;MUELLER, THOMAS:;;;24502,50
121168430165;99;49;00;;MUELLER, THOMAS:;;;11400,00
121252422766;99;55;00;;MUELLER, THOMAS:;;;29520,00
071155429824;99;51;00;;MUELLER, THOMAS:;;;23747,50
081256428280;99;55;00;;MUELLER, THOMAS:;;;21160,00
140666411913;18;80;00;;MUELLER, THOMAS:;;;15256,00
030960413613;97;06;00;;MUELLER, THOMAS:;;;19085,00
160643409528;97;07;00;;MUELLER, THOMAS:;;;28875,00
030663404438;18;31;00;;MUELLER, THOMAS:;;;19800,00
090269406739;18;29;30;;MUELLER, THOMAS:;;;8950,00
300762416036;09;51;00;;MUELLER, THOMAS:;;;16500,00
160168417747;17;00;00;;MUELLER, THORALF:;;;8950,00
120462419931;18;29;30;;MUELLER, THORALF:;;;22440,00
010769401528;01;69;00;;MUELLER, THORALF:;;;2896,61
030371426328;98;82;00;;MUELLER, THORSTEN:;;;3020,00
191260430022;98;82;00;;MUELLER, TORSTEN:;;;20790,00
031261413029;08;06;00;;MUELLER, TORSTEN:;;;19965,00
200470414858;08;69;00;;MUELLER, TORSTEN:;;;9555,00
160667408925;06;65;00;;MUELLER, TORSTEN:;;;14210,00
291265409116;06;02;00;;MUELLER, TORSTEN:;;;16384,50
030867428263;14;00;61;;MUELLER, TORSTEN:;;;13860,00
030670401729;02;69;00;;MUELLER, TORSTEN:;;;3220,00
130171411429;94;03;00;;MUELLER, TORSTEN:;;;2918,39
011270419619;10;69;00;;MUELLER, TORSTEN:;;;3220,00
310371418922;10;69;00;;MUELLER, TORSTEN:;;;2870,00
240570418238;10;69;00;;MUELLER, TORSTEN:;;;6780,00
160167400847;01;69;00;;MUELLER, TORSTEN:;;;17280,00
150160403376;03;00;43;;MUELLER, UDO:;;;21285,00
180768415014;94;03;00;;MUELLER, UDO:;;;9510,00
291270400124;01;69;00;;MUELLER, ULF:;;;2896,61
130454411816;07;19;00;;MUELLER, ULLRICH:;;;24150,00
300651405027;04;00;47;;MUELLER, ULRICH:;;;23280,00
121050418611;10;06;00;;MUELLER, ULRICH:;;;22215,00
301049529734;98;18;00;;MUELLER, URSULA:;;;24687,50
090533509535;06;55;00;;MUELLER, URSULA:;;;21625,00
050763508216;94;03;00;;MUELLER, UTE:;;;15852,21
300363500644;01;96;43;;MUELLER, UTE:;;;7769,64
210457419821;98;82;00;;MUELLER, UWE:;;;23402,50
040961422799;98;18;00;;MUELLER, UWE:;;;11220,00
150460401823;98;50;00;;MUELLER, UWE:;;;18630,00
030852421536;98;83;00;;MUELLER, UWE:;;;24420,00
200460406117;04;19;00;;MUELLER, UWE:;;;24840,00
211155406130;04;08;00;;MUELLER, UWE:;;;18572,50
290962422733;12;08;00;;MUELLER, UWE:;;;18480,00
041252420912;12;06;00;;MUELLER, UWE:;;;19320,00
311268427219;99;43;00;;MUELLER, UWE:;;;13285,00
250269413111;18;32;00;;MUELLER, UWE:;;;9675,00
310159430051;18;71;20;;MUELLER, UWE:;;;23287,50
301158428238;97;07;00;;MUELLER, UWE:;;;22770,00
270955406446;30;61;00;;MUELLER, UWE:;;;17055,00
191161422772;96;15;13;;MUELLER, UWE:;;;17770,50
200332530084;99;14;00;;MUELLER, VERA:;;;24687,50
090853427416;14;03;00;;MUELLER, VOLKMAR:;;;21600,00
180636407231;94;03;00;;MUELLER, WALDEMAR:;;;23562,50
230637430030;94;03;00;;MUELLER, WALLFRIED:;;;24000,00
290752415367;08;15;00;;MUELLER, WALTER:;;;23460,00
091135529711;94;30;00;;MUELLER, WALTRAUT:;;;20250,00
250530430020;98;19;00;;MUELLER, WERNER:;;;42000,00
280532404819;97;01;00;;MUELLER, WERNER:;;;24000,00
060636407518;05;06;00;;MUELLER, WERNER:;;;20562,50
280134428217;14;80;00;;MUELLER, WERNER:;;;23095,00
110748422723;12;06;00;;MUELLER, WERNER:;;;23220,00
300147401828;02;00;42;;MUELLER, WERNER:;;;21000,00
150636400219;99;02;00;;MUELLER, WERNER:;;;30000,00
291034429742;97;08;00;;MUELLER, WERNER:;;;35250,00
191254429797;94;65;00;;MUELLER, WERNER:;;;19950,00
100731407210;96;15;14;;MUELLER, WERNER:;;;35250,00
090746407014;98;83;00;;MUELLER, WILFRIED:;;;24750,00
090453412231;08;00;56;;MUELLER, WILFRIED:;;;24752,50
090747412245;07;08;00;;MUELLER, WILFRIED:;;;22275,00
080531412212;07;99;00;;MUELLER, WILFRIED:;;;50250,00
160256400224;01;69;00;;MUELLER, WILFRIED:;;;16905,00
080540430244;98;83;00;;MUELLER, WINFRIED:;;;25500,00
270934418544;10;00;42;;MUELLER, WINFRIED:;;;36000,00
010447417519;09;00;41;;MUELLER, WINFRIED:;;;29250,00
061059401320;01;19;00;;MUELLER, WINFRIED:;;;21285,00
261063406729;99;02;00;;MUELLER, WOLF-DIETER:;;;19085,00
020536415370;97;01;00;;MUELLER, WOLFGANG:;;;42000,00
271046430101;04;08;00;;MUELLER, WOLFGANG:;;;24125,00
160333429232;14;00;61;;MUELLER, WOLFGANG:;;;23250,00
240228430012;15;06;00;;MUELLER, WOLFGANG:;;;42000,00
250944429767;15;00;49;;MUELLER, WOLFGANG:;;;24375,00
211239428935;14;78;00;;MUELLER, WOLFGANG:;;;33750,00
040441422904;12;08;00;;MUELLER, WOLFGANG:;;;23937,50
240742422840;12;06;00;;MUELLER, WOLFGANG:;;;23250,00
251157419011;10;00;43;;MUELLER, WOLFGANG:;;;22942,50
230635401324;01;06;26;;MUELLER, WOLFGANG:;;;22500,00
140354429890;99;43;00;;MUELLER, WOLFGANG:;;;20880,00
040748415119;99;09;00;;MUELLER, WOLFGANG:;;;28500,00
250151426531;94;65;00;;MUELLER, WOLFGANG:;;;27472,50
050350417551;09;00;41;;MUELLER, WOLFGANG:;;;23220,00
141256417719;09;07;00;;MUELLER, WOLFGANG:;;;25932,50
300449417411;09;06;00;;MUELLER, WOLFGANG:;;;23250,00
110549400230;01;19;00;;MUELLER, WOLFGANG:;;;23460,00
200740430058;94;03;00;;MUELLER, WOLFGANG:;;;24062,50
150146421324;95;45;00;;MUELLER, WOLFGANG:;;;22500,00
121249414618;99;78;00;;MUELLER, WOLFRAM:;;;33000,00
110358412263;07;08;00;;MUELLER-VON, HANS:;;;17451,25
180961520916;12;06;00;;MUELLING, PETRA:;;;11907,12
250869418215;18;35;00;;MUENCH, FRANK:;;;10287,08
020353424311;97;07;00;;MUENCH, LOTHAR:;;;25620,00
140537420346;11;55;00;;MUENCH, MANFRED:;;;31500,00
230470430783;15;69;00;;MUENCH, OLAF:;;;13285,00
190250416433;09;26;00;;MUENCH, REINHARD:;;;18955,00
171237418238;10;06;00;;MUENCH, SIEGFRIED:;;;28516,13
170169420330;11;69;00;;MUENCH, STEFAN:;;;9600,00
101167415336;08;69;00;;MUENCH, STEFFEN:;;;9875,00
270236420348;11;14;00;;MUENCH, WERNER:;;;24875,00
131145415324;08;12;00;;MUENCH, WILLI:;;;22492,34
281239429712;98;20;00;;MUENCHBERG, HORST:;;;23937,50
010369516027;99;53;00;;MUENCHBERG, KATRIN:;;;13500,00
200555505812;04;80;00;;MUENCHEBERG, EDELTRAUD:;;;17155,13
121255405814;04;06;00;;MUENCHEBERG, GERD:;;;22080,00
220156402718;02;20;00;;MUENCHOW, HARALD:;;;1725,00
080471405749;04;69;00;;MUENCHOW, SVEN:;;;2870,00
250862530191;18;29;00;;MUENCHOW, SYLVIA:;;;11315,54
190753406114;98;19;00;;MUENCHOW, WILFRIED:;;;24240,00
290440411922;07;06;00;;MUENCHOW, WOLFGANG:;;;21187,50
310169411516;18;35;00;;MUENDER, KRISTIAN:;;;9555,00
290961406168;04;00;48;;MUENN, RALF:;;;22880,00
220948406143;04;00;40;;MUENN, WILFRIED:;;;31822,50
180553508934;06;77;00;;MUENNICH, BETTINA:;;;18904,45
101148419040;94;11;00;;MUENNICH, DIETER:;;;24420,00
010431529719;15;00;40;;MUENNICH, GISELA:;;;26250,00
040837422791;08;40;00;;MUENNICH, HORST:;;;26250,00
190153408917;06;80;00;;MUENNICH, ULRICH:;;;18720,00
051058430040;99;40;00;;MUENNICH, UWE:;;;20355,00
250569413615;18;35;00;;MUENNING, DIRK:;;;9675,00
171236530121;98;83;00;;MUENSTER, ERIKA:;;;20625,00
120150415376;99;55;00;;MUENSTER, GERHARD:;;;23250,00
151037428214;94;03;00;;MUENSTER, GUENTER:;;;35250,00
250731429712;99;40;00;;MUENSTER, HORST:;;;39562,50
270130422759;12;06;00;;MUENSTER, MANFRED:;;;28687,50
281257430135;98;84;00;;MUENSTER, PETER:;;;20700,00
150957530196;96;15;03;;MUENSTER, VIOLA:;;;17857,86
311048415355;97;06;00;;MUENSTER, WERNER:;;;23187,50
100948405531;04;06;00;;MUENSTER, WOLFRAM:;;;23187,50
300952401353;01;14;00;;MUENSTERMANN, GERD:;;;19140,00
060156429830;05;65;00;;MUENTER, CHRISTIAN:;;;23460,00
161060430215;97;08;00;;MUENTER, FLORIAN:;;;18617,50
040663518928;15;18;00;;MUENZ, GABRIELE:;;;4500,00
160667422786;12;69;00;;MUENZ, RALF:;;;9675,00
301162424993;94;03;00;;MUENZ, UWE:;;;20460,00
151050430116;15;00;43;;MUENZBERG, PETER:;;;26640,00
260433429713;98;18;00;;MUENZEL, EGON:;;;27750,00
180449526315;96;15;13;;MUENZEL, INGE:;;;21960,00
050930430023;96;15;11;;MUENZEL, JOHANNES:;;;42000,00
300352417781;09;51;00;;MUENZEL, KLAUS-DIETER:;;;20760,00
250258430151;12;06;00;;MUENZEL, UWE:;;;19952,50
200660424213;01;77;00;;MUENZER, JENS:;;;17321,25
121258507445;01;77;00;;MUENZER, SYLVIA:;;;15975,90
100157419013;99;43;00;;MUENZNER, ANDREAS:;;;18630,00
080248422423;97;01;00;;MUENZNER, ARNOLD:;;;29000,04
071151428226;14;11;00;;MUENZNER, BERND:;;;23400,00
011134530187;98;83;00;;MUENZNER, BRUNHILDE:;;;20073,22
291244428254;14;08;00;;MUENZNER, DIETER:;;;24000,00
070534419023;99;43;00;;MUENZNER, EGON:;;;18497,50
030647528334;14;08;00;;MUENZNER, ELKE:;;;15696,00
200335429731;98;20;00;;MUENZNER, GUENTER:;;;30750,00
051067428241;97;08;00;;MUENZNER, INGO:;;;8950,00
250668427748;30;49;00;;MUENZNER, JENS:;;;1900,00
220639415425;94;30;00;;MUENZNER, KLAUS-DIETER:;;;30750,00
251040429734;99;43;00;;MUENZNER, REINER:;;;36375,00
080844529729;98;82;00;;MUENZNER, REINGARD:;;;19500,00
150264426724;14;40;00;;MUENZNER, RENE:;;;17063,00
160427428230;14;80;00;;MUENZNER, ROLF:;;;27000,00
140731428237;14;99;00;;MUENZNER, WERNER:;;;29250,00
100361522835;99;77;00;;MUERBE, MARION:;;;16357,86
220357430117;99;13;00;;MUERBE, ULLRICH:;;;23450,42
010370409368;06;69;00;;MUERNER, TORSTEN:;;;7130,00
131237428245;14;06;00;;MUESZIG, KLAUS:;;;24687,50
010360502745;99;77;00;;MUETHEL, KERSTIN:;;;14751,40
150569422871;12;69;00;;MUETZE, JENS-UWE:;;;12150,00
270142422799;30;33;00;;MUETZE, VOLKER:;;;18220,00
201252421245;12;06;00;;MUETZE, WOLFGANG:;;;20880,00
230437429756;97;01;00;;MUETZEL, MANFRED:;;;28500,00
211270404237;03;69;00;;MUFF, ALEXANDER:;;;2870,00
120139530234;30;74;00;;MUHL, ERIKA:;;;22320,00
140537430114;30;76;00;;MUHL, PETER:;;;26820,00
140165411026;07;06;00;;MUHL, TORSTEN:;;;16890,32
150869410848;18;32;00;;MUHME, ERIK:;;;9330,00
290264415026;99;43;00;;MUHRA, ERIK:;;;17792,50
070253429874;18;33;00;;MUHS, HANS-JOERG:;;;25200,00
271034411915;07;00;57;;MULKAU, DIETER:;;;28750,00
290150422754;94;30;00;;MULKE, ANDREAS:;;;22775,00
280859402436;02;20;00;;MULSOW, ANDREAS:;;;20460,00
120965409540;94;30;00;;MUMMERT, BERT:;;;16902,00
071262409538;97;06;00;;MUMMERT, FRED:;;;21945,00
151064424980;13;51;00;;MUMMERT, JO(E)RG:;;;17022,50
060470409213;06;69;00;;MUMMERT, MAIK:;;;9510,00
020365408538;04;06;00;;MUMMERT, PETER:;;;16417,50
301052415367;09;06;00;;MUMMERT, WILFRIED:;;;19920,00
271251521563;30;84;00;;MUMMHARDT, CHRISTINE:;;;22128,38
300460430158;15;69;00;;MUMMHARDT, WILFRIED:;;;20460,00
231249406156;04;06;00;;MUMOT, ROBERT:;;;20477,50
290465418610;10;51;00;;MUNCKE, HENDRICK:;;;16610,00
011040415380;30;47;00;;MUND, EBERHARD:;;;26202,00
230736530221;98;18;00;;MUND, INGRID:;;;24480,00
130662412258;07;65;00;;MUND, JOERG:;;;12661,54
070769426834;18;77;00;;MUND, RU(E)DIGER:;;;9812,42
151250411411;07;08;00;;MUND, ULLRICH:;;;24480,00
100748428915;14;00;53;;MUNDEL, ULRICH:;;;25860,00
270471415127;94;65;00;;MUNDIGL, ANDREAS:;;;2870,00
310852414834;08;07;00;;MUNDIGL, BERND:;;;24480,00
020356401924;02;08;00;;MUNDRY, WOLFGANG:;;;20010,00
220869422815;99;77;00;;MUNDT, ANDRE:;;;8300,00
080166415131;98;82;00;;MUNDT, ANDREAS:;;;16575,00
270161519625;11;96;61;;MUNDT, ANGELA:;;;17697,40
180869428252;18;33;00;;MUNDT, CARSTEN:;;;10500,00
080744428242;14;29;00;;MUNDT, EGON:;;;23250,00
010256407035;18;32;00;;MUNDT, FRANK:;;;36430,41
210249402136;02;99;00;;MUNDT, GERHARD:;;;25920,00
260752400838;30;38;00;;MUNDT, HELMUT:;;;15120,00
290769400620;01;69;00;;MUNDT, HENRIK:;;;2896,61
181036424964;97;08;00;;MUNDT, HORST:;;;23250,00
260259513249;99;77;00;;MUNDT, IRIS:;;;13040,32
080751502113;02;40;00;;MUNDT, JUTTA:;;;14506,06
260355400834;97;01;00;;MUNDT, KLAUS-DIETER:;;;20770,00
010956501516;01;00;48;;MUNDT, MARIANNE:;;;13384,51
200662400864;07;00;54;;MUNDT, NORBERT:;;;14190,00
041150429860;15;14;00;;MUNDT, REINHARD:;;;21825,00
181241524948;18;32;00;;MUNDT, ROSEMARIE:;;;21375,00
010455401525;01;00;48;;MUNDT, SIEGFRIED:;;;16215,00
020571402225;02;06;00;;MUNDT, THOMAS:;;;3510,00
230768430161;18;32;00;;MUNDT, THOMAS:;;;9675,00
301066428214;97;01;00;;MUNDT, TINO:;;;14026,07
260332425107;13;08;00;;MUNDT, WILFRIED:;;;25500,00
051251430069;99;09;00;;MUNDT, WOLFGANG:;;;24120,00
160371409515;18;40;00;;MUNITZK, GERD:;;;2720,00
071268409512;18;32;00;;MUNITZK, RALF:;;;9510,00
270768419647;18;32;00;;MUNK, ANDREAS:;;;9675,00
060349400719;01;26;00;;MUNK, FRANZ:;;;22500,00
220252419616;11;00;45;;MUNKEL, RALF:;;;22440,00
041267417716;09;00;51;;MUNKELT, DIRK:;;;15708,00
160745417721;09;00;40;;MUNKELT, GUENTER:;;;24000,00
180471420912;18;29;30;;MUNSCH, ANDRE:;;;3070,16
231048404816;12;00;44;;MUNSCH, ARNO:;;;21000,00
210447422795;12;80;00;;MUNSKY, HANS-GUNTHER:;;;20250,00
111263418827;11;00;44;;MUNZERT, ANDREAS:;;;20460,00
060563430302;15;80;00;;MUNZERT, FRANK:;;;16830,00
180848418813;10;80;00;;MUNZERT, GERHARD:;;;19054,05
301029430067;18;25;00;;MUNZERT, MANFRED:;;;26375,00
160664418212;10;77;00;;MUNZERT, OLAF:;;;16665,00
210655406116;17;00;00;;MUNZERT, RALF:;;;21220,00
070245419043;30;36;00;;MUNZERT, REINER:;;;15544,44
040658430016;98;20;00;;MUNZERT, UWE:;;;23115,00
220136530173;98;83;00;;MUNZERT, WALTRAUD:;;;23250,00
161169422737;18;35;00;;MUNZIG, ANDREAS:;;;6705,00
121142517713;09;77;00;;MURAWA, ANITA:;;;5002,50
040541417782;09;77;00;;MURAWA, HANS-DIETER:;;;21600,00
160743412222;99;09;00;;MUREGGER, DIETRICH:;;;33000,00
261267430093;98;27;00;;MURK, FRANK:;;;15532,00
190744429728;96;15;09;;MURK, HUGO:;;;35250,00
190147529712;94;30;00;;MURK, RENATE:;;;24000,00
281044401736;02;00;41;;MURR, JUERGEN:;;;19125,00
060264412948;97;01;00;;MURR, THORSTEN:;;;22440,00
140560415369;95;45;00;;MURRER, ALEXANDER:;;;21390,00
091238400822;01;53;00;;MURSCHALL, KURT:;;;24000,00
160153401822;04;00;42;;MUSAHL, ERWIN:;;;21531,88
150634422879;98;83;00;;MUSCALIK, HORST:;;;24000,00
310548400016;94;03;00;;MUSCH, FRITZ:;;;24250,00
100140429725;99;43;00;;MUSCHACK, HANS:;;;23250,00
280750504017;99;77;00;;MUSCHACK, INGRID:;;;21187,50
151032429744;96;15;08;;MUSCHEL, ROLF:;;;28500,00
150370404510;18;31;00;;MUSCHERT, HOLGER:;;;6705,00
271248400015;10;19;00;;MUSCHERT, ULLI:;;;25472,50
250665422247;12;19;00;;MUSCHICK, BERT:;;;20027,00
271054405328;04;06;00;;MUSCHKE, FRANK-DIETER:;;;20820,00
280658405315;04;08;00;;MUSCHKE, UWE:;;;19320,00
290564505218;04;06;00;;MUSCHKORGEL, HEIKE:;;;12581,18
060165408935;06;65;00;;MUSCHTER, FRANK:;;;15785,00
270855428111;14;99;00;;MUSCHTER, VOLKMAR:;;;26600,00
220152411414;11;22;00;;MUSIALEK, BRUNO:;;;24150,00
070438429723;99;26;00;;MUSIALEK, KLAUS-DIETER:;;;23250,00
040562419031;10;14;00;;MUSIOL, CARSTEN:;;;14496,43
141065419041;99;43;00;;MUSIOL, OLAF:;;;14882,69
221241419017;10;08;00;;MUSIOL, WINFRIED:;;;27000,00
110860425027;13;20;00;;MUSKE, HOLGER:;;;18760,00
260867523811;13;08;00;;MUSKE, MANUELA:;;;14544,00
041263424994;13;08;00;;MUSKE, RENE:;;;17160,00
050764404312;99;51;00;;MUSOLT, INGOLF:;;;19140,00
260454405729;04;40;00;;MUSOW, BERND-JUERGEN:;;;24840,00
211069400015;01;69;00;;MUSOW, THOMAS:;;;6806,61
181257506111;17;00;00;;MUSSEHL, BARBARA:;;;14805,01
120353403121;99;43;00;;MUSSEHL, DIETER:;;;20820,00
061163403123;12;00;44;;MUSSEHL, DIRK:;;;5184,00
240848429776;17;00;00;;MUSSEHL, HEINZ-PETER:;;;23437,50
040870406910;99;43;00;;MUSSEHL, JENS:;;;3620,00
030559403136;99;43;00;;MUSSEHL, JOACHIM:;;;19952,50
220257506911;99;43;00;;MUSSEHL, KARIN:;;;17258,42
210550403111;99;43;00;;MUSSEHL, ULRICH:;;;23040,00
140353407024;05;06;00;;MUSTER, HORST:;;;20820,00
230862401826;02;00;42;;MUSTIN, ROLAND:;;;13608,00
200159407313;18;28;00;;MUSTROPH, BODO:;;;21447,50
130840407313;05;00;48;;MUSTROPH, HELMUT:;;;17503,75
020866407314;05;08;00;;MUSTROPH, RALF:;;;15984,00
030868400713;01;06;26;;MUSWYK, HARTMUT:;;;13575,00
110451406466;04;20;00;;MUSZ, WILFRIED:;;;12180,41
020836520316;11;40;00;;MUSZBACH, INGE:;;;21000,00
301053404811;99;43;00;;MUSZLER, MANFRED:;;;21600,00
041159407422;05;06;00;;MUSZMANN, DIETMAR:;;;18572,50
300159419013;99;12;00;;MUTH, BERND:;;;19320,00
220235414514;08;96;00;;MUTH, GERHARD:;;;17681,25
190737415352;08;65;00;;MUTH, HARRY:;;;27000,00
070134514558;08;96;00;;MUTH, LIESELOTTE:;;;16301,25
130760415356;08;08;00;;MUTH, PETER:;;;21715,00
display stas;96;15;00;269/68, P:;MUTH, ROLF;1017;KOPPENSTR. 68;
310129430165;96;15;00;269/68, P:;MUTH, ROLF;1017;KOPPENSTR. 68;
230362427018;14;00;42;;MUTH, STEFFEN:;;;18590,00
210660424992;30;32;00;;MUTH, UWE:;;;20541,85
060856412247;07;51;00;;MUTHMANN, NORBERT:;;;23805,00
021064530219;99;77;00;;MUTSCHER, BEATE:;;;9510,39
210959421315;97;06;00;;MUTSCHER, DIETMAR:;;;20872,50
081149420523;94;65;00;;MUTSCHER, JOACHIM:;;;21562,50
011253520563;90;65;40;3684/82,;MUTSCHER, MONIKA;1130;HARNACKSTR. 26;
101263423918;99;77;00;;MUTSCHER, OLAF:;;;17062,84
270333429715;97;08;00;;MUTSCHER, REINER:;;;31500,00
240168425026;18;35;00;;MUTSCHER, STEFAN:;;;9675,00
010970421336;18;32;00;;MUTSCHINK, LARS:;;;2795,00
310156507519;97;06;00;;MUTSCHKE, CHRISTIANE:;;;20302,94
100134407212;05;00;47;;MUTSCHKE, ERHARDT:;;;25500,00
100155429824;97;06;00;;MUTSCHKE, PETER:;;;23040,00
060662430041;94;30;00;;MUTZ, DETLEV:;;;18705,50
150166530085;96;15;22;;MUTZ, KATHRIN:;;;566,67
231259430109;99;09;00;;MUTZ, MATTHIAS:;;;20175,00
310568408912;97;01;00;;MUTZ, MICHAEL:;;;8055,00
241169408919;06;14;00;;MUTZ, RICO:;;;12725,00
221253405712;04;06;00;;MUTZ, THOMAS:;;;22260,00
230562430211;15;18;00;;MUTZ, THOMAS:;;;20625,00
310750405734;15;09;00;;MUTZ, VIKTOR:;;;24922,50
091067422807;18;32;00;;MUTZE, JO(E)RG:;;;9675,00
010369422135;18;33;00;;MUTZE, STEFFEN:;;;2720,00
120561414749;10;18;00;;MYLIUS, BERND:;;;20856,00
181168407525;94;03;00;;MYRACH, MAIK:;;;10600,00
131157512295;99;77;00;;MYSLIWIEC, KARIN:;;;18378,89
091055410729;97;08;00;;MYSLIWIEC, PETER:;;;22186,34
050565430155;98;83;00;;MYSLOWITSCH, ANDRE:;;;16096,50Diese Liste beinhaltet die Namen von 90.598 Mitarbeitern des Ministeriums für Staatssicherheit der DDR. Die Liste ist nicht vollständig. Insbesondere Mitarbeiter der Führungsebene sind nicht enthalten.This is a list of 90.598 members of the secret police of East Germany (Ministry for State Security), the list isn’t complete, because the most of the high Officiers lieke Colonel and higher have destroyed the personal Informations in the last days of Eastern Germany.
| Listen der Stasimitarbeiter-hier findest Du sie! Was bedeuten die Zahlen? |
| |
1.Listen der Stasi-Diensteinheiten!
Bem.:hier kannst du die Nr.(6-stellig) der Dienststellen heraussuchen.
2.Liste der Stasi-Mitarbeiter (Hauptamtlich)
Bem.:Hoffentlich hast Du einen guten Rechner, denn die Liste ist erschreckend lang. Die ersten 6 Ziffern sind das Geburtsdatum + die nächsten 6 Ziffern = Dienstausweisnummer! Die zwei Ziffern hinter dem Geburtsdatum geben das Geschlecht an: 41 und 42 = Männlich, 51 und 52 = Weiblich! Wichtig für suchen und finden, sind die sechs Ziffern in den Semikolon vor den Namen: z.B. ;07;00;44; ! Das ist die Nummer der Dienststelle !
Also du suchst in der Liste der Dienststellen, die Nummer der Dienststelle, die Dich interessiert. Damit gehst Du in die Liste der Mitarbeiter und suchst Dir alle Mitarbeiter der entsprechenden Dienststelle heraus. Ich habe das für mein Wohnort getan und so alle Mitarbeiter gefunden. Ob die Liste Vollständig ist kann ich nicht einschätzen, aber zumindest er/kannte ich einige Exverräter . |






































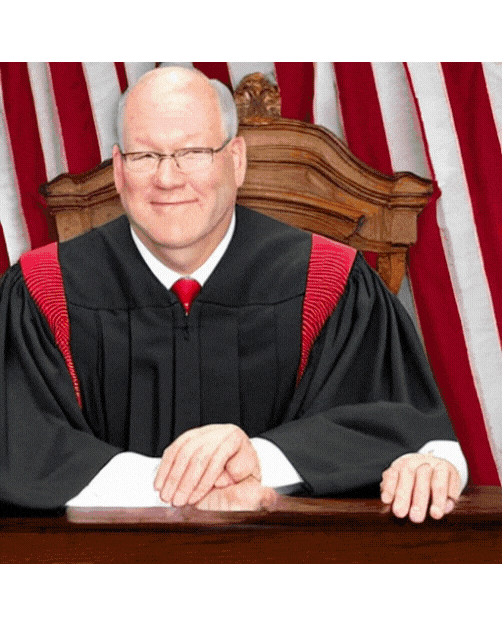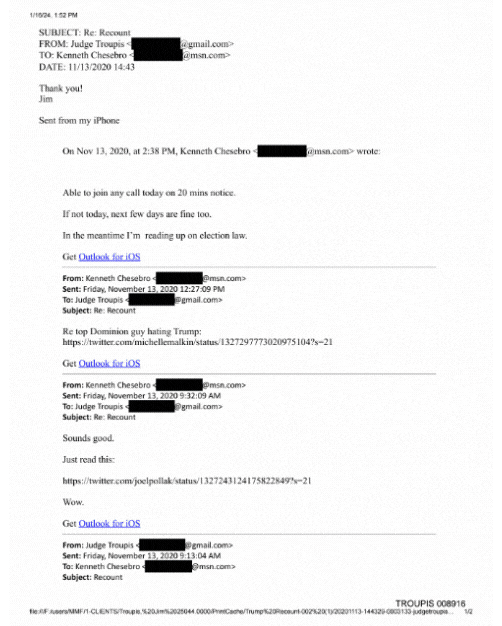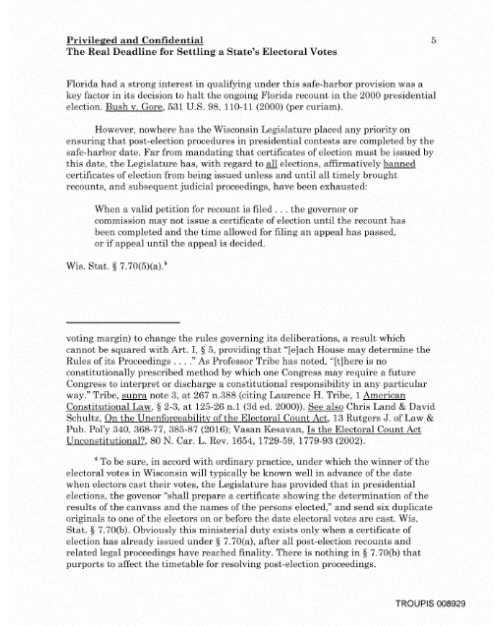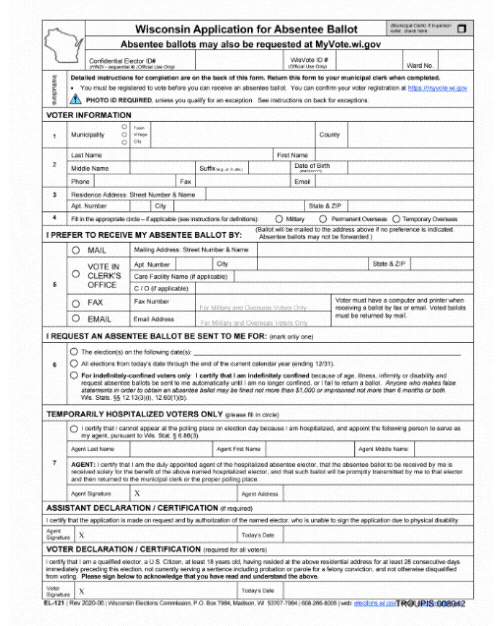

























%2Farc-anglerfish-arc2-prod-mco.s3.amazonaws.com%2Fpublic%2FWU3POGPIMFGENBBYSKUIW5UKNY.jpg&f=1&nofb=1)


























![[Image]](https://cryptome.org/2015-info/niamey/pict22.jpg)
![[Image]](https://cryptome.org/2015-info/niamey/pict20.jpg)
![[Image]](https://cryptome.org/2015-info/niamey/pict18.jpg)
![[Image]](https://cryptome.org/2015-info/niamey/pict17.jpg)
![[Image]](https://cryptome.org/2015-info/niamey/pict16.jpg)
![[Image]](https://cryptome.org/2015-info/niamey/pict14.jpg)
![[Image]](https://cryptome.org/2015-info/niamey/pict3.jpg)
![[Image]](https://cryptome.org/2015-info/niamey/pict4.jpg)
![[Image]](https://cryptome.org/2015-info/niamey/pict5.jpg)
![[Image]](https://cryptome.org/2015-info/niamey/pict9.jpg)
![[Image]](https://cryptome.org/2015-info/niamey/pict10.jpg)
![[Image]](https://cryptome.org/2015-info/niamey/pict6.jpg)
![[Image]](https://cryptome.org/2015-info/niamey/pict27.jpg)
![[Image]](https://cryptome.org/2015-info/niamey/pict44.jpg)
![[Image]](https://cryptome.org/2015-info/niamey/pict28.jpg)
![[Image]](https://cryptome.org/2015-info/niamey/pict45.jpg)
![[Image]](https://cryptome.org/2015-info/niamey/pict29.jpg)
![[Image]](https://cryptome.org/2015-info/niamey/pict30.jpg)
![[Image]](https://cryptome.org/2015-info/niamey/pict31.jpg)
![[Image]](https://cryptome.org/2015-info/niamey/pict32.jpg)
![[Image]](https://cryptome.org/2015-info/niamey/pict33.jpg)
![[Image]](https://cryptome.org/2015-info/niamey/pict34.jpg)
![[Image]](https://cryptome.org/2015-info/niamey/pict35.jpg)
![[Image]](https://cryptome.org/2015-info/niamey/pict36.jpg)
![[Image]](https://cryptome.org/2015-info/niamey/pict37.jpg)
![[Image]](https://cryptome.org/2015-info/niamey/pict39.jpg)
![[Image]](https://cryptome.org/2015-info/niamey/pict40.jpg)


![[Image]](https://cryptome.org/2016-info/trump-protect/pict23.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict25.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict26.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict27.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict28.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict12.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict11.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict17.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict18.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict10.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict15.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict14.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict0.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict1.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict3.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict19.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict20.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict21.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict22.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict2.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict4.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict5.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict6.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict7.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict8.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict9.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict13.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict16.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict24.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict33.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict34.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict31.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict36.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict35.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict32.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict29.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict30.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict37.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict38.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict39.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict40.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict41.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict42.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict43.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict44.jpg)
![[Image]](https://cryptome.org/2016-info/trump-protect/pict45.jpg)



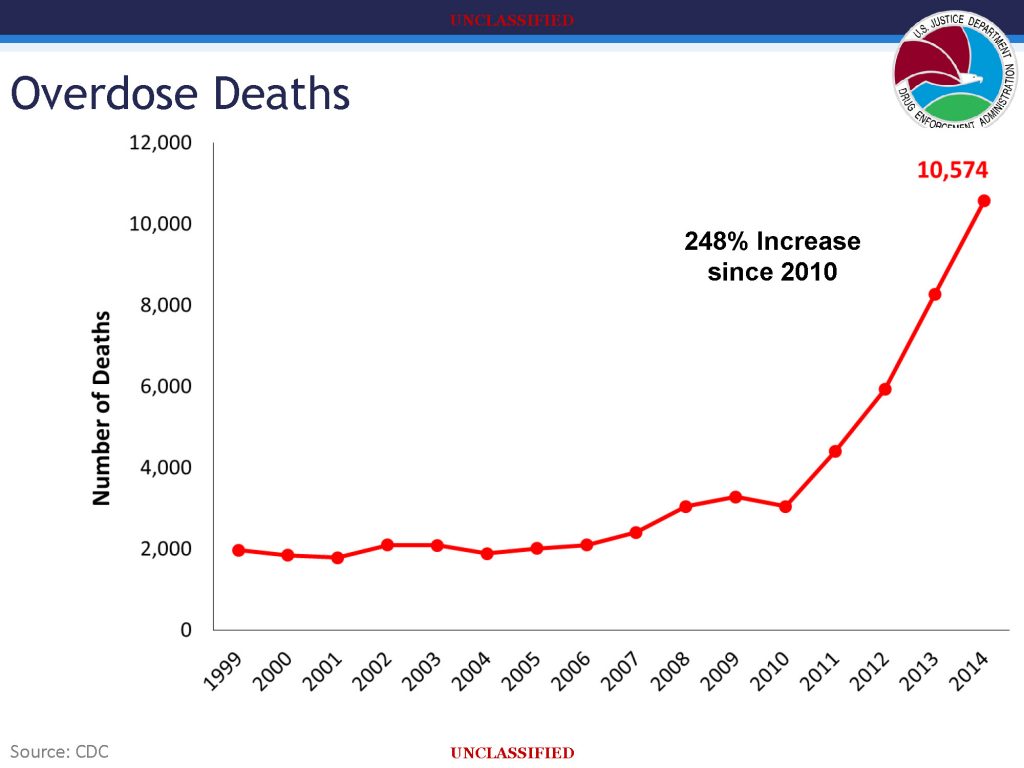
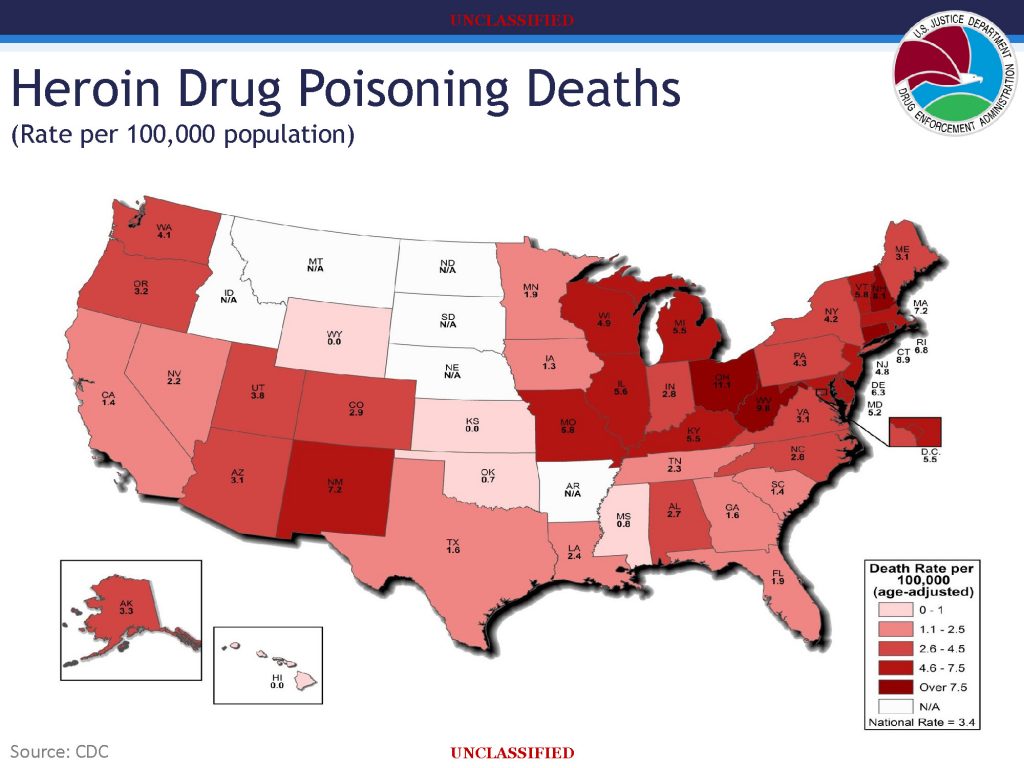
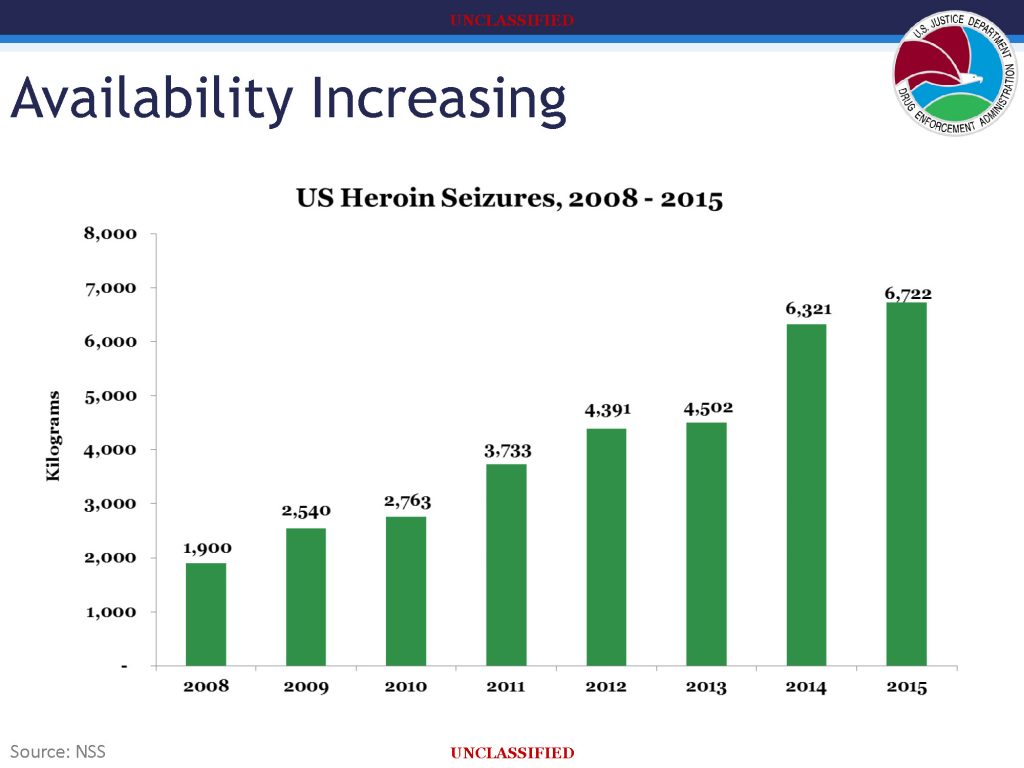
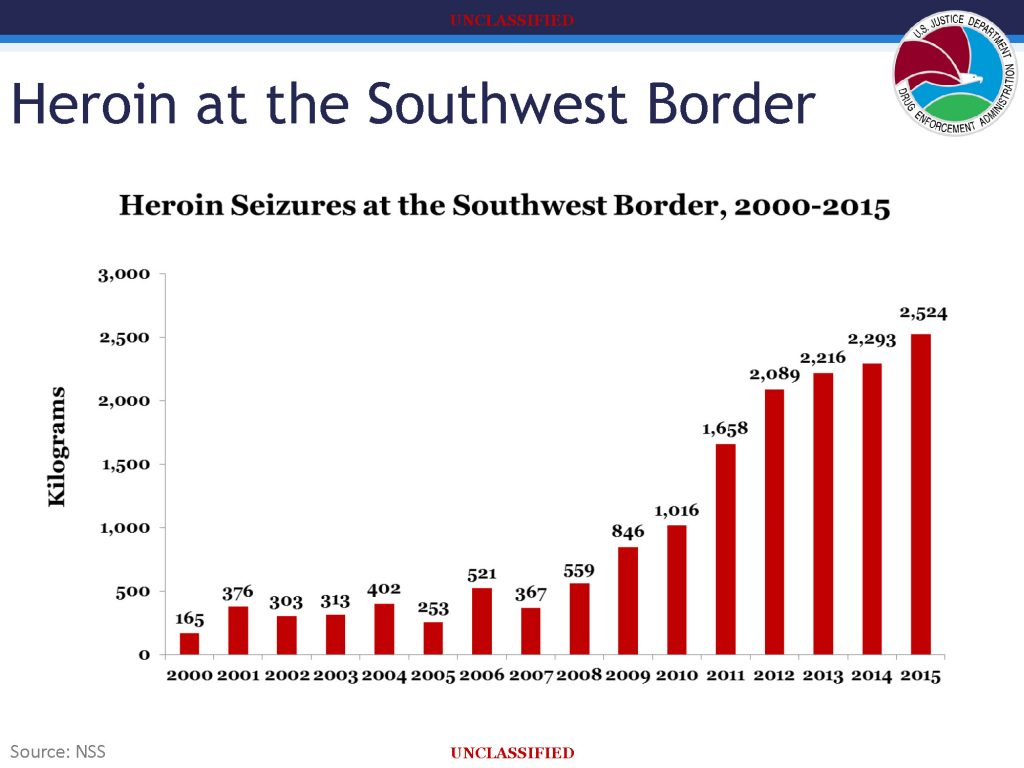
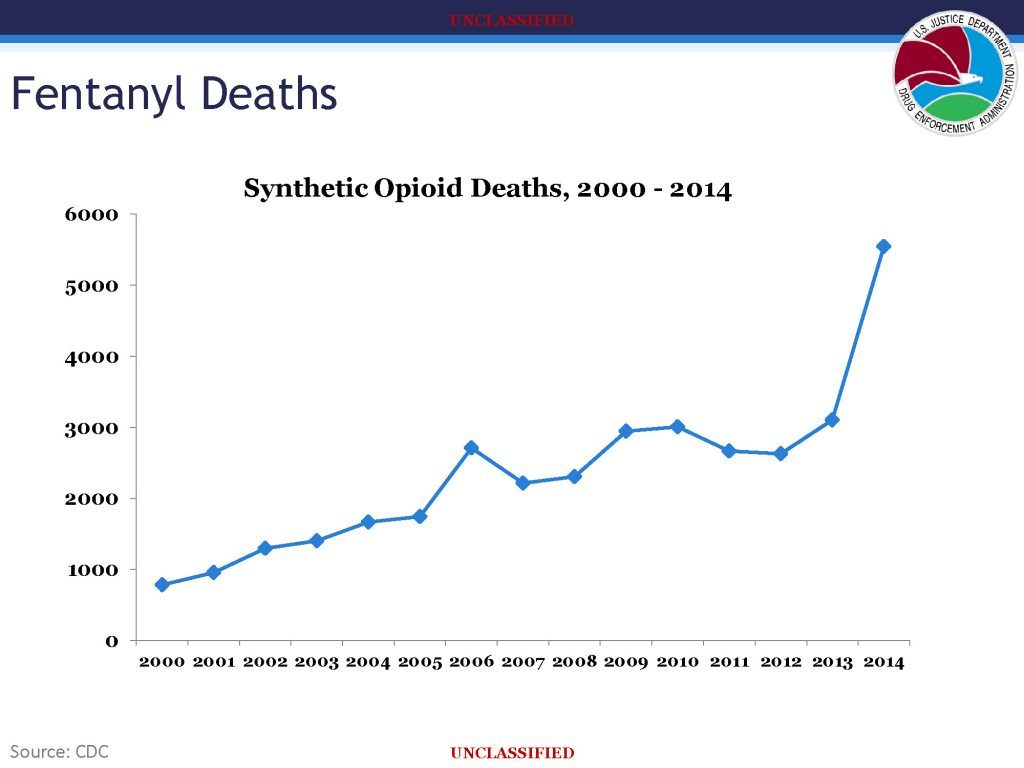



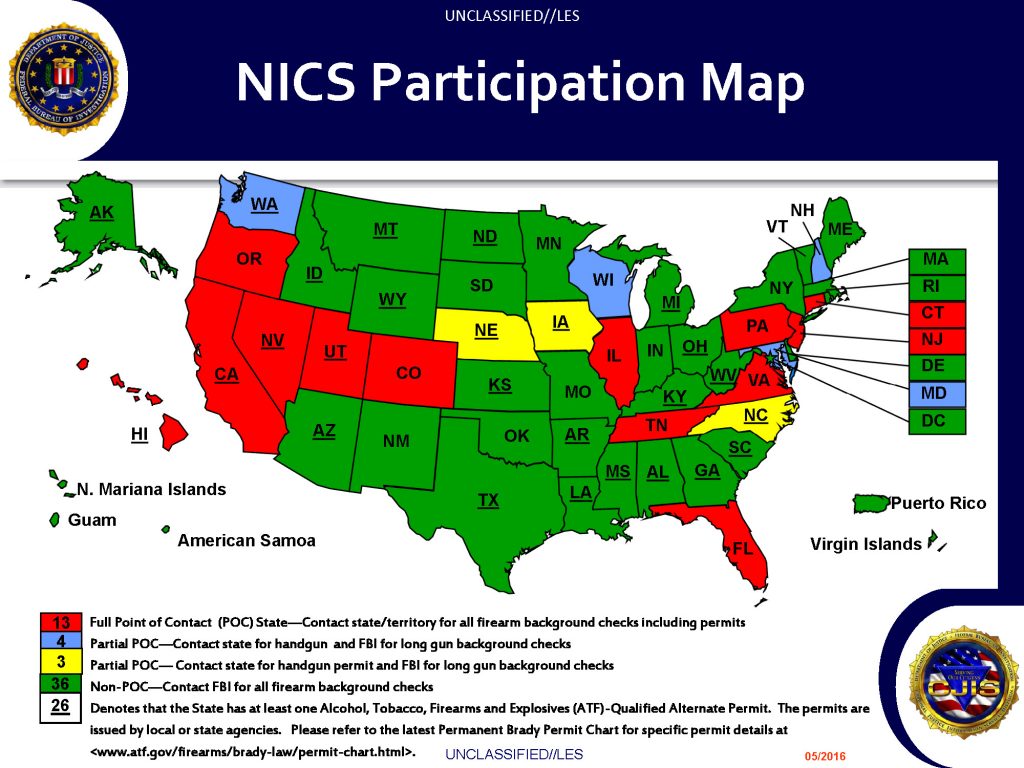

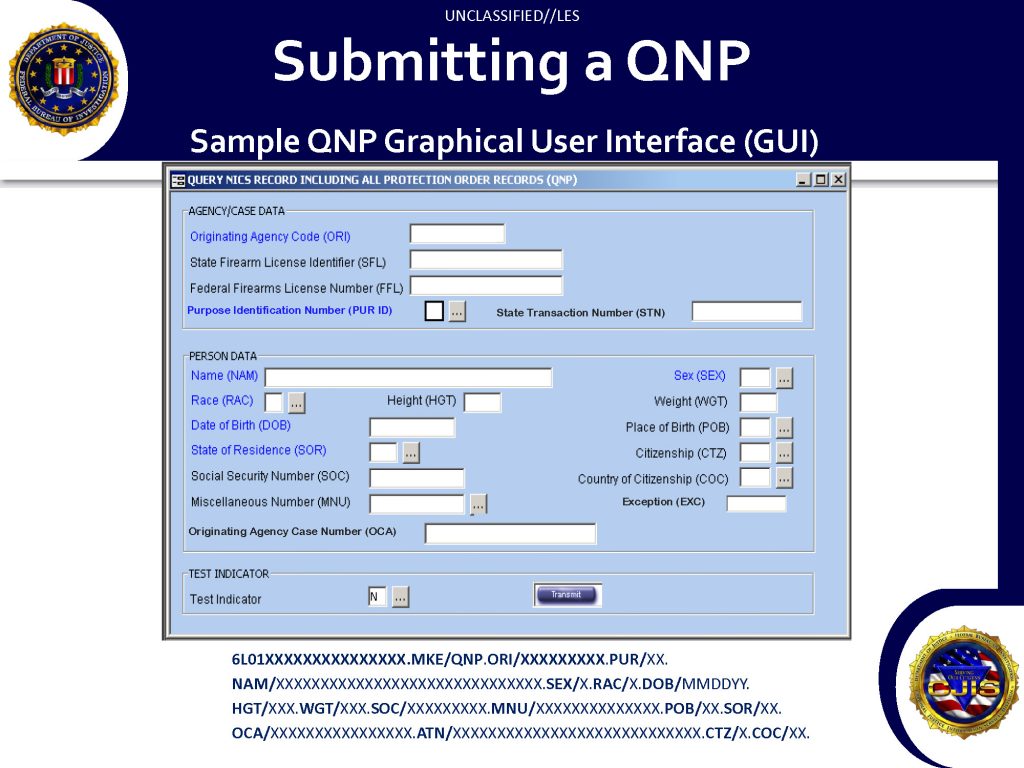
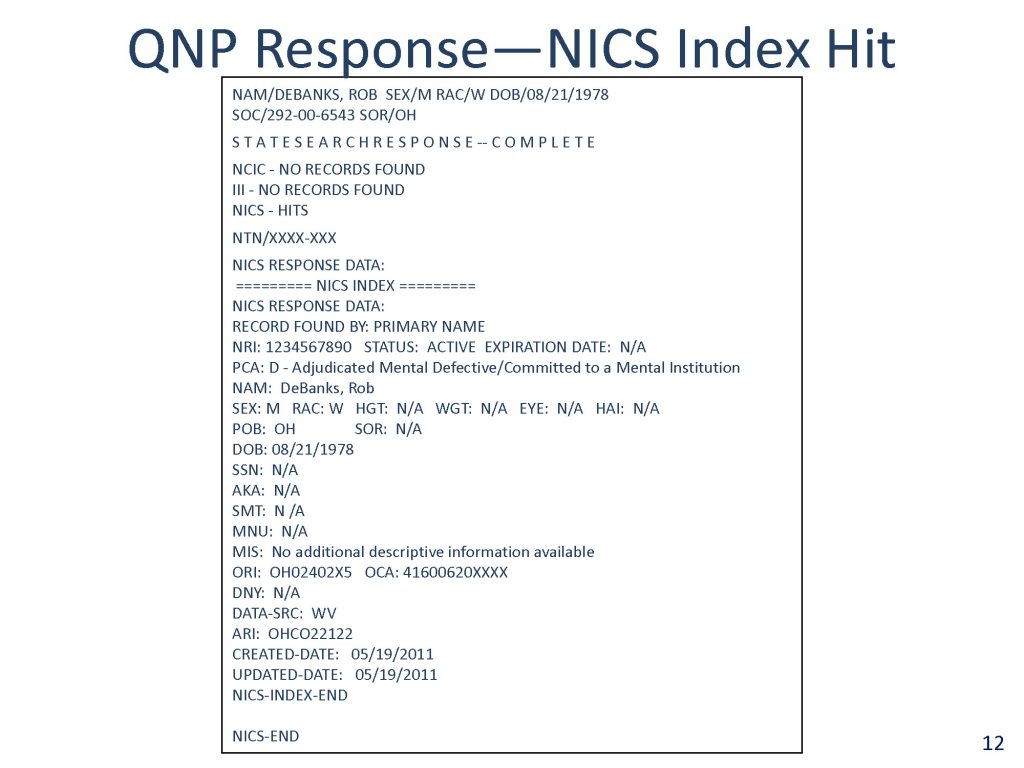



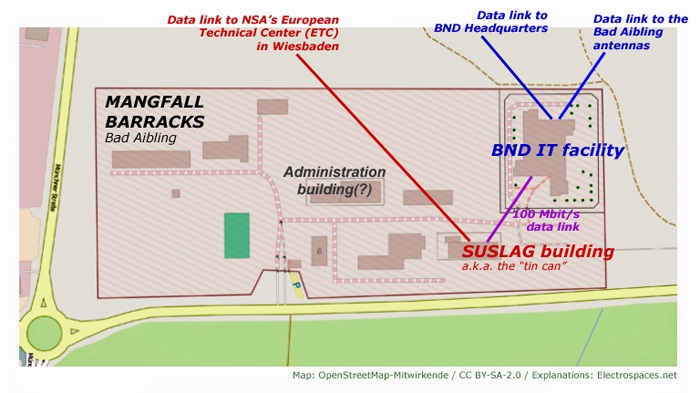
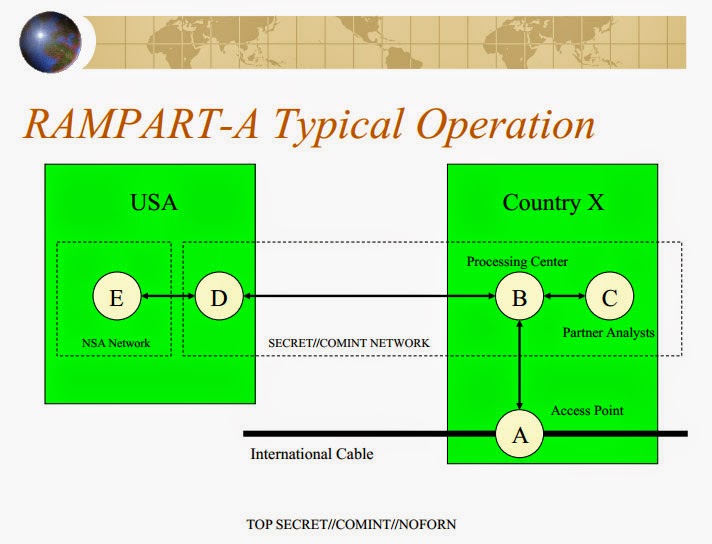
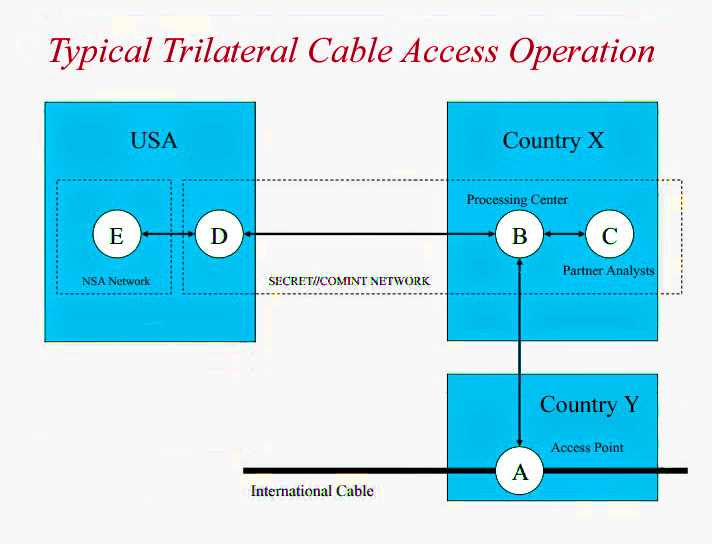
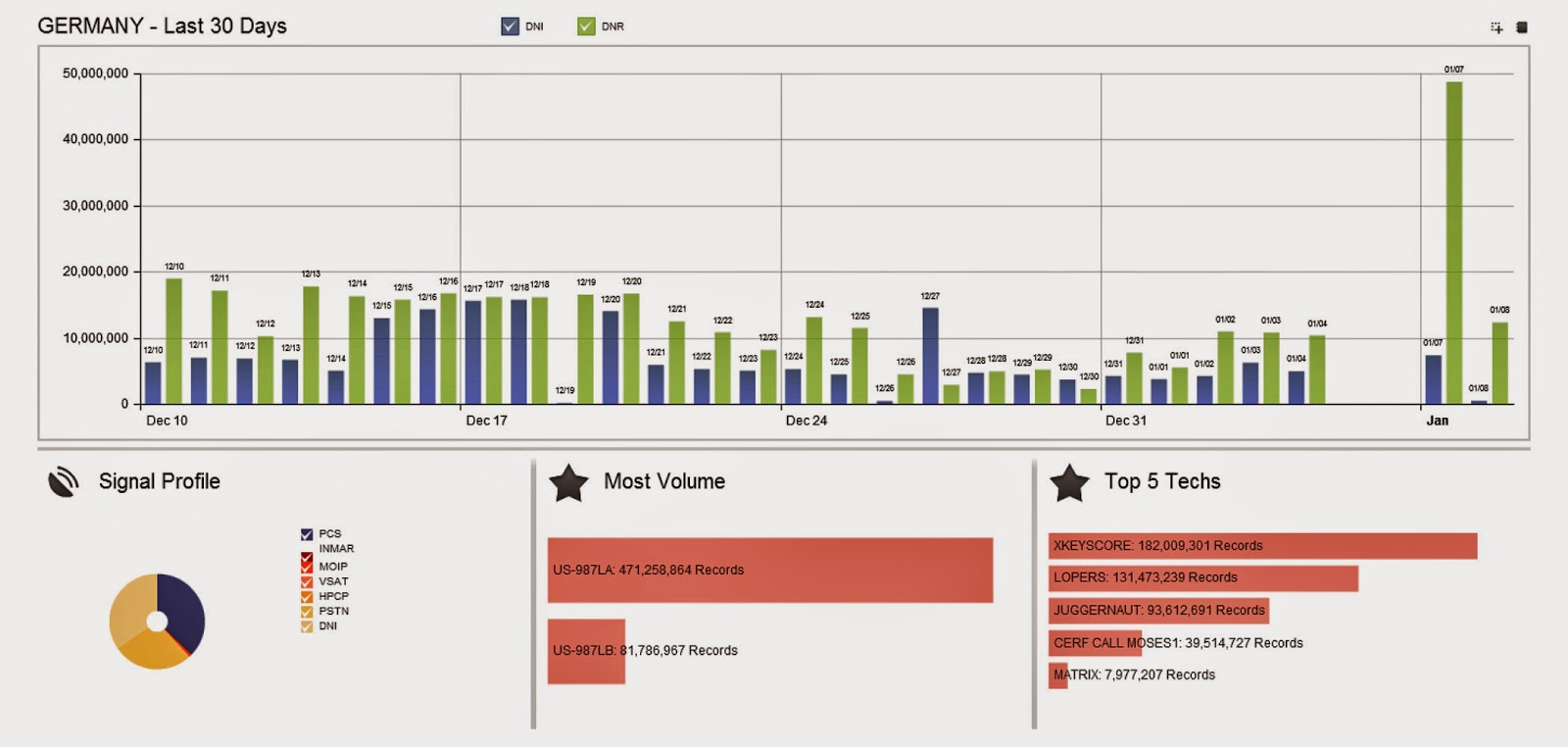










![[Image]](https://cryptome.org/2015-info/niamey/pict41.jpg)
![[Image]](https://cryptome.org/2016-info/us-sf-syria/pict55.jpg)
![[Image]](https://cryptome.org/2016-info/us-sf-syria/pict56.jpg)
![[Image]](https://cryptome.org/2016-info/us-sf-syria/pict38.jpg)
![[Image]](https://cryptome.org/2016-info/us-sf-syria/pict45.jpg)
![[Image]](https://cryptome.org/2016-info/us-sf-syria/pict42.jpg)
![[Image]](https://cryptome.org/2016-info/us-sf-syria/pict46.jpg)
![[Image]](https://cryptome.org/2016-info/us-sf-syria/pict41.jpg)
![[Image]](https://cryptome.org/2016-info/us-sf-syria/pict40.jpg)
![[Image]](https://cryptome.org/2016-info/us-sf-syria/pict39.jpg)
![[Image]](https://cryptome.org/2016-info/us-sf-syria/pict47.jpg)
![[Image]](https://cryptome.org/2016-info/us-sf-syria/pict37.jpg)
![[Image]](https://cryptome.org/2016-info/us-sf-syria/pict44.jpg)
![[Image]](https://cryptome.org/2016-info/us-sf-syria/pict48.jpg)
![[Image]](https://cryptome.org/2016-info/us-sf-syria/pict53.jpg)
![[Image]](https://cryptome.org/2016-info/us-sf-syria/pict54.jpg)
![[Image]](https://cryptome.org/2016-info/us-sf-syria/pict52.jpg)
![[Image]](https://cryptome.org/2016-info/us-sf-syria/pict51.jpg)
![[Image]](https://cryptome.org/2016-info/us-sf-syria/pict50.jpg)
![[Image]](https://cryptome.org/2016-info/us-sf-syria/pict36.jpg)
![[Image]](https://cryptome.org/2016-info/us-sf-syria/pict49.jpg)





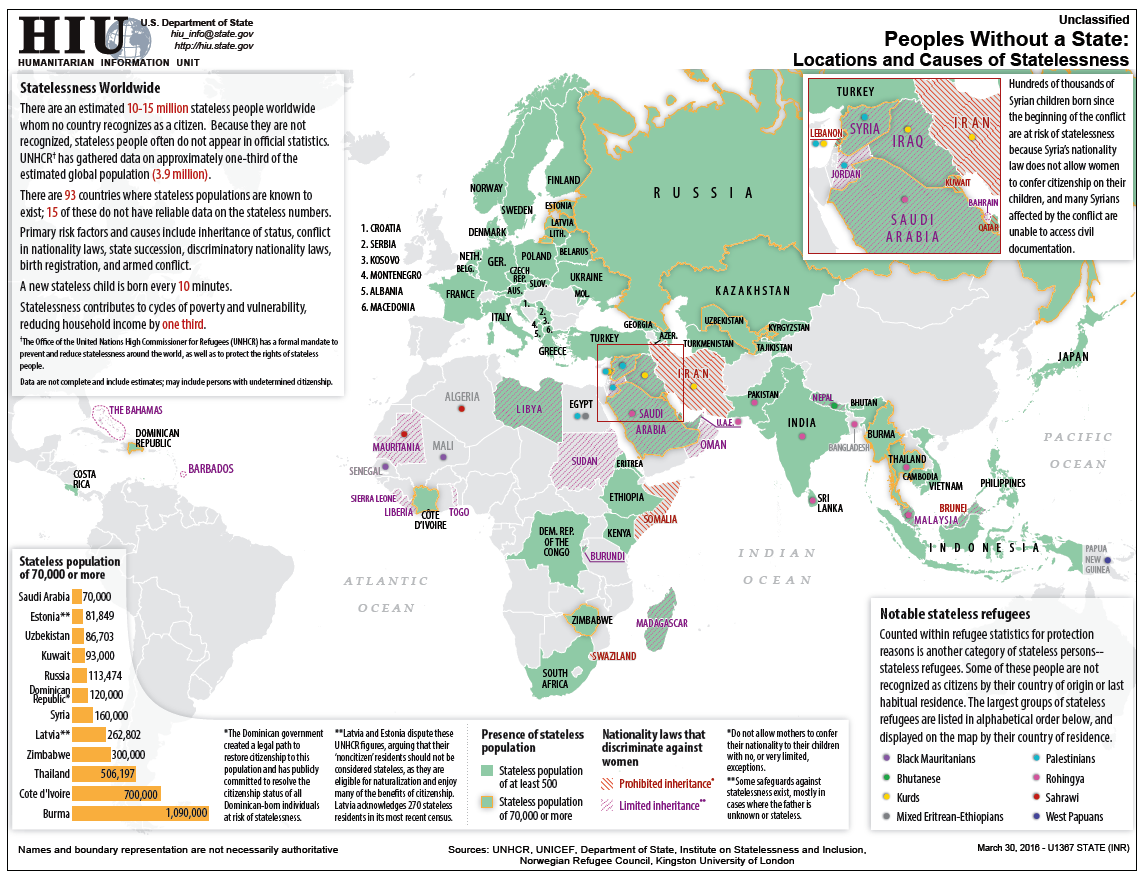
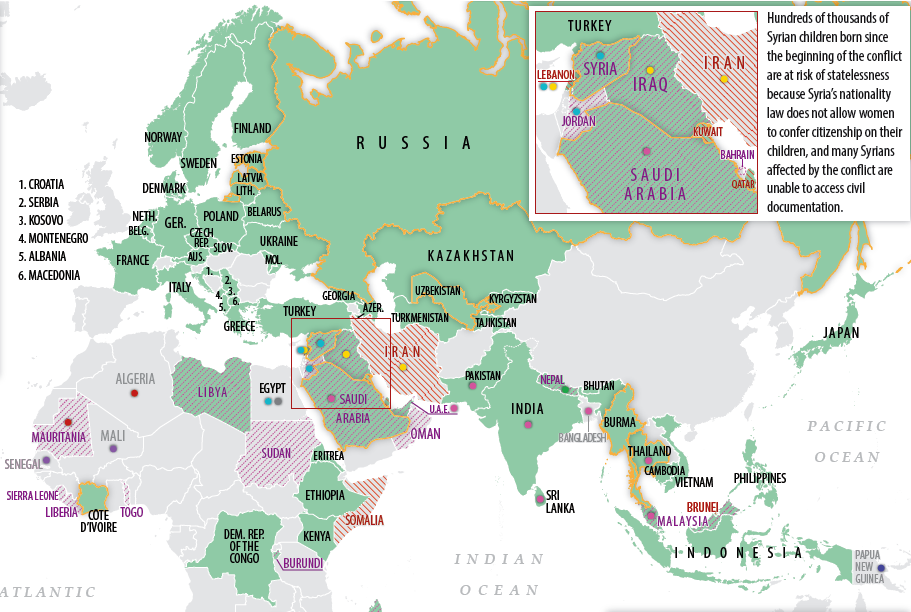


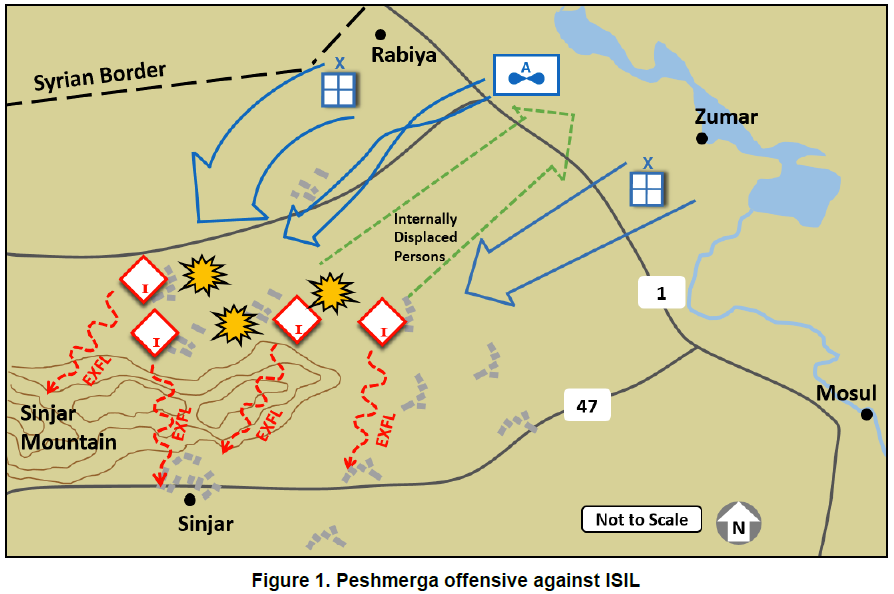

























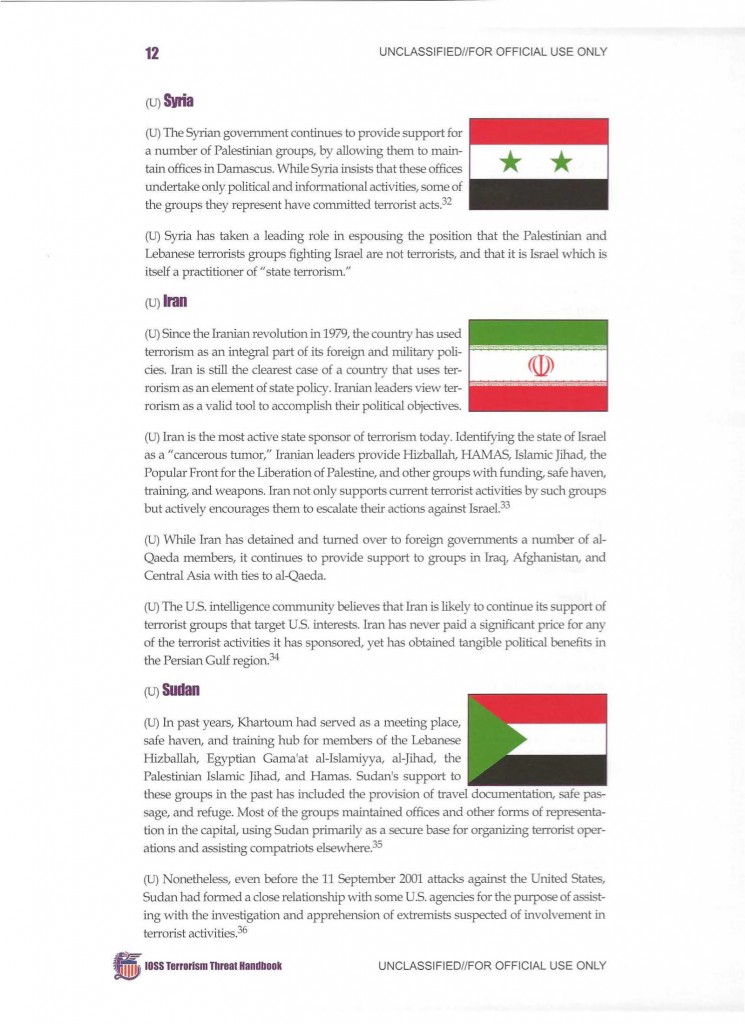




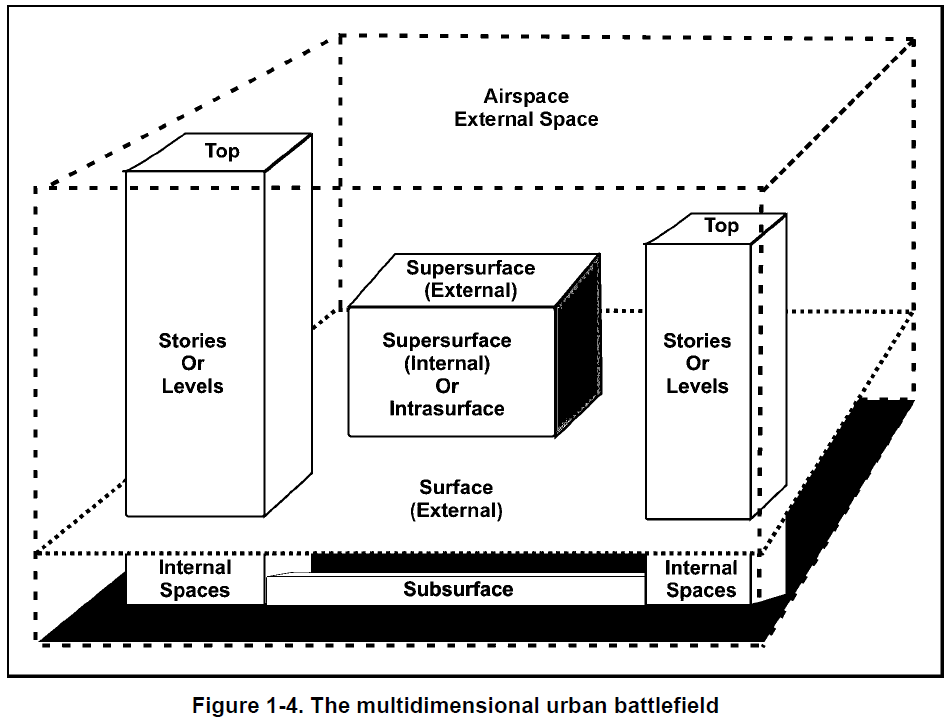


![[Image]](https://cryptome.org/2015-info/shenzhen/pict19.jpg)
![[Image]](https://cryptome.org/2015-info/shenzhen/pict20.jpg)
![[Image]](https://cryptome.org/2015-info/shenzhen/pict17.jpg)
![[Image]](https://cryptome.org/2015-info/shenzhen/pict16.jpg)
![[Image]](https://cryptome.org/2015-info/shenzhen/pict2.jpg)
![[Image]](https://cryptome.org/2015-info/shenzhen/pict3.jpg)
![[Image]](https://cryptome.org/2015-info/shenzhen/pict4.jpg)
![[Image]](https://cryptome.org/2015-info/shenzhen/pict5.jpg)
![[Image]](https://cryptome.org/2015-info/shenzhen/pict6.jpg)
![[Image]](https://cryptome.org/2015-info/shenzhen/pict7.jpg)
![[Image]](https://cryptome.org/2015-info/shenzhen/pict8.jpg)
![[Image]](https://cryptome.org/2015-info/shenzhen/pict9.jpg)
![[Image]](https://cryptome.org/2015-info/shenzhen/pict10.jpg)
![[Image]](https://cryptome.org/2015-info/shenzhen/pict11.jpg)
![[Image]](https://cryptome.org/2015-info/shenzhen/pict12.jpg)
![[Image]](https://cryptome.org/2015-info/shenzhen/pict13.jpg)
![[Image]](https://cryptome.org/2015-info/shenzhen/pict14.jpg)
![[Image]](https://cryptome.org/2015-info/shenzhen/pict15.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2015-info/risalpur/pict0.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2015-info/risalpur/pict1.jpg)


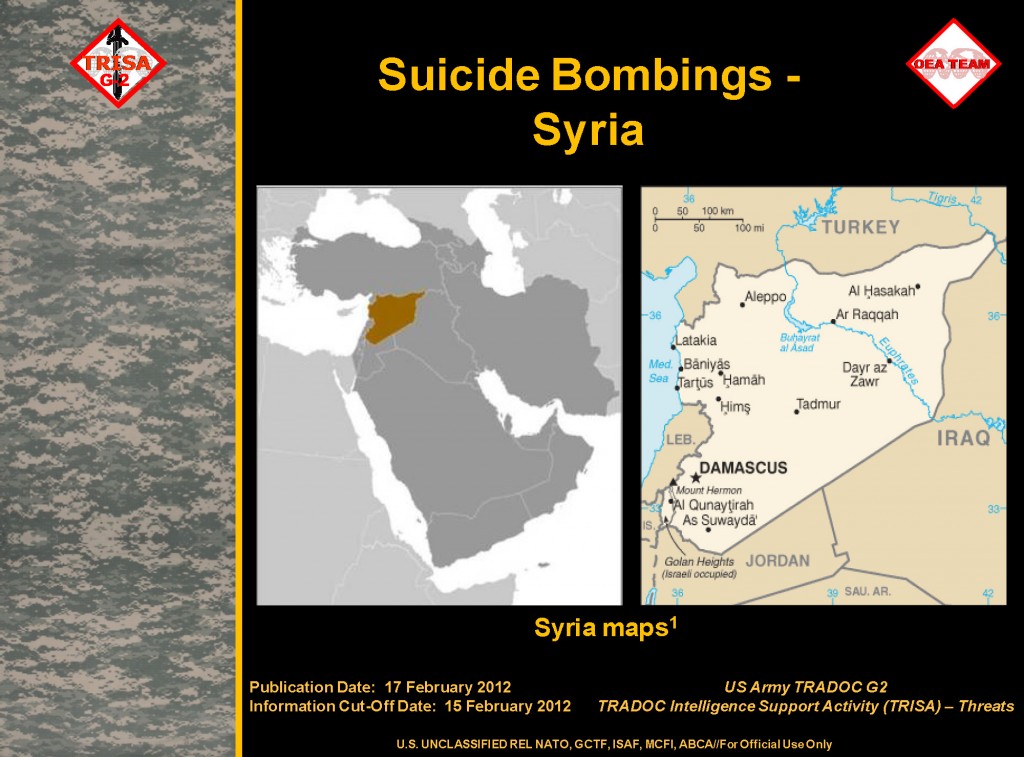


![[Image]](https://i0.wp.com/cryptome.org/2015-info/evgeny-buryakov/pict7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2015-info/evgeny-buryakov/pict0.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2015-info/evgeny-buryakov/pict5.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2015-info/evgeny-buryakov/pict2.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2015-info/evgeny-buryakov/pict1.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2015-info/evgeny-buryakov/pict3.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2015-info/evgeny-buryakov/pict4.jpg)












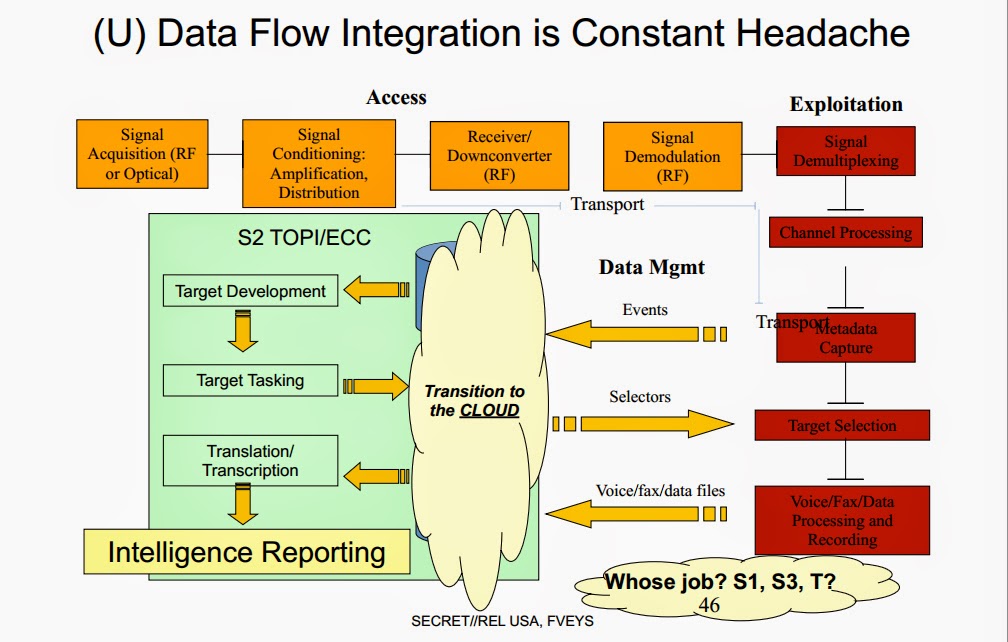






![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict38.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict0.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict19.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict23.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict22.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict18.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict21.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict42.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict40.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict30.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict28.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict24.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict4.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict41.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict37.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict39.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict6.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict11.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict13.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict2.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict29.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict5.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict32.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict31.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict14.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict17.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict20.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict9.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict43.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict44.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict12.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict36.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict27.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict25.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict26.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict3.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict34.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict35.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/assange-embassy/pict15.jpg)










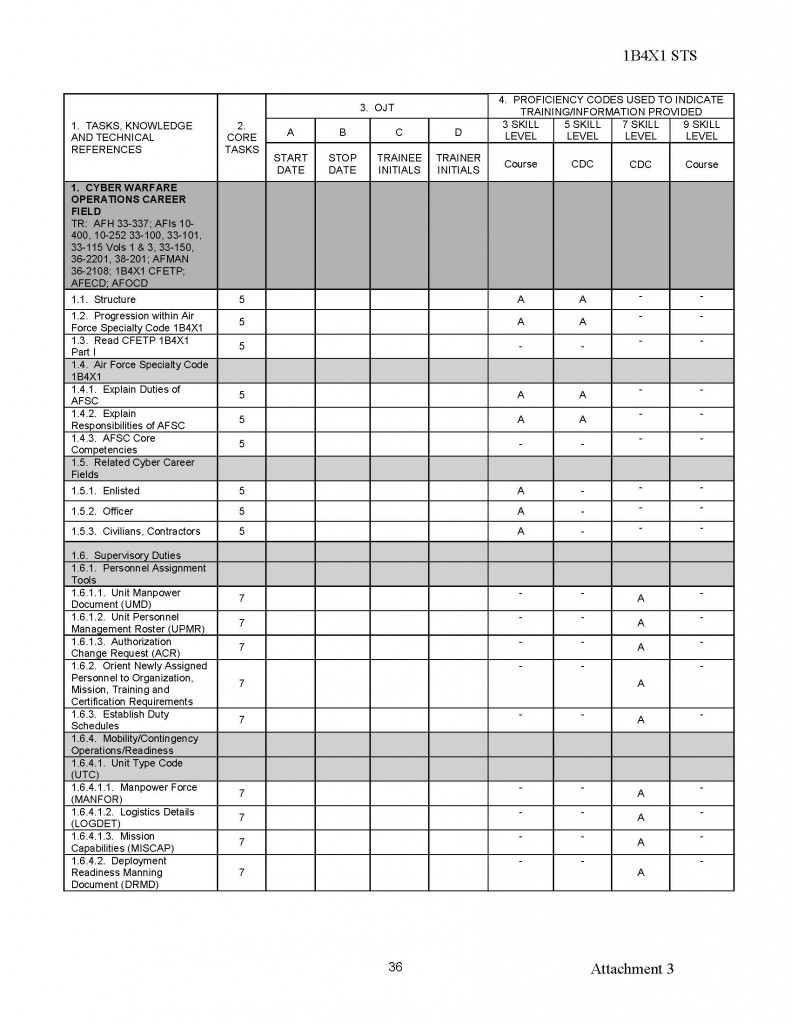
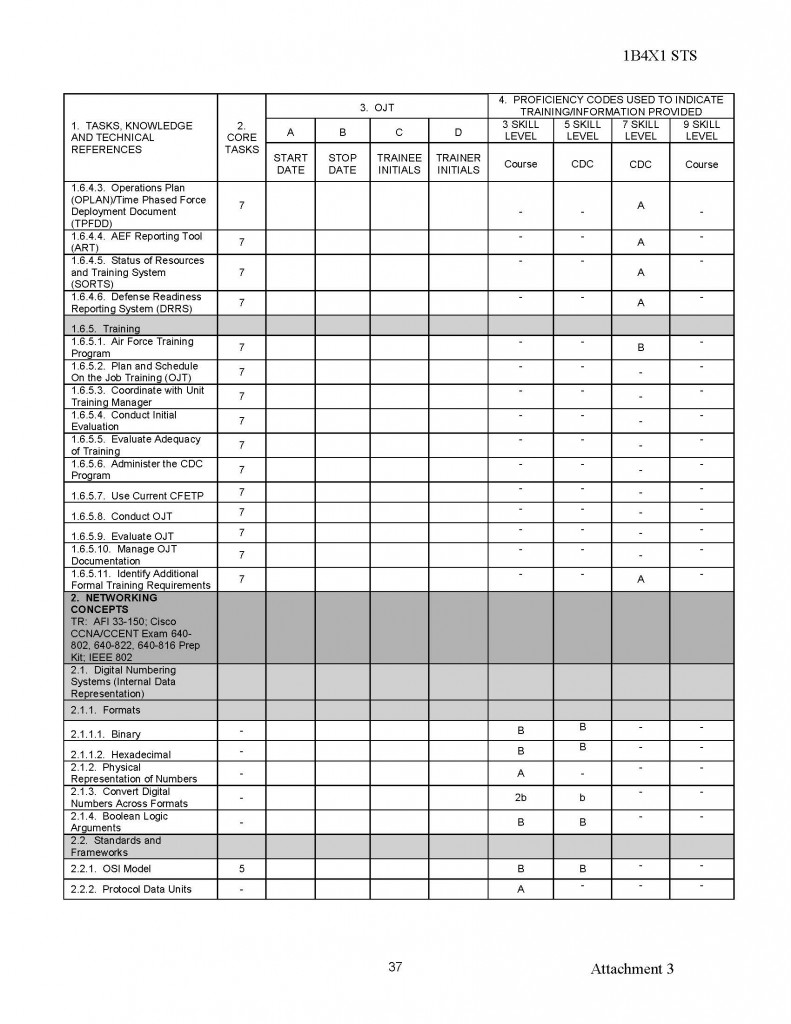
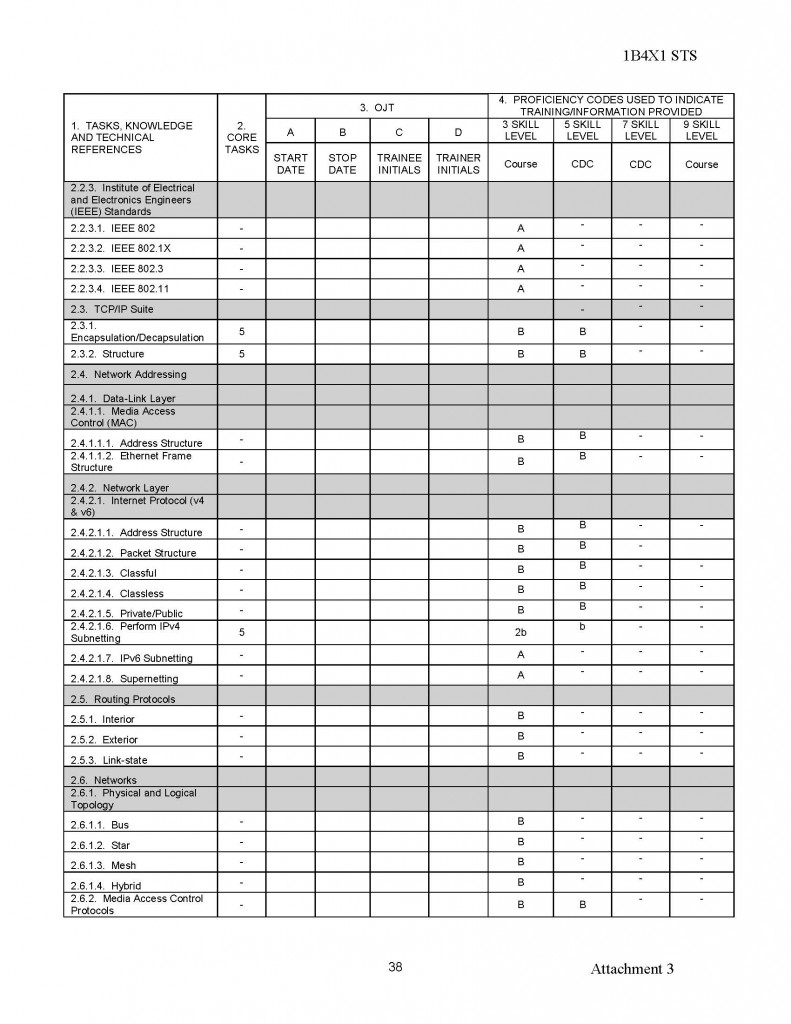
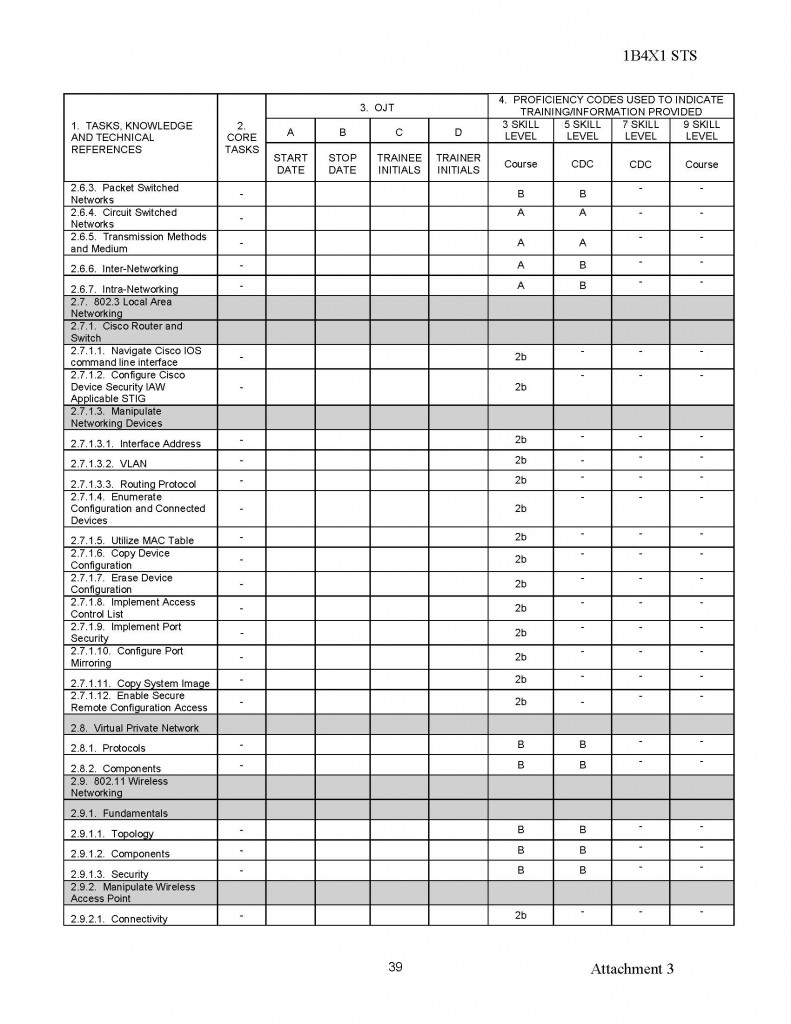
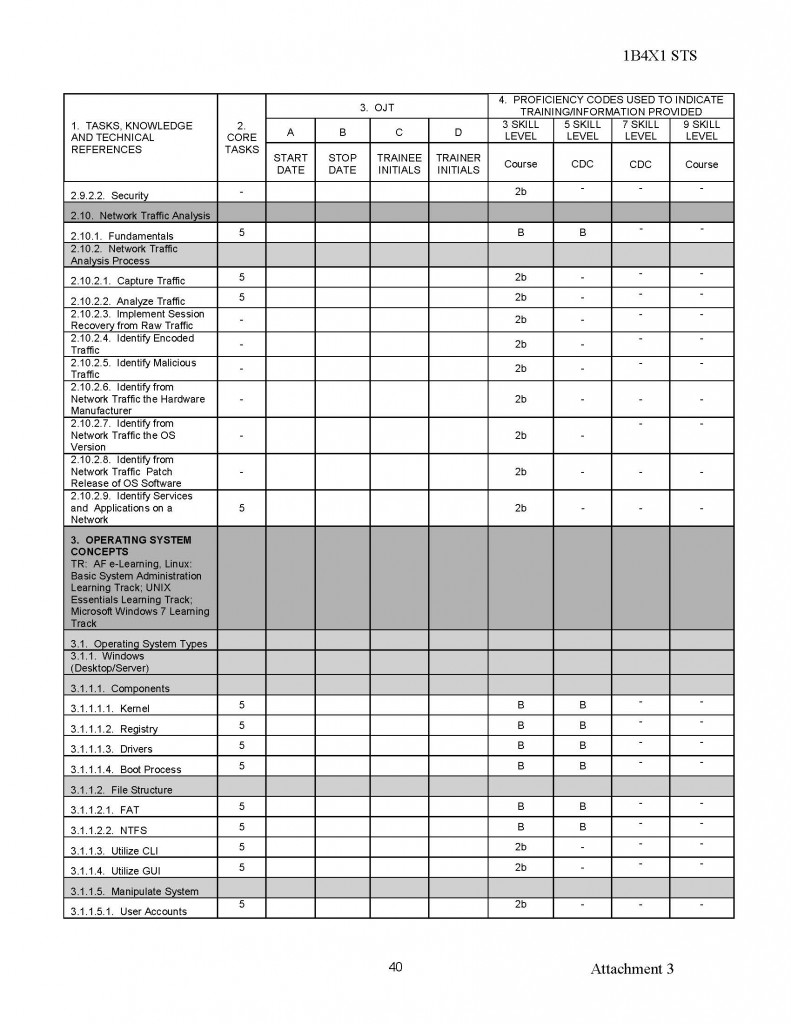
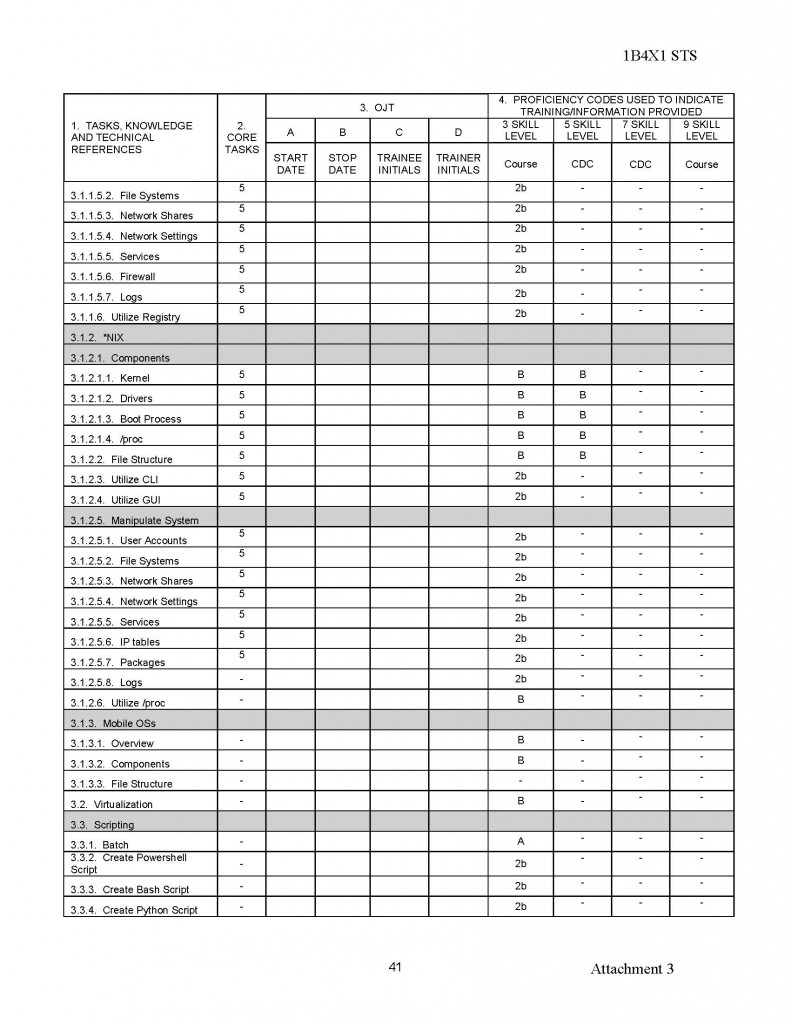
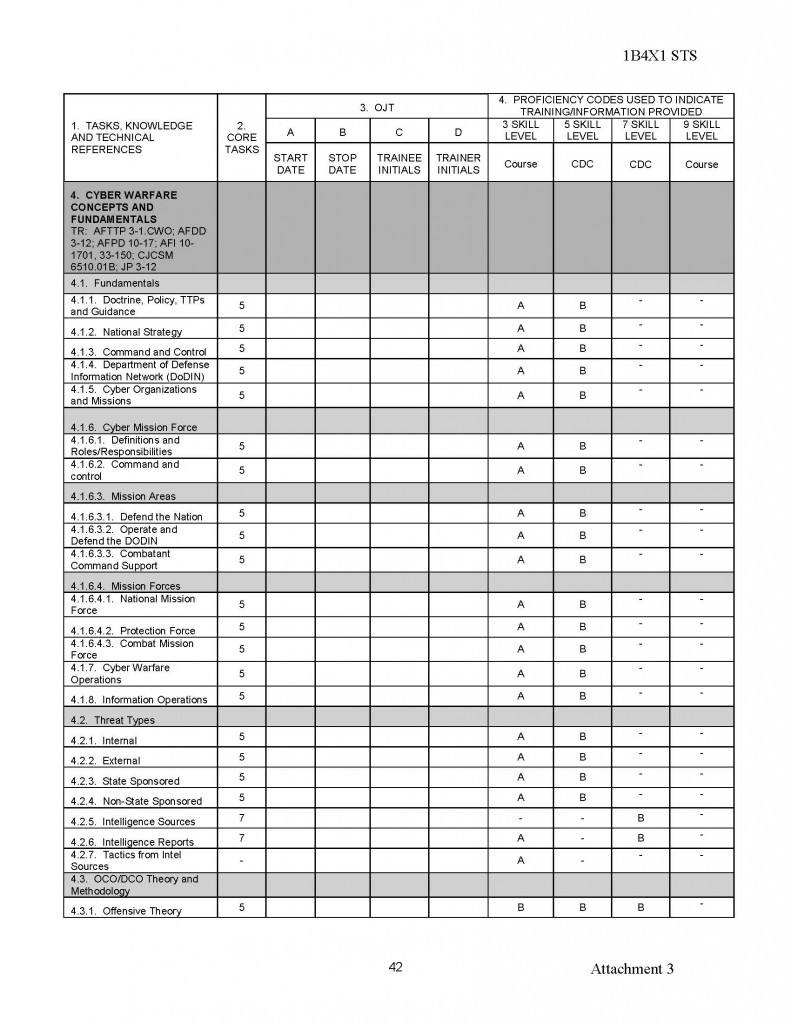
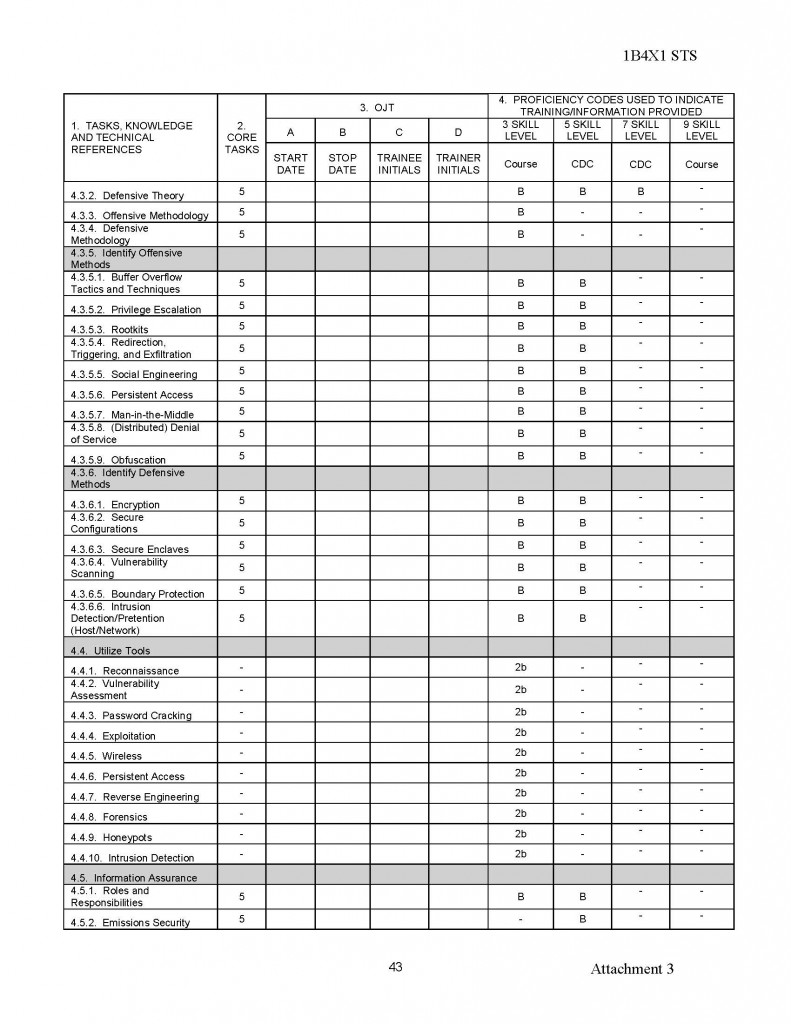
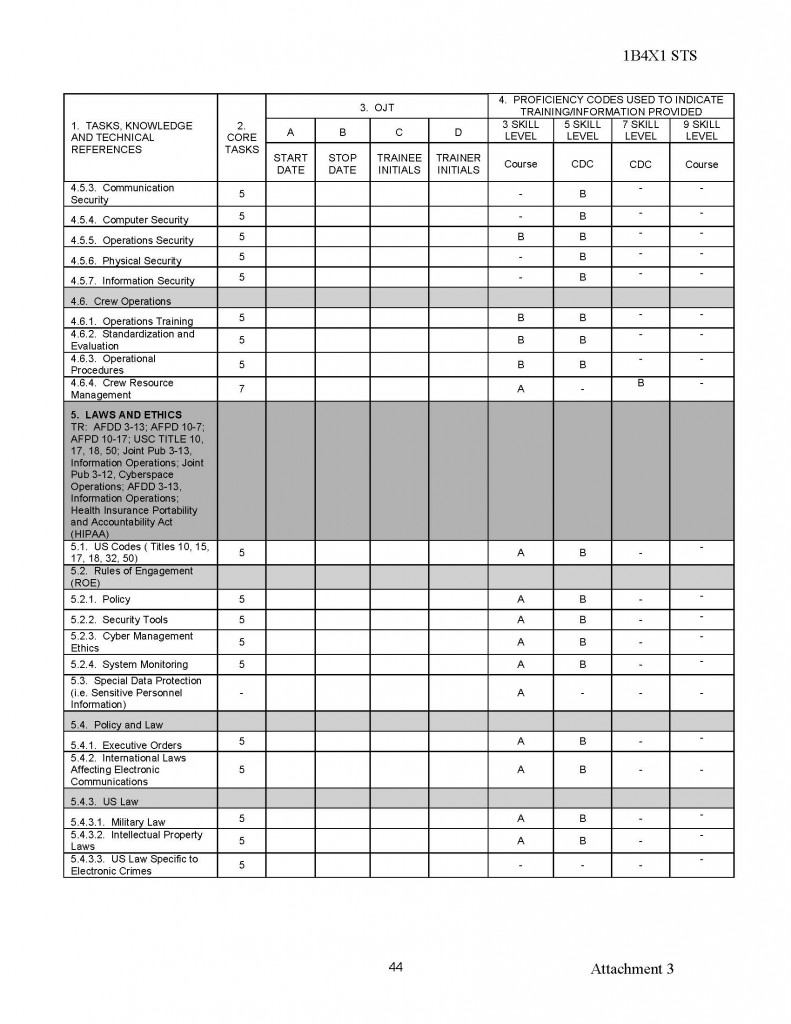
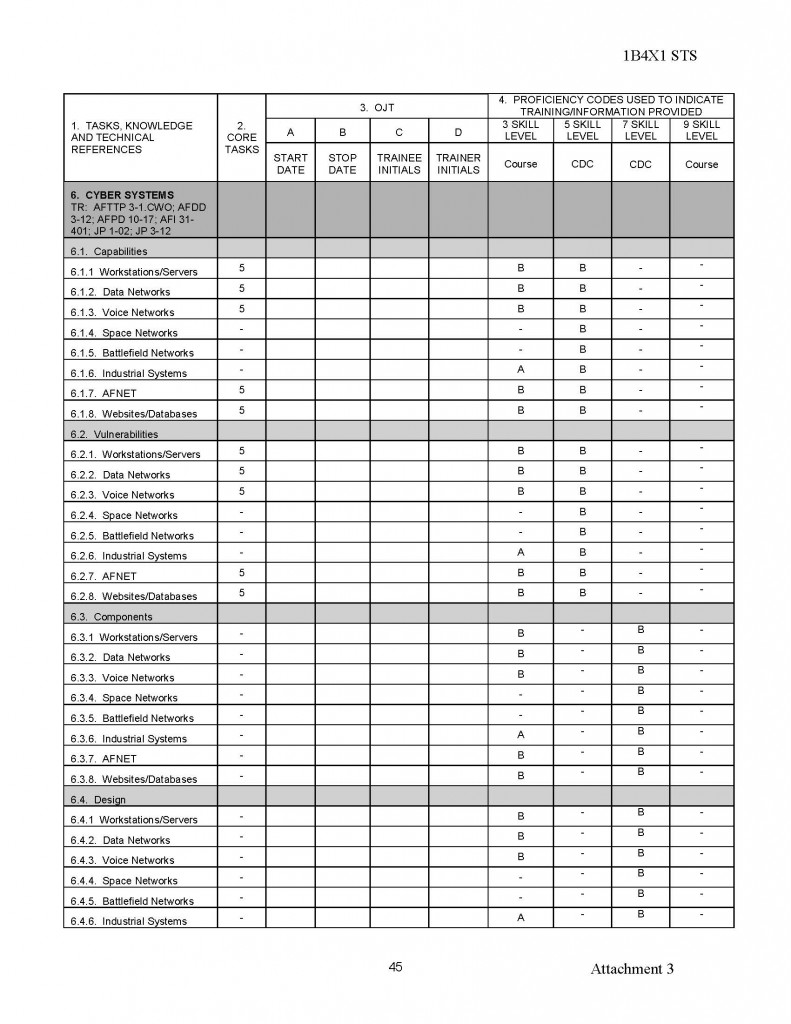
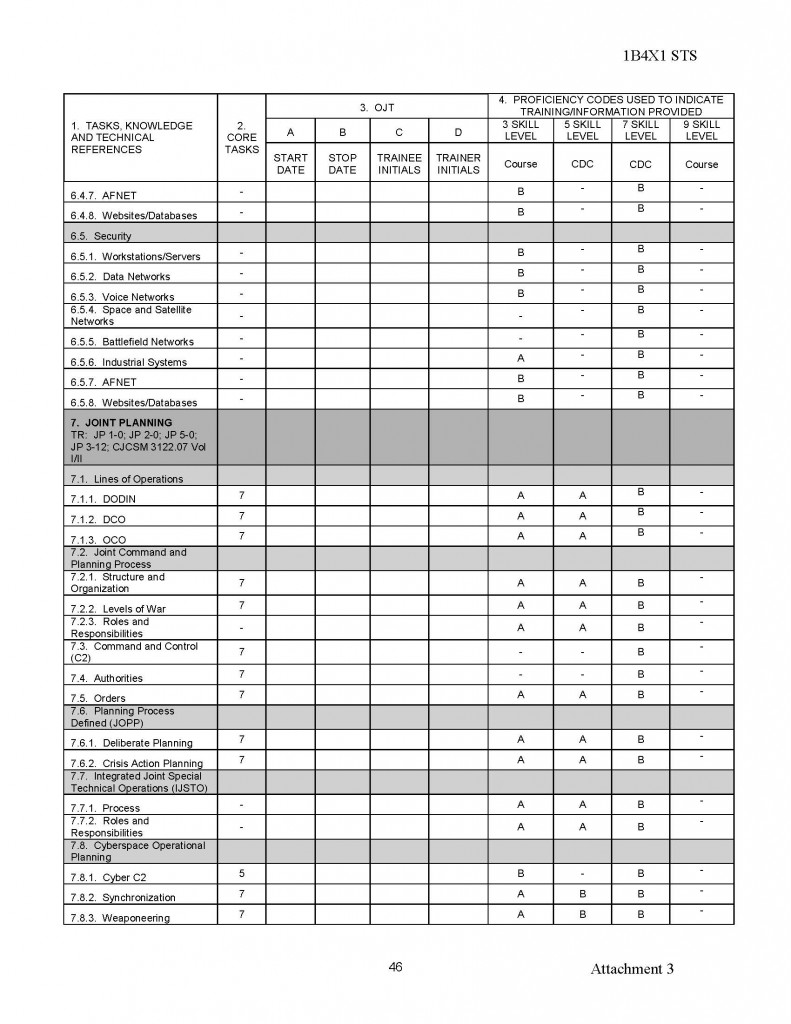
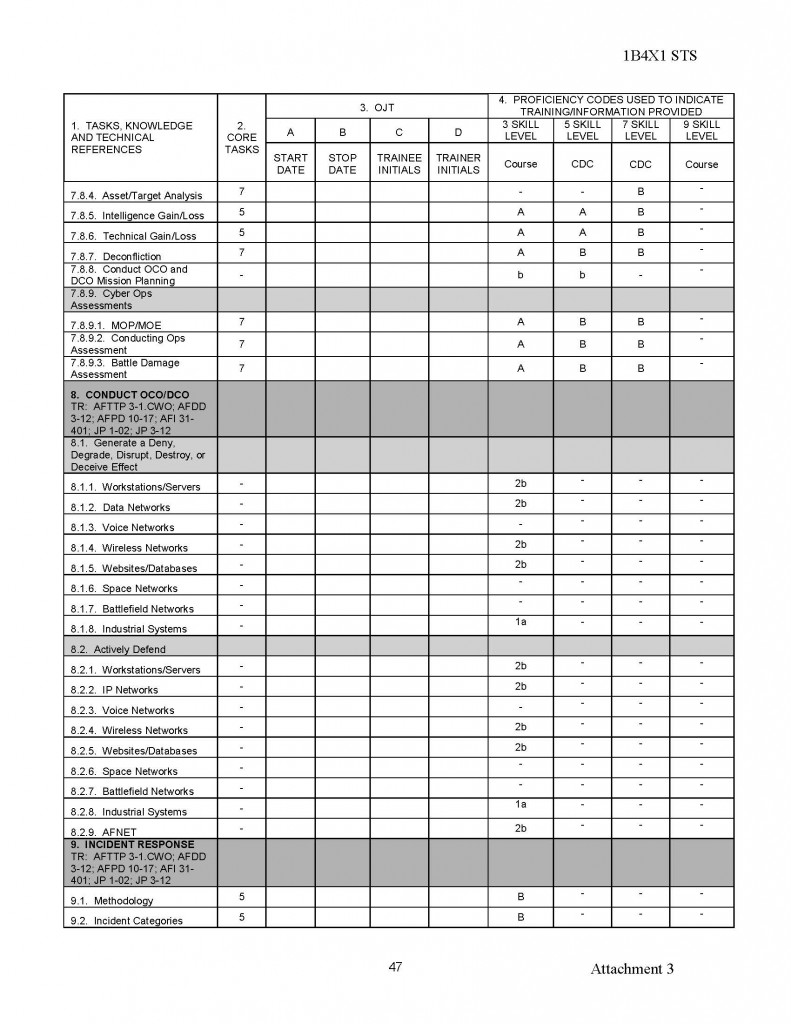
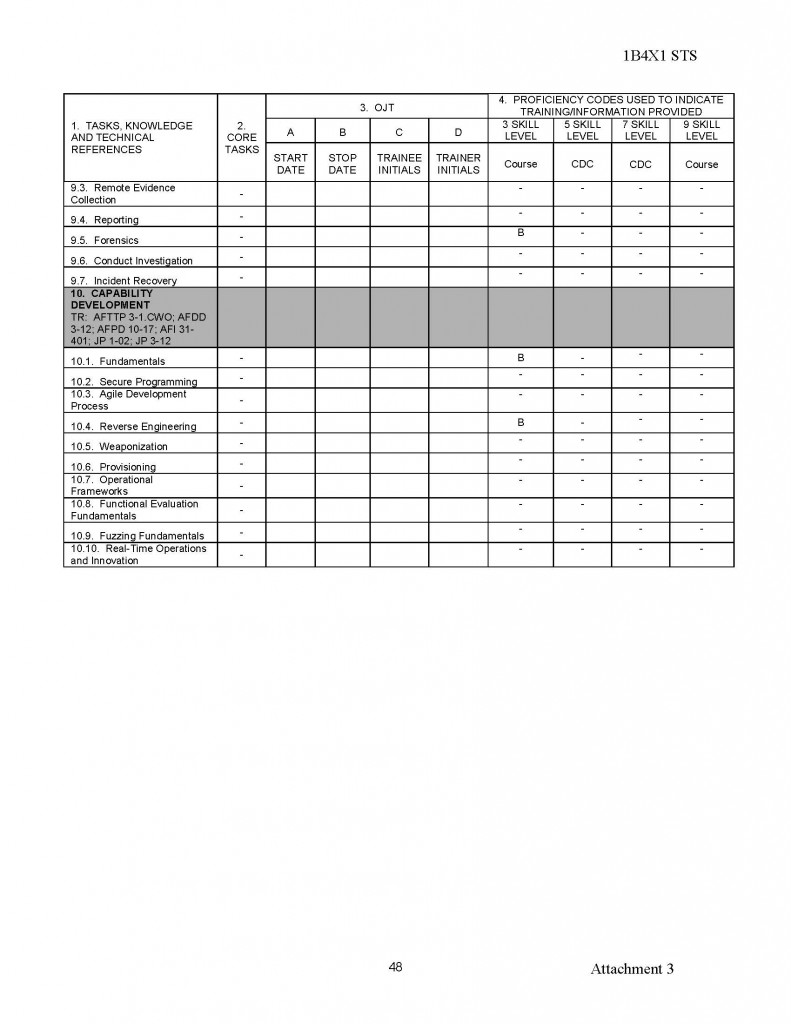

![[Image]](https://i0.wp.com/cryptome.org/2014/09/kensinger/pict7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014/09/kensinger/pict8.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014/09/kensinger/pict3.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014/09/kensinger/pict4.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014/09/kensinger/pict9.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014/09/kensinger/pict6.jpg)


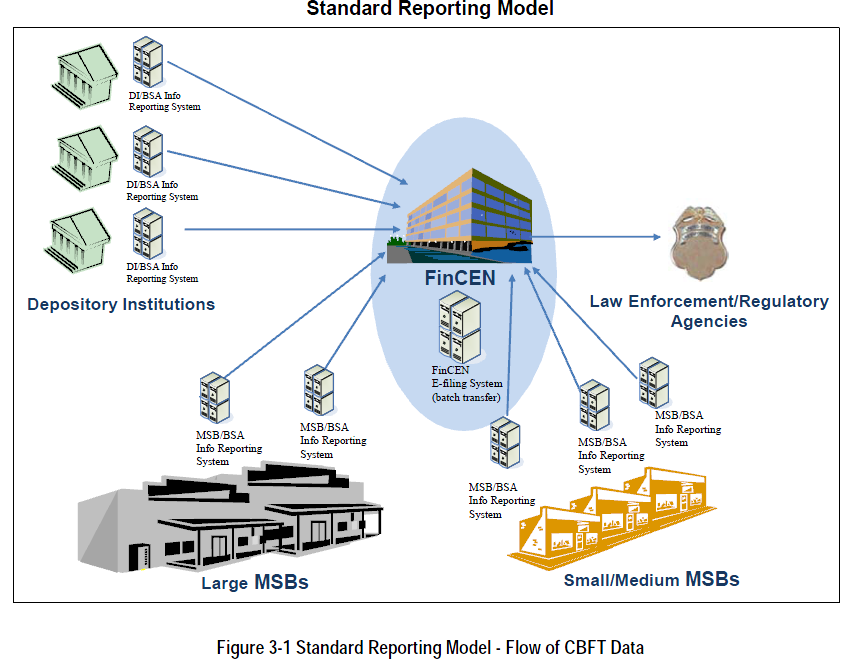
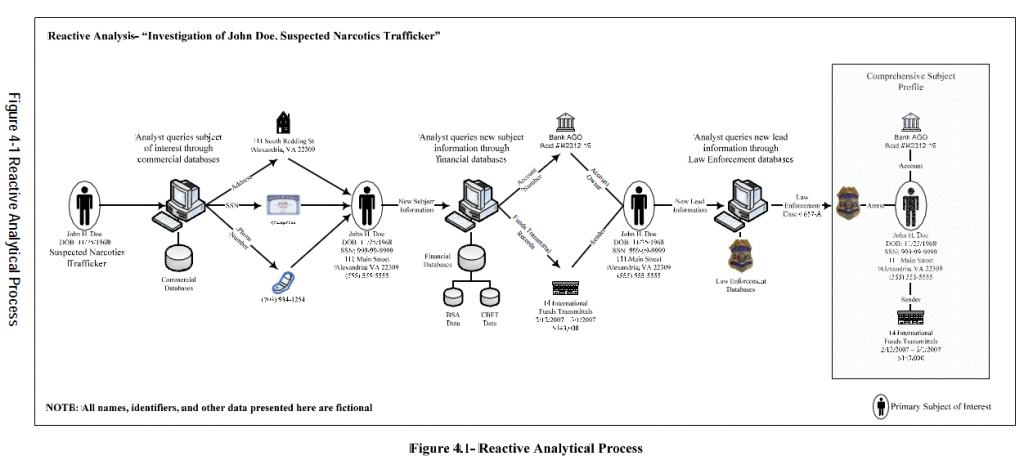
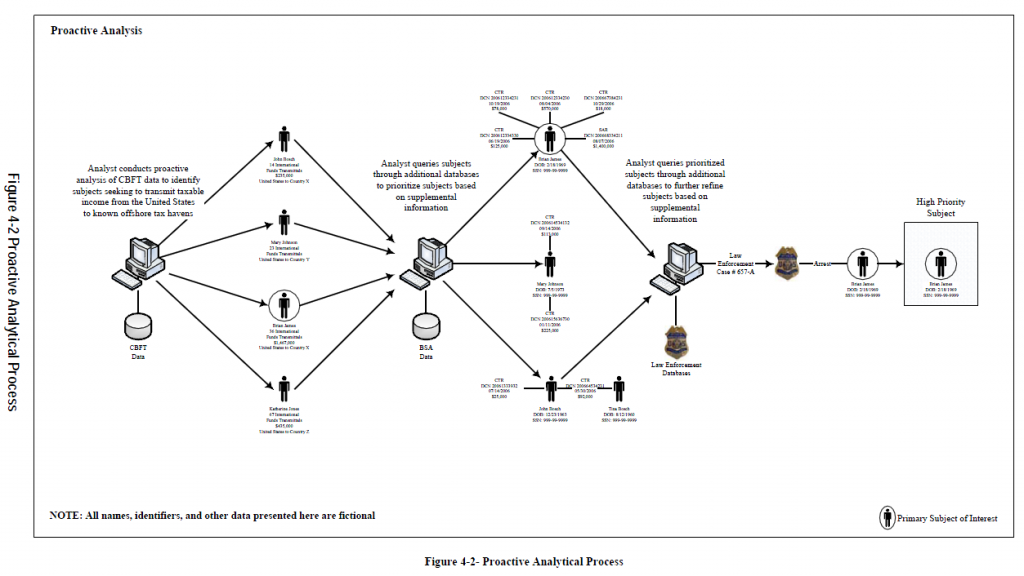

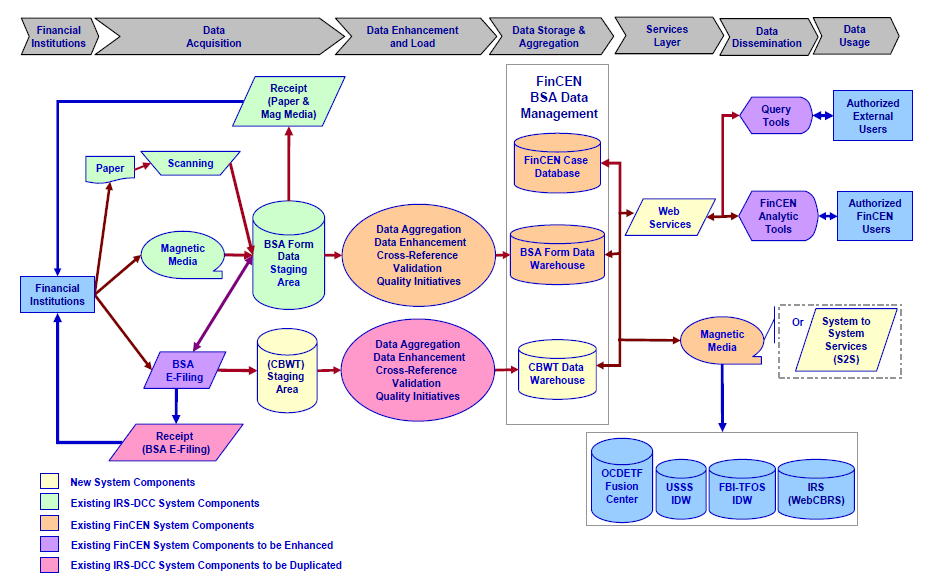

![[Image]](https://i0.wp.com/cryptome.org/2014-info/pu-pits/pict82.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/pu-pits/pict81.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/pu-pits/pict83.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/pu-pits/pict84.jpg)





![[Image]](https://i0.wp.com/cryptome.org/2014-info/daiichi-14-0323/pict62.jpg)


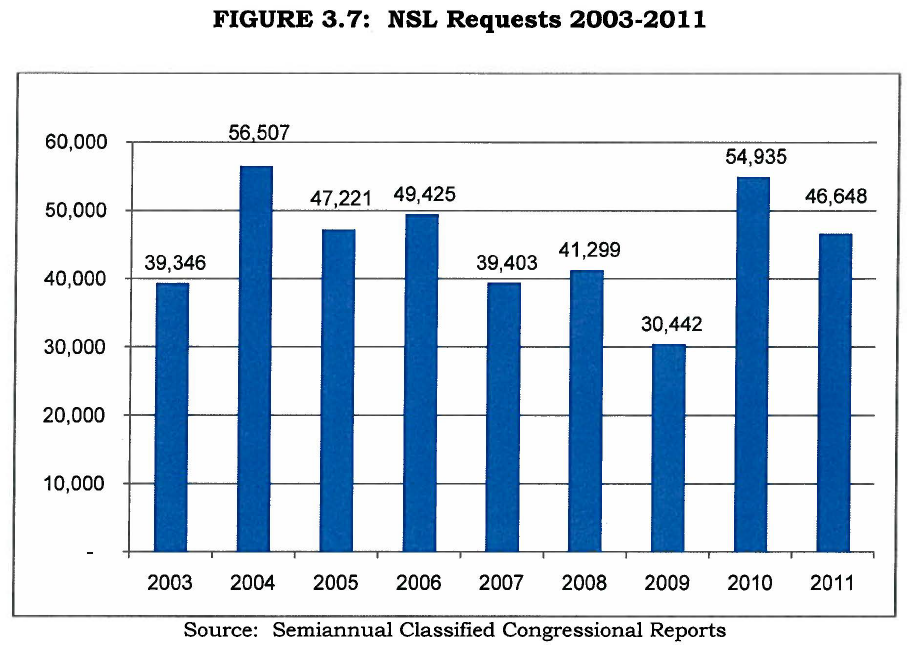

![[Image]](https://i0.wp.com/cryptome.org/2014/08/philby-spy-tools-46.jpg)

![[Image]](https://i0.wp.com/cryptome.org/2014/08/philby-spy-tools-47.jpg)





 Translation: A land / Where the air / Is like honey, / You can leave / And speed away carefree, — / But a land, / With which / You suffered together / Is in your heart permanently. [Vladimir Mayakovsky, “Good”] Happy Birthday!
Translation: A land / Where the air / Is like honey, / You can leave / And speed away carefree, — / But a land, / With which / You suffered together / Is in your heart permanently. [Vladimir Mayakovsky, “Good”] Happy Birthday!








![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict71.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict62.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict70.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict63.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict54.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict64.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict55.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict56.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict61.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict58.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict59.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict57.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict50.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict46.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict48.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict49.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict51.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict52.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict53.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict65.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict66.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict67.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict68.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict69.jpg)



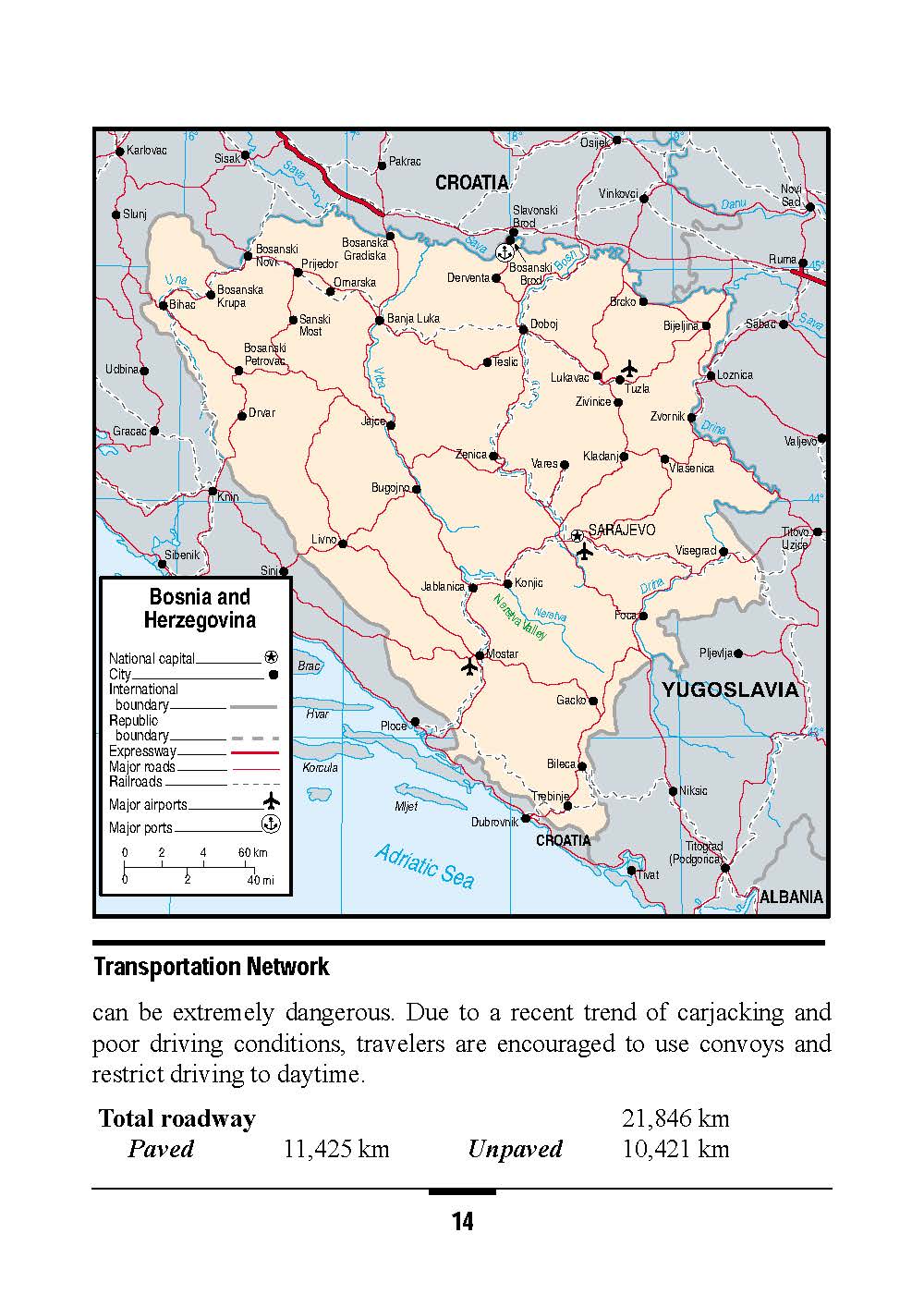
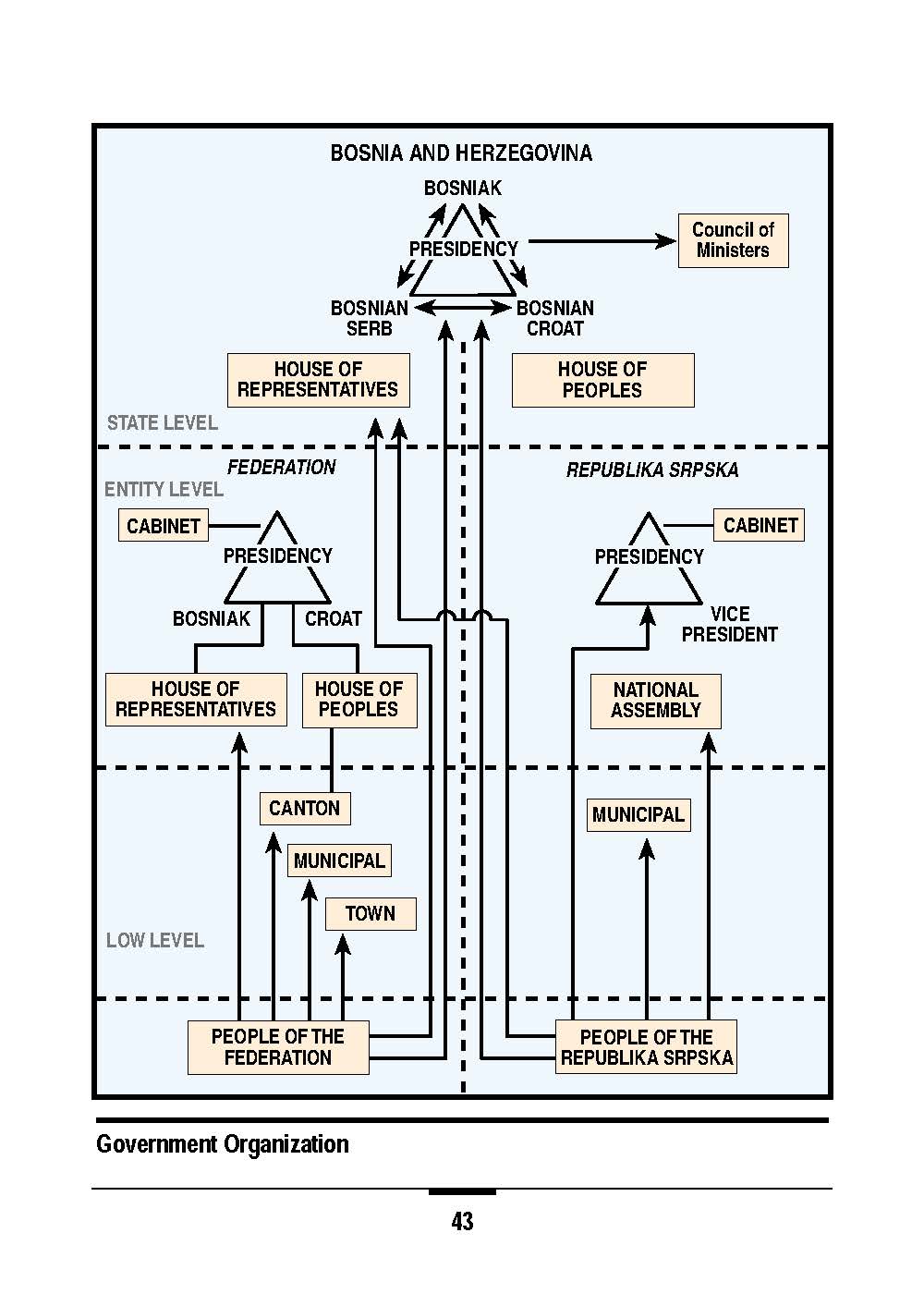


![[Image]](https://i0.wp.com/cryptome.org/2014-info/nsa-bad-abling/pict0.jpg)

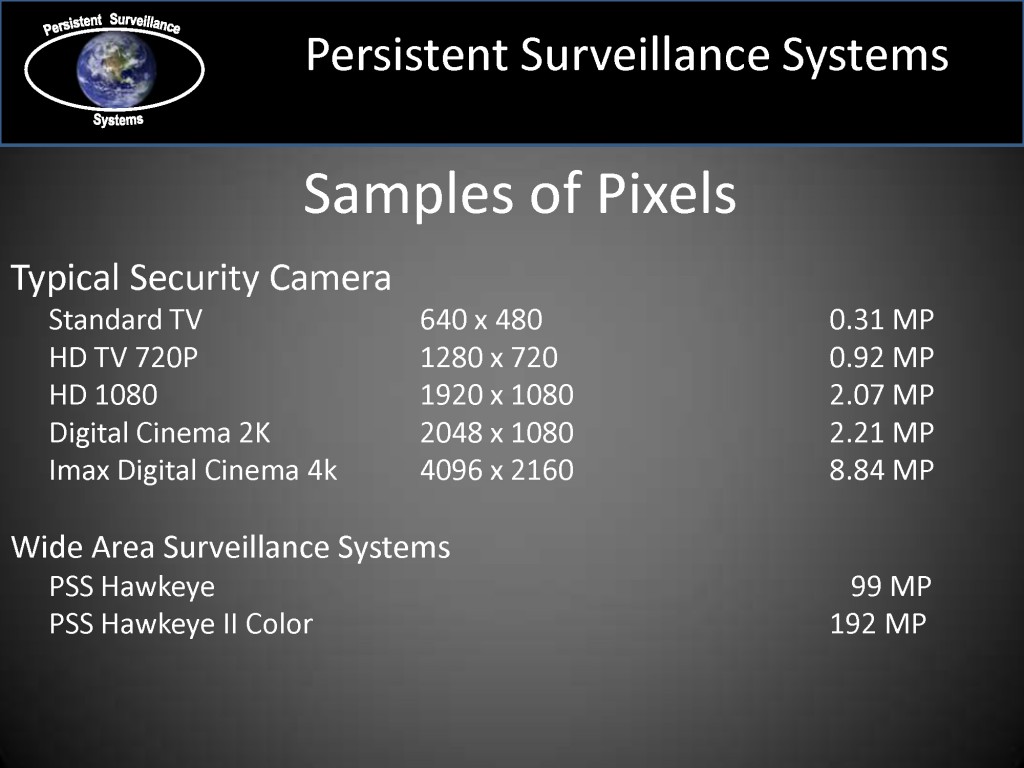

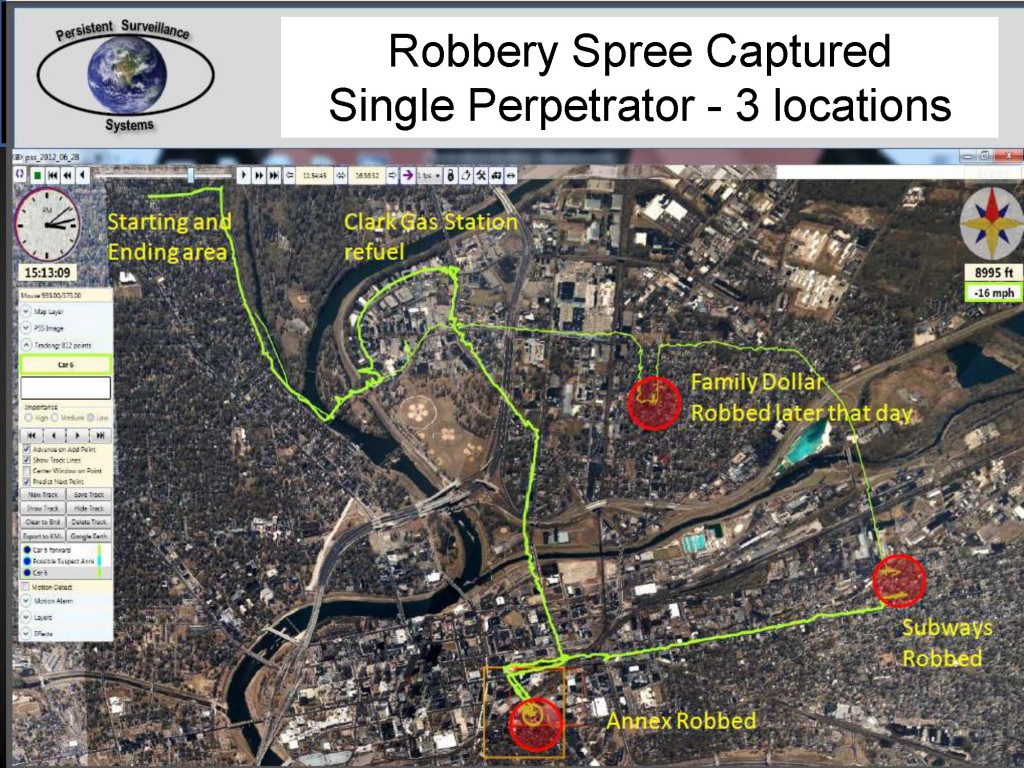
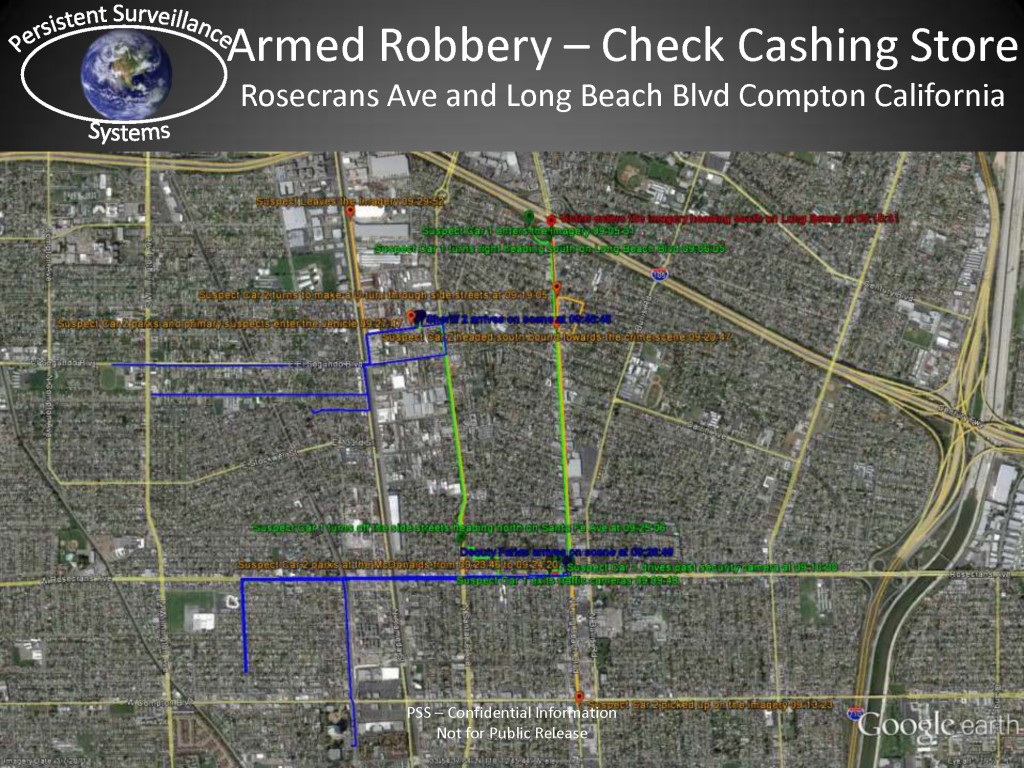


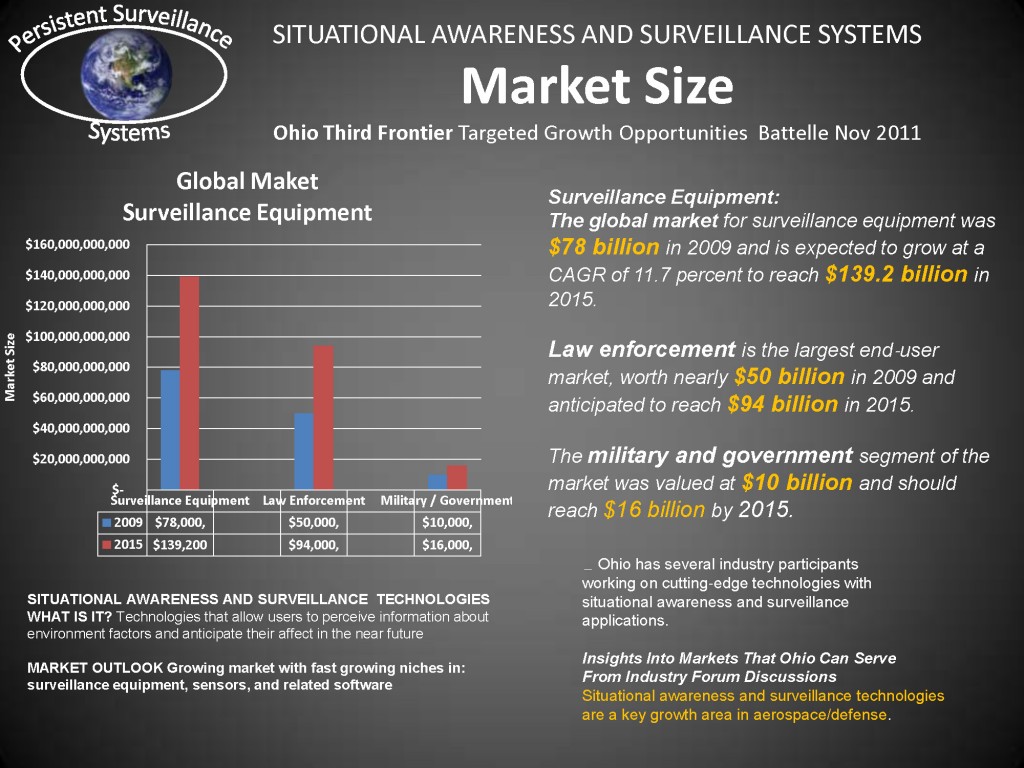

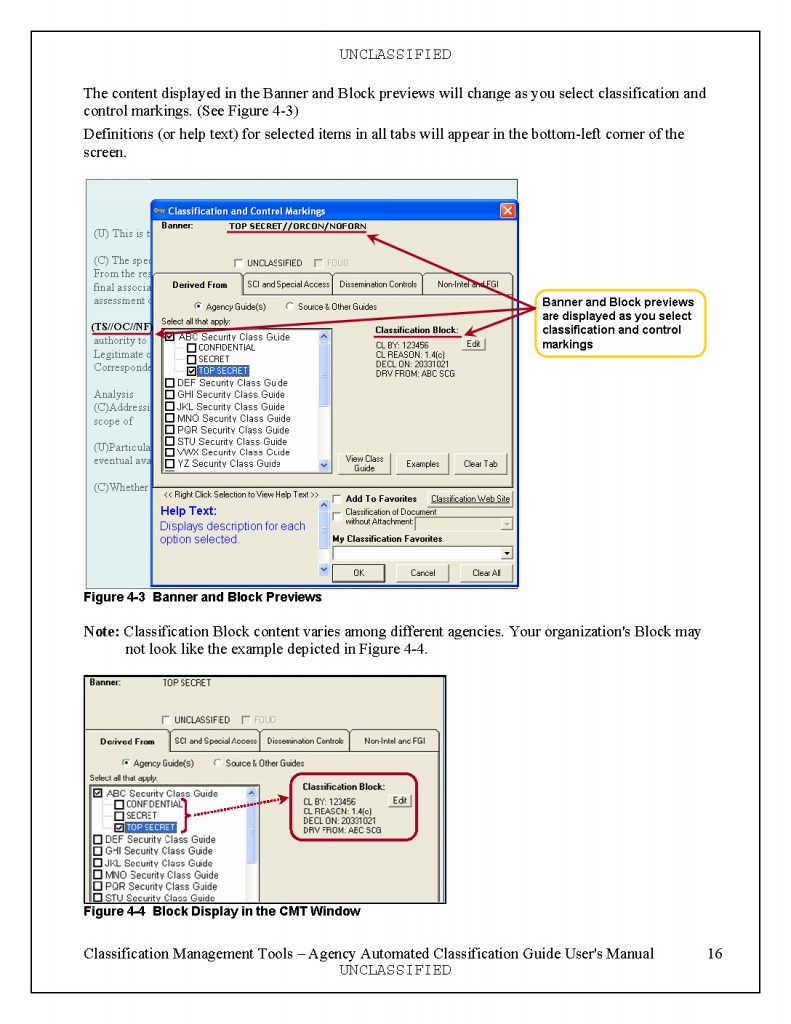
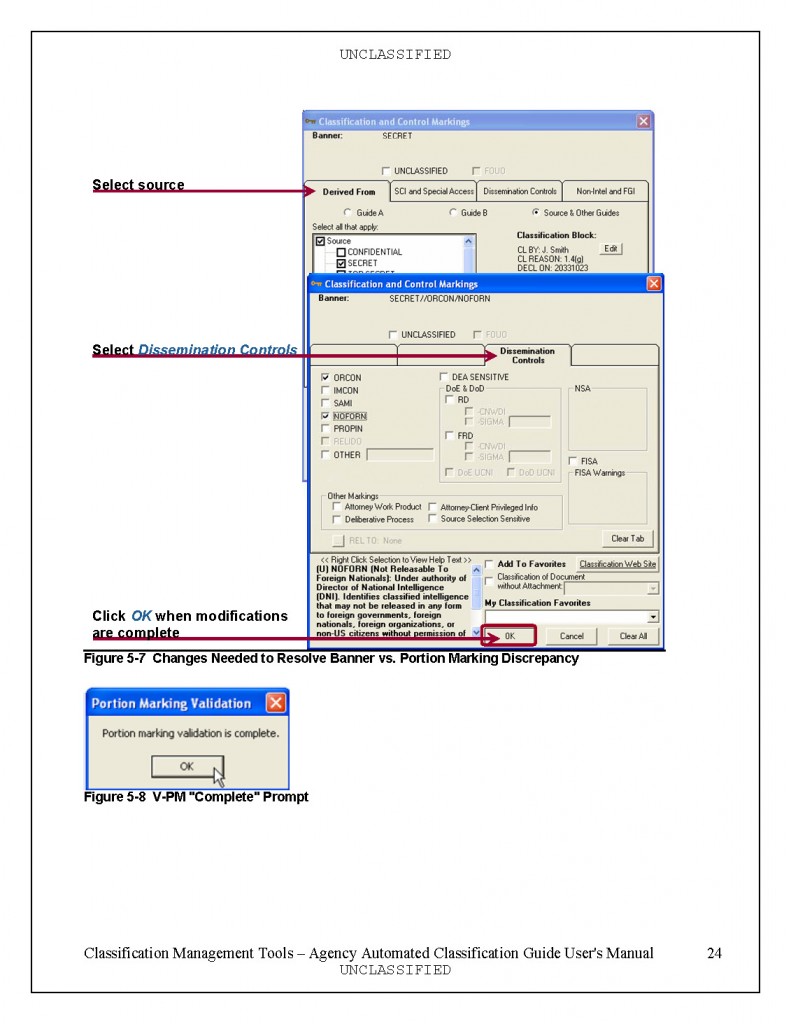


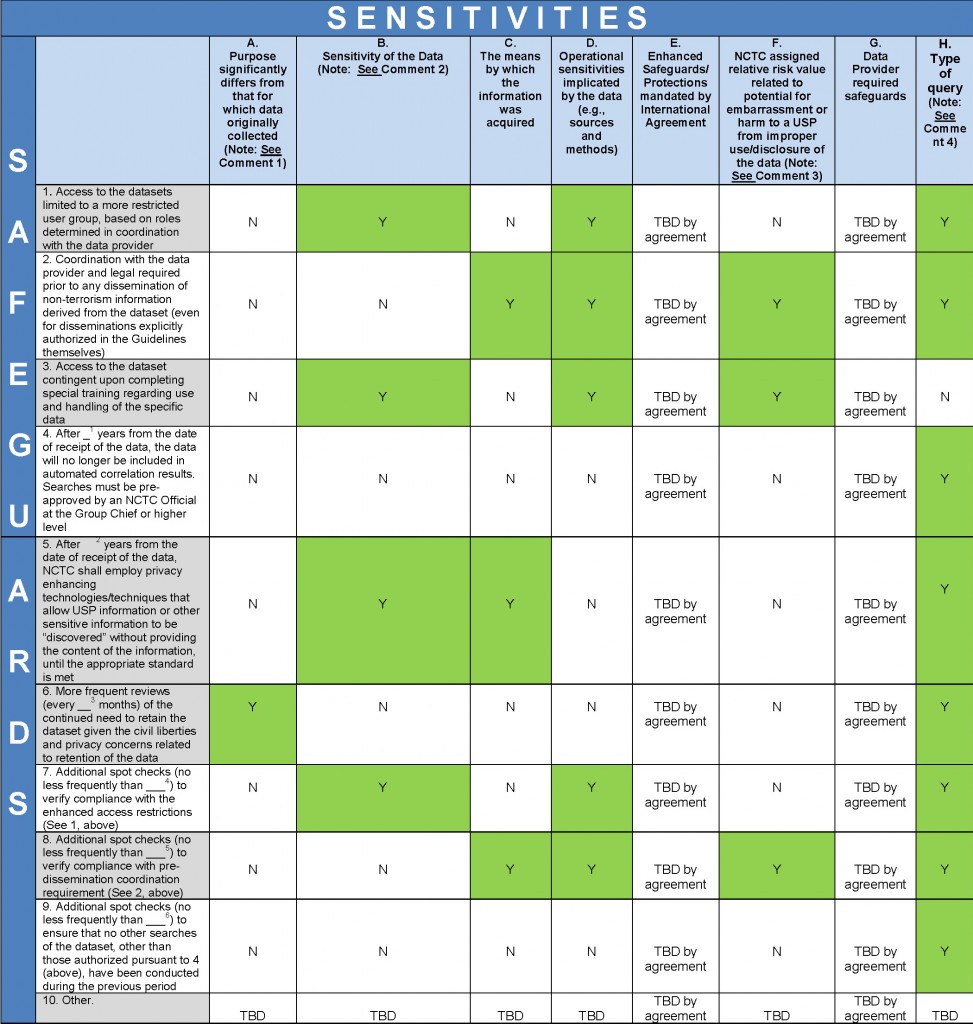



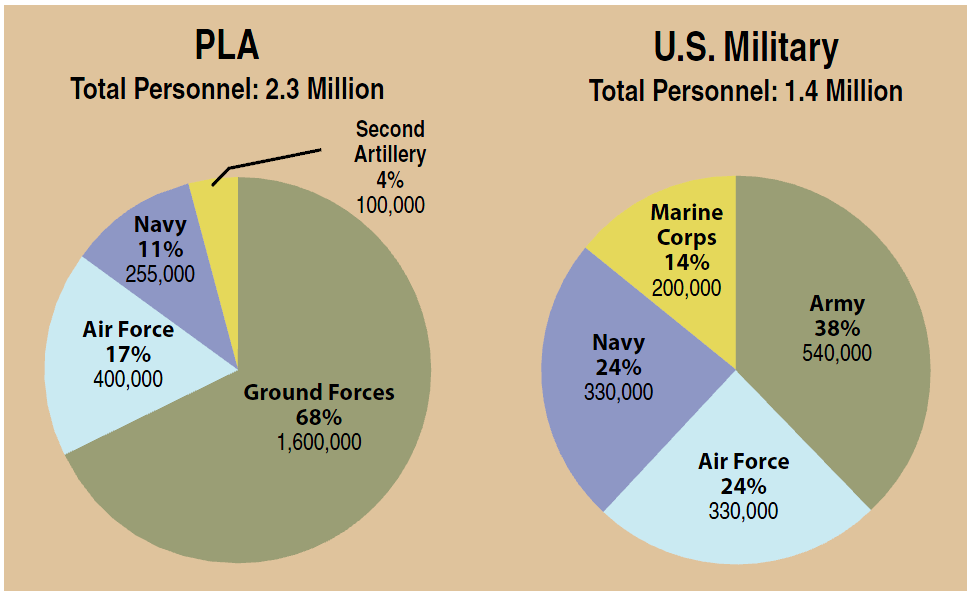

![[Image]](https://i0.wp.com/cryptome.org/2014-info/michael-rogers/pict23.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/michael-rogers/pict17.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/michael-rogers/pict20.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/michael-rogers/pict22.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/michael-rogers/pict19.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/michael-rogers/pict25.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/michael-rogers/pict24.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/michael-rogers/pict29.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/michael-rogers/pict26.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/michael-rogers/pict27.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/michael-rogers/pict28.jpg)






























































































































































































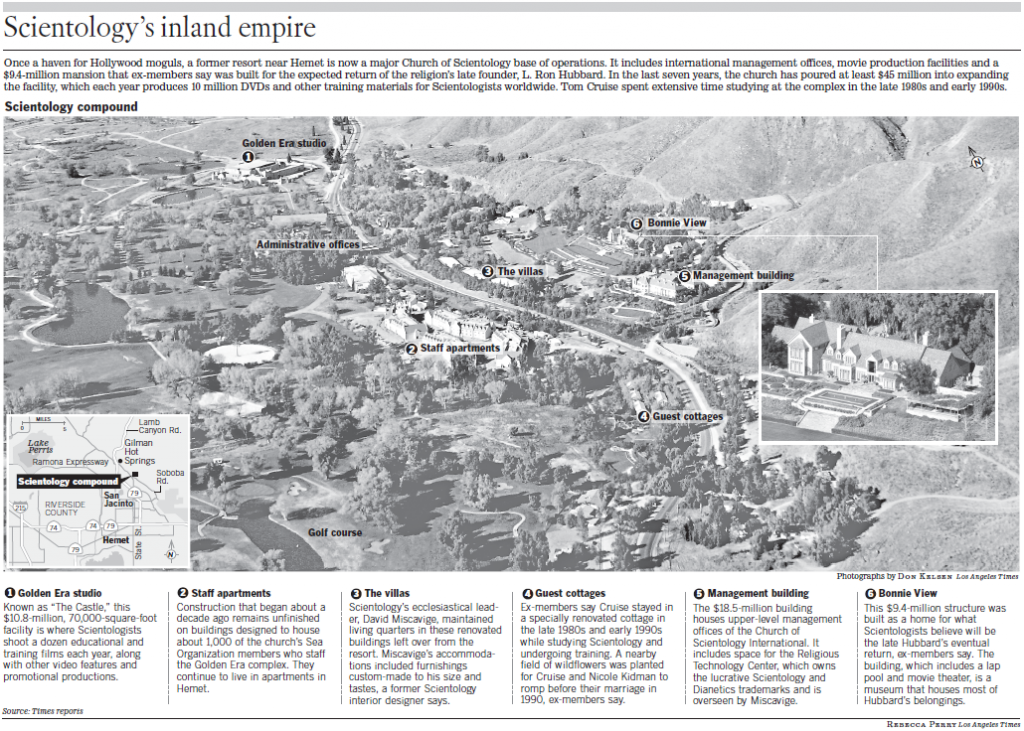
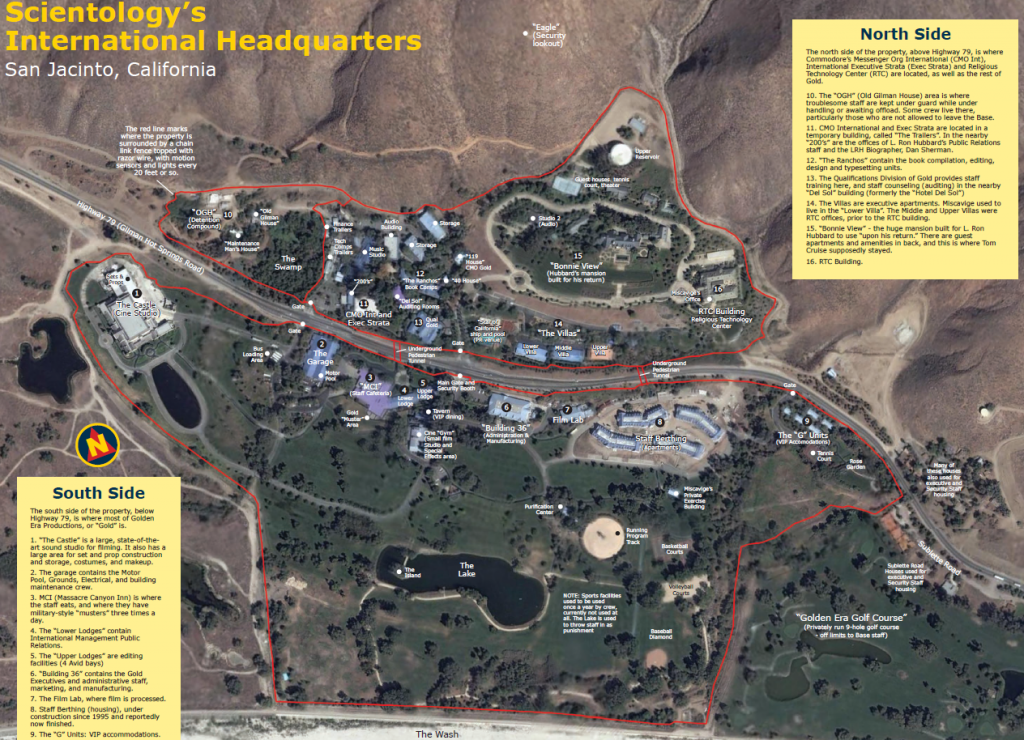













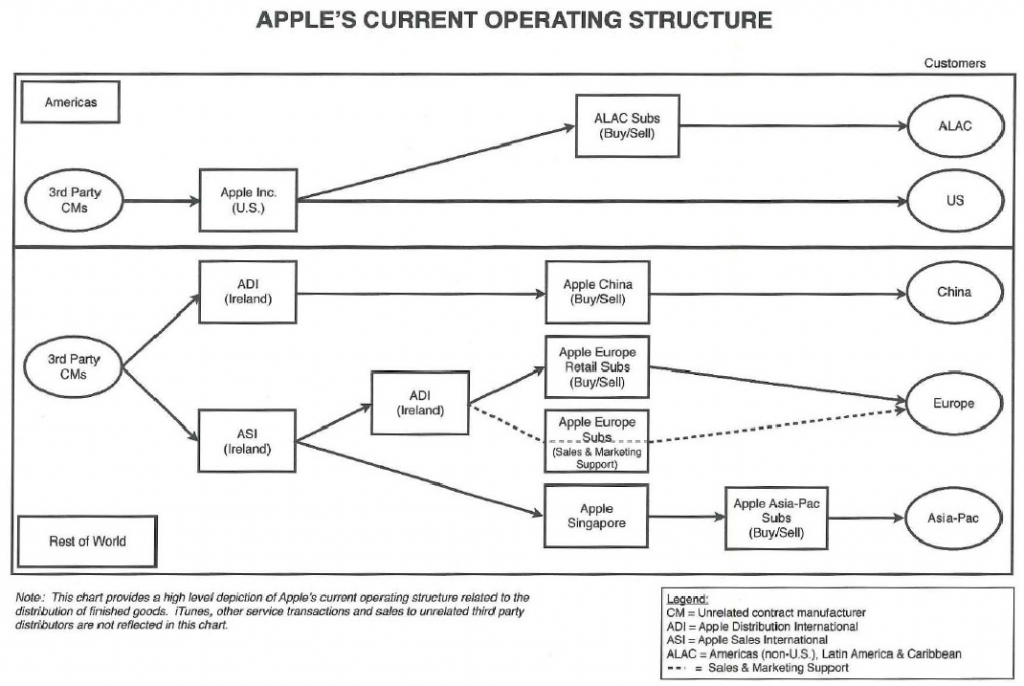








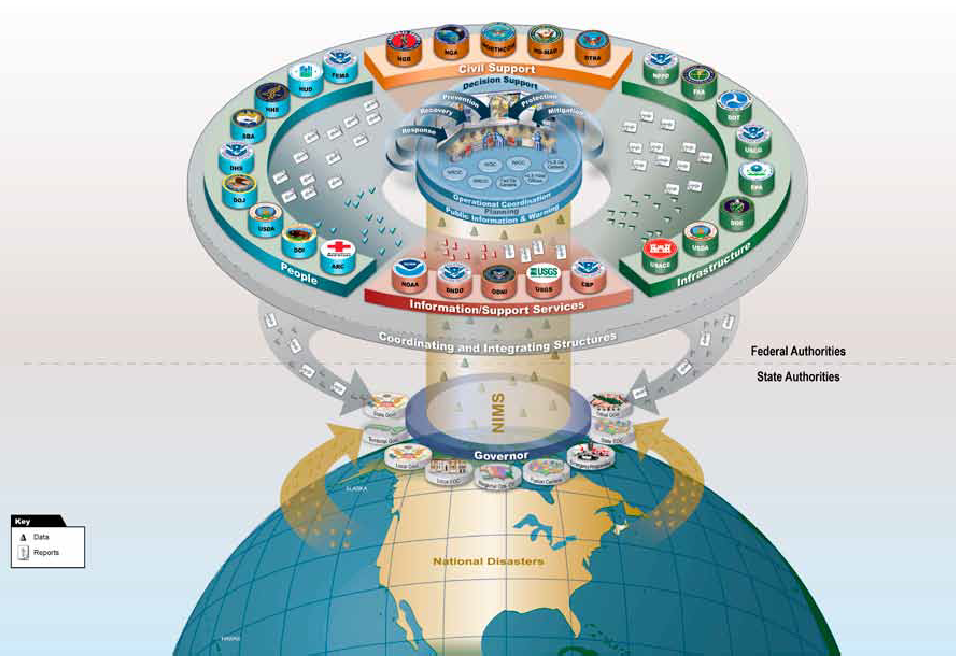
![[Image]](https://i0.wp.com/cryptome.org/2013-info/03/shabak-sites/pict25.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/03/shabak-sites/pict32.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/03/shabak-sites/pict26.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/03/shabak-sites/pict33.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/03/shabak-sites/pict28.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/03/shabak-sites/pict35.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/03/shabak-sites/pict27.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/03/shabak-sites/pict34.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/03/shabak-sites/pict31.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/03/shabak-sites/pict36.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/03/shabak-sites/pict29.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/03/shabak-sites/pict37.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/03/shabak-sites/pict30.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2013-info/03/shabak-sites/pict24.jpg)

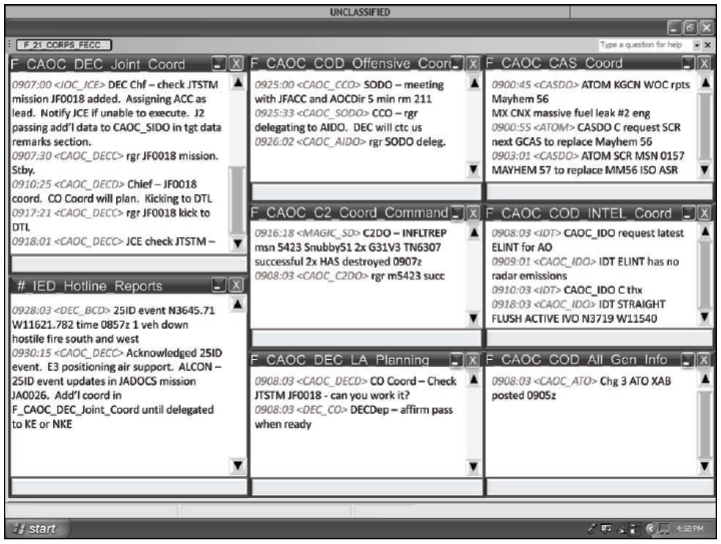




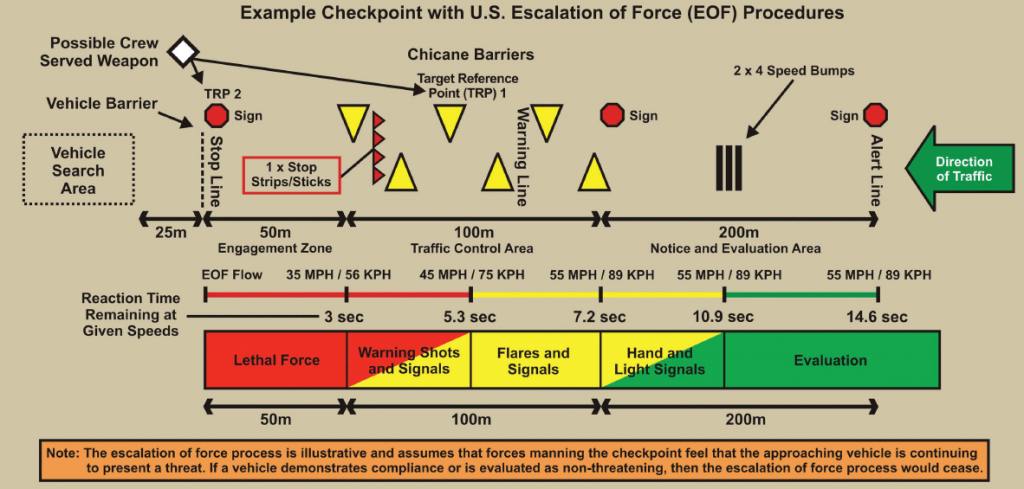





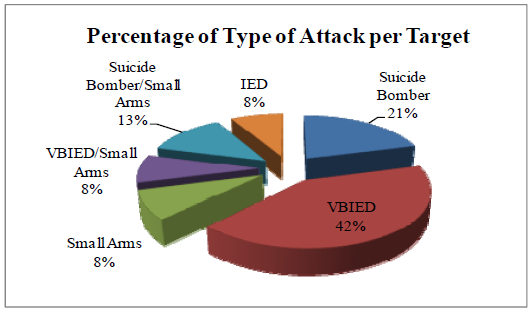



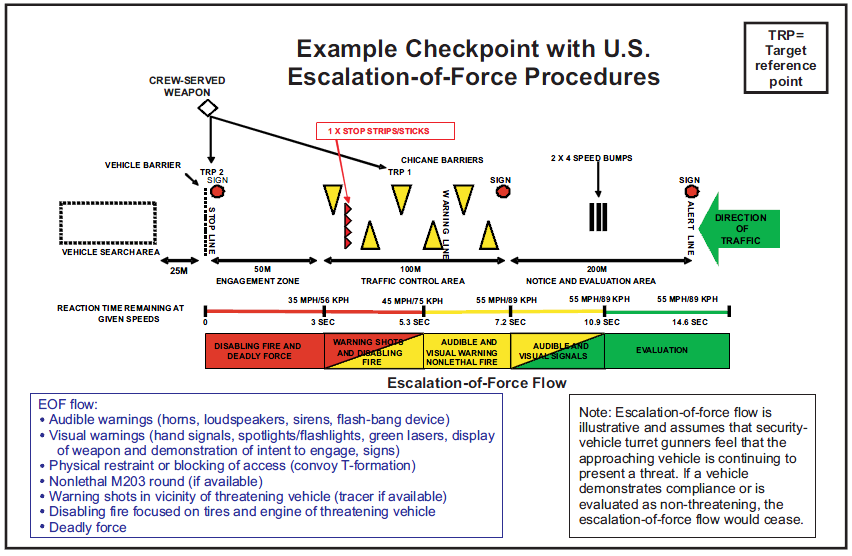





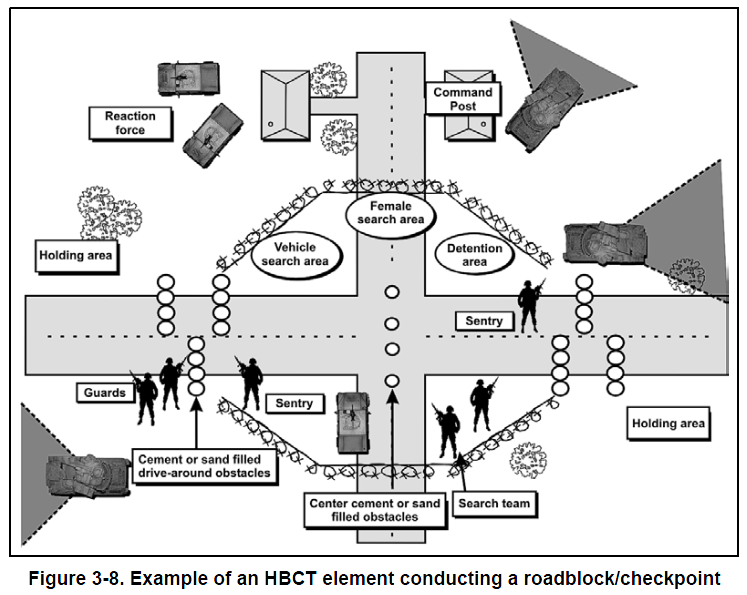
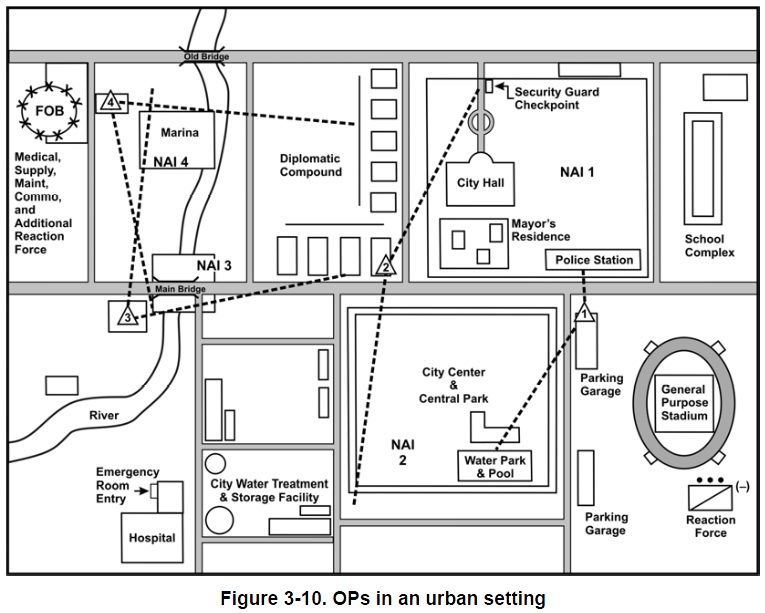
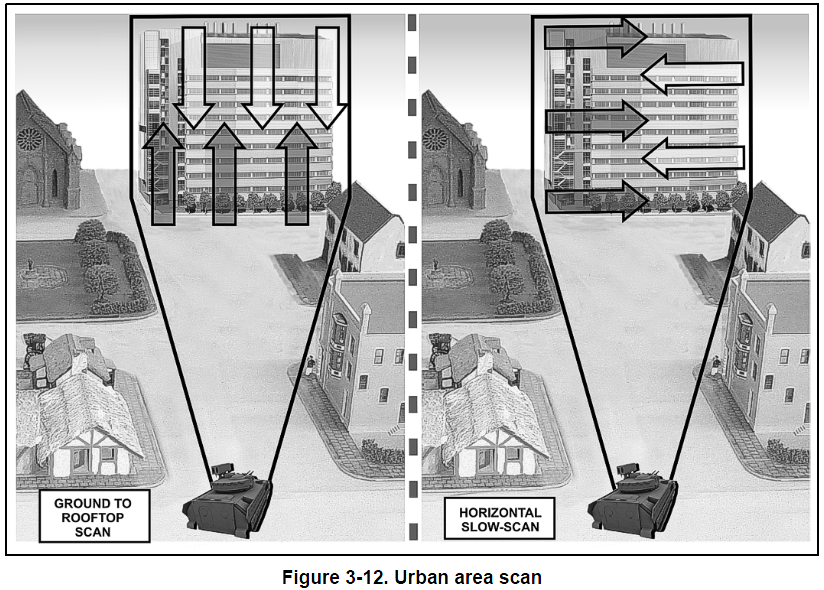
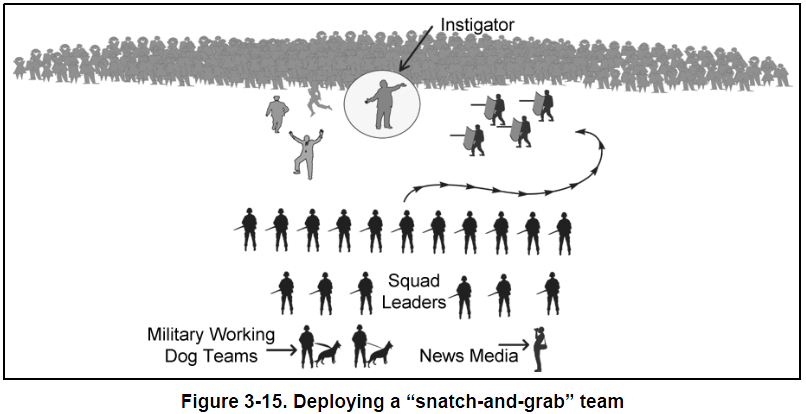

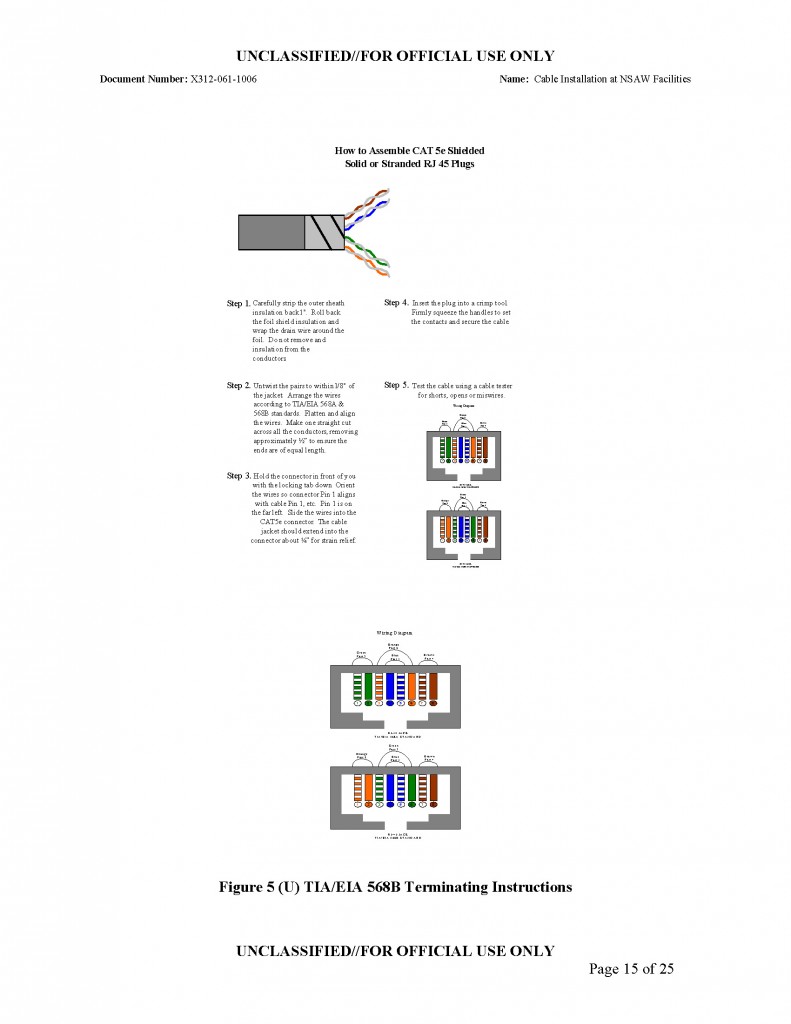


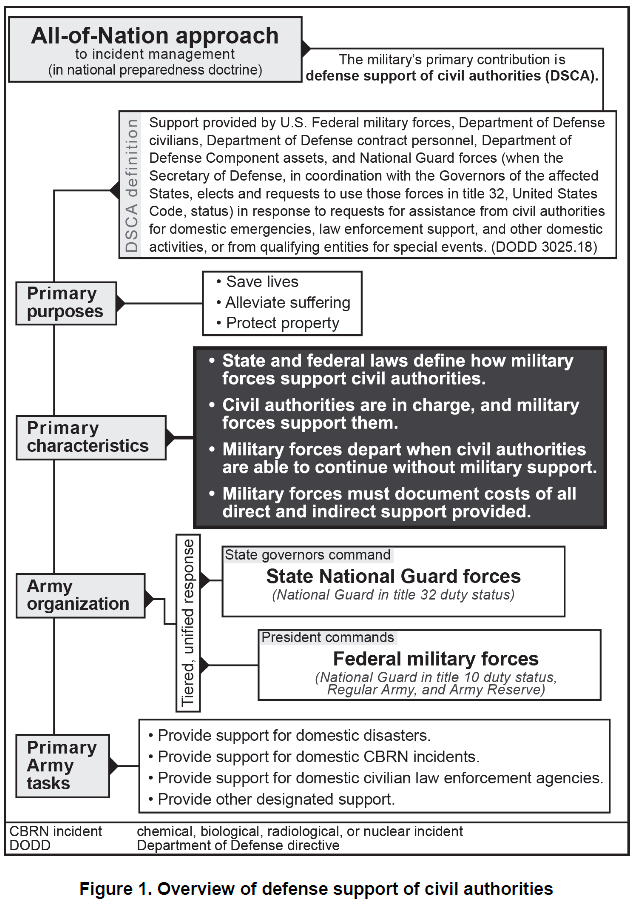



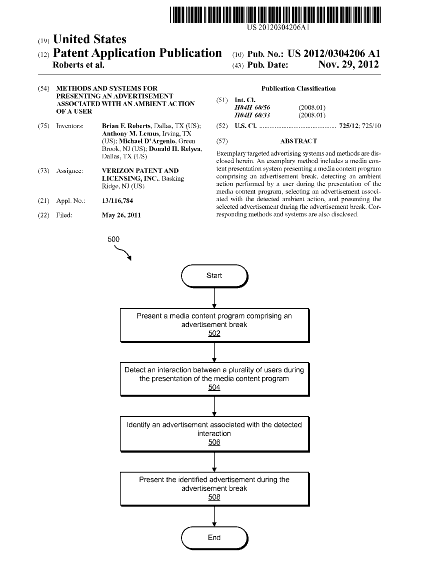


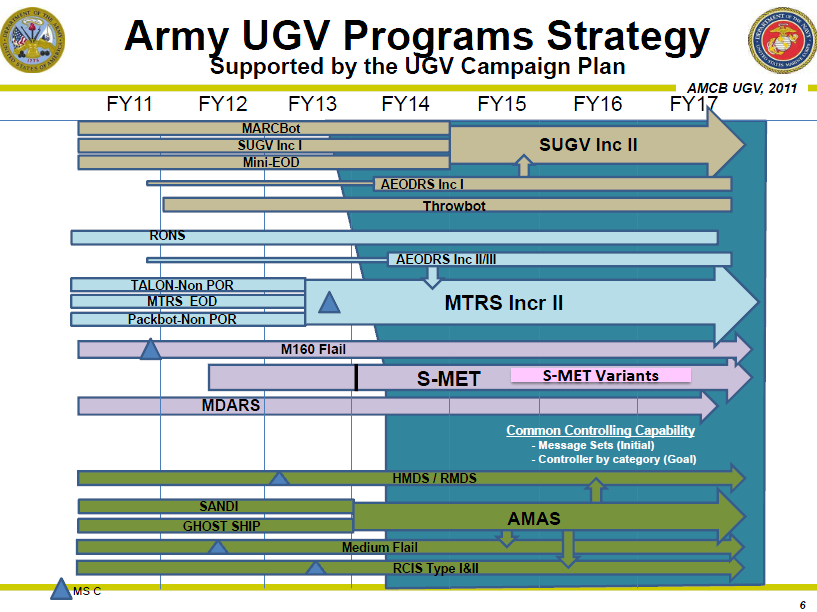







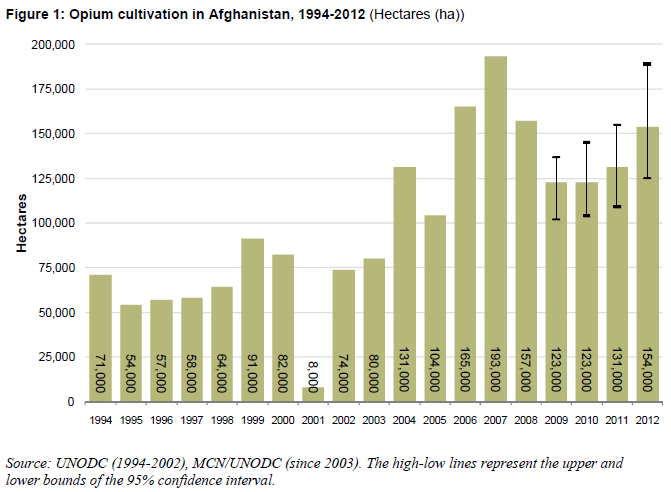
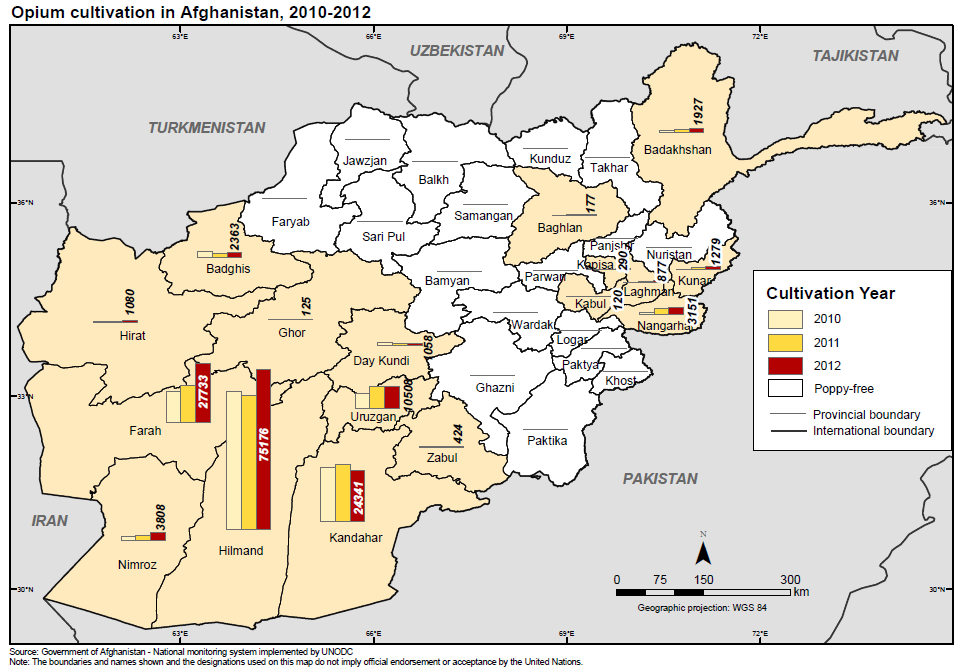


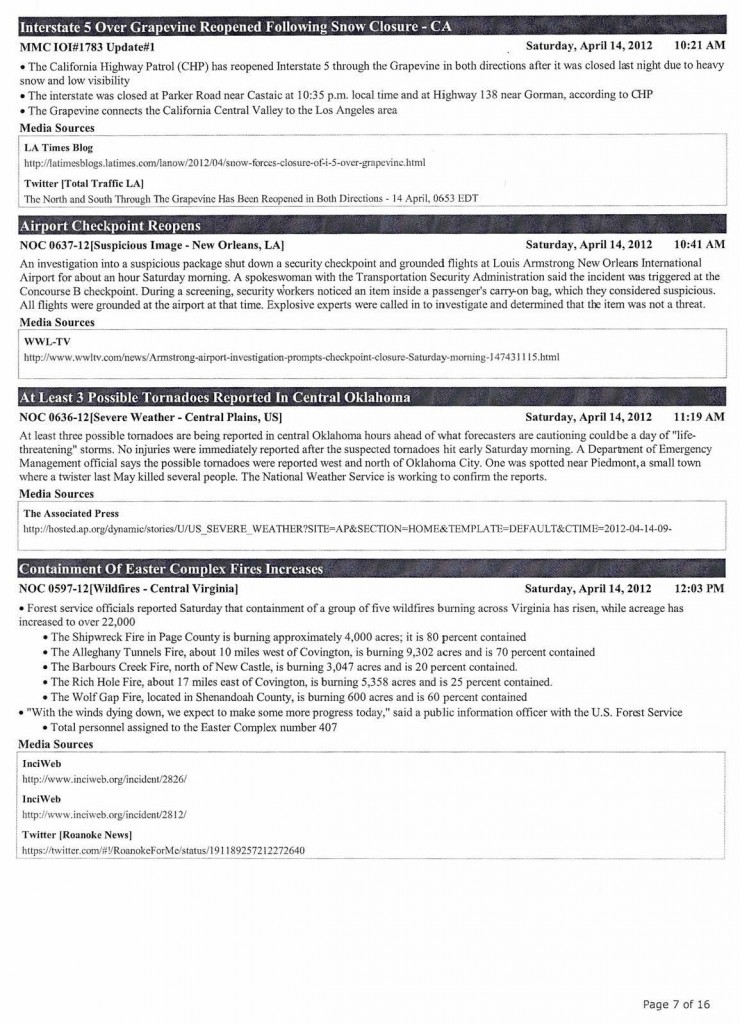

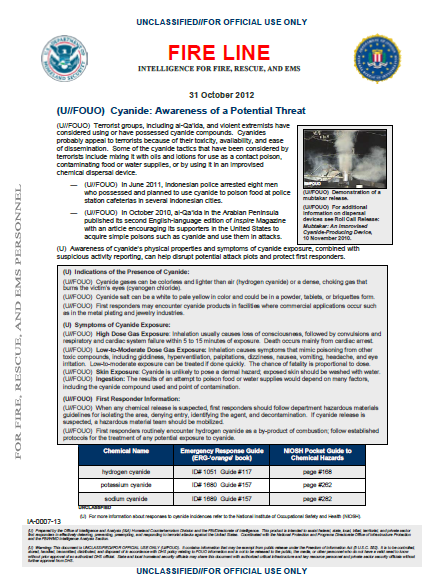

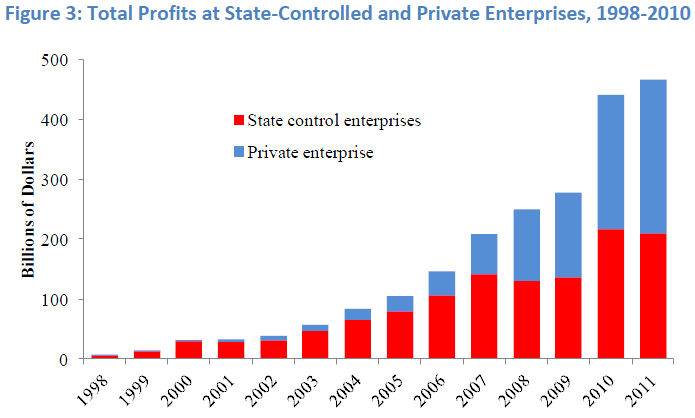
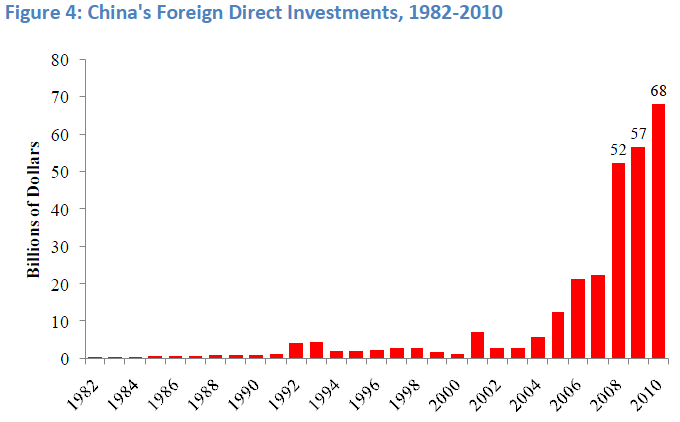

![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict33.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict34.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict35.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict36.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict37.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict38.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict39.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict40.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict41.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict42.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict43.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict44.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict45.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict46.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict48.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict47.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict51.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict49.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict50.jpg)

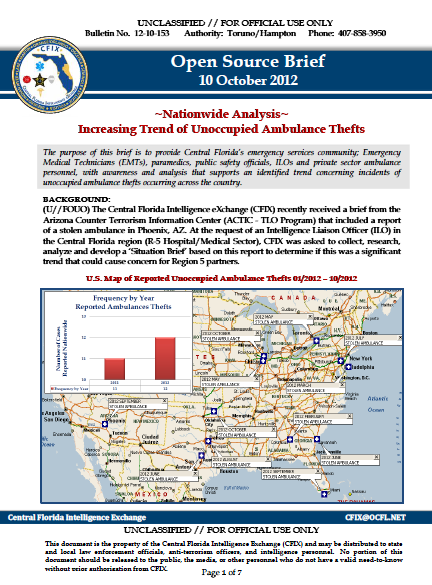
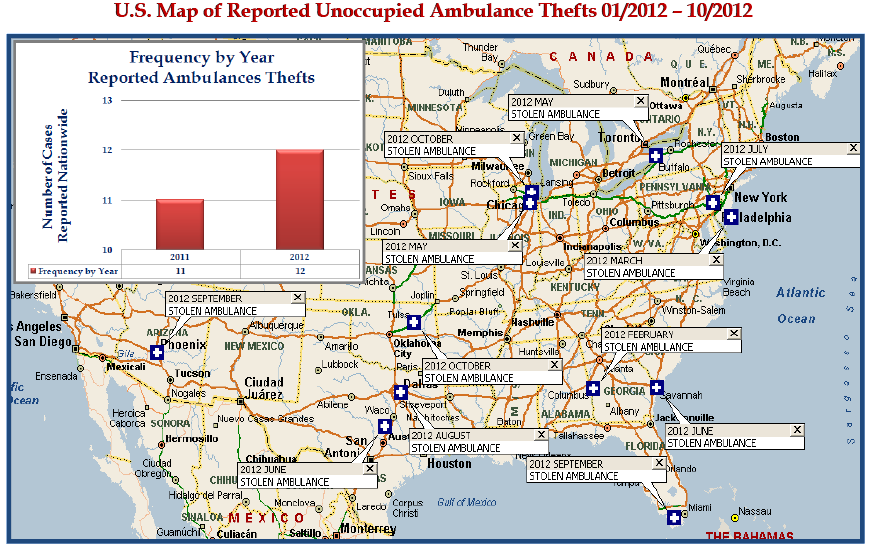










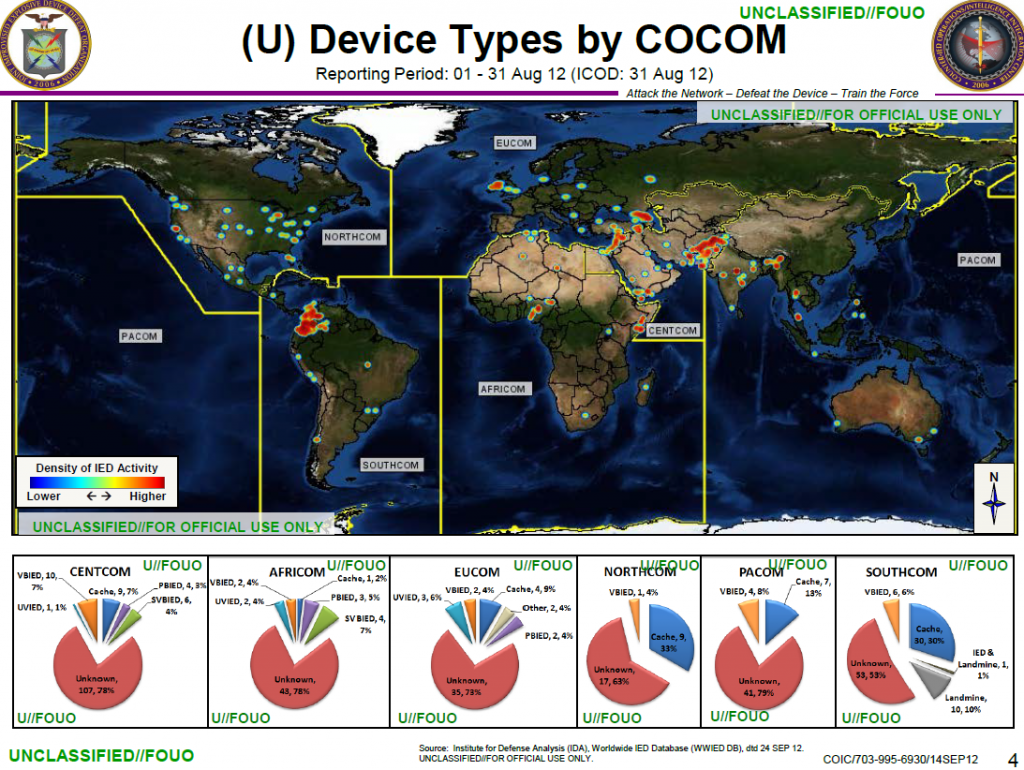
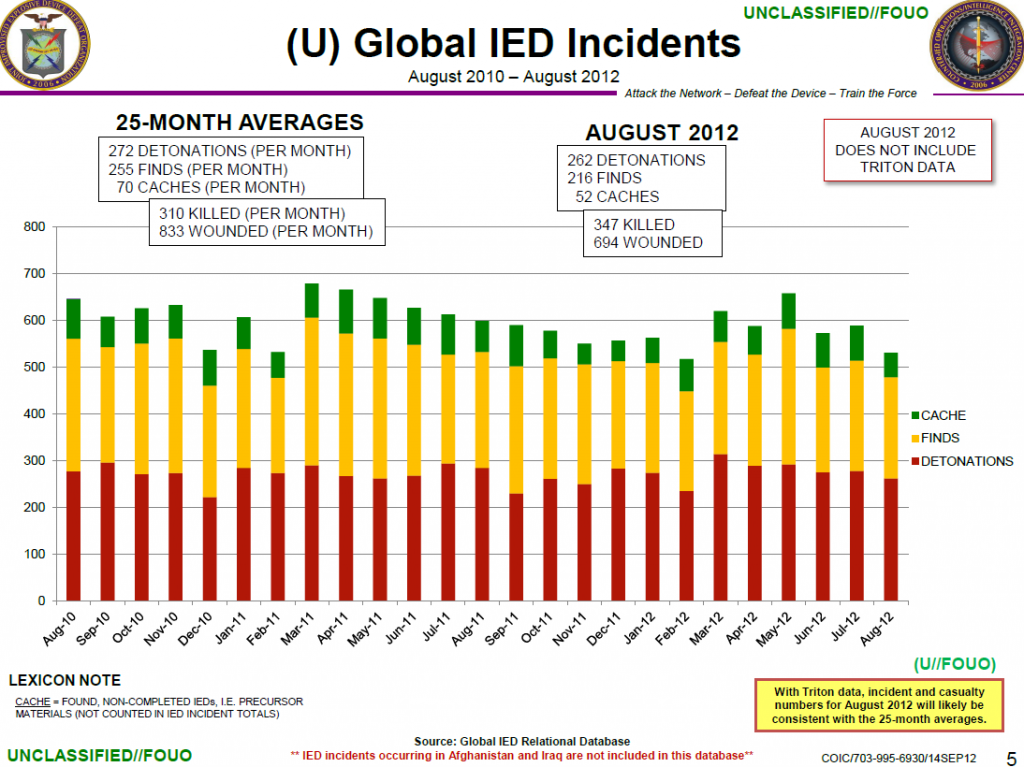
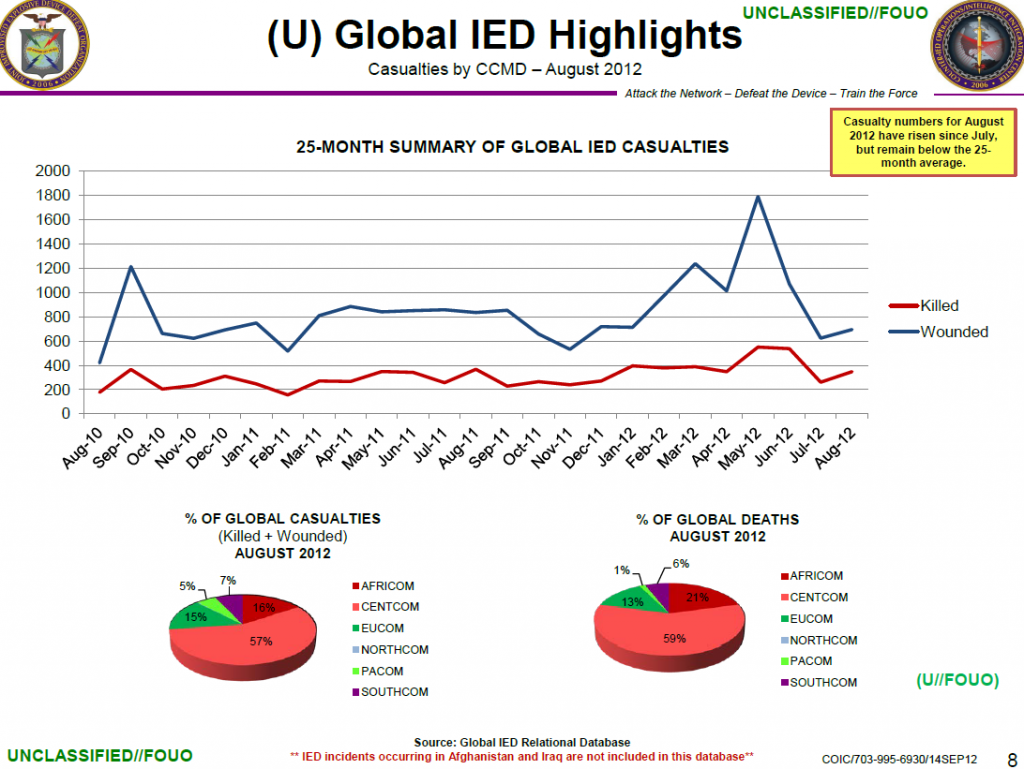
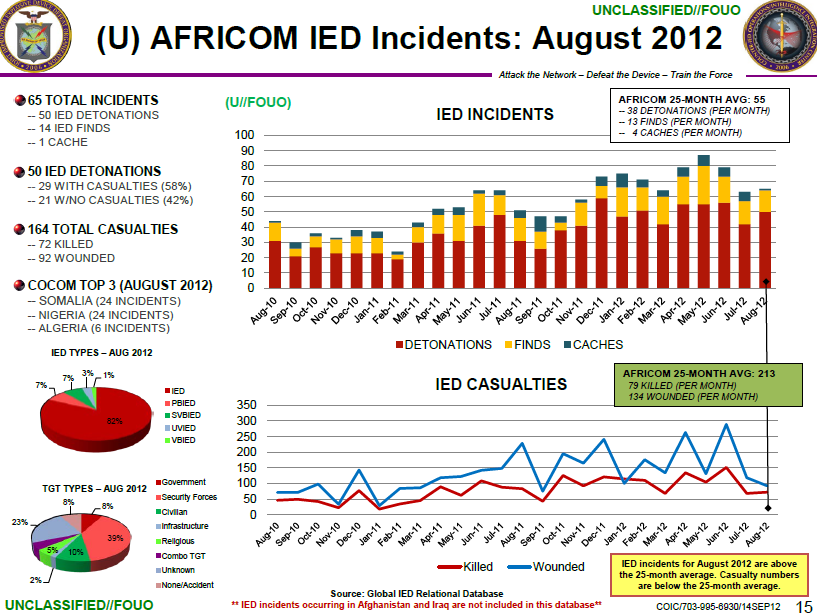
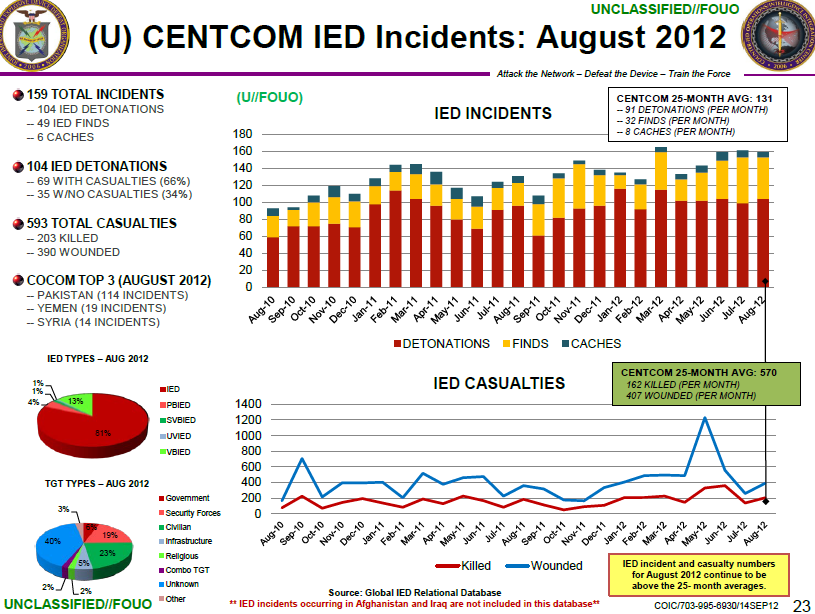
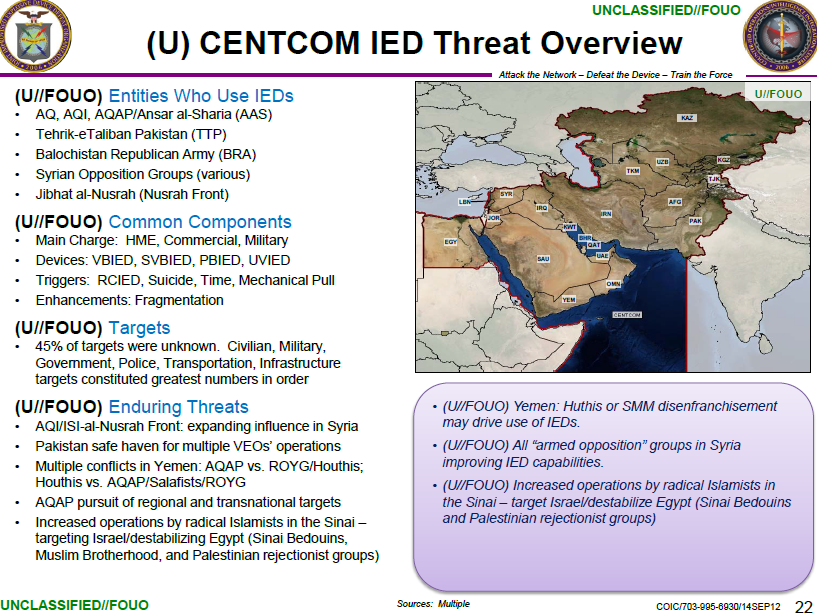



![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict58.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict62.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict51.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict52.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict63.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict54.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict53.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict64.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict35.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict36.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict37.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict38.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict39.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict50.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict65.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict44.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict43.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict42.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict40.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict41.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict45.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict46.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict47.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict48.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict49.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict61.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict34.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict33.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict30.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict29.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict32.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict31.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict60.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict59.jpg)

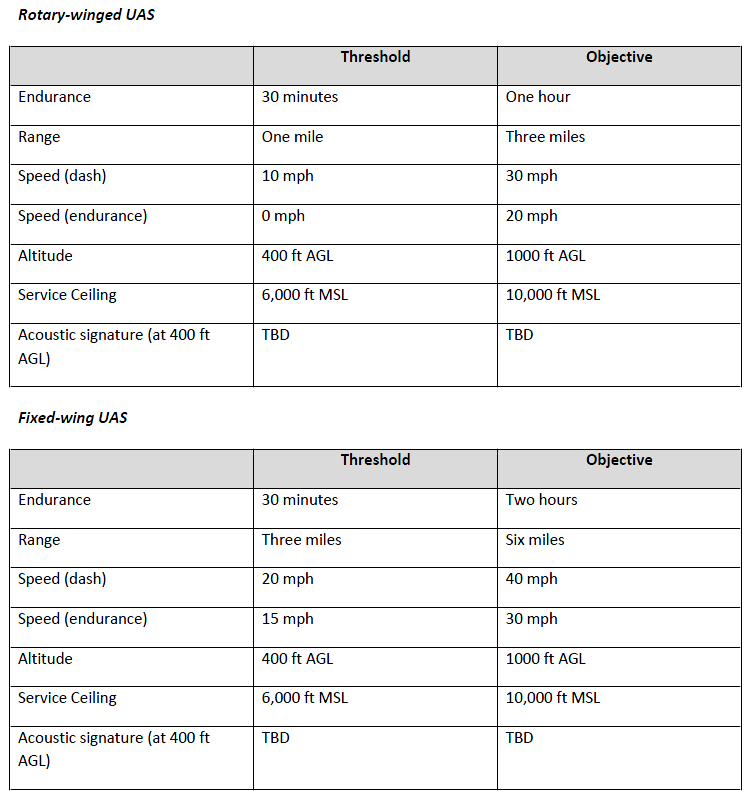

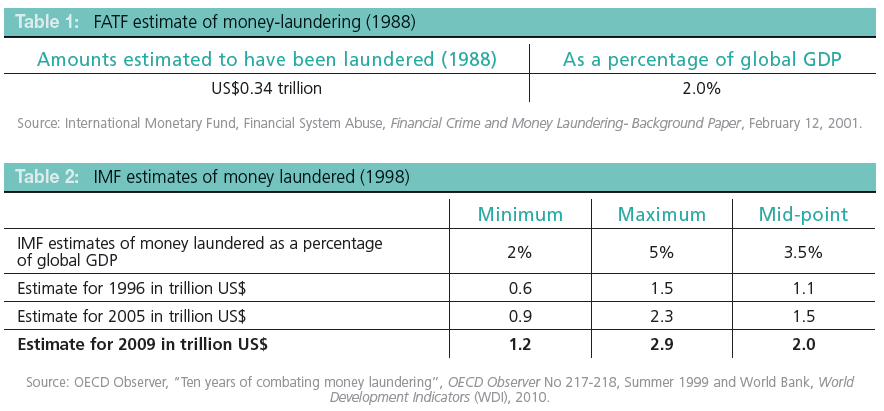
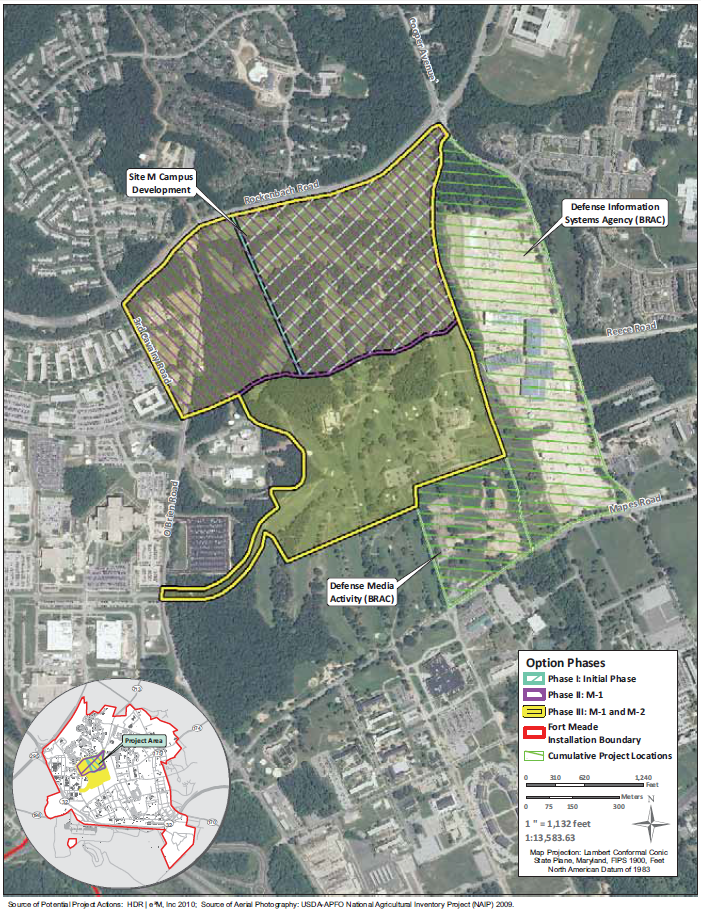
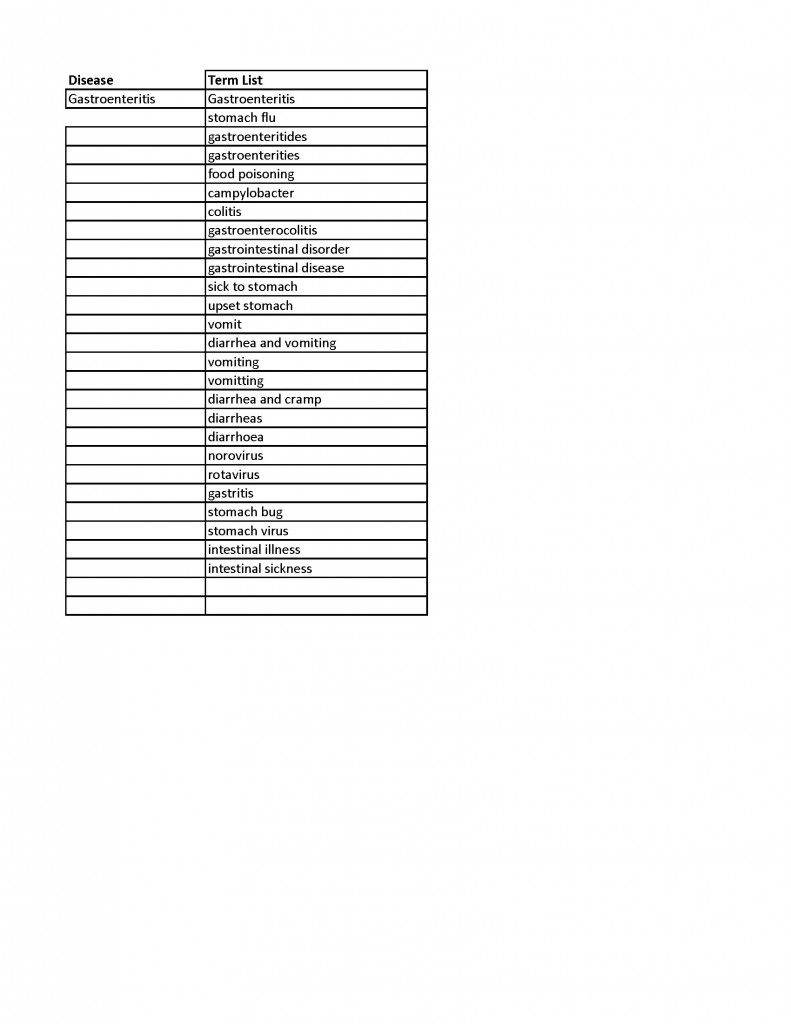





![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict2.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict3.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict62.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict63.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict0.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict71.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict1.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict4.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict64.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict65.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict5.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict66.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict67.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict70.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict68.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict69.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict6.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict8.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict9.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict11.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict12.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/uk-drones/pict52.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/uk-drones/pict59.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/uk-drones/pict60.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/uk-drones/pict53.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/uk-drones/pict58.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/uk-drones/pict54.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/uk-drones/pict55.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/uk-drones/pict57.jpg) A soldier of Bravo Company, 1 Rifles launches a Desert Hawk UAV (Unmanned Aerial Vehicle) from a WMIK Landrover during an operation near Garmsir, Afghanistan. Desert Hawk is a portable UAV surveillance system which provides aerial video reconnaissance. It has a flight time of approximately one hour, and can fly anywhere within a 10km radius of its ground control station. It has both day and night time (thermal imaging) capability. The equipment can be used for a variety of tasks, such as force protection for convoys and patrols, route clearance, base security, reconnaissance or target tracking. March 20, 2009. MoD
A soldier of Bravo Company, 1 Rifles launches a Desert Hawk UAV (Unmanned Aerial Vehicle) from a WMIK Landrover during an operation near Garmsir, Afghanistan. Desert Hawk is a portable UAV surveillance system which provides aerial video reconnaissance. It has a flight time of approximately one hour, and can fly anywhere within a 10km radius of its ground control station. It has both day and night time (thermal imaging) capability. The equipment can be used for a variety of tasks, such as force protection for convoys and patrols, route clearance, base security, reconnaissance or target tracking. March 20, 2009. MoD![[Image]](https://i0.wp.com/cryptome.org/2012-info/uk-drones/pict56.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/uk-drones/pict61.jpg)





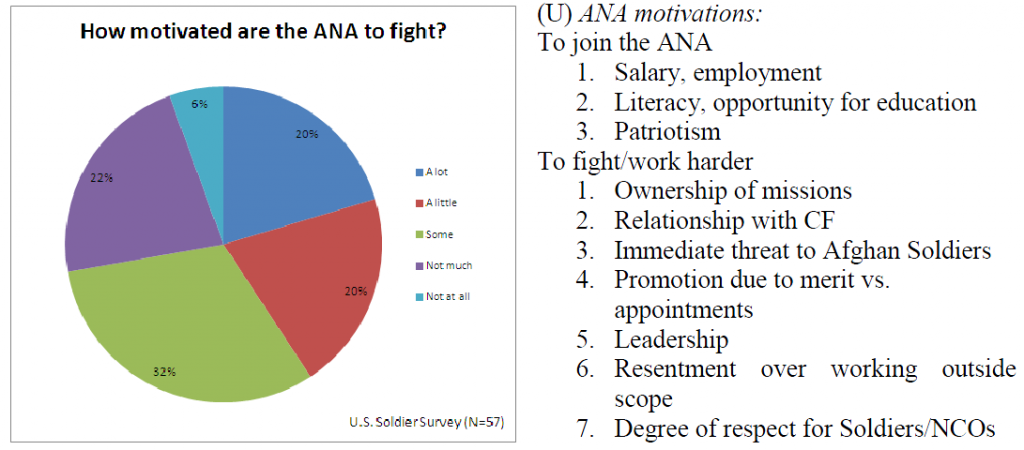

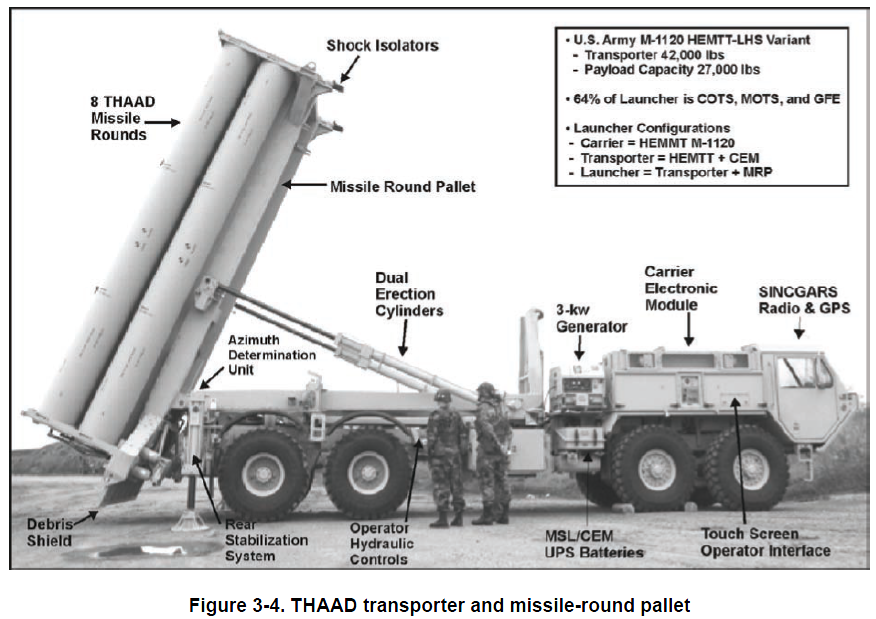


![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-07/pict106.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-07/pict103.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-07/pict104.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-07/pict105.jpg)
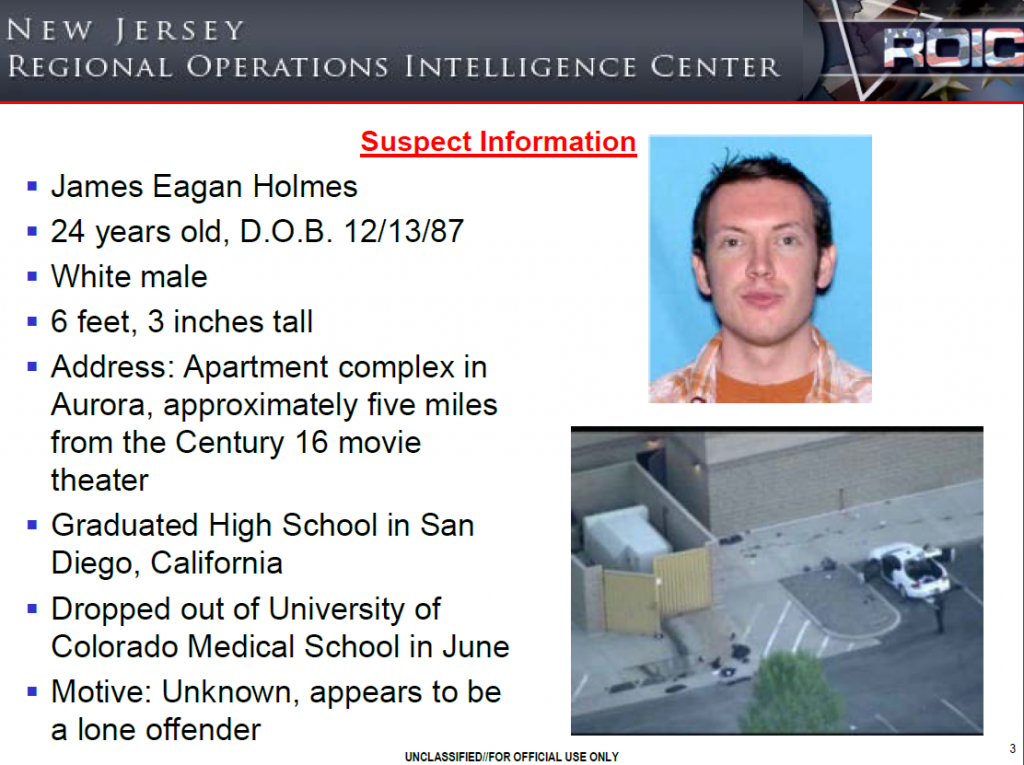







![[Image]](https://i0.wp.com/cryptome.org/2012/06/lulzsec-sneak-preview.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/dulles-mystery/pict22.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/dulles-mystery/pict23.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/dulles-mystery/pict24.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/dulles-mystery/pict35.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/dulles-mystery/pict21.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/dulles-mystery/pict31.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/dulles-mystery/pict30.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/dulles-mystery/pict29.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/dulles-mystery/pict27.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/dulles-mystery/pict28.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/dulles-mystery/pict25.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/dulles-mystery/pict26.jpg)










![[Image]](https://i0.wp.com/cryptome.org/eyeball/wny-mb/pict5.jpg) Modified Humvee vehicles from the 1st Battalion 200th Air Defense Artillery of the New Mexico National Guard are shown Friday, July 30, 2004, at the unit’s headquarters in Roswell, N.M. About 200 Guard members soon will bolster air defenses near Washington, D.C., in these modified vehicles, carrying up to 288 Stinger missiles. Each Humvee has a turret with 8 missile launchers on top, and there are 36 of the vehicles to be used under the Avenger weapons system, Air Defense Artillery, Maj. Ken Nava said Friday. (AP Photo/Roswell Daily Record, Andrew Poertner)
Modified Humvee vehicles from the 1st Battalion 200th Air Defense Artillery of the New Mexico National Guard are shown Friday, July 30, 2004, at the unit’s headquarters in Roswell, N.M. About 200 Guard members soon will bolster air defenses near Washington, D.C., in these modified vehicles, carrying up to 288 Stinger missiles. Each Humvee has a turret with 8 missile launchers on top, and there are 36 of the vehicles to be used under the Avenger weapons system, Air Defense Artillery, Maj. Ken Nava said Friday. (AP Photo/Roswell Daily Record, Andrew Poertner)![[Image]](https://i0.wp.com/cryptome.org/eyeball/wny-mb/pict6.jpg) Modified Humvee vehicles from the 1st Battalion 200th Air Defense Artillery of the New Mexico National Guard are shown Friday, July 30, 2004, at the unit’s headquarters in Roswell, N.M. About 200 Guard members soon will bolster air defenses near Washington, D.C., in these modified vehicles, carrying up to 288 Stinger missiles. Each Humvee has a turret with 8 missile launchers on top, and there are 36 of the vehicles to be used under the Avenger weapons system, Air Defense Artillery, Maj. Ken Nava said Friday. (AP Photo/Roswell Daily Record, Andrew Poertner)
Modified Humvee vehicles from the 1st Battalion 200th Air Defense Artillery of the New Mexico National Guard are shown Friday, July 30, 2004, at the unit’s headquarters in Roswell, N.M. About 200 Guard members soon will bolster air defenses near Washington, D.C., in these modified vehicles, carrying up to 288 Stinger missiles. Each Humvee has a turret with 8 missile launchers on top, and there are 36 of the vehicles to be used under the Avenger weapons system, Air Defense Artillery, Maj. Ken Nava said Friday. (AP Photo/Roswell Daily Record, Andrew Poertner)![[Image]](https://i0.wp.com/cryptome.org/eyeball/wny-mb/pict7.jpg) A military Humvee with an Avenger anti-aircraft missile launcher on top sits parked near the Pentagon Wednesday, Sept. 11, 2002. Defense Secretary Donald H. Rumsfeld ordered the launchers placed around Washignton as a “prudent precaution” on the first anniversary of the terrorist attack on the Pentagon. (AP Photo/J. Scott Applewhite)
A military Humvee with an Avenger anti-aircraft missile launcher on top sits parked near the Pentagon Wednesday, Sept. 11, 2002. Defense Secretary Donald H. Rumsfeld ordered the launchers placed around Washignton as a “prudent precaution” on the first anniversary of the terrorist attack on the Pentagon. (AP Photo/J. Scott Applewhite)![[Image]](https://i0.wp.com/cryptome.org/eyeball/wny-mb/pict18.jpg) Security and construction underway to enhance security is seen on Capitol Hill Wednesday, Feb. 12, 2003. Avenger anti-aircraft missiles have been stationed around Washington, along with extra radars, and the Air Force has stepped up its combat air patrols over the capital. (AP Photo/Terry Ashe)
Security and construction underway to enhance security is seen on Capitol Hill Wednesday, Feb. 12, 2003. Avenger anti-aircraft missiles have been stationed around Washington, along with extra radars, and the Air Force has stepped up its combat air patrols over the capital. (AP Photo/Terry Ashe)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/wny-mb/pict10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/wny-mb/pict8.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/wny-mb/pict9.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/wny-mb/pict11.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/wny-mb/pict12.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/wny-mb/pict13.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/wny-mb/pict14.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/exp30/pict0.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/exp30/pict1.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/exp30/pict2.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/exp30/pict3.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/exp30/pict4.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/exp30/pict5.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/exp30/pict6.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/exp30/pict8.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/exp30/pict15.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/exp30/pict13.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/exp30/pict7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/exp30/pict9.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/exp30/pict14.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/exp30/pict10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/exp30/pict11.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/exp30/pict12.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/exp30/pict16.jpg)









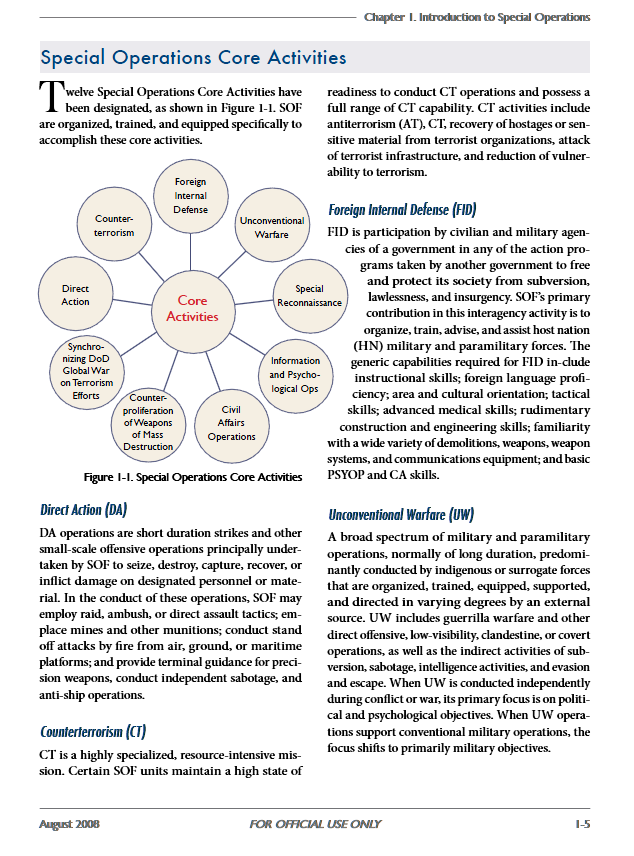

![[Image]](https://i0.wp.com/cryptome.org/2012-info/dprk-missile/pict19.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/dprk-missile/pict20.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/dprk-missile/pict21.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/dprk-missile/pict22.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/dprk-missile/pict23.jpg) A North Korean cameraman films a map with the site of launch pad of the rocket Unah-3 at the Tongchang-ri space center on April 8, 2012. North Korea’s long-range rocket is on its launch platform, AFP reporters said Sunday, as the regime again insisted it was to send a peaceful satellite and not a missile. The usually secretive North organised an unprecedented visit for foreign reporters to Tongchang-ri space centre in an effort to show its Unha-3 rocket is not a disguised ballistic missile, as claimed by the US and its allies. Getty
A North Korean cameraman films a map with the site of launch pad of the rocket Unah-3 at the Tongchang-ri space center on April 8, 2012. North Korea’s long-range rocket is on its launch platform, AFP reporters said Sunday, as the regime again insisted it was to send a peaceful satellite and not a missile. The usually secretive North organised an unprecedented visit for foreign reporters to Tongchang-ri space centre in an effort to show its Unha-3 rocket is not a disguised ballistic missile, as claimed by the US and its allies. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/dprk-missile/pict17.jpg) North Korean officials and foreign journalists leave the launch pad after a visit to see the rocket Unha-3 in Tangachai -ri space center on April 8, 2012. North Korea has confirmed their intentions to launch the rocket next week despite international condemnations. Getty
North Korean officials and foreign journalists leave the launch pad after a visit to see the rocket Unha-3 in Tangachai -ri space center on April 8, 2012. North Korea has confirmed their intentions to launch the rocket next week despite international condemnations. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/dprk-missile/pict18.jpg) The North Korean Unha-3 rocket is pictured at Tangachai -ri space center on April 8, 2012. North Korea has confirmed their intention to launch the rocket next week despite international condemnations. Getty
The North Korean Unha-3 rocket is pictured at Tangachai -ri space center on April 8, 2012. North Korea has confirmed their intention to launch the rocket next week despite international condemnations. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/dprk-missile/pict16.jpg) North Korean soldiers stand guard in front of the Unha-3 rocket at Tangachai -ri space center on April 8, 2012. North Korea has confirmed their intention to launch the rocket next week despite international condemnations. Getty
North Korean soldiers stand guard in front of the Unha-3 rocket at Tangachai -ri space center on April 8, 2012. North Korea has confirmed their intention to launch the rocket next week despite international condemnations. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/dprk-missile/pict14.jpg) Engineers are seen checking the Unha-3 (Milky Way 3) rocket sitting on a launch pad at the West Sea Satellite Launch Site, during a guided media tour by North Korean authorities in the northwest of Pyongyang April 8, 2012. North Korea has readied a rocket for a launch from a forested valley in its remote northwest this week that will showcase the reclusive state’s ability to fire a missile with the capacity to hit the continental United States. Picture taken April 8, 2012. Getty
Engineers are seen checking the Unha-3 (Milky Way 3) rocket sitting on a launch pad at the West Sea Satellite Launch Site, during a guided media tour by North Korean authorities in the northwest of Pyongyang April 8, 2012. North Korea has readied a rocket for a launch from a forested valley in its remote northwest this week that will showcase the reclusive state’s ability to fire a missile with the capacity to hit the continental United States. Picture taken April 8, 2012. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/dprk-missile/pict13.jpg) The North Korean rocket Unha-3 rocket is pictured at the Tongchang-ri space center on April 8, 2012. North Korea’s long-range rocket is on its launch platform, AFP reporters said Sunday, as the regime again insisted it was to send a peaceful satellite and not a missile. The usually secretive North organised an unprecedented visit for foreign reporters to Tongchang-ri space centre in an effort to show its Unha-3 rocket is not a disguised ballistic missile, as claimed by the US and its allies. Getty
The North Korean rocket Unha-3 rocket is pictured at the Tongchang-ri space center on April 8, 2012. North Korea’s long-range rocket is on its launch platform, AFP reporters said Sunday, as the regime again insisted it was to send a peaceful satellite and not a missile. The usually secretive North organised an unprecedented visit for foreign reporters to Tongchang-ri space centre in an effort to show its Unha-3 rocket is not a disguised ballistic missile, as claimed by the US and its allies. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/dprk-missile/pict15.jpg) Scientists are seen monitoring the Unha-3 (Milky Way 3) rocket in a control room at the West Sea Satellite Launch Site during a guided media tour by North Korean authorities in the northwest of Pyongyang April 8, 2012. North Korea has readied a rocket for a launch from a forested valley in its remote northwest this week that will showcase the reclusive state’s ability to fire a missile with the capacity to hit the continental United States. The Korean characters on the banner read “Let us occupy the high target of building a powerful nation by relying on the strength of science and technology!” Picture taken April 8, 2012. Reuters
Scientists are seen monitoring the Unha-3 (Milky Way 3) rocket in a control room at the West Sea Satellite Launch Site during a guided media tour by North Korean authorities in the northwest of Pyongyang April 8, 2012. North Korea has readied a rocket for a launch from a forested valley in its remote northwest this week that will showcase the reclusive state’s ability to fire a missile with the capacity to hit the continental United States. The Korean characters on the banner read “Let us occupy the high target of building a powerful nation by relying on the strength of science and technology!” Picture taken April 8, 2012. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/dprk-missile/pict24.jpg) Scientists are seen monitoring the Unha-3 (Milky Way 3) rocket in a control room at the West Sea Satellite Launch Site during a guided media tour by North Korean authorities in the northwest of Pyongyang April 8, 2012. North Korea has readied a rocket for a launch from a forested valley in its remote northwest this week that will showcase the reclusive state’s ability to fire a missile with the capacity to hit the continental United States. Picture taken April 8, 2012. Reuters
Scientists are seen monitoring the Unha-3 (Milky Way 3) rocket in a control room at the West Sea Satellite Launch Site during a guided media tour by North Korean authorities in the northwest of Pyongyang April 8, 2012. North Korea has readied a rocket for a launch from a forested valley in its remote northwest this week that will showcase the reclusive state’s ability to fire a missile with the capacity to hit the continental United States. Picture taken April 8, 2012. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/dprk-missile/pict0.jpg) Mobile Patriot missile launchers, center, are set up at a Japan Air Self-Defense Force base on Miyakojima island in Okinawa Prefecture, southwestern Japan, Monday, April 9, 2012 in preparation for North Korea’s rocket launch slated between April 12 and 16. North Korean space officials moved all three stages of a long-range rocket into position for a controversial launch, vowing to push ahead with their plan in defiance of international warnings against violating a ban on missile activity.
Mobile Patriot missile launchers, center, are set up at a Japan Air Self-Defense Force base on Miyakojima island in Okinawa Prefecture, southwestern Japan, Monday, April 9, 2012 in preparation for North Korea’s rocket launch slated between April 12 and 16. North Korean space officials moved all three stages of a long-range rocket into position for a controversial launch, vowing to push ahead with their plan in defiance of international warnings against violating a ban on missile activity.![[Image]](https://i0.wp.com/cryptome.org/2012-info/dprk-missile/pict1.jpg) U.S. Navy’s guided-missile cruiser USS Shiloh (CG 67) sails in the East China Sea, about 90 kilometers (56 miles) northeast of Miyakojima island in Okinawa Prefecture, southwestern Japan, Monday, April 9, 2012. North Korean space officials moved all three stages of a long-range rocket into position for a controversial launch slated between April 12 and 16 towards south over the East China Sea and the Pacific.
U.S. Navy’s guided-missile cruiser USS Shiloh (CG 67) sails in the East China Sea, about 90 kilometers (56 miles) northeast of Miyakojima island in Okinawa Prefecture, southwestern Japan, Monday, April 9, 2012. North Korean space officials moved all three stages of a long-range rocket into position for a controversial launch slated between April 12 and 16 towards south over the East China Sea and the Pacific.
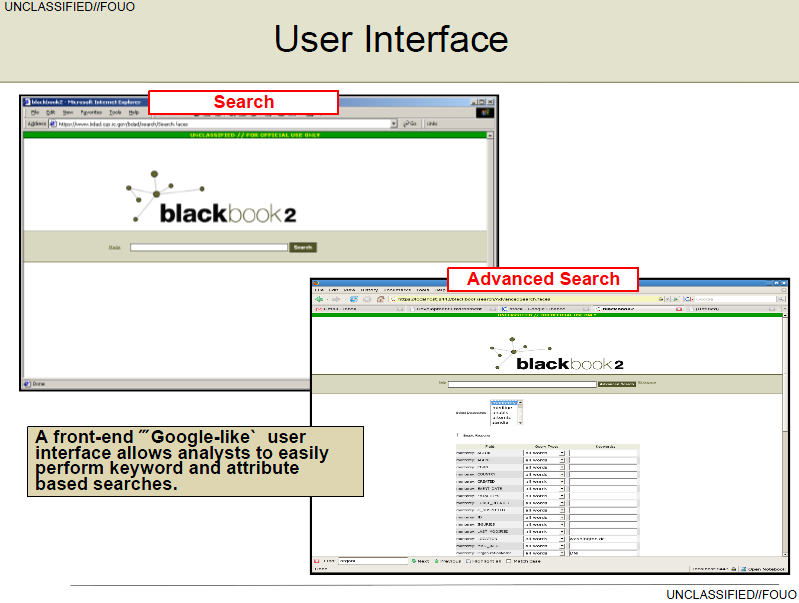
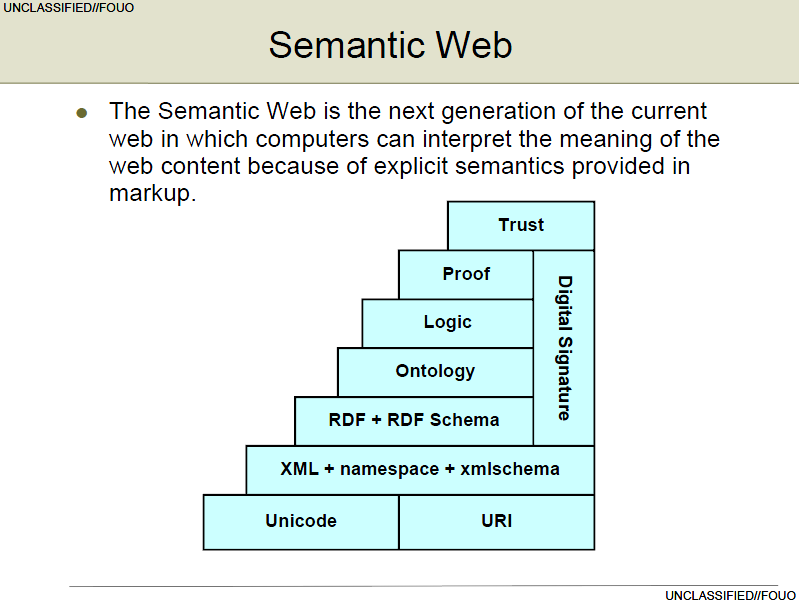
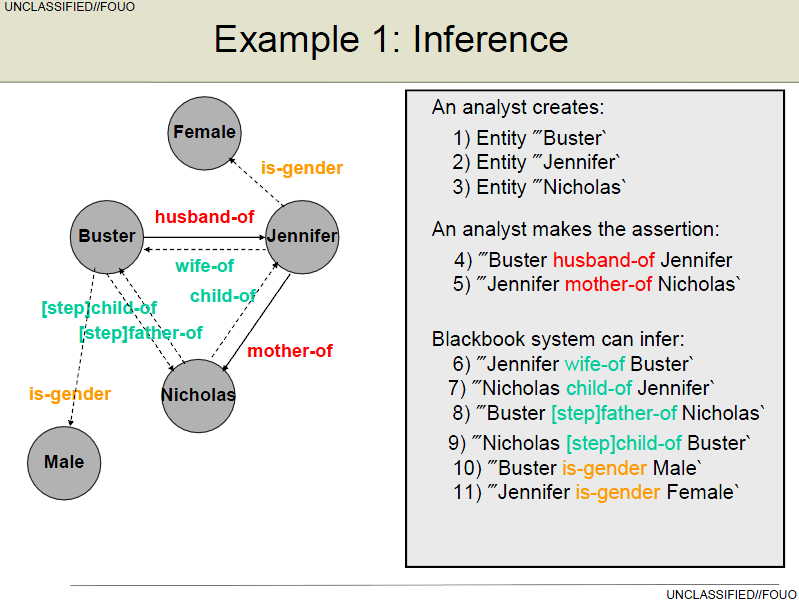

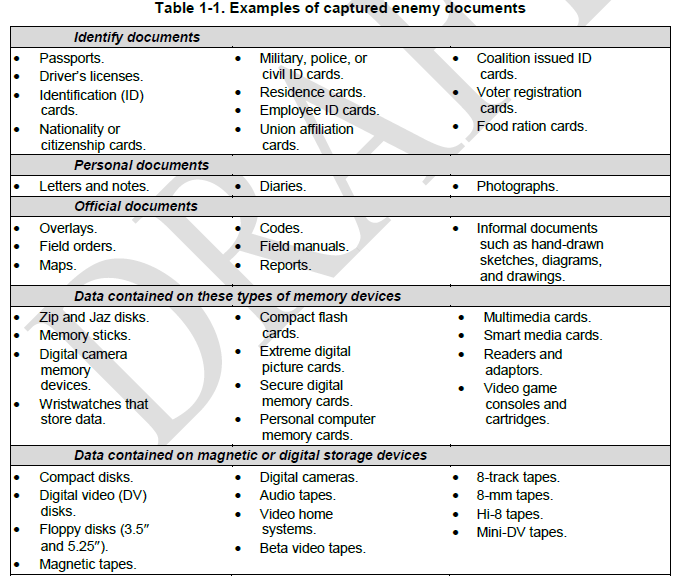
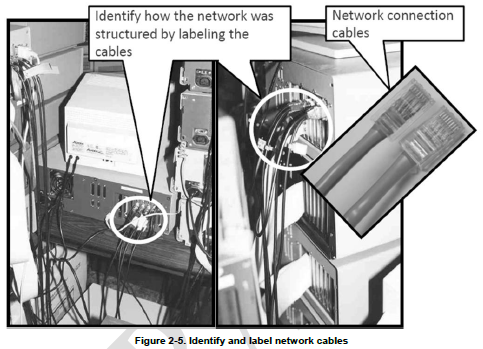


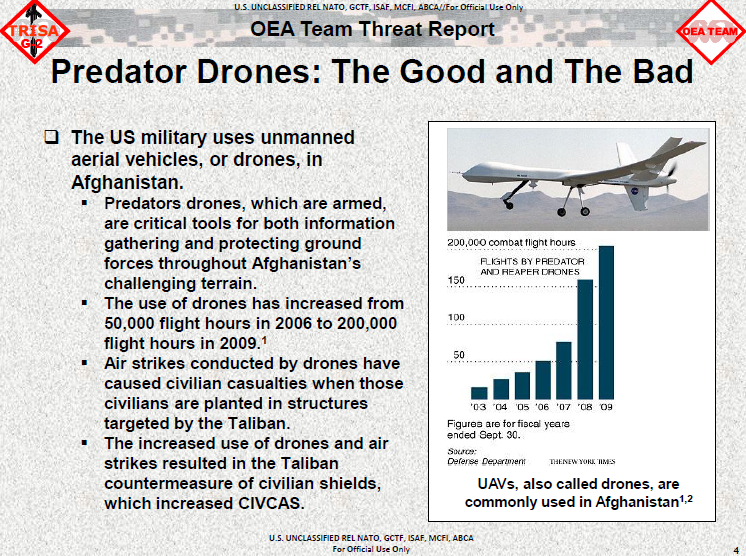

You must be logged in to post a comment.