James Atkinson to Expose Illegal Court Eavesdropping
Court documents related to the James Atkinson e-mail following:
27-June-2012-Niroula-orders.pdf (1.4)
top-secret-page-one-cobines.pdf (1.4MB)
Scan-14082012_00000.pdf (4.3MB)
Microsoft-Word-5-Feb-2012-Babble-Motion-Order-and-Declarations.pdf (103KB)
Microsoft-Word-5-Feb-2012-Jim-Declaration.pdf (57KB)
Courtfiling_for_Kaushal_Niroula_in_Pro_Per_Babble_41.pdf (160KB)
15-June-2012-James-Atkinson-Exhibits-and-Declarations-1.pdf (2.3MB)
11-June-2012-Court-Orders-for-James-Atkinson-TSCM-2.pdf (2.2MB)
Scan-25062012_00000-MInEavedrop1.pdf (1.6MB)
Mey-Tann-transcript.pdf (1.5MB)
Subject: My Services to the Court
Date: Fri, 17 Aug 2012 15:44:44 -0400
From: James M. Atkinson <jmatk[at]tscm.com>
Reply-To: jmatk[at]tscm.com
Organization: Granite Island Group
To: Kristine.Hinos[at]riverside.courts.ca.gov
Ms. Kristine Hinos
Superior Court of the State of California
County of Riverside, Indio Branch
Department 1B
Annex Court
82-675 Highway 111
Indio, CA 92201
Please forward a copy of this correspondence to the Honorable David B.
Downing, as soon as possible, as it involves a case (People v. Niroula,
INF064492) which is currently before the court.
Please consider this not to be an Ex Parte communication (at your
discretion), and it is requested that it not be placed under seal (at
your discretion). I would ask that copies be distributed to all of the
respective parties.
Your Honor, a matter has come before me which effects the operation of
your court, and which may affect the integrity of the proceedings in the
above captioned case. Also, I am relatively certain that the
information that I am in possession of, or which will be uncovered in my
work will result in a mistrial, and likely the Indictment before the
Grand Jury of several court officers, and members of law enforcement, and
likely the Defendants themselves.
Defendant Kashual Niroula has unsuccessfully attempted to retain my
services as a technical expert in this case, and I have provided him
with quotations for legitimate services that I could render in support
of this case.
However, to this day I have not been able to consummate any agreement
with Mr. Niroula for these services as he perpetually will not focus the
proposed services to the case at hand, and instead tries to get me to
fraudulently charge this court for services utterly unrelated to the
matter before you, but rather he blatantly tries to manipulate the Court
to order my consulting services outside of the scope of these proceedings,
and he seems to be trying to get the court to order me to work for free.
Nevertheless, as there have been no agreement between Mr. Niroula and
myself, and there is no acceptance of my offer (which was based on a
request by Mr. Niroula), there has been no consideration paid, although
Mr. Niroula has promised to pay me $7,000 per hour for certain services
(which I feel are illegal in nature, and which I refuse to be a part
of), but there has not yet been any form of consideration or payment to
me in any form. Further, he stated or inferred that he has hidden funds
from which he could pay me $7,000 per hour for my services, if I would
assist in him an escape attempt. I of course refused to assist him in
this illegal activity as well, which I now bring to the attention of this
court.
In addition, it must be brought to this courts attention that my normal
(and documented) base rate for a government entity or work on a criminal
case is $7500 per day, plus all out-of-pocket expenses. This is billed
on a door to door basis, and I normally work 14+ documented hours per
day, 7 days a week and bill bi-weekly against the retainer for the project.
This amount was made clear to Mr. Niroula several times verbally and in
writing. However, I offered to him that I would reduce my fee to an
hourly basis of $350 per hour, provided that 3220 hours as approved as
an initial cap, for the combined projects outlined is various sealed
document which have been signed by you and provided to me. I made it clear to
Mr. Niroula that if I was not engaged for the initial 3220 hours of work
then my rate would remain at $7500 per day.
Mr. Niroula then stated that the court would pay me $150 per hour, and
that he could engage me at that amount, but I did not accept his offer
and his proposed project description at that time as it appeared to
involve the commission of felonies on his behalf, which refused to be a
part in.
Also, I made if very clear to him that I will provide him no services of
any sort unless those services are well described and outlined in the
form of a signed and sealed order of this court, but also that the
estimated fee must be paid in advance of any work on the case. Also that
there must be 3 week advance notice of any and all travel in regards to
this case.
As the court has repeatedly, issued sealed orders for my for services,
and have not specified any other rate. I then have to assume that my
previously discussed and quoted rate of $7500 per day (plus all
expenses) will apply, I thus must assume that the court (through your
agent Kaushal Niroula) is willing to pay me $7500 per day for my work on
this case.
Based on the August 10, 2012 order alone this will be 187 days of work
at a daily rate of $7500 per day, for a initial fee of $1,403,572, plus
expenses (airfare and excess cargo costs of approximately $8,500),
lodging costs of roughly $46,750, office supplies of $5,600, office
machine costs of roughly $7800, and the purchase of 20 ea 6 TB
Thunderbolt Drives at a combined cost of $12,500 to perform the copying
function ordered by this court.
On top of this will be the actual hardware required to set up the “hive”
or “cloud” which will involve roughly $47,500 of materials costs, plus
the two demo machines at a cost of $12,800 each. Due to the nature of
the materials on these hard drive, it ill be necessary to mechanically
destroy them and to reduce them to molten metal as the completion of the
demonstration. This destruction will be performed by me using an
incendiary device which I will make form scratch called a “burning bar”
which will liquefy the hard drives in questions. The hard drives in or
associated with the computers will be removed and liquefied in the same
fashion. This molten metal will then be poured into a sand form in the
sign of a Roman cross.
Additionally, it is my understanding that the testimony in this case is
almost completed, and they by the time I actually get to California their
may be mere hours left in the trial, and thus I feel that Mr. Niroula is
running a scam on the court, and that he fully intends to cheat me out
of any expenses, or that he intends to force a last minute mistrial, and
then use the time before the new trial for me to render services.
As the court and Mr. Niroula has acquiesced to my $7,500 per day rate,
and has issued orders for me to perform services, but with an order which
neglects to specify the rate at which I will be paid, then the $7500 per
day previously discussed with Mr. Niroula is thus applied.
The fee for the services to be rendered based on the August 10, 2012
will thus be $1,403,572, plus $8,500 for transportation, plus $46,750
for lodging, and $86,200 for office supplies, office machines, storage
devices, and “HYDRA” computers.
Thusly, by way of a wire transfer or check from Riverside Country or
from one of Mr. Niroula (or Mr. Garcia’s) numerous hidden bank accounts,
or from the court in the amount of $1,544,022 payment in full must be
made in advance for services being rendered. This must be paid in full
before I will perform any work, supply any materials, or initiate travel
arrangements, or take any action in this case of any sort. I am amenable
for these funds to be provided to a court officer in Indio, and then
paid out against bi-weekly billing, or dispersion made to cover travel
and lodging. The court does have the authority to order the county to
place $1,544,022 with a local law firm or other officer of this court,
and then to release the funds to me as the work progresses.
I am amenable to working at a lower hourly or daily rate (if there is a
higher volume of work), but the court has so far been mute in defining
how much the court or the county is willing to pay. Mr. Niroula has
claimed that the court can pay only $150 per hour, and I am willing to
except that payment amount, provided the work is not unlawful, that the
work is detailed in a signed and sealed order from this court, and my
services are confined to those matters actually before this court.
Mr. Niroula has attempted to contract my services, and while me may be
representing himself in a criminal matter, I doubt that he has the
authority to contract with me on behalf of the county to develop a
software program which he intended to sell commercially. Please
understand that he wishes the country to pay me to develop a program
which he and Mr. Garcia will then sell for profit (which the county paid
for).
Further, as I am not an attorney, or clergy, or physician to Mr. Niroula
there can be no automatic privilege between he and I until the court
orders that that privilege takes place, or he provides me with a signed
contract for my service which invoke formal confidentiality, after which
the court would issue an order of formal privilege.
As your honor is well aware, I may have long hair, and I look like a
hippy, but I am nobody’s fool (which I believe were the exact words out
of your honors mouth).
Also, please be aware that it is not only your jail that has been
illicitly bugged, but also your own courtroom; including times then you
personally thought that you were having private discussions. Thus, this
matter should be further technically examined by an outside expert in
the field (such as myself), as you may have a near-term mistrial on your
hands, and you may have a grave situation of obstruction of justice by
the eavesdroppers, along other violations of your own rights.
I am in receipt of an order of the court dated August 10, 2012, but I
was not provided a copy of this order until 6:15 PM on August 14, 2012,
which also orders me to appear before this honorable court the day
before the order was provided to me. I also understand that your honor
was concerned when I was not before the court as ordered on August 13,
2012 as so ordered. But as the Defendant did not provide me with the
copy of the order until the 14th, is suggests that Mr. Niroula is
playing games and getting you to sign frivolous orders, merely to get
into the record that experts were ordered to come, but did not, as is
quite clear in this case. Indeed is could appear that Mr. Niroula is
playing this honorable court for the fool, and observation that I am
morally and ethically bound to bring to your attention.
Mr. Niroula never bothering to notify me of the ordered appearance in a
way that would allow me to comply unless I possess a time machine and
could go backwards a few days. The orders he has repeatedly gotten
signed as in fact frivolous and serve no legitimate purpose, and it
would appear they he is merely setting up the record for an appeal.
Mr. Niroula has not yet paid my for the services he requests, and as
you honor is aware the Thirteenth Amendment to the United States
Constitution officially forbids involuntary servitude, so that if
Mr. Niroula or the Court wishes me to provide goods and services,
I must be paid, and paid in advance.
I do need to be completely frank with the court, and to disclose that
Mr. Niroula and I have been utterly unsuccessful in consummating a
contract for services, and while there was a request for services was
made to me by Mr. Niroula, then an offer of services was made by me to Mr.
Niroula, the offer was then rejected by Mr Niroula who proposed and
requested a different service be rendered, which I refused to provide
out of my own ethical, moral and legal limitations. He then engaged in
repeatedly asking for different services, and we never reached the point
where a contract could even remotely be considered to be formed and there
as no actual acceptance of the offer, or any consideration given.
In short, request was made for an offer, an offer was then made in which
certain conditions applied, the offer as refused, and then another
counter-offer was made, which was declined, and this whole process repeated.
For example, Mr. Niroula has proposed that I assist him in an escape
plan by which he would escape from custody and flee the country, which I
refused to take part in, and which I here and now disclose to on a
matter of a forthcoming escape attempt/plan. Mr. Niroula proposes to
trick the court into placing him under house arrest by way of a GPS
tracking bracelet, then removing the GPS bracelet in such a way that the
removal would not be detected, and then to flee the country by way of a
jet aircraft. He proposed to me the chartering of a private aircraft (a
Citation X), with a range of roughly 3700 miles, but he has not yet
disclosed the intended destination country.
I have explained to Mr. Niroula that I will take no part in his escape
plans, or with providing him with any information whatsoever about
tamping with his or other peoples tracking bracelets. In the past (at
time periods before Mr. Niroula was arrested, or even in this country),
I have written and publicly published white papers and articles in
regards to flaws in “House Arrest” type of GPS tracking bracelets which
render then prone to false data, render them vulnerable to removal
without detection, and how wireless garage door openers and wireless
thermometers can interfere with the tracking bracelets and how an
offender can “slip the control of the tracking system” and then return
to it undetected at a later time with no indication that the device has
been subverted. Mr. Niroula has mentioned these writings to me
face-to-face, but I felt it would be irresponsible to discuss the
writings with him at this time, given his current incarceration
situation, and his stated express scheme to be place under the
constraint of such a system, which he had an interest in subverting.
Also, outside of a privileged relationship Mr. Niroula or his legal
runner (in early 2011) has repeatedly ask me to provide him with
information in regards to subverting the tracking of cellular
telephones, which I refused to share with him. He now attempts to gain
access to this same information under the guise of getting me to testify
in regards to “Cell Phone Tower Pinging Faking” as listed on line 14, on
page 2, of the order of this court dated August 10, 2011. While I am
happy to testify in court as to the methods used to track cell phone
movements, the intelligence analysis of this data, the use of this data
in criminal investigation, of the proper procurement of this technical
data from the cellular phone service providers, and how investigators
have tampered with or tainted evidence in the past, and how this
tampering or faking can be detected, and who there may be such tampering
in this case. But, I have not yet agreed to provide him this
information, or to study the records of the case, or to provide reports or
testimony on the matter.
Proposed Invoice For Technical Services
Based on the Order of this Court Dated August 10, 2012
(and received in to my hands on August 14, 2012)
To obtain a better idea of what the charges would be, for the services
described in the Order of this Court dated August 10, 2012, I have
broken down the tasks list in the order, and we will assume for the time
that an hourly rate of $150 per hour applies.
$37,500 - 250 hrs [at] $150 per hour – Review of all court transcripts, and
then coaching KN on TSCM and Electronic Surveillance Related Matters
face-to-face at the Indio Jail, and sit next to him at the Defendant
table in Superior Court for the duration of this trial. In court
testimony as to findings.
$24,000 - 160 hrs [at] $150 per hour – Review of Cell Phone Records, Tower
Dumps, and Cell Phone “Pings” and to review, testimony, reports and
transcripts. In court testimony as to findings.
$277,500 -1850 hrs [at] $150 per hour – Design, Program, and Compile a
program in C++ or Objective C on a Apple Computer called “HYDRA” to
simulate a computer based internet “hive” or “cloud”, and then to place
this program on a dedicated computer, and to populate this computer with
COURT SUPPLIED child pornography in the form of photographs and videos
of child having sex with other children, adults having sex with
children, which may include photographs and videos of the Defendants
themselves (or images created by the defendants for the purposes of
blackmail and extortion) in this and related cases having sex with
minors within the jurisdiction of this court, or of the Federal courts,
and also outside of the jurisdiction of the United States of America,
but with the files in question currently residing within the
jurisdiction of this court. Also to provide extensive court testimony
and demonstration as to findings.
As I already possess knowledge of the “HYDRA” product obtained outside
of a protected, privileged, or proprietary relationship. I have reason
to believe that I possess a working knowledge of the proposed operation
and function, and that based on my education, training, and experience I
have good reason that the secret to HYDRA is a vast library possessed by
Mr. Garcia and Mr. Niroula, and others, of a huge collection of child
pornography that has been amassed on hard drives by Daniel Garcia and
his Associates.
Thus, it would be improper for the court to order me to be compelled
into a business contract with Mr. Garcia as is ordered by the court in
it order dated August 10, 2012. Indeed, as an ethic matter I must
respectfully refuse to comply with the order of the court in regards to
signing any such contract confected by either Daniel Garcia or Kaushal
Niroula, and will recognize only a protective authored by the court and
order issue to me by this Honorable Court to perform this project, and
not to divulge the secrets of the program beyond that which is already
known to me.
Instead, a Protective Order from this court would be more proper in this
matter, which would protect only those secrets or details that I do not
already have knowledge of. This order would need to state that I already
hold a working knowledge of the Hydra program, in that I understand the
means and mechanism and algorithms which they intend to use, and how
they intend to use it, but also that at present the program itself does
not exist, merely the massive library of child pornography that will feed it.
Further, as I have good reason to believe that the “HYDRA” computer
program is in fact a massive library of child pornography which has been
compiled by the defendants, I thus request of this court issue a very specific
work order that permits me to possess this court provided child pornography
(from the computers and drives in police custody) for the sole purposes of
integrating it as raw data files into a program called HYDRA which I will
write or modify in order to comply with your order dated August 10, 2012.
Based on my prior education, and training, I have good reason to suspect
that the “HYDRA” project is in fact a mechanism to suspect fraud,
extortion, and a massive library of child pornography, with which the
defendants appear to intend to use extortion, fraud, and blackmail
against those adults who have taken part in the production and trafficking
in child pornography, to suggest that this includes videos and
photographs of child pornography actually produced by the defendants as
a tool of extortion and blackmail.
I would urge the court to tightly constrain what is done by the
Defendants with the data on the hard drives which the defendants intend
and propose to provide to me. For example, as the court will be paying
for the development of this program, and the Defendants merely supply raw
data (possession of which is a serious federal felony), and I would need
to perform this work directly for the court, and not for the defendants,
and as the county would be paying for the development, the county could
then claim ownership of the program, and once operational provide both
the data and the program to the State, County, of Federal Task Forces
which deal with child pornography issues.
Also, unless I have a specific order from this court that recognizes
that contraband child pornography is present on these hard drives and
data files, and the court authorized me to be in possession of this
materials I will formally refuse to have any part in the “HYDRA” project.
$54,000 - 360 hrs [at] $150 per hour - Technical investigation of the
computer and external hard drive and thumb drives of Daniel Garcia, to
detect and isolated eavesdropping software, or files that resulted from
eavesdropping. {120 hours to examine the computer itself, 240 hours to
examine the external hard drive). In court testimony and demonstration
as to findings.
$90,000 - 600 hrs [at] $150 per hour - Technical investigation of the
computer and wireless networks present in the courtroom, and the
evaluation of all computers active on the network segment which provides
connectivity to and from the courtroom, and to all computers thereon to
detect eavesdropping software or eavesdropping files. Then detect
illicit network eavesdropping and then to seize and mirror the computers
so identified, and to deliver these computer to the court. In court
testimony and demonstration as to findings.
Thusly, the proposed projects, at the $150 per hour rate will be $483,500,
plus expenses of $141,450 or a total of $624,950
This does not include the inspection of the Attorney-Client booths that
Mr. Niroula has also requested, nor the seized and examinations of GTL
computers and servers, which this court orders, but there was no mention
of payment in the orders these orders. Nor does there appear to have been
any proper requests from this court to the Federal Courts to request the
assistance of the U.S. Marshals nor of the Federal Courts as of yet.
I must also respectfully remind the court that I am physically located
in Massachusetts, and that the authority of this honorable court does
not extend beyond the borders of California. I am happy to provide
services to this court, but I also have to be paid for my service.
I do not work for free, nor can I be considered a fool.
Thank You for understanding,
Respectfully
James M. Atkinson
--
James M. Atkinson. President and Sr. Engineer
"Leonardo da Vinci of Bug Sweeps and Spy Hunting"
http://www.linkedin.com/profile/view?id=15178662
Granite Island Group http://www.tscm.com/
(978) 546-3803 jmatk[at]tscm.com
(978) 381-9111



![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict26.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict34.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict35.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict33.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict27.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict32.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict28.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict31.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict29.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict30.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict21.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict23.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict20.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict22.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict24.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict25.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict37.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict39.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict38.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict36.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict40.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict43.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict41.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict42.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict45.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict46.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict47.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict48.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict44.jpg)



![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-boundary.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-boundary3.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-boundary5.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-boundary4.jpg)

![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-pulpit-13.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-pulpit-12.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-pulpit-11.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-pulpit-09.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-pulpit-10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-pulpit-07.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-pulpit-06.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-pulpit-04.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-pulpit-05.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-pulpit-08.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-pulpit-03.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-pulpit-02.jpg)









![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict26.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict22.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict27.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict28.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict29.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict30.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict17.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict25.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict20.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict15.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict11.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict16.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict24.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict6.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict8.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict13.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict18.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict12.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict14.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict19.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict23.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict21.jpg)


















![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict173.jpg) Republican presidential candidate and former Massachusetts Governor Mitt Romney (L) and Rep. Paul Ryan (R-WI) (R) greet supporters during a campaign rally on August 11, 2012 in Manassas, Virginia. Mitt Romney kicked off a four day bus tour with an announcement of his running mate, Rep. Paul Ryan (R-WI).
Republican presidential candidate and former Massachusetts Governor Mitt Romney (L) and Rep. Paul Ryan (R-WI) (R) greet supporters during a campaign rally on August 11, 2012 in Manassas, Virginia. Mitt Romney kicked off a four day bus tour with an announcement of his running mate, Rep. Paul Ryan (R-WI).![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict165.jpg) Republican presidential candidate and former Massachusetts Governor Mitt Romney (L) and his running mate Rep. Paul Ryan (R-WI) wave to an overflow crowd before a campaign rally at Absolute Style furniture on August 12, 2012 in High Point, North Carolina. Mitt Romney continues his four day bus tour a day after announcing his running mate, Rep. Paul Ryan (R-WI).
Republican presidential candidate and former Massachusetts Governor Mitt Romney (L) and his running mate Rep. Paul Ryan (R-WI) wave to an overflow crowd before a campaign rally at Absolute Style furniture on August 12, 2012 in High Point, North Carolina. Mitt Romney continues his four day bus tour a day after announcing his running mate, Rep. Paul Ryan (R-WI).![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict162.jpg) Republican U.S. presidential candidate Mitt Romney greets supporters during a campaign stop at Absolute Style furniture store in High Point, North Carolina August 12, 2012.
Republican U.S. presidential candidate Mitt Romney greets supporters during a campaign stop at Absolute Style furniture store in High Point, North Carolina August 12, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict163.jpg) Republican presidential candidate and former Massachusetts Governor Mitt Romney greets an overflow crowd before a campaign rally at Absolute Style furniture on August 12, 2012 in High Point, North Carolina. Mitt Romney continues his four day bus tour a day after announcing his running mate, Rep. Paul Ryan (R-WI).
Republican presidential candidate and former Massachusetts Governor Mitt Romney greets an overflow crowd before a campaign rally at Absolute Style furniture on August 12, 2012 in High Point, North Carolina. Mitt Romney continues his four day bus tour a day after announcing his running mate, Rep. Paul Ryan (R-WI).![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict164.jpg) Republican vice presidential candidate Rep. Paul Ryan (R-WI) greets an overflow crowd before a campaign rally at Absolute Style furniture on August 12, 2012 in High Point, North Carolina. Mitt Romney continues his four day bus tour a day after announcing his running mate, Rep. Paul Ryan (R-WI).
Republican vice presidential candidate Rep. Paul Ryan (R-WI) greets an overflow crowd before a campaign rally at Absolute Style furniture on August 12, 2012 in High Point, North Carolina. Mitt Romney continues his four day bus tour a day after announcing his running mate, Rep. Paul Ryan (R-WI).![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict166.jpg) US Republican presidential candidate and former Massachusetts Governor Mitt Romney greets supporters prior to speaking during a campaign rally at Absolute Style furniture company in High Point, North Carolina, August 12, 2012. Romney and his running mate Wisconsin Representative Paul Ryan continue on the second day of a 4-day bus trip that will take Romney to 4 key swing states, Virginia, North Carolina, Florida and Ohio, and also to Ryan’s home state of Wisconsin.
US Republican presidential candidate and former Massachusetts Governor Mitt Romney greets supporters prior to speaking during a campaign rally at Absolute Style furniture company in High Point, North Carolina, August 12, 2012. Romney and his running mate Wisconsin Representative Paul Ryan continue on the second day of a 4-day bus trip that will take Romney to 4 key swing states, Virginia, North Carolina, Florida and Ohio, and also to Ryan’s home state of Wisconsin.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict167.jpg) Republican presidential candidate and former Massachusetts Governor Mitt Romney (R) looks on as his running mate Republican vice presidential candidate, U.S. Rep. Paul Ryan (R-WI) speaks to an overflow crowd outside of a campaign rally at the NASCAR Technical Institute on August 12, 2012 in Mooresville, North Carolina. Mitt Romney continues his four day bus tour a day after announcing his running mate, Rep. Paul Ryan (R-WI).
Republican presidential candidate and former Massachusetts Governor Mitt Romney (R) looks on as his running mate Republican vice presidential candidate, U.S. Rep. Paul Ryan (R-WI) speaks to an overflow crowd outside of a campaign rally at the NASCAR Technical Institute on August 12, 2012 in Mooresville, North Carolina. Mitt Romney continues his four day bus tour a day after announcing his running mate, Rep. Paul Ryan (R-WI).![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict168.jpg) Republican vice presidential candidate, U.S. Rep. Paul Ryan (R-WI) shakes hands with supporters after speaking with Republican presidential candidate and former Massachusetts Governor Mitt Romney during the Mooresville Victory Rally August 12, 2012 at NASCAR Technical Institute in Mooresville, North Carolina. Mitt Romney will make stops in Florida and Ohio during his four-day bus tour.
Republican vice presidential candidate, U.S. Rep. Paul Ryan (R-WI) shakes hands with supporters after speaking with Republican presidential candidate and former Massachusetts Governor Mitt Romney during the Mooresville Victory Rally August 12, 2012 at NASCAR Technical Institute in Mooresville, North Carolina. Mitt Romney will make stops in Florida and Ohio during his four-day bus tour.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict169.jpg) Republican presidential candidate and former Massachusetts Gov. Mitt Romney shakes hands with supporters after speaking at the Mooresville Victory Rally with his running mate Republican vice presidential candidate, U.S. Rep. Paul Ryan (R-WI) August 12, 2012 at NASCAR Technical Institute in Mooresville, North Carolina. Mitt Romney will make stops in Florida and Ohio during his four-day bus tour.
Republican presidential candidate and former Massachusetts Gov. Mitt Romney shakes hands with supporters after speaking at the Mooresville Victory Rally with his running mate Republican vice presidential candidate, U.S. Rep. Paul Ryan (R-WI) August 12, 2012 at NASCAR Technical Institute in Mooresville, North Carolina. Mitt Romney will make stops in Florida and Ohio during his four-day bus tour.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict170.jpg) Republican presidential candidate Mitt Romney, center, greets supporters at a rally Sunday, Aug. 12, 2012, in Mooresville, N.C. , at the NASCAR Technical Institute.
Republican presidential candidate Mitt Romney, center, greets supporters at a rally Sunday, Aug. 12, 2012, in Mooresville, N.C. , at the NASCAR Technical Institute.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict171.jpg) Republican presidential candidate, former Massachusetts Gov. Mitt Romney, and vice presidential running mate Rep. Paul Ryan, R-Wis. , left, greet supporters during a campaign event at the NASCAR Technical Institute, Sunday, Aug. 12, 2012, in Mooresville, N.C.
Republican presidential candidate, former Massachusetts Gov. Mitt Romney, and vice presidential running mate Rep. Paul Ryan, R-Wis. , left, greet supporters during a campaign event at the NASCAR Technical Institute, Sunday, Aug. 12, 2012, in Mooresville, N.C.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict174.jpg) In this photo provided by the U.S. Coast Guard, Republican Presidential candidate Mitt Romney, second from right, shakes a person’s hand during a campaign rally in Manassas, Va. , Saturday, Aug. 11, 2012. Romney announced Wisconsin Congressman Paul Ryan, second from left, as his running mate during an event in Norfolk, Va. , launching a bus tour promoting The Romney Plan For A Stronger Middle Class in Virginia.
In this photo provided by the U.S. Coast Guard, Republican Presidential candidate Mitt Romney, second from right, shakes a person’s hand during a campaign rally in Manassas, Va. , Saturday, Aug. 11, 2012. Romney announced Wisconsin Congressman Paul Ryan, second from left, as his running mate during an event in Norfolk, Va. , launching a bus tour promoting The Romney Plan For A Stronger Middle Class in Virginia.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict175.jpg) Members of the U.S. Secret Service are seen on the rooftop of a building near the site of a campaign rally for Republican presidential candidate, former Massachusetts Gov. Mitt Romney, in Manassas, Va. , Saturday, Aug. 11, 2012.
Members of the U.S. Secret Service are seen on the rooftop of a building near the site of a campaign rally for Republican presidential candidate, former Massachusetts Gov. Mitt Romney, in Manassas, Va. , Saturday, Aug. 11, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict176.jpg) Wisconsin Representative Paul Ryan greets supporters after US Republican presidential candidate and former Massachusetts Governor Mitt Romney announced Ryan as his vice presidential running mate during a campaign rally at the Nauticus Museum after touring the USS Wisconsin in Norfolk, Virginia, August 11, 2012. Romney and his new running mate embark on the first day of a 4-day bus trip that will take the White House hopefuls to 4 key swing states, Virginia, North Carolina, Florida and Ohio.
Wisconsin Representative Paul Ryan greets supporters after US Republican presidential candidate and former Massachusetts Governor Mitt Romney announced Ryan as his vice presidential running mate during a campaign rally at the Nauticus Museum after touring the USS Wisconsin in Norfolk, Virginia, August 11, 2012. Romney and his new running mate embark on the first day of a 4-day bus trip that will take the White House hopefuls to 4 key swing states, Virginia, North Carolina, Florida and Ohio.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict177.jpg) Republican presidential candidate, former Massachusetts Gov. Mitt Romney (R) and U.S. Rep. Paul Ryan (R-WI) wave as Ryan is announced as his vice presidential running mate aboard the USS Wisconsin August 11, 2012 in Norfolk, Virginia. Ryan, a seven term congressman, is Chairman of the House Budget Committee and provides a strong contrast to the Obama administration on fiscal policy.
Republican presidential candidate, former Massachusetts Gov. Mitt Romney (R) and U.S. Rep. Paul Ryan (R-WI) wave as Ryan is announced as his vice presidential running mate aboard the USS Wisconsin August 11, 2012 in Norfolk, Virginia. Ryan, a seven term congressman, is Chairman of the House Budget Committee and provides a strong contrast to the Obama administration on fiscal policy.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict178.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict179.jpg) US Republican presidential candidate and former Massachusetts Governor Mitt Romney and Wisconsin Representative Paul Ryan(2ndL) greet supporters after announcing Ryan as his vice presidential running mate during a campaign rally at the Nauticus Museum after touring the USS Wisconsin in Norfolk, Virginia, August 11, 2012. Romney and his new running mate embark on the first day of a 4-day bus trip that will take the White House hopefuls to 4 key swing states, Virginia, North Carolina, Florida and Ohio.
US Republican presidential candidate and former Massachusetts Governor Mitt Romney and Wisconsin Representative Paul Ryan(2ndL) greet supporters after announcing Ryan as his vice presidential running mate during a campaign rally at the Nauticus Museum after touring the USS Wisconsin in Norfolk, Virginia, August 11, 2012. Romney and his new running mate embark on the first day of a 4-day bus trip that will take the White House hopefuls to 4 key swing states, Virginia, North Carolina, Florida and Ohio.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict180.jpg) Republican presidential candidate, former Massachusetts Gov. Mitt Romney (C) arrives at the USS Wisconsin August 11, 2012 in Norfolk, Virginia. Mitt Romney will announce Rep. Paul Ryan (R-WI), a seven term congressman, as his Vice President pick. Ryan is Chairman of the House Budget Committee and provides a strong contrast to the Obama administration on fiscal policy.
Republican presidential candidate, former Massachusetts Gov. Mitt Romney (C) arrives at the USS Wisconsin August 11, 2012 in Norfolk, Virginia. Mitt Romney will announce Rep. Paul Ryan (R-WI), a seven term congressman, as his Vice President pick. Ryan is Chairman of the House Budget Committee and provides a strong contrast to the Obama administration on fiscal policy.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict181.jpg) Janna Ryan, wife of newly announced Republican vice presidential candidate, Wisconsin Rep. Paul Ryan, partially visible behind her, greets crowd members after her husband addressed the crowd Saturday, Aug. 11, 2012 in Norfolk, Va.
Janna Ryan, wife of newly announced Republican vice presidential candidate, Wisconsin Rep. Paul Ryan, partially visible behind her, greets crowd members after her husband addressed the crowd Saturday, Aug. 11, 2012 in Norfolk, Va.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict182.jpg) U.S. Secret Service agents guard the campaign bus of Republican presidential candidate and former Massachusetts Gov. Mitt Romney on August 10, 2012 in Norfolk, Virginia. Romney is kicking off a four-day bus tour that in addtion to Viriginia, will see the candidate visit Florida, North Carolina and Ohio.
U.S. Secret Service agents guard the campaign bus of Republican presidential candidate and former Massachusetts Gov. Mitt Romney on August 10, 2012 in Norfolk, Virginia. Romney is kicking off a four-day bus tour that in addtion to Viriginia, will see the candidate visit Florida, North Carolina and Ohio.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict183.jpg) The motorcade of Republican presidential candidate and former Massachusetts Gov. Mitt Romney drives towards Downtown Boston on August 10, 2012 in Belmont, Massachusetts. Mitt Romney visited his campaign headquarters a day before kicking off a four day bus tour that will visit Virginia, Florida, North Carolina and Ohio.
The motorcade of Republican presidential candidate and former Massachusetts Gov. Mitt Romney drives towards Downtown Boston on August 10, 2012 in Belmont, Massachusetts. Mitt Romney visited his campaign headquarters a day before kicking off a four day bus tour that will visit Virginia, Florida, North Carolina and Ohio.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict184.jpg) A U.S. Secret Service agent guards a door before Republican presidential candidate and former Massachusetts Gov. Mitt Romney arrived at his campaign headquarters on August 10, 2012 in Boston, Massachusetts. Mitt Romney visited his campaign headquarters a day before kicking off a four day bus tour that will visit Virginia, Florida, North Carolina and Ohio.
A U.S. Secret Service agent guards a door before Republican presidential candidate and former Massachusetts Gov. Mitt Romney arrived at his campaign headquarters on August 10, 2012 in Boston, Massachusetts. Mitt Romney visited his campaign headquarters a day before kicking off a four day bus tour that will visit Virginia, Florida, North Carolina and Ohio.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict185.jpg) Republican presidential candidate and former Massachusetts Gov. Mitt Romney departs an Upper East Side event in Manhattan on August 9, 2012 in New York City. Mitt Romney is visiting New York for fundraising events today before travelling to Boston.
Republican presidential candidate and former Massachusetts Gov. Mitt Romney departs an Upper East Side event in Manhattan on August 9, 2012 in New York City. Mitt Romney is visiting New York for fundraising events today before travelling to Boston.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict186.jpg) A secret service agent stands posted at a field as Republican presidential candidate and former Massachusetts Governor Mitt Romney meets with Iowa Secretary of Agriculture Bill Northey at a farm in Des Moines, Iowa August 8, 2012.
A secret service agent stands posted at a field as Republican presidential candidate and former Massachusetts Governor Mitt Romney meets with Iowa Secretary of Agriculture Bill Northey at a farm in Des Moines, Iowa August 8, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict187.jpg) Republican presidential candidate and former Massachusetts Governor Mitt Romney (back C) shakes hands with supporters during a campaign event at Central Campus High School in Des Moines, Iowa August 8, 2012.
Republican presidential candidate and former Massachusetts Governor Mitt Romney (back C) shakes hands with supporters during a campaign event at Central Campus High School in Des Moines, Iowa August 8, 2012.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict188.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict189.jpg) Republican presidential candidate and former Massachusetts Gov. Mitt Romney campaigns at Stepto’s BBQ Shack in Evansville, Ind. , Saturday, Aug. 4, 2012.
Republican presidential candidate and former Massachusetts Gov. Mitt Romney campaigns at Stepto’s BBQ Shack in Evansville, Ind. , Saturday, Aug. 4, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict190.jpg) Republican presidential candidate and former Massachusetts Gov. Mitt Romney greets supporters during a campaign event with Republican Governors at Basalt Public High School on August 2, 2012 in Basalt, Colorado. One day after returning from a six-day overseas trip to England, Israel and Poland, Mitt Romney is campaigning in Colorado before heading to Nevada.
Republican presidential candidate and former Massachusetts Gov. Mitt Romney greets supporters during a campaign event with Republican Governors at Basalt Public High School on August 2, 2012 in Basalt, Colorado. One day after returning from a six-day overseas trip to England, Israel and Poland, Mitt Romney is campaigning in Colorado before heading to Nevada.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict191.jpg) Republican presidential candidate and former Massachusetts Gov. Mitt Romney steps off of a picnic table after speaking to an overflow crowd during a campaign event at the Jefferson County Fairgrounds on August 2, 2012 in Golden, Colorado. One day after returning from a six-day overseas trip to England, Israel and Poland, Mitt Romney is campaigning in Colorado before heading to Nevada.
Republican presidential candidate and former Massachusetts Gov. Mitt Romney steps off of a picnic table after speaking to an overflow crowd during a campaign event at the Jefferson County Fairgrounds on August 2, 2012 in Golden, Colorado. One day after returning from a six-day overseas trip to England, Israel and Poland, Mitt Romney is campaigning in Colorado before heading to Nevada.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict193.jpg) U.S. Republican Presidential candidate Mitt Romney takes off his jacket as he walks to his limousine after visiting the Warsaw Uprising Memorial in Warsaw, July 31, 2012.
U.S. Republican Presidential candidate Mitt Romney takes off his jacket as he walks to his limousine after visiting the Warsaw Uprising Memorial in Warsaw, July 31, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict192.jpg) U.S. Republican presidential candidate, former Massachusetts Gov. Mitt Romney (C) talks with participants after his speech in the Hall of the University of Warsaw Library on July 31, 2012 in Warsaw, Poland. After visiting London, Israel, and the polish city of Gdansk, Romney visits the capital of Poland, Warsaw.
U.S. Republican presidential candidate, former Massachusetts Gov. Mitt Romney (C) talks with participants after his speech in the Hall of the University of Warsaw Library on July 31, 2012 in Warsaw, Poland. After visiting London, Israel, and the polish city of Gdansk, Romney visits the capital of Poland, Warsaw.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict194.jpg) U.S. Republican presidential candidate Mitt Romney (C) is surrounded by security as he walks in the center of Gdansk Old Town, July 30, 2012.
U.S. Republican presidential candidate Mitt Romney (C) is surrounded by security as he walks in the center of Gdansk Old Town, July 30, 2012.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict195.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict196.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict197.jpg) Republican presidential candidate and former Massachusetts Gov. Mitt Romney and his wife Ann board their charter plane in Tel Aviv, Israel as they travel to Poland, Monday, July 30, 2012.
Republican presidential candidate and former Massachusetts Gov. Mitt Romney and his wife Ann board their charter plane in Tel Aviv, Israel as they travel to Poland, Monday, July 30, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict198.jpg) U.S. Republican Presidential candidate Mitt Romney (C) arrives surrounded by security to deliver foreign policy remarks at Mishkenot Sha’ananim in Jerusalem, July 29, 2012.
U.S. Republican Presidential candidate Mitt Romney (C) arrives surrounded by security to deliver foreign policy remarks at Mishkenot Sha’ananim in Jerusalem, July 29, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict199.jpg) US Republican presidential candidate Mitt Romney greets people after placing a message, written on paper, in the ancient stones of the Western Wall in Jerusalem’s Old City on July 29, 2012, during the annual Tisha B’Av (Ninth of Av) fasting and a memorial day, commemorating the destruction of ancient Jerusalem temples. Romney is meeting Israeli leaders as he seeks to burnish his foreign policy credentials and portray himself as a better friend to Israel than President Barack Obama.
US Republican presidential candidate Mitt Romney greets people after placing a message, written on paper, in the ancient stones of the Western Wall in Jerusalem’s Old City on July 29, 2012, during the annual Tisha B’Av (Ninth of Av) fasting and a memorial day, commemorating the destruction of ancient Jerusalem temples. Romney is meeting Israeli leaders as he seeks to burnish his foreign policy credentials and portray himself as a better friend to Israel than President Barack Obama.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict200.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict201.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict202.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict203.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict204.jpg) Israeli security is seen after the motorcade of Republican presidential candidate and former Massachusetts Gov. Mitt Romney arrives at the King David Hotel in Jerusalem, Sunday, July 29, 2012.
Israeli security is seen after the motorcade of Republican presidential candidate and former Massachusetts Gov. Mitt Romney arrives at the King David Hotel in Jerusalem, Sunday, July 29, 2012. ![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict205.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict206.jpg) U.S. Republican Presidential candidate Mitt Romney is recognized by pedestrians at Grosvenor Place in London, July 27, 2012, as he was forced by gridlock traffic to walk from his hotel to the Irish Embassy to meet with Irish Prime Minister (Taoiseach) Enda Kenny.
U.S. Republican Presidential candidate Mitt Romney is recognized by pedestrians at Grosvenor Place in London, July 27, 2012, as he was forced by gridlock traffic to walk from his hotel to the Irish Embassy to meet with Irish Prime Minister (Taoiseach) Enda Kenny.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict207.jpg) U.S. Republican Presidential candidate Mitt Romney gets out of his SUV with a team of security as he arrives for a fundraising event in London, July 26, 2012.
U.S. Republican Presidential candidate Mitt Romney gets out of his SUV with a team of security as he arrives for a fundraising event in London, July 26, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict208.jpg) Republican presidential candidate, former Massachusetts Gov. Mitt Romney arrives for a private fundraiser in Buffalo N.Y. , on Friday, June 29, 2012.
Republican presidential candidate, former Massachusetts Gov. Mitt Romney arrives for a private fundraiser in Buffalo N.Y. , on Friday, June 29, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict209.jpg) A U.S. Secret Service agent carries his weapon as he looks out from a motorcade vehicle as Republican presidential candidate Mitt Romney, not pictured, arrives for a private campaign finance event in New York, Thursday, June 28, 2012.
A U.S. Secret Service agent carries his weapon as he looks out from a motorcade vehicle as Republican presidential candidate Mitt Romney, not pictured, arrives for a private campaign finance event in New York, Thursday, June 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict210.jpg) Secret Service vehicles escort the campaign bus of Republican presidential candidate, former Massachusetts Gov. Mitt Romney after leaving Yampa Valley Airport on May 28, 2012 in Yampa, Colorado. Mitt Romney will campaign in Colorado before heading to Las Vegas, Nevada.
Secret Service vehicles escort the campaign bus of Republican presidential candidate, former Massachusetts Gov. Mitt Romney after leaving Yampa Valley Airport on May 28, 2012 in Yampa, Colorado. Mitt Romney will campaign in Colorado before heading to Las Vegas, Nevada.
![[]](https://i0.wp.com/arcticready.com/PR-images/shell.gif)
![[]](https://i0.wp.com/arcticready.com/PR-images/whale_email1.jpg)








![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict154.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict153.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict152.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict135.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict136.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict137.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict138.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict140.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict144.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict139.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict142.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict141.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict143.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict145.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict147.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict148.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict146.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict149.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict150.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict151.jpg)

![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict14.jpg) U.S. President Barack Obama (3rd L) greets an Air Force officer before boarding Marine One helicopter on August 4, 2012 at Joint Base Andrews, Maryland. Obama is spending the weekend at Camp David.
U.S. President Barack Obama (3rd L) greets an Air Force officer before boarding Marine One helicopter on August 4, 2012 at Joint Base Andrews, Maryland. Obama is spending the weekend at Camp David.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict15.jpg) President Barack Obama shakes hands with supporters at the end of a campaign rally at Loudoun County High School on August 2, 2012 in Leesburg, Virginia. The president campaigned earlier in the day in Florida.
President Barack Obama shakes hands with supporters at the end of a campaign rally at Loudoun County High School on August 2, 2012 in Leesburg, Virginia. The president campaigned earlier in the day in Florida.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict16.jpg) President Barack Obama, center, greets supporters after speaking at a campaign event at Loudoun County High School, Thursday, Aug. 2, 2012 in Leesburg, Va. Obama was campaigning in Florida and Northern Virginia today.
President Barack Obama, center, greets supporters after speaking at a campaign event at Loudoun County High School, Thursday, Aug. 2, 2012 in Leesburg, Va. Obama was campaigning in Florida and Northern Virginia today.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict17.jpg) President Barack Obama greets supporters after speaking at a campaign event at Loudoun County High School, Thursday, Aug. 2, 2012 in Leesburg, Va. Obama spent the day campaigning in Florida and Northern Virginia.
President Barack Obama greets supporters after speaking at a campaign event at Loudoun County High School, Thursday, Aug. 2, 2012 in Leesburg, Va. Obama spent the day campaigning in Florida and Northern Virginia.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict19.jpg) A Secret Service Counter Sniper Team prepares to climb down a ladder from on top of a people mover after President Barack Obama aboard Air Force One landed at Dulles International Airport in Sterling, Va.. , Thursday, Aug. 2, 2012.
A Secret Service Counter Sniper Team prepares to climb down a ladder from on top of a people mover after President Barack Obama aboard Air Force One landed at Dulles International Airport in Sterling, Va.. , Thursday, Aug. 2, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict22.jpg) President Barack Obama greets supporters after a campaign event at Rollins College, Thursday, Aug. 2, 2012, in Winter Park, Fla.
President Barack Obama greets supporters after a campaign event at Rollins College, Thursday, Aug. 2, 2012, in Winter Park, Fla.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict21.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict23.jpg) President Barack Obama greets guests on the tarmac upon his arrival at Orlando International Airport, Thursday, Aug. 2, 2012, in Orlando, Fla. Obama is campaigning in Florida and Northern Virginia today.
President Barack Obama greets guests on the tarmac upon his arrival at Orlando International Airport, Thursday, Aug. 2, 2012, in Orlando, Fla. Obama is campaigning in Florida and Northern Virginia today.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict50.jpg) President Barack Obama stops to greet patrons at Lechonera El Barrio, a local restaurant in Orlando, Fla. , Thursday, Aug. 2, 2012. Obama is campaigning in Florida and Northern Virginia today.
President Barack Obama stops to greet patrons at Lechonera El Barrio, a local restaurant in Orlando, Fla. , Thursday, Aug. 2, 2012. Obama is campaigning in Florida and Northern Virginia today.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict53.jpg) President Barack Obama greets eight-year old Olivia Short after he departed from Air Force One upon his arrival in Orlando, Fla. , Thursday, Aug. 2, 2012.
President Barack Obama greets eight-year old Olivia Short after he departed from Air Force One upon his arrival in Orlando, Fla. , Thursday, Aug. 2, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict54.jpg) President Barack Obama is hugged by a supporter after speaking at a campaign event at Mansfield Central Park, Wednesday, Aug. 1, 2012, in Mansfield, Ohio. Obama is campaign in Ohio with stops in Mansfield and Akron today. [Secret Service ready to remove an arm from Obama’s back. Note three agents in the crowd.]
President Barack Obama is hugged by a supporter after speaking at a campaign event at Mansfield Central Park, Wednesday, Aug. 1, 2012, in Mansfield, Ohio. Obama is campaign in Ohio with stops in Mansfield and Akron today. [Secret Service ready to remove an arm from Obama’s back. Note three agents in the crowd.]![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict56.jpg) Marine One helicopter, with President Barack Obama aboard, takes off from Wall Street heliport in New York, Monday, July, 30, 2012. Obama traveled to New York for a private fundraiser. [Decoy helo at rear, fire truck at right, Coast Guard ship in the river.]
Marine One helicopter, with President Barack Obama aboard, takes off from Wall Street heliport in New York, Monday, July, 30, 2012. Obama traveled to New York for a private fundraiser. [Decoy helo at rear, fire truck at right, Coast Guard ship in the river.]![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict55.jpg) US President Barack Obama prepares to land at the Wall Street Helipad in New York on July 30, 2012. Obama is in New York to attend campaign events ahead of the November presidential election. [Two Marine transport at left, Secret Service agent on dock.]
US President Barack Obama prepares to land at the Wall Street Helipad in New York on July 30, 2012. Obama is in New York to attend campaign events ahead of the November presidential election. [Two Marine transport at left, Secret Service agent on dock.]
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict57.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict58.jpg) A Secret Service vehicle, left, and Air Force Security Forces vehicle follow Air Force One on the tarmac as it prepares to take-off with President Barack Obama aboard, at Andrews Air Force Base, Md. , Monday, July 30, 2012.
A Secret Service vehicle, left, and Air Force Security Forces vehicle follow Air Force One on the tarmac as it prepares to take-off with President Barack Obama aboard, at Andrews Air Force Base, Md. , Monday, July 30, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict59.jpg) U.S. First Lady Michelle Obama sits separated from the public during the basketball match between the U.S. and France for the London 2012 Olympic Games at the Basketball Arena in the Olympic Park at Stratford in east London July 29, 2012. [Michelle’s customary Secret Service at her right, and below.]
U.S. First Lady Michelle Obama sits separated from the public during the basketball match between the U.S. and France for the London 2012 Olympic Games at the Basketball Arena in the Olympic Park at Stratford in east London July 29, 2012. [Michelle’s customary Secret Service at her right, and below.]![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict60.jpg) US First Lady Michelle Obama (R) speaks with tennis player Venus Williams (top L) as they attend the women’s singles tennis match between Serbia’s Jelena Jankovic and Serena Williams of the US during the London 2012 Olympic Games at the All England Tennis Club in Wimbledon, southwest London, on July 28, 2012.
US First Lady Michelle Obama (R) speaks with tennis player Venus Williams (top L) as they attend the women’s singles tennis match between Serbia’s Jelena Jankovic and Serena Williams of the US during the London 2012 Olympic Games at the All England Tennis Club in Wimbledon, southwest London, on July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict61.jpg) U.S First Lady Michelle Obama, left, waves an American flag as she cheers on the U.S. swim team during the first day of finals at the 2012 Summer Olympics, Saturday, July 28, 2012, in London. At right is Summer Schlopy, host of Yahoo! Sports’ web series Elite Athlete Workout. [Two Secret Service at left.]
U.S First Lady Michelle Obama, left, waves an American flag as she cheers on the U.S. swim team during the first day of finals at the 2012 Summer Olympics, Saturday, July 28, 2012, in London. At right is Summer Schlopy, host of Yahoo! Sports’ web series Elite Athlete Workout. [Two Secret Service at left.]![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict62.jpg) Agents keep watch as U.S. President Barack Obama (C) walks to the Marine One helicopter before departing from a soccer field at the Madeira School after attending a campaign event at a nearby private residence in McLean, Virginia, July 27, 2012.
Agents keep watch as U.S. President Barack Obama (C) walks to the Marine One helicopter before departing from a soccer field at the Madeira School after attending a campaign event at a nearby private residence in McLean, Virginia, July 27, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict63.jpg) US President Barack Obama walk across a field after stepping off Marine One upon arrival at the Madeira School landing zone July 27, 2012 in McLean, Virginia. Obama is in McLean to attend campaign fundraisers.
US President Barack Obama walk across a field after stepping off Marine One upon arrival at the Madeira School landing zone July 27, 2012 in McLean, Virginia. Obama is in McLean to attend campaign fundraisers.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict64.jpg) President Barack Obama waves as he walks across the football field at Madeira school in McLean, Va. , Friday, July, 27, 2012. Obama Traveled to Northern Virginia for a private fundraiser.
President Barack Obama waves as he walks across the football field at Madeira school in McLean, Va. , Friday, July, 27, 2012. Obama Traveled to Northern Virginia for a private fundraiser.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict65.jpg) US First Lady Michelle Obama plays with children as part of her ‘Let’s Move-London’ event at the Winfield House in London on July 27, 2012, hours before the official start of the London 2012 Olympic Games. [SS at right.
US First Lady Michelle Obama plays with children as part of her ‘Let’s Move-London’ event at the Winfield House in London on July 27, 2012, hours before the official start of the London 2012 Olympic Games. [SS at right.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict66.jpg) U.S. first lady Michelle Obama plays with schoolchildren during a ‘Let’s Move!’ event for about 1,000 American military children and American and British students at the U.S. ambassador’s residence in London, ahead of the 2012 Summer Olympics, Friday, July 27, 2012. [Two Secret Service in suits to hide weapons; at center, female.]
U.S. first lady Michelle Obama plays with schoolchildren during a ‘Let’s Move!’ event for about 1,000 American military children and American and British students at the U.S. ambassador’s residence in London, ahead of the 2012 Summer Olympics, Friday, July 27, 2012. [Two Secret Service in suits to hide weapons; at center, female.]![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict67.jpg) U.S. Secret Service keeps watch as President Barack Obama departs the New Orleans area in Air Force One at Louis Armstrong International Airport in Kenner, La. , Wednesday, July 25, 2012. Obama delivered remarks at the National Urban League 2012 Annual Conference and attended campaign events in New Orleans.
U.S. Secret Service keeps watch as President Barack Obama departs the New Orleans area in Air Force One at Louis Armstrong International Airport in Kenner, La. , Wednesday, July 25, 2012. Obama delivered remarks at the National Urban League 2012 Annual Conference and attended campaign events in New Orleans.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict68.jpg) President Barack Obama walks over to greet people after arriving at Boeing Field in Seattle, Tuesday, July 24, 2012.
President Barack Obama walks over to greet people after arriving at Boeing Field in Seattle, Tuesday, July 24, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict69.jpg) US President Barack Obama greets wellwishers upon arrival on Air Force One at Portland International Airport in Portland, Oregon, July 24, 2012. Obama is traveling to attend campaign events and fundraisers.
US President Barack Obama greets wellwishers upon arrival on Air Force One at Portland International Airport in Portland, Oregon, July 24, 2012. Obama is traveling to attend campaign events and fundraisers.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict70.jpg) Supporters walk in a line across the tarmac to greet President Barack Obama on his arrival at Boeing Field Tuesday, July 24, 2012, in Seattle. Obama is scheduled to attend a pair of campaign fund-raisers in the area.
Supporters walk in a line across the tarmac to greet President Barack Obama on his arrival at Boeing Field Tuesday, July 24, 2012, in Seattle. Obama is scheduled to attend a pair of campaign fund-raisers in the area.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict71.jpg) President Barack Obama heads to his limousine after stopping at the Gateway Breakfast House in Portland, Ore. , Tuesday, July 24, 2012.
President Barack Obama heads to his limousine after stopping at the Gateway Breakfast House in Portland, Ore. , Tuesday, July 24, 2012.

![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict78.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict61.jpg) Local residents clash with the police in front of a local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu province July 28, 2012. Chinese officials cancelled an industrial waste pipeline project on Saturday after anti-pollution demonstrators occupied the government office in eastern China, destroying computers and overturning cars. The demonstration was the latest in a string of protests sparked by fears of environmental degradation and highlights the social tensions the government in Beijing faces as it approaches a leadership transition this year.
Local residents clash with the police in front of a local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu province July 28, 2012. Chinese officials cancelled an industrial waste pipeline project on Saturday after anti-pollution demonstrators occupied the government office in eastern China, destroying computers and overturning cars. The demonstration was the latest in a string of protests sparked by fears of environmental degradation and highlights the social tensions the government in Beijing faces as it approaches a leadership transition this year.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict60.jpg) A police officer bleeds after clashing with local residents in front of a local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.
A police officer bleeds after clashing with local residents in front of a local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict30.jpg) A woman, with her face covered in blood, is helped by demonstrators after clashes with police during protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.
A woman, with her face covered in blood, is helped by demonstrators after clashes with police during protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict62.jpg) Local residents, holding banner which reads “Against the Oji Paper Group, protect our homeland”, shout as they gather to protest against plans for a water discharge project in Qidong, China Saturday, July 28, 2012.
Local residents, holding banner which reads “Against the Oji Paper Group, protect our homeland”, shout as they gather to protest against plans for a water discharge project in Qidong, China Saturday, July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict63.jpg) A group of protesters overturn a car near the local government office compound in the coastal city of Qidong, near Shanghai, in the eastern China province of Jiangsu on July 28, 2012.
A group of protesters overturn a car near the local government office compound in the coastal city of Qidong, near Shanghai, in the eastern China province of Jiangsu on July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict64.jpg) Local residents gather around scattered documents and an overturned car during a protest against plans for a water discharge project in Qidong, China Saturday, July 28, 2012.
Local residents gather around scattered documents and an overturned car during a protest against plans for a water discharge project in Qidong, China Saturday, July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict65.jpg) Local residents surround a vehicle after they overturned it, as they gather to protest against plans for a water discharge project in Qidong, China Saturday, July 28, 2012.
Local residents surround a vehicle after they overturned it, as they gather to protest against plans for a water discharge project in Qidong, China Saturday, July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict66.jpg) Armed police officers head to the local government office building where local residents gathered to protest against plans for a water discharge project in Qidong, China Saturday, July 28, 2012.
Armed police officers head to the local government office building where local residents gathered to protest against plans for a water discharge project in Qidong, China Saturday, July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict67.jpg) Local residents stand on smashed cars as they occupy the local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.
Local residents stand on smashed cars as they occupy the local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict52.jpg) Police beat a protestor on the ground (not pictured) outside the local government offices in the coastal city of Qidong, near Shanghai, in the eastern China province of Jiangsu on July 28, 2012.
Police beat a protestor on the ground (not pictured) outside the local government offices in the coastal city of Qidong, near Shanghai, in the eastern China province of Jiangsu on July 28, 2012.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict53.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict81.jpg) This photo taken on July 28, 2012 shows police putting a protester’s T-shirt over his head (C) after they detained him outside the local government offices in Qidong in the eastern China province of Jiangsu. The coastal city of Qidong, near Shanghai, seemed calm on July 29 a day after local officials announced a waste water pipeline project from the paper mill, which belongs to Japanese company Oji Paper, would be ‘permanently cancelled’.
This photo taken on July 28, 2012 shows police putting a protester’s T-shirt over his head (C) after they detained him outside the local government offices in Qidong in the eastern China province of Jiangsu. The coastal city of Qidong, near Shanghai, seemed calm on July 29 a day after local officials announced a waste water pipeline project from the paper mill, which belongs to Japanese company Oji Paper, would be ‘permanently cancelled’.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict47.jpg) A police officer is thrown to the ground by protesters near the local government office building Saturday July 28, 2012 in Qidong, Jiangsu Province, China. Authorities in eastern China dropped plans for a water-discharge project Saturday after thousands of protesters angry about pollution took to the streets, in the latest of many such confrontations in a country where three decades of rapid economic expansion have come at an environmental price.
A police officer is thrown to the ground by protesters near the local government office building Saturday July 28, 2012 in Qidong, Jiangsu Province, China. Authorities in eastern China dropped plans for a water-discharge project Saturday after thousands of protesters angry about pollution took to the streets, in the latest of many such confrontations in a country where three decades of rapid economic expansion have come at an environmental price.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict51.jpg) Protesters and police clash outside the local government offices in Qidong in the eastern China province of Jiangsu on July 28, 2012.
Protesters and police clash outside the local government offices in Qidong in the eastern China province of Jiangsu on July 28, 2012.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict45.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict50.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict44.jpg) A line of paramilitary police makes its way through protesters outside the local government offices in Qidong in the eastern China province of Jiangsu on July 28, 2012.
A line of paramilitary police makes its way through protesters outside the local government offices in Qidong in the eastern China province of Jiangsu on July 28, 2012.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict68.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict69.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict73.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict55.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict41.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict49.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict71.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict72.jpg) Police officers guard the local government office building Saturday July 28, 2012 in Qidong, Jiangsu Province, China.
Police officers guard the local government office building Saturday July 28, 2012 in Qidong, Jiangsu Province, China.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict40.jpg) Protesters stand as police officers guard the local government office building Saturday July 28, 2012 in Qidong, Jiangsu Province, China.
Protesters stand as police officers guard the local government office building Saturday July 28, 2012 in Qidong, Jiangsu Province, China.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict48.jpg) Vehicles damaged by protesters are seen at the local government office building Saturday July 28, 2012 in Qidong, Jiangsu Province, China.
Vehicles damaged by protesters are seen at the local government office building Saturday July 28, 2012 in Qidong, Jiangsu Province, China.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict42.jpg) A protester stands in front of a lines of riot police officers Saturday July 28, 2012 in Qidong, Jiangsu Province, China.
A protester stands in front of a lines of riot police officers Saturday July 28, 2012 in Qidong, Jiangsu Province, China.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict46.jpg) Protesters, right, confront with police officers, left, near the local government office building Saturday July 28, 2012 in Qidong, Jiangsu Province, China.
Protesters, right, confront with police officers, left, near the local government office building Saturday July 28, 2012 in Qidong, Jiangsu Province, China.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict21.jpg) A demonstrator fights with a police officer in front of the local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012. Angry demonstrators occupied a government office in eastern China on Saturday, destroying computers and overturning cars parked outside in a violent protest against an industrial waste pipeline they said would poison their coastal waters. The demonstration was the latest in a string of protests sparked by fears of environment degradation and highlights the social tensions the government in Beijing is having to deal with as it approaches a leadership transition this year. About a 1,000 protesters marched through the coastal city of Qidong, about one hour north of Shanghai by car, shouting slogans against the plan to build a pipeline through the city that would empty waste from a nearby paper factory into the sea.
A demonstrator fights with a police officer in front of the local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012. Angry demonstrators occupied a government office in eastern China on Saturday, destroying computers and overturning cars parked outside in a violent protest against an industrial waste pipeline they said would poison their coastal waters. The demonstration was the latest in a string of protests sparked by fears of environment degradation and highlights the social tensions the government in Beijing is having to deal with as it approaches a leadership transition this year. About a 1,000 protesters marched through the coastal city of Qidong, about one hour north of Shanghai by car, shouting slogans against the plan to build a pipeline through the city that would empty waste from a nearby paper factory into the sea.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict27.jpg) Protesters beat a policeman (C) during a protest outside the local government offices in Qidong in the eastern China province of Jiangsu on July 28, 2012. Thousands of demonstrators protested against alleged pollution from a paper factory in this easten China city and clashed with police after they seized bottles of liquor and wine from the offices along with cartons of cigarettes, items which Chinese officials frequently receive as bribes.
Protesters beat a policeman (C) during a protest outside the local government offices in Qidong in the eastern China province of Jiangsu on July 28, 2012. Thousands of demonstrators protested against alleged pollution from a paper factory in this easten China city and clashed with police after they seized bottles of liquor and wine from the offices along with cartons of cigarettes, items which Chinese officials frequently receive as bribes.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict28.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict26.jpg) Protesters beat a policeman (C) during a protest outside the local government offices in Qidong in the eastern China province of Jiangsu on July 28, 2012. Thousands of demonstrators protested against alleged pollution from a paper factory in this easten China city and clashed with police after they seized bottles of liquor and wine from the offices along with cartons of cigarettes, items which Chinese officials frequently receive as bribes.
Protesters beat a policeman (C) during a protest outside the local government offices in Qidong in the eastern China province of Jiangsu on July 28, 2012. Thousands of demonstrators protested against alleged pollution from a paper factory in this easten China city and clashed with police after they seized bottles of liquor and wine from the offices along with cartons of cigarettes, items which Chinese officials frequently receive as bribes.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict29.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict31.jpg) Local residents occupy a local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.
Local residents occupy a local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict23.jpg) Local residents push over a police vehicle as they gather to protest against plans for a water discharge project in Qidong, China Saturday, July 28, 2012. The government in the city announced on its official website Saturday that the plans were scrapped amid opposition by local residents, who are concerned over potential pollution.
Local residents push over a police vehicle as they gather to protest against plans for a water discharge project in Qidong, China Saturday, July 28, 2012. The government in the city announced on its official website Saturday that the plans were scrapped amid opposition by local residents, who are concerned over potential pollution.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict24.jpg) A police car lies overturned as protesters occupy a government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.
A police car lies overturned as protesters occupy a government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict22.jpg) A local resident squats on a destroyed car after demonstrators occupied the local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.
A local resident squats on a destroyed car after demonstrators occupied the local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict25.jpg) Demonstrators stand inside a destroyed office at the local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012. Angry demonstrators occupied a government office in eastern China on Saturday, destroying computers and overturning cars in a violent protest against an industrial waste pipeline they said would poison their coastal waters.
Demonstrators stand inside a destroyed office at the local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012. Angry demonstrators occupied a government office in eastern China on Saturday, destroying computers and overturning cars in a violent protest against an industrial waste pipeline they said would poison their coastal waters.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict32.jpg) Police officers stands next to a damaged police car after demonstrators occupied the local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.
Police officers stands next to a damaged police car after demonstrators occupied the local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict37.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict20.jpg) A demonstrator smashes a car window during a protest against an industrial waste pipeline under construction in front of the local government building in Qidong, Jiangsu Province July 28, 2012.
A demonstrator smashes a car window during a protest against an industrial waste pipeline under construction in front of the local government building in Qidong, Jiangsu Province July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict19.jpg) Demonstrators smash a car in front of the local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.
Demonstrators smash a car in front of the local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict18.jpg) Local residents gather to protest against plans for a water discharge project in Qidong, China Saturday, July 28, 2012. The government in the city announced on its official website Saturday that the plans were scrapped amid opposition by local residents, who are concerned over potential pollution. AP
Local residents gather to protest against plans for a water discharge project in Qidong, China Saturday, July 28, 2012. The government in the city announced on its official website Saturday that the plans were scrapped amid opposition by local residents, who are concerned over potential pollution. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict17.jpg) Local residents gather to protest against plans for a water discharge project in Qidong, China Saturday, July 28, 2012. The government in the city announced on its official website Saturday that the plans were scrapped amid opposition by local residents, who are concerned over potential pollution.
Local residents gather to protest against plans for a water discharge project in Qidong, China Saturday, July 28, 2012. The government in the city announced on its official website Saturday that the plans were scrapped amid opposition by local residents, who are concerned over potential pollution.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict16.jpg) Local residents protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.
Local residents protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict33.jpg) Local residents marche during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.
Local residents marche during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict36.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict34.jpg) Police officers try to calm the crowd during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.
Police officers try to calm the crowd during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict35.jpg) Local residents occupy the local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.
Local residents occupy the local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict54.jpg) Protesters gather on rooftops to shout slogans outside the local government offices in the coastal city of Qidong, near Shanghai, in the eastern China province of Jiangsu on July 28, 2012.
Protesters gather on rooftops to shout slogans outside the local government offices in the coastal city of Qidong, near Shanghai, in the eastern China province of Jiangsu on July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict56.jpg) People standing on cars hold a banner as other protestors shout slogans inside the local government office compound in the coastal city of Qidong, near Shanghai, in the eastern China province of Jiangsu on July 28, 2012.
People standing on cars hold a banner as other protestors shout slogans inside the local government office compound in the coastal city of Qidong, near Shanghai, in the eastern China province of Jiangsu on July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict57.jpg) Protestor shout slogans and hold placards outside the local government offices in the coastal city of Qidong, near Shanghai, in the eastern China province of Jiangsu on July 28, 2012.
Protestor shout slogans and hold placards outside the local government offices in the coastal city of Qidong, near Shanghai, in the eastern China province of Jiangsu on July 28, 2012.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict74.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012/07/report-infra-damage-bc.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012/07/report-infra-damage2.jpg)

![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict77.jpg) Nick Warner, director-general of Australia’s Secret Intelligence Service (ASIS), prepares to give a speech at the National Portrait Gallery in Canberra on July 19, 2012. Australia’s top spy warned of the ‘very real threat’ from extremists, in the first public address by the head of the country’s Secret Intelligence Service (ASIS) in its 60-year history.
Nick Warner, director-general of Australia’s Secret Intelligence Service (ASIS), prepares to give a speech at the National Portrait Gallery in Canberra on July 19, 2012. Australia’s top spy warned of the ‘very real threat’ from extremists, in the first public address by the head of the country’s Secret Intelligence Service (ASIS) in its 60-year history.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict76.jpg) Nick Warner (C), director-general of Australia’s Secret Intelligence Service (ASIS), gets wired up before giving a speech at the National Portrait Gallery in Canberra on July 19, 2012. Australia’s top spy warned of the ‘very real threat’ from extremists, in the first public address by the head of the country’s Secret Intelligence Service (ASIS) in its 60-year history.
Nick Warner (C), director-general of Australia’s Secret Intelligence Service (ASIS), gets wired up before giving a speech at the National Portrait Gallery in Canberra on July 19, 2012. Australia’s top spy warned of the ‘very real threat’ from extremists, in the first public address by the head of the country’s Secret Intelligence Service (ASIS) in its 60-year history.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict78.jpg) Nick Warner, director-general of Australia’s Secret Intelligence Service (ASIS), speaks at the National Portrait Gallery in Canberra on July 19, 2012. Australia’s top spy warned of the ‘very real threat’ from extremists, in the first public address by the head of the country’s Secret Intelligence Service (ASIS) in its 60-year history.
Nick Warner, director-general of Australia’s Secret Intelligence Service (ASIS), speaks at the National Portrait Gallery in Canberra on July 19, 2012. Australia’s top spy warned of the ‘very real threat’ from extremists, in the first public address by the head of the country’s Secret Intelligence Service (ASIS) in its 60-year history.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict108.jpg) Director Richard Fadden waits to testify before the Commons public safety committee on Parliament Hill in Ottawa May 31, 2012.
Director Richard Fadden waits to testify before the Commons public safety committee on Parliament Hill in Ottawa May 31, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict92.jpg) French intelligence national coordinator, Ange Mancini, leaves after a meeting with French Justice on March 29, 2012 in Paris.
French intelligence national coordinator, Ange Mancini, leaves after a meeting with French Justice on March 29, 2012 in Paris.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict93.jpg) French intelligence national coordinator, Ange Mancini arrives at the Elysee presidential palace in Paris, on March 27, 2012 to take part in a meeting with French President, magistrates and policemen who took part in the investigations following the shooting of seven persons and in the siege of self-proclaimed Islamist Mohamed Merah’s flat in Toulouse. Mohamed Merah was killed during the RAID police special forces unit assault after a 32-hour siege on March 21.
French intelligence national coordinator, Ange Mancini arrives at the Elysee presidential palace in Paris, on March 27, 2012 to take part in a meeting with French President, magistrates and policemen who took part in the investigations following the shooting of seven persons and in the siege of self-proclaimed Islamist Mohamed Merah’s flat in Toulouse. Mohamed Merah was killed during the RAID police special forces unit assault after a 32-hour siege on March 21.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict101.jpg) General Director of National Police (DGPN) Frederic Pechenard (L) and his Principal private secretary Robert Martin (C) speak with director of the French Intelligence agency, the Central Directorate of Interior Intelligence (DCRI) Bernard Squarcini (R) as they inaugurate the France’s Milipol global security trade fair on October 18, 2011 in Paris. Milipol Paris 2011, welcoming more than 1,000 exhibiting companies from 43 countries, runs until October 21.
General Director of National Police (DGPN) Frederic Pechenard (L) and his Principal private secretary Robert Martin (C) speak with director of the French Intelligence agency, the Central Directorate of Interior Intelligence (DCRI) Bernard Squarcini (R) as they inaugurate the France’s Milipol global security trade fair on October 18, 2011 in Paris. Milipol Paris 2011, welcoming more than 1,000 exhibiting companies from 43 countries, runs until October 21.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict117.jpg) Director of the NZSIS Warren Tucker reads out a prepared statement regarding Ahmed Zaoui, September 13, 2007.
Director of the NZSIS Warren Tucker reads out a prepared statement regarding Ahmed Zaoui, September 13, 2007.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict96.jpg) Syria’s President Bashar al-Assad (R) meets Russian Foreign Minister Sergei Lavrov (2nd R) with Russian Foreign Intelligence Service chief Mikhail Fradkov (L) in Damascus February 7, 2012, in this handout photograph released by Syria’s national news agency SANA. Lavrov began talks with Syrian President Bashar al-Assad on Tuesday by saying Moscow wants Arab peoples to live in peace and the Syrian leader is aware of his responsibility, Russian news agency RIA reported.
Syria’s President Bashar al-Assad (R) meets Russian Foreign Minister Sergei Lavrov (2nd R) with Russian Foreign Intelligence Service chief Mikhail Fradkov (L) in Damascus February 7, 2012, in this handout photograph released by Syria’s national news agency SANA. Lavrov began talks with Syrian President Bashar al-Assad on Tuesday by saying Moscow wants Arab peoples to live in peace and the Syrian leader is aware of his responsibility, Russian news agency RIA reported.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict81.jpg) The Director General of the British domestic security and counter-intelligence service MI5 Jonathan Evans, right, sits beside the head of the British foreign intelligence service, the Secret Intelligence Service (SIS), MI6, Sir John Sawers, left, as they listen in the front row of the audience during a speech by Britain’s Foreign Secretary William Hague at the Foreign Office in London, Wednesday, Nov. 16, 2011. Hague’s speech was on Secret Intelligence, praising the work of agencies, stressing the importance of framework of law, values and accountability.
The Director General of the British domestic security and counter-intelligence service MI5 Jonathan Evans, right, sits beside the head of the British foreign intelligence service, the Secret Intelligence Service (SIS), MI6, Sir John Sawers, left, as they listen in the front row of the audience during a speech by Britain’s Foreign Secretary William Hague at the Foreign Office in London, Wednesday, Nov. 16, 2011. Hague’s speech was on Secret Intelligence, praising the work of agencies, stressing the importance of framework of law, values and accountability.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict82.jpg) The Director General of the British domestic security and counter-intelligence service MI5 Jonathan Evans, right, chats with the head of the British foreign intelligence service, the Secret Intelligence Service (SIS), MI6, Sir John Sawers, left, as they sit in the front row of the audience before the start of a speech by Britain’s Foreign Secretary William Hague at the Foreign Office in London, Wednesday, Nov. 16, 2011. Hague’s speech was on Secret Intelligence, praising the work of agencies, stressing the importance of framework of law, values and accountability.
The Director General of the British domestic security and counter-intelligence service MI5 Jonathan Evans, right, chats with the head of the British foreign intelligence service, the Secret Intelligence Service (SIS), MI6, Sir John Sawers, left, as they sit in the front row of the audience before the start of a speech by Britain’s Foreign Secretary William Hague at the Foreign Office in London, Wednesday, Nov. 16, 2011. Hague’s speech was on Secret Intelligence, praising the work of agencies, stressing the importance of framework of law, values and accountability.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict83.jpg) The Director General of the British domestic security and counter-intelligence service MI5 Jonathan Evans, second left, sits beside the head of the British foreign intelligence service, the Secret Intelligence Service (SIS), MI6, Sir John Sawers, left, as they listen with other officials in the front row of the audience during a speech by Britain’s Foreign Secretary William Hague at the Foreign Office in London, Wednesday, Nov. 16, 2011. Hague’s speech was on Secret Intelligence, praising the work of agencies, stressing the importance of framework of law, values and accountability.
The Director General of the British domestic security and counter-intelligence service MI5 Jonathan Evans, second left, sits beside the head of the British foreign intelligence service, the Secret Intelligence Service (SIS), MI6, Sir John Sawers, left, as they listen with other officials in the front row of the audience during a speech by Britain’s Foreign Secretary William Hague at the Foreign Office in London, Wednesday, Nov. 16, 2011. Hague’s speech was on Secret Intelligence, praising the work of agencies, stressing the importance of framework of law, values and accountability.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict107.jpg) John Brennan, Assistant to the President for Homeland Security and Counterterrorism, speaks at the Intelligence and National Security Alliance conference in Washington, Wednesday, Sept. 7, 2011.
John Brennan, Assistant to the President for Homeland Security and Counterterrorism, speaks at the Intelligence and National Security Alliance conference in Washington, Wednesday, Sept. 7, 2011.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict89.jpg) Director of National Intelligence James R. Clapper leaves a joint closed door meeting with the Senate and House Intelligence Committee on Capitol Hill, on June 7, 2012 in Wasington, DC. The joint Intelligence committee met with Clapper to discuss administration leaks of classified information.
Director of National Intelligence James R. Clapper leaves a joint closed door meeting with the Senate and House Intelligence Committee on Capitol Hill, on June 7, 2012 in Wasington, DC. The joint Intelligence committee met with Clapper to discuss administration leaks of classified information.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict90.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict91.jpg) James R. Clapper, Director of the National Intelligence Agency, talks with guests during a luncheon hosted by U.S. Secretary of State Hillary Clinton, to honor President of the Republic of the Philippines Benigno S. Aquino III, at the Department of State, on June 8, 2012 in Washington, DC. Later today President Aquino is scheduled to meet with U.S. President Barack Obama at the White House.
James R. Clapper, Director of the National Intelligence Agency, talks with guests during a luncheon hosted by U.S. Secretary of State Hillary Clinton, to honor President of the Republic of the Philippines Benigno S. Aquino III, at the Department of State, on June 8, 2012 in Washington, DC. Later today President Aquino is scheduled to meet with U.S. President Barack Obama at the White House.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict95.jpg) Witnesses are seated as the US Senate Intelligence Committee holds a full committee hearing on ‘World Wide Threats.’ on January 31, 2012 on Capitol Hill in Washington, DC. Witnesses include: Director of National Intelligence James Clapper; CIA Director David Petraeus; FBI Director Robert Mueller; Defense Intelligence Agency Director Lt. Gen. Ronald Burgess; National Counter terrorism Center Director Matthew Olsen; Assistant Secretary of State for Intelligence and Research Philip Goldberg; and Homeland Security Undersecretary for Intelligence and Analysis Caryn Wagner.
Witnesses are seated as the US Senate Intelligence Committee holds a full committee hearing on ‘World Wide Threats.’ on January 31, 2012 on Capitol Hill in Washington, DC. Witnesses include: Director of National Intelligence James Clapper; CIA Director David Petraeus; FBI Director Robert Mueller; Defense Intelligence Agency Director Lt. Gen. Ronald Burgess; National Counter terrorism Center Director Matthew Olsen; Assistant Secretary of State for Intelligence and Research Philip Goldberg; and Homeland Security Undersecretary for Intelligence and Analysis Caryn Wagner.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict98.jpg) FBI Director Robert Mueller, testifies before the US Senate Intelligence Committee during a full committee hearing on ‘World Wide Threats.’ on January 31, 2012 on Capitol Hill in Washington, DC.
FBI Director Robert Mueller, testifies before the US Senate Intelligence Committee during a full committee hearing on ‘World Wide Threats.’ on January 31, 2012 on Capitol Hill in Washington, DC.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict99.jpg) CIA Director David Petraeus, testifies before the US Senate Intelligence Committee during a full committee hearing on ‘World Wide Threats.’ on January 31, 2012 on Capitol Hill in Washington, DC.
CIA Director David Petraeus, testifies before the US Senate Intelligence Committee during a full committee hearing on ‘World Wide Threats.’ on January 31, 2012 on Capitol Hill in Washington, DC.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict110.jpg) Assistant Secretary of State for Intelligence and Research Philip Goldberg testifies before the Senate Select Committee on Intelligence on Capitol Hill January 31, 2012 in Washington, DC. The committee met to hear testimony on the topic of ‘World Wide Threats.’
Assistant Secretary of State for Intelligence and Research Philip Goldberg testifies before the Senate Select Committee on Intelligence on Capitol Hill January 31, 2012 in Washington, DC. The committee met to hear testimony on the topic of ‘World Wide Threats.’![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict112.jpg) Homeland Security Undersecretary for Intelligence and Analysis Caryn Wagner testifies before the Senate Select Committee on Intelligence on Capitol Hill January 31, 2012 in Washington, DC. The committee met to hear testimony on the topic of ‘World Wide Threats.’
Homeland Security Undersecretary for Intelligence and Analysis Caryn Wagner testifies before the Senate Select Committee on Intelligence on Capitol Hill January 31, 2012 in Washington, DC. The committee met to hear testimony on the topic of ‘World Wide Threats.’![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict97.jpg) National Counterterrorism Center Director Matthew Olsen testifies before the Senate Select Committee on Intelligence on Capitol Hill January 31, 2012 in Washington, DC. The committee met to hear testimony on the topic of ‘World Wide Threats.’
National Counterterrorism Center Director Matthew Olsen testifies before the Senate Select Committee on Intelligence on Capitol Hill January 31, 2012 in Washington, DC. The committee met to hear testimony on the topic of ‘World Wide Threats.’![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict116.jpg) Director of Defense Intelligence Agency Army Lt. Gen. Ronald Burgess testifies on Capitol Hill in Washington, Thursday, Feb. 2, 2012, before the House Intelligence Committee hearing on worldwide threats.
Director of Defense Intelligence Agency Army Lt. Gen. Ronald Burgess testifies on Capitol Hill in Washington, Thursday, Feb. 2, 2012, before the House Intelligence Committee hearing on worldwide threats.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict113.jpg) National Security Agency Director Gen. Keith Alexander speaks about cybersecurity and the new threats posed to the U.S. economy and military at the American Enterprise Institute July 9, 2012 in Washington, DC. Alexander is also the commander of the U.S. Cyber Command and chief at the Central Security Service, with responsibility for national foreign intelligence, combat support and U.S. national security information system protection. Alexander said that in cyberspace ‘the probability for crisis is mounting,’ and that now is the time for putting into place strong policies and rules for operations and defense.
National Security Agency Director Gen. Keith Alexander speaks about cybersecurity and the new threats posed to the U.S. economy and military at the American Enterprise Institute July 9, 2012 in Washington, DC. Alexander is also the commander of the U.S. Cyber Command and chief at the Central Security Service, with responsibility for national foreign intelligence, combat support and U.S. national security information system protection. Alexander said that in cyberspace ‘the probability for crisis is mounting,’ and that now is the time for putting into place strong policies and rules for operations and defense.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict87.jpg) National Security Agency Director Gen. Keith Alexander speaks about cybersecurity and the new threats posed to the U.S. economy and military at the American Enterprise Institute July 9, 2012 in Washington, DC. Alexander is also the commander of the U.S. Cyber Command and chief at the Central Security Service, with responsibility for national foreign intelligence, combat support and U.S. national security information system protection. Alexander said that in cyberspace ‘the probability for crisis is mounting,’ and that now is the time for putting into place strong policies and rules for operations and defense.
National Security Agency Director Gen. Keith Alexander speaks about cybersecurity and the new threats posed to the U.S. economy and military at the American Enterprise Institute July 9, 2012 in Washington, DC. Alexander is also the commander of the U.S. Cyber Command and chief at the Central Security Service, with responsibility for national foreign intelligence, combat support and U.S. national security information system protection. Alexander said that in cyberspace ‘the probability for crisis is mounting,’ and that now is the time for putting into place strong policies and rules for operations and defense.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict88.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict100.jpg) John Sano, Deputy Director of the C.I.A’s national clandestine service attends an international conference focused on a solution for Camp Ashraf in Iraq, which is home to thousands of outlawed Iranian regime opponents, on January 20, 2012 in Paris.
John Sano, Deputy Director of the C.I.A’s national clandestine service attends an international conference focused on a solution for Camp Ashraf in Iraq, which is home to thousands of outlawed Iranian regime opponents, on January 20, 2012 in Paris.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict86.jpg) Retired Gen. Michael Hayden, former Central Intelligence Agency and National Security Agency Director, speaks during the launch of the 2012 Failed States Index (FSI), on July 13, 2012 in Washington, DC. The FSI is a report that is released annually and highlights current trends in social, economic and political pressures that affect all states in the international community.
Retired Gen. Michael Hayden, former Central Intelligence Agency and National Security Agency Director, speaks during the launch of the 2012 Failed States Index (FSI), on July 13, 2012 in Washington, DC. The FSI is a report that is released annually and highlights current trends in social, economic and political pressures that affect all states in the international community.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict102.jpg) New York Police Department Commissioner Ray Kelly (C) takes part in his morning intelligence briefing with the Deputy Commissioner for Counterterrorism, Richard Daddario (L), and Deputy Commissioner of Intelligence, David Cohen (R) inside of the Executive Command Center at NYPD headquarters in New York August 5, 2011. The NYPD has worked since 9/11 on a long-term project to permanently increase vigilance in Lower Manhattan and Midtown, home to prominent financial institutions and national landmarks. Picture taken August 5, 2011.
New York Police Department Commissioner Ray Kelly (C) takes part in his morning intelligence briefing with the Deputy Commissioner for Counterterrorism, Richard Daddario (L), and Deputy Commissioner of Intelligence, David Cohen (R) inside of the Executive Command Center at NYPD headquarters in New York August 5, 2011. The NYPD has worked since 9/11 on a long-term project to permanently increase vigilance in Lower Manhattan and Midtown, home to prominent financial institutions and national landmarks. Picture taken August 5, 2011.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict104.jpg) New York Police Department Commissioner Ray Kelly (R) takes part in his morning intelligence briefing with the Deputy Commissioner for Counterterrorism Richard Daddario (C) and Deputy Commissioner of Intelligence David Cohen (L) inside of the Executive Command Center at NYPD headquarters in New York August 5, 2011. The NYPD has worked since 9/11 on a long-term project to permanently increase vigilance in Lower Manhattan and Midtown, home to prominent financial institutions and national landmarks. Picture taken August 5, 2011.
New York Police Department Commissioner Ray Kelly (R) takes part in his morning intelligence briefing with the Deputy Commissioner for Counterterrorism Richard Daddario (C) and Deputy Commissioner of Intelligence David Cohen (L) inside of the Executive Command Center at NYPD headquarters in New York August 5, 2011. The NYPD has worked since 9/11 on a long-term project to permanently increase vigilance in Lower Manhattan and Midtown, home to prominent financial institutions and national landmarks. Picture taken August 5, 2011.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict105.jpg) New York Police Department Commissioner Ray Kelly (L) takes part in his morning intelligence briefing with the Deputy Commissioner of Public Information, Paul Browne, and Deputy Commissioner of Intelligence, David Cohen (R) inside of the Executive Command Center at NYPD headquarters in New York August 5, 2011. The NYPD has worked since 9/11 on a long-term project to permanently increase vigilance in Lower Manhattan and Midtown, home to prominent financial institutions and national landmarks. Picture taken August 5, 2011.
New York Police Department Commissioner Ray Kelly (L) takes part in his morning intelligence briefing with the Deputy Commissioner of Public Information, Paul Browne, and Deputy Commissioner of Intelligence, David Cohen (R) inside of the Executive Command Center at NYPD headquarters in New York August 5, 2011. The NYPD has worked since 9/11 on a long-term project to permanently increase vigilance in Lower Manhattan and Midtown, home to prominent financial institutions and national landmarks. Picture taken August 5, 2011.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict106.jpg) New York Police Department Commissioner Ray Kelly (C) takes part in his morning intelligence briefing with the Deputy Commissioner for Counter-terrorism Richard Daddario (R) and Deputy Commissioner of Intelligence David Cohen (L) inside the Executive Command Center at the NYPD headquarters in New York August 5, 2011. The NYPD has worked since 9/11 on a long-term project to permanently increase vigilance in Lower Manhattan and Midtown, home to prominent financial institutions and national landmarks. Picture taken August 5, 2011.
New York Police Department Commissioner Ray Kelly (C) takes part in his morning intelligence briefing with the Deputy Commissioner for Counter-terrorism Richard Daddario (R) and Deputy Commissioner of Intelligence David Cohen (L) inside the Executive Command Center at the NYPD headquarters in New York August 5, 2011. The NYPD has worked since 9/11 on a long-term project to permanently increase vigilance in Lower Manhattan and Midtown, home to prominent financial institutions and national landmarks. Picture taken August 5, 2011.














![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-07/pict106.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-07/pict103.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-07/pict104.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-07/pict105.jpg)




 Alle Pläne schon in der Tasche: Titelbild der Doktorarbeit
Alle Pläne schon in der Tasche: Titelbild der Doktorarbeit Ein Ferienhaus von Schalck-Golodkowski. Von mehr als 200 Tarnfirmen ließ sich gut leben.
Ein Ferienhaus von Schalck-Golodkowski. Von mehr als 200 Tarnfirmen ließ sich gut leben. Beschaffte das Geld für 5000 Tonnen Äpfel: Alexander Schalck-Golodkowski
Beschaffte das Geld für 5000 Tonnen Äpfel: Alexander Schalck-Golodkowski
 Der große Devisenbeschaffer endete vor dem Untersuchungsausschuss des Deutschen Bundestages
Der große Devisenbeschaffer endete vor dem Untersuchungsausschuss des Deutschen Bundestages
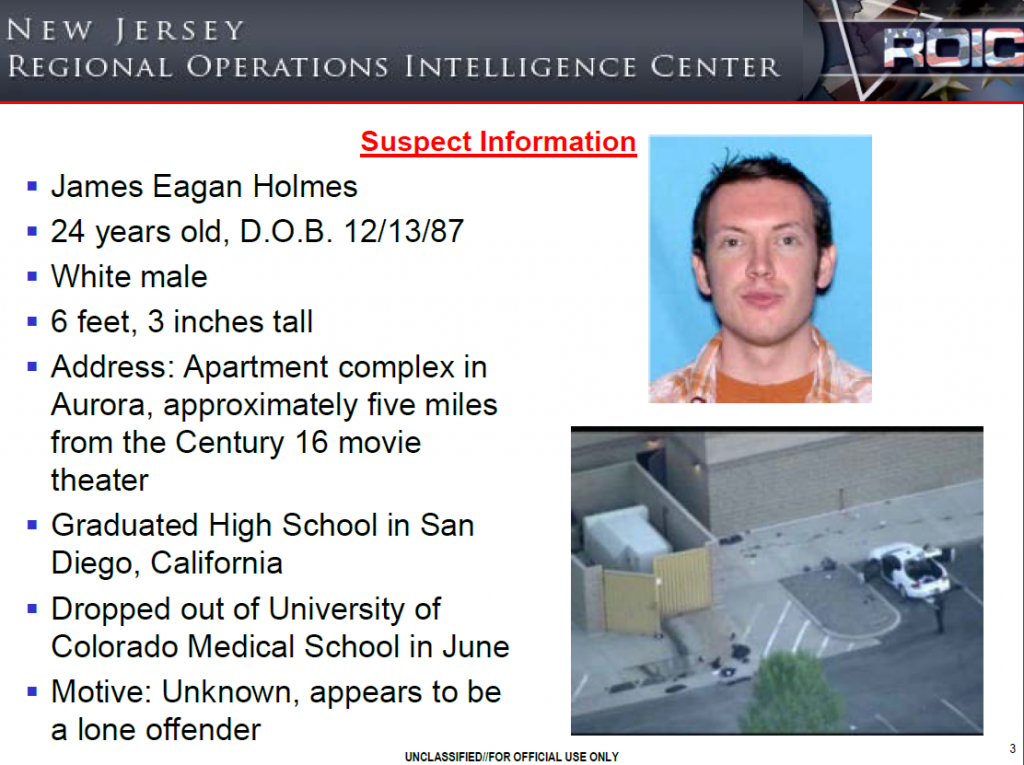




 Deep Throat, Berlin, berichtet: „Das Mastermind hinter allen „GoMoPa“-Aktionen ist der „Anlegerschutzanwalt“ Jochen Resch. Er hat auch Meridian Capital erpresst, schickt aber immer die Handlanger wie Klaus-Dieter Maurischat vor. Nur vorbestrafte Serienbetrüger wie Maurischat lassen sich zu solchen Straftaten instrumentalisieren. Resch hat auch den Terminus „Cyberstalker“ aus den USA importiert. Maurischat kann das aufgrund mangelnder Bildung sogar nicht einmal korrekt schreiben.“
Deep Throat, Berlin, berichtet: „Das Mastermind hinter allen „GoMoPa“-Aktionen ist der „Anlegerschutzanwalt“ Jochen Resch. Er hat auch Meridian Capital erpresst, schickt aber immer die Handlanger wie Klaus-Dieter Maurischat vor. Nur vorbestrafte Serienbetrüger wie Maurischat lassen sich zu solchen Straftaten instrumentalisieren. Resch hat auch den Terminus „Cyberstalker“ aus den USA importiert. Maurischat kann das aufgrund mangelnder Bildung sogar nicht einmal korrekt schreiben.“
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict99.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict82.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict83.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict92.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict87.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict84.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict85.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict86.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict88.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict91.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict89.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict90.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict98.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict93.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict96.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict97.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict94.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict101.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/ru-art31-protest/pict100.jpg)

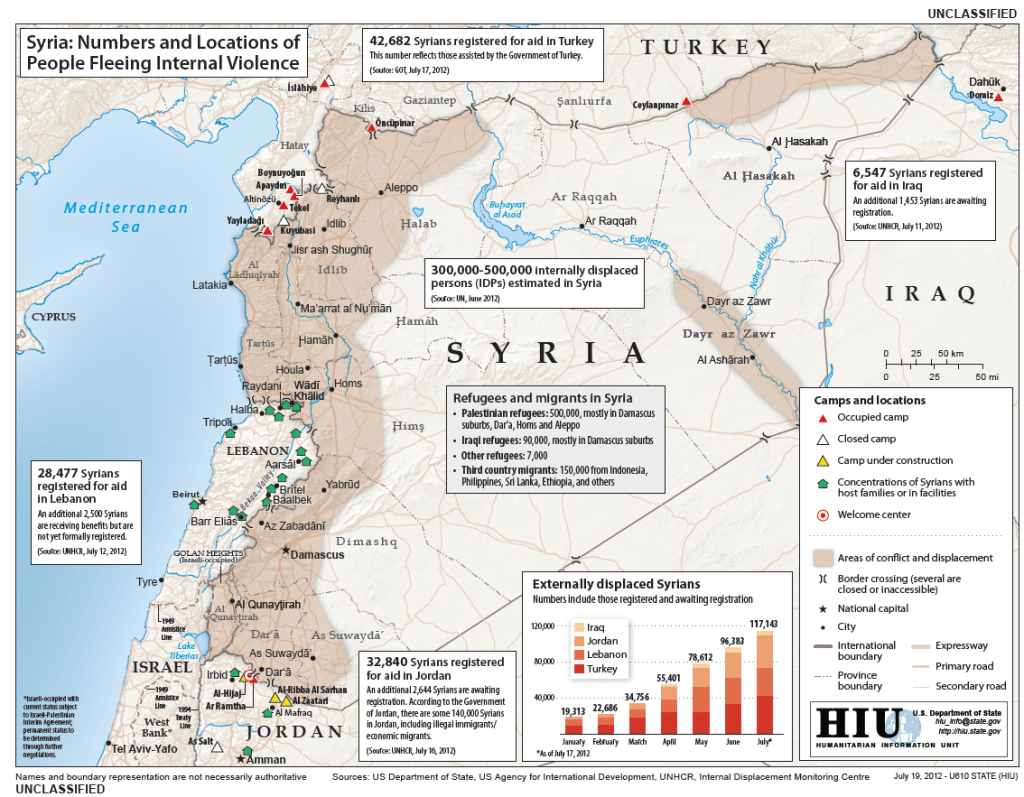



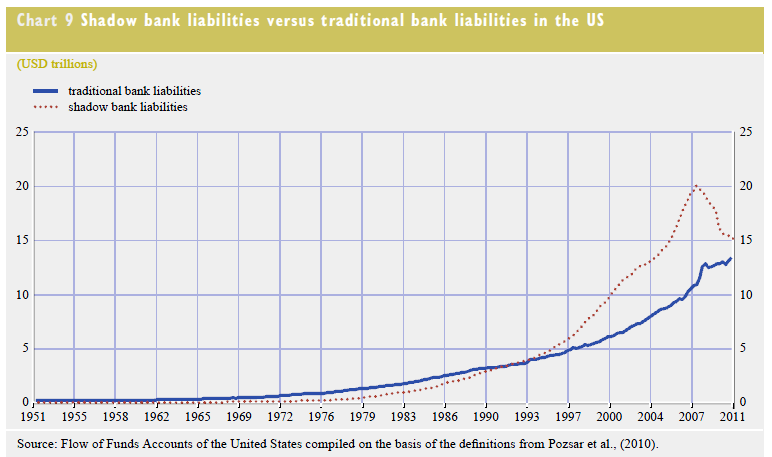


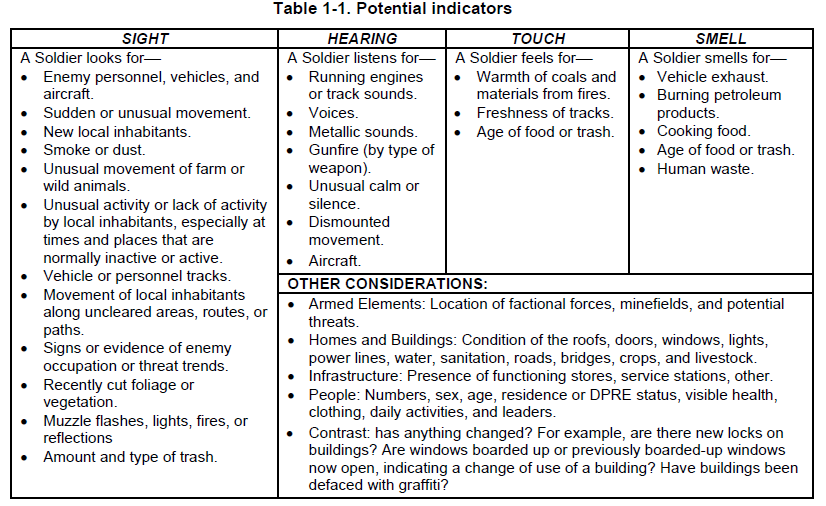
![[Image]](https://i0.wp.com/cryptome.org/2012-info/wh-obl-recycle/pict2.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/wh-obl-recycle/pict3.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/wh-obl-recycle/pict4.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/wh-obl-recycle/pict5.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/wh-obl-recycle/pict6.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/wh-obl-recycle/pict7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/wh-obl-recycle/pict8.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/wh-obl-recycle/pict9.jpg)




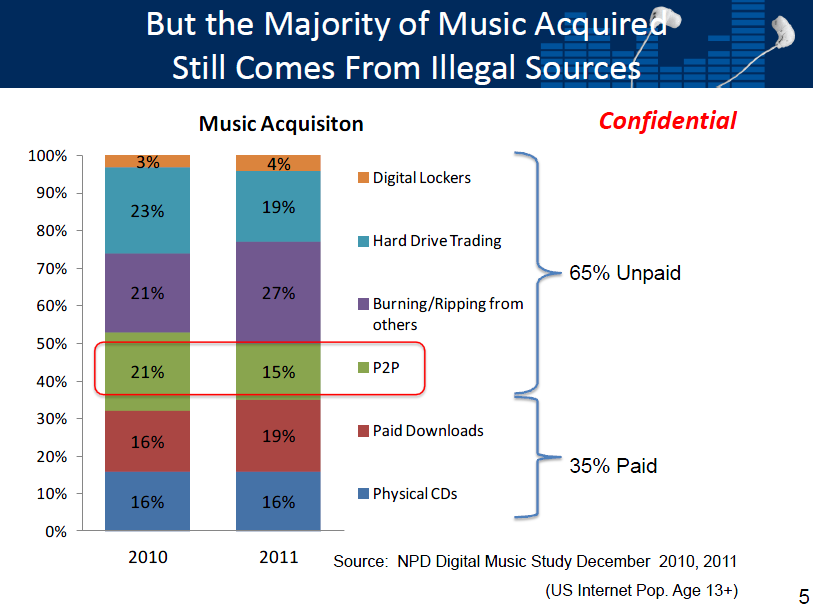





![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict26.jpg) A man wearing a mask of Spanish Prime Minister Mariano Rajoy protest during a demonstration organized by Unions on July 19, 2012 in Barcelona, against the government’s welfare cuts. In the latest measures to lower Spain’s deficit, conservative Prime Minister Mariano Rajoy announced 65 billion euros’ ($80 billion) worth of savings measures. Getty
A man wearing a mask of Spanish Prime Minister Mariano Rajoy protest during a demonstration organized by Unions on July 19, 2012 in Barcelona, against the government’s welfare cuts. In the latest measures to lower Spain’s deficit, conservative Prime Minister Mariano Rajoy announced 65 billion euros’ ($80 billion) worth of savings measures. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict46.jpg) A street performer dressed as an character from the science fiction film Avatar walks among the crowds near Mexico City’s main plaza, the Zocalo, Friday, July 13, 2012. Street performers, many dressed in costumes, gathered to protest in the historic downtown area where once they were allowed to perform but are now run off by police. AP
A street performer dressed as an character from the science fiction film Avatar walks among the crowds near Mexico City’s main plaza, the Zocalo, Friday, July 13, 2012. Street performers, many dressed in costumes, gathered to protest in the historic downtown area where once they were allowed to perform but are now run off by police. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict44.jpg) An anti-government demonstrator holds a molotov cocktail during clashes in the village of Sitra, south of Manama, Bahrain July 13, 2012. Dozens of demonstrators marched in an attempt to protest under the slogan ”Challenge Friday”, challenging the authorities after the government banned the protest. On Thursday, the Ministry of Interior issued a statement saying that the ministry is looking into venues where protests can be held. Reuters
An anti-government demonstrator holds a molotov cocktail during clashes in the village of Sitra, south of Manama, Bahrain July 13, 2012. Dozens of demonstrators marched in an attempt to protest under the slogan ”Challenge Friday”, challenging the authorities after the government banned the protest. On Thursday, the Ministry of Interior issued a statement saying that the ministry is looking into venues where protests can be held. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict51.jpg) An animal rights activist wearing an elephant-shaped headpiece arrives holding a placard for a protest in front of the Staples Center in Los Angeles, on July 11, 2012 in California, on the opening day of the Ringling Bros. and Barnum & Bailey Circus. Representatives of PETA, Animal Defenders International, In Defense of Animals, Last Chance for Animals, and the Animal Protection and Rescue League participated with a message for prospective circusgoers: Don’t go. Getty
An animal rights activist wearing an elephant-shaped headpiece arrives holding a placard for a protest in front of the Staples Center in Los Angeles, on July 11, 2012 in California, on the opening day of the Ringling Bros. and Barnum & Bailey Circus. Representatives of PETA, Animal Defenders International, In Defense of Animals, Last Chance for Animals, and the Animal Protection and Rescue League participated with a message for prospective circusgoers: Don’t go. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict40.jpg) A member of the Sikh community takes part in a protest against the Pakistani government in New Delhi on July 15, 2012. Sikh protesters demanded the immediate release of Indian national Sarabjit Singh who is currently held in a Pakistani prison. Sarabjit Singh is a high-profile prisoner who has spent two decades in solitary confinement on death row in Lahore after being convicted for his role in a string of bombings. Getty
A member of the Sikh community takes part in a protest against the Pakistani government in New Delhi on July 15, 2012. Sikh protesters demanded the immediate release of Indian national Sarabjit Singh who is currently held in a Pakistani prison. Sarabjit Singh is a high-profile prisoner who has spent two decades in solitary confinement on death row in Lahore after being convicted for his role in a string of bombings. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict42.jpg) An Israeli protester wearing a Guy Fawkes mask and Pharaoh headpiece chains his hand as he holds a slogan which reads in Hebrew ‘The justice is like Pharaoh’ during a demonstration in the Mediterranean coastal city of Tel Aviv on July 14, 2012 to mark the first anniversary of last summer’s social justice demonstrations that swept the country to protest the spiralling cost of living. Getty
An Israeli protester wearing a Guy Fawkes mask and Pharaoh headpiece chains his hand as he holds a slogan which reads in Hebrew ‘The justice is like Pharaoh’ during a demonstration in the Mediterranean coastal city of Tel Aviv on July 14, 2012 to mark the first anniversary of last summer’s social justice demonstrations that swept the country to protest the spiralling cost of living. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict11.jpg) Demonstrators march against student tuition hikes and Bill 78 in downtown Montreal, Quebec July 22, 2012. The mass demonstration, which is quickly becoming a monthly protest in Montreal since it started around six months ago, has drawn tens of thousands of people to protest in the city. Reuters
Demonstrators march against student tuition hikes and Bill 78 in downtown Montreal, Quebec July 22, 2012. The mass demonstration, which is quickly becoming a monthly protest in Montreal since it started around six months ago, has drawn tens of thousands of people to protest in the city. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict13.jpg) A woman wears an old police helmet during a protest by firefighters and police officers against government austerity measures in Valencia July 23, 2012. Reuters
A woman wears an old police helmet during a protest by firefighters and police officers against government austerity measures in Valencia July 23, 2012. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict12.jpg) A member of the movement ‘YoSoy#132’ takes part in a protest against the election results at Reforma avenue, in Mexico City, on July 22, 2012. The movement is protesting against Enrique Pena Nieto, candidate of the Institutional Revolutionary Party (PRI), who declared victory in the presidential election, after the first official results showed him with 38 percent of the vote. The candidate for the leftist coalition Progressive Movement of Mexico, Andres Manuel Lopez Obrador, the winner’s nearest rival, refused to concede the race to Pena Nieto until the official final results be released, claiming to have data showing different results. Getty
A member of the movement ‘YoSoy#132’ takes part in a protest against the election results at Reforma avenue, in Mexico City, on July 22, 2012. The movement is protesting against Enrique Pena Nieto, candidate of the Institutional Revolutionary Party (PRI), who declared victory in the presidential election, after the first official results showed him with 38 percent of the vote. The candidate for the leftist coalition Progressive Movement of Mexico, Andres Manuel Lopez Obrador, the winner’s nearest rival, refused to concede the race to Pena Nieto until the official final results be released, claiming to have data showing different results. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict14.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict15.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict16.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict17.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict18.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict19.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict20.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict22.jpg) Juan Antonio Torres, 42, a social worker and member of the Comisiones Obreras (CCOO), lies in a coffin while wearing a mask of Spain’s Prime Minister Mariano Rajoy during a protest march against austerity measures in Malaga, southern Spain, July 19, 2012. Hundreds of thousands of Spaniards marched against the centre-right government’s latest austerity measures on Thursday evening, following more than a week of demonstrations across the country. Reuters
Juan Antonio Torres, 42, a social worker and member of the Comisiones Obreras (CCOO), lies in a coffin while wearing a mask of Spain’s Prime Minister Mariano Rajoy during a protest march against austerity measures in Malaga, southern Spain, July 19, 2012. Hundreds of thousands of Spaniards marched against the centre-right government’s latest austerity measures on Thursday evening, following more than a week of demonstrations across the country. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict23.jpg) Firemen shouts slogans as they march during a protest against government austerity measures in Madrid July 19, 2012. A protest movement against the centre-right Spanish government’s latest austerity measures swelled on Thursday as public sector workers stepped up demonstrations in Madrid and around the country after more than a week of spontaneous action. The placard reads, “Our cut will be with a guillotine”. Reuters
Firemen shouts slogans as they march during a protest against government austerity measures in Madrid July 19, 2012. A protest movement against the centre-right Spanish government’s latest austerity measures swelled on Thursday as public sector workers stepped up demonstrations in Madrid and around the country after more than a week of spontaneous action. The placard reads, “Our cut will be with a guillotine”. Reuters
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict25.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict24.jpg) A demonstrator dresses as an skeleton during a protest against government austerity measures in Madrid July 19, 2012. A protest movement against the centre-right Spanish government’s latest austerity measures swelled on Thursday as public sector workers stepped up demonstrations in Madrid and around the country after more than a week of spontaneous action. The placard reads, “Market, money management thieves”. Reuters
A demonstrator dresses as an skeleton during a protest against government austerity measures in Madrid July 19, 2012. A protest movement against the centre-right Spanish government’s latest austerity measures swelled on Thursday as public sector workers stepped up demonstrations in Madrid and around the country after more than a week of spontaneous action. The placard reads, “Market, money management thieves”. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict27.jpg) A woman performs during a protest against the health care system in Bogota, Colombia, on July 19, 2012, requiring the dismantling of the Health Promotion Companies (EPS). Colombian President Juan Manuel Santos announced Thursday a package of drastic measures to save the health sector, threatened with bankruptcy because of debts incurred by the EPS. Getty
A woman performs during a protest against the health care system in Bogota, Colombia, on July 19, 2012, requiring the dismantling of the Health Promotion Companies (EPS). Colombian President Juan Manuel Santos announced Thursday a package of drastic measures to save the health sector, threatened with bankruptcy because of debts incurred by the EPS. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict28.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict29.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict31.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict30.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict32.jpg) A woman carries a gallows rope with the pictures Yahya Mohammed Abdullah Saleh (R), nephew of former Yemeni President Ali Abdullah Saleh, and Saleh’s son Ahmed Ali Abdullah Saleh, during a protest outside the home of Yemeni President Abd-Rabbu Mansour Hadi, to demand the dismissal of the rest of the Saleh’s family members, in Sanaa July 19, 2012. Reuters
A woman carries a gallows rope with the pictures Yahya Mohammed Abdullah Saleh (R), nephew of former Yemeni President Ali Abdullah Saleh, and Saleh’s son Ahmed Ali Abdullah Saleh, during a protest outside the home of Yemeni President Abd-Rabbu Mansour Hadi, to demand the dismissal of the rest of the Saleh’s family members, in Sanaa July 19, 2012. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict33.jpg) Hungarian rescue workers remove Greenpeace activists from the roof of a local petrol station in Budapest on July 19, 2012, during an action of Greenpeace’s Hungarian and foreign activists to protest against the Shell Oil Company’s plans to drill in the Arctic. Getty
Hungarian rescue workers remove Greenpeace activists from the roof of a local petrol station in Budapest on July 19, 2012, during an action of Greenpeace’s Hungarian and foreign activists to protest against the Shell Oil Company’s plans to drill in the Arctic. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict35.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict36.jpg) A Filipino woman protester gives vegetables to an activist wearing a mask of Uncle Sam while another with a mask of Philippine President Benigno Aquino III joins a symbolic protest outside the gates of the Malacanang Presidential Palace in Manila, Philippines on Tuesday, July 17, 2012. The protest aims to symbolize President Aquino and the U.S. of depriving and cheating Filipinos. AP
A Filipino woman protester gives vegetables to an activist wearing a mask of Uncle Sam while another with a mask of Philippine President Benigno Aquino III joins a symbolic protest outside the gates of the Malacanang Presidential Palace in Manila, Philippines on Tuesday, July 17, 2012. The protest aims to symbolize President Aquino and the U.S. of depriving and cheating Filipinos. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict37.jpg) Firefighters and other government employees take part in a demonstration against the Spanish government’s latest austerity measures, in front of the Spanish Parliament (Las Cortes) in Madrid, on July 16, 2012. Several hundreds government workers, including police officers, firefighters, and healthcare workers, joined the spontaneous protest after conservative Prime Minister Mariano Rajoy announced, on July 13, the latest measures to lower Spain’s deficit, a 65-billion-euro (80 billion USD) austerity package involving among other things an increase in the VAT (TVA) tax and cuts in unemployment benefits. Getty
Firefighters and other government employees take part in a demonstration against the Spanish government’s latest austerity measures, in front of the Spanish Parliament (Las Cortes) in Madrid, on July 16, 2012. Several hundreds government workers, including police officers, firefighters, and healthcare workers, joined the spontaneous protest after conservative Prime Minister Mariano Rajoy announced, on July 13, the latest measures to lower Spain’s deficit, a 65-billion-euro (80 billion USD) austerity package involving among other things an increase in the VAT (TVA) tax and cuts in unemployment benefits. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict38.jpg) A demonstrator holds up a sign during a protest in Tel Aviv July 15, 2012, against the economic policies of Israel’s conservative government and to show solidarity with Moshe Silman, who sustained serious burns after he poured flammable liquid on himself and lit it at another protest on Saturday. The sign reads in Hebrew “Bibi you burned me too”, referring to Israel’s Prime Minister Benjamin Netanyahu by his nickname. Reuters
A demonstrator holds up a sign during a protest in Tel Aviv July 15, 2012, against the economic policies of Israel’s conservative government and to show solidarity with Moshe Silman, who sustained serious burns after he poured flammable liquid on himself and lit it at another protest on Saturday. The sign reads in Hebrew “Bibi you burned me too”, referring to Israel’s Prime Minister Benjamin Netanyahu by his nickname. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict39.jpg) Israelis block a highway as they march through the streets to protest rising housing costs on July 15, 2012 in Tel Aviv, Israel. Growing discontent among Israelis over housing prices and other social inequalities have spurred marches, boycotts and labor strikes in the Jewish state. An Israeli man set himself on fire during the march for social justice protest yesterday. Getty
Israelis block a highway as they march through the streets to protest rising housing costs on July 15, 2012 in Tel Aviv, Israel. Growing discontent among Israelis over housing prices and other social inequalities have spurred marches, boycotts and labor strikes in the Jewish state. An Israeli man set himself on fire during the march for social justice protest yesterday. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict41.jpg) In this Sunday, July 15, 2012 photo, Lebanese women sit at a protest camp set up by Sheik Ahmad Assir, a harline Sunni cleric, in the southern port city of Sidon, Lebanon. Assir has set up the camp in the middle of a key road in Sidon, declaring it an uprising against Hezbollah’s weapons. Assir is taking aim at Hezbollah at a vulnerable time for the group when it faces the possible downfall of its crucial ally, President Bashar Assad in Syria. Assir may not be a direct threat to Hezbollah, but the willingness to publicly confront it underlines the dangers the group faces as it tries to retain the power and influence it has built up over the past 30 years in the face of the Syria crisis. AP
In this Sunday, July 15, 2012 photo, Lebanese women sit at a protest camp set up by Sheik Ahmad Assir, a harline Sunni cleric, in the southern port city of Sidon, Lebanon. Assir has set up the camp in the middle of a key road in Sidon, declaring it an uprising against Hezbollah’s weapons. Assir is taking aim at Hezbollah at a vulnerable time for the group when it faces the possible downfall of its crucial ally, President Bashar Assad in Syria. Assir may not be a direct threat to Hezbollah, but the willingness to publicly confront it underlines the dangers the group faces as it tries to retain the power and influence it has built up over the past 30 years in the face of the Syria crisis. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict43.jpg) A protester stands in front of Malaysia Islamic Party flag (PAS) during a protest march to the National Palace to to hand out a memorandum in protest of the listing of Malaysia’s Felda Global in Kuala Lumpur, Malaysia, Saturday, July 14, 2012. The Malaysian palm oil firm Felda Global surged 20 percent in its trading debut on June 28, as investors cheered on the world’s second largest Initial Public Offering (IPO) after Facebook. Felda’s listing plans were initially met with resistance from the farmers who partly owned the firm and feared the loss of control of an asset they had invested in for generations. AP
A protester stands in front of Malaysia Islamic Party flag (PAS) during a protest march to the National Palace to to hand out a memorandum in protest of the listing of Malaysia’s Felda Global in Kuala Lumpur, Malaysia, Saturday, July 14, 2012. The Malaysian palm oil firm Felda Global surged 20 percent in its trading debut on June 28, as investors cheered on the world’s second largest Initial Public Offering (IPO) after Facebook. Felda’s listing plans were initially met with resistance from the farmers who partly owned the firm and feared the loss of control of an asset they had invested in for generations. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict45.jpg) A street performer dressed as a Minotaur walks among the crowds near Mexico City’s main plaza, the Zocalo, Friday, July 13, 2012. Street performers, many dressed in costumes, gathered to protest in the historic downtown area where once they were allowed to perform but are now run off by police. AP
A street performer dressed as a Minotaur walks among the crowds near Mexico City’s main plaza, the Zocalo, Friday, July 13, 2012. Street performers, many dressed in costumes, gathered to protest in the historic downtown area where once they were allowed to perform but are now run off by police. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/masque-protests/pict47.jpg) A worker in a mask marches holding a sign which reads, “No to Conga, no to mine,” in solidarity with the anti-mining protest in Cajamarca, Lima July 12, 2012. More than 1,000 members of the General Confederation of Workers of Peru (CGTP), who marched in solidarity with the anti-mining protest, also protested against Peru’s President Ollanta Humala’s government and demanded better pay conditions. The Cajamarca region is still under state of emergency a week after five people died and 21 were injured in clashes between police and protesters against Newmont’s $5 billion gold mine project, known as Conga. Reuters
A worker in a mask marches holding a sign which reads, “No to Conga, no to mine,” in solidarity with the anti-mining protest in Cajamarca, Lima July 12, 2012. More than 1,000 members of the General Confederation of Workers of Peru (CGTP), who marched in solidarity with the anti-mining protest, also protested against Peru’s President Ollanta Humala’s government and demanded better pay conditions. The Cajamarca region is still under state of emergency a week after five people died and 21 were injured in clashes between police and protesters against Newmont’s $5 billion gold mine project, known as Conga. Reuters
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-02-05/pict10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-02-05/pict5.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-02-05/pict2.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-02-05/pict3.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-02-05/pict9.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-02-05/pict4.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-02-05/pict6.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-02-05/pict7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-02-05/pict8.jpg)










![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict41.jpg) U.S. President Barack Obama greets people gathered on the sidewalk after stopping for food at Skyline Chili in Cincinnati, July 16, 2012. Obama flew on Monday to Cincinnati for election campaign events. Reuters
U.S. President Barack Obama greets people gathered on the sidewalk after stopping for food at Skyline Chili in Cincinnati, July 16, 2012. Obama flew on Monday to Cincinnati for election campaign events. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict39.jpg) US President Barack Obama greets wellwishers upon arrival on Air Force One at Cincinnati Northern Kentucky International Airport in Boone, Kentucky, July 16, 2012, enroute to attend campaign events in Cincinnati, Ohio. Getty
US President Barack Obama greets wellwishers upon arrival on Air Force One at Cincinnati Northern Kentucky International Airport in Boone, Kentucky, July 16, 2012, enroute to attend campaign events in Cincinnati, Ohio. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict38.jpg) President Barack Obama passes his jacket to White House Trip Director Marvin Nicholson before heading over to greet people after arriving at Northern Kentucky International Airport in Boone, Ky. , Monday, July 16, 2012. Obama is spending the day campaigning in Cincinnati. AP
President Barack Obama passes his jacket to White House Trip Director Marvin Nicholson before heading over to greet people after arriving at Northern Kentucky International Airport in Boone, Ky. , Monday, July 16, 2012. Obama is spending the day campaigning in Cincinnati. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict40.jpg) U.S. Secret Service members use a golf cart while providing protection for President Barack Obama while he golfs at the Army installation’s course July 15, 2012 in Ft. Belvoir, Virginia. Obama also campaigned in Virginia, a state he won in 2008, on Saturday, holding events in Fairfax and Glen Allen. Getty
U.S. Secret Service members use a golf cart while providing protection for President Barack Obama while he golfs at the Army installation’s course July 15, 2012 in Ft. Belvoir, Virginia. Obama also campaigned in Virginia, a state he won in 2008, on Saturday, holding events in Fairfax and Glen Allen. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict31.jpg) US President Barack Obama greets supporters are he arrives at a campaign event on July 14, 2012 at Centreville High School in Clifton, Virginia. Getty
US President Barack Obama greets supporters are he arrives at a campaign event on July 14, 2012 at Centreville High School in Clifton, Virginia. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict32.jpg) U.S. President Barack Obama arrives at a campaign rally at Centreville High School in Clifton, Virginia, July 14, 2012. Obama travelled to Virginia on Saturday for campaign events. Reuters
U.S. President Barack Obama arrives at a campaign rally at Centreville High School in Clifton, Virginia, July 14, 2012. Obama travelled to Virginia on Saturday for campaign events. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict28.jpg) President Barack Obama walks up a set of stairs during a campaign rally at Centreville High School in Clifton, Va. , a Washington suburb, on Saturday, July 14, 2012. AP
President Barack Obama walks up a set of stairs during a campaign rally at Centreville High School in Clifton, Va. , a Washington suburb, on Saturday, July 14, 2012. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict35.jpg) People hold signs protesting against U.S. President Barack Obama along Obama’s motorcade route on his way to a campaign rally at Centreville High School in Clifton, Virginia, July 14, 2012. Obama travelled to Virginia on Saturday for campaign events. Reuters
People hold signs protesting against U.S. President Barack Obama along Obama’s motorcade route on his way to a campaign rally at Centreville High School in Clifton, Virginia, July 14, 2012. Obama travelled to Virginia on Saturday for campaign events. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict30.jpg) President Barack Obama laughs while campaigning under the pouring rain at the historic Walkerton Tavern & Gardens in Glen Allen, Va. , near Richmond Saturday, July 14, 2012. It is in the Congressional district represented by House Majority Leader Eric Cantor, R-Va. , a key county in a crucial swing state of the presidential election. AP
President Barack Obama laughs while campaigning under the pouring rain at the historic Walkerton Tavern & Gardens in Glen Allen, Va. , near Richmond Saturday, July 14, 2012. It is in the Congressional district represented by House Majority Leader Eric Cantor, R-Va. , a key county in a crucial swing state of the presidential election. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict26.jpg) U.S. President Barack Obama greets supporters at the end of his ”A Vision for Virginia’s Middle Class” campaign event July 14, 2012 at Walkerton Tavern in Glen Allen, Virginia. On the last day of his two-day campaign across Virginia, Obama continue to discuss his plan to restore middle class security and urged Congress to act on extending tax cuts to middle class families. Getty
U.S. President Barack Obama greets supporters at the end of his ”A Vision for Virginia’s Middle Class” campaign event July 14, 2012 at Walkerton Tavern in Glen Allen, Virginia. On the last day of his two-day campaign across Virginia, Obama continue to discuss his plan to restore middle class security and urged Congress to act on extending tax cuts to middle class families. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict27.jpg) President Barack Obama campaigns during the pouring rain at the historic Walkerton Tavern & Gardens in Glen Allen, Va. , near Richmond, Saturday, July 14, 2012. AP
President Barack Obama campaigns during the pouring rain at the historic Walkerton Tavern & Gardens in Glen Allen, Va. , near Richmond, Saturday, July 14, 2012. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict37.jpg) Protesters line an entrance route to a campaign event where President Barack Obama is scheduled to speak at the historic Walkerton Tavern & Gardens in Glen Allen, Va. , near Richmond Saturday, July 14, 2012. AP
Protesters line an entrance route to a campaign event where President Barack Obama is scheduled to speak at the historic Walkerton Tavern & Gardens in Glen Allen, Va. , near Richmond Saturday, July 14, 2012. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict36.jpg) Conservative local residents protest prior to U.S. President Barack Obama’s ”A Vision for Virginia’s Middle Class” campaign event July 14, 2012 at Walkerton Tavern in Glen Allen, Virginia. On the last day of his two-day campaign across Virginia, Obama continue to discuss his plan to restore middle class security and urged the Congress to act on extending tax cuts to middle class families. Getty
Conservative local residents protest prior to U.S. President Barack Obama’s ”A Vision for Virginia’s Middle Class” campaign event July 14, 2012 at Walkerton Tavern in Glen Allen, Virginia. On the last day of his two-day campaign across Virginia, Obama continue to discuss his plan to restore middle class security and urged the Congress to act on extending tax cuts to middle class families. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict29.jpg) President Barack Obama removes his jacket upon his arrival at Washington Dulles International Airport in Chantilly, Va. , Saturday, July 14, 2012, for a campaign event in the vicinity. AP
President Barack Obama removes his jacket upon his arrival at Washington Dulles International Airport in Chantilly, Va. , Saturday, July 14, 2012, for a campaign event in the vicinity. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict25.jpg) US President Barack Obama boards his limousine after greeting well-wishers upon arrival July 14, 2012 at Richmond International Airport in Richmond, Virginia. Obama is in Virginia to attend campaign events. Getty
US President Barack Obama boards his limousine after greeting well-wishers upon arrival July 14, 2012 at Richmond International Airport in Richmond, Virginia. Obama is in Virginia to attend campaign events. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict33.jpg) Secret Service members keep watch in front of Air Force One shortly before US President Barack Obama’s departure on July 14, 2012 at Richmond International Airport in Richmond, Virginia. Obama is in Virginia to attend campaign events. Getty
Secret Service members keep watch in front of Air Force One shortly before US President Barack Obama’s departure on July 14, 2012 at Richmond International Airport in Richmond, Virginia. Obama is in Virginia to attend campaign events. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict1.jpg) US President Barack Obama hold up a tomato during a stop at Berry’s Produce on July 14, 2012 in Mechanicsville, Virginia. Obama is campaigning in Virginia ahead of the November presidential election. Getty
US President Barack Obama hold up a tomato during a stop at Berry’s Produce on July 14, 2012 in Mechanicsville, Virginia. Obama is campaigning in Virginia ahead of the November presidential election. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict0.jpg) President Barack Obama shakes hands as he arrives at the Richmond International Airport in Richmond, Va. , Saturday, July 14, 2012. AP
President Barack Obama shakes hands as he arrives at the Richmond International Airport in Richmond, Va. , Saturday, July 14, 2012. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict14.jpg) President Barack Obama greets the crowd after a campaign stop at the historic Fire Station No.1, in downtown Roanoke, Virginia, Friday, July 13, 2012. Obama traveled to southwest Virginia to discuss choice in this election between two fundamentally different visions on how to grow the economy, create middle-class jobs and pay down the debt. AP
President Barack Obama greets the crowd after a campaign stop at the historic Fire Station No.1, in downtown Roanoke, Virginia, Friday, July 13, 2012. Obama traveled to southwest Virginia to discuss choice in this election between two fundamentally different visions on how to grow the economy, create middle-class jobs and pay down the debt. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict15.jpg) President Barack Obama greets the crowd during a campaign stop at the historic Fire Station No.1, in downtown Roanoke, Va. , Friday, July 13, 2012. Obama traveled to southwest Virginia to discuss choice in this election between two fundamentally different visions on how to grow the economy, create middle-class jobs and pay down the debt. AP
President Barack Obama greets the crowd during a campaign stop at the historic Fire Station No.1, in downtown Roanoke, Va. , Friday, July 13, 2012. Obama traveled to southwest Virginia to discuss choice in this election between two fundamentally different visions on how to grow the economy, create middle-class jobs and pay down the debt. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict16.jpg) President Barack Obama greets people after arriving at Roanoke Regional Airport in Roanoke, Va. , Friday, July 13, 2012. Obama is spending the day campaigning in Virginia. AP
President Barack Obama greets people after arriving at Roanoke Regional Airport in Roanoke, Va. , Friday, July 13, 2012. Obama is spending the day campaigning in Virginia. AP
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict20.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict18.jpg) President Barack Obama greets people after arriving at Roanoke Regional Airport in Roanoke, Va. , Friday, July 13, 2012. Obama is spending the day campaigning in Virginia. AP
President Barack Obama greets people after arriving at Roanoke Regional Airport in Roanoke, Va. , Friday, July 13, 2012. Obama is spending the day campaigning in Virginia. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict19.jpg) President Barack Obama arrives at the Roanoke Airport on Air Force One on the campaign trail, Friday, July 13, 2012 in Roanoke, Va. AP
President Barack Obama arrives at the Roanoke Airport on Air Force One on the campaign trail, Friday, July 13, 2012 in Roanoke, Va. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict17.jpg) President Barack Obama greets people after arriving at Roanoke Regional Airport in Roanoke, Va. , Friday, July 13, 2012. Obama is spending the day campaigning in Virginia. AP
President Barack Obama greets people after arriving at Roanoke Regional Airport in Roanoke, Va. , Friday, July 13, 2012. Obama is spending the day campaigning in Virginia. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict22.jpg) President Barack Obama greets the crowd after speaking at a campaign event at Phoebus High School in Hampton, Va. , Friday, July 13, 2012. Obama is spending the day in Virginia campaigning. AP
President Barack Obama greets the crowd after speaking at a campaign event at Phoebus High School in Hampton, Va. , Friday, July 13, 2012. Obama is spending the day in Virginia campaigning. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict21.jpg) President Barack Obama greets the crowd after speaking at a campaign event at Phoebus High School in Hampton, Va. , Friday, July 13, 2012. Obama is spending the day in Virginia campaigning. AP
President Barack Obama greets the crowd after speaking at a campaign event at Phoebus High School in Hampton, Va. , Friday, July 13, 2012. Obama is spending the day in Virginia campaigning. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict24.jpg) President Barack Obama arrives to speak at a campaign event at Phoebus High School in Hampton, Va. , Friday, July 13, 2012. Obama is spending the day in Virginia campaigning. AP
President Barack Obama arrives to speak at a campaign event at Phoebus High School in Hampton, Va. , Friday, July 13, 2012. Obama is spending the day in Virginia campaigning. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict12.jpg) U.S. President Barack Obama (C) greets supporters at the end of his ‘A Vision for Virginia’s Middle Class’ campaign event July 13, 2012 at Green Run High School in Virginia Beach, Virginia. Obama discussed his plan to restore middle class security and urged the Congress to act on extending tax cuts to middle class families. Getty
U.S. President Barack Obama (C) greets supporters at the end of his ‘A Vision for Virginia’s Middle Class’ campaign event July 13, 2012 at Green Run High School in Virginia Beach, Virginia. Obama discussed his plan to restore middle class security and urged the Congress to act on extending tax cuts to middle class families. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict13.jpg) U.S. President Barack Obama (R) greets supporters at the end of his ‘A Vision for Virginia’s Middle Class’ campaign event July 13, 2012 at Green Run High School in Virginia Beach, Virginia. Obama discussed his plan to restore middle class security and urged the Congress to act on extending tax cuts to middle class families. Getty [Two Secret Service in “hands ready” position.
U.S. President Barack Obama (R) greets supporters at the end of his ‘A Vision for Virginia’s Middle Class’ campaign event July 13, 2012 at Green Run High School in Virginia Beach, Virginia. Obama discussed his plan to restore middle class security and urged the Congress to act on extending tax cuts to middle class families. Getty [Two Secret Service in “hands ready” position.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict2.jpg) President Barack Obama reaches out to shake hands at a campaign event at Green Run High School in Virginia Beach, Va. , Friday, July 13, 2012. Obama is spending the day in Virginia campaigning. AP
President Barack Obama reaches out to shake hands at a campaign event at Green Run High School in Virginia Beach, Va. , Friday, July 13, 2012. Obama is spending the day in Virginia campaigning. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict3.jpg) President Barack Obama heads to his car after greeting people after arriving at Norfolk International Airport in Norfolk, Va. , Friday, July 13, 2012. AP
President Barack Obama heads to his car after greeting people after arriving at Norfolk International Airport in Norfolk, Va. , Friday, July 13, 2012. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict4.jpg) President Barack Obama is surrounded by secret service as he greets people after arriving at Norfolk International Airport in Norfolk, Va. , Friday, July 13, 2012. AP
President Barack Obama is surrounded by secret service as he greets people after arriving at Norfolk International Airport in Norfolk, Va. , Friday, July 13, 2012. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict6.jpg) President Barack Obama heads to his car after greeting people after arriving at Norfolk International Airport in Norfolk, Va. , Friday, July 13, 2012. AP
President Barack Obama heads to his car after greeting people after arriving at Norfolk International Airport in Norfolk, Va. , Friday, July 13, 2012. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict5.jpg) President Barack Obama meets with supporters after arriving aboard Air Force One at the Norfolk International Airport in Norfolk, Va. , Friday, July 13, 2012. AP
President Barack Obama meets with supporters after arriving aboard Air Force One at the Norfolk International Airport in Norfolk, Va. , Friday, July 13, 2012. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict7.jpg) President Barack Obama meets with supporters after arriving aboard Air Force One at the Norfolk International Airport in Norfolk, Va. , Friday, July 13, 2012. AP
President Barack Obama meets with supporters after arriving aboard Air Force One at the Norfolk International Airport in Norfolk, Va. , Friday, July 13, 2012. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict8.jpg) President Barack Obama walks to Air Force One at Andrews Air Force Base in Md. , Friday, July 13, 2012, enroute to Virginia for a series of campaign events. AP
President Barack Obama walks to Air Force One at Andrews Air Force Base in Md. , Friday, July 13, 2012, enroute to Virginia for a series of campaign events. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict9.jpg) Members of the media exit a house alongside US President Barack Obama’s SUV holding in the driveway as Obama meets with Jason McLaughlin, principal of Center Point-Urbana High School, his wife, Ali, an account manager for a document scanning company, and their 4-year-old son Cooper, on middle class tax cuts at their home in Cedar Rapids, Iowa, July 10, 2012. Getty
Members of the media exit a house alongside US President Barack Obama’s SUV holding in the driveway as Obama meets with Jason McLaughlin, principal of Center Point-Urbana High School, his wife, Ali, an account manager for a document scanning company, and their 4-year-old son Cooper, on middle class tax cuts at their home in Cedar Rapids, Iowa, July 10, 2012. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict34.jpg) Secret Service agents guard the door of the home of Jason and Ali McLaughlin while President Barack Obama visits with them in Cedar Rapids, Iowa, Tuesday, July 10, 2012. AP
Secret Service agents guard the door of the home of Jason and Ali McLaughlin while President Barack Obama visits with them in Cedar Rapids, Iowa, Tuesday, July 10, 2012. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict10.jpg) U.S. President Barack Obama arrives in Cedar Rapids, Iowa, July 10, 2012. Obama flew to Iowa for an event pushing for the extension of Bush-era tax cuts due to expire at the end of 2012. Reuters
U.S. President Barack Obama arrives in Cedar Rapids, Iowa, July 10, 2012. Obama flew to Iowa for an event pushing for the extension of Bush-era tax cuts due to expire at the end of 2012. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict11.jpg) President Barack Obama heads to his car after getting ice cream at Deb’s Ice Cream & Deli in Cedar Rapids, Iowa, Tuesday, July 10, 2012. AP
President Barack Obama heads to his car after getting ice cream at Deb’s Ice Cream & Deli in Cedar Rapids, Iowa, Tuesday, July 10, 2012. AP






![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0711/pict8.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0711/pict0.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0711/pict1.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0711/pict2.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0711/pict3.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0711/pict6.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-0711/pict5.jpg)





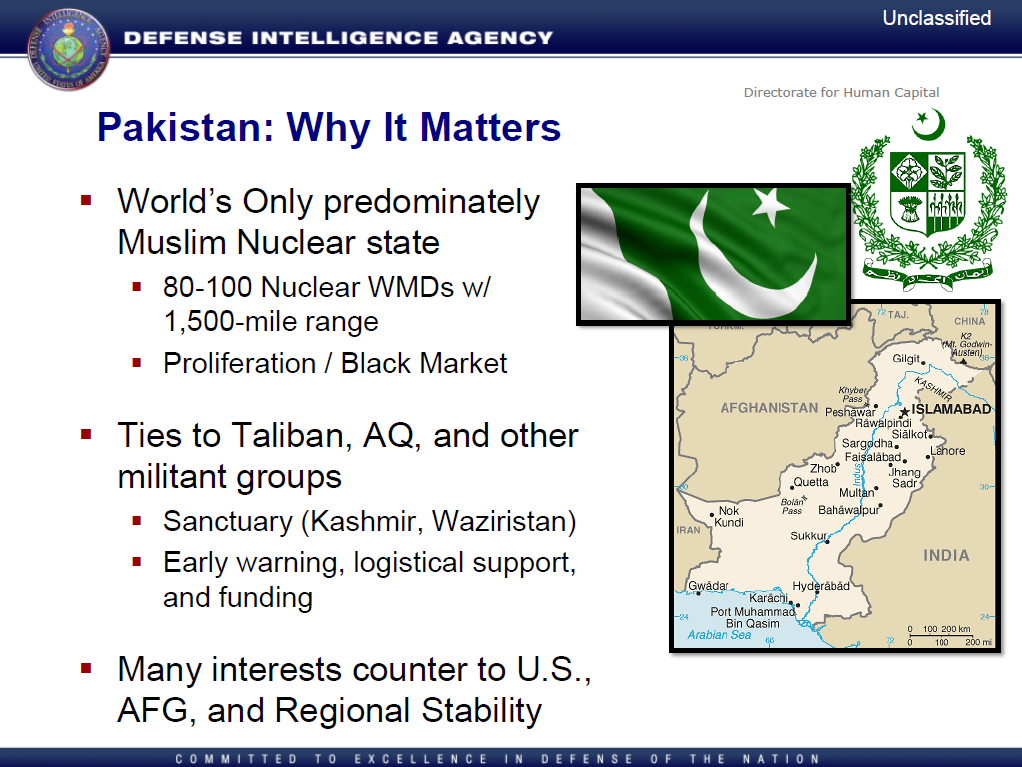

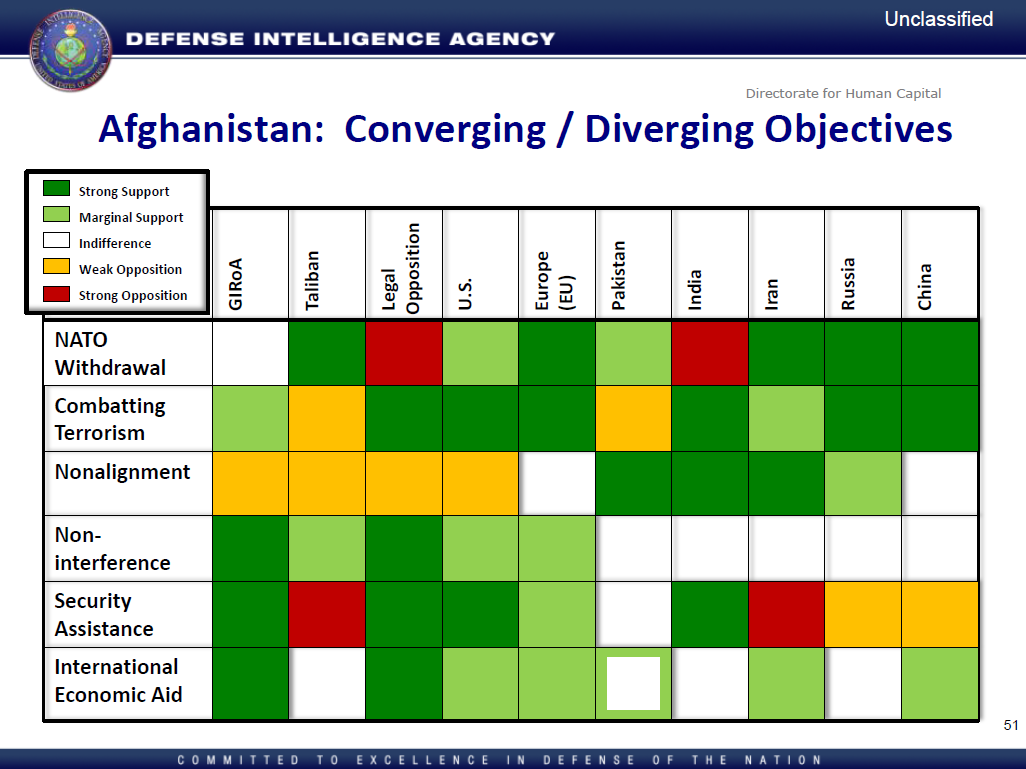

You must be logged in to post a comment.