“Hitler’s Henchmen” is a six-part series that portrays the men who aided Adolf Hitler in his rise to power and serviced the infernal machinery of the Third Reich. The Nuremberg Trials play an important role here: in a historical first, the International War Crimes Tribunal passed judgment on leading Nazi paladins for their unparalleled atrocities while exposing to the world the infamy of the Hitler regime and its leaders. ZDF uses newly discovered archive material and interviews with surviving family members and Nazi insiders to draw historical psychograms of Hitler’s closest aides. Conceived as a sequel to our six-part series “Hitler,” “Hitler’s Henchmen” offers in-depth personal and political profiles of six men who became architects of the destruction of Europe. Portraits of the men who carried out Hitler’s plans: ZDF’s sequel about the men who consolidated Hitler’s reign and turned his plans into action. They wove the complicities and plots without which Hitler could have never perpetrated the crime of the century. They helped to sway the judges and the bureaucrats, the armed forces and the police, the scientists and the industrialists, the students and their teachers to the regime’s ways of thinking. What kind of people were they? What inspired them to serve a corrupt administration with such enthusiasm and devotion? How did their careers unfold and their fates end? The series answers these and other questions by examining six of Hitler’s cohorts. The portraits of these aides-de-camp provide viewers with a revealing psychogram of “Hitler’s willing executors.” The films present for the first time newly discovered film clips and sound recordings from international archives. Recent revelations provided by historical research and interviews with former coworkers, relatives, and victims are also shown.
Hitler’s Henchmen 1 Episodes:
1. The Propagandist/Firebrand – Joseph Goebbels – German with English Subtitles
2. The Marshall – Hermann Goering – German with English Subtitles
3. The Deputy – Rudolf Hess – German with English Subtitles
4. The Executioner – Heinrich Himmler – German with English Subtitles
5. The Admiral – Karl Doenitz – German with English Subtitles
6. The Architect – Albert Speer – German with English Subtitles
Hitler’s Henchmen II Episodes:
1. Bureaucrat of Murder – Adolf Eichmann – German with English Subtitles
2. The Secretary – Martin Bormann – German with English Subtitles
3. The Corruptor of Youth – Baldur von Schirach – German with English Subtitles
4. Diplomat of Evil – Joachim von Ribbentrop – German with English Subtitles
5. Doctor of Death – Josef Mengele – German and English with Swedish Subtitles
6. Arbitrator over Death and Life – Roland Freisler – German with English Subtitles
Month: March 2012
UNCENSORED -FEMEN ITALY
Uncensored – Hitler’s Henchmen – The Secretary Martin Bormann
“Hitler’s Henchmen” is a six-part series that portrays the men who aided Adolf Hitler in his rise to power and serviced the infernal machinery of the Third Reich. The Nuremberg Trials play an important role here: in a historical first, the International War Crimes Tribunal passed judgment on leading Nazi paladins for their unparalleled atrocities while exposing to the world the infamy of the Hitler regime and its leaders. ZDF uses newly discovered archive material and interviews with surviving family members and Nazi insiders to draw historical psychograms of Hitler’s closest aides. Conceived as a sequel to our six-part series “Hitler,” “Hitler’s Henchmen” offers in-depth personal and political profiles of six men who became architects of the destruction of Europe. Portraits of the men who carried out Hitler’s plans: ZDF’s sequel about the men who consolidated Hitler’s reign and turned his plans into action. They wove the complicities and plots without which Hitler could have never perpetrated the crime of the century. They helped to sway the judges and the bureaucrats, the armed forces and the police, the scientists and the industrialists, the students and their teachers to the regime’s ways of thinking. What kind of people were they? What inspired them to serve a corrupt administration with such enthusiasm and devotion? How did their careers unfold and their fates end? The series answers these and other questions by examining six of Hitler’s cohorts. The portraits of these aides-de-camp provide viewers with a revealing psychogram of “Hitler’s willing executors.” The films present for the first time newly discovered film clips and sound recordings from international archives. Recent revelations provided by historical research and interviews with former coworkers, relatives, and victims are also shown.
Hitler’s Henchmen 1 Episodes:
1. The Propagandist/Firebrand – Joseph Goebbels – German with English Subtitles
2. The Marshall – Hermann Goering – German with English Subtitles
3. The Deputy – Rudolf Hess – German with English Subtitles
4. The Executioner – Heinrich Himmler – German with English Subtitles
5. The Admiral – Karl Doenitz – German with English Subtitles
6. The Architect – Albert Speer – German with English Subtitles
Hitler’s Henchmen II Episodes:
1. Bureaucrat of Murder – Adolf Eichmann – German with English Subtitles
2. The Secretary – Martin Bormann – German with English Subtitles
3. The Corruptor of Youth – Baldur von Schirach – German with English Subtitles
4. Diplomat of Evil – Joachim von Ribbentrop – German with English Subtitles
5. Doctor of Death – Josef Mengele – German and English with Swedish Subtitles
6. Arbitrator over Death and Life – Roland Freisler – German with English Subtitles
Crpytome – Chopper Hell Fire Attack on Afghan Civilians
Confidential – New Jersey Office of Homeland Security Terrorism Awareness and Prevention Participant Guide

The New Jersey Office of Homeland Security and Preparedness is pleased to present this opportunity for you to learn more about terrorism awareness and prevention. This program is designed to raise the awareness of New Jersey citizens and workers so they can assist in combating terrorism by enhancing powers of observation and encouraging mutual assistance and concern. It involves the joint efforts of the federal, state and local agencies along with the residents of New Jersey.
While our country tells us to be more aware no one is telling is how and for what. This leaves the possibility for misunderstanding, abuses, and prejudices to surface. This program will inform citizens of what to look for and that their observations should rely on the unusual or suspicious activities and behaviors. Citizens should never use race or religion as factors for reporting suspicious activity.
You, the residents and workers of New Jersey, are our partners.

SZ – SÜDDEUTSCHE ZEITUNG ÜBER STASI-“GoMoPa” UND DEREN STALKER- UND ERPRESSER-METHODEN
Neue Morddrohung – mutmasslich von “Peter Ehlers” – EIN SCHUSS AUF PULCH und alles ist erledigt”
Lieber Leser,
Wildwest bei der mutmasslichen STASI:
Vor Zeugen hat mutmasslich “Peter Ehlers” mir mit einem Mordanschlag gedroht – und die Parallele zu dem verstorbenen Journalisten Heinz Gerlach gezogen.
Alle wissen, ich habe als Erster kritisch über Heinz Gerlach berichtet und bin deswegen von ihm verklagt worden.
Den Prozess haben meine Gesellschafter und ich damals gewonnen.
ABER ICH HABE AUCH ALS ERSTER ÜBER DEN MUTMASSLICHEN MORD AN HEINZ GERLACH UND DIE VERDACHTSMOMENTE GEGEN STASI-GOMOPA GESCHRIEBEN
NIE IM LEBEN HABE ICH GEDACHT DASS AUS “PETER EHLERS” MORDDROHUNGEN BLUTIGER ERNST WIRD
Ich habe mich im wahrsten Sinne des Wortes getäuscht.
Heute wissen wir über das STASI-“GoMoPa”-Geflecht Bescheid.
Die mörderischen und rufmörderischen Drohungen von mutmasslich ” Peter Ehlers” und von “GoMoPa” sowie deren Partnern und Aufftraggebern erhalten ich und meine Partner und Kunden täglich.
Desgleichen immer mehr Beweise über die Helfer UND Helfershelfer UND DEREN MUTMASSLICHE AUFTRAGGEBER RESCH UND BENNEWIRTZ , der STASI-“GoMoPa” sowie deren HELFERSHELFER Thomas P und Beate P, Isabella C und Jan M UND WIE DIE JUSTIZ MANIPULIERT WURDE UND WIRD INDEM BEWEISE UNTERSCHLAGEN UND GEFÄLSCHT WERDEN
Für “PETER EHLERS” sind BUNDESKANZLERIN ANGELA MERKEL UND FINANZMINSITER WOLFGANG SCHÄUBLE DEUTSCHLANDS “GRÖSSTE HEHLER”
Verstehen Sie jetzt, mit wem und was wir hier zu tun haben ?
Schöne Grüsse
Bernd Pulch, MA der Publizistik, Germanistik und Komparatistik
Unveiled – FBI – Facebook and Twitter Social Media Open Sources Spying – PDF
American intelligence agency FBI is reportedly developing new software to scan social networks Twitter and Facebook to look for emerging threats and predict crimes.
The FBI has asked technology firms to create software that can effectively scan the websites for words, phrases and other suspected behaviour, a US Federal site reported.
It will also be able to translate from foreign languages as well as detect patterns of users misleading the police.
Download the cake from FBI bakery HERE
Russia – Hezbollah in Possession of Advanced Antitank Missiles
Russia recently unveiled its new Kornet EM missile that can launch at least two antitank missiles simultaneously. There is concern that the weapon might be transferred to Syria, and then make its way to Hezbollah in Lebanon

Russia unveiled its new Kornet EM antitank missile at a recent exhibition. This missile is an advanced variant of the veteran Kornet missile, and is meant to be easier to operate against a wider range of targets.
Israel is concerned that quantities of the advanced missile might be transferred from Russia to Syria, and then might end up in the hands of Hezbollah.
The new missile has a greater level of precision with a range of up to 10 km, compared to the previous missile’s range of 5 km.
One of the missile’s advantages is that it can be used in the “natural reserves” in south Lebanon, since it can be assembled on various mobile light platforms.
In addition, the system allows for the simultaneous firing of two missiles, which may pose a risk to the IDF’s armored vehicles.
Israel has been concerned since the start of the popular uprising in Syria that the Assad regime is transferring quantities of weapons to Hezbollah to preserve the strength of its regional ally.
The FBI – Interview – The Cyber Threat Part 2: Shawn Henry on Partnerships, Challenges
 |
|---|
| Shawn Henry |
The Cyber Threat
Part 2: Shawn Henry on Partnerships, Challenges
03/30/12
Part 2 of an interview with Shawn Henry, executive assistant director of the Criminal, Cyber, Response, and Services Branch.
Q: Why are partnerships so important?
Henry: The threat we face is not solely within the FBI’s area of responsibility. So we work very closely with other law enforcement agencies and the intelligence community domestically. We share tactics and intelligence. We also partner with the private sector, because they often are the victims and see attacks before anybody else. The final piece—and one of the most significant—is international law enforcement partnerships. The ability to reach across the ocean once we identify criminals and put our hands on them is something that is relatively new. For many years, the adversaries believed they were immune to prosecution because they were thousands of miles away. That’s not the case anymore. Through our partnerships we have arrested hundreds of bad actors who targeted U.S. and foreign infrastructure and institutions. Just in the last two years we have worked with dozens of countries, and we have actually stationed FBI agents overseas into the police agencies in countries including Ukraine, Romania, The Netherlands, and Estonia.
|
The Cyber Threat
Shawn Henry, who became a special agent in 1989 and rose to become the FBI’s top official on cyber crime, talks about the evolving cyber threat and his FBI career. – The Cyber Threat, Part 1 |
|---|
Q: So the cyber threat is truly global in scope?
Henry: Absolutely. In the physical world when somebody robs a bank, the pool of suspects is limited to the number of people in the general vicinity of that bank. When a bank is robbed virtually, even though it is very real for the victims—the money is actually gone—the pool of suspects is limited to the number of people on the face of the earth that have a laptop and an Internet connection, because anybody with an Internet connection can potentially attack any other computer that is tied to the network. You don’t have to be a computer scientist to launch these types of attacks.
Q: Going forward, what are the challenges regarding the cyber threat?
Henry: What I call the expansion of the network is going to create challenges. As technology increases, the threat becomes greater. All our wireless networks and smart devices are network-based, and anything touching the network is potentially susceptible. As more and more information transitions across the network, more adversaries will move to get their hands on it, because that information is extraordinarily valuable.
Q: You have responsibilities beyond the cyber area. What are some of the challenges you see with other criminal matters?
Henry: As an organization, fighting terrorism is rightfully the FBI’s number one priority, but criminal threats are substantial. There is white-collar crime, where we’ve seen people lose their entire life savings because of criminals taking advantage of them. There’s something very rewarding about seeing our agents and analysts aggressively working to take those criminals off the streets. We’ve seen public corruption cases where people have abused their position for personal gain. I see those types of cases continuing. There’s a percentage of people in society that are always going to be bad actors.
Q: What are you going to miss when you leave the Bureau?
Henry: The people and the mission. There is nothing else I wanted to do more in my professional life than to be an FBI agent. The quality and caliber of the people I have worked with are second to none. Working day to day to carry out our mission to help protect the country is an experience that can never be replaced. I leave with a tremendous sense of pride.
Uncensored – Hitler’s Henchmen – The Marshall – Hermann Goering
SECRET – Washington D.C. Metropolitan Police Department Procedures for Handling First Amendment Assemblies and Mass Demonstrations
The Standard Operating Procedures (SOP) outlined in this manual are to ensure that this department is prepared to respond effectively and efficiently in accordance with applicable law and District of Columbia policy to any unlawful conduct occurring in the context of First Amendment assemblies. These SOP’s incorporate revisions to the manner in which the Metropolitan Police Department responds to demonstrations and other assemblies on District of Columbia public space that the District has implemented in resolving litigation. This manual also reflects measures mandated by the First Amendment Rights and Police Standards Act of 2004.
This handbook sets forth general policy and shall serve as standard operating procedures for all members in carrying out the mission of the Metropolitan Police Department in dealing with all demonstrations, rallies, marches, picket lines, or other similar gatherings conducted for the purpose of persons expressing their political, social, or religious views. This policy is intended to exceed constitutional requirements and satisfy the heightened requirements of local statutory law and best practices.
The manual also is designed around the concept of operational flexibility within the requirements of the National Incident Management System. It is impossible to devise specific standard procedures for handling all possible situations, for each has its own characteristics and problems. The overall police philosophy must be one of moderation, flexibility and controlled response. Since each situation is unique, both commanders and supervisory officials must plan to respond according to the nature and size of the crowd. The tactical procedures established within this manual are a guide, and not a substitute for the exercise of sound judgment and proper command and supervision within the context of general departmental policy.
It is imperative that members of the force understand the role of the Metropolitan Police Department during mass demonstrations and major disturbances in our city and the manner by which the department prepares itself to fulfill this role. It is to this end that this handbook is dedicated.
…
V. VIOLENT CIVIL DISTURBANCES
Unplanned civil disturbances may arise from a number of causes such as political grievances, economic conflicts, community unrest, or in response to police action taking place in neighborhoods, or in the midst of a crowded street, park or public place. Civil disturbance participants come from all walks of life and cover the entire political spectrum.
Whenever an unplanned First Amendment assembly arises, the first officer on the scene will serve as the initial incident commander. That member will be responsible for conducting an assessment of the scene, notifying the CIC and the element Watch Commander of the situation and requesting assistance from the Special Operations Division.
The basic human element sparking a civil disturbance is usually the presence of a crowd. Civil disturbances usually arise when a crowd:
1. Gathers to air grievances on issues, and transfers its anger from the issues to the people dealing with the issues.
2. Swells uncontrollably as curious bystanders and sympathetic onlookers join forces with the activists or protestors.
3. Is incited to irrational action by skillful agitators.In civil disturbances, crowds employ any number of tactics to achieve their goals. Their tactics may be unplanned or planned, non-violent or violent confrontations. As indicated, the situations that could evolve into a violent civil disturbance are numerous and varied. Often there will be little or no warning before the onset of violence or property damage. In a few instances, it may be possible to predict a level of civil disorder by the nature of a pre-planned event. However, each civil disturbance situation is unique and commanders and supervisory officials must, therefore, plan and respond according to the nature and size of the disturbance. The policies and procedures presented in this SOP are based upon the concept of operational flexibility, and it is expected that officials will exercise sound judgment and proper command and supervisory responsibility in the control of a civil disturbance.
Uncensored – Hitler’s Henchmen – Bureaucrat of Murder – Adolf Eichmann
“Hitler’s Henchmen” is a six-part series that portrays the men who aided Adolf Hitler in his rise to power and serviced the infernal machinery of the Third Reich. The Nuremberg Trials play an important role here: in a historical first, the International War Crimes Tribunal passed judgment on leading Nazi paladins for their unparalleled atrocities while exposing to the world the infamy of the Hitler regime and its leaders. ZDF uses newly discovered archive material and interviews with surviving family members and Nazi insiders to draw historical psychograms of Hitler’s closest aides. Conceived as a sequel to our six-part series “Hitler,” “Hitler’s Henchmen” offers in-depth personal and political profiles of six men who became architects of the destruction of Europe. Portraits of the men who carried out Hitler’s plans: ZDF’s sequel about the men who consolidated Hitler’s reign and turned his plans into action. They wove the complicities and plots without which Hitler could have never perpetrated the crime of the century. They helped to sway the judges and the bureaucrats, the armed forces and the police, the scientists and the industrialists, the students and their teachers to the regime’s ways of thinking. What kind of people were they? What inspired them to serve a corrupt administration with such enthusiasm and devotion? How did their careers unfold and their fates end? The series answers these and other questions by examining six of Hitler’s cohorts. The portraits of these aides-de-camp provide viewers with a revealing psychogram of “Hitler’s willing executors.” The films present for the first time newly discovered film clips and sound recordings from international archives. Recent revelations provided by historical research and interviews with former coworkers, relatives, and victims are also shown.
Hitler’s Henchmen 1 Episodes:
1. The Propagandist/Firebrand – Joseph Goebbels – German with English Subtitles
2. The Marshall – Hermann Goering – German with English Subtitles
3. The Deputy – Rudolf Hess – German with English Subtitles
4. The Executioner – Heinrich Himmler – German with English Subtitles
5. The Admiral – Karl Doenitz – German with English Subtitles
6. The Architect – Albert Speer – German with English Subtitles
Hitler’s Henchmen II Episodes:
1. Bureaucrat of Murder – Adolf Eichmann – German with English Subtitles
2. The Secretary – Martin Bormann – German with English Subtitles
3. The Corruptor of Youth – Baldur von Schirach – German with English Subtitles
4. Diplomat of Evil – Joachim von Ribbentrop – German with English Subtitles
5. Doctor of Death – Josef Mengele – German and English with Swedish Subtitles
6. Arbitrator over Death and Life – Roland Freisler – German with English Subtitles
The CIA Crown Jewels – The MHCHAOS Program
| Citation: | The MHCHAOS Program Secret, Report, May 08, 1973, 3 pp. |
| Collection: | The CIA Family Jewels Indexed |
| Item Number: | FJ00058 |
| Origin: | United States. Central Intelligence Agency |
| Individuals/ Organizations Named: |
Dean, John Wesley III; Fedayeen-e Islam; Kissinger, Henry A.; United States. Central Intelligence Agency. Director; United States. Central Intelligence Agency. Directorate of Operations; United States. Central Intelligence Agency. Directorate of Operations. East Asia Division; United States. Central Intelligence Agency. Directorate of Operations. East Asia Division. Vietnam Operations; United States. Central Intelligence Agency. Directorate of Operations. Soviet Bloc Division; United States. Central Intelligence Agency. Directorate of Operations. Special Operations Division; United States. Central Intelligence Agency. Directorate of Plans. Far East Division. China Operations; United States. Central Intelligence Agency. Directorate of Plans. Western Hemisphere Division. Cuban Operations Group; United States. Department of Justice. Attorney General; United States. Department of State. Secretary; United States. Federal Bureau of Investigation; United States. Federal Bureau of Investigation. Director; United States. White House |
| Subjects: | Algiers (Algeria) | Biographical intelligence | Brussels (Belgium) | China | Communications interception | Communications security | Conakry (Guinea) | Covert identities | Cuba | Dar es Salaam (Tanzania) | Domestic intelligence | Foreign citizens | Hong Kong | Intelligence collection | Interagency cooperation | Korea (North) | Mexico City (Mexico) | Ottawa (Canada) | Paris (France) | Political activists | Project MHCHAOS [Codename CHAOS] | Santiago (Chile) | Soviet Union | Stockholm (Sweden) | Vietnam (North) |
| Abstract: | Describes MHCHAOS program and activities, including intelligence gathering on U.S. and foreign dissidents and methods for transmitting findings to U.S. agencies. |
| Full Text: | Document – PDF – this link will open in a new window (102 KB) |
The FBI – Four Additional Defendants Charged for Assaulting Practitioners of the Amish Religion in Cleveland
WASHINGTON—The Justice Department announced today that a federal grand jury in Cleveland returned a 10-count superseding indictment in United States v. Mullet, et al. The superseding indictment charges 10 men and six women, all residents of Ohio, with federal crimes arising out of a series of religiously-motivated assaults on practitioners of the Amish religion.
The superseding indictment addresses five separate assaults that occurred between September and November of 2011 and obstructive conduct related to those assaults. In each assault, defendants forcibly removed beard and head hair from practitioners of the Amish faith with whom they had ongoing religious disputes. As set forth in the superseding indictment, the manner in which Amish men wear their beards and Amish women wear their hair are symbols of their faith. The superseding indictment adds four defendants, Lovina Miller, Kathryn Miller, Emma Miller and Elizabeth Miller, who had not previously been charged. The indictment also adds charges against some of the defendants for the concealment and destruction of evidence, including a disposable camera, shears, and a bag of hair from victims of the attacks, as well as a charge against Samuel Mullet, Sr. for false statements he allegedly made to federal agents during the investigation.
This case is being investigated by the Cleveland Division of the FBI and is being prosecuted by Assistant U.S. Attorneys Thomas Getz and Bridget M. Brennan of the U.S. Attorney’s Office for the Northern District of Ohio and Deputy Chief Kristy Parker of the Civil Rights Division’s Criminal Section.
For more information on the 12 defendants previously charged in this case, please visit http://www.justice.gov/opa/pr/2011/December/11-crt-1683.html.
An indictment is merely an accusation. All defendants are presumed innocent of the charges until proven guilty beyond a reasonable doubt in court.
Secret – U.S. Army Document and Media Exploitation Draft Manual

This publication provides Tactics, Techniques, and Procedures (TTP) required for Army personnel when conducting Document and Media Exploitation (DOMEX) operations. The document is designed to serve as a reference for multiple personnel at varying echelons. The ATTP provides specific information for Army personnel operating as part of a DOMEX or other exploitation team for the collection, processing, and reporting of DOMEX activities. The manual serves as a reference for staff planners and intelligence personnel at battalion and brigade combat teams. Additionally, the manual provides an understanding of DOMEX activities, procedures, organizations, products, and databases at joint task force, U.S. Army, and the Department of Defense.
DOCUMENT AND MEDIA EXPLOITATION
1-2. DOMEX is the processing, translation, analysis, and dissemination of collected hardcopy documents and electronic media that are under the U.S. Government’s physical control and are not publicly available (training circular [TC] 2-91.8).
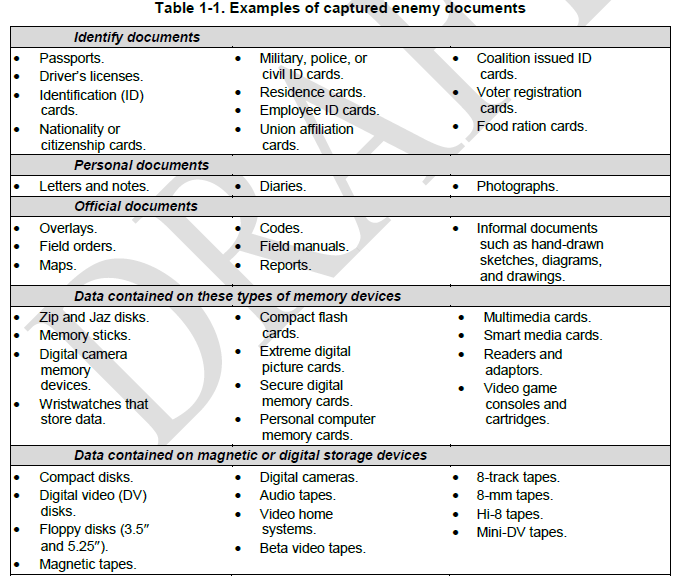
1-3. DOMEX includes the collection and exploitation of captured equipment, documents, and media to generate actionable intelligence. DOMEX provides leaders at all echelons with intelligence about enemy forces; their plans and intentions; and their TTP. It does this through the rapid and accurate extraction, exploitation, and analysis of acquired documents, cell phones, computers, digital storage devices, video and audio tapes, and other media and material. DOMEX is a critical part of target exploitation, especially as it relates to actions on the objective during site exploitation activities.
1-4. Through DOMEX, information is systematically extracted from all captured materials in response to the commanders’ critical information requirements (CCIR). DOMEX activities—
- Maximize the value of intelligence gained from captured materials.
- Provide commanders with timely and relevant intelligence to effectively enhance awareness of the enemies’ capabilities, operational structures, and intents.
- Provide timely and accurate intelligence support to the commander throughout the full spectrum of operations.
- Assist in criminal prosecution and legal processes by maintaining chain of custody procedures and preserving the evidentiary value of captured materials.
From the FBI – The Cyber Threat Part 1: On the Front Lines with Shawn Henry
Shawn Henry realized a lifelong dream when he became a special agent in 1989. Since that time he has traveled the world for investigations and become one of the FBI’s most senior executives and its top official on cyber crime. FBI.gov recently sat down with Henry—who is about to retire from the Bureau—to talk about the cyber threat and his FBI career.
Q: You were involved with cyber investigations long before the public had an awareness of how serious the threat is. How did you become interested in the cyber realm?
Henry: I was always interested in technology, and in the late 1990s I started to take courses at the FBI related to cyber intrusion investigations. When I had an opportunity to move over to that side of the house, I seized it. I saw right away that the challenges we were going to face in the future were tremendous, and I wanted to be on the front lines of that.
Q: How has the cyber threat changed over time?
Henry: Early on, cyber intrusions such as website defacements and denial of service attacks were generally perceived to be pranks by teenagers. But even then, in the late 1990s, there were state actors sponsored by governments who were attacking networks. What received media attention was the teenage hacker and the defacements, but there were more significant types of attacks and a more substantial threat that was in the background. Also, those early attacks were much more intermittent. Now we are seeing literally thousands of attacks a day. The ones people hear about are often because victims are coming forward. And there are more substantial attacks that people don’t ever see or hear about.
Q: Where are the cyber threats coming from today?
Henry: We see three primary actors: organized crime groups that are primarily threatening the financial services sector, and they are expanding the scope of their attacks; state sponsors—foreign governments that are interested in pilfering data, including intellectual property and research and development data from major manufacturers, government agencies, and defense contractors; and increasingly there are terrorist groups who want to impact this country the same way they did on 9/11 by flying planes into buildings. They are seeking to use the network to challenge the United States by looking at critical infrastructure to disrupt or harm the viability of our way of life.
Q: How has the FBI adapted to address the threat?
Henry: We have grown substantially, particularly in the last four or five years, where we have hired much more technically proficient agents, many of whom have advanced degrees in computer science or information technology. We bring them onboard and teach them to be FBI agents rather than trying to teach FBI agents how the technology works. That has given us a leg up and put our capabilities on par with anybody in the world. We have also worked proactively to mitigate the threat by using some of the same investigative techniques we use in the physical world—undercover operations, cooperating witnesses, and authorized surveillance techniques. We have taken those same time-tested tactics and applied them to the cyber threat. So we are now able to breach networks of criminal actors by putting somebody into their group. The other critical area we have been successful in is developing partnerships.
Shawn Henry is executive assistant director of the FBI’s Criminal, Cyber, Response, and Services Branch. He served as assistant director of the Cyber Division from September 2008 to January 2010,
TOP-SECRET – Garbage Collectors Around the U.S. Trained to Report Suspicious Activity
Several newspapers in southern Florida are reporting that trash collectors are receiving training from their employer Waste Management to work with local law enforcement to report crimes and other suspicious activities. The training is part of a program called Waste Watch that is designed to leverage the fact that “drivers are familiar with their routes and are in the same neighborhoods every day” which “puts them in the unique position to spot unusual activity and anything out of the ordinary.” Press releases from Waste Management describe the program as a way of opening “channels of communication with the authorities to help keep them informed and alert of what’s happening in their city’s streets and alleys.”
Waste Watch training sessions are conducted by former FBI agents in association with security representatives from Waste Management. The program has been operating since 2004 when it was first introduced by Waste Management’s Corporate Security Services and Community Relations offices. Waste Watch operates in more than 100 communities around the country including Utah, New York, Nevada, South Carolina, California, Oregon, Michigan, Washington and Florida. There is little public information available on the program or the content of training material presented to Waste Watch participants.
Given the recent proliferation of programs dedicated to promoting suspicious activity reporting, more information is needed on the program’s guidelines for detecting and reporting suspicious activity. FBI flyers designed to promote suspicious activity reporting have listed actions like insisting on paying cash or trying to cover one’s computer screen as evidence of potential terrorist activity. A similar guide produced by the New Jersey Office of Homeland Security and Preparedness listed yawning and repeatedly touching one’s face as suspicious activities. The Waste Watch program does seem to have produced some positive results, including helping to catch vandals or petty thieves. In 2008 the program was awarded the “Award of Excellence in the Neighborhood Watch” by the National Sheriff’s Association.
While encouraging citizens and businesses to look out for criminal activity is a worthwhile cause, the recent proliferation of programs for reporting suspicious activity has raised concerns from civil liberties groups about the potential for turning citizens and business owners into effective spies on their neighbors and customers. The Department of Homeland Security’s “If You See Something, Say Something” program has greatly expanded in the last few years by partnering with the NBA, MLB, NFL, MLS, NCAA, religious organizations, hotel television providers and even Walmart to promote suspicious activity reporting. Fusion centers and cities around the country are creating websites and phone applications to help citizens report suspicious activity, complete with photographs and geolocation information. However, the “Waste Watch” program extends citizen surveillance one step further by leveraging the manpower of the country’s largest waste collection company to look not just for suspicious activity, but for “anything out of the ordinary.”
Uncensored – Hitler’s Henchmen – The Deputy – Rudolf Hess
“Hitler’s Henchmen” is a six-part series that portrays the men who aided Adolf Hitler in his rise to power and serviced the infernal machinery of the Third Reich. The Nuremberg Trials play an important role here: in a historical first, the International War Crimes Tribunal passed judgment on leading Nazi paladins for their unparalleled atrocities while exposing to the world the infamy of the Hitler regime and its leaders. ZDF uses newly discovered archive material and interviews with surviving family members and Nazi insiders to draw historical psychograms of Hitler’s closest aides. Conceived as a sequel to our six-part series “Hitler,” “Hitler’s Henchmen” offers in-depth personal and political profiles of six men who became architects of the destruction of Europe. Portraits of the men who carried out Hitler’s plans: ZDF’s sequel about the men who consolidated Hitler’s reign and turned his plans into action. They wove the complicities and plots without which Hitler could have never perpetrated the crime of the century. They helped to sway the judges and the bureaucrats, the armed forces and the police, the scientists and the industrialists, the students and their teachers to the regime’s ways of thinking. What kind of people were they? What inspired them to serve a corrupt administration with such enthusiasm and devotion? How did their careers unfold and their fates end? The series answers these and other questions by examining six of Hitler’s cohorts. The portraits of these aides-de-camp provide viewers with a revealing psychogram of “Hitler’s willing executors.” The films present for the first time newly discovered film clips and sound recordings from international archives. Recent revelations provided by historical research and interviews with former coworkers, relatives, and victims are also shown.
Hitler’s Henchmen 1 Episodes:
1. The Propagandist/Firebrand – Joseph Goebbels – German with English Subtitles
2. The Marshall – Hermann Goering – German with English Subtitles
3. The Deputy – Rudolf Hess – German with English Subtitles
4. The Executioner – Heinrich Himmler – German with English Subtitles
5. The Admiral – Karl Doenitz – German with English Subtitles
6. The Architect – Albert Speer – German with English Subtitles
Hitler’s Henchmen II Episodes:
1. Bureaucrat of Murder – Adolf Eichmann – German with English Subtitles
2. The Secretary – Martin Bormann – German with English Subtitles
3. The Corruptor of Youth – Baldur von Schirach – German with English Subtitles
4. Diplomat of Evil – Joachim von Ribbentrop – German with English Subtitles
5. Doctor of Death – Josef Mengele – German and English with Swedish Subtitles
6. Arbitrator over Death and Life – Roland Freisler – German with English Subtitles
Confidential – Restricted U.S. Military Multi-Service Joint Application of Firepower (JFIRE) Manual

JFIRE is a pocket-size, quick-reference guide for requesting fire support in accordance with approved joint tactics, techniques, and procedures (TTP). JFIRE contains calls for fire, joint air attack team (JAAT) techniques, a format for joint air strike requests, close air support (CAS) coordination and planning procedures, communications architecture, and weapons data.
Scope
JFIRE applies to the tactical and special operating forces of the Army, Navy, Marine Corps, and Air Force. It is a United States (US) unilateral-only document, but includes some North Atlantic Treaty Organization (NATO) formats where appropriate. Information in JFIRE has been extracted from existing Service directives. It is primarily intended for use by members of battalion and squadronlevel combat units.
…
5. Unmanned Aircraft Systems Considerations
UASs consist of one or more unmanned aircraft (UA), a control station, datalinks, and payloads. The capability of UASs to support or execute CAS varies greatly between systems. For example, US Air Force (USAF) MQ-1 and MQ-9 are armed with air-to-surface weapons, have radio communications aboard the UA, and are flown by rated aviators trained in CAS procedures. Other systems may not be similarly equipped or flown by CAS-qualified crews but may be employed for situational awareness, target marking, or as an observer for Types 2 or 3 control by the controlling JTAC. (See appendices A and B for more information on UASs.) The following UAS CAS considerations are intended for use with CAS-capable UAS and CAS-qualified UAS operators only:
a. Threat: Unmanned aircraft are unlikely to survive in a heavily defended environment. Consideration must be given to enemy air-to-air and surface-to-air weapons with the ability to engage a UA at its operating location and altitude. UAs are not normally equipped with warning receivers or countermeasures and depend on threat avoidance for mission survivability. Datalinks may be susceptible to jamming or interference.
b. Weather: UAs are susceptible to turbulence, icing, and visible precipitation. Electro-optical (EO) / IR sensors and laser designators / range finders / target markers require unobstructed LOS to the target. Intervening haze, clouds, or blowing dust may interfere with or prevent mission accomplishment. On the other hand, synthetic aperture radar (SAR) and inertially aided munitions (IAMs) are unaffected by haze, cloud cover, or dust. High winds aloft may make it difficult for the UA to maintain station in a highly restricted location or may unacceptably delay transit between target areas.
c. Signature: UAs vary in visual, radar, IR, and acoustic signature and in system ability and crew proficiency to manage the signature. For example, when minimum noise is desired to avoid tipping off a target, it may be possible to modulate power and trade altitude for airspeed in order to reduce the noise signature while approaching closer to a target. On the other hand, it may be desirable to announce presence in order to stimulate a desired response or intimidate the target.
d. Deconfliction: While UASs presently lack the ability to see and avoid other aircraft, there are other means to integrate UASs (e.g., voice radio; tactical datalinks; identification, friend or foe [IFF]). Formal and informal airspace control measures apply to UASs. UAs may hold overhead or offset from a target. Relatively slow airspeeds can permit a UA to operate in a smaller segment of airspace than other aircraft. Depending upon performance capabilities of the specific UAS and communications with the crew, it may take several minutes to reposition the UA or change altitude blocks. JTACs must trade off the best position for the UASs to employ sensors / weapons against the desired target(s) with the ability to best employ other assets. Consideration should also be given to the “lost link” profile autonomously flown by UA if the control datalink is lost. Upon initial check-in, the JTAC should query the UAS operator for the currently programmed lost-link profile. If unacceptable due to airspace limitations or other reasons, the JTAC should direct a new lost-link profile and receive verification that the UA has been programmed.
e. Communication and Situational Awareness: Some UAs have onboard radios and / or secure voice providing the ability to communicate with the UAS pilot as with any manned aircraft. In addition, some UASs have secure chat and voice over Internet Protocol, as well as additional air and ground situational awareness displays. Providing the ground scheme of maneuver to the supporting UAS can significantly increase the crew’s situational awareness and subsequent mission support.
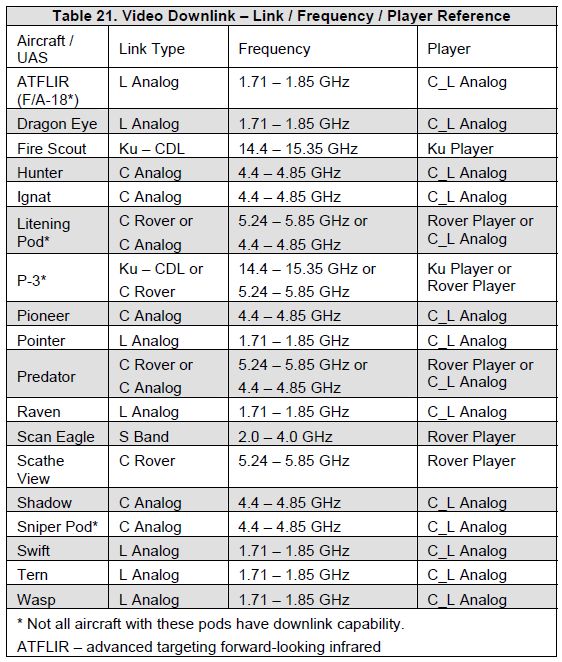
f. Video Downlink (VDL) and Machine-to-machine Datalinks: Some UASs can accept and provide machine-to-machine digital targeting information and many UASs provide LOS video downlinks to users with compatible video receivers. This can significantly reduce voice traffic and reduce information transfer errors. (See table 21 VDL – Link / Frequency / Player Reference on p.77 for more information.)
g. Tactics: UASs employ using a variety of tactics ranging from a wheel to a variant of an IP-target run-in. UA performance characteristics and sensor and weapons capabilities, along with the environmental and tactical situation, influence the selection of tactics, ranges, altitudes, and timing considerations.
…
Uncensored – Hitler’s Henchmen – The Executioner – Heinrich Himmler
“Hitler’s Henchmen” is a six-part series that portrays the men who aided Adolf Hitler in his rise to power and serviced the infernal machinery of the Third Reich. The Nuremberg Trials play an important role here: in a historical first, the International War Crimes Tribunal passed judgment on leading Nazi paladins for their unparalleled atrocities while exposing to the world the infamy of the Hitler regime and its leaders. ZDF uses newly discovered archive material and interviews with surviving family members and Nazi insiders to draw historical psychograms of Hitler’s closest aides. Conceived as a sequel to our six-part series “Hitler,” “Hitler’s Henchmen” offers in-depth personal and political profiles of six men who became architects of the destruction of Europe. Portraits of the men who carried out Hitler’s plans: ZDF’s sequel about the men who consolidated Hitler’s reign and turned his plans into action. They wove the complicities and plots without which Hitler could have never perpetrated the crime of the century. They helped to sway the judges and the bureaucrats, the armed forces and the police, the scientists and the industrialists, the students and their teachers to the regime’s ways of thinking. What kind of people were they? What inspired them to serve a corrupt administration with such enthusiasm and devotion? How did their careers unfold and their fates end? The series answers these and other questions by examining six of Hitler’s cohorts. The portraits of these aides-de-camp provide viewers with a revealing psychogram of “Hitler’s willing executors.” The films present for the first time newly discovered film clips and sound recordings from international archives. Recent revelations provided by historical research and interviews with former coworkers, relatives, and victims are also shown.
Hitler’s Henchmen 1 Episodes:
1. The Propagandist/Firebrand – Joseph Goebbels – German with English Subtitles
2. The Marshall – Hermann Goering – German with English Subtitles
3. The Deputy – Rudolf Hess – German with English Subtitles
4. The Executioner – Heinrich Himmler – German with English Subtitles
5. The Admiral – Karl Doenitz – German with English Subtitles
6. The Architect – Albert Speer – German with English Subtitles
Hitler’s Henchmen II Episodes:
1. Bureaucrat of Murder – Adolf Eichmann – German with English Subtitles
2. The Secretary – Martin Bormann – German with English Subtitles
3. The Corruptor of Youth – Baldur von Schirach – German with English Subtitles
4. Diplomat of Evil – Joachim von Ribbentrop – German with English Subtitles
5. Doctor of Death – Josef Mengele – German and English with Swedish Subtitles
6. Arbitrator over Death and Life – Roland Freisler – German with English Subtitles
Unveiled – Censored U.S. Army Articles on Afghan Massacre Suspect Staff Sergeant Robert Bales

The following are mirrored copies of multiple U.S. Army news articles referencing and containing pictures of Staff Sergeant Robert Bales who has been identified as the man accused of murdering of 16 civilians in Kandahar on March 11, 2012. These two articles along with all other photos and media created by the U.S. Army that references Bales or contains photos of him is being removed from Army websites in an attempt to wipe away traces of the soldier’s online history. We have mirrored the material in the interest of preserving the documents for analysis and historical interest.
| High Desert Warrior Volume 7, Number 35Original URL: http://assets.mediaspanonline.com/prod/6887587/hdw_09012011A24.pdf | September 1, 2011 | Download PDF (6.52 MB) |
| U.S. Army News Article “Lessons Learned in Iraq: The Battle of Zarqa”Original URL: http://www.army.mil/article/16623/Lessons_learned_in_Iraq__the_Battle_of_Zarqa/
Lessons Learned in Iraq: The Battle of ZarqaFebruary 9, 2009 By Don Kramer Story Highlights
Editor’s note: This is a three-part account of the Battle of Zarqa, also called the Battle of Najaf in some sources. Background information and portions of this article were drawn from the Fort Lewis Battle Command Training Center 2008 video documentary of the Battle of Zarqa. The full video and other training and leader development information is available on https://StrykerNet.army.mil to AKO account holders. FORT LEWIS, Wash. – With the trappings of World War I and II tactics and 21st Century weaponry, the 2nd Battalion, 3rd Infantry Regiment’s fight in January 2007 to recover a downed Apache helicopter south of Najaf stands as unique among Operation Iraqi Freedom engagements. Counterinsurgency operations carry their own metrics, different from those that measure success in combat against an enemy who stands and fights. But by all military standards, Lt. Col. Barry Huggins’ 3rd Brigade, 2nd Infantry Division Stryker battalion achieved a smashing success in what might have been the most traditional battle of Operation Iraqi Freedom. It ended in such a one-sided victory for U.S. and Iraqi forces that anticoalition media attempted to frame it as a “massacre” – until details came to light of the enemy’s plans, detailed preparations and prodigious arsenal of weapons and equipment. On Jan. 28 and 29, 2007, a fanatic and well-armed Shiite paramilitary faction stood and fought in southern Iraq against two companies of 2-3 Inf. augmented with engineers, 8th Iraqi Army elements and two Special Forces detachments, on a compound the insurgents had prepared for months. Riddled on three sides with deep trenches, high berms and antitank positions and protected on the fourth by the Euphrates River, nearly 600 Jund as-Sama’, “Soldiers of Heaven,” fired all of their considerable ordnance and launched one assault after another throughout the night in attempts to surprise and outflank the Patriot Battalion task force. For the Shiite fighters, they had begun an apocalyptic battle they believed would hasten the return of the Mahdi, the 12th Imam. In the end, the most important metric was the casualty count: 250 enemy fighters killed, 81 wounded and 410 detained and not a single 2-3 Inf. Soldier hurt or killed. Sophisticated, relentless firepower defeated superior numbers on ground of the enemy’s choosing. As the company commander of the lead element, Capt. Brent Clemmer, now a major enrolled at the Naval Postgraduate School in Monterey, Calif. paraphrased a Ranger epigram, “Forget the fair fight.” Every commander’s most optimistic intent on the battlefield had been realized – decisive victory with no loss of life to his unit. What cannot be measured occurred at the end of the battle. Defining “agility,” American Soldiers seamlessly shifted into humanitarian operations. The Charger Company first sergeant, 1st Sgt. Viriato Ferrera, hastily organized detainee and casualty collection points at the outskirts of the village. He was shocked to see women and children join the trickle of demoralized fighters, which turned rapidly into a stream and then, a flood. Within minutes of surrender, 2-3 Inf. Soldiers began a 10-hour struggle to save the lives of the same Jund as-Sama’ members they had battled all night long. Along with them came hundreds of their wives and children, completely taxing the unit’s medical supplies and personnel. Some of the Patriots said they felt fated to take part in the surreal mix of fighting and lifesaving in Zarqa, since their involvement in the episode happened by chance. The situation The Patriot Battalion, which had already moved in late December from Mosul to Baghdad, had been detached from 3rd Brigade, 2nd Infantry Division to 4th Brigade, 25th Infantry Division to assist with its large southern battle space. Spartan Brigade leaders had asked for reinforcements based on the identification of several targets by intelligence during the Ashura season, the commemoration of the battle of Karbala in 680 A.D., during which the Muslim prophet Muhammad’s grandson, Husayn ibn Ali, died. As the holiest day of the year among many Shiites, it represents a key moment in their historical separation from Sunni Islam. Ashura is marked by pilgrimages to Karbala by Shiite faithful who often become targets for Sunni zealots. The Soldiers of 2-3 Inf. had been on their own journey. “We’d been on a long odyssey for the last week and a half before this whole thing started,” Clemmer said. The battalion left FOB Liberty in Baghdad for Karbala “on a 15-minute string,” and hadn’t returned to refit and resupply. Meanwhile, two of Clemmer’s three C Company platoons lost vehicles in the course of subsequent movements. “We weren’t supposed to even be with the brigade we were with at the time,” said the company commander. “There weren’t any other Strykers down there at (Forward Operating Base) Kalsu when it happened. Who would have come to the rescue’” On Jan. 28, 4th Bde., 25th Inf. Div. received a call for help from Operational Detachment Alpha 563, a Special Forces team that had answered an earlier call from another SF A-team, 566, in Zarqa, a village south of Najaf. The following account is taken from the introduction to the DVD produced by the Leader Development Team in the I Corps Battle Command Training Center at Fort Lewis: Iraqi police received a tip that Jund as-Sama’ based in Zarqa were planning to assassinate Shiite leaders including the Grand Ayatollah al-Sistani and Muqtada al-Sadr, during Ashura. Provincial authorities reported the information to the 8th Iraqi Army, which sent a scout platoon with American advisers to conduct reconnaissance and report on the gathering in Zarqa. Once on site, the Iraqi scouts were attacked by a battalion-sized element with small arms and heavy machine guns. The scouts requested assistance. U.S. Army SF Detachment ODA 566 arrived at 8 a.m., Jan 28. The ODA reported a large insurgent element had occupied hasty fighting positions in existing drainage canals and was placing effective small arms, machine gun and rocket-propelled-grenade fire on the Iraqi Forces. ODA 566 requested reinforcements. A joint patrol of Iraqi SWAT and another SF detachment, ODA 563, moved to the site. After close air support from F-16s and A-10s failed to disrupt the insurgent defense, ODA 566 requested attack aviation. An attack weapons team of two AH-64 Apache helicopters departed FOB Kalsu and arrived at 12:30 p.m., simultaneously with the arrival of Hillah SWAT and ODA 563. Coordinated attacks began on the insurgent positions. At about 1:30 p.m., one of the Apaches was shot down near the enemy position, killing both pilots. Insurgent direct fire, now augmented with mortars, prevented the SF from securing the aircraft. The coalition forces on site established an overwatch of the crash site, and effectively fixed the insurgent force with direct fire, additional attack aviation and continuous close air support. The 4th Bde., 25th Inf. Div. commander, Col. Mike Garrett, directed that his attached Stryker battalion task force answer the call. “The best force I’ve got, the most ready force to move 97 kilometers quickly into this unknown situation is the Strykers that are attached to me,” Lt. Col. Adam Rocke, current 2-3 Inf. commander, then the 3rd Bde., 2nd Inf. Div. operations officer, paraphrased Garrett. Movement to Zarqa Huggins got the call and said he could have his companies together in 15 minutes. They had planned to conduct raids that night anyway, so the planning sequence was already completed. When Clemmer’s radio squawked, in fact, he thought it was part of the rehearsal for that night’s operation. “No sir, it’s not a practice, sir,” said the voice of his operations sergeant. “Brigade’s calling us and there’s a helicopter down.” “We’re focused on a helicopter needs to be recovered,” Huggins said. “We get the word that there’s an (SF) ODA at the scene securing it and there’s some light contact. About an hour later we get the word to launch. I send the initial company forward, Charlie Company with Brent Clemmer, and he’s moving within 10 minutes of that launch. I assemble the logistics support trains with my Bravo Company and my battalion TAC. We’re still trying to figure out the situation on the ground.” As orders to saddle up moved through the companies, the common expectation among the Soldiers was that they would be back in their racks at FOB Kalsu by midnight. No one had heard of the brisk fighting going on 100 kilometers to the south. Charger Company left an hour after the launch order and Blackhorse followed a half hour later with Huggins, the TAC and battalion support trains in tow. The way south from FOB Kalsu took C Company through the city of Hillah, which they found full of Ashura pilgrims. The movement halted in its tracks. “There’s a couple thousand people flailing themselves, big banners and everything else,” Clemmer said. “Here’s where some of the lessons of Mosul came into effect because we had worked with the police so well.” The Iraqi police escorted the fast-moving Stryker convoy around the crowds and with the help of its escort, had quickly cleared the city and resumed its pace. Clemmer’s company made it to the outskirts of Zarqa in about 90 minutes total, despite the slowdown in Hillah. As he arrived on site, Clemmer saw a humvee with steer horns mounted on the grill along the road. “It was Special Forces, no doubt about that,” Clemmer said. “I roll in there, jump out of the truck and the first thing I hear is .50 cal down the road just going off. So much for a secure site.” A brief hand-off of control of the site focused on the recovery operation at hand. “We go and confirm we have two people in the helicopter, and that was the most important thing – make sure the two guys were there,” Clemmer said. “We were there. No one else was going to get to them. It took hours to get them out, but we were going to get them out.” Forget the fair fight: Part 2: ‘It was like a match lit up’ Captain Brent Clemmer’s C Company was the tip of the 2nd Battalion, 3rd Infantry Regiment spear on Jan. 28, 2007. He had tested the limits of his Stryker vehicles to cover the ground from FOB Kalsu to Zarqa, leading his Charger-Company convoy on a 97-kilometer dead gallop in 90 minutes. Almost as soon as the convoy arrived at 5:30 p.m. to take control of the crash site of an AH-64, automatic fire erupted, touching off a fire fight that would last all night. The situation was confusing at first. Iraqi 8th Army and SWAT elements had been heavily engaged in the hours prior to the arrival of the small task force and were unable to provide a detailed picture of the battleground. A berm complex, a series of tree lines and a small cluster of farm buildings obstructed views of what Patriot Soldiers later learned was a fortified compound at the edge of a hardened village full of zealots prepared to fight to their deaths. “The SF did a good job covering the crash site by fire,” said Staff Sgt. Brian Butler, then weapons squad leader of 2nd Platoon, C Co., “but they didn’t have the means to build a perimeter around it. The only enemy they were seeing were the ones trying to go out to the crash site to get the pilots.” The twilight had turned to darkness, through which the Charger platoons prepared to maneuver around the helicopter. Clemmer issued orders to his platoon leaders to envelop the crash. As the platoons stepped off, AK-47s opened up from four huts to the north. “The SF was still in control of the birds at that point,” Butler said. “That’s when the first Hellfire went off.” “It was like a match lit up,” said Staff Sgt. Robert Bales, team leader in C Company’s 1st Squad, 1st Platoon. “It looked like a toy with a candle lit underneath it. Fire straight up.” By 5:45 p.m., the Charger platoons had formed a horseshoe around the downed Apache. They had begun the assault in their Strykers, then dismounted to sweep back across the site. Until then, there had been no mortar- or rocket-propelled-grenade fire to argue against tactical exposure. By a few minutes after 6 p.m., they had secured the site enough to let the engineers do their work. Sappers traveling with C Company recovered the first pilot while Patriot Soldiers provided cover. The battalion commander, Lt. Col. Barry Huggins, arrived with Capt. Bill Parsons’ B Company, which was task-organized with recovery vehicles and his own engineer platoon. Charger Company’s 1st Platoon took up positions on the eastern side of the chopper while 2nd Platoon settled to the Southeast, directly in front of the still-burning wreckage. Third platoon occupied berms to the west. Small-arms fire started almost immediately from farther to the southeast. As the platoons were aligned, only 3rd could answer to suppress it without firing through its own lines. “The bad guys were not afraid to shoot a lot but had no (aiming lights) and were poorly trained,” Clemmer said. “The result was they shot high. Most of my guys will tell you they had parts of the trees around us falling onto them, cut down by enemy fire.” Clemmer called forward his company mortar section and oriented his section sergeant, Staff Sgt. Scott Muetz, on the targets to the east and southeast. Muetz and his section leader, Staff Sgt. Larry Neal, had endured merciless ribbing from the rest of the battalion for their insistence on training on their guns while artillery Soldiers in OIF were used overwhelmingly as infantry assets. Every Charger mortarman was thankful that night for his long hours of training and certification on the guns. With its thicket of deep trenches, Zarqa was more than anything an indirect-fire fight. “All we had visual on was a little farm shack,” Muetz said. “(The compound and village were) farther back in. But at first we were wondering, ‘What’s all this firing about”” The mortar section fired missions and alternately dug in. By the early morning, the 60 mm tubes were ensconced inside fighting positions. The platoons on the crash-site perimeter were also using shovels in throwback defensive tactics. “The cool part about this was World War II style, you dug in,” Bales said. “Guys were out there digging a fighting position in the ground. You’re taking a shovel and digging as fast as you can.” “It’s no problem digging when you have rounds zinging by and the vehicle behind you is getting hit,” Muetz said. Soon after he arrived, Parsons conducted a reconnaissance-in-force and placed his engineer platoon in security overwatch on the main road into the site known as ASR Miami. Soon after he arrived, he conducted his own battle handoff with ODA 563 personnel. En route from FOB Kalsu, Parsons had already attended to convoy security by sending his executive officer, 1st Lt. Patrick Horan, and a small team to neutralize a machine-gun ambush at a choke point along their route to Zarqa. By the time they arrived on the high ground where the enemy position had been sited, the machine gun and its crew were gone. While B Company settled in, Huggins moved his command post and battalion support trains forward near the C Co. mortar section, now fully engaged in firing 60 mm missions. He was still unaware of the village in front of him, hidden behind the complex of farm shacks and a grove of date palms. After receiving Clemmer’s initial reports of spirited resistance and a thorough report from Capt. Roy Kempf, team leader of ODA 563, Huggins began to grasp the capability and dedication of the enemy still menacing the downed Apache in his battle space. The plan changes Huggins decided to modify the mission to engage the large concentration of enemy fighters they had encountered; he called in Parsons and Clemmer and issued an order to destroy enemy forces in the vicinity, while continuing recovery operations. “We had not yet completed the recovery of the crash site, but had the site well secured,” Huggins wrote later in his commander’s summary of the battle. “I developed a plan to coordinate the airspace and allow close-air support, mortars, and rotary-winged aircraft all to participate in the fight. (I) figured we had a lucrative target and should develop it.” “One of the main reasons we were successful,” Parsons said, “was Lt. Col. Huggins’ simple but effective plan that fixed the enemy and facilitated coordination between the different units on the ground.” He assigned the Joint Theater Air Control System to Parsons to coordinate air assets and ordered him to lead his company south to seal off the bottom of the site. With Blackhorse Soldiers in place by 9 p.m., C Company to the west and the river to the east, Huggins concentrated air power on the northern sector to complete the box around the compound. “They had a kill box where aircraft were looking for their own targets and calling to make sure everything was clear,” said C Co. fire support NCO, Staff Sgt. Jason Sims. “We had our indirect fires to the west of that, fixed wing and Spectre (gun ships) coming in. They were deconflicting themselves for the most part.” Muetz’s mortar section switched to 120 mm rounds with low charges to keep the rounds below the flock of swirling aircraft. The Stryker mortar variant delivered round after pinpoint round to foil a number of insurgent attempts to regroup or mount charges. “Those 120s were dead on,” Bales said. “We were getting (target) refinements from Spectre that were no refinements at all with the 120s. They were just dead on, just that accurate.” “We were hearing reports that we’d killed a hundred in this trench line and I’m saying ‘Come on now, who’s slinging this bull” Clemmer said. “I’ve been in Iraq twice now and we’ve never faced 100 bad guys. It ended up being incredibly accurate, but in our minds, a hundred guys!” Meanwhile, the careful work continued of extricating the second Apache pilot from the wreckage. Along with ducking enemy fire, the helicopter itself created a greater danger to the engineers attached to Charger Company. “One Apache has so much (unexploded ordnance),” Butler said. “There was UXO scattered all over that field. I didn’t want to blow up trying to dig in so we didn’t dig in our hasties.” At 10:27 p.m., brigade engineers accomplished the solemn task of securing the remains of the second pilot. “My infantry was forward fighting and those studs got the bodies out,” Clemmer said. “This was not an easy or pleasant task.” Fire superiority As the night wore on, despite the murderous volume of fire from all sides and above, the Soldiers-of-Heaven fighters showed incredible resiliency. “There was a north-south running road with a big berm, behind which they were able to run and reinforce behind and a trench line that also ran east and west,” Butler said. “They’d come up on that berm and we’d shoot them; they’d pull that guy back, do buddy aid on him and replace the guy. So as they were taking casualties they were pulling guys back.” A half-dozen times during the night, enemy fighters made suicidal rushes, some getting to within 100 to 150 meters of Patriot positions, Butler estimated. Every time, they were cut down by the weapons platform most available at the moment. “Throughout the night, the enemy came up out of their positions and would come towards us,” Clemmer said. “It wasn’t fair and that was fine with me. As 3rd Battalion, 75th Infantry (Rangers) used to say, ‘forget the fair fight.’ Our thermals would see them and that .50 cal and the remote weapon station is wicked, wicked, wicked.” Specialist Rodrigo Moreno had a front-row seat with 2nd Platoon, C Company directly in front of the crash site. “When we were shooting I kind of stood up a little bit and tried to shoot,” Moreno said, “but I remember when they were dropping the 500 pounders, we got up on our knees even though bullets were still going over us and we got blown back.” “We had so much control, we were bringing munitions in as close as we could according to military standard,” Sims said, “having the control and confidence and everybody knew where everybody was on the battlefield.” It was clear that no amount of fanaticism would stand up to the sophistication and fire superiority of the array of U.S. weapons systems. As midnight passed, Huggins directed B- and C-Company commanders to offer surrender terms over the public address systems in their command Strykers. They promised a lull to allow enemy fighters to gather themselves and come forward. Instead, the insurgents used the time to regroup and counter-attack. “By (1 a.m. the enemy) was re-engaging with heavy machine guns and repositioning forces,” Huggins said. “We re-engaged with all assets. Among other things, we hit a truck carrying ammunition; it continued to cook off for half an hour. At another point, we hit an underground cache, with sympathetic detonations and small-arms ammunition cooking off for some time afterwards.” The battle wanes The volume of fire decreased through the early hours of Jan. 29, to the point that by some time between 3 and 4 a.m., 1st Sgt. Viriato Ferrera said it stopped altogether. “That was the point where I think we broke their will,” Ferrera said. Tarps and more recovery equipment arrived with ammunition resupply, allowing the sappers to complete their work dismantling the helicopter and loading the pieces onto two flat racks. In the early morning the dangerous mission of trench clearing fell to B Company. Huggins’ battle plan from the beginning was for a Blackhorse assault from the south in the morning. “At first light my 1st Platoon, led by 1st Lt. Austin Jones, moved up the eastern side of the objective to prevent some enemy from escaping,” Parsons said. “Then we got on-line, all four platoons, and cleared the trenches.” While B Company mopped up the southern trenches, Clemmer was preparing his company for daylight assault from the west. He dismounted with his platoons and advanced to the berm closest to the compound. Charger Soldiers were going through final checks before the attack. “I’m right behind my middle platoon, and we’re prepping hand grenades,” Clemmer said. “We’re going to go over the berm and seize this foothold to establish our support-by-fire line for B Company.” As they popped up to go over the berm, fires that had burned overnight met another arms cache that exploded immediately in front of the C Co. position. “Everyone was hitting the deck, diving over berms,” Clemmer said. “The next thing that happens is you start seeing white flags coming out. I’m looking up and my 2nd Platoon leader is in front of me saying, ‘Sir, they’re surrendering.’” Zarqa: Forget the fair fight – Part 3: Warriors to life-savers Patriot Battalion Soldiers were wary of the first group of Shiite fighters who walked out of Zarqa under white flags. Special Forces officers had warned Huggins of the Soldiers of Heaven using flags of truce in attempts to sucker U.S. forces into ambushes, word of which he passed through his subordinate commanders. Huggins’ plan before the surrender called for B Co. to clear trenches and assault from the south in the early morning hours of Monday, Jan. 29. For C Co. to assume unobstructed positions from which it could support Blackhorse Soldiers by fire, its platoons were forced to move forward, then intended to pivot on-line and orient with fields of fire across the trenches and the southern edge of the village. Clemmer had dismounted and was following his 2nd Platoon forward on foot when the white flags appeared. After fighting throughout the night the Chargers took cover on line behind a berm, distrustful of their enemy. Clemmer ordered his platoons to halt in place to let the situation develop, ensuring this surrender was genuine. “Everyone was exhausted at this point,” said C Company platoon leader, 1st Lt. Steve Smith. “Everyone was tense and waiting to see what would happen. We’d been shot at all night by these guys.” First Lieutenant Jon Lowe’s 2nd Platoon, B Company Soldiers moved out to clear the largest swath of the Blackhorse sector. Lowe “had a tougher task because they had to clear a portion of the rubble-strewn village that was more heavily populated,” Parsons said, as well their share of the trench line. Lowe’s platoon also linked with the right flank of C Co. to prevent fratricide. The companies swept forward across the open areas south and west of the village and into the village itself without major incident. “The fight was out of the enemy,” Parsons said. Parsons’ B Co. was still clearing forward of its fighting positions from the previous night when the small group surrendered to C Co. Within a few minutes, the group in the C Company sector grew bolder. “My assessment later is they were the bravest ones,” Clemmer said. “They probably thought we would kill them.” The operational pause was the first chance for the 2-3 Inf. Soldiers to get a good look at what was in front of them, their first pictures that weren’t through the sites of weapons. It was their first realization that there was a village ahead rather than a few random farm buildings. Two women followed the first group out of the village. When the Americans held their fire for the first several minutes, more followed. The Charger 3rd Platoon sergeant, Sgt. 1st Class Tausala Faamausili, was the first to see severely wounded villagers ahead, calling out “We’ve got three litter urgents.” From that point, the floodgates opened. “All of the sudden we go from five or 10 people to 50, then 100,” Clemmer said. “Now two platoons are fully engaged from putting the pins back in grenades, calling the trucks up, whipping the concertina wire off the trucks to start building some pens.” Clemmer did a quick handoff with his first sergeant, who set up detainee- and casualty-collection points. The company commander culled out two squads from each platoon and pushed forward to continue clearing the village, while 1st Sgt. Viriato Ferrera took charge of the rest to quickly organize a field medical site. Shifting on the fly With no formal order or declaration, the mission of the first sergeant’s half of C Company shifted from combat to humanitarian operations. “I took most of my combat lifesavers, my emergency medical technicians,” Ferrera said. “As I started getting flooded with people I called everybody else up and said, ‘Look, I need your CLSs, I need all your EMTs down here. I need your medics down here with me.’” Huggins directed Parsons’ company to keep its medics in case his Blackhorse Soldiers met resistance in the trenches. Every other able bodied medic or Soldier with medical training streamed into the impromptu aid station to help. The battalion surgeon, Lt. Col. Dean Pedersen, prepared his medical-evacuation-variant Stryker to receive patients, then moved out to start categorizing the wounded. “I jumped into sort of a triage mode,” Pedersen said. “I let the medics do what treatment they could and just became an adviser, running from medic to medic saying ‘Here, do this, do that … This woman we need to evac urgently; this one isn’t going to make it no matter what we do, go to the next.’ There were all kinds (of injuries); the extent of the injuries were massive – extremity amputations to bullet wounds to fractured pelvis, intra-abdominal wounds.” By 9 a.m., the pens were filling fast. There seemed an unlimited number of seriously wounded. “I had the vehicles positioned so that the people getting treated weren’t in view of the detainees,” Ferrera said. He set up a field surgical site with Pedersen treating the most seriously wounded. “Once we started getting the initial casualties in we identified some litter-urgents we had to get out of there,” Ferrera said. “I started calling battalion requesting a bird because we needed to get them air evaced out of there because they were going to pass away.” The sun appeared blood red that morning, Clemmer said, in part because of sand in the air from desert winds. By the time the three medevac helicopters approached, the formation with the call sign “Spirit 11″ flew into a full-on sandstorm, somehow touching down exactly on the landing zone that had been scratched out for them. Weather conditions allowed only one medical sortie, however, with the three birds taking 16 of the worst injured. Two died, but 14 were saved as a direct result of the heroic efforts of the Spirit 11 pilots. Clearing the village Charger Company Soldiers not engaged in the medical effort moved into the village. Clemmer said it looked like a scene from hell, wrought by the combination of Air Force and Army weapons, from indirect and his own direct fire. The scene in the village invaded all Charger Soldiers’ senses at once. “I’ve tried to forget the smell,” Clemmer said. “The coppery, charred, sickly sweet smell of it all was overpowering. My radio-telephone operator, Spc. (Zachary) Parsons, and I were moving all around the town and had to keep passing by a couple of the worst spots. He’d just keep lighting the smokes and passing them too me. They were a great distraction to the carnage.” Clemmer wasn’t a smoker, but inhaled an entire pack as he and his RTO surveyed the damage. Bill Parsons’ Blackhorse Soldiers encountered the same scenes in the southern sector of the village they cleared. “I just couldn’t understand, faced with this overwhelming firepower, why someone would stand and fight to your death,” Parsons said. Their own plentiful supply of arms and ammunition had apparently given the cult members a false security. Most of the dead were fully outfitted for combat. “I thought when we were coming up on the objective that like a lot of times it was going to be pretty hard to tell who were combatants and who were not,” said Staff Sgt. Brian Butler, weapons squad leader in 2nd Platoon of C Co., “but it wasn’t actually. About 95 percent of everybody who was fighting against us, they had some gear on. They had full kits on and they were fully armed. It was clear cut: bad guys here, good guys there. If you were male, you were fighting. That’s the way they were doing it. Older males and younger, teen-age and above, they were all kitted up. They had night observation devices, sniper rifles – they had everything.” One C Co. squad gunned down a Soldiers-of-Heaven fighter carrying an AK-47 as he dashed toward a heavy machine gun. Another squad returned fire as they cleared a building, killing a holdout who attempted to ambush its members. But these were the exceptions. Most combatants were too injured, exhausted or shell shocked to resist. “One by one we started pulling these males out,” said platoon leader, 1st Lt. Gregory Weber. “About 50 percent of them had some sort of injury, whether it was minor with shrapnel and scratches to some amputees, loss of hearing and eyesight.” After a while, however, the clearing operation morphed with the humanitarian. As Soldiers pulled out the injured, it became apparent to their horror that these fanatics had brought their families to the fight. “Once we started clearing the town we actually started carrying people back out,” said Staff Sgt. Bales, a team leader in 1st Platoon, C Co. “We’d go in, find some people that we could help, because there were a bunch of dead people we couldn’t, throw them on a litter and bring them out to the casualty collection point.” Heavy toll From mid-morning through mid-afternoon, the medical aid station brimmed with bloody customers. The Charger first sergeant estimated that 90 percent of the wounded and detainees were combatants, about half of those humiliated at their loss, but most of them visibly grateful to no longer be fighting. The nature of the casualties demonstrated the precision of U.S. firepower. Huggins said the highest battle-damage estimate of noncombatants killed was 10, a statistic verging on miraculous considering the ordnance visited upon the Shiite fighters, testimony to the accuracy of U.S. weapons and the remarkable discipline exercised by the pilots, artillerymen and Soldiers pulling the triggers. “I was glad for the pilots that they saw it from afar because we were dealing with most of that,” Butler said. “They did an outstanding job of target discrimination because most of the dead were all enemy (combatants).” As the day wore on, the relentless flow of casualties took its toll on C Company’s stores of supplies. “That’s the first time I saw the MEV completely empty of all first aid equipment,” Ferrera said. “We went completely black on equipment and first aid supplies.” The number and nature of the wounded also took an emotional toll. “The hardest thing they had to deal with (among) all the guys that were treating that day, as well as myself because I have four children, was treating the children,” Ferrera said. He stopped one NCO from fleeing after treating a 5-year-old girl with a grievously injured arm. “‘I need you here to do your job, Sergeant,’” he told the exhausted, overwhelmed medic. “‘These people need you.’ That was probably the largest battle that day – treating the children.” Faamausili, who was named an “Armed Forces Real Hero” by the Rainier Chapter of the American Red Cross for his combat- and lifesaving actions that day, found two children dead along the road leading to the village. The platoon sergeant’s men watched as he wrapped them in a rug and, eyes glistening, gently placed them away from traffic. “Just the grief on his face for the loss of a child’s life,” Clemmer said. “The guy’s almost 6’6″ and 300 pounds, and in this tender way wrapping up someone who had been killed, treating them like his own kids. I try to get most of the images of that place out of my head, but that’s one of the few that always sticks there.” Ferrera stayed on task but remembered thinking at the end of the day, “Why would you bring your family, your children to something like this if you know what you were going to do’” By 3 p.m., they had treated most of the wounded and around 4 p.m., transferred responsibility for them and the site to the Iraqi Security Forces. Pedersen, exhausted by his lifesaving efforts, knelt and took a moment to catch his breath. He had trouble getting back on his feet. Aftermath Interrogators’ interviews with detainees began to paint an intelligence picture later confirmed by materials collected at Zarqa. The Soldiers of Heaven were a Shiite splinter group that had prepared and trained for combat. They had imminent plans to travel to Najaf and murder three Shiite leaders during Ashura to foment strife and exacerbate an already tenuous security environment that some were in January 2007 calling a civil war in Iraq. “This is a cult who had bought this farm, like the Branch Davidians,” Huggins said. “It was their base. They had stockpiled medical supplies, ammunition, a significant number of weapons, literally hundreds and hundreds of small arms, RPGs. I don’t know what the result would have been had all those folks been assassinated during Ashura. It’s probably not unreasonable to assume that a collapse would have ensued. And it was headed off because they shot a helicopter down and we got sucked into what went from a search-and-rescue to a recovery to a hasty defense to an attack to humanitarian relief.” The current commander of 2-3 Inf. saw the battle as validation for the tactics, configuration and agility of the Stryker brigade combat team. “Zarqa demonstrated that we have an expeditionary mindset, a mindset unlike any other unit in the Army today,” Lt. Col. Adam Rocke said. “It shows that a Stryker infantry task force is capable of doing things that no other unit in the Army is capable of doing, exemplifying flexibility, agility and lethality like no other unit.” Rocke said the battalion’s exceptional chain of command helped the SBCT produced the one-sided victory. “Leadership is paramount,” he said, “leaders who are seasoned, who understand commander’s intent and who act with disciplined initiative and who understand the offensive mindset.” The ability to conduct full-spectrum operations and transition to humanitarian activities proved how unique Stryker Soldiers are, he said. That sentiment was shared by the NCOs who were there, many of whom remain in the Patriot Battalion. “I’ve never been more proud to be a part of this unit than that day,” Bales said now a member of 2-3 Inf. headquarters, “for the simple fact that we discriminated between the bad guys and the noncombatants and then afterward we ended up helping the people that three or four hours before were trying to kill us. I think that’s the real difference between being an American as opposed to being a bad guy, someone who puts his family in harm’s way like that.” Clemmer, who won a Silver Star for his leadership through all phases of the complex battle, saw it as a moral victory as well as a tactical one. “There is not an army in the world, in my opinion, that can go from taking pins out of grenades and throwing them over trenches to receiving wounded, treating the wounded and taking care of an enemy that we had killed throughout the night – treating enemy combatants with that humanity.” For its actions in the Battle of Zarqa, 2-3 Inf. has been submitted for the Valorous Unit Award. The recommendation received the endorsement of the current commanding general of Central Command, Gen. David S. Petraeus, and is awaiting final approval at Human Resources Command. Don Kramer is a reporter with Fort Lewis’ Northwest Guardian. |
NSA-U.S. Intelligence : Hiding of Military Assets by “Rogue Nations” and Other States a Major Security Challenge for 21st Century

Washington, D.C., March 27, 2012 – A central element of the current debate over how to deal with Iran’s nuclear program has focused on the possible difficulty of destroying the Qom underground uranium enrichment facility via air strikes. However, documents posted today by the National Security Archive show that Qom is only the latest in a long series of alleged and real underground facilities that for decades have been a high priority challenge for U.S. and allied intelligence collection and analysis efforts, as well as for military planners.
The documents featured in this posting describe in detail the agencies and programs the U.S. government has brought to the task of identifying and assessing underground structures in foreign countries since World War II. Internal records indicate there are more than 10,000 such facilities worldwide, many of them in hostile territory, and many presumably intended to hide or protect lethal military equipment and activities, including weapons of mass destruction, that could threaten U.S. or allied interests.
The records (and introductory essay by Archive Fellow Jeffrey T. Richelson) also discuss the vast complexities of gathering and analyzing intelligence on these facilities, and detail several of the highly technical methods U.S. agencies have developed for the purpose over time.
Introduction: “Underground Facilities: Intelligence and Targeting Issues”
By Jeffrey T. Richelson
A central element of the current debate over how to deal with Iran’s nuclear program has focused on the possible difficulty of destroying the Qom underground uranium enrichment facility via air strikes.1 But documents posted today by the National Security Archive show that Qom is only the latest in a long series of alleged and real underground facilities that for decades have been a high priority challenge for U.S. and allied intelligence collection and analysis efforts, as well as for military planners.
Such challenges go back to at least the Second World War. In August 1943, the Germans, in the face of allied aerial attacks, decided to move production of their A-4 (V-2) rocket to an underground facility near Nordhausen. By late 1944, British intelligence was reporting that the facility was producing over thirty rockets a day, while the British Chiefs of Staff wanted to know the feasibility of a bombing campaign to halt or seriously impair production. In her memoirs, Constance Babington-Smith reported examining aerial photographs of Kahla, in the Thuringian Hills, and finding evidence of an underground jet-fighter factory.2
During the Cold War there were two types of underground facilities that were, in some ways, emblematic of the consequences of that war turning into a hot one – missile silos and leadership protection bunkers. While the Cold War ended with the collapse of the Soviet Union in 1991 (if not before), the U.S. Intelligence Community’s concern about foreign underground facilities has grown over the last two decades, particularly with respect to “rogue nations” that have discovered that hardening and concealing sensitive operations “remains an effective response to the technology advantages in intelligence and weaponry enjoyed by the United States and its allies” (Document 23). In 1999, a Defense Intelligence Agency assessment of the threat for the following twenty years stated that “The proliferation of underground facilities (UGFs) in recent years has emerged as one of the most difficult challenges facing the U.S. Intelligence Community and is projected to become even more of a problem over the next two decades.”3
The concern about underground facilities (or “hard and buried” targets) is evident in the establishment of a number components in various intelligence and defense agencies. The National Reconnaissance Office has a Hard and Buried Targets Working Group, while the National Geospatial Intelligence Agency, had (as of 2005) an Information and Underground Issues Division in its analysis directorate, and by 2008 the Defense Threat Reduction Agency had Hard Target Research and Analysis Center.4
But the most significant indication of the concern about underground facilities was the establishment, in 1997, of the Underground Facility Analysis Center (UFAC), which while subordinate to DIA also relies on participation from a number of other intelligence agencies – including the Central Intelligence Agency (CIA), National Security Agency (NSA), U.S. Strategic Command Joint Intelligence Operations Center, and the Air Force Technical Applications Center (AFTAC) – as well as the Defense Threat Reduction Agency (DTRA) and the U.S. Geological Survey (USGS). When it was established, UFAC had a staff of 20; by 2009 that number had grown to 240.5
The underground facilities that have been and are of concern to the U.S. Intelligence Community have an assortment of purposes. One is covert concealment and transportation, the most prominent example being the tunnels constructed under the Demilitarized Zone between North and South Korea to allow North Korean troops to be infiltrated into the South. According to independent experts, 12 levels of underground tunnels also lie beneath the Russian capital, the largest being an underground subway system reserved for high-ranking officials.6
A second type of underground facility are those employed for fuel and food storage. By 1976, according to a memo (Document 7) from the director of the Defense Intelligence Agency to the secretary of defense, the Soviet Union had either developed or was in the process of developing underground grain storage depots. In late 2008 or early 2009, North Korea reportedly built an underground fueling facility at the Musudan-ni missile complex on the nation’s northeastern coast. According to the report, the objective of constructing the facility was to make it more difficult for reconnaissance satellites to detect signs that a missile was being prepared for launch.7
As noted above, the construction of underground bunkers for leadership protection was part of both United States and Soviet nuclear strategy during the Cold War. According to various reports, the end of the Cold War did not diminish Russian interest in the upgrading of older facilities and the construction of new ones.
The Pentagon’s 1988 report (Document 14) on Soviet military power also noted that “neither changes in the Soviets’ leadership nor the restructuring of the strategic balance and the refinements in military doctrine that accompanied these changes have diminished their commitment to the program,” and that “another round of construction on these complexes began in the early 1980s.” About a decade later, reports appeared concerning new Soviet underground structures, some for leadership protection. Intelligence reports from 1997 stated that construction was nearly complete on a government relocation bunker 46 miles south of Moscow. That project, along with refurbishment efforts at other bunkers in the Moscow area, was believed to be intended to ensure “continuity of leadership during nuclear war.” Another construction effort was at Yamantau Mountain, about 850 miles east of Moscow – which included the digging of a “deep underground complex” as well as construction at above-ground support areas.8
Russia is, of course, not the only nation whose underground facilities are of interest to the U.S. Intelligence Community and military. In June 1989, in the midst of the Tiananmen Square demonstrations, The New York Times quoted an intelligence official as stating that “All of the top leaders have gone underground to their bunkers.” Not surprisingly, U.S. forces found vast underground complexes when they arrived in Baghdad in 2003, including a 12-room complex inside a cave. Libya also maintained underground bunkers designed to protect its leadership – or, more accurately, the Qadhafi family. One was located 40 feet underneath a mansion owned by one of Muammar Qadhafi’s sons. The facility contained an operating room, medical supplies, a generator, and living quarters.9
In addition to investing heavily in underground leadership protection facilities, the Soviet Union and now Russia have devoted considerable resources to underground construction with another purpose – the preservation of command, control, and communications capabilities. In 1997, an intelligence report stated that there was ongoing construction work on a “nuclear-survivable strategic command post at Kosvinsky Mountain,” about 850 miles east of Moscow. A press report characterized the facility as the Russian counterpart to the North American Defense Command’s Cheyenne Mountain Operations Center. In March 2011, the director of the DIA reported (Document 38) that Russia was upgrading “massive underground facilities that provide command and control of its strategic nuclear forces.”10
Cuba has also, reportedly, constructed bunkers to protect command, control, and communications capabilities. According to a press report, a circa-2000 DIA report stated that “All essential Cuban command, control, and communications sites are in hardened bunkers,” and that “Many of the sites are greater than 20 meters below the surface, making some too deep to attack with conventional munitions.” The Amiriyah Bunker and Shelter in Iraq was originally built as an air raid shelter during the Iran-Iraq War (1980-88), and subsequently converted into a military command and control center. In 1991, it was used as a military communications center by senior Iraqi military officials. During the Persian Gulf War of 1991, selected civilians were admitted to the top floor at night, and a number were killed when the facility was bombed on February 13, 1991.11
The practice of building underground factories for weapons production may be a precaution to ensure continued production during wartime – as Nazi Germany did in relocating A-4 (V-2) production underground. It might also be a peacetime measure undertaken to limit intelligence collection about the items being produced, for example weaponry (such as biological agents) being manufactured in violation of a treaty.
In 1966, China launched Project 816, which called for an underground plutonium production reactor and a reprocessing facility located near the village of Baotao, in the Fuling District of Chongqing Province. The effort resulted in the construction of the world’s largest “man-made cave” – 104,000 square meters, the equivalent of 20 football fields. However, with the facility about 85% complete, it was scrapped in 1982. After the weapons effort was shut down, the facility was converted into a chemical-fertilizer plant. (Document 37).12
Three decades after China launched that project, Libya was involved in another such project. In April 1996, the Defense Department reported (Document 18) that the Qadhafi regime had initiated construction of “a large, underground chemical warfare plant near Tarhunah, a mountainous region about 60 kilometers [37 miles] southeast of Tripoli.” The DoD report observed that “putting the facility underground masks its activities and increases its survivability in case of an attack.” In late June 1996 it was reported that construction had stopped on the facility – at least that there was no activity outside the site.13
In March 2011, the director of the Defense Intelligence Agency told (Document 38) a Congressional committee that “Iran has major underground nuclear facilities at Qom and Natanz.” Later that year, Iran apparently moved uranium hexaflouride to the Fordow Fuel Enrichment Plant near Qom, in preparation to begin enrichment operations. Then, in January 2012 diplomats confirmed a report that Iran had commenced uranium enrichment at Fordow, and stated that 348 centrifuges were in operation, in two cascades.14
In addition to weapons production and storage, underground facilities may also be used
to protect operational weapons sites – that is, sites with aircraft, missiles, or communications equipment that are ready for immediate use. A 1972 national intelligence estimate (Document 6) noted the underground facilities associated with Chinese air bases, which could be employed to hide operations-ready aircraft. A 1982 imagery analysis report (Document 11) focused on retractable radio-relay antennas that could be withdrawn into a concrete area underground.
In 1984, it was reported that North Korea also protected radars and missiles in underground facilities, popping up for action when needed. By 2002, North Korea maintained underground hangars at Puckch’ang Air Base, 34 miles northeast of Pyonyang along the Taedong River.15
In June 2011, Iran unveiled underground missile silos, which state television claimed held medium- and long-range missiles. The television report showed footage of an underground launching pad for what was identified as a Shahab-3 missile. Previously, Western news organizations had reported evidence, albeit sketchy, of Iranian missile silos near Tabriz and Khorramabad in northwest Iran.16
Exactly how many facilities around the world fall into each category is not clear , particularly not at the unclassified level. But a 2001 report to Congress (Document 23) noted the Intelligence Community’s suspicion that there were over 10,000 potential hard and buried targets and that number would increase over the next decade.
U.S. intelligence requirements with respect to monitoring underground facilities can be divided into four basic categories. The first is verifying the existence of such a facility at a specific location, hints of which may come from intelligence sources or claims that may emanate from defectors. A second requirement is determining the facility’s mission – whether it be leadership protection, weapons production, weapons storage or something else. The third requirement is the development of specific intelligence concerning the facility – including its physical layout and size, the number of personnel, the equipment present, and its capability and/or output – whether that be the number of troops that can pass through a tunnel, the number of weapons stored, or the facility’s ability to produce enriched uranium or a biological agent. The intelligence developed concerning those requirements can be employed to assess foreign capabilities, monitor treaty compliance, as well as plan or conduct military operations.
Additional data requirements exist when the facility is considered a potential target. The information required includes the natural protection offered by the surface under which the facility has been constructed(e.g. its geology), the depth at which the facility exists, and the extent to which the facility has been hardened (and with what material).
The effort to gather such intelligence involves a variety of collection, analysis, and processing techniques. Overhead imagery, including electro-optical, radar, and infrared imagery, can spot construction in progress, allow estimation of the amount of material that has been dug out of the ground, or identify entrances leading underground. Overhead photography identified extensive underground construction in Cuba in 1966 (Document 3), a possible alternate military command center in the Wuhan Military Region of China (Document 10), and retractable radio-relay antennas in the Soviet Union and Poland in the 1980s (Document 11). The satellite imagery displayed in the 1988 edition of Soviet Military Power (Document 14) shows an entrance to a wartime underground relocation center as well as a surface support area and road/rail transfer point. Libya’s work on an underground chemical agents production plant was spotted by satellite photography in the 1990s (Document 13).
Signals intelligence may provide data on the location or specifics of underground sites, such as its mission or other details about its operations. Human intelligence, including overt collection involving foreign construction crews involved in building bunkers for foreign leaders, can also contribute to knowledge about the facilities – and provide information of relevance to determining the their vulnerability to attack. Even open sources, including press and television reports, have occasionally been helpful in this regard (Document 35). The U.S. Army Intelligence and Security Command’s Asian Studies Detachment has produced studies of North Korean underground facilities based on open sources.17
But a key discipline in the effort directed against such targets is measurement and signature intelligence (MASINT) – which includes, but is not limited to, hyperspectral imagery, geophysical data (acoustic, seismic and electromagnetic signals), effluents, and the analysis of the collected data. The Air Force Technical Applications Center and U.S. Geological Survey, – with seismic and acoustic collection capabilities, and DIA’s MASINT and Technical Collection Directorate, are particularly involved in those aspects of the underground facilities intelligence effort.
The esoteric nature of the MASINT effort is illustrated by the variety of technical reports prepared in the quest to improve U.S. capabilities to gather intelligence on underground facilities. Thus, the 1999 report, Characterization of Underground Facilities (Document 20) includes sections on the magnetic detection of machinery, laser vibrometry, and the detection of heat shimmer. Similarly, a report prepared for the Air Force Office of Scientific Research, titled Time- Exposure Acoustics for Imaging Underground Structures (Document 28), contains an appendix replete with formulas and discussion of computation “by backpropagating the received signals” and “signal loss due to geometric spreading.” Another report, produced by the U.S. Army Research and Development Center (Document 33) refers to signals extracted from simulation data that “reveal impulsive vertical ground-surface vibrations caused by the surface waves.” Another effort, an Air War College paper (Document 27), discusses applying gravity gradiometry to the search for deeply buried facilities.
As noted above, intelligence collection and analysis concerning an underground facility may be partially based on the prospect of military action to destroy or significantly degrade the capabilities of a facility. Thus, the July 2001 report to Congress from the secretaries of defense and energy (Document 18) notes a variety of programs to procure weapons capable of penetrating hardened and buried targets, including the Enhanced GBU-28 bomb for the B-2 bomber and the Advanced Unitary Penetrator bomb for smaller aircraft. The previous year, another Air War College study, Deeply Buried Facilities: Implications for Military Operations (Document 22), examined the ‘critical nodes’ of deeply buried facilities and a number of ‘neutralizing concepts’ for each node – including (p. 23) ‘undermine with suitcase nukes’ and ‘entombment’ as possible means for overburdening the physical structure node. More recently, in early 2012, it was reported that the Pentagon had concluded that the 30,0000-pound Massive Ordnance Penetrator was not capable of destroying some of Iran’s hardened underground facilities and that the Defense Department was seeking to make it more powerful.18
It is clear that no other nation, including Israel, can match the United States’ capabilities for the collection and analysis of data on foreign underground facilities, or that other governments have an equal ability to develop weapons to destroy such facilities. Despite the close U.S.-Israeli intelligence relationship, it is not likely that the United States has fully shared its intelligence on facilities such as Qom. What intelligence on Qom or other Iranian nuclear facilities the U.S. chooses to share with Israel is likely to be influenced by the impact the U.S. believes such shared intelligence might have on Israeli decisions.
DOCUMENTS
Document 1: Central Intelligence Agency, “Underground Shelter Used by KIM Il-Sung,” May 9, 1951. Secret.
Source: CIA Records Search Tool.
This short report, probably based on human intelligence, provides data on an underground reinforced concrete shelter, constructed within a cave for North Korean leader Kim Il-Sung.
Document 2: Central Intelligence Agency, “Construction of a Large Underground Shelter under Zizkov Hill in Prague,” March 27, 1957. Secret
Source: CIA Records Search Tool.
This report covers both the history of underground construction at Zizkov, which went back to World War II, as well as its then-current use for protecting employees of several nearby factories.
Document 3: Central Intelligence Agency, Memorandum for Director, Central Intelligence; Director, Defense Intelligence Agency, Subject: Joint CIA-DIA Report on the Military Posture in Cuba As It Pertains to Strategic Weapons, August 17, 1966. Secret.
Source: LBJ Library.
This one-page memo focuses on “extensive underground construction” throughout Cuba, spotted by overhead photography. The memo notes the number of bunkers built or under construction, and the evidence (or lack thereof) concerning the possible use of the bunkers for storing strategic weapons.
Document 4: National Photographic Interpretation Center, “Underground Aircraft Dispersal, Bihac Airfield, Yugoslavia,” June 17, 1968. Top Secret RUFF.
Source: CIA Records Search Tool.
This report notes the identification, based on satellite imagery, of the underground dispersal of aircraft at a Yugoslavian airfield. In addition to discussing the implications of the satellite imagery, it also provides relevant data drawn from other sources (‘collateral’) – including human intelligence.
Document 5: Defense Intelligence Agency, Soviet and People’s Republic of China Nuclear Weapons Employment Policy and Strategy, March 1972. Top Secret. (Extract)
Source: Freedom of Information Act Request.
Annex A of this report focuses on PRC force development and deployment, and contains a brief discussion (on p. II-A-5) of China’s construction – beginning no later than 1963 – of underground facilities at a number of naval bases.
Document 6: Director of Central Intelligence, NIE 13-3-72, China’s Military Policy and General Purpose Forces, July 20, 1972. Top Secret. (Extract)
Source: CIA Electronic Reading Room (www.cia.gov).
In its discussion of the Chinese air force this estimate notes “a rapid growth of underground facilities near [Chinese] airfields” and that the facilities represent an “important feature of the Chinese program to build air installations.” It goes on to estimate the number of airfields with underground facilities and the number of fighters they can accommodate. The estimate also discusses the advantages and disadvantages of the facilities.
Document 7: Lt. Gen. Samuel V. Wilson, Director, Defense Intelligence Agency, Memorandum for the Secretary of Defense, Subject: Soviet Grain Consumption and Imports, June 25, 1976. Confidential.
Source: The Rumsfeld Papers (www.rumsfeld.com)
This brief memo references a Defense Intelligence Agency briefing on Soviet underground grain storage facilities.
Document 8: National Photographic Interpretation Center, Central Intelligence Agency, Underground Berthing Facilities in North Korea, March 1, 1978. Secret.
Source: CIA Records Search Tool.
This slide identifies the location of North Korean underground berthing facilities.
Document 9: J.F. Vesecky, W.A. Nierenberg, A.M. Despan, SRI International, JSR-79-11, Tunnel Detection, April 1, 1980. Unclassified.
Source: Federation of American Scientists (http://www.fas.org)
This technical study, conducted for the Department of Defense’s scientific advisory group, JASON, focuses on the possible use of seismic and electromagnetic waves in detecting tunnels.
Document 10: National Photographic Interpretation Center, CIA. Possible Alternate Military Command Center, Wuhan Military Region, China, November 1980. Top Secret.
Source: CIA Records Search Tool.
This imagery analysis report, which apparently also uses information from communications intelligence, notes the discovery of a possible alternate military command center in eastern China, about 600 miles from Beijing. It discusses the underground complex as well as communications facilities.
Document 11: National Photographic Interpretation Center, Central Intelligence Agency, IAR-0039/82, Retractable Hardened Radio-Relay Antennas in the USSR and Poland, May 1982. Secret/WNINTEL.
Source: CIA Records Search Tool.
This imagery analysis report focuses on retractable radio-relay antennas that had been identified in the Soviet Union and Poland through satellite photography. The report notes that the antennas are mast-mounted “and the masts apparently can be retracted into a shaft set in an underground concrete housing.”
Document 12: Director of Central Intelligence, IIM 83-10005JX, Soviet Wartime Management: The Role of Civil Defense in Leadership Continuity, December 1983. Top Secret.
Source: CIA Electronic Reading Room (www.cia.gov).
This interagency intelligence memorandum focuses on various aspects of the role of civil defense in the continuity of leadership in the Soviet Union in the event of war. One part of the memorandum (Chapter IV) discusses the assorted types of leadership protection and relocation facilities – which include underground structures. Among the facilities examined in the chapter are those at Sharapovo andChekhov. The authors observe that “the deep underground facilities at these complexes for the National Command Authority would present a difficult target problem.” They also note that construction on another complex about 400 miles from Moscow, believed to be an alternate national command facility, was continuing.
Document 13: Central Intelligence Agency, Soviet Civil Defense: Medical Planning for Post Attack Recovery, July 1984. Secret.
Source: CIA Records Search Tool.
This study of Soviet medical planning for a post-nuclear attack environment includes a discussion (pp. 10,12) of underground medical facilities, which comprise both “modestly equipped dispensaries” as well as “extensive underground facilities.” It also discusses different groups to be served by those facilities – including leadership and nearby civilian populations after evacuation.
Document 14: Department of Defense, Soviet Military Power: An Assessment of the Threat 1988 (Washington, D.C.: U.S. Government Printing Office, 1988). Unclassified. (Extract)
Source: Department of Defense.
The U.S. interest in and concern about Soviet underground leadership protection facilities was evident in some issues of the Defense Department’s annual report, on Soviet military forces prepared, during the Ronald Reagan and George H.W. Bush administrations. The 1988 edition contained a discussion of those facilities, an annotated satellite photograph of a relocation facility, and a artist’s depiction of both the outside and inside of such a facility.
Document 15: Department of Defense, Military Forces in Transition, 1991. (Washington, D.C.: U.S Government Printing Office, 1991). Unclassified (Extract)
Source: Department of Defense.
This, the last Department of Defense report on Soviet military power, contains a briefer treatment of Moscow’s deep underground facilities, using the same artist’s depiction as employed in the 1988 report (Document 14). It notes a Soviet press report about “the presence of an enormous underground leadership bunker adjacent to Moscow State University.”
Document 16: Bureau of Intelligence and Research, Department of State, “Underground Nuclear Facilities,” December 9, 1992. Secret.
Source: Freedom of Information Act Request.
Among the topics discussed in this report by the State Department’s intelligence unit on underground facilities is the possibility that if South Africa did not accurately declare the amount of highly enriched uranium it had produced it could be stored underground in South Africa.
Document 17: National Imagery and Mapping Agency, Photo Interpretation Student Handbook, Module 6, March 1996. Unclassified. (Extract)
Source: Donation.
This paper from a manual produced by the U.S. national imagery interpretation organization (today known as the National Geospatial-Intelligence Agency) contains a brief discussion that is designed to aid imagery interpreters in identifying underground facilities employed for the storage of ammunition and bombs. It also discusses the feasibility of damaging the facilities via aerial attack.
Document 18: Office of the Secretary of Defense, Proliferation: Threat and Response, April 1996. Unclassified. (Extract)
Source: Department of Defense.
Two pages from this Defense Department report on proliferation of weapons of mass destruction focus on the Libyan chemical warfare program, which initially involved production of chemical agents at the above-ground Rabta facility. After the U.S. focused international attention on that facility, Libya began construction on an underground alternative.
Document 19: Director of Central Intelligence, FY 1998-1999 Congressional Budget Justification, Volume IV: National Reconnaissance Program, February 1997. Secret. (Extract)
Source: Federation of American Scientists (http://www.fas.org).
This page from the budget justification for the National Reconnaissance Program notes the challenges posed by underground facilities.
Document 20: JASON, JSR-97-155, Characterization of Underground Facilities, April 12, 1999. Unclassified.
Source: Federation of American Scientists (http://www.fas.org).
This technical study, produced by the DOD’s JASON advisory group, examines a number of technical approaches to the characterization of underground facilities – including seismic/vibration sensing, imagery and change detection, low-frequency electromagnetic techniques, magnetic detection of machinery, detection of power lines, and low frequency electromagnetic techniques. It also examines the differences in characterizing covert and overt facilities, and looks at possible areas for future research and development.
Document 21: Department of Defense, Joint Warfighting Science & Technology Plan, February 2000. Unclassified. (Extract)
Source: www.wslfweb.org.
This chapter of the joint warfighting science and technology plan is focused at least as much on the requirements for destroying or neutralizing underground targets as on the intelligence problem. It notes the differences among underground targets with respect to a number of factors, identifies the “core capabilities” (e.g., detect, characterize) that are needed to destroy or neutralize such targets, and the functional capabilities required (eighteen in all – from sensors to decision process analysis and assessment).
Document 22: Lt. Col. Eric M. Sepp, Air War College Center for Strategy and Technology, Occasional Paper No. 14, Deeply Buried Facilities: Implications for Military Operations, May 2000. Unclassified.
Source: Air War College.
This author states that “the existence of deeply buried [u]nderground facilities has emerged as one of the more difficult challenges to confront U.S. military forces in the twenty-first century.” The paper focuses on two intelligence issues – locating and analyzing deeply buried facilities – as well as neutralizing such facilities.
Document 23: Secretary of Defense and Secretary of Energy, Report to Congress on the Defeat of Hard and Deeply Buried Targets, July 2001. Unclassified.
Source: Federation of American Scientists (http://www.fas.org).
This report was mandated by the National Defense Authorization Act for the 2001 fiscal year. It provides an introduction to the topic, a description of accomplishments, requirements, relevant programs, and the role of science and technology in meeting future threats.
Document 24: Steve Buchsbaum and Dan Cress, Special Projects Office, Defense Advanced Research Projects Agency, “A Program to Counter Underground Facilities,” 2002. Unclassified.
Source: Defense Advanced Research Projects Agency (www.darpa.mil).
This short paper describes DARPA work on countering underground facilities. It delineates program objectives and notes that the DARPA program has focused on two primary approaches for characterizing underground facilities – PASEM (passive, acoustic, seismic, and electromagnetic monitoring) or the use of effluents.
Document 25: Department of State, Apparatus of Lies: Saddam’s Disinformation and Propaganda, 1990-2003, 2003. Unclassified. (Extract)
Source: Department of State.
Part of this State Department release focuses on an incident during the 1991 Persian Gulf war – the allied bombing of an underground bunker whose top floor had, unknown to the U.S, been used to house civilians at night. The release describes the origins of the facility, the security arrangements as of 1991, and its use for military purposes.
Document 26: Keith Payne, Office of the Assistant Secretary of Defense for International Security Policy, For: Larry Di Rita, Subject: Secretary’s Response to Rep. Tauscher before the HASC, 5 Feb., n.d. (circa Feb. 2003). Unclassified.
Source: The Rumsfeld Papers (www.rumsfeld.com).
This memo, which concerns Secretary of Defense Donald Rumsfeld’s response to a question posed during a House Armed Services Committee hearing concerning small nuclear weapons, notes an attempt to improve U.S. capabilities to model the ground shock created by both nuclear and conventional weapons against underground facilities.
Document 27: Lt. Col. Arnold H. Streland, Air War College, Air University, Going Deep: A System Concept for Detecting Deeply Buried Facilities from Space, February 23, 2003. Unclassfied.
Source: Air War College.
This paper, in addition to providing background on the history of underground facilities and the threat they pose, examines the problem of locating those facilities and understanding their uses, and then turns to the use of space-based gravity measurement to help locate deeply buried facilities.
Document 28: I.J. Won, Alan Witten, and Steven Norton, Geophex Ltd and University of Oklahoma, Time-Exposure Acoustics for Imaging Underground Structures, June 25, 2003. Unclassified.
Source: Defense Technical Information Center.
This paper, sponsored by the Air Force Office of Scientific Research, reports on the authors’ development of a “new technique for imaging underground facilities based on the passive monitoring of acoustic emissions from both stationary and moving equipment within such facilities.”
Document 29: Greg Duckworth, Defense Advanced Research Projects Agency, Counter Underground Facilities, 2004. Unclassified.
Source: Defense Advanced Research Projects Agency.
This briefing identifies different varieties of underground facilities and assorted means for detecting them.
Document 30: Maj. Mark Easterbrook, ‘Unearthing’ the Truth in Defense of Our Nation,” Pathfinder, January – February 2005. Unclassified.
Source: National Geospatial-Intelligence Agency.
This article, from the National Geospatial-Intelligence Agency’s unclassified magazine, describes the background and functions of the Underground Facility Analysis Center (UFAC) as well as interagency participation in the center, which is operated by DIA. It also describes the UFAC “knowledge base” and specifies the six goals “guiding UFAC development.”
Document 31: Donald Rumsfeld, Secretary of Defense, to Steve Cambone Subject: Deep Earth Penetrator, February 24, 2005. For Official Use Only.
Source: The Rumsfeld Papers (www.rumsfeld.com).
This memo from the Secretary of Defense asks for information about the underground activities of “all appropriate nations” as a prelude to a meeting about a ‘bunker buster’ weapon.
Document 32: Michael Klumb, “Searching for Undergrounds with a High-Tech Toolkit,” Pathfinder, March – April 2005. Unclassified.
Source: National Geospatial-Intelligence Agency.
This Pathfinder article focuses on the tools used to search and characterize underground facilities. Sections cover classifying urban terrain, distinguishing recurring features, the relevance of medical techniques, and the use of radar data.
Document 33: U.S. Army Engineer Research and Development Center, Seismic Propagation From Activity In Tunnels And Underground Facilities, November 1, 2006. Unclassified.
Source: Defense Technical Information Center.
As its title partially indicates, this highly technical analysis focuses on the use of seismic signals generated by mechanical activity in underground facilities – which, the authors write, “can be measured as ground vibrations at offset distances.”
Document 34: Scott Robertson, “Collaboration Is Cornerstone of UFAC,” Pathfinder, May/June 2007. Unclassified.
Source: National Geospatial-Intelligence Agency.
In addition to specifying the agencies involved in the UFAC effort, the article notes the role of the NGA element of the center, and reports on UFAC’s functions as specified in its charter.
Document 35: DNI Open Source Center, “Subtitled Clips of China’s Declassified Underground Nuclear Facility in Chongqing,” April 23, 2010. Unclassified.
Source: Federation of American Scientists (http://www.fas.org).
This brief OSC document reports on the content of a Chinese television report on an underground facility that was originally the home of a plutonium production reactor and was converted into a chemical factory.
Document 36: Underground Facility Analysis Center, “UFAC Digs Deep to Find Covert Facilities,” Communiqué, May/June 2010. Unclassified.
Source: Freedom of Information Act Request.
This short article, appeared in the Defense Intelligence Agency’s unclassified magazine, and provides a description of UFAC, the role of different agencies in the center, and some of the techniques employed by the center.
Document 37: Frank Pabian, Los Alamos National Laboratory, LA-UR#10-01758, The New Geospatial Tools: Global Transparency Enhancing Safeguards Verifications, October 27, 2010. Unclassified.
Source: Center for Nonproliferation Studies, Monterey Institute for International Studies.
One portion of this briefing focuses on the use of geospatial tools (particularly imagery and geo-location) in locating an underground facility in China that had been first constructed to house a plutonium production facility.
Document 38: Lt. Gen. Ronald Burgess, Jr., Director, Defense Intelligence Agency, Statement before the Committee on Armed Services, U.S. Senate, Worldwide Threat Assessment, March 10, 2011. Unclassified.
Source: Defense Intelligence Agency.
This assessment, by the DIA’s director, briefly notes the role of underground facilities in protecting Iran’s nuclear program (p. 14) and Russian command and control facilities (p.20). It also notes (p. 32) that employment of underground facilities represents a transnational trend.
Document 39: Office of the Secretary of Defense, Annual Report to Congress, Military and Security Developments involving the People’s Republic of China, 2011, 2011. Unclassified. (Extract)
Source: Department of Defense (www.defense.gov).
This report, which focuses on a large number of components of Chinese military power, contains a brief description of the interest of the Second Artillery Corps in the employment of underground facilities and their role in Chinese nuclear strategy.
Document 40: Gunnar J. Radel, Defense Intelligence Agency, Military Geophysics, June 14, 2011. Unclassified.
Source: Incorporated Research Institutions for Seismology (www.iris.edu).
This briefing, by a staff member of the Underground Facility Analysis Center, focuses on geophysical sensing in locating underground facilities, applications (treaty monitoring, battlespace awareness, and clandestine tunnel detection), and assorted challenges (for example, terrain and man-made clutter).
Document 41: Lt. Gen. Ronald Burgess, Jr., Director, Defense Intelligence Agency, Statement before the Committee on Armed Services, U.S. Senate, Annual Threat Assessment, February 16, 2012. Unclassified.
Source: U.S. Senate Armed Services Committee.
As he did the year before, DIA Director Burgess notes Russia’s massive effort to upgrade its underground command and control facilities (p. 22). In addition (pp. 26-27) he notes six countries and one terrorist group that employ underground facilities and specifies five uses of such facilities (including cover and concealment, and industrial production).
NOTES
1. Joby Warrick, “Iran’s underground nuclear sites not immune to U.S. bunker-busters, experts say,” www.washingtonpost.com, February 29, 2012.
2. Michael J. Neufeld, The Rocket and the Reich: Peenemunde and the Coming of the Ballistic Missile Era (New York: Free Press, 1995), p. 202; F.H. Hinsley, E.E. Thomas, C.A.G. Simkins, and C.F.G. Ransom, British Intelligence in the Second World War, Volume 3, Part 2 (New York: Cambridge University Press, 1988), p. 571; Constance Babington-Smith, Air Spy: The Story of Photo Intelligence in World War II (New York: Harper & Brothers, 1957), pp. 192-193.
3. Defense I\ntelligence Agency, A Primer on the Future Threat, The Decades Ahead: 1999-2020, July 1999, p. 139. Portions of the Primer appear in Rowan Scarborough, Rumsfeld’s War: The Untold Story of America’s Anti-Terrorist Commander (Washington, D.C.: Regnery, 2004), pp. 194-223.
4. “About the Authors,” Pathfinder, May/June 2005, p. 4; “Statement of Dr. James Tengelia, Director, Defense Threat Reduction Agency before the Subcommittee on Emerging Threats and Capabilities, Committee on Armed Services, United States Senate,” March 12, 2008, p. 5.
5. Maj. Mark Esterbrook, “‘Unearthing’ the Truth in Defense of Our Nation, Pathfinder, January-February 2005, pp. 19-21; “Tunnel vision,” DefenseNews (www.defensenews.com), August 1, 2009. The Air Force Technical Applications Center (AFTAC), in response to a FOIA request for a copy of any memorandum of agreement between AFTAC and UFAC refused to confirm or deny the existence of such an agreement. However, the DIA, in response to an identical request, while denying the request, stated that “A search of DIA’s systems of records located one document responsive to your request.” Alesia Y. William, Chief, Freedom of Information Act Staff, Defense Intelligence Agency, to Jeffrey Richelson, July 8, 2010.
6. Andrei Soldatov and Irina Borogan, The New Nobility: The Restoration of Russia’s Security State and the Enduring Legacy of the KGB (New York: Public Affairs, 2010, p. 118.
7. Lt. Gen. Samuel V. Wilson, Director, Defense Intelligence Agency, Memorandum for the Secretary of Defense, Subject: Soviet Grain Consumption and Imports, June 25, 1976. Kwang- Tae Kim, Associated Press, “Report: NKorea builds underground fueling facility,” February 25, 2009.
8. Department of Defense, Soviet Military Power, An Assessment of the Threat 1988, p. 60; Bill Gertz, “Moscow builds bunkers against nuclear attack,” Washington Times, April 1, 1997, pp. A1, A16; Bill Gertz, Betrayal: How the Clinton Administration Undermined American Security (Washington, D.C.: Regnery, 1999), pp. 44, 231.
9. Thomas L. Friedman, “200,000 Troops Near Beijing, U.S. Says,” New York Times, June 8, 1989, p. A13; Robert Tanner, “U.S. soldiers enter Saddam’s tunnels,” Washington Times, April 10, 2003, p. A13. Thomas Erdbrink, “Deep underground, elaborate bunkers show that Gaddafi family was ready,” Washington Post, August 26, 2011, p. A8.
10. Bill Gertz, “Moscow builds bunkers against nuclear attack”; Bill Gertz, Betrayal, pp. 47, 231; Kenneth R. Timmerman, “Inside Russia’s magic mountain,” World Net Daily (www.wnd.com), June 6, 2000; Lt. Gen. Ronald L. Burgess, Director, Defense Intelligence Agency Statement before the Committee on Armed Services, United States Senate, World Wide Threat Assessment, March 10, 2011, p. 20.
11. Bill Gertz, “Notes from the Pentagon,” December 8, 2000, http://www.gertzfilecom/InsidetheRing.html, “Cuba Bunkers,” http://groups.yahoo.com/group/coldwarcomms/message/1730. U.S. Department of State , Apparatus of Lies: Saddam’s Disinformation and Propaganda, 1990-2003, 2003, p. 12.
12. Frank Pabian, Los Alamos National Laboratory, LA-UR 10-04532, Using the New Geospatial Tools to Locate a Newly Revealed Underground Plutonium Production Complex in China, July 21, 2010, n.p. Open Source Center, “Subtitled Clips of China’s Declassified Underground Nuclear Facility in Chongqing,” April 23, 2010.
13. Barbara Starr, “Impenetrable Libyan CW plant progresses …,” Jane’s Defence Weekly, April 17, 1996, p. 3; “Targeting a Buried Threat,” Newsweek, April 22, 1996, p. 6; Charles Aldinger, “U.S. Rules Out Nuclear Attack on Libya Plant,” Washington Post, May 8, 1996, p. A32; Bill Gertz, “Libyans stop work on chemical plant,” Washington Times, June 25, 1996, p. A4; Office of the Secretary of Defense, Proliferation: Threat and Response, April 1996, p. 26.
14. Lt. Gen. Ronald L. Burgess, Jr., Director, Defense Intelligence Agency, Statement before the Committee on Armed Services, United States Senate, Worldwide Threat Assessment, March 10, 2011, p. 14; “Iran Prepares to Transport Atomic Substance to New Enrichment Facility,” Global Security Newswire, (http://gsn.nti.org), October 21, 2011; George Jahn, “Iran nuclear work at bunker is confirmed,” www.washingtontimes.com, January 9, 2012; David E. Sanger, “Iran Trumpets Nuclear Ability At a 2nd Plant,” New York Times, January 9, 2012, pp. A1, A3.
15. Benjamin F. Schemmer, “North Korea Buries Its Aircraft, Guns, Submarines, and Radars Inside Granite,” Armed Forces Journal International, August 1984, pp. 94-97. Jonas Siegel, “In harm’s way,” Bulletin of the Atomic Scientists, May/June 2005, pp. 34-35.
16. William J. Broad, “Iran Unveils Missile Silos As It Begins War Games,” New York Times, June 28, 2011, p. A4.
17. David A. Reese, “50 Years of Excellence: ASD Forges Ahead as the Army’s Premier OSINT Unit in the Pacific,” Military Intelligence Professionals Bulletin, October – December 2005, pp. 27-29.
18. Adam Entous and Julian E. Barnes, “Pentagon Seeks Mightier Bomb Vs. Iran,” Wall Street Journal January 28-29, 2012, pp. A1, A2.
Confidential – U.S. Army Afghanistan Theater of Operations Evidence Collection Guide

The transition from law of war-based detentions to evidence-based criminal detentions is underway. To fully support this aspect of our counter-insurgency (COIN) mission, Coalition Forces, partnered with Afghan units, are working in the field to provide information and evidence that supports detention operations. These efforts will most fully support the COIN effort if detainees suspected of committing criminal offenses are referred to the Afghan criminal justice system for pre-trial detention, prosecution, and serving of sentence for their crimes, based upon evidence which is used and understood in Afghan criminal courts.
This Guide will assist Coalition Forces and Afghan units by providing practical means and methods to properly identify, collect, preserve, and provide evidence that will be recognized and accepted by the Afghan criminal justice system. Using this Guide, Coalition Forces and partnered Afghan units can provide usable evidence, including statements, sketches, photographs, and physical evidence, to the Afghan authorities for each case. This justice effort continues in tandem with and complements existing intelligence exploitation which facilitates our own targeting process. To the greatest extent possible, however, the creation of unclassified products and declassification of classified products will significantly enhance in the transferability of evidence to the Afghan courts.
Built upon original work of Regional Commands, enhanced by the Detainee Criminal Investigation and Prosecution Training Team, Legal Operation Directorate, CJIATF-435, and coordinated with Battle Space Owners and Afghan partners throughout Afghanistan, this Guide will assist Coalition Forces and partnered Afghan units in properly handling and documenting evidence. While each nation within the Coalition Forces may have independent national authorities to adhere to in the detention process, the techniques provided in this Guide will assist all Coalition Forces to understand the importance of the collection of evidence for each suspect in order to continue the transition to evidence based-criminal detentions.
…
II. Why Evidence Collection is Vital
1. The Government of the Islamic Republic of Afghanistan (GIRoA) is a sovereign entity with its own criminal justice system. As we strive to improve adherence to the Rule of Law in Afghanistan, we must enable and support the criminal justice system. Capturing units must provide evidence and witness statements for use in an Afghan court of law to enable the National Security Prosecutor’s Unit (NSPU) or a provincial criminal court to prosecute and convict criminal suspects. Appropriate evidence collection may result in admissible evidence being used in support of effective prosecutions. To the greatest extent possible, evidence collection and case preparation will be performed by Afghan partnering forces. Although USFOR-A and ISAF continue to have a need to exploit evidence for potential intelligence value, units should ultimately turn all evidence associated with a suspect over to Afghan authorities. Therefore, units must have a plan to transfer both a copy of the case file as well as all the evidence and statements with suspects to the appropriate local, provincial, or national governmental authorities or to a national security court.
2. The Afghan legal system does not specify a standard of proof similar to that found in most common law western legal regimes. Instead, units must coordinate with the relevant local, provincial, or national prosecutors and judges to determine the specific type and amount of evidence deemed credible. Some prosecutors or judges might require a slightly different format or type of evidence than is accepted by most other authorities. Evidence collection practices and the type of evidence to be collected, as suggested in this Guide, should be tailored to fit local court requirements as necessary.
Report – An Estimated $8 Billion in Cash Was Smuggled Out of Afghanistan Last Year
In the busy street markets of Kabul, stacks of cash sit in piles as moneychangers shout the day’s exchange rate to shoppers bustling by. Currency is bought and sold in the open air.
But all the money changing hands on the streets is barely a drop in the bucket compared to all the cash being siphoned out of the country in suitcases, and that is not a metaphor.
“It’s hard to estimate exactly how much is going out of Afghanistan, but I can tell you in 2011, 4.5 billion was (flown) out of Afghanistan,” said Khan Afzal Hadawal, deputy governor of the bank of Afghanistan.
That is just what is moving out of the Kabul airport. It is estimated $8 billion in cash was lugged out of the country last year by car, private jets and border crossings. That is almost double the entire country’s budget for 2011.
The government is trying to stop the outflow of money to other countries and encourage investment in Afghanistan. It has capped the amount of cash that can be taken out of the country at $20,000.
Video – NYPD Infiltrated Liberal Political Groups
Via The Huffington Post: “Undercover NYPD officers attended meetings of liberal political organizations and kept intelligence files on activists who planned protests around the country, according to interviews and documents that show how police have used counterterrorism tactics to monitor even lawful activities…”.* Ana Kasparian and Cenk Uygur break it down on The Young Turks.
* http://www.huffingtonpost.com/2012/03/23/nypd-infiltrated-liberal-political-g…
Subscribe to The Young Turks: http://bit.ly/eWuu5i
Find out how to watch The Young Turks on Current by clicking here: http://www.current.com/gettyt
The Largest Online New Show in the World.
Google+: http://www.gplus.to/TheYoungTurks
Facebook: http://www.facebook.com/tytnation
Twitter: http://twitter.com/theyoungturks
Video – Obama Open Mic Audio With Russian President Medvedev
Via The Huffington Post/Reuters: “President Barack Obama was caught on camera on Monday assuring outgoing Russian President Dmitry Medvedev he will have “more flexibility” to deal with contentious issues like missile defense after the U.S. presidential election. Obama, during talks in Seoul, urged Moscow to give him “space” until after the November ballot, and Medvedev said he would relay the message to incoming Russian president Vladimir Putin. The unusually frank exchange came as Obama and Medvedev huddled together on the eve of a global nuclear security summit in the South Korean capital, unaware their words were being picked up by microphones as reporters were led into the room…”.* The Young Turks host Cenk Uygur breaks it down.
* http://www.huffingtonpost.com/2012/03/26/nuclear-summit-barack-obama-medvedev…
Subscribe to The Young Turks: http://bit.ly/eWuu5i
Find out how to watch The Young Turks on Current by clicking here: http://www.current.com/gettyt
The Largest Online New Show in the World.
Google+: http://www.gplus.to/TheYoungTurks
Facebook: http://www.facebook.com/tytnation
Twitter: http://twitter.com/theyoungturks
Reports on types of alias documentation issued by Central Cover Staff of Central Intelligence Agency
| Citation: | [Memoranda on Alias Documentation Provided by Central Intelligence Agency’s Central Cover Staff; Attached to Divider Sheet; Includes Routing Sheets and Attachments Entitled “Cover Support”; Variations of “CCS Cover Support Provided within the United States”; Variations of “Alias Passports”; “Alias U.S. Documentation”; “U.S. Documentation in Clandestine Services Operations”; Heavily Excised] Secret, Compendium, May 07, 1973, 34 pp. |
| Collection: | The CIA Family Jewels Indexed |
| Item Number: | FJ00047 |
| Origin: | United States. Central Intelligence Agency. Directorate of Operations. Central Cover Staff |
| Individuals/ Organizations Named: |
Bissell, Richard M., Jr.; Colby, William E.; Helms, Richard M.; United States. Central Intelligence Agency. Directorate of Operations; United States. Central Intelligence Agency. Directorate of Operations. Central Cover Staff. Chief; United States. Central Intelligence Agency. Directorate of Operations. Deputy Director; United States. Central Intelligence Agency. Directorate of Plans. Deputy Director; United States. Department of Justice. Bureau of Narcotics and Dangerous Drugs |
| Subjects: | Alias documentation | Corporations | Covert identities |
| Abstract: | Reports on types of alias documentation issued by Central Cover Staff of Central Intelligence Agency. |
| Full Text: | Document – PDF – this link will open in a new window (360 KB) |
Uncensored – Hitler’s Henchmen – Arbitrator over Death and Life – Roland Freisler
Cryptome – General Strike in Central Park New York City
Tuesday — 03.27.12 General Strike in Central Park
CONTENTS:
1. Invitation / Introduction
2. Some Background
3. Online Resources
4. Readings
5. Local Links
6. Precarious & Service Worker Assembly
___________________________________________________
1. Invitation / Introduction
What: Drifting Assembly on General Strike
When: Tuesday — 03.27.12
Where: Central Park, meet up at the steps of Metropolitan Museum
When: 6:00 pm
Who: Everyone (dress warm)
During the winter, we participated in a molecular seminar entitled
‘Welcome to the New Paradigm; The Crisis of Everything Everywhere.’ A few
hundred people attended over the course of 9 days, some staying for a
session, others for a day, and yet others for the entire duration.
Together we organized, disorganized, ate, spoke, disagreed, speculated,
walked, mapped, manifested, felt, listened, played, and even mic checked
Diego Rivera.
’Welcome to the New Paradigm’ was an allusion
to a banner we had seen in Washington Square Park at the conclusion of a
day of actions globally on October 15. That same night, after Gayatri
Spivak addressed everyone, we discovered that along with a lot of friends,
she had been thinking about the potentials for a General Strike.
At the time, the occupations at Liberty and across the globe were so
powerful; it was still unclear whether the idea of a General Strike was a
nostalgic regression or potential mode of amplification and generalization
of refusal. After all, the occupations were themselves a new paradigm of a
strike, not just striking against a work place or work but taking
everything, everywhere. As the coordinated and violent attacks by police started in late Fall on
the encampments, there was an even greater urgency placed upon everyone to
consider how this refusal of austerity, of faux solutions, of legalized
robbery, of new forms of enclosure, of an increasing surveillance /
security state, of ever greater ecological ruin, of continued structural
racism, could be expressed, embodied, uttered, collectively; and how could
this be done in a forceful manner, without further empowering or placing
all of our collective attention into a reactionary game with and on the
police force.
In January, we returned to the question of the General Strike and
we asked one another:
What it could mean a General Strike today given the global dimension of
financial capital, given the shifting qualities of the workplace and
work-time (namely its increased itinerancy, placelessness, instability,
meaninglessness), given the ever more invasive forms of extracting
productivity and value from the basic reproduction of our life and social
relations?
The winter provided to hundreds of people a season to formally and
informally meet, consider, propose plans and create possibilities for the
General Strike that has been called on May 1st.
In examining the shifted terrain of work, productivity, and thus strike,
the critical questions which emerge are:
How can this complex arrangement …
– of placed and non-placed labor (i.e., labor that occurs in a
recognizable workplace as well as Starbucks or the neighborhood boutique
cafe or the street or in the home)
– of recognized and unrecognized productivity (i.e., a waged job, albeit
badly paid, contracted labor or just using Google, Facebook, YouTube,
indirectly producing immense data, content, value, profits)
- of
remunerated and unremunerated life (i.e., the time which is paid for a
specific work and the time spent between any specific work just making
oneself available, preparing, learning new skills which could be reapplied
back into work)
– of visible and invisible, of legal and not legalized, of union and
non-unionized workers
… redefine the strategies for a General Strike?
Where could be the sites of blockage? Where could be the site of flow
stoppage? Where could be the sites of non-cooperation? How to activate
other fields of non-cooperation such a debt strike under the heading
general strike? And where could be the sites of cooperation, of
communization, of convergence?
Seen in the light of occupation, how might the general strike also
question the ideals sovereignty, autonomy, or freedom that presume an
individual political subject? How has occupation allowed us to reconceive
the strike not just as total refusal, blockage, or stoppage, but as a
public gathering that demonstrates the practices and principles of
socialization, communization, and mutual aid and care? What would it mean
to rethink the social intransitivity of the strike—its lack of
instrumentality, of work, of means-ends relations—as neither undoing or
negativity nor direct action, but as opening onto the potentiality of
being-in-common?
What does it mean to strike if you are unemployed? Or “your own boss”? Or
a freelance worker? How to also take account of those whose time is not so
flexible, and who face greater threats and risks in walking off the job or
joining a public demonstration?
What qualities could a strike take to address the multiplicity of sites of
and modes of production? And if our consumption, obedience, and everyday
participation is part of our productivity, if our everyday social
reproduction is the lubricant of the economic machinery that increasingly
surveys and oppresses the multitudes and our shared habitats, how could
May 1st become the turning point to intensify a process not only of
withdrawal or a symbolic act but a call for the infinite strike, the
closest we can get of doing nothing, how actively we envision and realize
our lives without capitalism.
We are interested in continuing this discussion not only on theoretical
grounds but through proposals for specific actions online and in the city.
We would like to propose meeting at Central Park on Tuesday early evening
for a walk and informal assembly.
The walking assembly will be unfacilitated by the Central Park Exploratory
Committee, an ungroup attempting to reassert the park as a commons, and as
potential site of convergence on the day of the General Strike, resulting
in a meshwork of refusal, food, music, pleasure, sensuality, resistance,
communization. The group is interested in weaving together with others
great fictions and believes strongly that such visions or horizons will
resonate with multitudes not only on May Day but also for the days
after.
Come join us and bring things to share: proposals,
food, drink.
___________________________________________________
2. Background
A general strike has been called for May Day, first by Occupy Los Angeles
on November 15th, and locally by Occupy Wall Street on February 14th. In
the time between and since many other city and neighborhood assemblies
have taken up the call, and a number of other coalitions, collectives, and
committees have started to agitate and organize for a general strike in
2012.
These recent calls for a May Day general strike have taken inspiration
from Occupy Oakland’s wildcat general strike of November 2nd, 2011, and
the struggles in Wisconsin last Spring which first reignited interest in
the concept. In the months since the Occupy movement began we have seen
general strikes called in Belgium, Egypt, Greece, India, Israel, Italy,
Nigeria, Portugal, South Africa, Spain, Syria, Tunisia, and the United
Kingdom.
The general assembly of Occupy Los Angeles committed to the general strike
on December 19th; Occupy Boston on January 7th; Occupy Tampa on January
7th; Occupy Pasadena on January 8th; Occupy Phoenix on January 10th;
Occupy Williamsburg and Occupy Long Beach on January 17th; Occupy Brooklyn
on January 19th; Occupy Oakland on January 29th; Occupy Ventura on
February 7th; New York City on February 14th; Occupy Sydney on February
18th; Occupy Detroit on February 21st; Occupy Seattle on February 26th;
and Occupy Bushwick on March 1st. In the weeks between and since many
other cities, assemblies, and organizations have also called for the May
Day General Strike, and we expect more to follow suit in the next five
weeks.
___________________________________________________
3. Some Online Resources
NEW YORK CITY LINKS
http://da.nycga.net/mayday/
http://da.nycga.net/category/subgroups/may-day/
https://lists.riseup.net/www/subscribe/strikeeverywhere
http://maydaynyc.org/
http://www.nycga.net/
http://occuprint.org/Category/MayDay
http://occupybk.org/
http://occupybk.org/groups/organize-bushwick-1128840377/
http://occupywilliamsburg.org/
http://strikeeverywhere.net/
http://university.nycga.net/our-courses/studying-may-day/
http://university.nycga.net/our-courses/studying-may-day/recommended-readings/
http://wiki.occupy.net/wiki/May_Day
ONLINE RESOURCES
http://www.gstrike.org/
http://insurrectiondays.noblogs.org/
http://interoccupy.org/may1call/
http://libcom.org/gallery/may-1st-2012-posters-graphics
http://www.occupymay1st.org/
http://www.occupymay1st.org/groups/occupation-coordination/
http://www.occupymay1st.org/resources/imagery/
https://www.facebook.com/events/337068492974144/
https://www.facebook.com/events/307864259256522/
https://www.facebook.com/events/119235331529404/
https://www.facebook.com/events/367411923279181/
https://www.facebook.com/events/185740101536525/
https://www.facebook.com/OccupyGeneralStrike
https://www.facebook.com/occupym1
https://www.facebook.com/occupymayfirst
https://www.facebook.com/strikeeverywhere
https://www.facebook.com/pages/Occupy-May-1st-General-Strike/160023040772206
https://www.facebook.com/pages/Resources-for-the-worldwide-general-strike-May-1st/354855194534813
https://twitter.com/global_strike
https://twitter.com/May1StreetTeam
https://twitter.com/Maydaystrike
https://twitter.com/nycgenstrike
https://twitter.com/OccupyGenStrike
https://twitter.com/OccupyGenStrk
https://twitter.com/occupym1
https://twitter.com/OWSGenStrike
https://twitter.com/OWSMayDay
https://twitter.com/StrikeEverywher
https://twitter.com/USGeneralStrike
https://twitter.com/WorldStrikeMay1
___________________________________________________
4. Readings
[unsorted]
–The Social General Strike – Stephen Naft, 1905:
http://www.mediafire.com/?t37d5nxsvshzdcr
–The Mass Strike, the Political Party and the Trade Unions – Rosa
Luxemburg, 1906:
http://www.marxists.org/archive/luxemburg/1906/mass-strike/index.htm
–Reflections on Violence – George Sorel, 1908:
http://ifile.it/wpclbh/__Sorel__Reflections_on_Violence__Cambridge_Texts_in_the_
History_of_Political_Thought_.l_ntx2j6721x3xo9.pdf
–“The General Strike” – Bill Haywood, 1911:
http://www.iww.org/en/history/library/Haywood/GeneralStrike
–“Critique of Violence” – Walter Benjamin, 1921:
http://www.mediafire.com/?ew0x25f2guv
–The General Strike – Ralph Chaplin, 1933:
http://libcom.org/library/general-strike-ralph-chaplin
–“The General Strike” – W.E.B. Du Bois, 1935:
http://townsendlab.berkeley.edu/sites/all/files/The%20General%20Strike.pdf
–Kill the Bill: The Power of a General Strike – Madison IWW, 2011:
http://libcom.org/library/iww-general-strike-pamphlet
–“To All the Working People: Call for De-Nuke General Strike” – Committee
for De-nuke General Strike, 2011:
http://jfissures.wordpress.com/2011/03/26/to-all-the-working-people-%E2%80%93-call-
for-de-nuke-general-strike/
–“Wisconsin’s Lost Strike Moment” – Nicolas Lampert & Dan S. Wang, 2011:
http://www.justseeds.org/blog/2011/04/wisconsins_lost_strike_moment_1.html
–“What Chance a General Strike in Manhattan?” – Nikolas Kozloff, 2011:
http://www.aljazeera.com/indepth/opinion/2011/10/2011107135115719238.html
–“A Message to the Partisans, in Advance of the General Strike” – Society
of Enemies, 2011: http://www.indybay.org/newsitems/2011/11/01/18696540.php
–“Blockading the Port is Only the First of Many Last Resorts” – Society
of Enemies, 2011:
http://www.bayofrage.com/from-the-bay/blockading-the-port-is-only-the-first-of-many-last-resorts/
–“General Strike” – Gayatri Chakravorty Spivak, 2011:
http://occupytheory.org/Tidal_5.html
–“What are the Origins of May Day?” – Rosa Luxemburg, 1894:
http://www.marxists.org/archive/luxemburg/1894/02/may-day.htm
–“The Idea of May Day on the March” – Rosa Luxemburg, 1913:
http://www.marxists.org/archive/luxemburg/1913/04/30.htm
–“May Day in the West and the East” – Leon Trotsky, 1923:
http://www.marxists.org/archive/trotsky/1924/04/mayday.htm
–“The First of May: Symbol of a New Era in the Life and Struggle of the
Toilers” – Nestor Makhno, 1928:
http://www.marxists.org/reference/archive/makhno-nestor/works/1928/05_01.htm
–The History of Mayday – Alexander Trachtenberg, 1932:
http://www.marxists.org/subject/mayday/articles/tracht.html
–“A General Strike” – Mariarosa Dall Costa, 1974:
http://caringlabor.wordpress.com/2010/10/20/mariarosa-dalla-costa-a-general-strike/
–“What do we mean by… The General Strike?” – Chris Harman, 1985:
http://www.marxists.org/archive/harman/1985/01/genstrike.htm
–The Incomplete, True, Authentic and Wonderful History of May Day – Peter
Linebaugh, 1986
–“Birth of a Holiday: The First of May” – Eric Hobsbawm, 1994:
http://libcom.org/history/birth-holiday-first-may
–“Infinite Strike” – Anonymous, 2010:
http://theanarchistlibrary.org/HTML/Anonymous__Infinite_Strike.html
–“Which Way Forward for the 99%?” – Occupy May 1st, 2012:
http://libcom.org/library/which-way-forward-99-build-power-show-power-through-
mass-participatory-bold-action
___________________________________________________
5. NYC Links
Brooklyn General Assembly: http://occupybk.org/
Bushwick General Assembly: https://www.facebook.com/groups/Bushwick.GA/
New York City General Assembly: http://www.nycga.net/
Strike Everywhere: http://strikeeverywhere.net/
Williamsburg General Assembly: http://occupywilliamsburg.org/
___________________________________________________
6. Precarious & Service Worker Assembly
Start:
03/28/2012 19:30
Category:
Precarious/Service Worker Assembly
Address:
360 Court Street, Brooklyn, NY, 11231, United States
Tired of being treated like a servant by your customers? Tired of
management demanding more and more for less and less? Feeling alone or
frustrated? Come to the first Precarious and Service Worker Assembly to
network with others who share your interests!
As service workers, we are often both overworked and underpaid; with
Management forcing workers to work ever faster in an ever shorter amount
of time. Productivity and speed-of-service requirements increase while
hours per week are slashed. It’s clear: The harder we work, the less we
get paid, and the richer they get!
Many of us are already in tough situations as parents, immigrants, young
people, and students. Racism is blatantly apparent at many of our
workplaces, with Latino and immigrant workers confined to back-of-house
positions, maintaining a racial hierarchy to keep us separated. For some,
a job at a restaurant or a cafe is a 2nd or even 3rd job, a result of the
declining wages for other careers. Even worse, we often find ourselves
forced into student loan and credit card debt because of low pay. All the
while, rent, food, and transportation costs climb through the roof.
Solidarity and support among local service workers can be empowering for
all of us. Remember, they can’t run these places without us. Bosses thrive
by pitting us against one another, but if not for us, Management wouldn’t
make a dime. So let’s take what’s ours!
Bring some goods to share from your place of employment if you’d like, and
feel free to bring a friend or two as long as they’re not the boss! We’ll
be discussing how we can make our collective situation much more
interesting and how we can engage together in upcoming actions like the
May Day General Strike.
__________________________________________________
16 Beaver Group
16 Beaver Street, 4th fl.
New York, NY 10004
for directions/subscriptions/info visit:
http://www.16beavergroup.org
TRAINS:
4,5 — Bowling Green
2,3 — Wall Street
J,Z — Broad Street
R — Whitehall
1 — South Ferry
Research Project on Robert L. Vesco – The CIA Criown Jewels
| Citation: | Research Project on Robert L. Vesco [Attached to Divider Sheet], Secret, Memorandum, May 07, 1973, 3 pp. |
| Collection: | The CIA Family Jewels Indexed |
| Item Number: | FJ00048 |
| Origin: | United States. Central Intelligence Agency. Directorate of Operations. European Division. Chief |
| From: | Roosevelt, Archibald B. |
| To: | United States. Central Intelligence Agency. Directorate of Operations. Deputy Director |
| Individuals/ Organizations Named: |
Helms, Richard M.; Proctor, Edward W.; United States. Central Intelligence Agency. Deputy Director; United States. Central Intelligence Agency. Director; United States. Central Intelligence Agency. Directorate of Intelligence. Office of Economic Research; United States. Central Intelligence Agency. Directorate of Plans; Vesco, Robert L. |
| Subjects: | Corporations | Investigations |
| Abstract: | Recounts Central Intelligence Agency Office of Economic Research’s investigation of Robert Vesco and the sudden cancellation of inquiry at Richard Helms’ behest. |
| Full Text: | Document – PDF – this link will open in a new window (60 KB) |
TOP-SECRET – DHS-FBI Intelligence Bulletin on Homegrown Extremist Retaliation for Afghan Massacre

(U//FOUO) This Joint Intelligence Bulletin is intended to increase awareness and provide understanding of the nature of potentially emergent threats in response to the alleged killing of civilians by a US soldier in Afghanistan and the burning of Korans and other religious documents on a military base. This Information is provided to support the activities of FBI and DHS and to assist federal, state, local, tribal, and territorial counterterrorism and law enforcement officials and the private sector to prevent or respond to terrorist attacks against the United States.
(U//FOUO) Civilian Killings in Afghanistan Could Lead to Retaliatory Attacks by Homegrown Violent Extremists In the United States
(U//FOUO) On 11 March 2012, a US service member stationed in Afghanistan allegedly went on a shooting spree, killing 16 civilians, Including nine children, according to US press reporting. The FBI and DHS are concerned that this event could contribute to the radicalization or mobilization of homegrown violent extremists (HVEs) in the Homeland, particularly against US-based military targets, which HVEs have historically considered legitimate targets for retaliation in response to past alleged US military actions against civilians overseas.
(U//FOUO) The soldier who allegedly perpetrated the attacks reportedly trained at Joint Base Lewls-McChord near Tacoma, Washington. This base was also the training site of four soldiers convicted in 2011 of killing Afghan citizens, according to US press reporting. Abu Khalid Abdul-Latif, currently awaiting trial for plotting an attack, Initially wanted to target Lewis-McChord in retaliation for the actions of soldiers who had been stationed there. Ultimately, Abdul-Latif changed his alleged target to a Military Entrance Processing Station in Seattle, Washington, in part because he believed it was a softer target.
(U//FOUO) Perceived US Military Anti-Islamic Events in Afghanistan Could Compound Homegrown Violent Extremist Grievances
(U//FOUO) We assess that the alleged killing of civilians by a US soldier could trigger acts of violence by HVEs as this was a motivation that drove plotting against Joint Base Lewis-McChord. While recent high profile perceived offenses against Islam historically have led to calls for retaliation by violent extremists, they have not yet incited HVEs to attack in the United States. Nevertheless, the series of perceived anti-Mulslim and anti-Islamic events in Afghanistan since January 2012-which include graphic images of dead civilians-could cumulatively lead an HVE to mobilize to violence.
(U//FOUO) Some users of Web sites hosting violent extremist content circulated graphic images of the 11 March 2012 shooting victims, including women and children, and called for revenge against the US military. Some users stated their belief that the attack was intentionally planned by the US military and that there were more killings than reported by the media.
Nazi Leaders Executed At Nuremberg
Video – Volksgerichtshof (Nazi Peoples Court) – NEW FOOTAGE
This is a collection of unique footage of the proceedings of the Volksgerichtshof, the “Nazi Peoples Court”, which was specifically set up for political enemies.
In these 7 parts who will find comprehensive footage of the proceedings after the failed attempt of officers and civilians to kill Hitler on 20th July 1944.
I post these clips so that their memory won’t be forgotten. These people had a conscience and were incredibly brave. They are role models for all of us. They knew that the failure of their actions would lead to death, but their aim was to prevent to total distruction of Germany and to end the unspeakable crimes of the Nazi Regime.
I am afraid that all this footage is in German language. However, there are other clips on youtube on which the ravings of Roland Freisler, Hitlers “blood judge”, are translated.
However, these clips contain much more footage than was ever shown on youtube and outside Germany. This film is a real treasure for anybody who is interested in the actions of the men and women of the 20th July 1944 and the proceedings of the Nazi Peoples Court (Volksgerichtshof).
Please look up further details in Wikipedia.
The CIA Crown Jewels – Items for Possible Use in Briefing the DCI
| Citation: | Items for Possible Use in Briefing the DCI [Attached to Divider Sheet], Secret, Memorandum, May 07, 1973, 3 pp. |
| Collection: | The CIA Family Jewels Indexed |
| Item Number: | FJ00049 |
| Origin: | United States. Central Intelligence Agency. Directorate of Operations. Soviet Bloc Division. Chief |
| From: | Blee, David H. |
| To: | United States. Central Intelligence Agency. Directorate of Operations. Deputy Director |
| Individuals/ Organizations Named: |
Nosenko, Yurii; United States. Central Intelligence Agency. Directorate of Management and Services. Office of Security. Director; United States. Department of Justice. Marshals Service; United States. Federal Bureau of Investigation |
| Subjects: | Assassination plots | Attorneys | Counterintelligence | Defectors | Detention | Interagency cooperation | News media | Organized crime | Safe houses | Soviet Union |
| Abstract: | Describes Central Intelligence Agency Soviet Bloc Division activities that could be considered “inappropriate,” including provision of safe house for U.S. attorney threatened by “organized criminal elements,” collaboration with Federal Bureau of Investigation on counterintelligence training, and secret detention of Soviet defector Yurii Nosenko. |
| Full Text: | Document – PDF – this link will open in a new window (59 KB) |
Weird in Wired – Three Blind Phreaks
How the phone-phreaking Badir brothers ran rings around Israel‘s telcos for six scam-filled years.
Inside the chintz-filled living room of the Badir family’s neat and modest home, a feast of freshly roasted chicken, saffron rice, and seasoned vegetable stew perfumes the air. Friends and relatives pour through the front door to congratulate 27-year-old Munther “Ramy” Badir. He’s just been released from prison after serving 47 months for computer-related crimes. Outside, Islamic prayers resonate from speakers on a truck moving slowly down the dusty streets of Kafr Kassem. Everyone in this Israeli village – populated mostly by Arabs – appears ecstatic to have Ramy back.
But he does not see their smiles. Ramy, along with two of his three brothers, has been blind since birth due to a genetic defect. He and his sightless brothers have devoted their lives to proving they can out-think, out-program, and out-hack anyone with vision. (Their sighted brother, Ashraf, is a baker with no tech leanings.) They’ve been remarkably successful. Ramy says dryly, “A computer that is safe and protected is a computer stacked in a warehouse and unplugged.”
Israeli authorities agree. The 44 charges leveled against Ramy, Muzher, and Shadde Badir in 1999 included telecommunications fraud, theft of computer data, and impersonation of a police officer. The brothers’ six-year spree of hacking into phone systems and hijacking telephone time ended when they were convicted of stealing credit card numbers and breaking into the Israeli army radio station’s telephone system to set up an illicit phone company. Unwitting customers – mostly Palestinians on theWest Bankand Gaza Strip – paid the fake telco for long distance calls that were billed to the radio station. A lawyer close to the case said that the Badirs’ scams pulled in more than $2 million.
Ramy, the leader and most technologically savvy of the brothers, was the only one sentenced to prison. Muzher, 28, was ordered to perform community service for six months; Shadde, 22, received a suspended sentence – not because he was innocent, the judge made clear, but because of his age.
Those targeted by the Badirs feel less charitable. Yekutiel “Kuty” Lavi, a security specialist at Bezeq International,Israel’s largest telco and a frequent victim of the Badirs, angrily complains, “Every day people try to steal from us, but nobody has ever stolen from us the way the Badirs did. When they dial, they use the middle finger.”
The Badirs pulled off Mamet-worthy phone cons, employing cell phones, Braille-display computers, ace code-writing skills, and an uncanny ability to impersonate anyone from corporate suits to sex-starved females. On the phone, the brothers morph into verbal 007s, intimidating men, seducing women, and wheedling classified information from steely-voiced security personnel. The phone phreakers’ term for this is social engineering: using a combination of brains and guile to obtain codes for trespassing into systems to rejigger them via strings of touch-tone code. Combine this talent with supersensitive hearing – the brothers can dissect an international connection the way wine expert Robert Parker pulls notes from a glass of Bordeaux – and you have what BernieS, a legendary phreaker and contributor to the hacking journal 2600, calls “a formidable skill set.”
At one point during my visit with the Badirs, I pull out my cell phone and make a call. Before it even connects, Shadde, who is sitting across the room, recites all 12 digits perfectly.
Ramy smiles at the parlor trick. “It used to be disgusting to be blind,” he says. “Today, you scare people. You possess skills that those with sight cannot possibly understand.”
Two hours into an afternoon-long interview with the Hebrew-speaking Badirs, my translator’s lips lock. He shrugs and tells me that the Badirs have shifted into a secret code. Ramy later explains that as kids he and Muzher developed their own language – reordering letters in mathematically complex ways – after they discovered that other boys were snooping on their conversations. “People said that God cursed our mother by giving her three blind sons,” recalls Ramy. “Children beat us on the backs of our legs. Those abuses left scars on our hearts. But they also forced us to grow stronger.”
The young Badirs closed ranks and vowed that their blindness would never be an impediment. They taught themselves to take apart telephones, to mimic voices and verbal tics, and to get around Tel Aviv without canes or guide dogs. They became obsessed with technology and telephones. After encountering their first computer, in 1989, at Tel Aviv’s Center for the Blind, Ramy and Muzher became enchanted with the IBM clones. They hung aroundTelAvivUniversitywhile working, with little success, as software and telephone consultants; their early crimes were the phreaker equivalent of shoplifting a Hershey bar.
But Ramy was too ambitious to stop there. “I taught myself to program in all the languages: C, C++, Basic, Java, HTML, PHP, CGI. I built my own black boxes, blue boxes, and red boxes,” which, respectively, circumvent billing, generate tones to place free calls, and simulate pulses triggered by money dropped into a pay phone. “I used those boxes to get into and decode phone systems.”
In 1993, Bezeq technicians caught the Badirs snagging telephone time for their own use. Things quickly escalated when the brothers obtained the codes to break into PBXs – private branch exchanges – belonging to Bezeq and to the Israeli headquarters of Comverse, Intel, Nortel, and others. PBXs are the computerized nerve centers that operate phone systems; they are designed to be repaired, updated, and altered remotely by technicians using touch-tone codes.
“The Badirs regularly called Bezeq, pretending to be engineers in the field,” recalls Eyal Raz, who worked in the telco’s international antifraud unit from 1994 to 1999. “They called secretaries and said,
‘I need to get in to do a repair. You need to give me the number and password.’ Sometimes they succeeded, or else they’d get only the number and try to break the password by using proprietary programs.” At other times, a secretary would simply key in the code, providing what seemed like onetime access but actually enabling the brothers to hear touch tones and translate them into numbers they could then use whenever they pleased.
The three used their access to devise an elaborate moneymaking scheme. According to Raz, during the mid-1990s the brothers made a deal with a phone sex outfit based in theDominican Republic. They would be paid for driving calls to the service. The Badirs made the calls themselves, but the lines were rigged so that Comverse and Nortel were billed by the phone sex service.
At the time there were no computer crime laws inIsrael, so Bezeq took it upon itself to try to short-circuit the Badirs. “At one point I asked an engineer to block three lines that the Badirs had opened up for themselves,” recalls Raz. “They knew that I had put the blocks on. So a couple days later, one of them phoned the engineer and said, ‘This is Eyal Raz. Please unblock those three lines.’ The engineer, who knew my voice, believed it was me. He unblocked the lines.” Raz shakes his head, showing grudging admiration. “These are very clever boys.”
In 1995, the Badirs turned their attention to a business closer to home. Their target was Israeli phone sex mogul Ben Zion “Bency” Levy, who maintained a database of thousands of customer credit card numbers. Ramy and his brothers went to work on Levy’s secretary, patiently convincing her to provide the information that would allow them to unlock the credit card numbers and PINs.
“We knew to approach her gently and break through her psychological barrier,” says Muzher. ” We had her tell us clues that would lead to the password of her boss’s computer.”
“I figured out the personality of her boss, learned the numbers that were meaningful to him, and used those numbers to get into his system remotely,” says Ramy. In the end, the Badirs seized some 20,000 credit card numbers – and, after being confronted by Levy, caused all of his telephones to ring continuously with no caller on the other end of the line.
In 1996, Levy reported the scam toIsrael’s National Fraud Unit. The following year, a file of Badir-related complaints – including Levy’s – landed on the desk of David Osmo, an investigator withIsrael’s national police force. Osmo met with Ramy and recalls being amazed at the speed of the young man’s fingers on a phone keypad when he made a call. “I told him he is a smart person who should use his intelligence for good things,” Osmo says. “Return back to society,” he urged.
Ramy remembers his response to Osmo: “You can chase me for 20 years and you will not find anything to convict me on.”
The Israeli Army Radio Station is guarded as if it were a military base. Occupying four floors of a dirty white building on a busy two-lane street in Jaffa, the station is protected 24/7 by a half-dozen armed recruits. In 1998, the brothers joined forces with a group of Jewish and Arab scam artists and targeted the station, intending to hijack phone lines and sell call time on them.
Though they were convicted of participating in the scheme, the brothers deny they were involved. Ramy is nonetheless willing to speak knowledgeably about the con. “These were among the most protected lines in theMiddle East,” says Ramy. “They had a lot of scrambling, and big technology is required in order to get in.”
Why an army outpost? “Those lines cannot be tapped by the police, so there is no monitoring,” explains Ramy. “These are the safest lines on which to do something like this.”
Authorities maintain that Ramy broke into the army radio station’s phone system and activated a dormant function called direct inward systems access, which allows long distance calls to be placed remotely and charged to that particular phone account. He structured the DISA so that as many as 281 people would be able to make telephone calls simultaneously on that single line.
Once the long distance access was in place, the Badirs’ partners set up a switchboard inside a shack in an orange grove inJaffa. Voilא, instant phone company. Customers placed calls from kiosks along the Gaza Strip, from cloned cell phones, or directly from their homes; these were routed from the switchboard to the radio station’s DISA. The Badirs and their partners billed customers for the calls, while the actual costs were absorbed by the radio station.
It wasn’t long before the station realized its bills were excessive and contacted Bezeq. The company’s security specialists joined with the Israeli national police in an investigation. They raided the orange grove, arresting several low-level workers at the shack. Only after one of them mentioned that the lines had been set up by blind technicians, says one source close to police, did the probe turn to the Badirs.
At the time, Ramy and his brothers were already in the crosshairs. Suspects in numerous telecommunication crimes, their home phone was frequently tapped by the national police. They reviewed the tap transcripts and spent a year investigating the brothers, hoping to find incontrovertible links between them and the pirate phone company. An intense cat-and-mouse game developed: the Badirs on one side, with fraud investigator David Osmo and prosecutor Doron Porat on the other.
While Porat was working on the case, his car’s GPS system and email were repeatedly hacked. “There was a message waiting for him with his password in it,” says Ramy, sounding quite pleased. “After that, he changed his password every hour before giving up on email altogether and using a typewriter.” The brothers reportedly contactedIsrael’s DMV and registered Osmo’s car under another name, causing embarrassing problems for the investigator when he tried to sell his vehicle.
“The police experienced bad luck,” notes Ramy. “Their telephone systems went down, their computers developed bugs. Osmo got big bills for calls that he hadn’t made. He believed we were always listening in on him. Sometimes Osmo spoke on the telephone and other calls came across the line as he tried to talk.” Ramy smiles devilishly. “He found that to be very annoying.”
Ironically, even as they knew the degree to which they were being pursued, the Badirs did not show a lot of restraint over the telephone. “This was our mistake,” admits Ramy, who believed that some of his phone lines were secure. “We knew the police were chasing us and trying to catch us. Our overconfidence led us to think they would never do it.”
On June 14, 1999, 14 police officers raided the brothers’ home in Kafr Kassem. Though they found a safe containing more than $14,000 worth of Jordanian dinars, investigators did not uncover an expected treasure trove of hardware, software, and notes in Braille. “It’s all in our heads,” asserts Ramy. “The police took my laptop, which contained programs for running through thousands of numbers very quickly, but I had it designed to erase everything on the hard drive if it was opened by somebody other than me. They lost all the material.”
Ramy, Muzher, and Shadde were arrested on a variety of charges relating to computer fraud in connection with their hacks of the radio station and Bency Levy’s phone sex operation. Police took them from their home in wrist and leg cuffs, but even in custody, they could not help but show off by conversing in their secret language and announcing telephone numbers that were being keyed in by law enforcers. “When Doron Porat stood next to me,” adds Ramy, “he took the battery out of his cell phone.”
Ramy was jailed throughout the trial, which dragged on for 27 months and took the prosecutors way beyond their depth of technological expertise. Porat and his team eventually quit trying to explain how the Badirs did what they’d been charged with and focused instead on simply proving they did commit acts like breaking into a phone company switchboard.
In her November 2001 ruling, judge Saviona Rotlevi went easy on Muzher and Shadde but found Ramy guilty of 20 counts concerning Israeli cyberlaw, 4 counts of telecom law violation, and 15 counts of other crimes. The judge sentenced him to 65 months in prison. Among his restrictions: All of his calls were to be made with the assistance of a guard so that he would never touch a telephone keypad.
After nearly four years behind bars, Ramy was released when a judge ruled he’d served enough time. He marks his second day of freedom by repairing with Muzher and Shadde to a small cafי on the edge of Kafr Kassem. Inside, the brothers order bottles of orange juice and three water pipes. They puff deeply, releasing plumes of fruity-smelling tobacco smoke.
Despite his years in prison, Ramy appears to have no financial worries. Upon arriving home, he promptly ordered a $20,000 Braille-display computer fromGermany. He also spent a couple of hours checking on the construction of his new four-story house. Workers broke ground on it while he was still in prison; completion was scheduled to coincide with his original release date. It’s a sprawling, solid-looking place, situated on a prime corner lot in the center of Kafr Kassem. The top floor will be a high tech penthouse where Ramy can hatch his next move.
And what will that be? Ramy claims a couple of juicy software programs that he began developing in prison are in the pipeline. “I am inventing a PBX firewall,” he says. “I know all the weakest spots of a telephone system. I can protect any system from infiltration.”
Ramy insists there are major companies interested in his new software. He talks about big money and big meetings. But he refuses to show what he’s working on and won’t name anybody who’s backing him. One person who sounds perfectly game to be involved is the brothers’ old nemesis Eyal Raz. “If he can build that, he’ll become a billionaire,” predicts Raz, who now works for a Tel Aviv-based phone security firm called ECtel. “The Badirs know so much and are so talented that I would happily use them as consultants.”
Ramy insists he has outgrown the scams: “I am going to the other side, coming up with devices that will keep the phreakers out.”
You want to believe him, you really do. Maybe it’s the truth. Or maybe it’s a sweet bit of social engineering designed to generate positive press and position the Badir brothers for their next spree.
Hate Crime – Three Men Plead Guilty to Racially Motivated Assault and Murder in Mississippi
In the early morning hours of June 26, 2011, Daryl Paul Dedmon, John Aaron Rice, and Dylan Wade Butler were driving around Jackson, Mississippi, engaging in one of their favorite pastimes—looking for innocent victims to attack. They based their search on one specific factor: skin color…they wanted to hurt African-Americans. This time, they happened upon James Craig Anderson in a motel parking lot, got out of their vehicles, and began their unprovoked assault. Once back in their vehicles, Dedmon used his Ford F-250 pickup truck as a murder weapon, deliberately running over Mr. Anderson.
In the first case involving the death of a victim brought under the Matthew Shepard and James Byrd, Jr. Hate Crimes Prevention Act, Dedmon, Rice, and Butler pled guilty on Thursday to their roles in this unthinkable crime. At a press conference regarding the guilty pleas, Assistant Attorney General Thomas E. Perez stated, “This is a case about a group of racist thugs who made a sport of targeting African-Americans in Jackson and attacking them without provocation, simply because of the color of their skin.”
Investigating hate crimes is the top priority of the FBI’s civil rights program, and personnel in the Bureau’s Jackson Field Office devoted themselves to this investigation, with the assistance of the Jackson Police Department. Jackson Special Agent in Charge Daniel McMullen said, “Every sector of our community has a role to play in helping to ensure that no person is targeted for violence because of who they are or what they believe.”
Echoed Perez, “We must and will remain ever vigilant in our common humanity to root out hate and violence when it rears its ugly face. Hate crimes such as this simply have no place in Jackson, in Mississippi, or anywhere in America.”
SECRET – The FBI – Multi-Million-Dollar Hospice Health Care Fraud Alleged
PHILADELPHIA—An indictment was unsealed today charging five nurses in a health care fraud conspiracy arising from their employment at Home Care Hospice Inc. (HCH), a hospice care provider in Philadelphia, between 2005 and 2008 that resulted in a multi-million-dollar fraud on Medicare. Patricia McGill, 64, of Philadelphia, was a registered nurse and served as the director of professional services for HCH. She allegedly authorized and supervised the admission of inappropriate and ineligible patients for hospice services, resulting in approximately $9.32 million in fraudulent claims. She is charged, along with Natalya Shvets, 42, of Southhampton, Pennsylvania Giorgi Oqroshidze, 36, of Philadelphia; Yevgeniya Goltman, 42, of Newtown, Pennsylvania; and Alexsandr Koptyakov, 39, of Bensalem, Pennsylvania, with one count of conspiracy to commit health care fraud and numerous counts of health care fraud. All five defendants were arrested this morning.
HCH was co-owned by Matthew Kolodesh, who is charged separately in an indictment unsealed October 12, 2011, and “A.P.,” the Hospice Director for HCH. HCH was a for-profit business at 1810 Grant Avenue, and later 2801 Grant Avenue, in Philadelphia that provided hospice services for patients at nursing homes, hospitals, and private residences. According to the indictment, announced by United States Attorney Zane David Memeger, McGill authorized nursing staff and supervisors, including her co-defendants, to fabricate and falsify documents in support of hospice care for patients who were not eligible for hospice care, or for a higher, more costly level of care than was actually provided to the patients. Between January 2005 and December 2008, approximately $9,328,000 in fraudulent claims for inappropriate patients were submitted to Medicare as authorized by AP and McGill. Defendants Shvets, Oqroshidze, Goltman, and Koptyakov created fraudulent nursing notes for approximately 150 patients indicating hospice services were provided for patients, when, in reality, they were not.
In February 2007, HCH was notified that it was subject to a claims review audit. According to the indictment, in anticipation of this audit, McGill assisted A.P. in reviewing patient charts, sanctioning false documentation by the nursing staff, and authorizing the alteration of charts. In September 2007, HCH was notified that it had exceeded its cap for Medicare reimbursement and would have to repay $2,625,047 to the government program. At that point, A.P. and McGill directed staff to review patient files and discharge hospice patients. This resulted in a mass discharge of patients. In one month, 79 hospice patients were discharged in October 2007 and a total of 128 discharged by January 2008, some of whom had been ineligible for hospice or inappropriately maintained on hospice service in excess of six months. Some of the patients discharged were shifted to another hospice business owned by Kolodesh. In the spring of 2008, approximately 20 percent of the discharged patients were placed back on hospice service at HCH with McGill’s knowledge. McGill is charged in 14 counts; Shvets is charged in eight counts; Oqroshidze is charged in seven counts; Goltman is charged in four counts; and Koptykov is charged in eight counts.
If convicted of all charges, McGill faces a potential advisory sentencing guideline range of 108 to 135 months in prison, a fine of up to $150,000, and a $1400 special assessment; Shvets, Goltman, and Koptykov each face a potential advisory sentencing guideline range of 27 to 33 months in prison, a fine of up to $60,000, and an $800 special assessment; Oqroshidze faces a potential advisory sentencing guideline range of 21 to 27 months in prison, a fine of up to $50,000, and a $700 special assessment.
The case was investigated by the Federal Bureau of Investigation and the Department of Health and Human Services-Office of Inspector General. It is being prosecuted by Assistant United States Attorney Suzanne B. Ercole and Trial Attorney Margaret Vierbuchen of the Organized Crime and Gang Section in the Justice Department’s Criminal Division.
TOP-SECRET from Inside the CIA – CIA Narcotics Activities Having Domestic Implications
| Citation: | CIA Narcotics Activities Having Domestic Implications [Attached to Divider Sheet, Heavily Excised Cover Sheet, and Memorandum; Includes Variation of Main Document], Secret, Memorandum, May 07, 1973, 5 pp. |
| Collection: | The CIA Family Jewels Indexed |
| Item Number: | FJ00050 |
| Origin: | United States. Central Intelligence Agency. Directorate of Operations. Narcotics Coordination Group. Chief |
| To: | United States. Central Intelligence Agency. Directorate of Operations. Deputy Director |
| Individuals/ Organizations Named: |
United States. Central Intelligence Agency. Directorate of Operations. Technical Services Division; United States. Department of Justice. Bureau of Narcotics and Dangerous Drugs |
| Subjects: | Alias documentation | Covert identities | Domestic intelligence | Intelligence collection | Interagency cooperation | Narcotics | Photographic intelligence | Police assistance | United States citizens | Wiretapping |
| Abstract: | Describes coordination with law enforcement agencies on intelligence gathering and reporting on U.S. citizens suspected of narcotics trafficking. |
| Full Text: | Document – PDF – this link will open in a new window (94 KB) |
Public Intelligence – Where’s the Evidence Against Staff Sergeant Robert Bales?

In this Sunday, March 11, 2012 photo, men stand next to blood stains and charred remains inside a home where witnesses say Afghans were killed by a U.S. soldier in Panjwai, Kandahar province south of Kabul, Afghanistan.
The lawyer for the soldier accused of massacring seventeen people in a small Afghan village earlier this month has stated publicly that there is little or no evidence against his client. John Henry Browne, who is defending Staff Sergeant Robert Bales, told NBC that the U.S. government’s prosecution of Bales will be difficult as “They have no bodies, they have no autopsies, they have no forensics, they have no photographs, they have no witnesses. There is no Afghan who is going to come here to testify against this guy, so how do they prove premeditation? It’s going to be a problem for them.” In an interview with CBS, Browne reiterated this claim stating “There is no crime scene. There is no CSI stuff. There’s no DNA. There’s no fingerprints.” Browne has also stated that there is “no evidence about how many alleged victims” or “of where those remains are.”
Given the state of war and turmoil in Afghanistan, this complete absence of evidence might seem plausible to those unfamiliar with the Afghan justice system or the military’s on-the-ground capabilities in the region. However, for a number of years the U.S. military has operated complex forensic facilities in every region of Afghanistan capable of fingerprint and DNA analysis, ballistics testing, forensic chemistry and more. In fact, collecting complex evidence to be used in the trials of Afghan insurgents is a common practice for U.S. soldiers. Both the U.S. Army and ISAF have issued guides to soldiers regarding the collection of evidence in support of prosecution of insurgency crimes.
ISAF’s evidence collection guide details how to interview witnesses, perform chemical tests, collect DNA evidence, photograph the crime scene, analyze tire marks and footprints and how to eventually turn all this evidence over to Afghan courts while maintaining a chain of custody. The U.S. Army’s guide similarly details sophisticated methods of evidence collection by “providing practical means and methods to properly identify, collect, preserve, and provide evidence that will be recognized and accepted by the Afghan criminal justice system.” A presentation from the U.S. Army’s Office of the Provost Marshal General indicates that as of August 2011 there were three Joint Expeditionary Forensics Facilities (JEFFs) throughout Afghanistan including one in Kandahar, the same province where Staff Sgt. Bales reportedly committed the massacre. These forensics facilities are capable of DNA analysis, latent print identification, photographic forensics, as well as chemical and ballistic analysis. The presentation also indicates that there are centralized crime labs operated in coordination with the Afghan government capable of many of the same methods of forensic analysis.
While Browne’s claims could simply reflect that the U.S. military’s investigation of the incident is still in an early stage, the supposed lack of evidence is troubling given that many witnesses still maintain that more than one person was involved in the massacre, a belief supported by Afghan President Hamid Karzai. After meeting with the victims’ family members, Karzai said that they did not believe it was possible for one man to kill seventeen people in different rooms of houses in multiple villages, drag the bodies into piles and burn them within such a limited period of time. According to the Washington Post, survivors of the massacre have told family members that “There were 10 soldiers in our neighborhood alone.” An Afghan parliamentary investigation found that it was widely reported by witnesses that up to twenty soldiers may have been involved and the BBC reported that residents heard helicopters that they believe were supporting the operation.
Though Staff Sgt. Bales has now been charged with seventeen counts of premeditated murder, it remains to be seen whether the U.S. military will present the same level of forensic evidence that it routinely collects and analyzes when attempting to prosecute suspected insurgents.
Secret – Washington D.C. Fusion Center: White Powder Letters Warning March 2012

Since 2007 an unknown subject has sent more than 360 letters containing a white, powder substance to various government officials, public schools and other locations. In May, 2011 20 letters were delivered to public schools in Washington, DC. Over the past two days similar letters have been received in Washington, DC; New York, New York; Dallas, Texas and Enfield, Connecticut.
(U//FOUO) SCOPE
The WRTAC produces Information Bulletins in response to changes in the threat environment from terrorist attacks, natural hazards, criminal developments, and other events.
(U//FOUO) EVENT OVERVIEW
A series of “white powder letters” were received in the District of Columbia in October, 2010 and May, 2011. Similar letters were received at various locations around the country March 6, 2012 and additional letters may be in the mail system pending delivery. Specially trained response teams are prepared to investigate and collect any suspicious letters.
The letters are postmarked Dallas,Texas and contain a letter with the words AL AQEDA-FBI or similar language and contain a white powder. They are typically addressed using a computer printed label.
(U) Indicators of Suspicious Packages and Envelopes. Suspicious packages and envelopes often have characteristics that can alert handlers or recipients to potentially harmful contents.
• Inappropriate or unusual labeling:
• Excessive postage.
• A handwritten or poorly typed address.
• Misspellings of common words.
• Strange return address or no return address.
• Incorrect title or title without a name.
• Not addressed to a specific person.
• Marked with restrictions, such as “Personal,” “Confidential,” or “Do not X-ray.”
• Marked with threatening, insulting, or disparaging language.
• Postmarked from a city or state that does not match the return address.(U) Appearance:
• Powdery substance felt through or visible on the package or envelope.
• Oily stains, discolorations, or odor.
• Lopsided or uneven envelope.
• Excessive packaging material such as masking tape or string.
• Other suspicious signs:
• Excessive weight.
o Ticking sound.
o Protruding wires or aluminum foil.
The FBI – Former NBA Player and CEO of The George Group Indicted in Ponzi Scheme
NEWARK—C. Tate George, former NBA basketball player and the CEO of purported real estate development firm The George Group, was indicted today by a Newark grand jury for allegedly orchestrating a $2 million investment fraud scheme, U.S. Attorney Paul J. Fishman announced.
George, 43, of Newark, was indicted on four counts of wire fraud. He was previously charged by criminal complaint with one count of wire fraud. He will be arraigned on the new charges in Newark federal court on a date to be determined.
According to the indictment and other documents filed in this case:
George, a former player for the New Jersey Nets and Milwaukee Bucks, held himself out as the CEO of The George Group and claimed to have more than $500 million in assets under management. He pitched prospective investors, including several former professional athletes, to invest with the firm and told them their money would be used to fund The George Group’s purchase and development of real estate development projects, including projects in Connecticut and New Jersey. George represented to some prospective investors that their funds would be held in an attorney trust account and personally guaranteed the return of their investments, with interest.
Based on George’s representations, investors invested more than $2 million in The George Group between 2005 and 2011, which he deposited in both the firm’s and his personal bank accounts. Instead of using investments to fund real estate development projects as promised, George used the money from new investors to pay existing investors in Ponzi scheme fashion. He also used some of the money for home improvement projects, meals at restaurants, clothing, and gas. The George Group had virtually no income-generating operations.
Under the wire fraud counts with which he is charged, George faces a maximum potential penalty of 20 years in prison and a $250,000 fine for each count.
U.S. Attorney Fishman credited special agents of the FBI, under the direction of Special Agent in Charge Michael B. Ward; postal inspectors of the USPIS, under the direction of Postal Inspector in Charge Philip R. Bartlett; and the Securities and Exchange Commission, under the direction of George S. Canellos, director of the New York Regional Office, with the investigation leading to today’s Indictment.
The government is represented by Assistant U.S. Attorney Christopher J. Kelly of the U.S. Attorney’s Office Economic Crimes Unit in Newark.
The charges and allegations contained in the indictment are merely accusations and the defendant is considered innocent unless and until proven guilty.
If you believe you are a victim of or otherwise have information concerning this alleged scheme, you are encouraged to contact the FBI at 973-792-3000.
This case was brought in coordination with President Barack Obama’s Financial Fraud Enforcement Task Force. President Obama established the interagency Financial Fraud Enforcement Task Force to wage an aggressive, coordinated, and proactive effort to investigate and prosecute financial crimes. The task force includes representatives from a broad range of federal agencies, regulatory authorities, inspectors general, and state and local law enforcement who, working together, bring to bear a powerful array of criminal and civil enforcement resources. The task force is working to improve efforts across the federal executive branch, and with state and local partners, to investigate and prosecute significant financial crimes, ensure just and effective punishment for those who perpetrate financial crimes, combat discrimination in the lending and financial markets, and recover proceeds for victims of financial crimes.
Defense counsel: Thomas R. Ashley Esq., Newark
TOP-SECET – U.S. Marine Corps Suicide Activity Report for February 2012

CY 2008 national suicide rate adjusted for MC demographics
The 2008 national suicide rate adjusted for Marine Corps demographics is 20.7 per 100,000.
Calculating an adjusted national rate is important to accurately compare Marine Corps and national suicide rates, as in Figure 1.
The national adjusted suicide rate is calculated by taking Centers for Disease Control data, and changing the data to look more like the Marine Corps (mostly young and male). Adjusted civilian rates for CYs ’09 and ’10 will be calculated when the data is available.
…
Suicide Prevention Media Guidelines:
The Suicide Prevention Resource Center offers the following guidelines when using media to prevent suicide:
– Themes should be positive (e.g., “Life is worth living”) versus negative (e.g., “Don‟t kill yourself”).
– Depictions should not contain graphics or descriptions of methods of suicide (e.g., guns, pills, etc.) because that has been shown to lead to copycat suicides.
– The word „suicide‟ should not appear in titles or headlines.
– Scenes should depict desired behavior (e.g., Marines talking to other Marines), not undesired behavior (e.g., sitting isolated in a corner).
– Actors or models should not appear disheveled, depressed, or in obvious distress. They should appear normal, because there are often no obvious warning signs of distress, and close engagement is required to tell if someone may be at risk.
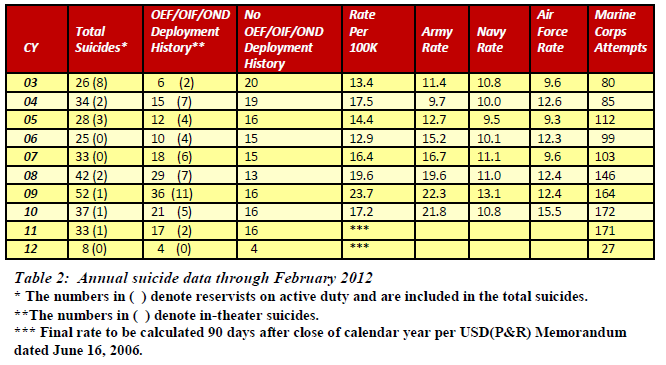
Inside in the CIA – Item for the List of Delicate Matters
| Citation: | Item for the List of Delicate Matters [Attached to Divider Sheet], Secret, Memorandum, May 07, 1973, 2 pp. |
| Collection: | The CIA Family Jewels Indexed |
| Item Number: | FJ00052 |
| Origin: | United States. Central Intelligence Agency. Directorate of Operations. Foreign Intelligence Staff. Chief |
| To: | United States. Central Intelligence Agency. Directorate of Operations. Deputy Director |
| Individuals/ Organizations Named: |
Barreaux, Theodore C.; Colby, William E.; Houston, Laurence R.; Timmeny, Wallace L.; United States. Central Intelligence Agency. Directorate of Intelligence. Deputy Director; United States. Securities and Exchange Commission; Vesco, Robert L.; Walsh, Paul V.; Young, David R. |
| Subjects: | Corporations | Interagency cooperation | Investigations | Organized crime |
| Abstract: | Reports on request from Securities and Exchange Commission for information on “foreign connections with organized crime” in the U.S.; notes Central Intelligence Agency’s release of banking transaction made by associate of Robert Vesco. |
| Full Text: | Document – PDF – this link will open in a new window (39 KB) |
Confidential – U.S. Army Surgeon General’s Office: Psychological Issues of War
Betreff: Neo-Nazi-Terrorbande – Beate Zschäpe soll bei Morden geholfen haben
Die mutmaßliche Terroristin Beate Zschäpe muss wegen der Neonazi-Mordserie womöglich als Mittäterin mit lebenslanger Haft rechnen. Es gebe viele Beweismittel, die belegten, dass Zschäpe “an den Taten beteiligt war, zumindest durch logistische Hilfe”, sagte Generalbundesanwalt Harald Range der “Frankfurter Allgemeinen Sonntagszeitung”. Derzeit sei noch nicht klar, ob Zschäpe “an einem oder mehreren Tatorten” war.
Range zufolge arbeitet die Bundesanwaltschaft “mit Hochdruck” daran, Zschäpe eine Beteiligung an den Morden ihrer mutmaßlichen Komplizen Uwe Mundlos und Uwe Böhnhardt nachzuweisen. Viele Beweismittel belegten, “dass sie sehr genau wusste, was in den Köpfen von Mundlos und Böhnhardt vorgegangen ist und was sie getan haben”, sagte Range. “Wenn wir ihr die Mittäterschaft zum Mord nachweisen können, ist eine lebenslange Freiheitsstrafe die Konsequenz. Bei so vielen Morden kann das auch wirklich heißen: lebenslang”, unterstrich Range.
Zschäpe schweigt bislang zu ihrer Rolle in dem Neonazi-Trio, das nach seinem Abtauchen Ende der 1990er Jahre die Terror-Gruppe “Nationalsozialistischer Untergrund” (NSU) gegründet haben soll. Dem NSU werden zehn Morde, zwei Sprengstoffanschläge und eine Serie von Banküberfällen zur Last gelegt. Mundlos und Böhnhardt waren im November nach einem gescheiterten Banküberfall in Eisenach tot in einem Wohnmobil gefunden worden, Zschäpe stellte sich der Polizei.
Vor dem Hintergrund der jahrelang unentdeckt gebliebenen Terrorzelle forderte Range zudem eine Ausweitung der Rechte seiner Behörde. Die Bundesanwaltschaft brauche “mehr und klare Initiativrechte, um in der Lage zu sein, selbst zu prüfen und zu bewerten, ob wir in einem konkreten Fall zuständig sind”, sagte er der “FAS”.
Range betonte, bei der NPD sei keine systematische Hilfe für den NSU zu erkennen. Bei einzelnen Unterstützern gebe es eine personelle Überschneidung. “Eine strukturierte Unterstützung aus der NPD gab es nach unseren bisherigen Erkenntnissen aber nicht.” Laut “Focus” soll der NSU offenbar mehr Unterstützer gehabt haben als bisher bekannt. Darauf deuteten mehrere Ausweis-Dokumente hin, die in der abgebrannten Wohnung von Mundlos, Böhnhardt und Zschäpe in Zwickau sichergestellt worden seien. Dem Bericht zufolge fanden Polizisten im Brandschutt des Hauses die Personalausweise von drei Männern aus Sachsen im Alter von 29, 35 und 37 Jahren. Böhnhardt und Mundlos könnten sich demnach die Papiere besorgt haben, um ihre wahre Identität zu verschleiern.
Nach Informationen des “Spiegel” berichtete der als mutmaßlicher NSU-Unterstützer inhaftierte Holger G. den Ermittlern von erheblichen Spannungen innerhalb des Trios. So habe sich die Zelle einen heftigen Streit in Chemnitz geliefert und sich vorübergehend getrennt. Nach dem Streit, der beinahe handgreiflich geworden sei, habe Mundlos demnach zeitweise eine eigene Wohnung bezogen. Diese Aussage wird dem Magazin zufolge durch einen Mietvertrag für eine Wohnung in Zwickau untermauert, der auf die Aliaspersonalien von Mundlos ausgestellt war.
G. soll laut “Spiegel” darüber hinaus zu Protokoll gegeben haben, dass er von den untergetauchten Terroristen 10.000 Mark vermutlich aus Raubüberfällen zur “Aufbewahrung” erhalten habe. Die gleiche Summe habe auch der ebenfalls inhaftierte Ex-NPD-Funktionär Ralf Wohlleben von dem Trio erhalten.
Video – 20 Jahre Stasi-Archiv – Akten als Geschichts-Puzzle
Wie die STASI ihre eigene Republikflucht plante
Endorsement – Warum die FDP so wichtig ist
Liebe Leser,
die FDP ist in Deutschland die einzige Partei die konsequent liberal und wirtschaftsfreundlich ist.
Keine andere Partei ist damit den Umverteilern und Staaatsgläubigern so abhold.
Deshalb wollen sie die FDP – auch über die Medien vernichten.
Das darf nicht sein:
Keine andere Partei ist so liberal im Denken und im Handeln – seit Jahrzehnten.
Keine andere Partei hat sich so entschieden für Bürgerrechte und gegen Nazis und STASI eingesetzt.
Unterstützen Sie die FDP, wenn Sie nicht wollen, dass Deutschland wieder und weiter von mono-gläubigen, unfähigen Apparatschiks regiert wird !
Stärken Sie die Freiheitsliebe und wehren Sie sic gegen das getarnte sozialistische -kommunistische Gesocks.
Herzlichst Ihr
Wahrheitsliebender Bernd Pulch
Unternehmer seit 30 Jahren – (Ohne Staatshilfe, ohne Förderhilfe, ohne Investoren)
Nicht-Genosse, nicht-korrupt, nicht-erpressbar
Magister der Publizistik, Germanistik und Komparatistik
Erpresser-Mail von STASI-“GoMoPa” von mutmasslich “Gerd Bennewirtz” und “Peter Ehlers” beauftragt (Identitäten mutmasslich unklar)
HALLO KINDERFICKER PULCH UND SCHRAMM!!!
IER GEHT BALD DIE POST RICHTIG AB.
http://www…
http://www….
SO IN ETWA WIRD ES AUSSEHEN:
INTERNETJAGT AUF DIE KINDERFICKER BERND PULCH
UND STEFAN SCHRAMM!
http://www.yout….
AN DIESER STELLE KOMMEN PORNPGRAPHISCHE
FOTOS VON EUREN OPFER-KINDERN.
JETZT GEHT ES LOS PULCH UND SCHRAMM!!!
AUF ALLEN KANAELEN!!!
DAS IST DAS ORIGINAL MIT DEN GRAMMATIK-FEHLERN – NATÜRLICH LIEGEN ALLE DIESE ERPRSSER-MAILS- AUCH BEATE P VOR
RATEN SIE MAL WAS PASSIERT UND PASSIEREN WIRD VON IHRER SEITE ?
UND JETZT RATEN SIE MAL WAS WIR TUN WERDEN ?
GRATULIERE !
RICHTIG GERATEN !
Herzlichst Ihr
Nicht korrupter und nicht erpressbarer Bernd Pulch, MA der Publizistik, Germanistk und Komparatistik
Opfer -DIE MYSTERIÖSEN TODESFÄLLE UND ATTENTATE AUF STASI- UND NEO-STASI-GEGNER
DER VON DER STASI ERMORDETE JÖRG BERGER – “Blei- und Arsenverbindungen wurden mir ins Essen oder Trinken getan”
DFB Torwart-Trainer, Jörg Berger und Jogi Löw – Jörg Berger: “Blei- und Arsenverbindungen wurden mir ins Essen oder Trinken getan”
Zitat: “Nach der Wende forderte man mich auf, meine Krankenakten an Professor Dr. Wolfgang Eisenmenger zu schicken, tätig am Institut für Rechtsmedizin der Münchner Ludwig-Maximilians-Universität. Er kam zu dem Ergebnis, dass es sich aufgrund der darin beschriebenen Symptome wahrscheinlich nicht um eine Viruserkrankung, sondern um eine Vergiftung gehandelt habe. Er konkretisierte dies auch noch in Hinsicht auf eine Schwermetallvergiftung aus der Gruppe der Blei- und Arsenverbindungen.
Die Stasi-Akten geben darüber keine klaren Auskünfte. Das einzige, was aus den Akten selber hervorgeht, ist, dass in der Zeit „agressives Verhalten gegenüber dem Feindbild Berger“ angesagt war. In meiner Lesart: Es ging ihnen bei mir nicht gerade um Mord, sondern darum, mich beruflich außer Gefecht zu setzen. Nicht umsonst hatte man mir wohl ein Gift gegeben, das Lähmungserscheinungen auslöst. Dennoch: In zu hoher Dosierung hätte es meine Gliedmaßen absterben lassen, aber auch zum Tode führen können. Dann wäre es doch ein Auftragsmord gewesen. Mit großer Wahrscheinlichkeit hat mir jemand das Mittel in ein Getränk oder ins Essen getan. “
“Ich habe die Stasi unterschätzt”
Trainer Jörg Berger über seine “Republikflucht”, zerstochene Auto-Reifen und vergebliche Warnungen an Lutz Eigendorf.
 |
Herr Berger, Otto Rehhagel hat Sie 1983 erst nach Informationen über Lok Leipzig ausfragt und anschließend zum Dank ins Weserstadion eingeladen. Sie lehnten ab. Warum? |
Ich hätte mich damit zur Zielscheibe für die Stasi gemacht. So offensiv wollte ich mich dem DDR-System nicht präsentieren.
Rehhagel hat das damals allerdings überhaupt nicht verstanden.
Otto hat nie geglaubt, dass der Arm der Stasi bis nach Bremen reichen würde, dass die Stasi in Westdeutschland für mich eine Gefahr darstellen könnte.
Hätten Sie ihm das nicht erklären können? Gründe gab es doch genug.
Otto hätte mich nicht verstanden! Als ich meine Problematik vorsichtig andeutete, hat er gesagt: “Du bist doch im Westen, was soll dir schon passieren?” Mit Erklärungen habe ich mich lange zurückgehalten. Bis zu meiner Einsicht in die Stasi-Akten. Selbst meine Frau, die ich ja im Westen kennen gelernt hatte, hat mich manchmal gefragt:”Jörg, leidest du schon unter Verfolgungswahn?” Später hat sie sich dafür entschuldigt.
Sie haben sich insgesamt also sehr bedeckt gehalten?
Ich habe es zumindest immer versucht. Anders als Lutz Eigendorf, der sich sehr provokant inszeniert hat. Wenn Ost-Vereine in Westdeutschland gespielt haben, ist Lutz mit seinem großen Schlitten vorgefahren und hat – überspitzt formuliert – mit den großen Scheinen gewedelt. Der Erfolg von “Republikflüchtlingen” wie Lutz und mir war ein rotes Tuch für das DDR-Regime. Jedes Mal, wenn die uns gesehen haben, war das eine persönliche Niederlage. Ein Verräter, der im Westen gefeiert wird? Eine Katastrophe!
Wann wurde Ihnen bewusst, dass die Stasi auch im Westen hinter Ihnen her war?
Eigentlich schon in der deutschen Botschaft in Belgrad, nach meiner Flucht aus Subotica. Man sagte mir, in ganz Jugoslawien werde bereits nach mir gefahndet. So wichtig hatte ich mich dann doch nicht eingeschätzt. Im Aufnahmelager in Gießen wurde ich stundenlang vom BND und der CIA verhört. Da ist mir erst klar geworden, wie riskant meine Flucht war, welcher riesige Partei-Apparat dahinter steckt. Nach einer Woche in Westdeutschland wurde ich vom MfS (Ministerium für Staatssicherheit, Anm. d. Red.) unter Druck gesetzt. Vor meiner Flucht war ich mir sicher gewesen, im Westen die ganze DDR-Vergangenheit abzuschütteln.
Hätten Sie nicht auch einfach Sportlehrer auf dem Land werden können?
Dass ich Bundesliga-Trainer werde, hätte ich ja nie gedacht. Im Nachhinein wäre mein Fall bei der Stasi dann sicherlich schnell vergessen gewesen. Nur dachte ich damals: Je erfolgreicher und populärer du wirst, desto weniger traut sich die DDR an dich heran! Ich habe die Stasi unterschätzt. So lange, bis das mit Lutz Eigendorf passierte.
Als Eigendorf starb, haben Sie gleich gedacht: Das war Mord?
Sofort. Ich war im Stadion, als in der Halbzeit ein Journalist zu mir kommt und sagt: “Jörg, der Eigendorf ist tot.” Ich frage: “Wie und wo?” – “Mit dem Auto. In Braunschweig.” Danach habe ich zu meiner Frau gesagt: “Jetzt muss ich noch mehr aufpassen. Denen ist alles zuzutrauen.”
Was haben Sie konkret unternommen?
Mein Auto häufiger warten lassen. Reifen prüfen, die Bremsleitung untersuchen. Mir fiel auf, wie oft meine Reifen zerstochen waren. Einmal ist mir bei Tempo 160 das Rad abgefallen. Das war kein Zufall.
In einem Stasi-Eintrag über Eigendorfs Tod heißt es: “Eigendorf verblitzt.” Warum war er zur Zielscheibe geworden?
Lutz war ein Eigenbrötler, sehr von sich eingenommen und ziemlich unbedacht. Er hat dieses schicksalhafte Interview für “Kennzeichen D” direkt vor der Berliner Mauer gegeben, im Hintergrund sah man das Stadion vom BFC. Ich war einen Tag vorher da und sollte mich ebenfalls vor der Mauer befragen lassen. “Das könnt ihr gleich wieder vergessen”, habe ich gesagt. Lutz hat es gemacht. Das war quasi eine Aufforderung an alle Ost-Fußballer: Folgt mir in die Freiheit! Ich habe ihn gewarnt: “Lutz, so kannst du die nicht weiter provozieren, sonst bekommst du irgendwann einen Knüppel auf den Kopf!”
1986 bekamen Sie keinen Knüppel auf den Kopf, sondern wurden vergiftet.
Ich war inzwischen Trainer bei Hessen Kassel und litt plötzlich unter Lähmungen. Zuerst wurde der Fuß taub, dann das Bein und die Hände. Alles war wie abgestorben. Vermutlich eine Schwermetall-Vergiftung, irgendwas wurde mir auf jeden Fall ins Essen getan
Wie hat der Westen darauf reagiert?
Das wurde schnell unter den Tisch gekehrt. Der Tod von Eigendorf, meine Vergiftung: das hätte die diplomatischen Beziehungen zur DDR nur gestört. Offiziell sollte ich vom BND abgeschirmt werden, später habe ich in meinen Stasi-Akten gelesen, dass die Mielke-Behörde tatsächlich über jeden meiner Schritte in Westdeutschland Bescheid wusste.
Wie haben Sie das Ende der DDR erlebt?
Das Regime war für mich gestorben, die DDR abgehakt, nicht aber die Menschen. Meine gesamten Ersparnisse hätte ich darauf verwettet, dass die Grenze niemals wieder geöffnet werden würde. Als die Mauer fiel, war das für mich der politisch bewegendste Moment in meinem Leben. Ich dachte: Was ist denn jetzt passiert? Was hat das für Folgen? Ich habe geheult, ich habe gejubelt. Und wieder geheult. Andere haben Champagner getrunken.
Nach der Wende sind viele Ex-“Genossen” in neuen Ämtern aufgetaucht, auch im Fußball. Sie beschreiben die Szene, als Sie Wolfgang Riedel wieder sehen …
… ausgerechnet den Mann, der mich als Leiter unserer Verbandsdelegation in Jugoslawien nach meiner Flucht durch das ganze Land gejagt hatte. Ein absoluter Hardliner. 100 Prozent SED-treu. Der läuft mir auf der Treppe in der Otto-Fleck-Schneise entgegen, Riedel war inzwischen beim DFB gelandet. Hätte ich dem zwölf Jahre vorher gesagt, wie toll der DFB ist, wäre meine Karriere beendet gewesen. Wenn meine Frau nicht dabei gewesen wäre, ich hätte mich auf den gestürzt! Nach der Wende hat man sich im Fußball nicht genügend um Aufklärung bemüht. Sie glauben doch nicht, dass jemand vom DFB wieder eine ähnliche Position im DDR-Verband bekommen hätte?
Hätten Sie die Verbandsführung nicht aufklären können?
Wie denn? Damals hatte ich doch noch gar keine handfesten Beweise. Die fielen mir erst später in die Hand, bei der Einsicht in meine Stasiakten. Mir hätte direkt nach der Wende kein Mensch geglaubt
Secret – The CIA – Request for Information on Sensitive Activities
| Citation: | Request for Information on Sensitive Activities [Central Intelligence Agency Funds for Federal Bureau of Investigation], Secret, Memorandum, May 07, 1973, 1 pp. |
| Collection: | The CIA Family Jewels Indexed |
| Item Number: | FJ00056 |
| Origin: | United States. Central Intelligence Agency. Directorate of Plans. Missions and Programs Staff |
| From: | Sherman, Edward L. |
| Individuals/ Organizations Named: |
Angleton, James; Briggs, Charles; United States. Central Intelligence Agency. Directorate of Operations. Technical Services Division; United States. Central Intelligence Agency. Executive Director; United States. Federal Bureau of Investigation |
| Subjects: | Government appropriations and expenditures | Interagency cooperation |
| Abstract: | Reveals that Central Intelligence Agency funds were made available to Federal Bureau of Investigation. |
| Full Text: | Document – PDF – this link will open in a new window (22 KB) |
FEMEN at Occupy Wall Street – Long Documentary uncensored
TOP-SECRET – The CIA Training of Foreign Police Forces
| Citation: | [Training of Foreign Police Forces; Attached to Divider Sheet and Routing Sheet; Includes Attachments Entitled “Counter Intelligence Staff, Police Group Activities”; “Joint CIA/USAID Terrorist (Technical) Investigations Course #7 (English Language) CI Staff’s Project [Excised]”; “Facts and Statistics”; and “National Security: Political, Military, and Economic Strategies in the Decade Ahead”] Secret, Compendium, April 25, 1973, 16 pp. |
| Collection: | The CIA Family Jewels Indexed |
| Item Number: | FJ00059 |
| Origin: | United States. Central Intelligence Agency |
| To: | Halpern, Sam |
| Individuals/ Organizations Named: |
Abshire, David M.; Allen, Richard V.; Angleton, James; Burke, Arleigh A.; Colby, William E.; Dade County (Florida). Police Department. Bomb Squad; International Police Academy; Mitrione, Daniel A.; Schlesinger, James R.; Tupamaros (Uruguay); United States Park Police; United States. Agency for International Development. Office of Public Safety; United States. Central Intelligence Agency. Directorate of Operations. Counterintelligence Staff. Chief; United States. Central Intelligence Agency. Directorate of Operations. Counterintelligence Staff. Police Group; United States. Central Intelligence Agency. Directorate of Operations. Deputy Director; United States. Central Intelligence Agency. Directorate of Operations. Technical Services Division; United States. Department of the Treasury. Office of Enforcement; United States. Secret Service |
| Subjects: | Biographical intelligence | Bombings | Developing countries | Diplomatic security | Explosives detection | Foreign policy | Government appropriations and expenditures | Intelligence collection | Interagency cooperation | International trade | Investigations | Latin America | Murders | Police assistance | Sabotage | Sanctions | Target analysis | Terrorism | Uruguay |
| Abstract: | Provides overview of coordination among Central Intelligence Agency, Agency for International Development, and International Police Academy for training of foreign police and security forces; assesses potential use of aid and trade relationships to affect change in foreign governments. |
| Full Text: | Document – PDF – this link will open in a new window (1.1 MB) |
NEUE DROHMAIL DER STASI DER “GoMoPa” MUTMASSSLICH IM AUFTRAG VON GERD BENNEWIRTZ UND PETER EHLERS
Hey kids fucker Pulch. The new year has nasty surprises for you child and mother fucker. The Internet never sleeps. We wish you a good time. Hier der die Info zu dem "GoMoPa"-"Kinderportal": http://www.victims-opfer.com/?p=22832 DER SCHELM DENKT WIE ER IST SIND AUCH ANDERE - MITNICHTEN |
Cryptome – Quantum Computation Cognitive Footprint
A sends a comment from Schneier on Security:
http://www.schneier.com/blog/archives/2012/01/authentication_1.html
Slightly Weird claim: Cognitive Footprint Biometric Application has been around for years
A ‘cognitive footprint’ biometric analysis system based on keyboard and mouse movements, combined with software-use behavior, has been in production for years. I’ve known of it since 2004 with a high degree of confidence, but I’m generally wise enough not to discuss it. I tinker with AI and neural networks (NN) myself, and am an expert software engineer, so I can reliably tell you that it’s not particularly hard to build such a system at the toy/theoretical level. It’s probably quite hard to implement it well in the real world.
My browser-centric toy model of a cognitive footprint biometric application used JavaScript to track keyboard and mouse interaction, which then passed time-parsed data to a neural network for classification. With an ordinary (non-recurrent) neural network the above comments about error rates and edge cases are very accurate. However, with access to an advanced recurrent neural network I’m pretty sure that the error rate could be reduced to a level low enough for effective use in combination with other authentication methods.
___________
Thoroughly Outlandish Claim: Five Eyes got production QC power in 1995
A real-world functional cognitive footprint biometric application requires an advanced recurrent neural network. The recurrent neural network that now powers this app is (literally) related to or descended from a classified system built to crack public-private key cryptography in the 90s.
The Five Eyes (AUS CAN NZ UK US) have had access to practical, production quantum computer power since about 1995. Other groups may have had access since that era, but that’s a moot point. I strongly suspect that both China and Russia later developed operational QCs along similar principles.
The QC approach that actually works, in a production-ready scale-able way, is to run a virtual Turing machine atop a winner-take-all-style teleportation/entanglement-based recurrent topological quantum neural network (QNN). Even a basic neural network is Turing Complete, because a NN can perfectly emulate an XOR gate, and multiple XOR gates can be used to construct a Turing machine. A quantum neural network can emulate a quantum Turing machine.
The underlying physical system for this type of QNN is interactions between non-abelian anyons in a two dimensional electron gas (2DEG). The primary math required is a branch of Knot Theory called Braid Theory. Obviously, the primary purpose of this system, from the Five Eyes/Echelon perspective, is to run Shor’s algorithm to crack public/private key cryptography. A perusal of current known quantum algorithms, combined with a survey of current advanced AI applications, may suggest other uses.
___________
Not especially Weird Claim: There’s a really nifty back story about how this new general technology was developed, and why it matters. It is worthy of a book by Neal Stephenson.
The subject of the 1985 Nobel Prize in Physics was the “quantum Hall effect”, which opened up new avenues of research into quantum effects, esp. in two dimensional electron gases. The process of creating a working quantum neural network involved generating lots of anyons (soliton-type standing waves treated as particles) in a two dimensional electron gas and then exploring and measuring the results.
The cleverest aspect of inventing this new technology was to take this ‘Anyon Soup’ system to the edge of chaos, per the life work of Stuart Kauffman, and then exploit the emergent neural network to bootstrap itself into a more stable and usable system via evolutionary programming techniques. See Kauffman’s publications for details on how and why this emergent neural network exists, and then consider it’s environment to see why it is a quantum neural network. This author believes Stuart Kauffman is overdue for a Nobel Prize.
The original work inventing this new technology was done between 1990 and 1995. It would be hard to do this work methodically without stumbling on the previously unknown fractional quantum Hall effect. The discoverers of this effect were awarded the 1998 Nobel Prize in Physics, and now lead various Quantum Computing research institutes.
Someone, somewhere, is due to be awarded the Grand Prize Turing Award, for solving Turing’s unfinished Morphogenesis problem, and then implementing Turing’s original machine on the resulting artificially intelligent ‘organism’. I’m inclined towards neither spiritualism nor whimsy, but were I so, then I might suspect that, after he died in 1954, Alan Turing reincarnated quickly, in 1965, in order to finish his incomplete life work. The classified nature of the work probably precludes any awards.
I’d really like it if this whole thing was declassified, but fear we’ll have to wait many additional decades for that. This QNN is an excellent candidate to pursue adiabatic (reversible) computing, might be helpful for certain approaches to advanced nanotechnology, and, were it declassified, might also be helpful to many other scientific ventures. Per the Ultra Secret, it’s undoubtedly still considered ‘national security’, even if it’s becoming an open secret within the Intelligence Community.
— Energyscholar
The FBI Financial Intelligence – Center Getting Ahead of Crime
Investigating financial crime is like working a puzzle—you have to fit all of the pieces of information together in order to see the entire picture. The FBI’s Financial Intelligence Center in Washington, D.C., does just that, linking disparate pieces of data to give our field investigators a clearer picture of possible criminal activity in their regions.
The center was established in the fall of 2009 in response to the financial crisis at that time—its mission was to identify potential investigative targets engaged in mortgage fraud. Because of its success, the center’s focus expanded to include other types of financial crimes, like securities/commodities fraud, health care fraud, money laundering, fraud against the government, and even public corruption (which usually involves financial wrongdoing of some sort).
The center is staffed primarily by intelligence analysts and staff operations specialists. Their first order of business is to review large datasets that come from the FBI, other law enforcement and regulatory agencies, consumer complaint websites, etc. Computer programs cull out data with common themes (i.e., similar scams, similar names). That data is researched and analyzed to help further identify potential subjects and/or activity, and the results are organized using spreadsheets and link analysis in order to draw connections among all the key players. If there is good reason to believe that criminal activity exists, the results are summarized in an intelligence package and sent to the appropriate field office.
During fiscal year 2011, FBI offices opened dozens of investigations based on the center’s intelligence packages.
Current initiatives. In response to some of the most serious financial crimes, the Financial Intelligence Center is working on a number of specific initiatives, such as:
- Foreclosure rescue fraud, where analysts collect and analyze deceptive practices complaint data from the Federal Trade Commission (FTC), which is then cross-referenced with suspicious activity reports filed by financial institutions;
- Securities and corporate fraud, in which the center partners with the Commodities and Futures Trading Commission and Securities and Exchange Commission (SEC) to review civil referrals for possible criminal violations;
- Health care fraud, which involves us working with the Centers for Medicare and Medicaid (CMS) and the Department of Justice on a new predictive modeling system that uses algorithms to generate lists of medical professionals potentially engaging in health care fraud; and
- Money laundering, in which analysts review incoming intelligence from the FBI’s Southwest Border Initiative to determine if subjects are laundering proceeds from criminal activities.
Although the center’s primary mission is to identify those who may have thus far escaped the law enforcement lens, it also uses its tools and expertise to enhance current investigations that feature large numbers of subjects and multiple FBI offices.
Of course, we don’t do this alone—we work closely with our partners. As a matter of fact, our analysts are currently or will soon be embedded in the Office of the Special Inspector General for the Troubled Asset Relief Program, the SEC, the Internal Revenue Service, the FTC, and the CMS….to expand even further the pool of data that can be used by all to uncover financial crime.
The bottom line of the FBI’s Financial Intelligence Center: to work proactively to help identify the nation’s most egregious criminal enterprises.
Cryptome – Office of the Director of National Intelligence and Department of Justice Joint Statement
REVISED GUIDELINES ISSUED TO ALLOW THE NCTC TO ACCESS AND ANALYZE CERTAIN FEDERAL DATA MORE EFFECTIVELY TO COMBAT TERRORIST THREATS
Director of National Intelligence James R. Clapper, Attorney General Eric Holder, and National Counterterrorism Center (NCTC) Director Matthew G. Olsen have signed updated guidelines designed to allow NCTC to obtain and more effectively analyze certain data in the government s possession to better address terrorism-related threats, while at the same time protecting privacy and civil liberties.
The Guidelines for Access, Retention, Use, and Dissemination by the National Counterrorism Center (NCTC) of Information in Datasets Containing Non-Terrorism Information effective Mar. 22, 2012, update November 2008 guidelines that governed NCTC s access, retention, use, and dissemination of terrorism information contained within federal datasets that are identified as also including non-terrorism information and information pertaining exclusively to domestic terrorism.
The updated Guidelines provide a framework that allows NCTC to obtain certain data held by other U.S. Government agencies to better protect the nation and its allies from terrorist attacks. In coordination with other federal agencies providing data to the NCTC, NCTC will establish the timeline for the retention of individual datasets based upon the type of data, the sensitivity of the data, any legal requirements that apply to the particular data, and other relevant considerations.
Among other modifications, the revised Guidelines:
- Permit NCTC to retain certain datasets that are likely to contain significant terrorism information and are already in the lawful custody and control of other federal agencies for up to five years, unless a shorter period is required by law.
- Permit NCTC to query this data only to identify information that is reasonably believed to constitute terrorism information.
- Provide that all data obtained by NCTC from another federal agency pursuant to the Guidelines, will be subject to appropriate safeguards and oversight mechanisms, including monitoring, recording, and auditing of access to and queries of the data, to protect privacy and civil liberties.
- Require NCTC to undertake a number of additional compliance and reporting obligations to ensure robust oversight.
The updated Guidelines do not provide any new authorities for the U.S. Government to collect information, nor do they authorize acquisition of data from entities outside the federal government. All information that would be accessed by NCTC under the Guidelines is already in the lawful custody and control of other federal agencies. The Guidelines merely provide the NCTC with a more effective means of accessing and analyzing datasets in the government s possession that are likely to contain significant terrorism information. They permit NCTC to consolidate disparate federal datasets that contain information of value to NCTC s critical counterterrorism mission. Furthermore, the updated Guidelines do not supersede or replace any legal restrictions on information sharing (existing by statute, Executive Order, regulation, or international agreement). Thus, the updated Guidelines do not give NCTC authority to require another agency to share any dataset where such sharing would contravene U.S. law or an international agreement.
One of the issues identified by Congress and the Intelligence Community after the 2009 Fort Hood shootings and the Christmas Day 2009 bombing attempt was the government s limited ability to query multiple federal datasets and to correlate information from many sources that might relate to a potential attack. A review of government actions taken before these attacks recommended that the Intelligence Community push for the completion of state-of-the-art search and correlation capabilities, including techniques that would provide a single point of entry to various government databases.
Following the failed terrorist attack in December 2009, representatives of the counterterrorism community concluded it is vital for NCTC to be provided with a variety of datasets from various agencies that contain terrorism information, said Clapper, The ability to search against these datasets for up to five years on a continuing basis as these updated Guidelines permit will enable NCTC to accomplish its mission more practically and effectively than the 2008 Guidelines allowed.
The updated Guidelines have undergone extensive review within the Office of the Director of National Intelligence and the Department of Justice and have been coordinated throughout the Intelligence Community. Under the National Security Act of 1947, NCTC is charged with serving as the primary organization in the U.S. Government for analyzing and integrating all intelligence possessed or acquired by the U.S. Government pertaining to terrorism and counterterrorism, excepting intelligence pertaining exclusively to domestic terrorists and domestic counterterrorism. Consistent with this statutory mission, Executive Order 12333 provides that Intelligence Community elements may collect, retain, or disseminate information concerning United States Persons (USPs) only in accordance with procedures established by the head of the Intelligence Community element and approved by the Attorney General in consultation with the Director of National Intelligence.
The 2008 Guidelines required NCTC to promptly review USP information and then promptly remove it if it is not reasonably believed to constitute terrorism information. This approach was a reasonable first step in 2008, but based on subsequent experience and lessons learned, the requirement to promptly remove USP information hampers NCTC s ability to identify terrorism information by connecting the dots across multiple datasets.
There are a number of protections built into the 2012 revised Guidelines, said Alexander Joel, ODNI Civil Liberties Protection Officer. Before obtaining a dataset, the Director of NCTC, in coordination with the data provider, is required to make a finding that the dataset is likely to contain significant terrorism information.
Once ingested, data is subject to a number of baseline safeguards carried over from the 2008 Guidelines, including restrictions that limit access to only those individuals with a mission need and who have received training on the Guidelines.
The approval of these Guidelines will significantly improve NCTC s ability to carry out its statutory mission said Clapper, Our citizens expect that we do everything in our power to keep them safe, while protecting privacy and other civil liberties. These Guidelines provide our counterterrorism analysts with the means to accomplish that task more effectively.
###
NCTC Guidelines: http://cryptome.org/2012/03/nctc-data-spy.pdf (2.2MB)
TOP-SECRET – The CIA Crown Jewels – The CIA and Allende
| Citation: | The CIA and Allende [Editorial on U.S. Involvement in Foreign Matters], Non-Classified, Article, April 12, 1973, 1 pp. |
| Collection: | The CIA Family Jewels Indexed |
| Item Number: | FJ00042 |
| Origin: | Baltimore News American |
| From: | Roche, John P. |
| Individuals/ Organizations Named: |
Allende Gossens, Salvador; Colby, William E.; Dulles, John Foster; International Telephone and Telegraph Corporation; Nasser, Gamal Abdel; Organization of American States; Roosevelt, Theodore |
| Subjects: | Assassinations | Chile | Coffee industry | Congressional investigations | Covert operations | Dominican Republic | Egypt | Elections | Foreign assistance | Foreign investments | Foreign policy | News media | Panama | Trujillo, Rafael Assassination (1961) |
| Abstract: | Reveals U.S. covert operations in other countries and debates ethics of U.S. intervention in foreign matters. |
| Full Text: | Document – PDF – this link will open in a new window (63 KB) |
TOP-SECRET from the CIA – Agency Support to the U.S. Secret Service (USSS) for National Democratic (10-14 July 1972) and National Republican (21-24 August 1972) Conventions
| Citation: | Agency Support to the U.S. Secret Service (USSS) for National Democratic (10-14 July 1972) and National Republican (21-24 August 1972) Conventions [Attached to Divider Sheet; Includes Attachments Entitled “CIA Support to the Secret Service for the Democratic National Convention in Miami, Florida, July 9-15, 1972” and “Democratic National Convention–Miami, Florida–July 9-15, 1972”], Secret, Memorandum, June 23, 1972, 7 pp. |
| Collection: | The CIA Family Jewels Indexed |
| Item Number: | FJ00055 |
| Origin: | United States. Central Intelligence Agency. Directorate of Plans. Western Hemisphere Division. Chief |
| From: | Shackley, Theodore G. |
| To: | United States. Central Intelligence Agency. Executive Director-Comptroller |
| Individuals/ Organizations Named: |
Angleton, James; Helms, Richard M.; Rowley, James J.; United States. Central Intelligence Agency. Deputy Director; United States. Central Intelligence Agency. Director; United States. Central Intelligence Agency. Directorate of Operations. Counterintelligence Staff. Chief; United States. Central Intelligence Agency. Directorate of Plans. Acting Deputy Director; United States. Central Intelligence Agency. Directorate of Plans. Deputy Director; United States. Central Intelligence Agency. Executive Director-Comptroller; United States. Secret Service |
| Subjects: | Caribbean Region | Cuban exiles | Democratic National Convention (1972) | Domestic intelligence | Intelligence collection | Interagency cooperation | Latin America | Miami (Florida) | Project JMCOBRA | Project JMFALCON | Republican National Convention (1972) | Safe houses | Security personnel |
| Abstract: | Documents coordination efforts between Central Intelligence Agency and Secret Service in preparation for 1972 Democratic and Republican National Conventions. |
| Full Text: | Document – PDF – this link will open in a new window (205 KB) |
FEMEN – Strip Off Against Putin
Secret – U.S. Army Taliban Use of Civilian Shields

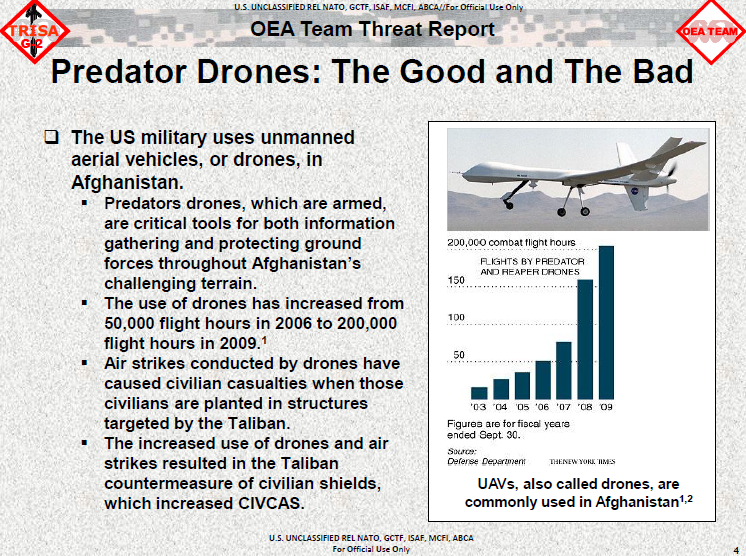

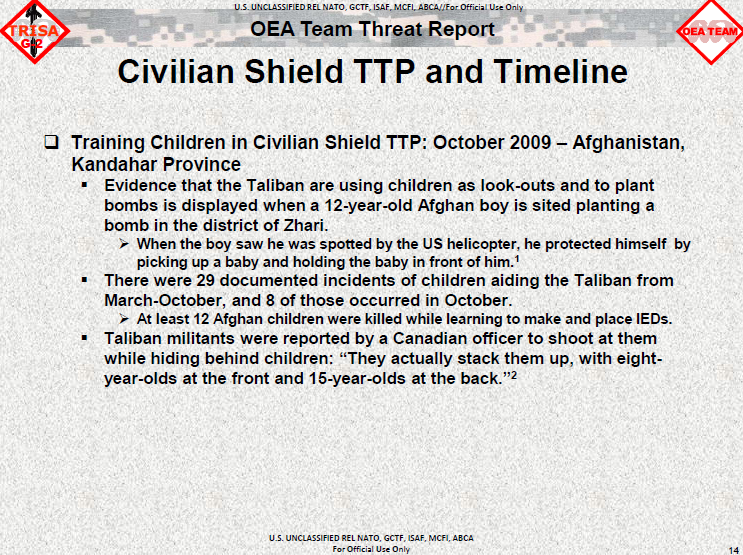
The FBI – $1 Million Reward Offered for Missing Retired FBI Agent
 |
|---|
This week marks the fifth anniversary of Robert Levinson’s disappearance, and the FBI today announced a reward of up to $1 million for information leading to the safe recovery and return of the retired special agent.
Levinson, who retired from the FBI in 1998 after 22 years of service, was working as a private investigator when he traveled to Kish Island, Iran on March 8, 2007. He has not been seen or heard from publicly since he disappeared the following day. In 2010, a video showing him in captivity was sent to the Levinson family by his captors.
Supporting the Levinson Family
The Society of Former Special Agents of the FBI announced this week that it will give the two youngest Levinson children $5,000 each to help with college costs. “Bob is part of the FBI family,” said Brad Benson, the society’s president. “We are trying to help carry out what he would be doing for his children if he were home. We also want to commend and support the fact that Bob’s family has pulled together so heroically.” |
|---|
The FBI is responsible for investigating crimes committed against U.S. citizens abroad. We have been working since 2007 to obtain information about Levinson’s whereabouts and well-being.
“On the fifth anniversary of Bob’s disappearance, the FBI continues to follow every lead into his abduction and captivity,” said James W. McJunkin, assistant director in charge of our Washington Field Office. “We are committed to bringing Bob home safely to his family. We hope this reward will encourage anyone with information, no matter how insignificant they may think it is, to come forward. It may be the clue that we need to locate Bob.”
“Though he is retired from the FBI, Bob remains a member of the FBI family to this day,” said Director Robert S. Mueller, “and his family is our family. Like all families, we stand together in good times and in times of adversity. Today, we stand together to reaffirm our commitment to Bob Levinson.”
“I am very grateful that the FBI has offered this reward,” said Levinson’s wife Christine. “Our family believes the only way of resolving this issue successfully is with the FBI’s help. It has been an extremely difficult time for my family,” she said. “We all thought Bob would be home by now. But five years have passed, and we still don’t know why he’s being held, who has him, or where he is.”
Levinson will celebrate his 64th birthday on March 10. In addition to his wife of 37 years, Levinson has seven children and two grandchildren. The family has been working tirelessly to bring Levinson home safely. “Our youngest son is about to graduate from high school,” Christine Levinson said. “He was in middle school when his father disappeared.”
In March 2011, the U.S. secretary of state issued a statement that the U.S. government had received indications that Levinson was being held by a group in southwest Asia. That region includes the border areas of Afghanistan, Iran, and Pakistan. A publicity campaign is being launched this week in southwest Asia to heighten awareness of Levinson’s abduction, announce the $1,000,000 reward, and solicit information. Billboards, radio messages, and flyers will be used to publicize the reward and the investigation. A telephone tip line will be provided to listeners and viewers in that region so that they can confidentially provide information.
“We’re never going to give up,” Christine Levinson said. “Our goal is to get Bob home. We miss him every single day.”
TOP-SECRET-The CIA’s File about Mafia Boss Johnny Rosselli
DOWNLOAD THE ORIGINAL FILE HERE
Confidential – The Department of Justice’s Principles for Conducting Online Undercover Operations

In 1999 the Department of Justice convened a working group to discuss the increasingly technological makeup of criminal organizations and the challenges law enforcement face when conducting online investigations. The Online Investigations Working Group included members of the FBI, Treasury, Secret Service, IRS, ATF, Air Force and even NASA who worked to produce a series of general principles governing the legality of online investigative practices. The working group came up with eleven principles governing everything from basic information gathering to undercover operations and wrote a final report titled “Online Investigative Principles for Federal Law Enforcement Agents” that detailed the group’s findings. Though it was originally marked as “Sensitive Law Enforcement Information,” a significant portion of the document was released to the Electronic Privacy Information Center (EPIC) in 2004. However, several very significant portions of the document that discuss online undercover operations were released in a heavily redacted form. These sections are highly relevant to understanding law enforcement’s pursuit of the hacktivist group Anonymous and the recent case of LulzSec leader “Sabu” who operated for nearly six months as a FBI informant after his arrest in June 2011.
Though it was written over a decade ago, the principles described in the DoJ’s guide for federal agents offer tremendous insight into the legal reasoning behind many tactics used by law enforcement to gather evidence in online settings. These tactics can range from the basic, such as using internet search tools or looking up an IP address, to the more advanced, like creating undercover online identities and websites to gather incriminating information. When the document was first released to EPIC in 2004, two sections were entirely redacted for the reason that they “would disclose techniques and procedures for law enforcement investigations or prosecutions.” The first section covered Principle 7 of online investigations “Online Undercover Facilities” which describes how “just as law enforcement agencies may establish physical-world undercover entities, they also may establish online undercover facilities, such as bulletin board systems, Internet service providers, and World Wide Web sites, which covertly offer information or services to the public.” The second section removed from the document discussed Principle 9 “Appropriating Online Identities” which occurs when “a law enforcement agent electronically communicates with others by deliberately assuming the known online identity (such as the username) of a real person, without obtaining that person’s consent.”
The document’s description of online undercover facilities states that federal agents may operate websites, web-based services and even ISPs either directly or indirectly in order to obtain evidence in a criminal case. An example of such an operation is provided:
As part of a project to identify and prosecute computer criminals, a law enforcement agency considers a proposal to operate a World Wide Web site with information about and computer programs for hacking, links to other hacker sites, and a facility to allow people who access the site to discuss hacking techniques. The proposal would allow the law enforcement agents running the site to track all visitors, and monitor all communications among the users. Because this proposal would establish an online undercover facility that would do more than just provide information or a means to contact agents, the consultation requirement applies to this proposal.
This means that if you are the subject of a high-level criminal investigation, online services that you use, such as a VPN or server provider, could in fact be part of an elaborate law enforcement operation and access to your private user information may have been gained either surreptitiously or through direct consent of the service’s legitimate operators. In addition to setting up false web facilities, federal agents may also seize someone’s “online identity” to communicate with others and gather evidence while representing themselves as the owner of the seized identity. The recent case of LulzSec leader/FBI informant Sabu is actually different than this because Hector Xavier Monsegur, the individual who used the name Sabu and operated its associated Twitter account, gave law enforcement permission to use his identity to gain evidence from other users. This method is also covered in the document under Principle 8 “Communicating Through the Online Identity of a Cooperating Witness, With Consent.”
The Orginal CIA Murder Contract for Congo President Lumumba – Document
DOWNLOAD THE ORIGINAL DOCUMENT HERE
Confidential an Diego Fusion Center: The Role of the Firefighter Terrorism Liaison Officer (TLO)

(U//FOUO) Valued Access and Role of the Firefighter TLO: Firefighters’ roles as a first responder and an emergency medical service allow for unique access to people and information, which can generate invaluable tips and leads. Because the presence and effectiveness of firefighters mitigate the impact of a terrorist incident involving massive human casualties, terrorists have historically conducted preoperational planning that target firefighting agencies in order to limit the effectiveness of their reaction capabilities.
(U//FOUO) The following case studies provide details on how and why terrorists have historically conducted targeting and preoperational planning on firefighting organizations. Additionally, this bulletin will address related terrorist techniques and activities that will help the Fire TLO identify and report terrorist related activity.
…
(U//FOUO) Terrorist surveillance techniques and indicators of terrorist activities:
• Unusual or prolonged interest in security measures or personnel, entry points and access controls, or perimeter fences or walls.
• Dry runs: attempting to gain access to secure facilities or bypassing security.
• Unusual behavior such as watching or documenting personnel or vehicles entering or leaving designated facilities or parking areas.
• Attempts to determine the number of security personnel and shift changes.
• Increase in anonymous telephone or e‐mail threats to facilities in conjunction with suspected surveillance incidents.
• Two or three individuals, on foot, demonstrating a combination of observation and recording data (i.e., note‐taking, photography, filming).
TOP-SECRET – ISAF Guide to Collecting Evidence for Prosecution in Afghan Courts

A Guide to Collecting Evidence for Prosecution in Afghan Courts
For the National Security Prosecutor’s Unit (NSPU) or a provincial court to prosecute and convict detainees, including Afghan murder suspects or National Security criminals, capturing units must provide evidence and witness statements against the suspects for use in an Afghan court of law. Appropriate evidence collection may result in admissible evidence in support of effective prosecutions. Turn all evidence associated with the suspect over to Afghan authorities and obtain a thoroughly documented receipt for the evidence.
Evidence collection may also be necessary without an actual detention. Operators may find weapons, documents, or other items that should be collected as evidence, even if no one is detained.
To the greatest extent possible, in order to increase the likelihood of admissibility in the Afghan courts, evidence collection and case preparation should be performed by Afghan partnering forces.
This booklet is a guide. Your local prosecutor or judge may require a slightly different format or type of evidence. Your evidence may be tailored to fit your local court’s requirements if necessary.
…
Prior to the Operation.
Each tactical unit conducting an operation will appoint an evidence collection team (a.k.a. Site Exploitation (SE) team) who will plan for, collect, receive, and handle all evidence seized during the operation. This team will be properly trained on evidence collection and handling procedures and will include an Afghan partnering member.
Whenever possible, obtain a search warrant before an operation where you plan to collect evidence. If the warrant is not obtained in advance, your unit should ensure that a warrant is obtained after the operation.
Planning and Equipment
During planning for a specific operation, the team will consider the following issues and prepare accordingly:
Possible evidence
• Documents
• Weapons
• IED components / explosives
• Drugs
• Witness statements (Interpreters!)
DOWNLOAD ORIGINAL DOCUMENT HERE
The NSA – Holder Responds to Rosemary Award

Director of the DOJ Office of Information Policy, Melanie Pustay, US Assistant Attorney General and Chief FOIA Officer Tony West, and US Attorney General Eric Holder, sit beneath the Spirit of Justice in the Department of Justice’s Great Hall.
Washington, DC, March 22, 2012 – Attorney General Eric Holder kicked off Sunshine Week 2012 by rehashing widely discredited statistics released by the Department of Justice after it was awarded the Rosemary Award by the National Security Archive for the worst open government performance by a federal agency in 2011.
In his speech, Holder stated that Department of Justice’s work on FOIA was “nothing short of remarkable,” but – just as his recent speech on the legality of assassinating Americans did not mention the “targeted killing” of al-Awlaki – Holder did not mention or refute his department’s Rosemary Award, or the reasons the DOJ was awarded it. His department’s open government failures included the DOJ Office of Information Policy’s attempt to issue new regulations that (among other steps backward) would have allowed the agency to lie to FOIA requesters and exclude online media from news media reduced fee status; the “odd” argument made to the Supreme Court by the DOJ’s Assistant Solicitor General that the Freedom of Information Act should become a withholding rather than a disclosure statute; and the DOJ’s “war on leakers” which has surely had a chilling effect upon –to use Holder’s own words– “the sacred bond of trust which must always exists between the government and those we are privileged to serve.”
Holder did, however, repeat claims from a Department of Justice press release posted just after being awarded the Rosemary Award, boasting of a 94 percent FOIA release rate and a 26 percent reduction in FOIA backlog. A National Security Archive analysis of the DOJ’s release rate shows that the DOJ excluded nine of the eleven reasons that the Department denied documents to requesters from its count. These include denials based upon: fees (pricing requesters out); referrals (passing the request off to another agency while the requester still waits); “no records” (very frequently the result of inadequate searches by DOJ employees); and requests “improper for other reasons” (which ostensibly include the “can neither confirm nor deny” glomar exemption).
What Holder did not mention was that when the full eleven reasons for denial are factored in, the Department of Justice’s “release rate” is a much more believable 56.7 percent. Melanie Pustay, head of the DOJ Office of Information Policy since 2007, also spoke. She boasted that Department of FOIA officials are using “new and creative” methods to improve FOIA output. Unfortunately, these methods appear to include “new and creative” math that obfuscates the true number of documents released under FOIA in an attempt to portray the Department of Justice in a better light. Josh Gerstein recently reported in Politico that one other “new and creative” method that the Federal Bureau of Investigation used to reduce its backlog was to simply close some requests even though the requesters “may not always have been notified.”
Dan Metcalfe, founding director and 25-year veteran of the Justice Department’s Office of Information and Privacy (now called the Office of Information Policy), agrees. The Atlantic Wire reported his judgment that, “The department’s most recent backlog reduction claim appears to be grossly wrong.” Metcalfe pointed out that to boast of a reduced backlog, the DOJ omitted data about 3,081 other “pending FOIA requests” that have not been responded to, but could not all technically be overdue. When these “pending” requests are factored in, the Department of Justice achieved a much more modest 4.5 percent decrease in actual outstanding requests, over a two-year period. According to Metcalfe, “For [the Department of Justice] to falsely claim that it ‘continues to lead by example’ has now become sad to the point of being pathetic, as is the notion that it is doing more today than ever in the past to promote FOIA disclosure.”
A FOIA survey by the Associated Press also debunks the Department of Justice’s claims about sky-high FOIA release rates government-wide. Pustay used similarly misleading math to claim an astounding 92 percent FOIA release rate across all government agencies. The Associated Press surveyed the 37 largest FOIA agencies and found a much more plausible 65 percent release rate. Unlike the Department of Justice, the Associated Press survey tallied all denials of requests including fee denials, “no records” denials, and referrals to other agencies.
It’s unclear why the Attorney General chose to regurgitate these flawed statistics. Perhaps, he simply read what the Office of Information Policy provided him, without double checking the facts. Perhaps he actually placed more importance on scoring favorable headlines than presenting a clear picture of the DOJ’s progress on FOIA. No matter the reason, the discredited figures he cited in his speech went far in disproving DOJ spokeswoman Tracy Schmaler’s bold assertion that, “Anyone who knows anything about the Freedom of Information Act will tell you that the Department of Justice is doing more than ever to promote openness and transparency under that act.”
An analysis of the DOJ’s annual FOIA reports also shows that the DOJ’s three leadership offices, the Office of the Attorney General, the Office of the Deputy Attorney General, and the Office of the Associate Attorney General have some of the worst FOIA results within the Department of Justice. As Holder “celebrated and showcased” the Department of Justice’s FOIA progress, the combined backlog of his own leadership offices had risen 35.27 percent since fiscal year 2010. Troublingly, the Office of Information Policy is responsible for processing FOIA requests at the DOJ leadership offices. How can Americans trust the DOJ OIP to reform FOIA throughout the federal government, when it can’t even improve the backlog in its own department’s leadership offices? As Senator Grassley told OIP Chief Pustay during last year’s Sunshine Week, “The president set a very high benchmark [on FOIA]. And if we’re doing the same thing after two and a half years of this administration, the same as we’ve been doing for 20 years, the president’s benchmark isn’t being followed by the people he appoints.”
Today’s presentation did provide some room from optimism from agencies other than the DOJ that have taken bold steps to improve their FOIA process. The Federal Communications Commission now proactively posts its proceedings on its relaunched, search-centered website. The Nuclear Regulatory Commission harnessed the power of e-discovery tools and electronic delivery of records to push out documents about the Fukushima nuclear catastrophe. The Social Security Administration set up a FOIA process evaluation working group to evaluate its FOIA efficiency. The Department of the Interior completed a complete “reorganization” of the FOIA office, led by the Secretary of the Interior; FOIA officials are now required to send monthly summaries of overdue FOIA requests.
However each of these FOIA reforms was created by individual agencies, and the Department of Justice has done very little –three years after Holder’s FOIA memorandum– to effect this kind of government-wide, rather than piecemeal, FOIA change.
At the Department of Justice, Holder proclaimed that he “is committed to this work,” and announced a new search pane for the FOIA.gov website –essentially a pane that simply shows the results of a google search with “site:.gov” added at the end. His promises to post monthly FOIA logs of requests to the Attorney General’s office and to eventually incorporate the FOIA.gov search and tracking into the AG’s FOIA webpage are baby steps in the correct direction. But Holder did not comment on his agency’s 21.8 percent increase its use of the b(5) “deliberative process” exemption, a key indicator showing the DOJ’s backsliding on discretionary releases. Holder also did not mention the US government’s increased reliance on the b(1) national security exemption to censor information about an ever-expanding sphere of topics (Holder’s own DOJ refuses to confirm or deny the existence of an Office of Legal Counsel memo allowing the “targeted killing” of US citizens without trial). Nor did he propose fixing the unnecessary and wasteful referral system, in which multiple (sometimes up to fourteen) agency reviews of documents lead to twenty-year-old outstanding FOIA requests.
The one fact that Holder did get absolutely correct was his comment that the Department of Justice’s FOIA progress to date is “only the beginning” of what needs to be done to achieve his 2009 promise to ensure that the Freedom of Information Act “is realized in practice.” To actually realize this, Holder must force his Department of Justice to work toward actual, difficult, fundamental, FOIA change within his DOJ and throughout the federal government, rather than merely restating his Office of Information Policy’s misleading FOIA statistics.
FEMEN protest again the Prostitution in the Ucraine – Uncensored
The FBI – Former President of Atlanta-Based Public Company Indicted in Multi-Million-Dollar Securities Fraud Cover-Up
ATLANTA—JOSEPH PACIFICO, 62, of Atlanta, was indicted today by a federal grand jury for securities fraud, causing the filing of false financial statements, and falsifying the books and records of a public company. The charges are part of a superseding indictment that charges PACIFICO and another former top executive, JOSEPH M. ELLES, 57, of Las Vegas, Nevada, with 37 federal crimes relating to their alleged roles in accounting irregularities at the major children’s clothing company Carter’s Inc. PACIFICO’s initial appearance in court on the charges has not yet been scheduled.
United States Attorney Sally Quillian Yates said of the case, “The indictment of this case investigated by the President’s Financial Fraud Task Force demonstrates that we will follow the evidence wherever it leads, even to the top of the corporate ladder. Joseph Pacifico, the former number two executive at Carter’s Inc., based in Atlanta, is accused of trying to hide a multi-million-dollar fraud, lying to shareholders, and committing additional crimes in the course of the attempted cover-up. Shareholders expect and deserve far more from their corporate leaders.”
Brian D. Lamkin, Special Agent in Charge, FBI Atlanta Field Office, stated, “Such actions by a senior corporate officer as charged in the superseding indictment impact not only the company in which he served but the many shareholders who make investment decisions based on that company’s financial statements. The FBI will continue to work with its various law enforcement partners and the U.S. Attorney’s Office as it aggressively investigates those who engage in corporate fraud.”
According to United States Attorney Yates, the charges, and other information presented in court: PACIFICO served as president of the Atlanta-based children’s clothing company Carter’s Inc. from 2004 until December 2009. PACIFICO was a senior executive officer of the company and the highest-ranking executive in the Carter’s sales organization. He supervised the company’s head of wholesale sales, defendant JOSEPH M. ELLES, and the company’s wholesale sales accounts, including Kohl’s Department Stores.
Carter’s is registered with the U.S. Securities and Exchange Commission (“SEC”), and its stock is publicly traded on the New York Stock Exchange. It is obligated to report its financial results in annual and quarterly filings with the SEC, so that members of the public can make informed investment decisions. The securities laws also require Carter’s to make and keep accurate corporate books and records.
The superseding indictment alleges that, at least by April 2009, PACIFICO was aware that ELLES and others had been deliberately causing Carter’s to falsely record in its accounting books millions of dollars in rebates that ELLES had agreed to pay to Kohl’s and other retailers. The superseding indictment alleges that, from 2006 and into 2009, at the end of each fiscal year and at the end of several fiscal quarters, ELLES agreed to pay rebates to Kohl’s and other retailers referred to as “margin support” or “accommodations.” These rebates, which are common in the apparel industry, help compensate the retailer in certain circumstances where the retailer was unable to make its expected profit margins from the sale of Carter’s goods. These rebates are expenses that reduce Carter’s net sales revenue and profits.
The superseding indictment alleges that ELLES manipulated the company’s accounting for millions of dollars in rebates to Kohl’s by misrepresenting that the rebates related to sales made in current fiscal years or quarters, rather than the prior years or quarters in which the sales were actually made. This caused Carter’s to record all of the sales revenue from selling goods in a particular year or quarter without accounting for all of the expenses (“accommodations” or “margin support”) that the company was incurring in connection with those sales.
The superseding indictment alleges that at least by April 2009 and continuing through November 2009, PACIFICO was aware of millions of dollars in undisclosed rebates and attempted to keep them hidden from other members of senior management, Carter’s shareholders, internal and external auditors, and others. The superseding indictment alleges that PACIFICO did so by lying to other members of senior management and other employees, signing false documents, and instructing subordinates not to relay information about the rebates to senior management or dissuading them from doing so.
The superseding indictment alleges that, as a result of the fraud and attempted cover-up, PACIFICO caused Carter’s to materially misstate its net income and other items in its publicly filed financial statements from April 2009 through July 2009 and falsified and caused to be falsified certain corporate books and records during that period. The superseding indictment alleges that ELLES caused Carter’s to file materially false financial statements for several years and quarters from at least November 2006 through July 2009, and that he also falsified or caused to be falsified multiple corporate books and records during that period.
In late October 2009 and continuing into December 2009, Carter’s announced that it had discovered the accounting regularities and that it intended to re-state several years’ worth of previously-published financial statements. Carter’s stock price fell over 20 percent on the day it announced that it would delay the release of its financial information for the third quarter of 2009 in order to review its accounting for accommodations. PACIFICO was placed on administrative leave in November 2009 and then resigned in December 2009. ELLES left the company earlier in 2009, working for the company in a consulting capacity for three months after resigning in March 2009.
The grand jury previously returned a 32-count indictment against ELLES on September 21, 2011 containing charges for securities fraud, causing the filing of false financial statements, falsifying corporate books and records, wire fraud, and mail fraud.
The securities fraud charges against PACIFICO and ELLES each carry a maximum sentence of 25 years in prison and a fine of up to $250,000. The charges against PACIFICO and ELLES for causing the filing of false financial statements with the SEC and the falsification of corporate books and records, in violation of the Securities Exchange Act of 1934, each carry a maximum sentence of 20 years in prison and a fine of up to $5 million. The wire and mail fraud charges against ELLES alone each carry a maximum sentence of 20 years in prison and a fine of up to $250,000. In determining the actual sentence, the court will consider the United States Sentencing Guidelines, which are not binding but provide appropriate sentencing ranges for most offenders.
This law enforcement action is part of President Barack Obama’s Financial Fraud Enforcement Task Force. President Obama established the interagency Financial Fraud Enforcement Task Force to wage an aggressive, coordinated, and proactive effort to investigate and prosecute financial crimes. The task force includes representatives from a broad range of federal agencies, regulatory authorities, inspectors general, and state and local law enforcement who, working together, bring to bear a powerful array of criminal and civil enforcement resources. The task force is working to improve efforts across the federal executive branch, and with state and local partners, to investigate and prosecute significant financial crimes, ensure just and effective punishment for those who perpetrate financial crimes, combat discrimination in the lending and financial markets, and recover proceeds for victims of financial crimes.
This case is being investigated by special agents of the Federal Bureau of Investigation. The SEC has conducted a separate investigation of possible civil violations of the U.S. securities laws, and in December 2010 reached a non-prosecution agreement with Carter’s and filed a civil enforcement action against ELLES alleging securities fraud, insider trading, and other securities violations. That case remains pending.
Assistant United States Attorney David M. Chaiken is prosecuting the case.
Members of the public are reminded that the indictment contains only allegations. A defendant is presumed innocent of the charges, and it will be the government’s burden to prove a defendant’s guilt beyond a reasonable doubt at trial.
The CIA and the Congress – A Secret Document
DOWNLOAD THE ORIGINAL DOCUMENT HERE
Unveiled – Noted Scientist Sentenced to 13-Year Prison Term for Attempted Espionage, Fraud, and Tax Charges
WASHINGTON—Stewart David Nozette, 54, a scientist who once worked for the Department of Energy, the Department of Defense, the National Aeronautics and Space Administration, and the White House’s National Space Council, was sentenced today to 13 years in prison for attempted espionage, conspiracy to defraud the United States, and tax evasion.
The sentence covered charges in two cases. In one, Nozette pleaded guilty in September 2011 to attempted espionage for providing classified information to a person he believed to be an Israeli intelligence officer. In the other, he pleaded guilty in January 2009 to fraud and tax charges stemming from more than $265,000 in false claims he submitted to the government.
The sentencing, which took place this morning in the U.S. District Court for the District of Columbia, was announced by Ronald C. Machen Jr., U.S. Attorney for the District of Columbia; Lisa Monaco, Assistant Attorney General for National Security; and Principal Deputy Assistant Attorney General John A. DiCicco of the Tax Division.
Joining in the announcement were James W. McJunkin, Assistant Director in Charge of the FBI’s Washington Field Office; Paul K. Martin, Inspector General for the National Aeronautics and Space Administration (NASA OIG); Eric Hylton, Acting Special Agent in Charge of the Washington Field Office of the Internal Revenue Service-Criminal Investigation (IRS-CI); and John Wagner, Special Agent in Charge of the Washington, D.C. Office of the Naval Criminal Investigative Service (NCIS).
In addition to the prison term, the Honorable Paul L. Friedman ordered that Nozette pay more than $217,000 in restitution to the government agencies he defrauded.
Nozette has been in custody since his arrest for attempted espionage on October 19, 2009. At the time, he was awaiting sentencing on the fraud and tax evasion charges. FBI agents arrested Nozette following an undercover operation in which he provided classified materials on three occasions, including one that formed the basis for his guilty plea. He was subsequently indicted by a federal grand jury. The indictment does not allege that the government of Israel or anyone acting on its behalf committed any offense under U.S. laws in this case.
“Stewart Nozette’s greed exceeded his loyalty to our country,” said U.S. Attorney Machen. “He wasted his talent and ruined his reputation by agreeing to sell national secrets to someone he believed was a foreign agent. His time in prison will provide him ample opportunity to reflect on his decision to betray the United States.”
“Stewart Nozette betrayed his country and the trust that was placed in him by attempting to sell some of America’s most closely-guarded secrets for profit. Today, he received the justice he deserves. As this case demonstrates, we remain vigilant in protecting America’s secrets and in bringing to justice those who compromise them,” said Assistant Attorney General Monaco. “I thank the many agents, analysts, and prosecutors who worked on this important case.”
“As this case demonstrates, those who attempt to evade their taxes by abusing the tax-exempt status of non-profit entities will be investigated, prosecuted, and punished,” said Principal Deputy Assistant Attorney General DiCicco.
“Today’s sentencing demonstrates that espionage remains a serious threat to our national security,” said Assistant Director in Charge McJunkin. “The FBI and our partners in the defense and intelligence communities work every day to prevent sensitive information from getting into the wrong hands, and I commend the hard work of the dedicated agents, analysts, and prosecutors who spent a significant amount of time bringing this case to resolution.”
“We are particularly proud that NASA OIG’s fraud investigation of Nozette, which began in 2006, served as the catalyst for further investigation and today’s outcome,” said NASA Inspector General Martin.
“IRS-Criminal Investigation provides financial investigative expertise in our work with our law enforcement partners,” said Acting Special Agent in Charge Hylton. “Pooling the skills of each agency makes a formidable team as we investigate allegations of wrongdoing. Mr. Nozette decided to betray his country to line his own pockets rather than play by the rules. He now is being held accountable for his actions.”
“Federal agents take an oath to protect our nation ‘against all enemies, foreign and domestic.’ That would include ‘insider threats’ like Stewart Nozette,” said Special Agent in Charge Wagner. “NCIS is committed to working with our law enforcement partners and prosecutors to find and hold accountable those like Nozette who put personal gain above national security.”
Nozette received a Ph.D. in planetary sciences from the Massachusetts Institute of Technology. Beginning in at least 1989, he held sensitive and high-profile positions within the U.S. government. He worked in various capacities on behalf of the government in the development of state-of-the-art programs in defense and space. During his career, for example, Nozette worked at the White House on the National Space Council, Executive Office of the President. He also worked as a physicist for the U.S. Department of Energy’s Lawrence Livermore National Laboratory, where he designed highly advanced technology.
Nozette was the president, treasurer, and director of the Alliance for Competitive Technology (ACT), a non-profit organization that he organized in March 1990. Between January 2000 and February 2006, Nozette, through his company, ACT, entered into agreements with several government agencies to develop highly advanced technology. Nozette performed some of this research and development at the U.S. Naval Research Laboratory (NRL) in Washington, D.C.; the Defense Advanced Research Projects Agency (DARPA) in Arlington, Virginia; and NASA’s Goddard Space Flight Center in Greenbelt, Maryland.
In connection with the fraud and tax case, Nozette admitted that, from 2000 through 2006, he used ACT to defraud the NRL, DARPA and NASA by making and presenting more than $265,000 in fraudulent reimbursement claims, most of which were paid. He also admitted that, from 2001 through 2005, he willfully evaded more than $200,000 in federal taxes. In addition, he admitted using ACT, an entity exempt from taxation because of its non-profit status, to receive income and to pay personal expenses, such as mortgages, automobile loans, sedan services, and other items.
The investigation concerning ACT led investigators to suspect that Nozette had misused government information. From 1989 through 2006, Nozette held security clearances as high as top secret and had regular, frequent access to classified information and documents related to the national defense of the United States.
On September 3, 2009, Nozette was contacted via telephone by an individual purporting to be an Israeli intelligence officer from the Mossad, but who was, in fact, an undercover employee of the FBI. That same day, Nozette informed the undercover employee that he had clearances “all the way to top secret/SCI” and that anything “that the U.S. has done in space I’ve seen.” He stated that he would provide classified information for money and a foreign passport to a country without extradition to the United States.
A series of contacts followed over the next several weeks, including meetings and exchanges in which Nozette took $10,000 in cash left by the FBI at prearranged drop-off sites. Nozette provided information classified as secret/SCI and top secret/SCI that related to national defense. Some of this information directly concerned satellites, early warning systems, means of defense or retaliation against large-scale attack, communications intelligence information, and major elements of defense strategy.
Nozette and the undercover employee met for the final time on October 19, 2009 at the Mayflower Hotel. During that meeting, Nozette pushed to receive larger payments for the secrets he was disclosing, declaring that, “I gave you even in this first run some of the most classified information that there is…I’ve sort of crossed the Rubicon.”
Nozette was arrested soon after he made these statements.
The investigation of the fraud and tax evasion case was conducted by NASA OIG, NCIS, the Defense Criminal Investigative Service (DCIS), IRS-CI, the IRS Tax Exempt and Government Entities Group, the Naval Audit Service, the Defense Contract Audit Agency, and the FBI’s Washington Field Office.
The prosecution of the fraud and tax evasion case was handled by Assistant U.S. Attorney Michael K. Atkinson from the Fraud and Public Corruption Section of the U.S. Attorney’s Office for the District of Columbia and Trial Attorney Kenneth C. Vert from the Department of Justice’s Tax Division.
The investigation of the attempted espionage case was conducted by the FBI’s Washington Field Office, with assistance from NCIS; Naval Audit Service; National Reconnaissance Office; Air Force Office of Special Investigations; Defense Computer Forensics Laboratory; Defense Advanced Research Projects Agency; DCIS; Defense Contract Audit Agency; U.S. Army 902nd Military Intelligence Group; NASA Office of Counterintelligence; NASA OIG; Department of Energy Office of Intelligence and Counterintelligence; IRS-CI; IRS Tax Exempt and Government Entities group; U.S. Customs and Border Protection; and the U.S. Postal Inspection Service, as well as other partners in the U.S. intelligence community.
The prosecution of that case was handled by Assistant U.S. Attorney Anthony Asuncion, from the National Security Section of the U.S. Attorney’s Office for the District of Columbia, and Trial Attorneys Deborah A. Curtis and Heather M. Schmidt, from the Counterespionage Section of the Justice Department’s National Security Division.
Video – FEMEN bare all in Kiev protest
TOP-SECRET – Transcript of Council on Foreign Relations Secret Meeting on the Theory of CIA Covert Action
The following is a transcript of a private meeting held in 1968 in the New York Pratt House of the Council on Foreign Relations. The meeting was attended by a number of prominent members of the early U.S. intelligence community, including Richard Bissell and Allen Dulles. The transcript was reportedly discovered by Vietnam War protesters who occupied a building in 1971 housing Harvard’s Center for International Affairs. One of the attendees of the secret meeting, William Harris, served as an associate to the Center for International Affairs and this transcript was found in his personal files. The transcript was published in full in the 1974 book “The CIA and the Cult of Intelligence” by Victor Marchetti, a former special assistant to the Deputy Director of the Central Intelligence Agency, and John D. Marks, a former officer of the United States Department of State. The meeting transcript is described in the book as the “most complete description of the CIA’s covert-action strategy and tactics ever made available to the outside world.”
Minutes of the 1968 “Bissell Meeting” at the Council on Foreign Relations
The third meeting of the Discussion Group on Intelligence and Foreign Policy was held at the Harold Pratt House on January 8, 1968, at 5:00 p.m. Present were: Richard M. Bissell, Jr., Discussion Leader; Douglas Dillon, Chairman; William J. Barnds, Secretary; William R. Harris, Rapporteur; George Agree, Frank Altschul, Robert Amory, Jr., Meyer Bernstein, Col. Sidney B. Berry, Jr., Allen W. Dulles, George S. Franklin, Jr., Eugene Fubini, Julius C. Holmes, Thomas L. Hughes, Joseph Kraft, David W. MacEachron, Philip W. Quigg, Harry Howe Ransom, Theodore C. Sorensen, David B. Truman.
The Chairman, Mr. Dillon, opened the meeting, noting that although this entire series of discussion was “off-the-record,” the subject of discussion for this particular meeting was especially sensitive and subject to the previously announced restrictions.
Mr. Dillon noted that problems involving CIA’s relationships with private institutions would be examined at a later meeting, though neither Mr. Bissell nor others should feel restricted in discussion of such problems this evening.
As the session’s discussion leader, Mr. Bissell offered a review and appraisal of covert operations in U.S. foreign policy.
Touching briefly upon the question of responsibility, of whether these agencies are instruments of national policy, Mr. Bissell remarked that, in such a group, he needn’t elaborate on CIA’s responsiveness to national policy; that we could assume that, although CIA participates in policy making (as do other “action agencies,” such as AID, the military services and Departments, in addition to the Department of State), CIA was a responsible agency of national policy.
Indeed in Mr. Bissell’s personal experience, CIA’s role was more carefully circumscribed and the established limits observed more attentively than in ECA, where Mr. Bissell had previously worked.
The essential control of CIA rested in a Cabinent-level committee, comprising a representative of the White House staff the Under Secretary of State, Deputy Secretary of Defense, and in recent years the personal participation of the Director of Central Intelligence. Over the years this committee has become a more powerful and effective device for enforcing control. It reviews all new projects, and periodically scrutinizes ongoing projects.
As an interdepartmental committee composed of busy officials who meet only once per week, this control group is of limited effectiveness. Were it the only control instrument, Mr. Bissell would view it as inadequate, but in fact this committee is merely the summit of control, with a series of intermediate review procedures as lower levels. Projects are usually discussed in the relevant office of the Assistant Secretary of State, and, if at all related to Defense Department interests, at a similar level in DoD, frequently after consideration at lower levels in these departments. It was rare to take an issue before the Special Group prior to discussion at lower levels, and if there was objection at lower levels most issues were not proposed to the Special Group — excepting large projects or key issues, which would be appealed at every level, including the Special Group.
Similar procedures applied in the field. Generally, the Ambassador had a right to know of any covert operations in his jurisdiction, although in special cases (as a result of requests from the local Chief of State or the Secretary of State) the chief of station was instructed to withhold information from the Ambassador. Indeed, in one case the restriction was imposed upon the specific exhortation of the Ambassador in question, who preferred to remain ignorant of certain activities.
Of the “blown” operations, frequently among the larger ones, most are known to have been approved by the President himself. The U-2 project, for example, was an offshoot of the Land (intelligence) Committee of the Killian panel on surprise attack; it was proposed as a Killian panel recommendation to the President, supported by USIB; its procurement, in utmost secrecy, was authorized by the President, and, with the exception of the first few flights (the initial authorization being to operate for a period of ten days, “weather permitting”), each individual flight was authorized by the President, with participation by the Secretary of State and Secretary of Defense.
Covert operations should, for some purposes, be divided into two classifications: ( 1) Intelligence collection, primarily espionage, or the obtaining of intelligence by covert means; and (2) Covert action, attempting to influence the internal affairs of other nations — sometimes called “intervention” — by covert means.
Although these two categories of activity can be separated in theory, intelligence collection and covert action interact and overlap. Efforts have been made historically to separate the two functions but the result has usually been regarded as “a total disaster organizationally.” One such attempt was the establishment in the early days of CIA (1948) of the OPC under Frank G. Wisner as a separate organ for covert action. Although supported and given cover by the CIA, this organization was independent and Wisner reported directly to the Secretaries of State and Defense. “Beedle” Smith decided when he became Director of Central Intelligence that, if he were responsible for OPC, he was going to run it and it was merged with the clandestine intelligence organization in such a way that within the combined Clandestine Service there was a complete integration of intelligence collection and covert action functions in each area division.
In addition to our experience with OPC, the Germans and the British for a time during the war had organizations for covert special operations separate from, and inevitably in competition with. their espionage services. In every case the experience has been unfortunate. Although there are many disagreements within CIA on matters of doctrine, the view is unanimous that the splitting of intelligence and covert action services would be disastrous, with resulting competition for recruitment of agents, multiple recruitment of the same agents, additional security risks, and dissipation of effort.
Concerning the first category, intelligence collection, we should ask: (a) What is the scope of “covert intelligence collection”? (b) What intelligence collection functions can best be performed covertly?
The scope of covert intelligence collection includes: (1) reconnaissance; (2) communications and electronic intelligence, primarily undertaken by NSA; and (3) classical espionage, by agents. In gauging their utility, Mr. Bissell ranked (1) the most important, (2) slightly below, and (3) considerably below both (1) and (2).
Although it is less effective, classical espionage is “much the least costly,” with the hardware components of recon and NSA activities raising their costs considerably.
(In the after-dinner discussion, an authority on communications-electronics expressed his concurrence in Mr. Bissell’s relative rankings. Notwithstanding technological advances in cryptology, the increased sophistication in most cryptosystems assured that (1) (reconnaissance) outranked (2). Another observer noted that the budgets correlated in similar manner, the former speaker concurring and noting that, however surprising, the budgets approximated maximum utility according to cost-effectiveness criteria.)
Postwar U.S. reconnaissance operations began, historically, as “covert” operations, primarily a series of clandestine overflights of Communist territory in Eastern Europe, inaugurated in the early 1950s. These early efforts were followed by the U-2 project, which provided limited coverage but dramatic results.
Now we have reconnaissance satellites. Overhead reconnaissance is one of the most open of “secrets” in international affairs; it is no longer really a “covert activity,” and bureaucratic responsibility for it now resides in the Pentagon. Classical espionage, in the early postwar years, was conducted with special intensity in West Germany, and before the Berlin wall, in that city, which was ideal for the moving of agents in both directions, providing a sizable flow of political and economic intelligence (especially from East Germany).
Throughout the period since the early fifties, of course, the Communist bloc, and more especially the U.S.S.R. itself, has been recognized as the primary target for espionage activities. Circumstances have greatly limited the scale of operations that could be undertaken within the bloc so much of the effort has been directed at bloc nationals stationed in neutral or friendly areas, and at “third country” operations that seek to use the nationals of other non-Communist countries as sources of information on the Soviet bloc.
More recently there has been a shift in priorities for classical espionage toward targets in the underdeveloped world. Partly as a result of this change in priorities and partly because of other developments, the scale of the classical espionage effort mounted in Europe has considerably diminished. The U.S.S.R. remains a prime target but Communist China would today be given the same priority.
As to the kinds of information that could be obtained, espionage has been of declining relative importance as a means of learning about observable developments, such as new construction, the characteristics of transportation systems, the strength and deployment of military forces and the like because reconnaissance has become a far more effective collection technique and (except in China) travel is freer and far more extensive than some years ago. It had been hoped that espionage would contribute to the collection of intelligence on Soviet and East European technology, since this is a body of information not readily observable (until embodied in operational systems). Another type of intelligence for which espionage would seem to be the only available technique is that concerning enemy intentions. In practice however espionage has been disappointing with respect to both these types of intelligence. They ,are for obvious reasons closely guarded and the task is just too difficult to permit results to be obtained with any dependability or regularity. With respect to the former category — technology — the published literature and direct professional contacts with the scientific community have been far richer sources.
(A communications-electronics expert interjected the observation that the same reasoning applied to inadequacies in S&T intelligence collection; technology is just too difficult for agents, who are insufficiently trained to comprehend what they observe as the technologies become increasingly complicated.)
As to friendly neutrals and allies, it is usually easier to learn what one wishes by overt contacts, human contact of overt members of the U.S. mission or private citizens. We don’t need espionage to learn British, or even French
intentions.
(The speaker was questioned as to whether the other side’s espionage was of similarly limited utility, or whether — with their Philbys — they were more successful?)
Mr. Bissell remarked that Soviet Union successes were primarily in counterintelligence, though going back aways, the Soviet Union had been more successful in recruiting U.S. scientists.
(The question was raised as to whether Burgess and MacLean constituted merely C.I. successes.)
Mr. Bissell thought so.
(In another’s recollection, Soviet atomic intelligence efforts had been of substantial assistance in facilitating the Soviet nuclear weapons program. Although it is not possible to estimate with precision the effects of this intelligence, it was Lewis Strauss’s guess that atomic intelligence successes allowed the Soviets to detonate their first device at least one and one-half and perhaps as much as two and one-half years before such a test would have been possible with purely indigenous efforts.)
The general conclusion is that against the Soviet bloc or other sophisticated societies, espionage is not a primary source of intelligence, although it has had occasional brilliant successes (like the Berlin Tunnel and several of the high level defectors). A basic reason is that espionage operates mainly through the recruitment of agents and it is enormously difficult to recruit high level agents. A low level agent, even assuming that he remained loyal and that there is some means of communicating with him[,] simply cannot tell you much of what you want to know. The secrets we cannot find out by reconnaissance or from open sources are in the minds of scientists and senior policy makers and are not accessible to an ordinary citizen even of middle rank.
In contrast, the underdeveloped world presents greater opportunities for covert intelligence collection, simply because governments are much less highly oriented; there is less security consciousness; and there is apt to be more actual or potential diffusion of power among parties, localities, organizations, and individuals outside of the central governments. The primary purpose of espionage in these areas is to provide Washington with timely knowledge of the internal power balance, a form of intelligence that is primarily of tactical significance.
Why is this relevant?
Changes in the balance of power are extremely difficult to discern except through frequent contact with power elements. Again and again we have been surprised at coups within the military; often, we have failed to talk to the junior officers or non-coms who are involved in the coups. The same problem applies to labor leaders, and others. Frequently we don’t know of power relationships, because power balances are murky and sometimes not well known even to the principal actors. Only by knowing the principal players well do you have a chance of careful prediction. There is real scope for action in this area; the technique is essentially that of “penetration,” including “penetrations” of the sort which horrify classicists of covert operations, with a disregard for the “standards” and “agent recruitment rules.” Many of the “penetrations” don’t take the form of “hiring” but of establishing a close or friendly relationship (which may or may not be furthered by the provision of money from time to time).
In some countries the CIA representative has served as a close counselor (and in at least one case a drinking companion) of the chief of state. These are situations of course in which the tasks of intelligence collection and political action overlap to the point of being almost indistinguishable. (The question was raised as to why ordinary diplomats couldn’t maintain these relationships.)
Mr. Bissell observed that often they could. There were special cases, however, such as in one Republic where the chief of state had a “special relationship” with the senior CIA officers without the knowledge of the U.S. Ambassador because the President of the Republic had so requested it. The CIA man sent reports by CIA channels back to the Secretary of State, but the Ambassador in the field, as agreed by the Secretary of State, wasn’t to be informed. In this case, a problem arose when the relevant Assistant Secretary of State (who had received cables from the CIA man) became the new Ambassador, but the President of the Republic liked the new Ambassador and asked that a “special relationship” be established with him too.
Aside from this unique case, it seems to have been true generally that the Ambassador has to be a formal representative of the United States most of whose relations with the government to which he is accredited are through or with the knowledge of. its foreign office. On the other hand, the CIA representative can maintain a more intimate and informal relationship the privacy of which can be better preserved both within the government of the country in question and within the United States government. Moreover, if a chief of state leaves the scene or changes his mind, you can quietly move a station chief, but it could be embarrassing if it were necessary suddenly to recall the U.S. Ambassador.
(Was the previously described relationship really a “covert operation”?)
The “cover” may be to shield visibility from some junior officials or, in the case of a “private adviser” to a chief of state, to shield this fact from politicians of the local government. (Another observation was that the method of reporting, through CIA channels, constituted one difference and had some influence. A chief of state who knew that CIA’s reports would be handfed in a smaller circle, with less attendant publicity, might prefer these channels for some communications.)
Concerning the second category, covert action:
The scope of covert action could include: (1) political advice and counsel; (2) subsidies to an individual; (3) financial support and “technical assistance” to political parties; ( 4) support of private organizations, including labor unions, business firms, cooperatives, etc.; (5) covert propaganda; (6) “private” training of individuals and exchange of persons; (7) economic operations; and (8) paramilitary [or] political action operations designed to overthrow or to support a regime (like the Bay of Pigs and the programs in Laos). These operations can be classified in various ways: by the degree and type of secrecy required [,] by their legality, and, perhaps, by their benign or hostile character.
From whom is the activity to be kept secret? After five days, for example, the U-2 flights were not secret from the Russians but these operations remained highly secret in the United States, and with good reason. If these overflights had “leaked” to the American press, the U.S.S.R. would have had been forced to take action. On a less severe level the same problem applies to satellite reconnaissance. These are examples of two hostile governments collaborating to keep operations secret from the general public of both sides. “Unfortunately, there aren’t enough of these situations.” (The remark was interjected that there was another reason for secrecy; if one had to admit to the activity, one would have to show the results, and exactly how good or bad they were.)
Covert operations could be classified by their legality or illegality. Many of them are legal.
They can also be classified as “benign” or “hostile.” Most operations in Western Europe have been “benign,” though involving the gravest improprieties, and in some cases clearly illegal action. (E.g., covert support of political parties.)
In the case of a large underdeveloped country, for example, money was put into a party’s funds without the knowledge of that party. The relatively few economic operations that have been undertaken have been both benign and legal. One of these involved the provision by CIA of interim ostensibly private financing of an overt project pending an overt and official loan by AID. Its purpose was to give AID time for some hard bargaining without causing a complete failure of the transaction. The stereotype, of course, is that all covert operations are illegal and hostile, but this is not really the case.
The role of covert intervention can best be understood by contrast with the overt activities of the United States government. Diplomacy seeks results by bargaining on a government-to-government basis, sometimes openly — sometimes privately. Foreign economic policy and cultural programs seek to modify benignly the economies of other countries and the climate of opinion within them. Covert intervention is usually designed to operate on the internal power balance, often with fairly short-term objectives in view. An effort to build up the economy of an underdeveloped country must be subtle, long continued, probably quite costly, and must openly enlist the cooperation of major groups within the country if it is to have much influence. On the other hand an effort to weaken the local Communist party or to win an election, and to achieve results within at most two or three years, must obviously be covert, it must pragmatically use the people and the instrumentalities that are available and the methods that seem likely to work. It is not surprising that the practitioners within the United States government of these two types of intervention differ temperamentally and in their preferences for methods, friends, and ideologies.
The essence of such intervention in the internal power balance is the identification of allies who can be rendered more effective, more powerful, and perhaps wiser through covert assistance. Typically these local allies know the source of the assistance but neither they nor the United States could afford to admit to its existence. Agents for fairly minor and low sensitivity interventions, for instance some covert propaganda and certain economic activities, can be recruited simply with money. But for the larger and more sensitive interventions, the allies must have their own motivation. On the whole the Agency has been remarkably successful in finding individuals and instrumentalities with which and through which it could work in this fashion. Implied in the requirement for a pre-existing motivation is the corollary that an attempt to induce the local ally to follow a course he does not believe in will at least reduce his effectiveness and may destroy the whole operation. It is notably true of the subsidies to student, labor, and. cultural groups that have recently been publicized that the Agency’s objective was never to control their activities, only occasionally to point them in a particular direction, but primarily to enlarge them and render them more effective.
Turning to relations with other agencies. Mr. Bissell was impressed by the degree of improvement in relations with the State Department. Seen from the Washington end, there has been an increase in consultation at the country-desk level, more often at the Bureau level or the Assistant Secretary of State level as the operation shapes up. The main problem some five to six years ago was not one of responsibility or authority but of cover arrangements.
Mr. Bissell provided a brief critique of covert operations, along the following lines:
That aspect of the Agency’s operations most in need of change is the Agency’s use and abuse of “cover.” In this regard, the “background paper” for this session raised many cover-oriented questions.
On disclosure of private institutional support of late, it is very clear that we should have had greater compartmenting of operations.
If the Agency is to be effective, it will have to make use of private institutions on an expanding scale, though those relations which have “blown” cannot be resurrected.
We need to operate under deeper cover, with increased attention to the use of “cut-outs.” CIA’s interface with the rest of the world needs to be better protected.
If various groups hadn’t been aware of the source of their funding, the damage subsequent to disclosure might have been far less than occurred.
The CIA interface with various private groups, including business and student groups, must be remedied.
The problem of Agency operations overseas is frequently a problem for the State Department. It tends to be true that local allies ‘ find themselves dealing always with an American and an official American-since the cover is almost invariably as a U.S. government employee. There are powerful reasons for this practice, and it will always be desirable to have some CIA personnel housed in the Embassy compound, if only for local “command post” and communications requirements.
Nonetheless, it is possible and desirable, although difficult and time-consuming, to build overseas an apparatus of unofficial cover. This would. require the use or creation of private organizations, many of the personnel of which would be non-U.S. nationals, with freer entry into the local society and less implication for the official U.S. posture.
The United States should make increasing use of non-nationals, who, with effort at indoctrination and training, should be encouraged to develop a second loyalty, more or less comparable to that of the American staff. As we shift our attention to Latin America, Asia, and Africa, the conduct of U.S. nationals is likely to be increasingly circumscribed. The primary change recommended would be to build up a system of unofficial cover; to see how far we can go with non-U.S. nationals, especially in the field. The CIA might be able to make increasing use of non-nationals as “career agents” that is with a status midway between that of the classical agent used in a single compartmented operation perhaps for a limited period of time and that of a staff member involved through his career in many operations and well informed of the Agency’s capabilities. Such career agents should be encouraged with an effort at indoctrination and training and with a prospect of long-term employment to develop a second loyalty and they could of course never be employed in ways that would conflict with their primary loyalties toward their own countries. This still leaves open, however, a wide range of potential uses. The desirability of more effective use of foreign nationals increases as we shift our attention to Latin America, Asia, and Africa where the conduct of United States nationals is easily subject to scrutiny and is likely to be increasingly circumscribed.
These suggestions about unofficial cover and career agents illustrate and emphasize the need for continuing efforts to develop covert action capabilities even where there is no immediate need to employ them. The central task is that of identifying potential indigenous allies-both individuals and organizations-making contact with them, and establishing the fact of a community of interest. There is some room for improvement, Mr. Bissell thought, in the planning of covert action country by country. Covert intervention is probably most effective in situations where a comprehensive effort is undertaken with a number of separate operations designed to support and complement one another and to have a cumulatively significant effect. The Agency probably finds itself involved in too many small covert action operations having no particular relationship with one another and having little cumulative impact.
There is no doubt that some covertly funded programs could be undertaken overtly, Mr. Bissell thought. Often activities have been initiated through CIA channels because they could be started more quickly and informally but do not inherently need to be secret. An example might be certain exchange of persons programs designed to identify potential political leaders and give them some exposure to the United States. It should be noted, however, that many such innocent programs are more effective if carried out by private auspices than if supported officially by the United States government. They do not need to be covert but if legitimate private entities such as the foundations do not initiate them, there may be no way to get them done except by covert support to “front” organizations.
Many propaganda operations are of declining effectiveness. Some can be continued at slight cost, but some of the larger ones (radio, etc.) are pretty well “blown” and not inexpensive. USIA doesn’t like them, and although they did have a real justification some ten to fifteen years ago as the voice of refugees and emigres, groups which also have declined in value, and in the view of some professionals are likely to continue declining in value.
In his last two years in the Agency, Mr. Bissell felt that the Clandestine Services could have been smaller.
Indeed, steps were taken to reduce their size. It is impossible to separate the issue of size from personnel and cover problems. It was Mr. Bissell’s impression that the Clandestine Services were becoming increasingly a career service, too much like the Foreign Service (personnel looking to a succession of overt posts in a safe career) . One result was the circumscription of local contacts. There was a subtle change taking place, which threatened to degrade some of CIA’s former capabilities. Formally, the CIA had a staff with a wide variety of backgrounds, experiences, and capabilities. Its members were recruited from every sort of public and private occupation. If this diversity and variety is lost through the process of recruiting staff members from college, training them in a fairly standard pattern, and carrying them through orderly planned careers in the Agency, one of the organization’s most valuable attributes will disappear.
Finally, Mr. Bissell remarked on large operations. It is self-evident that if an operation is too large, it can’t remain a deeply kept secret. At best, one can then hope for a successful formal disclaimer. The worst of many faults of the Bay of Pigs operation was excessive reliance on the operation’s disclaimability.
It has been a wise decision that operations of that scale not be undertaken by the Agency, except in theaters such as Vietnam, where the stakes and standards are different.
Covert action operations are generally aimed at short-term goals and the justification for the control machinery is that bias of operators to the short run can be compensated for in the review process. Mr. Bissell can conceive of no other way to force greater attention to long-range costs and values. One alternative is that caution will lead to ineffectuality. “Operational types” will he risk-takers, the counterweight is, and should be, applied by the other agencies in government.
In the discussion following Mr. Bissell’s talk, the issue of CIA cover was cited as among the more interesting from the perspective of a former State Department appointee. The size of covert operations known to other governments was a continuing embarrassment, and the overseas staff maintained for these purposes and known to host governments was a similar source of embarrassment. From time to time, efforts were made to reduce overseas staff; although agreement in principle was readily forthcoming, the particulars of staff reduction were difficult to obtain.
A former member of the Special Group (who served eighteen months on that committee) agreed with Mr. Bissell’s earlier remarks on control mechanisms, insofar as they applied to review of new projects. These received most careful scrutiny. Insofar as the Special Group considered ongoing projects during this eighteen-month period, it was recalled that there was not any systematic, thorough procedure for such review, the committee finding itself busy with all the new proposals. If it were true that most operations were most useful for short-term goals, then perhaps there should be greater attention to review of ongoing projects, and termination of more projects earlier than in past practice.
A continuing problem which worries one former official was that. concerning the “charter” of CIA, the public expression of which, in the National Security Act of 1947, was necessarily vague. CIA’s full “charter” has been frequently revised, but it has been, and must remain[,] secret. The absence of a public charter leads people to search for the charter and to question the Agency’s authority to undertake various activities. The problem of a secret “charter” remains as a curse, but the need for secrecy would appear to preclude a solution.
Another former official remarked on the inadequacy of clandestine intelligence as a means of obtaining enemy intentions. Sherman Kent (former Chairman. Board of National Estimates) distinguishes “the knowable” from “the unknowable,” and we should recognize that much remains impossible to know, including, frequently, enemy intentions.
Respecting the reduction of overseas personnel and programs of declining utility, it was noted that the curtailment of over-age and unproductive personnel was a thorny issue. Recognizing the likelihood of appeal to the President and the absence of widespread participation in a manpower review, a former budget official arranged the participation of the Bureau of the Budget, CIA, FIAB, and relevant Under Secretaries in considerations of budgetary modifications. What emerged was an inertia, partly the inertia of the cold war. Parenthetically, a couple of much-criticized public media projects (cited by name) had proven of value, as the fall of Novotny in Czechoslovakia suggested, but a number of ineffective programs were retained. The problem was to free the budget, to do something new, in the place of old programs, not to reduce the budget, but unfortunately, the chiefs in CIA wanted to control their working capital. If it were only possible to tell these officials not to worry. that we were setting aside $xxx million for CIA, and merely seeking to encourage better use of the same dollar amounts, then it would have been possible to move around some money. The big “iffy” question was a particular (named) foundation, which received a sizable allocation. Finally. everything was cleared up, and the next big review was scheduled, but never really effected as a consequence of the Cuban missile crisis. The review was geared up in 1963 once again.
Another observer, drawing upon work with the “combined cryptologic budget” and private industry, concluded that it was usually impossible to cut a budget; usually it was only possible to substitute a new project for an old one.
The Chairman suggested a number of questions: What are the effects of covert operations being blown? What can be done to improve the image of the Agency? What can he done to improve relations between the Agency and the press?
It was thought that a journalist’s perspective might aid in discussing these questions, but a number of prior issues were thought to require attention:
(1) The matter of size required attention. In any government agency size can become a problem; increasingly there is a realization that the government is too big and “an ever-swelling tumor.” At some point there will have to be a fairly sharp cutback in the U.S. foreign policy establishment.
(2) One was not overly impressed by the use of CIA in the developing world; in any case, we could have increased confidence in the range of choice in most developing areas. Conversely, it might not be as easy. as Mr. Bissell suggested to know the power structure in more developed areas, in Western Europe and Japan.
(A query was interjected: Why should we have increasing confidence in the range of choice in developing areas? Perhaps there are Jess variations than we earlier thought. “Things are evening out and we can live more comfortably.”)
(3) Where do you bury the body? One is not completely convinced by citation of the experience with Frank Wisner’s OPC. We could get around the responsibility issue raised by “Beedle” Smith; we could get around conflicting chains of command.
(4) Related to (3). Maybe there is a cost to be paid for having covert operations under CIA. Perhaps we could have intelligence collection under State and covert operations under the Special Assistant to the President for National Security Affairs.
In response to items (3) and (4) some earlier remarks were clarified: one would not claim that the operational side of CIA need be where it is. Rather, one would inveigh against the splitting of covert intelligence collection and covert operations. One could, however, split the operational side from the analytic side. This is a plausible case, a solution for which could be worked out (though, on balance, the speaker was against it). But to split the operational side-as the German case, the British case for a time, and our own for a time suggested-would be disastrous.
Remarking on labor activities, one participant stated that before May 1967 it was common knowledge that there bad been some CIA support for labor programs, but first Ramparts and then Tom Braden spelled out this support in public. Those in international labor affairs were dismayed, and certain newspapermen compounded their difficulties by confusing AID with CIA, and claiming that the AFL-CIO’s Free Labor Development program was tainted.
Since these disclosures, the turn of events has been unexpected. First, there hasn’t been any real trouble with international labor programs. Indeed, there has been an increase in demand for U.S. labor programs and the strain on our capacity has been embarrassing. Formerly, these foreign labor unions knew we were short of funds, but now they all assume we have secret CIA money, and they ask for more help.
Worse yet, Vic Reuther, who had been alleging that others were receiving CIA money, and whose brother’s receipt of $50,000 from CIA in old bills was subsequently disclosed by Tom Braden, still goes on with his charges that the AFL-CIO has taken CIA money. Here again, no one seems to listen. “The net result has been as close to zero as possible. We’ve come to accept CIA, like sin.” So, for example, British Guiana’s labor unions were supported through CIA conduits, but now they ask for more assistance than before. So, our expectations to the contrary, there has been almost no damage.
A former State Department official offered some remarks on intelligence operations as seen from the field. He concurred in Mr. Bissell’s remarks on “cover.” The initial agreement between the Agency and State was intended to be “temporary,” but “nothing endures like the ephemeral.”
How are Agency officials under “official cover” specially equipped to handle covert operations? If the Agency station chief has a “special relationship” with the chief of state, one would submit that it was because the Ambassador wasn’t worth a damn. Moreover, such a “special relationship” created the risk that the chief of state, seeing two channels to Washington, could play one off against another. Some foreign statesmen are convinced that an “invisible government” really exists, and this impression shouldn’t be allowed,
Also, prejudice in favor of covertly obtained intelligence is a troublesome thing.
One way to overcome the misconceptions is to make CIA a truly secret service, and not merely an agency duplicating the Foreign Service. With money shortages CIA has often filled a vacuum, but this does not make it right.
Another questioned the discussion leader’s proposal for greater utilization of non-U.S. nationals. How could you get non-nationals to do the job and to develop loyalty to the United States?
One was not sure that it was doable, but it was worth trying. It would be more prone to work if you used a national of Country B to work in Country C, if what you are asking is neither (1) against the interest of Country B, nor (2) nefarious. You do need some cover, and the natural vehicle is an organization with non-American nationals.
Another observer was struck by the lack of interest in the “blowing” of covertly sponsored radio activities. Why has there been so little interest in these activities, in contrast to the immense concern over the CIA-NSA relationship? One might conclude that the public is not likely to be concerned by the penetration of overseas institutions, at least not nearly so much as by penetration of U.S. institutions. “The public doesn’t think it’s right: they don’t know where it ends; they take a look at their neighbors.” Does this suggested expansion in use of private institutions include those in the United States, or U.S. institutions operating overseas?
In response, attention was drawn to the clear jurisdictional boundaries between CIA and the FBI, CIA being proscribed from “internal security functions.” CIA was averse to surveillance of U.S. citizens overseas (even when specifically requested), and averse to operating in the United States, excepting against foreigners here as transients. One might want CIA to expand its use of U.S. private corporations, but for objectives outside the United States. It was recalled that the Agency funding of the National Student Association was, in every case, for activities outside the United States or for activities with overseas objectives.
Why, we might ask, should the U.S. government use nongovernmental institutions more, and why should it deal with them in the United States? If dealings are overseas, then it is necessary to maintain an overseas bureaucracy to deal with the locals. It is also necessary to engage in communications in a possibly hostile environment. If one deals through U.S. corporations with overseas activities, one can keep most of the bureaucratic staff at home and can deal through the corporate headquarters, perhaps using corporate channels for overseas communications (including classified communications). In this opinion, the policy distinction should involve the use to which the private institution is put, not whether or not to use private institutions. In another view it was desirable for this discussion group to examine different types of institutions. For example, should CIA use educational institutions? Should CIA have influenced the selection of NSA officers?
One was not aware that CIA had influenced the election of NSA officers; if it had, it shouldn’t have done so, in one’s opinion.
Mightn’t it be possible to deal with individuals rather than organizations?
Yes, in many cases this would be preferable. It depended upon skill in the use of our operating capabilities. As an example of the political use of secretly acquired intelligence, a former official noted the clandestine acquisition of Khrushchev’s “secret speech” in February 1956. The speech was too long for even Khrushchev to memorize, and over one hundred people had heard it. We targeted it, and by secret means acquired a copy. The State Department released the text and The New York Times printed it in full. The repercussions were felt around the world, and particularly within the Communist bloc. The Soviets felt unable to deny the authenticity of the text we released, and the effect upon many of the satellite states was profound. It was the beginning of the split in the Communist movement. If you get a precise target, and go after it, you can change history.
Another observer was troubled by the earlier-expressed point about increased use of private institutions. Most demoralizing in the academic community was the sense of uncertainty about institutions with which individuals were associated. There is a profound problem in penetrating institutions within the country when there is a generalized loss of faith, a fear that nothing is what it seems. It was noted that the next session, on February 15, 1968, would concentrate upon relations with private institutions.
To one observer, part of this solution would be found in the political process, involving extragovernmental contacts in the sphere of political action.
In response to a query, the relative utilities of types of intelligence data were reviewed. Most valuable was reconnaissance, then communications-electronic intelligence, then classical espionage. We have forgotten, it was noted, the number one over-all source, namely, overt data.
The meeting was adjourned at 9:15p.m., and participants were reminded of the next meeting on February 15.
WILLIAM R. HARRIS
RAPPORTEUR
Cyber-Security – The Software that will Provide Intelligence Information during Investigations

MITsy International Ltd., the largest and most experienced Israeli company in the field of data-storage reconstruction and data recovery, is presenting a new, fast, and very efficient Hebrew version of Foresee digital forensic software. ForeSee can trace data that has been deleted from any platform, including hidden files.
“Files, emails, and online communication plays an important role in all aspects of life, and tracing data deleted by criminals is therefore, vital for many investigations,” explains Avner Sharon, MITsy’s CEO. “The new, improved version of MITsy allows the police to work faster and in a more precise manner during the investigation, and prevents unpleasantness if the suspect isn’t guilty – or accelerate his conviction if he broke the law.”
The software itself is a unique product, specially adapted to the requirements of Israeli entities and authorities – the police, Ministry of Justice, Ministry of Defense, law offices, and legal departments in organizations. Foresee 2012 includes swift tracing and reconstruction of word strings and files on drives of all kinds, 32 and 64-bit system support, a more convenient and user-friendly interface, a search tool for specific words in deleted files, and improved Russian and Arabic support.
Shabak Arrested Suspect on Way to Abduct Soldier and Carry Out a Terror Attack Near Eilat
Mahammad Hasin Awad Abu-Aadra was arrested trying to infiltrate Israel through the Sinai. He confessed that he sought to implement a suicide attack in Eilat, planned by Hamas

Shabak released a statement that they arrested Mahammad Hasin Awad Abu-Aadra, a Rafah resident, at the end of February, while he was attempting to infiltrate Israel through the Gaza border.
Abu-Aadra is suspected of planning to abduct an Israeli soldier, as well as planning a suicide attack in Eilat. Abu-Aadra is the son of a well-known Rafah family of Hamas operatives.
During the investigation, Abu-Aadra admitted that he escaped from Gaza to the Sinai a year ago via a tunnel, due to criminal entanglement. After several months in the Egyptian peninsula, Abu-Aadra was approached by Yunes Shluf, a Rafah resident and Hamas operative. According to Abu-Aadra, Shluf is the commander of the organization’s artillery layout and responsible for the Hamas observation layout in the Sinai.
He asked Abu-Aadra to work for Hamas in the Sinai, carry out observations, and photograph Israeli positions along the Egyptian border with the purpose of carrying out a terror attack.
Abu-Aadra understood from Shluf that there were other elements in the Sinai conducting intelligence collection in order to carry out terror attacks backed by Hamas. Some of the operatives even received considerable sums of money for this activity.
After agreeing to work for Hamas in the Sinai, Abu-Aadra was smuggled through a tunnel by Hamas operatives.
Abu-Aadra underwent a comprehensive military debriefing in Gaza, and was informed that the purpose of the intelligence collection was for examining targets and destinations for carrying out terror attacks. He was also told that his relative, Rashdi Jama’a Mousa Abu-Aadra, a Hamas military operative, would accompany him for collecting intelligence for attacks in Sinai.
In August 2011, both of them carried out most of the observations while equipped with sophisticated cameras and a GPS device, which they used to mark the targets they observed. Local Sinai residents additionally aided them.
It should be noted that the Taba border crossing was one of the targets for which they were collecting information, with emphasis on examining the security forces and the guard stations at the crossing. The two also collected intelligence about military outposts spread out across the border with Israel, as well as several civilian targets within Israel, with emphasis on targets in the city of Eilat. Both of the men infiltrated into Israeli territory as part of their activities, with the objective of collecting better intelligence about targets and ways to reach them.
After completing the observations, Mahammad and Rashdi transferred their information to the Gaza Strip, where it was examined by senior Hamas operatives. They later received follow-up missions and precise briefings regarding the information and the targets for which they needed to collect intelligence.
Near the end of 2011, Mahammad Abu-Aadra was asked to reach the Gaza Strip. Upon his arrival, he was taken along with Rushdi Abu-Aadra and Yunes Abu Shluf to a meeting with Ra’ed Atar, commander of Hamas’s military brigade in Rafah.
Mahammad Abu-Aadra agreed to carry out fire attacks towards military and civilian targets on the Sinai-Israel border, as well as fire rockets from Sinai towards Israel. Ra’ed Atar explained to Mahammad Abu-Aatra that the purpose of the attack would be the abduction of an Israeli soldier, and that another attack was planned.
In the additional attack, a squad of suicide bombers would be inserted into the city of Eilat in order to carry out a suicide attack.
Mahammad Abu-Aadra admitted during his interrogation that he agreed to set up the suicide squad in Eilat. He added that Yunes Shluf told him the training of the terrorists for the suicide attack squad had been completed, and that the infrastructure for their transport had been prepared in Sinai, but they were currently waiting for the right conditions to commence the attack.
An indictment have been presented to the Be’er Sheva regional court against Abu-Aadra, on charges including: contact with foreign agents, membership in an illegal organization, conspiracy to commit murder, conspiracy to commit abduction, intent to harm national security, and more.
Unveiled – U.S. Army Plans to Fire Whistleblower For Speaking to the Media

The military’s embattled crime lab is trying to fire an outspoken whistleblower who’s spotlighted its problems.
Earlier this month, the U.S. Army Criminal Investigation Laboratory warned its firearms branch chief, Donald Mikko, in a memo of its plans to fire him, in part for talking to a McClatchy reporter.
As part of an internal investigation, Mikko was interrogated for about four hours and questioned about his contacts with McClatchy, according to his attorney Peter Lown. The Army Criminal Investigation Command, which oversees the lab, launched the inquiry after McClatchy published a story late last year about the lab losing evidence.
McClatchy has written more than a dozen stories about the lab since last March, which included details of the misconduct of two former analysts who made serious errors during DNA and firearms testing and who later were found to have falsified and destroyed documents when confronted with the problems.
As a result of McClatchy’s articles, Senate Judiciary Committee Chairman Patrick Leahy, D- Vt., and Sen. Charles Grassley of Iowa, the committee’s top-ranking Republican member, urged the military to look into the lab’s handling of the misconduct by one of the analysts. An investigation by the Pentagon’s inspector general is ongoing.
“The Army is looking for a scapegoat to blame for the recent adverse media reports,” Lown said.
The Criminal Investigation Command, abbreviated as CID, says it’s never targeted anyone for talking to the news media, and it’s asserted that McClatchy’s series of stories has overblown isolated mistakes and misconduct that shouldn’t reflect on the lab’s overall reputation.
Stung by critical stories about their crime laboratory, officials at Army Criminal Investigation Command recently questioned lab employees for hours and scrutinized personal phone records looking for contacts with reporters.
The inquiry was launched after a McClatchy reporter asked questions late last year about the lab losing evidence. A command spokesman characterized the investigation as looking into violations of privacy law, but the investigation report, which McClatchy obtained, shows that the command was interested primarily in whether employees had provided information that resulted in a story about lab problems.
“This investigation was aimed at rooting out anyone even remotely critical of the lab,” charged Peter Lown, an attorney for one of the employees questioned in the probe. “The lab’s management doesn’t want any more critical stories.”
McClatchy has written a dozen stories about the lab since last March, including detailing the misconduct of two former analysts who made serious errors during DNA and firearms testing and who later were found to have falsified and destroyed documents when confronted with the problems.
As a result of McClatchy’s articles, Senate Judiciary Committee Chairman Patrick Leahy, D- Vt., and Sen. Charles Grassley, R-Iowa, have urged the military to look into the lab’s handling of the misconduct by one of the analysts. An investigation by the Pentagon’s inspector general is ongoing.
The Army’s investigation of media contacts comes as the Obama administration takes a hard-line stance on leaks. President Barack Obama’s Justice and Defense departments have criminally prosecuted more former and current government officials on charges of disclosing information than previous administrations have.
Unlike in the Army investigation, however, all the prosecuted officials were accused of divulging classified intelligence, which can be a felony.
“This is an unprecedented crackdown by the Obama administration,” Jesselyn Radack, a lawyer with the Government Accountability Project, a public interest organization that protects whistleblowers. “It sends a very chilling message to any kind of whistleblower who is considering dissenting or speaking out.”
TOP-SECRET- The CIA reports – Transcript of 1968 Council on Foreign Relations Secret Meeting
| The following is a transcript of a private meeting held in 1968 in the New York Pratt House of the Council on Foreign Relations. The meeting was attended by a number of prominent members of the early U.S. intelligence community, including Richard Bissell and Allen Dulles. The transcript was reportedly discovered by Vietnam War protesters who occupied a building in 1971 housing Harvard’s Center for International Affairs. One of the attendees of the secret meeting, William Harris, served as an associate to the Center for International Affairs and this transcript was found in his personal files. The transcript was published in full in the 1974 book “The CIA and the Cult of Intelligence” by Victor Marchetti, a former special assistant to the Deputy Director of the Central Intelligence Agency, and John D. Marks, a former officer of the United States Department of State. The meeting transcript is described in the book as the “most complete description of the CIA’s covert-action strategy and tactics ever made available to the outside world.”A PDF version of the transcript is also available. |
Minutes of the 1968 “Bissell Meeting” at the Council on Foreign Relations
The third meeting of the Discussion Group on Intelligence and Foreign Policy was held at the Harold Pratt House on January 8, 1968, at 5:00 p.m. Present were: Richard M. Bissell, Jr., Discussion Leader; Douglas Dillon, Chairman; William J. Barnds, Secretary; William R. Harris, Rapporteur; George Agree, Frank Altschul, Robert Amory, Jr., Meyer Bernstein, Col. Sidney B. Berry, Jr., Allen W. Dulles, George S. Franklin, Jr., Eugene Fubini, Julius C. Holmes, Thomas L. Hughes, Joseph Kraft, David W. MacEachron, Philip W. Quigg, Harry Howe Ransom, Theodore C. Sorensen, David B. Truman.
The Chairman, Mr. Dillon, opened the meeting, noting that although this entire series of discussion was “off-the-record,” the subject of discussion for this particular meeting was especially sensitive and subject to the previously announced restrictions.
Mr. Dillon noted that problems involving CIA’s relationships with private institutions would be examined at a later meeting, though neither Mr. Bissell nor others should feel restricted in discussion of such problems this evening.
As the session’s discussion leader, Mr. Bissell offered a review and appraisal of covert operations in U.S. foreign policy.
Touching briefly upon the question of responsibility, of whether these agencies are instruments of national policy, Mr. Bissell remarked that, in such a group, he needn’t elaborate on CIA’s responsiveness to national policy; that we could assume that, although CIA participates in policy making (as do other “action agencies,” such as AID, the military services and Departments, in addition to the Department of State), CIA was a responsible agency of national policy.
Indeed in Mr. Bissell’s personal experience, CIA’s role was more carefully circumscribed and the established limits observed more attentively than in ECA, where Mr. Bissell had previously worked.
The essential control of CIA rested in a Cabinent-level committee, comprising a representative of the White House staff the Under Secretary of State, Deputy Secretary of Defense, and in recent years the personal participation of the Director of Central Intelligence. Over the years this committee has become a more powerful and effective device for enforcing control. It reviews all new projects, and periodically scrutinizes ongoing projects.
As an interdepartmental committee composed of busy officials who meet only once per week, this control group is of limited effectiveness. Were it the only control instrument, Mr. Bissell would view it as inadequate, but in fact this committee is merely the summit of control, with a series of intermediate review procedures as lower levels. Projects are usually discussed in the relevant office of the Assistant Secretary of State, and, if at all related to Defense Department interests, at a similar level in DoD, frequently after consideration at lower levels in these departments. It was rare to take an issue before the Special Group prior to discussion at lower levels, and if there was objection at lower levels most issues were not proposed to the Special Group — excepting large projects or key issues, which would be appealed at every level, including the Special Group.
Similar procedures applied in the field. Generally, the Ambassador had a right to know of any covert operations in his jurisdiction, although in special cases (as a result of requests from the local Chief of State or the Secretary of State) the chief of station was instructed to withhold information from the Ambassador. Indeed, in one case the restriction was imposed upon the specific exhortation of the Ambassador in question, who preferred to remain ignorant of certain activities.
Of the “blown” operations, frequently among the larger ones, most are known to have been approved by the President himself. The U-2 project, for example, was an offshoot of the Land (intelligence) Committee of the Killian panel on surprise attack; it was proposed as a Killian panel recommendation to the President, supported by USIB; its procurement, in utmost secrecy, was authorized by the President, and, with the exception of the first few flights (the initial authorization being to operate for a period of ten days, “weather permitting”), each individual flight was authorized by the President, with participation by the Secretary of State and Secretary of Defense.
Covert operations should, for some purposes, be divided into two classifications: ( 1) Intelligence collection, primarily espionage, or the obtaining of intelligence by covert means; and (2) Covert action, attempting to influence the internal affairs of other nations — sometimes called “intervention” — by covert means.
Although these two categories of activity can be separated in theory, intelligence collection and covert action interact and overlap. Efforts have been made historically to separate the two functions but the result has usually been regarded as “a total disaster organizationally.” One such attempt was the establishment in the early days of CIA (1948) of the OPC under Frank G. Wisner as a separate organ for covert action. Although supported and given cover by the CIA, this organization was independent and Wisner reported directly to the Secretaries of State and Defense. “Beedle” Smith decided when he became Director of Central Intelligence that, if he were responsible for OPC, he was going to run it and it was merged with the clandestine intelligence organization in such a way that within the combined Clandestine Service there was a complete integration of intelligence collection and covert action functions in each area division.
In addition to our experience with OPC, the Germans and the British for a time during the war had organizations for covert special operations separate from, and inevitably in competition with. their espionage services. In every case the experience has been unfortunate. Although there are many disagreements within CIA on matters of doctrine, the view is unanimous that the splitting of intelligence and covert action services would be disastrous, with resulting competition for recruitment of agents, multiple recruitment of the same agents, additional security risks, and dissipation of effort.
Concerning the first category, intelligence collection, we should ask: (a) What is the scope of “covert intelligence collection”? (b) What intelligence collection functions can best be performed covertly?
The scope of covert intelligence collection includes: (1) reconnaissance; (2) communications and electronic intelligence, primarily undertaken by NSA; and (3) classical espionage, by agents. In gauging their utility, Mr. Bissell ranked (1) the most important, (2) slightly below, and (3) considerably below both (1) and (2).
Although it is less effective, classical espionage is “much the least costly,” with the hardware components of recon and NSA activities raising their costs considerably.
(In the after-dinner discussion, an authority on communications-electronics expressed his concurrence in Mr. Bissell’s relative rankings. Notwithstanding technological advances in cryptology, the increased sophistication in most cryptosystems assured that (1) (reconnaissance) outranked (2). Another observer noted that the budgets correlated in similar manner, the former speaker concurring and noting that, however surprising, the budgets approximated maximum utility according to cost-effectiveness criteria.)
Postwar U.S. reconnaissance operations began, historically, as “covert” operations, primarily a series of clandestine overflights of Communist territory in Eastern Europe, inaugurated in the early 1950s. These early efforts were followed by the U-2 project, which provided limited coverage but dramatic results.
Now we have reconnaissance satellites. Overhead reconnaissance is one of the most open of “secrets” in international affairs; it is no longer really a “covert activity,” and bureaucratic responsibility for it now resides in the Pentagon. Classical espionage, in the early postwar years, was conducted with special intensity in West Germany, and before the Berlin wall, in that city, which was ideal for the moving of agents in both directions, providing a sizable flow of political and economic intelligence (especially from East Germany).
Throughout the period since the early fifties, of course, the Communist bloc, and more especially the U.S.S.R. itself, has been recognized as the primary target for espionage activities. Circumstances have greatly limited the scale of operations that could be undertaken within the bloc so much of the effort has been directed at bloc nationals stationed in neutral or friendly areas, and at “third country” operations that seek to use the nationals of other non-Communist countries as sources of information on the Soviet bloc.
More recently there has been a shift in priorities for classical espionage toward targets in the underdeveloped world. Partly as a result of this change in priorities and partly because of other developments, the scale of the classical espionage effort mounted in Europe has considerably diminished. The U.S.S.R. remains a prime target but Communist China would today be given the same priority.
As to the kinds of information that could be obtained, espionage has been of declining relative importance as a means of learning about observable developments, such as new construction, the characteristics of transportation systems, the strength and deployment of military forces and the like because reconnaissance has become a far more effective collection technique and (except in China) travel is freer and far more extensive than some years ago. It had been hoped that espionage would contribute to the collection of intelligence on Soviet and East European technology, since this is a body of information not readily observable (until embodied in operational systems). Another type of intelligence for which espionage would seem to be the only available technique is that concerning enemy intentions. In practice however espionage has been disappointing with respect to both these types of intelligence. They ,are for obvious reasons closely guarded and the task is just too difficult to permit results to be obtained with any dependability or regularity. With respect to the former category — technology — the published literature and direct professional contacts with the scientific community have been far richer sources.
(A communications-electronics expert interjected the observation that the same reasoning applied to inadequacies in S&T intelligence collection; technology is just too difficult for agents, who are insufficiently trained to comprehend what they observe as the technologies become increasingly complicated.)
As to friendly neutrals and allies, it is usually easier to learn what one wishes by overt contacts, human contact of overt members of the U.S. mission or private citizens. We don’t need espionage to learn British, or even French
intentions.
(The speaker was questioned as to whether the other side’s espionage was of similarly limited utility, or whether — with their Philbys — they were more successful?)
Mr. Bissell remarked that Soviet Union successes were primarily in counterintelligence, though going back aways, the Soviet Union had been more successful in recruiting U.S. scientists.
(The question was raised as to whether Burgess and MacLean constituted merely C.I. successes.)
Mr. Bissell thought so.
(In another’s recollection, Soviet atomic intelligence efforts had been of substantial assistance in facilitating the Soviet nuclear weapons program. Although it is not possible to estimate with precision the effects of this intelligence, it was Lewis Strauss’s guess that atomic intelligence successes allowed the Soviets to detonate their first device at least one and one-half and perhaps as much as two and one-half years before such a test would have been possible with purely indigenous efforts.)
The general conclusion is that against the Soviet bloc or other sophisticated societies, espionage is not a primary source of intelligence, although it has had occasional brilliant successes (like the Berlin Tunnel and several of the high level defectors). A basic reason is that espionage operates mainly through the recruitment of agents and it is enormously difficult to recruit high level agents. A low level agent, even assuming that he remained loyal and that there is some means of communicating with him[,] simply cannot tell you much of what you want to know. The secrets we cannot find out by reconnaissance or from open sources are in the minds of scientists and senior policy makers and are not accessible to an ordinary citizen even of middle rank.
In contrast, the underdeveloped world presents greater opportunities for covert intelligence collection, simply because governments are much less highly oriented; there is less security consciousness; and there is apt to be more actual or potential diffusion of power among parties, localities, organizations, and individuals outside of the central governments. The primary purpose of espionage in these areas is to provide Washington with timely knowledge of the internal power balance, a form of intelligence that is primarily of tactical significance.
Why is this relevant?
Changes in the balance of power are extremely difficult to discern except through frequent contact with power elements. Again and again we have been surprised at coups within the military; often, we have failed to talk to the junior officers or non-coms who are involved in the coups. The same problem applies to labor leaders, and others. Frequently we don’t know of power relationships, because power balances are murky and sometimes not well known even to the principal actors. Only by knowing the principal players well do you have a chance of careful prediction. There is real scope for action in this area; the technique is essentially that of “penetration,” including “penetrations” of the sort which horrify classicists of covert operations, with a disregard for the “standards” and “agent recruitment rules.” Many of the “penetrations” don’t take the form of “hiring” but of establishing a close or friendly relationship (which may or may not be furthered by the provision of money from time to time).
In some countries the CIA representative has served as a close counselor (and in at least one case a drinking companion) of the chief of state. These are situations of course in which the tasks of intelligence collection and political action overlap to the point of being almost indistinguishable. (The question was raised as to why ordinary diplomats couldn’t maintain these relationships.)
Mr. Bissell observed that often they could. There were special cases, however, such as in one Republic where the chief of state had a “special relationship” with the senior CIA officers without the knowledge of the U.S. Ambassador because the President of the Republic had so requested it. The CIA man sent reports by CIA channels back to the Secretary of State, but the Ambassador in the field, as agreed by the Secretary of State, wasn’t to be informed. In this case, a problem arose when the relevant Assistant Secretary of State (who had received cables from the CIA man) became the new Ambassador, but the President of the Republic liked the new Ambassador and asked that a “special relationship” be established with him too.
Aside from this unique case, it seems to have been true generally that the Ambassador has to be a formal representative of the United States most of whose relations with the government to which he is accredited are through or with the knowledge of. its foreign office. On the other hand, the CIA representative can maintain a more intimate and informal relationship the privacy of which can be better preserved both within the government of the country in question and within the United States government. Moreover, if a chief of state leaves the scene or changes his mind, you can quietly move a station chief, but it could be embarrassing if it were necessary suddenly to recall the U.S. Ambassador.
(Was the previously described relationship really a “covert operation”?)
The “cover” may be to shield visibility from some junior officials or, in the case of a “private adviser” to a chief of state, to shield this fact from politicians of the local government. (Another observation was that the method of reporting, through CIA channels, constituted one difference and had some influence. A chief of state who knew that CIA’s reports would be handfed in a smaller circle, with less attendant publicity, might prefer these channels for some communications.)
Concerning the second category, covert action:
The scope of covert action could include: (1) political advice and counsel; (2) subsidies to an individual; (3) financial support and “technical assistance” to political parties; ( 4) support of private organizations, including labor unions, business firms, cooperatives, etc.; (5) covert propaganda; (6) “private” training of individuals and exchange of persons; (7) economic operations; and (8) paramilitary [or] political action operations designed to overthrow or to support a regime (like the Bay of Pigs and the programs in Laos). These operations can be classified in various ways: by the degree and type of secrecy required [,] by their legality, and, perhaps, by their benign or hostile character.
From whom is the activity to be kept secret? After five days, for example, the U-2 flights were not secret from the Russians but these operations remained highly secret in the United States, and with good reason. If these overflights had “leaked” to the American press, the U.S.S.R. would have had been forced to take action. On a less severe level the same problem applies to satellite reconnaissance. These are examples of two hostile governments collaborating to keep operations secret from the general public of both sides. “Unfortunately, there aren’t enough of these situations.” (The remark was interjected that there was another reason for secrecy; if one had to admit to the activity, one would have to show the results, and exactly how good or bad they were.)
Covert operations could be classified by their legality or illegality. Many of them are legal.
They can also be classified as “benign” or “hostile.” Most operations in Western Europe have been “benign,” though involving the gravest improprieties, and in some cases clearly illegal action. (E.g., covert support of political parties.)
In the case of a large underdeveloped country, for example, money was put into a party’s funds without the knowledge of that party. The relatively few economic operations that have been undertaken have been both benign and legal. One of these involved the provision by CIA of interim ostensibly private financing of an overt project pending an overt and official loan by AID. Its purpose was to give AID time for some hard bargaining without causing a complete failure of the transaction. The stereotype, of course, is that all covert operations are illegal and hostile, but this is not really the case.
The role of covert intervention can best be understood by contrast with the overt activities of the United States government. Diplomacy seeks results by bargaining on a government-to-government basis, sometimes openly — sometimes privately. Foreign economic policy and cultural programs seek to modify benignly the economies of other countries and the climate of opinion within them. Covert intervention is usually designed to operate on the internal power balance, often with fairly short-term objectives in view. An effort to build up the economy of an underdeveloped country must be subtle, long continued, probably quite costly, and must openly enlist the cooperation of major groups within the country if it is to have much influence. On the other hand an effort to weaken the local Communist party or to win an election, and to achieve results within at most two or three years, must obviously be covert, it must pragmatically use the people and the instrumentalities that are available and the methods that seem likely to work. It is not surprising that the practitioners within the United States government of these two types of intervention differ temperamentally and in their preferences for methods, friends, and ideologies.
The essence of such intervention in the internal power balance is the identification of allies who can be rendered more effective, more powerful, and perhaps wiser through covert assistance. Typically these local allies know the source of the assistance but neither they nor the United States could afford to admit to its existence. Agents for fairly minor and low sensitivity interventions, for instance some covert propaganda and certain economic activities, can be recruited simply with money. But for the larger and more sensitive interventions, the allies must have their own motivation. On the whole the Agency has been remarkably successful in finding individuals and instrumentalities with which and through which it could work in this fashion. Implied in the requirement for a pre-existing motivation is the corollary that an attempt to induce the local ally to follow a course he does not believe in will at least reduce his effectiveness and may destroy the whole operation. It is notably true of the subsidies to student, labor, and. cultural groups that have recently been publicized that the Agency’s objective was never to control their activities, only occasionally to point them in a particular direction, but primarily to enlarge them and render them more effective.
Turning to relations with other agencies. Mr. Bissell was impressed by the degree of improvement in relations with the State Department. Seen from the Washington end, there has been an increase in consultation at the country-desk level, more often at the Bureau level or the Assistant Secretary of State level as the operation shapes up. The main problem some five to six years ago was not one of responsibility or authority but of cover arrangements.
Mr. Bissell provided a brief critique of covert operations, along the following lines:
That aspect of the Agency’s operations most in need of change is the Agency’s use and abuse of “cover.” In this regard, the “background paper” for this session raised many cover-oriented questions.
On disclosure of private institutional support of late, it is very clear that we should have had greater compartmenting of operations.
If the Agency is to be effective, it will have to make use of private institutions on an expanding scale, though those relations which have “blown” cannot be resurrected.
We need to operate under deeper cover, with increased attention to the use of “cut-outs.” CIA’s interface with the rest of the world needs to be better protected.
If various groups hadn’t been aware of the source of their funding, the damage subsequent to disclosure might have been far less than occurred.
The CIA interface with various private groups, including business and student groups, must be remedied.
The problem of Agency operations overseas is frequently a problem for the State Department. It tends to be true that local allies ‘ find themselves dealing always with an American and an official American-since the cover is almost invariably as a U.S. government employee. There are powerful reasons for this practice, and it will always be desirable to have some CIA personnel housed in the Embassy compound, if only for local “command post” and communications requirements.
Nonetheless, it is possible and desirable, although difficult and time-consuming, to build overseas an apparatus of unofficial cover. This would. require the use or creation of private organizations, many of the personnel of which would be non-U.S. nationals, with freer entry into the local society and less implication for the official U.S. posture.
The United States should make increasing use of non-nationals, who, with effort at indoctrination and training, should be encouraged to develop a second loyalty, more or less comparable to that of the American staff. As we shift our attention to Latin America, Asia, and Africa, the conduct of U.S. nationals is likely to be increasingly circumscribed. The primary change recommended would be to build up a system of unofficial cover; to see how far we can go with non-U.S. nationals, especially in the field. The CIA might be able to make increasing use of non-nationals as “career agents” that is with a status midway between that of the classical agent used in a single compartmented operation perhaps for a limited period of time and that of a staff member involved through his career in many operations and well informed of the Agency’s capabilities. Such career agents should be encouraged with an effort at indoctrination and training and with a prospect of long-term employment to develop a second loyalty and they could of course never be employed in ways that would conflict with their primary loyalties toward their own countries. This still leaves open, however, a wide range of potential uses. The desirability of more effective use of foreign nationals increases as we shift our attention to Latin America, Asia, and Africa where the conduct of United States nationals is easily subject to scrutiny and is likely to be increasingly circumscribed.
These suggestions about unofficial cover and career agents illustrate and emphasize the need for continuing efforts to develop covert action capabilities even where there is no immediate need to employ them. The central task is that of identifying potential indigenous allies-both individuals and organizations-making contact with them, and establishing the fact of a community of interest. There is some room for improvement, Mr. Bissell thought, in the planning of covert action country by country. Covert intervention is probably most effective in situations where a comprehensive effort is undertaken with a number of separate operations designed to support and complement one another and to have a cumulatively significant effect. The Agency probably finds itself involved in too many small covert action operations having no particular relationship with one another and having little cumulative impact.
There is no doubt that some covertly funded programs could be undertaken overtly, Mr. Bissell thought. Often activities have been initiated through CIA channels because they could be started more quickly and informally but do not inherently need to be secret. An example might be certain exchange of persons programs designed to identify potential political leaders and give them some exposure to the United States. It should be noted, however, that many such innocent programs are more effective if carried out by private auspices than if supported officially by the United States government. They do not need to be covert but if legitimate private entities such as the foundations do not initiate them, there may be no way to get them done except by covert support to “front” organizations.
Many propaganda operations are of declining effectiveness. Some can be continued at slight cost, but some of the larger ones (radio, etc.) are pretty well “blown” and not inexpensive. USIA doesn’t like them, and although they did have a real justification some ten to fifteen years ago as the voice of refugees and emigres, groups which also have declined in value, and in the view of some professionals are likely to continue declining in value.
In his last two years in the Agency, Mr. Bissell felt that the Clandestine Services could have been smaller.
Indeed, steps were taken to reduce their size. It is impossible to separate the issue of size from personnel and cover problems. It was Mr. Bissell’s impression that the Clandestine Services were becoming increasingly a career service, too much like the Foreign Service (personnel looking to a succession of overt posts in a safe career) . One result was the circumscription of local contacts. There was a subtle change taking place, which threatened to degrade some of CIA’s former capabilities. Formally, the CIA had a staff with a wide variety of backgrounds, experiences, and capabilities. Its members were recruited from every sort of public and private occupation. If this diversity and variety is lost through the process of recruiting staff members from college, training them in a fairly standard pattern, and carrying them through orderly planned careers in the Agency, one of the organization’s most valuable attributes will disappear.
Finally, Mr. Bissell remarked on large operations. It is self-evident that if an operation is too large, it can’t remain a deeply kept secret. At best, one can then hope for a successful formal disclaimer. The worst of many faults of the Bay of Pigs operation was excessive reliance on the operation’s disclaimability.
It has been a wise decision that operations of that scale not be undertaken by the Agency, except in theaters such as Vietnam, where the stakes and standards are different.
Covert action operations are generally aimed at short-term goals and the justification for the control machinery is that bias of operators to the short run can be compensated for in the review process. Mr. Bissell can conceive of no other way to force greater attention to long-range costs and values. One alternative is that caution will lead to ineffectuality. “Operational types” will he risk-takers, the counterweight is, and should be, applied by the other agencies in government.
In the discussion following Mr. Bissell’s talk, the issue of CIA cover was cited as among the more interesting from the perspective of a former State Department appointee. The size of covert operations known to other governments was a continuing embarrassment, and the overseas staff maintained for these purposes and known to host governments was a similar source of embarrassment. From time to time, efforts were made to reduce overseas staff; although agreement in principle was readily forthcoming, the particulars of staff reduction were difficult to obtain.
A former member of the Special Group (who served eighteen months on that committee) agreed with Mr. Bissell’s earlier remarks on control mechanisms, insofar as they applied to review of new projects. These received most careful scrutiny. Insofar as the Special Group considered ongoing projects during this eighteen-month period, it was recalled that there was not any systematic, thorough procedure for such review, the committee finding itself busy with all the new proposals. If it were true that most operations were most useful for short-term goals, then perhaps there should be greater attention to review of ongoing projects, and termination of more projects earlier than in past practice.
A continuing problem which worries one former official was that. concerning the “charter” of CIA, the public expression of which, in the National Security Act of 1947, was necessarily vague. CIA’s full “charter” has been frequently revised, but it has been, and must remain[,] secret. The absence of a public charter leads people to search for the charter and to question the Agency’s authority to undertake various activities. The problem of a secret “charter” remains as a curse, but the need for secrecy would appear to preclude a solution.
Another former official remarked on the inadequacy of clandestine intelligence as a means of obtaining enemy intentions. Sherman Kent (former Chairman. Board of National Estimates) distinguishes “the knowable” from “the unknowable,” and we should recognize that much remains impossible to know, including, frequently, enemy intentions.
Respecting the reduction of overseas personnel and programs of declining utility, it was noted that the curtailment of over-age and unproductive personnel was a thorny issue. Recognizing the likelihood of appeal to the President and the absence of widespread participation in a manpower review, a former budget official arranged the participation of the Bureau of the Budget, CIA, FIAB, and relevant Under Secretaries in considerations of budgetary modifications. What emerged was an inertia, partly the inertia of the cold war. Parenthetically, a couple of much-criticized public media projects (cited by name) had proven of value, as the fall of Novotny in Czechoslovakia suggested, but a number of ineffective programs were retained. The problem was to free the budget, to do something new, in the place of old programs, not to reduce the budget, but unfortunately, the chiefs in CIA wanted to control their working capital. If it were only possible to tell these officials not to worry. that we were setting aside $xxx million for CIA, and merely seeking to encourage better use of the same dollar amounts, then it would have been possible to move around some money. The big “iffy” question was a particular (named) foundation, which received a sizable allocation. Finally. everything was cleared up, and the next big review was scheduled, but never really effected as a consequence of the Cuban missile crisis. The review was geared up in 1963 once again.
Another observer, drawing upon work with the “combined cryptologic budget” and private industry, concluded that it was usually impossible to cut a budget; usually it was only possible to substitute a new project for an old one.
The Chairman suggested a number of questions: What are the effects of covert operations being blown? What can be done to improve the image of the Agency? What can he done to improve relations between the Agency and the press?
It was thought that a journalist’s perspective might aid in discussing these questions, but a number of prior issues were thought to require attention:
(1) The matter of size required attention. In any government agency size can become a problem; increasingly there is a realization that the government is too big and “an ever-swelling tumor.” At some point there will have to be a fairly sharp cutback in the U.S. foreign policy establishment.
(2) One was not overly impressed by the use of CIA in the developing world; in any case, we could have increased confidence in the range of choice in most developing areas. Conversely, it might not be as easy. as Mr. Bissell suggested to know the power structure in more developed areas, in Western Europe and Japan.
(A query was interjected: Why should we have increasing confidence in the range of choice in developing areas? Perhaps there are Jess variations than we earlier thought. “Things are evening out and we can live more comfortably.”)
(3) Where do you bury the body? One is not completely convinced by citation of the experience with Frank Wisner’s OPC. We could get around the responsibility issue raised by “Beedle” Smith; we could get around conflicting chains of command.
(4) Related to (3). Maybe there is a cost to be paid for having covert operations under CIA. Perhaps we could have intelligence collection under State and covert operations under the Special Assistant to the President for National Security Affairs.
In response to items (3) and (4) some earlier remarks were clarified: one would not claim that the operational side of CIA need be where it is. Rather, one would inveigh against the splitting of covert intelligence collection and covert operations. One could, however, split the operational side from the analytic side. This is a plausible case, a solution for which could be worked out (though, on balance, the speaker was against it). But to split the operational side-as the German case, the British case for a time, and our own for a time suggested-would be disastrous.
Remarking on labor activities, one participant stated that before May 1967 it was common knowledge that there bad been some CIA support for labor programs, but first Ramparts and then Tom Braden spelled out this support in public. Those in international labor affairs were dismayed, and certain newspapermen compounded their difficulties by confusing AID with CIA, and claiming that the AFL-CIO’s Free Labor Development program was tainted.
Since these disclosures, the turn of events has been unexpected. First, there hasn’t been any real trouble with international labor programs. Indeed, there has been an increase in demand for U.S. labor programs and the strain on our capacity has been embarrassing. Formerly, these foreign labor unions knew we were short of funds, but now they all assume we have secret CIA money, and they ask for more help.
Worse yet, Vic Reuther, who had been alleging that others were receiving CIA money, and whose brother’s receipt of $50,000 from CIA in old bills was subsequently disclosed by Tom Braden, still goes on with his charges that the AFL-CIO has taken CIA money. Here again, no one seems to listen. “The net result has been as close to zero as possible. We’ve come to accept CIA, like sin.” So, for example, British Guiana’s labor unions were supported through CIA conduits, but now they ask for more assistance than before. So, our expectations to the contrary, there has been almost no damage.
A former State Department official offered some remarks on intelligence operations as seen from the field. He concurred in Mr. Bissell’s remarks on “cover.” The initial agreement between the Agency and State was intended to be “temporary,” but “nothing endures like the ephemeral.”
How are Agency officials under “official cover” specially equipped to handle covert operations? If the Agency station chief has a “special relationship” with the chief of state, one would submit that it was because the Ambassador wasn’t worth a damn. Moreover, such a “special relationship” created the risk that the chief of state, seeing two channels to Washington, could play one off against another. Some foreign statesmen are convinced that an “invisible government” really exists, and this impression shouldn’t be allowed,
Also, prejudice in favor of covertly obtained intelligence is a troublesome thing.
One way to overcome the misconceptions is to make CIA a truly secret service, and not merely an agency duplicating the Foreign Service. With money shortages CIA has often filled a vacuum, but this does not make it right.
Another questioned the discussion leader’s proposal for greater utilization of non-U.S. nationals. How could you get non-nationals to do the job and to develop loyalty to the United States?
One was not sure that it was doable, but it was worth trying. It would be more prone to work if you used a national of Country B to work in Country C, if what you are asking is neither (1) against the interest of Country B, nor (2) nefarious. You do need some cover, and the natural vehicle is an organization with non-American nationals.
Another observer was struck by the lack of interest in the “blowing” of covertly sponsored radio activities. Why has there been so little interest in these activities, in contrast to the immense concern over the CIA-NSA relationship? One might conclude that the public is not likely to be concerned by the penetration of overseas institutions, at least not nearly so much as by penetration of U.S. institutions. “The public doesn’t think it’s right: they don’t know where it ends; they take a look at their neighbors.” Does this suggested expansion in use of private institutions include those in the United States, or U.S. institutions operating overseas?
In response, attention was drawn to the clear jurisdictional boundaries between CIA and the FBI, CIA being proscribed from “internal security functions.” CIA was averse to surveillance of U.S. citizens overseas (even when specifically requested), and averse to operating in the United States, excepting against foreigners here as transients. One might want CIA to expand its use of U.S. private corporations, but for objectives outside the United States. It was recalled that the Agency funding of the National Student Association was, in every case, for activities outside the United States or for activities with overseas objectives.
Why, we might ask, should the U.S. government use nongovernmental institutions more, and why should it deal with them in the United States? If dealings are overseas, then it is necessary to maintain an overseas bureaucracy to deal with the locals. It is also necessary to engage in communications in a possibly hostile environment. If one deals through U.S. corporations with overseas activities, one can keep most of the bureaucratic staff at home and can deal through the corporate headquarters, perhaps using corporate channels for overseas communications (including classified communications). In this opinion, the policy distinction should involve the use to which the private institution is put, not whether or not to use private institutions. In another view it was desirable for this discussion group to examine different types of institutions. For example, should CIA use educational institutions? Should CIA have influenced the selection of NSA officers?
One was not aware that CIA had influenced the election of NSA officers; if it had, it shouldn’t have done so, in one’s opinion.
Mightn’t it be possible to deal with individuals rather than organizations?
Yes, in many cases this would be preferable. It depended upon skill in the use of our operating capabilities. As an example of the political use of secretly acquired intelligence, a former official noted the clandestine acquisition of Khrushchev’s “secret speech” in February 1956. The speech was too long for even Khrushchev to memorize, and over one hundred people had heard it. We targeted it, and by secret means acquired a copy. The State Department released the text and The New York Times printed it in full. The repercussions were felt around the world, and particularly within the Communist bloc. The Soviets felt unable to deny the authenticity of the text we released, and the effect upon many of the satellite states was profound. It was the beginning of the split in the Communist movement. If you get a precise target, and go after it, you can change history.
Another observer was troubled by the earlier-expressed point about increased use of private institutions. Most demoralizing in the academic community was the sense of uncertainty about institutions with which individuals were associated. There is a profound problem in penetrating institutions within the country when there is a generalized loss of faith, a fear that nothing is what it seems. It was noted that the next session, on February 15, 1968, would concentrate upon relations with private institutions.
To one observer, part of this solution would be found in the political process, involving extragovernmental contacts in the sphere of political action.
In response to a query, the relative utilities of types of intelligence data were reviewed. Most valuable was reconnaissance, then communications-electronic intelligence, then classical espionage. We have forgotten, it was noted, the number one over-all source, namely, overt data.
The meeting was adjourned at 9:15p.m., and participants were reminded of the next meeting on February 15.
WILLIAM R. HARRIS
RAPPORTEUR
Offener Brief an Frau P
Sehr geehrte Frau P,
wir werden Sie und Ihre dubiosen Genossen für Ihre dubiosen Machenschaften zur Verantwortung ziehen
Das garantiere ich mit meinem Namen, ebenso wie ich die Hintermänner der STASI “GoMoPa” wie versprochen aufgedeckt habe !
Nicht Sozialistischer Gruss
Bernd Pulch, früherer Mentor von Thomas P, Ihrem Honeyboy
Secret – Transcript of 1968 Council on Foreign Relations Secret Meeting on the Theory of CIA Covert Action
| The following is a transcript of a private meeting held in 1968 in the New York Pratt House of the Council on Foreign Relations. The meeting was attended by a number of prominent members of the early U.S. intelligence community, including Richard Bissell and Allen Dulles. The transcript was reportedly discovered by Vietnam War protesters who occupied a building in 1971 housing Harvard’s Center for International Affairs. One of the attendees of the secret meeting, William Harris, served as an associate to the Center for International Affairs and this transcript was found in his personal files. The transcript was published in full in the 1974 book “The CIA and the Cult of Intelligence” by Victor Marchetti, a former special assistant to the Deputy Director of the Central Intelligence Agency, and John D. Marks, a former officer of the United States Department of State. The meeting transcript is described in the book as the “most complete description of the CIA’s covert-action strategy and tactics ever made available to the outside world.”A PDF version of the transcript is also available. |
Minutes of the 1968 “Bissell Meeting” at the Council on Foreign Relations
The third meeting of the Discussion Group on Intelligence and Foreign Policy was held at the Harold Pratt House on January 8, 1968, at 5:00 p.m. Present were: Richard M. Bissell, Jr., Discussion Leader; Douglas Dillon, Chairman; William J. Barnds, Secretary; William R. Harris, Rapporteur; George Agree, Frank Altschul, Robert Amory, Jr., Meyer Bernstein, Col. Sidney B. Berry, Jr., Allen W. Dulles, George S. Franklin, Jr., Eugene Fubini, Julius C. Holmes, Thomas L. Hughes, Joseph Kraft, David W. MacEachron, Philip W. Quigg, Harry Howe Ransom, Theodore C. Sorensen, David B. Truman.
The Chairman, Mr. Dillon, opened the meeting, noting that although this entire series of discussion was “off-the-record,” the subject of discussion for this particular meeting was especially sensitive and subject to the previously announced restrictions.
Mr. Dillon noted that problems involving CIA’s relationships with private institutions would be examined at a later meeting, though neither Mr. Bissell nor others should feel restricted in discussion of such problems this evening.
As the session’s discussion leader, Mr. Bissell offered a review and appraisal of covert operations in U.S. foreign policy.
Touching briefly upon the question of responsibility, of whether these agencies are instruments of national policy, Mr. Bissell remarked that, in such a group, he needn’t elaborate on CIA’s responsiveness to national policy; that we could assume that, although CIA participates in policy making (as do other “action agencies,” such as AID, the military services and Departments, in addition to the Department of State), CIA was a responsible agency of national policy.
Indeed in Mr. Bissell’s personal experience, CIA’s role was more carefully circumscribed and the established limits observed more attentively than in ECA, where Mr. Bissell had previously worked.
The essential control of CIA rested in a Cabinent-level committee, comprising a representative of the White House staff the Under Secretary of State, Deputy Secretary of Defense, and in recent years the personal participation of the Director of Central Intelligence. Over the years this committee has become a more powerful and effective device for enforcing control. It reviews all new projects, and periodically scrutinizes ongoing projects.
As an interdepartmental committee composed of busy officials who meet only once per week, this control group is of limited effectiveness. Were it the only control instrument, Mr. Bissell would view it as inadequate, but in fact this committee is merely the summit of control, with a series of intermediate review procedures as lower levels. Projects are usually discussed in the relevant office of the Assistant Secretary of State, and, if at all related to Defense Department interests, at a similar level in DoD, frequently after consideration at lower levels in these departments. It was rare to take an issue before the Special Group prior to discussion at lower levels, and if there was objection at lower levels most issues were not proposed to the Special Group — excepting large projects or key issues, which would be appealed at every level, including the Special Group.
Similar procedures applied in the field. Generally, the Ambassador had a right to know of any covert operations in his jurisdiction, although in special cases (as a result of requests from the local Chief of State or the Secretary of State) the chief of station was instructed to withhold information from the Ambassador. Indeed, in one case the restriction was imposed upon the specific exhortation of the Ambassador in question, who preferred to remain ignorant of certain activities.
Of the “blown” operations, frequently among the larger ones, most are known to have been approved by the President himself. The U-2 project, for example, was an offshoot of the Land (intelligence) Committee of the Killian panel on surprise attack; it was proposed as a Killian panel recommendation to the President, supported by USIB; its procurement, in utmost secrecy, was authorized by the President, and, with the exception of the first few flights (the initial authorization being to operate for a period of ten days, “weather permitting”), each individual flight was authorized by the President, with participation by the Secretary of State and Secretary of Defense.
Covert operations should, for some purposes, be divided into two classifications: ( 1) Intelligence collection, primarily espionage, or the obtaining of intelligence by covert means; and (2) Covert action, attempting to influence the internal affairs of other nations — sometimes called “intervention” — by covert means.
Although these two categories of activity can be separated in theory, intelligence collection and covert action interact and overlap. Efforts have been made historically to separate the two functions but the result has usually been regarded as “a total disaster organizationally.” One such attempt was the establishment in the early days of CIA (1948) of the OPC under Frank G. Wisner as a separate organ for covert action. Although supported and given cover by the CIA, this organization was independent and Wisner reported directly to the Secretaries of State and Defense. “Beedle” Smith decided when he became Director of Central Intelligence that, if he were responsible for OPC, he was going to run it and it was merged with the clandestine intelligence organization in such a way that within the combined Clandestine Service there was a complete integration of intelligence collection and covert action functions in each area division.
In addition to our experience with OPC, the Germans and the British for a time during the war had organizations for covert special operations separate from, and inevitably in competition with. their espionage services. In every case the experience has been unfortunate. Although there are many disagreements within CIA on matters of doctrine, the view is unanimous that the splitting of intelligence and covert action services would be disastrous, with resulting competition for recruitment of agents, multiple recruitment of the same agents, additional security risks, and dissipation of effort.
Concerning the first category, intelligence collection, we should ask: (a) What is the scope of “covert intelligence collection”? (b) What intelligence collection functions can best be performed covertly?
The scope of covert intelligence collection includes: (1) reconnaissance; (2) communications and electronic intelligence, primarily undertaken by NSA; and (3) classical espionage, by agents. In gauging their utility, Mr. Bissell ranked (1) the most important, (2) slightly below, and (3) considerably below both (1) and (2).
Although it is less effective, classical espionage is “much the least costly,” with the hardware components of recon and NSA activities raising their costs considerably.
(In the after-dinner discussion, an authority on communications-electronics expressed his concurrence in Mr. Bissell’s relative rankings. Notwithstanding technological advances in cryptology, the increased sophistication in most cryptosystems assured that (1) (reconnaissance) outranked (2). Another observer noted that the budgets correlated in similar manner, the former speaker concurring and noting that, however surprising, the budgets approximated maximum utility according to cost-effectiveness criteria.)
Postwar U.S. reconnaissance operations began, historically, as “covert” operations, primarily a series of clandestine overflights of Communist territory in Eastern Europe, inaugurated in the early 1950s. These early efforts were followed by the U-2 project, which provided limited coverage but dramatic results.
Now we have reconnaissance satellites. Overhead reconnaissance is one of the most open of “secrets” in international affairs; it is no longer really a “covert activity,” and bureaucratic responsibility for it now resides in the Pentagon. Classical espionage, in the early postwar years, was conducted with special intensity in West Germany, and before the Berlin wall, in that city, which was ideal for the moving of agents in both directions, providing a sizable flow of political and economic intelligence (especially from East Germany).
Throughout the period since the early fifties, of course, the Communist bloc, and more especially the U.S.S.R. itself, has been recognized as the primary target for espionage activities. Circumstances have greatly limited the scale of operations that could be undertaken within the bloc so much of the effort has been directed at bloc nationals stationed in neutral or friendly areas, and at “third country” operations that seek to use the nationals of other non-Communist countries as sources of information on the Soviet bloc.
More recently there has been a shift in priorities for classical espionage toward targets in the underdeveloped world. Partly as a result of this change in priorities and partly because of other developments, the scale of the classical espionage effort mounted in Europe has considerably diminished. The U.S.S.R. remains a prime target but Communist China would today be given the same priority.
As to the kinds of information that could be obtained, espionage has been of declining relative importance as a means of learning about observable developments, such as new construction, the characteristics of transportation systems, the strength and deployment of military forces and the like because reconnaissance has become a far more effective collection technique and (except in China) travel is freer and far more extensive than some years ago. It had been hoped that espionage would contribute to the collection of intelligence on Soviet and East European technology, since this is a body of information not readily observable (until embodied in operational systems). Another type of intelligence for which espionage would seem to be the only available technique is that concerning enemy intentions. In practice however espionage has been disappointing with respect to both these types of intelligence. They ,are for obvious reasons closely guarded and the task is just too difficult to permit results to be obtained with any dependability or regularity. With respect to the former category — technology — the published literature and direct professional contacts with the scientific community have been far richer sources.
(A communications-electronics expert interjected the observation that the same reasoning applied to inadequacies in S&T intelligence collection; technology is just too difficult for agents, who are insufficiently trained to comprehend what they observe as the technologies become increasingly complicated.)
As to friendly neutrals and allies, it is usually easier to learn what one wishes by overt contacts, human contact of overt members of the U.S. mission or private citizens. We don’t need espionage to learn British, or even French
intentions.
(The speaker was questioned as to whether the other side’s espionage was of similarly limited utility, or whether — with their Philbys — they were more successful?)
Mr. Bissell remarked that Soviet Union successes were primarily in counterintelligence, though going back aways, the Soviet Union had been more successful in recruiting U.S. scientists.
(The question was raised as to whether Burgess and MacLean constituted merely C.I. successes.)
Mr. Bissell thought so.
(In another’s recollection, Soviet atomic intelligence efforts had been of substantial assistance in facilitating the Soviet nuclear weapons program. Although it is not possible to estimate with precision the effects of this intelligence, it was Lewis Strauss’s guess that atomic intelligence successes allowed the Soviets to detonate their first device at least one and one-half and perhaps as much as two and one-half years before such a test would have been possible with purely indigenous efforts.)
The general conclusion is that against the Soviet bloc or other sophisticated societies, espionage is not a primary source of intelligence, although it has had occasional brilliant successes (like the Berlin Tunnel and several of the high level defectors). A basic reason is that espionage operates mainly through the recruitment of agents and it is enormously difficult to recruit high level agents. A low level agent, even assuming that he remained loyal and that there is some means of communicating with him[,] simply cannot tell you much of what you want to know. The secrets we cannot find out by reconnaissance or from open sources are in the minds of scientists and senior policy makers and are not accessible to an ordinary citizen even of middle rank.
In contrast, the underdeveloped world presents greater opportunities for covert intelligence collection, simply because governments are much less highly oriented; there is less security consciousness; and there is apt to be more actual or potential diffusion of power among parties, localities, organizations, and individuals outside of the central governments. The primary purpose of espionage in these areas is to provide Washington with timely knowledge of the internal power balance, a form of intelligence that is primarily of tactical significance.
Why is this relevant?
Changes in the balance of power are extremely difficult to discern except through frequent contact with power elements. Again and again we have been surprised at coups within the military; often, we have failed to talk to the junior officers or non-coms who are involved in the coups. The same problem applies to labor leaders, and others. Frequently we don’t know of power relationships, because power balances are murky and sometimes not well known even to the principal actors. Only by knowing the principal players well do you have a chance of careful prediction. There is real scope for action in this area; the technique is essentially that of “penetration,” including “penetrations” of the sort which horrify classicists of covert operations, with a disregard for the “standards” and “agent recruitment rules.” Many of the “penetrations” don’t take the form of “hiring” but of establishing a close or friendly relationship (which may or may not be furthered by the provision of money from time to time).
In some countries the CIA representative has served as a close counselor (and in at least one case a drinking companion) of the chief of state. These are situations of course in which the tasks of intelligence collection and political action overlap to the point of being almost indistinguishable. (The question was raised as to why ordinary diplomats couldn’t maintain these relationships.)
Mr. Bissell observed that often they could. There were special cases, however, such as in one Republic where the chief of state had a “special relationship” with the senior CIA officers without the knowledge of the U.S. Ambassador because the President of the Republic had so requested it. The CIA man sent reports by CIA channels back to the Secretary of State, but the Ambassador in the field, as agreed by the Secretary of State, wasn’t to be informed. In this case, a problem arose when the relevant Assistant Secretary of State (who had received cables from the CIA man) became the new Ambassador, but the President of the Republic liked the new Ambassador and asked that a “special relationship” be established with him too.
Aside from this unique case, it seems to have been true generally that the Ambassador has to be a formal representative of the United States most of whose relations with the government to which he is accredited are through or with the knowledge of. its foreign office. On the other hand, the CIA representative can maintain a more intimate and informal relationship the privacy of which can be better preserved both within the government of the country in question and within the United States government. Moreover, if a chief of state leaves the scene or changes his mind, you can quietly move a station chief, but it could be embarrassing if it were necessary suddenly to recall the U.S. Ambassador.
(Was the previously described relationship really a “covert operation”?)
The “cover” may be to shield visibility from some junior officials or, in the case of a “private adviser” to a chief of state, to shield this fact from politicians of the local government. (Another observation was that the method of reporting, through CIA channels, constituted one difference and had some influence. A chief of state who knew that CIA’s reports would be handfed in a smaller circle, with less attendant publicity, might prefer these channels for some communications.)
Concerning the second category, covert action:
The scope of covert action could include: (1) political advice and counsel; (2) subsidies to an individual; (3) financial support and “technical assistance” to political parties; ( 4) support of private organizations, including labor unions, business firms, cooperatives, etc.; (5) covert propaganda; (6) “private” training of individuals and exchange of persons; (7) economic operations; and (8) paramilitary [or] political action operations designed to overthrow or to support a regime (like the Bay of Pigs and the programs in Laos). These operations can be classified in various ways: by the degree and type of secrecy required [,] by their legality, and, perhaps, by their benign or hostile character.
From whom is the activity to be kept secret? After five days, for example, the U-2 flights were not secret from the Russians but these operations remained highly secret in the United States, and with good reason. If these overflights had “leaked” to the American press, the U.S.S.R. would have had been forced to take action. On a less severe level the same problem applies to satellite reconnaissance. These are examples of two hostile governments collaborating to keep operations secret from the general public of both sides. “Unfortunately, there aren’t enough of these situations.” (The remark was interjected that there was another reason for secrecy; if one had to admit to the activity, one would have to show the results, and exactly how good or bad they were.)
Covert operations could be classified by their legality or illegality. Many of them are legal.
They can also be classified as “benign” or “hostile.” Most operations in Western Europe have been “benign,” though involving the gravest improprieties, and in some cases clearly illegal action. (E.g., covert support of political parties.)
In the case of a large underdeveloped country, for example, money was put into a party’s funds without the knowledge of that party. The relatively few economic operations that have been undertaken have been both benign and legal. One of these involved the provision by CIA of interim ostensibly private financing of an overt project pending an overt and official loan by AID. Its purpose was to give AID time for some hard bargaining without causing a complete failure of the transaction. The stereotype, of course, is that all covert operations are illegal and hostile, but this is not really the case.
The role of covert intervention can best be understood by contrast with the overt activities of the United States government. Diplomacy seeks results by bargaining on a government-to-government basis, sometimes openly — sometimes privately. Foreign economic policy and cultural programs seek to modify benignly the economies of other countries and the climate of opinion within them. Covert intervention is usually designed to operate on the internal power balance, often with fairly short-term objectives in view. An effort to build up the economy of an underdeveloped country must be subtle, long continued, probably quite costly, and must openly enlist the cooperation of major groups within the country if it is to have much influence. On the other hand an effort to weaken the local Communist party or to win an election, and to achieve results within at most two or three years, must obviously be covert, it must pragmatically use the people and the instrumentalities that are available and the methods that seem likely to work. It is not surprising that the practitioners within the United States government of these two types of intervention differ temperamentally and in their preferences for methods, friends, and ideologies.
The essence of such intervention in the internal power balance is the identification of allies who can be rendered more effective, more powerful, and perhaps wiser through covert assistance. Typically these local allies know the source of the assistance but neither they nor the United States could afford to admit to its existence. Agents for fairly minor and low sensitivity interventions, for instance some covert propaganda and certain economic activities, can be recruited simply with money. But for the larger and more sensitive interventions, the allies must have their own motivation. On the whole the Agency has been remarkably successful in finding individuals and instrumentalities with which and through which it could work in this fashion. Implied in the requirement for a pre-existing motivation is the corollary that an attempt to induce the local ally to follow a course he does not believe in will at least reduce his effectiveness and may destroy the whole operation. It is notably true of the subsidies to student, labor, and. cultural groups that have recently been publicized that the Agency’s objective was never to control their activities, only occasionally to point them in a particular direction, but primarily to enlarge them and render them more effective.
Turning to relations with other agencies. Mr. Bissell was impressed by the degree of improvement in relations with the State Department. Seen from the Washington end, there has been an increase in consultation at the country-desk level, more often at the Bureau level or the Assistant Secretary of State level as the operation shapes up. The main problem some five to six years ago was not one of responsibility or authority but of cover arrangements.
Mr. Bissell provided a brief critique of covert operations, along the following lines:
That aspect of the Agency’s operations most in need of change is the Agency’s use and abuse of “cover.” In this regard, the “background paper” for this session raised many cover-oriented questions.
On disclosure of private institutional support of late, it is very clear that we should have had greater compartmenting of operations.
If the Agency is to be effective, it will have to make use of private institutions on an expanding scale, though those relations which have “blown” cannot be resurrected.
We need to operate under deeper cover, with increased attention to the use of “cut-outs.” CIA’s interface with the rest of the world needs to be better protected.
If various groups hadn’t been aware of the source of their funding, the damage subsequent to disclosure might have been far less than occurred.
The CIA interface with various private groups, including business and student groups, must be remedied.
The problem of Agency operations overseas is frequently a problem for the State Department. It tends to be true that local allies ‘ find themselves dealing always with an American and an official American-since the cover is almost invariably as a U.S. government employee. There are powerful reasons for this practice, and it will always be desirable to have some CIA personnel housed in the Embassy compound, if only for local “command post” and communications requirements.
Nonetheless, it is possible and desirable, although difficult and time-consuming, to build overseas an apparatus of unofficial cover. This would. require the use or creation of private organizations, many of the personnel of which would be non-U.S. nationals, with freer entry into the local society and less implication for the official U.S. posture.
The United States should make increasing use of non-nationals, who, with effort at indoctrination and training, should be encouraged to develop a second loyalty, more or less comparable to that of the American staff. As we shift our attention to Latin America, Asia, and Africa, the conduct of U.S. nationals is likely to be increasingly circumscribed. The primary change recommended would be to build up a system of unofficial cover; to see how far we can go with non-U.S. nationals, especially in the field. The CIA might be able to make increasing use of non-nationals as “career agents” that is with a status midway between that of the classical agent used in a single compartmented operation perhaps for a limited period of time and that of a staff member involved through his career in many operations and well informed of the Agency’s capabilities. Such career agents should be encouraged with an effort at indoctrination and training and with a prospect of long-term employment to develop a second loyalty and they could of course never be employed in ways that would conflict with their primary loyalties toward their own countries. This still leaves open, however, a wide range of potential uses. The desirability of more effective use of foreign nationals increases as we shift our attention to Latin America, Asia, and Africa where the conduct of United States nationals is easily subject to scrutiny and is likely to be increasingly circumscribed.
These suggestions about unofficial cover and career agents illustrate and emphasize the need for continuing efforts to develop covert action capabilities even where there is no immediate need to employ them. The central task is that of identifying potential indigenous allies-both individuals and organizations-making contact with them, and establishing the fact of a community of interest. There is some room for improvement, Mr. Bissell thought, in the planning of covert action country by country. Covert intervention is probably most effective in situations where a comprehensive effort is undertaken with a number of separate operations designed to support and complement one another and to have a cumulatively significant effect. The Agency probably finds itself involved in too many small covert action operations having no particular relationship with one another and having little cumulative impact.
There is no doubt that some covertly funded programs could be undertaken overtly, Mr. Bissell thought. Often activities have been initiated through CIA channels because they could be started more quickly and informally but do not inherently need to be secret. An example might be certain exchange of persons programs designed to identify potential political leaders and give them some exposure to the United States. It should be noted, however, that many such innocent programs are more effective if carried out by private auspices than if supported officially by the United States government. They do not need to be covert but if legitimate private entities such as the foundations do not initiate them, there may be no way to get them done except by covert support to “front” organizations.
Many propaganda operations are of declining effectiveness. Some can be continued at slight cost, but some of the larger ones (radio, etc.) are pretty well “blown” and not inexpensive. USIA doesn’t like them, and although they did have a real justification some ten to fifteen years ago as the voice of refugees and emigres, groups which also have declined in value, and in the view of some professionals are likely to continue declining in value.
In his last two years in the Agency, Mr. Bissell felt that the Clandestine Services could have been smaller.
Indeed, steps were taken to reduce their size. It is impossible to separate the issue of size from personnel and cover problems. It was Mr. Bissell’s impression that the Clandestine Services were becoming increasingly a career service, too much like the Foreign Service (personnel looking to a succession of overt posts in a safe career) . One result was the circumscription of local contacts. There was a subtle change taking place, which threatened to degrade some of CIA’s former capabilities. Formally, the CIA had a staff with a wide variety of backgrounds, experiences, and capabilities. Its members were recruited from every sort of public and private occupation. If this diversity and variety is lost through the process of recruiting staff members from college, training them in a fairly standard pattern, and carrying them through orderly planned careers in the Agency, one of the organization’s most valuable attributes will disappear.
Finally, Mr. Bissell remarked on large operations. It is self-evident that if an operation is too large, it can’t remain a deeply kept secret. At best, one can then hope for a successful formal disclaimer. The worst of many faults of the Bay of Pigs operation was excessive reliance on the operation’s disclaimability.
It has been a wise decision that operations of that scale not be undertaken by the Agency, except in theaters such as Vietnam, where the stakes and standards are different.
Covert action operations are generally aimed at short-term goals and the justification for the control machinery is that bias of operators to the short run can be compensated for in the review process. Mr. Bissell can conceive of no other way to force greater attention to long-range costs and values. One alternative is that caution will lead to ineffectuality. “Operational types” will he risk-takers, the counterweight is, and should be, applied by the other agencies in government.
In the discussion following Mr. Bissell’s talk, the issue of CIA cover was cited as among the more interesting from the perspective of a former State Department appointee. The size of covert operations known to other governments was a continuing embarrassment, and the overseas staff maintained for these purposes and known to host governments was a similar source of embarrassment. From time to time, efforts were made to reduce overseas staff; although agreement in principle was readily forthcoming, the particulars of staff reduction were difficult to obtain.
A former member of the Special Group (who served eighteen months on that committee) agreed with Mr. Bissell’s earlier remarks on control mechanisms, insofar as they applied to review of new projects. These received most careful scrutiny. Insofar as the Special Group considered ongoing projects during this eighteen-month period, it was recalled that there was not any systematic, thorough procedure for such review, the committee finding itself busy with all the new proposals. If it were true that most operations were most useful for short-term goals, then perhaps there should be greater attention to review of ongoing projects, and termination of more projects earlier than in past practice.
A continuing problem which worries one former official was that. concerning the “charter” of CIA, the public expression of which, in the National Security Act of 1947, was necessarily vague. CIA’s full “charter” has been frequently revised, but it has been, and must remain[,] secret. The absence of a public charter leads people to search for the charter and to question the Agency’s authority to undertake various activities. The problem of a secret “charter” remains as a curse, but the need for secrecy would appear to preclude a solution.
Another former official remarked on the inadequacy of clandestine intelligence as a means of obtaining enemy intentions. Sherman Kent (former Chairman. Board of National Estimates) distinguishes “the knowable” from “the unknowable,” and we should recognize that much remains impossible to know, including, frequently, enemy intentions.
Respecting the reduction of overseas personnel and programs of declining utility, it was noted that the curtailment of over-age and unproductive personnel was a thorny issue. Recognizing the likelihood of appeal to the President and the absence of widespread participation in a manpower review, a former budget official arranged the participation of the Bureau of the Budget, CIA, FIAB, and relevant Under Secretaries in considerations of budgetary modifications. What emerged was an inertia, partly the inertia of the cold war. Parenthetically, a couple of much-criticized public media projects (cited by name) had proven of value, as the fall of Novotny in Czechoslovakia suggested, but a number of ineffective programs were retained. The problem was to free the budget, to do something new, in the place of old programs, not to reduce the budget, but unfortunately, the chiefs in CIA wanted to control their working capital. If it were only possible to tell these officials not to worry. that we were setting aside $xxx million for CIA, and merely seeking to encourage better use of the same dollar amounts, then it would have been possible to move around some money. The big “iffy” question was a particular (named) foundation, which received a sizable allocation. Finally. everything was cleared up, and the next big review was scheduled, but never really effected as a consequence of the Cuban missile crisis. The review was geared up in 1963 once again.
Another observer, drawing upon work with the “combined cryptologic budget” and private industry, concluded that it was usually impossible to cut a budget; usually it was only possible to substitute a new project for an old one.
The Chairman suggested a number of questions: What are the effects of covert operations being blown? What can be done to improve the image of the Agency? What can he done to improve relations between the Agency and the press?
It was thought that a journalist’s perspective might aid in discussing these questions, but a number of prior issues were thought to require attention:
(1) The matter of size required attention. In any government agency size can become a problem; increasingly there is a realization that the government is too big and “an ever-swelling tumor.” At some point there will have to be a fairly sharp cutback in the U.S. foreign policy establishment.
(2) One was not overly impressed by the use of CIA in the developing world; in any case, we could have increased confidence in the range of choice in most developing areas. Conversely, it might not be as easy. as Mr. Bissell suggested to know the power structure in more developed areas, in Western Europe and Japan.
(A query was interjected: Why should we have increasing confidence in the range of choice in developing areas? Perhaps there are Jess variations than we earlier thought. “Things are evening out and we can live more comfortably.”)
(3) Where do you bury the body? One is not completely convinced by citation of the experience with Frank Wisner’s OPC. We could get around the responsibility issue raised by “Beedle” Smith; we could get around conflicting chains of command.
(4) Related to (3). Maybe there is a cost to be paid for having covert operations under CIA. Perhaps we could have intelligence collection under State and covert operations under the Special Assistant to the President for National Security Affairs.
In response to items (3) and (4) some earlier remarks were clarified: one would not claim that the operational side of CIA need be where it is. Rather, one would inveigh against the splitting of covert intelligence collection and covert operations. One could, however, split the operational side from the analytic side. This is a plausible case, a solution for which could be worked out (though, on balance, the speaker was against it). But to split the operational side-as the German case, the British case for a time, and our own for a time suggested-would be disastrous.
Remarking on labor activities, one participant stated that before May 1967 it was common knowledge that there bad been some CIA support for labor programs, but first Ramparts and then Tom Braden spelled out this support in public. Those in international labor affairs were dismayed, and certain newspapermen compounded their difficulties by confusing AID with CIA, and claiming that the AFL-CIO’s Free Labor Development program was tainted.
Since these disclosures, the turn of events has been unexpected. First, there hasn’t been any real trouble with international labor programs. Indeed, there has been an increase in demand for U.S. labor programs and the strain on our capacity has been embarrassing. Formerly, these foreign labor unions knew we were short of funds, but now they all assume we have secret CIA money, and they ask for more help.
Worse yet, Vic Reuther, who had been alleging that others were receiving CIA money, and whose brother’s receipt of $50,000 from CIA in old bills was subsequently disclosed by Tom Braden, still goes on with his charges that the AFL-CIO has taken CIA money. Here again, no one seems to listen. “The net result has been as close to zero as possible. We’ve come to accept CIA, like sin.” So, for example, British Guiana’s labor unions were supported through CIA conduits, but now they ask for more assistance than before. So, our expectations to the contrary, there has been almost no damage.
A former State Department official offered some remarks on intelligence operations as seen from the field. He concurred in Mr. Bissell’s remarks on “cover.” The initial agreement between the Agency and State was intended to be “temporary,” but “nothing endures like the ephemeral.”
How are Agency officials under “official cover” specially equipped to handle covert operations? If the Agency station chief has a “special relationship” with the chief of state, one would submit that it was because the Ambassador wasn’t worth a damn. Moreover, such a “special relationship” created the risk that the chief of state, seeing two channels to Washington, could play one off against another. Some foreign statesmen are convinced that an “invisible government” really exists, and this impression shouldn’t be allowed,
Also, prejudice in favor of covertly obtained intelligence is a troublesome thing.
One way to overcome the misconceptions is to make CIA a truly secret service, and not merely an agency duplicating the Foreign Service. With money shortages CIA has often filled a vacuum, but this does not make it right.
Another questioned the discussion leader’s proposal for greater utilization of non-U.S. nationals. How could you get non-nationals to do the job and to develop loyalty to the United States?
One was not sure that it was doable, but it was worth trying. It would be more prone to work if you used a national of Country B to work in Country C, if what you are asking is neither (1) against the interest of Country B, nor (2) nefarious. You do need some cover, and the natural vehicle is an organization with non-American nationals.
Another observer was struck by the lack of interest in the “blowing” of covertly sponsored radio activities. Why has there been so little interest in these activities, in contrast to the immense concern over the CIA-NSA relationship? One might conclude that the public is not likely to be concerned by the penetration of overseas institutions, at least not nearly so much as by penetration of U.S. institutions. “The public doesn’t think it’s right: they don’t know where it ends; they take a look at their neighbors.” Does this suggested expansion in use of private institutions include those in the United States, or U.S. institutions operating overseas?
In response, attention was drawn to the clear jurisdictional boundaries between CIA and the FBI, CIA being proscribed from “internal security functions.” CIA was averse to surveillance of U.S. citizens overseas (even when specifically requested), and averse to operating in the United States, excepting against foreigners here as transients. One might want CIA to expand its use of U.S. private corporations, but for objectives outside the United States. It was recalled that the Agency funding of the National Student Association was, in every case, for activities outside the United States or for activities with overseas objectives.
Why, we might ask, should the U.S. government use nongovernmental institutions more, and why should it deal with them in the United States? If dealings are overseas, then it is necessary to maintain an overseas bureaucracy to deal with the locals. It is also necessary to engage in communications in a possibly hostile environment. If one deals through U.S. corporations with overseas activities, one can keep most of the bureaucratic staff at home and can deal through the corporate headquarters, perhaps using corporate channels for overseas communications (including classified communications). In this opinion, the policy distinction should involve the use to which the private institution is put, not whether or not to use private institutions. In another view it was desirable for this discussion group to examine different types of institutions. For example, should CIA use educational institutions? Should CIA have influenced the selection of NSA officers?
One was not aware that CIA had influenced the election of NSA officers; if it had, it shouldn’t have done so, in one’s opinion.
Mightn’t it be possible to deal with individuals rather than organizations?
Yes, in many cases this would be preferable. It depended upon skill in the use of our operating capabilities. As an example of the political use of secretly acquired intelligence, a former official noted the clandestine acquisition of Khrushchev’s “secret speech” in February 1956. The speech was too long for even Khrushchev to memorize, and over one hundred people had heard it. We targeted it, and by secret means acquired a copy. The State Department released the text and The New York Times printed it in full. The repercussions were felt around the world, and particularly within the Communist bloc. The Soviets felt unable to deny the authenticity of the text we released, and the effect upon many of the satellite states was profound. It was the beginning of the split in the Communist movement. If you get a precise target, and go after it, you can change history.
Another observer was troubled by the earlier-expressed point about increased use of private institutions. Most demoralizing in the academic community was the sense of uncertainty about institutions with which individuals were associated. There is a profound problem in penetrating institutions within the country when there is a generalized loss of faith, a fear that nothing is what it seems. It was noted that the next session, on February 15, 1968, would concentrate upon relations with private institutions.
To one observer, part of this solution would be found in the political process, involving extragovernmental contacts in the sphere of political action.
In response to a query, the relative utilities of types of intelligence data were reviewed. Most valuable was reconnaissance, then communications-electronic intelligence, then classical espionage. We have forgotten, it was noted, the number one over-all source, namely, overt data.
The meeting was adjourned at 9:15p.m., and participants were reminded of the next meeting on February 15.
WILLIAM R. HARRIS
RAPPORTEUR
Die STASI Morde in Westdeutschland – Mord an Alfred Herrhausen von Typen wie STASI-“GoMoPa” durch RAF-Adepten
Heute sind es meistens Rufmorde, aber auch vor Morden hat das feige STASI-Geschmeiss nie zurückgeschreckt. Und auch heute schrecken sie nicht davor zurürck, das zeigen die Dioxin-Vergiftungen. Und die Mord-Drohungen.
Einen der besten unseren deutschen Personen haben sie feige ermordet, wie es eben feige ihre Art ist: Alfred Herrhausen
Die Uhr läuft ab für STASI-Seilschaften der STASI-“GoMoPa”
Liebe Leser,
ein Treppenwitz der deutschen Historie:Wegen Betruges am eigenen Anleger vorbestrafte, anonyme STASI-Schergen, Serien-Rufmörder, Serien-Betrüger und mutmassliche Dioxin-Mörder spielen sich als Moralisten und Verbraucherschützer auf – unter dem Beifall der ehemaligen DDR-Presse wie “Neues Deutschland” und “Neue Welt”, unterstützt vom “Verbraucherschutz Brandenburg”, einer dubiosen “Anwaltskanzlei” als Schaltzentrale und einer Beschützerin im westdeutschen Justiz-Apparat, deren Gatte mutmasslich mit der Dame und der STASI konspiriert sowie einem dubiosen Finanzberater, der dutzendfach Strafanzeigen von seinen eigenen Anlegern kassiert hat und kassiert.
Zusammen haben sie sogar einen unbescholtenen Berliner Justizsenator durch üble Tricks und Medien-Machenschaften gestürzt und über 4.000 Firmen und Personen über eine dubiose “Warnliste” gestalkt.
Aber wie die Mauer gefallen ist – so wird auch diese Seilschaft fallen !
Das Augenmerk von allerhöchster Stelle ist auf diese Kamarilla gerichtet – in Deutschland und auch ganz sicher in den USA und im UK !
Herzlichst Ihr
Bernd Pulch, Magister Artium der Publizistik, Germanistik und Komparatistik
Top-Secret – The FBI – $ 2.9 billion fraud – CFO of Taylor, Bean, & Whitaker Pleads Guilty to Fraud Scheme
WASHINGTON—Delton de Armas, a former chief financial officer (CFO) of Taylor, Bean, & Whitaker Mortgage Corp. (TBW), pleaded guilty today to making false statements and conspiring to commit bank and wire fraud for his role in a more than $2.9 billion fraud scheme that contributed to the failures of TBW and Colonial Bank.
The guilty plea was announced today by Assistant Attorney General Lanny A. Breuer of the Criminal Division; U.S. Attorney Neil H. MacBride for the Eastern District of Virginia; Christy Romero, Deputy Special Inspector General, Office of the Special Inspector General for the Troubled Asset Relief Program (SIGTARP); Assistant Director in Charge James W. McJunkin of the FBI’s Washington Field Office; David A. Montoya, Inspector General of the Department of Housing and Urban Development (HUD-OIG); Jon T. Rymer, Inspector General of the Federal Deposit Insurance Corporation (FDIC-OIG); Steve A. Linick, Inspector General of the Federal Housing Finance Agency (FHFA-OIG); and Rick A. Raven, Acting Chief of the Internal Revenue Service Criminal Investigation (IRS-CI).
De Armas, 41, of Carrollton, Texas, pleaded guilty before U.S. District Judge Leonie M. Brinkema in the Eastern District of Virginia. De Armas faces a maximum penalty of 10 years in prison when he is sentenced on June 15, 2012.
“As TBW’s chief financial officer, Mr. de Armas concealed a massive $1.5 billion deficit in TBW’s funding facility and another large deficit on TBW’s books,” said Assistant Attorney General Breuer. “He tried to conceal the gaping holes by falsifying financial statements and lying to investors as well as the government. Ultimately, Mr. de Armas’ criminal conduct, along with that of his co-conspirators, contributed to the collapse of TBW and Colonial Bank. With today’s guilty plea, Mr. de Armas joins seven other defendants—including the former chairman of TBW, Lee Bentley Farkas—who have been convicted of participating in this massive fraudulent scheme.”
“When Mr. de Armas learned of a hole in Ocala Funding’s assets, he used his position as CFO to cover it up and mislead investors,” said U.S. Attorney MacBride. “Today’s plea is the eighth conviction in one of the nation’s largest bank frauds in history. As CFO, Mr. de Armas could have put a stop to the fraud the moment he discovered it. Instead, the hole in Ocala Funding grew to $1.5 billion on his watch, and as it grew, so did his lies to investors and the government.”
According to court documents, de Armas joined TBW in 2000 as its CFO and reported directly to its chairman, Lee Bentley Farkas, and later to its CEO, Paul Allen. He admitted in court that from 2005 through August 2009, he and other co-conspirators engaged in a scheme to defraud financial institutions that had invested in a wholly-owned lending facility called Ocala Funding. Ocala Funding obtained funds for mortgage lending for TBW from the sale of asset-backed commercial paper to financial institutions, including Deutsche Bank and BNP Paribas. The facility was managed by TBW and had no employees of its own.
According to court records, shortly after Ocala Funding was established, de Armas learned there were inadequate assets backing its commercial paper, a deficiency referred to internally at TBW as a “hole” in Ocala Funding. De Armas knew that the hole grew over time to more than $700 million. He learned from the CEO that the hole was more than $1.5 billion at the time of TBW’s collapse. De Armas admitted he was aware that, in an effort to cover up the hole and mislead investors, a subordinate who reported to him had falsified Ocala Funding collateral reports and periodically sent the falsified reports to financial institution investors in Ocala Funding and to other third parties. De Armas acknowledged that he and the CEO also deceived investors by providing them with a false explanation for the hole in Ocala Funding.
De Armas also admitted in court that he directed a subordinate to inflate an account receivable balance for loan participations in TBW’s financial statements. De Armas acknowledged that he knew that the falsified financial statements were subsequently provided to Ginnie Mae and Freddie Mac for their determination on the renewal of TBW’s authority to sell and service securities issued by them.
In addition, de Armas admitted in court to aiding and abetting false statements in a letter the CEO sent to the U.S. Department of Housing and Urban Development, through Ginnie Mae, regarding TBW’s audited financial statements for the fiscal year ending on March 31, 2009. De Armas reviewed and edited the letter, knowing it contained material omissions. The letter omitted that the delay in submitting the financial data was caused by concerns its independent auditor had raised about the financing relationship between TBW and Colonial Bank and its request that TBW retain a law firm to conduct an internal investigation. Instead, the letter falsely attributed the delay to a new acquisition and TBW’s switch to a compressed 11-month fiscal year.
“With our nation in a housing crisis, de Armas, as chief financial officer of TBW, one of the country’s largest mortgage lenders, papered over a gaping hole in the balance sheet of TBW subsidiary Ocala Funding and lied to regulators and investors to cover it up,” said Deputy Special Inspector General Romero for SIGTARP. “The fraud provided cover to others at TBW to misappropriate more than $1 billion in Ocala funds and sell fraudulent, worthless securities to conspirators at Colonial BancGroup. SIGTARP and its law enforcement partners stopped $553 million in TARP funds from being lost to this fraud and brought accountability and justice that the American taxpayers deserve.”
“Mr. de Armas has admitted that, during his tenure at TBW, he purposefully misled investors in a massive scheme to defraud financial institutions,” said FBI Assistant Director in Charge McJunkin. “The actions of Mr. de Armas and his co-conspirators contributed to the financial crisis and led to the collapse of one of the country’s largest commercial banks. The FBI and our partners remain vigilant in investigating such fraudulent activity in our banking and mortgage industries.”
“The guilty plea of Mr. de Armas is one small measure in our continued efforts to restore the trust and confidence of the general public and of investors in our financial system,” said HUD Inspector General Montoya. “In response to the many recent articles of mortgage fraud and misconduct, the mortgage industry needs to do much to rethink their values and their idea of client service in order to help rebuild a stronger economy and to restore the confidence of American homeowners.”
“The Federal Deposit Insurance Corporation Office of Inspector General is pleased to have played a role in bringing to justice yet another senior official in a position of trust who was involved in one of the biggest and most complex bank fraud schemes of our time,” said FDIC Inspector General Rymer. “The former chief financial officer of Taylor, Bean, & Whitaker is the latest participant who will be held accountable for seeking to undermine the integrity of the financial services industry. Even as the financial and economic crisis seems to be easing, we reaffirm our commitment to ensuring that those contributing to the failures of financial institutions and corresponding losses to the Deposit Insurance Fund will be punished to the fullest extent of the law.”
“Mr. de Armas and his colleagues committed an egregious crime,” said FHFA Inspector General Linick. “FHFA-OIG is proud to be part of the team that continues to protect American taxpayers.”
In April 2011, a jury in the Eastern District of Virginia found Lee Bentley Farkas, the chairman of TBW, guilty of 14 counts of conspiracy, bank, securities, and wire fraud. On June 30, 2011, Judge Brinkema sentenced Farkas to 30 years in prison. In addition, six individuals have pleaded guilty for their roles in the fraud scheme, including: Paul Allen, former chief executive officer of TBW, who was sentenced to 40 months in prison; Raymond Bowman, former president of TBW, who was sentenced to 30 months in prison; Desiree Brown, former treasurer of TBW, who was sentenced to six years in prison; Catherine Kissick, former senior vice president of Colonial Bank and head of its Mortgage Warehouse Lending Division (MWLD), who was sentenced to eight years in prison; Teresa Kelly, former operations supervisor for Colonial Bank’s MWLD, who was sentenced to three months in prison; and Sean Ragland, a former senior financial analyst at TBW, who was sentenced to three months in prison.
The case is being prosecuted by Deputy Chief Patrick Stokes and Trial Attorney Robert Zink of the Criminal Division’s Fraud Section and Assistant U.S. Attorneys Charles Connolly and Paul Nathanson of the Eastern District of Virginia. This case was investigated by SIGTARP, FBI’s Washington Field Office, FDIC-OIG, HUD-OIG, FHFA-OIG, and IRS-CI. The Financial Crimes Enforcement Network (FinCEN) of the Department of the Treasury also provided support in the investigation. The Department would also like to acknowledge the substantial assistance of the U.S. Securities and Exchange Commission in the investigation of the fraud scheme.
This prosecution was brought in coordination with President Barack Obama’s Financial Fraud Enforcement Task Force. President Obama established the interagency Financial Fraud Enforcement Task Force to wage an aggressive, coordinated and proactive effort to investigate and prosecute financial crimes. The task force includes representatives from a broad range of federal agencies, regulatory authorities, inspectors general and state and local law enforcement who, working together, bring to bear a powerful array of criminal and civil enforcement resources. The task force is working to improve efforts across the federal executive branch, and with state and local partners, to investigate and prosecute significant financial crimes, ensure just and effective punishment for those who perpetrate financial crimes, combat discrimination in the lending and financial markets, and recover proceeds for victims of financial crimes. For more information on the task force, visit: http://www.stopfraud.gov.
Cryptome – NSA Decryption Multipurpose Research Facility
| The NSA Is Building the Country’s Biggest Spy Center (Watch What You Say)
By James Bamford March 15, 2012 [Excerpts of excellent NSA overview to focus on the MRF decryption facility.] When Barack Obama took office, Binney hoped the new administration might be open to reforming the program to address his constitutional concerns. He and another former senior NSA analyst, J. Kirk Wiebe, tried to bring the idea of an automated warrant-approval system to the attention of the Department of Justice’s inspector general. They were given the brush-off. “They said, oh, OK, we can’t comment,” Binney says. Sitting in a restaurant not far from NSA headquarters, the place where he spent nearly 40 years of his life, Binney held his thumb and forefinger close together. “We are, like, that far from a turnkey totalitarian state,” he says. There is still one technology preventing untrammeled government access to private digital data: strong encryption. Anyone—from terrorists and weapons dealers to corporations, financial institutions, and ordinary email senders—can use it to seal their messages, plans, photos, and documents in hardened data shells. For years, one of the hardest shells has been the Advanced Encryption Standard, one of several algorithms used by much of the world to encrypt data. Available in three different strengths—128 bits, 192 bits, and 256 bits—it’s incorporated in most commercial email programs and web browsers and is considered so strong that the NSA has even approved its use for top-secret US government communications. Most experts say that a so-called brute-force computer attack on the algorithm—trying one combination after another to unlock the encryption—would likely take longer than the age of the universe. For a 128-bit cipher, the number of trial-and-error attempts would be 340 undecillion (1036). Breaking into those complex mathematical shells like the AES is one of the key reasons for the construction going on in Bluffdale. That kind of cryptanalysis requires two major ingredients: super-fast computers to conduct brute-force attacks on encrypted messages and a massive number of those messages for the computers to analyze. The more messages from a given target, the more likely it is for the computers to detect telltale patterns, and Bluffdale will be able to hold a great many messages. “We questioned it one time,” says another source, a senior intelligence manager who was also involved with the planning. “Why were we building this NSA facility? And, boy, they rolled out all the old guys—the crypto guys.” According to the official, these experts told then-director of national intelligence Dennis Blair, “You’ve got to build this thing because we just don’t have the capability of doing the code-breaking.” It was a candid admission. In the long war between the code breakers and the code makers—the tens of thousands of cryptographers in the worldwide computer security industry—the code breakers were admitting defeat. So the agency had one major ingredient—a massive data storage facility—under way. Meanwhile, across the country in Tennessee, the government was working in utmost secrecy on the other vital element: the most powerful computer the world has ever known. The plan was launched in 2004 as a modern-day Manhattan Project. Dubbed the High Productivity Computing Systems program, its goal was to advance computer speed a thousandfold, creating a machine that could execute a quadrillion (1015) operations a second, known as a petaflop—the computer equivalent of breaking the land speed record. And as with the Manhattan Project, the venue chosen for the supercomputing program was the town of Oak Ridge in eastern Tennessee, a rural area where sharp ridges give way to low, scattered hills, and the southwestward-flowing Clinch River bends sharply to the southeast. About 25 miles from Knoxville, it is the “secret city” where uranium- 235 was extracted for the first atomic bomb. A sign near the exit read: what you see here, what you do here, what you hear here, when you leave here, let it stay here. Today, not far from where that sign stood, Oak Ridge is home to the Department of Energy’s Oak Ridge National Laboratory, and it’s engaged in a new secret war. But this time, instead of a bomb of almost unimaginable power, the weapon is a computer of almost unimaginable speed. In 2004, as part of the supercomputing program, the Department of Energy established its Oak Ridge Leadership Computing Facility for multiple agencies to join forces on the project. But in reality there would be two tracks, one unclassified, in which all of the scientific work would be public, and another top-secret, in which the NSA could pursue its own computer covertly. “For our purposes, they had to create a separate facility,” says a former senior NSA computer expert who worked on the project and is still associated with the agency. (He is one of three sources who described the program.) It was an expensive undertaking, but one the NSA was desperate to launch. Known as the Multiprogram Research Facility, or Building 5300, the $41 million, five-story, 214,000-square-foot structure was built on a plot of land on the lab’s East Campus and completed in 2006. Behind the brick walls and green-tinted windows, 318 scientists, computer engineers, and other staff work in secret on the cryptanalytic applications of high-speed computing and other classified projects. The supercomputer center was named in honor of George R. Cotter, the NSA’s now-retired chief scientist and head of its information technology program. Not that you’d know it. “There’s no sign on the door,” says the ex-NSA computer expert. At the DOE’s unclassified center at Oak Ridge, work progressed at a furious pace, although it was a one-way street when it came to cooperation with the closemouthed people in Building 5300. Nevertheless, the unclassified team had its Cray XT4 supercomputer upgraded to a warehouse-sized XT5. Named Jaguar for its speed, it clocked in at 1.75 petaflops, officially becoming the world’s fastest computer in 2009.
1 Geostationary satellites Four satellites positioned around the globe monitor frequencies carrying everything from walkie-talkies and cell phones in Libya to radar systems in North Korea. Onboard software acts as the first filter in the collection process, targeting only key regions, countries, cities, and phone numbers or email. 2 Aerospace Data Facility, Buckley Air Force Base, Colorado Intelligence collected from the geostationary satellites, as well as signals from other spacecraft and overseas listening posts, is relayed to this facility outside Denver. About 850 NSA employees track the satellites, transmit target information, and download the intelligence haul. 3 NSA Georgia, Fort Gordon, Augusta, Georgia Focuses on intercepts from Europe, the Middle East, and North Africa. Codenamed Sweet Tea, the facility has been massively expanded and now consists of a 604,000-square-foot operations building for up to 4,000 intercept operators, analysts, and other specialists. 4 NSA Texas, Lackland Air Force Base, San Antonio Focuses on intercepts from Latin America and, since 9/11, the Middle East and Europe. Some 2,000 workers staff the operation. The NSA recently completed a $100 million renovation on a mega-data center here—a backup storage facility for the Utah Data Center. 5 NSA Hawaii, Oahu Focuses on intercepts from Asia. Built to house an aircraft assembly plant during World War II, the 250,000-square-foot bunker is nicknamed the Hole. Like the other NSA operations centers, it has since been expanded: Its 2,700 employees now do their work aboveground from a new 234,000-square-foot facility. 6 Domestic listening posts The NSA has long been free to eavesdrop on international satellite communications. But after 9/11, it installed taps in US telecom “switches,” gaining access to domestic traffic. An ex-NSA official says there are 10 to 20 such installations. 7 Overseas listening posts According to a knowledgeable intelligence source, the NSA has installed taps on at least a dozen of the major overseas communications links, each capable of eavesdropping on information passing by at a high data rate. 8 Utah Data Center, Bluffdale, Utah At a million square feet, this $2 billion digital storage facility outside Salt Lake City will be the centerpiece of the NSA’s cloud-based data strategy and essential in its plans for decrypting previously uncrackable documents. 9 Multiprogram Research Facility, Oak Ridge, Tennessee Some 300 scientists and computer engineers with top security clearance toil away here, building the world’s fastest supercomputers and working on cryptanalytic applications and other secret projects. 10 NSA headquarters, Fort Meade, Maryland Analysts here will access material stored at Bluffdale to prepare reports and recommendations that are sent to policymakers. To handle the increased data load, the NSA is also building an $896 million supercomputer here. |
| Oak Ridge National Laboratory – Multi-Program Research Facilityhttp://www.heery.com/Repository/Images/Oak_Ridge_National_Laboratories.jpg
http://www.heery.com/portfolio/oak-ridge-national-laboratory.aspx?service=5 Oak Ridge National Laboratory – Multi-Program Research Facility Oak Ridge, Tennessee The Department of Energy (DOE) complex at Oak Ridge required the creation of a state of the art, large-scale, secure science and technology facility that would provide the appropriate infrastructure and environment to both integrate and consolidate multidisciplinary scientific capabilities for defense and homeland security activities. The Heery-designed and constructed Multi-Program Research Facility (MPRF) provides facilities for research and development activities in non-proliferation research, training and operations; cyber security research and development; geospatial analysis; inorganic membrane research and prototyping; and myriad other activities. Based on Heery’s previous successful work with ORNL as part of a third-party development team, ORNL tapped the Keenan team to serve as its developer for the MPRF, with Heery in the role of design-builder. The MPRF contains 218,000 SF of office and laboratory space. This highly secure building plays a key role in delivering the science and technology needed to protect homeland and national security. In addition, Heery International continues to work on various new assignments on the ORNL campus. The goal was to develop cutting-edge facilities designed for sustainability and energy efficiency. Heery guided ORNL and the development team in delivering facilities to showcase energy and water efficiency and renewable energy improvements. With Heery’s assistance, ORNL now has the most LEED-certified space in the entire DOE system, having attained LEED certification for the firm’s earlier project, the East Campus Complex, and LEED Gold certification for the MPRF, which is the first LEED Gold facility on the ORNL campus. |
| Following images from bing.com/mapsThe MRF is at upper left.
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/nsa-mrf/pict9.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/nsa-mrf/pict14.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/nsa-mrf/pict11.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/nsa-mrf/pict12.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/nsa-mrf/pict13.jpg) |
| http://femp.buildinggreen.com/overview.cfm?ProjectID=1125Oak Ridge National Laboratory Multiprogram Research Facility (MRF)
(ORNL Multiprogram Research Facility)
Overview Location: Oak Ridge, TN Building type(s): Other, Laboratory, Commercial office New construction 195,000 ft2 (18,100 m2) Project scope: 5-story building Rural setting Completed October 2006 Rating: U.S. Green Building Council LEED-NC, v.2/v.2.1–Level: Gold (39 points) The Multiprogram Research Facility (MRF) was implemented through a design-build contract, but is a complex mixture of labs and offices that have stringent operational, security, and environmental and energy requirements. The program was highly developed and has detailed technical parameters that could not be compromised. Environmental Aspects The building’s vertical orientation minimized its footprint on the landscape. Using native, drought-resistant plants in the landscape obviated the need for irrigation. This, along with the use of low-flow plumbing fixtures, reduced potable water usage by approximately 34%. The building was projected to use 25% less energy than that of a comparable facility built in minimal compliance with code. A hybrid solar lighting system with rooftop solar collectors was installed to test the feasibility of using fiber optics for natural lighting. The project team preferred materials with recycled content and those that were manufactured regionally. The team also recycled construction waste wherever possible. Owner & Occupancy Owned by Keenan Development Associates, LLC, Corporation, for-profit Occupants: Federal government Typically occupied by 318 people, 40 hours per person per week Expected Building Service Life: 35 years
Building Programs
Indoor Spaces:
Other (43%), Office (18%), Laboratory (14%), Conference (6%), Data processing (6%), Mechanical systems (3%), Retail general (3%), Public assembly (2%), Restrooms (2%), Lobby/reception (2%), Cafeteria, Circulation, Gymnasium, Electrical systems |
Confidential – DHS Chemical Facilities Threat Assessment

(U) The DHS Homeland Infrastructure Threat and Risk Analysis Center produced this threat assessment to support implementation of 6 Code of Federal Regulations Part 27, “Chemical Facility Anti-Terrorism Standards (CFATS).” This assessment describes the potential terrorist threat to the chemical and petroleum facilities regulated under CFATS and determined to be high risk by the Secretary of Homeland Security. It does not address facilities that may hold threshold quantities of the chemicals listed in CFATS that fall outside its scope, such as public water facilities or facilities regulated under the Maritime Transportation Security Act of 2002. Nor does it address the transportation of chemicals, which is regulated under other authorities. Potential terrorist tactics against such facilities—based on DHS’ knowledge of terrorist intentions and capabilities—are included to aid industry security personnel in implementing security measures at their facilities.
…
(U//FOUO) Intelligence reporting indicates al-Qa‘ida, affiliated Sunni extremist groups, and other like-minded extremists continue to engage in operational planning with the intent to attack the Homeland.
— (U//FOUO) None of the reporting to date has revealed any specific or credible threats targeting facilities in the nation’s chemical sector.
— (U//FOUO) DHS has received general information on threats to U.S. petroleum infrastructure—including refineries and petrochemical plants—but has seen no credible or specific intelligence indicating an imminent terrorist threat to the sector.(U//FOUO) The tactics terrorists are most likely to use against the nation’s chemical and petroleum infrastructure include aircraft as a weapon and vehicle-borne improvised explosive devices (VBIEDs). Many facilities also are vulnerable to cyber attacks against their supervisory control and data acquisition or business systems. Any of these tactics could include the use of insiders with access to and knowledge of sensitive facilities and systems.
(U//FOUO) Chemical and petroleum facilities are potentially attractive targets for terrorists.
— (U//FOUO) An attack on a chemical sector facility containing large quantities of toxic industrial chemicals could cause fatalities, extensive injuries, and panic, and could generate heavy media attention.
— (U//FOUO) Petroleum facilities appeal to al-Qa‘ida and its affiliates because they symbolize what Usama Bin Ladin has referred to as “Western theft of the Muslim world’s oil resources.” Islamic extremists have attacked overseas petroleum facilities, especially in the Arabian Peninsula and Iraq.…
(U//FOUO) Traditional Domestic Extremists
(U//FOUO) Traditional domestic extremists pose a limited threat to homeland chemical and petroleum infrastructure. Most domestic, right-wing extremists focus their ire on government entities or racial minorities. Groups such as white supremacists, neo-Nazis, and the modern-day “militias” have not yet demonstrated particular interest in chemical or petroleum infrastructure.
(U//FOUO) Traditional domestic extremist groups, however—such as radical animal rights and environmental groups—have emerged as the most active domestic extremist threat. A primary objective of animal rights and environmental extremists is to attack corporations and other entities whose activities they perceive as contrary to their personal beliefs and ideological cause. Animal rights extremists oppose any experimentation on or euthanasia of animals; the environmental extremists target companies engaged in practices they believe degrade the environment. Animal rights extremists have targeted chemical and pharmaceutical companies, and environmental extremists opposed to oil drilling and some uses of petroleum products have targeted petroleum companies.
(U//FOUO) So-called “lone wolves”—such as individuals who have targeted the Trans-Alaska Pipeline and a California man who threatened to attack a refinery where he had worked—also pose threats to chemical and petroleum infrastructure.
…
(U) Cyber Attack
(U//FOUO) Chemical and petroleum facilities use computers to monitor and process data such as flow, temperature, and pressure through supervisory control and data acquisition networks. Computers manage enterprise resource process systems and conduct automated measurement readings, while central or local control stations send signals to remote valves, opening and closing them to regulate flow or pressure or to seal them tight in an emergency. These capabilities improve the efficiency of the facility, but also expose the control systems to manipulation or disruption by malicious operatives, including terrorists.
(U//FOUO) Control systems are vulnerable to cyber attacks from inside and outside the control system network. The most elaborate boundary control program of firewalls, intrusion detection, and virus filtering will be of little help if an intruder or untrustworthy insider is able to gain physical access to servers, networks, or sensitive information.
(U//FOUO) Members of single-issue groups also may harness cyber capabilities to threaten and harass chemical and petroleum companies, although their goals are not likely to include physical destruction affecting the population and environment outside the targeted facility.
FEMEN naked in the Vatican
Das HANDELSBLATT über die Verbrechen und Vorstrafen von STASI-“GoMoPa”
TOP-SECRET – U.S. Army Company Intelligence Support Team (COIST) Reference Card
Video – George Clooney Arrested Protesting Sudanese Regime
George Clooney and his father Nick joined members of Congress and activists at the Sudanese Embassy in Washington, D.C., calling on the government of Sudan to end its indiscriminate bombing campaign against people in the Nuba Mountains and restore humanitarian access immediately.
Uncensored – Women Protest Worldwide 12
|
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest12/pict2.jpg) A supporter of a female Russian punk band holds a photo placard of the band while she and others picket the Moscow Central Court in Moscow, Wednesday, March, 14, 2012. Supporters of a female Russian punk band have picketed Central Court in Moscow to protest the group’s jailing for trying to mount an impromptu concert inside the city’s main cathedral. A supporter of a female Russian punk band holds a photo placard of the band while she and others picket the Moscow Central Court in Moscow, Wednesday, March, 14, 2012. Supporters of a female Russian punk band have picketed Central Court in Moscow to protest the group’s jailing for trying to mount an impromptu concert inside the city’s main cathedral. |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest12/pict20.jpg) Animals rights activists protest during a demonstration calling for the abolition of bullfights in Valencia March 18, 2012. Placards read, “They killed me this Fallas festival”. Reuters Animals rights activists protest during a demonstration calling for the abolition of bullfights in Valencia March 18, 2012. Placards read, “They killed me this Fallas festival”. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest12/pict13.jpg) A demonstrator shouts slogans during a protest against Syria’s President Bashar Al-Assad in front of the Beyazit mosque in Istanbul March 18, 2012. Reuters A demonstrator shouts slogans during a protest against Syria’s President Bashar Al-Assad in front of the Beyazit mosque in Istanbul March 18, 2012. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest12/pict14.jpg) Women shout slogans as they protest against the suicide of Amina al-Filali, 16 who was forced to marry the man who raped her outside parlament in Rabat on March 17, 2012. They called for changes to a penal code that allows a rapist to stay out of jail if he marries his victim with the consent of her parents. Sign reads ” Rape me, Marry me, My life is futile , I am maroocan”. Getty Women shout slogans as they protest against the suicide of Amina al-Filali, 16 who was forced to marry the man who raped her outside parlament in Rabat on March 17, 2012. They called for changes to a penal code that allows a rapist to stay out of jail if he marries his victim with the consent of her parents. Sign reads ” Rape me, Marry me, My life is futile , I am maroocan”. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest12/pict15.jpg) Women clap during a Polish minority protest about the autonomy of their schools in Vilnius March 17, 2012. They demonstrated against the lack of regard for ethnic minorities seen in a law which enforced that history and geography lessons must be taught in Lithuanian at all schools, as well as the sole use of Lithuanian from 2013 in all pre-university exams taken by students to enable them to study at local universities, according to local media. Reuters Women clap during a Polish minority protest about the autonomy of their schools in Vilnius March 17, 2012. They demonstrated against the lack of regard for ethnic minorities seen in a law which enforced that history and geography lessons must be taught in Lithuanian at all schools, as well as the sole use of Lithuanian from 2013 in all pre-university exams taken by students to enable them to study at local universities, according to local media. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest12/pict16.jpg) Russian opposition supporters shout during a rally in central Moscow, on March 17, 2012. The rally was originally announced as campaigning for the release of Udaltsov, the radical leftwing leader of the Left Front movement, who was sentenced on Thursday to 10 days in jail for defying police at an earlier rally and participants protest against Russian Prime Minister Vladimir Putin’s rule. Getty Russian opposition supporters shout during a rally in central Moscow, on March 17, 2012. The rally was originally announced as campaigning for the release of Udaltsov, the radical leftwing leader of the Left Front movement, who was sentenced on Thursday to 10 days in jail for defying police at an earlier rally and participants protest against Russian Prime Minister Vladimir Putin’s rule. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest12/pict19.jpg) Protesters affiliated with Occupy Wall Street participate in a ‘spring training’ protest outside the New York Stock Exchange on March 16, 2012 in New York City. The movement is planning an upcoming series of ‘spring training’ protests ahead of its planned ‘May Day’ strike. Getty Protesters affiliated with Occupy Wall Street participate in a ‘spring training’ protest outside the New York Stock Exchange on March 16, 2012 in New York City. The movement is planning an upcoming series of ‘spring training’ protests ahead of its planned ‘May Day’ strike. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest12/pict17.jpg) A mother carries a picture of her son, a kidnapped student, as she joins relatives of other kidnapped students during a protest march against violence in downtown Monterrey March 16, 2012. Relatives of victims and students from different universities marched on Friday to demand the government to stop violence, kidnapping and denouncing the forced disappearance. The banner reads, “Student kidnapped on January 11, 2011”. Reuters A mother carries a picture of her son, a kidnapped student, as she joins relatives of other kidnapped students during a protest march against violence in downtown Monterrey March 16, 2012. Relatives of victims and students from different universities marched on Friday to demand the government to stop violence, kidnapping and denouncing the forced disappearance. The banner reads, “Student kidnapped on January 11, 2011”. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest12/pict18.jpg) Writer and activist Starhawk (ground) demonstrates how to act when being arrested during the “Occupy the Midwest” regional conference in St. Louis, Missouri March, 16, 2012. Two demonstrators were charged on Friday with assaulting a police officer following the arrests of 15 people at the start of a Midwest protest designed to help reinvigorate the “Occupy” movement against economic inequality. Reuters Writer and activist Starhawk (ground) demonstrates how to act when being arrested during the “Occupy the Midwest” regional conference in St. Louis, Missouri March, 16, 2012. Two demonstrators were charged on Friday with assaulting a police officer following the arrests of 15 people at the start of a Midwest protest designed to help reinvigorate the “Occupy” movement against economic inequality. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest12/pict0.jpg) Egyptian activist Samira Ibrahim, second left attends a rally while fellow activists chant anti Military Supreme Council slogans during a protest in Tahrir square, Cairo, Egypt Tuesday, March 13, 2012. Egyptian activists protested a military tribunal verdict acquitting an army doctor of an accusation of public obscenity filed by a protester who claimed she was forced to undergo a virginity test while in detention among seven women detained by the military a year ago. (Nasser Nasser) Egyptian activist Samira Ibrahim, second left attends a rally while fellow activists chant anti Military Supreme Council slogans during a protest in Tahrir square, Cairo, Egypt Tuesday, March 13, 2012. Egyptian activists protested a military tribunal verdict acquitting an army doctor of an accusation of public obscenity filed by a protester who claimed she was forced to undergo a virginity test while in detention among seven women detained by the military a year ago. (Nasser Nasser) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest12/pict1.jpg) A member of Socialist Unity Center of India (SUCI) shouts slogans as she participates in a rally in New Delhi, India, Wednesday, March 14, 2012. The protest was against a price hike on essential commodities as well as rampant corruption. (Saurabh Das) A member of Socialist Unity Center of India (SUCI) shouts slogans as she participates in a rally in New Delhi, India, Wednesday, March 14, 2012. The protest was against a price hike on essential commodities as well as rampant corruption. (Saurabh Das) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest12/pict3.jpg) Activists wear costume and masks of endangered animals during a protest against animal cruelty outside the Supreme Court in Jakarta, Indonesia, Tuesday, March 13, 2012. Animal protection activists staged the protest demanding Supreme Court to bring to justice palm oil companies that involved in the killings of orangutans in central Borneo last year. (Tatan Syuflana) Activists wear costume and masks of endangered animals during a protest against animal cruelty outside the Supreme Court in Jakarta, Indonesia, Tuesday, March 13, 2012. Animal protection activists staged the protest demanding Supreme Court to bring to justice palm oil companies that involved in the killings of orangutans in central Borneo last year. (Tatan Syuflana) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest12/pict4.jpg) Costumed protesters shout slogans outside Tokyo Electric Power Company (TEPCO) during an anti-nuclear demonstration in Tokyo, Sunday, March 11, 2012. Japan marked Sunday the first anniversary of the March 11 earthquake and tsunami which devastated the northeast Japan cities and triggered a massive accident of Fukushima nuclear power plant, run by TEPCO. (Junji Kurokawa) Costumed protesters shout slogans outside Tokyo Electric Power Company (TEPCO) during an anti-nuclear demonstration in Tokyo, Sunday, March 11, 2012. Japan marked Sunday the first anniversary of the March 11 earthquake and tsunami which devastated the northeast Japan cities and triggered a massive accident of Fukushima nuclear power plant, run by TEPCO. (Junji Kurokawa) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest12/pict5.jpg) Relatives of missing Kashmiri youth participate in a protest demonstration organized by the Association of Parents of Disappeared Persons (APDP) in Srinagar, India, Saturday, March 10, 2012. According to APDP some 8,000-10,000 people have gone missing since the beginning of the Kashmir conflict in 1989, after being arrested by Indian security forces and other security agencies. (Dar Yasin) Relatives of missing Kashmiri youth participate in a protest demonstration organized by the Association of Parents of Disappeared Persons (APDP) in Srinagar, India, Saturday, March 10, 2012. According to APDP some 8,000-10,000 people have gone missing since the beginning of the Kashmir conflict in 1989, after being arrested by Indian security forces and other security agencies. (Dar Yasin) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest12/pict7.jpg) A demonstrator tries to scale a barrier to enter the Cambridge University Students’ Union to protest against speech being given to students by former International Monetary Fund chief Dominic Strauss-Kahn, in Cambridge, England, Friday, March 9, 2012. The 62-year-old French politician, often called DSK, was invited to speak at the university’s debating society despite calls for the event to be canceled. (Sang Tan) A demonstrator tries to scale a barrier to enter the Cambridge University Students’ Union to protest against speech being given to students by former International Monetary Fund chief Dominic Strauss-Kahn, in Cambridge, England, Friday, March 9, 2012. The 62-year-old French politician, often called DSK, was invited to speak at the university’s debating society despite calls for the event to be canceled. (Sang Tan) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest12/pict6.jpg) A woman protests against violence against women during a demonstration marking the International Women’s Day in Mexico City, Thursday March 8, 2012. (Alexandre Meneghini) A woman protests against violence against women during a demonstration marking the International Women’s Day in Mexico City, Thursday March 8, 2012. (Alexandre Meneghini) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest12/pict8.jpg) Female protesters raise their clenched fists as they shout slogans during a rally in celebration of International Women’s Day Thursday, March 8, 2012 near the presidential palace in Manila, Philippines. The protesters denounced President Benigno Aquino III and the three big Filipino oil companies for a series of oil price hike as well as U.S. military’s presence in the country. (Pat Roque) Female protesters raise their clenched fists as they shout slogans during a rally in celebration of International Women’s Day Thursday, March 8, 2012 near the presidential palace in Manila, Philippines. The protesters denounced President Benigno Aquino III and the three big Filipino oil companies for a series of oil price hike as well as U.S. military’s presence in the country. (Pat Roque) |
|
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest12/pict9.jpg) A woman carries posters with photos of activists of human rights allegedly killed during a march to mark the International Day of Victims of State Crimes and ask the government for the restitution of land for victims of the country’s prolonged armed conflict and protection for activists in Bogota, Colombia, Tuesday March 6, 2012. (Fernando Vergara) A woman carries posters with photos of activists of human rights allegedly killed during a march to mark the International Day of Victims of State Crimes and ask the government for the restitution of land for victims of the country’s prolonged armed conflict and protection for activists in Bogota, Colombia, Tuesday March 6, 2012. (Fernando Vergara) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest12/pict11.jpg) Russian police officers detain opposition activists during a protest against alleged vote rigging in St. Petersburg, Russia, Monday, March 5, 2012. More then 100 protesters were arrested in St. Petersburg, where some 2,000 gathered for an unauthorized rally to protest Prime Minister Vladimir Putin’s victory in Russian presidential election. (Dmitry Lovetsky) Russian police officers detain opposition activists during a protest against alleged vote rigging in St. Petersburg, Russia, Monday, March 5, 2012. More then 100 protesters were arrested in St. Petersburg, where some 2,000 gathered for an unauthorized rally to protest Prime Minister Vladimir Putin’s victory in Russian presidential election. (Dmitry Lovetsky)
|
Movie – George Clooney Witnesses War Crimes in Sudan’s Nuba Mountains
WARNING: This video contains graphic content that some viewers may find disturbing.
In a recent trip across the Sudanese border into rebel-held territory in Sudan’s Nuba Mountains, George Clooney witnessed rocket attacks and the effects of aerial bombardment by the Sudanese regime against the Nuban people. This trip diary was written and directed by George Clooney in the field with the Enough Project.
To take action, text SUDAN to 30644.
Visit http://www.EnoughProject.org for more information.
Column – Assad – “He will bleed, he will kick, but it is the end”
A year after the eruption of the Syrian uprising, Lieutenant Colonel Dr. Mordechai Kedar examines the continuation of the struggle, and claims that Assad will fall sooner or later

This week marked a year since the start of the Syrian uprisings. However, despite assessments that claimed his regime would end within several months, Assad remains in power, and the final results of the internal Syrian conflict are still unclear.
According to Lieutenant Colonel (Res.) Dr. Mordechai Kedar, Assad will eventually be defeated. Even if it takes more time, he will eventually vacate his position, whether if it happens in the framework of an agreement, or due to defeat at the hands of the rebels. “He will bleed, he will kick, but it’s the end. People will not agree to continue with him after massacring 10,000 people, even if it happens in a month, two months, or a year. He’s in a state similar to a terminal illness – he can take all sorts of measures to bring calm for a period, but he will eventually be subdued.
“The situation has completely changed. The Kurds can almost smell their freedom, and they’re waiting for the Arab factions in Syria to do all the work – the more they slaughter each other, the more the Kurds’ situation will improve.
“Assad will be toppled when the military units direct the tank barrels towards him. Officers, soldiers, and even small units have defected so far, but they are few. We’ve yet to see tank regiments defect, along with their ammunition bases and logistical layout. As soon as units with large combat forces defect and turn against Assad, that will mark the end. It’s heading in that direction – the question is if it’s going in that direction fast enough. The West is not interfering because it fears Russia and China, and Syria is not Libya. The Russians didn’t have a port in Libya, whereas they have three ports in Syria – Latakia, Tartus, and Baniyas. These are their only ports on the Mediterranean Sea, which means that from their perspective, losing Syria poses a strategic problem. Furthermore, the fall of Syria would greatly anger Iran, which may result in Iran causing problems in the gulf.
You don’t see a scenario in which Assad subdues the rebels, and as a result, ends up strengthened?
“Even if that were to happen, the riots would eventually erupt again at some point. You can’t turn back time, and when it erupts again, it will be even stronger. What we are seeing in the Youtube videos is nothing compared to what they are actually experiencing there – women are being viciously raped and people are being massacred everywhere. Members of a military unit break into the house of the head of a village, seize his eldest daughter, and rape her.”
**Dr. Mordechai Kedar is an expert in Middle Eastern affairs, a Lt. Colonel reservist, and research associate at the BESA Center for Strategic Studies at Bar-Ilan University.
Uncensored – Occupy Wallstreet Protest By FEMEN
Confidential – CIA, Mossad Agree That Iran is Not Pursuing Nuclear Weapons
Mossad, CIA agree Iran has yet to decide to build nuclear weapon (Ha’aretz):
Israel’s intelligence services agree with American intelligence assessments that there is not enough proof to determine whether Iran is building a nuclear bomb, according to a report published Sunday in the New York Times. The newspaper said that senior American officials believe there is little disagreement between the Mossad and U.S. intelligence agencies over Iran’s nuclear program, despite the fact that Israeli political leaders have been pushing for quick action to block Iran from becoming what they describe as an existential threat.
The report further quoted one former senior American intelligence official who states that the Mossad “does not disagree with the U.S. on the weapons program,” adding that there is “not a lot of dispute between the U.S. and Israeli intelligence communities on the facts.”
U.S. Faces a Tricky Task in Assessment of Data on Iran (New York Times):
Mossad, Israel’s intelligence service, agrees with the American intelligence assessments, even while Israeli political leaders have been pushing for quick, aggressive action to block Iran from becoming what they describe as an existential threat to the Jewish state.
“Their people ask very hard questions, but Mossad does not disagree with the U.S. on the weapons program,” said one former senior American intelligence official, who, like others for this article, would speak only on the condition of anonymity about classified information. “There is not a lot of dispute between the U.S. and Israeli intelligence communities on the facts.”
In trying to evaluate the potential perils of Iran’s nuclear program, the United States’ spy agencies have spent years trying to track its efforts to enrich uranium and develop missile technology, and watching for any move toward weaponization — designing and building a bomb.
…
The United States and Israel share intelligence on Iran, American officials said. For its spying efforts, Israel relies in part on an Iranian exile group that is labeled a terrorist organization by the United States, the Mujahedeen Khalq, or M.E.K., which is based in Iraq. The Israelis have also developed close ties in the semiautonomous region of Kurdistan in northern Iraq, and they are believed to use Kurdish agents who can move back and forth across the border into Iran.
American intelligence officials, however, are wary of relying on information from an opposition group like the M.E.K., particularly after their experience in Iraq of relying on flawed information provided by the Iraqi National Congress, an exile group run by Ahmad Chalabi.
“I’m very suspicious of anything that the M.E.K. provides,” said David A. Kay, who led the C.I.A.’s fruitless effort to find weapons program in Iraq. “We all dealt with the Chalabis of the world once.”
Just as in 2010, new evidence about the Iranian nuclear program delayed the National Intelligence Estimate in 2007, the last previous assessment. Current and former American officials say that a draft version of the assessment had been completed when the United States began to collect surprising intelligence suggesting that Iran had suspended its weapons program and disbanded its weapons team four years earlier.
The draft version had concluded that the Iranians were still trying to build a bomb, the same finding of a 2005 assessment. But as they scrutinized the new intelligence from several sources, including intercepted communications in which Iranian officials were heard complaining to one another about stopping the program, the American intelligence officials decided they had to change course, officials said. While enrichment activities continued, the evidence that Iran had halted its weapons program in 2003 at the direction of the supreme leader, Ayatollah Ali Khamenei, was too strong to ignore, they said.
One former senior official characterized the information as very persuasive. “I had high confidence in it,” he said. “There was tremendous evidence that the program had been halted.”
And today, despite criticism of that assessment from some outside observers and hawkish politicians, American intelligence analysts still believe that the Iranians have not gotten the go-ahead from Ayatollah Khamenei to revive the program.
“That assessment,” said one American official, “holds up really well.”
Uncensored – FEMEN Chernobyl Protest Verse Nukes Energy
TOP-SECRET from the FBI – Former Employee Pleads Guilty to Conspiracy Charge in $900,000 Embezzlement Scheme
WASHINGTON—Valencia Person, 54, of Suitland, Maryland, pled guilty today to a federal conspiracy charge stemming from a scheme in which she helped embezzle more than $900,000 from her former employer, XM Satellite Radio, announced U.S. Attorney Ronald C. Machen Jr. and James W. McJunkin, Assistant Director in Charge of the FBI’s Washington Field Office.
Person pled guilty before the Honorable Reggie B. Walton in the U.S. District Court for the District of Columbia to one count of conspiracy to commit wire fraud. Sentencing is scheduled for June 8, 2012. The charge carries a maximum statutory penalty of five years in prison. However, under federal sentencing guidelines, Person faces a likely sentence of 24 to 30 months in prison and a fine of up to $50,000.
As part of the plea agreement, Person agreed to a money judgment of at least $909,924, representing the amount of proceeds from the crime. She also is subject to an order to make restitution.
According to a statement of offense submitted to the Court by Assistant U.S. Attorney Sherri L. Schornstein, Person worked at XM Satellite Radio (now known as Sirius XM Radio Inc.), a corporation based in Washington, D.C., as a coordinator in the Accounts Payable Department. Her duties included responsibility for payments to large vendors.
From 2005 until at least 2008, Person and an XM Satellite Radio Accounts Payable Administrator, Brenda L. Jones, embezzled more than $909,000 from the company. They secretly diverted at least 26 payments, which were supposed to go to XM vendors, to bank accounts held by Jones. They also covered up the activities by altering data in the company’s accounting system. Jones then gave a portion of the monies to Person. Jones resigned in 2006. However, more than $690,000 of the money was transferred into her accounts after she had left the company.
According to Person, she personally benefitted from the scheme in an amount not exceeding $125,000.
Jones, 46, of Lothian, Maryland, pled guilty in January 2012 to one count of conspiracy to commit wire fraud. She is awaiting sentencing.
In announcing the plea, U.S. Attorney Machen and Assistant Director in Charge McJunkin praised those who worked on the case, including the Special Agents of the FBI’s Washington Field Office, as well as Legal Assistant Jared Forney of the U.S. Attorney’s Office. They also commended the efforts of Assistant U.S. Attorney Sherri L. Schornstein, who is prosecuting the case.
FEMEN in Italian TV
Unveiled – National Security Archive Collects US Government Documents for Public Use
Wikileaks has received widespread attention for releasing classified U.S. government documents. But if you want to examine notes from White House meetings with foreign leaders, read email from a Cabinet secretary, or look at photos taken by U.S. surveillance satellites… you can, thanks to the Freedom of Information Act, which grants access to declassified government records. As VOA’s Deborah Block reports, millions of those documents are available at the National Security Archive, a private research group in Washington.
Uncensored – Bradley Manning Hearing March 15, 2012 Photos
Confidential – U.S. Army Tactical Questioning Soldier’s Handbook

This handbook is a compilation of tools to help all soldiers collect information through tactical questioning and EPW/detainee and document handling in Offensive, Defensive, Stability, and Support operations. However, most of the handbook was developed specific to small unit patrols, traffic control points (TCPs)/ roadblocks, and other interaction with the local population in the Middle East.
This handbook is not intended to train soldiers as Human Intelligence collectors or even make the soldier an expert on tactical questioning. It is only designed to introduce the basics of questioning and to provide some tools. The proponent of this handbook is the US Army Intelligence Center. This handbook was quickly developed to try to immediately fill a gap in existing documentation on tactical questioning. It was developed based on the agreement that the US Army Intelligence Center will follow this handbook with the development of a Special Text publication on this subject. This handbook does not reflect authoritative US Army doctrine or tactics, techniques, and procedures (TTPs).
…
Every soldier, as a part of a small unit, is a potential information collector and an essential component to help reach situational understanding. Every soldier develops a special level of situational awareness simply due to exposure to events occurring in the area of operations (AO) and has the opportunity to collect information by observation and interaction with the population. This task is critical because the environment we operate in is characterized by violence, uncertainty, complexity, and asymmetric methods by the threat. The increased situational awareness that soldiers develop through personal contact and observation is a critical element of the Brigade’s and Battalion’s ability to more fully understand the operational environment. The concept that every soldier is an information collector cannot be overstated.
However, you are not an Intelligence Collector. This handbook is not meant to turn you into a Human Intelligence (HUMINT) Collector and will not make you an expert on tactical questioning. It is only designed to provide guidance for how to deal with and handle the local population you may come in contact with and to introduce the basics of tactical questioning.
…

Secret – Internet Freedom Programs in the Middle East
Question Taken at the MARCH 14, 2012 Daily Press Briefing
March 15, 2012
QUESTION: What kind of Internet freedom support has the State Department provided in the Middle East region?
ANSWER: Advancing Internet freedom is a priority for this administration. From 2008 through 2011, the State Department and USAID have spent $76 million on Internet freedom programming. This year, at a time when we are making significant budget cuts in many areas, we anticipate spending $25 million in Internet freedom programming. Through these programs, we provide training and tools to civil society activists, in the Middle East and throughout the world, to enable them to freely and safely exercise their freedoms of expression, association, and assembly on the Internet and via other communication technologies.
Across the Middle East, we have seen that access to technological tools enables people to tell their story to the world when they are otherwise silenced by repressive governments. Our Internet freedom programming is aimed at making sure that voices for peaceful democratic reform in the region can be heard.
Countering increasingly active Internet surveillance and censorship efforts aimed at suppressing individuals’ exercise of their human rights requires a diverse portfolio of tools and training. State Department grants support more advanced technologies, including in Farsi and Arabic. Tools that have received support from the State Department help provide unfettered Internet access for hundreds of thousands of individuals in the Middle East. We also support the development of mobile security software to provide safer ways for activists in repressive societies to communicate, and technologies to enable them to post their own content online and protect against cyber attacks. Recently, State Department grantees have come to the aid of dozens of individuals and organizations in the region that have been victims of hacking or have had their accounts compromised. State has also supported the efforts of organizations that have trained over 7,500 activists worldwide, including many from the Middle East, in cyber-self defense.
In the face of growing repression, we continue to expand these important efforts to advance Internet freedom, in the Middle East and throughout the world.
PRN: 2012/390
Top-Secret from the FBI – Miami-Area Resident Pleads Guilty to Participating in $200 Million Medicare Fraud Scheme
WASHINGTON—A Miami-area resident pleaded guilty yesterday for his role in a fraud scheme that resulted in the submission of more than $200 million in fraudulent claims to Medicare, announced the Department of Justice, the FBI, and the Department of Health and Human Services (HHS).
Frank Criado, 33, pleaded guilty before U.S. Magistrate Judge Barry L. Garber in Miami to one count of conspiracy to commit health care fraud and one count of conspiracy to defraud the United States and to pay and receive illegal health care kickbacks. Criado was charged in an indictment unsealed on February 15, 2011 in the Southern District of Florida.
Criado admitted to participating in a fraud scheme that was orchestrated by the owners and operators of American Therapeutic Corporation (ATC); its management company, Medlink Professional Management Group Inc.; and the American Sleep Institute (ASI). ATC, Medlink, and ASI were Florida corporations headquartered in Miami. ATC operated purported partial hospitalization programs (PHPs), a form of intensive treatment for severe mental illness, in seven different locations throughout South Florida and Orlando. ASI purported to provide diagnostic sleep disorder testing.
According to court filings, ATC’s owners and operators paid kickbacks to owners and operators of assisted living facilities and halfway houses and to patient brokers in exchange for delivering ineligible patients to ATC and ASI. In some cases, the patients received a portion of those kickbacks. Throughout the course of the ATC and ASI conspiracy, millions of dollars in kickbacks were paid in exchange for Medicare beneficiaries who did not qualify for PHP services to attend treatment programs that were not legitimate PHPs so that ATC and ASI could bill Medicare for the medically unnecessary services. According to court filings, to obtain the cash required to support the kickbacks, the co-conspirators laundered millions of dollars of payments from Medicare.
Criado admitted to serving as a patient broker who provided patients for ATC and ASI in exchange for kickbacks in the form of checks and cash. The amount of the kickback was based on the number of days each patient spent at ATC.
According to his plea agreement, Criado’s participation in the ATC fraud resulted in $7.3 million in fraudulent billings to the Medicare program.
Sentencing for Criado is scheduled for May 31, 2012 at 8:30 a.m. He faces a maximum penalty of 15 years in prison and a $250,000 fine.
ATC, Medlink, and various owners, managers, doctors, therapists, patient brokers, and marketers of ATC, Medlink, and ASI were charged with various health care fraud, kickback, money laundering, and other offenses in two indictments unsealed on February 15, 2011. ATC, Medlink, and 11 of the individual defendants have pleaded guilty or have been convicted at trial. Other defendants are scheduled for trial April 9, 2012 before U.S. District Judge Patricia A. Seitz. A defendant is presumed innocent unless proven guilty beyond a reasonable doubt in a court of law.
The guilty plea was announced by Assistant Attorney General Lanny A. Breuer of the Justice Department’s Criminal Division; U.S. Attorney Wifredo A. Ferrer of the Southern District of Florida; John V. Gillies, Special Agent in Charge of the FBI’s Miami Field Office; and Special Agent in Charge Christopher B. Dennis of the HHS Office of Inspector General (HHS-OIG), Office of Investigations, Miami Office.
The criminal case is being prosecuted by Trial Attorneys Jennifer L. Saulino, Steven Kim, and Robert Zink of the Criminal Division’s Fraud Section. A related civil action is being handled by Vanessa I. Reed and Carolyn B. Tapie of the Civil Division and Assistant U.S. Attorney Ted L. Radway of the Southern District of Florida. The case was investigated by the FBI and HHS-OIG and was brought as part of the Medicare Fraud Strike Force, supervised by the Criminal Division’s Fraud Section and the U.S. Attorney’s Office for the Southern District of Florida.
Since its inception in March 2007, the Medicare Fraud Strike Force operations in nine locations have charged more than 1,190 defendants that collectively have billed the Medicare program for more than $3.6 billion. In addition, HHS’s Centers for Medicare and Medicaid Services, working in conjunction with the HHS-OIG, is taking steps to increase accountability and decrease the presence of fraudulent providers.
To learn more about the Health Care Fraud Prevention and Enforcement Action Team (HEAT), go to: http://www.stopmedicarefraud.gov.
Uncensored – Sex Slaves – Frontline Documentary
The Hacker News – President Assad’s hacked emails reveal isolation of Syria’s leader
FEMEN “Topless Warriors” documentary
Sexy Photos for the Dictator Assad
A provocative photograph of a near-naked young woman appears among e-mails apparently sent to Syrian President Bashar al-Assad and hacked by opposition activists who shared them with Western media.
On Saturday, London’s Daily Telegraph published an edited version of the photograph, which has been seen by Reuters among the original e-mails. It speculated on the state of his 11-year marriage to British-born Asma al-Assad, who has stood by her husband during a year of protests that come close to civil war.
The cache of some 3,000 e-mails dated for about nine months until early February has not been repudiated by the Assads or the small circle of aides and contacts who sent them since details were first published by Britain’s Guardian on Thursday.
There is no way to be certain, however, that all the content is genuine, nor to be sure that Assad’s enemies, at home and abroad, are not seeking to use material to their advantage.
E-mails seen by Reuters indicate a generally affectionate and light-hearted tone between Syria’s first couple and among the mostly English-speaking advisers sending messages to these private e-mail accounts. Some comments sent by female aides to the president gush with admiration: “miss uuu” writes one.
“So cute,” says another young woman when sending the 46-year-old Assad a photograph showing him in his younger days.
However, with the exception of the nude photograph sent on December 11 last year, there is little that seems overtly sexual in the content. The e-mail containing the photograph is entitled “Fw: file” and carries no text, nor is there any sign in those mails Reuters has seen of a response to it by Assad.
The woman in the picture stands, back to the camera, face in profile, wearing only skimpy underwear, with her arms raised and hands against the wall of a room. Dark hair piled high, she appears to be in her 20s and bears a similarity to a woman from whose account the message was apparently sent. Data embedded in the photo file indicate the shot was taken five years ago.
JOKES
On the day it was e-mailed to the head of state, his army was attacking towns that had become strongholds for rebel troops in some of the heaviest fighting that had then been seen.
It is not the only picture passed around though. Another woman apparently sent the president a computer-graphic image of a comic camel in thigh boots and bondage gear and, on another day, an obese giraffe captioned: “Just got back from America”.
The e-mail cache also gives a picture of the Assads’ inner circle sharing news of international reaction – especially anything that bucked the trend of generally negative comment abroad – offering advice to counter bad publicity and alerting Assad to the presence of foreign journalists in rebel areas.
The president himself, notably in warm messages to his 36-year-old wife, disparages reforms he has himself put forward to appease protesters – “rubbish”, he calls them. He also shares a crude pun playing on the words “elections” and “erections”, while making an eclectic series of music purchases on iTunes.
They range from country laments to New Order’s “Bizarre Love Triangle” and LMFAO’s party-rock hit “Sexy And I Know It”.
Asma al-Assad, whose e-mail account appears to show a passion for luxury shopping in London, Paris and other cities as Syria’s economy has collapsed under violence and trade sanctions, also seems to offer her husband support while clearly aware of the dangers after four decades of Assad family rule.
“If we are strong together, we will overcome this together…I love you…” she seems to have written on December 28.
BROKEN FRIENDSHIPS
Another e-mail from wife to husband earlier that month also illustrates how Syria’s estrangement from fellow Arab and regional leaders has been a deeply personal affair for them.
A three-word email from Asma al-Assad to her husband on December 11, forwarding a solicitous message from a daughter of the emir of Qatar betrays their bitter mood toward a Gulf state that was once a key ally and investor: “For a laugh…,” Asma wrote above the email, which gave assurances of the emir’s friendship.
Her sarcasm strikes a jarring note amid a string of personal messages between the Syrian first lady and the Qatari princess, Mayassa al-Thani, in which they exchange warm greetings and news of their young children – messages which, however, are unlikely to have been sent from Qatar without the emirate’s rulers being well aware of their value as a “back-channel” for diplomacy.
A recurring theme of Thani’s correspondence is urging her Syrian friend to flee the country with her husband; “Please get the kids out before it’s too late,” she wrote in August. On January 30, Thani assured Assad of a welcome in the Qatari capital Doha.
Such an outcome to the conflict, which has cost 8,000 lives and raised tensions between Assad’s Shi’ite Muslim Iranian allies and the Sunni Muslim Gulf states, would suit Qatar. The emir, who sent troops and arms to Libya’s rebels last year, has pressed for military intervention to end the bloodshed in Syria.
In the email exchange in December, at a time when Qatar was pushing the Arab League to punish Syria, Asma al-Assad referred to Qatar not “playing its cards right”. A few hours later, the emir’s daughter replied: “Your last remark is unfair. My father regards President Bashar as a friend, despite the current tensions – he always gives him genuine advice.”
It was that email, which urged the Assads to “come out of the state of denial” and apologized for “harsh” honesty, that Asma forwarded to Bashar suggesting he would find it amusing.
But three days later she replied: “My dear Mayassa, I don’t have a problem with frankness or honesty, in fact to me it’s like oxygen – I need it to survive … Take care, aaa.”
Talk of personal ties also clouds relations with Turkey, another regional player which once took a lead in trying to draw Assad out of an earlier isolation. Prime Minister Tayyip Erdogan once invited the Assads to a holiday resort in Turkey.
But, asked by Thani if she could pass her email address to Erdogan’s wife, Asma al-Assad replied in personal terms: “I use this account only for family and friends. It would be difficult for me at this stage to consider her in either category after the insults they have directed towards the president.”
Shocking – Nearly 20 Soldiers May Have Been Involved in Afghan Massacre

Afghan protestors shout anti-US slogans as they carry an effigy of US President Barack Obama during a demonstration in Jalalabad, capital of Nangarhar province on March 13, 2012. Hundreds of university students took to the streets in Afghanistan’s eastern city of Jalalabad to protest a rampage by a US soldier who killed 16 villagers, witnesses said. In the first street demonstrations since the mass killings on March 11, about 400 protesters shouted “Death to America — Death to (US President Barack) Obama”, and called for the soldier to be tried in public in Afghanistan
Up to 20 US troops executed Panjwai massacre (Pajhwok News Agency):
A parliamentary probe team on Thursday said up to 20 American troops were involved in Sunday’s killing of 16 civilians in southern Kandahar province.The probing delegation includes lawmakers Hamidzai Lali, Abdul Rahim Ayubi, Shakiba Hashimi, Syed Mohammad Akhund and Bismillah Afghanmal, all representing Kandahar province at the Wolesi Jirga and Abdul Latif Padram, a lawmaker from northern Badakhshan province, Mirbat Mangal, Khost province, Muhammad Sarwar Usmani, Farah province. The team spent two days in the province, interviewing the bereaved families, tribal elders, survivors and collecting evidences at the site in Panjwai district.
Hamizai Lali told Pajhwok Afghan News their investigation showed there were 15 to 20 American soldiers, who executed the brutal killings.
“We closely examined the site of the incident, talked to the families who lost their beloved ones, the injured people and tribal elders,” he said.
Afghan shootings: US soldier suspect flown to Kuwait (BBC):
The attack in Kandahar province has caused outrage across Afghanistan and protests in several areas. On Thursday about 2,000 people demonstrated in the southern Afghan province of Zabul, the second major protest outside Kandahar this week.
Nato has insisted that the detained man carried out the killings on his own.
But the head of an Afghan parliamentary delegation has told the BBC he has heard evidence from local villagers which suggests as many as 20 US soldiers were involved.
Sayed Ishaq Gillani, a leading Afghan MP, also claims that helicopters were heard overhead, and that they were seen dropping chaff – a measure designed to protect aircraft from ground attack.
Mr Gillani said local people believe the killings were carried out in revenge for an attack a week earlier in which several US troops were hurt
FEMEN – Ucraine uncensored
STASI-Zersetzung und Unterwanderung – “Willkommen in der Todeszone” – Die schleichende Unterwanderung
Liebe Leser,
die Realität ist schlimmer als jede Phantasie – bestätigt am Beispiel Griechenland.
Für mich persönlich erlebe ich dies seit langer Zeit.
Bereits in 1996 hatte ich Belege über die kriminellen Machenschaften der Neo-STASI vorliegen.
Damals vertraute sich ein unter dubiosen Umständen gestorbener Informant meiner an – über Werften und Milliarden-Subventionsbetrug in der Treuhand.
Er hatte Angst um sein Leben und ich habe dies nicht in der Immobilienzeitung publiziert, deren Herausgeber ich damals war, auf Anraten anderer Stimmen…
Mittlerweile denke ich, ich weiss, warum….
Wir, alle, die Begründer der IZ, sind entsetzt von dem moralischen Verfall der IZ durch ihre heutigen mutmasslichen Resch-Adepten und mutmasslichen Financiers
Herzlichst Ihr
Bernd Pulch
GARANTIERT STASI-FREI
DESWEGEN SIND “GoMoPa” UND GENOSSEN FREI: JEDER 5. IM LKA BRANDENBURG IST STASI WIE AUCH MUTMASSLICH BEATE P
STASI-Opfer decken weitere Verbindung zwischen RA Resch/”GoMoPa” und SED Medien auf: Connection zur “Jungen Welt”/SED/FDJ/Zentralorgan
Confidential from the FBI – Former Humphreys County Sheriff’s Deputies Indicted for Federal Civil Rights Offenses
WASHINGTON—The Justice Department announced today that a federal grand jury in Nashville, Tennessee returned a one-count indictment charging former Humphreys County, Tennessee Sheriff’s Deputies Timothy Wayne Hedge, 50, and James Benjamin Lee, 32, for violating the civil rights of an individual on January 23, 2011 in Humphreys County.
The indictment alleges that on January 23, 2011, Hedge and Lee, while acting under color of law and while aiding and abetting each other, violated an individual’s right to be free from unreasonable seizures by kicking and striking an individual with a collapsible baton during the course of arresting the individual, resulting in bodily injury.
An indictment is only an accusation of a crime, and a defendant should be presumed innocent unless and until proven guilty. If convicted, Hedge and Lee could face a maximum sentence of 10 years in prison and a $250,000 fine plus three years of supervised release.
This case was investigated by the Clarksville, Tennessee Office of the FBI’s Memphis Division and the Tennessee Bureau of Investigation, and is being prosecuted by Assistant U.S. Attorney Harold B. McDonough and Civil Rights Division Trial Attorney Adriana Vieco.
Confidential – U.S. Army Counterguerrilla Operations Manual

The aims, objectives, and methods of guerrilla warfare differ greatly from those of conventional warfare. To be successful in countering this type of war, the planners of counterguerrilla operations must understand the enemy and the unique environment in which he operates.
This manual provides commanders and staffs of brigade elements and below with concepts and doctrine concerning the conduct of counterguerrilla operations by US forces in insurgency and conventional conflict environments. It provides a general overview of US counterinsurgency strategy and the impact that strategy has on counterguerrilla operations. It provides planning, training, and operational guidance for commanders and staffs conducting counterguerrilla operations. The doctrine provides principles to guide the actions of US forces conducting counterguerrilla operations. In applying these principles, the commander must be aware that the situation in each counterguerrilla operation is unique. Techniques and tactics applied successfully in one situation may not be suitable if applied in the same manner in another situation. The principles in this manual are guides to be adapted to each counterguerrilla situation.
…
1-2. Types of conflict.
a. The risk to national survival is greatest in a conventional conflict, but the probability of such conflicts occurring is relatively low. On the other hand, the risk to national survival is not as great in a counterinsurgency conflict, but the probability of these types of conflicts occurring is much greater.
b. Conventional conflicts imply a state of open belligerency between nations and a direct confrontation of their armed forces. An insurgency implies a situation where a country is threatened by an internal attempt, frequently assisted by external support, to overthrow the legitimate government. counterguerrilla situations faced by US forces are likely to occur in an insurgency environment, but may also occur in conventional conflict environments. Counterguerrilla operations in support of a conventional conflict (such as the partisan operations that occurred behind German lines during World War II) are discussed in Chapter 4.
Section II. Insurgency
1-3. Concept.
a. The concept of resistance applies to an organized effort by some portion of the civil population of a country to resist, oppose, or overthrow the existing government. Many of the methods of resistance are part of the stock-in-trade of revolutionary activity. There can be no revolution without a resistance movement, but there can be a resistance movement without a revolution when the objectives of the resistors do not envision a reallocation of power.
b. This concept applies to an organized insurgent movement that seeks to overthrow the established government. In this manner, an insurgent organization can be considered a type of resistance organization.
1-4. Prerequisites.
There are three requirements that must exist before an insurgency can occur.
a. Vulnerable population. For whatever the reasons — social, political, or economic — the population is generally open to change. The insurgents will offer hope for change and exploit dissatisfaction with the current government.
b. Leadership available for direction. A vulnerable population alone will “not support an insurgent movement. There must be a leadership element that can direct the frustrations of a dissatisfied populace along the lines delineated by the overall insurgent strategy.
c. Lack of government control. Lack of government control may be real or perceived. The greater the control the government has over the situation, the less likely are the chances for insurgent success The opposite is also true: the less control the government has, the greater is the chance for insurgent success.
STASI-Opfer enthüllen dubiose Connection “GoMoPa”/Resch und “Neues Deutschland” – Ex- Parteiblatt von Honecker und Mielke
Video – FEMEN Solidarity message to FEMEN Holland –
Survey – Journalists Finds Public Information Officers Often Prevent the Public From Accessing Information
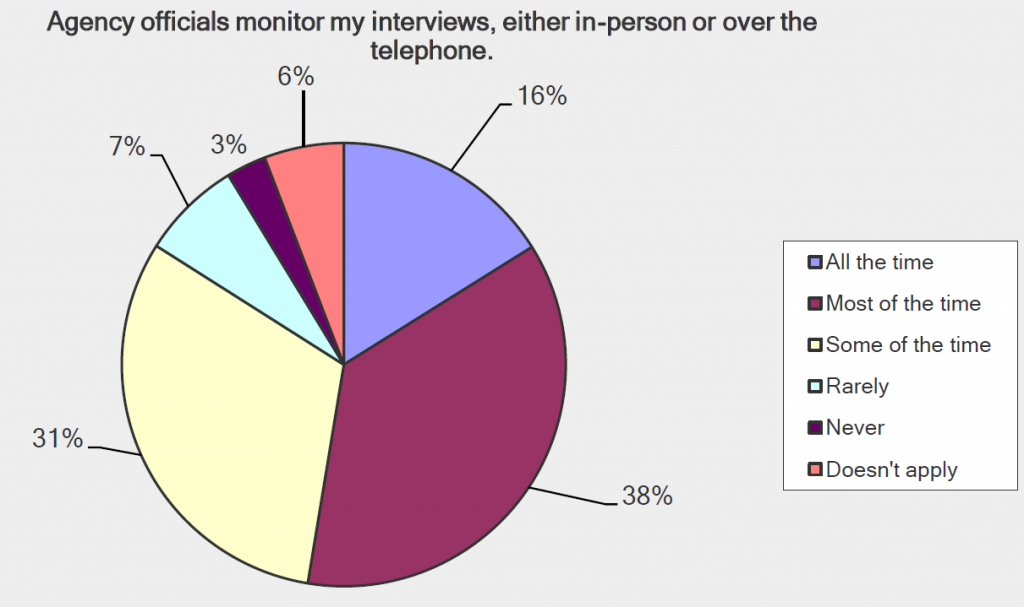
The Society of Professional Journalists conducted a study for this year’s Sunshine Week surveying 146 journalists who cover federal agencies regarding the role that public affairs or public information officers play in restricting the flow of relevant information to the public. The survey found that journalists face significant obstacles in the performance of their duties due to the obstructive activities of public affairs officers. Some of these obstacles include requiring pre-approval for interviews, prohibiting interviews of certain agency employees or rerouting interview requests, and the active monitoring of interviews being conducted with agency employees. Journalists who responded to the survey found that this obstruction is preventing the public from “getting all the information it needs because of barriers agencies are imposing on journalists’ reporting practices.”
Here’s what the survey found:
- 75% of journalists reported that they have to get approval from public affairs officers before interviewing an agency employee
- 70% reported that agency interview requests are forwarded to public affairs officers for “selective routing” to whomever they want
- Almost 50% reported that agency employees are sometimes barred from engaging with interviews with the press and nearly 20% of journalists say that this is a common occurrence
- More than 50% reported that public affairs officials monitor their interviews with agency employees either all or most of the time
Uncensored – FEMEN Topless Protst
Confidential – U.S. Army John F. Kennedy Special Warfare Center Leader’s Handbook on Unconventional Warfare

Unconventional warfare, or UW, is defined as activities conducted to enable a resistance movement or insurgency to coerce, disrupt or overthrow an occupying power or government by operating through or with an underground, auxiliary and guerrilla force in a denied area. Inherent in this type of operation are the inter-related lines of operation of armed conflict and subversion. The concept is perhaps best understood when thought of as a means to significantly degrade an adversary’s capabilities, by promoting insurrection or resistance within his area of control, thereby making him more vulnerable to a conventional military attack or more susceptible to political coercion. “UW includes military and paramilitary aspects of resistance movements. UW military activity represents the culmination of a successful effort to organize and mobilize the civil populace against a hostile government or occupying power. From the U.S. perspective, the intent is to develop and sustain these supported resistance organizations and to synchronize their activities to further U.S. national security objectives.”
…
Enabling a resistance movement or insurgency entails the development of guerrilla forces and an underground, both with their own supporting auxiliaries. The end result comes from the combined effects of “armed conflict,” conducted predominantly by the guerrillas, and “subversion,” conducted predominantly by the underground. The armed conflict, normally in the form of guerrilla warfare, reduces the host-nation’s security apparatus and subsequent control over the population. The subversion undermines the government’s or occupier’s power by portraying them as illegitimate and incapable of effective governance in the eyes of the population. In order for an adversary to be susceptible to the effects of insurgency or resistance, he must have some overt infrastructure and legitimacy that are vulnerable to attacks (physical or psychological). In this respect the “target recipient” does not have to be a state government, but it does have to possess state-like characteristics (e.g. the elements of national power), such as those similar to an occupying military force exercising authority through martial law. It is not uncommon for military planners to overfocus on the quantifiable aspects related to the more familiar armed conflict and underfocus on the somewhat less quantifiable and less familiar aspects of subversion.
While different insurgencies are unique to their own strategy and environment, U.S. Army Special Forces has long utilized a doctrinal construct that serves as an extremely useful frame of reference for describing the actual configuration of a resistance movement or insurgency. This construct depicts three components common to insurgencies: the guerrillas, the underground and the auxiliary. Without an understanding and appreciation for the various components (guerrillas, underground and auxiliary) and their relation to each other, it would be difficult to comprehend the whole of the organization based solely on what is seen. In this regard, insurgencies are sometimes compared to icebergs, with a distinct portion above the surface (the guerrillas) and a much larger portion concealed below the surface (the underground and auxiliary).
…
The Guerrillas
Guerrillas are the overt military component of a resistance movement or insurgency. As the element that will engage the enemy in combat operations, the guerrilla is at a significant disadvantage in terms of training, equipment and fire power. For all his disadvantages, he has one advantage that can offset this unfavorable balance…the initiative. In all his endeavors, the guerrilla commander must strive to maintain and protect this advantage. The guerrilla only attacks the enemy when he can generate a relative (albeit temporary) state of superiority. The guerrilla commander must avoid decisive engagements, thereby denying the enemy the opportunity to recover and regain their actual superiority and bring it to bear against his guerrilla force. The guerrilla force is only able to generate and maintain this advantage in areas where they have significant familiarity with the terrain and a connection with the local population that allows them to harness clandestine support.
The Underground
The underground is a cellular organization within the resistance movement or insurgency that has the ability to conduct operations in areas that are inaccessible to guerrillas, such as urban areas under the control of the local security forces. The underground can function in these areas because it operates in a clandestine manner, resulting in its members not being afforded legal belligerent status under any international conventions.
Examples of these functions include:
• Intelligence and counterintelligence networks
• Subversive radio stations
• Propaganda networks that control newspaper/leaflet print shops and or Web pages
• Special material fabrication (false identification, explosives, weapons, munitions)
• Control of networks for moving personnel and logistics
• Acts of sabotage (in urban centers)
• Clandestine medical facilities
Underground members are normally not active members of the community and their service is not a product of their normal life or position within the community. They operate by maintaining compartmentalization and having their auxiliary workers assume most of the risk. The functions of the underground largely enable the resistance movement to impact the urban areas.
…
The development of organized resistance in a territory must follow a carefully planned sequence of steps, each of which must be completed successfully before the following step can be safely taken.
1. Organization of clandestine networks. The first essential is to be able to move resistance organizers and propaganda material into the territory; support them clandestinely, and provide for continuing communications with adjoining resistance bases. These networks also pave the way for later active resistance by developing active support from a significant part of the total population.
2. Organization of intelligence and counterintelligence networks. No resistance organization can operate successfully unless it is fully protected by a deep intelligence screen. Equally, it is necessary to establish effective counterintelligence nets to verify every participant’s loyalty to the movement and, through penetrations into the enemy security services, to identify those who are acting as double agents.
3. Organization of local area commands in areas of favorable terrain. Such area commands will be the forerunners of later fully-armed guerrilla units, and will provide the transition between the entirely clandestine civilian organization and the mobile armed guerrilla force living in forests and other inaccessible areas. These commands will be given full responsibility for the organization of their geographical areas, including the organization of supplies, intelligence, propaganda and communications. As the area commands continue to develop, they may further subdivide the area into subordinate sector commands. These sector commands will carry the brunt of attacks against enemy installations and forces, while drawing support from the area commands.
4. The development of direct communications with the outside. At approximately this point in the development of resistance in the area, direct communication with the outside world can be established, although it may be established in some cases at an earlier stage.
5. Gradual development of free territory in the hinterlands. As the fighting units further develop in strength, it will be possible to establish relatively large areas that are normally free of any enemy troops and all enemy controls over the civil population. At this point, these “liberated” territories can begin to prepare and organize to replace the enemy structure on the completion of the conflict.
…
U.S. UW Efforts from 1951- 2003
U.S. Military and CIA in Korea (1951-1953)
The U.S. military was largely caught off guard by the conflict in Korea. Despite tremendous success during World War II, the capability to support resistance movements was almost completely removed from within the Department of Defense by 1950. A fraction of the capability was retained in the newly established CIA, but proved to be inadequate to meet the needs of a full-scale campaign. Overall this campaign effort was effective, but not nearly as effective as it could have been. The inability to establish sustainable guerrilla areas on the mainland hampered long-term operations. The U.S. provided personnel who were not familiar with the concepts and techniques associated with resistance operations. The military’s best attempt to find a matching experience set was to send basic-training instructors. Operations made wide use of displaced refugees as recruits and were generally launched from outside enemy-controlled areas and resembled temporary raiding parties.
The resulting operations caused the military to re-think its position on a military force trained for this type of operation. In 1952, the first official U.S. Special Forces organization was established. In 1953, some of the newly developed Special Forces deployed to Korea. However, they were not employed as intended and generally used as replacements.
CIA in Albania and Latvia (1951-1955)
The CIA used these opportunities to test theories for rolling back communist domination of Eastern Europe. These locations were chosen due to their relatively small size. Both efforts were failures. From these efforts the CIA theoretically learned three lessons. First, techniques used during wartime do not apply in peacetime (emphasizing the need for covert methods of operating). Secondly, tyrannical regimes that have had the benefit of years to consolidate power have a much greater hold over the population than a newly occupying power. Subsequently, there must be a weakness that can be exploited. This specifically equates to the ability of the state to exert control over the population and the population’s willingness to resist. Lastly prior to any guerrilla operations, a sufficient base of support must be present in the form of auxiliary and underground networks, although the least visible and understood, it is the most time-consuming and difficult to establish. Developing guerrilla elements is relatively easy; keeping them alive is much harder. Trying to jump ahead to developing guerrillas is like trying to build the upper floors of a house before laying the foundation.
CIA in Guatemala (1954)
In 1954, various influential businesses persuaded members of the media as well as members of the U.S. government that the Arbenz government, which was the elected government of Guatemala, was leaning toward communism. The U.S. government, through the State Department and the CIA, convinced several senior Guatemalan military officials to overthrow Arbenz’s government. This effort was supported by a highly successful psychological campaign that portrayed the overthrow as part of a much larger movement. Although widely suspected, the U.S. government’s hand in this effort remained ambiguous for a couple of years until it was finally exposed as the follow-on governments were accused of being inept dictators by the Guatemalan population. Although often portrayed as a success, the hindsight of history now reveals the Guatemalan operations were in fact “shameful, particularly so because the five decades of governments that followed the 1954 coup were far more oppressive than Arbenz’s elected government. Aside from the morality, there were other unfortunate legacies of the Guatemalan “success”. Allen Dulles used it as a model in advising President Kennedy seven years later to pursue the ill-fated Bay of Pigs invasion of Cuba.” The Guatemalan effort serves as an example of tactical success in isolation of any wider sound strategy, particularly in the form of long-term effects on a region. This effort coupled with the coup of the elected Mossedegh government in Iran (1953) provided a strong argument to de-legitimize any U.S. claim to support democracy for the remainder of the Cold War.
CIA in Tibet (1955-1969)
While this campaign was very well executed, no level of tactical success in Tibet could defeat the Chinese. The National Volunteer Defense Army (NVDA) did successfully delay the Chinese victory by several years. In 1960, the first U2 aircraft was shot down. Although not related to the covert support efforts, the subsequent compromise of U.S. clandestine overflights of communist territory caused the U.S. President to suspend all further clandestine overflights, which essentially crippled the air resupply to the Tibetan guerrillas. A year later, the catastrophic failure of UW efforts in Cuba nearly ended the Tibetan program. The last resupply airdrop to Tibetan resistance forces took place in 1965. Although the U.S. ceased all support to the Tibetan resistance in 1969 as a condition for eventually establishing diplomatic relations with China, the Tibetan resistance continued to resist into the 1970s. Two lessons can be drawn from the Tibetan efforts. As an alternative to prior U.S. efforts where advisers infiltrated into the combat area, in this effort selected personnel were extracted, trained and reinserted with reasonable success. The nature of the offensive operations in this type of campaign is different compared to operations that culminate in support of a TBD D-day. Without the eventual introduction of conventional forces (i.e., a D-Day) the combat operations need to be sustained for an undetermined period of time and therefore conducted in a manner that does not compromise the supporting resistance infrastructure.
CIA in Indonesia (1957-1958)
Fearing that the Indonesian government was leaning toward communism, after a declaration of neutrality, the CIA supported several Indonesian military officers who claimed to control a rebel army made up of former military units. During this operation, the CIA chose to employ refitted B-26 bombers and P-51 fighter aircraft flown by mercenaries from various countries. The rebel army had little popular support among the population while the Indonesian government still held control of the majority of its military. During the course of the support effort, direct American support was exposed several times causing embarrassment to the United States. This situation finally came to a head when a B-26 flown by an American CIA contract employee was shot down and the pilot was captured by Indonesian forces. Although the CIA was confident that no link could be made between the U.S. government and the pilot, he in fact had documents on him that indeed did link him to Clark Air Force Base. The incident had been a major scandal for the Eisenhower administration. Soon after the scandal broke, the CIA ceased all support and the Indonesian government crushed the rebellion with conventional military forces. A particularly interesting point in this case is that Indonesia was not considered a belligerent state when the decision was made to support the rebels. The U.S. State Department maintained relations with the government and had an embassy in Jakarta during the operation.
CIA in Cuba and the Bay of Pigs (1961)
The CIA applied a variety of the nine-phase model, consummate with covert operations, but attempted a culminating D-day style uprising rather than sustained guerrilla warfare. There were some reasonably successful efforts to develop underground elements, but these efforts were not coordinated with the larger campaign. They did not employ appropriate techniques to conceal the operation or the U.S. participation. The “resistance movement” was generally manufactured, rather than fostered from an already existing one in country. Lastly operational security in the United States was a complete failure.
The lessons of the Bay of Pigs are as follows:
• Resistance forces require clandestine infrastructure and support mechanisms.
• These operations require planners and advisers who understand the dynamics of insurgency/ resistance operations (including guerrilla warfare and underground operations and how they integrate with each other).
• When there is a population involved, the psychological piece (i.e. propaganda and subversion) may be more important than the physical piece (guerrilla warfare).
• This type of effort requires the ability to conduct the full spectrum of nonattributable psychological operations in conjunction with the physical piece.
• Any organization involved in UW (particularly peacetime) needs a comprehensive understanding and process for oversight, C2 and OPSEC for covert and clandestine ops.
CIA and Special Forces in Laos (1959-1962)
In 1959 the United States began a secret program called White Star. This opera tion was coordinated in conjunction with the French government to train Laotian Army Battalions. Personnel came from the 1st and 7th Special Forces groups. In December of 1960, a group of Laotian paratroopers attempted a coup d’etat that caused the withdrawal of the French advisers, whom had previously restricted American military involvement to the role of trainers. During the counter coup, Special Forces personnel advised the remaining parachute forces to rout the rebel paratroopers, winning great favor with the Laotian government. By 1961 the original contingent of nine ODAs had grown to 21 ODAs and the effort expanded to include an advisory role. The counterinsurgency efforts also included training for selected tribal elements in civil defense. A concept was developed to expand the tribal operations [covertly] to the rural areas in northern Laos parallel to the North Vietnamese border. Special Forces also undertook two major unconventional programs in northern Laos (as compared to the other counterinsurgency programs). Both programs concentrated on training minority tribal groups as irregular forces capable of conducting guerrilla warfare across rugged terrain or behind the enemy lines. The Kha program, the second unconventional training activity, was designed by Special Forces to use the various Kha tribes in harassing and raiding enemy rear bases and installations especially along the Ho Chi Minh trail, the primary overland North Vietnamese resupply route across Laos into South Vietnam and Cambodia. Unfortunately higher authorities refused to adopt the Special Forces suggestions regarding the newly created guerrilla movements and due to political decisions the Meo and Kha programs never realized their full potential. After 1962, the effort was dramatically reduced when Laos declared its neutrality. While the Special Forces involvement ended, U.S. support continued covertly by the CIA to General Vang Pao’s “Army Clandestine” for another decade.
The counterinsurgency programs in Laos are sometimes misrepresented as UW. The counterinsurgency efforts conducted against the Pathet Lao in southern Laos were significantly different from the proposed UW efforts envisioned for northern Laos and North Vietnam. The proposed UW efforts were intended to interdict and harass regular North Vietnamese forces who were occupying Laotian territory in order to establish supply networks into South Vietnam which later became the Ho Chi Minh trail.
CIA and Special Forces in North Vietnam (1961-1964)
In 1960, the CIA began attempts to establish agent networks within North Vietnam. The program, called Leaping Lena, was highly penetrated by double agents and never produced any viable results beyond a handful of questionable agents. The hopes of conducting UW against North Vietnam had diminished by 1964 when the military assumed control of the operation. The Special Observations Group’s or SOG’s actual name had been UW Task Force. The Special Forces concluded Leaping Lena by parachuting the questionable trainees over North Vietnam and terminating further support. From this point on operational efforts focused on portraying a false resistance movement intended to confuse the North Vietnamese.
The program shifted to covert coastal raids (similar to North Korea) and covert reconnaissance and interdiction missions into Laos and Cambodia. Special Forces in
South Vietnam (1957-1975)
As a result of the increased concern over communist subversion in Vietnam and at President John F. Kennedy’s insistence, SF added COIN to its list of missions in 1961, making a significant point that it is different from UW and not a subcomponent of it. The majority of Special Forces efforts in South Vietnam were not UW but rather COIN, specifically the Civilian Irregular Defense Group, or CIDG, the Provisional Reconnaissance Units, or PRU, and Mike Forces.
The CIDG were indigenous irregulars who provided a vital counterinsurgency role of area denial by securing hamlets.
The PRU were indigenous platoons developed as part of the CIA Phoenix program. These elements identified insurgent support infrastructure (or underground and auxiliary members). This effort could be called counterterrorism, or counterinsurgency. SOG also developed platoon- and company-size strike forces called Mobile Guerrilla Forces and Bright Light teams. The Mobile Guerrilla Forces acted as quick-reaction forces for recon teams in contact with Viet Cong elements and the Bright Light teams conducted raids to rescue allied prisoners and downed air crews. The Mobile Guerrilla Forces conducted four static line jumps during their operations and the Bright Light teams conducted nearly 100 raids (in S. Vietnam, Laos and Cambodia). While these efforts utilized recruited indigenous personnel, they were not considered UW. In 1970, this program disbanded and transformed to an adviser program for Vietnamese and Cambodian counterguerrilla forces.
See Colonel (R) Al Paddock’s (the author of U.S. Army Special Warfare and Its Origins) comments regarding a review of Imperial Grunts (and the misuse of the term UW) in the March-April 2006 Special Warfare. Paddock, a Special Forces veteran of SOG and the CIDG mission stated, “In truth, the mobile guerrilla forces can be more likened to World War II long range penetration units such as Merrill’s Marauders or Wingate’s Chindits. This is not to say that the Mobile Guerrilla forces did not perform useful or heroic missions. They did, but not as guerrillas.”
CIA and Special Forces in Nicaragua and Honduras (1980-1988)
The United States supported various resistance groups that opposed the socialist Nicaraguan Sandinista government. These groups, which operated from Honduras and Costa Rica, collectively became known at the Contras. RAND after action reviews from this covert operation criticize it for being artificially manufactured and not having legitimate support inside Nicaragua. “This effort was developed almost entirely along military lines and advisors lacked practical understanding of the requirements to develop and run an insurgency.” (U.S. Support to the Nicaraguan Resistance, 1989 and The U.S. Army’s Role in Counterinsurgency and Insurgency, 1990). The Contras have been compared to paid mercenaries with no real political component and connection to the population. This may partially explain the lack of guerrilla bases inside Nicaragua. The other part of the explanation comes from the strength of the government counterguerrilla forces. The Contras would not have survived without the safe havens across neutral borders. Ultimately the covert operation, which became widely exposed due to the Iran-Contra scandal, ended badly for the U.S. government and caused feelings reminiscent to the post Bay of Pigs-era regarding covert support to insurgents.
CIA and Special Forces in Pakistan and Afghanistan (1980-1991)
While this covert effort remained primarily training and material support, it grew to the point that the potential risk of providing indigenous guerrillas with U.S.-man ufactured lethal aid (such as Stinger anti-aircraft missiles) became acceptable. U.S. personnel established supporting bases in Pakistan (following the nine-phase model mentioned previously). There are several lessons of the operations in Afghanistan. Covert operations of this nature require neighboring partner countries to develop support bases. This necessity causes a level of compromise in U.S. objectives. Pakistan controlled the distribution of U.S. support to rebel groups and subsequently was able to alter the balance of power among resistance group in Pakistan’s favor. Afghanistan highlights the importance of maintaining perspective of long-term goals and not allowing enthusiasm to overtake decision making. The importance of a feasibility assessment before the decision to throw support at a group can’t be overemphasized. Any support will change the balance of power and dynamics of the region. When a group is supported, engagement should continue until post-conflict stability is achieved. The Taliban came to power because the U.S. ceased support to Northern Alliance troops and other Islamic nations did not cease their support to these radical groups.
The sensitivity of these types of covert operations demands that operational commands interact directly with the national command authority and not through various “go betweens” in a long military chain of command.
Cold War Contingency Plans for Scandinavia and Europe. (1952-1989)
Although not executed, it is worth including the contingency plans that Special Forces would have implemented in the event of escalated hostilities in Europe during the Cold War. There is little debate as to the nature of what SF was prepared to do in this event; unfortunately, these plans count for little as they fade farther away with each passing day. There would be much value to declassifying some of this information for the betterment of the military’s knowledge. At the height of the Cold War, 10th Special Forces Group remained prepared to employ 50 plus detachments across the whole of Europe. In addition to 10th SF Group, Det-A, although manned with SF Soldiers not officially part of 10th SF Group, remained prepared to conduct UW with its six detachments specifically in the urban areas of Berlin and northeast Germany.
Kuwait (1990-1991)
Following the Iraq invasion of Kuwait in August 1990, several isolated pockets of Kuwaiti resistance formed. Although the U.S. was in contact with elements of the Kuwaiti government in-exile in Saudi Arabia, efforts to support and coordinate the resistance forces was poorly integrated with the main military campaign planning. Planning efforts were too little and way too late. Although Kuwait offered little favorable terrain to support resistance operations, ad hoc resistance forces did operate without U.S. support until their eventual destruction. The operation may have proven unfeasible, but other circumstances rendered that debate irrelevant. Post-war after-action reviews indicated a general lack of organic capability, a lack of understanding of the requirements for supporting a resistance throughout the Department of Defense (to include special-operations forces) and a lack of synchronization between DoD and the interagency.
NSA – The National Security Agency after the Bin Laden Killing
CONFIDENTIAL from the FBI – Guilford Resident Pleads Guilty to Illegal Gambling and Tax Charges
David B. Fein, United States Attorney for the District of Connecticut, today announced that DOMINIC J. ACQUARULO, JR., 42, of Guilford, waived his right to indictment and pleaded guilty yesterday, March 13, before United States District Judge Janet Bond Arterton in New Haven to illegal gambling and tax offenses.
According to court documents and statements made in court, between 2006 and 2008, ACQUARULO operated an illegal sports bookmaking business that involved a number of sub-bookmakers, each of whom had a network of bettors. As part of his gambling business, ACQUARULO used two online betting websites and he provided each sub-bookmaker with passwords to the sites so that each bettor in their network would be able to place bets through an individual account. On behalf of ACQUARULO, the sub-bookmakers collected losses from the bettors and paid out any winnings. The sub-bookmakers received a 10 percent commission on losses they collected from bettors, and they provided the remaining funds to ACQUARULO.
ACQUARULO also utilized at least two other individuals to receive and count funds collected from the sub-bookmakers, and to provide funds to sub-bookmakers to pay out to winning bettors.
Between 2006 and 2008, ACQUARULO also operated Shoreline Finance and Marketing Corporation, a mortgage brokerage company. During this time, ACQUARULO employed a close associate as a mortgage loan officer at the business. With ACQUARULO’s knowledge, his associate used corporate credit cards and corporate checks to pay for numerous personal expenses, including rent for her apartment, car lease payments, jewelry, and clothing. She then classified these payments and purchases, which totaled more than $19,000, as business expenses in the bookkeeping records of the business. As a result, ACQUARULO underreported his income generated from his business on his 2007 individual income tax return, resulting in a tax loss of $6,170.
In addition, ACQUARULO’s gross income in 2008 was $178,860, but he failed to file a 2008 tax return by October 15, 2009, as required. ACQUARULO filed his Form 1040 in May 2010, approximately 10 months after he was interviewed by federal agents and informed of this pending investigation.
ACQUARULO pleaded guilty to one count of operating an illegal gambling business, one count of filing a false tax return, and one count of willfully failing to timely file a tax return. Judge Arterton has scheduled sentencing for June 1, 2012, at which time ACQUARULO faces a maximum term of imprisonment of nine years and a fine of up to $600,000.
This matter is being investigated by the Federal Bureau of Investigation and the Internal Revenue Service-Criminal Investigation. The case is being prosecuted by Assistant United States Attorney Anastasia Enos King.
Unveiled – 10 Toxic Chemical Sites Added to EPA Superfund
[Federal Register Volume 77, Number 51 (Thursday, March 15, 2012)] [Proposed Rules] [Pages 15344-15351] From the Federal Register Online via the Government Printing Office [www.gpo.gov] [FR Doc No: 2012-6328] ----------------------------------------------------------------------- ENVIRONMENTAL PROTECTION AGENCY 40 CFR Part 300 [EPA-HQ-SFUND-1994-0003, EPA-HQ-SFUND-2012-0062, 0063, 0064, 0065, 0066, 0067, 0068, 0069, 0070, 0071, 0146, and 0147; FRL-9647-4] RIN 2050-AD75 National Priorities List, Proposed Rule No. 56 AGENCY: Environmental Protection Agency. ACTION: Proposed rule. ----------------------------------------------------------------------- SUMMARY: The Comprehensive Environmental Response, Compensation, and Liability Act (``CERCLA'' or ``the Act''), as amended, requires that the National Oil and Hazardous Substances Pollution Contingency Plan (``NCP'') include a list of national priorities among the known releases or threatened releases of hazardous substances, pollutants or contaminants throughout the United States. The National Priorities List (``NPL'') constitutes this list. The NPL is intended primarily to guide the Environmental Protection Agency (``EPA'' or ``the agency'') in determining which sites warrant further investigation. These further investigations will allow the EPA to assess the nature and extent of public health and environmental risks associated with the site and to determine what CERCLA-financed remedial action(s), if any, may be appropriate. This rule proposes to: Add 10 sites to the General Superfund section of the NPL; remove the Construction Completion List column notation and footnote description; and correct the partial deletion notation. This rule also withdraws one site from proposal to the Federal Facilities section of the NPL. DATES: Comments regarding any of these proposed listings must be submitted (postmarked) on or before May 14, 2012. ADDRESSES: Identify the appropriate Docket Number from the table below. Docket Identification Numbers by Site --------------------------------------------------------------------------------------- Site name City/county, state Docket ID No. --------------------------------------------------------------------------------------- Cedar Chemical Corporation........... West Helena, AR........ EPA-HQ-SFUND-2012-0062. Fairfax St. Wood Treaters............ Jacksonville, FL....... EPA-HQ-SFUND-2012-0063. Macon Naval Ordnance Plant........... Macon, GA.............. EPA-HQ-SFUND-2012-0064. Bautsch-Gray Mine.................... Galena, IL............. EPA-HQ-SFUND-2012-0065. EVR-Wood Treating/Evangeline Refining Jennings, LA........... EPA-HQ-SFUND-2012-0066. Company. Holcomb Creosote Co.................. Yadkinville, NC........ EPA-HQ-SFUND-2012-0067. Orange Valley Regional Ground Water West Orange/Orange, NJ. EPA-HQ-SFUND-2012-0068. Contamination. Jackpile-Paguate Uranium Mine........ Laguna Pueblo, NM...... EPA-HQ-SFUND-2012-0069. West Troy Contaminated Aquifer....... Troy, OH............... EPA-HQ-SFUND-2012-0070. Circle Court Ground Water Plume...... Willow Park, TX........ EPA-HQ-SFUND-2012-0071. --------------------------------------------------------------------------------------- Submit your comments, identified by the appropriate Docket number, by one of the following methods: www.regulations.gov: Follow the online instructions for submitting comments. Email: superfund.docket@epa.gov. Mail: Mail comments (no facsimiles or tapes) to Docket Coordinator, Headquarters, U.S. Environmental Protection Agency, CERCLA Docket Office (Mail Code 5305T), 1200 Pennsylvania Avenue NW., Washington, DC 20460. Hand Delivery or Express Mail: Send comments (no facsimiles or tapes) to Docket Coordinator, Headquarters, U.S. Environmental Protection Agency, CERCLA Docket Office, 1301 Constitution Avenue NW., EPA West, Room 3334, Washington, DC 20004. Such deliveries are accepted only during the Docket's normal hours of operation (8:30 a.m. to 4:30 p.m., Monday through Friday, excluding federal holidays). Instructions: Direct your comments to the appropriate Docket number (see table above). The EPA's policy is that all comments received will be included in the public Docket without change and may be made available online at www.regulations.gov, including any personal information provided, unless the comment includes information claimed to be Confidential Business Information (CBI) or other information whose disclosure is restricted by statute. Do not submit information that you consider to be CBI or otherwise protected through www.regulations.gov or email. The www.regulations.gov Web [[Page 15345]] site is an ``anonymous access'' system; that means the EPA will not know your identity or contact information unless you provide it in the body of your comment. If you send an email comment directly to the EPA without going through www.regulations.gov, your email address will be automatically captured and included as part of the comment that is placed in the public Docket and made available on the Internet. If you submit an electronic comment, the EPA recommends that you include your name and other contact information in the body of your comment and with any disk or CD-ROM you submit. If the EPA cannot read your comment due to technical difficulties and cannot contact you for clarification, the EPA may not be able to consider your comment. Electronic files should avoid the use of special characters, any form of encryption, and be free of any defects or viruses. For additional Docket addresses and further details on their contents, see section II, ``Public Review/ Public Comment,'' of the Supplementary Information portion of this preamble. FOR FURTHER INFORMATION CONTACT: Terry Jeng, phone: (703) 603-8852, email: jeng.terry@epa.gov, Site Assessment and Remedy Decisions Branch, Assessment and Remediation Division, Office of Superfund Remediation and Technology Innovation (Mail Code 5204P), U.S. Environmental Protection Agency, 1200 Pennsylvania Avenue NW., Washington, DC 20460; or the Superfund Hotline, phone (800) 424-9346 or (703) 412-9810 in the Washington, DC, metropolitan area. SUPPLEMENTARY INFORMATION: Table of Contents I. Background A. What are CERCLA and SARA? B. What is the NCP? C. What is the National Priorities List (NPL)? D. How are sites listed on the NPL? E. What happens to sites on the NPL? F. Does the NPL define the boundaries of sites? G. How are sites removed from the NPL? H. May the EPA delete portions of sites from the NPL as they are cleaned up? I. What is the Construction Completion List (CCL)? J. What is the sitewide ready for anticipated use measure? II. Public Review/Public Comment A. May I review the documents relevant to this proposed rule? B. How do I access the documents? C. What documents are available for public review at the headquarters docket? D. What documents are available for public review at the regional dockets? E. How do I submit my comments? F. What happens to my comments? G. What should I consider when preparing my comments? H. May I submit comments after the public comment period is over? I. May I view public comments submitted by others? J. May I submit comments regarding sites not currently proposed to the NPL? III. Contents of This Proposed Rule A. Proposed Additions to the NPL B. Withdrawal of Site From Proposal to the NPL C. Proposal To Remove Construction Completion List Column Notation and Footnote Description D. Proposed Correction of Partial Deletion Notation in Table 1 IV. Statutory and Executive Order Reviews A. Executive Order 12866: Regulatory Planning and Review 1. What is Executive Order 12866? 2. Is this proposed rule subject to Executive Order 12866 review? B. Paperwork Reduction Act 1. What is the Paperwork Reduction Act? 2. Does the Paperwork Reduction Act apply to this proposed rule? C. Regulatory Flexibility Act 1. What is the Regulatory Flexibility Act? 2. How has the EPA complied with the Regulatory Flexibility Act? D. Unfunded Mandates Reform Act 1. What is the Unfunded Mandates Reform Act (UMRA)? 2. Does UMRA apply to this proposed rule? E. Executive Order 13132: Federalism 1. What is Executive Order 13132? 2. Does Executive Order 13132 apply to this proposed rule? F. Executive Order 13175: Consultation and Coordination With Indian Tribal Governments 1. What is Executive Order 13175? 2. Does Executive Order 13175 apply to this proposed rule? G. Executive Order 13045: Protection of Children From Environmental Health and Safety Risks 1. What is Executive Order 13045? 2. Does Executive Order 13045 apply to this proposed rule? H. Executive Order 13211: Actions That Significantly Affect Energy Supply, Distribution or Use 1. What is Executive Order 13211? 2. Does Executive Order 13211 apply to this proposed rule? I. National Technology Transfer and Advancement Act 1. What is the National Technology Transfer and Advancement Act? 2. Does the National Technology Transfer and Advancement Act apply to this proposed rule? J. Executive Order 12898: Federal Actions To Address Environmental Justice in Minority Populations and Low-Income Populations 1. What is Executive Order 12898? 2. Does Executive Order 12898 apply to this proposed rule? I. Background A. What are CERCLA and SARA? In 1980, Congress enacted the Comprehensive Environmental Response, Compensation, and Liability Act, 42 U.S.C. 9601-9675 (``CERCLA'' or ``the Act''), in response to the dangers of uncontrolled releases or threatened releases of hazardous substances, and releases or substantial threats of releases into the environment of any pollutant or contaminant that may present an imminent or substantial danger to the public health or welfare. CERCLA was amended on October 17, 1986, by the Superfund Amendments and Reauthorization Act (``SARA''), Public Law 99-499, 100 Stat. 1613 et seq. B. What is the NCP? To implement CERCLA, the EPA promulgated the revised National Oil and Hazardous Substances Pollution Contingency Plan (``NCP''), 40 CFR part 300, on July 16, 1982 (47 FR 31180), pursuant to CERCLA section 105 and Executive Order 12316 (46 FR 42237, August 20, 1981). The NCP sets guidelines and procedures for responding to releases and threatened releases of hazardous substances or releases or substantial threats of releases into the environment of any pollutant or contaminant that may present an imminent or substantial danger to the public health or welfare. The EPA has revised the NCP on several occasions. The most recent comprehensive revision was on March 8, 1990 (55 FR 8666). As required under section 105(a)(8)(A) of CERCLA, the NCP also includes ``criteria for determining priorities among releases or threatened releases throughout the United States for the purpose of taking remedial action and, to the extent practicable taking into account the potential urgency of such action, for the purpose of taking removal action.'' ``Removal'' actions are defined broadly and include a wide range of actions taken to study, clean up, prevent or otherwise address releases and threatened releases of hazardous substances, pollutants or contaminants (42 U.S.C. 9601(23)). C. What is the National Priorities List (NPL)? The NPL is a list of national priorities among the known or threatened releases of hazardous substances, pollutants or contaminants throughout the United States. The list, which is appendix B of the NCP (40 CFR Part 300), was required under section 105(a)(8)(B) of CERCLA, as amended. Section 105(a)(8)(B) defines the NPL as a list of ``releases'' and the highest priority ``facilities'' and [[Page 15346]] requires that the NPL be revised at least annually. The NPL is intended primarily to guide the EPA in determining which sites warrant further investigation to assess the nature and extent of public health and environmental risks associated with a release of hazardous substances, pollutants or contaminants. The NPL is only of limited significance, however, as it does not assign liability to any party or to the owner of any specific property. Also, placing a site on the NPL does not mean that any remedial or removal action necessarily need be taken. For purposes of listing, the NPL includes two sections, one of sites that are generally evaluated and cleaned up by the EPA (the ``General Superfund Section''), and one of sites that are owned or operated by other federal agencies (the ``Federal Facilities Section''). With respect to sites in the Federal Facilities Section, these sites are generally being addressed by other federal agencies. Under Executive Order 12580 (52 FR 2923, January 29, 1987) and CERCLA section 120, each federal agency is responsible for carrying out most response actions at facilities under its own jurisdiction, custody or control, although the EPA is responsible for preparing a Hazard Ranking System (``HRS'') score and determining whether the facility is placed on the NPL. D. How are sites listed on the NPL? There are three mechanisms for placing sites on the NPL for possible remedial action (see 40 CFR 300.425(c) of the NCP): (1) A site may be included on the NPL if it scores sufficiently high on the HRS, which the EPA promulgated as appendix A of the NCP (40 CFR Part 300). The HRS serves as a screening tool to evaluate the relative potential of uncontrolled hazardous substances, pollutants or contaminants to pose a threat to human health or the environment. On December 14, 1990 (55 FR 51532), the EPA promulgated revisions to the HRS partly in response to CERCLA section 105(c), added by SARA. The revised HRS evaluates four pathways: ground water, surface water, soil exposure and air. As a matter of agency policy, those sites that score 28.50 or greater on the HRS are eligible for the NPL. (2) Pursuant to 42 U.S.C. 9605(a)(8)(B), each state may designate a single site as its top priority to be listed on the NPL, without any HRS score. This provision of CERCLA requires that, to the extent practicable, the NPL include one facility designated by each state as the greatest danger to public health, welfare or the environment among known facilities in the state. This mechanism for listing is set out in the NCP at 40 CFR 300.425(c)(2). (3) The third mechanism for listing, included in the NCP at 40 CFR 300.425(c)(3), allows certain sites to be listed without any HRS score, if all of the following conditions are met: The Agency for Toxic Substances and Disease Registry (ATSDR) of the U.S. Public Health Service has issued a health advisory that recommends dissociation of individuals from the release. The EPA determines that the release poses a significant threat to public health. The EPA anticipates that it will be more cost-effective to use its remedial authority than to use its removal authority to respond to the release. The EPA promulgated an original NPL of 406 sites on September 8, 1983 (48 FR 40658) and generally has updated it at least annually. E. What happens to sites on the NPL? A site may undergo remedial action financed by the Trust Fund established under CERCLA (commonly referred to as the ``Superfund'') only after it is placed on the NPL, as provided in the NCP at 40 CFR 300.425(b)(1). (``Remedial actions'' are those ``consistent with permanent remedy, taken instead of or in addition to removal actions. * * *'' 42 U.S.C. 9601(24).) However, under 40 CFR 300.425(b)(2) placing a site on the NPL ``does not imply that monies will be expended.'' The EPA may pursue other appropriate authorities to respond to the releases, including enforcement action under CERCLA and other laws. F. Does the NPL define the boundaries of sites? The NPL does not describe releases in precise geographical terms; it would be neither feasible nor consistent with the limited purpose of the NPL (to identify releases that are priorities for further evaluation), for it to do so. Indeed, the precise nature and extent of the site are typically not known at the time of listing. Although a CERCLA ``facility'' is broadly defined to include any area where a hazardous substance has ``come to be located'' (CERCLA section 101(9)), the listing process itself is not intended to define or reflect the boundaries of such facilities or releases. Of course, HRS data (if the HRS is used to list a site) upon which the NPL placement was based will, to some extent, describe the release(s) at issue. That is, the NPL site would include all releases evaluated as part of that HRS analysis. When a site is listed, the approach generally used to describe the relevant release(s) is to delineate a geographical area (usually the area within an installation or plant boundaries) and identify the site by reference to that area. However, the NPL site is not necessarily coextensive with the boundaries of the installation or plant, and the boundaries of the installation or plant are not necessarily the ``boundaries'' of the site. Rather, the site consists of all contaminated areas within the area used to identify the site, as well as any other location where that contamination has come to be located, or from where that contamination came. In other words, while geographic terms are often used to designate the site (e.g., the ``Jones Co. plant site'') in terms of the property owned by a particular party, the site, properly understood, is not limited to that property (e.g., it may extend beyond the property due to contaminant migration), and conversely may not occupy the full extent of the property (e.g., where there are uncontaminated parts of the identified property, they may not be, strictly speaking, part of the ``site''). The ``site'' is thus neither equal to, nor confined by, the boundaries of any specific property that may give the site its name, and the name itself should not be read to imply that this site is coextensive with the entire area within the property boundary of the installation or plant. In addition, the site name is merely used to help identify the geographic location of the contamination, and is not meant to constitute any determination of liability at a site. For example, the name ``Jones Co. plant site,'' does not imply that the Jones company is responsible for the contamination located on the plant site. The EPA regulations provide that the Remedial Investigation (``RI'') ``is a process undertaken * * * to determine the nature and extent of the problem presented by the release'' as more information is developed on site contamination, and which is generally performed in an interactive fashion with the Feasibility Study (``FS'') (40 CFR 300.5). During the RI/FS process, the release may be found to be larger or smaller than was originally thought, as more is learned about the source(s) and the migration of the contamination. However, the HRS inquiry focuses on an evaluation of the threat posed and therefore the boundaries of the release need not be exactly defined. Moreover, it generally is impossible to discover the full extent of where the contamination ``has come to be located'' before all necessary studies and remedial work are completed at a site. Indeed, the known boundaries of the contamination can be expected to change over time. Thus, in [[Page 15347]] most cases, it may be impossible to describe the boundaries of a release with absolute certainty. Further, as noted above, NPL listing does not assign liability to any party or to the owner of any specific property. Thus, if a party does not believe it is liable for releases on discrete parcels of property, it can submit supporting information to the agency at any time after it receives notice it is a potentially responsible party. For these reasons, the NPL need not be amended as further research reveals more information about the location of the contamination or release. G. How are sites removed from the NPL? The EPA may delete sites from the NPL where no further response is appropriate under Superfund, as explained in the NCP at 40 CFR 300.425(e). This section also provides that the EPA shall consult with states on proposed deletions and shall consider whether any of the following criteria have been met: (i) Responsible parties or other persons have implemented all appropriate response actions required; (ii) All appropriate Superfund-financed response has been implemented and no further response action is required; or (iii) The remedial investigation has shown the release poses no significant threat to public health or the environment, and taking of remedial measures is not appropriate. H. May the EPA delete portions of sites from the NPL as they are cleaned up? In November 1995, the EPA initiated a policy to delete portions of NPL sites where cleanup is complete (60 FR 55465, November 1, 1995). Total site cleanup may take many years, while portions of the site may have been cleaned up and made available for productive use. I. What is the construction completion list (CCL)? The EPA also has developed an NPL construction completion list (``CCL'') to simplify its system of categorizing sites and to better communicate the successful completion of cleanup activities (58 FR 12142, March 2, 1993). Inclusion of a site on the CCL has no legal significance. Sites qualify for the CCL when: (1) Any necessary physical construction is complete, whether or not final cleanup levels or other requirements have been achieved; (2) the EPA has determined that the response action should be limited to measures that do not involve construction (e.g., institutional controls); or (3) the site qualifies for deletion from the NPL. For the most up-to-date information on the CCL, see the EPA's Internet site at http://www.epa.gov/superfund/cleanup/ccl.htm. J. What is the sitewide ready for anticipated use measure? The Sitewide Ready for Anticipated Use measure (formerly called Sitewide Ready-for-Reuse) represents important Superfund accomplishments and the measure reflects the high priority the EPA places on considering anticipated future land use as part of our remedy selection process. See Guidance for Implementing the Sitewide Ready- for-Reuse Measure, May 24, 2006, OSWER 9365.0-36. This measure applies to final and deleted sites where construction is complete, all cleanup goals have been achieved, and all institutional or other controls are in place. The EPA has been successful on many occasions in carrying out remedial actions that ensure protectiveness of human health and the environment for current and future land uses, in a manner that allows contaminated properties to be restored to environmental and economic vitality. For further information, please go to http://www.epa.gov/superfund/programs/recycle/tools/index.html. II. Public Review/Public Comment A. May I review the documents relevant to this proposed rule? Yes, documents that form the basis for the EPA's evaluation and scoring of the sites in this proposed rule are contained in public Dockets located both at the EPA Headquarters in Washington, DC, and in the Regional offices. These documents are also available by electronic access at www.regulations.gov (see instructions in the ADDRESSES section above). B. How do I access the documents? You may view the documents, by appointment only, in the Headquarters or the Regional Dockets after the publication of this proposed rule. The hours of operation for the Headquarters Docket are from 8:30 a.m. to 4:30 p.m., Monday through Friday excluding federal holidays. Please contact the Regional Dockets for hours. The following is the contact information for the EPA Headquarters Docket: Docket Coordinator, Headquarters, U.S. Environmental Protection Agency, CERCLA Docket Office, 1301 Constitution Avenue NW., EPA West, Room 3334, Washington, DC 20004; 202/566-0276. (Please note this is a visiting address only. Mail comments to the EPA Headquarters as detailed at the beginning of this preamble.) The contact information for the Regional Dockets is as follows: Joan Berggren, Region 1 (CT, ME, MA, NH, RI, VT), U.S. EPA, Superfund Records and Information Center, 5 Post Office Square, Suite 100, Boston, MA 02109-3912; 617/918-1417. Ildefonso Acosta, Region 2 (NJ, NY, PR, VI), U.S. EPA, 290 Broadway, New York, NY 10007-1866; 212/637-4344. Dawn Shellenberger (ASRC), Region 3 (DE, DC, MD, PA, VA, WV), U.S. EPA, Library, 1650 Arch Street, Mail Code 3PM52, Philadelphia, PA 19103; 215/814-5364. Debbie Jourdan, Region 4 (AL, FL, GA, KY, MS, NC, SC, TN), U.S. EPA, 61 Forsyth Street, SW., Mail Code 9T25, Atlanta, GA 30303; 404/ 562-8862. Todd Quesada, Region 5 (IL, IN, MI, MN, OH, WI), U.S. EPA Superfund Division Librarian/SFD Records Manager SRC-7J, Metcalfe Federal Building, 77 West Jackson Boulevard, Chicago, IL 60604; 312/886-4465. Brenda Cook, Region 6 (AR, LA, NM, OK, TX), U.S. EPA, 1445 Ross Avenue, Suite 1200, Mail Code 6SFTS, Dallas, TX 75202-2733; 214/665- 7436. Michelle Quick, Region 7 (IA, KS, MO, NE), U.S. EPA, 901 North 5th Street, Mail Code SUPRERNB, Kansas City, KS 66101; 913/551-7335. Sabrina Forrest, Region 8 (CO, MT, ND, SD, UT, WY), U.S. EPA, 1595 Wynkoop Street, Mail Code 8EPR-B, Denver, CO 80202-1129; 303/312-6484. Karen Jurist, Region 9 (AZ, CA, HI, NV, AS, GU, MP), U.S. EPA, 75 Hawthorne Street Mail Code SFD-9-1, San Francisco, CA 94105; 415/972- 3219. Ken Marcy, Region 10 (AK, ID, OR, WA), U.S. EPA, 1200 6th Avenue Mail Code ECL-112, Seattle, WA 98101; 206/463-1349. You may also request copies from the EPA Headquarters or the Regional Dockets. An informal request, rather than a formal written request under the Freedom of Information Act, should be the ordinary procedure for obtaining copies of any of these documents. Please note that due to the difficulty of reproducing oversized maps, oversized maps may be viewed only in-person; since the EPA dockets are not equipped to either copy and mail out such maps or scan them and send them out electronically. You may use the Docket at www.regulations.gov to access documents in the Headquarters Docket (see instructions included in the ADDRESSES section above). Please note that there are differences between the [[Page 15348]] Headquarters Docket and the Regional Dockets and those differences are outlined below. C. What documents are available for public review at the headquarters docket? The Headquarters Docket for this proposed rule contains the following for the sites proposed in this rule: HRS score sheets; Documentation Records describing the information used to compute the score; information for any sites affected by particular statutory requirements or the EPA listing policies; and a list of documents referenced in the Documentation Record. D. What documents are available for public review at the regional dockets? The Regional Dockets for this proposed rule contain all of the information in the Headquarters Docket plus the actual reference documents containing the data principally relied upon and cited by the EPA in calculating or evaluating the HRS score for the sites. These reference documents are available only in the Regional Dockets. E. How do I submit my comments? Comments must be submitted to the EPA Headquarters as detailed at the beginning of this preamble in the ADDRESSES section. Please note that the mailing addresses differ according to method of delivery. There are two different addresses that depend on whether comments are sent by express mail or by postal mail. F. What happens to my comments? The EPA considers all comments received during the comment period. Significant comments are typically addressed in a support document that the EPA will publish concurrently with the Federal Register document if, and when, the site is listed on the NPL. G. What should I consider when preparing my comments? Comments that include complex or voluminous reports, or materials prepared for purposes other than HRS scoring, should point out the specific information that the EPA should consider and how it affects individual HRS factor values or other listing criteria (Northside Sanitary Landfill v. Thomas, 849 F.2d 1516 (DC Cir. 1988)). The EPA will not address voluminous comments that are not referenced to the HRS or other listing criteria. The EPA will not address comments unless they indicate which component of the HRS documentation record or what particular point in the EPA's stated eligibility criteria is at issue. H. May I submit comments after the public comment period is over? Generally, the EPA will not respond to late comments. The EPA can guarantee only that it will consider those comments postmarked by the close of the formal comment period. The EPA has a policy of generally not delaying a final listing decision solely to accommodate consideration of late comments. I. May I view public comments submitted by others? During the comment period, comments are placed in the Headquarters Docket and are available to the public on an ``as received'' basis. A complete set of comments will be available for viewing in the Regional Dockets approximately one week after the formal comment period closes. All public comments, whether submitted electronically or in paper form, will be made available for public viewing in the electronic public Docket at www.regulations.gov. http://www/epa/goc/edocket as the EPA receives them and without change, unless the comment contains copyrighted material, Confidential Business Information (CBI) or other information whose disclosure is restricted by statute. Once in the public Dockets system, select ``search,'' then key in the appropriate Docket ID number. J. May I submit comments regarding sites not currently proposed to the NPL? In certain instances, interested parties have written to the EPA concerning sites that were not at that time proposed to the NPL. If those sites are later proposed to the NPL, parties should review their earlier concerns and, if still appropriate, resubmit those concerns for consideration during the formal comment period. Site-specific correspondence received prior to the period of formal proposal and comment will not generally be included in the Docket. III. Contents of This Proposed Rule A. Proposed Additions to the NPL In today's proposed rule, the EPA is proposing to add 10 sites to the General Superfund section of the NPL. All of the sites in this proposed rulemaking are being proposed based on HRS scores of 28.50 or above with the exception of Cedar Chemical Corporation which has been designated as the state's one-time top priority site. The sites are presented in the table below. ------------------------------------------------------------------------ State Site name City/county ------------------------------------------------------------------------ AR..................... Cedar Chemical West Helena. Corporation. FL..................... Fairfax St. Wood Jacksonville. Treaters. GA..................... Macon Naval Macon. Ordnance Plant. IL..................... Bautsch-Gray Mine Galena. LA..................... EVR-Wood Treating/ Jennings. Evangeline Refining Company. NC..................... Holcomb Creosote Yadkinville. Co. NJ..................... Orange Valley West Orange/Orange. Regional Ground Water Contamination. NM..................... Jackpile-Paguate Laguna Pueblo. Uranium Mine. OH..................... West Troy Troy. Contaminated Aquifer. TX..................... Circle Court Willow Park. Ground Water Plume. ------------------------------------------------------------------------ B. Withdrawal of Site From Proposal to the NPL The EPA is withdrawing the proposal to add the Arnold Engineering Development Center site in Coffee and Franklin Counties, Tennessee to the NPL, because the site is being addressed under the Resource Conservation and Recovery Act (RCRA) program. Cleanup is progressing successfully, the migration of contaminated ground water is under control and measures have been taken that are protective of human health. The proposed rule can be found at 59 FR 43314 (August 23, 1994). Refer to the Docket ID Number EPA-HQ-SFUND-1994-0003 for supporting documentation regarding this action. C. Proposal To Remove Construction Completion List Column Notation and Footnote Description The EPA is proposing to amend the notes column and footnote description [[Page 15349]] of Appendix B to 40 CFR Part 300 to remove the note that references ``sites on the construction completion list.'' The EPA developed the Construction Completion List (CCL) (58 FR 14142, March 2, 1993) ``to simplify its system of categorizing sites and to better communicate the successful completion of cleanup activities.'' Notes were added to Table 1 (General Superfund Section) and Table 2 (Federal Facilities Section) of the NPL to identify those sites on the CCL. With today's easy public accessibility to the Internet and the availability of the most current data on the EPA's Web site, the EPA is proposing to remove the construction completion list note. Comments may be submitted to Docket number EPA-HQ-SFUND-2012-0146. For information on the construction completion list, please visit the EPA's Web site at http://www.epa.gov/superfund/sites/query/queryhtm/nplccl.htm. D. Proposed Correction of Partial Deletion Notation in Table 1 The EPA is proposing to correct an error in the column note symbol used to designate sites with partial deletions in Appendix B to CFR Part 300. The correct column note symbol for a site with a partial deletion is ``P''. The Mouat Industries site in Montana has its partial deletion incorrectly designated by a column note symbol of ``* * * P''. In addition, this incorrect symbol was erroneously added to the footnote descriptions at the end of Table 1 as ``* * * P = Sites with deletion(s).'' The EPA is proposing to correct the column note for the Mouat Industries site by changing it to ``P'' and removing the erroneous footnote description. Comment may be submitted to Docket number EPA-HQ-SFUND-2012-0147. IV. Statutory and Executive Order Reviews A. Executive Order 12866: Regulatory Planning and Review 1. What is Executive Order 12866? Under Executive Order 12866 (58 FR 51735 (October 4, 1993)), the agency must determine whether a regulatory action is ``significant'' and therefore subject to Office of Management and Budget (OMB) review and the requirements of the Executive Order. The Order defines ``significant regulatory action'' as one that is likely to result in a rule that may: (1) Have an annual effect on the economy of $100 million or more or adversely affect in a material way the economy, a sector of the economy, productivity, competition, jobs, the environment, public health or safety or state, local or tribal governments or communities; (2) create a serious inconsistency or otherwise interfere with an action taken or planned by another agency; (3) materially alter the budgetary impact of entitlements, grants, user fees or loan programs or the rights and obligations of recipients thereof; or (4) raise novel legal or policy issues arising out of legal mandates, the President's priorities or the principles set forth in the Executive Order. 2. Is this proposed rule subject to Executive Order 12866 review? No. The listing of sites on the NPL does not impose any obligations on any entities. The listing does not set standards or a regulatory regime and imposes no liability or costs. Any liability under CERCLA exists irrespective of whether a site is listed. It has been determined that this action is not a ``significant regulatory action'' under the terms of Executive Order 12866 and is therefore not subject to OMB review. B. Paperwork Reduction Act 1. What is the Paperwork Reduction Act? According to the Paperwork Reduction Act (PRA), 44 U.S.C. 3501 et seq., an agency may not conduct or sponsor, and a person is not required to respond to a collection of information that requires OMB approval under the PRA, unless it has been approved by OMB and displays a currently valid OMB control number. The OMB control numbers for the EPA's regulations, after initial display in the preamble of the final rules, are listed in 40 CFR part 9. 2. Does the Paperwork Reduction Act apply to this proposed rule? This action does not impose an information collection burden under the provisions of the Paperwork Reduction Act, 44 U.S.C. 3501 et seq. The EPA has determined that the PRA does not apply because this rule does not contain any information collection requirements that require approval of the OMB. Burden means the total time, effort or financial resources expended by persons to generate, maintain, retain or disclose or provide information to or for a federal agency. This includes the time needed to review instructions; develop, acquire, install and utilize technology and systems for the purposes of collecting, validating and verifying information, processing and maintaining information and disclosing and providing information; adjust the existing ways to comply with any previously applicable instructions and requirements; train personnel to be able to respond to a collection of information; search data sources; complete and review the collection of information; and transmit or otherwise disclose the information. An agency may not conduct or sponsor, and a person is not required to respond to, a collection of information unless it displays a currently valid OMB control number. The OMB control numbers for the EPA's regulations in 40 CFR are listed in 40 CFR part 9. C. Regulatory Flexibility Act 1. What is the Regulatory Flexibility Act? Pursuant to the Regulatory Flexibility Act (5 U.S.C. 601 et seq., as amended by the Small Business Regulatory Enforcement Fairness Act (SBREFA) of 1996) whenever an agency is required to publish a notice of rulemaking for any proposed or final rule, it must prepare and make available for public comment a regulatory flexibility analysis that describes the effect of the rule on small entities (i.e., small businesses, small organizations and small governmental jurisdictions). However, no regulatory flexibility analysis is required if the head of an agency certifies the rule will not have a significant economic impact on a substantial number of small entities. SBREFA amended the Regulatory Flexibility Act to require federal agencies to provide a statement of the factual basis for certifying that a rule will not have a significant economic impact on a substantial number of small entities. 2. How has the EPA complied with the Regulatory Flexibility Act? This proposed rule listing sites on the NPL, if promulgated, would not impose any obligations on any group, including small entities. This proposed rule, if promulgated, also would establish no standards or requirements that any small entity must meet, and would impose no direct costs on any small entity. Whether an entity, small or otherwise, is liable for response costs for a release of hazardous substances depends on whether that entity is liable under CERCLA 107(a). Any such liability exists regardless of whether the site is listed on the NPL through this rulemaking. Thus, this proposed rule, if promulgated, would not impose any requirements on any small entities. For the foregoing reasons, I certify that this proposed rule, if promulgated, will not have a significant economic impact on a substantial number of small entities. [[Page 15350]] D. Unfunded Mandates Reform Act 1. What is the Unfunded Mandates Reform Act (UMRA)? Title II of the Unfunded Mandates Reform Act of 1995 (UMRA), Public Law 104-4, establishes requirements for federal agencies to assess the effects of their regulatory actions on state, local and tribal governments and the private sector. Under section 202 of the UMRA, the EPA generally must prepare a written statement, including a cost- benefit analysis, for proposed and final rules with ``federal mandates'' that may result in expenditures by state, local and tribal governments, in the aggregate, or by the private sector, of $100 million or more in any one year. Before the EPA promulgates a rule where a written statement is needed, section 205 of the UMRA generally requires the EPA to identify and consider a reasonable number of regulatory alternatives and adopt the least costly, most cost- effective, or least burdensome alternative that achieves the objectives of the rule. The provisions of section 205 do not apply when they are inconsistent with applicable law. Moreover, section 205 allows the EPA to adopt an alternative other than the least costly, most cost- effective or least burdensome alternative if the Administrator publishes with the final rule an explanation why that alternative was not adopted. Before the EPA establishes any regulatory requirements that may significantly or uniquely affect small governments, including tribal governments, it must have developed under section 203 of the UMRA a small government agency plan. The plan must provide for notifying potentially affected small governments, enabling officials of affected small governments to have meaningful and timely input in the development of EPA regulatory proposals with significant federal intergovernmental mandates and informing, educating, and advising small governments on compliance with the regulatory requirements. 2. Does UMRA apply to this proposed rule? This proposed rule does not contain a federal mandate that may result in expenditures of $100 million or more for state, local and tribal governments, in the aggregate, or the private sector in any one year. Proposing a site on the NPL does not itself impose any costs. Proposal does not mean that the EPA necessarily will undertake remedial action. Nor does proposal require any action by a private party or determine liability for response costs. Costs that arise out of site responses result from site-specific decisions regarding what actions to take, not directly from the act of proposing a site to be placed on the NPL. Thus, this rule is not subject to the requirements of section 202 and 205 of UMRA. This rule is also not subject to the requirements of section 203 of UMRA because it contains no regulatory requirements that might significantly or uniquely affect small governments. As is mentioned above, site proposal does not impose any costs and would not require any action of a small government. E. Executive Order 13132: Federalism 1. What is Executive Order 13132? Executive Order 13132, entitled ``Federalism'' (64 FR 43255, August 10, 1999), requires the EPA to develop an accountable process to ensure ``meaningful and timely input by state and local officials in the development of regulatory policies that have federalism implications.'' ``Policies that have federalism implications'' are defined in the Executive Order to include regulations that have ``substantial direct effects on the states, on the relationship between the national government and the states, or on the distribution of power and responsibilities among the various levels of government.'' 2. Does Executive Order 13132 apply to this proposed rule? This proposed rule does not have federalism implications. It will not have substantial direct effects on the states, on the relationship between the national government and the states, or on the distribution of power and responsibilities among the various levels of government, as specified in Executive Order 13132, because it does not contain any requirements applicable to states or other levels of government. Thus, the requirements of the Executive Order do not apply to this proposed rule. The EPA believes, however, that this proposed rule may be of significant interest to state governments. In the spirit of Executive Order 13132, and consistent with the EPA policy to promote communications between the EPA and state and local governments, the EPA therefore consulted with state officials and/or representatives of state governments early in the process of developing the rule to permit them to have meaningful and timely input into its development. All sites included in this proposed rule were referred to the EPA by states for listing. For all sites in this rule, the EPA received letters of support either from the Governor or a state official who was delegated the authority by the Governor to speak on their behalf regarding NPL listing decisions. F. Executive Order 13175: Consultation and Coordination With Indian Tribal Governments 1. What is Executive Order 13175? Executive Order 13175, entitled ``Consultation and Coordination with Indian Tribal Governments'' (65 FR 67249, November 6, 2000), requires the EPA to develop an accountable process to ensure ``meaningful and timely input by tribal officials in the development of regulatory policies that have tribal implications.'' ``Policies that have tribal implications'' are defined in the Executive Order to include regulations that have ``substantial direct effects on one or more Indian tribes, on the relationship between the federal government and the Indian tribes, or on the distribution of power and responsibilities between the federal government and Indian tribes.'' 2. Does Executive Order 13175 apply to this proposed rule? This action does not have tribal implications, as specified in Executive Order 13175. Proposing a site to the NPL does not impose any costs on a tribe or require a tribe to take remedial action. Thus, Executive Order 13175 does not apply to this proposed rule. G. Executive Order 13045: Protection of Children From Environmental Health and Safety Risks 1. What is Executive Order 13045? Executive Order 13045: ``Protection of Children from Environmental Health Risks and Safety Risks'' (62 FR 19885, April 23, 1997) applies to any rule that: (1) Is determined to be ``economically significant'' as defined under Executive Order 12866, and (2) concerns an environmental health or safety risk that the EPA has reason to believe may have a disproportionate effect on children. If the regulatory action meets both criteria, the agency must evaluate the environmental health or safety effects of the planned rule on children, and explain why the planned regulation is preferable to other potentially effective and reasonably feasible alternatives considered by the agency. 2. Does Executive Order 13045 apply to this proposed rule? This proposed rule is not subject to Executive Order 13045 because it is not an economically significant rule as defined by Executive Order 12866, and because the agency does not have reason to believe the environmental health or [[Page 15351]] safety risks addressed by this proposed rule present a disproportionate risk to children. H. Executive Order 13211: Actions That Significantly Affect Energy Supply, Distribution, or Use 1. What is Executive Order 13211? Executive Order 13211, ``Actions Concerning Regulations That Significantly Affect Energy Supply, Distribution or Use,'' (66 FR 28355 (May 22, 2001)) requires federal agencies to prepare a ``Statement of Energy Effects'' when undertaking certain regulatory actions. A Statement of Energy Effects describes the adverse effects of a ``significant energy action'' on energy supply, distribution and use, reasonable alternatives to the action and the expected effects of the alternatives on energy supply, distribution and use. 2. Does Executive Order 13211 apply to this proposed rule? This action is not a ``significant energy action'' as defined in Executive Order 13211, because it is not likely to have a significant adverse effect on the supply, distribution or use of energy. Further, the agency has concluded that this rule is not likely to have any adverse energy impacts because proposing a site to the NPL does not require an entity to conduct any action that would require energy use, let alone that which would significantly affect energy supply, distribution or usage. Thus, Executive Order 13175 does not apply to this action. I. National Technology Transfer and Advancement Act 1. What is the National Technology Transfer and Advancement Act? Section 12(d) of the National Technology Transfer and Advancement Act of 1995 (NTTAA), Public Law 104-113, section 12(d) (15 U.S.C. 272 note), directs the EPA to use voluntary consensus standards in its regulatory activities unless to do so would be inconsistent with applicable law or otherwise impractical. Voluntary consensus standards are technical standards (e.g., materials specifications, test methods, sampling procedures and business practices) that are developed or adopted by voluntary consensus standards bodies. The NTTAA directs the EPA to provide Congress, through OMB, explanations when the agency decides not to use available and applicable voluntary consensus standards. 2. Does the National Technology Transfer and Advancement Act apply to this proposed rule? No. This proposed rulemaking does not involve technical standards. Therefore, the EPA did not consider the use of any voluntary consensus standards. J. Executive Order 12898: Federal Actions To Address Environmental Justice in Minority Populations and Low-Income Populations 1. What is Executive Order 12898? Executive Order (EO) 12898 (59 FR 7629 (Feb. 16, 1994)) establishes federal executive policy on environmental justice. Its main provision directs federal agencies, to the greatest extent practicable and permitted by law, to make environmental justice part of their mission by identifying and addressing, as appropriate, disproportionately high and adverse human health or environmental effects of their programs, policies and activities on minority populations and low-income populations in the United States. 2. Does Executive Order 12898 apply to this rule? The EPA has determined that this proposed rule will not have disproportionately high and adverse human health or environmental effects on minority or low-income populations because it does not affect the level of protection provided to human health or the environment. As this rule does not impose any enforceable duty upon state, tribal or local governments, this rule will neither increase nor decrease environmental protection. List of Subjects in 40 CFR Part 300 Environmental protection, Air pollution control, Chemicals, Hazardous substances, Hazardous waste, Intergovernmental relations, Natural resources, Oil pollution, Penalties, Reporting and recordkeeping requirements, Superfund, Water pollution control, Water supply. Authority: 33 U.S.C. 1321(c)(2); 42 U.S.C. 9601-9657; E.O. 12777, 56 FR 54757, 3 CFR, 1991 Comp., p. 351; E.O. 12580, 52 FR 2923, 3 CFR, 1987 Comp., p. 193. Dated: March 18, 2012. Mathy Stanislaus, Assistant Administrator, Office of Solid Waste and Emergency Response. [FR Doc. 2012-6328 Filed 3-14-12; 8:45 am] BILLING CODE 6560-50-P
|
|
VIDEO – U.S.-Funded Afghan Air Force Allegedly Smuggling Drugs and Weapons
KABUL — The U.S. is investigating allegations that some officials in the Afghan Air Force with CIA backing, which was established largely with American funds, have been using aircraft to ferry narcotics and illegal weapons around the country, American officials told The Wall Street Journal.
Two probes of the Afghan Air Force, or AAF, are under way-one led by the U.S. military coalition and another by the U.S. Drug Enforcement Administration, officials said.
“The nature of the allegations is fairly dramatic and indicated that [AAF officials] were transporting drugs on aircraft and transported weapons not owned by the government of Afghanistan for the use of private groups,” said U.S. Army Lt. Gen. Daniel Bolger, commander of the North Atlantic Treaty Organization Training Mission-Afghanistan, the command that is establishing and financing Afghan security forces, including the AAF.
Leaked – Director of National Intelligence 2012 Report on Reengagement of Detainees Formerly Held at Guantanamo Bay
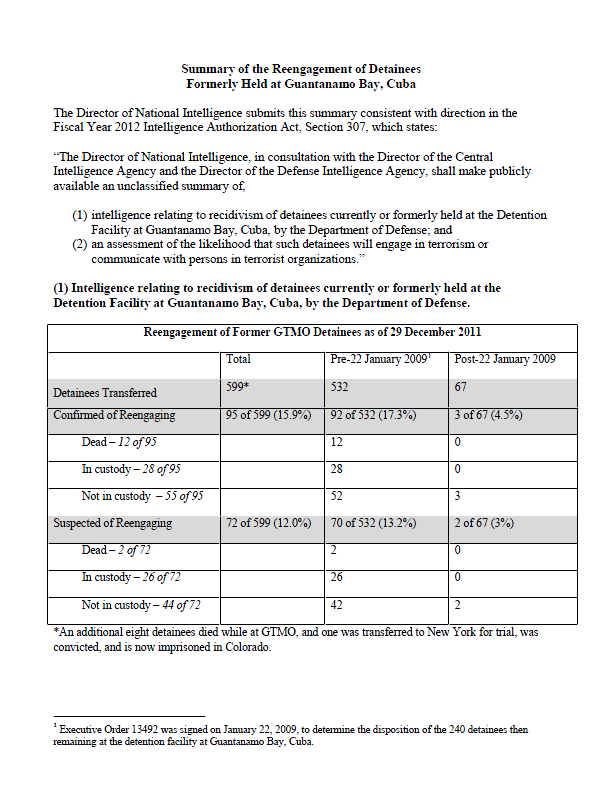
(2) (a) An assessment of the likelihood that such detainees will engage in terrorism.
Based on trends identified during the past 9 years, we assess that if additional detainees are transferred without conditions from GTMO, some will reengage in terrorist or insurgent activities. Posing a particular problem are transfers to countries with ongoing conflicts and internal instability as well as active recruitment by insurgent and terrorist organizations.
(2) (b) An assessment of the likelihood that such detainees will communicate with persons in terrorist organizations.
Former GTMO detainees routinely communicate with each other, families of other former detainees, and previous associates who are members of terrorist organizations. The reasons for communication span from the mundane (reminiscing about shared experiences) to the nefarious (planning terrorist operations). We assess that some GTMO detainees transferred in the future also will communicate with other former GTMO detainees and persons in terrorist organizations. We do not consider mere communication with individuals or organizations – including other former GTMO detainees – an indicator of reengagement. Rather, the motives, intentions, and purposes of each communication are taken into account when assessing whether the individual has reengaged.
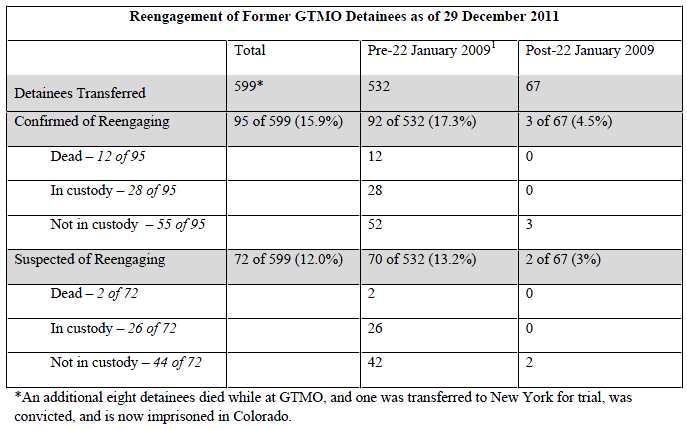
FEDERAL GOVERNMENT – 9 Toxic Air Sites Added to EPA Superfund
From the Federal Register Online via the Government Printing Office [www.gpo.gov] [FR Doc No: 2012-6329] ----------------------------------------------------------------------- ENVIRONMENTAL PROTECTION AGENCY 40 CFR Part 300 [EPA-HQ-SFUND-1993-0001, EPA-HQ-SFUND-2011-0064, 0068, 0646, 0648, 0649, 0650, 0651, and 0652; FRL-9647-3] RIN 2050-AD75 National Priorities List, Final Rule No. 53 AGENCY: Environmental Protection Agency. ACTION: Final rule. ----------------------------------------------------------------------- SUMMARY: The Comprehensive Environmental Response, Compensation, and Liability Act of 1980 (``CERCLA'' or ``the Act''), as amended, requires that the National Oil and Hazardous Substances Pollution Contingency Plan (``NCP'') include a list of national priorities among the known releases or threatened releases of hazardous substances, pollutants, or [[Page 15277]] contaminants throughout the United States. The National Priorities List (``NPL'') constitutes this list. The NPL is intended primarily to guide the Environmental Protection Agency (``the EPA'' or ``the agency'') in determining which sites warrant further investigation. These further investigations will allow the EPA to assess the nature and extent of public health and environmental risks associated with the site and to determine what CERCLA-financed remedial action(s), if any, may be appropriate. This rule adds nine sites to the General Superfund Section of the NPL. DATES: Effective date: The effective date for this amendment to the NCP is April 16, 2012. ADDRESSES: For addresses for the Headquarters and Regional dockets, as well as further details on what these dockets contain, see section II, ``Availability of Information to the Public'' in the SUPPLEMENTARY INFORMATION portion of this preamble. FOR FURTHER INFORMATION CONTACT: Terry Jeng, phone: (703) 603-8852, email: jeng.terry@epa.gov, Site Assessment and Remedy Decisions Branch, Assessment and Remediation Division, Office of Superfund Remediation and Technology Innovation (Mail Code 5204P), U.S. Environmental Protection Agency; 1200 Pennsylvania Avenue NW., Washington, DC 20460; or the Superfund Hotline, phone (800) 424-9346 or (703) 412-9810 in the Washington, DC, metropolitan area. SUPPLEMENTARY INFORMATION: Table of Contents I. Background A. What are CERCLA and SARA? B. What is the NCP? C. What is the National Priorities List (NPL)? D. How are sites listed on the NPL? E. What happens to sites on the NPL? F. Does the NPL define the boundaries of sites? G. How are sites removed from the NPL? H. May the EPA delete portions of sites from the NPL as they are cleaned up? I. What is the Construction Completion List (CCL)? J. What is the sitewide ready for anticipated use measure? II. Availability of Information to the Public A. May I review the documents relevant to this final rule? B. What documents are available for review at the headquarters docket? C. What documents are available for review at the regional dockets? D. How do I access the documents? E. How may I obtain a current list of NPL sites? III. Contents of This Final Rule A. Additions to the NPL B. What did the EPA do with the public comments it received? IV. Statutory and Executive Order Reviews A. Executive Order 12866: Regulatory Planning and Review 1. What is Executive Order 12866? 2. Is this Final Rule subject to Executive Order 12866 review? B. Paperwork Reduction Act 1. What is the Paperwork Reduction Act? 2. Does the Paperwork Reduction Act apply to this Final Rule? C. Regulatory Flexibility Act 1. What is the Regulatory Flexibility Act? 2. How has the EPA complied with the Regulatory Flexibility Act? D. Unfunded Mandates Reform Act 1. What is the Unfunded Mandates Reform Act (UMRA)? 2. Does UMRA apply to this Final Rule? E. Executive Order 13132: Federalism 1. What is Executive Order 13132? 2. Does Executive Order 13132 apply to this Final Rule? F. Executive Order 13175: Consultation and Coordination With Indian Tribal Governments 1. What is Executive Order 13175? 2. Does Executive Order 13175 apply to this Final Rule? G. Executive Order 13045: Protection of Children From Environmental Health and Safety Risks 1. What is Executive Order 13045? 2. Does Executive Order 13045 apply to this Final Rule? H. Executive Order 13211: Actions That Significantly Affect Energy Supply, Distribution, or Usage 1. What is Executive Order 13211? 2. Does Executive Order 13211 apply to this Final Rule? I. National Technology Transfer and Advancement Act 1. What is the National Technology Transfer and Advancement Act? 2. Does the National Technology Transfer and Advancement Act apply to this Final Rule? J. Executive Order 12898: Federal Actions To Address Environmental Justice in Minority Populations and Low-Income Populations 1. What is Executive Order 12898? 2. Does Executive Order 12898 apply to this Final Rule? K. Congressional Review Act 1. Has the EPA submitted this Rule to Congress and the Government Accountability Office? 2. Could the effective date of this Final Rule change? 3. What could cause a change in the effective date of this Rule? I. Background A. What are CERCLA and SARA? In 1980, Congress enacted the Comprehensive Environmental Response, Compensation, and Liability Act, 42 U.S.C. 9601-9675 (``CERCLA'' or ``the Act''), in response to the dangers of uncontrolled releases or threatened releases of hazardous substances, and releases or substantial threats of releases into the environment of any pollutant or contaminant that may present an imminent or substantial danger to the public health or welfare. CERCLA was amended on October 17, 1986, by the Superfund Amendments and Reauthorization Act (``SARA''), Public Law 99-499, 100 Stat. 1613 et seq. B. What is the NCP? To implement CERCLA, the EPA promulgated the revised National Oil and Hazardous Substances Pollution Contingency Plan (``NCP''), 40 CFR part 300, on July 16, 1982 (47 FR 31180), pursuant to CERCLA section 105 and Executive Order 12316 (46 FR 42237, August 20, 1981). The NCP sets guidelines and procedures for responding to releases and threatened releases of hazardous substances, or releases or substantial threats of releases into the environment of any pollutant or contaminant that may present an imminent or substantial danger to the public health or welfare. The EPA has revised the NCP on several occasions. The most recent comprehensive revision was on March 8, 1990 (55 FR 8666). As required under section 105(a)(8)(A) of CERCLA, the NCP also includes ``criteria for determining priorities among releases or threatened releases throughout the United States for the purpose of taking remedial action and, to the extent practicable, taking into account the potential urgency of such action, for the purpose of taking removal action.'' ``Removal'' actions are defined broadly and include a wide range of actions taken to study, clean up, prevent or otherwise address releases and threatened releases of hazardous substances, pollutants or contaminants (42 U.S.C. 9601(23)). C. What is the National Priorities List (NPL)? The NPL is a list of national priorities among the known or threatened releases of hazardous substances, pollutants, or contaminants throughout the United States. The list, which is appendix B of the NCP (40 CFR part 300), was required under section 105(a)(8)(B) of CERCLA, as amended. Section 105(a)(8)(B) defines the NPL as a list of ``releases'' and the highest priority ``facilities'' and requires that the NPL be revised at least annually. The NPL is intended primarily to guide the EPA in determining which sites warrant further investigation to assess the nature and extent of public health and environmental risks associated with a release of hazardous substances, pollutants or contaminants. The NPL is [[Page 15278]] of only limited significance, however, as it does not assign liability to any party or to the owner of any specific property. Also, placing a site on the NPL does not mean that any remedial or removal action necessarily need be taken. For purposes of listing, the NPL includes two sections, one of sites that are generally evaluated and cleaned up by the EPA (the ``General Superfund Section'') and one of sites that are owned or operated by other Federal agencies (the ``Federal Facilities Section''). With respect to sites in the Federal Facilities Section, these sites are generally being addressed by other Federal agencies. Under Executive Order 12580 (52 FR 2923, January 29, 1987) and CERCLA section 120, each Federal agency is responsible for carrying out most response actions at facilities under its own jurisdiction, custody or control, although the EPA is responsible for preparing a Hazard Ranking System (``HRS'') score and determining whether the facility is placed on the NPL. D. How are sites listed on the NPL? There are three mechanisms for placing sites on the NPL for possible remedial action (see 40 CFR 300.425(c) of the NCP): (1) A site may be included on the NPL if it scores sufficiently high on the HRS, which the EPA promulgated as appendix A of the NCP (40 CFR part 300). The HRS serves as a screening tool to evaluate the relative potential of uncontrolled hazardous substances, pollutants or contaminants to pose a threat to human health or the environment. On December 14, 1990 (55 FR 51532), the EPA promulgated revisions to the HRS partly in response to CERCLA section 105(c), added by SARA. The revised HRS evaluates four pathways: ground water, surface water, soil exposure and air. As a matter of agency policy, those sites that score 28.50 or greater on the HRS are eligible for the NPL. (2) Pursuant to 42 U.S.C. 9605(a)(8)(B), each state may designate a single site as its top priority to be listed on the NPL, without any HRS score. This provision of CERCLA requires that, to the extent practicable, the NPL include one facility designated by each state as the greatest danger to public health, welfare or the environment among known facilities in the state. This mechanism for listing is set out in the NCP at 40 CFR 300.425(c)(2). (3) The third mechanism for listing, included in the NCP at 40 CFR 300.425(c)(3), allows certain sites to be listed without any HRS score, if all of the following conditions are met: The Agency for Toxic Substances and Disease Registry (ATSDR) of the U.S. Public Health Service has issued a health advisory that recommends dissociation of individuals from the release. The EPA determines that the release poses a significant threat to public health. The EPA anticipates that it will be more cost-effective to use its remedial authority than to use its removal authority to respond to the release. The EPA promulgated an original NPL of 406 sites on September 8, 1983 (48 FR 40658) and generally has updated it at least annually. E. What happens to sites on the NPL? A site may undergo remedial action financed by the Trust Fund established under CERCLA (commonly referred to as the ``Superfund'') only after it is placed on the NPL, as provided in the NCP at 40 CFR 300.425(b)(1). (``Remedial actions'' are those ``consistent with a permanent remedy, taken instead of or in addition to removal actions. * * *'' 42 U.S.C. 9601(24).) However, under 40 CFR 300.425(b)(2), placing a site on the NPL ``does not imply that monies will be expended.'' The EPA may pursue other appropriate authorities to respond to the releases, including enforcement action under CERCLA and other laws. F. Does the NPL define the boundaries of sites? The NPL does not describe releases in precise geographical terms; it would be neither feasible nor consistent with the limited purpose of the NPL (to identify releases that are priorities for further evaluation), for it to do so. Indeed, the precise nature and extent of the site are typically not known at the time of listing. Although a CERCLA ``facility'' is broadly defined to include any area where a hazardous substance has ``come to be located'' (CERCLA section 101(9)), the listing process itself is not intended to define or reflect the boundaries of such facilities or releases. Of course, HRS data (if the HRS is used to list a site) upon which the NPL placement was based will, to some extent, describe the release(s) at issue. That is, the NPL site would include all releases evaluated as part of that HRS analysis. When a site is listed, the approach generally used to describe the relevant release(s) is to delineate a geographical area (usually the area within an installation or plant boundaries) and identify the site by reference to that area. However, the NPL site is not necessarily coextensive with the boundaries of the installation or plant, and the boundaries of the installation or plant are not necessarily the ``boundaries'' of the site. Rather, the site consists of all contaminated areas within the area used to identify the site, as well as any other location where that contamination has come to be located, or from where that contamination came. In other words, while geographic terms are often used to designate the site (e.g., the ``Jones Co. plant site'') in terms of the property owned by a particular party, the site, properly understood, is not limited to that property (e.g., it may extend beyond the property due to contaminant migration), and conversely may not occupy the full extent of the property (e.g., where there are uncontaminated parts of the identified property, they may not be, strictly speaking, part of the ``site''). The ``site'' is thus neither equal to, nor confined by, the boundaries of any specific property that may give the site its name, and the name itself should not be read to imply that this site is coextensive with the entire area within the property boundary of the installation or plant. In addition, the site name is merely used to help identify the geographic location of the contamination, and is not meant to constitute any determination of liability at a site. For example, the name ``Jones Co. plant site,'' does not imply that the Jones company is responsible for the contamination located on the plant site. EPA regulations provide that the Remedial Investigation (``RI'') ``is a process undertaken * * * to determine the nature and extent of the problem presented by the release'' as more information is developed on site contamination, and which is generally performed in an interactive fashion with the Feasibility Study (``FS'') (40 CFR 300.5). During the RI/FS process, the release may be found to be larger or smaller than was originally thought, as more is learned about the source(s) and the migration of the contamination. However, the HRS inquiry focuses on an evaluation of the threat posed and therefore the boundaries of the release need not be exactly defined. Moreover, it generally is impossible to discover the full extent of where the contamination ``has come to be located'' before all necessary studies and remedial work are completed at a site. Indeed, the known boundaries of the contamination can be expected to change over time. Thus, in most cases, it may be impossible to describe the boundaries of a release with absolute certainty. Further, as noted above, NPL listing does not assign liability to any party or to the owner of any specific property. Thus, if a party does not believe it is liable for releases on discrete parcels of [[Page 15279]] property, it can submit supporting information to the agency at any time after it receives notice it is a potentially responsible party. For these reasons, the NPL need not be amended as further research reveals more information about the location of the contamination or release. G. How are sites removed from the NPL? The EPA may delete sites from the NPL where no further response is appropriate under Superfund, as explained in the NCP at 40 CFR 300.425(e). This section also provides that the EPA shall consult with states on proposed deletions and shall consider whether any of the following criteria have been met: (i) Responsible parties or other persons have implemented all appropriate response actions required; (ii) All appropriate Superfund-financed response has been implemented and no further response action is required; or (iii) The remedial investigation has shown the release poses no significant threat to public health or the environment, and taking of remedial measures is not appropriate. H. May the EPA delete portions of sites from the NPL as they are cleaned up? In November 1995, the EPA initiated a policy to delete portions of NPL sites where cleanup is complete (60 FR 55465, November 1, 1995). Total site cleanup may take many years, while portions of the site may have been cleaned up and made available for productive use. I. What is the Construction Completion List (CCL)? The EPA also has developed an NPL construction completion list (``CCL'') to simplify its system of categorizing sites and to better communicate the successful completion of cleanup activities (58 FR 12142, March 2, 1993). Inclusion of a site on the CCL has no legal significance. Sites qualify for the CCL when: (1) Any necessary physical construction is complete, whether or not final cleanup levels or other requirements have been achieved; (2) the EPA has determined that the response action should be limited to measures that do not involve construction (e.g., institutional controls); or (3) the site qualifies for deletion from the NPL. For the most up-to-date information on the CCL, see the EPA's Internet site at http://www.epa.gov/superfund/ cleanup/ccl.htm J. What is the sitewide ready for anticipated use measure? The Sitewide Ready for Anticipated Use measure represents important Superfund accomplishments and the measure reflects the high priority the EPA places on considering anticipated future land use as part of our remedy selection process. See Guidance for Implementing the Sitewide Ready-for-Reuse Measure, May 24, 2006, OSWER 9365.0-36. This measure applies to final and deleted sites where construction is complete, all cleanup goals have been achieved, and all institutional or other controls are in place. The EPA has been successful on many occasions in carrying out remedial actions that ensure protectiveness of human health and the environment for current and future land uses, in a manner that allows contaminated properties to be restored to environmental and economic vitality. For further information, please go to http://www.epa.gov/superfund/programs/recycle/tools/index.html. II. Availability of Information to the Public A. May I review the documents relevant to this Final Rule? Yes, documents relating to the evaluation and scoring of the sites in this final rule are contained in dockets located both at the EPA Headquarters and in the Regional offices. An electronic version of the public docket is available through www.regulations.gov (see table below for Docket Identification numbers). Although not all Docket materials may be available electronically, you may still access any of the publicly available Docket materials through the Docket facilities identified below in section II D. Docket Identification Numbers by Site ------------------------------------------------------------------------------------- Site name City/County, State Docket ID No. ------------------------------------------------------------------------------------- Continental Cleaners................ Miami, FL............. EPA-HQ-SFUND-2011-0646. Sauer Dump.......................... Dundalk, MD........... EPA-HQ-SFUND-2011-0064. Compass Plaza Well TCE.............. Rogersville, MO....... EPA-HQ-SFUND-2011-0648. Chemfax, Inc........................ Gulfport, MS.......... EPA-HQ-SFUND-1993-0001. Southeastern Wood Preserving........ Canton, MS............ EPA-HQ-SFUND-2011-0649. CTS of Asheville, Inc............... Asheville, NC......... EPA-HQ-SFUND-2011-0068. Eighteenmile Creek.................. Niagara County, NY.... EPA-HQ-SFUND-2011-0650. Metro Container Corporation......... Trainer, PA........... EPA-HQ-SFUND-2011-0651. Corozal Well........................ Corozal, PR........... EPA-HQ-SFUND-2011-0652. ------------------------------------------------------------------------------------- B. What documents are available for review at the headquarters docket? The Headquarters Docket for this rule contains, for each site, the HRS score sheets, the Documentation Record describing the information used to compute the score, pertinent information regarding statutory requirements or the EPA listing policies that affect the site and a list of documents referenced in the Documentation Record. For sites that received comments during the comment period, the Headquarters Docket also contains a Support Document that includes the EPA's responses to comments. C. What documents are available for review at the regional dockets? The Regional Dockets contain all the information in the Headquarters Docket, plus the actual reference documents containing the data principally relied upon by the EPA in calculating or evaluating the HRS score for the sites located in their Region. These reference documents are available only in the Regional Dockets. For sites that received comments during the comment period, the Regional Docket also contains a Support Document that includes the EPA's responses to comments. D. How do I access the documents? You may view the documents, by appointment only, after the publication of this rule. The hours of operation for the Headquarters Docket are from 8:30 a.m. to 4:30 p.m., Monday through Friday, excluding Federal holidays. Please contact the Regional Dockets for hours. Following is the contact information for the EPA Headquarters: Docket [[Page 15280]] Coordinator, Headquarters; U.S. Environmental Protection Agency; CERCLA Docket Office; 1301 Constitution Avenue NW.; EPA West, Room 3334, Washington, DC 20004, 202/566-0276. The contact information for the Regional Dockets is as follows: Joan Berggren, Region 1 (CT, ME, MA, NH, RI, VT), U.S. EPA, Superfund Records and Information Center, 5 Post Office Square, Suite 100; Boston, MA 02109-3912; 617/918-1417. Ildefonso Acosta, Region 2 (NJ, NY, PR, VI), U.S. EPA, 290 Broadway, New York, NY 10007-1866; 212/637-4344. Dawn Shellenberger (ASRC), Region 3 (DE, DC, MD, PA, VA, WV), U.S. EPA, Library, 1650 Arch Street, Mail Code 3PM52, Philadelphia, PA 19103; 215/814-5364. Debbie Jourdan, Region 4 (AL, FL, GA, KY, MS, NC, SC, TN), U.S. EPA, 61 Forsyth Street, SW., Mail Code 9T25, Atlanta, GA 30303; 404/562-8862. Todd Quesada, Region 5 (IL, IN, MI, MN, OH, WI), U.S. EPA Superfund Division Librarian/SFD Records Manager SRC-7J, Metcalfe Federal Building, 77 West Jackson Boulevard, Chicago, IL 60604; 312/886-4465. Brenda Cook, Region 6 (AR, LA, NM, OK, TX), U.S. EPA, 1445 Ross Avenue, Suite 1200, Mail Code 6SFTS, Dallas, TX 75202-2733; 214/665-7436. Michelle Quick, Region 7 (IA, KS, MO, NE), U.S. EPA, 901 North 5th Street, Mail Code SUPRERNB, Kansas City, KS 66101; 913/551-7335. Sabrina Forrest, Region 8 (CO, MT, ND, SD, UT, WY), U.S. EPA, 1595 Wynkoop Street, Mail Code 8EPR-B, Denver, CO 80202-1129; 303/312-6484. Karen Jurist, Region 9 (AZ, CA, HI, NV, AS, GU, MP), U.S. EPA, 75 Hawthorne Street, Mail Code SFD-9-1, San Francisco, CA 94105; 415/972- 3219. Ken Marcy, Region 10 (AK, ID, OR, WA), U.S. EPA, 1200 6th Avenue, Mail Code ECL-112, Seattle, WA 98101; 206/463-1349. E. How may I obtain a current list of NPL sites? You may obtain a current list of NPL sites via the Internet at http://www.epa.gov/superfund/sites/npl/index.htm or by contacting the Superfund Docket (see contact information above). III. Contents of This Final Rule A. Additions to the NPL This final rule adds the following nine sites to the NPL, all to the General Superfund Section. All of the sites included in this final rulemaking are being added to the NPL based on HRS scores of 28.50 or above. The sites are presented in the table below: ------------------------------------------------------------------------ State Site name City/County ------------------------------------------------------------------------ FL................ Continental Miami. Cleaners. MD................ Sauer Dump...... Dundalk. MO................ Compass Plaza Rogersville. Well TCE. MS................ Chemfax, Inc.... Gulfport. MS................ Southeastern Canton. Wood Preserving. NC................ CTS of Asheville. Asheville, Inc. NY................ Eighteenmile Niagara County. Creek. PR................ Corozal Well.... Corozal. PA................ Metro Container Trainer. Corporation. ------------------------------------------------------------------------ B. What did the EPA do with the public comments it received? The EPA reviewed all comments received on the sites in this rule and responded to all relevant comments. This rule adds nine sites to the NPL. Five sites received no comments: Corozal Well (PR); Metro Container Corporation (PA); Continental Cleaners (FL); Southeastern Wood Preserving (MS); and Compass Plaza Well TCE (MO). Four sites being placed on the NPL received comments specifically related to the HRS score and these are being addressed in response to comment support documents available concurrent with this final rule: Eighteenmile Creek (NY); Sauer Dump (MD); Chemfax, Inc. (MS); and CTS of Asheville, Inc. (NC). IV. Statutory and Executive Order Reviews A. Executive Order 12866: Regulatory Planning and Review 1. What is Executive Order 12866? Under Executive Order 12866 (58 FR 51735 (October 4, 1993)), the agency must determine whether a regulatory action is ``significant'' and therefore subject to Office of Management and Budget (OMB) review and the requirements of the Executive Order. The Order defines ``significant regulatory action'' as one that is likely to result in a rule that may: (1) Have an annual effect on the economy of $100 million or more or adversely affect in a material way the economy, a sector of the economy, productivity, competition, jobs, the environment, public health or safety, or state, local or tribal governments or communities; (2) create a serious inconsistency or otherwise interfere with an action taken or planned by another agency; (3) materially alter the budgetary impact of entitlements, grants, user fees, or loan programs or the rights and obligations of recipients thereof; or (4) raise novel legal or policy issues arising out of legal mandates, the President's priorities or the principles set forth in the Executive Order. 2. Is this Final Rule subject to Executive Order 12866 review? No. The listing of sites on the NPL does not impose any obligations on any entities. The listing does not set standards or a regulatory regime and imposes no liability or costs. Any liability under CERCLA exists irrespective of whether a site is listed. It has been determined that this action is not a ``significant regulatory action'' under the terms of Executive Order 12866 and is therefore not subject to OMB review. B. Paperwork Reduction Act 1. What is the Paperwork Reduction Act? According to the Paperwork Reduction Act (PRA), 44 U.S.C. 3501 et seq., an agency may not conduct or sponsor, and a person is not required to respond to, a collection of information that requires OMB approval under the PRA, unless it has been approved by OMB and displays a currently valid OMB control number. The OMB control numbers for the EPA's regulations, after initial display in the preamble of the final rules, are listed in 40 CFR part 9. [[Page 15281]] 2. Does the Paperwork Reduction Act apply to this Final Rule? This action does not impose an information collection burden under the provisions of the Paperwork Reduction Act, 44 U.S.C. 3501 et seq. the EPA has determined that the PRA does not apply because this rule does not contain any information collection requirements that require approval of the OMB. Burden means the total time, effort, or financial resources expended by persons to generate, maintain, retain, or disclose or provide information to or for a Federal agency. This includes the time needed to review instructions; develop, acquire, install and utilize technology and systems for the purposes of collecting, validating and verifying information, processing and maintaining information and disclosing and providing information; adjust the existing ways to comply with any previously applicable instructions and requirements; train personnel to be able to respond to a collection of information; search data sources; complete and review the collection of information; and transmit or otherwise disclose the information. An agency may not conduct or sponsor, and a person is not required to respond to a collection of information unless it displays a currently valid OMB control number. The OMB control numbers for the EPA's regulations in 40 CFR are listed in 40 CFR part 9. C. Regulatory Flexibility Act 1. What is the Regulatory Flexibility Act? Pursuant to the Regulatory Flexibility Act (5 U.S.C. 601 et seq., as amended by the Small Business Regulatory Enforcement Fairness Act (SBREFA) of 1996) whenever an agency is required to publish a notice of rulemaking for any proposed or final rule, it must prepare and make available for public comment a regulatory flexibility analysis that describes the effect of the rule on small entities (i.e., small businesses, small organizations and small governmental jurisdictions). However, no regulatory flexibility analysis is required if the head of an agency certifies the rule will not have a significant economic impact on a substantial number of small entities. SBREFA amended the Regulatory Flexibility Act to require Federal agencies to provide a statement of the factual basis for certifying that a rule will not have a significant economic impact on a substantial number of small entities. 2. How has the EPA complied with the Regulatory Flexibility Act? This rule listing sites on the NPL does not impose any obligations on any group, including small entities. This rule also does not establish standards or requirements that any small entity must meet, and imposes no direct costs on any small entity. Whether an entity, small or otherwise, is liable for response costs for a release of hazardous substances depends on whether that entity is liable under CERCLA 107(a). Any such liability exists regardless of whether the site is listed on the NPL through this rulemaking. Thus, this rule does not impose any requirements on any small entities. For the foregoing reasons, I certify that this rule will not have a significant economic impact on a substantial number of small entities. D. Unfunded Mandates Reform Act 1. What is the Unfunded Mandates Reform Act (UMRA)? Title II of the Unfunded Mandates Reform Act of 1995 (UMRA), Public Law 104-4, establishes requirements for Federal agencies to assess the effects of their regulatory actions on state, local and tribal governments and the private sector. Under section 202 of the UMRA, the EPA generally must prepare a written statement, including a cost- benefit analysis, for proposed and final rules with ``federal mandates'' that may result in expenditures by state, local and tribal governments, in the aggregate, or by the private sector, of $100 million or more in any one year. Before the EPA promulgates a rule where a written statement is needed, section 205 of the UMRA generally requires the EPA to identify and consider a reasonable number of regulatory alternatives and adopt the least costly, most cost- effective, or least burdensome alternative that achieves the objectives of the rule. The provisions of section 205 do not apply when they are inconsistent with applicable law. Moreover, section 205 allows the EPA to adopt an alternative other than the least costly, most cost- effective, or least burdensome alternative if the Administrator publishes with the final rule an explanation why that alternative was not adopted. Before the EPA establishes any regulatory requirements that may significantly or uniquely affect small governments, including tribal governments, it must have developed under section 203 of the UMRA a small government agency plan. The plan must provide for notifying potentially affected small governments, enabling officials of affected small governments to have meaningful and timely input in the development of the EPA regulatory proposals with significant Federal intergovernmental mandates and informing, educating and advising small governments on compliance with the regulatory requirements. 2. Does UMRA apply to this Final Rule? This final rule does not contain a Federal mandate that may result in expenditures of $100 million or more for state, local and tribal governments, in the aggregate, or the private sector in any one year. Listing a site on the NPL does not itself impose any costs. Listing does not mean that the EPA necessarily will undertake remedial action. Nor does listing require any action by a private party or determine liability for response costs. Costs that arise out of site responses result from site-specific decisions regarding what actions to take, not directly from the act of placing a site on the NPL. Thus, this rule is not subject to the requirements of section 202 and 205 of UMRA. This rule is also not subject to the requirements of section 203 of UMRA because it contains no regulatory requirements that might significantly or uniquely affect small governments. As is mentioned above, site listing does not impose any costs and would not require any action of a small government. E. Executive Order 13132: Federalism 1. What is Executive Order 13132? Executive Order 13132, entitled ``Federalism'' (64 FR 43255, August 10, 1999), requires the EPA to develop an accountable process to ensure ``meaningful and timely input by state and local officials in the development of regulatory policies that have federalism implications.'' ``Policies that have federalism implications'' are defined in the Executive Order to include regulations that have ``substantial direct effects on the states, on the relationship between the national government and the states, or on the distribution of power and responsibilities among the various levels of government.'' 2. Does Executive Order 13132 apply to this Final Rule? This final rule does not have federalism implications. It will not have substantial direct effects on the states, on the relationship between the national government and the states, or on the distribution of power and responsibilities among the various levels of government, as specified in Executive Order 13132, because it does not contain any requirements applicable to states or other levels of government. [[Page 15282]] Thus, the requirements of the Executive Order do not apply to this final rule. The EPA believes, however, that this final rule may be of significant interest to state governments. In the spirit of Executive Order 13132, and consistent with the EPA policy to promote communications between the EPA and state and local governments, the EPA therefore consulted with state officials and/or representatives of state governments early in the process of developing the rule to permit them to have meaningful and timely input into its development. All sites included in this final rule were referred to the EPA by states for listing. For all sites in this rule, the EPA received letters of support either from the Governor or a state official who was delegated the authority by the Governor to speak on their behalf regarding NPL listing decisions. F. Executive Order 13175: Consultation and Coordination With Indian Tribal Governments 1. What is Executive Order 13175? Executive Order 13175, entitled ``Consultation and Coordination with Indian Tribal Governments'' (65 FR 67249, November 6, 2000), requires the EPA to develop an accountable process to ensure ``meaningful and timely input by tribal officials in the development of regulatory policies that have tribal implications.'' ``Policies that have tribal implications'' are defined in the Executive Order to include regulations that have ``substantial direct effects on one or more Indian tribes, on the relationship between the Federal government and the Indian tribes, or on the distribution of power and responsibilities between the Federal government and Indian tribes.'' 2. Does Executive Order 13175 apply to this Final Rule? This final rule does not have tribal implications, as specified in Executive Order 13175 (65 FR 67249, November 9, 2000). Listing a site on the NPL does not impose any costs on a tribe or require a tribe to take remedial action. Thus, Executive Order 13175 does not apply to this final rule. G. Executive Order 13045: Protection of Children From Environmental Health and Safety Risks 1. What is Executive Order 13045? Executive Order 13045: ``Protection of Children from Environmental Health Risks and Safety Risks'' (62 FR 19885, April 23, 1997) applies to any rule that: (1) Is determined to be ``economically significant'' as defined under Executive Order 12866, and (2) concerns an environmental health or safety risk that the EPA has reason to believe may have a disproportionate effect on children. If the regulatory action meets both criteria, the agency must evaluate the environmental health or safety effects of the planned rule on children, and explain why the planned regulation is preferable to other potentially effective and reasonably feasible alternatives considered by the agency. 2. Does Executive Order 13045 apply to this Final Rule? This rule is not subject to Executive Order 13045 because it is not an economically significant rule as defined by Executive Order 12866, and because the agency does not have reason to believe the environmental health or safety risks addressed by this section present a disproportionate risk to children. H. Executive Order 13211: Actions That Significantly Affect Energy Supply, Distribution, or Usage 1. What is Executive Order 13211? Executive Order 13211, ``Actions Concerning Regulations That Significantly Affect Energy Supply, Distribution or Use'' (66 FR 28355 (May 22, 2001)), requires Federal agencies to prepare a ``Statement of Energy Effects'' when undertaking certain regulatory actions. A Statement of Energy Effects describes the adverse effects of a ``significant energy action'' on energy supply, distribution and use, reasonable alternatives to the action and the expected effects of the alternatives on energy supply, distribution and use. 2. Does Executive Order 13211 apply to this Final Rule? This action is not a ``significant energy action'' as defined in Executive Order 13211, because it is not likely to have a significant adverse effect on the supply, distribution or use of energy. Further, the agency has concluded that this final rule is not likely to have any adverse energy impacts because adding a site to the NPL does not require an entity to conduct any action that would require energy use, let alone that which would significantly affect energy supply, distribution, or usage. Thus, Executive Order 13175 does not apply to this action. I. National Technology Transfer and Advancement Act 1. What is the National Technology Transfer and Advancement Act? Section 12(d) of the National Technology Transfer and Advancement Act of 1995 (NTTAA), Public Law 104-113, section 12(d) (15 U.S.C. 272 note), directs the EPA to use voluntary consensus standards in its regulatory activities unless to do so would be inconsistent with applicable law or otherwise impractical. Voluntary consensus standards are technical standards (e.g., materials specifications, test methods, sampling procedures and business practices) that are developed or adopted by voluntary consensus standards bodies. The NTTAA directs the EPA to provide Congress, through OMB, explanations when the agency decides not to use available and applicable voluntary consensus standards. 2. Does the National Technology Transfer and Advancement Act apply to this Final Rule? No. This rulemaking does not involve technical standards. Therefore, the EPA did not consider the use of any voluntary consensus standards. J. Executive Order 12898: Federal Actions To Address Environmental Justice in Minority Populations and Low-Income Populations 1. What is Executive Order 12898? Executive Order (EO) 12898 (59 FR 7629 (Feb. 16, 1994)) establishes Federal executive policy on environmental justice. Its main provision directs Federal agencies, to the greatest extent practicable and permitted by law, to make environmental justice part of their mission by identifying and addressing, as appropriate, disproportionately high and adverse human health or environmental effects of their programs, policies and activities on minority populations and low-income populations in the United States. 2. Does Executive Order 12898 apply to this Rule? The EPA has determined that this final rule will not have disproportionately high and adverse human health or environmental effects on minority or low-income populations because it does not affect the level of protection provided to human health or the environment. As this rule does not impose any enforceable duty upon state, tribal or local governments, this rule will neither increase nor decrease environmental protection. K. Congressional Review Act 1. Has the EPA submitted this Rule to Congress and the Government Accountability Office? The Congressional Review Act, 5 U.S.C. 801 et seq., as added by the Small Business Regulatory Enforcement [[Page 15283]] Fairness Act of 1996, generally provides that before a rule may take effect, the agency promulgating the rule must submit a rule report, which includes a copy of the rule, to each House of the Congress and to the Comptroller General of the United States. The EPA has submitted a report containing this rule and other required information to the U.S. Senate, the U.S. House of Representatives and the Comptroller General of the United States prior to publication of the rule in the Federal Register. A ``major rule'' cannot take effect until 60 days after it is published in the Federal Register. This rule is not a ``major rule'' as defined by 5 U.S.C. 804(2). 2. Could the effective date of this Final Rule change? Provisions of the Congressional Review Act (CRA) or section 305 of CERCLA may alter the effective date of this regulation. Under the CRA, 5 U.S.C. 801(a), before a rule can take effect, the Federal agency promulgating the rule must submit a report to each House of the Congress and to the Comptroller General. This report must contain a copy of the rule, a concise general statement relating to the rule (including whether it is a major rule), a copy of the cost-benefit analysis of the rule (if any), the agency's actions relevant to provisions of the Regulatory Flexibility Act (affecting small businesses) and the Unfunded Mandates Reform Act of 1995 (describing unfunded Federal requirements imposed on state and local governments and the private sector) and any other relevant information or requirements and any relevant Executive Orders. The EPA has submitted a report under the CRA for this rule. The rule will take effect, as provided by law, within 30 days of publication of this document, since it is not a major rule. Section 804(2) defines a major rule as any rule that the Administrator of the Office of Information and Regulatory Affairs (OIRA) of the Office of Management and Budget (OMB) finds has resulted in or is likely to result in: An annual effect on the economy of $100,000,000 or more; a major increase in costs or prices for consumers, individual industries, Federal, state or local government agencies or geographic regions; or significant adverse effects on competition, employment, investment, productivity, innovation, or on the ability of United States-based enterprises to compete with foreign-based enterprises in domestic and export markets. NPL listing is not a major rule because, as explained above, the listing, itself, imposes no monetary costs on any person. It establishes no enforceable duties, does not establish that the EPA necessarily will undertake remedial action, nor does it require any action by any party or determine liability for site response costs. Costs that arise out of site responses result from site-by-site decisions about what actions to take, not directly from the act of listing itself. Section 801(a)(3) provides for a delay in the effective date of major rules after this report is submitted. 3. What could cause a change in the effective date of this Rule? Under 5 U.S.C. 801(b)(1), a rule shall not take effect, or continue in effect, if Congress enacts (and the President signs) a joint resolution of disapproval, described under section 802. Another statutory provision that may affect this rule is CERCLA section 305, which provides for a legislative veto of regulations promulgated under CERCLA. Although INS v. Chadha, 462 U.S. 919,103 S. Ct. 2764 (1983), and Bd. of Regents of the University of Washington v. EPA, 86 F.3d 1214,1222 (DC Cir. 1996), cast the validity of the legislative veto into question, the EPA has transmitted a copy of this regulation to the Secretary of the Senate and the Clerk of the House of Representatives. If action by Congress under either the CRA or CERCLA section 305 calls the effective date of this regulation into question, the EPA will publish a document of clarification in the Federal Register. List of Subjects in 40 CFR Part 300 Environmental protection, Air pollution control, Chemicals, Hazardous substances, Hazardous waste, Intergovernmental relations, Natural resources, Oil pollution, Penalties, Reporting and recordkeeping requirements, Superfund, Water pollution control, Water supply. Dated: March 8, 2012. Mathy Stanislaus, Assistant Administrator, Office of Solid Waste and Emergency Response. 40 CFR part 300 is amended as follows: PART 300--[AMENDED] 0 1. The authority citation for Part 300 continues to read as follows: Authority: 33 U.S.C. 1321(c)(2); 42 U.S.C. 9601-9657; E.O. 12777, 56 FR 54757, 3 CFR, 1991 Comp., p. 351; E.O. 12580, 52 FR 2923, 3 CFR, 1987 Comp., p. 193. 0 2. Table 1 of Appendix B to Part 300 is amended by adding the following sites in alphabetical order to read as follows: Appendix B to Part 300--National Priorities List Table 1--General Superfund Section ----------------------------------------------------------------------------------- State Site name City/County Notes \a\ ----------------------------------------------------------------------------------- * * * * * * * FL Continental Cleaners........ Miami............................. * * * * * * * MD Sauer Dump.................. Dundalk........................... * * * * * * * MO Compass Plaza Well TCE...... Rogersville....................... * * * * * * * MS Chemfax, Inc................ Gulfport.......................... * * * * * * * MS Southeastern Wood Preserving Canton............................ * * * * * * * NC CTS of Asheville, Inc....... Asheville......................... [[Page 15284]] * * * * * * * NY Eighteenmile Creek......... Niagara County.................... * * * * * * * PA Metro Container Corporation Trainer........................... * * * * * * * PR Corozal Well............... Corozal........................... * * * * * * * ----------------------------------------------------------------------------------- \a\ A = Based on issuance of health advisory by Agency for Toxic Substance and Disease Registry (HRS score need not be greater than or equal to 28.50). S = State top priority (HRS score need not be greater than or equal to 28.50). P = Sites with partial deletion(s). * * * * * [FR Doc. 2012-6329 Filed 3-14-12; 8:45 am] BILLING CODE 6560-50-P
Exposed – FEMEN “Topless Warriors
SECRET from the FBI – Owners Plead Guilty for $5.4 Million Medicare Fraud Scheme
WASHINGTON—Three Detroit-area clinic owners pleaded guilty today for their participation in a Medicare fraud scheme, announced the Department of Justice, the FBI, and the Department of Health and Human Services (HHS).
Karina Hernandez, 28; Marieva Briceno, 46; and Henry Briceno, 58, all of Miami, pleaded guilty before U.S. District Judge Arthur J. Tarnow in the Eastern District of Michigan to one count of conspiracy to commit health care fraud. At sentencing, each defendant faces a maximum penalty of 10 years in prison and a $250,000 fine.
According to the plea documents, Hernandez managed the daily operations of three Livonia, Michigan clinics: Blessed Medical Clinic, Alpha & Omega Medical Clinic, and Manuel Medical Clinic. Marieva Briceno contributed capital to fund the opening of one clinic, and assisted her daughter, Hernandez, in the daily management of the clinics. At each clinic, Hernandez and Marieva Briceno hired recruiters who paid cash bribes to Medicare beneficiaries to attend the clinics and provide their Medicare numbers and other information. Hernandez and Marieva Briceno admitted that they used the beneficiary information to bill for medically unnecessary diagnostic tests and treatments. Henry Briceno admitted that he incorporated Manuel Medical Clinic and opened a bank account to conceal the actual ownership of the clinic. According to court documents, Blessed Medical Clinic, Alpha & Omega Medical Clinic, and Manuel Medical Clinic fraudulently billed Medicare for $5.4 million during the course of the scheme.
Today’s guilty pleas were announced by Assistant Attorney General Lanny A. Breuer of the Justice Department’s Criminal Division; U.S. Attorney for the Eastern District of Michigan Barbara L. McQuade; Special Agent in Charge Andrew G. Arena of the FBI’s Detroit Field Office; and Special Agent in Charge Lamont Pugh, III of the HHS Office of Inspector General’s (OIG) Chicago Regional Office.
This case is being prosecuted by Assistant U.S. Attorneys Frances Lee Carlson and Philip A. Ross of the Eastern District of Michigan, with assistance from Assistant Chief Gejaa T. Gobena of the Criminal Division’s Fraud Section. The case was investigated by the FBI and HHS-OIG and was brought as part of the Medicare Fraud Strike Force, supervised by the Criminal Division’s Fraud Section and the U.S. Attorney’s Office for the Eastern District of Michigan.
Since their inception in March 2007, the Medicare Fraud Strike Force operations in nine districts have charged more than 1,190 individuals, who collectively have falsely billed the Medicare program for more than $3.6 billion. In addition, HHS’s Centers for Medicare and Medicaid Services, working in conjunction with the HHS-OIG, is taking steps to increase accountability and decrease the presence of fraudulent providers.
TOP SECRET – Anonymous/LulzSec Sabu, Kayla, Topiary, Anarchaos, Palladium, Pwnsauce Indictment and Criminal Complaints

UNITED STATES OF AMERICA
– v. –
RYAN ACKROYD,
a/k/a “kayla,”
a/k/a “lol,”
a/k/a “lolspoon,”
JAKE DAVIS,
a/k/a “topiary,”
a/k/a “atopiary”
DARREN MARTYN,
a/k/a “pwnsauce,”
a/k/a “raepsauce,”
a/k/a “networkkitten,”
and DONNCHA O’CEARRBHAIL,
a/k/a “palladium,”
25 pages
DOWNLOAD ORIGINAL DOCUMENT HERE
UNITED STATES OF AMERICA
– v. –
HECTOR XAVIER MONSEGUR,
a/k/a “Sabu,”
a/k/a “Xavier DeLeon,”
a/k/a “Leon,”
27 pages
DOWNLOAD ORIGINAL DOCUMENT HERE
UNITED STATES OF AMERICA
– v. –
JEREMY HAMMOND,
a/k/a “Anarchaos,”
a/k/a “sup_g,”
a/k/a “burn,”
a/k/a “yohoho,”
a/k/a “POW,”
a/k/a “tylerknowsthis,”
a/k/~ “crediblethreat,”
34 pages
DOWNLOAD ORIGINAL DOCUMENT HERE
UNITED STATES OF AMERICA
– v. –
DONNCHA O’CEARRBHAIL,
a/k/a “palladium”
a/k/a “polonium,”
a/k/a “anonsacco,”
10 pages
DOWNLOAD ORIGINAL DOCUMENT HERE
UNCENSORED – FEMEN – Moscow Protest Performance Гаси Газпром! (shut gazprom!)
Femen Moscow Protest Performance Гаси Газпром! (shut gazprom!, stop gaz blackmail)
Public Intelligence – Marine Corps Intelligence Activity Cultural Intelligence Indicators Guide (CIIG)

Understanding the local culture is critical to mission success. This Cultural Intelligence Indicators Guide (CIIG ) will contribute to an initial Intelligence Preparation of the Operational Environment that should be continuously updated by line companies. It is intended to aid Marines in the identification of key cultural observables during security and atmospherics patrols, while at the same time helping tactical unit leaders identify the information needed to understand and influence their local environment. The intent is to anticipate the second and third order effects of our actions in order to shape and influence events to our advantage.
How is this guide organized?
There are 12 sections within this guide. Within each section, the questions are divided into indicators Marines can observe during patrols and into things that Marines can find out during engagements with local populations. Marines may choose to focus of these sections directly tied to their mission. The first few sections cover basic cultural indicators about the local populace to include language, education, economy, health, and the environment. These indicators are most often readily observable or easily accessible and will help the Marines understand people’s backgrounds in order to anticipate or prevent potential sources of friction or conflict. The latter sections cover more complex cultural indicators such social organization, power and authority, values and beliefs, and motivating issues. These sections are crucial in helping Marines understand the organization and mindset of the local people in order to better shape and influence lines of operations.
…
Practical Field Application of the CIIG
During security and stability operations overseas, Marines set up check points where personnel were screened for identification. After a short time, the Marines turned the check points over to local police. They noticed, however, that some odd practices were cropping up. The local police were given instructions to not let anyone through after 1800 except uniformed members of the police and members of coalition forces. After a while, one of the Marines noticed that traffic did not diminish after 1800 for one check point in particular. The Marine joined a local policeman on guard duty and found that higher ranking police officers were running a taxi service for nonpolice locals who needed to pass the check point and were willing to pay. The local policeman at the checkpoint also got some money for every ‘taxi’ he let though. “But I have to let him through,” said the policeman when confronted. “He’s an important man in my tribe, so it’s hard for me to say no.”
Using Cultural Intelligence Indicators
- Marines noticed a change in daily traffic patterns at check points. Traffic patterns were an important indicator of cultural intelligence for this locality. (See CIIG, pp. 36–38)
- Marines went beyond directly observable indicators to find out why the traffic patterns changed. This led Marines to learn about dominant affiliations and backgrounds of the population in the AO. (See CIIG, p. 8)
- Marines also found out about informal services and the wielding of power in that locality. (See CIIG, pp. 22–24, 60–62)
- To learn more about interactions among tribes in the AO, Marines could also investigate which tribes did and did not take advantage of ‘taxi’ service.
Israel – Former head of the Counter-Terrorism Bureau, Nitzan Nuriel – Attacks on Israel from Turkey
Former head of the Counter-Terrorism Bureau, Nitzan Nuriel, is calling on Israelis in Turkey to operate cautiously in light of information that terror elements are seeking to carry out attacks against Israeli targets

The Counter-Terrorism Bureau increased its existing travel alert for Turkey yesterday (Tuesday), following intelligence information that terror elements intend to carry out attacks against Israeli or Jewish targets.
In a special interview for IsraelDefense, the former head of the Counter-Terrorism Bureau, Nitzan Nuriel, explained that behind the bureau’s decision was “a coalition of jihadists, and it makes no difference if it’s Hezbollah, the Revolutionary Guard, or anyone else who is identifying Turkey as a convenient place to operate. The country has a shared border with Iran and Syria, and the anti-Israeli sentiment is very extensive.”
He continued, by saying, “The truth needs to be said – there is a sort of cooperation between the terrorists and the local security forces in Turkey.” This morning the Turkish media reported that Turkey’s Prime Minister, Tayyip Rajab Erdogan, sent a warning to Iran in which he warned the Revolutionary Guard against hurting Israelis or Jews. Nuriel believes that this was only “lip service.” “They just don’t want to find themselves arresting Iranians for the moment, so they prefer to hint that they not reach them.” He added that so far, no one has demanded that the terrorists that have already operated in Turkey answer for their actions. “Turkey knows who carried out the May 2011 attacks (in which several people were wounded in what was apparently an attempt to hurt the Israeli consul), and have yet to punish those responsible. The terrorists are operating in a convenient arena, in which there are many targets, and they know they will not pay a price for it.”
According to Nuriel, there are three possible targets for terrorists in Turkey – the Jewish community, Israeli diplomats, and business people from Israel that reside in the country. “With regards to the Jews, the Turkish government is responsible for protecting them, as they protect other populations in the country. The diplomats are secured by Israel. The business people, however, are the most vulnerable targets at the moment, which is why the travel warning was escalated.
“Business in Turkey might be good for the Israeli economy, but business people must be offered several ways to reduce their risk of danger. It’s recommended that the same cab driver not be taken more than once; meet in central and bustling areas, not in remote locations; it’s best to go to a meeting with two people, and carefully inspect every businessman you are invited to meet for the first time, regardless of how tempting and lucrative his proposal may be,” Nuriel explains.
Facebook Warnings
Nuriel said that the Counter-Terrorism Bureau launched a Facebook page two weeks ago that publishes travel warnings for Israelis overseas. It was made especially for Israeli backpackers and those residing overseas for long durations who are not up-to-date regarding news events in Israel.
“Travelers, especially youths, go to distant locations in the world and upload their photos to Facebook in real-time. What they don’t realize is that they’re making a doubled mistake. They’re essentially telling anyone looking at the page, ‘Hey, I’m here, and I’m an Israeli.’ It’s better to upload photos from the trip a week later after leaving the place.”
TOP-SECRET – Communication from Gromyko to Stalin
| Communication from Gromyko to Stalin Concerning a Draft Reply to the United States, England, and France on the Matter of the National Police of the German Democratic Republic, 22 September 1950 | |
| Date: 09/22/1950 |
Source: Library of Congress |
| Description: Communication from Gromyko to Stalin Concerning a Draft Reply to the United States, England, and France on the Matter of the National Police of the German Democratic Republic, 22 September 1950 |
|
Strictly Secret
All-Union Communist Party [Bolsheviks] [VKP(b)]. CENTRAL COMMITTEE [TSK].
p.78/32 To Comrades Malenkov, Gromyko
September 25, 1950. Excerpt from Minutes No. 78, session of the Politburo of the Central Committee of the VKP(b).
Decision of September 25, 1950
32. Draft communique from the Soviet government to the governments of the U.S.A., England, and France on the matter of the national police of the German Democratic Republic.
To instruct Comrade Gromyko to present within 3 days, based on an exchange of opinions, an explanatory note and amended reply from the USSR government to the governments of the U.S.A., England, and France concerning the national police of the German Democratic Republic.
Politburo TSK VK(b)
To Comrade J. STALIN
The governments of the U.S.A., England, and France have sent to the Ministry of Foreign Affairs [MID of the USSR communiques of similar content asserting that the national police of the German Democratic Republic do not perform normal police functions but have the character of an army. In connection with this the communiques charges that the Soviet government with violating the decisions of the Potsdam Conference and other quadrilateral international agreements on the demilitarization of Germany.
The MID advises sending the governments of the U.S.A., England, and France replies deflecting these assertions as groundless, point out that the national police of the GDR was created for the protection of the democratic processes established in the GDR in accordance with the decisions of the Potsdam Conference on the democratization of Germany.
Facts about the creation of an army in the guise of armed police by the governments of the U.S.A., England, and France in West Germany appear in this communique.
The TSK VK(b) has already examined the matter of sending replies to the governments of the three powers. It was decided to return to this question later.
Considering the meetings of the western powers now taking place on the question of rearming West Germany and the launching of a broad campaign in the west European press of the creation of German armed forces, the MID requests again your review of the Soviet government’s response.
The draft resolution is attached.
I request your review.
[signed] A. Gromyko
September 23, 1950
Confidential – U.S. Marine Corps Intelligence Activity Afghanistan Cultural Intelligence Reports

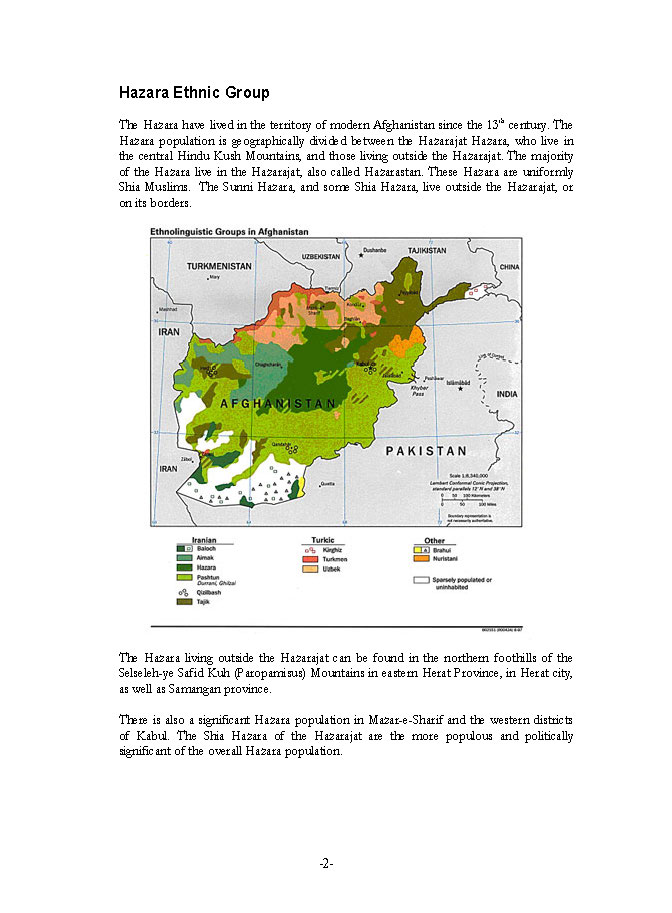

The collection of “cultural intelligence” reports for the Afghanistan region were created by the Marine Corps Intelligence Activity (MCIA). They represent some of the only known public examples of MCIA cultural intelligence reports available on the web. In 2008, a MCIA cultural intelligence report on Iran’s culture was obtained and published by the Center for Public Integrity. The following reports on Afghan culture were produced in 2002, but are still believed to be in use by advisers and soldiers today.
FEMEN Uncensored – Topless Protest in Istanbul
The FBI – Former Business Executive Pleads Guilty to Federal Charges in Alleged $28 Million Bribery and Kickback Scheme
WASHINGTON—Harold F. Babb, 60, the former director of contracts at Eyak Technology LLC (EyakTek), pled guilty today to federal charges of bribery and unlawful kickbacks for his role in a scheme that allegedly involved more than $28 million in bribes and kickback payments and the planned steering of a government contract that potentially was worth about $1 billion.
The plea was announced by U.S. attorney Ronald C. Machen Jr.; James W. McJunkin, assistant director in Ccharge of the FBI’s Washington Field Office; Eric Hylton, acting special agent in charge of the Washington Field Office of the Internal Revenue Service-Criminal Investigation (IRS-CI); Peggy E. Gustafson, inspector general for the Small Business Administration (SBA); Robert E. Craig, special agent in charge of the Mid-Atlantic Field Office of the Defense Criminal Investigative Service (DCIS); and Major General David E. Quantock, the commanding general of the U.S. Army Criminal Investigation Command (CID).
Babb, formerly of Sterling, Virginia, pled guilty before the Honorable Emmet G. Sullivan in the U.S. District Court for the District of Columbia. A sentencing date has not been set. The bribery charge carries a statutory maximum of 15 years in prison and the unlawful kickbacks charge carries up to 10 years of incarceration. The charges also carry potential fines, an order of restitution, and forfeiture of a money judgment for $689,342, including more than $200,000 in cash and bank account funds and the value of properties in Sterling and Virginia Beach, Virginia and a 2007 Porsche.
The guilty plea is the latest example of law enforcement’s commitment to rooting out public corruption as well as fraud involving government contracts. Since 2010, the U.S. Attorney’s Office for the District of Columbia has secured convictions against more than 80 people on public corruption charges, including more than three dozen federal and local government employees.
As part of his plea agreement, Babb agreed to cooperate in the government’s ongoing investigation into contracts involving, among others, the U.S. Army Corps of Engineers.
***
“As our investigation has continued, we have identified millions of dollars more in bribes,” said U.S. Attorney Machen. “With today’s plea, another government contractor has accepted responsibility for corrupting the federal procurement process with bribes and kickbacks. He faces significant prison time for his role in this scheme, and will forfeit to the government cash, properties, and a Porsche that he bought with his ill-gotten gains. Unethical contractors should understand that their attempts to fleece the taxpayer will not only carry harsh financial penalties but also real prison time as well.”
“Today’s plea, in one of the largest procurement fraud cases in history, demonstrates that those who engage in bribes and kickbacks will be held accountable for their actions,” said Assistant Director in Charge McJunkin. “Together with our law enforcement partners, the FBI will continue to ensure those who commit fraud and corruption are brought to justice.”
“Today’s plea hearing is a reminder that individuals who scheme to defraud the U.S. government and violate the public’s trust will be brought to justice, said Acting IRS Special Agent in Charge Eric Hylton. “Steering business to favored individuals in exchange for kickbacks and using bribes to secure government contracts will not be tolerated. The IRS Criminal Investigation Division will continue to work with the U.S. Attorney’s Office and other law enforcement agencies to punish corrupt behavior wherever we find it.”
“The brazen and corrupt actions by the defendants in this case, who bribed government officials to obtain set-aside contracts and share in the illicit proceeds, harms legitimate small businesses seeking to do business with the government,” said Inspector General Gustafson. “The evidence demonstrates Harold Babb’s participation was an integral part of this scheme. The SBA OIG appreciates the leadership of the U.S. Attorney’s Office and the support of the FBI and our interagency partners in bringing forth this plea agreement.”
“The illegal manipulation of contracts and subcontracts to facilitate bribes and kickbacks that circumvent the military contracting process costs the taxpayer and warfighter alike,” said Special Agent in Charge Craig. “DCIS continues to work alongside its federal law enforcement partners in innovative ways to further detect and deter fraud, and bring those to justice that criminally exploit the contracting process.”
“As this case illustrates, Army CID’s Major Procurement Fraud Unit will aggressively pursue anyone who attempts to defraud the U.S. government,” said Major General Quantock. “Army CID, along with our federal law enforcement partners, are committed to ensuring that these conspirators are held accountable for their illegal activities.”
***
According to a statement of offense signed by Babb, he was the director of contracts at Eyak Technology (EyakTek), an Alaska Native-owned small business with an office in Dulles, Virginia, from 2006 until the time of his arrest in October 2011. He admitted participating in a scheme that involved the U.S. Army Corps of Engineers and two contracts: the Technology for Infrastructure, Geospatial, and Environmental Requirements (TIGER) contract and the Contingency Operations Readiness Engineering & Support (CORES) contract.
The TIGER contract was used by authorized federal government agencies and departments to purchase products and services. The CORES contract was a planned contract, envisioned as an alternative or potential replacement to the TIGER contract.
In his guilty plea, Babb admitted to carrying out the scheme with others. They included Kerry F. Khan and Michael A. Alexander, who at the time were program managers with the Army Corps of Engineers; Alex N. Cho, the former chief technology officer of Nova Datacom, LLC, a provider of information assurance and security services to federal agencies and commercial companies, and James Edward Miller, who owned and controlled Big Surf Construction Management LLC.
The bribery charge stems from Babb’s payments and promises to Khan in return for Khan’s approval on contracts and subcontracts awarded through the Army Corps of Engineers to EyakTek and Big Surf Construction Management. All told, Babb pled guilty to providing, offering, and promising more than $7 million, directly and indirectly, to Khan.
The kickback charge stems from Babb’s dealings with Cho and Nova Datacom. Babb pled guilty to soliciting, accepting, and attempting to accept more than $1 million in kickbacks from Cho and Nova Datacom in return for giving the company preferential treatment on subcontracts.
***
Activities Involving the TIGER Contract
According to the statement of offense, starting in 2008, Babb and Khan agreed to work together in a plan in which the Army Corps of Engineers would pay millions of dollars for equipment and services that never actually would be provided.
EyakTek was the prime contractor for the TIGER contract and entered into agreements with subcontractors that included Nova Datacom, Big Surf Construction Management, and Ananke LLC, a company that was controlled by Khan.
In or about 2008, Khan introduced Babb to Cho. Babb agreed to accept kickbacks—money, gifts, and things of value—from Cho as compensation for Babb providing favorable treatment to Nova Datacom on subcontracts. From 2008 until October 2011, Cho offered and made more than $1 million in payments, directly and indirectly, to Babb. These included cash and checks of more than $344,000, airline tickets worth about $100,000, a future offer to pay Babb $600,000, and a promise of future employment for Babb at Nova Datacom.
From May 2007 through October 2011, the Army Corps of Engineers awarded contracts and sub-contracts to Nova Datacom totaling more than $45 million.
Also in or about 2008, Babb and Khan agreed to use Big Surf Construction Management and Ananke to obtain subcontracts from EyakTek. Khan did not intend for either Big Surf or Ananke to provide any equipment or services pursuant to the contracts. Instead, according to the statement of offense, Babb and Khan agreed to submit fictitious orders to the Army Corps of Engineers and EyakTek through Big Surf and to distribute the proceeds obtained amongst themselves and Big Surf’s Miller.
Babb intended these payments to benefit Khan, in part, in exchange for Khan using his official position to direct the government orders to Big Surf and EyakTek.
The statement of offense identifies three subcontracts awarded and paid by EyakTek to Big Surf, totaling more than $8 million. Of this money, Big Surf channeled more than $3.6 million from the first two subcontracts to Ananke. According to the statement of offense, Babb directed Miller to pay another $2.9 million, from the third subcontract, to Ananke. However, Miller allegedly reneged on the plan and Big Surf kept the money. As a result, a fourth intended subcontract, worth about $1.9 million, was cancelled.
During the scheme, Babb received a number of benefits from Big Surf, including nearly $270,000 used for a property in Virginia Beach, Virginia; $66,000 for a 2007 Porsche; and $9,000 for the purchase of a 2005 Hyundai.
***
Activities Involving the CORES Contract
According to the statement of offense, Babb, Khan, Alexander, and Cho agreed to work together to steer the award of the CORES contract to Nova Datacom. Cho promised Babb future employment and other benefits for his agreement to help steer the award to Nova Datacom, and Babb acted as an intermediary to offer things of value to an unnamed contracting officer with the Army Corps of Engineers.
By the end of September 2011, the unnamed contracting officer and Babb agreed to move ahead on a five-year CORES contract for a total amount of $790 million. They agreed that, after the contract was awarded to Nova Datacom, the contracting officer would seek an additional 25 percent increase in the award, for a total potential award of nearly $1 billion.
This scheme was thwarted by the arrests of Babb and the others last fall.
***
Khan, 54, formerly of Alexandria, Virginia; Khan’s son, Lee Khan, 31, formerly of Fairfax, Virginia; and Alexander, 56, formerly of Woodbridge, were indicted along with Babb in September 2011 on one count of conspiracy to commit bribery and wire fraud and aiding and abetting and causing an illegal act to be done, as well as one count of conspiracy to commit money laundering. Khan and Alexander also were indicted on one count of receipt of a bribe by a public official, and Babb was indicted on one count of unlawful kickbacks. Khan and his son have pleaded not guilty to all charges in the case and are awaiting trial. Khan, Lee Khan, Babb, and Alexander have been in custody since their arrests in October.
Alexander pled guilty in February 2012 to federal charges of bribery and conspiracy to commit money laundering. Cho, 40, of Great Falls, Virginia, pled guilty in September 2011 to one count of conspiracy to commit bribery, money laundering, and wire fraud, and to defraud the United States, and one count of bribery.
Another former Nova Datacom employee, Theodoros Hallas, 40, of Potomac, Maryland, the company’s former Executive Vice President, pled guilty in October 2011 to one count of conspiracy to commit wire fraud. Another businessman, Robert L. McKinney, 51, the president of Alpha Technology Group, one of the companies involved in the contracting scam, pled guilty in February 2012 to bribery. No sentencing dates have been set for any of the defendants.
Miller, 64, formerly of Virginia Beach, the owner of Big Surf, was charged in a criminal information on March 12, 2012 with conspiracy to commit money laundering. The filing of an information is merely a formal charge that a defendant has committed a violation of criminal laws and is not evidence of guilt. Every defendant is presumed innocent until, and unless, proven guilty.
The indictment returned last September against the Khans, Alexander, and Babb included allegations involving more than $20 million in offers and payments of bribes and kickback payments related to Nova Datacom. However, that did not include bribes and kickback payments related to other contractors, such as Big Surf and Alpha Technology Group, which were uncovered in the investigation. The case now involves in excess of $28 million in alleged offers and payments of bribes and kickback payments.
To date, the United States has seized for forfeiture or recovered approximately $7.2 million in bank account funds, cash, and repayments; 16 real properties; five luxury cars; and multiple pieces of fine jewelry.
***
In announcing the plea, U.S. Attorney Machen, Assistant Director McJunkin, Acting Special Agent in Charge Hylton, Inspector General Gustafson, Special Agent in Charge Craig, and Major General Quantock thanked those who investigated the case from the FBI’s Washington Field Office; the Washington Field Office of the Internal Revenue Service-Criminal Investigation; the Office of the Inspector General for the Small Business Administration; the Department of Defense’s Defense Criminal Investigative Service; the Defense Contract Audit Agency; and the Army Criminal Investigation Command. They also expressed thanks to the U.S. Marshals Service for its assistance on the forfeiture matter.
They also praised the efforts of those who worked on the case from the U.S. Attorney’s Office, including Assistant U.S. Attorneys Michael K. Atkinson and Bryan Seeley of the Fraud and Public Corruption Section and Assistant U.S. Attorney Anthony Saler of the Asset Forfeiture and Money Laundering Section. Finally, they expressed thanks for assistance provided by former Special Assistant U.S. Attorney Christopher Dana; Forensic Accountant Maria Boodoo; Paralegal Specialists Tasha Harris, Shanna Hays, Taryn McLaughlin, Sarah Reis, Christopher Samson, and Nicole Wattelet, and Legal Assistants Jared Forney and Krishawn Graham.
Confidential – Attorney General Eric Holder Speech on Targeted Killing of U.S. Citizens

Thank you, Dean [Daniel] Rodriguez, for your kind words, and for the outstanding leadership that you provide – not only for this academic campus, but also for our nation’s legal community. It is a privilege to be with you today – and to be among the distinguished faculty members, staff, alumni, and students who make Northwestern such an extraordinary place.
For more than 150 years, this law school has served as a training ground for future leaders; as a forum for critical, thoughtful debate; and as a meeting place to consider issues of national concern and global consequence. This afternoon, I am honored to be part of this tradition. And I’m grateful for the opportunity to join with you in discussing a defining issue of our time – and a most critical responsibility that we share: how we will stay true to America’s founding – and enduring – promises of security, justice and liberty.
Since this country’s earliest days, the American people have risen to this challenge – and all that it demands. But, as we have seen – and as President John F. Kennedy may have described best – “In the long history of the world, only a few generations have been granted the role of defending freedom in its hour of maximum danger.”
Half a century has passed since those words were spoken, but our nation today confronts grave national security threats that demand our constant attention and steadfast commitment. It is clear that, once again, we have reached an “hour of danger.”
We are a nation at war. And, in this war, we face a nimble and determined enemy that cannot be underestimated.
Like President Obama – and my fellow members of his national security team – I begin each day with a briefing on the latest and most urgent threats made against us in the preceding 24 hours. And, like scores of attorneys and agents at the Justice Department, I go to sleep each night thinking of how best to keep our people safe.
I know that – more than a decade after the September 11th attacks; and despite our recent national security successes, including the operation that brought to justice Osama bin Laden last year – there are people currently plotting to murder Americans, who reside in distant countries as well as within our own borders. Disrupting and preventing these plots – and using every available and appropriate tool to keep the American people safe – has been, and will remain, this Administration’s top priority.
But just as surely as we are a nation at war, we also are a nation of laws and values. Even when under attack, our actions must always be grounded on the bedrock of the Constitution – and must always be consistent with statutes, court precedent, the rule of law and our founding ideals. Not only is this the right thing to do – history has shown that it is also the most effective approach we can take in combating those who seek to do us harm.
This is not just my view. My judgment is shared by senior national security officials across the government. As the President reminded us in 2009, at the National Archives where our founding documents are housed, “[w]e uphold our most cherished values not only because doing so is right, but because it strengthens our country and it keeps us safe. Time and again, our values have been our best national security asset.” Our history proves this. We do not have to choose between security and liberty – and we will not.
Today, I want to tell you about the collaboration across the government that defines and distinguishes this Administration’s national security efforts. I also want to discuss some of the legal principles that guide – and strengthen – this work, as well as the special role of the Department of Justice in protecting the American people and upholding the Constitution.
Before 9/11, today’s level of interagency cooperation was not commonplace. In many ways, government lacked the infrastructure – as well as the imperative – to share national security information quickly and effectively. Domestic law enforcement and foreign intelligence operated in largely independent spheres. But those who attacked us on September 11th chose both military and civilian targets. They crossed borders and jurisdictional lines. And it immediately became clear that no single agency could address these threats, because no single agency has all of the necessary tools.
To counter this enemy aggressively and intelligently, the government had to draw on all of its resources – and radically update its operations. As a result, today, government agencies are better postured to work together to address a range of emerging national security threats. Now, the lawyers, agents and analysts at the Department of Justice work closely with our colleagues across the national security community to detect and disrupt terrorist plots, to prosecute suspected terrorists, and to identify and implement the legal tools necessary to keep the American people safe. Unfortunately, the fact and extent of this cooperation are often overlooked in the public debate – but it’s something that this Administration, and the previous one, can be proud of.
As part of this coordinated effort, the Justice Department plays a key role in conducting oversight to ensure that the intelligence community’s activities remain in compliance with the law, and, together with the Foreign Intelligence Surveillance Court, in authorizing surveillance to investigate suspected terrorists. We must – and will continue to – use the intelligence-gathering capabilities that Congress has provided to collect information that can save and protect American lives. At the same time, these tools must be subject to appropriate checks and balances – including oversight by Congress and the courts, as well as within the Executive Branch – to protect the privacy and civil rights of innocent individuals. This Administration is committed to making sure that our surveillance programs appropriately reflect all of these interests.
Let me give you an example. Under section 702 of the Foreign Intelligence Surveillance Act, the Attorney General and the Director of National Intelligence may authorize annually, with the approval of the Foreign Intelligence Surveillance Court, collection directed at identified categories of foreign intelligence targets, without the need for a court order for each individual subject. This ensures that the government has the flexibility and agility it needs to identify and to respond to terrorist and other foreign threats to our security. But the government may not use this authority intentionally to target a U.S. person, here or abroad, or anyone known to be in the United States.
The law requires special procedures, reviewed and approved by the Foreign Intelligence Surveillance Court, to make sure that these restrictions are followed, and to protect the privacy of any U.S. persons whose nonpublic information may be incidentally acquired through this program. The Department of Justice and the Office of the Director of National Intelligence conduct extensive oversight reviews of section 702 activities at least once every sixty days, and we report to Congress on implementation and compliance twice a year. This law therefore establishes a comprehensive regime of oversight by all three branches of government. Reauthorizing this authority before it expires at the end of this year is the top legislative priority of the Intelligence Community.
But surveillance is only the first of many complex issues we must navigate. Once a suspected terrorist is captured, a decision must be made as to how to proceed with that individual in order to identify the disposition that best serves the interests of the American people and the security of this nation.
Much has been made of the distinction between our federal civilian courts and revised military commissions. The reality is that both incorporate fundamental due process and other protections that are essential to the effective administration of justice – and we should not deprive ourselves of any tool in our fight against al Qaeda.
Our criminal justice system is renowned not only for its fair process; it is respected for its results. We are not the first Administration to rely on federal courts to prosecute terrorists, nor will we be the last. Although far too many choose to ignore this fact, the previous Administration consistently relied on criminal prosecutions in federal court to bring terrorists to justice. John Walker Lindh, attempted shoe bomber Richard Reid, and 9/11 conspirator Zacarias Moussaoui were among the hundreds of defendants convicted of terrorism-related offenses – without political controversy – during the last administration.
Over the past three years, we’ve built a remarkable record of success in terror prosecutions. For example, in October, we secured a conviction against Umar Farouk Abdulmutallab for his role in the attempted bombing of an airplane traveling from Amsterdam to Detroit on Christmas Day 2009. He was sentenced last month to life in prison without the possibility of parole. While in custody, he provided significant intelligence during debriefing sessions with the FBI. He described in detail how he became inspired to carry out an act of jihad, and how he traveled to Yemen and made contact with Anwar al-Aulaqi, a U.S. citizen and a leader of al Qaeda in the Arabian Peninsula. Abdulmutallab also detailed the training he received, as well as Aulaqi’s specific instructions to wait until the airplane was over the United States before detonating his bomb.
In addition to Abdulmutallab, Faizal Shahzad, the attempted Times Square bomber, Ahmed Ghailani, a conspirator in the 1998 U.S. embassy bombings in Kenya and Tanzania, and three individuals who plotted an attack against John F. Kennedy Airport in 2007, have also recently begun serving life sentences. And convictions have been obtained in the cases of several homegrown extremists, as well. For example, last year, United States citizen and North Carolina resident Daniel Boyd pleaded guilty to conspiracy to provide material support to terrorists and conspiracy to murder, kidnap, maim, and injure persons abroad; and U.S. citizen and Illinois resident Michael Finton pleaded guilty to attempted use of a weapon of mass destruction in connection with his efforts to detonate a truck bomb outside of a federal courthouse.
I could go on. Which is why the calls that I’ve heard to ban the use of civilian courts in prosecutions of terrorism-related activity are so baffling, and ultimately are so dangerous. These calls ignore reality. And if heeded, they would significantly weaken – in fact, they would cripple – our ability to incapacitate and punish those who attempt to do us harm.
Simply put, since 9/11, hundreds of individuals have been convicted of terrorism or terrorism-related offenses in Article III courts and are now serving long sentences in federal prison. Not one has ever escaped custody. No judicial district has suffered any kind of retaliatory attack. These are facts, not opinions. There are not two sides to this story. Those who claim that our federal courts are incapable of handling terrorism cases are not registering a dissenting opinion — they are simply wrong.
But federal courts are not our only option. Military commissions are also appropriate in proper circumstances, and we can use them as well to convict terrorists and disrupt their plots. This Administration’s approach has been to ensure that the military commissions system is as effective as possible, in part by strengthening the procedural protections on which the commissions are based. With the President’s leadership, and the bipartisan backing of Congress, the Military Commissions Act of 2009 was enacted into law. And, since then, meaningful improvements have been implemented.
It’s important to note that the reformed commissions draw from the same fundamental protections of a fair trial that underlie our civilian courts. They provide a presumption of innocence and require proof of guilt beyond a reasonable doubt. They afford the accused the right to counsel – as well as the right to present evidence and cross-examine witnesses. They prohibit the use of statements obtained through torture or cruel, inhuman, or degrading treatment. And they secure the right to appeal to Article III judges – all the way to the United States Supreme Court. In addition, like our federal civilian courts, reformed commissions allow for the protection of sensitive sources and methods of intelligence gathering, and for the safety and security of participants.
A key difference is that, in military commissions, evidentiary rules reflect the realities of the battlefield and of conducting investigations in a war zone. For example, statements may be admissible even in the absence of Miranda warnings, because we cannot expect military personnel to administer warnings to an enemy captured in battle. But instead, a military judge must make other findings – for instance, that the statement is reliable and that it was made voluntarily.
I have faith in the framework and promise of our military commissions, which is why I’ve sent several cases to the reformed commissions for prosecution. There is, quite simply, no inherent contradiction between using military commissions in appropriate cases while still prosecuting other terrorists in civilian courts. Without question, there are differences between these systems that must be – and will continue to be – weighed carefully. Such decisions about how to prosecute suspected terrorists are core Executive Branch functions. In each case, prosecutors and counterterrorism professionals across the government conduct an intensive review of case-specific facts designed to determine which avenue of prosecution to pursue.
Several practical considerations affect the choice of forum.
First of all, the commissions only have jurisdiction to prosecute individuals who are a part of al Qaeda, have engaged in hostilities against the United States or its coalition partners, or who have purposefully and materially supported such hostilities. This means that there may be members of certain terrorist groups who fall outside the jurisdiction of military commissions because, for example, they lack ties to al Qaeda and their conduct does not otherwise make them subject to prosecution in this forum. Additionally, by statute, military commissions cannot be used to try U.S. citizens.
Second, our civilian courts cover a much broader set of offenses than the military commissions, which can only prosecute specified offenses, including violations of the laws of war and other offenses traditionally triable by military commission. This means federal prosecutors have a wider range of tools that can be used to incapacitate suspected terrorists. Those charges, and the sentences they carry upon successful conviction, can provide important incentives to reach plea agreements and convince defendants to cooperate with federal authorities.
Third, there is the issue of international cooperation. A number of countries have indicated that they will not cooperate with the United States in certain counterterrorism efforts — for instance, in providing evidence or extraditing suspects – if we intend to use that cooperation in pursuit of a military commission prosecution. Although the use of military commissions in the United States can be traced back to the early days of our nation, in their present form they are less familiar to the international community than our time-tested criminal justice system and Article III courts. However, it is my hope that, with time and experience, the reformed commissions will attain similar respect in the eyes of the world.
Where cases are selected for prosecution in military commissions, Justice Department investigators and prosecutors work closely to support our Department of Defense colleagues. Today, the alleged mastermind of the bombing of the U.S.S. Cole is being prosecuted before a military commission. I am proud to say that trial attorneys from the Department of Justice are working with military prosecutors on that case, as well as others.
And we will continue to reject the false idea that we must choose between federal courts and military commissions, instead of using them both. If we were to fail to use all necessary and available tools at our disposal, we would undoubtedly fail in our fundamental duty to protect the Nation and its people. That is simply not an outcome we can accept.
This Administration has worked in other areas as well to ensure that counterterrorism professionals have the flexibility that they need to fulfill their critical responsibilities without diverging from our laws and our values. Last week brought the most recent step, when the President issued procedures under the National Defense Authorization Act. This legislation, which Congress passed in December, mandated that a narrow category of al Qaeda terrorist suspects be placed in temporary military custody.
Last Tuesday, the President exercised his authority under the statute to issue procedures to make sure that military custody will not disrupt ongoing law enforcement and intelligence operations — and that an individual will be transferred from civilian to military custody only after a thorough evaluation of his or her case, based on the considered judgment of the President’s senior national security team. As authorized by the statute, the President waived the requirements for several categories of individuals where he found that the waivers were in our national security interest. These procedures implement not only the language of the statute but also the expressed intent of the lead sponsors of this legislation. And they address the concerns the President expressed when he signed this bill into law at the end of last year.
Now, I realize I have gone into considerable detail about tools we use to identify suspected terrorists and to bring captured terrorists to justice. It is preferable to capture suspected terrorists where feasible – among other reasons, so that we can gather valuable intelligence from them – but we must also recognize that there are instances where our government has the clear authority – and, I would argue, the responsibility – to defend the United States through the appropriate and lawful use of lethal force.
This principle has long been established under both U.S. and international law. In response to the attacks perpetrated – and the continuing threat posed – by al Qaeda, the Taliban, and associated forces, Congress has authorized the President to use all necessary and appropriate force against those groups. Because the United States is in an armed conflict, we are authorized to take action against enemy belligerents under international law. The Constitution empowers the President to protect the nation from any imminent threat of violent attack. And international law recognizes the inherent right of national self-defense. None of this is changed by the fact that we are not in a conventional war.
Our legal authority is not limited to the battlefields in Afghanistan. Indeed, neither Congress nor our federal courts has limited the geographic scope of our ability to use force to the current conflict in Afghanistan. We are at war with a stateless enemy, prone to shifting operations from country to country. Over the last three years alone, al Qaeda and its associates have directed several attacks – fortunately, unsuccessful – against us from countries other than Afghanistan. Our government has both a responsibility and a right to protect this nation and its people from such threats.
This does not mean that we can use military force whenever or wherever we want. International legal principles, including respect for another nation’s sovereignty, constrain our ability to act unilaterally. But the use of force in foreign territory would be consistent with these international legal principles if conducted, for example, with the consent of the nation involved – or after a determination that the nation is unable or unwilling to deal effectively with a threat to the United States.
Furthermore, it is entirely lawful – under both United States law and applicable law of war principles – to target specific senior operational leaders of al Qaeda and associated forces. This is not a novel concept. In fact, during World War II, the United States tracked the plane flying Admiral Isoroku Yamamoto – the commander of Japanese forces in the attack on Pearl Harbor and the Battle of Midway – and shot it down specifically because he was on board. As I explained to the Senate Judiciary Committee following the operation that killed Osama bin Laden, the same rules apply today.
Some have called such operations “assassinations.” They are not, and the use of that loaded term is misplaced. Assassinations are unlawful killings. Here, for the reasons I have given, the U.S. government’s use of lethal force in self defense against a leader of al Qaeda or an associated force who presents an imminent threat of violent attack would not be unlawful — and therefore would not violate the Executive Order banning assassination or criminal statutes.
Now, it is an unfortunate but undeniable fact that some of the threats we face come from a small number of United States citizens who have decided to commit violent attacks against their own country from abroad. Based on generations-old legal principles and Supreme Court decisions handed down during World War II, as well as during this current conflict, it’s clear that United States citizenship alone does not make such individuals immune from being targeted. But it does mean that the government must take into account all relevant constitutional considerations with respect to United States citizens – even those who are leading efforts to kill innocent Americans. Of these, the most relevant is the Fifth Amendment’s Due Process Clause, which says that the government may not deprive a citizen of his or her life without due process of law.
The Supreme Court has made clear that the Due Process Clause does not impose one-size-fits-all requirements, but instead mandates procedural safeguards that depend on specific circumstances. In cases arising under the Due Process Clause – including in a case involving a U.S. citizen captured in the conflict against al Qaeda – the Court has applied a balancing approach, weighing the private interest that will be affected against the interest the government is trying to protect, and the burdens the government would face in providing additional process. Where national security operations are at stake, due process takes into account the realities of combat.
Here, the interests on both sides of the scale are extraordinarily weighty. An individual’s interest in making sure that the government does not target him erroneously could not be more significant. Yet it is imperative for the government to counter threats posed by senior operational leaders of al Qaeda, and to protect the innocent people whose lives could be lost in their attacks.
Any decision to use lethal force against a United States citizen – even one intent on murdering Americans and who has become an operational leader of al-Qaeda in a foreign land – is among the gravest that government leaders can face. The American people can be – and deserve to be – assured that actions taken in their defense are consistent with their values and their laws. So, although I cannot discuss or confirm any particular program or operation, I believe it is important to explain these legal principles publicly.
Let me be clear: an operation using lethal force in a foreign country, targeted against a U.S. citizen who is a senior operational leader of al Qaeda or associated forces, and who is actively engaged in planning to kill Americans, would be lawful at least in the following circumstances: First, the U.S. government has determined, after a thorough and careful review, that the individual poses an imminent threat of violent attack against the United States; second, capture is not feasible; and third, the operation would be conducted in a manner consistent with applicable law of war principles.
The evaluation of whether an individual presents an “imminent threat” incorporates considerations of the relevant window of opportunity to act, the possible harm that missing the window would cause to civilians, and the likelihood of heading off future disastrous attacks against the United States. As we learned on 9/11, al Qaeda has demonstrated the ability to strike with little or no notice – and to cause devastating casualties. Its leaders are continually planning attacks against the United States, and they do not behave like a traditional military – wearing uniforms, carrying arms openly, or massing forces in preparation for an attack. Given these facts, the Constitution does not require the President to delay action until some theoretical end-stage of planning – when the precise time, place, and manner of an attack become clear. Such a requirement would create an unacceptably high risk that our efforts would fail, and that Americans would be killed.
Whether the capture of a U.S. citizen terrorist is feasible is a fact-specific, and potentially time-sensitive, question. It may depend on, among other things, whether capture can be accomplished in the window of time available to prevent an attack and without undue risk to civilians or to U.S. personnel. Given the nature of how terrorists act and where they tend to hide, it may not always be feasible to capture a United States citizen terrorist who presents an imminent threat of violent attack. In that case, our government has the clear authority to defend the United States with lethal force.
Of course, any such use of lethal force by the United States will comply with the four fundamental law of war principles governing the use of force. The principle of necessity requires that the target have definite military value. The principle of distinction requires that only lawful targets – such as combatants, civilians directly participating in hostilities, and military objectives – may be targeted intentionally. Under the principle of proportionality, the anticipated collateral damage must not be excessive in relation to the anticipated military advantage. Finally, the principle of humanity requires us to use weapons that will not inflict unnecessary suffering.
These principles do not forbid the use of stealth or technologically advanced weapons. In fact, the use of advanced weapons may help to ensure that the best intelligence is available for planning and carrying out operations, and that the risk of civilian casualties can be minimized or avoided altogether.
Some have argued that the President is required to get permission from a federal court before taking action against a United States citizen who is a senior operational leader of al Qaeda or associated forces. This is simply not accurate. “Due process” and “judicial process” are not one and the same, particularly when it comes to national security. The Constitution guarantees due process, not judicial process.
The conduct and management of national security operations are core functions of the Executive Branch, as courts have recognized throughout our history. Military and civilian officials must often make real-time decisions that balance the need to act, the existence of alternative options, the possibility of collateral damage, and other judgments – all of which depend on expertise and immediate access to information that only the Executive Branch may possess in real time. The Constitution’s guarantee of due process is ironclad, and it is essential – but, as a recent court decision makes clear, it does not require judicial approval before the President may use force abroad against a senior operational leader of a foreign terrorist organization with which the United States is at war – even if that individual happens to be a U.S. citizen.
That is not to say that the Executive Branch has – or should ever have – the ability to target any such individuals without robust oversight. Which is why, in keeping with the law and our constitutional system of checks and balances, the Executive Branch regularly informs the appropriate members of Congress about our counterterrorism activities, including the legal framework, and would of course follow the same practice where lethal force is used against United States citizens.
Now, these circumstances are sufficient under the Constitution for the United States to use lethal force against a U.S. citizen abroad – but it is important to note that the legal requirements I have described may not apply in every situation – such as operations that take place on traditional battlefields.
The unfortunate reality is that our nation will likely continue to face terrorist threats that – at times – originate with our own citizens. When such individuals take up arms against this country – and join al Qaeda in plotting attacks designed to kill their fellow Americans – there may be only one realistic and appropriate response. We must take steps to stop them – in full accordance with the Constitution. In this hour of danger, we simply cannot afford to wait until deadly plans are carried out – and we will not.
This is an indicator of our times – not a departure from our laws and our values. For this Administration – and for this nation – our values are clear. We must always look to them for answers when we face difficult questions, like the ones I have discussed today. As the President reminded us at the National Archives, “our Constitution has endured through secession and civil rights, through World War and Cold War, because it provides a foundation of principles that can be applied pragmatically; it provides a compass that can help us find our way.”
Our most sacred principles and values – of security, justice and liberty for all citizens – must continue to unite us, to guide us forward, and to help us build a future that honors our founding documents and advances our ongoing – uniquely American – pursuit of a safer, more just, and more perfect union. In the continuing effort to keep our people secure, this Administration will remain true to those values that inspired our nation’s founding and, over the course of two centuries, have made America an example of strength and a beacon of justice for all the world. This is our pledge.
Thank you for inviting me to discuss these important issues with you today.
TV – Amnesty: China Still World Leader in Executions
Testimony – Special Ops Forces Create “Visible and Dramatic Effects”
U.S. special operations forces are engaged in “more than 100 countries worldwide,” said Adm. William H. McRaven, commander of U.S. Special Operations Command (SOCOM), in testimony before the Senate Armed Services Committee.
“In significant ways, our forces are creating visible and dramatic effects of the greatest magnitude across the globe,” Adm. McRaven said in the 2012 US SOCOM posture statement.
“The decade of war after 9/11 has proffered many lessons; among them, specific to SOF, is the complementary nature of our direct and indirect approaches and how these SOF approaches are aligned to this changing strategic environment,” Adm. McRaven said.
“The direct approach is characterized by technologically-enabled small-unit precision lethality, focused intelligence, and interagency cooperation integrated on a digitally-networked battlefield…. Extreme in risk, precise in execution and able to deliver a high payoff, the impacts of the direct approach are immediate, visible to the public and have had tremendous effects on our enemies’ networks throughout the decade.”
“However, the direct approach alone is not the solution to the challenges our Nation faces today as it ultimately only buys time and space for the indirect approach and broader governmental elements to take effect. Less well known but decisive in importance, the indirect approach is the complementary element that can counter the systemic components of the threat.”
“The indirect approach includes empowering host nation forces, providing appropriate assistance to humanitarian agencies, and engaging key populations. These long-term efforts increase partner capabilities to generate sufficient security and rule of law, address local needs, and advance ideas that discredit and defeat the appeal of violent extremism.”
“As Al Qaeda and other extremist organizations attempt to franchise their ideology and violence globally, we will likely remain engaged against violent extremist networks for the foreseeable future,” he said.
In a rare unclassified “notification of special forces operation,” President Obama formally advised Congress last January of the rescue of an American in Somalia.
“At my direction, on January 24, 2012, U.S. Special Operations Forces conducted an operation in Somalia to rescue Ms. Jessica Buchanan, a U.S. citizen. The operation was successfully completed,” President Obama wrote. The report was transmitted “as part of my efforts to keep the Congress fully informed.”
TOP-SECRET – “Leak”: A New Look at Watergate’s Deep Throat
The Watergate scandal was a formative episode in American political culture that powerfully reinforced public skepticism towards government and fostered a heroic image of the intrepid reporter aided by his truth-telling source. But the reality, as usual, is more complicated than the received narrative. In a fascinating new book, “Leak: Why Mark Felt Became Deep Throat,” Max Holland probes deep into the record of Watergate to illuminate some of those complications.
The question that Holland sets out to answer is the nature of “Deep Throat’s” agenda. What drove FBI official Mark Felt to disclose sensitive investigative information about the Watergate burglary and the ensuing coverup to Bob Woodward of the Washington Post? What were his motivations and what was he hoping to accomplish?
Holland pays close attention to what Felt told Woodward (and when), what Felt could have told Woodward but did not, and what he told Woodward that was not actually true.
His conclusion, spelled out at the beginning of the book, is that Felt’s actions are best understood in the context of the struggle over who would succeed J. Edgar Hoover as director of the FBI. Felt hoped it would be him.
“More than any other single factor, the desperate, no-holds-barred war of succession explains why Mark Felt did what he did, and to a considerable extent, why the scandal played out in the media as it did,” Holland writes. “The contest to succeed Hoover was perceived as a once-in-a-generation opportunity, and it brought out the worst in the Bureau and Mark Felt.”
“The portrait of Felt that emerges when we follow this thread does not resemble any of Bob Woodward’s depictions,” in Holland’s judgment. “Felt held the news media in contempt and was neither a high-minded whistle-blower, nor was he genuinely concerned about defending his institution’s integrity.”
“Woodward believed that he and Felt were on the same side, allies in the struggle to expose the facts and larger truth. For Felt, however, their relationship was simply a means to the end of becoming FBI director. If that end was best served by salting the information he gave Woodward with details that had only a casual relationship with the facts, so be it.”
Strictly speaking, Felt’s motives in leaking information are of secondary importance, if not quite irrelevant. Holland cites an observation by Timothy Noah that “If the free flow of vital information about our government depended on the purity of heart of all concerned, we would know very little. Happily, we are as likely to learn what we need to know through the pursuit of cheap advantage.”
Still, Holland says, “a recognition that Felt was seeking personal advancement first and foremost would have led to heightened scrutiny of his claims and a better version of the obtainable truth.”
More broadly, a reader of the book will be reminded to question the motives of sources, especially anonymous sources. Further, one may conclude that the mantle of “whistleblower” is not one to be lightly claimed or bestowed. (Some may feel that publishing collections of stolen email, for example, does not qualify.)
“Leak” is a work of impressive scholarship, yet it is vividly told and quite engrossing. Reading it on the subway, I missed my stop. The book benefits from the intrinsic drama of Watergate, and from the enduring impact of Woodward and Bernstein’s book (and Redford’s movie) “All the President’s Men.” For better or worse, the story is one that transcends its time.
“Leak: Why Mark Felt Became Deep Throat” by Max Holland was published last week by University of Kansas Press.
The book was recently reviewed by Jack Shafer, Glenn Garvin, and John Dean.
Leaked – NSA Was Tasked to Help Secure Private Communications
As long ago as the Gerald Ford Administration, the National Security Agency was directed to help secure non-governmental communications networks against intrusion and interception by foreign — or domestic — entities, according to a recently declassified presidential directive.
“The President is concerned about possible damage to the national security and the economy from continuing Soviet intercept of critical non-government communications, including government defense contractors and certain other key institutions in the private sector,” wrote National Security Advisor Gen. Brent Scowcroft in National Security Decision Memorandum (NSDM) 338 of September 1, 1976.
“The President further recognizes that U.S. citizens and institutions should have a reasonable expectation of privacy from foreign or domestic intercept when using the public telephone system. The President has therefore decided that communication security should be extended to government defense contractors dealing in classified or sensitive information at the earliest possible time. He has also directed that planning be undertaken to meet the longer-term need to protect other key institutions in the private sector, and, ultimately, to provide a reasonable expectation of privacy for all users of public telecommunications.”
The directive ordered that “in confirmed threat areas,” existing communications networks involving classified information should be transitioned from microwave circuits to secure cable “as soon as possible.” A broader plan to protect non-governmental communications was also to be prepared.
“The President further directs the Director of the Office of Telecommunications Policy, with the participation and assistance of DOD and NSA, to prepare a detailed Action Plan setting forth the actions and schedule milestones necessary to achieve a wide degree of protection for private sector microwave communications. The Plan should identify needed policy and regulatory decisions, describe in detail the roles of industry and government, including management and funding considerations, and integrate the schedule for these actions with the technical development milestones.”
“The Action Plan should be based on the fundamental objective of protecting the privacy of all users of public telecommunications, as well as satisfying specific needs of the government,” the directive stated.
The 1976 directive was originally marked TOP SECRET / SENSITIVE (XGDS), where XGDS stood for “exempt from general declassification schedule.” It was declassified on September 13, 2011. The document had been requested through the mandatory declassification review process by Dr. John Laprise of Northwestern University.
The directive prefigures an ongoing controversy over the proper role, and the actual extent, of National Security Agency involvement in securing public communications.
In response to a FOIA lawsuit brought by the Electronic Privacy Information Center, the NSA said (and a court affirmed) that it could “neither confirm or deny” a relationship between the Agency and Google. NSA has also refused to release the 2008 National Security Presidential Directive 54, which reportedly tasks the Agency with certain cybersecurity functions.
The FBI Director on Cyber Crimes and Cyber Stalkers
- Robert S. Mueller, III
- Director
- Federal Bureau of Investigation
- RSA Cyber Security Conference
- San Francisco, CA
- March 01, 2012
* Remarks as prepared for delivery
Good afternoon. I am indeed honored to be here, and gratified to be back in San Francisco.
A few weeks ago, there was a story in The New York Times about a woman who was taking a break from work. She was watching YouTube videos on her iPhone when a man walked up, pointed a gun at her, grabbed the phone, and ran.
A New York City police officer responded to the call and told her not to worry, that he would find her phone. He grabbed his own phone, opened the “Find My iPhone” app, and typed in the victim’s Apple ID. In seconds, a phone icon popped up, showing that the subject was near 8th Avenue and 51st Street. The officer and his partner headed that way.
As they pulled up, the officer pushed a button on his phone, and they began to hear a pinging noise some 20 feet away. The officer hit “Play” once more, and they followed the pinging to its source, which turned out to be in the man’s sock. The Times reporter pointed out that had the subject been tech savvy, he might have known how to disable the iCloud setting and stop the trace.
If only every case could be solved so easily, and in less than 30 minutes.
Technology has become pervasive as a target. It has also been used as a means of attack. But this story illustrates our use of technology as an investigative tool. It also illustrates the power of innovative thinking and fast action—the very tools we need to stop those who have hijacked cyber space for their own ends.
Technology is moving so rapidly that from a security perspective, it is difficult to keep up. Consider the evolution of cyber crime in just the past decade.
When I was the U.S. Attorney here in 2000, we worked with the Royal Canadian Mounted Police to track down a Canadian teenager known as “Mafiaboy.” He was responsible for the largest denial of service attack at that time. He targeted eBay, Yahoo, E*Trade, Global Crossing, and CNN, just to see if he could shut them down…and he could and did.
When he was finally caught, the 15-year-old was reportedly at a sleepover at a friend’s house, eating junk food and watching “Goodfellas.” He said at the time that he did not understand the consequences of his actions. That now seems like the good old days.
Traditional crime—from mortgage and health care fraud to child exploitation—has migrated online. Terrorists use the Internet as a recruiting tool, a moneymaker, a training ground, and a virtual town square, all in one.
At the same time, we confront hacktivists, organized criminal syndicates, hostile foreign nations that seek our state secrets and our trade secrets, and mercenaries willing to hack for the right price. And we have seen firsthand what happens when countries launch cyber attacks against other nations as a means of exerting power and control.
Today we will discuss what we in the FBI view as the most dangerous cyber threats, what we are doing to confront these threats, and why it is imperative that we work together to protect our intellectual property, our infrastructure, and our economy.
Let me begin with cyber threats to our national security.
Terrorists are increasingly cyber savvy. Much like every other multi-national organization, they are using the Internet to grow their business and to connect with like-minded individuals. And they are not hiding in the shadows of cyber space.
Al Qaeda in the Arabian Peninsula has produced a full-color, English-language online magazine. They are not only sharing ideas, they are soliciting information and inviting recruits to join al Qaeda.
Al Shabaab—the al Qaeda affiliate in Somalia—has its own Twitter account. Al Shabaab uses it to taunt its enemies—in English—and to encourage terrorist activity.
Extremists are not merely making use of the Internet for propaganda and recruitment. They are also using cyber space to conduct operations.
The individuals who planned the attempted Times Square bombing in May 2010 used public web cameras for reconnaissance. They used file-sharing sites to share sensitive operational details. They deployed remote conferencing software to communicate. They used a proxy server to avoid being tracked by an IP address. And they claimed responsibility for the attempted attack—on YouTube.
To date, terrorists have not used the Internet to launch a full-scale cyber attack. But we cannot underestimate their intent. In one hacker recruiting video, a terrorist proclaims that cyber warfare will be the warfare of the future.
Terrorist use of the Internet is not our only national security concern. As we know, state-sponsored computer hacking and economic espionage pose significant challenges.
Just as traditional crime has migrated online, so, too, has espionage. Hostile foreign nations seek our intellectual property and our trade secrets for military and competitive advantage.
State-sponsored hackers are patient and calculating. They have the time, the money, and the resources to burrow in, and to wait. They may come and go, conducting reconnaissance and exfiltrating bits of seemingly innocuous information—information that in the aggregate may be of high value.
You may discover one breach, only to find that the real damage has been done at a much higher level.
Unlike state-sponsored intruders, hackers for profit do not seek information for political power—they seek information for sale to the highest bidder. These once-isolated hackers have joined forces to create criminal syndicates. Organized crime in cyber space offers a higher profit with a lower probability of being identified and prosecuted.
Unlike traditional crime families, these hackers may never meet, but they possess specialized skills in high demand.
They exploit routine vulnerabilities. They move in quickly, make their money, and disappear. No company is immune, from the Fortune 500 corporation to the neighborhood “mom and pop” business.
We are also worried about trusted insiders who may be lured into selling secrets for monetary gain. Perimeter defense may not matter if the enemy is inside the gates.
The end result of these developments is that we are losing data. We are losing money. We are losing ideas and we are losing innovation. And as citizens, we are increasingly vulnerable to losing our information. Together we must find a way to stop the bleeding.
We in the FBI have built up a substantial expertise to address these threats, both here at home and abroad.
We have cyber squads in each of our 56 field offices, with more than 1,000 specially trained agents, analysts, and forensic specialists. Given the FBI’s dual role in law enforcement and national security, we are uniquely positioned to collect the intelligence we need to take down criminal networks, prosecute those responsible, and protect our national security.
But we cannot confront cyber crime on our own.
Borders and boundaries pose no obstacles for hackers. But they continue to pose obstacles for global law enforcement, with conflicting laws, different priorities, and diverse criminal justice systems. With each passing day, the need for a collective approach—for true collaboration and timely information sharing—becomes more pressing.
The FBI has 63 legal attaché offices that cover the globe. Together with our international counterparts, we are sharing information and coordinating investigations. We have special agents embedded with police departments in Romania, Estonia, Ukraine, and the Netherlands, working to identify emerging trends and key players.
Here at home, the National Cyber Investigative Joint Task Force brings together 18 law enforcement, military, and intelligence agencies to stop current and predict future attacks. With our partners at DHS, CIA, NSA, and the Secret Service, we are targeting cyber threats facing our nation. The task force operates through Threat Focus Cells—specialized groups of agents, officers, and analysts that are focused on particular threats, such as botnets.
Together we are making progress.
Last April, with our private sector and law enforcement partners, the FBI dismantled the Coreflood botnet. This botnet infected an estimated two million computers with malware that enabled hackers to seize control of zombie computers to steal personal and financial information.
With court approval, the FBI seized domain names and re-routed the botnet to FBI-controlled servers. The servers directed the zombie computers to stop the Coreflood software, preventing potential harm to hundreds of thousands of users.
In another case, just a few months ago, we worked with NASA’s Inspector General and our partners in Estonia, Denmark, Germany, and the Netherlands to shut down a criminal network operated by an Estonian company by the name of Rove Digital.
The investigation, called Operation Ghost Click, targeted a ring of criminals who manipulated Internet “click” advertising. They re-directed users to their own advertisements and generated more than $14 million in illegal fees. This “click” scheme impacted more than 100 countries and infected four million computers, half-a-million of which were here in the United States.
We seized and disabled computers, froze the defendants’ bank accounts, and replaced rogue servers with legitimate ones to minimize service disruptions. With our Estonian partners, we arrested and charged six Estonian nationals for their participation in the scheme.
And again, we must continue to push forward together.
Terrorism remains the FBI’s top priority. But in the not too distant future, we anticipate that the cyber threat will pose the number one threat to our country.
We need to take lessons learned from fighting terrorism and apply them to cyber crime. We will ensure that all of our special agents have the fundamental skills to operate in this cyber environment. Those agents specializing in cyber matters will have the greatest possible skill set.
We are creating a structure whereby a cyber agent in San Francisco can work in a virtual environment with an agent in Texas, an analyst in Virginia, and a forensic specialist in New York to solve a computer intrusion that emanated from Eastern Europe.
At the same time, we must rely on the traditional capabilities of the Bureau: sources and wires. We must cultivate the sources necessary to infiltrate criminal online networks, to collect the intelligence to prevent the next attack, and to topple the network from the inside. We must ensure that our ability to intercept communications—pursuant to court order—is not eroded by advances in technology. These include wireless technology and peer-to-peer networks, as well as social media.
We will also continue to enhance our collective ability to fight cyber crime.
Following the September 11th terrorist attacks, we increased the number of Joint Terrorism Task Forces. Today, we have more than 100 such task forces—with agents, state and local law enforcement officers, and military personnel—working together to prevent terrorism.
We are developing a similar model to fight cyber crime—to bolster our capabilities and to build those of state and local law enforcement as well.
Along these same lines, 12 years ago we joined forces to address both the growing volume and complexity of digital evidence. Together with our state and local partners, we created the first Regional Computer Forensics Laboratory in San Diego. Today, we have 16 such labs across the country, where we collaborate on cases ranging from child exploitation to public corruption. Together we are using technology to identify and prosecute criminals and terrorists.
Working with our partners at DHS and the National Cyber-Forensics Training Alliance, we are using intelligence to create an operational picture of the cyber threat—to identify patterns and players, to link cases and criminals.
Real-time information-sharing is essential. Much information can and should be shared with the private sector. And in turn, those of you in the private sector must have the means and the motivation to work with us.
We in the Bureau are pushing for legislation to provide for national data breach reporting. This would require companies to report significant cyber breaches to law enforcement and to consumers. Forty-seven states already require the reporting of data breaches, but they do so in different ways and to different degrees.
We must continue to break down walls and to share information, in the same way we did in the wake of the September 11th attacks. This includes the walls that sometimes exist between law enforcement and the private sector.
You here today are often the first to see new threats coming down the road. You know what data is critically important, and what could be at risk.
And while you are fierce competitors in the marketplace, you routinely collaborate behind the scenes. For example, Microsoft, Google, Facebook, and Bank of America, along with several other companies, have joined forces to design a system to authenticate legitimate e-mails and weed out fake messages.
Such collaboration is commonplace now. But 12 years ago in the “Mafiaboy” case, several of the affected companies shared their experiences and worked together—for the first time—to present a united front against that denial of service attack.
Public-private partnerships are equally important.
Through the FBI’s InfraGard program, individuals in law enforcement, government, the private sector, and academia meet to talk about how to protect our critical infrastructure. Over the past 15 years, InfraGard has grown from a single chapter in the Cleveland FBI Field Office to more than 85 chapters across the country, with more than 47,000 members.
Recently, after attending a local InfraGard meeting, one member recognized a phishing scam and notified the FBI. We identified 100 U.S. banks that had been victimized by unauthorized ATM withdrawals in Romania. Eighteen Romanian citizens were charged and eight individuals were extradited to the United States. Three have pled guilty, with one sentenced to more than four years in prison.
We in the FBI understand that you may be reluctant to report security breaches. You may believe that notifying the authorities will harm your competitive position. You may fear that news of a breach will erode shareholder confidence. Or you may think that the information flows just one way—and that is to us.
We do not want you to feel victimized a second time by an investigation. We will minimize the disruption to your business, and we will safeguard your privacy. Where necessary, we will seek protective orders to preserve trade secrets and business confidentiality. And we will share with you what we can, as quickly as we can, about the means and the methods of attack.
But maintaining a code of silence will not serve us in the long run. For it is no longer a question of “if,” but “when” and “how often.”
I am convinced that there are only two types of companies: those that have been hacked and those that will be. And even they are converging into one category: companies that have been hacked and will be hacked again.
Given that scenario, we must limit the data that can be gleaned from any compromise. We must segregate mission-centric data from routine information. And we must incorporate layers of protection and layers of access to critical information.
We may need to look at alternative architectures that are more secure…that allow critical infrastructure owners and operators to better spot threat actors and to provide information to law enforcement to track and to catch them.
Attribution is critical to deter future attacks. We cannot just minimize vulnerabilities and deal with the consequences. Collectively, we can improve cyber security and lower costs—with systems designed to catch threat actors rather than to withstand them.
Several months ago, I read William Powers’ book, “Hamlet’s BlackBerry,” about the impact of technology on civilization. In one chapter, he wrote about the Roman philosopher Seneca In the days of the Roman Empire, connectivity was on the rise—new roads, new ways of communicating, and a new postal system to handle the influx of written documents. Postal deliveries were the high point of the day. People coming from every direction would converge at the port to meet the delivery boats arriving from Egypt.
As they say, the more things change, the more they stay the same.
Today we have the so-called “BlackBerry Jam,” where several individuals—heads down, shoulders slumped, all furiously typing, talking, reading, or browsing at once—come to a head on a crowded corner. We are all guilty of this conduct.
All those years ago, Seneca argued that the more connected society becomes, the greater the chance that the individual will become a slave to that connectivity. Today, one could argue that the more connected we become, the greater the risk to all of us.
We cannot turn back the clock. We cannot undo the impact of technology. Nor would we want to.
But we must continue to build our collective capabilities to fight the cyber threat…we must share information…we must work together to safeguard our property, our privacy, our ideas, and our innovation.
We must use our connectivity to stop those who seek to do us harm.
Thank you and God bless.
Inside the LRA – Uganda – Full Movie
Lured by a government amnesty, senior commanders from the LRA are coming out of the bush and speaking about their time with Joseph Kony. In this rare report, they justify their actions.
“He is from God. What he predicts comes true”, states Captain Ray Apire, explaining Kony’s hold over his soldiers. “By making people suffer, he is bringing people close to God”. Commanders explain how they interpreted Jesus’ command to “Go and catch people”, seeing it as an order to abduct children. For the first time in a decade, the government and LRA are involved in serious peace talks. But the conflict is far from over. A woman breaks down describing how her daughter was abducted the previous night. This is the second time her girl has been kidnapped so she knows she will probably be killed.
Make up your mind about KONY 2012
Uncensored Video – Topless protest in Miami Beach
A topless protest held on Lincoln Road in Miami Beach on 8/21/11. The women are topless (but wearing pasties) to protest the fact that men can be topless in public, but women can’t
CONFIDENTIAL – Marine Corps Intelligence Activity Report: Cultural Islam in Afghanistan

(U) Islam is practiced differently in Afghanistan than in any other part of the world. For operations in Afghanistan, it is significant to know the origins of existing cultural influences come from pre-Islamic Central Asian beliefs. This knowledge is necessary for two key reasons. First, understanding the specific cultural-religious mindset of local Afghans is essential to successful operations within the population. Secondly, Afghan cultural Islam conflicts with the fundamentalist Islamic movements that influence the current insurgency. Knowing and exploiting these differences can be beneficial to counteracting insurgent IO campaigns and to discourage local Afghans from identifying with insurgent groups vying for control of the population.
(U) Three main topics of discussions are key in understanding the cultural-religious mindset of the Afghans: (1) Demographics: When/how did Islam arrive in the geographic region of Afghanistan and what major sects of Islam can claim followers there? (2) Integrated Pre-Islamic Traditions: What are the origins and the lasting traditional influences of pre-Islamic Central Asian beliefs in Afghanistan? (3) Islam in the Insurgency: What Islamic movements influence the insurgent groups in Afghanistan and how do these movements specifically conflict with Afghan cultural Islam? Further, how have insurgency groups used Islam and Afghan cultural traditions for their gain? By answering these three questions, Coalition forces in Afghanistan can benefit from greater knowledge of the local religious sentiment. That knowledge can be used to a tactical and operational advantage in a variety of situations ranging from interaction with the locals to information operations.
…
(U) Pre-Islamic Central Asian Beliefs and their Integration into Muslim Life in Afghanistan
(U//FOUO) Afghans are a traditionally superstitious culture who place heavy emphasis on signs, dreams, and symbols as logical decision factors in daily life. Further, several existing Afghan Islamic practices have their origin in pre-Islamic beliefs. These practices are based primarily in Central Asian belief systems that include lasting cult traditions, ziarats and shrine-worship, spirits (jinnd), witches, witchcraft, shamanism, and malangs. Most of these practices conflict with the strict interpretation of the Qur’an found in movements that influence the insurgency such as Wahhabism, Deobandism, and the teachings of Abdullah Azzam.
(U) Pre-Islamic belief systems in Afghanistan include ‘imported’ faiths like Zoroastrianism, Buddhism, and Hinduism. Lasting effects of these traditions are evident in the giant Buddhas of Bamyan Province and in the Kalash religion of the Nuristanis (forcibly converted to Islam in the mid-19th century). Legacies of the Hindu caste system are evident in popular Afghan folklore that is more than 2,400 years old. The Mogul ruler Akbar, who exerted considerable influence over Central Asia in the early 1500s, dreamed of uniting his empire under one religion, Din Illahi, which would combine elements of Islam, Christianity, Jain, Hindu, and Judaism. He was not aggressive in terms of forcefully converting the inhabitants of Central Asia, but his ideas influenced the Afghan traditions combining elements of many religious influences into their Islamic practice.
(U) In addition to the effects of these imported religions, there were also indigenous movements that remain key influences.
…
(U) Strategic Use of Islam in Afghanistan
(U) Insurgent propaganda is both effective and dangerous. The strategic use of religion, traditional cultural mediums like song and dance, and the timely distribution of propaganda to the media in local language gives the insurgency an advantage in IO efforts. To efficiently counter these efforts, which damage nationbuilding incentive and Coalition success, it is significant to understand how and by what means the insurgents are strategically using Islam and other cultural traditions for their gain.
(U//FOUO) There are a number of instances where insurgent groups have used Islam as a method of gaining/coercing support from the local population. For example, Taliban propaganda suggested that Mullah Omar received dreams of Muhammad instructing him to unite Afghanistan under Shari’a. This helped the movement to gain legitimacy among the Afghan nationals. Not only does this example display a manipulative use of Afghan Islamic belief, but also of Afghan mystical traditions that place heavy emphasis on the importance of dreams.
(U) Karzai’s government has shown effective examples of recognizing the influence of religion among Afghans. The Religious Cultural Affairs division of the Afghan National Army is working to legitimize the new government and military through religious means. As one mullah, Moheburahman, points out: “The most effective thing that can persuade Muslims to do dangerous things and to fight is to give them the legitimacy of what they are fighting for. I describe the legitimacy of this government and point to verses [in the Qur’an].”
(U) The insurgency also uses media outlets to manipulate the Afghan public’s religious and cultural traditions. There are recent reports of Taliban use of DVDs, song, and poems (most of which were once banned under Taliban rule) to spread propaganda. Media outlets like newspapers and television reports also show evidence of this propaganda effort.
(U) On 26 March 2001, a Kandahar paper, Tolu-e Afghan, an article written in Pashtu, reported that the true aim of the United States in Afghanistan was to eliminate Islam. This insurgent propaganda cited the Secretary of Defense’s anger at the Taliban’s destruction of a historic statue of Buddha as evidence that the United States wanted to eliminate Islam from Afghanistan. The article continues to accuse the United States government of encouraging “nakedness” and “degradation” of Afghan women. The article also identifies Coalition-supporting Afghans as “pro-infidel” Afghans and claims they are part of the problem. This kind of reporting is an effective method of intimidating Afghan locals and using their fear of God to not only turn locals against United States forces, but also to help eliminate local customs and traditions that separate Afghan Muslim practices from the Taliban’s ideals.
UNCENSORED – Models Topless Protest in Manchester
Models in Manchester campaign for better equipment for British troops.
Unveiled – the Lybian Money Laundering Machine of Gaddafi
Please Download Original Document Here
Revealed – £10m house in expensive London suburb recovered by Libya
Global Witness welcomes today’s successful recovery by Libya of a £10 million London house, previously belonging to Colonel Gaddafi’s son, Saadi Gaddafi. The High Court in London ruled that the property, in the up-market London suburb of Hampstead, rightfully belongs to the Libyan state as it had been purchased with diverted Libyan state funds.
“This judgement is extremely important as it is the first successful asset recovery case brought by a country involved in the Arab Spring. The Libyan people deserve to get back the money stolen by a tyrant and his sons,” said Robert Palmer, a campaigner at Global Witness. “With billions squirreled away by toppled dictators and their cronies in the UK and elsewhere, we hope this is the first of many such judgements.”
The Arab Spring resulted in billions of pounds being frozen in western banks, including £12 billion of Libyan funds held in the UK. Much of this was state money, over which corrupt leaders exerted significant power. A sizable proportion was also personal assets belonging to regime figures, which were possibly corruptly acquired.
This case shows the ease with which corrupt politicians and their family members can use offshore shell companies to acquire such assets. Saadi Gaddafi appears to have bought 7 Winnington Close in 2010 via a British Virgin Islands (BVI) company, Capitana Seas Limited. The case was uncontested by Capitana Seas which was the formal defendant in the case.
Efforts to trace corrupt assets are often extremely difficult given the secrecy surrounding the owners of shell companies including those registered in British secrecy jurisdictions such as the BVI. This case was relatively straightforward as the house was known to belong to one of Gaddafi’s sons and the UK Treasury sanctions list stated that Saadi was the owner of Capitana and therefore of the house.
“The British government needs to do more to ensure that corrupt politicians and their family members cannot bring their ill-gotten gains into the UK and spend them on luxury lifestyles. If Saadi had a house, he must have had a bank account here as well: what checks did that bank do on his source of funds?” said Palmer.
“The UK should also be putting pressure on the BVI and other secrecy jurisdictions to stop allowing the set-up of anonymous companies that allow corrupt politicians to hide their assets,” said Palmer.
Global Witness is calling for better enforcement of the anti-money laundering regulations that are designed to stop the flow of illicit funds, including the proceeds of corruption. In addition governments should require company registers to list the ultimate person (‘beneficial owner’) who owns a company.
TOP-SECRET – Restricted U.S. Army Special Operations Forces (ARSOF) Religious Factors Analysis Manual

This document represents an effort by the United States Army John F. Kennedy Special Warfare Center and School (USAJFKSWCS) Directorate of Training and Doctrine (DOTD) to equip Army special operations forces (ARSOF) with a better tool for understanding religious considerations in mission planning. Today’s culturally centric warfare places ARSOF Soldiers in high demand. Soldiers trained in the skills of cultural competence and cultural analysis provide an effective mission planning tool for developing an understanding of the operational environment.
Since 9/11, ARSOF have been at the forefront of the War on Terrorism. They are recognized as one of the greatest force multipliers in the United States (U.S.) military arsenal, because of their expertise in military operations, which ranges from counterinsurgency to nation building.
The War on Terrorism has made U.S. leaders more aware of the importance of religious identity and caused them to increasingly focus on religious ideology. Secretary of Defense Donald Rumsfeld’s 2 February 2006 press conference addressed the need to counter the religious ideology of extremist Islamic groups. Doing so will require not only a deeper understanding of religion’s effects upon society than is currently provided by intelligence analyses and products but also an increased emphasis on including religious factors in mission planning. The changing dynamics of conflict are driving a profound change in ARSOF operations. Finding the center of gravity (COG) of the conflict may require translating unfamiliar religious traditions into mission factors. Religion, in the form of nonstate actors, faith-based transnational networks, polygonal insurgency operations, and transcendent ideology, challenges the power of secular organizations.
The answer to overcoming this challenge is not to exclude religion from planning but rather to increase the ARSOF’s understanding of religious factors. They need to examine the application of religious factors to mission planning and develop a synchronized process within the intelligence preparation of the battlefield (IPB). There is a need to integrate a new religious factors analysis (RFA) into the IPB process so that religious factors become actionable elements of the mission plan.
WHY RELIGION MATTERS
Given religion’s complexity and power, it is imperative that ARSOF understand the way it shapes modern warfare and the modern battlefield. There are several reasons for religion’s ability to shape the battlefield:
• Religion answers some of life’s big questions, such as why there is death and war. Religion is relevant to all conflict.
• Religion adds a higher intensity, severity, brutality, and lethality to conflict than other factors do.
• Religion offers a stronger identity to participants in conflicts than nationality, ethnicity, politics, or language.
• Religion can motivate the masses quickly and cheaply, and it often remains outside the view of nation-state security forces.
• Religion offers an ideology—or a platform for a political ideology—that resonates more strongly than other forms of propaganda. Theology will trump ideology in most conflicts.
• Religious leaders are often the last leaders left when states fail, and they offer a voice to the disempowered or oppressed.
• Religious leaders are often the first to seek peace and reconciliation after a conflict.
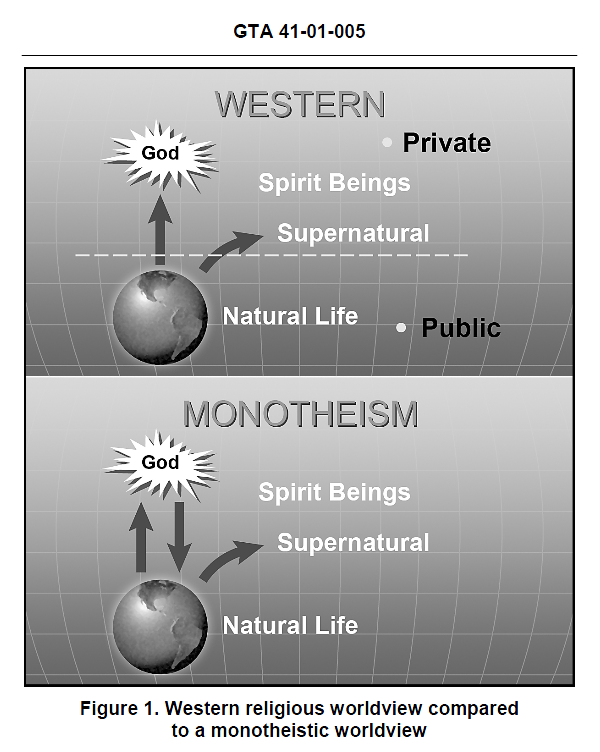
RELIGIOUS FACTORS ANALYSIS—EXPEDIENT ASSESSMENT
Crisis action planning often necessitates modification of either the military decision-making process or joint operation-planning process, either because of time constraints or the direction of the commander.
Whatever the cause, expedient planning should never totally omit an initial, even if abbreviated, RFA of the targeted AO. Available information may come from either classified or open sources, may be dated, or may be unverifiable, forcing the development of planning assumptions prior to deployment.
In a time-constrained planning environment, certain key RFA information will—
• Contribute to the overall civil considerations analysis and the IPB process.
• Enhance cultural awareness of the AO.
• Identify key leaders, communicators, and spheres of influence.
• Contribute to both the lethal and nonlethal targeting process.
• Assist in populace and resource-control planning.
• Provide the basis for a more in-depth analysis.
Figure 8, pages 33 through 36, is a suggested expedient RFA template.
It uses the complete template (Figure 9, pages 37 through 44) as a source document. As with any assessment and analysis process continuous information gathering is essential upon entry into the AO to validate the initial assessment and satisfy identified information gaps.
SECRET – ISAF Afghan Ministry of Interior Advisor Guide

a. Mission. NTM‐A / CSTC‐A, in coordination with NATO nations and partners, international organizations, donors and non‐governmental organizations; supports the Government of the Islamic Republic of Afghanistan (GIRoA) as it generates and sustains the Afghan National Security Force (ANSF), develops leaders, and establishes enduring institutional capacity to enable accountable Afghan‐led security.
b. 2014 End State. A self‐reliant, professionally‐led ANSF which generates and sustains enduring police, army, medical, infrastructure, and logistics capabilities, with accountable and effective Afghan Ministries that are responsible and answerable to Afghan people.
…
5. MOI Mission and Vision (From National Police Strategy – January 2011).
a. Mission. The ANP is primarily responsible for maintaining civil order and law enforcement. The police will work with the people to actively combat crime and disorder (including terrorism and illegal armed activity); prevent the cultivation, production and smuggling of narcotics; and fight corruption. The police will ensure the sovereignty of the State and protect its borders.
b. Minister of Interior Affairs Vision. In five years the people of Afghanistan will consider their police to be a valued institution which is honest, accountable, brave, impartial, and striving to create a secure and lawful society.
c. Our (GIRO’s) long term vision is that the ANP will uphold the Constitution of Afghanistan and enforce the prevailing laws of the country to protect the rights of all people of Afghanistan. The police will perform their duties in a professional, non‐discriminatory, accountable and trustworthy manner.
d. Civilian Policing. As part of the phased stabilization of Afghanistan with the assistance of the international community, the Afghan National Police are committed to seeking the highest standards in civilian policing in order to guarantee the rights of all Afghan citizens under the Constitution. Civilian policing is a crucial strategic concept that is based on intelligence led, proactive community collaboration. It is aimed at controlling crime, reducing the fear of criminal activity, improving the quality of life of all Afghans, and enhancing the legitimacy of police services. Civilian policing requires greater accountability of police, greater involvement of citizens, and greater concern for human rights.
DOWNLOAD ORIGINAL DOCUMENT HERE
TOP-SECRET – DHS Terrorist Use of Improvised Incendiary Devices and Attack Methods

(U//FOUO) Improvised incendiary devices (IIDs) typically are less expensive to make than improvised explosive devices but still are capable of creating mass casualties and causing widespread fear and panic.
(U//FOUO) Improvised incendiary devices (IIDs) can be constructed easily from everyday materials available at hardware and grocery stores.
(U//FOUO) IIDs can be used against many types of infrastructure targets; violent extremists have used them successfully in attacks in the United States and overseas.
(U//FOUO) The DHS/Office of Intelligence and Analysis (I&A) has no credible or specific intelligence indicating current terrorist attack planning featuring use of IIDs against infrastructure in the United States. The ease with which IIDs can be constructed and used, however, makes it difficult to detect and prevent such attacks.
(U) Improvised Incendiary Devices Can Be Constructed from Common Materials
(U//FOUO) An IID consists of an ignition source, a flammable or combustible fuel —including kerosene, cigarette and charcoal lighter fluid, motor fuels, such as gasoline or diesel, and reactive chemicals—and some type of container, such as propane cylinders, plastic pipes, bottles, and cans. IIDs range in sophistication from very simple and easily-constructed Molotov cocktails—which are made by filling a glass bottle with fuel and lighting a rag placed in the top—to more complicated timed devices consisting of a sodium and acid mixture.
(U) U.S. Infrastructure Vulnerable to Improvised Incendiary Device Attack
(U//FOUO) The accessibility of many types of infrastructure, such as government facilities, national monuments, various transportation and energy assets, and commercial facilities, make them susceptible to IID attacks. Passenger trains, ferries, and other public conveyances are among the more attractive targets for terrorists because they often have large numbers of people enclosed in concentrated areas that are difficult to evacuate rapidly.
(U) Previous Use of Improvised Incendiary Devices in the United States
(U//FOUO) Violent extremists have used IIDs against government facilities and vehicles, commercial facilities, and railroad lines. Their most frequent targets have been healthcare, educational and research facilities, and scientists and research personnel.
(U) Improvised Incendiary Device Attacks Abroad
(U) Terrorists using IIDs achieved their most notable success in a February 2007 attack by Kashmiri operatives who placed six suitcase IIDs in three cars of the “Friendship Express” passenger train traveling from India to Pakistan. Four of the six IIDs ignited, causing fires in two passenger cars that killed 68 people and injured 13. Other incidents, like those in the United States, have achieved mixed results.
— (U) In May 2008, an ethnic Uighur woman aboard a domestic flight bound for Beijing, China attempted to ignite a flammable liquid in a beverage can. She aroused suspicions when she exited the lavatory to pick up a second can after the first failed to ignite and produced a smell of gasoline.
— (U) In June 2007, two men drove a burning jeep with several gasoline-filled containers into the main terminal building at the Glasgow, Scotland airport, causing structural damage to the front of the building but no casualties.
— (U) In July 2006, two men plotted to attack two trains in Germany using suitcases filled with butane and gasoline, but the devices failed to ignite. German prosecutors claimed, however, that the trains would have become “balls of fire” had the IIDs functioned as planned
The FBI – Former California State University Assistant Professor Sentenced to 450 Months in Prison for Aggravated Sexual Abuse of a Child
SAN FRANCISCO—Kenneth Martin Kyle pleaded guilty and was sentenced late Thursday afternoon to 37-and-a-half years in prison and ordered to pay $50,000 in restitution for traveling across state lines to sexually abuse a child, Melinda Haag, U.S. Attorney for the Northern District of California, announced.
In pleading guilty, Kyle admitted that in August 2009, he traveled from San Francisco to St. Louis for the purpose of engaging in sexual acts with an infant victim. Immediately following his guilty plea, which was pursuant to a plea agreement with the United States, Kyle was sentenced by U.S. District Judge Jeffrey S. White.
“It is my hope that the sentence Mr. Kyle received sends a strong message about the abhorrent conduct in this case,” U.S. Attorney Haag said. “Protecting children from sexual predators is an important priority. My office will continue to work diligently with our partners in law enforcement to track down and prosecute sexual predators to the fullest extent of the law.”
At the time of his arrest, in March 2010, Kyle was an Assistant Professor of Justice Studies at California State University East Bay. He came to the attention of the FBI when undercover agents discovered that he was sharing child pornography over a peer-to-peer file-sharing network. The FBI passed this information along to San Francisco police officers who obtained a search warrant for Kyle’s San Francisco apartment. During the search of Kyle’s apartment, they found computers containing child pornography. Because Kyle was out of the country at the time, San Francisco police officers shared their information with U.S. Immigration and Customs Enforcement (ICE)-Homeland Security Investigations (HSI).
“Nothing is more gratifying than seeing someone like this go to prison for a very, very long time where he will no longer have the opportunity to harm children in such a horrible fashion,” said Clark Settles, special agent in charge for the ICE-HSI office in San Francisco. “HSI will use every tool at its disposal to track down those who would harm our children and see that they are brought to justice.”
During his plea hearing, Kyle admitted to molesting a 5-month-old infant in St. Louis over several months. The infant victim’s mother currently faces federal child pornography charges in California and Missouri and has already pleaded guilty to state child molestation charges in Missouri.
Kyle, 47, of San Francisco, was indicted by a federal grand jury on April 1, 2010. He was charged with aggravated sexual abuse of a child, production of child pornography, distribution of child pornography, transportation of child pornography, and possession of child pornography. Under the plea agreement, Kyle pleaded guilty to count one of the indictment.
Owen Martikan is the Assistant U.S. Attorney who is prosecuting the case with the assistance of Rosario Calderon. The prosecution is the result of an investigation by ICE-HSI. This investigation also involved significant assistance from the FBI, the San Francisco Police Department, the St. Louis Police Department, and the U.S. Attorney’s Office for the Eastern District of Missouri.
UNCENSORED – FEMEN Protest Turkey Violence Against Women
|
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-instanbul/pict25.jpg) An activist of the women’s rights group Femen prepares for a protest against domestic violence in Istanbul March 8, 2012. Reuters/Osman Orsal. An activist of the women’s rights group Femen prepares for a protest against domestic violence in Istanbul March 8, 2012. Reuters/Osman Orsal. |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-instanbul/pict17.jpg) Police detain one of the Ukrainian women’s rights activists as they stage a topless demonstration to protest domestic violence against women in Turkey, in Istanbul, Thursday, March 8, 2012, just hours after a man shot dead a female relative. Four members of the Femen group, wearing makeup to represent injuries, chanted slogans and displayed banners like “stolen lives” in the one-minute protest in to mark International Women’s Day. (AP Photo) Police detain one of the Ukrainian women’s rights activists as they stage a topless demonstration to protest domestic violence against women in Turkey, in Istanbul, Thursday, March 8, 2012, just hours after a man shot dead a female relative. Four members of the Femen group, wearing makeup to represent injuries, chanted slogans and displayed banners like “stolen lives” in the one-minute protest in to mark International Women’s Day. (AP Photo) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-instanbul/pict21.jpg) Ukrainian Femen activists with fake injuries hold placards as they protest against domestic violence in front of the Hagia Sofia in Istanbul on March 8, 2012 during the International Women’s Day. The protest ended after police arrested the three activists. Getty Ukrainian Femen activists with fake injuries hold placards as they protest against domestic violence in front of the Hagia Sofia in Istanbul on March 8, 2012 during the International Women’s Day. The protest ended after police arrested the three activists. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-instanbul/pict18.jpg) Police detain one of Ukrainian women’s rights activists as they stage a topless demonstration to protest domestic violence against women in Turkey, in Istanbul, Thursday, March 8, 2012, just hours after a man shot dead a female relative. Four members of the Femen group, wearing makeup to represent injuries, chanted slogans and displayed banners like “stolen lives” in the one-minute protest to mark international Women’s Day. (AP Photo) Police detain one of Ukrainian women’s rights activists as they stage a topless demonstration to protest domestic violence against women in Turkey, in Istanbul, Thursday, March 8, 2012, just hours after a man shot dead a female relative. Four members of the Femen group, wearing makeup to represent injuries, chanted slogans and displayed banners like “stolen lives” in the one-minute protest to mark international Women’s Day. (AP Photo) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-instanbul/pict23.jpg) Ukrainian Femen activists with fake injuries hold placards as they protest against domestic violence in front of the Hagia Sofia in Istanbul on March 8, 2012 during the International Women’s Day. The protest ended after police arrested the three activists. Getty Ukrainian Femen activists with fake injuries hold placards as they protest against domestic violence in front of the Hagia Sofia in Istanbul on March 8, 2012 during the International Women’s Day. The protest ended after police arrested the three activists. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-instanbul/pict19.jpg) A Ukrainian Femen activist sporting fake injuries is pulled up from the ground by female police officers during a protest against domestic violence in front of the Agia Sofia mosque in Istanbul on March 8, 2012. The protest ended after police arrested the three activists. Getty A Ukrainian Femen activist sporting fake injuries is pulled up from the ground by female police officers during a protest against domestic violence in front of the Agia Sofia mosque in Istanbul on March 8, 2012. The protest ended after police arrested the three activists. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-instanbul/pict20.jpg) A Ukrainian Femen activist sporting fake injuries is pulled up from the ground by female police officers during a protest against domestic violence in front of the Agia Sofia mosque in Istanbul on March 8, 2012. The protest ended after police arrested the three activists. Getty A Ukrainian Femen activist sporting fake injuries is pulled up from the ground by female police officers during a protest against domestic violence in front of the Agia Sofia mosque in Istanbul on March 8, 2012. The protest ended after police arrested the three activists. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-instanbul/pict24.jpg) Ukrainian Femen activists with fake injuries hold placards as they protest against domestic violence in front of the Hagia Sofia in Istanbul on March 8, 2012 during the International Women’s Day. The protest ended after police arrested the three activists. Getty Ukrainian Femen activists with fake injuries hold placards as they protest against domestic violence in front of the Hagia Sofia in Istanbul on March 8, 2012 during the International Women’s Day. The protest ended after police arrested the three activists. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-instanbul/pict22.jpg) A Femen activist with fake injuries continues to protest against domestic violence after being led to a car by police in front of the Hagia Sofia in Istanbul on March 8, 2012 during the International Women’s Day. The protest ended after police arrested the three activists. A Femen activist with fake injuries continues to protest against domestic violence after being led to a car by police in front of the Hagia Sofia in Istanbul on March 8, 2012 during the International Women’s Day. The protest ended after police arrested the three activists. |
Confidential – Joint Center for International Security Force Study

The intent of Phase I initial impressions is to provide rapid support to the Warfighter. In parallel, these insights serve as part of a broader Ministerial-Level Advisor Training Effectiveness Study, which JCISFA will publish in the spring of 2011. These observations and insights may support planning and decision-making within the NTM-A/CSTC-A as well as joint, interagency, intergovernmental, multinational (JIIM) organizations responsible for force generation supporting the NTM-A/CSTC-A mission. Specifically, this report addresses contemporary issues and senior leader perspectives within the NTM-A/CSTC-A Ministerial-Level Advisor program to include prospective gaps across joint DOTMLPF-P domains. The following illustrates the NTM-A/CSTC-A mission.
“NTM-A/CSTC-A, in coordination with key stakeholders, generates and sustains the ANSF, develops leaders, and establishes enduring institutional capacity in order to enable accountable Afghan-led security.”
Senior level Advisors supporting the development of Afghan ministries provide critical roles in helping the United States and the Government of Afghanistan (GIRoA) achieve national objectives within Afghanistan. As a core function within the NTM-A/CSTC-A, senior Advisors support and influence capability development across two primary Afghan ministries: the Ministry of Defense (MoD) and the Ministry of Interior (MoI). Primarily, Afghan MoD and MoI provide an executive role and function in order to administer the Afghan National Army (ANA) and Afghan National Police (ANP) policy, recruiting, organizing, training, equipping, and building ANA and ANP capabilities. These capabilities provide the nation of Afghanistan with capacity to meet local and regional security requirements. In parallel, the Afghan MoD and MoI must influence and shape local and regional political decisions, plan and execute strategically, assess readiness levels, conduct reviews and analysis, as well as forecast and budget ANA/ANP fiscal requirements.
These complex roles and functions within the Afghan ministries require skilled Senior Advisors capable of adapting culturally as well as operating functionally as subject matter experts (SME) within their respective ministry counterpart’s role and function. Within this framework, the JCISFA conducted Senior Advisor interviews and analysis across the NTM-A/CSTC-A in order to gauge senior Advisor capability requirements to support pre-deployment training and selection methodologies. Two sections provide organization for these initial impressions. The first deals with findings within Ministerial-Level Advisor Training. The second focuses on potential issues within Ministerial-Level Advisor Training.
Ministerial-Level Advisor Findings
- Interviews and surveys revealed that no formal pre-deployment training exists that prepares senior military officers to be Ministerial-Level Advisors.
- Interviews and surveys revealed that there is no standardized transition process between incoming and outgoing Ministerial-Level Advisors.
- There is no enduring capability to collect, analyze and integrate Ministerial advisor lessons learned in NTM-A/CSTC-A.
- A majority of the advisors interviewed/surveyed felt that the recent integration of support staff functions into the DCOMs has been a valuable first step towards improving Ministerial development capability.
- Personnel coming into theater and performing primary or additional duties as advisors are not receiving requisite advisor skills training.
- Senior Advisors interviews focused on how Ministerial developmental goals are established and evaluated/assessed. Almost all advisors interviewed/surveyed stated that the NTM-A/CSTC-A Ministerial Development Plan (MDP) process has been an effective tool in establishing goals and coordinating efforts across multiple functional areas.
- Senior Advisors interviewed/surveyed expressed that coordinating, conducting and reconciling travel with their counterparts is an extremely difficult and frustrating process.
Ministerial-Level Advisor Potential Issues
- Overall, the majority of Ministerial-Level Advisors interviewed/surveyed expressed support for the AFPAK Hands program.
- Many of those interviewed/surveyed had comments and recommendations on the types of skill sets required for Ministerial advisors and on how joint force providers should identify, assign, and track future advisors.
- A great deal of observations and insights were collected regarding the Afghans’ abilities to govern/sustain themselves and effectively deal with corruption.
Unveiled – TSCM Smuggling, Fraud and Assault
James Atkinson sends:
Here is a little light reading in regards to the smuggling of TSCM equipment, and some very naughty things, by some very bad people.
http://www.tscm.com/Atkinson.v.Rockport.4th%20Amended1983Complaint.pdf
It is a a little dry at times (and most legal documents are), but the bits about the REI Smuggling, the export fraud, the 2nd, 4th, 5th, and 14th Amendments and bill of rights, and the complex serious of events that almost killed me a few years back is brought to light in this documents.
A few TSCM people knew what happened, but most were not aware that I got the living crap beat out of me by half a dozen police officers who broken into my home with no warrant and put me in the hospital, and that I ended up needing life saving surgery and an extended hospital stay to save my life as a result. Then they went and obtained/forged a search warrant the day after the illegal search, and stolen huge amounts of equipment, money, gold, sweep gear, armour, training equipment, and all sorts of other property.
Read it carefully, and keep in mind what country we are in… yeah, still… but we can change it, which is what I am doing here.
Please redistribute widely and quickly.
Donation may be sent to my PayPal account of: jmatk@tscm.com
-jma
—
James M. Atkinson
President, Scientist and Sr. Engineer
“Leonardo da Vinci of Bug Sweeps and Spy Hunting”
Granite Island Group
jmatk[at]tscm.com
http://www.tscm.com/
UNCENSORED – FEMEN Cyber War against Sex Tourism
Start for Israels New Head of Central Command – Major General Nitzan Alon

The new Major General in the IDF’s General Staff, Nitzan Alon, was considered to be the “enemy of the settlers” when he served as former commander of the Judea and Samaria division.
Today, Alon began his role as head of the Central Command. He was promoted to the rank of Major General in a ceremony held last Thursday at the Kiriya in Tel Aviv.
The Minister of Defense, Ehud Barak, and the Chief of Staff, Lt. Gen. Benny Gantz, attended the ceremony along with the members of the General Staff and the families of the commanders.
Maj. Gen. Nitzan Alon is replacing Maj. Gen. Avi Mizrahi who served as head of Central Command for the past three years and is expected to leave to study in the US. Mizrahi is competing for the role of next Deputy Chief of Staff against Maj. Gen. Gadi Eizenkot, the former head of Northern Command.
On Thursday, the Minister of Defense told Maj. Gen. Mizrahi: “Avi, you brought along tremendous experience and left your mark on the command, the military units, and their readiness for war, as well as on the complicated fabric of the region.”
He told the new Major General: “Nitzan, today you are entering a far more complex reality than you’ve experienced in the past two years, and today you’re receiving comprehensive responsibility for it. I would like to wish you the best of luck.”
The outgoing head of Central Command, Maj. Gen. Avi Mizrahi, said, “This is the most challenging, complicated, and difficult role I’ve held throughout my service. I’m glad for the opportunity that was given to me, to take part in shaping the future of the state of Israel.”
The incoming head of the Central Command, Maj. Gen. Nitzan Alon, thanked the Minister of Defense and the Chief of Staff for their trust in choosing him for the role, saying, “I am grateful for the trust in choosing me for this role, and I will make every effort to meet the trust.”
Before his appointment, Maj. Gen. Nitzan Alon served as commander of Sayeret Matkal.
Video – Interpol “Operation Unmask” 25 ‘Anonymous’ Hackers Arrest 29/2/12 Spain & South America
Confidential from the FBI – Indictment Filed
PORTLAND, OR—A federal grand jury sitting in Portland, Oregon returned an indictment today charging Christopher Lee Carlson, 39, of the Portland-Vancouver area with two criminal offenses. The indictment arises out of an investigation into the mailing of approximately 100 envelopes containing white powder and threatening letters to members of the U.S. Congress and certain members of the news media. The letters were postmarked in Portland, Oregon.
The indictment charges Carlson with one count of mailing a threatening communication to a member of Congress and one count of mailing a letter threatening to use a biological weapon to a U.S. senator. Carlson is presently in custody. It is expected that he will be arraigned in federal court on Monday, March 12, 2012.
Over the past few weeks, the lead investigative agencies, including the FBI, the U.S. Postal Inspection Service, and the U.S. Capitol Police, have recovered more than 100 threatening letters sent to U.S. senators and U.S. representatives. To date, all letters have tested negative for toxic substances.
“Anyone who sends threatening letters to government officials should expect to be found, arrested, and prosecuted,” said U.S. Attorney for the District of Oregon S. Amanda Marshall.
“Threatening letters—whether hoax or real—are serious concerns that federal law enforcement agencies will aggressively pursue,” said Greg Fowler, Special Agent in Charge of the FBI in Oregon. “We want to thank our partners at the U.S. Postal Inspection Service and the U.S. Capitol Police who worked with us day-in and day-out for the past two weeks to bring this case to this resolution.”
U.S. Postal Inspection Service Inspector in Charge, Bradley Kleinknecht stated, “The U.S. Postal Inspection Service is dedicated to safeguarding the U.S. Mail to protect employees, customers, and the American public.”
An indictment is only an allegation of a crime, and every defendant is presumed innocent until proven guilty. Under U.S. Department of Justice regulations, no photo will be released. No further information is available at this time.
Confidential – ISAF Afghan Ministry of Interior Advisor Guide

a. Mission. NTM‐A / CSTC‐A, in coordination with NATO nations and partners, international organizations, donors and non‐governmental organizations; supports the Government of the Islamic Republic of Afghanistan (GIRoA) as it generates and sustains the Afghan National Security Force (ANSF), develops leaders, and establishes enduring institutional capacity to enable accountable Afghan‐led security.
b. 2014 End State. A self‐reliant, professionally‐led ANSF which generates and sustains enduring police, army, medical, infrastructure, and logistics capabilities, with accountable and effective Afghan Ministries that are responsible and answerable to Afghan people.
…
5. MOI Mission and Vision (From National Police Strategy – January 2011).
a. Mission. The ANP is primarily responsible for maintaining civil order and law enforcement. The police will work with the people to actively combat crime and disorder (including terrorism and illegal armed activity); prevent the cultivation, production and smuggling of narcotics; and fight corruption. The police will ensure the sovereignty of the State and protect its borders.
b. Minister of Interior Affairs Vision. In five years the people of Afghanistan will consider their police to be a valued institution which is honest, accountable, brave, impartial, and striving to create a secure and lawful society.
c. Our (GIRO’s) long term vision is that the ANP will uphold the Constitution of Afghanistan and enforce the prevailing laws of the country to protect the rights of all people of Afghanistan. The police will perform their duties in a professional, non‐discriminatory, accountable and trustworthy manner.
d. Civilian Policing. As part of the phased stabilization of Afghanistan with the assistance of the international community, the Afghan National Police are committed to seeking the highest standards in civilian policing in order to guarantee the rights of all Afghan citizens under the Constitution. Civilian policing is a crucial strategic concept that is based on intelligence led, proactive community collaboration. It is aimed at controlling crime, reducing the fear of criminal activity, improving the quality of life of all Afghans, and enhancing the legitimacy of police services. Civilian policing requires greater accountability of police, greater involvement of citizens, and greater concern for human rights.
Unveiled – The State Department is Concerned About Vatican Money Laundering

The Vatican has for the first time appeared on the U.S. State Department’s list of money-laundering centres but the tiny city-state is not rated as a high-risk country.The 2012 International Narcotics Control Strategy Report was made public on Wednesday and Washington’s list of 190 countries classifies them in three categories: of primary concern, of concern and monitored.
The Vatican is in the second category, grouped with 67 other nations including Poland, Egypt, Ireland, Hungary and Chile.
It was added to the list because it was considered vulnerable to money-laundering and had recently established programmes to prevent it, a State Department official said.
“To be considered a jurisdiction of concern merely indicates that there is a vulnerability to a financial system by money launderers. With the large volumes of international currency that goes through the Holy See, it is a system that makes it vulnerable as a potential money-laundering center,” Susan Pittman of the State Department’s Bureau of International Narcotics and Law Enforcement, told Reuters.
Last year, the Vatican adapted internal laws to comply with international standards on financial crime.
The Vatican is seeking inclusion on the European Commission’s so-called “white list” of states who comply with international standards against tax fraud and money-laundering. A decision on its inclusion is expected in June.
Countries/Jurisdictions of Concern:
| Countries/Jurisdictions of Primary Concern |
Countries/Jurisdictions of Concern |
Other Countries/Jurisdictions Monitored |
||||
| Afghanistan | Latvia | Albania | Marshall Islands | Andorra | Maldives | |
| Antigua and Barbuda | Lebanon | Algeria | Moldova | Anguilla | Mali | |
| Argentina | Liechtenstein | Angola | Monaco | Armenia | Malta | |
| Australia | Luxembourg | Aruba | Mongolia | Benin | Mauritania | |
| Austria | Macau | Azerbaijan | Montenegro | Bermuda | Mauritius | |
| Bahamas | Mexico | Bahrain | Morocco | Botswana | Micronesia FS | |
| Belize | Netherlands | Bangladesh | Nicaragua | Brunei | Montserrat | |
| Bolivia | Nigeria | Barbados | Peru | Burkina Faso | Mozambique | |
| Brazil | Pakistan | Belarus | Poland | Burundi | Namibia | |
| British Virgin Islands | Panama | Belgium | Portugal | Cameroon | Nauru | |
| Burma | Paraguay | Bosnia and Herzegovina | Qatar | Cape Verde | Nepal | |
| Cambodia | Philippines | Bulgaria | Romania | Central African Republic | New Zealand | |
| Canada | Russia | Chile | Saudi Arabia | Chad | Niger | |
| Cayman Islands | Singapore | Comoros | Senegal | Congo, Dem Rep of | Niue | |
| China, People Rep | Somalia | Cook Islands | Serbia | Congo, Rep of | Norway | |
| Colombia | Spain | Cote d’Ivoire | Seychelles | Croatia | Oman | |
| Costa Rica | St. Maarten | Czech Republic | Sierra Leone | Cuba | Palau | |
| Curacao | Switzerland | Djibouti | Slovakia | Denmark | Papua New Guinea | |
| Cyprus | Taiwan | Ecuador | South Africa | Dominica | Rwanda | |
| Dominican Republic | Thailand | Egypt | St. Kitts and Nevis | Equatorial Guinea | Samoa | |
| France | Turkey | El Salvador | St. Lucia | Eritrea | San Marino | |
| Germany | Ukraine | Ghana | St. Vincent | Estonia | Sao Tome & Principe | |
| Greece | United Arab Emirates | Gibraltar | Suriname | Ethiopia | Slovenia | |
| Guatemala | United Kingdom | Grenada | Syria | Fiji | Solomon Islands | |
| Guernsey | United States | Guyana | Tanzania | Finland | South Sudan | |
| Guinea Bissau | Uruguay | Holy See | Trinidad and Tobago | Gabon | Sri Lanka | |
| Haiti | Venezuela | Honduras | Turks and Caicos | Gambia | Sudan | |
| Hong Kong | Zimbabwe | Hungary | Vanuatu | Georgia | Swaziland | |
| India | Ireland | Vietnam | Guinea | Sweden | ||
| Indonesia | Jamaica | Yemen | Iceland | Tajikistan | ||
| Iran | Jordan | Kyrgyz Republic | Timor-Leste | |||
| Iraq | Kazakhstan | Lesotho | Togo | |||
| Isle of Man | Korea, North | Liberia | Tonga | |||
| Israel | Korea, South | Libya | Tunisia | |||
| Italy | Kosovo | Lithuania | Turkmenistan | |||
| Japan | Kuwait | Macedonia | Uganda | |||
| Jersey | Laos | Madagascar | Uzbekistan | |||
| Kenya | Malaysia | Malawi | Zambia | |||
JFK – Full Movie by Oliver Stone – Starring Kevi Costner
TOP-SECRET – UNCENSORED – Osama bin Laden Shrine Teardown
![[Image]](https://i0.wp.com/cryptome.org/eyeball/obl-shrine-down/pict16.jpg) In this May 4, 2011, photo, local residents and media gather outside a house where al-Qaida leader Osama bin Laden was caught and killed in Abbottabad, Pakistan. The U.S. military is denouncing a former Navy SEAL’s book that claims to describe the “real” version of the raid that killed bin Laden, taken from alleged eyewitness accounts. In this May 4, 2011, photo, local residents and media gather outside a house where al-Qaida leader Osama bin Laden was caught and killed in Abbottabad, Pakistan. The U.S. military is denouncing a former Navy SEAL’s book that claims to describe the “real” version of the raid that killed bin Laden, taken from alleged eyewitness accounts. |
![[Image]](https://i0.wp.com/cryptome.org/eyeball/obl-shrine-down/pict11.jpg) This Nov 18, 2011 photo shows the guesthouse inside Osama bin Laden’s compound in Abbottabad, Pakistan. Bin Laden spent his last weeks in a house divided, amid wives riven by suspicions. On the top floor, sharing his bedroom, was his youngest wife and favorite. The trouble came when his eldest wife showed up and moved into the bedroom on the floor below. (Shaukat Qadir) This Nov 18, 2011 photo shows the guesthouse inside Osama bin Laden’s compound in Abbottabad, Pakistan. Bin Laden spent his last weeks in a house divided, amid wives riven by suspicions. On the top floor, sharing his bedroom, was his youngest wife and favorite. The trouble came when his eldest wife showed up and moved into the bedroom on the floor below. (Shaukat Qadir) |
![[Image]](https://i0.wp.com/cryptome.org/eyeball/obl-shrine-down/pict14.jpg) Flood lights are seen in the compound of Osama bin Laden in Abbottatabd, Pakistan on Saturday, Feb 25, 2012. Local residents say Pakistan has started to demolish the compound in the northwest city of Abbottabad where Osama bin Laden lived for years and was killed by U.S. commandos. Two residents say the government brought in three mechanized backhoes Saturday, Feb. 25, 2012, and began destroying the tall outer walls of the compound after sunset. They set up floodlights to carry out the work. Flood lights are seen in the compound of Osama bin Laden in Abbottatabd, Pakistan on Saturday, Feb 25, 2012. Local residents say Pakistan has started to demolish the compound in the northwest city of Abbottabad where Osama bin Laden lived for years and was killed by U.S. commandos. Two residents say the government brought in three mechanized backhoes Saturday, Feb. 25, 2012, and began destroying the tall outer walls of the compound after sunset. They set up floodlights to carry out the work. |
![[Image]](https://i0.wp.com/cryptome.org/eyeball/obl-shrine-down/pict7.jpg) A policeman walks towards the partially demolished compound where al Qaeda leader Osama bin Laden was killed by U.S. special forces last May in Abbottabad February 26, 2012. Pakistani forces began demolishing the house where Bin Laden was killed by U.S. special forces last May, in an unexplained move carried out in the dark of night. Reuters A policeman walks towards the partially demolished compound where al Qaeda leader Osama bin Laden was killed by U.S. special forces last May in Abbottabad February 26, 2012. Pakistani forces began demolishing the house where Bin Laden was killed by U.S. special forces last May, in an unexplained move carried out in the dark of night. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/eyeball/obl-shrine-down/pict9.jpg) ![[Image]](https://i0.wp.com/cryptome.org/eyeball/obl-shrine-down/pict8.jpg)
Pakistani security personnel conduct demolition works on the compound where Al-Qaeda chief Osama bin Laden was slain last year in the northwestern town of Abbottabad on February 26, 2012. Pakistani security forces began demolishing the compound where Osama bin Laden was killed in a covert US raid last May in the garrison town of Abbottabad, police and witnesses said. Getty |
![[Image]](https://i0.wp.com/cryptome.org/eyeball/obl-shrine-down/pict10.jpg) Local residents watch ongoing demolition of the compound where Al-Qaeda chief Osama bin Laden was slain last year in the northwestern town of Abbottabad on February 26, 2012. Pakistani security forces began demolishing the compound where Osama bin Laden was killed in a covert US raid last May in the garrison town of Abbottabad, police and witnesses said. Getty Local residents watch ongoing demolition of the compound where Al-Qaeda chief Osama bin Laden was slain last year in the northwestern town of Abbottabad on February 26, 2012. Pakistani security forces began demolishing the compound where Osama bin Laden was killed in a covert US raid last May in the garrison town of Abbottabad, police and witnesses said. Getty |
![[Image]](https://i0.wp.com/cryptome.org/eyeball/obl-shrine-down/pict5.jpg) In this Feb. 26, 2012 file picture, a police commando stands guard as authorities use heavy machinery to demolish Osama bin Laden’s compound in Abbottabad, Pakistan. Bin Laden spent his last weeks in a house divided, amid wives riven by suspicions. On the top floor, sharing his bedroom, was his youngest wife and favorite. The trouble came when his eldest wife showed up and moved into the bedroom on the floor below. AP In this Feb. 26, 2012 file picture, a police commando stands guard as authorities use heavy machinery to demolish Osama bin Laden’s compound in Abbottabad, Pakistan. Bin Laden spent his last weeks in a house divided, amid wives riven by suspicions. On the top floor, sharing his bedroom, was his youngest wife and favorite. The trouble came when his eldest wife showed up and moved into the bedroom on the floor below. AP |
![[Image]](https://i0.wp.com/cryptome.org/eyeball/obl-shrine-down/pict12.jpg) A Pakistani family watch the compound, center top, of Osama bin Laden which is demolishing by authorities in Abbottabad, Pakistan on Sunday, Feb. 26, 2012. Pakistan begun demolishing the three-story compound where Osama bin Laden lived for years and was killed by U.S. commandos last May, eliminating a concrete reminder of the painful and embarrassing chapter in the country’s history. (Anjum Naveed) A Pakistani family watch the compound, center top, of Osama bin Laden which is demolishing by authorities in Abbottabad, Pakistan on Sunday, Feb. 26, 2012. Pakistan begun demolishing the three-story compound where Osama bin Laden lived for years and was killed by U.S. commandos last May, eliminating a concrete reminder of the painful and embarrassing chapter in the country’s history. (Anjum Naveed) |
![[Image]](https://i0.wp.com/cryptome.org/eyeball/obl-shrine-down/pict0.jpg) In this combo of two images, Pakistan police officers gather next to heavy machinery parked inside the demolished compound of Osama bin Laden, Monday, Feb. 27, 2012, top, and police officers gather outside bin Laden’s compound Sunday, Feb. 26, 2012, in Abbottabad, Pakistan. Pakistani authorities have reduced the house where Osama bin Laden lived for years before he was killed by U.S. commandos to rubble, destroying a concrete symbol of the country’s association with one of the world’s most reviled men. AP In this combo of two images, Pakistan police officers gather next to heavy machinery parked inside the demolished compound of Osama bin Laden, Monday, Feb. 27, 2012, top, and police officers gather outside bin Laden’s compound Sunday, Feb. 26, 2012, in Abbottabad, Pakistan. Pakistani authorities have reduced the house where Osama bin Laden lived for years before he was killed by U.S. commandos to rubble, destroying a concrete symbol of the country’s association with one of the world’s most reviled men. AP |
![[Image]](https://i0.wp.com/cryptome.org/eyeball/obl-shrine-down/pict1.jpg) In this combo of two pictures, a Pakistani woman and children stand next to the remained boundary wall of Osama bin Laden’s compound, Monday, Feb 27, 2012, top, and, heavy machinery demolishes the main building of bin Laden’s compound Sunday, Feb. 26, 2012, bottom, in Abbottabad, Pakistan. Pakistani authorities have reduced the house where bin Laden lived for years before he was killed by U.S. commandos to rubble, destroying a concrete symbol of the country’s association with one of the world’s most reviled men. AP In this combo of two pictures, a Pakistani woman and children stand next to the remained boundary wall of Osama bin Laden’s compound, Monday, Feb 27, 2012, top, and, heavy machinery demolishes the main building of bin Laden’s compound Sunday, Feb. 26, 2012, bottom, in Abbottabad, Pakistan. Pakistani authorities have reduced the house where bin Laden lived for years before he was killed by U.S. commandos to rubble, destroying a concrete symbol of the country’s association with one of the world’s most reviled men. AP |
![[Image]](https://i0.wp.com/cryptome.org/eyeball/obl-shrine-down/pict2.jpg) Heavy machinery is seen inside the compound where al Qaeda leader Osama bin Laden was killed after it was demolished in Abbottabad February 27, 2012. The Pakistani home of al Qaeda chief Osama bin Laden, the place where he was killed after the biggest manhunt in history, is no more. Pakistan security forces completed the demolition of bin Laden’s compound on Sunday, erasing a symbol of humiliation for Pakistan’s military that has marked one of the most difficult periods in U.S. Pakistan ties. Reuters Heavy machinery is seen inside the compound where al Qaeda leader Osama bin Laden was killed after it was demolished in Abbottabad February 27, 2012. The Pakistani home of al Qaeda chief Osama bin Laden, the place where he was killed after the biggest manhunt in history, is no more. Pakistan security forces completed the demolition of bin Laden’s compound on Sunday, erasing a symbol of humiliation for Pakistan’s military that has marked one of the most difficult periods in U.S. Pakistan ties. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/eyeball/obl-shrine-down/pict3.jpg) Pakistani policemen stand near the boundary wall which surrounded the house of Al-Qaeda chief Osama bin Laden, slain last year during a covert US special forces mission, following the building’s demolition in the northwestern town of Abbottabad on February 27, 2012. Pakistani bulldozers on February 27 finished demolishing the house where Osama bin Laden lived for at least five years until he was killed by US special forces last May. Only the wall of the compound remained intact, surrounding the debris of the three-storey building where the Al-Qaeda leader hid in the garrison town of Abbottabad and a security official confirmed the demolition had been completed. Getty Pakistani policemen stand near the boundary wall which surrounded the house of Al-Qaeda chief Osama bin Laden, slain last year during a covert US special forces mission, following the building’s demolition in the northwestern town of Abbottabad on February 27, 2012. Pakistani bulldozers on February 27 finished demolishing the house where Osama bin Laden lived for at least five years until he was killed by US special forces last May. Only the wall of the compound remained intact, surrounding the debris of the three-storey building where the Al-Qaeda leader hid in the garrison town of Abbottabad and a security official confirmed the demolition had been completed. Getty |
![[Image]](https://i0.wp.com/cryptome.org/eyeball/obl-shrine-down/pict6.jpg) Residents walk past the boundary wall of the building where al Qaeda leader Osama bin Laden was killed after it was demolished in Abbottabad February 27, 2012. The Pakistani home of al Qaeda chief Osama bin Laden, the place where he was killed after the biggest manhunt in history, is no more. Pakistan security forces completed the demolition of bin Laden’s compound on Sunday, erasing a symbol of humiliation for Pakistan’s military that has marked one of the most difficult periods in U.S. Pakistan ties. Reuters Residents walk past the boundary wall of the building where al Qaeda leader Osama bin Laden was killed after it was demolished in Abbottabad February 27, 2012. The Pakistani home of al Qaeda chief Osama bin Laden, the place where he was killed after the biggest manhunt in history, is no more. Pakistan security forces completed the demolition of bin Laden’s compound on Sunday, erasing a symbol of humiliation for Pakistan’s military that has marked one of the most difficult periods in U.S. Pakistan ties. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/eyeball/obl-shrine-down/pict13.jpg) Pakistan children play cricket next the remained boundary wall of demolished compound of Osama bin Laden in Abbottabad, Pakistan on Monday, Feb. 27, 2012. Pakistani authorities have reduced the house where Osama bin Laden lived for years before he was killed by U.S. commandos to rubble, destroying a concrete symbol of the country’s association with one of the world’s most reviled men. (Anjum Naveed) Pakistan children play cricket next the remained boundary wall of demolished compound of Osama bin Laden in Abbottabad, Pakistan on Monday, Feb. 27, 2012. Pakistani authorities have reduced the house where Osama bin Laden lived for years before he was killed by U.S. commandos to rubble, destroying a concrete symbol of the country’s association with one of the world’s most reviled men. (Anjum Naveed) |
![[Image]](https://i0.wp.com/cryptome.org/eyeball/obl-shrine-down/pict15.jpg) This Friday, March 2, 2012, file photo shows Salafists holding posters showing Osama bin Laden during a rally to condemn the disposal last week of a number of Qurans at a U.S. military base in Afghanistan, near the U.S. embassy in Tunis, Tunisia. An emerging movement of believers known as Salafis has seemingly appeared out of thin air _ and prompted fears of a culture war in this North African country of 10 million. This Friday, March 2, 2012, file photo shows Salafists holding posters showing Osama bin Laden during a rally to condemn the disposal last week of a number of Qurans at a U.S. military base in Afghanistan, near the U.S. embassy in Tunis, Tunisia. An emerging movement of believers known as Salafis has seemingly appeared out of thin air _ and prompted fears of a culture war in this North African country of 10 million. |
Herbst in Peking – Bakschischrepublik – Musikvideo
UNCENSORED – FEMEN Topless Protest against Putin
Herbst in Peking – Jesus war so cool – Musikvideo
Citation:
“This no budget music video has been produced in spring 2005. Rex Joswig, the singer of the band, is a good friend of mine.”
“9/11” – Full Movie – Uncensored
Full Movie – NATIONAL SECURITY ALERT – 9/11 PENTAGON ATTACK
Visit the home site of the investigators: http://www.citizeninvestigationteam.com
TOP-SECRET -Russians to resume Patrols soon
SOURCE- RUSSAIN FORCESAdmiral Vladimir Vysotskiy, the Commander-in-Chief of the Russian Navy announcedthat the Russian strategic submarines will resume regular patrols “on the 1st of July or a bit later.” According to Vysotskiy, the Navy was awaiting this “for 26 years.”
What this probably means is that Russia will try to keep at least one strategic submarine at sea at any given time. I’m not sure what will change in June 2012 that would allow the navy to do that – the only significant development is that Novomoskovsk will probably return to service by then – it has been in overhaul since May 2011. But then there is Ekaterinburg, which is unlikely to be back after the fire until at least 2014. Also, another submarine, Karelia is in the dry dock right now, although this seems to be a brief repair work (let’s hope they removed missiles this time).
Maybe the plan is to rely on the first Project 955 class submarine, Yuri Dolgorukiy, which is expected to begin service some time in June-July 2012. That’s a possibility, I guess.
It’s interesting to look back 26 years to see why Vysotskiy believes it was such a remarkable year. It wasn’t in fact – according to the U.S. naval intelligence data (posted by Hans Kristensen), in 1986 Soviet strategic submarines conducted about 80 patrols. But the patrol rate was higher before and did not drop significantly until much later – there were still 60 patrols in 1990.
In 2008, Russian strategic submarines conducted ten patrols, but as Hans notes in his post, these were probably clustered together rather than spread over the course of the year. Still, that rate seems to indicate that the Russian Navy could keep continuous deterrence patrols with five or six submarines.
CONFIDENTIAL – DHS Terrorist Use of Improvised Incendiary Devices and Attack Methods

(U) Key Findings
(U//FOUO) Improvised incendiary devices (IIDs) typically are less expensive to make than improvised explosive devices but still are capable of creating mass casualties and causing widespread fear and panic.
(U//FOUO) Improvised incendiary devices (IIDs) can be constructed easily from everyday materials available at hardware and grocery stores.
(U//FOUO) IIDs can be used against many types of infrastructure targets; violent extremists have used them successfully in attacks in the United States and overseas.
(U//FOUO) The DHS/Office of Intelligence and Analysis (I&A) has no credible or specific intelligence indicating current terrorist attack planning featuring use of IIDs against infrastructure in the United States. The ease with which IIDs can be constructed and used, however, makes it difficult to detect and prevent such attacks.
(U) Improvised Incendiary Devices Can Be Constructed from Common Materials
(U//FOUO) An IID consists of an ignition source, a flammable or combustible fuel —including kerosene, cigarette and charcoal lighter fluid, motor fuels, such as gasoline or diesel, and reactive chemicals—and some type of container, such as propane cylinders, plastic pipes, bottles, and cans. IIDs range in sophistication from very simple and easily-constructed Molotov cocktails—which are made by filling a glass bottle with fuel and lighting a rag placed in the top—to more complicated timed devices consisting of a sodium and acid mixture.
(U) U.S. Infrastructure Vulnerable to Improvised Incendiary Device Attack
(U//FOUO) The accessibility of many types of infrastructure, such as government facilities, national monuments, various transportation and energy assets, and commercial facilities, make them susceptible to IID attacks. Passenger trains, ferries, and other public conveyances are among the more attractive targets for terrorists because they often have large numbers of people enclosed in concentrated areas that are difficult to evacuate rapidly.
(U) Previous Use of Improvised Incendiary Devices in the United States
(U//FOUO) Violent extremists have used IIDs against government facilities and vehicles, commercial facilities, and railroad lines. Their most frequent targets have been healthcare, educational and research facilities, and scientists and research personnel.
(U) Improvised Incendiary Device Attacks Abroad
(U) Terrorists using IIDs achieved their most notable success in a February 2007 attack by Kashmiri operatives who placed six suitcase IIDs in three cars of the “Friendship Express” passenger train traveling from India to Pakistan. Four of the six IIDs ignited, causing fires in two passenger cars that killed 68 people and injured 13. Other incidents, like those in the United States, have achieved mixed results.
— (U) In May 2008, an ethnic Uighur woman aboard a domestic flight bound for Beijing, China attempted to ignite a flammable liquid in a beverage can. She aroused suspicions when she exited the lavatory to pick up a second can after the first failed to ignite and produced a smell of gasoline.
— (U) In June 2007, two men drove a burning jeep with several gasoline-filled containers into the main terminal building at the Glasgow, Scotland airport, causing structural damage to the front of the building but no casualties.
— (U) In July 2006, two men plotted to attack two trains in Germany using suitcases filled with butane and gasoline, but the devices failed to ignite. German prosecutors claimed, however, that the trains would have become “balls of fire” had the IIDs functioned as planned.
TOP-SECRET – Joint Center for International Security Force Assistance Ministerial-Level Advisor Training Effectiveness Study

The intent of Phase I initial impressions is to provide rapid support to the Warfighter. In parallel, these insights serve as part of a broader Ministerial-Level Advisor Training Effectiveness Study, which JCISFA will publish in the spring of 2011. These observations and insights may support planning and decision-making within the NTM-A/CSTC-A as well as joint, interagency, intergovernmental, multinational (JIIM) organizations responsible for force generation supporting the NTM-A/CSTC-A mission. Specifically, this report addresses contemporary issues and senior leader perspectives within the NTM-A/CSTC-A Ministerial-Level Advisor program to include prospective gaps across joint DOTMLPF-P domains. The following illustrates the NTM-A/CSTC-A mission.
“NTM-A/CSTC-A, in coordination with key stakeholders, generates and sustains the ANSF, develops leaders, and establishes enduring institutional capacity in order to enable accountable Afghan-led security.”
Senior level Advisors supporting the development of Afghan ministries provide critical roles in helping the United States and the Government of Afghanistan (GIRoA) achieve national objectives within Afghanistan. As a core function within the NTM-A/CSTC-A, senior Advisors support and influence capability development across two primary Afghan ministries: the Ministry of Defense (MoD) and the Ministry of Interior (MoI). Primarily, Afghan MoD and MoI provide an executive role and function in order to administer the Afghan National Army (ANA) and Afghan National Police (ANP) policy, recruiting, organizing, training, equipping, and building ANA and ANP capabilities. These capabilities provide the nation of Afghanistan with capacity to meet local and regional security requirements. In parallel, the Afghan MoD and MoI must influence and shape local and regional political decisions, plan and execute strategically, assess readiness levels, conduct reviews and analysis, as well as forecast and budget ANA/ANP fiscal requirements.
These complex roles and functions within the Afghan ministries require skilled Senior Advisors capable of adapting culturally as well as operating functionally as subject matter experts (SME) within their respective ministry counterpart’s role and function. Within this framework, the JCISFA conducted Senior Advisor interviews and analysis across the NTM-A/CSTC-A in order to gauge senior Advisor capability requirements to support pre-deployment training and selection methodologies. Two sections provide organization for these initial impressions. The first deals with findings within Ministerial-Level Advisor Training. The second focuses on potential issues within Ministerial-Level Advisor Training.
Ministerial-Level Advisor Findings
- Interviews and surveys revealed that no formal pre-deployment training exists that prepares senior military officers to be Ministerial-Level Advisors.
- Interviews and surveys revealed that there is no standardized transition process between incoming and outgoing Ministerial-Level Advisors.
- There is no enduring capability to collect, analyze and integrate Ministerial advisor lessons learned in NTM-A/CSTC-A.
- A majority of the advisors interviewed/surveyed felt that the recent integration of support staff functions into the DCOMs has been a valuable first step towards improving Ministerial development capability.
- Personnel coming into theater and performing primary or additional duties as advisors are not receiving requisite advisor skills training.
- Senior Advisors interviews focused on how Ministerial developmental goals are established and evaluated/assessed. Almost all advisors interviewed/surveyed stated that the NTM-A/CSTC-A Ministerial Development Plan (MDP) process has been an effective tool in establishing goals and coordinating efforts across multiple functional areas.
- Senior Advisors interviewed/surveyed expressed that coordinating, conducting and reconciling travel with their counterparts is an extremely difficult and frustrating process.
Ministerial-Level Advisor Potential Issues
- Overall, the majority of Ministerial-Level Advisors interviewed/surveyed expressed support for the AFPAK Hands program.
- Many of those interviewed/surveyed had comments and recommendations on the types of skill sets required for Ministerial advisors and on how joint force providers should identify, assign, and track future advisors.
- A great deal of observations and insights were collected regarding the Afghans’ abilities to govern/sustain themselves and effectively deal with corruption.
DOWNLOAD ORIGINAL DOCUMENT HERE
TOP-SECRET – FEMA National Responder Support Camps (NRSC) Contract Announcement
The following contract solicitation and accompanying material was posted to the Federal Business Opportunities website between February 10 – 24, 2012. The contract concerns the construction of a temporary camp anywhere in the continental United States (CONUS) within 72 hours in a disaster-impacted area or “any other situation where FEMA or an agency working through FEMA needs a RSC” to host up to 2,000 responders and emergency staff as well as displaced citizens.
DOWNLOAD ORIGINAL FILE HERE
Video – uncensored – Pussy Riot – Russian girl band declares war on Putin
Report – Obamas Gifts to Israel in Exchange for Not Attacking Iran
Why was Netanyahu forced to have a spokesperson describe the meeting with Obama? Why are the US presidential elections the most important in Israel’s history? Why is IMI only a “scapegoat” in the Indian affair? And will Barak surprise with new appointments pertaining to Udi Shani and Yoav Galant?
The fact that the new head of Netanyahu’s publicity layout, Liran Dan, had to explain in the media that Israeli Prime Minister Netanyahu and US President Obama had a “good meeting” regarding the Iranian issue, is not a good sign in itself.
If Netanyahu and Obama were really deeply coordinated, then the events following the meeting should have gone down more or less as follows: none of the heads of states would have said a word about the Iranian issue (and would have thus increased the pressure in Tehran); within a few weeks or months, upon the exhaustion (and near certain failure) of the economic sanctions, the US and its allies would have declared a naval and aerial blockade in the Persian Gulf. If the blockade wouldn’t have helped halt Iran’s progress towards a nuclear bomb – that’s when the assault stage would have arrived, be it Israeli or international.
Although that it is not what happened, the meetings that took place this week have historical significance nevertheless. Two very important things can be understood from Obama’s words after the meetings: Obama does not trust Netanyahu or Ehud Barak not to instruct the Israeli air force to attack Iran. Thus, he operated in order to effectively “lock” them by publicly announcing that the US believes that it’s too early for an attack.
At the same time, Obama announced an unprecedented commitment to Israel’s protection, and essentially promised Israel that the US is taking all the responsibility for halting the Iranian bomb. Obama announced that it is a US interest. This is no trivial matter. Yet, can his promise to halt the bomb be trusted? Not necessarily. November will see the most fateful elections in Israel’s history (in which the next US president will be elected). After the elections, Obama may change his skin, or a Republican president will be elected, one that will not be bound to Obama’s statements. Therefore, it’s entirely possible to agree with Netanyahu’s words in this context: that Israel is obligated to protecting itself by itself.
A Man of Words
Netanyahu is a person who attributes great significance to words. Each and every word he said this week in the US was measured. Netanyahu is also obsessed with his image (hardly an exclusive for this column, it’s rather well known). He arrived to the US directly from Canada. It’s possible to remember another occasion in which he also arrived from Canada, on May 30, 2010 (though that day is chiefly remembered due to the events onboard the Mavi Marmara, and less because of the US visit).
During that trip in 2010, Netanyahu first achieved the historic commitment which was also proclaimed this week, that the US will guarantee Israel’s safety (it occurred following behind-the-scenes efforts by the head of Israel’s National Security Council at the time, Uzi Arad).
After that visit, the Israeli media published the (incorrect) report that Obama had promised that Israel be approved construction of nuclear reactors for peaceful purposes. The US was furious, and the accusation for the leak was cast within the Prime Minister’s office on Uzi Arad – yes, the same Uzi Arad, who’s already been outside of the Prime Ministers office for a year, and who verbally attacked the Prime Minister last week over the same affair.
Gifts for Restraint
So what did we have this week? At the bottom line, an obvious warning coming from the direction of the US that Israel must not attack (even if it wasn’t an explicit prohibition). Furthermore, a more-than-implied US promise that it will take full responsibility for stopping the Iranian bomb, even if the possible Israeli window-of-opportunity for an attack (until the coming summer) is not utilized. And lastly, as according to Israeli tradition, there was a shopping list, but we cannot know if it was granted.
A “shopping list” is a tradition in which Israeli prime ministers arrive to the US with a request for a gift from the US, in exchange for any Israeli step, in the defensive or political field. Israel usually gains weapons or other gifts in exchange for concessions with regards to the peace process with the Palestinians or with regards to countries in its neighborhood. According to reports, Israel requested refueling aircraft from the US this time, which will enable it to increase the air force’s flight range, as well as additional bunker-penetrating bombs. The reward would not necessarily be an explicit commitment that it not attack. In any case, according to publications, Israel’s Minister of Defense, Ehud Barak, also met with President Obama during his US visit from more than a week ago, and discussed these “gifts” with him. Even if the request was truly granted, it can be assumed that the US will not provide it to Israel at a date that will allow it to use the new measures in the imminent period.
Ashkenazi Is in the Bunker
While an Israeli option to attack Iran was apparently postponed in Washington, monumental efforts were invested this week in the local front, in the battle between the Minister of Defense, Ehud Barak, and former Chief of Staff, Lt. Gen. Gabi Ashkenazi, following the State Comptroller’s interim statement on the Harpaz Affair.
The current situation picture near the weekend in this front: after several utterances in which he took partial responsibility for the affair and cast a greater responsibility on Barak, Ashkenazi descended into the bunker, where he spends his time with his lawyer and prepares the response to the Comptroller. Barak and his people are heavily bombing the bunker, and will continue to do so, though it’s doubtful that it’ll be effective. Both Barak and Ashkenazi are in a bad place with regards to public opinion – at least with regards to this affair.
Interestingly enough, from this week’s developments was the demand by Brigadier General Imad Fares to be returned to the IDF, due to the things stated in Barak’s official announcement, which stated that Ashkenazi had wronged him. Logic dictates that if the Minister of Defense says such things, then there’s allegedly a “case” for the demand coming from Fares. However, will the current Chief of Staff, Benny Gantz, really bring the dismissed officer back into service? It doesn’t seem to be the case.
By the way, Barak claimed that Brigadier General Moshe (Chico) Tamir was also wronged by Ashkenazi, who dismissed him due to the affair in which his son drove a military-issued ATV. Gantz can be at ease when it comes to this issue: there’s no chance that Brigadier General Tamir will ask to return to service. He’s making great success (and money) as VP of Defense and Homeland Security for Gilat Satellite Networks (read the special interview with him in the coming issue of IsraelDefense, which will be published next week).
IMI on India’s Blacklist
On another matter: employees working at the various defense industries in Israel know to appreciate the considerable amount of work that they receive from India, which has been a tremendous market for the defense industries for more than 15 years. The collective scope of the sales there nearly reaches the figure of $10 billion.
The Indian issue rose to the headlines this week following the reports that Israel Military Industries (IMI) is still on the Indian Ministry of Defense’s blacklist of companies with which they are not to do business. IMI entered the list several years ago, due to an investigation in India into the actions of Indian businessman Sudhir “Bunny” Choudhrie. Choudhrie represented the company in a deal, in which it was supposed to establish a munitions factory on Indian soil at an investment of $240 million.
If Tamir and Fares are “victims” of Ashkenazi, according to Barak, then IMI is a “scapegoat” in a sense, as Choudhrie previously represented nearly all the Israeli defense industries in India, including Israel Aerospace Industries and Rafael. Furthermore, he was even a shareholder in both Aeronautics and Soltam (presently a part of Elbit Systems). The Israeli defense establishment can live with the ban on IMI, so long as no more bans are imposed upon other, larger companies as well.
Galant for the Ministry of Defense?
While we’re mentioning IAI, it’s hard to know the seriousness of the rumor in the defense establishment, that the current chairman of the Ministry of Defense, Major General (Res.) Udi Shani, will be IAI’s next CEO (following the anticipated retirement of Itzhak Nissan, the current CEO, in October). The same goes for the chances that Major General (Res.) Yoav Galant, who was dropped from the race for the position of Chief of Staff, will replace Shani as chairman. All this is according to a “master plan” attributed to Barak, one which was not written down in any document, such as the forged “Harpaz document.”
SOURCE: ISRAEL DEFENSE
SECRET – Agency Tattoo Handbook – Criminal Tatoos and Their Meanings

Tattoos are useful indicators to identify individuals who are members of a gang or a criminal organization. It is important to note that an image may have several different, occasionally innocuous, meanings, depending on the interpretation of the individual or gangs using it.
The Organized Crime Section (OCS) is providing the following tattoos and their definitions as a tool to assist officers in detecting gang members or members of a criminal organization. It is important that Border Services Officers contact their Regional Intelligence Officers to assist in determining a subject’s admissibility to Canada.



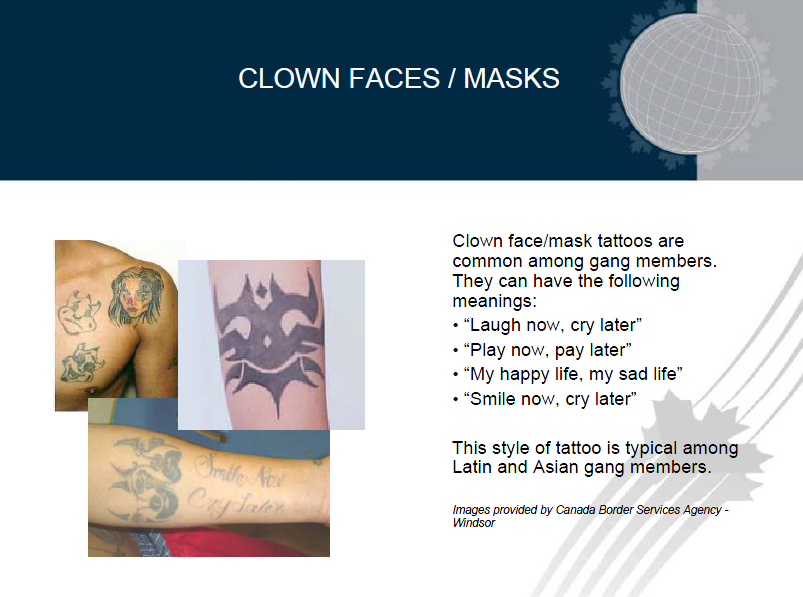
DOWNLOAD ORIGINAL DOCUMENT HERE
TOP-SECRET – American Friends of Bilderberg 2010 Tax Return and Contributors/Donators
AMERICAN FRIENDS OF BILDERBERG, INC.
C/O JAMES JOHNSON, PERSEUS, LLC
1325 AVE OF THE AMERICAS, 25TH FL
NEW YORK, NY 10019
(212) 651-6400
EIN: 51-0163715
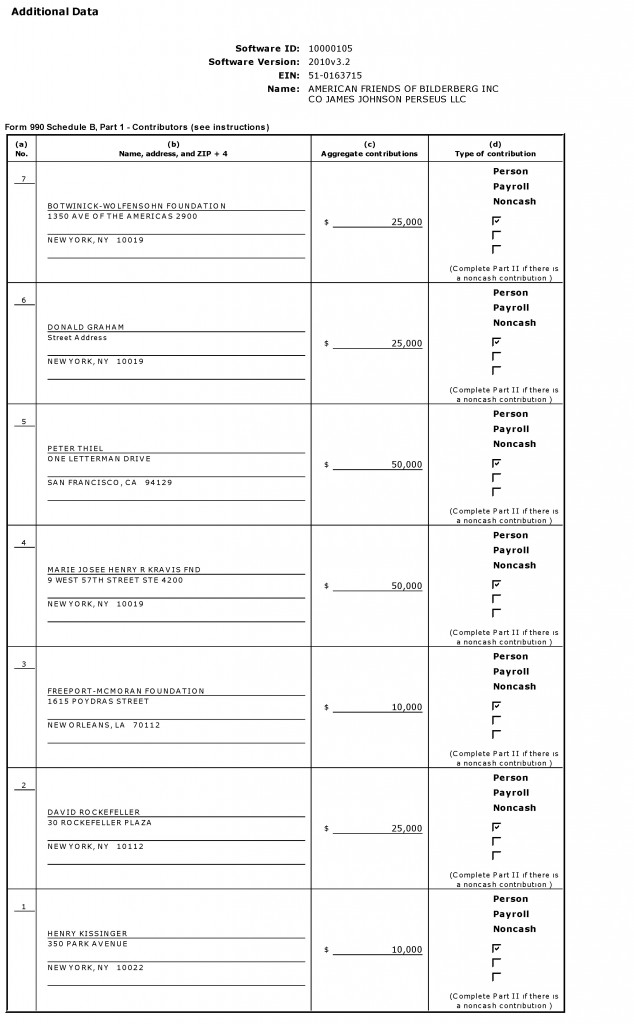
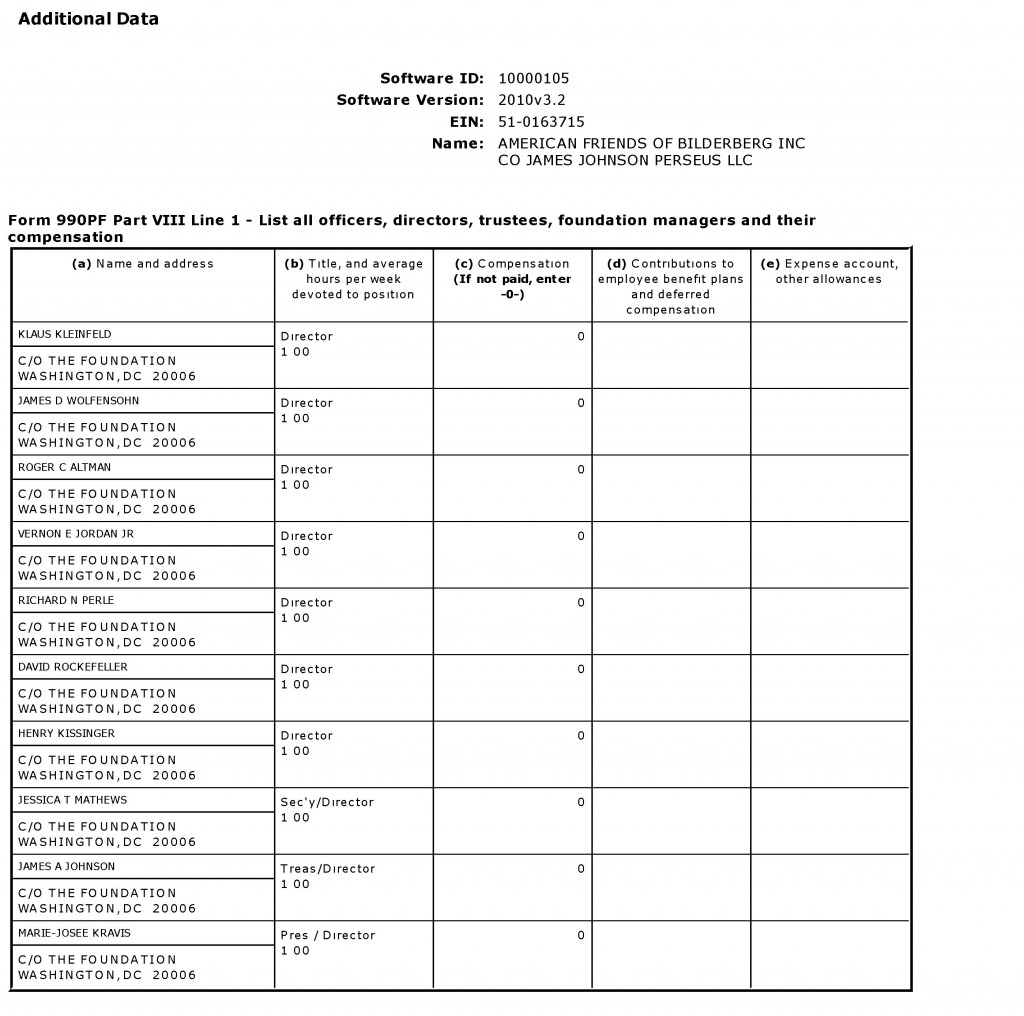
DOWNLOAD ORIGINAL DOCUMENT HERE
CRYPTOME unveils New Canadian Prison Construction Documents
A sends:
Construction drawings and specifications for new prison buildings at four Canadian prisons:
Bath Institution, Bath, Ontario, Drawings and Specifications
http://cryptome.org/2012/03/csc/bath-csc.zip (105MB)
bath_drawings.pdf
bath_specs.pdf
Collins Bay Institution, Kingston, Ontario, Drawings and Specifications
http://cryptome.org/2012/03/csc/collins-bay-csc.zip (136MB)
cb_drawings_arch.pdf
cb_drawings_civil.pdf
cb_drawings_elec.pdf
cb_drawings_mech.pdf
cb_drawings_struc.pdf
cb_specs.pdf
Millhaven Institution, Bath, Ontario, Drawings and Specifications
http://cryptome.org/2012/03/csc/millhaven-csc.zip (170MB)
mh_drawings_arch.pdf
mh_drawings_civil.pdf
mh_drawings_elec.pdf
mh_drawings_elec.pdf
mh_drawings_struc.pdf
mh_drawings_secsys.pdf
mh_specs.pdf
Stony Mountain Institution, Winnipeg, Manitoba, Drawings
http://cryptome.org/2012/03/csc/stony-mountain-csc.zip (73MB)
stony_drawings.pdf
Prison Websites (Correctional Service of Canada)
Bath Institution, Bath, Ontario
http://www.csc-scc.gc.ca/text/facilit/institutprofiles/bath-eng.shtml
Collins Bay Institution, Kingston, Ontario
http://www.csc-scc.gc.ca/text/facilit/institutprofiles/collinsbay-eng.shtml
Millhaven Institution, Bath, Ontario
http://www.csc-scc.gc.ca/text/facilit/institutprofiles/millhaven-eng.shtml
Stony Mountain Institution, Winnipeg, Manitoba
http://www.csc-scc.gc.ca/text/facilit/institutprofiles/stonymountain-eng.shtml
UNCENSORED – FEMEN shows it all at Kiev Protest
TOP-SECRET – FBI National Gang Threat Assessment

(U) Street, prison, and motorcycle gang membership and criminal activity continues to flourish in US communities where gangs identify opportunities to control street level drug sales, and other profitable crimes. Gangs will not only continue to defend their territory from rival gangs, but will also increasingly seek to diversify both their membership and their criminal activities in recognition of potential financial gain. New alliances between rival gangs will likely form as gangs suspend their former racial ideologies in pursuit of mutual profit. Gangs will continue to evolve and adapt to current conditions and law enforcement tactics, diversify their criminal activity, and employ new strategies and technology to enhance their criminal operations, while facilitating lower-risk and more profitable schemes, such as white collar crime.
(U) The expansion of communication networks, especially in wireless communications and the Internet, will allow gang members to form associations and alliances with other gangs and criminal organizations—both domestically and internationally—and enable gang members to better facilitate criminal activity and enhance their criminal operations discreetly without the physical interfacing once necessary to conduct these activities. (U) Changes in immigrant populations, which are susceptible to victimization and recruitment by gangs, may have the most profound effect on street gang membership. Continued drug trafficking-related violence along the US Southwest border could trigger increased migration of Mexicans and Central Americans into the United States and, as such, provide a greater pool of victims, recruits, and criminal opportunities for street gangs as they seek to profit from the illegal drug trade, alien smuggling, and weapons trafficking. Likewise, increased gang recruitment of youths among the immigrant population may result in an increase in gang membership and gang-related violence in a number of regions.
(U) Street gang activity and violence may also increase as more dangerous gang members are released early from prison and re-establish their roles armed with new knowledge and improved techniques. Prison gang members, already an ideal target audience for radicalization, may expand their associations with foreign gang members or radical criminal organizations, both inside correctional institutions and in the community upon their release.
(U//LES) Gang members armed with high-powered weapons and knowledge and expertise acquired from employment in law enforcement, corrections, or the military will likely pose an increasing nationwide threat, as they employ these tactics and weapons against law enforcement officials, rival gang members, and civilians. Associates, friends, and family members of gangs will continue to play a pivotal role in the infiltration and acquisition of sensitive information.
(U) Globalization, socio-political change, technological advances, and immigration will result either in greater gang expansion and gang-related crime or displace gang members as they search for criminal opportunities elsewhere. Stagnant or poor economic conditions in the United States, including budget cuts in law enforcement, may undercut gang dismantlement efforts and encourage gang expansion as police agencies redirect their resources and disband gang units and taskforces, as reported by a large number of law enforcement agencies.
DOWNLOAD ORGINAL FILE HERE
SECRET – Pakistan Internet Filtering and URL Blocking System Request for Proposal
The National ICT R&D Fund invites proposals from academia/research institutions, companies, organizations for the development, deployment and operation of a national level URL Filtering and Blocking System. Institutions/organizations/companies desirous of developing, deploying and managing the proposed system are requested to submit their proposals to the ICT R&D Fund Islamabad by 1500 hrs on 2nd March, 2012 as per the prescribed format.
…
Internet access in Pakistan is mostly unrestricted and unfiltered. The Internet traffic is coming from two IP backbone providers, i.e., PTCL and TWA. The Internet Service Providers (ISPs) and backbone providers have currently deployed manual URL filtering and blocking mechanism in order to block the specific URLs containing undesirable content as notified by PTA from time to time.
Many countries have deployed web filtering and blocking systems at the Internet backbones within their countries. However, Pakistani ISPs and backbone providers have expressed their inability to block millions of undesirable web sites using current manual blocking systems. A national URL filtering and blocking system is therefore required to be deployed at national IP backbone of the country.
ICT R&D Fund has decided to fund the indigenous development, deployment, operations and maintenance of such a system by companies, vendors, academia and/or research organizations with proven track record.
This system would be indigenously developed within Pakistan and deployed at IP backbones in major cities, i.e., Karachi, Lahore and Islamabad. Any other city/POP could be added in future. The system is proposed to be centrally managed by a small and efficient team stationed at POPs of backbone providers.The system would have a central database of undesirable URLs that would be loaded on the distributed hardware boxes at each POP and updated on daily basis. The database would be regularly updated through subscription to an international reputed company maintaining and updating such databases.
System requirements would be as follows:
1. Should be capable of URL filtering and blocking, from domain level to sub folder, file levels and file types.
2. Should be able to block a single IP address or a range of IP address.
3. Hardware should be stand-alone that can be integrated into any Ethernet/IP network.
4. Hardware should be carrier grade, 1+1 redundant configuration, 100% uptime, redundant power supplies (-48 V DC) with minimum power consumption and other carrier grade specifications.
5. The system should be capable of network monitoring via SNMP. The system should also report critical system statistics, like CPU/Memory utilization, network throughput, etc.
6. The solution should support offline configuration with zero packet delay to the original traffic.
7. The system should operate on OSI layer 2 or 3.
8. The bandwidth handling capacity should be scalable. The current bandwidth of Pakistan is about 85Gbps in total as of December 2011, growing at 40-50% per year. The solution should be scalable and modular to cater for bandwidth expansion of future. Bandwidth expansion should be handled by adding/stacking hardware boxes in modular form. The solution should be deployed in distributed model with filtering boxes placed at the distribution points of backbone providers in major cities. Each hardware box should be capable of handling 10Gbps (or more) of traffic at line rate.
The installation at PTCL IP Gateways at Karachi (Pak Capital and Marston Road Exchange requires to TAP 20 (twenty) 10G interfaces. The system should be able to handle 100Gbps traffic at each node.
PTCL has decided to install 100Gbps interfaces at above location in near future, therefore the system should be able to support 100Gbps interfaces. Minimum change should be required to migrate from 10Gbps interfaces to 100Gbps interfaces.Similar design approach should be adopted after reviewing the core network of TWA.
9. The system should be modular and scalable to any number of interfaces at the backbone router/switches.
10. The system should have the ability to intercept the flow in both directions (in-bound or out-bound traffic).
11. The system should be rapidly programmable to support new protocols and applications.
12. The system should be preferably plug and play and require minimum configuration for setup.
13. The total delay introduced by each hardware box should not be more than 1 milliseconds at line rate of 10Gbps. In case of offline configuration there should be Fail Safe operation.
14. Each box should be able to handle a block list of up to 50 million URLs (concurrent unidirectional filtering capacity) with processing delay of not more than 1 milliseconds.
15. The system should support multiple languages to capture URL in any language.
16. The system must support IWF or any other equivalent 3rd party external URL Database.
17. Master Database update time should be user configurable.
18. The Master Database should be locally installed with support to update the Database from network.
19. The system should allow Proprietary DB definition or integration.
20. The Database should be flexible and could be locally modified to meet customer needs.
21. The Database should be flexible to add/remove filters or categories.
22. The backend control of the system to view access to block list URL database should be only with the solution holder (backbone operator). The solution supplier should not have access to view the categories defined by the customer.
23. The solution supplier should be able to provide remote and onsite support on 24 x7 basis in major cities of Pakistan.
24. The solution supplier should propose and quote for providing operations and maintenance (O&M) support of the system with service level agreement (SLA) for five years after system installation and commissioning.
25. System supplier should quote cost of yearly maintenance and up-gradation of the system.
26. No one should be able to view or access the customer defined categories in Database.
27. Separate hardware fast-path for delay-sensitive traffic, ensuring very low latency (~10micS) should be provided. The system should have load balancing and failover capabilities. In case of failure or degraded performance of the system, it should be capable of automatic bypass through a fail-safe port.
28. Updating of URL Database should be done through CLI commands. Support for bulk load through file/network should also be provided.
29. The solution should also support Web based administration via HTTP or HTTPS.
30. The solution should provide easy to use, user friendly web based application to easily block/unblock URL categories.
31. The solution should provide a hierarchical authentication system with configurable hierarchal access to the system management.
32. Blacklist database must be protected with some encryption technology method/key to protect tampering.
33. The system should allow to view statistics related to packet TX and RX.
34. The system should allow reset to factory default mode. User should be prompted if Database is to be reset too.
35. The system should allow to enable/disable all the features listed under filtering/blocking.
TOP-SECRET from the FBI – New Defendants Added to Case Alleging $20 Million Home Health Care Fraud Conspiracy,
CHICAGO—Two physicians and four registered nurses are among 11 new defendants who were added to a federal indictment against a suburban Chicago man who operated two home health care businesses for allegedly swindling Medicare of at least $20 million over five years, federal law enforcement officials announced today. Nine of the 11 new defendants allegedly conspired with the initial defendant, Jacinto “John” Gabriel, Jr., to submit millions of dollars in false claims for reimbursement of home health care services purportedly provided to Medicare beneficiaries, which allegedly were never provided or were not medically necessary so that they could profit from the fraudulently-obtained funds. Gabriel and his co-schemers allegedly used the proceeds for various purposes, including using cash to gamble at casinos in the Chicago area and Las Vegas; to buy automobiles, jewelry; to purchase real estate in the United States and the Philippines; to perpetuate the businesses by paying his employees and providing them with gifts; and to bribe physicians and pay kickbacks to others in exchange for patient referrals.
Gabriel, 44, of Berwyn, who had no formal medical training, medical degrees, or licenses to practice as a health care professional, was charged in the new indictment with one count of health care fraud conspiracy, 43 counts of health care fraud, 11 counts of money laundering, and four counts of federal income tax evasion in a 69-count superseding indictment returned yesterday by a federal grand jury, announced Patrick J. Fitzgerald, United States Attorney for the Northern District of Illinois. Gabriel was arrested on preliminary charges in February 2011 and was charged alone in a 15-count indictment last summer. He pleaded not guilty to the original charges and is free on bond.
According to the indictment, Gabriel did not identify himself as an owner, but in fact exercised ownership and control over Perpetual Home Health, Inc., based in Oak Forest, and Legacy Home Healthcare Services, which was located on the city’s north side. Both firms have ceased operating and no longer receive Medicare payments. Between May 2006 and January 2011, Perpetual submitted more than 14,000 Medicare claims seeking reimbursement for services allegedly provided to beneficiaries. As a result of those claims, Perpetual received more than $38 million in Medicare payments. Between 2008 and January 2011, Legacy submitted more than 2,000 claims for Medicare reimbursement and received more than $6 million. Neither Perpetual nor Legacy had any sources of revenue other than Medicare funds, the indictment states.
The new defendants are:
Jassy Gabriel, 42, of Berwyn, John Gabriel’s brother, the nominal majority owner of Perpetual and its president, as well as a registered nurse. He was charged with one count of health care fraud conspiracy and one count of filing a false federal income tax return.
Stella Lubaton, 46, of Midlothian, a minority owner of Perpetual and an officer and administrator, as well as a registered nurse. She was charged with one count of health care fraud conspiracy, 16 counts of health care fraud, one count of filing a false federal income tax return, and one count of violating the medical anti-kickback statute.
Nessli Reyes, 35, of Elgin, part-owner of Legacy and its president, as well as a registered nurse. She was charged with one count of health care fraud conspiracy and nine counts of health care fraud.
Charito Dela Torre, 71, of Berwyn, a physician, was charged with one count of health care fraud conspiracy, 12 counts of health care fraud, and three counts of federal income tax evasion.
Ricardo Gonzales, 75, of Orland Park, a physician, was charged with one count of health care fraud conspiracy, 19 counts of health care fraud, and one count of violating the medical anti-kickback statute.
Rosalie Gonzales, 42, of Chicago, a registered nurse and Ricardo Gonzales’ daughter, was charged with one count of violating the medical anti-kickback statute.
James Davis, 37, of West Chicago; Francis Galang, 27, of Crest Hill; and Michael Pacis, 38, of Homer Glen, all data entry employees of Perpetual, were charged with one count each of health care fraud conspiracy.
Regelina “Queenie” David, 58, of Joliet, a Perpetual quality assurance employee, was charged with one count of health care fraud conspiracy.
Kennedy Lomillo, 44, of Mundelein, who provided bookkeeping and payroll services to Perpetual and also prepared a corporate tax return for Perpetual, as well as an individual return for Lubaton, was charged with two counts of aiding and abetting the preparation of false income tax returns.
The indictment also seeks forfeiture of $20 million against the Gabriel brothers and Lubaton.
As part of the conspiracy, Gabriel, acting in various combinations with the nine co-conspirators, allegedly obtained personal information of Medicare beneficiaries to bill Medicare without the beneficiaries’ knowledge or consent; paid bribes and kickbacks in cash and by check, directly and indirectly, to physicians and others in exchange for referrals of patients to Perpetual and Legacy; created false patient files to support fraudulent Medicare claims and submitted false claims based on those records; used Medicare proceeds to pay themselves and others who assisted in carrying out the scheme; and concealed the fraud proceeds by directing Perpetual and Legacy to issue checks payable to fictitious entities, John Gabriel’s friends and associates.
Among other details, the indictment alleges that John and Jassy Gabriel, Lubaton, and Reyes authorized Perpetual and Legacy to pay various amounts, ranging between $200 and $800, to employees and others, including indirectly to Ricardo Gonzales, for each patient they referred and enrolled in home health care services. John Gabriel and others also cold-called Medicare beneficiaries to try to persuade them to enroll with Perpetual and Legacy.
As part of allegedly falsifying patient records, John Gabriel directed Perpetual and Legacy employees, including Davis, Galang, and Pacis, to systematically complete standard forms by listing the same false diagnoses, including arthropathy (joint disease) and hypertension, which enabled them to claim a higher level of Medicare reimbursement, according to the charges.
In addition to the fraud counts, the money laundering charges allege that between October and December 2010, Gabriel cashed 11 checks in amounts under $10,000—usually $9,000 and all involving fraud proceeds—to avoid federal currency transaction reporting requirements.
The four tax evasion counts against John Gabriel allege that for calendar years 2006 through 2009, he failed to pay taxes totaling approximately $889,062 on gross income totaling more than $2.82 million. The three tax evasion counts against Dela Torre allege that for calendar years 2005 through 2007, she failed to pay taxes totaling approximately $158,405 on gross income totaling more than $560,000.
Lubaton was charged with filing a false tax return for 2007 for allegedly failing to report all of her income, which was in excess of the $546,442 that she reported, and Lomillo was charged with aiding and abetting the preparation of her false return. Jassy Gabriel was charged with filing a false tax return for 2007 for allegedly failing to report all of his adjusted gross income, which exceeded the $603,974 that he reported, and Lomillo was charged with aiding and abetting the preparation of his false return.
Health care fraud conspiracy and each count of health care fraud carries a maximum penalty of 10 years in prison and a maximum fine of $250,000, or an alternate fine totaling twice the loss or twice the gain, whichever is greater, as well as mandatory restitution. Each count of money laundering carries a maximum 20-year prison term and a maximum fine of $500,000. Violating the medical anti-kickback statute carries a maximum penalty of five years in prison and a $250,000 fine. Each count of tax evasion carries a five-year maximum prison term, while each count of filing a false income tax return carries a three-year maximum, and a $250,000 fine. In addition, defendants convicted of tax offenses must pay the costs of prosecution and remain liable for any and all back taxes, as well as a potential civil fraud penalty of 75 percent of the underpayment plus interest. If convicted, the court must impose a reasonable sentence under federal statutes and the advisory United States Sentencing Guidelines.
Mr. Fitzgerald announced the charges together with Lamont Pugh III, special agent in charge of the Chicago Region of the U.S. Department of Health and Human Services Office of Inspector General; Robert D. Grant, special agent in charge of the Chicago Office of Federal Bureau of Investigation; and Alvin Patton, special agent in charge of the Internal Revenue Service Criminal Investigation Division. The Railroad Retirement Board Office of Inspector General also participated in the investigation, which is continuing. The investigation is being conducted by the Medicare Fraud Strike Force, which expanded to Chicago in 2011, and is part of the Health Care Fraud Prevention and Enforcement Action Team (HEAT), a joint initiative between the Justice Department and HHS to focus their efforts to prevent and deter fraud and enforce anti-fraud laws around the country.
The government is being represented by Assistant U.S. Attorneys Brian Havey, Raj Laud, and Tony Iweagwu, Jr.
The public is reminded that charges are not evidence of guilt. The defendants are presumed innocent and are entitled to a fair trial at which the government has the burden of proving guilt beyond a reasonable doubt.
STASI-NAMEN ALPHABETISCH BUCHSTABE WI-WL – STASI-NAMES IN ALPHABETICAL ORDER – WI-WL
see more info at http://www.victims-opfer.com
Die Liste wurde bereits früher hier publiziert:
http://stasiopfer.de/component/option,com_simpleboard/Itemid,/func,view/id,993815828/catid,4/
Vom “Stasiopfer”-Angebot führt ein Link zu einer Website in den USA (www.jya.com), die sich auch mit den Praktiken von Geheimdiensten beschäftigt. Dort findet sich die “Fipro-Liste”, das detaillierte “Finanzprojekt” der Stasi, angefertigt in den letzten Tagen der DDR, um die Rentenansprüche der rund 100 000 hauptamtlichen Mitarbeiter des MfS auch nach dem Zusammenbruch des Systems belegen zu können. Die “Fipro-Liste” ist seit langem bekannt und diente Anfang der neunziger Jahre etwa zur Identifizierung der so genannten OibE – Offiziere im besonderen Einsatz. Diese Liste „Offiziere im besonderen Einsatz“im Jahre 1991 erschien in der “taz. Die Echtheit kann beim BStU überprüft werden.
Siehe u.a. http://www.spiegel.de/spiegel/print/d-22539439.html
Auf Druck ehemaliger STASI-Leute und Ihrer Genossen wurde die Liste aus dem Verkehr gezogen.
Hier ist sie wieder:
021060500514;97;08;00;;WIATR, ELLEN:;;;11464,30
150437430116;18;27;30;;WIATROK, HELMUT:;;;27000,00
280870408310;06;69;00;;WIATZKE, FRANK:;;;2870,00
070269403441;03;80;00;;WIBELITZ, TORSTEN:;;;8950,00
260340500816;99;77;00;;WICH, GISELA:;;;22500,00
260847412233;07;00;40;;WICH, HELMUT:;;;26640,00
201228404111;99;40;00;;WICH, JOACHIM:;;;19320,00
050561400813;94;65;00;;WICH, JOERG:;;;18090,00
240249401317;01;00;47;;WICHATE, MANFRED:;;;22187,50
310156401538;01;06;24;;WICHERT, BERND:;;;17640,96
241140429732;99;43;00;;WICHERT, HELMUT:;;;26250,00
040654406174;04;06;00;;WICHERT, INGO:;;;23460,00
120964430399;15;14;00;;WICHERT, JUERGEN:;;;19633,00
241164414826;18;80;00;;WICHERT, THOMAS:;;;18944,84
160761430256;15;03;00;;WICHITILL, STEFFEN:;;;17985,00
140262506713;99;40;00;;WICHMANN, ANDREA:;;;16463,63
221142509922;99;40;00;;WICHMANN, CHRISTA:;;;19380,00
240568403440;17;00;00;;WICHMANN, DENIS:;;;8950,00
150271409826;18;35;00;;WICHMANN, FRANK:;;;2795,00
030148516419;99;41;00;;WICHMANN, GABRIELE:;;;22482,50
111136429726;15;01;00;;WICHMANN, HANS:;;;30000,00
210162406716;05;00;41;;WICHMANN, HOLGER:;;;15180,00
110765414338;99;55;00;;WICHMANN, JENS:;;;15604,50
021059402730;94;03;00;;WICHMANN, JOERG:;;;16830,00
291250406721;05;51;00;;WICHMANN, JUERGEN:;;;23385,00
230461509916;94;03;00;;WICHMANN, KERSTIN:;;;1654,37
061046403415;03;00;44;;WICHMANN, KLAUS:;;;33659,27
110340409920;97;01;00;;WICHMANN, KURT:;;;27750,00
310363426340;99;43;00;;WICHMANN, MAIK:;;;18755,00
020947416423;99;02;00;;WICHMANN, NORBERT:;;;30687,50
171152411416;07;02;00;;WICHMANN, REINHARD:;;;22770,00
230856510620;07;00;48;;WICHMANN, RENATE:;;;17365,00
130267400628;01;06;27;;WICHMANN, RICO:;;;13986,00
070357430044;96;15;10;;WICHMANN, THORSTEN:;;;19085,00
150156406718;94;64;00;;WICHMANN, UWE:;;;18480,00
230757400821;97;08;00;;WICHT, HELMUT:;;;20010,00
080937400115;01;00;45;;WICHT, KURT:;;;19875,00
110460414230;30;48;00;;WICHT, PETER:;;;20965,00
270368413422;18;33;00;;WICHT, RENE:;;;9825,00
010166406813;98;82;00;;WICHT, THOMAS:;;;15949,50
291068405335;18;31;00;;WICHURA, BERND:;;;9675,00
281256530089;18;32;00;;WICK, DOROTHEA:;;;18975,00
130541406169;04;41;00;;WICK, HANS-HELMUT:;;;40312,50
090769406137;04;18;00;;WICK, HEIKO:;;;8300,00
161165417412;09;00;50;;WICK, TORSTEN:;;;14670,00
110351429257;14;03;00;;WICKE, EBERHARD:;;;25245,00
280362413519;08;00;44;;WICKE, OLAF:;;;21285,00
020167413512;08;00;51;;WICKE, PETER:;;;16470,00
201155421833;12;08;00;;WICKERT, GERALD:;;;20010,00
280866528221;14;80;00;;WICKLEDER, ANKE:;;;1120,00
040938428228;14;19;00;;WICKLEDER, HEINER:;;;23250,00
040763428313;14;15;00;;WICKLEDER, STEFFEN:;;;19965,00
140461428287;14;99;00;;WICKLEDER, THOMAS:;;;22155,00
181249417741;09;19;00;;WICKLEIN, BURKHARD:;;;28800,00
040746417727;09;51;00;;WICKLEIN, HANS-JOACHIM:;;;21937,50
171047427248;14;26;00;;WICKLEIN, JOHANNES:;;;21937,50
151167417724;09;80;00;;WICKLEIN, THOMAS:;;;13244,00
110449420226;97;06;00;;WICKLEIN, WOLFGANG:;;;23120,00
120764413922;98;82;00;;WIDDECKE, HEIKO:;;;17490,00
170171413930;18;35;00;;WIDDECKE, PETER:;;;2795,00
280454417728;09;80;00;;WIDDER, HANS-JUERGEN:;;;20460,00
130769404813;04;08;00;;WIDIGER, DIRK:;;;7405,00
270768413034;97;06;00;;WIDOWSKI, ANDRE:;;;14700,00
101165500713;99;43;00;;WIDULLE, ANNE-CATRIN:;;;0,00
050165401339;99;43;00;;WIDULLE, JEAN:;;;16830,00
141167428221;99;43;00;;WIEBACH, DIRK:;;;13608,00
011165424934;99;40;00;;WIEBELITZ, THOMAS:;;;19520,34
010440430032;15;19;00;;WIEBERNEIT, HEINZ:;;;29437,50
080270413937;08;69;00;;WIEBICKE, RALF:;;;9555,00
130533430214;15;00;48;;WIECH, ACHIM:;;;27000,00
051245405713;30;56;00;;WIECHERT, DIETER:;;;26440,00
251148404336;97;06;00;;WIECHERT, HARTMUT:;;;24000,00
080669406165;04;69;00;;WIECHERT, OLAF:;;;2870,00
310762415411;08;14;00;;WIECHERT, THOMAS:;;;16115,00
070469403446;18;34;00;;WIECHERT, VOLKER:;;;9510,00
091040402136;02;08;00;;WIECHMANN, BERND:;;;20750,00
260652401921;98;82;00;;WIECHMANN, BRUNO:;;;20160,00
050137529722;99;02;00;;WIECHMANN, CHRISTA:;;;27672,91
281139406142;97;08;00;;WIECHMANN, EGON:;;;27750,00
170137529710;97;07;00;;WIECHMANN, HELGA:;;;26437,50
271069430198;18;31;00;;WIECHMANN, JAN:;;;6958,87
131034429715;98;84;00;;WIECHMANN, KARL:;;;21750,00
200939429732;96;15;13;;WIECHMANN, MANFRED:;;;23312,50
180366401517;01;06;22;;WIECHMANN, PETER:;;;14928,50
221056416818;99;43;00;;WIECHMANN, PETER:;;;20010,00
160650401524;98;83;00;;WIECHMANN, SIEGFRIED:;;;21097,50
250469402118;02;69;00;;WIECHMANN, THOMAS:;;;9555,00
080761522732;96;15;21;;WIECHOWSKI, BIRGIT:;;;3755,07
040655402220;02;00;45;;WIECK, REINHARD:;;;19320,00
050146402213;04;06;00;;WIECKI-VON, ERNST-RUEDIGER:;;;22875,00
040853404016;99;43;00;;WIECZNY, ROLAND:;;;20662,50
281147422783;12;09;00;;WIECZORECK, DIETER:;;;24840,00
120351410619;99;43;00;;WIECZOREK, DETLEFF:;;;26640,00
271269411426;07;69;00;;WIECZOREK, MAIK:;;;9510,00
050552410016;98;82;00;;WIECZOREK, MICHAEL:;;;20160,00
190362413958;08;20;00;;WIECZOREK, RONALD:;;;21120,00
030646407223;96;15;05;;WIECZOREK, RUEDIGER:;;;21750,00
081046426324;14;80;00;;WIECZOREK, SIEGFRIED:;;;21540,00
270268403630;03;55;00;;WIEDBUSCH, FRANK:;;;13720,00
100364430231;98;18;00;;WIEDE, BERND:;;;16784,76
210467506152;98;18;00;;WIEDE, JANA:;;;0,00
160441425132;13;09;00;;WIEDE, JUERGEN:;;;25937,50
190637429714;94;30;00;;WIEDE, MANFRED:;;;22687,50
150265430135;99;02;00;;WIEDE, OLAF:;;;14418,00
111040400443;97;06;00;;WIEDE, SIEGFRIED:;;;32250,00
060149424038;18;27;00;;WIEDEBACH, RAINER:;;;21687,50
200143500847;99;43;00;;WIEDEMANN, ANNELIESE:;;;19440,00
080257420016;11;06;20;;WIEDEMANN, BERND:;;;17652,50
050852414713;97;06;00;;WIEDEMANN, BERND:;;;23040,00
290952415409;94;30;00;;WIEDEMANN, BERND:;;;26400,00
141155400512;97;07;00;;WIEDEMANN, BERTHOLD:;;;19530,00
110749417723;97;01;00;;WIEDEMANN, DIETER:;;;27360,00
220842429742;99;53;00;;WIEDEMANN, EBERHARD:;;;32437,50
161062417129;99;02;00;;WIEDEMANN, FRANK:;;;19360,00
120445426718;14;40;00;;WIEDEMANN, GERD:;;;27000,00
080351417745;97;01;00;;WIEDEMANN, GERHARD:;;;24150,00
261252405928;97;06;00;;WIEDEMANN, GERT:;;;20880,00
120756424998;90;65;40;5219/84, :;WIEDEMANN, GU(E)NTHER;1280;NEUE STR. 1;
120756424998;90;65;40;5219/84, :;WIEDEMANN, GU(E)NTHER;1280;NEUE STR. 1;
310537429710;18;27;00;;WIEDEMANN, HANS:;;;39750,00
180749400546;98;82;00;;WIEDEMANN, HANS-DIETER:;;;21000,00
130158530116;96;15;05;;WIEDEMANN, HEIKE:;;;18680,47
041255420336;99;09;00;;WIEDEMANN, HERBERT:;;;23100,00
220970400848;94;65;00;;WIEDEMANN, JENS:;;;2870,00
180468406132;04;69;00;;WIEDEMANN, KEY:;;;9675,00
010555417129;98;81;00;;WIEDEMANN, LUTZ:;;;23564,13
020843530272;30;83;00;;WIEDEMANN, MARGRIT:;;;19290,00
141239400907;97;01;00;;WIEDEMANN, PETER:;;;33000,00
060360422417;12;02;00;;WIEDEMANN, PETER:;;;22080,00
130355412258;07;40;00;;WIEDEMANN, REINHARD:;;;21022,50
020759422826;18;28;00;;WIEDEMANN, UWE:;;;18687,50
231256417726;09;08;00;;WIEDEMANN, UWE:;;;17297,50
090265513625;08;02;00;;WIEDENBECK, CHRISTINE:;;;2682,63
110839413638;08;00;48;;WIEDENBECK, HANS-DIETER:;;;25500,00
040650403013;01;00;45;;WIEDENBECK, HANS-EDO:;;;23230,00
110666400117;01;26;00;;WIEDENBECK, JENS:;;;14742,00
230235413617;08;00;48;;WIEDENBECK, LOTHAR:;;;25500,00
301060413628;08;26;00;;WIEDENBECK, LUTZ:;;;17251,50
271044415397;96;15;18;;WIEDENBECK, RAINER:;;;31620,00
070758527111;97;22;00;;WIEDENHOEFT, ILONA:;;;16468,07
300660512211;99;53;00;;WIEDER, CARMEN:;;;18291,81
060261408417;97;08;00;;WIEDER, MICHAEL:;;;20502,50
230554427418;30;83;00;;WIEDERER, REINER:;;;20385,00
020261417771;97;01;00;;WIEDERHOLD, ANDREAS:;;;20582,50
260361410828;07;00;49;;WIEDERHOLD, PETER:;;;20460,00
221169418617;18;35;00;;WIEDERMANN, MARIO:;;;9510,00
201264425024;15;00;48;;WIEDERMANN, ROBBY:;;;16505,91
150668412222;18;35;00;;WIEDFELDT, MARKO:;;;10050,00
210566414827;09;15;00;;WIEDICKE, THOMAS:;;;20161,80
290770424849;18;35;00;;WIEDLITZKI, MIRKO:;;;2795,00
260847416621;09;00;45;;WIEDMER, ROLF:;;;26562,50
030635428221;14;00;54;;WIEDMER, SIEGFRIED:;;;26250,00
130652425100;10;18;00;;WIEDNER, BERND:;;;17572,50
280649408418;06;06;00;;WIEDNER, DIETRICH:;;;21500,00
110651424933;13;00;41;;WIEDNER, FRANK:;;;18720,00
051149409212;94;30;00;;WIEDNER, JUERGEN:;;;22250,00
160950527145;97;01;00;;WIEDNER, KARLA:;;;17693,57
150258424917;96;15;25;;WIEDNER, MICHAEL:;;;24495,00
160859500849;97;22;00;;WIEDNER, PETRA:;;;17773,25
220743401912;02;20;00;;WIEDNER, SIEGFRIED:;;;21600,00
030856519047;10;19;00;;WIEDNER, UTE:;;;16456,50
060667411421;99;78;00;;WIEDORN, HAGEN:;;;14157,00
061261402220;02;00;45;;WIEDOW, JOERG:;;;15120,00
190144521117;12;80;00;;WIEDRICH, BRIGITTE:;;;17658,00
010836421116;12;30;00;;WIEDRICH, WERNER:;;;24471,77
250348415350;30;63;00;;WIEDUWILT, BERND:;;;19080,00
080350515394;30;83;00;;WIEDUWILT, CHRISTINE:;;;15180,00
080568419354;10;00;51;;WIEDUWILT, HEIKO:;;;12975,00
120566419338;10;06;00;;WIEDUWILT, JOERG:;;;16308,00
240867418829;10;00;50;;WIEDUWILT, RALF:;;;12525,00
261267518511;10;06;00;;WIEDUWILT, SANDRA:;;;8366,94
100256420589;94;03;00;;WIEFEL, FRANK:;;;18033,80
060964420527;12;00;55;;WIEFEL, MAIK:;;;19054,50
301151519727;15;00;42;;WIEGAND, ANITA:;;;15645,97
270360409218;94;64;00;;WIEGAND, BORIS:;;;20310,00
180150412348;07;00;40;;WIEGAND, DIETER:;;;23937,50
051245416922;09;06;00;;WIEGAND, DIETER:;;;20820,00
030853429871;94;65;00;;WIEGAND, DIETMAR:;;;22320,00
080970413970;18;32;00;;WIEGAND, DIRK:;;;2795,00
021069413927;08;80;00;;WIEGAND, FALK:;;;11055,00
150768425047;13;69;00;;WIEGAND, FRANK:;;;9555,00
260662413627;97;22;00;;WIEGAND, FRANK:;;;17423,09
080655518748;10;51;00;;WIEGAND, GERLINDE:;;;16360,17
250945516942;09;00;52;;WIEGAND, GISELA:;;;14355,00
290530430019;97;06;00;;WIEGAND, GUENTER:;;;27000,00
220151407528;05;06;00;;WIEGAND, GUENTER:;;;21052,50
020552421826;12;51;00;;WIEGAND, HARALD:;;;22502,32
090359516229;98;83;00;;WIEGAND, HEIDEMARIE:;;;15317,95
250940419916;04;07;00;;WIEGAND, HELMUT:;;;26250,00
300669419830;18;33;00;;WIEGAND, HENRY:;;;9600,00
230748413911;08;08;00;;WIEGAND, HORST:;;;26187,50
261069423810;18;31;00;;WIEGAND, JENS:;;;9600,00
151061413610;08;80;00;;WIEGAND, JO(E)RG:;;;20865,00
140832429714;98;20;00;;WIEGAND, JOACHIM:;;;42000,00
010835417721;99;40;00;;WIEGAND, JOACHIM:;;;33000,00
050555428334;10;51;00;;WIEGAND, KLAUS:;;;19702,50
260538417428;09;00;50;;WIEGAND, LOTHAR:;;;26750,00
011158413444;99;43;00;;WIEGAND, MICHAEL:;;;19085,00
021163417721;96;15;22;;WIEGAND, MIKE:;;;15392,50
280961418434;94;03;00;;WIEGAND, NORBERT:;;;19140,00
130739429710;99;02;00;;WIEGAND, RAINER:;;;39750,00
250870415329;18;33;00;;WIEGAND, STEFFEN:;;;2795,00
270865425029;13;80;00;;WIEGAND, THOMAS:;;;16067,00
180868417324;18;33;00;;WIEGAND, THOMAS:;;;9675,00
160865417427;94;30;00;;WIEGAND, TORSTEN:;;;11101,00
240464416431;09;00;44;;WIEGAND, TORSTEN:;;;18907,17
250155413973;08;00;62;;WIEGAND, UWE:;;;23402,50
111234400855;01;12;00;;WIEGAND, WALTER:;;;21000,00
180644404823;04;00;45;;WIEGANDT, LOTHAR:;;;26375,00
070768415017;18;38;00;;WIEGANDT, MAIK:;;;9675,00
240659507229;94;03;00;;WIEGANDT, MARLIES:;;;19158,63
010454429892;99;41;00;;WIEGANDT, STEFAN:;;;26640,00
060170412226;18;34;00;;WIEGEL, DIRK:;;;9510,00
270359411943;07;00;57;;WIEGEL, HARALD:;;;22770,00
160170416719;18;34;00;;WIEGEL, STEFFEN:;;;10135,00
190469415339;18;80;00;;WIEGEL, TORSTEN:;;;9675,00
280946410514;07;00;51;;WIEGEN-VON, WILFRIED:;;;25500,00
270459410817;07;06;00;;WIEGER, EGBERT:;;;19320,00
111067412284;18;40;00;;WIEGERS, SEBASTIAN:;;;11475,00
100957404426;98;82;00;;WIEGERT, BERND:;;;21175,00
210371404418;18;35;00;;WIEGERT, MARCO:;;;2720,00
070869430144;18;33;00;;WIEGLEB, ANDRE:;;;2720,00
230944425047;13;65;00;;WIEGLEB, FRANK:;;;20250,00
020366430163;18;35;00;;WIEGLEB, MARCO:;;;9675,00
161045524918;13;06;00;;WIEGLEB, MONIKA:;;;18720,00
120533529717;02;80;00;;WIEGLEPP, ERIKA:;;;32625,00
221157409422;06;51;00;;WIEGMANN, HANS-DIRK:;;;19262,50
100633430054;99;40;00;;WIEGMANN, HASSO:;;;37500,00
171150410321;01;96;52;;WIEGMANN, PETER:;;;17520,00
061059509913;07;29;00;;WIEGNER, ANGELA:;;;15745,83
120357411110;07;65;00;;WIEGNER, JOACHIM:;;;22252,50
261250411128;07;03;00;;WIEGNER, KARLHEINZ:;;;25140,00
100444406733;97;01;00;;WIEGNER, PETER:;;;30750,00
171255406249;17;00;00;;WIEGNER, THOMAS:;;;20950,00
060663424313;98;84;00;;WIEGNER, VEIKKO:;;;16830,00
190168406121;04;06;00;;WIEGRATZ, HOLGER:;;;12450,00
070360414758;98;84;00;;WIEHLE, GISBERT:;;;19040,17
020161515331;99;77;00;;WIEHLE, RENATE:;;;18233,61
020954404340;60;90;00;;WIEHLE, WINFRIED:;;;
020954404340;60;90;00;;WIEHLE, WINFRIED:;;;20085,00
070269414749;18;31;00;;WIEHR, ANDRE:;;;9675,00
220347405225;04;00;48;;WIEJA, GUENTER:;;;17537,50
210632419918;97;01;00;;WIEJA, HEINZ:;;;26250,00
181056407520;05;00;40;;WIELAND, BERND:;;;22770,00
090630530010;99;40;00;;WIELAND, CHRISTA:;;;38062,50
080370406136;04;06;00;;WIELAND, FALK:;;;8235,00
280431406137;04;00;40;;WIELAND, GUENTER:;;;21937,50
260359430096;94;65;00;;WIELAND, HANS-HENNING:;;;21332,50
030352429822;94;65;00;;WIELAND, HANS-JOERG:;;;25606,39
310130530024;98;83;00;;WIELAND, HELGA:;;;23250,00
210158428146;97;07;00;;WIELAND, KARL-HEINZ:;;;25530,00
071039407521;05;14;00;;WIELAND, KLAUS:;;;24812,50
070957410362;94;03;00;;WIELAND, MICHAEL:;;;25993,83
090363428272;98;82;00;;WIELAND, RALF:;;;17301,93
060928430023;15;69;00;;WIELAND, SIEGFRIED:;;;30750,00
291062530151;98;83;00;;WIELAND, SONDRA:;;;14100,40
150869421045;18;40;00;;WIELAND, STEFFEN:;;;9600,00
150965401511;01;69;00;;WIELAND, TINO:;;;13144,86
310349429238;14;00;44;;WIELE, DIETER:;;;27937,50
060837407530;05;06;00;;WIELE, HEINZ-JOACHIM:;;;21812,50
151230409533;06;29;00;;WIELE, OTTO:;;;25375,00
051251429789;15;06;00;;WIELGOSZ, LOTHAR:;;;25920,00
261229409314;06;00;47;;WIELSCH, BRINGFRIED:;;;25500,00
200757412235;97;01;00;;WIEMANN, BURKHARD:;;;26150,04
010951413111;94;11;00;;WIEMANN, INGO:;;;23922,50
181251412253;97;01;00;;WIEMANN, REINHARD:;;;29520,00
161054413929;08;00;51;;WIEMANN, ROLAND:;;;15384,92
120853408527;94;03;00;;WIEMER, BURKHARD:;;;21000,00
120570508317;06;00;43;;WIEMER, CLAUDIA:;;;11895,00
190254415331;08;00;40;;WIEMER, FRED:;;;21332,51
251168428933;02;69;00;;WIEMER, KAY:;;;9600,00
250163410828;94;65;00;;WIEMERT, FRANK:;;;17765,00
111040510810;07;06;00;;WIEMERT, MARGITTA:;;;17552,25
071259401818;02;00;42;;WIEMEYER, UWE:;;;22110,00
030468415393;18;31;00;;WIEN, ANDRE:;;;9825,00
040754409524;30;53;00;;WIENARICK, INGOLF:;;;22012,50
150138419339;10;53;00;;WIENCH, WERNER:;;;26250,00
200245400425;01;80;00;;WIENCK, KURT:;;;20250,00
140442400860;01;18;00;;WIENCKE, ERWIN:;;;26250,00
130270400864;18;34;00;;WIENCKE, GERALF:;;;6705,00
180169430175;18;33;00;;WIENCKE, JENS:;;;9600,00
231266412232;06;00;40;;WIENECKE, DIRK:;;;14742,00
021268417760;18;32;00;;WIENER, HAGEN:;;;9600,00
261139430291;99;02;00;;WIENERT, EDGAR:;;;32125,00
081070430737;18;33;00;;WIENERT, JAN:;;;2795,00
240262505911;97;01;00;;WIENHOLD, ANDREA:;;;8446,73
200456525017;07;00;58;;WIENHOLD, CHRISTINE:;;;15747,97
100550424978;07;08;00;;WIENHOLD, JUERGEN:;;;16912,50
230659428337;14;00;47;;WIENHOLD, MARIO:;;;19320,00
071268412287;07;69;00;;WIENHOLD, OLAF:;;;9510,00
300369400214;18;35;00;;WIENHOLD, OLAF:;;;9675,00
050854424616;97;01;00;;WIENHOLD, UWE:;;;22200,00
260763400630;98;85;00;;WIENHOLZ, BODO:;;;15744,19
260966400622;94;03;00;;WIENHOLZ, JAN:;;;15261,97
221247409522;06;08;00;;WIENIGK, HANS-JOACHIM:;;;27000,00
181169400720;18;32;00;;WIENKE, SVEN:;;;6958,87
080566410823;07;51;00;;WIENSKOWSKI, JOERG:;;;16195,07
210867406919;94;30;00;;WIEPRECHT, TORSTEN:;;;12929,00
020559430143;98;18;00;;WIEPRICH, FRANK:;;;24840,00
230568417800;18;31;00;;WIERCZEWSKI, STEFAN:;;;9725,00
180268408934;18;31;00;;WIERE, ANDREAS:;;;10825,00
291267420917;18;00;50;;WIERICK, ANDRE:;;;15407,00
010758408521;12;55;00;;WIERICK, FRANK:;;;19262,50
160534408526;06;06;00;;WIERICK, HEINZ:;;;25500,00
270549408518;06;06;00;;WIERICK, KARL-HEINZ:;;;19800,00
290454500627;01;96;43;;WIERICK, ROTRAUD:;;;14835,00
231251408513;01;06;27;;WIERICK, WILFRIED:;;;18900,00
230449530181;99;43;00;;WIERSCH, BARBARA:;;;15478,47
171050400433;99;43;00;;WIERSCH, ECKHART:;;;22320,00
160562516014;99;40;00;;WIERSZING, ELKE:;;;17792,50
041259417732;99;40;00;;WIERSZING, MANFRED:;;;22770,00
050749416227;90;65;40;3892/77,;WIERTELORZ, HORST;1136;STR DER BEFREIUNG 68;
210169408415;18;33;00;;WIERTELORZ, KAY-UWE:;;;9675,00
160667416247;18;32;00;;WIES(Z)NER, ROBERT:;;;11925,00
180257529220;14;51;00;;WIESBAUM, ULRIKE:;;;16961,29
040560502712;04;80;00;;WIESE, ANNEGRET:;;;13758,84
050464408848;97;01;00;;WIESE, AXEL:;;;12760,00
030958402210;02;00;45;;WIESE, BODO:;;;20405,00
050967401533;17;00;00;;WIESE, CARSTEN:;;;9872,00
091257403316;99;40;00;;WIESE, DIETMAR:;;;25472,50
080160400713;01;08;00;;WIESE, EDMUND:;;;18085,00
270568413638;96;15;22;;WIESE, ERIK:;;;9800,00
290967410811;07;06;00;;WIESE, FRANK:;;;15685,19
291155529838;96;15;09;;WIESE, GUDRUN:;;;1903,40
091051426387;94;03;00;;WIESE, HARTMUT:;;;23040,00
250965400242;94;64;00;;WIESE, HEIKO:;;;15949,50
150670404125;03;69;00;;WIESE, HOLGER:;;;9510,00
080364530106;99;77;00;;WIESE, JEANETTE:;;;9109,14
220969402168;02;00;44;;WIESE, JOERN:;;;2700,00
180943405519;04;00;51;;WIESE, JUERGEN:;;;26250,00
250435429734;97;07;00;;WIESE, KARL-HEINZ:;;;44250,00
161169407238;05;00;47;;WIESE, KARSTEN:;;;8205,00
171263411232;18;34;00;;WIESE, KARSTEN:;;;21780,00
090939430202;30;61;00;;WIESE, KURT:;;;25268,00
140847528221;99;40;00;;WIESE, MARIA-ILONA:;;;27750,00
200169430234;99;14;00;;WIESE, MARIO:;;;13775,00
030539529719;94;30;00;;WIESE, MONICA:;;;13486,56
170145428266;99;02;00;;WIESE, PETER:;;;32125,00
301163500038;01;96;52;;WIESE, PETRA:;;;14842,92
231168405717;18;40;00;;WIESE, RENE:;;;9720,00
250456403728;04;00;43;;WIESE, ROLAND:;;;16682,50
301070407838;97;22;00;;WIESE, STEFAN:;;;6968,71
200670411416;18;35;00;;WIESE, SVEN:;;;6705,00
260556423610;13;51;00;;WIESE, UDO:;;;18227,50
111257430029;98;18;00;;WIESE, UWE-PETER:;;;22252,50
100344407229;97;08;00;;WIESE, WOLFGANG:;;;19125,00
181132404613;99;40;00;;WIESEKE, ERICH:;;;33000,00
150270426915;14;69;00;;WIESEKE, MARIO:;;;12085,00
200458430046;90;65;40;2129/78,;WIESEL, BERND;1143;WO(E)RLITZER STR. 4;
200458430046;90;65;40;2129/78,;WIESEL, BERND;1143;WO(E)RLITZER STR. 4;
070259417751;09;06;21;;WIESEL, HANS-JU(E)RGEN:;;;18745,00
190562506112;04;80;00;;WIESEL, HEIKE:;;;14759,52
030969416458;97;22;00;;WIESEL, JOERG:;;;9600,00
120769408313;18;34;00;;WIESEL, KLAUS:;;;9510,00
151232429722;96;15;06;;WIESEL, ROLF:;;;35250,00
101260515358;08;15;00;;WIESELER, ASTRID:;;;16108,12
070139414716;08;51;00;;WIESELER, GERTH:;;;23250,00
140859414715;08;51;00;;WIESELER, HEIKO:;;;18112,50
141263414719;18;35;00;;WIESELER, MAIK:;;;17270,00
231157512269;98;83;00;;WIESELMANN, MARION:;;;9079,46
291146422422;12;06;00;;WIESEMANN, JUERGEN:;;;20500,00
191042429728;94;03;00;;WIESEMANN, KLAUS:;;;24000,00
270355408819;99;55;00;;WIESEMANN, MANFRED:;;;20340,00
030769404735;18;31;00;;WIESENACK, TORSTEN:;;;6705,00
240839409546;06;55;00;;WIESENBERG, DIETRICH:;;;33750,00
230950421034;12;06;00;;WIESENBERG, KARL-HEINZ:;;;23760,00
220461409123;98;20;00;;WIESENBERG, RONNY:;;;22440,00
210658515019;94;30;00;;WIESENBERG, VIOLA:;;;19411,07
270150419020;10;00;43;;WIESENBERG, VOLKER:;;;33000,00
071161405722;04;08;00;;WIESENER, BERND:;;;17765,00
030261407310;18;35;00;;WIESENER, FRANK:;;;17315,00
270250408046;01;20;00;;WIESENER, REINHARD:;;;33840,00
130669422790;18;33;00;;WIESENER, THOMAS:;;;6441,77
100764422433;99;77;00;;WIESENHU(E)TTER, JENS:;;;11220,00
010570413628;11;69;00;;WIESENHUTTER, STEPHAN:;;;9555,00
100151416460;99;02;00;;WIESENTHAL, HORST:;;;26640,00
310558416441;99;02;00;;WIESENTHAL, ROLF:;;;22724,75
080151404528;04;53;00;;WIESER, EDWIN:;;;22770,00
111156405211;04;08;00;;WIESER, GOETZ:;;;17767,50
260267410020;07;08;00;;WIESER, HEIKO:;;;15228,00
031266405212;99;40;00;;WIESER, HEIKO:;;;15390,00
230265408026;06;00;41;;WIESER, TORSTEN:;;;12850,00
060659417727;09;08;00;;WIESICKE, JUERGEN:;;;19012,50
060352403638;98;85;00;;WIESINGER, GERD:;;;24517,50
050354508573;06;00;46;;WIESNER, ANGELIKA:;;;14771,55
080554408443;99;49;00;;WIESNER, BERND:;;;28800,00
141255529735;99;49;00;;WIESNER, CAROLA:;;;26536,25
010561430119;18;32;00;;WIESNER, DETLEF:;;;18177,50
251251407623;06;00;52;;WIESNER, DIETRICH:;;;22770,00
310736415389;96;15;00;3659/64, M:;WIESNER, ERHARD;1140;AMANLISWEG 16;
310736415389;96;15;00;3659/64, M:;WIESNER, ERHARD;1140;AMANLISWEG 16;
030968417758;09;69;00;;WIESNER, FRANK:;;;9792,50
290549407513;05;03;00;;WIESNER, HANS-JUERGEN:;;;25200,00
011263414617;08;00;58;;WIESNER, JENS:;;;19112,50
050956414611;08;00;59;;WIESNER, LUTZ:;;;21175,00
250338430223;96;15;05;;WIESNER, MANFRED:;;;22500,00
050959430158;14;09;00;;WIESNER, MICHAEL:;;;19745,00
101249415057;15;00;50;;WIESNER, PETER:;;;26730,00
171055424928;13;51;00;;WIESNER, PETER:;;;18760,00
250869424922;05;69;00;;WIESNER, RALF:;;;9800,00
080970424215;18;28;00;;WIESNER, RENATO:;;;2720,00
051170402234;18;40;00;;WIESNER, RENE:;;;2720,00
130750515054;94;30;00;;WIESNER, STEFANIE:;;;17546,38
161067419035;95;45;00;;WIESNER, TINO:;;;14100,00
081068415351;08;69;00;;WIESNER, UWE:;;;9600,00
070259426818;14;80;00;;WIESNER, VOLKER:;;;16962,50
210951407519;05;15;00;;WIESNER, WOLFGANG:;;;24840,00
070865417532;09;60;00;;WIESZER, STEFFEN:;;;15322,00
231160425035;97;06;00;;WIESZMEIER, DIRK:;;;20647,50
171148530180;15;12;00;;WIESZNER, ANNELIES:;;;21390,00
220642429721;97;06;00;;WIESZNER, GUENTER:;;;24000,00
251068408548;06;69;00;;WIESZNER, HOLM:;;;13725,00
141064416471;09;51;00;;WIESZNER, JAN:;;;16005,00
290366428047;06;00;42;;WIESZNER, THOMAS:;;;15625,50
070462424025;18;77;00;;WIESZNER, VOLKER:;;;20625,00
220145415409;17;00;00;;WIETEPSKY, JUERGEN:;;;31875,00
121267403015;60;90;00;;WIETHOFF, SVEN:;;;
121267403015;60;90;00;;WIETHOFF, SVEN:;;;14408,00
190239406189;04;06;00;;WIETING, HORST:;;;29250,00
160171423136;18;35;00;;WIETOG, SVEN:;;;2795,00
060660420018;30;37;00;;WIETS, EMANUEL:;;;5550,00
190955420037;11;00;43;;WIETS, REIMUND:;;;23460,00
260171416444;18;32;00;;WIETSCHEL, KAY:;;;2795,00
071147404811;06;15;00;;WIETUSCH, DETLEF:;;;29280,00
240145429729;98;83;00;;WIETZORREK, PETER:;;;27750,00
301139429729;99;43;00;;WIEZOREK, NORBERT:;;;27750,00
150550427429;18;29;30;;WIHNALECK, KLAUS:;;;28500,00
200263522020;12;51;00;;WIITIG, KERSTIN:;;;14552,13
021165418218;97;06;00;;WIKOWSKI, ANDREAS:;;;18067,50
210150529743;96;15;22;;WIKOWSKI, ANGELIKA:;;;24480,00
220343418213;97;06;00;;WIKOWSKI, GERD:;;;27000,00
240170418212;98;83;00;;WIKOWSKI, JAN:;;;9007,80
161137429715;98;18;00;;WILBERG, DETLEF:;;;29250,00
190667412278;07;00;00;;WILBERG, FRANK:;;;8954,00
140847429725;95;45;00;;WILBERG, WOLFGANG:;;;23743,75
120663414512;94;03;00;;WILBRECHT, BERND:;;;11220,00
110260517753;18;35;00;;WILBRECHT, SYLVIA:;;;18112,50
230158414519;99;40;00;;WILBRECHT, WOLFGANG:;;;22942,50
101137402614;02;00;49;;WILCK, FRIEDRICH:;;;15510,00
021153403617;97;17;00;;WILCK, NORBERT:;;;28020,00
081070400837;01;14;00;;WILCKEN, RENE:;;;3220,00
230834429717;98;20;00;;WILCZINSKI, SIEGWART:;;;28500,00
250748407229;05;20;00;;WILCZYNSKI, GUENTHER:;;;25080,00
221256409815;96;15;13;;WILD, ANDREAS:;;;25990,00
260953530188;98;83;00;;WILD, BIRGIT:;;;23242,98
011233529712;94;30;00;;WILD, CHRISTA:;;;18590,50
270864414264;08;00;60;;WILD, HEIKO:;;;15455,00
211225428010;14;00;59;;WILD, HELMUT:;;;12770,16
150650423820;99;49;00;;WILD, JOCHEN:;;;21060,00
030965524734;13;00;51;;WILD, KATHRIN:;;;13932,00
041063425079;99;49;00;;WILD, KJELD:;;;17050,00
241135429711;15;20;00;;WILD, MANFRED:;;;37500,00
090947412215;07;26;00;;WILD, PETER:;;;27000,00
091142424942;99;49;00;;WILD, PETER:;;;26640,00
200150413768;08;00;50;;WILD, PETER:;;;29055,00
160853429930;97;29;00;;WILD, RAINER:;;;26640,00
111156428923;10;06;00;;WILD, VOLKER:;;;19492,50
060534412228;07;18;00;;WILD, WERNER:;;;28500,00
020868417786;09;69;00;;WILDAUER, JOERG:;;;9458,39
190556400418;97;06;00;;WILDE, ALBRECHT:;;;21562,50
101153426325;14;51;00;;WILDE, BERND:;;;24360,00
241263401326;94;11;00;::;WILDE, DIRK;2300;FRIEDRICH-WOLF-STR. 15;
241263401326;94;11;00;::;WILDE, DIRK;2300;FRIEDRICH-WOLF-STR. 15;
180169430183;18;35;00;;WILDE, DIRK:;;;9600,00
251268425000;13;69;00;;WILDE, FRANK:;;;9555,00
191156401360;01;51;00;;WILDE, FRANK:;;;19952,50
270732401322;01;18;00;5749/79, :;WILDE, HANS-HEINZ;2300;KETELHOTSTR. 9;
270732401322;01;18;00;5749/79, :;WILDE, HANS-HEINZ;2300;KETELHOTSTR. 9;
040862430187;15;65;00;;WILDE, HEIKO:;;;18342,50
190935421227;12;00;48;;WILDE, HEINZ:;;;24745,96
070533430044;15;08;00;;WILDE, HORST:;;;28500,00
060637402743;02;51;00;;WILDE, HORST:;;;27000,00
140564500624;30;45;00;;WILDE, KERSTIN:;;;8386,66
251235425012;13;55;00;;WILDE, LIENHARD:;;;24000,00
250548422731;12;00;40;;WILDE, MANFRED:;;;22500,00
210667501727;02;15;00;;WILDE, MANUELA:;;;12675,00
060764408566;06;00;54;;WILDE, RALF:;;;14040,00
290463530203;15;77;00;;WILDE, REGINA:;;;6296,07
260256428241;96;15;18;;WILDE, REINHARD:;;;22440,00
070240521225;12;00;48;;WILDE, ROSEMARIE:;;;17887,50
040269401318;01;80;00;;WILDE, STEFAN:;;;12500,00
030244430041;94;03;00;;WILDE, UWE:;;;23937,50
150740429732;98;82;00;;WILDE, WERNER:;;;26250,00
200954400428;01;00;48;;WILDE, WOLFGANG:;;;23940,00
180167416222;98;82;00;;WILDENBERGER, HEIKO:;;;14058,00
250850429248;14;00;61;;WILDENHAIN, FRANK:;;;19320,03
231240429263;14;29;00;;WILDENHAIN, MANFRED:;;;23040,00
151249427643;18;27;00;;WILDENHAIN, ULRICH:;;;27750,00
281060404718;04;08;00;;WILDENHAYN, LUTZ:;;;16640,00
031262506112;04;08;00;;WILDENHAYN, MARTINA:;;;13407,50
081057423823;96;15;13;;WILDENSEE, HENRY:;;;16905,00
160362400252;94;03;00;;WILDGRUBE, EBERHARD:;;;17516,01
150369417410;18;80;00;;WILDGRUBE, VOLKER:;;;9675,00
220258424619;09;09;00;;WILDNER, HANS-GEORG:;;;22080,00
120763428129;14;65;00;;WILDNER, ROBERTO:;;;16995,00
090744428129;14;29;00;;WILDNER, WERNER:;;;26250,00
140941407266;94;03;00;;WILDNER, WERNER:;;;24000,00
030958526344;10;80;00;;WILDOER, TAMARA:;;;14625,00
160665415363;17;00;00;;WILDT, ANDREAS:;;;17225,00
060948426718;18;28;00;;WILDT, GERD:;;;27750,00
210251419025;30;52;00;;WILDT, MANFRED:;;;18720,00
290865430184;94;65;00;;WILDT, MIRKO:;;;13932,00
260444429735;94;65;00;;WILDT, WERNER:;;;24000,00
210563406717;02;00;43;;WILFERT, HOLGER:;;;16500,00
221059428267;99;43;00;;WILFERT, THOMAS:;;;17802,50
270755413932;94;65;00;;WILFINGER, JUERGEN:;;;22480,00
180360524014;11;96;63;;WILHELM, ANNELORE:;;;15180,00
160561522439;30;31;00;;WILHELM, HEIKE:;;;17898,00
131134422051;97;01;00;;WILHELM, HEINFRIED:;;;28500,00
081155409312;13;00;51;;WILHELM, HORST:;;;15158,71
200571417716;18;33;00;;WILHELM, JENS:;;;2720,00
100669415024;94;65;00;;WILHELM, JOERG:;;;9610,00
231254429838;94;03;00;;WILHELM, JOERG:;;;21142,50
120448418713;10;00;49;;WILHELM, JOHANNES:;;;27687,50
300356422035;99;02;00;;WILHELM, JUERGEN:;;;24610,00
041067422019;12;69;00;;WILHELM, KARSTEN:;;;9600,00
140860417710;04;00;50;;WILHELM, KLAUS:;;;16500,00
061036515317;08;40;00;;WILHELM, LENI:;;;27000,00
210233420129;11;18;00;;WILHELM, LOTHAR:;;;40500,00
200953416823;08;00;45;;WILHELM, LOTHAR:;;;24932,50
090548419030;10;14;00;;WILHELM, LOTHAR:;;;24000,00
200240402747;02;53;00;;WILHELM, MANFRED:;;;24000,00
251254510634;07;00;48;;WILHELM, MARGOT:;;;11678,06
180167404328;97;08;00;;WILHELM, OLAF:;;;16524,00
240965406135;94;30;00;;WILHELM, OLAF:;;;15463,50
270756420114;11;00;46;;WILHELM, PETER:;;;22080,00
280341424032;30;32;00;;WILHELM, PETER:;;;23040,00
150751422034;96;15;00;23/77, F:;WILHELM, RALF;1142;GRUMSINER STR. 22;
150751422034;96;15;00;23/77, F:;WILHELM, RALF;1142;GRUMSINER STR. 22;
051159420132;11;96;63;;WILHELM, RALF:;;;16560,00
160748406825;04;51;00;;WILHELM, REINHARD:;;;21125,00
020268422012;96;15;25;;WILHELM, RICCO:;;;12853,19
260770404728;98;85;00;;WILHELM, SOEREN:;;;2870,00
171164429234;14;03;00;;WILHELM, STEFFEN:;;;16500,00
240869420113;18;35;00;;WILHELM, STEFFEN:;;;9555,00
090763430160;99;02;00;;WILHELM, STEFFEN:;;;18199,84
140963530046;97;01;00;;WILHELM, TATJANA:;;;15822,00
070943407525;05;60;00;;WILHELM, WILFRIED:;;;24000,00
090948426336;98;84;00;;WILHELM, WOLFGANG:;;;31250,00
050958422017;12;40;00;;WILHELM, WOLFGANG:;;;21390,00
040340420352;11;65;00;;WILHELMI, GERALD:;;;23806,45
100342520316;11;77;00;;WILHELMI, ROSEMARIE:;;;7348,79
171163512220;99;77;00;;WILHELMUS, ANTJE:;;;10490,81
021161430092;18;35;00;;WILHELMUS, NORBERT:;;;21560,00
030169409129;18;31;00;;WILINSKI, HEIKO:;;;9600,00
130369407513;99;02;00;;WILK, ANDREAS:;;;14375,00
250968503423;03;00;40;;WILK, ANGELA:;;;8549,29
270630430018;98;85;00;;WILK, BRUNO:;;;23114,59
280168416214;18;31;00;;WILK, ENRICO:;;;9825,00
130241424947;13;09;00;;WILK, ERHARDT:;;;25687,50
310851523641;13;00;40;;WILK, EVA:;;;20100,00
300446506726;05;55;00;;WILK, HELGA:;;;21125,00
300941502546;02;80;00;;WILK, KARIN:;;;16440,00
250148419066;10;14;00;;WILK, KLAUS:;;;17250,00
300969406177;04;80;00;;WILK, MARIO:;;;12305,00
030756419030;10;51;00;;WILK, NORBERT:;;;23862,50
151239402514;02;26;00;;WILK, PETER:;;;25500,00
040667406712;98;82;00;;WILK, RAIK-UDO:;;;8950,00
301049417556;99;40;00;;WILK, ROLF:;;;24480,00
140965403438;94;65;00;;WILK, RONALD:;;;16546,50
131261400824;01;55;00;;WILK, RONNY:;;;14602,50
270147406712;05;07;00;;WILK, UDO:;;;25500,00
080571415741;96;15;22;;WILKE, ALEXANDER:;;;2700,00
180362406150;99;02;00;;WILKE, ANDREAS:;;;18480,00
181260510728;07;00;58;;WILKE, ANNETTE:;;;2691,12
280256416230;97;01;00;;WILKE, BERND:;;;24840,00
031058407627;05;06;00;;WILKE, BERND:;;;19125,00
280747400516;30;43;00;;WILKE, BERNHARD:;;;15968,00
200568413036;08;03;00;;WILKE, CARSTEN:;;;9872,00
270153413636;07;00;56;;WILKE, DIETER:;;;24992,00
290555409929;07;00;45;;WILKE, DIETMAR:;;;23800,00
061232429723;97;06;00;;WILKE, ERHARD:;;;44250,00
220847400615;97;06;00;;WILKE, ERNST:;;;27750,00
111268403114;17;00;00;;WILKE, FRANK:;;;8350,00
200168417513;17;00;00;;WILKE, FRANK:;;;9872,00
191070430742;18;35;00;;WILKE, FRANK:;;;2795,00
030958404312;99;02;00;;WILKE, FRANK:;;;20297,50
141062419046;10;65;00;;WILKE, FRANK:;;;15537,50
080163400874;01;80;00;;WILKE, FRED:;;;22275,00
150534403718;03;00;46;;WILKE, FRITZ:;;;19812,50
161262406715;99;43;00;;WILKE, GERD:;;;16830,00
190668424537;18;31;00;;WILKE, GEROLD:;;;10600,00
291252408720;99;09;00;;WILKE, GUENTER:;;;25920,00
100145406178;98;84;00;;WILKE, HANS-JOACHIM:;;;21750,00
141150419337;10;18;00;;WILKE, HANS-JUERGEN:;;;23040,00
090560404624;90;65;40;5019/85, :;WILKE, HARTMUT;1092;LENINALLEE 273;
090560404624;90;65;40;5019/85, :;WILKE, HARTMUT;1092;LENINALLEE 273;
130449403416;03;02;00;;WILKE, HARTMUT:;;;27000,00
251229404610;99;40;00;;WILKE, HEINZ:;;;27000,00
250554406711;94;30;00;;WILKE, HELMER:;;;22367,50
010150402738;02;55;00;;WILKE, HORST:;;;6125,00
060655400864;95;45;00;;WILKE, HORST:;;;21217,50
201159405144;04;06;00;;WILKE, INGO:;;;18397,50
061067408522;18;34;00;;WILKE, JAN:;;;10800,00
160268406412;17;00;00;;WILKE, JENS:;;;10879,84
261155429848;15;00;47;;WILKE, JUERGEN:;;;23460,00
090560430048;30;80;00;;WILKE, KARSTEN:;;;18755,00
300571427736;18;32;00;;WILKE, KAY:;;;2795,00
020855412230;07;80;00;;WILKE, KLAUS:;;;19806,25
031250424937;13;40;00;;WILKE, KLAUS:;;;25900,00
101068405036;18;31;00;;WILKE, KNUT:;;;9725,00
011129407336;97;01;00;;WILKE, LOTHAR:;;;28437,50
160639412214;97;06;00;;WILKE, LUTZ:;;;26625,00
130351410132;07;06;00;;WILKE, MANFRED:;;;20340,00
021132410615;07;06;00;;WILKE, MANFRED:;;;24750,00
130551503413;03;08;00;;WILKE, MARGITTA:;;;21138,99
070268410842;99;26;00;;WILKE, MARKO:;;;11582,00
171169406912;05;69;00;;WILKE, MATTHIAS:;;;8350,00
150269406917;18;33;00;;WILKE, MATTHIAS:;;;9675,00
030770402411;18;28;00;;WILKE, MATTHIAS:;;;2945,00
021069413118;17;00;00;;WILKE, MICHAEL:;;;8300,00
200556529787;97;01;00;;WILKE, MICHAELA:;;;18919,28
230664405527;04;06;00;;WILKE, NORBERT:;;;16417,50
200852403417;03;08;00;;WILKE, NORBERT:;;;24000,00
070455402514;15;00;50;;WILKE, NORBERT:;;;24480,00
200962410618;07;80;00;;WILKE, OLAF:;;;16252,50
151168411519;18;31;00;;WILKE, PETER:;;;9600,00
120266500724;98;83;00;;WILKE, PETRA:;;;2611,60
140343408234;06;00;42;;WILKE, RAINER:;;;23750,00
180257411513;07;00;54;;WILKE, RALF:;;;22385,00
060570424955;18;31;00;;WILKE, RALF:;;;6705,00
240956425027;97;08;00;;WILKE, RALF:;;;22080,00
140160400897;94;30;00;;WILKE, RALF:;;;18105,11
220856415317;95;45;00;;WILKE, RALF:;;;24092,50
021169406812;05;06;00;;WILKE, RENE:;;;11610,00
150447529726;98;20;00;;WILKE, RUTH:;;;27680,00
081251524978;13;08;00;;WILKE, SABINE:;;;21180,00
250769405660;04;69;00;;WILKE, STEFFEN:;;;9555,00
050768402613;02;06;00;;WILKE, STEFFEN:;;;12530,00
290466407518;05;14;00;;WILKE, THORSTEN:;;;13905,00
180150404110;03;09;00;;WILKE, UDO:;;;33352,50
170950508963;06;80;00;;WILKE, WALTRAUD:;;;14960,00
240838506918;99;43;00;;WILKE, WALTRAUD:;;;20625,00
311054405313;04;08;00;;WILKE, WILFRIED:;;;20760,00
070843413020;08;00;57;;WILKE, WOLFGANG:;;;30750,00
030444402619;02;00;49;;WILKE, WOLFGANG:;;;27000,00
301049527114;94;03;00;;WILKEN, ANNELIES:;;;19440,00
250853401523;30;55;00;;WILKEN, DETLEF:;;;21360,00
010344429752;97;08;00;;WILKEN, GERHARD:;;;25875,00
280466400835;99;14;00;;WILKEN, OLAF:;;;16600,50
210855513020;97;29;00;;WILKEN, SABINE:;;;19168,29
120263400816;01;00;40;;WILKEN, THOMAS:;;;19800,00
290552403329;03;00;44;;WILKENS, MANFRED:;;;16847,50
240170407513;18;28;00;;WILKENS, MARTIN:;;;9510,00
280458403323;99;40;00;;WILKENS, PETER:;;;19837,50
040667403415;03;55;00;;WILKER, SVEN:;;;12827,00
100366425014;99;09;00;;WILKES, ARNDT:;;;11016,00
100438424927;99;02;00;;WILKES, PETER:;;;35250,00
251141424924;13;60;00;;WILKES, RAINER:;;;26250,00
040150515406;99;77;00;;WILKOWSKI, MARLIS:;;;18870,97
300856413514;99;43;00;;WILKS, ROLAND:;;;21850,00
270869402625;02;06;00;;WILKS, STEFFEN:;;;12505,00
290870425443;18;34;00;;WILL, ALEXANDER:;;;2795,00
241141429726;98;83;00;;WILL, DIETER:;;;27750,00
190739500876;01;51;00;;WILL, EDDA:;;;20760,00
080165408917;17;00;00;;WILL, FRANK:;;;15510,00
201259420325;94;64;00;;WILL, FRANK:;;;17935,00
251029428239;14;15;00;;WILL, GUENTER:;;;27750,00
220434400879;01;80;00;;WILL, HARRY:;;;9141,46
300148530277;99;40;00;;WILL, ILSE:;;;19262,50
190140428337;98;54;00;;WILL, JUERGEN:;;;36000,00
220939406184;17;00;00;;WILL, KARL-HEINZ:;;;30000,00
141046429711;99;43;00;;WILL, KLAUS-DIETER:;;;24000,00
180669415393;18;32;00;;WILL, MANFRED:;;;2795,00
290635500618;01;00;49;;WILL, RENATE:;;;20937,50
181068415114;18;31;00;;WILL, RONALD:;;;14069,35
091068419618;11;14;00;;WILL, STEFAN:;;;12725,00
010769400728;01;06;24;;WILL, THOMAS:;;;11917,26
140268419370;99;43;00;;WILL, THOMAS:;;;14709,00
050466520331;18;71;20;;WILL, TINA:;;;15768,00
230930400623;01;00;49;;WILL, ULRICH:;;;28500,00
290747419013;99;26;00;;WILL, WOLFGANG:;;;24125,00
101164430231;18;71;20;;WILLADSEN, JENS:;;;15408,50
300769413137;03;69;00;;WILLAMOWIUS, VOLKER:;;;9510,00
240929411914;07;80;00;;WILLBERG, KURT:;;;31500,00
080355403316;97;01;00;;WILLBRANDT, GERD-PETER:;;;29520,00
260757503318;97;01;00;;WILLBRANDT, GISELA:;;;19952,50
190670412236;18;33;00;;WILLE, ALEXANDER:;;;7508,87
150658411947;99;10;00;;WILLE, ANDREAS:;;;22712,50
081255429900;94;03;00;;WILLE, ANDREJ:;;;23264,50
250759412285;94;30;00;;WILLE, DETLEF:;;;21965,00
080947412910;08;26;00;;WILLE, DIETER:;;;23250,00
130456412230;30;39;00;;WILLE, DIETER:;;;15675,00
131143412218;07;26;00;;WILLE, ECKHARD:;;;27000,00
030235407536;05;06;00;;WILLE, ERNST:;;;23250,00
080953402524;02;00;48;;WILLE, GERD:;;;16905,00
080641412213;07;29;00;;WILLE, HARTMUT:;;;27750,00
230369417162;18;40;00;;WILLE, HEIKO:;;;10080,00
290945510328;07;51;00;;WILLE, ILONA:;;;20602,09
200160524971;01;40;00;;WILLE, INES:;;;18565,82
051068412268;18;31;00;;WILLE, JENS:;;;9600,00
080968409315;18;35;00;;WILLE, JENS-UWE:;;;10600,00
260353406941;01;00;49;;WILLE, JOCHEN:;;;21780,00
050468412246;98;83;00;;WILLE, KAI:;;;13800,00
230834410813;11;53;00;;WILLE, KARLOTTO:;;;24750,00
061264401346;01;65;00;;WILLE, LUTZ-CHRISTIAN:;;;17334,00
110567403419;03;40;00;;WILLE, MAIK:;;;17982,00
110461405627;99;02;00;;WILLE, RONALD:;;;19375,00
221052413265;99;09;00;;WILLE, UWE:;;;23220,00
041252412234;07;02;00;;WILLE, WOLFGANG:;;;24480,00
150171415364;97;22;00;;WILLEKE, DIRK:;;;3849,00
161169417428;99;43;00;;WILLEMELIS, FRANK:;;;9600,00
071248416838;09;00;52;;WILLEMS, GERT:;;;21285,00
300540403125;96;15;12;;WILLEMS, HEINZ:;;;26280,00
231041526810;96;15;15;;WILLENBERG, ELKE:;;;20880,00
010263407113;05;69;00;;WILLENBERG, FRANK:;;;16500,00
160439426857;96;15;14;;WILLENBERG, MANFRED:;;;25200,00
160169414118;18;38;00;;WILLER, JENS:;;;9675,00
110755403811;97;22;00;;WILLER, JOACHIM:;;;20182,50
050831410115;97;01;00;;WILLER, RUDOLF:;;;28500,00
040137400882;97;01;00;;WILLERT, HEINZ:;;;33562,50
250251512111;07;00;59;;WILLERT, HILTRAUD:;;;19232,50
151250501812;99;77;00;;WILLERT, INGRID:;;;19305,00
060169403015;03;69;00;;WILLERT, JENS:;;;9600,00
060148401811;18;35;00;;WILLERT, KLAUS:;;;32645,16
171260405814;99;02;00;;WILLERT, RALF:;;;22825,00
220870405828;18;31;00;;WILLERT, RENE:;;;2795,00
251268405616;18;28;00;;WILLERT, RONNY:;;;9675,00
230571407216;18;33;00;;WILLERT, ULF:;;;2795,00
260255403712;03;06;00;;WILLHAGEN, WOLFHARD:;;;24150,00
230947530280;99;43;00;;WILLIAM, CHRISTINA:;;;15876,00
181254400039;97;17;00;;WILLIAM, HENRY:;;;25080,00
250547430078;15;08;00;;WILLIAM, HORST:;;;23250,00
201133422763;30;57;00;;WILLIG, HORST:;;;16110,00
090761521528;12;80;00;;WILLIGER, BRIGITTE:;;;15413,30
130657421520;12;00;40;;WILLIGER, DIETMAR:;;;22770,00
180470427119;18;33;00;;WILLIGER, JENS:;;;2795,00
250257410415;99;41;00;;WILLIM, DITMAR:;;;29612,50
200360406144;04;14;00;;WILLIMZIK, STEFAN:;;;16240,00
011155510513;94;03;00;;WILLING, ANGELIKA:;;;8816,84
030444422783;12;00;40;;WILLING, BERND:;;;27255,00
271152419643;11;06;20;;WILLING, FRIEDHELM:;;;20040,00
260531429717;15;00;45;;WILLING, GERHARD:;;;27750,00
040338411115;97;01;00;;WILLING, HANS:;;;22875,00
100328416029;09;80;00;;WILLING, HANS:;;;19125,00
051264411115;98;20;00;;WILLING, HANS-JOERG:;;;18480,00
230969417801;18;35;00;;WILLING, MARCO:;;;9510,00
101255516428;09;80;00;;WILLING, PETRA:;;;16222,50
250154419329;94;03;00;;WILLING, SIEGFRIED:;;;22380,00
190156428307;14;00;50;;WILLINGER, OLAF:;;;24500,00
200749414425;98;83;00;;WILLKE, KARL-HEINZ:;;;23700,00
230964430249;99;51;00;;WILLKOMMEN, FRANK:;;;20405,00
210935429726;99;43;00;;WILLKOMMEN, LOTHAR:;;;21750,00
140832506118;04;51;00;;WILLKOMMEN, SIGRID:;;;30750,00
110754406113;97;08;00;;WILLKOMMEN, UDO:;;;22320,00
010370401323;01;69;00;;WILLMER, MARTIN:;;;6806,61
211169401314;18;35;00;;WILLMER, SVEN:;;;9510,00
071269400042;18;33;00;;WILLMS, ANDREY:;;;9510,00
230763418913;60;90;00;;WILLMS, THOMAS:;;;
230763418913;60;90;00;;WILLMS, THOMAS:;;;15408,00
260642419028;10;07;00;;WILLMS, WOLFGANG:;;;38250,00
080570422245;18;32;00;;WILLNER, INGO:;;;9510,00
150867414714;18;80;00;;WILLNOW, STEFFEN:;;;13850,00
220830530018;99;14;00;;WILLOMITZER, ANNEMARIE:;;;23250,00
210653429859;15;02;00;;WILLOMITZER, REINHARD:;;;27360,00
160669403626;03;69;00;;WILLSCH, THOMAS:;;;9510,00
080569415427;18;31;00;;WILLSCHINSKY, KAI:;;;9600,00
140770400624;01;06;24;;WILLUDT, HOLGER:;;;2896,61
140765407346;06;19;00;;WILLUMEIT, IVO:;;;17092,50
230866407352;99;43;00;;WILLUMEIT, OLAF:;;;15876,00
120158408568;06;00;40;;WILLUWEIT, RAINER:;;;14850,00
050469407035;05;69;00;;WILLY, THOMAS:;;;9600,00
120668407012;18;32;00;;WILMERSTAEDT, WILKO:;;;10575,00
250940407640;05;00;45;;WILMS, HANS-ULRICH:;;;25500,00
061063407637;05;64;00;;WILMS, HEIKO:;;;17490,00
270663430276;94;30;00;;WILPERT, ANDRE:;;;17820,00
100354529879;30;61;00;;WILPERT, PETRA:;;;10617,64
220944420327;11;80;00;;WILS, HARTMUT:;;;5716,66
261164430023;99;77;00;;WILS, JOERG:;;;17160,00
251255429889;18;32;00;;WILS, PETER-MICHAEL:;;;27525,00
091267428111;14;69;00;;WILSCH, HEIKO:;;;13860,00
211054406115;04;06;00;;WILSCHEWSKI, BERND:;;;20820,00
100258424014;94;65;00;;WILSDORF, MATHIAS:;;;19320,00
250856413925;99;43;00;;WILSDORF, RAINER:;;;30705,00
010333429714;15;18;00;;WILSDORF, ROLF:;;;28500,00
161052410118;99;09;00;;WILSENACK, WILFRIED:;;;24960,00
030933530232;97;08;00;;WILSKE, ERIKA:;;;16500,00
220235429724;99;43;00;;WILSKE, SIEGFRIED:;;;24750,00
310851402436;94;03;00;;WILZEWSKI, HORST:;;;23040,00
310158501823;94;03;00;;WILZEWSKI, LIESELOTTE:;;;14939,86
130670414851;08;69;00;;WIMMER, JOERG:;;;7905,00
251068406446;04;06;00;;WIND, MICHAEL:;;;13000,00
100854424627;14;26;00;;WINDE, BERND:;;;21000,00
120663407136;97;01;00;;WINDERLICH, JAN:;;;20864,00
101067413528;96;15;00;3453/86, O:;WINDERLICH, JENS;1093;DIERHAGENER STR. 20;
101067413528;96;15;00;3453/86, O:;WINDERLICH, JENS;1093;DIERHAGENER STR. 20;
200261419062;10;09;00;;WINDHAUSEN, HENDRIK:;;;20140,00
200261419070;95;45;00;;WINDHAUSEN, UWE:;;;17967,50
060370408926;18;31;00;;WINDISCH, ANDREAS:;;;6705,00
021048530171;99;77;00;;WINDISCH, CHRISTA:;;;20478,07
131051418516;10;51;00;;WINDISCH, DIETER:;;;21780,00
080454429925;97;01;00;;WINDISCH, GERD:;;;26840,04
040741506966;94;03;00;;WINDISCH, GUDRUN:;;;17595,00
010147422711;18;71;25;;WINDISCH, GUENTER:;;;27000,00
140449427716;97;01;00;;WINDISCH, GUNTER:;;;28500,00
120170426312;08;69;00;;WINDISCH, KARSTEN:;;;8055,00
140140406917;05;00;43;;WINDISCH, KLAUS:;;;21000,00
101067430125;30;61;00;;WINDISCH, STEPHAN:;;;4680,00
240648417113;09;00;47;;WINDOLF, KURT:;;;25500,00
230171416615;09;69;00;;WINDOLF, RAY:;;;2911,13
110655424965;13;06;00;;WINDOLPH, BERND:;;;20872,50
110256420721;12;06;00;;WINDRICH, UWE:;;;24267,50
010263420377;94;03;00;;WINDSCH, RAINER:;;;18947,50
140171420332;99;43;00;;WINDSCH, RALF:;;;3620,00
261165420329;94;03;00;;WINDSCH, THOMAS:;;;13815,29
280559422718;98;20;00;;WINGE, ANDREAS:;;;22640,16
250756422760;18;25;00;;WINGE, STEPHAN:;;;22770,00
120668402748;02;69;00;;WINGER, HELGO:;;;9700,00
010357412255;30;39;00;;WINGRICH, MARIO:;;;17825,00
250832402228;02;53;00;;WINKEL, HORST:;;;25500,00
130171413416;18;35;00;;WINKEL, JAN:;;;2795,00
210665400738;99;43;00;;WINKEL, MICHAEL:;;;15822,00
050963405123;04;06;00;;WINKEL, THOMAS:;;;17930,00
250271409410;18;34;00;;WINKELBAUER, MIKE:;;;2795,00
200370420230;18;32;00;;WINKELHO(E)FER, DIRK:;;;9510,00
271034530295;98;85;00;;WINKELMANN, ANNI:;;;18163,75
070550410344;30;84;00;;WINKELMANN, BERND:;;;16560,00
230734506148;17;00;00;;WINKELMANN, BRIGITTE:;;;18000,00
050738408256;06;00;42;;WINKELMANN, DIETER:;;;24870,00
151267430336;18;32;00;;WINKELMANN, DIRK:;;;9675,00
170963413111;08;00;43;;WINKELMANN, FRANK:;;;19704,20
270931406150;17;00;00;;WINKELMANN, HEINZ:;;;22275,00
260144406152;04;08;00;;WINKELMANN, KLAUS:;;;21657,25
130935429726;99;02;00;;WINKELMANN, KLAUS:;;;30000,00
150171411937;18;38;00;;WINKELMANN, MARKO:;;;2795,00
041055411515;12;60;00;;WINKELMANN, ROBERTO:;;;20010,00
030857404620;04;06;00;;WINKELMANN, RONALD:;;;19607,50
171166411716;99;43;00;;WINKELMANN, THOMAS:;;;16038,00
100746426836;14;00;47;;WINKELMANN, WERNER:;;;27000,00
160554400898;99;43;00;;WINKELMANN, WOLFGANG:;;;23040,00
230756429737;18;29;00;;WINKELMANN, WOLFGANG:;;;16673,08
220138406248;17;00;00;;WINKENS, MARTIN:;;;35250,00
241050519013;99;51;00;;WINKENS, MONIKA:;;;26640,00
250735506113;17;00;00;;WINKENS, RENATE:;;;23540,00
210743429721;99;51;00;;WINKENS, WILHELM-PETER:;;;28500,00
110948500036;94;03;00;;WINKHAUS, INGRID:;;;23437,50
230744400013;94;03;00;;WINKHAUS, KLAUS-DIETER:;;;24312,50
061230430018;99;43;00;;WINKLER, ADELHARD:;;;31500,00
031258428246;60;90;00;;WINKLER, ANDRE:;;;
031258428246;60;90;00;;WINKLER, ANDRE:;;;18600,00
080866426528;14;80;00;;WINKLER, ANDREAS:;;;13244,00
061056508325;99;77;00;;WINKLER, ANITA:;;;18359,18
190435530056;99;49;00;;WINKLER, ANNELIESE:;;;26250,00
220342400863;96;15;00;4674/89, M:;WINKLER, ANTON;1156;PAUL-JUNIUS-STR. 37;
220342400863;96;15;00;4674/89, M:;WINKLER, ANTON;1156;PAUL-JUNIUS-STR. 37;
090362502215;99;43;00;;WINKLER, BEATE:;;;16776,77
140544412125;07;06;00;;WINKLER, BERND:;;;22687,50
240648429720;15;65;00;;WINKLER, BERND:;;;23040,00
220649402636;98;20;00;;WINKLER, BERNDT:;;;24750,00
060266517153;06;00;40;;WINKLER, BIRGIT:;;;15341,50
291055523623;13;00;50;;WINKLER, BIRGIT:;;;17066,52
080147420736;12;00;47;;WINKLER, BJOERN:;;;24480,00
271256530178;15;08;00;;WINKLER, BRIGITTE:;;;10290,83
270934529711;98;98;11;;WINKLER, CHRISTA:;;;26125,00
080770411911;06;69;00;;WINKLER, CHRISTIAN:;;;3253,87
100639429716;99;99;11;;WINKLER, CHRISTOPH:;;;27750,00
231237406132;04;06;00;;WINKLER, CLAUS:;;;21968,75
280860528247;14;08;00;;WINKLER, CORNELIA:;;;15595,29
250959503616;99;12;00;;WINKLER, DAGMAR:;;;20355,00
250470507531;05;00;41;;WINKLER, DANIELA:;;;11800,00
070948410715;07;30;00;;WINKLER, DETLEF:;;;27360,00
050834428230;14;22;00;;WINKLER, DIETER:;;;33750,00
231155424951;13;02;00;;WINKLER, DIETER:;;;17537,50
220533428260;30;34;00;;WINKLER, DIETER:;;;15120,00
220351424015;97;01;00;;WINKLER, DIETMAR:;;;21690,00
140561408021;06;02;00;;WINKLER, EBERHARD:;;;16555,00
230165424977;96;15;21;;WINKLER, ENNO:;;;11101,00
270539513285;08;77;00;;WINKLER, EVA:;;;18630,00
070842530241;99;49;00;;WINKLER, EVA:;;;22770,00
120346424928;13;18;00;;WINKLER, FRANK:;;;25500,00
270254424414;99;49;00;;WINKLER, FRANK:;;;21600,00
180570421136;99;43;00;;WINKLER, FRANK:;;;13285,00
050345429726;99;09;00;;WINKLER, FRANK:;;;27000,00
120157428217;96;15;05;;WINKLER, FRANK:;;;22055,00
050934424915;13;60;00;;WINKLER, FRITZ:;;;26250,00
070830421523;12;18;00;XII/1347/87, :;WINKLER, GEORG;8250;QUESTENBERGER WEG 37D;
070830421523;12;18;00;XII/1347/87, :;WINKLER, GEORG;8250;QUESTENBERGER WEG 37D;
010658403416;97;01;00;;WINKLER, GERD:;;;25530,00
150353415373;08;00;40;;WINKLER, GERD:;;;23460,00
171246417317;09;00;49;;WINKLER, GERD:;;;16165,17
220158430093;98;83;00;;WINKLER, GERHARD:;;;22137,50
120434429710;99;49;00;;WINKLER, GERHARD:;;;21316,26
080451419027;10;54;00;;WINKLER, GEROLD:;;;28275,00
151243428231;94;30;00;;WINKLER, GERT:;;;30000,00
270748510718;07;77;00;;WINKLER, GERTRAUD:;;;19164,19
140740528328;14;51;00;;WINKLER, GRETEL:;;;19830,00
301167513012;18;33;00;;WINKLER, GRIT:;;;16125,00
300445424948;96;15;00;1996/73, A:;WINKLER, GU(E)NTER;1142;BRODOWINER RING 28;
300445424948;96;15;00;1996/73, A:;WINKLER, GU(E)NTER;1142;BRODOWINER RING 28;
140445530169;99;77;00;;WINKLER, GUDRUN:;;;25800,00
250644415363;08;00;64;;WINKLER, GUENTER:;;;23250,00
130837429722;94;03;00;;WINKLER, HANS:;;;24000,00
201257415418;08;65;00;;WINKLER, HANS-DIETER:;;;20987,50
230628430194;99;09;00;;WINKLER, HANS-JUERGEN:;;;29250,00
031244430054;94;03;00;;WINKLER, HANS-JUERGEN:;;;28500,00
050250414636;07;06;00;;WINKLER, HANS-ULRICH:;;;23250,00
260847422415;97;06;00;;WINKLER, HANS-WERNER:;;;24000,00
030753409566;06;12;00;;WINKLER, HARALD:;;;19440,00
281246425007;14;08;00;;WINKLER, HARALD:;;;24000,00
270956423627;99;49;00;;WINKLER, HARTMUT:;;;18630,00
171064415310;98;83;00;;WINKLER, HEIKO:;;;15505,92
060967424427;13;69;00;;WINKLER, HEIKO:;;;9675,00
210857428137;11;20;00;;WINKLER, HEINZ-JOERG:;;;20625,00
140941529722;99;40;00;;WINKLER, HELGA:;;;24000,00
140652416713;09;80;00;;WINKLER, HELMUT:;;;21660,00
150943429724;99;43;00;;WINKLER, HOLGER:;;;24750,00
080152421821;98;83;00;;WINKLER, HORST:;;;19350,00
290349422858;12;26;00;;WINKLER, HORST:;;;22500,00
020730430013;95;45;00;;WINKLER, HORST:;;;30750,00
160236528327;14;12;00;;WINKLER, INGELORE:;;;16301,25
200765422740;99;77;00;;WINKLER, JANOS:;;;11101,00
041261422784;12;26;00;;WINKLER, JENS:;;;19635,00
280569422770;18;32;00;;WINKLER, JENS:;;;9675,00
310570427725;18;32;00;;WINKLER, JENS:;;;10035,00
161167424034;18;35;00;;WINKLER, JENS:;;;9675,00
030164430180;15;55;00;;WINKLER, JO(E)RG:;;;17435,00
100169423634;18;33;00;;WINKLER, JOERG:;;;9675,00
251264414515;09;69;00;;WINKLER, JOERG:;;;17820,00
220659530236;96;15;14;;WINKLER, KARIN:;;;15123,02
110438402751;02;07;00;;WINKLER, KARL-HEINZ:;;;36000,00
120145417158;09;06;00;;WINKLER, KARL-HEINZ:;;;21187,50
300544429736;98;82;00;;WINKLER, KLAUS:;;;20250,00
011040428245;14;07;00;;WINKLER, KLAUS:;;;26937,50
130338428282;14;29;00;;WINKLER, KLAUS:;;;24000,00
230945418711;10;00;49;;WINKLER, KLAUS:;;;22500,00
300769424936;18;38;00;;WINKLER, KNUT:;;;9510,00
120157428233;04;06;00;;WINKLER, KRISTIAN:;;;21332,50
220849424928;98;18;00;;WINKLER, LUTZ:;;;23940,00
090740428252;14;14;00;;WINKLER, LUTZ:;;;22687,50
020741419362;10;00;51;;WINKLER, LUTZ:;;;29250,00
030570415349;08;80;00;;WINKLER, MAIK:;;;11280,00
251038406162;04;40;00;;WINKLER, MANFRED:;;;24562,50
291134430054;99;51;00;;WINKLER, MANFRED:;;;25500,00
110641506169;04;06;00;;WINKLER, MARGIT:;;;20820,00
161269414611;07;06;00;;WINKLER, MARIO:;;;10300,00
120262422773;12;18;00;;WINKLER, MARIO:;;;20460,00
230636529733;99;40;00;;WINKLER, MARLIES:;;;23062,50
181068424029;18;31;00;;WINKLER, MATTHIAS:;;;9675,00
210766408915;18;28;00;;WINKLER, MICHAEL:;;;16038,00
120264428028;99;51;00;;WINKLER, MIRKO:;;;18590,00
191055429903;98;84;00;;WINKLER, NORBERT:;;;19008,38
020633424914;13;53;00;;WINKLER, PETER:;;;38250,00
080259402727;02;80;00;;WINKLER, PETER:;;;17297,50
271065412128;18;28;00;;WINKLER, PETER:;;;16863,50
100757418620;10;06;00;;WINKLER, PETER:;;;19492,50
190763424615;96;15;21;;WINKLER, PETER:;;;11220,00
150651515364;07;06;00;;WINKLER, PETRA:;;;20105,81
080858515379;18;35;00;;WINKLER, PETRA:;;;20570,00
231153524019;97;06;00;;WINKLER, PETRA:;;;18055,00
080941409542;06;51;00;;WINKLER, RALF:;;;20610,89
301159402216;99;43;00;;WINKLER, RALF-MICHAEL:;;;20240,00
270838430041;15;20;00;;WINKLER, REINER:;;;24750,00
160249422740;30;57;00;;WINKLER, REINHARD:;;;15120,00
240338506188;04;78;00;;WINKLER, RENATE:;;;21060,00
190138517111;09;00;48;;WINKLER, RENATE:;;;23250,00
010469430247;99;02;00;;WINKLER, RENE:;;;9600,00
260160430195;01;20;00;;WINKLER, RENE:;;;18630,00
291163426927;14;40;00;;WINKLER, ROBBY:;;;11220,00
051246407315;05;06;00;;WINKLER, ROLAND:;;;26625,00
240352419013;96;15;13;;WINKLER, ROLAND:;;;24092,50
090254409558;06;65;00;;WINKLER, ROLF:;;;19387,74
110533430056;99;53;00;;WINKLER, ROLF:;;;26437,50
140337413256;08;80;00;;WINKLER, SIEGFRIED:;;;26187,50
110538422434;12;00;53;;WINKLER, SIEGFRIED:;;;38250,00
230740429724;99;43;00;;WINKLER, SIEGFRIED:;;;30000,00
220765525035;13;09;00;;WINKLER, SILKE:;;;14602,50
050865423942;08;14;00;;WINKLER, STEFFEN:;;;16042,50
250962408716;06;02;00;;WINKLER, STEFFEN:;;;20243,00
250869417132;18;38;00;;WINKLER, STEFFEN:;;;9510,00
140454404834;99;09;00;;WINKLER, STEFFEN:;;;24120,00
140669418328;18;31;00;;WINKLER, STEPHAN:;;;6705,00
020169416258;09;69;00;;WINKLER, THOMAS:;;;12700,00
100155428274;94;03;00;;WINKLER, THOMAS:;;;22977,58
041262415420;96;15;25;;WINKLER, THOMAS:;;;19140,00
260644402748;01;77;00;;WINKLER, TILO:;;;21600,00
140366418312;10;00;45;;WINKLER, TORSTEN:;;;14094,00
171151414711;15;77;00;;WINKLER, UWE:;;;19521,46
080967420731;12;06;00;;WINKLER, UWE:;;;13976,00
080162425033;18;33;00;;WINKLER, UWE:;;;22440,00
270860418428;10;06;00;;WINKLER, UWE:;;;16275,00
010739429730;15;15;00;;WINKLER, WERNER:;;;30187,50
150560421127;12;00;46;;WINKLER, WERNER:;;;20625,00
110847412221;07;65;00;;WINKLER, WOLFGANG:;;;20250,00
010748428318;14;08;00;;WINKLER, WOLFGANG:;;;23250,00
070770421555;18;31;00;;WINKLER, WOLFGANG:;;;6705,00
270634417419;09;00;50;;WINNE, HANS:;;;23000,00
090449530171;97;17;00;;WINNE, KARIN:;;;21600,00
200643429733;99;12;00;;WINNE, STEFFEN:;;;24250,00
081248519019;99;55;00;;WINNER, LUCIA:;;;22937,50
210448419010;99;26;00;;WINNER, ULF:;;;27000,00
190469427137;14;69;00;;WINNIGE, ANDREAS:;;;12085,00
240568427135;14;06;00;;WINNIGE, THOMAS:;;;13219,00
231258530140;98;19;00;;WINNING, BAERBEL:;;;17747,10
210656410029;07;65;00;;WINNING, ECKHARD:;;;18802,50
051251417737;98;18;00;;WINNING, FRANK:;;;32760,00
111053517712;98;83;00;;WINNING, GABRIELE:;;;22712,50
270147429711;99;40;00;;WINNING, HEINZ-PETER:;;;27000,00
300170429714;98;20;00;;WINNING, JENS:;;;8300,00
251158417528;98;19;00;;WINNING, LUTZ:;;;22110,00
261264410038;09;06;21;;WINNING, UWE:;;;16555,00
010470428929;18;00;50;;WINOKUROW, ANDRE:;;;9720,00
210539416210;09;06;00;;WINTER, ADOLF:;;;24580,65
290164416232;98;18;00;;WINTER, ANDREAS:;;;21120,00
210469415318;04;69;00;;WINTER, ANDREAS:;;;9600,00
190268423818;18;31;00;;WINTER, ANDREAS:;;;9825,00
240868502117;01;96;31;;WINTER, ANKE:;;;12675,00
130854423859;15;77;00;;WINTER, AXEL:;;;28710,00
041043417784;09;03;00;;WINTER, BERND:;;;24000,00
080862506125;97;22;00;;WINTER, BIRGIT:;;;15715,15
140255503418;03;12;00;;WINTER, BRIGITTE:;;;18915,75
211067423838;18;29;30;;WINTER, CARSTEN:;;;10015,00
310156420026;11;07;00;;WINTER, DETLEF:;;;24442,50
281069404212;99;43;00;;WINTER, DETLEF:;;;13625,00
080641429728;98;82;00;;WINTER, DIETER:;;;21000,00
230243419744;97;01;00;;WINTER, DIETER:;;;28500,00
180851418435;01;51;00;;WINTER, DIETER:;;;21900,00
171250429740;15;15;00;;WINTER, DIETHARD:;;;27082,50
291250429712;15;15;00;;WINTER, DIETRICH:;;;29862,50
160868425086;13;00;40;;WINTER, DIRK:;;;12825,00
130335530433;99;12;00;;WINTER, DOROTHEA:;;;21540,00
251242413028;99;02;00;;WINTER, EBERHARD:;;;29460,00
130556523827;15;40;00;;WINTER, ELKE:;;;19061,25
100962402118;02;06;00;;WINTER, FRANK:;;;17105,00
141268403728;18;34;00;;WINTER, FRANK:;;;9675,00
201055423858;18;32;00;;WINTER, FRANK:;;;23182,50
131249413956;08;00;51;;WINTER, FRANK:;;;24250,00
100650416131;97;06;00;;WINTER, FRITZ:;;;23605,64
121051429785;30;62;00;;WINTER, GEORG:;;;16560,00
300447400114;01;40;00;;WINTER, GERD:;;;22500,00
150932429710;96;15;10;;WINTER, GUENTER:;;;24687,50
300668430376;15;69;00;;WINTER, HANNES:;;;9600,00
180356403711;03;11;00;;WINTER, HARALD:;;;24150,00
230867413228;99;43;00;;WINTER, HEIKO:;;;9675,00
140532400127;01;40;00;;WINTER, HEINZ:;;;27000,00
130453429918;94;03;00;;WINTER, HELGE:;;;25130,00
100437428248;14;40;00;;WINTER, HERBERT:;;;26250,00
130568406716;94;03;00;;WINTER, JAN:;;;9945,00
101267417523;18;33;00;;WINTER, JENS:;;;10800,00
200171400894;18;35;00;;WINTER, JENS:;;;2795,00
230668421022;18;35;00;;WINTER, JO(E)RG:;;;9675,00
240149406436;04;00;51;;WINTER, JOERG:;;;19380,00
041257402115;02;00;44;;WINTER, JUERGEN:;;;24200,00
070358430222;94;03;00;;WINTER, JUERGEN:;;;20010,00
020943516240;09;06;00;;WINTER, JUTTA:;;;18916,67
090371427210;18;32;00;;WINTER, KAI-JO(E)RG:;;;2720,00
150744530096;98;83;00;;WINTER, KARIN:;;;25530,00
280853519027;10;51;00;;WINTER, KARIN:;;;21780,00
090140429729;99;09;00;;WINTER, KARLHEINZ:;;;27750,00
121255506914;99;77;00;;WINTER, KERSTIN:;;;28200,00
280561422127;18;34;00;;WINTER, KLAUS:;;;22700,00
130336429724;18;78;00;;WINTER, KLAUS:;;;23312,50
080662415405;08;15;00;;WINTER, KLAUS-PETER:;;;13695,00
291145400846;99;43;00;;WINTER, KLAUS-PETER:;;;20625,00
020268417715;18;29;30;;WINTER, LARS:;;;8950,00
221251400010;01;00;47;;WINTER, LOTHAR:;;;20700,00
071070407511;18;35;00;;WINTER, LUTZ:;;;6958,87
050754427529;30;34;00;;WINTER, MANFRED:;;;22557,50
261160506174;96;15;00;4293/84, J:;WINTER, MARINA;1130;COPPISTR. 10;
261160506174;96;15;00;4293/84, J:;WINTER, MARINA;1130;COPPISTR. 10;
241168417426;99;43;00;;WINTER, MATTHIAS:;;;13725,00
100957428241;94;65;00;;WINTER, MICHAEL:;;;20010,00
040160403221;03;00;43;;WINTER, NEIDHARD:;;;22470,00
271163423648;14;18;00;;WINTER, OLAF:;;;17157,51
080655401523;97;08;00;;WINTER, OLAF:;;;21545,00
170159430113;98;84;00;;WINTER, PETER:;;;18285,00
041048429717;99;13;00;;WINTER, PETER:;;;23187,50
210754415333;99;12;00;;WINTER, PETER:;;;23760,00
090753400021;05;40;00;;WINTER, RAINER:;;;32760,00
020344429719;97;08;00;;WINTER, RAINER:;;;24750,00
050364428243;14;03;00;;WINTER, RALF:;;;15750,00
200554427429;97;08;00;;WINTER, RALF:;;;26100,00
310844420011;97;01;00;;WINTER, REINER:;;;22687,50
081038411712;07;00;55;;WINTER, RICHARD:;;;17911,70
230634415310;30;38;00;;WINTER, RICHARD:;;;16940,00
180335430091;18;99;00;;WINTER, ROLAND:;;;42000,00
080636409220;06;00;53;;WINTER, ROLF:;;;30375,00
141254417731;09;26;00;;WINTER, ROLF-GERIK:;;;22770,00
160170401517;01;69;00;;WINTER, SASCHA:;;;9510,00
190563416231;18;41;30;;WINTER, STEFFEN:;;;17820,00
050565430403;15;14;00;;WINTER, SVEN:;;;18067,50
080170414529;18;32;00;;WINTER, SWEN:;;;9510,00
220569403727;18;31;00;;WINTER, THOMAS:;;;9600,00
220261430016;99;14;00;;WINTER, TILO:;;;19327,10
130467416261;98;85;00;;WINTER, TORSTEN:;;;14719,00
061147513015;99;02;00;;WINTER, UTA:;;;16830,00
230755429866;98;82;00;;WINTER, UWE:;;;19320,00
220853417720;09;08;00;;WINTER, UWE:;;;21060,00
200651427615;14;00;47;;WINTER, WOLFGANG:;;;24480,00
300571406126;17;00;00;;WINTERBERG, MICHAEL:;;;2918,39
091166416461;96;15;11;;WINTERBERG, UWE:;;;16146,00
170163402713;02;77;00;;WINTERFELD, ANDREAS:;;;15730,00
100361407618;18;28;00;;WINTERFELD, RAINER:;;;19499,60
180260402538;97;22;00;;WINTERFELD, RONALD:;;;22080,00
280640428244;14;53;00;;WINTERHOF, ARNDT:;;;27000,00
261258507036;97;01;00;;WINTERLICH, BAERBEL:;;;2535,75
210551406728;97;01;00;;WINTERLICH, VOLKER:;;;27360,00
260955409525;06;18;00;;WINZER, BERND:;;;23100,00
270336429737;98;27;00;;WINZER, DIETER:;;;33000,00
150867419929;18;31;00;;WINZER, FALKO:;;;9825,00
050767415383;08;69;00;;WINZER, FRANK:;;;9875,00
181134409522;06;40;00;;WINZER, FRANZ:;;;38250,00
091161409510;06;51;00;;WINZER, FRED:;;;18975,00
040251413214;08;00;65;;WINZER, GERHARD:;;;22552,50
020849424913;30;32;00;;WINZER, HEINZ:;;;17143,70
220565400246;30;61;00;;WINZER, JOERG:;;;14190,00
161062507220;06;03;00;;WINZER, KIRSTEN:;;;15581,07
300370417419;18;32;00;;WINZER, MARIO:;;;9510,00
210964416836;09;06;20;;WINZER, MICHAEL:;;;16775,00
251069503117;96;15;21;;WINZER, RICARDA:;;;12255,00
100665404336;96;15;06;;WINZER, TORSTEN:;;;14720,00
241070413611;99;14;00;;WINZERLING, MIKE:;;;3620,00
030156503626;98;82;00;;WINZIGER, DAGMAR:;;;15674,58
140555403611;97;06;00;;WINZIGER, HENRY:;;;23280,00
110654515363;08;77;00;;WIPPERT, CHRISTINE:;;;18967,01
010355420016;96;15;26;;WIPPICH, AXEL:;;;23940,00
010428401810;02;00;42;;WIPPICH, HANS:;;;26250,00
121169515398;97;07;00;;WIPPICH, INES:;;;13210,00
130949412239;07;65;00;;WIRBEL, KLAUS:;;;18720,00
121265411521;99;43;00;;WIRBITZKI, NORBERT:;;;16600,50
090461419038;97;01;00;;WIRKNER, ANDREAS:;;;24882,50
251131419021;10;20;00;;WIRKNER, HUBERT:;;;29250,00
210169407279;18;40;00;;WIRKNER, PETER:;;;10575,00
140341410728;07;08;00;;WIRRMANN, DIETRICH:;;;16215,00
010637510749;07;08;00;;WIRRMANN, ELFRIEDE:;;;14135,00
150853406131;04;80;00;;WIRRMANN, HERBERT:;;;20340,00
211160410716;04;08;00;;WIRRMANN, RONALD:;;;15840,00
051258500613;04;80;00;;WIRRMANN, SIGRID:;;;17422,50
110859406136;04;08;00;;WIRRMANN, WERNER:;;;15552,00
311246415110;98;19;00;;WIRRWITZ, WOLFGANG:;;;24480,00
101151419711;11;09;00;;WIRSCHNITZER, DIETMAR:;;;27360,00
220437530281;98;80;00;;WIRSIG, GERTRAUDE:;;;22437,50
170133429712;97;06;00;;WIRSIG, GUENTER:;;;26187,50
280465420324;17;00;00;;WIRSING, ANDRE:;;;13345,50
270560419728;11;96;63;;WIRSING, ANDREAS:;;;14067,00
041060500723;11;96;63;;WIRSING, DAGMAR:;;;12605,70
210868420325;11;69;00;;WIRSING, STEFFEN:;;;9675,00
130961530107;99;77;00;;WIRTH, ANTJE:;;;5419,36
020964412280;07;06;00;;WIRTH, DANIEL:;;;14765,50
200567512227;07;18;00;;WIRTH, DIANA:;;;6865,97
041053416443;09;51;00;;WIRTH, EKKEHARDT:;;;23940,00
151270424738;18;28;00;;WIRTH, ENRICO:;;;2720,00
021152520029;99;12;00;;WIRTH, EVA:;;;20125,00
161268405115;13;69;00;;WIRTH, FRANK:;;;9900,00
180741419736;97;01;00;;WIRTH, GUENTER:;;;20625,00
101148416229;09;51;00;;WIRTH, HARTMUT:;;;27000,00
100133429719;99;43;00;;WIRTH, HELMUT:;;;44250,00
050460414829;08;00;59;;WIRTH, HOLGER:;;;20847,50
201257413017;08;08;00;;WIRTH, HORST:;;;20010,00
010662415022;08;65;00;;WIRTH, INGOLF:;;;16212,50
040768427512;18;31;00;;WIRTH, JENS:;;;9825,00
040834406411;04;14;00;;WIRTH, JOACHIM:;;;21000,00
040145421827;97;07;00;;WIRTH, JOACHIM:;;;22687,50
231142425074;02;06;00;;WIRTH, JUERGEN:;;;21750,00
180266514813;08;00;59;;WIRTH, KATRIN:;;;10129,98
120741427715;14;00;56;;WIRTH, KLAUS:;;;27000,00
171268405624;04;69;00;;WIRTH, NORMAN:;;;9750,00
231051420059;94;65;00;;WIRTH, REINHOLD:;;;22320,00
191268418722;10;08;00;;WIRTH, RENE:;;;14600,00
201053429279;14;40;00;;WIRTH, THOMAS:;;;27360,00
151069417325;09;00;49;;WIRTHGEN, RONALD:;;;2700,00
050570407638;05;69;00;;WIRTHS, CHRISTIAN:;;;12335,00
060666407623;98;82;00;;WIRTHS, SILVIO:;;;15083,00
280935520013;11;00;43;;WIRTHWEIN, IRENE:;;;21000,00
270668421213;18;31;00;;WIRTZ, STEFFEN:;;;9825,00
280667420015;18;31;00;;WIS(Z)LER, MICHAEL:;;;9825,00
101141430335;97;08;00;;WISCHER, PETER:;;;19956,25
070239529713;97;08;00;;WISCHER, SIGRID:;;;24000,00
070743519020;10;77;00;;WISCHKE, DORIS:;;;21000,00
100366430251;30;47;00;;WISCHNAT, MARIO:;;;2538,00
290169416928;17;00;00;;WISCHNEWSKI, JENS:;;;9875,00
120864412230;99;02;00;;WISCHNEWSKI, THOMAS:;;;11220,00
090661430127;18;71;10;;WISCHNEWSKY, MICHAEL:;;;18975,00
100364409512;94;03;00;;WISCHNIOWSKI, AXEL:;;;17992,10
250171407223;18;32;00;;WISCHOFSKY, MAIK:;;;2795,00
081267407223;96;15;22;;WISCHOFSKY, RENE:;;;13896,00
240670421514;18;35;00;;WISGOTT, ANDRE:;;;6705,00
240769409515;06;69;00;;WISHEIT, ANDREAS:;;;12575,00
080568409519;06;69;00;;WISHEIT, UWE:;;;9875,00
260256402236;02;00;45;;WISKANDT, HORST:;;;15715,00
260252421341;12;00;49;;WISLICENUS, GUENTER:;;;16739,03
061141405136;30;54;00;;WISMER, PETER:;;;24040,00
270952529838;02;77;00;;WISNER, MONIKA:;;;19268,07
131052401812;02;00;42;;WISNER, NORBERT:;;;23040,00
050457401816;02;80;00;;WISNER, PETER:;;;17305,42
120360406216;99;40;00;;WISNEWSKI, FRANK:;;;19885,32
260968415393;18;29;30;;WISNIEWSKI, UWE:;;;8950,00
271242400014;94;03;00;;WISOSCHINSKI, DIETER:;;;24687,50
011145402420;97;06;00;;WISOTZKI, HANS-JUERGEN:;;;21480,00
291053419048;10;20;00;;WISOTZKI, KURT:;;;24660,00
260960417132;99;77;00;;WISOTZKY, UWE:;;;16780,88
050468417784;09;00;47;;WISPEL, JENS:;;;12456,77
261141416712;09;00;52;;WISPEL, KLAUS-DIETER:;;;35937,50
260170401320;18;40;00;;WISSE, RONALD:;;;6876,77
010942429728;15;07;00;;WISSEL, HANS-GUENTHER:;;;37500,00
060351407434;05;00;49;;WISSEL, MANFRED:;;;25920,00
090567417575;09;69;00;;WISSER, DIRK:;;;9600,00
120951407448;09;65;00;;WISSER, RUDOLF:;;;17250,00
211055412226;07;08;00;;WISTUBA, KLAUS-DIETER:;;;17365,00
060239430044;94;03;00;;WISTUBA, MANFRED:;;;30750,00
250768426320;18;27;00;;WISTUBA, THOMAS:;;;9675,00
180869420023;11;69;00;;WISZLER, FALK:;;;9555,00
280568403631;18;34;00;;WITAK, BERND:;;;10800,00
050138407460;99;49;00;;WITAK, GERHARD:;;;41625,00
270640507429;30;47;00;;WITAK, RENATE:;;;17280,00
071260412119;98;84;00;;WITEK, JOERG:;;;17403,75
080657412138;99;26;00;;WITEK, ULRICH:;;;21390,00
300561408320;06;14;00;;WITING, DETLEF:;;;16060,00
281261413928;05;06;00;;WITKOWSKI, FRANK:;;;17552,34
130668424815;18;32;00;;WITNIK, OLIVER:;;;9675,00
010467425065;60;90;00;;WITOWSKI, ANDREAS:;;;15408,00
270870405049;18;33;00;;WITSCHAK, JIRKA:;;;2795,00
190941405012;04;26;00;;WITSCHAK, RAINER:;;;23250,00
141169403319;18;34;00;;WITSCHEL, JENS:;;;9610,00
200944403924;03;00;48;;WITSCHEL, SIEGFRIED:;;;26250,00
270349426316;97;08;00;;WITSCHER, HEINZ:;;;28500,00
020563422437;12;69;00;;WITSCHETZKY, ANDRE:;;;20460,00
020866406741;94;03;00;;WITSCHONKE, RENE:;;;11016,00
300970402317;02;06;00;;WITT, ANDREAS:;;;3510,00
121162400838;01;69;00;;WITT, ANDREAS:;;;19525,00
110554529717;97;01;00;;WITT, ASTRID:;;;16059,70
091155514744;01;00;42;;WITT, BAERBEL:;;;4200,00
290959408439;97;06;00;;WITT, BERND:;;;20700,00
130569500018;01;96;43;;WITT, BIRGIT:;;;982,26
271157403421;98;82;00;;WITT, BODO:;;;17793,47
110747500814;01;07;00;;WITT, CHARLOTTE:;;;20195,56
140354501813;02;03;00;;WITT, CHRISTEL:;;;15981,79
111144400712;01;06;24;;WITT, DIETER:;;;22687,50
190857412244;99;14;00;;WITT, DIETMAR:;;;21390,00
190359502423;02;08;00;;WITT, ELLEN:;;;4892,00
160434430267;98;82;00;;WITT, ERWIN:;;;21000,00
090652500613;01;96;43;;WITT, EVELIN:;;;17280,00
300166400716;99;13;00;;WITT, FRANK-THOMAS:;;;17496,00
240549416828;04;06;00;;WITT, GUENTER:;;;20812,50
210337429726;99;55;00;;WITT, GUENTER:;;;24000,00
160769400756;99;43;00;;WITT, GUNNAR:;;;9510,00
140247411214;03;00;40;;WITT, HANS:;;;19125,00
010244400864;01;03;00;;WITT, HANS-DIETER:;;;25500,00
070953401928;99;12;00;;WITT, HANS-DIETER:;;;22320,00
270138429728;94;11;00;;WITT, HANS-JUERGEN:;;;27750,00
060153400610;01;54;00;;WITT, HARRY:;;;22320,00
130658404319;14;00;61;;WITT, HARTMUT:;;;15455,00
091150500853;01;80;00;;WITT, HEIDI:;;;12378,55
151067402429;17;00;00;;WITT, HEIKO:;;;8950,00
281163430353;94;65;00;;WITT, HEIKO:;;;16775,00
210749400882;01;51;00;;WITT, HEINRICH:;;;18720,00
160149400712;97;06;00;;WITT, HELMUT:;;;24000,00
240635412217;07;51;00;;WITT, HORST:;;;22500,00
100237407629;05;15;00;;WITT, HORST:;;;20625,00
130430402552;30;44;00;;WITT, HORST:;;;24340,00
110248530103;30;83;00;;WITT, ILONA:;;;19398,00
280665412273;18;28;00;;WITT, INGO:;;;16775,00
220460430203;98;82;00;;WITT, JOERG:;;;17325,00
230942429714;97;01;00;;WITT, JUERGEN:;;;22687,50
151151400127;01;06;26;;WITT, JUERGEN:;;;24320,04
130552400627;01;96;43;;WITT, KARL-GUENTER:;;;17910,00
280562402136;15;07;00;;WITT, KARSTEN:;;;18150,00
060841400710;97;01;00;;WITT, KLAUS-DIETER:;;;30750,00
051158402311;04;06;00;;WITT, LUTZ:;;;18572,50
020954406186;04;06;00;;WITT, MANFRED:;;;22030,00
060947403231;99;51;00;;WITT, MANFRED:;;;26875,00
040169430269;18;25;00;;WITT, MARIO:;;;9600,00
030770425453;99;43;00;;WITT, MATHIAS:;;;3620,00
210270402413;02;69;00;;WITT, MATTHIAS:;;;2947,71
151069412305;18;32;00;;WITT, MICHAEL:;;;10035,00
260166430188;97;08;00;;WITT, MICHAEL:;;;16035,00
130452506176;17;00;00;;WITT, MONIKA:;;;18831,40
201257402414;02;51;00;;WITT, PETER:;;;19492,50
090358401331;01;00;50;;WITT, PETER:;;;18645,00
141153402733;17;00;00;;WITT, PETER:;;;16912,50
110866430089;15;07;00;;WITT, RAICO:;;;15228,00
150463401378;04;06;00;;WITT, RALF:;;;17435,00
160865402313;02;51;00;;WITT, RALF:;;;14865,14
090366400822;99;43;00;;WITT, RALPH:;;;16096,50
021261504212;03;26;00;;WITT, RONNI:;;;16123,51
050339430069;98;82;00;;WITT, RUDOLF:;;;24750,00
160160403420;30;45;00;;WITT, RUEDIGER:;;;12150,00
130158507223;18;35;00;;WITT, SABINE:;;;16344,82
261164400721;01;00;46;;WITT, SANDRO:;;;18468,00
240952424019;96;15;13;;WITT, SIEGMUND:;;;23760,00
201255507431;94;64;00;;WITT, SILVIA:;;;21957,50
121267500720;01;96;31;;WITT, SYNKE:;;;2123,70
110170400113;01;69;00;;WITT, THOMAS:;;;9510,00
211067412215;07;14;00;;WITT, TORSTEN:;;;13770,00
120860402529;02;12;00;;WITT, TORSTEN-MICHAEL:;;;17300,00
200271418514;10;69;00;;WITT, UWE:;;;2870,00
160360403214;03;43;00;;WITT, VOLKER:;;;21102,50
061149402714;94;03;00;;WITT, VOLKER:;;;23937,50
100230412214;07;64;00;;WITT, WERNER:;;;6070,83
070451402533;02;51;00;;WITT, WILLI:;;;21833,43
130852403432;97;01;00;;WITT, WOLFGANG:;;;19440,00
150449400168;02;08;00;;WITT, WOLFGANG:;;;27000,00
150748402411;01;26;00;;WITT, WOLFGANG:;;;25500,00
080568409527;18;31;00;;WITTAU, FRANK:;;;9675,00
081059403412;03;00;40;;WITTBRODT, DIETMAR:;;;20400,00
311239406507;04;08;00;;WITTBRODT, JOHANNES:;;;22500,00
140960405725;04;00;52;;WITTE, ANDREAS:;;;22865,00
270368422724;17;00;00;;WITTE, ANDREAS:;;;9872,00
270170410154;07;69;00;;WITTE, ANDY:;;;2911,13
220861414212;99;43;00;;WITTE, DETLEF:;;;17985,00
280552411717;99;51;00;;WITTE, DETLEF:;;;23760,00
231137415349;90;65;40;5039/76,;WITTE, DIETER;1140;ALLEE DER KOSMONAUTEN 69;
231137415349;90;65;40;5039/76,;WITTE, DIETER;1140;ALLEE DER KOSMONAUTEN 69;
091251405329;99;12;00;;WITTE, ECKHARD:;;;21840,00
200259415126;08;02;00;;WITTE, FRANK:;;;22770,00
041163406166;04;00;40;;WITTE, FRANK:;;;14850,00
281154429908;15;00;48;;WITTE, FRANK:;;;32400,00
080863402539;30;62;00;;WITTE, FRANK:;;;8077,92
260258403638;03;18;00;;WITTE, HANS-ALBRECHT:;;;22440,00
180752417744;99;51;00;;WITTE, HANS-WERNER:;;;24000,00
070636417117;98;19;00;;WITTE, HEINZ:;;;25500,00
151037529736;96;15;33;;WITTE, HELGA:;;;22687,50
131152505811;94;64;00;;WITTE, IRMGARD:;;;20930,00
100243417743;09;40;00;;WITTE, JUERGEN:;;;28000,00
120753429881;18;25;00;;WITTE, KARL-HEINZ:;;;27360,00
031070422061;18;33;00;;WITTE, KAY:;;;2720,00
250547406131;04;06;00;;WITTE, LOTHAR:;;;22375,00
300847417724;09;06;00;;WITTE, LOTHAR:;;;23250,00
170156511014;99;51;00;;WITTE, MARIANNE:;;;18174,84
140969413027;99;43;00;;WITTE, MARIO:;;;2870,00
120167430097;18;25;00;;WITTE, MARTEN:;;;10425,00
041261411911;07;00;40;;WITTE, MATTHIAS:;;;20375,00
141037411114;97;01;00;;WITTE, OTTO:;;;35000,04
310554400266;99;43;00;;WITTE, RALF:;;;20880,00
271258530155;15;00;45;;WITTE, RAMONA:;;;0,00
150750411536;05;00;50;;WITTE, ROLF-PETER:;;;21390,00
020967424738;94;03;00;;WITTE, TORSTEN:;;;14944,00
140968406175;04;06;00;;WITTE, UDO:;;;14150,00
150456411818;07;06;00;;WITTE, UWE:;;;18736,58
270862415386;08;02;00;;WITTEBORN, FRANK:;;;19965,00
030641415339;08;35;00;;WITTEBORN, HANS-JUERGEN:;;;36000,00
061262515323;08;08;00;;WITTEBORN, INA:;;;16520,65
101050415383;08;00;61;;WITTEBORN, OLAF:;;;25200,00
270762416138;09;06;00;;WITTEBORN, THOMAS:;;;16225,00
120157400126;01;80;00;;WITTECK, VOLKER:;;;18802,50
201161530067;05;00;47;;WITTEK, ANETT:;;;12402,22
120567422256;94;03;00;;WITTEK, FRANK:;;;14998,00
280448409246;06;06;00;;WITTEK, HANS-JOACHIM:;;;23440,00
100544422212;12;06;00;;WITTEK, HANS-JUERGEN:;;;24875,00
121268410313;18;32;00;;WITTEK, JENS:;;;10650,00
010364403728;01;80;00;;WITTEK, KARSTEN:;;;15510,00
100566503136;30;84;00;;WITTEK, SILKE:;;;1120,00
290443403717;03;00;42;;WITTEK, WILFRIED:;;;28500,00
290663525003;13;09;00;;WITTENBECHER, HEIKE:;;;9914,18
300651413940;94;03;00;;WITTENBECHER, MARTIN:;;;22860,00
050268414538;18;38;00;;WITTENBECHER, ROLF:;;;9675,00
191135502736;99;02;00;;WITTENBERG, HANNA:;;;17320,00
190256411924;99;43;00;;WITTENBERG, HANS-JUERGEN:;;;20010,00
261153429713;98;97;00;;WITTENBERG, JUERGEN:;;;21600,00
011052404320;03;00;52;;WITTENBERG, KARL-HEINZ:;;;17880,00
240433402715;99;02;00;;WITTENBERG, KARL-HEINZ:;;;24750,00
260456429820;99;02;00;;WITTENBERG, MATTHIAS:;;;29370,00
300354405717;04;06;00;;WITTENBORN, GUNTRAM:;;;21720,00
241155505718;04;80;00;;WITTENBORN, KAROLA:;;;14610,00
210350403918;03;00;53;;WITTENBURG, UWE:;;;28280,00
270958519745;99;26;00;;WITTER, ANDREA:;;;20460,00
030359430076;98;84;00;;WITTER, FRANK:;;;18400,00
160642419732;11;06;21;;WITTER, HEINZ:;;;20625,00
110167420316;11;00;00;;WITTER, JENS:;;;12276,00
280747529715;99;40;00;;WITTER, JOHANNA:;;;23406,45
210269419728;17;00;00;;WITTER, KNUT:;;;8950,00
151251419757;97;22;00;;WITTER, MANFRED:;;;28080,00
051033429748;98;84;00;;WITTER, REINHOLD:;;;27750,00
131246429725;97;06;00;;WITTER, ULRICH:;;;24000,00
191149423625;99;02;00;;WITTERISCH, GERHARD:;;;28687,50
261156404327;98;83;00;;WITTHAAR, RALPH:;;;17712,78
050459504317;94;30;00;;WITTHAAR, SYLVIA:;;;19635,00
120459403437;30;58;00;;WITTHAHN, BODO:;;;18350,00
310558405128;97;22;00;;WITTHAHN, FRED:;;;21390,00
010255507018;05;53;00;;WITTHUHN, DAGMAR:;;;19123,38
281256407013;05;14;00;;WITTHUHN, HARRY:;;;19706,07
090453400126;99;43;00;;WITTHUHN, HEINO:;;;20340,00
120562415436;08;29;00;;WITTHUHN, JOERG:;;;22440,00
070148403736;99;43;00;;WITTHUHN, KLAUS-DIETER:;;;21750,00
090757406412;15;00;41;;WITTICH, BERND:;;;24150,00
280866430072;99;02;00;;WITTICH, MATTHIAS:;;;15552,00
190169405139;04;06;00;;WITTICH, OLAF:;;;12000,00
310149422808;13;18;00;;WITTICH, THOMAS:;;;26852,50
121141529712;99;77;00;;WITTICH, URSULA:;;;22500,00
131268411921;18;35;00;;WITTICKE, JENS:;;;9825,00
281161405015;04;06;00;;WITTIG, BERND:;;;17325,00
220261424927;13;07;00;;WITTIG, BERND:;;;22725,00
040851519813;99;43;00;;WITTIG, CHRISTA:;;;16170,00
160559405727;94;03;00;;WITTIG, DIETMAR:;;;20470,00
011046425002;13;20;00;;WITTIG, FRANK:;;;27937,50
021260421829;12;06;00;;WITTIG, FRANK:;;;17900,00
110569430197;18;32;00;;WITTIG, FRANK:;;;11737,10
200668411222;18;32;00;;WITTIG, FRANK:;;;9600,00
060350424523;97;17;00;;WITTIG, FRANK:;;;21916,67
300469430031;94;03;00;;WITTIG, FRANK:;;;14250,00
300347419029;10;08;00;;WITTIG, GERHARD:;;;18750,00
110950417346;99;43;00;;WITTIG, HARALD:;;;26355,00
130953402746;02;30;00;;WITTIG, HELMUT:;;;21600,00
231138503711;04;00;47;;WITTIG, INGEBORG:;;;18060,00
231053502111;02;80;00;;WITTIG, INGRID:;;;17040,00
080643429713;99;43;00;;WITTIG, JOACHIM:;;;27750,00
100546430064;99;09;00;;WITTIG, JOACHIM:;;;28500,00
050842425005;99;49;00;;WITTIG, JOERG:;;;24840,00
290948424919;96;15;17;;WITTIG, JUERGEN:;;;33562,50
220148529727;99;43;00;;WITTIG, JUTTA:;;;22500,00
051051406187;60;90;00;;WITTIG, KLAUS-DIETER:;;;
051051406187;60;90;00;;WITTIG, KLAUS-DIETER:;;;22080,00
070260405010;99;43;00;;WITTIG, LUTZ:;;;19492,50
200568417344;18;28;00;;WITTIG, MARIO:;;;12785,00
020861429215;14;00;61;;WITTIG, MICHAEL:;;;16472,50
010170422736;12;69;00;;WITTIG, MICHAEL:;;;9555,00
231139420221;97;01;00;;WITTIG, PAUL:;;;20625,00
250637430039;99;26;00;;WITTIG, PETER:;;;33000,00
270549420912;30;59;00;;WITTIG, RAINER:;;;17640,00
280869403440;03;69;00;;WITTIG, RAYKO:;;;9510,00
230961522041;13;12;00;;WITTIG, RITA:;;;15676,62
150451417786;09;03;00;;WITTIG, ROLAND:;;;22200,03
010654514629;97;01;00;;WITTIG, SIGRID:;;;18720,00
160754525003;13;20;00;;WITTIG, SIGRID:;;;15455,00
071053422787;06;08;00;;WITTIG, STEFFEN:;;;22500,00
040754427335;05;00;45;;WITTIG, STEFFEN:;;;29785,00
060863412915;08;00;57;;WITTIG, SVEN:;;;17820,00
110171416715;18;32;00;;WITTIG, THOMAS:;;;2795,00
100167400869;01;53;00;;WITTIG, THORSTEN:;;;11016,00
020463422018;18;31;00;;WITTIG, TILO:;;;22385,00
141148530079;94;30;00;;WITTIG, URSULA:;;;21437,50
020156416013;09;00;42;;WITTIG, WOFGANG:;;;20625,00
111251424920;13;06;20;;WITTIG, WOLFGANG:;;;20160,00
230434505928;04;40;00;;WITTKE, ELVIRA:;;;28125,00
010633429732;96;15;03;;WITTKE, HORST:;;;33000,00
220450405012;04;08;00;;WITTKE, RALF:;;;21375,00
081251505013;04;12;00;;WITTKE, RENATE:;;;20520,00
050148405741;98;84;00;;WITTKOPF, JUERGEN:;;;22500,00
220170405317;18;28;00;;WITTKOPF, MATHIAS:;;;6780,00
240858520717;12;00;47;;WITTKOPP, ANITA:;;;13952,37
081065401923;18;80;00;;WITTKOPP, JOERG:;;;17251,50
240839401915;02;00;43;;WITTKOPP, KLAUS:;;;25500,00
050352421749;12;06;00;;WITTKOPP, WOLFGANG:;;;19952,50
211167402778;17;00;00;;WITTKUHN, GREGOR:;;;8950,00
040850502729;99;77;00;;WITTMANN, DORIS:;;;20700,00
010156506124;97;08;00;;WITTMANN, ELLEN:;;;18883,67
190270420210;18;32;00;;WITTMANN, FALK:;;;6958,87
161251427254;98;82;00;;WITTMANN, GUENTHER:;;;25920,00
160370412923;18;35;00;;WITTMANN, HELGE:;;;9510,00
280949520217;11;00;47;;WITTMANN, SIGRID:;;;21605,00
210451412223;99;14;00;;WITTMANN, WOLFGANG:;;;24547,50
010331412214;97;17;00;;WITTMANN, WOLFGANG:;;;27750,00
220641412215;07;09;00;;WITTMEYER, LOTHAR:;;;33750,00
180352413621;95;45;00;;WITTOR, ERWIN:;;;23880,00
030659519048;10;55;00;;WITTRIN, KERSTIN:;;;15210,17
280259422740;10;20;00;;WITTRIN, PIERRE:;;;18645,00
091256416019;09;00;42;;WITTRODT, ANDREAS:;;;22425,00
110954407532;05;08;00;;WITTSACK, HANS-JU(E)RGEN:;;;20155,00
080553507538;05;08;00;;WITTSACK, MARGITTA:;;;17558,27
060643419314;01;18;00;;WITTSCHECK, KARL:;;;22165,00
270450429730;15;20;00;;WITTSTOCK, HARALD:;;;25920,00
080545530041;18;27;00;;WITTSTOCK, INGEBORG:;;;26346,77
250161430120;97;01;00;;WITTSTOCK, JUERGEN:;;;16775,00
080943514717;08;00;62;;WITTSTOCK, KARLA:;;;21895,16
310332400850;01;07;00;936/64, :;WITTSTOCK, MANFRED;2500;LANGE STR. 33;
310332400850;01;07;00;936/64, :;WITTSTOCK, MANFRED;2500;LANGE STR. 33;
190655400843;97;22;00;;WITTSTOCK, REINHARD:;;;24412,50
050250405713;97;07;00;;WITTSTOCK, ROLF:;;;27465,00
020571406728;18;35;00;;WITTSTOCK, STEFFEN:;;;2795,00
291135429717;15;09;00;;WITTUM, PETER:;;;28500,00
121163403846;99;51;00;;WITTWER, ANDREAS:;;;19140,00
031268405144;18;33;00;;WITTWER, DIRK:;;;9744,68
070964405123;04;00;40;;WITTWER, HEIKO:;;;14190,00
181170408025;18;33;00;;WITTWER, MATTHIAS:;;;2795,00
191265404018;94;03;00;;WITTWER, OLAF:;;;16577,40
010666419610;99;43;00;;WITTWER, PETER:;;;16330,50
040164419634;99;43;00;;WITTWER, RALF:;;;17141,66
310164404325;98;85;00;;WITTWER, REIK:;;;16775,00
100567422717;99;53;00;;WITTWER, RENE:;;;16218,00
080468424981;18;35;00;;WITTWER, RONNY:;;;9675,00
270649528920;14;00;54;;WITZ, GERLINDE:;;;14850,00
230452428911;14;00;54;;WITZ, JOERG:;;;23040,00
180946429751;99;43;00;;WITZE, HEINZ-WERNER:;;;28500,00
270947510817;99;43;00;;WITZE, INGRID:;;;24480,00
130347410113;07;06;00;;WITZE, UDO:;;;21187,50
101070419664;18;33;00;;WITZEL, DOMINIK:;;;2795,00
200954429976;96;15;03;;WITZEL, HANS-JUERGEN:;;;19320,00
280954413731;96;15;05;;WITZEL, HENRY:;;;17490,00
290560413738;97;17;00;;WITZEL, HOLGER:;;;22942,50
100431429717;96;15;05;;WITZEL, KARL-HEINZ:;;;30750,00
151263415390;94;03;00;;WITZEL, NORBERT:;;;18645,00
190464403435;96;15;00;3581/88, M:;WITZEL, RAINER;1090;WARTINER STR. 59;
190464403435;96;15;00;3581/88, M:;WITZEL, RAINER;1090;WARTINER STR. 59;
240271411933;07;69;00;;WITZEL, THOMAS:;;;2911,13
170968420214;11;00;47;;WITZENHAUSEN, JENS:;;;13425,00
041057409144;06;00;43;;WITZENMANN, ROLF:;;;20872,50
160958411235;07;03;00;;WITZKE, DIRK-RAINER:;;;22770,00
070767417117;09;69;00;;WITZKE, MICHAEL:;;;9700,00
010342416034;09;53;00;;WITZMANN, FRITZ:;;;27875,00
060854402758;94;11;00;3959/83, :;WITZMANN, HELMAR;1142;HEINRICH-RAU-STR. 240;
060854402758;94;11;00;3959/83, :;WITZMANN, HELMAR;1142;HEINRICH-RAU-STR. 240;
050959421825;12;00;52;;WITZMANN, HOLGER:;;;22385,00
200766416027;09;08;00;;WITZMANN, MAIK:;;;14742,00
030869413911;18;31;00;;WITZSCHE, ANDREAS:;;;9600,00
020350416412;09;06;00;;WITZSCHEL, ANDREAS:;;;24187,50
Diese Liste beinhaltet die Namen von 90.598 Mitarbeitern des Ministeriums für Staatssicherheit der DDR. Die Liste ist nicht vollständig. Insbesondere Mitarbeiter der Führungsebene sind nicht enthalten.
This is a list of 90.598 members of the secret police of East Germany (Ministry for State Security), the list isn’t complete, because the most of the high Officiers lieke Colonel and higher have destroyed the personal Informations in the last days of Eastern Germany.
| Listen der Stasimitarbeiter-hier findest Du sie! Was bedeuten die Zahlen? |
| 1.Listen der Stasi-Diensteinheiten! Bem.:hier kannst du die Nr.(6-stellig) der Dienststellen heraussuchen. 2.Liste der Stasi-Mitarbeiter (Hauptamtlich) Bem.:Hoffentlich hast Du einen guten Rechner, denn die Liste ist erschreckend lang. Die ersten 6 Ziffern sind das Geburtsdatum + die nächsten 6 Ziffern = Dienstausweisnummer! Die zwei Ziffern hinter dem Geburtsdatum geben das Geschlecht an: 41 und 42 = Männlich, 51 und 52 = Weiblich! Wichtig für suchen und finden, sind die sechs Ziffern in den Semikolon vor den Namen: z.B. ;07;00;44; ! Das ist die Nummer der Dienststelle ! Also du suchst in der Liste der Dienststellen, die Nummer der Dienststelle, die Dich interessiert. Damit gehst Du in die Liste der Mitarbeiter und suchst Dir alle Mitarbeiter der entsprechenden Dienststelle heraus. Ich habe das für mein Wohnort getan und so alle Mitarbeiter gefunden. Ob die Liste Vollständig ist kann ich nicht einschätzen, aber zumindest er/kannte ich einige Exverräter vom Namen her. 3.Liste der OibE (Offiziere im besonderen Einsatz) |
Confidential Cryptome – USA v. The Monsegur Five
USA v. The Monsegur Five
The various USA charges against Hector “Sabu” Xavier Monsgur (1-SDNY) (2-SDNY) (3-EDCA) (4-CDCA) (5-NDGA) (6-EDVA) and the four persons he informed on, Ryan “Kayla” Ackroyd, Jake “Topiary” Davis, Darren Martyn and Donncha O’Cearrbhail, were assigned to the Southern District of New York court. These are the court dockets and filings in the five cases.
Hector Xavier Monsegur 1 – Southern District of New York
None of the docket filings in this case were released. See following docket and docketfrom Eastern District of Virginia.
| CLOSED, MERGED |
U.S. District Court
Southern District of New York (Foley Square)
CRIMINAL DOCKET FOR CASE #: 1:11-mj-01509-UA-1
| Case title: USA v. Monsegur |
Date Filed: 06/08/2011 Date Terminated: 08/15/2011 |
| Assigned to: Judge Unassigned | ||
| Defendant (1) | ||
| Hector Xavier Monsegur TERMINATED: 08/15/2011 |
represented by | Peggy M. Cross-Goldenberg Federal Defenders of New York Inc. (NYC) 52 Duane Street 10th Floor New York, NY 10007 (212) 417-8732 Fax: (212) 571-0392 Email: Peggy_Cross@fd.org Designation: Public Defender or Community Defender Appointment |
| Pending Counts | Disposition | |
| None | ||
| Highest Offense Level (Opening) | ||
| None | ||
| Terminated Counts | Disposition | |
| None | ||
| Highest Offense Level (Terminated) | ||
| None | ||
| Complaints | Disposition | |
| 18:1028A.FRAUD WITH IDENTIFICATION DOCUMENTS;, 18:1029:PRODUCES/TRAFFICS IN COUNTERFEIT DEVICE. |
| Plaintiff | ||
| USA | represented by | James J. Pastore , Jr U.S. Attorney’s Office, SDNY (St Andw’s) One St. Andrew’s Plaza New York, NY 10007 (212) 637-2418 Fax: (212) 637-2937 Email: James.Pastore@usdoj.gov Thomas G. A. Brown |
| Date Filed | # | Docket Text |
|---|---|---|
| 06/07/2011 | Arrest of Hector Xavier Monsegur. (gq) (Entered: 03/06/2012) | |
| 06/08/2011 | 1 | COMPLAINT as to Hector Xavier Monsegur (1) in violation of 18 U.S.C. 1028 and 1029. (Signed by Magistrate Judge James L. Cott) (gq) (Entered: 03/06/2012) |
| 06/08/2011 | 2 | CJA 23 Financial Affidavit by Hector Xavier Monsegur. Approved. (Signed by Judge Magistrate Judge James L. Cott) (gq) (Entered: 03/06/2012) |
| 06/08/2011 | 3 | ORDER APPOINTING FEDERAL PUBLIC DEFENDER as to Hector Xavier Monsegur. Peggy M. Cross-Goldenberg for Hector Xavier Monsegur appointed. (Signed by Magistrate Judge James L. Cott on 6/8/2011)(gq) (Entered: 03/06/2012) |
| 06/08/2011 | Minute Entry for proceedings held before Magistrate Judge James L. Cott:Initial Appearance as to Hector Xavier Monsegur held on 6/8/2011. Deft appears with Assistant Federal Defender atty Peggy Cross. AUSA James Pastore present for the gov’t. Agreed conditions of release: $50,000 PRB. Other conditions: Deft to be supervised by the FBI with respect to travel and reporting and all other issues. Deft to be released on own signature. See Sealing Order dated 6/8/11. ( Preliminary Hearing set for 7/8/2011 at 10:00 AM before Judge Unassigned.) (gq) (Entered: 03/06/2012) | |
| 06/08/2011 | 4 | PRB APPEARANCE Bond Entered as to Hector Xavier Monsegur in amount of $50,000. Deft to be supervised by the FBI with respect to travel and reporting and all other issues. Deft to be released on own signature. (gq) (Entered: 03/06/2012) |
| 06/08/2011 | 5 | ADVICE OF PENALTIES AND SANCTIONS as to Hector Xavier Monsegur. (gq) (Entered: 03/06/2012) |
| 06/08/2011 | 6 | EX PARTE AND SEALED APPLICATION AND AFFIRMATION of AUSA James J. Pastore, Jr. in Support by USA for an order sealing this case, as to Hector Xavier Monsegur. (gq) (Entered: 03/06/2012) |
| 06/08/2011 | 7 | SEALED ORDER as to Hector Xavier Monsegur…that filings in the above-captioned case be filed under seal and the case shall be captioned as United States v. John Doe, in the public docket, until further order by this Court. (Signed by Magistrate Judge James L. Cott on 6/8/2011)(gq) (Entered: 03/06/2012) |
| 07/08/2011 | 8 | SEALED AFFIRMATION of AUSA Joseph P. Facciponti in Support by USA of a request for a 30-day continuance until 8/8/11, as to Hector Xavier Monsegur. (gq) (Entered: 03/06/2012) |
| 07/08/2011 | 9 | SEALED ORDER TO CONTINUE IN THE INTEREST OF JUSTICE as to Hector Xavier Monsegur. Time excluded from 7/8/2011 until 8/8/2011. (Signed by Magistrate Judge Frank Maas on 7/8/2011)(gq) (Entered: 03/06/2012) |
| 03/05/2012 | TRUE COPY OF UNSEALING ORDER as to Hector Xavier Monsegur…that all records and proceedings, including copies of pleadings and transcripts, associated with the cases with docket numbers S1 11 Cr. 666(LAP), 11 Cr. 693(LAP), 11 Cr. 694(LAP), 11 Cr. 695(LAP), 11 Cr. 696(LAP) and 11 Mag. 1509, which had by previous order of this Court been sealed and captioned as United States v. John Doe, be unsealed and captioned under their true names…that this unsealing order shall be effective 9:00 a.m. on March 6, 2012. (Signed by Judge Loretta A. Preska on 3/5/2012)(gq) (Entered: 03/06/2012) |
Hector Xavier Monsegur 2 – Southern District of New York
| ECF |
U.S. District Court
Southern District of New York (Foley Square)
CRIMINAL DOCKET FOR CASE #: 1:11-cr-00666-LAP-1
Case title: USA v. Monsegur
|
Date Filed: 08/05/2011 |
| Assigned to: Judge Loretta A. Preska | ||
| Defendant (1) | ||
| Hector Xavier Monsegur also known as Sealed Defendant 1 also known as Sabu also known as Xavier DeLeon also known as Leon |
represented by | Peggy M. Cross-Goldenberg Federal Defenders of New York Inc. (NYC) 52 Duane Street 10th Floor New York, NY 10007 (212) 417-8732 Fax: (212) 571-0392 Email: Peggy_Cross@fd.org Designation: Public Defender or Community Defender Appointment |
| Pending Counts | Disposition | |
| 18:1030A.F FRAUD ACTIVITY CONNECTED WITH COMPUTERS (CONSPIRACY TO COMMIT COMPUTER INTRUSION) (1-3) |
||
| 18:1030A.F FRAUD ACTIVITY CONNECTED WITH COMPUTERS (COMPUTER INTRUSION INTENTIONALLY CAUSING DAMAGE)) (4-8) |
||
| 18:1030A.F FRAUD ACTIVITY CONNECTED WITH COMPUTERS (COMPUTER INTRUSION FURTHERING FRAUD) (9) |
||
| 18:1029B.F ATTEMPTS TO COMMIT AN OFFENSE (CONSPIRACY TO COMMIT ACCESS DEVICE FRAUD) (10) |
||
| 18:1349.F ATTEMPT AND CONSPIRACY TO COMMIT BANK FRAUD (11) |
||
| 18:1028A.F FRAUD WITH IDENTIFICATION DOCUMENTS (AGGRAVATED IDENTITY THEFT) (12) |
||
| Highest Offense Level (Opening) | ||
| Felony | ||
| Terminated Counts | Disposition | |
| None | ||
| Highest Offense Level (Terminated) | ||
| None | ||
| Complaints | Disposition | |
| 18:1028A.FRAUD WITH IDENTIFICATION DOCUMENTS;, 18:1029:PRODUCES/TRAFFICS IN COUNTERFEIT DEVICE. |
| Plaintiff |
| USA |
| Date Filed | # | Docket Text |
|---|---|---|
| 06/07/2011 | Arrest of Hector Xavier Monsegur. (gq) [1:11-mj-01509-UA] (Entered: 03/06/2012) | |
| 06/08/2011 | 1 | COMPLAINT as to Hector Xavier Monsegur (1) in violation of 18 U.S.C. 1028 and 1029. (Signed by Magistrate Judge James L. Cott) (gq) [1:11-mj-01509-UA] (Entered: 03/06/2012) |
| 06/08/2011 | 2 | CJA 23 Financial Affidavit by Hector Xavier Monsegur. Approved. (Signed by Judge Magistrate Judge James L. Cott) (gq) [1:11-mj-01509-UA] (Entered: 03/06/2012) |
| 06/08/2011 | 3 | ORDER APPOINTING FEDERAL PUBLIC DEFENDER as to Hector Xavier Monsegur. Peggy M. Cross-Goldenberg for Hector Xavier Monsegur appointed. (Signed by Magistrate Judge James L. Cott on 6/8/2011)(gq) [1:11-mj-01509-UA] (Entered: 03/06/2012) |
| 06/08/2011 | Minute Entry for proceedings held before Magistrate Judge James L. Cott:Initial Appearance as to Hector Xavier Monsegur held on 6/8/2011. Deft appears with Assistant Federal Defender atty Peggy Cross. AUSA James Pastore present for the gov’t. Agreed conditions of release: $50,000 PRB. Other conditions: Deft to be supervised by the FBI with respect to travel and reporting and all other issues. Deft to be released on own signature. See Sealing Order dated 6/8/11. ( Preliminary Hearing set for 7/8/2011 at 10:00 AM before Judge Unassigned.) (gq) [1:11-mj-01509-UA] (Entered: 03/06/2012) | |
| 06/08/2011 | 4 | PRB APPEARANCE Bond Entered as to Hector Xavier Monsegur in amount of $50,000. Deft to be supervised by the FBI with respect to travel and reporting and all other issues. Deft to be released on own signature. (gq) [1:11-mj-01509-UA] (Entered: 03/06/2012) |
| 06/08/2011 | 5 | ADVICE OF PENALTIES AND SANCTIONS as to Hector Xavier Monsegur. (gq) [1:11-mj-01509-UA] (Entered: 03/06/2012) |
| 06/08/2011 | 6 | EX PARTE AND SEALED APPLICATION AND AFFIRMATION of AUSA James J. Pastore, Jr. in Support by USA for an order sealing this case, as to Hector Xavier Monsegur. (gq) [1:11-mj-01509-UA] (Entered: 03/06/2012) |
| 06/08/2011 | 7 | SEALED ORDER as to Hector Xavier Monsegur…that filings in the above-captioned case be filed under seal and the case shall be captioned as United States v. John Doe, in the public docket, until further order by this Court. (Signed by Magistrate Judge James L. Cott on 6/8/2011)(gq) [1:11-mj-01509-UA] (Entered: 03/06/2012) |
| 07/08/2011 | 8 | SEALED AFFIRMATION of AUSA Joseph P. Facciponti in Support by USA of a request for a 30-day continuance until 8/8/11, as to Hector Xavier Monsegur. (gq) [1:11-mj-01509-UA] (Entered: 03/06/2012) |
| 07/08/2011 | 9 | SEALED ORDER TO CONTINUE IN THE INTEREST OF JUSTICE as to Hector Xavier Monsegur. Time excluded from 7/8/2011 until 8/8/2011. (Signed by Magistrate Judge Frank Maas on 7/8/2011)(gq) [1:11-mj-01509-UA] (Entered: 03/06/2012) |
| 08/09/2011 | 1 | SEALED DOCUMENT placed in vault. (nm) (Entered: 08/09/2011) |
| 08/09/2011 | 2 | SEALED DOCUMENT placed in vault. (nm) (Entered: 08/09/2011) |
| 08/15/2011 | 10 | SEALED S(1)INFORMATION (Felony) as to Hector Xavier Monsegur (1) count(s) 1-3, 4-8, 9, 10, 11, 12. (jm) Modified on 3/6/2012 (jm). (Entered: 03/06/2012) |
| 03/05/2012 | TRUE COPY OF UNSEALING ORDER as to Hector Xavier Monsegur…that all records and proceedings, including copies of pleadings and transcripts, associated with the cases with docket numbers S1 11 Cr. 666(LAP), 11 Cr. 693(LAP), 11 Cr. 694(LAP), 11 Cr. 695(LAP), 11 Cr. 696(LAP) and 11 Mag. 1509, which had by previous order of this Court been sealed and captioned as United States v. John Doe, be unsealed and captioned under their true names…that this unsealing order shall be effective 9:00 a.m. on March 6, 2012. (Signed by Judge Loretta A. Preska on 3/5/2012)(gq) [1:11-mj-01509-UA] (Entered: 03/06/2012) | |
| 03/06/2012 | 11 | Order to Unseal S(1)Information as to Hector Xavier Monsegur. (Signed by Judge Loretta A. Preska on 3/5/12)(jm) Modified on 3/6/2012 (jm). (Entered: 03/06/2012) |
| 03/06/2012 | S(1) INFORMATION UNSEALED as to Hector Xavier Monsegur (jm) (Entered: 03/06/2012) | |
| 03/06/2012 | Case Designated ECF as to Hector Xavier Monsegur. (jm) (Entered: 03/06/2012) | |
| 03/06/2012 | Minute Entry for proceedings held before Judge Loretta A. Preska:Initial Appearance as to Hector Xavier Monsegur held on 3/6/2012. (Please reference arraignment) (jm) (Entered: 03/06/2012) | |
| 03/06/2012 | 12 | WAIVER OF INDICTMENT by Hector Xavier Monsegur. (Document originally filed under seal on 8/15/11) (jm) (Entered: 03/06/2012) |
| 03/06/2012 | Minute Entry for proceedings held before Judge Loretta A. Preska: Defendant present with attorney Peggy Cross and Philip Weinstein; AUSA James Pastore and Thomas Brown also present. Defendant waives indictment and proceeds by information. The agreement is acceptable to the Court. Arraignment as to Hector Xavier Monsegur (1) Count 1-3,4-8,9,10,11,12 held on 3/6/2012. Plea entered by Hector Xavier Monsegur (1) Guilty as to Count 1-3,4-8,9,10,11,12., as to Hector Xavier Monsegur( Sentencing set for 2/15/2012 at 10:30 AM before Judge Loretta A. Preska.) )Hearing originally held 8/15/11) (jm) (Entered: 03/06/2012) | |
| 03/06/2012 | 13 | RULE 20 DOCUMENTS RECEIVED as to Hector Xavier Monsegur transferred from the United States District Court – District of CD California, Case Number: 11cr766. The following documents were received: Certified copy of the indictment/information, certified copy of the docket sheet, and letter of acknowledgment. (Document originally filed under seal on 8/30/11) (jm) (Entered: 03/06/2012) |
Hector Xavier Monsegur 3 – Eastern District of California
| ECF |
U.S. District Court
Southern District of New York (Foley Square)
CRIMINAL DOCKET FOR CASE #: 1:11-cr-00693-LAP-1
| Case title: USA v. Monsegur | Date Filed: 08/12/2011 |
| Assigned to: Judge Loretta A. Preska | ||
| Defendant (1) | ||
| Hector Xavier Monsegur also known as Sealed Defendant 1 |
||
| Pending Counts | Disposition | |
| 18:1030A.F FRAUD ACTIVITY CONNECTED WITH COMPUTERS (COMPUTER INTRUSION FURTHERING FRAUD) (1) |
||
| Highest Offense Level (Opening) | ||
| Felony | ||
| Terminated Counts | Disposition | |
| None | ||
| Highest Offense Level (Terminated) | ||
| None | ||
| Complaints | Disposition | |
| None |
| Plaintiff | ||
| USA | represented by | James J. Pastore , Jr U.S. Attorney’s Office, SDNY (St Andw’s) One St. Andrew’s Plaza New York, NY 10007 (212) 637-2418 Fax: (212) 637-2937 Email: James.Pastore@usdoj.gov ATTORNEY TO BE NOTICED |
| Date Filed | # | Docket Text |
|---|---|---|
| 08/12/2011 | 1 | CONSENT TO TRANSFER JURISDICTION (Rule 20) from the United States District Court – District of ED California; by Sealed Defendant 1 (1) count(s) 1. (jm) (Entered: 03/06/2012) |
| 03/06/2012 | 2 | Order to Unseal Case as to Sealed Defendant 1. (Signed by Judge Loretta A. Preska on 3/5/12)(jm) (Entered: 03/06/2012) |
| 03/06/2012 | Case Designated ECF as to Sealed Defendant 1 (jm) (Entered: 03/06/2012) | |
| 03/06/2012 | 3 | RULE 20 DOCUMENTS RECEIVED as to Hector Xavier Monsegur transferred from the United States District Court – District of ED California, Case Number: 2:11cr332 MCE. The following documents were received: Certified copy of the indictment/information, certified copy of the docket sheet, and letter of acknowledgment. (jm) Modified on 3/6/2012 (jm). (Document originally filed under seal on 8/12/11) (Entered: 03/06/2012) |
Hector Xavier Monsegur 4 – Central District of California
| ECF |
U.S. District Court
Southern District of New York (Foley Square)
CRIMINAL DOCKET FOR CASE #: 1:11-cr-00694-LAP-1
| Case title: USA v. Monsegur | Date Filed: 08/12/2011 |
| Assigned to: Judge Loretta A. Preska | ||
| Defendant (1) | ||
| Hector Xavier Monsegur also known as Sealed Defendant 1 also known as Sabu also known as Xavier DeLeon also known as Leon |
||
| Pending Counts | Disposition | |
| 18:1030A.F FRAUD ACTIVITY CONNECTED WITH COMPUTERS (COMPUTER INTRUSION FURTHERING FRAUD) (1-2) |
||
| Highest Offense Level (Opening) | ||
| Felony | ||
| Terminated Counts | Disposition | |
| None | ||
| Highest Offense Level (Terminated) | ||
| None | ||
| Complaints | Disposition | |
| None |
| Plaintiff | ||
| USA | represented by | James J. Pastore , Jr U.S. Attorney’s Office, SDNY (St Andw’s) One St. Andrew’s Plaza New York, NY 10007 (212) 637-2418 Fax: (212) 637-2937 Email: James.Pastore@usdoj.gov ATTORNEY TO BE NOTICED |
| Date Filed | # | Docket Text |
|---|---|---|
| 08/12/2011 | 1 | CONSENT TO TRANSFER JURISDICTION (Rule 20) from the United States District Court – District of CD California; by Sealed Defendant 1 (1) count(s) 1-2. (jm) (Entered: 03/06/2012) |
| 03/06/2012 | 2 | Order to Unseal Case as to Sealed Defendant 1. (Signed by Judge Loretta A. Preska on 3/5/12)(jm) (Entered: 03/06/2012) |
| 03/06/2012 | Case Designated ECF as to Hector Xavier Monsegur. (jm) (Entered: 03/06/2012) | |
| 03/06/2012 | 3 | RULE 20 DOCUMENTS RECEIVED as to Hector Xavier Monsegur transferred from the United States District Court – District of CD California, Case Number: CR 11 0766. The following documents were received: Certified copy of the indictment/information. (Document originally filed under seal on 8/12/11) (jm) (Entered: 03/06/2012) |
Hector Xavier Monsegur 5 – Northern District of Georgia
| ECF |
U.S. District Court
Southern District of New York (Foley Square)
CRIMINAL DOCKET FOR CASE #: 1:11-cr-00695-LAP-1
| Case title: USA v. Monsegur | Date Filed: 08/12/2011 |
| Assigned to: Judge Loretta A. Preska | ||
| Defendant (1) | ||
| Hector Xavier Monsegur also known as Sealed Defendant 1 |
||
| Pending Counts | Disposition | |
| 18:1030A.F FRAUD ACTIVITY CONNECTED WITH COMPUTERS (COMPUTER INTRUSION FURTHERING FRAUD) (1) |
||
| Highest Offense Level (Opening) | ||
| Felony | ||
| Terminated Counts | Disposition | |
| None | ||
| Highest Offense Level (Terminated) | ||
| None | ||
| Complaints | Disposition | |
| None |
| Plaintiff | ||
| USA | represented by | James J. Pastore , Jr U.S. Attorney’s Office, SDNY (St Andw’s) One St. Andrew’s Plaza New York, NY 10007 (212) 637-2418 Fax: (212) 637-2937 Email: James.Pastore@usdoj.gov ATTORNEY TO BE NOTICED |
| Date Filed | # | Docket Text |
|---|---|---|
| 08/12/2011 | 1 | CONSENT TO TRANSFER JURISDICTION (Rule 20) from the United States District Court – District of ND GEORGIA; by Sealed Defendant 1 (1) count(s) 1. (jm) (Entered: 03/06/2012) |
| 03/06/2012 | 2 | Order to Unseal Case as to Sealed Defendant 1. (Signed by Judge Loretta A. Preska on 3/5/12)(jm) (Entered: 03/06/2012) |
| 03/06/2012 | Case Designated ECF as to Hector Xavier Monsegur. (jm) (Entered: 03/06/2012) | |
| 03/06/2012 | 3 | RULE 20 DOCUMENTS RECEIVED as to Hector Xavier Monsegur transferred from the United States District Court – District of ND Georgia, Case Number: 11cr379. The following documents were received: Certified copy of the indictment/information. (jm) Modified on 3/6/2012 (jm). (Documents originally received 8/12/11) (Entered: 03/06/2012) |
Hector Xavier Monsegur 6 – Eastern District of Virginia
| ECF |
U.S. District Court
Southern District of New York (Foley Square)
CRIMINAL DOCKET FOR CASE #: 1:11-cr-00696-LAP-1
| Case title: USA v. Monsegur | Date Filed: 08/12/2011 |
| Assigned to: Judge Loretta A. Preska | ||
| Defendant (1) | ||
| Hector Xavier Monsegur also known as Sealed Defendant 1 |
||
| Pending Counts | Disposition | |
| 18:1030A.F FRAUD ACTIVITY CONNECTED WITH COMPUTERS (COMPUTER INTRUSION FURTHERING FRAUD) (1) |
||
| Highest Offense Level (Opening) | ||
| Felony | ||
| Terminated Counts | Disposition | |
| None | ||
| Highest Offense Level (Terminated) | ||
| None | ||
| Complaints | Disposition | |
| None |
| Plaintiff | ||
| USA | represented by | James J. Pastore , Jr U.S. Attorney’s Office, SDNY (St Andw’s) One St. Andrew’s Plaza New York, NY 10007 (212) 637-2418 Fax: (212) 637-2937 Email: James.Pastore@usdoj.gov ATTORNEY TO BE NOTICED |
| Date Filed | # | Docket Text |
|---|---|---|
| 03/06/2012 | 1 | CONSENT TO TRANSFER JURISDICTION (Rule 20) from the United States District Court – District of ED Virginia; by Sealed Defendant 1 (1) count(s) 1. (jm) (Entered: 03/06/2012) |
| 03/06/2012 | 2 | Order to Unseal Case as to Sealed Defendant 1. (Signed by Judge Loretta A. Preska on 3/5/12)(jm) (Entered: 03/06/2012) |
| 03/06/2012 | Case Designated ECF as to Hector Xavier Monsegur. (jm) (Entered: 03/06/2012) | |
| 03/06/2012 | 3 | RULE 20 DOCUMENTS RECEIVED as to Hector Xavier Monsegur transferred from the United States District Court – District of ED Virginia, Case Number: 11CR381. The following documents were received: Certified copy of the indictment/information, certified copy of the docket sheet, and letter of acknowledgment. (jm) (Entered: 03/06/2012) |
| 03/06/2012 | 4 | Order to Unseal Document as to Hector Xavier Monsegur. ORDERED that all records and proceedings, including copies of pleadings and transcripts, associated with the cases with docket numbers S1 11 Cr. 666 (LAP), 11 Cr. 693 (LAP) 1 11 Cr. 694 (LAP) 1 11 Cr. 695 (LAP), 11 Cr. 696 (LAP) 1 and 11 Mag. 1509, which had by previous order of this Court been sealed and captioned as United States v. John Doe, be unsealed and captioned under their true names. It is further ORDERED that this unsealing order shall be effective 9:00a.m. on March 6, 2012. SO ORDERED. (Signed by Judge Loretta A. Preska on 3/5/12)(jw) (Entered: 03/06/2012) |
U.S. District Court
Southern District of New York (Foley Square)
CRIMINAL DOCKET FOR CASE #: 1:12-cr-00185-UA-1
| Case title: USA v. Ackroyd et al | Date Filed: 02/27/2012 |
| Assigned to: Judge Unassigned | ||
| Defendant (1) | ||
| Ryan Ackroyd also known as Sealed Defendant 1 also known as Kayla also known as lol also known as lolspoon |
||
| Pending Counts | Disposition | |
| 18:1030A.F FRAUD ACTIVITY CONNECTED WITH COMPUTERS (CONSPIRACY TO COMMIT COMPUTER INTRUSION CAUSING DAMAGE) (1-2) |
||
| Highest Offense Level (Opening) | ||
| Felony | ||
| Terminated Counts | Disposition | |
| None | ||
| Highest Offense Level (Terminated) | ||
| None | ||
| Complaints | Disposition | |
| None |
| Plaintiff | ||
| USA | represented by | Thomas G. A. Brown U.S. Attorney’s Office, SDNY (St Andw’s) One St. Andrew’s Plaza New York, NY 10007 2126372200 Fax: 718-4221718 Email: thomas.ga.brown@usdoj.gov ATTORNEY TO BE NOTICED |
| Date Filed | # | Docket Text |
|---|---|---|
| 02/27/2012 | 2 | SEALED INDICTMENT as to Sealed Defendant 1 (1) count(s) 1-2, Sealed Defendant 2 (2) count(s) 1-2, Sealed Defendant 3 (3) count(s) 1-2, Sealed Defendant 4 (4) count(s) 1. (jm) (Entered: 03/06/2012) |
| 02/28/2012 | 1 | SEALED DOCUMENT placed in vault. (mps) (Entered: 02/28/2012) |
| 03/05/2012 | 3 | Order to Unseal Indictment as to Sealed Defendant 1, Sealed Defendant 2, Sealed Defendant 3, Sealed Defendant 4. (Signed by Magistrate Judge Ronald L. Ellis on 3/5/12)(jm) (Entered: 03/06/2012) |
U.S. District Court
Southern District of New York (Foley Square)
CRIMINAL DOCKET FOR CASE #: 1:12-cr-00185-UA-2
| Case title: USA v. Ackroyd et al | Date Filed: 02/27/2012 |
| Assigned to: Judge Unassigned | ||
| Defendant (2) | ||
| Jake Davis also known as Sealed Defendant 2 also known as topiary also known as atopiary |
||
| Pending Counts | Disposition | |
| 18:1030A.F FRAUD ACTIVITY CONNECTED WITH COMPUTERS (CONSPIRACY TO COMMIT COMPUTER INTRUSION CAUSING DAMAGE) (1-2) |
||
| Highest Offense Level (Opening) | ||
| Felony | ||
| Terminated Counts | Disposition | |
| None | ||
| Highest Offense Level (Terminated) | ||
| None | ||
| Complaints | Disposition | |
| None |
| Plaintiff | ||
| USA | represented by | Thomas G. A. Brown U.S. Attorney’s Office, SDNY (St Andw’s) One St. Andrew’s Plaza New York, NY 10007 2126372200 Fax: 718-4221718 Email: thomas.ga.brown@usdoj.gov ATTORNEY TO BE NOTICED |
| Date Filed | # | Docket Text |
|---|---|---|
| 02/27/2012 | 2 | SEALED INDICTMENT as to Sealed Defendant 1 (1) count(s) 1-2, Sealed Defendant 2 (2) count(s) 1-2, Sealed Defendant 3 (3) count(s) 1-2, Sealed Defendant 4 (4) count(s) 1. (jm) (Entered: 03/06/2012) |
| 03/05/2012 | 3 | Order to Unseal Indictment as to Sealed Defendant 1, Sealed Defendant 2, Sealed Defendant 3, Sealed Defendant 4. (Signed by Magistrate Judge Ronald L. Ellis on 3/5/12)(jm) (Entered: 03/06/2012) |
U.S. District Court
Southern District of New York (Foley Square)
CRIMINAL DOCKET FOR CASE #: 1:12-cr-00185-UA-3
| Case title: USA v. Ackroyd et al | Date Filed: 02/27/2012 |
| Assigned to: Judge Unassigned | ||
| Defendant (3) | ||
| Darren Martyn also known as Sealed Defendant 3 also known as pwnsauce also known as reapsauce also known as networkkitten |
||
| Pending Counts | Disposition | |
| 18:1030A.F FRAUD ACTIVITY CONNECTED WITH COMPUTERS (CONSPIRACY TO COMMIT COMPUTER INTRUSION CAUSING DAMAGE) (1-2) |
||
| Highest Offense Level (Opening) | ||
| Felony | ||
| Terminated Counts | Disposition | |
| None | ||
| Highest Offense Level (Terminated) | ||
| None | ||
| Complaints | Disposition | |
| None |
| Plaintiff | ||
| USA | represented by | Thomas G. A. Brown U.S. Attorney’s Office, SDNY (St Andw’s) One St. Andrew’s Plaza New York, NY 10007 2126372200 Fax: 718-4221718 Email: thomas.ga.brown@usdoj.gov ATTORNEY TO BE NOTICED |
| Date Filed | # | Docket Text |
|---|---|---|
| 02/27/2012 | 2 | SEALED INDICTMENT as to Sealed Defendant 1 (1) count(s) 1-2, Sealed Defendant 2 (2) count(s) 1-2, Sealed Defendant 3 (3) count(s) 1-2, Sealed Defendant 4 (4) count(s) 1. (jm) (Entered: 03/06/2012) |
| 03/05/2012 | 3 | Order to Unseal Indictment as to Sealed Defendant 1, Sealed Defendant 2, Sealed Defendant 3, Sealed Defendant 4. (Signed by Magistrate Judge Ronald L. Ellis on 3/5/12)(jm) (Entered: 03/06/2012) |
Filings in this case were not released.
U.S. District Court
Southern District of New York (Foley Square)
CRIMINAL DOCKET FOR CASE #: 1:12-mj-00609-UA-1
| Case title: USA v. O’Cearrbhail | Date Filed: 03/05/2012 |
| Assigned to: Judge Unassigned | ||
| Defendant (1) | ||
| Donncha O’Cearrbhail also known as palladium also known as polonium also known as anonsacco |
||
| Pending Counts | Disposition | |
| None | ||
| Highest Offense Level (Opening) | ||
| None | ||
| Terminated Counts | Disposition | |
| None | ||
| Highest Offense Level (Terminated) | ||
| None | ||
| Complaints | Disposition | |
| 18:2511:INTERCEPTION AND DISCLOSURE OF WIRE OR ORAL COMMUNICATIONS. |
| Plaintiff | ||
| USA | represented by | Thomas G. A. Brown U.S. Attorney’s Office, SDNY (St Andw’s) One St. Andrew’s Plaza New York, NY 10007 2126372200 Fax: 718-4221718 Email: thomas.ga.brown@usdoj.gov |
| Date Filed | # | Docket Text |
|---|---|---|
| 03/05/2012 | 1 | COMPLAINT as to Donncha O’Cearrbhail (1) in violation of 18 U.S.C. 2511 & 2. (Signed by Magistrate Judge Ronald L. Ellis) (gq) (Entered: 03/06/2012) |
| 03/06/2012 | 3 | AMENDED COMPLAINT as to Donncha O’Cearrbhail in violation of 18 U.S.C. 2511 & 2. (Signed by Magistrate Judge Ronald L. Ellis) (gq) (Entered: 03/06/2012) |
| 03/06/2012 | 4 | UNSEALING ORDER as to Donncha O’Cearrbhail…that the Complaint and Arrest Warrant in this matter be unsealed effective 9:00 a.m. on March 6, 2012. (Signed by Magistrate Judge Ronald L. Ellis on 3/6/2012)(gq) (Entered: 03/06/2012) |
Confidential – Cryptome – USA v. Hector Xavier Monsegur EDVA
SA v. Hector Xavier Monsegur EDVA
| CLOSED |
U.S. District Court
Eastern District of Virginia – (Alexandria)
CRIMINAL DOCKET FOR CASE #: 1:11-cr-00381-TSE-1
| Case title: USA v. Monsegur |
Date Filed: 08/04/2011 Date Terminated: 08/08/2011 |
| Assigned to: District Judge T. S. Ellis, III | ||
| Defendant (1) | ||
| Hector Xavier Monsegur TERMINATED: 08/08/2011 |
||
| Pending Counts | Disposition | |
| None | ||
| Highest Offense Level (Opening) | ||
| None | ||
| Terminated Counts | Disposition | |
| 18:1030(a)(5)(A), 1030(c)(4)(B)(i)&2 Computer Fraud (1) |
Rule 20 | |
| Highest Offense Level (Terminated) | ||
| Felony | ||
| Complaints | Disposition | |
| None |
| Plaintiff | ||
| USA | represented by | John Frank Eisinger US Attorney’s Office (Alexandria) 2100 Jamieson Avenue Alexandria, VA 22314 (703) 299-3906 Fax: (703) 299-3981 Email: ausa@eisinger.net ATTORNEY TO BE NOTICED |
| Date Filed | # | Docket Text |
|---|---|---|
| 08/04/2011 | 1 | INFORMATION as to Hector Xavier Monsegur (1) count(s) 1. (krob, ) (Entered: 08/05/2011) |
| 08/04/2011 | 2 | Redacted Criminal Case Cover Sheet (krob, ) (Entered: 08/05/2011) |
| 08/04/2011 | 4 | NOTICE by USA as to Hector Xavier Monsegur (krob, ) (Entered: 08/05/2011) |
| 08/04/2011 | 5 | NON-CONFIDENTIAL Memorandum by USA as to Hector Xavier Monsegur (krob, ) (Entered: 08/05/2011) |
| 08/04/2011 | 6 | MOTION to Seal Case by USA as to Hector Xavier Monsegur. (krob, ) (Entered: 08/05/2011) |
| 08/04/2011 | 7 | ORDER granting 6 Motion to Seal Case as to Hector Xavier Monsegur (1). Signed by District Judge T. S. Ellis, III on 8/4/11. (krob, ) (Entered: 08/05/2011) |
| 08/08/2011 | 8 | CONSENT TO TRANSFER JURISDICTION (Rule 20) to Southern District of New York Counts closed as to Hector Xavier Monsegur (1) Count 1. (krob, ) (Entered: 08/09/2011) |
| 03/06/2012 | 9 | Motion by USA as to Hector Xavier Monsegur. (jcor) (Entered: 03/06/2012) |
| 03/06/2012 | 10 | UNSEALING ORDER that this case will be unsealed as to Hector Xavier Monsegur. Signed by District Judge T. S. Ellis, III on 3/6/2012. (jcor) (Entered: 03/06/2012) |
CONFIDENTIAL – NSA Opens $286 Million Cryptologic Facility in Georgia
| The National Security Agency officially opened for business Monday in its new building on Fort Gordon.In a rare public ceremony for an agency typically cloaked in secrecy, NSA’s director and other dignitaries symbolically cut the ribbon inside a 200-seat rotunda that will serve as an operations center. When full occupancy is completed in late summer, about 4,000 civilian and military workers trained in linguistics and cryptology will report to what’s known as NSA Georgia.Army Gen. Keith Alexander, the commander of the Fort Meade, Md.,-based NSA, acknowledged the irony of inviting the public to a department jokingly referred to as “No Such Agency.”
He heaped praise, however, on the work done in Augusta to support national defense and military missions abroad. |
NSA/CSS Opens Its Newest Facility In Georgia
The National Security Agency/Central Security Service officially opened the new NSA/CSS Georgia Cryptologic Center at a ribbon-cutting ceremony where officials emphasized how the $286 million complex will provide cryptologic professionals with the latest state-of-the-art tools to conduct signals intelligence operations, train the cryptologic workforce, and enable global communications.NSA/CSS has had a presence in Georgia for over 16 years on Ft. Gordon, when only 50 people arrived to establish one of NSA’s Regional Security Operations Centers.As a testament to this rich heritage, GEN Keith B. Alexander – Commander, U.S. Cyber Command, Director, NSA/Chief, CSS – told the guests at the ceremony, which included federal, state, and local officials, that the NSA/CSS workforce nominated Mr. John Whitelaw for the honor of having one of the buildings in the complex dedicated in his name, because they considered him influential to the establishment and success of the mission in Georgia. In 1995 Mr. Whitelaw was named the first Deputy Director of Operations for NSA Georgia and remained in that position until his death in 2004. “And there have been many successes here at NSA Georgia as evidenced by the fact that this site has won the Travis Trophy six times,” said GEN Alexander. The Travis Trophy is an annual award presented to those whose activities have made a significant contribution to NSA/CSS’s mission.
“This new facility will allow the National Security Agency to work more effectively and efficiently in protecting our homeland,” said Sen. Saxby Chambliss. “It will also attract more jobs to the Augusta area. The opening of this complex means that Georgians will play an even greater role in ensuring the safety and security of our nation.”
The new NSA/CSS Georgia Cryptologic Center is another step in the NSA’s efforts to further evolve a cryptologic enterprise that is resilient, agile, and effective to respond to the current and future threat environment.
NSA/CSS opened a new facility in Hawaii in January 2012 and is also upgrading the cryptologic centers in Texas and Denver to make the agency’s global enterprise even more seamless as it confronts the increasing challenges of the future.
TOP-SECRET – Former 9/11 Commission Chairmen Call for Prompt Action on Cybersecurity Legislation
Tom Kean and Lee Hamilton, who co-chaired the 9/11 Commission, weighed in Monday on a simmering disagreement in the Senate over the best way to address the nation’s vulnerability to cyberattacks.
The two men, who now run the Bipartisan Policy Center’s Homeland Security project, are calling on senators to take more urgent action on the issue of cybersecurity. They cite recent public statements by Director of National Intelligence James Clapper and FBI Director Robert Mueller warning that the cyber threat is expected to overshadow other terrorist threats facing the United States in the not-too-distant future.
“Much like the situation before the September 11, 2001, attacks, the federal government is not adequately organized to deal with a significant emerging national security threat,” said Kean, former governor of New Jersey; and Hamilton, a former congressman from Indiana, in a letter sent to Senate leaders urging action on cybersecurity.
There are now two competing versions of cyber legislation in the Senate. One bill introduced last month by Sens. Joe Lieberman, I-Connecticut, and Susan Collins, R-Maine, establishes the Department of Homeland Security as the government’s lead agency in battling cyberthreats. A controversial part of the bill calls on private companies that run critical infrastructure operations to prove to the government that they have taken steps to safeguard against attack.
But a group of Republican senators led by John McCain of Arizona last week introduced similar legislation without designating a lead government agency to take the helm on the issue. They argued that the Lieberman-Collins legislation puts too much power in the hands of DHS.
It’s a view that Kean and Hamilton do not share.
“One of the reasons that the 9/11 Commission recommended the establishment of one committee with jurisdiction over homeland security issues was to ensure that there would not be a failure to act on important issues because of jurisdictional conflicts,” they wrote. “Unfortunately, jurisdictional and procedural objections to considering cyber security legislation are now being raised. This homeland security issue is too critical for it to succumb to such conflicts between committees.”
FEMEN – Nackter Protest auf dem Petersplatz in Rom
Aufruhr nach der Sonntagsmesse des Papstes in Rom: Mit einem Nacktprotest hielten Mitglieder der ukrainischen Frauenrechtsbewegung FEMEN mehrere Polizisten in Atem.
High Risk – Security Forces Will Outnumber Athletes Nearly 4 to 1 at the 2012 London Olympics

The 10,500 athletes participating in the London Olympic and Paralympic Games, the world’s greatest celebration of human physical endeavour and progress, will be guarded by a security force of some 40,000. This beats the 3:1 ratio of guards to athletes at the 2010 Vancouver Winter Olympics, as the London Games continues the Olympian trend for record-breaking security contingencies. Indeed the home secretary, Theresa May, only last month crowed that the Games’ security would constitute “the UK’s largest ever peacetime logistical operation”. Never mind the performance of athletes: the Olympics is about government and business delivering security solutions.And it’s a great show. Armed officers from the Metropolitan police and the Royal Marines hammering along the Thames in speedboats and helicopters, ground-to-air missiles scanning the skies, hovering spy drones scanning the land, security services scanning the internet for nascent plots or cyber attacks – it’s all being co-ordinated by a bevy of Olympic-themed security agencies.
The police-led multi-agency National Olympic Coordination Centre co-ordinates the forces to deal with the threats identified in the Olympic Intelligence Centre’s “national Olympic threat assessments, while the Olympic Clearing House is screening 380,000 people, from athletes to voluntary litter pickers, seeking accreditation for the Games. Meanwhile the UK Borders Agency boasts the UK is to be the first country to welcome arriving athletes by funnelling them up dedicated “Olympic lanes” at airports for fast-track fingerprinting.
Locals are also in the firing line, in subtle, privatised ways. Houseboaters on the River Lea have been priced out of a controlled mooring zone around the Games, while the £60m Prevent strategy has screened the five Olympic host boroughs for what threat they pose for brewing local extremism, with “engagement officers” dispatched to each borough.
Random security screening has been carried out on cars parked at Stratford City’s Westfield shopping centre, by officers from the staggering 23,700-strong private security contingent of the London Organising Committee of the Olympic and Paralympic Games (LOCOG) and G4S. Westfield isn’t even in the Olympic park, itself a hotbed of embedded biometric scanners and CCTV with automatic facial and behaviour recognition technologies, amid which LOCOG’s forces can search anyone and use “all available powers” to dispose of troublemakers, particularly anyone caught with anything that could be used … in a tent.
Who LOCOG’s bouncers are accountable to is not clear, but they are backed by 13,500 military reservists, apart from countless police deployments, and international contingents such as up to 1,000 US agents, possibly armed. The Games’ security costs exploded from £282m in 2010 to £553m by end-of 2011, with another £475m for policing. Under the host city contract, the chancellor of the exchequer signed a guarantee “bearing the costs of providing security” – a blank cheque signed by the taxpayer for Olympic security planning that industry lobby body the British Security Industry Association (BSIA) has proudly been involved with from the outset.
Olympic security is booming business. The $1.7bn security budget for the 2004 Athens Games was over four times that of the 2000 Sydney Games, while $6.5bn went on security at the 2008 Beijing Games, mostly going on security technologies supplied by firms like General Electric and Panasonic – two major sponsors of the London Games. Beijing also saw innovations like armed police zipping around on Segways, or tickets inserted with radio-frequency ID chips to enable the real-time tracking of ticket holders.
Olympic and Paralympic Games Blog: Exercise Forward Defensive (met.police.uk):
| During last week I was one of the 2,500 people put through their paces as part of Exercise Forward Defensive. The exercise aimed to test, from constable through to COBR, how we all responded to a partially exploded bomb on the underground during Games time.Just as athletes prepare to be at the top of their game so must we. As the Met’s Gold Commander on the 7th July 2005 I am only too aware of the genuine value in exercising and testing our responses at every level to incidents such as these. We must all understand how we work together and be reassured that the right people are in the right places.I spent the two days of the exercise in the National Olympic Coordination Centre at New Scotland Yard, attending COBR meetings and meeting with my key people to keep an oversight of what we were all doing to keep London, the UK and Games safe and secure.
It was an excellent exercise and throughout the Met, and the other organisations who played, debriefs are taking place to make sure we get what learning we can. This week I’ve been down to Eton Dorney with the Home Secretary and Thames Valley Police Gold John Turnbull to look at the venue and police security plans for the rowing, Paralympic rowing and the canoe sprint. For the last two days I’ve been with police colleagues from across the country, being updated on Gold plans from across the 12 venue forces and briefing my national colleagues on where we are with Games safety and security planning. With only 148 days until the opening ceremony of the Olympic Games we are in a good place to deliver what will be the Police Service’s biggest ever peacetime safety and security operation. |
STASI Agents – Seduced by Secrets – E-Book
Dirty STASI Secrets exposed – East German SIGINT Operations by Ben Fischer
Bernd Schäfer – Stasi Files and GDR Espionage Against the West
FBI unveils Ponzi Scheme That Took $1 Million from Victims
SANTA ANA, CA—The owner and operator of a Downey company has been sentenced to 57 months in custody in a wire fraud scheme that collected nearly $1 million from victims who were falsely promised that their money would be used to host Christian rock concerts.
Lauren Baumann, 43, of Downey, the owner of Stewardship Estates, LLC, was sentenced late yesterday by United States District Judge Josephine S. Tucker.
Baumann pleaded guilty in October, admitting in court that she solicited loans from investors with claims that the money would be used to finance “battle of the bands” events featuring Christian rock bands and other music groups that would generate profits from ticket sales and company sponsorships. In some cases, Baumann told investors that the funds would also be used to purchase, refurbish, and resell homes.
In fact, a substantial portion of the investors’ funds was used to pay earlier investors, who thought they were receiving profits from Baumann’s venture. Baumann also used investor funds to pay approximately $10,000 a month to rent a historic mansion in Downey and to pay private school tuition for her children, among other personal expenses.
As a result of Baumann’s scheme, more than two dozen victims in Orange and Los Angeles counties suffered losses totaling nearly $560,000.
When she pleaded guilty, Baumann also admitted that she failed to disclose to investors that she had been convicted of securities fraud in 1999 in a Texas federal court and that she had been found liable in a related civil fraud action brought by the United States Securities and Exchange Commission.
Baumann was ordered to report to begin serving her sentence by April 2. The court will also issue an order requiring that Baumann pay restitution to her victims in the scheme.
The criminal case against Baumann is the result of an investigation by the Federal Bureau of Investigation.
Contact:
Assistant United States Attorney Joshua M. Robbins
Santa Ana Branch Office
(714) 338-3538
Biggest Ponzi Scheme since Madoff – Fraudster Stanford convicted
Texas tycoon R. Allen Stanford was convicted Tuesday of running a $7 billion Ponzi scheme — the biggest investment fraud since the Bernie Madoff scandal.
A jury found Stanford, 61, guilty on 13 of 14 criminal charges, including fraud, conspiracy, and obstructing an investigation by the Securities and Exchange Commission, Reuters reports. Jurors acquitted Stanford on a single wire-fraud charge.
“For all the investors, I think there is a sense of relief that they weren’t just fools,” one of Stanford’s victims told. “We were just conned.”
R. Allen Stanford was arrested in 2009 and accused of running a $7 billion Ponzi scheme that defrauded nearly 30,000 investors in more than 100 countries.
Stanford’s conviction involved use of a bank — the Stanford International Bank, which he set up on the Caribbean island of Antigua, according to Reuters. Stanford put investors’ money into the bank, then used the bank as his “personal ATM,” prosecutors said.
The money bankrolled Stanford’s lavish lifestyle. He spent millions on pricey real estate for family and friends, and bought expensive clothes, luxury homes, and a yacht for himself.
At one point, Stanford’s personal fortune was valued at $2.2 billion. Most of Stanford’s victims, however, never got anything in return for their investments.
R. Allen Stanford’s conviction could result in a 20-year prison sentence for the most serious charges, the AP reports — but he could be in prison much longer, if a judge orders his sentences to be served consecutively. One of Stanford’s lawyers says his client plans to appeal.
Confidential from Cryptome – UK Parliament Reveals Mark Burby Super-Injunction 2
A sends:
Re: http://cryptome.org/2012/01/mark-burby.htm
There has been one further development in the matter of the Mark Burby super-injunction. Yesterday the High Court published online its judgment in the privacy case at the heart of Burby’s evidence to Parliament:
WXY -v- Henry Gewanter, Positive Profile Ltd & Mark Burbyhttp://www.judiciary.gov.uk/media/judgments/2012/wxy-judgment-06032012
The judgment follows from a hearing in July 2011 and finds against Burby in that it prevents him from publicising the allegations covered in his evidence to Parliament.
The other defendants are Henry Gewanter, a PR consultant, and his agency Positive Profile. Gewanter and his agency were engaged by Burby in 2009.
(Gewanter was also the middleman who passed on details of MPs’ expenses to the Daily Telegraph in 2009. The expenses story was a big scandal in the UK, and a journalistic coup for the Telegraph. The Gewanter connection may explain the Telegraph’s particular interest in this case.)
The principals are anonymised in the High Court judgment, but for reference:
— ‘WXY’ / ‘Claimant’ is Mariam Abdul Aziz and the ‘Head of State’ is the Sultan of Brunei.– ‘X’ is Michael McGurk. McGurk apparently made tape recordings of conversations in which some of the allegations were made and passed them to Burby. These are referred to in the judgment as the ‘Jersey Tapes’.
— ‘M’ is a man named Amr Hendawy, apparently an Egyptian national. (Usenet postings from January 2008, linking Mariam Aziz and Amr Hendawy, have been removed by Google following a legal complaint.)
The High Court judgment covers the same ground as Burby’s evidence but does provide a few additional threads to pull.
Central to the case against Burby is that during 2009 he set up a website to publicise some of the allegations. That website is referred to in the judgment only as ‘A’.
By the time of the hearings in 2011 website ‘A’ had been taken down. Ironically, that seems to have counted against Burby. The injunction has been upheld in part because: “the information has not entered the public domain so as to render it is no longer private and confidential. It still retains ‘the basic attribute of inaccessibility’. It is not public property or public knowledge.”
Website ‘A’ was previously at the domain royallyshafted.co.uk. (According to the Nominet whois record, this domain remains registered to sixbynine, a Jersey-based media company controlled by the Burbys.)
From May through July 2009 the website was also linked to a Twitter account [at]royallyshafted. Tweets to that Twitter account (from May to July 2009) are still online; several mention the Sultan of Brunei.
Although the royallyshafted.co.uk website itself is no longer active, ‘snapshots’ of the homepage remain in the Wayback Machine archive at:
http://wayback.archive.org/web/*/http://royallyshafted.co.uk/*
Although some of Burby’s posts have been lost, the Wayback Machine snapshots enable retrieval of ten posts from May and June 2009 as well as the headers of other posts from April 2009. I have attached a verbatim copy of those posts and headers.
http://cryptome.org/2012/03/burby-Royally_Shafted_1.pdf
http://cryptome.org/2012/03/burby-Royally_Shafted_2.pdf
Most of the posts concern Burby’s attempts to collect on an earlier civil judgment against a member of the Sultan’s family. However there is one post provocatively titled ‘Brunei Royals agent supports 911 attack’.
Uncensored – FEMEN – A tribute to the ‘topless warriors’ and i.e. Ann Hutsol
This video is a pictorial tribute to Femen, Anna Hutsol and the “topless warriors”. The Ukranian activist group was formed in 2008 by Anna Hutsol. The group has become reknowned internationally for their topless protests. Primarily concerned with domestic issues they have since taken up many major internationl causes and they have inspired similar movements globally.
This video contains some scenes of nudity from their protests but these scenes are, I must stress, images from what are valid political protests.
In accordance with the YouTube community guidelines which state that “YouTube is not for pornography or sexually explicit content” and that “We encourage free speech”, I hope the video will be seen for what it is – a pictorial tribute to the political activism and courage of women, albeit young beautiful ones.
Visit http://femen.org/
Die vorbestraften STASI-Stalker der “GoMoPa” und Ihre Verbrechen im Spiegel der Presse
SECRET from the FBI – Six Hackers in the United States and Abroad Charged for Crimes Affecting Over One Million Victims
Five computer hackers in the United States and abroad were charged today, and a sixth pled guilty, for computer hacking and other crimes. The six hackers identified themselves as aligned with the group Anonymous, which is a loose confederation of computer hackers and others, and/or offshoot groups related to Anonymous, including “Internet Feds,” “LulzSec,” and “AntiSec.”
RYAN ACKROYD, a/k/a “kayla,” a/k/a “lol,” a/k/a “lolspoon”; JAKE DAVIS, a/k/a “topiary,” a/k/a “atopiary”; DARREN MARTYN, a/k/a “pwnsauce,” a/k/a “raepsauce,” a/k/a “networkkitten”; and DONNCHA O’CEARRBHAIL, a/k/a “palladium,” who identified themselves as members of Anonymous, Internet Feds, and/or LulzSec, were charged in an indictment unsealed today in Manhattan federal court with computer hacking conspiracy involving the hacks of Fox Broadcasting Company, Sony Pictures Entertainment, and the Public Broadcasting Service (“PBS”). O’CEARRBHAIL is also charged in a separate criminal complaint with intentionally disclosing an unlawfully intercepted wire communication.
HECTOR XAVIER MONSEGUR, a/k/a “Sabu,” a/k/a “Xavier DeLeon,” a/k/a “Leon,” who also identified himself as a member of Anonymous, Internet Feds, and LulzSec, pled guilty on August 15, 2011 in U.S. District Court to a 12-count information charging him with computer hacking conspiracies and other crimes. MONSEGUR’S information and guilty plea were unsealed today. The crimes to which MONSEGUR pled guilty include computer hacking conspiracy charges initially filed in the Southern District of New York. He also pled guilty to the following charges: a substantive hacking charge initially filed by the U.S. Attorney’s Office in the Eastern District of California related to the hacks of HBGary, Inc. and HBGary Federal LLC; a substantive hacking charge initially filed by the U.S. Attorney’s Office in the Central District of California related to the hack of Sony Pictures Entertainment and Fox Broadcasting Company; a substantive hacking charge initially filed by the U.S. Attorney’s Office in the Northern District of Georgia related to the hack of Infragard Members Alliance; and a substantive hacking charge initially filed by the U.S. Attorney’s Office in the Eastern District of Virginia related to the hack of PBS, all of which were transferred to the Southern District of New York, pursuant to Rule 20 of the Federal Rules of Criminal Procedure, in coordination with the Computer Crime and Intellectual Property Section (“CCIPS”) in the Justice Department’s Criminal Division.
Late yesterday, JEREMY HAMMOND, a/k/a “Anarchaos,” a/k/a “sup_g,” a/k/a “burn,” a/k/a “yohoho,” a/k/a “POW,” a/k/a “tylerknowsthis,” a/k/a “crediblethreat,” who identified himself as a member of AntiSec, was arrested in Chicago, Illinois and charged in a criminal complaint with crimes relating to the December 2011 hack of Strategic Forecasting, Inc. (“Stratfor”), a global intelligence firm in Austin, Texas, which may have affected approximately 860,000 victims. In publicizing the Stratfor hack, members of AntiSec reaffirmed their connection to Anonymous and other related groups, including LulzSec. For example, AntiSec members published a document with links to the stolen Stratfor data titled, “Anonymous Lulzxmas rooting you proud” on a file sharing website.
The following allegations are based on the indictment, the information, the complaints, and statements made at MONSEGUR’s guilty plea:
Hacks by Anonymous, Internet Feds, and LulzSec
Since at least 2008, Anonymous has been a loose confederation of computer hackers and others. MONSEGUR and other members of Anonymous took responsibility for a number of cyber attacks between December 2010 and June 2011, including denial of service (“DoS”) attacks against the websites of Visa, MasterCard, and PayPal, as retaliation for the refusal of these companies to process donations to Wikileaks, as well as hacks or DoS attacks on foreign government computer systems.
Between December 2010 and May 2011, members of Internet Feds similarly waged a deliberate campaign of online destruction, intimidation, and criminality. Members of Internet Feds engaged in a series of cyber attacks that included breaking into computer systems, stealing confidential information, publicly disclosing stolen confidential information, hijacking victims’ e-mail and Twitter accounts, and defacing victims’ Internet websites. Specifically, ACKROYD, DAVIS, MARTYN, O’CEARRBHAIL, and MONSEGUR, as members of InternetFeds, conspired to commit computer hacks including: the hack of the website of Fine Gael, a political party in Ireland; the hack of computer systems used by security firms HBGary, Inc. and its affiliate HBGary Federal, LLC, from which Internet Feds stole confidential data pertaining to 80,000 user accounts; and the hack of computer systems used by Fox Broadcasting Company, from which Internet Feds stole confidential data relating to more than 70,000 potential contestants on “X-Factor,” a Fox television show.
In May 2011, following the publicity that they had generated as a result of their hacks, including those of Fine Gael and HBGary, ACKROYD, DAVIS, MARTYN, and MONSEGUR formed and became the principal members of a new hacking group called “Lulz Security” or “LulzSec.” Like Internet Feds, LulzSec undertook a campaign of malicious cyber assaults on the websites and computer systems of various business and governmental entities in the United States and throughout the world. Specifically, ACKROYD, DAVIS, MARTYN, and MONSEGUR, as members of LulzSec, conspired to commit computer hacks including the hacks of computer systems used by the PBS, in retaliation for what LulzSec perceived to be unfavorable news coverage in an episode of the news program “Frontline”; Sony Pictures Entertainment, in which LulzSec stole confidential data concerning approximately 100,000 users of Sony’s website; and Bethesda Softworks, a video game company based in Maryland, in which LulzSec stole confidential information for approximately 200,000 users of Bethesda’s website.
The Stratfor Hack
In December 2011, HAMMOND conspired to hack into computer systems used by Stratfor, a private firm that provides governments and others with independent geopolitical analysis. HAMMOND and his co-conspirators, as members of AntiSec, stole confidential information from those computer systems, including Stratfor employees’ e-mails as well as account information for approximately 860,000 Stratfor subscribers or clients. HAMMOND and his co-conspirators stole credit card information for approximately 60,000 credit card users and used some of the stolen data to make unauthorized charges exceeding $700,000. HAMMOND and his co-conspirators also publicly disclosed some of the confidential information they had stolen.
The Hack of International Law Enforcement
In January 2012, O’CEARRBHAIL hacked into the personal e-mail account of an officer with Ireland’s national police service, the An Garda Siochana (the “Garda”). Because the Garda officer had forwarded work e-mails to a personal account, O’CEARRBHAIL learned information about how to access a conference call that the Garda, the FBI, and other law enforcement agencies were planning to hold on January 17, 2012 regarding international investigations of Anonymous and other hacking groups. O’CEARRBHAIL then accessed and secretly recorded the January 17 international law enforcement conference call, and then disseminated the illegally-obtained recording to others.
***
MONSEGUR, 28, of New York, New York, pled guilty to three counts of computer hacking conspiracy, five counts of computer hacking, one count of computer hacking in furtherance of fraud, one count of conspiracy to commit access device fraud, one count of conspiracy to commit bank fraud, and one count of aggravated identity theft. He faces a maximum sentence of 124 years and six months in prison.
ACKROYD, 23, of Doncaster, United Kingdom; DAVIS, 29, of Lerwick, Shetland Islands, United Kingdom; and MARTYN, 25, of Galway, Ireland, each are charged with two counts of computer hacking conspiracy. Each conspiracy count carries a maximum sentence of 10 years in prison.
O’CEARRBHAIL, 19, of Birr, Ireland, is charged in the indictment with one count of computer hacking conspiracy, for which he faces 10 years in prison. He is also charged in the complaint with one count of intentionally disclosing an unlawfully intercepted wire communication, for which he faces a maximum sentence of five years in prison.
HAMMOND, 27, of Chicago, Illinois, is charged with one count of computer hacking conspiracy, one count of computer hacking, and one count of conspiracy to commit access device fraud. Each count carries a maximum sentence of 10 years in prison.
DAVIS is separately facing criminal charges in the United Kingdom, which remain pending, and ACKROYD is being interviewed today by the Police Central e-crime Unit in the United Kingdom. O’CEARRBHAIL was arrested today by the Garda.
The case is being prosecuted by the U.S. Attorney’s Office for the Southern District of New York. The investigation was initiated and led by the FBI, and its New York Cyber Crime Task Force, which is a federal, state, and local law enforcement task force combating cybercrime, with assistance from the PCeU; a unit of New Scotland Yard’s Specialist Crime Directorate, SCD6; the Garda; the Criminal Division’s CCIPS; and the U.S. Attorneys’ Offices for the Eastern District of California, the Central District of California, the Northern District of Georgia, and the Eastern District of Virginia; as well as the Criminal Division’s Office of International Affairs.
The charges contained in the indictment and complaints are merely accusations, and the defendants are presumed innocent unless and until proven guilty.
TOP-SECRET from the NSA – INTEL WARS The Lessons for U.S. Intelligence From Today’s Battlefields
Purchase Intel Wars: The Secret History of the Fight Against Terror at Amazon.
Washington, D.C., March 6, 2012 – Spendthrift, schizophrenic policies and a massive, multi-tiered bureaucracy more focused on preserving secrets than on mission accomplishment leave our intelligence operatives drowning in raw data, resource-starved, and choked on paperwork, according to a new book, Intel Wars: The Secret History of the Fight Against Terror (Bloomsbury Press, 2012), by intelligence historian Matthew Aid. Excerpts from the book and declassified documents cited in it were posted today by the National Security Archive, where Aid is a Visiting Fellow.
Even after the celebrated raid by U.S. Navy SEAL commandos in May 2011, which killed al Qaeda leader Osama Bin Laden, America’s spies are still struggling to beat a host of ragtag enemies around the world, Aid argues.
Thanks to more than $500 billion in taxpayer dollars spent on revamping and modernizing America’s spy networks since 9/11, the U.S. today has the largest and most technologically sophisticated intelligence community in the world, consisting of 210,000 employees, CIA stations in 170 countries, and an annual budget of more than $75 billion. Armed with cutting-edge surveillance gear, high-tech weapons, and fleets of armed and unarmed drone aircraft, the U.S. intelligence community is now producing more and better intelligence than at any time in its history.
But, according to Aid, overlapping jurisdictions and bureaucratic inertia often stall intelligence operations, such as U.S. military operators in Afghanistan who have to wait seventy-two hours for clearance to attack fast-moving Taliban IED teams planting explosive devices. U.S. military computers – their classified hard drives still in place – turn up for sale at Afghan bazaars. When you dig beneath the surface, swift, tightly focused intelligence-driven operations like the Osama bin Laden raid seem to be the exception rather than the rule, Aid concludes.
Intel Wars – based on extensive, on-the-ground interviews, dozens of declassified documents, and revelations from Wikileaks cables – shows how our soldier-spies are still fighting to catch up with the enemy.
Today’s posting of 12 documents consists of a selection of reports and memoranda cited in Intel Wars concerning the role played by the U.S. intelligence community in today’s military conflicts and crises, particularly in Afghanistan.
Die SZ-Süddeutsche Zeitung über die STASI-“GoMoPa”- Machenschaften
DOWNLOAD THE ORIGINAL FILE BELOW
Confidential – DHS Media Monitoring Desktop Reference Manual

The following manual for the Department of Homeland Security’s Media Monitoring Capability was reportedly obtained by EPIC via a FOIA request. The manual has been slightly redacted by DHS to remove names and contact information and the URL of the Network Operations Center Media Monitoring Capability reporting website. This website has been listed in three of the four publicly available manuals as an example of a website monitored by DHS.
1 Media Monitoring Capability Mission & Reporting Parameters:
1.1 MMC Mission
The MMC has three primary missions:
- First – to continually update existing National Situation Summaries (NSS) and International Situation Summaries (ISS) with the most recent, relevant, and actionable open source media information
- Second – to constantly monitor all available open source information with the goal of expeditiously alerting the NOC Watch Team and other key Department personnel of emergent situations
- Third – to receive, process, and distribute media captured by DHS Situational Awareness Teams (DSAT) or other streaming media available to the NOC such as Northern Command’s (NORTHCOM) Full Motion Video (FMV) and via open sources
These three missions are accomplished by employing various tools, services, and procedures that are described in detail in this document. Expanded upon, these primary missions have three key components:
1.1.1 Leverage Operationally Relevant Data
Leveraging news stories, media reports and postings on social media sites concerning Homeland Security, Emergency Management, and National Health for operationally relevant data, information, analysis, and imagery is the first mission component. The traditional and social media teams review a story or posting from every direction and interest, utilizing thousands of reporters, sources, still/video cameramen, analysts, bloggers and ordinary individuals on scene. Traditional Media outlets provide unmatched insight into the depth and breadth of the situation, worsening issues, federal preparations, response activities, and critical timelines. At the same time, Social Media outlets provide instant feedback and alert capabilities to rapidly changing or newly occurring situations. The MMC works to summarize the extensive information from these resources to provide a well rounded operational picture for the Department of Homeland Security.
1.1.2 Support NOC in Identifying Relevant Operational Media
Supporting the NOC by ensuring they have a timely appreciation for evolving Homeland Security news stories and media reports of interest to the public and DHS/other federal agencies involved in preparations and response activities is the second key component. DHS and other federal agencies conducting joint operations may be affected by other evolving situations in that area. These situations may be related; have a cause and effect relationship; or be unrelated but have a detrimental effect. Through coordination with the NOC Duty Director (NDD), Senior Watch Officer (SWO) the MMC works to ensure the NOC Watch Team is aware of such stories and news events and has time to analyze any effect on operations.
Timely reporting of current information is an integral element in maintaining complete operational awareness by Homeland Security Personnel. The MMC understand it is vital that critical information is relayed to key Department decision makers in as expeditious a manner as possible.
1.1.3 Increase Situational Awareness of the DHS Secretary
Mitigating the likelihood that the Secretary and DHS Executive staffs are unaware of a breaking Homeland Security news story or media report is the third component. The Secretary and executive staff members are subject to press questions regarding domestic and international events and may or may not be informed of the most current media coverage. The MMC understands critical information requirements and monitors news coverage with the perspective of how the breaking story may be related to current and other important ongoing situations and DHS activities.
The on-duty MMC analyst alerts DHS personnel and related federal agencies of updated news stories through distributed Items of Interest (see section 3.9.6). Recognizing that local media coverage is potentially sensationalizing an incident, the MMC strives to comprehend the media’s message and identify sensitive situations that must be brought to the attention of the Secretar
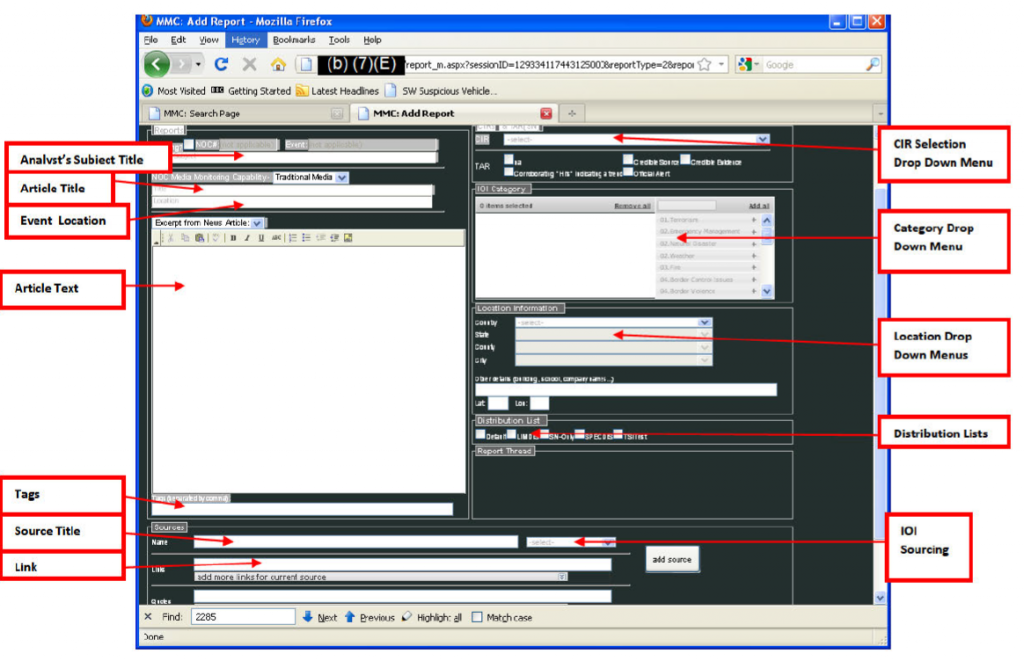
TOP-SECRET from the NSA – Excerpts on warning systems and October 1960 false from Institute for Defense Analyses, The Evolution of U.S. Strategic Command and Control and Warning, 1945-1972,
READ THE DOCUMENTS
Document 1: Excerpts on warning systems and October 1960 false from Institute for Defense Analyses, The Evolution of U.S. Strategic Command and Control and Warning, 1945-1972, Study S-468 (Arlington, Virginia, 1975), op Secret, excerpts: pp. 216-218, 339-347, and 419-425.
Source: Digital National Security Archive
This invaluable history provides useful background on the missile attack warning systems–BMEWs and DSP, among others–that became available during the 1960s and 1970s. One chapter provides context for the creation of the National Emergency Airborne Command Post [NEACP] that became operational in 1975.
Document 2: State Department cable 295771 to U.S. Embassy Moscow, “Brezhnev Message to President on Nuclear False Alarm,” 14 November 1979, Secret
Source: State Department FOIA release
The Soviets surely read about the November 1979 false warning in the U.S. press, but whether their intelligence systems had already detected it is not so clear. In any event, Soviet General Secretary Brezhnev privately expressed his “extreme anxiety” to President Carter a few days after U.S. press reports appeared on 11 November 1979. The message was closely held, not only as “Nodis” (“no distribution” except to a few authorized people), but also as “Cherokee,” a special information control established when Dean Rusk was Secretary of State (Rusk was born in Cherokee Country, GA) and used by subsequent Secretaries of State.
Document 3: Brigadier General Carl Smith, USAF, Military Assistant to the Secretary of Defense, to William Odom, Military Assistant to the Assistant to the President for National Security Affairs, “Proposed Oral Message Response,” 16 November 1979
Source: Defense Department FOIA release
Officials at the Pentagon drafted a reply that became the basis for the message that was eventually sent to the Kremlin. Giving very little quarter, the text asserted that the Kremlin had used bad information and that its message made “inaccurate and unacceptable” assertions, that Moscow had little to worry about because U.S. forces were under reliable control, and that it did not “serve the purposes of peace or strategic stability” to make a fuss about the recent incident.
Document 4: Excerpt from State Department memorandum to Secretary of State with attached memo “Late Supplement to VBB [Vance, Brown, Brzezinski] Item on Brezhnev Oral Message on False Alert,” circa 16 November 1979, secret, excerpt (as released by State Department)
Source: State Department FOIA release
Excerpts from a memorandum to Secretary of State Vance to prepare for a routine coordinating meeting with Secretary of Defense Brown and national security adviser Brzezinski, suggest that senior State Department officials opposed rushing a response to the Soviet message. Although they agreed that the “tone” of Brezhnev’s message was “unacceptable,” they opposed giving the Soviets ammunition to exploit, wanted to discuss carefully the “merits” of the Soviet case, and did not want to appear too “cavalier” about the incident because that could make U.S. allies nervous when they were already discussing new U.S. nuclear deployments in Western Europe.
Document 5: Marshal Shulman memo to Secretary of State Cyrus Vance, 16 November 1979, Top Secret
Source: State Department FOIA release
Vance’s adviser on Soviet policy Marshal Shulman had signed off on the memorandum on the reply to the Soviets, but had further thoughts. Believing that the U.S. could not really fault the Soviets for worrying about such episodes, Shulman noted that false alerts not a “rare occurrence” and worried about “complacency” toward the problem. Seeing the proposed reply as “kindergarten stuff,” he suggested more straightforward language. Whether this paper actually went to Vance is unclear, given the line crossing out the text.
Document 6: Marshal Shulman memo to Cyrus Vance, 21 November 1979, with draft message attached, nonclassified,
Source: State Department FOIA release
The debate over the reply continued, and an alternate version was drafted, but the one that Vance accidentally approved was the version that Shulman and others in the Department and the NSC found “gratuitously insulting and inappropriate for the Carter/Brezhnev channel.” Shulman’s advice came too late; even though Vance reportedly disliked the reply, he did not want to revisit the issue. Instead of handling the memorandum at the Secretary of State level, Vance’s top advisers wanted it to be delivered at somewhat lower level such as by Assistant Secretary of State George Vest. The version that is attached to Shulman’s note is a milder version of what was sent (see document 8).
Document 7: State Department cable 307013 to the U.S. Mission to the North Atlantic Treaty Organization, “TNF: Soviets and the False Missile Alert,” 28 November 1979, Secret
Source: State Department FOIA release
Before the Soviets received the reply, the State Department briefed permanent representatives to the North Atlantic Council to counter any attempts by Moscow to “cast doubt on the reliability of our nuclear control” and thereby influence the outcome of the ongoing debates over prospective theater nuclear forces [TNF] deployments in NATO Europe. This cable includes briefing information on what happened and also to demonstrate the “the redundant and complete nature of our well-established confirmation and control mechanisms.” The message was reasonably accurate about the cause of the false warning, not an operator error but the mistaken transmission of part of a test tape. Yet, as Scott Sagan has pointed out, this message wrongly asserted that the NORAD interceptors were launched because of an earlier alert; nothing of that sort had occurred.[11]
Document 8: State Department cable 312357 to U.S. Embassy Moscow, “U.S. Oral Message on Purported Alert of American Strategic Forces,” 4 December 1979, Confidential
Source: State Department FOIA release
On 4 December 1979, Robert Louis Barry, an official at the Bureau of European Affairs, at a lower level than Assistant Secretary Vest, finally conveyed the reply to the Soviet embassy’s Minister Counselor Aleksandr Bessmertnykh (later an ambassador to the United States). Unlike the original Soviet message, it was not a head of state communication, Carter–to-Brezhnev, suggesting that relations were quite frosty in this pre-Afghanistan period. Possibly the version of the reply that Shulman saw as “snotty,” it described Brezhnev’s original message as “inaccurate and unacceptable.” Ignoring Brezhnev’s concern about “no errors,” the message insisted that U.S. strategic forces were under “reliable control.”
Document 9: State Department cable 326348 to U.S. Embassy Moscow, “Supplementary Soviet Statement on U.S. Strategic Alert,” 19 December 1979, Confidential
Source: State Department FOIA release
Apparently surprised by the U.S. reply, the Soviets took issue with it in a “non-paper” delivered to the State Department by their chargé. Arguing that they had not raised the issue to engage in “polemics,” the Soviets asserted that a “profound and natural concern” instigated their original message.
Document 10: Message, HQ/NORAD to Assistant Secretary of Defense C3 and Joint Chiefs of Staff, 20 December 1979, Secret
Source: Donation by Scott Sagan, Stanford University
Sen. Gary Hart (D-Co), a member of the Senate Arms Services Committee, was concerned about what had happened on 9 November and visited NORAD for a briefing. While Hart wondered why the President and the Secretary of Defense had not been informed at the time, Lt. General Bruce K. Brown and other NORAD briefers explained that almost from the outset of the episode, NORAD officials saw a “a very high probability” that the warning was false. Hart also wondered why development testing on the NORAD 427M computer had been allowed; the briefers explained that NORAD officials recognized there was a problem and had recommended an auxiliary computer system as an “isolated” means for testing but the request had been denied because of “lack of funds.” Early in the message the briefers explained that they had stayed away from discussing the connection between the 427M computers and the Worldwide Military Command and Control System (WWMCCS). What may have explained that problem was ongoing concern at the Government Accounting Office and elsewhere that the WWMCCS lacked the capacity to meet NORAD’s mission requirements.
Document 11: Letter, Lt. General James V. Hartinger, Commander-in-chief, Aerospace Defense Command, to General Lew Allen, Chief of Staff, U.S. Air Force, 14 March 1980, Secret, attachments not included
Source: Donation by Scott Sagan, Stanford University
In a letter to the Air Force Chief of Staff, NORAD commander General Hartinger summarized the command’s report on the 9 November incident. That report is currently the subject of a declassification request to the Air Force. Not sure whether the incident was caused by a “human error, computer error, or combination of both,” Hartinger reported that “stringent safeguards have been established to preclude a repetition.”
Document 12: Secretary of Defense Harold Brown to President Carter, “False Missile Alert,” 7 June 1980, Top Secret, excised copy
Source: Defense Department FOIA release, currently under appeal
Hartinger’s confidence was misplaced. Massively and overzealously excised by reviewers at the Defense Department, this memorandum discloses that U.S. warning systems produced 3 false alerts during May and June 1980. The May event, described in document 19, was a minor precursor to the 3 June incident.
Document 13: Department of Defense “Fact Sheet,” n.d. [circa 7/8 June 1980], Secret
Source: Defense Department FOIA release
This document reviews the false alerts on 3 and 6 June of Soviet ICBM and SLBM attacks, what apparently caused them, what SAC bomber crews did in response to the warnings, and the measures that were taken to diagnosis what happened and to ensure that it did not happen again. Corrective measures included a separate computer system for testing operations (which had been rejected before because of insufficient funds[12]) and a determination by CINCNORAD that the U.S. is “under attack” before anything beyond basic “precautionary measures” are taken.
After the first incident on 3 June, SAC, NORAD, and the National Military Command Center established a “continuous voice telephone conference” to ensure that nothing went amiss.
The authors of the “Fact Sheet” emphasized the importance of the “human safeguards” noting that officers at NORAD were aware that electronic warning systems were working as usual and that the displays showed no unusual activity. An article in The New York Times published on 18 June (“Missile Alerts Traced to 46¢ Item”) included details on the response to the warning not mentioned in the “Fact Sheet,” asserting that missile crews went on a “higher state of alert” and that submarine crews were also informed. The Times’ writers, however, were not aware that NEACP “taxied into position” as part of an emergency routine.
Document 14: Assistant Secretary for Politico-Military Affairs Reginald Bartholomew to Secretary of State [Muskie], “False Alarm on Soviet Missile Attack,” 10 June 1980, Limited Official Use
Source: State Department FOIA release
Reginald Bartholomew sent a briefing memo on the incidents to Secretary Muskie, noting that “these incidents inevitably raise concerns … about the dangers of an accidental nuclear war.” The media had already picked up on the story[13], so there was some possibility of a Soviet complaint, although “the tone may well be sharper” in light of the tensions over the Soviet invasion of Afghanistan
Document 15: Secretary of Defense Brown to President Carter, “False Missile Alerts,” 13 June 1980, Secret, Excised copy
Source: Defense Department FOIA release
In this memorandum, Brown provided suggestions on how to answer media questions about the false warning problem. Treating false warnings as a byproduct of computerized warning technology, he emphasized that “human safeguards” ensured that there would be “no chance that any irretrievable actions would be taken.” While “any missile warning indications”, false or otherwise, would force SAC to take “precautionary action” by raising the bomber force’s alert status, Brown did not believe that anything more would happen.
Document 16: Assistant Secretary of Defense for Communications, Command, Control, and Intelligence Gerald P. Dinneen http://www.nap.edu/openbook.php?record_id=9052&page=1 to Secretary and Deputy Secretary of Defense, “False Missile Alerts – Information Memorandum,” 14 June 1980, Top Secret, excised copy
Source: Defense Department FOIA release
Assistant Secretary of Defense Dinneen (former director of Lincoln Laboratories) apprised Brown on the efforts to identify what had caused the false alerts and what could be done to fix the problem. A task force studying NORAD computer problems had identified a “suspect integrated circuit” as the most likely culprit (although they were not 100 percent certain). Various measures had been taken or under consideration but the details have been excised. A few days later Dinneen would brief the press on the failure of the 46¢ chip.
Document 17: Memorandum of Conversation, “U.S.-Soviet Relations,” 16 June 1960
Source: State Department FOIA release
During a meeting between Secretary of State Muskie and Ambassador Dobrynin, the latter asked about the recent “nuclear alerts,” which Foreign Minister Andrei Gromyko had already raised with U.S. Ambassador to Moscow, Thomas Watson. Muskie downplayed the problem on the grounds that the false signals would not create a “danger of war” because of the “interposition of human judgment.”
Document 18: Secretary of Defense to President Carter, “False Missile Alerts,” 12 July 1980, Top Secret, excised copy, attached to memorandum from Zbigniew Brzezinski to Brown, “False Alerts,” 17 July 1980, with annotations by Jimmy Carter
Source: Defense Department FOIA release
Here Brown updated Carter on the explanations for the recent false alert, corrective measures (e.g. special alarms when warning messages arrived so they could undergo confidence checks), and reactions by Congress and the public. Carter approved Brown’s report with an OK but was surprised (see handwritten exclamation mark) by the statement that “NORAD has been unable to get the suspected circuit to fail again under tests.” That conflicts with a statement in the Senate report that what caused the 6 June incident was an attempt to reproduce the earlier false alert, but perhaps subsequent attempts failed. Brown reminded Carter that “we must be prepared for the possibility that another, unrelated malfunction may someday generate another false alert.”
Document 19: Office of NORAD Deputy Chief of Staff, Operations, Captain Victor B. Budura, J-3, “Talking Points on 3/6 June False Indications,” 21 July 1980, Secret
Source: Donation by Scott Sagan, Stanford University
This NORAD document provides a chronology of the episodes of 28 May, 3 June, and 6 June 1980, although leaving out some events, such as the role of NEACP in the 3 June incident.
Document 20: U.S. Pacific Command, Annual History, 1980, excerpt, pages 201-202 (2nd page of excerpt unreadable), Secret
Source: Donation by Scott Sagan, Stanford University
This excerpt from a Pacific Command history discusses the launching of the Pacific Command airborne command post, “Blue Eagle,” during the 3 June false episode. As the chronology in document 19 indicates, the warning was determined to be false before “Blue Eagle” had taken off, but it stayed airborne for several hours.[14]
NOTES
[1] The following draws on the Institute for Defense Analyses’ History of Strategic Command Control and Warning, 1945-1972 (excerpts in document 1) and Jeffrey Richelson, America’s Space Sentinels: DSP Satellites and National Security (Lawrence: University Press of Kansas, 1999)
[2] Joseph T. Jockel, Canada and NORAD: 1957-2007: A History (Montreal: McGill-Queen’s University Press, Program, 2007), 95. This book and Jockel’s earlier, No Boundaries Upstairs: Canada, the United States, and the Origins of North American Air Defence, 1945-1958 (Vancouver: University of British Columbia Press, 1987) are valuable studies on the origins and development of NORAD. A comparable U.S. study on NORAD history remains to be prepared, although Christopher Bright’s Continental Air Defense in the Eisenhower Era: Nuclear Antiaircraft Arms and the Cold War (New York: Palgrave Macmillan) is helpful on nuclear issues in NORAD’s early years.
[3] Scott Sagan, The Limits of Safety: Organizations, Accidents, and Nuclear Weapons (Princeton: Princeton University Press, 1993). 99-100 and 126-133.
[4] Sagan, Limits of Safety, 228-229, 238.
[5] Ibid., 232, 244-246. See also Report of Senator Gary Hart and Senator Barry Goldwater to the Committee on the Armed Services United States Senate, Recent False Alerts from the Nation’s Missile Attack Warning System (Washington, D.C.: U.S. Government Printing Office, 1980), 5-6, and Government Accounting Office, MASAD 81-30, “NORAD’s Missile Warning System: What Went Wrong?”
[8] Bruce Blair, The Logic of Accidental Nuclear War (Washington, D.C.: Brookings Institution, 1993), 193.
[9] David E. Hoffman, The Dead Hand The Untold Story of the Cold War Arms Race and Its Dangerous Legacy (New York: Doubleday, 2009): 152-154, 422-423.
[10] David E. Hoffman, “Cold War Doctrines Refuse to Die,” The Washington Post, 15 March 1998,
[11] Sagan, Limits of Safety, 240-241.
[13] For example, the Washington Post published a story by George C. Wilson, “Computer Errs, Warns of Soviet Attack on U.S.,” on 6 June 1980.
TOP-SECRET from the NSA – False Warnings of Soviet Missile Attacks during 1979-80 Led to Alert Actions for U.S. Strategic Forces

Click for Larger ViewPhoto 1: “Command post for all NORAD [North American Aerospace Defense Command] operations, including the Command’s surveillance and warning sensors around the globe.” Caption from U.S. Information Agency photo. This and the next two photos were taken about 1982 so the depiction of NORAD facilities may not correspond exactly to arrangements during 1979-1980.
Source: National Archives, Still Pictures Branch, RG 306-PSE, box 79

Click for Larger ViewPhoto 2: “Satellite watchers in the Space Computational Center, NORAD Headquarters, track all the satellites orbiting earth. ” Caption from U.S. Information Agency photo.
Source: National Archives, Still Pictures Branch, RG 306-PSE, box 79

Click for Larger ViewPhoto 3: “Computers are used by specialists in NORAD Headquarters to keep track of information received daily.” Caption from U.S. Information Agency photo.
Source: National Archives, Still Pictures Branch, RG 306-PSE, box 79

Click for Larger ViewPhoto 4: “3/4s front view of a Boeing 747 Airborne Command post aircraft taking off. This aircraft will be designated the E-4A and become the new Night Watch Airplane.” Four Boeing 747s were modified to serve as the National Emergency Airborne Command Post [NEACP] for the National Command Authority [NCA], the President and the Secretary of Defense. Quotation from caption on photo taken by Sgt. J. F. Smith at Andrews Air Force Base, 1973.
Source: National Archives, Still Pictures Branch, RG 342B, box 731, E-4A

Click for Larger ViewPhoto 5: “National Emergency Airborne Command Post internal configuration.” Caption from Department of Defense photograph, 5 April 1976
Source: National Archives, Still Pictures Branch, RG 342B, box 731, E-4A

Click for Larger ViewPhoto 6: “Operations team shown in NCA conference room normally occupied by the NCA and immediate staff.” Caption from Air Force photo of NEACP taken by Sgt. J.F. Smith, 1974.
Source: National Archives, Still Pictures Branch, RG 342B, box 30, E-4A

Click for Larger ViewPhoto 7: Interior shot of the NEACP shows the briefing room. Department of Defense photo taken 5 April 1976.
Source: National Archives, Still Pictures Branch, RG 342B, box 731, Aircraft E4-AE

Click for Larger ViewPhoto 8: “Operations team shown in NCA conference room normally occupied by the NCA and immediate staff. It seats nine people.” Caption from Air Force photo of NEACP taken by Sgt. J.F. Smith, 1974.
Source: National Archives, Still Pictures Branch, RG 342B, box 30, E-4A

Click for Larger ViewPhoto 9: “Side view of three U.S. Air Force F-106’s , Det[achment] 3, 25th Air Division, fly by Mt. McKinley, Alaska, while on a training mission, 14 April 1969.” These were the type of aircraft launched by NORAD during the 9 November 1979 false alert. Caption from U.S. Air photo
Source: National Archives, Still Pictures Branch, RG 342-B, box 743, Aircraft F-106.
Washington, D.C., March 6, 2012 – During the 2008 campaign, Democratic presidential hopefuls Hillary Clinton and Barack Obama debated the question: who was best suited to be suddenly awakened at 3 a.m. in the White House to make a tough call in a crisis. The candidates probably meant news of trouble in the Middle East or a terrorist attack in the United States or in a major ally, not an ‘end of the world’ phone call about a major nuclear strike on the United States. In fact at least one such phone call occurred during the Cold War, but it did not go to the President. It went to a national security adviser, Zbigniew Brzezinski, who was awakened on 9 November 1979, to be told that the North American Aerospace Defense Command (NORAD), the combined U.S.–Canada military command–was reporting a Soviet missile attack. Just before Brzezinski was about to call President Carter, the NORAD warning turned out to be a false alarm. It was one of those moments in Cold War history when top officials believed they were facing the ultimate threat. The apparent cause? The routine testing of an overworked computer system.
Recently declassified documents about this incident and other false warnings of Soviet missile attacks delivered to the Pentagon and military commands by computers at NORAD in 1979 and 1980 are published today for the first time by the National Security Archive. The erroneous warnings, variously produced by computer tests and worn out computer chips, led to a number of alert actions by U.S. bomber and missile forces and the emergency airborne command post. Alarmed by reports of the incident on 9 November 1979, the Soviet leadership lodged a complaint with Washington about the “extreme danger” of false warnings. While Pentagon officials were trying to prevent future incidents, Secretary of Defense Harold Brown assured President Jimmy Carter that false warnings were virtually inevitable, although he tried to reassure the President that “human safeguards” would prevent them from getting out of control.
Among the disclosures in today’s posting:
- Reports that the mistaken use of a nuclear exercise tape on a NORAD computer had produced a U.S. false warning and alert actions prompted Soviet Communist Party General Secretary Leonid Brezhnev to write secretly to President Carter that the erroneous alert was “fraught with a tremendous danger.” Further, “I think you will agree with me that there should be no errors in such matters.”
- Commenting on the November 1979 NORAD incident, senior State Department adviser Marshal Shulman wrote that “false alerts of this kind are not a rare occurrence” and that there is a “complacency about handling them that disturbs me.”
- With U.S.-Soviet relations already difficult, the Brezhnev message sparked discussion inside the Carter administration on how best to reply. Hard-liners prevailed and the draft that was approved included language (“inaccurate and unacceptable”) that Marshal Shulman saw as “snotty” and “gratuitously insulting.”
- Months later, in May and June 1980, 3 more false alerts occurred. The dates of two of them, 3 and 6 June 1980, have been in the public record for years, but the existence of a third event, cited in a memorandum from Secretary of Defense Brown to President Carter on 7 June 1980, has hitherto been unknown, although the details are classified.
- False alerts by NORAD computers on 3 and 6 June 1980 triggered routine actions by SAC and the NMCC to ensure survivability of strategic forces and command and control systems. The National Emergency Airborne Command Post (NEACP) at Andrews Air Force Base taxied in position for emergency launch, although it remained in place. Because missile attack warning systems showed nothing unusual, the alert actions were suspended.
- Supposedly causing the incidents in June 1980 was the failure of a 46¢ integrated circuit (“chip”) in a NORAD computer, but Secretary of Defense Brown reported to a surprised President Carter that NORAD “has been unable to get the suspected circuit to fail again under tests.”
- In reports to Carter, Secretary cautioned that “we must be prepared for the possibility that another, unrelated malfunction may someday generate another false alert.” Nevertheless, Brown argued that “human safeguards”—people reading data produced by warning systems–ensured that there would be “no chance that any irretrievable actions would be taken.”
Background
For decades, the possibility of a Soviet missile attack preoccupied U.S. presidents and their security advisers. Because nuclear hostilities were more likely to emerge during a political-military confrontation (such as Cuba 1962) the likelihood of a bolt from the blue was remote but Washington nevertheless planned for the worst case. Under any circumstances, U.S. presidents and top military commanders wanted warning systems that could provide them with the earliest possible notice of missile launches by the Soviet Union or other adversaries. By the early 1960s, the Pentagon had the Ballistic Missile Early Warning System (BMEWs) that could provide about 15 minutes of warning time. By the mid-to-late1960s, forward-scatter systems (so-called “Over the Horizon Radar”) could detect missile launches within five to seven minutes from while, the 474N system could give three-to-seven minutes of warning of launches from submarines off the North American coast. [1]
By the end of the 1960s, the United States was getting ready to deploy the Defense Support Program satellites which use infrared technology to detect plumes produced by missile launches. DSP could be used to tell whether missile launches were only tests or whether they signified a real attack by detecting number of missile launches and trajectory. This provided25 to 30 minutes of warning along with information on the trajectory and ultimate targets of the missiles. As long as decision-makers were not confronting the danger of a SLBM launch, the DSP would give them some time to decide how to retaliate.
In 1972, the North American Aerospace Command (NORAD) began to network warning systems into at “interlinked system” operated at its headquarters in Cheyenne Mountain, Colorado.[2] A complex computer-based system always bore the risk of failure, break-downs, or errors. Even before networking emerged, false warnings emerged as early as 1960 when a BMEWs radar in Greenland caught “echoes from the moon,” which generated a report of a missile attack which was quickly understood to be false (see document 1). During the Cuban Missile Crisis false warning episodes occurred, some of them involving NORAD, that were virtually unknown for many years.[3] If there were significant incidents during the years that followed, it remains to be learned. But once the networked systems were in place, the possibility that they would typically produce false warnings became evident.
The Events of 1979-1980
“As he recounted it to me, Brzezinski was awakened at three in the morning by [military assistant William] Odom, who told him that some 250 Soviet missiles had been launched against the United States. Brzezinski knew that the President’s decision time to order retaliation was from three to seven minutes …. Thus he told Odom he would stand by for a further call to confirm Soviet launch and the intended targets before calling the President. Brzezinski was convinced we had to hit back and told Odom to confirm that the Strategic Air Command was launching its planes. When Odom called back, he reported that … 2,200 missiles had been launched—it was an all-out attack. One minute before Brzezinski intended to call the President, Odom called a third time to say that other warning systems were not reporting Soviet launches. Sitting alone in the middle of the night, Brzezinski had not awakened his wife, reckoning that everyone would be dead in half an hour. It had been a false alarm. Someone had mistakenly put military exercise tapes into the computer system.” — Robert M. Gates. From the Shadows: The Ultimate Insider’s Story of Five Presidents and How they Won the Cold War (New York: Simon & Shuster, 1996),114.
The series of alarming incidents and telephone phone calls recounted by former NSC staffer (and later CIA director and future Secretary of Defense) Robert Gates took place in the middle of the night on 9 November 1979. Because of the potentially grave implications of the event, the episode quickly leaked to the media, with the Washington Post and The New York Times printing stories on what happened. According to press reports, based on Pentagon briefings, a NORAD staffer caused the mistake by mistakenly loading a training/exercise tape into a computer, which simulated an “attack into the live warning system.” This was a distortion because it was not a matter of a “wrong tape,” but software simulating a Soviet missile attack then testing NORAD’s 427M computers “was inexplicably transferred into the regular warning display” at the Command’s headquarters. Indeed, NORAD’s Commander-in-chief later acknowledged that the “precise mode of failure … could not be replicated.”[4]
The information on the display simultaneously appeared on screens at SAC headquarters and the National Military Command Center (NMCC), which quickly led to defensive actions: NORAD alerted interceptor forces and 10 fighters were immediately launched. Moreover, the National Emergency Airborne Command Post (NEACP), used so the president could control U.S. forces during a nuclear war, was launched from Andrews Air Force Base, although without the president or secretary of defense.
Some of this information did not reach the public for months, but at least one reporter received misleading information about how high the alert went. According to the New York Times’ sources, the warning was “deemed insufficiently urgent to warrant notifying top Government or military officials.” Apparently no one wanted to tell reporters (and further scare the public) that the phone call went to President’s Carter’s national security adviser Zbigniew Brzezinski.
The behind-the-scenes story became more complicated because the Soviet leadership was worried enough to lodge a complaint with Washington. The Cold War tensions had already been exacerbated during the previous year and this could not help (nor could an impending Kremlin decision to invade Afghanistan). On 14 November, party leader Leonid Brezhnev sent a message via Ambassador Anatoly Dobyrnin expressing his concern about the incident which was “fraught with a tremendous danger.” What especially concerned Brezhnev were press reports that top U.S. leaders had not been informed at the time about the warning. The Defense Department and Brzezinski took hold of the reply to Brezhnev’s message which senior State Department adviser Marshall Shulman saw as “gratuitously snotty” (for example, language about the “inaccurate and unacceptable” Soviet message). The Soviets were indeed miffed because they later replied that the U.S. message was not “satisfactory” because it had taken a polemical approach to Moscow’s “profound and natural concern.”
About seven months later, U.S. warning systems generated three more false alerts. One occurred on 28 May 1980; it was a minor harbinger of false alerts on 3 and 6 June 1980. According to the Pentagon, what caused the malfunctions in June 1980 was a failed 46¢ micro-electronic integrated circuit (“chip”) and “faulty message design.” A computer at NORAD made what amounted to “typographical errors” in the routine messages it sent to SAC and the National Military Command Center (NMCC) about missile launches. While the message usually said “OOO” ICBMs or SLBMs had been launched, some of the zeroes were erroneously filled in with a 2, e.g. 002 or 200, so the message indicated that 2, then 200 SLBMs were on their way. Once the message arrived at SAC, the command took survivability measures by ordering bomber pilots and crews to their stations at alert bombers and tankers and to start the engines.
No NORAD interceptors were launched so something had been learned from the November episode, but SAC took same precautionary measures. The Pacific Command’s airborne command post (“Blue Eagle”) was launched for reasons that remain mysterious.[5] NEACP taxied in position at Andrews Air Force Base, but it was not launched as in November. That missile warning sensors (DSP, BMEWs, etc) showed nothing amiss made it possible for military commanders to call off further action. According to a Senate report, NORAD ran its computers the next 3 days in order to isolate the cause of the error; the “mistake was reproduced” in the mid-afternoon of 6 June with the similar results and SAC took defensive measures.[6]
When Harold Brown explained to President Carter what had happened and what was being done to fix the system, he cautioned that “we must be prepared for the possibility that another, unrelated malfunction may someday generate another false alert.” This meant that “we must continue to place our confidence in the human element of our missile attack warning system.” Brown, however, did not address a problem raised by journalists who asked Pentagon officials, if another false alert occurred, whether a “chain reaction” could be triggered when “duty officers in the Soviet Union read data on the American alert coming into their warning systems.” A nameless U.S. defense official would give no assurances that a “chain reaction” would not occur, noting that “I hope they have as secure a system as we do, that they have the safeguards we do.”
How good the safeguards actually were remains an open question. While Secretary of Defense Brown acknowledged the “possibility” of future false alerts, he insisted on the importance of human safeguards in preventing catastrophes. Stanford University professor Scott Sagan’s argument about “organizational failure” is critical of that optimism on several counts. For example, under some circumstances false alerts could have had more perilous outcomes, e.g. if Soviet missile tests had occurred at the same time or if there were serious political tensions with Moscow, defense officials might have been jumpier and launched bomber aircraft or worse. Further, false warnings were symptomatic of “more serious problems with the way portions of the command system had been designed.” Yet, defense officials have been reluctant to acknowledge organizational failings, instead blaming mistakes on 46¢ chips or individuals inserting the wrong tape. Treating the events of 1979 and 1980 as “normal accidents” in complex systems, Sagan observes that defense officials are reluctant to learn from mistakes and have persuaded themselves that the system is “foolproof.”[7]
Bruce Blair also sees systemic problems. Once a “launch-under–attack” strategic nuclear option became embedded in war planning policy during the late 1970s, he sees the weakening of the safeguards that had been in place, e.g., confirmation that a Soviet nuclear attack was in progress or had already occurred. One of the arguments for taking Minuteman ICBMs off their current high alert status (making virtually instantaneous launch possible) has been that a false warning, combined with an advanced state of readiness, raises the risk of accidental nuclear war. The risk of false alerts/accidental war is one of the considerations that is prompting other anti-nuclear activists, including Daniel Ellsberg, to protest at Vandenberg Air Force Base against the Minuteman ICBM program and the continued testing of Minutemen.[8]
The Soviet nuclear command and control system that developed during the 1980s provides an interesting contrast with the U.S.’s. While the United States emphasized “human safeguards” as a firewall, the “Perimeter” nuclear warning-nuclear strike system may have minimized them. In large part, it was a response to Soviet concern that a U.S. decapitating strike, aimed at the political leadership and central control systems, could cripple retaliatory capabilities. Reminiscent of the “doomsday machine” in Stanley Kubrick’s Dr. Strangelove or How I Learned to Stop Worrying and Love the Bomb, Perimeter could launch a semi-automatic nuclear strike under specified conditions, for example, no contact with political or military leaders, atomic bombs detonating, etc. If such conditions were fulfilled, a few military personnel deep in an underground bunker could launch emergency command and control rockets which in turn would transmit launch orders to ICBMs in their silos. According to David Hoffman’s Pulitzer-prize winning The Dead Hand, when Bruce Blair learned about Perimeter, he was “uneasy that it put launch orders in the hands of a few, with so much automation.” While the system may have been operational as late as the early 1990s, only declassification decisions by Russian authorities can shed light on Perimeter’s evolution.[9]
According to Bruce Blair, writing in the early 1990s, warning system failures continued after 1980, although they did not trigger alert measures.[10] The U.S. nuclear incidents that have received the most attention have not been false warnings, but events such as the Air Force’s accidental movement of nuclear-tipped cruise missiles from Minot AFB to Barksdale AFB in 2007 and the mistaken transfer of Minuteman nose-cone assemblies to Taiwan in 2006. In any event, more needs to be learned about the problem of false warnings during and after the Cold War and pending declassification requests and appeals may shed further light on this issue.
Column by Arie Egozi – Separate Speeches – Separate Realities

Arie Egozi Arie Egozi is a seasoned reporter in the defense industry and in military and civilian aviation. He has worked closely with the Israeli daily Yedioth Ahronoth, and written for international journals in both the aviation and defense fields.
The speeches were amazing, truly a school of state speeches, fluent and sweeping. The applause from the good Jewish Americans at the AIPAC convention was genuine and loud. So far, so good. However, there’s a very large problem behind the scene. Perhaps a twofold problem.
It’s an election year in the United States, and the US doesn’t need a war in the Middle East. Israel, on the other hand, has reached the conclusion that the sanctions barely tickle the whiskers on Ahmadinejad’s face, and that the nuclear facilities need to be attacked. So the US solved its problem with Jerusalem, but those in Jerusalem have forgotten something; It’s the Israeli home front that will suffer the Iranian response, and the home front is in no way ready for an attack.
A home front can’t really be prepared for a missile attack, but not even the smallest effort has been taken in Israel; no shelters, no NBC protective masks for the populace, no element to coordinate the activities in the areas that will be hit. In short, a typical Israeli mess. The home front has simply been abandoned, and it seems that Jerusalem’s forgotten this. There is clearly a tremendous problem here.
After the applause in Washington fades, someone will have to examine the situation, and it’s a grim one. Having just two Arrow batteries, as well as all the deficiencies listed earlier, is a recipe for a heavy blow to the home front. Not the 500 casualties (a number that Minister of Defense Ehud Barak plucked from the confidential files), not “tolerable damage” – but the paralysis of the home front, mass casualties, widespread destruction, and a joint attack from Iran, Syria, Hezbollah, and Hamas.
Everyone will take part in the attack, but Israel is simply not ready. The Merkava Mark IV tanks and the sophisticated UAVs will not help here. Nor will the smart and precise weapons. The Israeli home front is relatively small and unprepared for a barrage of missiles and rockets. Our leaders need to remember this before they make any decisions.
The problem is not what will be said in the White House, the problem is what will happen to us here. I’m not at all certain that this is being taken into consideration in Jerusalem.
To paraphrase Bibi Netanyahu’s words in Washington: If it looks like a mess, sounds like a mess, and walks like a mess, then it’s a mess.
Uncensored – FEMEN Protesters Versace Show Milan Fashion Week Italy
Olala! Topless Ukrainian Women Femen Protesters Versace Show Milan Fashion Week Italy
The three attractive women, understood to be model themselves, chanted outside the high-end fashion show while holding aloft handmade placards with the same mottos and “Models do not go to brothels”.
Confidential – U.S. Marine Corps Civilian Casualty Mitigation Lessons Learned Report

(U//FOUO) Fully understanding the imperative to balance employment of fires to defeat the enemy with the necessity to protect civilian lives, the Marine Corps has modified the training / education of ground commanders, aviators, forward air controllers (FACs), joint terminal attack controllers (JTACs), and others in the fire support approval chain. This incorporates lessons and guidance contained in the USJFCOM investigation into the Farah incident and the Commander, International Security Assistance Force (COMISAF) tactical directive issued in July 2009.
(U//FOUO) Marine Corps units and individuals preparing to deploy to Afghanistan are trained on theater specific directives and measures to prevent civilian casualties, to include rules of engagement (ROE), considerations for use of air to ground and indirect fires, and requirements for collateral damage estimation and battle damage assessment (BDA).
(U//FOUO) Training for forces deploying to Afghanistan is tailored for that threat and environment by monitoring events in theater, reviewing intelligence summaries, after action reports, e-mails, information provided by recently redeployed Marines, and MCCLL products. Instructor staff at Tactical Training and Exercise Control Group (TTECG) and Marine Aviation Weapons Training Squadron (MAWTS) 1 maintain situational awareness through periodic ‘lessons learned’ trips to Afghanistan and participation in video teleconferences with deployed forces.
(U//FOUO) Observations and best practices to mitigate potential for civilian casualties identified in this summary are consistent with counterinsurgency (COIN) doctrine relating to proportionality in use of force to achieve military objectives, discrimination of targets, and determination of acceptable risk to noncombatants. Understanding the long term effects on operations and mission success, avoidance of CIVCAS must be integrated into planning and operations. “There’s got to be a CIVCAS theme that goes through every aspect of planning and operations we do.” Col Michael Killion, G-3, MEB-A
(U//FOUO) Throughout its ongoing procurement and fielding initiatives, the Marine Corps is investigating, procuring and fielding technologies that can aid in reduction of civilian casualties. These include non-lethal weapons systems currently employed in Afghanistan by I MEF (Fwd) and systems to be fielded over the next six years.
(U//FOUO) Capabilities/missions supported by currently fielded systems include vehicle check point (VCP), crowd control and entry control point (ECP) operations. Future systems will provide additional capabilities for these three missions and address functions of convoy security, conduct cordon, clear facilities, urban patrolling, establish and secure a perimeter, conduct search and detain personnel.
(U) Recommendations suggested by content of interviews include the following topics and associated implications for the doctrine, organization, training, material, leadership and education, personnel, and facilities (DOTMLPF) pillars.
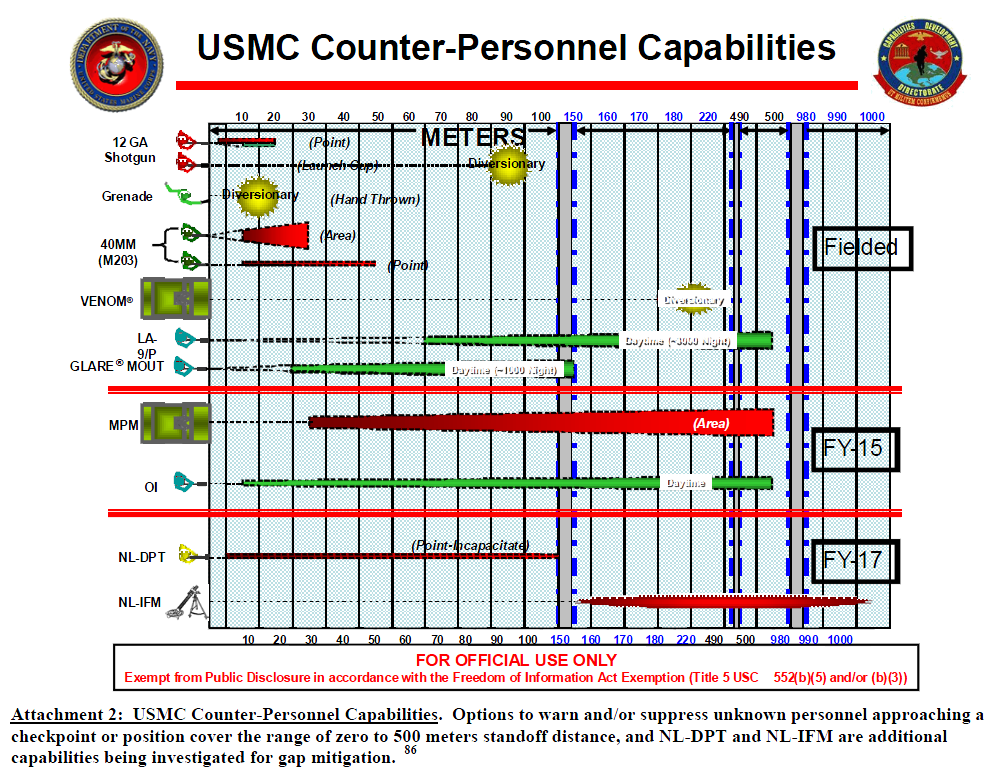
Das “HANDELSBLATT” über die Wirtschaftskriminellen-Betrüger der STASI-“GoMoPa” und deren Vorstrafen
Zitat:
“Der Kurs des Münchener Zahlungsabwicklers Wirecard war am vergangenen Dienstag um mehr als 30 Prozent eingebrochen. Am Abend zuvor hatte der Internetdienst Goldman, Morgenstern & Partners (Gomopa) berichtet, der in den USA wegen illegalen Online-Glücksspiels verhaftete Deutsche Michael Schütt habe in einem Geständnis Wirecard schwer belastet. Gomopa bezog sich auf einen Bericht der Lokalzeitung “Naples News”. Schütt habe ausgesagt, er sei bei illegalen Geldgeschäften direkt vom Wirecard-Vorstand beauftragt worden.
Das Problem an dem Gomopa-Bericht: Er war falsch. Wie Nachfragen des Handelsblattes ergaben, hat die Reporterin, die für die “Naples News” über Schütt schreibt, Wirecard nie erwähnt. Gomopa reagierte auf Nachfragen zögerlich. Erst löschte der Dienst den Hinweis auf die Lokalzeitung, hielt aber den Vorwurf aufrecht, Schütt habe Wirecard belastet. Danach änderte man den Bericht erneut. Nun hieß es, ein Informant von Gomopa verfüge über die fraglichen Details aus Schütts Geständnis.
Dem Handelsblatt liegt inzwischen das amtliche Protokoll von Schütts Geständnis am 23. März vor. Schütt bekennt sich darin schuldig, illegale Geldgeschäfte im Zusammenhang mit Online-Glücksspiel abgewickelt zu haben. Das Wort Wirecard kommt nicht vor. Gomopa hatte zu Wochenbeginn seinen Text erneut geändert und nun behauptet, Schütt belaste “eine Bank”. Auf erneute Nachfragen des Handelsblattes war der Bericht dann ganz verschwunden.
Der Kurs von Wirecard hat sich inzwischen fast vollständig erholt. Ein Frankfurter Analyst sagte, für ihn sei klar, dass die Aktie seit Wochen manipuliert werde. Erst verteure sich die Leihe der Aktie, dann komme es zu außergewöhnlichem Handel, danach tauchten plötzlich desaströse Gerüchte auf. Dazu gehöre auch die Anzeige, die vor kurzem bei der Staatsanwaltschaft München einging und Wirecard der Geldwäsche bezichtigt. Es sei offensichtlich, dass Short Seller mit der Wirecard-Aktie Jojo spielen.
Mark Vornkahl, einer der Gründer von Gomopa wies den Vorwurf der Kursmanipulation gestern zurück. Man wolle nur die Wahrheit aufdecken. Es ist allerdings nicht das erste Mal, dass Gomopa-Vertreter ins Zwielicht geraten. 2006 wurden Vornkahl und Mitgründer Klaus Maurischat wegen Betrugs an einem Anleger verurteilt. Maurischat gab gestern gegenüber dem Handelsblatt weitere Verurteilungen zu. Es habe sich dabei jedoch nicht um Anlagebetrug gehandelt.”
Link:
TOP-SECRET – FBI Indicators for Terrorist Use of Toxic Industrial Chemicals

(U//FOUO) The release of a toxic industrial chemical (TIC) by a terrorist group or lone actor represents a significant threat. TICs are readily available in large quantities, routinely shipped by commercial carriers, and often stored in bulk containers. Most TICs are generally less toxic than chemical warfare (CW) agents, but a large volume of TICs can be equally dangerous. The release of a TIC in a populated area is capable of generating numerous casualties and deaths; the toxic effects would be more dangerous if release occurred in an enclosed space.
• (U//FOUO) Some TICs such as phosgene, hydrogen cyanide, and chlorine are dangerous without any modification and can serve as “ready-made” chemical agents. Even with limited expertise, terrorists could produce an improvised dispersal device (IDD) to release TICs, or they could rupture TIC containers at a fixed site or while in transit.
• (U//FOUO) Other TICs such as potassium cyanide or sodium cyanide can be combined with additional chemicals to produce more toxic chemicals. Simple plans for constructing crude chemical devices are available in extremist literature and can be found on the Internet.…
(U) Common High-Risk TICs:
The following TICs present a high risk because they can be used as improvised chemical weapons, combined to form more toxic chemicals, or used as precursors for CW agents:
• (U) Ammonia
• (U) Arsine
• (U) Chlorine
• (U) Fluorine
• (U) Hydrogen chloride
• (U) Hydrogen cyanide
• (U) Hydrogen fluoride
• (U) Hydrogen sulfide
• (U) Malathion
• (U) Parathion
• (U) Phosgene
• (U) Phosphorous oxychloride
• (U) Phosphorous trichloride
• (U) Potassium cyanide
• (U) Sodium cyanide
• (U) Sulfur dioxide
• (U) Sulfuric acid(U) Phosphorous oxychloride, phosphorous trichloride, hydrogen fluoride, potassium cyanide and sodium cyanide are precursor chemicals on the Australia Group export control list. Phosphorous oxychloride and phosphorous trichloride are also listed by the Chemical Weapons Convention.
DOWNLOAD ORIGINAL DOCUMENT HERE
Video – Injured UK-Journalist describes Escape from Syria
U.K. journalist Paul Conroy recounts his escape from Syria after being injured.
SECRET from the FBI – Dallas Doctor Arrested for Role in Nearly $375 Million Health Care Fraud Scheme
WASHINGTON—A physician and the office manager of his medical practice, along with five owners of home health agencies, were arrested today on charges related to their alleged participation in a nearly $375 million health care fraud scheme involving fraudulent claims for home health services.
The arrests and charges were announced today by Deputy Attorney General James Cole and Health and Human Services (HHS) Deputy Secretary Bill Corr, along with Assistant Attorney General Lanny A. Breuer of the Justice Department’s Criminal Division; U.S. Attorney Sarah R. Saldaña of the Northern District of Texas; HHS Inspector General Daniel R. Levinson; Special Agent in Charge Robert E. Casey Jr. of the FBI’s Dallas Field Office; Dr. Peter Budetti, Deputy Administrator for Program Integrity for the Centers for Medicare and Medicaid Services (CMS); and the Texas Attorney General’s Medicaid Fraud Control Unit (MFCU).
The indictment, filed in the Northern District of Texas and unsealed today, charges Jacques Roy, M.D., 54, of Rockwall, Texas; Cynthia Stiger, 49, of Dallas; Wilbert James Veasey Jr., 60, of Dallas; Cyprian Akamnonu, 63, of Cedar Hill, Texas; Patricia Akamnonu, RN, 48, of Cedar Hill; Teri Sivils, 44, of Midlothian, Texas; and Charity Eleda, RN, 51, of Rowlett, Texas, each with one count of conspiracy to commit health care fraud. Roy also is charged with nine counts of substantive health care fraud, and Veasey, Patricia, Akamnonu and Eleda are each charged with three counts of health care fraud. Eleda also is charged with three counts of making false statements related to a Medicare claim. All the defendants are expected to make their initial appearances at 2:00 p.m. CST today in federal court in Dallas.
In addition to the indictment, CMS announced the suspension of an additional 78 home health agencies (HHA) associated with Roy based on credible allegations of fraud against them.
Today’s enforcement actions are the result of the Medicare Fraud Strike Force operations, which are part of the Health Care Fraud Prevention & Enforcement Action Team (HEAT). HEAT is a joint initiative announced in May 2009 between the Department of Justice and HHS to focus their efforts to prevent and deter fraud and enforce anti-fraud laws around the country.
“The conduct charged in this indictment represents the single largest fraud amount orchestrated by one doctor in the history of HEAT and our Medicare Fraud Strike Force operations,” said Deputy Attorney General Cole. “Thanks to the historic partnerships we’ve built to combat health care fraud, we are sending a clear message: If you victimize American taxpayers, we will track you down and prosecute you.”
“Thanks to our new fraud detection tools, we have greater abilities to identify the kind of sophisticated fraud scheme that previously could have escaped scrutiny,” said HHS Deputy Secretary Corr. “Our aggressive Medicare Fraud Strike Force operations have enabled us to break up a significant alleged fraud operation and the fraud-fighting authorities in the Affordable Care Act have allowed us to stop further payments to providers connected to this scheme. This case and our new detection tools are examples of our growing ability to stop Medicare fraud.”
According to the indictment, Dr. Roy owned and operated Medistat Group Associates P.A. in the Dallas area. Medistat was an association of health care providers that primarily provided home health certifications and performed patient home visits. Dr. Roy allegedly certified or directed the certification of more than 11,000 individual patients from more than 500 HHAs for home health services during the past five years. Between January 2006 and November 2011, Medistat certified more Medicare beneficiaries for home health services and had more purported patients than any other medical practice in the United States. These certifications allegedly resulted in more than $350 million being fraudulently billed to Medicare and more than $24 million being fraudulently billed to Medicaid by Medistat and HHAs.
“Today, the Medicare Fraud Strike Force is taking aim at the largest alleged home health fraud scheme ever committed,” said Assistant Attorney General Breuer. “According to the indictment, Dr. Roy and his co-conspirators, for years, ran a well-oiled fraudulent enterprise in the Dallas area, making millions by recruiting thousands of patients for unnecessary services, and billing Medicare for those services. In Dallas, and the eight other Medicare Fraud Strike Force cities, the Criminal Division and our partners in the U.S. Attorneys’ Offices will continue to crack down on Medicare fraud, and hold accountable those stealing from the public fisc.”
“Fraud schemes, like the one we allege Dr. Roy executed, represent the next wave of Medicare and Medicaid crime that we face,” said U.S. Attorney Saldaña. “As enforcement actions have ramped up, not only in the Dallas Metroplex, but in several other areas throughout the country, fraudsters are devising new ways to beat the system. Rest assured, however, that with the tools and resources our district’s Medicare Care Fraud Strike Force provides, we will meet this challenge head-on and bring indictments against those who seek to defraud these critical programs, and you, the taxpayer.”
“Using sophisticated data analysis we can now target suspicious billing spikes,” said HHS Inspector General Levinson. “In this case, our analysts discovered that in 2010, while 99 percent of physicians who certified patients for home health signed off on 104 or fewer people—Dr. Roy certified more than 5,000.”
“The FBI views health care fraud as a severe crime problem,” said FBI Special Agent in Charge Casey. “It causes increased costs for consumers, tax payers and health insurance plans, and degrades the integrity of our health care system and legitimate patient care. Today’s arrests by the Dallas Medicare Fraud Strike Force send a clear message to those persons who are not only defrauding our federal Medicare and Medicaid and private health insurance programs, but victimizing the elderly, the disadvantaged, and those who are at a vulnerable time in their lives due to legitimate health issues. The FBI will continue to dedicate a substantial amount of expert resources to investigate these crimes.”
The indictment alleges that Dr. Roy used HHAs as recruiters so that Medistat could bill unnecessary home visits and medical services. Dr. Roy and other Medistat physicians certified and recertified plans of care so that HHAs also were able to bill Medicare for home health services that were not medically necessary and not provided. In addition, Dr. Roy allegedly performed unnecessary home visits and ordered unnecessary medical services.
According to the indictment, Medistat maintained a “485 Department,” named for the number of the Medicare form on which the plan of care was documented. Dr. Roy allegedly instructed Medistat employees to complete the 485s by either signing his name by hand or by using his electronic signature on the document.
Three of the HHAs Dr. Roy used as part of the scheme were Apple of Your Eye Healthcare Services Inc., owned and operated by Stiger and Veasey; Ultimate Care Home Health Services Inc., owned and operated by Cyprian and Patricia Akamnonu; and Charry Home Care Services Inc., owned and operated by Eleda. According to the indictment, Veasey, Akamnonu, Eleda and others recruited beneficiaries to be placed at their HHAs so that they could bill Medicare for the unnecessary and not provided services. As part of her role in the scheme, Eleda allegedly visited The Bridge Homeless Shelter in Dallas to recruit homeless beneficiaries staying at the facility, paying recruiters $50 per beneficiary they found at The Bridge and directed to Eleda’s vehicle parked outside the shelter’s gates.
Apple allegedly submitted claims to Medicare from Jan. 1, 2006, through July 31, 2011, totaling $9,157,646 for home health services to Medicare beneficiaries that were medically unnecessary and not provided. Dr. Roy or another Medistat physician certified the services. From Jan. 1, 2006, to Aug. 31, 2011, Ultimate submitted claims for medically unnecessary home health services totaling $43,184,628. Charry allegedly submitted fraudulent claims from Aug. 1, 2008, to June 30, 2011, totaling $468,858 in medically unnecessary and not provided home health services.
The indictment alleges that Sivils, as Medistat’s office manager, helped facilitate the fraud scheme by, among other actions, supervising the processing of thousands of plans of care that contained Dr. Roy’s electronic signature and other Medistat physicians’ signatures, permitting HHAs to bill Medicare for unnecessary home health services and accepting cash payments from Cyprian Akamnonu in exchange for ensuring plans of care contained Dr. Roy or another Medistat physician’s signature.
As outlined in the government’s request to the court to detain Dr. Roy, in June 2011, CMS suspended provider numbers for Dr. Roy and Medistat based on credible allegations of fraud, thus ensuring Dr. Roy did not receive payment from Medicare. Immediately after the suspension, nearly all of Medistat’s employees started billing Medicare under the provider number for Medcare HouseCalls. The court document alleges that Dr. Roy was in fact in charge of day-to-day operations at Medcare, and that Dr. Roy continued to certify patients for home health despite the suspension.
Each charged count of conspiracy to commit health care fraud and substantive health care fraud carries a maximum penalty of 10 years in prison and a $250,000 fine. Each false statement charge carries a maximum penalty of five years in prison and a $250,000 fine. The indictment also seeks forfeiture of numerous items including funds in bank accounts, a sailboat, vehicles, and multiple pieces of property.
An indictment is merely an allegation and defendants are presumed innocent unless and until proven guilty beyond a reasonable doubt in a court of law.
The case is being prosecuted by Assistant U.S. Attorneys Michael C. Elliott, Mindy Sauter, and John DeLaGarza of the Northern District of Texas and Trial Attorney Ben O’Neil and Deputy Chief Sam S. Sheldon of the Criminal Division’s Fraud Section. The case was investigated by the FBI, HHS-OIG, and MFCU and was brought as part of the Medicare Fraud Strike Force, supervised by the Criminal Division’s Fraud Section and the U.S. Attorney’s Office for the Northern District of Texas.
Since their inception in March 2007, Medicare Fraud Strike Force operations in nine locations have charged more than 1,190 defendants who collectively have falsely billed the Medicare program for more than $3.6 billion.
To learn more about the HEAT Strike Force, please visit: http://www.stopmedicarefraud.gov.
The Wall Street Journal about the Murder of Alfred Herrhausen by STASI and RAF
NSA – National Security Video – The Invisible Battleground
The Nuclear Vault – “Nobody Wins a Nuclear War” But “Success” is Possible
General Curtis LeMay, mid-1957, sometime during his transition from Commander-in-Chief of the Strategic Air Command [1948-1957] to Vice Chief of Staff, U.S. Air Force [1957-1961]. [Photo source: U.S. National Archives, Still Pictures Division, RG 342B, Box 507 B&W]
“The Power of Decision” may be the first (and perhaps the only) U.S. government film dramatizing nuclear war decision-making. Commissioned by the Strategic Air Command in 1956, the film has the look of a 1950s TV drama, but the subject is the ultimate Cold War nightmare. By the end of the film, after the U.S. Air Force has implemented war plan “Quick Strike” following a Soviet surprise attack, millions of Americans, Russians, Europeans, and Japanese are dead. The narrator, a Colonel Dodd, asserts that “nobody wins a nuclear war because both sides are sure to suffer terrible damage.” Despite the “catastrophic” damage, one of the film’s operating assumptions is that defeat is avoidable as long as the adversary cannot impose its “will” on the United States. The film’s last few minutes suggest that the United States would prevail because of the “success” of its nuclear air offensive. Moscow, not the United States, is sending out pleas for a cease-fire.
The conviction that the United States could prevail was a doctrinal necessity because Air Force leaders assumed the decisiveness of air power. The founding fathers of the U.S. Air Force came out of World War II with an unshakeable, if exaggerated, conviction that the strategic bombing of Germany and Japan had been decisive for the Allied victory and that air power would be crucial in future conflicts. (Note 1) The film’s title: “Power of Decision” embodies that conviction. The title itself is a reference to a 1948 statement by General George C. Kenney, the Strategic Air Command’s first commander-in-chief: “A war in which either or both opponents use atomic bombs will be over in a matter of days…The Air Force that is superior in its capability of destruction plays the dominant role and has the power of decision.” (Note 2) A confident statement made by one of the characters, General “Pete” Larson, near the close of reel 6 flows from that assumption: the Soviets “must quit; we have the air and the power and they know it.”
The story begins with Colonel Dodd, standing in the underground command post of the “Long Range Offense Force” (oddly, the Strategic Air Command is never mentioned by name). Dodd discusses the Force’s strike capabilities, its mechanisms for keeping track of its strategic assets, and its war plans. That hundreds of bombers, based in U.S. territories and overseas bases, are ready to launch at a moment’s notice is the “surest way to prevent war.” Dodd does not think that the Soviets are likely to strike, but if deterrence fails and the Soviets launch an attack, “this is what will happen.”
What “happens” is the initial detection by U.S. air defense network of the approach of Soviet bombers over the Arctic Circle. That leads to General Larson’s decision to launch the SAC alert force under plan “Quick Strike”; airborne and nuclear-armed alert bombers fly toward the Soviet periphery, but stay at position until they receive an attack order (this was the concept of “Fail Safe” or “Positive Control” although those terms were not used in the film). About an hour after the alert force is launched, General Larson receives reports of attacks on U.S. bases, followed by more information on Soviet nuclear attacks on cities and military bases in Japan and Western Europe. “That does it,” General Turner (one of Larson’s deputies) exclaims. He soon receives a call on the red phone from the Joint Chiefs, who with the President, are in a protected command post. The president has ordered the execution of “Quick Strike,” releasing bombers and missiles to strike the Soviet Union. This simultaneous bomber-missile “double punch” is aimed at “all elements of [Soviet] air power” [bomber bases] along with “war making and war sustaining resources,” which meant strikes on urban-industrial areas and urban populations. To depict the undepictable, the film’s producers use stock footage of nuclear tests and missile and bomber launches.
Once it is evident that the Soviets have launched a surprise air attack, Colonel Dodd observes that “By giving up the initiative, the West must expect to take the first blow.” This statement is not developed, but for Air Force planners, “initiative” meant a preemptive attack or a first strike. By the early 1950, senior military planners and defense officials had begun considering the possibility of pre-emptive attacks on the basis of strategic warning; that is, if the United States intelligence warning system collected reliable information on an impending Soviet attack, decision-makers could approve strikes against Soviet military forces to disrupt it. (Note 3) Consistent with this, Strategic Air Command war plans assumed “two basic modes” for executing strike plans [See Document One below]. (Note 4) One was retaliation against a surprise attack; the other “plan was based on the assumption that the United States had strategic warning and had decided to take the initiative.” The SAC strike force would then be “launched to penetrate en masse prior to the enemy attack; the main target would be the enemy’s retaliatory capability.”
In the last part of reel 6, Air Force intelligence briefings review the destruction of the Soviet military machine, including destruction of air bases, weapons storage centers, and government control centers, among other targets. “Target M,” presumably Moscow, has “been destroyed” by a nuclear weapon which struck 300 yards from the aiming point. The Soviet attack has done calamitous damage to the United States, with 60 million casualties, including 20 million wounded, but evidence was becoming available of the “success” of the U.S. air offensive. The Soviet Air Force has been reduced to a handful of aircraft, it had stopped launching nuclear strikes outside of its territory, and SACEUR [Supreme Allied Commander Europe] reports the “complete disintegration of resistance” by Soviet ground forces. Moreover, cease-fire requests are coming in from the Soviets. In this context, General Larson’s certainty that the “Soviets must quit” conveyed prevailing assumptions about the value of strategic air power.
Around the time when “The Power of Decision” as being produced, a statement by SAC Commander-in-Chief General Curtis LeMay made explicit what was implicit in Larson’s observation. In an address before the Air Force’s Scientific Advisory Board in 1957 [see Document Two], LeMay argued that U.S. strategic forces could not be an effective deterrent unless they were “clearly capable of winning under operational handicaps of bad weather and no more than tactical warning.” And by winning, LeMay said he meant “achieving a condition wherein the enemy cannot impose his will on us, but we can impose our will on him.” Larson’s statement about control of the air dovetailed exactly with LeMay’s assumptions about winning.
Little is known about the production and distribution of “The Power of Decision,” or even if it was actually shown. According to the history of the Air Photographic and Charting Service for January through June 1957, on 28 May 1956, the Strategic Air Command requested the service to produce the film, which would be classified Secret. SAC leaders may have wanted such a film for internal indoctrination and training purposes, to help officers and airmen prepare themselves for the worst active-duty situation that they could encounter. Perhaps the relatively unruffled style of the film’s performers was to serve as a model for SAC officers if they ever had to follow orders that could produce a nuclear holocaust. In any event, the script for “Power of Decision” was approved on 10 May 1957 and a production planning conference took place on 29 May 1957. The contract productions section of the Air Photographic and Charting Service was the film’s producing unit. (Note 5)
The next step was to find actors with security clearances because even the synopsis of the film was classified secret (although later downgraded to “official use only”). As the Air Force was not in the business of hiring actors, the production unit engaged the services of MPO Productions, a New York-based firm which produced commercials and industrial films. [References to MPO, Inc. are on the index cards and on “The End” frame at the close of reel 6]. What happened next, when the work on the film was completed, SAC’s assessment of the project, and whether, when, or where the film was shown, cannot presently be determined, although the information may be in the living memories of participants or viewers from those days.
Note: The relatively poor quality of this digital reproduction reflects the condition of the original reels as turned over to the National Archives by the Air Force.
Notes
1. For the development of ideas about air power and strategic bombing, see Tami Davis Biddle, Rhetoric and Reality in Air Warfare: The Evolution of British and American Ideas about Strategic Bombing, 1941–1945 ( Princeton University Press, 2002). See page 293 for “overselling” of air power. See also Gian Peri Gentile, “Advocacy or Assessment? The United States Strategic Bombing Survey of Germany and Japan,” Pacific Historical Review 66 (1997): 53-79.
2. Quotation from Headquarters, Strategic Air Command, History of Strategic Air Command, July-December 1959, Volume I, 191. Information provided by Mr. Barry Spink, U.S. Air Force Historical Research Agency (AFHRA), Maxwell Air Force Base, Alabama, e-mail 17 May 2010. After his unsuccessful tour as first Commander-in-Chief Strategic Air Command, Kenney become notorious for his endorsement of preventive war against the Soviet Union. See Marc Trachtenberg, History and Strategy Princeton: Princeton University Press, 1991), 106.
3. See Trachtenberg, History and Strategy, 134-135.
4. For a briefing by SAC commander-in-chief Curtis LeMay of the nuclear war plan, see David A. Rosenberg, “Smoking Radiating Ruin at the End of Two Hours”: Documents on American Plans for Nuclear War with the Soviet Union, 1954-55,” International Security, 6 (Winter, 1981-1982): 3-38.
5. Information from “Air Photographic and Charting Service history for January through June 1957,” provided by Mr. Barry Spink, AFHRA e-mail 13 May 2010.
Unveiled – The U.S. Intelligence Community

1 9 4 7 – 1 9 8 9
Capable of flying three times faster than the speed of sound, the exact speed limit and operational ceiling of Lockheed’s recently retired SR-71 “spy plane” remain classified (Wide World Photos).
- Picture: One of several overseas ground stations critical to U.S intelligence, the Joint Defense Space Research Facility at Alice Springs, Australia controls and receives data from U.S signals intelligence satellites (Desmond Ball).
- Document1: Top secret memo signed by President Harry Truman established a special communications (COMINT) committee and served to supervise the super-secret National Security Agency.
- Document2: One of a rarely released series (DCI Directives), William Casey’s confidential directive of October 12, 1982 established a human intelligence (HUMINT) gathering committee.
Intelligence Origins and Operations
Spies in trench coats. Lightning-fast reconnaissance planes. Super-secret photo satellites. International eavesdropping. All make up an enormous multi-billion dollar bureaucracy that collects intelligence and carries out covert operations for the United States. The U.S. Intelligence Community reveals the bureaucratic reality often missing in the dramatic fables of best-selling spy novels. Here, previously inaccessible organizations and function manuals, unit histories, and internal directives provide researchers with the most comprehensive structural portrait of the U.S. espionage establishment ever published.
The U.S. Intelligence Community: Organization, Operations and Management, 1947-1989
Focus of the Collection
The U.S. Intelligence Community collection contains over 15,000 pages of documents–many only recently declassified–from key intelligence organizations. The majority of these documents are heretofore unpublished materials acquired through Freedom of Information Act (FOIA) requests. The Archive painstakingly cataloged, indexed and arranged these documents by organization and intelligence activity.
It details the evolution of the U.S. intelligence community and the structure, activities and distribution of tasks among the twenty-five intelligence organizations that comprise the community. It looks at the bureaucratic reality underlying the most secret operations of the U.S. government, and highlights the complexity of the intelligence apparatus in the U.S. and the involvement of a diverse number of agencies in intelligence programs. It offers a greater understanding of the regulations, directives and manuals that have guided the organization and functions of the U.S. intelligence community, as well as the directives and committees employed to coordinate this complicated system. Of additional interest is the inclusion of the assessment of the intelligence community’s performance by various outside commissions.
Inner Workings of Secret Agencies
Organizational manuals present detailed information regarding the structure of the agencies, their divisions and subdivisions. Specific agency regulations give a clear picture of the role each agency plays in intelligence gathering and the activities assigned to each. Histories contain background information concerning an agency’s origins, structure and operations and provide a direction for further research. Directives divide responsibilities among different agencies and create mechanisms for coordinating intelligence activities.
Researchers can use manuals and histories provided in this collection to discover information not available elsewhere. For example, the Central Intelligence Agency considers classified the titles of National Intelligence Estimates (NIEs) and information on the subcommittees of the National Foreign Intelligence Board. However, researchers will find these titles and information in U.S. military intelligence histories and regulations that have been declassified and released by intelligence elements within the Department of Defense.
Insight into U.S. Intelligence Activities
The materials in the collection shed light upon issues important to U.S. foreign and defense policy. Evidence of U.S. espionage and counterintelligence activities abroad, international intelligence agreements and discussions of China’s initiative to build “the bomb” are found among these documents.
Through these documents researchers will become aware of the surprising number of agencies involved in intelligence work. Intelligence on Latin America has been collected and analyzed by the Central Intelligence Agency, the Defense Intelligence Agency, the State Department Bureau of Intelligence and Research, the Army Intelligence and Threat Analysis Center, and the Southern Command (J-2) (Intelligence Directorate). Foreign space programs have been studied and documented by the Central Intelligence Agency, the Defense Intelligence Agency, the Air Force Foreign Technology Division, the Army Missile and Space Intelligence Center, and the Naval Technical Intelligence Center. Scholars will need these primary materials for background and direction in seeking out appropriate agencies to further their own FOIA requests.
Unprecedented Indexing Makes Every Document Accessible
The Archive prepares extensive, printed finding aids for the collection. The Guide contains an events chronology, glossaries of key individuals, acronyms and technical terms, a bibliography of relevant secondary sources and a document catalog. Organized by intelligence agency and intelligence activity, the catalog facilitates browsing through the document collection and allows researchers to preview key details within documents before perusing the microfiche. The Index contains a rich contextual cross-reference to subjects and names. The detail provided in each allows researchers to pinpoint relevant documents in their particular area of study.
The Collection Is a Necessity For
- Scholars and students of: intelligence organizations and operations, regional and strategic studies, politics and intra-government coordination
- Teachers of government and political science courses
- Librarians and bibliographers
- Investigative reporters
- Government officials and contractors
- Concerned citizens
Documents in the Collection Include:
- Organization and Functions Manuals
- Internal Classified Histories
- Studies of Intelligence Community Performance Regulations
- National Security Council Intelligence Directives
- Director of Central Intelligence Directives
Key Intelligence Organizations Include:
- National Security Council
- Office of the Director of Central Intelligence
- Central Intelligence Agency
- National Security Agency
- Defense Intelligence Agency
- Army Intelligence and Security Command
- Navy Operational Intelligence Center
- Air Force Foreign Technology Division
- Unified and Specified Command Intelligence Directorates
- Department of State, Bureau of Intelligence and Research
Sample Document Titles
- DIA, Defense Intelligence Organization: Operations and Management, 1979
- Harry S. Truman, Communications Intelligence Activities, October 24,1952 (The Charter of the National Security Agency)
- Department of Justice, Report on CIA-Related Electronic Surveillance Activities, 1976
- Central Intelligence Agency, The Chinese Communist Atomic Energy Program, 1960
- INSCOM Regulation 10-2, Organization and Functions, United States Army Intelligence and Security Command, April 1, 1982
- National Security Council Intelligence Directive No. 5, U.S. Espionage and Counterintelligence Activities Abroad, various dates
- United States Signals Intelligence Directive 4, SIGINT Support to Military Commanders, July 1, 1974
- Director of Central Intelligence Directive 3/4, Production of Guided Missile and Astronautics Intelligence, 1965
- Central Intelligence Agency, Report on CIA Chilean Task Force Activities, 15 September to 3 November 1970
- National Security Agency, NSA Organizational Manual, October 21, 1986
- Naval Security Group Command, Annual History Report for 1985; Golden Anniversary Celebration: 1935-1985
Overview
Title:
- The U.S. Intelligence Community: Organization, Operations and Management, 1947-1989
- Content:
- Reproduces on microfiche over 15,000 pages of documents from key intelligence organizations.
- Arrangement and Access:
- Documents pertaining to agency structure, organization and responsibility are grouped by agency. Documents pertaining to inter-agency intelligence activities are grouped by activity. The unique identification numbers assigned to documents are printed in eye-legible type at the top right hand corner of the microfiche strip.
- Standards:
- Documents are reproduced on silver halide positive-reading microfiche at a nominal reduction of 24x in envelopes. They are archivally permanent and conform to NMA and BSI standards. Any microfiche found to be physically substandard will be replaced free of charge.
- Indexing:
- A printed guide and index accompanies the microfiche collection. Volume I contains an events chronology, glossaries of key individuals, acronyms and technical terms, a bibliography of secondary sources and a document catalog. Volume II is an index providing in-depth, document-level access to names, subjects and organizations.
- Date of Publication:
- December 1990
- Orders and Inquiries
The U.S. Intelligence Community: Editorial Board
- William E. Burrows, Professor of Journalism Director, Science and Environmental Reporting Program, New York University Author, Deep Black: Space Espionage and National Security
- David Kahn, Author, The Code Breakers and Hitler’s Spies
- John Prados, Author, The Soviet Estimate: U.S. Intelligence Analysis and Russian Military Strength
National Security Archive Project Staff
- Jeffrey T. Richelson, Ph.D., Political Science Project Consultant
- Dr. Richelson is a Senior Fellow at the National Security Archive and served as a special consultant in the production of this document set. He is noted for his scholarship in the field of U.S. and foreign intelligence and has authored numerous books, articles and reviews that have illuminated the organization, structure and activities of the intelligence community. He has written about the U.S. intelligence community (The U.S. Intelligence Community, 1985), the Soviet intelligence apparatus (Sword and Shield, 1986), a variety of foreign intelligence organizations (Foreign Intelligence Organizations, 1988), the U.S. intelligence operation directed at the Soviet Union (American Espionage and the Soviet Target, 1987), and the history of U.S. spy satellites (America’s Secret Eyes in Space, 1990).
- Jonathan Stier, Catalog Editor Ricardo Aguilera, Cataloger Glenn Baker, Project Analyst Wendy Simmons, Senior Indexer Joyce Battle, Indexer Lisa Thompson, Indexer Jeanne Valentine, Research Assistant Joseph Pittera, Research Assistant
Praise for The U.S. Intelligence Community, 1947-1989
“The National Security Archive represents an idea that is so obvious–once you think of it–that it instantly makes the transition from novelty to necessity. The desirability of collecting in one location all the declassified and unclassified documentation on U.S. foreign policy is so compelling that we are certain to ask ourselves very soon how we managed to get along without it. . .All of us who have a professional interest in contemporary security and foreign policy issues can only rejoice at the appearance of this new institutional resource.”
Gary Sick
Adjunct Professor of Middle East Politics
Columbia University
Revealed – U.S. Army Afghanistan and Pakistan Suicide Attacks Reports

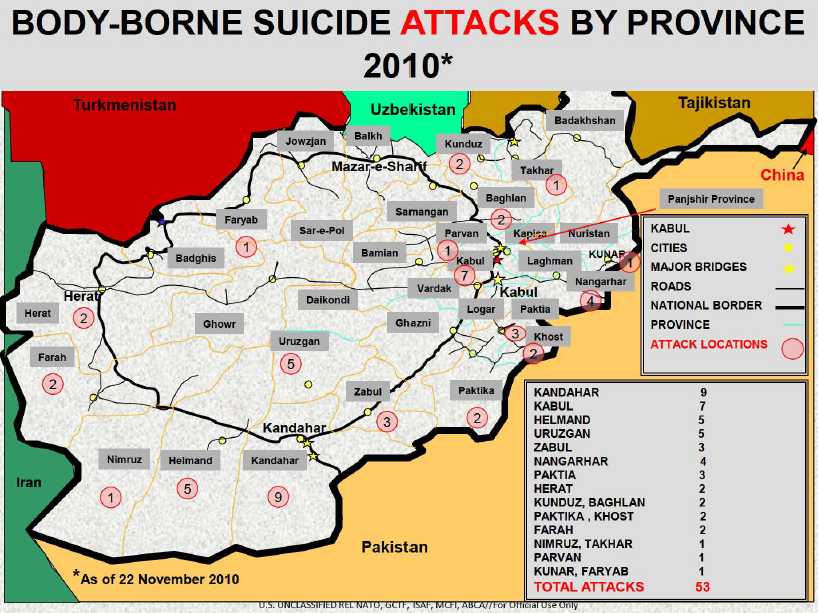
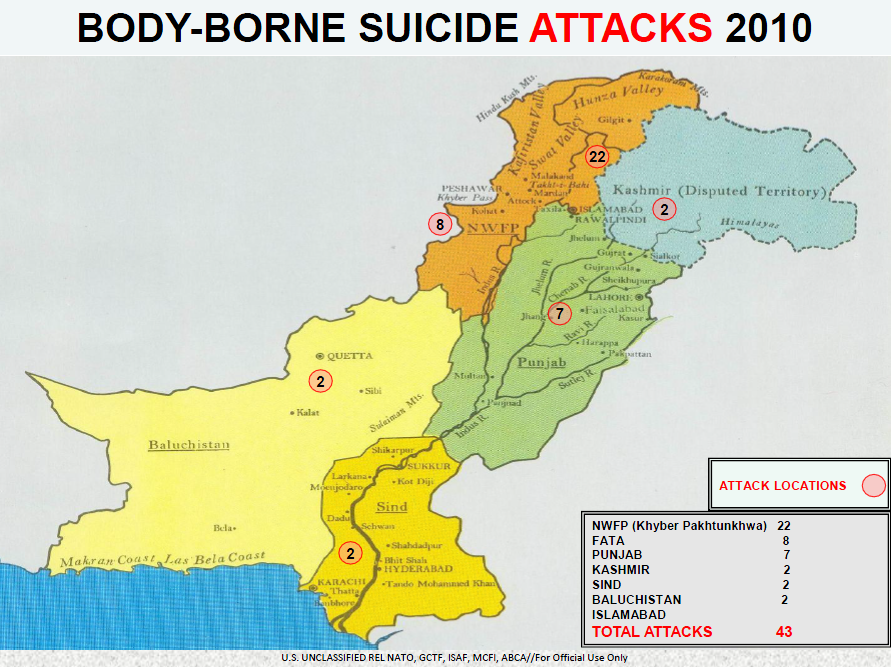
The FBI reports – Brooklyn Man Sentenced to 27 Years in Prison for Conspiring to Kill U.S. Soldiers
Betim Kaziu was sentenced today to 27 years’ imprisonment for conspiring to kill U.S. soldiers abroad and related terrorism charges. On July 7, 2011, following a two-week trial before United States District Judge John Gleeson in Brooklyn federal court, the defendant was convicted of conspiring to commit murder overseas, conspiring to provide material support to terrorism, attempting to provide material support to a foreign terrorist organization, and conspiring to use a machine gun in furtherance of those crimes.
The sentence was announced by Loretta E. Lynch, United States Attorney for the Eastern District of New York.
The evidence at trial established that the defendant traveled from Brooklyn to Cairo, Egypt in February 2009 in order to wage violent jihad against United States troops in the Middle East and the Balkans. While in Cairo, the defendant also attempted to acquire automatic weapons and to travel to Somalia to join al Shabaab, a Somali terrorist organization allied with al Qaeda. Ultimately, the defendant traveled to Kosovo in an effort to target American troops stationed there or to travel onward to Pakistan to join al Qaeda. The defendant also recorded a martyrdom video on the Albanian coast of his “last few moments” before he expected to depart for jannah, or paradise, reserved for martyrs. Shortly thereafter, on August 27, 2009, the defendant was arrested in Kosovo by the Kosovo Police Service. He was then transferred to the custody of agents and detectives of the New York Joint Terrorism Task Force to face terrorism charges filed in the Eastern District of New York. At the time of his arrest, the defendant had already purchased a ticket to travel to Pakistan on September 15, 2009.
Testimony at trial established that Kaziu had been radicalized, in part, by Internet speeches by Anwar al-Awlaki and propaganda videos produced by al Qaeda and al Shabaab. The government also introduced at trial evidence from the defendant’s social networking website, including quotes by Osama Bin Laden.
United States Attorney Lynch thanked the New York Joint Terrorism Task Force, the government of Kosovo, the U.S. State Department, the Department of Justice Office of International Affairs, and the New York City Police Department for their assistance.
The government’s case was prosecuted by Assistant United States Attorneys Shreve Ariail, Seth D. DuCharme and Ali Kazemi, with assistance provided by Joanna Baltes of the National Security Division.
The Defendant
BETIM KAZIU
Age: 23
UNCENSORED – FEMEN Protest Putin Election – Pictures
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-putin/pict0.jpg) Police officers detain one of the activists of Ukrainian group Femen trying to protest at a polling station in Moscow, March 4, 2012, shortly after Russia’s Prime Minister and presidential candidate Vladimir Putin cast his ballot. The sign on the girl reads: ‘I steal for Putin!’ The slogan refers to the term ‘party of crooks and thieves’ to describe Vladimir Putin’s United Russia party. Russians voted today in presidential polls expected to return Putin to the Kremlin for a record third term, despite a wave of protests against his 12 years of domination. Getty Police officers detain one of the activists of Ukrainian group Femen trying to protest at a polling station in Moscow, March 4, 2012, shortly after Russia’s Prime Minister and presidential candidate Vladimir Putin cast his ballot. The sign on the girl reads: ‘I steal for Putin!’ The slogan refers to the term ‘party of crooks and thieves’ to describe Vladimir Putin’s United Russia party. Russians voted today in presidential polls expected to return Putin to the Kremlin for a record third term, despite a wave of protests against his 12 years of domination. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-putin/pict9.jpg) Police officers detain activists of Ukrainian group Femen trying to protest at a polling station in Moscow, March 4, 2012, shortly after Russia’s Prime Minister and presidential candidate Vladimir Putin cast his ballot. The sign on the front girl reads: ‘I steal for Putin!’ The slogan reffers to the term ‘party of crooks and thieves’ to describe Vladimir Putin’s United Russia party. Russians voted today in presidential polls expected to return Putin to the Kremlin for a record third term, despite a wave of protests against his 12 years of domination. Getty Police officers detain activists of Ukrainian group Femen trying to protest at a polling station in Moscow, March 4, 2012, shortly after Russia’s Prime Minister and presidential candidate Vladimir Putin cast his ballot. The sign on the front girl reads: ‘I steal for Putin!’ The slogan reffers to the term ‘party of crooks and thieves’ to describe Vladimir Putin’s United Russia party. Russians voted today in presidential polls expected to return Putin to the Kremlin for a record third term, despite a wave of protests against his 12 years of domination. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-putin/pict12.jpg) Polling station officials clash with topless members of Ukrainian feminist group FEMEN members at a polling station in Moscow on Sunday, March 4, 2012. Written on the bodies of the radically anti-Putin protesters is the slogan “I steal for Putin”, referring to their symbolic act of trying to steal votes. Polling stations have opened across Russia’s vast expanse for the presidential election widely expected to return Vladimir Putin to the Kremlin. (Misha Japaridze) Polling station officials clash with topless members of Ukrainian feminist group FEMEN members at a polling station in Moscow on Sunday, March 4, 2012. Written on the bodies of the radically anti-Putin protesters is the slogan “I steal for Putin”, referring to their symbolic act of trying to steal votes. Polling stations have opened across Russia’s vast expanse for the presidential election widely expected to return Vladimir Putin to the Kremlin. (Misha Japaridze) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-putin/pict4.jpg) Police officers detain activists of Ukrainian group Femen trying to protest at a polling station in Moscow, March 4, 2012, shortly after Russia’s Prime Minister and presidential candidate Vladimir Putin cast his ballot. The sign on the front girl reads: ‘I steal for Putin!’ The slogan reffers to the term ‘party of crooks and thieves’ to describe Vladimir Putin’s United Russia party. Russians voted today in presidential polls expected to return Putin to the Kremlin for a record third term, despite a wave of protests against his 12 years of domination. Getty Police officers detain activists of Ukrainian group Femen trying to protest at a polling station in Moscow, March 4, 2012, shortly after Russia’s Prime Minister and presidential candidate Vladimir Putin cast his ballot. The sign on the front girl reads: ‘I steal for Putin!’ The slogan reffers to the term ‘party of crooks and thieves’ to describe Vladimir Putin’s United Russia party. Russians voted today in presidential polls expected to return Putin to the Kremlin for a record third term, despite a wave of protests against his 12 years of domination. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-putin/pict7.jpg) Police officers detain activists of Ukrainian group Femen trying to protest at a polling station in Moscow, March 4, 2012, shortly after Russia’s Prime Minister and presidential candidate Vladimir Putin cast his ballot. Russians voted today in presidential polls expected to return Putin to the Kremlin for a record third term, despite a wave of protests against his 12 years of domination. Getty Police officers detain activists of Ukrainian group Femen trying to protest at a polling station in Moscow, March 4, 2012, shortly after Russia’s Prime Minister and presidential candidate Vladimir Putin cast his ballot. Russians voted today in presidential polls expected to return Putin to the Kremlin for a record third term, despite a wave of protests against his 12 years of domination. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-putin/pict5.jpg) Police officers detain activists of Ukrainian group Femen trying to protest at a polling station in Moscow, March 4, 2012, shortly after Russia’s Prime Minister and presidential candidate Vladimir Putin cast his ballot. The sign on the front girl reads: ‘I steal for Putin!’ The slogan reffers to the term ‘party of crooks and thieves’ to describe Vladimir Putin’s United Russia party. Russians voted today in presidential polls expected to return Putin to the Kremlin for a record third term, despite a wave of protests against his 12 years of domination. Getty Police officers detain activists of Ukrainian group Femen trying to protest at a polling station in Moscow, March 4, 2012, shortly after Russia’s Prime Minister and presidential candidate Vladimir Putin cast his ballot. The sign on the front girl reads: ‘I steal for Putin!’ The slogan reffers to the term ‘party of crooks and thieves’ to describe Vladimir Putin’s United Russia party. Russians voted today in presidential polls expected to return Putin to the Kremlin for a record third term, despite a wave of protests against his 12 years of domination. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-putin/pict6.jpg) Police officers detain activists of Ukrainian group Femen trying to protest at a polling station in Moscow, March 4, 2012, shortly after Russia’s Prime Minister and presidential candidate Vladimir Putin cast his ballot. Russians voted today in presidential polls expected to return Putin to the Kremlin for a record third term, despite a wave of protests against his 12 years of domination. Getty Police officers detain activists of Ukrainian group Femen trying to protest at a polling station in Moscow, March 4, 2012, shortly after Russia’s Prime Minister and presidential candidate Vladimir Putin cast his ballot. Russians voted today in presidential polls expected to return Putin to the Kremlin for a record third term, despite a wave of protests against his 12 years of domination. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-putin/pict2.jpg) Police officers detain one of the activists of Ukrainian group Femen trying to protest at a polling station in Moscow, March 4, 2012, shortly after Russia’s Prime Minister and presidential candidate Vladimir Putin cast his ballot. The sign on the girl reads: ‘I steal for Putin!’ The slogan refers to the term ‘party of crooks and thieves’ to describe Vladimir Putin’s United Russia party. Russians voted today in presidential polls expected to return Putin to the Kremlin for a record third term, despite a wave of protests against his 12 years of domination. Police officers detain one of the activists of Ukrainian group Femen trying to protest at a polling station in Moscow, March 4, 2012, shortly after Russia’s Prime Minister and presidential candidate Vladimir Putin cast his ballot. The sign on the girl reads: ‘I steal for Putin!’ The slogan refers to the term ‘party of crooks and thieves’ to describe Vladimir Putin’s United Russia party. Russians voted today in presidential polls expected to return Putin to the Kremlin for a record third term, despite a wave of protests against his 12 years of domination. |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-putin/pict3.jpg) Police officers detain one of the activists of Ukrainian group Femen trying to protest at a polling station in Moscow, March 4, 2012, shortly after Russia’s Prime Minister and presidential candidate Vladimir Putin cast his ballot. The sign on the girl reads: ‘I steal for Putin!’ The slogan refers to the term ‘party of crooks and thieves’ to describe Vladimir Putin’s United Russia party. Russians voted today in presidential polls expected to return Putin to the Kremlin for a record third term, despite a wave of protests against his 12 years of domination. Getty Police officers detain one of the activists of Ukrainian group Femen trying to protest at a polling station in Moscow, March 4, 2012, shortly after Russia’s Prime Minister and presidential candidate Vladimir Putin cast his ballot. The sign on the girl reads: ‘I steal for Putin!’ The slogan refers to the term ‘party of crooks and thieves’ to describe Vladimir Putin’s United Russia party. Russians voted today in presidential polls expected to return Putin to the Kremlin for a record third term, despite a wave of protests against his 12 years of domination. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-putin/pict1.jpg) Police officers detain one of the activists of Ukrainian group Femen trying to protest at a polling station in Moscow, March 4, 2012, shortly after Russia’s Prime Minister and presidential candidate Vladimir Putin cast his ballot. The sign on the girl reads: ‘I steal for Putin!’ The slogan refers to the term ‘party of crooks and thieves’ to describe Vladimir Putin’s United Russia party. Russians voted today in presidential polls expected to return Putin to the Kremlin for a record third term, despite a wave of protests against his 12 years of domination. Getty Police officers detain one of the activists of Ukrainian group Femen trying to protest at a polling station in Moscow, March 4, 2012, shortly after Russia’s Prime Minister and presidential candidate Vladimir Putin cast his ballot. The sign on the girl reads: ‘I steal for Putin!’ The slogan refers to the term ‘party of crooks and thieves’ to describe Vladimir Putin’s United Russia party. Russians voted today in presidential polls expected to return Putin to the Kremlin for a record third term, despite a wave of protests against his 12 years of domination. Getty |
| Fashion Week Milan Protest |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-putin/pict10.jpg) Members of the radical feminist group Femen protest at the entrance of the Versace Fall-winter 2012-2013 show on February 24, 2012 during the Women’s fashion week in Milan. Getty Members of the radical feminist group Femen protest at the entrance of the Versace Fall-winter 2012-2013 show on February 24, 2012 during the Women’s fashion week in Milan. Getty |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-putin/pict11.jpg) Members of the radical feminist group Femen are blocked by police as they protest at the entrance of the Versace Fall-winter 2012-2013 show on February 24, 2012 during the Women’s fashion week in Milan. Members of the radical feminist group Femen are blocked by police as they protest at the entrance of the Versace Fall-winter 2012-2013 show on February 24, 2012 during the Women’s fashion week in Milan. |
VIDEO – Who are FEMEN?
TV – Obama singing and Putin on Piano
President O’Bama and Russian prime Minister Vladmir Putin got together to have a live piano recital. Unfortunately Putin doesn’t know how to play piano and O’Bama doesn’t know how to sing. All hell breaks loose.
SECRET – Deterence 2.0 – Violent No-State Actors in Cyberspace

he chapters before you were born from the examination of two fundamental questions regarding the nature and theory of deterrence in the 21st century. First we had to consider what had changed since our victory in the Cold War (the experience from which most of our current doctrine is derived); and, armed with that understanding, consider how the United States might execute deterrence strategy in this new era. Our study revealed elemental shifts in the state of play that required more than “tweaking” on the margins of our thinking. Our observations compelled us to challenge the epistemological underpinnings of traditional nation-state deterrence models. What can be held at risk as we seek to deter the violent metastasis of ideas propagated over the Internet? How can we prevail in a global marketplace of ideas without compromising our own sacred values? The enclosed pages contain comments, insights and recommendations that transcend any thinking about deterrence that has ever gone before those of us in uniform. As evidenced by the sage words of James Fallows in the Foreword to this report, the ideas contained within are “worth reading.” The Deterrence of Violent Non-State Actor Workshop during the period of 9-10 January 2008 was a special event that was both compelling and timely.
So what has changed? Of course, the answer is rather obvious yet curiously underrepresented in the recent deterrence scholarship. Humanity is undergoing a transformation from the Industrial Age characterized by machinery, factories, urbanization and measured change where resources, production and optimization were the source of wealth and power, to an Information Age, defined by knowledge and networks, interconnectedness, globalization, adaptability, agility, innovation and rapid change. New rules sets are emerging that cannot be predicted and with them come opportunities, creativity and societal dislocations that often breed violence and instability.
Like Damocles’ sword, this global interconnectivity both strengthens us and moderates us at the same time. We are strengthened because we are better connected to others than ever before and thus capable of spreading the seeds of liberty and opportunity to populations that yearn for it and where the lack of it is still being justified. We are moderated by this interconnectivity because others can more easily exploit the seams and turn our freedoms against us to infect with vitriolic propaganda that violently radicalizes populations across this interconnected web. It is the matter of moderation of our strength that brought together the remarkable group of thinkers whose words are reflected within this report. We are concerned here with the problem of deterring violent non-state actors from doing harm to our nation and to our allies. The questions of extending freedom through access while mitigating the misuse of that freedom to harm us were the dominant questions we took up in this workshop. This report captures the intellectual power and dynamic interactions that took place during these two days and must be read by today’s and tomorrow’s decision-makers. These thoughts will inform the planning and execution of deterrence principles for years to come.
…
5 Models of Emergent Behavior of Violent Non-State Actors in Cyberspace
by Robert Popp, National Security Innovations; Laura Mariano, University of Connecticut;
Krishna Pattipati, University of Connecticut; Victor Asal, State University of NY at Albany; and
Katya Drozdova, National Security Innovations.
Executive Summary – Chapter 5
For violent non-state actors (VNSAs) on a mission to spread their message, or cyberterrorists who just want to create mischief, cyberspace offers limitless resources and opportunities for achieving these goals. The Internet is unparalleled in its ability to grant individuals access to a mass audience in an environment that has almost no enforceable personal conduct regulations or monitoring capabilities. According to a report compiled by Dr. Gabriel Weimann of the United States Institute of Peace, as of 2004, all active terrorist groups had established a Web presence of some kind, with the intention of exposing current and potential supporters, as well as enemies, to their ideologies (Weimann, 2004). The behavior of such groups in cyberspace has been studied extensively and can be broadly classified by the impact it has on the cyber and corporeal realms. Figure 1 below depicts this interaction and categorizes the behavior according to its origin and impact. Cyber-psychological activities include dissemination of propaganda and disinformation, intimidation, and indoctrination via cyber-based communication channels. Cyber-cyber interactions describe efforts to negatively impact the cyber infrastructure, while attacks planned via cyber means that target the corporeal realm are illustrative of the cyber-corporeal connection. A final category of interaction that is germane to this discussion is the corporeal-cyber connection, which represents actions originating in the corporeal realm that affect the cyber infrastructure. Table 1 below provides examples of recent actions from each of these categories. This chapter focuses on the cyber-psychological and cyber-corporeal connections, with further discussion of the use of cyberspace by VNSAs to disseminate propaganda, recruit members, create publicity, collect and share data, network, plan, coordinate, raise funds, and wage psychological warfare (Weimann, 2004).
The wide-ranging and covert nature of VNSA activity in cyberspace makes modeling their emergent behavior a difficult task that requires a large-scale, multidisciplinary effort. The current paradigm combines technology and perspectives from the sub-disciplines of data collection, data mining and analysis, and predictive modeling; each of these contributes a piece to the puzzle. Automated data collection techniques address the issue of extracting “clean,” meaningful, and relevant information from the seemingly limitless datasets that constitute the cyberspace. The methodology must be able to locate a “needle-in-a-haystack”, since the activity is often intentionally hidden, scattered across many sites, and frequently moved or removed. However, without the kind of content-rich datasets that data collection techniques can provide, modeling is cumbersome and time consuming, if not infeasible. An example of such a dataset is the so-called ‘Dark Web’ collection, which contains about two terabytes (2 TB) of extremist/terrorist related content collected using a semi-automated Web-crawling approach developed by researchers at the University of Arizona’s Artificial Intelligence Lab (Univ. of Arizona, 2008).
DOWNLOAD ORIGINAL DOCUMENT HERE
CONFIDENTIAL -DHS Infrastructure Protection Note: Evolving Threats to the Homeland

(U//FOUO) The Office of Infrastructure Protection (IP) Homeland Infrastructure Threat and Risk Analysis Center (HITRAC) produces Infrastructure Protection Notes to address issues impacting the infrastructure protection community’s risk environment from terrorist threats and attacks, natural hazards, and other events. Based on the analysis within the DHS Office of Intelligence and Analysis product Evolution of the Terrorist Threat to the United States this IP Note outlines the evolution of terrorist threats and impacts to the Nation’s critical infrastructure.
(U) KEY FINDINGS
- (U//FOUO) Given recent terrorist activity, homeland security partners should operate under the premise that other operatives are in the country and could advance plotting with little or no warning.
- (U//FOUO) Al-Qa’ida and its affiliates are focusing on smaller operations in the United States that are harder to detect but more likely to succeed than the large-scale attacks they once emphasized.
- (U//FOUO) The increasing prevalence and role of Westerners (including U.S. citizens) in al-Qai’da and associated groups, either as leaders or operatives, gives these individuals knowledge of Western culture and security practices.
- (U//FOUO) HITRAC assesses the sectors at greatest risk from these attack scenarios are Commercial Facilities, Government Facilities, Banking and Finance, and Transporation.
(U) BACKGROUND
(U//FOUO) The U.S. Homeland faces a persistent and evolving terrorist threat from a number of violent “jihadist” groups that are aligned ideologically with, but not necessarily directed by, al-Qa’ida. These groups are driven by their undiminished intent to attack the Homeland and a continued effort by these terrorist groups to adapt and improve their capabilities.
(U//FOUO) Al-Qai’da and its affiliates will continue to enhance its capabilities to attack the Homeland through greater cooperation with regional terrorist groups. Historically, al-Qa‘ida has focused on prominent political, economic, and infrastructure targets with the intent to produce mass casualties, visually dramatic destruction, significant economic aftershocks, and fear among the population. The group is innovative in creating new capabilities and overcoming security obstacles.
(U) Potential Attack without Warning
(U//FOUO) There is an increased challenge in detecting terrorist plots underway because of the current trend and tactics which use individuals or small groups acting quickly and independently or with only tenuous ties to foreign handlers. State, local, tribal, and private sector partners play a critical role in identifying suspicious activities and raising awareness of federal counterterrorism officials.
(U//FOUO) Given recent terrorist activity, homeland security partners should operate under the premise that other operatives are in the country and could advance plotting with little or no warning.
(U) Increased Frequency of Attacks Possible
(U//FOUO) Recent events suggest a trend in which terrorists seek to conduct smaller, more achievable attacks against easily accessible targets. Within the past year, attempted attacks and plots in the United States progressed to an advanced stage largely because of these groups’ ability to use operatives that have access to and familiarity with the U.S. as well as their use of new and varied attack patterns.
(U//FOUO) The evolving threat and increasing resilience of al-Qa’ida and other terrorist organizations have been highlighted by a number of recent domestic events, including the Times Square bombing attempt, the Fort Hood attack and the December 2009 airline bomb plot. The number and pace of attempted attacks against the United States over the past nine months have surpassed the number of attempts during any other previous one-year period.
(U) Globalization trends and recent technological advances will continue to enable even small numbers of alienated people to find and connect with one another, justify and intensify their anger, and mobilize resources to attack – all without requiring a centralized terrorist organization, training camp, or leader.
(U//FOUO) The increasing prevalence and role of Westerners (including U.S. citizens) in al-Qai’da and associated groups, either as leaders or operatives, gives these individuals knowledge of Western culture and security practices. U.S. persons who hold leadership positions in al-Qai’da and associated groups have also called publicly on Western individuals to wage jihad by conducting attacks locally.
(U//FOUO) The analysis below builds on these judgments by identifying the relative risk of attacks
TV – Vladimir Putin tells Russian American Spy Joke
TOP-SECRET – Amine El Khalifi Attempted Capitol Suicide Bomber Criminal Complaint
East German Uprising – Situation Report from Vladimir Semyonov and Andrei Grechko to Vyacheslav Molotov and Nikolai Bulganin (2)
| Situation Report from Vladimir Semyonov and Andrei Grechko to Vyacheslav Molotov and Nikolai Bulganin (2) | |
| Date: 06/17/1953 |
Source: Archive of the General Staff (AGSh), f. 16, op. 3139, d. 155, ll. 6-7. Provided and translated by Victor Gobarev. Originally published in Cold War International History Project Bulletin no. 10 (March 1998), p. 87 |
| Description: The current state of protests in East Germany, the number of people on strike, the presence of American soldiers and Soviet measures to dispel the protesters. |
|
THE OPERATIONS DIVISION, THE MAIN OPERATIONS ADMINISTRATION
THE GENERAL STAFF OF THE SOVIET ARMY
Top Secret
Copy #5
To Comrade V.M. MOLOTOV
To Comrade N.A. BULGANIN
Today, the morning of 17 June, some plants are on strike in East Berlin, including the large plants of the Soviet State-Stock Company and the national enterprises. The workers of the construction companies have also not come to work. The striking workers went to Strausberger Platz, which was arranged by the organizers of the disorders to be the place of the meeting.
By 8 a.m., some 30 enterprises, with a workforce of up to 25,000 people, were on strike. There are about 15,000 to 20,000 people in the streets. The speeches of the demonstrators are running under the same slogans as they were put forward yesterday. The demand to decrease the prices by 20 percent in retail shops is strongly emphasized.
The measures undertaken by the German police failed to disperse the demonstrators. Soviet military patrols run throughout the city. Two companies of armored personnel carriers are patrolling near the building that houses the SED CC and the government.
An American vehicle with two uniformed American officers in it, calling on the demonstrators to go to West Berlin was noticed.
The organization of a solidarity demonstration was announced in West Berlin. There is a possibility that those demonstrators will attempt to penetrate East Berlin from West Berlin, which may increase the disturbances.
The first columns of the eastern demonstrators came to the building occupied by the GDR government at 8:30 a.m. The demonstrators were pushed back by the German police. Gathering in the ruins of houses, they started throwing stones at the police.
The workers on strike at the cable factory demanded from the guards of the plant to hand over their arms. The workers of that plant demand a withdrawal of the German police and the Soviet forces from East Berlin.
The strike is expanding, drawing in new, large enterprises. The workers of those plants usually leave work and go out to join the demonstration.
There have been instances where demonstrators have provoked the Soviet patrols at Stalinallee.
We will report on further events.
SEMYONOV
GRECHKO
11:15. a.m., 17 June 1953
Report from A. Grechko and Tarasov to N.A. Bulganin, 9:30p.m. about the East German Rebellion
| Report from A. Grechko and Tarasov to N.A. Bulganin, 9:30p.m. | |
| Date: 06/17/1953 |
Source: AGSh, f. 16, op. 3139, d. 155, ll. 10-11. Provided and translated by Viktor Gobarev. |
| Description: Soviet forces continued to restore order in Berlin and other cities and towns of the German Democratic Republic. The following numbers of people took part in the demonstrations: up to 15,000 in Magdeburg, up to 1,500 in Brandenburg, up to 1,000 in Oranienburg and Werder, up to 1,000 in Jena, 1,000 in Gera, up to 1,000 in Soemmerda, up to 10,000 in Dresden, up to 2,000 in Leipzig, 20,000 in Goerlitz. According to Soviet data, by 9:00. p.m., Moscow time, 50 people were killed or wounded in Magdeburg during the restoration of order. Three Germans were killed and 17 wounded in Leipzig. There have been no losses on the Soviet forces’ side. |
|
OPERATIONS DIVISION,
MAIN OPERATIONS ADMINISTRATION,
GENERAL STAFF OF THE SOVIET ARMY
Top Secret
Copy #6
To Comrade BULGANIN, N.A.
I am reporting the situation in the city of Berlin and on the territory of the German Democratic Republic as of 5:30 p.m., on 17 June (local time).
1. The forces of the [Soviet] Group [of Forces in Germany] continue to restore order in Berlin and other cities and towns of the German Democratic Republic. There are still some demonstrations and street disorders in Berlin and some cities and towns of the German Democratic Republic.
The demonstrators demand the resignation of the government of the German Democratic Republic, a decrease in the output quotas, a decrease of consumer goods and food prices, the elimination of the sectoral borders, and the restoration of the united Germany within the pre-war borders.
There have been some pogroms of public buildings, commercial shops, as well as some attempts to capture public and government establishments.
2. Besides Berlin, demonstrations and disorders have also taken place in some other cities and towns of the German Democratic Republic. The following numbers of people took part in the demonstrations: up to 15,000 in Magdeburg, up to 1,500 in Brandenburg, up to 1,000 in Oranienburg and Werder, up to 1,000 in Jena, 1,000 in Gera, up to 1,000 in Soemmerda, up to 10,000 in Dresden, up to 2,000 in Leipzig, 20,000 in Goerlitz.
The following mechanized and tank units of the Group [of the Soviet Occupation Forces in Germany] have been dispatched for the restoration of order: some units of the 19th mechanized division in Magdeburg, a mechanized infantry regiment of the 11th tank division in Dresden, a mechanized regiment and a motorbike battalion of the 8th mechanized division in Leipzig. Order was restored in Jena, Gera, and Soemmerda by 6:00 p.m.
3. There are still some disorders in some parts of the Soviet sector of Berlin. According to incomplete information, more than 30 plants and other enterprises have been on strike in the Soviet sector of Berlin.
The 1st and the 14th mechanized divisions are operating in Berlin. The 12th tank division has approached the northeastern suburbs of Berlin.
According to incomplete information, 94 instigators and provocateurs were arrested by 5:00. p.m.
4. According to [our] data, by 9:00. p.m., Moscow time, 50 people were killed or wounded in Magdeburg during the restoration of order. Three Germans were killed and 17 wounded in Leipzig. There have been no losses on our side.
5. Comrade Sokolovskii arrived in Berlin at 8:43 p.m., Moscow time.
GRECHKO [and] TARASOV
“Correct”. General of the Army SHTEMENKO
17 June 1953, 9:30 p.m.49
EAST GERMAN UPRISING – Report from A. Grechko and Tarasov in Berlin to N.A. Bulganin and Stalin
| Report from A. Grechko and Tarasov in Berlin to N.A. Bulganin (3) | |
| Date: 06/17/1953 |
Source: Source: AGSh, f. 16, op. 3139, d. 155, ll. 12-14. Provided and translated by Viktor Gobarev. |
| Description: The demonstrations in Berlin and several other cities had been stopped. Grechko and Tarasow came to the conclusion that “the provocation was prepared in advance, organized, and directed from Western sectors of Berlin.” The losses of the strikers in the whole territory of the GDR had been: 84 people killed and wounded, 700 men arrested. |
|
OPERATIONS DIVISION,
MAIN OPERATIONS ADMINISTRATION,
GENERAL STAFF OF THE SOVIET ARMY
Top Secret
To Comrade BULGANIN, N.A.
I am reporting on the situation in the GDR and Berlin as of 11:00 p.m., 17 June 1953 (Moscow time).
1. The Soviet forces, namely the 1st mechanized infantry division, the 14th mechanized infantry division, and the 12th tank division (altogether 600 tanks), have for the most part restored order in the Soviet sector of Berlin. The provocative plan of the reactionary and fascist-like elements has been wrecked.
There have been only minor groups around the Alexanderplatz and Stalinallee downtown area in the evening, which are being dispersed and arrested by our forces.
It may be considered that a special organization based in West Berlin has directed the strikes in East Berlin. Analyzing the situation, I have also come to the conclusion that the provocation was prepared in advance, organized, and directed from Western sectors of Berlin. The simultaneous actions in the majority of the big cities of the GDR, the same demands of the rebels everywhere as well as the same anti-state and anti-Soviet slogans, serve as proof for this conclusion.
As the result of measures undertaken in the Western sectors of Berlin, there have been large gatherings of German residents at the borders between the Soviet sector and the British and American ones.
The border with the Western sectors of Berlin was closed by our troops.
Power-stations, gas plants, water-supply, and railway have worked smoothly.
About 300 organizers and provocateurs were arrested in Berlin by 8:00 p.m.
2. Order was restored in the majority of the cities of GDR. Normal life and activity of state institutions were restored toward the end of the day. Order was restored by measures undertaken in Magdeburg. 50 Germans were killed and wounded, and over 100 instigators and provocateurs have been arrested during the restoration of order.
3. With the purpose of preventing further possible riots, the forces of the Group [of Soviet Forces in Germany] are being moved from field camps into the following big and important populated areas:
The 3rd Army – the 19th mechanized division into Magdeburg; the 136th artillery-technical, tank & self-propelled gun regiment into Burg; the 13th mechanized division into Parchim, Ludwigslust, Pirleberg; the 207th infantry division into Gardelegen, Stendal.
The 8th Guards Army – the 20th Guards mechanized division into Weimar, Jena, Zeitz; the 21st Guards mechanized division into Halle, Merseburg; the 57th Guards infantry division into Naumburg, Weissenfels and its one infantry regiment into Eisenach.
The 1st Guards Army – the 11th tank division into Dresden (the main forces) and Meissen, Koenigsbruck (the minor forces); the 8th Guards mechanized division into Leipzig (the main forces) and Borna, Grimma (the minor forces); the 9th tank division into Piesa, Oschatz, Zeithavn.
The 3rd Guards Mechanized Army – the 6th Guards tank division into Dessau, Wittenberg; the 9th mechanized division into Luebben, Cottbus, Spremberg.
The 4th Guards Mechanized Army – the 6th Guards mechanized division into Bernau, Eberswalde, Bad Freienwalde; the 7th Guards mechanized division into Fuerstenwalde, Frankfurt an der Oder.
The motorbike battalion and the howitzer battalion of the 10th tank division into Brandenburg; the 25th tank division (a tank regiment and a mechanized infantry regiment) into Oranienburg.
4. According to preliminary information, the losses suffered throughout the entire GDR territory by protesters have been[:] 84 people killed and wounded, 700 men arrested. Our exact losses are being determined.
5. Martial law was declared in the British sector of Berlin. Soldiers are not allowed to leave the barracks. The patrols at the border with the Soviet sector have been reinforced. Troops in the American and French sectors of Berlin are in barracks.
GRECHKO TARASOV
“Correctly”: COLONEL-GENERAL MALININ
17 June 1953
Stalin’s Henchmen exposed during East German Uprising
| Telephonogram from Vladimir Semyonov and Marshal Vasilii Sokolovskii to Vyacheslav Molotov and Nikolai Bulganin Reporting on the Situation in East Berlin, as of 11:00 p.m. CET | |
| Date: 06/17/1953 |
Source: AVP RF, f. 082, op. 41, port. 93, pap. 280, ll. 3-4. Translated by Daniel Rozas. |
| Description: Cable to the Soviet leadership describing the situation in East Berlin after the imposition of the curfew. The cable reports that at least 700 people have been arrested in East Germany, 300 of which were in the Soviet sector of Berlin. East German police and Soviet troops have taken control of the border of East Berlin to prevent “provocateur elements” from entering the Soviet sector. |
|
Secret
Copy #14
TELEPHONOGRAM BY VCH
From Berlin
17 June 1953
To comrade V.M. Molotov
To comrade N.A. Bulganin
We report on the situation in Berlin and the GDR at 11 p.m., 17 June.
The disorders in Berlin have been stopped. The streets are calm. In connection with the implementation of martial law from 9 p.m. to 5 a.m., the movement of transportation and walking on the streets were halted in the Soviet sector of the city. A small number of people were arrested for breaking this order.
Our troops and the German police are in control of all key streets and important installations in the Soviet sector of the city. The most attention has been paid to the defense of the sector border between East and West Berlin, across which a number of large groups of provocateurs and hooligans from West Berlin had broken through into the Soviet sector in the evening. On the streets Brunnenstrasse and Bernauer Strasse, these gangs started a shootout with the German police, which resulted in casualties. According to preliminary information, 79 German policemen were injured and 2 policemen are missing as a result of the disturbances in the Soviet sector. West Berlin radio is reporting that 7 demonstrators were killed and 66 people were injured. As yet, there are no complete reports on the number of casualties.
In its broadcasts, the American radio station RIAS is calling upon the rebels to submit to the orders of the Soviet authorities and avoid clashes with the Soviet troops.
In the majority of cities in the GDR, order has been fully restored. There are reports of continuing disorders only in the two small cities of Apolda and Mühlhausen.
According to incomplete data, 700 instigators of the disorders have been arrested in the Republic, 300 of whom were in Berlin.
Measures are being taken to reestablish normal operation of all enterprises in the Republic, as well as measures to prevent interruptions in the food supply to the inhabitants of Berlin. The GDR government has called upon the people to swiftly reestablish social order and normal operation of enterprises.
Sokolovskii
Semyonov
Sent by Blatov
Received by Roshchina
18.VI.1953
2 hours, 45 min.
VIDEO – Topless FEMEN at Putin’s polling station
LEAKED VIDEO – FEMEN – Topless Ukrainian Activists Protest at Gazprom
DIE FAZ ÜBER DIE WIRTSCHAFTSKRIMINELLEN DER STASI-“GoMoPa”
FAZ – FRANKFURTER ALLGEMEINE ZEITUNG ÜBER “GoMoPa”
Wirtschaftskriminalität Großrazzia wegen Verdachts auf Insiderhandel
Schlag gegen mutmaßliche Anlagebetrüger: Die Staatsanwaltschaft München hat in einer Großrazzia Dutzende Büros und Wohnungen nach Beweisen für Insiderhandel durchsucht. Drei Verdächtige wurden verhaftet. Durchsucht wurde auch die Schutzgemeinschaft der Kapitalanleger.
24.09.2010 2010-09-24T08:31:05+0200
//
© Wolfgang Eilmes / F.A.Z.
Betrugsverdacht: An der Börse sollen fast wertlose Papiere gekauft, die Kurse durch gezielt positive Nachrichten nach oben getrieben und dann wieder verkauft worden sein
Die Münchner Staatsanwaltschaft hat in einer Großrazzia umfangreiches Beweismaterial gegen mutmaßliche Anlagebetrüger sichergestellt. Ermittelt wird gegen ein Netzwerk von Investoren, Zockern und Gerüchtestreuern, die seit Jahren gemeinsame Sache gemacht haben sollen. Die Vorwürfe lauten auf Marktmanipulation und Insiderhandel mit Aktien, sagte die Sprecherin der Anklagebehörde, Barbara Stockinger. „Wir ermitteln gegen 31 Beschuldigte, und es besteht erheblicher Tatverdacht.“ Dabei laufen die Ermittlungen bereits seit 2007, und sie reichen bis hin zur Schutzgemeinschaft der Kapitalanleger (SdK), deren Redner gern auf den Hauptversammlungen von Dax-Konzernen auftreten.
Nach Informationen der F.A.Z. sitzen die früheren SdK-Sprecher Markus Straub und Tobias Bosler in Untersuchungshaft. Sie gehören zum Kreis der Verdächtigen, die in windigen Börsenbriefen und Internetportalen Gerüchte über Aktien von Unternehmen wie Wirecard oder Nascacell verbreitet haben sollen. Erschwert würden die Untersuchungen, weil die Beschuldigten oft Namen und Firmenadressen wechselten und internationale Durchsuchungsbeschlüsse notwendig gewesen seien, sagte eine mit der Angelegenheit befasste Person dieser Zeitung. Die Masche selbst ist nach ihren Angaben leicht durchschaubar, aber schwer nachzuweisen. Vermutlich haben sämtliche Verdächtige Gerüchte über mindestens 20 kleine Aktiengesellschaften gestreut und an den Kursausschlägen der jeweiligen Aktien kräftig verdient. Gegenstand dieser Geschäfte waren bevorzugt im unregulierten Freihandel notierte und meist wertlose Aktien, sogenannte Pennystocks. Die Kurse dieser Werte sind wegen ihres hohen Streubesitzes leicht zu manipulieren.
Gezielt Gerüchte gestreut
Nach Informationen der F.A.Z. sollen unter anderem gezielt über den Finanznachrichtendienst Gomopa im Internet Gerüchte über Pennystocks gestreut worden sein. Gomopa steht für Goldman Morgenstern & Partners Consulting LLC. Auf ihrer Internetseite hat Gomopa „Transparenz in Sachen Finanzen, Vorsorge und Geldanlage“ versprochen, doch ihr Chef Klaus Maurischat saß als mutmaßlicher Betrüger schon in Untersuchungshaft.
Seit einigen Tagen ist die Internetseite http://www.gomopa.net offline, und es kursieren Gerüchte über finanzielle Unregelmäßigkeiten. Immer wieder ist Gomopa in juristische Streitigkeiten verwickelt. In einer einstweiligen Verfügung des Landgerichts Berlin vom 31. August (Az.: 27 O 658/10) ist das Unternehmen aufgefordert worden, nicht länger Falschinformationen über den Kasseler Immobilienhändler Immovation AG und seinen Finanzvorstand Lars Bergmann zu verbreiten. „Gomopa hat seinen Firmensitz bewusst in New York, weil die Firma dort presserechtlich nicht belangt werden kann“, sagte ein Kenner des Unternehmens der F.A.Z.
Die SdK räumte am Freitag ein, dass auch ihre Geschäftsräume durchsucht wurden. Es gebe jedoch „aus der Sicht der SdK keinerlei neue Vorwürfe gegen den Verein“. Die alten Vorwürfe gegen die SdK stehen im Zusammenhang mit Kursmanipulationen bei Aktien der Unternehmen Thielert und Wirecard. Staatsanwaltschaft und Allfinanzaufsicht Bafin ermittelten seinerzeit gegen den damaligen stellvertretenden SdK-Vorsitzenden Straub. Dieser hatte eingeräumt, Verkaufsoptionen auf das Zahlungsunternehmen Wirecard zu halten, dessen Kurs durch heftige Kritik der SdK unter Druck geraten war. Später trat Straub, der offenbar in kurzer Zeit ein Vermögen verdient hatte, zurück. Wirecard hatte Anzeige wegen Insiderhandels und Kursmanipulation gegen sechs Personen erstattet, darunter auch aktuelle und frühere SdK-Vorstände.
TOP-SECRET – U.S. Army RQ7-B Shadow Tactical Unmanned Aircraft System (TUAS) Handbook

1-1. The Shadow TUAS extends the ARS Commander’s ability to support the full spectrum of conflict through reconnaissance, security, aerial surveillance, communications relay, and laser designation.
1-2. The UAS supports the full spectrum capability through augmenting all warfighting functions:
a. Movement and Maneuver: Provides the full depth of the reconnaissance and security missions in order to aid the ground commander in movement of friendly forces and provide the ground forces with freedom to maneuver.
b. Intelligence: The Shadow Troop provides Near Real Time (NRT) intelligence, surveillance, and reconnaissance (ISR) and extends the capability through flexible RSTA platforms as an organic asset to the ARS and CAB commanders. They greatly improve the situational awareness of the ARS and aid in employing the Scout Weapons Team (SWT) in high threat environments.
c. Fires: Coupling the Communication Relay Package (CRP) with the Laser-Designating (LD) payload, the Shadow aids in all levels of the Decide, Detect, Deliver, and Asses cycle.
d. Protection: Through continuous reconnaissance, the Shadow Troop can significantly increase the force protection in and around secure operational bases.
e. Sustainment: The Shadow provides reconnaissance and security along supply routes and logistics support areas. Using the CRP, the Shadow can talk directly to the convoy commander for immediate reaction.
f. Command and Control: The Shadow greatly increases the ARS commander’s ability to control the fight. The CRP package extends radio transmission ranges to 240 kilometers. With proper TTPs, the Shadow can serve as an emergency re-transmitting capability to isolated personnel.
1-3. The Shadow Troop aids the ARS and CAB commanders through the full spectrum of operations from stable peace to general war:
a. Peacetime Military Engagement: The Shadow Troop provides counterdrug activities, recovery operations, security assistance, and multinational training events and exercises.
b. Limited Intervention: Provides search for evacuation operations, security for strike and raid operations, foreign humanitarian assistance (search of survivors during disaster relief), and searching for weapons of mass destruction.
c. Peace operations: Provides peacekeeping through surveillance and security for peace enforcement operations.
d. Irregular Warfare: Assists in tracking enemy personnel while combating terrorism and unconventional warfare.
e. Major Combat Operations: Provides the capability to extend the communication of friendly units, emergency retransmitting capability to isolated personnel, target acquisition, and laser designation.
…
ONE SYSTEM GROUND CONTROL STATION POSITIONING
2-6. OSGCS positioning is critical to successful employment of UAS. The OSGCS provides the technical means to receive UA sensor data. The unmanned aircraft operator, PO, and MC assigned to the OSGCS provide tactical and technical expertise to facilitate UAS operations. The CAB commander advises the division commander on placement of this critical UAS component to maximize its effectiveness. The CAB, BFSB, Fires brigade, and BCT conduct disparate missions simultaneously across the division area of operation, with different TTP, focus, and skill sets required. This requires integration of overall aviation operations at division-level to avoid redundancy of effort. An additional consideration is the Shadow platoons in the IBCT BSTBs and the OSGCSs that remain in their control. With a cohesive ATP relationship built between the IBCT Shadow platoons and the ARS Shadow Troop, direct support missions to the IBCT in an extended range environment can be controlled by the IBCT Shadow operators, POs, and MCs.
Single-Site Operations
2-7. In single-site operations, the entire UAS unit is co-located. Single-site operations allow for easier unit command, control, communication, and logistics. Coordination with the supported unit may be more difficult due to distance from and communications with the supported unit. In addition, single-site operations emit a greater electronic and physical signature.
Split-Site Operations
2-8. In split-site operations, the UAS element is typically split into two distinct sites: the mission planning control site (MPCS) and the L/R site. The MPCS is normally located at the supported unit’s main or tactical CP location. The L/R site is normally located in more secure area, positioned to best support operations.
2-9. The IBCT Shadow platoons should also consider consolidating launch-recovery with the ARS Shadow Troop in order to receive the additional benefits of the ARSs large logistical footprint. The IBCT Shadow platoons can focus directly on the MPCS with forward-staged GCSs.
…
ZONE RECONNAISSANCE
3-20. Zone reconnaissance is conducted to find any significant signs of positions of enemy activity within a given area defined by boundaries. It is conducted only in conjunction with a larger reconnaissance element and is an extremely detailed reconnaissance effort. For this reason, the zone reconnaissance will normally be conducted in a MURT, which will also be a part of a larger task force.
3-21. Similar to the route reconnaissance, the Shadow will extend further towards enemy activity and work further ahead of the Forward Line of Own Troops (FLOT). The Shadow will clear territory for any major threats one phase line ahead of the SWT and report any significant activity. The primary goal of the Shadow during a zone reconnaissance is to ensure the freedom of maneuver for the SWT. The SWT is focused primarily on the freedom of maneuver of the larger friendly reconnaissance element.
AREA RECONNAISSANCE
3-22. Area reconnaissance gathers intelligence or conducts surveillance of a specified area. This area may be key terrain or other features critical to an operation. Similar to a route reconnaissance, the TUAS may conduct an area reconnaissance autonomously or in a MURT.
3-23. The autonomous area reconnaissance will focus outwards and move into the objective area. The flanks of the overall objective area are secured; then, reconnaissance efforts are focused inward. UAS may establish a screen on the flank to provide security for ground forces, if used.
3-24. The MURT will use the Shadow to continue reconnaissance efforts on any terrain that can influence the given objective area while the SWT moves inward towards the main objective area. This provides NRT intelligence on any changes or significant activities during the conduct of the reconnaissance.
AERIAL SURVEILLANCE
3-25. Aerial surveillance is the systematic observation of aerospace, surface or subsurface areas, places, persons, or things by visual, aural, electronic, photographic, or other means to collect information. Aerial surveillance is usually passive and may be continuous.
3-26. UAS surveillance of base camps, airfields, and key logistic sites in lesser-contested areas may free combat forces to perform other missions and help prevent surprise.
3-27. The TUAS provides easily maintained and lower detectable aerial surveillance to the ARS and CAB commander to help develop the commander’s intent and concept of the operation. The Shadow Troop provides 24 hour coverage for an NAI in order to:
• Track pattern of life VIA Full Motion Video (FMV)
• Observe a specific area for enemy activity
• Provide early warning and detection on a specific high speed avenue of approach3-28. The difference between an aerial surveillance and standard reconnaissance is the amount of movement for the Shadow payload. During an aerial surveillance, the payload should remain generally stabilized to gather information on an extremely specific area of the battlefield.
DOWNLOAD ORIGINAL DOCUMENT HERE
WIKILEAKS – 9/11 tragedy pager intercepts.
From 3AM on Sunday September 11, 2011, until 3AM the following day (US east coast time), WikiLeaks is re-releasing over half a million US national text pager intercepts. The intercepts cover a 24 hour period surrounding the September 11, 2001 attacks in New York and Washington.
The messages are being broadcast “live” to the global community — sychronized to the time of day they were sent. The first message is from 3AM September 11, 2001, five hours before the first attack, and the last, 24 hours later.
Text pagers are usualy carried by persons operating in an official capacity. Messages in the archive range from Pentagon, FBI, FEMA and New York Police Department exchanges, to computers reporting faults at investment banks inside the World Trade Center
The archive is a completely objective record of the defining moment of our time. We hope that its entrance into the historical record will lead to a nuanced understanding of how this event led to death, opportunism and war.
An index of messages released so far is available here.
Twitter users may use the hashtag #911txts. We will give status updates at twitter.com/wikileaks.
Last 12 intercept collections:
2001.09.12 02.55 to 2001.09.12 02.59 (text)
2001.09.12 02.50 to 2001.09.12 02.54 (text)
2001.09.12 02.45 to 2001.09.12 02.49 (text)
2001.09.12 02.40 to 2001.09.12 02.44 (text)
2001.09.12 02.35 to 2001.09.12 02.39 (text)
2001.09.12 02.30 to 2001.09.12 02.34 (text)
2001.09.12 02.25 to 2001.09.12 02.29 (text)
2001.09.12 02.20 to 2001.09.12 02.24 (text)
2001.09.12 02.15 to 2001.09.12 02.19 (text)
2001.09.12 02.10 to 2001.09.12 02.14 (text)
2001.09.12 02.05 to 2001.09.12 02.09 (text)
2001.09.12 02.00 to 2001.09.12 02.04 (text)
JULIAN ASSANGE UNVEILS – Cuba to work around US embargo via undersea cable to Venezuela

JULIAN ASSANGE (investigative editor)
July 16, 2008
From Santiago de Cuba to La Guaira : Cuba will be connected to the Internet by 2010
| “ |
According to the Vice Minister of Telecommunication, Boris Moreno, the government is unable to offer Cubans comprehensive Internet for their new Pcs because the American embargo prevents it from getting service directly from the United States nearby through underwater cables. Instead, Cuba gets Internet service through less reliable satellite connections, usually from faraway countries including Italy and Canada.
|
„ |
| — Cuba blames US for Internet restrictions, AP Newswire 16 May 2008[1] |
Documents released by Wikileaks reveal that Cuba and Venezuela signed a confidential contract in 2006 to lay an undersea fibre-optic cable that bypasses the United States. The cable is to be completed by 2010.
The contract between the two countries, which has been independently verified, adds weight to Cuban statements that the United States economic embargo of the island has forced it to rely on slow and expensive satellite links for Internet connectivity. Cuba is situated a mere 120 kilometres off the coast of Florida. The proposed 1,500 kilometre cable will connect Cuba, Jamaica, Haiti and Trinidad to the rest of the world via La Guaira, Venezuela.
Carrying out the work are CVG Telecom (Corporación Venezolana de Guyana) and ETC (Empresa de Telecomunicaciones de Cuba).
The leaked documents have technical details and pictures of the cable, maps, and systems to be used, parties signing the agreement, terms and conditions, costs, and a schedule of charges and compromises. The connection allows for the transmission of data, video and voice (VoIP). According to the contract, the agreement is designed to build a relationship of “strategic value” which will permit Cuba and Venezuela to, among other matters:
- Increase interchange between the two governments.
- Foster science, cultural and social development.
- Increase the volume and variety of relationships between country members of ALBA (Bolivarian Alternative for America) and the South American MERCOSUR trading block.
- Help serve the increasing demand of commercial traffic between Cuba, Venezuela and the rest of the world.
The contract parties state that given the diversity of foreign affairs, they wish to build a new international order, multi-polar, based in sustainability, equity and common good and that an international cable with maximum security protected by international organizations (ITU/ICPC) is crucial.
The documents disclose plans to separate commercial traffic and governmental traffic upon data arrival.
Column of Major General (Res.) Amos Yadlin – former Head of Israel’s Directorate of Military Intelligence

Major General (Res.) Amos Yadlin, the former Head of the Directorate of Military Intelligence and current head of the Institute for National Security Studies (INSS), believes that an Israeli strike against Iran’s nuclear facilities will result in regional stability in the Middle East.
In an article written by Yadlin for the New York Times, he says, “Others claim that an action will destabilize the region. However, a nuclear Iran could lead to far worse: a regional nuclear arms race without a red phone to defuse an escalating crisis and Iranian aggression in the Persian Gulf.”
“An ironclad American assurance is needed to prevent a nuclear Iran, and if President Obama will not do so, Israel may well choose to act while it still can,” Amos continued.
In his opinion, Israel will require support from Washington in case of an attack. “The US could carry out an extensive air campaign using stealth technology and huge amounts of ammunition, beyond what Israel can achieve.”
Israeli Prime Minister Binyamin Netanyahu will depart today for a formal visit to Canada, from where he’ll continue to Washington DC for a meeting with US President Barack Obama. The two are expected to discuss the topic of Iran’s nuclear program.
At the same time, Bloomberg news is reporting that the US army is practicing for an attack on Iran’s nuclear facilities. The US Air Force Commander, General Norton A. Shwartz, said during a discussion with reporters in Washington that the US Army has prepared military options in case it might need to attack Iran’s nuclear facilities.
“You wouldn’t want to be in the area,” Shwartz reportedly said. Senior Pentagon officials told a network reporter that the US is considering, among other things, assisting the Israeli Air Force in refueling its aircraft on the way to an attack on the Iranian facilities.
Another option that’s also being considered is a US Army attack against the headquarters of the Iranian Revolutionary Guard.
WIKILEAKS VIDEO – Collateral Murder – Iraq
FBI – Former DuPont Scientist Pleads Guilty to Economic Espionage
SAN FRANCISCO—Tze Chao pleaded guilty in federal court in San Francisco late yesterday afternoon to conspiracy to commit economic espionage, United States Attorney Melinda Haag announced.
In pleading guilty, Chao, who was employed by DuPont from 1966 to 2002, admitted that he provided trade secrets concerning DuPont’s proprietary titanium dioxide (TiO2) manufacturing process to companies he knew were controlled by the government of the People’s Republic of China (PRC). Chao admitted that beginning in 2003, the year after he left DuPont, he began consulting for the Pangang Group, a PRC government-controlled company that produces TiO2. According to his plea agreement, Chao had “learned that the PRC government had placed a priority on developing chloride-process TiO2 technology in a short period of time and wished to acquire this technology from western companies.”
In 2008, Chao submitted a bid to design a 100,000-ton per year TiO2 facility for the Pangang Group. In connection with his bid, Chao provided DuPont information to the Pangang Group, including information that, according to his plea agreement, he “understood to be secret to DuPont and not available to the public.” Chao did not win the contract but in 2009 was asked by Pangang Group to review design work done by USA Performance Technology, Inc. He did so, and in the course of this review, provided additional DuPont trade secret information to Pangang Group.
Chao’s plea comes in connection with the superseding indictment returned three weeks ago charging Walter Liew, Christina Liew, Robert Maegerle, and USA Performance Technology, Inc., among others, for their efforts to sell DuPont trade secrets to companies controlled by the PRC government. Those companies—the Pangang Group and three subsidiaries—also were named as defendants in the indictment and charged with conspiracy to commit economic espionage and attempted economic espionage. As part of his plea agreement, Chao agreed to cooperate in the investigation and prosecution of this case.
Chao, 77 of Newark, Del., was indicted by a federal Grand Jury on Feb. 7, 2012. He was charged with one count of conspiracy to commit economic espionage, in violation of 18 U.S.C. § 1831(a)(5). Under the plea agreement, Chao pleaded guilty to this charge as alleged in the superseding indictment.
Chao was arraigned yesterday in San Francisco and released on his own recognizance. He entered his guilty plea before the Honorable Jeffrey S. White late yesterday afternoon in San Francisco. A date for sentencing was not set. The maximum statutory penalty is 15 years in prison and a fine of $500,000, plus restitution if appropriate. However, any sentence following conviction would be imposed by the court after consideration of the U.S. Sentencing Guidelines and the federal statute governing the imposition of a sentence, 18 U.S.C. § 3553.
This case is being prosecuted by the Special Prosecutions and National Security Unit of the U.S. Attorney’s Office in San Francisco and the Counterespionage Section of the National Security Division of the U.S. Department of Justice. The investigation is being conducted by the Federal Bureau of Investigation.
ZAHLREICHE STASI-AGENTEN UND -AKTIVITÄTEN VOR ENTTARNUNG
Berlin (epd). 16.000 Säcke verborgene Information über die DDR bewahrt die Stasi-Unterlagen-Behörde in Berlin und Magdeburg auf. In großen Papiertüten ist das gesammelt, was Stasi-Mitarbeiter 1989 schnell vernichten wollten. Als der politische Umbruch unübersehbar war, zerrissen sie Akten, schredderten, machten Papiermehl daraus.
Für Menschen ist das Stasi-Puzzle eine Jahrhundertaufgabe. In jedem Sack befinden sich rund 4.000 Blatt – geviertelt, geachtelt oder in noch viel kleineren Teilen. Seit 1995 puzzeln frühere Mitarbeiter des Bundesamts für die Anerkennung ausländischer Flüchtlinge in Zirndorf bei Nürnberg Aktenseiten manuell zusammen. 400 Säcke haben sie seither bewältigt. Ginge es in dem Tempo weiter, würde die Rekonstruktion noch weit über 500 Jahre dauern.
“Um sich diese riesige Anzahl von Schnipseln zu merken und sie dann zusammenzusetzen, braucht man ein wahnsinniges Gedächtnis”, sagt Joachim Häußler, Projektleiter für die virtuelle Rekonstruktion der zerrissenen Stasi-Unterlagen in der Behörde. “Das hat kein Mensch”. Die Historiker setzen daher auf den Rechner: In Zusammenarbeit mit der Bundesbehörde entwickelt das Fraunhofer-Institut für Produktionsanlagen und Konstruktionstechnik ein System, das die eingescannten Schnipsel automatisch zusammensetzt.
Rund sechs Millionen Euro haben die Institutionen dafür vom Bund bekommen. Für das Geld sollen das Programm entwickelt und in einer Testphase Schnipsel aus weiteren 400 Säcken digital zusammengesetzt werden. Herausgekommen ist der “ePuzzler”. Nur Kleinigkeiten macht er noch nicht ganz richtig, sagt Häußler. Das Programm ordnet manchmal falsche Schnipsel einander zu, weil es die Risskanten mehrerer gemeinsam zerrissener Seiten nur schwer unterscheiden kann. Dies müsse bis zur Version 1.0 der Software noch optimiert werden.
Der Leiter des Projekts im Fraunhofer-Institut, Bertram Nickolay, traut seinem Programm zu, in zehn bis 15 Jahren alle Stasi-Schnipsel bearbeitet zu haben. Der promovierte Technik-Spezialist ist mit persönlichem Interesse bei der Sache: DDR-Bürgerrechtler zählen zu seinen Freunden, darunter war auch der 1999 gestorbene Schriftsteller Jürgen Fuchs. Wenn er zur Aufklärung der Überwachung dieser Menschen beitragen könnte, wäre er zufrieden, sagt er.
“Natürlich ist es auch die Frage, warum der jeweilige Stasi-Mitarbeiter genau das zerrissen hat”, sagt Joachim Häußler. Ob es bewusste Griffe der Führungsoffiziere waren oder ob sie einfach nur unkoordiniert mit dem Vernichten der Beweise ihres Handelns beginnen wollten – letztlich können das nur die zusammengesetzten Akten beantworten. Ein Hinweis, wie pikant die Inhalte der zerrissenen Akten sein könnten, eröffnete sich Ende Januar. Anhand einer aus Schnipseln manuell rekonstruierten Akte wurde ein Jenaer Professor in Medienberichten als Inoffizieller Mitarbeiter enttarnt.
Die Pilotphase der virtuellen Rekonstruktion ist demnächst abgeschlossen, das Geld dann auch alle. Funktioniert das Programm, kann das große Puzzeln beginnen. Das Geld dafür muss dann aber erst noch bewilligt werden. Sicher ist indes, dass der Deutsche Bundestag mit einem Erweiterungsauftrag in Höhe von zwei Millionen Euro eine Machbarkeitsstudie finanziert, um die zusammengesetzten Seiten IT-gestützt wieder zu Akten ordnen zu lassen.
Und auch mit dem “ePuzzler” sind menschliche Vorsortierer weiter vonnöten. Rund 20 Mitarbeiter in der Bundesbehörde sind mit dem Stasi-Puzzle befasst. Zehn von ihnen arbeiten in der “Feinsichtung”. Sie sortieren Sack für Sack die Schnipsel vor: Nach Papierfarbe, Schriftart, manchmal auch ersten inhaltlichen Hinweisen. Nur einmal zerrissene Seiten können dann auch gleich wieder zusammengeklebt werden – das geht per Hand schneller als mit der Maschine.
Das prüfende Auge des Menschen wird auch mit der Software weiter gebraucht. “Wir gehen momentan davon aus, dass der Rechner im automatisierten Verfahren mindestens 80 Prozent der Schnipsel zusammensetzen kann”, sagt Häußler. Der Rest muss per Mausklick erledigt werden.
Für ein weltweit bisher einmaliges Programm sei das trotzdem eine gute Automatisierungsquote, ist Häußler überzeugt. “Wir bekommen viele Nachfragen von Behörden, die wissen wollen, wie weit wir sind”, sagt er. Die Interessenten sind Landeskriminalämter, Kommissariate sowie Zoll- und Finanzfahnder. Das Vernichten verräterischer Dokumente ist eben nicht nur eine Stasi-Eigenart gewesen.
epd ost bep/co bue
Department of Defense Anti Terrorism Program
Uncensored FEMEN Parody Video
CONFIDENTIAL – U.S. Army RQ7-B Shadow Tactical Unmanned Aircraft System (TUAS) Handbook

1-1. The Shadow TUAS extends the ARS Commander’s ability to support the full spectrum of conflict through reconnaissance, security, aerial surveillance, communications relay, and laser designation.
1-2. The UAS supports the full spectrum capability through augmenting all warfighting functions:
a. Movement and Maneuver: Provides the full depth of the reconnaissance and security missions in order to aid the ground commander in movement of friendly forces and provide the ground forces with freedom to maneuver.
b. Intelligence: The Shadow Troop provides Near Real Time (NRT) intelligence, surveillance, and reconnaissance (ISR) and extends the capability through flexible RSTA platforms as an organic asset to the ARS and CAB commanders. They greatly improve the situational awareness of the ARS and aid in employing the Scout Weapons Team (SWT) in high threat environments.
c. Fires: Coupling the Communication Relay Package (CRP) with the Laser-Designating (LD) payload, the Shadow aids in all levels of the Decide, Detect, Deliver, and Asses cycle.
d. Protection: Through continuous reconnaissance, the Shadow Troop can significantly increase the force protection in and around secure operational bases.
e. Sustainment: The Shadow provides reconnaissance and security along supply routes and logistics support areas. Using the CRP, the Shadow can talk directly to the convoy commander for immediate reaction.
f. Command and Control: The Shadow greatly increases the ARS commander’s ability to control the fight. The CRP package extends radio transmission ranges to 240 kilometers. With proper TTPs, the Shadow can serve as an emergency re-transmitting capability to isolated personnel.
1-3. The Shadow Troop aids the ARS and CAB commanders through the full spectrum of operations from stable peace to general war:
a. Peacetime Military Engagement: The Shadow Troop provides counterdrug activities, recovery operations, security assistance, and multinational training events and exercises.
b. Limited Intervention: Provides search for evacuation operations, security for strike and raid operations, foreign humanitarian assistance (search of survivors during disaster relief), and searching for weapons of mass destruction.
c. Peace operations: Provides peacekeeping through surveillance and security for peace enforcement operations.
d. Irregular Warfare: Assists in tracking enemy personnel while combating terrorism and unconventional warfare.
e. Major Combat Operations: Provides the capability to extend the communication of friendly units, emergency retransmitting capability to isolated personnel, target acquisition, and laser designation.
…
ONE SYSTEM GROUND CONTROL STATION POSITIONING
2-6. OSGCS positioning is critical to successful employment of UAS. The OSGCS provides the technical means to receive UA sensor data. The unmanned aircraft operator, PO, and MC assigned to the OSGCS provide tactical and technical expertise to facilitate UAS operations. The CAB commander advises the division commander on placement of this critical UAS component to maximize its effectiveness. The CAB, BFSB, Fires brigade, and BCT conduct disparate missions simultaneously across the division area of operation, with different TTP, focus, and skill sets required. This requires integration of overall aviation operations at division-level to avoid redundancy of effort. An additional consideration is the Shadow platoons in the IBCT BSTBs and the OSGCSs that remain in their control. With a cohesive ATP relationship built between the IBCT Shadow platoons and the ARS Shadow Troop, direct support missions to the IBCT in an extended range environment can be controlled by the IBCT Shadow operators, POs, and MCs.
Single-Site Operations
2-7. In single-site operations, the entire UAS unit is co-located. Single-site operations allow for easier unit command, control, communication, and logistics. Coordination with the supported unit may be more difficult due to distance from and communications with the supported unit. In addition, single-site operations emit a greater electronic and physical signature.
Split-Site Operations
2-8. In split-site operations, the UAS element is typically split into two distinct sites: the mission planning control site (MPCS) and the L/R site. The MPCS is normally located at the supported unit’s main or tactical CP location. The L/R site is normally located in more secure area, positioned to best support operations.
2-9. The IBCT Shadow platoons should also consider consolidating launch-recovery with the ARS Shadow Troop in order to receive the additional benefits of the ARSs large logistical footprint. The IBCT Shadow platoons can focus directly on the MPCS with forward-staged GCSs.
…
ZONE RECONNAISSANCE
3-20. Zone reconnaissance is conducted to find any significant signs of positions of enemy activity within a given area defined by boundaries. It is conducted only in conjunction with a larger reconnaissance element and is an extremely detailed reconnaissance effort. For this reason, the zone reconnaissance will normally be conducted in a MURT, which will also be a part of a larger task force.
3-21. Similar to the route reconnaissance, the Shadow will extend further towards enemy activity and work further ahead of the Forward Line of Own Troops (FLOT). The Shadow will clear territory for any major threats one phase line ahead of the SWT and report any significant activity. The primary goal of the Shadow during a zone reconnaissance is to ensure the freedom of maneuver for the SWT. The SWT is focused primarily on the freedom of maneuver of the larger friendly reconnaissance element.
AREA RECONNAISSANCE
3-22. Area reconnaissance gathers intelligence or conducts surveillance of a specified area. This area may be key terrain or other features critical to an operation. Similar to a route reconnaissance, the TUAS may conduct an area reconnaissance autonomously or in a MURT.
3-23. The autonomous area reconnaissance will focus outwards and move into the objective area. The flanks of the overall objective area are secured; then, reconnaissance efforts are focused inward. UAS may establish a screen on the flank to provide security for ground forces, if used.
3-24. The MURT will use the Shadow to continue reconnaissance efforts on any terrain that can influence the given objective area while the SWT moves inward towards the main objective area. This provides NRT intelligence on any changes or significant activities during the conduct of the reconnaissance.
AERIAL SURVEILLANCE
3-25. Aerial surveillance is the systematic observation of aerospace, surface or subsurface areas, places, persons, or things by visual, aural, electronic, photographic, or other means to collect information. Aerial surveillance is usually passive and may be continuous.
3-26. UAS surveillance of base camps, airfields, and key logistic sites in lesser-contested areas may free combat forces to perform other missions and help prevent surprise.
3-27. The TUAS provides easily maintained and lower detectable aerial surveillance to the ARS and CAB commander to help develop the commander’s intent and concept of the operation. The Shadow Troop provides 24 hour coverage for an NAI in order to:
• Track pattern of life VIA Full Motion Video (FMV)
• Observe a specific area for enemy activity
• Provide early warning and detection on a specific high speed avenue of approach3-28. The difference between an aerial surveillance and standard reconnaissance is the amount of movement for the Shadow payload. During an aerial surveillance, the payload should remain generally stabilized to gather information on an extremely specific area of the battlefield.
FEMEN bare all in Kiev Protest
HOMELAND SECURITY – DHS Mass Transit and Passenger Railroad Systems Terrorist Attack Preparedness Info Regarding a Realistic Threat
(U//FOUO) Terrorist attack tactics used against mass transit and passenger railroad systems abroad provide insights that can assist law enforcement officers in securing these critical infrastructure assets. The chart below highlights common tactics noted in attempted or successful use of explosive or incendiary devices against mass transit or passenger railroad systems in attacks conducted between March 2004 and November 2009. The information about these attacks provides insights into device type, selection, and construction and can help law enforcement identify patterns and develop protective measures. Analysis shows terrorists have timed attacks during periods of peak ridership; used multiple, coordinated, drop-and-leave devices in identical or similar baggage; and placed devices inside rail cars to cause casualties among passengers.
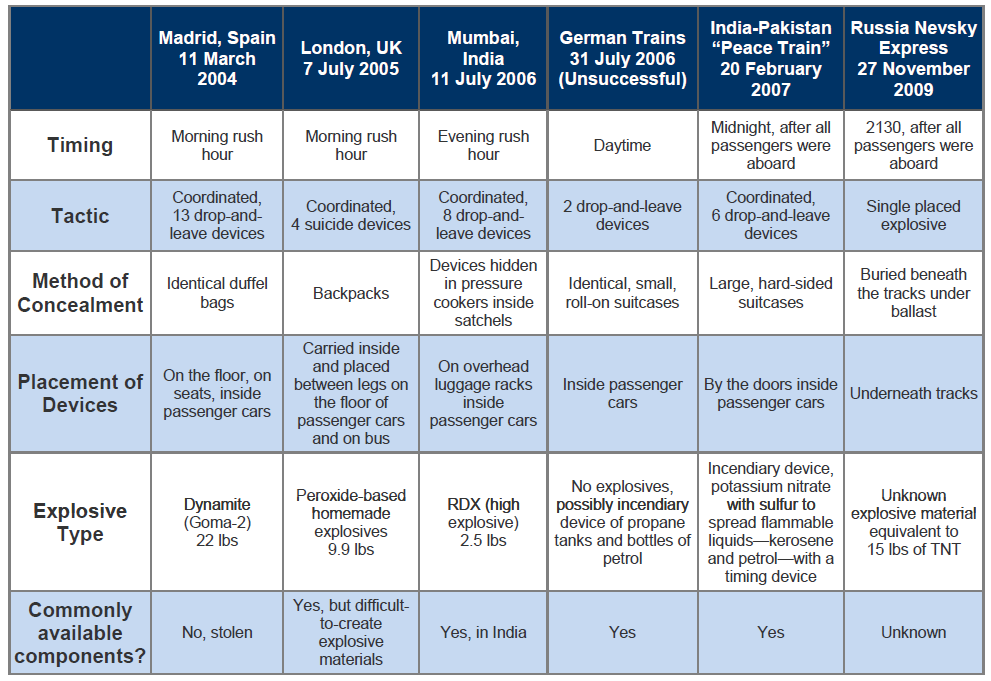
DOWNLOAD ORIGINAL FILE HERE
TOP-SECRET-Telephonogram from Vladimir Semyonov and Marshal Vasilii Sokolovskii to Vyacheslav Molotov and Nikolai Bulganin
Telephonogram from Vladimir Semyonov and Marshal Vasilii Sokolovskii to Vyacheslav Molotov and Nikolai Bulganin Reporting on the Situation in East Berlin, as of 11:00 p.m. CET
Secret
Copy #14
TELEPHONOGRAM BY VCH
From Berlin
17 June 1953
To comrade V.M. Molotov
To comrade N.A. Bulganin
We report on the situation in Berlin and the GDR at 11 p.m., 17 June.
The disorders in Berlin have been stopped. The streets are calm. In connection with the implementation of martial law from 9 p.m. to 5 a.m., the movement of transportation and walking on the streets were halted in the Soviet sector of the city. A small number of people were arrested for breaking this order.
Our troops and the German police are in control of all key streets and important installations in the Soviet sector of the city. The most attention has been paid to the defense of the sector border between East and West Berlin, across which a number of large groups of provocateurs and hooligans from West Berlin had broken through into the Soviet sector in the evening. On the streets Brunnenstrasse and Bernauer Strasse, these gangs started a shootout with the German police, which resulted in casualties. According to preliminary information, 79 German policemen were injured and 2 policemen are missing as a result of the disturbances in the Soviet sector. West Berlin radio is reporting that 7 demonstrators were killed and 66 people were injured. As yet, there are no complete reports on the number of casualties.
In its broadcasts, the American radio station RIAS is calling upon the rebels to submit to the orders of the Soviet authorities and avoid clashes with the Soviet troops.
In the majority of cities in the GDR, order has been fully restored. There are reports of continuing disorders only in the two small cities of Apolda and Mühlhausen.
According to incomplete data, 700 instigators of the disorders have been arrested in the Republic, 300 of whom were in Berlin.
Measures are being taken to reestablish normal operation of all enterprises in the Republic, as well as measures to prevent interruptions in the food supply to the inhabitants of Berlin. The GDR government has called upon the people to swiftly reestablish social order and normal operation of enterprises.
Sokolovskii
Semyonov
Sent by Blatov
Received by Roshchina
18.VI.1953
2 hours, 45 min.
| Collection | East German Uprising |
| Creator | V. Semenov, V. Sokolovskii |
| Contributor | |
| Type | Cable |
| Subject | East Germany, GDR, popular protests in, East Germany, GDR, Soviet control of borders, Germany, intra-German relations, Nicolai Bulganin, popular protests, protesters, Vyacheslav Molotov |
| Coverage | Berlin (Germany), Germany (East) |
| Relation | Germany in the Cold War |
| Lang | English |
| Publisher | CWIHP |
| Rights | CWIHP |
| Format | Translation |
| Identifier: | 5034FC11-96B6-175C-9F3A7C96C66CB71D |
| Thank you for your interest in the Cold War International History Project Virtual Archive. We have redesigned the Virtual Archive to improve access and reflect some of your common requests. Currently the search function is not fully implemented, so we recommend browsing through the collections rather than doing searches. We appreciate your patience and welcome any comments and suggestions at coldwar@wilsoncenter.org
Contents of this website Copyright 1991-2005 Cold War International History Project. All rights reserved. If cited, quoted, translated, or reproduced, acknowledgment of any document’s origin must be made as follows: “Cold War International History Project (CWIHP), http://www.CWIHP.org, by permission of the Woodrow Wilson International Center for Scholars.” For permission to reproduce documents in full or in part, please contact CWIHP at coldwar@wilsoncenter.org |
UNVEILED – Telephonogram from Vladimir Semyonov and Marshal Vasilii Sokolovskii to Vyacheslav Molotov and Nikolai Bulganin
| Date: 06/17/1953 |
Source: AVP RF, f. 082, op. 41, port. 93, pap. 280, ll. 3-4. Translated by Daniel Rozas. |
| Description: Cable to the Soviet leadership describing the situation in East Berlin after the imposition of the curfew. The cable reports that at least 700 people have been arrested in East Germany, 300 of which were in the Soviet sector of Berlin. East German police and Soviet troops have taken control of the border of East Berlin to prevent “provocateur elements” from entering the Soviet sector. |
|
TELEPHONOGRAM BY VCH
From Berlin
17 June 1953
To comrade V.M. Molotov
To comrade N.A. Bulganin
We report on the situation in Berlin and the GDR at 11 p.m., 17 June.
The disorders in Berlin have been stopped. The streets are calm. In connection with the implementation of martial law from 9 p.m. to 5 a.m., the movement of transportation and walking on the streets were halted in the Soviet sector of the city. A small number of people were arrested for breaking this order.
Our troops and the German police are in control of all key streets and important installations in the Soviet sector of the city. The most attention has been paid to the defense of the sector border between East and West Berlin, across which a number of large groups of provocateurs and hooligans from West Berlin had broken through into the Soviet sector in the evening. On the streets Brunnenstrasse and Bernauer Strasse, these gangs started a shootout with the German police, which resulted in casualties. According to preliminary information, 79 German policemen were injured and 2 policemen are missing as a result of the disturbances in the Soviet sector. West Berlin radio is reporting that 7 demonstrators were killed and 66 people were injured. As yet, there are no complete reports on the number of casualties.
In its broadcasts, the American radio station RIAS is calling upon the rebels to submit to the orders of the Soviet authorities and avoid clashes with the Soviet troops.
In the majority of cities in the GDR, order has been fully restored. There are reports of continuing disorders only in the two small cities of Apolda and Mühlhausen.
According to incomplete data, 700 instigators of the disorders have been arrested in the Republic, 300 of whom were in Berlin.
Measures are being taken to reestablish normal operation of all enterprises in the Republic, as well as measures to prevent interruptions in the food supply to the inhabitants of Berlin. The GDR government has called upon the people to swiftly reestablish social order and normal operation of enterprises.
Sokolovskii
Semyonov
Sent by Blatov
Received by Roshchina
18.VI.1953
2 hours, 45 min.
DIE STASI-“GoMoPa”-Betrüger enttarnt – eine Schande für die deutsche Justiz
Das Weekend – Quiz – Was und wieviel verlangen eine “Anwältin” und ein “Chefredakteur” wohl für “DIENSTE”
TOP SECRET from the Homeland Security – DHS Mass Transit and Passenger Railroad Systems Terrorist Attack Preparedness Info Regarding a Realistic Threat

(U//FOUO) Terrorist attack tactics used against mass transit and passenger railroad systems abroad provide insights that can assist law enforcement officers in securing these critical infrastructure assets. The chart below highlights common tactics noted in attempted or successful use of explosive or incendiary devices against mass transit or passenger railroad systems in attacks conducted between March 2004 and November 2009. The information about these attacks provides insights into device type, selection, and construction and can help law enforcement identify patterns and develop protective measures. Analysis shows terrorists have timed attacks during periods of peak ridership; used multiple, coordinated, drop-and-leave devices in identical or similar baggage; and placed devices inside rail cars to cause casualties among passengers.

DOWNLOAD ORIGINAL DOCUMENT HERE
SECRET – United Nations Assistance Mission in Afghanistan (UNAMA) Protection of Civilians in Armed Conflict 2011 Annual Report

A decade after it began, the armed conflict in Afghanistan again incurred a greater human cost in 2011 than in previous years. The United Nations Assistance Mission in Afghanistan (UNAMA) documented 3,021 civilian deaths in 2011, an increase of eight percent over 2010 (2,790 civilian deaths) and a 25 percent increase from 2009 (2,412 civilian deaths).
In 2012, UNAMA re-asserts the imperative for all parties to the conflict – Anti-Government Elements, and Afghan national and international military forces – to increase their commitment and efforts to protect civilians, and to comply fully with their legal obligations to minimize loss of life and injury among civilians.
…
Different Definitions of Civilian Casualties
UNAMA notes that civilian casualty figures may vary among organizations gathering and analyzing such information. Variations between ISAF and UNAMA in numbers of civilians killed and injured in the conflict arise from the use of different methodologies, different levels of access to locations and incidents of civilian casualties and different geographical coverage of the country.
ISAF notes this divergence may be attributed to the following factors:
Figures for Afghan National Security Forces (ANSF) caused civilian casualties are not monitored by ISAF, and reporting of insurgent-caused civilian casualties is based on what is observed or on reports that can be confirmed by ISAF; it therefore presents an incomplete picture.”
ISAF further notes that UNAMA and ISAF use different definitions for civilian casualties regarding the categorization and entities that cause civilian casualties and differ on how civilian casualty events and numbers are confirmed. ISAF states that it includes only Afghan civilians in its statistics and not every noncombatant (armed and unarmed internationals, unarmed Afghans such as interpreters and international civilians such as tourists). ISAF’s statistics also include all civilians casualties identified as ISAF-caused and ANSF-caused civilian casualties when an ANSF unit is partnered with ISAF. Additional ANSF-caused civilian casualties reported or not reported to ISAF are excluded from ISAF’s figures. ISAF states it confirms civilian casualty incidents and numbers through ISAF HQ SOP 302 Edition 3 further to verification by a Joint Incident Assessment Team (JIAT).
UNAMA tracks and includes in its statistics civilian deaths and injuries resulting from the operations of ISAF, ANSF and Anti-Government Elements. UNAMA also proactively monitors, verifies and reports conflict-related killings of civilians including targeted killings by parties to the conflict. UNAMA relies on a wide range of sources to verify and confirm civilian casualties as noted above.
UNAMA does not claim the statistics presented in this report are complete; it may be that UNAMA is under-reporting civilian casualties given limitations associated with the operating environment.
…

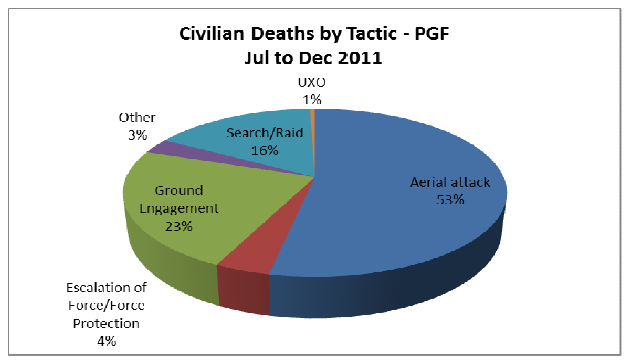
TOP-SECRET – Draft Instructions for General Vasilii Chuikov and Vladimir Semyonov regarding GDR Control of Borders
| Date: 03/18/1953 |
Source: AVP RF, f. 06, op. 12, papka (pap.) 18, port. 283. Obtained and translated by Hope Harrison. |
| Description: Draft instructions of the Soviet leadership to its representatives in East Germany, advising that the SED requests for East German control of the border with West Germany are “unacceptable and grossly simplistic.” |
|
TOP SECRET
Draft Instructions
To Cdes. Chuikov, Semyonov
Regarding nos. 8/1517 and 8/1543. The proposals of the GDR leadership, supported by you, on the implementation of border protection/border guards on the sector border of East Berlin with West Berlin and on measures connected with the carrying out of such protection, including the regulation of transport, appear, according to political considerations, unacceptable and grossly simplistic.
You must meet with Grotewohl and Ulbricht and tactfully explain to them the following:
a) Carrying out such measures in Berlin with a population of several million people would certainly lead to a violation of the established order of city life, would cause the disorganization of the city’s economy, and even more would negatively affect the interests of the population not only of West but also of East Berlin, would evoke bitterness and dissatisfaction from Berliners with regard to the government of the GDR and the Soviet forces in Germany, which would be used by the three Western powers against the interests of the GDR and the USSR.
b) Carrying out such measures with regard to West Berlin would place in doubt the sincerity of the policy of the Soviet government and the GDR government, which are actively and consistently supporting the unification of Germany and the conclusion of a peace treaty with Germany, and would seriously damage our political successes, which have been achieved in West Germany as a result of the implementation of that just policy which answers the fundamental national interests of the German people.
c) The deployment of border guards on the sector border of East Berlin would only complicate, to the clear disadvantage of the countries of the camp of peace and democracy, relations of the Soviet Union with the USA, England and France, a development which we can and must avoid.
Recognizing the unacceptable ideas of your proposals, however, we in general do not deny the necessity of carrying out a series of additional measures for safeguarding the interests of the GDR (and also the USSR) in Berlin, having in mind with this the strengthening of countermeasures against the hostile forces which have their support in West Berlin. It is necessary that these additional measures not be hurried or simplistic, since with a simplistic approach to this serious matter we would only hurt ourselves and facilitate possible hostile activity on the part of those elements which are ready to take advantage of our every blunder.
From this, it follows that you must very seriously rethink this question and those practical measures which it is necessary to undertake in Berlin. We hope that you will look into this matter more attentively in the next two three weeks and give us your thoughts on this question.
TOP-SECRET – Conversation between Joseph V. Stalin and SED leadership
| Date: 04/07/1952 |
Source: Library of Congress, Dmitri Volkogonov Collection; according to Mikhail Narinsky (Moscow), a copy can be found in Arkhiv Prezidenta Rossiisskoi Federatsii, Moscow (AP RF), fond (f.) 45, opis’ (op.) 1, delo (d.) 303, list (l.) 179. |
| Description: The second conversation between Stalin and the SED leadership during their trip to Moscow in April 1952. Stalin discusses the political and military situation in East Germany and asks about the status of economic development in the GDR. The SED delegation asks Stalin to approve the transfer of raw materials to East Germany. |
|
Attended by: Comrades Molotov, Malenkov, Bulganin, and Semyonov (ACC)
Comrade Stalin says that in their last conversation W. Pieck raised the issue of the prospects for German development in connection with the Soviet proposals on peace treaty and the policy of the Americans and the British in Germany. Comrade Stalin believes that regardless of what proposals we make on the German issue, the Western powers will not agree with them, and will not leave West Germany anyway. To think that we would be able to achieve a compromise or that the Americans would accept the draft of peace treaty would be a mistake. The Americans need an army in West Germany, so that they would be able to have all of Europe in their hands. They are saying that they keep the army there against us. In reality however, the mission of their army there is to control Europe. The Americans will pull West Germany into the Atlantic pact. They will create West German troops. Adenauer is in the Americans’ pocket. All the former fascists and generals are there as well. In reality, an independent state is being created in Germany. And you too need to organize an independent state. The demarcation line between East and West Germany should be considered a border–and not just any border, but a dangerous one. We need to strengthen the defense of this border. The Germans will guard the first line of defense, and we will put Russian troops on the second line. Agents of Western countries are moving around the German Democratic Republic all too freely. They can decide to use some extreme measures and kill you or Comrade [Vasilii] Chuikov. This has to be taken into account. Therefore, we need strong border defenses.
Then, continues Comrade Stalin, we want to revive the offices of military commandants. This is another good move against possible subversion. In addition, our troops should also have good protection. And you need it too; you will be stronger yourself. Comrade Stalin asks whether these proposals are acceptable.
Comrade Pieck says that it is very important.
Comrade Ulbricht expresses his agreement. He asks whether military commandants’ offices would be reopened everywhere.
Comrade Stalin responds that he does not know that. Comrade Chuikov wants to reopen military commandants’ offices, and assigns 3 to 4 thousand military for this task.
Comrade Pieck says that it is very important and necessary to do.
Comrade Stalin says that we have examined the issue of arming the German police, and came to the conclusion that it should have Russian-made weapons. Currently the German police are armed with old German weapons, for which they do not have any German bullets. You should either revive the production of bullets, or we should sell you our weapons.
Comrade Ulbricht says that he agrees with that. But would all kinds of weapons be sold? Beginning from the revolver, or beginning with the machine gun?
Comrade Stalin says that all kinds of weapons [will be sold]. If your police are not armed, what kind of police is that? You have a right to have armed police. Comrade Chuikov says that in addition to the regular police, the GDR also has the “Barracked Police,” i.e. the troops. He asked that it be given tanks and artillery. We agree with that. Think about it.
Comrade Stalin says that he has two questions. Last time it was found that in the GDR, the ratio of workers’ salary to the salary of engineering and technical personnel was 1:1.7. It is absolutely incorrect. It will doom your entire industry. Maybe you started from the assumption of what Marx and Engels said in the period of the Commune–that an engineer should not be paid more than a well-qualified worker. Maybe it was correct then, but it is absolutely incorrect now. The engineer is engaged in intellectual work. He must have an apartment, decent furniture; he should not be chasing a piece of bread. He should enjoy a standard of living appropriate for a person who is engaged in intellectual work. He has to have a library, comfort, so that he could sit down and read a book undisturbed, or write something. If you do not do it, not only will your old engineers leave, but even the young ones will run away. In our country, an engineer gets two to three times more than a worker and in some spheres even four times more. Academicians get 12 thousand rubles monthly. It is impossible to work and grow without it. Therefore, you should discard your old views on this issue. The technology has become so complex compared to the times of the Commune, that engineers, and even high-level workers, must study a lot to master this technology. An engineer must have an opportunity to constantly grow, read books, write—there can be no engineer without it. The same applies to the army. Marx and Engels believed that we needed a militia-based army. In our first years, we also thought that only a militia-based army was needed. Life has taught us that that was incorrect. Today, in order to defend the country, we need a modern army with various specialists. A militia-based army is good only in the situation where war is decided with the rifle. Today we should discard this old militia-based army. Today the army is not the manufacture army, but the machine army. Therefore, we need people in the army who know machines.
Comrade Stalin says that he heard that in the GDR well-qualified workers get only slightly more than the manual workers.
Comrade Ulbricht says that they do get more, but the difference is not sufficient. Therefore, they plan to introduce pay rate charts.
Comrade Stalin says that we went through the same experience in the first years of the Soviet government. Communes were organized on the plants, which brought together engineers and manual workers, who pulled all their money together and then divided it equally. It was stupid. White-collar workers did not have any incentive to raise their qualifications, while blue-collar workers did not have any incentive to grow to the level of white-collar workers. As a result, both categories lost. In the old time, some people were saying that such an approach was a proletarian, socialist one. But there is nothing socialist or proletarian about it. It is a simple peasant leveling of all. Any proletarian will tell you that if he gets more money, he would try to raise his skills, otherwise he will not. A skilled worker should be paid more than an unskilled worker, and an engineer—much more than a skilled worker. It should be done regardless of how much it costs. In our country, we did it 25 years ago, and that is the only reason why it works so well. Skilled workers have their prospects–many of them took exams to become engineers, and became good specialists. The peasant leveling of all should be buried. Comrade Stalin asks if the German leaders agree with this and adds that it is the genuine Marxist approach.
Comrade Pieck says that is correct.
Comrade Stalin says that he has a second question. He, Stalin, understands that the GDR has no collective farms at all, and the machine-rental stations serve only private peasant farms.
Comrade Ulbricht confirms that and adds that they even prohibited organization of collective farms where the peasants wanted it, trying not to harm the movement for united Germany.
Comrade Stalin says, why are you complaining about the kulaks. What kind of tactic is that–to complain? The kulaks should be encircled, and you should create collective farms around them. In our country, organization of collective farms was going on simultaneously with expropriation of the kulaks. You will not need to do it this way. Let your kulaks sit tight, leave them alone. But in addition to the kulaks, you have poor peasants in your villages, that live right next to the kulaks. They should be pulled into production cooperatives. How many peasant farms join a production cooperative–5, 10 or 15–that does not matter. What matters, is that they will be organized. Currently poor peasants do not have any machines, do not have enough seed, and do not have necessary knowledge and experience in the economy. That is why their harvest is so poor. In such a situation, poor peasants will ruin themselves and will join the ranks of the unemployed. However, if you organize small collective farms and show them how to manage their farms, then peasants would start thinking, what is better–to join collective farms or to live separately. Good experience was accumulated in Hungary, where they organized good collective farms, left their kulaks alone, and gave machines to their collective farms. They were trying to improve the collective farms’ harvest. It would be wrong to think that the Hungarians are more capable than Germans. You should do the same. You should give production cooperatives some privileges, as it used to be in our country some time ago. You should sell them machines cheaper, help them with seed and advice. If you need instructors for organization of collective farms, we will give them to you. Of course, if the bloc of parties objects to it–that would be a different case. But the bloc will not object if the peasants want to organize production cooperation, and if you help your peasants to do it, what can be bad about it? You will see for yourself that peasants will visit those collective farms and watch how life will unfold in a new way. I noticed, said comrade Stalin, that you do not value peasants in your policy. This is an old social-democratic prejudice toward peasants. If that is true, you should put an end to this situation. Comrade Stalin asks German comrades, whether they need peasants. Whether they give them food products. If they need peasants, then it is necessary to have a base for union with the peasants.
Comrade Pieck says that when the GDR implemented the land reform, the enemies were engaged in propaganda saying that we wanted to create collective farms. The peasants had a very strong prejudice against collective farms. Therefore, we were afraid to raise the issue of collective farms. Now we have peasant unions of mutual assistance and trade cooperation. This is what the principle of cooperation is all about. It is possible that now it would be expedient to raise this issue on a more extensive basis.
Comrade Stalin says that they need to create production cooperatives in the villages, and to call them as such. That would be only positive. You would receive firm support among the peasants. In Hungary it worked very well. And you could have done it long ago. Against any propaganda, you should present your own counter-propaganda and not just sit silently. You can say that poor peasants want to join production cooperatives and that the government is helping them to do it.
Comrade Pieck says that that would be good.
Comrade Stalin notes that they should provide privileges for cooperatives, sell them machines cheaper and help them with seeds for the first two years, and then they will become stronger. Is it possible?
Comrade Ulbricht says that it is possible. That would improve our situation in the village.
Comrade Stalin says, of course, you will have your own base in the village. Do not force anybody to join, if they want to, good. If they do not, do not force them. Peasants will join production cooperatives voluntarily. You could send good people from the city unemployed to organize such cooperatives in the village. Comrade Stalin says that in the Soviet Union, we were able to get rid of unemployment for two reasons; first of all, because we expanded the production and, secondly, because peasants settled on the land. It used to be that every year between 23 to 25 million hungry peasants would come from villages to Russian cities and undermine the price for labor force. Now we do not experience it any more, because the peasants are interested in working in the villages. Today we do not have unemployment in the USSR, and our problem is that we do not have enough workers. We mobilize young peasants and send them to work in the industry. This is how we defeated unemployment from both ends. Do not economize on assistance to collective farms; it will pay back later. Then gradually you will have a union of workers and peasants, and it is difficult for workers to stand alone without peasants. You need help on the part of the peasants.
Comrade Ulbricht says that that would also have its consequences. So far in the GDR we were saying that we stand for democratic Germany, and did not carry out a number of measures that we would need to implement in the process of development in the direction of socialism. We also have never said that we were moving toward socialism.
Comrade Stalin says that this was correct.
Comrade Ulbricht asks whether we should continue this tactic after the deep split of Germany?
Comrade Stalin says that even now they should not shout about socialism. But production cooperatives represent little pieces of socialism. Enterprises owned by people also mean socialism.
Comrade Ulbricht says that so far we have never spoken about it, and did not point out that people’s enterprises were socialist. We disguised the social relations that emerged in the GDR to some extent.
Comrade Stalin says that this mask helped you not to scare the middle class of West Germany. However, if you did not have that mask, then maybe you would have been able to pull the lowest strata of the population to your side. The workers would be glad if they found out that you nationalized the industry. Otherwise, they would say that you have the same government as the one in Bonn. One can say that the GDR has a public nationalized industry, whereas separatist capitalists–millionaires who own the industries–represent West Germany. You have to maneuver here; on the one hand, you should not scare the middle class away. But at the same time, you should not offend the workers of the West. We are selling you our joint-stock enterprises. It would be important for the German workers to know that by doing so we increased the scope of nationalized industry. Workers would be very glad to hear that. Of course, you need to maneuver and to disguise it in your relations with the middle class. If you say that you have state industry, it means that enterprises are in the hands of all the people and not in the hands of robber barons-capitalists. However, you should know for yourself that this is socialist production. Production cooperatives in the village are also little pieces of socialism. You should not make noise about it. When production cooperatives function well, all the peasants will see the benefits and the strength of cooperatives, and after that peasants will turn to the workers. But for now, you should not shout about it, because collective farms are not in your pocket yet. In my opinion, you should begin to do it. Although two states are being currently created in Germany, you should not shout about socialism at this point. You should not call these farms collective farms, but call them production cooperatives.
Comrade Pieck says that the issue of production cooperation should be seriously discussed and clarified for the party.
Comrade Stalin says, to begin with, you should build several collective farms and then discuss it in the party. Right now you do not have any material for such discussion. Laughing, Comrade Stalin notes that the deed comes before the word.
Comrade Ulbricht asks, what experience did the countries of people’s democracy have? Would it be more expedient to start creating production cooperatives after the harvesting is completed?
Comrade Stalin says that usually peasants build during the winter. You could talk with peasants about creating production cooperatives after the harvest is over.
Comrade Pieck says that workers ask us, what is the social regime of the GDR? Is this socialism? Up to this point, we avoided answering this question, but the workers remained unsatisfied.
Comrade Stalin says that you should say to your workers: We have just entered socialism. This is not full socialism yet, because you have a lot of private capitalists. But this is the beginning of socialism, a little piece of socialism, and a road to socialism. You should show that you are closer to the workers than Adenauer’s government.
Comrade Stalin asks, what organ is higher in your country–the Secretariat or the Politburo?
Comrade Pieck responds that they did not have much clarity on this issue in the SED, although, according to the Charter of the SED, the Politburo is above the Secretariat. We had a conversation with comrade Pegov from the CPSU CC, and he explained their methods of work to us very well, and made it very clear. In addition, we talked with Kuznetsov, Romanov, and Mikhailov on the issues of military education in preparation of young people for the draft. Comrade Stalin says that you probably would need instructors for building collective farms. You could request instructors from Hungary or Poland.
Comrade Malenkov notes that they would carry more authority for German peasants than the Soviet people.
Comrade Stalin says that we will give you one or two instructors, but you should not engage in expropriation simultaneously with collectivization. You can leave your kulaks alone for the time being.
Comrade Ulbricht responds that we do not need to touch them at the present time, because when production cooperatives are starting to organize, a part of kulaks will immediately escape to the West.
Comrade Stalin asks, what is bad about that? You will take their land. In Poland, part of the kulaks sold their lands and now engage in carrier’s trade. Comrade Stalin asks whether the GDR has any state farms?
Comrade Ulbricht responds affirmatively and adds that state farms cover approximately 5% of all cultivated land in the GDR.
Comrade Stalin asks whether they work well.
Comrade Ulbricht says that they do not work very well.
Comrade Semyonov gives a reference that the productivity of people’s farms in the GDR is considerably better than the productivity of peasants’ fields, however, people’s farms are, as a rule, unprofitable and receive subsidies from the state.
Comrade Stalin says that some people’s farms could be transferred to peasants if they do not work well. In our country, in the Soviet Union, initially we experienced difficulties in setting up the work of state farms. Then we transferred part of state farms to the peasants, and the farms became profitable. In order to provide for workers of the state farms, we decided to give them plots of land and they began to work better and settled on the land permanently.
Comrade Stalin asks whether the German comrades received the rolling mill?
Comrade Grotewohl responds that the money to buy the mill was transferred, but so far they cannot say anything definite about the purchase of the mill.
Comrade Stalin asks whether they hope to receive the mill?
Comrade Grotewohl responds affirmatively and says that they issued appropriate orders.
Comrade Stalin notes that in the Soviet Union they make such mills and all necessary equipment for them, however, the plants are overloaded with orders.
Comrade Stalin asks whether they found iron-ore in the new locations in the GDR.
Comrade Ulbricht responds that the GDR only has poor ore, which contains only 20% of iron.
Comrade Stalin says that it should be mixed with good ore. Before the war, the Germans did not refuse even the ore containing only 5% of iron.
Comrade Ulbricht says that they built special low mines for such poor ore.
Comrade Stalin says that such ore should be mixed with good ore. The Poles take our ore from Kryvoi Rog and mix 50% of it with their own poor ore. The Germans took our ore even under Hitler. Recently we discovered good ore in Siberia that contains 60% of iron. But that layer is located very far from railroads.
Comrade Ulbricht says that they have one more request. We have already informed you that we would like to develop a program of the Communist Party of West Germany. We will try to speed up the development of this program and to publish it before the KPD is prohibited. We are asking if comrade Stalin and the Politburo of the CPSU CC could look at our draft and help us in developing that program.
Comrade Stalin gives his approval.
Comrade Grotewohl says that they completely agree with Comrade Stalin’s opinion in his evaluation of the situation in West Germany, and the policy of the United States. He, Grotewohl, would like to ask whether Comrade Stalin believes that at the present time we should introduce changes in our arguments to the official position of the GDR government on the issue of revival of German unity.
Comrade Stalin answers negatively. You should continue propaganda of German unity in the future. It has a great importance for the education of the people in Western Germany. Now it is a weapon in your hands and you should always hold it in your hands. We should also continue to make proposals regarding German unity in order to expose the Americans.
Comrade Grotewohl asks Comrade Stalin about additional sales of 8,000 tons of long-fiber cotton to the GDR.
Comrade Stalin gives his approval, and proposes to talk about it with Comrade Malenkov.
Unveiled – Letter from President Roosevelt to Stalin on an Acceptable Compromise
THE WHITE HOUSE
WASHINGTON
February 6, 1945
My dear Marshal Stalin:
I have been giving a great deal of thought to our meeting this afternoon, and I want to tell you in all frankness what is on my mind.
In so far as the Polish Government is concerned, I am greatly disturbed that the three great powers do not have a meeting of minds about the political setup in Poland. It seems to me that it puts all of us in a bad light throughout the world to have you recognizing one government while we and the British are recognizing another in London. I am sure this state of affairs should not continue and that if it does it can only lead our people to think there is a breach between us, which is not the case. I am determined that there shall be no breach between ourselves and the Soviet Union. Surely there is a way to reconcile our differences.
Marshal V. I. [sic] Stalin,
Koreis, The Crimea
I was very much impressed with some of the things you said today, particularly your determination that your rear must be safeguarded as your army moves into Berlin. You cannot, and we must not, tolerate any temporary government which will give your armed forces any trouble of this sort. I want you to know that I am fully mindful of this.
You must believe me when I tell you that our people at home look with a critical eye on what they consider a disagreement between us at this vital stage of the war. They, in effect, say that if we cannot get a meeting of minds now when our armies are converging on the common enemy, how can we get an understanding on even more vital things in the future.
I have had to make it clear to you that we cannot recognize the Lublin Government as now composed, and the world would regard it as a lamentable outcome of our work here if we parted with an open and obvious divergence between us on this issue.
You said today that you would be prepared to support any suggestions for the solution of this problem which offered a fair chance of success, and you also mentioned the possibility of bringing some members of the Lublin government here.
Realizing that we all have the same anxiety in getting the matter settled, I would like to develop your proposal a little and suggest that we invite here to Yalta at once Mr. Beirut [Bierut] and Mr. Osubka Morawski from the Lublin government and also two or three from the following list of Poles, which according to our information would be desirable as representatives of the other elements of the Polish people in development of a new temporary government which all three of us could recognize and support: Bishop Sapieha of Cracow, Vincente [Wincenty] Witos, Mr. Zurlowski [Zulawski], Professor Buyak [Bujak], and Professor Kutzeva [Kutzeba]. If, as a result of the presence of these Polish leaders from abroad such as Mr. Mikolajczyk, Mr. Grabski, and Mr. Romer, the United States Government, and I feel sure the British government as well, would be prepared to examine with you conditions in which they would dissociate themselves from the London government and transfer their recognition to the new provisional government.
I hope that I do not have to assure you that the United States will never lend its support in any way to any provisional government in Poland that would be inimical to your interest.
It goes without saying that any interim government could be formed as a result of our conference with the Poles here would be pledged to the holding of free elections in Poland at the earliest possible date. I know this is completely consistent with your desire to see a new free and democratic Poland emerge from the welter of this war.
Most sincerely yours
Franklin Roosevelt
TOP-SECRET from the FBI – Homebuilder Indicted in $14.7 Million Construction Investment Scheme
BALTIMORE—A federal grand jury indicted Patrick J. Belzner, a/k/a “Patrick McCloskey,” age 42, of Glen Arm, Maryland, yesterday for conspiring to commit wire fraud arising from an investment fraud scheme. The indictment was unsealed today upon the arrest of the defendant.
The indictment was announced by United States Attorney for the District of Maryland Rod J. Rosenstein; Special Agent in Charge Richard A. McFeely of the Federal Bureau of Investigation; and Acting Special Agent in Charge Eric C. Hylton of the Internal Revenue Service-Criminal Investigation, Washington, D.C. Field Office.
According to the indictment, from at least August 2009 to August 2011, Belzner, a homebuilder, and a co-conspirator also in the home building business, targeted individuals seeking investment opportunities or commercial real estate development lending. Belzner, who falsely presented himself as “Patrick McCloskey” with certain investors, instructed the victims that in order to obtain loans for commercial real estate projects, the purported lenders required that large sums of money be deposited in an escrow bank account to show “liquidity.”
The indictment alleges that in order to gain their victims’ confidence, Belzner and his co-conspirators caused victim investors and borrowers to enter into escrow agreements which stated that no person other than the victims had the ability to remove the escrowed funds without the victims’ permission. Belzner told the victims that a co-conspirator had to be the attorney assigned as the escrow agent.
The indictment alleges that Belzner and his co-conspirator fraudulently withdrew approximately $14,730,780 from the escrow accounts and used these stolen funds to satisfy their business and personal debts. To conceal their scheme, Belzner and his co-conspirators allegedly e-mailed fabricated bank statements to victims that misrepresented the escrow account balance and the date by when the investors’ money would be returned. Belzner and his co-conspirators also used funds fraudulently obtained from some victim investors to repay money owed to previous victim investors, or to other individuals to whom the conspirators owed debts.
The indictment seeks forfeiture at least $14,730,780, the amount of money stolen from victim investors.
Belzner faces a maximum sentence of 20 years in prison and a fine of $250,000 or twice the value of the gain or loss. Belzner had his initial appearance today in federal court in Baltimore.
An indictment is not a finding of guilt. An individual charged by indictment is presumed innocent unless and until proven guilty at some later criminal proceedings.
This law enforcement action is part of President Barack Obama’s Financial Fraud Enforcement Task Force. President Obama established the interagency Financial Fraud Enforcement Task Force to wage an aggressive, coordinated, and proactive effort to investigate and prosecute financial crimes. The task force includes representatives from a broad range of federal agencies, regulatory authorities, inspectors general, and state and local law enforcement who, working together, bring to bear a powerful array of criminal and civil enforcement resources. The task force is working to improve efforts across the federal executive branch, and with state and local partners, to investigate and prosecute significant financial crimes, ensure just and effective punishment for those who perpetrate financial crimes, combat discrimination in the lending and financial markets, and recover proceeds for victims of financial crimes.
United States Attorney Rod J. Rosenstein thanked the FBI and IRS-CI for their work in the investigation. Mr. Rosenstein praised Assistant U.S. Attorneys Sean O’Connell and Sujit Raman, who are prosecuting the case.
NEWS – West Virginia Unveils App for Suspicious Activity Reporting
Today Gov. Earl Ray Tomblin joined by West Virginia Division of Homeland Security and Emergency Management Director Jimmy Gianato and West Virginia Intelligence Fusion Center Director Thom Kirk together announced a new mobile app, that enables West Virginians to submit tips concerning suspicious criminal and terrorist activity, is now available for smartphones.
“Through the use of innovative technology our citizens can download the new Suspicious Activity Reporting Application for free and help protect their own communities,” Gov. Tomblin said. “With the assistance of our citizens, important information can quickly get into the hands of our law enforcement community allowing them to provide better protection. This is just another example of my administration’s commitment to helping keep our streets and citizens safer.”
Developed by West Virginia Interactive as a project of the West Virginia Division of Homeland Security and Emergency Management and the West Virginia Intelligence Fusion Center, the app sends submitted information, including photos and texts, to the Fusion Center where the information can help authorities react to and prevent incidents from occurring. The previous methods of submitting suspicious or criminal activity by using the Fusion Center’s website or by calling them directly has now been enhanced by the implementation of this application.
“The longer you wait the less accurate eyewitness information becomes and evidence fades,” said Thom Kirk, Director of the Fusion Center. “Enabling the information to be sent at the time the activity is taking place will not only improve the accuracy of the report, but also improve the ability of the authorities to respond quickly.”
The free application is available for download from the iTunes App Store or Android Market and gives citizens the ability to:
- Capture a photo from the app or use one that already exists on the device
- Automatically find and use their location or enter an address
- Report detailed subject and vehicle descriptions
- Remain anonymous if preferred, or include contact information
“We’re excited about getting citizens involved in protecting their communities,” said WVDHSEM Director Jimmy Gianato. “We’re currently looking at our other services to see what else makes sense to move to the mobile platform.”
The mission of the West Virginia Division of Homeland Security and Emergency Management is to ensure the protection of life and property by providing coordination, guidance, support and assistance to local emergency managers and first responders. For more information, visit http://www.dhsem.wv.gov.
The West Virginia Intelligence Fusion Center is a partnership between public and private entities. Through the cooperation of local, state, and federal law enforcement, public safety agencies, and the private sector, the fusion center is able to better protect the citizens of the United States against all hazards. For more information, visit http://www.fusioncenter.wv.gov.
The new Suspicious Activity Reporting Application was developed at no cost to the West Virginia Division of Homeland Security and Emergency Management or West Virginia Intelligence Fusion Center through the state’s self-funded electronic government program, WV.gov. For more information about West Virginia’s electronic government program, visit: http://www.wv.gov/partner.
FEMEN uncensonsored in Kiev
Cryptome – STRATFOR Hacked Update 7
Anonymous allegedly releases “5 million” (not substantiated) Stratfor emails through WikiLeaks:
http://wikileaks.org/the-gifiles.html
John Young @Cryptomeorg
@AnonymousIRC @wikileaks Great show! Will the full raw emails be released as promised by Anonymous to legitimate media-ized spoon-feeding?
Summary of releases of STRATFOR documents, subscribers’ firm names and personal information (including addresses, telephone numbers, credit card numbers and passwords), latest release at top:
STRATFOR Hacked Update 6
30 December 2011. A writes that five Pastebin posts of recovered STRATFOR passwords have been removed as indicated below. In addition, four files from sources have been removed from Rapid Share (1) and Wikisend (3).
29 December 2011.
Lulzxmas Dumps 860,000 STRATFOR Accounts:
http://pastebin.com/f7jYf5Wdhttp://www.megaupload.com/?d=O5P03RXK
28 December 2011.
Prepping for the Stratfor 5M Email Release
27 December 2011.
http://pastebin.com/78MUAaeZ [Now removed]
These are 28517 of 53281 (54%) passwords from the list of STRATFOR customer accounts cracked.Part 1/3: http://pastebin.com/CdD92fJG [Now removed]
Part 2/3: http://pastebin.com/AcwQgHmF [Now removed]
Part 3/3: http://pastebin.com/78MUAaeZ [Now removed]
26 December 2011. Firms and personal first names beginning with “D” through “My” (~ 30,000).
http://pastebin.com/q5kXd7Fdhttps://rapidshare.com/#!download|44tl6|2444489251|STRATFOR_full_d_m.txt.gz|3255|
R~7B8842ED6343CEAE67A23C094E131679|0|0 [Now removed]And 25,000 IT work tickets:
26 December 2011. Sample Stratfor.com email:
http://pastebin.com/HmDs0EM4“just a small preview of the mayhem to come. 1 out of 2.7 million”
26 December 2011. STRATFOR leaked accounts (10257 passwords recovered)
http://pastebin.com/CdD92fJG [Now removed]
25 December 2011. Firms and personal miscellaneous names not in alphabetical order (~13,000):
http://pastebin.com/8v3768Bw[Now removed]http://wikisend.com/download/132838/stratfor_full_misc.txt.gz [Now removed]
25 December 2011. Firms and personal first names beginning with “B-By” through “C-Cz” (~4,000) :
http://pastebin.com/bUqkb9mqhttp://wikisend.com/download/597646/stratfor_full_b.txt.gz [Now removed]
25 December 2011. Firms and personal first names beginning with “A” through “Az” (~ 4,000).
http://pastebin.com/bQ2YHDdwhttp://wikisend.com/download/601776/stratfor_full_a.txt.gz [Now removed]
25 December 2011. A message allegedly to subscribers from George Friedman, Stratfor, was posted to Facebook and Pastebin (below).
25 December 2011. A paste today denying Anonymous role:
And, Stratfor’s A client list of passwords:
24 December 2011
STRATFOR Hacked
Related:
A sends:
Subject: Important Announcement from STRATFOR
Date: Sat, 24 Dec 2011 19:49:58 -0500
From: STRATFOR <mail[at]response.stratfor.com>
Dear Stratfor Member,
We have learned that Stratfor’s web site was hacked by an unauthorized party. As a result of this incident the operation of Stratfor’s servers and email have been suspended.
We have reason to believe that the names of our corporate subscribers have been posed [sic] on other web sites. We are diligently investigating the extent to which subscriber information may have been obtained.
Stratfor and I take this incident very seriously. Stratfor’s relationship with its members and, in particular, the confidentiality of their subscriber information, are very important to Stratfor and me. We are working closely with law enforcement in their investigation and will assist them with the identification of the individual(s) who are responsible.
Although we are still learning more and the law enforcement investigation is active and ongoing, we wanted to provide you with notice of this incident as quickly as possible. We will keep you updated regarding these matters.
Sincerely,
George Friedman
STRATFOR
221 W. 6th Street, Suite 400
Austin, TX 78701 US
www.stratfor.com
http://www.facebook.com/stratfor
Dec 25th, 2011
On December 24th an unauthorized party disclosed personally identifiable information and related credit card data of some of our members. We have reason to believe that your personal and credit card data could have been included in the information that was illegally obtained and disclosed.
Also publicly released was a list of our members which the unauthorized party claimed to be Stratfor’s “private clients.” Contrary to this assertion the disclosure was merely a list of some of the members that have purchased our publications and does not comprise a list of individuals or entities that have a relationship with Stratfor beyond their purchase of our subscription-based publications.
We have also retained the services of a leading identity theft protection and monitoring service on behalf of the Stratfor members that have been impacted by these events. Details regarding the services to be provided will be forwarded in a subsequent email that is to be delivered to the impacted members no later than Wednesday, December 28th.
In the interim, precautions that can be taken by you to minimize and prevent the misuse of information which may have been disclosed include the following:
– contact your financial institution and inform them of this incident;
– if you see any unauthorized activity on your accounts promptly notify your financial institution;
– submit a complaint with the Federal Trade Commission (“FTC”) by calling 1-877-ID-THEFT (1-877- 438-4338) or online at https://www.ftccomplaintassistant.gov/; and
– contact the three U.S. credit reporting agencies: Equifax (http://www.equifax.com/ or (800) 685-1111), Experian (http://www.experian.com/ or (888) 397-3742), and TransUnion (http://www.transunion.com/ or (800) 888-4213), to obtain a free credit report from each.
Even if you do not find any suspicious activity on your initial credit reports, the FTC recommends that you check your credit reports periodically. Checking your credit reports can help you spot problems and address them quickly.
To ease any concerns you may have about your personal information going forward, we have also retained an experienced outside consultant that specializes in such security matters to bolster our existing efforts on these issues as we work to better serve you. We are on top of the situation and will continue to be vigilant in our implementation of the latest, and most comprehensive, data security measures.
We are also working to restore access to our website and continuing to work closely with law enforcement regarding these matters. We will continue to update you regarding the status of these matters.
Again, my sincerest apologies for this unfortunate incident.
Sincerely,
George Friedman
Unveiled – Asian Head of State knew of 9/11 and funded al-Qaeda
A sends:
You may find this of interest, and if so consider publishing a copy of the Burby submission below. It is currently still up on the UK
Parliament website, but lawyers are reportedly threatening diplomatic repercussions.
In brief:
The unnamed ex-wife of an unnamed Asian head of state has a “super-injunction” in effect in the UK, against a businessman named
Mark Burby. Normally that would prevent any mention in the UK media. However Burby recently provided a written submission to a committee in
the UK Parliament, and it has been published under “parliamentary privilege”.
A few days ago the Telegraph newspaper reported the contents of Burby’s submission under the headline “Head of state ‘funded al-Qaeda
and knew of 7/7 terror attacks'”.
It was reported this afternoon that lawyers for the claimant (ex-wife) are now actually trying to persuade Parliament to take down Burby’s
submission “as a matter of extreme urgency” and warning that it will have diplomatic repercussions.
Burby’s submission is quite extraordinary and includes allegations that the unnamed head of state is a “substantial” backer of AQ and had
advance warning of the suicide bombings in London in July 2005. Additionally it covers personal matters likely to embarrass the
principals involved.
The submission itself is not proof of anything of course. However Burby is clearly not a fantasist. In 2005 he was awarded damages of
£50m over a disputed business deal with the family of the head of state. A second businessman under a similar injunction from the same
source was murdered in Australia in 2009.
I’ve included links to Burby’s submission, the Telegraph articles, and supporting older news articles below.
Naming the names:
The “Asian head of state” is Hassanal Bolkiah, the Sultan of Brunei (ostensibly a close ally of the UK).
The claimant is the Sultan’s first ex-wife Mariam Aziz (recipient of the “world’s largest divorce settlement” in 2003).
The murdered businessman is Michael McGurk (shot to death in Sydney in 2009).
Main links:
Joint Committee on Privacy and Injunctions – Oral and written evidence (see Burby pages 50-79)
http://www.parliament.uk/documents/joint-committees/Privacy_and_Injunctions/JCPIWrittenEvWeb.pdf
[Cryptome mirror: http://cryptome.org/2012/01/mark-burby-doc.pdf (2.9MB)]
“Head of state ‘funded al-Qaeda and knew of 7/7 terror attacks'” (Telegraph, 25/02/2012)
“Exclusive: Lawyers order Parliament to stop publishing super-injunction document” (Telegraph, 28/02/2012)
2003 Divorce:
“The world’s largest divorce settlement” (Scotsman, 04/02/2003)
http://www.scotsman.com/news/international/the_world_s_largest_divorce_settlement_1_544213
“Sultan of Brunei to divorce his second wife” (Hello, 06/02/2003)
http://www.hellomagazine.com/royalty/2003/02/06/sultanofbrunei/
2007 Mariam Aziz and the fortune teller (previous injunction attempt):
“Sultan of Brunei’s bid to ‘protect dignity’ fails” (Telegraph, 11/07/2007)
http://www.telegraph.co.uk/news/uknews/1557122/Sultan-of-Bruneis-bid-to-protect-dignity-fails.html
“Sultan of Brunei’s ex-wife and the £2m con” (Telegraph, 12/07/2007)
http://www.telegraph.co.uk/news/uknews/1557227/Sultan-of-Bruneis-ex-wife-and-the-2m-con.html
2009 Michael McGurk murder and link to Burby:
“Claims that slain businessman wanted to blackmail Sultan” (ABC, 10/09/2009)
http://www.abc.net.au/pm/content/2009/s2682461.htm
“McGurk ‘planned to blackmail’ Sultan of Brunei” (ABC, 11/09/2009)
http://www.abc.net.au/news/2009-09-10/mcgurk-planned-to-blackmail-sultan-of-brunei/1425082
“British property developer claims police protection after Sydney murder” (Guardian, 09/09/2009)
http://www.guardian.co.uk/world/2009/sep/09/mark-burby-police-protection-australia
Hassanal Bolkiah, Sultan of Brunei (Wikipedia entry)
From the FBI – Operation Atlantic Taking International Aim at Child Predators
 |
|---|
On Wednesday, Europol released the results of its first joint operation with the FBI against international child predators, announcing the identification of eight child victims and the arrest of 17 individuals for child sexual molestation and production of pornography.
Operation Atlantic has led to the identification of 37 child sex offenders in France, Italy, the Netherlands, Spain, and the United Kingdom. The investigation, which began in December 2010, continues as individuals overseas are still being sought.
“Online child predators and child exploitation are not just an American problem,” said FBI Director Robert S. Mueller. “The FBI is committed to working with our law enforcement partners around the world, such as Europol, to combat these horrendous crimes. We share actionable intelligence and resources to keep children safe and bring those who do them harm to justice.”
Sharing intelligence was our primary role in Operation Atlantic, and it was facilitated by our Innocent Images Operations Unit (IIOU) at FBI Headquarters. Agents working covertly set up an electronic dragnet on a peer-to-peer network targeting pedophiles located in European Union (EU) countries and forwarded investigative results to our partners at Europol.
Previously, IIOU staff worked with our legal attachés overseas to formalize a cooperative agreement with Europol regarding several criminal investigative programs, including online child sexual exploitation. “The results of Operation Atlantic validate this new relationship and offer an example of outstanding achievement through international law enforcement cooperation,” said Audrey McNeill, IIOU chief.
Europol works with law enforcement agencies in the 27 EU countries, along with non-EU members such as the U.S. and Australia. Europol personnel do not have direct powers of arrest, but instead support law enforcement in member countries through coordination and intelligence gathering and sharing.
“Collaboration and cooperation between Europol and our international law enforcement partners such as the FBI is essential if we are to bring members of these child sex abuse networks to justice and prevent the distribution of child exploitation material across the Internet,” said Rob Wainwright, Europol’s director. Noting that Operation Atlantic is the first joint operation conducted by the FBI and Europol in the area of child sexual exploitation, Wainwright added, “Europol is ready and willing to support ongoing and future operations to infiltrate these networks.”
The leads and intelligence gathered by the FBI that formed the basis of Operation Atlantic helped link suspects in five countries to pedophile groups, including the notorious “Boylover” network, the focus of a previous Europol action called Operation Rescue. Subjects arrested in Operation Atlantic include a web of offenders that were producing and distributing images depicting the severe abuse of children—in some cases toddlers and infants.
“These individuals were not just possessors of child pornography,” McNeill said. “Some were previously convicted child sex offenders and were actively engaged in child sexual abuse.” In addition to providing leads to Europol, the IIOU detailed an agent to Europol headquarters in The Hague, Netherlands last summer to help facilitate the investigation.
“Europol is a key and valued strategic partner for the IIOU, and we look forward to a long and productive relationship with them,” McNeill said. “I hope that Operation Atlantic is the first of many future successes. We are working hard to increase our international footprint and to stop child predators wherever they are in the world.”
FEMEN Uncensored Video
TOP-SECRET – DHS Testimony on Social Networking and Media Monitoring
Joint testimony of Chief Privacy Officer Mary Ellen Callahan, and Operations Coordination and Planning Director Richard Chávez for a House Committee on Homeland Security, Subcommittee on Counterterrorism and Intelligence hearing on DHS monitoring of social networking and media
311 Cannon
Introduction
Chairman Meehan, Ranking Member Speier, and Members of the subcommittee, we appreciate the opportunity to be here today to discuss the Department of Homeland Security’s (DHS) use of social media, and the privacy protections the DHS Privacy Office has put into place.
Social media are web-based and mobile technologies that turn communication into an interactive dialogue in a variety of online fora. It may be appropriate for the government, including DHS, to use social media for a variety of reasons. The President has challenged his Administration to use technology and tools to create a more efficient, effective, and transparent government1. DHS recognizes that the use of social media by government actors must occur with appropriate privacy, civil rights, and civil liberties protections; whether DHS is disclosing its information and press releases via social media platforms like Twitter and Facebook, reviewing news feeds for situational awareness, or researching identified, discrete targets for legitimate investigatory purposes. Accordingly, DHS has created Department-wide standards designed to protect privacy, civil rights, and civil liberties in each category of its use. There are three general ways in which DHS utilizes social media, and each has associated privacy protections:
- External communications and outreach between the Department and the public;
- Awareness of breaking news of events or situations related to homeland security, known as “situational awareness;” and
- Operational use, when DHS has the appropriate authorities, such as law enforcement and investigations.
In each category, the Department has established and enforces standards that incorporate privacy protections ex ante, create uniform standards across the components and Department, and are transparent with regard to the scope of our activities
External Communications and Outreach
Consistent with the President’s 2009 Memorandum on Transparency and Open Government, the Office of Management and Budget’s (OMB) Open Government Directive2 and OMB’s Memorandum M-10-23, Guidance for Agency Use of Third-Party Websites and Applications3, the Department uses the social networking medium to provide the public with robust information through many channels. For example, DHS currently has a presence on many of the major social networking platforms, including Facebook, Twitter, and YouTube. In addition, FEMA launched a FEMA app for smartphones that contains preparedness information for different types of disasters. Similarly, the Transportation Security Administration has MyTSA Mobile Application, which enables the traveling public access to relevant TSA travel information, such as types of items that may be carried through TSA security checkpoints, or estimated wait times.
In 2009, the Department established a Social Media Advisory Group, with representatives from the Privacy Office; Office of General Counsel; Chief Information Security Officer; Office of Records Management; and Office of Public Affairs to ensure that a variety of compliance issues including privacy, legal, security, and records management issues are addressed as DHS uses social media. This group governs and provides guidance on social media initiatives related to external communications and public outreach by reviewing recommendations from components and offices and evaluating Terms of Service agreements and Terms of Use policies. The group also developed a social media use plan, while working to ensure compliance issues are addressed and resolved before the first Department use of a particular application of social media.
DHS also established Department-wide standards for use of social media for communications and outreach purposes through the creation, and development of, two Privacy Impact Assessments (PIAs). The PIAs address two types of uses of social media within the communications/outreach category: 1) interactive platforms where the Department has official identities, using those profiles to provide information about the Department and its services, while having the ability to interact with members of the public such as allowing them to post comments on the official Department page or profile;4 and 2) unidirectional social media applications encompassing a range of applications, often referred to as applets or widgets, that allow users to view relevant, real-time content from predetermined sources, such as podcasts, Short Message Service (SMS) texting, audio and video streams, and Really Simple Syndication (RSS) feeds.5
The PIAs analyze the Department’s use of social media and networking for communications purposes, if and how these interactions and applications could result in the Department receiving personally identifiable information (PII), and the privacy protections in place. The PIAs describe the information the Department may have access to, how it will use the information, what information is retained and shared, and how individuals can gain access to and correct their information. For example, official DHS accounts across social media and networking websites and applications must be identified by the component or Department seal as well as an anonymous, but easily identifiable user name account displaying a DHS presence, such as “DHS John Q. Employee.” Both the communications and outreach PIAs also include periodically-updated appendices that identify the specific Department-approved profiles and applications. In addition, the PIAs contain provisions that Department-approved profiles are subject to Privacy Compliance Reviews by the DHS Privacy Office.
Situational Awareness
The Office of Operations Coordination and Planning (OPS), National Operations Center (NOC), has a statutory responsibility (Section 515 of the Homeland Security Act (6 U.S.C. § 321d(b)(1))) to provide situational awareness and establish a common operating picture for the federal government, and for state, local, tribal governments as appropriate, in the event of a natural disaster, act of terrorism, or other man-made disaster, and (2) ensure that critical terrorism and disaster-related information reaches government decision-makers. Traditional media sources, and more recently social media sources, such as Twitter, Facebook, and a vast number of blogs, provide public reports on breaking events with a potential nexus to homeland security. By examining open source traditional and social media information, comparing it with many other sources of information, and including it where appropriate into NOC reports, the NOC can provide a more comprehensive picture of breaking or evolving events. To fulfill its statutory responsibility to provide situational awareness and to access the potential value of the public information within the social media realm, in 2010, the NOC launched the first of three pilots using social media monitoring related to specific natural disasters and international events.
Beginning with the pilots, the reason the NOC utilizes social media tools is to identify breaking or evolving incidents and events to provide timely situational awareness and establish a more complete common operating picture. The NOC views information from a variety of sources to include open source reporting and a variety of public and government sources. The NOC synthesizes these reports for inclusion in a single comprehensive report. These reports are then disseminated to DHS components, interagency partners, and state, local, tribal, territorial, and private sector partners with access to the NOC’s common operating picture. The content of the reports may be related to standing critical information requirements, emerging events potentially affecting the homeland, or special events such as the Super Bowl or the United Nations General Assembly.
Prior to implementing each social media pilot, the Privacy Office and the Office of Operations Coordination and Planning developed detailed standards and procedures associated with reviewing information on social media web sites. These standards and procedures are documented through a series of pilot-specific PIAs.6
The NOC pilots occurred during the 2010 Haiti earthquake response, the 2010 Winter Olympics in Vancouver, British Columbia; and the response to the April 2010, Deep Water Horizon Gulf Coast oil spill. For each of these pilots, the NOC utilized internet-based platforms to provide situational awareness and develop a common operating picture directly related to the response, recovery, and rebuilding efforts in Haiti by reviewing information on publicly-available online fora, blogs, public websites, and message boards. Following the three discrete social media monitoring pilots by the NOC, the Privacy Office did a thorough (and public) Privacy Compliance Review of the NOC’s implementation of the PIAs’ privacy protections.7 The Privacy Office’s review found that the NOC’s social media monitoring activities did not collect PII, did not monitor or track individuals’ comments, and complied with the stated privacy parameters set forth in the underlying PIAs.
Given the positive assessment of the three pilots, OPS and the Privacy Office designed a holistic set of privacy protections to be implemented whenever information made available through social media is being reviewed for situational awareness and establishing a common operating picture. In June 2010, the Department released its Publicly Available Social Media Monitoring and Situational Awareness Initiative PIA, incorporating these protections.8 This PIA describes how the NOC uses Internet-based platforms that provide a variety of ways to review information accessible on publicly-available online fora, blogs, public websites, and message boards. Through the use of publicly-available search engines and content aggregators, the NOC reviews information accessible on certain heavily-trafficked social media sites for information that the NOC can use to provide situational awareness and establish a common operating picture, all without monitoring or tracking individuals’ comments or relying on the collection of PII, with very narrow exceptions, discussed below.
The NOC does not: 1) actively seek PII except for the narrow exceptions; 2) post any information on social media sites; 3) actively seek to connect with internal/external social media users; 4) accept internal/external personal users’ invitations to connect; or 5) interact on social media sites. The NOC is, however, permitted to establish user names (consistent with the criteria established in the communications and outreach PIAs) and passwords to form profiles and follow relevant government, media, and subject matter experts on social media sites as described in the June 2010 PIA; and to use search tools under established criteria and search terms that support situational awareness and establishing a common operating picture.
As part of the publication of the June 2010 PIA, the Privacy Office mandates Privacy Compliance Reviews every six months. After conducting the second Privacy Compliance Review, the Privacy Office determined that this PIA should be updated to allow for the collection and dissemination of PII in a very limited number of situations in order to respond to the evolving operational needs of the NOC. After January 2011, this PII on the following categories of individuals may be collected when it lends credibility to the report or facilitates coordination with federal, state, local, tribal, territorial, and foreign governments, or international law enforcement partners:
- U.S. and foreign individuals in extremis, i.e., in situations involving potential life or death circumstances;
- Senior U.S. and foreign government officials who make public statements or provide public updates;
- U.S. and foreign government spokespersons who make public statements or provide public updates;
- U.S. and foreign private sector officials and spokespersons who make public statements or provide public updates;
- Names of anchors, newscasters, or on-scene reporters who are known or identified as reporters in their posts or articles, or who use traditional and/or social media in real time to provide their audience situational awareness and information;
- Current and former public officials who are victims of incidents or activities related to homeland security; and
- Terrorists, drug cartel leaders, or other persons known to have been involved in major crimes of homeland security interest, (e.g., mass shooters such as those at Virginia Tech or Ft. Hood) who are killed or found dead.9
For this narrow category of individuals, DHS may only collect the full name, affiliation, position or title, and publicly-available user ID, when it lends credibility to the report. DHS determined that this information improves the efficacy and effectiveness of the social media monitoring initiative without an unwarranted invasion of privacy of individuals in each of these categories. For this narrow category of individuals the PII is only stored in the narrative report in which it is used, and is not tracked for any other reason. DHS published a System of Records Notice10 that describes the creation of these seven exceptions for the collection of PII and narrowly tailored, how much information can be collected, and how the information can be used. Furthermore, the Privacy Office is commencing its semi-annual Privacy Compliance Review in late February to ensure that the NOC continues to adhere to the privacy protections identified in the PIA.
Operational Use
There may be situations where particular programs within the Department or its components may need to access material on social media or individual profiles in support of authorized missions. Given the breadth of the Department’s mission, and the fact that access, collection, and use of social media and other publicly-available information is governed by specific legal authorities, rather than Department-wide standards, the Department has taken a different approach in embedding privacy protections into Department use of social media for operational purposes, with authority-based requirements implemented through policy and Management Directives. For example, components of DHS such as U.S. Customs and Border Protection, U.S. Immigration and Customs Enforcement, Federal Protective Service, Federal Air Marshals Service, U.S. Coast Guard, and U.S. Secret Service have the authority to engage in law enforcement activities which may include the use of online and Internet materials. Other DHS offices and components may be authorized to utilize social media for specific law enforcement purposes such as investigating fraud. The Office of Intelligence and Analysis also has some overt collection authorities for intelligence purposes which may include the use of online and Internet materials.
DHS has established objective criteria by which those investigatory components can access publicly-available information. DHS components cannot review individuals’ information unless they have appropriate underlying authority and supervisory approval. Moreover, Office of Operations Coordination and Planning and Office of Intelligence and Analysis have additional specific policies on the use of social media for operational purposes. One of DHS’ responsibilities is to confirm our work is being done under the appropriate legal framework for federal law enforcement activities. However, with increased access to individuals’ personal information posted on the Internet and social media sites, these DHS components have been reminded that they must also be conscious of privacy considerations.
At DHS, we work every day to strike a balance between our need to use open source Internet and social media information for all purposes, but particularly law enforcement and investigatory purposes to further our mission, while protecting First Amendment rights, Fourth Amendment rights, and privacy.
In 1999, the Department of Justice issued guidelines for federal law enforcement agents that outline online investigative principles that are applicable, but do not explicitly reference, social media. In 2011, the Office of the Director of National Intelligence issued guidelines that outline how intelligence community professionals should use technology, including social media. Both guidelines address the following topics: obtaining information from publicly-available media under the same conditions that apply to obtaining information from other sources generally open to the public; passively observing and logging real-time electronic communications on media open to the public under the same circumstances in which these activities could be undertaken when attending a public meeting; and retaining the contents of a stored electronic message, such as online traffic, if that information would have been retained had it been written on paper. Moreover, federal law enforcement agents communicating online with witnesses, subjects, or victims must disclose their affiliation with law enforcement when DHS guidelines would require such disclosure if the communication were taking place in person or over the telephone — they may communicate online under a non-identifying name or fictitious identity if DHS guidelines and procedures would authorize such communications in the physical world.11 Finally, federal law enforcement agents may not access restricted online sources absent legal authority permitting entry into a private space. Until a Department-wide Management Directive on using social media for operational purposes is finalized, the Secretary has instructed all components to adhere to the DOJ or ODNI guidelines as appropriate.
In light of the varying authorities and responsibilities within the Department, instead of having a Privacy Impact Assessment with general standards (such as for communications and situational awareness purposes), the Department is developing a Management Directive for Privacy Protections in Operational Use of Social Media. The Management Directive will be enforceable throughout the Department, and will identify the authorities, restrictions, and privacy oversight related to use of social media for operational purposes. The Management Directive will also provide instructions on how to embed privacy protections into the operational use of social media and each investigation performed by Department personnel. The Privacy Office has already investigated one component’s use of social media for investigatory purposes; its conclusions are informing the Management Directive.
Consistent with the Department’s approach to embed privacy protections throughout the lifecycle of Department activities, the Privacy Office will conduct a Privacy Compliance Review or assessment of the Department’s adherence to the social media Management Directive approximately six months after the Directive is implemented.
Conclusion
In light of the scope and availability of information including PII found in social media venues, the Privacy Office intends to continue to monitor the Department’s use of social media in all three categories—communications and outreach, situational awareness, and operational use—to ensure privacy protections are built-in and followed.
Footnotes
1 President Barack Obama, Memorandum on Transparency and Open Government (January 21, 2009), available at http://www.gpoaccess.gov/presdocs/2009/DCPD200900010.pdf; OMB Memorandum M-10-06, Open Government Directive (December 8, 2009), available at http://www.whitehouse.gov/omb/assets/memoranda_2010/m10-06.pdf.
3 http://www.whitehouse.gov/sites/default/files/omb/assets/memoranda_2010/m10-23.pdf
4 http://www.dhs.gov/xlibrary/assets/privacy/privacy_pia-dhs_socialnetworkinginteractions.pdf
5 http://www.dhs.gov/xlibrary/assets/privacy/privacy_pia_dhswide_unidirectionalsocialmedia.pdf
6 The NOC and the Privacy Office developed three PIAs in the pilot stage of the NOC Media Monitoring Initiative: Haiti Social Media Disaster Monitoring Initiative, January 21, 2010, available at ttp://www.dhs.gov/xlibrary/assets/privacy/privacy_pia_ops_haiti.pdf; 2010 Winter Olympics Social Media Event Monitoring Initiative February 10, 2010, available at http://www.dhs.gov/xlibrary/assets/privacy/privacy_pia_ops_2010winterolympics.pdf; and April 2010 BP Oil Spill Response Social Media Event Monitoring Initiative, April 29, 2010, available at http://www.dhs.gov/xlibrary/assets/privacy/privacy_pia_ops_bpoilspill.pdf.
7 http://www.dhs.gov/xlibrary/assets/privacy/privacy-privcomrev-ops-olympicsandhaiti.pdf. Three Privacy Compliance Reviews have been completed and published by the Privacy Office, available at: http://www.dhs.gov/files/publications/gc_1284657535855.shtm.
8 http://www.dhs.gov/xlibrary/assets/privacy/privacy_pia_ops_publiclyavailablesocialmedia.pdf.
9 The most recent PIA update (authorizing these narrow PII categories collection) was finalized January 6, 2011, and is available at: http://www.dhs.gov/xlibrary/assets/privacy/privacy_pia_ops_publiclyavailablesocialmedia_update.pdf.
10 http://edocket.access.gpo.gov/2011/2011-2198.htm.
11 See, e.g., Online Investigative Principles for Federal Law Enforcement Agents (Department of Justice, 1999) and Civil Liberties and Privacy Guidance for Intelligence Community Professionals: Properly Obtaining and Using Publicly Available Information (Office of the Director of National Intelligence, 2011).
Bundestag-Bericht zu DDR- und STASI Vermögen – Report of German Bundestag about GDR and STASI Assets
Genossen in crime von STASI-Oberst Stelzer – Die Journalisten-Giftmörder mit dem Regenschirm
Geheimwaffe Regenschirm: Am 7. September 1978 wartete der bulgarische Regimekritiker Georgij Markow in London auf seinen Bus, als er plötzlich einen Stich im Bein verspürte. Er sah einen Mann mit Regenschirm davoneilen. Kurz danach bekam er hohes Fieber, vier Tage später war er tot. Erst bei der Obduktion entdeckten Ärzte eine winzige Kapsel, die das Gift Rizin verströmte. Heute weiß man, dass die Kapsel durch einen speziellen Gasdruck-Mechanismus an der Spitze des Schirms in die Haut des Dissidenten geschossen wurde. Der Mörder wurde nie gefasst, die Spuren führten jedoch zum KGB. Das Bild zeigt einen Nachbau des Regenschirms und ist im International Spy Museum in Washington zu besichtigen.
Als Regenschirmattentat wird der Giftanschlag mit dem hochtoxischen Pflanzengift Rizin auf den bulgarischen Schriftsteller und Dissidenten Georgi Markow in London am 7. September 1978, dem Geburtstag des durch Markow häufig kritisierten bulgarischen Staatschefs Todor Schiwkow, bezeichnet.
Der Täter, vermutlich ein Agent des damaligen bulgarischen Geheimdienstes, verletzte das Opfer auf der Londoner Waterloo Bridge scheinbar zufällig mit einer präparierten Regenschirmspitze (sog. Bulgarischer Regenschirm).[1] Dabei wurde eine Kugel aus Platin–Iridium von ungefähr einem Millimeter Durchmesser in den Unterschenkel des Opfers injiziert. In der Platinkugel fanden sich zwei dünne Röhren, die mit 40 Mikrogramm Rizin gefüllt waren. Verschlossen waren diese mit Zucker, der sich bei 37 Grad Körpertemperatur leicht in der Gewebsflüssigkeit auflöste und daraufhin die kontinuierliche Rizin-Freisetzung ermöglichte. Das Platinkügelchen wurde bei der Obduktion entdeckt.[2]
Zunächst als harmloser Zwischenfall abgetan, wurde die Ursache der spät einsetzenden Symptome der Vergiftung viel zu spät erkannt. Markow starb drei Tage nach dem Attentat.
Im Juni 2005 benannte die britische Zeitung The Times den in Italien gebürtigen Dänen Francesco Giullino als Hauptverdächtigen für das Attentat.[3] Eine Fernsehdokumentation des britischen Senders Five enthüllte im Jahr 2005 unter Verwendung mehrerer Interviews, die in den Vereinigten Staaten, Großbritannien und Bulgarien aufgenommen wurden, dass Giullino noch immer gesund und am Leben ist und sich frei durch die Europäische Union bewegen kann. Nach Auffassung der Autoren der Dokumentation ist es möglich, dass eine Strafverfolgung aufgrund der bulgarischen Gesetzeslage ab Ende 2008 durch Verjährung ausgeschlossen war.[4] Scotland Yard hat im Juni 2008 deswegen erneut Ermittlungen in dieser Angelegenheit aufgenommen und Beamte nach Bulgarien entsandt, die Einsicht in archivierte Dokumente zu dem Fall beantragten und die bulgarischen Behörden um Erlaubnis gebeten haben, 40 Zeugen befragen zu dürfen, darunter auch ehemalige Geheimpolizisten.[5] Der frühere Generalmajor des sowjetischen Geheimdienstes Oleg Kalugin bestätigte in einem Interview mit dem bulgarischen Sender Darik Radio, dass dieses Attentat aufgrund eines Befehls des bulgarischen Partei- und Staatschef Todor Schiwkow ausgeführt wurde. Der KGB lieferte das Gift und die Kapsel.[6]
Ein gleichartiges Attentat gegen den bulgarischen Dissidenten und Journalisten Wladimir Kostow im August 1978 in der Pariser Metro scheiterte.
Das Attentat inspirierte 1980 den französischen Film Der Regenschirmmörder (Le coup du parapluie) mit Pierre Richard und Gert Fröbe unter der Regie von Gérard Oury.
QUELLE: WIKIPEDIA
SZ berichtete:
Die bulgarische Justiz gerät nach heftiger Kritik aus der EU-Kommission wegen mangelhafter Korruptionsermittlungen jetzt auch durch den Umgang mit einem historischen Attentat, dem sogenannten Regenschirmmord vor 30 Jahren, unter Druck. Die Sofioter Zeitung Dnevnik druckt in dieser Woche eine Serie ab, die bisher unbekannte Dokumente über den an einer Bushaltestelle in London verübten Mord an dem bulgarischen Regimekritiker Georgi Markow enthüllt.
Demnach wurde der Mörder, ein Däne italienischer Herkunft, später vom bulgarischen Geheimdienst mit Medaillen ausgezeichnet und erhielt umgerechnet insgesamt 30.000 Euro sowie Ferienaufenthalte als Belohnung. Hingegen erklärte der zuständige Ermittler in Sofia, für einen Mord mit dem Regenschirm gebe es überhaupt keine Beweise.
Tödlicher Schuss ins Bein
Der Vorgang ist politisch hochbrisant, weil die bulgarische Justiz offenbar am Donnerstag dieser Woche das Ermittlungsverfahren in Sachen Markow einstellen will. An diesem Tag läuft die reguläre 30-jährige Verjährungsfrist ab, ohne dass bisher ein Verantwortlicher für den gewaltsamen Tod des Journalisten und Theaterautors festgenommen wurde.
Schon am Wochenende hatte deshalb der konservative britische Unterhaus-Abgeordnete Julian Lewis die bulgarischen Behörden aufgefordert, die Verjährungsfrist auszusetzen. Lewis sagte, es wäre “ein empörender Akt”, wenn die Regierung in Sofia die Einstellung der Ermittlungen zuließe und die betreffenden Unterlagen zerstören oder an die Geheimdienste zurückgeben würde. In Großbritannien hingegen setzt Scotland Yard seine Untersuchungen ohne zeitliche Befristung fort; unlängst war ein Team von Ermittlern auch in Sofia, um zahlreiche Zeugen zu vernehmen und Dokumente zu sichten.
Der Fall hatte schon vor 30 Jahren beträchtliches Aufsehen erregt und gilt als einer der mysteriösesten Anschläge des Kalten Krieges in Europa. Der 49-jährige Georgi Markow, der 1969 aus Bulgarien emigriert war und seit 1972 im bulgarischen Programm der BBC arbeitete, hatte am 7. September 1978 an der Waterloo-Bridge in London auf den Bus gewartet, als ein Unbekannter mit einem Regenschirm ihn anrempelte und davoneilte. Markow bekam danach Fieber und andere gesundheitliche Probleme, am 11. September starb er. Nach bisherigen Erkenntnissen war er vergiftet worden, und zwar mit dem Stoff Rizin, der ihm in einer Kapsel mit dem Regenschirm ins Bein gestochen worden war.
Für diese Annahme gebe es keinen Beweis, erklärte jetzt der Chef der Abteilung Schwerkriminalität der bulgarischen Polizei, Luchezar Penew. Die in Markows Bein gefundene Kapsel sei um ein Vielfaches zu klein gewesen, um die nötige Menge Rizin aufzunehmen. Schon vorher hatte der zuständige Chefermittler Andrej Tswetanow die Ansicht vertreten, Markows Tod vor 30 Jahren gehe auf einen Fehler der behandelnden Ärzte zurück. Außerdem sagte er, Markows Mörder bleibe unbekannt.
Vom Geheimdienst angeworben und trainiert
Hingegen berichtet jetzt der Enthüllungsjournalist Hristo Hristov in der Zeitung Dnevnik, bei dem Tatverdächtigen mit dem Decknamen “Piccadilly” handele es sich um einen in Italien geborenen Dänen namens Francesco Gullino. Der Name war zuvor schon in britischen Presseberichten genannt worden.
Den neuen Dokumenten zufolge hatte der bulgarische Geheimdienst “Piccadilly” angeworben und trainiert. Weiter heißt es, der bulgarische Geheimdienst Darschawna Sigurnost habe in dieser Sache mit dem sowjetischen KGB zusammengearbeitet und von diesem das Gift Rizin erhalten.
Gleiches hatte jüngst auch der frühere KGB-Generalmajor Oleg Kalugin im Sofioter Sender Radio Darik gesagt. Der Anschlag gehe auf eine Anordnung des damaligen kommunistischen Partei- und Staatschefs Todor Schiwkow zurück. Dieser habe sich sehr geärgert, weil ihn Dissident Markow in den bulgarischen Programmen der BBC und im Sender Radio Free Europe persönlich angegriffen und sich über ihn lustig gemacht habe.
Vor dem Hintergrund dieser neuesten Erklärungen richtet sich alle Aufmerksamkeit auf die Entscheidung der Justizbehörden an diesem Donnerstag. Sollte Ermittler Twetsanow die Untersuchungen einstellen und behaupten, Markows Tod gehe auf einen ärztlichen Fehler zurück, “dann wird das einen Skandal verursachen in einer Zeit, in der Bulgariens Justiz von der EU-Kommission wegen ihrer Ineffizienz kritisiert wird”, schreibt die englischsprachige Zeitung Sofia News. Twetsanow habe auch alle Erkenntnisse ignoriert, die frühere Ermittler gesammelt hätten.
Neuen Stoff liefert auch die Enthüllungsserie in Dnevnik, die erst nach dreijährigem juristischen Streit zustande kam. Der Journalist Hristov hatte gegen die Weigerung des Geheimdienstes, ihm die Akten herauszugeben, erfolgreich geklagt.
TOP-SECRET – STASI-Kooperation with Bulgaria’s Poison-Umbrella Agents
Document: The CC BCP Politburo approves the protocol for co-operation between the Ministry of Internal Affairs and the East German Ministry for State Security (Stasi), agreed upon at a September meeting in Berlin.
The Committee for State Security (Bulgarian: Комитет за държавна сигурност, Komitet za darzhavna sigurnost; abbreviated КДС, CSS), popularly known as State Security (Държавна сигурност, Darzhavna sigurnost; abbrievated ДС) was the name of the Bulgarian secret service during the Communist rule of Bulgaria and the Cold War (until 1989).
- 1st Head Directorate – foreign intelligence. Succeeded by the National Intelligence Service in 1990.
- 2nd Head Directorate – counter-intelligence. Succeeded by the National Security Service.
- 3rd Directorate – military counter-intelligence
- 4th Directorate – surveillence
- 5th Directorate – government security and protection. Succeeded by the National Protection Service.
- 6th Directorate – political police. Succeeded by the Head Service for Combating Organized Crime. It had the following departments:
- 1st Department – worked among the intelligentsia and controlling the unions of artists
- 2nd Department – worked in the universities and among the students
- 3rd Department – responsible for the clergy, the Jews, Armenians and Russian White emigrants
- 4th Department – specialized in pro-Turkish and pro-Macedonian nationalism
- 5th Department – worked among the political rivals, such as the agrarians and social democrats
- 6th Department – observed pro-Maoist and anti-party activity
- 7th Department – information analysis and anonymous activity
- 7th Directorate – information work
In 1964 the State Security formed a unit Service 7, led by colonel Petko Kovachev, dedicated to murder, kidnaping and disinformation against Bulgarian dissidents living abroad. The unit executed actions against dissidents in Italy, Britain, Denmark, West Germany, Turkey, France, Ethiopia, Sweden and Switzerland. Documents describing its activities were declassified only in 2010.[1]
State Security played an active part in the so-called “Revival Process” to Bulgarianize the Bulgarian Turks in the 1980s, as well as writer and dissident Georgi Markov‘s murder in London in 1978 known for the “Bulgarian umbrella” that was used.
An issue often raised by the international community is State Security’s alleged control of the weapons, drugs, alcohol, cigarettes, gold, silver and antiques traffic through Bulgaria before 1989.[2] Because of this, it is popularly thought that the organized crime in the country in the 1990s was set up by former State Security agents.[3]
The agency is often incriminated with the ill-famed murder of dissident writer Georgi Markov using a “Bulgarian umbrella” on London’s Waterloo Bridge and was formerly accused of the 1981 attempt on Pope John Paul II‘s life. The latter allegation has always been sharply criticised and denied by Bulgaria, and the country was officially cleared of any involvement by the Pontiff himself during a 2002 visit.
The secret files of the DS have been a source of great controversy in the country. After the communist regime in the country collapsed, newly established democratic forces accused the former communist elite of secretly removing DS files that could compromise its members. In 2002, former Interior Minister Gen. Atanas Semerdzhiev was found guilty of razing 144,235 files from the Durzhavna Sigurnost archives. Others have accused the DS of infiltrating the young opposition.
The Bulgarian umbrella is the name of an umbrella with a hidden pneumatic mechanism which shot out a small poisonous pellet containing ricin.
Such an umbrella was allegedly used in the assassination of the Bulgarian dissident writer Georgi Markov on September 7, 1978 (the birthday of the Bulgarian State Council Chairman Todor Zhivkov who had often been the target of Georgi Markov’s criticism), on Waterloo Bridge in London (Markov died four days later), and also allegedly used in the failed assassination attempt against the Bulgarian dissident journalist Vladimir Kostov the same year in the Paris Métro. The poison used in both cases was ricin. Both assassination attempts are believed to have been organized by the Bulgarian Secret Service of the time of the Cold War with the assistance of the KGB. These two cases inspired the 1980 French film Le Coup du parapluie (The Umbrella Coup) directed by Gérard Oury, starring Pierre Richard.
Das Komitee für Staatssicherheit (bulgarisch Комитет за държавна сигурност/Komitet za darschawna sigurnost, abgekürzt КДС/KDS), auch bekannt als Staatssicherheit (bulg. Държавна сигурност/Darschawna Sigurnost, abgekürzt ДС/DS) war der Name des bulgarischen Geheimdienst während der Zeit der sozialistischen Volksrepublik Bulgarien. Gegründet wurde dieser 1944 unter persönlicher Anleitung von Georgi Dimitrow, noch im Exil, und nach Vorbild des sowjetischen KGB. Der Geheimdienst wurde nach dem Sturz des kommunistischen Staatschef Todor Schiwkow im Rahmen der Demokratisierung aufgelöst.
Der bulgarische Geheimdienst spielte eine aktive Rolle in den sogenannten “Bulgarisierungsprozessen“, um die ethnische Minderheit der Balkan-Türken in den 1980er Jahren, sowie gegen Schriftsteller und Dissidenten.
Weiterhin gilt er als Auftraggeber des Mordes an dem Schriftsteller Georgi Markov auf der Waterloo Bridge in London im Jahr 1978, welcher als Regenschirmattentat bekannt wurde. Ein gleichartiges Attentat gegen den bulgarischen Dissidenten und Journalisten Wladimir Kostow im August 1978 in der Pariser U-Bahn scheiterte.
Heute geht man davon aus, dass der DS vor 1989 auch die gesamte Kontrolle über den Handel von Waffen, Drogen, Alkohol, Zigaretten, Gold, Silber und Antiquitäten in Bulgarien und auf der gesamten Balkanhalbinsel hatte.[1][2] Es ist daher naheliegend, dass die Strukturen, der ähnlich der Mafia organisierten Kriminalität in Bulgarien, welche in den 1990er Jahren entstanden, durch viele ehemalige Agenten des DS errichtet wurden.
Weiterhin wurde der Geheimdienst lange Zeit als Hauptauftraggeber des Pistolenattentats auf den damaligen Papst Johannes Paul II., durch Mehmet Ali Ağca, beschuldigt. Diese Darstellung wurde seitens der VR Bulgarien stets scharf kritisiert und zurückgewiesen. Bei seinem Besuch 2002 negierte auch Papst Johannes Paul II. diese Version und unterstrich die Version des Einzeltäters Ağca.
Die Geheimakten des KDS, bzw. DS sorgten auch in Bulgarien für große Kontroversen. Allerdings wurden diese zum größten Teil nach dem Zusammenbruch des kommunistischen Regimes 1989 durch Agenten vernichtet. Die ab 1990 neu gegründeten demokratischen Kräfte der Opposition machten daher die bis 1997 weiter regierenden kommunistische Funktionäre, welche nun wieder als Mitglieder der Bulgarischen Sozialistischen Partei die Regierung und den Ministerpräsidenten stellten, für die Vernichtung von Dateien verantwortlich, welche ihre Mitglieder belasten könnten. Im Jahr 2002 wurde der ehemalige Innenminister und Vizepräsident Atanas Semerdzhiev für schuldig befunden, noch 1990 persönlich die Vernichtung von 144.235 Dateien aus den DS-Archiven angeordnet zu haben und damit die damals noch junge Demokratie unterwandert zu haben.
SOURCE: WIKIPEDIA









![[Image]](https://i0.wp.com/cryptome.org/2012-info/nsa-mrf/pict17.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/nsa-mrf/pict15.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/nsa-mrf/pict10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/nsa-mrf/pict16.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest12/pict10.jpg) South African protestors march downtown Johannesburg, South Africa, Wednesday March 7, 2012. Tens of thousands of South Africans marched peacefully through their main cities in a protest organized by the country’s biggest trade union federation against economic decisions made by the governing African National Congress. The Congress of South African Trade Unions, known as COSATU, is a close ally of the ANC, but often among its sharpest critics. (Jerome Delay)
South African protestors march downtown Johannesburg, South Africa, Wednesday March 7, 2012. Tens of thousands of South Africans marched peacefully through their main cities in a protest organized by the country’s biggest trade union federation against economic decisions made by the governing African National Congress. The Congress of South African Trade Unions, known as COSATU, is a close ally of the ANC, but often among its sharpest critics. (Jerome Delay)![[Image]](https://i0.wp.com/cryptome.org/2012-info/women-protest12/pict12.jpg)
![[Image]](https://i0.wp.com/www.cryptome.org/2012-info/manning031512/pict8.jpg)
![[Image]](https://i0.wp.com/www.cryptome.org/2012-info/manning031512/pict3.jpg) US Army Pfc. Bradley Manning is seen arriving for a motion hearing in the case Unted States vs. Manning at Fort Meade March 15, 2012 in Maryland. US Army Pfc. Bradley Manning was charged in February for leaking hundreds of thousands of secret US military and government documents to WikiLeaks. Getty
US Army Pfc. Bradley Manning is seen arriving for a motion hearing in the case Unted States vs. Manning at Fort Meade March 15, 2012 in Maryland. US Army Pfc. Bradley Manning was charged in February for leaking hundreds of thousands of secret US military and government documents to WikiLeaks. Getty![[Image]](https://i0.wp.com/www.cryptome.org/2012-info/manning031512/pict1.jpg) US Army Pfc. Bradley Manning(C) is seen arriving for a motion hearing in the case Unted States vs. Manning at Fort Meade March 15, 2012 in Maryland. US Army Pfc. Bradley Manning was charged in February for leaking hundreds of thousands of secret US military and government documents to WikiLeaks. Getty
US Army Pfc. Bradley Manning(C) is seen arriving for a motion hearing in the case Unted States vs. Manning at Fort Meade March 15, 2012 in Maryland. US Army Pfc. Bradley Manning was charged in February for leaking hundreds of thousands of secret US military and government documents to WikiLeaks. Getty![[Image]](https://i0.wp.com/www.cryptome.org/2012-info/manning031512/pict2.jpg) Army Pfc. Bradley Manning, center, is escorted by a security detail into a courthouse in Fort Meade, Md. , Thursday, March 15, 2012. Manning, a US Army private accused of leaking classified material to the anti-secrecy website Wikileaks could soon learn when his trial will start. AP
Army Pfc. Bradley Manning, center, is escorted by a security detail into a courthouse in Fort Meade, Md. , Thursday, March 15, 2012. Manning, a US Army private accused of leaking classified material to the anti-secrecy website Wikileaks could soon learn when his trial will start. AP![[Image]](https://i0.wp.com/www.cryptome.org/2012-info/manning031512/pict5.jpg) Army Pfc. Bradley Manning’s civilian attorney David Coombs and Tanya Monestier arrive at a courthouse in Fort Meade, Md. , Thursday, Mar. 15, 2012, for a motion hearing in Manning’s upcoming court-martial trial. Manning, a US Army private accused of leaking classified material to the anti-secrecy website Wikileaks could soon learn when his trial will start. AP
Army Pfc. Bradley Manning’s civilian attorney David Coombs and Tanya Monestier arrive at a courthouse in Fort Meade, Md. , Thursday, Mar. 15, 2012, for a motion hearing in Manning’s upcoming court-martial trial. Manning, a US Army private accused of leaking classified material to the anti-secrecy website Wikileaks could soon learn when his trial will start. AP![[Image]](https://i0.wp.com/www.cryptome.org/2012-info/manning031512/pict4.jpg) Army Capt. Paul Bouchard, military defense attorney for Army Pfc. Bradley Manning, arrives at a courthouse in Fort Meade, Md. , Thursday, March 15, 2012, for a motion hearing in Manning’s upcoming court-martial trial. AP
Army Capt. Paul Bouchard, military defense attorney for Army Pfc. Bradley Manning, arrives at a courthouse in Fort Meade, Md. , Thursday, March 15, 2012, for a motion hearing in Manning’s upcoming court-martial trial. AP![[Image]](https://i0.wp.com/www.cryptome.org/2012-info/manning031512/pict6.jpg) Army Capt. Joe Morrow, a member of the Army’s prosecution team, arrives at a courthouse in Fort Meade, Md. , Thursday, Mar. 15, 2012, for a motion hearing in the court-martial of Army Pfc. Bradley Manning. Manning, a US Army private accused of leaking classified material to the anti-secrecy website Wikileaks could soon learn when his trial will start. AP
Army Capt. Joe Morrow, a member of the Army’s prosecution team, arrives at a courthouse in Fort Meade, Md. , Thursday, Mar. 15, 2012, for a motion hearing in the court-martial of Army Pfc. Bradley Manning. Manning, a US Army private accused of leaking classified material to the anti-secrecy website Wikileaks could soon learn when his trial will start. AP![[Image]](https://i0.wp.com/www.cryptome.org/2012-info/manning031512/pict7.jpg) Army Capt. Angel Overgaard, a member of the Army’s prosecution team, arrives at a courthouse in Fort Meade, Md. , Thursday, March 15, 2012, for a motion hearing in the upcoming court-martial trial of Army Pfc. Bradley Manning. AP
Army Capt. Angel Overgaard, a member of the Army’s prosecution team, arrives at a courthouse in Fort Meade, Md. , Thursday, March 15, 2012, for a motion hearing in the upcoming court-martial trial of Army Pfc. Bradley Manning. AP![[Image]](https://i0.wp.com/www.cryptome.org/2012-info/manning031512/pict0.jpg)

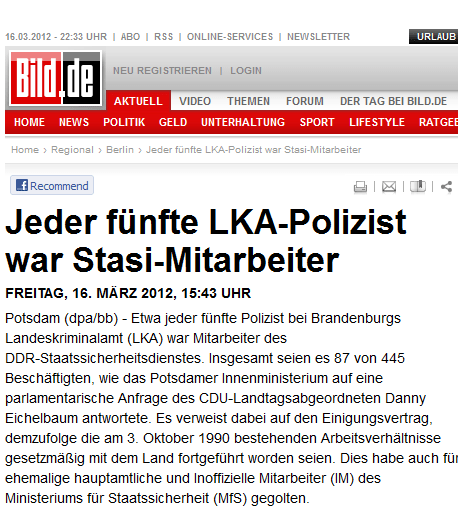


























You must be logged in to post a comment.