Washington, D.C., April 26, 2013 – Since at least 1997, the National Security Agency (NSA) has been responsible for developing ways to attack hostile computer networks as part of the growing field of Information Warfare (IW), according to a recently declassified internal NSA publication posted today by the non-governmental National Security Archive (“the Archive”) at The George Washington University. Declaring that “the future of warfare is warfare in cyberspace,” a former NSA official describes the new activity as “sure to be a catalyst for major change” at the super-secret agency.
The document is one of 98 items the Archive is posting today that provide wide-ranging background on the nature and scope of U.S. cyber activities.
Activities in cyberspace — both defensive and offensive — have become a subject of increasing media and government attention over the last decade, although usually the focus has been on foreign attacks against the United States, most notably the Chinese government’s reported exploitation of U.S. government, commercial and media computer networks. At the same time, the apparent U.S.-Israeli created Stuxnet worm, designed to damage Iranian centrifuges, has put the spotlight on the United States’ own clandestine cyber efforts.
The NSA’s new assignment as of 1997, known as Computer Network Attack (CNA), comprises “operations to disrupt, deny, degrade or destroy” information in target computers or networks, “or the computers and networks themselves,” according to the NSA document.
Today’s posting by the Archive highlights various aspects of U.S. cyberspace activities and concerns going back to the late 1970s. The documents — obtained from government and private websites as well as Freedom of Information Act requests — originate from a wide variety of organizations. These include the White House and National Security Council, the National Security Agency, the Departments of Defense, Energy, and Homeland Security, the military services, the General Accounting/ Government Accountability Office, and the Congressional Research Service — as well as three private organizations (Project 2049, Mandiant Corporation, and Symantec).
Source: Department of Homeland Security (see Document 52).
Among the highlights of the documents are:
The NSA’s earlier concerns about the vulnerability of sensitive computer systems to either viruses or compromise through foreign intelligence service recruitment of computer personnel (Document 1, Document 2, Document 3, Document 4, Document 9)
The Secretary of Defense’s March 1997 authorization of the National Security Agency to conduct computer network attack operations (Document 11)
Detailed discussions of Chinese computer network exploitation activities (Document 66, Document 79, Document 83)
Analyses of the Stuxnet worm (Document 40, Document 42, Document 44, Document 88)
Extensive treatments of intelligence collection concerning U.S. technologies through computer network exploitation (Document 18, Document 55, Document 63)
* * *
Cyberspace and U.S. National Security
By Jeffrey T. Richelson
In an October 2012 speech (Document 78), then-Secretary of Defense Leon Panetta told a group of business executives that “a cyber attack perpetrated by nation states [or] violent extremist groups could be as destructive as the terrorist attack on 9/11,” and raised the prospect of a “cyber Pearl Harbor.” In his February 2013 State of the Union address, President Barack Obama asserted that “our enemies are … seeking the ability to sabotage our power grid, our financial institutions, our air traffic control systems.” Later that month, Director of National Intelligence James R. Clapper led off his annual threat assessment (Document 90) appearance before the Senate Select Committee on Intelligence with a discussion of the Intelligence Community’s assessment of the cyber threat.1
Stuxnet: “The world’s first precision cybermunition.” Source: Department of Homeland Security (see Document 52)
Concern about the potential damage of cyber attack did not originate in the current administration. Even before the establishment of the computer connectivity of the current Internet-era, there was concern, including in the National Security Agency, about the threat of computer viruses (Document 1, Document 2, Document 3, Document 4, Document 5, Document 6) or the vulnerability of computer systems due to recruitment efforts by hostile intelligence services (Document 9). More recently, the William J. Clinton and George W. Bush administrations focused on the connection between cyberspace and national security, issued policy directives, and considered and/or authorized both public and covert actions.
Occasionally, some of those concerns have been met with skepticism. Critiques have included the assertion that the very structure of the Internet means it is not subject to a ‘Pearl Harbor’ type attack — that is, an attack at single point. The association of power outages in the northeastern United States in 2003 and Brazil in 2007 with cyberattacks has been challenged by reviewers and experts — who point to studies that concluded there were other, more mundane, causes. One writer has asserted that cyberwar is not here, and that it is not coming. Additional issues that have been raised include the lack of disclosed evidence with regard to more extreme claims concerning the threat, the dangers of threat inflation (including facilitating the expenditure on ‘cyber pork’), and the extent to which the costs of other types of criminal activity (such as car theft) dwarf the cost of cyber crime.2 What is indisputable, however, is the dramatic increase in attention — both in the U.S. Government and private industry — to activities in cyberspace in the last decade — which has been reflected in both media coverage and the release of private and government documents.
Attacks & Exercises
Source: Defense Science Board. See Document 81.
Significant attention has been devoted, in both the classified and unclassified realms, to actual attacks as well as exercises that have sought to determine the vulnerability of key government and infrastructure systems to attack.
The Government Accounting Office (renamed the Government Accountability Office in 2004) reported (Document 6) that between April 1990 and May 1991, a period that encompassed Operations Desert Shield and Desert Storm, computer hackers from the Netherlands penetrated 34 Department of Defense sites. According to that report, the hackers were able to access “unclassified, sensitive information” concerning military personnel, logistics, and weapons systems development. The report also asserted that, particularly during times of international conflict, “such information … can be highly sensitive.”
In March and April 1994, according to GAO reports (Document 10a, Document 10b), the Air Force’s Rome Laboratory, in upstate New York, was targeted by a pair of hackers (a 16-year old British student and a 22-year old Israeli technician) who, using “Trojan Horse” and “sniffer” programs, managed to take control of the lab’s networks. In addition to taking all of the lab’s 33 subnetworks offline for several days, the hackers also stole air tasking order research data and gained access to systems at NASA’s Goddard Space Flight Center, Wright Patterson Air Force Base, and a variety of defense contractors.
Source: Defense Science Board. See Document 81.
In February 1998, several Department of Defense networks were attacked through a commonly understood vulnerability in the Solaris (UNIX-based) computer system — the investigation of which was designated SOLAR SUNRISE. The attack involved probing Defense Department servers to determine if the vulnerability existed, and then exploiting it — entering the system and planting a program to collect data. The hackers, ultimately discovered to be two California high school students, also mounted at least a second intrusion to extract data from the penetrated computers.3
In 2003, a series of computer intrusions were directed against the U.S. Defense Information Systems Agency (DISA), the U.S. Redstone Arsenal, the Army Space and Strategic Defense Command, and several DoD contractors – but they apparently went undetected for several months. That series of intrusions was labeled TITAN RAIN, and Defense Department investigators believed it to have originated in China. In June 2006, Department of Energy officials acknowledged that the names of and personal information of more than 1,500 National Nuclear Security Administration (NNSA) employees had been stolen due to network intrusion that apparently began in 2004.4
Another set of attacks that attracted attention (Document 27) was directed against former Soviet-controlled territories, and was widely believed to have been the work of the Russian government. On July 20, 2008, the Georgian president’s website was subjected to a denial-of-service attack. On August 8, a coordinated, distributed denial-of-service attack occurred on other Georgian government websites. At that time, Russian forces were engaged in combat with Georgian forces. Additional cyber attacks on Lithuanian and Kyrgzstan targets took place in June 2008 and January 2009, respectively. The attack on Lithuanian websites occurred three days after that country passed legislation outlawing the use of Soviet and communist symbols, while the January 2009 attack took place on the same day that Russia tried to pressure Kyrgyzstan to revoke U.S. access to the Bishkek airbase being used as a transit point for supplies to Afghanistan.5
Since that time there have been numerous reports of cyber incidents. Included have been a series of attacks on global energy targets, dubbed NIGHT DRAGON, a 2012 cyber attack on the Saudi Arabian state-owned Aramco oil company, and cyber attacks on U.S. banks and companies — attacks alleged to have been the responsibility of Iran.6
Along with the actual intrusions that have been taking place for over two decades, the United States has also conducted a number of exercises and studies in an attempt to assess the extent of computer network vulnerability. The first exercise, designated ELIGIBLE RECEIVER, was conducted over 90 days in 1997, and involved a Red Team consisting of 35 individuals. Simulated, and apparently successful, cyber attacks were made against government and private power and communications networks in Oahu, Los Angeles, Colorado Springs, St. Louis, Chicago, Detroit, Washington, D.C., Fayetteville, and Tampa. The head of the Pentagon’s Joint Task Force – Computer Network Defense, wrote that the exercise “clearly demonstrated our lack of preparation for a coordinated cyber and physical attack on our critical military and civilian infrastucture.”7
A subsequent exercise, designated LIVEWIRE, was conducted by the Department of Homeland Security. In 2005, the CIA’s Information Operations Center conducted a three-day exercise, codenamed SILENT HORIZON. The objective of the exercise was to practice defending against a cyber attack that would be on the same scale as the September 11, 2001, events, and would target both governmental and private sectors.8
Intelligence and Threat Assessments
Intelligence/threat assessments concerning cyberspace include estimates of the current and projected future cyber capabilities and activities of a variety of nations and groups. They can also include assessments of the specific threats faced by government and private organizations in relation to the current state of cyber security.
In late 2012 and early 2013, several press sources reported that a national intelligence estimate focused on worldwide cyber activities had either been completed or was in the process of completion. An earlier estimate was produced in February 2004: NIE-2004-01D/I, Cyber Threats to the Information Infrastructure. An additional national intelligence product was produced for the Office of the Director of National Intelligence (ODNI) by the Intelligence Science Board – a January 2008 report titled Technical Challenges of the National Cyber Initiative. 9
None of those products has been released, even in redacted form. Estimates and assessments which have been released include those produced by the Congressional Research Service, the Defense Security Service, a ODNI component, and a contractor for the U.S.-China Security and Economic Review Commission. In 2007, the CRS examined (Document 24), inter alia, examples of vulnerabilities that terrorists might decide to exploit in attempting a coordinated cyberattack and ways that terrorists might be improving their cyber skills. The report, Terrorist Capabilities for Cyberattack: Overview and Policy Issues, noted different views concerning the ability of Al-Qaeda (or other terrorist groups) to launch a significant cyberattack and the related danger of a “Digital Pearl Harbor.” It also noted a CIA assessment, provided in April 2002 to the Senate Select Committee on Intelligence, that “cyberwarfare attacks against the U.S. critical infrastructure will become a viable option for terrorists as they become more familiar with the technology required for the attacks.”
A 2004 assessment of the intelligence threat (Document 18), particularly from nations or others seeking to conduct economic espionage was produced by the Interagency OPSEC Support Staff. One chapter focuses on ‘Computers and the Internet’. In addition to providing a history of Internet security and discussing the relationship between website content and operational security, it also explores the roots of network vulnerability and eight outsider attack techniques – including scanning, packet sniffing, and malware.
Several unclassified assessments (Document 26, Document 43, Document 63) by the Defense Security Service have focused on foreign attempts to acquire advanced U.S. technology. The most recent version (Document 63), as with previous versions, examines a variety of methods for acquiring information on U.S. technologies — including “suspicious network activity,” which was the most prevalent collection method for “entities originating from East Asia and the Pacific.”
A similar type of assessment (Document 55) was produced in October 2011 by the Office of the National Counterintelligence Executive, a component of the Office of the Director of National Intelligence. The report, Foreign Spies Stealing US Economic Secrets in Cyberspace, examines the vulnerability of US technologies and trade secrets to cyberspace operations, the threat from specific collectors (including Russia, China, and U.S. partners), and the outlook for the future (including both “near certainties” and “possible game changers”).
Key assessments of Chinese computer network exploitation that are in the public domain have been produced either by contractors in response to tasking from the U.S.-China Economic and Security Review Commission or by private organizations. In October 2009, the review commission released Capability of the People’s Republic of China to Conduct Cyber Warfare and Computer Network Exploitation (Document 30). It examined Chinese computer network exploitation activities, strategy and operations during a military conflict, key entities in Chinese computer network operations, cyber-espionage, an operational profile of an advanced cyber intrusion and a chronology of alleged Chinese computer network exploitation activities.
A second report (Document 66), also produced for the U.S.-China review commission, and released in 2012, Occupying the High Ground, focused on Chinese capabilities for computer network exploitation. It included a look at the key entities and institutions supporting Chinese computer network operations, potential risks to the U.S. telecommunications supply chain, and the risks and reality of collaboration between U.S. and Chinese information security firms. Along with the reports for the review commission, two private organizations have produced detailed reports on PRC computer espionage activities. In 2012, a research group focused on China released a study (Document 79) based on open sources and computer-based investigations, examining the roles of several PLA organizations in cyber operations, including the Third Department of the PLA General Staff Department, its 2nd Bureau as well as its Beijing North Computer Center. Early the next year, the Mandiant computer security company released its study (Document 83) on the 2nd Bureau — which discussed the tasking of the unit, its past espionage operations, attack lifecycle, and the unit’s infrastructure and personnel.
In contrast to the extensive public documents concerning China’s computer attack and exploitation activities, far less has appeared concerning similar Iranian activities. In 2012, Director of National Intelligence James Clapper did characterize them as “dramatically increasing in recent years in depth and complexity.” 10 A hearing in 2012 featured statements on Iranian cyber activities from two members of Congress and two non-governmental experts. (Document 71a, Document 71b, Document 71c, Document 71d).
Directives, Strategies, Policies, and Plans
While a number of presidential directives in earlier years addressed subjects such as communications security and information security, Presidential Decision Directive 63 (Document 12), Critical Infrastructure Protection, signed by President William J. Clinton on May 22, 1998, focused on protecting both “physical and cyber-based systems essential to the minimum operations of the economy and government.” Among the steps Clinton directed was the establishment of a National Infrastructure Assurance Plan, increased intelligence collection and analysis devoted to the cyber threat, and creation of a National Infrastructure Protection Center.
The George W. Bush administration produced a number of classified as well as unclassified documents concerning cyberspace. The first, National Security Presidential Directive 16 (NSPD-16) was reported to have been issued in July 2002 and provide guidelines for the conduct of offensive cyber operations. A public document, The National Strategy to Secure Cyberspace (Document 16), was released in February 2003 and was followed by the classified NSPD-38, with the same title, of July 7, 2004. A third classified directive, NSPD-54, Cyber Security and Monitoring, was issued on January 8, 2008. 11
President Obama has signed two Presidential Policy Directives concerning cybersecurity — the still classified PPD-20 (title unknown) and PPD-21, “Critical Infrastructure Security and Resilience” (Document 86) — the latter following the failure of two proposed pieces of cybersecurity legislation to make it through Congress. Its key components are its delineation of roles and responsibilities, of officials and agencies, its identification of three strategic imperatives, and its direction to the Secretary of Homeland Security on steps to take to implement the directive. Issued the same day was an executive order (Document 87) that focused solely on critical infrastructure cybersecurity — including information sharing, reduction of cyber risk, and identification of critical infrastructure at greatest risk.
On May 8, 2009, the White House issued the results of its cyberspace policy review — Cyberspace Policy Review: Assuring a Trusted and Resilient Information and Communications Infrastructure (Document 28). It produced a plan that included establishing performance metrics, preparing a cybersecurity response plan, and instituting a national public awareness and education campaign to promote cybersecurity. In May 2011 the White House released its International Strategy for Cyberspace: Prosperity, Security, and Openness in a Networked World (Document 46), which discussed the building of U.S. cyberspace policy, the future of cyberspace, as well as U.S. policy priorities and concludes with the a discussion of the implementation of U.S. strategy. Then, in early 2013, along with PPD-21 and the related executive order, the administration released Administration Strategy on Mitigating the Theft of U.S. Trade Secrets (Document 82). Part of the strategy concerns mitigating cyber theft and describes four action items – diplomatic efforts, voluntary practices by industry, enhancing domestic law enforcement operations, improving domestic legislation, and promoting public awareness.
Numerous departments also have produced cyber strategy documents at various levels of classification. In 2006, the Chairman of the Joint Chiefs of Staff produced the National Military Strategy for Cyberspace Operations (Document 23), which was classified Secret. Its introduction described it as the “comprehensive strategy of the U.S. Armed Forces to ensure U.S. military superiority in cyberspace.” Since released under the Freedom of Information Act, the document identified four strategic priorities in implementing the strategy – including gaining and maintaining the initiative to operate within adversary decision cycles and integrating cyber capabilities across the full range of military operations using cyberspace. In July 2011, that strategy was replaced by the unclassified Department of Defense Strategy for Operating in Cyberspace (Document 50) — which noted five strategic initiatives with regard to DoD operations in cyberspace. Those initiatives include treating cyberspace as an operational domain with regard to organization, training, and equipment as well as employing new concepts to protect DoD networks and systems.
The individual military services and their components have also produced their own policy and planning documents concerning cyberspace activities. In February 2010, the Army’s Training and Doctrine Command published an unclassified pamphlet (Document 33) on how cyber operations would be integrated into the full spectrum of Army operations. The next year, the Air Force produced Air Force Doctrine Document 3-12, Cyberspace Operations (Document 60), which included a discussion of the design, planning, execution, and assessment of cyberspace operations.
Civilian departments have also produced their own strategy documents — such as the Department of Homeland Security’s November 2011 Blueprint for a Secure Cyber Future (Document 58), which listed four cybersecurity goals (including reducing exposure to cyber risk and increasing resilience) and nine means for achieving those goals.
In addition to presidential directives, departmental directives also serve to state policies as well as assign responsibilities. Thus, the 2006 DoD Directive 3600.01 (Document 22), “Information Operations,” assigned the Assistant Secretary of Defense for Networks and Information Integration responsibilities with regard to computer network defense — a responsibility since assumed by the department’s Chief Information Officer.. A January 2010 directive (Document 31) focuses on protection of unclassified Defense Department information that passes through or resides on Defense Industrial Base information systems and networks.
The Department of Energy has also issued its own directives concerning cybersecurity — including a September 2010 directive (Document 36) on the department’s cybersecurity management policy, including a statement of objectives, principles, responsibilities, and implementation, as well as a May 2011 directive (Document 48) which stipulates that the department’s cybersecurity policy be based on a risk management approach.
Organizations
U.S. government organizations involved in cyberspace activities (excluding those involved in evaluating programs) can be found in the Intelligence Community, Department of Defense, and several civilian departments or agencies – including the Federal Bureau of Investigation and the Department of Homeland Security.
The most senior U.S. official concerned with the analysis of intelligence concerning foreign cyber capabilities and activities is a member of the DNI’s National Intelligence Council — the National Intelligence Officer for Cyber Issues — a position first established in May 2011. Sometime in the late 1990s, an Information Operations Center was established within the CIA’s Directorate of Operations (now the National Clandestine Service). It absorbed some of the functions of the Directorate of Science and Technology’s Clandestine Information Technology Office. The office was officially described as being responsible for addressing “collection capabilities within emerging information technologies.” The Center’s Analysis Group is located in the Directorate of Intelligence and evaluates foreign threats to U.S. computer systems, particularly those that support critical infrastructure. 1 2
The National Security Agency’s involvement in cyber security is a consequence of its long-time role in insuring first communications and then information security for various components of the government and private sector as well as its need to insure the security of the computers it has relied on heavily for decades (e.g. Document 2, Document 3, Document 4). Its role in computer network exploitation – of gathering electronic “data at rest” is a natural extension of its signals intelligence role of gathering “data in motion.” In March 1997, according to an article (Document 11) by a former deputy director, it was also assigned the mission of computer network attack.
A major step in the organization of U.S. cyberspace activities, indicative of an upgrade in attention, occurred in late June 2009, when Secretary of Defense Robert Gates ordered (Document 29) the establishment of a unified U.S. Cyber Command subordinate to the U.S. Strategic Command. In his memo Gates noted that he would recommend to the president that he appoint the director of the National Security Agency as commander of the Cyber Command, that the command would reach initial operating capability by October 2009 and full operating capability by October 2010. He also directed disestablishment of STRATCOM’s Joint Task Force — Global Network Operations (JTF-GNO) and Joint Functional Component Command — Network Warfare (JFCC-NW) prior to the new command reaching full capability. In addition, Gates wrote that his memorandum “reinforces, but does not expand, USSTRATCOM authorities and responsibilities for military cyberspace operations.”
According to a brief fact sheet (Document 38), the Cyber Command is responsible for planning, coordinating, and conducting the operations and defense of specified Department of Defense information networks.” It also, when directed, conducts “full-spectrum military cyberspace operations.” Its current headquarters organization, as depicted in an organization chart (Document 92), was released in April 2013.
Subordinate to the Cyber Command are its component commands — Army Forces Cyber Command; the 24th Air Force (a component of the Air Force Space Command); the U.S. Fleet Cyber Command (Document 69), which oversees the Navy Information Operations Command; the Navy Cyber Warfare Development Group; the Navy Cyber Defense Operations Command; and the Marine Forces Cyber Command.
In June 2002, the Director of the FBI established a Cyber Division. The division is responsible for coordinating and supervising the FBI’s investigation of federal violations “in which the Internet, computer systems, or networks are exploited as the principal instruments or targets of terrorist organizations, foreign government-sponsored intelligence operations, or criminal activity, and for which the use of such systems is essential to that activity.” 13
The Department of Homeland Security established the National Cyber Security Division (NCSD) in June 2003 “to serve as the national focal point for cybersecurity and to coordinate implementation of the February 2003 national cyberspace strategy (Document 16). Its mission (Document 52) is to “serve as the Federal Government’s lead in assessing, mitigating and responding to cyber risks in collaboration with Federal, State and local governments, the private sector, academia, and international partners.”
Cybersecurity White Papers
The most public aspect of U.S. activities in cyberspace centers around standard cybersecurity operations. In addition to documents such as presidential and departmental directives or strategy documents that stipulate cybersecurity goals, objectives or specific activities, there are a variety of other relevant documents.
Included are a number of “white papers” which described cybersecurity efforts. In March 2010, the White House released The Comprehensive National Cybersecurity Initiative (Document 34), which described details of the initiative launched in the previous administration and provided details of a dozen different components of the effort. In February 2010, the Department of Homeland Security released a paper (Document 32) describing various cybersecurity activities — such as the operation of the EINSTEIN intrusion detection system. In July 2011 a DHS official briefed his audience (Document 52) on a variety of topics — including the department’s National Cyber Security Division, hacking activities directed at both government and private organizations, the Stuxnet worm, and the NIGHT DRAGON exploitation effort, and cybersecurity advisory activities.
Computer Network Exploitation
Computer network exploitation (CNE) has been defined (Document 22) as “enabling operations and intelligence collection to gather data from target or adversary automated information systems or networks.” Such exploitation operations can be intended to produce information about the computer systems and networks as a prelude to a network attack or as another method of gathering economic or military intelligence. 14
CNE operations are examined in a number of intelligence threat assessments, including the Defense Security Service (Document 26, Document 43, Document 63) assessments, as well as the report by the Office of the National Counterintelligence Executive. (Document 55). As noted above, Chinese CNE operations are discussed in two reports (Document 30, Document 66) for the U.S-China review commission as well as the reports by Project 2049 (Document 79) and the Mandiant Corporation (Document 83). In addition, an Army War College paper (Document 72) also examines Chinese cyber, including CNE, capabilities.
Computer Network Attack
Computer Network Attack (CNA) has been defined (Document 22) as “operations to disrupt, deny, degrade or destroy information resident in computers and computer networks, or the computers and networks themselves. According to former NSA official William B Black Jr. (Document 11), on March 3, 1997, the Secretary of Defense officially delegated to the National Security Agency the authority to develop CNA techniques. Prior to U.S.-led airstrikes against the Qaddafi government in March 2011, the U.S. reportedly considered a cyber offensive designed to disrupt and even disable the Libyan government’s air-defense system.15
What is widely believed to be the product of a joint U.S-Israeli CNA operation was the worm Stuxnet — part of a U.S. CNA effort designated OLYMPIC GAMES.16 The worm was reported to have infected Iranian industrial control systems at the Natanz nuclear facility and damaged Iranian centrifuges. While there has been no official U.S. or Israeli confirmation of their involvement in the operation, it has been the subject of reports by the RAND Corporation (Document 42) and Congressional Research Service (Document 40) as well as the Symantec computer security corporation.
The CRS paper (Document 40), The Stuxnet Computer Worm: Harbinger of an Emerging Warfare Capability, provides an overview of the worm, an exploration of possible developers and future users, a discussion of whether Iran was the intended target, as well as coverage of industrial control systems vulnerabilities and critical infrastructure, national security implications, and issues for Congress. RAND’s study, A Cyberworm that Knows No Boundaries (Document 42), explores the issues raised by the Stuxnet case, the vulnerabilities exploited, the difficulties in defending against such malware, and the problems posed by organizational and legal restrictions. It also provides a short assessment of the status of U.S. defensive capabilities and efforts required to improve those capabilities.
Symantec’s initial analysis (Document 44) provided a technical analysis of the worm, exploring the attack scenario, timeline, Stuxnet architecture, installation, load point, command and control, propagation methods, payload exports, payload resources, and other topics. A subsequent Symantec report (Document 88) stated that the company had “discovered an older version of Stuxnet that can answer questions about its evolution.”
Computer Network Defense
See Document 23.
Computer network defense is defined in the DoD Information Operations directive (Document 22) as “actions taken to protect, monitor, analyze, detect, and respond to unauthorized activity within DoD information systems and computer networks.” Those actions can include counterintelligence, law enforcement, and other military capabilities. The first of these is the subject of one classified DoD directive (Document 41) — “Counterintelligence (CI) Activities in Cyberspace.” That directive makes clear that those activities include not only counterintelligence collection and support but offensive counterintelligence operations.
Techniques for computer network defense are also the subject of two Naval Postgraduate School theses. A 2003 thesis (Document 17) explores the feasibility of employing deception against cyberterrorists, where cyberterrorists are defined by two criteria – that the aim of launching unlawful attacks or threatening such attacks on computers, networks, and the information stored in them is to intimidate or coerce a government or its people in pursuit of political or social objectives, and that the activities result either in violence against persons or property or cause enough harm to generate fear.
A 2008 thesis (Document 25) examines what the author believes to be the key elements of deterrence in cyberspace – including denial, the development and demonstration of overt punishment techniques, the establishment of thresholds, and the development and articulation of national policy – and the prospects for cyber deterrence.
Audits and Evaluations
Audits and evaluations of cybersecurity and other cyberspace operations have been conducted by the GAO and the inspectors general of the Defense, Energy, Homeland Security, and Justice departments.
The inspector general of the Department of Homeland Security produced a classified report, released with redactions (Document 54), which examined the department’s capability to share cyber threat information with other federal agencies and the private sector. A subsequent classified report, also released with redactions in August 2012 (Document 75), addressed the department’s international cybersecurity program and noted areas that could be targeted for improvement — including developing a strategic implementation plan for foreign engagement and improving communications between the U.S. Computer Emergency Readiness Team and foreign entities.
The Department of Energy’s inspector general issued a report (Document 56) in October 2011 on the department’s unclassified cybersecurity program, which examined whether that program provided sufficient protection of its data and information systems. According to the report, corrective actions for only 11 of 35 cyber security weaknesses identified in the inspector general’s 2010 report had been completed. It also reported that there was a 60 percent growth in identified weaknesses over the 2010 report. In early 2013, the department’s inspector general issued a report (Document 84) on the cybersecurity program at the Los Alamos National Laboratory.
The Justice Department’s inspector general produced a 2011 audit report (Document 45) on the FBI’s ability to address the national security cyber intrusion threat. It reported on the FBI’s efforts in developing and operating the National Cyber Investigative Joint Task Force, and the ability of the FBI field offices to investigate national security cyber cases.
The GAO also produced a report (Document 47), released in May 2011, that evaluated the extent to which the Department of Defense and the U.S. Cyber Command had provided the military services with adequate guidance with respect to roles and responsibilities, command and control relationships, and mission requirements and capabilities with regard to cyberspace operations. Other GAO reports have examined continued challenges facing DoD (Document 49) and protection of critical infrastructure (Document 51, Document 62). A 2012 GAO report (Document 70) assessed the cyber threats to federal and other computer systems and vulnerabilities present in federal information systems and supporting critical infrastructure. A February 2013 report (Document 85) focused on the challenges facing the federal government in producing a strategic approach to cybersecurity.
Some GAO evaluations have focused on cybersecurity issues with respect to single components of critical U.S. infrastructure – including the electricity grid (Document 74), and pipelines (Document 76). The GAO’s report on securing the electricity grid examines cyber threats to the grid, actions taken to prevent attacks, and remaining challenges. The office’s pipeline study cybersecurity risks, U.S. pipeline security initiatives, and the adequacy of voluntary pipeline cybersecurity.
Legal Issues
The increasing attention to cyberspace issues has also been reflected in the examination of associated legal issues — both in law journals and government documents.17
In November 1999, the Office of the General Counsel of the Department of Defense issued a second edition of An Assessment of International Legal Issues in Information Operations (Document 13). The section “Application to Computer Network Attacks” (pp.16-23) concludes with a one-paragraph assessment which begins, “It is far from clear the extent to which the world community will regard computer network attacks as ‘armed attacks’ or ‘uses of force,’ and how the doctrines of self-defense and countermeasures will be applied to computer network attacks.” More recently, an Air Force instruction (Document 53) specifies the responsibilities of different Air Force components for legal reviews of weapons and cyber capabilities as well as the content of such reviews.
Legal issues have also been examined by the Congressional Research Service. In a March 2012 paper (Document 65), CRS explored Fourth Amendment, civil liberties, and privacy issues related to the protection of critical infrastructure and the sharing of cybersecurity information — as well as the possibility of conflicts between state and federal cybersecurity law. Another CRS study (Document 73) examines possible cyber-related changes to 28 different statutes.
The question of whether the U.S. Cyber Command had sufficient legal authority to carry out its mission was the catalyst for an exchange of letters (Document 68a, Document 68b, Document 68c), beginning in March 2012, between Senator John McCain (R-AZ) and General Keith B. Alexander, Director of the National Security Agency and the commander of the U.S. Cyber Command. In his initial letter McCain posed six questions, while in his second letter he notes a number of disagreements with the content of Alexander’s responses.
The Documents
Document 1: [Deleted], National Security Agency, “Computer Operating System Vulnerabilities,” Cryptolog, VI, 3 (March 1979). Unclassified.
Source: http://www.nsa.gov
This article, which appeared in a classified NSA journal, explores seven common computer operating system vulnerabilities, several penetration techniques, defensive measures, and future research areas.
Document 2: Robert J. Hanyok, National Security Agency, “Some Reflections on the Reality of Computer Security,” Cryptolog, IX, 6-7 (June-July 1982). Confidential.
Source: http://www.nsa.gov
The author of this article argues that while computer users at NSA have been confident that the security of their systems is “ironclad and invulnerable” the reality is quite different. He then notes a number of user practices and implementation problems that make those systems vulnerable.
Document 3: [Deleted], “Computer Virus Infections: Is NSA Vulnerable?,” Cryptologic Quarterly, 4, 3 (Fall 1985). Top Secret.
Source: http://www.nsa.gov
This paper examines the nature of computer viruses, whether there is an algorithm to determine whether a program is infected with a virus, different classes of attack (including compromise, spoofing, and denial of service), and solutions.
Document 4: [Deleted], “A First Generation Technical Viral Defense,” Cryptologic Quarterly, 7, 2 (Summer 1988). Secret.
Source: http://www.nsa.gov
This paper examines a defense, involving encryption, that can be used to respond to the detection of a computer virus — and means for checking the effectiveness of the response.
Document 5: General Accounting Office, GAO/IMTEC-89-57, Computer Security: Virus Highlights Need for Improved Internet Management, June 1989. Unclassified.
The catalyst for this report was a November 1988 computer virus that caused thousands of computers, in the United States and overseas, to shut down. The report provides details on some of the networks disrupted by the virus, the means of infection, and notes the vulnerabilities highlighted by the incident.
Document 6: General Accounting Office, GAO/T-IMTEC-92-5, Computer Security: Hackers Penetrate DOD Computer Systems, November 20, 1991. Unclassified.
Source: http://www.gao.gov
This testimony of a GAO official concerns his division’s investigation of the attacks by Dutch hackers on Army, Navy, and Air Force computer systems — which the official characterizes as containing unclassified but sensitive information — during Operation Desert Storm/Shield. It examines how the hackers penetrated the systems, agency responses, and the need for greater attention to computer security.
Document 7: Richard Sylvester, National Security Agency, “NSA and Computer Viruses,” Cryptolog, XIX, 3 (1992). Unclassified/For Official Use Only.
Source: http://www.nsa.gov
This one-page article reports NSA classification guidelines with respect to any discussion of computer viruses with regard to NSA systems. Classification of specific facts ranged from Unclassified to Top Secret/Handle Via Comint Channels Only.
Document 8: [Deleted], National Security Agency, “Global Network Intelligence and Information Warfare: SIGINT and INFOSEC in Cyberspace,” Cryptolog, XXI,1 (1995). Top Secret/Handle Via Comint Channels Only.
Source: http://www.nsa.gov
This heavily-redacted article extends beyond cyber issues, but does note that “sophisticated telecommunications and data networks … make it possible to deny and degrade a potential adversary’s command and control communications and sensitive commercial and diplomatic communications from great distances with little or no risk to life and limb.”
Document 9: [Deleted], “Out of Control,” Cryptologic Quarterly, Special Edition, 15, 1996. Secret.
Source: http://www.nsa.gov
This article, in another National Security Agency journal, discusses the threat to computer systems containing classified information via human intelligence operations directed at systems administrators. A largely redacted section is titled “”Foreign Intelligence Services Are Already Targeting Computer Personnel,” while the final section offers recommendations on how to address the problem.
Document 10a: Government Accounting Office, GAO/AIMD- 96-84, Information Security: Computer Attacks at Department of Defense Pose Increasing Risks, May 22, 1996. Unclassified.
Document 10b: Jack L. Brock, General Accounting Office, GAO/T-AIMD-96-92, Information Security: Computer Attacks at Department of Defense Pose Increasing Risks, May 22, 1996. Unclassified.
Source: http://www.gao.gov
This report and testimony by a GAO official reports on an examination of hacker attacks on Defense Department computer systems, including a 1994 episode that involved over 150 attempts to access the computer systems of Rome Laboratory — which resulted in the theft of air tasking research data and damage to the laboratory’s air tasking order research project “beyond repair,” according to lab officials. The report and testimony also discuss the challenges faced by DoD in securing its computer systems.
Document 11: William B. Black, National Security Agency, “Thinking Out Loud About Cyberspace,” Cryptolog, XXIII, 1 (Spring 1997). Secret.
Source: http://www.nsa.gov
This article, by a senior NSA official, notes that NSA was assigned the mission of computer network attack in March 1997, and argues that the world was on the verge of a new age — “the information age” — and that the future of war would be warfare in cyberspace.
Document 12: William J. Clinton, Presidential Decision Directive/NSC-63, Subject: Critical Infrastructure Protection, May 22, 1998. For Official Use Only/Unclassified.
Source: Federation of American Scientists (www.fas.org)
The introduction to this directive notes that the military and economy of the United States are “increasingly reliant upon certain critical infrastructures and upon cyber-based information systems.” The remainder of the 18-page directive specifies the President’s intent “to assure the continuity and validity of critical infrastructures” in the face of physical or cyber threats, states a national goal, delineates a public-private partnership to reduce vulnerability, states guidelines, specifies structure and organization, discusses protection of Federal government critical infrastructures, orders a NSC subgroup to produce a schedule for the completion of a variety of tasks, and directs that an annual implementation report be produced.
Document 13: Office of General Counsel, Department of Defense, An Assessment of International Legal Issues in Information Operations, Second Edition, November 1999. Unclassified.
Source: http://www.dod.gov
The introduction to this assessment notes that information operations includes information attack which, in turn, includes computer network attack. It goes on to consider the implications of a variety of domestic and international laws and treaties with regard to information operations.
Document 14: Steven A. Hildreth, Congressional Research Service, Cyberwarfare, June 19, 2001. Unclassified.
Source: http://www.fas.org
This report discusses the definition of cyberwarfare, and contains three case studies — including the Rome Laboratory incident (Document 8a, Document 8b) and two exercises — and, inter alia, reviews U.S policy and doctrine, organization, and legal issues. It also discusses selected foreign views and activities with regard to cyberwar.
Document 15: Michael Vatis, ESDP Discussion Paper-2002-04, Cyber Attacks: Protecting America’s Security Against Digital Threats, John F. Kennedy School of Government, Harvard University, June 2002. Not classified.
Source: Belfer Center for Science and International Affairs, Harvard University (www.beflercenter.hks.harvard.edu)
This paper, written by the first director of the Federal Bureau of Investigation’s National Infrastructure Protection Center, examines: the range of cyber attackers (including insiders, criminal groups, virus writers, foreign intelligence services, foreign military organizations, terrorists, “hacktivists,” and recreational hackers), types of cyber attacks, the international component of cyber attacks, the federal response to cyber attacks, Presidential Decision Directives 62 and 63, and the policy of the George H.W. Bush administration. Vatis also offers recommendations concerning cyber research and development, alert status during conflict, and identifying best practices related to cyber security.
Document 16: The White House, The National Strategy to Secure Cyberspace, February 2003. Unclassified.
Source: http://www.us-cert.gov
This 76-page document discusses the strategy’s strategic objectives (including preventing cyber attacks against critical U.S. infrastructures), the government’s role in cyber security, the anticipated role of the Department of Homeland Security in cyber security, and five critical priorities for cyberspace security (including a national cyberspace security response system and international cooperation). A classified National Security Presidential Directive (NSPD-38), with the identical title, was issued on July 7, 2004.
Document 17: Kheng Lee Gregory Tran, Naval Postgraduate School, Confronting Cyberterrorism with Cyber Deception, December 2003. Unclassified.
Source: Dudley Knox Library, Naval Postgraduate School (www.nps.edu/library)
This master’s thesis examines the possibility of using deception to defeat or mitigate the damage from cyberterrorism. It examines, inter alia, the cyberterrorism threat, the values and risks of deception, nine varieties of cyber deception (including concealment, camouflage, false and planted information, ruses, and feints) and cyber defense, and the pitfalls of cyber defense.
Document 18: Interagency OPSEC Support Staff, Intelligence Threat Handbook, June 2004. Unclassified.
Source: Author’s Collection
The scope of this handbook is broader than cybersecurity, but one section — Computers and the Internet — addresses the history of Internet security, threats to computer network security, roots of network vulnerability, outsider attack techniques, insider attack techniques, and countermeasures.
Document 19: Office of Inspector General, Department of Homeland Security, OIG-04-29, Progress and Challenges in Securing the Nation’s Cyberspace, July 2004. Unclassified.
Source: http://www.dhs.gov
This document reports on the inspector general’s evaluation of the Department of Homeland Security’s efforts to implement The National Strategy to Secure Cyberspace (Document 14). It notes “major accomplishments” — including the creation of a Computer Emergency Readiness Team, creation of the National Cyber Alert System, and sponsorship of the National Cyber Security Summit. It also notes “a number of challenges to address long-term cyber threats and vulnerabilities” — including the DHS National Cybersecurity Division’s need to prioritize its initiatives, identify resources required to carry out its mission, and develop strategic implementation plans.
Document 20: President’s Information Technology Advisory Committee, Report to the President, Cyber Security: A Crisis of Prioritization, February 2005. Unclassified.
Source: http://www.nitrd.gov/pitac/reports
The two main chapters of this report, prior to the concluding chapter, address the importance of cyber security and examine federal cyber security research and development efforts. In its concluding chapter the committee states its findings and recommendations with regard to federal funding for fundamental research in civilian cyber security, the cyber security research community, technology transfer efforts, and the coordination and oversight of federal cyber security research and development.
Document 21: Donald Rumsfeld, to Steve Cambone, Subject: Cyber Attack Issue, November 04, 2005, Unclassified/FOUO .
Source: http://www.rumsfeld.com
In this “snowflake” directed to his under secretary for intelligence, Rumsfeld suggests that Cambone consider establishing a group to review organization, budgeting, and presentation issues with regard to cyber attacks.
Document 22: Department of Directive O-3600.01, Subject: Information Operations, August 14, 2006. Unclassified/For Official Use Only.
Source: Department of Defense Freedom of Information Act Release
This directive states Department of Defense policy and responsibilities with regard to information operations (defined as the integrated deployment of electronic warfare, computer network operations, psychological operations, military deception, and operations security). Among those whose responsibilities are identified is the Assistant Secretary of Defense for Networks and Information Integration.
Document 23: Chairman of the Joint Chiefs of Staff, The National Military Strategy for Cyberspace Operations, December 2006. Secret.
Source: Department of Defense Freedom of Information Act Release.
This strategy document was issued to provide guidelines to the Defense Department — including military service organizations, the unified commands, and DoD components (including agencies, field activities and other entities) — with regard to planning, executing, and allocating resources for cyberspace operations. Its main chapters focus on the strategic context, threats and vulnerabilities, strategic considerations, the military strategic framework, and implementation and assessment. Several enclosures address topics such as examples of threats and threat actors, examples of vulnerabilities, and strategic priorities and outcomes.
Document 24: John Rollins and Clay Wilson, Congressional Research Service, Terrorist Capabilities for Cyberattack: Overview and Policy Issues, January 22, 2007. Unclassified.
Source: http://www.fas.org
This study examines possible terrorists’ objectives in conducting cyberattacks, computer vulnerabilities that might make cyberattack against the U.S. homeland’s critical infrastructure viable, and emerging computer and technical skills of terrorists. It also examines the cybersecurity efforts of several government agencies, changing concerns about cyberattack, and a number of additional issues concerning terrorist or criminal cyber activities.
Document 25: Ryan J. Moore, Naval Postgraduate School, Prospects for Cyber Deterrence, December 2008. Unclassified.
Source: http://www.nps.edu/library
The author of this thesis argues that with “more sectors of critical national infrastructure [being] interconnected in cyberspace,” the risk to national security from cyberattack “has increased dramatically.” He explores the fundamentals of strategic deterrence, the evolving cyber threat, deterrence strategy in cyberspace, and the prospects for cyber deterrence.
Document 26: Defense Security Service, Targeting U.S. Technologies: A Trend Analysis of Reporting from Defense Industry, 2009. Unclassified.
Source: http://www.dss.mil
This assessment of foreign attempts to illicitly acquire U.S. technologies concerns a variety of techniques, including “suspicious internet activity” — which includes, but is not limited to “confirmed intrusion, attempted intrusion, [and] computer network attack.”
Document 27: Major William C. Ashmore, School of Advanced Military Studies, United States Army Command and General Staff, Impact of Alleged Russian Cyber Attacks, 2009. Unclassified.
Source: http://www.dtic.mil/dtic/fr/fulltext/u2/a504991.pdf
This monograph was written to examine the implications of alleged Russian cyber attacks against Estonia and Georgia for the Russian Federation, former Soviet satellites, and international organizations.
Document 28: The White House, Cyberspace Policy Review: Assuring a Trusted and Resilient Information and Communications Infrastructure, May 8, 2009. Unclassified.
Source: The White House (www.whitehouse.gov)
This paper reports the results of a presidentially-directed 60-day comprehensive review to evaluate U.S. policies and organizational structures related to cybersecurity. The review produced seven main conclusions which included: “The Nation is at a crossroads,” “The status quo is no longer acceptable,” “The United States cannot succeed in securing cyberspace if it works in isolation,” and “The Federal government cannot entirely delegate or abrogate its role in securing the Nation from a cyber incident or accident.”
Document 29: Robert M. Gates, Memorandum to Secretaries of the Military Departments, Subject: Establishment of a Subordinate Unified U.S. Cyber Command Under U.S. Strategic Command for Military Cyberspace Operations, June 23, 2009. Unclassified.
Source: http://www.dod.gov
This memo from the Secretary of Defense directs the commander of the U.S. Strategic Command to establish a U.S. Cyber Command and that the command reach an initial operating capability by October 2009 and a full operating capability by October 2010. It also informs the recipients of the Secretary’s plan to recommend to the president that the National Security Agency director also become commander of the Cyber Command.
Document 30: Bryan Krekel, Northrop Grumman, Capability of the People’s Republic of China to Conduct Cyber Warfare and Computer Network Exploitation, October 9, 2009. Unclassified .
Source: Air University (www.au.af.mil)
This study, prepared for the U.S.-China Economic and Security Review Commission, focuses largely on Chinese computer network exploitation (CNE) as a strategic intelligence collection tool. It examines Chinese CNE operations strategy and operations during conflict, key entities in Chinese computer network operations, cyber-espionage, an operational profile of an advanced cyber intrusion, and a chronology of alleged Chinese computer network exploitation events.
Document 31: Department of Defense, DoD Instruction 5205.13, Subject: Defense Industrial Base (DIB) Cyber Security/Information Assurance (CS/IA) Activities, January 29, 2010. Unclassified.
Source: http://www.dtic.mil/whs/directives/corres/pdf/520513p.pdf
This Defense Department instruction states policy, establishes responsibilities, and delegates authority with regard to the protection of unclassified DoD information that passes through or resides on unclassified Defense Industrial Base information systems and networks.
Document 32: Department of Homeland Security, Computer Network Security & Privacy Protection, February 19, 2010. Unclassified.
Source: http://www.dhs.gov
This white paper describes the Department of Homeland Security’s computer network security activities, which includes the operation of the EINSTEIN intrusion detection systems — including the systems collection methods and the implications for privacy protection. It also discusses topics such as oversight and compliance, the role of the National Security Agency, and future program development.
Document 33: U.S. Army Training and Doctrine Command, TRADOC Pamphlet 525-7-8, The United States Army’s Cyberspace Operations Concept Capability Plan, 2016-2028, February 22, 2010. Unclassified.
Source: http://www.fas.org
This pamphlet explores how “the Army’s future force in 2016-2028 will leverage cyberspace and CyberOps” and how CyberOps (which is specified to consist of four components — cyberwarfare, cyber network operations, cyber support, and cyber situational awareness) will be integrated into full spectrum operations.
Document 34: The White House, The Comprehensive National Cybersecurity Initiative, March 2, 2010. Unclassified.
Source: http://www.whitehouse.gov
The release of this document by the Obama White House revealed details of the cybersecurity initiative launched during the previous administration. It provides basic details of twelve different components of the initiative — which include intrusion detection and prevention systems across the federal government, coordination and redirection of research and development efforts, enhancing situational awareness, increasing the security of classified networks, developing enduring deterrence strategies, and defining the role of the federal government for extending cybersecurity into critical infrastructure domains.
Document 35: Keith Alexander, Director, National Security Agency, Advanced Questions for Lieutenant General Keith Alexander, USA Nominee for Commander, United States Cyber Command, April15, 2010. Unclassified.
Source: http://www.fas.org
This 32-page documents consists of 28 questions (some with multiple parts) posed to, and answered by, General Alexander in advance of his appearance before the Senate Armed Services Committee with respect to his nomination to head the newly formed U.S. Cyber Command.
Document 36: Department of Energy, DOE P 205.1, Subject: Departmental Cyber Security Management Policy, September 23, 2010. Unclassified.
Source: http://www.energy.gov
This Department of Energy policy directive covers the six components of the department’s cyber security management policy — its objectives, guiding principles, core functions, mechanisms, responsibilities, and implementation.
Document 37: Janet Napolitano and Robert Gates (signators), Memorandum of Agreement Between the Department of Homeland Security and the Department of Defense Regarding Cybersecurity, September 27, 2010. Unclassified.
Source: http://www.dhs.gov
The purpose of the agreement, signed by the Secretaries of Homeland Security and Defense, is specified as establishing the terms by which the two departments “will provide personnel, equipment, and facilities” in order to increase interdepartmental collaboration in strategic planning as well as operational activities concerning cybersecurity.
Document 38: Department of Defense, Cyber Command Fact Sheet, October 13, 2010. Unclassified.
Source: http://www.dod.gov
This fact sheet provides basic information about the U.S. Cyber Command — including its mission, focus, and components.
Document 39: JASON, JSR-10-102, Science of Cyber-Security, November 2010. Unclassified.
Source: http://www.fas.org
This report, by the Defense Department’s JASON scientific advisory group, was a response to the department’s request that the group examine whether there were underlying fundamental principles that would make it possible to adopt a more scientific approach to the issue of cybersecurity. The sciences they examine for possible guidance are economics, meteorology, medicine, astronomy, and agriculture.
Document 40: Paul K. Kerr, John Rollins, and Catherine A. Theohary, Congressional Research Service, The Stuxnet Computer Worm: Harbringer of an Emerging Warfare Capability, December 9, 2010. Unclassified.
Source: http://www.fas.org
This short paper provides an overview of the Stuxnet worm, an exploration of possible developers and future users, a discussion of whether Iran was the intended target, as well as industrial control systems vulnerabilities and critical infrastructure, national security implications, and issues for Congress.
Document 41: Department of Defense, DoD Instruction S-5240.23, Subject: Counterintelligence (CI) Activities in Cyberspace, December 13, 2010. Secret.
Source: Department of Defense Freedom of Information Act Release.
According to this instruction, DoD counterintelligence activities in cyberspace are to be directed against foreign intelligence services and international terrorist organizations. The two key portions of the instruction define the responsibilities of DoD components and establish procedures for counterintelligence activities. While much of the segment concerning procedures is redacted in the declassified version, the table of contents indicates three different types of CI-related activities in cyberspace: counterintelligence support, counterintelligence collection, and offensive counterintelligence operations (OFCO).
Document 42: Isaac R. Porsche III, Jerry M. Sollinger, and Shawn McKay, RAND Corporation, A Cyberworm that Knows no Boundaries, 2011. Unclassified.
Source: http://www.rand.org
The catalyst for this paper were the reports of the Stuxnet worm (Document 40). It explores issues raised by “sophisticated yet virulent malware” — including the nature of the threats, the vulnerabilities exploited and the difficulties in defending against Stuxnet-type worms, and the problems posed by organizational and legal restrictions. It also provides a short assessment of the status of U.S. defensive capabilities and efforts required to improve those capabilities.
Document 43: Defense Security Service, Targeting U.S. Technologies: A Trend Analysis of Reporting from Defense Industry, 2011. Unclassified.
Source: http://www.dss.mil
This report updates the Defense Security Service’s 2009 assessment of foreign attempts to illicitly acquire U.S. technologies, and concerns a variety of techniques, including “suspicious internet activity.” It notes a high level of suspicious network activity “in the form of cyber intrusion attempts directed at cleared contractor networks.”
Document 44: Nicolas Falliere, Liam O. Murchu, and Eric Chien, Symantec, W 32. Stuxnet Dossier, Version 1.4, February 2011. Not classified.
Source: http://www.symantec.com
This study, prepared by the Symantec computer security firm, provides a technical analysis of the Stuxnet malware — exploring the attack scenario, timeline, Stuxnet architecture, installation, load point, command and control, propagation methods, payload exports, payload resources and other topics.
Document 45: Office of the Inspector General, Department of Justice, Audit Report 11-22, The Federal Bureau of Investigation’s Ability to Address the National Security Cyber Intrusion Threat , April 2011. Secret.
Source: http://www.justice.gov/oig/reports/FBI/a1122r.pdf
The audit which is the subject of this report was conducted to evaluate the FBI’s efforts in developing and operating the National Cyber Investigative Joint Task Force in response to the national security cyber threat, and assess the FBI field offices’ capabilities to investigate national security cyber cases.
Document 46: The White House, International Strategy for Cyberspace: Prosperity, Security, and Openness in a Networked World, May 2011. Unclassified.
Source: http://www.whitehouse.gov
This policy document discusses the process of building U.S. cyberspace policy, the future of cyberspace (including the preferences of the U.S. and its role in achieving its preferred outcomes), and U.S. policy priorities (with regard to economic issues, network protection, law enforcement, and several additional issues). It concludes with a discussion of U.S. implementation of its strategy.
Document 47: Government Accountability Office, GAO-11-421, Defense Department Cyber Efforts: More Detailed Guidance Needed to Ensure Military Services Develop Appropriate Cyberspace Capabilities, May 2011. Unclassified.
Source: http://www.gao.gov
This study was conducted to determine the extent to which the Defense Department and U.S. Cyber Command had provided the military services with adequate guidance with respect to roles and responsibilities, command and control relationships, and mission requirements and capabilities with regard to cyberspace operations.
Document 48: Department of Energy, DOE O 205.1B, Subject: Department of Energy Cyber Security Program, May 16, 2011. Unclassified .
Source: http://www.energy.gov
This Energy department order states requirements for the department’s Cyber Security Program, which requires a risk management approach. It also specifies the responsibilities of over a dozen department components or officers in formulating and implementing the program.
Document 49: Government Accountability Office, GAO-11-75, Department of Defense Cyber Efforts: DOD Faces Challenges In Its Cyber Activities, July 2011. Unclassified.
Source: http://www.gao.gov
This is an unclassified version of a previously classified report. It examines DoD’s organization for addressing cybersecurity threats as well as assessing the extent to which the Defense Department had developed a joint doctrine for cyberspace operations, assigned command and control responsibilities, and identified and addressed key capability gaps involving cyberspace operations.
Document 50: Department of Defense, Department of Defense Strategy for Operating in Cyberspace, July 2011. Unclassified .
Source: http://www.defense.gov
The core of this strategy document is the discussion of five strategic initiatives with regard to DoD operations in cyberspace — treating cyberspace as an operational domain with regard to organization, training, and equipment; employing new defense operations concepts to protect DoD networks and systems; collaboration with other U.S. government departments and the private sector; cooperation with U.S. allies and international partners; and leveraging “the nation’s ingenuity” through the cyber work force and technological innovation.
Document 51: Gregory C. Wilshusen, Government Accountability Office, GAO-11-865T, Cybersecurity: Continued Attention Needed to Protect Our Nation’s Critical Infrastructure, July 26, 2011. Unclassified.
Source: http://www.gao.gov
The focus of this study is the federal role in enhancing cybersecurity related to the private sector’s operation of critical infrastructure. It describes cyber threats facing cyber-reliant critical infrastructures; discusses recent federal government actions, taken in cooperation with the private sector, to identify and protect such infrastructures; and identifies challenges to the protection of those infrastructures.
Document 52: Bradford Willke, Department of Homeland Security, Moving Toward Cyber Resilience, July 27, 2011. Unclassified.
Source: Pubic Intelligence (http://info.publicintelligence.net/DHS-CyberResilience.pdf)
This briefing covers a number of topics, including the origins, organization, and mission of the DHS National Cyber Security Division, hacking activities directed at a number of government and private entities (the CIA, Booz Allen Hamilton, Lockheed Martin), the Stuxnet worm, an effort designated Night Dragon that involved cyber-theft of sensitive information from international oil and energy companies, and cyber security advisory activities.
Document 53: Department of the Air Force, Air Force Instruction 51-402, Legal Reviews of Weapons and Cyber Capabilities, July 27, 2011. Unclassified.
Source: http://www.fas.org
This instruction focuses on the responsibilities of different Air Force components for legal reviews of weapons and cyber capabilities, as well as the contents of such reviews.
Document 54: Office of Inspector General, Department of Homeland Security, Review of the Department of Homeland Security’s Capability to Share Cyber Threat Information (Redacted), September 2011, Unclassified.
Source: http://www.dhs.gov
The Fiscal Year 2010 Intelligence Authorization Act required the inspectors general of the Intelligence Community and DHS to provide Congress with an assessment of how cyber threat information is being shared among federal agencies and the private sector, the means used to share classified cyber threat information, and the effectiveness of the sharing and distribution of cyber threat information. In addition to providing such an assessment, the Inspector General made three recommendations to DHS.
Document 55: National Counterintelligence Executive, Foreign Spies Stealing US Economic Secrets in Cyberspace: Report to Congress on Foreign Economic Collection and Industrial Espionage, 2009-2011 , October 2011. Unclassified.
Source: http://www.ncix.gov
This report, produced by a component of the Office of the Director of National Intelligence, consists of three major sections. One is the vulnerability of U.S. technologies and trade secrets to cyberspace operations and the appeal of cyberspace collection. Another examines the threat from specific collectors, including Russia, China, and U.S. partners. The third provides an outlook for the future, divided between sections on “near certainties” and “possible game changers.”
Document 56: Office of Inspector General, Department of Energy, DOE/IG-0856, Evaluation Report: The Department’s Unclassified Cyber Security Program – 2011, October 2011. Unclassified.
Source: http://www.dhs.gov
The Federal Information Security Management Act of 2002 required an independent evaluation to determine whether the Department of Energy’s unclassified cyber security program adequately protected its data and information systems. According to the report, corrective actions for only 11 of 35 cybersecurity weaknesses identified in the inspector general’s 2010 report had been completed. In addition, there was a 60 percent growth in identified weakness over the 2010 report.
Document 57: Department of Homeland Security, Preventing and Defending Against Cyber Attacks, October 2011. Unclassified.
Source: http://www.dhs.gov
This DHS paper focuses on the department’s efforts in assisting federal executive branch civilian departments with securing their unclassified computer networks. It reports on the department’s efforts with respect to cybersecurity coordination and research, cybersecurity initiatives and exercises, the promotion of public awareness of cybersecurity, cybersecurity workforce development, and privacy and civil liberties issues.
Document 58: Department of Homeland Security, Blueprint for a Secure Cyber Future: The Cybersecurity Strategy for the Homeland Security Enterprise, November 2011. Unclassified.
Source: http://www.dhs.gov
This blueprint contains two main components. It lists four cybersecurity goals (reducing exposure to cyber risk, ensuring priority response and recovery, maintaining shared situational awareness, and increasing resilience) — to be attained through nine objectives. Secondly, it specifies four goals for strengthening the cyber system (to be attained via eleven objectives).
Document 59: Department of Defense, Department of Defense Cyberspace Policy Report: A Report to Congress Pursuant to the National Defense Authorization Act for Fiscal Year 2011, Section 934 , November 2011. Unclassified.
Source: http://www.dod.gov
This 14-page document describes the legal and policy issues associated with cyberspace, reports on decisions of the secretary of defense, and notes that there are no plans to update the National Military Strategy for Cyberspace Operations (Document 23) but that the Department of Defense Strategy for Operating in Cyberspace (Document 50) would provide strategy guidance. In addition, it describes the use and application of cyber modeling and simulation.
Document 60: United States Air Force, Air Force Doctrine Document 3-12, Cyberspace Operations, November 30, 2011. Unclassified.
Source: http://www.e-publishing/af.mil
This document examines cyberspace fundamentals (including U.S. national policy and the challenges of cyberspace operations); command and organization (including a description of U.S. cyberspace organizations as well as command and control of cyberspace operations); and the design, planning, execution, and assessment of cyberspace operations.
Document 61: National Science and Technology Council, Executive Office of the President, Trustworthy Cyberspace: Strategic Plan for the Federal Cybersecurity Research and Development Program, December 2011. Unclassified .
Source: http://www.cyber.st.dhs.gov
This plan specifies four interconnected priorities for U.S. government agencies that conduct or sponsor research and development in cybersecurity. The priorities are organized along four lines: inducing change, developing scientific foundations, accelerating transition to practice, and maximizing research impact.
Document 62: Government Accountability Office, GAO-12-92, Critical Infrastructure Protection: Cybersecurity Guidance Is Available but More Can Be Done to Promote Its Use, December 2011. Unclassified.
Source: http://www.gao.gov
This GAO report examines the use of cybersecurity guidance in seven critical infrastructure sectors (including banking and finance, energy, and nuclear reactors) from national and international organizations. It reports that while such guidance is being employed, sector officials do not believe it is comprehensive, and DHS and other sector-specific agencies have not identified key cybersecurity guidance applicable to each of their critical infrastructure sectors.
Document 63: Defense Security Service, Targeting U.S. Technologies: A Trend Analysis of Reporting from Defense Industry, 2012. Unclassified.
Source: http://www.dss.mil
The main focus of this report, by the Pentagon’s Defense Security Service, is not cybersecurity but the attempts to gather information on U.S. technologies — by whatever method. However, as did previous DSS reports (Document 26, Document 43), it does discuss “suspicious network activity” (SNA) as one acquisition method. It notes that SNA is “the most prevalent collection method for entities originating from East Asia and the Pacific,” although it is no higher than fifth with regard to collection methods associated with other regions.
Document 64: 624th Operations Center, Intelligence Surveillance & Reconnaissance Division, Air Force Space Command, Cyber Threat Bulletin, 2012 Top Ten Cyber Threats, January 9, 2012. Unclassified/For Official Use Only.
Source: http://www.publicintelligence.net
This bulletin passes along the conclusions of the McAfee computer security firm concerning the top 10 cyber threats for the coming year. The top five are attacking mobile devices, embedded hardware, “legalized” spam, industrial attacks, and hacktivism.
Document 65: Mark Mateski, Cassandra M. Trevino, Cynthia K. Veitch, John Michalski, J. Mark Harris, Scott Maruoka, and Jason Frye, Sandia National Laboratories, SAND 2012-2427, Cyber Threat Metrics, March 2012. Unclassified.
Source: http://www.fas.org
This report was prepared in support of the DHS cyber-risk and vulnerability assessment program intended to aid federal civilian executive branch agencies. It reviews alternative cyber threat metrics and models that might be employed in any operational threat assessment.
Document 66: Bryan Krekel, Patton Adams, George Bakos, Northrup Grumman, Occupying the Information High Ground: Chinese Capabilities for Computer Network Espionage and Cyber Espionage, March 7, 2012. Unclassified.
Source: http://www.uscc.gov
This report, prepared for the U.S.-China Economic and Security Review Commission, focuses on six topics: information warfare strategy, Chinese use of network warfare against the United States, key entities and institutions supporting Chinese computer network operations (the Third and Fourth Departments of the Peoples Liberation Army’s General Staff Department), potential risks to the U.S. telecommunications supply chain, the comparison between criminal and state-sponsored network exploitation, and the risks and reality of collaboration between U.S. and Chinese information security firms.
Document 67: Edward C. Liu, Gina Stevens, Kathleen Ann Ruane, Alissa M. Dolan, and Richard M. Thompson II, Congressional Research Service, Cybersecurity: Selected Legal Issues, March 14, 2012. Unclassified.
Source: http://www.fas.org
The authors of this report address legal issues related to the protection of critical infrastructure, the protection of federal networks (including Fourth Amendment as well as civil liberties and privacy issues), and the sharing of cybersecurity information. In addition, the authors explore the possibility of federal cybersecurity law preempting state law.
Document 68a: John McCain to General Keith B. Alexander, Letter, March 29, 2012. Unclassified.
Document 68b: Keith B. Alexander, Commander, U.S. Cyber Command to The Honorable John McCain, May 3, 2012. Unclassified/For Official Use Only.
Document 68c: John McCain to General Keith B. Alexander, May 9, 2012. Unclassified.
Sources: http://www.washingtonpost.com, http://www.federalnewsradio.com, http://blog.zwillgencom
This series of letters begins with Senator John McCain (R-Az.) writing to Cyber Command chief Keith Alexander concerning the issue of whether the U.S. government needs additional authorities to deter and defend against cyber attacks. Alexander’s May 3 letter contains responses to the six questions posed by McCain in his March 29 letter. In turn, McCain’s May 9 letter notes a number of disagreements with the content of Alexander’s responses.
Document 69: Office of the Chief of Naval Operations, OPNAV Instruction 5450.345, Subj: Mission, Functions, and Tasks for Commander, U.S. Fleet Cyber Command and Commander, U.S. Tenth Fleet, April 4, 2012. Unclassified.
Source: http://doni.daps.dla.mil/Directives
This instruction specifies the authorities and missions of the U.S. Fleet Cyber Command, as well as the relationship between the commander, Fleet Cyber Command, and the commander, U.S. Tenth Fleet. It also specifies a number of Navy entities under the administrative control of the Fleet Cyber Command — including the Navy Information Operations Command (which conducts signals intelligence operations), the Navy Cyber Warfare Development Group, and the Navy Cyber Defense Operations Command.
Document 70: Gregory C. Wilshusen, Government Accountability Office, GAO-12-666T, Cybersecurity: Threats Impacting the Nation, April 24, 2012. Unclassified.
Source: http://www.gao.gov
This report describes GAO’s assessment of cyber threats posed to federal and other computer systems, and vulnerabilities present in federal information systems and supporting critical infrastructure. It also describes reported cyber incidents and their impacts. It characterizes the number of cybersecurity incidents reported by federal agencies as rising and that “recent incidents illustrate that these pose serious risk.”
Document 71a: Pat Meehan, Statement to Subcommittee on Counterterrorism and Intelligence and Subcommittee on Cybersecurity, Infrastructure Protection and Security Technologies, “Iranian Cyber Threat to the U.S. Homeland,” April 26, 2012. Unclassified.
Document 71b: Dan Lungren, Statement to Subcommittee on Counterterrorism and Intelligence and Subcommittee on Cybersecurity, Infrastructure Protection and Security Technologies, “Iranian Cyber Threat to the U.S. Homeland,” April 26, 2012. Unclassified.
Document 71c: Frank J. Cilluffo, Director, Homeland Security Policy Institute, George Washington University, Statement to Subcommittee on Counterterrorism and Intelligence and Subcommittee on Cybersecurity, Infrastructure Protection and Security Technologies, “The Iranian Cyber Threat to the United States,” April 26, 2012.
Document 71d: Ilan Berman, American Foreign Policy Council, Statement to Subcommittee on Counterterrorism and Intelligence and Subcommittee on Cybersecurity, Infrastructure Protection and Security Technologies, “The Iranian Cyber Threat to the U.S. Homeland,” April 26, 2012. Unclassified.
Source: http://homeland.house.gov
Substantial attention has been devoted to Chinese cyberwarfare activities in the reports of private and government organizations as well as in Congressional hearings. While Iranian cyber activities were noted in the 2012 testimony of Director of National Intelligence James Clapper, who characterized them as “dramatically increasing in recent years in depth and complexity,” they have received less attention that those of the People’s Republic of China. These hearings, before a subcommittee of the House Committee on Homeland Security, involve assessments of the Iranian cyber threat by two Congressmen and representatives of two private organizations.
Document 72: Colonel Jayson M. Spade, U.S. Army War College, Information as Power: China’s Cyber Power and America’s National Security, May 2012. Unclassified.
Source: U.S. Army War College (www.carlisle.army.mil)
This research paper examines the growth of Chinese cyber capabilities — including those for offensive, defensive, and computer network exploitation operations. It also compares China’s capacity and potential in cyberspace to United States efforts with regard to cybersecurity. In addition, the author suggests a number of steps to improve U.S. cybersecurity policy.
Document 73: Eric A. Fischer, Congressional Research Service, Federal Laws Relating to Cybersecurity: Discussion of Proposed Revisions, June 29, 2012. Unclassified.
Source: http://www.fas.org
This analysis contains an introduction reviewing the then-current legislative framework on cybersecurity, executive branch actions, and legislative proposals. It then discusses proposed cybersecurity-related revisions to 28 different statutes — from the Posse Comitatus Act of 1879 to the Intelligence Reform and Terrorism Prevention Act of 2004.
Document 74: Gregory C. Wilshusen, Government Accountability Office, GAO-12-962T, Cybersecurity: Challenges in Securing the Electricity Grid, July 17, 2012. Unclassified.
Source: http://www.gao.gov
This testimony, by a GAO official, concerns cyber threats to critical infrastructure — including the electricity grid — as well as actions taken to prevent cyber attacks on the grid and challenges that remain. Mr. Wilshusen notes the actions taken by a number of entities (including the North American Electric Reliability Corporation, the National Institute of Standards and Technology, and the Federal Energy Regulatory Commission), and identifies challenges such as a focus by utilities on regulatory compliance instead of comprehensive security and the lack of electricity metrics for evaluating cybersecurity.
Document 75: Office of Inspector General, Department of Homeland Security, OIG-12-112, DHS Can Strengthen Its International Cybersecurity Program (Redacted) , August 2012. Unclassified.
Source: http://www.dhs.gov
This is an unclassified version of a DHS inspector general report. In addition to reviewing actions taken to establish relationships with international cybersecurity entities, the report notes four areas that could be targeted for improvement — developing a strategic implementation plan for foreign engagement, streamlining the National Programs and Protection Directorate’s (NPPD) international affairs program and processes, improving communication between the U.S. Computer Emergency Readiness Team and foreign entities, and strengthening NPPD information sharing capabilities.
Document 76: Paul W. Parfomak, Congressional Research Service, Pipeline Cybersecurity: Federal Policy, August 16, 2012. Unclassified.
Source: http://www.fas.org
As a means of aiding Congressional consideration of possible measures to enhance pipeline security, this report examines pipeline security risks (including general security threats, supervisory control and data acquisition (SCADA) security risks, and cyber threats to U.S. pipelines), U.S. pipeline security initiatives, and the adequacy of voluntary pipeline cybersecurity.
Document 77: Brian McKeon, Executive Secretary, National Security Staff, The White House, Memorandum, Subject: Papers Deputies Committee Meeting on Executive Order on Improving Critical Infrastructure Cybersecurity Practices, September 28, 2012 w/atts: Discussion Paper for Deputies Committee Meeting on Executive Order on Improving Critical Infrastructure Cybersecurity Practices; Draft Executive Order on Improving Critical Infrastructure Cybersecurity Practices. Unclassified.
Source: http://www.lawfareblog.com
In the face of Congressional rejection of the Administration’s proposed cybersecurity legislation, work began on producing an executive order intended to accomplish the desired objectives. The first attachment (Tab A) to the covering memo discusses the key components of the cybersecurity legislation as well as how the executive order relies on current agency authorities to accomplish those objectives. The second attachment is a draft of the executive order.
Document 78: Leon E. Panetta, Secretary of Defense, “Defending the Nation from Cyber Attack,” Speech to Business Executives for National Security, October 11, 2012. Unclassified.
Source: http://www.defense.gov
In this speech, Secretary Panetta warns of the possibility of a “cyber Pearl Harbor” — which could involve the derailing of passenger trains, contamination of the water supply in major cities, or the shutdown of the power grid across large parts of the country.
Document 79: Mark A. Stokes and L.C. Russell Hsiao, Project 2049 Institute, Countering Chinese Cyber Operations: Opportunities and Challenges for U.S. Interests, October 29, 2012. Not classified.
Source: http://project2049.net
This report, by a private organization, examines the role of several Chinese organizations — including the Third Department of the PLA General Staff Department, its Second Bureau, and its Beijing North Computing Center — in cyber operations. It also explores a number of possible reactions — including deception, an international code of conduct, an Asian cyber defense alliance, and what the report terms a “forceful response.”
Document 80: Richard Colbaugh and Kristin Glass, Sandia National Laboratories, SAND2012-10177, Proactive Defense for Evolving Cyber Threats, November 2012. Unclassified.
Source: http://www.fas.org
This technical/mathematical analysis seeks to characterize “the predictability of attack/defender coevolution” — which is then used to create a framework for designing proactive defenses for large networks.
Document 81: Defense Science Board, Resilient Military Systems and the Advanced Cyber Threat, January 2013. Unclassified.
Source: http://www.acq.osd.mil/reports
This report (consisting of eleven chapters and six appendices) examines and evaluates the Defense Department’s defensive and offensive cyber operations. It concludes that DoD cyber security practices “have not kept up” with the tactics of cyber adversaries. It characterizes the threat as “serious” and “insidious” and objects that current Defense Department actions are “fragmented,” intelligence against targeting of DoD systems is “inadequate,” and that “with present capabilities and technology it is not possible to defend with confidence against the most sophisticated cyber attacks.”
Document 82: The White House, Administration Strategy on Mitigating the Theft of U.S. Trade Secrets, February 2013. Unclassified.
Source: http://www.publicintelligence.net
This document describes the administration strategy on mitigating the theft of U.S. trade secrets — including those stolen through cyber operations. It describes four action items — involving diplomatic efforts, promoting voluntary practices by private industry, enhancing domestic law enforcement operations, improving domestic legislation, and promoting public awareness.
Document 83: Mandiant, APT 1: Exposing One of China’s Cyber Espionage Units, February 2013. Not classified.
Source: http://www.mandiant.com
As a result of its investigation into computer security breaches around the world, Mandiant identified 20 groups designated Advanced Persistent Threat (APT) groups. The focus of this report is APT 1 — which the report concludes is the People Liberation Army’s Unit 61398 — the military unit cover designator for the 2nd Bureau of the Third Department of the PLA General Staff Department (also discussed in Document 79). The key elements of the report are the discussions of tasking to the unit, its past espionage operations, attack lifecycle, and the unit’s infrastructure and personnel.
Document 84: Office of Inspector General, Department of Energy, DOE/IG-0880, Audit Report, Management of Los Alamos National Laboratory’s Cyber Security Program, February 2013. Unclassified.
Source: http://www.energy.gov
Based on its audit of the Los Alamos National Laboratory’s (LANL) cyber security practices, the DoE inspector general observes that “LANL had made significant improvements to its cybersecurity program in recent years,” but that there were continuing concerns for several reasons – including a failure to address the full set of “critical and high-risk vulnerabilities.” The inspector general also makes three recommendations to improve LANL cybersecurity.
Document 85: Government Accountability Office, GAO-13-187, Cybersecurity: National Strategy, Roles, and Responsibilities Need to Be Better Defined and More Effectively Implemented, February 2013. Unclassified.
Source: http://www.gao.gov
This study reports a 782-percent increase in cybersecurity incidents between 2006 and 2012. It examines the challenges facing the federal government in producing a strategic approach to cybersecurity and the degree to which the “national cybersecurity strategy adheres to desirable characteristics for such a strategy.”
Document 86: The White House, Presidential Policy Directive/PPD-21, Subject: Critical Infrastructure Security and Resilience, February 12, 2013. Unclassified.
Source: http://www.whitehouse.gov
This directive states basic U.S. policy with regard to the protection and recovery of critical infrastructure from both physical and cyber attacks. The key components are its delineation of roles and responsibilities of officials and agencies, its identification of three strategic imperatives, and its direction to the Secretary of Homeland Security on steps to implement the directive.
Document 87: The White House, Executive Order – Improving Critical Infrastructure Cybersecurity, February 12, 2013. Unclassified.
Source: Federal Register, 78, 33 (February 19, 2013)
In contrast to PPD-21 (Document 86) this executive order focuses solely on critical infrastructure cybersecurity. It address cybersecurity information sharing, a framework to reduce cyber risk to critical infrastructure, and the identification of critical infrastructure at greatest risk.
Document 88: Geoff McDonald, Liam O. Murchu, Stephen Doherty, and Eric Chien, Symantec Corporation, Stuxnet 0.5: The Missing Link, February 26, 2013. Not classified.
Source: http://www.symantec.com
This analysis follows up on Symantec’s earlier examination of the Stuxnet worm (Document 44, also see Document 40). It reports that Symantec “discovered an older version of Stuxent that can answer the questions about [its] evolution.”
Document 89: Eric A. Fischer, Edward C. Liu, John Rollins, and Catherine A. Theohary, Congressional Research Service, The 2013 Cybersecurity Executive Order: Overview and Considerations for Congress, March 1, 2013. Unclassified.
Source: http://www.fas.org
This paper identifies a number of types of individuals or groups that are considered threats to cybersecurity. It also provides an overview of President Obama’s executive order (Document 87), considers the question of the scope of presidential authority, and examines the relationship between the executive order and legislative proposals.
Document 90: James R. Clapper, Director of National Intelligence, Worldwide Threat Assessment of the US Intelligence Community, Statement for the Record to the Senate Select Committee on Intelligence, March 12, 2013. Unclassified.
Source: http://www.dni.gov
In his annual worldwide threat assessment, Director of National Intelligence James Clapper begins with a discussion of global threats, and his discussion of global threat with an examination of the cyber threat. Specific topics addressed include the risk to U.S. critical infrastructure, the impact on U.S. economic and national security, information control and internet governance, and the activities of hacktivists and cybercrimnals.
Document 91: General Keith Alexander, Commander, United States Cyber Command, Statement before the Senate Committee on Armed Services, March 12, 2013. Unclassified.
Source: http://www.armed-services-senate.gov
In this statement, Alexander describes the organization and personnel strength of the Cyber Command, the strategic landscape, the command’s priorities, and plans for the future.
Document 92: U.S. Cyber Command, U.S. Cyber Command Organization Chart, n.d., Unclassified.
Source: U.S. Strategic Command Freedom of Information Act Release
This chart depicts the headquarters organizational structure of U.S. Cyber Command as of April 2013.
NOTES
1. Leon Panetta, Address to Business Executives for National Security, “Defending the Nation from Cyber Attack,” October 11, 2012, http://www.defense.gov; Barack Obama, “Remarks by the President in the State of the Union Address,” February 12, 2013, http://www.whitehouse.gov; James R. Clapper, Statement for the Record, Worldwide Threat Assessment of the US Intelligence Community, March 12, 2013, pp. 1-3, http://www.dni.gov; “Senate Armed Services Committee Gets Grim Briefing on Cyber Threats,” March 20, 2013, http://www.matthewaid.com.
2. See Ted Lewis, “Cyber Insecurity: Black Swan or Headline?,” Homeland Security Watch (www.hlswatch.com), February 8, 2013; Ryan Singel, “Richard Clarke’s Cyberware: File Under Fiction, http://www.wired.com, April 22, 2010; John Arquilla, “Panetta’s Wrong About a Cyber ‘Pearl Harbor’, http://www.foreignpolicy.com, November 19, 2012; Jerry Brito and Tate Watkins, “Loving the Cyber Bomb?: The Dangers of Threat Inflation in Cybersecurity Policy,” Homeland National Security Journal, Vol. 3, 2011, pp. 39-83; Thomas Rid, “Cyber War Will Not Take Place,” Journal of Strategic Studies, 35, 1 (February 2012), pp. 5-32; Ronald Bailey, “Cyberwar Is Harder Than It Looks,” Reason, May 2011, pp. 50-51.
3. Steven A. Hildreth, Congressional Research Service, Cyberwarfare , June 19, 2001, p. CRS-4
4. John Rollins and Clay Wilson, Congressional Research Service, Terrorist Capabilities for Cyberattack: Overview and Policy Issues , January 22, 2007,pp. CRS-16-17.
5. Major William C. Ashmore, United States Army Command and General Staff College, Impact of Alleged Russian Cyber Attacks , 2009, pp. 11-14.
6. McAfee, Global Energy Cyberattacks: “Night Dragon”, February 10, 2011; “Three Saudis Sent to Prison for Stealing Info From Aramco Computer Systems,” http://www.matthewaid.com,March 19, 2013; Ellen Nakashima, “Iran blamed for cyberattacks on U.S. banks and companies,”www.washingtonpost.com, September 21, 2012.
7. Michael Vatis, Cyber Atttacks: Protecting America’s Security against Digital Threats,” ESDP Discussion Paper ESDP-2002-04, John F. Kennedy School of Government, Harvard University, June 2002, p. 15, n.42.
8. Ted Bridis, “‘Silent Horizon’ war games wrap up for the CI A,” http://www.usatoday.com,May 26,2005
9. Chairman of the Joint Chiefs of Staff, The National Military Strategy for Cyberspace Operations , December 2006, p. C-2.
10. James R. Clapper, Director of National Intelligence, Unclassified Statement for the Record on the Worldwide Threat Assessment for the Senate Select Committee on Intelligence , January 31, 2012, p. 8.
11. “National Security Presidential Directives [NSPD] George W. Bush Administration,”www.fas.org, accessed March 30, 2013.
12. “Sean Kanuck – National Intelligence Officer for Cyber Issues, Office of the Director of National Intelligence,” http://www.security-innovation.org/bios, accessed April 5, 2013; Jeffrey T. Richelson, The U.S. Intelligence Community (Boulder, Co.: Westview, 2011), pp. 23, 29;”The Information Operations Center Analysis Group (IOC/AG),” http://www.cia.gov, accessed April7, 2013; John Rollins and Clay Wilson, Congressional Research Service, Terrorist Capabilities for Cyberattack: Overview and Policy Issues, January 22, 2007, p. CRS-8.
13. Jana D. Monroe, Federal Bureau of Investigation, “Testimony before House Judiciary Committee, Subcommittee on Courts, the Internet and Intellectual Property,” June 17, 2002,www.fbi.gov/news/testimony/the-fbis-cyber-division; “Cyber Division,” http://www.fbigovs.gov/311132.asp, accessed March 31, 2013.
14. A computer virus designated FLAME has been reported to have been designed to gather information needed for the U.S. and Israel to employ the Stuxnet worm. See Ellen Nakishima, Greg Miller, and Julie Tate, “U.S., Israel developed Flame computer virus to slow Iranian nuclear efforts, officials say,” http://www.washingtonpostcom, June 19, 2012; Kim Zetter, “Meet ‘Flame,’ The Massive Spy Malware Infiltrating Iranian Computers,” http://www.wired.com, May 28, 2012.
15. Eric Schmitt and Thom Shanker, “U.S. Weighed Use of Cyberattacks To Weaken Libya,” New York Times, October 18, 2011, pp. A1, A7.
16. David E. Sanger, Confront and Conceal: Obama’s Secret Wars and Surprising Use of American Power (New York: Crown, 2012), pp. 188-225; Marc Ambinder and D.B. Grady, Deep State: Inside the Government Secrecy Industry (New York: Wiley, 2013), pp. 261-279.
17. Some law review articles include David E. Graham, “Cyber Threats and the Law of War,” Journal of National Security Law and Policy , 4, 2010, pp. 87-102; Matthew C. Waxman, “Cyber-Attack and the Use of Force: Back to the Future, Article 2(4),” Yale Journal of International Law, 36, 2011, pp. 421-459; Eric Talbot Jensen, “Computer Attacks on Critical National Infrastructure,” Stanford Journal of International Law, 38, 2002, pp. 207-240.








































![[Image]](https://i0.wp.com/cryptome.org/nsa-nassau.jpg)






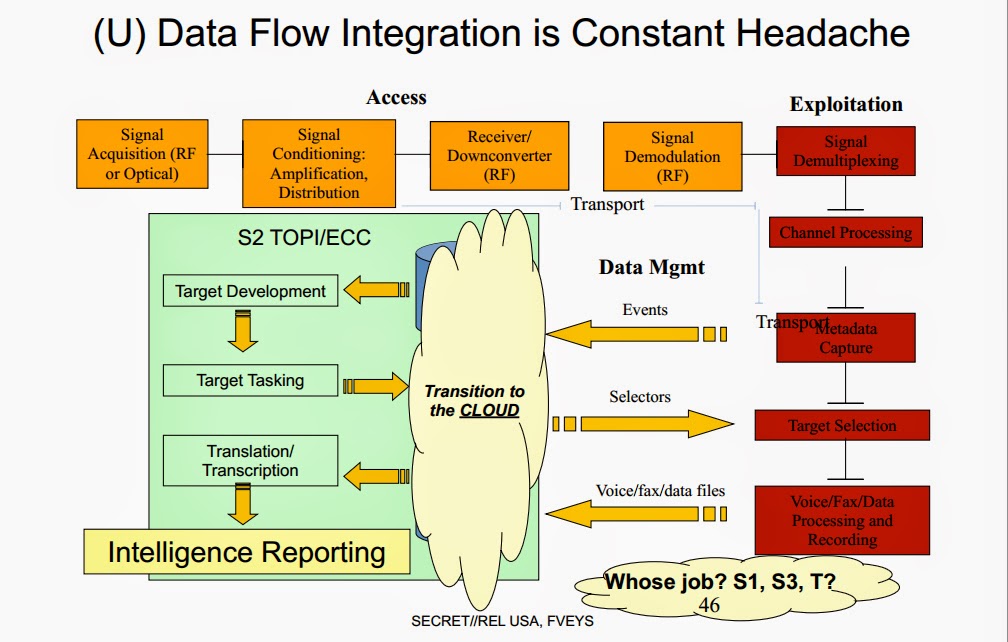


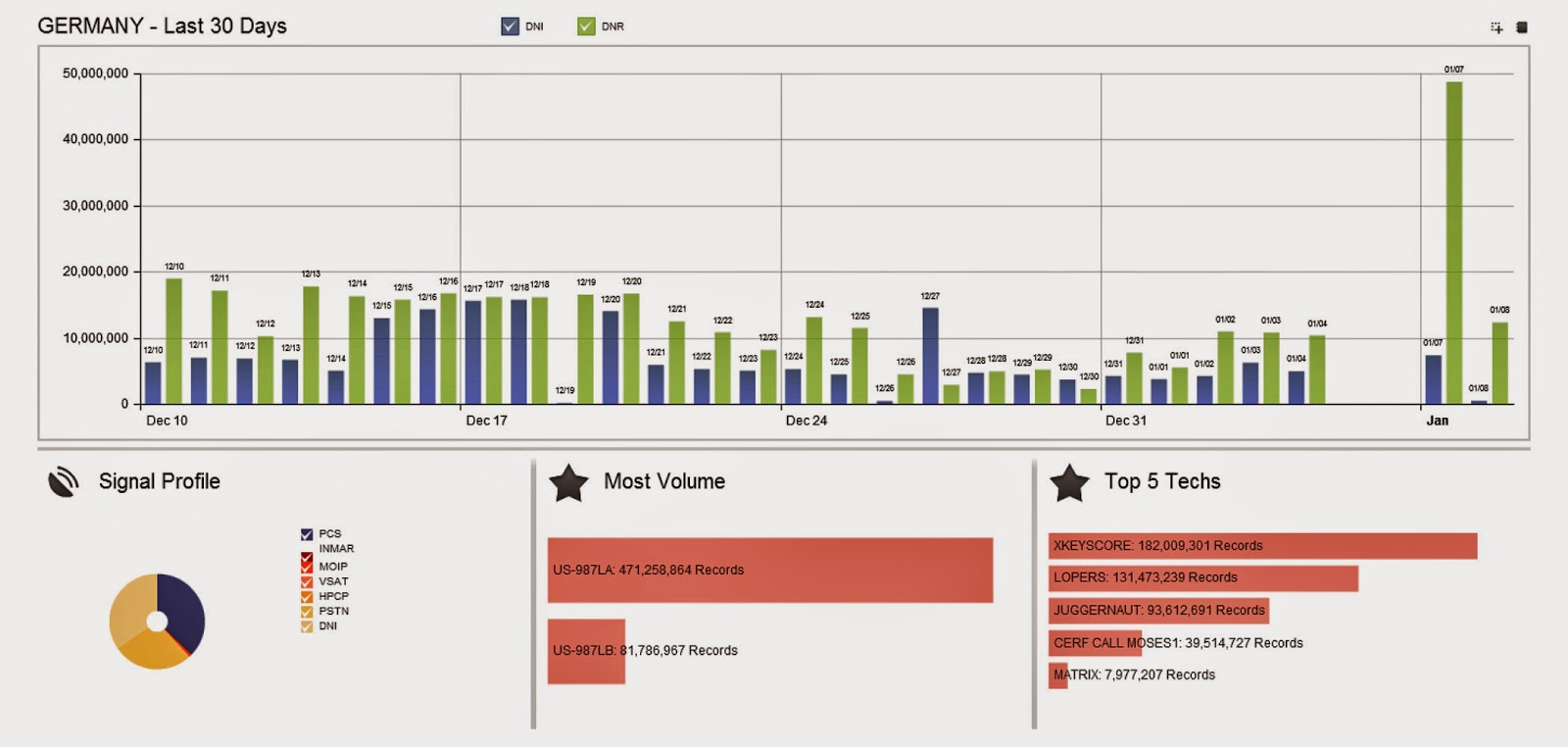











![[Image]](https://i0.wp.com/cryptome.org/2014-info/nsa-bad-abling/pict0.jpg)

























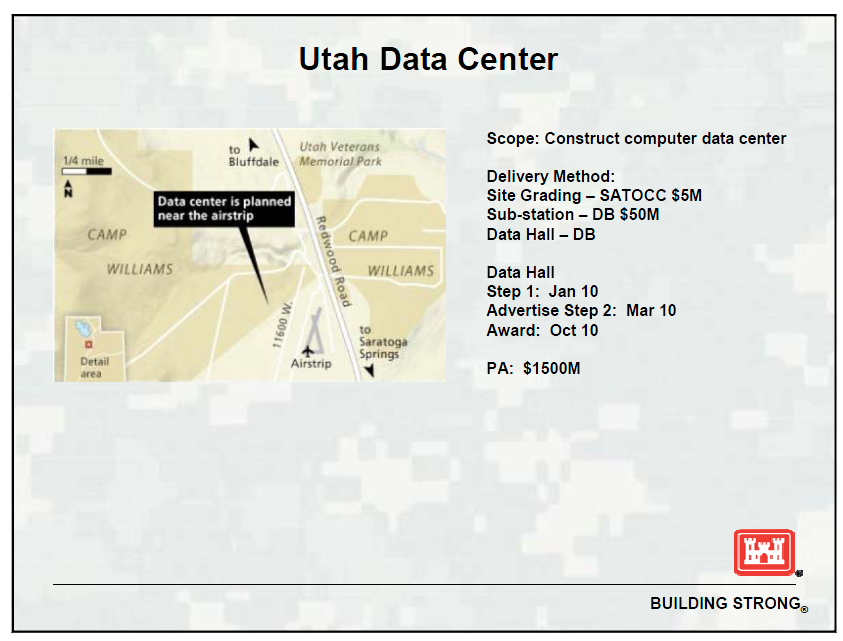


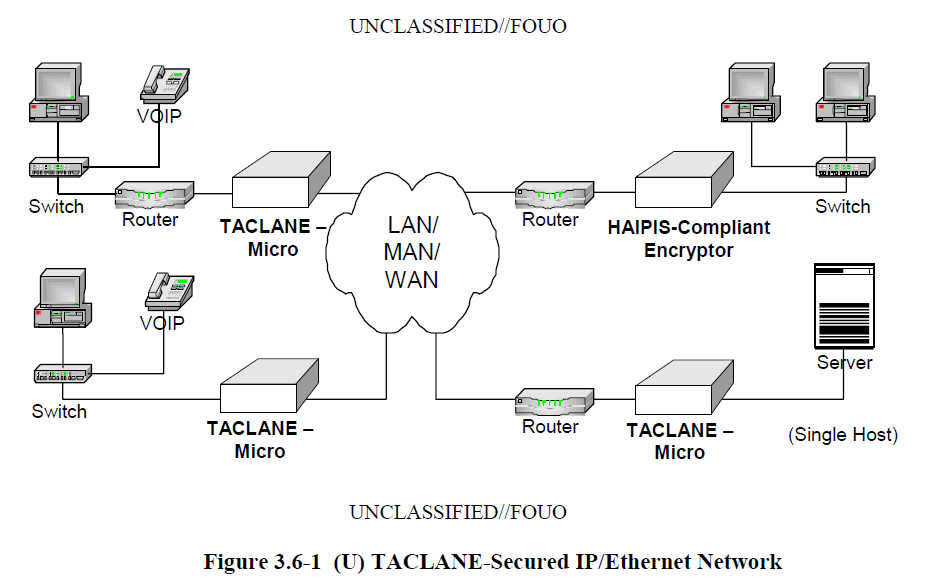


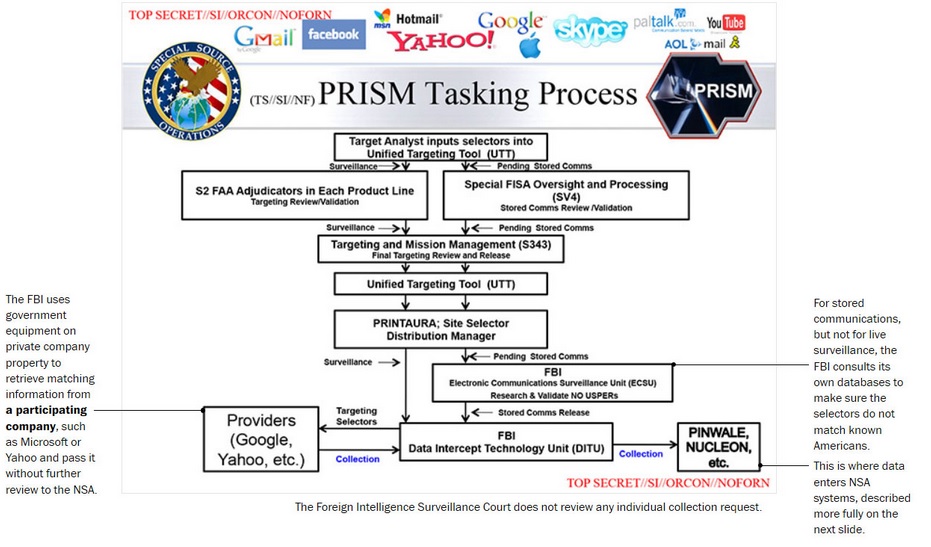
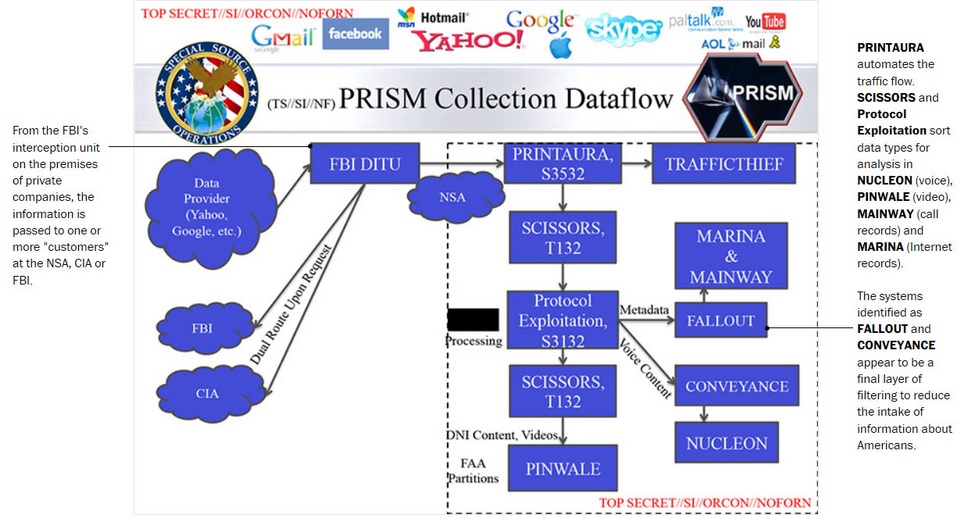



You must be logged in to post a comment.