Vol. 76 Tuesday, No. 225 November 22, 2011 Part II Department of State ———————————————————————– 22 CFR Parts 120, 123, 124, et al. Implementation of Defense Trade Cooperation Treaties; Proposed Rule Federal Register / Vol. 76, No. 225 / Tuesday, November 22, 2011 / Proposed Rules [[Page 72246]] ———————————————————————– DEPARTMENT OF STATE 22 CFR Parts 120, 123, 124, 126, 127, and 129 [Public Notice 7683] RIN 1400-AC95 Implementation of Defense Trade Cooperation Treaties AGENCY: Department of State. ACTION: Proposed rule. ———————————————————————– SUMMARY: The Department of State is proposing to amend the International Traffic in Arms Regulations (ITAR) to implement the Defense Trade Cooperation Treaty between the United States and Australia and the Defense Trade Cooperation Treaty between the United States and the United Kingdom, and identify via a supplement the defense articles and defense services that may not be exported pursuant to the Treaties. Additionally, the Department of State proposes to amend the section pertaining to the Canadian exemption to reference the new supplement, and, with regard to Congressional certification, the Department of State proposes to add Israel to the list of countries and entities that have a shorter certification time period and a higher dollar value reporting threshold. DATES: The Department of State will accept comments on this proposed rule until December 22, 2011. ADDRESSES: Interested parties may submit comments within 30 days of the date of the publication by any of the following methods: Email: DDTCResponseTeam@state.gov with the subject line, Regulatory Change–Treaties. Persons with access to the Internet may also view and comment on this notice by searching for its RIN on the U.S. Government regulations Web site at http://www.regulations.gov. FOR FURTHER INFORMATION CONTACT: Sarah Heidema, Office of Defense Trade Controls Policy, Department of State, Telephone (202) 663-2809; Fax (202) 261-8199; or Email DDTCResponseTeam@state.gov. ATTN: Regulatory Change–Treaties. SUPPLEMENTARY INFORMATION: ———————————————————————— ITAR Part Proposed change ———————————————————————— Part 120…………………….. Section 120.19 revised to clarify meaning of reexport or retransfer; new Sec. Sec. 120.33 and 120.34 added to provide definitions of the Defense Trade Cooperation Treaties between the United States and Australia and the U.K., respectively; new Sec. Sec. 120.35 and 120.36 added to define the implementing arrangements pursuant to the Treaties between the United States and Australia and the United States and the U.K., respectively. Part 123…………………….. Clarifying edits made throughout section and references to new proposed Sec. Sec. 126.16 and 126.17 added; Israel added to Sec. 123.9(e). Part 124…………………….. Sec. 124.11 revised to add Israel to the list of countries and entities subject to the 15-day time period regarding Congressional certification. Part 126…………………….. Clarifying edits made throughout section; Sec. 126.5(b) revised to reference the new supplement to part 126, consequently, Sec. Sec. 126.5(b)(1)-(21) are removed; Sec. 126.16 added to describe the exemption pursuant to the Defense Trade Cooperation Treaty between the United States and Australia; Sec. 126.17 added to describe the exemption pursuant to the Defense Trade Cooperation Treaty between the United States and the United Kingdom; Supplement No. 1 to part 126 added. Part 127…………………….. Clarifying edits made throughout section; revised to make reference to new proposed Sec. Sec. 126.16 and 126.17. Part 129…………………….. Sections 129.6(b)(2), 129.7(a)(1)(vii), and 129.7(a)(2) revised to include Israel in the listing of countries and entities. ———————————————————————— These proposed amendments are pursuant to the Security Cooperation Act of 2010 (Pub. L. 111-266), with the inclusion of other proposed changes. Title I of the Security Cooperation Act, the Defense Trade Cooperation Treaties Implementation Act of 2010, implements the Defense Trade Cooperation Treaty between the United States and Australia, done at Sydney, Australia, on September 5, 2007; and the Defense Trade Cooperation Treaty between the United States and the United Kingdom, done at Washington, DC and London on June 21 and 26, 2007, respectively (collectively referred to herein as the “Treaties”). We propose a supplement to part 126 that will identify those defense articles and defense services exempt from the scope of the Treaties. These proposed amendments would affect parts 120, 123, 126, and 127, with new sections in part 126 describing the licensing exemptions pursuant to the Treaties. Title III of the Security Cooperation Act creates for Israel a status in law similar to the North Atlantic Treaty Organization (NATO), the member countries of NATO, Australia, Japan, New Zealand, and the Republic of Korea concerning certification to the Congress. Pursuant to the proposed change, we would require certification for transfers to Israel prior to granting any license or other approval for transactions of major defense equipment sold under a contract in the amount of $25,000,000 or more (currently required for amounts of $14,000,000 or more), or for defense articles and defense services sold under a contract in the amount of $100,000,000 or more (currently required for amounts of $50,000,000 or more), and provided the transfer does not include any other countries. The change would also shorten from thirty (30) to fifteen (15) calendar days the certification time period during which approval may not be granted. This proposed amendment would affect parts 123, 124, and 129. Additionally, we are revising Sec. 126.5, describing the Canadian exemption, to reference the proposed supplement to part 126. This proposed amendment would affect part 126. Section by section identification of the proposed changes follows. We are revising the authority citation for part 120 to include Public Law 111-266; section 120.1 to reference the Treaties as authorities; and section 120.19 to clarify the meaning of reexport or retransfer. In Sec. 120.28, we are correcting an outdated reference (Shipper’s Export Declaration) to refer to the Electronic Export Information. We are proposing new Sec. Sec. 120.33 and 120.34 to provide definitions of the Defense Trade Cooperation Treaties between the United States and Australia and the U.K., respectively. Also, we are proposing new Sec. Sec. 120.35 and 120.36 to define the implementing arrangements pursuant to the Treaties between the United States and Australia and the United States and the U.K., respectively. The proposed change in Sec. 123.4 replaces the word “export” with the word “exporter.” In the last sentence in [[Page 72247]] Sec. 123.9(a), “a person” will replace “exporters,” and we are adding “destination” as an item that must be determined prior to the submission of an application or the claiming of an exemption. We are adding a note following this section. We are revising section 123.9(b) to expand the reference to documents, and to reference the new proposed Sec. Sec. 126.16 and 126.17. We are adding clarifying language to Sec. Sec. 123.9(c), (c)(1), and (c)(2); and adding the language of the current (c)(4) to (c)(3). New language pertaining to new Sec. Sec. 126.16 and 126.17 will comprise a new (c)(4). We are removing and reserving section 123.9(d). We are adding Israel to the list of countries and entities in Sec. 123.9(e); citing the new Sec. Sec. 126.16 and 126.17 in Sec. 123.9(e)(1); and adding clarifying language to Sec. Sec. 123.9(e)(3) and (e)(4). We are adding Israel to the list of countries and entities in Sec. Sec. 123.15(a)(1), (a)(2), and (b). We are adding Australia and the United Kingdom to Sec. 123.16(a), and reference to the Electronic Export Information replaces reference to the Shipper’s Export Declaration in this section and in Sec. 123.16(b)(1)(iii). We are clarifying documents in Sec. 123.16(b)(2)(vi), and adding new Sec. Sec. 123.16(c) and (d) referencing the new Sec. Sec. 126.16 and 126.17. Section 123.22(b)(2) replaces references to the Shipper’s Export Declaration with the Electronic Export Information. We are revising the title and text for Sec. 123.26. We are revising the authority citation for part 124 to include Public Law 111-266. We are revising section 124.11 to add Israel to the list of countries and entities subject to the 15-day time period regarding Congressional certification. We are revising the authority citation for part 126 to include Public Law 111-266, and revising section 126.1(e) for clarification. We are adding a section (e)(1), to contain the current requirement found in (e) to notify the Directorate of Defense Trade Controls of any transactions that contravene the prohibitions of Sec. 126.1(a). We are reserving section (e)(2). We are revising section 126.3 to change “Director” to “Managing Director” and “Office” to “Directorate.” We are replacing references to Shipper’s Export Declaration with Electronic Export Information in Sec. 126.4(d). We are revising section 126.5(a) to change “Port Director” to “Port Directors.” We are revising section 126.5(b) to reference the new supplement to part 126; consequently, we are removing Sec. Sec. 126.5(b)(1)-(21). We are removing and reserving section 126.5(c) (defense services not subject to exemption will be covered by the new supplement to part 126). We are revising Section 126.5(d) to change “re-transfer” to “retransfer,” and revising Sec. 126.5(d)(2) Note 2 to reference the proposed new supplement to part 126. We are adding the terms “criminal complaint” and “other criminal charge” to Sec. 126.7(a)(3), and adding clarifying language to Sec. 126.7(a)(7). We are revising section 126.13(a) to include reference to Sec. 123.9; revising Sec. 126.13(a)(1) to add the terms “criminal complaint” and “other criminal charge”; and revising Sec. 126.13(a)(4) to include reference to Sec. 123.9. We are proposing section 126.16 to describe the exemption pursuant to the Defense Trade Cooperation Treaty between the United States and Australia, and proposing Sec. 126.17 to describe the exemption pursuant to the Defense Trade Cooperation Treaty between the United States and the United Kingdom. We are proposing the addition of Supplement No. 1 to part 126, and this provision will delineate those items of the U.S. Munitions List that are outside the scope of the exemptions established by the Treaties and the Canadian exemptions at Sec. 126.5. We are revising the authority citation for part 127 to include Public Law 111-266. We are revising section 127.1 to make reference, where appropriate, to new proposed Sec. Sec. 126.16 and 126.17, and we are providing clarifying language, leading to the inclusion of a new proposed Sec. 127.1(e). We are adding the words “or attempt to use” in Sec. 127.2(a); “subchapter” will replace “section” in Sec. 127.2(b); we are adding “reexport” and “retransfer to Sec. 127.2(b)(1); adding “Electronic Export Information filing” to Sec. 127.2(b)(2); and proposing a new Sec. 127.2(b)(14). We are adding clarifying language to Sec. 127.3(a); adding the words “or by exemption” to Sec. 127.4(a); adding the words “or claim of an exemption” to Sec. 127.4(c); and proposing new Sec. 127.4(d). We are revising section 127.7(a) to remove the words “for which a license or approval is required by this subchapter.” In Sec. 127.10(a), we are modifying the word “approval” with addition of the word “written.” We are proposing new Sec. 127.12(b)(5). We are revising the structure of Sec. 127.12(d), removing an unnecessary level, and expanding the example list for “shipping documents”. We are revising sections 129.6(b)(2), 129.7(a)(1)(vii), and 129.7(a)(2) to include Israel in the listing of countries and entities. Regulatory Analysis and Notices Administrative Procedure Act The Department of State is of the opinion that controlling the import and export of defense services is a foreign affairs function of the United States Government and that rules implementing this function are exempt from Sec. 553 (Rulemaking) and Sec. 554 (Adjudications) of the Administrative Procedure Act. Although the Department is of the opinion that this proposed rule is exempt from the rulemaking provisions of the APA, the Department is publishing this proposed rule with a 30-day provision for public comment and without prejudice to its determination that controlling the import and export of defense services is a foreign affairs function. Regulatory Flexibility Act Since this proposed amendment is not subject to the notice-and- comment procedures of 5 U.S.C. 553, it does not require analysis under the Regulatory Flexibility Act. Unfunded Mandates Reform Act of 1995 This proposed amendment does not involve a mandate that will result in the expenditure by State, local, and tribal governments, in the aggregate, or by the private sector, of $100 million or more in any year and it will not significantly or uniquely affect small governments. Therefore, no actions were deemed necessary under the provisions of the Unfunded Mandates Reform Act of 1995. Executive Order 13175 The Department of State has determined that this proposed amendment will not have tribal implications, will not impose substantial direct compliance costs on Indian tribal governments, and will not pre-empt tribal law. Accordingly, the requirement of Executive Order 13175 does not apply to this proposed amendment. Small Business Regulatory Enforcement Fairness Act of 1996 This proposed amendment has been found not to be a major rule within the meaning of the Small Business Regulatory Enforcement Fairness Act of 1996. Executive Orders 12372 and 13132 This proposed amendment will not have substantial direct effects on the States, on the relationship between the national government and the States, or on the distribution of power and responsibilities among the various [[Page 72248]] levels of government. Therefore, in accordance with Executive Order 13132, it is determined that this proposed amendment does not have sufficient federalism implications to require consultations or warrant the preparation of a federalism summary impact statement. The regulations implementing Executive Order 12372 regarding intergovernmental consultation on Federal programs and activities do not apply to this proposed amendment. Executive Order 12866 The Department is of the opinion that restricting defense articles exports is a foreign affairs function of the United States Government and that rules governing the conduct of this function are exempt from the requirements of Executive order 12866. However, the Department has nevertheless reviewed this regulation to ensure its consistency with the regulatory philosophy and principles set forth in that Executive Order. Executive Order 12988 The Department of State has reviewed this proposed amendment in light of sections 3(a) and 3(b)(2) of Executive Order 12988 to eliminate ambiguity, minimize litigation, establish clear legal standards, and reduce burden. Executive Order 13563 The Department of State has considered this rule in light of Executive Order 13563, dated January 18, 2011, and affirms that this regulation is consistent with the guidance therein. Paperwork Reduction Act This proposed amendment does not impose any new reporting or recordkeeping requirements subject to the Paperwork Reduction Act, 44 U.S.C. Chapter 35. List of Subjects 22 CFR Parts 120, 123, 124, and 126 Arms and Munitions, Exports. 22 CFR Part 127 Arms and Munitions, Crime, Exports, Penalties, Seizures and Forfeitures. 22 CFR Part 129 Arms and Munitions, Exports, Brokering. Accordingly, for the reasons set forth above, Title 22, Chapter I, Subchapter M, parts 120, 123, 124, 126, 127, and 129 are proposed to be amended as follows: PART 120–PURPOSE AND DEFINITIONS 1. The authority citation for Part 120 is revised to read as follows: Authority: Secs. 2, 38, and 71, Pub. L. 90-629, 90 Stat. 744 (22 U.S.C. 2752, 2778, 2797); 22 U.S.C. 2794; E.O. 11958, 42 FR 4311; E.O. 13284, 68 FR 4075; 3 CFR, 1977 Comp. p. 79; 22 U.S.C. 2651a; Pub. L. 105-261, 112 Stat. 1920; Pub. L. 111-266. 2. Section 120.1 is amended by revising paragraphs (a), (c), and (d) to read as follows: Sec. 120.1 General authorities and eligibility. (a) Section 38 of the Arms Export Control Act (22 U.S.C. 2778), as amended, authorizes the President to control the export and import of defense articles and defense services. The statutory authority of the President to promulgate regulations with respect to exports of defense articles and defense services was delegated to the Secretary of State by Executive Order 11958, as amended. This subchapter implements that authority. Portions of this subchapter also implement the Defense Trade Cooperation Treaty between the United States and Australia and the Defense Trade Cooperation Treaty between the United States and the United Kingdom. (Note, however, that the Treaties are not the source of authority for the prohibitions in part 127, but instead are the source of one limitation on the scope of such prohibitions.) By virtue of delegations of authority by the Secretary of State, these regulations are primarily administered by the Deputy Assistant Secretary of State for Defense Trade and Regional Security and the Managing Director of Defense Trade Controls, Bureau of Political-Military Affairs. * * * * * (c) Receipt of Licenses and Eligibility. (1) A U.S. person may receive a license or other approval pursuant to this subchapter. A foreign person may not receive such a license or other approval, except as follows: (i) A foreign governmental entity in the United States may receive an export license or other export approval; (ii) A foreign person may receive a reexport or retransfer approval; and (iii) A foreign person may receive a prior approval for brokering activities. Requests for a license or other approval other than by a person referred to in paragraphs (c)(1)(i) and (c)(1)(ii) will be considered only if the applicant has registered with the Directorate of Defense Trade Controls pursuant to part 122 or 129 of this subchapter, as appropriate. (2) Persons who have been convicted of violating the criminal statutes enumerated in Sec. 120.27 of this subchapter, who have been debarred pursuant to part 127 or 128 of this subchapter, who are subject to indictment or are otherwise charged (e.g., by information) for violating the criminal statutes enumerated in Sec. 120.27 of this subchapter, who are ineligible to contract with, or to receive a license or other form of authorization to import defense articles or defense services from any agency of the U.S. Government, who are ineligible to receive an export license or other approval from any other agency of the U.S. Government, or who are subject to a Department of State policy of denial, suspension or revocation under Sec. 126.7(a) of this subchapter, or to interim suspension under Sec. 127.8 of this subchapter, are generally ineligible to be involved in activities regulated under this subchapter. (d) The exemptions provided in this subchapter do not apply to transactions in which the exporter, any party to the export (as defined in Sec. 126.7(e) of this subchapter), any source or manufacturer, broker or other participant in the brokering activities, is generally ineligible as set forth above in paragraph (c) of this section, unless prior written authorization has been granted by the Directorate of Defense Trade Controls. 3. Section 120.19 is revised to read as follows: Sec. 120.19 Reexport or retransfer. Reexport or retransfer means the transfer of defense articles or defense services to an end-use, end-user, or destination not previously authorized by license, written approval, or exemption pursuant to this subchapter. 4. Section 120.28 is amended by revising paragraph (b)(2) to read as follows: Sec. 120.28 Listing of forms referred to in this subchapter. * * * * * (b) * * * (2) Electronic Export Information filed via the Automated Export System. * * * * * 5. Section 120.33 is added to read as follows: Sec. 120.33 Defense Trade Cooperation Treaty between the United States and Australia. Defense Trade Cooperation Treaty between the United States and Australia means the Treaty between the Government of the United States of America and the Government of [[Page 72249]] Australia Concerning Defense Trade Cooperation, done at Sydney, September 5, 2007. For additional information on making exports pursuant to this treaty, see Sec. 126.16 of this subchapter. 6. Section 120.34 is added to read as follows: Sec. 120.34 Defense Trade Cooperation Treaty between the United States and the United Kingdom. Defense Trade Cooperation Treaty between the United States and the United Kingdom means the Treaty between the Government of the United States of America and the Government of the United Kingdom of Great Britain and Northern Ireland Concerning Defense Trade Cooperation, done at Washington DC and London, June 21 and 26, 2007. For additional information on making exports pursuant to this treaty, see Sec. 126.17 of this subchapter. 7. Section 120.35 is added to read as follows: Sec. 120.35 Australia Implementing Arrangement. Australia Implementing Arrangement means the Implementing Arrangement Pursuant to the Treaty between the Government of the United States of America and the Government of Australia Concerning Defense Trade Cooperation, done at Washington, March 14, 2008, as it may be amended. 8. Section 120.36 is added to read as follows: Sec. 120.36 United Kingdom Implementing Arrangement. United Kingdom Implementing Arrangement means the Implementing Arrangement Pursuant to the Treaty between the Government of the United States of America and the Government of the United Kingdom of Great Britain and Northern Ireland Concerning Defense Trade Cooperation, done at Washington DC, February 14, 2008, as it may be amended. PART 123–LICENSES FOR THE EXPORT OF DEFENSE ARTICLES 9. The authority citation for part 123 continues to read as follows: Authority: Secs. 2, 38, and 71, Pub. L. 90-629, 90 Stat. 744 (22 U.S.C. 2752, 2778, 2797); 22 U.S.C. 2753; E.O. 11958, 42 FR 4311; 3 CFR, 1977 Comp. p. 79; 22 U.S.C. 2651a; 22 U.S.C. 2776; Pub. L. 105- 261, 112 Stat. 1920; Sec 1205(a), Pub. L. 107-228. 10. Section 123.4 is amended by revising paragraph (d) introductory text to read as follows: Sec. 123.4 Temporary import license exemptions. * * * * * (d) Procedures. To the satisfaction of the Port Directors of U.S. Customs and Border Protection, the importer and exporter must comply with the following procedures: * * * * * 11. Section 123.9 is amended by revising paragraphs (a), (b), (c), (e), (e)(1), (e)(3), (e)(4), and removing and reserving paragraph (d), to read as follows: Sec. 123.9 Country of ultimate destination and approval of reexports or retransfers. (a) The country designated as the country of ultimate destination on an application for an export license, or in an Electronic Export Information filing where an exemption is claimed under this subchapter, must be the country of ultimate end use. The written approval of the Directorate of Defense Trade Controls must be obtained before reselling, transferring, reexporting, retransferring, transshipping, or disposing of a defense article to any end-user, end-use, or destination other than as stated on the export license, or in the Electronic Export Information filing in cases where an exemption is claimed under this subchapter, except in accordance with the provisions of an exemption under this subchapter that explicitly authorizes the resell, transfer, reexport, retransfer, transshipment, or disposition of a defense article without such approval. A person must determine the specific end-user, end-use, and destination prior to submitting an application to the Directorate of Defense Trade Controls or claiming an exemption under this subchapter. Note to paragraph (a): In making the aforementioned determination, a person is expected to review all readily available information, including information available to the public generally as well as information available from other parties to the transaction. (b) The exporter shall incorporate the following statement as an integral part of the bill of lading, airway bill, or other shipping documents and the invoice whenever defense articles or defense services are to be exported or transferred pursuant to a license, other written approval, or an exemption under this subchapter, other than the exemptions contained in Sec. 126.16 and Sec. 126.17 of this subchapter (Note: for exports made pursuant to Sec. 126.16 or Sec. 126.17 of this subchapter, see Sec. 126.16(j)(5) or Sec. 126.17(j)(5)): “These commodities are authorized by the U.S. Government for export only to [country of ultimate destination] for use by [end-user]. They may not be transferred, transshipped on a non- continuous voyage, or otherwise be disposed of, to any other country or end-user, either in their original form or after being incorporated into other end-items, without the prior written approval of the U.S. Department of State.” (c) Any person requesting written approval from the Directorate of Defense Trade Controls for the reexport, retransfer, other disposition, or change in end use, end user, or destination of a defense article or defense service initially exported or transferred pursuant to a license or other written approval, or an exemption under this subchapter, must submit all the documentation required for a permanent export license (see Sec. 123.1 of this subchapter) and shall also submit the following: (1) The license number, written authorization, or exemption under which the defense article or defense service was previously authorized for export from the United States (Note: For exports under exemptions at Sec. 126.16 or Sec. 126.17 of this subchapter, the original end- use, program, project, or operation under which the item was exported must be identified.); (2) A precise description, quantity, and value of the defense article or defense service; (3) A description and identification of the new end-user, end-use, and destination; and (4) With regard to any request for such approval relating to a defense article or defense service initially exported pursuant to an exemption contained in Sec. 126.16 or Sec. 126.17 of this subchapter, written request for the prior approval of the transaction from the Directorate of Defense Trade Controls must be submitted: (i) By the original U.S. exporter, provided a written request is received from a member of the Australian Community, as identified in Sec. 126.16 of this subchapter, or the United Kingdom Community, as identified in Sec. 126.17 of this subchapter (where such a written request includes a written certification from the member of the Australian Community or the United Kingdom Community providing the information set forth in this subsection); or (ii) By a member of the Australian Community or the United Kingdom Community, where such request provides the information set forth in this section. (d) [Reserved] (e) Reexports or retransfers of U.S.-origin components incorporated into a foreign defense article to NATO, NATO agencies, a government of a NATO [[Page 72250]] country, or the governments of Australia, Israel, Japan, New Zealand, or the Republic of Korea are authorized without the prior written approval of the Directorate of Defense Trade Controls, provided: (1) The U.S.-origin components were previously authorized for export from the United States, either by a license, written authorization, or an exemption other than those described in either Sec. 126.16 or Sec. 126.17 of this subchapter; * * * * * (3) The person reexporting the defense article provides written notification to the Directorate of Defense Trade Controls of the retransfer not later than 30 days following the reexport. The notification must state the articles being reexported and the recipient government. (4) The original license or other approval of the Directorate of Defense Trade Controls did not include retransfer or reexport restrictions prohibiting use of this exemption. 12. Section 123.15 is amended by revising paragraphs (a)(1), (a)(2), and (b) to read as follows: Sec. 123.15 Congressional certification pursuant to Section 36(c) of the Arms Export Control Act. (a) * * * (1) A license for the export of major defense equipment sold under a contract in the amount of $14,000,000 or more, or for defense articles and defense services sold under a contract in the amount of $50,000,000 or more, to any country that is not a member of the North Atlantic Treaty Organization (NATO), or Australia, Israel, Japan, New Zealand, or the Republic of Korea that does not authorize a new sales territory; or (2) A license for export to a country that is a member country of the North Atlantic Treaty Organization (NATO), or Australia, Israel, Japan, New Zealand, or the Republic of Korea, of major defense equipment sold under a contract in the amount in the amount of $25,000,000 or more, or for defense articles and defense services sold under a contract in the amount of $100,000,000 or more, and provided the transfer does not include any other countries; or * * * * * (b) Unless an emergency exists which requires the proposed export in the national security interests of the United States, approval may not be granted for any transaction until at least 15 calendar days have elapsed after receipt by the Congress of the certification required by 22 U.S.C. 2776(c)(1) involving the North Atlantic Treaty Organization, or Australia, Israel, Japan, New Zealand, or the Republic of Korea or at least 30 calendar days have elapsed for any other country; in the case of a license for an export of a commercial communications satellite for launch from, and by nationals of, the Russian Federation, Ukraine, or Kazakhstan, until at least 15 calendar days after the Congress receives such certification. * * * * * 13. Section 123.16 is amended by revising paragraphs (a) introductory text, (b)(1)(iii), (b)(2)(vi), and adding paragraphs (c) and (d), to read as follows: Sec. 123.16 Exemptions of general applicability. (a) The following exemptions apply to exports of unclassified defense articles for which no approval is needed from the Directorate of Defense Trade Controls. These exemptions do not apply to: Proscribed destinations under Sec. 126.1 of this subchapter; exports for which Congressional notification is required (see Sec. 123.15 of this subchapter); MTCR articles; Significant Military Equipment (SME); and may not be used by persons who are generally ineligible as described in Sec. 120.1(c) of this subchapter. All shipments of defense articles, including but not limited to those to and from Australia, Canada, and the United Kingdom, require an Electronic Export Information (EEI) filing or notification letter. If the export of a defense article is exempt from licensing, the EEI filing must cite the exemption. Refer to Sec. 123.22 of this subchapter for EEI filing and letter notification requirements. (b) * * * (1) * * * (iii) The exporter certifies in the EEI filing that the export is exempt from the licensing requirements of this subchapter. This is done by writing, “22 CFR 123.16(b)(1) and the agreement or arrangement (identify/state number) applicable”; and * * * * * (2) * * * (vi) The exporter must certify on the invoice, the bill of lading, air waybill, or shipping documents and in the EEI filing that the export is exempt from the licensing requirements of this subchapter. This is done by writing “22 CFR 123.16(b)(2) applicable”. * * * * * (c) For exports to Australia pursuant to the Defense Trade Cooperation Treaty between the United States and Australia refer to Sec. 126.16 of this subchapter. (d) For exports to the United Kingdom pursuant to the Defense Trade Cooperation Treaty between the United States and the United Kingdom refer to Sec. 126.17 of this subchapter. 14. Section 123.22 is amended by revising paragraph (b)(2) to read as follows: Sec. 123.22 Filing, retention, and return of export licenses and filing of export information. * * * * * (b) * * * (2) Emergency shipments of hardware that cannot meet the pre- departure filing requirements. U.S. Customs and Border Protection may permit an emergency export of hardware by truck (e.g., departures to Mexico or Canada) or air, by a U.S. registered person, when the exporter is unable to comply with the Electronic Export Information (EEI) filing timeline in paragraph (b)(1)(i) of this section. The applicant, or an agent acting on the applicant’s behalf, in addition to providing the EEI using the AES, must provide documentation required by the U.S. Customs and Border Protection and this subchapter. The documentation provided to the U.S. Customs and Border Protection at the port of exit must include the External Transaction Number (XTN) or Internal Transaction Number (ITN) for the shipment and a copy of a notification to the Directorate of Defense Trade Controls stating that the shipment is urgent accompanied by an explanation for the urgency. The original of the notification must be immediately provided to the Directorate of Defense Trade Controls. The AES filing of the export information when the export is by air must be at least two hours prior to any departure from the United States; and, when a truck shipment, at the time when the exporter provides the articles to the carrier or at least one hour prior to departure from the United States, when the permanent export of the hardware has been authorized for export: * * * * * 15. Section 123.26 is revised to read as follows: Sec. 123.26 Recordkeeping for exemptions. Any person engaging in any export, reexport, transfer, or retransfer of a defense article or defense service pursuant to an exemption must maintain records of each such export, reexport, transfer, or retransfer. The records shall include the following information: A description of the defense article, including technical data, or defense service; the name and address of the end-user and other available contact information (e.g., telephone number and electronic mail address); the name of the natural person [[Page 72251]] responsible for the transaction; the stated end-use of the defense article or defense service; the date and time of the transaction; the Electronic Export Information (EEI) Internal Transaction Number (ITN); and the method of transmission. The person using or acting in reliance upon the exemption shall also comply with any additional recordkeeping requirements enumerated in the text of the regulations concerning such exemption. * * * * * PART 124–AGREEMENTS, OFF-SHORE PROCUREMENT AND OTHER DEFENSE SERVICES 16. The authority citation for part 124 continues to read as follows: Authority: Secs. 2, 38, and 71, Pub. L. 90-629, 90 Stat. 744 (22 U.S.C. 2752, 2778, 2797); E.O. 11958, 42 FR 4311; 3 CFR 1977 Comp. p. 79; 22 U.S.C. 2651a; 22 U.S.C. 2776; Pub. L. 105-261. 17. Section 124.11 is amended by revising paragraph (b) to read as follows: Sec. 124.11 Congressional certification pursuant to Section 36(d) of the Arms Export Control Act. * * * * * (b) Unless an emergency exists which requires the immediate approval of the agreement in the national security interests of the United States, approval may not be granted until at least 15 calendar days have elapsed after receipt by the Congress of the certification required by 22 U.S.C. 2776(d)(1) involving the North Atlantic Treaty Organization, any member country of that Organization, or Australia, Israel, Japan, New Zealand, or the Republic of Korea or at least 30 calendar days have elapsed for any other country. Approvals may not be granted when the Congress has enacted a joint resolution prohibiting the export. * * * * * PART 126–GENERAL POLICIES AND PROVISIONS 18. The authority citation for part 126 is revised to read as follows: Authority: Secs. 2, 38, 40, 42, and 71, Pub. L. 90-629, 90 Stat. 744 (22 U.S.C. 2752, 2778, 2780, 2791, and 2797); E.O. 11958, 42 FR 4311; 3 CFR, 1977 Comp. p. 79; 22 U.S.C. 2651a; 22 U.S.C. 287c; E.O. 12918, 59 FR 28205; 3 CFR, 1994 Comp. p. 899; Sec. 1225, Pub. L. 108-375; Sec. 7089, Pub. L. 111-117; Pub. L. 111-266. 19. Section 126.1 is amended by revising paragraph (e) to read as follows: Sec. 126.1 Prohibited exports, imports, and sales to or from certain countries. * * * * * (e) Proposed sales. No sale, export, transfer, reexport, or retransfer and no proposal to sell, export, transfer, reexport, or retransfer any defense articles or defense services subject to this subchapter may be made to any country referred to in this section (including the embassies or consulates of such a country), or to any person acting on its behalf, whether in the United States or abroad, without first obtaining a license or written approval of the Directorate of Defense Trade Controls. However, in accordance with paragraph (a) of this section, it is the policy of the Department of State to deny licenses and approvals in such cases. (1) Duty to Notify: Any person who knows or has reason to know of such a proposed or actual sale, export, transfer, reexport, or retransfer of such articles, services, or data must immediately inform the Directorate of Defense Trade Controls. Such notifications should be submitted to the Office of Defense Trade Controls Compliance, Directorate of Defense Trade Controls. (2) [Reserved] * * * * * 20. Section 126.3 is revised to read as follows: Sec. 126.3 Exceptions. In a case of exceptional or undue hardship, or when it is otherwise in the interest of the United States Government, the Managing Director, Directorate of Defense Trade Controls, may make an exception to the provisions of this subchapter. 21. Section 126.4 is amended by revising paragraph (d) to read as follows: Sec. 126.4 Shipments by or for United States Government agencies. * * * * * (d) An Electronic Export Information (EEI) filing, required under Sec. 123.22 of this subchapter, and a written statement by the exporter certifying that these requirements have been met must be presented at the time of export to the appropriate Port Directors of U.S. Customs and Border Protection or Department of Defense transmittal authority. A copy of the EEI filing and the written certification statement shall be provided to the Directorate of Defense Trade Controls immediately following the export. 22. Section 126.5 is amended by removing and reserving paragraph (c) and revising paragraphs (a), (b), (d) introductory text, and Notes 1 and 2, to read as follows: Sec. 126.5 Canadian exemptions. (a) Temporary import of defense articles. Port Directors of U.S. Customs and Border Protection and postmasters shall permit the temporary import and return to Canada without a license of any unclassified defense articles (see Sec. 120.6 of this subchapter) that originate in Canada for temporary use in the United States and return to Canada. All other temporary imports shall be in accordance with Sec. Sec. 123.3 and 123.4 of this subchapter. (b) Permanent and temporary export of defense articles. Except as provided in Supplement No. 1 to part 126 of this subchapter and for exports that transit third countries, Port Directors of U.S. Customs and Border Protection and postmasters shall permit, when for end-use in Canada by Canadian Federal or Provincial governmental authorities acting in an official capacity or by a Canadian-registered person for return to the United States, the permanent and temporary export to Canada without a license of unclassified defense articles and defense services identified on the U.S. Munitions List (22 CFR 121.1). The exceptions noted above are subject to meeting the requirements of this subchapter, to include 22 CFR 120.1(c) and (d), parts 122 and 123 (except insofar as exemption from licensing requirements is herein authorized) and Sec. 126.1, and the requirement to obtain non-transfer and use assurances for all significant military equipment. For purposes of this section, “Canadian-registered person” is any Canadian national (including Canadian business entities organized under the laws of Canada), dual citizen of Canada and a third country other than a country listed in Sec. 126.1, and permanent resident registered in Canada in accordance with the Canadian Defense Production Act, and such other Canadian Crown Corporations identified by the Department of State in a list of such persons publicly available through the Internet Web site of the Directorate of Defense Trade Controls and by other means. (c) [Reserved] (d) Reexports/retransfer. Reexport/retransfer in Canada to another end user or end use or from Canada to another destination, except the United States, must in all instances have the prior approval of the Directorate of Defense Trade Controls. Unless otherwise exempt in this subchapter, the original exporter is responsible, upon request from a Canadian-registered person, for obtaining or providing reexport/ retransfer approval. In any instance when the U.S. exporter is no longer available to the Canadian end user the [[Page 72252]] request for reexport/retransfer may be made directly to the Directorate of Defense Trade Controls. All requests must include the information in Sec. 123.9(c) of this subchapter. Reexport/retransfer approval is acquired by: * * * * * Notes to Sec. 126.5: 1. In any instance when the exporter has knowledge that the defense article exempt from licensing is being exported for use other than by a qualified Canadian-registered person or for export to another foreign destination, other than the United States, in its original form or incorporated into another item, an export license must be obtained prior to the transfer to Canada. 2. Additional exemptions exist in other sections of this subchapter that are applicable to Canada, for example Sec. Sec. 123.9, 125.4, and 124.2, that allow for the performance of defense services related to training in basic operations and maintenance, without a license, for certain defense articles lawfully exported, including those identified in Supplement No. 1 to part 126 of this subchapter. 23. Section 126.7 is amended by revising the section heading and paragraphs (a)(3), (a)(7) and (e) introductory text to read as follows: Sec. 126.7 Denial, revocation, suspension, or amendment of licenses and other approvals. (a) * * * (3) An applicant is the subject of a criminal complaint, other criminal charge (e.g., an information), or indictment for a violation of any of the U.S. criminal statutes enumerated in Sec. 120.27 of this subchapter; or * * * * * (7) An applicant has failed to include any of the information or documentation expressly required to support a license application, exemption, or other request for approval under this subchapter, or as required in the instructions in the applicable Department of State form or has failed to provide notice or information as required under this subchapter; or * * * * * (e) Special definition. For purposes of this subchapter, the term “Party to the Export” means: * * * * * 24. Section 126.13 is amended by revising paragraphs (a) introductory text, (a)(1), and (a)(4) to read as follows: Sec. 126.13 Required information. (a) All applications for licenses (DSP-5, DSP-61, DSP-73, and DSP- 85), all requests for approval of agreements and amendments thereto under part 124 of this subchapter, and all requests for other written authorizations (including requests for retransfer or reexport pursuant to Sec. 123.9 of this subchapter) must include a letter signed by a responsible official empowered by the applicant and addressed to the Directorate of Defense Trade Controls, stating whether: (1) The applicant or the chief executive officer, president, vice- presidents, other senior officers or officials (e.g., comptroller, treasurer, general counsel) or any member of the board of directors is the subject of a criminal complaint, other criminal charge (e.g., an information), or indictment for or has been convicted of violating any of the U.S. criminal statutes enumerated in Sec. 120.27 of this subchapter since the effective date of the Arms Export Control Act, Public Law 94-329, 90 Stat. 729 (June 30, 1976); * * * * * (4) The natural person signing the application, notification or other request for approval (including the statement required by this subsection) is a citizen or national of the United States, has been lawfully admitted to the United States for permanent residence (and maintains such lawful permanent residence status under the Immigration and Nationality Act, as amended (8 U.S.C. 1101(a), section 101(a)20, 60 Stat. 163), or is an official of a foreign government entity in the United States, or is a foreign person making a request pursuant to Sec. 123.9 of this subchapter. * * * * * 25. Section 126.16 is added to read as follows: Sec. 126.16 Exemption pursuant to the Defense Trade Cooperation Treaty between the United States and Australia. (a) Scope of exemption and required conditions. (1) Definitions. (i) An export means, for purposes of this section only, the initial movement of defense articles or defense services from the United States Community to the Australian Community. (ii) A transfer means, for purposes of this section only, the movement of a defense article or defense service, previously exported, by a member of the Australian Community within the Australian Community, or between a member of the United States Community and a member of the Australian Community. (iii) Retransfer and reexport have the meaning provided in Sec. 120.19 of this subchapter. (iv) Intermediate consignee means, for purposes of this section, an entity or person who receives defense articles, including technical data, but who does not have access to such defense articles, for the sole purpose of effecting onward movement to members of the Approved Community. (2) Persons or entities exporting or transferring defense articles or defense services are exempt from the otherwise applicable licensing requirements if such persons or entities comply with the regulations set forth in this section. Except as provided in Supplement No. 1 to part 126 of this subchapter, Port Directors of U.S. Customs and Border Protection and postmasters shall permit the permanent and temporary export without a license to members of the Australian Community (see paragraph (d) of this section regarding the identification of members of the Australian Community) of defense articles and defense services not listed in Supplement No. 1 to part 126, for the end-uses specifically identified pursuant to paragraphs (e) and (f) of this section. The purpose of this section is to specify the requirements to export, transfer, reexport, retransfer, or otherwise dispose of a defense article or defense service pursuant to the Defense Trade Cooperation Treaty between the United States and Australia. (3) Export. In order for an exporter to export a defense article or defense service pursuant to the Defense Trade Cooperation Treaty between the United States and Australia, all of the following conditions must be met: (i) The exporter must be registered with the Directorate of Defense Trade Controls and must be eligible, according to the requirements and prohibitions of the Arms Export Control Act, this subchapter, and other provisions of United States law, to obtain an export license (or other forms of authorization to export) from any agency of the U.S. Government without restriction (see paragraphs (b) and (c) of this section for specific requirements); (ii) The recipient of the export must be a member of the Australian Community (see paragraph (d) of this section regarding the identification of members of the Australian Community). Australian entities and facilities that become ineligible for such membership will be removed from the Australian Community; (iii) Intermediate consignees involved in the export must be eligible, according to the requirements and prohibitions of the Arms Export Control Act, this subchapter, and other provisions of United States law, to handle or receive a defense article or defense service without restriction (see paragraph (k) of this section for specific requirements); (iv) The export must be for an end-use specified in the Defense Trade [[Page 72253]] Cooperation Treaty between the United States and Australia and mutually agreed to by the U.S. Government and the Government of Australia pursuant to the Defense Trade Cooperation Treaty between the United States and Australia and the Implementing Arrangement thereto (the Australia Implementing Arrangement) (see paragraphs (e) and (f) of this section regarding authorized end-uses); (v) The defense article or defense service is not excluded from the scope of the Defense Trade Cooperation Treaty between the United States and Australia (see paragraph (g) of this section and Supplement No. 1 to part 126 of this subchapter for specific information on the scope of items excluded from export under this exemption) and is marked or identified, at a minimum, as “Restricted USML” (see paragraph (j) of this section for specific requirements on marking exports); (vi) All required documentation of such export is maintained by the exporter and recipient and is available upon the request of the U.S. Government (see paragraph (l) of this section for specific requirements); and (vii) The Department of State has provided advance notification to the Congress, as required, in accordance with this section (see paragraph (o) of this section for specific requirements). (4) Transfers. In order for a member of the Australian Community to transfer a defense article or defense service under the Defense Trade Cooperation Treaty between the United States and Australia, all of the following conditions must be met: (i) The defense article or defense service must have been previously exported in accordance with paragraph (a)(3) of this section or transitioned from a license or other approval in accordance with paragraph (i) Transitions of this section; (ii) The transferor and transferee of the defense article or defense service are members of the Australian Community (see paragraph (d) of this section regarding the identification of members of the Australian Community) or the United States Community (see paragraph (b) for information on the United States Community/approved exporters); (iii) The transfer is required for an end-use specified in the Defense Trade Cooperation Treaty between the United States and Australia and mutually agreed to by the United States and the Government of Australia pursuant to the terms of the Defense Trade Cooperation Treaty between the United States and Australia and the Australia Implementing Arrangement (see paragraphs (e) and (f) of this section regarding authorized end-uses); (iv) The defense article or defense service is not identified in paragraph (g) of this section and Supplement No. 1 to part 126 of this subchapter as ineligible for export under this exemption, and is marked or otherwise identified, at a minimum, as “Restricted USML” (see paragraph (j) of this section for specific requirements on marking exports); (v) All required documentation of such transfer is maintained by the transferor and transferee and is available upon the request of the U.S. Government (see paragraph (l) of this section for specific requirements); and (vi) The Department of State has provided advance notification to the Congress in accordance with this section (see paragraph (o) of this section for specific requirements). (5) This section does not apply to the export of defense articles or defense services from the United States pursuant to the Foreign Military Sales program. (b) Authorized exporters. The following persons compose the United States Community and may export defense articles and defense services pursuant to the Defense Trade Cooperation Treaty between the United States and Australia: (1) Departments and agencies of the U.S. Government, including their personnel, with, as appropriate, a security clearance and a need- to-know; and (2) Nongovernmental U.S. persons registered with the Directorate of Defense Trade Controls and eligible, according to the requirements and prohibitions of the Arms Export Control Act, this subchapter, and other provisions of United States law, to obtain an export license (or other forms of authorization to export) from any agency of the U.S. Government without restriction, including their employees acting in their official capacity with, as appropriate, a security clearance and a need-to-know. (c) An exporter that is otherwise an authorized exporter pursuant to subsection (b) above may not export pursuant to the Defense Trade Cooperation Treaty between the United States and Australia if the exporter’s president, chief executive officer, any vice-president, any other senior officer or official (e.g., comptroller, treasurer, general counsel); any member of the board of directors of the exporter; any party to the export; or any source or manufacturer is ineligible to receive export licenses (or other forms of authorization to export) from any agency of the U.S. Government. (d) Australian Community. For purposes of the exemption provided by this section, the Australian Community consists of the Australian entities and facilities identified as members of the Approved Community through the Directorate of Defense Trade Controls Web site at the time of a transaction under this section; Australian entities and facilities that become ineligible for such membership will be removed from the Australian Community. (e) Authorized End-uses. The following end-uses, subject to subsection (f), are specified in the Defense Trade Cooperation Treaty between the United States and Australia: (1) United States and Australian combined military or counter- terrorism operations; (2) United States and Australian cooperative security and defense research, development, production, and support programs; (3) Mutually determined specific security and defense projects where the Government of Australia is the end-user; or (4) U.S. Government end-use. (f) Procedures for identifying authorized end-uses pursuant to paragraph (e) of this section: (1) Operations, programs, and projects that can be publicly identified will be posted on the Directorate of Defense Trade Controls’ Web site; (2) Operations, programs, and projects that cannot be publicly identified will be confirmed in written correspondence from the Directorate of Defense Trade Controls; or (3) U.S. Government end-use will be identified specifically in a U.S. Government contract or solicitation as being eligible under the Treaty. (4) No other operations, programs, projects, or end-uses qualify for this exemption. (g) Items eligible under this section. With the exception of items listed in Supplement No. 1 to part 126 of this subchapter, defense articles and defense services may be exported under this section subject to the following: (1) An exporter authorized pursuant to paragraph (b)(2) of this section may market a defense article to the Government of Australia if that exporter has been licensed by the Directorate of Defense Trade Controls to export (as defined by Sec. 120.17 of this subchapter) the identical type of defense article to any foreign person. (2) The export of any defense article specific to the existence of (e.g., reveals the existence of or details of) anti-tamper measures made at U.S. Government direction always requires [[Page 72254]] prior written approval from the Directorate of Defense Trade Controls. (3) U.S.-origin classified defense articles or defense services may be exported only pursuant to a written request, directive, or contract from the U.S. Department of Defense that provides for the export of the classified defense article(s) or defense service(s). (4) Defense articles specific to developmental systems that have not obtained written Milestone B approval from the Department of Defense milestone approval authority are not eligible for export unless such export is pursuant to a written solicitation or contract issued or awarded by the Department of Defense for an end-use identified pursuant to paragraphs (e)(1), (2), or (4) of this section. (5) Defense articles excluded by paragraph (g) of this section or Supplement No. 1 to part 126 of this subchapter (e.g., USML Category XI(a)(3) electronically scanned array radar) that are embedded in a larger system that is eligible to ship under this section (e.g., a ship or aircraft) must separately comply with any restrictions placed on that embedded defense article under this subsection. The exporter must obtain a license or other authorization from the Directorate of Defense Trade Controls for the export of such embedded defense articles (for example, USML Category XI(a)(3) electronically scanned array radar systems that are exempt from this section that are incorporated in an aircraft that is eligible to ship under the this section continue to require separate authorization from the Directorate of Defense Trade Controls for their export, transfer, reexport, or retransfer). (6) No liability shall be incurred by or attributed to the U.S. Government in connection with any possible infringement of privately owned patent or proprietary rights, either domestic or foreign, by reason of an export conducted pursuant to this section. (7) Sales by exporters made through the U.S. Government shall not include either charges for patent rights in which the U.S. Government holds a royalty-free license, or charges for information which the U.S. Government has a right to use and disclose to others, which is in the public domain, or which the U.S. Government has acquired or is entitled to acquire without restrictions upon its use and disclosure to others. (h) Transfers, Retransfers, and Reexports. (1) Any transfer of a defense article or defense service not exempted in Supplement No. 1 to part 126 of this subchapter by a member of the Australian Community (see paragraph (d) of this section for specific information on the identification of the Community) to another member of the Australian Community or the United States Community for an end-use that is authorized by this exemption (see paragraphs (e) and (f) of this section regarding authorized end-uses) is authorized under this exemption. (2) Any transfer or other provision of a defense article or defense service for an end-use that is not authorized by the exemption provided by this section is prohibited without a license or the prior written approval of the Directorate of Defense Trade Controls (see paragraphs (e) and (f) of this section regarding authorized end-uses). (3) Any retransfer or reexport, or other provision of a defense article or defense service by a member of the Australian Community to a foreign person that is not a member of the Australian Community, or to a U.S. person that is not a member of the United States Community, is prohibited without a license or the prior written approval of the Directorate of Defense Trade Controls (see paragraph (d) of this section for specific information on the identification of the Australian Community). (4) Any change in the use of a defense article or defense service previously exported, transferred, or obtained under this exemption by any foreign person, including a member of the Australian Community, to an end-use that is not authorized by this exemption is prohibited without a license or other written approval of the Directorate of Defense Trade Controls (see paragraphs (e) and (f) of this section regarding authorized end-uses). (5) Any retransfer, reexport, or change in end-use requiring such approval of the U.S. Government shall be made in accordance with Sec. 123.9 of this subchapter. (6) Defense articles excluded by paragraph (g) of this section or Supplement No. 1 to part 126 of this subchapter (e.g., USML Category XI(a)(3) electronically scanned array radar) that are embedded in a larger system that is eligible to ship under this section (e.g., a ship or aircraft) must separately comply with any restrictions placed on that embedded defense article unless otherwise specified. A license or other authorization must be obtained from the Directorate of Defense Trade Controls for the retransfer, reexport or change in end-use of any such embedded defense article (for example, USML Category XI(a)(3) electronically scanned radar systems that are exempt from this section that are incorporated in an aircraft that is eligible to ship under the this section continue to require separate authorization from the Directorate of Defense Trade Controls for their export, transfer, reexport, or retransfer). (7) A license or prior approval from the Directorate of Defense Trade Controls is not required for a transfer, retransfer, or reexport of an exported defense article or defense service under this section, if: (i) The transfer of defense articles or defense services is made by a member of the United States Community to Australian Department of Defense (ADOD) elements deployed outside the Territory of Australia and engaged in an authorized end-use (see paragraphs (e) and (f) of this section regarding authorized end-uses) using ADOD transmission channels or the provisions of this section (Note: For purposes of paragraph (h)(7)(i)-(iv), per Section 9(9) of the Australia Implementing Arrangement, “ADOD Transmission channels” includes electronic transmission of a defense article and transmission of a defense article by an ADOD contracted carrier or freight forwarder that merely transports or arranges transport for the defense article in this instance.); (ii) The transfer of defense articles or defense services is made by a member of the United States Community to an Approved Community member (either U.S. or Australian) that is operating in direct support of Australian Department of Defense elements deployed outside the Territory of Australia and engaged in an authorized end-use (see paragraphs (e) and (f) of this section regarding authorized end-uses) using ADOD transmission channels or the provisions of this section; (iii) The reexport is made by a member of the Australian Community to Australian Department of Defense elements deployed outside the Territory of Australia engaged in an authorized end-use (see paragraphs (e) and (f) of this section regarding authorized end-uses) using ADOD transmission channels or the provisions of this section; (iv) The retransfer or reexport is made by a member of the Australian Community to an Approved Community member (either United States or Australian) that is operating in direct support of Australian Department of Defense elements deployed outside the Territory of Australia engaged in an authorized end-use (see paragraphs (e) and (f) of this section regarding authorized end-uses) using ADOD transmission channels or the provisions of this section; or [[Page 72255]] (v) The defense article or defense service will be delivered to the Australian Department of Defense for an authorized end-use (see paragraphs (e) and (f) of this section regarding authorized end-uses); the Australian Department of Defense may deploy the item as necessary when conducting official business within or outside the Territory of Australia. The item must remain under the effective control of the Australian Department of Defense while deployed and access may not be provided to unauthorized third parties. (8) U.S. persons registered, or required to be registered, pursuant to part 122 of this subchapter and Members of the Australian Community must immediately notify the Directorate of Defense Trade Controls of any actual or proposed sale, retransfer, or reexport of a defense article or defense service on the U.S. Munitions List originally exported under this exemption to any of the countries listed in Sec. 126.1 of this subchapter, any citizen of such countries, or any person acting on behalf of such countries, whether within or outside the United States. Any person knowing or having reason to know of such a proposed or actual sale, reexport, or retransfer shall submit such information in writing to the Office of Defense Trade Controls Compliance, Directorate of Defense Trade Controls. (i) Transitions. (1) Any previous export of a defense article under a license or other approval of the U.S. Department of State remains subject to the conditions and limitations of the original license or authorization unless the Directorate of Defense Trade Controls has approved in writing a transition to this section. (2) If a U.S. exporter desires to transition from an existing license or other approval to the use of the provisions of this section, the following is required: (i) The U.S. exporter must submit a written request to the Directorate of Defense Trade Controls, which identifies the defense articles or defense services to be transitioned, the existing license(s) or other authorizations under which the defense articles or defense services were originally exported; and the Treaty-eligible end- use for which the defense articles or defense services will be used. Any license(s) filed with U.S. Customs and Border Protection should remain on file until the exporter has received approval from the Directorate of Defense Trade Controls to retire the license(s) and transition to this section. When this approval is conveyed to U.S. Customs and Border Protection by the Directorate of Defense Trade Controls, the license(s) will be returned to the Directorate of Defense Trade Controls by U.S. Customs and Border Protection in accordance with existing procedures for the return of expired licenses in Sec. 123.22(c) of this subchapter. (ii) Any license(s) not filed with U.S. Customs and Border Protection must be returned to the Directorate of Defense Trade Controls with a letter citing the Directorate of Defense Trade Controls’ approval to transition to this section as the reason for returning the license(s). (3) If a member of the Australian Community desires to transition defense articles received under an existing license or other approval to the processes established under the Treaty, the Australian Community member must submit a written request to the Directorate of Defense Trade Controls, either directly or through the original U.S. exporter, which identifies the defense articles or defense services to be transitioned, the existing license(s) or other authorizations under which the defense articles or defense services were received, and the Treaty-eligible end-use (see paragraphs (e) and (f) of this section regarding authorized end-uses) for which the defense articles or defense services will be used. The defense article or defense service shall remain subject to the conditions and limitations of the existing license or other approval until the Australian Community member has received approval from the Directorate of Defense Trade Controls to transition to this section. (4) Authorized exporters identified in paragraph (b)(2) of this section who have exported a defense article or defense service that has subsequently been placed on the list of exempted items in Supplement No. 1 to part 126 of this subchapter must review and adhere to the requirements in the relevant Federal Register notice announcing such removal. Once removed, the defense article or defense service will no longer be subject to this section, such defense article or defense service previously exported shall remain on the U.S. Munitions List and be subject to the International Traffic in Arms Regulations unless the applicable Federal Register notice states otherwise. Subsequent reexport or retransfer must be made pursuant to Sec. 123.9 of this subchapter. (5) Any defense article or defense service transitioned from a license or other approval to treatment under this section must be marked in accordance with the requirements of paragraph (j) of this section. (j) Marking of Exports. (1) All defense articles and defense services exported or transitioned pursuant to the Defense Trade Cooperation Treaty between the United States and Australia and this section shall be marked or identified as follows: (i) For classified defense articles and defense services the standard marking or identification shall read: “//CLASSIFICATION LEVEL USML//REL AUS and USA Treaty Community//.” For example, for defense articles classified SECRET, the marking or identification shall be “// SECRET USML//REL AUS and USA Treaty Community//.” (ii) Unclassified defense articles and defense services exported under or transitioned pursuant to this section shall be AUS classified as “Restricted USML” and, the standard marking or identification shall read “//RESTRICTED USML//REL AUS and USA Treaty Community//.” (2) Where defense articles are returned to a member of the United States Community identified in paragraph (b) of this section, any defense articles AUS classified and marked or identified pursuant to paragraph j(1)(ii) of this section as “//RESTRICTED USML//REL AUS and USA Treaty Community//” shall no longer be AUS classified and such marking or identification shall be removed; and (3) The standard marking and identification requirements are as follows: (i) Defense articles (other than technical data) shall be individually labeled with the appropriate identification detailed in paragraphs (j)(1) and (j)(2) of this section; or, where such labeling is impracticable (e.g., propellants, chemicals), shall be accompanied by documentation (such as contracts or invoices) clearly associating the defense articles with the appropriate markings as detailed above; (ii) Technical data (including data packages, technical papers, manuals, presentations, specifications, guides and reports), regardless of media or means of transmission (physical or electronic), shall be individually labeled with the appropriate identification detailed in paragraphs (j)(1) and (j)(2) of this section; or, where such labeling is impracticable (oral presentations), shall have a verbal notification clearly associating the technical data with the appropriate markings as detailed above; and (4) Contracts and agreements for the provision of defense services shall be identified with the appropriate identification detailed in paragraphs (j)(1) and (j)(2) of this section. (5) The exporter shall incorporate the following statement as an integral part [[Page 72256]] of all shipping documentation (airway bill, bill of lading, manifest, packing documents, delivery verification, invoice, etc.) whenever defense articles are to be exported: “These commodities are authorized by the U.S. Government for export only to Australia for use in approved projects, programs or operations by members of the Australian Community. They may not be retransferred or reexported or used outside of an approved project, program or operation, either in their original form or after being incorporated into other end-items, without the prior written approval of the U.S. Department of State.” (k) Intermediate Consignees. (1) Unclassified exports under this section may only be handled by: (i) U.S. intermediate consignees who are: (A) Exporters registered with the Directorate of Defense Trade Controls and eligible; (B) Licensed customs brokers who are subject to background investigation and have passed a comprehensive examination administered by U.S. Customs and Border Protection; or (C) Commercial air freight and surface shipment carriers, freight forwarders, or other parties not exempt from registration under Sec. 129.3(b)(3) of this subchapter that are identified at the time of export as being on the list of Authorized U.S. Intermediate Consignees, which is available on the Directorate of Defense Trade Controls’ Web site. (ii) Australian intermediate consignees who are: (A) Members of the Australian Community; or (B) Freight forwarders, customs brokers, commercial air freight and surface shipment carriers, or other Australian parties that are identified at the time of export as being on the list of Authorized Australian Intermediate Consignees, which is available on the Directorate of Defense Trade Controls’ Web site. (2) Classified exports must comply with the security requirements of the National Industrial Security Program Operating Manual (DoD 5220.22-M and supplements or successors). (l) Records. (1) All exporters authorized pursuant to paragraph (b)(2) of this section who export pursuant to the Defense Trade Cooperation Treaty between the United States and Australia and this section shall maintain detailed records of all exports, imports, and transfers made by that exporter of defense articles or defense services subject to the Defense Trade Cooperation Treaty between the United States and Australia and the requirements of this section. Exporters shall also maintain detailed records of any reexports and retransfers approved or otherwise authorized by the Directorate of Defense Trade Controls of defense articles or defense services subject to the Defense Trade Cooperation Treaty between the United States and Australia and the requirements of this section. These records shall be maintained for a minimum of five years from the date of export, import, transfer, reexport, or retransfer and shall be made available upon request to the Directorate of Defense Trade Controls, U.S. Immigration and Customs Enforcement, or U.S. Customs and Border Protection, or any other authorized U.S. law enforcement officer. Records in an electronic format must be maintained using a process or system capable of reproducing all records on paper. Such records when displayed on a viewer, monitor, or reproduced on paper, must exhibit a high degree of legibility and readability. (For the purpose of this section, “legible” and “legibility” mean the quality of a letter or numeral that enables the observer to identify it positively and quickly to the exclusion of all other letters or numerals. “Readable” and “readability” means the quality of a group of letters or numerals being recognized as complete words or numbers.) These records shall consist of the following: (i) Port of entry/exit; (ii) Date/time of export/import; (iii) Method of export/import; (iv) Commodity code and description of the commodity, including technical data; (v) Value of export; (vi) Reference to this section and justification for export under the Treaty; (vii) End-user/end-use; (viii) Identification of all U.S. and foreign parties to the transaction; (ix) How the export was marked; (x) Classification of the export; (xi) All written correspondence with the U.S. Government on the export; (xii) All information relating to political contributions, fees, or commissions furnished or obtained, offered, solicited, or agreed upon as outlined in paragraph (m) of this section; (xiii) Purchase order or contract; (xiv) Technical data actually exported; (xv) The Internal Transaction Number for the Electronic Export Information filing in the Automated Export System; (xvi) All shipping documentation (airway bill, bill of lading, manifest, packing documents, delivery verification, invoice, etc.); and (xvii) Statement of Registration (Form DS-2032). (2) Filing of export information. All exporters of defense articles and defense services under the Defense Trade Cooperation Treaty between the United States and Australia and the requirements of this section must electronically file Electronic Export Information (EEI) using the Automated Export System citing one of the four below referenced codes in the appropriate field in the EEI for each shipment: (i) 126.16(e)(1): used for exports in support of United States and Australian combined military or counter-terrorism operations (the name or an appropriate description of the operation shall be placed in the appropriate field in the EEI, as well); (ii) 126.16(e)(2): used for exports in support of United States and Australian cooperative security and defense research, development, production, and support programs (the name or an appropriate description of the program shall be placed in the appropriate field in the EEI, as well); (iii) 126.16(e)(3): used for exports in support of mutually determined specific security and defense projects where the Government of Australia is the end-user (the name or an appropriate description of the project shall be placed in the appropriate field in the EEI, as well); or (iv) 126.16(e)(4): used for exports that will have a U.S. Government end-use (the U.S. Government contract number or solicitation number (e.g., “U.S. Government contract number XXXXX”) shall be placed in the appropriate field in the EEI, as well). Such exports must meet the required export documentation and filing guidelines, including for defense services, of Sec. 123.22(a), (b)(1), and (b)(2) of this subchapter. (m) Fees and Commissions. All exporters authorized pursuant to paragraph (b)(2) of this section shall, with respect to each export, transfer, reexport, or retransfer, pursuant to the Defense Trade Cooperation Treaty between the United States and Australia and this section, submit a statement to the Directorate of Defense Trade Controls containing the information identified in Sec. 130.10 of this subchapter relating to fees, commissions, and political contributions on contracts or other instruments valued in an amount of $500,000 or more. (n) Violations and Enforcement. (1) Exports, transfers, reexports, and retransfers that do not comply with the conditions prescribed in this section will constitute violations of the Arms Export Control Act and this subchapter, [[Page 72257]] and are subject to all relevant criminal, civil, and administrative penalties (see Sec. 127.1 of this subchapter), and may also be subject to other statutes or regulations. (2) U.S. Immigration and Customs Enforcement and U.S. Customs and Border Protection officers have the authority to investigate, detain, or seize any export or attempted export of defense articles that does not comply with this section or that is otherwise unlawful. (3) The Directorate of Defense Trade Controls, U.S. Immigration and Customs Enforcement, U.S. Customs and Border Protection, and other authorized U.S. law enforcement officers may require the production of documents and information relating to any actual or attempted export, transfer, reexport, or retransfer pursuant to this section. Any foreign person refusing to provide such records within a reasonable period of time shall be suspended from the Australian Community and ineligible to receive defense articles or defense services pursuant to the exemption under this section or otherwise. (o) Procedures for Legislative Notification. (1) Exports pursuant to the Defense Trade Cooperation Treaty between the United States and Australia and this section by any person identified in paragraph (b)(2) of this section shall not take place until 30 days after the Directorate of Defense Trade Controls has acknowledged receipt of a Form DS-4048 (entitled, “Projected Sales of Major Weapons in Support of Section 25(a)(1) of the Arms Export Control Act”) from the exporter notifying the Department of State if the export involves one or more of the following: (i) A contract or other instrument for the export of major defense equipment in the amount of $25,000,000 or more, or for defense articles and defense services in the amount of $100,000,000 or more; (ii) A contract or other instrument for the export of firearms controlled under Category I of the U.S. Munitions List of the International Traffic in Arms Regulations in an amount of $1,000,000 or more; (iii) A contract or other instrument, regardless of value, for the manufacturing abroad of any item of significant military equipment; or (iv) An amended contract or other instrument that meets the requirements of paragraphs (o)(1)(i)-(o)(1)(iii) of this section. (2) The Form DS-4048 required in paragraph (o)(1) of this section shall be accompanied by the following additional information: (i) The information identified in Sec. 130.10 and Sec. 130.11 of this subchapter; (ii) A statement regarding whether any offset agreement is proposed to be entered into in connection with the export and a description of any such offset agreement; (iii) A copy of the signed contract or other instrument; and (iv) If the notification is for paragraph (o)(1)(ii) of this section, a statement of what will happen to the weapons in their inventory (for example, whether the current inventory will be sold, reassigned to another service branch, destroyed, etc.). (3) The Department of State will notify the Congress of exports that meet the requirements of paragraph (o)(1) of this section. 26. Section 126.17 is added to read as follows: Sec. 126.17 Exemption pursuant to the Defense Trade Cooperation Treaty between the United States and the United Kingdom. (a) Scope of exemption and required conditions. (1) Definitions. (i) An export means, for purposes of this section only, the initial movement of defense articles or defense services from the United States to the United Kingdom Community. (ii) A transfer means, for purposes of this section only, the movement of a defense article or defense service, previously exported, by a member of the United Kingdom Community within the United Kingdom Community, or between a member of the United States Community and a member of the United Kingdom Community. (iii) Retransfer and reexport have the meaning provided in Sec. 120.19 of this subchapter. (iv) Intermediate consignee means, for purposes of this section, an entity or person who receives defense articles, including technical data, but who does not have access to such defense articles, for the sole purpose of effecting onward movement to members of the Approved Community. (2) Persons or entities exporting or transferring defense articles or defense services are exempt from the otherwise applicable licensing requirements if such persons or entities comply with the regulations set forth in this section. Except as provided in Supplement No. 1 to part 126 of this subchapter, Port Directors of U.S. Customs and Border Protection and postmasters shall permit the permanent and temporary export without a license to members of the United Kingdom Community (see paragraph (d) of this section regarding the identification of members of the United Kingdom Community) of defense articles and defense services not listed in Supplement No. 1 to part 126, for the end-uses specifically identified pursuant to paragraphs (e) and (f) below. The purpose of this section is to specify the requirements to export, transfer, reexport, retransfer, or otherwise dispose of a defense article or defense service pursuant to the Defense Trade Cooperation Treaty between the United States and the United Kingdom. (3) Export. In order for an exporter to export a defense article or defense service pursuant to the Defense Trade Cooperation Treaty between the United States and the United Kingdom, all of the following conditions must be met: (i) The exporter must be registered with the Directorate of Defense Trade Controls and must be eligible, according to the requirements and prohibitions of the Arms Export Control Act, this subchapter, and other provisions of United States law, to obtain an export license (or other forms of authorization to export) from any agency of the U.S. Government without restriction (see paragraphs (b) and (c) of this section for specific requirements); (ii) The recipient of the export must be a member of the United Kingdom Community (see paragraph (d) of this section regarding the identification of members of the United Kingdom Community). United Kingdom entities and facilities that become ineligible for such membership will be removed from the United Kingdom Community; (iii) Intermediate consignees involved in the export must be eligible, according to the requirements and prohibitions of the Arms Export Control Act, this subchapter, and other provisions of United States law, to handle or receive a defense article or defense service without restriction (see paragraph (k) of this section for specific requirements); (iv) The export must be for an end-use specified in the Defense Trade Cooperation Treaty between the United States and the United Kingdom and mutually agreed to by the U.S. Government and the Government of the United Kingdom pursuant to the Defense Trade Cooperation Treaty between the United States and the United Kingdom and the Implementing Arrangement thereto (United Kingdom Implementing Arrangement) (see paragraphs (e) and (f) of this section regarding authorized end-uses); (v) The defense article or defense service is not excluded from the scope of the Defense Trade Cooperation Treaty between the United States and the United Kingdom (see paragraph (g) of this section and Supplement No. 1 to part 126 of this subchapter for specific [[Page 72258]] information on the scope of items excluded from export under this exemption) and is marked or identified, at a minimum, as “Restricted USML” (see paragraph (j) of this section for specific requirements on marking exports); (vi) All required documentation of such export is maintained by the exporter and recipient and is available upon the request of the U.S. Government (see paragraph (l) of this section for specific requirements); and (vii) The Department of State has provided advance notification to the Congress, as required, in accordance with this section (see paragraph (o) of this section for specific requirements). (4) Transfers. In order for a member of the United Kingdom Community to transfer a defense article or defense service under the Defense Trade Cooperation Treaty between the United States and the United Kingdom, all of the following conditions must be met: (i) The defense article or defense service must have been previously exported in accordance with paragraph (a)(3) of this section or transitioned from a license or other approval in accordance with paragraph (i) Transfers of this section; (ii) The transferor and transferee of the defense article or defense service are members of the United Kingdom Community (see paragraph (d) of this section regarding the identification of members of the United Kingdom Community) or the United States Community (see paragraph (b) of this section for information on the United States Community/approved exporters); (iii) The transfer is required for an end-use specified in the Defense Trade Cooperation Treaty between the United States and the United Kingdom and mutually agreed to by the United States and the Government of United Kingdom pursuant to the terms of the Defense Trade Cooperation Treaty between the United States and the United Kingdom and the United Kingdom Implementing Arrangement (see paragraphs (e) and (f) of this section regarding authorized end-uses); (iv) The defense article or defense service is not identified in paragraph (g) of this section and Supplement No. 1 to part 126 of this subchapter as ineligible for export under this exemption, and is marked or otherwise identified, at a minimum, as “Restricted USML” (see paragraph (j) of this section for specific requirements on marking exports); (v) All required documentation of such transfer is maintained by the transferor and transferee and is available upon the request of the U.S. Government (see paragraph (l) of this section for specific requirements); and (vi) The Department of State has provided advance notification to the Congress in accordance with this section (see paragraph (o) of this section for specific requirements). (5) This section does not apply to the export of defense articles or defense services from the United States pursuant to the Foreign Military Sales program. (b) Authorized exporters. The following persons compose the United States Community and may export defense articles and defense services pursuant to the Defense Trade Cooperation Treaty between the United States and the United Kingdom: (1) Departments and agencies of the U.S. Government, including their personnel, with, as appropriate, a security clearance and a need- to-know; and (2) Nongovernmental U.S. persons registered with the Directorate of Defense Trade Controls and eligible, according to the requirements and prohibitions of the Arms Export Control Act, this subchapter, and other provisions of United States law, to obtain an export license (or other forms of authorization to export) from any agency of the U.S. Government without restriction, including their employees acting in their official capacity with, as appropriate, a security clearance and a need-to-know. (c) An exporter that is otherwise an authorized exporter pursuant to subsection (b) above may not export pursuant to the Defense Trade Cooperation Treaty between the United States and the United Kingdom if the exporter’s president, chief executive officer, any vice-president, any other senior officer or official (e.g., comptroller, treasurer, general counsel); any member of the board of directors of the exporter; any party to the export; or any source or manufacturer is ineligible to receive export licenses (or other forms of authorization to export) from any agency of the U.S. Government. (d) United Kingdom Community. For purposes of the exemption provided by this section, the United Kingdom Community consists of the United Kingdom entities and facilities identified as members of the Approved Community through the Directorate of Defense Trade Controls’ Web site at the time of a transaction under this section; non- governmental United Kingdom entities and facilities that become ineligible for such membership will be removed from the United Kingdom Community. (e) Authorized End-uses. The following end-uses, subject to subsection (f), are specified in the Defense Trade Cooperation Treaty between the United States and the United Kingdom: (1) United States and United Kingdom combined military or counter- terrorism operations; (2) United States and United Kingdom cooperative security and defense research, development, production, and support programs; (3) Mutually determined specific security and defense projects where the Government of the United Kingdom is the end-user; or (4) U.S. Government end-use. (f) Procedures for identifying authorized end-uses pursuant to paragraph (e) of this section: (1) Operations, programs, and projects that can be publicly identified will be posted on the Directorate of Defense Trade Controls’ Web site; (2) Operations, programs, and projects that cannot be publicly identified will be confirmed in written correspondence from the Directorate of Defense Trade Controls; or (3) U.S. Government end-use will be identified specifically in a U.S. Government contract or solicitation as being eligible under the Treaty. (4) No other operations, programs, projects, or end-uses qualify for this exemption. (g) Items eligible under this section. With the exception of items listed in Supplement No. 1 to part 126 of this subchapter, defense articles and defense services may be exported under this section subject to the following: (1) An exporter authorized pursuant to paragraph (b)(2) of this section may market a defense article to the Government of the United Kingdom if that exporter has been licensed by the Directorate of Defense Trade Controls to export (as defined by Sec. 120.17 of this subchapter) the identical type of defense article to any foreign person. (2) The export of any defense article specific to the existence of (e.g., reveals the existence of or details of) anti-tamper measures made at U.S. Government direction always requires prior written approval from the Directorate of Defense Trade Controls. (3) U.S.-origin classified defense articles or defense services may be exported only pursuant to a written request, directive, or contract from the U.S. Department of Defense that provides for the export of the classified defense article(s) or defense service(s). (4) Defense articles specific to developmental systems that have not obtained written Milestone B approval from the Department of Defense milestone approval authority are not [[Page 72259]] eligible for export unless such export is pursuant to a written solicitation or contract issued or awarded by the Department of Defense for an end-use identified pursuant to paragraphs (e)(1), (2), or (4) of this section. (5) Defense articles excluded by paragraph (g) of this section or Supplement No. 1 to part 126 of this subchapter (e.g., USML Category XI (a)(3) electronically scanned array radar) that are embedded in a larger system that is eligible to ship under this section (e.g., a ship or aircraft) must separately comply with any restrictions placed on that embedded defense article under this subsection. The exporter must obtain a license or other authorization from the Directorate of Defense Trade Controls for the export of such embedded defense articles (for example, USML Category XI (a)(3) electronically scanned array radar systems that are exempt from this section that are incorporated in an aircraft that is eligible to ship under the this section continue to require separate authorization from the Directorate of Defense Trade Controls for their export, transfer, reexport, or retransfer). (6) No liability shall be incurred by or attributed to the U.S. Government in connection with any possible infringement of privately owned patent or proprietary rights, either domestic or foreign, by reason of an export conducted pursuant to this section. (7) Sales by exporters made through the U.S. Government shall not include either charges for patent rights in which the U.S. Government holds a royalty-free license, or charges for information which the U.S. Government has a right to use and disclose to others, which is in the public domain, or which the U.S. Government has acquired or is entitled to acquire without restrictions upon its use and disclosure to others. (8) Defense articles and services specific to items that appear on the European Union Dual Use List (as described in Annex 1 to EC Council Regulation No. 428/2009) are not eligible for export under the Defense Trade Cooperation Treaty between the United States and the United Kingdom. (h) Transfers, Retransfers, and Reexports. (1) Any transfer of a defense article or defense service not exempted in Supplement No.1 to part 126 of this subchapter by a member of the United Kingdom Community (see paragraph (d) of this section for specific information on the identification of the Community) to another member of the United Kingdom Community or the United States Community for an end-use that is authorized by this exemption (see paragraphs (e) and (f) of this section regarding authorized end-uses) is authorized under this exemption. (2) Any transfer or other provision of a defense article or defense service for an end-use that is not authorized by the exemption provided by this section is prohibited without a license or the prior written approval of the Directorate of Defense Trade Controls (see paragraphs (e) and (f) of this section regarding authorized end-uses). (3) Any retransfer or reexport, or other provision of a defense article or defense service by a member of the United Kingdom Community to a foreign person that is not a member of the United Kingdom Community, or to a U.S. person that is not a member of the United States Community, is prohibited without a license or the prior written approval of the Directorate of Defense Trade Controls (see paragraph (d) of this section for specific information on the identification of the United Kingdom Community). (4) Any change in the use of a defense article or defense service previously exported, transferred, or obtained under this exemption by any foreign person, including a member of the United Kingdom Community, to an end-use that is not authorized by this exemption is prohibited without a license or other written approval of the Directorate of Defense Trade Controls (see paragraphs (e) and (f) of this section regarding authorized end-uses). (5) Any retransfer, reexport, or change in end-use requiring such approval of the U.S. Government shall be made in accordance with Sec. 123.9 of this subchapter. (6) Defense articles excluded by paragraph (g) of this section or Supplement No. 1 to part 126 of this subchapter (e.g., USML Category XI (a)(3) electronically scanned array radar systems) that are embedded in a larger system that is eligible to ship under this section (e.g., a ship or aircraft) must separately comply with any restrictions placed on that embedded defense article unless otherwise specified. A license or other authorization must be obtained from the Directorate of Defense Trade Controls for the retransfer, reexport or change in end-use of any such embedded defense article (for example, USML Category XI(a)(3) electronically scanned array radar systems that are exempt from this section that are incorporated in an aircraft that is eligible to ship under the this section continue to require separate authorization from the Directorate of Defense Trade Controls for their export, transfer, reexport, or retransfer). (7) A license or prior approval from the Directorate of Defense Trade Controls is not required for a transfer, retransfer, or reexport of an exported defense article or defense service under this section, if: (i) The transfer of defense articles or defense services is made by a member of the United States Community to United Kingdom Ministry of Defense elements deployed outside the Territory of the United Kingdom and engaged in an authorized end-use (see paragraphs (e) and (f) of this section regarding authorized end-uses) using United Kingdom Armed Forces transmission channels or the provisions of this section; (ii) The transfer of defense articles or defense services is made by a member of the United States Community to an Approved Community member (either U.S. or U.K.) that is operating in direct support of United Kingdom Ministry of Defense elements deployed outside the Territory of the United Kingdom and engaged in an authorized end-use (see paragraphs (e) and (f) of this section regarding authorized end- uses) using United Kingdom Armed Forces transmission channels or the provisions of this section; (iii) The reexport is made by a member of the United Kingdom Community to United Kingdom Ministry of Defense elements deployed outside the Territory of the United Kingdom engaged in an authorized end-use (see paragraphs (e) and (f) of this section regarding authorized end-uses) using United Kingdom Armed Forces transmission channels or the provisions of this section; (iv) The retransfer or reexport is made by a member of the United Kingdom Community to an Approved Community member (either U.S. or U.K.) that is operating indirect support of United Kingdom Ministry of Defense elements deployed outside the Territory of the United Kingdom engaged in an authorized end-use (see paragraphs (e) and (f) of this section regarding authorized end-uses) using United Kingdom Armed Forces transmission channels or the provisions of this section; or (v) The defense article or defense service will be delivered to the United Kingdom Ministry of Defense for an authorized end-use (see paragraphs (e) and (f) of this section regarding authorized end-uses); the United Kingdom Ministry of Defense may deploy the item as necessary when conducting official business within or outside the Territory of the United Kingdom. The item must remain under the effective control of the United [[Page 72260]] Kingdom Ministry of Defense while deployed and access may not be provided to unauthorized third parties. (8) U.S. persons registered, or required to be registered, pursuant to part 122 of this subchapter and Members of the United Kingdom Community must immediately notify the Directorate of Defense Trade Controls of any actual or proposed sale, retransfer, or reexport of a defense article or defense service on the U.S. Munitions List originally exported under this exemption to any of the countries listed in Sec. 126.1 of this subchapter, any citizen of such countries, or any person acting on behalf of such countries, whether within or outside the United States. Any person knowing or having reason to know of such a proposed or actual sale, reexport, or retransfer shall submit such information in writing to the Office of Defense Trade Controls Compliance, Directorate of Defense Trade Controls. (i) Transitions. (1) Any previous export of a defense article under a license or other approval of the U.S. Department of State remains subject to the conditions and limitations of the original license or authorization unless the Directorate of Defense Trade Controls has approved in writing a transition to this section. (2) If a U.S. exporter desires to transition from an existing license or other approval to the use of the provisions of this section, the following is required: (i) The U.S. exporter must submit a written request to the Directorate of Defense Trade Controls, which identifies the defense articles or defense services to be transitioned, the existing license(s) or other authorizations under which the defense articles or defense services were originally exported; and the Treaty-eligible end- use for which the defense articles or defense services will be used. Any license(s) filed with U.S. Customs and Border Protection should remain on file until the exporter has received approval from the Directorate of Defense Trade Controls to retire the license(s) and transition to this section. When this approval is conveyed to U.S. Customs and Border Protection by the Directorate of Defense Trade Controls, the license(s) will be returned to the Directorate of Defense Trade Controls by U.S. Customs and Border Protection in accord with existing procedures for the return of expired licenses in Sec. 123.22(c) of this subchapter. (ii) Any license(s) not filed with U.S. Customs and Border Protection must be returned to the Directorate of Defense Trade Controls with a letter citing the Directorate of Defense Trade Controls’ approval to transition to this section as the reason for returning the license(s). (3) If a member of the United Kingdom Community desires to transition defense articles received under an existing license or other approval to the processes established under the Treaty, the United Kingdom Community member must submit a written request to the Directorate of Defense Trade Controls, either directly or through the original U.S. exporter, which identifies the defense articles or defense services to be transitioned, the existing license(s) or other authorizations under which the defense articles or defense services were received, and the Treaty-eligible end-use (see paragraphs (e) and (f) of this section regarding authorized end-uses) for which the defense articles or defense services will be used. The defense article or defense service shall remain subject to the conditions and limitations of the existing license or other approval until the United Kingdom Community member has received approval from the Directorate of Defense Trade Controls to transition to this section. (4) Authorized exporters identified in paragraph (b)(2) of this section who have exported a defense article or defense service that has subsequently been placed on the list of exempted items in Supplement No. 1 to part 126 of this subchapter must review and adhere to the requirements in the relevant Federal Register notice announcing such removal. Once removed, the defense article or defense service will no longer be subject to this section, such defense article or defense service previously exported shall remain on the U.S. Munitions List and be subject to the International Traffic in Arms Regulations unless the applicable Federal Register notice states otherwise. Subsequent reexport or retransfer must be made pursuant to Sec. 123.9 of this subchapter. (5) Any defense article or defense service transitioned from a license or other approval to treatment under this section must be marked in accordance with the requirements of paragraph (j) of this section. (j) Marking of Exports. (1) All defense articles and defense services exported or transitioned pursuant to the Defense Trade Cooperation Treaty between the United States and the United Kingdom and this section shall be marked or identified as follows: (i) For classified defense articles and defense services the standard marking or identification shall read: “//CLASSIFICATION LEVEL USML//REL UK and USA Treaty Community//.” For example, for defense articles classified SECRET, the marking or identification shall be “// SECRET USML//REL UK and USA Treaty Community//.” (ii) Unclassified defense articles and defense services exported under or transitioned pursuant to this section shall be UK classified as “Restricted USML” and, the standard marking or identification shall read “//RESTRICTED USML//REL UK and USA Treaty Community//.” (2) Where defense articles are returned to a member of the United States Community identified in paragraph (b) of this section, any defense articles UK classified and marked or identified pursuant to paragraph j(1)(ii) as “//RESTRICTED USML//REL UK and USA Treaty Community//” no longer be UK classified and such marking or identification shall be removed; and (3) The standard marking and identification requirements are as follows: (i) Defense articles (other than technical data) shall be individually labeled with the appropriate identification detailed in paragraphs (j)(1) and (j)(2) of this section; or, where such labeling is impracticable (e.g., propellants, chemicals), shall be accompanied by documentation (such as contracts or invoices) clearly associating the defense articles with the appropriate markings as detailed above; (ii) Technical data (including data packages, technical papers, manuals, presentations, specifications, guides and reports), regardless of media or means of transmission (physical or electronic), shall be individually labeled with the appropriate identification detailed in paragraphs (j)(1) and (j)(2) of this section; or, where such labeling is impracticable (oral presentations), shall have a verbal notification clearly associating the technical data with the appropriate markings as detailed above; and (4) Contracts and agreements for the provision of defense services shall be identified with the appropriate identification detailed in paragraphs (j)(1) and (j)(2) of this section. (5) The exporter shall incorporate the following statement as an integral part of all shipping documentation (airway bill, bill of lading, manifest, packing documents, delivery verification, invoice, etc.) whenever defense articles are to be exported: “These commodities are authorized by the U.S. Government for export only to United Kingdom for use in approved projects, programs or operations by members of the United Kingdom [[Page 72261]] Community. They may not be retransferred or reexported or used outside of an approved project, program, or operation, either in their original form or after being incorporated into other end-items, without the prior written approval of the U.S. Department of State.” (k) Intermediate Consignees. (1) Unclassified exports under this section may only be handled by: (i) U.S. intermediate consignees who are: (A) Exporters registered with the Directorate of Defense Trade Controls and eligible; (B) Licensed customs brokers who are subject to background investigation and have passed a comprehensive examination administered by U.S. Customs and Border Protection; or (C) Commercial air freight and surface shipment carriers, freight forwarders, or other parties not exempt from registration under Sec. 129.3(b)(3) of this subchapter that are identified at the time of export as being on the list of Authorized U.S. Intermediate Consignees, which is available on the Directorate of Defense Trade Controls’ Web site. (ii) United Kingdom intermediate consignees who are: (A) Members of the United Kingdom Community; or (B) Freight forwarders, customs brokers, commercial air freight and surface shipment carriers, or other United Kingdom parties that are identified at the time of export as being on the list of Authorized United Kingdom Intermediate Consignees, which is available on the Directorate of Defense Trade Controls’ Web site. (2) Classified exports must comply with the security requirements of the National Industrial Security Program Operating Manual (DoD 5220.22-M and supplements or successors). (l) Records. (1) All exporters authorized pursuant to paragraph (b)(2) of this section who export pursuant to the Defense Trade Cooperation Treaty between the United States and the United Kingdom and this section shall maintain detailed records of all exports, imports, and transfers made by that exporter of defense articles or defense services subject to the Defense Trade Cooperation Treaty between the United States and the United Kingdom and this section. Exporters shall also maintain detailed records of any reexports and retransfers approved or otherwise authorized by the Directorate of Defense Trade Controls of defense articles or defense services subject to the Defense Trade Cooperation Treaty between the United States and the United Kingdom and this section. These records shall be maintained for a minimum of five years from the date of export, import, transfer, reexport, or retransfer and shall be made available upon request to the Directorate of Defense Trade Controls, U.S. Immigration and Customs Enforcement, or U.S. Customs and Border Protection, or any other authorized U.S. law enforcement officer. Records in an electronic format must be maintained using a process or system capable of reproducing all records on paper. Such records when displayed on a viewer, monitor, or reproduced on paper, must exhibit a high degree of legibility and readability. (For the purpose of this section, “legible” and “legibility” mean the quality of a letter or numeral that enables the observer to identify it positively and quickly to the exclusion of all other letters or numerals. “Readable” and “readability” means the quality of a group of letters or numerals being recognized as complete words or numbers.) These records shall consist of the following: (i) Port of entry/exit; (ii) Date/time of export/import; (iii) Method of export/import; (iv) Commodity code and description of the commodity, including technical data; (v) Value of export; (vi) Reference to this section and justification for export under the Treaty; (vii) End-user/end-use; (viii) Identification of all U.S. and foreign parties to the transaction; (ix) How the export was marked; (x) Classification of the export; (xi) All written correspondence with the U.S. Government on the export; (xii) All information relating to political contributions, fees, or commissions furnished or obtained, offered, solicited, or agreed upon as outlined in subsection (m) below; (xiii) Purchase order or contract; (xiv) Technical data actually exported; (xv) The Internal Transaction Number for the Electronic Export Information filing in the Automated Export System; (xvi) All shipping documentation (airway bill, bill of lading, manifest, packing documents, delivery verification, invoice, etc.); and (xvii) Statement of Registration (Form DS-2032). (2) Filing of export information. All exporters of defense articles and defense services under the Defense Trade Cooperation Treaty between the United States and the United Kingdom and this section must electronically file Electronic Export Information (EEI) using the Automated Export System citing one of the four below referenced codes in the appropriate field in the EEI for each shipment: (i) 126.16(e)(1): Used for exports in support of United States and United Kingdom combined military or counter-terrorism operations (the name or an appropriate description of the operation shall be placed in the appropriate field in the EEI, as well); (ii) 126.16(e)(2): Used for exports in support of United States and United Kingdom cooperative security and defense research, development, production, and support programs (the name or an appropriate description of the program shall be placed in the appropriate field in the EEI, as well); (iii) 126.16(e)(3): Used for exports in support of mutually determined specific security and defense projects where the Government of the United Kingdom is the end-user (the name or an appropriate description of the project shall be placed in the appropriate field in the EEI, as well); or (iv) 126.16(e)(4): Used for exports that will have a U.S. Government end-use (the U.S. Government contract number or solicitation number (e.g., “U.S. Government contract number XXXXX”) shall be placed in the appropriate field in the EEI, as well). Such exports must meet the required export documentation and filing guidelines, including for defense services, of Sec. 123.22(a), (b)(1), and (b)(2) of this subchapter. (m) Fees and Commissions. All exporters authorized pursuant to paragraph (b)(2) of this section shall, with respect to each export, transfer, reexport, or retransfer, pursuant to the Defense Trade Cooperation Treaty between the United States and the United Kingdom and this section, submit a statement to the Directorate of Defense Trade Controls containing the information identified in Sec. 130.10 of this subchapter relating to fees, commissions, and political contributions on contracts or other instruments valued in an amount of $500,000 or more. (n) Violations and Enforcement. (1) Exports, transfers, reexports, and retransfers that do not comply with the conditions prescribed in this section will constitute violations of the Arms Export Control Act and this subchapter, and are subject to all relevant criminal, civil, and administrative penalties (see Sec. 127.1 of this subchapter), and may also be subject to other statutes or regulations. (2) U.S. Immigration and Customs Enforcement and U.S. Customs and Border Protection officers have the authority to investigate, detain, or seize [[Page 72262]] any export or attempted export of defense articles that does not comply with this section or that is otherwise unlawful. (3) The Directorate of Defense Trade Controls, U.S. Immigration and Customs Enforcement, U.S. Customs and Border Protection, and other authorized U.S. law enforcement officers may require the production of documents and information relating to any actual or attempted export, transfer, reexport, or retransfer pursuant to this section. Any foreign person refusing to provide such records within a reasonable period of time shall be suspended from the United Kingdom Community and ineligible to receive defense articles or defense services pursuant to the exemption under this section or otherwise. (o) Procedures for Legislative Notification. (1) Exports pursuant to the Defense Trade Cooperation Treaty between the United States and the United Kingdom and this section by any person identified in paragraph (b)(2) of this section shall not take place until 30 days after the Directorate of Defense Trade Controls has acknowledged receipt of a Form DS-4048 (entitled, “Projected Sales of Major Weapons in Support of Section 25(a)(1) of the Arms Export Control Act”) from the exporter notifying the Department of State if the export involves one or more of the following: (i) A contract or other instrument for the export of major defense equipment in the amount of $25,000,000 or more, or for defense articles and defense services in the amount of $100,000,000 or more; (ii) A contract or other instrument for the export of firearms controlled under Category I of the U.S. Munitions List of the International Traffic in Arms Regulations in an amount of $1,000,000 or more; (iii) A contract or other instrument, regardless of value, for the manufacturing abroad of any item of significant military equipment; or (iv) An amended contract or other instrument that meets the requirements of paragraphs (o)(1)(i)-(o)(1)(iii) of this section. (2) The Form DS-4048 required in paragraph (o)(1) of this section shall be accompanied by the following additional information: (i) The information identified in Sec. 130.10 and Sec. 130.11 of this subchapter; (ii) A statement regarding whether any offset agreement is proposed to be entered into in connection with the export and a description of any such offset agreement; (iii) A copy of the signed contract or other instrument; and (iv) If the notification is for paragraph (o)(1)(ii) of this section, a statement of what will happen to the weapons in their inventory (for example, whether the current inventory will be sold, reassigned to another service branch, destroyed, etc.). (3) The Department of State will notify the Congress of exports that meet the requirements of paragraph (o)(1) of this section. 27. Supplement No. 1 is added to Part 126 read as follows: Supplement No. 1 * —————————————————————————————————————- (CA) Sec. (AS) Sec. (UK) Sec. USML category Exclusion 126.5 126.16 126.17 —————————————————————————————————————- I-XXI……………………………….. Classified defense articles and X X X services. See Note 1. I-XXI……………………………….. Defense articles listed in the X X X Missile Technology Control Regime (MTCR) Annex. I-XXI……………………………….. U.S. origin defense articles ………. X X and services used for marketing purposes and not previously licensed for export in accordance with this subchapter. I-XXI……………………………….. Defense services for or X ………. ………. technical data related to defense articles identified in this supplement as excluded from the Canadian exemption. I-XXI……………………………….. Any transaction involving the X ………. ………. export of defense articles and services for which congressional notification is required in accordance with Sec. 123.15 and Sec. 124.11 of this subchapter. I-XXI……………………………….. U.S. origin defense articles ………. X X and services specific to developmental systems that have not obtained written Milestone B approval from the U.S. Department of Defense milestone approval authority, unless such export is pursuant to a written solicitation or contract issued or awarded by the U.S. Department of Defense for an end use identified in subsections (e)(1), (2), or (4) of Sec. 126.16 or Sec. 126.17 of this subchapter and is consistent with other exclusions of this supplement. I-XXI……………………………….. Nuclear weapons strategic X ………. ………. delivery systems and all components, parts, accessories, and attachments specifically designed for such systems and associated equipment. I-XXI……………………………….. Defense articles and services ………. X X specific to the existence or method of compliance with anti- tamper measures made at U.S. Government direction. I-XXI……………………………….. Defense articles and services ………. X X specific to reduced observables or counter low observables in any part of the spectrum. See Note 2. I-XXI……………………………….. Defense articles and services ………. X X specific to sensor fusion beyond that required for display or identification correlation. See Note 3. I-XXI……………………………….. Defense articles and services ………. X X specific to the automatic target acquisition or recognition and cueing of multiple autonomous unmanned systems. I-XXI……………………………….. Nuclear power generating ………. ………. X equipment or propulsion equipment (e.g. nuclear reactors), specifically designed for military use and components therefore, specifically designed for military use. See also Sec. 123.20 of this subchapter. I-XXI……………………………….. Libraries (parametric technical ………. ………. X databases) specially designed for military use with equipment controlled on the USML. I-XXI……………………………….. Defense services or technical X ………. ………. data specific to applied research as defined in Sec. 125.4(c)(3) of this subchapter, design methodology as defined in Sec. 125.4(c)(4) of this subchapter, engineering analysis as defined in Sec. 125.4(c)(5) of this subchapter, or manufacturing know-how as defined in Sec. 125.4(c)(6) of this subchapter. [[Page 72263]] I-XXI……………………………….. Defense services that are not X ………. ………. based on a written arrangement (between the U.S. exporter and the Canadian recipient) that includes a clause requiring that all documentation created from U.S. origin technical data contain the statement that “This document contains technical data, the use of which is restricted by the U.S. Arms Export Control Act. This data has been provided in accordance with, and is subject to, the limitations specified in Sec. 126.5 of the International Traffic In Arms Regulations (ITAR). By accepting this data, the consignee agrees to honor the requirements of the ITAR”. I…………………………………… Defense articles and services X ………. ………. related to firearms, close assault weapons, and combat shotguns. II(k)……………………………….. Software source code related to ………. X X Categories II(c), II(d), or II(i). See Note 4. II(k)……………………………….. Manufacturing know-how related X X X to Category II(d). See Note 5. III…………………………………. Defense articles and services X ………. ………. related to ammunition for firearms, close assault weapons, and combat shotguns listed in Category I. III…………………………………. Defense articles and services ………. ………. X specific to ammunition and fuse setting devices for guns and armament controlled in Category II. III(e)………………………………. Manufacturing know-how related X X X to Categories III(d)(1) or III(d)(2) and their specially designed components. See Note 5. III(e)………………………………. Software source code related to ………. X X Categories III(d)(1) or III(d)(2). See Note 4. IV………………………………….. Defense articles and services X X X specific to man-portable air defense systems (MANPADS). See Note 6. IV………………………………….. Defense articles and services ………. ………. X specific to rockets, designed or modified for non-military applications that do not have a range of 300 km (i.e., not controlled on the MTCR Annex). IV………………………………….. Defense articles and services ………. X X specific to torpedoes. IV………………………………….. Defense articles and services ………. ………. X specific to anti-personnel landmines. IV(i)……………………………….. Software source code related to ………. X X Categories IV(a), IV(b), IV(c), or IV(g). See Note 4. IV(i)……………………………….. Manufacturing know-how related X X X to Categories IV(a), IV(b), IV(d), or IV(g) and their specially designed components. See Note 5. V…………………………………… The following energetic ………. ………. X materials and related substances:. a. TATB (triaminotrinitrobenzene) (CAS 3058-38-6) b. Explosives controlled in USML Category V(a)(32) or V(a)(33) c. Iron powder (CAS 7439-89-6) with particle size of 3 micrometers or less produced by reduction of iron oxide with hydrogen d. BOBBA-8 (bis(2- methylaziridinyl)2-(2- hydroxypropanoxy) propylamino phosphine oxide), and other MAPO derivatives e. N-methyl-p-nitroaniline (CAS 100-15-2) f. Trinitrophenylmethyl- ………. ………. ………. nitramine (tetryl) (CAS 479-45- 8) V(c)(7)……………………………… Pyrotechnics and pyrophorics ………. ………. X specifically formulated for military purposes to enhance or control radiated energy in any part of the IR spectrum. V(d)(3)……………………………… Bis-2, 2-dinitropropylnitrate ………. ………. X (BDNPN). VI………………………………….. Defense Articles specific to ………. ………. X equipment specially designed or configured to be installed in a vehicle for military ground, marine, airborne or space applications, capable of operating while in motion and of producing or maintaining temperatures below 103 K (-170 [deg]C). VI………………………………….. Defense Articles specific to ………. ………. X superconductive electrical equipment (rotating machinery and transformers) specially designed or configured to be installed in a vehicle for military ground, marine, airborne, or space applications and capable of operating while in motion. This, however, does not include direct current hybrid homopolar generators that have single-pole normal metal armatures which rotate in a magnetic field produced by superconducting windings, provided those windings are the only superconducting component in the generator. VI………………………………….. Defense articles and services ………. X X specific to naval technology and systems relating to acoustic spectrum control and awareness. See Note 10. VI(a)……………………………….. Nuclear powered vessels…….. X X X VI(c)……………………………….. Defense articles and services ………. X X specific to submarine combat control systems. VI(d)……………………………….. Harbor entrance detection ………. ………. X devices. VI(e)……………………………….. Defense articles and services X X X specific to naval nuclear propulsion equipment. See Note 7. VI(g)……………………………….. Technical data and defense X X X services for gas turbine engine hot sections related to Category VI(f). See Note 8. VI(g)……………………………….. Software source code related to ………. X X Categories VI(a) or VI(c). See Note 4. VII…………………………………. Defense articles specific to ………. ………. X equipment specially designed or configured to be installed in a vehicle for military ground, marine, airborne, or space applications, capable of operating while in motion and of producing or maintaining temperatures below 103 K (-170 [deg]C). [[Page 72264]] VII…………………………………. Defense articles specific to ………. ………. X superconductive electrical equipment (rotating machinery and transformers) specially designed or configured to be installed in a vehicle for military ground, marine, airborne, or space applications and capable of operating while in motion. This, however, does not include direct current hybrid homopolar generators that have single-pole normal metal armatures which rotate in a magnetic field produced by superconducting windings, provided those windings are the only superconducting component in the generator. VII…………………………………. Armored all wheel drive ………. ………. X vehicles, other than vehicles specifically designed or modified for military use, fitted with, or designed or modified to be fitted with, a plough or flail for the purpose of land mine clearance. VII(e)………………………………. Amphibious vehicles………… ………. ………. X VII(f)………………………………. Technical data and defense X X X services for gas turbine engine hot sections. See Note 8. VIII………………………………… Defense articles specific to ………. ………. X equipment specially designed or configured to be installed in a vehicle for military ground, marine, airborne, or space applications, capable of operating while in motion and of producing or maintaining temperatures below 103 K (-170 [deg]C). VIII………………………………… Defense articles specific to ………. ………. X superconductive electrical equipment (rotating machinery and transformers) specially designed or configured to be installed in a vehicle for military ground, marine, airborne, or space applications and capable of operating while in motion. This, however, does not include direct current hybrid homopolar generators that have single-pole normal metal armatures which rotate in a magnetic field produced by superconducting windings, provided those windings are the only superconducting component in the generator. VIII(a)……………………………… All Category VIII(a) items….. X ………. ………. VIII(b)……………………………… Defense articles and services ………. X X specific to gas turbine engine hot section components and digital engine controls. See Note 8. VIII(f)……………………………… Developmental aircraft, engines X ………. ………. and components identified in Category VIII(f). VIII(g)……………………………… Ground Effect Machines (GEMS).. ………. ………. X VIII(i)……………………………… Technical data and defense X X X services for gas turbine engine hot sections related to Category VIII(b). See Note 8. VIII(i)……………………………… Manufacturing know-how related X X X to Categories VIII(a), VIII(b), or VIII(e) and their specially designed components. See Note 5. VIII(i)……………………………… Software source code related to ………. X X Categories VIII(a) or VIII(e). See Note 4. IX………………………………….. Training or simulation ………. ………. X equipment for MANPADS. See Note 6. IX(e)……………………………….. Software source code related to ………. X X Categories IX(a) or IX(b). See Note 4. IX(e)……………………………….. Software that is both ………. ………. X specifically designed or modified for military use and specifically designed or modified for modeling or simulating military operational scenarios. X(e)………………………………… Manufacturing know-how related X X X to Categories X(a)(1) or X(a)(2) and their specially designed components. See Note 5. XI(a)……………………………….. Defense articles and services ………. X X specific to countermeasures and counter-countermeasures See Note 9. XI………………………………….. Defense articles and services ………. X X specific to naval technology and systems relating to acoustic spectrum control and awareness. See Note 10. XI(b) XI(c) XI(d)…………………….. Defense articles and services ………. X X specific to communications security (e.g., COMSEC and TEMPEST). XI(d)……………………………….. Software source code related to ………. X X Category XI(a). See Note 4. XI(d)……………………………….. Manufacturing know-how related X X X to Categories XI(a)(3) or XI(a)(4) and their specially designed components. See Note 5. XII…………………………………. Defense articles and services ………. X X specific to countermeasures and counter-countermeasures. See Note 9. XII(c)………………………………. Defense articles and services X ………. ………. specific to XII(c) articles, except any 1st- and 2nd- generation image intensification tubes and 1st- and 2nd-generation image intensification night sighting equipment. End items in XII(c) and related technical data limited to basic operations, maintenance, and training information as authorized under the exemption in Sec. 125.4(b)(5) of this subchapter may be exported directly to a Canadian Government entity. XII(c)………………………………. Technical data or defense X X X services for night vision equipment beyond basic operations, maintenance, and training data. However, the AS and UK Treaty exemptions apply when such export is pursuant to a written solicitation or contract issued or awarded by the U.S. Department of Defense for an end use identified in subsections (e)(1), (2), or (4) of Sec. 126.16 or Sec. 126.17 of this subchapter and is consistent with other exclusions of this supplement. XII(f)………………………………. Manufacturing know-how related X X X to Category XII(d) and their specially designed components. See Note 5. XII(f)………………………………. Software source code related to ………. X X Categories XII(a), XII(b), XII(c), or XII(d). See Note 4. XIII(b)……………………………… Defense articles and services ………. X X specific to Military Information Security Assurance Systems. [[Page 72265]] XIII(c)……………………………… Defense articles and services ………. ………. X specific to armored plate manufactured to comply with a military standard or specification or suitable for military use. See Note 11. XIII(d)……………………………… Carbon/carbon billets and ………. ………. X performs which are reinforced in three or more dimensional planes, specifically designed, developed, modified, configured or adapted for defense articles. XIII(f)……………………………… Structural materials……….. ………. ………. X XIII(g)……………………………… Defense articles and services ………. ………. X related to concealment and deception equipment and materials. XIII(h)……………………………… Energy conversion devices other ………. ………. X than fuel cells. XIII(i)……………………………… Metal embrittling agents……. ………. ………. X XIII(j)……………………………… Defense articles and services ………. X X related to hardware associated with the measurement or modification of system signatures for detection of defense articles as described in Note 2. XIII(k)……………………………… Defense articles and services ………. X X related to tooling and equipment specifically designed or modified for the production of defense articles identified in Category XIII(b). XIII(l)……………………………… Software source code related to ………. X X Category XIII(a). See Note 4. XIV…………………………………. Defense articles and services ………. X X related to toxicological agents, including chemical agents, biological agents, and associated equipment. XIV(a) XIV(b) XIV(d) XIV(e) XIV(f)……… Chemical agents listed in X ………. ………. Category XIV(a), (d) and (e), biological agents and biologically derived substances in Category XIV(b), and equipment listed in Category XIV(f) for dissemination of the chemical agents and biological agents listed in Category XIV(a), (b), (d), and (e). XV(a)……………………………….. Defense articles and services X X X specific to spacecraft/ satellites. However, the Canadian exemption may be used for commercial communications satellites that have no other type of payload. XV(b)……………………………….. Defense articles and services ………. X X specific to ground control stations for spacecraft telemetry, tracking, and control. XV(c)……………………………….. Defense articles and services ………. X X specific to GPS/PPS security modules. XV(c)……………………………….. Defense articles controlled in X ………. ………. XV(c) except end items for end use by the Federal Government of Canada exported directly or indirectly through a Canadian- registered person. XV(d)……………………………….. Defense articles and services X X X specific to radiation-hardened microelectronic circuits. XV(e)……………………………….. Anti-jam systems with the X ………. ………. ability to respond to incoming interference by adaptively reducing antenna gain (nulling) in the direction of the interference. XV(e)……………………………….. Antennas having any of the following: (a) Aperture (overall dimension of the radiating portions of the antenna) greater than 30 feet; (b) All sidelobes less than or equal to -35 dB relative to the peak of the main beam; or (c) Designed, modified, or X ………. ………. configured to provide coverage area on the surface of the earth less than 200 nautical miles in diameter, where “coverage area” is defined as that area on the surface of the earth that is illuminated by the main beam width of the antenna (which is the angular distance between half power points of the beam). XV(e)……………………………….. Optical intersatellite data X ………. ………. links (cross links) and optical ground satellite terminals. XV(e)……………………………….. Spaceborne regenerative X ………. ………. baseband processing (direct up and down conversion to and from baseband) equipment. XV(e)……………………………….. Propulsion systems which permit X ………. ………. acceleration of the satellite on-orbit (i.e., after mission orbit injection) at rates greater than 0.1 g. XV(e)……………………………….. Attitude control and X ………. ………. determination systems designed to provide spacecraft pointing determination and control or payload pointing system control better than 0.02 degrees per axis. XV(e)……………………………….. All specifically designed or X ………. ………. modified systems, components, parts, accessories, attachments, and associated equipment for all Category XV(a) items, except when specifically designed or modified for use in commercial communications satellites. XV(e)……………………………….. Defense articles and services ………. X X specific to spacecraft and ground control station systems (only for telemetry, tracking and control as controlled in XV(b)), subsystems, components, parts, accessories, attachments, and associated equipment. XV(f)……………………………….. Technical data and defense X X X services directly related to the other defense articles excluded from the exemptions for Category XV. XVI…………………………………. Defense articles and services X X X specific to design and testing of nuclear weapons. XVI(c)………………………………. Nuclear radiation measuring X ………. ………. devices manufactured to military specifications. XVI(e)………………………………. Software source code related to ………. X X Category XVI(c). See Note 4. XVII………………………………… Classified articles and defense X X X services not elsewhere enumerated. See Note 1. XVIII……………………………….. Defense articles and services ………. X X specific to directed energy weapon systems. XX………………………………….. Defense articles and services X X X related to submersible vessels, oceanographic, and associated equipment. XXI…………………………………. Miscellaneous defense articles X X X and services. —————————————————————————————————————- [[Page 72266]] Note 1: Classified defense articles and services are not eligible for export under the Canadian exemptions. U.S. origin defense articles and services controlled in Category XVII are not eligible for export under the UK Treaty exemption. U.S. origin classified defense articles and services are not eligible for export under either the UK or AS Treaty exemptions except when being released pursuant to a U.S. Department of Defense written request, directive or contract that provides for the export of the defense article or service. Note 2: The phrase “any part of the spectrum” includes radio frequency (RF), infrared (IR), electro-optical, visual, ultraviolet (UV), acoustic, and magnetic. Defense articles related to reduced observables or counter reduced observables are defined as: a. Signature reduction (radio frequency (RF), infrared (IR), Electro-Optical, visual, ultraviolet (UV), acoustic, magnetic, RF emissions) of defense platforms, including systems, subsystems, components, materials, (including dual-purpose materials used for Electromagnetic Interference (EM) reduction) technologies, and signature prediction, test and measurement equipment and software and material transmissivity/reflectivity prediction codes and optimization software. b. Electronically scanned array radar, high power radars, radar processing algorithms, periscope-mounted radar systems (PATRIOT), LADAR, multistatic and IR focal plane array-based sensors, to include systems, subsystems, components, materials, and technologies. Note 3: Defense Articles related to sensor fusion beyond that required for display or identification correlation is defined as techniques designed to automatically combine information from two or more sensors/sources for the purpose of target identification, tracking, designation, or passing of data in support of surveillance or weapons engagement. Sensor fusion involves sensors such as acoustic, infrared, electro optical, frequency, etc. Display or identification correlation refers to the combination of target detections from multiple sources for assignment of common target track designation. Note 4: Software source code beyond that source code required for basic operation, maintenance, and training for programs, systems, and/or subsystems is not eligible for use of the UK or AS Treaty Exemptions, unless such export is pursuant to a written solicitation or contract issued or awarded by the U.S. Department of Defense for an end use identified in subsections (e)(1), (2), or (4) of Sec. 126.16 or Sec. 126.17 of this subchapter and is consistent with other exclusions of this supplement. Note 5: Manufacturing know-how, as defined in Sec. 125.4(c)(6) of this subchapter, is not eligible for use of the UK or AS Treaty Exemptions, unless such export is pursuant to a written solicitation or contract issued or awarded by the U.S. Department of Defense for an end use identified in subsections (e)(1), (2), or (4) of Sec. 126.16 or Sec. 126.17 of this subchapter and is consistent with other exclusions of this supplement. Note 6: Defense Articles specific to Man Portable Air Defense Systems (MANPADS) includes missiles which can be used without modification in other applications. It also includes production equipment specifically designed or modified for MANPAD systems, as well as training equipment specifically designed or modified for MANPAD systems. Note 7: Naval nuclear propulsion plants includes all of USML Category VI(e). Naval nuclear propulsion information is technical data that concerns the design, arrangement, development, manufacture, testing, operation, administration, training, maintenance, and repair of the propulsion plants of naval nuclear-powered ships and prototypes, including the associated shipboard and shore-based nuclear support facilities. Examples of defense articles covered by this exclusion include nuclear propulsion plants and nuclear submarine technologies or systems; nuclear powered vessels (see USML Categories VI and XX). Note 8: Examples of gas turbine engine hot section exempted defense article components and technology are combustion chambers/liners; high pressure turbine blades, vanes, disks and related cooled structure; cooled low pressure turbine blades, vanes, disks and related cooled structure; advanced cooled augmenters; and advanced cooled nozzles. Examples of gas turbine engine hot section developmental technologies are Integrated High Performance Turbine Engine Technology (IHPTET), Versatile, Affordable Advanced Turbine Engine (VAATE), Ultra- Efficient Engine Technology (UEET). Note 9: Examples of countermeasures and counter-countermeasures related to defense articles not exportable under the AS or UK Treaty exemptions are: a. IR countermeasures; b. Classified techniques and capabilities; c. Exports for precision radio frequency location that directly or indirectly supports fire control and is used for situation awareness, target identification, target acquisition, and weapons targeting and Radio Direction Finding (RDF) capabilities. Precision RF location is defined as angle of arrival accuracy of less than five degrees (RMS) and RF emitter location of less than ten percent range error; d. Providing the capability to reprogram; and e. Acoustics (including underwater), active and passive countermeasures, and counter-countermeasures Note 10: Examples of defense articles covered by this exclusion include underwater acoustic vector sensors; acoustic reduction; off-board, underwater, active and passive sensing, propeller/propulsor technologies; fixed mobile/floating/powered detection systems which include in-buoy signal processing for target detection and classification; autonomous underwater vehicles capable of long endurance in ocean environments (manned submarines excluded); automated control algorithms embedded in on-board autonomous platforms which enable (a) group behaviors for target detection and classification, (b) adaptation to the environment or tactical situation for enhancing target detection and classification; “intelligent autonomy” algorithms which define the status, group (greater than 2) behaviors, and responses to detection stimuli by autonomous, underwater vehicles; and low frequency, broad-band “acoustic color,” active acoustic “fingerprint” sensing for the purpose of long range, single pass identification of ocean bottom objects, buried or otherwise. (Controlled under Category XI(a), (1) and (2) and in (b), (c), and (d)). Note 11: The defense articles include constructions of metallic or non-metallic materials or combinations thereof specially designed to provide protection for military systems. The phrase “suitable for military use” applies to any articles or materials which have been tested to level IIIA or above IAW NIJ standard 0108.01 or comparable national standard. This exclusion does not include military helmets, body armor, or other protective garments which may be exported IAW the terms of the AS or UK Treaties. —————————————————————————————————————- * An “X” in the chart indicates that the item is excluded from use under the exemption referenced in the top of the column. An item excluded in any one row is excluded regardless of whether other rows may contain a description that would include the item. PART 127–VIOLATIONS AND PENALTIES 28. The authority citation for part 127 is revised to read to as follows: Authority: Secs. 2, 38, and 42, Public Law 90-629, 90 Stat. 744 (22 U.S.C. 2752, 2778, 2791); E.O. 11958, 42 FR 4311; 3 CFR, 1977 Comp., p. 79; 22 U.S.C. 401; 22 U.S.C. 2651a; 22 U.S.C. 2779a; 22 U.S.C. 2780; Pub. L. 111-266. 29. Section 127.1 is revised to read as follows: Sec. 127.1 Violations. (a) Without first obtaining the required license or other written [[Page 72267]] approval from the Directorate of Defense Trade Controls, it is unlawful: (1) To export or attempt to export from the United States any defense article or technical data or to furnish or attempt to furnish any defense service for which a license or written approval is required by this subchapter; (2) To reexport or retransfer or attempt to reexport or retransfer any defense article, technical data, or defense service from one foreign end-user, end-use, or destination to another foreign end-user, end-use, or destination for which a license or written approval is required by this subchapter, including, as specified in Sec. 126.16(h) and Sec. 126.17(h) of this subchapter, any defense article, technical data, or defense service that was exported from the United States without a license pursuant to any exemption under this subchapter; (3) To import or attempt to import any defense article whenever a license is required by this subchapter; (4) To conspire to export, import, reexport, retransfer, furnish or cause to be exported, imported, reexported, retransferred or furnished, any defense article, technical data, or defense service for which a license or written approval is required by this subchapter. (b) It is unlawful: (1) To violate any of the terms or conditions of a license or approval granted pursuant to this subchapter, any exemption contained in this subchapter, or any rule or regulation contained in this subchapter. (2) To engage in the business of brokering activities for which registration and a license or written approval is required by this subchapter without first registering or obtaining the required license or written approval from the Directorate of Defense Trade Controls. For the purposes of this subchapter, engaging in the business of brokering activities requires only one occasion of engaging in an activity as reflected in Sec. 129.2(b) of this subchapter. (3) To engage in the United States in the business of either manufacturing or exporting defense articles or furnishing defense services without complying with the registration requirements. For the purposes of this subchapter, engaging in the business of manufacturing or exporting defense articles or furnishing defense services requires only one occasion of manufacturing or exporting a defense article or furnishing a defense service. (c) Any person who is granted a license or other approval or who acts pursuant to an exemption under this subchapter is responsible for the acts of employees, agents, and all authorized persons to whom possession of the defense article or technical data has been entrusted regarding the operation, use, possession, transportation, and handling of such defense article or technical data abroad. All persons abroad subject to U.S. jurisdiction who obtain temporary or permanent custody of a defense article exported from the United States or produced under an agreement described in part 124 of this subchapter, and irrespective of the number of intermediate transfers, are bound by the regulations of this subchapter in the same manner and to the same extent as the original owner or transferor. (d) A person with knowledge that another person is then ineligible pursuant to Sec. Sec. 120.1(c) or 126.7 of this subchapter may not, directly or indirectly, in any manner or capacity, without prior disclosure of the facts to, and written authorization from, the Directorate of Defense Trade Controls: (1) Apply for, obtain, or use any export control document as defined in Sec. 127.2(b) of this subchapter for such ineligible person; or (2) Order, buy, receive, use, sell, deliver, store, dispose of, forward, transport, finance, or otherwise service or participate in any transaction which may involve any defense article or the furnishing of any defense service for which a license or approval is required by this subchapter or an exemption is available under this subchapter for export, where such ineligible person may obtain any benefit therefrom or have any direct or indirect interest therein. (e) No person may knowingly or willfully cause, or aid, abet, counsel, demand, induce, procure, or permit the commission of, any act prohibited by, or the omission of any act required by, 22 U.S.C. 2778 and 2779, or any regulation, license, approval, or order issued thereunder. 30. Section 127.2 is amended by revising paragraphs (a), (b) introductory text, (b)(1), (b)(2), and adding (b)(14), to read as follows: Sec. 127.2 Misrepresentation and omission of facts. (a) It is unlawful to use or attempt to use any export or temporary import control document containing a false statement or misrepresenting or omitting a material fact for the purpose of exporting, transferring, reexporting, retransferring, obtaining, or furnishing any defense article, technical data, or defense service. Any false statement, misrepresentation, or omission of material fact in an export or temporary import control document will be considered as made in a matter within the jurisdiction of a department or agency of the United States for the purposes of 18 U.S.C. 1001, 22 U.S.C. 2778, and 22 U.S.C. 2779. (b) For the purpose of this subchapter, export or temporary import control documents include the following: (1) An application for a permanent export, reexport, retransfer, or a temporary import license and supporting documents. (2) Shipper’s Export Declaration or an Electronic Export Information filing. * * * * * (14) Any other shipping document that has information related to the export of the defense article or defense service. 31. Section 127.3 is revised to read as follows: Sec. 127.3 Penalties for violations. Any person who willfully: (a) Violates any provision of Sec. 38 or Sec. 39 of the Arms Export Control Act (22 U.S.C. 2778 and 2779) or any rule or regulation issued under either Sec. 38 or Sec. 39 of the Act, or any undertaking specifically required by part 124 of this subchapter; or (b) In a registration, license application, or report required by Sec. 38 or Sec. 39 of the Arms Export Control Act (22 U.S.C. 2778 and 2779) or by any rule or regulation issued under either section, makes any untrue statement of a material fact or omits a material fact required to be stated therein or necessary to make the statements therein not misleading, shall upon conviction be subject to a fine or imprisonment, or both, as prescribed by 22 U.S.C. 2778(c). 32. Section 127.4 is amended by revising paragraphs (a) and (c), and adding paragraph (d), to read as follows: Sec. 127.4 Authority of U.S. Immigration and Customs Enforcement and U.S. Customs and Border Protection officers. (a) U.S. Immigration and Customs Enforcement and U.S. Customs and Border Protection officers may take appropriate action to ensure observance of this subchapter as to the export or the attempted export of any defense article or technical data, including the inspection of loading or unloading of any vessel, vehicle, or aircraft. This applies whether the export is authorized by license or by written approval issued under this subchapter or by exemption. * * * * * (c) Upon the presentation to a U.S. Customs and Border Protection Officer of a license or written approval, or claim of an exemption, authorizing the export [[Page 72268]] of any defense article, the customs officer may require the production of other relevant documents and information relating to the proposed export. This includes an invoice, order, packing list, shipping document, correspondence, instructions, and the documents otherwise required by the U.S. Customs and Border Protection or U.S. Immigration and Customs Enforcement. (d) If an exemption under this subchapter is used or claimed to export, transfer, reexport or retransfer, furnish, or obtain a defense article, technical data, or defense service, law enforcement officers may rely upon the authorities noted above, additional authority identified in the language of the exemption, and any other lawful means to investigate such a matter. 33. Section 127.7 is amended by revising paragraph (a) to read as follows: Sec. 127.7 Debarment. (a) Debarment. In implementing Sec. 38 of the Arms Export Control Act, the Assistant Secretary of State for Political-Military Affairs may prohibit any person from participating directly or indirectly in the export, reexport and retransfer of defense articles, including technical data, or in the furnishing of defense services for any of the reasons listed below and publish notice of such action in the Federal Register. Any such prohibition is referred to as a debarment for purposes of this subchapter. The Assistant Secretary of State for Political-Military Affairs shall determine the appropriate period of time for debarment, which shall generally be for a period of three years. However, reinstatement is not automatic and in all cases the debarred person must submit a request for reinstatement and be approved for reinstatement before engaging in any export or brokering activities subject to the Arms Export Control Act or this subchapter. * * * * * 34. Section 127.10 is amended by revising paragraph (a) to read as follows: Sec. 127.10 Civil penalty. (a) The Assistant Secretary of State for Political-Military Affairs is authorized to impose a civil penalty in an amount not to exceed that authorized by 22 U.S.C. 2778, 2779a, and 2780 for each violation of 22 U.S.C. 2778, 2779a, and 2780, or any regulation, order, license, or written approval issued thereunder. This civil penalty may be either in addition to, or in lieu of, any other liability or penalty which may be imposed. * * * * * 35. Section 127.12 is amended by adding paragraph (b)(5), and revising paragraph (d), to read as follows: Sec. 127.12 Voluntary disclosures. * * * * * (b) * * * (5) Nothing in this section shall be interpreted to negate or lessen the affirmative duty pursuant to Sec. Sec. 126.1(e), 126.16(h)(5), and 126.17(h)(5) of this subchapter upon persons to inform the Directorate of Defense Trade Controls of the actual or proposed sale, export, transfer, reexport, or retransfer of a defense article, technical data, or defense service to any country referred to in Sec. 126.1 of this subchapter, any citizen of such country, or any person acting on its behalf. * * * * * (d) Documentation. The written disclosure should be accompanied by copies of substantiating documents. Where appropriate, the documentation should include, but not be limited to: (1) Licensing documents (e.g., license applications, export licenses, and end-user statements), exemption citation, or other authorization description, if any; (2) Shipping documents (e.g., Shipper’s Export Declarations; Electronic Export Information filing, including the Internal Transaction Number), air waybills, and bills of laden, invoices, and any other associated documents); (3) Any other relevant documents must be retained by the person making the disclosure until the Directorate of Defense Trade Controls requests them or until a final decision on the disclosed information has been made. * * * * * PART 129–REGISTRATION AND LICENSING OF BROKERS 36. The authority citation for part 129 continues to read as follows: Authority: Sec. 38, Pub. L. 104-164, 110 Stat. 1437, (22 U.S.C. 2778). 37. Section 129.6 is amended by revising paragraph (b)(2) to read as follows: Sec. 129.6 Requirements for License/Approval. * * * * * (b) * * * (2) Brokering activities that are arranged wholly within and destined exclusively for the North Atlantic Treaty Organization, any member country of that Organization, Australia, Israel, Japan, New Zealand, or the Republic of Korea, except in the case of the defense articles or defense services specified in Sec. 129.7(a) of this subchapter, for which prior approval is always required. 38. Section 129.7 is amended by revising paragraphs (a)(1)(vii) and (a)(2) to read as follows: Sec. 129.7 Prior Approval (License). (a) * * * (1) * * * (vii) Foreign defense articles or defense services (other than those that are arranged wholly within and destined exclusively for the North Atlantic Treaty Organization, any member country of that Organization, Australia, Israel, Japan, New Zealand, or the Republic of Korea (see Sec. Sec. 129.6(b)(2) and 129.7(a)). (2) Brokering activities involving defense articles or defense services covered by, or of a nature described by part 121, of this subchapter, in addition to those specified in Sec. 129.7(a), that are designated as significant military equipment under this subchapter, for or from any country not a member of the North Atlantic Treaty Organization, Australia, Israel, Japan, New Zealand, or the Republic of Korea whenever any of the following factors are present: * * * * * Dated: November 7, 2011. Ellen O. Tauscher, Under Secretary, Arms Control and International Security, Department of State. [FR Doc. 2011-29328 Filed 11-21-11; 8:45 am] BILLING CODE 4710-25-P



























![[Image]](https://i0.wp.com/cryptome.org/2012/11/paula-kranz/pict22.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012/11/paula-kranz/pict24.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012/11/paula-kranz/pict23.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict5.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict1.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict2.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict3.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict8.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict9.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict11.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict12.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict13.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict14.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict15.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict16.jpg) U.S. first lady Michelle Obama, center left, walks with friends and security during a visit to Ronda in southern Spain, Saturday, Aug. 7, 2010. AP
U.S. first lady Michelle Obama, center left, walks with friends and security during a visit to Ronda in southern Spain, Saturday, Aug. 7, 2010. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict17.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict18.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict19.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict20.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict6.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict4.jpg)
![[Image]](https://i0.wp.com/cryptome.org/katy-perry-milwaukee.jpg)


![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict14.jpg) U.S. President Barack Obama (3rd L) greets an Air Force officer before boarding Marine One helicopter on August 4, 2012 at Joint Base Andrews, Maryland. Obama is spending the weekend at Camp David.
U.S. President Barack Obama (3rd L) greets an Air Force officer before boarding Marine One helicopter on August 4, 2012 at Joint Base Andrews, Maryland. Obama is spending the weekend at Camp David.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict15.jpg) President Barack Obama shakes hands with supporters at the end of a campaign rally at Loudoun County High School on August 2, 2012 in Leesburg, Virginia. The president campaigned earlier in the day in Florida.
President Barack Obama shakes hands with supporters at the end of a campaign rally at Loudoun County High School on August 2, 2012 in Leesburg, Virginia. The president campaigned earlier in the day in Florida.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict16.jpg) President Barack Obama, center, greets supporters after speaking at a campaign event at Loudoun County High School, Thursday, Aug. 2, 2012 in Leesburg, Va. Obama was campaigning in Florida and Northern Virginia today.
President Barack Obama, center, greets supporters after speaking at a campaign event at Loudoun County High School, Thursday, Aug. 2, 2012 in Leesburg, Va. Obama was campaigning in Florida and Northern Virginia today.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict17.jpg) President Barack Obama greets supporters after speaking at a campaign event at Loudoun County High School, Thursday, Aug. 2, 2012 in Leesburg, Va. Obama spent the day campaigning in Florida and Northern Virginia.
President Barack Obama greets supporters after speaking at a campaign event at Loudoun County High School, Thursday, Aug. 2, 2012 in Leesburg, Va. Obama spent the day campaigning in Florida and Northern Virginia.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict19.jpg) A Secret Service Counter Sniper Team prepares to climb down a ladder from on top of a people mover after President Barack Obama aboard Air Force One landed at Dulles International Airport in Sterling, Va.. , Thursday, Aug. 2, 2012.
A Secret Service Counter Sniper Team prepares to climb down a ladder from on top of a people mover after President Barack Obama aboard Air Force One landed at Dulles International Airport in Sterling, Va.. , Thursday, Aug. 2, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict22.jpg) President Barack Obama greets supporters after a campaign event at Rollins College, Thursday, Aug. 2, 2012, in Winter Park, Fla.
President Barack Obama greets supporters after a campaign event at Rollins College, Thursday, Aug. 2, 2012, in Winter Park, Fla.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict21.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict23.jpg) President Barack Obama greets guests on the tarmac upon his arrival at Orlando International Airport, Thursday, Aug. 2, 2012, in Orlando, Fla. Obama is campaigning in Florida and Northern Virginia today.
President Barack Obama greets guests on the tarmac upon his arrival at Orlando International Airport, Thursday, Aug. 2, 2012, in Orlando, Fla. Obama is campaigning in Florida and Northern Virginia today.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict50.jpg) President Barack Obama stops to greet patrons at Lechonera El Barrio, a local restaurant in Orlando, Fla. , Thursday, Aug. 2, 2012. Obama is campaigning in Florida and Northern Virginia today.
President Barack Obama stops to greet patrons at Lechonera El Barrio, a local restaurant in Orlando, Fla. , Thursday, Aug. 2, 2012. Obama is campaigning in Florida and Northern Virginia today.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict53.jpg) President Barack Obama greets eight-year old Olivia Short after he departed from Air Force One upon his arrival in Orlando, Fla. , Thursday, Aug. 2, 2012.
President Barack Obama greets eight-year old Olivia Short after he departed from Air Force One upon his arrival in Orlando, Fla. , Thursday, Aug. 2, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict54.jpg) President Barack Obama is hugged by a supporter after speaking at a campaign event at Mansfield Central Park, Wednesday, Aug. 1, 2012, in Mansfield, Ohio. Obama is campaign in Ohio with stops in Mansfield and Akron today. [Secret Service ready to remove an arm from Obama’s back. Note three agents in the crowd.]
President Barack Obama is hugged by a supporter after speaking at a campaign event at Mansfield Central Park, Wednesday, Aug. 1, 2012, in Mansfield, Ohio. Obama is campaign in Ohio with stops in Mansfield and Akron today. [Secret Service ready to remove an arm from Obama’s back. Note three agents in the crowd.]![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict56.jpg) Marine One helicopter, with President Barack Obama aboard, takes off from Wall Street heliport in New York, Monday, July, 30, 2012. Obama traveled to New York for a private fundraiser. [Decoy helo at rear, fire truck at right, Coast Guard ship in the river.]
Marine One helicopter, with President Barack Obama aboard, takes off from Wall Street heliport in New York, Monday, July, 30, 2012. Obama traveled to New York for a private fundraiser. [Decoy helo at rear, fire truck at right, Coast Guard ship in the river.]![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict55.jpg) US President Barack Obama prepares to land at the Wall Street Helipad in New York on July 30, 2012. Obama is in New York to attend campaign events ahead of the November presidential election. [Two Marine transport at left, Secret Service agent on dock.]
US President Barack Obama prepares to land at the Wall Street Helipad in New York on July 30, 2012. Obama is in New York to attend campaign events ahead of the November presidential election. [Two Marine transport at left, Secret Service agent on dock.]
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict57.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict58.jpg) A Secret Service vehicle, left, and Air Force Security Forces vehicle follow Air Force One on the tarmac as it prepares to take-off with President Barack Obama aboard, at Andrews Air Force Base, Md. , Monday, July 30, 2012.
A Secret Service vehicle, left, and Air Force Security Forces vehicle follow Air Force One on the tarmac as it prepares to take-off with President Barack Obama aboard, at Andrews Air Force Base, Md. , Monday, July 30, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict59.jpg) U.S. First Lady Michelle Obama sits separated from the public during the basketball match between the U.S. and France for the London 2012 Olympic Games at the Basketball Arena in the Olympic Park at Stratford in east London July 29, 2012. [Michelle’s customary Secret Service at her right, and below.]
U.S. First Lady Michelle Obama sits separated from the public during the basketball match between the U.S. and France for the London 2012 Olympic Games at the Basketball Arena in the Olympic Park at Stratford in east London July 29, 2012. [Michelle’s customary Secret Service at her right, and below.]![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict60.jpg) US First Lady Michelle Obama (R) speaks with tennis player Venus Williams (top L) as they attend the women’s singles tennis match between Serbia’s Jelena Jankovic and Serena Williams of the US during the London 2012 Olympic Games at the All England Tennis Club in Wimbledon, southwest London, on July 28, 2012.
US First Lady Michelle Obama (R) speaks with tennis player Venus Williams (top L) as they attend the women’s singles tennis match between Serbia’s Jelena Jankovic and Serena Williams of the US during the London 2012 Olympic Games at the All England Tennis Club in Wimbledon, southwest London, on July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict61.jpg) U.S First Lady Michelle Obama, left, waves an American flag as she cheers on the U.S. swim team during the first day of finals at the 2012 Summer Olympics, Saturday, July 28, 2012, in London. At right is Summer Schlopy, host of Yahoo! Sports’ web series Elite Athlete Workout. [Two Secret Service at left.]
U.S First Lady Michelle Obama, left, waves an American flag as she cheers on the U.S. swim team during the first day of finals at the 2012 Summer Olympics, Saturday, July 28, 2012, in London. At right is Summer Schlopy, host of Yahoo! Sports’ web series Elite Athlete Workout. [Two Secret Service at left.]![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict62.jpg) Agents keep watch as U.S. President Barack Obama (C) walks to the Marine One helicopter before departing from a soccer field at the Madeira School after attending a campaign event at a nearby private residence in McLean, Virginia, July 27, 2012.
Agents keep watch as U.S. President Barack Obama (C) walks to the Marine One helicopter before departing from a soccer field at the Madeira School after attending a campaign event at a nearby private residence in McLean, Virginia, July 27, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict63.jpg) US President Barack Obama walk across a field after stepping off Marine One upon arrival at the Madeira School landing zone July 27, 2012 in McLean, Virginia. Obama is in McLean to attend campaign fundraisers.
US President Barack Obama walk across a field after stepping off Marine One upon arrival at the Madeira School landing zone July 27, 2012 in McLean, Virginia. Obama is in McLean to attend campaign fundraisers.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict64.jpg) President Barack Obama waves as he walks across the football field at Madeira school in McLean, Va. , Friday, July, 27, 2012. Obama Traveled to Northern Virginia for a private fundraiser.
President Barack Obama waves as he walks across the football field at Madeira school in McLean, Va. , Friday, July, 27, 2012. Obama Traveled to Northern Virginia for a private fundraiser.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict65.jpg) US First Lady Michelle Obama plays with children as part of her ‘Let’s Move-London’ event at the Winfield House in London on July 27, 2012, hours before the official start of the London 2012 Olympic Games. [SS at right.
US First Lady Michelle Obama plays with children as part of her ‘Let’s Move-London’ event at the Winfield House in London on July 27, 2012, hours before the official start of the London 2012 Olympic Games. [SS at right.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict66.jpg) U.S. first lady Michelle Obama plays with schoolchildren during a ‘Let’s Move!’ event for about 1,000 American military children and American and British students at the U.S. ambassador’s residence in London, ahead of the 2012 Summer Olympics, Friday, July 27, 2012. [Two Secret Service in suits to hide weapons; at center, female.]
U.S. first lady Michelle Obama plays with schoolchildren during a ‘Let’s Move!’ event for about 1,000 American military children and American and British students at the U.S. ambassador’s residence in London, ahead of the 2012 Summer Olympics, Friday, July 27, 2012. [Two Secret Service in suits to hide weapons; at center, female.]![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict67.jpg) U.S. Secret Service keeps watch as President Barack Obama departs the New Orleans area in Air Force One at Louis Armstrong International Airport in Kenner, La. , Wednesday, July 25, 2012. Obama delivered remarks at the National Urban League 2012 Annual Conference and attended campaign events in New Orleans.
U.S. Secret Service keeps watch as President Barack Obama departs the New Orleans area in Air Force One at Louis Armstrong International Airport in Kenner, La. , Wednesday, July 25, 2012. Obama delivered remarks at the National Urban League 2012 Annual Conference and attended campaign events in New Orleans.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict68.jpg) President Barack Obama walks over to greet people after arriving at Boeing Field in Seattle, Tuesday, July 24, 2012.
President Barack Obama walks over to greet people after arriving at Boeing Field in Seattle, Tuesday, July 24, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict69.jpg) US President Barack Obama greets wellwishers upon arrival on Air Force One at Portland International Airport in Portland, Oregon, July 24, 2012. Obama is traveling to attend campaign events and fundraisers.
US President Barack Obama greets wellwishers upon arrival on Air Force One at Portland International Airport in Portland, Oregon, July 24, 2012. Obama is traveling to attend campaign events and fundraisers.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict70.jpg) Supporters walk in a line across the tarmac to greet President Barack Obama on his arrival at Boeing Field Tuesday, July 24, 2012, in Seattle. Obama is scheduled to attend a pair of campaign fund-raisers in the area.
Supporters walk in a line across the tarmac to greet President Barack Obama on his arrival at Boeing Field Tuesday, July 24, 2012, in Seattle. Obama is scheduled to attend a pair of campaign fund-raisers in the area.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict71.jpg) President Barack Obama heads to his limousine after stopping at the Gateway Breakfast House in Portland, Ore. , Tuesday, July 24, 2012.
President Barack Obama heads to his limousine after stopping at the Gateway Breakfast House in Portland, Ore. , Tuesday, July 24, 2012.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict41.jpg) U.S. President Barack Obama greets people gathered on the sidewalk after stopping for food at Skyline Chili in Cincinnati, July 16, 2012. Obama flew on Monday to Cincinnati for election campaign events. Reuters
U.S. President Barack Obama greets people gathered on the sidewalk after stopping for food at Skyline Chili in Cincinnati, July 16, 2012. Obama flew on Monday to Cincinnati for election campaign events. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict39.jpg) US President Barack Obama greets wellwishers upon arrival on Air Force One at Cincinnati Northern Kentucky International Airport in Boone, Kentucky, July 16, 2012, enroute to attend campaign events in Cincinnati, Ohio. Getty
US President Barack Obama greets wellwishers upon arrival on Air Force One at Cincinnati Northern Kentucky International Airport in Boone, Kentucky, July 16, 2012, enroute to attend campaign events in Cincinnati, Ohio. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict38.jpg) President Barack Obama passes his jacket to White House Trip Director Marvin Nicholson before heading over to greet people after arriving at Northern Kentucky International Airport in Boone, Ky. , Monday, July 16, 2012. Obama is spending the day campaigning in Cincinnati. AP
President Barack Obama passes his jacket to White House Trip Director Marvin Nicholson before heading over to greet people after arriving at Northern Kentucky International Airport in Boone, Ky. , Monday, July 16, 2012. Obama is spending the day campaigning in Cincinnati. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict40.jpg) U.S. Secret Service members use a golf cart while providing protection for President Barack Obama while he golfs at the Army installation’s course July 15, 2012 in Ft. Belvoir, Virginia. Obama also campaigned in Virginia, a state he won in 2008, on Saturday, holding events in Fairfax and Glen Allen. Getty
U.S. Secret Service members use a golf cart while providing protection for President Barack Obama while he golfs at the Army installation’s course July 15, 2012 in Ft. Belvoir, Virginia. Obama also campaigned in Virginia, a state he won in 2008, on Saturday, holding events in Fairfax and Glen Allen. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict31.jpg) US President Barack Obama greets supporters are he arrives at a campaign event on July 14, 2012 at Centreville High School in Clifton, Virginia. Getty
US President Barack Obama greets supporters are he arrives at a campaign event on July 14, 2012 at Centreville High School in Clifton, Virginia. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict32.jpg) U.S. President Barack Obama arrives at a campaign rally at Centreville High School in Clifton, Virginia, July 14, 2012. Obama travelled to Virginia on Saturday for campaign events. Reuters
U.S. President Barack Obama arrives at a campaign rally at Centreville High School in Clifton, Virginia, July 14, 2012. Obama travelled to Virginia on Saturday for campaign events. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict28.jpg) President Barack Obama walks up a set of stairs during a campaign rally at Centreville High School in Clifton, Va. , a Washington suburb, on Saturday, July 14, 2012. AP
President Barack Obama walks up a set of stairs during a campaign rally at Centreville High School in Clifton, Va. , a Washington suburb, on Saturday, July 14, 2012. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict35.jpg) People hold signs protesting against U.S. President Barack Obama along Obama’s motorcade route on his way to a campaign rally at Centreville High School in Clifton, Virginia, July 14, 2012. Obama travelled to Virginia on Saturday for campaign events. Reuters
People hold signs protesting against U.S. President Barack Obama along Obama’s motorcade route on his way to a campaign rally at Centreville High School in Clifton, Virginia, July 14, 2012. Obama travelled to Virginia on Saturday for campaign events. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict30.jpg) President Barack Obama laughs while campaigning under the pouring rain at the historic Walkerton Tavern & Gardens in Glen Allen, Va. , near Richmond Saturday, July 14, 2012. It is in the Congressional district represented by House Majority Leader Eric Cantor, R-Va. , a key county in a crucial swing state of the presidential election. AP
President Barack Obama laughs while campaigning under the pouring rain at the historic Walkerton Tavern & Gardens in Glen Allen, Va. , near Richmond Saturday, July 14, 2012. It is in the Congressional district represented by House Majority Leader Eric Cantor, R-Va. , a key county in a crucial swing state of the presidential election. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict26.jpg) U.S. President Barack Obama greets supporters at the end of his ”A Vision for Virginia’s Middle Class” campaign event July 14, 2012 at Walkerton Tavern in Glen Allen, Virginia. On the last day of his two-day campaign across Virginia, Obama continue to discuss his plan to restore middle class security and urged Congress to act on extending tax cuts to middle class families. Getty
U.S. President Barack Obama greets supporters at the end of his ”A Vision for Virginia’s Middle Class” campaign event July 14, 2012 at Walkerton Tavern in Glen Allen, Virginia. On the last day of his two-day campaign across Virginia, Obama continue to discuss his plan to restore middle class security and urged Congress to act on extending tax cuts to middle class families. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict27.jpg) President Barack Obama campaigns during the pouring rain at the historic Walkerton Tavern & Gardens in Glen Allen, Va. , near Richmond, Saturday, July 14, 2012. AP
President Barack Obama campaigns during the pouring rain at the historic Walkerton Tavern & Gardens in Glen Allen, Va. , near Richmond, Saturday, July 14, 2012. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict37.jpg) Protesters line an entrance route to a campaign event where President Barack Obama is scheduled to speak at the historic Walkerton Tavern & Gardens in Glen Allen, Va. , near Richmond Saturday, July 14, 2012. AP
Protesters line an entrance route to a campaign event where President Barack Obama is scheduled to speak at the historic Walkerton Tavern & Gardens in Glen Allen, Va. , near Richmond Saturday, July 14, 2012. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict36.jpg) Conservative local residents protest prior to U.S. President Barack Obama’s ”A Vision for Virginia’s Middle Class” campaign event July 14, 2012 at Walkerton Tavern in Glen Allen, Virginia. On the last day of his two-day campaign across Virginia, Obama continue to discuss his plan to restore middle class security and urged the Congress to act on extending tax cuts to middle class families. Getty
Conservative local residents protest prior to U.S. President Barack Obama’s ”A Vision for Virginia’s Middle Class” campaign event July 14, 2012 at Walkerton Tavern in Glen Allen, Virginia. On the last day of his two-day campaign across Virginia, Obama continue to discuss his plan to restore middle class security and urged the Congress to act on extending tax cuts to middle class families. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict29.jpg) President Barack Obama removes his jacket upon his arrival at Washington Dulles International Airport in Chantilly, Va. , Saturday, July 14, 2012, for a campaign event in the vicinity. AP
President Barack Obama removes his jacket upon his arrival at Washington Dulles International Airport in Chantilly, Va. , Saturday, July 14, 2012, for a campaign event in the vicinity. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict25.jpg) US President Barack Obama boards his limousine after greeting well-wishers upon arrival July 14, 2012 at Richmond International Airport in Richmond, Virginia. Obama is in Virginia to attend campaign events. Getty
US President Barack Obama boards his limousine after greeting well-wishers upon arrival July 14, 2012 at Richmond International Airport in Richmond, Virginia. Obama is in Virginia to attend campaign events. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict33.jpg) Secret Service members keep watch in front of Air Force One shortly before US President Barack Obama’s departure on July 14, 2012 at Richmond International Airport in Richmond, Virginia. Obama is in Virginia to attend campaign events. Getty
Secret Service members keep watch in front of Air Force One shortly before US President Barack Obama’s departure on July 14, 2012 at Richmond International Airport in Richmond, Virginia. Obama is in Virginia to attend campaign events. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict1.jpg) US President Barack Obama hold up a tomato during a stop at Berry’s Produce on July 14, 2012 in Mechanicsville, Virginia. Obama is campaigning in Virginia ahead of the November presidential election. Getty
US President Barack Obama hold up a tomato during a stop at Berry’s Produce on July 14, 2012 in Mechanicsville, Virginia. Obama is campaigning in Virginia ahead of the November presidential election. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict0.jpg) President Barack Obama shakes hands as he arrives at the Richmond International Airport in Richmond, Va. , Saturday, July 14, 2012. AP
President Barack Obama shakes hands as he arrives at the Richmond International Airport in Richmond, Va. , Saturday, July 14, 2012. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict14.jpg) President Barack Obama greets the crowd after a campaign stop at the historic Fire Station No.1, in downtown Roanoke, Virginia, Friday, July 13, 2012. Obama traveled to southwest Virginia to discuss choice in this election between two fundamentally different visions on how to grow the economy, create middle-class jobs and pay down the debt. AP
President Barack Obama greets the crowd after a campaign stop at the historic Fire Station No.1, in downtown Roanoke, Virginia, Friday, July 13, 2012. Obama traveled to southwest Virginia to discuss choice in this election between two fundamentally different visions on how to grow the economy, create middle-class jobs and pay down the debt. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict15.jpg) President Barack Obama greets the crowd during a campaign stop at the historic Fire Station No.1, in downtown Roanoke, Va. , Friday, July 13, 2012. Obama traveled to southwest Virginia to discuss choice in this election between two fundamentally different visions on how to grow the economy, create middle-class jobs and pay down the debt. AP
President Barack Obama greets the crowd during a campaign stop at the historic Fire Station No.1, in downtown Roanoke, Va. , Friday, July 13, 2012. Obama traveled to southwest Virginia to discuss choice in this election between two fundamentally different visions on how to grow the economy, create middle-class jobs and pay down the debt. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict16.jpg) President Barack Obama greets people after arriving at Roanoke Regional Airport in Roanoke, Va. , Friday, July 13, 2012. Obama is spending the day campaigning in Virginia. AP
President Barack Obama greets people after arriving at Roanoke Regional Airport in Roanoke, Va. , Friday, July 13, 2012. Obama is spending the day campaigning in Virginia. AP
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict20.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict18.jpg) President Barack Obama greets people after arriving at Roanoke Regional Airport in Roanoke, Va. , Friday, July 13, 2012. Obama is spending the day campaigning in Virginia. AP
President Barack Obama greets people after arriving at Roanoke Regional Airport in Roanoke, Va. , Friday, July 13, 2012. Obama is spending the day campaigning in Virginia. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict19.jpg) President Barack Obama arrives at the Roanoke Airport on Air Force One on the campaign trail, Friday, July 13, 2012 in Roanoke, Va. AP
President Barack Obama arrives at the Roanoke Airport on Air Force One on the campaign trail, Friday, July 13, 2012 in Roanoke, Va. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict17.jpg) President Barack Obama greets people after arriving at Roanoke Regional Airport in Roanoke, Va. , Friday, July 13, 2012. Obama is spending the day campaigning in Virginia. AP
President Barack Obama greets people after arriving at Roanoke Regional Airport in Roanoke, Va. , Friday, July 13, 2012. Obama is spending the day campaigning in Virginia. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict22.jpg) President Barack Obama greets the crowd after speaking at a campaign event at Phoebus High School in Hampton, Va. , Friday, July 13, 2012. Obama is spending the day in Virginia campaigning. AP
President Barack Obama greets the crowd after speaking at a campaign event at Phoebus High School in Hampton, Va. , Friday, July 13, 2012. Obama is spending the day in Virginia campaigning. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict21.jpg) President Barack Obama greets the crowd after speaking at a campaign event at Phoebus High School in Hampton, Va. , Friday, July 13, 2012. Obama is spending the day in Virginia campaigning. AP
President Barack Obama greets the crowd after speaking at a campaign event at Phoebus High School in Hampton, Va. , Friday, July 13, 2012. Obama is spending the day in Virginia campaigning. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict24.jpg) President Barack Obama arrives to speak at a campaign event at Phoebus High School in Hampton, Va. , Friday, July 13, 2012. Obama is spending the day in Virginia campaigning. AP
President Barack Obama arrives to speak at a campaign event at Phoebus High School in Hampton, Va. , Friday, July 13, 2012. Obama is spending the day in Virginia campaigning. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict12.jpg) U.S. President Barack Obama (C) greets supporters at the end of his ‘A Vision for Virginia’s Middle Class’ campaign event July 13, 2012 at Green Run High School in Virginia Beach, Virginia. Obama discussed his plan to restore middle class security and urged the Congress to act on extending tax cuts to middle class families. Getty
U.S. President Barack Obama (C) greets supporters at the end of his ‘A Vision for Virginia’s Middle Class’ campaign event July 13, 2012 at Green Run High School in Virginia Beach, Virginia. Obama discussed his plan to restore middle class security and urged the Congress to act on extending tax cuts to middle class families. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict13.jpg) U.S. President Barack Obama (R) greets supporters at the end of his ‘A Vision for Virginia’s Middle Class’ campaign event July 13, 2012 at Green Run High School in Virginia Beach, Virginia. Obama discussed his plan to restore middle class security and urged the Congress to act on extending tax cuts to middle class families. Getty [Two Secret Service in “hands ready” position.
U.S. President Barack Obama (R) greets supporters at the end of his ‘A Vision for Virginia’s Middle Class’ campaign event July 13, 2012 at Green Run High School in Virginia Beach, Virginia. Obama discussed his plan to restore middle class security and urged the Congress to act on extending tax cuts to middle class families. Getty [Two Secret Service in “hands ready” position.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict2.jpg) President Barack Obama reaches out to shake hands at a campaign event at Green Run High School in Virginia Beach, Va. , Friday, July 13, 2012. Obama is spending the day in Virginia campaigning. AP
President Barack Obama reaches out to shake hands at a campaign event at Green Run High School in Virginia Beach, Va. , Friday, July 13, 2012. Obama is spending the day in Virginia campaigning. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict3.jpg) President Barack Obama heads to his car after greeting people after arriving at Norfolk International Airport in Norfolk, Va. , Friday, July 13, 2012. AP
President Barack Obama heads to his car after greeting people after arriving at Norfolk International Airport in Norfolk, Va. , Friday, July 13, 2012. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict4.jpg) President Barack Obama is surrounded by secret service as he greets people after arriving at Norfolk International Airport in Norfolk, Va. , Friday, July 13, 2012. AP
President Barack Obama is surrounded by secret service as he greets people after arriving at Norfolk International Airport in Norfolk, Va. , Friday, July 13, 2012. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict6.jpg) President Barack Obama heads to his car after greeting people after arriving at Norfolk International Airport in Norfolk, Va. , Friday, July 13, 2012. AP
President Barack Obama heads to his car after greeting people after arriving at Norfolk International Airport in Norfolk, Va. , Friday, July 13, 2012. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict5.jpg) President Barack Obama meets with supporters after arriving aboard Air Force One at the Norfolk International Airport in Norfolk, Va. , Friday, July 13, 2012. AP
President Barack Obama meets with supporters after arriving aboard Air Force One at the Norfolk International Airport in Norfolk, Va. , Friday, July 13, 2012. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict7.jpg) President Barack Obama meets with supporters after arriving aboard Air Force One at the Norfolk International Airport in Norfolk, Va. , Friday, July 13, 2012. AP
President Barack Obama meets with supporters after arriving aboard Air Force One at the Norfolk International Airport in Norfolk, Va. , Friday, July 13, 2012. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict8.jpg) President Barack Obama walks to Air Force One at Andrews Air Force Base in Md. , Friday, July 13, 2012, enroute to Virginia for a series of campaign events. AP
President Barack Obama walks to Air Force One at Andrews Air Force Base in Md. , Friday, July 13, 2012, enroute to Virginia for a series of campaign events. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict9.jpg) Members of the media exit a house alongside US President Barack Obama’s SUV holding in the driveway as Obama meets with Jason McLaughlin, principal of Center Point-Urbana High School, his wife, Ali, an account manager for a document scanning company, and their 4-year-old son Cooper, on middle class tax cuts at their home in Cedar Rapids, Iowa, July 10, 2012. Getty
Members of the media exit a house alongside US President Barack Obama’s SUV holding in the driveway as Obama meets with Jason McLaughlin, principal of Center Point-Urbana High School, his wife, Ali, an account manager for a document scanning company, and their 4-year-old son Cooper, on middle class tax cuts at their home in Cedar Rapids, Iowa, July 10, 2012. Getty![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict34.jpg) Secret Service agents guard the door of the home of Jason and Ali McLaughlin while President Barack Obama visits with them in Cedar Rapids, Iowa, Tuesday, July 10, 2012. AP
Secret Service agents guard the door of the home of Jason and Ali McLaughlin while President Barack Obama visits with them in Cedar Rapids, Iowa, Tuesday, July 10, 2012. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict10.jpg) U.S. President Barack Obama arrives in Cedar Rapids, Iowa, July 10, 2012. Obama flew to Iowa for an event pushing for the extension of Bush-era tax cuts due to expire at the end of 2012. Reuters
U.S. President Barack Obama arrives in Cedar Rapids, Iowa, July 10, 2012. Obama flew to Iowa for an event pushing for the extension of Bush-era tax cuts due to expire at the end of 2012. Reuters![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect47/pict11.jpg) President Barack Obama heads to his car after getting ice cream at Deb’s Ice Cream & Deli in Cedar Rapids, Iowa, Tuesday, July 10, 2012. AP
President Barack Obama heads to his car after getting ice cream at Deb’s Ice Cream & Deli in Cedar Rapids, Iowa, Tuesday, July 10, 2012. AP
![[Image]](https://i0.wp.com/cryptome.org/2012/04/cia-john3/pict27.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012/04/cia-john3/pict26.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012/04/cia-john3/pict25.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/wh-missile/pict1.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/wh-missile/pict0.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/wh-missile/pict4.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/wh-missile/pict5.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/wh-missile/pict2.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/wh-missile/pict3.jpg)



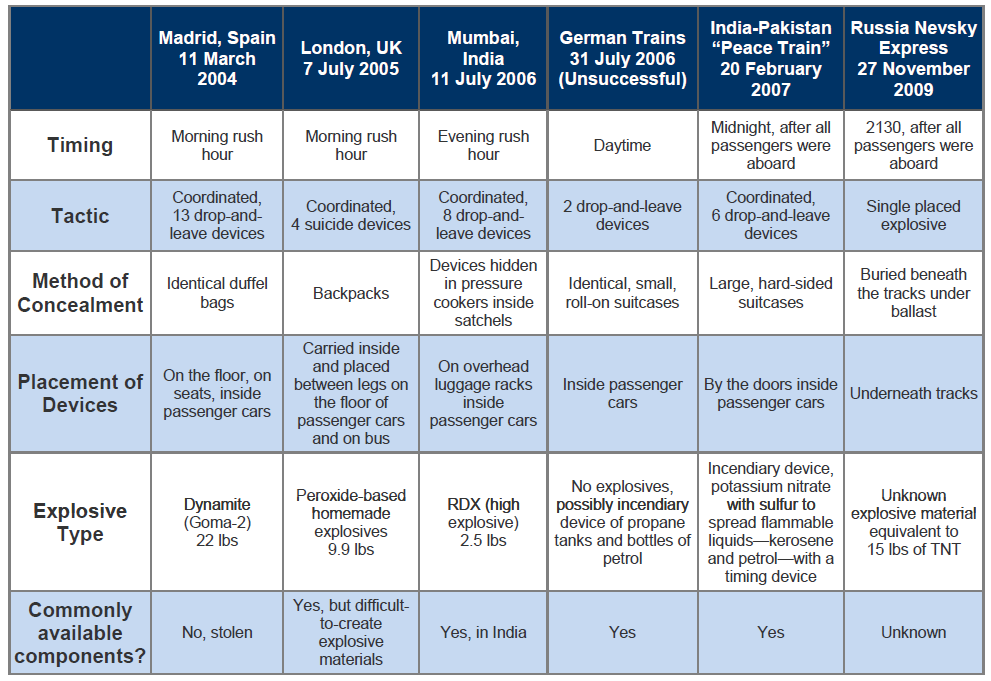







![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict40.jpg) President Barack Obama and Orlando, Fla. Mayor Buddy Dyer, right, walk over to greet onlookers after arriving at Orlando International Airport in Orlando, Fla., Thursday, Jan. 19, 2012. (Haraz N. Ghanbari)
President Barack Obama and Orlando, Fla. Mayor Buddy Dyer, right, walk over to greet onlookers after arriving at Orlando International Airport in Orlando, Fla., Thursday, Jan. 19, 2012. (Haraz N. Ghanbari)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict41.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict42.jpg) President Barack Obama shakes hands with people waiting to greet him on the tarmac as he steps off of Air Force One at Hickam Air Force Base in Friday, Dec. 23, 2011, in Honolulu. (Carolyn Kaster)
President Barack Obama shakes hands with people waiting to greet him on the tarmac as he steps off of Air Force One at Hickam Air Force Base in Friday, Dec. 23, 2011, in Honolulu. (Carolyn Kaster)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict43.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict44.jpg) President Barack Obama visits with patron at PetsMart, Wednesday, Dec. 21, 2011, in Alexandria, Va., where he shopped with his dog Bo. (Carolyn Kaster)
President Barack Obama visits with patron at PetsMart, Wednesday, Dec. 21, 2011, in Alexandria, Va., where he shopped with his dog Bo. (Carolyn Kaster)![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict50.jpg) President Barack Obama, accompanied by his security personnel, walks through a White House gate prior to crossing Pennsylvania Avenue heading to the Blair House to attend a holiday party, Friday, Dec. 9, 2011, in Washington. (Carolyn Kaster)
President Barack Obama, accompanied by his security personnel, walks through a White House gate prior to crossing Pennsylvania Avenue heading to the Blair House to attend a holiday party, Friday, Dec. 9, 2011, in Washington. (Carolyn Kaster)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict51.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict52.jpg) President Barack Obama greets people on the tarmac upon his arrival at Kansas City International Airport, Tuesday, Dec. 6, 2011, in Kansas City , Mo. (Carolyn Kaster)
President Barack Obama greets people on the tarmac upon his arrival at Kansas City International Airport, Tuesday, Dec. 6, 2011, in Kansas City , Mo. (Carolyn Kaster)![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict46.jpg) In this Nov. 30, 2011, file photo, President Barack Obama walks to his motorcade with members of security after visiting with Patrick and Donna Festa in their Scranton, Pa. home.
In this Nov. 30, 2011, file photo, President Barack Obama walks to his motorcade with members of security after visiting with Patrick and Donna Festa in their Scranton, Pa. home.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict47.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict48.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict53.jpg) President Barack Obama greets members of the Towson University football team during half time as he and first lady Michelle Obama, not seen, attend the Oregon State versus Towson NCAA college basketball game at Towson University Saturday, Nov. 26, 2011, in Towson, Md. (Carolyn Kaster)
President Barack Obama greets members of the Towson University football team during half time as he and first lady Michelle Obama, not seen, attend the Oregon State versus Towson NCAA college basketball game at Towson University Saturday, Nov. 26, 2011, in Towson, Md. (Carolyn Kaster)![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict54.jpg) As Secret Service agents watch, President Barack Obama embraces a girl following an address where he remarked on the American Jobs Act, Tuesday, Nov. 22, 2011, at Central High School in Manchester, N.H. (Charles Krupa)
As Secret Service agents watch, President Barack Obama embraces a girl following an address where he remarked on the American Jobs Act, Tuesday, Nov. 22, 2011, at Central High School in Manchester, N.H. (Charles Krupa)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict55.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict56.jpg) President Barack Obama arrives in Manchester, N.H., Tuesday, Nov. 22, 2011. President Obama will travel to Manchester High School Central to discuss the American Jobs Act. (Cheryl Senter)
President Barack Obama arrives in Manchester, N.H., Tuesday, Nov. 22, 2011. President Obama will travel to Manchester High School Central to discuss the American Jobs Act. (Cheryl Senter)![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict57.jpg) U.S. President Barack Obama walks as he attends the East Asia Summit at Nusa Dua, Bali, Indonesia on Saturday Nov. 19, 2011. (Aaron Favila)
U.S. President Barack Obama walks as he attends the East Asia Summit at Nusa Dua, Bali, Indonesia on Saturday Nov. 19, 2011. (Aaron Favila)![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict58.jpg) President Barack Obama greets Australian troops during a visit to the Royal Army Air Force Base in Darwin, Australia, Thursday, Nov. 17, 2011. (Charles Dharapak)
President Barack Obama greets Australian troops during a visit to the Royal Army Air Force Base in Darwin, Australia, Thursday, Nov. 17, 2011. (Charles Dharapak)![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict59.jpg) President Barack Obama talks with Medal of Honor recipient John Baca before the start of the Carrier Classic NCAA basketball game between North Carolina and Michigan State on the flight deck of the USS Carl Vinson in Coronado, Calif., Friday, Nov. 11, 2011. (Susan Walsh)
President Barack Obama talks with Medal of Honor recipient John Baca before the start of the Carrier Classic NCAA basketball game between North Carolina and Michigan State on the flight deck of the USS Carl Vinson in Coronado, Calif., Friday, Nov. 11, 2011. (Susan Walsh)![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict60.jpg) President Barack Obama and French President Nicolas Sarkozy walk together after arriving at an event outside City Hall in Cannes, France, Friday, Nov. 4, 2011. The two leaders were at a memorial to World Wars I and II. (Susan Walsh)
President Barack Obama and French President Nicolas Sarkozy walk together after arriving at an event outside City Hall in Cannes, France, Friday, Nov. 4, 2011. The two leaders were at a memorial to World Wars I and II. (Susan Walsh)![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict61.jpg) President Barack Obama arrives to speak about managing student debt during an event at the University of Colorado Denver Downtown Campus in Denver, Wednesday, Oct. 26, 2011. Denver is the final stop on a three-day trip to the West Coast for fundraising and speeches promoting his American Jobs Act. (Susan Walsh)
President Barack Obama arrives to speak about managing student debt during an event at the University of Colorado Denver Downtown Campus in Denver, Wednesday, Oct. 26, 2011. Denver is the final stop on a three-day trip to the West Coast for fundraising and speeches promoting his American Jobs Act. (Susan Walsh)![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict62.jpg) President Barack Obama walks out of Roscoe’s House of Chicken and Waffles in Los Angeles, Monday, Oct. 24, 2011, with Rep. Karen Bass, D-Calif., after ordering a snack. Obama is on a three-day trip to the West Coast. (Susan Walsh)
President Barack Obama walks out of Roscoe’s House of Chicken and Waffles in Los Angeles, Monday, Oct. 24, 2011, with Rep. Karen Bass, D-Calif., after ordering a snack. Obama is on a three-day trip to the West Coast. (Susan Walsh)![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict63.jpg) President Barack Obama greets after exiting Air Force One after arriving at McCarran International Airport in Las Vegas Monday, Oct. 24, 2011. (John Gurzinski)
President Barack Obama greets after exiting Air Force One after arriving at McCarran International Airport in Las Vegas Monday, Oct. 24, 2011. (John Gurzinski)![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict64.jpg) President Barack Obama talks on the phone as he greets people outside the Reid’s House Restaurant in Reidsville, N.C., Tuesday, Oct. 18, 2011. Obama is on a three-day bus tour promoting the American Jobs Act. (Susan Walsh)
President Barack Obama talks on the phone as he greets people outside the Reid’s House Restaurant in Reidsville, N.C., Tuesday, Oct. 18, 2011. Obama is on a three-day bus tour promoting the American Jobs Act. (Susan Walsh)![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict66.jpg) President Barack Obama poses for a photo after speaking at West Wilkes High School in Millers Creek, N.C., on Monday, Oct. 17, 2011. (Terry Renna)
President Barack Obama poses for a photo after speaking at West Wilkes High School in Millers Creek, N.C., on Monday, Oct. 17, 2011. (Terry Renna)![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict67.jpg) President Barack Obama walks to his bus after stopping at the Countryside Barbeque in Marion in N.C., Monday, Oct. 17, 2011. Obama is on a three-day bus tour promoting the American Jobs Act. (Susan Walsh)
President Barack Obama walks to his bus after stopping at the Countryside Barbeque in Marion in N.C., Monday, Oct. 17, 2011. Obama is on a three-day bus tour promoting the American Jobs Act. (Susan Walsh)![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict68.jpg) President Barack Obama walks around his bus at Asheville Regional Airport in Fletcher, N.C., Monday, Oct. 17, 2011, to begin his three-day bus tour promoting the American Jobs Act. (Susan Walsh)
President Barack Obama walks around his bus at Asheville Regional Airport in Fletcher, N.C., Monday, Oct. 17, 2011, to begin his three-day bus tour promoting the American Jobs Act. (Susan Walsh)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect45/pict69.jpg)
![[Image]](https://i0.wp.com/cryptome.org/0006/cia-john2/pict31.jpg) “This is a composite of several images of the President and his national security team during a series of meetings in the Situation Room of the White House discussing the mission against Osama bin Laden on Sunday, May 1. We put this together so in addition to the previous, now iconic image of this day, people might have a better sense of what it’s like in presidential meetings of historic significance.” (Official White House Photo by Pete Souza)
“This is a composite of several images of the President and his national security team during a series of meetings in the Situation Room of the White House discussing the mission against Osama bin Laden on Sunday, May 1. We put this together so in addition to the previous, now iconic image of this day, people might have a better sense of what it’s like in presidential meetings of historic significance.” (Official White House Photo by Pete Souza)![[Image]](https://i0.wp.com/cryptome.org/0006/cia-john2/pict32.jpg)
![[Image]](https://i0.wp.com/cryptome.org/0006/cia-john2/pict33.jpg)
![[Image]](https://i0.wp.com/cryptome.org/0004/cia-john/pict26.jpg) President Barack Obama and Vice President Joe Biden, along with members of the national security team, receive an update on the mission against Osama bin Laden in the Situation Room of the White House, May 1, 2011. (Official White House Photo by Pete Souza)
President Barack Obama and Vice President Joe Biden, along with members of the national security team, receive an update on the mission against Osama bin Laden in the Situation Room of the White House, May 1, 2011. (Official White House Photo by Pete Souza)
![[Image]](https://i0.wp.com/cryptome.org/0004/cia-john/pict27.jpg)
![[Image]](https://i0.wp.com/cryptome.org/0004/cia-john/pict29.jpg)

![[Image]](https://i0.wp.com/cryptome.org/0004/cia-john/pict28.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-moron/pict2.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-moron/pict3.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-moron/pict4.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict1.jpg) On his first day in office, President Barack Obama speaks with a foreign leader in the Oval Office, Jan. 21, 2009. (Official White House Photo by Pete Souza)
On his first day in office, President Barack Obama speaks with a foreign leader in the Oval Office, Jan. 21, 2009. (Official White House Photo by Pete Souza)![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict0.jpg) President Barack Obama places a phone call at his desk in the Oval Office, Jan. 23, 2009. (Official White House Photo by Pete Souza) [This is a Raytheon IST secure phone.
President Barack Obama places a phone call at his desk in the Oval Office, Jan. 23, 2009. (Official White House Photo by Pete Souza) [This is a Raytheon IST secure phone. ![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict4.jpg) President Barack Obama meets with Interior Secretary Ken Salazar aboard Air Force One during a flight to Denver, Col., Feb. 17, 2009. (Official White House Photo by Pete Souza) [Desk phone is a
President Barack Obama meets with Interior Secretary Ken Salazar aboard Air Force One during a flight to Denver, Col., Feb. 17, 2009. (Official White House Photo by Pete Souza) [Desk phone is a ![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict8.jpg) [Phone at Oval Office seating area] President Obama has a briefing with a staff member prior to a phone call in the Oval Office, March 13, 2009. (Official White House Photo by Pete Souza)
[Phone at Oval Office seating area] President Obama has a briefing with a staff member prior to a phone call in the Oval Office, March 13, 2009. (Official White House Photo by Pete Souza)![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict11.jpg) President Barack Obama is seen at a meeting with his staff April 5, 2009, aboard Air Force One on a flight from Prague, Czech Republic en route to Ankara, Turkey. (Official White House Photo by Pete Souza)
President Barack Obama is seen at a meeting with his staff April 5, 2009, aboard Air Force One on a flight from Prague, Czech Republic en route to Ankara, Turkey. (Official White House Photo by Pete Souza)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict12.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict13.jpg) President Barack Obama works with Jon Favreau, director of speechwriting, on the President’s Normandy speech aboard Air Force One enroute to Paris on June 5, 2009. (Official White House photo by Pete Souza)
President Barack Obama works with Jon Favreau, director of speechwriting, on the President’s Normandy speech aboard Air Force One enroute to Paris on June 5, 2009. (Official White House photo by Pete Souza)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict14.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict15.jpg) President Barack Obama confers with Senior Advisor David Axelrod and Press Secretary Robert Gibbs at their hotel in Moscow, Russia, July 6, 2009. (Official White House Photo by Pete Souza) [Enlarged from small image.]
President Barack Obama confers with Senior Advisor David Axelrod and Press Secretary Robert Gibbs at their hotel in Moscow, Russia, July 6, 2009. (Official White House Photo by Pete Souza) [Enlarged from small image.]![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict16.jpg) President Barack Obama meets with John Brennan, Assistant to the President for Counterterrorism and Homeland Security, in the Oval Office, Jan. 4, 2010. (Official White House photo by Pete Souza) [Two phones, top for secure, bottom White House phone system.]
President Barack Obama meets with John Brennan, Assistant to the President for Counterterrorism and Homeland Security, in the Oval Office, Jan. 4, 2010. (Official White House photo by Pete Souza) [Two phones, top for secure, bottom White House phone system.]
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict17.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict18.jpg) “This is a rare look inside the President’s Treaty Room office in the private residence of the White House. He was making a call to Poland Prime Minister Donald Tusk.” (Official White House photo by Pete Souza)
“This is a rare look inside the President’s Treaty Room office in the private residence of the White House. He was making a call to Poland Prime Minister Donald Tusk.” (Official White House photo by Pete Souza)![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict19.jpg) March 29, 2009. “It was a Sunday night in the Oval Office. The auto task force listened to the President before he made phone calls to alert key people about his plan to set deadlines for General Motors and Chrysler overhauls that was to be announced the next morning.” (Official White House photo by Pete Souza)
March 29, 2009. “It was a Sunday night in the Oval Office. The auto task force listened to the President before he made phone calls to alert key people about his plan to set deadlines for General Motors and Chrysler overhauls that was to be announced the next morning.” (Official White House photo by Pete Souza)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict20.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict21.jpg) President Barack Obama meets with Rep. Dennis Kucinich, D-Ohio, aboard Air Force One en route to Cleveland, Ohio, March 15, 2010. (Official White House Photo by Pete Souza) [The desk phone is a
President Barack Obama meets with Rep. Dennis Kucinich, D-Ohio, aboard Air Force One en route to Cleveland, Ohio, March 15, 2010. (Official White House Photo by Pete Souza) [The desk phone is a ![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict22.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict23.jpg) President Barack Obama checks his BlackBerry as he walks along the Colonnade to the Oval Office, March 18, 2010. (Official White House Photo by Pete Souza)
President Barack Obama checks his BlackBerry as he walks along the Colonnade to the Oval Office, March 18, 2010. (Official White House Photo by Pete Souza)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict24.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict25.jpg) President Barack Obama talks on the phone with a Member of Congress while en route to a health care event at George Mason University in Fairfax, Va., March 19, 2010. Assistant to the President for Legislative Affairs Phil Schiliro rides with the President. (Official White House Photo by Pete Souza) [A sends ” [The device between the seats under the seal is unknown. Not all presidential vehicles have it. There is a phone in the console.]
President Barack Obama talks on the phone with a Member of Congress while en route to a health care event at George Mason University in Fairfax, Va., March 19, 2010. Assistant to the President for Legislative Affairs Phil Schiliro rides with the President. (Official White House Photo by Pete Souza) [A sends ” [The device between the seats under the seal is unknown. Not all presidential vehicles have it. There is a phone in the console.]
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict2.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict27.jpg) President Barack Obama talks on the phone in a holding room at Oakley Lindsay Center in Quincy, Ill., April 28, 2010. Mona Sutphen, deputy chief of staff for policy, sits at right. (Official White House Photo by Pete Souza) [Phones are L-3 STE model:
President Barack Obama talks on the phone in a holding room at Oakley Lindsay Center in Quincy, Ill., April 28, 2010. Mona Sutphen, deputy chief of staff for policy, sits at right. (Official White House Photo by Pete Souza) [Phones are L-3 STE model: ![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict28.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict29.jpg) President Barack Obama talks on the phone with German Chancellor Angela Merkel to discuss the economic situation in Europe, prior to the Hampton University commencement in Hampton, Va., Sunday, May 9, 2010. (Official White House Photo by Pete Souza)
President Barack Obama talks on the phone with German Chancellor Angela Merkel to discuss the economic situation in Europe, prior to the Hampton University commencement in Hampton, Va., Sunday, May 9, 2010. (Official White House Photo by Pete Souza)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict30.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict31.jpg) President Barack Obama talks with Alyssa Mastromonaco, director of scheduling and advance, in the Outer Oval Office, May 24, 2010. (Official White House Photo by Pete Souza) [Three types of phones sets, perhaps for three different systems.]
President Barack Obama talks with Alyssa Mastromonaco, director of scheduling and advance, in the Outer Oval Office, May 24, 2010. (Official White House Photo by Pete Souza) [Three types of phones sets, perhaps for three different systems.]![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-phones/pict32.jpg) President Barack Obama prepares for foreign leader phone calls with Nigerian President Goodluck Jonathan and Japanese Prime Minister designate Naoto Kan, in the Oval Office, Saturday, June 5, 2010. Pictured, from left, are Michelle Gavin, senior director for African Affairs, Puneet Talwar, senior director for Iraq, Iran and the Gulf States, John Buchanan (on phone), director of operations and deputy director of the White House Situation Room, and National Security Advisor Gen. James Jones. (Official White House Photo by Pete Souza) [A phone technician apparently arranging a secure hook-up.]
President Barack Obama prepares for foreign leader phone calls with Nigerian President Goodluck Jonathan and Japanese Prime Minister designate Naoto Kan, in the Oval Office, Saturday, June 5, 2010. Pictured, from left, are Michelle Gavin, senior director for African Affairs, Puneet Talwar, senior director for Iraq, Iran and the Gulf States, John Buchanan (on phone), director of operations and deputy director of the White House Situation Room, and National Security Advisor Gen. James Jones. (Official White House Photo by Pete Souza) [A phone technician apparently arranging a secure hook-up.]



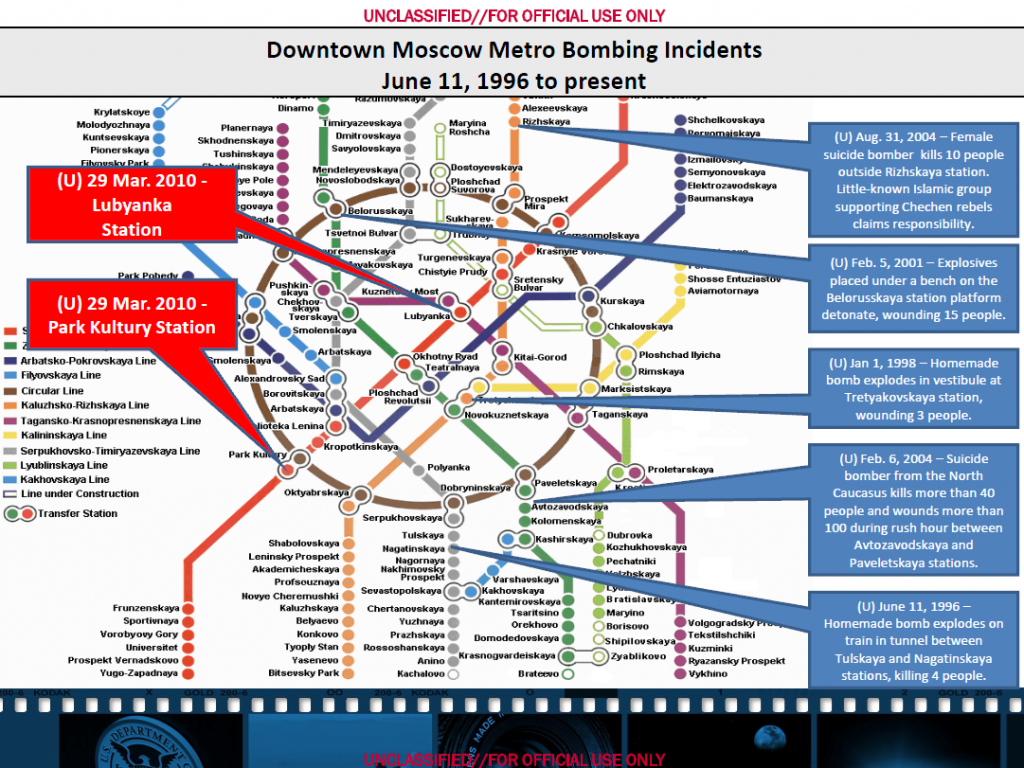













You must be logged in to post a comment.