July 6, 2011 in Russia
This “previously confidential list of people and organizations found to be involved in laundering money and funding terrorism” was presented by Rossiyskaya Gazeta, the Russian-government owned newspaper. It was originally compiled by the Russian Ministry of Justice. A rough, Google translation is also presented [in brackets] alongside the headings in Russian.
Организации и физические лица, включенные в перечень на основании подпунктов 1 – 3 пункта 2.1 статьи 6 Федерального закона от 7 августа 2001 г. N 115-ФЗ “О противодействии легализации (отмыванию) доходов, полученных преступным путем, и финансированию терроризма”
[Organizations and individuals included in the list by virtue of subsections 1 – 3 of paragraph 2.1 of Article 6 of the Federal Law of 7 August 2001 N 115-FZ “On Combating Legalization (Laundering) of Proceeds from Crime and Terrorist Financing”]
Организации [Organizations]
1. АЛЬ-КАИДА В СТРАНАХ ИСЛАМСКОГО МАГРИБА (ПРЕЖНЕЕ НАЗВАНИЕ САЛАФИСТСКАЯ ГРУППА ПРОПОВЕДИ И ДЖИХАДА)*.
2. АСБАТ АЛЬ-АНСАР*.
3. БАЗА (АЛЬ-КАИДА)*.
4. БРАТЬЯ-МУСУЛЬМАНЕ (АЛЬ-ИХВАН АЛЬ-МУСЛИМУН)*.
5. ВЫСШИЙ ВОЕННЫЙ МАДЖЛИСУЛЬ ШУРА ОБЪЕДИНЕННЫХ СИЛ МОДЖАХЕДОВ КАВКАЗА*.
6. ГРУППА ДЖАМААТ МУВАХИДОВ.
7. ДВИЖЕНИЕ ТАЛИБАН*.
8. ДЖУНД АШ-ШАМ*.
9. ДОМ ДВУХ СВЯТЫХ (АЛЬ-ХАРАМЕЙН)*.
10. ИМАРАТ КАВКАЗ (КАВКАЗСКИЙ ЭМИРАТ)*.
11. ИСЛАМСКАЯ ГРУППА (АЛЬ-ГАМАА АЛЬ-ИСЛАМИЯ)*.
12. ИСЛАМСКАЯ ГРУППА (ДЖАМААТ-И-ИСЛАМИ)*.
13. ИСЛАМСКАЯ ПАРТИЯ ТУРКЕСТАНА (бывшее ИСЛАМСКОЕ ДВИЖЕНИЕ УЗБЕКИСТАНА)*.
14. ИСЛАМСКИЙ ДЖИХАД-ДЖАМААТ МОДЖАХЕДОВ*.
15. КАБАРДИНО-БАЛКАРСКАЯ РЕГИОНАЛЬНАЯ ОБЩЕСТВЕННАЯ ОРГАНИЗАЦИЯ СОВЕТ СТАРЕЙШИН БАЛКАРСКОГО НАРОДА КБР; ИНН: 0721013951; Рег.номер: 1060700000118; г. Нальчик Кабардино-Балкарская Республика, пр. Ленина, д. 7 “а”, офис 110.
16. КОНГРЕСС НАРОДОВ ИЧКЕРИИ И ДАГЕСТАНА*.
17. ЛАШКАР-И-ТАЙБА*.
18. МЕЖДУНАРОДНАЯ РЕЛИГИОЗНАЯ ОРГАНИЗАЦИЯ НУРДЖУЛАР.
19. МЕЖДУНАРОДНОЕ ОБЩЕСТВЕННОЕ ОБЪЕДИНЕНИЕ НАЦИОНАЛ-СОЦИАЛИСТИЧЕСКОЕ ОБЩЕСТВО (НСО, НС).
20. МЕЖДУНАРОДНОЕ РЕЛИГИОЗНОЕ ОБЪЕДИНЕНИЕ АТ-ТАКФИР ВАЛЬ-ХИДЖРА.
21. МЕЖДУНАРОДНОЕ РЕЛИГИОЗНОЕ ОБЪЕДИНЕНИЕ ТАБЛИГИ ДЖАМААТ.
22. МЕЖРЕГИОНАЛЬНАЯ ОБЩЕСТВЕННАЯ ОРГАНИЗАЦИЯ ДВИЖЕНИЕ ПРОТИВ НЕЛЕГАЛЬНОЙ ИММИГРАЦИИ.
23. МЕЖРЕГИОНАЛЬНАЯ ОБЩЕСТВЕННАЯ ОРГАНИЗАЦИЯ НАЦИОНАЛ-БОЛЬШЕВИСТСКАЯ ПАРТИЯ.
24. МЕЖРЕГИОНАЛЬНОЕ ОБЩЕСТВЕННОЕ ДВИЖЕНИЕ АРМИЯ ВОЛИ НАРОДА.
25. МЕЖРЕГИОНАЛЬНОЕ ОБЩЕСТВЕННОЕ ОБЪЕДИНЕНИЕ ДУХОВНО-РОДОВАЯ ДЕРЖАВА РУСЬ.
26. МЕЖРЕГИОНАЛЬНОЕ ОБЩЕСТВЕННОЕ ОБЪЕДИНЕНИЕ ФОРМАТ-18.
27. МЕСТНАЯ ОРГАНИЗАЦИЯ ГОРОДА КРАСНОДАРА ПИТ БУЛЬ (PIT BULL); г. Краснодар, ул. Гудимы, д. 32, кв. 99.
28. МЕСТНАЯ РЕЛИГИОЗНАЯ ОРГАНИЗАЦИЯ АСГАРДСКАЯ СЛАВЯНСКАЯ ОБЩИНА ДУХОВНОГО УПРАВЛЕНИЯ АСГАРДСКОЙ ВЕСИ БЕЛОВОДЬЯ ДРЕВНЕРУССКОЙ ИНГЛИИСТИЧЕСКОЙ ЦЕРКВИ ПРАВОСЛАВНЫХ СТАРОВЕРОВ-ИНГЛИНГОВ; г. Омск; г.Омск, ул.Ивана Воронкова, 29-а.
29. МЕСТНАЯ РЕЛИГИОЗНАЯ ОРГАНИЗАЦИЯ СВИДЕТЕЛИ ИЕГОВЫ ТАГАНРОГ.
30. МЕСТНАЯ РЕЛИГИОЗНАЯ ОРГАНИЗАЦИЯ СЛАВЯНСКАЯ ОБЩИНА КАПИЩА ВЕДЫ ПЕРУНА ДУХОВНОГО УПРАВЛЕНИЯ АСГАРДСКОЙ ВЕСИ БЕЛОВОДЬЯ ДРЕВНЕРУССКОЙ ИНГЛИИСТИЧЕСКОЙ ЦЕРКВИ ПРАВОСЛАВНЫХ СТАРОВЕРОВ-ИНГЛИНГОВ; г. Омск; г.Омск, ул.Ивана Воронкова, 29-а.
31. МОСКОВСКАЯ ГОРОДСКАЯ ОРГАНИЗАЦИЯ МЕЖРЕГИОНАЛЬНОГО ОБЩЕСТВЕННОГО ДВИЖЕНИЯ СЛАВЯНСКИЙ СОЮЗ.
32. ОБЩЕСТВЕННОЕ НЕЗАРЕГИСТРИРОВАННОЕ ОБЪЕДИНЕНИЕ ГРУППА РАДА ЗЕМЛИ КУБАНСКОЙ ДУХОВНО РОДОВОЙ ДЕРЖАВЫ РУСЬ; г. Краснодар, ул. Коммунаров, д. 221.
33. ОБЩЕСТВЕННОЕ ОБЪЕДИНЕНИЕ АХТУБИНСКОЕ НАРОДНОЕ ДВИЖЕНИЕ К БОГОДЕРЖАВИЮ.
34. ОБЩЕСТВЕННОЕ ОБЪЕДИНЕНИЕ КУЗБАССКАЯ ОБЩЕСТВЕННАЯ ОРГАНИЗАЦИЯ СЛАВЯНСКИЙ МИР.
35. ОБЩЕСТВЕННОЕ ОБЪЕДИНЕНИЕ ОМСКАЯ ОРГАНИЗАЦИЯ ОБЩЕСТВЕННОГО ПОЛИТИЧЕСКОГО ДВИЖЕНИЯ РУССКОЕ НАЦИОНАЛЬНОЕ ЕДИНСТВО.
36. ОБЩЕСТВО ВОЗРОЖДЕНИЯ ИСЛАМСКОГО НАСЛЕДИЯ (ДЖАМИЯТ ИХЬЯ АТ-ТУРАЗ АЛЬ-ИСЛАМИ)*.
37. ОБЩЕСТВО СОЦИАЛЬНЫХ РЕФОРМ (ДЖАМИЯТ АЛЬ-ИСЛАХ АЛЬ-ИДЖТИМАИ)*.
38. ОБЪЕДИНЕННЫЙ ВИЛАЙАТ КАБАРДЫ, БАЛКАРИИ И КАРАЧАЯ.
39. ПАРТИЯ ИСЛАМСКОГО ОСВОБОЖДЕНИЯ (ХИЗБ УТ-ТАХРИР АЛЬ-ИСЛАМИ)*.
40. ПРИМОРСКАЯ РЕГИОНАЛЬНАЯ ПРАВОЗАЩИТНАЯ ОБЩЕСТВЕННАЯ ОРГАНИЗАЦИЯ СОЮЗ СЛАВЯН; ИНН: 2540087611; Рег. номер: 1082500000318; 690019, г. Владивосток, ул. Алеутская, д. 45А, офис 120.
41. РЕГИОНАЛЬНОЕ ОБЩЕСТВЕННОЕ ОБЪЕДИНЕНИЕ НАЦИОНАЛ-СОЦИАЛИСТИЧЕСКАЯ РАБОЧАЯ ПАРТИЯ РОССИИ (НСРПР).
42. РЕЛИГИОЗНАЯ ГРУППА БЛАГОРОДНЫЙ ОРДЕН ДЬЯВОЛА.
43. РЕЛИГИОЗНАЯ ГРУППА КРАСНОДАРСКАЯ ПРАВОСЛАВНАЯ СЛАВЯНСКАЯ ОБЩИНА “ВЕК РА” (ВЕДИЧЕСКОЙ КУЛЬТУРЫ РОССИЙСКИХ АРИЕВ) СКИФСКОЙ ВЕСИ РАССЕНИИ.
44. РЕЛИГИОЗНАЯ ОРГАНИЗАЦИЯ МУЖСКАЯ ДУХОВНАЯ СЕМИНАРИЯ ДУХОВНОЕ УЧРЕЖДЕНИЕ ПРОФЕССИОНАЛЬНОГО РЕЛИГИОЗНОГО ОБРАЗОВАНИЯ ДРЕВНЕРУССКОЙ ИНГЛИИСТИЧЕСКОЙ ЦЕРКВИ ПРАВОСЛАВНЫХ СТАРОВЕРОВ-ИНГЛИНГОВ; г. Омск; г. Омск, ул. Ивана Воронкова, 29-а.
45. РЯЗАНСКАЯ ГОРОДСКАЯ ОБЩЕСТВЕННАЯ ПАТРИОТИЧЕСКАЯ ОРГАНИЗАЦИЯ РУССКОЕ НАЦИОНАЛЬНОЕ ЕДИНСТВО.
46. СВЯЩЕННАЯ ВОЙНА (АЛЬ-ДЖИХАД ИЛИ ЕГИПЕТСКИЙ ИСЛАМСКИЙ ДЖИХАД)*.
Физические лица [Individuals]
1. АБАЕВ АЛИХАН АБДИЕВИЧ*, 19.12.1986 г.р., с. Сельментаузе Веденского района ЧИАССР.
2. АБАЕВ АСЛАНБЕК БАУДИНОВИЧ*, 29.05.1983 г.р., г. Грозный ЧИАССР.
3. АБАКАРОВ МАГОМЕД ГАСАНОВИЧ*, 12.07.1983 г.р., ст. Бороздиновская Шелковского района ЧИАССР.
4. АБАСИЛОВ МАГОМЕД ПАХРУДИНОВИЧ*, 27.02.1972 г.р., с. Стальское Кизилюртовского района Республики Дагестан.
5. АБДЕЛЬ АЗИЗ МАХАММЕД АБДЕЛЬ ВАХАТ*, 07.09.1959 г.р., г. Мосул, Ирак.
6. АБДРАХМАНОВ АДЛАН АМСАДОВИЧ*, 03.07.1975 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
7. АБДУЛАЕВ ПАТАХ МАГОМЕДОВИЧ*, 18.02.1973 г.р., с. Гимры Унцукульского района Республики Дагестан.
8. АБДУЛАЕВ ШАМИЛЬ ХАРОНОВИЧ*, 18.01.1980 г.р., с. Уч-Арал Талды-Курганской области Казахской ССР.
9. АБДУЛВАГАБОВ РУСЛАН КАЗБЕКОВИЧ*, 09.05.1978 г.р., ст. Каргалинская Шелковского района ЧИАССР.
10. АБДУЛВАГАПОВ САЙД-МАГОМЕД АБУТАЛИПОВИЧ*, 31.07.1980 г.р., с. Шаами-Юрт ЧИАССР.
11. АБДУЛВАХАБОВ РУСЛАН МИЦИЕВИЧ*, 29.01.1980 г.р., с. Закан-Юрт Ачхой-Мартановского района ЧИАССР.
12. АБДУЛКАДЫРОВ АБДУЛКАДЫР ГАДЖИЕВИЧ*, 07.09.1959 г.р., с. Кудали Гунибского района Республики Дагестан.
13. АБДУЛКАДЫРОВ РУСЛАН РАМЗАНОВИЧ*, 23.07.1980 г.р., с. Урус-Мартан Урус-Мартановского района Чеченской Республики.
14. АБДУЛКАДЫРОВ ШАМСУДИ САЙТХУСЕЙНОВИЧ*, 06.03.1981 г.р., с. Яшкуль Яшкульского района Калмыцкой АССР.
15. АБДУЛКАРИМОВ МАГОМЕД УСМАНОВИЧ*, 21.01.1974 г.р., с. Муцалаул Хасавюртовского района Республики Дагестан.
16. АБДУЛЛАЕВ АДАМ МОЛДИЕВИЧ (АБДУЛАЕВ АДАМ МОЛДИЕВИЧ)*, 20.05.1985 г.р., с. Алхан-Юрт Урус-Мартановского района ЧИАССР (20.05.1985 г.р., с. Алхан-Юрт Урус-Мартановского района ЧИАССР).
17. АБДУЛМАЖИДОВ АХМАД ДЕНИЕВИЧ*, 25.10.1981 г.р., с. Алхан-Юрт Урус-Мартановского района ЧИАССР.
18. АБДУЛХАДЖИЕВ ЗЕЛИМХАН ЗАНДИЕВИЧ*, 31.07.1975 г.р., г. Грозный ЧИАССР.
19. АБДУРАЗАКОВ АБДУРАЗАК МАГОМЕДОВИЧ*, 22.01.1961 г.р., г. Буйнакск Республики Дагестан.
20. АБДУРАЗАКОВ МУРАД САЛИМОВИЧ*, 23.11.1968 г.р., с. Хоточ Гунибского района Республики Дагестан.
21. АБДУРАХМАНОВ АСЛАМБЕК САЙХАНОВИЧ*, 21.06.1975 г.р., с. Курчалой ЧИАССР.
22. АБДУРАХМАНОВ ТУРПАЛ АЛИ ИЗМУТДИНОВИЧ*, 04.11.1966 г.р., с. Замьяны Астраханской обл.
23. АБДУРАХМАНОВ ШАМИЛЬ ХАНСОЛТАЕВИЧ*, 15.11.1990 г.р., с. Байтарки Ножай-Юртовского района ЧИАССР.
24. АБДУРАШИДОВ МОХМАТСЕЛАХ АБДУЛВАХИДОВИЧ*, 14.08.1965 г.р., с. Кошкельды Гудермесского района Чеченской Республики.
25. АБЖАВАТОВ АРТУР АБАКАРОВИЧ*, 26.11.1983 г.р., г. Махачкала Республики Дагестан.
26. АБСАЛИМОВ РУСТАМ САПИРОВИЧ*, 28.08.1976 г.р., г. Махачкала Республики Дагестан.
27. АБУБАКАРОВ ИЛЬЯС АХМЕТОВИЧ*, 24.10.1984 г.р., г. Грозный Чеченской Республики.
28. АБУБАКАРОВ ИЛЬЯС МУСАЕВИЧ*, 14.09.1979 г.р., с. Мескер-Юрт Шалинского р-на ЧИАССР.
29. АБУБАКАРОВ ЛЕМА ДЕНИСОЛТАНОВИЧ*, 10.05.1974 г.р., с. Ахкинчу-Борзой Ножай-Юртовского района ЧИАССР.
30. АБУБАКАРОВ РИЗАВДИ СУЛТАНОВИЧ*, 29.11.1982 г.р., п. Чограйский Арзгирского района Ставропольского края.
31. АБУБАКАРОВ РИЗВАН СУЛТАНОВИЧ*, 17.01.1977 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
32. АБУБАКАРОВ РУСЛАН САЛАУДИНОВИЧ*, 14.09.1965 г.р., г. Токмак Киргизской АССР.
33. АБУБАКАРОВ РУСЛАНБЕК БУСАНИЕВИЧ*, 27.05.1979 г.р., с. Знаменское Надтеречного района ЧИАССР.
34. АБУБАКАРОВ САИДХАСАН НАЖМУДИЕВИЧ*, 09.06.1981 г.р., с. Шали Шалинского района ЧИАССР.
35. АБУБАКАРОВ САЙД-ХАМЗАТ АДАМОВИЧ*, 02.01.1979 г.р., с. Дуба-Юрт Шалинского района ЧИАССР.
36. АБУЕВ САИД МУСАЕВИЧ*, 08.05.1973 г.р., г. Тимер-Тау Карагалинской области Республики Казахстан.
37. АБУЕВ ХАСАН АБУСУЛТАНОВИЧ*, 21.12.1963 г.р., с. Тевзан Веденского р-на ЧИАССР.
38. АБУХАНОВ АЛИК ШАХИДОВИЧ*, 31.08.1960 г.р., с. Махкеты Введенского района ЧИАССР.
39. АВДАДАЕВ РУСТАМ ХАМЗАТОВИЧ*, 20.02.1979 г.р., с. Гойское Урус-Мартановского района ЧИАССР.
40. АГАЕВ ТАХИР ХАЛАДОВИЧ*, 08.08.1977 г.р., с. Байтарки Ножай-Юртовского района ЧИАССР.
41. АГАМИРЗАЕВ АБДУЛХАМИД МУТАЛИПОВИЧ*, 16.05.1985 г.р., с. Советское Советского района ЧИАССР.
42. АГАМИРЗАЕВ АРТУР МУТАЛИПОВИЧ*, 26.07.1981 г.р., с. Нохч-Келой Советского района ЧИАССР.
43. АГУЕВ МАГОМЕД-ЭМИ МОВЛАЕВИЧ*, 09.07.1986 г.р., с. Новые Атаги Шалинского района ЧИАССР.
44. АГУЕВ МОВЛИД МАМАЕВИЧ*, 29.07.1970 г.р., с. Мескеты Ножай-Юртовского района ЧИАССР.
45. АДАЕВ ЕВГЕНИЙ АБУЯЗИТОВИЧ*, 12.03.1984 г.р., х. Овчинников Дубовского р-на Ростовской обл.
46. АДАЕВ ЗЕЛИМХАН ВАЛЕРЬЕВИЧ*, 24.03.1974 г.р., с. Ножай-Юрт Ножай-Юртовского района ЧИАССР.
47. АДАМОВ АБУДАРДЫ МАГАМЕДОВИЧ*, 25.07.1973 г.р., с. Арбузинка Балкашинского р-на Целиноградской области Республики Казахстан.
48. АДАМОВ МАЙРБЕК МАГОМЕДОВИЧ*, 07.04.1957 г.р., с. Чулактау Джамбульской области Казахской ССР.
49. АДЖИНИЯЗОВ КАЙТАРБИ СЕЙДАЛИЕВИЧ*, 22.12.1974 г.р., с. Тукуй-Мектеб Нефтекумского района Ставропольского края.
50. АДИЛЬГЕРЕЕВ ИСМАИЛ АБДУЛАЕВИЧ*, 24.04.1970 г.р., г. Буйнакск Республики Дагестан.
51. АДУЕВ РАМЗАН АЛАУДИНОВИЧ*, 27.09.1983 г.р., г. Грозный ЧИАССР.
52. АЖГЕЛЬДИЕВ ЭНВЕР МАГОМЕДОВИЧ*, 10.09.1983 г.р., а. Кизыл-Юрт Хабезского района Ставропольского края.
53. АЗИЕВ АЛИХАН МОВЛАЕВИЧ*, 31.07.1982 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
54. АЗИЕВ ИМРАН ЛЕЧИЕВИЧ*, 01.06.1973 г.р., с. Старая Сунжа Грозненского р-на ЧИАССР.
55. АЗИЕВ РИЗВАН ЛЕЧИЕВИЧ*, 21.03.1979 г.р., с. Старая Сунжа Грозненского района (возможно г. Грозный) ЧИАССР.
56. АЗИЕВ САИД-АХМЕД МУХИДОВИЧ*, 20.12.1977 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
57. АЗИЕВ ХАЖМУРАД ЯКУБОВИЧ*, 29.09.1968 г.р., с. Автуры Шалинского района ЧИАССР.
58. АЗИЕВ ХАМЗАТ БАДРУДИНОВИЧ*, 14.09.1983 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
59. АЗИЕВ ХАРОН ЛЕЧИЕВИЧ*, 15.01.1975 г.р., с. Совяжа-Юрт Грозненского района ЧИАССР.
60. АЗИЕВ ШАМХАН МУХИДОВИЧ*, 10.08.1979 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
61. АЗИЕВ ЮНУС ЛЕЧИЕВИЧ*, 08.09.1981 г.р., с. Советское Советского района ЧИАССР.
62. АЗИЗОВ АЛЕКСЕЙ АЛЫМЖАНОВИЧ*, 10.11.1982 г.р., с. Никольское Гатчинского района Ленинградской области.
63. АЗИМОВ АНЗОР ЗИЯУДИНОВИЧ*, 14.09.1982 г.р., с. Ушкалой Советского района ЧИАССР.
64. АЙБАЗОВ ОТАРИЙ АЛИЕВИЧ*, 26.05.1971 г.р., ст. Сторожевая Зеленчукского района Ставропольского края.
65. АЙБАЗОВ РАШИД ХАСАНОВИЧ*, 15.02.1980 г.р., г. Усть-Джегута Карачаево-Черкесской Республики.
66. АЙГУМОВ СУЛЕЙМАН САЙД-ХАСАНОВИЧ*, 27.01.1981 г.р., с. Побединское ЧИАССР.
67. АЙДАЕВ ИБРАГИМ ГОГЛАЕВИЧ*, 15.11.1977 г.р., г. Грозный ЧИАССР.
68. АЙДАМИРОВ ВАХИТ КАЧАЕВИЧ*, 22.11.1964 г.р., с. Агишбатой Веденского района ЧИАССР.
69. АЙСУМОВ ЗАУРБЕК АСЛАМБЕКОВИЧ*, 24.09.1990 г.р., с. Шали Шалинского района ЧИАССР.
70. АЙТАЕВ АЛИ САЛМАНОВИЧ*, 16.11.1973 г.р., с. Киров-Юрт Введенского района ЧИАССР.
71. АЙТАМИРОВ ЗЕЛИМХАН ИСЛАМХАНОВИЧ*, 10.01.1964 г.р., с. Татай-Хутор Ножай-Юртовского района ЧИАССР.
72. АЙТУКАЕВ АЛИБЕК ЮНУСОВИЧ*, 24.01.1979 г.р., с. Хамавюрт Хасавюртовского района ДАССР.
73. АЙТУКАЕВ МЯХЬДИ МОВСАЕВИЧ*, 23.10.1984 г.р., ст. Дубовская Шелковского района Чеченской Республики.
74. АКАВОВ ЗАУР ГУСЕЙНОВИЧ*, 11.08.1973 г.р., г. Махачкала ДАССР.
75. АКАЕВ СУПЬЯН ХАСУЕВИЧ*, 04.03.1976 г.р., с. Катыр-Юрт Ачхой-Мартановского района ЧИАССР.
76. АКБУЛАТОВ АСЛАН САЛМАНОВИЧ*, 15.05.1972 г.р., с. Побединское Грозненского района ЧИАССР.
77. АКИЕВ АДАМ АЮБОВИЧ*, 01.07.1955 г.р., с. Джатсай Ильичевского района Ю-Казахстанской области.
78. АКИШИН ВИТАЛИЙ НИКОЛАЕВИЧ*, 07.05.1969 г.р., г. Дятьково Брянской области.
79. АЛАЕВ АСЛАН САЙДАХМАДОВИЧ*, 13.06.1978 г.р., с. Нижний Герзель Гудермесского района ЧИАССР.
80. АЛАЕВ ХАСАИН АБДУЛХАНОВИЧ*, 15.05.1976 г.р., с. Нижний Герзель Гудермесского района ЧИАССР.
81. АЛАРХАНОВ МАГОМЕД ЭДАМОВИЧ*, 05.11.1973 г.р., с. Суворов-Юрт Гудермесского района ЧИАССР.
82. АЛАУДИНОВ АЛАШ АЛЬВИЕВИЧ*, 07.03.1960 г.р., Чири-Юрт Шалинского района ЧИАССР.
83. АЛДАМОВ АЛИХАН ЛЕЧИЕВИЧ*, 05.10.1977 г.р., с. Советское Советского района ЧИАССР.
84. АЛДАМОВ АСЛАН ЛЕЧАЕВИЧ*, 24.07.1976 г.р., с. Золотуха Актюбинского района Астраханской области.
85. АЛДАНОВ ХАБИБ МАГОМЕДОВИЧ*, 13.09.1975 г.р., с. Верхний Дженгутай Буйнакского района ДАССР.
86. АЛЕКПЕРОВ МУСА НУХБАБАЕВИЧ*, 15.03.1972 г.р., с. Побегайловка Минераловодского района Ставропольского края.
87. АЛЕКСАНДРОВ НИКОЛАЙ ГЕННАДЬЕВИЧ*, 09.11.1982 г.р., г. Новочебоксарск Чувашской Республики.
88. АЛЕКСЕЙЧИК СЕРГЕЙ АЛЕКСАНДРОВИЧ*, 18.04.1978 г.р., г. Чимкент Республики Казахстан.
89. АЛЕРОЕВ ИБРАГИМ ХУСЕНОВИЧ*, 19.06.1976 г.р., с. Пседах Малгобекского района ЧИАССР.
90. АЛЕРОЕВ ХАЛИД СУЛТАНОВИЧ*, 03.02.1974 г.р., с. Пседах Малгобекского района Республики Ингушетия.
91. АЛИ СОЙТЕКИНОГЛЫ*, 10.02.1977 г.р., Карасу, Турция.
92. АЛИБАЕВ МАРСЕЛЬ УРАЛОВИЧ*, 09.07.1974 г.р., п. Уфимский Хайбуллинского района Республики Башкортостан.
93. АЛИБИЕВ РАМАЗАН ИЛЬМАТИЕВИЧ*, 21.08.1976 г.р., с. Эдиссия Курского района Ставропольского края.
94. АЛИДИБИРОВ ЗАГИДГАДЖИ МАГОМЕДОВИЧ*, 20.12.1960 г.р., с. Алак Ботлихского района Республики Дагестан.
95. АЛИЕВ АБДУЛЛА УВАЙСОВИЧ*, 28.01.1984 г.р., с. Билихуль Джувалинского района Джамбульской области КазССР.
96. АЛИЕВ АСЛАН БАЛАУДИНОВИЧ*, 08.01.1987 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
97. АЛИЕВ АСЛАН ЮНУСОВИЧ*, 07.10.1981 г.р., г. Грозный ЧИАССР.
98. АЛИЕВ БАУДИН РУСЛАНОВИЧ*, 15.02.1983 г.р., с. Ачхой-Мартан ЧИАССР.
99. АЛИЕВ ИСА ХУСЕЙНОВИЧ*, 24.04.1987 г.р., с.Золотуха Ахтубинского района Астраханской области.
100. АЛИЕВ РУСЛАН БОРИСОВИЧ*, 02.01.1974 г.р., г. Малгобек Республики Ингушетия.
101. АЛИЕВ СУЛТАН ВАХАЕВИЧ*, 05.01.1959 г.р., с. Алхазурово Урус-Мартановского района ЧИАССР.
102. АЛИЕВ ТИМУРЛАН АЙГУНОВИЧ*, 04.12.1964 г.р., г. Буйнакск Республики Дагестан.
103. АЛИЕВ ХУСАЙН АБДУЛРЕШИДОВИЧ*, 24.12.1979 г.р., с. Ножай-Юрт Ножай-Юртовского района Чеченской Республики.
104. АЛИЛОВ ОМАР МАГОМЕДОВИЧ*, 20.07.1962 г.р., с. Вихли Кулинского района Республики Дагестан.
105. АЛИЛОВА СОФИЯ МАГОМЕДОВНА*, 10.03.1986 г.р., с. Кули Кулинского р-на Республики Дагестан.
106. АЛИСУЛТАНОВ ВАХИТ АЛИХАДЖИЕВИЧ*, 24.12.1984 г.р., с. Курчалой ЧИАССР.
107. АЛИСУЛТАНОВ РАШИД ТАГИРОВИЧ*, 03.09.1982 г.р., с. Чонтаул Кизилюртовского района Республики Дагестан.
108. АЛИСУЛТАНОВ САЙХАН АЛИХАНОВИЧ*, 16.10.1988 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
109. АЛИСХАНОВ АСЛАН ВАХАЕВИЧ*, 10.08.1981 г.р., ст. Вознесеновская Малгобекского района ЧИАССР.
110. АЛИХАДЖИЕВ АСЛАН МОВЛАЕВИЧ*, 10.01.1982 г.р., с. Зоны Шатойского района Чеченской Республики.
111. АЛИХАДЖИЕВ ИСА ШАМИЛЕВИЧ*, 14.09.1978 г.р., с. Автуры Шалинского района Чеченской Республики.
112. АЛИХАНОВ АБИЛЬ АЗИМОВИЧ*, 22.10.1989 г.р., пос. Заволжский Палласовского района Волгоградской области.
113. АЛИХАНОВ БЕСЛАН ЗИНУЛБЕКОВИЧ*, 06.02.1984 г.р., с. Сержень-Юрт Шалинского района ЧИАССР.
114. АЛСОЛТАНОВ МУСА ОЛХАЗУРОВИЧ*, 06.10.1983 г.р., поселок Татал Юстинского района Калмыкской АССР.
115. АЛХАЗУРОВ ГАЙИРБЕК КАРИМОВИЧ*, 07.12.1977 г.р., ст. Курдюковская Шелковского района Чечено-Ингушской АССР.
116. АЛХАНОВ МАГОМЕД ХАСАНОВИЧ*, 24.10.1982 г.р., с. Надтеречное, Надтеречного р-на ЧИАССР.
117. АЛХАНОВ ОМАР АБУБАКАРОВИЧ*, 08.01.1977 г.р., г. Грозный ЧИАССР.
118. АЛХАНОВ РУСЛАН ГУМАХАЕВИЧ*, 15.09.1969 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
119. АЛХОТОВ АРТЕМ ЯКУБОВИЧ*, 17.11.1983 г.р., с. Байтарки Ножай-Юртовского района ЧИАССР.
120. АЛЬ-ЖУНАЙДИ АММАР МАХМУД*, 01.05.1975 г.р., г. Хеврон, Палестина.
121. АЛЬБУКАЕВ АНЗОР ДУКВАХОВИЧ*, 08.09.1984 г.р., с. Валерик Ачхой-Мартановского района ЧИАССР.
122. АЛЬДАГИР АМИН БУТРОС*, 27.04.1964 г.р., г. Хама Сирийской Арабской Республики.
123. АЛЬМУРЗАЕВ АЛИ АЛИЕВИЧ*, 09.07.1958 г.р., г. Караганда КазССР.
124. АЛЬМУРЗИЕВ АЛАУДИН ОСМАНОВИЧ*, 14.08.1980 г.р., г. Нальчик Кабардино-Балкарской АССР.
125. АМАГОВ РУСЛАН МУХМАТСАНИЕВИЧ*, 25.01.1978 г.р., ст. Орджоникидзевская Сунженского района ЧИАССР.
126. АМАЕВ МУХМАД МАЛИКОВИЧ*, 10.04.1978 г.р., с. Новотерское Наурского района ЧИАССР.
127. АМАЕВ РИЗВАН РАМЗАНОВИЧ*, 25.06.1972 г.р., г. Аргун ЧИАССР.
128. АМАЕВ ШАРПУДИН ЛЕЧИЕВИЧ*, 20.08.1958 г.р., с. Гехи Урус-Мартановского района ЧИАССР.
129. АМАНКАЕВ АЛИМХАН КАЙТЕРБИЕВИЧ*, 08.01.1977 г.р., с. Токуй-Мектеб Ногайского района Республики Дагестан.
130. АМРИЕВ ЗУРАБ СУЛУМБЕКОВИЧ*, 15.05.1981 г.р., г. Грозный ЧИАССР.
131. АНАСОВ САИДБЕК КУРБАНОВИЧ*, 15.12.1981 г.р., с. Энгель-Юрт Гудермесского района ЧИАССР.
132. АНДРЕЕВ АНДРЕЙ АЛЕКСАНДРОВИЧ*, 24.10.1984 г.р., станица Смоленская Северского р-на Краснодарского края.
133. АНДРЕЕВ РОМАН ВЛАДИМИРОВИЧ*, 24.07.1960 г.р., г. Гатчина Ленинградской области.
134. АНЧИН АЛЕКСАНДР АРКАДЬЕВИЧ*, 26.07.1982 г.р., п. Удачный Мирнинского района Якутской АССР.
135. АПАЕВ ЮНУС АХМЕДОВИЧ*, 06.10.1986 г.р., с. Валерик Ачхой-Мартановского района ЧИАССР.
136. АРАХОВ АРКАДИЙ АЛИКОВИЧ*, 11.11.1976 г.р., г. Елгава Латвийской ССР.
137. АРСАЕВ АНЗОР АСАНОВИЧ*, 04.02.1980 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
138. АРСАЕВ ИБРАГИМ ВИСИРПАШАЕВИЧ*, 02.11.1979 г.р., г. Хасавюрт ДАССР.
139. АРСАЕВ МАСХУД ЮНАДИЕВИЧ*, 04.12.1974 г.р., с. Мескеты Ножай-Юртовского района ЧИАССР.
140. АРСАМАКОВ ШАМИЛЬ ВАХИДОВИЧ (ВАХИТОВИЧ)*, 21.11.1978 г.р., с. Ведучи Сунженского района ЧИАССР.
141. АРСАМИКОВ АЛИХАН АБДУЛАЕВИЧ*, 14.04.1984 г.р., с. Шали Шалинского района Чеченской Республики.
142. АРСАМИКОВ АНЗОР САЛАУДИНОВИЧ*, 08.08.1983 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
143. АРСАМИКОВ РУСТАМ САЛАУДИНОВИЧ*, 16.11.1978 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
144. АРСАМИРЗУЕВ ЗЕЛИМХАН АЕЛЬЕВИЧ*, 08.10.1984 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
145. АРСАНОВ ВИСХАН ИСАЕВИЧ*, 20.02.1988 г.р., с. Курчалой Шалинского района ЧИАССР.
146. АРСАНОВ РУСЛАН ИСАЕВИЧ*, 25.12.1977 г.р., с. Курчалой Шалинского района ЧИАССР.
147. АРСАНУКАЕВ ЗУБАЙРА ЭЛИЕВИЧ*, 17.03.1987 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
148. АРСАНУКАЕВ МОВСАР ХАСАНОВИЧ*, 01.07.1978 г.р., г. Аргун ЧИАССР.
149. АРСАНУКАЕВ МУСЛИМ ВАХАЕВИЧ*, 24.10.1975 г.р., с. Побединское Грозненского района Чеченской Республики.
150. АРСАНУКАЕВ УМАЛТ МУСАЕВИЧ*, 19.01.1973 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
151. АРСАХАНОВ ХАСАН АХМЕТОВИЧ*, 30.12.1988 г.р., с. Хамби-Ирзи Ачхой-Мартановского района ЧИАССР.
152. АРСЕЛЬГОВ МУХАМЕД-АЛИ ЮСУПОВИЧ*, 09.05.1976 г.р., с. Насыр-Корт Назрановского района ЧИАССР.
153. АРСЛАНБЕКОВ АЛЬБЕРТ АРСЛАНБЕКОВИЧ*, 15.11.1978 г.р., п. Дубки гор. Кизилюрт Республики Дагестан.
154. АРСЛАНОВ ЮСУП АБДУРАХМАНОВИЧ*, 08.08.1968 г.р., с. Карамахи Буйнакского района Республики Дагестан.
155. АРСНУКАЕВ РУСЛАН ВАХАЕВИЧ*, 14.10.1976 г.р., с. Катар-Юрт Ачхой-Мартановского района ЧИАССР.
156. АРСТЕМИРОВ РАСУЛ ШЕДИТОВИЧ*, 24.04.1982 г.р., с. Киров-Юрт Веденского района ЧИАССР.
157. АРХАГОВ РУСТАМ РУСЛАНОВИЧ*, 26.05.1983 г.р., аул Кара-Паго Прикубанского района Карачаево-Черкесской Республики.
158. АРЦАЕВ ИБРАГИМ ВИСИРПАШАЕВИЧ*, 02.11.1979 г.р., г. Хасавюрт Республики Дагестан.
159. АРЦУЕВ АХМЕД АБДУЛАЕВИЧ (АРЦУЕВ АРТУР АБДУЛАЕВИЧ)*, 08.07.1979 г.р., с. Ново-Шарой Ачхой-Мартановского района ЧИАССР (08.07.1979 г.р., с. Ново-Шарой Ачхой-Мартановского района ЧИАССР).
160. АСЕЛЬДЕРОВ МАГОМЕД ГУСЕНОВИЧ*, 18.06.1979 г.р., с.Карамахи Буйнакского района Республики Дагестан.
161. АСЕЛЬДЕРОВ ЮСУП ГУСЕЙНОВИЧ*, 24.03.1974 г.р., с.Карамахи Буйнакского района Республики Дагестан.
162. АСЛАМБЕКОВ СУЛТАН МУМАДИЕВИЧ*, 24.11.1975 г.р., с. Агишты Веденского района ЧИАССР.
163. АСЛАМКАДИРОВ БОРЗ-АЛИ ЭЛЬМАНОВИЧ*, 07.07.1971 г.р., с. Агишбатой Чеченской Республики.
164. АСЛАНБЕКОВ МАГАДЫ СУЛТАНОВИЧ*, 09.12.1974 г.р., с. Ачхой-Мартан ЧИАССР.
165. АСЛАНБЕКОВ РУСЛАН МУХТАРОВИЧ*, 23.07.1983 г.р., с. Дубовское Дубовского района Ростовской области.
166. АСТАМИРОВ АСЛАН РАМЗАНОВИЧ*, 02.04.1977 г.р., г. Грозный ЧИАССР.
167. АСТАМИРОВ ИЛЕС ИСАЕВИЧ*, 05.01.1975 г.р., г. Грозный Чечено-Ингушской АССР.
168. АСУХАНОВ СОСЛАН АБУБАКАРОВИЧ*, 25.03.1984 г.р., г. Аргун ЧИАССР.
169. АСХАБАЛИЕВ ШАМИЛЬ МАГОМЕДОВИЧ*, 10.07.1975 г.р., г. Махачкала Республики Дагестан.
170. АСХАБОВ АДАМ ГЕБЕРТУЕВИЧ*, 23.02.1984 г.р., х. Фомин Заветинского района Ростовской области.
171. АСХАБОВ АДАМ ИСАЕВИЧ*, 07.02.1977 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
172. АСХАБОВ РУСЛАН ДАЙДАЛОВИЧ*, 27.08.1968 г.р., с. Майколь Кустанаевской области КССР.
173. АТАБИЕВ РАШИД ХАСАНОВИЧ*, 21.07.1980 г.р., г. Усть-Джегута Ставропольского края КЧАО.
174. АТАЕВ КАЗБЕК МАГОМЕДОВИЧ*, 31.01.1978 г.р., г. Малгобеке ЧИАССР.
175. АТГИРИЕВ ТУРПАЛАЛИ АЛАУДИНОВИЧ*, 08.05.1969 г.р., с. Аллерой Шалинского района ЧИАССР.
176. АТНАЗОВ САИД-ХУСЕЙН МАГОМЕДОВИЧ*, 20.12.1981 г.р., г. Грозный ЧИАССР.
177. АТСАЛАМОВ ЮНАДИ АДАМОВИЧ*, 28.09.1978 г.р., с. Вярды Советского района ЧИАССР.
178. АТУЕВ ИСЛАМ ИМХАДЖИЕВИЧ*, 28.07.1976 г.р., г. Аргун ЧИАССР.
179. АУШЕВ МАГОМЕД МУССИЕВИЧ*, 16.09.1978 г.р., г. Грозный ЧИАССР.
180. АХАЕВ ЭЛЬБЕК ЛУЛУЕВИЧ*, 01.04.1963 г.р., с. Ца-Ведено Веденского района Чеченской Республики.
181. АХМАДОВ АЛЬВИ АБДУЛБЕКОВИЧ*, 31.10.1978 г.р., с. Старая Сунжа Грозненского района ЧИАССР.
182. АХМАДОВ РИЗВАН ЛЕЧАЕВИЧ*, 20.04.1977 г.р., с. Кулары Грозненского района ЧИАССР.
183. АХМАДОВ РУСЛАН ИСРАИЛОВИЧ*, 08.12.1966 г.р., с. Исти-Су Гудермесского района ЧИАССР.
184. АХМАДОВ ХАВАЖИ ХАСАНОВИЧ*, 29.12.1978 г.р., с. Мескер-Юрт Шалинского района ЧИАССР.
185. АХМАДОВ ХАСАМБЕК САЙД-АРБИЕВИЧ*, 12.03.1975 г.р., с. Батурино Чапаевского района Уральской области.
186. АХМАДОВ ХАСАН САЛАУДЫНОВИЧ*, 21.03.1977 г.р., с. Гойты Урус-Мартановского района Чеченской Республики.
187. АХМАДХАНОВ ЗАЙНДИ УМАРОВИЧ*, 22.07.1948 г.р., Джамбульская область Республики Казахстан.
188. АХМАДХАНОВ ТИМУР ШЕЙХ-АХМЕДОВИЧ*, 24.09.1975 г.р., г. Гудермес Чеченской Республики.
189. АХМАТОВ РУСЛАН ИМРАНОВИЧ*, 09.01.1971 г.р., п. Горагорск Надтеречного района ЧИАССР.
190. АХМЕДОВ СУЛТАН АЛИЕВИЧ*, 17.11.1981 г.р., с. Замай-Юрт Ножай-Юртовского района ЧИАССР.
191. АХМЕДОВ ШАВКАТ РАВИЛЬЕВИЧ*, 22.09.1985 г.р., п. Бустон Матчинского района Ленинабадской обл. Таджикской ССР.
192. АХМЕРХАДЖИЕВ АЮБ ТИМИРХАДЖИЕВИЧ*, 24.06.1971 г.р., ст. Гребенская Шелковского района ЧИАССР.
193. АХМЕТСАФИН МУСА ШАРИФОВИЧ*, 10.05.1977 г.р., г. Белорецк.
194. АЦАЕВ АДАМ ТАУСОВИЧ*, 15.10.1975 г.р., пос. Краснокунский Краснокунского района Павлодарской области.
195. АШАХАНОВ КАХИМ ИСРАПИЛОВИЧ*, 24.12.1984 г.р., ст. Наурская Наурского района ЧИАССР.
196. АШАХАНОВ РУСЛАН САЙПАЕВИЧ*, 30.10.1972 г.р., с. Самашки Ачхой-Мартановского р-на Чеченской Республики.
197. АШИКОВ ШАМИЛЬ БАГАВДИНОВИЧ*, 25.08.1971 г.р., с. Гуниб Гунибского района Республики Дагестан.
198. АЮБОВ ИМАЛИ ВИСАРХАДЖИЕВИЧ*, 22.06.1978 г.р., пос. Новогрозненский Гудермесского района ЧИАССР.
199. БАДАЕВ АНЗОР МАГОМЕДОВИЧ*, 29.05.1985 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
200. БАДАШЕВ АЛХАЗУР ШАМИЛЬЕВИЧ*, 24.07.1975 г.р., г. Грозный ЧИАССР.
201. БАДУЕВ САЙДМАГОМЕД ХУСЕЙНОВИЧ*, 19.05.1986 г.р., с. Урус-Мартан ЧИАССР.
202. БАДУРГОВ ЗЕЛИМХАН МАГОМЕДОВИЧ*, 10.06.1982 г.р., Ачхой-Мартановский район ЧИАССР.
203. БАЗАЕВ ШЕМИЛЬ ЖАМЛЕЙНОВИЧ*, 24.02.1976 г.р., г. Шали ЧИАССР.
204. БАЗУЕВ УМАР УЛЬБИЕВИЧ*, 27.01.1977 г.р., г. Эмба Мугаджарского района Казахской ССР.
205. БАЗУРКАЕВ АСЛАНБЕК ВАХАЕВИЧ*, 15.03.1975 г.р., с. Исти-Су Гудермесского района ЧИАССР.
206. БАЗУРКАЕВ СУЛТАН АБДУЛАЕВИЧ*, 06.01.1963 г.р., с. Баматюрт Хасавюртовского района Республики Дагестан.
207. БАЙДАРОВ ШАМХАН ХАВАЖЕВИЧ*, 16.10.1977 г.р., г. Грозный ЧИАССР.
208. БАЙДУЛАЕВ АНЗОР АЛХАЕВИЧ*, 29.10.1987 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
209. БАЙДУЛАЕВ ДОККА АЛХАЕВИЧ*, 17.05.1980 г.р., с. Алхан-Кала Грозненского р-на ЧИАССР.
210. БАЙДУЛАЕВ КАЗБЕК ДЖАЛАУДИНОВИЧ*, 23.09.1988 г.р., хутор Страховский Новоанинского района Волгоградской области.
211. БАЙЗУРКАЕВ АРТУР АБУЕВИЧ*, 05.12.1981 г.р., г. Новый Узень Мангышлакской области КазССР.
212. БАЙМУРАТОВ АРИБИЙ АБДУЛЛАЕВИЧ*, 26.01.1987 г.р., с. Борагангечу Хасавюртовского района ДАССР.
213. БАЙМУРЗАЕВ УМАР АЛИЕВИЧ*, 02.04.1983 г.р., с. Макажой Веденского района ЧИАССР.
214. БАЙРАМУКОВ МУРАТБИ АЙГУФОВИЧ*, 08.06.1976 г.р., ст. Сторожевая Зеленчукского района Карачаево-Черкесской Республики.
215. БАЙСАГУРОВ АБДУЛАХИ ШАРИПОВИЧ*, 27.10.1986 г.р., с. Курчалой Шалинского района ЧИАССР.
216. БАЙСАЕВ УМАР ДАУДОВИЧ*, 24.04.1977 г.р., х. Мокро-Соленый Цимлянского района Ростовской обл.
217. БАЙСИЕВ ИСЛАМ ХАМАДОВИЧ*, 21.10.1991 г.р., с. Хаттуни Веденского района Чеченской Республики.
218. БАЙСУЕВ МАХДИ МУСАЕВИЧ*, 25.10.1978 г.р., с. Энгель-Юрт Гудермесского района ЧИАССР.
219. БАЙСУРОВ КАЗБЕК АБУХОЕВИЧ*, 21.06.1980 г.р., с. Курчалой ЧИАССР.
220. БАЙТАЕВ БЕСЛАН ХУСАИНОВИЧ*, 19.10.1975 г.р., с. Самашки Ачхой-Мартановского р-на ЧИАССР.
221. БАЙТАЛАЕВ МУСЛОВ ХАЙДАРОВИЧ*, 06.05.1985 г.р., с. Дарго Веденского района ЧИАССР.
222. БАЙТУКАЕВ АНЗОР ЗАЙНДИЕВИЧ*, 12.06.1980 г.р., с. Мескер-Юрт ЧИАССР.
223. БАЙЧОРОВ АРСЕН АХМАТОВИЧ*, 08.01.1984 г.р., г. Карачаевск Карачаево-Черкесской Республики.
224. БАКАЕВ АХДАН БАУДОВИЧ*, 06.10.1980 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
225. БАКАЕВ ИДРИС САЙДАЕВИЧ*, 23.02.1971 г.р., ст. Наурская Наурского района ЧИАССР.
226. БАКАЕВ МАГДАН БАУДИНОВИЧ*, 09.11.1970 г.р., с. Энбексий-Карабулакский Алакульского р-на Талды-Курганской обл.
227. БАКАЛОВ МАГОМЕД ХАСАНОВИЧ*, 19.09.1979 г.р., с. Н.Атаги Шалинского района ЧИАССР.
228. БАКАШЕВ ДЖАМБУЛАТ ДЕНИЛБЕКОВИЧ*, 24.07.1984 г.р., с. Ведено Веденского района ЧИАССР.
229. БАКИЕВ ШАМИЛЬ АХМАТОВИЧ*, 06.10.1981 г.р., с. Маловодное Энбекшиказахского района Алма-Атинской области Казахской ССР.
230. БАЛАЕВ ТАМИРЛАН ТУРУЕВИЧ*, 02.10.1970 г.р., с. Харачой Веденского района ЧИАССР.
231. БАЛАНТАЕВ ВЛАДИМИР АЛЕКСАНДРОВИЧ*, 22.06.1973 г.р., г. Кемерово.
232. БАЛТИЕВ УМАЛТ ДЖАМЛАЙЛОВИЧ*, 26.11.1983 г.р., с. Шали Шалинского района Чеченской Республики.
233. БАЛУЕВ ИСМАИЛ ИСХАКОВИЧ*, 16.12.1974 г.р., г. Нальчик, с. Хасанья Кабардино-Балкарской Республики.
234. БАНТАЕВ АРБИ ХОЖ-БАУДИНОВИЧ*, 28.08.1981 г.р., с. Комсомольское Гудермесского района ЧИАССР.
235. БАРАКАЕВ ШАРАБДИН САМОВДИНОВИЧ*, 16.09.1973 г.р., с. Брагуны Гудермесского района ЧИАССР.
236. БАРАХАЕВ ХАМИТ АХИЯДОВИЧ*, 28.03.1954 г.р., г. Караганда Казахской ССР.
237. БАРАХОЕВ ИССА АХЪЯДОВИЧ*, 20.06.1968 г.р., с. Сурхахи Республики Ингушетия.
238. БАРЗАКОВ МАГОМЕД МАХМУДОВИЧ*, 13.05.1966 г.р., с. Мескиты Ножай-Юртовского района ЧИАССР.
239. БАРЗИГОВ ЛЕЧИ АХЪЯДОВИЧ*, 08.07.1979 г.р., с. Далготой Шалинского района ЧИАССР.
240. БАРКИНХОЕВ АБУБУКАР ХАДЖИБИКАРОВИЧ*, 24.08.1982 г.р., с. Сурхахи Назрановского района ЧИАССР.
241. БАРКИНХОЕВ РУСЛАН ЗЕЛИМХАНОВИЧ*, 21.06.1984 г.р., г. Есиль Есильского района Тургайской области Казахской ССР.
242. БАСАЕВ АЛХАЗУР САЛМАНОВИЧ*, 17.07.1962 г.р., с. Мартан-Чу Урус-Мартановского района ЧИАССР.
243. БАСАЕВ АЛЬВИ МУСАЕВИЧ*, 25.09.1968 г.р., с. Мартан-Чу Урус-Мартановского района ЧИАССР.
244. БАСАЕВ ВИС-АЛИ ХОЖАХМЕДОВИЧ*, 29.10.1972 г.р., с. Грушевое Урус-Мартановского района ЧИАССР.
245. БАСХАНОВ ИСЛАМ МУРТАНОВИЧ*, 19.11.1980 г.р., с. Побединское Грозненского района ЧИАССР.
246. БАСХАНОВ РУСТАМ МАХАМЕДОВИЧ*, 21.06.1984 г.р., с. Новое Солкушино Наурского района ЧИАССР.
247. БАТАГОВ МАГМЕД АРБИЕВИЧ*, 03.08.1981 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
248. БАТАЕВ АСЛАН ЛОМ-АЛИЕВИЧ*, 19.09.1984 г.р., с. Урус-Мартан ЧИАССР.
249. БАТАЕВ АХМЕД РАХМАНОВИЧ*, 15.04.1982 г.р., с. Урус-Мартан ЧИАССР.
250. БАТАЕВ ВИСИТ НУРДИЕВИЧ*, 03.11.1985 г.р., г. Аргун Чеченской Республики.
251. БАТАЕВ РУСЛАН ХОЖАЕВИЧ*, 29.03.1970 г.р., ст. Сары-Су Шелковского района ЧИАССР.
252. БАТАЕВ ТУРКО САЛМАНОВИЧ*, 20.12.1986 г.р., г. Грозный ЧИАССР.
253. БАТАЕВ УМАР ИСАЕВИЧ*, 17.08.1981 г.р., с. Ачхой-Мартановского района ЧИАССР.
254. БАТАКОВ ВАХИТ СУПЬЯНОВИЧ*, 03.08.1973 г.р., с. Брагуны Гудермесского района ЧИАССР.
255. БАТАЛОВ АЛИХАН СУЛТАНОВИЧ*, 05.08.1979 г.р., с. Серноводск Сунженского района ЧИАССР.
256. БАТАЛОВ АСЛАМБЕК ХАСЕЙНОВИЧ*, 11.03.1968 г.р., г. Аргун Шалинского р-на Чеченской Республики.
257. БАТАЛОВ ИДРИС ЭМАЛИЕВИЧ*, 24.06.1981 г.р., с. Джалка Гудермесского района ЧИАССР.
258. БАТАЛОВ РУСТАМ МАГОМЕДОВИЧ*, 25.05.1972 г.р., г. Южно-Сухокумск Республики Дагестан.
259. БАТАЛОВ ХАМЗАТ ЗАЙНДИЕВИЧ*, 31.03.1981 г.р., с. Серноводск Сунженского района ЧИАССР.
260. БАТУКАЕВ САЙДБЕК СИДИКОВИЧ*, 22.04.1987 г.р., с. Ведено Веденского района ЧИАССР.
261. БАТЧАЕВ АЛИМ СУЛЕЙМАНОВИЧ*, 07.08.1972 г.р., ст. Сторожевая Зеленочукского района Карачаево-Черкесской Республики.
262. БАТЫРОВ БАТЫР ГАДЖИЕВИЧ*, 02.01.1947 г.р., с. Карамахи Буйнакского района Республики Дагестан.
263. БАТЫРОВ СУЛЕЙМАН ГАДЖИЕВИЧ*, 21.06.1963 г.р., с. Карамахи Буйнакского района Республики Дагестан.
264. БАХАЕВ АХМЕД РАМЗАНОВИЧ*, 22.09.1975 г.р., г. Грозный Чеченской Республики.
265. БАХАЕВ РОМАН МАХМУДОВИЧ*, 24.05.1976 г.р., с. Серноводск ЧИАССР.
266. БАХАЕВ ХАМЗАТ ХАРОНОВИЧ*, 15.09.1976 г.р., х. Фомин Заветинского района Ростовской области.
267. БАХАРЧИЕВ МАГОМЕД САИДСЕЛИМОВИЧ*, 19.11.1972 г.р., с. Серноводск Сунженского района ЧИАССР.
268. БАХАРЧИЕВ РУСЛАН САЙДАМИНОВИЧ*, 24.02.1978 г.р., село Промысловка Лимановского р-на Астраханской обл.
269. БАХВАЛОВ АЛЕКСЕЙ ЕВГЕНЬЕВИЧ*, 17.09.1975 г.р., г. Ленинград.
270. БАХТИЕВ АСЛАН МУСАЕВИЧ*, 13.09.1976 г.р., с. Альтиево Назрановского района ЧИАССР.
271. БАЦАЕВ АБДУЛСАЙД ЖАПАРОВИЧ*, 23.04.1966 г.р., с. Зандак Ножай-Юртовского района ЧИАССР.
272. БАЦИЕВ ДАУД ДОККАЕВИЧ*, 13.05.1983 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
273. БАЦИЕВ ИСЛАМ САЙДАХМАТОВИЧ*, 20.10.1977 г.р., г. Хасавюрт ДАССР.
274. БАЦИЕВ РУСЛАН АНАТОЛЬЕВИЧ*, 23.03.1978 г.р., г. Хасавюрт Республики Дагестан.
275. БАЧАЕВ ИСЛАМ ИСАЕВИЧ*, 21.11.1983 г.р., с. Серноводск Сунженского района ЧИАССР.
276. БАЧАЕВ МУСА УСМАНОВИЧ*, 05.03.1983 г.р., с. Старая Сунжа Грозненского района ЧИАССР.
277. БАЧАЕВ МУСЛИМ ИСАЕВИЧ*, 19.12.1977 г.р., с. Серноводск Сунженского района ЧИАССР.
278. БАЧИГОВ АКРАМАН ХАРУНОВИЧ*, 04.04.1986 г.р., с. Цаца Светлояровского района Волгоградской области.
279. БАШЕЛУТСКОВ ДАВИД ВАГАРШАКОВИЧ*, 17.01.1991 г.р., село Ахалкалаки Ахалкалакского района Республики Грузия.
280. БАШИРОВ БИСЛАН ВАХАЕВИЧ*, 31.01.1982 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
281. БАШТАРОВ АДАМ МУСАЕВИЧ*, 08.02.1984 г.р., г. Грозный ЧИАССР.
282. БЕГЕЛЬДИЕВ ТАХИР ХАЙРЕТДИНОВИЧ*, 05.11.1974 г.р., с. Кара-Тюбе Нефтекумского района Ставропольского края.
283. БЕГИТОВ АСЛАНБЕК СОСЛАНБЕКОВИЧ*, 01.06.1965 г.р., с. Хал-Калой Советского района ЧИАССР.
284. БЕЙДУЛЛАЕВ ЗАУР ТЕМРАЗОВИЧ*, 27.02.1985 г.р., г. Махачкала ДАССР.
285. БЕКАЕВ КАЗБЕК ШАМСУДИЕВИЧ*, 24.01.1979 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
286. БЕКМУРЗАЕВ РАСАМБЕК СУЛЕЙМАНОВИЧ*, 17.09.1980 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
287. БЕКОВ ИССА УВАЙСОВИЧ*, 27.10.1972 г.р., с. Верхние Ачалуки Малгобекского района ЧИАССР.
288. БЕКСУЛТАНОВ МОВСАР ВАХАЕВИЧ*, 09.11.1983 г.р., г. Грозный ЧИАССР.
289. БЕКСУЛТАНОВ РУСЛАН ВАХАЕВИЧ*, 30.01.1983 г.р., с. Мирный Курского района Ставропольской области.
290. БЕЛАШЕВ ВЛАДИМИР ИЛЬИЧ*, 30.07.1961 г.р., г. Кунгур Пермской области.
291. БЕЛИЕВ РУСЛАН ХУМАЙДОВИЧ*, 12.12.1979 г.р., г. Хасавюрт ДАССР.
292. БЕЛКИН ДМИТРИЙ НИКОЛАЕВИЧ*, 27.01.1976 г.р., п. Шишино Топкинского р-на Кемеровской области.
293. БЕЛОВ АЛЕКСАНДР ВАСИЛЬЕВИЧ*, 08.07.1979 г.р., г. Зеленодольск Республики Татарстан.
294. БЕЛОЗЕРОВ АЛЕКСЕЙ ВИКТОРОВИЧ*, 26.03.1980 г.р., с. Красный Городок Сергиевского района Самарской области.
295. БЕРГОЕВ СУЛИМ АБДУЛАЕВИЧ*, 16.08.1975 г.р., с. Катыр-Юрт Ачхой-Мартановского района ЧИАССР.
296. БЕРИЕВ АСЛАНБЕК МАКШЕРИПОВИЧ*, 26.05.1974 г.р., ст. Ильиноская Грозненского района ЧИАССР.
297. БЕРСАНОВ ЛЕММА МУСАЕВИЧ*, 18.08.1985 г.р., г. Грозный ЧИАССР.
298. БЕРСАНОВ ЛОМ-АЛИ ЛОМАЕВИЧ*, 02.02.1982 г.р., с. Алхан-Кала Грозненского района ЧИАССР.
299. БЕРСАНОВ ЛОМ-АЛИ МУСАЕВИЧ*, 18.08.1985 г.р., г. Грозный ЧИАССР.
300. БЕРСАНОВ САИД-ХУСЕЙН МУСАЕВИЧ*, 01.05.1977 г.р., с. Дуба-Юрт Шалинского района Чеченской Республики.
301. БЕТАЛМИРЗАЕВ АСЛАН МОВЛАДОВИЧ*, 08.06.1975 г.р., совхоз “Коммунизм” Амангельдинского района Тургайкой обл. КазССР.
302. БЕТЕРГИРАЕВ ЗАУР ХИЗИРОВИЧ*, 28.05.1981 г.р., с. Шали ЧИАССР.
303. БЕЦИЕВ ХАСАН ЭМИЕВИЧ*, 03.04.1976 г.р., с. Ведено Веденского района Чеченской Республики.
304. БИБУЛАТОВ БАДРУДИ ШАХАЕВИЧ*, 07.12.1972 г.р., с. Элистанжи Веденского района ЧИАССР.
305. БИБУЛАТОВ САЙХАН АЛГАЗИРОВИЧ*, 21.07.1982 г.р., с. Ачхой-Мартан ЧИАССР.
306. БИДАГОВ РУСЛАН МАГОМЕДОВИЧ*, 17.06.1978 г.р., с. Карамахи Буйнакского района Республики Дагестан.
307. БИДЖИЕВ ХАЗРЕТ РАКАЕВИЧ*, 06.07.1960 г.р., пос. Красноводский Республики Казахстан.
308. БИДИЕВ ЯКУБ АХМЕДОВИЧ*, 30.09.1979 г.р., с. Дышне-Ведено Веденского района ЧИАССР. Возможно 1970 г.р.
309. БИКАЕВ АДАМ КЮРАЕВИЧ*, 08.05.1978 г.р., с. Алхан-Кала ЧИАССР.
310. БИКТИМИРОВ РУСЛАН САЛАВАТОВИЧ*, 14.07.1975 г.р., д. Ялчикаево Кумертауского района Республики Башкортостан.
311. БИЛАЛОВ КАЗБЕК ИСАЕВИЧ*, 10.04.1982 г.р., с. Согунты Ножай-Юртовского района ЧИАССР.
312. БИЛЬТАЕВ ХАСАН ДУКВАЕВИЧ*, 27.05.1983 г.р., с. Валерик Ачхой-Мартановского района ЧИАССР.
313. БИНИНИ ДЖОН (САУДАНИ ЕСЕФ САИДОВИЧ)*, 01.09.1975 г.р., г. Лондон (Великобритания) (18.09.1969 г.р., г. Константин (Алжир)).
314. БИССАМИРОВ ШАМИЛЬ ВАХАЕВИЧ*, 03.12.1976 г.р., с. Кошкельды Гудермесского района ЧИАССР.
315. БИТАЕВ СУЛИМ РУСЛАНОВИЧ*, 10.02.1981 г.р., г. Грозный ЧИАССР.
316. БИТИЕВ АЛИХАН ШАМИЛЬЕВИЧ*, 13.12.1976 г.р., с. Черный Яр Черноярского района Астраханской области.
317. БИТИЕВ АСЛАН ШАМХАНОВИЧ*, 14.06.1969 г.р., с. Верхний Наур Надтеречного р-на Чеченской Республики.
318. БИТИЕВ ЗЕЛИМХАН ШАМИЛЬЕВИЧ*, 29.04.1979 г.р., пос. Большой Царын Октябрьского района Калмыкской АССР.
319. БИХАЕВ АНАРБЕК АХМЕДОВИЧ*, 16.09.1962 г.р., г. Аргун ЧИАССР.
320. БЛОХИН АЛЕКСАНДР ЮРЬЕВИЧ*, 06.12.1980 г.р., д. Горушки Яранского района Кировской области.
321. БОГАТЫРЕВ ИСА АБУЯЗИТОВИЧ*, 28.09.1991 г.р., г. Грозный ЧИАССР.
322. БОДРОВ МИХАИЛ АЛЕКСАНДРОВИЧ*, 27.03.1985 г.р., д. Верховая Рыбинского района Красноярского края.
323. БОЛТУКАЕВ МЕХДИН УМАРПАШАЕВИЧ*, 26.02.1990 г.р., с. Аллерой Ножай-Юртовского района ЧИАССР.
324. БОПАЕВ ШАМХАН ЮСАЕВИЧ*, 23.05.1980 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
325. БОРИСОВ АНДРЕЙ ИВАНОВИЧ*, 26.03.1968 г.р., Тюменская область.
326. БОСТАНОВ АСЛАН РУСЛАНОВИЧ*, 29.01.1980 г.р., г. Карачевск КЧАО.
327. БОСТАНОВ МАРАТ ИСЛАМОВИЧ*, 05.02.1964 г.р., с. Кызыл-Покун Малокарачаевского р-на КЧАО.
328. БОТАЕВ СУЛТАН ШАМСУДИНОВИЧ*, 23.04.1982 г.р., с. Чонтаул Кизилюртовского района Республики Дагестан (23.04.1982 г.р., г. Хасавюрт Республики Дагестан).
329. БУГАЕВ АЛЬБЕК САЛИЕВИЧ*, 06.02.1978 г.р., г. Урус-Мартан Урус-Мартановского района ЧИАССР.
330. БУГАЕВ КЮРИ ЛЕЧИЕВИЧ*, 16.08.1973 г.р., г. Гудермес ЧИАССР.
331. БУГАЕВ РАИДИН ЯМУДИНОВИЧ*, 29.05.1978 г.р., г. Махачкала Республики Дагестан.
332. БУЛАХ ВИТАЛИЙ ЕВГЕНЬЕВИЧ*, 20.07.1963 г.р., г. Армавир Краснодарского края.
333. БУРМАСОВ СЕРГЕЙ ПАВЛОВИЧ*, 10.06.1983 г.р., п. Санболи Амурского района Хабаровского края.
334. БУРЧАЛОВ КАМИЛЬ МАГОМЕДОВИЧ*, 16.08.1959 г.р., г. Бухара Узбекской ССР.
335. БУСЫРЕВ СЕРГЕЙ НИКОЛАЕВИЧ*, 30.09.1970 г.р., г. Ленинград.
336. БУШТУРОВ ТУРПАЛБЕК ШААЕВИЧ*, 15.03.1955 г.р., с. Бегень Баскарагайского района Павлодарской области.
337. БУШУЕВ ЗУРАБ НЕДИРСУЛТАНОВИЧ*, 18.09.1979 г.р., с. Ножай-Юрт Ножай-Юртовского района ЧИАССР.
338. ВАКУЕВ МАРАТ САЛАМБЕКОВИЧ*, 27.03.1976 г.р., г. Аргун ЧИАССР.
339. ВАЛИТОВ МАРС МАРАТОВИЧ*, 14.12.1967 г.р., г. Уфа Республики Башкортостан.
340. ВАЛИТОВ РАИЛЬ РАМИЛЕВИЧ*, 04.04.1981 г.р., г. Туймазы Республики Башкортостан.
341. ВАНГАШЕВ СУЛИМ МУСАЕВИЧ*, 10.12.1975 г.р., с. Катыр-Юрт Ачхой-Мартановского района ЧИАССР.
342. ВАРАЕВ МАЙРБЕК ВИЙСАЕВИЧ*, 01.07.1975 г.р., п. Яшкуль Яшкульского района Калмыцкой АССР.
343. ВАРЛАКОВ АЛЕКСАНДР АЛЕКСАНДРОВИЧ*, 21.04.1971 г.р., г. Свердловск.
344. ВАХАЕВ АРБИ ХУСЕЙНОВИЧ*, 11.11.1976 г.р., г. Грозный Чеченской Республики.
345. ВАХАЕВ МАГДАН ХОЗАЕВИЧ*, 11.06.1986 г.р., с. Урус-Мартан ЧИАССР.
346. ВАХАЕВ ТИМУР ДАДАШЕВИЧ*, 25.05.1976 г.р., г. Грозный Чеченской Республики.
347. ВАХИДОВ ВАХИД ШАМХАНОВИЧ*, 14.03.1976 г.р., с. Урус-Мартан Урус-Мартановского р-на ЧИАССР.
348. ВАЦАНАЕВ МУХАММЕД-ШЕРИП МАГОМЕДОВИЧ*, 19.07.1969 г.р., с. Дышне-Ведено Веденского района ЧИАССР.
349. ВАШАЕВ АБУБАКАР СУЛТАНОВИЧ*, 20.06.1965 г.р., с. Автуры Шалинского района ЧИАССР.
350. ВАШАЕВ ЗЕЛИМХАН СУЛТАНОВИЧ*, 10.10.1969 г.р., с. Автуры Шалинского района ЧИАССР.
351. ВЕДЕРНИКОВ ВЛАДИМИР АЛЕКСАНДРОВИЧ*, 30.01.1984 г.р., Чистопольского района Республики Татарстан.
352. ВЕЗЕРХАНОВ АСЛАНБЕК ВАХИДОВИЧ*, 25.08.1978 г.р., с. Кургалой Шалинского района ЧИАССР.
353. ВИДАЕВ ХИЗАР ЛОМЭЛЬЕВИЧ*, 18.11.1987 г.р., с. Урус-Мартан ЧИАССР.
354. ВИСАЕВ АПТИ УВАЙСОВИЧ*, 01.05.1985 г.р., г. Грозный ЧИАССР.
355. ВИСАИТОВ АДАМ АЛИЕВИЧ*, 30.01.1957 г.р., с. Джусалы Кармакчинского района Кзыл-Ординской области Казахской ССР.
356. ВИСАИТОВ АСЛАН МОВЛДИЕВИЧ*, 27.02.1974 г.р., с. Серноводск Сунженского района ЧИАССР.
357. ВИСИХАНОВ РУСЛАН ЗИНАУДИНОВИЧ*, 04.12.1979 г.р., с. Елтай Индерского района Гурьевской области Казахской ССР.
358. ВИСЛОГУЗОВ ДМИТРИЙ СЕРГЕЕВИЧ*, 20.09.1980 г.р., г. Бийск Алтайского края.
359. ВИТУШЕВ УМАР ЗАЙНАЛОВИЧ*, 17.10.1977 г.р., с. Новый Шарой Ачхой-Мартановского района ЧИАССР.
360. ВИЧИГОВ РУСТАМ РУСЛАНОВИЧ*, 14.12.1982 г.р., с. Ачхой-Мартан ЧИАССР.
361. ВИШНЯКОВ АРТУР ВЛАДИМИРОВИЧ*, 30.10.1987 г.р., п. Шексна Вологодской области.
362. ВЛАДОВСКИЙ МИХАИЛ АЛЕКСАНДРОВИЧ*, 23.03.1983 г.р., г. Грозный Чеченской Республики.
363. ВЛАСОВ ВЛАДИМИР СЕРГЕЕВИЧ*, 29.07.1956 г.р., г. Москва.
364. ВОРОНОВ ДМИТРИЙ ВИКТОРОВИЧ*, 26.09.1969 г.р., г. Грозный Чеченская Республика.
365. ВЫШЕГУРОВ МАГОМЕД УМАРОВИЧ*, 04.08.1972 г.р., г. Орджоникидзе СОАССР.
366. ГАБАЕВ ИСЛАМ РУСЛАНОВИЧ*, 19.01.1989 г.р., с. Ведено Веденского района ЧИАССР.
367. ГАБДРАХМАНОВ РИНАТ РИФОВИЧ*, 24.12.1968 г.р., г. Уфа Республики Башкортостан.
368. ГАБДУЛХАКОВ ДАНИЛ ЛЯБИБОВИЧ*, 18.05.1982 г.р., г. Усинск Республики Коми.
369. ГАДАЕВ АНЗОР АБДУЛБЕКОВИЧ*, 04.10.1983 г.р., с. Мескер-Юрт Шалинского района ЧИАССР.
370. ГАДАЕВ МАГОМЕД КАЗБЕКОВИЧ*, 06.11.1984 г.р., с. Закан-Юрт Ачхой-Мартановского района ЧИАССР.
371. ГАДАМУРОВ АЛИХАН АДАМОВИЧ*, 21.08.1985 г.р., с. Косиновка Обоянского района Курской области.
372. ГАДЖИАКАЕВ МАГОМАДЗАГИР УМАКАЕВИЧ*, 07.01.1975 г.р., с. Доргели Карабудахкентского района ДАССР.
373. ГАДЖИБАГОМЕДОВ МУСА ГАДЖИБАГОМЕДОВИЧ*, 28.02.1972 г.р., с. Карамахи Буйнакского района ДАССР.
374. ГАДЖИЕВ МАГОМЕД АБДУСАЛИМОВИЧ*, 18.10.1968 г.р., г. Избербаше ДАССР.
375. ГАДЖИЕВ ХАБИБ САИДБЕГОВИЧ*, 10.12.1966 г.р., с. Хвайни-Кунда Цумадинского района Республики Дагестан.
376. ГАЗИЕВ БИСЛАН ХАРОНОВИЧ*, 17.08.1977 г.р., с. Катыр-Юрт Ачхой-Мартановского района ЧИАССР.
377. ГАЗИЕВ ЗАУРБЕК МАСХУДОВИЧ*, 15.04.1981 г.р., с. Пролетарское Грозненского района ЧИАССР.
378. ГАЗИЕВ КАЗБЕК РАМЗАНОВИЧ*, 24.12.1972 г.р., с. Дышне-Ведено Веденского района ЧИАССР.
379. ГАЗИЗОВ ИЛЬЯС АХМЕТХАФИЗОВИЧ*, 16.03.1960 г.р., п. Лесхоз Сабинского района Республики Татарстан.
380. ГАИРБЕКОВ ГАЗИМАГОМЕД ГАИРБЕКОВИЧ*, 26.07.1977 г.р., с. Кванада Цумадинского района Республики Дагестан.
381. ГАИРБЕКОВ МАГОМЕД ГАИРБЕКОВИЧ*, 06.02.1976 г.р., с. Кванада Цумадинского района Республики Дагестан.
382. ГАЙГЕРАЕВ УМАР МАГОМЕДОВИЧ*, 08.01.1983 г.р., с. Ачхой-Мартан ЧИАССР.
383. ГАЙТАМИРОВ АДАМ АЛИЕВИЧ*, 19.08.1976 г.р., с. Шаро-Аргун Шатойского района Чеченской Республики.
384. ГАЙТУКАЕВ ДЖАМАЛАЙ ИСАЕВИЧ*, 03.02.1979 г.р., с. Ленинское Ерментауского р-на Целиноградской обл. КазССР.
385. ГАЙХАНОВ МУСА МИНКАИЛОВИЧ*, 26.03.1953 г.р., п. Кадамжай Фрунзенского района Ошской области КиргССР.
386. ГАКАЕВ МАГОМЕД-ХУСЕЙН УМАРОВИЧ*, 18.05.1977 г.р., г. Грозный ЧИАССР.
387. ГАКАЕВ РОМАН ДЖАНДАРОВИЧ*, 01.10.1978 г.р., ст. Червленая Шелковского района ЧИАССР.
388. ГАМАДАЕВ ГАМЗАТ ЗАЛИМХАНОВИЧ*, 12.08.1980 г.р., с. Новолакское Новолакского района Республики Дагестан.
389. ГАМАДАЕВ ГИЛАНИ ЗАЛИМХАНОВИЧ*, 19.12.1978 г.р., с. Новолакское Новолакского района Республики Дагестан.
390. ГАМАДАЕВ ЗАЛИМХАН МАГОМЕДОВИЧ*, 20.08.1936 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
391. ГАМАЕВ АСЛАНБЕК ОСМАНОВИЧ*, 30.01.1978 г.р., с. Новые-Атаги ЧИАССР.
392. ГАМАЕВ ИСА МАЙРБЕКОВИЧ*, 04.11.1978 г.р., с. Ушкалой ЧИАССР.
393. ГАМИДОВ МАГОМЕДРАСУЛ МЕДЖИДОВИЧ*, 01.03.1952 г.р., с. Карамахи Буйнакского района ДАССР.
394. ГАНАЕВ ИСРАПИЛ АДАМОВИЧ*, 30.01.1987 г.р., с. Мескер-Юрт Шалинского района ЧИАССР.
395. ГАНАТОВ ХАМЗАТ ДАУДОВИЧ*, 17.09.1967 г.р., с. Ведучи Советского района ЧИАССР.
396. ГАНИЕВ РУСТАМ СУЛУМБЕКОВИЧ*, 01.12.1979 г.р., с. Чемульга Сунженского района ЧИАССР.
397. ГАНИШИВ АБДУЛГАНИ ЮСУПОВИЧ*, 05.01.1988 г.р., г. Грозный Чеченской Республики.
398. ГАПАРХОЕВ ИССА МАКШАРИПОВИЧ*, 28.09.1974 г.р., ст. Орджоникидзевская Сунженского района ЧИАССР.
399. ГАПАРХОЕВ МАЙРБЕК МАГОМЕДОВИЧ*, 12.08.1984 г.р., г. Назрань ЧИАССР.
400. ГАПОНОВ МАКСИМ АЛЕКСАНДРОВИЧ*, 06.06.1973 г.р., г. Ташкент Республики Узбекистан.
401. ГАСТЕМИРОВ РОМАН МАГОМЕДОВИЧ*, 10.03.1979 г.р., г. Грозный ЧИАССР.
402. ГАСТИЕВ ИСЛАМ ИБРАГИМОВИЧ*, 03.02.1984 г.р., с. Ведено Веденского района ЧИАССР.
403. ГАТИЕВ НАРИМАН ХИЗИРИЕВИЧ*, 07.01.1967 г.р., с. Османюрт Хасавюртовского района ДАССР.
404. ГАЦАЕВ РАМЗАН САЙД-БЕКОВИЧ*, 15.07.1989 г.р., с. Захино Пушко-Горского района Псковской области.
405. ГАЯНОВ БУЛАТ МАРСОВИЧ*, 24.07.1972 г.р., г. Туймазы Республики Башкортостан.
406. ГАЯНОВ САЛАВАТ МАРСОВИЧ*, 15.08.1976 г.р., г. Туймазы Республики Башкортостан.
407. ГЕЗИХАДЖИЕВ ХАМЗАТ МАХЧАЕВИЧ*, 18.07.1969 г.р., с. Мескеты Ножай-Юртовского района ЧИАССР.
408. ГЕРИМСУЛТАНОВ АСЛАН БЕДИЕВИЧ*, 02.11.1975 г.р., ст. Гребенская Шелковского района ЧИАССР.
409. ГЕРИХАНОВ МУСЛИМ МУСАЕВИЧ*, 27.09.1974 г.р., г. Аргун ЧИАССР.
410. ГИГИЕВ ЛЕЧИ БАУДИНОВИЧ*, 08.06.1954 г.р., г. Текели Талды-Курганской области Казахской ССР.
411. ГИМРАНОВ РУСТАМ РАВИЛОВИЧ*, 04.05.1987 г.р., р.п. Нижняя Мактама Альметьевского района ТАССР.
412. ГИНАЕВ АСЛАМБЕК ЖУНАЙДОВИЧ*, 31.12.1976 г.р., ст. Калиновская Наурского района ЧИАССР.
413. ГИНАЕВ ТИМУР МУРАТОВИЧ*, 20.05.1984 г.р., с. Ведено Веденского района ЧИАССР.
414. ГЛЕБОВ КОНСТАНТИН ВИКТОРОВИЧ*, 26.04.1979 г.р., г. Владивосток.
415. ГОЙДЕНКО РУСЛАН АЛЕКСАНДРОВИЧ*, 04.09.1977 г.
416. ГОЙЛАБИЕВ САЛВАДИ НУРАДИЕВИЧ*, 29.03.1987 г.р., с. Байтарки Ножай-Юртовского района ЧИАССР.
417. ГОЛОВНЕВ ЕВГЕНИЙ НИКОЛАЕВИЧ*, 14.05.1989 г.р., г. Красноярск.
418. ГОЛОДОК СЕРГЕЙ АЛЕКСАНДРОВИЧ*, 02.04.1962 г.р., д. Гальки Крупского р-на Минской обл. Республики Беларусь.
419. ГОРЧАКОВ ВАДИМ МИХАЙЛОВИЧ*, 27.06.1985 г.р., г. Одинцово Московской обл.
420. ГОЧИЯЕВ РАМАЗАН ХАНАФИЕВИЧ*, 08.12.1965 г.р., ст. Сторожевая Зеленчукского района Карачаево-Черкесской Республики.
421. ГРИЦКЕВИЧ НИКОЛАЙ ПАВЛОВИЧ*, 20.12.1959 г.р., г. Лунинец Брестской области.
422. ГУБАРЕВ ПАВЕЛ АЛЕКСЕЕВИЧ*, 19.02.1987 г.р., г. Омск.
423. ГУБКИН ИГОРЬ ВЛАДИМИРОВИЧ*, 25.01.1964 г.р., г. Благовещенск Амурской области.
424. ГУДАЕВ АЛИХАН ИМРАНОВИЧ*, 01.03.1981 г.р., с. Советское Приозерного р-на Калмыцкой АССР.
425. ГУДКОВ АЛЕКСЕЙ ГЕНАДЬЕВИЧ*, 05.01.1978 г.р., пос. Могойтуй Агинско-Бурятского АО Читинской области.
426. ГУМАРОВ РАВИЛЬ ШАФИЕВИЧ*, 22.11.1962 г.р., г. Кушва Свердловской области.
427. ГУМЕРОВ ИЛЬГАМ ШАКИРОВИЧ*, 16.03.1966 г.р., д. Чувашский Брод Алькеевского р-н Республики Татарстан.
428. ГУПОЛОВИЧ АЛЕКСАНДР ИВАНОВИЧ*, 17.02.1966 г.р., г. Донецк Ростовской области.
429. ГУЦИЕВ РИЗВАН МАГДАНОВИЧ*, 11.09.1966 г.р., с. Серноводск Сунженского района ЧИАССР.
430. ГУЧИГОВ РУСТАМ ВАХАЕВИЧ*, 03.11.1977 г.р., г. Урус-Мартан Урус-Мартановского района ЧИАССР.
431. ДАДАЕВ АМАЙ ДАУТОВИЧ*, 30.01.1989 г.р., ст. Наурская Наурского района ЧИАССР.
432. ДАДАЕВ ИЛЬМАН ИМРАНОВИЧ*, 26.02.1984 г.р., с. Ачхой-Мартан ЧИАССР.
433. ДАДАЕВ ЛЕЧА СУЛТАНОВИЧ*, 21.02.1982 г.р., г. Грозный ЧИАССР.
434. ДАДАЕВ МУСА УСМАНОВИЧ*, 20.09.1981 г.р., с. Надтеречное Надтеречного р-на ЧИАССР.
435. ДАДАЕВ РАСУЛ АРБИЕВИЧ*, 16.05.1985 г.р., с. Березовка Нелидовского района Калининской области.
436. ДАДАЕВ РУСЛАН МАГОМЕДОВИЧ*, 30.10.1969 г.р., с. Алхазурово Урус-Мартановского района ЧИАССР.
437. ДАДАЕВ ХАЗИР ЛЕЧИЕВИЧ*, 01.07.1968 г.р., с. Шали Шалинского р-на ЧИАССР.
438. ДАДАШЕВА АСЕТ МОВЛАГАДИНОВНА*, 03.04.1963 г.р., с. Дачу-Борзой Грозненского р-на ЧИАССР.
439. ДАЕВ АХЪЯД АСХАБОВИЧ*, 04.08.1982 г.р., г. Урус-Мартан ЧИАССР.
440. ДАЙДАЕВ ДЖАМИЛЬ ШАМСОЛТОВИЧ*, 27.07.1982 г.р., с. Урус-Мартан ЧИАССР.
441. ДАЙЗИЕВ МАГОМЕДШАПИ ЮСУПОВИЧ*, 24.05.1959 г.р., с. Карамахи Буйнарского района ДАССР.
442. ДАКАЕВ АХМЕД ИЗРАИЛОВИЧ*, 22.07.1980 г.р., с. Энгель-Юрт Гудермесского района ЧИАССР.
443. ДАКАЕВ СУЛЕЙМАН СЕБЕРОВИЧ*, 18.08.1976 г.р., с. Ленинское Наурского района ЧИАССР.
444. ДАКАЕВ ЮСУП АХЯТОВИЧ*, 20.02.1990 г.р., с. Ремонтное Ростовской области.
445. ДАКАШЕВ РУСТАМ УЗГЕНБАЕВИЧ*, 01.11.1980 г.р., г. Аргун ЧИАССР.
446. ДАЛЬЦАЕВ МУСА ТАТИЕВИЧ*, 02.04.1958 г.р., с. Новотерское Наурского р-на ЧИАССР.
447. ДАМАЕВ РУСТАМ РИЗВАНОВИЧ*, 28.02.1984 г.р., с. Урус-Мартан ЧИАССР.
448. ДАМХАЕВ УСАМА МУСАЕВИЧ*, 25.12.1977 г.р., с. Ведено Веденского района ЧИАССР.
449. ДАНАШЕВ РАМЗАН АБУЯЗИТОВИЧ*, 08.10.1971 г.р., с. Ведено Введенского района ЧИАССР.
450. ДАНДАЕВ АРБИ ХАМЗАТОВИЧ*, 01.02.1974 г.р., г. Грозный ЧИАССР.
451. ДАНДАЕВ ИСА МУМАДИЕВИЧ*, 17.04.1973 г.р., с. Дуба-Юрт ЧИАССР.
452. ДАНДАЕВ МАГОМЕД АДЛАНОВИЧ*, 22.05.1980 г.р., г. Урус-Мартан ЧИАССР.
453. ДАРАЕВ РАМЗАН ДАЛХАДОВИЧ*, 08.01.1963 г.р., с. Герменчук Шалинского района ЧИАССР.
454. ДАСАЕВ ТИМУР МОВЛИДОВИЧ*, 07.12.1979 г.р., с. Ачхой-Мартан ЧИАССР. Возможно 1974 г.р.
455. ДАТАГАЕВ АЛИ ХУСАИНОВИЧ*, 17.06.1980 г.р., с. Курчалой Шалинского района ЧИАССР.
456. ДАУДОВ АХМЕД ХОЖБАУДЫЕВИЧ*, 09.11.1979 г.р., с. Курчалой Шалинского района ЧИАССР.
457. ДАУДОВ МАХМУД АЛАУДИЕВИЧ*, 24.06.1984 г.р., г. Грозный ЧИАССР.
458. ДАУДОВ РУСЛАН САИДСАЛАХАНОВИЧ*, 24.12.1970 г.р., с. Дуба-Юрт Шалинского района ЧИАССР.
459. ДАУДОВ САЛАМБЕК СУЛТАНОВИЧ*, 19.02.1974 г.р., с. Шали Шалинского района ЧИАССР.
460. ДАУРБЕКОВ МАГОМЕД САЛИМХАНОВИЧ*, 04.10.1980 г.р., г. Назрань ЧИАССР.
461. ДАУТМЕРЗАЕВ РИЗВАН АХМАЕВИЧ*, 29.10.1980 г.р., г. Гудермес ЧИАССР.
462. ДАХАЕВ ВАХИТ ШЕРИПУЕВИЧ*, 22.06.1978 г.р., с. Автуры Шалинского района ЧИАССР.
463. ДАЦИЕВ БЕСЛАН ИСАЕВИЧ*, 07.06.1982 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
464. ДАШАЕВ КАИМ ШАМСУДИЕВИЧ*, 08.01.1982 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
465. ДАШАЕВ ТАГИР ШАМСУДИЕВИЧ*, 14.04.1984 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
466. ДАШТАЕВ ИДРИС ИБРАГИМОВИЧ*, 03.05.1977 г.р., нас. пункт Новые Атаги Шалинского района ЧИАССР.
467. ДАШУКАЕВ ВАХИД ВАХАЕВИЧ*, 28.04.1974 г.р., г. Грозный ЧИАССР.
468. ДЕБИРОВ ИСМАИЛ ХУМАИДОВИЧ*, 27.04.1971 г.р., г. Хасавюрт ДАССР.
469. ДЕДИЕВ АСЛАН СЕЛИМОВИЧ*, 10.03.1974 г.р., с. Пролетарское Грозненского района ЧИАССР.
470. ДЕККУШЕВ АДАМ ОСМАНОВИЧ*, 03.02.1962 г.р., г. Карачаевск Карачаево-Черкесской автономной области Ставропольского края.
471. ДЕМЕЛЬХАНОВ АХМЕД РУСЛАНОВИЧ*, 10.10.1983 г.р., г. Грозный ЧИАССР.
472. ДЕМЕЛЬХАНОВ РАУФ ВЯЧЕСЛАВОВИЧ*, 29.06.1985 г.р., г. Грозный ЧИАССР.
473. ДЕНИЕВ РАМЗАН СУЛТАНОВИЧ*, 06.11.1972 г.р., с. Эрсеной Веденского района ЧИАССР.
474. ДЕНИСУЛТАНОВ ЗАУРБЕК ИСМАИЛОВИЧ*, 04.11.1977 г.р., село Плодовитое Малодербетовского района Республики Калмыкия.
475. ДЕРБИШЕВ АЮБ АХМЕДОВИЧ*, 10.12.1983 г.р., с. Кулары Грозненского района ЧИАССР.
476. ДЕЦИЕВ МАУЛАТ МАСУДОВИЧ*, 03.05.1987 г.р., г. Чимкент КазССР.
477. ДЖАБАЕВ РАМЗАН ШАХРУДИНОВИЧ*, 16.04.1958 г.р., с. Алхан Ножай-Юртовского района ЧИАССР.
478. ДЖАБАЕВ САИД-МАГОМЕД АЛИЕВИЧ*, 21.05.1975 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
479. ДЖАБАРОВ ХАМЗАТ ХАМИДОВИЧ*, 18.06.1977 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
480. ДЖАБРАИЛОВ АДАМ МАГОМЕДОВИЧ*, 01.01.1979 г.р., н.п. Курчалой ЧИАССР.
481. ДЖАБРАИЛОВ АЛИК ЛЕШАЕВИЧ*, 10.08.1976 г.р., г. Грозный ЧИАССР.
482. ДЖАБРАИЛОВ АНВАР ПОХАРУДИНОВИЧ*, 10.12.1981 г.р., с. Замай-Юрт Ножай-Юртовского района ЧИАССР.
483. ДЖАБРАИЛОВ ЗЕЛИМХАН МУХОДИНОВИЧ*, 07.09.1978 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
484. ДЖАБРАИЛОВ ИСЛАМ ОБУ-АЛИЕВИЧ*, 19.12.1989 г.р., с. Ведено Веденского района ЧИАССР.
485. ДЖАБРАИЛОВ ЛЕМИ БЕТИЕВИЧ*, 03.09.1967 г.р., с. Джагларги Ножай-Юртовского района ЧИАССР.
486. ДЖАБРАИЛОВ МАГОМЕДГАДЖИ НУРМАГОМЕДОВИЧ*, 04.05.1976 г.р., с. Сильди Цумадинского района ДАССР.
487. ДЖАБРАИЛОВ РАМЗАН ХУМИДОВИЧ*, 10.02.1979 г.р., г. Шали ЧИАССР.
488. ДЖАБРАИЛОВ УСМАН ЗЕЛИМХАНОВИЧ*, 07.04.1986 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
489. ДЖАБРАИЛОВА ТУИТА АБУКОСУМОВНА*, 24.07.1967 г.р., с. Элистанжи Введенского района ЧИАССР.
490. ДЖАЛМАШВИЛИ АРСЕН ЮРЬЕВИЧ*, 03.06.1986 г.р., п. Николаевский Тарбагатаевского района Бурятской АССР.
491. ДЖАМУЛАЕВ ТАМЕРЛАН АХМЕДОВИЧ*, 07.06.1982 г.р., г. Гудермес ЧИАССР.
492. ДЖАНТЕМИРОВ ДОККА СУЛУМБЕКОВИЧ*, 27.05.1974 г.р., г. Грозный ЧИАССР.
493. ДЖАНТУЕВ ТАХИР ХУСЕЙНОВИЧ*, 27.12.1979 г.р., г. Тырнауз Кабардино-Балкарской Республики.
494. ДЖАНХОВАТОВ МАГОМЕД БАДРУДИНОВИЧ*, 10.08.1956 г.р., с. Кадар Буйнакского района Республики Дагестан.
495. ДЖАНХОТОВ АЛВИ АХМАДГИРЕЕВИЧ*, 25.05.1960 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
496. ДЖАНХОТОВ САЛЕХ УСМАНОВИЧ*, 15.02.1985 г.р., с. Кулары Грозненского района ЧИАССР.
497. ДЖАСУЕВ ИМРАН ИДРИСОВИЧ*, 20.12.1985 г.р., г. Грозный ЧИАССР.
498. ДЖАУТХАНОВ СУЛТАН САЛАМОВИЧ*, 27.09.1976 г.р., п. Ойсхара Гудермесского района ЧИАССР.
499. ДЖАЦАЕВ ТУРПАЛ ХАМИДОВИЧ*, 04.12.1966 г.р., с. Курчалой Шалинского района ЧИАССР.
500. ДЖАШЕЕВ ДЖАТДАЙ БАТДАЛОВИЧ (ДЖАШЕЕВ ДЖАТДАЙ БОРИСОВИЧ)*, 21.03.1969 г.р., а. Эльтаркач Усть-Джегутинского района Ставропольского края КЧАО.
501. ДЖВАРИДЗЕ ДАВИД ЛАВРЕНТЬЕВИЧ*, 12.04.1974 г.р., г. Вале Республики Грузия.
502. ДЖИГУЕВ АМХАД МОГИТОВИЧ*, 19.10.1986 г.р., с. Ушкалой Советского района ЧИАССР.
503. ДЖУМАГИШИЕВ АБДУЛЛЯЛИМ АХМАТОВИЧ*, 10.06.1981 г.р., с. Сары-Су Шелковского района ЧИАССР.
504. ДЖУРАЕВ АЛИШЕР МАМАРАСУЛОВИЧ*, 19.06.1978 г.р., пос. им. Исаева Колхозабадского района Халтонской области Республики Таджикистан.
505. ДЖУРАЕВ УМЕДЖОН МИРЗОАХМАДОВИЧ*, 14.10.1980 г.р., г. Худжант Республики Таджикистан.
506. ДЗАНГИЕВ МУСА БОРИСОВИЧ*, 12.09.1972 г.р., с. Алхасты Сунженского района Республики Ингушетия.
507. ДЗЕЙТОВ АДАМ РУКМАНОВИЧ*, 21.12.1983 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
508. ДЗЕЙТОВ АДЛАН РУКМАНОВИЧ*, 17.08.1978 г.р., х. Веселый Ачхой-Мартановского района Чеченской Республики.
509. ДЗЕЙТОВ САЛМАН РУХМАНОВИЧ*, 08.01.1980 г.р., хутор Веселый Ачхой-Мартановского ЧИАССР.
510. ДЗУБАЙРАЕВ АЛИ ЛЕЧИЕВИЧ*, 29.03.1989 г.р., с. Элистанжи Веденского района ЧИАССР.
511. ДИБИРОВ ДЖАФАР АБДУЛЛАЕВИЧ*, 25.06.1972 г.р., с. Терекли-Мектеб Ногайского р-на Республики Дагестан.
512. ДИКИЕВ СИДИК ГИЛАНИЕВИЧ*, 09.11.1974 г.р., с. Д-Ведено ЧИАССР.
513. ДИНАЕВ ВАХИ АБУБАКАРОВИЧ*, 01.09.1975 г.р., с. Дышне-Ведено Веденского района Чеченской Республики.
514. ДОВЛЕТБИЕВ ИДРИС МОВСАРОВИЧ*, 30.12.1984 г.р., с. Чири-Юрт ЧИАССР.
515. ДОЛГИХ АНАТОЛИЙ ВЛАДИМИРОВИЧ*, 11.03.1976 г.р., с. Бегишево Вагайского р-на Тюменской области.
516. ДОМБАЕВ АСЛАН РУСЛАНОВИЧ*, 07.03.1977 г.р., с. Толстой-Юрт Грозненского района ЧИАССР.
517. ДОТМЕРЗОЕВ МАЙРБЕК ВЛАДИМИРОВИЧ*, 18.11.1986 г.р., ст. Троицкая Сунженского района ЧИАССР.
518. ДРОБОТОВ АЛЕКСЕЙ ВАСИЛЬЕВИЧ*, 16.07.1960 г.р., г. Миллерово Ростовской области.
519. ДРОЗДОВСКАЯ АННА ЮРЬЕВНА*, 27.01.1984 г.р., г. Ярославль.
520. ДУБАЕВ АНЗОР РУСЛАНОВИЧ*, 13.08.1986 г.р., г. Грозный ЧИАССР.
521. ДУБАЕВ БЕСЛАН РИЗВАНОВИЧ*, 23.01.1987 г.р., с. Урус-Мартан ЧИАССР.
522. ДУДАЕВ ХУСЕЙН ЭЛИДОВИЧ*, 20.03.1976 г.р., г. Грозный Чеченской Республики.
523. ДУДУЕВ КАЧАК БИЛАЛОВИЧ*, 29.09.1954 г.р., с. Советское Базаркурголинского района Республики Киргизия.
524. ДУДУЕВА МАРЕТА САЛАВДИНОВНА*, 26.03.1984 г.р., ст. Шелковская Шелковского района Чеченской Республики.
525. ДУДУШЕВ ИБРАГИМ ВАХАХАЖИЕВИЧ*, 15.05.1966 г.р., с. Дышне-Ведено Веденского района Чеченской Республики.
526. ДУЖИЕВ АРСЛАН САДАХМЕДОВИЧ*, 09.06.1973 г.р., с. Ножай-Юрт Ножай-Юртовского района Чеченской Республики.
527. ДУКАЕВ АХМЕД ШАРАНИЕВИЧ*, 25.07.1983 г.р., с. Шали ЧИАССР.
528. ДУКАЕВ ИСА АЛХАЗУРОВИЧ*, 09.04.1968 г.р., с. Кади-Юрт Гудермесского района Чеченской Республики.
529. ДУКУЕВ ИСА СУЛТАНОВИЧ*, 21.01.1986 г.р., г. Гудермес ЧИАССР.
530. ДУКУШОВ АБУ-УМАР УСАМОВИЧ*, 30.05.1983 г.р., с. Урд-Юхой Советского района ЧИАССР.
531. ДУЛАЕВ АХМЕД САИД-ХЕСЕЙНОВИЧ*, 12.11.1980 г.р., с. Памятой Шатойского района ЧИАССР.
532. ДУЛАЕВ МАГОМЕД ВАХАЕВИЧ*, 20.10.1983 г.р., г. Аргун ЧИАССР.
533. ДУЛАТОВ ШАМИЛЬ САЛАУДИНОВИЧ*, 25.05.1980 г.р., с. Большая Мартыновка Мартыновского района Ростовской области.
534. ДУНДАЕВА РАЙСА ДОККАЕВНА*, 11.06.1973 г.р., г. Грозный Чеченской Республики.
535. ДУРАЕВ АСЛАНБЕК ЛЕМАЕВИЧ*, 06.08.1969 г.р., г. Грозный ЧИАССР.
536. ДУРИЕВ АЛИ АБДУЛХАМИДОВИЧ*, 13.05.1977 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
537. ДЫШНИЕВ МАГОМЕД ХУСЕЙНОВИЧ*, 04.02.1982 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
538. ДЬЯЧКОВ АЛЕКСАНДР СЕРГЕЕВИЧ*, 05.10.1980 г.р., п. Октябрьский Устьянского района Архангельской области.
539. ЕДАЕВ ИБРАГИМ РУСЛАНОВИЧ*, 11.11.1983 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
540. ЕДАЕВ РУСЛАН МАГОМЕДОВИЧ*, 07.02.1982 г.р., г. Грозный ЧИАССР.
541. ЕДИСУЛТАНОВ АСЛАН ВАХАЕВИЧ*, 13.11.1975 г.р., с. Белгатой Шалинского района ЧИАССР.
542. ЕПИФАНОВ ПАВЕЛ НИКОЛАЕВИЧ*, 24.08.1976 г.р., г. Грозный ЧИАССР.
543. ЕПРИНЦЕВ НИКОЛАЙ БОРИСОВИЧ*, 08.07.1978 г.р., ст. Исправная Зеленчукского р-на Карачаево-Черкесской Республики.
544. ЕСИН АРТЕМ СЕРГЕЕВИЧ*, 08.03.1981 г.р., г. Чистополь Татарской АССР.
545. ЕФРЕМОВ АНДРЕЙ АНАТОЛЬЕВИЧ*, 15.07.1971 г.р., г. Витебск Республики Беларусь.
546. ЕШУРКАЕВ МУСЛИМ НУРДЫЕВИЧ*, 28.03.1989 г.р., с. Побединское Грозненского района ЧИАССР.
547. ЖАБРАИЛОВ АСЛАН РОМАНОВИЧ*, 15.02.1983 г.р., с. Караванное Лиманского района Астраханской области.
548. ЖАБРАИЛОВ ХИЗИР АЛИЕВИЧ*, 08.05.1980 г.р., с. Аллерой Шалинского района ЧИАССР.
549. ЖАМАЛДАЕВ ЗАУРБЕК АЛХАЗУРОВИЧ*, 01.06.1985 г.р., с. Серноводск Сунженского района ЧИАССР.
550. ЖАНТУЕВ МАГОМЕД ЖАМАЛОВИЧ*, 25.08.1974 г.р., г. Нальчик Кабардино-Балкарской Республики.
551. ЖАПКАЕВ ШАРКАН ИСАЕВИЧ*, 19.12.1974 г.р., с. Хаттуни Веденского района ЧИАССР.
552. ЖАРКОВ СЕРГЕЙ ВЛАДИМИРОВИЧ*, 12.06.1985 г.р., г. Череповец Вологодской области.
553. ЖЕБРАИЛОВ ИБРАГИМ ШУДДИЕВИЧ*, 19.09.1984 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
554. ЖИДАЕВ САЛАМБЕК ИСАНОВИЧ*, 29.10.1982 г.р., с. Ширди-Мохк Веденского района ЧИАССР.
555. ЖИЛИНСКИЙ КИРИЛЛ ВЛАДИМИРОВИЧ*, 26.06.1982 г.р., г. Луга Ленинградской области.
556. ЖУКОВЦОВ ВАЛЕРИЙ ВИТАЛЬЕВИЧ*, 10.04.1988 г.р., г. Москва.
557. ЗАВЛИЕВ КАЗБЕК ГАРСОЛТОВИЧ*, 25.09.1984 г.р., с. Ачхой-Мартан Ачхой-Мартановского р-на ЧИАССР.
558. ЗАГАЛАЕВ МОВСАР АНАСОВИЧ*, 23.12.1966 г.р., с. Дарго Веденского района ЧИАССР.
559. ЗАГРЕТДИНОВ МАРАТ АЛЬБЕРТОВИЧ*, 03.06.1985 г.р., г. Азнакаево Республики Татарстан.
560. ЗАИТОВ ВИСАНИ НУРИТОВИЧ*, 02.08.1970 г.р., п. Горагорск Надтеречного района Чеченской Республики.
561. ЗАЙНАГУТДИНОВ РУСТЕМ РАФИКОВИЧ*, 20.10.1971 г.р., г. Салават Республики Башкортостан.
562. ЗАЙНАЛОВ АПТИ РАМЗАНОВИЧ*, 30.06.1980 г.р., с. Ведено ЧИАССР.
563. ЗАЙНУДИНОВ ИСА ИСАЕВИЧ*, 27.12.1938 г.р., с. Кудали Гунибского района ДАССР.
564. ЗАЙЦЕВ АЛЕКСЕЙ ВЛАДИМИРОВИЧ*, 17.11.1971 г.р., г. Томск.
565. ЗАКАЕВ ИБРАГИМ ХУСАЙНОВИЧ*, 25.11.1973 г.р., ст. Галюгаевская Курского района Ставропольского края.
566. ЗАКИРОВ ИЛЬШАТ ШАУКАТОВИЧ*, 22.06.1962 г.р., с. Олуяз Мамадышского района Республики Татарстан.
567. ЗАКРАИЛОВ РУСТАМ ХОЖАХМЕДОВИЧ*, 25.07.1980 г.р., с. Старые Атаги Грозненского района ЧИАССР.
568. ЗАКРИЕВ АРБИ САИДАЛИЕВИЧ*, 21.09.1979 г.р., ст. Николавская Наурского р-на Чеченской Республики.
569. ЗАКРИЕВ НУРДЫ ЯРАГИЕВИЧ*, 15.05.1952 г.р., Каратальский район Алма-Атинской области КССР.
570. ЗАКРИЕВ РАСУЛ АБДУЛВАДУДОВИЧ*, 02.04.1974 г.р., г. Хасавюрт Дагестанской АССР.
571. ЗАКРИЕВ СУЛТАН ШАЙАХМАТОВИЧ*, 19.11.1986 г.р., с. Нурадилово Хасавюртовского района ДАССР.
572. ЗАМТИЕВ ЛЕМА ШАМИЛЬЕВИЧ*, 02.10.1985 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
573. ЗАРИПОВ РАДИК РАМИЛОВИЧ*, 08.10.1985 г.р., с. Большие Кибячи Сабинского района ТАССР.
574. ЗАХАРКИН ВЛАДИМИР ВАЛЕРЬЕВИЧ*, 18.02.1975 г.р., ст. Червленая Шелковского района Чеченской Республики.
575. ЗЕЛЕМХАНОВ ИБРАГИМ МАГАМЕДОВИЧ*, 27.09.1989 г.р., г. Грозный ЧИАССР.
576. ЗЕУШЕВ ЭДУАРД ИСМАИЛОВИЧ*, 02.09.1977 г.р., г. Тырныауз КБР.
577. ЗИЗАЕВ АПТИ АБДУРАХМАНОВИЧ*, 06.05.1981 г.р., г. Урус-Мартан ЧИАССР.
578. ЗИННУРОВ РАУФ РАШИТОВИЧ*, 09.02.1978 г.р., с. Возжаевка Белогородского района Амурской области.
579. ЗИЯВУДИНОВ ЗИЯВУДИН КУРБАНОВИЧ*, 02.05.1977 г.р., с. Кикуни Гергебельского района Республики Дагестан.
580. ЗУБАЙРАЕВ САЙД-АХМЕД САЙДЕМИЕВИЧ*, 24.10.1979 г.р., с. Побединское Грозненского р-на Чеченской Республики.
581. ЗУЛКАРНАЕВ МУСЛИМ ЗАЙНДИЕВИЧ*, 18.07.1977 г.р., с. Муцалаул Хасавюртовского района РеспубликиДагестан.
582. ЗУХАЙРАЕВ АСЛАН НАГАЕВИЧ*, 12.09.1974 г.р., с. Сержен-Юрт Шалинского района ЧИАССР.
583. ЗУХАЙРАЕВ МУСА АЛИЕВИЧ*, 02.05.1974 г.р., г. Грозный ЧИАССР.
584. ЗЯЛИЛОВ ИЛЬНАР ИЛЬЯСОВИЧ*, 27.09.1980 г.р., г. Казань ТАССР.
585. ИБАЕВ РУСЛАН ЛОМ-АЛИЕВИЧ*, 11.11.1983 г.р., с. Старые Атаги Грозненского района ЧИАССР.
586. ИБАКОВ ЯСАВИЙ БУХАРЕВИЧ*, 01.09.1970 г.р., ст. Наурская ЧИАССР.
587. ИБРАГИМОВ АЛИХАН АДНАНОВИЧ*, 21.09.1980 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
588. ИБРАГИМОВ АРБИ ШАХИДОВИЧ*, 19.05.1974 г.р., с. Серноводск Сунженского района ЧИАССР.
589. ИБРАГИМОВ АХМЕД МАМАТОВИЧ*, 01.08.1976 г.р., с. Катыр-Юрт Ачхой-Мартановского района ЧИАССР.
590. ИБРАГИМОВ БИСЛАН МАСХУДОВИЧ*, 27.12.1976 г.р., г. Урус-Мартан Урус-Мартановского района ЧИАССР.
591. ИБРАГИМОВ ДАУД ВАХОДОВИЧ*, 07.12.1982 г.р., с. Урус-Мартан ЧИАССР.
592. ИБРАГИМОВ РУСЛАН ДЖАВАДИЕВИЧ*, 27.07.1982 г.р., г. Грозный ЧИАССР.
593. ИГОЛКИН МИХАИЛ ВИТАЛЬЕВИЧ*, 03.07.1974 г.р., г. Пермь.
594. ИДИГОВ ЗЕЛИМХАН АЛХАЗУРОВИЧ*, 09.06.1977 г.р., с. Старые-Атаги Грозненского района ЧИАССР.
595. ИДИГОВ РАМЗАН АСРУДИНОВИЧ*, 29.06.1979 г.р., с. Курчалой Шалинского района Чеченской Республики.
596. ИДРИСОВ БЕКМИРЗА АХМЕДОВИЧ*, 06.02.1984 г.р., с. Ялхой-Мохк Ножай-Юртовского района ЧИАССР.
597. ИДРИСОВ СУЛБАН СУЛТАНОВИЧ*, 03.06.1983 г.р., г. Шали ЧИАССР.
598. ИДРИСОВ ТИМУР САЙПИЕВИЧ*, 03.11.1974 г.р., г. Аргун ЧИАССР.
599. ИЖАЕВ МОВСАР САЛМАНОВИЧ*, 15.05.1983 г.р., с. Валерик Ачхой-Мартановского района ЧИАССР.
600. ИЗМАЙЛОВ ВАХА РУСЛАНОВИЧ*, 26.11.1983 г.р., г. Назрань ЧИАССР.
601. ИЛИЕВ ИССА ДАВИДОВИЧ*, 11.06.1976 г.р., с. Камбилеевское Пригородного района Северо-Осетинской АССР.
602. ИЛЬЯСОВ АБДУЛМАЛИК АБДУЛХАДЖИЕВИЧ*, 09.02.1959 г.р., с. Мирзааки Узгенский район Ошская область Киргизской ССР.
603. ИЛЬЯСОВ БАХРУДЫ ЗЕМЕЛЬЕВИЧ*, 24.05.1966 г.р., г. Гудермес ЧИАССР (24.05.1953 г.).
604. ИЛЬЯСОВ МУСЛИМ ЯРАГИЕВИЧ*, 09.11.1972 г.р., г. Шали ЧИАССР.
605. ИЛЯСОВ РАСУЛ КУРБАНОВИЧ*, 26.07.1985 г.р., с. Ведено Веденского района ЧИССР.
606. ИНАЛОВ АСЛАМБЕК АБУЯЗИТОВИЧ*, 05.06.1982 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
607. ИНАЛОВ ТИМУР АБУЯЗИТОВИЧ*, 02.09.1988 г.р., с. Ачхой-Мартан ЧИАССР.
608. ИОНОВ РУСЛАН ГАЗРАИЛЕВИЧ*, 31.08.1980 г.р., г. Усть-Джегута Карачаево-Черкесской Республики.
609. ИРИСБИЕВ ВАХИД ХАМИДОВИЧ*, 12.04.1973 г.р., с. Байрамаул Хасавюртовского р-на Республики Дагестан.
610. ИРИСБИЕВ МАГОМЕД УМАРПАШАЕВИЧ*, 02.08.1979 г.р., г. Гудермес Чечено-Ингушской АССР.
611. ИРИСХАНОВ ГЕЛАНИ УМАР-АЛИЕВИЧ*, 09.08.1983 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
612. ИРИСХАНОВ ИЛЕС ГИЛАНИЕВИЧ*, 22.06.1965 г.р., г. Аргун ЧИАССР.
613. ИРИСХАНОВ ЛЕМА УМАР-АЛИЕВИЧ*, 07.08.1978 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
614. ИСАЕВ АЛИХАН АЗИЗОВИЧ*, 1983 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
615. ИСАЕВ ИСЛАМ ДЕНИЕВИЧ*, 09.05.1984 г.р., Целиноградская область КазССР.
616. ИСАЕВ ЛЕМА ЯХЪЯЕВИЧ*, 30.04.1983 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
617. ИСАЕВ РАМЗАН УАХИТОВИЧ*, 08.08.1979 г.р., ст. Вознесеновка Малгобекского района ЧИАССР.
618. ИСАЕВ САИД-МАГОМЕД ЛЕЧАЕВИЧ*, 18.04.1978 г.р., с. Ачхой-Мартан ЧИАССР.
619. ИСАЕВ САЛАМБЕК МУСАЕВИЧ*, 14.11.1987 г.р., с. Бурнов Джувалинского района Джамбульской области КазССР.
620. ИСАЕВ ХАСАН БУКУЛИЕВИЧ*, 11.05.1967 г.р., с. Липовка Урус-Мартановского района ЧИАССР.
621. ИСАКОВ АБДУЛКАДЫР МАГОМЕДОВИЧ*, 12.03.1965 г.р., с. Комсомольское Кизилюртовского района Республики Дагестан.
622. ИСАКОВ АСЛАНБЕК МОВЛДЫЕВИЧ*, 08.05.1983 г.р., с. Урус-Мартан Урус-Мартановского района Чеченской Республики.
623. ИСАКОВ БЕСЛАН УРУХМАНОВИЧ*, 07.12.1978 г.р., с. Бережновка Николаевского района Волгоградской области.
624. ИСАКОВ ВАЛИД САИД-АХМЕТОВИЧ*, 12.08.1972 г.р., с. Рошни-Чу Урус-Мартановского района ЧИАССР.
625. ИСАКОВ КАХРАМОН ЭРГАШЕВИЧ*, 23.03.1970 г.р., г. Ташкент Республики Узбекистан.
626. ИСАКОВ ШИРЛАМ ШИРВАНЬЕВИЧ*, 19.10.1979 г.р., г. Грозный ЧИАССР.
627. ИСЛАМОВ ЛЕЧИ СИРАЕВИЧ*, 28.05.1961 г.р., с. Алхазурово Урус-Мартановского района ЧИАССР.
628. ИСЛАМОВ САИД МАГОМЕДОВИЧ*, 31.01.1977 г.р., с. Кислово Быковского района Волгоградской обл.
629. ИСЛАМОВ УСМАН МУСАЕВИЧ*, 17.12.1979 г.р., г. Аргун Шалинского района ЧИАССР.
630. ИСМАИЛОВ АСЛАН БАУДИНОВИЧ*, 11.11.1978 г.р., г. Грозный Чеченской Республики.
631. ИСМАИЛОВ АХМЕД ИМРАНОВИЧ*, 24.06.1974 г.р., г. Чимкент Казахской ССР.
632. ИСМАИЛОВ ИСЛАМ ИСАЕВИЧ*, 29.04.1987 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
633. ИСМАИЛОВ ИСМАИЛ МАГОМЕДОВИЧ*, 03.09.1949 г.р., с. Леваши Левашинского р-на Республики Дагестан.
634. ИСМАИЛОВ КАЗБЕК ВАХИДОВИЧ*, 09.06.1977 г.р., с. Аллерой Ножай-Юртовского района ЧИАССР.
635. ИСМАИЛОВ МУХТАРПАША ХУМАИДОВИЧ*, 11.01.1972 г.р., с. Борагангечу Хасавюртовского района Республики Дагестан.
636. ИСМАИЛОВ САИД-ХУСАЙН ЛЕЧИЕВИЧ*, 16.09.1985 г.р., с. Белгатой Шалинского района ЧИАССР.
637. ИСМАИЛОВ ШАМХАН ШАМСУДИНОВИЧ*, 12.09.1983 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
638. ИСРАИЛОВ ВАХИТ ХАСЕНОВИЧ*, 12.10.1983 г.р., с. Суворов-Юрт Гудермесского района ЧИАССР.
639. ИСРАИЛОВ ВИСХАН ВАЛИДОВИЧ*, 17.01.1988 г.р., с. Центарой Ножай-Юртовского района ЧИАССР.
640. ИСРАИЛОВ ФАРИД ХАЙРУЛАЕВИЧ*, 12.10.1980 г.р., с. Ведено Веденского района ЧИАССР.
641. ИСРАИЛОВ ХАБИБ ХАВАЖИЕВИЧ*, 16.01.1985 г.р., с. Макажой Веденского района ЧИАССР.
642. ИСРАПИЛОВ АБУ-СЕЛИМ АБУ-МУСЛИМОВИЧ*, 08.01.1976 г.р., с. Рошни-Чу Урус-Мартановского района ЧИАССР.
643. ИСРАПИЛОВ ИБРАГИМ АХМАДОВИЧ*, 13.01.1960 г.р., с. Сюжи Советского района ЧИАССР.
644. ИСТАМУЛОВ БЕКСОЛТ ШИРВАНИЕВИЧ*, 14.03.1979 г.р., с. Ведено Веденского района ЧИАССР.
645. ИСУПХАДЖИЕВ АДАМ ВАХАЕВИЧ*, 13.11.1985 г.р., г. Грозный ЧИАССР.
646. ИСУПХАДЖИЕВ САЙДАМИН АЛМАНОВИЧ*, 25.11.1976 г.р., ст. Калиновская Наурского района ЧИАССР.
647. ИЦАРАЕВ ИСА МАГОМЕДОВИЧ*, 29.11.1976 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
648. ИШКОВ РУСЛАН НАВИЛЬЕВИЧ*, 11.09.1979 г.р., г. Чистополь Республики Татарстан.
649. ИШМУРАТОВ ТИМУР РАВИЛЕВИЧ*, 05.06.1975 г.р., г. Азнакаево Республики Татарстан.
650. КАБИЛОВ БУХАРИ ГЕЛАНИЕВИЧ*, 30.07.1982 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
651. КАБЫЛОВ АДЛАН АДАМОВИЧ*, 26.12.1979 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
652. КАВТАРАШВИЛИ АСЛАН АЛЕКСАНДРОВИЧ*, 22.04.1982 г.р., с. Джоколо Ахметского района Грузинской ССР.
653. КАДИЕВ САИД-САЛАХ ХОЗУЕВИЧ*, 10.02.1974 г.р., с. Шатой Шатойского района ЧИАССР.
654. КАДИСОВ АЛАШ АТОВХАДЖИЕВИЧ*, 02.10.1977 г.р., с. Зандак Ножай-Юртовского района ЧИАССР.
655. КАДЫРОВ АЛИ МОВДАЕВИЧ*, 18.10.1979 г.р., с. Нижний Герзель Гудермесского района ЧИАССР.
656. КАЗАНЧЕВ АСЛАНБЕК ЮРЬЕВИЧ*, 08.11.1971 г.р., г. Нальчик Кабардино-Балкарской Республики.
657. КАЗБУЛАТОВ ШАМИЛЬ КАСИМОВИЧ*, 10.06.1972 г.р., с. Кара-Тюбе Нефтекумского района Ставропольского края.
658. КАЗНИН ОЛЕГ ВАЛЕНТИНОВИЧ*, 02.04.1963 г.
659. КАИМОВ ИЛЬЯС БАУДИНОВИЧ*, 03.04.1984 г.р., г. Грозный ЧИАССР.
660. КАИМОВ ИСА ЛОМ-АЛИЕВИЧ*, 11.07.1985 г.р., г. Грозный ЧИАССР.
661. КАИМОВ МОЛДЫ ЛОМ-АЛИЕВИЧ*, 26.02.1976 г.р., с. Побединское Грозненского района ЧИАССР.
662. КАЛИМУЛЛИН НАФИС МУЗАГИТОВИЧ*, 12.01.1959 г.р., с. Урсаево Азнакаевского района Республики Татарстан.
663. КАМАЛЕТДИНОВ АЙРАТ ГАМИЛОВИЧ*, 26.04.1976 г.р., г. Набарежные Челны ТАССР.
664. КАМЕНИЧЕНКО СЕРГЕЙ СЕРГЕЕВИЧ*, 24.10.1975 г.р., ст. Ассиновская Сунженского района ЧИАССР.
665. КАНАЕВ САИД САЙД-МАГОМЕДОВИЧ*, 14.03.1984 г.р., с. Захарово Рязанской области.
666. КАНТАЕВ АНЗОР ЮСУПОВИЧ*, 10.10.1972 г.р., с. Ачхой-Мартан Ачхой-Матрановского района ЧИАССР.
667. КАНТАЕВ КАЗБЕК МАЙРБЕКОВИЧ*, 21.06.1980 г.р., с. Ачхой-Мартан ЧИАССР.
668. КАНТАЕВ РАДЖУ ХАМЗАНОВИЧ*, 28.09.1982 г.р., с. Ачхой-Мартан Ачхой-Мартановского р-на ЧИАССР.
669. КАППУШЕВ АЛИ АНЗАУРОВИЧ*, 28.11.1967 г.р., с. Учкекен Малокарачаевского района Карачаево-Черкесской Республики.
670. КАРАСОВ ТИМУР МУРЗАБЕКОВИЧ*, 07.11.1975 г.р., а. Адыге-Хабль Адыге-Хабльского района Ставропольского края Карачаево-Черкесской Республики (КЧАО).
671. КАРИМОВ ИСА АБДУЛАЕВИЧ*, 23.12.1970 г.р., с. Побединское Грозненского района Чеченской Республики.
672. КАРПЕНКО ВИКТОР ЯКОВЛЕВИЧ*, 09.01.1950 г.р., с. Воронцовка Фрунзенской обл. Кыргызской ССР.
673. КАРТУЕВ УВАЙС МАХМУДОВИЧ*, 13.01.1960 г.р., с. Комсомольское Урус-Мартановского района Чеченской Республики.
674. КАСАТКИНА СВЕТЛАНА ВИКТОРОВНА*, 16.02.1963 г.р., г. Йошкар-Ола.
675. КАСЫМАХУНОВ ЮСУП САЛИМАХУНОВИЧ*, 15.10.1964 г.р., г. Андижан Республики Узбекистан.
676. КАТАЕВ АБУБАКАР ЭЛЬМУРЗАЕВИЧ*, 01.07.1979 г.р., селение Батаюрт Хасавюртовского района Республики Дагестан.
677. КАТАЕВ АХМЕД ВАХАЕВИЧ*, 27.03.1980 г.р., с. Алхан-Кала Грозненского района ЧИАССР.
678. КАТАЕВ САИД-ЭМИН УВАЙСОВИЧ*, 27.12.1984 г.р., с. Старые Атаги Грозненского района ЧИАССР.
679. КАТЧИЕВ РАШИД АБРЕКЗАУРОВИЧ*, 28.08.1974 г.р., с. Учкент Малокарачаевского района Карачаево-Черкесской Республики.
680. КАЦИЕВ СУЭЛДЫ РУСЛАНОВИЧ*, 12.06.1976 г.р., г. Грозный ЧИАССР.
681. КЕРЕЙТОВ РУСЛАН ЮНУСОВИЧ*, 14.04.1977 г.р., а. Эркен-Халк Адыге-Хабльского района Карачаево-Черкесской Республики.
682. КЕЧЕРУКОВ ОЙСУЛ КАЗИ-МАГОМЕДОВИЧ*, 02.01.1966 г.р., с. Учкекен Малокарачаевского района Ставропольского края.
683. КИБИЧОВ РИЗВАН САЛМАНОВАИЧ*, 01.12.1969 г.р., с. Мескеты Ножай-Юртовского района ЧИАССР.
684. КИЛАТ КОНСТАНТИН ВЛАДИМИРОВИЧ*, 27.03.1976 г.р., г. Красноводск Туркменской ССР.
685. КИМ ВАЛЕРИЙ САНГИЛЬЕВИЧ*, 14.10.1976 г.р., пос. Быков Долинского р-на Сахалинской области.
686. КИРИЕНКО КОНСТАНТИН БОРИСОВИЧ*, 13.05.1975 г.р., г. Барнаул Алтайского края.
687. КИРИЛЛОВ ИГОРЬ АНАТОЛЬЕВИЧ*, 05.05.1975 г.р., г. Томск.
688. КЛЕВАЧЕВ МИХАИЛ МИХАЙЛОВИЧ*, 30.03.1958 г.р., г. Москва.
689. КЛИМУК СЕРГЕЙ АЛЕКСАНДРОВИЧ*, 09.12.1970 г.р., пос. Первое Мая Илийского района Алма-Атинской области Казахской ССР.
690. КЛОЧКОВ РУСЛАН СЕРГЕЕВИЧ*, 04.01.1976 г.р., пос. Первомайский Тамбовской области.
691. КОВАЛЬЧУК ФЕДОР СЕРГЕЕВИЧ*, 06.03.1981 г.р., г. Полярные Зори Мурманской обл.
692. КОВРАЕВ АХМЕД МАГОМЕДОВИЧ*, 29.04.1977 г.р., г. Грозный ЧИАССР.
693. КОВРАЕВ ВАХИД ВАХАЕВИЧ*, 15.12.1974 г.р., с. Кулары Грозненского района Чечено-Ингушской АССР.
694. КОВРАЕВ ВИСХАДЖИ ВИСИТАЕВИЧ*, 18.04.1982 г.р., с. Цоци-Юрт Курчалоевского района Чеченской Республики.
695. КОВРАЕВ РАМЗАН АВАЛУЕВИЧ*, 20.12.1969 г.р., г. Грозный ЧИАССР.
696. КОВРАЕВ РУСЛАН МАХМУДОВИЧ*, 03.06.1977 г.р., с. Урус-Мартан Урус-Мартановского р-на Чечено-Ингушской АССР.
697. КОДЗОЕВ МАГОМЕД МАЖИТОВИЧ*, 18.04.1975 г.р., г. Назрань ЧИАССР.
698. КОЗРОЕВ РАМАЗАН ДЖАБРАИЛОВИЧ*, 07.02.1974 г.р., ст. Гребенская Шелковского района ЧИАССР.
699. КОЙТЕМИРОВ АБДУЛГАСАН МАГОМЕДКАМИЛОВИЧ*, 22.02.1969 г.р., с. Н. Казанище ДАССР.
700. КОЙЧУЕВ РУСЛАН НУРПАШАЕВИЧ*, 01.12.1977 г.р., пос. Н.Сулак Кизилюртовского района Республики Дагестан.
701. КОЙЧУЕВ РУСЛАН ХАНАПИЕВИЧ*, 09.11.1969 г.р., г. Усть-Джегута Карачаево-Черкесской Республики.
702. КОКУНАЕВ РУСТАМ АЛЬБЕКОВИЧ*, 06.03.1986 г.р., с. Ачхой-Мартан ЧИАССР.
703. КОЛЧИН ЮРИЙ НИКОЛАЕВИЧ*, 08.04.1968 г.р., г. Дятьково Брянской области.
704. КОРНИЕНКО ГЕННАДИЙ АДАМОВИЧ*, 27.06.1950 г.р., г. Киселевск Кемеровской области.
705. КОРОВИН РУСЛАН МУМАДИЕВИЧ*, 18.07.1983 г.р., г. Грозный Чечено-Ингушской АССР.
706. КОРОЛЕВ НИКОЛАЙ ВАЛЕНТИНОВИЧ*, 31.03.1981 г.р., г. Москва.
707. КОРОЛЕВ СЕРГЕЙ ЕВГЕНЬЕВИЧ*, 12.11.1984 г.р., г. Сокольники Новомосковского района Тульской области.
708. КОРПЕНКО АЛЕКСАНДР ИННОКЕНТЬЕВИЧ*, 10.01.1979 г.р., г. Усть-Кута Иркутской области.
709. КОСАРИМ АНАТОЛИЙ ПЕТРОВИЧ*, 16.02.1961 г.р., п. Крещенский Гордеевского района Брянской области.
710. КОСИЛОВ СЕРГЕЙ ПЕТРОВИЧ*, 16.12.1953 г.р., г. Фатеж Фатежский район Курской области.
711. КОСТАРЕВ ОЛЕГ ВЛАДИМИРОВИЧ*, 25.04.1986 г.р., г. Глазов Удмуртской АССР.
712. КОСТЕНКО НИКОЛАЙ НИКОЛАЕВИЧ*, 20.09.1974 г.р., д. Лукошкино Топкинского района Кемеровской области.
713. КОСТОЕВ МАГОМЕТ БИСУЛТАНОВИЧ*, 29.07.1970 г.р., г. Орджоникидзе СО АССР.
714. КОСУМОВ ХАВАЖ ХУСЕЙНОВИЧ*, 01.02.1978 г.р., г. Аргун ЧИАССР.
715. КРЫМШАМХАЛОВ ЮСУФ ИБРАГИМОВИЧ*, 16.11.1966 г.р., п. Эркен-Шахар Адыге-Хабльского района Ставропольского края.
716. КУБАЧЕВ АХМЕД МОХМАДОВИЧ*, 20.10.1981 г.р., с. Чернокозово Наурского района ЧИАССР.
717. КУДАЕВ АХМЕД РУСЛАНОВИЧ*, 18.05.1985 г.р., г. Грозный ЧИАССР.
718. КУЖУЛОВ АРТУР ГАСАНОВИЧ*, 02.01.1980 г.р., ст. Шелковская Шелковского р-на ЧИАССР.
719. КУЖУЛОВ ИСМАИЛ ИМАНОВИЧ*, 28.06.1966 г.р., с. Эшилхатой Веденского района ЧИАССР.
720. КУЛАЕВ АРТУР ХАЛИТОВИЧ*, 30.07.1980 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
721. КУЛАЕВ НУРПАШИ АБУРГКАШЕВИЧ*, 28.10.1980 г.р., с. Энгеной Ножай-Юртовского района ЧИАССР.
722. КУЛИНИЧ ПАВЕЛ ВАЛЕНТИНОВИЧ*, 17.08.1973 г.р., г. Миасс Челябинской области.
723. КУЛЬВИНЕЦ АНАТОЛИЙ АЛЕКСАНДРОВИЧ*, 02.06.1972 г.р., г. Грозный Чеченской Республики.
724. КУПРИЯНОВ КИРИЛЛ АРНОЛЬДОВИЧ*, 28.11.1973 г.р., Ленинград.
725. КУРАМШИН АДЕЛЬ РУСТЭМОВИЧ*, 09.08.1982 г.р., г. Бугульма Республики Татарстан.
726. КУРАШЕВ НАСРУДИН ВАХИДОВИЧ*, 18.01.1982 г.р., с. Советское Советского района ЧИАССР.
727. КУРГАНОВ ЛАСХАН МАМБЕТОВИЧ*, 24.06.1982 г.р., ст. Щелкозаводская Шелковского района ЧИАССР.
728. КУРЕБЕДА НАТАЛЬЯ ВАЛЕНТИНОВНА*, 13.09.1975 г.р., г. Челябинск.
729. КУРКАЕВ СОСЛАН ХАСАНОВИЧ*, 11.05.1979 г.р., г. Чарск Семипалатинской области КазССР.
730. КУРКАЕВ ХУСЕН АХМЕДОВИЧ*, 29.06.1975 г.р., с. Слепцовская ЧИАССР.
731. КУЧАВА ЕЛГУДЖА ВАХТАНГОВИЧ*, 10.07.1977 г.р., с. Дэнвери Целенджихского района Грузинской ССР.
732. ЛАБАЗАНОВ АСЛАНБЕК СУЛТАНОВИЧ*, 28.04.1971 г.р., с. Советское Советского района Чеченской Республики.
733. ЛАБАЗАНОВ МАНСУР АХЪЯТОВИЧ*, 14.03.1979 г.р., ст. Ишерская Наурского района ЧИАССР.
734. ЛАБАЗАНОВ РИЗВАН ИСАЕВИЧ*, 26.09.1976 г.р., с. Алхан-Кала Грозненского района ЧИАССР.
735. ЛАВАРСЛАНОВ ХАЙБУЛА ЛАВАРСЛАНОВИЧ*, 18.09.1940 г.р., с. Карамахи Буйнакского района Республики Дагестан.
736. ЛАВРЕНОВ ВИТАЛИЙ ВЛАДИМИРОВИЧ*, 25.04.1983 г.р., г. Ленинград.
737. ЛАТЫПОВ САЛАВАТ МИРЗАГИТОВИЧ*, 16.02.1975 г.р., г. Ангрен Ташкентской области Республики Узбекистан.
738. ЛЕЛИЕВ АРСЕН ВИСИРПАШАЕВИЧ*, 24.09.1973 г.р., г. Хасавюрт Республики Дагестан.
739. ЛЕЛИЕВ ТАХИР ВИСИРПАШАЕВИЧ*, 20.04.1983 г.р., г. Хасавюрт Хасавюртовского р-на Республики Дагестан.
740. ЛЕЧИЕВ СУПЬЯН МУСАЕВИЧ*, 02.10.1980 г.р., с. Галайты Ножай-Юртовского района ЧИАССР.
741. ЛИМОНОВ КОНСТАНТИН МИХАЙЛОВИЧ*, 22.03.1976 г.р., пос. Пролетарье Верхотурского района Свердловской области.
742. ЛИСИЦИНА ЮЛИЯ СЕРГЕЕВНА*, 01.07.1982 г.р., г. Усть-Илимск Иркутской области.
743. ЛИХАНОВ АНДРЕЙ ВИКТОРОВИЧ*, 09.08.1978 г.р., г. Зыряновск Восточно-Казахстанской области.
744. ЛОБАЧЕВ ВЛАДИМИР ВЛАДИМИРОВИЧ*, 12.09.1970 г.р., х. Черни Усть-Донецкого района Ростовской области.
745. ЛОЛОХОЕВ МАГОМЕД КУРЕЙШОВИЧ*, 17.07.1978 г.р., с. Экажево Назрановского района Чечено-Ингушской АССР.
746. ЛОМАЕВ МУСА УМУРСОЛТОВИЧ*, 04.06.1981 г.р., г. Грозный Чеченской Республики.
747. ЛОРСАНОВ ИСЛАМ АБДУЛ-МУТАЛИПОВИЧ*, 20.09.1983 г.р., Ачхой-Мартановский район ЧИАССР.
748. ЛОРСАНОВ РУСЛАН ЭМДИЕВИЧ*, 07.02.1983 г.р., г. Грозный ЧИАССР.
749. ЛУКМАНОВ АЙРАТ РАЗИФОВИЧ, 27.09.1974 г.р., г. Дюртюли Республики Башкортостан.
750. ЛУКОЖЕВ ИСЛАМ БАЗДЖИГИТОВИЧ*, 22.01.1975 г.р., с. Тукуй-Мектеб Нефтекумского района Ставропольского края.
751. ЛУКЬЯНЧИКОВ ВИКТОР ВАСИЛЬЕВИЧ*, 08.01.1951 г.р., г. Волчанск Карпинский район Свердловской области.
752. ЛУЛУГОВ СЕРГЕЙ САЙДАЛИЕВИЧ*, 01.09.1955 г.р., с. Конкринка Шартандинского района Акмолинской области КазССР.
753. ЛУЛУЕВ УСПА БАЙДИНОВИЧ*, 08.08.1959 г.р., с. Эшилхатой Веденского района ЧИАССР.
754. ЛУХМЫРИН СТАНИСЛАВ АНДРЕЕВИЧ*, 12.04.1990 г.р., г. Волгоград.
755. ЛЫСОГОР СЕРГЕЙ ВЛАДИМИРОВИЧ*, 31.08.1970 г.р., г. Приморско-Ахтарск Приморско-Ахтарского р-на Краснодарского края.
756. МААЗИЕВ МАКАМАГОМЕД МАГОМЕДШАПИЕВИЧ*, 23.09.1963 г.р., с. Губден Карабудахкентского района Республики Дагестан.
757. МААЛОВ РУСЛАН ШАМСУДИНОВИЧ*, 28.09.1970 г.р., с. Айти-Мохк Ножай-Юртовского района ЧИАССР.
758. МАГАМАДОВ АРСЕН РАМАЗАНОВИЧ*, 23.07.1983 г.р., с. Знаменское Надтеречного района ЧИАССР.
759. МАГАМАДОВ ВАХИ ДУТАЕВИЧ*, 23.02.1986 г.р., с. Катыр-Юрт Ачхой-Мартановского района Чеченской Республики.
760. МАГАМАДОВ ТЕМИРХАН УСМАНОВИЧ*, 06.05.1980 г.р., п. Ики-Бурул Ики-Бурульского района Калмыцкой АССР.
761. МАГАМЕРЗУЕВ ТАХИР САЙДУЛАЕВИЧ*, 19.09.1974 г.р., с. Серноводск ЧИАССР.
762. МАГЕМЕДОВ АДАМ СЕИДИМИЕВИЧ*, 04.10.1981 г.р., г. Гудермес ЧИАССР.
763. МАГОМАДОВ АРСЕН СУЛЕЙМАНОВИЧ*, 20.01.1986 г.р., с. Ачхой-Мартан ЧИАССР.
764. МАГОМАДОВ АСЛАН МАВЛАДОВИЧ*, 09.03.1972 г.р., с. Знаменское Надтеречного р-на ЧИАССР.
765. МАГОМАДОВ АЮБ САИД-АХМЕДОВИЧ*, 06.02.1982 г.р., с. Шовхал-Берды Ножай-Юртовского района ЧИАССР.
766. МАГОМАДОВ БЕСЛАН ЗИЯВДИЕВИЧ*, 23.05.1975 г.р., с. Урус-Мартан ЧИАССР.
767. МАГОМАДОВ ВИСХАН ГЕЛАНИЕВИЧ*, 11.11.1984 г.р., г. Грозный ЧИАССР.
768. МАГОМАДОВ ДЖАБРАИЛ САЙД-ЭМИЕВИЧ*, 04.10.1987 г.р., с. Курчалой ЧИАССР.
769. МАГОМАДОВ ИСЛАМ ШАХИДОВИЧ*, 25.08.1980 г.р., г. Грозный ЧИАССР.
770. МАГОМАДОВ РАСУ ВАХАЕВИЧ*, 18.03.1977 г.р., г. Грозный ЧИАССР.
771. МАГОМАДОВ РИЗВАН РАМАЗАНОВИЧ*, 29.05.1978 г.р., с. Новый-Шарой Ачхой-Мартановского р-на ЧИАССР.
772. МАГОМАДОВ САИД-ЭМИ САЙДАНОВИЧ*, 20.09.1978 г.р., г. Балхаш Эжезказганской области Казахской АССР.
773. МАГОМАДОВ ХУСЕЙН ИСАЕВИЧ*, 23.01.1979 г.р., с. Урус-Мартан ЧИАССР.
774. МАГОМАЗОВ РУСТАМ АБАКАРОВИЧ*, 18.01.1981 г.р., ст. Бороздиновская Шелковского района ЧИАССР.
775. МАГОМЕДОВ АБДУРАХИМ ОМАРОВИЧ*, 15.01.1943 г.р., с. Саситли Цумадинского района ДАССР.
776. МАГОМЕДОВ АХМЕД МАГОМЕДОВИЧ*, 19.03.1976 г.р., г. Махачкала Республики Дагестан.
777. МАГОМЕДОВ БИСЛАН ДАДАЕВИЧ*, 28.08.1978 г.р., ст. Шелковская Шелковского района ЧИАССР.
778. МАГОМЕДОВ ГАСАН АСИЛДЕРОВИЧ*, 19.09.1968 г.р., с. Гунха Ботлихского района Республики Дагестан.
779. МАГОМЕДОВ ЗАЙНУТДИН АБДУРАХМАНОВИЧ*, 05.10.1963 г.р., с. Куппа Левашинского района Республики Дагестан.
780. МАГОМЕДОВ МАГОМЕД-САЙГИД МАГОМЕДРАСУЛОВИЧ (МАГОМЕДОВ МАГОМЕДСАЙГИД МАГОМЕДРАСУЛОВИЧ)*, 16.08.1972 г.р., с. Губден Карабудахкентского района Республики Дагестан (16.08.1972 г.р., с. Каясула Нефтекумского района Ставропольского края).
781. МАГОМЕДОВ МАГОМЕДРАСУЛ ГАЗИДИБИРОВИЧ*, 10.01.1958 г.р., с. Тлондод Цумадинского района Дагестанской АССР.
782. МАГОМЕДОВ МУСЛИМ МУСАЕВИЧ*, 22.10.1985 г.р., с. Киров-Юрт Веденского района ЧИАССР.
783. МАГОМЕДОВ УВАЙС АБДУЛМУСЛИМОВИЧ*, 25.05.1970 г.р., с. Зубутли-Миатли Кизилюртовского района Республики Дагестан.
784. МАГОМЕДОВ УМАХАН РАМАЗАНОВИЧ*, 12.09.1967 г.р., с. Лобко Левашинского района ДАССР.
785. МАГОМЕДОВ ЮСУП БАГАУТДИНОВИЧ*, 05.02.1971 г.р., с. Ташкапур Левашинского района Республика Дагестан.
786. МАГОМЕДШАФИЕВ ЗАВИР МАГОМЕДНАБИЕВИЧ*, 29.09.1988 г.р., г. Махачкала Республики Дагестан.
787. МАДАГОВ МАГОМЕД МОВЛАДИЕВИЧ*, 28.10.1985 г.р., с. Гехи Урус-Мартановского района Чеченской Республики.
788. МАДАЕВ АДНАН ИСАЕВИЧ*, 06.10.1985 г.р., с. Урус-Мартан ЧИАССР.
789. МАДАЕВ АХМЕД РИЗВАНОВИЧ*, 31.10.1976 г.р., с. Знаменское Надтеречного района ЧИАССР.
790. МАДАЕВ ГИЛАНИ САЛАМУЕВИЧ*, 12.08.1967 г.р., с. Шали Шалинского района ЧИАССР.
791. МАДАЕВ УЗУМ-ХАЖИ САЙТАМ-ЗАТОВИЧ*, 14.12.1980 г.р., с. Курчалой Курчалоевского района Чеченской Республики.
792. МАДАРОВ ИСРАИЛ ИСАЕВИЧ*, 04.04.1988 г.р., с. Шали Шалинского р-на ЧИАССР.
793. МАЖИЕВ ХУСЕЙН ИБРАГИМОВИЧ*, 21.11.1971 г.р., г. Аргун ЧИАССР.
794. МАЗАЕВ АКРАМАН ЛОМАЛИЕВИЧ*, 12.09.1986 г.р., с. Ведено Веденского района ЧИАССР.
795. МАЗУЕВ АДЛАН САИД-ХАСАНОВИЧ*, 30.06.1984 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
796. МАЗУЕВ АРСЕН САЙД-ХАСАНОВИЧ*, 05.02.1975 г.р., с. Самашки Ачхой-Мартановского р-на ЧИАССР.
797. МАКАЕВ ИСА АЭЛЕЕВИЧ*, 29.05.1981 г.р., с. Урус-Мартан ЧИАССР.
798. МАКАЕВ МУСЛИМ САИД-АХМЕДОВИЧ*, 07.12.1979 г.р., с. Катыр-Юрт Ачхой-Мартановского р-на Чеченской Республики.
799. МАКАЕВ ЮНУС МОЛДИНОВИЧ*, 09.09.1978 г.р., с. Алхан-Кала Грозненского района ЧИАССР.
800. МАКАРЕНКО АНДРЕЙ ВИКТОРОВИЧ*, 18.07.1962 г.р., г. Киселевск Кемеровской области.
801. МАКСИМЕНКО СЕРГЕЙ ЛЕОНИДОВИЧ*, 17.07.1966 г.р., г. Владивосток Приморского края.
802. МАКУЕВ РУСЛАН АЛАУДИНОВИЧ*, 27.05.1974 г.р., с. Самашки ЧИАССР.
803. МАЛИКОВ ЗЕЛИМХАН СУЛЕЙМАНОВИЧ*, 02.12.1985 г.р., с. Ачхой-Мартан ЧИАССР.
804. МАЛЬСАГОВ АЛИ АХМЕТОВИЧ*, 11.02.1987 г.р., г. Грозный ЧИАССР.
805. МАЛЬСАГОВ ИСЛАМ ВАХИТОВИЧ*, 13.03.1972 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
806. МАЛЬСАГОВ УМАР АХМЕТОВИЧ*, 20.11.1984 г.р., с. Урус-Мартан ЧИАССР.
807. МАМАЕВ АРТУР ЗАПИРОВИЧ*, 06.10.1974 г.р., г. Махачкала ДАССР.
808. МАМАЕВ РУСЛАН РАСУЛОВИЧ*, 21.09.1974 г.р., с. Хамавюрт Хасавюртовского района ДАССР.
809. МАМАКАЕВ ЗАУР МУСАЕВИЧ*, 15.12.1982 г.р., с. Герменчук Шалинского района ЧИАССР.
810. МАМЕДОВ САЙД-МАГОМЕД АБУАЗИТОВИЧ*, 15.06.1977 г.р., г. Грозный ЧИАССР.
811. МАМСУРОВ ХАРОН АЛАУДЫЕВИЧ*, 31.01.1985 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
812. МАМЧУЕВ ХАСАН КЕМАЛОВИЧ*, 10.07.1970 г.р., ст. Каладжинская Лабинского района Краснодарского края.
813. МАНИЯ МУРТАЗИ ГВАНДЖИЕВИЧ*, 07.02.1966 г.р., с. Бзыбь Гагрского района Абхазской АССР.
814. МАНТАГОВ АРСЛАНБЕК НАЙБИРСОЛТАНОВИЧ*, 24.01.1977 г.р., с. Хамавюрт Хасавюртовского района Республики Дагестан.
815. МАНФИРОВ ВАДИМ СЕРГЕЕВИЧ*, 17.06.1982 г.р., г. Кемерово.
816. МАРЗАГИШИЕВ РУСТАМ АЙНОДИНОВИЧ*, 24.07.1976 г.р., с. Бурунское Шелковского района ЧИАССР.
817. МАРКОВ ВЛАДИСЛАВ АЛЕКСЕЕВИЧ*, 12.04.1983 г.р., п. Коммунар Гатчинского района Ленинградской области.
818. МАРКУЕВ АЮБХАН СУЛТАНОВИЧ*, 27.10.1983 г.р., с. Шали Чеченской Республики.
819. МАСЛОВ ДМИТРИЙ ВИКТОРОВИЧ*, 27.03.1973 г.р., г. Закаменск Бурятской АССР.
820. МАСЛОВ ИВАН НИКОЛАЕВИЧ*, 13.07.1986 г.р., г. Пошехонье Ярославской области.
821. МАСТАЕВ АСЛАН ХУСЕЙНОВИЧ*, 20.11.1965 г.р., п. Горагорский Надтеречного района ЧИАССР.
822. МАСХУДОВ УМАТХАДЖИ АЛИЕВИЧ*, 07.12.1987 г.р., г. Грозный ЧИАССР.
823. МАТАЕВ СУПЬЯН САИДГАЛИЕВИЧ*, 18.08.1980 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
824. МАТВЕЕВ АЛЕКСЕЙ НИКОЛАЕВИЧ*, 18.04.1971 г.р., г. Кострома.
825. МАТВЕЕВ ЕВГЕНИЙ ВАЛЕРЬЕВИЧ*, 03.10.1976 г.р., г. Кострома.
826. МАТУЕВ МОВЛДИ АБУЕВИЧ*, 18.11.1977 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
827. МАХАЕВ ХУСЕЙН МАГОМЕДОВИЧ*, 24.02.1985 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
828. МАХАМАДОВ АЛМАН ИМРАНОВИЧ*, 01.10.1975 г.р., с. Дуба-Юрт Шалинского района Чеченской Республики.
829. МАХАТАЕВ АХАТ ТЕМИРСУЛТАНУЛЫ*, 27.07.1978 г.р., с. Советское Ленгерского района Чимкентской области Казахской ССР.
830. МАХАУРИ АЗАМАТ РУСЛАНОВИЧ*, 24.06.1985 г.р., ст. Ассиновская Сунженского р-на ЧИАССР.
831. МАХАУРИ АСЛАН МАХМАТГИРИЕВИЧ*, 08.10.1985 г.р., с. Ачхой-Мартан Ачхой-Мартановского р-на ЧИАССР.
832. МАХМУДОВ ЮСУП УМАРОВИЧ*, 30.07.1973 г.р., п. Новогрозненский Гудермесского района Чеченской Республики.
833. МАХМУЕВ ЗЕЛИМХАН АБДУРАШИДОВИЧ*, 20.06.1989 г.р., ст. Калиновская Наурского района ЧИАССР.
834. МАХНЫЧЕВ ВЛАДИМИР АЛЕКСЕЕВИЧ*, 10.07.1970 г.р., ст. Орджоникидзевская Сунженского района Республики Ингушетия.
835. МАХУШЕВ РУСТАМ ВАСИЛЬЕВИЧ*, 02.12.1977 г.р., с. Керла-Юрт Грозненского района ЧИАССР.
836. МАЦАЕВ МАГОМЕД ЛАУДИЕВИЧ*, 08.02.1977 г.р., г. Грозный ЧИАССР.
837. МАЦИЕВ СУЛТАН ДЕЛЕМБЕКОВИЧ*, 13.10.1974 г.р., г. Грозный ЧИАССР.
838. МЕДИЕВ ТАМЕРЛАН ХАЛИДОВИЧ*, 15.12.1986 г.р., с. Хиди-Хутор Ножай-Юртовского района ЧИАССР.
839. МЕДОВ ЗЕЛИМХАН ХУСЕЙНОВИЧ*, 02.02.1981 г.р., с. Сагопши Малгобекского района Республики Ингушетия.
840. МЕЖИДОВ ИСМАИЛ АЙНДИНОВИЧ*, 04.01.1987 г.р., с. Улус-Керт Советского района ЧИАССР.
841. МЕЖИЕВ АБУБАКАР ДОРГУЕВИЧ*, 14.04.1970 г.р., с. Ищерское Наурского района ЧИАССР.
842. МЕЖИЕВ АЛИХАН САЙД-АХМЕДОВИЧ*, 29.10.1978 г.р., с. Махкеты Веденского района ЧИАССР.
843. МЕЖИЕВ АХЯД САЙД-АХМЕДОВИЧ*, 09.09.1969 г.р., с. Махкеты Веденского района ЧИАССР.
844. МЕЖИЕВ ЛЕМА ЛЕЧИЕВИЧ*, 22.11.1988 г.р., с. Садовое Грозненского района ЧИАССР.
845. МЕЖИЕВ МУСА МОВЛАЕВИЧ*, 21.05.1977 г.р., совхоз “Подгорный” Курсавского района Ставропольского края.
846. МЕЖИЕВ РУСТАМ СУПЬЯНОВИЧ*, 17.09.1975 г.р., с. Серноводск Сунженского района ЧИАССР.
847. МЕЗЕНЦЕВ ВИКТОР ВИКТОРОВИЧ*, 19.07.1966 г.р., г. Ишим Тюменской области.
848. МЕРЖОЕВ АЙДИ МАГОМЕДОВИЧ*, 18.08.1979 г.р., с. Бамут Ачхой-Мартановского района ЧИАССР.
849. МЕРЖОЕВ АНЗОР УСМАНОВИЧ*, 28.07.1985 г.р., с. Бамут Ачхой-Мартановского района ЧИАССР.
850. МЕРЖОЕВ КАЗБЕК ОМАРОВИЧ*, 06.11.1981 г.р., с. Бамут Ачхой-Мартановского района ЧИАССР.
851. МЕРКУЛОВ АЛЕКСЕЙ ВЛАДИМИРОВИЧ*, 18.01.1974 г.р., г. Лесичанск Луганской области Украинской ССР.
852. МЕШИЕВ МАГОМЕД УСМАНОВИЧ*, 29.01.1985 г.р., с. Ведено ЧИАССР.
853. МИГАЕВ ИЛЬЯ ВАСИЛЬЕВИЧ*, 10.12.1980 г.р., хутор Веселый Веселовского района Ростовской области.
854. МИГАЛЬ СТАНИСЛАВ ВИКТОРОВИЧ*, 11.12.1973 г.р., г. Камень-на-Оби Алтайского края.
855. МИЗАЕВ АДАМ РАМЗАНОВИЧ*, 05.07.1979 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
856. МИЛЮКОВ АЛЕКСАНДР АРКАДЬЕВИЧ*, 31.08.1977 г.р., г. Назарово Красноярского края.
857. МИНИН АНДРЕЙ ИВАНОВИЧ*, 28.12.1972 г.р., г. Саратов.
858. МИНКАЕВ ИБРАГИМ УМАРОВИЧ*, 10.07.1989 г.р., с. Курчалой Шалинского района ЧИАССР.
859. МИНКАИЛОВ РАСУЛ НИКОЛАЕВИЧ*, 17.11.1978 г.р., с. Новое Солкушино Наурского района ЧИАССР.
860. МИНСУЛТАНОВ АЛИ ИБРАГИМОВИЧ*, 22.03.1979 г.р., с. Ленинаул Казбековского р-на Республики Дагестан.
861. МИРОШКИН ИГОРЬ ДМИТРИЕВИЧ*, 10.10.1970 г.р., г. Норильск Красноярского края.
862. МИТАЕВ СУПЬЯН МУСАЕВИЧ*, 19.04.1979 г.р., г. Гудермес ЧИАССР.
863. МИТАЛАЕВ АСЛАНБЕК НАИБОВИЧ*, 21.06.1979 г.р., с. Ведено Веденского района ЧИАССР.
864. МИТАЛАЕВ ХУСЕЙН УМАРОВИЧ*, 13.02.1977 г.р., с. Ведено Веденского района Чеченской Республики.
865. МИТИГОВ МУСА ВАДУТОВИЧ*, 27.09.1978 г.р., с. Хамавюрт Хасавюртовского района ДССР.
866. МИХАЛОВ ГЕЛАНИ ЗАЙНДИЕВИЧ*, 28.09.1985 г.р., с. Радужное Грозненского района ЧИАССР.
867. МИХАЛОВ ХАВАЖИ ЗЕУДЫЕВИЧ*, 23.10.1984 г.р., с. Побединское Грозненского района ЧИАССР.
868. МИХЕЕВ АЛЕКСАНДР МИХАЙЛОВИЧ*, 06.02.1964 г.р., г. Сельцо Брянской области.
869. МИХЕЕВ ИВАН ВЛАДИМИРОВИЧ*, 01.02.1985 г.р., г. Киров.
870. МОГУШКОВ РУСЛАН АХЪЯЕВИЧ*, 14.05.1976 г.р., с. Насыр-Корт Назрановского района ЧИАССР.
871. МОРОЗОВ РОМАН ИВАНОВИЧ*, 24.11.1974 г.р., село Лебедин Шполянского р-на Черкасской области.
872. МУДАЕВ ДЖАМАЛАЙ ЛЕЧИЕВИЧ*, 07.10.1984 г.р., с. Курчалой Шалинского района ЧИАССР.
873. МУДУШОВ ВАХА-АЛИ САЙДСЕЛИМОВИЧ*, 27.03.1970 г.р., с. Согунты Ножай-Юртовского района ЧИАССР.
874. МУДУШОВ РАСУЛ РУХМАДОВИЧ*, 09.06.1984 г.р., с. Согунты Ножай-Юртовского района ЧИАССР.
875. МУЖАХОЕВА ЗАРЕМА МУСАЕВНА*, 09.02.1980 г.р., станица Ассиновская Сунженского района ЧИАССР.
876. МУЗАЕВ АДАМ ИДРИСОВИЧ*, 21.10.1979 г.р., с. Энгель-Юрт Гудермесского района ЧИАССР.
877. МУЗАЕВ АСЛАН МОВЛДЫЕВИЧ*, 04.04.1977 г.р., н.п. Гой-Чу Урус-Мартановского района ЧИАССР.
878. МУЗАЕВ АХМЕД ВАХИТОВИЧ*, 25.09.1986 г.р., с. Серноводск Сунженского района ЧИАССР.
879. МУЗИЕВ ЭЛЬМАДИ НУРАДИЛОВИЧ*, 28.02.1972 г.р., с. Хасавюрт ДАССР.
880. МУЛАЕВ ИСА МУГУМАТОВИЧ*, 21.01.1987 г.р., с. Труновское Ставропольского края.
881. МУЛАСАНОВ МИХАИЛ ТАЙМАЗХАНОВИЧ*, 20.08.1970 г.р., ст. Шелковская Шелковского района ЧИАССР.
882. МУЛУЕВ РОМАН ЭМИЕВИЧ*, 07.01.1986 г.р., с. Гуни Введенского района ЧИАССР.
883. МУЛЬКАЕВ РАСУЛ РАШИТОВИЧ*, 16.11.1979 г.р., ст. Галюгаевской Курского района Ставропольского края.
884. МУНАЕВ МАГОМЕД АПТИЕВИЧ*, 08.10.1982 г.р., г. Грозный ЧИАССР.
885. МУНАПОВ ЭДИЛБЕК ДАНИЛБЕКОВИЧ*, 18.08.1981 г.р., ст. Шелковская Шелковского района ЧИАССР.
886. МУРДАЛОВ АСЛАН МУСАЕВИЧ*, 02.01.1975 г.р., с. Урус-Мартан ЧИАССР.
887. МУРДАШЕВ ВАХИТ ЛАКАЕВИЧ*, 01.12.1955 г.р., г. Караганда Казахской ССР.
888. МУРЖАХАТОВ АДАМ ИСРАИЛОВИЧ*, 07.10.1982 г.р., с. Зандак Ножай-Юртовского района ЧИАССР.
889. МУРТАЗАЛИЕВ РУСЛАН МУСАЕВИЧ*, 09.01.1984 г.р., ст. Николаевская Наурского района Чеченской Республики.
890. МУРТАЗАЛИЕВА ЗАРА ХАСАНОВНА*, 04.09.1983 г.р., станица Наурская Чеченской Республики.
891. МУРТАЗОВ МАГОМЕД АБДУРАХМАНОВИЧ*, 07.02.1977 г.р., г. Грозный ЧИАССР.
892. МУРТУЗАЛИЕВ ЗУБАЙРУ ОМАРОВИЧ*, 23.11.1949 г.р., с. Леваши Левашинского р-на Республики Дагестан.
893. МУСАБЕКОВ РАГИМХАН ДУВАНБЕКОВИЧ*, 12.07.1972 г.р., с. Стальск Кизилюртовского района ДАССР.
894. МУСАЕВ АДЛАН АЛИЕВИЧ*, 20.11.1979 г.р., г. Грозный ЧИАССР.
895. МУСАЕВ АСЛАН РУСЛАНОВИЧ*, 22.10.1977 г.р., с. Гехи Урус-Мартановского района Чеченской Республики.
896. МУСАЕВ ДЖАМАЛ ХАВАЖИЕВИЧ*, 13.05.1985 г.р., ст. Ильиновская Грозненского района ЧИАССР.
897. МУСАЕВ ДОККИ ДОРШЕВИЧ*, 21.12.1970 г.р., пос. с/х 23 съезда КПСС Джездзинского района Карагандинской области Казахской ССР.
898. МУСАЕВ ИБРАГИМ ШЕРВАНИЕВИЧ*, 30.06.1974 г.р., с. Урус-Мартан ЧИАССР.
899. МУСАЕВ СУЛТАН САЙДБЕКОВИЧ*, 21.12.1981 г.р., с. Старые Атаги Грозненского района ЧИАССР.
900. МУСАЕВ УМАР ЗАЙДХАМЗАТОВИЧ*, 22.09.1982 г.р., с. Самашки Ачхой-Мартановского р-на ЧИАССР.
901. МУСАЛАЕВ ГУСЕЙН ХИЗРИЕВИЧ*, 18.05.1980 г.р., г. Махачкала ДАССР.
902. МУСАЛОВ ГАДЖИМУРАД ШАМИЛОВИЧ*, 28.02.1978 г.р., с. Согратль Гунибского района ДАССР.
903. МУСРАПИЛОВ АДАМ УВАЙСОВИЧ*, 08.10.1973 г.р., с. Гуни Веденского района ЧИАССР.
904. МУСХАНОВ АДАМ МОВЛДИЕВИЧ*, 24.09.1982 г.р., с. Урус-Матран Урус-Мартановского района ЧИАССР.
905. МУСХАНОВ МАГОМЕД МУСУЕВИЧ*, 28.05.1986 г.р., пос. Долинский Грозненского района ЧИАССР.
906. МУТАЕВ БИСЛАН РУСЛАНОВИЧ*, 25.07.1983 г.р., г. Урус-Мартан Урус-Мартановский район ЧИАССР.
907. МУТАЕВ ИСМАИЛ ПАТАХОВИЧ*, 24.06.1981 г.р., г. Гудермес ЧИАССР.
908. МУТАЛИПОВ АСХАБ АДАМОВИЧ*, 12.02.1967 г.р., с. Ца-Ведено Веденского района ЧИАССР.
909. МУТАШЕВ ОСМАН АБУБАКАРОВИЧ*, 08.08.1975 г.р., п. Маныч Ики-Бурульского района Республики Калмыкия.
910. МУТИЕВ ИСА АХМЕТОВИЧ*, 22.12.1985 г.р., с. Новотеречное Наурского района Чеченской Республики.
911. МУТУСХАНОВ МАГОМЕД ГАБАРОВИЧ*, 04.01.1968 г.р., г. Грозный ЧИАССР.
912. МУХАЕВ МЕХТИ МАХМУДОВИЧ*, 20.03.1958 г.р., с. Самашки ЧИАССР.
913. МУХАМЕДОВ НАЗАР МИДХАТОВИЧ*, 06.02.1970 г.р., с. Боз Бозского района Андижанской обл. Республики Узбекистан.
914. МУХАНИН ВЛАДИМИР ВАСИЛЬЕВИЧ*, 10.10.1972 г.р., г. Уфа.
915. МУХТАРОВ БЕСЛАН ВАХАЕВИЧ*, 16.02.1978 г.р., с. Урус-Мартан ЧИАССР.
916. МУХТАРОВ МАГОМЕД СИРАЖУТДИНОВИЧ*, 27.10.1960 г.р., с. Куппа Левашинского района Республики Дагестан.
917. МУЦАЕВ БЕКХАН АДАМОВИЧ*, 14.11.1987 г.р., с. Старая Сунжа ЧИАССР.
918. МУЦАЛХАНОВ МУССА МУСЛИМОВИЧ*, 01.11.1979 г.р., с. Урус-Мартан ЧИАССР.
919. МУЦАЛХАНОВ РИЗВАН МУСЛИМОВИЧ*, 14.11.1977 г.р., с. Танги-Чу Урус-Мартановского района ЧИАССР.
920. МУЦОЛЬГОВ ЗАУР МАГОМЕДОВИЧ*, 14.09.1981 г.р., г. Назрань Республики Ингушетия.
921. МЫЛЬНИКОВ АНАТОЛИЙ ВИКТОРОВИЧ*, 12.12.1946 г.р., г. Ивано-Франковск.
922. НАБИУЛЛИН МУХАММАД ГАЙНУЛЛОВИЧ*, 16.10.1979 г.р., п. Раевский Альшеевского района Республики Башкортостан.
923. НАГИМАТОВ СЕРГЕЙ ИСКАНДЫРОВИЧ*, 18.10.1977 г.р., с. Березовка Брединского района Челябинской области.
924. НАЖАЕВ ШАХ ХАЛИАРОВИЧ*, 20.01.1967 г.р., с. Надтеречное Надтеречного района ЧИАССР.
925. НАЗАРОВ ВЯЧЕСЛАВ ВИТАЛЬЕВИЧ*, 17.10.1970 г.р., г. Рубцовск Алтайского края.
926. НАКОНЕЧНЫЙ ИГОРЬ ЕВГЕНЬЕВИЧ*, 07.01.1966 г.р., г. Уфа Республики Башкортостан.
927. НАКРАЕВ ЭДИЛБЕК ЛЕМАЕВИЧ*, 02.08.1980 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
928. НАСИПОВ РИЗВАН АБДУКАДЫРОВИЧ*, 19.12.1978 г.р., с. Рубежное Наурского р-на ЧИАССР.
929. НАСУРОВ ВАЛИД ХАСМАГАМЕДОВИЧ*, 30.03.1982 г.р., г. Гудермес ЧИАССР.
930. НАСУХАНОВ ИСМАИЛ АХИЯТОВИЧ*, 26.08.1984 г.р., с. Надтеречное Надтереченского района ЧИАССР.
931. НАШАЕВ АЛИХАН АЛЬВИЕВИЧ*, 20.03.1980 г.р., с. Катыр-Юрт Ачхой-Мартановского района ЧИАССР.
932. НАШАЕВ УМАР РАМЗАНОВИЧ*, 25.04.1985 г.р., с. Ведено Веденского района ЧИАССР.
933. НЕВСКАЯ ОЛЬГА АЛЕКСАНДРОВНА*, 09.09.1978 г.р., г. Волжский Волгоградской области.
934. НЕДУЕВ РИЗВАН ИЛЬЯСОВИЧ*, 27.08.1966 г.р., с. Мескер-Юрт Шалинского района ЧИАССР.
935. НЕИЗВЕСТНЫЙ ИВАН АЛЕКСАНДРОВИЧ*, 14.02.1984 г.р., с. Эхаби Охинского района Сахалинской области.
936. НЕМЦЕВ СЕРГЕЙ ВАСИЛЬЕВИЧ*, 16.02.1985 г.р., г. Комсомольск-на-Амуре Хабаровского края.
937. НЕСМЕЯНОВ АНДРЕЙ АЛЕКСАНДРОВИЧ*, 31.05.1970 г.р., г. Миасс Челябинской области.
938. НЕСТЕРОВ ВЯЧЕСЛАВ АЛЕКСАНДРОВИЧ*, 10.04.1981 г.р., г. Таштагол Кемеровской области.
939. НЕСТЕРОВ СЕРГЕЙ АЛЕКСАНДРОВИЧ*, 03.03.1974 г.р., г. Котлас Архангельской области.
940. НИГОМАЕВ АЛЕКСЕЙ НИКОЛАЕВИЧ*, 26.03.1961 г.р., д. Гарюшка Куединского района Пермской области.
941. НИКИТИН СЕРГЕЙ ЮРЬЕВИЧ*, 07.05.1980 г.р., г. Ленинград.
942. НОВОЖИЛОВ АНДРЕЙ НИКОЛАЕВИЧ*, 02.03.1962 г.р., г. Дно Псковской области.
943. НУКАЕВ МАМЕД АХМЕДОВИЧ*, 12.10.1970 г.р., с. Чилгир Яшкульского района Республики Калмыкия.
944. НУКАЕВ ХАМЗАТ ВАХАЕВИЧ*, 05.07.1968 г.р., с. Дуба-Юрт Шалинского р-на ЧИАССР.
945. НУРГАЛИЕВ САЛАВАТ МАЛИКОВИЧ*, 20.04.1979 г.р., с. Суюндюк Бакалинского района Республики Башкирия.
946. НУРИЧЕВ АСЛАМБЕК АБУЯЗИТОВИЧ*, 15.08.1978 г.р., с. Пролетарское Грозненского района ЧИАССР.
947. НУРМАГОМЕДОВ ЗАКИР ХАМИДОВИЧ*, 04.01.1976 г.р., с. Кижани Ботлиховского района Республики Дагестан.
948. НУРМАГОМЕДОВ МАГОМЕД БАГАУТДИНОВИЧ*, 13.06.1979 г.р., с. Хаджалмахи Левашинского района Республика Дагестан.
949. НУРМУХАМЕТОВ ТАГИР ИЛЬДАРОВИЧ*, 10.11.1984 г.р., г. Казань Республики Татарстан.
950. НУЦАЛОВ АРСЕН МУХТАРПАШАЕВИЧ*, 04.01.1980 г.р., с. Казмааул Хасавюртовского р-на Республики Дагестан.
951. ОГАНЕСЯН ГРИГОРИЙ ГУРГЕНОВИЧ*, 24.04.1969 г.р., с. Эдиссия Курского района Ставропольского края.
952. ОЗДИЕВ ИБРАГИМ МАМУРИЕВИЧ*, 18.02.1989 г.р., с. Ведено Веденского района ЧИАССР.
953. ОЗДИЕВ ХАМИД НУРИДОВИЧ*, 04.01.1986 г.р., с. Ведено Веденского района ЧИАССР.
954. ОЗДИЕВ ХАСАН ХАМЗАТОВИЧ*, 01.12.1980 г.р., с. Терси Кайского района Красноярского края.
955. ОЗДОЕВ АДАМ МАГОМЕТОВИЧ*, 21.03.1980 г.р., г. Назрань ЧИАССР.
956. ОЗДОЕВ АЛИХАН МАГОМЕДОВИЧ*, 26.11.1977 г.р., г. Владикавказ РСО-Алания.
957. ОЗДОЕВ АСЛАН МУСТАФАЕВИЧ*, 31.07.1975 г.р., г. Владикавказ РСО-Алания.
958. ОМАРДИБИРОВ МУРАД МАГОМЕДОВИЧ*, 17.06.1972 г.р., г. Каспийск Республики Дагестан.
959. ОМЕЛЬЧЕНКО ОЛЕГ НИКОЛАЕВИЧ*, 09.12.1974 г.р., г. Азов Ростовской области.
960. ОПАРИН ДЕНИС НИКОЛАЕВИЧ*, 19.04.1979 г.р., г. Мончегорск Мурманской области.
961. ОРЗУМИЕВ ИЛЕС АБУСУЛТАНОВИЧ*, 18.03.1979 г.р., с. Нижний Герзель Гудермесского района ЧИАССР.
962. ОСМАЕВ АДАМ ЖАМАЛАЙЛОВИЧ*, 12.11.1978 г.р., с. Ачхой-Мартан Ачхой-Мартановского р-на ЧИАССР.
963. ОСМАНОВ МАГОМЕД АБУТАЛИМОВИЧ*, 10.02.1962 г.р., с. Губден Карабудахкентского района Республики Дагестан.
964. ОСУПОВ АЛЬБЕРТ АБУЕЗИТОВИЧ*, 12.07.1985 г.р., с. Ведено Веденского района ЧИАССР.
965. ОТЕГЕНОВ ТИМУР РЕЙЗАЕВИЧ*, 20.06.1973 г.р., с. Иргаклы Степновского района Ставропольского края.
966. ОТЕМИСОВ ЭСМАНБЕТ ЯМАКОВИЧ*, 14.06.1967 г.р., с. Червленные Буруны Ногайского района Республики Дагестан.
967. ОТЕПОВ НАРИМАН ОРАЗБИЕВИЧ*, 18.04.1976 г.р., с. Иргаклы Степновского района Ставропольского края.
968. ОХАЕВ ЛЕМ САЛМАНОВИЧ*, 07.07.1974 г.р., г. Грозный ЧИАССР.
969. ОЧАРХАДЖИЕВ ДЖАБРАИЛ НАИМСОЛТАЕВИЧ*, 07.01.1982 г.р., с. Ишхой-Юрт Гудермесского района ЧИАССР.
970. ОЧЕРХАДЖИЕВ АСЛАН ИБРАГИМОВИЧ*, 26.08.1979 г.р., г. Грозный ЧИАССР.
971. ПАВЛИКОВ ЭДУАРД ВИКТОРОВИЧ*, 02.03.1972 г.р., г. Златоуст Челябинской области.
972. ПАДАЕВ ИСЛАМ МУХАМЕТСАЛЫЕВИЧ*, 30.03.1985 г.р., с. Чонтаул Кизилюртовского района Республики Дагестан.
973. ПАК АЛЕКСАНДР АЛЕКСАНДРОВИЧ*, 20.06.1979 г.р., с. Стародубское Долинского р-на Сахалинской области.
974. ПАНИН АНДРЕЙ КОНСТАНТИНОВИЧ*, 22.06.1980 г.р., г. Норильск Красноярского края.
975. ПЕТРИЧЕНКО ДМИТРИЙ АЛЕКСАНДРОВИЧ*, 26.09.1979 г.р., г. Дрезден Республика Германия.
976. ПИВОВАРОВ ДМИТРИЙ ВИТАЛЬЕВИЧ*, 04.10.1974 г.р., г. Гудермес ЧИАССР.
977. ПИДИЕВ АДАМ МУСТАФАЕВИЧ*, 16.12.1979 г.р., ст. Орджоникидзевская ЧИАССР.
978. ПИРОВ ИСКАНДАР КУРБОНАЛИЕВИЧ*, 31.03.1984 г.р., с. Курбаншахи Восейского района Кулябской области Республики Таджикистан.
979. ПЛЮСНИН ДЕНИС АЛЕКСАНДРОВИЧ*, 05.04.1991 г.р., д. Середина Юрьянского района Кировской области.
980. ПОЗДЯЕВ АЛЕКСЕЙ НИКОЛАЕВИЧ*, 30.03.1963 г.р., с. Ст. Турдаки Кочкуровского района Республики Мордовия.
981. ПОЛИКАРПОВ ВЛАДИМИР СЕРГЕЕВИЧ*, 16.04.1976 г.р., с. Косой Брод Полевского района Свердловской области.
982. ПОЛЫНЦЕВ ГРИГОРИЙ АЛЕКСАНДРОВИЧ*, 28.11.1979 г.р., г. Нукус Республики Каракалпакия.
983. ПОНАРЬИН МАКСИМ АЛЕКСАНДРОВИЧ*, 15.11.1976 г.р., г. Будапешт Венгерской Народной Республики.
984. ПОПОВ МИХАИЛ КОНСТАНТИНОВИЧ*, 06.08.1977 г.р., г. Новосибирск.
985. ПОТЕХИН ЕВГЕНИЙ ПЕТРОВИЧ*, 26.03.1978 г.р., п. Мохнатушка г. Барнаула Алтайского края.
986. ПРИВЕДЕННАЯ ЮЛИЯ АНАТОЛЬЕВНА*, 23.05.1974 г.р., г. Стерлитамак Башкирской АССР.
987. ПРОСВЕТОВ ЕВГЕНИЙ ВИКТРОВИЧ*, 13.08.1976 г.р., г. Комсомольск-на-Амуре Хабаровского края.
988. ПРОЦЕНКО ВЯЧЕСЛАВ НИКОЛАЕВИЧ*, 23.09.1958 г.р., ст. Октябрьская Павловского района Краснодарского края.
989. ПРОЩАВАЕВ ВЯЧЕСЛАВ ВИКТОРОВИЧ*, 01.07.1973 г.р., пос. Сокол Долинского р-на Сахалинской области.
990. ПУХТЕЕВ АЛЕКСЕЙ АЛЕКСАНДРОВИЧ*, 22.08.1982 г.р., д. Большуха Кировского района Калужской обл.
991. РАБАДАНОВ РИЗВАНУЛЛА МАММАЕВИЧ*, 01.01.1972 г.р., с. Гинти Акушинского района ДАССР.
992. РАДЧЕНКО ВЛАДИМИР ГЕННАДЬЕВИЧ*, 06.12.1958 г.р., с. Дмитриевка Ижморского района Кемеровской области.
993. РАЖАПОВ РУСЛАН АБДУЛ-ВАХИДОВИЧ*, 28.08.1966 г.р., с. Бачи-Юрт Шалинского р-на ЧИАССР.
994. РАЖИПОВ МУСТАПА МАГОМЕДШАПИЕВИЧ*, 02.07.1965 г.р., с. Карамахи Буйнакского района Республики Дагестан.
995. РАЗЗАКОВ ХАФИЗ ХАМЗАЕВИЧ*, 05.09.1975 г.р., ст. Зиадин Пахтачийского Самаркандской области Республики Узбекистан.
996. РАКС НАДЕЖДА ГЕОРГИЕВНА*, 13.01.1973 г.р., г. Ровно Республики Украина.
997. РАСКОВАЛОВ АЛЕКСЕЙ ВЯЧЕСЛАВОВИЧ*, 21.01.1964 г.р., г. Верхняя Пышма Свердловской области.
998. РАСУЕВ АДАМ ИБРАГИМОВИЧ*, 30.12.1986 г.р., с. Урус-Мартан Урус-Мартановского района Чеченской Республики.
999. РАФИКОВ ДИАС АЛЬБЕРДОВИЧ*, 31.05.1986 г.р., г. Казань.
1000. РАХИМОВ АРСЕН ХАМЗАТОВИЧ*, 03.05.1978 г.р., г. Грозный ЧИАССР.
1001. РЕВТОВ ПАВЕЛ ИВАНОВИЧ*, 05.01.1979 г.р., г. Кустанай Кахахской ССР.
1002. РОЗОВ ДМИТРИЙ ВАЛЕРЬЕВИЧ*, 25.08.1982 г.р., г. Ленинград.
1003. РОМАНОВА ЛАРИСА ВАЛЕРЬЕВНА*, 23.04.1974 г.р., г. Москва.
1004. РЯДИНСКИЙ ВИТАЛИЙ НИКОЛАЕВИЧ*, 15.08.1976 г.р., п. Никитинка Боровского района Кустанайской области Казахской ССР.
1005. САБИРОВ АЗАТ ФАНИСОВИЧ*, 06.02.1987 г.р., г. Брежнев ТАССР (г. Набережные Челны Республики Татарстан).
1006. САБИТОВ РАФАЭЛЬ РИФГАТОВИЧ*, 18.06.1985 г.р., г. Казань Республики Татарстан.
1007. САБИТОВ РАФИС РИФГАТОВИЧ*, 26.07.1978 г.р., г. Казань.
1008. САВЕЛЬЕВ ЕВГЕНИЙ АНАТОЛЬЕВИЧ*, 05.01.1984 г.р., г. Белорецк.
1009. САВЧЕНКО ИГОРЬ АНАТОЛЬЕВИЧ*, 03.05.1972 г.р., пос. Лазаревское, г. Сочи Краснодарского края.
1010. САГАИПОВ ШАМХАН ШАРПУДИНОВИЧ*, 03.07.1977 г.р., с. Чири-Юрт Шалинского района Чеченской Республики.
1011. САГАРИЕВ РУСТАМ ШАМСУДИНОВИЧ*, 16.11.1980 г.р., г. Грозный ЧИАССР.
1012. САДАЕВ МАГОМЕД ХАМЗАТОВИЧ*, 21.08.1975 г.р., г. Грозный ЧИАССР.
1013. САДУЕВ СУЛТАН ШАХРАДИЕВИЧ*, 07.03.1968 г.р., г. Аргун Чеченской Республики.
1014. САДЫКОВ АРТУР ХАКИМОВИЧ*, 12.03.1979 г.р., г. Кизляр ДАССР.
1015. САДЫКОВ РАМЗАН РИЗВАНОВИЧ*, 30.08.1976 г.р., г. Грозный Чеченской Республики.
1016. САЗОНОВ ЕВГЕНИЙ АЛЕКСАНДРОВИЧ*, 28.12.1976 г.р., с. Орой Акшинского района Читинской области.
1017. САИДБЕКОВ МАГОМЕД ГАДЖИЕВИЧ*, 06.01.1949 г.р., с. Эчеда Цумадинского района Республики Дагестан.
1018. САИДОВ АСЛАН ХАМЗАТОВИЧ*, 19.12.1988 г.р., с. Автуры ЧИАССР.
1019. САИДОВ МАГОМЕД РАМЗАНОВИЧ*, 21.12.1981 г.р., с. Автуры Шалинского района ЧИАССР.
1020. САИДОВ МАХМУД СУЛЕЙМАНОВИЧ*, 27.10.1978 г.р., ст. Старощедринская Шелковского района ЧИАССР.
1021. САИЕВ ИБРАГИМ БЕКСАЛТАНОВИЧ*, 29.12.1982 г.р., пос. Новогрозненский Гудермесского района ЧИАССР.
1022. САИЕВ ЛЕМА МАЗЛАКОВИЧ*, 18.01.1969 г.р., г. Элиста Калмыкской АССР.
1023. САИТОВ РАСУЛ АХМЕДОВИЧ*, 04.02.1985 г.р., с. Ведено Веденского района ЧИАССР.
1024. САЙБАТАЛОВ МАРАТ ТЕМЕРБУЛАТОВИЧ*, 05.05.1972 г.р., г. Тюмень.
1025. САЙГИДОВ САЙГИД НУРМАГОМЕДОВИЧ*, 16.07.1979 г.р., с. Сильди Цумадинского района Республики Дагестан.
1026. САЙДАЕВ БАДРУДИ АЛАУДЫЕВИЧ*, 05.12.1972 г.р., с. Хиди-Хутор Ножай-Юртовского района ЧИАССР.
1027. САЙДАЕВ ХАСАН ГОЦУЕВИЧ*, 26.08.1956 г.р., с. Ново-Павловка Кызыл-Аскеровского района Киргизской ССР.
1028. САЙДАЛИЕВ АЛИХАН ОБУСУПЬЯНОВИЧ*, 21.11.1976 г.р., с. Энгеной Ножай-Юртовского района ЧИАССР.
1029. САЙДУЛАЕВ АДНАН ИСАЕВИЧ*, 28.08.1977 г.р., с. Алхан-Кала Грозненского района Чеченской Республики.
1030. САЙДУЛАЕВ АРТУР ИСАЕВИЧ*, 12.12.1983 г.р., с. Алхан-Кала Грозненского района ЧИАССР.
1031. САЙДУЛАЕВ АСЛАНБЕК ЗАУДИЕВИЧ*, 06.11.1976 г.р., с. Майртуп Шалинского района ЧИАССР.
1032. САЙДУЛАЕВ МУСА ЗУДИНОВИЧ*, 01.03.1972 г.р., с. Майртуп Шалинского района ЧИАССР.
1033. САЙДУМОВ МУСА САЛАМУЕВИЧ*, 05.12.1976 г.р., с. Дышне-Ведено Веденского района ЧИАССР.
1034. САЙТАМУЛОВ АЛИ БАЙТЕМИРОВИЧ*, 02.08.1977 г.р., г. Хасавюрт Республика Дагестан.
1035. САЛАВАТОВ ШАМСУДИН ДАДАШЕВИЧ*, 30.01.1971 г.р., с. Автуры Шалинского р-на ЧИАССР.
1036. САЛАМОВ БАЙ-АЛИ САИД-ЭМИЕВИЧ*, 11.06.1987 г.р., с. Курчалой Шалинского района ЧИАССР.
1037. САЛАТАЕВ АБУБАКАР БАВАДИЕВИЧ*, 13.09.1969 г.р., с. Ялхой-Мохк Ножай-Юртовского района ЧИАССР.
1038. САЛАТАЕВ ИБРАГИМ САЛАМБЕКОВИЧ*, 23.06.1977 г.р., г. Аргун ЧИАССР.
1039. САЛАТАЕВ ИЛЬЯС ДАЛАМБЕКОВИЧ*, 15.03.1972 г.р., г. Гудермес ЧИАССР.
1040. САЛИХОВ АЛИСУЛТАН САПИЮЛАЕВИЧ*, 06.11.1969 г.р., Гунибский район ДАССР.
1041. САЛИХОВ БАГАУТДИН САПИЮЛАЕВИЧ*, 30.03.1972 г.р., г. Буйнакск ДАССР.
1042. САЛМУРЗАЕВ МАГОМЕД ШАМАНОВИЧ*, 27.12.1980 г.р., х. Семечный Дубовского района Ростовской области.
1043. САЛПАГАРОВ ДАХИР МЕКЕРОВИЧ*, 04.01.1964 г.р., аул Джегута Усть-Джегутского района Карачаево-Черкесской Республики.
1044. САЛПАГАРОВ МУРАТ КОРНЕЕВИЧ*, 18.09.1965 г.р., ст. Сторожевая Зеленчукского района Карачаево-Черкесской Республики.
1045. САЛПАГАРОВ ХЫЗЫР МЕКЕРОВИЧ*, 08.01.1959 г.р., а. Джегута Усть-Джегутинского района Карачаево-Черкесской Республики.
1046. САЛСАНОВ УМАР САЛМАНОВИЧ*, 20.07.1976 г.р., с. Валерик Ачхой-Мартановского района Чечено-Ингушской АССР.
1047. САМБИЕВ АЙНДИ МУТАЕВИЧ*, 16.12.1977 г.р., с. Улус-Керт Советского р-на ЧИАССР.
1048. САМБИЕВ ИСА СОНТАЕВИЧ*, 24.05.1964 г.р., с. Липовка Урус-Мартановского района ЧИАССР.
1049. САМБИЕВ МОВСАР МУТАЕВИЧ*, 28.02.1984 г.р., с. Улус-Керт Советского р-на ЧИАССР.
1050. САНГАРИЕВ ЗЕЛИМХАН РАМЗАНОВИЧ*, 16.08.1986 г.р., с. Уштобе Каратальского района Талды-Курганской области КазССР.
1051. САНГАРИЕВ РУСЛАН АБУСОЛТОВИЧ*, 13.05.1977 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
1052. САНГИРАЕВ САЛАМБЕК ШАРПУДИНОВИЧ*, 13.10.1988 г.р., с. Новые-Атаги Шалинского района ЧИАССР.
1053. САРАЛИЕВ АЛИ УВАЙСОВИЧ*, 27.07.1970 г.р., с. Гехи Урус-Мартановского р-на Чеченской Республики.
1054. САРДАЛОВ АДАМ АХМЕДОВИЧ*, 31.07.1982 г.р., с. Троицкое Целинного района Калмыцкой АССР.
1055. САРДАЛОВ МАМЕД МЕРЖУЕВИЧ*, 22.04.1972 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
1056. САРДАЛОВ СУЛИМАН ТАУСОВИЧ (САРДАЛОВ СУЛЕЙМАН ТАУСОВИЧ)*, 08.12.1986 г.р., г. Грозный ЧИАССР (1986 г.).
1057. САРДАЛОВ УМАР АХМЕДОВИЧ*, 18.07.1984 г.р., пос. Первомайское Яшкульского района Калмыкской АССР.
1058. САРИЕВ УМАР ВЛАДИМИРОВИЧ*, 03.07.1966 г.р., с. Усть-Джегута Карачаево-Черкесской Республики.
1059. САТАБАЕВ ТИМУР ВИСИТАЕВИЧ*, 30.07.1976 г.р., с. Урус-Мартан Урус-Мартановского р-на ЧИАССР.
1060. САТИАДЖИЕВ МУЖАИД АЛЕВДИНОВИЧ (САТИ-АДЖИЕВ МУЖАИД АЛИРДИНОВИЧ; САТИ-АДЖИЕВ МУЖАИД АЛИВДИНОВИЧ)*, 05.04.1959 г.р., г. Хасавюрт ДАССР.
1061. СВЕТЛИЧНЫЙ ЮРИЙ ВАЛЕРЬЕВИЧ*, 02.04.1980 г.р., г. Киселевск Кемеровской области.
1062. СЕЛИМОВ АСЛАНБЕК СЛАВДИНОВИЧ*, 28.04.1975 г.р., с. Новосельское Хасавюртовского района ДАССР.
1063. СЕМАНОВ АЛЕКСЕЙ СЕРГЕЕВИЧ*, 29.11.1973 г.р., Емецкий с/с Холмогорского района Архангельской области.
1064. СЕНИН ИГОРЬ МИХАЙЛОВИЧ*, 22.09.1965 г.р., г. Москва.
1065. СЕРИТХАНОВ АДАМ ЗАЙНАЛБЕКОВИЧ*, 26.05.1984 г.р., с. Джалагаш Джалагашского района Кзыл-Ординской области Казахской АССР.
1066. СЕРСУЛТАНОВ АДАМ АХМЕДОВИЧ*, 02.01.1985 г.р., г. Грозный ЧИАССР.
1067. СЕТОВ АСКЕР НУРБИЕВИЧ*, 13.09.1982 г.р., аул Шовгеновский Шовгеновского района Республики Адыгея.
1068. СИГАЧЕВ ДМИТРИЙ ИГОРЕВИЧ*, 10.02.1977 г.р., г. Москва.
1069. СИДЕЛЬНИК ВЛАДИМИР ЕВГЕНЬЕВИЧ*, 18.02.1962 г.р., г. Армавир Краснодарского края.
1070. СИНЯЧКИН АЛЕКСЕЙ МИХАЙЛОВИЧ*, 12.08.1986 г.р., деревня Алешино Касимовского района Рязанской обл.
1071. СИРАЖДИНОВ ЛЕЧИ СУЛТАНОВИЧ*, 26.02.1976 г.р., с. Нижний Герзель Гудермесского района ЧИАССР.
1072. СИТАЕВ ЕВГЕНИЙ АЛЕКСАНДРОВИЧ*, 14.04.1983 г.р., станица Смоленская Северского р-на Краснодарского края.
1073. СИТНИКОВ ЮРИЙ АЛЕКСАНДРОВИЧ*, 31.10.1971 г.р., с. Филипповка Кунгурского района Пермской обл.
1074. СКВОРЦОВ ГЕННАДИЙ ГЕННАДЬЕВИЧ*, 09.03.1979 г.р., г.п. Чунский Иркутской области.
1075. СКЛЯР ВАЛЕРИЙ ВАСИЛЬЕВИЧ*, 17.09.1965 г.р., г. Фрунзе Республики Киргизия.
1076. СКОЛОТЯН РОМАН ПАВЛОВИЧ*, 07.10.1978 г.р., г. Березняки Пермской области.
1077. СКОРОВ ЕВГЕНИЙ СЕРГЕЕВИЧ*, 13.04.1987 г.р., г. Иркутск.
1078. СМОРОДНИКОВ НИКОЛАЙ ВИКТОРОВИЧ*, 14.07.1978 г.р., п. Карымское Карымского р-на Читинской обл.
1079. СОБРАЛИЕВ ХАМПАША ХАМЗАТОВИЧ*, 05.01.1972 г.р., с. Ца-Ведено Веденского района ЧИАССР.
1080. СОВМИЗ РУСЛАН АСЛАНОВИЧ*, 16.06.1983 г.р., а. Козет Тахтамукайского района Республики Адыгея.
1081. СОКОЛОВ ВАЛЕРИЙ АНАТОЛЬЕВИЧ*, 22.06.1966 г.р., г. Рыбинск.
1082. СОКОЛОВ ИГОРЬ ЛЕОНИДОВИЧ*, 05.09.1970 г.р., г. Тверь.
1083. СОЛСАНОВ МАМЕД АХМЕДОВИЧ*, 29.06.1979 г.р., с. Чернокозово Наурского района ЧИАССР.
1084. СОЛТАМУРАДОВ РУСТАМ БАТЫРСУЛТАНОВИЧ*, 13.03.1978 г.р., ст. Гребенская Шелковского района ЧИАССР.
1085. СОЛТАХАНОВ УМАР АСЛАМБЕКОВИЧ*, 03.01.1982 г.р., с. Лиман Лиманского района Астраханской области.
1086. СОЛТМУРАДОВ ИСЛАМ АРБИЕВИЧ*, 09.07.1977 г.р., с. Мескер-Юрт Шалинского района Чеченской Республики.
1087. СОЛТУХАНОВ ХИЗИР БУВАЙСАРИЕВИЧ*, 23.03.1983 г.р., с. Автуры Шалинского района ЧИАССР.
1088. СОРОКИН СЕРГЕЙ АНАТОЛЬЕВИЧ*, 23.01.1975 г.р., г. Вязьма Смоленской области.
1089. СОСЛАМБЕКОВ ШАМИЛЬ ШАХИДОВИЧ*, 28.03.1981 г.р., г. Грозный ЧИАССР.
1090. СОЮПОВ МУСЛИМ РАМЗАНОВИЧ*, 20.01.1982 г.р., с. Закон-Юрт Ачхой-Мартановского района ЧИАССР.
1091. СТРУГАНОВ ВИЛОР ВИКТОРОВИЧ*, 24.09.1962 г.р., г. Мариинск Кемеровской области.
1092. СУГАИПОВ АРСЕН ПАЗЛУДИНОВИЧ*, 11.09.1982 г.р., с. Племзавод Ногайского района ДАССР.
1093. СУГАТИЕВ АНЗОР ИСАЕВИЧ*, 17.01.1979 г.р., г. Гудермес ЧИАССР.
1094. СУГАЮНОВ ГАДЕЛЬ МАХМУДЖАНОВИЧ*, 08.04.1985 г.р., г. Азнакаево Республики Татарстан.
1095. СУЛАЙМАНОВ САЛМАН АЮБОВИЧ*, 24.08.1984 г.р., с. Ленинаул Казбековского р-на Республики Дагестан.
1096. СУЛЕБАНОВ ДЖАБРАИЛ АКАЕВИЧ*, 14.10.1960 г.р., с. Карамахи Буйнакского района ДАССР.
1097. СУЛЕЙМАНОВ АСХАБ АБДУЛВАХИДОВИЧ*, 21.09.1985 г.р., с. Успеновка Ленгерского района Чимкентской области КазССР.
1098. СУЛЕЙМАНОВ АХМЕД АЛИЕВИЧ*, 04.10.1974 г.р., с. Бачи-Юрт Шалинского района ЧИАССР.
1099. СУЛЕЙМАНОВ ВАЛИД АЛАВДИНОВИЧ*, 27.07.1974 г.р., с. Тазен-Кала Веденского района ЧИАССР, возможно г. Грозный.
1100. СУЛЕЙМАНОВ МАЙР-АЛИ МАЙРБЕКОВИЧ*, 19.05.1984 г.р., с. Автуры Шалинского района ЧИАССР.
1101. СУЛЕЙМАНОВ РУСЛАН ХАМИДОВИЧ*, 17.11.1968 г.р., г. Шали Шалинского района Чеченской Республики.
1102. СУЛЕЙМАНОВ РУСТАМ ВИСРАИЛОВИЧ*, 18.06.1987 г.р., с. Нурадилова Хасавюртовского района ДАССР.
1103. СУЛЕЙМАНОВ ХУСЕЙН УАЙСОВИЧ*, 12.08.1977 г.р., г. Грозный ЧИАССР.
1104. СУЛЕМАНОВ СУЛТАН ВАХАЕВИЧ*, 30.04.1977 г.р., с. Гойты Урус-Мартановского района Чеченской Республики.
1105. СУЛИМАНОВ АДАМ АЮБОВИЧ*, 19.02.1964 г.р., с. Шали ЧИАССР.
1106. СУЛИМАНОВ ШАРПУДИ ВАХАЕВИЧ*, 30.06.1966 г.р., с. Сержень-Юрт Шалинского района ЧИАССР.
1107. СУЛТАНГЕРИЕВ БЕСЛАН АДЛАНОВИЧ*, 26.09.1987 г.р., с. Урус-Мартан ЧИАССР.
1108. СУЛТАНМУРАДОВ МУСЛИМ АБДУРАХМАНОВИЧ*, 26.01.1987 г.р., с. Ахар Новолакского района ДАССР.
1109. СУЛТАНОВ АСЛАН МАГОМЕТОВИЧ*, 11.07.1980 г.р., ст. Ассиновская Сунженского района ЧИАССР.
1110. СУЛТАНОВ ВАХА МАГОМЕДОВИЧ*, 04.09.1985 г.р., ст. Ассиновская Сунженского района ЧИАССР.
1111. СУЛТАНОВ МУССА МОВСАРОВИЧ*, 11.11.1979 г.р., с. Мескер-Юрт Шалинского района Чеченской Республики.
1112. СУЛТАНОВ ХАЛИД АХМЕДОВИЧ*, 01.12.1982 г.р., с. Майское Сырдарьинского района Кзыл-Ординской области.
1113. СУЛТУХАНОВ УМАР САЙД-ХАМЗАТОВИЧ*, 27.07.1983 г.р., г. Грозный ЧИАССР.
1114. СУНАЕВ МАХМУД АБДУЛБАСИРОВИЧ*, 27.07.1963 г.р., с. В. Казанище Буйнакского района Республики Дагестан.
1115. СУНГУРОВ АБДУРАХМАН ЯНУРОВИЧ*, 07.12.1974 г.р., с. Хуна Лакского района ДАССР.
1116. СУСАРИЕВ АРСАН АЛАУДИНОВИЧ*, 17.03.1976 г.р., с. Серноводское Сунженского района Чеченской Республики.
1117. СУСЛИКОВ АЛЕКСАНДР ВЛАДИМИРОВИЧ*, 24.01.1958 г.р., г. Москва.
1118. СУСХАНОВ ИСЛАМ РУСЛАНОВИЧ*, 30.11.1984 г.р., г. Грозный ЧИАССР.
1119. СУЮПОВ УСМАН АЛЬВИЕВИЧ*, 20.07.1974 г.р., с. Гехи-Чу Урус-Мартановского района ЧИАССР.
1120. СЫСКЕВИЧ ДМИТРИЙ ВЛАДИМИРОВИЧ*, 16.06.1972 г.р., г. Томск.
1121. ТАВГАЗОВ СОСЛАН АРАМОВИЧ*, 06.09.1982 г.р., с. Коста-Хетагурова Карачаевского района Карачаево-Черкесской Республики.
1122. ТАВСУЛТАНОВ ИСА АХМЕДОВИЧ*, 19.10.1987 г.р., пос. Рассвет Ленинского р-на Волгоградской обл.
1123. ТАВСУЛТАНОВ САИД СЕЛИМ-АЛИМОВИЧ*, 27.06.1976 г.р., с. Ачхой-Мартан ЧИАССР.
1124. ТАЗАБАЕВ ЛЕЧИ СУЛТАНОВИЧ*, 20.05.1986 г.р., с. Ведено Веденского района ЧИАССР.
1125. ТАЗУЕВ САЙДИ ПАДИШАХОВИЧ*, 20.01.1952 г.р., с. Константино Вишневский район Акмолинской области Казахской ССР.
1126. ТАЗУРКАЕВ АХМЕД САЙДУЛАЕВИЧ*, 04.07.1980 г.р., с. Ачхой-Мартан ЧИАССР.
1127. ТАЗУРКАЕВ ОЛХАЗАР АБДУРОХМАНОВИЧ*, 08.03.1966 г.р., с. Катыр-Юрт Ачхой-Мартановского района ЧИАССР.
1128. ТАЙМАСОВ МАГОМЕДШАРИП АБДУЛМУСЛИМОВИЧ*, 22.04.1975 г.р., с. Губден Карабудахкентского района Республики Дагестан.
1129. ТАЙМАСХАНОВ РИЗВАН ТАГИРОВИЧ*, 10.04.1979 г.р., г. Гудермес ЧИАССР.
1130. ТАЙМАСХАНОВА ФАТИМА ДАНИЛБЕКОВНА*, 28.04.1973 г.р., г. Аргун Шалинского района ЧИАССР.
1131. ТАЙСУМОВ РИЗВАН БАЛАВДИЕВИЧ*, 06.11.1979 г.р., с. Ялхой-Мохк Курчалоевского района ЧИАССР.
1132. ТАЙСУМОВ ХИЗИР ХУСАИНОВИЧ*, 27.02.1983 г.р., г. Грозный ЧИАССР.
1133. ТАКАЕВ МОВСАР АРБИЕВИЧ*, 03.08.1982 г.р., г. Грозный ЧИАССР.
1134. ТАЛГАЕВ ИМРАН ШИРВАНИЕВИЧ*, 20.08.1971 г.р., г. Урус-Мартан ЧИАССР.
1135. ТАЛХАДОВ РОМАН ХАСБУЛАТОВИЧ*, 28.12.1968 г.р., х. Клинков станицы Мекенской Наурского района ЧИАССР.
1136. ТАЛХИГОВ ЗАУРБЕК ЮНУСОВИЧ*, 22.07.1977 г.р., с. Шали Шалинского района ЧИАССР.
1137. ТАМИМДАРОВ ШАМИЛ ГАМБАРОВИЧ*, 12.08.1958 г.р., с. Сюльте Илишевского района Республики Башкортостан.
1138. ТАРАМОВ АДАМ АПТИЕВИЧ*, 05.01.1975 г.р., с. Старые Атаги Грозненского района ЧИАССР.
1139. ТАРАСУНОВ МУРАДИН ИОСИФОВИЧ*, 29.03.1972 г.р., а. Псыж Прикубанского района Ставропольского края.
1140. ТАРМАЛИЕВ АСЛАНБЕК МОВЛИДОВИЧ*, 12.08.1977 г.р., с. Катыр-Юрт Ачхой-Мартановского района ЧИАССР.
1141. ТАСАЕВ МАГОМЕД СЕРГЕЕВИЧ*, 05.02.1987 г.р., с. Сельментаузен Веденского района ЧИАССР.
1142. ТАСУЕВ АХМЕД АБДУЛСАИТОВИЧ*, 11.11.1980 г.р., г. Грозный ЧИАССР.
1143. ТАСУЕВ ИЛЬЯС ХАСАНОВИЧ*, 16.05.1979 г.р., с. Советское Приозерного района Республики Калмыкии.
1144. ТАТАЕВ АБДУРАХМАН ШАМИЛЬЕВИЧ*, 30.06.1963 г.р., с. Курчалой Шалинского района ЧИАССР.
1145. ТАТАЕВ АСЛАН ШАМИЛЬЕВИЧ*, 29.01.1971 г.р., с. Курчалой Шалинского района ЧИАССР.
1146. ТАТАЕВ АТА АБАКАРОВИЧ*, 10.12.1971 г.р., г. Махачкала ДАССР.
1147. ТАТАЕВ ГУСЕЙН ХАМЗАТОВИЧ*, 16.01.1977 г.р., с. Османюрт Хасавюртовского района ДАССР.
1148. ТАТАЕВ ДАУР ЮСУПОВИЧ*, 29.06.1976 г.р., с. Дойкура-Эвл Грозненского района ЧИАССР.
1149. ТАТАЕВ ИМРАН ЛЕЧАЕВИЧ*, 20.10.1986 г.р., с. Ачхой-Мартан ЧИАССР.
1150. ТАТАЕВ ТУРПАЛ РУСЛАНОВИЧ*, 09.10.1980 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
1151. ТАТАЛОВ ХАСАН ЛОМАЛИЕВИЧ*, 03.08.1970 г.р., с. Степное Гудермесского района ЧИАССР.
1152. ТАУШЕВ АРСЛАН КАДРАЛИЕВИЧ*, 18.06.1973 г.р., ст. Шелковская ЧИАССР.
1153. ТАШАЕВ АРБИ ИМАЛИЕВИЧ*, 16.03.1976 г.р., г. Гудермес ЧИАССР.
1154. ТАШУЕВ РУСЛАН АСЛАМБЕКОВИЧ*, 29.11.1979 г.р., с. Автуры Шалинского района ЧИАССР.
1155. ТЕБЕКОВ ЭЖЕР МИХАЙЛОВИЧ*, 07.01.1986 г.р., с. Бельтир Кош-Агачского р-на Алтайского края.
1156. ТЕГАЕВ АСЛАН УВАЙСОВИЧ*, 26.12.1984 г.р., с. Котлован Удомельского района Калининской области РФ.
1157. ТЕГАЕВ ТАМЕРЛАН УМАР-ЭЛИЕВИЧ*, 25.09.1980 г.р., с. Алхан-Кала Грозненского р-на ЧИАССР.
1158. ТЕКЕЕВ ЭНВЕР ХАСАНОВИЧ*, 05.11.1963 г.р., с. Садовое Киргизской ССР.
1159. ТЕМИРБИЕВ МАХМУД ГУДАБЕРТОВИЧ*, 13.09.1979 г.р., г. Владикавказ Республики Северная Осетия – Алания.
1160. ТЕМИРБИЕВ МОВСАР АБДУЛ-ВАГАПОВИЧ*, 07.12.1977 г.р., г. Владикавказ Республики Северная Осетия-Алания.
1161. ТЕМИРБУЛАТОВ САЛМАН САИДОВИЧ*, 19.12.1972 г.р., пос. Новогрозный Гудермесского района ЧИАССР.
1162. ТЕМИРБУЛАТОВ СУЛТУМБЕК СУЛТАНОВИЧ*, 04.02.1979 г.р., с. Шали Шалинского района ЧИАССР.
1163. ТЕМИРСУЛТАНОВ АРСЕН ЗУВАДИЕВИЧ*, 10.08.1988 г.р., г. Хасавюрт ДАССР.
1164. ТЕМИРСУЛТАНОВ ВАХА АБДРАХМАНОВИЧ*, 20.02.1979 г.р., с. Уманцево Саринского района Калмыцкой АССР.
1165. ТЕМИРСУЛТАНОВ ИДРИС РАМЗАНОВИЧ*, 14.10.1978 г.р., с. Суворов-Юрт Гудермесского района ЧИАССР.
1166. ТЕМИРСУЛТАНОВ ХАМЗАТ АБДРАХМАНОВИЧ*, 11.05.1979 г.р., с. Октябрьское Шалинского района ЧИАССР.
1167. ТЕПСАЕВ ХУСЕЙН ВАГИДОВИЧ*, 01.04.1967 г.р., с. Гойты Урус-Мартановского района ЧИАССР.
1168. ТЕРХОЕВ ЗАУР ВАХАЕВИЧ*, 17.02.1990 г.р., ст. Орджоникидзевская Сунженского района ЧИАССР.
1169. ТИЛИЕВ ИСА ХАМЗАТОВИЧ*, 24.03.1975 г.р., г. Гудермес ЧИАССР.
1170. ТИМАЕВ ОСМАН РАМАЗАНОВИЧ*, 21.11.1983 г.р., с. Покровское Хасавюртовского района Республики Дагестан.
1171. ТИМАРБУЛАТОВ СУЛЕЙМАН АХЪЯДОВИЧ*, 19.11.1979 г.р., с. Катар-Юрт Ачхой-Мартановского района ЧИАССР.
1172. ТИМЕРБУЛАТОВ МЕХИД МАГОМЕДОВИЧ*, 06.05.1970 г.р., с. Кади-Юрт Гудермесского района Чеченской Республики.
1173. ТИМИРБУЛАТОВ САЛАУДИН ХАСМАГАМАДОВИЧ*, 01.01.1960 г.р., с. Борзой Советского района ЧИАССР.
1174. ТИМКИН ИГОРЬ ВЛАДИМИРОВИЧ*, 09.06.1981 г.р., с. Поспелиха Алтайского края.
1175. ТИМКО АЛЕКСАНДР АЛЕКСАНДРОВИЧ*, 20.12.1977 г.р., п. Южный (г. Городовиковск) Городовиковского р-на Республики Калмыкия.
1176. ТИМОШИН СЕРГЕЙ СЕРГЕЕВИЧ*, 30.05.1981 г.р., г. Харьков Украинской ССР.
1177. ТИПСУРКАЕВ ИБРАГИМ СЕРГЕЕВИЧ*, 20.10.1983 г.р., с. Урус-Мартан ЧИАССР.
1178. ТИТАЕВ ВИСИТА ВАХИДОВИЧ*, 03.10.1985 г.р., г. Аргун ЧИАССР.
1179. ТИХОМИРОВ ИЛЬЯ ЮРЬЕВИЧ*, 26.07.1986 г.р., г. Москва.
1180. ТИХОНОВ ВИКТОР ИВАНОВИЧ*, 08.12.1954 г.р., г. Новосибирск.
1181. ТЛЕПСУК ЮРИЙ АСХАДОВИЧ*, 08.10.1981 г.р., г. Краснодар.
1182. ТЛИАП АСЛАН ХАЗРЕТОВИЧ*, 26.01.1983 г.р., г. Краснодар.
1183. ТЛИСОВ АЗАМАТ АЛИ-МУРЗОВИЧ*, 12.06.1978 г.р., пос. Кавказский Прикубанского района Ставропольского края.
1184. ТОВСУЛТАНОВ ИБРАГИМ МАГОМЕТ-САЛИЕВИЧ*, 02.11.1984 г.р., с. Алхан-Кала Грозненского района ЧИАССР.
1185. ТОДИКОВ ГЕННАДИЙ ГЕОРГИЕВИЧ*, 16.06.1938 г.р., г. Черемхово Иркутской области.
1186. ТОКАРЬ АЛЕКСАНДР МИХАЙЛОВИЧ*, 01.08.1983 г.р., п. Невская Дубровка Всеволжского района Ленинградской области.
1187. ТОСУЕВ МАХАРБИ ЗАКРИЕВИЧ*, 02.02.1977 г.р., ст. Курдюковская Шелковского района ЧИАССР.
1188. ТОТЧИЕВ АДАМ ИСАЕВИЧ*, 02.01.1981 г.р., с. Серноводское Сунженского района ЧИАССР.
1189. ТОФАН ВИТАЛИЙ ВАСИЛЬЕВИЧ*, 16.06.1983 г.р., с. Сиротское Ширяевского района Одесской области УССР.
1190. ТУГАНБАЕВ МУРАТБИЙ МАХАМБЕТОВИЧ*, 21.12.1979 г.р., ст. Преградная Урупского района КЧАО.
1191. ТУПЕЙКО БОРИС СЕРГЕЕВИЧ*, 25.05.1973 г.р., г. Душанбе Республики Таджикистан.
1192. ТУРАЕВ АСЛАНБЕК АРБИЕВИЧ*, 07.10.1969 г.р., с. Рошни-Чу Урус-Мартановского района ЧИАССР.
1193. ТУРАЕВ ОБУСАЛАХ ГАЗАЛИЕВИЧ*, 01.04.1966 г.р., с. Агишбатой Чеченской Республики.
1194. ТУРЛУЕВ РУСТАМ БАРДЕЛОВИЧ*, 23.06.1975 г.р., с. Соцы-Алды Акульского района Талды-Курганского района Казахской ССР.
1195. ТУРЛУЕВ УСАМ РУКМАНОВИЧ*, 22.07.1980 г.р., пос. Новогрозненский Гудермесского района ЧИАССР.
1196. ТУРПУЛХАНОВ ИСЛАМ ЛЕЧАЕВИЧ*, 14.09.1980 г.р., с. Урус-Мартан Чечено-Ингушской АССР.
1197. ТУРШАЕВ МАГОМЕД ОМАРОВИЧ*, 13.11.1986 г.р., пос. Никольский Енотаевского района Астраханской области.
1198. ТУТАЕВ ТИМУР АПТИЕВИЧ*, 24.12.1984 г.р., г. Грозный ЧИАССР.
1199. ТУХАШЕВ ИСЛАМ ШАМИЛЬЕВИЧ*, 22.05.1981 г.р., с. Ведено Веденского района Чеченской Республики.
1200. ТЭППО АЛЕКСАНДР НИКОЛАЕВИЧ*, 10.04.1975 г.р., г. Новосибирск.
1201. ТЯГАЕВ ЗЕЛИМХАН ИСАЕВИЧ*, 19.03.1985 г.р., с. Ново-Георгиевска Тарумского района Дагестанской АССР.
1202. УЗДЕНОВ МИКАИЛ ИБРАГИМОВИЧ*, 27.06.1979 г.р., селение Ленинаул Казбековского района Республики Дагестан.
1203. УЛАБАЕВ МИКАИЛ ДОШАЕВИЧ*, 17.01.1971 г.р., с. Алхан-Кала Чеченской Республики.
1204. УЛЬБИЕВ АСЛАН ВАХИДОВИЧ*, 31.07.1981 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
1205. УМАЕВ ХУСЕЙН ВАХАЕВИЧ*, 20.07.1966 г.р., с. Алхан-Юрт Урус-Мартановского района ЧИАССР.
1206. УМАЛАТОВ ВАХА СУПЕНОВИЧ*, 25.03.1981 г.р., с. Подгорное Надтеречного района ЧИАССР.
1207. УМАНЦЕВ СЕМЕН ГРИГОРЬЕВИЧ*, 24.12.1984 г.р., ст. Шелковская Шелковского района ЧИАССР.
1208. УМАРОВ АДАМ РУСЛАНОВИЧ*, 02.12.1988 г.р., с. Ачхой-Мартан ЧИАССР.
1209. УМАРОВ ЗЕЛИМХАН АХМЕДОВИЧ*, 15.07.1981 г.р., г. Грозный ЧИАССР.
1210. УМАРОВ МОВСАР ИБРАГИМОВИЧ*, 30.05.1986 г.р., ст. Орджоникидзевская Сунженского района ЧИАССР.
1211. УМАРОВ МУРАД ХОЖБАХУДИЕВИЧ*, 30.12.1984 г.р., с. Беной-Ведено Ножай-Юртовского района ЧИАССР.
1212. УМАРОВ РАМЗАН ХАМЗАТОВИЧ*, 18.02.1989 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
1213. УМАРОВ САЛЕХ РУСЛАНОВИЧ*, 24.12.1974 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
1214. УМАРОВ СОСЛАН САЙХАНОВИЧ*, 21.03.1980 г.р., с. Бамут Ачхой-Мартановского района ЧИАССР.
1215. УМАРОВ УСМАН ХАДЖИЕВИЧ*, 20.05.1963 г.р., с. Кенхи Советского района ЧИАССР.
1216. УМАРПАШАЕВ ИСЛАМ ИРИСБАЕВИЧ*, 11.02.1986 г.р., с. Зандак Ножай-Юртовского района ЧИАССР.
1217. УМАРХАЖИЕВ ИСА ДЖЕБРОИЛОВИЧ*, 29.05.1980 г.р., с. Зандак Ножай-Юртовского района ЧИАССР.
1218. УМАХАНОВ АДАМ ГИХОЕВИЧ*, 18.10.1983 г.р., г. Грозный ЧИАССР.
1219. УМАХАНОВ ШАМИЛЬ ГАСАНАЛИЕВИЧ*, 23.11.1964 г.р., г. Махачкала Республики Дагестан.
1220. УРБАКОВ СЕРГЕЙ МИХАЙЛОВИЧ*, 24.10.1970 г.р., г. Улан-Удэ.
1221. УСАЕВ АДРАХИН ТУРПАЛОВИЧ*, 15.01.1976 г.р., с. Н.- Курчали Веденского района ЧИАССР.
1222. УСМАНОВ АПТИ ИСАЕВИЧ*, 07.06.1973 г.р., с. Знаменское Надтеречного района ЧИАССР.
1223. УСМАНОВ АХМЕД ЗАЙНДИЕВИЧ*, 29.07.1975 г.р., г. Аргун ЧИАССР.
1224. УСМАНОВ ЛОМАЛИ ГИЛАЕВИЧ*, 26.03.1985 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
1225. УСМАНОВ РАСУЛ МОУДИЕВИЧ*, 08.11.1987 г.р., г. Грозный ЧИАССР.
1226. УСМАНОВ ТИМУР ЛЕЧИЕВИЧ*, 27.10.1979 г.р., с. Автуры ЧИАССР.
1227. УСМАНОВ ХАМПАША ШЕРИЕВИЧ*, 06.09.1978 г.р., с. Курчалой Курчалоевского района ЧИАССР.
1228. УСПАНОВ АХМЕД АБДУЛ-КЕРИМОВИЧ*, 03.01.1981 г.р., с. Осакаровка Карагандинской области Казахской ССР.
1229. УСПАНОВ ИМРАН ВАХИДОВИЧ*, 08.10.1975 г.р., с. Чемульга Сунженского района ЧИАССР.
1230. УСТАЕВ КЮРИ АХМЕДОВИЧ*, 22.07.1981 г.р., с. Ачхой-Мартан ЧИАССР.
1231. УСТАЕВ РУСТАМ САЙД-АХМЕТОВИЧ*, 26.03.1983 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
1232. УСТАРХАНОВ КАЗБЕК САЛМАНОВИЧ*, 01.06.1982 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
1233. УЦАЕВ АБУ ИСМАИЛОВИЧ*, 12.06.1981 г.р., с. Шали ЧИАССР.
1234. УЦМИГОВ АСЛАН ХУСЕЙНОВИЧ*, 16.01.1978 г.р., ст. Старогладовская Шелковского района ЧИАССР.
1235. ФАЙЗУЛИН ФАРХАТ РИЗАЕВИЧ*, 14.02.1966 г.р., пос. Балезино Балезинского района Удмуртской АССР.
1236. ФАЙРУЗОВ РАФИС АТЛАСОВИЧ*, 05.01.1986 г.р., г. Азнакаево Республики Татарстан.
1237. ФАРЗАЛИЕВ КАЗБЕК ХАЧМАСОВИЧ*, 06.01.1976 г.р., г. Дербент Республики Дагестан.
1238. ФЕДОРЕНКО ИЛЬЯ ВЛАДИМИРОВИЧ*, 27.05.1983 г.р., с. Среднее Верховского района Орловской области.
1239. ФИЛИН СЕРГЕЙ ВИТАЛЬЕВИЧ*, 23.12.1968 г.р., г. Магадан.
1240. ФРАНЦУЗОВ ТАУКАН КАЗИМОВИЧ*, 22.10.1962 г.р., а. Нижняя Теберда Карачаевского р-на КЧАО.
1241. ХАБИЛАЕВ ИСЛАМ САПАРБЕКОВИЧ*, 15.10.1983 г.р., д. Ильятино Бологовского района Калининской области.
1242. ХАДЖАЕВ РИЗВАН САЛАУДИЕВИЧ*, 25.02.1983 г.р., с. Ачхой-Мартан Ачхой-Мартановского р-на ЧИАССР.
1243. ХАДЖАЛИЕВ ИСРАИЛ ВИСАМУРАДОВИЧ*, 19.04.1979 г.р., г. Ленинаул Казбековского р-на ДАССР.
1244. ХАДЖАЛИЕВ САИД ХИЗАРОВИЧ*, 29.06.1978 г.р., с. Гойты Урус-Мартановского района ЧИАССР.
1245. ХАДЖИЕВ АДАМ МОГДАНОВИЧ*, 28.11.1985 г.р., г. Чимкент КазССР.
1246. ХАДЖИЕВ АЛХАСТ САЙДСЕЛИМОВИЧ*, 02.06.1976 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
1247. ХАДЖИЕВ МУРАД ТАУЗОВИЧ*, 30.07.1981 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
1248. ХАДЖИЕВ РАМЗАН ЗАЙНУЛЛАЕВИЧ*, 12.04.1974 г.р., с. Алпатово Наурского района ЧИАССР.
1249. ХАДЖИЕВ УМАР ИБРАГИМОВИЧ*, 09.05.1977 г.р., ст. Наурская ЧИАССР.
1250. ХАДЖИМУРАДОВ ВИСХАН УМАРОВИЧ*, 02.07.1979 г.р., г. Грозный ЧИАССР.
1251. ХАДЗИЕВ УМАР БАГАУДИНОВИЧ*, 29.04.1984 г.р., г. Владикавказ РСО-Алания.
1252. ХАДИЗОВ МУРАД ДЖАМИРЗОЕВИЧ*, 16.03.1982 г.р., с. Ачхой-Мартан ЧИАССР.
1253. ХАДИСОВ РУСЛАН РАМЗАНОВИЧ*, 24.10.1976 г.р., ст. Каргалинская Щелковского р-на ЧИАССР.
1254. ХАДИСОВ ШАМИЛЬ УСМАНОВИЧ*, 13.12.1981 г.р., с. Ачхой-Мартан Ачхой-Мартановского р-на ЧИАССР.
1255. ХАЖБАХМАДОВ УМАР МУСАЕВИЧ*, 08.07.1986 г.р., с. Киселевка Заветинского района Ростовской области.
1256. ХАЖМАГАМАЕВ ЛЕЧИ ЗУБАЙРАЕВИЧ*, 21.01.1985 г.р., с. Зандак Ножай-Юртовского района ЧИАССР.
1257. ХАЗАМОВ МАГОМЕДЗАГИД АБДУЛАЕВИЧ*, 21.03.1973 г.р., с. Согратль Гунибского района ДАССР.
1258. ХАЗБУЛАТОВ АБУБАКАР МАЛАТОВИЧ*, 20.12.1982 г.р., с. Надтеречное Надтеречного р-на ЧИАССР.
1259. ХАЗБУЛАТОВ АСЛАН ИБРАГИМОВИЧ*, 07.11.1984 г.р., г. Грозный ЧИАССР.
1260. ХАЙДАЕВ ХУМАЙД АБДУЛХАМИДОВИЧ*, 20.09.1979 г.р., с. Ишхой-Юрт Гудермесского района ЧИАССР.
1261. ХАЙДЕРХАНОВ АЛЬВИ ЛЕЧЕВИЧ*, 26.08.1979 г.р., г. Аргун ЧИАССР.
1262. ХАЙРУЛЛИН ВИЛЬСУР РАФИЛЕВИЧ*, 22.04.1982 г.р., пос. Кукмор Кукморского района Республики Татарстан.
1263. ХАЙХАРОЕВ АХЪЯД АЛАУДИНОВИЧ*, 17.10.1975 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
1264. ХАЙХАРОЕВ ИМРАН УМАРОВИЧ*, 30.07.1976 г.р., с. Солдатско-Степное Быковского района Волгоградской обл.
1265. ХАКИМОВ АЛИ МАГОМЕДОВИЧ*, 19.08.1980 г.р., г. Урус-Мартан ЧИАССР.
1266. ХАКИМОВ БУЛАТ БИБОЛТОВИЧ*, 27.07.1982 г.р., х. Павловка Курсавского района Ставропольского края.
1267. ХАКИМОВ МАГОМЕД УСАМОВИЧ*, 21.09.1987 г.р., с. Сельментаузен Веденского района ЧИАССР.
1268. ХАКИМОВ МОВСАР АВАЛУЕВИЧ*, 12.12.1975 г.р., с. Алхан-Юрт Урус-Мартановского района ЧИАССР.
1269. ХАЛАЕВ РУСЛАН САЛАУДИНОВИЧ*, 07.06.1984 г.р., с. Новые Атаги Шалинского района ЧИАССР.
1270. ХАЛАЕВ ШАРУДИН БАДРУДИНОВИЧ*, 07.04.1979 г.р., с. Новые Атаги Шалинского района ЧИАССР.
1271. ХАЛЕТОВ УМАР АБДУРАХМАНОВИЧ*, 24.04.1980 г.р., с. Аралбай Джангильдинского района Тургайской области Казахской АССР.
1272. ХАЛИМОВ ВАХИД ХАМЕДОВИЧ*, 22.03.1984 г.р., с. Кулары ЧИАССР.
1273. ХАЛЬДИХОРОЕВ МАЛИД ИСРАПИЛОВИЧ*, 26.09.1976 г.р., пос. Октябрьский Грозненского района ЧИАССР.
1274. ХАМБУРАЕВ МАГОМЕД МАКШАРИПОВИЧ*, 13.11.1984 г.р., ст. Орджоникидзевская ЧИАССР.
1275. ХАМЗАЕВ МАЙРБЕК РУСЛАНОВИЧ*, 11.12.1981 г.р., с. Урус-Мартан Урус-Мартановского р-на ЧИАССР.
1276. ХАМЗАЛАТОВ АСЛАН ХАМИТОВИЧ*, 14.03.1981 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
1277. ХАМЗАТОВ АДЛАН МАГОМЕД-САЛИХОВИЧ*, 31.10.1984 г.р., с. Самашки (с. Ачхой-Мартан) Ачхой-Мартановского района ЧИАССР.
1278. ХАМЗАТОВ АЛЬВИ АЛАУДИНОВИЧ*, 13.12.1966 г.р., с. Чистопольское Алакульского района Алма-атинской области КазССР.
1279. ХАМЗАТОВ ИЛЕС АЛАУДИНОВИЧ*, 06.06.1974 г.р., с. Самашки ЧИАССР.
1280. ХАМЗАТОВ ИСМАИЛ АЛАУДИЕВИЧ*, 01.05.1979 г.р., с. Самашки Ачхой-Мартановского района ЧИАССР.
1281. ХАМЗАТХАНОВ РАХИМ АДДИЕВИЧ*, 04.09.1979 г.р., с. Ца-Ведено Веденского р-на ЧИАССР.
1282. ХАМИЕВ ЛОРС НОХЧОЕВИЧ*, 11.01.1984 г.р., г. Грозный ЧИАССР.
1283. ХАМИСБИЕВ НАЗИРБЕК АЛИФТИНОВИЧ*, 08.03.1981 г.р., с. Виноградное Грозненского района ЧИАССР.
1284. ХАМСТХАНОВ ХАСАН ИЛЕСОВИЧ*, 04.12.1980 г.р., с. Катар-Юрт Ачхой-Мртановского района ЧИАССР.
1285. ХАМУРАДОВ АЛИ-ХАН МАУСАРОВИЧ*, 20.08.1982 г.р., с. Старокозинка Мичуринского района Тамбовской области.
1286. ХАМУРЗАЕВ МАРТАН УСМАНОВИЧ*, 03.01.1984 г.р., с. Ачхой-Мартан Ачхой-Мартановского р-на ЧИАССР.
1287. ХАМХОЕВ МАГОМЕД ГАБОЕВИЧ*, 03.12.1978 г.р., с. Яндаре Назрановского района ЧИАССР.
1288. ХАНИЕВ УМАР ИСАЕВИЧ*, 07.07.1984 г.р., с. Октябрьское Пригородного района РСО-Алания.
1289. ХАНОВ МАГОМЕД АХМЕДОВИЧ*, 14.02.1966 г.р., с. Куппа Левашинского р-на ДАССР.
1290. ХАНТАЕВ ЗАУРБЕК РАМЗАНОВИЧ*, 16.12.1981 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
1291. ХАРАТОКОВ ЭДУАРД МУХАМЕДОВИЧ*, 15.10.1981 г.р., а. Кубина Усть-Джегутинского района Карачаево-Черкесской Республики.
1292. ХАРИХАНОВ АНЗОР МАГОМЕДАЛИЕВИЧ*, 04.09.1985 г.р., г. Грозный Чеченской Республики.
1293. ХАРОНОВ СУЛИМАН ХАМИДОВИЧ*, 28.03.1978 г.р., с. Бешил-Ирзу Ножай-Юртовского района ЧИАССР.
1294. ХАСАЕВ ВАХА АХМЕТОВИЧ*, 09.05.1980 г.р., с. Н. Янгуль Ставропольского края.
1295. ХАСАНОВ АЗАТ ДАМИРОВИЧ*, 20.12.1977 г.р., с. Малые Болгояры Апастовского района ТАССР.
1296. ХАСАНОВ АЛМАЗ ДАМИРОВИЧ*, 20.12.1977 г.р., дер. Малые Болгояры Апастовского района ТАССР.
1297. ХАСАНОВ ИСА МАГОМЕДОВИЧ*, 28.08.1985 г.р., с. Шалажи Урус-Мартановского района ЧИАССР.
1298. ХАСАНОВ МАГАМЕД ВАХАЕВИЧ*, 20.03.1961 г.р., с. Урус-Мартан ЧИАССР.
1299. ХАСАНЬШИН ДАНИЛ РАФАИЛОВИЧ*, 16.11.1977 г.р., г. Ташкент Республики Узбекистан.
1300. ХАСАРБИЕВ ИСЛАМ ДЕНИЛОВИЧ*, 20.10.1972 г.р., г. Грозный ЧИАССР.
1301. ХАСАРОВ МАГОМЕД СУЛУМБЕКОВИЧ*, 20.05.1979 г.р., с. Ачхой-Мартан ЧИАССР.
1302. ХАСАХАНОВ САЛМАН ВАЛИТОВИЧ*, 01.01.1981 г.р., г. Грозный ЧИАССР.
1303. ХАСБУЛАТОВ АБДУЛА МАГОМЕДОВИЧ*, 30.07.1969 г.р., с. Карамахи Буйнакского района ДАССР.
1304. ХАСБУЛАТОВ АБУБАКАР МАЛАТОВИЧ*, 20.12.1982 г.р., с. Надтеречное Надтеречного района ЧИАССР.
1305. ХАСБУЛАТОВ АХМАД ИССАКОВИЧ*, 25.09.1973 г.р., с. Дуба-Юрт Шалинского района Чеченской Республики.
1306. ХАСБУЛАТОВ ГАСАН ХАСБУЛАТОВИЧ*, 19.02.1958 г.р., с. Карамахи Буйнакского района ДАССР.
1307. ХАСБУЛАТОВ ЗАКАРЬЯ МАГОМЕДОВИЧ*, 13.12.1975 г.р., с. Карамахи Буйнакского района Республики Дагестан.
1308. ХАСБУЛАТОВ РУСЛАН ХАМЗАИТОВИЧ*, 05.01.1980 г.р., с. Ножай-Юрт Ножай-Юртовского района ЧИАССР.
1309. ХАСИЕВ РУСЛАН ДУКВАХАЕВИЧ*, 04.07.1980 г.р., с. Валерик Ачхой-Мартановского района ЧИАССР.
1310. ХАСИЕВ ХАМЗАТ БАУДИНОВИЧ*, 23.11.1956 г.р., с. Дуба-Юрт Шалинского района Чеченской Республики.
1311. ХАСИЕВА ЯХА МУТАГИРОВНА*, 23.09.1956 г.р., КазССР.
1312. ХАСУХАНОВ ИСЛАМ ШАЙХ-АХМЕДОВИЧ*, 29.11.1954 г.р., с. Ворошиловское Ворошиловского района Киргизской ССР.
1313. ХАТАЕВ АЛИХАН НЕБИЮЛАЕВИЧ*, 04.06.1987 г.р., с. Дарго Веденского района ЧИАССР.
1314. ХАТУЕВ АБДУРАХМАН МОВСАРОВИЧ*, 22.12.1952 г.р., г. Караганда КазССР.
1315. ХАТУЕВ БИСЛАН АБУЯЗИТОВИЧ*, 11.04.1972 г.р., с. Орехово Ачхой-Мартановского района ЧИАССР.
1316. ХАТУЕВ НУР-МАГОМЕД ШАХИДОВИЧ*, 16.05.1967 г.р., с. Гойты Урус-Мартановского района ЧИАССР (1966 г.).
1317. ХАЦИЕВ БЕЛАН ВИСАНГИРЕЕВИЧ*, 18.06.1978 г.р., г. Джамбул Казахской ССР.
1318. ХАЧЛАЕВ ТАМИРЛАН ИЛЬЯСОВИЧ*, 08.06.1974 г.р., г. Хасавюрт ДАССР.
1319. ХАЧУКАЕВ ИЗРАИЛ САЛМАНОВИЧ*, 02.01.1980 г.р., г. Грозный ЧИАССР.
1320. ХАЧУКАЕВ ИМРАН САЙД-АХМЕДОВИЧ*, 16.02.1972 г.р., с. Новый-Шарой Ачхой-Мартановского района ЧИАССР.
1321. ХАЧУКАЕВ ЭРШТХО СУЛТАНОВИЧ*, 02.02.1983 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
1322. ХАШУМОВ РАШИД АМИРБЕКОВИЧ*, 08.02.1979 г.р., с. Эникали Ножай-Юртовского района ЧИАССР.
1323. ХИДЕРЛЕЗОВ РАСУЛ СОЛТАНСАИДОВИЧ*, 30.06.1982 г.р., г. Хасавюрт Республики Дагестан.
1324. ХИДИРБЕКОВ МАГОМЕДСОЛТАН МАГОМЕДСАИДОВИЧ*, 17.05.1965 г.р., с. Манас Карабудахкентского района ДАССР.
1325. ХИДИРОВ АРСЕН МАГОМЕДНАБИЕВИЧ*, 07.12.1974 г.р., г. Махачкала ДАССР.
1326. ХИЗИРОВ УМАР ИМРАНОВИЧ*, 16.05.1977 г.р., с. Дуба-Юрт Шалинского р-на ЧИАССР.
1327. ХИЗРИЕВ ЗЕЛИМХА МУСЛИМОВИЧ*, 28.04.1978 г.р., с/х Дюрский Новокузнецкого района Саратовской области.
1328. ХИЗРИЕВ ИДРИС БУХАЙСЕРОВИЧ*, 12.01.1977 г.р., с. Кургалой Шалинского района Чеченской Республики.
1329. ХИЗРИЕВ ИЛЕС ВАХИТОВИЧ*, 17.01.1982 г.р., с. Автуры Шалинского района ЧИАССР.
1330. ХИЗРИЕВ РУСТАМ ВИСИРКОВИЧ*, 22.09.1978 г.р., с. Курчалой Шалинского района ЧИАССР.
1331. ХИРИХАНОВ ИБРАГИМ ЛЕЧАЕВИЧ*, 28.11.1982 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
1332. ХИСИМИКОВ САИД-МАГОМЕД ХАМЗАЕВИЧ*, 14.03.1980 г.р., г. Грозный Чечено-Ингушской АССР.
1333. ХИТИЕВА ЗАРГАН БАУДИНОВНА*, 23.02.1957 г.р., г. Кызыл-Орда Казахской ССР.
1334. ХИХОЕВ ХУСЕЙН ОМАРОВИЧ*, 02.11.1978 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
1335. ХОЖАЕВ АНЗОР АХМЕТОВИЧ*, 14.09.1988 г.р., с. Пригородное Грозненского района ЧИАССР.
1336. ХОЗЯИНОВ ДМИТРИЙ ВЛАДИМИРОВИЧ*, 22.10.1979 г.р., г. Нарьян-Мар Архангельской области.
1337. ХРАМЦОВ СЕРГЕЙ АНАТОЛЬЕВИЧ*, 07.11.1978 г.р., пос. Светлый Котельнического района Кировской области.
1338. ХУБИЕВ АРАСУЛ ПАВЛОВИЧ*, 02.07.1977 г.р., с. Важное Усть-Джегутинского р-на Карачаево-Черкесской Республики.
1339. ХУБИЕВ ТАМБИЙ АНАТОЛЬЕВИЧ*, 25.04.1977 г.р., с. Учкекен Малокарачаевского района Карачаево-Черкесской Республики.
1340. ХУГУЕВ ХАЛИД ХАСМАГОМАДОВИЧ*, 01.01.1956 г.р., пос. Чу Джамбульской области Казахской ССР.
1341. ХУДОЯРОВ ЗАЙНАДИН АЛИМХАНОВИЧ*, 22.08.1979 г.р., с. Коби Шелковского района ЧИАССР.
1342. ХУДУЛОВ ВИСХАДЖИ ХУСАЙИНОВИЧ*, 06.06.1974 г.р., с. Бильты Ножай-Юртовского района ЧИАССР.
1343. ХУСАИНОВ АБДУЛ-МЕЛИК НАЖМУДИНОВИЧ*, 05.05.1967 г.р., с. Киров-Юрт Веденского района ЧИАССР.
1344. ХУСАИНОВ БЕСЛАН НАЖМУДИНОВИЧ, 10.12.1977 г.р., с. Киров-Юрт Веденского района ЧИАССР.
1345. ХУСАИНОВ УМАР БИЛАЛОВИЧ*, 06.04.1987 г.р., ст. Курдюковская ЧИАССР.
1346. ХУСЕЙНОВ АЛИ ХАЛИДОВИЧ*, 10.04.1979 г.р., с. Новый Шарой Ачхой-Мартановского района ЧИАССР.
1347. ХУТИЕВ АБДУЛРАХИМ ХАЖБЕКАРОВИЧ*, 07.01.1978 г.р., с. Октябрьское Пригородного района РСО-Алания.
1348. ХУТОВ АНЗОР ЭЛЬВЕРОВИЧ*, 21.11.1978 г.р., ст. Ессентукская Предгорного района Ставропольского края.
1349. ХУТОВ РУЗАЛИ ЭЛЬВЕРОВИЧ*, 27.01.1977 г.р., совхоз Кисловодский Предгорного района Ставропольского края.
1350. ХУЦАЕВ ДУКВАХА ИСАЕВИЧ*, 15.07.1985 г.р., с. Ачхой-Мартан ЧИАССР.
1351. ХУЦАЕВ РУСТАМ ИСАЕВИЧ*, 11.07.1980 г.р., с. Урус-Мартан ЧИАССР.
1352. ЦАКАЕВ АЛИ САЙД-ХУСЕНОВИЧ*, 04.01.1977 г.р., с. Татай-Хутор Ножай-Юртовского района ЧИАССР.
1353. ЦАКАЕВ АМХАД УМАРСОЛТАЕВИЧ*, 24.03.1988 г.р., с. Татай-Хутор Ножай-Юртовского района Чеченской Республики.
1354. ЦАКАЕВ БЕСЛАН САИД-ХУСЕЙНОВИЧ*, 03.11.1983 г.р., с. Татай-Хутор Ножай-Юртовского района ЧИАССР.
1355. ЦАХИГОВ МАГОМЕД ВАХИДОВИЧ*, 22.12.1976 г.р., с. Гойты Урус-Мартановского района Чеченской Республики.
1356. ЦАЦАЕВА МАЛИКАТ АДАМОВНА*, 25.05.1952 г.р., с. Садовое Московского района КиргССР.
1357. ЦВИГУН ВАЛЕРИЙ ВЛАДИМИРОВИЧ*, 20.08.1982 г.р., г. Набережные Челны Татарской АССР.
1358. ЦЕЧОЕВ АДАМ АХМЕТОВИЧ*, 29.09.1976 г.р., ст. Орджоникидзевская Сунженского района Республики Ингушетия.
1359. ЦЕЧОЕВ МАГОМЕД-ХАМИД РУСЛАНОВИЧ*, 02.10.1974 г.р., г. Назрань Республики Ингушетия.
1360. ЦИНАЕВ МУРАД МАГОМЕДОВИЧ*, 10.09.1984 г.р., с. Ачхой-Мартан Ачхой-Мартановского р-на ЧИАССР.
1361. ЦИЦАЕВ РУСТАМ ИЛЬЯСОВИЧ*, 05.12.1982 г.р., г. Шали Шалинского района ЧИАССР.
1362. ЦИЦИЕВ РАМЗАН МАГОМЕДОВИЧ*, 18.03.1982 г.р., с. Ножай-Юрт Ножай-Юртовского района ЧИАССР.
1363. ЦОКАЛАЕВ МАГОМЕД ЛЕЧАЕВИЧ*, 21.05.1988 г.р., с. Ачхой-Мартан ЧИАССР.
1364. ЦУРАЕВ САЙД-ХАСАН УВАЙСОВИЧ*, 12.08.1980 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
1365. ЦУРОВ АДАМ МУССАЕВИЧ*, 05.07.1980 г.р., п. Карца Промышленного района г. Владикавказа РСО-Алания.
1366. ЦУРОВ РУСТАМ ЮНУСОВИЧ*, 12.08.1979 г.р., г. Владикавказ Республики Северная Осетия-Алания.
1367. ЦУРОЕВ АХМЕТ АЛИХАНОВИЧ*, 30.07.1979 г.р., г. Назрань Республики Ингушетия.
1368. ЧАБДАЕВ БИСЛАН УСАМОВИЧ*, 02.10.1973 г.р., х. Бударка Котельниковского района Волгоградской области.
1369. ЧАГАЕВ САЛМАН АСЛАХОВИЧ*, 28.07.1975 г.р., с. Шалажи Урус-Мартановского района ЧИАССР.
1370. ЧАГИЛОВ АЛИБЕК МУХТАРОВИЧ*, 06.09.1976 г.р., г. Карачаевск Карачаево-Черкесской Республики.
1371. ЧАГИЛОВ РУСТАМ РУСЛАНОВИЧ*, 14.06.1978 г.р., г. Карачаевск Карачаево-Черкесской Республики.
1372. ЧАКАЕВ АЮБ САЙДАХМЕТОВИЧ*, 05.09.1981 г.р., г. Гудермес ЧИАССР.
1373. ЧАЛАЕВ ИСЛАМ ТУРГУНБАЕВИЧ*, 07.06.1986 г.р., с. Симсир Ножай-Юртовского района ЧИАССР.
1374. ЧАЛАЕВ СУЛИМАН ХАСАНБЕКОВИЧ*, 06.07.1976 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
1375. ЧАМАЕВ АХМЕД МУХАДИНОВИЧ*, 18.11.1975 г.р., с. А. Шерипова ЧИАССР.
1376. ЧАНИЕВ АХМЕД ШАБАЗГИРЕЕВИЧ*, 10.09.1966 г.р., д. Горно-Слинкино Тюменской области.
1377. ЧАРАЕВ МАГОМЕД ХУСЕЙНОВИЧ*, 08.03.1986 г.р., с. Курчалой Шалинского района ЧИАССР.
1378. ЧАУШЕВ ОСМАН БОРИСОВИЧ*, 12.11.1977 г.р., а. Эльбурган Хабезского района Ставропольского края.
1379. ЧАХКИЕВ РУСЛАН МАГОМЕТОВИЧ*, 25.01.1978 г.р., с. Куртат Пригородного района Республики Северная Осетия-Алания.
1380. ЧЕРНОБРОВКИН ВИТАЛИЙ АЛЕКСАНДРОВИЧ*, 28.09.1975 г.р., г. Чита.
1381. ЧЕРНОВ АЛЕКСЕЙ АНАТОЛЬЕВИЧ*, 13.07.1977 г.р., с. Ламки Узловского района Тульской области.
1382. ЧЕРНЯВСКИЙ ЮРИЙ ВЛАДИМИРОВИЧ*, 04.10.1968 г.р., г. Приозерск Карагандинской области Казахской ССР.
1383. ЧЕСНОКОВ ВЯЧЕСЛАВ ВЛАДИМИРОВИЧ*, 23.11.1963 г.р., г. Свердловск.
1384. ЧИМАЕВ АНЗОР ВАХАЕВИЧ*, 05.03.1978 г.р., г. Грозный Чеченской Республики.
1385. ЧИНТАГОВ РАДЖИ МАГОМЕДОВИЧ*, 21.02.1986 г.р., с. Ачхой-Мартан Ачхой-Мартановского района ЧИАССР.
1386. ЧИСТЯКОВ АЛЕКСАНДР ИВАНОВИЧ*, 25.03.1982 г.р., пгт. Пойковский Нефтеюганского района Тюменской области.
1387. ЧИТАЕВ СУРХО АЛИЕВИЧ*, 10.09.1980 г.р., г. Грозный ЧИАССР.
1388. ЧУДАЛОВ МУСЛИМ МУСАЕВИЧ*, 11.10.1979 г.р., г. Грозный (с. Аллерой Шалинского района) ЧИАССР.
1389. ЧУНЧАЕВ САЙПУДИ ЛЕЧАЕВИЧ*, 23.06.1977 г.р., с. Урус-Мартан ЧИАССР.
1390. ЧУПАЛАЕВ САИД-МАГОМЕД ЦУГАЕВИЧ*, 04.04.1957 г.р., с. Ириновка Урджарского р-на Семипалатинской области Казахской ССР.
1391. ШАВАЕВ МАГОМЕД НАИПОВИЧ*, 13.12.1975 г.р., г. Грозный ЧИАССР.
1392. ШАВАЕВ МУРАТ ИСМАИЛОВИЧ*, 17.02.1975 г.р., г. Нальчик Кабардино-Балкарской Республики.
1393. ШАВХАЛОВ ИБРАГИМ САЙДАХМЕДОВИЧ*, 23.08.1987 г.р., г. Хасавюрт ДАССР.
1394. ШАВХАЛОВ РАМЗАН РУСЛАНОВИЧ*, 08.10.1980 г.р., с. Алхан-Кала ЧИАССР.
1395. ШАГАЛИЕВ ИЛЬШАТ ИСМАГИЛОВИЧ*, 04.07.1986 г.р., г. Набережные Челны Республики Татарстан.
1396. ШАДУКАЕВ РИЗВАН БУКАЕВИЧ*, 09.08.1968 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
1397. ШАИПОВ МАГОМЕД ВАХАЕВИЧ*, 09.04.1983 г.р., с. Урус-Мартан Урус-Мартановского района Чеченской Республики.
1398. ШАИПОВ ТИМУР СУРПАШЕВИЧ*, 10.03.1984 г.р., г. Хасавюрт Республики Дагестан.
1399. ШАИПОВ ШАМХАН ШАМСУДИНОВИЧ*, 17.05.1977 г.р., п. Маныч Ики-Бурульского района Республики Калмыкия.
1400. ШАЙДУЛЛИН ИЛЬМИР ИЛЬГИЗОВИЧ*, 31.10.1983 г.р., г. Азнакаево Республики Татарстан.
1401. ШАЙДУЛЛИН РУСТЕМ ИЛЬГИЗОВИЧ*, 26.02.1987 г.р., г. Азнакаево Республики Татарстан.
1402. ШАЙЛИЕВ ХАЛИС СУЛТАНОВИЧ*, 21.01.1967 г.р., г. Карачаевск Карачаево-Черкесской Республики.
1403. ШАЙХИЕВ ШИРВАНИ ХАСМАГОМЕДОВИЧ*, 14.08.1951 г.р., с. Кара-Кочкар Ошской области Киргизской ССР.
1404. ШАЙХУТДИНОВ ФАНИС АГЛЯМОВИЧ*, 27.06.1965 г.р., с. Агерзе Азнакаевского района ТАССР.
1405. ШАЛАЕВ АЙНДИ ЗАИНДИЕВИЧ*, 19.12.1974 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
1406. ШАМАЕВ АЛЬВИ АИНДЫЕВИЧ*, 18.09.1984 г.р., г. Грозный ЧИАССР.
1407. ШАМАНОВ ТИМУР КАЗБЕКОВИЧ*, 28.01.1975 г.р., г. Песчаный Приютненского района Калмыцкой АССР.
1408. ШАМСАДОВ ИСА МУСАЕВИЧ*, 10.09.1986 г.р., с. Советское Советского района ЧИАССР.
1409. ШАМСАДОВ СУПЬЯН МУХАДИНОВИЧ*, 14.08.1969 г.р., с. Тазбичи Советского района ЧИАССР.
1410. ШАМСАДОВ ТИМУР МАГОМЕДОВИЧ*, 01.06.1981 г.р., г. Грозный ЧИАССР.
1411. ШАМСУДИНОВ АСЛАНБЕК АЗИЗОВИЧ*, 20.12.1972 г.р., с. Танги-Чу ЧИАССР.
1412. ШАМУРЗАЕВ МАГОМЕД САЛМАНОВИЧ*, 12.07.1974 г.р., с. Комсомольское Гудермесского района ЧИАССР.
1413. ШАМХАЛОВ ШАМИЛЬ ЮСУПОВИЧ*, 12.12.1979 г.р., г. Махачкала Республики Дагестан.
1414. ШАРГО МАКСИМ МАКСИМОВИЧ*, 04.10.1974 г.р., г. Петропавловск-Камчатский.
1415. ШАХГИРИЕВ РУСЛАН АБАЕВИЧ*, 21.11.1964 г.р., с. Агишбатой Веденского района Чеченской Республики.
1416. ШЕВЛЯКОВ АНАТОЛИЙ ЮРЬЕВИЧ*, 06.11.1984 г.р., г. Грозный ЧИАССР.
1417. ШЕЙХОВ БАММАТХАН КАМИЛОВИЧ*, 04.04.1964 г.р., г. Буйнакск Республики Дагестан.
1418. ШЕПИЕВ АСЛАН АХЪЯЕВИЧ*, 08.05.1969 г.р., с. Джалка Гудермесского района ЧИАССР.
1419. ШЕПИЕВ РУДОЛЬФ АЛЕКСАНДРОВИЧ*, 11.07.1980 г.р., ст. Каргалинская Шелковского района ЧИАССР.
1420. ШИДИЕВ РИЗВАН ШУДИЕВИЧ*, 11.07.1987 г.р., с. Гуни Веденского района ЧИАССР.
1421. ШИМАЕВ ХАСУ АЙНДИЕВИЧ*, 20.04.1982 г.р., с. Урус-Мартан Урус-Мартановского района Чеченской Республики.
1422. ШИХОВ АЗАТ ФАТТАХОВИЧ*, 11.04.1978 г.р., с. Ульт-Ягун Сургутского района Тюменской области.
1423. ШИШХАНОВ МАЙРБЕК ОМАРОВИЧ*, 23.09.1983 г.р., с. Ачхой-Мартан Ачхой-Мартановского р-на ЧИАССР.
1424. ШОВХАЛОВ ВИСХАН ВАХИТОВИЧ*, 28.06.1986 г.р., д. Волково Артинского района Свердловской области.
1425. ШОВХАЛОВ РУСЛАН САЛАМУВИЧ*, 11.03.1977 г.р., совхоз Джетикульский Джамбутинского района Уральской области КазССР.
1426. ШУКУРОВ ИЛХОМ ИБРАГИМОВИЧ*, 06.12.1976 г.р., г. Карши Кашкадарьинской области Республики Узбекистан.
1427. ШУКУРОВ ШЕРАЛИ ИБРАГИМОВИЧ*, 17.07.1974 г.р., г. Карши Кашкадарьинской области Республики Узбекистан.
1428. ШУМИЛКИН АЛЕКСАНДР ЕВГЕНЬЕВИЧ*, 23.11.1970 г.р., с. Первомайский Перелюбского района Саратовской области.
1429. ЩЕРБОВ СЕРГЕЙ ВАСИЛЬЕВИЧ*, 09.10.1977 г.р., с. Ярославичи Подпорожского района Ленинградской области.
1430. ЩУКИН ДМИТРИЙ АЛЕКСАНДРОВИЧ*, 14.02.1979 г.р., г. Витебск Республики Беларусь.
1431. ЭДИЛСУЛТАНОВ РАМЗАН МАК-МАГОМЕДОВИЧ*, 25.10.1980 г.р., с. Курчалой Шалинского района ЧИАССР.
1432. ЭДИЛСУЛТАНОВ РУСЛАН МАГОМЕДОВИЧ*, 09.05.1967 г.р., с. Курчалой Шалинского района ЧИАССР.
1433. ЭДИЛЬСУЛТАНОВ ХУСЕЙН КУСУЕВИЧ*, 14.03.1961 г.р., с. Курчалой Шалинского района ЧИАССР.
1434. ЭЖИЕВ РУСТАМ ХАМИДОВИЧ*, 21.01.1972 г.р., с. Сержень-Юрт Шалинского района.
1435. ЭЗЕРХАНОВ АХМЕТ РАСУЛОВИЧ*, 07.03.1985 г.р., г. Грозный ЧИАССР.
1436. ЭЗИРХАНОВ САЙД-ЭМИ САЙД-АХМЕДОВИЧ*, 02.03.1985 г.р., с. Кошкельды Гудермесского района ЧИАССР.
1437. ЭКЗЕКОВ МУРАТ УМАРОВИЧ*, 28.05.1979 г.р., г. Черкесск Карачаево-Черкесской Республики.
1438. ЭКТУМАЕВ ЗАУРБЕК МУХАРБЕКОВИЧ*, 30.08.1980 г.р., х. Веселый Ачхой-Мартановского района ЧИАССР.
1439. ЭКТУМАЕВ ИСЛАМ СУЛЕЙМАНОВИЧ*, 31.05.1982 г.р., ст. Орджоникидзевская Сунженского района ЧИАССР.
1440. ЭКТУМАЕВ МУСЛИМ МАГОМЕДОВИЧ*, 27.06.1977 г.р., с. Бамут Ачхой-Мартановского района ЧИАССР.
1441. ЭЛАЕВ АДЛАН САЛМАНОВИЧ*, 01.10.1972 г.р., с. Дай ЧИАССР.
1442. ЭЛЖУРКАЕВ АСЛАН АРБИЕВИЧ*, 04.11.1986 г.р., г. Грозный ЧИАССР.
1443. ЭЛИХАДЖИЕВ ДАНИЛХАН СУЛЕЙМАНОВИЧ*, 17.07.1984 г.р., с. Курчалой Курчалоевского района ЧИАССР.
1444. ЭЛИХАНОВ ИБРАГИМ ТУХАНОВИЧ*, 19.11.1985 г.р., п. Новогрозненский Гудермесского района ЧИАССР.
1445. ЭЛИХАНОВ МАГОМЕД АЙСАЕВИЧ*, 18.01.1985 г.р., с. Новые Атаги Шалинского района ЧИАССР.
1446. ЭЛИХАНОВ РУСЛАН АБУБАКАРОВИЧ*, 11.06.1983 г.р., с. Ялхой-Мохк Ножай-Юртовского района ЧИАССР.
1447. ЭЛИХАНОВ РУСТАМ ИСАЕВИЧ*, 25.09.1986 г.р., с. Каримово Бижбуляжского района Башкирской АССР.
1448. ЭЛИХАНОВ САЙД-ХУСЕЙН ХАСАНОВИЧ*, 20.10.1978 г.р., село Бачи-Юрт Шалинского района ЧИАССР.
1449. ЭЛЬГЕРЕЕВ РОМАН ЭЛЛИЕВИЧ*, 04.10.1977 г.р., г. Гудермес ЧИАССР.
1450. ЭЛЬДАРОВ МАГОМЕД ИСАЕВИЧ*, 03.10.1979 г.р., г. Грозный ЧИАССР.
1451. ЭЛЬКАНОВ ОСМАН САЙДАХМАТОВИЧ*, 31.03.1982 г.р., п. Новый Карачай Карачаевского района Карачаево-Черкесской Республики.
1452. ЭЛЬМУРЗАЕВ АРСЛАН МАМАСОЛЕБОВИЧ*, 15.03.1976 г.р., ст. Шелковская ЧИАССР.
1453. ЭЛЬМУРЗАЕВ АСЛАНБЕК ХАМЗАТОВИЧ*, 10.08.1979 г.р., с. Зоны Советского района Чеченской Республики.
1454. ЭЛЬМУРЗАЕВ КАЗБЕК АБДУЛ-ВАХАБОВИЧ*, 19.11.1983 г.р., г. Аргун ЧИАССР.
1455. ЭЛЬМУРЗАЕВ МАХМА МАГОМЕДОВИЧ*, 01.09.1953 г.р., г. Усть-Каменогорск КазССР.
1456. ЭЛЬМУРЗАЕВ САИД ШАМАНОВИЧ*, 07.12.1981 г.р., г. Грозный ЧИАССР.
1457. ЭЛЬМУРЗИЕВ МУССА КУРЕЙШЕВИЧ*, 20.06.1968 г.р., г. Орджоникидзе Республики Северная Осетия.
1458. ЭЛЬСАЕВ ТИМУР КЮРАЕВИЧ*, 04.10.1987 г.р., с. Ачхой-Мартан ЧИАССР.
1459. ЭЛЬСИЕВ ЮНАДИ СУЛТАНОВИЧ*, 29.11.1979 г.р., с. Урус-Мартан ЧИАССР.
1460. ЭЛЬХАДЖИЕВ АНЗОР СУЛТАНБЕКОВИЧ*, 13.09.1979 г.р., с. Хамавюрт Хасавюртовского района ДагАССР.
1461. ЭЛЬХОДЖИЕВ АЗАМАТ СУЛТАНБЕКОВИЧ*, 23.02.1982 г.р., с. Хамавюрт Хасавюртовского района ДагАССР.
1462. ЭРЗАНУКАЕВ МОХМАД ИНДАРБЕКОВИЧ*, 20.01.1987 г.р., с. Агишты Веденского района ЧИАССР.
1463. ЭРСАБИЕВ АЛЬВИ АНДИЕВИЧ*, 25.11.1988 г.р., г. Грозный Чеченской Республики.
1464. ЭРСИМИКОВ ИБРАГИМ БИСЛАНОВИЧ*, 12.07.1983 г.р., г. Аргун ЧИАССР.
1465. ЭСАЕВ РАХМАН РАМЗАНОВИЧ*, 01.05.1988 г.р., с. Ведено ЧИАССР.
1466. ЭСАМБАЕВ ХАСМАГОМЕД ХАМИДОВИЧ*, 21.04.1960 г.р., с. Ачеришки Ножай-Юртовского района ЧИАССР.
1467. ЭСКАРБИЕВ ВИСЛАН ВАХАРПАШАЕВИЧ*, 01.08.1976 г.р., с. Гиляны Ножай-Юртовского района ЧИАССР.
1468. ЭСКЕРХАНОВ АЙНДИ САЙПУДИНОВИЧ*, 01.01.1982 г.р., с. Советское Советского района ЧИАССР.
1469. ЭСКЕРХАНОВ САЛМАН ТАРХАНОВИЧ*, 26.09.1970 г.р., с. Кулары Грозненского район ЧИАССР.
1470. ЭСКИРХАНОВ ЭЛИ САЛАМОЕВИЧ*, 14.04.1974 г.р., с. Сарай Новороссийского района Актюбинской области КазССР.
1471. ЮНУСОВ АСЛАМБЕК ИДРИСОВИЧ*, 19.04.1979 г.р., с. Побединское Грозненского района Чеченской Республики.
1472. ЮНУСОВ АСЛАН АНДИЕВИЧ*, 23.07.1976 г.р., совхоз Алгайский Новоузенского района Саратовской области.
1473. ЮНУСОВ ДЖАБРАИЛ МАЙРБЕКОВИЧ*, 29.03.1970 г.р., станица Калиновская Наурского р-на ЧИАССР.
1474. ЮНУСОВ ДУКВАХИ ИЙСАЕВИЧ*, 13.10.1978 г.р., г. Грозный ЧИАССР.
1475. ЮНУСОВ РАМЗАН ДАУДОВИЧ*, 24.06.1984 г.р., с. Ачхой-Мартан Ачхой-Мартановского р-на ЧИАССР.
1476. ЮНУСОВ РУСЛАН ИЙСАЕВИЧ*, 14.11.1974 г.р., г. Грозный ЧИАССР.
1477. ЮНУСОВ ЮСУП РАМЗАНОВИЧ*, 21.07.1978 г.р., с. Курчали Веденского района ЧИАССР.
1478. ЮСУПОВ АЛИ СУЛТАНОВИЧ*, 01.06.1974 г.р., с. Новые-Атаги Шалинского района ЧИАССР.
1479. ЮСУПОВ АЛИБЕК АЙНДЫЕВИЧ*, 25.04.1983 г.р., с. Урус-Мартан Урус-Мартановского района ЧИАССР.
1480. ЮСУПОВ АЛИБЕК ХУСАИНОВИЧ*, 19.08.1978 г.р., с. Урус-Мартановского р-на ЧИАССР.
1481. ЮСУПОВ АМХАД СУЛТАНОВИЧ*, 22.01.1981 г.р., с. Майртуп Шалинского района ЧИАССР.
1482. ЮСУПОВ АРЗУ МАГОМЕДОВИЧ*, 17.02.1985 г.р., с. Суворов-Юрт Гудермесского района ЧИАССР.
1483. ЮСУПОВ ВАХМУРАД АЙНУТДИНОВИЧ*, 06.08.1984 г.р., г. Хасавюрт Республики Дагестан.
1484. ЮСУПОВ ВИСИТА ВАХИТОВИЧ*, 02.02.1988 г.р., г. Гудермес ЧИАССР.
1485. ЮСУПОВ ИМРАН БОЙСУЕВИЧ*, 01.01.1983 г.р., с. Кошкельды Гудермесского района ЧИАССР.
1486. ЮСУПОВ ИСЛАМ АБУЕВИЧ*, 04.10.1986 г.р., с. Чири-Юрт Шалинского района ЧИАССР.
1487. ЮСУПОВ КАЗБЕК САЛМАНОВИЧ*, 20.02.1981 г.р., с. Урус-Мартан ЧИАССР.
1488. ЮСУПОВ МАХМАД ГИЛАНИЕВИЧ*, 22.06.1982 г.р., с. Новые-Атаги ЧИАССР.
1489. ЮСУПОВ РАСАНБЕК ХАМИДОВИЧ*, 06.11.1984 г.р., с. Ножай-Юрт Ножай-Юртовского района ЧИАССР.
1490. ЮСУПОВ СКАНДАРБЕК СУЛТАНОВИЧ*, 20.12.1955 г.р., колхоз им. Крупской Сталинского района Фрунзенской области Киргизской ССР.
1491. ЮСУПОВ СУЛУМБЕК АХМЕДОВИЧ*, 21.05.1985 г.р., с. Бешил-Ирзой Ножай-Юртовского района Чеченской Республики.
1492. ЮСУПОВ ХАВАЖ ХАМИДОВИЧ*, 04.04.1986 г.р., с. Аллерой Ножай-Юртовского района ЧИАССР.
1493. ЮСУПОВ ХАМЗАТ САЙДАЕВИЧ*, 05.07.1957 г.р., с. Кандыковка Шемонайхинского района Восточно-Казахстанской области КазССР.
1494. ЮШАЕВ СУЛИМА САЛМАНОВИЧ*, 17.09.1981 г.р., г. Гудермес ЧИАССР.
1495. ЯКОВЛЕВ АНДРЕЙ ЮРЬЕВИЧ*, 05.01.1970 г.р., г. Армавир Краснодарского края.
1496. ЯКОВЛЕВ ЕВГЕНИЙ ИВАНОВИЧ*, 10.10.1960 г.р., д. Кошноруй Канашского района Чувашской Республики.
1497. ЯКУБОВ АСЛАН НАСРУДИЕВИЧ*, 15.05.1970 г.р., с. Шали Шалинского района ЧИАССР.
1498. ЯКУЕВ ЗАУРБЕК НАБИУЛЛЫЕВИЧ*, 30.11.1981 г.р., с. Рубежное Наурского р-на ЧИАССР.
1499. ЯКУШЕВ РОМАН ВЛАДИМИРОВИЧ*, 03.07.1982 г.р., г. Алексин Тульской области.
1500. ЯЛХОРОЕВ ДЖАБРАИЛ УМАТ-ГИРЕЕВИЧ*, 30.11.1970 г.р., г. Грозный ЧИАССР.
1501. ЯНДАРБИЕВ ЗЕЛИМХАН АБДУЛ-МУСЛИМОВИЧ*, 12.09.1951 г.р., Верхубинский район Восточно-Казахской области Казахской ССР.
1502. ЯНДИЕВ АЛИЯ СУЛТАНОВИЧ*, 20.09.1975 г.р., г. Назрань ЧИАССР.
1503. ЯРМОЛАТОВ РАМЗАН ВАХИТОВИЧ*, 02.12.1983 г.р., с. Автуры ЧИАССР.
1504. ЯРМОЛАТОВ УМАР ВАХИТОВИЧ*, 06.07.1987 г.р., г. Шали ЧИАССР.
1505. ЯСАКОВ РЕШЕД ИБРАГИМОВИЧ*, 23.02.1972 г.р., с. Кади-Юрт Гудермесского района ЧИАССР.
1506. ЯСУЕВ АСЛАНБЕК ШАРПУДИЕВИЧ*, 26.12.1984 г.р., с. Старые Атаги Грозненского района ЧИАССР.
1507. ЯСУЕВ МОВЛАДИ САИД-МАГОМЕДОВИЧ*, 21.10.1984 г.р., с. Улус-Керт Советского р-на ЧИАССР.
1508. ЯХЪЯЕВ ЯКУБ ИСМАИЛОВИЧ*, 09.03.1974 г.р., х. Мирный Дубовского района Ростовской области.
1509. ЯХЬЯЕВ ДУК-ВАХА ИДРИСОВИЧ*, 03.02.1974 г.р., г. Урус-Мартан ЧИАССР.
1510. ЯШУЕВ ТАМЕРЛАН САЙДМАГОМЕДОВИЧ*, 03.08.1983 г.р., н.п. Кошкельды Гудермесского района ЧИАССР.
Примечание: 1. Отмечены (*) организации и физические лица, в отношении которых имеются сведения об их причастности к терроризму.
[Note: 1. Individuals and organizations marked (*) indicate that there is evidence of their involvement in terrorism.]


















































































 Political Parties in Afghanistan
Political Parties in Afghanistan


















 U.S. Espionage and Intelligence: Organization, Operations, and Management, 1947-1996 publishes together for the first time recent unclassified and newly declassified documents pertaining to the organizational structure, operations, and management of the U.S. intelligence community over the last fifty years, cross-indexed for maximum accessibility. This set reproduces on microfiche 1,174 organizational histories, memoranda, manuals, regulations, directives, reports, and studies, representing over 36,102 pages of documents from the Office of the Director of Central Intelligence, the Central Intelligence Agency, National Reconnaissance Office, National Security Agency, Defense Intelligence Agency, military service intelligence organizations, National Security Council and other organizations. U.S. Espionage and Intelligence presents a unique look into the internal workings of America’s intelligence community. The documents gathered here shed further light on U.S. intelligence organization and activities during the Cold War, and describe the consolidation and reevaluation of the intelligence community in the post-Cold War era. They are drawn from diverse sources, including the National Archives, manuscript collections in the Library of Congress, court files of major espionage prosecutions, presidential libraries, and most importantly, Freedom of Information Act requests. The result of this effort is an authoritative documents publication which, together with the National Security Archive’s previous collection on the structure and operations of the U.S. intelligence community,
U.S. Espionage and Intelligence: Organization, Operations, and Management, 1947-1996 publishes together for the first time recent unclassified and newly declassified documents pertaining to the organizational structure, operations, and management of the U.S. intelligence community over the last fifty years, cross-indexed for maximum accessibility. This set reproduces on microfiche 1,174 organizational histories, memoranda, manuals, regulations, directives, reports, and studies, representing over 36,102 pages of documents from the Office of the Director of Central Intelligence, the Central Intelligence Agency, National Reconnaissance Office, National Security Agency, Defense Intelligence Agency, military service intelligence organizations, National Security Council and other organizations. U.S. Espionage and Intelligence presents a unique look into the internal workings of America’s intelligence community. The documents gathered here shed further light on U.S. intelligence organization and activities during the Cold War, and describe the consolidation and reevaluation of the intelligence community in the post-Cold War era. They are drawn from diverse sources, including the National Archives, manuscript collections in the Library of Congress, court files of major espionage prosecutions, presidential libraries, and most importantly, Freedom of Information Act requests. The result of this effort is an authoritative documents publication which, together with the National Security Archive’s previous collection on the structure and operations of the U.S. intelligence community,


![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict13.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict11.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict12.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict14.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict4.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict5.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict8.jpg)































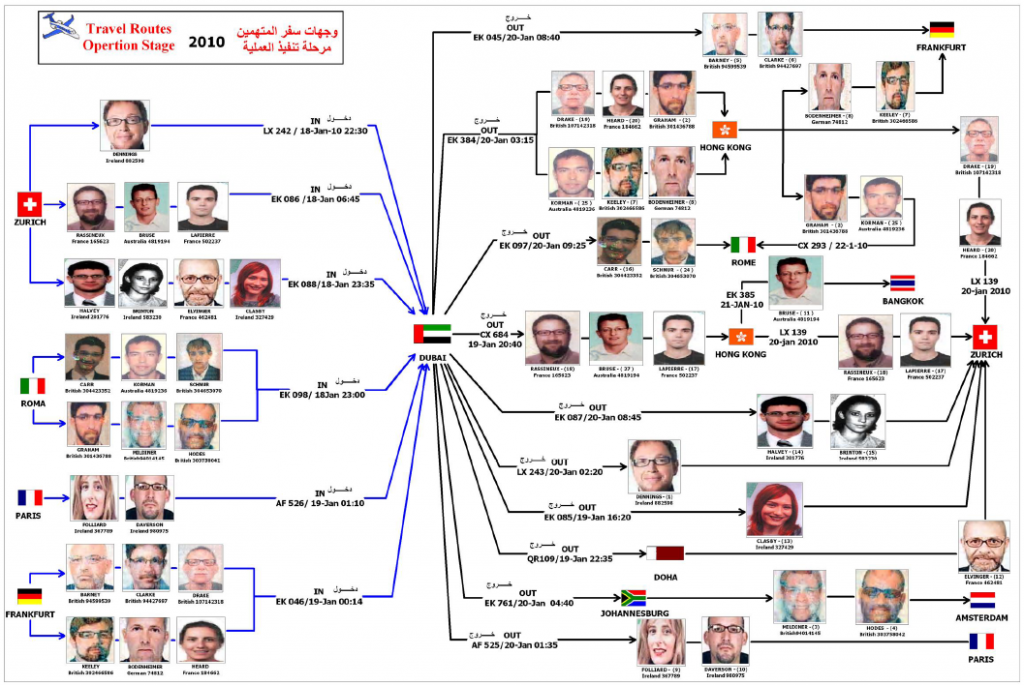

























![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111911/pict0.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111911/pict1.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111911/pict3.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111911/pict4.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111911/pict5.jpg)















 In His Own Words “Mr. So and So, I understand that you’re going to whip any FBI agent that walks into your store. I’m not armed, but I wanted to let you know if you would like to whip me, let’s get started…”
In His Own Words “Mr. So and So, I understand that you’re going to whip any FBI agent that walks into your store. I’m not armed, but I wanted to let you know if you would like to whip me, let’s get started…”



 Intimidation…vandalism…assault…rape…murder. These are crimes by anyone’s definition. But add an element of bias against the victims—because of their race or religion, for example—and these traditional crimes become hate crimes.
Intimidation…vandalism…assault…rape…murder. These are crimes by anyone’s definition. But add an element of bias against the victims—because of their race or religion, for example—and these traditional crimes become hate crimes.







![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict26.jpg) An official from the Tokyo Electric Power Co. (TEPCO), wearing a protective suit and mask, uses a plastic covered megaphone to speak to fellow TEPCO workers and journalists as they drive towards the crippled Fukushima Dai-ichi nuclear power station in Okuma, Japan, Saturday, Nov. 12, 2011. Conditions at Japan’s wrecked Fukushima nuclear power plant, devastated by a tsunami in March, were slowly improving to the point where a “cold shutdown” would be possible as planned, officials said on Saturday during a tour of the facility. The nuclear reactor buildings were still surrounded by crumpled trucks, twisted metal fences, and large, dented water tanks. Smaller office buildings around the reactors were left as they were abandoned on March 11, when the tsunami hit.
An official from the Tokyo Electric Power Co. (TEPCO), wearing a protective suit and mask, uses a plastic covered megaphone to speak to fellow TEPCO workers and journalists as they drive towards the crippled Fukushima Dai-ichi nuclear power station in Okuma, Japan, Saturday, Nov. 12, 2011. Conditions at Japan’s wrecked Fukushima nuclear power plant, devastated by a tsunami in March, were slowly improving to the point where a “cold shutdown” would be possible as planned, officials said on Saturday during a tour of the facility. The nuclear reactor buildings were still surrounded by crumpled trucks, twisted metal fences, and large, dented water tanks. Smaller office buildings around the reactors were left as they were abandoned on March 11, when the tsunami hit.![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict25.jpg) Japanese police man a checkpoint near the edge of the contaminated exclusion zone around the crippled Fukushima Dai-ichi nuclear power station near Okuma, Fukushima prefecture, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)
Japanese police man a checkpoint near the edge of the contaminated exclusion zone around the crippled Fukushima Dai-ichi nuclear power station near Okuma, Fukushima prefecture, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict13.jpg) A deserted street inside the contaminated exclusion zone around the crippled Fukushima Daiichi nuclear power plant is seen from bus windows in Fukushima prefecture, November 12, 2011.
A deserted street inside the contaminated exclusion zone around the crippled Fukushima Daiichi nuclear power plant is seen from bus windows in Fukushima prefecture, November 12, 2011.![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict22.jpg) A deserted field and buildings inside the contaminated exclusion zone around the crippled Fukushima Dai-ichi nuclear power station are seen through a bus window near Okuma, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)
A deserted field and buildings inside the contaminated exclusion zone around the crippled Fukushima Dai-ichi nuclear power station are seen through a bus window near Okuma, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict23.jpg) An official from the Tokyo Electric Power Co., right, and an unidentified man, both wearing protective suits and masks ride on a bus as they pass by the crippled Fukushima Dai-ichi nuclear power station, seen through the window, in Okuma, Japan, Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)
An official from the Tokyo Electric Power Co., right, and an unidentified man, both wearing protective suits and masks ride on a bus as they pass by the crippled Fukushima Dai-ichi nuclear power station, seen through the window, in Okuma, Japan, Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict20.jpg) Officials from the Tokyo Electric Power Co. and Japanese journalists look at the crippled Fukushima Dai-ichi nuclear power station from bus windows in Okuma, Japan Saturday, Nov. 12, 2011. Media allowed into Japan’s tsunami-damaged nuclear power plant for the first time Saturday saw a striking scene of devastation: twisted and overturned vehicles, crumbling reactor buildings and piles of rubble virtually untouched since the wave struck more than eight months ago. (David Guttenfelder, Pool)
Officials from the Tokyo Electric Power Co. and Japanese journalists look at the crippled Fukushima Dai-ichi nuclear power station from bus windows in Okuma, Japan Saturday, Nov. 12, 2011. Media allowed into Japan’s tsunami-damaged nuclear power plant for the first time Saturday saw a striking scene of devastation: twisted and overturned vehicles, crumbling reactor buildings and piles of rubble virtually untouched since the wave struck more than eight months ago. (David Guttenfelder, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict19.jpg) A view of Tokyo Electric Power Co’s tsunami-crippled Fukushima Daiichi nuclear power plant in Fukushima prefecture November 12, 2011. (David Guttenfelder, Pool)
A view of Tokyo Electric Power Co’s tsunami-crippled Fukushima Daiichi nuclear power plant in Fukushima prefecture November 12, 2011. (David Guttenfelder, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict2.jpg) The crippled Fukushima Daiichi nuclear power plant’s No.4, No.3, No.2 and No.1 (R-L) reactor buildings are seen from bus windows in Fukushima prefecture November 12, 2011. Reuters
The crippled Fukushima Daiichi nuclear power plant’s No.4, No.3, No.2 and No.1 (R-L) reactor buildings are seen from bus windows in Fukushima prefecture November 12, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict3.jpg) The crippled Fukushima Daiichi nuclear power plant is seen from bus windows in Fukushima prefecture, November 12, 2011. Reuters
The crippled Fukushima Daiichi nuclear power plant is seen from bus windows in Fukushima prefecture, November 12, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict21.jpg) The Unit 4 reactor building of the crippled Fukushima Dai-ichi nuclear power station is seen through a bus window in Okuma, Japan Saturday, Nov. 12, 2011. Media allowed into Japan’s tsunami-damaged nuclear power plant for the first time Saturday saw a striking scene of devastation: twisted and overturned vehicles, crumbling reactor buildings and piles of rubble virtually untouched since the wave struck more than eight months ago. (David Guttenfelder, Pool)
The Unit 4 reactor building of the crippled Fukushima Dai-ichi nuclear power station is seen through a bus window in Okuma, Japan Saturday, Nov. 12, 2011. Media allowed into Japan’s tsunami-damaged nuclear power plant for the first time Saturday saw a striking scene of devastation: twisted and overturned vehicles, crumbling reactor buildings and piles of rubble virtually untouched since the wave struck more than eight months ago. (David Guttenfelder, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict32.jpg) The Unit 4 reactor building of the crippled Fukushima Dai-ichi nuclear power station is seen through a bus window in Okuma, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)
The Unit 4 reactor building of the crippled Fukushima Dai-ichi nuclear power station is seen through a bus window in Okuma, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict27.jpg) Broken vehicles are abandoned outside Unit 4 turbine building at the crippled Fukushima Dai-ichi nuclear power station as they are observed from inside a bus in Okuma, Fukushima Prefecture, Japan, Saturday, Nov. 12, 2011.
Broken vehicles are abandoned outside Unit 4 turbine building at the crippled Fukushima Dai-ichi nuclear power station as they are observed from inside a bus in Okuma, Fukushima Prefecture, Japan, Saturday, Nov. 12, 2011.![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict0.jpg) The crippled Fukushima Daiichi nuclear power plant’s upper part of the No.3 reactor building is seen from a bus window in Fukushima prefecture, November 12, 2011. Reuters
The crippled Fukushima Daiichi nuclear power plant’s upper part of the No.3 reactor building is seen from a bus window in Fukushima prefecture, November 12, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict29.jpg) The crippled Fukushima Dai-ichi nuclear power station is seen through a bus window in Okuma, Japan Saturday, Nov. 12, 2011. Media allowed into Japan’s tsunami-damaged nuclear power plant for the first time Saturday saw a striking scene of devastation: twisted and overturned vehicles, crumbling reactor buildings and piles of rubble virtually untouched since the wave struck more than eight months ago. (David Guttenfelder, Pool)
The crippled Fukushima Dai-ichi nuclear power station is seen through a bus window in Okuma, Japan Saturday, Nov. 12, 2011. Media allowed into Japan’s tsunami-damaged nuclear power plant for the first time Saturday saw a striking scene of devastation: twisted and overturned vehicles, crumbling reactor buildings and piles of rubble virtually untouched since the wave struck more than eight months ago. (David Guttenfelder, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict4.jpg) The crippled Fukushima Daiichi nuclear power plant is seen from bus windows in Fukushima prefecture, November 12, 2011. Reuters
The crippled Fukushima Daiichi nuclear power plant is seen from bus windows in Fukushima prefecture, November 12, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict16.jpg) The crippled Fukushima Daiichi nuclear power plant is seen from bus windows in Fukushima prefecture, November 12, 2011. Reuters
The crippled Fukushima Daiichi nuclear power plant is seen from bus windows in Fukushima prefecture, November 12, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict24.jpg) Crushed piping is observed from inside a bus at the crippled Fukushima Dai-ichi nuclear power station in Okuma, Fukushima Prefecture, Japan, Saturday, Nov. 12, 2011. Media allowed into Japan’s tsunami-damaged nuclear power plant for the first time Saturday saw a striking scene of devastation: twisted and overturned trucks, crumbling reactor buildings and piles of rubble virtually untouched since the wave struck more than eight months ago. (Ikuro Aiba, Pool)
Crushed piping is observed from inside a bus at the crippled Fukushima Dai-ichi nuclear power station in Okuma, Fukushima Prefecture, Japan, Saturday, Nov. 12, 2011. Media allowed into Japan’s tsunami-damaged nuclear power plant for the first time Saturday saw a striking scene of devastation: twisted and overturned trucks, crumbling reactor buildings and piles of rubble virtually untouched since the wave struck more than eight months ago. (Ikuro Aiba, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict31.jpg) Units five and six of the Fukushima Dai-ichi nuclear power station are seen through a bus window in Futaba, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)
Units five and six of the Fukushima Dai-ichi nuclear power station are seen through a bus window in Futaba, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict28.jpg) Members of the media, wearing protective suits, interview Japan’s Minister of the Environment, Goshi Hosono, and Chief of the Fukushima Dai-ichi nuclear power plant, Masao Yoshida, inside the emergency operation center at the crippled nuclear power station in Okuma, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)
Members of the media, wearing protective suits, interview Japan’s Minister of the Environment, Goshi Hosono, and Chief of the Fukushima Dai-ichi nuclear power plant, Masao Yoshida, inside the emergency operation center at the crippled nuclear power station in Okuma, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict33.jpg) Tokyo Electric Power Co. employees work inside the emergency operation center at the crippled Fukushima Dai-ichi nuclear power station in Okuma, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)
Tokyo Electric Power Co. employees work inside the emergency operation center at the crippled Fukushima Dai-ichi nuclear power station in Okuma, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)






 “Today, with the flip of a switch, the FBI and our partners dismantled the Rove criminal enterprise. Thanks to the collective effort across the U.S. and in Estonia, six leaders of the criminal enterprise have been arrested and numerous servers operated by the criminal organization have been disabled. Additionally, thanks to a coordinated effort of trusted industry partners, a mitigation plan commenced today, beginning with the replacement of rogue DNS servers with clean DNS servers to keep millions online, while providing ISPs the opportunity to coordinate user remediation efforts.”
“Today, with the flip of a switch, the FBI and our partners dismantled the Rove criminal enterprise. Thanks to the collective effort across the U.S. and in Estonia, six leaders of the criminal enterprise have been arrested and numerous servers operated by the criminal organization have been disabled. Additionally, thanks to a coordinated effort of trusted industry partners, a mitigation plan commenced today, beginning with the replacement of rogue DNS servers with clean DNS servers to keep millions online, while providing ISPs the opportunity to coordinate user remediation efforts.”![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict18.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict19.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict2.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict1.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict3.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict4.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict5.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict20.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict6.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict9.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict11.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict12.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict21.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict13.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict14.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict15.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict16.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111011/pict17.jpg)





 An Oregon man recently pled guilty to operating an unlicensed money transmittal business that illegally moved more than $172 million in and out of the United States.
An Oregon man recently pled guilty to operating an unlicensed money transmittal business that illegally moved more than $172 million in and out of the United States. 


















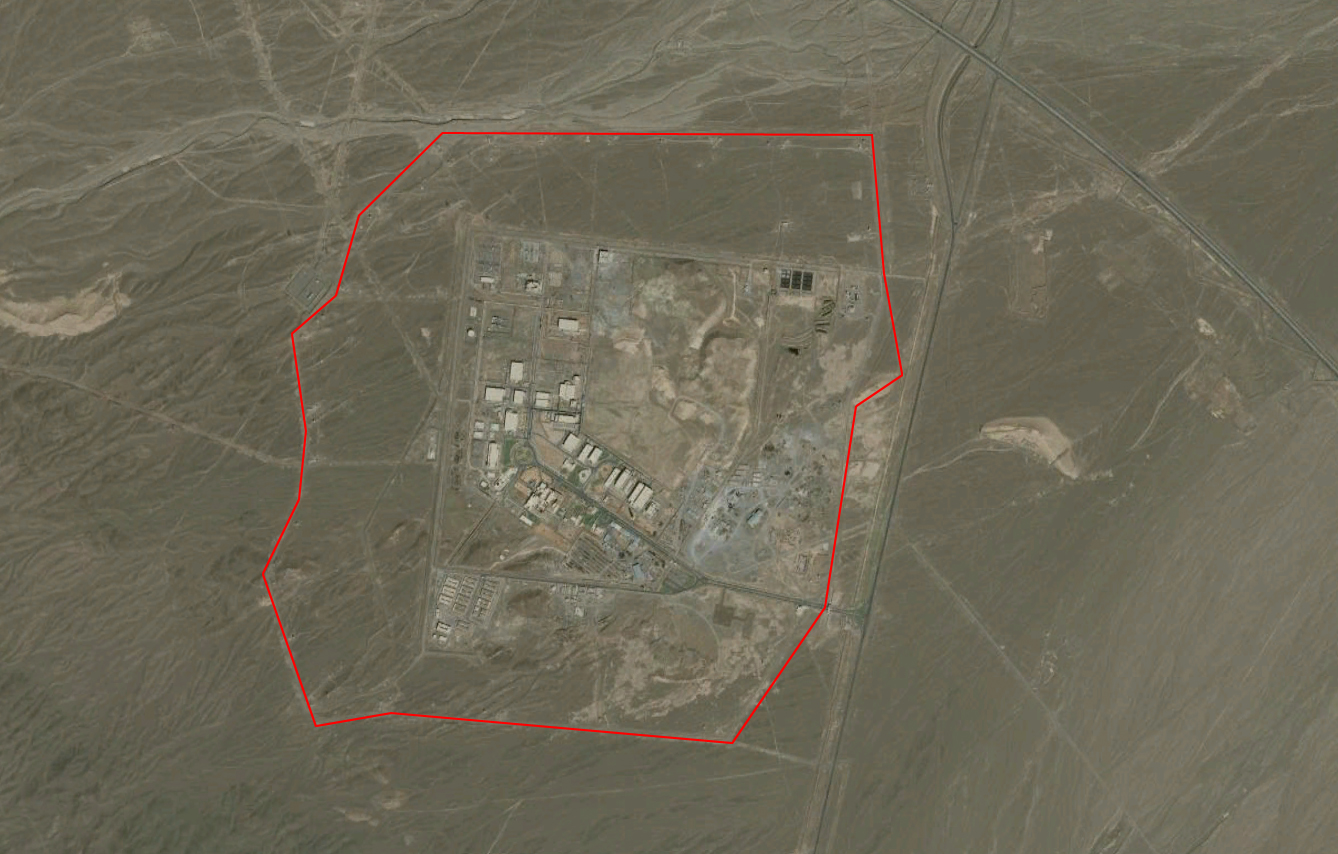
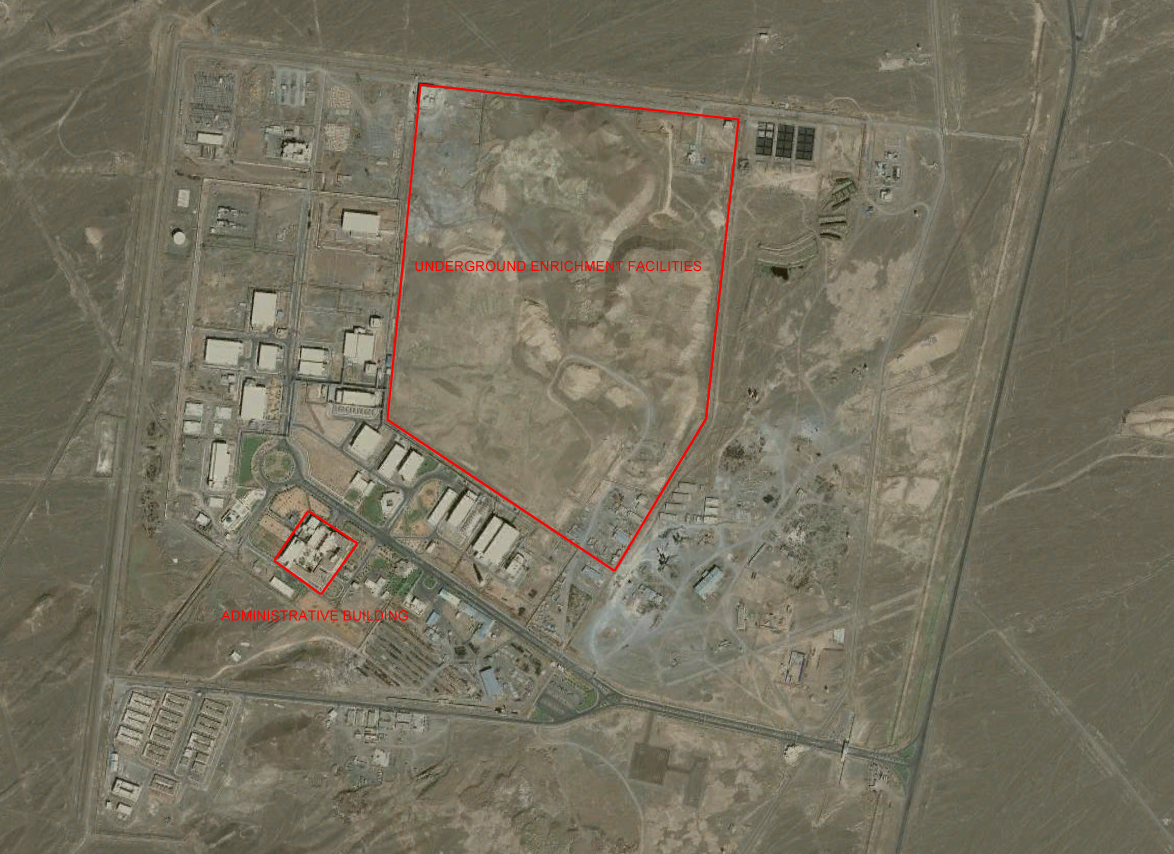
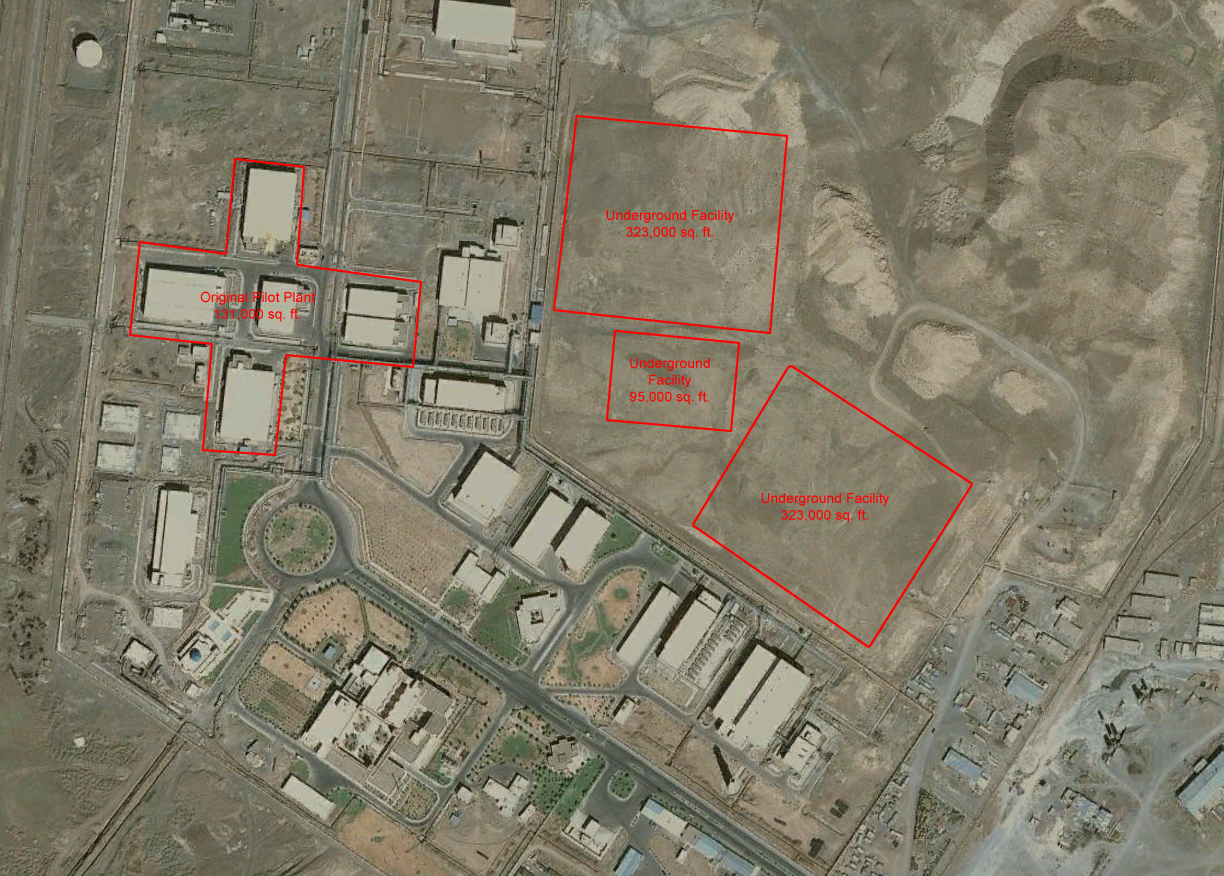


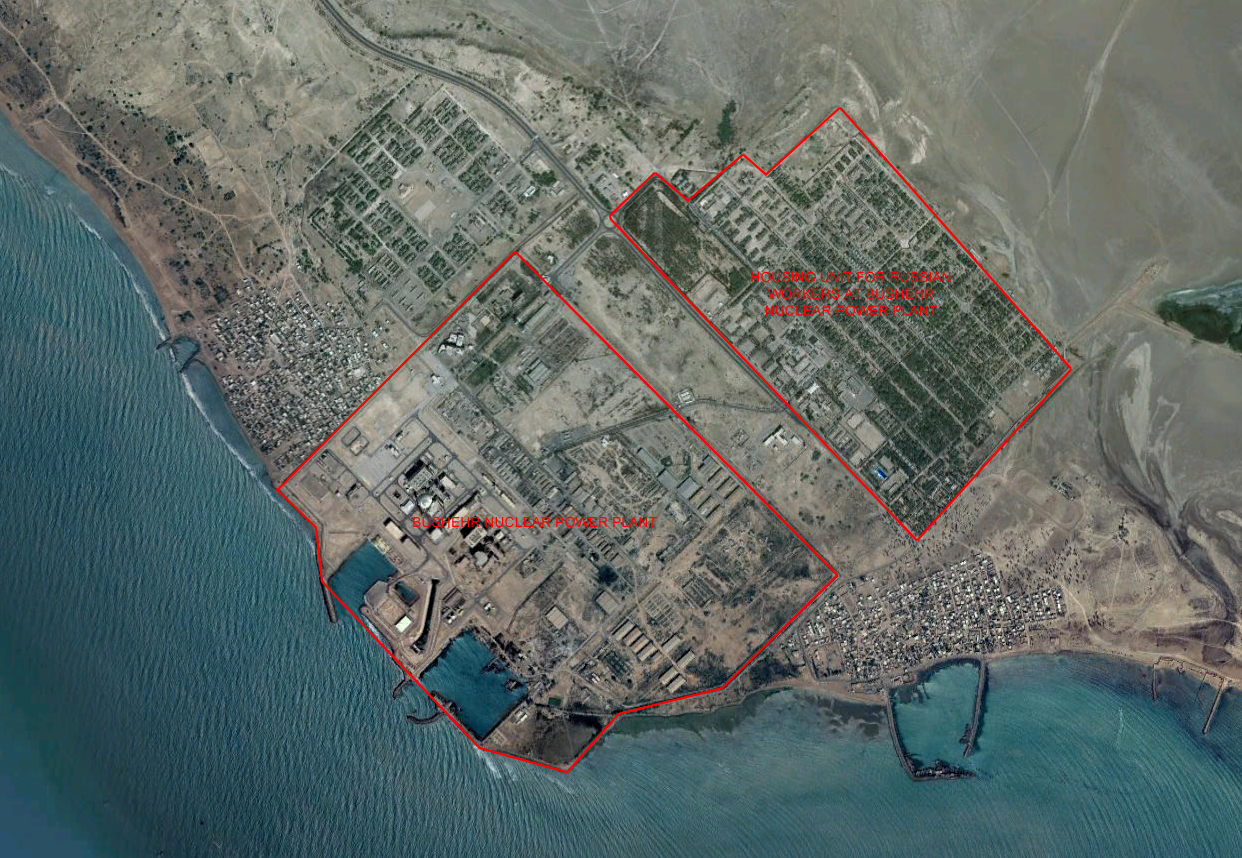










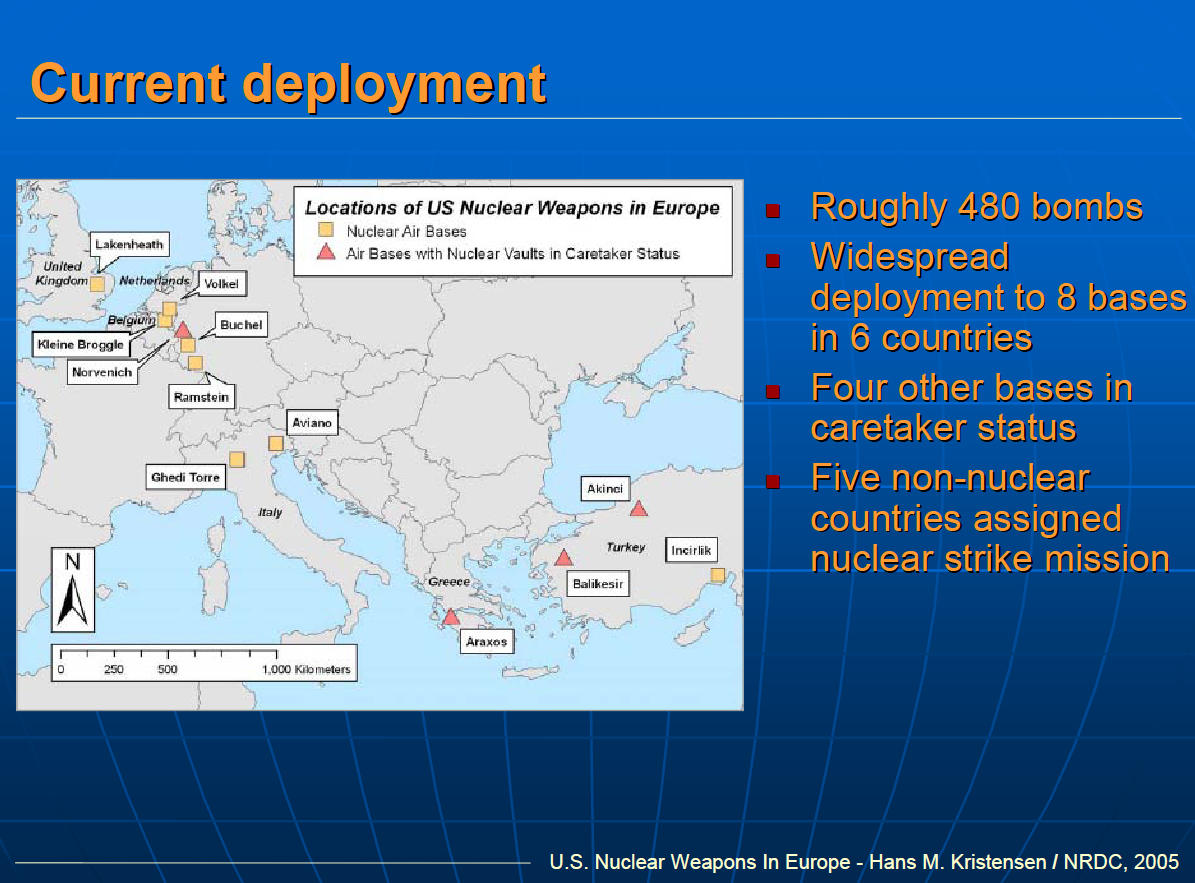

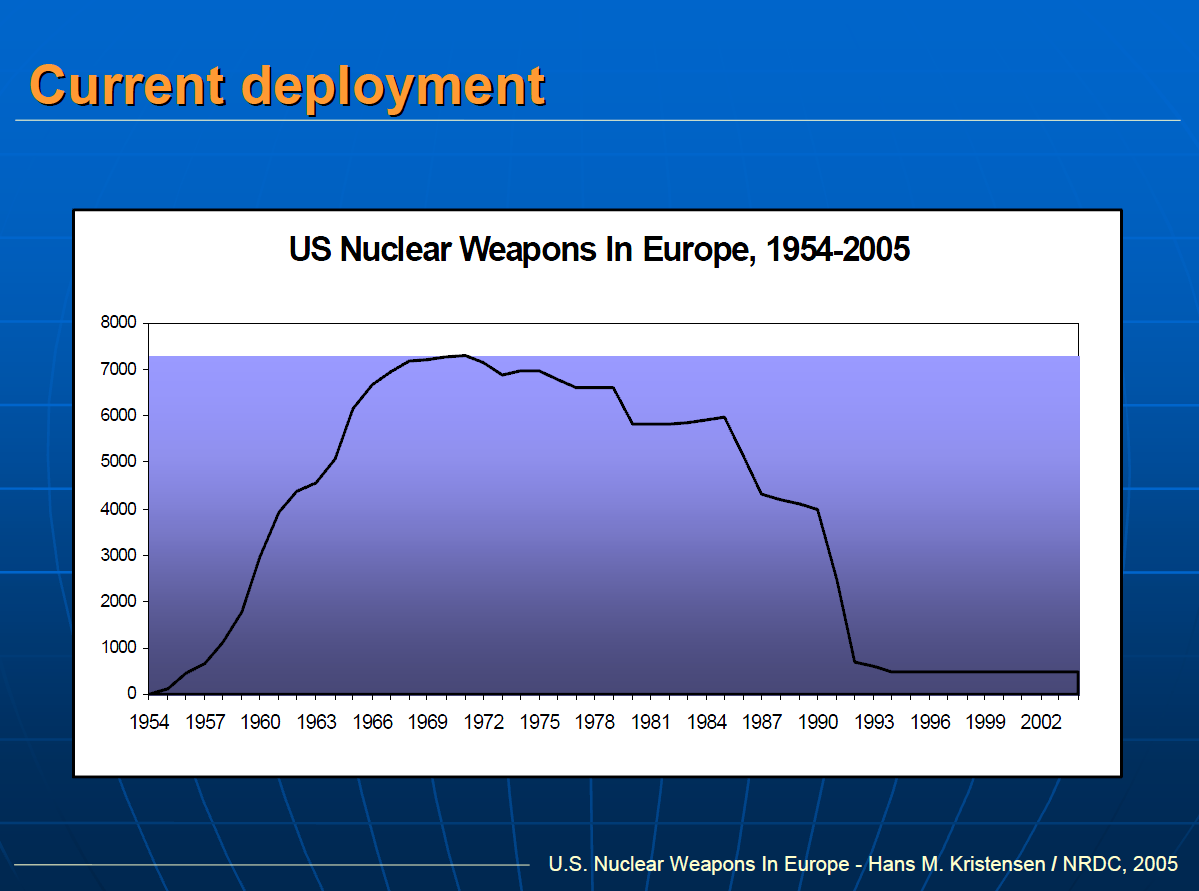
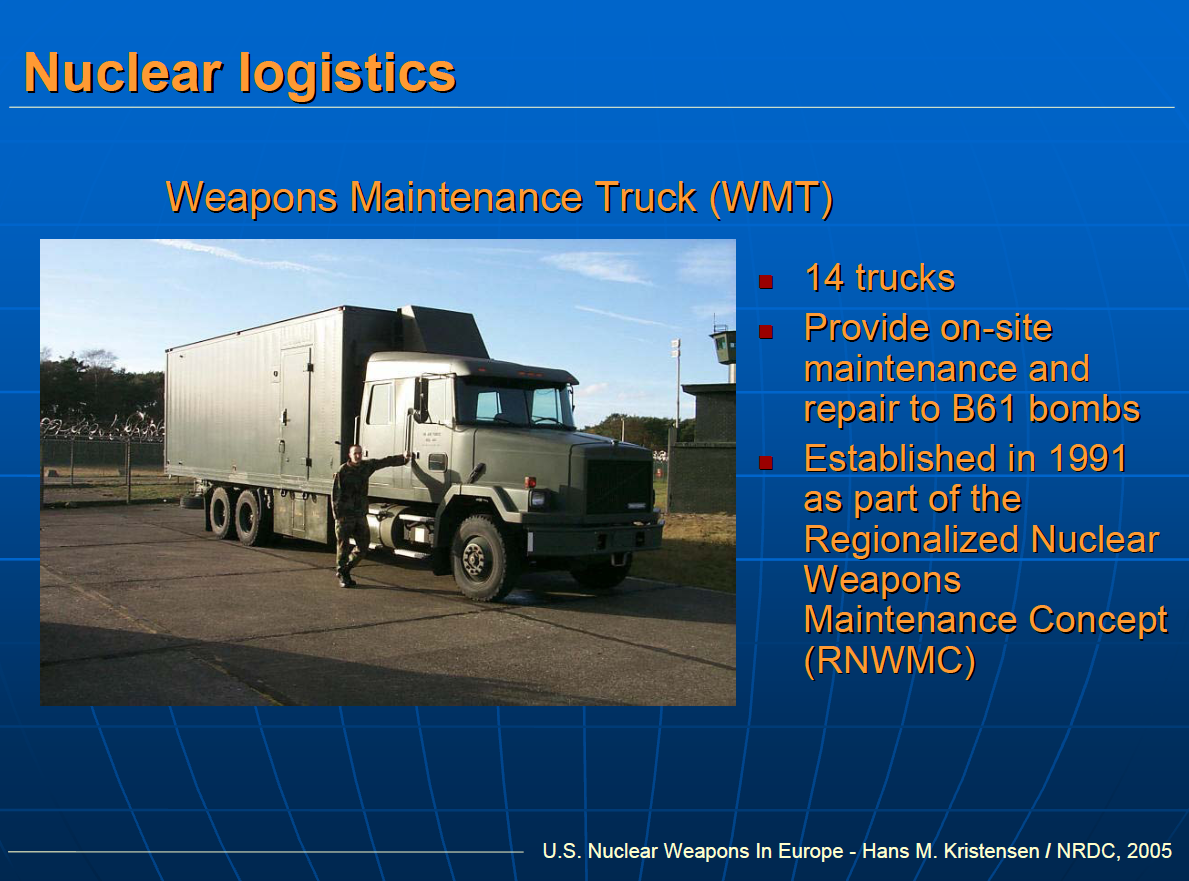
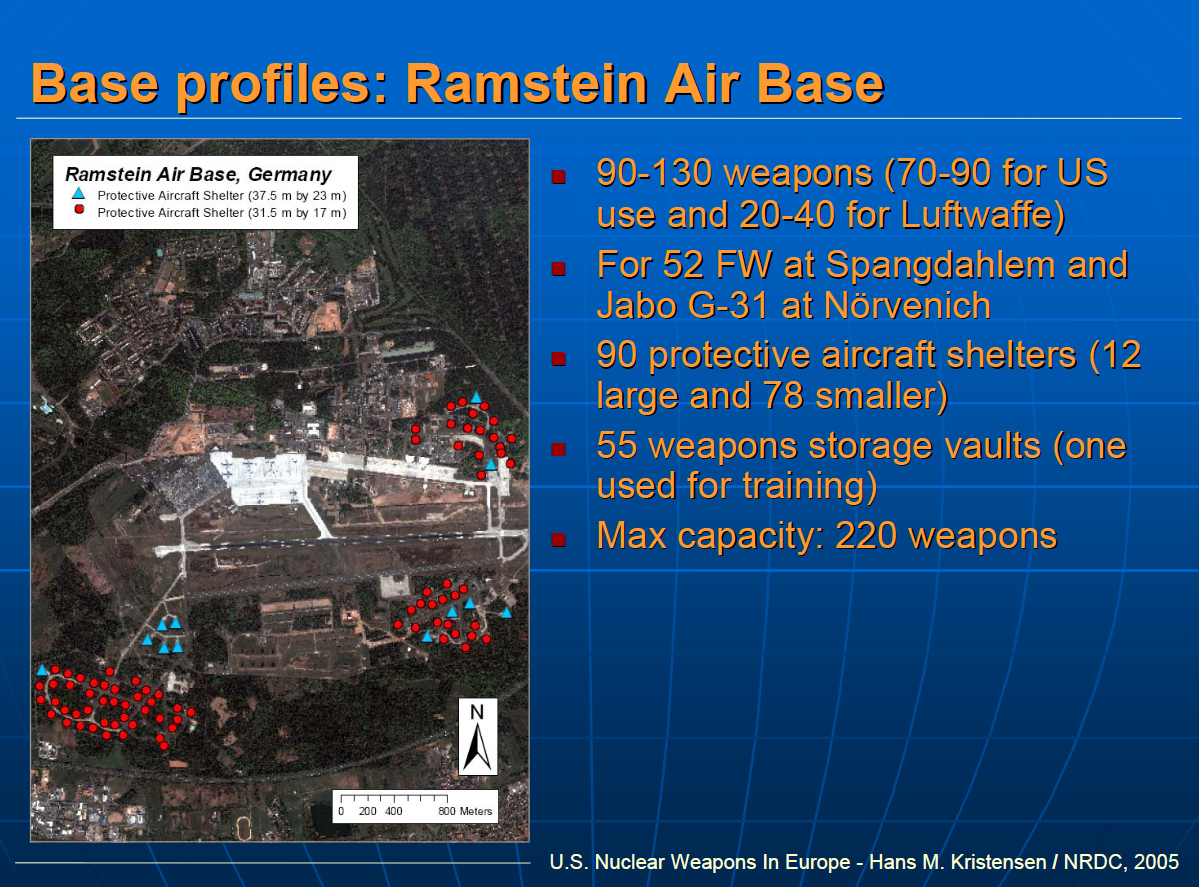




























 The new collection also sheds light on the role of U.S. intelligence agencies in Colombia’s conflict—both the close cooperation with Colombian security forces evident in the Task Force as well as the highly-sensitive U.S. intelligence operations that targeted the Colombian government itself. Key information about links between the Task Force and the Pepes was derived from U.S. intelligence sources that closely monitored meetings between the Colombian president and his top security officials.
The new collection also sheds light on the role of U.S. intelligence agencies in Colombia’s conflict—both the close cooperation with Colombian security forces evident in the Task Force as well as the highly-sensitive U.S. intelligence operations that targeted the Colombian government itself. Key information about links between the Task Force and the Pepes was derived from U.S. intelligence sources that closely monitored meetings between the Colombian president and his top security officials.






![[Image]](https://i0.wp.com/cryptome.org/eyeball/public-debt/pict131.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/public-debt/pict132.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/public-debt/pict133.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/public-debt/pict134.jpg)
 Citizens of Trujillo gather at a memorial for the victims (
Citizens of Trujillo gather at a memorial for the victims (

 Gen. Mario Montoya Uribe announces his resigation as Colombian Army Commander in November 2008. (Photo credit:
Gen. Mario Montoya Uribe announces his resigation as Colombian Army Commander in November 2008. (Photo credit: 
![[Image]](https://i0.wp.com/cryptome.org/0005/schmidle/pict25.jpg)
![[Image]](https://i0.wp.com/cryptome.org/0005/schmidle/pict27.jpg)
![[Image]](https://i0.wp.com/cryptome.org/0005/schmidle/pict30.jpg)
![[Image]](https://i0.wp.com/cryptome.org/0005/schmidle/pict31.jpg)
![[Image]](https://i0.wp.com/cryptome.org/0005/schmidle/pict29.jpg)
![[Image]](https://i0.wp.com/cryptome.org/0005/schmidle/pict32.jpg)
![[Image]](https://i0.wp.com/cryptome.org/0005/schmidle/pict26.jpg)
![[Image]](https://i0.wp.com/cryptome.org/0005/schmidle/pict28.jpg)
 U.S. Secretary of Defense Donald Rumsfeld (center) and U.S. Ambassador to Afghanistan, Robert Finn are given a tour of the U.S. Embassy compound in Kabul, Afghanistan on April 27, 2002. OSD Package No. A07D-00238 (DOD Photo by Robert D. Ward)
U.S. Secretary of Defense Donald Rumsfeld (center) and U.S. Ambassador to Afghanistan, Robert Finn are given a tour of the U.S. Embassy compound in Kabul, Afghanistan on April 27, 2002. OSD Package No. A07D-00238 (DOD Photo by Robert D. Ward)
















![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi091211/pict0.jpg)

























![[Image]](https://i0.wp.com/cryptome.org/eyeball/undersea-spy/pict30.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/undersea-spy/pict24.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/undersea-spy/pict27.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/undersea-spy/pict28.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/undersea-spy/pict29.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/undersea-spy/pict32.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/undersea-spy/pict31.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/undersea-spy/pict36.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/undersea-spy/pict33.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/undersea-spy/pict34.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/undersea-spy/pict35.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/chile-protest4/pict47.jpg) Riot police hit students with their batons during a 48-hour national strike at Santiago August 25, 2011. Protesters battled police in Chile’s capital on Thursday, the second day of a two-day strike against unpopular President Sebastian Pinera that was marked by sporadic looting but had no impact on the vital mining sector. Reuters
Riot police hit students with their batons during a 48-hour national strike at Santiago August 25, 2011. Protesters battled police in Chile’s capital on Thursday, the second day of a two-day strike against unpopular President Sebastian Pinera that was marked by sporadic looting but had no impact on the vital mining sector. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/chile-protest4/pict46.jpg) Workers, students and citizens attend a 48-hour national strike at Santiago August 25, 2011. Protesters scuffled with police in the Chilean capital on Thursday, the second of a two-day strike against unpopular President Sebastian Pinera marked by sporadic looting, though the linchpin mining sector was not affected. Reuters
Workers, students and citizens attend a 48-hour national strike at Santiago August 25, 2011. Protesters scuffled with police in the Chilean capital on Thursday, the second of a two-day strike against unpopular President Sebastian Pinera marked by sporadic looting, though the linchpin mining sector was not affected. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/chile-protest4/pict48.jpg) A demonstrator is detained by riot policemen during a 48-hour national strike at Santiago August 25, 2011. Protesters scuffled with police in the Chilean capital on Thursday, the second of a two-day strike against unpopular President Sebastian Pinera marked by sporadic looting, though the linchpin mining sector was not affected. Reuters
A demonstrator is detained by riot policemen during a 48-hour national strike at Santiago August 25, 2011. Protesters scuffled with police in the Chilean capital on Thursday, the second of a two-day strike against unpopular President Sebastian Pinera marked by sporadic looting, though the linchpin mining sector was not affected. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/chile-protest4/pict44.jpg) Carlos Burgos, who says he was shot at by the Chilean police, shows his wound in the Penalolen neighbourhood in Santiago August 26, 2011, where 16-year-old Manuel Gutierrez was shot dead during a 48-hour national strike against President Sebastian Pinera. Gutierrez died early on Friday after he was shot a day earlier in massive protests in the capital against the unpopular Pinera, the first fatality in months of social unrest. Police said he was shot in the chest as protesters battled them overnight in Santiago, in the aftermath of a 48-hour national strike against Pinera marked by violent clashes and sporadic looting. Reuters
Carlos Burgos, who says he was shot at by the Chilean police, shows his wound in the Penalolen neighbourhood in Santiago August 26, 2011, where 16-year-old Manuel Gutierrez was shot dead during a 48-hour national strike against President Sebastian Pinera. Gutierrez died early on Friday after he was shot a day earlier in massive protests in the capital against the unpopular Pinera, the first fatality in months of social unrest. Police said he was shot in the chest as protesters battled them overnight in Santiago, in the aftermath of a 48-hour national strike against Pinera marked by violent clashes and sporadic looting. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/chile-protest4/pict45.jpg) Students march toward the Chilean consulate in Buenos Aires on August 25, 2011, supporting the Chilean students in their claim for free education and against Chile’s President Sebastian Pinera. Getty
Students march toward the Chilean consulate in Buenos Aires on August 25, 2011, supporting the Chilean students in their claim for free education and against Chile’s President Sebastian Pinera. Getty![[Image]](https://i0.wp.com/cryptome.org/info/chile-protest4/pict36.jpg) A demonstrator stands next to a burning barricade on the second day of a national strike in Santiago, Chile, Thursday Aug. 25, 2011. Chileans marched Thursday, demanding profound changes in the country’s heavily centralized and privatized form of government. Union members, students, government workers and Chile’s center-left opposition parties joined the nationwide two-day strike. (Roberto Candia)
A demonstrator stands next to a burning barricade on the second day of a national strike in Santiago, Chile, Thursday Aug. 25, 2011. Chileans marched Thursday, demanding profound changes in the country’s heavily centralized and privatized form of government. Union members, students, government workers and Chile’s center-left opposition parties joined the nationwide two-day strike. (Roberto Candia)![[Image]](https://i0.wp.com/cryptome.org/info/chile-protest4/pict41.jpg) Riot police detain a woman during a protest of public workers and students for the massive layoffs of government employees in Santiago, Chile, Thursday, Aug. 26, 2010. (Aliosha Marquez)
Riot police detain a woman during a protest of public workers and students for the massive layoffs of government employees in Santiago, Chile, Thursday, Aug. 26, 2010. (Aliosha Marquez)![[Image]](https://i0.wp.com/cryptome.org/info/chile-protest4/pict32.jpg) Police and protesters clash in front of the Gratitud Nacional Church during the second day of a national strike in Santiago, Chile, Thursday Aug. 25, 2011. Chileans marched Thursday, demanding profound changes in the country’s heavily centralized and privatized form of government. Union members, students, government workers and Chile’s center-left opposition parties joined the nationwide two-day strike. (Sebastian Silva)
Police and protesters clash in front of the Gratitud Nacional Church during the second day of a national strike in Santiago, Chile, Thursday Aug. 25, 2011. Chileans marched Thursday, demanding profound changes in the country’s heavily centralized and privatized form of government. Union members, students, government workers and Chile’s center-left opposition parties joined the nationwide two-day strike. (Sebastian Silva)![[Image]](https://i0.wp.com/cryptome.org/info/chile-protest4/pict38.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/chile-protest4/pict35.jpg) Riot police detain a protester near La Moneda presidential palace during the second day of a national strike in Santiago, Chile, Thursday Aug. 25, 2011. Chileans are demanding profound changes in the country’s heavily centralized and privatized form of government. Union members, students, government workers and Chile’s center-left opposition parties joined the nationwide two-day strike. (Victor R. Caivano)
Riot police detain a protester near La Moneda presidential palace during the second day of a national strike in Santiago, Chile, Thursday Aug. 25, 2011. Chileans are demanding profound changes in the country’s heavily centralized and privatized form of government. Union members, students, government workers and Chile’s center-left opposition parties joined the nationwide two-day strike. (Victor R. Caivano)![[Image]](https://i0.wp.com/cryptome.org/info/chile-protest4/pict31.jpg) Protesters throw stones at an armored police vehicle spraying tear gas during the second day of a national strike in Santiago, Chile, Thursday Aug. 25, 2011. Chileans marched Thursday, demanding profound changes in the country’s heavily centralized and privatized form of government. Union members, students, government workers and Chile’s center-left opposition parties joined the nationwide two-day strike. (Sebastian Silva)
Protesters throw stones at an armored police vehicle spraying tear gas during the second day of a national strike in Santiago, Chile, Thursday Aug. 25, 2011. Chileans marched Thursday, demanding profound changes in the country’s heavily centralized and privatized form of government. Union members, students, government workers and Chile’s center-left opposition parties joined the nationwide two-day strike. (Sebastian Silva)![[Image]](https://i0.wp.com/cryptome.org/info/chile-protest4/pict42.jpg) A police officer on horseback rides past a bus stop set on fire by demonstrators on the second day of a national strike in Santiago, Chile, Thursday Aug. 25, 2011. Chileans marched Thursday, demanding profound changes in the country’s heavily centralized and privatized form of government. Union members, students, government workers and Chile’s center-left opposition parties joined the nationwide two-day strike. (Luis Hidalgo)
A police officer on horseback rides past a bus stop set on fire by demonstrators on the second day of a national strike in Santiago, Chile, Thursday Aug. 25, 2011. Chileans marched Thursday, demanding profound changes in the country’s heavily centralized and privatized form of government. Union members, students, government workers and Chile’s center-left opposition parties joined the nationwide two-day strike. (Luis Hidalgo)![[Image]](https://i0.wp.com/cryptome.org/info/chile-protest4/pict33.jpg) A protester kicks a tear gas canister during clashes with police in the second day of a national strike in Santiago, Chile, Thursday Aug 25, 2011. Chileans marched Thursday, demanding profound changes in the country’s heavily centralized and privatized form of government. Union members, students, government workers and Chile’s center-left opposition parties joined the nationwide two-day strike. (Jose Miguel Rojas)
A protester kicks a tear gas canister during clashes with police in the second day of a national strike in Santiago, Chile, Thursday Aug 25, 2011. Chileans marched Thursday, demanding profound changes in the country’s heavily centralized and privatized form of government. Union members, students, government workers and Chile’s center-left opposition parties joined the nationwide two-day strike. (Jose Miguel Rojas)![[Image]](https://i0.wp.com/cryptome.org/info/chile-protest4/pict34.jpg) A protester throws stones at an armored police vehicle after clashes broke out during a march on the second day of a national strike in Santiago, Chile, Thursday Aug. 25, 2011. Chileans marched Thursday, demanding profound changes in the country’s heavily centralized and privatized form of government. Union members, students, government workers and Chile’s center-left opposition parties joined the nationwide two-day strike. (Victor R. Caivano)
A protester throws stones at an armored police vehicle after clashes broke out during a march on the second day of a national strike in Santiago, Chile, Thursday Aug. 25, 2011. Chileans marched Thursday, demanding profound changes in the country’s heavily centralized and privatized form of government. Union members, students, government workers and Chile’s center-left opposition parties joined the nationwide two-day strike. (Victor R. Caivano)![[Image]](https://i0.wp.com/cryptome.org/info/chile-protest4/pict37.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/chile-protest4/pict40.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/chile-protest4/pict50.jpg) Nearly one million people, including whole families, gathered at the Parque O’Higgins in a demonstration called “Family Sunday for Education”, organised by University students, high schools and the College of Teachers. Chile. 21st August 2011 Demotix
Nearly one million people, including whole families, gathered at the Parque O’Higgins in a demonstration called “Family Sunday for Education”, organised by University students, high schools and the College of Teachers. Chile. 21st August 2011 Demotix![[Image]](https://i0.wp.com/cryptome.org/eyeball/voa/pict38.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/voa/pict29.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/voa/pict23.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/voa/pict24.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/voa/pict25.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/voa/pict22.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/voa/pict36.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/voa/pict26.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/voa/pict37.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/voa/pict27.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/voa/pict30.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/voa/pict31.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/voa/pict32.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/voa/pict33.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/voa/pict34.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/voa/pict35.jpg)

![[Image]](https://i0.wp.com/cryptome.org/eyeball/tsa-series-03/pict29.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/tsa-series-03/pict24.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/tsa-series-03/pict25.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/tsa-series-03/pict22.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/tsa-series-03/pict23.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/tsa-series-03/pict27.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/tsa-series-03/pict28.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi082911/pict31.jpg) Dust-sampling Opening of Reactor Building of Unit 1, Fukushima Daiichi Nuclear Power Station pictured on August 28, 2011. Released August 30, 2011 by TEPCO. (Tokyo Electric Power Co.)
Dust-sampling Opening of Reactor Building of Unit 1, Fukushima Daiichi Nuclear Power Station pictured on August 28, 2011. Released August 30, 2011 by TEPCO. (Tokyo Electric Power Co.)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi082911/pict30.jpg) Dust-sampling Opening of Reactor Building of Unit 2, Fukushima Daiichi Nuclear Power Station pictured on August 29, 2011. Released August 30, 2011 by TEPCO. (Tokyo Electric Power Co.)
Dust-sampling Opening of Reactor Building of Unit 2, Fukushima Daiichi Nuclear Power Station pictured on August 29, 2011. Released August 30, 2011 by TEPCO. (Tokyo Electric Power Co.)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi082911/pict32.jpg) Checking inside of the reactor containment vessel of Unit 4, Fukushima Daini Nuclear Power Station. Opening an airlock door for workers. Pictured on August 29, 2011. Released August 30, 2011 by TEPCO. (Tokyo Electric Power Co.)
Checking inside of the reactor containment vessel of Unit 4, Fukushima Daini Nuclear Power Station. Opening an airlock door for workers. Pictured on August 29, 2011. Released August 30, 2011 by TEPCO. (Tokyo Electric Power Co.)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/tsa-series-01/pict4.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/tsa-series-01/pict7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/tsa-series-01/pict8.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/tsa-series-01/pict9.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/tsa-series-01/pict11.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/tsa-series-01/pict12.jpg)

















































































 Why was the revolution non-violent? One of the many subplots of the new compilation is the fact that, despite the authorities’ initial use of force to break up the November demonstrations, the Velvet Revolution and similar events in other East European states (with the notable exception of Romania) were allowed to take place without Moscow resorting to bloody repression to keep its clients in power. An earlier National Security Archive
Why was the revolution non-violent? One of the many subplots of the new compilation is the fact that, despite the authorities’ initial use of force to break up the November demonstrations, the Velvet Revolution and similar events in other East European states (with the notable exception of Romania) were allowed to take place without Moscow resorting to bloody repression to keep its clients in power. An earlier National Security Archive 





























 Today’s posting includes the internal Soviet deliberations leading up to the summit, full transcripts of the two leaders’ discussions, the Soviet record of negotiations with top American diplomats, and other historic records being published for the first time.
Today’s posting includes the internal Soviet deliberations leading up to the summit, full transcripts of the two leaders’ discussions, the Soviet record of negotiations with top American diplomats, and other historic records being published for the first time. Under the Treaty, the Soviet Union destroyed 889 of its intermediate-range missiles and 957 shorter-range missiles, and the U.S. destroyed 677 and 169 respectively. These were the missiles with very short flight time to targets in the Soviet Union, which made them “most likely to spur escalation to general nuclear war from any local hostilities that might erupt.” (
Under the Treaty, the Soviet Union destroyed 889 of its intermediate-range missiles and 957 shorter-range missiles, and the U.S. destroyed 677 and 169 respectively. These were the missiles with very short flight time to targets in the Soviet Union, which made them “most likely to spur escalation to general nuclear war from any local hostilities that might erupt.” (



















You must be logged in to post a comment.