
Report of the Select Committee on Assassinations of the U.S. House of Representatives
C. The Committee believes, on the basis of the evidence available to it, that President John F. Kennedy was probably assassinated as a result of a conspiracy. The Committee is unable to identify the other gunman or the extent of the conspiracy.
Go to the footnotes for this chapter.
- The committee believes, on the basis of the evidence available to it, that the Soviet Government was not involved in the assassination of President Kennedy
- The committee believes, on the basis of the evidence available to it, that the Cuban Government was not involved in the assassination of President Kennedy
- The committee believes, on the basis of the evidence available to it, that anti-Castro Cuban groups, as groups, were not involved in the assassination of President Kennedy, but that the available evidence does not preclude the possibility that individual members may have been involved
- The committee believes, on the basis of the evidence available to it, that the national syndicate of organized crime, as a group, was not involved in the assassination of President Kennedy, but that the available evidence does not preclude the possibility that individual members may have been involved
- The Secret Service, Federal Bureau of Investigation, and Central Intelligence Agency were not involved in the assassination of President Kennedy
Supreme Court Justice Oliver Wendell Holmes once simply defined conspiracy as “a partnership in criminal purposes.” (1) That definition is adequate. Nevertheless, it may be helpful to set out a more precise definition. If two or more individuals agreed to take action to kill President Kennedy, and at least one of them took action in furtherance of the plan, and it resulted in President Kennedy’s death, the President would have been assassinated as a result of a conspiracy.
The committee recognizes, of course, that while the work “conspiracy” technically denotes only a “partnership in criminal purposes,” it also, in fact, connotes widely varying meanings to many people, and its use has vastly differing societal implications depending upon the sophistication, extent and ultimate purpose of the partnership. For example, a conspiracy to assassinate a President might be a complex plot orchestrated by foreign political powers; it might be the scheme of a group of American citizens dissatisfied with particular governmental policies; it also might be the plan of two largely isolated individuals with no readily discernible motive.
Conspiracies may easily range, therefore, from those with important implications for social or governmental institutions to those with no major societal significance. As the evidence concerning the probability that President Kennedy was assassinated as a result of a “conspiracy” is analyzed, these various connotations of the word “conspiracy” and distinctions between them ought to be constantly borne in mind. Here, as elsewhere, words must be used carefully, lest people be misled.1
A conspiracy cannot be said to have existed in Dealey Plaza unless evidence exists from which, in Justice Holmes’ words, a “partnership in criminal purposes” may be inferred. The Warren Commission’s conclusion that Lee Harvey Oswald was not involved in a conspiracy to assassinate the President was, for example, largely based on its findings of the absence of evidence of significant association (2) between Oswald and other possible conspirators and no physical evidence of conspiracy.(3) The Commission reasoned, quite rightly, that in the absence of association or physical evidence, there was no conspiracy.
Even without physical evidence of conspiracy at the scene of the assassination, there would, of course, be a conspiracy if others assisted Oswald in his efforts. Accordingly, an examination of Oswald’s associates is necessary. The Warren Commission recognized that a first premise in a finding of conspiracy may be a finding of association. Because the Commission did not find any significant Oswald associ-
1It might be suggested that because of the widely varying meanings attached to the word “conspiracy,” it ought to be avoided. Such a suggestion, however, raises another objection– the search for euphemistic variations can lead to a lack of candor. There is virtue in seeing something for what it is, even if the plain truth causes discomfort.
Page 96
ates, it was not compelled to face the difficult questions posed by such a finding. More than association is required to establish conspiracy. There must be at least knowing assistance or a manifestation of agreement to the criminal purpose by the associate.
It is important to realize, too, that the term “associate” may connote widely varying meanings to different people. A person’s associate may be his next door neighbor and vacation companion, or it may be an individual he has met only once for the purpose of discussing a contract for a murder. The Warren Commission examined Oswald’s past and concluded he was essentially a loner. (4) It reasoned, therefore, that since Oswald had no significant associations with persons who could have been involved with him in the assassination, there could not have been a conspiracy. (5)
With respect to Jack Ruby, 2 the Warren Commission similarly found no significant associations, either between Ruby and Oswald or between Ruby and others who might have been conspirators with him. (8) In particular, it found no connections between Ruby and organized crime, and it reasoned that absent such associations, there was no conspiracy to kill Oswald or the president. (9)
The committee conducted a three-pronged investigation of conspiracy in the Kennedy assassination. On the basis of extensive scientific analysis and an analysis of the testimony of Dealey Plaza witnesses, the committee found there was a high probability that two gunmen fired at President Kennedy.
Second, the committee explored Oswald’s and Ruby’s contact for any evidence of significant associations. Unlike the Warren Commission, it found certain of these contacts to be of investigative significance. The Commission apparently had looked for evidence of conspiratorial association. Finding none on the face of the associations it investigated, it did not go further. The committee, however, conducted a wider ranging investigation. Notwithstanding the possibility of a benign reason for contact between Oswald or Ruby and one of their associates, the committee examined the very fact of the contact to see if it contained investigative significance. Unlike the Warren Commission, the committee took a close look at the associates to determine whether conspiratorial activity in the assassination could have been possible, given what the committee could learn about the associates, and whether the apparent nature of the contact should, therefore, be examined more closely. 3
Third, the committee examined groups– political organizations, national governments and so on–that might have had the motive, opportunity and means to assassinate the President.
The committee, therefore, directly introduced the hypothesis of conspiracy and investigated it with reference to known facts to determine if it had any bearing on the assassination.
2The Warren Commission devoted its Appendix XVI to a biography of Jack Ruby in which his family background, psychological makeup, education and business activities were considered. While the evidence was sometimes contradictory, the Commission found that Ruby grew up in Chicago, the son of Jewish immigrants; that he lived in a home disrupted by domestic strife; (6) that he was troubled psychologically as a youth and not educated beyond high school; and that descriptions of his temperament ranged from “mild mannered” to “violent.”(7) In 1963, Ruby was 52 and unmarried. He ran a Dallas nightclub but was not particularly successful in business. His acquaintances included a number of Dallas police officers who frequented his nightclub, as well as other types of people who comprised his clientele.
3The committee found associations of both Ruby and Oswald that were unknown to the Warren Commission.
Page 97
The committee examined a series of major groups or organizations that have been alleged to have been involved in a conspiracy to assassinate the President. If any of these groups or organizations, as a group, had been involved in the assassination, the conspiracy to assassinate President Kennedy would have been one of major significance.
As will be detailed in succeeding sections of this report, the committee did not find sufficient evidence that any of these groups or organizations were involved in a conspiracy in the Kennedy assassination. Accordingly, the committee concluded, on the basis of the evidence available to it, that the Soviet government, the Cuban government, anti-Castro Cuban groups, and the national syndicate of organized crime were not involved in the assassination. Further, the committee found that the Secret Service, the Federal Bureau of Investigation, and the Central Intelligence Agency were not involved in the assassination.
Based on the evidence available to it, the committee could not preclude the possibility that individual members of anti-Castro Cuban groups or the national syndicate of organized crime were involved in the assassination. There was insufficient evidence, however, to support a finding that any individual members were involved. The ramifications of a conspiracy involving such individuals would be significant, although of perhaps less import than would be the case if a group itself, the national syndicate, for example had been involved.
The committee recognized that a finding that two gunmen fired simultaneously at the President did not, by itself, establish that there was a conspiracy to assassinate the President. It is theoretically possible that the gunmen were acting independently, each totally unaware of the other. It was the committee’s opinion, however, that such a theoretical possibility is extremely remote. The more logical and probable inference to be drawn from two gunmen firing at the same person at the same time and in the same place is that they were acting in concert, that is, as a result of a conspiracy.
The committee found that, to be precise and loyal to the facts it established, it, was compelled to find that President Kennedy was probably killed as a result of a conspiracy. The committee’s finding that President Kennedy was probably assassinated as a result of a conspiracy was premised on four factors:
(1) Since the Warren Commission’s and FBI’s investigation into the possibility of a conspiracy was seriously flawed, their failure to develop evidence of a conspiracy could not be given independent weight.
(2) The Warren Commission was, in fact, incorrect in concluding that Oswald and Ruby had no significant associations, and therefore its finding of no conspiracy was not reliable.
(3) While it cannot be inferred from the significant associations of Oswald and Ruby that any of the major groups examined by the committee were involved in the assassination, a more limited conspiracy could not be ruled out.
(4) There was a high probability that a second gunman, in fact, fired at the President. At the same time, the committee candidly stated, in expressing it finding of conspiracy in the Kennedy assassination, that it was “unable to identify the other gunman or the extent of the conspiracy.
Page 98
The photographic and other scientific evidence available to the committee was insufficient to permit the committee to answer these questions. In addition, the committee’s other investigative efforts did not develop evidence from which Oswald’s conspirator or conspirators could be firmly identified. It is possible, of course, that the extent of the conspiracy was so limited that it involved only Oswald and the second gunman. The committee was not able to reach such a conclusion, for it would have been based on speculation, not evidence. Aspects of the investigation did suggest that the conspiracy may have been relatively limited, but to state with precision exactly how small was not possible. Other aspects of the committee’s investigation did suggest, however, that while the conspiracy may not have involved a major group, it may not have been limited to only two people. These aspects of the committee’s investigation are discussed elsewhere.
If the conspiracy to assassinate President Kennedy was limited to Oswald and a second gunman, its main societal significance may be in the realization that agencies of the U.S. Government inadequately investigated the possibility of such a conspiracy. In terms of its implications for government and society, an assassination as a consequence of a conspiracy composed solely of Oswald and a small number of persons, possibly only one, and possibly a person akin to Oswald in temperament and ideology, would not have been fundamentally different from an assassination by Oswald alone. 4
4If the conspiracy was, in fact, limited to Oswald, the second gunman, and perhaps one or two others, the committee believes it was possible they shared Oswald’s left-wing political disposition. A consistent pattern in Oswald’s life (see section A 5) was a propensity for actions with political overtones. It is quite likely that an assassination conspiracy limited to Oswald and a few associates was in keeping with that pattern.
Further it is possible that associates of Oswald in the Kennedy assassination had been involved with him in earlier activities. Two possibilities: the attempt on the life of Gen. Edwin A. Walker in April 1963 and the distribution of Fair Play for Cuba Committee literature in August 1963. With respect to the Walker incident, there was substantial evidence that Oswald did the shooting (section A 5), although at the time of the shooting it was not sufficient to implicate Oswald or anyone else. It was not until after the Kennedy assassination that Oswald became a suspect in the Walker attack, based on the testimony of his widow Marina. Marina’s characterization of Oswald is more consistent with his having shot at Walker alone than his having assistance, although at the time of the shooting there was testimony that tended to indicate more than one person was involved. Further, it is not necessary to believe all of what Marina said about the incident or to believe that Oswald told her all there was to know, since either of them might have been concealing the involvement of others.
According to a general offense report of the Dallas police, Walker reported at approximately 9:10 p.m. on April 10, 1963, that a bullet had been fired through a first floor window of his home at 4011 Turtle Creek Boulevard, Dallas. Detectives subsequently found that a bullet had first shattered a window, then gone through a wall and had landed on a stack of papers in an adjoining room. In their report the detectives described the bullet as steel-jacketed, of unknown caliber.
Police located a 14-year-old boy in Walker’s neighborhood who said that after hearing the shot, he climbed a fence and looked into an alley to the rear of Walker’s home. The boy said he then saw some men speeding down the alley in a light green or light blue Ford, either a 1959 or 1960 model. He said he also saw another car, a 1958 Chevrolet, black with white down the side, in a church parking lot adjacent to Walker’s house. The car door was open, and a man was bending over the back seat, as though he was placing something on the floor of the car.
On the night of the incident, police interviewed Robert Surrey, an aide to Walker. Surrey said that on Saturday, April 6, at about 9 p.m., he had seen two men sitting in a dark purple or brown 1963 Ford at the rear of Walker’s house. Surrey also said the two men got out of the car and walked around the house. Surrey said he was suspicious and followed the car, noting that it carried no license plate.
If it could be shown that Oswald had associates in the attempt on General Walker, they would be likely candidates as the grassy knoll gunmen. The committee recognized, however, that this is speculation, since the existence, much less identity, of an Oswald associate in the Walker shooting was hardly established. Further, the committee failed in its effort to develop productive leads in the Walker shooting.
With respect to the Cuba literature incident, Oswald was photographed with two associates distributing pro-Castro pamphlets in August 1963. As a result of a fight with anti-Castro Cubans, Oswald was arrested, but his associates were not. Of the two associates, only one was identified in the Warren Commission investigation (Warren Report, p. 292). Although the second associate was clearly portrayed in photographs (see Pizzo Exhibits 453-A and 453-B. Warren Commission Report, Vol. XXI, p. 139), the Commission was unable to identify him, as was the case with the committee.
Page 99
Top of Page
1. THE COMMITTEE BELIEVES, ON THE BASIS OF THE EVIDENCE AVAILABLE TO IT, THAT THE SOVIET GOVERNMENT WAS NOT INVOLVED IN THE ASSASSINATION OF PRESIDENT KENNEDY
Go to the footnotes for this section.
- United States-Soviet Relations
- The Warren Commission investigation
- The committee’s investigation
- Oswald in the U.S.S.R.
- Treatment of defectors by the Soviet Government
- Yuri Nosenko
- Opinions of other defectors
- Marina Oswald
- Response of the Soviet Government
- Summary of the evidence
With the arrest of Lee Harvey Oswald in the assassination of President Kennedy, speculation arose over the significance of Oswald’s defection to the Soviet Union from October 1959 to June 1962, and his activities while living in that country. Specifically, these troubling questions were asked:
Had Oswald been enlisted by the KGB, the Soviet secret police?.
Could the assassination have been the result of a KGB plot?(1)
Top of Page
(a) United States-Soviet relations
To put these concerns in context, it is necessary to look at Soviet-American relations in the 1960’s. United States-Soviet relations had, in fact, been turbulent during the Kennedy Presidency. There had been major confrontations: over Berlin, where the wall had come to symbolize the barrier between the two superpowers; and over Cuba, where the emplacement of Soviet missiles had nearly started World War III. (2)
A nuclear test-ban treaty in August 1963 seemed to signal detente, but in November, tension was building again, as the Soviets harassed, American troop movements to and from West Berlin.(3) And Cuba was as much an issue as ever. In Miami, on November 18, President Kennedy vowed the United States would not countenance the establishment of another Cuba in the Western Hemisphere.(4)
Top of Page
(b) The Warren Commission investigation
The Warren Commission considered the possibility of Soviet complicity in the assassination, but it concluded there was no evidence of it.(5) In its report, the Commission noted that the same conclusion had been reached by Secretary of State Dean Rusk and Secretary of Defense Robert McNamara, among others.(6)Rusk testified before the Commission on June 10, 1964:
I have seen no evidence that would indicate to me that the Soviet Union considered that it had any interest in the removal of President Kennedy …I can’t see how it could be to the interest of the Soviet Union to make any such effort.
Top of Page
(c) The committee’s investigation
The committee, in analyzing Oswald’s relationship to Russian intelligence, considered:
Statements of both Oswald and his wife, Marina, about their life in the Soviet Union;(7)
Documents provided by the Soviet Government to the Warren Commission concerning Oswald’s residence in the Soviet Union; (8)
Statements by Soviet experts in the employ, current or past, of the Central Intelligence Agency;(9)
Files on other defectors to the Soviet Union; (10) and
Statements by defectors from the Soviet Union to the United States. (11)
Page 100
Top of Page
(1) Oswald in the U.S.S.R.—The committee reviewed the documents Oswald wrote about his life in the Soviet Union, including his diary and letters to his mother, Marguerite, and brother, Robert. They paralleled, to a great extent, the information in documents provided to the Warren Commission by the Soviet Government after the assassination. (13) These documents were provided to the Commission in response to its request that the Soviet Government give the Commission any “available information concerning the activities of Lee Harvey Oswald during his residence from 1959 to 1962 in the Soviet Union, in particular, copies of any official records concerning him.”(14)
Two sets of documents, totaling approximately 140 pages, were turned over to the Commission by the Soviets in November 1963 and in May 1964.(15) They were routine, official papers. None of them appeared to have come from KGB files, and there were no records of interviews of Oswald by the KGB, nor were there any surveillance reports. Unfortunately, the authenticity of the documents could not be established. The signatures of Soviet officials, for example, were illegible.(16)
Nevertheless, the Soviet documents and Oswald’s own statements give this account of Oswald’s stay in the Soviet Union:
He lived there from October 1959 to June 1962.
He attempted suicide on learning he would not be permitted to remain in the U.S.S.R.
He worked in a radio plant in Minsk.
He met and married Marina.
He was originally issued a residence visa for stateless persons and later issued a residence visa for foreigners.
He obtained exit visas for himself and his family before departing the Soviet Union.
Neither the documents nor Oswald’s own statements indicate that he was debriefed or put under surveillance by the KGB.
The committee interviewed U.S. officials who specialize in Soviet intelligence, asking them what treatment they would have expected Oswald to have received during his defection. (17) For the most part, they suspected that Oswald would have routinely been debriefed by the KGB and that many persons who came in contact with Oswald in the U.S.S.R. would have been connected with the KGB.(18)
Top of Page
(2) Treatment of defectors by the Soviet Government.—The committee examined the CIA and FBI files on others who had defected in the same period as Oswald and who had eventually returned to the United States.(19) The purpose was to determine the frequency of KGB contact and whether the treatment of Oswald appeared to be significantly different from the norm. The defectors studied by the committee were selected because their backgrounds and other characteristics were similar to Oswald’s, on the theory that their treatment by the KGB could be expected to parallel that of Oswald, if he was not a special case, a recruited assassin, for example.
The examination of the defector files was inconclusive, principally because the case of nearly every defector was unique. (20) In addition, the files available on the experiences of the defectors were often not adequate to extract meaningful data for the purpose of this investiga-
Page 101
tion, since, they were compiled for other reasons. (21) As to contacts with the KGB, the experiences of American defectors appeared to have varied greatly. Some reported daily contact with Soviet intelligence agents, while others did not mention ever having been contacted or debriefed.(22)
Top of Page
(3) Yuri Nosenko.–Of all the areas investigated by the committee with respect to possible Soviet involvement in the assassination, none seemed as potentially rewarding as an examination of statements made by KGB officers who had defected to the United States. In determining how the KGB treats American defectors, an ex-KGB officer would certainly be of great interest. In this regard, the committee had access to three such men, one of whom, Yuri Nosenko, claimed to possess far more than general information about American defectors.
In January 1964,5 Nosenko, identifying himself as a KGB officer, sought asylum in the United States. (23) He claimed to have worked in the KGB Second Chief Directorate whose functions, in many respects, are similar to those of the FBI.(24) According to Nosenko, while working in 1959 in a KGB department dealing with American tourists, he learned of a young American who sought to defect to the Soviet Union. The American was Lee Harvey Oswald. (25)
Nosenko stated he had worked extensively on the Oswald case, and he provided the FBI and CIA with data pertaining to Oswald’s request to defect and remain in the Soviet Union, the initial rejection of that request by the KGB, Oswald’s suicide attempt and a subsequent decision to permit him to remain in Russia. (26) Although the KGB, according to Nosenko, was well aware of Oswald, it made no attempt to debrief or interview him.(27) Never was any consideration given by the KGB to enlist Oswald into the Soviet intelligence service. (28)
The committee was most interested in Nosenko’s claim that in 1963, after Oswald was arrested in the assassination, he had an opportunity to see the KGB file on the suspected assassin. As a result, Nosenko said, he was able to state categorically that Oswald was not a Soviet agent and that no officer of the KGB had ever interviewed or debriefed him. (29)
Nosenko’s testimony, however, did not settle the question of Soviet complicity in the assassination. From the time of his defection, some U.S. intelligence officers suspected Nosenko was on a disinformation mission to mislead the American Government. Since other CIA officials believed Nosenko was a bona fide defector, a serious disagreement at the top level of the Agency resulted. (30)
The Warren Commission found itself in the middle of the Nosenko controversy–and in a quandary of its own, since the issue of Nosenko’s reliability bore significantly on the assassination investigation.(31) If he was telling the truth, the Commission could possibly write off Soviet involvement in a conspiracy. 6 If, on the other hand, Nosenko was lying, the Commission would be faced with a dilemma. While a deceitful Nosenko would not necessarily point to Soviet complicity, it would leave the issue in limbo. The Warren Commission
5Nosenko had first contacted the U.S.Government in June 1962.
6The Commission as well as the committee recognized that Nosenko could have been candid and that the connection between Oswald and the KGB could have been compartmentalized, that is, known only to a few people, not including Nosenko.
Page 102
chose not to call Nosenko as a witness or to mention him in its report, apparently because it could not resolve the issue of his reliability. (32)
The committee, on the other hand, reviewed all available statements and files pertaining to Nosenko. (33) It questioned Nosenko in detail about Oswald, finding significant inconsistencies in statements he had given the FBI, CIA and the committee. (34) For example, Nosenko told the committee that the KGB had Oswald under extensive surveillance, including mail interception, wiretap and physical observation. Yet, in 1964, he told the CIA and FBI there had been no such surveillance of Oswald.(35) Similarly, in 1964, Nosenko indicated there had been no psychiatric examination of Oswald subsequent to his suicide attempt, while in 1978 he detailed for the committee the reports he had read about psychiatric examinations of Oswald.(36)
The committee also found that the CIA had literally put Nosenko in solitary confinement from 1964 to 1968. (37) Strangely, while he was interrogated during this period, he was questioned very little about Oswald. (38) The Agency did not seem to realize Nosenko’s importance to an investigation of the assassination. While Richard Helms, then the CIA’s Deputy Director for Plans, did tell Chief Justice Warren about Nosenko, the Agency’s interest in him seemed to be largely limited to its own intelligence-gathering problem: did the KGB send Nosenko to the United States to deceive the CIA on many matters, only one of them perhaps related to the assassination? (39)
In the end, the committee, too, was unable to resolve the Nosenko matter. The fashion in which Nosenko was treated by the Agency–his interrogation and confinement–virtually ruined him as a valid source of information on the assassination. Nevertheless, the committee was certain Nosenko lied about Oswald–whether it was to the FBI and CIA in 1964, or to the committee in 1978, or perhaps to both.(40)
The reasons he would lie about Oswald range from the possibility that he merely wanted to exaggerate his own importance to the disinformation hypothesis with its sinister implications.
Lacking sufficient evidence to distinguish among alternatives, 7 the committee decided to limit its conclusion to a characterization of Nosenko as an unreliable source of information about the assassination, or, more specifically, as to whether Oswald was ever contacted, or placed under surveillance, by the KGB.
Top of Page
(4) Opinions of other defectors.–In addition to interviewing Nosenko, the committee questioned two other former KGB officers who had defected to the United States. While neither could base an opinion on any personal experience with that part of the KGB in which Nosenko said he had served, both said that Oswald would have been of interest to the Soviet intelligence agency, that he would have been debriefed and that he may have been kept under surveillance.(41)
Top of Page
(5) Marina Oswald.–The committee not only considered a possible connection between Oswald and the KGB, it also looked into charges that his widow, Marina, was an agent of the KGB, or that she at least influenced her husband’s actions in the assassination on orders from
7Beyond those reasons for falsification that can be attributed to Nosenko himself, there has been speculation that the Soviet Government, while not involved in the assassination, sent Nosenko on a mission to allay American fears. Hence, while his story about no connection between Oswald and the KGB might be false, his claim of no Soviet involvement in the assassination would be truthful.
Page 103
Soviet officials. The committee examined Government files on Marina, it questioned experts on Soviet affairs and former KGB officers, and it took testimony from Marina herself.(42) The committee could find no evidence to substantiate the allegations about Marina Oswald Porter.
Mrs. Porter testified before the committee that Oswald had never been contacted directly by the KGB, though she assumed that he and she alike had been under KGB surveillance when they lived in the Soviet Union.
Top of Page
(6) Response of the Soviet Government.–Finally, the committee attempted to obtain from the Soviet Government any information on Oswald that it had not provided to the Warren Commission. In response to a committee request relayed by the State Department, the Soviet Government informed the committee that all the information it had on Oswald had been forwarded to the Warren Commission. (43)
The committee concluded, however, that it is highly probable that the Soviet Government possessed information on Oswald that it has not provided to the U.S. Government. It would be the extensive information that most likely was gathered by a KGB surveillance of Oswald and Marina while they were living in Russia. It is also quite likely that the Soviet Government withheld files on a KGB interview with Oswald. 8
Top of Page
(d) Summary of the evidence
Its suspicions notwithstanding, the committee was led to believe, on the basis of the available evidence, that the Soviet Government was not involved in the assassination. In the last, analysis, the Committee agreed with the testimony of former Secretary of State Dean Rusk. To wit, there is no evidence that the Soviet Government had any interest in removing President Kennedy, nor is there any evidence that it planned to take advantage of the President’s death before it happened or attempted to capitalize on it after it occurred. In fact, the reaction of the Soviet Government as well as the Soviet people seemed to be one of genuine shock and sincere grief. The committee believed, therefore, on the basis of the evidence available to it, that the Soviet Government was not involved in the assassination.
Top of Page
2. THE COMMITTEE BELIEVES, ON THE BASIS OF THE EVIDENCE AVAILABLE TO IT, THAT THE CUBAN GOVERNMENT WAS NOT INVOLVED IN THE ASSASSINATION OF PRESIDENT KENNEDY
Go to the footnotes for this section.
- United States-Cuban relations
- Bay of Pigs
- Cuban Missile Crisis
- Earlier investigations of Cuban complicity
- The Warren Commission investigation
- The U.S. Senate investigation
- The CIA’s response to the Senate
- The committee’s analysis of the CIA task force report
- AMLASH
- CIA-Mafia plots
- Summary of the evidence
- Cubana Airlines flight allegation
- Gilberto Policarpo Lopez allegation
- Other allegations
- The committee’s trip to Cuba
- Deficiencies of the 1963-64 investigation
- Summary of the findings
When the leader of a great nation is assassinated, those initially suspected always include his adversaries. When President John F. Kennedy was struck down by rifle fire in Dallas in November 1963, many people suspected Cuba and its leader, Fidel Castro Ruz, of involvement in the assassination, particularly after it was learned that Lee Harvey Oswald, the alleged assassin, had sought to travel to Cuba in September 1963.(1) To evaluate those suspicions properly, it is
8The committee concluded that it should not necessarily be inferred from the failure of the Soviet Government to cooperate with the committee that it was involved in the assassination. Just as agencies of the U.S. intelligence community are reluctant to share their confidential files, a similar response might be expected to come from the KGB. The Soviet Government, it could be argued, would have little to gain and much to lose by turning over its files. While the committee recognized the logic of this argument, it regretted that the Soviet Government, in the interest of historical truth, did not cooperate.
Page 104
necessary to look at Cuban-American relations in the years immediately before and after President Kennedy took office.
Top of Page
(a) United States-Cuban relations
The triumphant arrival of Fidel Castro in Havana on, January 1, 1959, marking a victorious climax of file revolution he had led, was initially heralded in the United States as well as in Cuba. Castro was hailed as a champion of the people, a man who would lead a free and democratic Cuba. While some suspected that Castro had Communist leanings, the majority of the American public supported him. (2) The appointment of Philip Bonsal as U.S. Ambassador to Cuba, replacing Earl E.T. Smith, who was personally wary of Castro, was a clear signal that the United States was interested in amicable relations with the revolutionary government. On appointing Bonsal, President Eisenhower expressed the hope for an “ever closer relationship between Cuba and the United States.”(3)
By the end of 1959, however, United States-Cuban relations had deteriorated to the point that there was open hostility between the two countries. (4) President Kennedy was to inherit the problem in 1961, and by the time of his assassination on November 22, 1963, the antagonism had developed into a serious international crisis.
To begin with, the United States deplored the mass executions of officials of the Batista government that Castro had deposed. (5) In reply, Castro charged that the United States had never voiced objections to killing and torture by Batista. He said the trials and sentences would continue. (6) In his revolutionary economic policies. Castro took steps that severely challenged the traditional role of the United States. In March 1959, the Cuban Government took over the United States-owned Cuban Telephone Co. in May. U.S. companies were among those expropriated in the Cuban Government’s first large-scale nationalization action, also in May, the agrarian reform law resulted in the expropriation of large landholdings, many of them U.S.-owned. (7)
Vice President Nixon met with Castro in Washington in April. Castro left the meeting convinced that Nixon was hostile. For his part, Nixon recommended to President Eisenhower that the United States take measures to quash the Cuban revolution. (8)
Disillusionment with Castro also spread to significant elements of the Cuban populace. In June, the chief of the Cuban Air Force, Maj. Pedro Diaz Lanz, fled to the United States, charging there was Communist influence in the armed forces and the Government of Cuba. (9) A few weeks later, Manuel Urrutria Lleo, the President of Cuba, stated on Cuban national television that communist was not concerned with the welfare of the people and that it constituted a throat to the revolution. In the succeeding flurry of events, President Urrutria resigned after Castro accused him of “actions bordering on treason.”(10)
By the summer of 1960, Castro had seized more than $700 million in U.S. property; the Eisenhower administration had canceled the Cuban sugar quota; Castro was cementing his relations with the Soviet Union, having sent his brother Raul on a visit to Moscow, Ernesto “Che” Guevara, a top Castro lieutenant, had proclaimed publicly that the revolution was on a course set by Marx; and CIA Director Allen Dulles had said in a speech that communist had pervaded Castro’s
Page 105
revolution. (11) On March 17, 1960, President Eisenhower quietly authorized the CIA to organize, train, and equip Cuban refugees as a guerrilla force to overthrow Castro. (12)
On January 2, 1961, the United States broke diplomatic relations with Cuba.(13) A period of increased tension followed. It was marked by an exchange of bitter statements by the new U.S. President, John F. Kennedy, and the Cuban Premier. Castro charged CIA complicity in counterrevolutionary activity against his Government and publicly predicted an imminent U.S. invasion. (14)In his state of the Union address on January 30, Kennedy said:
In Latin America, Communist agents seeking to exploit that region’s peaceful revolution of hope have established a base on Cuba, only 90 miles from our shores. Our objection with Cuba is not over the people’s drive for a better life. Our objection is to their domination by foreign and domestic tyrannies….
President Kennedy said further that “…Communist domination in this hemisphere can never be negotiated.” (15)
Top of Page
(1) Bay of Pigs.–After much deliberation, President Kennedy gave the go-ahead for a landing of anti-Castro Cubans, with U.S. support, at the Bay of Pigs on the southern coast of Las Villas Province. It was launched on April 17, 1961, but it was thwarted by Cuban troops, said to have been commanded by Castro himself. (16)
On President Kennedy’s orders, no U.S. military personnel actually fought on Cuban soil, but U.S. sponsorship of the landing was readily apparent. President Kennedy publicly acknowledged “sole responsibility” for the U.S. role in the abortive invasion. (17)
After the Bay of Pigs debacle, the tension continued to escalate. As early as April 20, President Kennedy reaffirmed, in a speech to the American Society of Newspaper Editors, that the United States was resolved not to abandon Cuba to communism.(18) On May 1, Secretary of State Dean Rusk told the Senate Foreign Relations Subcommittee on Latin American Affairs that if the Castro regime engaged in acts of aggression, the United States would “defend itself.” (19) On May 17, the House of Representatives passed a resolution declaring Cuba to be “a clear and present danger” to the Western Hemisphere. (20) Throughout 1961 and 1962, U.S. policy was to subject Cuba to economic isolation and to support stepped-up raids by anti-Castro guerrillas, many of which were planned with the assassination of Castro and other Cuban officials as a probable consequence, if not a specific objective. (21) The Cuban Government, in turn, assumed often correctly– that the raids were instigated and directed by the U.S. Government.(22) In preparation for another large-scale attack, the Castro regime sought and received increased military support from the Soviet Union.(23)
Top of Page
(2) Cuban missile crisis.–All-out war between the United States and the U.S.S.R. was narrowly averted in the Cuban missile crisis in the fall of 1962. On October 22, President Kennedy announced that U.S. photographic reconnaissance flights had discovered that work was underway in Cuba on offensive missile sites with a nuclear strike capability. (24) On October 23, the President issued a proclamation impos-
Page 106
ing a quarantine on the delivery of offensive weapons to Cuba, to be enforced by a U.S. naval blockade. (25)
Negotiations conducted between the United States and the Soviet Union resulted in an end to the immediate crisis on November 20, 1962.(26) To most observers, President Kennedy had won the confrontation with Castro and Soviet leader Nikita Khrushchev.9 War had been averted, however narrowly. Russian IL-28 bombers were to be withdrawn from Cuba, and progress was being made on the removal of offensive missiles and other weapons.(27) The Soviets and the Cubans gained a “no invasion” pledge that was conditional upon a United Nations inspection to verify that Soviet offensive weapons had been removed from Cuba. (28) Because Castro never allowed the inspection, the United States never officially made the reciprocal pledge not to invade Cuba.(29)
There is evidence that by the fall of 1963, informal overtures for better United States-Cuban relations had been authorized by President Kennedy. (30) Talks between United States and Cuban officials at the United Nations were under consideration. In addition, the United States had attempted in the period after the missile crisis to stem the anti-Castro raids by, at least publicly, refusing to sanction them.(31) But covert action by the United States had neither ceased nor escaped Castro’s notice, and the rhetoric indicated that the crisis could explode anew at any time. (32)
On September 7, 1963, in an interview with Associated Press reporter Daniel Harker, Castro warned against the United States “aiding terrorist plans to eliminate Cuban leaders,” and added that U.S. leaders would be in danger if they promoted any attempt to eliminate the leaders of Cuba. (33)On November 18, in Miami, Fla., just 4 days before his assassination, President Kennedy stated:
…what now divides Cuba from my Country …is the fact that a small band of conspirators has stripped the Cuban people of their freedom and handed over the independence and sovereignty of the Cuban nation to forces beyond this hemisphere. They have made Cuba a victim of foreign imperialism, an instrument of the policy of others. a weapon in an effort dictated by external powers to subvert the other American Republics. This, and this alone, divides us. (34)
Top of Page
(b) Earlier investigations of Cuban complicity
When President Kennedy was assassinated on November 22, 1963, the basic outlines of the recent history of United States-Cuban relations, if not the specific details, were known to every American who even occasionally read a newspaper. Thus, when speculation arose as to the possibility of conspiracy, Fidel Castro and his Communist government were natural suspects. While rationality may have precluded any involvement of the Cuban Government, the recognition that Castro had been among the late President’s most prominent enemies compelled such speculation.
9When it became known to anti-Castro Cuban exiles that Kennedy had agreed to stop the raids on Cuba, the exiles considered the Kennedy-Khrushchev deal anything but a victory. To them, it was another betrayal (see section C 3 for details).
Page 107
Top of Page
(1) The Warren Commission investigation.–Investigative efforts into the background of Lee Harvey Oswald led to an early awareness of his Communist and pro-Castro sympathies, his activities in support of the Fair Play for Cuba Committee, and a trip he made in September 1963 to Mexico City where he visited the Soviet Embassy and the Cuban consulate. (35)
All of this information had been gathered prior to the beginning of the Warren Commission’s investigation, and it was sufficient to alert the Commission to the need to investigate the possibility of a conspiracy initiated or influenced by Castro. The report of the Warren Commission reflects that it was indeed considered, especially with respect to the implications of Oswald’s Mexico City trip. (36) In addition, the Warren Commission reviewed various specific allegations of activity that suggested Cuban involvement, concluding, however, that there had been no such conspiracy. (37) For the next few years, suspicions of Cuban involvement in the assassination were neither widespread nor vocal. Nevertheless, beginning with a 1967 column by Drew Pearson and Jack Anderson, press reports that suggested Castro’s involvement in the assassination began to circulate once again. (38) Specifically, they posed the theory that President Kennedy might have been assassinated in retaliation for CIA plots against the life of the Cuban leader.
Top of Page
(2) The U.S. Senate investigation.–Thereafter, the Senate Select Committee to Study Governmental Operations with Respect to Intelligence Activities was formed to investigate the performance of the CIA and other U.S. intelligence agencies.(39) The Senate committee detailed two general types of operations that the CIA had directed against Castro. One, referred to as the AMLASH operation, involved the CIA’s relationship with an important Cuban figure (code-named AMLASH) who,(40) while he was trusted by Castro, professed to the CIA that he would be willing to organize a coup against the Cuban leader. The CIA was in contact with AMLASH from March 1961 until June 1965. (41) A second plot documented by the Senate committee was a joint effort by the CIA and organized crime in America. It was initiated in 1960 in a conversation between the agency’s Deputy Director for Plans, Richard Bissell, and the Director of Security, Col. Sheffield Edwards. According to the Senate committee, this operation lasted until February 1963. (42)
The Senate committee concluded from its review of the joint operations of the CIA and organized crime that “…Castro probably would not have been certain that the CIA was behind the underworld attempts.” (43) Nor, in the view of the Senate committee, would Castro have distinguished between the CIA-underworld plots and the numerous other plots by Cuban exiles which were not affiliated in any way with the CIA. (44) By emphasizing these two conclusions, the Senate committee apparently intended to suggest that the efforts by the CIA and organized crime to eliminate Castro would not have resulted any retaliation against officials of the United States.(45)
The Senate committee identified the AMLASH operation as being “clearly different” from the CIA-underworld plots.(46) It was still in progress at the time of the assassination, and it could clearly be traced to the CIA, since AMLASH’s proposed coup had been endorsed
Page 108
by the CIA, with the realization that the assassination of Castro might be a consequence.(47) Nevertheless, the Senate committee found “…no evidence that Fidel Castro or others in the Cuban Government plotted President Kennedy’s assassination in retaliation for U.S. operations against Cuba.”(48) The Senate committee left the door open, however, starting, “…the investigation should continue in certain areas, and for that reason (the committee) does not reach any final conclusions.” (49)
Top of Page
(3) The CIA’s response to the Senate.–In response to publication of the report of the Senate committee, a special internal CIA task force was assigned in 1977 to investigate and evaluate the critical questions that had been raised. The task force first considered the retaliation thesis. It advanced the position that the Senate committee had essentially ignored the history of adversarial relations between the United States and Cuba which, if provocation were the issue, provided adequate grounds to support a theory of possible retaliation without the necessity of reaching for specific Agency programs such as the Mafia and AMLASH plots. (50) In essence, the task force report suggests, those plots were only one aspect of a large picture and in themselves were not sufficient to have provoked retaliation. (51).
The 1977 CIA task force then specifically responded to the Senate committee with respect to the AMLASH operation:
Whatever the relationship with AMLASH, following the death of President Kennedy, there is every indication that during President Kennedy’s life AMLASH had no basis for believing that he had CIA support for much of anything. Were he a provocateur reporting to Castro, or if he was merely careless and leaked what he knew, he had no factual basis for leaking or reporting any actual CIA plot directed against Castro. (52)
With respect to the CIA-sponsored organized crime operations, the CIA task force noted:
It is possible that the CIA simply found itself involved in providing additional resources for independent operations that the syndicate already had underway …[I]n a sense CIA may have been piggy-backing on the syndicate and in addition to its material contributions was also providing an aura of official sanction. (53)
The task force argued, therefore, that the plots should have been seen as Mafia, not CIA, endeavors.
A conclusion of the Senate committee had been that further investigation was warranted, based in part on its finding that the CIA had responded inadequately to the Warren Commission’s request for all possible relevant information. The CIA had not told the Commission of the plots. (54)In response, the 1977 CIA task force observed:
While one can understand today why the Warren Commission limited its inquiry to normal avenues of investigation, it would have served to reinforce the credibility of its effort had it taken a broader view of the matter. CIA, too, could have considered in specific terms what most saw in general terms– the possibility of Soviet or Cuban involvement in the JFK
Page 109
assassination because of the tensions of the time …The Agency should have taken broader initiatives, then, as well. That CIA employees at the time felt–as they obviously did– that the activities about which they knew had no relevance to the Warren Commission inquiry does not take the place of a record of conscious review. (55)
Top of Page
(c) The committee’s analysis of the CIA task force report
The committee believed its mandate compelled it to take a new look at the question of Cuban complicity in the assassination.
The Warren Commission had expressed its view, as follows:
…the investigation of the Commission has thus produced no evidence that Oswald’s trip to Mexico was in any way connected with the assassination of President Kennedy, nor has it uncovered evidence that the Cuban Government had any involvement in the assassination. (56)
There are two ways that this statement may be read:
The Warren Commission’s investigation was such that had a conspiracy existed, it would have been discovered, and since it was not, there was no conspiracy.
The Warren Commission’s investigation, limited as it was, simply did not find a conspiracy.
Although the Commission inferred that the first interpretation was the proper one, the committee investigated the possibility that the second was closer to the truth.
Similarly, the committee investigated to see if there was a factual basis for a finding made by the Senate Select Committee that the CIA plots to assassinate Castro could have given rise to crucial leads that could have been pursued in 1963 and 1964, or, at a minimum, would have provided critical additional impetus to the Commission’s investigation. (57)
As previously noted, although the 1977 CIA Task Force Report at least nominally recognized that the Agency, in 1962-64, “… could have considered in specific terms what most saw then in general terms– the possibility of Soviet or Cuban involvement in the assassination because of the tensions of the time,” and that the Agency “should have taken broader initiatives then,” the remainder of the Task Force Report failed to specify what those broader initiatives should have been or what they might have produced. It did, however, enumerate four areas for review of its 1963-64 performance:
Oswald’s travel to and from the U.S.S.R.;
Oswald’s Mexico visit in September-October 1963;
The CIA’s general extraterritorial intelligence collection requirements; and
Miscellaneous leads that the Senate committee alleged the Agency had failed to pursue. (58)
The 1977 Task Force Report reviewed the question of Agency operations directed at Cuba, including, in particular, the Mafia and AMLASH plots.(59) In each area, the report concluded that the Agency’s 1963-64 investigation was adequate and could not be faulted, even with the benefit of hindsight.(60) The task force uncritically accepted the Senate committee’s conclusions where they were favor-
Page 110
able to the Agency, 10 and it critically rejected the Senate committee’s conclusions (as in the case of AMLASH) wherever some possible investigative oversight was suggested. (62)
The 1977 Task Force Report, in sum, did little more than suggest that any theoretically “broader initiatives” the Agency could have taken in 1963-64 would have uncovered nothing. They would only have served to head off outside criticism. That conclusion is illustrated in the following passage of the report:
…[our] findings are essentially negative. However, it must be recognized that CIA cannot be as confident of a cold trail in 1977 as it could have been in 1964; this apparent fact will be noted by the critics of the Agency, and by those who have found a career in the questions already asked and yet to be asked about the assassination of President Kennedy. (63)
The committee, of course, realized that the CIA’s 1977 review might be correct, that broader initiatives might only have been window dressing and would have produced nothing of substance. But the 1977 report failed to document that fact, if it were a fact. For example, it provided no detailed resume of the backgrounds of those CIA case officers, Cubans and Mafia figures who plotted together to kill Castro.
There is nothing in the report on the activities of the anti-Castro plotters during the last half of 1963. If the Agency had been truly interested in determining the possible investigative significance to the Kennedy assassination of such CIA-Cuban-Mafia associations, the committee assumed it would have directed its immediate attention to such activities in that period.
The task force report also noted that even without its taking broader initiatives, the CIA still sent general directives to overseas stations and cited, as an example, a cable which read:
Tragic death of President Kennedy requires all of us to look sharp for any unusual intelligence development. Although we have no reason to expect anything of a particular military nature, all hands should be on the quick alert for the next few days while the new President takes over the reins.(64)
The report, reasoned that the CIA’s tasking of its stations was “necessarily general,” since little was known at the time about which it could be specific. (65)
The CIA task force further noted that 4 days after this general cable was sent, a follow-up request for any available information was sent to 10 specific stations. The task force argued, in any event, that such general requirements for intelligence-gathering would have been adequate, since “relevant information on the subject” would have been reported anyway. (66)
Conspicuously absent from such self-exculpatory analysis was any detailed discussion of what specific efforts the Agency’s stations actually made to secure “relevant information” about the assassination.
10For example, with respect to the Agency’s investigation of Oswald’s trip to Russia, the report summarily concluded, “Book V of the SSC Final Report, in not criticizing the Agency’s performance in this aspect of the investigation, seems to have accepted it as adequate, and it will not be detailed here.” (61)
Page 111
For example, it became generally known that in 1963 the CIA had a station in Florida through which it monitored the activities of most of the anti-Castro Cuban groups operating in the United States. While the Florida station was mentioned, the task force report failed to make a comprehensive analysis of what requirements were placed on the station and the station’s response. It might have been expected that the station would have been required to contact and debrief all of its Cuban sources. In addition, the station should have been asked to use all of its possible sources to determine if any operatives in the anti-Castro Cuban community had information about possible Cuban Government involvement or about any association between Oswald and possible Cuban Government agents. Further, the station, or possibly other units of the CIA, should have been tasked to attempt to reconstruct the details of the travels and activities of known pro-Castro Cuban operatives in the United States for 60 or 90 days prior to the assassination. (Such undertakings might have been made without specific cables or memoranda requiring them. The Task Force Report implied such efforts were taken by the stations “on their own initiative.” (67) But the Task Force Report failed to document or even discuss the details of such efforts or the responses of the stations to CIA headquarters.)
The committee found that the CIA’s 1977 Task Force Report was little more than an attempted rebuttal of the Senate Select Committee’s criticisms, and not a responsible effort to evaluate objectively its own 1963-64 investigation or its anti-Castro activities during the early 1960’s or to assess their significance vis-a-vis the assassination.
The committee made an effort to evaluate these questions through its own independent investigation. In investigating the implications of the CIA plots and the Warren Commission’s ignorance of them, the committee conducted interviews, depositions and hearings for the purpose of taking testimony from pertinent individuals, conducted interviews in Mexico and Cuba, and reviewed extensive files at the CIA and FBI. (68)
Top of Page
(1) AMLASH.—Turning first to the AMLASH operation, the committee received conflicting testimony as to whether, prior to the Kennedy assassination, it was considered to be an assassination plot. Former CIA Director Richard M. Helms, in his testimony before the committee, stated that the AMLASH operation was not designed to be an assassination plot. (69) And, as already indicated, the 1977 Task Force Report concluded that AMLASH had “no factual basis for leaking or reporting any actual Central Intelligence Agency plot directed against Castro” during President Kennedy’s life.(70)
The committee, however, noted that such characterizations were probably both self-serving and irrelevant. The committee found that the evidence confirmed the Senate committee’s report that AMLASH himself envisioned assassination as an essential first step in any overthrow of Castro. (71) It also noted that it was Castro’s point of view, not the Agency’s, that would have counted.
The CIA’s files reflect that as early as August 1962, AMLASH spoke to his CIA case officer about being interested in the “…sabotage of an oil refinery and the execution of a top ranking Castro subordinate, of the Soviet Ambassador and of Castro himself.”(72) The case officer,
Page 112
in his report, while stating he made no commitments to AMLASH, acknowledged that he did tell AMLASH”…schemes like he envisioned certainly had their place, but that a lot of coordination, planning, information-collection, et cetera, were necessary prerequisites to insure the value and success of such plans.”(73) Further, cables between the case officer and CIA headquarters reflected that the Agency decided not to give AMLASH a “physical elimination mission as [a] requirement,” but that it was something “he could or might try to carry out on his own initiative.”(74) Thus, the CIA’s relationship with AMLASH at least left him free to employ assassination in the coup he was contemplating. That relationship could also have been viewed by Castro as one involving the CIA in his planned assassination.
Ultimately, the CIA also provided AMLASH with the means of assassination and assurances that the U.S. Government would back him in the event his coup was successful.(75) CIA files reflect that AMLASH returned to Cuba shortly after the August 1962 meetings. (76) He next left Cuba and met with a CIA officer in September 1963. At that time, the CIA learned that AMLASH had not abandoned his intentions and that he now wanted to know what the U.S. “plan of action” was. (77) On October 11, the case officer cabled headquarters that AMLASH was determined to make the attempt on Castro with or without U.S. support.(78) On October 21, he reported that AMLASH wanted assurance that the United States would support him if his effort was successful.(79) On October 29, Desmond FitzGerald, chief of the Special Affairs Staff, met with AMLASH, representing himself as a spokesman for Attorney General Robert Kennedy. FitzGerald gave AMLASH the assurance he had asked for, (80) although the CIA has argued that the support did not specifically include assassination.
At the end of the meeting, according to the case officer’s memorandum, AMLASH asked for “technical support” which, according to FitzGerald’s memory, was described by AMLASH as being a high-powered rifle, or other weapon, to kill Castro. (81) Although the CIA files reflect that AMLASH did not receive the assurances of pre-assassination “technical support” he had asked for on October 29, the matter was further discussed, at least within the Agency, and on November 20 AMLASH was told that the meeting he “had requested” had been granted. (82) The technical support, as the Senate committee reported, was actually offered to AMLASH on November 22, 1963, the day President Kennedy was assassinated. (83)
Whether CIA officials chose to characterize their activity as an assassination plot, it is reasonable to infer that had Castro learned about the meetings between AMLASH and the CIA, he could also have learned of AMLASH’s intentions, including the fact that his assassination would be a natural and probable consequence of the plot. In a deposition to the committee, Joseph Langosch, in 1963 the Chief of Counterintelligence for the CIA’s Special Affairs Staff,(84) recalled that, as of 1962, it was highly possible that Cuban intelligence was aware of AMLASH and his association with the CIA.(85) (SAS was responsible for CIA operations against the Government of Cuba and as such was in charge of the AMLASH operation. (86))
Page 113
The committee was unable to determine if that possibility was a reality. The Cuban Government informed the committee that it had come to believe that AMLASH was in fact Rolando Cubela (based upon its construction of a profile from biographic information on AMLASH made public by the Senate committee).(87) It stated it did not know of Cubela’s intentions until 1966. (88) The committee was unable to confirm or deny the validity of the Cuban Government’s belief that AMLASH was Cubela. Nevertheless, the committee considered the statement that, if Cubela were AMLASH, the Cuban Government did not know of his intentions until 1966. On this point, the committee was unable to accept or reject the Cuban Government’s claim with confidence. The committee merely noted that the statement was corroborated by other information known about the dates of Cubela’s arrest and trial in Cuba and the charges against him. The Cuban Government’s position must, however, be recognized as potentially self-serving, since it must be assumed the Cuban Government would be inclined not to reveal any knowledge it may have had about AMLASH’s assassination plans and the CIA prior to November 22, 1963. If it had indicated it knew, it would have contributed to the credibility of the Senate’s theories about possible Cuban involvement in the assassination as a retaliatory act. (89)
The committee, while in Cuba, spoke to Rolando Cubela, who was serving a life sentence for acts against the Cuban Government. He confirmed the statements of the Cuban Government to the committee(90) that he did not give the Cuban Government any information that would have led it to believe that the CIA was involved in a plot on Castro’s life in 1963. In considering Cubela’s testimony, the committee took into account the possible influence of his confinement. After reviewing all the available evidence, the committee concluded that Castro may well have known about the AMLASH plot by November 22, 1963, and, if so, he could have either documented or assumed it was backed by the United States and that it was directed at his life. The committee believed that the details of the AMLASH operation should have been provided to the Warren Commission, since the Commission might have been able to develop leads to participants in the Kennedy assassination. At a minimum, the existence of the plot, if it had been brought to the Commissions attention, would have served as a stimulus in the 1963-64 investigation.
In conclusion, the committee believed a description of the activities of participants in the AMLASH plot should have been provided to the Warren Commission. It based this not only on the possibility that the plots could have increased Castro’s motivation to conspire to assassinate President Kennedy (assuming he, in fact, was privy to the plot prior to November 22, 1963), but also because knowledge of the AMLASH plot might have increased the interest of the CIA, FBI, and Warren Commission in a more thorough investigation of the question of Cuban conspiracy. In stating this view, the committee did not reject the suggestion in the CIA’s 1977 Task Force Report that Castro already had significant motivation to assassinate President Kennedy, even if he were not aware of the AMLASH plot. The committee noted however, that to the extent that that thesis was true, it did not negate the conclusion that the AMLASH plot was relevant
Page 114
and that information about it should have been supplied to the Warren Commission. If it had been made available, it might have affected the course of the investigation.
Top of Page
(2) CIA-Mafia Plots.–Turning next to the CIA-Mafia plots, the committee found in its investigation that organized crime probably was active in attempts to assassinate Castro, independent of any activity it engaged in with the CIA, as the 1977 Task Force Report had suggested. (91) The committee found that during the initial stages of the joint operation, organized crime decided to assist the CIA for two reasons: CIA sponsorship would mean official sanction and logistical support for a Castro assassination; and a relationship with the CIA in the assassination of a foreign leader could be used by organized crime as leverage to prevent prosecution for unrelated offenses. (92) During the latter stages of the CIA-Mafia operation, from early 1962, to early 1963, however, organized crime may no longer have been interested in assassinating Castro. (93) The Soviet influence in Cuba had rendered the prospect of regaining the old Havana territory less likely, and there were fortunes to be made in the Bahamas and elsewhere.(94) There is reason to speculate that the Mafia continued to appear to participate in the plots just to keep the CIA interested, in hopes of preventing prosecution of organized crime figures and others involved in the plots. (95)
This theory is supported by the actions of Robert Maheu, an FBI agent turned private investigator who had acted as a CIA-organized crime go-between, and John Roselli, a Mafia principal in the plots. (96) Maheu, for example, was the subject of an FBI wiretap investigation in Las Vegas in the spring of 1962. He had installed a telephone wiretap, which he claimed was done as a favor to Mafia chieftain Sam Giancana, who was also involved in the anti-Castro plots.(97) Maheu’s explanation to the FBI was that the tap was placed as part of a CIA effort to obtain Cuban intelligence information through organized crime contacts. The CIA corroborated Maheu’s story, and the case was not prosecuted. (98) In addition, in 1966, Maheu used his contacts with the CIA to avoid testifying before a Senate committee that was conducting hearings into invasion of privacy. (99)
As for Roselli, the committee considered it significant that public revelations about the plots corresponded with his efforts to avoid deportation in 1966 and 1971 and to escape prosecution for illegal gambling activities in 1967.(100) It was Roselli who managed the release of information about the plots and who proposed the so-called turnaround theory of the Kennedy assassination (Cuban exiles hired by the Mafia as hit men, captured by Castro. were forced to “turn around” and murder President Kennedy). (101) The committee found it quite plausible that Roselli would have manipulated public perception of the facts of the plots, then tried to get the CIA to intervene in his legal problems as the price for his agreeing to make no further disclosures.
The allegation that President Kennedy was killed as a result of a Mafia-CIA plot that was turned around by Castro was passed to Drew Pearson and Jack Anderson by Washington attorney Edward P. Mor-
Page 115
gan; its ultimate source was Roselli.(102) The committee found little credibility in such an explanation for the President’s death because, if for no other reason, it would have been unnecessarily risky. The committee determined from CIA files that, in 1963, the Cuban Government had agents of its own in nearly every country of the Western Hemisphere, including the United States, who undoubtedly would have been more dependable for such an assignment. Even if Castro had wanted to minimize the chance of detection by using hired non-Cuban killers, it appeared unlikely to the committee that he would have tried to force Mafia members or their Cuban exile confederates to engage in the assassination of an American head of state.
The committee found it more difficult to dismiss the possibility that the Mafia, while it was not turned around by Castro, might have voluntarily turned around with him. By late 1962 and 1963, when the underworld leaders involved with the CIA in the plots had perhaps lost their motivation to assassinate Castro, they had been given sufficient reason by the organized crime program of the Department of Justice to eliminate President Kennedy. The committee’s investigation revealed that Mafia figures are rational, pragmatic “businessmen” who often realine their associations and form partnerships with ex-enemies when it is expedient.(103) While Castro, by 1963, was an old enemy of organized crime, it was more important that both Castro and the Mafia were ailing financially, chiefly as a result of pressures applied by the Kennedy administration. (104) Thus, they had a common motive that might have made an alliance more attractive than a split based on mutual animosity.
By 1963 also, Cuban exiles bitterly opposed to Castro were being frustrated by the Kennedy administration. (105) Many of them had come to conclude that the U.S. President was an obstacle requiring elimination even more urgently than the Cuban dictator.(106) The Mafia had been enlisted by the CIA because of its access to anti-Castro Cuban operatives both in and out of Cuba.(107) In its attempt to determine if the Mafia plot associations could have led to the assassination, the committee, therefore, recognized that Cuban antagonism toward President Kennedy did not depend on whether the Cubans were pro- or anti-Castro.
The committee found that the CIA-Mafia-Cuban plots had all the elements necessary for a successful assassination conspiracy–people, motive and means, and the evidence indicated that the participants might well have considered using the resources at their disposal to increase their power and alleviate their problems by assassinating the President. Nevertheless, the committee was ultimately frustrated in its attempt to determine details of those activities that might have led to the assassination–identification of participants, associations, timing of events and so on. Many of the key figures of the Castro plots had, for example, since died or, as in the case of both Giancana and Roselli, had been murdered.
The committee was also unable to confirm in its investigation the findings of the Senate committee and the CIA that there were reasons to discount the dangers to President Kennedy that may have resulted from CIA associations with the Mafia in anti-Castro activities, The
Page 116
committee did not agree with the Senate committee that Castro would not have blamed President Kennedy for the CIA-Mafia plots against his life. They were formulated in the United States, and the history of United States-Cuban relations shows that when Castro erred in his assumptions, it was in the direction of attributing more, not less, responsibility for attempts to depose him to U.S. Government actions than might have been merited.
In its 1977 Task Force Report, the CIA commented on this reality:
The United States provided a haven and base for Cuban exiles, who conducted their independent operations against the Castro government. Some of these exiles had the support of CIA, as well as from other elements of the U.S. Government, and still others had support from private sources. With or without official U.S. support these exiles spoke in forceful Latin terms about what they hoped to do. The Cuban intelligence services had agents in the exile community in America and it is likely that what they reported back to Havana assigned to CIA responsibility for many of the activities under consideration, whether CIA was involved or not. (108)
From its investigation of documents and from the testimony of officials and others, the committee decided that the Senate committee was probably mistaken in its conclusion that the CIA-Mafia plots were less significant than the AMLASH plot. In the judgment of the committee, the CIA-Mafia plots, like the AMLASH plot, should have been aggressively explored as part of the 1963-64 investigation of the assassination of President Kennedy. At that time, it might still have been possible to determine precise dates of trips, meetings, telephone communications: and financial transactions, and the participants in these potentially pertinent transactions could have been questioned. At least in this one respect, the committee must concur with a sentiment expressed in the 1977 CIA Task Force Report:
Today, the knowledge of the persons involved directly in the various Cuban operations in the period preceding President Kennedy’s death cannot be recaptured in the form that it existed then. These persons are scattered, their memories are blurred by time, and some are dead. (109)
The committee, moreover, was unable to accept the conclusion of the CIA and the Senate committee that the CIA-Mafia plots were irrelevant because they had been terminated in February 1963, several months before the assassination. The record is clear that the relationships created by the plots did not terminate, nor had the threat to Castro abated by that time. There is insufficient evidence to conclude that the inherently sinister relationships had become benign by November 22, 1963.
In June 1963, according to the interim report of the Senate committee, Roselli had dinner with William Harvey, chief of the CIA’s Cuban Task Force.(110) CIA files show that Roselli continued to maintain direct contact with Harvey at least until 1967, and he was in touch, at least indirectly, with the Agency’s Chief of the Operational Support Branch. Office of Security, as late as 1971. (111) The Task Force Report itself alluded to information that, as late as June
Page 117
1964, gangster elements in Miami were offering $150,000 for Castro’s life, an amount mentioned to the syndicate representatives by CIA case officers at an earlier date.” (112)
In the absence of documentation of the activities of Mafia plot participants between February 1963 and November 22, 1963–which had not been obtained in earlier investigations, and the committee was able to do no better–the committee found it difficult to dismiss the CIA-Mafia plots, even assuming they had been terminated in February 1963, as of no consequence to the events in Dallas on November 22, 1963. The plots, in short, should have been made known to the Warren Commission. If they had been investigated in 1964, they might have provided insights into what happened in Dallas and resolved questions that have persisted.
Top of Page
(3) Summary of the evidence–By its conclusions about the AMLASH operation and the CIA-Mafia plots–that they were of possible consequence to the assassination investigation and therefore should have been revealed to the Warren Commission–the committee did not intend to imply it had discovered a link to the assassination. To the contrary, the committee was not able to develop evidence that President Kennedy was murdered in retaliation for U.S. activities against Castro. What the committee did determine, however, was that there was no basis, in terms of relevance to the assassination, for the CIA to decide that the AMLASH operation and the CIA-Mafia plots were of no significance to the Warren Commission’s investigation. On the other hand, the possibility that President Kennedy was assassinated in retaliation for anti-Castro activities of the CIA should have been considered quite pertinent, especially in light of specific allegations of conspiracy possibly involving supporters of the Cuban leader.
Top of Page
(d) Cubana Airlines flight allegation
The committee considered specific allegations of conspiracy involving supporters of Castro.
One such charge, referred to in book V of the Senate select committee’s report, concerns a Cubana Airlines flight from Mexico City to Havana on the evening of November 23, 1963. (113) It had been alleged that the flight was delayed 5 hours, awaiting the arrival at 9:30 p.m. of a private twin-engined aircraft.(114) The aircraft was supposed to have deposited an unidentified passenger who boarded the Cubans flight without clearing customs and traveled to Havana in the pilot’s cabin. (115)
The Senate committee reported that the Cubana flight departed at 10 p.m. This committee checked the times of key events that night by reviewing extensive investigative agency documents. It found the following facts:
The Cubana flight was on the ground in Mexico City for a total of only about 4 hours and 10 minutes and thus could not have been delayed five hours. (116) The Cubana flight had departed for Havana at 8:30 p.m., about an hour before the arrival of the private aircraft reportedly carrying a mysterious passenger, so he could not have taken the flight. (117)
Page 118
The committee found that extensive records of flight arrivals and departures at the Mexico City airport were available and deemed it doubtful that the alleged transfer of a passenger from a private aircraft to the Cubana flight could have gone unnoticed, had it occurred. (118) The committee concluded, therefore, that the transfer did not occur.
Top of Page
(e) Gilberto Policarpo Lopez allegation
More troubling to the committee was another specific allegation discussed by the Senate committee. It concerned a Cuban-American named Gilberto Policarpo Lopez.(119) According to the account, Lopez obtained a tourist card in Tampa, Fla., on November 20, 1963, entered Mexico at Nuevo Laredo on November 23, and flew from Mexico City to Havana on November 27. (12O) Further, Lopez was alleged to have attended a meeting of the Tampa chapter of the Fair Play for Cuba Committee on November 17, 1963, and at a December meeting of the chapter, Lopez was reported to be in Cuba. (12l)
The committee first examined the CIA files on Policarpo Lopez.(122) They reflect that in early December 1963, CIA headquarters received a classified message stating that a source had requested “urgent traces on U.S. citizen Gilberto P. Lopez.” (123) According to the source, Lopez had arrived in Mexico on November 23 enroute to Havana and had disappeared with no record of his trip to Havana. The message added that Lopez had obtained tourist card No. 24553 in Tampa on November 20, that he had left Mexico for Havana November 27 on Cubana Airlines, and that his U.S. passport number was 310162.(124)
In another classified message of the same date, it was reported that the FBI had been advised that Lopez entered Mexico on November 27 at Nuevo Laredo. (125)
Two days later these details were added: Lopez had crossed the border at Laredo, Tex., on November 23; registered at the Roosevelt Hotel in Mexico City on November 25; and departed Mexico on November 27 on a Cubana flight for Havana. (126) Another dispatch noted that Lopez was the only passenger on Cubans flight 465 on November 27 to Havana. (127) It said he used a U.S. passport and Cuban courtesy visa. It noted, too: “Source states the timing and circumstances surrounding subject’s travel through Mexico and departure for Havana are suspicious.” It was this dispatch that alerted headquarters to the source’s “urgent” request for all available data on Lopez. (128)
The same day as the dispatch, headquarters sent a cable identifying the Cuban-American as Gilberto Policarpo Lopez, born January 26, 1940. It added that Lopez was not identical with a Gilberto Lopez who had been active in pro-Castro groups in Los Angeles. (129)
Headquarters was also told that there existed a “good” photograph of Lopez, showing him wearing dark .glasses. A copy of the photograph with “27 November 1963” stamped on the back was found in his CIA file by committee investigators in 1978. (130)
In March 1964, CIA headquarters received a classified message: a source had reported in late February that an American citizen named
Page 119
Gilberto Lopes 11 had been involved in the Kennedy assassination; that Lopes had entered Mexico on foot from Laredo, Tex., on November 13 carrying U.S. passport 319962, which had been issued July 13, 1960; that he had been issued Mexican travel form B24553 in Nuevo Laredo; that Lopes had proceeded by bus to Mexico City “where he entered the Cuban Embassy”; and that he left the Cuban Embassy on November 27 and was the only passenger on flight 465 for Cuba. (132)
The following day, a classified message was sent to headquarters stating that the information “jibes fully with that provided station by in early December 1963.” (133)
A file had been opened on Lopez at headquarters on December 16, 1963. (134) It contained a “Review of [material omitted] file on U.S. Citizen” by an operations officer of the responsible component of the agency. In the review, the file was classified as a “counterintelligence case, (that is, involving a foreign intelligence or security service).” The date of entry of that category in the agency’s records is indicated as January 22, 1975. (135)
The committee also reviewed an FBI investigation of Gilberto Policarpo Lopez in Key West, Fla., contained in a report dated August 1964.(136)
In an interview, Lopez’ cousin, Guillermo Serpa Rodriguez, had said that Lopez had come to the United States soon after Castro came to power, stayed about a year and returned to Cuba because he was homesick. He returned to the United States in 1960 or 1961 fearing he would be drafted into the Cuban militia. (137)
The FBI also interviewed an American woman Lopez had married in Key West. She listed companies where he had been employed, including a construction firm in Tampa. She also said he began suffering from epileptic attacks, was confined for a time at Jackson Memorial Hospital in Miami in early 1963, and was treated by doctors in Coral Gables and Key West. She said she believed the epilepsy was brought on by concern for his family in Cuba. (138)
Lopez’ wife said she received a letter from him in about November 1963, saying he had returned to Cuba once more. She said she had been surprised, although he had mentioned returning, to Cuba before he left for Tampa in November 1963. In a later letter, Lopez told his wife he had received financial assistance for his trip to Cuba from an organization in Tampa. His wife explained that he would not have been able to pay for the trip without help. She said, however, he had not had earlier contacts with Cuban refugee organizations. (139)
11The committee noted the discrepancies in this message, as follows: the spelling of Lopes, for Lopez; the November 13 date and passport number 319962, issued July 13, 1960; and Lopez entering Mexico on foot. In its 1977 Task Force Report, the CIA cited the several “inaccuracies,” as they had been repeated in the report of the Senate Select Committee, as reason to refute the report itself. The TFR pointed out that Lopez’ name had been misspelled “Lopes,” that it had Lopez entering Mexico on foot, when the CIA had information that he had traveled by automobile; that it listed incorrect digits for Lopez’ passport number; that it stated that Lopez’ Mexican tourist visa had been issued in Nuevo Laredo, not Tampa; and it reported that he had stayed at the Cuban Embassy. Based on these inaccuracies, the TFR concluded, “the source was patently and extensively misinformed.” The TFR therefore discounted the March cable that held that the information “jibed” with what the CIA’s source had earlier reported. (131)
The discrepancies pointed out in the TFR were apparently intended to explain why the CIA had not taken more aggressive investigative steps to determine whether there had been a connection between Lopez and the assassination.
Page 120
Rodriguez said Lopez left Key West in late 1963 for Tampa with the hope of being able to return to Cuba, explaining he was afraid he would be drafted into the U.S. military. Rodriguez said Lopez had not been involved in pro-Castro activity in Key West, but that he was definitely pro-Castro, and he had once gotten into a fistfight over his Castro sympathies. (140)
The FBI had previously documented that Lopez had actually been in contact with the Fair Play for Cuba Committee and had attended a meeting in Tampa on November 20, 1963. In a March 1964 report, it recounted that at a November 17 meeting of the Tampa FPCC, Lopez had said he had not been granted permission to return to Cuba but that he was awaiting a phone call about his return to his homeland.
In that March report, a Tampa FPCC member was quoted as saying she called a friend in Cuba on December 8, 1963, and was told that Lopez had arrived safely. She also said that the Tampa chapter of the FPCC had given Lopez about $190 for the trip to Cuba and that he had gone to Cuba by way of Mexico because he did not have a passport. (141)
The March 1964 FBI report stated that Lopez did have a U.S. passport– it had been issued in January 1960 and was numbered 310162. His Mexican tourist card was numbered M8-24553 and was issued November 20, 1963 in Tampa. The report also confirmed that Lopez entered Mexico via Laredo, Tex., by automobile on November 23, and he departed for Havana on November 27, the only passenger on a Cubana flight. He was carrying a Cuban courtesy visa.(142)
Lopez’ FBI file contained a memorandum from the Tampa office. Dated October 26, 1964, it read:
It is felt that information developed regarding the subject is not sufficient to merit consideration for the Security Index. (143)
The only information transmitted by the FBI to the Warren Commission, the committee determined, concerned a passport check on Lopez. Information sent to the Commission by the FBI on the Tampa chapter of the FPCC did not contain information on Lopez’ activities. The CIA apparently did not provide any information to the Warren Commission on Lopez. (144) The committee concurred with the Senate Select Committee that this omission was egregious, since sources had reported within a few days of the assassination that the circumstances surrounding Lopez’ travel to Cuba seemed “suspicious.” Moreover, in March 1964, when the Warren Commission’s investigation was in its most active stage, there were reports circulating that Lopez had been involved in the assassination.
In its 1977 Task Force Report, the CIA responded to the charges of the Senate committee. It claimed that the agency had carried its investigation of Lopez as far as it could, having questioned a Cuban defector about him. (145) The committee found that the absence of access to additional sources of information was not an adequate explanation for the agency’s failure to consider more seriously the suspicions of its sources or to report what information it did have to the Warren Commission. Attempts in the Task Force Report to denigrate the information that was provided on Lopez were not an adequate substitute for enabling the Warren Commission itself to pursue the leads more aggressively.
Page 121
From the information gathered by the FBI, there appeared to be plausible reasons both for Lopez’ desire to return to Cuba and for his solicitation of financial aid from the Tampa FPCC chapter. Lopez’ contacts in Florida appeared to have been innocent and not connected with the assassination, and while there was a suggestion in the Senate committee’s report that Lee Harvey Oswald also was in contact with the Tampa FPCC chapter, the committee could find no evidence of it. Nor could the committee find any evidence that Oswald was in contact with Lopez.
Lopez’ association with the Fair Play for Cuba Committee, however, coupled with the facts that the dates of his travel to Mexico via Texas coincide with the assassination, plus the reports in Mexico that Lopez’ activities were “suspicious,” all amount to a troublesome circumstance that the committee was unable to resolve with confidence.
Top of Page
(f) Other allegations
The committee also pursued allegations of Cuban complicity that were not suggested by the investigation of the Senate committee. For example, it looked into an allegation by one Autulio Ramirez Ortiz, who hijacked an aircraft to Cuba in 1961. Ramirez claimed that while being held by the Cuban Government, he worked in an intelligence facility where he found a dossier on Lee Harvey Oswald. (146) It was labeled the “Oswald-Kennedy” file and contained a photograph of “Kennedy’s future assassin.”(147) In the Spanish language manuscript of a book he wrote Ramirez claimed the Oswald file read, in part “… The KGB has recommended this individual …He is a North American, married to an agent of the Soviet organism who has orders to go and reside in the United States. Oswald is an adventurer. Our Embassy in Mexico has orders to get in contact with him. Be very careful.”(148)
The committee, in executive session, questioned Ramirez, who had been returned to the United States to serve a 20-year Federal sentence for hijacking.(149) He testified he was unable to describe the photograph he had allegedly seen and that the writing in the file was in Russian, a language he does not speak. (150)
The committee sought from the FBI and CIA independent evidence of the accuracy of Ramirez’ allegations, but there was no corroboration of the existence of an “Osvaldo-Kennedy” file to be found. On the other hand, in every instance where there was independent evidence of allegations made by Ramirez (the identities of Cuban officials named by him, for example) Ramirez’ statements were found to be accurate.(151)
In the end, however, the committee was forced to dismiss Ramirez’ story about the “Osvaldo-Kennedy” file. The decisive factor was the committee’s belief that the Cuban intelligence system in the 1961-63 period was too sophisticated to have been infiltrated by Ramirez in the manner he had described. While some details of his story could be corroborated, the essential aspects of his allegation were incredible.
The committee also considered the allegation that appeared in an article in a 1967 issue of the National Enquirer, written by a British freelancer named Comer Clark.(152) Purportedly based on an exclusive interview with Castro, it quoted the Cuban President as admitting to having heard of threats by Oswald to assassinate president
Page 122
Kennedy. According to Clark, Castro told him that while at the Cuban consulate in Mexico City in September 1963, Oswald vowed he would kill the President. (153)
On a trip to Havana in April 1978, the committee met with President Castro and asked him about the charge. Castro denied there had ever been an interview with Clark.(154) He also suggested that had such a threat been overheard by Cuban officials, they and he would have been morally obligated to transmit it to U.S. authorities.(155)
The committee did not agree that the Cuban Government would have been obligated to report the threat. Nothing in the evidence indicated that the threat should have been taken seriously, if it had occurred, since Oswald had behaved in an argumentative and obnoxious fashion during his visit to the consulate. (156) Cuban officials would have been justified, the committee reasoned, to have considered the threat an idle boast, deserving no serious attention.
The accuracy of Clark’s account was also undermined by the committee’s investigation of his background. Clark had been the author of articles with such sensational titles as “British Girls as Nazi Sex Slaves,” “I Was Hitler’s Secret Love” and “German Plans to Kidnap the Royal Family.” The committee was unable to question Clark himself, as he had since died. (157)
Despite the committee’s doubts about the Clark interview with Castro, it was informed that the substance of it had been independently reported to the U.S. Government. A highly confidential but reliable source reported that Oswald had indeed vowed in the presence of Cuban consulate officials to assassinate the President. (158)
This information prompted the committee to pursue the report further in file reviews and interviews. The files that were reviewed included records of conversations of relevant people at appropriate times and places. Only one of them provided any possible corroboration. It was the record of a reported conversation by an employee of the Cuban Embassy named Luisa Calderon. (159) The absence of other corroboration must be considered significant.
A blind memorandum 12provided by the CIA to the committee contained Calderon’s pertinent remarks:
1. A reliable source reported that on November 22, 1963, several hours after the assassination of President John F. Kennedy, Luisa Calderon Carralero, a Cuban employee of the Cuban Embassy in Mexico City, and believed to be a member of the Cuban Directorate General of Intelligence (DGI), discussed news of the assassination with an acquaintance. Initially, when asked if she had heard the latest news, Calderon replied, in what appeared to be a joking manner, “Yes, of course, I knew almost before Kennedy.”
2. After further discussion of the news accounts about the assassination, the acquaintance asked Calderon what else she had learned. Calderon replied that they [assumed to refer to personnel of the Cuban Embassy] learned about it a little while ago. (160)
12there is no indication on a blind memorandum of either origin or destination.
Page 123
Luisa Calderon’s statements on the day of the assassination could be construed as either an indication of foreknowledge or mere braggadocio. The preponderance of the evidence led the committee to find that it was braggadocio. While the committee attempted to interview Calderon in Cuba, it was unable to, since she was ill. (161) Nevertheless, it forwarded interrogatories to her, which she responded to denying foreknowledge of the assassination.(162) The committee also interviewed other employees of the Cuban consulate in Mexico City in 1963 all of whom denied the allegation.(163) While it may be argued that they had a reason to do so because of Castro’s view that the Cuban Government would have had a moral obligation to report the threat had it occurred, these officials, in the committee’s judgment, indicated by their demeanor that they were testifying truthfully.
The committee also made a judgment about the risk that would have been incurred by Cubans had they testified falsely on this issue or by those who might have orchestrated their false testimony. Based on newspaper reporting alone, the Cuban Government might reasonably have believed that the committee had access to extensive information about conversations in the Cuban consulate in Mexico City and that such information might have provided convincing evidence of a coverup. To have been caught in a lie in public testimony in the United States 13 would have been a major embarrassment for the Cuban Government, one that might have implied more than moral responsibility for failing to report a threat against President Kennedy in advance of the assassination.
On balance, the committee did not believe that Oswald voiced a threat to Cuban officials. However reliable the confidential source may be, the committee found it to be in error in this instance.
The committee investigated other aspects of Oswald’s trip to Mexico City in September 1963 to see if it could develop information that bore on the question of a Cuban conspiracy. It considered the claim by the Cuban consul in Mexico City in 1963, Eusebio Azcue, that a man posing as Oswald applied for a Cuban visa. 14It also investigated two plausible, though unsubstantiated, allegations of activities that had not previously been publicly revealed:
That of a Mexican author, Elena Garro de Paz, who claimed that Oswald and two companions had attended a “twist” party at the home of Ruben Duran, brother-in-law of Silvia Duran, the secretary of Cuban consul Azcue who dealt with Oswald when he applied at the consulate for a Cuban visa.(164)
That of a Mexican named Oscar Contreras who, in 1967, claimed he had met Oswald on the campus of the National Autonomous University of Mexico. (165)
The committee conducted extensive interviews with respect to these allegations. (166)
The significance of the Elena Garro allegation, aside from its pointing to Oswald associations in Mexico City that the Warren Commis-
13In addition to a tape-recorded interview with President Castro in Havana, the committee heard testimony in public hearing from two former Cuban counsuls in Mexico City, Eusebio Azcue and Alfredo Mirabel, and it tape-recorded an interview with Silvia Duran, a secretary at the Cuban Consulate in Mexico City in 1963 who had had one or more encounters with Oswald.
14Details of the issue of an alleged Oswald imposter are presented in section I D 4.
Page 124
sion did not investigate, lay in her description of one of the companions as gaunt and blond-haired. (167) These are characteristics that both Azcue and Silvia Duran attributed to the visitor to the Cuban consulate who identified himself as Lee Harvey Oswald. (168) Even though “gaunt and blond-haired” did not describe Oswald, Duran said that the American visitor was the man later arrested in the assassination of the President. (169) Azcue, on the other hand, insisted that the visitor was not the individual whose published photograph was that of Oswald. (170)
The committee was unable to obtain corroboration for the Elena Garro allegation, although Silvia Duran did confirm that there was a “twist” party at her brother-in-law’s home in the fall of 1963 and that Elena Garro was there. (171) She denied, however, that Oswald was there, insisting that she never saw Oswald outside of the Cuban consulate.(172) The committee was unable to check the story with official U.S. investigative agencies because they failed to pursue it, even though they were aware of it in 1964.15
The committee’s investigation was sufficient, however, to develop a conclusion that the Elena Garro allegation had warranted investigation when it was first received by the CIA in October 1964. Even in the late 1960’s, at a time when Garro and others were available for questioning, there was still the potential for sufficient corroboration 16 to make the allegation worth pursuing. Further, while the allegation did not specifically show a Cuban conspiracy, it did indicate significant Oswald associations that were not known to the Warren Commission.
The other Oswald association in Mexico City that might have proven significant, had it been pursued, was the one alleged by Oscar Contreras, a student at the National Autonomous University of Mexico. The committee made an effort to investigate this allegation. Silvia Duran, for example, admitted to the committee. that she had advised Oswald he might obtain a Cuban visa if he could get a letter of recommendation from a Mexican in good standing with the Cuban revolutionary hierarchy. (175) The committee also learned that the chairman of the philosophy department at the National Autonomous University, Ricardo Guerra, held seminars from time to time at the Duran home on Kant, Hegel, and Marx. (176) The committee speculated that these circumstances might explain why Oswald contacted Contreras, who reported to Mexican authorities that Oswald approached him in Sept-
15The committee’s investigation in Mexico City was further inhibited by the refusal of the CIA to make available its sources on the Elena Garro allegation, and, as a committee of the U.S. Congress in a foreign country, it was bound by a decision of the Mexican Government to permit its citizens to decide individually if they wished to meet with committee representatives (173)
The CIA, moreover, had failed to pursue the Elena Garro allegation adequately in 1964. A review of the CIA file indicated that the allegation was treated skeptically because Agency officials apparently considered Elena Garro to be other than totally rational. Inquiries of sources were ordered, but the files do not indicate that any responses were actively solicited or, in fact, received. The Agency files on this aspect of the case are devoid of any substance that would suggest an active CIA investigation.
The committee did ultimately locate Elena Garro in Europe, but attempts by telephone to persuade her to come to the United States to testify did not succeed (174).
16Elena Garro maintained that after the assassination she wanted to report her story to authorities but that she was warned of possible danger by a man named Manuel Calvillo. Elena Garro, alleged that Calvillo placed her in the Hotel Vermont in Mexico City where she remained for several days. In 1967, the CIA did in fact receive confirmation of Elena Garro’s stay at the Hotel Vermont immediately after the assassination.
Page 125
tember 1963 following a roundtable discussion at the school of philosophy. 17
The committee’s attempts to contact Contreras were frustrated. On two occasions, the Mexican Government said he would be available for an interview, but neither materialized. The committee also was unable to contract Guerra. who in 1978 was Mexico’s Ambassador to East Germany. (177) The significance of the Contreras allegation, therefore, remains largely indeterminate.
The committee also pondered what deductions might be drawn from Azcue’s conviction that the man who applied for a Cuban visa was not Oswald. One possibility considered, although ultimately rejected by the committee, was that there was a sinister association between Oswald and the Castro regime that Azcue was attempting to conceal.
The committee weighed the evidence on both sides of the Oswald-at-the-Cuban-consulate issue:
That it was Oswald was indicated by the testimony of Silvia Duran and Alfredo Mirabal, who was in the process of succeeding Azcue as Cuban consul when the visit occurred in late September 1963. They both identified Oswald from post-assassination photographs as the man who applied for a Cuban visa.
That it was not Oswald was a possibility raised by the committee’s inability to secure a photograph of him entering or leaving the Soviet Embassy or the Cuban consulate. The committee obtained evidence from the Cuban Government that such photographs were being taken routinely in 1963. Further, the committee found that Oswald paid at least five visits to the Soviet Embassy or the Cuban consulate. 18 (178)
The committee also sought to understand the significance of a Secret Service investigation of threats against President Kennedy by pro-Castro Cubans. In April 1961, for example, when the President and Mrs. Kennedy were scheduled to address a special meeting of the Council of the Organization of American States, the State Department reported that Cuba would be represented by one Quentin Pino Machado. Machado, a Cuban diplomat, described as a character of ill repute, armed and dangerous, ultimately did not attend the meeting. (179)
On November 27, 1963, a Miami Secret Service informant told Special Agent Ernest Aragon that if the assassination involved an international plot in which Castro had participated, then Castro’s agent in the plot would have been Machado, a well-known terrorist. There were
17The Contreras story, as in the case of the Elena Garro allegation, was not adequately pursued when it first came to the attention of the CIA in 1967. At that time, the Agency was informed by the U.S. Consul in Tampico, Mexico, that Contreras had passed the information to him. An Agency employee later discussed the matter in more detail with the Consul and then met with Contreras himself. The CIA confirmed that Contreras had been a student in 1963 and was politically a strong supporter of Fidel Castro. The Contreras story was considered, according to Agency files, to be the first significant development in the investigation of the Kennedy assassination after 1965. Nevertheless, no attempt was made to determine who Contreras’ associates were or how Oswald might have contacted him. Instead, the case was simply reported to the FBI. According to FBI files, no follow-up investigation was conducted.
18The committee believed that photographs of Oswald might have been taken and subsequently lost or destroyed. The committee did obtain a photograph of a man whose description seemed to match that given by Azcue and Duran of the “gaunt and blond-haired” visitor to the Cuban consulate. They each stated, however, that he was not the man they had described as the one who, in the name of Lee Harvey Oswald, had applied for a visa to Cuba.
Page 126
rumors in the Miami Cuban community at the time that Machado had been assigned to escort Oswald from Texas to Cuba after the assassination. The plan went awry, the report continued, because Oswald had not been wearing clothing of a prearranged color and because of the shooting of Dallas Patrolman J.D. Tippit.(180)
The reports on Machado, along with other suspicions of Castro complicity in the assassination, were forwarded only in brief summary form by the Secret Service to the Warren Commission. The committee could find no record of follow-up action. (181) The committee’s investigation of actions by the Secret Service subsequent to the assassination, however, revealed the most extensive work of the Agency to have been in response to reports of pro-Castro Cuban involvement. (182)
Top of Page
(g) The committee’s trip to Cuba
The committee took its investigation to Cuba in the spring and summer of 1978. It sought information on numerous allegations, such as those mentioned above, and it put to President Castro the question of Cuban involvement in the assassination. The committee found the Cuban Government to be cooperative, both in supplying written reports and documents in response to questions and by making a number of its citizens available for interviews. (183) While the committee was unable to interview Luisa Calderon personally, the Cuban Government did permit its former consuls in Mexico City, Eusebio Azcue and Alfredo Mirabal, to come to Washington to testify in a public hearing of the committee. (184)
In response to the question of Cuban complicity in the assassination, Castro replied:
That [the Cuban Government might have been involved in the President’s death] was insane. From the ideological point of view it was insane. And from the political point of view, it was a tremendous insanity. I am going to tell you here that nobody, nobody ever had the idea of such things. What would it do? We just tried to defend our folks here, within our territory. Anyone who subscribed to that idea would have been judged insane …absolutely sick. Never, in 20 years of revolution, I never heard anyone suggest nor even speculate about a measure of that sort, because who could think of the idea of organizing the death of the President of the United States. That would have been the most perfect pretext for the United States to invade our country. which is what I have tried to prevent for all these years, in every possible sense. Since the United States is much more powerful than we are, what could we gain from a war with the United States? The United States would lose nothing. The destruction would have been here. (185)
Castro added:
I want to tell you that the death of the leader does not change the system. It has never done that. (186)
In the interview, Castro also commented on his speech of September 7, 1963, which on its face might have been viewed as an indication
Page 127
that Castro may have been prompted to retaliate for a CIA-inspired attempt on his life:
So, I said something like those plots start to set a very bad precedent, a very serious one–that could become a boomerang against the authors of those actions …but I did not mean to threaten by that. I did not mean even that …not in the least …but rather, like a warning that we knew; that we had news about it; and that to set those precedents of plotting the assassination of leaders of other countries would be a very bad precedent …something very negative. And, if at present, the same would happen under the same circumstances, I would have no doubt in saying the same as I said [then] because I didn’t mean a threat by that. I didn’t say it as a threat. I did not mean by that that we were going to take measures–similar measures– like a retaliation for that. We never meant that because we knew that there were plots. For 3 years, we had known there were plots against us. So the conversation came about very casually, you know; but I would say that all these plots or attempts were part of the everyday life.(187)
Finally, President Castro noted that although relations between the United States and Cuba were strained during the Kennedy administration, by 1963 there were definite hopes for reconciliation. (188)
The committee confirmed from the historic record that, in 1963, the Cuban Government made several overtures. While, for the most part, Kennedy did not respond favorably, he did, in November, direct that the possibility of holding talks be explored by United Nations Delegate William Atwood with Cuban United Nations Ambassador Carlos Lechuga. (189) There was also reason to believe that French journalist Jean Daniel was asked by Kennedy to relay a peace message to Castro.(190) At least, that was how Castro interpreted it when he met with Daniel on November 20, 1963. (191)
In his interview with the committee, Castro referred to these two developments toward rapprochement, as he viewed them, suggesting that he would not have had a motive to eliminate President Kennedy. Instead, it would have been to his advantage, Castro insisted, to have pursued the prospect for better relations that had been portended. (192)
Top of Page
(h) Deficiencies of the 1963-64 investigation
In attempting to resolve the question of possible Cuban conspiracy, the committee concluded that a definitive answer had to come, if at all, largely from the investigation conducted in 1963-64 by the Warren Commission and the FBI and CIA. What the committee was able to do 15 years later could fill in important details, but it could not make up for basic insufficiencies. Unfortunately, the committee found that there were in fact significant deficiencies in the earlier investigation. The Warren Commission knew far less than it professed to know about Oswald’s trip to Mexico and his possible association with pro-Castro agents in Mexico and elsewhere. This was true, in part, because the Commission had demanded less of the FBI and CIA than called for in its mandate. (193)
Page 128
For its part, the FBI mechanically ran out thousands of leads, but it failed to make effective use of its Cuban Section of the Domestic Intelligence Division or to develop and systematically pursue investigative hypotheses of possible Cuban complicity. It must be said that the FBI generally exhausted its resources in confirming the case against Lee Harvey Oswald as the lone assassin, a case that Director J. Edgar Hoover, at least, seemed determined to make within 24 hours of the assassination. (194)
With respect to the CIA, the committee determined that it could have been better equipped to investigate the question of Cuban complicity. 19 The CIA had, at the time, only limited access to Cuban intelligence defectors, and most of its information sources inside Cuba were better equipped to report on economic developments and troop movements than on political decisions, especially sensitive ones, such as those involving political assassination.(198)
As the CIA admitted in its 1977 Task Force Report, it could have taken “broader initiatives” in pursuing the investigation. The committee found that such initiatives could have included more comprehensive instructions on debriefing Cuban sources and more explicit tasking of stations for specific investigative efforts.
With respect to the CIA’s investigation of possible Cuban complicity, however, the committee found that the Agency’s shortcomings were not attributable to any improper motive. The committee found that the CIA did generally gather and analyze the information that came to its attention regarding possible Cuban involvement, at least until the Warren Commission made its report in 1964. Indeed, the committee noted that the Agency acted not only out of dedication, but out of a specific motivation related to Cuba. The officers, agents and employees in the Cuba-related divisions had devoted their careers to the overthrow of Castro, and evidence of his participation in the assassination, if it had existed and could have been brought to light, would have vindicated their long-frustrated efforts, of not, in fact, led directly to a U.S. invasion of Cuba and destruction of the Castro regime.
That being said, the committee did not ignore the possibility that certain CIA officials who were aware that close scrutiny of U.S.-Cuban relations in the early 1960’s could have inadvertently exposed the CIA-Mafia plots against Castro, might have attempted to prevent the CIA’s assassination investigation or that of the Warren Commission from delving deeply into the question of Cuban complicity. The committee determined, however, that only CIA Deputy Director Richard Helms would have been in a position to have had both the requisite knowledge and the power to accomplish such a coverup, and it was satisfied, on the basis of its investigation, that it was highly unlikely he in fact did so. (199)
19With respect to the incident at the home of Sylvia Odio in Dallas (see sec. C 3), the CIA had developed since 1963 the ability to identify from physical descriptions possible intelligence agents who may have been involved. In fact, at the committee’s request, the CIA attempted to identify Odio’s visitors, and it determined that they may have been members of Cuban intelligence. (195) The committee showed photographs supplied by the CIA to Odio who stated they did not appear to be the visitors in question. (196) The committee came to the conclusion that had she been shown photographs in 1963, when the event was clearer in her mind, she might have been able to make an identification. It is also regrettable that the CIA did not make use of a defector from Cuba who had worked in intelligence and who might have been able to identify the Odio visitors. (197)
Page 129
While noting the deficiencies in the CIA assassination investigation, the committee was impressed with certain overseas capabilities of the CIA in 1963. The Agency had, for example, comprehensive coverage of anti-Castro Cuban groups that, in turn, had extensive information sources in and out of Cuba. (200) Thus, while it was flawed in certain specific respects, the committee concluded that the CIA assassination investigation could, in fact, be relied on–with only limited reservations– as a general indicator of possible Cuban involvement. That investigation found no evidence of Cuban complicity.
Top of Page
(i) Summary of the findings
While the committee did not take Castro’s denials at face value, it found persuasive reasons to conclude that the Cuban Government was not involved in the Kennedy assassination. First, by 1963 there were prospects for repairing the hostility that had marked relations between the two countries since Castro had come to power. Second, the risk of retaliation that Cuba would have incurred by conspiring in the assassination of an American President must have canceled out other considerations that might have argued for that act. President Castro’s description of the idea as “insane” is appropriate. And there was no evidence indicating an insane or grossly reckless lack of judgment on the part of the Cuban Government. Third, the CIA had both the motive to develop evidence of Cuban involvement and access to at least substantial, if incomplete, information bearing on relevant aspects of it, had such involvement existed. Its absence, therefore, must be weighed in the balance. Finally, the Cuban Government’s cooperation with this committee in the investigation must be a factor in any judgment. In conclusion, the committee found, on the basis of the evidence available to it, that the Cuban Government was not involved in the assassination of President Kennedy.
Top of Page
3. THE COMMITTEE BELIEVES, ON THE BASIS OF THE EVIDENCE AVAILABLE TO IT, THAT ANTI-CASTRO CUBAN GROUPS, AS GROUPS, WERE NOT INVOLVED IN THE ASSASSINATION OF PRESIDENT KENNEDY, BUT THAT THE AVAILABLE EVIDENCE DOES NOT PRECLUDE THE POSSIBILITY THAT INDIVIDUAL MEMBERS MAY HAVE BEEN INVOLVED
Go to the footnotes for this section.
- The anti-Castro perspective
- The missile crisis and its aftermath
- Attitude of anti-Castro Cubans toward Kennedy
- The committee investigation
- Homer S. Echevarria
- Antonio Veciana Blanch
- Silvia Odio
- Oswald and the anti-Castro Cubans
- Oswald in New Orleans
- Oswald in Clinton, La
- David Ferrie
- 544 Camp Street
- A committee analysis of Oswald in New Orleans
- Summary of the evidence
The committee investigated possible involvement in the assassination by a number of anti-Castro Cuban groups and individual activists for two primary reasons:
First, they had the motive, based on what they considered President Kennedy’s betrayal of their cause, the liberation of Cuba from the Castro regime; the means, since they were trained and practiced in violent acts, the result of the guerrilla warfare they were waging against Castro; and the opportunity, whenever the President, as he did from time to time, appeared at public gatherings, as in Dallas on November 22, 1963.
Second, the committee’s investigation revealed that certain associations of Lee Harvey Oswald were or may have been with anti-Castro activists.
The committee, therefore, paid close attention to the activities of anti-Castro Cubans–in Miami, where most of them were concentrated and their organizations were headquartered,(1) and in New Orleans
Page 130
and Dallas, where Oswald, while living in these cities in the months preceding the assassination, reportedly was in contact with anti-Castro activists.(2)
The Warren Commission did not, of course, ignore Oswald’s ties to anti-Castroites. From the evidence that was available in 1964, two Warren Commission staff attorneys, W. David Slawson and William Coleman, went so far as to speculate that Oswald, despite his public posture as a Castro sympathizer, might actually have been an agent of anti-Castro exiles.(3)Indeed, pressing for further investigation of the possibility, they wrote a memorandum which read in part:
The evidence here could lead to an anti-Castro involvement in the assassination on some sort of basis as this: Oswald could have become known to the Cubans as being strongly pro-Castro. He made no secret of his sympathies, so the anti-Castro Cubans must have realized that law enforcement authorities were also aware of Oswald’s feelings and that, therefore, if he got into trouble, the public would also learn of them …Second, someone in the anti-Castro organization might have been keen enough to sense that Oswald had a penchant for violence …On these facts, it is possible that some sort of deception was used to encourage Oswald to kill the President when he came to Dallas …The motive of this would, of course, be the expectation that after the President was killed, Oswald would be caught or at least his identity ascertained, the law enforcement authorities and the public would blame the assassination on the Castro government, and a call for its forceful overthrow would be irresistible…. (4)
While it is seemingly in contradiction of Oswald’s personal character and known public posture, the committee seriously considered, therefore, the possibility of an anti-Castro conspiracy in the assassination (perhaps with Oswald unaware of ifs true nature). It is appropriate to begin that consideration with an examination of the history of United States-Cuban relations from the perspective of the anti-Castro movement, beginning with the victorious end of the revolution on January 1, 1959. (5)
Top of Page
(a) The anti-Castro Cuban perspective
The anti-Castro movement began not long after Fidel Castro assumed control of Cuba. (6) at first, the Cuban people cheered the revolution and its leader for the defeat of the dictatorial Batista regime, but it was not long before many former supporters found reason to condemn the new premier’s policies and politics. (7) Many Cubans were deeply disillusioned when it became apparent that the Castro government was renouncing the country’s long affiliation with the United States and moving closer to the Soviet Union. (8) As Castro’s preference for Marxism became evident, underground opposition movements were born. (9) They survived for a time within Cuba, but as the effectiveness of Castro’s militia system was recognized, they retreated to the exile communities of Miami and other cities in the United States. (10)
The U.S. Government was responsive to the efforts of exiles to remove a Communist threat from the Caribbean, only 90 miles from the
Page 131
Florida coast, and to recapture business investments lost to the nationalization of industry in Cuba. (11) An official, yet covert, program to train and equip exiles determined to overthrow Castro was sanctioned by President Eisenhower and his successor, President Kennedy, and carried out by the American intelligence agencies, particularly the Central Intelligence Agency. (12). The Cuban exiles, dependent on the United States for arms and logistical support, had little choice but to put their trust in Washington. (13)
Their trust collapsed however, at the Bay of Pigs on April 17, 1961, when an exile invasion of Cuba was annihilated by Castro’s troops. (14) The failure of American airpower to support the landing shattered the confidence of the anti-Castro Cubans in the U.S. Government.(15) They blamed President Kennedy, and he publicly accepted responsibility for the defeat. (16)
President Kennedy’s readiness to take the blame for the Bay of Pigs served to intensify the anger of the exiles.(17) In executive session before the committee, Manuel Antonio Varona, who in 1961 was the head of the united exile organization, the Revolutionary Democratic Front, told of a tense and emotional encounter with the President at the White House, as hope for the invasion was fading.(18) “We were not charging Mr. Kennedy with anything,” Varona testified.(19) “We knew he was not in charge of the military efforts directly. Nevertheless, President Kennedy told us he was the one–the only one responsible.” (20)
A noted Cuban attorney, Mario Lazo, summed up Cuban feeling toward President Kennedy in his book, “Dagger in the Heart”:
The Bay of Pigs was wholly self-inflicted in Washington. Kennedy told the truth when he publicly accepted responsibility… The heroism of the beleaguered Cuban Brigade had been rewarded by betrayal, defeat, death for many of them, long and cruel imprisonment for the rest. The Cuban people …had always admired the United States as strong, rich, generous–but where was its sense of honor and the capacity of its leaders? (21)
President Kennedy was well aware of the bitter legacy of the Bay of Pigs debacle. Far from abandoning the Cuban exiles, he set out to convince them of his loyalty to their cause. One of the most emotionally charged events of his relationship with the Cuban exiles occurred on December 29, 1962, at the Orange Bowl in Miami. (22) He had come to welcome the survivors of the invasion force, Brigade 2506, the 1,200 men who had been ransomed from Cuba after almost 20 months in prison.(23) The President was presented with the brigade flag in a dramatic and tumultuous scene.
The euphoria was false and misleading. Although the Cuban exiles cheered President Kennedy that day, there also coursed through the crowd a bitter resentment among some who felt they were witnessing a display of political hypocrisy. Later, it would be claimed that the brigade feeling against President Kennedy was so strong that the presentation nearly did not take place, and it would be alleged (incorrectly, as it turned out) that the brigade flag given to Kennedy was actually a replica.(25)
Page 132
It is not possible to know fully how the Bay of Pigs defeat changed President Kennedy’s attitude toward Cuba, but when journalists Taylor Branch and George Crile wrote in Harper’s Magazine about a massive infusion of U.S. aid to clandestine anti-Castro operations in the wake of the Bay of Pigs, they titled their article, “The Kennedy Vendetta.”(26) What is known is that the period between the Bay of Pigs and the Cuban missile crisis in October 1962 can be characterized as the high point of anti-Castro activity. (27) Miami, the center of the exile community, became a busy staging ground for armed infiltrations Cuba.(28) While not every raid was supported or even known about in advance by Government agencies, the United States played a key role in monitoring, directing and supporting the anti-Castro Cubans. (29) Although this effort was cloaked in secrecy, most Cubans in the exile community knew what was happening and who was supporting the operations. (30)
Top of Page
(1) The missile crisis and its aftermath.–At the time of the missile crisis in October 1962, the Cuban exiles were initially elated at the prospect of U.S. military action that might topple the Castro regime.(31) In the end, it seemed to the world that President Kennedy had the best of the confrontation with Castro and Soviet leader Nikita Khrushchev by demanding, and getting, the withdrawal of offensive missiles and bombers from Cuba. From the exiles’ perspective, however, they had been compromised, since as part of the bargain, President Kennedy made a pledge not to invade Cuba. 20 (32)
Anti-Castro forces in the United States were all the more embittered in the spring of 1963 when the Federal Government closed down many of their training camps and guerrilla bases. (34) In cases where government raids intercepted the illegal arms transfers, weapons were confiscated and arrests were made.(35) Some anti-Castro operations did continue, however, right up to the time of the assassination, though the committee. found that U.S. backing had by that time been reduced. (36)
Top of Page
(2) Attitude of anti-Castro Cubans toward Kennedy.–President Kennedy’s popularity among the Cuban exiles had plunged deeply by 1963. Their bitterness is illustrated in a tape recording of a meeting of anti-Castro Cubans and right-wing Americans in the Dallas suburb of Farmer’s Branch on October 1, 1963. (37) In it, a Cuban identified as Nestor Castellanos vehemently criticized the United States and blamed President Kennedy for the U.S. Government’s policy of “non-interference” with respect to the Cuban issue. (38)Holding a copy of the September 26 edition of the Dallas Morning News, featuring a front-page account of the President’s planned trip to Texas in November, Castellanos vented his hostility without restraint:
CASTELLANOS. …we’re waiting for Kennedy the 22d, buddy. We’re going to see him in one way or the other. We’re going to give him the works when he gets in Dallas. Mr. good ol’ Kennedy. I wouldn’t even call him President Kennedy He stinks.
20The United States never actually signed the pledge, since it was conditioned on United Nations inspection of the weapons withdrawal that Castro would not honor. The fine point of signing the pledge was of little importance to the Cuban exiles, however, who could point out later that no invasion did, in fact, occur. (33)
Page 133
QUESTIONER. Are you insinuating that since this downfall came through the leader there [Castro in Cuba], that this might come to us …?
CASTELLANOS. Yes ma’am, your present leader. He’s the one who is doing everything right now to help the United States to become Communist.21 (39)
Top of Page
(b) The committee investigation
The committee initiated its investigation by identifying the most violent and frustrated anti-Castro groups and their leaders from among the more than 100 Cuban exile organizations in existence in November 1963. (40) These groups included Alpha 66, the Cuban Revolutionary Junta (JURE), Commandos L, the Directorio Revolutionary Estudiantil (DRE), the Cuban Revolutionary Council (CRC) which included the Frente Revolucionario Democratico (FRD), the Junta del Gobierno de Cuba en el Exilio (JGCE), the 30th of November, the International Penetration Forces (InterPen), the Revolutionary Recovery Movement (MRR), and the Ejercito Invasor Cubano (EIC).(41) Their election evolved both from the committee’s independent field investigation and the examination of the files and records maintained by the Federal and local agencies then monitoring Cuban exile activity. These agencies included local police departments, the FBI, the CIA, the Bureau of Narcotics and Dangerous Drugs (now the Drug Enforcement Administration, or DEA), the Customs Service, the Immigration and Naturalization Service and the Department of Defense.
The groups that received the committee’s attention were “action groups”–those most involved in military actions and propaganda campaigns. Unlike most others, they did not merely talk about anti-Castro operations, they actually carried out infiltrations into Cuba, planned, and sometimes attempted, Castro’s assassination, and shipped arms into Cuba. These were also the groups whose leaders felt most betrayed by U.S. policy toward Cuba and by the President; they were also those whose operations were frustrated by American law enforcement efforts after the missile crisis.
Top of Page
(1) Homer S. Echevarria.—For the most part the committee found that the anti-Castro Cuban leaders were more vociferous than potentially violent in their tirades against the President. Nevertheless, it was unable to conclude with certainty that all of the threats were benign. For example, one that the committee found particularly disturbing especially so, since it was not thoroughly looked into in the 1963-64 investigation came to the attention of the Secret Service within days of the President’s death, prompting the Acting Special Agent-in-Charge of the Chicago field office to write an urgent memorandum indicating he had received reliable information of “a group in the Chicago area who [sic] may have a connection with the J.F.K. assassination.”(43) The memorandum was based on a tip from an informant who reported a conversation on November 21, 1963, with a Cuban activist named Homer S. Echevarria.(44) They were discussing an illegal arms sale, and Echevarria was quoted as saying his group now
21The committee uncovered no evidence that linked Castellanos to the assassination. His speech is quoted to illustrate the depth of feeling that existed in the Cuban exile community in 1963.
Page 134
had “plenty of money” and that his backers would proceed “as soon as we take care of Kennedy.” (45)
Following the initial memorandum, the Secret Service instructed its informant to continue his association with Echevarria and notified the Chicago FBI field office. (46) It learned that Echevarria might have been a member of the 30th of November anti-Castro organization, that he was associated with Juan Francisco Blanco-Fernandez, military director of the DRE, and that the arms deal was being financed through one Paulino Sierra Martinez by hoodlum elements in Chicago and elsewhere.(47)
Although the Secret Service recommended further investigation, the FBI initially took the position that the Echevarria case “was primarily a protection matter and that the continued investigation would be left to the U.S. Secret Service,” (48) and that the Cuban group in question was probably not involved in illegal activities. (49) The Secret Service initially was reluctant to accept this position, since it had developed evidence that illegal acts were, in fact, involved. (50) Then, on November 29, 1963, President Johnson created the Warren Commission and gave the FBI primary investigative responsibility in the assassination.(51) Based on its initial understanding that the President’s order meant primary, not exclusive, investigative responsibility, the Secret Service continued its efforts;(52) but when the FBI made clear that it wanted the Secret Service to terminate its investigation, (53) it did so, turning over its files to the FBI. (54) The FBI, in turn, did not pursue the Echevarria case. (55)
While it was unable to substantiate the content of the informant’s alleged conversations with Echevarria or any connection to the events in Dallas, the committee did establish that the original judgment of the Secret Service was correct, that the Echevarria case did warrant a thorough investigation. It found, for example, that the 30th of November group was backed financially by the Junta del Gobierno de Cuba en el Exilio (JGCE), a Chicago-based organization run by Paulino Sierra Martinez.(56) JGCE was a coalition of many of the more active anti-Castro groups that had been rounded in April 1963; it was dissolved soon after the assassination. 22 (57) Its purpose was to back the activities of the more militant groups, including Alpha 66 and the Student Directorate, or DRE, both of which had reportedly been in contact with Lee Harvey Oswald. (58) Much of JGCE’s financial support, moreover, allegedly came from individuals connected to organized crime. (59)
As it surveyed the various anti-Castro organizations, the committee focused its interest on reported contacts with Oswald. Unless an association with the President’s assassin could be established, it is doubtful that it could be shown that the anti-Castro groups were involved in the assassination. The Warren Commission, discounting the recommendations of Slawson and Coleman, had either regarded these contacts as insignificant or as probably not having been made or else was not aware of them. (60) The committee could not so easily dismiss them.
22The committee established– though it could make no judgment about there having been a connection– that many of the anti-Castro Cuban groups ceased their operations at about the time of President Kennedy’s assassination. The Echevarria allegation is also discussed in section I D (1)(b) infra.
Page 135
Top of Page
(2) Antonio Veciana Blanch.–The committee devoted a significant portion of its anti-Castro Cuban investigation to an alleged contact with Oswald that had been reported by Antonio Veciana Blanch, the founder of Alpha 66 which, throughout 1962 and most of 1963, was one of the most militant of the exile groups. (61) Its repeated hit-and-run attacks had drawn public criticism from President Kennedy in the spring of 1963, to which Veciana replied, “We are going to attack again and again.”
Veciana claimed to have had the active support of the CIA, and in 1976 he reported to a Senate investigator that from 1960 to 1973 his adviser, whom he believed to be a representative of the CIA, was known to him as Maurice Bishop. (62) Veciana stated that over their 13-year association, he and Bishop met on over 100 occasions and that Bishop actually planned many Alpha 66 operations. (63) He also said that he knew the man only, as Maurice Bishop and that all of their contacts were initiated by Bishop. (64)
Veciana said that Bishop had guided him in planning assassination attempts of Castro in Havana in 1961 and in Chile in 1971; that Bishop had directed him to organize Alpha 66 in 1962; and that Bishop, on ending their relationship in 1973, had paid him $253,000 in cash for his services over the years. (65) Veciana also revealed that at one meeting with Bishop in Dallas in late August or early September 1963, a third party at their meeting was a man he later recognized as Lee Harvey Oswald. (66)
Veciana also indicated to the committee that subsequent to the assassination, he had been contacted by Bishop, who was aware that Veciana had a relative in Cuban intelligence in Mexico.(67) Bishop, according to Veciana, offered to pay Veciana’s relative a large sum of money if he would say that it was he and his wife who had met with Oswald in Mexico City.(68) Veciana said he had agreed to contact his relative, but he had been unable to do so. (69)
The committee pursued the details of Veciana’s story, particularly the alleged meeting with Oswald. It conducted numerous file reviews and interviews with associates and former associates of Veciana, to try to confirm the existence of a Maurice Bishop or otherwise assess Veciana’s credibility. On a trip to Cuba, the committee interviewed Veciana’s relative, the Cuban intelligence agent.
While the committee was unable to find corroboration for the contacts with Bishop, it did substantiate other statements by Veciana. For example, he did organize an attempted assassination of Castro in Havana in 1961, (70) and he probably did participate in another plot against Castro in Chile in 1971. (71) That Veciana was the principal organizer of the militant Alpha 66 organization was a matter of record. (72)
The committee went to great lengths in its unsuccessful effort to substantiate the existence of Bishop and his alleged relationship with Oswald. It reviewed CIA files, but they showed no record of such an agent or employee. It circulated a sketch via the national news media, but no one responded with an identification. (73) It pursued a lead originating with the Senate investigation that a former chief of the CIA’s Western Hemisphere Division of the Directorate of Operations bore a resemblance to the Bishop sketch.(74) The committee arranged for
Page 136
a chance meeting between Veciana and the CIA officer, who had since retired. (75) Veciana said he was not Bishop. (76) In an executive session of the committee, the retired officer testified under oath that he had never used the name Maurice Bishop, had never known anyone by that name and had never known Veciana. (77) Veciana, also before a committee executive session, testified the officer was not Bishop although he bore a “physical similarity.”23 (78)
A former Director of the CIA, John McCone, and an agent who had participated in covert Cuban operations, each told the committee they recalled that a Maurice Bishop had been associated with the Agency, though neither could supply additional details.(80) Subsequently, McCone was interviewed by CIA personnel, and he told them that his original testimony to the committee had been in error. (81) The agent did confirm, however, even after a CIA reinterview, that he had seen the man known to him as Maurice Bishop three or four times at CIA headquarters in the early 1960’s. (82) He did not know his organizational responsibilities, and he had not known him personally. (83) The agent also testified that he had been acquainted with the retired officer who had been chief of the Western Hemisphere Division and that he was not Bishop. (84)
The committee also requested flies on Bishop from the FBI and Department of Defense, with negative results.(85) It did discover, however, that Army intelligence had an operational interest in Veciana as a source of information on Alpha 66 activities, and that Veciana complied, hoping to be supplied in return with funds and weapons. (86) Veciana acknowledged his contacts with the Army, but he stated that the only relationship those contacts had to Bishop was that he kept Bishop informed of them. (87)
The CIA’s files reflected that the Agency had been in contact with Veciana three times during the early 1960’s, but the Agency maintained it offered him no encouragement.(88) (The committee could discover only one piece of arguably contradictory evidence–a record of $500 in operational expenses, given to Veciana by a person with whom the CIA had maintained a long-standing operational relationship. (89) The CIA further insisted that it did not at any time assign a case officer to Veciana. 24 (90)
The committee was left with the task of evaluating Veciana’s story, both with respect to the existence of Maurice Bishop and the alleged meeting with Oswald, by assessing Veciana’s credibility. It found several reasons to believe that Veciana had been less than candid:
23The committee suspected that Veciana was lying when he denied that the retired CIA officer was Bishop. The committee recognized that Veciana had an interest in renewing his anti-Castro operations that might have led him to protect the officer from exposure as Bishop so they could work together again. For his part, the retired officer aroused the committee’s suspicion when he told the committee he did not recognize Veciana as the founder of Alpha 66, especially since the officer had once been deeply involved in Agency anti-Castro operations. Further, a former CIA case officer who was assigned from September 1960 to November 1962 to the JM/WAVE station in Miami told the committee that the retired officer had in fact used the alias, Maurice Bishop. The committee also interviewed a former assistant of the retired officer but he could not recall his former superior ever having used the name or having been referred to as Bishop. (79)
24The committee found it probable that some agency of the United States assigned a case officer to Veciana, since he was the dominant figure in an extremely active anti-Castro organization. The committee established that the CIA assigned case officers to Cuban revolutionaries of less importance than Veciana, though it could not draw from that alone an inference of CIA deception of the committee concerning Veciana, since Bishop could well have been in the employ of one of the military intelligence agencies or even perhaps of some foreign power.
Page 137
First, Veciana waited more than 10 years after the assassination to reveal his story.
Second, Veciana would not supply proof of the $253,000 payment from Bishop, claiming fear of the Internal Revenue Service.
Third, Veciana could not point to a single witness to his meetings with Bishop, much less with Oswald.
Fourth, Veciana did little to help the committee identify Bishop.
In the absence of corroboration or independent substantiation, the committee could not, therefore, credit Veciana’s story of having met with Lee Harvey Oswald.
Top of Page
(3) Silvia Odio. The incident of reported contact between Oswald and anti-Castro Cubans that has gained the most attention over the years involved Silvia Odio, a member of the Cuban Revolutionary Junta, or JURE. (91) Mrs. Odio had not volunteered her information to the FBI.(92) The FBI initially contacted Mrs. Odio after hearing of a conversation she had had with her neighbor in which she described an encounter with Lee Harvey Oswald. (93) Subsequently, in testimony before the Warren Commission, she said that in late September 1963, three men came to her home in Dallas to ask for help in preparing a fundraising letter for JURE.(94) She stated that two of the men appeared to be Cubans, although they also had characteristics that she associated with Mexicans. (95) The two individuals, she remembered, indicated that their “war” names were “Leopoldo” and “Angelo.”(96) The third man, an American, was introduced to her as “Leon Oswald,” and she was told that he was very much interested in the anti-Castro Cuban cause. (97)
Mrs. Odio stated that the men told her that they had just come from New Orleans and that they were then about to leave on a trip. (98) The next day, one of the Cubans called her on the telephone and told her that it had been his idea to introduce the American into the underground “…because he is great, he is kind of nuts.” (99) The Cuban also said that the American had been in the Marine Corps and was an excellent shot, and that the American had said that Cubans “…don’t have any guts …because President Kennedy should have been assassinated after the Bay of Pigs, and some Cubans should have done that, because he was the one that was holding the freedom of Cuba actually.”(100) Mrs. Odio claimed the American was Lee Harvey Oswald. (101)
Mrs. Odio’s sister, who was in the apartment at the time of the visit by the three men and who stated that she saw them briefly in the hallway when answering the door, also believed that the American was Lee Harvey Oswald. (102) Mrs. Odio fixed the date of the alleged visit as being September 26 or 27.(103) She was positive that the visit occurred prior to October 1. (104)
The Warren Commission was persuaded that Oswald could not have been in Dallas on the dates given by Mrs. Odio. (105) Nevertheless, it requested the FBI to conduct further investigation into her allegation, and it acknowledged that the FBI had not completed its Odio investigation at the time its report was published in September 1964. (106)
How the Warren Commission treated the Odio incident is instructive. In the summer of 1964, the FBI was pressed to dig more deeply into the Odio allegation. (107) On July 24, chief counsel J. Lee Rankin,
Page 138
in a letter to FBI Director J. Edgar Hoover, noted, “… the Commission already possesses firm evidence that Lee Harvey Oswald was on a bus traveling from Houston, Tex., to Mexico City, Mexico, on virtually the entire day of September 26.”(108) J. Wesley Liebeler, the Warren Commission assistant counsel who had taken Mrs. Odio’s deposition, disagreed, however, that there was firm evidence of Oswald’s bus trip to Mexico City. (109) In a memorandum to another Commission attorney, Howard Willens, on September 14, 1964, Liebeler objected to a section of the Warren Report in which it was stated there was strong evidence that Oswald was on a bus to Mexico on the date in question.(110) Liebeler argued, “There really is no evidence at all that [Oswald] left Houston on that bus.”(111) Liebeler also argued that the conclusion that there was “persuasive” evidence that Oswald was not in Dallas on September 24, 1963, a day for which his travel was unaccounted, was “too strong.” (112) Liebeler urged Willens to tone down the language, of the report,(113) contending in his memorandum:”There are problems. Odio may well be right. The Commission will look bad if it turns out that she is.” (114)
On August 23, 1964, Rankin again wrote to Hoover to say, “It is a matter of some importance to the Commission that Mrs. Odio’s allegation either be proved or disproved.” (115) Rankin asked that the FBI attempt to learn the identities of the three visitors by contacting members of anti-Castro groups active in the Dallas area, as well as leaders of the JURE organization. (116) He asked the FBI to check the possibility that Oswald had spent the night of September 24, in a hotel in New Orleans, after vacating his apartment. (117) Portions of this investigation, which were inconclusive in supporting the Warren Commission’s contention that Mrs. Odio was mistaken, were not sent to Rankin until November 9,(118) at which time the final report already had been completed. (119)
The FBI did attempt to alleviate the “problems.” In a report dated September 26, it reported the interview of Loran Eugene Hall who claimed he had been in Dallas in September 1963, accompanied by two men fitting the general description given by Silvia Odio, and that it was they who had visited her. (120) Oswald, Hall said, was not one of the men.(121) Within a week of Hall’s statement, the other two men Hall said had accompanied him. Lawrence Howard and William Seymour, were interviewed.(122) They denied ever having met Silvia Odio. (123) Later, Hall himself retracted his statement about meeting with Mrs. Odio. (124)
Even though the Commission could not show conclusively that Oswald was not at the Odio apartment, and even though Loran Hall’s story was an admitted fabrication, the Warren report published this explanation of the Odio incident:
While the FBI had not yet completed its investigation into this matter at the time the report went to press, the Commission has concluded that Lee Harvey Oswald was not at Mrs. Odio’s apartment in September 1963. (125)
Not satisfied with that conclusion, the committee conducted interviews with and took depositions from the principals–Silvia Odio,(126) members of her family,(127) and Dr. Burton Einspruch,
Page 139
(128) her psychiatrist. (Mrs. Odio had contacted Dr. Einspruch for consultation about problems that could not be construed to affect her perception or credibility.) (129) The committee also set up a conference telephone call between Dr. Einspruch in Dallas and Silvia Odio in Miami, during which she related to him the visit of the three men. (130) Mrs. Odio and Dr. Einspruch concurred that she had told him of the nighttime meeting shortly after its occurrence, but prior to the president’s assassination.(131)
Loran Hall testified before the committee in executive session on October 5, 1977; Howard and Seymour were interviewed.(132) The FBI agent who wrote up the Hall story also testified before the committee. (133) From a review of FBI files, the committee secured a list of persons who belonged to the Dallas Chapter of JURE, and the committee attempted to locate and interview these individuals. Additionally, staff investigators interviewed the leader of JURE, Manolo Ray, who was residing in Puerto Rico. (134)
Further, the committee secured photographs of scores of pro-Castro and anti-Castro activists who might have fit the descriptions of the two individuals who, Mrs. Odio said, had visited her with Oswald. (135) The committee also used the resources of the CIA which conducted a check on all individuals who used the “war” names of “Leopoldo” and “Angelo”, and the name “Leon”, or had similar names. (136) An extensive search produced the names and photographs of three men who might possibly have, been in Dallas in September 1963. (137) These photographs were shown to Mrs. Odio, but she was unable to identify them as the men she had seen. (138)
The committee was inclined to believe Silvia Odio. From the evidence provided in the sworn testimony of the witnesses, it appeared that three men did visit her apartment in Dallas prior to the Kennedy assassination and identified themselves as members of an anti-Castro organization. Based on a judgment of the credibility of Silvia and Annie Odio, one of these men at least looked like Lee Harvey Oswald and was introduced to Mrs. Odio as Leon Oswald.
The committee did not agree with the Warren Commission’s conclusion that Oswald could not have been in Dallas at the requisite time. Nevertheless, the committee itself could reach no definite conclusion on the specific date of the visit. It could have been as early as September 24, the morning of which Oswald was seen in New Orleans,(139) but it was more likely on the 25th, 26th or 27th of September. If it was on these dates, then Oswald had to have had access to private transportation to have traveled through Dallas and still reached Mexico City when he did, judging from other evidence developed by both the Warren Commission and the committee. (140)
Top of Page
(c) Oswald and anti-Castro Cubans
The committee recognized that an association by Oswald with anti-Castro Cubans would pose problems for its evaluation of the assassin and what might have motivated him. In reviewing Oswald’s life, the committee found his actions and values to have been those of a self-proclaimed Marxist who would be bound to favor the Castro regime in Cuba, or at least not advocate its overthrow. For this reason, it did not seem likely to the committee that Oswald would have allied
Page 140
himself with an anti-Castro group or individual activist for the sole purpose of furthering the anti-Castro cause. The committee recognized the possibility that Oswald might have established contacts with such groups or persons to implicate the anti-Castro movement in the assassination. Such an implication might have protected the Castro regime and other left-wing suspects, while resulting in an intensive investigation and possible neutralization of the opponents of Castro. It is also possible, despite his alleged remark about killing Kennedy, that Oswald had not yet contemplated the President’s assassination at the time of the Odio incident, or if he did, that his assassination plan had no relation to his anti-Castro contacts, and that he was associating with anti-Castro activists for some other unrelated reason. A variety of speculations are possible, but the committee was forced to acknowledge frankly that, despite its efforts, it was unable to reach firm conclusions as to the meaning or significance of the Odio incident to the President’s assassination.
Top of Page
(1) Oswald in New Orleans.–Another contact by Lee Harvey Oswald with anti-Castro Cuban activists that was not only documented, but also publicized at the time in the news media, occurred when he was living in New Orleans in the summer of 1963, an especially puzzling period in Oswald’s life. His actions were blatantly pro-Castro, as he carried a one-man Fair Play for Cuba Committee crusade into the streets of a city whose Cuban population was predominantly anti-Castro. Yet Oswald’s known and alleged associations even at this time included Cubans who were of an anti-Castro persuasion and their anti-Communist American supporters.
New Orleans was Oswald’s home town; he was born there on October 18, 1939.(141) In April 1963, shortly after the Walker shooting, he moved back, having lived in Fort Worth and Dallas since his return from the Soviet Union the previous June.(142) He spent the first 2 weeks job hunting, staying with the Murrets, Lillian and Charles, or “Dutz,” as he was called, the sister and brother-in-law of Oswald’s mother, Marguerite. (143) After being hired by the Reily Coffee Co. as a maintenance man, he sent for his wife Marina and their baby daughter, who were still in Dallas, and they moved into an apartment on Magazine Street.
In May, Oswald wrote to Vincent T. Lee, national director of the Fair Play for Cuba Committee, expressing a desire to open an FPCC chapter in New Orleans and requesting literature to distribute. (145) He also had handouts printed, some of which were stamped “L. H. Oswald, 4907 Magazine Street,” others with the alias, “A. J. Hidell, P.O. Box 30016,” still others listing the FPCC address as 544 Camp Street. (146)
In letters written earlier that summer and spring to the FPCC headquarters in New York, Oswald had indicated that he intended to rent an office.(147) In one letter he mentioned that he had acquired a space but had been told to vacate 3 days later because the building was to be remodeled. The Warren Commission failed to discover any record of Oswald’s having rented an office at 544 Camp and concluded he had fabricated the story. (149)
In investigating Oswald after the assassination, the Secret Service learned that the New Orleans chapter of the Cuban Revolutionary
Page 141
Council (CRC), an anti-Castro organization, had occupied an office at 544 Camp Street for about 6 months during 1961-62.(150) At that time, Sergio Arcacha Smith was the official CRC delegate for the New Orleans area.(151) Since the CRC had vacated the building 15 months before Oswald arrived in New Orleans, the Warren Commission concluded that there was no connection with Oswald.(152) Nevertheless, the riddle of 544 Camp Street persisted over the years.
Oswald lost his job at the Reily Coffee Co. in July, and his efforts to find another were futile.(153) Through the rest of the summer, he filed claims at the unemployment office.
On August 5, Oswald initiated contact with Carlos Bringuier, a delegate of the Directorio Revolucionario Estudiantil (DRE).(155) According to his testimony before the Warren Commission, Bringuier was the only registered member of the group in New Orleans. (156) Bringuier also said he had two friends at the time, Celso Hernandez and Miguel Cruz, who were also active in the anti-Castro cause. (157) Oswald reportedly told Bringuier that he wished to join the DRE, offering money and assistance to train guerrillas.(158) Bringuier, fearful of an infiltration attempt by Castro sympathizers or the FBI, told Oswald to deal directly with DRE headquarters in Miami. (159) The next day, Oswald returned to Bringuier’s store and left a copy of a Marine training manual with Rolando Pelaez, Bringuier’s brother-in-law. (160)
On August 9, Bringuier learned that a man was carrying a pro-Castro sign and handing out literature on Canal Street. (161) Carrying his own anti-Castro sign, Bringuier, along with Hernandez and Cruz, set out to demonstrate against the pro-Castro sympathizer. (162) Bringuier recognized Oswald and began shouting that he was a traitor and a Communist.(163) A scuffle ensued, and police arrested all participants.(164) Oswald spent the night in jail.(165) On August 12, he pleaded guilty to disturbing the peace and was fined $10. (166) The anti-Castro Cubans were not charged. (167)
During the incident with Bringuier, Oswald also encountered Frank Bartes, the New Orleans delegate of the CRC from 1962-64.(168) After Bringuier and Oswald were arrested in the street scuffle, Bartes appeared in court with Bringuier. (169) According Bartes, the news media surrounded Oswald for a statement after the hearing. (170) Bartes then engaged in an argument with the media and Oswald because the Cubans were not being given an opportunity to present their anti-Castro views. (171)
On August 16, Oswald was again seen distributing pro-Castro literature.(172) A friend of Bringuier, Carlos Quiroga, brought one of Oswald’s leaflets to Bringuier and volunteered to visit Oswald and feign interest in the FPCC in order to determine Oswald’s motives. (173) Quiroga met with Oswald for about an hour.(174) He learned that Oswald had a Russian wife and spoke Russian himself. Oswald gave Quiroga an application for membership in the FPCC chapter, but Quiroga noted he did not seem intent on actually enlisting members. (175)
Oswald’s campaign received newspaper, television, and radio coverage. (176) William Stuckey, a reporter for radio station WDSU who had been following the FPCC, interviewed Oswald on August 17 and
Page 142
proposed a television debate between Oswald and Bringuier, to be held on August 21. (177) Bringuier issued a press release immediately after the debate, urging the citizens of New Orleans to write their Congressmen demanding a congressional investigation of Lee Harvey Oswald.(178)
Oswald largely passed out of sight from August 21 until September 17, the day he applied for a tourist card to Mexico.(179) He is known to have written letters to left-wing political organizations, and he and Marina visited the Murrets on Labor Day. (180) Marina said her husband spent his free time reading books and practicing with his rifle. (181)
Top of Page
(2) Oswald in Clinton, La.–While reports of some Oswald contacts with anti-Castro Cubans were known at the time of the 1964 investigation, allegations of additional Cuba-related associations surfaced in subsequent years. As an example, Oswald reportedly appeared in August-September 1963 in Clinton, La., where a voting rights demonstration was in progress. The reports of Oswald in Clinton were not, as far as the committee could determine, available to the Warren Commission, although one witness said he notified the FBI when he recognized Oswald from news photographs right after the assassination.25 (182) In fact, the Clinton sightings did not publicly surface until 1967, when they were introduced as evidence in the assassination investigation being conducted by New Orleans District Attorney Jim Garrison.(184) In that investigation, one suspect, David W. Ferrie, a staunch anti-Castro partisan, died within days of having been named by Garrison; the other, Clay L. Shaw, was acquitted in 1969.(185) Aware that Garrison had been fairly criticized for questionable tactics, the committee proceeded cautiously, making sure to determine on its own the credibility of information coming from his probe. The committee found that the Clinton witnesses were credible and significant. They each were interviewed or deposed, or appeared before the committee in executive session. While there were points that could be raised to call into question their credibility, it was the judgment of the committee that they were telling the truth as they knew it.
There were six Clinton witnesses, among them a State representative, a deputy sheriff and a registrar of voters. (186) By synthesizing the testimony of all of them, since they each contributed to the overall account, the committee was able to piece together the following sequence of events.
Clinton, La. about 130 miles from New Orleans, is the county seat of East Feliciana Parish. In the late summer of 1963 it was targeted by the Congress of Racial Equality for a voting rights campaign. (187) Oswald first showed up in nearby Jackson, La., seeking employment at East Louisiana State Hospital, a mental institution. (188) Apparently on advice that his job would depend on his becoming a registered voter, Oswald went to Clinton for that purpose (although the committee could find no record that he was successful. (189)
In addition to the physical descriptions they gave that matched that of Oswald, other observations of the witnesses tended to substanti-
25Reeves Morgan, a member of the Louisiana Legislature, testified he was called back by the FBI a few days later and asked what Oswald had been wearing. He said he was not contacted again. The FBI had not record of Morgan’s call. (183)
Page 143
ate their belief that he was, in fact, the man they saw. For example, he referred to himself as “Oswald,” and he produced his Marine Corps discharge papers as identification.(190) Some of the witnesses said that Oswald was accompanied by two older men whom they identified as Ferrie and Shaw. (191) If the witnesses were not only truthful but accurate as well in their accounts, they established an association of an undetermined nature between Ferrie, Shaw and Oswald less than 3 months before the assassination.
Top of Page
(3) David Ferrie.–The Clinton witnesses were not the only ones who linked Oswald to Ferrie. On November 23, the day after the assassination, Jack S. Martin, a part-time private detective and police informant, told the office of the New Orleans District Attorney that a former Eastern Airlines pilot named David Ferrie might have aided Oswald in the assassination. (192) Martin had known Ferrie for over 2 years, beginning when he and Ferrie had performed some investigative work on a case involving an illegitimate religious order in Louisville, Ky. (193) Martin advised Assistant New Orleans District Attorney Herman Kohlman that he suspected Ferrie might have known Oswald for some time and that Ferrie might have once been Oswald’s superior officer in a New Orleans unit of the Civil Air Patrol.(194) Martin made further allegations to the FBI on November 25.(195) He indicated he thought he once saw a photograph of Oswald and other CAP members when he visited Ferrie’s home and that Ferrie might have assisted Oswald in purchasing a foreign firearm.(196) Martin also informed the FBI that Ferrie had a history of arrests and that Ferrie was an amateur hypnotist, possibly capable of hypnotizing Oswald. (197)
The committee reviewed Ferrie’s background. He had been fired by Eastern Airlines,(198) and in litigation over the dismissal, which continued through August 1963, he was counseled by a New Orleans attorney named G. Wray Gill. (199) Ferrie later stated that in March 1960, he and Gill made an agreement whereby Gill would represent Ferrie in his dismissal dispute in return for Ferrie’s work as an investigator on other cases. (200) One of these cases involved deportation proceedings against Carlos Marcello, the head of the organized crime network in Louisiana and a client of Gill.26 (201) Ferrie also said he had entered into a similar agreement with Guy Banister, a former FBI agent (Special Agent-in-Charge in Chicago) who had opened a private detective agency in New Orleans. (203)
Top of Page
(4) 544 Camp Street.–Banister’s firm occupied an office in 1963 in the Newman Building at 531 Lafayette Street. (204) Another entrance to the building was at 544 Camp Street, the address Oswald had stamped on his Fair Play for Cuba Committee handouts. (205) During the summer of 1963, Ferrie frequented 544 Camp Street regularly as a result of his working relationship with Banister. (206)
Another occupant of the Newman Building, was the Cuban Revolutionary Council, whose chief New Orleans delegate until 1962 was Ser-
26The committee learned that Ferrie’s associations with Marcello might have begun earlier. An unconfirmed U.S. border Patrol report indicated that in February 1962, Ferrie piloted an airplane that returned Marcello to the United States following his ouster from the country by Federal agents in April 1961, as part of the Kennedy administration’s crackdown on organized crime. Marcello denied to the committee in executive session that Ferrie flew him out of Latin America, saying that he flew commercial airlines. Records do not exist that can confirm or refute this contention. (202)
Page 144
gio Arcacha Smith. (207) He was replaced by Luis Rabel who, in turn, was succeeded by Frank Bartes.(208) The committee interviewed or deposed all three CRC New Orleans delegates. (209) Arcacha said he never encountered Oswald and that he left New Orleans when he was relieved of his CRC position in early 1962. (210) Rabel said he held the post from January to October 1962, but that he likewise never knew or saw Oswald and that the only time he went to the Newman Building was to remove some office materials that Arcacha had left there. (211) Bartes said the only time he was in contact with Oswald was in their courtroom confrontation, that he ran the CRC chapter from an office in his home and that he never visited an office at either 544 Camp Street or 531 Lafayette Street. (212)
The committee, on the other hand, developed information that, in 1961, Banister, Ferrie, and Arcacha were working together in the anti-Castro cause. Banister, a fervent anti-Communist, was helping to establish Friends of Democratic Cuba as an adjunct to the New Orleans CRC chapter run by Arcacha in an office in the Newman Building. (213) Banister was also conducting background investigations of CRC members for Arcacha.(214) Ferrie, also strongly anti-Communist and anti-Castro, was associated with Arcacha (and probably Banister) in anti-Castro activism. (215)
On November 22, 1963, Ferrie had been in a Federal courtroom in New Orleans in connection with legal proceedings against Carlos Marcello.27 (216) That night he drove, with two young friends, to Houston, Tex. then to Galveston on Saturday, November 23, and back to New Orleans on Sunday. (218) Before reaching New Orleans, he learned from a telephone conversation with G. Wray Gill that Martin had implicated him in the, assassination.(219) Gill also told Ferrie about the rumors that he and Oswald had served together in the CAP and that Oswald supposedly had Ferrie’s library card in his possession when he was arrested in Dallas.(220) When he got to his residence, Ferrie did not go in, but sent in his place one of his companions on the trip, Alvin Beauboeuf.(221) Beauboeuf and Ferrie’s roommate, Layton Martens, were detained by officers from the district attorney’s office. (222) Ferrie drove to Hammond, La, and spent the night with a friend. (223)
On Monday, November 25, Ferrie turned himself in to the district attorney’s office where he was arrested on suspicion of being involved in the assassination. (224) In subsequent interviews with New Orleans authorities, the FBI and the Secret Service, Ferrie denied ever having known Oswald or having ever been involved in the assassination. (225) He stated that in the days preceding, November 22, he had been working intensively for Gill on the Marcello case. (226) Ferrie said he was in New Orleans on the morning of November 22, at which time Marcello was acquitted in Federal court of citizenship falsification. (227) He stated that he took the weekend trip to Texas for relaxation.(228) Ferrie acknowledged knowing Jack Martin, stating that Martin resented him for forcibly removing him from Gill’s office earlier that year. (229)
27With Ferrie’s employer G. Wray Gill as his counsel, Marcello was successfully resisting any attempt by the Government to have him legally deported or convicted of a crime. (217)
Page 145
The FBI and Secret Service investigation into the possibility that Ferrie and Oswald head been associated ended a few days later.(230) A Secret Service report concluded that the information provided by Jack Martin that Ferrie had been associated with Oswald and had trained him to fire, a rifle was “without foundation.” (231) The Secret Service report went on to state that on November 26, 1963, the FBI had informed the Secret Service that Martin had admitted that his information was a “figment of his imagination.” 28(232) The investigation of Ferrie was subsequently closed for lack of evidence against him.(234)
Top of Page
(5) A committee analysis of Oswald in New Orleans.—The Warren Commission had attempted to reconstruct a daily chronology of Oswald’s activities in New Orleans during the summer of 1963, and the committee used it, as well as information arising from critics and the Garrison investigation, to select events and contacts that merited closer analysis. Among these were Oswald’s confrontation with Carlos Bringuier and with Frank Bartes, his reported activities in Clinton, La., and his ties, if any, to Guy Banister, David Ferrie, Sergio Arcacha Smith and others who frequented the office building at 544 Camp Street. The committee deposed Carlos Bringuier and interviewed or deposed several of his associates. (235) It concluded that there had been no relationship between Oswald and Bringuier and the DRE with the exception of the confrontation over Oswald’s distribution of pro-Castro literature. The committee was not able to determine why Oswald approached the anti-Castro Cubans, but it tended to concur with Bringuier and others in their belief that Oswald was seeking to infiltrate their ranks and obtain information about their activities.
As noted, the committee believed the Clinton witnesses to be telling the truth as they knew it. It was, therefore, inclined to believe that Oswald was in Clinton, La., in late August, early September 1963, and that he was in the company of David Ferrie, if not Clay Shaw. The committee was puzzled by Oswald’s apparent association with Ferrie, a person whose anti-Castro sentiments were so distant from those of Oswald, the Fair Play for Cuba Committee campaigner. But the relationship with Ferrie may have been significant for more than its anti-Castro aspect, in light of Ferrie’s connection with G. Wray Gill and Carlos Marcello.
The committee also found that there was at least possibility that Oswald and Guy Banister were acquainted. The following facts were considered:
The 544 Camp Street address stamped on Oswald’s FPCC handouts was that of the building where Banister had his office;
Ross Banister told the committee that his brother had seen Oswald handing out FPCC literature during the summer of 1963; (236) and
Banister’s secretary, Delphine Roberts, told the committee she saw Oswald in Banister’s office on several occasions, the first being
28It appeared to the committee that the FBI overstated Martin’s recantation in its information to the Secret Service. Martin had cautioned the FBI that he had no evidence to support his suspicions but that he believed they merited investigation. (233)
Page 146
when he was interviewed for a job during the summer of 1963.29 (237)
The committee learned that Banister left extensive files when he died in 1964.(238) Later that year, they were purchased by the Louisiana State Police from Banister’s widow.(239) According to Joseph Cambre of the State police, Oswald’s name was not the subject of any file, but it was included in a file for the Fair Play for Cuba Committee.(240) Cambre said the FPCC file contained newspaper clippings and a transcript, of a radio program on which Oswald had appeared. (241) The committee was not able to review Banister’s files, since they had been destroyed pursuant to an order of the superintendent of Louisiana State Police that all files not part of the public record or pertinent to ongoing criminal investigations be burned. (242)
Additional evidence that Oswald may have been associated or acquainted with Ferrie and Banister was provided by the testimony of Adrian Alba, proprietor of the Crescent City Garage which was next door to the Reily Coffee Co. where Oswald had worked for a couple of months in 1963. (The garage and the coffee company were both located less than a block from 544 Camp Street.) Although Alba’s testimony on some points was questionable, he undoubtedly did know Oswald who frequently visited his garage, and the committee found no reason to question his statement that he had often seen Oswald in Mancuso’s Restaurant on the first floor of 544 Camp. (243) Ferrie and Banister also were frequent customers at Mancuso’s. (244)
Top of Page
(6) Summary of the evidence.–In sum, the committee did not believe that an anti-Castro organization was involved in a conspiracy to assassinate President Kennedy. Even though the committee’s investigation did reveal that in 1964 the FBI failed to pursue intelligence reports of possible anti-Castro involvement as vigorously as it might have, the committee found it significant that it discovered no information in U.S. intelligence agency files that would implicate anti-Castroites. Contact between the intelligence community and the anti-Castro movement was close, so it is logical to suppose that some trace of group involvement would have been detected had it existed.
The committee also thought it significant that it received no information from the Cuban Government that would implicate anti-Castroites. The Cubans had dependable information sources in the exile communities in Miami, New Orleans, Dallas and other U.S. cities, so there is high probability that Cuban intelligence would have been aware of any group involvement by the exiles. Following the assassination, the Cuban Government would have had the highest incentive to report participation by anti-Castroites, had it existed to its knowledge, since it would have dispelled suspicions of pro-Castro Cuban involvement.
The committee was impressed with the cooperation it received from the Cuban Government, and while it acknowledged this cooperation might not have been forthcoming in 1964, it concluded that, had such information existed in 1978, it would have been supplied by Cuban officials.
On the other hand, the committee noted that it was unable to preclude from its investigation the possibility that individuals with anti-
29The committee did not credit the Roberts’ testimony standing alone. It came late in the investigation and without corroboration or independent substantiation, and much of Roberts’ other testimony lacked credibility.
Page 147
Castro leanings might have been involved in the assassination. The committee candidly acknowledged, for example that it could not explain Oswald’s associations–nor at this late date fully determine their extent–with anti-Castro Cubans. The committee remained convinced that since Oswald consistently demonstrated a left-wing Marxist ideology, he would not have supported the anti-Castro movement. At the same time, the committee noted that Oswald’s possible association with Ferrie might be distinguishable, since it could not be simply termed an anti-Castro association. Ferrie and Oswald may have had a personal friendship unrelated to Cuban activities. Ferrie was not Cuban, and though he actively supported the anti-Castro cause, he had other interests. For one, he was employed by Carlos Marcello as an investigator. (245) (It has been alleged that Ferrie operated a service station in 1964 the franchise for which was reportedly paid by Marcello.) (246) The committee concluded, therefore, that Oswald’s most significant apparent anti-Castro association, that with David Ferrie, might in fact not have been related to the Cuban issue.
In the end, the committee concluded that the evidence was sufficient to support the conclusion that anti-Castro Cuban groups, as groups, were not involved in the assassination, but it could not preclude the possibility that individual members may have been involved.
Top of Page
4.THE COMMITTEE BELIEVES, ON THE BASIS OF THE EVIDENCE AVAILABLE TO IT, THAT THE NATIONAL SYNDICATE OF ORGANIZED CRIME AS A GROUP, WAS NOT INVOLVED IN THE ASSASSINATION OF PRESIDENT KENNEDY, BUT THAT THE AVAILABLE EVIDENCE DOES NOT PRECLUDE THE POSSIBILITY THAT INDIVIDUAL MEMBERS MAY HAVE BEEN INVOLVED
Go to the footnotes for this section.
- The Warren Commission investigation
- The committee investigation
- Ruby and organized crime
- Ruby and the Dallas Police Department
- Other evidence relating to Ruby
- Involvement of organized crime
- Analysis of the 1963-64 investigation
- Carlos Marcello
- Santos Trafficante
- James R. Hoffa
- Summary and analysis of the evidence
Lee Harvey Oswald was fatally shot by Jack Ruby at 11:21 a.m on Sunday, November 24, 1963, less than 48 hours after President Kennedy was assassinated. While many Americans were prepared to believe that Oswald had acted alone in shooting the President, they found their credulity strained when they were asked to accept a conclusion that Ruby, too, had not acted as part of a plot. As the Warren Commission observed,
…almost immediately speculation arose that Ruby had acted on behalf of members of a conspiracy who had planned the killing of President Kennedy and wanted to silence Oswald. (1).
The implications of the murder of Oswald are crucial to an understanding of the assassination itself. Several of the logical possibilities should be made explicit:
Oswald was a member of a conspiracy, and he was killed by Ruby, also a conspirator, so that he would not reveal the plot.
Oswald was a member of a conspiracy, yet Ruby acted alone, as he explained, for personal reasons.
Oswald was not a member of a conspiracy as far as Ruby knew, but his murder was an act planned by Ruby and others to take justice into their own hands.
Page 148
Both Oswald and Ruby acted alone or with the assistance of only one or two confederates, but there was no wider conspiracy, one that extended beyond the immediate participants.
If it is determined that Ruby acted alone, it does not necessarily follow that there was no conspiracy to murder the President. But if Ruby was part of a sophisticated plot to murder Oswald, there would be troublesome implications with respect to the assassination of the President. While it is possible to develop an acceptable rationale of why a group might want to kill the President’s accused assassin, even though its members were not in fact involved in the assassination, it is difficult to make the explanation sound convincing. There is a possibility, for example, that a Dallas citizen or groups of citizens planned the murder of Oswald by Ruby to revenge the murders of President Kennedy or Patrolman J.D. Tippit, or both. Nevertheless, the brief period of time between the two murders, during which the vengeful plotters would have had to formulate and execute Oswald’s murder, would seem to indicate the improbability of such an explanation. A preexisting group might have taken action within 48 hours, but it is doubtful that a group could have planned and then carried out Oswald’s murder in such a short period of time.
Top of Page
(a) The Warren Commission investigation
The Warren Commission looked at Ruby’s conduct and associations from November 21 through November 24 to determine if they reflected a conspiratorial relationship with Oswald.(2) It found no “… grounds for believing that Ruby’s killing of Oswald was part of a conspiracy.”(3) It accepted as true his explanation that his conduct reflected “genuine shock and grief” and strong affection for President Kennedy and his family. (4) As for numerous phone contacts Ruby had with underworld figures in the weeks preceding the assassination, the Commission believed his explanation that they had to do with his troubles with the American Guild of Variety Artists, rather than reflecting any sinister associations that might have been related to the President’s assassination. (5)
The Commission also found no evidence that Ruby and Oswald had ever been acquainted, although the Commission acknowledged that they both lived in the Oak Cliff section of Dallas, had post office boxes at the terminal annex, and had possible but tenuous third party links. These included Oswald’s landlady, Earlene Roberts, whose sister, Bertha Cheek, had visited Ruby at his nightclub on November 18, (6) and a fellow boarder at Oswald’s roominghouse, John Carter, who was friendly with a close friend and employee of Ruby, Wanda Killam.(7).
The Commission also looked to Ruby’s ties to other individuals or groups that might have obviated the need for direct contact with Oswald near the time of the assassination. Ruby was found not to be linked to pro- or anti-Castro Cuban groups;(8) he was also found not to be linked to “illegal activities with members of the organized underworld.”(9) The Commission noted that Ruby “disclaimed that he was associated with organized criminal activities,” and it did not find reason to disbelieve him. (10) The evidence “fell short” of demonstrating that Ruby “was significantly affiliated with organized crime.”(11) He was, at worst, “familiar, if not friendly” with some
Page 149
criminal elements, but he was not a participant in “organized criminal activity.” (12) Consequently, the Commission concluded that “the evidence does not establish a significant link between Ruby and organized crime? (13) And in its central conclusion about Jack Ruby, the Commission stated that its investigation had “yielded no evidence that Ruby conspired with anyone in planning or executing the killing of Lee Harvey Oswald.”(14) For the Warren Commission, therefore, Ruby’s killing of Oswald had no implications for Oswald’s killing of the President.
Top of Page
(b) The committee investigation
Like the Warren Commission, the committee was deeply troubled by the circumstances surrounding the murder of the President’s accused assassin. It, too, focused its attention on Jack Ruby, his family and his associates. Its investigation, however, was not limited to Ruby, Oswald and their immediate world. The committee’s attention was also directed to organized crime and those major figures in it who might have been involved in a conspiracy to kill the President because of the Kennedy administration’s unprecedented crackdown on them and their illicit activities.
Top of Page
(1) Ruby and organized crime.–The committee, as did the Warren Commission, recognized that a primary reason to suspect organized crime of possible involvement in the assassination was Ruby’s killing of Oswald. For this reason, the committee undertook an extensive investigation of Ruby and his relatives, friends and associates to determine if there was evidence that Ruby was involved in crime, organized or otherwise, such as gambling and vice, and if such involvement might have been related to the murder of Oswald.
The evidence available to the committee indicated that Ruby was not a “member” of organized crime in Dallas or elsewhere, although it showed that he had a significant number of associations and direct and indirect contacts with underworld figures, a number of whom were connected to the most powerful La Cosa Nostra leaders. Additionally, Ruby had numerous associations with the Dallas criminal element. The committee examined the circumstances of a well-known episode in organized crime history in which representatives of the Chicago Mafia attempted in, 1947, a move into Dallas, facilitated by the bribery of members of the Dallas sheriff’s office. (15) The Kefauver committee of the U.S. Senate, during, its extensive probe of organized crime in the early 1950’s, termed this attempt by the Chicago syndicate to buy protection from the Dallas authorities an extraordinary event, one of the more brazen efforts made during that postwar period of criminal expansion.
In the years since the assassination, there had been allegations that Ruby was involved in organized crime’s 1947 attempt to move into Dallas, perhaps as a frontman for the Chicago racketeers. (16) During discussions of the bribe offer, Dallas Sheriff Steve Guthrie secretly taped conversations in which the Chicago mob representative outlined plans for its Dallas operation. (17) They spoke of establishing a nightclub as a front for illegal gambling. It happens that Ruby moved from Chicago to Dallas in 1947 and began operating a number of nightclubs. (18) While the FBI and the Warren Commission were aware in 1964 of the alleged links between Ruby and those involved in the
Page 150
bribery attempt, a thorough investigation of the charges was not undertaken. (19)
The committee frankly realized that because this incident occurred years in the past, it would be difficult, if not impossible, to answer all the allegations fully and finally. Nevertheless, the committee was able to develop substantial evidence from tape recordings made by the sheriff’s office, detailed law enforcement documents and the testimony of knowledgeable witnesses.
As a result, the committee concluded that while Ruby and members of his family were acquainted with individuals who were involved in the incident, including Chicago gangsters who had moved to Dallas, and while Ruby may have wished to participate, there was no solid evidence that he was, in fact, part of the Chicago group. (20) There was also no evidence available that Ruby was to have been involved in the proposed gambling operation had the bribery attempt been successful, or that Ruby came to Dallas for that purpose. (21)
The committee found it reasonable to assume that had Ruby been involved in any significant way, he would probably have been referred to in either the tape recordings or the documentation relating to the incident, but a review of that available evidence failed to disclose any reference to Ruby. (22) The committee, however, was not able to interview former Sheriff Guthrie, the subject of the bribery attempt and the one witness who maintained to the FBI in 1963-64 that Ruby was significantly involved in the Chicago syndicate plan.1 (23)
The committee also examined allegations that, even before the 1947 move to Dallas, Ruby had been personally acquainted with two professional killers for the organized crime syndicate in Chicago, David Yaras and Lenny Patrick. (25) The committee established that Ruby, Yaras and Patrick were in fact acquainted during Ruby’s years in Chicago, particularly in the 1930’s and 1940’s.(26) Both Yaras and Patrick admitted, when questioned by the FBI in 1964, that they did know Ruby, but both said that they had not had any contact with him for 10 to 15 years. (27) Yaras and Patrick further maintained they had never been particularly close to Ruby, had never visited him in Dallas and had no knowledge of Ruby being connected to organized crime. (28) Indeed, the Warren Commission used Patrick’s statement as a footnote citation in its report to support its conclusion that Ruby did not have significant syndicate associations. (29)
On the other hand, the committee established that Yaras and Patrick were, in fact, notorious gunmen, having been identified by law enforcement authorities as executioners for the Chicago mob(30) and closely associated with Sam Giancana, the organized crime leader in Chicago who was murdered in 1975. Yaras and Patrick are believed to have been responsible for numerous syndicate executions, including the murder of James Ragan, a gambling wire service owner. (31) The evidence implicating Yaras and Patrick in syndicate activities is unusually reliable.(32) Yaras, for example, was overheard in a 1969, electronic surveillance discussing various underworld murder con-
1With reference to Guthrie’s claim that Ruby’s name had been mentioned frequently in the discussions with Chicago underworld representatives, the committee’s review of the tape recordings failed to disclose such references. Portions of the tapes were unintelligible and two entire recordings were discovered by investigators in 1964 to be missing, so the evidence was not conclusive.
Page 151
tracts he had carried out and one he had only recently been assigned. While the committee found no evidence that Ruby was associated with Yaras or Patrick during the 50’s or 1960’s, (33) it concluded that Ruby had probably talked by telephone to Patrick during the summer of 1963. (34)
While Ruby apparently did not participate in the organized crime move to Dallas is 1947, he did establish himself as a Dallas nightclub operator around that time. His first club was the Silver Spur, which featured country and western entertainment. Then he operated the Sovereign, a private club that failed and was converted into the Carousel Club, a burlesque house with striptease acts. Ruby, an extroverted individual, acquired numerous friends and contacts in and around Dallas, some of whom had syndicate ties.
Included among Ruby’s closest friends was Lewis McWillie. McWillie moved from Dallas to Cuba in 1958 and worked in gambling casinos in Havana until 1960.(35) In 1978, McWillie was employed in Las Vegas, and law enforcement files indicate he had business and personal ties to major organized crime figures, including Meyer Lansky and Santos Trafficante. (36)
Ruby traveled to Cuba on at least one occasion to visit McWillie. (37) McWillie testified to the committee that Ruby visited him only once in Cuba, and that it was a social visit.(38) The Warren Commission concluded this was the only trip Ruby took to Cuba,(39) despite documentation in the Commission’s own files indicating Ruby made a second trip.
Both Ruby and McWillie claimed that Ruby’s visit to Cuba was at McWillie’s invitation and lasted about a week in the late summer or early fall of 1959. (41) The committee, however, obtained tourist cards from the Cuban Government that show Ruby entered Cuba on August 8, 1959, left on September 11, reentered on September 12 and left again on September 13, 1959.(42) These documents supplement records the committee obtained from the Immigration and Naturalization Service (INS) indicating that Ruby left Cuba on September 11, 1959, traveling to Miami, returned to Cuba on September 12, and traveled on to New Orleans on September 13, 1959.(43) The Cuban Government could not state with certainty that the commercial airline flights indicated by the INS records were the only ones Ruby took during the period.(44)
Other records obtained by the committee indicate that Ruby was in Dallas at times during the August 8 to September 11, 1959, period. (45) He apparently visited his safe deposit box on August 21, met with FBI Agent Charles W. Flynn on August 31,2 and returned to the safe deposit box on September 4. (47) Consequently, if the tourist card documentation, INS, FBI and bank records are all correct, Ruby had to have made at least three trips to Cuba. While the records appeared to be accurate, they were incomplete. The committee was unable to determine, for example, whether on the third trip, if it occurred, Ruby
2In March 1959, Ruby told the FBI he wished to assist the Bureau by supplying on a confidential basis criminal information that had come to his attention. Between April and October 1959, Ruby met with Agent Flynn eight times and gave him a small bit of information about thefts and related offenses. On November 6, 1959, Flynn wrote that Ruby’s information had not been particularly helpful, that further attempts to develop Ruby as a PCI (potential criminal informant) would be fruitless and that the file on Ruby should be closed (46).
Page 152
traveled by commercial airline or some other means. Consequently, the committee could not rule out the possibility that Ruby made more trips during this period or at other times.
Based on the unusual nature of the l-day trip to Miami from Havana on September 11-12 and the possibility of at least one additional trip to Cuba, the committee concluded that vacationing was probably not the purpose for traveling to Havana, despite Ruby’s insistence to the Warren Commission that his one trip to Cuba in 1959 was a social visit. (48) The committee reached the judgment that Ruby most likely was serving as a courier for gambling interests when he traveled to Miami from Havana for 1 day, then returned to Cuba for a day, before flying to New Orleans.(49)This judgement is supported by the following:
McWillie had made previous trips to Miami on behalf of the owners of the Tropicana, the casino for which he worked, to deposit funds; (50)
McWillie placed a call to Meyer Panitz, a gambling associate in Miami, to inform him that Ruby was coming from Cuba, resulting in two meetings between Panitz and Ruby; (51)
There was a continuing need for Havana casino operators to send their assets out of Cuba to protect them from seizure by the Castro government; (52) and
The 1-day trip from Havana to Miami was not explained by Ruby, and his testimony to the Warren Commission about his travels to Cuba was contradictory.(53)
The committee also deemed it likely that Ruby at least met various organized crime figures in Cuba, possibly including some who had been detained by the Cuban government. (54) In fact, Ruby told the Warren Commission that he was later visited in Dallas by McWillie and a Havana casino owner and that they had discussed the gambling business in Cuba. 3 (55)
As noted by the Warren Commission, an exporter named Robert McKeown alleged that Ruby offered in 1959 to purchase a letter of introduction to Fidel Castro in hopes of securing the release of three individuals being held in a Cuban prison. (57) McKeown also claimed Ruby contacted him about a sale of jeeps to Cuba. 4 (58) If McKeown’s allegations were accurate, they would support a judgment that Ruby’s travels to Cuba were not merely for a vacation. (The committee was unable to confirm or refute McKeown’s allegations. In his appearance before the committee in executive session, however, McKeown’s story did not seem to be credible, based on the committee’s assessment of his demeanor.(61)
It has been charged that Ruby met with Santos Trafficante in Cuba sometime in 1959.(62) Trafficante, regarded as one of the Nation’s most powerful organized crime figures, was to become a key participant in Castro assassination attempts by the Mafia and the CIA from 1960 to 1963.(63) The committee developed circumstantial evidence
3Earlier, though both he and McWillie denied it, Ruby apparently sent a coded message to McWillie in Havana, containing various sets of numerals, a communication Ruby transmitted to McWillie via McWillie’s girlfriend (56).
4Ruby denied this to the Warren Commission, stating he did not have sufficient contacts to obtain jeeps at the time. (59) The Warren Commission noted that Ruby “made preliminary inquiries, as a middleman” in regard to the possible sale of jeeps in Cuba, but stated that he “was merely pursuing a moneymaking opportunity.”(60)
Page 153
that makes a meeting between Ruby and Trafficante a distinct possibility,(64) but the evidence was not sufficient to form a final conclusion as to whether or not such a meeting took place.
While allegations of a Ruby link to Trafficante had previously been raised, mainly due to McWillie’s alleged close connections to the Mafia leader, it was not until recent years that they received serious attention. Trafficante had long been recognized by law enforcement officials as a leading member of the La Cosa Nostra, but he did not become the object of significant public attention in connection with the assassination of the President until his participation in the assassination plots against Castro was disclosed in 1975.
In 1976, in response to a freedom of information suit, the CIA declassified a State Department cablegram received from London on November 28, 1963. It read:
On 26 November 1963, a British Journalist named John Wilson, and also known as Wilson-Hudson, gave information to the American Embassy in London which indicated that an “American gangster-type named Ruby” visited Cuba around 1959. Wilson himself was working in Cuba at that time and was jailed by Castro before he was deported.
In prison in Cuba, Wilson says he met an American gangster-gambler named Santos who could not return to the U.S.A. …Instead he preferred to live in relative luxury in a Cuban prison. While Santos was in prison, Wilson says, Santos was visited frequently by an American gangster type named Ruby. (65)
Several days after the CIA had received the information, the Agency noted that there were reports that Wilson-Hudson was a “psychopath” and unreliable. The Agency did not conduct an investigation of the information, and the Warren Commission was apparently not informed of the cablegram. The former staff counsel who directed the Commission’s somewhat limited investigation of organized crime told the committee that since the Commission was never told of the CIA’s use of the Mafia to try to assassinate Castro from 1960 to 1963, he was not familiar with the name Santos Trafficante in 1964. (66)
The committee was unable to locate John Wilson-Hudson (According to reports, he had died.) Nor was the committee able to obtain independent confirmation of the Wilson-Hudson allegation. The committee was able, however, to develop corroborative information to the effect that Wilson-Hudson was incarcerated at the same detention camp in Cuba as Trafficante. (67)
On June 6, 1959, Trafficante and others who controlled extensive gambling interests in Cuba were detained as part of a Castro government policy that would subsequently lead to the confiscation of all underworld holding in Cuba.(68) They were held in Trescornia, a minimum security detention camp. (69) According to documentation supplied by the Cuban Government, Trafficante was released from Trescornia on August 18, 1959. (70) Tourist card documentation, also obtained by the committee, as well as various Warren Commission documents, indicate Ruby’s first trip to Cuba began on August 1959.(71) Thus, Ruby was in Cuba during part of the final days of Trafficante’s detention at Trescornia.(72)
Page 154
McWillie testified before the committee that he had visited another detainee at Trescornia during that period, and he recalled possibly seeing Trafficante there. McWillie claimed, however, he did not say more than “hello” to him. (73) McWillie further testified it was during that period that Ruby visited him in Havana for about a week, and that Ruby tagged along with him during much of his stay. (74) McWillie told the committee that Ruby could have gone with him to visit Trescornia, although he doubted that Ruby did so.(75) McWillie testified that he could not clearly recall much about Ruby’s visit. (76)
Jose Verdacia Verdacia, a witness made available for a committee interview by the Cuban Government, was the warden at Trescornia in August 1959.(77) Verdacia told the committee that he could not recall the name John Wilson-Hudson, but he could remember a British journalist who had worked in Argentina, as had Wilson-Hudson, who was detained at Trescornia. (78)
In his own public testimony before the committee, Trafficante testified that he did not remember Ruby ever having visited him at Trescornia. Trafficante stated,
There was no reason for this man to visit me. I have never seen this man before. I have never been to Dallas, I never had no contact with him. I don’t see why he was going to come and visit me. (79)
Trafficante did, however, testify that he could recall an individual fitting British journalist John Wilson-Hudson’s description, and he stated that the man was among those who were held in his section at Trescornia. (80)
The importance of a Ruby-Trafficante meeting in Trescornia should not be overemphasized. The most it would show would be a meeting, at that a brief one. No one has suggested that President Kennedy’s assassination was planned at Trescornia in 1959. At the same time, a meeting or an association, even minor, between Ruby and Trafficante would not have been necessary for Ruby to have been used by Trafficante to murder Oswald. (81) Indeed, it is likely that such a direct contact would have been avoided by Trafficante if there had been a plan to execute either the President or the President’s assassin, but, since no such plot could have been under consideration in 1959, there would not have been a particular necessity for Trafficante-to avoid contact with Ruby in Cuba.
The committee investigated other aspects of Ruby’s activities that might have shown an association with organized crime figures. An extensive computer analysis of his telephone toll records for the month prior to the President’s assassination revealed that he either placed calls to or received calls from a number of individuals who may be fairly characterized as having been affiliated, directly or indirectly, with organized crime. (82) These included Irwin Weiner a Chicago bondsman well know as a frontman for organized crime and the Teamsters Union;(83) Robert “Barney” Baker, a lieutenant of James R. Hoffa and associate of several convicted organized crime executioners:(84) Nofio J. Pecora, a lieutenant of Carlos Marcello, the Mafia boss in Louisiana (85) Harold Tannenbaum, a New Orleans French Quarter nightclub manager who lived in a trailer park owned
Page 155
by Pecora;(86) McWillie, the Havana gambler;(87) and Murray “Dusty” Miller, a Teamster deputy of Hoffa and associate of various underworld figures.(88) Additionally, the committee concluded that Ruby was also probably in telephonic contact with Mafia executioner Lenny Patrick sometime during the summer of 1963. (89) Although no such call was indicated in the available Ruby telephone records, Ruby’s sister, Eva Grant, told the Warren Commission that Ruby had spoken more than once of having contacted Patrick by telephone during that period. (90)
The committee found that the evidence surrounding the calls was generally consistent–at least to the times of their occurrence–with the explanation that they were for the purpose of seeking assistance in a labor dispute. (91) Ruby, as the operator of two nightclubs, the Carousel and the Vegas, had to deal with the American Guild of Variety Artists (AGVA), an entertainers union.(92) Ruby did in fact have a history of labor problems involving his striptease performers, and there was an ongoing dispute in the early 1960’s regarding amateur performers in Dallas area nightclubs.(93) Testimony to the committee supported the conclusion that Ruby’s phone calls were, by and large, related to his labor troubles. (94) In light of the identity of some of the individuals, however, the possibility of other matters being discussed could not be dismissed.(95)
In particular, the committee was not satisfied with the explanations of three individuals closely associated with organized crime who received telephone calls from Ruby in October or November 1963. (96)
Weiner, the Chicago bondsman, refused to discuss his call from Ruby on October 26, 1963, with the FBI in 1964,(97) and he told a reporter in 1978 that the call had nothing to do with labor problems.(98) In his executive session testimony before the committee, however, Weiner stated that he had lied to the reporter, and he claimed that he and Ruby had, in fact discussed a labor dispute. (99) The committee was not satisfied with Weiner’s explanation of his relationship with Ruby. Weiner suggested Ruby was seeking a bond necessary to obtain an injunction in his labor troubles, yet the committee could find no other creditable indication that Ruby contemplated seeking court relief, nor any other explanation for his having to go to Chicago for such a bond. (100)
Barney Baker told the FBI in 1964 that he had received only one telephone call from Ruby (on Nov. 7, 1963) during which he had curtly dismissed Ruby’s plea for assistance in a nightclub labor dispute.(101) The committee established, however, that Baker received a second lengthy call from Ruby on November 8.(102) The committee found it hard to believe that Baker, who denied the conversation ever took place, could have forgotten it. (103)
The committee was also dissatisfied with the explanation of a call Ruby made on October 30, 1963, to the New Orleans trailer park office of Nofio J. Pecora, the long-time Marcello lieutenant.(104) Pecora told the committee that only he would have answered his phone and that he never spoke with Ruby or took a message from him.(105) The committee considered the possibility that the call was actually for Harold Tannenbaum, a mutual friend of Ruby and
Page 156
Pecora who lived in the trailer park, although Pecora denied he would have relayed such a message. (106)
Additionally, the committee found it difficult to dismiss certain Ruby associations with the explanation that they were solely related to his labor problems. For example, James Henry Dolan, a Dallas AGVA representative, was reportedly an acquaintance of both Carlos Marcello and Santos Trafficante.(107) While Dolan worked with Ruby on labor matters, they were also allegedly associated in other dealings, including a strong-arm attempt to appropriate the proceeds of a one-night performance of a stage review at the Adolphus Hotel in Dallas called “Bottoms Up.” (108) The FBI, moreover, has identified Dolan as an associate of Nofio Pecora. (109) The committee noted further that reported links between AGVA and organized crime figures have been the subject of Federal and State investigations that have been underway for years.5 (110) The committee’s difficulties in separating Ruby’s AGVA contacts from his organized crime connections was, in large degree, based on the dual roles that many of his associates played. 6
In assessing the significance of these Ruby contacts, the committee noted, first of all, that they should have been more thoroughly explored in 1964 when memories were clearer and related records (including, but not limited to, additional telephone toll records) were available. Further, while there may be persuasive arguments against the likelihood that the attack on Oswald would have been planned in advance on the telephone with an individual like Ruby, the pattern of contacts did show that individuals who had the motive to kill the President also had knowledge of a man who could be used to get access to Oswald in the custody of the Dallas police. In Ruby, they also had knowledge of a man who had exhibited a violent nature and who was in serious financial trouble. The calls, in short, established knowledge and possible availability, if not actual planning.
Top of Page
(2) Ruby and the Dallas Police Department. The committee also investigated the relationship between Ruby and the Dallas Police Department to determine whether members of the department might have helped Ruby get access to Oswald for the purpose of shooting him.(111) Ruby had a friendly and somewhat unusual relationship with the Dallas Police Department, both collectively and with individual officers, but the committee found little evidence of any significant influence by Ruby within the force that permitted him to engage in illicit activities.(112) Nevertheless, Ruby’s close relationship with one or more members of the police force may have been a factor in his entry to the police basement on November 24, 1963. (113)
Both the Warren Commission and a Dallas Police Department investigative unit concluded that Ruby entered the police basement on November 24, 1963, between 11:17 a.m., when he apparently sent a telegram, and 11:21, when he shot Oswald, via the building’s Main Street ramp as a police vehicle was exiting, thereby fortuitously
5According to FBI records, AGVA has been used frequently by members of organized crime as a front for criminal activities.
6Although it was dissatisfied with the explanations it received for these calls, the committee also noted that the individuals called may have been reluctant to admit that Ruby was seeking their assistance in an illegal effort to settle his labor problems.
Page 157
creating a momentary distraction.(114) The committee, however, found that Ruby probably did not come down the ramp,(115) and that his most likely route was an alleyway located next to the Dallas Municipal Building and a stairway leading to the basement garage of police headquarters. (116)
The conclusion reached by the Warren Commission that Ruby entered the police basement via the ramp was refuted by the eyewitness testimony of every witness in the relevant area only Ruby himself excepted. (117) It was also difficult for the committee to reconcile the ramp route with the 55-second interval (derived from viewings of the video tapes of the Oswald murder) from the moment the police vehicle started up the ramp and the moment Ruby shot Oswald. (118) Ruby would have had to come down the ramp after the vehicle went up, leaving him less than 55 seconds to get down the ramp and kill Oswald.
Even though the Warren Commission and the Dallas police investigative unit were aware of substantial testimony contradicting the ramp theory, (119) they arrived at their respective conclusions by relying heavily on Ruby’s own assertions and what they perceived to be the absence of a plausible alternative route. (120)
The committee’s conclusion that Ruby entered from the alley was supported by the fact that it was much less conspicuous than the alternatives,(121) by the lack of security in the garage area and along the entire route,(122) and by the testimony concerning the security of the doors along the alley and stairway route. (123) This route would also have accommodated the 4-minute interval from Ruby’s departure from a Western Union office near police headquarters at 11:17 a.m. to the moment of the shooting at 11:21.(124)
Based on a review of the evidence, albeit circumstantial, the committee believed that Ruby’s shooting of Oswald was not a spontaneous act, in that it involved at least some premeditation.(125) Similarly, the Committee believed that it was less likely that Ruby entered the police basement without assistance, even though the assistance may have been provided with no knowledge of Ruby’s intentions. The assistance may have been in the form of information about plans for Oswald’s transfer or aid in entering the building or both.7 (126)
The committee found several circumstances significant in its evaluation of Ruby’s conduct. It considered in particular the selectively recalled and self-serving statements in Ruby’s narration of the events of the entire November 22-24 weekend in arriving at its conclusions. (127) It also considered certain conditions and events. The committee was troubled by the apparently unlocked doors along the stairway route and the removal of security guards from the area of the garage nearest the stairway shortly before the shooting;(128) by a Saturday night telephone call from Ruby to his closest friend, Ralph Paul, in which Paul responded to something Ruby said by asking him if he was crazy;(129) and by the actions and statements of several Dallas police officers, particularly those present when Ruby was initially interrogated about the shooting of Oswald. (130)
7While the Warren Commission did not make reference to it in its report, Ruby refused in his first interviews with the FBI, Secret Service and the Dallas police to indicate how he entered the basement or whether anyone had assisted him. In later interviews, Ruby state he had walked down the ramp.
Page 158
There is also evidence that the Dallas Police Department withheld relevant information from the Warren Commission concerning Ruby’s entry to the scene of the Oswald transfer.(131) For example, the fact that a polygraph test had been given to Sergeant Patrick Dean in 1964 was never revealed to the Commission, even though Dean was responsible for basement security and was the first person to whom Ruby explained how he had entered the basement.(132) Dean indicated to the committee that he had “failed” the test, but the committee was unable to locate a copy of the actual questions, responses and results. (133)
Top of Page
(3) Other evidence relating to Ruby.—The committee noted that other Ruby activities and movements during the period immediately following the assassination–on November 22 and 23–raised disturbing questions. For example, Ruby’s first encounter with Oswald occurred over 36 hours before he shot him. Ruby was standing within a few feet of Oswald as he was being moved from one part of police headquarters to another just before midnight on November 22.(134) Ruby testified that he had no trouble entering the building, and the committee found no evidence contradicting his story. The committee was disturbed, however, by Ruby’s easy access to headquarters and by his inconsistent accounts of his carrying a pistol. In an FBI interview on December 25, 1963, he said he had the pistol during the encounter with Oswald late in the evening of November 22. But when questioned about it by the Warren Commission, Ruby replied, “I will be honest with you. I lied about it. It isn’t so, I didn’t have a gun.” (135) Finally, the committee was troubled by reported sightings of Ruby on Saturday, November 23, at Dallas police headquarters and at the county jail at a time when Oswald’s transfer to the county facility had originally been scheduled. These sightings, along with the one on Friday night, could indicate that Ruby was pursuing Oswald’s movements throughout the weekend.
The committee also questioned Ruby’s self-professed motive for killing Oswald, his story to the Warren Commission and other authorities that he did it out of sorrow over the assassination and sympathy for the President’s widow and children. Ruby consistently claimed there had been no other motive and that no one had influenced his act. (136) A handwritten note by Ruby, disclosed in 1967, however, exposed Ruby’s explanation for the Oswald slaying as a fabricated legal ploy. (137) Addressed to his attorney, Joseph Tonahill, it told of advice Ruby had received from his first lawyer. Tom Howard, in 1963: “Joe, you should know this. Tom Howard told me to say that I shot Oswald so that Caroline and Mrs. Kennedy wouldn’t have to come to Dallas to testify. OK?” (138)
The committee examined a report that Ruby was at Parkland Hospital shortly after the fatally wounded President had been brought there on November 22, 1963. Seth Kantor, a newsman then employed by Scripps-Howard who had known Ruby, later testified to the Warren Commission that he had run into him at Parkland and spoken with him briefly shortly before the President’s death was announced. (139) While the Warren Commission concluded that Kantor was mistaken.(14O) the committee determined he probably was not. The committee was impressed by the opinion of Burr W. Griffin, the
Page 159
Warren Commission counsel who directed the Ruby investigation and wrote the Ruby section of the Warren report. Griffin told the committee he had come to believe, in light of evidence subsequently brought out, that the Commission conclusion about Kantor’s testimony was wrong.(141)
Subsequent to Ruby’s apprehension, he was given a polygraph examination by the FBI in which he denied that he had been involved with any other person in killing Oswald, or had been involved in any way in the assassination of President Kennedy.(142) The Warren Commission stated it did not rely on this examination in drawing conclusions, although it did publish a transcript of the examination.(143) The FBI in 1964 also expressed dissatisfaction with the test,(144) based on the circumstances surrounding its administration. A panel of polygraph experts reviewed the examination for the committee and concluded that it was not validly conducted or interfered.(145) Because there were numerous procedural errors made during the test, the committee’s panel was unable to interpret the examination.(146)
Finally, the committee analyzed the finances of Ruby and of his family to determine if there was any evidence of financial profit from his killing of the accused assassins.(147) It was an analysis the Warren Commission could not perform so soon after the assassination. (148) Some financial records, including tax returns, could not be legally obtained by the committee without great difficulty, and others no longer existed. (149) Nevertheless, on the basis of the information that it did obtain, the committee uncovered no evidence that Ruby or members of his family profited from the killing of Oswald. (150) Particular allegations concerning the increased business and personal incomes of Ruby’s brother Earl were investigated, but the committee found no link between Earl Ruby’s finances and the Oswald slaying. (151) Earl Ruby did say he had been approached by the Chicago bondsman and associate of organized crime figures, Irwin Weiner, who made a business proposition to him in 1978. the day before Earl Ruby was to testify before the committee. (152) Earl Ruby said he declined the offer,(153) while Weiner denied to the committee he ever made it. (154) The committee was not able to resolve the difference between the two witnesses.
Top of Page
(4) Involvement of organized crime.—In contrast to the Warren Commission, the committee’s investigation of the possible involvement of organized crime in the assassination was not limited to an examination of Jack Ruby. The committee also directed its attention to organized crime itself.
Organized crime is a term of many meanings. It can be used to refer to the crimes committed by organized criminal groups–gambling, narcotics, loan-sharking, theft and fencing, and the like.(155) It can also be used to refer to the criminal group that commit those crimes. (156) Here, a distinction may be drawn between an organized crime enterprise that engages in providing illicit goods and services and an organized crime syndicate that regulates relations between individual enterprises–allocating territory, settling personal disputes, establishing gambling payoffs, etc. (157) Syndicates, too, are of different types. They may be metropolitan, regional, national or interna-
Page 160
tional in scope; they may be limited to one field of endeavor–for example, narcotics- or they may cover a broad range of illicit activities. (158).
Often, but not always, the term organized crime refers to a particular organized crime syndicate, variously known as the Mafia or La Cosa Nostra,(159) and it is in this sense that the committee has used the phrase. This organized crime syndicate was the principal target of the committee investigation. (160)
The committee found that by 1964 the fundamental structure and operations of organized crime in America had changed little since the early 1950’s, when, after conducting what was then the most extensive investigation of organized crime in history, the Kefauver committee concluded:
1. There is a nationwide crime syndicate known as the Mafia, whose tentacles are found in many large cities. It has international ramifications which appear most clearly in connection with the narcotics traffic.
2. Its leaders are usually found in control of the most lucrative rackets in their cities.
3. There are indications of a centralized direction and control of these rackets, but leadership appears to be in a group rather than in a single individual.
4. The Mafia is the cement that helps to bind the …syndicate of New York and the …syndicate of Chicago as well as smaller criminal gangs and individual criminals through the country.
5. The domination of the Mafia is based fundamentally on “muscle” and “murder.” The Mafia is a secret conspiracy against law and order which will ruthlessly eliminate anyone who stands in the way of its success in any criminal enterprise in which it is interested. It will destroy anyone who betrays its secrets. It will use any means available–political influence, bribery, intimidation, et cetera, to defeat any attempt on the part of law enforcement to touch its top figures…. (161)
The committee reviewed the evolution of the national crime syndicate in the years after the Kefauver committee and found continuing vitality, even more sophisticated techniques, and an increased concern for the awareness by law enforcement authorities of the danger it posed to the Nation. (162)In 1967, after having conducted a lengthy examination of organized crime in the United States, the President’s Crime Commission offered another description of the power and influence of the American underworld in the 1960’s:
Organized crime is a society that seeks to operate outside the control of the American people and their governments. It involves thousands of criminals, working within structures as complex as those of any large corporation, subject to laws more rigidly enforced than those of legitimate governments. Its actions are not impulsive but rather the result of intricate conspiracies, carried on over many years and aimed at gaining control over whole fields of activity in order to amass huge profits.(163)
Page 161
An analysis by the committee revealed that the Kennedy administration brought about the strongest effort against organized crime that had ever been coordinated by the Federal Government.(164) John and Robert Kennedy brought to their respective positions as President and Attorney General an unprecedented familiarity with the threat of organized crime–and a commitment to prosecute its leaders– based on their service as member and chief counsel respectively of the McClellan Committee during its extensive investigation of labor racketeering in the late 1950’s. (165) A review of the electronic surveillance conducted by the FBI from 1961 to 1964 demonstrated that members of La Cosa Nostra, as well as other organized crime figures, were quite cognizant of the stepped-up effort against them, and they placed responsibility for it directly upon President Kennedy and Attorney General Kennedy. (166)
During this period, the FBI had comprehensive electronic coverage of the major underworld figures, particularly those who comprised the commission. 8(167) The committee had access to and analyzed the product of this electronic coverage; it reviewed literally thousands of pages of electronic surveillance logs that revealed the innermost workings of organized crime in the United States. (168) The committee saw in stark terms a record of murder, violence, bribery, corruption, and an untold variety of other crimes. (169) Uniquely among congressional committees, and in contrast to the Warren Commission, the committee became familiar with the nature and scope of organized crime in the years before and after the Kennedy assassination, using as its evidence the words of the participants themselves.
An analysis of the work of the Justice Department before and after the tenure of Robert Kennedy as Attorney General also led to the conclusion that organized crime directly benefited substantially from the changes in Government policy that occurred after the assassination. (170) That organized crime had the motive, opportunity and means to kill the President cannot be questioned. (171) Whether it did so is another matter.
In its investigation of the decisionmaking process and dynamics of organized crime murders and intrasyndicate assassinations during the early 1960’s. the committee noted the extraordinary web of insulation, secrecy, and complex machinations that frequently surrounded organized crime leaders who ordered such acts.(172)In testimony before the Senate on September 25, 1963, 2 months before his brother’s assassination, Attorney General Kennedy spoke of the Government’s continuing difficulty in solving murders carried out by organized crime elements, particularly those ordered by members of the La Cosa Nostra commission. Attorney General Kennedy testified that:
…because the members of the Commission, the top members, or even their chief lieutenants, have insulated themselves from the crime itself, if they want to have somebody knocked off, for instance, the top man will speak to somebody who will speak to somebody else who will speak to somebody else and order it. The man who actually does the gun work, who might
8The ruling council of 9 to 12 Mafia leaders who collectively rule the national crime syndicate
Page 162
get paid $250 or $500, depending on how important it is, perhaps nothing at all he does not know who ordered it. To trace that back is virtually impossible. (173)
The committee studied the Kennedy assassination in terms of the traditional forms of violence used by organized crime and the historic pattern of underworld slayings. While the murder of the President’s accused assassin did in fact fit the traditional pattern–a shadowy man with demonstrable organized crime connections shoots down a crucial witness–the method of the President’s assassination did not resemble the standard syndicate killing.(174) A person like Oswald-young, active in controversial political causes, apparently not subject to the internal discipline of a criminal organization–would appear to be the least likely candidate for the role of Mafia hit man, especially in such an important murder. Gunmen used in organized crime killings have traditionally been selected with utmost deliberation and care, the most important considerations being loyalty and a willingness to remain silent if apprehended. These are qualities best guaranteed by past participation in criminal activities. (175)
There are, however, other factors to be weighed in evaluating the method of possible operation in the assassination of President Kennedy. While the involvement of a gunman like Oswald does not readily suggest organized crime involvement, any underworld attempt to assassinate the President would in all likelihood have dictated the use of some kind of cover, a shielding or disguise. (176) The committee made the reasonable assumption that an assassination of a President by organized crime could not be allowed to appear to be what it was.
Traditional organized crime murders are generally committed through the use of killers who make no effort to hide the fact that organized crime was responsible for such murders or “hits.”(177) While syndicate-authorized hits are usually executed in such a way that identification of the killers is not at all likely, the slayings are nonetheless committed in what is commonly referred to as the “gangland style.”(178) Indeed, an intrinsic characteristic of the typical mob execution is that it serves as a self-apparent message, with the authorities and the public readily perceiving the nature of the crime as well as the general identity of the group or gang that carried it out.(179)
The execution of a political leader–most particularly a President would hardly be a typical mob execution and might well necessitate a different method of operation. The overriding consideration in such an extraordinary crime would be the avoidance of any appearance of organized crime complicity. (180)
In its investigation, the committee noted three cases, for the purposes of illustration, in which the methodology employed by syndicate figures was designed to insulate and disguise the involvement of organized crime. (181) These did not fit the typical pattern of mob killings, as the assassination of a President would not. (182) While the a typical cases did not involve political leaders, two of the three were attacks on figures in the public eye. (183)
In the first case, the acid blinding of investigative reporter Victor Riesel in April 1956, organized crime figures in New York used a complex series of go-betweens to hire a petty thief and burglar to
Page 163
commit the act. (184) Thus, the assailant did not know who had actually authorized the crime for which he had been recruited. (185) The use of such an individual was regarded as unprecedented, as he had not been associated with the syndicate, was a known drug user, and outwardly appeared to be unreliable.(186) Weeks later, Riesel’s assailant was slain by individuals who had recruited him in the plot. (187)
The second case, the fatal shooting of a well-known businessman, Sol Landie, in Kansas City, Mo., on November 22, 1970, involved the recruitment, through several intermediaries, of four young Black men by members of the local La Cosa Nostra family.(188) Landie had served as a witness in a Federal investigation of gambling activities directed by Kansas City organized crime leader Nicholas Civella. The men recruited for the murder did not know who had ultimately ordered the killing, were not part of the Kansas City syndicate, and had received instructions through intermediaries to make it appear that robbery was the motive for the murder. (189) All of the assailants and two of the intermediaries were ultimately convicted.
The third case, the shooting of New York underworld leader Joseph Columbo before a crowd of 65,000 people in June 1971, was carried out by a young Black man with a petty criminal record, a nondescript loner who appeared to be alien to the organized crime group that had recruited him through various go-betweens.(190) The gunman was shot to death immediately after the shooting of Columbo, a murder still designated as unsolved. (191) (Seriously wounded by a shot to the head, Columbo lingered for years in a semiconscious state before he died in 1978.)
The committee found that these three cases, each of which is an exception to the general rule of organized crime executions, had identifiable similarities.(192) Each case was solved, in that the identity of the perpetrator of the immediate act became known. (193) In two of the cases, the assailant was himself murdered soon after the crime.(194) In each case, the person who wanted the crime accomplished recruited the person or persons who made the attack through more than one intermediary.(195) In each case, the person suspected of inspiring the violence was a member of, or connected to, La Cosa Nostra. (196) In each case, the person or persons hired were not professional killers, and they were not part of organized criminal groups. (197) In each case, the persons recruited to carry out the acts could be characterized as dupes or tools who were being used in a conspiracy they were not fully aware of. (198) In each case, the intent was to insulate the organized crime connection, with a particular requirement for disguising the true identity of the conspirators, and to place the blame on generally nondescript individuals. (199) These exceptions to the general rule of organized crime violence made it impossible for the committee to preclude, on the basis of an analysis of the method of the assassination, that President Kennedy was killed by elements of organized crime. (200)
In its investigation into the possibility that organized crime elements were involved in the President’s murder, the committee examined various internal and external factor that bear on whether organized crime leaders would have considered, planned and executed an assas-
Page 164
sination conspiracy. (201) The committee examined the decisionmaking process that would have been involved in such a conspiracy, and two primary propositions emerged. (202) The first related to whether the national crime syndicate would have authorized and formulated a conspiracy with the formal consent of the commission, the ruling council of Mafia leaders. (203) The second related to whether an individual organized crime leader, or possibly a small combination of leaders, might have conspired to assassinate the President through unilateral action, that is, without the involvement of the leadership of the national syndicate. (204)
The most significant evidence that organized crime as an institution or group was not involved in the assassination of President Kennedy was contained in the electronic surveillance of syndicate leaders conducted by the FBI in the early 1960’s. (205) As the President’s Crime Commission noted in 1967, and as this committee found through its review of the FBI surveillance, there was a distinct hierarchy and structure to organized crime. (206) Decisions of national importance were generally made by the national commission, or at least they depended on the approval of the commission members. (207) In 1963, the following syndicate leaders served as members of the commission: Vito Genovese, Joseph Bonanno, Carlo Gambino, and Thomas Lucchese of New York City; Stefano Magaddino of Buffalo; Sam Giancana of Chicago; Joseph Zerilli of Detroit; Angelo Bruno of Philadelphia and Raymond Patriarca of Providence. (208) The committee’s review of the surveillance transcripts and logs, detailing the private conversations of the commission members and their associates, revealed that there were extensive and heated discussions about the serious difficulties the Kennedy administration’s crackdown on organized crime was causing. (209)
The bitterness and anger with which organized crime leaders viewed the Kennedy administration are readily apparent in the electronic surveillance transcripts, with such remarks being repeatedly made by commission members Genovese, Giancana, Bruno, Zerilli, Patriarca and Magaddino.(210) In one such conversation in May 1962, a New York Mafia member noted the intense Federal pressure upon the mob, and remarked, “Bob Kennedy won’t stop today until he puts us all in jail all over the country. Until the commission meets and puts its foot down, things will be at a standstill.”(211) Into 1963, the pressure was continuing to mount, as evidenced by a conversation in which commission member Magaddino bitterly cursed Attorney General Kennedy and commented on the Justice Department’s increasing knowledge of the crime syndicates inner workings, stating, “They know everything under the sun. They know who’s back of it–they know there is a commission. We got to watch right now–and stay as quiet as possible.” (212)
While the committee’s examination of the electronic surveillance program revealed no shortage of such conversations during that period, the committee found no evidence in the conversations of the formulation of any specific plan to assassinate the President. (213) Nevertheless, that organized crime figures did discuss possible violent courses of action against either the President or his brother, Attorney Gen-
Page 165
eral Robert F. Kennedy–as well as the possible repercussions of such action-can be starkly seen in the transcripts.(214)
One such discussion bears quoting at length. It is a conversation between commission member Angelo Bruno of Philadelphia and an associate Willie Weisburg, on February 8, 1962. (215)In the discussion, in response to Weisburg’s heated suggestion that Attorney General Kennedy should be murdered, Bruno cautioned that Kennedy might be followed by an even worse Attorney General:
WEISBURG. See what Kennedy done. With Kennedy, a guy should take a knife, like all them other guys, and stab and kill the [obscenity], where he is now. Somebody should kill the [obscenity], I mean it. This is true. Honest to God. It’s about time to go. But I tell you something. I hope I git a week’s notice, I’ll kill. Right in the [obscenity] in the White House. Somebody’s got to rid of this [obscenity].
BRUNO. Look, Willie, do you see there was a king, do you understand. And he found out that everybody was saying that he was a bad king. This is an old Italian story. So, he figured. Let me go talk to the old woman. She knows everything. So he went to the old wise woman. So he says to her: “I came here because I want your opinion.” He says: “Do you think I’m a bad king? She says: “No, I think you are a good king.” He says: “Well how can everybody says I’m a bad king?” She says: “Because they are stupid. They don’t know.” He says: Well how come, why do you say I’m a good king?” “Well,” she said, “I knew your great grandfather. He was a bad king. I knew your grandfather. He was worse. I knew your father. He was worse than them. You, you are worse than them, but your son, if you die, your son is going to be worse than you. So its better to be with you.” [All laugh.] So Brownell–former Attorney General–was bad. He was no [obscenity] good. He was this and that.
WEISBURG. Do you know what this man is going to do? He ain’t going to leave nobody alone.
BRUNO. I know he ain’t. But you see, everybody in there was bad. The other guy was good because the other guy was worse. Do you understand? Brownell came. He was no good. He was worse than the guy before.
WEISBURG. Not like this one.
BRUNO. Not like this one. This one is worse. right? If something happens to this guy…[laughs]. (216)
While Angelo Bruno had hoped to wait out his troubles, believing that things might get better for him as time went by, such was not to be the case during the Kennedy administration. The electronic surveillance transcripts disclosed that by mid 1963, Bruno was privately making plans to shut down his syndicate operations and leave America, an unprecedented response by a commission member to Federal law enforcement pressure.(217)
Another member of the mob commission, Stefano Magaddino, voiced similar anger toward the President during that same period. (218) In October 1963, in response to a Mafia family member’s
Page 166
remark that President Kennedy “should drop dead,” Magaddino exploded, “They should kill the whole family, the mother and father too. When he talks he talks like a mad dog, he says, my brother the Attorney General.” (219)
The committee concluded that had the national crime syndicate, as a group, been involved in a conspiracy to kill the President, some trace of the plot would have been picked up by the FBI surveillance of the commission. (220) Consequently, finding no evidence in the electronic surveillance transcripts of a specific intention or actual plan by commission members to have the President assassinated, the committee believed it was unlikely that it existed. The electronic surveillance transcripts included extensive conversations during secret meetings of various syndicate leaders, set forth many of their most closely guarded thoughts and actions, and detailed their involvement in a variety of other criminal acts, including murder.(221) Given the far-reaching possible consequences of an assassination plot by the commission, the committee found that such a conspiracy would have been the subject of serious discussion by members of the commission, and that no matter how guarded such discussions might have been, some trace of them would have emerged from the surveillance coverage. (222) It was possible to conclude, therefore, that it is unlikely that the national crime syndicate as a group, acting under the leadership of the commission, participated in the assassination of President Kennedy.(223)
While there was an absence of evidence in the electronic surveillance materials of commission participation in the President’s murder, there was no shortage of evidence of the elation and relief of various commission members over his death.(224) The surveillance transcripts contain numerous crude and obscene comments by organized crime leaders, their lieutenants, associates and families regarding the assassination of President Kennedy.(225) The transcripts also reveal an awareness by some mob leaders that the authorities might be watching their reactions. (226) On November 25, 1963, in response to a lieutenant’s remark that Oswald “was an anarchist …a Marxist Communist,” Giancana exclaimed, “He was a marksman who knew how to shoot.”(227) On November 29, 1963, Magaddino cautioned his associates not to joke openly about the President’s murder, stating, “You can be sure that the police spies will be watching carefully to see what we think and say about this.” (228) Several weeks later, during a discussion between Bruno and his lieutenants, one participant remarked of the late President, “It is too bad his brother Bobby was not in that car too.”(229)
While the committee found it unlikely that the national crime syndicate was involved in the assassination, it recognized the possibility that a particular organized crime leader or a small combination of leaders, acting unilaterally, might have formulated an assassination conspiracy without the consent of the commission. (230)
In its investigation of the national crime syndicate, the committee noted factors that could have led an organized crime leader who was considering an assassination to withhold it from the national commission.(231) The committee’s analysis of the national commission disclosed that it was splintered by dissension and enmity in 1963. Rivalry between two blocks of syndicate families had resulted in a partial paralysis of the commission’s functions. (232)
Page 167
One significant reason for the disarray was, of course, the pressure being exerted by Federal law enforcement agencies. (233)In the fall of 1963, Attorney General Kennedy noted,
…in the past 2 years, at least three carefully planned commission meetings had to be called off because the leaders learned that we had uncovered their well-concealed plans and meeting places.
The Government’s effort got an unprecedented boost from the willingness of Joseph Valachi, a member of the “family” of commission member Vito Genovese of New York, to testify about the internal structure and activities of the crime syndicate, a development described by Attorney General Kennedy as “the greatest intelligence breakthrough” in the history of the Federal program against organized crime. (234) While it was not until August 1963 that Valachi’s identity as a Federal witness became public, the surveillance transcripts disclose that syndicate leaders were aware as early as the spring of 1963 that Valachi was cooperating with the Justice Department.(235) The transcripts disclose that the discovery that Valachi had become a Federal informant aroused widespread suspicion fear over the possibility of other leaks and informants within the upper echelons of the syndicate. (236) The televised Senate testimony by Valachi led to considerable doubt by syndicate leaders in other parts of the country as to the security of commission proceedings, with Genovese rapidly losing influence as a result of Valachi’s actions. (237)
The greatest source of internal disruption within the commission related to the discovery in early 1963 of a secret plan by commission member Joseph Bonanno to assassinate fellow members Carlo Gambino and Thomas Lucchese. (238) Bonanno’s assassination plan, aimed at an eventual takeover of the commission leadership, was discovered after one of the gunmen Bonanno had enlisted, Joseph Columbo, informed on him to the commission. (239) The Bonanno conspiracy, an unheard-of violation of commission rules, led to a long series of acrimonious deliberations that lasted until early 1964. (240) Bonanno refused to submit to the judgment of the commission, and his colleagues were sharply divided over how to deal with his betrayal, Gambino recommending that Bonanno be handled with caution, and Giancana urging that he be murdered.(241)
The committee concluded, based on the state of disruption within the commission and the questions that had arisen as to the sanctity of commission proceedings, that an individual organized crime leader who was planning an assassination conspiracy against President Kennedy might well have avoided making the plan known to the commission or seeking approval for it from commission members. (242) Such a course of unilateral action seemed to the committee to have been particularly possible in the case of powerful organized crime leaders who were well established, with firm control over their jurisdictions.(243)
The committee noted a significant precedent for such a unilateral course of action. In 1957, Vito Genovese engineered the assassination of Albert Anastasia, then perhaps the most feared Mafia boss in the country. (244) Six months earlier, Genovese’s men had shot and wounded Frank Costello, who once was regarded as the single most influential
Page 168
organized crime leader.(245) Both the Anastasia assassination and the Costello assault were carried out without the knowledge or consent of the national commission.(246) Genovese did, however, obtain approval for the crimes after the fact. (247) It was an extraordinary sequence of events that Attorney General Kennedy noted in September 1963, when he stated that Genovese “…wanted Commission approval for these acts–which he has received.” The Genovese plot against Anastasia and Costello and the ex post facto commission approval were integral events in the rise to dominance of organized crime figures for the years that followed. It directly led to the assemblage of national syndicate leaders at the Apalachin conference 3 weeks after the Anastasia murder, and to the rise of Carlo Gambino to a position of preeminence in La Costa Nostra. (248)
Top of Page
(5) Analysis of the 1963-64 investigation–In its investigation, the committee learned that fears of the possibility that organized crime was behind the assassination were more common among Government officials at the time than has been generally recognized. Both Attorney General Kennedy and President Johnson privately voiced suspicion about underworld complicity.(249) The Attorney General requested that any relevant information be forwarded directly to him, and there was expectation at the time that the recently created Warren Commission would actively investigate the possibility of underworld involvement. (250)
The committee found, however, that the Warren Commission conducted only a limited pursuit of the possibility of organized crime complicity. (251) As has been noted, moreover, the Warren Commission’s interest in organized crime was directed exclusively at Jack Ruby, and it did not involve any investigation of the national crime syndicate in general, or individual leaders in particular.(252) This was confirmed to the committee by J. Lee Rankin, the Commission’s general counsel, and by Burt W. Griffin, the staff counsel who conducted the Ruby investigation. (253) Griffin testified before the committee that “…the possibility that someone associated with the underworld would have wanted to assassinate the President… [was] not seriously explored” by the Warren Commission. (254)
The committee similarly learned from testimony and documentation that the FBI’s investigation of the President’s assassination was also severely limited in the area of possible organized crime involvement. While the committee found that the Bureau was uniquely equipped, with the Special Investigative Division having been formed 2 years earlier specifically to investigate organized crime, the specialists and agents of that Division did not play a significant role in the assassination investigation. (255) Former Assistant FBI Director Courtney Evans, who headed the Special Investigative Division, told the committee that the officials who directed the investigation never consulted him or asked for any participation by his Division.(256) Evans recalled, “I know they sure didn’t come to me. We had no part in that that I can recall.” (257) Al Staffeld, a former FBI official who supervised the day-to-day operations of the Special Investigative Division, told the committee that if the FBI’s organized crime specialists had been asked to participate, “We would have gone at it in every damn way possible.”(258)
Page 169
Ironically, the Bureau’s own electronic surveillance transcripts revealed to the committee a conversation between Sam Giancana and a lieutenant, Charles English, regarding the FBI’s role in investigating President Kennedy’s assassination. (259). In the December 3, 1963 conversation, English told Giancana:”I will tell you something, in another 2 months from now, the FBI will be like it was 5 years ago. They won’t be around no more. They say the FBI will get it (the investigation of the President’s assassination). They’re gonna start running down Fair Play for Cuba, Fair Play for Matsu. They call that more detrimental to the country than us guys.”(260)
The committee found that the quality and scope of the investigation into the possibility of an organized crime conspiracy in the President’s assassination by the Warren Commission and the FBI was not sufficient to uncover one had it existed. The committee also found that it was possible, based on an analysis of motive, means and opportunity, that an individual organized crime leader, or a small combination of leaders, might have participated in a conspiracy to assassinate President Kennedy. The committee’s extensive investigation led it to conclude that the most likely family bosses of organized crime to have participated in such a unilateral assassination plan were Carlos Marcello and Santos Trafficante. (261) While other family bosses on the commission were subjected to considerable coverage in the electronic surveillance program, such coverage was never applied to Marcello and almost never to Trafficante. (262)
Top of Page
(6) Carlos Marcello.–The committee found that Marcello had the motive, means and opportunity to have President John F. Kennedy assassinated, (263) though it was unable to establish direct evidence of Marcello’s complicity.
In its investigation of Marcello, the committee identified the presence of one critical evidentiary element that was lacking with the other organized crime figures examined by the committee: credible associations relating both Lee Harvey Oswald and Jack Ruby to figures having a relationship, albeit tenuous, with Marcello’s crime family or organization. (264) At the same time, the committee explicitly cautioned: association is the first step in conspiracy; it is not identical to it, and while associations may legitimately give rise to suspicions, a careful distinction must always be drawn between suspicions suspected and facts found.
As the long-time La Cosa Nostra leader in an area that is based in New Orleans but extends throughout Louisiana and Texas, Marcello was one of the prime targets of Justice Department efforts during the Kennedy administration.(265) He had, in fact, been temporarily removed from the country for a time in 1961 through deportation proceedings personally expedited by Attorney General Kennedy. (266) In his appearance before the committee in executive session, Marcello exhibited an intense dislike for Robert Kennedy because of these actions, claiming that he had been illegally “kidnaped”by Government agents during the deportation. (267)
While the Warren Commission devoted extensive attention to Oswald’s background and activities, the committee uncovered significant details of his exposure to and contacts with figures associated
Page 170
with the underworld of New Orleans that apparently had escaped the Commission.(268) One Such relationship actually extended into Oswald’s own family through his uncle, Charles “Dutz” Murret, a minor underworld gambling figure.(269) The committee discovered that Murret, who served as a surrogate father of sorts throughout much of Oswald’s life in New Orleans, was in the 1940’s and 1950’s and possibly until his death in 1964: an associate of significant organized crime figures affiliated with the Marcello organization. (270)
The committee established that Oswald was familiar with his uncle’s underworld activities and had discussed them with his wife, Marina, in 1963.(271) Additionally, the committee found that Oswald’s mother, Marguerite Oswald, was acquainted with several men associated with lieutenants in the Marcello organization. One such acquaintance, who was also an associate of Dutz Murret, reportedly served as a personal aide or driver to Marcello at one time. (272) In another instance, the committee found that an individual connected to Dutz Murret, the person who arranged bail for Oswald following his arrest in August 1963 for a street disturbance, was an associate of two of Marcello’s syndicate deputies. (One of the two, Nofio Pecora, as noted, also received a telephone call from Ruby on October 30, 1963, according to the committee’s computer analysis of Ruby’s phone records.) (273)
During the course of its investigation, the committee developed several areas of credible evidence and testimony indicating a possible association in New Orleans and elsewhere between Lee Harvey Oswald and David W. Ferrie, a private investigator and even, perhaps, a pilot for Marcello before and during 1963.(274) From the evidence available to the committee, the nature of the Oswald-Ferrie association remained largely a mystery. The committee established that Oswald and Ferrie apparently first came into contact with each other during Oswald’s participation as a teenager in a Civil Air Patrol unit for which Ferrie served as an instructor, although Ferrie, when he was interviewed by the FBI after his detainment as a suspect in the assassination,(275) denied any past association with Oswald.
In interviews following the assassination, Ferrie stated that he may have spoken in an offhand manner of the desirability of having President Kennedy shot, but he denied wanting such a deed actually to be done.(276) Ferrie also admitted his association with Marcello and stated that he had been in personal contact with the syndicate leader in the fall of 1963. He noted that on the morning of the day of the President’s death he was present with Marcello at a courthouse in New Orleans. (277) In his executive session testimony before the committee, Marcello acknowledged that Ferrie did work for his lawyer, G. Wray Gill, on his case, but Marcello denied that Ferrie worked for him or that their relationship was close. (278) Ferrie died in 1967 of a ruptured blood vessel at the base of the brain, shortly after he was named in the assassination investigation of New Orleans District Attorney Jim Garrison.
The committee also confirmed that the address 544 Camp Street, that Oswald had printed on some Fair Play for Cuba Committee handouts in New Orleans, was the address of a small office building
Page 171
where Ferrie was working on at least a part-time basis in 1963. The Warren Commission stated in its report that despite the Commission’s probe into why Oswald used this return address on his literature, “investigation has indicated that neither the Fair Play for Cuba Committee nor Lee Oswald ever maintained an office at that address.” (280)
The committee also established associations between Jack Ruby and several individuals affiliated with the underworld activities of Carlos Marcello. (281) Ruby was a personal acquaintance of Joseph Civello, the Marcello associate, who allegedly headed organized crime activities in Dallas; he also knew other individuals who have been linked with organized crime, including a New Orleans nightclub figure, Harold Tannenbaum, with whom Ruby was considering going into partnership in the fall of 1963. (282) 9
The committee examined a widely circulated published account that Marcello made some kind of threat on the life of President Kennedy in September 1962 at a meeting at his Churchill Farms estate outside New Orleans.(284) It was alleged that Marcello shouted an old Sicilian threat, “Livarsi na petra di la scarpa!” “Take the stone out of my shoe!” against the Kennedy brothers, stating that the President ways going to be assassinated. He spoke of using a “nut” to carry out the murder. (285)
The committee established the origin of the story and identified the informant who claimed to have been present at the meeting during which Marcello made the threat.(286) The committee also learned that even though the FBI was aware of the informant’s allegations over a year and half before they were published in 1969, and possessed additional information indicating that the informant may in fact have met with Marcello in the fall of 1962, a substantive investigation of the information was never conducted. (287) Director Hoover and other senior FBI officials were aware that FBI agents were initiating action to “discredit” the informant, without having conducted a significant investigation of his allegations. (288) Further, the committee discovered that the originating office relied on derogatory information from a prominent underworld figure in the ongoing effort to discredit the informant (289) An internal memorandum to Hoover noted that another FBI source was taking action to discredit the informant, “in order that the Carlos Marcello incident would be deleted from the book that first recounted the information. (290)
The committee determined that the informant who gave the account of the Marcello threat was in fact associated with various underworld figures, including at least one person well-acquainted with the Marcello organization.(291) The committee noted, however, that as a consequence of his underworld involvement, the informant had a questionable reputation for honesty and may not be a credible source of information. (292)
9Law enforcement files have long contained information suggesting that Joseph Campisi, a restaurant owner in Dallas, occupied a position in organized crime. The committee’s investigation did not confirm or refute the allegation, but it did establish that Ruby visited Campisi’s restaurant on the evening of November 21 and that Ruby was visited in jail after the shooting of Oswald by Campisi and his wife. Further, Campisi acknowledged a long-standing business and personal relationship with Marcello. (283)
Page 172
The committee noted further that it is unlikely that an organized crime leader personally involved in an assassination plot would discuss it with anyone other than his closest lieutenants, although he might be willing to discuss it more freely prior to a serious decision to undertake such an act. In his executive session appearance before the committee, Marcello categorically denied any involvement in organized crime or the assassination of President Kennedy. Marcello also denied ever making any kind of threat against the President’s life.(293)
As noted, Marcello was never the subject of electronic surveillance coverage by the FBI. The committee found that the Bureau did make two attempts to effect such surveillance during the early 1960’s, but both attempts were unsuccessful.(294) Marcello’s sophisticated security system and close-knit organizational structure may have been a factor in preventing such surveillance. 10 A former FBI official knowledgeable about the surveillance program told the committee, “That was our biggest gap …. With Marcello, you’ve got the one big exception in our work back then. There was just no way of penetrating that area. He was too smart.”(296)
Any evaluation of Marcello’s possible role in the assassination must take into consideration his unique stature within La Cosa Nostra. The FBI determined in the 1960’s that because of Marcello’s position as head of the New Orleans Mafia family (the oldest in the United States, having first entered the country in the 1880’s), the Louisiana organized crime leader had been endowed with special powers and privileges not accorded to any other La Cosa Nostra members. (297) As the leader of “the first family” of the Mafia in America, according to FBI information, Marcello has been the recipient of the extraordinary privilege of conducting syndicate operations without having to seek the approval of the national commission.(298)
Finally, a caveat, Marcello’s uniquely successful career in organized crime has been based to a large extent on a policy of prudence; he is not reckless. As with the case of the Soviet and Cuban Governments, a risk analysis indicated that he would be unlikely to undertake so dangerous a course of action as a Presidential assassination. Considering that record of prudence, and in the absence of direct evidence of involvement, it may be said that it is unlikely that Marcello was in fact involved in the assassination of the President. On the basis of the evidence available to it, and in the context of its duty to be cautious in its evaluation of the evidence, there is no other conclusion that the committee could reach. On the other hand, the evidence that he had the motive and the evidence of links through associates to both Oswald and Ruby, coupled with the failure of the 1963-64 investigation to explore adequately possible conspiratorial activity in the assassination, precluded a judgment by the committee that Marcello and his associates were not involved.
Top of Page
(7) Santos Trafficante.–The committee also concentrated its attention on Santos Trafficante, the La Cosa Nostra leader in Florida. The
10In addition Marcello was considered by his FBI case agent to be a legitimate businessman, which may account for the fact that the case agent was less than enthusiastic about pressing an investigation of the Louisiana Mafia leader. (295)
Page 173
committee found that Trafficante, like Marcello, had the motive, means, and opportunity to assassinate President Kennedy. (299)
Trafficante was a key subject of the Justice Department crackdown on organized crime during the Kennedy administration, with his name being added to a list of the top 10 syndicate leaders targeted for investigation. (300) Ironically, attorney General Kennedy’s strong interest in having Trafficante prosecuted occurred during the same period in which CIA officials, unbeknownst to the Attorney General, were using Trafficante’s services in assassination plots against the Cuban chief of state, Fidel Castro. (301)
The committee found that Santos Trafficante’s stature in the national syndicate of organized crime, notably the violent narcotics trade, and his role as the mob’s chief liaison to criminal figures within the Cuban exile community, provided him with the capability of formulating an assassination conspiracy against President Kennedy. Trafficante had recruited Cuban nationals to help plan and execute the CIA’s assignment to assassinate Castro. (The CIA gave the assignment to former FBI Agent Robert Maheu, who passed the contract along to Mafia figures Sam Giancana and John Roselli. They, in turn, enlisted Trafficante to have the intended assassination carried out.) (302)
In his testimony before the committee, Trafficante admitted participating in the unsuccessful CIA conspiracy to assassinate Castro, an admission indicating his willingness to participate in political murder. (303) Trafficante testified that he worked with the CIA out of a patriotic feeling for his country, an explanation the committee did not accept, at least not as his sole motivation. (304)
As noted, the committee established a possible connection between Trafficante and Jack Ruby in Cuba in 1959. (305) It determined there had been a close friendship between Ruby and Lewis McWillie, who, as a Havana gambler, worked in an area subject to the control of the Trafficante Mafia family. (306) Further, it assembled documentary evidence that Ruby made at least two, if not three or more, trips to Havana in 1959 when McWillie was involved in underworld gambling operations there. (307) Ruby may in fact have been serving as a courier for underworld gambling interests in Havana, probably for the purpose of transporting funds to a bank in Miami. (308)
The committee also found that Ruby had been connected with other Trafficante associates–R. D. Matthews, Jack Todd, and James Dolan– all of Dallas. (309)
Finally, the committee developed corroborating evidence that Ruby may have met with Trafficante at Trescornia prison in Cuba during one of his visits to Havana in 1959, as the CIA had learned but had discounted in 1964. (310) While the committee was not able to determine the purpose of the meeting, there was considerable evidence that it did take place.(311)
During the course of its investigation of Santos Trafficante, the committee examined an allegation that Trafficante had told a prominent Cuban exile, Jose Aleman, that President Kennedy was going to be assassinated. (312) According to Aleman, Trafficante made the statement in a private conversation with him that took place sometime in September 1962. (313) In an account of the alleged conversation pub-
Page 174
lished by the Washington Post in 1976, Aleman was quoted as stating that Trafficante had told him that President Kennedy was “going to be hit.” (314) Aleman further stated, however, that it was his impression that Trafficante was not the specific individual who was allegedly planning the murder. (315) Aleman was quoted as having noted that Trafficante had spoken of Teamsters Union President James Hoffa during the same conversation, indicating that the President would “get what is coming to him” as a result of his administration’s intense efforts to prosecute Hoffa. (316)
During an interview with the committee in March 1977, Aleman provided further details of his alleged discussion with Trafficante in September 1962.(317) Aleman stated that during the course of the discussion, Trafficante had made clear to him that he was not guessing that the President was going to be killed. Rather he did in fact know that such a crime was being planned.(318) In his committee interview, Aleman further stated that Trafficante had given him the distinct impression that Hoffa was to be principally involved in planning the Presidential murder. (319)
In September 1978, prior to his appearance before the committee in public session. Aleman reaffirmed his earlier account of the alleged September 1962 meeting with Trafficante. Nevertheless, shortly before his appearance in public session, Aleman informed the committee staff that he feared for his physical safety and was afraid of possible reprisal from Trafficante or his organization. In this testimony, Aleman changed his professed understanding of Trafficante’s comments. Aleman repeated under oath that Trafficante had said Kennedy was “going to be hit, but he then stated it was his impression that Trafficante may have only meant the President was going to be hit by “a lot of Republican votes” in the 1964 election, not that he was going to be assassinated. (320)
Appearing before the committee in public session on September 28, 1978, Trafficante categorically denied ever having discussed any plan to assassinate President Kennedy. (321) Trafficante denied any foreknowledge of or participation in the President’s murder. (322) While stating that he did in fact know Aleman and that he had met with him on more than one occasion in 1962, Trafficante denied Aleman’s account of their alleged conversation about President Kennedy, and he denied ever having made a threatening remark against the President.(323)
The committee found it difficult to understand how Aleman could have misunderstood Trafficante during such a conversation, or why he would have fabricated such an account. Aleman appeared to be a reputable person, who did not seek to publicize his allegations, and he was well aware of the potential danger of making such allegations against a leader of La Costa Nostra. The committee noted, however, that Aleman’s prior allegations and testimony before the committee had made him understandably fearful for his life.
The committee also did not fully understand why Aleman waited so many years before publicly disclosing the alleged incident. While he stated in 1976 that be had reported Trafficante’s alleged remarks about the President to FBI agents in 1962 and 1963, the committee’s review
Page 175
of Bureau reports on his contacts with FBI agents did not reveal a record of any such disclosure or comments at the time. (324) Additionally, the FBI agent who served as Aleman’s contact during that period denied ever being told such information by Aleman.
Further, the committee found it difficult to comprehend why Trafficante, if he was planning or had personal knowledge of an assassination plot, would have revealed or hinted at such a sensitive matter to Aleman. It is possible that Trafficante may have been expressing a personal opinion, “The President ought to be hit,” but it is unlikely in the context of their relationship that Trafficante would have revealed to Aleman the existence of a current plot to kill the president. As previously noted with respect to Carlos Marcello, to have attained his stature as the recognized organized crime leader of Florida for a number of years. Trafficante necessarily had to operate in a characteristically calculating and discreet manner. The relationship between Trafficante and Aleman, a business acquaintance, does not seem to have been close enough for Trafficante to have mentioned or alluded to such a murder plot. The committee thus doubted that Trafficante would have inadvertently mentioned such a plot. In sum, the committee believed there were substantial factors that called into question the validity of Aleman’s account.
Nonetheless, as the electronic surveillance transcripts of Angelo Bruno, Stefano Magaddino and other top organized crime leaders make clear, there were in fact various underworld conversations in which the desirability of having the President assassinated was discussed. (325) There were private conversations in which assassination was mentioned, although not in a context that indicated such a crime had been specifically planned.(326) With this in mind, and in the absence of additional evidence with which to evaluate the Aleman account of Trafficante’s alleged 1962 remarks, the committee concluded that the conversation, if it did occur as Aleman testified, probably occurred in such a circumscribed context.
As noted earlier, the committee’s examination of the FBI’s electronic surveillance program of the early 1960’s disclosed that Santos Trafficante was the subject of minimal, in fact almost nonexistent, surveillance coverage. (327) During one conversation in 1963, overheard in a Miami restaurant, Trafficante had bitterly attacked the Kennedy administration’s efforts against organized crime, making obscene comments about “Kennedy’s right-hand man” who had recently coordinated various raids on trafficante gambling establishments.(328) In the conversation, Trafficante stated that he was under immense pressure from Federal investigators, commenting “I know when I’m beat, you understand? (329) Nevertheless, it was not possible to draw conclusions about Trafficante actions based on the electronic surveillance program since the coverage was so limited. Finally, as with Marcello, the committee noted that Trafficante’s cautious character is inconsistent with his taking the risk of being involved in an assassination plot against the President. The committee found, in the context of its duty to be cautious in its evaluation of the evidence, that it is unlikely that Trafficante plotted to kill the President, although it could not rule out the possibility of such participation on the basis of available evidence.
Page 176
Top of Page
(8) James R. Hoffa.–During the course of its investigation, the committee also examined a number of areas of information and allegations pertaining to James R. Hoffa and his Teamsters Union and underworld associates. The long and close relationship between Hoffa and powerful leaders of organized crime, his intense dislike of John and Robert Kennedy dating back to their role in the McClellan Senate investigation, together with his other criminal activities, led the committee to conclude that the former Teamsters Union president had the motive, means and opportunity for planning an assassination attempt upon the life of President John F. Kennedy.
The committee found that Hoffa and at least one of his Teamster lieutenants, Edward Partin, apparently did, in fact, discuss the planning of an assassination conspiracy against President Kennedy’s brother, Attorney General Robert F. Kennedy, in July or August of 1962.(330) Hoffa’s discussion about such an assassination plan first became known to the Federal Government in September 1962, when Partin informed authorities that he had recently participated in such a discussion with the Teamsters president. (331)
In October 1962, acting under the orders of Attorney General Kennedy, FBI Director Hoover authorized a detailed polygraph examination of Partin. (332) In the examination, the Bureau concluded that Partin had been truthful in recounting Hoffa’s discussion of a proposed assassination plan.(333) Subsequently, the Justice Department developed further evidence supporting Partin’s disclosures, indicating that Hoffa had spoken about the possibility of assassinating the President’s brother on more than one occasion. (334)
In an interview with the committee, Partin reaffirmed the account of Hoffa’s discussion of a possible assassination plan, and he stated that Hoffa had believed that having the Attorney General murdered would be the most effective way of ending the Federal Government’s intense investigation of the Teamsters and organized crime.(335) Partin further told the committee that he suspected that Hoffa may have approached him about the assassination proposal because Hoffa believed him to be close to various figures in Carlos Marcello’s syndicate organization.(336) Partin, a Baton Rouge Teamsters official with a criminal record, was then a leading Teamsters Union official in Louisiana. Partin was also a key Federal witness against Hoffa in the 1964 trial that led to Hoffa’s eventual imprisonment. (337)
While the committee did not uncover evidence that the proposed Hoffa assassination plan ever went beyond its discussion, the committee noted the similarities between the plan discussed by Hoffa in 1962 and the actual events of November 22, 1963. While the committee was aware of the apparent absence of any finalized method or plan during the course of Hoffa’s discussion about assassinating Attorney General Kennedy, he did discuss the possible use of a lone gunman equipped with a rifle with a telescopic sight, (338) the advisability of having the assassination committed somewhere in the South, (339) as well as the potential desirability of having Robert Kennedy shot while riding in a convertible. (34O) While the similarities are present, the committee also noted that they were not so unusual as to point ineluctably in a particular direction. President Kennedy himself, in fact, noted that he was vulnerable to rifle fire before his Dallas trip. Nevertheless, references
Page 177
to Hoffa’s discussion about having Kennedy assassinated while riding in a convertible were contained in several Justice Department memoranda received by the Attorney General and FBI Director Hoover in the fall of 1962.(341) Edward Partin told the committee that Hoffa believed that by having Kennedy shot as he rode in a convertible, the origin of the fatal shot or shots would be obscured. (342) The context of Hoffa’s discussion with Partin about an assassination conspiracy further seemed to have been predicated upon the recruitment of an assassin without any identifiable connection to the Teamsters organization or Hoffa himself.(343) Hoffa also spoke of the alternative possibility of having the Attorney General assassinated through the use of some type of plastic explosives. (344)
The committee established that President Kennedy himself was notified of Hoffa’s secret assassination discussion shortly after the Government learned of it. The personal journal of the late President’s friend, Benjamin C. Bradlee, executive editor of the Washington Post, reflects that the President informed him in February 1963 of Hoffa’s discussion about killing his brother. (345) Bradlee noted that President Kennedy mentioned that Hoffa had spoken of the desirability of having a silenced weapon used in such a plan. Bradlee noted that while he found such a Hoffa discussion hard to believe “the President was obviously serious” about it. (346)
Partly as a result of their knowledge of Hoffa’s discussion of assassination with Partin in 1962, various aides of the late President Kennedy voiced private suspicions about the possibility of Hoffa complicity in the President’s assassination.(347) The committee learned that Attorney General Robert F. Kennedy and White House Chief of Staff Kenneth O’Donnell contacted several associates in the days immediately following the Dallas murder to discuss the possibility of Teamsters Union or organized crime involvement. (348)
As noted in the account of Ruby’s telephone records, the committee confirmed the existence of several contacts between Ruby and associates of Hoffa during the period of October and November 1963,(349) including one Hoffa aide whom Robert Kennedy had once described as one of Hoffa’s most violent lieutenants. (350) Those associates, Barney Baker, Irwin Weiner and Dusty Miller, stated that Ruby had been in touch with them for the sole purpose of seeking assistance in a nightclub labor dispute. (351)
The committee learned that Attorney General Kennedy and his aides arranged for the appointment of Charles Shaffer, a Justice Department attorney, to the Warren Commission staff in order that the possibility of Teamster involvement be watched. Shaffer confirmed to the committee that looking into Hoffa was one purpose of his appointment.(352)
Yet, partly as a result of the Commission’s highly circumscribed approach to investigating possible underworld involvement, as well as limited staff resources, certain areas of possible information relating to Hoffa–such as the Ruby telephone calls–were not the subject of in-depth investigation.(353) Nevertheless, in a lengthy Commission memorandum prepared for the CIA in February 1964, the Teamsters Union had been listed first on a list of potential groups to be investigated in probing “ties between Ruby and others who might have been interested in the assassination of President Kennedy.” (354)
Page 178
During the course of its investigation, the committee noted the existence of other past relationships between Ruby and associates of Hoffa, apart from those disclosed by a review of the Ruby phone records. Two such figures were Paul Dorfman, the Chicago underworld figure who was instrumental in Hoffa’s rise to power in the labor movement, and David Yaras, the reputed organized crime executioner whose relationship to Ruby dated back to their early days in Chicago. (355)
The committee also confirmed that another Teamsters official, Frank Chavez, had spoken to Hoffa about murdering Robert Kennedy in early 1967, shortly before Hoffa went to Federal prison. (356) During that incident, Hoffa reportedly sharply rebuked his aide, telling him that such a course of action was dangerous and should not be considered. (357)
In an interview with a newsman several weeks before his disappearance and presumed murder, Hoffa denied any involvement in the assassination of President Kennedy, and he disclaimed knowing anything about Jack Ruby or his motivations in the murder of Oswald. Hoffa also denied that he had ever discussed a plan to assassinate Robert Kennedy. (358)
As in the cases of Marcello and Trafficante, the committee stressed that it uncovered no direct evidence that Hoffa was involved in a plot on the President’s life, much less the one that resulted in his death in Dallas in November 1963. In addition, and as opposed to the cases of Marcello and Trafficante, Hoffa was not a major leader of organized crime. Thus, his ability to guarantee that his associates would be killed if they turned Government informant may have been somewhat less assured. Indeed, much of the evidence tending to incriminate Hoffa was supplied by Edward Grady Partin, a Federal Government informant who was with Hoffa when the Teamster president was on trial in October 1962 in Tennessee for violating the Taft-Hartley Act. 11
It may be strongly doubted, therefore, that Hoffa would have risked anything so dangerous as a plot against the President at a time that he knew he was under active investigation by the Department of Justice.12
Finally, a note on Hoffa’s character. He was a man of strong emotions who hated the President and his brother, the Attorney General. He did not regret the President’s death, and he said so publicly. Nevertheless, Hoffa was not a confirmed murderer, as were various organized crime leaders whose involvement the committee considered, and he cannot be placed in that category with them, even though he had extensive associations with them. Hoffa’s associations with such organized crime leaders grew out of the nature of his union and the industry whose workers it represented. Organized crime and the violence of the labor movement were facts of life for Hoffa; they were part of the milieu in which he grew up and worked. But when he encountered the only specific plot against a Kennedy that came to the attention of the committee (the suggestion from Frank Chavez), he rejected it.
11Hoffa was in fact facing charges of trying to bribe the jury in his 1962 trial in Tennessee on November 22, 1963. The case was scheduled to go to trial in January 1964. Hoffa was ultimately convicted and sentenced to a prison term. Partin was the Government’s chief witness against him.
12The committee found no evidence to indicate that Hoffa was under electronic surveillance.
Page 179
The committee concluded, therefore, that the balance of the evidence argued that it was improbable that Hoffa had anything to do with the death of the President.
Top of Page
(c) Summary and analysis of the evidence
The committee also believed it appropriate to reflect on the general question of the possible complicity of organized crime members, such as Trafficante or Marcello, in the Kennedy assassination, and to try to put the evidence it had obtained in proper perspective.
The significance of the organized crime associations developed by the committee’s investigation speaks for itself, but there are limitations that must be noted. That President Kennedy’s assassin and the man who, in turn, murdered him can be tied to individuals connected to organized crime is important for one reason: for organized crime to have been involved in the assassination, it must have had access to Oswald or Ruby or both.
The evidence that has been presented by the committee demonstrates that Oswald did, in fact, have organized crime associations. Who he was and where he lived could have come to the attention of those in organized crime who had the motive and means to kill the President. Similarly, there is abundant evidence that Ruby was knowledgeable about and known to organized crime elements. Nevertheless, the committee felt compelled to stress that knowledge or availability through association falls considerably short of the sort of evidence that would be necessary to establish criminal responsibility for a conspiracy in the assassination. It is also considerably short of what a responsible congressional committee ought to have before it points a finger in a legislative context.
It must also be asked if it is likely that Oswald was, in fact, used by an individual such as Marcello or Trafficante in an organized crime plot. Here, Oswald’s character comes into play. As the committee noted, it is not likely that Oswald was a hired killer; it is likely that his principal motivation in the assassination was political. Further, his politics have been shown to have been generally leftwing, as demonstrated by such aspects of his life as his avowed support of Fidel Castro. Yet the organized crime figures who had the motive and means to murder the President must be generally characterized as rightwing and anti-Castro. Knitting these two contradictory strands together posed a difficult problem. Either the assassination of President Kennedy was essentially an apolitical act undertaken by Oswald with full or partial, knowledge of who he was working for–which would be hard to believe–or Oswald’s organized crime contacts deceived him about their true identity and motivation, or else organized crime was not involved.
From an organized crime member’s standpoint, the use of an assassin with political leanings inconsistent with his own would have enhanced his insulation from identification with the crime. Nevertheless, it would have made the conspiracy a more difficult undertaking, which raises questions about the likelihood that such a conspiracy occurred. The more complicated a plot becomes, the less likely it will work. Those who rationally set out to kill a king, it may be argued, first design a plot that will work. The Oswald plot did in fact work, at
Page 180
least for 15 years, but one must ask whether it would have looked workable 15 years ago. Oswald was an unstable individual. Shortly before the assassination, for example, he delivered a possibly threatening note to the Dallas FBI office. With his background, he would have been an immediate suspect in an assassination in Dallas, and those in contact with him would have known that. Conspirators could not have been assured that Oswald or his companion would be killed in Dealey Plaza; they could not be sure that they could silence them. The plot, because of Oswald’s involvement, would hardly have seemed to be a low risk undertaking.
The committee weighed other factors in its assessment of Oswald, his act and possible co-conspirators. It must be acknowledged that he did, in the end, exhibit a high degree of brutal proficiency in firing the shot that ended the President’s life, and that, as an ex-marine, that proficiency may have been expected. In the final analysis, it must be admitted that he accomplished what he set out to do.
Further, while Oswald exhibited a leftist political stance for a number of years, his activities and associations were by no means exclusively leftwing. His close friendship with George de Mohrenschildt, an oilman in Dallas with rightwing connections, is a case in point. Additionally, questions have been raised about the specific nature of Oswald’s pro-Castro activities. It has been established that on at least one occasion in 1963, he offered his services for clandestine paramilitary actions against the Castro regime, though, as has been suggested, he may have merely been posing as an anti-Castro activist.
That the evidence points to the possibility that Oswald was also associated in 1963 with David Ferrie, the Marcello operative who was openly and actively anti-Castro, is troubling, too. Finally, the only Cuba-related activities that have ever been established at 544 Camp Street, New Orleans, the address of an office building that Oswald stamped on some of his Fair Play for Cuba Committee handouts, were virulently anti-Castro in nature.
Thus, the committee was unable to resolve its doubts about Lee Harvey Oswald. While the search for additional information in order to reach an understanding of Oswald’s actions has continued for 15 years, and while the committee developed significant new details about his possible organized crime associations, particularly in New Orleans, the President’s assassin himself remains not fully understood. The committee developed new information about Oswald and Ruby, thus altering previous perceptions, but the assassin and the man who murdered him still appear against a backdrop of unexplained, or at least not fully explained, occurrences, associations and motivations.
The scientific evidence available to the committee indicated that it is probable that more than one person was involved in the President’s murder. That fact compels acceptance. And it demands re-examination of all that was thought to be true in the past. Further, the committee’s investigation of Oswald and Ruby showed a variety of relationships that may have matured into an assassination conspiracy. Neither Oswald nor Ruby turned out to be “loners,” as they had been painted in the 1964 investigation. Nevertheless, the committee frankly acknowledged that it was unable firmly to identify the other gunman or the nature and extent of the conspiracy.
Page 181
Top of Page
5. THE SECRET SERVICE, FEDERAL BUREAU OF INVESTIGATION, AND CENTRAL INTELLIGENCE AGENCY WERE NOT INVOLVED IN THE ASSASSINATION OF PRESIDENT KENNEDY
- The Secret Service
- Connally testimony
- Choice of motorcade route
- Allegation a Secret Service agent was on the grassy knoll
- Conclusion
- The Federal Bureau of Investigation
- Early rumors that Oswald was an informant
- The Hosty entry in Oswald’s address book
- FBI contacts with Oswald (Fort Worth, 1962)
- FBI contacts with Oswald (New Orleans, 1963)
- FBI contacts with Oswald (Dallas, 1963)
- The destruction of Oswald’s note
- Conclusion
- The Central Intelligence Agency
- CIA personnel in the Soviet Russia Division
- CIA personnel abroad
- Oswald’s CIA file
- Why the delay in opening Oswald’s 201 file?
- Why was he carried as Lee Henry Oswald in his 201 file?
- The meaning of “AG” under “Other identification” in Oswald’s 201 file
- Why was Oswald’s 201 file restricted?
- Were 37 documents missing from Oswald’s 201 file?
- Did the CIA maintain a dual filing system on Oswald?
- Did Oswald ever participate in a CIA counterintelligence project?
- Did the CIA ever debrief Oswald?
- The Justice Department’s failure to prosecute Oswald
- Oswald’s trip to Russia via Helsinki and his ability to obtain a visa in 2 days
- Oswald’s contact with Americans in the Soviet Union
- Alleged intelligence contacts after Oswald returned from Russia
- Alleged intelligence implications of Oswald’s military service
- Oswald’s military intelligence file
- The Oswald photograph in Office of Naval Intelligence files
- Oswald in Mexico City
- Conclusion
As the symbolic leader of the Nation, the President means many things to many people. His loss is keenly felt; it is a traumatic event. The President is also more than the symbolic leader of the Nation; in fact, he holds both political and military power, and his death is an occasion for its transfer. It was, therefore, understandable that in foreign. and domestic speculation at the time of President Kennedy’s assassination, there was a suggestion of complicity by agencies of the U.S. Government. This was one of the principal reasons for the Warren Commission’s creation.
With the publication of the Commission’s report, the question was quieted, if not completely stilled. Nevertheless, critics continued to imply that the Secret Service, the FBI or the CIA had somehow been involved in the tragedy in Dallas, and the Warren Commission itself came to be viewed by some as part of a Government effort to conceal the truth. With the revelation of the illegal domestic programs of the FBI and the foreign assassination plots of the CIA by the Senate Select Committee to Study Governmental Operations with Respect to Intelligence Activities in 1976, speculation was rekindled that Government itself may have been involved in the President’s death.
The committee carefully considered various charges of Government complicity and coverup. A major portion of its resources were devoted to examining a variety of allegations directed at the Secret Service, the FBI, and the CIA as well as the Warren Commission. As the investigation proceeded, the committee carefully sought evidence that Government agents had foreknowledge of an assassination, took advantage of it after the event, or afterwards covered up information relevant to ascertaining the truth. The committee made a conscientious effort, for example, to determine if the autopsy materials were authentic. Had they been tampered with, it would have raised the most serious of questions. The committee also carefully assessed the performance of the Secret Service in the planning and execution of the Dallas trip for signs that it may have actively sought to bring about the President’s death. In addition, the committee carefully examined the relationship, if any, that Lee Harvey Oswald might have had with various governmental agencies, particularly the FBI and CIA. Over the years, there has been speculation that. Oswald might have been an FBI informant or an agent of the CIA. However Oswald is seen–patsy or perpetrator–his relationship to the agencies of the Government was crucial to assessing the question of Government complicity. If he had had a relationship with one or more of the agencies, serious issues would be raised. If he had not, the question would be less pressing.
Top of Page
(a) The Secret Service
Go to the footnotes for this section.
The committee’s investigation of alleged Secret Service complicity in the assassination was primarily, although not, exclusively, concerned with two questions. One, did the Secret Service facilitate the shooting by arranging a motorcade route that went through the heart of downtown Dallas and past the Texas School Book Depository? Two, did
Page 182
any Secret Service personnel engage in conduct at the site of the assassination that might indicate complicity in the assassination? The committee’s investigation involved extensive file reviews, interviews, depositions, and hearings. Former White House personnel, Secret Service agents, Dallas Police Department officers, Texas public officials and private citizens who had witnessed the assassination were interviewed or questioned. In addition, relevant files and documents of former White House staff, the Secret Service, and the Dallas Police Department pertaining to the planning of the motorcade route were reviewed. These included the Secret Service’s contingency plans for the Dallas trip that set forth scheduling, security factors and related considerations for the motorcade route.
Top of Page
(1) Connally testimony.—Governor John B. Connally testified at a public hearing that he first heard of the possibility of a Presidential trip to Texas during his gubernatorial campaign in the spring of 1962, when Vice President Johnson told him the President wanted to make a fundraising visit to the State. (1) Connally said he discussed the trip with the President himself in El Paso, Tex., in June 1963, and in October he went to the White House to help formulate plans.(2) According to former White House aides, President Kennedy expressed a desire to make use of a motorcade during the trip,(3) since he had found it a useful political instrument during his campaign for the Presidency. Further, the Dallas luncheon engagement under discussion involved only a limited speaking appearance, and Kennedy believed a motorcade would broaden his public exposure. (4)
The decision to use a motorcade was opposed initially by Governor Connally, who testified that he thought it would fatigue the President. (5) Frank Erwin, executive secretary of the Texas Democratic Committee, also opposed the motorcade, but for a different reason. He testified that because of Adlai Stevenson’s ugly confrontation with rightwing extremists only weeks earlier, he was concerned about the possibility of a similar embarrassing and potentially difficult situation.(6) These objections, however, were overruled by the White House. (7)
Top of Page
(2) Choice of the motorcade route.–Once the motorcade decision was made, the choice of a route was dependent more upon the selection of a site for the President’s luncheon speech than upon security considerations. The White House staff at first favored the Dallas Women’s Building near the Dallas County Fairgrounds because its capacity was greater than that of the alternative site, the Trade Mart, a commercial center with more limited facilities. (8) The White House staff felt that the Women’s Building would have permitted more of the President’s supporters to attend.
According to Jerry Bruno, a White House advance man, the route to the Women’s Building would have led the motorcade to proceed along Main Street eastward to the Fairgrounds, which lay to the southeast of the business district. Access to Main Street on the west side of Dealey Plaza would have been by a cloverleaf from the expressway. Using this route, the motorcade would have proceeded at a relatively high speed (40 to 50 mph) into Dealey Plaza and it would maintain this speed until it reached the intersection of Main and Houston Streets where crowds would have gathered. (9)Had it taken
Page 183
this route, the motorcade would not have passed directly in front of the Texas School Book Depository at the slow (approximately 11 mph) speed that it did enroute to the Trade Mart.
In his testimony, Forrest Sorrels, the special agent-in-charge of the Dallas Secret Service office in 1963, indicated that the Secret Service also preferred the Women’s Building as the luncheon site because, as a single story structure, it would have been easier to secure than the Trade Mart.(10) For political reasons, however, Governor Connally insisted on the Trade Mart,1 (11) and the White House acquiesced to his wishes so it could avoid a dispute with the Governor, whose assistance was needed to assure the political success of the trip.(12)
Accordingly, a motorcade to the Trade Mart was planned, and since the purpose of the motorcade was to permit the President to greet well-wishers in downtown Dallas, the route that was chosen was west along Main, right on Houston, then left on Elm Street, proceeding past the book depository, and through Dealey Plaza. Main Street, according to Governor Connally, had been the usual route for ceremonial occasions,(13) such as a procession in 1936 although in the opposite direction–in honor of President Roosevelt, the last President to have traveled through Dallas in a motorcade.
While the Secret Service was consulted regarding alternative luncheon sites, its role in the ultimate decisionmaking process was secondary to that of Governor Connally and the White House staff. (14) Similarly, once the actual motorcade route had been set, also without significant Secret Service input, it was the White House staff, not the Secret Service, who made the decision to publish the route in Dallas newspapers. Presidential aides wanted to assure maximum public exposure for President Kennedy. (15)
The committee found no evidence, therefore, suggesting that the selection of a motorcade route involved. Secret Service complicity in a plot to assassinate the President.2 (18)
Top of Page
(3) Allegation a Secret Service agent was on the grassy knoll.- After the assassination, several witnesses stated they had seen or encountered Secret Service agents behind the stockade fence situated on the grassy knoll area and in the Texas School Book Depository. (19) Other witnesses reported Secret Service agents leaving the motorcade and running to various locations in Dealey Plaza. (20) Warren Commission critics have alleged that these Secret Service agents either participated in the assassination itself or were involved in a coverup of the evidence. (21)
None of the witnesses interviewed by the committee was able provide further corroborating information concerning their original statements. The majority, however, indicated that they were mistaken in their original interpretation of events.(22) Committee interviews or depositions with 11 of the 16 agents3 who were on duty with the motorcade and with their supervisors produced evidence that only one
1Connally in effect indicated he would not support the fundraising visit if the Trade Mart was not the luncheon site.
2The decision not to use a bubble top on the President’s limousine was made by White House staff aides just minutes before the motorcade got underway. The Secret Service was not involved in the decision. (16) The bubble top, in any event, was not a bulletproof barrier designed to protect the limousine occupants. It served merely to shield them from inclement weather. (17)
3One of the agents not interviewed had died. Affidavits were obtained from the remaining four.
Page 184
agent had left the motorcade at any time prior to the arrival at Parkland Hospital. This agent, Thomas “Lem” Johns, had been riding in Vice President Johnson’s follow-up car. In an attempt to reach Johnson’s limousine, he had left the car at the sound of shots and was momentarily on his own in Dealey Plaza, though he was picked up almost immediately and taken to Parkland Hospital.(23) In every instance, therefore, the committee was able to establish the movement and the activities of Secret Service agents. Except for Dallas Agent-in-Charge Sorrels, who helped police search the Texas School Book Depository, no agent was in the vicinity of the stockade fence or inside the book depository on the day of the assassination.(24)
Significantly, most of the witnesses who made identifications of Secret Service personnel stated that they had surmised that any plainclothed individual in the company of uniformed police officers must have been a Secret Service agent. (25) Because the Dallas Police Department had numerous plainclothes detectives on duty in the Dealey Plaza area,(26) the committee considered it possible that they were mistaken for Secret Service agents.
One witness who did not base his Secret Service agent identification merely upon observing a plainclothesman in the presence of uniformed police officers was Dallas police officer Joseph M. Smith. Smith, who had been riding as a motorcycle escort in the motorcade, ran up the grassy knoll immediately after the shooting occurred. He testified to the Warren Commission that at that time he encountered a man who stated that he was a Secret Service agent and offered supporting credentials. Smith indicated that he did not examine these credentials closely, and he then proceeded to search the area unsuccessfully for suspicious individuals. (27)
The committee made an effort to identify the person who talked to Patrolman Smith. FBI Special Agent James P. Hosty stated that Frank Ellsworth, then an agent for the Alcohol, Tobacco and Firearms Bureau of the Treasury Department, had indicated that he had been in the grassy knoll area and for some reason had identified himself to someone as a Secret Service agent. (28) The committee deposed Ellsworth, who denied Hosty’s allegation. (29)
The committee did obtain evidence that military intelligence personnel may have identified themselves as Secret Service agents or that they might have been misidentified as such. Robert E. Jones, a retired Army lieutenant colonel who in 1963 was commanding officer of the military intelligence region that encompassed Texas, told the committee that from 8 to 12 military intelligence personnel in plainclothes were assigned to Dallas to provide supplemental security for the President’s visit. He indicated that these agents had identification credentials and, if questioned, would most likely have stated that they were on detail to the Secret Service. (30)
The committee sought to identify these agents so that they could be questioned. The Department of Defense, however, reported that a search of its files showed “no records …indicating any Department of Defense Protective Services in Dallas.”(31) The committee was unable to resolve the contradiction.
Top of Page
(4) Conclusion.–Based on its entire investigation, the committee found no evidence of Secret Service complicity in the assassination.
Page 185
Top of Page
(b) The Federal Bureau of Investigation
Go to the footnotes for this section.
In the weeks that followed the assassination, it was alleged in several newspaper articles that Lee Harvey Oswald had been an FBI informant. Consequently, the Warren Commission expended considerable effort addressing the question. Testimony was taken from FBI Director J. Edgar Hoover, Assistant to the Director Alan H. Belmont, and FBI Special Agents John W. Fain, John L. Quigley and James P. Hosty, Jr. (1) “All declared, in substance, that Oswald was not an informant or agent of the FBI, and that he did not act in any other capacity for the FBI, and that no attempt was made to recruit him in any capacity.” In addition, “Director Hoover and each Bureau agent, who according to the FBI would have been responsible for or aware of any attempt to recruit Oswald …provided the Commission with sworn affidavits to this effect.”1 This testimony was corroborated by the Warren Commission’s independent review of FBI files. (3)
Nevertheless, the allegation that Oswald was associated in some capacity with the FBI persisted. (4) There are three main reasons for this that may be traced to actions by the Bureau.
First, Oswald’s address book contained the name, address, telephone number and automobile license plate number of Special Agent James P. Hoary. That entry has been a source of controversy, especially since this information was not contained in an FBI report to the Warren Commission in December 1963, one that purportedly contained the contents of the address book.
Second, based on FBI contacts with Oswald in Fort Worth in 1962 and New Orleans and Dallas in 1963, rumors that he was an informant for the Bureau continued to circulate.
Third, shortly after the assassination, Dallas FBI agent Hosty destroyed a note that had been delivered to his office allegedly by Oswald shortly before the assassination. When that conduct was finally made public in 1975 it aroused great suspicions, especially since it had not been previously revealed, even to the Warren Commission. (5)
The committee attempted to investigate each of the alleged links between Oswald and the FBI. It conducted extensive file reviews, interviews, depositions, and hearings. Testimony was taken from present and former FBI officials and employees as well as from private citizens claiming to have relevant information. On occasion, formal explanations were sought directly from the FBI. Even though the testimony of two special agents of the FBI appeared to be seriously lacking credibility on two of the major issues (the destruction of the Oswald note and the omission of Hosty’s name from a report purporting to contain a list of the entries in Oswald’s notebook), the results of the committee’s investigation were consistent with the conclusions reached by the Warren Commission. The committee found no credible evidence that Oswald was an FBI informant.
Top of Page
(1) Early rumors that Oswald was an informant–Shortly after the assassination of President Kennedy, rumors that Oswald had been an
1Nine of the 10 affidavits executed by FBI agents denying that Oswald had been an informant were revised before the FBI submitted them to the Warren Commission. It had been alleged that these affidavits may have been materially altered. The committee found that none of the affidavits had been materially altered before delivery to the Warren Commission. The essential difference between the preliminary drafts and the final affidavits was that the drafts were witnessed by fellow FBI agents, whereas the final affidavits were witnessed by notaries public. In a few instances, minor changes of words of phrases were made, although none affected substance. (2)
Page 186
FBI informant began to circulate. This allegation was discussed in articles by Joseph C. Goulden, Alonzo Hudkins, and Harold Feldman, among others. (6) The committee’s review of these articles indicated that they set forth the rumors and speculation concerning the informant issue, but they offered no direct evidence supporting the allegation. Moreover, Hudkins admitted to the committee that his involvement with the issue began when he and another newsman discussed by telephone a mythical FBI payroll number for Oswald in order to test their suspicion that they were under FBI surveillance. Hudkins told the committee that he was subsequently contacted by the FBI and asked what he knew about Oswald’s alleged informant status, and that shortly afterward a newspaper article appeared in which the FBI denied any relationship with Oswald. (7) Neither Hudkins nor Goulden was able to give the committee any additional information that would substantiate the informant allegation. (8) The committee was unable to locate Feldman.
Top of Page
(2) The Hosty entry in Oswald’s address book.– After the assassination, Dallas police found Oswald’s address book among his possessions and turned it over to the FBI in Dallas. It contained FBI Special Agent Hosty’s name, address, telephone number and car license plate number.(9) Dallas FBI agents recorded some of the entries in the address book and, on December 23, 1963, sent a report to the Warren Commission. This report, however, did not include the Hosty entry.2 (10)
The committee’s review of the December 23 report established in likelihood that page 25 of that document, the page that logically would have contained the Hosty entry had it been properly included,3 had been retyped. The page was numbered in the upper left-hand corner, whereas all other pages of the report–save page 1, the retyping of which had been clearly recorded–were numbered at the bottom center. In addition, the horizontal margins of page 25 were unusually wide.
The former special agent who had coordinated the FBI’s Dallas investigation and had submitted the December 23, 1963, report, testified in a committee executive session that he had ordered the contents of Oswald’s notebook transcribed for the purpose of indicating any investigative leads. (11) The agent acknowledged that page 25 of the report would have contained the Hosty entry had it been included, and that both the numbering of that page and its unusually wide horizontal margins indicated it had been retyped.(12) Nevertheless, he stated that the page had not been retyped to mislead anyone, and indicated that the only reason the Hosty entry had been omitted from his report was because the original office memorandum setting out investigative leads generated from Oswald’s address book had failed to include it. (13)
A second special agent, the one who had prepared the original office memorandum that was incorporated into the December 23, 1963, re-
2On January 25, 1964, the FBI independently questioned the Dallas office concerning the omission and later sent to the Warren Commission a report, dated February 11, 1964, that did include the Hosty entry. In addition, in a letter dated January 27, 1964, the FBI informed the Commission of the inclusion of the Hosty data in Oswald’s address book.
3This determination was based on a comparison of the other entries from Oswald’s address book that did appear on page 25.
Page 187
port, testified that the Hosty entry had not been included because it was not considered to be of significance as an investigative lead. (14) This agent contended it had already been known that Hosty had called at the home of Ruth and Michael Paine looking for Oswald prior to the assassination, so the entry of his name and related data in Oswald’s book would not have been of potential evidentiary value. (15)
The committee did not accept the explanation that the Hosty entry was omitted from the report because it was not of lead significance, since the FBI’s December 23, 1963, report included other entries from Oswald’s address book that clearly had no legal significance at the time. For example, by December 23, it was generally known that the Oswalds had been living at the Paine home, yet the Ruth Paine address book entry was included in the report. (16) Similarly, a Robert W. Oswald entry that referred to Oswald’s brother would not have been significant as a lead at that time. (17) Numerous other examples could be given. (18) Moreover, the agent who prepared the memorandum failed to include in it several entries that he acknowledged could not automatically be dismissed as lacking in lead significance (e.g., numbers and letters of the alphabet whose meaning was not then known). (19)
Finally, in the December 23 report that was given to the Warren Commission, the FBI did not indicate that the report of the address book’s contents had been limited to those items of lead significance.4 (20)
When the committee apprised the FBI of the testimony of the two agents (first, the agent who coordinated the investigation; second, the one who prepared the memorandum that was incorporated in the December 23 report), the Bureau initiated its own inquiry. It produced an FBI airtel (an interoffice telegram) dated December 11, 1963, that seemed to verify that the second agent’s original instructions were to set out investigative leads, rather than to transcribe the complete contents of the address book. (21) The FBI investigation also led to the discovery of a “tickler” copy of the December 23 report that did contain the Hosty entry on page 25. 5 (22) The two agents were then reinterviewed by FBI investigators.
Based on his review and analysis of FBI documents, the second agent substantially revised the testimony he had given the committee. He told the Bureau investigators that since his assignment was to review the information contained in Oswald’s address book and to set out appropriate leads where necessary, he initially reproduced by dictation those entries in the address book that he thought might require investigative action. He recalled that he was vitally concerned with accuracy; consequently, he initially included the Hosty entry. Nevertheless, he explained that when he later had time to determine what investigative work remained to be done with regard to the address book he decided that it was not necessary to include the Hosty data in his second dictation of an investigative “lead sheet.” (23)
4The agent who prepared the memorandum testified he did not know it would be incorporated in other reports and sent to the Warren Commission. The agent who coordinated the investigation was the one who actually prepared the report for transmission to the Warren Commission.
5The term “tickler” refers to a copy of a report that is placed in a file for the purpose of reminding the file keeper of further action that must be taken with respect to the subject of the report.
Page 188
A December 8, 1977, report of the FBI interview with the second agent records his recollection in further detail:
He specifically recalls that by the time of the second dictation, he had had the opportunity to check on the Hosty entry to the extent that he was aware of Hosty’s visits to the Paine residence and that the address book entry reflected the Dallas FBI Field Office telephone number and the license number of the Government vehicle assigned to Hosty.
Upon learning these facts, he was convinced that the Hosty entry was not required in a “lead sheet” since it did not require further investigative attention. In addition, he was unofficially aware, through office conversations, that Hosty was being criticized not only in the media, but also by the FBI hierarchy, for his conduct of the Oswald case. Since he realized that a “lead sheet” would receive wide dissemination in the Dallas Field Office, he was doubly convinced that the Hosty data should not be included in the “lead sheet”– Hosty’s connection to the Oswald case was officially known and had been explained in previous reports, and, furthermore, he did not wish to cause Hosty any unnecessary unpleasantness or exposure. At that time he never considered that Hosty might have been a target of Lee Harvey Oswald, and, further, any contention that Hosty was involved in an assassination conspiracy would have been so preposterous that he would not even have thought of it. He, therefore, did not dictate the Hosty data and thereby excluded it from the product of his second dictation which was, in effect, an office memorandum to be used only as a “lead worksheet.” He also never considered that the “lead sheet” might have been converted to a report insert and disseminated outside the FBI. Had he known it would be, he would have considered that the memorandum or “lead sheet” should have reflected all the entries in the address book, to include Hosty’s name, since to do otherwise would not have been an accurate reporting of the entire contents of the address book.
He could not recall specifically what may have occasioned the redoing of page 25 after the second dictation, but it is possible that it became necessary because either he or someone else noticed that the “Ministry of Finances of the U.S.S.R.” information should have been attributed to the Fame page in the address book as was the “Katya Ford” and “Declan Ford” information. This error was made by him during his first dictation and may have persisted through the second dictation, thereby necessitating an additional change which caused page 25, to be numbered as it appears in the December 23, 1963, report.
[The second agent] concluded by stating that his recall of these events was triggered only by a review and discussion of all the pertinent documents retrieved. Until viewing the tickler version of the address book contents which reproduced the entries more identically than the “lead sheet” version with its editorializations, he had no specific recall with regard to his first dictation. (24)
Page 189
When the first agent was reinterviewed by the FBI, he was unable to explain the origin of the headquarters tickler copy. In addition, after reviewing the December 11, 1963, FBI headquarters airtel to the Dallas office, he indicated that, contrary to his earlier recollection, he never instructed the second agent to transcribe the address book. That order had apparently been issued by another special agent. (25)
Bureau interviews with the former special-agent-in-charge of the Dallas office in 1963 and six other special agents who were involved in the assassination investigation generated no additional information concerning how the tickler copy of the December 23, 1963, report on the contents of the address book came to reside in FBI headquarters. Nor did they shed new light on the circumstances surrounding the omission of the Hosty entry from the copy of the report that was sent to the Warren Commission. Laboratory tests for fingerprints were inconclusive. (26) They did not indicate who had worked on the tickler copy of the December 23 report. Laboratory tests did determine, however, that the typewriter used to prepare page 25 of the December 23 report had also been used to prepare all but 10 pages of the report.
The committee also sought testimony from Special Agent Hosty concerning the circumstances by which his name was entered in Oswald’s notebook and why this particular entry might have been omitted from the December 23, 1963, report. Hosty stated that he had been assigned to internal security cases on both Lee Harvey Oswald and his wife Marina. (27) He recalled that he spoke briefly to Marina Oswald twice during the first week of November 1963 and that he had had no other contacts with her. (28) On this first occasion, he had given Ruth Paine, with whom Marina Oswald was residing, his name and telephone number and had told her to call him if she had any information on Oswald to give him.(29) It was Hosty’s belief that Ruth Paine probably gave this information to Oswald. Hosty added that Oswald could have obtained the address of the Dallas FBI office from the front page of any Dallas telephone book. (30) Hosty believed that during his second visit to the residence, while he was talking to Ruth Paine, Marina Oswald went outside and copied his license plate number. (31) He suggested that Oswald may have wanted this data so he could write his self-serving letter of protest to the Soviet Embassy in Washington.(32) In addition, he stated that it is possible that Oswald wanted this information so that he could complain to the FBI in Dallas. (33) Hosty indicated that he could think of no good reason for withholding the references to him in Oswald’s address book from the report on the address book that was sent to the Warren Commission, as this information was already well-known at the Dallas Police Department.(34) The committee also learned that Hosty dictated two memoranda in December 1963 that included the fact that his name and address were in Oswald’s address book. In addition, FBI headquarters was aware of the Hosty entry in the address book; it had been made public by the media, and the FBI had advised the Warren Commission of it on January 27, 1964.
Based on all this evidence, the committee concluded that there was no plan by the FBI to withhold the Hosty entry in Oswald’s address book for sinister reasons. This conclusion was based on several factors,
Page 190
the most important of which was the discovery of the tickler copy of the December 23, 1963 report.6
The committee considered the fact, on the other hand, that information about the entry was withheld. One explanation might be that it was unintentional, although the evidence was also consistent with an explanation that one or more Dallas FBI agents sought to protect Hosty from personal embarrassment by trying–ineffectually, as it turned out to exclude his name from the reporting. The committee, though it deemed the incident regrettable, found it to be trivial in the context of the entire investigation.
Top of Page
(3) FBI contacts with Oswald (Fort Worth, 1962).–Oswald was interviewed twice by FBI agents in Fort Worth in 1962 shortly after his return from the Soviet Union. (35) Special Agent Fain, who had been assigned the Oswald internal security case in Fort Worth, and Special Agent Burnett Tom Carter conducted the initial Oswald interview at the Fort Worth FBI office on June 26, 1962. In his report of this interview, Fain described Oswald as cold, arrogant and uncooperative. He also reported that when asked if he would be willing to submit to a polygraph examination, Oswald refused without giving a reason.(36)
On August 16, 1962, Fain and Special Agent Arnold J. Brown reinterviewed Oswald, this time in Fain’s automobile near Oswald’s Fort Worth residence. (37) The fact that the interview was conducted in Fain’s car has been cited as an indication that Oswald was being developed as an informant.
Fain, Carter, and Brown submitted affidavits to the Warren Commission asserting Oswald was not an informant.(38) All three were interviewed by the committee, and they affirmed their previous positions.
Fain told the committee that in the first encounter, Oswald displayed a bad attitude and gave incomplete answers (39) while Carter remembered Oswald as arrogant, uncooperative, and evasive. (40) Fain said the second contact was necessitated by Oswald’s bad attitude and incomplete answers in the first interview. In the second interview, Fain explained, Oswald invited him and Brown into his home, but decided to conduct the interview in his car so not to upset or frighten Oswald’s wife.(41) Brown told the committee that his memory was hazy, but he did recall that he and Fain met Oswald as he was returning from work and that they interviewed him in or near Fain’s car, possibly for the sake of convenience. (42)
The committee found the statements of these three FBI agents credible. They had legitimate reasons for contacting Oswald because his background suggested he might be a threat to the internal security of the United States. They corroborated each other’s accounts of the two interviews of Oswald, and their statements were entirely consistent with reports written shortly after these interviews occurred. Given Oswald’s documented unwillingness to cooperate, there was little reason to believe that he would have been considered by these agents for use as an informant.
6The leadership of the FBI as of 1978, was deserving of credit, in the committee’s estimate, for its efforts to find the truth about the Hosty entry in Oswald’s address book. The committee doubted that the tickler copy of the December 23 memorandum would have been found if FBI officials had not been interested in resolving the issue.
Page 191
Top of Page
(4) FBI contacts with Oswald (New Orleans, 1963).–The committee interviewed the special agent in charge of the FBI office in New Orleans in 1963 and three special agents who handled the Oswald case in that city, and it found their statements that Oswald had not been an FBI informant to be credible.
Harry Maynor, the special agent in charge of the New Orleans FBI office in 1963, explained that if Oswald had been an FBI informant in New Orleans, he would have known about it because of his supervisory position; if Oswald had been paid for any information, would have approved the payments. Maynor noted that he had submitted an affidavit to the Warren Commission in which he had stated that no effort was made to develop Oswald as an informant.(43)
Similarly, former Special Agent Milton Kaack, who had been assigned the FBI security investigation of Oswald, told the committee that Oswald had never been an FBI informant. Kaack explained that if Oswald had been an FBI informant, he would have known about it by virtue of having been assigned the internal security case on him.7 (44)
The statements of Maynor, Kaack, and two other former FBI employees were considered in the context of allegations made by three witnesses, William S. Walter, Orest Pena, and Adrian Alba.
On August 9, 1963, Oswald was arrested in New Orleans for disturbing the peace after he had gotten into a fight with anti-Castro Cubans while distributing Fair Play for Cuba Committee leaflets. FBI Special Agent John L. Quigley interviewed Oswald the following day in a New Orleans jail. (45) Quigley’s willingness to meet with Oswald in jail has been cited as evidence that Oswald was an FBI informant. Moreover, in connection with this incident, William S. Walter, who was an FBI security clerk in New Orleans in 1963, told the committee that he had been on duty on the day this interview occurred. In response to Quigley’s request for a file check on Oswald, he had determined that the New Orleans FBI office maintained both a security file and an informant file on Oswald.
In a committee interview, Quigley, who had submitted an affidavit to the Warren Commission asserting that, Oswald had not been an FBI informant, (47) reaffirmed his position. He explained that he interviewed Oswald at Oswald’s request, and that he then checked the file indices at the New Orleans office and found that Oswald was the subject of a security investigation assigned to Special Agent Kaack. He advised that the indices check provided no indication that Oswald had ever been an FBI informant. He added that if Oswald had been an informant, he would have known about it by virtue of this indices search. (48)
The committee could find no independent basis for verifying Walter’s testimony about an Oswald informant file, but another allegation made by him, unrelated to the informant issue, led the committee to reject his testimony in its entirety. In a committee deposition, Walter stated that on November 17, 1963, while he was on night duty as an FBI security clerk, he received a teletype from FBI headquarters warning of a possible assassination attempt against President Ken-
7The committee asked Kaack why he had not submitted an affidavit to this effect to the Warren Commission. In response, Kaack indicated that this had not been done because no one had requested it.
Page 192
nedy during the forthcoming trip to Dallas on November 22 or 23, 1963. (49) Walter recalled that the teletype was addressed to all special agents in charge of FBI field offices and that it instructed them to contact criminal, racial and hate group informants in order to determine whether there was any basis for the threat.(50) Walter contended that this teletype was removed from the New Orleans FBI office files soon after the Kennedy assassination. (51)
Walter admitted that he did not publicly allege the existence of this telephone until 1968 (52) At that time, the FBI instituted an investigation that failed to find any corroboration for Walter’s story. According to the Bureau, no record of a teletype or any other kind of communication reporting that there would be an attempt to assassinate President Kennedy in Texas could be found. Over 50 FBI employees of the New Orleans FBI office were interviewed by the Bureau, and none of them stated that they had any knowledge of any such teletype. (53) In 1975, the Bureau reinvestigated the teletype allegation after Walter claimed he had retained a replica of the teletype and that it had been sent to all FBI field offices. The FBI examined the text of the alleged replica and determined that it varied in format and wording from the standard. The Bureau also reported that searches at each of its 59 field offices yielded no evidence indicating the existence of such a teletype. (54)
Walter advised the committee that he did not know of anyone who could definitely substantiate his teletype allegation, although he suggested that his former wife, Sharon Covert, who also had worked for the FBI in New Orleans, might be able to do so. (55) Sharon Covert, however, advised the committee that she could not support any of Walter’s allegations against the FBI and that Walter had never mentioned his allegations to her during their marriage. (56)
New Orleans Special Agent in Charge Maynor also denied that he had been contacted by Walter in regard to an assassination threat. (57)
More fundamentally, however, the committee was led to distrust Walter’s account of the assassination teletype because of his claim that it had been addressed to the special agents in charge of every FBI field office. The committee found it difficult to believe that such a message could have been sent without someone 15 years later–a special agent in charge or an employee who might have seen the teletype– coming forward in support of Walter’s claim. The committee declined to believe that that many employees of the FBI would have remained silent for such a long time. Instead, the committee was led to question Walter’s credibility. The committee concluded that Walter’s allegations were unfounded.
Orest Pena, a bar owner in New Orleans, testified that during the early 1960’s he was an FBI informant who reported to Special Agent Warren D. deBrueys.(58) He told the committee that on several occasions he saw Oswald in the company of deBrueys and other Government agents in a restaurant and that he believed Oswald and deBrueys knew each other very well.8 Finally, Pena alleged that Special Agent
8In this regard, William Walter testified that after the assassination of President Kennedy he found a single file pertaining to Oswald in SAC Harry G. Maynor’s locked file cabinet. Walter stated that he did not recall the title of the file, and acknowledged that it may not have been an informant file, but he remembered that the name of FBI Special Agent Warren D. deBrueys appeared on the file jacket. As noted, the committee did not find Walter to be a credible witness.
Page 193
deBrueys was “transferred” to Dallas at the same time Oswald was “transferred” there. He added that he was “very, very, very sure” that deBrueys went to Dallas before the assassination of President Kennedy. (59)
Pena maintained that a few days before he went to testify before the Warren Commission, deBrueys threatened him physically and warned him not to make any accusations against him. Pena also stated that Warren Commission staff counsel Wesley J. Liebeler did not cooperate with him and did not let him talk freely, so he decided to “keep [his] mouth shut.” (60)
In testimony before the committee, deBrueys denied that Oswald was his informant, that he had ever met Oswald, or that he had ever knowingly talked to him by telephone.(61) He acknowledged that he did use Pena informally as an occasional source of information because of his position as a bar owner in New Orleans, but he declined to characterize Pena as an informant because of the absence of any systematic reporting relationship. (62) He also denied having threatened Pena prior to Pena’s Warren Commission testimony. (63) Finally, deBrueys testified that he was transferred to Dallas in 1963, but that this was the result of a temporary assignment to assist in the assassination investigation. (64) The transfer did not coincide with Oswald’s move from New Orleans to the Dallas area.9
FBI files served to corroborate relevant aspects of deBrueys’ testimony. DeBrueys’ personal file indicates that the only time he was transferred to Dallas was to work on the assassination investigation, and that he was in Dallas from November 23, 1963, until January 24, 1964. In addition, there is no Bureau record of Pena ever having served as an informant. This, too, supported deBrueys’ testimony that Pena was never used on any systematic basis as a source of information.
Pena, moreover, was unable to explain adequately why he waited until 1975 to make this allegation, and he declined to testify specifically that Oswald was, in fact, an FBI informant. Pena’s responses to committee questions on the informant issue and others were frequently evasive. (65) The committee found, therefore, that he was not a credible witness.
Adrian Alba testified before the committee that he was an employee and part owner of the Crescent City Garage in New Orleans and that in the summer of 1963 he had become acquainted with Oswald, who worked next door at the Reily Coffee Co. (66) He related that one day an FBI agent entered his garage and requested to use one of the Secret Service cars garaged there. The FBI agent showed his credentials, and Alba allowed him to take a Secret Service car, a dark green Studebaker. Later that day or the next day, Alba observed the FBI agent in the car handing a white envelope to Oswald in front of the Reily Coffee Co, There was no exchange of words. Oswald, in a bent position, turned away from the car window and held the envelope close
9The committee also asked deBrueys why he did not submit an affidavit to the Warren Commission on the informant issue. deBrueys testified that he was surprised not to have been called upon to submit an affidavit to the Warren Commission. He believed that he had signed an affidavit on the informant issue at Bureau headquarters within the past few years, but no longer recalled the specifics of this action. The Bureau informed the committee that, pursuant to regulations, deBrueys had submitted to the U.S. Attorney General a written synopsis of his testimony before the Senate Select Committee on Intelligence. In this synopsis, deBrueys stated that he had denied under oath that Oswald was his informant or that he had ever knowingly spoken to Oswald.
Page 194
to his chest as he walked toward the Reily Coffee Co. Alba believed that he observed a similar transaction a day or so later as he was returning from lunch, but on this occasion he was farther away and failed to see what was handed to Oswald. Alba did not recall when the Secret Service car was returned or by whom. He never questioned Oswald about these incidents. (67)
Alba did not relate his account of the transactions between Oswald and the FBI agent when he testified before the Warren Commission. (68). He told the committee in 1978 that he first remembered these incidents in 1970, when his memory was triggered by a television commercial showing a merchant running to and from a taxi to assist a customer. (69)
The committee examined Alba’s records for possible corroboration. These records indicated that in 1963 several Secret Service agents had signed out two Studebakers, a Ford and a Chevrolet at various times, but the records did not indicate that any FBI agents had signed out any of these cars. (70)
The committee regarded Alba’s testimony, at least on this point, to be of doubtful reliability and outweighed by the evidence provided by the former FBI personnel stationed in New Orleans.
Top of Page
(5) FBI contacts with Oswald (Dallas, 1963).–According to a 1964 FBI memorandum, an FBI agent, later identified as Will Hayden Griffin of the Dallas field office, allegedly stated in 1964 that Oswald was definitely an FBI informant and that FBI files in Washington would prove that fact.(71) Griffin, however, advised the committee that he had never made such an allegation. Moreover, in 1964, he had executed an affidavit specifically denying this allegation. (72) Griffin’s position is consistent with that of other Dallas FBI personnel.
J. Gordon Shanklin, who was special-agent-in-charge of the Dallas FBI office in 1963, submitted an affidavit to the Warren Commission in which he denied that Oswald was an FBI informant.(73) In a committee interview, he again stated that Oswald was never an informant for the FBI in Dallas and he added he had not even heard of Oswald prior to President Kennedy’s assassination. (74)
Special Agent James P. Hosty, Jr., testified that Oswald had not been an FBI informant. (75) Hosty had submitted an affidavit to this effect to the Warren Commission.10 Hosty told the committee that he had never interviewed Oswald before the assassination of President Kennedy. From his testimony, it appeared that his only contacts with Oswald had been indirect, in the form of two occasions that he had conversed with Marina Oswald and Ruth Paine. He added that Oswald was neither an informant for Special Agent Fain in Fort Worth nor an informant for any FBI agent in New Orleans. Had Oswald been an informant in either case, Hosty insisted he would have known about it by virtue of having been assigned the internal security case on Oswald in Dallas. (76)
Hosty also addressed the purported Griffin allegation. He testified to the committee that Griffin knew that Jack Ruby had been a poten-
10In addition to Hosty and Shanklin, several other FBI agents in Dallas executed affidavits for the Warren Commission denying that Oswald was an informant: Assistant Special-Agent-in-Charge Kyle G. Clark, former Special-Agent-in-Charge Curtis O. Lynum, and Special Agent Kenneth C. Howe.
Page 195
tial criminal informant for the FBI in Dallas. He suggested that someone could have heard Griffin talking about Ruby’s contacts with the FBI and might then have repeated the story with the mistaken assertion that Griffin was talking about Oswald. (77)
In support of Hosty’s explanation, Shanklin stated to the committee that the Dallas office did send the potential criminal informant file on Ruby to FBI headquarters in Washington after the Kennedy assassination. He added that he did not know whether this file was sent to the Warren Commission. 11 (78) Griffin told the committee in a second interview that soon after the Kennedy assassination he learned that the FBI in Dallas had approached Ruby in order to obtain information from him. He advised that, although his recollection was unclear, he might have seen an FBI informant file on Ruby and then may have talked to persons outside the Bureau about the FBI’s contacts with Ruby.
Top of Page
(6) The destruction of Oswald’s note.–Approximately 2 or 3 weeks before the assassination of President Kennedy, Oswald allegedly delivered a note addressed to Hosty at the FBI office in Dallas. (80) The varying accounts of the note’s contents suggest that it was threatening or complaining in tone, ordering Hosty to stop bothering Oswald’s wife.(81) Several hours after Oswald was murdered by Jack Ruby, Hosty, according to his own admission, destroyed the note after having been instructed to do so by J. Gordon Shanklin, the special-agent-in-charge of the Dallas FBI office. (82) Shanklin denied that he knew anything about the note until a reporter asked him about it in 1975. (83) Between 1963 and 1975, the existence of the note and its destruction were kept secret by the Dallas FBI Office.
In his committee testimony, Hosty stated that the note, according to his memory, did not contain Oswald’s name and that he first determined that the note might have been from Oswald on the day of the assassination of President Kennedy. Hosty explained that soon after Oswald’s arrest, he was instructed to sit in on the interrogation of Oswald at the Dallas Police Department, and that when he identified himself to Oswald, Oswald became upset and stated that Hosty had been bothering his wife, Marina. Hosty suggested that Special-Agent-in-Charge Shanklin, who was told by another FBI agent about Oswald’s reaction to Hosty, probably made the same connection between Oswald and the anonymous note. Hosty advised that he was surprised that Shanklin wanted him to destroy the note because the note’s contents were not particularly significant.
Hosty recalled that the note was complaining in tone, but that it contained no threats and did not suggest that Oswald was prone to violence. Hosty stated that he destroyed the note because Shanklin, his superior, ordered him to do so. When asked what motivation Oswald might have had for writing this note, Hosty suggested that Oswald might have wanted to prevent Hosty from contacting his wife because he was afraid that she would tell Hosty about Oswald’s trip to Mexico in the fall of 1963 and of his attempt to shoot Gen. Edwin Walker in the spring of 1963. (85)
11The committee found no evidence that this file was ever sent to the Warren Commission, although details of the association were furnished by the Commission by letter.
Page 196
The committee regarded the incident of the note as a serious impeachment of Shanklin’s and Hosty’s credibility. It noted, however, that the note, if it contained threats in response to FBI contacts with Oswald’s wife, would have been evidence tending to negate an informant relationship. The committee noted further the speculative nature of its findings about the note incident. Because the note had been destroyed, it was not possible to establish with confidence what its contents were.
Top of Page
(7) Conclusion–In summary, although there have been many allegations of an Oswald-FBI informant relationship, there was no credible evidence that Oswald was ever an informant for the Bureau. Absent a relationship between Oswald and the FBI, grounds for suspicions of FBI complicity in the assassination become remote.
Top of Page
(c) The Central Intelligence Agency 1
Go to the footnotes for this section.
In 1964, the CIA advised the Warren Commission that the Agency had never had a relationship of any kind with Lee Harvey Oswald. Testifying before the Commission, CIA Director John A. McCone indicated that:
Oswald was not an agent, employee, or informant of the Central Intelligence Agency. The Agency never contacted him, interviewed him, talked with him, or solicited any reports or information from him, or communicated with him directly or in any other manner …Oswald was never associated or connected directly or indirectly in any way whatsoever with the Agency. (1)
McCone’s testimony was corroborated by Deputy Director Richard M. Helms. (2) The record reflects that once these assurances had been received, no further efforts were made by the Warren Commission to pursue the matter.
Recognizing the special difficulty in investigating a clandestine agency, the committee sought to resolve the issue of Oswald’s alleged association with the CIA by conducting an inquiry that went beyond taking statements from two of the Agency’s most senior officials. The more analytical approach used by the committee consisted of a series of steps:
First, an effort was made to identify circumstances in Oswald’s life or in the way his case was handled by the CIA that possibly suggested an intelligence association.
Then, the committee undertook an intensive review of the pertinent files, including the CIA’s 144-volume Oswald file and hundreds of others from the CIA, FBI, Department of State, Department of Defense and other agencies.
Based on these file reviews, a series of interviews, depositions and executive session hearings was conducted with both Agency and non-Agency witnesses. The contacts with present and former CIA personnel covered a broad range of individuals, including staff and division chiefs, Clandestine case officers, area desk officers, research analysts, secretaries and clerical assistants. In total, more
1For a brief history of the CIA and description of its organizational structure, see Section I D 4 infra.
Page 197
than 125 persons, including at least 50 present and former CIA employees, were questioned.2
The results of this investigation confirmed the Warren Commission testimony of McCone and Helms. There was no indication in Oswald’s CIA file that he had ever had contact with the Agency. Finally, taken in their entirety, the items of circumstantial evidence that the committee had selected for investigation as possibly indicative of an intelligence association did not support the allegation that Oswald had an intelligence agency relationship.
This finding, however, must be placed in context, for the institutional characteristics–in terms of the Agency’s strict compartmentalization and the complexity of its enormous filing system–that are designed to prevent penetration by foreign powers have the simultaneous effect of making congressional inquiry difficult. For example, personnel testified to the committee that a review of Agency files would not always indicate whether an individual was affiliated with the Agency in any capacity. (3) Nor was there always an independent means of verifying that all materials requested from the Agency had, in fact, been provided. Accordingly, any finding that is essentially negative in nature–such as that Lee Harvey Oswald was neither associated with the CIA in any way, nor ever in contact with that institution–should explicitly acknowledge the possibility of oversight.
To the extent possible, however, the committee’s investigation was designed to overcome the Agency’s security-oriented institutional obstacles that potentially impede effective scrutiny of the CIA. The vast majority of CIA files made available to the committee were reviewed in undeleted form.(4) These files were evaluated both for their substantive content and for any potential procedural irregularities suggestive of possible editing or tampering. After review, the files were used as the basis for examination and cross-examination of present and former Agency employees. Each of the present and former Agency employees contacted by the committee was released from his secrecy oath by the CIA insofar as questions relevant to the committee’s legislative mandate were concerned. Because of the number of Agency personnel who were interrogated,(5) it is highly probable that significant inconsistencies between the files and witnesses’ responses would have been discovered by the committee.
During the course of its investigation, the committee was given access by the CIA to information based on sensitive sources and methods that are protected by law from unauthorized disclosure. The committee noted that in some circumstances disclosure of such information in detail would necessarily reveal the sensitive sources and methods by which it was acquired. With respect to each item of such information, the committee carefully weighed the possible advancement of public understanding that might accrue from disclosure of the details of the information against the possible harm that might be done to the national interests and the dangers that might result to individuals. To
2The committee also attempted to identify CIA employees who may have had the motive, means and opportunity to assassinate President Kennedy. In this regard, no useful information was generated from selected file reviews. An effort was also made to locate a man identified as Maurice Bishop who was said to have been a CIA officer who had been seen in the company of Lee Harvey Oswald. The effort to find “Bishop” was likewise unsuccessful.
Page 198
the extent required by the balancing process, sections of this report were written in a somewhat conclusionary manner in order to continue the protection of such classified information.
Top of Page
(1) CIA personnel in the Soviet Russia Division.3–Since Oswald spent time in the Soviet Union, a subject of special attention by the committee was the Russia-related activities of the CIA. In addition to obtaining testimony from former Directors McCone and Helms, the committee interviewed the chiefs of the Soviet Russia Division from 1959 to 1963. In each case, the committee received a categorical denial of any association of the CIA with Oswald. (6)
To investigate this matter further, the committee interviewed the persons who had been chiefs or deputy chiefs during 1959-62 of the three units within the Soviet Russia Division that were responsible respectively for clandestine activities, research in support of clandestine activities, and the American visitors program. 4 The heads of the clandestine activity section stated that during this period the CIA had few operatives in the Soviet Union and that Oswald was not one of them. Moreover, they stated that because of what they perceived to be his obvious instability, Oswald would never have met the Agency’s standards for use in the field 5 (7) The heads of the Soviet Russia Division’s section that sought the cooperation of visitors to the Soviet Union informed the committee that they met with each person involved in their program and that Oswald was not one of them.(8) These officials also advised the committee that “clean-cut” collegiate types tended to be used in this program, and that Oswald did not meet this criterion.(9) Finally, the officers in charge of the Soviet Russia Division’s research section in support of clandestine activities indicated that, had Oswald been contacted by the Agency, their section would probably have been informed, but that this, in fact, never occurred. (10)
Top of Page
(2) CIA personnel abroad.–Turning to particular allegations, the committee investigated the statement of former CIA employee James Wilcott, who testified in executive session that shortly after the assassination of President Kennedy he was advised by fellow employees at a CIA post abroad that Oswald was a CIA agent who had received financial disbursements under an assigned cryptonym.6 (11) Wilcott explained that he had been employed by the CIA as a finance officer from 1957 until his resignation in 1966. In this capacity, he
3Classified analyses of these issues, written in undeleted form, are in the committee’s files.
4The visitors program sought the cooperation, for limited purposes, of carefully selected persons traveling in the Soviet Union. For this unit, only the years 1959-61 were covered. Nevertheless, since every American traveler who was involved in this program was contacted before visiting the Soviet Union, the relevant year for Lee Harvey Oswald was 1959, the year he departed from the United States.
5One officer acknowledged the remote possibility that an individual could have been run by someone as part of a “vest pocket” (private or personal) operation without other Agency officials knowing about it. But even this possibility, as it applies to Oswald, was negated by the statement of the deputy chief of the Soviet Russia clandestine activities section. He commented that in 1963 he was involved in a review of every clandestine operation ever run in the Soviet Union, and Oswald was not involved in any of these cases.
6A cryptonym us a code designation for an agency project, program or activity or an organization, agency or individual (for whom a legal signature is not required) having a sensitive operational relationship with the agency. Cryptonyms are used in communications only to the extent necessary to protect sensitive information from disclosure to unauthorized persons. They are used (1) when disclosure of the true identity of persons, organizations or activities would be detrimental to the interest of the U.S. Government or to the persons, organizations or activities concerned; or (2) to prevent disclosure of a sensitive operational relationship with the agency.
Page 199
served as a fiscal account assistant on the support staff at a post abroad from June 1960 to June 1964. In addition to his regular responsibilities, he had performed security duty on his off-hours in order to supplement his income. This put him in contact with other employees of the post who would come by the office and engage in informal conversations. On the day after President Kennedy’s assassination, Wilcott claimed he was informed by a CIA case officer that Oswald was an agent.(12) He further testified that he was told that Oswald had been assigned a cryptonym and that Wilcott himself had unknowingly disbursed payments for Oswald’s project. (13) Although Wilcott was unable to identify the specific case officer who had initially informed him of Oswald’s agency relationship, he named several employees of the post abroad with whom he believed he had subsequently discussed the allegations. (14)
Wilcott advised the committee that after learning of the alleged Oswald connection to the CIA, he never rechecked official Agency disbursement records for evidence of the Oswald project. He explained that this was because at that time he viewed the information as mere shop talk and gave it little credence. (15) Neither did he report the allegations to any formal investigative bodies, as he considered the information hearsay.(16) Wilcott was unable to recall the agency cryptonym for the particular project in which Oswald had been involved, (17) nor was he familiar with the substance of that project. In this regard, however, because project funds were disbursed on a code basis, as a disbursement officer he would not have been apprised of the substantive aspects of projects.
In an attempt to investigate Wilcott’s allegations, the committee interviewed several present and former CIA employees selected on the basis of the position each had held during the years 1954-64. Among the persons interviewed were individuals whose responsibilities covered a broad spectrum of areas in the post abroad, including the chief and deputy chief of station, as well as officers in finance, registry, the Soviet Branch and counterintelligence.
None of these individuals interviewed had ever seen any documents or heard any information indicating that Oswald was an agent. (18) This allegation was not known by any of them until it was published by critics of the Warren Commission in the late 1960’s.(19) Some of the individuals, including a chief of counterintelligence in the Soviet Branch, expressed the belief that it was possible that Oswald had been recruited by the Soviet KGB during his military tour of duty overseas, as the CIA had identified a KGB program aimed at recruiting U.S. military personnel during the period Oswald was stationed there. (20) An intelligence analyst whom Wilcott had specifically named as having been involved in a conversation about the Oswald allegation told the committee that he was not in the post abroad at the time of the assassination.(21) A review of this individual’s office of personnel file confirmed that, in fact, he had been transferred from the post abroad to the United States in 1962. (22) The chief of the post abroad from 1961 to 1964 stated that had Oswald been used by the Agency he certainly would have learned about it.(23) Similarly, almost all those persons interviewed who
Page 200
worked in the Soviet Branch of that station indicated they would have known if Oswald had, in fact, been recruited by the CIA when he was overseas.(24) These persons expressed the opinion that, had Oswald been recruited without their knowledge, it would have been a rare exception contrary to the working policy and guidelines of the post abroad. (25)
Based on all the evidence, the committee concluded that Wilcott’s allegation was not worthy of belief.
Top of Page
(3) Oswald’s CIA file.–The CIA has long acknowledged that prior to the president’s assassination, it had a personality file on Oswald, that is, a file that contained data about Oswald as an individual. This file, which in Agency terminology is referred to as a 201 file, was opened on December 9, 1960. (26) The Agency explained that 201 files are opened when a person is considered to be of potential intelligence or counterintelligence significance.(27) The opening of such a file is designed to serve the purpose of placing certain CIA information pertaining to that individual in one centralized records system. The 201 file is maintained in a folder belonging to the Directorate for Operations, the Agency component responsible for clandestine activities.(28)
The existence of a 201 file does not necessarily connote any actual relationship or contact with the CIA. For example, the Oswald file was opened, according to the Agency, because as an American defector, he was considered to be of continuing intelligence interest.(29) Oswald’s file contained no indication that he had ever had a relationship with the CIA. Nevertheless, because the committee was aware of one instance (in an unrelated case) where an Agency officer had apparently contemplated the use of faked files with forged documents, (30) special attention was given to procedural questions that were occasioned by this file review.
Top of Page
(4) Why the delay in opening Oswald’s 201 file?–A confidential State Department telegram dated October 31, 1959, sent from Moscow to Washington and forwarded to the CIA, reported that Oswald, a recently discharged Marine, had appeared at the U.S. Embassy in Moscow to renounce his American citizenship and “has offered Soviets any information he has acquired as [an] enlisted radar operator.”(31) At least three other communications of a confidential nature that gave more detail on the Oswald case were sent to the CIA in about the same time period.(32) Agency officials questioned by the committee testified that the substance of the October 31, 1959, cable was sufficiently important to warrant the opening of a 201 file.(33) Oswald’s file was not, however, opened until December 9, 1960.(34)
The committee requested that the CIA indicate where documents pertaining to Oswald had been disseminated internally and stored prior to the opening of his 201 file. The agency advised the committee that because document dissemination records of relatively low national security significance are retained for only a 5-year period, they were no longer in existence for the years 1959-63. (35) 8 Consequently, the Agency was unable to explain either when these documents had been received or by which component.
8None of these documents were classified higher than confidential
Page 201
An Agency memorandum, dated September 18, 1975, indicates that Oswald’s file was opened on December 9, 1960, in response to the receipt of five documents: two from the FBI, two from the State Department and one from the Navy. (36) This explanation, however, is inconsistent with the presence in Oswald’s file of four State Department documents dated in 1959 and a fifth dated May 25, 1960. It is, of course, possible that the September 18, 1975, memorandum is referring to State Department documents that were received by the Directorate for Plans 9 in October and November of 1960 and that the earlier State Department communications had been received by the CIA’s Office of Security but not the Directorate for Plans. In the absence of dissemination record however, the issue could not be resolved.
The September 18, 1975, memorandum also states that Oswald’s file was opened on December 9, 1960, as a result of his “defection” to the U.S.S.R. on October 31, 1959 and renewed interest in Oswald brought about by his queries concerning possible reentry into the United States.”(37) There is no indication, however, that Oswald expressed to any U.S. Government official an intention to return to the United States until mid-February 1961. (38) Finally, reference to the original form that was used to start a file on Oswald did not resolve this issue because the appropriate space that would normally indicate the “source document” that initiated the action referred to an Agency component rather than to a dated document. 10 (39)
The committee was able to determine the basis for opening Oswald’s file on December 9, 1960, by interviewing and then deposing the Agency employee who was directly responsible for initiating the opening action. This individual explained that the CIA had received a request from the State Department for information concerning American defectors. After compiling the requested information, she responded to the inquiry and then opened a 201 file on each defector involved. (40)
This statement was corroborated by review of a State Department letter which indicated that such a request, in fact, had been made of the CIA on October 25, 1960. Attached to the State Department letter was a list of known defectors; Oswald’s name was on that list. The CIA responded to this request on November 21, 1960, by providing the requested information and adding two names to the State Department’s original list. (41)
Significantly, the committee reviewed the original State Department list and determined that files were opened in December 1960 for each of the five (including Oswald) who did not have 201 files prior to receipt of the State Department inquiry. In each case, the slot for “source document” referred to an Agency component rather than to a dated document.(42)
Even so, this analysis only explained why a file on Oswald was finally opened; it did not explain the seemingly long delay in opening of the file. To determine whether such a delayed opening was unusual, the committee reviewed the files of 13 of the 14 persons on the CIA’s November 21 1960, response to the State Department and
9The Directorate for Plans was the predecessor of the Directorate of Operations.
10The Agency indicated that it is customary to refer to a component when the opening action is taken on that component’s authority.
Page 202
of 16 other defectors (from an original list of 380) who were American-born, had defected during the years 1958-63, and who had returned to the United States during that same time period. Of 29 individuals whose files were reviewed, 8 had been the subject of 201 files prior to the time of their defection. In only 4 of the remaining cases were 201 files opened at the time of defection. The files on the 17 other defectors were opened from 4 months to several years after the defection. (43) At the very least, the committee’s review indicated that during 1958-63, the opening of a file years after a defection was not uncommon. In many cases, the opening was triggered by some event, independent of the defection, that had drawn attention to the individual involved.
Top of Page
(5) Why was he carried as Lee Henry Oswald in his 201 file?
Oswald’s 201 file was opened under the name Lee Henry Oswald. (44) No Agency witness was able to explain why. All agency personnel however, including the person who initiated the file opening, testified that this must have been occasioned innocently by bureaucratic error.(45) Moreover, the committee received substantial testimony to the effect that this error would not-have prevented the misnamed file from being retrieved from the CIA’s filing system during a routine name trace done under the name Lee Harvey Oswald. (46)
Top of Page
(6) The meaning of “AG” under “Other Identification” in Oswald’s 201 file.—The form used to initiate the opening of a 201 file for Lee Harvey Oswald contains the designation AG in a box marked “Other Identification.” Because this term was considered to be of potential significance in resolving the issue of Oswald’s alleged Agency relationship, the CIA was asked to explain its meaning.
The Agency’s response indicated that “AG” is the OI (“Other Identification”) code meaning “actual or potential defectors to the East or the Sino/Soviet block including Cuba,” and that anyone so described could have the OI code “AG.” This code was reportedly added to Oswald’s opening form because of the comment on the form that he had defected to the Soviet Union in 1959. (47)
An Agency official, who was a Directorate of Operations records expert and for many years one who had been involved in the CIA’s investigation of the Kennedy assassination, gave the committee a somewhat different explanation of the circumstances surrounding the term “AG” and its placement on Oswald’s opening form. This individual testified that “AG” was an example of a code used to aid in preparing computer listings of occupational groupings or intelligence affiliations. He explained that these codes always used two letters and that, in this case, the first letter “A” must have represented communism, while the second letter would represent some category within the Communist structure.(48)
His recollection was that at the time of the assassination, the “AG” code was not yet in existence because there were no provisions then in effect within the Agency for indexing American defectors. He recalled that it was only during the life of the Warren Commission that the CIA realized that its records system lacked provisions for indexing an individual such as Oswald. Consequently, the CIA revised its records manual to permit the indexing of American defectors and established a code for its computer system to be used for that category. Although
Page 203
this witness did not know when the notation “AG” was added to Oswald’s opening sheet, he presumed that it must have been following the addition of the American defector code, thus placing the time somewhere in the middle of the Warren Commission’s investigation. He explained that it was difficult to determine when any of the notations on the opening sheet had been made, since it was standard procedure to update the forms whenever necessary so that they were as reflective as possible of the available information.11 (49)
Finally, this witness testified that the regulations regarding the use of this occupation and intelligence code specifically prohibited indicating that a particular person was either an employee of the Agency or someone who was used by the Agency. This prohibition was designed to prevent anyone from being able to produce any kind of categorical listing of CIA employees, contacts or connections.(50)
Top of Page
(7) Why was Oswald’s 201 file restricted?–The form used to initiate the opening of Oswald’s 201 file contains a notation indicating that the file was to be “restricted”. (51) This indication was considered potentially significant because of the CIA’s practice of restricting access to agents’ files to persons on a “need-to-know” basis. Further investigation revealed, however, that restricting access to a file was not necessarily indicative of an relationship with the CIA.
The individual who actually placed the restriction on Oswald’s file testified that this was done simply to allow her to remain aware of any developments that might have occurred with regard to the file.(52) The restriction achieved this purpose because any person seeking access to the file would first have to notify the restricting officer, at which time the officer would be apprised of any developments.
This testimony was confirmed by a CIA records expert who further testified that had the file been permanently charged to a particular desk or case officer, as well as restricted, the possibility of a relationship with the CIA would have been greater. (53) There is no indication on Oswald’s form that it had been placed on permanent charge.
Finally, the committee reviewed the files of four other defectors that had been opened at the same time and by the same person as Oswald’s, and determined that each of the files had been similarly restricted. Each of these other individuals was on the lists of defectors that had been exchanged by the CIA and State Department. None of the files pertaining to these other defectors had any evidence suggestive of a possible intelligence agency association.
Top of Page
(8) Were 37 documents missing from Oswald’s 201 file?— In the course of reviewing Oswald’s 201 file, the committee discovered an unsigned memorandum to the Chief of Counterintelligence. Research and Analysis, dated February 20, 1964, which stated that 37 documents were missing from Oswald’s 201 file.(54) According to the memorandum, this statement was based on a comparison of a machine listing of documents officially recorded as being in the 201 file and those documents actually physically available in the file. (55) While the memorandum mentioned that such a machine listing was attached, no such attachment was found in the 201 file at the time of the committee’s
11The CIA, after considering this witness’ recollection of the origin of the AG code, adhered to its original position regarding this issue.
Page 204
review. The memorandum itself bears the classification “Secret Eyes Only” and was one of the documents that had been fully withheld from release under the Freedom of Information Act. (56)
In response to a committee inquiry, the CIA advised that, because Oswald’s file had been so active during the course of the Warren Commission investigation, up-to-date machine listings were produced periodically. On this basis, the Agency stated that
…it must be assumed that whoever was responsible for maintaining the Oswald file brought this file up-to-date by locating the 37 documents and placing them in the file. (57)
Because this response was incomplete, the author of the memorandum was deposed. He testified that once a document had been registered into a 201 file by the Agency’s computer system, physical placement of the document in the file was not always necessary. (58) On this basis, he explained, the items listed in the memorandum were not missing but rather had either been routinely placed in a separate file because of their sensitivity or were being held by other individuals who needed them for analytical purposes. (59) He further stated that in the course of his custodianship of Oswald’s file, he had requested perhaps as many as 100 computer listings on the contents of the Oswald file. While there had been many instances in which one or more documents had been charged out to someone, he stated that he had never discovered that any documents were actually missing. (60) According to his testimony, the 37 documents were, in fact, available, but they were not located in the file at the time. (61) The committee regarded this to be a plausible explanation.
Top of Page
(9) Did the CIA maintain a dual filing system on Oswald?— The committee was aware of the possibility that a dual filing system (one innocuous file and one that contained operational detail of a relationship with the CIA) could have been used to disguise a possible relationship between Oswald and the Agency. This awareness became a concern with the discovery that at least two Agency officers had contemplated the use of faked files and forged documents to protect the ZR Rifle project from disclosure.12(62) The implications of this discovery in terms of the possibility that the Oswald file might also have been faked were disturbing to the committee.
In the Oswald case, two items were scrutinized because they were potentially indicative of a dual filing system. The first was a photograph of Oswald that had been taken in Minsk in 1961; the second was a copy of a letter that had been written to Oswald by his mother during his stay in the Soviet Union. At the time of President Kennedy’s assassination, both of these items were in the CIA’s possession, but neither was in Oswald’s 201 file.
The photograph of Oswald taken in Minsk shows him posing with several other people. According to the CIA, the picture was found after the assassination as a result of a search of the Agency’s graphics files for materials potentially relevant to Oswald’s stay in the Soviet
12ZR Rifle was an executive action (assassination of foreign leader) program unrelated to the Oswald case. Former CIA Director Helms testified that the assassination aspect of ZR Rifle was never implemented and, in fact, was discontinued as soon as it was brought to his attention. (63)
Page 205
Union.(64) The Agency advised that this photograph, as well as several others not related to Oswald, were routinely obtained in 1962 from some tourists by the CIA’s Domestic Contacts Division, an Agency component that regularly sought information on a nonclandestine basis from Americans traveling abroad in Communist countries. (65)
Committee interviews with the tourists in question confirmed that the photograph, along with 159 other photographic slides, had routinely been made available to the Domestic Contacts Division. Neither tourist had heard of Oswald prior to the assassination or knew which photographs had been of interest to the Agency. (66)
CIA records indicate that only 5 of the 160 slides initially made available were retained. (67) Committee interviews with the two CIA employees who had handled the slides for the Domestic Contacts Division established that Oswald had not been identified at the time that these photographic materials were made available.(68) One of these employees stated that the Oswald picture had been retained because it depicted a Soviet Intourist guide; the other employee indicated that the picture had been kept because it showed a crane in the background.(69) Of these two employees, the one who worked at CIA headquarters (and therefore was in a position to know) indicated that the photograph of Oswald had not been discovered until a post-assassination search of the Minsk graphics file for materials pertaining to Oswald. (70)
Accordingly, this photograph was not evidence that the CIA maintained a dual filing system with respect to Oswald. The picture apparently was kept in a separate file until 1964, when Oswald was actually identified to be one of its subjects.
The committee’s investigation of a copy of a letter to Oswald from his mother that was in the Agency’s possession similarly did not show any evidence of a dual filing system. This letter, dated July 6, 1961 and sent by Marguerite Oswald, was intercepted as a result of a CIA program (71) known as HT-Lingual,13 the purpose of which was to obtain intelligence and counterintelligence information from letters sent between the United States and Russia. Typically, intercepted letters and envelopes would be photographed and then returned to the mails.(72)
In response to a committee inquiry, the CIA explained that because of HT-Lingual’s extreme sensitivity, all materials generated as a result of mail intercepts were stored in a separate project file that was maintained by the counterintelligence staff.(73) Consequently, such items were not placed in 201 files. This explanation was confirmed by the testimony of a senior officer from the counterintelligence staff who had jurisdiction over the HT-Lingual project files 14 (74)
Top of Page
(10) Did Oswald ever participate in a CIA counterintelligence project?— The committee’s review of HT-Lingual files pertaining to
13The HT-Lingual program was no longer in effect in 1978. Prior to that time, it had been found to be illegal
14Since Oswald was known to have sent or received more than 50 communications during his stay in the Soviet Union, the committee also questioned why the Agency ostensibly had just one letter in its possession directly related to Oswald. In essence, the Agency’s response suggested that HT-Lingual only operated 4 days a week, and, even then, proceeded on a sampling basis.
Page 206
the Oswald case 15 resulted in the discovery of reproductions of four index cards, two with reference to Lee Harvey Oswald and two to Marina Oswald, which were dated after the assassination of President Kennedy. The pages containing the reproductions of these cards were stamped “Secret Eyes Only.” (75)
The first card regarding Lee Harvey Oswald, dated November 9, 1959, states that Oswald is a recent defector to the U.S.S.R. and a former marine. It also bears the notation “CI/Project/RE” and some handwritten notations. (76) The second card on Oswald places him in Minsk. It contains background information on him and states that he “reportedly expresses a desire for return to the United States under certain conditions.” This card is dated August 7, 1961, and also bears the notation “Watch List.” (77) These cards, particularly the reference to “CI/Project/RE,” raised the question of whether Oswald was, in fact, involved in some sort of counterintelligence project for the CIA.
The committee questioned former employees of the CIA who may have had some knowledge pertaining to the HT-Lingual project in general and these cards in particular. Some of these employees recognized the cards as relating to the HT-Lingual project, but were unable to identify the meaning of the notation, “CI/Project/RE.” (78)
One employee, however, testified that the “CI Project” was “simply a name of convenience that was used to describe the HT-Lingual project”; (79) another testified that “CI Project” was the name of the component that ran the HT-Lingual project. This person also explained that “RE” represented the initials of a person who had been a translator of foreign language documents and that the initials had probably been placed there so that someone could come back to the translator if a question arose concerning one of the documents.(80) Another employee indicated that the “Watch List” notation on the second card referred to persons who had been identified as being of particular interest with respect to the mail intercept program. (81)
The committee requested the CIA to provide an explanation for the terms “CI/Project/RE” and “Watch List” and for the handwritten notations appearing on the index cards. In addition, the committee requested a description of criteria used in compiling a “Watch List?”
With respect to the meaning of the notation “CI/Project/RE,” the CIA explained that there existed an office within the counterintelligence staff that was known as “CI/Project,” a cover title that had been used to hide the true nature of the office’s functions. In fact, this office was responsible for the exploitation of the material produced by the HT-Lingual project. The Agency further explained that “RE” represented the initials of a former employee. (82)
In responding to a request for the criteria used in compiling a “Watch List,” the CIA referred to a section of the “Report to the President by the Commission on CIA Activities Within the United States,” which states:
15Although the Agency had only one Oswald letter in its possession, the HT-Lingual files were combed after the assassination for additional materials potentially related to him. Approximately 30 pieces of correspondence that were considered potentially related to the investigation of Oswald’s case (even though not necessarily directly related to Oswald) were discovered. None of these was ultimately judged by the CIA to be of any significance. These materials, however, were stored in a separate Oswald HT-Lingual file.
Page 207
Individuals or organizations of particular intelligence interest (one should also add counterintelligence interest) were specified in watch lists provided to the mail project by the counterintelligence staff, by other CIA components, and by the FBI. The total number of names on the Watch List varied, from time to time, but on the average, the list included approximately 300 names, including about 100 furnished by the FBI. The Watch List included the names of foreigners and of U.S. citizens. (83)
Thus, the full meaning of the notation is that on November 9, 1959, an employee whose initials were RE placed Oswald’s name on the “Watch List” for the HT-Lingual project for the reason stated on the card–that Oswald was a recent defector to the U.S.S.R. and a former Marine.(84)
The response went on to state that the handwritten number, No. 7-305, which also appears on the first card, is a reference to the communication from the CI staff to the Office of Security, expressing the CI staff’s interest in seeing any mail to or from Oswald in the Soviet Union. Finally, the other handwritten notation, “N/R-RI, 20 Nov. 59” signifies that a name trace run through the central records register indicates that there was no record for Lee Oswald as of that date.16 (85)
The Agency’s explanation of the meaning of the second card was that on August 7, 1961, the CIA staff officer who opened the Oswald 201 file requested that Oswald’s name be placed on the “Watch List” because of Oswald’s expressed desire to return to the United States, as stated on the card. The handwritten notation indicates, in this instance, that Oswald’s name was deleted from the “Watch List” on May 28, 1962.(86)
With reference to the two cards on Marina Oswald, the Agency stated that her name was first placed on the “Watch List” on November 26, 1963, because she was the wife of Lee Harvey Oswald. The second card served the purpose of adding the name Marina Oswald Porter to the “Watch List” on June 29, 1965, after she had remarried. Both names were deleted from the list as of May 26, 1972. (87)
Thus the statements of former CIA employees were corroborated by the Agency’s response regarding the explanation of the index cards in the CIA’s HT-Lingual files pertaining to Oswald. The explanations attested that the references on the cards were not demonstrative of an Agency relationship with Oswald, but instead were examples of notations routinely used in connection with the HT-Lingual project.
Top of Page
(11) Did the CIA ever debrief Oswald?–The CIA has denied ever having had any contact with Oswald,(88) and its records are consistent with this position. Because the Agency has a Domestic Contacts Division that routinely attempts to solicit information on a nonclandestine basis from Americans traveling abroad,(89) the absence of any record indicating that Oswald, a returning defector who had worked in a Minsk radio factory, had been debriefed has been con-
16This, of course, is contrary to the Agency’s record that indicates the receipt of a telegram concerning Oswald on Oct. 31, 1959, and of two telegrams from the Navy concerning him on Nov. 3 and 4, 1959.
Page 208
sidered by Warren Commission critics to be either inherently unbelievable (that is, the record was destroyed) or indicative that Oswald had been contacted through other than routine Domestic Contact Division channels. (90)
After reviewing the Agency’s records pertaining to this issue, the committee interviewed the former chief of an Agency component responsible for research related to clandestine operations within the Soviet Union. He had written a November 25, 1963, memorandum indicating that, upon Oswald’s return from the Soviet Union, he had considered “the laying of interviews [on him] through the [Domestic Contacts Division] or other suitable channels.”17(91) The officer indicated that Oswald was considered suspect because the Soviets appeared to have been very solicitous of him. For this reason, a nonclandestine contact, either by the Domestic Contacts Division or other “suitable channels” such as the FBI or the Immigration and Naturalization Service, was considered.(92) The officer stated, however, that to his knowledge no contact with Oswald was ever made. Moreover, if a debriefing had occurred, the officer stated that he would have been informed. Finally, he said that Oswald was considered a potential lead, but only of marginal importance, and therefore the absence of a debriefing was not at all unusual. (93)
The committee interviewed five other Agency employees who were in a position to have discussed Oswald in 1962 with the author of this memorandum, including the person who replaced the author of the memorandum as chief of the research section. None of them could recall such a discussion.(94) Interviews with personnel from the Soviet Russia Division’s clandestine operations section, the visitors program and the clandestine activity research section failed to result in any evidence suggesting that Oswald had been contacted at any time by the CIA.(96)
The author of the November 25, 1963, memorandum also informed the committee that the CIA maintained a large volume of information on the Minsk radio factory in which Oswald had worked. This information was stored in the Office of Research and Reports.(96)
Another former CIA employee, one who had worked in the Soviet branch of the Foreign Documents Division of the Directorate of Intelligence in 1962, advised the committee that he specifically recalled collecting intelligence regarding the Minsk radio plant. In fact, this individual claimed that during the summer of 1962 he reviewed a contact report from representatives of a CIA field office who had interviewed a former marine who had worked at the Minsk radio plant following his defection to the U.S.S.R. This defector, whom the employee believed may have been Oswald, had been living with his family in Minsk. (97)
The employee advised the committee that the contact report had been filed in a volume on the Minsk radio plant that should be retrievable from the Industrial Registry Branch, then a component of the Office of Central Reference. Accordingly, the committee requested that the CIA provide both the contact report and the volume of ma-
17The November 25, 1963 memorandum indicates that the possibility of an Oswald contact was discussed during the summer of 1960, but the author indicated that the conversation actually took place during the summer of 1962, shortly before his transfer to a new assignment. During the summer of 1960, the author was not on active assignment.
Page 209
terials concerning the Minsk radio plant. A review by the committee of the documents in the volumes on the Minsk radio plant, however, failed to locate any such contact report. (98)
Since the Minsk radio plant seemed to be a logical subject of CIA concern, the committee theorized that questions about it would have been included in the debriefing of defectors. The committee therefore asked the Agency for a statement regarding its procedures for debriefing defectors. In response, the CIA stated that between 1958 and 1963 it had no procedure for systematically debriefing overseas travelers, including returning defectors. Instead, the Agency relied upon the FBI both to make such contacts and report any significant results.(99)
To investigate this question further, the committee reviewed the files of 22 other defectors to the Soviet Union (from an original list of 380) who were born in America and appeared to have returned to the United States between 1958 and 1963.18 Of these 22 individuals, only 4 were interviewed at any time by the CIA. These four instances tended to involve particular intelligence or counterintelligence needs, but this was not always the case. (100)
Based on this file review, it appeared to the committee that, in fact, the CIA did not contact returning defectors in 1962 as a matter of standard operating procedure. For this reason, the absence of any Agency contact with Oswald on his return from the Soviet Union could not be considered unusual, particularly since the FBI did fulfill its jurisdictional obligation to conduct defector interviews.(101)
Top of Page
(12) The Justice Department’s failure to prosecute Oswald.— When Oswald appeared at the U.S. Embassy on October 31, 1959, to renounce his American citizenship, he allegedly threatened to give the Soviets information he had acquired as a Marine Corps radar operator.(102) The committee sought to determine why the Justice Department did not prosecute Oswald on his return to the United States for his offer to divulge this kind of information.
A review of Oswald’s correspondence with the American Embassy in Moscow indicates that on February 13, 1961, the embassy received a letter in which Oswald expressed a “desire to return to the United States if …some agreement [could be reached] concerning the dropping of any legal proceedings against [him].” (103) On February 28, 1961, the embassy sought guidance from the State Department concerning Oswald’s potential liability to criminal prosecution.(104)
The State Department, however, responded on April 13, 1961, that it was not in a position to advise Mr. Oswald whether upon his desired return to the United States he may be amenable to prosecution for any possible offenses committed in violation of the laws of the United States….(105)
In May 1961 Oswald wrote the embassy demanding a “full guarantee” against the possibility of prosecution.(106) He visited with Embassy Consul Richard Snyder on July 16, 1961, and denied that he had ever given any information to the Soviets. (107) Snyder advised
18An effort was made to review only the files of those who had defected between 1958 and 1963. Not all of the 22 defectors, however, met this criterion.
Page 210
Oswald on an informal basis that, while no assurances could be given, the embassy did not perceive any basis for prosecuting him. (108)
There is no record that the State Department ever gave Oswald any assurances that he would not be prosecuted. Upon his return to the United States, Oswald was interviewed twice by the FBI. On each occasion, he denied ever having given information to the Soviet Union. (109)
In response to a committee request, the Department of Justice indicated that prosecution of Oswald was never considered because his file contained no evidence that he had ever revealed or offered to reveal national defense information to the Soviet Union.(110)In a subsequent response, the Department acknowledged the existence of some evidence that Oswald had offered information to the Soviet Union, but stated that there were, nevertheless, serious obstacles to a possible prosecution:
It [the Department file] does contain a copy of an FBI memorandum, dated July 3, 1961, which is recorded as having been received in the Justice Department’s Internal Security Division on December 10, 1963, which states that the files of the Office of Naval Intelligence contained a copy of a Department of State telegram, dated October 31, 1959, at Moscow. The telegram, which is summarized in the FBI report, quoted Oswald as having offered the Soviets any information he had acquired as a radar operator. The FBI report did not indicate that the information to which Oswald had access as a radar operator was classified.
Oswald returned to the United States on June 13, 1962. He was interviewed by the FBI on June 26, 1962, at Fort Worth, Tex., at which time he denied furnishing any information to the Soviets concerning his Marine Corps experiences. He stated that he never gave the Soviets any information which would be used to the detriment of the United States.
In sum, therefore, the only “evidence” that Oswald ever offered to furnish information to the Soviets is his own reported statement to an official at the U.S. Embassy in Moscow. That statement, of course, was contradicted by his denial to the FBI, upon his return to the United States, that he had ever made such an offer.
In the prosecution of a criminal case, the Government cannot establish a prima facie case solely on a defendant’s unsupported confession. The Government must introduce substantial independent evidence which would tend to establish the trustworthiness of the defendant’s statement. See, Opper v. United States 348 U.S. 84 (1954).
Accordingly, in the absence of any information that Oswald had offered to reveal classified information to the Soviets, and lacking corroboration of his statement that he had proferred information of any kind to the Russians, we did not consider his prosecution for violation of the espionage statutes 18 U.S.C. 793, 794. (111)
Page 211
Based upon this analysis, the committee could find no evidence that Oswald received favorable treatment from either the State Department or the Justice Department regarding the possibility of criminal prosecution.
Top of Page
(13) Oswald’s trip to Russia via London to Helsinki has been a a visa in 2 days.–Oswald’s trip from London to Helsinki has been a point of controversy. His passport indicates he arrived in Finland on October 10, 1959. The Torni Hotel in Helsinki, however, had him registered as a guest on that date, although the only direct flight from London to Helsinki landed at 11:33 p.m. that day. According to a memorandum signed in 1964 by Richard Helms, “[i]f Oswald had taken this flight, he could not normally have cleared customs and landing formalities and reached the Torni Hotel downtown by 2400 (midnight) on the same day.” (112) Further questions concerning this segment of Oswald’s trip have been raised because he had been able to obtain a Soviet entry visa within only 2 days of having applied for it on October 12, 1959.(113) 19
The committee was unable to determine the circumstances surrounding Oswald’s trip from London to Helsinki. Louis Hopkins, the travel agent who arranged Oswald’s initial transportation from the United States, stated that he did not know Oswald’s ultimate destination at the time that Oswald booked his passage on the freighter Marion Lykes.(114) Consequently, Hopkins had nothing to do with the London-to-Helsinki leg of Oswald’s trip. In fact, Hopkins stated that had he known Oswald’s final destination, he would have suggested sailing on another ship that would have docked at a port more convenient to Russia.(115) Hopkins indicated that Oswald did not appear to be particularly well-informed about travel to Europe. The travel agent did not know whether Oswald had been referred to him by anyone.(116).
A request for any CIA and Department of Defense files on Louis Hopkins resulted in a negative response. The committee was unable to obtain any additional sources of information regarding Oswald’s London-to-Helsinki trip.
The relative ease with which Oswald obtained his Soviet Union entry visa was more readily amenable to investigation. This issue is one that also had been of concern to the Warren Commission.(117) In a letter to the CIA dated May 25, 1964, J. Lee Rankin inquired about the apparent speed with which Oswald’s Soviet visa had been issued. Rankin noted that he had recently spoken with Abraham Chayes, legal adviser to the State Department, who maintained that at the time Oswald received his visa to enter Russia from the Soviet Embassy in Helsinki, normally at least 1 week would elapse between the time of a tourist’s application and the issuance of a visa. Rankin contended that if Chayes assessment was accurate, then Oswald’s ability to obtain his tourist visa in 2 days might have been significant. (118)
The CIA responded Rankin that the Soviet Consulate in Helsinki 1964. Helms wrote to Rankin that the Soviet Consulate in Helsinki
19Since Oswald arrived in Helsinki on October 10, 1959, which was a Saturday, it is assumed that his first opportunity to apply for a visa would have been on Monday, October 12
Page 212
was able to issue a transit visa (valid for 24 hours) to U.S. businessmen within 5 minutes, but if a longer stay were intended, at least 1 week was needed to process a visa application and arrange lodging through Soviet Intourist. (119) A second communication from Helms to Rankin, dated September 14, 1964, added that during the 1964 tourist season, Soviet consulates in at least some Western European cities issued Soviet tourist visas in from 5 to 7 days. (120)
In an effort to resolve this issue, the committee reviewed classified information pertaining to Gregory Golub, who was the Soviet Consul in Helsinki when Oswald was issued his tourist visa. This review revealed that, in addition to his consular activities, Golub was suspected of having been an officer of the Soviet KGB. Two American Embassy dispatches concerning Golub were of particular significance with regard to the time necessary for issuance of visas to Americans for travel into the Soviet Union. The first dispatch recorded that Golub disclosed during a luncheon conversation that:
Moscow had given him the authority to give Americans visas without prior approval from Moscow. He [Golub] stated that this would make his job much easier, and as long as he was convinced the American was “all right” he could give him a visa in a matter of minutes…(121)
The second dispatch, dated October 9, 1959, 1 day prior to Oswald’s arrival in Helsinki, illustrated that Golub did have the authority to issue visas without delay. The dispatch discussed a telephone contact between Golub and his consular counterpart at the American Embassy in Helsinki:
…Since that evening [September 4, 1959] Golub has only phoned [the U.S. consul] once and this was on a business matter. Two Americans were in the Soviet Consulate at the time and were applying for Soviet visas thru Golub. They had previously been in the American consulate inquiring about the possibility of obtaining a Soviet visa in 1 or 2 days. [The U.S. Consul] advised them to go directly to Golub and make their request, which they did. Golub phoned [the U.S. Consul] to state that he would give them their visas as soon as they made advance Intourist reservations. When they did this, Golub immediately gave them their visas ….20(122)
Thus, based upon these two factors, (1) Golub’s authority to issue visas to Americans without prior approval from Moscow, and (2) a demonstration of this authority, as reported in an embassy dispatch approximately 1 month prior to Oswald’s appearance at the Soviet Embassy, the committee found that the available evidence tends to support the conclusion that the issuance of Oswald’s tourist visa within 2 days after his appearance at the Soviet Consulate was not indicative of an American intelligence agency connection. 21
20Evidently Oswald had made arrangements with Intourist. On his arrival at the Moscow railroad station on October 16, he was met by an Intourist representative and taken to the Hotel Berlin where he registered as a student (123)
21If anything, Oswald’s ability to receive a Soviet entry visa so quickly was more indicative of a Soviet interest in him.
Page 213
Top of Page
(14) Oswald’s contact with Americans in the Soviet Union.– Priscilla Johnson McMillan, author of Marina and Lee,” became a subject of the committee’s inquiry because she was one of two American corespondents who had obtained an interview with Oswald during his stay in Moscow in 1959. The committee sought to investigate an allegation that her interview with Oswald may have been arranged by the CIA.(124)
John McVickar, a consul at the American Embassy, testified that he had discussed Oswald’s case with McMillan, and that he thought “…she might help us in communicating with him and help him in dealing with what appeared to be a very strong personal problem if she were able to talk with him.”(125) McVickar stated, however, that he had never worked in any capacity for the CIA, nor did he believe that McMillan had any such affiliation.(126) McVickar’s State Department and CIA files were consistent with his testimony that he had never been associated with the CIA.
McMillan gave the following testimony about the events surrounding her interview with Oswald. In November 1959 she had returned from a visit to the United States where she covered the Camp David summit meeting between President Eisenhower and Premier Khrushchev. On November 16, 1959, she went to the American Embassy to pick her mail for the first time since her return to the Soviet Union. The mail pickup facility was in a foyer near the consular office. Consular Officer John A. McVickar came out of this office and welcomed McMillan back to the Soviet Union. They exchanged a few words, and, as she was leaving, McVickar commented that at her hotel was an American who was trying to defect to the Soviet Union. McVickar stated that the American would not speak to “any of us,” but he might speak to McMillan because she was a woman. She recalled that as she was leaving, McVickar told her to remember that she was an American.(127)
McMillan proceeded to her hotel, found out the American’s room number, knocked on his door and asked him for an interview. The American, Lee Harvey Oswald, did not ask her into the room, but he did agree to talk to her in her room later that night. (128) No American Government official arranged the actual interview. McMillan met with Oswald just once. She believed that McVickar called her on November 17, the day after the interview, and asked her to supper. That evening they discussed the interview. McVickar indicated a general concern about Oswald and believed that the attitude of another American consular official might have pushed Oswald further in the direction of defection. McVickar indicated a personal feeling that it would be a sad thing for Oswald to defect in view of his age, but he did not indicate that this was the U.S. Government’s position. (129)
McMillan also testified that she had never worked for the CIA, nor had she been connected with any other Federal Government agency at the time of her interview with Oswald. (130) According to an affidavit that McMillan filed with the committee, her only employment with the Federal Government was as a 30-day temporary translator. (131).
Finally, McMillan testified that because of her background in Russian studies, she applied for a position with the CIA in 1952 as an
Page 214
intelligence analyst. The application, however, was withdrawn.(132) She acknowledged having been debriefed by an Agency employee in 1962 after returning from her third trip to the Soviet Union, but explained that this contact was in some way related to the confiscation of her notes by Soviet officials. (133)22
The committee’s review of CIA files pertaining to Ms. McMillan corroborated her testimony. There was no indication in these files suggesting that she had ever worked for the CIA. In fact, the Agency did not even debrief her after her first two trips to the Soviet Union. An interview with the former Agency official who had been deputy chief and then chief of the visitors program during the years 1958 to 1961 similarly indicated that McMillan had not been used by the CIA in the program. (134)
There was information in McMillan’s file indicating that on occasion during the years 1962-65 she had provided cultural and literary information to the CIA. None of this information was, however, suggestive in any way of a clandestine relationship. Accordingly, there was no evidence that McMillan ever worked for the CIA or received the Agency assistance in obtaining an interview with Oswald.23
Richard E. Snyder was the consular official in the U.S. Embassy in Moscow who handled the Oswald case. It was Snyder with whom Oswald had met in 1959 when he sought to renounce his American citizenship.(135) Two years later, when Oswald initiated his inquiries about returning to the United States, Snyder again became involved in the case.(136) Warren Commission critics have alleged that Snyder was associated in some way with the CIA during his service in the Moscow Embassy.(137)
In his committee deposition, Richard Snyder acknowledged that for a 11-month period during 1949-50 he worked for the CIA while he was on the waiting list for a foreign service appointment with the State Department. (138) Snyder testified, however, that since resigning from the CIA in March 1950, he had had no contact with the other than a letter written in 1970 or 1971 inquiring about employment on a contractual basis. (139)24
The committee reviewed Snyder’s files at the State Department, Defense Department and the CIA. Both the State Department and Defense Department files are consistent with his testimony. Snyder’s CIA file revealed that, at one time prior to 1974, it had been red flagged and maintained on a segregated basis. The file contained
22In her affidavit McMillan discussed the circumstances surrounding this encounter in some detail: “In November 1962, I had a conversation with a man who identified himself as a CIA employee…I agreed to see him in part because the confiscation of my papers and notes had utterly altered my situation– I now had no hope of returning to the U.S.S.R. and was free for the first time to write what I knew. I was preparing a series of articles for The Reporter which would contain the same information about which [the CIA employee] had expressed a desire to talk to me. Finally, during the latter part of my 1962 trip to the U.S.S.R., I had been under heavy surveillance and the KGB knew what Soviet citizens I had seen. Many of those I had talked to for the Reporter articles were Russian “liberals” (anti-Stalin and pro-Khrushchev). What reprisals might befall those whom I had interviewed I did not know, but since my notes were now part of the KGB files, I felt that it might help them if the CIA knew that which the KGB already knew. My meeting with– the CIA employee– which occurred at the Brattle Inn, Cambridge, was a reversal of my usual effort to avoid contact with the CIA, and the subject matter was confined to my impressions of the Soviet literary and cultural climate.”
23Nor was there any basis, based on McMillan’s testimony, CIA files or evidence provided by McMillan’s publisher, Harper and Row, to support the allegation that the CIA financed or was otherwise involved in publishing “Marina and Lee.”
24Snyder also denied contact with any other intelligence service while active as a foreign service officer.
Page 215
routing indicator that stated that the file had been red flagged because of a “DCI [Director of Central Intelligence] statement and a matter of cover” concerning Snyder.(140)
In response to a committee inquiry, the CIA indicated that the DCI statement presumably refers to comments which former Director Richard Helms had made in 1964 concerning the Oswald case, when Helms was Deputy Director for Plans25 The CIA also stated that Snyder’s file had been flagged at the request of DDO/CI (Directorate of Operations/Central Intelligence) to insure that all inquiries concerning Snyder would be referred to that office. The Agency was unable to explain the reference to “cover,” because, according to its records, Snyder had never been assigned any cover while employed. Further, the Agency stated that “[t]here is no record in Snyder’s official personnel file that he ever worked, directly or indirectly, in any capacity for the CIA after his resignation on 26 September 1950.”
The committee did not regard this explanation as satisfactory, especially since Snyder’s 201 file indicated that for approximately 1 year during 1956-57 he had been used by an Agency case officer as a spotter at a university campus because of his access to others who might be going to the Soviet Union, nor was the Agency able to explain specifically why someone considered it necessary to red flag the Snyder file.
The remainder of the Snyder file, however, is consistent, with his testimony before the committee concerning the absence of Agency contacts. In addition, the CIA personnel officer who handled Snyder’s case in 1950 confirmed that Snyder had, in fact, terminated his employment with the CIA at that time. Moreover, he added that Snyder had gone to the State Department as a bona fide employee without any CIA ties. (143) This position was confirmed by a former State Department official who was familiar with State Department procedures regarding CIA employees. In addition, this individual stated that at no time from 1959 to 1963 did the CIA use the State Department’s overseas consular positions as cover for CIA intelligence officers. (144)
The CIA’s failure to explain adequately the red-flagging of Snyder’s file was extremely troubling to the committee. Even so, based on Snyder’s sworn testimony, the review of his file and the statements of his former personnel officer, a finding that he was in contact with Oswald on behalf of the CIA was not warranted.
Dr. Alexis H. Davison was the U.S. Embassy physician in Moscow from May 1961 to May 1963. In May 1963, the Soviet Union declared him persona non grata in connection with his alleged involvement in the Penkovsky case. (145) After the assassination of President Kennedy, it was discovered that the name of Dr. Davison’s mother, Mrs. Hal Davison, and her Atlanta address were in Oswald’s address book under the heading “Mother of U.S. Embassy Doctor.”(146) In addition, it was determined that the flight that Oswald, his wife and child took from New York to Dallas on June 14, 1962, had stopped in Atlanta. (147) For this reason, it has been alleged that Dr. Davison was Oswald’s intelligence contact in Moscow. (148)
25Responding to a newspaper allegation that Oswald had met with CIA representatives in Moscow, Richard Helms wrote a memorandum to the Warren Commission on March 18, 1964, in which he stated the “desire to state for the record that the allegation carried in this press report is utterly unfounded as far as the CIA is concerned.” (141)
Page 216
In a committee interview, Dr. Davison stated that he had been a physician in the U.S. Air Force and was stationed in Moscow as the U.S. Embassy physician from May 1961 to May 1963. In this capacity, it was his duty to perform physical examinations on all Soviet immigrants to the United States. He recalled that most of these immigrants were elderly, but he remembers two young women, one who was a mathematics teacher from the south of Russia and one who was married to an American. The individual who was married to the American was frightened by the prospect of going to the United States. She stated that she was going to Texas with her husband. Davison told her that if she and her husband traveled through Atlanta on their way to Texas, his mother, a native-born Russian, would be happy to see her. He gave his mother’s name and address in Atlanta to the woman’s husband, who was “scruffy looking.” This was not an unusual thing to do, since his family had always very hospitable to Russians who visited Atlanta. In retrospect, he assumed that he gave his mother’s name and address to either Lee or Marina Oswald, but he was uncertain about this. (149)
After the assassination of President Kennedy, Davison was interviewed first by a Secret Service agent and later by an FBI agent in connection with the entry of his mother’s name and address in Oswald’s address book. The FBI agent also interviewed Davison’s mother, Natalia Alekseevna Davison. Davison indicated that the Secret Service and the FBI were the only Government agencies to interview him about his contact with the Oswalds. (150)
Davison stated that in connection with his assignment as U.S. Embassy physician in Moscow, he had received some superficial intelligence training. This training mainly involved lectures on Soviet life and instructions on remembering and reporting Soviet names and military activities. (151)
Davison admitted his involvement in the Penkovsky spy case. During his tour of duty in Moscow, Davison was asked by an Embassy employee, whose name he no longer remembered, to observe a certain lamppost on his daily route between his apartment and the Embassy and to be alert for a signal by telephone. Davison agreed, according to his instructions, if he ever saw a black chalk mark on the lamppost, or if he ever received a telephone call in which the caller blew into the receiver three times, he was to notify a person whose name he also no longer remembered. He was told nothing else about the operation. Davison performed his role for approximately 1 year. On just one occasion, toward the end of his stay in the Soviet Union, he observed the mark on the lamppost and his wife received the telephone signal. As instructed, he reported these happenings. Shortly thereafter, the Soviets reported that they had broken the Penkovsky spying operation. The Soviets declared Davison persona non grata just after he left Moscow, his tour of duty having ended. He did not recall any intelligence debriefings on the Penkovsky case. (152)
Davison denied under oath participating in any other intelligence work during his tour in Moscow. (153) The deputy chief of the CIA’s Soviet Russia clandestine activities section from 1960 to 1962 confirmed Davison’s position, characterizing his involvement in the Penkovsky case as a “one shot” deal. (154) In addition, a review of Davison’s CIA
Page 217
and Department of Defense files showed them to be consistent with his committee testimony.
Accordingly, there was as insufficient evidence for concluding that Dr. Davison was an intelligence contact for Oswald in Moscow.
Top of Page
(15) Alleged intelligence contacts after Oswald returned from Russia.–George de Mohrenschildt was an enigmatic man–a geologist-businessman who befriended Oswald in Texas in 1962,(155) thus causing considerable speculation based on the contrasting backgrounds of the two men. De Mohrenschildt, who committed suicide in 1977, was sophisticated and well educated, a man who moved easily among wealthy Texas oilmen and a circle of white Russians in Dallas many of whom were avowed conservatives. Oswald, because of his background and his Marxist ideological positions, was shunned by most of the people de Mohrenschildt counted among his friends.
In his Warren Commission testimony, de Mohrenschildt stated that he believed he had discussed Oswald with J. Walton Moore, whom he described as “a Government man–either FBI or Central Intelligence.”(156) He said that Moore was known as the head of the FBI in Dallas and that Moore had interviewed him in 1957 when he returned from a trip to Yugoslavia. (157) De Mohrenschildt indicated that he had asked Moore and Fort Worth attorney Max Clark about. Oswald, to reassure himself that it was “safe” for the de Mohrenschildts to assist him and was told by one of these persons, “The guy seems to be OK”(158) This admitted association with J. Walton Moore, an employee of the CIA, gave rise to the question of whether de Mohrenschildt had contacted Oswald on behalf of the CIA. (159)
In 1963 J. Walton Moore was employed by the CIA in Dallas in the Domestic Contacts Division. (160) According to Moore’s CIA personnel file, he had been assigned to the division in 1948. During the period April 1, 1963, to March 31, 1964, he was an overt CIA employee assigned to contact persons traveling abroad for the purpose of eliciting information they might obtain. He was not part of a covert or clandestine operation.
In an Agency memorandum dated April 13, 1977, contained in deMohrenschildt’s CIA file, Moore set forth facts to counter a claim that had been recently made by a Dallas television station that Oswald had been employed by the CIA and that Moore had known him. In that memorandum, Moore was quoted as saying that, according to his records, the last time he had talked with de Mohrenschildt was in the fall of 1961. Moore said that he had no recollection of any conversation with de Mohrenschildt concerning Oswald. The memorandum also said that Moore recalled only two occasions when he had met de Mohrenschildt–first, in the spring of 1958, to discuss a mutual interest in China, and then in the fall of 1961, when de Mohrenschildt and his wife showed films of their Latin American walking trip. (161)
Other documents in de Mohrenschildt’s CIA file, however, indicated more contact with Moore than was stated in the 1977 memorandum. In a memorandum dated May 1, 1964, submitted to the Acting Chief of the Domestic Contacts Division of the CIA, Moore stated that he had known de Mohrenschildt and his wife since 1957, at which time Moore obtained biographical data on de Mohrenschildt following his trip to Yugoslavia for the International Cooperation Administration. Moore
Page 218
also wrote in that 1964 memorandum that he had seen de Mohrenschildt several times in 1958 and 1959. De Mohrenschildt’s CIA file contained several reports submitted by de Mohrenschildt to the CIA on topics concerning Yugoslavia. (162)
De Mohrenschildt testified before the Warren Commission that he had never been in any respect an intelligence agent. (163) Further, the committee’s interview with Moore and its review of the CIA’s Moore and de Mohrenschildt files showed no evidence that de Mohrenschildt had ever been an American intelligence agent. (In this regard, the committee noted that during 1959-63, upon returning from trips abroad, as many as 25,000 Americans annually provided information to the CIA’s Domestic Contacts Division on a nonclandestine basis. (164) Such acts of cooperation should not be confused with an actual Agency relationship).26
Prior to visiting Mexico in September 1963, Oswald applied in New Orleans for a Mexican tourist card. The tourist card immediately preceding his in numerical sequence was issued on September 17, 1963, (167) to William G. Gaudet, a newspaper editor. Two days later, Gaudet departed on a 3- or 4-week trip to Mexico and other Latin American countries.(168) This happened to coincide with Oswald’s visit to Mexico City between September 27, 1963, and October 3, 1963.(169) After the assassination, Gaudet advised the FBI during an interview that he had once been employed by the CIA.(170) Speculation about Gaudet’s possible relationship with Oswald arose when it was discovered that the Warren Commission Report contained a list, provided by the Mexican Government, purporting to include all individuals who had been issued Mexican tourist cards at the same time as Oswald, a list that omitted Gaudet’s name. (171)
In a committee deposition, Gaudet testified that his contact with the CIA was primarily as a source of information (obtained during his trips abroad). In addition, he explained that he occasionally performed errands for the Agency. (172) Gaudet stated that his last contact with the CIA was in 1969, although the relationship had never been formally terminated. (173)
The committee reviewed Gaudet’s CIA file but found neither any record reflecting a contact between him and the Agency after 1961, nor any indication that he had “performed errands” for the CIA. A memorandum, dated January 23, 1976, also indicated the absence of any further contact after this time:
The Domestic Collections Division (DCD) has an inactive file on William George Gaudet, former editor and publisher of the Latin American Report. The file shows that Gaudet was a source of the New Orleans DCD (Domestic Contacts Division) Resident Office from 1948 to 1955 during which period he provided foreign intelligence information on Latin American political and economic conditions resulting from his extensive travel in South and Central America in pursuit
26De Mohrenschildt’s file also contains a reference to an occasion when he may have been involved in arranging a meeting between a Haitian bank officer and a CIA or Department of Defense official. (165) The Department of Defense official, when interviewed by the committee, stated that the meeting was arranged by Department of Defense officials and that de Mohrenschildt’s presence (in the company of his wife) was unanticipated. (166) The committee did not regard this incident as evidence of a CIA relationship.
Page 219
of journalistic interests. The file further indicates that Gaudet was a casual contact of the New Orleans Office between 1955 and 1961 when, at various times, he furnished fragmentary intelligence.(174)
Gaudet said he could not recall whether his trip to Mexico and other Latin American countries in 1963 involved any intelligence-related activity. (175) He was able to testify, however, that during that trip he did not encounter Oswald, whom he had previously observed on occasion at the New Orleans Trade Mart.(176)27 Gaudet stated that he was unaware at the time his Mexican tourist card was issued that it immediately preceded Oswald’s, and he could not recall having seen Oswald on that day.(177) Finally, Gaudet said he did not have any information concerning the omission of his name from the list published in the Warren Commission Report. (178)
Based upon this evidence, the committee did not find a basis for concluding that Gaudet had contacted Oswald on behalf of the CIA. Although there was a conflict between Gaudet’s testimony and his CIA file concerning the duration of his Agency contacts as well as the performance of errands, there was no indication from his file or testimony that Gaudet’s cooperation involved clandestine activity. Again, it should be stressed that the Domestic Contacts Division, which was the Agency component that was in touch with Gaudet, was not involved in clandestine operations.
Top of Page
(16) Alleged intelligence implications of Oswald’s military service— The committee reviewed Oswald’s military records because allegations that he had received intelligence training and had participated in intelligence operations during his term of Marine service.(179) Particular attention was given to the charges that Oswald’s early discharge from the corps was designed to serve as a cover for an intelligence assignment and that his records reflected neither his true security clearance nor a substantial period of service in Taiwan. These allegations were considered relevant to the question of whether Oswald had been performing intelligence assignments for military intelligence, as well as to the issue of Oswald’s possible association with the CIA.
Oswald’s Marine Corps records bear no indication that he ever received any intelligence training or performed any intelligence assignments during his term of service. As a Marine serving in Atsugi, Japan, Oswald had a security clearance of confidential, but never received a higher classification.(180) In his Warren Commission testimony, John E. Donovan, the officer who had been in charge of Oswald’s crew at the El Toro Marine base in California, stated that all personnel working in the radar center were required to have a minimum security clearance of secret (181) Thus, the allegation has been made that the security clearance of confidential in Oswald’s records is inaccurate. The committee however, reviewed files belonging to four enlisted men who had worked with Oswald either in Japan or California and found that each of them had a security clearance of confidential.(182) 28
27Gaudet testified that he had never met Oswald, although he had known of him prior to the assassination because Oswald had distributed literature near his office. Gaudet stated that on one occasion he observed Oswald speaking to Guy Bannister on a street corner.
28John E. Donovan, Oswald’s commanding officer, did have a security clearance of secret.
Page 220
It has been stated that Oswald claimed to have served in Taiwan. (183) The committee’s review of his military records, including unit diaries that were not previously studied by the Warren Commission, indicated, however, that he had not spent substantial time, if any, in Taiwan. These records show that, except for a 3 1/2 month period of service in the Philippines, Oswald served in Japan from September 12, 1957, until November 2, 1958. (184) Although Department of Defense records do indicate that MAG (Marine Air Group) 11, Oswald’s unit, was deployed to Taiwan on September 16, 1958, and remained in that area until April 1959, an examination of the MAG 11 unit diaries indicated that Oswald was assigned at that time to a rear echelon unit. (185) The term rear echelon does not, on its face, preclude service with the main unit in Taiwan, but the Department of Defense has specifically stated that “Oswald did not sail from Yokosuka, Japan on September 16, 1958. He remained aboard NAS Atsugi as part of the MAG-11 rear echelon.” 29(186)
Oswald’s records also reflect that on October 6, 1958, he was transferred within MAG 11 to a Headquarters and Maintenance Squadron subunit in Atsugi, Japan. (187) He reportedly spent the next week in the Atsugi Station Hospital. (188) On November 2, 1958, Oswald left Japan for duty in the United States. (189)
Accordingly, based upon a direct examination of Oswald’s unit diaries, as well as his own-military records, it does not appear that he had spent any time in Taiwan. This finding is contrary to that of the Warren Commission that Oswald arrived with his unit in Taiwan on September 30, 1958, and remained there somewhat less than a week,(190) but the Commission’s analysis apparently was made without access to the unit diaries of MAG 11.30
Moreover, even if Oswald, in fact, did make the trip with his unit to Taiwan, it is clear that any such service there was not for a substantial time. The unit arrived at Atsugi on September 30, 1958, and by November 2, 1958, Oswald had left from Japan to complete his tour of duty in the United States. (191)
Finally, with one exception, the circumstances surrounding Oswald’s rapid discharge from the military do not appear to have been unusual. Oswald was obligated to serve on active duty until December 7, 1959, but on August 17 he applied for a hardship discharge to support his mother. About 2 weeks later the application was approved. (193) 31
It appeared that Oswald’s hardship discharge application was processed so expeditiously because it was accompanied by all of the necessary documentation. In response to a committee inquiry, the Department of Defense stated that “… to a large extent, the time involved a processing hardship discharge applications depended on how well the individual member had prepared the documentation needed for
29This is contrary to statements attributed to Lieutenant Charles R. Rhodes by Edward J. Epstein in his book, “The Secret World of Lee Harvey Oswald.” Rhodes maintains, according to Epstein, that Oswald did make the trip with the main unit but was sent back to Japan on October 6, 1958.
30Similarly, a message sent on November 4, 1959, from the Chief of Naval Operations concerning Oswald, which states that he had “served with Marine Air Control Squadrons in Japan and Taiwan,” (191) may have been issued without checking unit diaries which indicated that Oswald had not been so deployed.
31By September 4, 1959, Oswald had been informed that he would be discharged on September 11, 1959. (194) This explains why he was able to tell passport officials on that day that he expected to depart the United States for Europe on September 21, 1959.
Page 221
consideration of his or her case.”(195) A review of Oswald’s case indicates that his initial hardship discharge application was accompanied by all of the requisite documentation. Oswald had met the, preliminary requirements of having made a voluntary contribution to the hardship dependent (his mother) and of applying for a dependent’s quarters allotment 32 to alleviate the hardship. (196) Even though all of the supporting affidavits for the quarters allotment had not been submitted at the time that the hardship discharge application was filed, the endorsements on the application indicated that the reviewing officers were aware that both the requisite voluntary contribution and the application for a quarters allotment had been made. (197) Moreover, that application was accompanied by two letters and two affidavits attesting to Marguerite Oswald’s inability to support herself. (198)
Documents provided to the committee by the American Red Cross indicate that Oswald had sought its assistance and therefore was probably well advised on the requisite documentation to support his claim.(199) Indeed, Red Cross officials interviewed Marguerite Oswald and concluded that she “could not be considered employable from an emotional standpoint.”(200) The Fort Worth Red Cross office indicated a quarters allotment was necessary for Marguerite Oswald, rather than a hardship discharge for Lee, and assisted her in the preparation of the necessary application documents.(201) Nevertheless, Oswald informed the Red Cross office in El Toro, Calif., where he was then stationed, that he desired to apply for a hardship discharge. (202)
The unusual aspect of Oswald’s discharge application was that, technically, his requisite application for a quarters allowance for his mother should have been disallowed because Marguerite’s dependency affidavit stated that Oswald had not contributed any money to her during the preceding year. (203) Even so, the first officer to review Oswald’s application noted in his endorsement, dated August 19, 1959, that “[a] genuine hardship exists in this case, and in my opinion approval of the ‘Q’ [quarters] allotment will not sufficiently alleviate this situation.”(204) This quotation suggests the possibility that applications for quarters allotments and hardship discharges are considered independently of one another. In addition, six other officers endorsed Oswald’s application.(205) The committee was able to contact three of the seven endorsing officers (one had died); two had no memory of the event,(206) and one could not recall any details. (207) The committee considered their absence of memory to be indicative of the Oswald, case having been handled in a routine manner.
Based on this evidence, the committee was not able to discern any unusual discrepancies or features in Oswald’s military record.
Top of Page
(17) Oswald’s military intelligence file.–On November 22, 1963, soon after the assassination, Lieutenant Colonel Robert E. Jones, operations officer of the U.S. Army’s 112th Military Intelligence Group Fort Sam Houston, San Antonio, Tex. contacted the FBI offices in San Antonio and Dallas and gave those offices detailed information concerning Oswald and A. J. Hidell, Oswald’s alleged alias. (208) This information suggested the existence of a military intelli-
32A dependent’s quarters allotment is one that is jointly paid to the dependent by the serviceman and the service.
Page 222
gence file on Oswald and raised the possibility that he had intelligence associations of some kind. (209)
The committee’s investigation revealed that military intelligence officials had opened a file on Oswald because he was perceived as a possible counterintelligence threat. Robert E. Jones testified before the committee that in June 1963 he had been serving as operations officer of the 112th Military Intelligence Group at Fort Sam Houston, Tex. 33 Under the group’s control were seven regions encompassing five States: Texas, Louisiana. Arkansas, New Mexico and Oklahoma. Jones was directly responsible for counterintelligence operations, background investigations, domestic intelligence and any special operations in this five-State area. (210) He believed that Oswald first came to his attention in mid-1963 through information provided to the 112th MIG by the New Orleans Police Department to the effect that Oswald had been arrested there in connection with Fair Play for Cuba Committee activities. (211) As a result of this information, the 112th Military Intelligence Group took an interest in Oswald as a possible counterintelligence threat.(212) It collected information from local agencies and the military central records facility, and opened a file under the names Lee Harvey Oswald and A.J. Hidell.(213) Placed in this file were documents and newspaper articles on such topics as Oswald’s defection to the Soviet Union, his travels there, his marriage to a Russian national, his return to the United States, and his pro-Cuba activities in New Orleans.
Jones related that on November 22, 1963, while in his quarters at Fort Sam Houston, he heard about the assassination of President Kennedy. (215) Returning immediately to his office, he contacted MIG personnel in Dallas and instructed them to intensify their liaisons with Federal, State and local agencies and to report back any information obtained. Early that afternoon, he received a telephone call from Dallas advising that an A.J. Hidell had been arrested or had come to the attention of law enforcement authorities. Jones checked the MIG indexes, which indicated that there was a file on Lee Harvey Oswald, also known by the name A. J. Hidell.(216) Pulling the file, he telephoned the local FBI office in San Antonio to notify the FBI that he had some information. (217) He soon was in telephone contact with the Dallas FBI office, to which he summarized the documents in the file. He believed that one person with whom he spoke was FBI Special-Agent-in-Charge J. Gordon Shanklin. He may have talked with the Dallas FBI office more than one time that day. (218)
Jones testified that his last activity with regard to the Kennedy assassination was to write an “after action” report that summarized the actions he had taken, the people he had notified and the times of notification. (219) In addition, Jones believed that this “after action” report included information obtained from reports filed by the military intelligence agents who performed liaison functions with the Secret Service in Dallas on the day of the assassination. (220) This “after action” report was then maintained in the Oswald file.(221) Jones did not contact, nor was he contacted by, any other law enforce-
33Questions had been raised about the contents of some FBI communications on November 22, 1963, that reflected information allegedly provided by military intelligence. In his testimony, Jones clarified several points and corrected several errors in these communications.
Page 223
ment or intelligence agencies concerning information that he could provide on Oswald. (222) To Jones’ knowledge, neither the FBI nor any law enforcement agency ever requested a copy of the military intelligence file on Oswald. (223) To his surprise, neither the FBI, Secret Service, CIA nor Warren Commission ever interviewed him. (224) No one ever directed him to withhold any information; on the other hand, he never came forward and offered anyone further information relevant to the assassination investigation because he “felt that the information that [he] had provided was sufficient and …a matter of record. …”(225)
The committee found Jones’ testimony to be credible. His statements concerning the contents of the Oswald file were consistent with FBI communications that were generated as a result of the information that he initially provided. Access to Oswald’s military intelligence file, which the Department of Defense never gave to the Warren Commission, was not possible because the Department of Defense had destroyed the file as part of a general program aimed at eliminating all of its files pertaining to nonmilitary personnel. In response to a committee inquiry, the Department of Defense gave the following explanation for the file’s destruction:
- Dossier AB 652876, Oswald, Lee Harvey, was identified for deletion from IRR (Intelligence Records and Reports) holdings on Julian date 73060 (1 March 1973) as stamped on the microfilmed dossier cover. It is not possible to determine the actual date when physical destruction was accomplished, but is credibly surmised that the destruction was accomplished within a period not greater than 60 days following the identification for deletion. Evidence such as the type of deletion record available, the individual clerk involved in the identification, and the projects in progress at the time of deletion, all indicate the dossier deletion resulted from the implementation of a Department of the Army, Adjutant General letter dated 1 June 1971, subject: Acquisition of Information Concerning Persons and Organizations not Affiliated with the Department of Defense (DOD) (Incl 1). Basically, the letter called for the elimination of files on non-DOD affiliated persons and organizations.
- It is not possible to determine who accomplished the actual physical destruction of the dossier. The individual identifying the dossier for deletion can be determined from the clerk number appearing on the available deletion record. The number indicates that Lyndall E. Harp was the identifying clerk. Harp was an employee of the IRR from 1969 until late 1973, at which time she transferred to the Defense Investigative Service, Fort Holdbird, Md., where she is still a civil service employee. The individual ordering the destruction or deletion cannot be determined. However, available evidence indicates that the dossier was identified for deletion under a set of criteria applied by IRR clerks to all files. The basis for these criteria were [sic] established in the 1 June 1971 letter. There is no indication that the dossier was specifically identified for review or deletion. All evidence shows that the file was
Page 224
reviewed as part of a generally applied program to eliminate any dossier concerning persons not affiliated with DOD.
- The exact material contained in the dossier cannot be determined at this time. However, discussions with all available persons who recall seeing the dossier reveal that it most probably included: newspaper clippings relating to pro-Cuban activities of Oswald, several Federal Bureau of Investigation reports, and possibly some Army counterintelligence reports. None of the persons indicated that they remember any significant information in the dossier. It should be noted here that the Army was not asked to investigate the assassination. Consequently, any Army-derived information was turned over to the appropriate civil authority.
- At the time of the destruction of the Oswald dossier, IRR was operating under the records disposal authority contained in the DOD Memorandum to Secretaries of the Military Departments, OASD(A), 9 February 1972, subject: Records Disposal Authority (Incl 2). The memorandum forwards National Archivist disposal criteria which is similar in nature to the requirements outlined in the 1 June 1971 instructions. It was not until 1975 that the Archivist changed the criteria to ensure non-destruction of investigative records that may be of historical value. (226)
Upon receipt of this information, the committee orally requested the destruction order relating to the file on Oswald. In a letter dated September 13, 1978, the General Counsel of the Department of the Army replied that no such order existed:
Army regulations do not require any type of specific order before intelligence files can be destroyed, and none was prepared in connection with the destruction of the Oswald file. As a rule, investigative information on persons not directly affiliated with the Defense Department can be retained in Army files only for short periods of time and in carefully regulated circumstances. The Oswald file was destroyed routinely in accordance with normal files management procedures, as are thousands of intelligence files annually.(227)
The committee found this “routine” destruction of the Oswald file extremely troublesome, especially when viewed in light of the Department of Defense’s failure to make this file available to the Warren Commission. Despite the credibility of Jones’ testimony, without access to this file, the question of Oswald’s possible affiliation with military intelligence could not be fully resolved.
Top of Page
(18) The Oswald photograph in Office of Naval Intelligence files.– The Office of Naval Intelligence’s (ONI) Oswald file contained a photograph of Oswald, taken at the approximate time of his Marine Corps induction. It was contained in an envelope that had on it the language “REC’D 14 November 1963” and “CIA 77978.” (228) These markings raised the possibility that Oswald had been in some way associated with the CIA.
In response to it committee inquiry, the Department of Defense stated that the photograph had been obtained by ONI as a result of
Page 225
an October 4, 1963 CIA request for two copies of the most recent photographs of Oswald so that an attempt could be made to verify his reported presence in Mexico City. The requested copies, however, were not made available to the CIA until after the President’s assassination.34 Because of the absence of documentation, no explanation could be given for how or when the Office of Naval Intelligence received this particular photograph of Oswald. (229)
The committee’s review of CIA cable traffic confirmed that cable No. 77978, dated October 24, 1963, was in fact a request for two copies of the Department of the Navy’s most recent photograph of Lee Henry [sic] Oswald. Moreover, review of other cable traffic corroborated the Agency’s desire to determine whether Lee Harvey Oswald had, in fact, been in Mexico City. (230)
The committee concluded, therefore, that the ONI photograph of Oswald bearing a reference to the CIA, was not evidence that Oswald was a CIA agent. Again, however, the destruction of the military file on Oswald prevented the committee from resolving the question of Oswald’s possible affiliation with military intelligence.
Top of Page
(19) Oswald in Mexico City.–The committee also considered whether Oswald’s activities in Mexico City in the fall of 1963 were indicative of a relationship between him and the CIA. This aspect of the committee’s investigation involved a complete review both of alleged Oswald associates and of various CIA operations outside of the United States. (231)
The committee found no evidence of any relationship between Oswald and the CIA. Moreover, the Agency’s investigative efforts prior to the assassination regarding Oswald’s presence in Mexico City served to confirm the absence of any relationship with him. Specifically, when apprised of his possible presence in Mexico City, the Agency both initiated internal inquiries concerning his background and, once informed of his Soviet experience, notified other potentially interested Federal agencies of his possible contact with the Soviet Embassy in Mexico City. (232)
Top of Page
Conclusion
Based on the committee’s entire investigation, it concluded that the Secret Service, FBI and CIA were not involved in the assassination. The committee concluded that it is probable that the President was assassinated as a result of a conspiracy. Nothing in the committee’s investigation pointed to official involvement in that conspiracy. While the committee frankly acknowledged that its investigation was not able to identify the members of the conspiracy besides Oswald, or the extent of the conspiracy, the committee believed that it did not include the Secret Service, Federal Bureau of Investigation, or Central Intelligence Agency.
34As noted, the military file on Oswald, presumably including the ONI photograph, was destroyed by the Department of Defense.
Bibliographic note: Web version based on the Report of the Select Committee on Assassinations of the U.S. House of Representatives, Washington, DC: United States Government Printing Office, 1979. 1 volume, 686 pages. The formatting of this Web version may differ from the original.


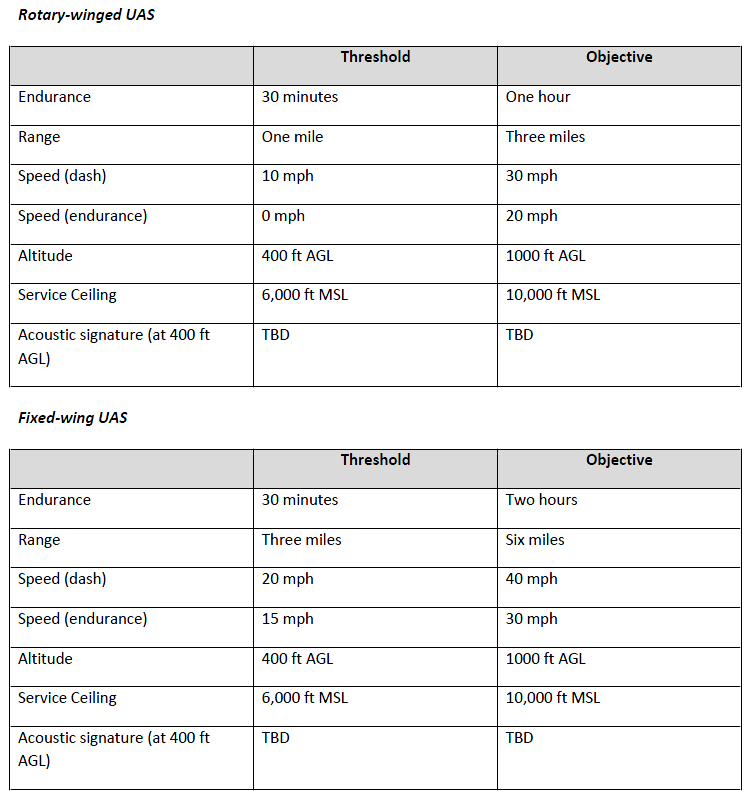
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-benghazi/pict20.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-benghazi/pict21.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-benghazi/pict22.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-benghazi/pict17.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-benghazi/pict14.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-benghazi/pict12.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-benghazi/pict11.jpg)

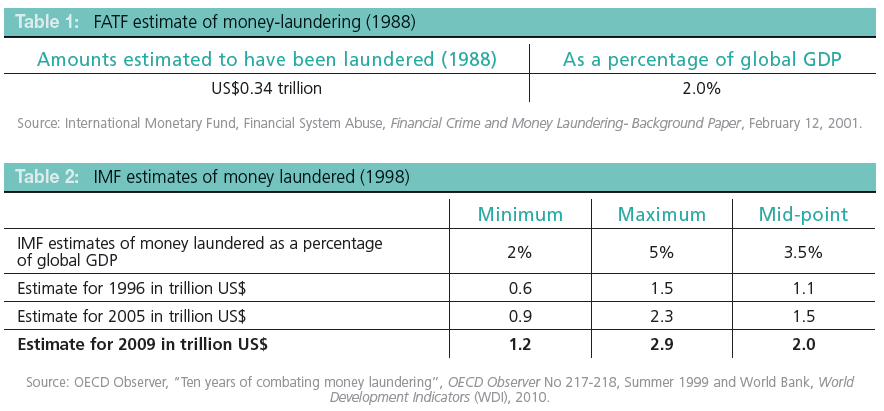
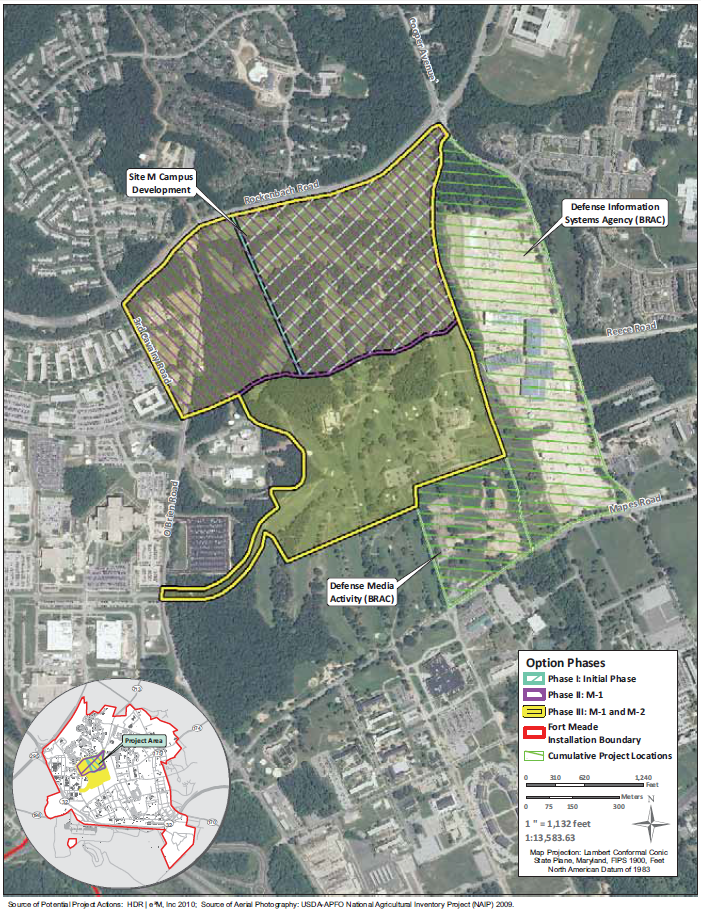
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obl-raid-mockup/pict20.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obl-raid-mockup/pict17.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obl-raid-mockup/pict16.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obl-raid-mockup/pict15.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obl-raid-mockup/pict18.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obl-raid-mockup/pict19.jpg)
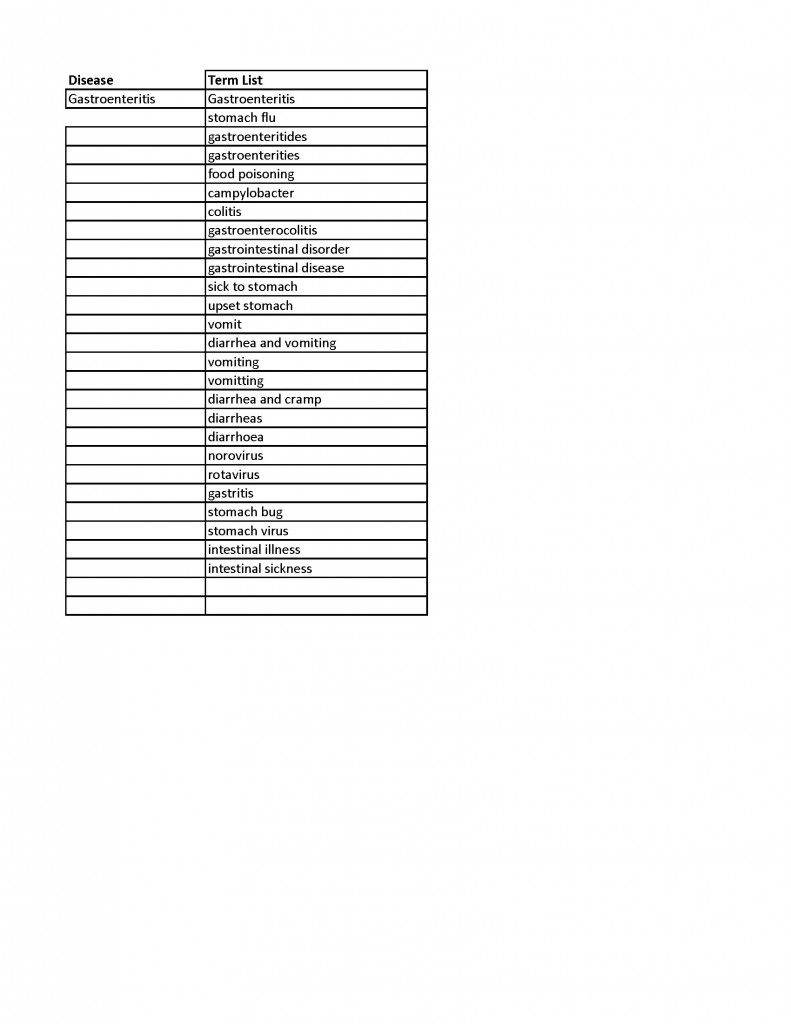






 October is National Cyber Security Awareness Month—for the ninth straight year. So what’s new?
October is National Cyber Security Awareness Month—for the ninth straight year. So what’s new?


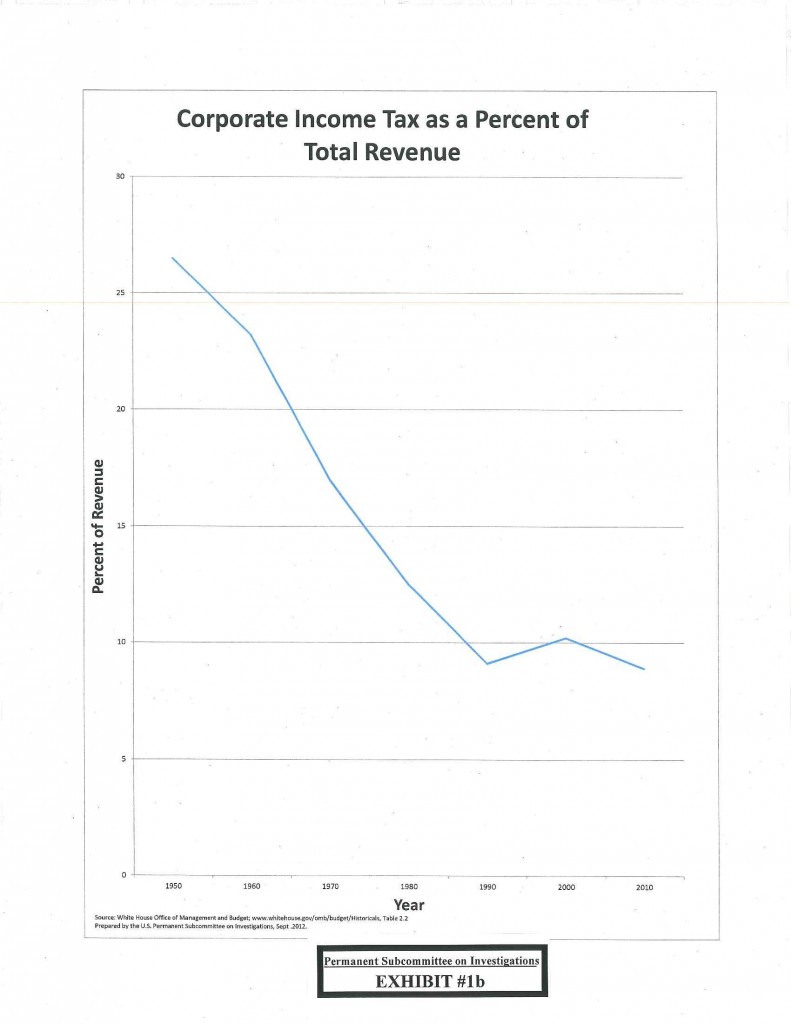
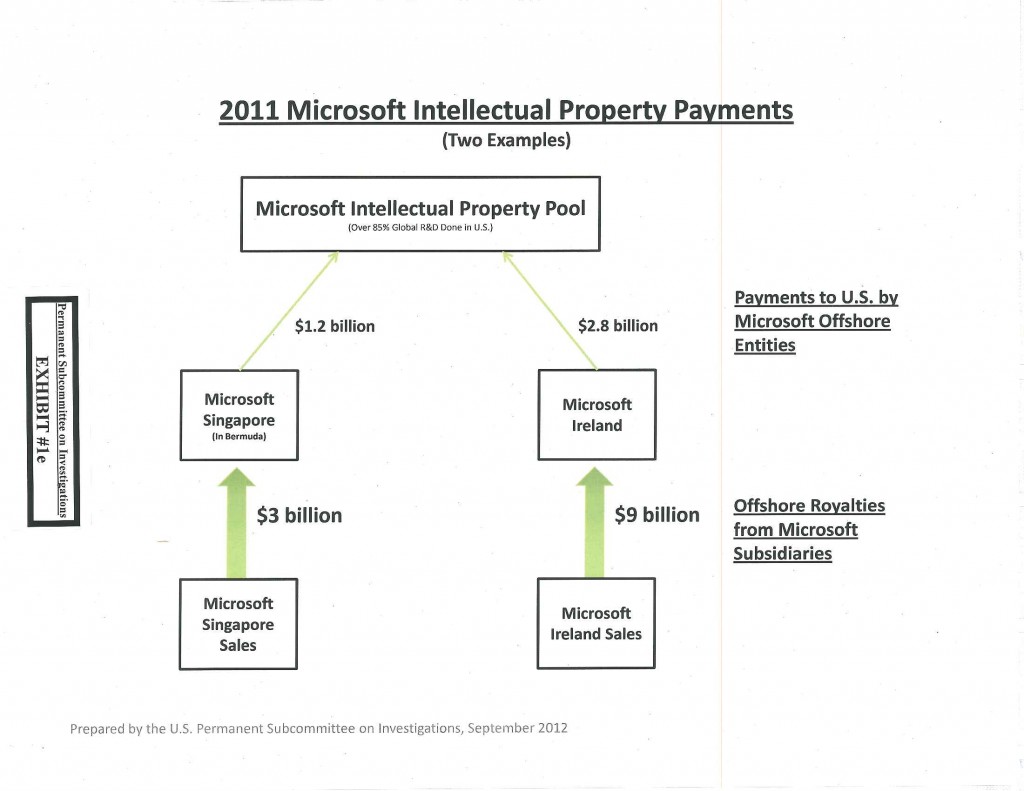




















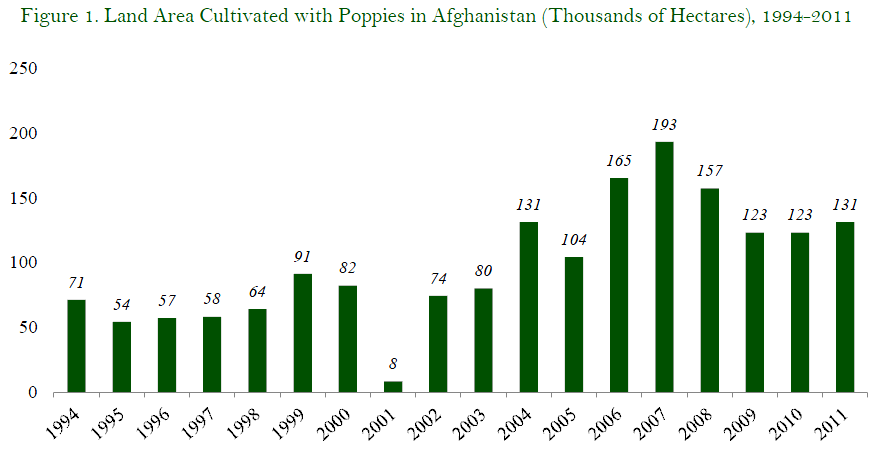


![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict2.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict3.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict62.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict63.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict0.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict71.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict1.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict4.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict64.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict65.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict5.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict66.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict67.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict70.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict68.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict69.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict6.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict8.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict9.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict11.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/camp-bastion/pict12.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/uk-drones/pict52.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/uk-drones/pict59.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/uk-drones/pict60.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/uk-drones/pict53.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/uk-drones/pict58.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/uk-drones/pict54.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/uk-drones/pict55.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/uk-drones/pict57.jpg) A soldier of Bravo Company, 1 Rifles launches a Desert Hawk UAV (Unmanned Aerial Vehicle) from a WMIK Landrover during an operation near Garmsir, Afghanistan. Desert Hawk is a portable UAV surveillance system which provides aerial video reconnaissance. It has a flight time of approximately one hour, and can fly anywhere within a 10km radius of its ground control station. It has both day and night time (thermal imaging) capability. The equipment can be used for a variety of tasks, such as force protection for convoys and patrols, route clearance, base security, reconnaissance or target tracking. March 20, 2009. MoD
A soldier of Bravo Company, 1 Rifles launches a Desert Hawk UAV (Unmanned Aerial Vehicle) from a WMIK Landrover during an operation near Garmsir, Afghanistan. Desert Hawk is a portable UAV surveillance system which provides aerial video reconnaissance. It has a flight time of approximately one hour, and can fly anywhere within a 10km radius of its ground control station. It has both day and night time (thermal imaging) capability. The equipment can be used for a variety of tasks, such as force protection for convoys and patrols, route clearance, base security, reconnaissance or target tracking. March 20, 2009. MoD![[Image]](https://i0.wp.com/cryptome.org/2012-info/uk-drones/pict56.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/uk-drones/pict61.jpg)

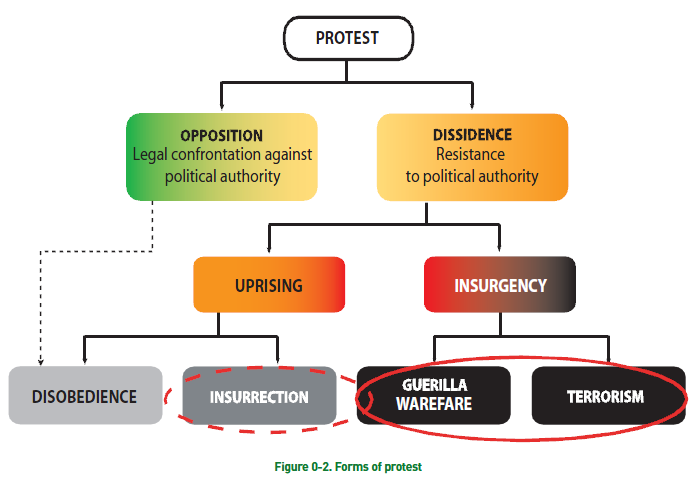










![[Image]](https://i0.wp.com/cryptome.org/2012-info/benghazi/pict8.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/benghazi/pict10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/benghazi/pict7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/benghazi/pict9.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/benghazi/pict15.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/benghazi/pict16.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/benghazi/pict12.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/benghazi/pict13.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/benghazi/pict14.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/benghazi/pict18.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/benghazi/pict17.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/benghazi/pict11.jpg)










 In den Akten der Staatssicherheit findet sich zum Fall Günter Litfin auch ein undatiertes Foto: Gedenkstein für Günter Litfin am Friedrich-List-Ufer, aufgestellt am 24.8.1962. Heute befindet sich der Gedenkstein an der Sandkrugbrücke in der Berliner Invalidenstraße. Quelle: BStU, MfS, HA IX, Fo 1673, Bild 88
In den Akten der Staatssicherheit findet sich zum Fall Günter Litfin auch ein undatiertes Foto: Gedenkstein für Günter Litfin am Friedrich-List-Ufer, aufgestellt am 24.8.1962. Heute befindet sich der Gedenkstein an der Sandkrugbrücke in der Berliner Invalidenstraße. Quelle: BStU, MfS, HA IX, Fo 1673, Bild 88









![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict129.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict128.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict130.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict131.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict132.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict133.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict134.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict135.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict136.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict137.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict138.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict139.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict140.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict141.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict142.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict143.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict144.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict145.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict146.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict114.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict113.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict116.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict120.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict115.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict117.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict119.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict118.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict123.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict122.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict124.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict125.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict126.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict127.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict121.jpg)


![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-dnc-2012/pict27.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-dnc-2012/pict36.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-dnc-2012/pict35.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-dnc-2012/pict34.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-dnc-2012/pict29.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-dnc-2012/pict31.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-dnc-2012/pict30.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-dnc-2012/pict32.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-dnc-2012/pict33.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-dnc-2012/pict28.jpg)




![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict49.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict107.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict108.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict109.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict50.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict51.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict106.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict11.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict15.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict17.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict18.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict19.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict12.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict14.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict2.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict3.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict4.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict1.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict0.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict5.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict6.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict8.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict9.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict13.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict110.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict111.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict104.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict105.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict102.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict96.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict97.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict98.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict99.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict100.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict101.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict103.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict82.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict83.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict84.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict85.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict112.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict86.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict87.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict88.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict89.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict90.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict91.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict93.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict94.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict95.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict92.jpg)


![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict81.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict61.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict63.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict52.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict55.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict53.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict54.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict66.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict60.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict56.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict57.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict58.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict59.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict62.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict67.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict68.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict69.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict70.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict71.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict72.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict73.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict74.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict75.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict76.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict79.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict77.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict78.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict80.jpg)
Na ja, Fakt ist, dass Wirecard ein Zahlungsdienstleister ist, der gut und gerne 60% seiner Umsätze mit Onlineglücksspielanbietern macht. Die Frage ist doch wer hinter dieser Bluetool Ltd steckt und der International Payment Systems die die Gelder über die Wirecard zu Schuett geschleust haben. Diese Nameh müssen der Wirecard ja bekannt sein. Solange hier keine Aufklärung passiert, denke ich stimmt bei der Wirecard was nicht. Und zum Nachdenken – wenn Schuett all dies nur erfunden hat und eine Story um die Wirecard strickt, dann müssten die Richter in USA doch sehr leichtgläubig sein. Wenn jemand nach einem Geständnis in USA gegen Kaution von 100K auf freien Fuss kommt, dann hat er kooperiert und die Hosen runter gelassen. Anzunhemen, der tanzt den Amis auf der Nase rum und bindet ihnen einen Bären auf, fällt mir schwer zu glauben. Die Amis kämpfen rigeros gegen illegales Online Glücksspiel, und ich denke, dass gegen Nennung der wahren Hintergründe der Zahlungen und deren Auftraggeber diese Kaution gewährt wurde. Auch machen die US Behörden keine Strafanzeige in DE wenn sie sich ihrer Sache nicht sicher sind. Und nochmals, wer sich nicht sicher ist, lässt seinen Hauptverdächtigen nicht frei. Ich denke wir sehen noch ordentlich “Bewegung” bei der Wirecard in den nächsten Wochen. Vielleicht auch ein paar plötzliche personelle Wechsel…
Cantaloop –
I’ve been looking into this story and am wondering where you get your information regarding Wirecards revs (60% onling gambling). Would you mind pointing me in the right direction?
Thanks!
Sarah
Warum kommt denn niemand darauf das Gomopa auch Informanten hat? Vielleicht drückte sich auch der Deinst nur falsch aus? Vielleicht hat auch die Journalistin in Florida am Telefon etwas anderes erzählt als sie es dem Handelsblatt berichtete? Jedenfalls ist die Pressemeldung bei Gomopa etwas geändert worden. Dass liest sich jetzt so:
eil er gegenüber dem Richter ein umfassendes Geständnis ablegte. Darin soll Schütt massiv die Wirecard AG beschuldigen.
Schütt soll nach Informationen eines Informanten ausgesagt haben: Er sei nur ein kleiner Geldbote. Einer von insgesamt fünf. Er habe lediglich im Auftrag und als Treuhänder für die Wirecard AG, insbesondere der Wirecard Bank AG, gearbeitet. Beauftragt wurde er hierzu direkt vom Vorstand der Wirecard AG, Herrn Rüdiger Trautmann (er hat den Vorstand am 31. Januar 2010 aus persönlichen Gründen inzwischen verlassen) und Herrn Dr. Markus Braun, Vorstandschef und zugleich Vertriebsvorstand der Wirecard AG.
Die Einzahlungen erfolgten dabei über Mastercard und Visacard und seien über die Wirecard Bank abgewickelt worden. Die Wirecard Bank hat bei beiden Karteninstituten den Status des Aquirierers. Wirecard habe ein “institutionelles System zur Abwicklung illegaler Zahlungen im Internet entwickelt”.
Konjunktiv ist angesagt! Schütt soll. Doppelte Absicherung bei Informationen eines Informanten. Gomopa ist also schon etwas zurückgerudert. Wie dem auch sei. Wo Rauch ist ist auch Feuer! Ich glaube das die Wircard da bis über beide Ohren drinn steckt! Vielleicht nicht gerade der Boss, aber die lassen machen.
Naja, das mag ja wohl sein, dass Gomopa Informanten hat, aber es lässt sich nirgendwo belegen, dass Schuett diese Aussagen gemacht haben soll. Ich bekomme in den nächsten Tagen/Wochen das genaue Gerichtsprotokoll, sobald es vom Gericht veröffentlich wurde, werde ich es hier online stellen.
Es kann schon sein, dass Schuett diese Aussagen gegenüber den Bundesbehörden gemacht, vor Gericht soll er das jedenfalls nicht gesagt haben.
Ich persönlich glaube nicht an eine Verwicklung von Wirecard, dann könnten Sie genauso auch alle anderen Banken verdächtigen. Viel mehr sollte mal hier ermittelt werden, wer sich hinter der Bluetool Ltd. bzw. deren Gesellschafter (sind Offshorefirmen) befindet. Zumindest muss es ja auch bei der Wirecard Aufzeichnungen geben, wer Zeichnungsberechtigter für das Bluetool Konto bei der Wirecard war. Wahrscheinlich nur ein Strohmann, aber hier kann die Staatsanwaltschaft ihre Ermittlungen ausweiten.
Momentan kommt es mir allerdings vor, als bewegt sich bisher keine deutsche Staatsanwaltschaft in dem Fall, nicht gegen Schuett und auch nicht gegen Bluetool.
http://www.usag24-betrug.com/index.php/gomopas-wirecard-behauptungen-zweifelhaft-schuett-hat-keinerlei-behauptungen-zu-wirecard-gemacht/
und in der FAZ:
Wirtschaftskriminalität Großrazzia wegen Verdachts auf Insiderhandel
Schlag gegen mutmaßliche Anlagebetrüger: Die Staatsanwaltschaft München hat in einer Großrazzia Dutzende Büros und Wohnungen nach Beweisen für Insiderhandel durchsucht. Drei Verdächtige wurden verhaftet. Durchsucht wurde auch die Schutzgemeinschaft der Kapitalanleger.
Von Henning Peitsmeier
24.09.2010 2010-09-24T08:31:05+0200
//
© Wolfgang Eilmes / F.A.Z.
Betrugsverdacht: An der Börse sollen fast wertlose Papiere gekauft, die Kurse durch gezielt positive Nachrichten nach oben getrieben und dann wieder verkauft worden sein
Die Münchner Staatsanwaltschaft hat in einer Großrazzia umfangreiches Beweismaterial gegen mutmaßliche Anlagebetrüger sichergestellt. Ermittelt wird gegen ein Netzwerk von Investoren, Zockern und Gerüchtestreuern, die seit Jahren gemeinsame Sache gemacht haben sollen. Die Vorwürfe lauten auf Marktmanipulation und Insiderhandel mit Aktien, sagte die Sprecherin der Anklagebehörde, Barbara Stockinger. „Wir ermitteln gegen 31 Beschuldigte, und es besteht erheblicher Tatverdacht.“ Dabei laufen die Ermittlungen bereits seit 2007, und sie reichen bis hin zur Schutzgemeinschaft der Kapitalanleger (SdK), deren Redner gern auf den Hauptversammlungen von Dax-Konzernen auftreten.
Nach Informationen der F.A.Z. sitzen die früheren SdK-Sprecher Markus Straub und Tobias Bosler in Untersuchungshaft. Sie gehören zum Kreis der Verdächtigen, die in windigen Börsenbriefen und Internetportalen Gerüchte über Aktien von Unternehmen wie Wirecard oder Nascacell verbreitet haben sollen. Erschwert würden die Untersuchungen, weil die Beschuldigten oft Namen und Firmenadressen wechselten und internationale Durchsuchungsbeschlüsse notwendig gewesen seien, sagte eine mit der Angelegenheit befasste Person dieser Zeitung. Die Masche selbst ist nach ihren Angaben leicht durchschaubar, aber schwer nachzuweisen. Vermutlich haben sämtliche Verdächtige Gerüchte über mindestens 20 kleine Aktiengesellschaften gestreut und an den Kursausschlägen der jeweiligen Aktien kräftig verdient. Gegenstand dieser Geschäfte waren bevorzugt im unregulierten Freihandel notierte und meist wertlose Aktien, sogenannte Pennystocks. Die Kurse dieser Werte sind wegen ihres hohen Streubesitzes leicht zu manipulieren.
Gezielt Gerüchte gestreut
Nach Informationen der F.A.Z. sollen unter anderem gezielt über den Finanznachrichtendienst Gomopa im Internet Gerüchte über Pennystocks gestreut worden sein. Gomopa steht für Goldman Morgenstern & Partners Consulting LLC. Auf ihrer Internetseite hat Gomopa „Transparenz in Sachen Finanzen, Vorsorge und Geldanlage“ versprochen, doch ihr Chef Klaus Maurischat saß als mutmaßlicher Betrüger schon in Untersuchungshaft.
Seit einigen Tagen ist die Internetseite http://www.gomopa.net offline, und es kursieren Gerüchte über finanzielle Unregelmäßigkeiten. Immer wieder ist Gomopa in juristische Streitigkeiten verwickelt. In einer einstweiligen Verfügung des Landgerichts Berlin vom 31. August (Az.: 27 O 658/10) ist das Unternehmen aufgefordert worden, nicht länger Falschinformationen über den Kasseler Immobilienhändler Immovation AG und seinen Finanzvorstand Lars Bergmann zu verbreiten. „Gomopa hat seinen Firmensitz bewusst in New York, weil die Firma dort presserechtlich nicht belangt werden kann“, sagte ein Kenner des Unternehmens der F.A.Z.
Die SdK räumte am Freitag ein, dass auch ihre Geschäftsräume durchsucht wurden. Es gebe jedoch „aus der Sicht der SdK keinerlei neue Vorwürfe gegen den Verein“. Die alten Vorwürfe gegen die SdK stehen im Zusammenhang mit Kursmanipulationen bei Aktien der Unternehmen Thielert und Wirecard. Staatsanwaltschaft und Allfinanzaufsicht Bafin ermittelten seinerzeit gegen den damaligen stellvertretenden SdK-Vorsitzenden Straub. Dieser hatte eingeräumt, Verkaufsoptionen auf das Zahlungsunternehmen Wirecard zu halten, dessen Kurs durch heftige Kritik der SdK unter Druck geraten war. Später trat Straub, der offenbar in kurzer Zeit ein Vermögen verdient hatte, zurück. Wirecard hatte Anzeige wegen Insiderhandels und Kursmanipulation gegen sechs Personen erstattet, darunter auch aktuelle und frühere SdK-Vorstände.
und das HANDELSBLATT:
Finanzaufsicht untersucht Kursachterbahn bei Wirecard
exklusiv Die Bundesanstalt für Finanzdienstleistungsaufsicht BaFin hat aufgrund der merkwürdigen Kursturbulenzen der Wirecard-Aktie eine förmliche Untersuchung des Falles eingeleitet. BaFin prüft mögliche Marktmanipulationen nach Falschbericht des Internetdienstes Gomopa. Zwei der Gomopa-Gründer wurden schon 2006 wegen Betrugs verurteilt
FRANKFURT. Die Bundesanstalt für Finanzdienstleistungsaufsicht BaFin hat aufgrund der merkwürdigen Kursturbulenzen der Wirecard-Aktie eine förmliche Untersuchung des Falles eingeleitet. “Wir prüfen, ob es Anhaltspunkte für Marktmanipulation in Aktien der Wirecard AG gibt”, sagte eine BaFin-Sprecherin. Zu Details könne sie sich jedoch nicht äußern.
Der Kurs des Münchener Zahlungsabwicklers Wirecard war am vergangenen Dienstag um mehr als 30 Prozent eingebrochen. Am Abend zuvor hatte der Internetdienst Goldman, Morgenstern & Partners (Gomopa) berichtet, der in den USA wegen illegalen Online-Glücksspiels verhaftete Deutsche Michael Schütt habe in einem Geständnis Wirecard schwer belastet. Gomopa bezog sich auf einen Bericht der Lokalzeitung “Naples News”. Schütt habe ausgesagt, er sei bei illegalen Geldgeschäften direkt vom Wirecard-Vorstand beauftragt worden.
Das Problem an dem Gomopa-Bericht: Er war falsch. Wie Nachfragen des Handelsblattes ergaben, hat die Reporterin, die für die “Naples News” über Schütt schreibt, Wirecard nie erwähnt. Gomopa reagierte auf Nachfragen zögerlich. Erst löschte der Dienst den Hinweis auf die Lokalzeitung, hielt aber den Vorwurf aufrecht, Schütt habe Wirecardbelastet. Danach änderte man den Bericht erneut. Nun hieß es, ein Informant von Gomopa verfüge über die fraglichen Details aus Schütts Geständnis.
Dem Handelsblatt liegt inzwischen das amtliche Protokoll von Schütts Geständnis am 23. März vor. Schütt bekennt sich darin schuldig, illegale Geldgeschäfte im Zusammenhang mit Online-Glücksspiel abgewickelt zu haben. Das Wort Wirecard kommt nicht vor. Gomopa hatte zu Wochenbeginn seinen Text erneut geändert und nun behauptet, Schütt belaste “eine Bank”. Auf erneute Nachfragen des Handelsblattes war der Bericht dann ganz verschwunden.
Der Kurs von Wirecard hat sich inzwischen fast vollständig erholt. Ein Frankfurter Analyst sagte, für ihn sei klar, dass die Aktie seit Wochen manipuliert werde. Erst verteure sich die Leihe der Aktie, dann komme es zu außergewöhnlichem Handel, danach tauchten plötzlich desaströse Gerüchte auf. Dazu gehöre auch die Anzeige, die vor kurzem bei der Staatsanwaltschaft München einging und Wirecard der Geldwäsche bezichtigt. Es sei offensichtlich, dass Short Seller mit der Wirecard-Aktie Jojo spielen.
Mark Vornkahl, einer der Gründer von Gomopa wies den Vorwurf der Kursmanipulation gestern zurück. Man wolle nur die Wahrheit aufdecken. Es ist allerdings nicht das erste Mal, dass Gomopa-Vertreter ins Zwielicht geraten. 2006 wurden Vornkahl und Mitgründer Klaus Maurischat wegen Betrugs an einem Anleger verurteilt. Maurischat gab gestern gegenüber dem Handelsblatt weitere Verurteilungen zu. Es habe sich dabei jedoch nicht um Anlagebetrug gehandelt.