Jesus of Nazareth,the son of God raised by a Jewish carpenter. Based on the gospel of Luke in the New Testament,here is the life of Jesus from the miraculous virgin birth to the calling of his disciples, public miracles and ministry, ending with his death by crucifixion at the hands of the Roman empire and resurrection on the third day
Category: BERND PULCH
The Christmas Blessing – Full Movie
With Neil Patrick Harris, Rebecca Gayheart, Angus T. Jones, Hugh Thompson
Max Lucado Story – Christmas Child (2003) – Full Movie
A life-sized nativity leads a man to learn about his past and lost family.
http://en.wikipedia.org/wiki/Christmas_Child
A Christmas Carol (1984 Full Film)
This Christmas Movie – Full Film
A Bride For Christmas – Full Movie
On The 2nd Day Of Christmas – Full Movie
Mickey’s Once Upon A Christmas : The Full Movie
Miley Cyrus Gets a BIG BOOTY HO for Her B’Day!
TOP-SECRET – FBI Pre-Deployment Checklist for Cyber Investigations
The following document was obtained from the website of the Oklahoma Bankers Association. The material is part of a collection of several documents provided to banks and financial institutions in the area by the local FBI Cyber Division office.
FBI Pre-deployment Checklist for Cyber Investigations
- 4 pages
- Law Enforcement Sensitive
- October 2012
INVESTIGATIVE TOOLS
The following investigative tools are available during incident response:
Investigative Interviews (subject, victim, witness)
The FBI can conduct interviews to gather information and evidence for an investigation.
Evidence Collection (technical and physical)
The FBI has the ability to collect evidence. This includes the ability to obtain forensic images of computer systems. The FBI utilizes its Computer Analysis Response Team (CART) program for collecting digital evidence.
Electronic Surveillance (consent, court-ordered, etc.)
The FBI has the ability, with proper legal authority, to conduct electronic surveillance.
Investigative Analysis
Cyber FBI agents and analysts are trained to conduct technical analysis in the field. This includes e-mail header analysis, network traffic analysis, and intrusion analysis. The FBI has specific units at FBI Headquarters to assist with highly technical or specialized analytical requests.
Malware analysis
The FBI developed a system called the Binary Analysis, Characterization, and Storage System (BACSS) which is used to triage malware identified in FBI investigations. Through this system, the FBI has the ability to cross-correlate malware events. If malware requires further, in-depth analysis, the FBI has specific units at FBI Headquarters to assist with this specialized analytical request.
Cyber Action Team (CAT) Deployment
The mission of the CAT is to deploy globally at the direction of Cyber Executive Management, in order to bring in-depth cyber expertise, specialized investigative skills, and direct connectivity to those cyber initiatives, investigations, and emergencies deemed critical and significant. These incidents are aligned with the FBI’s national priorities, and are defined primarily as intrusions into government, military, and commercial systems that have a direct and adverse effect on the national information infrastructure.
Legal Attaché Support
The FBI has Legal Attachés or LEGATS throughout the world to support the FBI’s mission. These LEGATS foster strategic partnerships to local law enforcement, intelligence, and security services agencies to facilitate information exchange and exploring joint operational opportunities.
National Cyber Investigative Joint Task Force (NCIJTF)
The NCIJTF is the national focal point for the U.S. government for the coordination, integration, and sharing of information related to all domestic cyber threat investigations. The NCIJTF is an alliance of peer agencies with complementary missions to protect national cyber interests as well as the political, economic, and overall vitality of our nation. Assignees from participating agencies have access to a unique, comprehensive view of the nation’s cyber situation while working together in a collaborative environment in which they maintain the authorities and operational/investigative responsibilities of their represented agencies.
Access to Legal Process
The FBI has access to legal process which can authorize subpoenas, search warrants, indictments, arrests, etc. In addition to legal process, the FBI can work through consent to obtain information or evidence in support of the investigation.
Review Current Field Office Collections and Investigations
The FBI has 56 field offices working cyber investigations. The combined information from all field office investigations offers an in-depth view of a threat not readily available through other databases.
PRE-DEPLOYMENT CHECKLIST
Prior to the FBI responding to a cyber incident, the items in the following checklist would greatly enhance the FBI’s ability to effectively further the investigation.
Network Inventory
Victims should provide as much information as possible regarding the inventory of computer systems and network components (i.e., workstations, servers, routers, switches, etc).
Software Inventory
Victims should provide as much information as possible regarding the inventory of software applications used in the organization (i.e., operating systems, application versions, proprietary applications).
Up-To-Date Network Topology Maps
Network topology maps should provide a current, functional understanding of the organization’s network.
Network- and Host-Based Incident Logs
These logs include, but are not limited to, web, proxy, IDS, VPN, DNS, database, remote access, and firewall logs.
Forensic Images of Compromised Hosts
If possible and your organization has the capability, obtain forensic images of identified compromised hosts. It is also recommended your organization maintains a log of activity for reference.
List of External and Internal IP Addresses
This list should include DNS, web server, proxies and workstations.
Physical Access Logs
These logs typically include video logs from security cameras, entry/exit access logs, keycard logs, and two-factor authentication logs.
Legal Banner and Computer Use Agreement
These legal items are essential to assure the data can legally be passed to the FBI.
Domain Infrastructure, Group Policy Hierarchy, and Access Control Details
These items can typically be provided by network/system administrators.
TMZ – Video – Candice Swanepoel’s Personal A** Washer!
TOP-SECRET- FBI Financial Sector Cyber Security Presentation
The following presentation on recent cyber attacks on the U.S. financial industry was obtained from the website of the Oklahoma Bankers Association. The presentation is part of a collection of several documents provided to banks and financial institutions in the area by the local FBI Cyber Division office.
FBI Financial Sector Cyber Security Presentation
- 11 pages
- For Official Use Only
- November 2012
Monty Python’s Flying Circus – Sex And Violence – Full Movie
Monty Python and the Holy Grail – Full Movie
Scrooge – Full Movie
Starring Seymour Hicks as the title character, Scrooge is a faithful adaptation of the classic Charles Dickens’ novel A Christmas Carol about a heartless miser who discovers the true meaning of Christmas when three ghosts visit him on Christmas Eve. Hicks co-wrote the screenplay to this film, which is a thoroughly entertaining and effective retelling of a familiar story
Sports Illustrated Swimsuit: Melissa Baker
SECRET-DHS Social Media Monitoring and Situational Awareness Initiative Privacy Compliance Review
The following privacy review of the DHS National Operations Center Publicly Available Social Media Monitoring and Situational Awareness Initiative was released November 8, 2012. This website has been listed in three of the four publicly available privacy impact assessments for the program as an example of a website monitored by DHS.
Privacy Compliance Review of the NOC Publicly Available Social Media Monitoring and Situational Awareness Initiative
- 25 pages
- November 8, 2012
The Office of Operations Coordination and Planning (OPS), National Operations Center (NOC), has statutory responsibility to (1) provide situational awareness and establish a common operating picture for the federal government, and for state, local, and tribal governments as appropriate, in the event of a natural disaster, act of terrorism, or other man-made disaster, and (2) ensure that critical terrorism and disaster-related information reaches government decisionmakers. Traditional media sources and, more recently, social media sources such as Twitter, Facebook, and a vast number of blogs provide public reports on breaking events with a potential nexus to homeland security. By examining open source traditional and social media information, comparing it with many other sources of information, and including it where appropriate into reports, the NOC can provide a more comprehensive picture of breaking or evolving events.
In January 2010, to help fulfill its statutory responsibility to provide situational awareness and to access the potential value of public information within the social media realm, the NOC launched the first of three Media Monitoring Capability (MMC) pilots using social media monitoring related to specific incidents and international events. The NOC pilots occurred during the 2010 Haiti earthquake response, the 2010 Winter Olympics in Vancouver, British Columbia, and the response to the 2010 Deepwater Horizon BP oil spill. Prior to implementation of each social media pilot, the DHS Privacy Office and OPS developed detailed standards and procedures for reviewing information on social media web sites. A series of pilotspecific Privacy Impact Assessments (PIA) document these standards and procedures. In June 2010, the Department released its Publicly Available Social Media Monitoring and Situational Awareness Initiative PIA, which incorporated these protections. OPS/NOC and PRIV subsequently updated the PIA in January 2011, and published a Privacy Act System of Records Act Notice (SORN) on February 1, 2011, to allow for the collection and dissemination of personally identifiable information (PII) in a very limited number of situations in order to respond to the evolving operational needs of OPS/NOC.
As of January 2011, the NOC may include PII on seven categories of individuals in an Item of Interest (hereinafter MMC Reports or Reports) when doing so lends credibility to the report or facilitates coordination with interagency or international partners. The seven categories as identified in the SORN are: “(1) U.S. and foreign individuals in extremis, i.e., in situations involving potential life or death circumstances; (2) senior U.S. and foreign government officials who make public statements or provide public updates; (3) U.S. and foreign government spokespersons who make public statements or provide public updates; (4) U.S. and foreign private sector officials and spokespersons who make public statements or provide public updates; (5) names of anchors, newscasters, or on-scene reporters who are known or identified as reporters in their posts or articles, or who use traditional and/or social media in real time to provide their audience situational awareness and information; (6) current and former public officials who are victims of incidents or activities related to homeland security; and (7) terrorists, drug cartel leaders, or other persons known to have been involved in major crimes of homeland security interest, who are killed or found dead.”
As documented in the January 2011 PIA Update, the NOC does not: (1) actively seek PII; (2) post any information on social media sites; (3) actively seek to connect with individuals, whether internal or external to DHS; (4) accept invitations to connect from individual social media users whether internal or external to DHS; or (5) interact with individuals on social media sites.
Privacy Compliance Reviews (PCR) are a key aspect of the layered privacy protections built into this initiative to ensure protections described in the PIAs are followed. Since the June 2010 PIA publication, PCRs have been conducted bi-annually. The DHS Privacy Office conducted this fifth PCR to assess compliance with the January 2011 PIA Update and February 2011 SORN. To address this objective, the DHS Privacy Office developed a questionnaire, interviewed OPS/NOC officials and analysts on issues raised by the NOC’s responses to the questionnaire, analyzed OPS/NOC guidance and standard operating procedures (SOP), and reviewed selected MMC Reports for compliance with the 2011 PIA Update.
…
TMZ Video – Kate Upton’s Sexy Antarctic Bikini Shoot!
Kate Upton stripped down to a tiny bikini for a Sports Illustrated photo shoot in the Antarctic… and the temperature hit 35 BELOW!!!
Important – WikiLeaks is Now Tax Deductible in U.S. and E.U.
Dear Friend of WikiLeaks This week sees the launch of the Freedom of the Press Foundation − a new initiative inspired by the fight against the two-year-long extra-judicial financial embargo imposed on WikiLeaks by U.S. financial giants including Visa, MasterCard, PayPal and the Bank of America. The Freedom of Press Foundation is tax deductible across America and takes credit cards, PayPal and google Checkout. The other week Wau Holland, who collect money for WikiLeaks in Germany, announced they are tax deductible across Europe and can take bank transfers. Make the most of your donation this Christmas and ensure it is tax deductible using one of these methods. Full press release on launch of Freedom of the Press Foundation: http://wikileaks.org/WikiLeaks-declares-war-on-banking.html Full Press release on Wau Holland tax deductibility: http://wikileaks.org/WikiLeaks-donations-now-tax.html All ways to donate: http://shop.wikileaks.org/donate https://wlfriends.org/ http://www.swedenversusassange.com/ http://www.bradleymanning.org/ http://freehammond.com/ http://freeanakata.se/index http://freeanons.org/
Jabberwocky (1977) – FULL FILM – Monty Phyton – Terry Gilliam
Storm of the Dead – Full Movie
http://viewster.com – watch MORE free movies on http://www.viewster.com When the Florida Panhandle is hit by a “Category 5” hurricane, the President of the United States has no choice but to reactivate the Florida Militia to restore order in the region. In their quest to restore stability to an unstable area, the Militia is ordered to ‘shoot looters’. When one of the looters tracked down and shot is the grandson of a Voodoo Queen, all hell breaks loose as she seeks revenge on the Militia.
Börse Online über “GoMoPa”-Betrüger und RA Jochen Resch
Curse of the Wolf – Full Movie
http://viewster.com – watch MORE free movies on http://www.viewster.com A young woman, Dakota has finally found a way to control her Lycanthrope metamorphosis and desires to live a normal life. All might be well if not for Dakota’s pack, who wants a different life for her to live in werewolf immortality and hunt with them forever! Dakota attempts to flee to the city and tries to hide from her pack and but they it aggressively seeks out Dakota in the city, where Dakota has enlisted the help of a shady nightclub owner and his hired assassins to help her combat her past. It becomes a battle where only the strongest will survive! Will Dakota break free from her past? Or will she succumb to the Curse of the Wolf!
Revealed – WikiLeaks declares war on banking blockade
|
Börse Online über die dubiosen vorbestraften “GoMoPa”- Chargen und deren Machenschaften
Sports Illustrated Swimsuit Video: Bar Refaeli
Unveiled – Moscow Protests 15 and 16 December 2012
Moscow Protests 15 and 16 December 2012
![[Image]](https://i0.wp.com/cryptome.org/2012-info/moscow-protests/pict8.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/moscow-protests/pict17.jpg)
Flickr, Person Behind the Scenes, Sergey Kukota (More March of Freedom, 15 December 2012, by this photographer)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/moscow-protests/pict5.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/moscow-protests/pict15.jpg)
Flickr, Person Behind the Scenes, Sergey Kukota
![[Image]](https://i0.wp.com/cryptome.org/2012-info/moscow-protests/pict12.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/moscow-protests/pict18.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/moscow-protests/pict19.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/moscow-protests/pict16.jpg)
Flickr, Person Behind the Scenes, Sergey Kukota
![[Image]](https://i0.wp.com/cryptome.org/2012-info/moscow-protests/pict6.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/moscow-protests/pict13.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/moscow-protests/pict9.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/moscow-protests/pict10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/moscow-protests/pict7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/moscow-protests/pict14.jpg)
Flickr, Person Behind the Scenes, Sergey Kukota
TMZ – 2 Hot Celebrities BOXING in a Strip Club!
SECRET – Minnesota Police Investigation of Officers Providing Drugs to Occupy Protesters
The following document contains files related to the Minnesota Bureau of Criminal Apprehension’s investigation into allegations that law enforcement officers participating in Drug Recognition Evaluator (DRE) courses provided drugs to sober people they had picked up from Peavey Plaza in downtown Minneapolis where protesters connected with Occupy Minnesota had been located since April 2012. The officers then used the intoxicated subjects for their training course, sometimes providing them with rewards like food or cigarettes, and then returned them to the Plaza. Though the investigation confirms many aspects of the story and a Sheriff’s Deputy admitted to the DRE course instructor that he had witnessed his partner in the course providing marijuana to subjects, the Minnesota Bureau of Criminal Apprehension found that there was insufficient evidence to sustain charges and obtain convictions against any of the officers involved. This was partly due to the fact that 29 former officers and employees associated with the program refused to testify, blocking the investigation. For more information on the file, see Dan Feidt’s article on the documents and watch the video report he helped produced in May 2012 which played a significant role in raising public awareness of the issue and spurring the investigation.
Minnesota Bureau of Criminal
Apprehension Drug Recognition Evaluator Investigation
- 513 pages
- September 2012
- 74.43 MB
The Bureau of Criminal Apprehension (BCA) has investigated allegations of law enforcement officers providing controlled substances to individuals as part of a drug recognition certification program. The investigation appeared to be professional and comprehensive. We have reviewed the allegations and for the reasons identified below have concluded that there is insufficient evidence to issue felony charges in this matter.
Background
The Drug Recognition Evaluator (DRE) course provides important training to law enforcement officers in Minnesota and throughout the country. DRE train officers to accurately identify specific drug impairment and, by observation, the characteristics and behaviors of drug impaired drivers. DRE helps officers detect and apprehend drug impaired drivers who endanger the public.
During April and May of 2012 the State Patrol conducted Drug Recognition Expert (DRE) training for law enforcement officers throughout Minnesota. The course began on April 2, 2012 with two weeks of classroom training. The classroom training occurred in White Bear Lake.
The classroom training was followed by certification training, which required students to go out into the streets to find people under the influence of drugs and evaluate them. The officer students were then supposed to persuade these individuals to voluntarily accompany them to a Richfield training facility where they would provide a urine sample. This sample would then be tested to determine whether the participant was impaired as the officer had believed, and if so, what drug had been ingested. To encourage cooperation, officers never recorded participants true names.
…
Source of Allegations
On May2, 2012 allegations were made in the local media that DRE officers were not just seeking already “high” people to participate in testing. Allegations were that officers were providing controlled substances to sober people so that they could become “high” and then participate in testing. One individual, Forest Oliver, claimed that he had participated three times in the DRE testing and DRE officers had given him marijuana on each occasion. Some of these allegations had appeared in previous days on YouTube.
In response to these allegations, instructors asked their class whether they had engaged in such conduct or had heard of any classmates doing so. They emphasized that DRE students should not provide potential test participants with controlled substances.
No DRE officer admitted in class to knowledge of such conduct. However, after class that day on May 3, 2102, Chisago Deputy Sheriff Andrew Mahowald told head instructor State Patrol Sgt. Ricardo (Rick) Munoz that he had witnessed his DRE partner, Hutchinson Officer Karl Willers, provide marijuana to test subjects. Mahowald coming forward with this information ultimately led to Hutchinson Police Chief Hatten requesting a BCA investigation of allegations regarding Hutchinson officers.
…
Death Hospital – SOVIA – Full Movie
http://viewster.com – watch MORE free movies on http://www.viewster.com Germany (2008) A dead woman revenges herself in an unusual manner. People seem to have no choice and are getting killed one by one. The horror begins, the police has no clue and a love story turns into tragedy. GERMAN version with English subtitles! Do you like this movie? Then why don’t you flatter it? https://flattr.com/thing/95899/Death-Hospital-Sovia
DER BEWEIS AUS DEM JAHR 2000: SO REGTE GRUNER und JAHR-TOCHTER, IPV, MICH AN, DEN TITEL “INVESTMENT” ZU LANCIEREN
DER BEWEIS AUS DEM JAHR 2000: SO REGTE GRUNER & JAHR-TOCHTER, IPV, MICH AN, DEN TITEL “INVESTMENT” AUCH IN DEUTSCHLAND ZU LANCIEREN. DESHALB HAT “PETER HLERS” MUTMASSLICH “GoMoPa” BEAUFTRAGT, MICH AUSZUSCHALTEN.
DANN HABE ICH ÜBER “GoMoPa” UND IHRE MUTMASSLICHEN PARTNER “PETER EHLERS” UND “GERD BENNEWIRTZ” RECHERCHIERT…
TMZ – Jessica Simpson — Something’s Fishy!
SECRET – DHS-FBI Bulletin: Cyanide Awareness
FIRE LINE INTELLIGENCE FOR FIRE, RESCUE, AND EMS
- 1 page
- For Official Use Only
- October 31, 2012
(U//FOUO) Terrorist groups, including al-Qa‘ida, and violent extremists have considered using or have possessed cyanide compounds. Cyanides probably appeal to terrorists because of their toxicity, availability, and ease of dissemination. Some of the cyanide tactics that have been considered by terrorists include mixing it with oils and lotions for use as a contact poison, contaminating food or water supplies, or by using it in an improvised chemical dispersal device.
— (U//FOUO) In June 2011, Indonesian police arrested eight men who possessed and planned to use cyanide to poison food at police station cafeterias in several Indonesian cities.
— (U//FOUO) In October 2010, al-Qa‘ida in the Arabian Peninsula published its second English-language edition of Inspire Magazine with an article encouraging its supporters in the United States to acquire simple poisons such as cyanide and use them in attacks.
(U) Awareness of cyanide’s physical properties and symptoms of cyanide exposure, combined with suspicious activity reporting, can help disrupt potential attack plots and protect first responders.
(U) Indications of the Presence of Cyanide:
(U//FOUO) Cyanide gases can be colorless and lighter than air (hydrogen cyanide) or a dense, choking gas that burns the victim’s eyes (cyanogen chloride).
(U//FOUO) Cyanide salt can be a white to pale yellow in color and could be in a powder, tablets, or briquettes form.
(U//FOUO) First responders may encounter cyanide products in facilities where commercial applications occur such as in the metal plating and jewelry industries.(U) Symptoms of Cyanide Exposure:
(U//FOUO) High Dose Gas Exposure: Inhalation usually causes loss of consciousness, followed by convulsions and respiratory and cardiac system failure within 5 to 15 minutes of exposure. Death occurs mainly from cardiac arrest.
(U//FOUO) Low-to-Moderate Dose Gas Exposure: Inhalation causes symptoms that mimic poisoning from other toxic compounds, including giddiness, hyperventilation, palpitations, dizziness, nausea, vomiting, headache, and eye irritation. Low-to-moderate exposure can be treated if done quickly. The chance of fatality is proportional to dose.
(U//FOUO) Skin Exposure: Cyanide is unlikely to pose a dermal hazard; exposed skin should be washed with water.
(U//FOUO) Ingestion: The results of an attempt to poison food or water supplies would depend on many factors, including the cyanide compound used and point of contamination.(U//FOUO) First Responder Information:
(U//FOUO) When any chemical release is suspected, first responders should follow department hazardous materials guidelines for isolating the area, denying entry, identifying the agent, and decontamination. If cyanide release is suspected, a hazardous material team should be mobilized.
(U//FOUO) First responders routinely encounter hydrogen cyanide as a by-product of combustion; follow established protocols for the treatment of any potential exposure to cyanide.
Last Chance – Full Movie
A hired assassin weighs his loyalty against his life after being dispatched to eliminate his latest target and falling for a beautiful woman with ties to the very man standing in the center of his crosshairs. Rob (Kristof Robinson) was always a professional, but this time the job has become personal. Realizing that the consequences of betraying his partner and disobeying his direct orders may result in death or worse, Rob attempts to remember what it meant to fight for something he truly believes in while carefully playing both sides and waiting for the perfect moment to play his hand.
A-Z- 2.000 STASI OFFIZIERE IM BESONDEREN EINSATZ OibE – “SCHLÄFERLISTE DER STASI IN WESTDEUTSCHLAND”- STASI-SLEEPER LIST A-Z
Become a Patron!
True Information is the most valuable resource and we ask you to give back.

This is the list of the STASI Agents waiting for their call to action in Western Europe from A-Z with their real names.
We have also published on this website new documents about Stratfor and their internal discussions about the STASI.
This is part of our cooperation with Wikileaks.
The Global Intelligence files were provided by Wikileaks.
This is part of our Investigative Partnership organised by WikiLeaks – the Data was obtained by WikiLeaks.
The STASI lists stem from the STASI itself. It is the so called “Fipro” list which was made to secure the pensions of the STASI Agents in Germany after the Reunification.
Below you find an explanation in German Language:
Die Liste wurde bereits früher hier publiziert:
http://stasiopfer.de/component/option,com_simpleboard/Itemid,/func,view/id,993815828/catid,4/
Vom “Stasiopfer”-Angebot führt ein Link zu einer Website in den USA (www.jya.com), die sich auch mit den Praktiken von Geheimdiensten beschäftigt. Dort findet sich die “Fipro-Liste”, das detaillierte “Finanzprojekt” der Stasi, angefertigt in den letzten Tagen der DDR, um die Rentenansprüche der rund 100 000 hauptamtlichen Mitarbeiter des MfS auch nach dem Zusammenbruch des Systems belegen zu können. Die “Fipro-Liste” ist seit langem bekannt und diente Anfang der neunziger Jahre etwa zur Identifizierung der so genannten OibE – Offiziere im besonderen Einsatz. Diese Liste „Offiziere im besonderen Einsatz“im Jahre 1991 erschien in der “taz. Die Echtheit kann beim BStU überprüft werden.
Siehe u.a. http://www.spiegel.de/spiegel/print/d-22539439.html
Auf Druck ehemaliger STASI-Leute und Ihrer Genossen wurde die Liste aus dem Verkehr gezogen.
Hier ist sie wieder:
Stasi Offiziere im besonderen Einsatz (abgekürzt OibE)
Stasi Schläfer Liste
Technische Hinweise:
Diese Daten stammen aus der OibE-Liste. Die Tabellen wurden von H.T. per OCR usw. in HTML gewandelt.
Die Datensätze sind – anders geordnet – auch Teilmenge der (‘HAMSTER’-Liste/MA_Stasi.txt). Dort sind die mit Adressen versehenen und meist gedoppelten Datensätze diejenigen der OibE.
OibE dürfen nicht mit Inoffiziellen Mitarbeitern (IM) verwechselt werden. Sie hatten im Gegensatz zu den IM [Ausnahme: HIM] ein Dienstverhältnis mit der Stasi und einen Kampfauftrag.
Die OibE sollten unter allen Umständen zum MfS stehen und mussten sich vor der “Abordnung” ins Zivilleben durch besondere ideologische Zuverlässigkeit auszeichnen. Deshalb fühlen sich viele dieser Überzeugungstäter wahrscheinlich heute noch der Stasi verpflichtet, leben aber ganz unauffällig. Man könnte sie auch als “Schläfer” bezeichnen.
Offiziere im besonderen Einsatz (abgekürzt OibE) waren hauptamtliche Mitarbeiter des Ministeriums für Staatssicherheit
Zudem kommen weitere STASI-Agenten in Westdeutschland, die noch besser getarnt wurden und deren Legenden sorgfältig aufbereitet wurden.
Viel schufen sich in den Wirren um 1989 eine neue Identität mit neuem Namen auch in Westdeutschland. Somit sind hier nur deren ALTE und RICHTIGE Namen erfasst.
Name, Vorname; Geb.-datum; DE: Zentrale, BV, KD; DE-Code; PLZ; Az. / Reg.-Nr.
Ackermann, Frank; 29.04.55; HVA; 961500; 1092; 4288/81, F
Ackermann, Kerstin; 22.02.58; HVA; 961500; 1092; 4288/81/1, F
Adelmeier, Lutz; 18.11.53; HVA; 961500; 1590; 650/75/12,
Ahrendt, Hans; 17.11.50; Abt. XI; 941100; 1092; 2382/74,
Amthor, Jürgen; 25.01.47; Abt. N; 906540; 1130; 7263/75,
Anschütz, Günter; 07.04.54; Abt. XI; 941100; 6110; 3454/86,
Antoni, Detlef; 02.06.59; HVA; 961500; 1162; 2110/84, F
Arlt, Frank; 12.03.58; HVA; 961500; 1140; 650/75/54,
Auerbach, Christel; 01.04.36; HVA; 961500; 1020; 79/74, B
Auerbach, Hans- Dieter; 25.03.37; HVA; 961500; 1020; 80/74, J
Aul, Claus; 28.09.62; HVA; 961500; 1150; 3776/85, F
Autenrieb, Eckbert; 02.06.56; Abt. N; 906540; 1095; 5785/82,
Badelt, Dieter; 17.01.37; Rostock VII; 010700; 2520; 4909/75,
Bahl, Reinhard; 10.03.48; HVA; 961500; 2800; 527/88, M
Baltruschat, Klaus; 27.07.34; HVA; 961500; 1170; 13222/60, X
Balzer, Christian; 28.10.51; Abt. N; 906540; 1115; 1690/76,
Bandermann, Hans-Rainer; 12.05.45; Abt. N; 906540; 1280; 4378/77,
Barnowsky, Wolfgang; 24.08.38; HVA; 961500; 1017; 962/83, M
Bartels, Klaus; 06.04.39; KD Stendal; 070054; 3500; BARTELS, KLAUS
Bartels, Uwe; 23.02.64; HVA; 961500; 1093; 5764/81/4, D
Barten, Günter; 27.11.38; Abt. XI; 941100; 1291; 179/78,
Barzik, Hans-Joachim; 30.08.46; HVA; 961500; 1190; 592/86, F
Barzik, Renate; 05.08.49; HVA; 961500; 1190; 592/86/1, F
Bassin, Dietrich; 28.04.34; BV Berlin XVIII; 151800; 1058; 1911/78,
Bauer, Gerhard; 29.08.47; Abt. N; 906540; 1140; 4254/77,
Bauer, Ralf; 04.06.64; HVA; 961500; 1144; 2858/84, F
Baumann, Manfred; 25.04.39; OD TU/H Dresden; 120058; 8045; XII/1353/87,
Baumann, Reinhard; 25.05.40; KD Pirna; 120052; 8300; XII/1359/87,
Bauschmann, Rolf-Jürgen; 19.04.57; Abt. N; 906540; 1095; 7575/80,
Bazyli, Dieter; 10.08.35; Frankfurt/O. IX; 050900; 1200; V/425/88,
Bäumler, Hans; 29.06.33; HVA; 961500; 1144; 21/77, F
Becker, Günter; 24.02.38; HVA; 961500; 1120; 2649/80, F
Becker, Heidrun; 30.03.52; HVA; 961500; 1090; 2850/78, J
Becker, Ralf-Ekkehard; 16.04.57; Abt. N; 906540; 1130; 5040/76,
Becke, Ronald; 07.03.57; HVA; 961500; 5062; 650/75/27,
Beier, Peter; 02.08.42; OD KKW Nord; 010050; 2200; 5678/84,
Beitz, Hans-Joachim; 07.10.37; Abt. XI; 941100; 1100; 2233/66,
Benjowski, Klaus; 22.08.35; HVA; 961500; 1162; 364/77, U
Benndorf, Roland; 11.03.57; Abt. N; 906540; 1142; 1787/81,
Berger, Andreas; 16.11.62; Abt. XI; 941100; 7065; 1713/89,
Bergmann, Holger; 23.04.60; HVA; 961500; 8291; 650/75/25,
Bergmann, Thomas; 04.04.54; HVA; 961500; 1144; 1439/89, F
Berliner, Kurt; 16.12.35; HVA; 961500; 1080; 1858/89, F
Berndt, Walter; 03.01.31; Abt. XI; 941100; 1017; 246/77,
Bernhardt, Hans; 30.05.28; HVA; 961500; 1195; 9831/61, F
Bernhardt, Hans-Joachim; 15.02.56; Abt. XI; 941100; 4370; 1709/89,
Bertholf, Manfred; 02.02.37; BV Berlin XVIII; 151800; 1055; 867/80,
Bertsch-Herzog, Herbert; 21.07.29; HVA; 961500; 1080; 3665/60/1, U
Betsch, Brigitt; 16.01.55; HVA; 961500; 1055; 5010/87, U
Betsch, Michael; 30.11.46; HVA; 961500; 1140; 2259/73,
Bettzieche, Frank; 21.10.54; HVA; 961500; 1093; 904/84, F
Bettzüge, Eberhard; 22.01.35; Abt. N; 906540; 1136; 1807/72
Beuster, Gerhard; 03.07.52; Abt. N; 906540; 1292; 7270/75,
Bevermann, Jürgen; 14.10.43; HVA; 961500; 1142; 209/81, F
Bewersdorf, Wolfram; 20.05.61; Abt. N; 906540; 1280; 3022/84,
Beyer, Alfred; 30.05.38; HVA; 961500; 1190; 528/88, M
Beyer, Andreas; 23.01.61; HVA; 961500; 1580; 650/75/55,
Bezdicek, Rolf-Dieter; 20.09.58; Abt. XI; 941100; 1120; 844/83,
Bienert, Peter; 10.08.42; Abt. N; 906540; 1020; 4110/79,
Bilke, Paul; 02.06.28; HVA; 961500; 1020; 9/76, X
Birgel, Artur; 25.01.35; HVA; 961500; 1020; 4207/84, 0
Birnbach, Steffen; 23.10.53; Karl-Marx-Stadt XX; 142000; 9081; K/3505/89,
Blank, Gerhard; 16.12.31; HVA; 961500; 1130; 3156/89, E
Blank, Monika; 12.10.39; HVA; 961500; 1130; 3156/89/1, E
Blaudzun,Alfred; 26.10.38; Rostock VI; 010600; 2500; 5011/86,
Blei, Holger; 08.05.57; HVA; 961500; 1055; 4644/80, J
Block, Gerhard; 04.11.52; Abt. XI; 941100; 3530; 5125/85,
Bloß, Rolf; 08.04.33; Dresden XVIII; 121800; 8019; XII/1344/87,
Blumenberg, Igor; 27.06.52; Abt. XI; 941100; 1130; 311/80,
Blum, Ines; 02.04.62; HVA; 961500; 1199; 2410/79, J
Blutnick, Harry; 27.01.36; HVA; 961500; 1020; 1653/87, F
Bock, Andre; 01.11.67; Abt. N; 906540; 1095; 5546/88,
Bogacz, Carsten; 10.11.58; HVA; 961500; 7513; 650/75/56,
Bohm, Peter; 24.10.45; HVA; 961500; 1144; 1671/87, F
Bohn, Detlef; 12.05.59; Abt. XI; 941100; 4070; 492/87,
Bohn, Steffi; 14.10.59; HVA; 961500; 4070; 492/87/1, F
Bohn, Wolfgang; 16.05.51; HVA; 961500; 1092; 2112/72, F
Bollmann, Lutz; 16.12.68; Abt. N; 906540; 1140; 5189/88,
Borchert, Detlef; 09.12.48; Abt. N; 906540; 1100; 255/73,
Borchert, Hans-Joachim; 19.11.54; HVA; 961500; 1142; 398/76, F
Bornschein, Horst; 20.04.30; Abt. XI; 941100; 1156; 3597/81,
Born, Joachim; 25.04.58; Abt. N; 906540; 1092; 4325/87,
Böhm, Jürgen; 22.11.44; HVA; 961500; 1142; 2660/79, M
Börnchen, Peter; 20.07.39; HVA; 961500; 1250; 30/70, A
Brada, Wolfgang; 15.11.50; HVA; 961500; 1130; 650/75/11,
Brade, Rolf; 21.07.42; Abt. XI; 941100; 1600; 271/68,
Brate, Andreas; 11.12.54; HVA; 961500; 1142; 3039/82, M
Brändel, Lothar; 19.04.35; KD Leipzig/Land; 130041; 4090; K, 4232/86,
Brendtner, Werner; 23.03.42; Rostock VII; 010700; 2520; 4733/88,
Bretschneider, Jens; 29.08.67; Karl-Marx-Stadt VIII; 140800; 9271; 182,
Bruhn, Siegfried; 28.11.50; HVA; 961500; 2520; 650/75/39,
Brunner, Manfred; 26.04.29; HVA; 961500; 1144; 1920/75, J
Bruns, Beate; 05.06.62; HVA; 961500; 1140; 6555/82, J
Brüning, Falk; 11.06.63; HVA; 961500; 1095; 4361/84, M
Burckhardt, Dietmar; 03.08.44; HVA; 961500; 1020; 3467/86, L
Burde, Hans-Joachim; 18.05.47; Abt. N; 906540; 1092; 2010/67,
Burkhardt, Marco; 12.10.59; HVA; 961500; 1142; 3887/83, E
Buschendorf, Lutz; 21.11.41; HVA; 961500; 1142; 3478/65, A
Bussin, Günter; 26.07.54; HVA; 961500; 1142; 3328/86, A
Büchner, Eckhard; 23.09.56; Abt. N; 906540; 1153; 3619/77,
Bürger, Heiderose; 05.05.50; Abt. N; 961500; 1140; 5764/81/3, D
Cantow, Hans-Gerhard; 11.01.44; HVA; 961500; 1143; 360/68, L
Christoph, Martin; 30.03.58; HVA; 961500; 9900; 650/75/26,
Claus, Werner; 29.03.26; HVA; 961500; 1017; 401/73, P
Cotte, Wolfgang; 16.11.51; HVA; 961500; 1600; 619/83, L
Czieselsky, Frank; 05.05.58; Abt. N; 906540; 1017; 2960/79,
Daum, Heinz; 09.09.35; BV Berlin VI; 150600; 1020; 4101/77,
Dau, Holger; 20.01.58; HVA; 961500; 1143; 7701/81, F
Dähn, Bernd; 23.07.48; Abt. XI; 941100; 1035; 97/75,
Degenhardt, Dieter; 12.07.31; HA VII; 970700; 1140; DEGENHARDT, DIETER
Dehmel, Wolfgang; 12.07.49; Abt. N; 906540; 1142; 7401/81,
Derlath, Bettina; 08.02.56; HVA; 961500; 1090; 5182/84, M
Deters, Frank; 10.11.67; Abt. N; 906540; 1950; 4649/87,
Deutscher, Peter; 16.07.47; HVA; 961500; 8019; 1382/89, M
Deysing, Gerd; 04.10.53; HVA; 961500; 1142; 650/75/58,
Diettrich, Günter; 06.05.53; Abt. N; 906540; 1281; 1794/80,
Dietrich, Matthias; 30.07.66; HVA; 961500; 1156; 4383/86, F
Dietrich, Reinhilde; 25.07.37; Abt. N; 906540; 1110; 5004/80,
Diettrich, Heidi; 14.11.54; Abt. N; 906540; 1281; 2002/87,
Dittrich, Michael; 09.11.46; Abt. XI; 941100; 1141; 99/75,
Dittrich, Wolfgang; 08.07.49; Abt. N; 906540; 1142; 1675/78,
Doegelsack, Uta; 20.01.63; Abt. N; 906540; 1093; 5808/84,
Donath, Martin; 03.04.51; HVA; 961500; 2520; 671/89, A
Dorgwarth, Reinhard; 10.11.48; Abt. N; 906540; 1280; 4379/77,
Dott, Bernd; 01.07.41; BV Berlin VII; 150700; 1180; 241/78,
Döbel, Holger; 07.04.61; Abt. N; 906540; 1143; 4865/81,
Döbereiner, Rene; 02.08.67; Karl-Marx-Stadt VIII; 140800; 9072; 175,
Drechsler, Peter; 06.06.57; HVA; 961500; 1136; 3594/74, F
Dreger, Uwe; 25.12.51; Abt. N; 906540; 1281; 7271/75,
Drexler, Andreas; 03.12.50; HVA; 961500; 1120; 4675/85, A
Dumke, Bodo; 21.03.51; BV Berlin VI; 150600; 1080; 1299/85,
Dybiona, Detlef; 21.05.60; Abt. XI; 941100; 3090; 494/87,
Dylla, Bernd; 07.03.57; Abt. XI; 941100; 6902; 767/86,
Ebedus, Dieter; 17.01.59; Abt. XI; 941100; 4350; 1819/87,
Eckert, Gerhard; 24.09.31; KD Eisenhüttenstadt; 050045; 1220; V/481/88,
Effenberger, Helga; 10.07.38; HVA; 961500; 1017; 19666/60/1, E
Effenberger, Rudolf; 13.01.33; HVA; 961500; 1017; 19666/60, E
Eggert, Asmus; 17.12.47; HVA; 961500; 1130; 2394/85, J
Eggestein, Dieter; 20.12.38; Rostock XVIII; 011800; 2520; 3862/81,
Ehrke, Hans-Jürgen; 17.01.42; Abt. N; 906540; 1090; 4025/79,
Ehrenberg, Rolland; 25.09.47; Frankfurt/O. IX; 050900; 1200; V/447/88,
Eichentopf, Marlis; 27.06.61; HVA; 961500; 5080; 5362/89, F
Eichhorn, Hans; 14.10.38; HVA; 961500; 1054; 1305/68, P
Eichner, Ulla; 02.04.42; HVA; 961500; 1092; 4218/84, F
Eisenhardt, Joachim; 05.09.58; Abt. N; 906540; 1095; 3413/78,
Elfert, Wolfgang; 08.05.56; Abt. XI; 941100; 1250; 448/80,
Elliger, Gabriele; 06.12.61; HVA; 961500; 1142; 650/75/59/1,
Elliger, Uwe; 08.05.58; HVA; 961500; 1142; 650/75/59,
Ende, Michael; 30.06.52; BV Berlin VII; 150700; 1092; 4977/79,
Engelmann, Frank; 03.08.42; HVA; 961500; 1140; 5681/86, M
Engelmann, Gabriele; 15.08.46; HVA; 961500; 1140; 3876/86, M
Englberger, Wolfgang; 24.06.43; HVA; 961500; 1020; 3760/87, U
Enke, Brigitte; 04.08.44; HVA; 961500; 1280; 650/75/50/1,
Enke, Dieter; 02.07.45; HVA; 961500; 1280; 650/75/50,
Escherich, Rolf; 18.01.40; HVA; 961500; 1156; 3039/62, F
Euen, Wolf; 19.02.44; KD Riesa; 120053; 8400; XlI/2673/87,
Ewald, Peter; 28.01.50; Abt. N; 906540; 1140; 3622/77,
Faber, Kurt; 30.07.27; Abt. XI; 941100; 1170; 8348/60,
Falkehagen, Bärbel; 10.04.56; Abt. N; 906540; 1130; 3412/78,
Falkenhagen, Ingo; 29.07.56; Abt. N; 906540; 1130; 2403/78,
Fauck, Alexa; 04.12.51; HVA; 961500; 1095; 3820/85/1, F
Fauck, Wolfgang; 21.01.50; HVA; 961500; 1095; 3820/85, F
Fähnrich, Alfred; 01.07.32; HA I; 970100; 1602; K, 4271/80
Fähnrich, Manfred; 29.03.33; Rostock XVIII; 011800; 2500; 549/60,
Fedtke, Simone; 02.03.66; HVA; 961500; 1092; 4462/81, A
Feige, Brigitte; 07.03.48; HVA; 961500; 1143; 592/88 F
Fell, Klaus; 30.05.35; Abt. N; 906540; 1092; 7259/75,
Fichtmüller, Jens; 06.03.67; HVA; 961500; 4850; 3641/88, O
Fickel, Michael; 30.01.61; HVA; 961500; 1140; 4276/83, J
Fiedler, Gunter; 16.09.51; HVA; 961500; 1034; 2113/72, F
Finsterbusch, Werner; 08.07.56; HVA; 961500; 1093; 5693/81, A
Fischer, Gerd; 21.02.61; HA VI; 970600; 1144; K, 3435/89
Fischer, Hans; 11.10.50; HVA; 961500; 1142; 505/83, O
Fischer, Hartmut; 25.04.52; HVA; 961500; 1250; 2256/73, F
Fischer, Horst; 03.02.32; HVA; 961500; 1600; 1573/85, K
Fischer, Horst; 03.05.46; KD Berlin-Köpenick; 150041; 1170; 2562/80,
Fischer, Karl-Heinz; 19.08.28; HVA; 961500; 1136; 2110/73, Z
Fischer, Klaus-Dieter; 06.12.44; Rostock XVIII; 011800; 2551; 3875/80,
Fischer, Marion; 02.08.52; HVA; 961500; 1142; 2779/84, O
Flister, Magrit; 20.02.56; HVA; 961500; 1020; 4561/87, U
Fox, Erhard; 04.12.52; Abt. XI; 941100; 2355; 5313/88,
Fraatz, Helmut; 06.07.31; HVA; 961500; 1156; 221/75, M
Franke, Lothar; 04.11.47; Abt. N; 906540; 1142; 5074/77,
Franke, Wilfried; 25.08.53; Rostock; 014300; 2500; 5952/84,
Franz, Bodo; 13.01.59; Abt. N; 906540; 1150; 1549/80,
Franz, Jürgen; 09.04.46; Abt. N; 906540; 1142; 2112/66,
Franz, Jürgen; 30.06.55; Abt. XI; 941100; 3250; 6588/81,
Frauenstein, Rolf; 14.07.52; HVA; 961500; 1143; 3166/78, J
Fränkler, Sabine; 10.02.61; HVA; 961500; 1020; 2264/86, U
Freese, Frank; 25.03.62; Abt. N; 906540; 1095; 2567/87,
Freitag, Ilona; 02.10.52; Dresden XIX; 121900; 8060; XII/2747/87,
Freund, Mario; 10.01.64; Abt. XI; 941100; 3038; 2759/89,
Freyberg, Rudolf; 23.09.35; Abt. N; 906540; 1055; 7260/75,
Freyer, Ingolf; 10.07.30; HVA; 961500; 1120; 1347/85, F
Freyer, Thorsten; 10.11.60; HVA; 961500; 1136; 650/75/40,
Frey, Rainer; 02.06.42; HVA; 961500; 7500; 1586/87, F
Frick, Dieter; 28.06.58; HVA; 961500; 1140; 4054/81, F
Friebe, Günter; 28.09.43; HVA; 961500; 1090; 1640/88, F
Friedel, Hartmut; 12.02.49; HVA; 961500; 1093; 231/78, J
Friedrich, Gerhard; 21.12.29; HA VI; 970600; 1034; K, 862/80
Friedrich, Joachim; 06.07.48; Abt. XI; 941100; 1141; 67/78,
Friedrich, Jörg; 30.06.64; HVA; 961500; 1193; 3925/86, F
Fritzsche, Harald; 14.08.57; Abt. XI; 941100; 1054;
Fruck, Gerhard; 13.05.35; Abt. N; 906540; 1136; 3706/73,
Fuchs, Eberhard; 04.10.50; HVA; 961500; 1153; 2879/78, J
Fuchs, Wolfgang; 18.11.53; HVA; 961500; 1156; 3547/82, M
Fungk, Torsten; 03.11.57; Abt. N; 906540; 1142; 2956/79,
Funke, Dieter; 20.01.38; HVA; 961500; 1080; 2929/61, F
Funk, Lutz; 22.09.57; HVA; 961500; 1095; 650/75/60,
Funk, Margret; 22.05.55; HVA; 961500; 1095; 650/75/60/1,
Füßler, Hubertus ; 10.01.56; HVA; 961500; 5080; 529/88, M
Füßl, Boris; 06.06.61; Abt. XI; 941100; 1018; 2417/88,
Fydrich, Erhard; 15.05.42; HVA; 961500; 1250; 593/86, F
Gableske, Gunther; 08.04.60; Abt. N; 906540; 1280; 7517/81,
Gallandt, Ronald; 16.08.57; Abt. N; 906540; 1280; 1788/78,
Gander, Jürgen; 31.08.47; Abt. N; 906540; 1156; 7275/75,
Gawlitza, Peter-Michael ; 07.12.46; HVA; 961500; 1142; 2505/65, G
Gäbler, Eveline; 23.08.56; Abt. N; 906540; 1281; 5155/88,
Gäbler, Ralf-Detlef ; 01.11.56; Abt. N; 906540; 1281; 3324/76,
Gehrt, Wolf-Rüdiger ; 26.01.56; Abt. N; 906540; 1090; 1840/79,
Geißenhöner, Bernd; 26.08.43; Abt. XI; 941100; 1092; 377/69,
Gerber, Jürgen; 05.05.49; Dresden XIX; 121900; 8020; XII/2666/87,
Gerber, Lutz; 19.01.61; Abt. N; 906540; 1140; 7472/80,
Gerhard, Henry; 23.02.32; KD Berlin-Köpenick; 150041; 1199; 1041/70,
Gerlach, Rainer; 25.02.53; HVA; 961500; 5080; 1477/87, F
Gerlach, Roland; 20.01.51; HVA; 961500; 1280; 4006/76, F
Gerstner, Christine; 01.07.43; HVA; 961500; 1136; 5255/85, D
Gerth, Peter; 21.05.54; Rostock XIX; 011900; 2540; 666/87,
Gielow, Hubert; 11.03.53; Abt. N; 906540; 1017; 2028/79,
Giesen, Gisela; 23.02.30; Abt. XI; 941100; 1197; 1866/69/2,
Gietl, Gottfried; 24.05.34; HVA; 961500; 1055; 18554/60, T
Gladitz, Dieter; 19.02.37; HVA; 961500; 1020; 3323/86, J
Gladitz, Edgar; 02.12.34; HVA; 961500; 1020; 2806/78, F
Gläßer, Axel; 18.07.57; Abt. N; 906540; 1020; 3100/80,
Glöckner, Hermann; 07.04.28; Dresden VI; 120600; 8060; XII/2657/87,
Goersch, Bärbel; 29.05.54; HVA; 961500; 1093; 5764/81/2, D
Golombek, Bernd; 30.07.62; Abt. XI; 941100; 1560; 5310/88,
Gompert, Dieter; 26.11.33; KD Strausberg; 050049; 1260; V/426/88,
Gorldt, Peter; 20.12.42; HVA; 961500; 9005; 530/88, M
Goutrie, Peter; 27.11.47; Abt. N; 906540; 1281; 3557/78,
Görke, Peter; 26.06.61; HVA; 961500; 1150; 921/83, F
Göthel, Jürgen ; 20.07.53; HVA; 961500; 1142; 8164/81, L
Grahmann, Dieter; 25.06.41; HVA; 961500; 1106; 5602/86, L
Gramß, Werner; 03.06.29; HVA; 961500; 1017; 2859/68, M
Grandel, Winfried; 12.03.43; KD Berlin-Köpenick; 150041; 1144; 3047/80,
Graßmann, Walter; 28.02.46; Abt. N; 906540; 1092; 2009/67,
Gräser, Rolf; 14.07.42; HVA; 961500; 1140; 662/88, M
Gräser, Ute; 24.02.63; HVA; 961500; 1140; 609/88, M
Greve, Bernd; 25.09.57; Abt. N; 906540; 1017; 5075/77,
Grieger, Angela; 11.05.63; HVA; 961500; 1185; 3973/81, O
Grigat, Alfred; 26.05.39; HVA; 961500; 2850; 3317/84, M
Grimmek, Norbert; 24.05.57; Abt. N; 906540; 1281; 4711/78,
Grimm, Peter; 03.11.41; HVA; 961500; 1156; 200/66, F
Grohmann, Achim; 15.02.54; HVA; 961500; 1100; 2518/88, F
Grohs, Michael; 19.10.53; HVA; 961500; 1143; 327/81, M
Gromes, Wilfried; 29.09.51; HVA; 961500; 1170; 1679/88, E
Großer, Jürgen; 27.01.59; HVA; 961500; 1607; 650/75/37,
Große, Hans-Peter ; 02.03.38; HVA; 961500; 1136; 2677/82, J
Großmann, Dietrich ; 24.09.41; Abt. XI; 941100; 1130; 2260/66,
Großmann, Gerald; 23.03.57; Abt. N; 906540; 1142; 1775/78,
Groß, Andreas; 29.11.55; Abt. XI; 941100; 9050; 6933/88,
Grotelüschen, Claus; 27.02.36; HVA; 961500; 1603; 2295/70, U
Grote, Konrad; 15.02.41; HVA; 961500; 1093; 1967/64, A
Groth, Rudi; 26.07.43; Abt. N; 906540; 1136; 1991/69,
Grotsch, Olaf; 21.05.63; Abt. N; 906540; 1092; 5152/88,
Gröpler, Peter; 12.06.44; HVA; 961500; 1020; 1643/68, O
Grötschel, Andrea; 28.09.57; HVA; 961500; 1540; 4463/84/1, F
Grötschel, Uwe; 28.12.58; HVA; 961500; 1540; 4463/84, F
Grube, Gerhard; 12.06.48; Abt. N; 906540; 1092; 4565/77,
Grunert, Joachim; 10.08.33; HVA; 961500; 1017; 3121/64, L
Gruner, Andreas; 22.03.58; Abt. XI; 941100; 1140; 479/83,
Gruner, Heidi; 09.09.59; HVA; 961500; 1156; 650/75/33/1,
Gruner, Michael; 28.07.55; HVA; 961500; 1156; 650/75/33,
Grünherz, Hans-Joachim; 07.04.45; Abt. XI; 941100; 1140; 3046/66,
Grütze, Regina; 18.07.55; BV Berlin XVIII; 151800; 1140; 763/86,
Gubsch, Volkmar; 19.08.52; KD Dresden/Stadt; 120040; 8038; XII/1357/87,
Gundermann, Dieter; 02.12.57; Abt. N; 906540; 1130; 2957/79,
Güntherodt, Ulrich; 28.04.46; HVA; 961500; 4090; 4273/89, M
Günther, Klaus; 06.08.55; HVA; 961500; 1130; 960/89, F
Günther, Norman; 19.11.65; HVA; 961500; 9900; 3734/88, Y
Haack, Jörg-Dieter; 06.09.52; Abt. N; 906540; 1110; 3718/76,
Haaser, Jutta; 23.11.33; Dresden VI; 120600; 8020; XII/2658/87,
Haase, Dieter; 27.06.31; Dresden IX; 120900; 8023; XII/2663/87,
Haberland, Lutz; 26.04.59; Abt. XI; 941100; 3038; 1894/87,
Hagenfeld, Wilfried; 18.02.40; HVA; 961500; 1020; 2990/76, M
Hagen, Rudolf; 24.02.39; Abt. N; 906540; 1136; 2075/76,
Hallfarth, Günter; 01.10.44; Abt. XI; 941100; 1092; 499/70/1,
Hallfarth, Renate; 20.01.48; Abt. XI; 941100; 1092; 499/70/2,
Hampel, Bärbel; 03.04.59; Abt. XI; 941100; 1280; 2563/86,
Hampel, Bernd; 23.03.56; Abt. N; 906540; 1280; 3388/76,
Hanke, Lutz; 04.02.56; HVA; 961500; 1195; 2378/88, F
Hanke, Peter; 21.10.53; HVA; 961500; 1143; 4174/88, A
Hantke, Gisela; 05.05.32; HVA; 961500; 1093; 3599/82, H
Hantke, Willi; 23.04.31; HVA; 961500; 1093; 6100/82, H
Harder, Dieter; 21.01.43; KD Riesa; 120053; 8400; XII/2674/87,
Hartmann, Andreas; 08.05.58; HVA; 961500; 1142; 650/75/52,
Hartmann, Gerd; 15.03.39; HVA; 961500; 1020; 647/87, A
Hartmann, Günter; 11.11.40; Abt. N; 906540; 1136; 1769/71,
Hasterok, Günter; 16.05.44; HVA; 961500; 1092; 1391/86, M
Hasterok, Hannelore; 07.05.50; HVA; 961500; 1092; 1737/87, F
Haude, Klaus-Dieter; 27.04.39; BV Berlin XVIII; 151800; 1020; 2978/81,
Hauschild, Dieter; 04.06.39; Rostock, Abt. Hafen; 011969; 2500; 5293/88,
Havlik, Lutz; 30.11.54; Abt. N; 906540; 1093; 5015/85,
Häber, Hermann; 02.04.48; HVA; 961500; 1143; 139/74, F
Hähn, Doris; 01.01.63; HVA; 961500; 1200; 5352/88, F
Hähn, Harald; 27.01.60; Abt. XI; 941100; 1200; 3455/86,
Härdrich, Horst; 03.07.38; Abt. XI; 941100; 1140; 3704/73,
Härtig, Uwe; 08.09.57; Abt. N; 906540; 1143; 3621/77,
Heckel, Reiner; 24.04.51; HVA; 961500; 1280; 2163/73, F
Heene, Edgar; 02.12.58; HVA; 961500; 2000; 1738/87, F
Heene, Elke; 12.02.60; HVA; 961500; 2000; 1738/87/1, F
Heerling, Frank; 01.09.62; Abt. N; 906540; 1130; 5017/85,
Heer, Carsten; 15.12.36; Abt. N; 906540; 1020; 454/73,
Heiliger, Ullrich; 20.05.57; Abt. N; 906540; 1120; 1856/86,
Heinicke, Frank; 26.05.56; Abt. N; 906540; 1017; 2564/86,
Heinrich, Guido; 26.06.66; Abt. N; 906540; 1590; 1159/89,
Heinrich, Peter; 29.04.40; HA XX; 982000; 1092; K, 3971/71
Hein, Jürgen; 20.12.54; HVA; 961500; 1152; 372/73, F
Hein, Winfried; 10.08.50; HVA; 961500; 1142; 3855/85, F
Heitfeld, Michael; 23.06.53; HVA; 961500; 1140; 4198/81, L
Hellmich, Kurt; 22.08.30; Rostock XVIII; 011800; 2520; 171/70,
Hellwig, Frank; 25.02.56; HVA; 961500; 1144; 650/75/41,
Helm, Michael; 19.04.59; Abt. XI; 941100; 9438; 589/88,
Hempel, Günter; 25.04.34; KD Eisenhüttenstadt; 050045; 1220; V/1001/88,
Hempel, Reinhard; 28.06.51; HVA; 961500; 1153; 1746/89, E
Hempel, Wolfgang; 02.07.53; Abt. N; 906540; 1020; 5015/77,
Henckel, Peter; 04.05.58; Abt. N; 906540; 1144; 3891/77,
Henke, Frank; 25.12.56; Abt. N; 906540; 1071; 3891/76,
Hennemann, Lutz; 29.09.50; Abt. N; 906540; 1100; 7269/75,
Hennig, Dietmar; 07.01.52; HVA; 961500; 1090; 1226/70, F
Henning, Friedrich; 11.05.35; HVA; 961500; 1017; 440/87, U
Henrion, Lothar; 07.01.41; KD Plauen; 140054; 9900; 1435/89,
Hentschke, Angelika; 19.07.51; HVA; 961500; 1153; 4189/89/1, F
Hentschke, Günther ; 08.01.51; HVA; 961500; 1153; 4189/89, F
Herbert, Roland; 10.10.43; HVA; 961500; 1020; 494/69, F
Herbst, Manfred; 09.10.33; HVA; 961500; 1156; 1087/84, U
Herder, Edeltraut; 27.07.31; HVA; 961500; 1020; 867/61, O
Herer, Erhard; 18.06.40; HVA; 961500; 1130; 4010/70, E
Herkendell, Karl-Heinz; 31.01.43; Abt. N; 906540; 1020; 3894/77,
Herkendell, Martha; 01.03.46; Abt. N; 906540; 1020; 4053/85,
Herold, Gerhard; 29.05.53; HVA; 961500; 1250; 4484/84, F
Herold, Monika; 28.08.52; HA VI; 970600; 1040; K, 3315/86
Herrmann, Alexander; 08.03.51; Abt. N; 906540; 1140; 3077/71,
Herrmann, Dietmar; 30.08.38; HA I; 970100; 8060; K, 5235/86
Herrmann, Günther; 28.01.30; HVA; 961500; 1020; 3627/74, A
Herschel, Steffen; 14.11.52; Abt. N; 906540; 1130; 1607/76,
Hertel, Ralf; 12.04.59; Abt. N; 906540; 1040; 2958/79,
Hertzsch, Wilfried; 10.07.43; HVA; 961500; 2591; 3906/83, M
Herzog, Peter; 08.04.47; HVA; 961500; 8600; 2872/87, M
Herz, Rudolf; 16.05.35; HVA; 961500; 1136; 4391/83, M
Hesse, Christina; 25.12.50; HVA; 961500; 1560; 4040/88, F
Hesse, Klaus; 09.09.47; HVA; 961500; 1136; 2032/72, J
Hesse, Rainer; 24.04.48; Abt. XI; 941100; 1560; 4484/87,
Hexamer, Rene; 10.04.57; HVA; 961500; 1197; 8082/81, F
Hielscher, Dirk; 26.01.56; HVA; 961500; 1092; 417/86, O
Hiersche, Eveline; 16.06.36; HVA; 961500; 1110; 3073/89, K
Hildebrandt, Fred; 23.12.57; HVA; 961500; 6060; 650/75/31,
Hildebrandt, Marion; 28.09.51; HVA; 961500; 1140; 3721/88/1, F
Hildebrandt, Michael; 03.08.52; HVA; 961500; 1140; 3721/88, F
Hildebrandt, Sonja; 07.02.54; HVA; 961500; 1165; 3020/76/26, M
Hildebrand, Hans-Jürgen ; 09.05.39; Frankfurt/O. VI; 050600; 1200; V/427/88,
Hildebrand, Norbert; 23.05.55; Abt. XI; 941100; 5600; 480/83,
Hille, Thomas; 27.04.61; Abt. N; 906540; 1055; 1356/84,
Hinterthan, Bernd; 25.11.41; Rostock VI; 010600; 2551; 1748/89,
Hinz, Hans-Jürgen; 18.01.43; Abt. XI; 941100; 1115; 410/70,
Hirsch, Jürgen; 31.07.54; Abt. XI; 941100; 1195; 2740/77,
Hirt, Sigurd; 05.07.42; Abt. XI; 941100; 1130; 1601/68,
Hitschler, Helmut; 22.07.58; ZAIG; 995300; 8010; K/4402/88,
Hofert, Michael; 02.09.59; HVA; 961500; 1093; 947/84, F
Hoffmann, Frank; 28.02.44; HVA; 961500; 1120; 1587/87, F
Hoffmann, Gunter; 03.11.54; HVA; 961500; 1140; 650/75/17,
Hoffmann, Hartmut; 06.08.51; Abt. XI; 941100; 1095; 6732/80,
Hoffmann, Ines; 03.11.61; HVA; 961500; 1140; 650/75/17/1,
Hofmann, Dieter; 18.04.39; HVA; 961500; 1162; 2607/84, F
Hofmann, Ellen; 03.10.54; Abt. N; 906540; 1280; 1680/81,
Hofmann, Udo; 20.02.41; HVA; 961500; 6019; 1492/86, F
Hohlfeld, Hartmut; 14.05.55; HVA; 961500; 1141; 2596/79, J
Hohnhold, Ulrich; 02.05.52; KD Fürstenwalde; 050047; 1240; V/453/88,
Hommel, Klaus; 14.09.52; HVA; 961500; 1142; 2503/77, F
Hoppe, Werner-Michael; 18.06.44; Abt. N; 906540; 1055; 2900/66,
Hornauer, Uwe; 16.08.46; HVA; 961500; 1092; 65/76, A
Hornemann, Rainer; 29.01.47; HVA; 961500; 1156; 1529/87, M
Hornig, Udo; 04.06.59; Abt. XI; 941100; 1140; 5850/84,
Horn, Jochen; 22.06.59; HVA; 961500; 1297; 2613/84, E
Höhl, Volker; 15.10.60; Abt. N; 906540; 1140; 1153/86,
Höhne, Siegfried; 10.10.39; KD Eisenhüttenstadt; 050045; 1220; V/1013/88,
Höhn, Marina; 22.03.60; HVA; 961500; 1150; 3022/89, A
Hölzel, Manfred; 29.05.39; Dresden VI; 120600; 8060; XII/1339/87,
Höppner, Matthias; 03.01.58; Abt. XI; 941100; 1143; 1710/89,
Hörnig, Klaus; 21.01.45; Abt. XI; 941100; 1092; 1903/72
Hösel, Karl; 08.11.35; Abt. XI; 941100; 1130; 434/68,
Hubatsch, Klaus; 02.12.55; HVA; 961500; 1143; 668/72, F
Hugel, Hans-Georg; 26.05.54; HVA; 961500; 1152; 4055/88, O
Huhn, Bernd; 02.12.52; HVA; 961500; 1142; 1565/86, M
Hundt, Thomas; 20.03.61; HVA; 961500; 1142; 650/75/62,
Hunger, Werner; 23.02.40; HVA; 961500; 1017; 415/81, F
Husung, Peter; 28.11.37; HVA; 961500; 1017; 2111/73, A
Huth, Andreas; 20.04.59; Dresden XIX; 121900; 8036; XII/2748/87,
Hübner, Henri; 18.11.58; Abt. N; 906540; 1034; 3892/79,
Hübner, Ina; 23.10.64; BV Berlin VI; 150600; 1090; K/4166/88,
Hübsch, Bernd; 20.09.43; HVA; 961500; 1080; 47/73, F
Hückel, Tino; 20.03.64; Abt. N; 906540; 1195; 3507/86,
Hühr, Bruno; 02.06.55; Abt. N; 906540; 1140; 3558/78,
Hüter, Rolf; 01.01.37; HVA; 961500; 1144; 2148/74, F
Ibold, Manfred; 10.08.51; HVA; 961500; 1100; 1904/73, F
Ickert, Winfried; 23.07.56; HVA; 961500; 1153; 650/75/8,
Ide, Hans-Heinrich; 27.09.41; Abt. N; 906540; 1156; 1611/76,
Illig, Gerald; 22.02.58; Abt. N; 906540; 1140; 2959/79,
Immermann, Gunter; 15.11.53; HVA; 961500; 1071; 959/89, F
Irmscher, Frank; 20.07.59; HVA; 961500; 1034; 2912/78, F
Jaenicke, Uwe; 23.06.53; HVA; 961500; 1156; 3057/89, F
Jahn, Heinz; 04.11.35; Rostock XIX; 011900; 2300; 3335/75,
Jahn, Klaus; 04.11.50; Abt. XI; 941100; 1120; 1515/75,
Jakowlow, Manfred; 29.03.50; Abt. N; 906540; 1281; 1058/86,
Janietz, Eberhard; 04.08.51; HVA; 961500; 1120; 2570/79, O
Janke, Erwin; 22.06.43; HVA; 961500; 7500; 3972/86, M
Jarchow, Hans-Jürgen; 06.04.44; HVA; 961500; 4850; 2355/88, M
Jasmann, Hans-Peter; 25.06.38; Rostock XIX; 011900; 2355; 4081/86,
Jautze, Stephan; 19.08.53; HVA; 961500; 1054; 2164/73, F
Jäger, Bernd; 04.11.47; Abt. XI; 941100; 1142; 245/77,
Jäger, Monika; 13.04.44; HVA; 961500; 1147; 618/86, M
Jäger, Siegfried; 10.01.43; HVA; 961500; 1147; 619/86, M
Jähne, Karsten; 24.06.57; HVA; 961500; 8060; 650/75/42,
Jähn, Rolf; 01.04.32; HVA; 961500; 1183; 187/61, J
Jedicke, Jürgen; 16.10.55; Abt. XI; 941100; 5060; 2415/88,
Jesse, Jan; 18.11.63; HVA; 961500; 1150; 503/82, M
John, Werner; 12.01.45; HVA; 961500; 9005; 2124/89, F
Jost, Rainer; 22.03.55; Karl-Marx-Stadt VIII; 140800; 9050; 167,
Jung, Herbert; 04.10.51; Abt. XI; 941100; 1600; 69/76,
Junkereit, Dieter; 14.05.62; Karl-Marx-Stadt VIII; 140800; 9050; 172,
Junkereit, Monika; 01.12.64; Karl-Marx-Stadt VIII; 140800; 9050; 173,
Jurisch, Hans; 11.08.32; HVA; 961500; 1130; 3730/66, K
Jürgens, Karl; 30.01.52; Abt. N; 906540; 1141; 1692/76,
Jürgens, Monika; 16.06.41; HVA; 961500; 3580; 2969/87, M
Jürgens, Peter; 13.03.41; HVA; 961500; 3580; 2968/87, M
Kaden, Horst; 13.01.35; Frankfurt/O. VI; 050600; 1200; V/430/88,
Kahl, Frank; 19.02.50; HVA; 961500; 8017; 2224/86, O
Kaiser, Karl; 16.12.36; Abt. N; 906540; 1136; 4568/77,
Kalbaß, Herbert; 21.10.34; Abt. XI; 941100; 1071; 8569/60,
Kappelmann, Jens; 08.07.53; HVA; 961500; 1160; 2972/76, F
Kappis, Peter; 14.12.49; KD Berlin-Treptow; 150046; 1093; 5320/88,
Karasch, Klaus-Dieter; 02.10.51; Abt. N; 906540; 1142; 5044/76,
Karlstedt, Manfred; 27.09.51; HVA; 961500; 1150; 1635/84, O
Kasper, Hans-Hendrik; 03.05.51; HVA; 961500; 1150; 2784/72, U
Kasper, Reiner; 16.01.56; Abt. N; 906540; 1130; 3472/76,
Kathert, Klaus; 03.06.49; Abt. N; 906540; 1292; 1354/71,
Keindorf, Thomas; 09.05.66; HVA; 961500; 1156; 3732/87, O
Kellermann, Harald; 26.04.51; HVA; 961500; 1140; 4691/89, L
Keller, Hans-Joachim; 22.10.38; HVA; 961500; 1020; 2245/73, M
Keller, Klaus; 25.01.36; HVA; 961500; 1600; 2332/73, M
Keller, Rolf; 25.10.57; HVA; 961500; 2000; 5743/84, M
Kellner, Axel; 05.01.40; Abt. XI; 941100; 1140; 759/66,
Kerlisch, Werner; 23.04.36; OD KKW Nord; 010050; 2200; 3477/73,
Kernchen, Eckehardt; 01.10.50; Abt. N; 906540; 1020; 5041/76,
Kettner, Bernd; 28.05.47; Rostock, Abt. Hafen; 011969; 2520; 4080/86,
Keyselt, Klaus; 30.04.51; HVA; 961500; 1142; 1938/75, F
Kießig, Horst; 02.05.37; HVA; 961500; 1156; 307/82, J
Kießling, Dirk; 11.03.69; Abt. N; 906540; 1092; 5156/88,
Kirchbach, Rene; 05.04.64; HVA; 961500; 8010; 5865/84, F
Kirchhof, Jens; 04.12.61; HVA; 961500; 1020; 650/75/72,
Kirchner, Marianne; 18.10.43; HVA; 961500; 1130; 4718/88/1, F
Kirchner, Wolfgang; 23.08.39; HVA; 961500; 1130; 4718/88, F
Kirmse, Udo; 24.02.39; HVA; 961500; 1136; 2824/84, X
Kirsten, Falko; 11.02.50; HVA; 961500; 1600; 2511/77, M
Kirst, Alfred; 08.03.34; HA VI; 970600; 1080; K/4428/87,
Kißig, Jochen; 11.05.53; KD Löbau; 120049; 8700; KISSIG, JOCHEN
Kittler, Manfred; 13.03.33; Dresden XVIII; 121800; 8251; XII/1346/87,
Kittler, Roland; 25.01.58; Abt. XI; 941100; 4020; 5311/88,
Klarner, Volkmar; 23.03.54; Abt. XI; 941100; 9900; 2305/85,
Kleiber, Thomas; 02.01.55; HVA; 961500; 1020; 4365/86, U
Kleinhempel, Heinz; 04.07.57; Leipzig XVIII; 131800; 7050; K/5409/88,
Klemcke, Hermann; 15.11.51; KD Schwedt; 050050; 1330; V/446/88,
Klemens, Leo; 25.03.27; HVA; 961500; 1532; 19522/60, X
Klemme, Jan; 03.02.67; Abt. N; 906540; 1142; 2976/86,
Klenz, Henry; 03.12.56; Abt. XI; 941100; 1130; 409/81,
Klingsieck, Ralf; 10.10.47; HVA; 961500; 1092; 1644/69, F
Klotzke, Jürgen; 05.07.48; HVA; 961500; 6908; 3914/85, A
Klutznik, Axel; 11.07.61; Abt. XI; 941100; 1580; :
Kluwe, Frank; 11.10.49; HVA; 961500; 1142; 465/74, F
Knackstedt, Hans-Jürgen; 02.03.41; Abt. XI; 941100; 1162; 40/69,
Knaupe, Henk; 14.10.65; HVA; 961500; 1090; 423/88, M
Knieling, Annelie; 09.11.50; HVA; 961500; 1115; 3167/78, U
Knobloch, Angelika; 11.07.49; Abt. N; 906540; 1281; 1997/77,
Knobloch, Hans-Uwe; 23.10.57; Abt. N; 906540; 1092; 2487/77,
Knorr, Hans-Joachim; 25.04.38; HVA; 961500; 1615; 304/80, M
Knoth, Uwe; 08.04.57; Abt. XI; 941100; 1100; 6461/82,
Knöller, Sergej; 24.10.63; HVA; 961500; 1095; 5000/87, F
Knötel, Ronald; 14.10.63; BV Magdeburg, Abt. XV; 071500; 3080; :
Kobel, Werner; 07.03.38; HVA; 961500; 1600; 4710/80, L
Kobuch, Norbert; 22.12.51; HVA; 961500; 1058; 4980/88, O
Kochanek, Wolfgang; 14.09.41; HVA; 961500; 1055; 389/74, A
Kochsiek, Jürgen; 15.03.41; Karl-Marx-Stadt VIII; 140800; 9050; 178,
Koch, Arno; 18.02.37; KD Görlitz; 120047; 8903; XII/2406/88,
Koch, Bernhard; 12.02.44; HVA; 961500; 1142; 1566/86, M
Koch, Helmut; 20.12.49; Abt. N; 906540; 1153; 5340/84,
Koch, Jutta; 16.06.32; Abt. XI; 941100; 1162; 2390/70,
Koch, Paul; 09.05.44; HVA; 961500; 1910; 4651/85, M
Koch, Wilhelm; 22.08.41; Abt. XI; 941100; 1115; 416/70,
Koderhold, Dieter; 25.06.47; Abt. N; 906540; 1140; 447/74,
Koglin, Mario; 11.08.66; HVA; 961500; 1110; 3900/85, M
Kohoutek, Sepp; 10.03.54; HVA; 961500; 1090; 4998/87, F
Kokscht, Thomas; 10.07.58; HVA; 961500; 1035; 836/77, F
Kolasinski, Helge; 04.04.63; Abt. N; 906540; 1054; 2220/83,
Kolleßer, Klaus; 11.03.51; HVA; 961500; 7072; 612/89, F
Kolleßer, Regina; 11.11.48; HVA; 961500; 7072; 6763/88, F
Kolletzky, Olaf; 08.07.54; Abt. XI; 941100; 9900; 862/83,
Konieczny, Frank; 04.09.44; HVA; 961500; 1600; 1762/89, N
Konnopka, Frank; 11.04.48; Abt. N; 906540; 1280; 5003/80,
Konnopka, Gudrun; 27.12.48; Abt. N; 906540; 1280; 4038/79,
Konschel, Peter; 30.03.49; Abt. N; 906540; 1280; 4054/85,
Kopius, Elke; 24.04.51; Abt. N; 906540; 1140; 1885/81,
Korn, Robert; 11.09.37; HVA; 961500; 1195; 43/63, L
Kosch, Bärbel; 07.08.60; HVA; 961500; 6500; 3153/89, F
Kosch, Gunter; 31.01.53; Abt. XI; 941100; 6500; 2414/88,
Kosin, Heinz; 07.03.26; HVA; 961500; 1020; 2148/72, U
Kowatzkl, Fred; 15.05.55; Abt. N; 906540; 1150; 4712/78,
Köhler, Erwin; 06.10.40; Frankfurt/O. XVIII; 051800; 1200; V/442/88,
Köhler, Klaus; 20.02.52; HVA; 961500; 1020; 2565/88, O
Köhler, Petra; 20.03.51; HVA; 961500; 1017; 318/78, E
Köhler, Wolfgang; 29.06.51; HVA; 961500; 1017; 3254/84, E
König, Hans; 23.05.36; Abt. N; 906540; 1136; 7261/75,
Körner, Manfred; 26.01.43; Dresden VI; 120600; 8019; XII/414/89,
Köster, Sven; 18.04.66; Abt. N; 906500; 1150; 4732/87,
Köster, Ulrich; 20.11.42; Abt. N; 906540; 1292; 1687/76,
Kraatz, Jens-Peter; 27.09.60; Abt. N; 906540; 1090; 7603/81,
Krahl, Frank-Michael; 03.03.50; Abt. N; 906540; 1130; 1614/75,
Krahmüller, Uwe; 14.12.65; HVA; 961500; 6018; 5265/85, Q
Krahn, Charlotte; 22.04.30; HVA; 961500; 1020; 46/72, U
Kramer, Bernd; 20.10.41; Karl-Marx-Stadt, BKG; 142900; 9005; K/6104/88
Krannich, Matthias; 20.03.57; Abt. XI; 941100; 1144; 5798/84,
Kranz, Herbert; 17.12.39; Abt. N; 906540; 1092; 9805/61,
Kranz, Rosmarie; 21.12.40; Abt. N; 906540; 1092; 4354/77,
Krause, Johannes; 24.10.49; Abt. XI; 941100; 1600; 3702/73,
Krauße, Günter; 25.05.37; HVA; 961500; 8360; 1498/87, F
Kraus, Bert; 03.03.61; HVA; 961500; 1143; 813/83, P
Kraus, Rudolf; 23.07.37; HVA; 961500; 1140; 340/81, F
Kreher, Ralf; 28.02.67; Abt. N; 906540; 9300; 1160/89,
Kreinberger, Rolf; 25.05.29; HVA; 961500; 1121; 2637/77, S
Krenz, Bianca; 23.12.62; HVA; 961500; 1120; 3899/86, U
Kresse, Lutz; 12.10.54; HVA; 961500; 2090; 2354/88, M
Krietsch, Sabine; 10.11.49; Abt. N; 906540; 1280; 1922/76,
Kringler, Paul; 02.07.28; KD Stralsund; 010047; 2300; 1110/73,
Krohn, Heinz Günter; 28.01.56; Abt. XI; 941100; 7033; 493/87,
Krone, Reinhard; 23.07.48; HVA; 961500; 4090; 3823/86, M
Kröpelin, Detlef; 01.11.56; HVA; 961500; 1142; 51/80, F
Krumpfert, Joachim; 15.02.49; Abt. N; 906540; 1034; 1763/76,
Kruse, Gerlinde; 02.10.54; Abt. XI; 941100; 1142; 4701/89,
Kruse, Peter; 07.01.46; Abt. N; 906540; 1142; 1989/76,
Krüger, Andreas; 11.04.61; Abt. N; 906540; 1130; 7148/81,
Krüger, Brigitte; 11.02.37; HVA; 961500; 1130; 3419/84/1, O
Krüger, Hans; 15.06.37; HVA; 961500; 1130; 3419/84, O
Krüger, Holger; 26.04.57; Abt. N; 906540; 1280; 3389/76,
Krüger, Horst; 05.10.43; Abt. N; 906540; 1034; 1622/76,
Krüger, Reinhard; 26.04.33; Abt. N; 906540; 1017; 7257/75,
Krüger, Uwe; 22.08.60; Abt. XI; 941100; 7513; 3385/84,
Krzebeck, Siegfried; 05.02.52; Abt. N; 906540; 1035; 1689/76,
Krzyzanowski, Claus; 28.11.53; Abt. N; 906540; 1130; 1926/76,
Kudernatsch, Matthias; 18.03.65; Abt. N; 906540; 1150; 5032/89,
Kulitzscher, Manfred; 30.05.32; Rostock XVIII; 011800; 2555; 1530/70,
Kunisch, Frank; 20.02.59; Abt. N; 906540; 1150; 4107/79,
Kunze, Alfred; 30.03.32; KD Eberswalde; 050044; 1298; V/429/88,
Kunze, Heinz; 08.05.37; Dresden XVIII; 121800; 8101; XII/1345/87,
Kunze, Wilfried; 01.04.45; BV Berlin XVIII; 151800; 1145; 2809/88,
Kunzmann, Frank; 08.06.53; HVA; 961500; 9050; 650/75/64,
Kupferschmidt, Erich; 23.07.52; Abt. N; 906540; 1140; 2808/79,
Kupferschmidt, Gudrun; 03.05.52; Abt. XI; 941100; 1140; :
Kupsch, Michael; 28.04.58; HVA; 961500; 1090; 2686/79, F
Kurjuweit, Karlheinz; 27.03.50; KD Angermünde; 050041; 1330; V/439/88,
Küchenmeister, Hartmut; 31.03.54; HVA; 961500; 1144; 5042/86, N
Kücken, Werner; 31.08.28; BV Berlin XVIII; 151800; 1421; 1143/70,
Kynast, Klaus; 29.04.55; HVA; 961500; 1150; 1043/84, A
Ladebeck, Bernd; 22.05.56; Abt. N; 906540; 1140; 4952/77,
Lagemann, Jürgen; 22.08.48; Abt. XI; 941100; 1140; 7/76,
Lamberz, Ulrich; 02.07.52; HVA; 961500; 1092; 234/73, F
Lamm, Hans-Joachim; 03.01.42; Dresden VI; 120600; 8020; XII/2655/87,
Langer, Achim; 09.03.56; Abt. N; 906540; 1130; 1864/78,
Langer, Karl; 06.10.34; Abt. N; 906540; 1297; 1796/80,
Lange, Frank; 31.12.50; Abt. XI; 941100; 1143; 2745/79,
Lange, Gerd; 15.12.60; HVA; 961500; 4300; 650/75/19,
Lange, Harald; 03.01.34; HVA; 961500; 1147; 2367/73, U
Lange, Karl-Heinz; 31.12.52; HVA; 961500; 1058; 107/75, F
Lange, Kathlen; 23.05.62; HVA; 961500; 4300; 1763/88, E
Lange, Matthias; 07.10.56; Abt. N; 906540; 1141; 3503/87,
Lange, Ralf; 15.08.60; HVA; 961500; 1100; 1433/85, J
Lange, Reiner; 12.06.36; HVA; 961500; 1017; 1046/67, M
Lauenroth, Hans-Peter; 08.08.61; HVA; 961500; 1136; 1078/81, F
Laue, Lutz; 25.02.53; Abt. N; 906540; 1143; 2528/82,
Laupert, Andrea; 16.09.61; HVA; 961500; 1140; 2816/80, O
Lätzer, Eberhard; 03.12.48; Abt. XI; 941100; 1140; 3700/73,
Lechelt, Arno; 24.06.44; Abt. XI; 941100; 1140; 8511/81,
Lehmann, Frank; 11.07.66; HVA; 961500; 7580; 3170/89, Q
Lehmann, Holger; 14.10.62; Abt. N; 906540; 1144; 6082/82,
Lehmann, Rainer; 08.03.49; HVA; 961500; 1150; 2987/77, J
Leibscher, Axel; 26.03.54; HVA; 961500; 7301; 650/75/65/,
Leinweber, Manfred; 04.03.42; HVA; 961500; 1136; 166/77, M
Leirich, Bernd; 02.06.55; Abt. XI; 941100; 2500; 2796/87,
Leistner, Dieter; 23.05.42; HVA; 961500; 1250; 3478/84, J
Lemke, Frank; 09.11.60; Abt. N; 906540; 1071; 3021/84,
Lemke, Sabine; 15.09.65; Abt. N; 906540; 1071; 969/86,
Lenhard, Peter; 27.09.51; Abt. N; 906540; 1140; 1906/71,
Leonhardt, Heiko; 12.01.66; Abt. N; 906540; 1130; 5391/86,
Lerche, Ruth; 12.03.33; HVA; 961500; 1092; 3899/63, U
Leuschner, Harald; 01.10.39; HVA; 961500; 1020; 3713/87, F
Leymann, Jan; 30.03.61; HVA; 961500; 1092; 3020/76/9, M
Liebholz, Gisela; 09.01.30; HVA; 961500; 1055; 225/78, U
Liedke, Peter; 04.12.50; HVA; 961500; 1140; 1476/87, F
Lieniger, Bruno; 01.11.31; Abt. XI; 941100; 1140; 4167/83,
Ließneck, Walter; 12.10.37; HVA; 961500; 1115; 1990/72, M
Lietz, Peter; 13.02.54; Abt. N; 906540; 1280; 1990/76,
Linck, Joachim; 27.02.48; HVA; 961500; 2330; 1528/87, M
Linck, Rita; 27.11.51; Abt. XI; 941100; 2330; 1533/87, M
Lindig, Hans-Dieter; 11.01.30; Rostock VI; 010600; 2540; 1397/86,
Lindner, Dietmar; 09.06.51; Abt. N; 906540; 1140; 1988/76,
Lindner, Steffen; 18.04.68; HVA; 961500; 1035; 3948/86, M
Linke, Gerald; 29.06.39; HVA; 961500; 6504; 3871/87, F
Linke, Marga; 01.09.39; HVA; 961500; 6504; 3871/87/1, F
Linke, Reinhard; 18.07.30; HVA; 961500; 1199; 153/72, J
Lippert, Bodo; 04.01.62; Abt. N; 906540; 1071; 7402/81,
Lißke, Birgit; 13.03.55; Karl-Marx-Stadt VIII; 140800; 9050; 177,
Lißke, Gerhard; 17.01.51; Karl-Marx-Stadt VIII; 140800; 9050; 176,
Lobedan, Gerd; 21.05.54; HVA; 961500; 1143; 3961/83, M
Lode, Harald; 06.10.53; HVA; 961500; 8036; 2429/88, M
Lohse, Gerd; 24.07.46; Abt. N; 906540; 1144; 2007/67,
Loos, Siegfried; 30.06.40; HVA; 961500; 9061; 1750/72, M
Lorenz, Jörg; 21.05.62; HVA; 961500; 1017; 5026/84, F
Lorenz, Werner; 01.01.34; HVA; 961500; 1595; 4626/79, F
Lorenz, Wolfgang; 03.05.54; HVA; 961500; 1143; 95/76, F
Loudovici, Armin; 12.10.39; HVA; 961500; 1190; 4331/86, F
Löbnitz, Wolfram; 26.08.57; HVA; 961500; 1195; 1371/77, F
Löwa, Werner; 30.05.54; HVA; 961500; 1093; 425/79, F
Lubs, Bodo; 14.03.53; Abt. XI; 941100; 2103; 2026/86,
Lucas, Karl-Heinz; 27.02.57; Abt. N; 906540; 1090; 3705/77,
Ludwig, Horst; 27.08.31; HVA; 961500; 1017; 2588/77, P
Ludwig, Lutz; 15.10.53; HVA; 961500; 1143; 2113/89, E
Lux, Klaus; 19.08.43; KD Wolgast; 010049; 2220; 5577/81,
Lübke, Brigitte; 22.04.41; Rostock XVIII; 011800; 2500; 1119/79,
Lübke, Klaus; 27.03.52; HVA; 961500; 1220; 650/75/22,
Lücke, Karl-Ernst; 17.10.37; Abt. XI; 941100; 1035; 769/86,
Lück, Michael; 16.07.60; Abt. XI; 941100; 7260; 3814/85,
Lüdecke, Olaf; 15.06.48; Abt. XI; 941100; 1092; 2747/79,
Lüneburg, Karsten; 31.07.60; Abt. N; 906540; 1142; 3079/83,
Maaske, Gudrun; 11.11.42; HVA; 961500; 1162; 1351/89, N
Maaske, Klaus; 26.07.39; HVA; 961500; 1162; 3997/85, N
Maaß, Uwe; 20.07.61; HVA; 961500; 1100; 1680/88, F
Maget, Gerhard; 18.12.51; HVA; 961500; 1142; 2576/77, F
Maigatter, Tino; 21.02.62; HVA; 961500; 1054; 2766/84, F
Malchow, Dieter; 19.07.54; HVA; 961500; 1110; 2730/89, F
Manikowski, Jürgen; 30.07.54; Abt. XI; 941100; 2540; 1607/88,
Maretzki, Peter; 27.03.57; HVA; 961500; 1093; 235/79, M
Marks, Stefan; 20.09.52; HVA; 961500; 1250; 2501/77, F
Marnitz, Andreas; 01.10.56; HVA; 961500; 1150; 3498/86, F
Marr, Donald; 10.04.37; Abt. XI; 941100; 1250; 8/74,
Masula, Jens; 23.08.64; HVA; 961500; 1152; 5863/84, F
Matros, Jürgen; 04.06.53; HVA; 961500; 1160; 4049/88, O
Mattner, Susanne; 02.12.61; Abt. N; 906540; 1140; 3966/82,
Matusch, Klaus-Dieter; 20.09.56; Abt. N; 906540; 1090; 3685/82,
Maudrich, Peter; 10.02.58; Abt. XI; 941100; 6502; 4705/85,
Maune, Monika; 16.06.59; Dresden VI; 120600; 8023; XII/1334/89,
May, Jürgen; 19.04.57; Abt. N; 906540; 1156; 1508/80,
Märkel, Günter; 01.06.41; Abt. N; 906540; 1130; 3325/76,
Märkel, Sigrid; 02.06.41; Abt. N; 906540; 1130; 5272/76,
Mehlhorn, Lutz-Rainer; 15.11.40; HVA; 961500; 1020; 1029/67, J
Meichsner, Matthias; 03.09.58; HVA; 961500; 1090; 4416/80, F
Meier, Bernd; 08.08.54; Dresden XIX; 121900; 8020; XII/2749/87,
Meier, Detlef; 23.09.51; Abt. N; 906540; 1150; 448/74,
Meilick, Bernd; 11.06.47; HVA; 961500; 1092; 419/81, M
Mekelburg, Michaela; 21.03.61; HVA; 961500; 1140; 1346/85/1, F
Menzel, Harri; 27.01.35; Rostock VII; 010700; 2520; 5951/84,
Menz, Harry; 27.05.38; HVA; 961500; 1136; 12487/60, A
Merkel, Thomas; 19.01.59; HVA; 961500; 1055; 424/82, M
Messerle, Peter; 05.06.53; HVA; 961500; 1195; 2784/73, F
Metelmann, Bernd; 16.05.56; Abt. N; 906540; 1130; 3390/76,
Meyer, Detlef; 09.08.52; KD Rostock; 010040; 2540; 379/88,
Meyer, Horst; 23.08.33; HVA; 961500; 1100; 1348/85, F
Meyer, Jürgen; 04.01.42; Abt. N; 906540; 1140; 2587/65,
Michaelis, Holger; 20.10.58; HVA; 961500; 1152; 2611/84, F
Michel, Günther; 07.06.51; Abt. N; 906540; 1093; 2407/77,
Mieley, Siegfried; 30.07.36; Frankfurt/O. VII; 050700; 1200; V/431/88,
Mielke, Klaus; 11.07.39; Abt. XI; 941100; 1055; 2899/68,
Miersch, Harald; 26.11.51; HVA; 961500; 1142; 174/79, M
Mihm, Guido; 11.07.70; HVA; 961500; 1035; 4666/89,
Milde, Jörg; 16.11.54; BV Berlin XVIII; 151800; 1136; 4199/80,
Mirtschink, Jürgen; 09.01.48; HVA; 961500; 1034; 1902/72, F
Mischner, Jörg; 24.11.64; HVA; 961500; 1150; 1716/89, I
Mittelberger, Andreas; 15.02.65; Abt. N; 906540; 1020; 5221/84,
Mitzscherling, Peter; 27.02.36; Abt. XI; 941100; 1136; 410/81,
Monatsch, Jörg; 17.12.67; Schwerin II; 020200; 2755; :
Montwill, Frank; 25.04.54; HVA; 961500; 1144; 5630/86, A
Möckel, Joachim; 12.02.45; HVA; 961500; 9050; 3757/87, F
Mrosk, Dieter; 01.11.43; Abt. XI; 941100; 1140; 211/74,
Muth, Rolf; 31.01.29; HVA; 961500; 1017; 269/68, P
Mutscher, Monika; 01.12.53; Abt. N; 906540; 1130; 3684/82,
Mühlbauer, Dietmar; 02.06.47; Abt. N; 906540; 1092; 374/75,
Mühle, Dieter; 07.03.40; KD Dresden/Stadt; 120040; 8010; XII/2671/87,
Müller, Bärbel; 12.03.41; HVA; 961500; 1170; 1675/84/1, C
Müller, Barbara; 22.09.52; Abt. XI; 941100; 2356; 1608/88/1,
Müller, Detlef; 04.02.58; HVA; 961500; 1020; 650/75/43,
Müller, Ernst-Peter; 24.07.40; HVA; 961500; 1170; 1675/84, C
Müller, Erwin; 19.07.44; Abt. N; 906540; 2081; 2626/65,
Müller, Hannelore; 22.06.46; Abt. N; 906540; 2081; 3339/78,
Müller, Heinz-Jürgen; 24.09.48; HVA; 961500; 2520; 499/87, F
Müller, Helga; 15.11.37; HVA; 961500; 1144; 5009/87, D
Müller, Helmut; 07.01.40; BV Berlin XVIII; 151800; 1080; 608/83,
Müller, Irina; 19.09.62; HVA; 961500; 1020; 650/75/43/1,
Müller, Johannes; 09.08.46; Abt. N; 906540; 1140; 2006/67,
Müller, Jürgen; 07.08.59; HVA; 961500; 7930; 650/75/23,
Müller, Jürgen; 25.07.53; Abt. N; 906540; 1090; 3490/83,
Müller, Matthias; 03.06.53; HVA; 961500; 7840; 4729/89, M
Müller, Peter; 06.06.37; Dresden XVIII; 121800; 8023; XII/1348/87,
Müller, Uwe; 02.12.63; HVA; 961500; 1136; 3791/85, F
Müller, Uwe; 07.10.54; Abt. XI; 941100; 2356; 1608/88,
Münchow, Frank; 19.02.61; Abt. XI; 941100; 2830;
Münzel, Heinz; 20.07.47; HVA; 961500; 1020; 167/78, K
Mütschard, Peter; 28.01.52; HVA; 961500; 7060; 650/75/35,
Nareike, Kurt; 28.09.37; Rostock VI; 010600; 2520; 5283/78,
Nathe, Rolf; 27.09.30; HVA; 961500; 1170; 8/75, J
Naue, Rainer; 14.03.56; Abt. N; 906540; 1130; 3077/83,
Naumann, Gerhard; 25.02.49; Cottbus XIX; 061900; 7500; K3504/89,
Naumann, Uwe; 15.07.56; HVA; 961500; 8321; 650/75/36,
Näther, Frank; 08.09.50; HVA; 961500; 1140; 2257/70, F
Neff, Gertrud; 25.04.31; Abt. XI; 941100; 1156; 8510/81,
Nehls, Jörg; 08.07.58; HVA; 961500; 1143; 2592/80, F
Nennhaus, Detlef; 30.06.47; Abt. N; 906540; 1140; 7264/75,
Nestler, Olaf; 26.05.63; Abt. N; 906540; 1040; 2080/82,
Neumann, Klaus-Dieter; 24.07.47; Abt. XI; 941100; 1400; 3386/71,
Nicicky, Stephan; 23.04.55; Abt. N; 906540; 1092; 1999/77,
Nier, Herbert; 28.08.54; HVA; 961500; 1100; 2477/75, F
Noculak, Johannes; 27.05.41; HVA; 961500; 1162; 113/74, L
Noetzel, Peter; 27.02.40; Abt. N; 906540; 1136; 1608/76,
Noffke, Bernd; 11.10.59; Abt. N; 906540; 1197; 5016/85,
Nöbel, Manfred; 29.11.32; BV Berlin XVIII; 151800; 1020; 1341/83,
Nölte, Joachim; 11.11.48; HVA; 961500; 1017; 2553/80, P
Nücklich, Horst; 03.06.35; Dresden, BKG; 122900; 8010; XII/2753/87,
Oelschlaeger, Wolfgang; 06.03.39; Abt. XI; 941100; 1162; 9802/61,
Oertel, Hans-Joachim; 07.12.54; HVA; 961500; 1120; 3561/88, E
Oertel, Ulrich; 12.01.51; HVA; 961500; 1156; 19/76, F
Ola, Heinz; 25.06.34; Abt. N; 906540; 1092; 3705/73,
Ondrej, Detlev; 31.01.52; Abt. XI; 941100; 1136; 3763/88,
Ondrej, Ilona ; 24.07.54; HVA; 961500; 1136; 3763/88/1, F
Ondrusch, Aribert; 11.06.52; HVA; 961500; 7063; 6372/81, U
Ostoike, Harry; 14.05.57; Abt. N; 906540; 1140; 6979/80,
Otto, Hans; 03.06.50; HVA; 961500; 1144; 4692/89, L
Paasch, Uwe; 26.02.58; Abt. XI; 941100; 7280; 2794/87,
Pach, Detlef; 08.03.44; Dresden VII; 120700; 8101; XII/1342/87,
Pahlke, Lothar; 30.07.42; HVA; 961500; 6850; 650/75/18,
Pahlke, Gudrun; 15.08.49; HVA; 961500; 6850; 650/75/18/1,
Pangsy, Reiner; 12.11.40; Abt. N; 906540; 1280; 2437/60,
Parke, Kerstin; 26.01.62; Abt. XI; 941100; 3018; 1894/87/1,
Paulick, Gunter; 30.06.57; HVA; 961500; 7513; 650/75/44,
Paul, Gerhard; 11.08.53; HVA; 961500; 1100; 2639/79, J
Paul, Werner; 28.04.52; Abt. N; 906540; 1150; 3893/77,
Pawlak, Norbert; 01.10.47; BV Berlin XX; 152000; 1140; 3005/84,
Päsler, Knut; 15.07.65; HVA; 961500; 2000; 5196/84, F
Pecher, Rudolf; 27.09.55; Abt. N; 906540; 1020; 7272/75,
Perschon, Andreas; 01.11.58; HVA; 961500; 1055; 1233/80, F
Petermann, Walter; 28.01.50; HVA; 961500; 1130; 4216/84, F
Peters, Joachim; 15.02.55; Abt. XI; 941100; 1580; 2797/87,
Petzold, Frank; 24.04.60; Abt. XI; 941100; 7840; 1711/89,
Pfarr, Wilfried; 04.09.38; HVA; 961500; 1080; 180/73, M
Philipp, Siegfried; 19.10.49; Abt. N; 906540; 1017; 3078/83,
Pieritz, Reiner; 10.06.49; Abt. XI; 941100; 1600; 3701/73,
Pierschel, Bernd; 25.02.40; HVA; 961500; 1280; 128/68, F
Pietschmann, Hans; 26.05.40; Dresden XVIII; 121800; 8010; XII/2665/87,
Piletzki, Doris; 20.04.54; Abt. N; 906540; 1120; 1603/76,
Pingel, Jürgen; 14.04.34; HVA; 961500; 1020; 250/81, M
Plogas, Lutz-Ulrich; 14.04.50; HVA; 961500; 1092; 3974/87, J
Plomann, Michael; 31.03.61; Abt. N; 906540; 1100; 3501/85,
Ploner, Ekhard; 08.06.30; HVA; 961500; 1020; 1041/67, M
Plumbohm, Ilona; 26.02.59; Abt. XI; 941100; 1092; 1844/88,
Pohl, Bernd; 07.11.52; Cottbus, Abt. KuSch; 064000; 7500; 1587/87,
Pohl, Heinrich; 05.10.53; ZAIG; 995300; 8036; K, 4401/88
Polcuch, Konrad; 03.12.53; HVA; 961500; 1055; 3671/88, M
Polcuch, Marion; 06.11.53; HVA; 961500; 1055; 3670/88, F
Polster, Claus; 07.07.50; HVA; 961500; 7034; 1530/87, M
Popp, Rudolf; 21.09.36; HVA; 961500; 1136; 4283/88, F
Porges, Brigitte; 09.06.49; HVA; 961500; 1280; 3137/89, F
Porges, Manfred; 18.12.45; HVA; 961500; 1280; 3136/89, F
Pötsch, Hans; 03.11.41; HVA; 961500; 1197; 112/76, M
Prade, Reiner; 19.09.56; HVA; 961500; 1145; 4527/87, A
Pratsch, Klaus; 21.07.39; HVA; 961500; 1017; 1331/63, T
Preißler, Steffen; 05.06.66; Abt. N; 906540; 8017; 1161/89,
Prestin, Uwe; 03.11.40; Abt. N; 906540; 1150; 7399/81,
Preusche, Dieter; 07.12.43; HVA; 961500; 1142; 6977/75, A
Proft, Andre; 09.10.63; HVA; 961500; 1017; 760/88, D
Prokop, Adolf; 02.02.39; AGM, Arbeitsgebiet R; 956024; 5066; K, 187/71
Propf, Ulrich; 12.06.57; HVA; 961500; 4350; 650/75/4,
Puchner, Albrecht; 05.07.53; Abt. N; 906540; 1200; 2319/84,
Puchta, Gerdt; 09.01.51; HVA; 961500; 2540; 1864/89, M
Pufe, Rainer; 21.02.52; Abt. N; 906540; 1140; 1514/75,
Püstel, Brigitte; 27.04.43; Abt. XI; 941100; 1100; 239/85,
Püwick, Heinz; 01.08.28; HVA; 961500; 1280; 330/85, T
Pyritz, Frank; 08.10.58; Abt. N; 906540; 1092; 2128/78,
Radke, Bernd; 29.09.46; Abt. N; 906540; 1280; 1604/76,
Radke, Gudrun; 24.06.47; Abt. N; 906540; 1280; 2286/74,
Radtke, Peter; 27.08.62; HVA; 961500; 1140; 2637/84, M
Radünz, Christine; 26.09.53; HVA; 961500; 1136; 2758/78, J
Rahn, Winfried; 25.04.57; Abt. N; 906540; 1090; 4142/79,
Ramme, Alwin; 12.03.32; HVA; 961500; 1017; 3321/71, U
Ramminger, Uwe; 04.01.54; Abt. XI; 941100; 8245; 3256/84,
Rasel, Klaus; 30.05.42; HVA; 961500; 1532; 650/75/45,
Rasmus, Hartmut; 04.02.43; Abt. XI; 941100; 5500; 702/86,
Ratschke, Lutz-Dieter; 04.12.53; Abt. N; 906540; 1034; 5042/76,
Ratzmann, Ingrid; 18.04.37; HVA; 961500; 1035; 1672/84, A
Rauch, Benno; 25.09.53; Abt. N; 906540; 1136; 4146/79,
Rauch, Hannelore; 24.12.50; HVA; 961500; 2794; 650/75/30/1,
Rauch, Helmut; 09.01.53; HVA; 961500; 1092; 574/72, F
Rauch, Lothar; 04.11.53; HVA; 961500; 2794; 650/75/30,
Redlich, Hans-Joachim; 27.09.41; BV Berlin XIX; 151900; 1150; 1091/79,
Redlinghöfer, Ilse; 28.07.37; HA III; 940300; 1162; K, 1858/88,
Regner, Karsten; 19.03.63; HVA; 961500; 1092; 4311/84, M
Reichelt, Werner; 10.12.35; Abt. XI; 941100; 1020; 2046/64,
Reichelt, Wolfgang; 24.04.38; Rostock XVIII; 011800; 2520; 189/71,
Reichel, Joachim; 06.07.44; HVA; 961500; 2500; 1863/89, M
Reichel, Manfred; 14.04.59; HVA; 961500; 1093; 3062/78, F
Reichel, Reinhard; 20.09.45; Abt. XI; 941100; 1080; 17/71,
Reichert, Bernd; 11.06.50; Abt. N; 906540; 1093; 2094/72,
Reif, Frank; 05.10.58; HVA; 961500; 6016; 650/75/20,
Reiß, Alfred; 06.10.34; HVA; 961500; 1020; 4242/60, J
Reiter, Hermann; 11.10.37; HVA; 961500; 1100; 186/77, J
Renner, Andreas; 16.04.59; HVA; 961500; 1153; 19/81, F
Renner, Lothar; 05.06.45; HVA; 961500; 1054; 136/71, J
Rennhack, Lutz-Peter; 12.11.54; HVA; 961500; 4730; 650/75/46,
Retzlaff, Gerd; 06.07.39; HVA; 961500; 1142; 2756/84, G
Reuter, Simone; 19.06.67; HVA; 961500; 1140; 4274/89, M
Ribbecke, Horst; 19.04.25; HA XVIII; 981800; 1017; RIBBECKE, HORST
Richter, Andre; 21.09.61; Abt. N; 906540; 1143; 5786/82,
Richter, Detlef; 02.05.57; Abt. N; 906540; 1093; 7135/80,
Richter, Norbert; 24.09.47; KD Freiberg; 140047; 9200; K/1724/89,
Richter, Reinhard; 27.02.52; HVA; 961500; 1035; 4349/84, O
Richter, Willi; 21.06.32; HVA; 961500; 1130; 3776/87, F
Riedel, Dieter; 24.11.52; HVA; 961500; 1140; 3848/81, M
Riedel, Dietmar; 19.02.52; HVA; 961500; 1020; 2970/87, M
Riedel, Erhard; 26.03.46; HA III; 940300; 1136; K, 2963/89
Riedel, Winfried; 27.05.40; HVA; 961500; 1017; 777/65, M
Riemer, Rudi; 04.03.32; Frankfurt/O. XVIII; 051800; 1200; V/443/88,
Riesner, Wolfgang; 12.06.50; Abt. N; 906540; 1136; 2279/74/1,
Riewe, Hartmut; 16.08.42; KD Wismar; 010048; 2402; 4910/75,
Ritzmann, Hartmut; 23.01.56; HVA; 961500; 1140; 1715/89, M
Roeßler, Jochen; 13.03.41; KD Dresden/Stadt; 120040; 8060; XII/2670/87,
Rolfs, Raimund; 16.10.57; HVA; 961500; 1136; 3891/83, F
Roll, Gerd; 05.09.55; HVA; 961500; 2200; 650/75/28,
Roloff, Herbert; 16.02.36; HVA; 961500; 1144; 1611/69, Q
Rosenkranz, Rudolf; 23.11.30; Rostock XVIII; 011800; 2565; 680/70,
Rosenthal, Ralf; 19.12.64; HVA; 961500; 1140; 5423/88, S
Rostek, Horst; 26.05.29; HVA; 961500; 1156; 18500/60, F
Rost, Andrea; 23.11.57; HVA; 961500; 1150; 4298/89, F
Rost, Dieter; 31.05.57; Abt. N; 906540; 1150; 7214/81,
Rothbauer, Edmund; 04.08.30; Frankfurt/O., SED-PO-Ltg.; 054100; 1200; V/432/88,
Roth, Andreas; 31.03.52; HVA; 961500; 1140; 121/69/35, AB
Roth, Hans-Jochen; 12.07.43; HVA; 961500; 1800; 1381/89, M
Rödel, Johannes; 05.07.33; HVA; 961500; 1614; 650/88, D
Röder, Detlev; 12.06.56; Abt. N; 906540; 1130; 744/88, N
Röder, Siegmar; 03.05.37; HVA; 961500; 1156; 18/67, S
Röhling, Thomas; 30.04.59; Abt. XI; 941100; 1035; 1649/82,
Röhl, Gerhard; 26.07.52; Abt. N; 906540; 1142; 1883/81,
Röhner, Bernd; 07.01.57; HVA; 961500; 1040; 4700/89, F
Römer, Heinz; 11.02.32; HVA; 961500; 1250; 5192/86, M
Römer, Lutz; 09.08.59; HVA; 961500; 1055; 3400/89, F
Rörster, Hans; 29.05.30; HVA; 961500; 1147; 1593/86, U
Rösch, Klaus; 28.04.41; Abt. XI; 941100; 1100; 9797/61,
Rösner, Andreas; 16.06.51; ZAIG; 995300; 8020; K, 2964/89
Rudolph, Peter; 05.10.29; HVA; 961500; 2520; 7095/60, A
Ruschel, Dietger; 15.08.43; HVA; 961500; 1140; 2111/72, F
Russ, Wolfgang; 08.01.48; HVA; 961500; 1153; 6983/75, M
Ruthenberg, Gerd-Wolfram; 08.11.53; HVA; 961500; 1093; 5714/81, L
Rücker, Frank; 20.01.63; HVA; 961500; 1130; 5361/89, F
Rücker, Ricarda; 21.05.66; HVA; 961500; 1130; 5361/89/1, F
Sacher, Hans; 06.11.26; HVA; 961500; 1162; 252/74, U
Sachse, Ingrid; 15.12.40; HVA; 961500; 1020; 580/89, F
Sachse, Manfred; 15.04.34; BV Berlin XX; 152000; 1193; 219/76,
Sahling, Frank; 12.07.50; HVA; 961500; 1136; 6908/82, F
Salm, Rainer; 11.05.58; HVA; 961500; 1143; 44/81, F
Salomon, Walter; 12.11.29; HVA; 961500; 1273; 2142/73, L
Salomo, Gerhard; 08.01.30; Dresden XX; 122000; 8023; XII/2667/87,
Salomo, Günther; 21.05.41; Dresden VI; 120600; 8060; XII/1885/89,
Sander, Gerhard; 25.05.52; HVA; 961500; 1093; 157/85, M
Sander, Rudolf; 14.11.33; HVA; 961500; 1188; 790/88, F
Sasse, Klaus-Jürgen; 01.12.42; Abteilung XI; 941100; 1092; 1339/68,
Sauer, Uwe; 09.05.58; Abt. N; 906540; 1150; 4551/77,
Sawatzki, Paul-Eckhard; 06.03.56; HVA; 961500; 1054; 2963/78, F
Schaarschmidt, Steffen; 06.10.58; Karl-Marx-Stadt VIII; 140800; 9001; 181,
Schade, Detlef; 10.11.57; Abt. N; 906540; 1090; 2195/82,
Schaffrath, Hans-Martin; 26.03.44; BV Berlin VI; 150600; 1156; 1352/75,
Scharfenberg, Anette; 02.12.63; Abt. N; 906540; 1093; 5559/83,
Schellenberger, Gerd; 11.11.50; BV Berlin XX; 152000; 1080; 3003/84,
Schemmel, Manfred; 18.02.54; Abt. XI; 941100; 7270; 2795/87,
Schering, Norbert; 24.03.55; HVA; 961500; 1195; 2729/89, A
Schiecke, Dieter; 12.10.54; HVA; 961500; 1153; 1960/75, M
Schiemann, Peter; 04.01.43; HVA; 961500; 1017; 693/86, E
Schiemann, Renate; 09.04.45; HVA; 961500; 1017; 693/86/1, E
Schierz, Rolf-Jörg; 13.02.61; Karl-Marx-Stadt VIII; 140800; 9050; 180,
Schilling, Aribert; 07.04.51; Abt. N; 906540; 1093; 3618/77,
Schilling, Klaus; 29.09.41; Leipzig VI; 130600; 7060; K, 1043/87
Schink, Peter; 30.12.55; HVA; 961500; 1130; 6659/80, M
Schlauß, Hannelore; 17.10.52; Abt. N; 906540; 1298; 5153/88,
Schleicher, Gerhard; 22.06.43; HVA; 961500; 1250; 36/77, M
Schlenkrich, Dieter; 07.05.41; Abt. N; 906540; 1092; 1253/65,
Schlesinger, Harald; 10.10.62; Abt. N; 906540; 1142; 5558/83,
Schliebe, Edda; 25.07.39; Abt. XI; 941100; 1130; 2758/89,
Schliesch, Erhard; 30.03.28; Dresden VII; 120700; 8060; XII/2660/87,
Schlinsog, Helfried; 16.06.44; HVA; 961500; 7022; 544/88, F
Schlinsog, Regina; 05.02.47; HVA; 961500; 7022; 544/88/02, F
Schlögl, Thomas; 01.08.64; Abt. N; 906540; 1141; 3020/84,
Schmidt-Bock, Peter; 04.05.56; Abt. N; 906540; 1142; 2962/79,
Schmidt, Andreas; 16.01.63; Abt. N; 906540; 1140; 5787/82,
Schmidt, Dietmar; 12.06.44; Abt. XI; 941100; 1093; 1276/73,
Schmidt, Eberhard; 22.09.47; HVA; 961500; 1280; 231/75, M
Schmidt, Gerd; 29.07.39; HVA; 961500; 5900; 551/86, F
Schmidt, Gudrun; 08.12.44; HVA; 961500; 4050; 1532/87, M
Schmidt, Hans-Dieter; 03.01.32; Dresden XVIII; 121800; 8019; XII/2664/87,
Schmidt, Hans-Dieter; 30.07.36; Frankfurt/O. XIX; 051900; 1200; V/449/88,
Schmidt, Hartmut; 10.02.62; Abt. N; 906540; 1136; 4050/82,
Schmidt, Joachim; 19.12.43; HVA; 961500; 4050; 1531/87, M
Schmidt, Klaus-Peter; 28.03.56; Abt. XI; 941100; 1600; 407/78,
Schmidt, Kuno; 10.01.37; Abt. XI; 941100; 1020; 1868/69,
Schmidt, Manfred; 04.08.54; HVA; 961500; 1100; 2616/80, U
Schmidt, Werner; 18.07.36; Kreisdienststelle [KD] Bautzen; 120042; 8609; XII/1355/87,
Schmidt, Wilfried; 14.10.52; HVA; 961500; 1093; 237/73, F
Schmiedke, Günter; 04.10.33; Frankfurt/O., BKG; 052900; 1200; V/436/88,
Schneider, Astrid; 24.03.51; HVA; 961500; 1140; 3353/86, F
Schneider, Günter; 08.10.54; HVA; 961500; 5800; 3470/85, M
Schneider, Günter; 26.07.41; Abt. N; 906540; 1136; 9806/61,
Schneider, Harald; 26.01.48; HVA; 961500; 1140; 4128/83, M
Schneider, Karl-Heinz; 24.12.34; HVA; 961500; 9900; 6857/82, M
Schneider, Lothar; 16.11.56; HVA; 961500; 1280; 1525/75, F
Schneider, Siegfried; 06.09.33; Frankfurt/O. XVIII; 051800; 1136; V/450/88,
Scholz, Gisela; 15.03.39; HVA; 961500; 1093; 5478/88, F
Schömann, Bodo; 12.12.61; Abt. XI; 941100; 1200; 5312/88,
Schönau, Lothar; 07.08.34; HVA; 961500; 1095; 3127/78, H
Schönau, Ruth; 23.02.33; HVA; 961500; 1095; 3127/78/1, H
Schönberg, Klaus; 27.12.51; Abt. XI; 941100; 9931; 3457/86,
Schönfeld, Dieter; 15.12.58; Abt. XI; 941100; 7570; 2806/89,
Schönfeld, Klaus; 14.09.41; HVA; 961500; 1136; 596/86, F
Schreyer, Harry; 16.01.38; HA I; 970100; 1185; K, 741/89
Schröder, Horst; 12.06.51; Abt. XI; 941100; 4090; 3458/86,
Schröter, Helmut; 14.08.35; KD Rostock; 010040; 2520; 552/75,
Schubert, Harry; 05.07.51; Abt. N; 906540; 1130; 3693/78,
Schubert, Thomas; 10.05.57; HVA; 961500; 1090; 4848/80, F
Schulke, Klaus-Peter; 06.12.41; Abt. N; 906540; 1092; 3953/76,
Schultze, Ralf; 30.04.56; HVA; 961500; 1150; 2306/74, F
Schulze, Alfred; 07.07.37; Abt. N; 906540; 1093; 4324/87,
Schulze, Frank; 09.07.60; HVA; 961500; 1197; 650/75/69,
Schulz, Dorelies; 11.03.49; HVA; 961500; 1136; 4640/89, M
Schulz, Michael; 03.03.65; Abt. N; 906540; 1140; 4909/86,
Schulz, Ronald; 22.08.61; HVA; 961500; 7700; 650/75/68,
Schulz, Udo; 30.03.58; HVA; 961500; 1143; 113/75, F
Schulz, Werner; 09.02.35; Frankfurt/O. XIX; 051900; 1200; V/437/88,
Schumacher, Michael; 13.04.57; Abt. N; 906540; 1090; 3819/79,
Schurz, Günter; 25.03.33; KD Dresden/Stadt; 120040; 8060; XII/2669/87,
Schuster, Bernd; 29.01.42; HVA; 961500; 1140; 61/67, M
Schußmann, Heike; 18.05.58; Abt. XI; 941100; 2000; 1712/89/1,
Schußmann, Klaus; 10.01.60; Abt. XI; 941100; 2000; 1712/89,
Schübel, Andreas; 03.10.61; HVA; 961500; 6301; 650/75/67,
Schütz, Harald; 19.09.32; HVA; 961500; 1153; 2580/65, K
Schwabe, Karl Heinz; 01.07.54; HVA; 961500; 1150; 234/79, J
Schwalbe, Manfred; 04.08.33; Frankfurt/O. XVIII; 051800; 1200; V/454/88,
Schwarzbach, Walter; 01.04.44; HVA; 961500; 1092; 5018/87, F
Schwarze, Lothar; 19.09.35; Dresden XVIII; 121800; 8020; XII/1352/87,
Schwarz, Frank; 19.01.56; Abt. N; 906540; 1093; 5327/80,
Schwarz, Stefan; 26.02.65; HVA; 961500; 1152; 1656/69/2, P
Schwenk, Wilfried; 03.02.55; HVA; 961500; 2620; 650/75/48,
Schwoch, Gerth; 28.06.51; Abt. N; 906540; 1140; 7274/75,
Schwunteck, Harald; 26.08.57; Abt. N; 906540; 8010; 2966/79,
Seckel, Peter; 11.09.60; HVA; 961500; 1143; 3543/81, F
Seckel, Wolfgang; 01.02.39; Karl-Marx-Stadt XX; 142000; 9005; K/3430/89,
Seeger, Regina; 22.03.51; HVA; 961500; 1140; 109/78, J
Seelig, Werner; 11.04.14; HVA; 961500; 1140; 1472/87, F
Seel, Ingolf; 31.07.57; HVA; 961500; 1035; 368/78, F
Seel, Uwe; 06.09.57; HVA; 961500; 1143; 3962/83, N
Seel, Werner; 28.12.32; HVA; 961500; 1142; 3502/61, T
Seibt, Eberhard; 31.08.36; Dresden VII; 120700; 8060; XII/1340/87,
Seibt, Rudolf; 15.09.30; Abt. N; 906540; 1092; 350/73,
Seibt, Siegfried; 24.04.34; Dresden II; 120200; 8021; XII/1338/87,
Seidel, Knut; 02.10.66; Karl-Marx-Stadt VIII; 140800; 9050; 174,
Seidel, Marga; 07.07.36; HVA; 961500; 1092; 2310/88/1, E
Seidel, Matthias; 15.08.59; HVA; 961500; 1017; 491/80, F
Seidel, Michael; 21.07.52; HVA; 961500; 1092; 581/89, U
Seidel, Wolfgang; 24.05.31; HVA; 961500; 1092; 2310/88, E
Seiffert,Reimar; 12.11.29; KD Eisenhüttenstadt; 050045; 1220; V/433/88,
Sellig, Dieter; 11.07.34; Abt. N; 906540; 1020; 7258/75,
Sell, Andreas; 28.06.54; HVA; 961500; 1095; 2311/88, O
Sendsitzky, Peter; 10.09.47; Abt. N; 906540; 1092; 3723/80,
Seyfarth, Stephan; 22.12.60; HVA; 961500; 1040; 4609/80, J
Siegert, Gerhard; 31.05.48; Abt. N; 906540; 1140; 3883/76,
Siegler, Werner; 01.11.52; HVA; 961500; 1400; 1485/87, O
Sievers, Reinhard; 14.10.49; Abt. N; 906540; 1140; 3822/77,
Siggelkow, Wolfgang; 03.11.60; Abt. XI; 941100; 2823; 590/88,
Sikorski, Joachim; 16.01.58; Abt. N; 906540; 1130; 5261/82,
Sikorski, Wolfgang; 27.11.49; Abt. N; 906540; 1156; 2309/73,
Simbrick, Joachim; 21.12.51; Abt. XI; 941100; 1153; 6462/82,
Sitte, Jutta; 06.08.38; HVA; 961500; 1055; 4139/88, M
Sitte, Kurt; 08.09.38; HVA; 961500; 1055; 3009/89, M
Skibinski, Udo; 24.11.42; HVA; 961500; 1020; 326/73, F
Skirde, Udo; 18.01.38; HVA; 961500; 1130; 890/82, T
Smetana, Rüdiger; 18.02.39; BV Berlin XVIII; 151800; 1136; 417/79,
Smiejczak, Jan-Peter; 16.04.64; HVA; 961500; 1156; 2833/87, M
Smolinski, Hans-Joachim; 21.05.53; Abt. N; 906540; 9300; 4070/79,
Sodann, Peter; 23.09.39; HVA; 961500; 7060; 3932/87, M
Sommerfeld, Dirk; 20.06.50; HVA; 961500; 1280; 1555/87, F
Sonnenfeld, Kurt; 25.04.44; Abt. N; 906540; 1017; 2262/87,
Sonntag, Peter; 18.03.55; HVA; 961500; 1092; 2817/80, M
Spangenberg, Heinz; 09.10.56; Abt. XI; 941100; 6550; 6665/82,
Spenke, Günter; 24.01.32; Abt. N; 906540; 1020; 4550/77,
Sperling, Achim; 29.10.56; HVA; 961500; 1130; 4681/79, F
Sprenger, Gisela; 01.06.54; HVA; 961500; 1020; 2633/88, J
Springer, Dieter; 23.06.34; KD Schwedt; 050050; 1330; V/435/88,
Staigies, Artur; 26.10.30; OD KKW Nord; 010050; 2220; 1022/84,
Standke, Michael; 04.11.54; Karl-Marx-Stadt VIII; 140800; 9023; 179,
Stange, Detlef; 20.02.59; Abt. N; 906540; 1115; 5547/88,
Stapff, Dirk; 08.03.63; HVA; 961500; 1090; 2612/84, F
Starick, Hartmuth; 02.08.52; Abt. XI; 941100; 1080; 8509/81,
Städtke, Hartmut; 20.05.56; Abt. N; 906540; 1140; 4029/79,
Steffin, Peter; 09.08.41; Rostock IX; 010900; 2520; 3762/82,
Steger, Ralph; 28.08.65; HVA; 961500; 1180; 2778/76/1, T
Stehr, Gerd; 29.03.58; Abt. XI; 941100; 1200; 3957/83,
Steinert, Joachim; 27.11.36; KD Rügen; 010046; 2355; 4028/86,
Steinmetz, Gerhard; 08.04.48; Abt. XI; 941100; 1017; 1904/72,
Steinmüller, Peter; 07.03.56; HVA; 961500; 1142; 1881/88, A
Stein, Peter; 05.02.61; Dresden XX; 122000; 8019; XII/2405/88,
Stein, Werner; 01.08.37; KD Berlin-Friedrichshain; 150040; 1197; 5579/88,
Stephan, Wolfgang; 29.06.37; KD Dresden/Stadt; 120040; 8060; XII/1358/87,
Sternberger, Dieter; 02.12.34; Abt. N; 906540; 1195; 1474/65/1,
Sternberger, Erika; 08.02.41; Abt. XI; 941100; 1195; 4586/85,
Steuding, Werner; 24.07.42; HA VI; 970600; 1190; K, 1042/87
Steyskal, Richard; 12.11.45; HVA; 961500; 1806; 650/75/53,
Stichler, Christian; 15.06.57; HVA; 961500; 1040; 3462/79, F
Stirzel, Werner; 10.06.34; KD Bautzen; 120042; 8600; XII/1354/87,
Stollmayer, Sabine; 10.03.51; HVA; 961500; 1293; 338/81, J
Stoll, Dietrich; 10.06.36; Rostock XVIII; 011800; 2551; 417/71,
Stopp, Helmar; 01.07.57; Abt. N; 906540; 1123; 5218/84,
Storbeck, Lutz; 30.09.59; HVA; 961500; 1095; 2769/84, F
Stoye, Andre; 28.11.60; HVA; 961500; 1152; 3261/84, F
Straube, Jost; 18.09.58; HVA; 961500; 1058; 3573/82, F
Strauhs, Rüdiger; 05.03.55; Abt. XI; 941100; 1017; 6370/81,
Strähler, Gisela; 28.02.42; Abt. N; 906540; 1281; 5150/88,
Strähler, Siegbert; 05.05.39; Abt. N; 906540; 1281; 5151/88,
Streda, Sylvia; 06.10.54; KD Schwedt; 050050; 1330; V/440/88,
Striegler, Ralf; 14.07.64; Abt. N; 906540; 1142; 1642/85,
Strischek, Erika; 11.11.49; HVA; 961500; 1035; 4270/78/1, N
Strischek, Rudolf; 23.08.45; HVA; 961500; 1035; 4270/78, N
Strobel, Günter; 02.04.36; HA I; 970100; 8312; K, 5809/82,
Stroth, Elke; 28.06.59; Abt. XI; 941100; 2760; 498/86/1,
Stroth, Heiko; 15.06.58; Abt. XI; 941100; 2760; 498/86,
Strutz, Reiner; 01.06.52; HVA; 961500; 2861; 309/76, F
Stuhl, Diethard; 02.03.61; Abt. XI; 941100; 6018; 591/88,
Stüdemann, Robert; 14.11.50; HVA; 961500; 1071; 1870/87, L
Stümer, Hans; 18.03.31; HVA; 961500; 1156; 3032/82, J
Stürmer, Gerlinde; 24.01.60; Abt. N; 906540; 1140; 2015/80,
Suhm, Rüdiger; 24.02.60; Abt. XI; 941100; 2831; 5346/85,
Swienty, Gerald; 25.03.51; Abt. XI; 941100; 1600; 2093/72,
Switalla, Heinz-Joachim; 12.01.46; HVA; 961500; 1017; 2105/73, O
Taubert, Gerald; 05.07.59; Abt. N; 906540; 1130; 5326/80,
Tausend, Klaus; 06.04.47; Abt. XI; 941100; 1142; 6987/75/1,
Teichmeyer, Lutz; 28.10.50; HVA; 961500; 1144; 1603/75, M
Tellbrun, Wolfgang; 09.07.47; Abt. N; 906540; 1140; 5133/76,
Telschow, Lieselotte; 24.03.35; HVA; 961500; 1136; 5181/84, U
Teuter, Maik; 21.12.64; Abt. N; 906540; 1280; 2729/86,
Thale, Klaus; 06.04.44; Abt. N; 906540; 1136; 666/66,
Thäter, Wolfgang; 23.02.45; KD Berlin-Weißensee; 150047; 1140; 1484/82,
Thiele, Horst; 26.09.34; HVA; 961500; 1093; 2481/88, F
Thiele, Ingrid; 04.08.38; HVA; 961500; 1093; 2481/88/1, F
Thiel, Manfred; 12.04.39; Abt. N; 906540; 1093; 9804/61,
Thomas, Heinz; 07.06.42; HVA; 961500; 6902; 3672/88, M
Thomas, Karsten; 18.02.62; HVA; 961500; 1153; 3407/84, F
Thomas, Manfred; 23.03.57; Abt. N; 906540; 1280; 3475/76,
Thomas, Nikita; 18.06.51; HVA; 961500; 1092; 650/75/32,
Thümmel, Elke; 25.12.56; HVA; 961500; 8060; 2528/88/1, F
Thümmel, Volker; 16.01.59; Abt. XI; 941100; 8060; 2528/88,
Thürasch, Carola; 01.11.59; HVA; 961500; 1597; 3849/86, F
Thürasch, Werner; 06.06.50; Abt. XI; 941100; 1597; 4417/84,
Tiede, Lars; 16.02.67; HVA; 961500; 2560; 2767/89, F
Tietsche, Frank; 25.06.55; HVA; 961500; 1141; 361/74, F
Tietz, Gisa; 14.03.47; HVA; 961500; 1092; 2428/79, O.
Tietz, Hans-Joachim; 27.01.47; HVA; 961500; 2000; 514/87, F
Tippmann, Falk; 12.06.53; Karl-Marx-Stadt VIII; 140800; 9050; 169,
Tkatsch, Ingo; 06.11.66; HVA; 961500; 1150; 2143/86, A
Tondock, Heinz; 08.02.30; HVA; 961500; 1156; 1601/75, M
Tornau, Andre; 15.10.65; Schwerin II; 020200; 2755; :
Treder, Gerd; 30.06.40; Rostock , Abt. Hafen; 011969; 2520; 3062/85,
Trenkmann, Ute; 20.09.52; HVA; 961500; 1156; 3904/86/1, F
Trenkmann, Wolfgang; 10.07.51; HVA; 961500; 1156; 3904/86, F
Triegel, Rainer; 17.01.62; Abt. N; 906540; 1034; 5788/82,
Trinks, Hartmut; 24.07.55; Abt. N; 906540; 1150; 3474/76,
Troisch, Andreas; 15.11.57; HVA; 961500; 1020; 2691/80, F
Trommler, Werner; 28.02.51; HVA; 961500; 1156; 957/89, F
Tschiharz, Ute; 03.05.58; HVA; 961500; 3540; 650/75/49/1,
Tschiharz, Wolfgang; 12.06.51; HVA; 961500; 3540; 650/75/49,
Tusche, Hans-Jürgen; 11.07.43; Abt. XI; 941100; 1020; 288/67,
Uher, Edgar; 09.11.52; HVA; 961500; 1142; 175/75, F
Uhlig, Andrea; 01.05.57; HVA; 961500; 1250; 2664/84, J
Uhlig, Gerd; 16.11.46; Abt. N; 906540; 1130; 2114/66,
Uhlig, Gunter; 17.10.52; Karl-Marx-Stadt VIII; 140800; 9044; 163,
Ulbrich, Fritz; 11.12.36; Abt. XI; 941100; 1095; 922/82,
Ullmann, Klaus; 16.10.51; Karl-Marx-Stadt VIII; 140800; 9001; 168,
Unger, Dieter; 29.12.52; HVA; 961500; 1156; 2427/74, F
Unger, Peter; 18.06.56; Abt. N; 906540; 1130; 5095/77,
Unmack, Franz; 01.08.48; HVA; 961500; 1055; 177/79, M
Unseld, Werner; 26.05.28; HVA; 961500; 4500; 18264/60, Y
Unterlauf, Diethard; 05.04.46; HVA; 961500; 9999; 337/77, O
Urban, Hartmut; 08.04.45; Abt. N; 906540; 1162; 1346/68,
Van Rossum, Ralf; 20.03.43; HVA; 961500; 9999; 2856/80, M
Vieweg, Jens-Uwe; 27.12.58; Abt. XI; 941100; 1200; 4706/85,
Vogel, Michael; 25.10.56; Abt. N; 906540; 1093; 1551/80,
Vogler, Reinhard; 15.07.49; HVA; 961500; 5820; 650/75/70,
Vogl, Hansjochen; 09.07.37; HVA; 961500; 1100; 6183/82/1, L
Vogt, Ditmar; 02.05.38; Abt. N; 906540; 1199; 5073/77,
Voigtländer, Christian; 03.12.47; HVA; 961500; 4090; 476/88, A
Voigtländer, Gunter; 25.06.52; HVA; 961500; 1055; 2769/87, F
Voigt, Armin; 22.10.51; Abt. XI; 941100; 1600; 412/77,
Voigt, Helmut; 15.02.50; HVA; 961500; 1017; 2482/88, F
Voigt, Knut; 01.08.48; HVA; 961500; 1156; 1430/85, M
Vollmeyer, Wolfgang; 10.10.50; HA VI; 970600; 1054; K, 4427/87
Vopel, Dieter; 03.01.35; HVA; 961500; 1090; 4083/81, M
Vopel, Elke; 26.03.47; Abt. XI; 941100; 1600; 417/70/2,
Vopel, Hans; 11.08.45; Abt. XI; 941100; 1600; 417/70/1,
Vorberg, Horst; 10.04.53; KD Zwickau; 140061; 9561; K/1436/89,
Voßwinkel, Hartmut; 29.04.50; HVA; 961500; 1140; 353/77, A
Völkel, Alfred; 20.06.31; HVA; 961500; 1113; 18556/60, E
Völkel, Heiko; 23.03.62; HVA; 961500; 1020; 2859/84, U
Völz, Andreas; 29.12.56; Abt. XI; 941100; 9900; 4170/83,
Vtelensky, Rainer; 04.11.44; OD KKW Nord; 010050; 2200; 2678/70,
Wadewitz, Volker; 04.08.57; HVA; 961500; 1034; 2472/79, F
Wagenknecht, Bernd; 20.12.40; HA IX; 990900; 1020; K, 5799/82
Wagner, Michael; 28.08.61; Abt. XI; 941100; 7065; 6932/88,
Wagner, Silke; 28.12.64; HVA; 961500; 7065; 6932/88/1, F
Walter, Isolde; 27.02.48; Rostock VIII; 010800; 1153; 2832/85,
Warncke, Claus-Dieter; 06.04.44; Abt. XI; 941100; 1140; 2496/74,
Warnecke, Siegfried; 27.12.59; Abt. N; 906540; 1142; 1985/79,
Warzel, Franz; 14.05.28; HVA; 961500; 1020; 181/73, M
Wächter, Wolfgang; 28.09.49; HVA; 961500; 9270; 650/75/16,
Wäckerle, Andrej; 03.04.50; HVA; 961500; 1092; 4683/79, M
Wähner, Jürgen; 28.04.56; Abt. N; 906540; 1093; 3473/76,
Weber, Dieter; 16.06.49; HVA; 961500; 1120; 1779/71, F
Weber, Frank; 06.10.50; KD Dresden/Land; 120041; 8270; XII/2668/87,
Weber, Gerd; 02.07.65; HVA; 961500; 1090; 3383/85, Q
Weber, Hans; 11.07.43; HVA; 961500; 1130; 192/73, X
Weber, Rainer; 06.11.45; HVA; 961500; 1110; 6794/82, O
Weber, Ulrich; 09.03.45; Abt. N; 906540; 1280; 1990/69,
Wedel, Kay; 07.03.64; Abt. N; 906540; 1144; 4933/86,
Weichman, Jürgen; 22.02.48; Abt. XI; 941100; 1156; 3212/77,
Weidehase, Jörg; 25.10.54; Abt. N; 906540; 1142; 3392/76,
Weigand, Andre; 09.04.68; HVA; 961500; 7024; 3118/89, S
Weigelt, Lutz; 22.01.56; Abt. N; 906540; 1280; 3391/76,
Weigel, Jens-Friedrich; 28.06.50; Abt. N; 906540; 1291; 7268/75,
Weigold, Dieter; 13.02.41; Abt. N; 906540; 1058; 2901/66,
Weihrauch, Heike; 11.07.59; HVA; 961500; 2050; 650/75/71/1,
Weinert, Gerhard; 06.10.39; KD Grimmen; 010044; 2300; 1608/70,
Weirich, Manfred; 11.06.38; Abt. N; 906540; 1020; 9798/61,
Weller, Jörg; 11.01.63; HVA; 961500; 1092; 1047/82, M
Welzel, Herbert; 30.04.44; Abt. N; 906540; 1281; 7265/75,
Welzel, Jürgen; 12.05.54; KD Greifswald; 010042; 2200; 617/83,
Wenzel, Joachim; 04.01.53; HVA; 961500; 1142; 5693/83, F
Wenzel, Joachim; 10.12.41; Abt. XI; 941100; 1400; 182/70,
Wenzel, Rolf; 13.05.47; Abt. XI; 941100; 1144; 1748/75,
Werner, Dietmar; 12.04.47; Abt. N; 906540; 1017; 376/69,
Werner, Günter; 31.01.37; HVA; 961500; 1160; 4553/85, H
Werner, Hartmut; 19.01.45; Abt. XI; 941100; 1156; 176/72,
Werner, Uwe; 04.08.61; HVA; 961500; 1143; 1577/86, F
Werner, Wolfgang; 17.11.35; HA VI; 970600; 1140; K, 505/87
Werner, Wolfgang; 24.08.56; Abt. N; 906540; 1020; 3884/76,
Wernicke, Günter; 10.07.49; Abt. XI; 941100; 1157; 98/75,
Wessendorf, Volker; 09.12.51; HVA; 961500; 1190; 1478/87, F
Wesser, Andrea; 20.04.64; HVA; 961500; 1100; 661/86, J
Westland, Jürgen; 08.01.51; Abt. XI; 941100; 1156; 2895/77,
Wetzel, Katrin; 29.03.60; HVA; 961500; 1145; 475/78, J
Wiedemann, Günther; 12.07.56; Abt. N; 906540; 1280; 5219/84,
Wiertelorz, Horst; 05.07.49; Abt. N; 906540; 1136; 3892/77,
Wiesel, Bernd; 20.04.58; Abt. N; 906540; 1143; 2129/78,
Wiesner, Erhard; 31.07.36; HVA; 961500; 1140; 3659/64, M
Wilde, Dirk; 24.12.63; Abt. XI; 941100; 2300; :
Wilde, Hans-Heinz; 27.07.32; Rostock XVIII; 011800; 2300; 5749/79,
Wilhelm, Ralf; 15.07.51; HVA; 961500; 1142; 23/77, F
Wilke, Hartmut; 09.05.60; Abt. N; 906540; 1092; 5019/85,
Winderlich, Jens; 10.10.67; HVA; 961500; 1093; 3453/86, O
Winkler, Anton; 22.03.42; HVA; 961500; 1156; 4674/89, M
Winkler, Georg; 07.08.30; Dresden XVIII; 121800; 8250; XII/1347/87,
Winkler, Günter; 30.04.45; HVA; 961500; 1142; 1996/73, A
Winter, Marina; 26.11.60; HVA; 961500; 1130; 4293/84, J
Witte, Dieter; 23.11.37; Abt. N; 906540; 1140; 5039/76,
Wittstock, Manfred; 31.03.32; Rostock VII; 010700; 2500; 936/64,
Witzel, Rainer; 19.04.64; HVA; 961500; 1090; 3581/88, M
Witzmann, Helmar; 06.08.54; Abt. XI; 941100; 1142; 3959/83,
Wokurka, Ulf; 31.10.62; HVA; 961500; 1055; 4228/83, F
Wolfsteller, Roland; 11.11.59; Abt. N; 906540; 2080; 1598/81,
Wolf, Barbara; 11.02.45; HVA; 961500; 1595; 804/83/1, F
Wolf, Jürgen; 15.10.51; Abt. XI; 941100; 1140; 2741/77,
Wolf, Klaus; 30.03.55; Abt. N; 906540; 1095; 2012/78,
Wolf, Matthias; 24.11.60; HVA; 961500; 1090; 3051/89, E
Wolf, Rainer; 22.02.59; Abt. N; 906540; 1130; 1548/80,
Wolf, Ulrich; 13.03.43; HVA; 961500; 1595; 804/83, F
Wolkenstein, Dietrich; 09.03.35; HVA; 961500; 1281; 962/64, M
Wolkenstein, Hubertus; 25.12.63; HVA; 961500; 1142; 6480/82, M
Wolkenstein, Renate; 23.08.33; HVA; 961500; 1281; 962/64/1, M
Worsch, Jürgen; 28.09.48; Abt. XI; 941100; 1140; 339/73,
Worsch, Ursula; 04.02.49; HVA; 961500; 1140; 339/73/2, E
Wotzka, Jörg-Michael; 27.07.47; KD Rostock; 010040; 2520; 3391/89,
Wöller, Klaus; 31.12.30; HVA; 961500; 1020; 2953/77, J
Wunderlich, Uwe; 06.05.60; Abt. N; 906540; 1140; 4037/79,
Würzburg, Gerd; 10.06.57; HVA; 961500; 1157; 421/79, F
Zapke, Helge-Jens; 01.10.67; Abt. N; 906540; 1156; 953/87,
Zech, Jürgen; 16.07.51; HVA; 961500; 1055; 4598/87, F
Zehl, Klaus; 07.01.38; Rostock VI; 010600; 2510; 553/75,
Zeiseweis, Ralf; 11.11.62; BV Berlin XX; 152000; 1140; 3299/88,
Zeiske, Tino; 27.07.61; HVA; 961500; 1143; 2614/84, F
Zellmer, Bernd; 04.12.55; Abt. N; 906540; 1136; 3620/77,
Zentsch, Peter; 28.08.41; Rostock, BKG; 012900; 2500; 2254/84,
Zetzsche, Jürgen; 16.10.52; Abt. N; 906540; 1144; 1753/80,
Ziegler, Frank; 15.11.63; HVA; 961500; 7010; 3341/86, S
Ziesche, Hans-Dieter; 16.01.60; HVA; 961500; 1017; 205/84, F
Ziese, Elvira; 09.10.54; Frankfurt/O. VI; 050600; 1200; V/441/88,
Zilm, Klaus; 03.03.51; HVA; 961500; 1601; 422/87, F
Zimmermann, Bernd; 07.08.39; HVA; 961500; 1080; 458/63, A
Zimmermann, Peter; 09.11.38; Frankfurt/O. XVIII; 051800; 1203; V/445/88,
Zimmermann, Werner; 05.03.46; Dresden VI; 120600; 8080; XII/1165/88,
Zobel, Frank; 03.04.67; HVA; 961500; 2003; 2842/89, J
Zobler, Günter; 06.09.36; HVA; 961500; 1120; 1826/88, A
Zurflüh, Joachim; 24.12.35; Abt. XI; 941100; 1150; 237/70,
Zwetz, Axel; 13.05.38; Abt. N; 906540; 1136; 958/65,
SECRET – U.S.-China Economic and Security Review Commission Analysis of Chinese Investments in the U.S. Economy

U.S.-China Economic and Security Review Commission Analysis of Chinese Investments in the U.S. Economy
- 156 pages
- October 2012
Once hardly noticeable, Chinese investments in U.S. companies are now rising sharply. Cumulative Chinese investments in U.S. companies remain modest compared to those of other major countries. However, a combination of “push and pull” factors are moving China’s annual investment levels closer to levels consistent with China’s current economic stature.
First, the Chinese government has made a conscious decision to diversify its foreign currency assets into hard assets. This has led to the creation of sovereign wealth funds that make portfolio investments in U.S. equities, private firms, and real estate.
Second, the Chinese government has altered its policy guidance toward foreign direct investment (FDI). Whereas it previously encouraged investments almost exclusively toward energy and resource acquisition in developing countries, it now also encourages investments in advanced countries. The government’s goals for these investments include securing energy and mineral resources and acquiring advanced technologies in industries where China wishes to leapfrog existing competitors.
Third, U.S. state governments and, to a lesser extent, the federal government are vigorously trying to attract Chinese greenfield investments in the hope of creating jobs and jump-starting local economies.
Fourth, Chinese investments are being drawn to the United States by the availability of financially weak firms, some of which possess potentially useful technologies for China.
Fifth, some firms that are already competitive with U.S. producers are investing to enhance their U.S. market shares or in response to trade remedies proceedings against unfair trade practices, such as Chinese subsidies.
Economic Benefits
On an aggregate basis, the economic benefits of Chinese investments in the United States have been modest. The precise benefit is difficult to measure due to the convoluted ownership structures of many Chinese investments and the time lags in official U.S. data. Still, based on a combination of official and private data, it is reasonable to conclude that jobs in Chinese-owned companies in the United States increased by 10,000 to 20,000 workers during the past five years.
While hardly significant relative to overall U.S. employment and even to jobs in other countries’ U.S. affiliates, any job creation is welcome given continued slackness in the U.S. labor market.
Chinese FDI in U.S. companies has helped stabilize some financially troubled firms. Portfolio investments by sovereign wealth funds also have helped the economy by solidifying the financial system and providing liquidity to certain property markets.
Chinese investments have occurred in all U.S. regions and in many sectors. According to one private data source, they have been especially prominent since 2007 in the Southwest, Great Lakes, Southeast, and Far West regions, and in the fossil fuels and chemicals, industrial machinery, and information technology industries. According to another private source, as well as government data, the financial sector is also a major recipient of Chinese FDI.
Policy Challenges
These welcome, though still modest, economic benefits are counterbalanced by policy challenges tied to Chinese FDI. First, U.S. affiliates of Chinese companies are not pure market actors and may be driven by state goals, not market forces. China’s outward investments are dominated by state-owned and state-controlled enterprises (SOEs). These entities are potentially disruptive because they frequently respond to policies of the Chinese government, which is the ultimate beneficial owner of U.S affiliates of China’s SOEs. Likewise, the government behaves like an owner, providing overall direction to SOE investments, including encouragement on where to invest, in what industries, and to what ends.
Second, SOEs may have unfair advantages relative to private firms when competing to purchase U.S. assets. SOEs benefit from substantial subsidies in China and their investments in developing countries also receive ample financial support from the national and sub-national governments, state-owned financial institutions and local governments. Government pronouncements out of China suggest that investments in the United States and other advanced countries will also receive ample financial support. This raises the possibility that Chinese largesse could determine market outcomes for purchases of U.S. businesses.
Third, an increased SOE presence may be harmful to the U.S. economy. In China, SOEs are a major force but as a group they are less efficient and profitable than private firms. To the extent that SOEs purchase U.S. companies on the basis of artificial advantages and operate inefficiently, they may not be beneficial to long-term U.S. economic performance.
Fourth, Chinese investments will create tensions related to economic security and national security if they behave in accordance with China’s industrial policy as articulated in the 12th Five Year Plan, government pronouncements, and official investment guidance. China’s current policy guidance directs firms to obtain leapfrog technologies to create national champions in key emerging industries, while investment guidance encourages technology acquisition, energy security, and export facilitation. Based on this juxtaposition, some will conclude that Chinese FDI in the United States is a potential Trojan horse. Indeed, this study describes three investments in new energy products after which production utilizing the desired technology was shifted to China.
Other FindingsU.S. data collection efforts related to FDI are substantial. However, they likely undercount Chinese FDI due to the complicated ownership structures of many Chinese investments. Moreover, although Chinese-owned companies report their data to the U.S. government, many data points are not publically disclosed due to standard U.S. reporting procedures that protect the identities of individual firms. This issue will resolve itself in the coming years if Chinese FDI grows as expected because limits on disclosure will no longer apply.
The United States is relatively open toward FDI, though there are some sectoral restrictions and a national security review undertaken by the Committee on Foreign Investment in the United States (CFIUS). There are a host of laws that subject foreign investors to rules on antitrust, foreign corrupt practices, and trade in arms and sensitive technology products. However, there is no procedure that explicitly considers issues related to economic security, one of the major concerns about Chinese FDI.
Portfolio investments in equities fall under the purview of the Securities and Exchange Commission (SEC). SEC disclosure requirements and practical considerations make it highly unlikely that Chinese SOEs could successfully collude to accumulate significant equity positions in important U.S. firms.
Reverse mergers offer a back door into U.S. capital markets but are not an effective way to acquire important U.S. assets. Indeed, the target of a reverse merger is typically a shell company devoid of meaningful assets. This technique is typically used by private firms that have difficulty accessing capital in China or by provincial SOEs trying to support restructuring efforts in China. There is no indication that any major SOE has used or plans to use this technique to enter the U.S. capital market.
The Chinese legal and regulatory framework for outward FDI requires approvals by three agencies at sub-national and/or national levels. For SOEs, the primary gatekeeper is the State-owned Assets Supervision and Administration Commission (SASAC), though for some investments approval from the State Council is required. The process is widely considered to be cumbersome and is being reformed to facilitate outward FDI.
…
TMZ Video – Anne Hathaway’s Vagina! — Amanda Seyfried Talks
TOP-SECRET-GAO Report: Strengthening Training Efforts to Counter Violent Extremism

Countering Violent Extremism: Additional Actions Could Strengthen Training Efforts
- 70 pages
- October 2012
The Department of Homeland Security (DHS) has identified and is communicating to its components and state and local partners topics that the training on countering violent extremism (CVE) it provides or funds should cover; in contrast, the Department of Justice (DOJ) has not identified what topics should be covered in its CVE-related training. According to a DHS official who leads DHS’s CVE efforts, identifying topics has helped to provide a logical structure for DHS’s CVE-related training efforts. According to DOJ officials, even though they have not specifically identified what topics should be covered in CVE-related training, they understand internally which of the department’s training is CVE-related and contributes either directly or indirectly to the department’s training responsibilities under the CVE national strategy. However, over the course of this review, the department generally relied upon the framework GAO developed for potential CVE-related training topics to determine which of its existing training was CVE-related. Further, because DOJ has not identified CVE-related training topics, DOJ components have had challenges in determining the extent to which their training efforts contribute to DOJ’s responsibilities under the CVE national strategy. In addition, officials who participated in an interagency working group focusing on ensuring CVE-related training quality stated that the group found it challenging to catalogue federal CVE-related training because agencies’ views differed as to what CVE-related training includes.
The majority of state and local participant feedback on training that DHS or DOJ provided or funded and that GAO identified as CVE-related was positive or neutral, but a minority of participants raised concerns about biased, inaccurate, or offensive material. DHS and DOJ collected feedback from 8,424 state and local participants in CVE-related training during fiscal years 2010 and 2011, and 77—less than 1 percent—provided comments that expressed such concerns. According to DHS and DOJ officials, agencies used the feedback to make changes where appropriate. DOJ’s Federal Bureau of Investigation (FBI) and other components generally solicit feedback for more formal, curriculum-based training, but the FBI does not require this for activities such as presentations by guest speakers because the FBI does not consider this to be training. Similarly, DOJ’s United States Attorneys’ Offices (USAO) do not require feedback on presentations and similar efforts. Nevertheless, FBI field offices and USAOs covered about 39 percent (approximately 9,900) of all participants in DOJ CVE-related training during fiscal years 2010 and 2011 through these less formal methods, yet only 4 of 21 FBI field offices and 15 of 39 USAOs chose to solicit feedback on such methods. GAO has previously reported that agencies need to develop systematic evaluation processes in order to obtain accurate information about the benefits of their training. Soliciting feedback for less formal efforts on a more consistent basis could help these agencies ensure their quality.
DOJ and DHS have undertaken reviews and developed guidance to help improve the quality of CVE-related training. For example, in September 2011, the DOJ Deputy Attorney General directed all DOJ components and USAOs to review all of their training materials, including those related to CVE, to ensure they are consistent with DOJ standards. In addition, in October 2011, DHS issued guidance that covers best practices for CVE-related training and informs recipients of DHS grants who use the funding for training involving CVE on how to ensure high-quality training. Since the departments’ reviews and efforts to implement the guidance they have developed are relatively new, it is too soon to determine their effectiveness.
…
Identifying Concerns about CVE-Related Training
To determine what concerns, if any, participants raised about CVE-related training, we reviewed course evaluations completed by participants of CVE-related training offered by DHS I&A, DHS Office for Civil Rights and Civil Liberties, DOJ BJA, and the FBI, and identified complaints or concerns about CVE-related training made formally in writing. We limited our analysis to training that was provided or funded by DHS or DOJ during fiscal years 2010 or 2011 and provided to a state or local entity (e.g., police department, community group, or fusion center). Two analysts independently reviewed 8,424 course evaluations from six training programs to consistently determine which ones included concerns or complaints. The analysts also assessed the nature of the concerns and complaints and assigned each complaint to one of three categories: (1) politically or culturally biased, (2) offensive, or (3) inaccurate. Where there were discrepancies between the analysts, they were resolved through supervisory review.
To identify formally submitted or documented complaints or concerns participants expressed, we asked DHS and DOJ to identify those submitted in writing to DHS or DOJ, or articulated to DHS or DOJ through other means but subsequently documented by the agency, from fiscal years 2010 through 2011. We also conducted keyword searches using LexisNexis and Google to identify concerns that were raised by either individuals or advocacy groups that were submitted in writing to DHS or DOJ. In addition, we interviewed representatives, including leaders, of select advocacy groups that raised concerns about CVE-related training to identify what concerns and complaints, if any, they submitted in writing to DHS or DOJ on behalf of training participants. The advocacy and civil liberties organizations we interviewed included the American Civil Liberties Union, the American-Arab Anti-Discrimination Committee, the Council on American Islamic Relations, and the Muslim Public Affairs Council. We selected these organizations based on their leadership in raising concerns we identified (e.g., by virtue of being the primary signatories) and upon the recommendation of other advocacy groups. These interviews also enabled us to confirm or obtain additional views on the formally documented complaints DHS or DOJ provided. Through these approaches, we identified a total of six letters of complaint regarding 18 alleged incidents of biased CVE and counterterrorism training that DHS or DOJ provided or funded during fiscal years 2010 and 2011. Given that the scope of this review is limited to CVE-related training provided to state and local officials and community members, and not training that is exclusively provided to federal officials, we determined that 7 of the alleged incidents described in five of the letters were relevant to this review. We also interviewed relevant DHS and DOJ officials to obtain their perspectives on the concerns raised in the written complaints and information on any actions agencies took in response to these incidents.
…
Raging Hormones – Full Movie
It’s said that women will take a boy’s mind of his schoolwork, and one young man finds out just how true that is in this frantic comedy. Peter Broadhurst (Topher Hopkins) is a high school senior whose mother Bev (Della Hobby) is bound and determined to see that her boy goes on to college. However, Bev isn’t quite sure how to pay Peter tuition, since her job at the supermarket barely covers food and rent on their space in the trailer park. Sally (Darlene Demko) is a local woman who has had her eye on Peter for some time, and while he’s had little experience with the opposite sex in the past, that quickly changes when Sally and her friend Randy (Rene Orobello) invite Peter over for some less-than-wholesome fun and games. Peter’s introduction to the world of kinky sex proves to be quite revelatory — to the point where Peter not only doesn’t care how college gets paid for, he doesn’t much care if he goes or not. Raging Hormones received the Audience Award as “Best Feature” at the 1999 New York International Independent Film and Video Festival, as well as a jury award as “Best Comedy.”
Cyberattacken der ANONYME STASI-SCHEI**HAUS-FLIEGEN – NOMEN EST OMEN
Liebe Leser,
jetzt helfen den GoMoPa-Stasi-Typen nur noch schwer kriminelle Cyberattacken !
Trotz serienmässiger Vorstrafen wegen Betruges und der zahlreicher anderer LKA, Kripo-,FBI-Ermittlungen werden die organisierten GoMoPa-STASI-Gangster Ihre unwahren Lügen gegen mich nicht löschen und stellen diese immer wieder neu ins Netz: Kein Wunder, denn ich habe die Verbrechen dieser organisierten Kriminellen aufgedeckt und werde dies weiter tun – im Interesse aller anständigen Mitglieder der menschlichen Gesellschaft !
Wie dumm diese STASI-Verbrecher zeigt sich in deren eigenen Texten: “Wie kann ein Magister eine Diplomarbeit schreiben” ? – wie in deren “Shithouse Fly Blog auf mich falsch dargelegt und natürlich haben die STASI-Kriminellen nicht den Hauch eines Beweises für irgendeine Behauptung – wir dagegen jede Menge und auch jede Menge Aktenzeichen gegen sie:
Zum Beispiel:
Klaus Maurischat ( Aktenzeichen Krefeld vom 24. April 2006; AZ: 28 Ls 85/05 – Am 24. April 2006 war die Verhandlung am Amtsgericht Krefeld in der Betrugssache: Mark Vornkahl / Klaus Maurischat ./. Dehnfeld. Aktenzeichen: 28 Ls 85/05, Klaus Maurischat, Lange Straße 38, 27313 Dörverden)
FAKT IST: Klaus Maurischat ist vorbestraft
Aktenzeichen Krefeld vom 24. April 2006; AZ: 28 Ls 85/05 – Am 24. April 2006 war die Verhandlung am Amtsgericht Krefeld in der Betrugssache: Mark Vornkahl / Klaus Maurischat ./. Dehnfeld. Aktenzeichen: 28 Ls 85/05, Klaus Maurischat, Lange Straße 38, 27313 Dörverden)
Sie wollen mich zwingen, mit ihren Lügen meine Berichterstattung gegen sie einzustellen – wie hier ersichtlich:
So wollte der Serienbetrüger Klaus Maurischat uns zwingen, die Berichterstattung über “GoMoPa” zu stoppen
Unser Bildtext: Klaus Maurischat: There is no Place like home
So wollte der Serienbetrüger Klaus Maurischat uns zwingen die Berichterstattung über den “NACHRICHTENDIENST” “GoMoPa” einzustellen
Meine Anmerkung: Sie lesen
den Original-Text mit den Original-Rechtschreibfehlern von Maurischat in chronologischer Reihenfolge von unten nach oben. “Unter den Linden” ist die Regus-Tarnadresse für den untergetauchten Serienbetrüger und Stasi-Ganoven. “SUMA” steht im Sprach-Jargon des “GoMoPa”-”NACHRICHTENDIENSTLERS” für Suchmaschine.
Zitat:
HAHAHAHAHAHAHAHAHAHAHAHAHAHAHA (MEINE ANTWORT)
> Was anderes fällt einem Hilfsschüler auch nicht ein! Wenn ich dich
> schnappe, dann haue ich dir die Fresse ein – mein Lieber! Merk dir
> das gut, du Kinderficker!
>
> Was sagt denn dein Freund Dr. XXX zu deinem handeln, Schwuchtel?
>
> > HAHAHAHAHAHAHAHAHAHAHAHAHAHAHA (MEINE ANTWORT)
> >
> > > Geiles Google Suchergebniss hast du mittlerweile. Das ist sowas von
> > > geil. Am besten ist dieser Beitrag zu Deiner Magisterarbeit, du
> > > Spinner:
> > >
> > > http://scheisshausfliege.wordpress.com/2011/01/29/die-diplomarbeit-des-magisters-bernd-pulch-ein-haufen-scheisse/
> > >
> > > Wenn du nicht aufhörst, wird niemand mehr ein Stück Brot von dir
> > > nehmen. Dein Name ist dan absolut durch. Glaub mir, wir verstehen da
> > > mehr von als du Schwachkopf!
> > >
> > > Im Übrigen kannst du mich stets gern persönlich treffen. Unter den
> > > Linden 21, Berlin – habe immer für dich Feigling Zeit! (TARN-ADRESSE)
> > >
> > > So – und nun überle wann du die Artikel über uns löschen willst,
> > > sonst mache ich die erste Seite der SUMA Ergebnisse mit deinen
> > > Einträgen voll.
Weitere Info zu den Verbrechen der organisierten Kriminellen der STASI “GoMoPa” aus Erich Mielkes Kloake auf http://www.victims-opfer.com
Und natürlich können die STASI-”GoMoPa” auch dumm-dreist fälschen:
http://www.victims-opfer.com/?p=26325
trotz serienmässiger Vorstrafen wegen Betruges und der zahlreicher anderer LKA, Kripo-,FBI-Ermittlungen werden die organisierten GoMoPa-STASI-Gangster Ihre unwahren Lügen gegen mich nicht löschen und stellen diese immer wieder neu ins Netz: Kein Wunder, denn ich habe die Verbrechen dieser organisierten Kriminellen aufgedeckt und werde dies weiter tun – im Interesse aller anständigen Mitglieder der menschlichen Gesellschaft !
Wie dumm diese STASI-Verbrecher zeigt sich in deren eigenen Texten: “Wie kann ein Magister eine Diplomarbeit schreiben” ? – wie in deren “Shithouse Fly Blog auf mich falsch dargelegt und natürlich haben die STASI-Kriminellen nicht den Hauch eines Beweises für irgendeine Behauptung – wir dagegen jede Menge und auch jede Menge Aktenzeichen gegen sie:
Zum Beispiel:
Klaus Maurischat ( Aktenzeichen Krefeld vom 24. April 2006; AZ: 28 Ls 85/05 – Am 24. April 2006 war die Verhandlung am Amtsgericht Krefeld in der Betrugssache: Mark Vornkahl / Klaus Maurischat ./. Dehnfeld. Aktenzeichen: 28 Ls 85/05, Klaus Maurischat, Lange Straße 38, 27313 Dörverden)
FAKT IST: Klaus Maurischat ist vorbestraft
Aktenzeichen Krefeld vom 24. April 2006; AZ: 28 Ls 85/05 – Am 24. April 2006 war die Verhandlung am Amtsgericht Krefeld in der Betrugssache: Mark Vornkahl / Klaus Maurischat ./. Dehnfeld. Aktenzeichen: 28 Ls 85/05, Klaus Maurischat, Lange Straße 38, 27313 Dörverden)
Sie wollen mich zwingen, mit ihren Lügen meine Berichterstattung gegen sie einzustellen – wie hier ersichtlich:
So wollte der Serienbetrüger Klaus Maurischat uns zwingen, die Berichterstattung über “GoMoPa” zu stoppen
Unser Bildtext: Klaus Maurischat: There is no Place like home
So wollte der Serienbetrüger Klaus Maurischat uns zwingen die Berichterstattung über den “NACHRICHTENDIENST” “GoMoPa” einzustellen
Meine Anmerkung: Sie lesen
den Original-Text mit den Original-Rechtschreibfehlern von Maurischat in chronologischer Reihenfolge von unten nach oben. “Unter den Linden” ist die Regus-Tarnadresse für den untergetauchten Serienbetrüger und Stasi-Ganoven. “SUMA” steht im Sprach-Jargon des “GoMoPa”-”NACHRICHTENDIENSTLERS” für Suchmaschine.
Zitat:
HAHAHAHAHAHAHAHAHAHAHAHAHAHAHA (MEINE ANTWORT)
> Was anderes fällt einem Hilfsschüler auch nicht ein! Wenn ich dich
> schnappe, dann haue ich dir die Fresse ein – mein Lieber! Merk dir
> das gut, du Kinderficker!
>
> Was sagt denn dein Freund Dr. XXX zu deinem handeln, Schwuchtel?
>
> > HAHAHAHAHAHAHAHAHAHAHAHAHAHAHA (MEINE ANTWORT)
> >
> > > Geiles Google Suchergebniss hast du mittlerweile. Das ist sowas von
> > > geil. Am besten ist dieser Beitrag zu Deiner Magisterarbeit, du
> > > Spinner:
> > >
> > > http://scheisshausfliege.wordpress.com/2011/01/29/die-diplomarbeit-des-magisters-bernd-pulch-ein-haufen-scheisse/
> > >
> > > Wenn du nicht aufhörst, wird niemand mehr ein Stück Brot von dir
> > > nehmen. Dein Name ist dan absolut durch. Glaub mir, wir verstehen da
> > > mehr von als du Schwachkopf!
> > >
> > > Im Übrigen kannst du mich stets gern persönlich treffen. Unter den
> > > Linden 21, Berlin – habe immer für dich Feigling Zeit! (TARN-ADRESSE)
> > >
> > > So – und nun überle wann du die Artikel über uns löschen willst,
> > > sonst mache ich die erste Seite der SUMA Ergebnisse mit deinen
> > > Einträgen voll.
Weitere Info zu den Verbrechen der organisierten Kriminellen der STASI “GoMoPa” aus Erich Mielkes Kloake auf http://www.victims-opfer.com
Und natürlich können die STASI-”GoMoPa” auch dumm-dreist fälschen:
http://www.victims-opfer.com/?p=26325
Liebe Leser,
trotz serienmässiger Vorstrafen wegen Betruges und der zahlreicher anderer LKA, Kripo-,FBI-Ermittlungen werden die organisierten GoMoPa-STASI-Gangster Ihre unwahren Lügen gegen mich nicht löschen und stellen diese immer wieder neu ins Netz: Kein Wunder, denn ich habe die Verbrechen dieser organisierten Kriminellen aufgedeckt und werde dies weiter tun – im Interesse aller anständigen Mitglieder der menschlichen Gesellschaft !
Wie dumm diese STASI-Verbrecher zeigt sich in deren eigenen Texten: “Wie kann ein Magister eine Diplomarbeit schreiben” ? – wie in deren “Shithouse Fly Blog auf mich falsch dargelegt und natürlich haben die STASI-Kriminellen nicht den Hauch eines Beweises für irgendeine Behauptung – wir dagegen jede Menge und auch jede Menge Aktenzeichen gegen sie:
Zum Beispiel:
Klaus Maurischat ( Aktenzeichen Krefeld vom 24. April 2006; AZ: 28 Ls 85/05 – Am 24. April 2006 war die Verhandlung am Amtsgericht Krefeld in der Betrugssache: Mark Vornkahl / Klaus Maurischat ./. Dehnfeld. Aktenzeichen: 28 Ls 85/05, Klaus Maurischat, Lange Straße 38, 27313 Dörverden)
FAKT IST: Klaus Maurischat ist vorbestraft
Aktenzeichen Krefeld vom 24. April 2006; AZ: 28 Ls 85/05 – Am 24. April 2006 war die Verhandlung am Amtsgericht Krefeld in der Betrugssache: Mark Vornkahl / Klaus Maurischat ./. Dehnfeld. Aktenzeichen: 28 Ls 85/05, Klaus Maurischat, Lange Straße 38, 27313 Dörverden)
Sie wollen mich zwingen, mit ihren Lügen meine Berichterstattung gegen sie einzustellen – wie hier ersichtlich:
So wollte der Serienbetrüger Klaus Maurischat uns zwingen, die Berichterstattung über “GoMoPa” zu stoppen
Unser Bildtext: Klaus Maurischat: There is no Place like home
So wollte der Serienbetrüger Klaus Maurischat uns zwingen die Berichterstattung über den “NACHRICHTENDIENST” “GoMoPa” einzustellen
Meine Anmerkung: Sie lesen
den Original-Text mit den Original-Rechtschreibfehlern von Maurischat in chronologischer Reihenfolge von unten nach oben. “Unter den Linden” ist die Regus-Tarnadresse für den untergetauchten Serienbetrüger und Stasi-Ganoven. “SUMA” steht im Sprach-Jargon des “GoMoPa”-”NACHRICHTENDIENSTLERS” für Suchmaschine.
Zitat:
HAHAHAHAHAHAHAHAHAHAHAHAHAHAHA (MEINE ANTWORT)
> Was anderes fällt einem Hilfsschüler auch nicht ein! Wenn ich dich
> schnappe, dann haue ich dir die Fresse ein – mein Lieber! Merk dir
> das gut, du Kinderficker!
>
> Was sagt denn dein Freund Dr. XXX zu deinem handeln, Schwuchtel?
>
> > HAHAHAHAHAHAHAHAHAHAHAHAHAHAHA (MEINE ANTWORT)
> >
> > > Geiles Google Suchergebniss hast du mittlerweile. Das ist sowas von
> > > geil. Am besten ist dieser Beitrag zu Deiner Magisterarbeit, du
> > > Spinner:
> > >
> > > http://scheisshausfliege.wordpress.com/2011/01/29/die-diplomarbeit-des-magisters-bernd-pulch-ein-haufen-scheisse/
> > >
> > > Wenn du nicht aufhörst, wird niemand mehr ein Stück Brot von dir
> > > nehmen. Dein Name ist dan absolut durch. Glaub mir, wir verstehen da
> > > mehr von als du Schwachkopf!
> > >
> > > Im Übrigen kannst du mich stets gern persönlich treffen. Unter den
> > > Linden 21, Berlin – habe immer für dich Feigling Zeit! (TARN-ADRESSE)
> > >
> > > So – und nun überle wann du die Artikel über uns löschen willst,
> > > sonst mache ich die erste Seite der SUMA Ergebnisse mit deinen
> > > Einträgen voll.
Weitere Info zu den Verbrechen der organisierten Kriminellen der STASI “GoMoPa” aus Erich Mielkes Kloake auf http://www.victims-opfer.com
Und natürlich können die STASI-”GoMoPa” auch dumm-dreist fälschen:
Sports Illustrated Swimsuit Video: Quiana Grant
Unveiled by Cryptome – Erik Prince and Retired FBI
A sends:
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict33.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict34.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict35.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict36.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict37.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict38.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict39.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict40.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict41.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict42.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict43.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict44.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict45.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict46.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict48.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict47.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict51.jpg) |
| Ellen Glasser 8111 San Rafael Dr. Jacksonville, Florida 32217 Home: (904) 619-1956 Cellular: (904) 472-6262OBJECTIVE: Applicant seeks part-time or fulltime position, using expertise in guidance, character education, security, or related area. BACKGROUND: Date of Birth: 02/24/56 EDUCATION: 1977 A.B. Duke University (Psychology) WORK EXPERIENCE: 1977-1982 State of North Carolina, Probation-Parole Officer 1982-2006 Federal Bureau of Investigation (FBI) 2006-2007 Substitute Teacher 2008-2009 Research Assistant, Florida Institute of Education 2009-Present Freelance Security Consultant HIGHLIGHTS, WORK EXPERIENCE: 1986 – 1990 Case Agent, Iran-Contra Investigation 1990 – 1993 Supervisor, Congressional Liaison, National Press Spokesperson 1993 – 1996 Supervisor, Western Washington State 1996 – 1999 Supervisor, Violent Crimes Program 1996 – 1999 Key FBI Agent in numerous high profile bank robbery, homicide, and extortion investigations 1999 – 2006 Foreign Counterintelligence; MISCELLANEOUS: 1975 – 1977 President, Duke Outing Club OTHER: Numerous awards and commendations. Details are available on request. Specialized Training: Crisis Management, Sensitivity & Diversity, Police Instructor, Critical Have passed General Knowledge, Professional Education, and Social Science tests |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict49.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/prince-fbi-retired/pict50.jpg) |
TMZ Video – Lindsay Lohan — Back to the Scene of the Crime!
SECRET – DHS U.S.-Canada Marine Transportation System Terrorist Threat Assessment

United States-Canada Marine Transportation System: Terrorist Threat Remains Low but Risks Persist
- 28 pages
- For Official Use Only
- April 11, 2011
- 3 MB
(//CAN U) This Assessment examines terrorist threats to the Marine Transportation System (MTS) relevant to the U.S. and Canadian maritime borders, and updates unclassified judgments from the 2007 Canadian Integrated Threat Assessment Centre (ITAC) product, “(//CAN U) Terrorist Threat to the Canadian Maritime Sector,” and the 2008 USCG Intelligence Coordination Center product, “(U//FOUO) National Maritime Terrorism Threat Assessment.” The information is provided in support of the activities of the Department and to assist federal, state, and local government counterterrorism and law enforcement officials in effectively deterring, preventing, preempting, or responding to maritime terrorist attacks against the United States and Canada.
(U//FOUO) This document provides an updated baseline for MTS threats to support the activities of the Department and assist other federal, state, and local government agencies and authorities; the private sector; and other entities, both in implementing joint U.S. and Canadian strategies for northern border security. Moreover, it assists the Department and other federal, state, and local government agencies and authorities; the private sector; and other entities in developing priorities for protective and support measures to address existing or emerging threats to the homeland related to maritime border security.
…
(U) Key Findings
(U//FOUO) While passenger vessels and terminals will likely remain potentially attractive targets for terrorist attacks, trends in overseas terrorist attacks and the lack of any reporting on maritime terrorist plots against the U.S.-Canada MTS suggests the threat to the majority of the system is low; violent extremists could attack U.S. and Canadian ferries and similar soft maritime targets with little or no warning.
— (U//FOUO) The capabilities of al-Qa‘ida and its sympathizers to conduct small boat waterborne improvised explosive device (WBIED) attacks against the U.S.-Canada MTS probably remain limited. When compared to other tactics, maritime attacks by al-Qa‘ida or its affiliates are rare and have only occurred in the Middle East and East Asia.† The transferability of this tactic to North America would be problematic given MTS governance and law enforcement that create a less permissive maritime environment.
— (U//FOUO) Terrorists probably would be reluctant to use containerized cargo to smuggle weapons of mass destruction (WMDs) into the United States or Canada because the loss of physical control of a valuable weapon would likely pose an unacceptable intervention risk. Nonetheless, this threat remains a low-probability, high impact scenario. We judge that terrorists would seriously consider other maritime means, such as small boats and bulk cargo shipments, to smuggle any available WMD or to conduct related waterside attacks in the United States or Canada if they had the opportunity. This judgment is primarily based on expert opinions from DHS officials, as well as assertions put forth by the Monterey Institute Center for Nonproliferation Studies and other academic or nongovernmental organizations.
(U//FOUO) Ferries and other passenger vessels remain vulnerable targets for terrorist attack. Although we have no credible reporting that any U.S. or Canadian ferry systems are the target of ongoing terrorist plotting, concerns are elevated because of the focus by al-Qa‘ida and its affiliates on attacking soft targets to cause mass casualties, the growth of internationally inspired and homegrown violent extremist (HVE) threats, and the paucity of preoperational indicators for ferry attacks. Moreover, terrorists might target ferries as a way to compensate for the increasing security measures protecting the aviation sector.
(U//FOUO) Past terrorist successes involving use of toxic industrial chemicals (TICs) in overseas conflicts may encourage attackers to attempt to weaponize large hazardous materials (HAZMAT) shipments moved in the MTS each day. Violent extremists have a limited ability to produce small improvised chemical weapons, but experimentation with these HAZMAT concoctions may eventually result in an evolutionary development of greater attack capabilities.
(U//FOUO) Terrorists and criminals almost certainly will continue their efforts to exploit the MTS to facilitate illegal entry of personnel or other criminal activities. Immigration and mariner document fraud, smuggling, and criminal activities along the waterfront require continuous law enforcement vigilance. Illicit actors may attempt to increase their circumvention of maritime security in North America because of enhanced land border security and air passenger screening.
(U//FOUO) Cyber attacks—regardless of motivation—will continue to represent only a marginal threat to automated ships and port facilities in North America, largely because of the complexity required for a successful attack. A paucity of information regarding such threats remains an enduring intelligence gap. Still, concerns related to maritime supply chain disruption perpetrated by disaffected employees or other insiders—particularly those with system administrator access—are the most frequently voiced by private sector security officials.
…
(U) MTS Overview and Vulnerabilities
(U//FOUO) The U.S.-Canada MTS consists of ocean, coastal, and inland waterways; ports; intermodal connections; vessels; and commercial, military, and recreational users. The system stretches from the Great Lakes-Saint Lawrence Seaway System—also known as the Great Lakes Marine Transportation System (GLMTS) westward—to the Pacific Ocean along the U.S.-Canada border.
— (U) Over 1.5 million passengers arrive in Canada annually, largely from the United States, and Canada’s ports handle a rapidly growing number of cruise ships.
— (U) Besides its ports, Canada also has 10 international ferry terminals, 19 interprovincial terminals, and nearly 300 intraprovincial terminals providing vital links both within and between the provinces. In 2008, Canada’s ferries carried more than 48 million passengers and approximately 18.3 million vehicles.
— (U//FOUO) According to TSA, more than 20,000 passenger vessels—including ferries, casinos, and harbor excursion vessels—carry more than 175 million passengers each year in U.S.-Canada waters.
(U//FOUO) The GLMTS is the heart of the U.S.-Canada MTS. The GLMTS is a vital binational waterborne transportation link for moving goods and people. The system encompasses the Saint Lawrence River and the five Great Lakes, and extends over 2,300 miles, encompassing eight states and two provinces with over 32 million citizens. The region produces 50 percent of all U.S. manufacturing output and two-thirds of Canada’s. This waterway is expected to increase in importance over this decade as both countries seek ways to ease highway and rail congestion, especially along North America’s east and west coasts and the midwest region.
Lady Frankenstein – Full Movie
This lurid but entertaining Italian/Spanish twist on the Frankenstein legend begins with Baron Frankenstein (Joseph Cotten) being assisted in his research by his sultry daughter Tania (Sara Bay). The doctor’s first attempt at a stitched-together creation results in a lumpy, pop-eyed monstrosity with little of the expected respect for its creator. In fact, the monster begins its rampage by murdering the Baron and escaping into the surrounding village. The younger Frankenstein returns from medical school with newly-acquired surgical expertise and a desire to follow in her late father’s footsteps. She soon begins work on a creation of her own by transplanting the brain of her brilliant but deformed assistant Charles (Paul Müller) into the body of a brawny handyman. The result is a handsome and powerful male creature not only capable of destroying the original monster, but virile enough to satisfy his creator’s overwhelming sexual appetites. Tania is apparently quite eager to test the latter, and she does quite frequently, as indicated in the film’s numerous softcore sex scenes. This lengthy romantic interlude is cut short when the first monster returns to finish what he started. Directed by Mel Welles (who B-movie fans will remember as Gravis Mushnik from Roger Corman’s cult classic Little Shop of Horrors), this film plays like a sexually-obsessed version of an early Hammer production.
“PETER EHLERS” “DAS INVESTMENT”: “BUNDESKANZLERIN ANGELA MERKEL UND BUNDESFINANZMINISTER WOLFGANG SCHÄUBLE SIND DEUTSCHLANDS BEKANNTESTE HEHLER!”
“Sind Bundeskanzlerin Angela Merkel und Finanzminister Wolfgang Schäuble Deutschlands bekannteste Hehler ?” „Sicher nein“, werden Sie jetzt sagen und fragen: „Wer behauptet diesen staatszersetzenden Schwachsinn ?“„Fonds & Friends-Herausgeber“ Peter Ehlers (wenn der Name stimmt ?) und der Ost-Berliner NACHRICHTENDIENST” “GoMoPa” bezeichneten die deutsche Bundeskanzlerin Angela Merkel und den deutschen Bundesfinanzminister Wolfgang Schäuble als “kriminelle Hehler” und als Deutschlands „bekannteste Hehler“. Original-Zitat Peter Ehlers (wenn denn wengistens der Name stimmt ?) : „Wolfgang Schäuble, Finanzminister unter Kanzlerin Angela Merkel. Beide sind sich nicht immer einig. Jetzt schon: Sie wollen als Staat, von deutschen Steuergeldern bezahlt, ein neues staatliches Geschäft eröffnen: Hehlerei.Peter Ehlers,Herausgeber DAS INVESTMENTEin Kommentar von Peter Ehlers, Herausgeber DAS INVESTMENTEin durchaus einträgliches Geschäft, das nur einen Haken hat: Es ist illegal. Schäuble hat dafür eine lustige Rechtsauffassung: Er sieht den Deal, den der damalige Finanzminister Peer Steinbrück („das beste Geschäft meines Lebens“) machte, für sich als Rechtfertigung. Frei nach dem billigen Motto: Wenn mein Vorgänger kriminell war, darf ich das ja wohl auch sein.“Das heisst nicht nur Schäuble handelt illegal und kriminell – im ganz grossen Stil, sondern auch die Vorgänger Ex-Bundes-Finanzminister Peer Steinbrück und Ex-Bundeskanzler gerhard Schröder…Und mich bezeichnet Peter Ehlers (wenn denn wengistens der Name stimmt ?) als “Internet-Terroristen”, „Erpresser“, „Gewohnheitsverbrecher“ und „Idioten“, ach ja meinen akademischen Titel Magister Artium täusche ich auch vor, sagen Peter Ehlers und GoMoPa, unisono..
Dies ist bezeichnet für die psychotische Wahnwelt dieser mutmasslich kommunistischen Delinquenten aus dem Osten Deutschlands.
Zum Tatbestand:
Im deutschen Strafrecht ist die Beamtenbeleidigung kein eigener Tatbestand. Ein Beamter ist hier nicht anders gestellt als ein anderer Bürger. Es handelt sich also um eine „normale“ Beleidigung gemäß § 185StGB.
Dennoch gibt es bei der Beleidigung eines Amtsträgers, der nicht zwingend Beamter sein muss, eine verfahrensrechtliche Besonderheit: Während die Straftat grundsätzlich nur auf Antrag des Verletzten verfolgt wird, kann gemäß § 194 Abs. 3 StGB bei Amtsträgern auch der Dienstvorgesetzte des Beleidigten den Strafantrag stellen:
„Ist die Beleidigung gegen einen Amtsträger, einen für den öffentlichen Dienst besonders Verpflichteten oder einen Soldaten der Bundeswehr während der Ausübung seines Dienstes oder in Beziehung auf seinen Dienst begangen, so wird sie auch auf Antrag des Dienstvorgesetzten verfolgt. Richtet sich die Tat gegen eine Behörde oder eine sonstige Stelle, die Aufgaben der öffentlichen Verwaltung wahrnimmt, so wird sie auf Antrag des Behördenleiters oder des Leiters der aufsichtführenden Behörde verfolgt. Dasselbe gilt für Träger von Ämtern und für Behörden der Kirchen und anderen Religionsgesellschaften des öffentlichen Rechts.“
Außerdem wird von der Staatsanwaltschaft in der Regel das öffentliche Interesse an der Strafverfolgung bejaht, so dass es weitaus seltener zur Verweisung auf den Privatklageweg oder zur Einstellung des Verfahrens nach § 153, 153a StPO kommt.
In der Praxis zieht die Beleidigung vor allem von (Polizei-)Beamten meist Geldstrafen nach sich. Bei mehrfach wegen solcher Delikte vorbestraften Personen sind in der Praxis schon kurze Freiheitsstrafen von z. B. 3 Monaten ohne Bewährung vorgekommen.
Fallbeispiel:
Beleidigung von Amtsträgern”Prozesse-Dieter” verurteilt“Prozesse-Dieter”, prozessfreudiger Sozialhilfeempfänger aus Ratingen, ist zu einem Jahr Haft verurteilt worden. Das Amtsgericht in Ratingen bei Düsseldorf sprach den als “König der Kläger” bekannt gewordenen ehemaligen 73-jährigen Sportlehrer wegen 44 Beleidigungen von Amtsträgern wie Beamten, Richtern und Rechtspflegern schuldig.
Per Postkarten hatte sie der Senior mit Fäkalausdrücken überzogen. Das Gericht setzte sich über den psychiatrischen Gutachter hinweg, der den Angeklagten als schuldunfähig eingestuft hatte, weil dieser an einer paranoiden Persönlichkeitsstörung leide.
Dies trifft möglicherweise auch auf die Delinquenten Peter Ehlers/”GoMoPa” zu.Zum Thema Wirecard und “GoMoPa” schreibt das “Handelsblatt:Finanzaufsicht untersucht Kursachterbahn bei Wirecard07.04.2010, 07:01 Uhrexklusiv Die Bundesanstalt für Finanzdienstleistungsaufsicht BaFin hat aufgrund der merkwürdigen Kursturbulenzen der Wirecard-Aktie eine förmliche Untersuchung des Falles eingeleitet. BaFin prüft mögliche Marktmanipulationen nach Falschbericht des Internetdienstes Gomopa. Zwei der Gomopa-Gründer wurden schon 2006 wegen Betrugs verurteilt.von Sönke Iwersen Der Kurs von Wirecard, einem Anbieter für elektronische Zahlungslöungen, ist am am vergangenen Dienstag nach Marktgerüchten heftig eingebrochen. Die BaFin prüft mögliche Manipulationen. Quelle: PressebildFRANKFURT. Die Bundesanstalt für Finanzdienstleistungsaufsicht BaFin hat aufgrund der merkwürdigen Kursturbulenzen der Wirecard-Aktie eine förmliche Untersuchung des Falles eingeleitet. “Wir prüfen, ob es Anhaltspunkte für Marktmanipulation in Aktien der Wirecard AG gibt”, sagte eine BaFin-Sprecherin. Zu Details könne sie sich jedoch nicht äußern.Der Kurs des Münchener Zahlungsabwicklers Wirecard war am vergangenen Dienstag um mehr als 30 Prozent eingebrochen. Am Abend zuvor hatte der Internetdienst Goldman, Morgenstern & Partners (Gomopa) berichtet, der in den USA wegen illegalen Online-Glücksspiels verhaftete Deutsche Michael Schütt habe in einem Geständnis Wirecard schwer belastet. Gomopa bezog sich auf einen Bericht der Lokalzeitung “Naples News”. Schütt habe ausgesagt, er sei bei illegalen Geldgeschäften direkt vom Wirecard-Vorstand beauftragt worden.Das Problem an dem Gomopa-Bericht: Er war falsch. Wie Nachfragen des Handelsblattes ergaben, hat die Reporterin, die für die “Naples News” über Schütt schreibt, Wirecard nie erwähnt. Gomopa reagierte auf Nachfragen zögerlich. Erst löschte der Dienst den Hinweis auf die Lokalzeitung, hielt aber den Vorwurf aufrecht, Schütt habe Wirecard belastet. Danach änderte man den Bericht erneut. Nun hieß es, ein Informant von Gomopa verfüge über die fraglichen Details aus Schütts Geständnis.Dem Handelsblatt liegt inzwischen das amtliche Protokoll von Schütts Geständnis am 23. März vor. Schütt bekennt sich darin schuldig, illegale Geldgeschäfte im Zusammenhang mit Online-Glücksspiel abgewickelt zu haben. Das Wort Wirecard kommt nicht vor. Gomopa hatte zu Wochenbeginn seinen Text erneut geändert und nun behauptet, Schütt belaste “eine Bank”. Auf erneute Nachfragen des Handelsblattes war der Bericht dann ganz verschwunden.Der Kurs von Wirecard hat sich inzwischen fast vollständig erholt. Ein Frankfurter Analyst sagte, für ihn sei klar, dass die Aktie seit Wochen manipuliert werde. Erst verteure sich die Leihe der Aktie, dann komme es zu außergewöhnlichem Handel, danach tauchten plötzlich desaströse Gerüchte auf. Dazu gehöre auch die Anzeige, die vor kurzem bei der Staatsanwaltschaft München einging und Wirecard der Geldwäsche bezichtigt. Es sei offensichtlich, dass Short Seller mit der Wirecard-Aktie Jojo spielen.Mark Vornkahl, einer der Gründer von Gomopa wies den Vorwurf der Kursmanipulation gestern zurück. Man wolle nur die Wahrheit aufdecken. Es ist allerdings nicht das erste Mal, dass Gomopa-Vertreter ins Zwielicht geraten. 2006 wurden Vornkahl und Mitgründer Klaus Maurischat wegen Betrugs an einem Anleger verurteilt. Maurischat gab gestern gegenüber dem Handelsblatt weitere Verurteilungen zu. Es habe sich dabei jedoch nicht um Anlagebetrug gehandelt.http://www.handelsblatt.com/finanzen/boerse-maerkte/boerse-inside/finanzaufsicht-untersucht-kursachterbahn-bei-wirecard/3406252.htmlUND SOLCHE TYPEN VERBREITEN WEITERE ENTEN AUS IRGENDEINEM SADDAM – ERDLOCH WÄHREND IN IHREM “VIRTUELLEN BÜRO” NUR EIN LEERER STUHL STEHT.Ich bin der Erbe unseres Familienbuches und damit das Oberhaupt unserer Familie Pulch. Unsere Familie hat seit Jahrunderten in Deutschland, USA und vielen anderen Ländern, erfolgreiche Unternehmer, Staatssekretäre, Banker, Richter, Anwälte, Politiker und auch Journalisten hervorgebracht. Wir lassen unseren guten Namen nicht durch vorbestrafte Anlagebetrüger, Cybermörder undStasi/NS-Kriminelle verunglimpfen. Deren Taten und Fäkalsprache sprechen für sich und bedürfen keiner ernsthaften Auseinandersetzung.Die bezahlten Betrüger sollen die Kapitalanlage-Verbrecher schützen.Darum geht es im Kern. Wie auch schon unterhttp://www.victims-opfer.comundhttp://sjb-fonds-opfer.com/?page_id=11764klar ersichtlich.Hier ist der Original-Bericht von MeridianCapitalhttp://webcache.googleusercontent.com/search?q=cache:8jmni-h2e_4J:www.maurischatinhaft.wordpress.com/+verhaftung+klaus+maurischat&cd=2&hl=de&ct=clnk&gl=de&source=www.google.deIchwerde die kriminellen Verantwortlichen und ihre kriminellen Helfershelfer bis zur letzten Konsequenz zur Verantwortung ziehen.Magister Bernd PulchPS Ich bedanke mich bei investment-on.com sowie allen anderen Medien für die Möglichkeit, die Dinge gerade zu rücken.
Sports Illustrated Swimsuit Video: Melissa Haro
TMZ – Video – Rihanna Gets Naked… AGAIN!
SECRECY NEWS – NRO RELEASES REDACTED BUDGET BOOK FOR FY 2013
The National Reconnaissance Office (NRO), the U.S. intelligence agency
that is responsible for developing and operating the nation's intelligence
satellites, has released a redacted version of its Congressional Budget
Justification Book for the current fiscal year in response to a Freedom of
Information Act request.
"NRO systems allow users to quickly focus multiple sensors on almost any
point on the globe to respond to emerging crises or operational
requirements and provide persistent, multi-INT coverage," the budget
document says.
"With these capabilities the NRO is an indispensable contributor to
national policymakers, the overall national intelligence effort, and the
war on terrorism and ongoing military operations.... In addition to their
primary intelligence missions, NRO systems increasingly support Homeland
Security requirements."
http://www.fas.org/irp/nro/fy2013cbjb.pdf
During the present budget year, the NRO said it is working "to improve the
responsiveness of existing systems." But it is also "developing new product
types integrating multi-platform, multi-INT, and multi-domain data to
maximize overhead performance and synergistically address the nation's
highest priority issues."
The agency told Congress it has had "successes developing new operational
concepts and sensor data processing tools enabling legacy satellites,
designed against different collection requirements and operating well
beyond their design lives, to effectively address current intelligence
problems."
The large majority of the NRO budget document has been redacted as
classified and was withheld from public disclosure. But meaningful
glimmers of fact or assertion can still be found in what has been released.
For example:
NRO said it has accomplished a "recent 88 percent reduction in
collection-to-analyst dissemination timelines."
NRO expects to complete 15,000 initial and periodic security clearance
reviews during the current fiscal year.
The budget document says the funding request for the NRO Inspector General
was cut by 37% this year. The NRO said this reduction could be managed
although sharp cuts in future budgets were discouraged: "There is no
greater time when an organization is in need of oversight than in times of
significantly decreasing budgets. It is during difficult fiscal decline
that fraud is most likely to occur, when management controls weaken, and
when unintended performance risks take root."
The current NRO research agenda includes efforts "to take advantage of
massive data sets, multiple data sources, and high-speed machine processing
to identify patterns without a priori knowledge or pattern definition; [as
well as] visualization and presentation of patterns for human
interpretation to enable identification of normal and abnormal behaviors to
detect, characterize, and identify elusive targets."
The redacted budget document devotes at least cursory attention to NRO
strategic planning, human resources, administration, facilities,
information technology, and research and development, among other topics.
Actual NRO budget numbers were not disclosed.
PRESIDENTIAL REORGANIZATION AUTHORITY, AND MORE FROM CRS
Noteworthy new and updated reports from the Congressional Research Service
that have not been made available to the public include the following.
Presidential Reorganization Authority: History, Recent Initiatives, and
Options for Congress, December 11, 2012:
http://www.fas.org/sgp/crs/misc/R42852.pdf
Presidential Appointee Positions Requiring Senate Confirmation and
Committees Handling Nominations, November 15, 2012:
http://www.fas.org/sgp/crs/misc/RL30959.pdf
Legal Protections for Subcontractors on Federal Prime Contracts, December
10, 2012:
http://www.fas.org/sgp/crs/misc/R41230.pdf
Loss of Federal Pensions for Members of Congress Convicted of Certain
Offenses, December 10, 2012:
http://www.fas.org/sgp/crs/misc/96-530.pdf
The National Defense Authorization Act for FY2012: Detainee Matters,
December 11, 2012:
http://www.fas.org/sgp/crs/natsec/R42143.pdf
"Gang of Four" Congressional Intelligence Notifications, November 19,
2012:
http://www.fas.org/sgp/crs/intel/R40698.pdf
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
Supercroc – Full Movie
A massive, man-eating crocodile is heading for the city, and it’s up to an elite team of soldiers to prevent the creature from feasting on the unsuspecting urbanites who live there.
Die Killer-Bibel“ Toxdat – die 900 Seiten-Mordstudie von „GoMoPa“-Mastermind und Resch-Protege´ STASI-Oberst Ehrenfried Stelzer
 (DAS INVESTMENT MAGAZIN – DAS ORIGINAL – IMMOBILIEN VERTRAULICH) DAS ORIGINAL) – Insider nennen ES die „Killer-Bibel“ – im Auftrag von Stasi Vizechef Gerhard Neiber verfasste „GoMoPa“-Mastermind, Ehrenfried Stelzer („Professor Mord“) eine präzise Studie, wie man am Besten den perfekten Mord begeht. (DAS INVESTMENT MAGAZIN – DAS ORIGINAL – IMMOBILIEN VERTRAULICH) DAS ORIGINAL) – Insider nennen ES die „Killer-Bibel“ – im Auftrag von Stasi Vizechef Gerhard Neiber verfasste „GoMoPa“-Mastermind, Ehrenfried Stelzer („Professor Mord“) eine präzise Studie, wie man am Besten den perfekten Mord begeht.
http://www.ddrgestapo.de/ Damit haben die Stelzer-Adepten des „NACHRICHTENDIENSTES“ „GoMoPa“ das richtige „Know-how“. Insider verdächtigen „GoMoPa“ des Mordes an Heinz Gerlach (siehe unten). Stasi-Oberst Ehrenfried Stelzer ist ein guter Bekannter, ja sogar „Oberster Anlegerschützer“ bei der DIAS, des „Anlegerschutz-Anwaltes“ Jochen Resch. In der ZDF-Dokumention „Sonderauftrag Mord. Die Geheimnisse der Stasi“Der tödliche Arm der DDR werden die tödlichen Taten der Stasi um den „Ersten Kriminologen der DDR“, Ehrenfried Stelzer, enthüllt. Die Ost-Geheimen setzten falsche Freunde auf ihn an. Peter H. einer von ihnen, begleitete Welsch mit Frau und Kind im Urlaub nach Israel. Dort mischte der Agent Rattengift ins Essen, was Welsch beinahe das Leben kostete. Im sogenannten Bulettenprozess wurde dieser Fall konkret juristisch aufgearbeitet. Und weil dies so ist, entspringt das Thema dieser guten und eindrucksvoll inszenierten ZDF-Dokumentation leider nicht einer blühenden Phantasie. Sondern gehört ins gesamtdeutsche Geschichtsbuch.“ Zuerst nahm der aus der DDR geflohene Fußballlehrer Jörg Berger nur ein Kribbeln in den Zehen wahr, dann in den ganzen Füßen und Händen. Hinzu kamen Fieber, Übelkeit und ein allgemeines Schwächegefühl. Hatte die Stasi ihn vergiftet? “Frisierte” Akten Wie weit ist die Stasi gegangen? Führende Stasi-Offiziere bestreiten bis heute Morde im Auftrag des Ministeriums für Staatssicherheit, der Nachweis ist schwierig. Viele Akten wurden kurz vor der Wende “frisiert”, brisantes Material hektisch vernichtet. Doch die Indizienkette, die Mordabsichten plausibel erscheinen lässt, wird immer dichter. Jörg Berger wird die Wahrheit nie erfahren. Im Juni dieses Jahres ist er an Krebs gestorben. In den Osten entführt Die Stasi experimentierte auch mit Sprengstoff. Für Übungszwecke wird ein Wartburg in die Luft gejagt (nachgestellte Spielszene). Wurde diese Erfahrungen auch bei Anschlägen im Westen “angewandt?” In der Stasiunterlagenbehörde in Berlin finden sich konkrete Mordplanungen: Der geflohene Grenzoffizier Rudi Thurow sollte 1963 mit einem 1.000 Gramm schweren Hammer erschlagen werden, bei einem anderen Fahnenflüchtigen plante die Stasi, einen Sprengsatz unter dem Sattel seines Mopeds zu montieren. Auch heute noch gehen die alten Seilschaften der Stasi, wie der „NACHRICHTENDIENST“ „GoMoPa“ mit Stasi-Methoen vor. Das beweisen auch ihre Droh-Emails gegen unsere Journalisten (siehe berndpulch.org). Informant: Wie die Stasi die Rentenkasse des „Klassenfeindes“ platt machen will Ein Informant der SJB-GoMoPa-Opfer spielte brisantes Material zu: „Wie die Stasi ihre eigene Republikflucht plante und durchführte oder Wie machen wir dem Klassenfeind seine Rentenkasse “platt”. Knabe: Sie muss neu geschrieben werden in Hinblick auf die Aktivitäten des DDR-Staatssicherheitsdienstes. Die Zeitgeschichtsforschung hat diese konspirative Dimension westdeutscher Vergangenheit bisher mit Schweigen übergangen. Doch egal, ob es um Politiker von FDP oder Grünen, die Friedensbewegung oder die 68er- Studentenrevolte geht – die Stasi hatte immer einen Fuß in der Tür. FOCUS: War die Arbeit des MfS tatsächlich so effektiv? Ihr Kollege Helmut Müller-Enbergs konstatiert, Aufwand und Ergebnis der Stasi-Spionage hätten nicht selten in krassem Missverhältnis gestanden. Knabe: Sicher hat es seitens der Stasi auch Wunschdenken über ihren Einfluss im Westen gegeben. Aber die Intensität der Unterwanderung ist erschreckend. Acht Bundestagsabgeordnete hatten MfS-Kontakte. Die Liste der als Informanten geführten Politiker reicht vom Berliner SDS-Sekretär Walter Barthel bis zum deutschlandpolitischen Sprecher der Grünen, Dirk Schneider. Mit ihrer Hilfe hatte es die DDR-Führung bis 1989 geschafft, im demokratischen Nachbarstaat zunehmend Akzeptanz zu finden bis hin zur Quasi-Anerkennung durch die Regierung.“ Zitatende Stattdessen gründet Stelzer den „NACHRICHTENDIENST“ „GoMoPa“, so der Insider Deep Throat. Jahrelang halten die Ermittler wie auch die Opfer die Gruppe um das „Aushängeschild“, den tatsächlich verurteilten Serienstraftäter nur für eine „normale“ Kriminellen-Bande. Die jüngsten Aufdeckungen zeigen indes, dass hier eine organisierte Gruppe die Wirtschaft unterwanderte. So traute sich in 2009 auch „GoMoPa“-Mastermind, Stasi-Obrist Ehrenfried Stelzer wieder in die Öffentlichkeit. Unser Rechtsstaat lässt es sogar zu, dass Stasi-Angehörige zur Desinformation siegessicher Siegfried Sievert oder Siegfried Siewert – das ist frei nach Hamlett hier die Dioxin-Frage. Ersterer ist der ehemalige Stasi-Agent und Dioxin-Nahrungsketten-Vergifter – letzterer Name das „Pseudonym“ von Klaus-Dieter Maurischat, dem serienmässig vorbestraften „NACHTRICHTENDIENST“-„GoMoPa“-Betrüge und Erpresser. Das Stasi-Problem war mit dem Zusammenbruch der DDR keineswegs beendet. Ehemalige Stasi-Mitarbeiter gelangten nach der Wende in höchste Positionen. In Brandenburg hatten es sogar mehrere ehemalige Stasi-Mitarbeiter bis in die aktuelle rot-rote Landesregierung geschafft, um dort die Regierung zu übernehmen. Auch in Sachsen-Anhalt könnten nach der Landtagswahl ehemalige Stasi-Mitarbeiter in die Regierung gelangen. Und auch in der Wirtschaft sind viele Stasi-Mitarbeiter in hohe Positionen gelangt. So auch der Herr Sievert. Doch was bezweckte dieser tatsächlich mit der Dioxinvergiftung? Handelte er wirklich aus Profitgier, oder war die bundesweite Vergiftung eine verspätete Rache der Stasi gegen den ehemaligen Klassenfeind? Auf Antrag von BILD gab die zuständige Birthler-Behörde die Unterlagen “Hiermit bescheinige ich den Erhalt von 100 Mark für geleistete Skrupel zeigte Sievert laut Stasi-Akte keine. Ein Führungsoffizier In der BRD ermitteln Staatsanwälte in 21 Fällen gegen Stasi-Offiziere wegen versuchten Mordes oder Verabredung zum Mord. Heinrich S. ist der einzige West-IM (“Rennfahrer”), der in diesem Zusammenhang verurteilt wird. Viereinhalb Jahre Haft kassiert er für die Beteiligung an den Stasi-Operationen “Fürst” und “Parasit”. Bei denen gibt Ost-Berlin die Aufträge, Grenzprovokateur Siegfried Sch. und Fluchthelfer Julius L. zu “liquidieren”. Beide Opfer überleben. Siegfried Sch., weil beim Überfall auf ihn (nach Karateschlägen) den Attentätern das Magazin aus der Pistole fällt. Er kann flüchten, gilt danach als verschwunden. Julius L. kommt davon, weil alle 19 Versuche eines angeheuerten Verbrechers (IM “Karate”) scheitern, eine Bombe an seinem Auto anzubringen. Mal findet er den Wagen nicht, mal gibt es zu viele Zeugen, mal fährt das Auto zu schnell weg. Der Sprengstoff stammt aus Ost-Berlin. Nach dem Verfahren gegen ihn verlässt IM “Karate” den Gerichtssaal als unschuldiger und freier Mann. Die Hauptangeklagten bleiben dem Prozessbeginn gleich fern. Mielke-Stellvertreter Gerhard Neiber hat es am Herzen. Stasi-General Albert Schubert leidet unter Bluthochdruck. Die Atteste sind unterschrieben von Ärzten aus Wandlitz. Bis heute wird darüber gestritten, wie der Begriff “Liquidierung” im Stasi-Jargon zu verstehen ist. Vor Gerichten behaupten fast alle MfS-Mitarbeiter, es habe in ihrem Sprachgebrauch generell nichts mit “töten” zu tun. Eher mit “unschädlich” machen. Der Führungsoffizier von “Rennfahrer” dagegen räumt ein, dass Siegfried Sch. und Julius L. “beseitigt” werden sollten. So sieht es auch der West-IM, dem Ost-Berlin insgesamt 374 000 Mark zahlt. Er habe die Weisung eindeutig als “Mord-Auftrag” verstanden. Ihn aber nie ausführen wollen. Angeblich will er die Opfer nur erschrecken… „Das Ministerium für Staatssicherheit hatte über 100 Spitzel auf die Unterwanderung westdeutscher Menschenrechtsorganisationen angesetzt. Ihre Akten liegen fast vollständig im Archiv der Gauck-Behörde. Die Inoffiziellen Mitarbeiter (IM) wurden noch 1989 aus der DDR in den Westen geschickt. Weite Bereiche der bundesdeutschen Gesellschaft wurden von der Stasi unterwandert. Ihre “Quellen” in Politik, Militär, Wirtschaft, Medien oder Wissenschaft … Die Historikerkommission zur Untersuchung der Unterwanderung der West-Berliner Polizei durch die Stasi wird voraussichtlich im Sommer ihre Ergebnisse präsentieren. Erst wenn Resultate vorlägen, könne darüber entschieden werden, ob es weitere Untersuchungen oder Überprüfungen geben müsse, sagte Polizeipräsident Dieter Glietsch. Der 27. April 1972. Willy Brandt ist wegen seiner Friedens-Politik (Entspannung, Öffnung) heftig umstritten. Abgeordnete der sozial-liberalen Koalition laufen über zu den Fraktionen von CDU und CSU. Rechnerisch hat die Union im Bundestag jetzt eine Mehrheit. Es kommt zum Misstrauensvotum gegen Brandt. Die CDU will ihren Fraktionsvorsitzenden Rainer Barzel zum Kanzler machen. Es schlägt eine der erfolgreichsten Stunden der Stasi. Ost-Berlin dreht am Rad der Geschichte, besticht die Abgeordneten Julius Steiner (CDU, IM “Theodor”) und Leo Wagner (CSU, IM “Löwe”). Beide kassieren jeweils 50 000 Mark. In Bonn gibt es den Eklat. Bei der geheimen Abstimmung bekommt Barzel nicht die erforderliche Mehrheit. Nur 247 Abgeordnete stimmen für ihn. Zwei weniger als erforderlich. Brandt bleibt Bundeskanzler. Und setzt seine Ost-Politik fort, für die er 1971 den Friedensnobelpreis bekam. Zwei Wochen später ist SED-Generalsekretär Honecker zu Gast beim Staatsbesuch in Rumänien. Er sagt stolz: “Wir haben noch kurz vor Behandlung des Misstrauensvotums bestimmte Maßnahmen getroffen, um die Regierung Brandt zu stützen. Und: “Es ist also die groteske Lage eingetreten, dass wir als die stärksten Helfer für die Stabilisierung von Brandt auftreten mussten.” Dann: “Wir haben das getan, weil diese Regierung selbstverständlich für uns alle angenehmer ist als eine Regierung unter Leitung von Barzel und Franz Josef Strauß.” 1974 tritt Brandt zurück. Die Bundesrepublik wird erschüttert von ihrem größten Spionagefall. Im Kanzleramt enttarnen Nachrichtendienste Top-Agent Günter Guillaume (47). Er ist Brandts persönlicher Referent, viel mit ihm auf Reisen (auch privat), hat Zugang zu Geheimakten, nimmt an Gesprächen im engen Kreis der politischen Macht teil. Guillaume soll Brandt zudem mit Frauen bekannt gemacht haben. Ermittler vermuten, dass Tonbänder von Brandts Liebesnächten in Ost-Berlin gelandet sind: “Der Kanzler ist erpressbar.” Brandt streitet das ab. Seit 1950 steht Hauptmann Guillaume in Diensten der Stasi. Er stammt aus Berlin. Bei der Festnahme sagt er forsch: “Ich bin Bürger der DDR und ihr Offizier. Respektieren Sie das!” Aufgeflogen ist Guillaume durch 17 Jahre alte Kurzwellen-Funksprüche aus Ost-Berlin, die der BND dechiffriert. Darin gratuliert das MfS seinem Spion zum Geburtstag, sendet Glückwünsche zur Geburt des Sohnes. Wegen Landesverrats verurteilt ihn das Gericht zu 13 Jahren, seine Ehefrau Christel (Sekretärin) zu 8 Jahren Knast. 1981 wird das Spionage-Paar ausgetauscht. Es kehrt nach Ost-Berlin zurück. Wie viele “IM” im Bundestag sitzen, ist unklar. In den “Rosenholz”-Dateien stehen für die Zeit zwischen 1969 und 1972 die Namen von 43 Abgeordneten. Viele sind ahnungslos. West-IM aus ihrem Umfeld “schöpfen” sie ab. Lediglich drei Abgeordnete sind laut Birthler-Behörde von 1969 bis 1972 “willentlich und wissentlich” Stasi-Informanten. Untersuchungen über andere Legislaturperioden gibt es nicht. Die Große Koalition lehnt 2007 ab, entsprechende Forschungsaufträge zu erteilen. Bekannt ist, dass Gerhard Fläming (SPD, lieferte tausend Dokumente) und Karl Wienand (SPD) Spitzel sind. Zu den drei IM-Abgeordneten gehört William Borm, von 1960 bis 1969 Berliner FDP-Landesvorsitzender. Er sitzt ab 1950 wegen “Kriegs- und Boykotthetze” in DDR-Haft, wird nach seiner Verpflichtungserklärung (IM “Olaf”) entlassen. Borm trifft sich regelmäßig mit Markus Wolf. Bei den Verabredungen fließt Krim-Sekt. Wolfs Leute schreiben Borms Bundestagsreden. In seinem Bonner Büro sitzt als Sekretärin Top-Agentin Johanna O. (“Sonja Lüneburg”). Sogar Borms Sekretär stellt das MfS. 1979 fordert der FDP-Mann die Anerkennung der DDR-Staatsbürgerschaft, er schimpft gegen die Nato, setzt sich für die Friedensbewegung ein. Vor seinem Tod 1987 wird Borm nicht enttarnt, bekommt das Bundesverdienstkreuz, ein Ehrengrab in Zehlendorf. In West-Berlin backt die Stasi kleinere Brötchen als in Bonn. Bis auf Dirk Schneider (IM “Ludwig”), der von 1983 bis 1985 aus Berlin für die Grünen in den Bundestag rotiert und den späteren Außenminister Joschka Fischer ausschnüffelt, gibt es keine wirklich spektakulären Fälle. Im Abgeordnetenhaus lauschen die SPD-Abgeordneten Ursula L. (IM “Purzel”) und Bodo T. (IM “Hans”) fürs MfS. Bodo T. zerbricht daran. Vorm Prozess 1995 begeht er Selbstmord. Auf die CDU und ihren Regierenden Eberhard Diepgen setzt die Stasi mehr als 80 Agenten an. Einer ist Bauunternehmer und IM “Delphin”, sitzt für die CDU in der BVV Neukölln (Diepgens Wahlkreis). “Delphin” plaudert in Ost-Berlin über taktische Einzelheiten im Wahlkampf, Diepgens Kritik an der Bundesregierung, die Vorstellungen des Regierenden über ein Treffen mit Erich Honecker. Nach der Wende wird das Spionage-Verfahren gegen IM “Delphin” gegen die Zahlung von 12 000 Mark eingestellt. SjB-GoMoPa-Opfer: Fakten und Fragen zu Heinz Gerlach & Peter Ehlers Heinz Friedrich, Sprecher der SJB-GoMoPa-Opfer, analysiert: „Fakt 1: Peter Ehlers war auf Heinz Gerlachs Beerdigung. Fakt 2: Wenige Monate vor Gerlachs Tod veranstaltete Ehlers mit Gerlach zusammen ein Seminar. Ein Novum. Fakt 3: Peter Ehlers hatte freien Zugang zu Heinz Gerlach. Fakt 5: Mit zwei Artikel entstand das Märchen von der Blutvergiftung von Heinz Gerlach: Mit den Methoden der Stasi arbeitet auch der äussert dubiose „Finanz- Als Heinz Gerlach dann die Zusammenhänge zwischen der mutmasslichen wie man bei Durchsicht der Seite http://www.akte-heinz-gerlach.info unschwer Diese Internet-Operations-Muster – so die SJB-Opfer – habe „Zum Tode von Heinz Gerlach » aus Uetersen (Kreis Pinneberg). Gemeint ist Siegfried Sievert, 58 dioxinverseuchte Industriefett sei versehentlich in die Produktion aufmerksam. Sie beobachtet sein „dekadentes Aussehen“, seine Etwa 150 000 Tonnen belastetes Futter könnten so in die Nahrungskette Fuchsgruber ist – nach Entgegennahme des Vorabhonorars – Opfer: „Nach Immovation und Estavis versucht GoMoPa nun DKB zu erpressen- GoMoPa-Hintermann RA Resch Die SJB-GoMoPa-Opfer behaupten: „Der abgetauchte Berliner Zweig der GoMoPa-Gangster will nun zusammen mit ihrem Hausanwalt RA Jochen Resch, Berlin, die DKB erpressen – so wie sie dies vorher mit Immovation versucht haben. Ein Insider: „Was glauben Sie, wer auf die Idee kam, die ominöse Briefkastenfirm Goldman, Morgenstern & Partner LLC, „GoMoPa“, einen angeblichen Zusammenschluss jüdischer Anwälte in den USA zu gründen und wer die vielen Anwälte wie RA Albrecht Saß, Hamburg, OLG Richter a.D. Matthias Schillo, Potsdam, und RA Thomas Schulte, Berlin, zur Reputationsaufbesserung aufbot ? Deep Throat: „Wie die CYBER-STASI anständige Bürger und Unternehmen per Rufmord in den gesundheitlichen und geschäftlichen RUIN treibt“ Deep Throat, Berlin, berichtet: „Das Mastermind hinter allen „GoMoPa“-Aktionen ist der „Anlegerschutzanwalt“ Jochen Resch. Resch hat auch Meridian Capital erpresst, schickt aber immer die Handlanger wie Klaus-Dieter Maurischat vor. Nur vorbestrafte Serienbetrüger wie Maurischat lassen sich zu solchen Straftaten instrumentalisieren. Er hat auch den Terminus „Cyberstalker“ aus den USA importiert. Maurischat kann das aufgrund mangelnder Bildung sogar nicht einmal korrekt schreiben.“ Der Selbstmord der populären Schauspielerin Choi Jin Sil entwickelt sich in Südkorea zu einer nationalen Affäre mit weitreichenden Konsequenzen. Diese betreffen vor allem das Internet, das von den südkoreanischen Behörden als Ursache des tragischen Ereignisses genannt wird. Wie die Zeitung International Herald Tribune berichtet, habe die Polizei mittlerweile nachweisen können, dass die Verzweiflungstat des Filmstars eine direkte Reaktion auf im Web verbreitete rufschädigende Gerüchte gewesen sei. Kurz nach dem Bekanntwerden des näheren Tathintergrunds brach im Parlament Südkoreas ein heftiger Streit über die bestehenden Internetregulierungsmaßnahmen aus. Während die Regierung den aktuellen Todesfall zum Anlass nimmt, um eine verschärfte Kontrolle des Internets zu fordern, lehnt die Opposition dies mit der Begründung ab, dass die bestehenden Gesetze gegen sogenanntes “Cybermobbing” völlig ausreichend seien. Die Cybermord-Opfer Lothar Berresheim, Dipl.-Ing. Paul Bösel, Andreas Decker, Herbert Ernst Meridian Capital, Bernd Pulch und Martin Sachs, klären über den kriminellen und serienmässig vorbestraften Ex-Gefängnissinsassen Klaus-Dieter Maurischat und seine GoMoPa-Erpresserbande auf: Deep Throat: „GoMoPa“ & Hintermänner: Erpressung, Einschüchterung, Rufmord und Mord „Erpressung, Einschüchterung, Rufmord und Mord“, sind wohl die täglichen Waffen des ominösen „NACHRICHTENDIENSTES“ „GoMoPa“ beichtet Deep Throat, ein Ex-Mitarbeiter des „NACHRICHTENDIENSTES“ „GoMoPa“. Der „NACHRICHTENDIENST“ „GoMoPa“: Neuer Angriff auf die Immobilienbranche – Ermittlungen der KRIPO: ST/0148943/2011 Trotz zahlreicher Strafanzeigen, serienmässiger Vorstrafen und der mutmasslichen Verwicklung in mindestens einen hochkarätigen Mordfall erdreistet sich der „NACHRICHTENDIENST“ „GoMoPa“ die Immobilienzene uter Druck setzen zu wollen. Wer waren wohl die oder Informant(en)? Dioxin-Täter: Die tödlichen Waffen des STASI „NACHRICHTENDIENSTES“: Der perfekte Mord Siegfried Sievert oder Siegfried Siewert – das ist frei nach Hamlett hier die Dioxin-Frage. Ersterer ist der ehemalige Stasi-Agent und Dioxin-Nahrungsketten-Vergifter – letzterer Name das „Pseudonym“ von Klaus-Dieter Maurischat, dem serienmässig vorbestraften „NACHTRICHTENDIENST“-„GoMoPa“-Betrüge und Erpresser. Der beinahe perfekte Dioxin-Mord So aber kam alles anders, als es um ein Haar hätte sein können. Viktor Juschtschenko, der liberale, westlich orientierte Präsidentschaft der Ukraine, ist zwar – für alle Welt sichtbar – entstellt und wird wohl noch jahrelang an den Folgen seiner Dioxinvergiftung zu leiden haben, aber er lebt. Aber es hätte um ein Haar anders kommen können. 5. September 2004, Geheimdienst Michael Zimpfer, seit drei Jahren Präsident des Aufsichtsrats des Rudolfinerhauses sowie Vorstand der Universitätsklinik für Anästhesie und Allgemeine Intensivmedizin, der bei Juschtschenkos Aufnahme anwesend war, berichtet, die Ärzte hätten sich zunächst nur auf eine „deskriptive Diagnostik“ beschränken müssen – so ungewöhnlich war das Krankheitsgeschehen. Demnach wurde Juschtschenko „in einem kritischen, aber nicht sterbenden Zustand“ eingeliefert. Die Erstdiagnose lautete auf „akutes Abdomen“ (akuter Bauch). Zunächst deutete nichts auf eine Vergiftung oder gar eine Dioxinvergiftung hin, wie sie etwa durch eine charakteristische Chlorakneerkrankung der Gesichtshaut erkennbar wird. Wohl zeigten sich im Gesicht des Patienten Hautrötungen, die von zwei hinzugezogenen Hautärzten zunächst als Rosacea, eine chronisch verlaufende Hauterkrankung unbekannter, vermutlich genetischer Ursache, gedeutet wurden. Weiters diagnostizierten die Mediziner einen Herpes zoster (Gürtelrose), eine leichte Gesichtslähmung sowie eine Ohrenentzündung. 11. September, Blutflecken im Darm Denn die Pankreatitis birgt in sich die Gefahr, dass sich die Entzündung „selbst propagiert“ und das Organ „verrückt spielt“, wie es Intensivmediziner Zimpfer formuliert. In solchen Fällen sondert die Bauchspeicheldrüse nicht mehr die üblichen Verdauungssekrete in den Darm ab, um den Speisebrei in seine Bestandteile aufzulösen, sondern beginnt, mittels gewebszersetzender Stoffe, seine Umgebung zu verdauen. Außerdem bestand auch Gefahr, dass die Leberfunktion zusammenbricht – für das behandelnde Ärzteteam ein Albtraum. Die Situation war umso dramatischer, als die Ursache von Juschtschenkos Erkrankung nach wie vor unbekannt war. Die Mediziner konnten vorerst nur versuchen, bekannte Erkrankungen nach und nach auszuschließen, wie etwa eine Fisch- oder eine andere Lebensmittelvergiftung, eine Immunerkrankung oder eine bakterielle oder virale Infektion. Aber im Blut fand sich bis auf den Herpes zoster keinerlei Erreger, auch ließ sich kein „Morbus“, also keinerlei Kombinationserkrankung, finden. Die Ärzte suchten, fanden aber nichts. Sie verabreichten dem Patienten Infusionen und organstabilisierende Medikamente. Aber damit war ihre Kunst auch schon zu Ende. 18. September, kritische Leberwerte 2. Oktober, unerträgliche Schmerzen Heute wissen sie, warum: Zwar gilt der Chefchemiker des Instituts für Gerichtsmedizin, Walter Vykudilik, allseits als hervorragender Detektiv mit der Pipette. (Er konnte unter anderem in den neunziger Jahren die von der „schwarzen Witwe“ Elfriede Blauensteiner mithilfe des Blutzuckermittels Euglucon begangenen Giftmorde an drei Pensionisten aufklären.) Aber es fehlen am gerichtsmedizinischen Institut jene Präzisionsgeräte, die man benötigt, um auch eine Dioxinvergiftung zu entdecken. „Man kann so eine Analyse ohne die entsprechenden Geräte, ohne die personellen und strukturellen Voraussetzungen nicht machen, das geht nicht“, sagt Vykudilik. 7. Oktober, ärztlicher Hilferuf Nach neuerlichem zehntägigem Aufenthalt im Rudolfinerhaus flog Juschtschenko, begleitet von Zimpfer und einer Wiener Ärztin, am 10. Oktober über Lemberg, wo Juschtschenko eine Wahlveranstaltung abhielt, nach Kiew, um sich dort in weitere ärztliche Behandlung zu begeben. Die Ärztin blieb als Beratungs- und Auskunftsperson in Kiew zurück. Nun behauptete der vom Westen unterstützte Juschtschenko auch im Parlament in Kiew, er sei von Regierungskreisen vergiftet worden, was nicht ohne Wirkung auf die öffentliche Meinung in der Ukraine blieb: Der Kandidat der Opposition legte in allen Umfragen deutlich zu und schien gute Aussichten zu haben, nach dem ersten Wahlgang am 31. Oktober in die für 20. November angesetzte Stichwahl zu kommen und seinen Hauptrivalen Viktor Janukowitsch, den Kandidaten des Regierungslagers, zu schlagen. Zum Beleg seiner Behauptung legte Juschtschenko jenes ärztliche Schreiben vor, das zu den erwähnten Erschütterungen unter den Ärzten des Rudolfinerhauses führte. 22. November, Dioxin-Verdacht Er verfüge zwar über keine toxikologische Evidenz zur Untermauerung seines Verdachts, aber seine Diagnose beziehe sich auf diese Bilder sowie auf den medizinischen Bericht, wonach Juschtschenko zwei Monate zuvor völlig gesund gewesen wäre. „Es gibt nur sehr wenige medizinische Konditionen, die innerhalb so kurzer Zeit zu dieser Art Veränderung führen können“, sagte Henry, der es für durchaus möglich hielt, dass eine einzige hohe Dosis Dioxin, versteckt im Essen, genügen würde, um jenen Effekt zu erzeugen, wie er nun in Juschtschenkos Gesicht zu sehen war. 11. Dezember, Dioxin-Bombe Unterdessen hatten die Ärzte an Juschtschenko appelliert, wieder zu kommen, um sich weiteren Untersuchungen zu unterziehen. Schon zuvor wurden ihm in Kiew neuerlich Blutproben abgenommen und von einem bei der Prozedur anwesenden Zeugen in einer eidesstattlichen Erklärung als von Juschtschenko stammend bestätigt. Diese Proben gingen an mehrere Labors, darunter an ein EU-Referenzlabor in Amsterdam. Am Samstag, den 11. Dezember platzte dann die Bombe: In einer internationalen Pressekonferenz gab das behandelnde Ärzteteam in Juschtschenkos Gegenwart die Analyse des Labors in Amsterdam bekannt: Demnach enthielten die Blutproben derart hohe Dioxinwerte, dass eine exakte Bestimmung vorerst unmöglich war. In der Vorwoche bestätigten zwei weitere EU-Referenzlabors, Juschtschenkos Blutproben würden Dioxinwerte zeigen, die etliche tausend Mal höher liegen als die im menschlichen Blut vorhandenen Normalwerte. Allerdings muss man bedenken, dass Juschtschenko eine außergewöhnliche, einmalige hohe Dosis Dioxin verabreicht bekam (50.000fach höher) und nicht über Jahre hinweg kein, gefährliche Dosen. Juschtschenkos Dioxinabbau darf daher nicht als Norm angesehen werden. Sein Körper ist trotz der ansehnlichen “Abbaukurve” nach wie vor verseucht. R.F., Berlin, ein intimer Kenner der RA-Kanzlei Resch und des „NACHRICHTENDIENSTES“ „GoMoPa“ legt nach: „Fast alle Texte der Webseite „GoMoPa“ werden in der Berliner Anwaltskanzlei von Resch verfasst. „NACHRICHTENDIENST“ „GoMoPa“ hat keine Redaktion. Die Aufgabe des vorbestraften Serienbetrügers Klaus Maurischat besteht vielmehr in der Bespitzelung und in der Erpressung. Intellektuell ist er gar nicht in der Lage, einen fehlerfreien Artikel zu schreiben. Meines Wissens her erhielt er seine Ausbildung bei der STASI. Aber selbst für den STASI-Obristen Ehrenfried Stelzer war er nur ein primitives Werkzeug.“ Resch: “Die meisten unserer Mandanten verfügen noch über eine Rechtsschutzversicherung. Aber, wie kommen Sie auf 10.000 bis 20.000 Euro Honorar, das sind doch Phantasiepreise?!” GoMoPa: Na, die Streitwerte liegen bei 100.000 Euro. Und wenn es dann durch alle Instanzen geht, über mehrere Jahre. Resch: “Wir haben Streitwerte um die 60.000 bis 80.000 Euro. Manchmal 100.000 Euro. An Gebühren kommen da höchstens 2.500 Euro zusammen. Und in einigen Fällen haben wir auch mittellosen Mandanten unentgeltlich geholfen.” GoMoPa: Aber 2.500 Euro reichen doch nicht, wenn es durch alle Instanzen geht. Resch: “Nein, dass reicht nicht. Aber der Verlierer zahlt alles und wir gewinnen meistens die Prozesse. Im Ergebnis nehmen wir es von den Reichen, wie Robin Hood.” GoMoPa: Nach eigenen Angaben im Internet bearbeiten Sie jährlich 2.500 Fälle, wie viele haben Sie schon gewonnen? Resch: “Wir, die 22 Resch-Rechtsanwälte, haben im Schnitt 2000 Fälle im Jahr. Die Zahl schwankt erheblich. Wir machen eine kostenlose Ersteinschätzung, ob wir den Fall überhaupt annehmen. Wir wollen gewinnen oder zu mindestens einen guten Vergleich erzielen können. Sonst lehnen wir ab! Über 90 Prozent unserer Prozesse gewinnen wir. Zunächst oft Musterverfahren, danach Vergleiche. In den letzten Monaten über tausend Vergleiche gegen Postbank und BAG. Ich kenne, mit Verlaub, keine Kanzlei, die über so lange Jahre so erfolgreich arbeitet. Für den Anleger, wohl gemerkt!! Klein und Mittelverdiener.” GoMoPa: Ihr Insiderwissen und Ihre Argumentationen auf Vorträgen und auf Ihren Internetseiten sind sehr beeindruckend. Und die Szenarien bis hin zum 30jährigen Schuldenturm, in dem man als Anlage-Geschädigter landen kann, sind beängstigend. Allerdings fußt Ihr gesamtes Argumentations-Konstrukt auf einer These, die Sie nirgendwo beweisen oder belegen. Sie behaupten einfach, dass eine Wohnung nicht zu dem Preis weiterverkauft werden kann, zu dem man diese gekauft hatte. Bitte belegen Sie diese These. Resch: “Versuchen Sie mal, ein von vornherein schlechtes Geschäft weiterzuverkaufen. Das geht nicht. Das Ganze läuft doch in Kurzfassung so ab. Vermittler rufen Telefonnummern aus Klicktel zwischen 15 und 21 Uhr der Reihe nach an. Die erste Frage lautet: Sind sie mit der Steuerpolitik einverstanden? Wer ist das schon? Die zweite Frage lautet: Wollen Sie jeden Monat 250 Euro haben? Wer will das nicht? Dann kommt der Vorschlag, die Lohnsteuern zu senken und das gewonnene Geld in eine Kapitalanlage zu investieren, eine vermietete Wohnung. Aus der Anlage könne man nach zehn Jahren aussteigen. Die Gemeinheit besteht darin, dass man 1.000 Euro Verluste haben muss und man nur von diesen 1.000 Euro Verlusten bei einem Steuersatz von 25 Prozent 250 Euro zurückbekommt. Man bleibt also auf 750 Euro Verlusten selbst sitzen, die man ja irgendwie aufbringen muss. Die reale Frage des Vermittlers hätte vollständig lauten müssen: Geben Sie mir 1.000 Euro, wenn ich Ihnen dafür 250 Euro gebe? Das würde natürlich keiner tun. Und der versprochene Ausstieg ist gar nicht möglich, weil man nicht mal so viel Geld bekommt, um den Kreditvertrag abzulösen. Sobald die Makler die Provision von 20 bis 30 Prozent in der Tasche haben, sind die Kunden nur noch Luft.” „Die Akte Resch“ – wird immer spannender – wie “The Firm” oder “Die Firma”, ein Roman von David Grisham, verfilmt mit Tom Cruise, aber diesmal leider wohl bittere Realität: „Die Akte Resch“ – wird immer spannender – wie “The Firm” oder “Die Firma”, ein Roman von David Grisham, verfilmt mit Tom Cruise, aber diesmal leider wohl bittere Realität: http://www.spiegel.de/spiegel/print/d-13502488.html Heute ist Ehrenfried Stelzers Vision Realität geworden. Stelzer und seine Mitstreiter und Nachfolger, haben es – 20 Jahre nach dem Fall der Mauer fast geschaft: Mit dem„NACHRICHTENDIENST“ „GoMoPa“ mutmasslich gesteuert von dem Berliner „Anlegerschutzanwalt“ Jochen Resch, einem wie er selber zugibt, langjährigen Bekannten, ja Intimus Stelzers, ist die CYBER-STASI entstanden, die ihre Gegner gnadenlos ausschaltet – „Wenn es sein muss auch mit Dioxin“, sagen Insider. An den Beispielen Meridian Capital und Immovation AG zeigt sich am Besten, wie der „NACHRICHTENDIENST“ „GoMoPa“ die Immobilienbramnche erpressen will und wie sich gegen die CYBER-STASI „GoMoPa“ wehrt. Das von „GoMoPa“ im Auftrag seiner dubiosen Hintermänner – Insider behaupten es sei, die Rechtsanwaltskanzlei Resch, Berlin, – verleumdete Unternehmen Immovation verfolgte eine offene Kommunikationsstrategie, das war der Schlüssel zu Erfolge gegen die Erpresser von der CYBER-STASI: „Erneut wehrt sich die Kasseler IMMOVATION Immobilien Handels AG, ein seit über zwei Jahrzehnten sehr erfolgreiches, bundesweit tätiges Unternehmen der Immobilienbranche, gegen die unverändert anhaltende Schmutzkampagne des sogenannten “Informationsdienstes” GoMoPa (mit Sitz im Ausland), dessen Gründer und “CEO” Klaus Maurischat ebenso wie Mitgründer Mark Vornkahl bereits wegen Betrugs verurteilt wurden. Der 2006 rechtskräftig verurteilte Maurischat gab sogar gegenüber dem Handelsblatt weitere Verurteilungen zu (Handelsblatt vom 07.04.2010), woraufhin das Handelsblatt wörtlich konkludierte: “Es ist allerdings nicht das erste Mal, dass GoMoPa-Vertreter ins Zwielicht geraten”. GoMoPa suggerierte am 16. August 2010 in einer “Pressemitteilung”, dass IMMOVATION-Vorstandsmitglied Lars Bergmann sogar für den Sturz und das Karriereende des früheren brandenburgischen Ministers Professor Dr. Kurt Schelter durch Immobiliengeschäfte verantwortlich zeichne. In diesem Zusammenhang verweist die IMMOVATION AG auf eine schriftliche Mitteilung von Professor Dr. Kurt Schelter vom 18. August 2010: “Diesen Zusammenhang gibt es nicht. Ich kenne Herrn Bergmann nicht und habe mit ihm persönlich keine Immobiliengeschäfte abgeschlossen. Mir ist auch nicht bekannt, dass Herr Bergmann etwa mit Verkäufern der von mir damals erworbenen Immobilien persönlich oder institutionell in Verbindung stand oder steht. Ich halte dies für ausgeschlossen.” Minister a.D. Professor Dr. Kurt Schelter Die IMMOVATION AG hat dieser eindeutigen Mitteilung von Herrn Professor Schelter nichts hinzuzufügen und unterstreicht erneut ihr volles Vertrauen in die Fähigkeit ihrer Klienten, Mitarbeiter und Vertriebspartner, sich selbst ein entsprechendes Bild von dieser Schmutzkampagne machen zu können, in der es dem Autor dieser verleumderischen GoMoPa-“Pressemitteilung” zudem nicht einmal gelang, das Amt des betreffenden Ministers korrekt zu bezeichnen: Im Gegensatz zu seiner Bezeichnung bei GoMoPa war Herr Professor Schelter nicht Finanzminister, sondern Minister der Justiz und für Europaangelegenheiten des Landes Brandenburg. Die IMMOVATION AG hat im Zusammenhang mit dieser und zahlreichen weiteren unzutreffenden Behauptungen in dieser “Pressemitteilung” heute, 24.08.2010, beim Landgericht Berlin eine einstweilige Verfügung u. a. gegen Goldmann Morgenstern&Partners Consulting LLC (New York) und die GoMoPa GmbH (Berlin) beantragt. Mit der Verfügung soll den Antragsgegnern untersagt werden, die grob diffamierende Pressemitteilung zu verbreiten oder verbreiten zu lassen.“ Und „Nach den höchsterfreulichen gerichtlichen Erfolgen gegen den u. a. von rechtskräftig verurteilten Betrügern betriebenen, im Ausland domizilierten “Informationsdienst” Gomopa geht die Kasseler IMMOVATION Immobilien Handels AG auch straf- und zivilrechtlich gegen den Wirtschaftsdetektiv Medard Fuchsgruber vor. Nunmehr aber kann niemand mehr bei „GoMoPa“ zustellen. Die Kriminalpolizei ermittelt: ST/0148943/2011 Und: „FAZ berichtet über Gomopa-Machenschaften Gezielt Gerüchte gestreut Meridian Capital lockte den Zuträger von „GoMoPa“- Erpresser in Berlin in eine Falle und erhielt von diesem dann die Info, wo sich Maurischat gerade aufhielt: „Seitens der Meridian Capital Enterprises Ltd. gab es überhaupt keine Reaktion auf den Erpressungsversuch von GOMOPA. Ende August 2008 auf dem Service http://www.gompa.net sind zahlreiche Artikel/Meldungen erscheinen, welche die Tätigkeit der Meridian Capital Enterprises Ltd. in einem sehr negativen Licht dargestellt haben. Nachdem die auf http://www.gomopa.net enthaltenen Informationen ausführlich und vollständig analysiert worden waren, ergab es sich, dass sie der Wahrheit nicht einmal in einem Punkt entsprechen und potenzielle und bereits bestehende Kunden der Meridian Capital Enterprises Ltd. in Bezug auf die von diesem Finanzinstitut geführten Geschäftstätigkeit irreführen. Infolge der kriminellen Handlugen von GOMOPA und der mit ihm kooperierenden Services und Blogs im Netz hat die Meridian Capital Enterprises Ltd. beachtliche und messbare geschäftliche Verluste erlitten. Die Meridian Capital Enterprises Ltd. hat nämlich in erster Linie eine wichtige Gruppe von potenziellen Kund verloren. Was sich aber als wichtiger ergab, haben sich die bisherigen Kunden von der Meridian Capital Enterprises Ltd. kaum abgewandt. Diejenigen Kunden haben unsere Dienstleitungen weiterhin genutzt und nutzen die immer noch. In Hinblick auf die bisherige Zusammenarbeit mit der Meridian Capital Enterprises Ltd., werden ihrerseits dem entsprechend keine Einwände erhoben . und hier http://othergomopa.blogspot.com/ aus dem Jahre 2009 und nicht wie die von „GoMoPa“gebastelte Fälschung aus 2010. Diese Vorgänge können gerne bei Meridian Capital überprüft und nachvollzogen werden. Der „NACHRICHTENDIENST“ „GoMoPA“ DIE CYBER-STASI DES 21. JAHRHUNDERTS „Lauschen, spähen, schnüffeln: Vor 60 Jahren wurde die DDR-Staatssicherheit gegründet. Mehr als 91.000 hauptamtliche und doppelt so viele inoffizielle Mitarbeiter garantierten der SED die Macht. Ein Geheimdienst im klassischen Sinn war der Apparat nie, eher schon eine kriminelle Vereinigung mit tödlichen Methoden“, schreibt die angesehene Tageszeitung „DIE WELT“. „Genau so verfährt auch der „NACHRICHTENDIENST“ „ GoMoPa“ , erläutert Rainer W. (Name wurde aus Sicherheitsgründen anonymisiert). Er war über mehrere Monate „inoffizieller“ Mitarbeiter des „NACHRICHTENDIENSTES“ „GoMoPa“, einem angeblichen Zusammenschluss jüdischer US-Rechtsanwälte namens Goldman, Morgenstern & Partner LLC, die noch nie jemand gesehen hat. Stattdessen sehen die Personen, die sich mit „GoMoPa“ beschäftigen nur die Totenkopfmaske stalinistischer STASI-Hacker, Erpresser und Cyberstalker. Rainer W.: „Die eigentlichen Köpfe von „GoMoPa“ sind meiner Meinung nach wohl RA Jochen Resch und STASI-Oberst Ehrenfried Stelzer. Maurischat (ein Deckname) hat nicht das Format so eine Organisation aufzuziehen.“ Seit Jahren schon vesuchen die vorbestraften Serien-Kriminellen um das „Aushängeschild“ Klaus-Dieter Maurischat die deutsche Wirtschaft zu infiltrieren. Doch erst seit dem mutmasslichen Mord an Heinz Gerlach und den monatelangen Attacken gegen Haus sind viele Fakten recherchiert und zu Tage gekommen. Vor allem über die Methoden des „NACHRICHTENDIENSTES“ – aber auch über dessen Hintermänner in Berlin, denn in New York existiert sowieso nur eine Briefkastenadresse und auch das „Büro“ in Berlin ist ein „virtuelles Regus-Büro“. Die Fassade soll den „NACHRICHTENDIENST“ tarnen. „DIE WELT“ schreibt: „40 Jahre lang, von der Gründung bis zu ihrer schrittweisen Auflösung zwischen Dezember 1989 und März 1990, war die Staatssicherheit der wichtigste Machtgarant der SED-Herrschaft. In dieser Zeit wucherte der Apparat immer mehr, bis schließlich mehr als 91.000 hauptamtliche Mitarbeiter für das MfS tätig waren. Von Arsen bis Zyankali: Themen Archiv Forum Links Kontakt Hilfe zum Ausdrucken 21.1.2002 Autoren: Christian Nitsche, Sabina Wolf Dieter Baumann ist nicht totzukriegen. Nach einer zweijährigen Dopingsperre geht er jetzt wieder an den Start. 1999 eine positive Dopingprobe. Dass er sich selbst gedopt hat, glauben heute nur noch seine Feinde. Und Feinde aus der ehemaligen DDR hatte er genug: Ebenso wie der Todesfall Heinz Gerlach zur Gänze aufgeklärt werden muss Insider Rainer W.:“Genau diese Methodenw erden heute von „GoMoPa“ und deren Hintermännern weider angewandt – natürlich verfeinert und mit Internet-Cyberstalking-Taktiken garniert. Hintergrund: Die Deutsche Kriminalpolizei hat weitere Ermittlungen gegen Damit sollen wohl DKB und andere „Zahlkandidaten“ in die Pflicht Zitat: Gerlach bietet dem Fondsinitiator eine Vorprüfung des Prospektes Scheidung war 2007) nach Holland und machte sich selbst zum Geschäftsführer. Heinz Gerlach ist zu einer Stellungnahme nicht bereit. bemerkenswert, weil Gerlach mit Vorliebe Finanzdienstleister gern als saufsicht hatte den drei Fonds Business Park Stuttgart, Carre Göttingen Der Anwalt: “Die SHB zauberte als Baron-Nachfolger für den ternehmerberater-Verträge abgeschlossen habe. Der Anwalt: “Die Anwälte haben mit Gerlach persönlich nichts zu „Der Anlegeranwalt Jochen Resch kommt neuerdings oft in den berinformation auch eine Bauträgergesellschaft, gegen die Anwalt Resch Demnach hat ein Arzt aus der Nähe von Münster die Firma aus Mit den Methoden der Stasi arbeitet auch der äussert dubiose „Finanz- Als Heinz Gerlach dann die Zusammenhänge zwischen der mutmasslichen wie man bei Durchsicht der Seite http://www.akte-heinz-gerlach.info unschwer Diese Internet-Operations-Muster – so die SJB-Opfer – habe „Zum Tode von Heinz Gerlach » aus Uetersen (Kreis Pinneberg). Gemeint ist Siegfried Sievert, 58 dioxinverseuchte Industriefett sei versehentlich in die Produktion aufmerksam. Sie beobachtet sein „dekadentes Aussehen“, seine Etwa 150 000 Tonnen belastetes Futter könnten so in die Nahrungskette Fuchsgruber ist – nach Entgegennahme des Vorabhonorars – Unternehmensinformation / Kurzprofil: INVESTMENT (das Original) erscheint mit einer deutschen Ausgabe, einer globalen Ausgabe und einer Asien-Ausgabe seit mehr als 10 Jahren als unabhängiges Magazin fürInvestoren und Finanzprofis. Dabei stehen die sogenannten “HNWI im Fokus”. Unterstützt durch das Wachstum der Börsenkapitalisierungen in den Schwellenländern stieg das Gesamtvermögen der weltweiten High Net Worth Individuals (HNWI – Privatpersonen mit Nettofinanzvermögen > 1 Mio. US-Dollar ohne Verbrauchsgüter und eigengenutzte Immobilien) im Jahr um 9,4% auf 40,7 Billionen US-Dollar. Dies geht aus dem von Merrill Lynch und Capgemini veröffentlichten zwölften, jährlich erscheinenden, World Wealth Report hervor. Die weltweite Anzahl der HNWI nahm 2007 um 6% auf 10,1 Millionen zu. Gleichzeitig stieg die Zahl der besonders wohlhabenden Personen (Ultra High Net Worth Individuals – UHNWI – Privatpersonen mit Nettofinanzvermögen > 30 Mio. US-Dollar ohne Verbrauchsgüter und eigengenutzte Immobilien) um 8,8%. Erstmals seit Bestehen dieses Reports wurde beim durchschnittlichen Finanzvermögen der HNWI die Schwelle von 4 Millionen US-Dollar überschritten. Aus sicherheitstechnischen Gründen geben wir zu unseren Mitarbeitern keine weiteren persönlichen Daten bekannt. siehe unseren Kreuzzug gegen Cyber Stalking *Magister Bernd M. Pulch (MA – Magister Artium) Abschluss des Studiums der Publizistik (Note 2) , Komparatistik (Note 1) und Germanistik (Note 1-2) 1988 Universität Mainz Magisterarbeit bei Professor Kepplinger über Dolf Zillmanns “Emotional Arousal Theory”1987, Mainz, 400 Seiten Sie können die Magisterarbeit bei uns zum Preis von nur € 99,- über das Kontaktformular bestellen. Die Zahlung erfolgt per Vorkasse. Die Lieferzeit beträgt ca. 14 Tage in Deutschland. Investment Magazin, Investment, Das Investment, Investment Magazine |
Wikileaks – Two Years of Cablegate as Bradley Manning Testifies for the First Time
|
TMZ – Australian DJs — A History of Irresponsible Prank Calls
Confidential – Barclays Resolution Plan
The Dodd-Frank Wall Street Reform and Consumer Protection Act requires that bank holding companies with total consolidated assets of $50 billion or more and nonbank financial companies designated by the Financial Stability Oversight Council for supervision by the Federal Reserve submit resolution plans annually to the Federal Reserve and the Federal Deposit Insurance Corporation (FDIC). Each plan, commonly known as a living will, must describe the company’s strategy for rapid and orderly resolution under the Bankruptcy Code in the event of material financial distress or failure of the company.
Companies subject to the rule are required to file their initial resolution plans in three groups and on a staggered schedule. Plans for the first group, which includes U.S. bank holding companies with $250 billion or more in total nonbank assets and foreign-based bank holding companies with $250 billion or more in total U.S. nonbank assets, must be submitted on or before July 2, 2012.
As required under section 243.8(c) of the Board’s Regulation QQ (12 CFR 243.8(c)), each resolution plan must be divided into a public section and a confidential section. The public sections available on the Board’s website have not been edited or reviewed by the Board and are provided exactly as submitted by the companies.
DOWNLOAD THE ORIGINAL DOCUMENT HERE:
Dream of a Warrior – Full Movie
The time travel drama Dream of a Warrior stars Leon Lai as Dean, a police officer who must travel back in time to save Rose, the daughter of the time machine’s inventor. Making matters more difficult is that fact that the brave man loves Rose, who is stuck in the past…and the time machine breaks.
BENNEWIRTZ ,”NUN GoMoPa”, VERSUCHT ERNEUT “GoMoPa”-KRITISCHE STELLEN LÖSCHEN ZU LASSEN
Dear madams, dear sirs, unfortunately I did not receive a reply concerning my request from July 1st from you yet. In this context I again want to point out the major wish of our customer SJB seeing the name removed from the entries mentioned below. It would be a great pleasure if you can manage the removal according to the wish of our customer. Thank you very much for your understanding. Please do not hesitate contacting me for further discussion. With kind regards, P. Schmitz Dein guter Ruf.de ---------- Forwarded message ---------- From: P. Schmitz <p.schmitz@deinguterruf.de> Date: 2011/7/1 Subject: Request To: office@ebizz.tv Dear madams, dear sirs, by order of our customer SJB Fonds Skyline OHG we are kindly asking you to remove some entries on your website thetvnet.com. The topicality and the correctness of these entries are no longer up to date. It is a major concern of our customer to see them removed: immobilien-vertraulich.com/law/7279-die-killer-bibel-toxdat--die-900-seiten-stasi-mordstudie-von-gomopa-mastermind-ehrenfried-stelzer.html immobilien-vertraulich.com/law/7277-sjb-fonds-opfer-sven-babyface-schmidt-als-chef-terrorist-von-europas-gefaehrlichster-internet-kriminellen-bande-enttarnt-.html immobilien-vertraulich.com/law/7268-der-beweis-tatsaechlich-vorbestrafter-serienbetrueger-klausmaurischat-gomopa-hat-eigenes-kinder-portal-.html immobilien-vertraulich.com/law/7264-die-killer-bibel-toxdat--die-900-seiten-stasi-mordstudie-von-gomopa-mastermind-ehrenfried-stelzer.html immobilien-vertraulich.com/law/7262-sjb-fonds-opfer-sven-babyface-schmidt-als-chef-terrorist-von-europas-gefaehrlichster-internet-kriminellen-bande-enttarnt-.html immobilien-vertraulich.com/law/7224-die-killer-bibel-toxdat-die-900-seiten-stasi-mordstudie-von-gomopa-mastermind-ehrenfried-stelzer.html immobilien-vertraulich.com/law/7223-opfer-sven-schmidt-als-chef-terrorist-von-europas-gefaehrlichster-internet-kriminellen-bande-enttarnt.html immobilien-vertraulich.com/law/7217-der-beweis-tatsaechlich-vorbestrafter-serienbetrueger-klausmaurischat-gomopa-hat-eigenes-kinder-portal-.html immobilien-vertraulich.com/law/7212-die-killer-bibel-toxdat-die-900-seiten-stasi-mordstudie-von-gomopa-mastermind-ehrenfried-stelzer.html immobilien-vertraulich.com/law/7210-opfer-sven-schmidt-als-chef-terrorist-von-europas-gefaehrlichster-internet-kriminellen-bande-enttarnt.html immobilien-vertraulich.com/law/7203-der-beweis-tatsaechlich-vorbestrafter-serienbetrueger-klausmaurischat-gomopa-hat-eigenes-kinder-portal-.html immobilien-vertraulich.com/law/7200-opfer-die-killer-bibel-toxdat-die-900-seiten-stasi-mordstudie-von-gomopa-mastermind-ehrenfried-stelzer.html immobilien-vertraulich.com/law/7189-opfer-die-killer-bibel-toxdat--die-900-seiten-stasi-mordstudie-von-gomopa-mastermind-ehrenfried-stelzer.html immobilien-vertraulich.com/law/7120--klaus-maurischats-gomopa-cybermoerder-leichen-und-falschmeldungen-plastern-ihren-weg--nicht-nur-im-internet.html immobilien-vertraulich.com/boerse-ipo-reit/7119--der-mehrfach-vorbestrafte-serienbetrueger-und-mutmassliche-paederast-klaus-maurischat-und-seine-neue-qwirecard-enteq.html We hope you can manage the removal of these entries according to the wish of our customer contemporarily. . These entries and similar ones cause major problems for our customer. We wanna thank you for your appreciation, for further information please visit our website deinguterruf.de. (the english version is still under construction). In case you are not the right receipt for this request, it would be very kind if you can name the correct person in charge. If you have further questions concerning this case or our services in general, please contact me. It would be a great pleasure to receive a positive feedback. With kind regards, -- Mit freundlichen Grüßen, P. Schmitz DEIN GUTER RUF.DE Ein Projekt der MoveVision GmbH Alfredstraße 341 45133 ESSEN Tel: 0201-2489452 E-mail: p.schmitz (at) deinguterruf.de MoveVision – GmbH - HRB 22121 Geschäftsführer: Martin Lux - Steuernummer: DE228746207 -- Mit freundlichen Grüßen, P. Schmitz DEIN GUTER RUF.DE Ein Projekt der MoveVision GmbH Alfredstraße 341 45133 ESSEN Tel: 0201-2489452 E-mail: p.schmitz (at) deinguterruf.de MoveVision – GmbH - HRB 22121 Geschäftsführer: Martin Lux - Steuernummer: DE228746207
SI Swimsuit Video – Selita
Confidential – Bank of New York – Mellon Resolution Plan
The Dodd-Frank Wall Street Reform and Consumer Protection Act requires that bank holding companies with total consolidated assets of $50 billion or more and nonbank financial companies designated by the Financial Stability Oversight Council for supervision by the Federal Reserve submit resolution plans annually to the Federal Reserve and the Federal Deposit Insurance Corporation (FDIC). Each plan, commonly known as a living will, must describe the company’s strategy for rapid and orderly resolution under the Bankruptcy Code in the event of material financial distress or failure of the company.
Companies subject to the rule are required to file their initial resolution plans in three groups and on a staggered schedule. Plans for the first group, which includes U.S. bank holding companies with $250 billion or more in total nonbank assets and foreign-based bank holding companies with $250 billion or more in total U.S. nonbank assets, must be submitted on or before July 2, 2012.
As required under section 243.8(c) of the Board’s Regulation QQ (12 CFR 243.8(c)), each resolution plan must be divided into a public section and a confidential section. The public sections available on the Board’s website have not been edited or reviewed by the Board and are provided exactly as submitted by the companies.
DOWNLOAD THE ORIGINAL DOCUMENT HERE:
TMZ – Katt Williams Slaps Target Employee IN THE FACE
Secrecy News – SENATE PUTS BRAKES ON DEFENSE CLANDESTINE SERVICE
The Senate moved last week to restrain the rapid growth of the Defense
Clandestine Service, the Pentagon's human intelligence operation.
Under a provision of the FY2013 defense authorization act that was
approved on December 4, the Pentagon would be prohibited from hiring any
more spies than it had as of last April, and it would have to provide
detailed cost estimates and program plans in forthcoming reports to
Congress.
"DoD needs to demonstrate that it can improve the management of
clandestine HUMINT before undertaking any further expansion," the Senate
Armed Services Committee wrote in a report on the new legislation.
http://www.fas.org/irp/congress/2012_cr/ndaa-dcs.html
Longstanding problems with defense human intelligence cited by the
Committee include: "inefficient utilization of personnel trained at
significant expense to conduct clandestine HUMINT; poor or non-existent
career management for trained HUMINT personnel; cover challenges; and
unproductive deployment locations."
The Committee noted further that "President Bush authorized 50 percent
growth in the CIA's case officer workforce, which followed significant
growth under President Clinton. Since 9/11, DOD's case officer ranks have
grown substantially as well. The committee is concerned that, despite this
expansion and the winding down of two overseas conflicts that required
large HUMINT resources, DOD believes that its needs are not being met."
Instead of an ambitious expansion, a tailored reduction in defense
intelligence spending might be more appropriate, the Committee said.
"If DOD is able to utilize existing resources much more effectively, the
case could be made that investment in this area could decline, rather than
remain steady or grow, to assist the Department in managing its fiscal and
personnel challenges," the Senate Committee wrote.
The Washington Post published a revealing account of Pentagon plans to
expand the size and reach of the defense human intelligence program in "DIA
sending hundreds more spies overseas" by Greg Miller, December 1.
Along with overhead surveillance, bolstering human intelligence has been
the focus of one of two major defense intelligence initiatives, said Under
Secretary of Defense (Intelligence) Michael G. Vickers last October. The
Defense Clandestine Service "enable[s] us to be more effective in the
collection of national-level clandestine human intelligence across a range
of targets of paramount interest to the Department of Defense," he said.
The latest issues of the U.S. Army's Military Intelligence Professional
Bulletin, released under the Freedom of Information Act, are available here
(in some very large pdf files):
http://www.fas.org/irp/agency/army/mipb/index.html
"A Short History of Army Intelligence" by Michael E. Bigelow of US Army
Intelligence and Security Command, dated July 2012, is available here:
http://www.fas.org/irp/agency/army/short.pdf
Newly updated doctrine from the Joint Chiefs of Staff includes Information
Operations, JP 3-13, 27 November 2012:
http://www.fas.org/irp/doddir/dod/jp3_13.pdf
and Joint Forcible Entry Operations, JP 3-18, 27 November 2012:
http://www.fas.org/irp/doddir/dod/jp3_18.pdf
The defense authorization bill approved by the Senate last week also
called upon the Pentagon to expedite the domestic use of unmanned aerial
systems (UAS) and their integration into National Airspace System (NAS).
"While progress has been made in the last 5 years [in integrating UASs
into domestic airspace], the pace of development must be accelerated," the
Senate Armed Services Committee said in its report on the bill. "Greater
cross-agency collaboration and resource sharing will contribute to that
objective."
"Without the ability to operate freely and routinely in the NAS, UAS
development and training -- and ultimately operational capabilities -- will
be severely impacted," the Senate Committee said.
http://www.fas.org/irp/congress/2012_cr/ndaa-uas.html
OPEN SOURCE TECHNOLOGIES FOR ARMS CONTROL
Members of the public are invited to develop and submit ideas to an essay
contest on the potential uses of open source information and technology to
support international arms control initiatives.
The State Department is sponsoring the contest in partnership with the
James Martin Center for Nonproliferation Studies and the Moscow-based
Center for Policy Studies.
http://cns.miis.edu/stories/121206_open_source_esssay_contest.htm
"The contest aims to harness the ingenuity of American and Russian
citizens to think creatively about innovative ways to use open source
information and communication technologies for arms control verification,
compliance monitoring, and monitoring of sensitive facilities," the CNS
said in its announcement.
While an essay contest is not a momentous undertaking, this one does seem
to represent a wholesome awareness that the underlying realities of
national security are changing in fundamental ways. It follows that
national security policies -- including classification policies and public
engagement -- need to adapt accordingly.
"Diplomacy today is very different than it was at the dawn of the nuclear
age," the State Department said. "More often diplomacy is happening in the
open, and at quicker speeds."
"The astonishing advancements in information and communication
technologies include new tools and capabilities that could help support
arms control transparency and compliance. This essay contest aims to
encourage more public participation, discussion and thought on arms
control," the State Department said.
There is already an impressive history of public participation in arms
control efforts, notably including the work of Thomas Cochran and the
Natural Resources Defense Council in demonstrating seismic monitoring for
verification of a low-threshold nuclear test ban.
IRAN'S BALLISTIC MISSILE PROGRAM, AND MORE FROM CRS
Noteworthy new and updated reports from the Congressional Research Service
that Congress has not made publicly available include the following.
Iran's Ballistic Missile and Space Launch Programs, December 6, 2012:
http://www.fas.org/sgp/crs/nuke/R42849.pdf
Syria's Chemical Weapons: Issues for Congress, December 5, 2012:
http://www.fas.org/sgp/crs/nuke/R42848.pdf
Egypt: Background and U.S. Relations, December 6, 2012:
http://www.fas.org/sgp/crs/mideast/RL33003.pdf
In Brief: Next Steps in the War in Afghanistan? Issues for Congress,
December 6, 2012:
http://www.fas.org/sgp/crs/natsec/R42137.pdf
Afghanistan Casualties: Military Forces and Civilians, December 6, 2012:
http://www.fas.org/sgp/crs/natsec/R41084.pdf
Detention of U.S. Persons as Enemy Belligerents, December 4, 2012:
http://www.fas.org/sgp/crs/natsec/R42337.pdf
Right to Work Laws: Legislative Background and Empirical Research,
December 6, 2012:
http://www.fas.org/sgp/crs/misc/R42575.pdf
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
Death of a Ghost Hunter – Full Movie
USA (2007) Renowned “ghost hunter”, Carter Simms is paid to conduct a paranormal investigation of a supposedly haunted house
A paranormal investigator determined to prove that there is life after death investigates the house where an unspeakable tragedy occurred in director Sean Tretta’s low-budget ghost story. The year was 2002. Carter Simms was a ghost hunter whose meticulous approach to studying the supernatural had earned her a $5000 offer to perform a paranormal investigation of the notorious “Masterson House.” Twenty years ago, respected Minister Joseph Masterson, is devoted wife, and their adorable daughter where ruthlessly slaughtered inside their family abode. To this day, the locals insist that the house where these unspeakable acts occurred is still haunted. After recruiting a videographer, a reporter, and a spiritual advocate to assist the investigation, Simms and her small crew settled prepared to prove once and for all whether “Masterson House” was truly haunted. Three days later, Simms was dead. What sinister events unfolded in that unholy house of death? In this film, viewers are invited to follow along on that fateful investigation and find out firsthand just what awful otherworldy force sent this seasoned ghost hunter to her grave.
DAS BETRUGSURTEIL GEGEN “BENNEWIRTZ” UND “PETER EHLERS” “GoMoPa”-PARTNER “MAURISCHAT” UND “VORNKAHL” WG BETRUGES AM EIGENEN ANLEGER
Über eine selbstgebaute Blogseite verbreiten die GoMoPa-Gangster eine gefälschte Stellung von Meridian Capital, um Verwirrung zu stiften.
Diese Blogseite existiert erst seit Dezember 2010.
Beweis:
http://www.hypestat.com/pressreleaser.org
Die Meridian Capital-Seite, das Original,
http://othergomopa.blogspot.com/
ist dagegen bereits seit2009 online
Beweis: Aussage Meridian Capital – das Unternehmen können Sie auch gerne direkt kontaktieren.
und
KLAUS DIETER MAURISCHAT IN DETENTION
Source: http://klaus-dieter-maurischat.blogspot.com/2009/01/klaus-dieter-maurischat-in-haft.html
Hintergrund: Die Verurteilung von Klaus Maurischat und Mark Vornkahl wegen Betruges am eigenen Anleger
Klaus Maurischat und Mark Vornkahl, Betreiber vonwww.gomopa.net: Am 24. April 2006 war die Verhandlung am Amtsgericht Krefeld in der Betrugssache: Mark Vornkahl / Klaus Maurischat ./. Dehnfeld. Aktenzeichen: 28 Ls 85/05 Klaus MaurischatLange Straße 3827313 Dörverden.Das in diesem Verfahren ausschließlich diese Betrugsache verhandelt wurde, ist das Urteil gegen Klaus Maurischat recht mäßig ausgefallen.Zusammenfassung der Verhandlung vom 24.04.2006 vor dem Schöffengericht des AG Krefeld in der Sache gegen Klaus Maurischat und Mark Vornkahl.Zur Hauptverhandlung erschienen:Richter Dr. Meister, 2 Schöffen,Staatsanwalt, Angeklagter Klaus Maurischat, vertr. durch RA Meier, Berlin; aus der U-Haft zur Verhandlung überführt.1. Eine Gerichtsvollzieherin stellt unter Ausschuss der Öffentlichkeit eine Urkunde an den Angeklagten Maurischat zu.2. Bei Mark Vornkahl wurde im Gerichtssaal eineTaschenpfändung vorgenommen.Beginn der HauptverhandlungDie Beklagten verzichten auf eine Einlassung zu Beginn.Nach Befragung des Zeugen Denfeld zum Sachverhalt wurde dieVerhandlung auf Wunsch der Staatsanwaltschaft und den Verteidigern unterbrochen.Der Angeklagte Maurischat gab nach Fortsetzung derHauptverhandlung Folgendes zu Protokoll:Er sähe ein, dass das Geld auf das falsche Konto gegangen sei und nicht dem eigentlichen Verwendungszweck zugeführt wurde. Das Geld sei aber zurückgezahlt worden und er distanziere sich ausdrücklich von einem Betrug.Schließung der BeweisaufnahmeDer Staatsanwalt verließt sein PlädoyerEr halte am Vorwurf des Betruges fest. Mit Hinweis auf die einschlägigen Vorstrafen des Angekl. Maurischatund auf laufende Ermittlungsverfahren, beantrage er ein Strafmaß von 1 Jahr und 6 Monaten.Er halte dem Angeklagten zu Gute, dass dieserWiedergutmachung geleistet habe, und dass dieser geständig war. Zudem läge die letzte Verurteilung wegen Betruges 11 Jahre zurück. Auch sei der Geschädigte nicht in existentielle Not geraten, wobei der Staatsanwalt nicht über noch laufende Verfahren hinweg sehen könne. Er läge aber dem Angeklagten Maurischat nahe, keine weiteren Aktivitäten im Bezirk der Staatsanwaltschaft Krefeld auszuüben, insbesondere möchte er, dass keine weiteren Anleger im Bezirk der Staatsanwaltschaft Krefeld durch GoMoPa akquiriert werden.Die Freiheitsstrafe soll zur Bewährung ausgesetzt werden.Plädoyer des Verteidigers des Angekl. Maurischat, Herrn RA MeierEr schließe sich, wie (in der Unterbrechung) vereinbart, dem Staatsanwalt an.Es stimme, dass sein Mandant Fehler in seiner Vergangenheit gemacht habe, und dass er auch diesmal einen Fehler begangen haben könnte, jedoch sei der Hinweis wichtig, dass sein Mandant aus diesen Fehlern gelernt habe.Der Angeklagte haben das letzte Wort.Maurischat sagt, es sei bereits alles gesagt worden.Unterbrechung zu Hauptverhandlung. Der Richter zieht sich mit den Schöffen zur Beratung zurück.Urteilsverkündung:Der Angeklagte wird des gemeinschaftlichen Betrugs für schuldig befunden.Der Angeklagte Klaus Maurischat wird zu einerFreiheitsstrafe von 1 Jahr und 6 Monaten verurteilt. Diese wird zur Bewährung ausgesetzt.Die Bewährungszeit wird auf 3 Jahre festgesetzt.Der Haftbefehl gegen Klaus Maurischat wird aufgehoben.Der Angeklagte trage die Kosten des Verfahrens.UrteilsbegründungDer Richter erklärt, dass eine Täuschung des Geschädigtenvorliegt und somit keine Untreue in Betracht kommen kann.Die Fragen, ob es sich um einen Anlagebetrug handele sei irrelevant. Er hält den Angeklagten die geleistete Wiedergutmachung zu Gute.Ebenso ist das Geständnis für die Angeklagten zu werten. Zudem liegt die letzte Verurteilung des Angeklagten Maurischat 11 Jahre zurück.Die Parteien verzichten auf Rechtsmittel. Das Urteil ist somit rechtskräftig.Mit dem heutigen Urteil endet ein Kapitel in derBetrugssache Goldman Morgenstern & Partners, Klaus Maurischat und Mark Vornkahl.Alle GoMoPa.net Verantwortlichen, Maurischat, Vornkahl und Henneberg sind nun vorbestrafte Abzocker und Betrüger und die Zukunft der Pseudoklitsche GoMoPa.net sieht duster aus.Mir dem Geständnis der beiden ABZOCKER MAURISCHAT UND VORNKAHL vor Gericht bricht ein jahrelangaufrechterhaltenes Lügengeflecht von einigen primitiven Betrügern zusammen. Gewohnheitsverbrecher und Denunzianten,die rechtschaffene Personen und Firmen in ihren Verbrecherforen kriminalisierten.
Confidential – Bank of America Resolution Plan
The Dodd-Frank Wall Street Reform and Consumer Protection Act requires that bank holding companies with total consolidated assets of $50 billion or more and nonbank financial companies designated by the Financial Stability Oversight Council for supervision by the Federal Reserve submit resolution plans annually to the Federal Reserve and the Federal Deposit Insurance Corporation (FDIC). Each plan, commonly known as a living will, must describe the company’s strategy for rapid and orderly resolution under the Bankruptcy Code in the event of material financial distress or failure of the company.
Companies subject to the rule are required to file their initial resolution plans in three groups and on a staggered schedule. Plans for the first group, which includes U.S. bank holding companies with $250 billion or more in total nonbank assets and foreign-based bank holding companies with $250 billion or more in total U.S. nonbank assets, must be submitted on or before July 2, 2012.
As required under section 243.8(c) of the Board’s Regulation QQ (12 CFR 243.8(c)), each resolution plan must be divided into a public section and a confidential section. The public sections available on the Board’s website have not been edited or reviewed by the Board and are provided exactly as submitted by the companies.
DOWNLOAD THE ORIGINAL DOCUMENT HERE:
TMZ – Erin Andrews Dissed by College Football Fans?
Confidential – Deutsche Bank Resolution Plan
The Dodd-Frank Wall Street Reform and Consumer Protection Act requires that bank holding companies with total consolidated assets of $50 billion or more and nonbank financial companies designated by the Financial Stability Oversight Council for supervision by the Federal Reserve submit resolution plans annually to the Federal Reserve and the Federal Deposit Insurance Corporation (FDIC). Each plan, commonly known as a living will, must describe the company’s strategy for rapid and orderly resolution under the Bankruptcy Code in the event of material financial distress or failure of the company.
Companies subject to the rule are required to file their initial resolution plans in three groups and on a staggered schedule. Plans for the first group, which includes U.S. bank holding companies with $250 billion or more in total nonbank assets and foreign-based bank holding companies with $250 billion or more in total U.S. nonbank assets, must be submitted on or before July 2, 2012.
As required under section 243.8(c) of the Board’s Regulation QQ (12 CFR 243.8(c)), each resolution plan must be divided into a public section and a confidential section. The public sections available on the Board’s website have not been edited or reviewed by the Board and are provided exactly as submitted by the companies.
DOWNLOAD THE ORIGINAL DOCUMENT HERE:
Bail Out – Full Movie – David Hasselhoff
David Hasselhoff plays one of three bounty hunters in search of a much-wanted criminal. The reward is astronomical, so it’s understandable that the cops want Hasselhoff and company to make themselves scarce. No matter what the law throws in their path, however, the three heroes will not be deterred. Bail Out costars Linda Blair and John Vernon. Though filmed in 1988, Bail Out wasn’t released until 1990, upon Hasselhoff’s success on television’s Baywatch.
DAS SYSTEM “GoMoPa”-Google
TMZ – Lindsay Lohan — The Wanted’s Newest Groupie?
Robin Hood – Full Movie – Douglas Fairbanks jr
This quirky animated take on the classic tale of Robin Hood finds Tom spying for the Sherriff of Nottingham and Prince John. When he realizes his employers have foul plans for Maid Marion, he enlists Jerry to help him save Maid Marion and bring the true king back safely.
Der “freiwillige” Beratungsvertrag zwischen “GoMoPa” und estavis
Die wichtigste Finanzierungsquelle von “GoMoPa” war laut der Teilhaberinformation auch eine Bauträgergesellschaft, gegen die Anwalt Resch im Auftrag von Anlegern vorgegangen war. Deren Muttergesellschaft Estavis schloss einen “freiwilligen Beratervertrag” mit “GoMoPa” – das ist das Strickmuster der Resch-”GoMoPa”-Vorgehensweise…
Schon eigenartig. Da hat Gomopa eine eigene GmbH in Berlin – eine 100 % Tochter der Goldman, Morgenstern & Partners LLC – schliesst aber Verträge mit Erfüllungsort Deutschland mit dem Gerichtsstand New York. Die GmbH bestand bereits zum Zeitpunkt des Vertragsabschlusses.
GoMoPa GmbH, Berlin(Unter den Linden 21, 10117 Berlin). Firma: GoMoPa GmbH Sitz / Zweigniederlassung: Berlin Gegenstand: Die wirtschaftliche Beratung, insbesondere des Mittelstandes, in der europäischen Gemeinschaft unter der Wortmarke GoMoPa. Dazu gehören die Präsentation von Firmen im Internet und anderen Medien, Vermietung von Werbeflächen auch im Internet, die Vermittlung von Handels- und Wirtschaftskontakten und Werbung auch über das Internet sowie das Bereitstellen von Informationen und Portalen im Internet. Stamm- bzw. Grundkapital: 50.000,00 EUR Vertretungsregelung: Ist ein Geschäftsführer bestellt, so vertritt er die Gesellschaft allein. Sind mehrere Geschäftsführer bestellt, wird die Gesellschaft gemeinschaftlich durch zwei Geschäftsführer oder durch einen Geschäftsführer in Gemeinschaft mit einem Prokuristen vertreten. Alleinvertretungsbefugnis kann erteilt werden. Geschäftsführer:; 1. Reski, Peter, *23.12.1952, Verden/Aller; mit der Befugnis die Gesellschaft allein zu vertreten mit der Befugnis Rechtsgeschäfte mit sich selbst oder als Vertreter Dritter abzuschließen Rechtsform: Gesellschaft mit beschränkter Haftung.
========================================================
BERATUNGSVERTRAG
Zwischen der
ESTAVIS AG
Uhlandstrasse 165
D-10719 Berlln
– im folgenden ESTAVIS genannt –
Und
Goldman, Morgenstern & Partners LLC.
575 Madison Avenue, 10th floor
New York, NY 10022-2511
USA
– im folgenden GoMoPa genannt –
I. AUFTRAG UND DURCHFÜHRUNG
1.1 ESTAVIS beauftragt GoMoPa mit der Erarbeitung elnes neuartigen Vertrlebskonzeptes für den Abverkauf Denkmalgeschützter
Immoblilien an eine entsprechende Klientel, die unter zur Hilfenahme des lnternets und unter Einhaltung verbraucherrechtlicher Auflagen geworben werden soll.
1.2. Dazu gehören: Vorschläge zur Herstetlung von Internetseiten und entsprechender Werbung, Kostenberatung, Überwachung
und Einholung entsprechender Angebote, Personalsuche, Verhandlungen mit affilablen Anbietern, Vermittlung von Consutern.
1.3 Die Durchführung erfolgt in enger und ständiger Abstimmung mit einem Vertreter des Vorstands der ESTAVIS AG, sowie
rechtlichen und steuerlichen Beratern der ESTAVIS. GoMoPa wird diesbezüglich entsprechende Vorschläge erarbeiten, die detalllierte und
schriftliche und mündliche Empfehlungen auf Basis der von ESTAVIS angestrebten Zlele beinhalten.
1.4 Weitere Beratungsleistungen GoMoPa’s bezlehen slch nicht auf Rechts- oder Steuerberatung, haben aber Unterhändler
Gespräche sowie die Vermittlung entsprechender Consulter zum Inhalt, jedoch ohne rechtsverbindliche Vollmacht.
2. HONORAR
2.1 Für die Erbringung der genannten Leistunqen zahlt die ESTAVIS an GOMOPA ein Honorar In Höhe von 75.000.- € (Fünfundsiebzigtausend Euro). Das Honorar lst fällig wie folqt:
2.2. Bis zum 21.08.2009 eine Abschlagszahlung In Höhe von 50.000.- Euro. Anschliessend jeweils zum Ende eines Monats (beginnend mit dem August) 5 Teilbeträge in Höhe von jeweils 5.000,- Euro gezahlt. Zahlungen erfolgen gegen Rechnunqsstellung.
2.3. Leistungen, dle eventuell darüber hlnaus zu erbringen sind (eventuelte Reisekosten, Spesen, zusätzliche Aufgaben und
Arbeiten) werden separat und ausschliesslich nach Absprache in Rechnung gestellt und von ESTAVIS gezahlt.
3. SCHLUSSBESTIMMUNGEN
3.1 Sind oder werden einzelne Bestimmungen dieser Vereinbarung unwirksam, so bleibt die Gültigkeit der Vereinbarung im
Übriqen unberührt. Ungültige Bestimmungen sind einvernehmlich durch solche zu ersetzen, die unter Berücksichtigung der Interessenlage den gewünschten wirtschaftlichen Zweck zu erreichen geeignet sind. Entsprechendes gilt für die Ausfüllung von
Lücken, die sich In dieser Verelnbarung etwa herausstellen könnten.
3.2 Aenderungen und Ergänzungen dieser Vereinbarung bedürfen zu ihrer Rechtswirksamkeit der Schriftform. Das Gleiche gilt für
ehe Abbedingung dieser Schriftformklausel.
3.3 Erfülllungsort und ausschliesslicher Gerichtsstand ist New York.
Berlln den, New York den, 13.08.20O9
ESTAVIS AG Goldman Morgenstern & Partners llc
Mozanovski F. Lanz Klaus Maurischat
Cryptome – NSA Tempest Control Plan
DOWNLOAD THE ORIGINAL DOCUMENT HERE:
TMZ – Bar Refaeli — Tweeting her Ass for the World to See!
Zane Grey’s Fighting Caravans – Full Movie
A young frontier scout helps guide a freight wagon train across the country, fighting off Indians and evil traders, while his two crusty companions try and save him from falling in love.
DER BEWEIS “DAS INVESTMENT MAGAZIN” DAS ORIGINAL IST ECHT
TMZ – Justin Bieber — Bangin’ MORE Victoria’s Secret Models
Justin Bieber performed at the Victoria’s Secret Fashion Show… and according to TMZ’s super hot guest host, Chrissy Teigen, all of those girls wanted a piece of the Biebs!!!
Exposed – Whistleblower Exposes Multi-Billion Dollar Securities Violations at Deutsche Bank

Deutsche Bank headquarters in Frankfurt, Germany
Financial Times: Deutsche Hid Up to $12Bn Losses, Say Staff
Summary: This explosive front-page article, along with a lengthy companion piece, details allegations of multi-billion-dollar fraud at Deutsche Bank. Three bank whistleblowers – including GAP client Eric Ben-Artzi – allege that the company’s “trades were valued in a way that hid billions in losses.” The piece is making major waves across the financial world.
Key Quote: But the three former employees told the SEC that this outcome does not mean the allegations should be forgotten. “If Lehman Brothers didn’t have to mark its books for six months it might still be in business,” says one of the men. “And if Deutsche had marked its books it might have been in the same position as Lehman.”
Related Article: Corporate Crime Reporter
Unveiled – Tepco Additional Compensation for Fukushima Voluntary Evacuees
|
SECRET – Central Florida Intelligence Exchange Unoccupied Ambulance Thefts Analysis
Central Florida Intelligence Exchange Nationwide Analysis: Increasing Trend of Unoccupied Ambulance Thefts
- 7 pages
- For Official Use Only
- October 10, 2012
(U//FOUO) The Central Florida Intelligence eXchange (CFIX) recently received a brief from the Arizona Counter Terrorism Information Center (ACTIC – TLO Program) that included a report of a stolen ambulance in Phoenix, AZ. At the request of an Intelligence Liaison Officer (ILO) in the Central Florida region (R-5 Hospital/Medical Sector), CFIX was asked to collect, research, analyze and develop a ‘Situation Brief’ based on this report to determine if this was a significant trend that could cause concern for Region 5 partners.
CASE STUDIES:
Chicago, (IL) – On October 09, 2012, a man took off in an ambulance parked in front of a hospital in Berwyn and drove 10 miles before being stopped by police. He stole the ambulance while paramedics assisted hospital staff with a patient. Two paramedics were suspended and may face disciplinary action for leaving the ambulance unattended and the keys inside. (Source: Chicago Tribune)
Tulsa, (OK) – On October 01, 2012, as paramedics were on a medical call at an apartment complex, an intoxicated man jumped in the ambulance and attempted to back up hitting three vehicles. Paramedics pulled him out of the driver’s seat. The man tried to run but paramedics held him until law enforcement arrived. He was arrested and booked into the Tulsa County Jail. (Source: KJRH News)
Phoenix, (AZ) – On September 21, 2012, a 26-year-old female (pictured below) stole an ambulance that was left running in front of a Phoenix hospital. An on-duty reserve officer spotted the ambulance; however, the suspect refused to stop. Officers also tried to negotiate using the ambulance radio. Officers finally stopped her by blocking the roads creating a barricade with their vehicles where she was arrested and taken into custody. (Source: ACTIC)
Monroe County, (FL) – On September 02, 2012, a 22-year-old suspect was arrested and charged after jumping into an ambulance and taking off. Officers spotted and pursued the ambulance that had its lights on but no siren after receiving reports that it was stolen. The suspect admitted to stealing the ambulance to gain attention from law enforcement after she was unable to locate her friend. (Source: Firehouse.com)
Dallas, (TX) – On August 26, 2012, a man stole an ambulance after paramedics left the engine idling as they searched for an injured person in an apartment complex. They never found the 9-1-1 caller and when they returned the ambulance was gone. Police tracked the vehicle back to the suspect, where he was arrested and charged. A pair of crutches and a backpack that did not belong to paramedics were also found inside the ambulance. (Source: dallasnew.com)
[Analyst Comment: Although officials from Dallas have not confirmed if the 9-1-1 caller was the same individual who stole the ambulance, paramedics and EMTs should be vigilant and aware of this activity, to prevent a crime of opportunity from occurring.]
Montgomery County, (PA) – On July 26, 2012, a suspect was caught on dashboard surveillance video (pictured right) after he jumped into an ambulance and drove off as EMTs were preparing to transport a patient to the hospital. Responder lights were still activated as the suspect prompted traffic to move and passed through the red lights. The suspect was able to monitor police transmissions with the radio equipment that was mounted in the ambulance console to avoid law enforcement. Law enforcement later found the ambulance abandoned in an apartment complex parking lot. (Source: ABC News)
Killeen, (TX) – On June 21, 2012, a man was arrested and charged for stealing an ambulance while paramedics were inside a residence responding to an emergency call. Shortly after the paramedics noticed the ambulance missing, the suspect came back to the residence, stepped out and walked away stating he just wanted to take a “joyride” in an ambulance. The suspect was arrested at the
scene. (Source: KWTX.com)Savannah, (GA) – On June 8, 2012, while under police supervision at a Georgia hospital, a man assaulted a deputy, stole an ambulance and led police on a low-speed pursuit. The suspect struggled with the deputy, attempted to remove a gun from his holster, climbed into an unlocked ambulance and then drove away. The officers attempted to stop the suspect by using stop sticks which flattened three tires, while the ambulance hit vehicles along the way. Patrol cars were also damaged, but no one was injured. (Source: WFMY News)
…
ANALYSIS:
(U//FOUO) In all of the ambulance theft cases analyzed in this brief, similar pre-incident indicators were identified. All of the documented cases had one or more of the following commonalities:
- The ambulance was left unattended;
- Keys were left in the ignition;
- The ambulance was left running;
- Many of the thieves were under the influence of drugs or alcohol; and
- Most thefts occurred while on scenes or parked on ambulance ramps at hospitals
IMPLICATIONS:
(U//FOUO) Although the cases included in this brief did not transpire within the Central Florida region, it implies that ambulance thefts could potentially occur in any jurisdiction where hospitals or ambulatory services are present. There are critical vulnerabilities associated with these thefts that could impact the emergency services sector, specifically pertaining to the safety of the public, homeland security concerns and monetary loss.
PUBLIC SAFETY ISSUES
(U//FOUO) The safety of the traveling public as well as pedestrians could be at risk if a subject takes off in an ambulance, especially when under the influence of drugs or alcohol. In most cases mentioned in this brief, crashes and injuries did occur due to speed and inexperience of the suspect driver. Another consideration is protocols for backup measures for a patient in need of immediate transport or care in the event an ambulance is stolen during a medical emergency. The equipment onboard or transport time may be critical for the patient’s care and may be the difference of a life or death situation.
HOMELAND SECURITY CONCERNS
(U//FOUO) The majority of theft cases involving ambulances typically conclude as an act of criminal behavior, usually involving intoxication. There are concerns however, among counterterrorism authorities that stolen ambulances could be cloned for carrying out terrorist attacks or other criminal/malicious activity. In 2008, for example, a paramedic working the Republican National Convention (RNC) in St. Paul, MN spotted an ambulance with unusual markings. When law enforcement searched the unlocked cloned ambulance, they found a large cache of weapons, as well as bags of urine and feces that potentially could have transitioned into a mass casualty event.
[Analyst Comment: Overseas, terrorists have also used stolen or cloned ambulances to carry out secondary and tertiary attacks as first responders arrive on scene. The threat to carry out similar attacks in the US has been widely discussed on extremist forums.]
…
A Farewell to Arms – Full Movie – Rock Hudson and Jennifer Jones
A tale of the love between ambulance driver Lt. Henry and Nurse Catherine Barkley during World War I
Farewell to Arms is the second film version of Ernest Hemingway’s World War One novel–and also the last film produced by David O. Selznick (Gone with the Wind). Rock Hudson plays an American serving in the Italian Army during the “War to End All Wars”. Jennifer Jones is his lover, a Red cross nurse. They have a torrid affair, which results in Jones’ pregnancy. As the months pass, Hudson and Jones lose contact with one another, and Jones believes that Hudson has forgotten her. But a battle-weary Hudson finally makes it to Switzerland, where Jones is hospitalized. The baby is stillborn, and Jones dies shortly afterward, murmuring that her death is “a dirty trick.” Filmed on a simpler scale in 1932 (with Gary Cooper and Helen Hayes starring), A Farewell to Arms was blown all out of proportion to “epic” stature for the 1957 remake–so much so that its original director, John Huston, quit the film in disgust. Still, the basic love story is touchingly enacted by Rock Hudson and Jennifer Jones.
DER “GoMoPa” ADRESSEN-FRIEDHOF BUCHSTABE A UND DIE GEFÄLSCHTEN MITGLIEDERZAHLEN
gomopa-friedhof-adressen-verwaltung
Download Link oben
Die gefälschten Mitgliederzaheln von “GoMoPa”.
Gomopa dürfte ohnehin ein Glaubwürdigkeitsproblem haben, denn der Dienst fiel mit falschen oder fragwürdigen Äußerungen auf. So gibt es laut Website 57 345 Mitglieder (Stand 21. September 2010). Die Mitgliedschaft ist bis auf einen einmonatigen Test kostenpflichtig. Einnahmen aus den Beiträgen beziffert Maurischat in seiner Information aber nur auf um die 5000 Euro. Selbst wenn alle Mitglieder die günstigste Variante gewählt haben, ergäben sich rechnerisch weit weniger als 1000 zahlende Mitglieder. Gomopa äußert sich dazu nicht.
Secrecy News – DETAINED LINGUIST SEEKS RELEASE FROM JAIL
James F. Hitselberger, a Navy contract linguist who was charged under the
Espionage Act for mishandling classified records, yesterday asked a court
to release him from pre-trial detention. His release would pose no hazard,
and he is not a flight risk, his public defenders said.
Mr. Hitselberg allegedly removed classified records from a secure facility
in Bahrain, and had previously donated classified materials to the Hoover
Institution, which maintains a James F. Hitselberger Collection. He is not
suspected of transmitting classified information to a foreign power. See
"Document Collector Charged Under Espionage Statute," Secrecy News,
November 7, 2012.
http://www.fas.org/blog/secrecy/2012/11/collector_charged.html
According to prosecutors, Mr. Hitselberger is a shadowy figure who might
vanish if released from custody. They urged that he be detained until
trial.
"For almost eight months, the defendant, James Hitselberger, has lived as
a fugitive," according to a November 29 government memorandum. "He speaks
multiple foreign languages, has an apparent network of friends and
acquaintances overseas, and is adept in adapting to foreign surroundings."
http://www.fas.org/sgp/jud/hitsel/112912-detention.pdf
But in a motion for reconsideration filed yesterday, defense attorneys
said that prosecutors had misrepresented the facts.
http://www.fas.org/sgp/jud/hitsel/120412-recon.pdf
Mr. Hitselberger "neither fled nor hid from law enforcement officials."
He "never tried to conceal his identity or location." Although government
officials had his contact information, "no government agent ever contacted
Mr. Hitselberger or asked him to return to the United States."
"The facts demonstrate that Mr. Hitselberger was not a fugitive, [and he]
cooperated with law enforcement in the investigation of his conduct... He
was never told that law enforcement agents required him to return to the
United States, and he did not 'flee' from law enforcement," defense
attorneys wrote.
Even prosecutors admitted that "Hitselberger has no history of violence.
Nor has the government's investigation revealed that he has tried to pass
any of the classified information he has acquired to a foreign power."
Under the circumstances, defense attorneys asked the court to release Mr.
Hitselberger from pre-trial detention into the custody of his family, and
under electronic monitoring.
"The evidence does not support a finding that Mr. Hitselberger would be a
substantial risk of flight or a danger to the community if released," they
wrote. "Mr. Hitselberger will comply with conditions of release and has
neither the passport necessary nor the will to flee."
The offenses allegedly committed by Mr. Hitselberger are undoubtedly
violations of classification policy. But the notion that they rise to the
level of multiple felonies is hard to credit, and suggests an excess of
zeal among prosecutors.
A status conference in the case will be held on December 13.
See also "Linguist charged with pilfering records seeks release" by Josh
Gerstein, Politico, December 5:
http://www.politico.com/blogs/under-the-radar/
HOW A BILL BECOMES A LAW, AND MORE FROM CRS
On January 6, 2013 Congress will convene to count electoral votes and to
formally certify the results of the last presidential election. The
process was detailed by the Congressional Research Service in "Counting
Electoral Votes: An Overview of Procedures at the Joint Session, Including
Objections by Members of Congress," November 30, 2012:
http://www.fas.org/sgp/crs/misc/RL32717.pdf
The declining economic condition of many state governments is examined by
CRS in "State Government Fiscal Stress and Federal Assistance," December 3,
2012:
http://www.fas.org/sgp/crs/misc/R41773.pdf
And for members of Congress who never had civics class, CRS explains how a
bill becomes a law in "Introduction to the Legislative Process in the U.S.
Congress," November 30, 2012:
http://www.fas.org/sgp/crs/misc/R42843.pdf
See also the elementary "Introduction to the Federal Budget Process,"
December 3, 2012:
http://www.fas.org/sgp/crs/misc/98-721.pdf
Other new and updated CRS reports that Congress has not made publicly
available include the following.
Congressional Salaries and Allowances, December 4, 2012:
http://www.fas.org/sgp/crs/misc/RL30064.pdf
Alternative Minimum Taxpayers by State: 2009, 2010, and Projections for
2012, December 4, 2012:
http://www.fas.org/sgp/crs/misc/RS22083.pdf
Offsets, Supplemental Appropriations, and the Disaster Relief Fund:
FY1990-FY2012, December 4, 2012:
http://www.fas.org/sgp/crs/misc/R42458.pdf
The Bayh-Dole Act: Selected Issues in Patent Policy and the
Commercialization of Technology, December 3, 2012:
http://www.fas.org/sgp/crs/misc/RL32076.pdf
Technology Transfer: Use of Federally Funded Research and Development,
December 3, 2012:
http://www.fas.org/sgp/crs/misc/RL33527.pdf
Industrial Competitiveness and Technological Advancement: Debate Over
Government Policy, December 3, 2012:
http://www.fas.org/sgp/crs/misc/RL33528.pdf
Cooperative R&D: Federal Efforts to Promote Industrial Competitiveness,
December 3, 2012:
http://www.fas.org/sgp/crs/misc/RL33526.pdf
IMF Reforms: Issues for Congress, December 4, 2012:
http://www.fas.org/sgp/crs/misc/R42844.pdf
China's Economic Conditions, December 4, 2012:
http://www.fas.org/sgp/crs/row/RL33534.pdf
Federal Emergency Management: A Brief Introduction, November 30, 2012:
http://www.fas.org/sgp/crs/homesec/R42845.pdf
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
Cryptome unveils – New Syrian Emails Hacked
A sends:
Most recent 7 days ago.
http://syria.ircdrama.us/ (List of the leaked e-mails)
http://par-anoia.net/releases.html (Anonymous)
http://par-anoia.net/assessment/sy/rnd-syr.tgz (Download link)
http://www.propublica.org/documents/item/522212-syrian-flight-manifests (Flight manifests for flights between Moscow and Damascus)
The leaked flight manifest refers to “30 ton” of banknotes. That is a US measure. Russian and Syrian usage is the metric system – “30 tonne” or “30,000 kg.” US aviation practice is to list weights in pounds, esp. fuel load and cargo load.
TOP-SECRET-U.S. Treasury Office Designated Nationals and Blocked Persons List

The following document contains the updated list of specially designated nationals as of November 5, 2012. The list includes individuals and companies “owned or controlled by, or acting for or on behalf of, targeted countries” as well as “terrorists and narcotics traffickers designated under programs that are not country-specific.” The list is available in other formats from the U.S. Treasury Office of Foreign Assets Control. H/T Carlton Purvis.
This publication of Treasury’s Office of Foreign Assets Control (“OFAC”) is designed as a reference tool providing actual notice of actions by OFAC with respect to Specially Designated Nationals and other persons (which term includes both individuals and entities) whose property is blocked, to assist the public in complying with the various sanctions programs administered by OFAC. The latest changes to the SDN List may appear here prior to their publication in the Federal Register, and it is intended that users rely on changes indicated in this document. Such changes reflect official actions of OFAC, and will be reflected as soon as practicable in the Federal Register under the index heading “Foreign Assets Control.” New Federal Register notices with regard to Specially Designated Nationals or blocked persons may be published at any time. Users are advised to check the Federal Register and this electronic publication routinely for additional names or other changes to the SDN List.
…
References following each SDN indicate the sanctions program pursuant to which the person has been designated or identified:
[BALKANS]: Western Balkans Stabilization Regulations, 31 C.F.R. part 588; Executive Order 13304, 68 FR 32315;
[BELARUS]: Executive Order 13405, 71 FR 35485;
[BPI-PA]: Blocked Pending Investigation, Patriot Act;
[BPI-SDNTK]: Blocked Pending Investigation, Foreign Narcotics Kingpin Sanctions Regulations, 31 C.F.R. part 598;
[BURMA]: Burmese Sanctions Regulations, 31 C.F.R. part 537; Executive Order 13448, 72 FR 60223; Executive Order 13464, 73 FR 24491;
[COTED]: Cote d’Ivoire Sanctions Regulations, 31 C.F.R. part 543;
[CUBA]: Cuban Assets Control Regulations, 31 C.F.R. part 515;
[DARFUR]: Darfur Sanctions Regulations, 31 C.F.R. part 546;
[DPRK]: Executive Order 13551;
[DRCONGO]: Democratic Republic of the Congo Sanctions Regulations, 31 C.F.R. part 547;
[FTO]: Foreign Terrorist Organizations Sanctions Regulations, 31 C.F.R. part 597;
[HRIT-SY]: Executive Order 13606 – Syria;
[HRIT-IR]: Executive Order 13606 – Iran;
[IFSR]: Iranian Financial Sanctions Regulations, 31 CFR part 561;
[IRAN]: Iranian Transactions Regulations, 31 CFR part 560;
[IRAN-HR]: Executive Order 13553;
[IRAQ2]: Executive Order 13315, 68 FR 52315; Executive Order 13350, 69 FR 46055;
[IRAQ3]: Executive Order 13438, 72 FR 39719;
[IRGC]: Iranian Financial Sanctions Regulations, 31 CFR Part 561
[ISA]: Iran Sanctions Act, Executive Order 13574;
[JADE]: Pub. L. 110-286, 122 Stat. 2632;
[LEBANON]: Executive Order 13441, 72 FR 43499;
[LIBERIA]: Former Liberian Regime of Charles Taylor Sanctions Regulations, 31 C.F.R. part 593;
[LIBYA2]: Libyan Sanctions, 31 C.F.R. part 570;
[NPWMD]: Weapons of Mass Destruction Proliferators Sanctions Regulations, 31 C.F.R. part 544;
[SDGT]: Global Terrorism Sanctions Regulations, 31 C.F.R. part 594;
[SDNT]: Narcotics Trafficking Sanctions Regulations, 31 C.F.R. part 536;
[SDNTK]: Foreign Narcotics Kingpin Sanctions Regulations, 31 C.F.R. part 598;
[SDT]: Terrorism Sanctions Regulations, 31 C.F.R. part 595;
[SOMALIA]: Somalia Sanctions Regulations, 31 C.F.R. part 551;
[SUDAN]: Sudanese Sanctions Regulations, 31 C.F.R. part 538;
[SYRIA]: Syrian Sanctions Regulations, 31 C.F.R. part 542; Executive Order 13399, 71 FR 25059; Executive Order 13460, 73 FR 8991;
[TCO]: Transnational Criminal Organizations Executive Order 13581; and
[ZIMBABWE]: Zimbabwe Sanctions Regulations, 31 C.F.R. part 541; Executive Order 13391, 70 FR 71201; Executive Order 13469, 73 FR 43841.
[561List]: Informational tag indicating that this designation is also listed on the List of Foreign Financial Institutions Subject to Part 561 (the “Part 561 List”)
DOWNLOAD THE ORIGINAL DOCUMENT HERE:
Meet John Doe – Full Movie
A man needing money agrees to impersonate a nonexistent person who said he’d be committing suicide as a protest, and a political movement begins
The first of director Frank Capra’s independent productions (in partnership with Robert Riskin), Meet John Doe begins with the end of reporter Ann Mitchell’s (Barbara Stanwyck) job. Fired as part of a downsizing move, she ends her last column with an imaginary letter written by “John Doe.” Angered at the ill treatment of America’s little people, the fabricated Doe announces that he’s going to jump off City Hall on Christmas Eve. When the phony letter goes to press, it causes a public sensation. Seeking to secure her job, Mitchell talks her managing editor (James Gleason) into playing up the John Doe letter for all it’s worth; but to ward off accusations from rival papers that the letter was bogus, they decide to hire someone to pose as John Doe: a ballplayer-turned-hobo (Gary Cooper), who’ll do anything for three squares and a place to sleep. “John Doe” and his traveling companion The Colonel (Walter Brennan) are ensconced in a luxury hotel while Mitchell continues churning out chunks of John Doe philosophy. When newspaper publisher D.B. Norton (Edward Arnold), a fascistic type with presidential aspirations, decides to use Doe as his ticket to the White House, he puts Doe on the radio to deliver inspirational speeches to the masses — ghost-written by Mitchell, who, it is implied, has become the publisher’s mistress. The central message of the Doe speeches is “Love Thy Neighbor,” though, conceived in cynicism, the speeches strike so responsive a chord with the public that John Doe clubs pop up all over the country. Believing he is working for the good of America, Cooper agrees to front the National John Doe Movement — until he discovers that Norton plans to exploit Doe in order to create a third political party and impose a virtual dictatorship on the country. The last of Capra’s “social statement” films, Meet John Doe posted a profit, although Capra and Riskin were forced to dissolve their corporation due to excessive taxes.
DIE FREI ERFUNDENEN LÜGEN VON “GoMoPa”, UND DEREN SCHEI*SHAUSFLIEGENBLOG, EXTREMNEWS,ETC: FALL PROFESSOR MINISTER SCHELTER
IMMOVATION AG: Frei erfundene Behauptungen des “Informationsdienstes” GoMoPa im Zusammenhang mit angeblichem Sturz des früheren brandenburgischen Ministers Prof. Schelter – Einstweilige Verfügung beantragt
TMZ – Kim Kardashian Causes a RIOT in the Middle East
FEMEN ATTACK COMPILATION VIDEO
TOP-SECRET – NATO Comprehensive Operations Planning Directive
The following is NATO’s allied command operations directive on comprehensive operations planning. Though unclassified, NATO doctrine and policy documents are not released to the public.
ALLIED COMMAND OPERATIONS COMPREHENSIVE OPERATIONS PLANNING DIRECTIVE COPD INTERIM V1.0
- 412 pages
- December 17, 2010
1-2. NATO’S Contribution to a Comprehensive Approach.
a. NATO recognises that that the military alone cannot resolve a crisis or conflict. There is a need for more deliberate and inclusive planning and action through established crisis management procedures that allow for both military and non-military resources and efforts to be marshalled with a greater unity of purpose. Adopting such a comprehensive approach to operations begins with inculcating a culture of active collaboration and transparency among those involved in crisis management.
b. The initiation of such an operation should lie in: the development of a shared understanding of overarching goals to resolve the crisis; facilitating the production of a broad multi-dimensional response on how to achieve the necessary objectives to reach the international “end state”; the delineation of lines of functional activities, where possible, and the responsibilities for them; identifying the effects to be achieved; and agreement in the leadership function for the overall international effort. For the Alliance, this includes the development of process and structures for effective co-ordination and cooperation with other actors, to allow each to complement and mutually reinforce the others’ efforts, ideally within an overall strategy agreed by the international community and legitimate local authorities.
c. Planning in a multi-dimensional environment generates particular challenges for both civilian and military actors. Experience shows that not only may there be no formally appointed lead agency to provide overall coordination, but that those organisations capable of reacting quickly are very often military in nature. In addition, some institutions may not wish to have formalised relationships with others. Thus, a comprehensive approach emerges through the determination of various actors to play their part to resolve a crisis. Pragmatism is often the way forward, as imperfect as this may be in an otherwise rules-based society. In this regard, unless otherwise authorised, it is not for NATO to offer itself as the lead coordinator. It is, however, right for all levels to look for opportunities for interaction and to collaborate actively under principles of mutual respect, trust, transparency and understanding, and a duty to share. Moreover it is incumbent on NATO, especially in the planning and early execution stages of an operation, to understand and to attempt to anticipate the needs and objectives of other potential contributors thus enabling subsequent coordination and cooperation.
1-3. Purpose.
a. Set within the context of a NATO contribution to a comprehensive approach, the purpose of this Allied Command Operations (ACO) Comprehensive Operations Planning Directive (COPD) is to outline the military procedures and responsibilities governing the preparation, approval, assessment, implementation and review of operations plans to enable a common approach to operations planning. This includes the associated documents which are required in order to execute the mission allocated to SACEUR and his subordinate joint force commanders.
b. The COPD provides a common framework for collaborative operations planning when defining NATO’s Contribution within a comprehensive approach philosophy. It is deliberately detailed, to support training, while giving experienced planners, at the strategic (Chapter 3) and operational (Chapter 4) levels, the necessary tools to fully appreciate all elements of the most complex crisis and produce high quality operations plans. It also covers details for the preparation, approval, promulgation, distribution, implementation, review and administration of operations plans documents necessary to execute the tasks allocated to SACEUR and his subordinate commanders. Its processes attempt to cover all expected scenarios; however, as planners become more familiar with the concepts of the COPD, it should be used to guide rather than slavishly followed.
c. Design, planning and execution are human matters where commanders lead and staff support. Intuition, experience and military judgement remain paramount and this directive provides the processes and tools to support commanders’ decision making at the strategic and operational levels. But the COPD is not an end in itself, merely a tool. Commander’s guidance at every level provides staff with the vision of how a challenge is to be tackled and provides subordinates with the freedom to operate within the broader context of the mission. For collaborative planning to work effectively, it is vital that planners, at each level, not only have a common understanding of the crisis situation and a common approach to developing the necessary plans to support NATO involvement, but also understand how the commander and staff operate at the next higher level so they are able to contribute to and influence the process.
d. Crises are dynamic and the planning process is iterative, influenced and crafted by the factors described earlier. Throughout the planning and execution process, there must be a continual review process to update the design, plan and execution of an operation. The detail provided in the COPD must not be mistaken as generating a requirement for a complex and detailed plan; rather, it is designed to help the planners develop a product of clarity and simplicity capable of providing the necessary guidance to execute the commander’s vision.
…
3-54. Plan StratCom.
a. Review Requirements for StratCom. StratCom must be an integral component of planning based on the mission-specific StratCom strategy adopted by the NAC. NATO’s Assistant Secretary General for Public Diplomacy (ASG PDD) oversees the formulation of the StratCom strategy through the SCPB, which includes representation from SecGen’s Private Office, PDD, NATO Spokesman, IMS StratCom, both StratCom and JFCs (as needed). Therefore, it is critically important that the SOPG be proactive in providing the necessary planning support in line with the strategic concept and in coordination with the supported JFC. Planning for StratCom, supported by the SCWG should include the following:
(1) Review NATO strategic and military strategic objectives and effects and assess the impact of military actions on the information environment.
(2) Further develop narratives, themes and master messages for different audiences.
(3) Determine StratCom aims and match to audiences and targets for StratCom effect.
(4) Establish responsibilities and arrangements for military support to Public Diplomacy, PA, Info Ops and PSYOPS.
(5) Develop criteria for the assessment of StratCom activities and the impact of military activities on the information environment.
(6) Coordinate StratCom activities with non-military and non-NATO entities.
(7) Ensure limitations are taken into account.
(8) Assess risks to achievement of the StratCom strategy and develop mitigation actions.
(9) Identify and establish required mechanisms to address issues of strategic and/or political importance, including but not limited to Civilian Casualties (CIVCAS) and counter-propaganda.b. Review NATO Strategic and Military Strategic objectives and desired effects. NATO strategic and military strategic objectives and desired effects are developed to ensure that NATO achieves its end state in an operation. NATO’s actions must be clearly understood to gain support from governments, populations and other groups in the theatre as well as to influence the actions of adversaries. StratCom must continually analyse the objective and desired effects in light of current strategic conditions to ensure that StratCom activities are coherent and integrated with military actions and contribute to desired effects for each phase of the operation.
c. Further develop narratives, themes and master messages for different Target Audiences. Based on their understanding of the different perspectives and biases of the different audiences, StratCom should develop an over-arching, resonating narrative, upon which themes and master messages can be based. StratCom must then refine the themes and master messages depending on the strategic conditions, taking into account target audience receptiveness, susceptibility and vulnerability to different historical, social, cultural, and religious references. This may include the necessity to establish agreed terminology to be used by all actors in the information environment when referring to adversaries and local populations. Red and green teams as well as systems analysts and other experts from the KD team may be able to assist.
d. Determine StratCom aims and match to audiences and targets in conjunction with an over-arching engagement strategy. The Alliance (and its Partners if applicable) must act in close concert in the delivery of agreed themes, messages and actions based on a planned and coordinated design to deliver specific StratCom aims. Where possible, other international actors, opinion formers and elites should be integrated into this approach through a coordinated engagement strategy at all levels within the wider local, regional and international public to promote support for NATO actions.
e. Develop criteria for the assessment of StratCom activities and the impact of military activities on the information environment. To assess the effectiveness of activities and messages in achieving the StratCom aims and contributing to the desired effects, StratCom must develop operations assessment criteria and measures of effectiveness within the larger cadre of the overall operations assessment effort. These should be closely coordinated with SHAPE strategic effects, Info Ops, PA and planning for the conduct of operations assessment at the strategic level.
f. Establish responsibilities and arrangements for military support to PD, PA, Info Ops and PSYOPS. On the basis of coordination with NATO IS and IMS, the supported JFC, and relevant cooperating non-NATO actors, StratCom, must clearly establish responsibilities and coordination mechanisms for the conduct of military activities in support of PD, PA, Info Ops and PSYOPS within the theatre.
g. Coordinate StratCom activities with relevant non-military and non-NATO actors. To promote coherence in StratCom among the non-military and relevant cooperating non-NATO actors, StratCom should arrange a suitable venue in consultation with the NATO SCPB, to coordinate and harmonise the principal aspects of StratCom activities in the theatre and within the wider international community. In particular, arrangements and mechanisms must be agreed that will allow regular coordination of information activities during the subsequent phases of the operation and in response to urgent information requirements as a result of events on the ground.
h. Ensure limitations are taken into account. There will likely be restraints and constraints imposed by political-level guidance and conditions in the JOA. These must be taken into account to ensure the StratCom effort remains focused and does not exceed the level of ambition of the nations.
i. Assess risks to StratCom strategy achievement and develop mitigation actions. Risks to achievement of the StratCom strategy can take many forms, including but not limited to message incoherence, information fratricide and rising expectations. These risks must be evaluated and mitigation actions planned against them.
j. Identify and establish required mechanisms to address issues of strategic and/or political importance. There is a need to identify and establish required mechanisms to address issues of strategic and/or political importance, including, but not limited to, civilian casualties (CIVCAS) and counter-propaganda. Mechanisms are required to address issues of political and/or strategic sensitivity to prevent an erosion or loss of NATO’s credibility and prevent the development of a gap between what NATO says and does and the perception of NATO at all levels. These mechanisms can take many forms, but two important issues are CIVCAS and propaganda. Responsive, thorough mechanisms for identifying, investigating and releasing information on all credible CIVCAS claims caused by NATO forces must be implemented and coordinated at all levels. Equally, implementation of a proactive counter propaganda mechanism coordinated at all levels is a must. Failure to do either of these mechanisms will result in a rapid loss of NATO’s credibility in the theatre and perhaps even within the wider international community.
Scrooge – Full Movie
Scrooge, the ultimate Victorian miser, hasn’t a good word for Christmas, though his impoverished clerk Cratchit and nephew Fred are full of holiday spirit. But in the night, Scrooge is visited by spirits of another color.
Starring Seymour Hicks as the title character, Scrooge is a faithful adaptation of the classic Charles Dickens’ novel A Christmas Carol about a heartless miser who discovers the true meaning of Christmas when three ghosts visit him on Christmas Eve. Hicks co-wrote the screenplay to this film, which is a thoroughly entertaining and effective retelling of a familiar story
Secret – Brooklyn Clinic Employee Pleads Guilty in Connection with $71 Million Medicare Fraud Scheme
WASHINGTON—A Brooklyn, New York resident pleaded guilty today to his role in a $71 million Medicare fraud scheme, announced Assistant Attorney General Lanny A. Breuer of the Justice Department’s Criminal Division, U.S. Attorney for the Eastern District of New York Loretta E. Lynch, Acting Assistant Director in Charge Mary E. Galligan of the FBI’s New York Field Office, and Special Agent in Charge Thomas O’Donnell of the U.S. Department of Health and Human Services Office of Inspector General (HHS-OIG).
Yuri Khandrius, 50, pleaded guilty today before U.S. District Judge Nina Gershon in the Eastern District of New York to one count of conspiracy to commit health care fraud, one count of health care fraud, and one count of conspiracy to pay kickbacks.
Khandrius was an employee of a clinic in Brooklyn that operated under three corporate names: Bay Medical Care PC, SVS Wellcare Medical PLLC and SZS Medical Care PLLC (Bay Medical clinic). According to court documents, owners, operators and employees of the Bay Medical clinic paid cash kickbacks to Medicare beneficiaries and used the beneficiaries’ names to bill Medicare for more than $71 million in services that were medically unnecessary or never provided. The defendants billed Medicare for a wide variety of fraudulent medical services and procedures, including physician office visits, physical therapy, and diagnostic tests.
According to the criminal complaint, the co-conspirators allegedly paid kickbacks to corrupt Medicare beneficiaries in a room at the clinic known as the “kickback room,” in which the conspirators paid approximately 1,000 kickbacks totaling more than $500,000 during a period of approximately six weeks from April to June 2010.
Khandrius admitted in court that he conspired with co-workers at Bay Medical to commit health care fraud and to pay cash kickbacks to Medicare beneficiaries as part of the scheme.
At sentencing, Khandrius faces a maximum penalty of 25 years in prison. Sentencing is scheduled for March 11, 2013.
In total, 16 individuals have been charged in the Bay Medical scheme, including two doctors, nine clinic owners/operators/employees, and five external money launderers. To date, 11 defendants have pleaded guilty for their roles in the conspiracy. Five individuals await trial before Judge Gershon on January 22, 2013.
The case is being prosecuted by Assistant U.S. Attorney Shannon Jones of the Eastern District of New York and Trial Attorney Sarah M. Hall of the Criminal Division’s Fraud Section. The case was investigated by the FBI and HHS-OIG.
The case was brought as part of the Medicare Fraud Strike Force, supervised by the Criminal Division’s Fraud Section and the U.S. Attorney’s Office for the Eastern District of New York. The Medicare Fraud Strike Force operations are part of the Health Care Fraud Prevention & Enforcement Action Team (HEAT), a joint initiative announced in May 2009 between the Department of Justice and HHS to focus their efforts to prevent and deter fraud and enforce current anti-fraud laws around the country.
Since its inception in March 2007, the Medicare Fraud Strike Force, now operating in nine cities across the country, has charged more than 1,480 defendants who have collectively billed the Medicare program for more than $4.8 billion. In addition, HHS’s Centers for Medicare and Medicaid Services, working in conjunction with HHS-OIG, is taking steps to increase accountability and decrease the presence of fraudulent providers.
To learn more about the Health Care Fraud Prevention and Enforcement Action Team (HEAT), go to: http://www.stopmedicarefraud.gov.
DER BEWEIS: DER MAGISTER-TITEL VON BERND PULCH IST ECHT
Liebe Leser,
hier der Beweis für meine Magisterarbeit auf der Webseite meines betreuenden Dozenten, Noelle-Neumann-Nachfolgers und LeiterS des
Institutes für Publizistik an der Universität Mainz, Dr. Hans Mathias Kepplinger:
Webseite:
http://www.kepplinger.de/node/50
am Institut für Publizistik der Universität Mainz
Magisterarbeiten N-Z
Neubauer, Frank Richard
Die Presse- und Öffentlichkeitsarbeit der Bundesvereinigung der deutschen Arbeitgeberverbände unter besonderer Berücksichtigung des Bereichs Lobbying
Oktober 1995
Neumann, Barbara
Welche Selektionsmöglichkeiten gibt es zu bestimmten Zeiten im Hörfunk? Eine Inhaltsanalyse des in Köln empfangbaren Hörfunkprogramms vom 15. bis 31. März 1983
Aug. 1984
Nickels, Margret
Zeit und Raum im Film
April 1981
Nicolai, Axel
Herkunftsprofile von Mitarbeitern in Werbeagenturen
Juni 1995
Nies, Ulrich
Die optische Darstellung von Helmut Schmidt und Hans-Dietrich Genscher in der Bildberichterstattung des STERN während der Bundestagswahlkämpfe 1980 und 1982/83
Oktober 1985
Nuppeney, Burkhard
Arbeitsplatzbeschreibung einer Zeitungsredaktion
1978
Obergethmann, Jörg
Die Darstellung von Sieg und Niederlage in der Sportberichterstattung deutscher und österreichischer Tageszeitungen
März 1986
Oechsner, Sibylle
Die Freiwillige Selbstkontrolle Fernsehen (FSF)
März 1994
Oess, Markus
Public Relations für Banken
November 1995
Ohl, Gabriela
Selbstdarstellung und Fremddarstellung von Politikern in Tageszei-tungen. Eine Inhaltsanalyse der Presseberichterstattung während des Bundestagswahlkampfes 1976
März 1980
Ohliger, Angelika
Berufswege von Studienabbrechern – Befragung ehemaliger Studenten der Publizistik
März 1980
Pankowski, Holger
Medien im Meinungsstreit – Die erste Frankfurter Oberbürgermeister-Direktwahl im Spiegel der lokalen Presse und des hessischen Fernsehens
1997
Patzer, Karl-Heinz
Theorien der Nachrichtenauswahl. Systematische Darstellung empirischer Studien
Dezember 1985
Peter, Susanne
Expertenurteile über ausgewählte Print- und TV-Medien
Juni 1998
Peterhanwahr, Ralf
Jockel Fuchs als Chefredakteur der rheinland-pfälzischen SPD-Zeitung “Die Freiheit” während der Jahre 1957-1962
Februar 1995
Peters, Elke
Die Presseberichterstattung vor dem Rücktritt von Ministerpräsident Filbinger
April 1983
Pfeifer, Andreas
Funktion und Wirkung der Typographie, Herkunft, Lesbarkeit und Anmutung lateinischer Druckschriften
Februar 1993
Piella, Wulf
Der Einfluß von Erwartungen auf die Berichterstattung nach einem Ereignis – Am Beispiel der Fußballberichterstattung regionaler Zeitungen
1996
Pleines, Harald
Qualifikation von Ratsmitgliedern – Am Beispiel von Rüsselsheim
Oktober 1982
Pohlmann, Dirk
Begriff des Intellektuellen
Januar 1990
Pöttgens, Stephanie
Franz Alt. Biographie eines Journalisten
Juni 1989
Preikschat, Alfred
Die aktuelle Berichterstattung über die Friedensbewegung. Eine Untersuchung der Tagespresse und des Hörfunks zur Validierung eines inhaltsanalytischen Verfahrens
April 1988
Pulch, Bernd
Dolf Zillmanns Studien zur ‘Emotional-Arousal-Theory’
Januar 1987
Puschatzky, Yvonne
Prominentenprofile. Eine Analyse des FAZ-Fragebogens
September 1996
Püttmann, Jürgen
Deutschsprachige Hörfunksendungen ausländischer Sender. Eine Inhaltsanalyse
Oktober 1988
Quoos, Swantje
Die Leser des Spiegel 1949-1994
September 1995
Rausch, Astrid
Lifestyle als Mittel der Zielgruppensegmentierung in der Werbung
August 1995
Reigber, Dieter
Die regionale/lokale Berichterstattung des ERSTEN PRIVATEN FERNSEHENS und der Tageszeitungen im Bereich des Kabelpilotprojekts Ludwigshafen/Vorderpfalz – Ein inter-/ intramedialer Vergleich
Mai 1989
Rethelford, Peter
Blockwerbung oder Einzelspotstreuung? Experimentelle Untersuchung zur Wirkungsweise alternativer TV-Publikationsweisen
März 1987
Riedl, Peter
Problemlösungskompetenz der Parteien und Thematisierung von Problemen im Landtagswahlkampf in Baden-Württemberg 1988
September 1990
Rindsfüsser, Karsten
Die Darstellung des Journalismus in Heinrich Bölls “Die verlorene Ehre der Katharina Blum”
Oktober 1993
Rode, Utta
Pressekonzentration und journalistische Qualität
März 1984
Rofalski, Peter
Die Umstrukturierung der Unternehmenskommunikation bei Hoechst
Februar 2000
Rosenthal, Matthias
Der Einfluß von Sympathie oder Antipathie auf das journalistische Verhalten von Tageszeitungsredakteuren bei Konflikten um Politiker
April 1987
Rössler, Bernhard
Product Placement oder Unterbrecherwerbung? Der Einfluß der Präsentationsform eines Werbereizes auf Erinnerung und Beurteilung
März 1994
Sauer, Heike
Geschäftsberichte von Kommunikationsmedium zur Unternehmensdarstellung
August 1992
Schäfer, Markus
Komik im Fernsehen – Entwicklung eines Analyseinstrumentes
September 1995
Schäfer-Talanga, Gudrun
Der Journalist Werner Holzer
April 1990
Schaus, Anabel
Selbstkritik von Journalisten und Wissenschaftlern
Juli 1992
Schermuly, Gabi
Die Gesundheitsreform in der Presse
Oktober 1993
Scheufele, Bertram
Die Skandalierung von Günter Krause
November 1996
Schilling, Rainer
Die internationale Diskussion um den “free flow of information”
Juli 1982
Schindler, Winfried
Fotografien von Ronald Reagan und Leonid Breschnew im STERN und TIME-MAGAZINE
Dezember 1985
Schlarb, Armin
Politische Instrumentalisierung der Medien. Literaturstudie zum Wandel der politischen Kommunikation in der Bundesrepublik Deutschland
Juni 1988
Schlüter, Elmar
Darstellung von Sexualmoral in den Massenmedien
Oktober 1985
Schmitt, Christiane
Die Entwicklung des “AIDS-Blut-Skandals” 1993
Dezember 1994
Schmitt, Iris
Motive für den Konsum von Horrorvideos bei Jugendlichen
Juli 1989
Schmitt-Egenolf, Andreas
Individualkommunikation in neuen Netzen – Technische und historische Entwicklung der Telematik sowie Überlegungen zu deren Stand und Perspektive in der Bundesrepublik Deutschland
Juli 1988
Schmitz, Lothar
Der Einfluß von Massenmedien auf die Relevanz von Urteilskriterien (Priming)
Februar 1993
Schneider, Hans-Jürgen
Der optische Eindruck von Politikern. Experimenteller Vergleich zwischen Fernseh- und Hörfunkauftritten von Schmidt, Genscher, Strauß und Kohl
Dezember 1983
Schraewer, Claudia
Rhetorische Mittel bei der Skandalierung von Linda Reisch
Juli 2000
Schreck, Jutta
Einzelfallstudien zur Pressekonzentration
August 1986
Schriefers, Annette
Ansichten der Bevölkerung zur Rolle und zur Arbeitsweise von Journalisten
März 1992
Schröter, Frauke
Die Nachrüstungsdebatte in der Prawda
Oktober 1985
Schuck, Petra
Mißbrauch von Pressefotos – Literaturbericht
Oktober 1985
Schué, Severin
Die Darstellung von Medizin im Fernsehen
Mai 1995
Schug, Markus
Vergleichende Untersuchung der Lokalberichterstattung der beiden Mainzer Tageszeitungen
Juni 1993
Schulze, Andreas
Kultursponsoring in Deutschland
Februar 1995
Schwarz, Michael
Das Fernsehen in Jamaica
August 1990
Schweizer, Marie-Theres
Die Jugendfilmarbeit im Dritten Reich
Juli 1982
Selbka, Iwona
Beiträge polnischer Wissenschaftler zur Kommunikationsforschung
August 1984
Semela, Eva
Welche ökonomischen Auswirkungen auf die öffentlich-rechtlichen Rundfunkanstalten besitzt die Einführung privaten Fernsehens?
September 1991
Sempert, Petra
Frageverhalten und Publikumsreaktion in Talkshows
Mai 1986
Severin, Petra
Geschlechterrollen und Lebensstile in der Werbung in Stern und Bunte von 1965 bis 1990. Eine Inhaltsanalyse der Werbeanzeigen in den beiden Zeitschriften Stern und Bunte
März 1991
Sidenstein, Ute
Gottfried Sello als Kunstkritiker in ‘Die Zeit’ von 1958 bis 1985
Oktober 1989
Siehl, Carsten
Virtuelle Realität. Grundlagen, Anwendungsbereiche und Kommunikationsaspekte einer neuen Medientechnologie
Juni 1995
Simons, Christian
Profil und Funktion der On-Air-Promotion. Eine Strukturanalyse der Programmwerbungen im deutschen Fernsehen
Juni 1996
Sinning, Hilka
Nachrichtenwerte – Die historische Entwicklung eines Forschungskonzeptes
Juli 1980
Spanier, Julia
Ausstrahlungseffekte von emotionalisierenden Werbespots
September 1993
Spiel, Ralph
Die Entwicklung der Filmtheater in der BRD seit 1970
Februar 1993
Staab, Christina
Der Bildungskandidat. Eine Analyse der Bewerbungsunterlagen zur Sendung ‘Der große Preis’
Dezember 1994
Staab, Joachim Friedrich
Der Einfluß der Pressestruktur auf die Berichterstattung über die Bundestagswahlen 1969-1983 aus der Sicht der Kandidaten
März 1985
Stein, Dorothee
Die Darstellung von Konrad Adenauer in der BRD während seiner Kanzlerzeit. Dargestellt am Beispiel der Berichterstattung der FAZ und des Nachrichtenmagazins Der Spiegel
Januar 1981
Stein, Simone
Horst Keller – Europa als Auftrag für einen Journalisten
Oktober 1994
Steinbach, Alexander
Präsentationselemente und Nachrichtenrezeption – Framing von Medieninhalten
September 1998
Steinborn, Annette
Die Bedeutung der Attributions-theorie für die Kommunikationswissenschaft
August 1986
Stienert, Heike
Vergleichende Analyse der Haus- und Kundenzeitschriften öffentlich-rechtlicher Rundfunkanstalten der Bundesrepublik Deutschland
November 1991
Stolz, Hans-Georg
Die redaktionelle Linie ausgewählter Publikationsorgane
August 1987
Storz, Sigrid
Der Einfluß von Bild und Text auf die Problemwahrnehmung und Ursachenzuschreibung von Fernsehzuschauern – Am Beispiel eines Beitrags über Umweltverschmutzung
Februar 1992
Strampe, Karsten
Gewerkschaftsarbeit im Rundfunk (Hörfunk und Fernsehen)
April 1980
Streicher, Jürgen
Der Stern und sein Gründer
März 1986
Streit, Achim
Gründe für Kommunikationskontrolle in Deutschland zwischen Reformation und Restauration
November 1986
Sturny, Dirk
Einfluß von Krisen-Typen auf Publikationsweisen. Eine Input-Output-Analyse anhand von zwei Beispielen
August 1997
Swoboda, Thilo
Der Einfluß von Medien auf politische Entscheidungen. Eine Befragung ehemaliger Bundestagsabgeordneter
August 1995
Szadzik, Carmen
Der Computer als Befragungsinstrument im persönlichen Interview und bei Selbstausfüllersystemen
Oktober 1993
Tesch, Roland
Die Wahrnehmung von Vergewaltigungsszenen im Fernsehen
Mai 1994
Topp, Elisabeth
Schemageleitete Rezeption von Hörfunk- und Zeitungsnachrichten
November 1991
Trares, Simone
Das “Luder” – eine Charaterfiktion der Boulevardpresse
April 2003
Tronsgard, Derek
Der Einfluss von Frames auf die Wirkung von Meldungen über die Gewalt gegen Ausländer
April 2003
Tscherner, Christine
Bedingungen von Thematisierungseffekten
September 1998
Tschullik, Astrid
Der publizistische Umgang von Journalisten mit Sozio- und Kultursponsoring
1994
Tullius, Christiane
Validierung von Inhaltsanalyse durch Tendenzeinschätzung
Oktober 1991
Unold, Michaela
Die Wirkung von Gewaltdarstellungen: Der relative Einfluß des Ereignisses – real vs. fiktional – bzw. der Darstellungsform – künstlich vs. natürlich – auf die Rezipienten
November 1989
Volb, Andrea
Journalisten-Preise in Deutschland
März 2000
Vollbracht, Matthias
Die Entwicklung der Werbeerlöse der öffentlich-rechtlichen Rundfunkanstalten in der Konkurrenz zu den privaten Anbietern
September 1993
Vondano, Ursula
Die kommunikationspolitischen Konzepte von CDU/CSU, SPD und FDP
Juli 1982
Wang, Yuquan
Entwicklung des chinesischen Fernsehens seit der Öffnungspolitik 1978
Januar 1999
Weiß, Christina
Image und Unternehmenskommunikation. Eine Image-Untersuchung über den Caritas-Verband Wiesbaden e.V.
Juli 1995
Weißbecker, Helga
Die Veränderungen der Themenschwerpunkte in den Hörfunk-Nachrichten des HR von 1955 bis 1985
Juni 1989
Wenderoth, Axel
Die wissenschaftliche Begleitforschung zu den Kabelpilotprojekten in Ludwigshafen, München, Dortmund und Berlin
Mai 1988
Weyand, Hans Arno
Redakteure von Anzeigenblättern
Dezember 1989
Winckler, Stefan
Der Journalist Gerhard Löwenthal
November 1994
Winkel, Julia
Von den Alternativzeitungen der 70er zu den Stadtmagazinen der 90er Jahre
März 1999
Winning, Karin
Konflikt zwischen Bild und Text. Experimentelle Untersuchung der Urteilsbildung
Januar 1985
Wolf, Marion
Die Mediennutzung in Deutschland seit 1945 – Eine Zusammenstellung von Literatur zu diesem Thema
April 1980
Wolf, Stefanie
Formale Gestaltung und inhaltliche Ausrichtung der FAZ, Welt, SZ 1951-1996
November 2001
Wolter, Renate
Zum Einfluß der bild- oder textorientierten Mediennutzung auf das Wissen und Verhalten von Vorschulkindern
November 1990
Wright, Claudia Sophie
Die Darstellung der Gentechnik in der Presse der USA. Eine vergleichende Analyse
März 1992
Zech, Stefan
Berufsverständnis von Motor-Journalisten
Juni 1993
Ziesemer, Dominique
Gründe für TV-Umschaltverhalten
April 1996
Zock, Peter
Planung und Realisierung der Unterhaltungssendung “Showfenster”
Mai 1991
Zwiebelberg, Martin
Die Darstellung von Rudolf Scharping in der Tagespresse
1997
Cryptome – Anonymous Hacks DEBKA.com
Anonymous Hacks DEBKA.com
Greetings Citizens of the world,
This is Anonymous.
DEBKA.com is an Israeli-Based News-Agency, which has tied relations with Israeli Intelligence Agency (MOSSAD) and Military sources, “Tongue of MOSSAD”. DEBKA first started around 2000 in purpose of polluting media with Zionist-Oriented news and rumors.
DEBKA also analyzes on how people react to news and information offered by the agency in their state of art laboratory. Using these methods the agency has got the ability to release news and rumors in subjects which have most impact in the eyes of readers and political figures.
We have managed to hack their systems and acquire highly sensitive information, including employees and authors personal information, labs details and of course their subscribers.
For now, we only release portion of what we have got which includes subscribers emails and passwords (Most of them are retired MOSSAD agents!!!). At the end we have a message for them:
THIS IS A WARNNING TO THOSE WHOM SUBSCRIBED TO DEBKA:
STOP SUPPORTING ZIONISM,
STOP SUPPORTING MASS-MURDUR,
STOP SUPPORTING KILLERS OF WOMEN AND CHILDREN.
WE WOULD PUBLISH MORE DETAILS AND INFORMATION IN FUTURE…
Target: http://www.debka-net-weekly.com/mailme.php?email=123@admin.com
Data Base: weekly
Table: users
Password email
----------------------------------------------------------------------
1439 yizraeli@zahav.net.il
FMLnWA bslater@netvision.net.il
palmira admin@debka.com
E6FZtf mepstein@aremet.com
KpQQu4 estelleroith@btinternet.com
hGEJML dachind@attglobal.net
Adler
PjpVKT estironi@bezeqint.net
jWpHCq gedit2@debka.com
12345 edit@debka.com
f8wKtE sharon.mikhailov@gmail.com
KvpYx8 sruben288?@a?l.com
mBDXtj john_erard@yahoo.com
zjDrin kirkvolkman@msn.com
O8Qrpm shulster@direcway.com
TKT6bd barbara@subacorp.com
3AYN3f csnobelen@csll.ca
saturn bsmith@advcourttech.com
LnEV5a flaifer@nyc.rr.com
zEwiu5 gldf4him@verizon.net
3WicZG themajor3@rcn.com
7o5yRh LARsubscription@paramountbio.com
No7c4G marsha.s.kantor@verizon.net
QDrRpP Noahgladstone@verizon.net
SVgQfE r.liebis@verizon.net
aSvu6V rlgotte@rcn.com
chochoma hosogold@hotmail.com
KDjbVq stanjoseph@verizon.net
RL8dQ1 wmcdo1@hughes.net
4R0TJn zs_ima@yahoo.com
WpRRS4 sutherland@charter.net
vinnie sndpaper@hotmail.com
iOk2YK dbsajet@xs4all.nl
CGA6Wz eric@cooperfund.com
hyO0c8 maher_90250@yahoo.com
qa9zFu aherbert@rodmanandrenshaw.com
20022002 d?nderson@loeb.com
wFiNUi mike@mgwelbel.com
murphy rifgroup@aol.com
Mindylou38 jiblais@dc.rr.com
3117 michael.gindi@mac.com
G2iyT7 crabtownprofs@comcast.net
CDSrUo brazil@inter.net.il
ug04NV alive@finishalive.com
bsmd drsalick@aol.com
sE758A zkatz@att.net.mx
2MDyHk ticitavi@aol.com
Kisyk8 hauknest@aol.com
BWrtJZ ttdoonan@hotmail.com
T5Kcne tom@corrigan.com
sT5BVU fherman@calix.com
a5bNEE somthinsmith@msn.com
0FBm30 jim@jbyrneco.com
tKa8z6 sandler@ccf.org
fSY7HR schulzepb@aol.com
KA1Mqe odd.sverre.hove@dagen.no
MSGACORN msgold@msn.com
cWEY45 aldo_b@inter.net.il
xJUNp4 david.wirtschafter@juno.com
M2C7sS llewis1007@aol.com
1931624 fjc@colsa.com
PGNjkX jason@xmiller.com
c1C3hY joe582@Bellsouth.net
xL5J9V johnburk@deskmedia.com
EVi1ny martyreit@csreit.com
presstek Rang1995@gmail.com
3Vsf1x exec@borealis.gi
cpkdHA silonde@bellsouth.net
LqK2pT tckrcr@aol.com
WZxqpN warrenschwar?z@accbrdbnd.com
cahfgr yk4000@ballade.plala.or.jp
tP1c7f oranim@usa.net
Shelidan billyo@microsoft.com
wr5x6c wmanag18@aol.com
dUhSeF dkufeld@aol.com
dragon godsart@bellsouth.net
2KjLCS lewinassoc@earthlink.net
uf7eK6 johnsoneb10@aol.com
yxfuXA jeirealty2@aol.com
yvMsQ8 harvey6@ix.netcom.com
SmileyElle lazyviking@centurytel.net
E7DQny twtspt@aol.com
8xFBW4 amermin@globenet.com.ph
99516 sspec99516@aol.com
cF3JSg bnesin@microgrit.com
RqR8Mg corevalue@comcast.net
1PhUyP randerson3@cox.net
LSSspu zippy20854@aol.com
EvbC2N ophir@speakeasy.net
9mH3Ub norm@theeisenberggroup.com
DDcMRJ njarendt@tds.net
This just has been started……. 🙂
We are Anonymous
We are Legion
We do not forgive.
We do not forget.
Israel, it is too late to expect us.
http://wikileak.ir/en/leaks/7/DEBKA+internal+informations+Hacked+%26+Leaked
#Anonymous #OpIsrael #DEBKALeak
TMZ – Lindsay Lohan — Pounding 2 LITERS of Vodka a Day!?
PUBLIC INTELLIGENCE – U.S. Army Law and Order Operations Publication
The following Army Tactics, Techniques and Procedures publication was released in June 2011 by the U.S. Army. A previous version of the document (FM 19-10) from January 1945 was titled “Military Police in Towns and Cities” and was “designed to furnish a guide for officers and enlisted men assigned the mission of patrolling civil communities”. The publication has been revised several times since then.
ATTP 3-39.10 (FM 19-10) LAW AND ORDER OPERATIONS
- 250 pages
- June 2011
- 3.8 MB
The establishment of full spectrum operations as the Army operational concept—and the shift to a doctrine where offense, defense, and stability or civil support are executed simultaneously and with equal emphasis—has been the catalyst in a major shift in thinking by military planners and commanders. Current doctrine and policy reinforce that the ultimate measure of success of any major operation is typically not realized through operations where offense and defense (traditional combat operations) are the dominant forms. Current doctrine establishes that stability operations and associated efforts to establish safe and secure environments culminating with a capable HN governing its own population, should be provided equal emphasis in military planning and execution. L&O operations are critical enablers to lines of effort supporting the creation of civil security and civil control necessary to achieve success.
Strategic and technological advances, geopolitical instability, and expanded threat spectrums have been the driving force for generating operational and organizational changes throughout the Army, to include the Military Police Corps Regiment. Army doctrine identifies four types of complex, interrelated, and emerging security challenges—irregular, traditional, catastrophic, and disruptive—to which U.S. forces will have to respond. The most immediate and pervasive threat the United States faces is the irregular security challenge. Irregular forces include insurgents, terrorists, and criminals who typically use asymmetric warfare and who benefit from conditions in areas throughout the world where HN governments are ineffective or nonexistent. The criminal threat can impact military operations and require commanders to commit forces and resources to minimize threat situations. To meet the challenges of current and future OEs, the modular military police structure is strategically mobile and provides operationally and tactically agile capabilities to respond to worldwide military police requirements.
L&O operations have historically been understood to consist of LE missions supporting U.S. military commanders and their efforts to police our military personnel, civilians, and family members working and residing on U.S. military posts, camps, and stations. (Posts, camps, and stations refer to any U.S. military installation, base, or other location within the United States and enduring installations, bases, or other locations outside the United States employed to support long-term military commitments and/or serve as power projection platforms.) U.S. Army doctrine has not historically focused on L&O operations outside of LE support to posts, camps, and stations. L&O support to the operational commander and the capabilities inherent within LE organizations have been largely disregarded within Army (and joint) doctrine. Recent conflicts and the nature of the threat within the OE have increased the relevance of L&O operations and LE capabilities in support of Army operations. The applications of L&O operations and the requirements for Army LE personnel to conduct these operations have grown tremendously as nation building and protracted stability operations have demonstrated the need for civil security and civil control as critical lines of effort within the larger effort to transfer authority to a secure and stable HN government.
Lessons learned from recent conflicts, coupled with task analysis conducted by the U.S. Army Military Police School (USAMPS), Fort Leonard Wood, Missouri, have resulted in an expanded doctrinal framework and understanding of L&O operations. The expanded framework does not establish new tasks within the L&O function, but identifies and documents missions and tasks in the revised doctrine that have historically been conducted by military police thought they have not been adequately documented within Army doctrine. Recent updates to military police keystone doctrine establish L&O as the primary military police function, shaping the actions and perspectives of military police in the conduct of all military police functions. These updates describe L&O operations within the context of two activities—policing and LE. Policing activities are general actions aimed at establishing order and stability within an area of operations (AO); LE activities are tied to the rule of law and require specific training and authority for the element or personnel performing the actions. While military police are uniquely qualified to conduct policing, these activities do not require personnel specifically trained for LE activities. LE activities require specific training and may only be conducted by LE personnel (military police, USACIDC special agents [SAs], or other trained and certified LE personnel).
Beyond support to posts, camps, and stations, the requirement for military police capabilities in training and supporting HN police is the most visible and resource-intensive L&O activity. Additionally, maneuver commanders recognize several key LE enablers that greatly enhance and contribute to mission success, including—
• Expertise in evidence collection that is critical to successful site exploitation.
• Biometric applications and modular forensic laboratories.
• Identification of critical civil information regarding the criminal environment, the HN police capability and capacity, and the local population which is obtained through integrated police intelligence operations.Whether conducting LE activities in support of posts, camps, and stations; supporting protection requirements; maintaining and restoring order in an effort to stabilize an AO; providing training and support to HN police; controlling populations; or supporting humanitarian relief operations, military police L&O capabilities are invaluable to the maneuver commander.
…
SUPPORT OF FULL SPECTRUM OPERATIONS
1-28. Army forces may execute a simultaneous and continuous combination of offensive, defensive, and stability or civil support operations (see FM 3-0). Military police L&O capabilities are relevant within all four elements of full spectrum operations by maintaining good order, enabling freedom of action, providing protection of the force, and shaping conditions for the successful transition from combat operations to civilian governance under the rule of law. Military police L&O support to full spectrum operations includes a wide range of missions and tasks that support uninterrupted movement, allow maneuver forces to preserve combat power so that it may be best applied at decisive points and times, and foster rapid transitions in operations. Throughout all operations, USACIDC elements conduct required criminal investigations regarding U.S. personnel, war crimes, detainee abuse, U.S. military civilian employees, contractor personnel, and other persons accompanying the force. USACIDC SAs may also be assigned to battalion, brigade, and higher-level staffs within the PM section to support L&O planning and police intelligence activities and to provide advice to the command on evidence collection and targeting. USACIDC SAs assigned or attached outside of the USACIDC command structure are not authorized to conduct felony LE investigative operations (see Army Regulation [AR] 195-2). Specific L&O-related tasks that support full spectrum operations include—
• Conducting police station operations.
• Conducting criminal investigations.
• Conducting traffic enforcement operations.
• Employing forensic capabilities.
• Conducting police engagement.
• Conducting temporary detention of personnel.
• Providing protective services for selected individuals and high-risk personnel security.
• Conducting critical site security.
• Providing customs support.
• Restoring and maintaining order.
• Conducting border control, security, and freedom of movement operations.
• Restoring public safety and order.
• Performing HN police training and support operations.
• Providing support to civil LE.1-29. Military police conduct L&O in support of full spectrum operations within three contexts or conditions, including support of—
• A commander’s internal efforts to maintain good order and discipline, such as providing support for posts, camps, and stations within the United States and its territories or on base camps and other operational sites in mature theaters of operation outside the United States. In this context, the application of the L&O function is focused internally at policing our own Soldiers and civilians and deterring, mitigating, and preventing criminal and terrorist threats. L&O within this context is critical to preserving combat power and enabling commanders to focus on their primary missions. Deliberate L&O operations are significantly reduced during operations in immature theaters and during operations off a base of operations. Minor infractions are typically handled by the chain of command without direct military police support. USACIDC conducts criminal investigations of major crimes (including those involving death, serious bodily injury, and war crimes) regardless of the environment or relative maturity of the theater of operations.
• A commander’s efforts to establish and maintain civil security and civil control within an HN to enable self-governance under the rule of law. This application is focused externally on policing and LE activities targeting the local population in an OE where HN policing and security capability is nonexistent or inadequate. The goal of any L&O operation within an HN is the eventual transition of all policing and LE functions to HN control.
• Local LE agencies within the United States or its territories in times of crisis during civil support operations. This may include—
• U.S. Army National Guard military police elements that regularly support their respective state governors in this function while operating as state assets under Title 32, U.S. Code (32 USC).
• U.S. Army Reserve and Regular Army military police elements, including federalized National Guard Soldiers, generally prohibited from direct participation in LE. (See FM 3-28 for additional information on civil support operations and a more complete discussion of the legal authorities and restrictions pertaining to military police L&O support to civilian LE authorities in the United States.)…
CIVIL SUPPORT OPERATIONS
1-41. Civil support is defined as DOD support to U.S. civil authorities for domestic emergencies and for designated law enforcement and other activities (FM 1-02). Civil support operations are domestic operations that address the consequences of man-made or natural accidents and incidents beyond the capabilities of civilian authorities (see FM 1). Civil support operations are conducted within the United States and its territories and are divided into the three broad categories of domestic emergencies, support of designated LE agencies, and other support activities (see FM 3-28).
Note. State and local governments have the primary responsibility for protecting life and property and maintaining L&O in the civilian community. Supplementary responsibility is vested by statute in specific agencies of the U.S. government other than the DOD.1-42. Civil support operations use Army forces to assist civil authorities as they prepare for, or respond to, crisis and relieve suffering. Typically, before civil support operations can be conducted with military personnel or resources, a formal request must be made by the civilian agency requiring support and approval given by the appropriate authority (see Department of Defense Directive [DODD] 5525.5). Civil support operations—
• Address the consequences of man-made or natural accidents or incidents.
• Normally occur after a Presidential declaration of a major disaster or an emergency.
• Are implemented only when response or recovery requirements are beyond the capabilities of civilian authorities, as determined by the Federal Emergency Management Agency or other lead federal agency.
• May be used to help civil authorities protect U.S. territory, population, and infrastructure against attacks. Other governmental agencies have primary responsibility for these areas. Army forces have specialized capabilities and may provide important resources and assistance in support of another lead federal agency.
• Are normally organized under the unified command and incident command system within the construct of the National Incident Management System.1-43. The primary purposes of civil support are to save lives, alleviate suffering, and protect property. These primary purposes are achieved through the following civil support tasks:
• Support for domestic disasters.
• Support for domestic chemical, biological, radiological, nuclear, and high-yield explosives (CBRNE) incidents.
• Support for domestic civil LE agencies.
• Other designated support.1-44. L&O operations by military police in civil support operations are typically limited to support tasks; 18 USC 1385 (the Posse Comitatus Act) specifically restricts the use of military forces to enforce civilian laws within the United States. There are exceptions to the Posse Comitatus Act, which can be enacted by the President or the Secretary of Defense during operations within the United States. The Posse Comitatus Act applies to military personnel operating under federal authority (10 USC). National Guard elements operating under state control (32 USC) are not restricted by the Posse Comitatus Act. After National Guard elements are mobilized under federal authority, they become subject to Posse Comitatus Act restrictions. (See FM 3-28 for additional information on civil support operations and a more complete discussion of the legal authorities and restrictions pertaining to military police L&O support to civilian LE authorities within the United States.)
Utopia – Full Movie – Stan Laurel – Oliver Hardy
In their very last feature film, Stan Laurel and Oliver Hardy travel to London so that Stan can claim his uncle’s inheritance. All of the cash has been eaten up by taxes, but at least Stan is able to claim a tax-free island and yacht that his uncle has left him. Boarding the yacht (actually a run-down tub) in Marseilles, Stan and Ollie set sail for their island in the company of stateless refugee Max Elloy, who signs on as a cook, and Italian bricklayer Adriano Rimoldi, a stowaway. The little party is nearly torn to bits by a storm at sea, but the yacht runs safely aground on a newly formed atoll. Its population is increased to five when nightclub singer Suzy Delair, fleeing her domineering naval-officer fiancé Luigi Tosi, takes refuge with the other castaways. Laurel & Hardy and their friends live an idyllic, Robinson Crusoe-like existence until Delair’s fiancé shows up. He announces he hasn’t come to claim her, but to investigate reports that the atoll is rich with uranium. Indeed it is, and soon every nation in the world is clamoring to claim the island’s radioactive deposits. Laurel and Hardy take quick action, declaring sovereignty over “Crusoeland.” They then devise an anarchic government over which Ollie presides. Stan is relegated to the position of “The People.” Comical chaos reigns when their “no laws, no taxes” policies attract the attention of various unsavory types, including rabble-rouser Michael Dalmatoff. Filmed over a period of 12 months, this expensive Franco-Italian co-production suffers from a too-complex plot, lazy direction, poor voice-over dubbing of the largely European supporting cast, and especially the horrible physical condition of Laurel, who was suffering from several life-threatening illnesses during filming. Fortunately, he regained his health after the production wrapped, as proven by his hale-and-hearty appearance on a 1954 installment of TV’s This Is Your Life. Though some disciples of Laurel and Hardy will have a great deal of difficulty sitting through Atoll K, it does contain a few isolated moments of pantomimic brilliance and first-rate sight gags. Originally running 98 minutes, Atoll K was judiciously pruned down to 82 minutes for its English-language release. In Great Britain, the film was titled Robinson Crusoeland, while it was released as Utopia in America.
Die Geschäftsführung der “GoMoPa” GmbH – angeblich in New York – mutmasslich in Verden
| Amtsgericht Charlottenburg (Berlin) Aktenzeichen: HRB 114153 BBekannt gemacht am: 07.03.2011 12:00 Uhr | |
| In () gesetzte Angaben der Anschriftund des Geschäftszweiges erfolgen
ohne Gewähr. |
|
| Veränderungen | |
| 03.03.2011 | |
| GoMoPa GmbH, Berlin, Unter den Linden 21, 10117 Berlin.Nicht mehr Geschäftsführer:; 1. Reski, Peter; Geschäftsführer:;
2. Vornkahl, Mark, *11.04.1973, New York/USA; mit der Befugnis die Gesellschaft allein zu vertreten mit der Befugnis Rechtsgeschäfte mit sich selbst oder als Vertreter Dritter abzuschließen. QUELLE: https://www.unternehmensregister.de /ureg/result.html;jsessionid=A13E0B7A14801B600FCB79BD27892BAE.www02-1?submitaction=showDocument&id=6898089 |
|
Unveiled – Julian Assange: Cryptographic Call to Arms
Julian Assange: Cryptographic Call to Arms
Excerpted from Cypherpunks: Freedom and the Future of the Internet, by Julian Assange with Jacob Appelbaum, Andy Müller-Maguhn and Jérémie Zimmermann. OR Books, New York, 2012, 186 pages, Paper. Buy online. Cryptome review of the book.
Pages 1-7.
INTRODUCTION: A CALL TO CRYPTOGRAPHIC ARMS
This book is not a manifesto. There is not time for that. This book is a warning.
The world is not sliding, but galloping into a new transnational dystopia. This development has not been properly recognized outside of national security circles. It has been hidden by secrecy, complexity and scale. The internet, our greatest tool of emancipation, has been transformed into the most dangerous facilitator of totalitarianism we have ever seen. The internet is a threat to human civilization.
These transformations have come about silently, because those who know what is going on work in the global surveillance industry and have no incentives to speak out. Left to its own trajectory, within a few years, global civilization will be a postmodern surveillance dystopia, from which escape for all but the most skilled individuals will be impossible. In fact, we may already be there.
While many writers have considered what the internet means for global civilization, they are wrong. They are wrong because they do not have the sense of perspective that direct experience brings. They are wrong because they have never met the enemy.
No description of the world survives first contact with the enemy.
We have met the enemy.
Over the last six years WikiLeaks has had conflicts with nearly every powerful state. We know the new surveillance state from an insider’s perspective, because we have plumbed its secrets. We know it from a combatant’s perspective, because we have had to protect our people, our finances and our sources from it. We know it from a global perspective, because we have people, assets and information in nearly every country. We know it from the perspective of time, because we have been fighting this phenomenon for years and have seen it double and spread, again and again. It is an invasive parasite, growing fat off societies that merge with the internet. It is rolling over the planet, infecting all states and peoples before it.
What is to be done?
Once upon a time in a place that was neither here nor there, we, the constructors and citizens of the young internet discussed the future of our new world.
We saw that the relationships between all people would be mediated by our new world, and that the nature of states, which are defined by how people exchange information, economic value, and force, would also change.
We saw that the merger between existing state structures and the internet created an opening to change the nature of states.
First, recall that states are systems through which coercive force flows. Factions within a state may compete for support, leading to democratic surface phenomena, but the underpinnings of states are the systematic application, and avoidance, of violence. Land ownership, property, rents, dividends, taxation, court fines, censorship, copyrights and trademarks are all enforced by the threatened application of state violence.
Most of the time we are not even aware of how close to violence we are, because we all grant concessions to avoid it. Like sailors smelling the breeze, we rarely contemplate how our surface world is propped up from below by darkness.
In the new space of the internet what would be the mediator of coercive force?
Does it even make sense to ask this question? In this otherworldly space, this seemingly platonic realm of ideas and information flow, could there be a notion of coercive force? A force that could modify historical records, tap phones, separate people, transform complexity into rubble, and erect walls, like an occupying army?
The platonic nature of the internet, ideas and information flows, is debased by its physical origins. Its foundations are fiber optic cable lines stretching across the ocean floors, satellites spinning above our heads, computer servers housed in buildings in cities from New York to Nairobi. Like the soldier who slew Archimedes with a mere sword, so too could an armed militia take control of the peak development of Western civilization, our platonic realm.
The new world of the internet, abstracted from the old world of brute atoms, longed for independence. But states and their friends moved to control our new world — by controlling its physical underpinnings. The state, like an army around an oil well, or a customs agent extracting bribes at the border, would soon learn to leverage its control of physical space to gain control over our platonic realm. It would prevent the independence we had dreamed of, and then, squatting on fiber optic lines and around satellite ground stations, it would go on to mass intercept the information flow of our new world — its very essence even as every human, economic, and political relationship embraced it. The state would leech into the veins and arteries of our new societies, gobbling up every relationship expressed or communicated, every web page read, every message sent and every thought googled, and then store this knowledge, billions of interceptions a day, undreamed of power, in vast top secret warehouses, forever. It would go on to mine and mine again this treasure, the collective private intellectual output of humanity, with ever more sophisticated search and pattern finding algorithms, enriching the treasure and maximizing the power imbalance between interceptors and the world of interceptees. And then the state would reflect what it had learned back into the physical world, to start wars, to target drones, to manipulate UN committees and trade deals, and to do favors for its vast connected network of industries, insiders and cronies.
But we discovered something. Our one hope against total domination. A hope that with courage, insight and solidarity we could use to resist. A strange property of the physical universe that we live in.
The universe believes in encryption.
It is easier to encrypt information than it is to decrypt it.
We saw we could use this strange property to create the laws of a new world. To abstract away our new platonic realm from its base underpinnings of satellites, undersea cables and their controllers. To fortify our space behind a cryptographic veil. To create new lands barred to those who control physical reality, because to follow us into them would require infinite resources.
And in this manner to declare independence.
Scientists in the Manhattan Project discovered that the universe permitted the construction of a nuclear bomb. This was not an obvious conclusion. Perhaps nuclear weapons were not within the laws of physics. However, the universe believes in atomic bombs and nuclear reactors. They are a phenomenon the universe blesses, like salt, sea or stars.
Similarly, the universe, our physical universe, has that property that makes it possible for an individual or a group of individuals to reliably, automatically, even without knowing, encipher something, so that all the resources and all the political will of the strongest superpower on earth may not decipher it. And the paths of encipherment between people can mesh together to create regions free from the coercive force of the outer state. Free from mass interception. Free from state control.
In this way, people can oppose their will to that of a fully mobilized superpower and win. Encryption is an embodiment of the laws of physics, and it does not listen to the bluster of states, even transnational surveillance dystopias.
It isn’t obvious that the world had to work this way. But somehow the universe smiles on encryption.
Cryptography is the ultimate form of non-violent direct action. While nuclear weapons states can exert unlimited violence over even millions of individuals, strong cryptography means that a state, even by exercising unlimited violence, cannot violate the intent of individuals to keep secrets from them.
Strong cryptography can resist an unlimited application of violence. No amount of coercive force will ever solve a math problem.
But could we take this strange fact about the world and build it up to be a basic emancipatory building block for the independence of mankind in the platonic realm of the internet? And as societies merged with the internet could that liberty then be reflected back into physical reality to redefine the state?
Recall that states are the systems which determine where and how coercive force is consistently applied.
The question of how much coercive force can seep into the platonic realm of the internet from the physical world is answered by cryptography and the cypherpunks’ ideals.
As states merge with the internet and the future of our civilization becomes the future of the internet, we must redefine force relations.
If we do not, the universality of the internet will merge global humanity into one giant grid of mass surveillance and mass control.
We must raise an alarm. This book is a watchman’s shout in the night.
On March 20, 2012, while under house arrest in the United Kingdom awaiting extradition, I met with three friends and fellow watchmen on the principle that perhaps in unison our voices can wake up the town. We must communicate what we have learned while there is still a chance for you, the reader, to understand and act on what is happening.
It is time to take up the arms of our new world, to fight for ourselves and for those we love.
Our task is to secure self-determination where we can, to hold back the coming dystopia where we cannot, and if all else fails, to accelerate its self-destruction.
— Julian Assange, London, October 2012
TMZ – How Can Jessica Simpson Be Pregnant AGAIN?
Secret – U.S. Special Operations Command Joint Civil Information Management Handbook and Manual
| Joint-CIM Tactical Handbook | April 2011 | 182 pages | Download (9.82 MB) |
| Joint-CIM User’s Manual | April 2011 | 262 pages | Download (4.35 MB) |
1.1 Handbook Purpose
The Joint Civil Information Management Tactical Handbook is designed to provide joint procedures and standardized formats for the collection and reporting of civil data to support the Joint Force Commander planning and execution of operations. The publication consolidates the Services’ best tactics, techniques and procedures.
1.2 Handbook Scope
The Joint Civil Information Management Tactical Handbook is applicable to all of the civil functional areas and sectors that comprise the civil operating environment across the full range of military operations.
The handbook is non-system specific. The manual procedures and forms contained here-in are to be treated as a base-line standard. Organizations equipped with any of the several available automated collection systems may need to apply additional techniques to account for the capability of their system.
1.3 Handbook Audience
The Joint Civil Information Management Tactical Handbook is intended for use by any organization with the responsibility to collect and report civil data in support of joint force planning and execution. Users include, but are not limited to tactical collectors, such as civil affairs teams, maritime civil affairs teams, civil liaison teams, provincial reconstruction teams, human terrain teams, engineers, military information support operations (MISO), maneuver forces, special operations forces, US interagency, and partner nations.
1.4 Joint-Civil Information Management (CIM) Process
The joint-CIM process standardizes actions that collectors already execute to manage civil information. Standardization enables collectors to train to the same standard and provides leaders the ability to prioritize efforts and manage expectations among stakeholders resulting in a clear vision of the civil environment for the commander.
Joint-CIM is the process whereby civil information is collected, consolidated in a central information system, and shared with the supported elements, higher headquarters, other US Government and Department of Defense (DOD) Agencies, international organizations, and non-governmental organizations (NGO).
Joint-CIM is a six-step process:
Planning – The process begins with planning. Planning develops plans to collect, consolidate and share. The plan to collect considers what data and information are necessary. The plan to consolidate informs how the collected data will be organized. The plan to share identifies what to share, and with whom.
Collection – This is a tested procedure that provides civil data to support the joint force commander’s civil information requirements.
Consolidation – This is a tested procedure for collating and processing data to produce civil information to support planning, analysis and sharing.
Analysis – This activity is situational assessment, sensemaking and projection. It supports the development of products requested by the joint force command.
Production – This activity organizes, based on requirements, analyzed civil information, event logs, status trackers, etc. into products that satisfy requirements.
Sharing – This is a tested procedure that supports the external and internal exchange of information to increase joint force commander and stakeholder situational awareness and situational understanding.
The joint civil information management process is executed at all echelons of war (tactical through strategic). Each step of the process is emphasized differently by echelon and organization. At the tactical level, efforts are focused on collection and sharing with consolidation and analysis being a secondary effort. While tactical collectors do perform all six of the JCIM Process Steps, the Tactical Handbook was written to specifically address collecting and sharing of civil data.
1.5 Collecting Civil Data
Complete, accurate, and timely collection of operationally relevant civil data is necessary for a reliable representation of the civil components of the operating environment. The ability to visualize and understand the civil components of the operating environment is a critical component of the commander’s military decision making process.
The joint force collects relevant civil data in three ways:
Information Search: Collecting data and information from the internet, printed media, or other civilian or military sources. This collection type is viewed as indirect collection. Information search might use data mining.
Civil Reconnaissance: Planned collection of focused and coordinated information by direct observation and evaluation of the operating environment.
Civil Engagements: Activity to engage one or more individuals in dialogue or cultural exchange. It is a participatory interaction, such as key leader engagement (KLE), mass engagement, and surveys between the collecting unit and the indigenous populations and institutions (IPI) in the operating environment.
David And Goliath – Orson Welles – Full Movie
The story of the film is adapted from the Old Testament: The Philistines declare war on the Israelites and wrench the Arch of the Allience from them. Saul, the king of Israel, listens meanwhile to the words of the prophets who tell him that the new king will be a young shepard called David. But still David has to fight the enemy in form of their mighty giant Goliath
Meridian Capital über Fälschungen der “GoMoPa”
Sehr geehrte Damen und Herren,
die Betrüger und durch uns inhaftierten Erpresser der GoMoPa versuchen mit einer gefälschten Presse-Mitteilung von sich abzulenken und einen investigativen Journalisten, Bernd Pulch, zu belasten.
Die Presse-Mitteilung auf pressreleaser.org ist eine Fälschung und die gesamte Webseite ist der GoMoPa zu zuordnen.
Hier noch einmal die tatäschlichen Geschehnisse:
Hier der Artikel von “GoMoPa” über Meridian Capital.
 „GoMopa“ schreibt:08.09.2008 „GoMopa“ schreibt:08.09.2008Weltweite Finanzierungen mit WidersprüchenDie Meridian Capital Enterprises Ltd. gibt an, weltweite Finanzierungen anbieten zu können und präsentiert sich hierbei auf aufwendig kreierten Webseiten. GOMOPA hat die dort gemachten Angaben analysiert und Widersprüche entdeckt.Der FirmensitzDer Firmensitz befindet sich laut eigener Aussage in Dubai, Vereinigte Arabische Emirate. In einem GOMOPA vorliegenden Schreiben der Meridian Capital Enterprises Ltd. heißt es jedoch, der Firmensitz sei in London. Auf der Homepage des Unternehmens taucht die Geschäftsadresse in der Londoner Old Broad Street nur als „Kundenabteilung für deutschsprachige Kunden“ auf. Eine weitere Adresse in der englischen Hauptstadt, diesmal in der Windsor Avenue, sei die „Abteilung der Zusammenarbeit mit Investoren“.Die Meridian Capital Enterprises ist tatsächlich als „Limited“ (Ltd.) mit Sitz in England und Wales eingetragen. Aber laut Firmenhomepage hat das Unternehmen seinen „rechtlichen Geschäftssitz“ in Dubai. Eine Abfrage beim Gewerbeamt Dubais (DED) zu dieser Firmierung bleibt ergebnislos.Bemerkenswert ist auch der vermeintliche Sitz in Israel. Auf der Webseite von Meridian Capital Enterprises heißt es: „Die Firma Meridian Capital Enterprises Ltd. ist im Register des israelischen Justizministeriums unter der Nummer 514108471, gemäß dem Gesellschaftsrecht von 1999, angemeldet.“ Hierzu Martin Kraeter, Gomopa-Partner und Prinzipal der KLP Group Emirates in Dubai: „Es würde keinem einzigen Emirati – geschweige denn einem Scheich auch nur im Traum einfallen, direkte Geschäfte mit Personen oder Firmen aus Israel zu tätigen. Und schon gar nicht würde er zustimmen, dass sein Konterfei auch noch mit vollem Namen auf der Webseite eines Israelischen Unternehmens prangt.“Auf der Internetseite sind diverse Fotos mit Scheichs an Konferenztischen zu sehen. Doch diese großen Tagungen und großen Kongresse der Meridian Capital Enterprises werden in den Pressearchiven der lokalen Presse Dubais mit keinem Wort erwähnt. Martin Kraeter: „ Ein ‚britisch-arabisch-israelisches bankfremdes Finanzinstitut sein zu wollen, wie die Meridian Capital Enterprises Ltd. es darstellt, ist mehr als zweifelhaft. So etwas gibt es schlicht und ergreifend nicht! Der Nahostkonflikt schwelt schon seit mehr als 50 Jahren. Hier in den Vereinigten Arabischen Emiraten (VAE) werden Israelis erst gar nicht ins Land gelassen. Israelische Produkte sind gebannt. Es gibt nicht einmal direkte Telefonverbindungen. Die VAE haben fast 70% der Wiederaufbaukosten des Libanon geschultert, nachdem Israel dort einmarschiert ist.“Zwei angebliche Großinvestitionen der Meridian Capital Enterprises in Dubai sind Investmentruinen bzw. erst gar nicht realisierte Projekte. Das Unternehmen wirbt mit ihrer finanziellen Beteiligung an dem Dubai Hydropolis Hotel und dem Dubai Snowdome. Der Aktivitätsstatus der Meridian Capital Enterprises Ltd. ist laut englischen Handelsregister (UK Companies House) „dormant“ gemeldet. Auf der Grundlage des englischen Gesellschaftsrechts können sich eingetragene Unternehmen selbst „dormant“ (schlafend) melden, wenn sie keine oder nur unwesentliche buchhalterisch zu erfassende Transaktionen vorgenommen haben. Dies ist angesichts der angeblichen globalen Investitionstätigkeit der Meridian Capital Ltd. sehr erstaunlich. Der Webauftritt Die Internetseite der MCE ist sehr aufwendig gestaltet, die Investitionen angeblich in Millionen- und Milliardenhöhe. Bei näherer Betrachtung der Präsentationselemente fällt jedoch auf, dass es sich bei zahlreichen veröffentlichen Fotos, die Veranstaltungen der Meridian Capital Enterprises dokumentieren sollen, meist um Fotos von Online-Zeitungen oder frei zugänglichen Medienfotos einzelner Institutionen handelt wie z.B. der Börse Dubai. Auf der Internetpräsenz befinden sich Videofilmchen, die eine frappierende Ähnlichkeit mit dem Werbematerial von NAKHEEL aufweisen, dem größten Bauträger der Vereinigten Arabischen Emirate. Doch den schillernden Videos über die berühmten drei Dubai Palmen „Jumeirah, Jebel Ali und Deira“ oder das Archipel „The World“ wurden offensichtlich selbstproduzierte Trailersequenzen der Meridian Capital Enterprises vorangestellt. Doch könnte es sich bei den Werbevideos um Fremdmaterial handeln. Auch die auf der Webseite wahllos platzierten Fotos von bekannten Sehenswürdigkeiten Dubais fungieren als Augenfang für den interessierten Surfer mit eigenem Finanzierungswunsch. Bei einem Volumen von 10 Millionen Euro oder höher präsentiert sich die Meridian Capital Enterprises Ltd. als der passende Investitionspartner. Das Unternehmen verfügt weltweit über zahlreiche Standorte: Berlin, London, Barcelona, Warschau, Moskau, Dubai, Riad, Tel Aviv, Hong Kong und New York. Aber nahezu alle Standorte sind lediglich Virtual Offices eines global arbeitenden Büroservice-Anbieters. „Virtual Office“ heißt im Deutschen schlicht „Briefkastenfirma“. Unter solchen Büroadressen sollen laut Meridian Capital Enterprises ganze Kommissionen ansässig sein, alles zum Wohle des Kunden.“ Zitatende |
Hier die Hintergründe der Erpressung:
Hier unsere Original-Stellungnahme:
Anfang Oktober 2008 erhielt einer der Arbeiter der Meridian Capital Enterprises Ltd. eine Meldung von einem anonymen Sender, dass in naher Zukunft – zuerst im Internet, dann im Fernsehen, im Radio und in der deutschen Presse – Informationen erscheinen, die die Funktionsweise und Tätigkeiten der Meridian Capital Enterprises Ltd. in einem äußerst negativen Licht darstellen. Der Mitarbeiter der Meridian Capital Enterprises Ltd. wurde also informiert, dass diese Meldungen/Nachrichten zweifelsohne deutlich das Aussehen und den guten Ruf der Firma Meridian Capital Enterprises Ltd. beeinträchtigen.
Der an dieser Stelle erwähnte „Gesprächspartner” hat den Arbeiter der Meridian Capital Enterprises Ltd. informiert, dass die Möglichkeit besteht die peinliche Situation zu vermeiden, indem die Meridian Capital Enterprises Ltd. auf das von der Person gezeigte Konto die Summe von 100.000,00 EUR überweist. Wie sich aber später zeigte, war der Herr Klaus Maurischat – dieser anonyme Gesprächspartner – „Gehirn“ und „Lider des GOMOPA“. Die Ermittlungen wurden angestellt durch die Bundeskriminalpolizei (Verfolgungs- und Ermittlungsorgan auf der Bundesebene) während des Ermittlungsverfahrens wegen einer finanziellen Erpressung, Betrügereien auch wegen der Bedrohungen, welche von Herrn Maurischat und seine Mitarbeiter praktiziert wurden sowie wegen Teilnahme anderer (Leiter der Internetservices und Moderatoren der Blogs) an diesem Prozedere. Diese Straftaten wurden begangen zu Schaden vieler Berufs- und Justizpersonen, darunter auch der Meridian Capital Enterprises Ltd. Die Opfer dieses Verbrechens sind in Deutschland, Österreich, der Schweiz, Spanien, Portugal, Großbritannien, den USA und Kanada sichtbar.
In diesem Moment taucht folgende Frage auf: Wie war die Reaktion der Meridian Capital Enterprises Ltd. auf die Forderungen seitens GOMOPA? Entsprach die Reaktion den Erwartungen von GOMOPA? Hat die Meridian Capital Enterprises Ltd. die geforderte Summe 100.000,00 EUR überwiesen?
Seites der Meridian Capital Enterprises Ltd. gab es überhaupt keine Reaktion auf den Erpressungsversuch von GOMOPA. Ende August 2008 auf dem Service http://www.gompa.net sind zahlreiche Artikel/Meldungen erscheinen, welche die Tätigkeit der Meridian Capital Enterprises Ltd. in einem sehr negativen Licht dargestellt haben. Nachdem die auf http://www.gomopa.net enthaltenen Informationen ausführlich und vollständig analysiert worden waren, ergab es sich, dass sie der Wahrheit nicht einmal in einem Punkt entsprechen und potenzielle und bereits bestehende Kunden der Meridian Capital Enterprises Ltd. in Bezug auf die von diesem Finanzinstitut geführten Geschäftstätigkeit irreführen. Infolge der kriminellen Handlugen von GOMOPA und der mit ihm kooperierenden Services und Blogs im Netz hat die Meridian Capital Enterprises Ltd. beachtliche und messbare geschäftliche Verluste erlitten. Die Meridian Capital Enterprises Ltd. hat nämlich in erster Linie eine wichtige Gruppe von potenziellen Kund verloren. Was sich aber als wichtiger ergab, haben sich die bisherigen Kunden von der Meridian Capital Enterprises Ltd. kaum abgewandt. Diejenigen Kunden haben unsere Dienstleitungen weiterhin genutzt und nutzen die immer noch. In Hinblick auf die bisherige Zusammenarbeit mit der Meridian Capital Enterprises Ltd., werden ihrerseits dem entsprechend keine Einwände erhoben .
GOMOPA hat so einen Verlauf der Ereignisse genau prognostiziert, dessen Ziel beachtliche und messbare geschäftliche durch die Meridian Capital Enterprises Ltd. erlittene Verluste waren. Der Verlauf der Ereignisse hat das Service GOMOPA mit Sicherheit gefreut. GOMOPA hat nämlich darauf gerechnet, dass die Stellung der Meridian Capital Enterprises Ltd. nachlässt und das Finanzinstitut die geforderte Summe (100.000,00 EUR) bereitstellt. Im Laufe der Zeit, als das ganze Prozedere im Netz immer populärer war, versuchte GOMOPA noch vier mal zu der Meridian Capital Enterprises Ltd. Kontakte aufzunehmen, indem es jedes mal das Einstellen dieser kriminellen „Kompanie” versprochen hat, wobei es jedes mal seine finanziellen Forderungen heraufsetzte. Die letzte für das Einstellen der „Kompanie“ gegen die Meridian Capital Enterprises Ltd. vorgesehene Quote betrug sogar 5.000.000,00 EUR (in Worten: fünfmilionen EURO). Die Meridian Capital Enterprises Ltd. konnte sich aber vor den ständig erhöhenden Forderungen seitens des Services GOMOPA behaupten.
Im Oktober 2008 traf die Leitung der Meridian Capital Enterprises Ltd. Entscheidung über die Benachrichtigung der Internationalen Polizei INTERPOL sowie entsprechender Strafverfolgungsorgane der BRD (die Polizei und die Staatsanwaltschaft) über den bestehenden Sachverhalt. In der Zwischenzeit meldeten sich bei der Meridian Capital Enterprises Ltd. zahlreiche Firmen und Korporationen, sogar Berufsperson wie Ärzte, Richter, Priester, Schauspieler und anderen Personen aus unterschiedlichen Ländern der Welt, die der Erpressung von GOMOPA nachgegeben und die geforderten Geldsummen überwiesen haben. Diese Personen gaben bereits Erklärungen ab, dass sie dies getan haben, damit man sie bloß endlich „in Ruhe lässt” und um unnötige Probleme, Schwierigkeiten und einen kaum begründbaren Ausklang vermeiden zu können. Die Opfer dieses kriminellen Vorgehens haben die Meridian Capital Enterprises Ltd. über unterschiedliche Geldsummen, welche verlangt wurden, informiert.
In einem Fall gab es verhältnismäßig kleine (um ein paar tausend EURO), in einem anderen Fall handelte es schon um beachtliche Summen (rund um paar Millionen EURO).
Zusätzlich wendeten sich an die Meridian Capital Enterprises Ltd. Firmen, welche dem GOMOPA noch keine „Gebühr” überweisen haben und bereits überlegen, ob sie dies tun sollen, oder nicht. Diese Firmen erwarteten von der Meridian Capital Enterprises Ltd. eine klare Stellungnahme sowie eine professionelle praktische Beratung, wie man sich in solch einer Lage verhalten soll und wie man diese Geldforderungen umgehen kann. Die Meridian Capital Enterprises Ltd. hat ausnahmslos allen Verbrechensopfern, welche sich bei unserer Firma gemeldet haben, eine Zusammenarbeit vorgeschlagen. Als oberste Aufgabe stellt sich diese Kooperation, gemeinsam entschlossene und wirksame Maßnahmen gegen GOMOPA, gegen andere Services im Netz sowie gegen alle Bloggers zu treffen, die an dem hier beschriebenen internationalen kriminellen Vorgehen mit GOMOPA-Führung teilnehmen.Auf unsere Bitte benachrichtigten alle mitbeteiligten Firmen die Internationale Polizei INTERPOL sowie ihre heimischen Verfolgungsorgane, u. a. die zuständige Staatsanwaltschaft und die Polizeibehörden über den bestehenden Sachverhalt.
In Hinblick auf die Tatsache, dass das verbrecherische Handeln von GOMOPA sich über viele Staaten erstreckte und dass die Anzahl der in der Bundesrepublik Deutschland erstatteten Anzeigen wegen der durch GOMOPA, Internetservices und Bloggers begangenen Straftaten, rasant wuchs – was zweifelsohne von einer weit gehenden kriminellen Wirkungskraft des GOMOPA zeugt – schlug die Internationale Wirtschaftspolizei INTERPOL der Meridian Capital Enterprises Ltd. vor, dass sich ihr Vertreter in Berlin mit dem Vertreter von GOMOPA trifft, um die „Zahlungsmodalitäten“ und Überweisung der Summe von 5.000.000,00 EUR zu besprechen. Dieser Schritt meinte, eine gut durchdachte und durch die Bundeskriminalpolizei organisierte Falle durchzuführen, deren Ziel die Festnahme der unter GOMOPA wirkenden internationalen Straftäter war.
Die koordinierten Schritte und Maßnahmen der Meridian Capital Enterprises Ltd. und anderer Beschädigter, geleitet von der Internationalen Wirtschaftspolizei INTERPOL, dem Bundeskriminalamt und der Staatsanwaltschaft der Bundesrepublik Deutschland haben zur Aus-, Einarbeitung und Durchführung der oben beschriebenen Falle beigetragen. Im November 2008 führte die in Berlin vorbereitete Falle zur Festnahme und Verhaftung des Vertreters des GOMOPA, der nach der Festnahme auf Herrn Klaus Maurichat – als den Hauptverantwortlichen und Anführer der internationalen kriminellen Gruppe GOMOPA verwies. Der Festgenommene benannte und zeigte der Bundeskriminalpolizei zugleich den aktuellen Aufenthaltsort des Herrn Klaus Maurischat. „Gehirn“ und Gründer dieser internationalen kriminellen Gruppe GOMOPA, Herr Klaus Maurischat wurde am selben Tag auch festgenommen und auf Frist verhaftet, wird bald in Anklagezustand gestellt, wird die Verantwortung für eigene Straftaten und die des Forums GOMOPA vor einem zuständigen Bundesgericht tragen. Die Meridian Capital Enterprises Ltd. unternahm bereits alle möglichen Schritte, damit Herr Klaus Maurischat auch auf der Anklagebank des zuständigen Gerichts des Vereinigten Königsreiches Großbritannien erscheint. Unter den beschädigten Berufs- und Justizpersonen aus Großbritannien, neben der Meridian Capital Enterprises Ltd. gibt es noch viele Opfer von GOMOPA…
Die dreisten Verbrecher wagen es unter http://www.pressreleaser.org, einer eigenen “GoMoPa”-Seite unsere Pressemitteilung oben zu verfälschen und unschuldige Personen zu belasten.
“GoMoPa” Boss is Jochen Resch
- May 15, 2011 – 1:15 pm
- Posted in Uncategorized
- Comments Off
Dear Readers,
after a thorough research we are sure that the real “GoMoPa” boss is Jochen Resch, lawyer in Berlin, Germany. He is the brain behind “GoMoPa” and responsable for blackmailing, extortion, racketeering, cybermurder and murder – in the tradition of the East German “Inteeligence” STASI that is why he called “GoMoPa” – Financial “Intelligence” Service .
Webmaster
Meridian Capital about GoMoPa
“GoMoPa” in detention
- May 13, 2011 – 1:02 pm
- Posted in Uncategorized
- Comments Off
Meridian Capital Enterprises Ltd.. unveils new criminal phenomena in network. In recently appeared on the net more often at the same time a new a very worrying phenomenon of criminal nature. Professional criminals groups in the network are taking part, to extortion, fraud, Erschwindeln relating to certain specifically selected companies and businesses are capable of. These criminals developed new methods and means, simply and in a short time to bereichern.Strategien and manifestations, which underlie this process are fairly simple. A criminal is looking to “carefully” on the Internet specific companies and corporations (victims of crime) and informed them in the next step, that of the business activities of such companies and corporations in the near future – first on the Internet then in other available mass media – numerous and very unfavorable information appears. At the same time, the criminals beat their future victims an effective means of reducing unnecessary difficulties and problems to escape the loss of good name and image of the company and corporate sector. These offenders are aware of that reputation, name and appearance of each company is a value in itself. It was therefore a value of what each company is prepared to pay any price. But the reason for difficulties and problems arising from the loss of good name and reputation result. The criminals and their victims are already aware that this loss is devastating consequences might have been the closing down of a particular business can enforce. It takes both to No as well as at large companies regard. The company is concerned that in virtually every industry in each country and cross-border activities sind.Das criminal procedure in the form of a blackmail on money, a fraud is becoming rapidly and globally, ie led cross-border and internationally. Among the victims of extortion, fraud is now looking both at home (domestic) and international corporations, the major emphasis on conservation, keeping and maintaining their reputation in the business according to their credibility lay. The criminals in the network have understood that maintaining an unassailable reputation and name of a company the unique ability to provide fast and easy enrichment forms. The above-mentioned criminal procedure is difficult to track because it is international in nature, and by overlapping or even nonexistent (fictional) professional and judicial persons in various countries and operated company wird.Diese offenders in the network publish it and disseminate false information about your victims on remote servers, which are not uncommon in many exotic countries. There are those countries in which serious gaps in the legal system, investigative and prosecution procedures are visible. As an example, at this point mention India werden. Mit criminals working in the network grid portals known leader of blogs with your seat-consciously or unconsciously, even in highly developed countries. For example, at this point, countries such as Germany, Austria, Switzerland, the United States, Britain, Spain or Portugal are mentioned. The below listed criminals were able to act unpunished today. As a symptom of such action appears here the activity and “effectiveness” of the company GOMOPA, which is on countries such as Germany, Switzerland, Austria, the United States, Britain, Spain and India. A good example of such an action is Mr. Klaus Mauri Chat – the leader and “brain” of the company GOMOPA with many already in force and criminal judgments “on his account”, which in this way for years and funded its maintenance in the industry almost unlimited activity. This status will change dramatically, however, including far and wide thanks to discontinued operations of the firm Meridian Capital Enterprises Ltd.. who would oppose such offenses addressed in the network. Other companies and corporations, in which the crime network and outside of this medium have fallen victim to contribute to combating such crimes bei.Die situation is changing, thanks to effective steps and the successful cooperation of the firm Meridian Capital Enterprises Ltd.. with the international police Interpol, with the federal agency (FBI) in the U.S., the Federal Criminal Police in Germany, with Scotland Yard in Britain, as well as with the Russian secret service FSB.Die Meridian Capital Enterprises Ltd.. – Together with other companies and cooperations, the victim of criminal activities of the network of crime have fallen – has undeniably already started to yield results. The fact that in recent weeks (November 2008) on the territory of the Federal Republic of Germany of the above-mentioned leaders and “brain” of the company GOMOPA, Mr Klaus Maurishat was arrested should not be ignored. The Meridian Capital Enterprises Ltd.. information available results clearly show that the next arrests of persons participating in this process in such countries as: Austria, Switzerland, Russia, Ukraine, Poland, Spain, Mexico, Portugal, Brazil, the USA, Canada, UK, Ireland , Australia, New Zealand and made in a.. The ultimate goal of Meridian Capital Enterprises Ltd.. and the other victims of crime in the network is to provide all participants in this criminal procedure before the competent court to lead. All professional and judicial persons, regardless of the seat and out of the business, which the above-described criminal action (fraud, extortion) to have fallen victim can of Meridian Capital Enterprises Ltd.. led company to join the goal set at all at this point the procedure described those associated in the public and the economic life out. II blacklist blackmail and with international fraudsters and their methods (opus operandi) in the following countries: 1 The Federal Republic Deutschland2. Dubai 3rd Russia 1st The Federal Republic of Germany GmbH GOMOPA, Goldman Morgenstern & Partners LLC., Goldman Morgenstern & Partners Consulting LLC, Wottle collection. In these firms are quite active following persons: – Klaus Mauri Chat ( “Father” and “brain” of the criminal organization responsible for countless final judgments have been achieved (arrested in Germany in November 2008) – Josef Rudolf Heckel ( “right hand “when Mr Klaus Mauri chat, denounced former banker who is excessive in many Bankschmuggeleien was involved.
The study of 900 pages named Toxdat by Ehrenfried Stelzer is the “Stasi Killer Bible”. It lists all kind of murder methods and concentrates on the most effective and untraceable.
“The toxdat study was ordered by Stasi Vice-President Gerhard Neiber, the second man in rank after boss Erich Mielke. The toxdat study was also the theoretical “story book” for the murder of the famous German watchdog and journalist Heinz Gerlach by former Stasi member under the guidance of “GoMoPa”,” an informer stated. “Ehrenfried stelzer” was nicknamed “Professor Murder” by his victims. Even close co-worker now compare him with the German SS”doctor” Mengele, “Dr. Death” from Auschwitz.
Only two articles let the German audience believe that the famous journalist and watchdog Heinz Gerlach died on natural courses by blood pollution.
For more Information the victims have launched a new site: http://www.victims-opfer.com
The first one, published only hours after the death of Mr Heinz Gerlach by the notorious “GoMoPa” (see article below) and a second 3 days later by a small German local newspaper, Weserbergland Nachrichten.
Many people including the hostile Gerlach website “Akte Heinz Gerlach” doubted that this man who had so many enemies and friends would die of natural causes without any previous warning. Rumours occured that Mr. Gerlach’s doctor doubted natural courses at all. After many critical voices discussed the issue a small website of a small German local newspaper – which never before had reported about Mr. Heinz Gerlach and which is not even in the region of Mr Gerlachs home – published that Mr Gerlach died of blood pollution. Weserbergland-Nachrichten published a long article about the deadly consequences of blood pollution and did not even name the source of such an important statement. It claimed only that somebody of Gerlachs inner circle had said this. It is a proven fact that after the collpase of the Eastern German Communist Regime many former Communist propaganda agents went to regional newspapers – often in Western Germany like Günther Schabowski did the man who opened the “Mauer”.
The theatre stage was set: One day later the hostile Gerlach website “Akte Heinz Gerlach” took the agenda publishing that Mr Gerlach had died for natural causes without any further research at all.
This was done by a website which for months and months and months reported everything about Mr. Gerlach.
Furthermore a research proves that the technical details regarding the website hosting of this hostile website “Akte Heinz Gerlach” proves that there are common details with the hosting of “GoMoPa” and their affiliates as proven by the SJB-GoMoPa-victims (see http://www.sjb-fonds-opfer.com)
Insiders believe that the murderers of Mr. Heinz Gerlach are former members of the Eastern German Terror Organisation “Stasi” with dioxins. They also believe that “GoMoPa” was part of the plot. At “GoMoPa”’ a person named Siegfried Siewers was officialy responsible for the press but never appeared in public. “GoMoPa”-victims say that this name was a cameo for “GoMoPa” frontrunner Klaus Maurischat who is controlled by the Stasi Top Agent Ehrenfried Stelzner, Berlin.
Siegfried Sievers, a former Stasi member is responsible for the pollution of millions Germanys for many years with dioxins. This was unveiled at 5th of January 2011 by German prosecutors.
The victims say that Maurischat (probably also a Stasi cameo) and Sievers were in contact as Sievers acted as Stasi Agent and was in fact already a specialist in dioxins under the Communist Terror Regime in Eastern Germany.
Furthermore the Stasi Top Agent Ehrenfried Stelzer disguised as Professor for Criminal studies during the Communist Regime at the Eastern Berlin Humboldt University.
Background:
The man behind the Berlin lawyer Jochen Resch and his activities is Ehrenfried Stelzer, former Stasi Top officer in Berlin and “Professor for Criminal Studies” at the Eastern Berlin Humboldt University during the Communist regime, the SJB-GoMoPa-victims say (www.sjb-fonds-opfer.com) is responsable for the killing of German watchdog and journalist Heinz Gerlach.
These informations stem from various sources who were close to the criminal organization of GoMoPa in the last years. The SJB-GoMoPa say that the well-known German watchdog and journalist Heinz Gerlach was killed by former Stasi members with dioxins. Polychlorinated dibenzodioxins (PCDDs), or simply dioxins, are a group of organic polyhalogenated compounds that are significant because they act as environmental pollutants. They are commonly referred to as dioxins for simplicity in scientific publications because every PCDD molecule contains a dioxin skeletal structure. Typically, the p-dioxin skeleton is at the core of a PCDD molecule, giving the molecule a dibenzo-p-dioxin ring system. Members of the PCDD family have been shown to bioaccumulate in humans and wildlife due to their lipophilic properties, and are known teratogens, mutagens, and confirmed (avered) human carcinogens. They are organic compounds.
Dioxins build up primarily in fatty tissues over time (bioaccumulate), so even small exposures may eventually reach dangerous levels. In 1994, the US EPA reported that dioxins are a probable carcinogen, but noted that non-cancer effects (reproduction and sexual development, immune system) may pose an even greater threat to human health. TCDD, the most toxic of the dibenzodioxins, is classified as a Group 1 carcinogen by the International Agency for Research on Cancer (IARC).
In 2004, a notable individual case of dioxin poisoning, Ukrainian politician Viktor Yushchenko was exposed to the second-largest measured dose of dioxins, according to the reports of the physicians responsible for diagnosing him. This is the first known case of a single high dose of TCDD dioxin poisoning, and was diagnosed only after a toxicologist recognized the symptoms of chloracne while viewing television news coverage of his condition.
German dioxin scandal: In January 2011 about 4700 German farms were banned from making deliveries after tests at the Harles und Jentzsch plant in the state of Schleswig-Holstein showed high levels of dioxin. Again this incident appears to involve PCBs and not PCDDs at all. Dioxin were found in animal feed and eggs in many farms. The person who is responsible for this, Siegfried Sievert is also a former Stasi Agent. At “GoMoPa” the notorious Eastern-Berlin press agency (see article below) one of the henchmen acted under the name of “Siegfried Siewert”.
Further evidence for the killing of Mr.Heinz Gerlach is provided by the SJB-GoMoPa-victims by analyzing the dubious role of former Stasi-Top-agent Ehrenfried Stelzer, also a former “Professor for Crime Studies” under the Communist regime in Eastern Germany and the dubious role of “detective” Medard Fuchsgruber. Both are closely tied to the dubious “GoMoPa” and Berlin lawyer Jochen Resch.
According to the SJB-GoMoPa-victims is Berlin lawyer Jochen Resch the mastermind of the criminal organization “GoMoPa2. The victims state that they have a source inside “GoMoPa” who helped them discover the shocking truth. The so-called “Deep Throat from Berlin” has information that Resch had the idea to found the criminal organization “GoMoPa” and use non-existing Jewish lawyers named Goldman, Morgenstern & Partner as camouflage. Their “office” in Madison Avenue, New York, is a mailbox. This is witnessed by a German Ex-Patriot, a lawyer, whose father, Heinz Gerlach, died under strange circumstances.
Resch seems to use “GoMoPa” as an instrument to blackmail parts of the German Property and Investment.
German authorities are under growing pressure to reopen investigations into at least a dozen suspicious deaths after the arrest of an alleged East German assassin cast new light on the communist regime. Stasi victims quoted a source saying “isolated units” had conducted operations that were “extremely well organised” and had “100 per cent logistical support” from the East German state.
A statement from prosecutors read: “The accused [Jurgen G] is suspected, as a member of a commando of the former DDR, of killing a number of people between 1976 and 1987 who from the point of view of the DDR regime had committed treason or were threatening to do so.”
Details of his Jurgen G’s arrest have been described in suitably florid terms, with the mass circulation tabloid Bild saying he was working at the Wolfsbruch marina near Rheinsberg in north-eastern Germany when a woman approached him. “Excuse me, is that your yellow Trabant in the car park? I just ran into it with my car,” she is said to have asked.
When he followed her to the car park, masked officers jumped out of vans and bushes and overpowered him in an operation worthy of the Stasi itself.
An eyewitness told Bild: “They blindfolded him and raced off in an unmarked car.”
Police across Germany are reported to be sifting through files to see who the victims may have been, and some intelligence officers are greeting the arrest of Jurgen G as a breakthrough.
Thomas Auerbach, who works for the Stasi file authority in Berlin and has written a book based on the death squad files, said: “These people were trained to make such murders look like accidents or suicides, even as ‘ordinary’ crimes such as robberies. They were real terror experts.”
The cases said to be linked to Jurgen G or his unit include many people involved with the commercial arm of the East German ruling socialist party, the SED (Socialist Unity Party).
Uwe Harms, the head of a Hamburg-based haulage firm which was part of a network of companies secretly owned by the SED, disappeared in March 1987 after conversations with various DDR functionaries. Six weeks later, his body was found in a plastic bag.
Weeks before his death he told friends that he felt he was being followed. After reunification, one of the other SED company heads said Mr Harms had been liquidated for refusing to allow his firm to be used to transport arms into East Germany.
Dieter Vogel, a businessman who had been jailed for life for spying for the CIA, was found suffocated in his cell in the East German prison Bautzen on March 9, 1982. The fact that he was due to be taken to the West in a spy swap arrangement just a few weeks later cast doubt on the suicide theory.
He had passed the names of several Stasi moles to the BND, West Germany’s heavily penetrated counter-intelligence service.
The Christian Democrat Union politician Uwe Barschel, 43, was found dead by magazine reporters in his bathtub in a hotel room in Geneva in October, 1987. He died of poisoning, but rumours that he was involved somehow in arms deals and the Stasi have clung to the case.
One of the more high-profile and enduring mysteries is that of Lutz Eigendorf, an East German footballer from the Stasi-backed Dynamo Berlin.
He fled to the West in 1979 amid great publicity. Four years later, he died after crashing his car into a tree on a straight stretch of road with blood alcohol levels way over the limit. Witnesses who had seen him earlier in the evening said he had not been drinking.
Most controversial though is the suggestion that the assassination squad was linked to the murder of a Swedish television reporter and her friend in 1984.
Cats Falk and her friend Lena Graens went missing on Nov 19, 1984. Their bodies were fished out of a Stockholm canal six months later.
Reports suggested a three-man assassination squad killed them, spiking their drinks with drugs, putting them into their car and pushing it into the Hammarby canal.
Shortly before her death, Cats Falk had reportedly uncovered a deal between an arms dealer and an East German firm.
Germany has recently undergone a wave of nostalgia for all things East German, dubbed Ostalgie, with colourful television shows featuring former DDR stars such as the ice skater Katerina Witt talking wistfully about socialist pop music.
A reassessment may be coming in the wake of the revelations.
Victims: The DDR-STASI MURDER GANG “GoMOPa” in murderoplot against Joerg Berger
The Stasi Murder Gang of „GoMoPa“ was involved in many trials to kill the popular East German soccer trainer Joerg Berger, Stasi victims tell in postings on their hompage http://www.sjb-fonds-opfer.com. Berger stated before his early death in his biography that they tried to pollute him with arsenic.
Arsenic and many of its compounds are especially potent poisons. Many water supplies close to mines are contaminated by these poisons. Arsenic disrupts ATP production through several mechanisms. At the level of the citric acid cycle, arsenic inhibits lipoic acid which is a cofactor for pyruvate dehydrogenase; and by competing with phosphate it uncouples oxidative phosphorylation, thus inhibiting energy-linked reduction of NAD+, mitochondrial respiration and ATP synthesis. Hydrogen peroxide production is also increased, which might form reactive oxygen species and oxidative stress. These metabolic interferences lead to death from multi-system organ failure, probably from necrotic cell death, not apoptosis. A post mortem reveals brick red coloured mucosa, owing to severe haemorrhage. Although arsenic causes toxicity, it can also play a protective role.[
Elemental arsenic and arsenic compounds are classified as “toxic” and “dangerous for the environment” in the European Union under directive 67/548/EEC. The International Agency for Research on Cancer (IARC) recognizes arsenic and arsenic compounds as group 1 carcinogens, and the EU lists arsenic trioxide, arsenic pentoxide and arsenate salts as category 1 carcinogens.
Arsenic is known to cause arsenicosis owing to its manifestation in drinking water, “the most common species being arsenate [HAsO42- ; As(V)] and arsenite [H3AsO3 ; As(III)]”. The ability of arsenic to undergo redox conversion between As(III) and As(V) makes its availability in the environment more abundant. According to Croal, Gralnick, Malasarn and Newman, “[the] understanding [of] what stimulates As(III) oxidation and/or limits As(V) reduction is relevant for bioremediation of contaminated sites (Croal). The study of chemolithoautotrophic As(III) oxidizers and the heterotrophic As(V) reducers can help the understanding of the oxidation and/or reduction of arsenic.
Treatment of chronic arsenic poisoning is easily accomplished. British anti-lewisite (dimercaprol) is prescribed in dosages of 5 mg/kg up to 300 mg each 4 hours for the first day. Then administer the same dosage each 6 hours for the second day. Then prescribe this dosage each 8 hours for eight additional days. However the Agency for Toxic Substances and Disease Registry (ATSDR) states that the long term effects of arsenic exposure cannot be predicted. Blood, urine, hair and nails may be tested for arsenic, however these tests cannot foresee possible health outcomes due to the exposure. Excretion occurs in the urine and long term exposure to arsenic has been linked to bladder and kidney cancer in addition to cancer of the liver, prostate, skin, lungs and nasal cavity.[
Occupational exposure and arsenic poisoning may occur in persons working in industries involving the use of inorganic arsenic and its compounds, such as wood preservation, glass production, nonferrous metal alloys and electronic semiconductor manufacturing. Inorganic arsenic is also found in coke oven emissions associated with the smelter industry.
THE DDR GESTAPO-STASI MURDER GANG responsable for the murder of Lutz Eigendorf
The talented Eigendorf played for East German side Dynamo Berlin.
He made his debut for the GDR in an August 1978 match against Bulgaria, immediately scoring his first two goals in a 2–2 draw. He went on to collect six caps, scoring three goals.[1] His final international was a February 1979 friendly match against Iraq.
On 20 March 1979, after a friendship match between Dynamo and West German club 1. FC Kaiserslautern in Gießen he fled to the west hoping to play for that team. But because of his defection he was banned from play for one year by UEFA and instead spent that time as a youth coach with the club.
This was not the first time an East German athlete had fled to the west, but it was a particularly embarrassing defection. Eigendorf’s club Dynamo was under the patronage of the Stasi, East Germany’s secretive state police, and subject to the personal attentions of the organisation’s head, Erich Mielke. He ensured that the club’s roster was made up of the country’s best players, as well as arranging for the manipulation of matches in Dynamo’s favour. After his defection Eigendorf openly criticised the DDR in the western media.
His wife Gabriele remained behind in Berlin with their daughter and was placed under constant police surveillance. Lawyers working for the Stasi quickly arranged a divorce and the former Frau Eigendorf re-married. Her new husband was eventually revealed as a Lothario – an agent of the state police whose role it was to spy on a suspect while romancing them.
In 1983 Eigendorf moved from Kaiserslautern to join Eintracht Braunschweig, all the while under the scrutiny of the Stasi who employed a number of West Germans as informants. On 5 March that year he was badly injured in a suspicious traffic accident and died within two days. An autopsy indicated a high blood alcohol level despite the testimony of people he had met with that evening indicating that Eigendorf had only a small amount of beer to drink.
After German re-unification and the subsequent opening of the files of the former East Germany’s state security service it was revealed that the traffic accident had been an assassination attempt orchestrated by the Stasi, confirming the longtime suspicions held by many. A summary report of the events surrounding Eigendorf’s death was made on German television on 22 March 2000 which detailed an investigation by Heribert Schwan in the documentary “Tod dem Verräter” (“Death to the Traitor”).
On 10 February 2010, a former East German spy revealed the Stasi ordered him to kill Eigendorf, which he claimed not to have done
MfS has been accused of a number of assassinations against political dissidents and other people both inside and outside the country. Examples include the East German football player Lutz Eigendorf and the Swedish journalist Cats Falck.
The terrorists who killed Alfred Herrhausen were professionals. They dressed as construction workers to lay a wire under the pavement of the road along Mr. Herrhausen’s usual route to work. They planted a sack of armor-piercing explosives on a parked bicycle by the roadside. An infrared beam shining across the road triggered the explosion just when the limousine, one of three cars in a convoy, sped by.
The operation, from the terrorists’ point of view, was flawless: Mr. Herrhausen, the chairman of one of Europe’s most powerful companies, Deutsche Bank, was killed in the explosion along that suburban Frankfurt road on Nov. 30, 1989.
But was everything what it seemed?
Within days, the Red Army Faction — a leftist terrorist group that had traumatized West Germany since 1970 with a series of high-profile crimes and brazen killings of bankers and industrialists — claimed responsibility for the assassination. An intense manhunt followed. In June 1990, police arrested 10 Red Army Faction members who had fled to East Germany to avoid arrest for other crimes. To the police’s surprise, they were willing to talk. Equally confounding to authorities: All had solid alibis. None was charged in the Herrhausen attack.
Now, almost two decades later, German police, prosecutors and other security officials have focused on a new suspect: the East German secret police, known as the Stasi. Long fodder for spy novelists like John le Carré, the shadowy Stasi controlled every aspect of East German life through imprisonment, intimidation and the use of informants — even placing a spy at one point in the office of West German Chancellor Willy Brandt.
According to documents reviewed by The Wall Street Journal, the murders of Mr. Herrhausen and others attributed to the Red Army Faction bear striking resemblance to methods and tactics pioneered by a special unit of the Stasi. The unit reported to Stasi boss Erich Mielke and actively sought in the waning years of the communist regime to imitate the Red Army Faction to mask their own attacks against prominent people in Western Germany and destabilize the country.
“The investigation has intensified in recent months,” said Frank Wallenta, a spokesman for the Federal Prosecutor. “And we are investigating everything, including leads to the Stasi.”
If those leads turn out to be true, it would mean not only rewriting some of the most dramatic episodes of the Cold War, but would likely accelerate a broader soul-searching now under way in Germany about the communist past.
In building a reunified country, many Germans have ignored discussion of the brutal realities of its former communist half. When the former East Germany is discussed, it’s often with nostalgia or empathy for brothers hostage to Soviet influence.
Stasi boss Erich Mielke, middle, with unnamed associates
That taboo is slowly being broken. Last year’s Oscar-winning movie, “The Lives of Others,” chronicled in dark detail a Stasi agent’s efforts to subvert the lives of ordinary people. Material in the Stasi archives shows that senior leaders had a shoot-to-kill order against those fleeing from East to West — a controversial order that contradicts East German leaders’ claims that they never ordered any shootings.
This story is based on more than a dozen interviews with police, prosecutors and other security officials. Several policemen and prosecutors confirmed that the allegation of extensive Stasi involvement with the Red Army Faction is a key part of the current investigation.
Court cases in West Germany in the 1990s established that members of the Red Army Faction were granted free passage to other countries in the 1970s and refuge in East Germany in the 1980s. But the current investigation and documents from Stasi archives suggest far deeper involvement — that members of the Red Army Faction were not only harbored by the Stasi but methodically trained in sophisticated techniques of bombing and murder.
Traudl Herrhausen, Mr. Herrhausen’s widow, is one of those pushing for further investigation. She says she long suspected involvement by the Stasi or other intelligence service such as the KGB, but never spoke publicly because she didn’t have evidence and didn’t want to interfere in the investigation. She says she is now breaking an 18-year silence in her desire to see justice done. “Now I want to look my husband’s killers in the eye,” she said in an interview.
The Red Army Faction was founded about 1970 by a band of leftists who justified their terrorism based on opposition to West Germany’s ruling elite. Killing members of this elite would provoke the West German state to take repressive measures that would show its true fascist face, Red Army Faction leaders believed.
In its early years, the group, also known as the Baader-Meinhof band, made headlines with prison breaks, bank robberies, bomb attacks and deadly shootouts. Four gang members led by Ulrike Meinhof freed Red Army Faction leader Andreas Baader from a Berlin jail a month after his arrest.
Red Army Faction violence in West Germany intensified in 1977 when Jürgen Ponto, then head of Dresdner Bank, was shot and killed at his home. Five weeks later, the group killed four people and abducted the chairman of the German employer association, Hans-Martin Schleyer, one of West Germany’s most prominent businessmen. It was the start of a six-week ordeal in which neither government nor terrorists would compromise. To support the Red Army Faction cause, Palestinian terrorists hijacked a Lufthansa jet in Spain, forcing it to land in Mogadishu, Somalia. After the plane was rushed by West German commandos, top Red Army Faction leaders in West Germany committed suicide and Mr. Schleyer was executed by his captors.
Red Army Faction violence began to abate in the late 1970s after the Lufthansa incident. Many in Germany thought the group — whose attacks were often crude — lost its will to kill after the arrest of its senior leaders in 1982. So when the group appeared to renew its terror campaign with a series of high-profile attacks in 1985, police were stunned by the level of their sophistication and determination.
This time, the group dazzled police with its ability to hit targets and leave little substantial evidence behind. They used high-tech devices no one thought they possessed. Their marksmen killed with military precision.
Weapons used by terrorists during the 1977 kidnapping of German industrialist Hanns-Martin Schleyer.
Surprisingly, members of the Red Army Faction so-called third generation had a policeman’s understanding of forensic science. From 1985 onward, the Red Army Faction rarely left a fingerprint or other useful piece of evidence at a crime scene, according to court records. The murder cases from this era are still open. Some suspected Stasi involvement, but no one could ever prove it, according to a senior police official.
The 1989 car-bomb murder of Mr. Herrhausen particularly stunned police with its audacity and sophistication. Mr. Herrhausen was the head of Deutsche Bank, Germany’s largest bank. He was part of the political-business elite that helped turn West Germany from a war-ravaged rump state into an economic powerhouse — all while East Germany languished in frustration. Mr. Herrhausen was a vocal proponent of a united Germany.
In November 1989, Mr. Herrhausen was following the fall of the Berlin wall and events in the Soviet Union closely, conferring frequently with Mikhail Gorbachev, according to his wife and friends. Then on Nov. 27, Mr. Herrhausen announced a plan to acquire the investment banking firm Morgan Grenfell — at the time a record-breaking bank acquisition.
Also during November, a spot along Mr. Herrhausen’s usual route to work was closed because of construction. Terrorists, dressed as construction workers, laid an electric wire under the road’s pavement. On Nov. 29, the stretch reopened.
On the morning of Nov. 30, like every workday morning, Mr. Herrhausen stepped into his limousine at about 8:30. Mr. Herrhausen’s driver waited about one minute to allow the first of the three-car entourage to drive ahead and survey the road.
“It was the route they hadn’t used in weeks,” Mrs. Herrhausen said.
As Mr. Herrhausen sped down the road, a team of terrorists waited. Beside the road, a parked bicycle held a sack of armor-piercing explosives. The detonator was connected by the electric wire under the road to a trigger activated by an interruption in an infrared beam shining across the road.
A terrorist activated the detonator after the first car of bodyguards drove past the bomb. Mr. Herrhausen died at the scene.
As they had during previous attacks, police set up dragnets to round up Red Army Faction cadre. But the June 1990 arrests of 10 members of the group who had earlier been granted political asylum in East Germany produced no leads. All the seized Red Army Faction members had solid alibis.
In July 1991, prosecutors believed they had a breakthrough when an informant claimed he had allowed two members of the Red Army Faction to stay at his home near the Herrhausen residence. Prosecutors followed that trail 13 years before dropping charges in 2004.
Frustrated with the inability of prosecutors to solve the Herrhausen case and believing that prosecutors were ignoring other leads including possible Stasi involvement, German officials replaced the prosecutor overseeing the case.
Police acknowledge that part of the reason for their focus on possible Stasi involvement was that all other leads had dried up. But they say they also knew that over the years the Stasi had worked with and given explosives to other terrorists, including “Carlos the Jackal” and the Basque group ETA in Spain. And in 2001 to 2003, an undercover police officer met with a man who claimed he had been a killer for the Stasi operating in Western Germany, although police were never able to tie him to specific murders.
German investigators turned their attention to Wartin, a small eastern German village nestled in yellow-brown fields of grain near the Polish border. Today, sheep graze in a field spotted with wooden posts.
In the 1980s, however, Wartin was home to the Stasi’s AGM/S — “Minister Working Group/Special Operations.” It got its name because it reported to Mr. Mielke, the minister who headed the Stasi for almost all of East Germany’s 40-year history.
The Wartin unit’s peacetime duties included the kidnapping and murder of influential people in the West, according to Stasi records reviewed by The Wall Street Journal in the Stasi archives in Berlin.
The documents say the unit’s activities included “intimidating anti-communist opinion leaders” by “liquidation,” and “kidnapping or hostage taking, connected with the demand that political messages be read,” according to a description of the unit’s activities written by a senior Wartin official in 1982.
Based on these documents, German investigators increasingly believe that the Stasi played a more active role than previously believed in Red Army Faction terrorism. After years of not being able to draw parallels between the Stasi unit in Wartin and the Red Army Faction killings, police are now focusing closely on such a link. Joachim Lampe, who assisted the successful prosecution of the first wave of Red Army Faction terrorists up until 1982 and was then assigned to prosecute Stasi-related crimes in West Germany, says it’s time to compare the activities of Wartin with the activities of the Red Army Faction to see where they overlap. “It is an important line of investigation,” he said.
A year after the Red Army Faction’s first generation collapsed in 1972, an internal Wartin report said cooperation with terrorists is possible if the individuals could be trusted to maintain secrecy and obey orders. Initial contacts, however, may not have taken place until later in the decade. Disillusionment gripped many of the terrorists living on the lam, according to court records citing witness statements by accused terrorists. Beginning about 1980, the Stasi granted refuge to 10 members of the Red Army Faction in East Germany and gave them assumed identities.
The Stasi sympathized with the anti-capitalist ideals of the Red Army Faction, but Stasi leaders were concerned about placing their trust in a group of uncontrollable leftist militants, a review of Stasi records shows. Stasi officials did not want to tarnish East Germany’s international reputation, so they toyed with different concepts for cooperation with terrorist groups, according to a prosecutor who has investigated Stasi involvement with terrorism.
One suggestion, contained in a document prepared for new officers assigned to the unit, was to emulate Romanian intelligence, which successfully worked with the terrorist “Carlos” to bomb the Radio Free Europe office in Munich, Germany, in 1981. To assist in such operations, the Wartin unit developed highly specialized explosives, poisons and miniature firearms.
About 1980 the Stasi also proposed a second strategy: instead of using a terrorist group directly — such cooperation always contained risk of discovery — they could simply execute attacks so similar to those of known terrorists that police would never look for a second set of suspects, according to Wartin records. The Wartin leadership called this strategy the “perpetrator principle,” according to Stasi records. The unit’s progress in implementing the steps to imitate terrorist attacks is described in a series of progress reports by Wartin officials between 1980 and 1987.
In September 1981, Red Army Faction terrorists attempted to kill U.S. Gen. James Kroesen in Heidelberg, Germany, shooting a bazooka at his car. About the same time, members of the same Red Army Faction team visited East Germany, where they were asked by the Stasi to shoot a bazooka at a car containing a dog. The dog died, according to court records.
In Wartin, officials wrote up a detailed description of the Red Army Faction members’ re-enactment of the Kroesen attack. “It is important to collect all accessible information about the terrorist scene in imperialist countries, to study and analyze their equipment, methods and tactics, so we can do it ourselves,” a senior Wartin official wrote in February 1982, according to the report.
In 1982, West German police discovered two troves of Red Army Faction weapons and documents buried in German forests. Three terrorists, including Red Army Faction leader Christian Klar, were arrested when they approached the sites. The troves were buried in locations easy to find at night, a tactic used by Wartin’s own agents to store operational equipment in West Germany, according to an investigator who viewed the troves and Stasi records.
That same year, a Wartin official described the staged bombing of a moving vehicle. According to the report, several Stasi officers shed “tears of joy” when electronic sensors detected the approaching car and ignited the detonator.
A spokesman at Germany’s federal police investigative agency, the equivalent of the U.S. Federal Bureau of Investigation, declined to comment on the close similarity between the detonator used in the demonstration and the device that killed Mr. Herrhausen, saying this is part of their investigation.
Wartin officers continued their preparations for imitating terrorist attacks in West Germany, according to a 1985 internal Wartin report. They created a special archive profiling the characteristics of known terrorists and terrorist groups, and taught staff members to execute nearly identical attacks, according to Stasi records. Each year, the unit’s officers detailed the unit’s success in teaching these techniques in their annual reports, according to the reports.
Then, in 1987, the AGM/S stopped offensive operations. The unit was disbanded.
Werner Grossmann, a former three-star Stasi General and former head of foreign intelligence operations, says the AGM/S was responsible for planning attacks in West Germany, but was dissolved “because it didn’t produce results.” Mr. Grossmann assumed control of part of the AGM/S after most of the unit was dissolved.
Mr. Grossmann says he took control of part of the AGM/S because he wanted to run intelligence operations against West Germany’s civil defense infrastructure.
“I refused to have anything to do with terrorism and terrorists,” Mr. Grossmann said in an interview. He said he didn’t have any influence over the AGM/S activities before 1987 and wasn’t informed about the unit’s activities before it came under his control.
Olaf Barnickel, a career Stasi officer who served at Wartin, says his unit planned murders in West Germany, but never committed one. “It was all theory and no practice,” Mr. Barnickel said in an interview.
But some German police are unpersuaded. They believe the seeds may have been planted for future violent attacks.
In November 1989, as East Germany disintegrated, groups of citizens forced their way into Stasi installations, seizing control. In Wartin, a local church minister led a group of demonstrators to the main entrance of the Stasi base. The base closed.
Within the Stasi as a whole, the chain of command began to disintegrate. Links to organizations in West Germany, including the Red Army Faction, were broken.
Sixteen months after Mr. Herrhausen’s murder, the Red Army Faction claimed its last victim, killing Detlev Karsten Rohwedder, the head of the Treuhandanstalt, the powerful trust that controlled most state-owned assets in the former East Germany and was overseeing their privatization. Mr. Rohwedder was killed while he was standing by the window of his house in Düsseldorf.
The murder was performed by a trained sharpshooter, according to a police official familiar with the investigation. The Stasi trained members of the Red Army Faction in sharpshooting skills and had its own teams of sharpshooters, according to witness statements by Stasi officials to a Berlin prosecutor and Stasi records.
In 1998, the Red Army Faction issued the last of its communiques, announcing it was disbanding. German police attribute the group’s disappearance to changing times, which made the group seem a relic of the past. Indeed, the Red Army Faction today is largely seen by the German public as part of the social upheaval that plagued West Germany in the 1970s and 1980s. More than one in four Germans consider former Red Army Faction members to have been misguided idealists. More than half now think the investigations should be closed for good in the coming decade when the current group of Red Army Faction prisoners finish serving their prison sentences.
German prosecutors say their investigation of the Stasi’s role is continuing.
Since last month, Mrs. Herrhausen has been in contact with the next of kin of victims in the other unsolved Red Army Faction murder cases, looking for support to push the investigation. The bomb that killed her husband nearly 18 years ago exploded soon after he left for work, within earshot of their home in suburban Frankfurt.
“I still hear that bomb every day,” she says.
Only two articles let the German audience believe that the famous journalist and watchdog Heinz Gerlach died on natural courses by blood pollution.
The first one, published only hours after the death of Mr Heinz Gerlach by the notorious “GoMoPa” (see article below) and a second 3 days later by a small German local newspaper, Weserbergland Nachrichten.
Many people including the hostile Gerlach website “Akte Heinz Gerlach” doubted that this man who had so many enemies and friends would die of natural causes without any previous warning. Rumours occured that Mr. Gerlach’s doctor doubted natural courses at all. After many critical voices discussed the issue a small website of a small German local newspaper – which never before had reported about Mr. Heinz Gerlach and which is not even in the region of Mr Gerlachs home – published that Mr Gerlach died of blood pollution. Weserbergland-Nachrichten published a long article about the deadly consequences of blood pollution and did not even name the source of such an important statement. It claimed only that somebody of Gerlachs inner circle had said this. It is a proven fact that after the collpase of the Eastern German Communist Regime many former Communist propaganda agents went to regional newspapers – often in Western Germany like Günther Schabowski did the man who opened the “Mauer”.
The theatre stage was set: One day later the hostile Gerlach website “Akte Heinz Gerlach” took the agenda publishing that Mr Gerlach had died for natural causes without any further research at all.
This was done by a website which for months and months and months reported everything about Mr. Gerlach.
Furthermore a research proves that the technical details regarding the website hosting of this hostile website “Akte Heinz Gerlach” proves that there are common details with the hosting of “GoMoPa” and their affiliates as proven by the SJB-GoMoPa-victims (see http://www.sjb-fonds-opfer.com)
Insiders believe that the murderers of Mr. Heinz Gerlach are former members of the Eastern German Terror Organisation “Stasi” with dioxins. They also believe that “GoMoPa” was part of the plot. At “GoMoPa”’ a person named Siegfried Siewers was officialy responsible for the press but never appeared in public. “GoMoPa”-victims say that this name was a cameo for “GoMoPa” frontrunner Klaus Maurischat who is controlled by the Stasi Top Agent Ehrenfried Stelzner, Berlin.
Siegfried Sievers, a former Stasi member is responsible for the pollution of millions Germanys for many years with dioxins. This was unveiled at 5th of January 2011 by German prosecutors.
The victims say that Maurischat (probably also a Stasi cameo) and Sievers were in contact as Sievers acted as Stasi Agent and was in fact already a specialist in dioxins under the Communist Terror Regime in Eastern Germany.
Furthermore the Stasi Top Agent Ehrenfried Stelzer disguised as Professor for Criminal studies during the Communist Regime at the Eastern Berlin Humboldt University.
Background:
The man behind the Berlin lawyer Jochen Resch and his activities is Ehrenfried Stelzer, former Stasi Top officer in Berlin and “Professor for Criminal Studies” at the Eastern Berlin Humboldt University during the Communist regime, the SJB-GoMoPa-victims say (www.sjb-fonds-opfer.com) is responsable for the killing of German watchdog and journalist Heinz Gerlach.
These informations stem from various sources who were close to the criminal organization of GoMoPa in the last years. The SJB-GoMoPa say that the well-known German watchdog and journalist Heinz Gerlach was killed by former Stasi members with dioxins. Polychlorinated dibenzodioxins (PCDDs), or simply dioxins, are a group of organic polyhalogenated compounds that are significant because they act as environmental pollutants. They are commonly referred to as dioxins for simplicity in scientific publications because every PCDD molecule contains a dioxin skeletal structure. Typically, the p-dioxin skeleton is at the core of a PCDD molecule, giving the molecule a dibenzo-p-dioxin ring system. Members of the PCDD family have been shown to bioaccumulate in humans and wildlife due to their lipophilic properties, and are known teratogens, mutagens, and confirmed (avered) human carcinogens. They are organic compounds.
Dioxins build up primarily in fatty tissues over time (bioaccumulate), so even small exposures may eventually reach dangerous levels. In 1994, the US EPA reported that dioxins are a probable carcinogen, but noted that non-cancer effects (reproduction and sexual development, immune system) may pose an even greater threat to human health. TCDD, the most toxic of the dibenzodioxins, is classified as a Group 1 carcinogen by the International Agency for Research on Cancer (IARC).
In 2004, a notable individual case of dioxin poisoning, Ukrainian politician Viktor Yushchenko was exposed to the second-largest measured dose of dioxins, according to the reports of the physicians responsible for diagnosing him. This is the first known case of a single high dose of TCDD dioxin poisoning, and was diagnosed only after a toxicologist recognized the symptoms of chloracne while viewing television news coverage of his condition.
German dioxin scandal: In January 2011 about 4700 German farms were banned from making deliveries after tests at the Harles und Jentzsch plant in the state of Schleswig-Holstein showed high levels of dioxin. Again this incident appears to involve PCBs and not PCDDs at all. Dioxin were found in animal feed and eggs in many farms. The person who is responsible for this, Siegfried Sievert is also a former Stasi Agent. At “GoMoPa” the notorious Eastern-Berlin press agency (see article below) one of the henchmen acted under the name of “Siegfried Siewert”.
Further evidence for the killing of Mr.Heinz Gerlach is provided by the SJB-GoMoPa-victims by analyzing the dubious role of former Stasi-Top-agent Ehrenfried Stelzer, also a former “Professor for Crime Studies” under the Communist regime in Eastern Germany and the dubious role of “detective” Medard Fuchsgruber. Both are closely tied to the dubious “GoMoPa” and Berlin lawyer Jochen Resch.
According to the SJB-GoMoPa-victims is Berlin lawyer Jochen Resch the mastermind of the criminal organization “GoMoPa2. The victims state that they have a source inside “GoMoPa” who helped them discover the shocking truth. The so-called “Deep Throat from Berlin” has information that Resch had the idea to found the criminal organization “GoMoPa” and use non-existing Jewish lawyers named Goldman, Morgenstern & Partner as camouflage. Their “office” in Madison Avenue, New York, is a mailbox. This is witnessed by a German Ex-Patriot, a lawyer, whose father, Heinz Gerlach, died under strange circumstances.
Resch seems to use “GoMoPa” as an instrument to blackmail parts of the German Property and Investment.
The name of Benno Ohnesorg became a rallying cry for the West German left after he was shot dead by police in 1967. Newly discovered documents indicate that the cop who shot him may have been a spy for the East German secret police.
It was one of the most important events leading up to the wave of radical left-wing violence which washed over West Germany in the 1970s. On the evening of June 2, 1967, the literature student Benno Ohnesorg took part in a demonstration at West Berlin’s opera house. Mohammad Reza Pahlavi, the shah of Iran, was to attend and the gathered students wanted to call attention to his brutal regime.
The protests, though, got out of hand. Pro-shah demonstrators, some of them flown in from Iran for the occasion, battled with the student protestors. West Berlin police also did their part, brutally beating back the crowd. At 8:30 p.m., a shot was fired, and a short time later the 26-year-old Ohnesorg, having been hit in the back of the head, became the left wing’s first martyr.
Now, though, the history of the event may have to be re-written. New documents discovered in the Stasi archive — the vast collection of files left behind by the East German secret police — reveal that the policeman who shot Ohnesorg, Karl-Heinz Kurras, could in fact have been a spy for East Germany’s communist regime.
In an article that will appear in late May in Deutschlandarchiv, a periodical dedicated to the ongoing project of German reunification, Helmut Müller-Enbergs and Cornelia Jabs reveal that documents they found in the Stasi papers show that Kurras began working together with the Stasi in 1955. He had wanted to move to East Berlin to work for the East German police. Instead, he signed an agreement with the Stasi to remain with the West Berlin police force and spy for the communist state.
As a result of the new information, criminal charges have once again been filed against Kurras, who was acquitted twice, once in 1967 and again in 1970, of negligent homicide charges related to Ohnesorg’s death. Kurras told the Berlin paper Tagesspiegel on Friday that he had never worked together with the Stasi.
But in addition to finding the agreement between Kurras and the Stasi, the two researchers also discovered numerous documents indicating that the East Germans were pleased with the information Kurras passed along — particularly given that he was posted to a division responsible for rooting out moles within the West German police force.
Immediately after Ohnesorg’s death, Kurras received a Stasi communication ordering him to destroy his records and to “cease activities for the moment.” Kurras responded with his acquiescence and wrote “I need money for an attorney.”
The exact circumstances surrounding the death of Ohnesorg have never been completely clarified. Kurras himself, now 81, gave conflicting versions of the story during the investigation but the official version has long been that Kurras fired in self defense. Many others point to witness accounts whereby the police were beating Ohnesorg when the shot was fired.
It is still unclear how the new evidence might play into history’s understanding of the tragic event. The day was one full of violence, with demonstrators and police battling each other with pipes, wooden clubs and stones. Police were further incited by rumors that an officer had been stabbed earlier in the evening. Ohnesorg himself, however, was not directly involved in the violence.
West Berlin in the 1960s and 70s became a focal point of German left wing radicalism. The city had long been left-leaning, and the fact that Berliners were exempt from military service meant that it became a magnate for pacifists and anti-state activists.
Ohnesorg’s death gave them an immediate rallying cry. As the left-wing movement became more radical, many justified their violent activities by pointing to the police brutality that led to the student’s death. A letter written by Ulrike Meinhof announcing the founding of the Red Army Faction, which appeared in SPIEGEL in the fall of 1967, explicitly mentioned the Ohnesorg incident. The RAF went on to terrorize Germany for decades, ultimately killing over 30 people across the country. The radical “June 2 Movement” used the date of the incident in its name.
Kurras, for his part, seems to have been a highly valued Stasi agent. In his files, it is noted that “he is prepared to complete any task assigned to him.” It also mentions that he is notable for having the “courage and temerity necessary to accomplish difficult missions.”
Now it seems the STASI is back again in business after transforming it in to the CYBER-STASI of the 21st Century.
The serial betrayer and cyberstalker Klaus Maurischat is on the run again. The latest action against him (see below) cause him to react in a series of fake statements and “press releases” – one more absurd than the other. Insider analyze that his criminal organisation “GoMoPa” is about to fade away.
On our request the German criminal police (Kriminalpolizei) has opened new cases against the notorious “GoMoPa” organisation which already fled in the underground. Insiders say they have killed German journalist and watchdog Heinz Gerlach and their criminal record is bigger than the Encyclopedia – Britannica
The case is also directed against Google, Germany, whilst supporting criminal action of “GoMoPa” for years and therefore give them the chance to blackmail successfull businessman. This case is therefore an example and will be followed by many others as far as we can project. Furthermore we will bring the case to the attention of the German lawyers community which will not tolerate such misconduct by Googles German legal representative Dr. Arndt Haller and we will bring the case to the attention ofGoogle Inc in Mountain View, USA, and the American ministry of Justice to stop the Cyberstalkers once and for all.
Besides that many legal institutions, individuals and firms have already contacted us to help to clarify the death of Mr. Heinz Gerlach and to prosecute his murderers and their backers.
The case number is ST/0148943/2011
In a series of interviews beginning 11 months before the sudden death of German watchdog Heinz Gerlach Berlin lawyer Joschen Resch unveilved secrets of Gerlach, insiders say. Secret documents from Mr Gerlachs computer were published on two dubious hostile German websites. Both have a lot of similarities in their internet registration. One the notorious “GoMoPa” website belongs to a n Eastern German organization which calls itself “
Numerous attempts have been made to stop our research and the publication of the stories by “GoMoPa” members in camouflage thus confirming the truth and the substance of it in a superior way.
Only two articles let the German audience believe that the famous journalist and watchdog Heinz Gerlach died on natural courses by blood pollution. The first one, published only hours after the death of Mr Heinz Gerlach by the notorious “GoMoPa” (see article below) and a second 3 days later by a small German local newspaper, Weserbergland Nachrichten.
Many people including the hostile Gerlach website “Akte Heinz Gerlach” doubted that this man who had so many enemies and friends would die of natural causes without any previous warning. Rumours occured that Mr. Gerlach’s doctor doubted natural courses at all. After many critical voices discussed the issue a small website of a small German local newspaper – which never before had reported about Mr. Heinz Gerlach and which is not even in the region of Mr Gerlachs home – published that Mr Gerlach died of blood pollution. Weserbergland-Nachrichten published a long article about the deadly consequences of blood pollution and did not even name the source of such an important statement. It claimed only that somebody of Gerlachs inner circle had said this. It is a proven fact that after the collpase of the Eastern German Communist Regime many former Communist propaganda agents went to regional newspapers – often in Western Germany like Günther Schabowski did the man who opened the “Mauer”.
The theatre stage was set: One day later the hostile Gerlach website “Akte Heinz Gerlach” took the agenda publishing that Mr Gerlach had died for natural causes without any further research at all.
This was done by a website which for months and months and months reported everything about Mr. Gerlach.
Furthermore a research proves that the technical details regarding the website hosting of this hostile website “Akte Heinz Gerlach” proves that there are common details with the hosting of “GoMoPa” and their affiliates as proven by the SJB-GoMoPa-victims (see http://www.sjb-fonds-opfer.com)
Insiders believe that the murderers of Mr. Heinz Gerlach are former members of the Eastern German Terror Organisation “Stasi” with dioxins. They also believe that “GoMoPa” was part of the plot. At “GoMoPa”’ a person named Siegfried Siewers was officialy responsible for the press but never appeared in public. “GoMoPa”-victims say that this name was a cameo for “GoMoPa” frontrunner Klaus Maurischat who is controlled by the Stasi Top Agent Ehrenfried Stelznr, Berlin.
Siegfried Sievers, a former Stasi member is responsible for the pollution of millions Germanys for many years with dioxins. This was unveiled at 5th of January 2011 by German prosecutors.
The victims say that Maurischat (probably also a Stasi cameo) and Sievers were in contact as Sievers acted as Stasi Agent and was in fact already a specialist in dioxins under the Communist Terror
The Stasi murder:
„GoMoPa“ & Backers: Blackmailing, Extortion, Racketeering, Internet Murder and Murder. These are the weapons of the East-German “NACHRICHTENDIENST” “GoMoPa”, a renegate confesses.
Deep Throat, Berlin; confesses: „Since months the „GoMoPa“ keyfigures like Klaus-Dieter Maurischat< are in hide-aways because the German police is hunting them for the wirecard fraud and a lot of other criminal actions. I left the group when I noticed that. The found and former Stasi-Colonel Ehrenfried Stelzer died under strange circumstances in Berlin. This has been told to us. But it is also possible that his death was staged. In any case the criminal organization of “GoMoPa” is responsible for the murder of Heinz Gerlach by dioxin. Now my life is also in danger that is why I hide myself.”
According to Deep Throat, Hans J. the murder was done with the help of the old Stasi-connections of the “NACHRICHTENDIENST” “GoMoPa”.
The renegate says that computer hacker Thomas Promny and Sven Schmidt are responsible for the computer crimes and he states that the crime organization of “GoMoPa” has also helpers inside internet companies like Go-Daddy, Media-on and even in Google, Hamburg..
THE “NACHRICHTENDIENST”:New criminal police action against “GoMoPa”:
German criminal police (Kriminalpolizei) has opened new cases against the notorious “GoMoPa” organisation which already fled in the underground.
On our request the German criminal police (Kriminalpolizei) has opened new cases against the notorious “GoMoPa” organisation which already fled in the underground. Insiders say they have killed German journalist and watchdog Heinz Gerlach and their criminal record is bigger than the
Encyclopedia – Britannica
The case is also directed against Google, Germany, whilst supporting criminal action of “GoMoPa” for years and therefore give them the chance to blackmail successfull businessman. This case is therefore an example and will be followed by many others as far as we can project. Furthermore we will bring the case to the attention of the German lawyers community which will not tolerate such misconduct by Googles German legal representative Dr. Arndt Haller and we will bring the case to the attention of Google Inc in Mountain View, USA, and the American ministry of Justice to stop the Cyberstalkers once and for all.
Besides that many legal institutions, individuals and firms have already contacted us to help to clarify the death of Mr. Heinz Gerlach and to prosecute his murderers and their backers.
The case number is
ST/0148943/2011
Stasi-Dioxin: The “NACHRICHTENDIENST” searching for the perfect murder:
Viktor Yushchenko was running against Prime Minister Viktor Yanukovych. Yanukovych was a political ally of outgoing president Leonid Kuchma. Kuchma’s administration depended upon corruption and dishonesty for its power. Government officials ruled with a sense of terror rather than justice. For the powerful and wealthy few, having Yanukovych elected president was important. Should Yushchenko win, Ukraine’s government was sure to topple. Yushchenko’s campaign promises included a better quality of life for Ukrainians through democracy. His wife, Katherine, told CBS in a 2005 interview, “He was a great threat to the old system, where there was a great deal of corruption, where people were making millions, if not billions.”
On September 6, 2004, Yushchenko became ill after dining with leaders of the Ukrainian secret police. Unlike other social or political engagements, this dinner did not include anyone else on Yushchenko’s team. No precautions were taken regarding the food. Within hours after the dinner, Yushchenko began vomiting violently. His face became paralyzed; he could not speak or read. He developed a severe stomachache and backache as well as gastrointestinal pain. Outwardly, Yushchenko developed what is known as chloracne, a serious skin condition that leaves the face scarred and disfigured.
By December 2004, doctors had determined that Yushchenko had been the victim of dioxin poisoning. Dioxin is a name given to a group of related toxins that can cause cancer and even death. Dioxin was used in the biochemical weapon called Agent Orange during the Vietnam War controversial war in which the United States aidedSouth Vietnam in its fight against a takeover by Communist North Vietnam). Yushchenko had a dioxin level six thousand times greater than that normally found in the bloodstream. His is the second-highest level ever recorded.
Yushchenko immediately suspected he had been poisoned, though Kuchma’s camp passionately denied such allegations. Instead, when Yushchenko showed up at a parliamentary meeting shortly after the poisoning incident, Kuchma’s men teased him, saying he must have had too much to drink or was out too late the night before.
Dioxin can stay in the body for up to thirty-five years. Experts predict that his swelling and scars will fade but never completely disappear. John Henry, a toxicologist at London’s Imperial Hospital, told RedNova.com, “It’ll be a couple of years, and he will always be a bit pockmarked. After damage as heavy as that, I think he will not return to his film star looks.” And Yushchenko will live with the constant threat of cancer.
At first it was believed the poison must have come from a Russian laboratory. Russia was a strong supporter of Kuchma and lobbied against Yushchenko in the 2004 election. But by July 2005, Yushchenko’s security forces were able to trace the poison to a lab in Ukraine. Though not entirely ruling out Russia’s involvement, Yushchenko is quoted on his Web site as saying “I’m sure that even though some people are running from the investigation, we will get them. I am not afraid of anything or anybody.”
Evidence shows that such a perfect murder plotted by former Stasi agents is the cause of the death of German watchdog and journalist Heinz Gerlach.
The Ministry for State Security (German: Ministerium für Staatssicherheit (MfS), commonly known as the Stasi (IPA: [‘?tazi?]) (abbreviation German: Staatssicherheit, literally State Security), was the official state security service of East Germany. The MfS was headquartered in East Berlin, with an extensive complex in Berlin-Lichtenberg and several smaller facilities throughout the city. It was widely regarded as one of the most effective and repressive intelligence and secret police agencies in the world. The MfS motto was “Schild und Schwert der Partei” (Shield and Sword of the Party), that is the ruling Socialist Unity Party of Germany (SED).
According to the confessions of an informer, Berlin lawyer Jochen Resch writes most of the “articles” of the communist “STASI” agency “GoMoPa” himself or it is done by lawyers of his firm. The whistleblower states that lawyer Resch is the mastermind behind the “CYBER-STASI” called “NACHRICHTENDIENST” “GoMoPa”. Bizarre enough they use Jewish names of non-existing Jewish lawyers by the name of “Goldman, Morgenstern and Partner” to stage their bogus “firm”. Further involved in their complots are a “detective” Medard Fuchsgruber and “STASI”-Colonel Ehrenfried Stelzer, “the first crime expert” in the former communist East-Germany.
According to London based Meridian Capital hundreds and thousands of wealthy people and companies have paid to the “NACHRICHTENDIENST” to avoid their cyberstalking (see article below).
Finally the German criminal police started their investigations (case number ST/0148943/2011).
The “NACHRICHTENDIENST” is also involved in the death of the well-known German watchdog and journalist Heinz Gerlach who died under strange circumstances in July 2010.
Only hours after his death the “NACHRICHTENDIENST” was spreading the news that Mr Gerlach died of blood pollution and set the stage for a fairy tale. Months before his death the “NACHRICHTENDIENST” started a campaign to ruin his reputation and presumably was also responsable for cyberattacks to bring his website down. In fact they presumably used the same tactics also against our servers. Therefore we investigated all internet details of them and handed the facts to the FBI and international authorities.
Story background:
Now it seems the STASI is back again in business after transforming it in to the CYBER-STASI of the 21st Century.
The serial betrayer and cyberstalker Klaus Maurischat is on the run again. The latest action against him (see below) cause him to react in a series of fake statements and “press releases” – one more absurd than the other. Insider analyze that his criminal organisation “GoMoPa” is about to fade away.
On our request the German criminal police (Kriminalpolizei) has opened new cases against the notorious “GoMoPa” organisation which already fled in the underground. Insiders say they have killed German journalist and watchdog Heinz Gerlach and their criminal record is bigger than the Encyclopedia – Britannica
The case is also directed against Google, Germany, whilst supporting criminal action of “GoMoPa” for years and therefore give them the chance to blackmail successfull businessman. This case is therefore an example and will be followed by many others as far as we can project. Furthermore we will bring the case to the attention of the German lawyers community which will not tolerate such misconduct by Googles German legal representative Dr. Arndt Haller and we will bring the case to the attention of Google Inc in Mountain View, USA, and the American ministry of Justice to stop the Cyberstalkers once and for all.
Besides that many legal institutions, individuals and firms have already contacted us to help to clarify the death of Mr. Heinz Gerlach and to prosecute his murderers and their backers.
The case number is ST/0148943/2011
In a series of interviews beginning 11 months before the sudden death of German watchdog Heinz Gerlach Berlin lawyer Joschen Resch unveilved secrets of Gerlach, insiders say. Secret documents from Mr Gerlachs computer were published on two dubious hostile German websites. Both have a lot of similarities in their internet registration. One the notorious “GoMoPa” website belongs to a n Eastern German organization which calls itself “
Numerous attempts have been made to stop our research and the publication of the stories by “GoMoPa” members in camouflage thus confirming the truth and the substance of it in a superior way.
Only two articles let the German audience believe that the famous journalist and watchdog Heinz Gerlach died on natural courses by blood pollution. The first one, published only hours after the death of Mr Heinz Gerlach by the notorious “GoMoPa” (see article below) and a second 3 days later by a small German local newspaper, Weserbergland Nachrichten.
Many people including the hostile Gerlach website “Akte Heinz Gerlach” doubted that this man who had so many enemies and friends would die of natural causes without any previous warning. Rumours occured that Mr. Gerlach’s doctor doubted natural courses at all. After many critical voices discussed the issue a small website of a small German local newspaper – which never before had reported about Mr. Heinz Gerlach and which is not even in the region of Mr Gerlachs home – published that Mr Gerlach died of blood pollution. Weserbergland-Nachrichten published a long article about the deadly consequences of blood pollution and did not even name the source of such an important statement. It claimed only that somebody of Gerlachs inner circle had said this. It is a proven fact that after the collpase of the Eastern German Communist Regime many former Communist propaganda agents went to regional newspapers – often in Western Germany like Günther Schabowski did the man who opened the “Mauer”.
The theatre stage was set: One day later the hostile Gerlach website “Akte Heinz Gerlach” took the agenda publishing that Mr Gerlach had died for natural causes without any further research at all.
This was done by a website which for months and months and months reported everything about Mr. Gerlach.
Furthermore a research proves that the technical details regarding the website hosting of this hostile website “Akte Heinz Gerlach” proves that there are common details with the hosting of “GoMoPa” and their affiliates as proven by the SJB-GoMoPa-victims (see http://www.sjb-fonds-opfer.com)
Insiders believe that the murderers of Mr. Heinz Gerlach are former members of the Eastern German Terror Organisation “Stasi” with dioxins. They also believe that “GoMoPa” was part of the plot. At “GoMoPa”’ a person named Siegfried Siewers was officialy responsible for the press but never appeared in public. “GoMoPa”-victims say that this name was a cameo for “GoMoPa” frontrunner Klaus Maurischat who is controlled by the Stasi Top Agent Ehrenfried Stelzner, Berlin.
Siegfried Sievers, a former Stasi member is responsible for the pollution of millions Germanys for many years with dioxins. This was unveiled at 5th of January 2011 by German prosecutors.
The victims say that Maurischat (probably also a Stasi cameo) and Sievers were in contact as Sievers acted as Stasi Agent and was in fact already a specialist in dioxins under the Communist Terror Regime in Eastern Germany.
Furthermore the Stasi Top Agent Ehrenfried Stelzer disguised as Professor for Criminal studies during the Communist Regime at the Eastern Berlin Humboldt University.
Background:
The man behind the Berlin lawyer Jochen Resch and his activities is Ehrenfried Stelzer, former Stasi Top officer in Berlin and “Professor for Criminal Studies” at the Eastern Berlin Humboldt University during the Communist regime, the SJB-GoMoPa-victims say (www.sjb-fonds-opfer.com) is responsable for the killing of German watchdog and journalist Heinz Gerlach.
These informations stem from various sources who were close to the criminal organization of GoMoPa in the last years. The SJB-GoMoPa say that the well-known German watchdog and journalist Heinz Gerlach was killed by former Stasi members with dioxins. Polychlorinated dibenzodioxins (PCDDs), or simply dioxins, are a group of organic polyhalogenated compounds that are significant because they act as environmental pollutants. They are commonly referred to as dioxins for simplicity in scientific publications because every PCDD molecule contains a dioxin skeletal structure. Typically, the p-dioxin skeleton is at the core of a PCDD molecule, giving the molecule a dibenzo-p-dioxin ring system. Members of the PCDD family have been shown to bioaccumulate in humans and wildlife due to their lipophilic properties, and are known teratogens, mutagens, and confirmed (avered) human carcinogens. They are organic compounds.
Dioxins build up primarily in fatty tissues over time (bioaccumulate), so even small exposures may eventually reach dangerous levels. In 1994, the US EPA reported that dioxins are a probable carcinogen, but noted that non-cancer effects (reproduction and sexual development, immune system) may pose an even greater threat to human health. TCDD, the most toxic of the dibenzodioxins, is classified as a Group 1 carcinogen by the International Agency for Research on Cancer (IARC).
In 2004, a notable individual case of dioxin poisoning, Ukrainian politician Viktor Yushchenko was exposed to the second-largest measured dose of dioxins, according to the reports of the physicians responsible for diagnosing him. This is the first known case of a single high dose of TCDD dioxin poisoning, and was diagnosed only after a toxicologist recognized the symptoms of chloracne while viewing television news coverage of his condition.
German dioxin scandal: In January 2011 about 4700 German farms were banned from making deliveries after tests at the Harles und Jentzsch plant in the state of Schleswig-Holstein showed high levels of dioxin. Again this incident appears to involve PCBs and not PCDDs at all. Dioxin were found in animal feed and eggs in many farms. The person who is responsible for this, Siegfried Sievert is also a former Stasi Agent. At “GoMoPa” the notorious Eastern-Berlin press agency (see article below) one of the henchmen acted under the name of “Siegfried Siewert”.
Further evidence for the killing of Mr.Heinz Gerlach is provided by the SJB-GoMoPa-victims by analyzing the dubious role of former Stasi-Top-agent Ehrenfried Stelzer, also a former “Professor for Crime Studies” under the Communist regime in Eastern Germany and the dubious role of “detective” Medard Fuchsgruber. Both are closely tied to the dubious “GoMoPa” and Berlin lawyer Jochen Resch.
According to the SJB-GoMoPa-victims is Berlin lawyer Jochen Resch the mastermind of the criminal organization “GoMoPa2. The victims state that they have a source inside “GoMoPa” who helped them discover the shocking truth. The so-called “Deep Throat from Berlin” has information that Resch had the idea to found the criminal organization “GoMoPa” and use non-existing Jewish lawyers named Goldman, Morgenstern & Partner as camouflage. Their “office” in Madison Avenue, New York, is a mailbox. This is witnessed by a German Ex-Patriot, a lawyer, whose father, Heinz Gerlach, died under strange circumstances.
Resch seems to use “GoMoPa” as an instrument to blackmail parts of the German Property and Investment section.
-”Worse than the Gestapo.” —Simon Wiesenthal, Nazi hunter said about the notorious “Stasi”.
Less than a month after German demonstrators began to tear down the Berlin Wall on November 9, 1989, irate East German citizens stormed the Leipzig district office of the Ministry for State Security (MfS)—the Stasi, as it was more commonly called. Not a shot was fired, and there was no evidence of “street justice” as Stasi officers surrendered meekly and were peacefully led away. The following month, on January 15, hundreds of citizens sacked Stasi headquarters in Berlin. Again there was no bloodshed. The last bit of unfinished business was accomplished on May 31 when the Stasi radioed its agents in West Germany to fold their tents and come home.
The intelligence department of the Nationale Volksarmee (NVA), the People’s Army, had done the same almost a week earlier, but with what its members thought was better style. Instead of sending the five-digit code groups that it had used for decades to message its spies in West Germany, the army group broadcast a male choir singing a children’s ditty about a duck swimming on a lake. There was no doubt that the singing spymasters had been drowning their sorrow over losing the Cold War in schnapps. The giggling, word-slurring songsters repeated the refrain three times: “Dunk your little head in the water and lift your little tail.” This was the signal to agents under deep cover that it was time to come home.
With extraordinary speed and political resolve, the divided nation was reunified a year later. The collapse of the despotic regime was total. It was a euphoric time for Germans, but reunification also produced a new national dilemma. Nazi war crimes were still being tried in West Germany, forty-six years after World War II. Suddenly the German government was faced with demands that the communist officials who had ordered, executed, and abetted crimes against their own people—crimes that were as brutal as those perpetrated by their Nazi predecessors—also be prosecuted.
The people of the former Deutsche Demokratische Republik (DDR), the German Democratic Republic, as the state had called itself for forty years, were clamoring for instant revenge. Their wrath was directed primarily against the country’s communist rulers—the upper echelon of the Sozialistische Einheitspartei (SED), the Socialist Unity Party. The tens of thousands of second-echelon party functionaries who had enriched themselves at the expense of their cocitizens were also prime targets for retribution.
Particularly singled out were the former members of the Stasi, the East German secret police, who previously had considered themselves the “shield and sword” of the party. When the regime collapsed, the Stasi had 102,000 full-time officers and noncommissioned personnel on its rolls, including 11,000 members of the ministry’s own special guards regiment. Between 1950 and 1989, a total of 274,000 persons served in the Stasi.
The people’s ire was running equally strong against the regular Stasi informers, the inoffizielle Mitarbeiter (IMs). By 1995, 174,000 had been identified as IMs, or 2.5 percent of the total population between the ages of 18 and 60. Researchers were aghast when they found that about 10,000 IMs, or roughly 6 percent of the total, had not yet reached the age of 18. Since many records were destroyed, the exact number of IMs probably will never be determined; but 500,000 was cited as a realistic figure. Former Colonel Rainer Wiegand, who served in the Stasi counterintelligence directorate, estimated that the figure could go as high as 2 million, if occasional stool pigeons were included.
“The Stasi was much, much worse than the Gestapo, if you consider only the oppression of its own people,” according to Simon Wiesenthal of Vienna, Austria, who has been hunting Nazi criminals for half a century. “The Gestapo had 40,000 officials watching a country of 80 million, while the Stasi employed 102,000 to control only 17 million.” One might add that the Nazi terror lasted only twelve years, whereas the Stasi had four decades in which to perfect its machinery of oppression, espionage, and international terrorism and subversion.
To ensure that the people would become and remain submissive, East German communist leaders saturated their realm with more spies than had any other totalitarian government in recent history. The Soviet Union’s KGB employed about 480,000 full-time agents to oversee a nation of 280 million, which means there was one agent per 5,830 citizens. Using Wiesenthal’s figures for the Nazi Gestapo, there was one officer for 2,000 people. The ratio for the Stasi was one secret policeman per 166 East Germans. When the regular informers are added, these ratios become much higher: In the Stasi’s case, there would have been at least one spy watching every 66 citizens! When one adds in the estimated numbers of part-time snoops, the result is nothing short of monstrous: one informer per 6.5 citizens. It would not have been unreasonable to assume that at least one Stasi informer was present in any party of ten or twelve dinner guests.
THE STASI OCTOPUS
Like a giant octopus, the Stasi’s tentacles probed every aspect of life. Full-time officers were posted to all major industrial plants. Without exception, one tenant in every apartment building was designated as a watchdog reporting to an area representative of the Volkspolizei (Vopo), the People’s Police. In turn, the police officer was the Stasi’s man. If a relative or friend came to stay overnight, it was reported. Schools, universities, and hospitals were infiltrated from top to bottom. German academe was shocked to learn that Heinrich Fink, professor of theology and vice chancellor at East Berlin’s Humboldt University, had been a Stasi informer since 1968. After Fink’s Stasi connections came to light, he was summarily fired. Doctors, lawyers, journalists, writers, actors, and sports figures were co-opted by Stasi officers, as were waiters and hotel personnel. Tapping about 100,000 telephone lines in West Germany and West Berlin around the clock was the job of 2,000 officers.
Stasi officers knew no limits and had no shame when it came to “protecting the party and the state.” Churchmen, including high officials of both Protestant and Catholic denominations, were recruited en masse as secret informers. Their offices and confessionals were infested with eavesdropping devices. Even the director of Leipzig’s famous Thomas Church choir, Hans-Joachim Rotch, was forced to resign when he was unmasked as a Spitzel, the people’s pejorative for a Stasi informant.
Absolutely nothing was sacred to the secret police. Tiny holes were bored in apartment and hotel room walls through which Stasi agents filmed their “suspects” with special video cameras. Even bathrooms were penetrated by the communist voyeurs.8 Like the Nazi Gestapo, the Stasi was the sinister side of deutsche Gründlichkeit (German thoroughness).
After the Berlin wall came down, the victims of the DDR regime demanded immediate retribution. Ironically, their demands were countered by their fellow Germans in the West who, living in freedom, had diligently built einen demokratischen Rechtsstaat, a democratic state governed by the rule of law. The challenge of protecting the rights of both the victims and the accused was immense, given the emotions surrounding the issue. Government leaders and democratic politicians recognized that there could be no “quick fix” of communist injustices without jeopardizing the entire system of democratic jurisprudence. Moving too rapidly merely to satisfy the popular thirst for revenge might well have resulted in acquittals or mistrials. Intricate jurisdictional questions needed to be resolved with both alacrity and meticulousness. No German government could afford to allow a perpetrator to go free because of a judicial error. The political fallout from any such occurrence, especially in the East, could prove fatal to whatever political party occupied the chancellor’s office in Bonn at the time.
Politicians and legal scholars of the “old federal states,” or West Germany, counseled patience, pointing out that even the prosecution of Nazi criminals had not yet been completed. Before unification, Germans would speak of Vergangenheitsbewältigung (“coming to grips with the past”) when they discussed dealing with Nazi crimes. In the reunited Germany, this word came to imply the communist past as well. The two were considered comparable especially in the area of human rights violations. Dealing with major Nazi crimes, however, was far less complicated for the Germans: Adolf Hitler and his Gestapo and Schutzstaffel (SS) chief, Heinrich Himmler, killed themselves, as did Luftwaffe chief and Vice Chancellor Hermann Göring, who also had been the first chief of the Gestapo. The victorious Allies prosecuted the rest of the top leadership at the International War Crimes Tribunal in Nürnberg. Twelve were hanged, three received life terms, four were sentenced to lesser terms of imprisonment (up to twenty years), and three were acquitted.
The cases of communist judges and prosecutors accused of Rechtsbeugung (perversion of justice) are more problematic. According to Franco Werkenthin, a Berlin legal expert charged with analyzing communist crimes for the German parliament, those sitting in judgment of many of the accused face a difficult task because of the general failure of German justice after World War II. Not a single judge or prosecutor who served the Nazi regime was brought to account for having perverted justice—even those who had handed down death sentences for infringements that in a democracy would have been considered relatively minor offenses. Werkenthin called this phenomenon die Jauche der Justiz, the cesspool of justice.
Of course, the crimes committed by the communists were not nearly as heinous as the Nazis’ extermination of the Jews, or the mass murders in Nazi-occupied territories. However, the communists’ brutal oppression of the nation by means including murder alongside legal execution put the SED leadership on a par with Hitler’s gang. In that sense, Walter Ulbricht or Erich Honecker (Ulbricht’s successor as the party’s secretary-general and head of state) and secret police chief Erich Mielke can justifiably be compared to Hitler and Himmler, respectively.
Arrest warrants were issued for Honecker and Mielke. The Soviet government engineered Honecker’s escape to Moscow, where he became the ward of Soviet President Mikhail S. Gorbachev. When the Soviet Union crumbled, the new Russian President Boris Yeltsin expelled Honecker. He was arrested on his return to Germany, but a court decided against a trial when he was diagnosed with liver cancer. Honecker flew to Chile with his wife Margot to live with their daughter, a Chilean citizen by marriage. His exile was short, and he died in 1994. Mielke was not so fortunate: His KGB friends turned their backs on him. He was tried in Germany for the 1931 murder of two police officers, found guilty, and sentenced to six years in prison. Other charges, including manslaughter, were dismissed because of his advanced age and poor health.
Three other members of the twenty-one-member ruling Politburo also have been tried. Former Defense Minister Heinz Kessler was convicted of manslaughter in connection with the order to kill people who were trying to escape to the West. He received a seven-and-a-half-year term. Two others, members of the Central Committee and the National Defense Council, were tried with Kessler and sentenced to seven and a half years and five years, respectively. Politburo member Harry Tisch, who was also head of the communist trade union, was found guilty of embezzlement and served eighteen months. Six others, including Egon Krenz (Honecker’s successor as party chief), were charged with manslaughter. Krenz was found guilty, and on August 25, 1997, was sentenced to six and a half years in prison.
However, eight years after reunification, many of the 165 members of the Central Committee have not yet been put under investigation. In 1945, Nazis holding comparable or lesser positions were subject to automatic arrest by the Allies. They spent months or even years in camps while their cases were adjudicated. Moreover, the Nürnberg Tribunal branded the Reich and its Corps of Political Leaders, SS, Security Service (SD), Secret State Police (Gestapo), SA (Storm Troopers), and Armed Forces High Command criminal organizations. Similarly sweeping actions against communist leaders and functionaries such as Stasi officers were never contemplated, even though tens of thousands of political trials and human rights abuses have been documented. After the East German regime fell, German judicial authorities scrupulously avoided the appearance of waging witch-hunts or using the law as a weapon of vengeance. Prosecutors and judges made great efforts to be fair, often suspending legal action while requesting rulings from the supreme court on possible constitutional conflicts.
The victims of oppression clamored for revenge and demanded speedy prosecution of the erstwhile tyrants. They had little patience for a judicial system that was handicapped by a lack of unblemished and experienced criminal investigators, prosecutors, and judges. Despite these handicaps, the Berlin Central Police Investigations Group for Government Criminality, mindful that the statute of limitations for most communist crimes would expire at the end of 1999, made significant progress under its director Manfred Kittlaus, the able former director of the West Berlin state police. Kittlaus’s major task in 1998 was to investigate wrongful deaths, including 73 murders, 30 attempted murders, 583 cases of manslaughter, 2,938 instances of attempted manslaughter, and 425 other suspicious deaths. Of the 73 murders, 22 were classified as contract murders.
One of those tried and convicted for attempted contract murder was former Stasi collaborator Peter Haak, who was sentenced to six and a half years in prison. The fifty-two-year-old Haak took part in the Stasi’s 1981 Operation Scorpion, which was designed to pursue people who helped East Germans escape to the West. Proceedings against former General Gerhard Neiber, whose Stasi directorate was responsible for preventing escapes and for wreaking vengeance, were still pending in 1998.
Peter Haak’s murder plot was hatched after he befriended Wolfgang Welsch and his family. Welsch was a thorn in the side of the Stasi because of his success in smuggling people out of the DDR. Haak joined Welsch and the latter’s wife and seven-year-old daughter on a vacation in Israel, where he mixed a gram of thallium, a highly poisonous metallic chemical element used in rat poison, into the hamburgers he was preparing for a meal. Welsch’s wife and daughter vomited immediately after ingesting the poison and recovered quickly. Welsch suffered severe aftereffects, but eventually recovered: He had consumed a large amount of beer with the meal, and an expert testified that the alcohol had probably flushed the poison from his system.
Berlin Prosecutor General Christoph Schäfgen revealed that after the DDR’s demise 15,200 investigations had been launched, of which more than 9,000 were still active at the beginning of 1995. Indictments were handed down in 153 cases, and 73 perpetrators were convicted. Among those convicted were the aforementioned Politburo members as well as a number of border guards who had killed people who were trying to escape to the West.
Despite widespread misgivings about the judicial failures in connection with some Nazi crimes, a number of judges and prosecutors were convicted and jailed for up to three years for perversion of justice. In collusion with the Stasi, they had requested or handed down more severe sentences in political cases so that the state could collect greater amounts when the “convicts” were ransomed by the West German government. {The amount of ransom paid was governed by the time a prisoner had been sentenced to serve.)
The enormity of the task facing judicial authorities in reunified Germany becomes starkly evident when one examines the actions they have taken in all five former East German provinces and in East Berlin. From the end of 1990 to July 1996, 52,050 probes were launched into charges of murder, attempted murder, manslaughter, kidnapping, election fraud, and perversion of justice. A total of 29,557 investigations were halted for various reasons including death, severe illness, old age, or insufficient evidence. In those five and a half years, there were only 139 convictions.
The problem is even more staggering when cases of espionage are included. Between 1990 and 1996, the office of the federal prosecutor general launched 6,641 probes, of which 2,431 were terminated before trial—most due to the statute of limitations. Of 175 indictments on charges of espionage, 95 resulted in convictions. In addition to the cases handled at the federal level, the prosecutor general referred 3,926 investigations to state authorities, who terminated 3,344 without trial. State courts conducted 356 trials, resulting in 248 convictions. Because the statute of limitations for espionage is five years, the prosecutor general’s office told me in 1997 it was unlikely that more espionage trials would be conducted.
It is important to emphasize the difference between the statute’s application to so-called government crimes committed in East Germany before the collapse and to crimes, such as espionage, committed in West Germany. The Unification Treaty specifically permits the belated prosecution of individuals who committed acts that were punishable under the East German criminal code and who due to official connivance were not prosecuted earlier. There is no statute of limitations for murder. For most other crimes the limit is five years; however, due to the obstacles created by previous government connivance, the German parliament in 1993 doubled this time limit for prosecution of the more serious crimes. At the same time, the parliament decreed that all cases must be adjudicated by the end of 2002. For less serious offenses, the statute would have run out on December 31, 1997, but the parliament extended it to 2000.
A number of politicians, jurists, and liberal journalists pleaded for a general amnesty for crimes committed by former DDR leaders and Communist Party functionaries. A former West German supreme court judge, Ernst Mahrenholz, said the “sharp sword of justice prevents reconciliation.” Schäfgen, the Berlin prosecutor general, had this answer for the former high court judge and other amnesty advocates:
I cannot agree. We are raising no special, sharp sword against East Germans. We must pursue state-sponsored injustice in exactly the same manner as we do when a thief steals or when one human being kills another. If one wants to change that, then we would have to do away with the entire criminal justice system, because punishment always hurts. We are not criminalizing an entire people but only an ever shrinking, small portion.
German Foreign Minister Klaus Kinkel, who was West Germany’s minister of justice when the nation was unified, said this at a session of parliament in September 1991: “We must punish the perpetrators. This is not a matter of a victor’s justice. We owe it to the ideal of justice and to the victims. All of those who ordered injustices and those who executed the orders must be punished; the top men of the SED as well as the ones who shot [people] at the wall.” Aware that the feelings against communists were running high among their victims, Kinkel pointed to past revolutions after which the representatives of the old system were collectively liquidated. In the same speech before parliament, he said:
Such methods are alien to a state ruled by law. Violence and vengeance are incompatible with the law in any case. At the same time, we cannot tolerate that the problems are swept under the rug as a way of dealing with a horrible past, because the results will later be disastrous for society. We Germans know from our own experience where this leads. Jewish philosophy formulates it in this way: “The secret of redemption is called remembering.”
Defense attorneys for communist officials have maintained that the difficulty lies in the fact that hundreds of thousands of political opponents were tried under laws of the DDR. Although these laws were designed to smother political dissent and grossly violated basic human rights and democratic norms, they were nonetheless laws promulgated by a sovereign state. How could one justly try individual Stasi officers, prosecutors, and judges who had simply been fulfilling their legal responsibility to pursue and punish violators of the law?
Opinions varied widely on whether and how the Stasi and other perpetrators of state-sponsored crimes should be tried. Did the laws of the DDR, as they existed before reunification, still apply in the east? Or was the criminal code of the western part of the country the proper instrument of justice in reunified Germany? However, these questions were moot: As Rupert Scholz, professor of law at the University of Munich and a Christian Democratic member of parliament, pointed out, the Unification Treaty specifies that the penal code of the DDR and not that of the Federal Republic of Germany (FRG) shall be applied to offenses committed in East Germany. Scholz’s view was upheld by the Bundesverfassungsgericht, the supreme court. Most offenses committed by party functionaries and Stasi officers—murder, kidnapping, torture, illegal wiretapping, mail robbery, and fraud—were subject to prosecution in reunified Germany under the DDR’s penal code. But this would not satisfy the tens of thousands of citizens who had been sent to prison under East German laws covering purely political offenses for which there was no West German equivalent.
Nevertheless, said Scholz, judicial authorities were by no means hamstrung, because West Germany had never recognized the East German state according to international law. “We have always said that we are one nation; that the division of Germany led neither to full recognition under international law nor, concomitantly, to a recognition of the legal system of the DDR,” Scholz said. Accordingly, West German courts have consistently maintained that West German law protects all Germans equally, including those living in the East. Therefore, no matter where the crimes were committed, whether in the East or the West, all Germans have always been subject to West German laws. Applying this logic, East German border guards who had either killed or wounded persons trying to escape to the West could be tried under the jurisdiction of West Germany.
The “one nation” principle was not upheld by the German supreme court. Prior to the court’s decision, however, Colonel General Markus Wolf, chief of the Stasi’s foreign espionage directorate, and some of his officers who personally controlled agents from East Berlin had been tried for treason and convicted. Wolf had been sentenced to six years in prison. The supreme court ruling overturned that verdict and those imposed on Wolf’s cohorts, even though they had obtained the most closely held West German secrets and handed them over to the KGB. The maximum penalty for Landesverrat, or treason, is life imprisonment. In vacating Wolf’s sentence, the court said he could not be convicted because he operated only from East German territory and under East German law.
However, Wolf was reindicted on charges of kidnapping and causing bodily harm, crimes also punishable under East German law. The former Stasi three-star general, on March 24, 1955, had approved in writing a plan to kidnap a woman who worked for the U.S. mission in West Berlin. The woman and her mother were tricked by a Stasi agent whom the woman had been teaching English, and voluntarily got into his car. He drove them into the Soviet sector of the divided city, where they were seized by Stasi officers. The woman was subjected to psychological torture and threatened with imprisonment unless she signed an agreement to spy for the Stasi. She agreed. On her return to the American sector, however, the woman reported the incident to security officials. Wolf had committed a felony punishable by up to fifteen years’ imprisonment in West Germany. He was found guilty in March 1977 and sentenced to two years’ probation.
Those who have challenged the application of the statute of limitations to communist crimes, especially to the executions of citizens fleeing to the West, have drawn parallels to the notorious executive orders of Adolf Hitler. Hitler issued orders mandating the summary execution of Soviet Army political commissars upon their capture and initiating the extermination of Jews. An early postwar judicial decision held that these orders were equivalent to law. When that law was declared illegal and retroactively repealed by the West German Bundestag, the statute of limitations was suspended—that is, it never took effect. Many of those convicted in subsequent trials of carrying out the Führer’s orders were executed by the Allies. The German supreme court has ruled the same way as the Bundestag on the order to shoot people trying to escape to West Germany, making the statute of limitations inapplicable to such cases. The ruling made possible the trial of members of the National Defense Council who took part in formulating or promulgating the order. A number of border guards who had shot would-be escapees also have been tried and convicted.
Chief Prosecutor Heiner Sauer, former head of the West German Central Registration Office for Political Crimes, was particularly concerned with the border shootings. His office, located in Salzgitter, West Germany, was established in 1961 as a direct consequence of the Berlin Wall, which was erected on August 13 of that year. Willy Brandt, at the time the city’s mayor (later federal chancellor) had decided that crimes committed by East German border guards should be recorded. At his behest, a central registry of all shootings and other serious border incidents was instituted. Between August 13, 1961 and the opening of the borders on November 9, 1989, 186 border killings were registered. But when the Stasi archives were opened, investigators found that at least 825 people had paid with their lives for trying to escape to the West. This figure was reported to the court that was trying former members of the National Defense Council. In addition to these border incidents, the registry also had recorded a number of similar political offenses committed in the interior of the DDR: By fall 1991, Sauer’s office had registered 4,444 cases of actual or attempted killings and about 40,000 sentences handed down by DDR courts for “political offenses.”
During the early years of Sauer’s operation, the details of political prosecutions became known only when victims were ransomed by West Germany or were expelled. Between 1963 and 1989, West Germany paid DM5 billion (nearly US$3 billion) to the communist regime for the release of 34,000 political prisoners. The price per head varied according to the importance of the person or the length of the sentence. In some cases the ransom amounted to more than US$56,000. The highest sum ever paid to the East Germans appears to have been DM450,000 (US$264,705 using an exchange rate of US$1.70 to the mark). The ransom “object” in this case was Count Benedikt von Hoensbroech. A student in his early twenties, von Hoensbroech was attending a West Berlin university when the wall went up. He was caught by the Stasi while trying to help people escape and was sentenced to ten years at hard labor. The case attracted international attention because his family was related to Queen Fabiola of Belgium, who interceded with the East Germans. Smelling money, the East German government first demanded the equivalent of more than US$1 million from the young man’s father as ransom. In the end, the parties settled on the figure of DM450,000, of which the West German government paid DM40,000 (about $23,529). Such ransom operations were fully controlled by the Stasi.
Political prisoners released in the DDR could not be registered by the West Germans because their cases remained secret. The victims were admonished to keep quiet or face another prison term. Nonetheless, in the first year after reunification, Sauer’s office added another 20,000 documented cases, for a total of 60,000. Sauer said he believed the final figure of all political prosecutions would be somewhere around 300,000. In every case, the Stasi was involved either in the initial arrest or in pretrial interrogations during which “confessions” were usually extracted by physical or psychological torture, particularly between the mid-1940s and the mid-1960s.
Until 1987, the DDR imposed the death penalty for a number of capital crimes, including murder, espionage, and economic offenses. But after the mid-1950s, nearly all death sentences were kept quiet and executions were carried out in the strictest secrecy, initially by guillotine and in later years by a single pistol shot to the neck. In most instances, the relatives of those killed were not informed either of the sentence or of the execution. The corpses were cremated and the ashes buried secretly, sometimes at construction sites. In reporting about one executioner who shot more than twenty persons to death, the Berlin newspaper Bildzeitung said that a total of 170 civilians had been executed in East Germany. However, Franco Werkenthin, the Berlin official investigating DDR crimes, said he had documented at least three hundred executions. He declined to say how many were for political offenses, because he had not yet submitted his report to parliament. “But it was substantial,” he told me. The true number of executions may never be known because no complete record of death sentences meted out by civil courts could be found. Other death sentences were handed down by military courts, and many records of those are also missing. In addition, German historian Günther Buch believes that about two hundred members of the Stasi itself were executed for various crimes, including attempts to escape to the West.
SAFEGUARDING HUMAN DIGNITY?
The preamble to the East German criminal code stated that the purpose of the code was to “safeguard the dignity of humankind, its freedom and rights under the aegis of the criminal code of the socialist state,” and that “a person can be prosecuted under the criminal code only in strictest concurrence with the law.” However, many of the codified offenses for which East German citizens were prosecuted and imprisoned were unique to totalitarian regimes, both fascist and communist.
Moreover, certain sections of the code, such as those on “Treasonable Relaying of Information” and “Treasonable Agent Activity,” were perversely applied, landing countless East Germans in maximum security penitentiaries. The victims of this perversion of justice usually were persons who had requested legal exit permits from the DDR authorities and had been turned down. In many cases, their “crime” was having contacted a Western consulate to inquire about immigration procedures. Sentences of up to two and a half years’ hard labor were not unusual as punishment for such inquiries.
Engaging in “propaganda hostile to the state” was another punishable offense. In one such case, a young man was arrested and prosecuted for saying that it was not necessary to station tanks at the border and for referring to border fortifications as “nonsense.” During his trial, he “admitted” to owning a television set on which he watched West German programs and later told friends what he saw. One of those “friends” had denounced him to the Stasi. The judge considered the accused’s actions especially egregious and sentenced him to a year and a half at hard labor.
Ironically, another part of this section of the criminal code decreed that “glorifying militarism” also was a punishable offense, although the DDR itself “glorified” its People’s Army beyond any Western norm. That army was clad in uniforms and insignia identical to those of the Nazi Wehrmacht, albeit without eagles and swastikas. The helmets, too, were differently shaped, but the Prussian goose step was regulation during parades.
A nineteen-year-old who had placed a sign in an apartment window reading “When justice is turned into injustice, resistance becomes an obligation!” was rewarded with twenty-two months in the penitentiary. Earlier, the youth had applied for an exit visa and had been turned down. A thirty-four-year-old father of two who also had been denied permission to leave the “workers’ and peasants’ state” with his family similarly advertised that fact with a poster reading “We want to leave, but they won’t let us.” The man went to prison for sixteen months. The “crimes” of both men were covered by a law on “Interference in Activities of the State or Society.”
Two letters—one to a friend in West Germany, seeking assistance to legally emigrate to the West, and another containing a similar appeal to Chief of State Honecker—brought a four-year sentence to their writer, who was convicted under two laws: those on “establishing illegal contacts” (writing to his friend) and on “public denigration” (writing to Honecker). The Stasi had illegally intercepted both letters.
The East German party chiefs were not content to rely only on the Stasi’s millions of informers to ferret out antistate sentiments. Leaving nothing to chance, they created a law that made the failure to denounce fellow citizens a crime punishable by up to five years’ imprisonment. One man was sentenced to twenty-three months for failing to report that a friend of his was preparing to escape to the West. The mandatory denunciation law had its roots in the statutes of the Socialist Unity Party, which were published in the form of a little red booklet. I picked up a copy of this booklet that had been discarded by its previous owner, a Stasi chauffeur, who had written “Ha, Ha” next to the mandate to “report any misdeeds, regardless of the person responsible, to leading party organs, all the way up to the Central Committee.”
Rupert Scholz, member of parliament and professor of law at the University of Munich, said many East Germans feel there is little determination among their Western brethren to bring the Stasi criminals to trial. “In fact, we already have heard many of them say that the peaceful revolution should have been a bloody one instead so they could have done away with their tormentors by hanging them posthaste,” Scholz told me.
The Reverend Joachim Gauck, minister to a Lutheran parish in East Germany, shared the people’s pessimism that justice would be done. Following reunification, Gauck was appointed by the Bonn government as its special representative for safeguarding and maintaining the Stasi archives. “We must at least establish a legal basis for finding the culprits in our files,” Gauck told me. “But it will not be easy. If you stood the millions of files upright in one line, they would stretch for 202 kilometers [about 121 miles]. In those files you can find an unbelievable number of Stasi victims and their tormentors.”
Gauck was given the mandate he needed in November 1991, when the German parliament passed a law authorizing file searches to uncover Stasi perpetrators and their informants. He viewed this legislation as first step in the right direction. With the evidence from Stasi files, the perpetrators could be removed from their public service jobs without any formal legal proceedings. Said Gauck: “We needed this law badly. It is not reasonable that persons who served this apparatus of oppression remain in positions of trust.”
See more at the journalist Bernd Pulch website http://www.berndpulch.org
TMZ – Kim Kardashian Meets with Middle East Diplomats!?
Orson Welles’ Macbeth – Full Movie
MORD-DROHUNG WG PUBLIKATION DER STASI-LISTEN MIT KLARNAMEN
PUBLIC INTELLIGENCE – Harris Corporation Wireless Surveillance Products Standard Terms and Conditions of Sale
The following is Harris Corporation’s standard terms and conditions for the sale of their wireless surveillance products including the AmberJack, StingRay, StingRay II, Harpoon and KingFish products. The terms and conditions document was included in a contract signed with Tempe, Arizona on October 8, 2012 for $60,321.15 worth of surveillance software, equipment and training. The contract has since been removed from the City of Tempe’s website. See also:
Harris Wireless Products Group Standard Terms and Conditions of Sale
- 11 pages
- June 25, 2012
Chimes At Midnight (1965) – Orson Welles – Full Movie
The aging King Henry IV watches disapprovingly as his son Hal (later Henry V) enjoys a rude and irresponsible life under the bloated and decadent Sir John Falstaff. The young prince dreads the not-too-distant day when he will have to chose between his opposed father figures…
Mutmasslich wie bei estavis – debis select “unterwirft sich “GoMoPa”, dem Exklusiv-”Nachrichten-Dienst” zu Heinz Gerlachs Todesursache
SECRECY NEWS – SECURING U.S. DIPLOMATIC FACILITIES, AND MORE FROM CRS
In almost every year since 2007, Congress appropriated less money for
diplomatic security than had been requested. In FY2012, the State
Department sought $2.9 billion for security, and Congress enacted $2.6
billion.
The diplomatic security function, including its funding profile, was
discussed in the light of recent attacks of U.S. diplomatic facilities in
Benghazi, Libya and elsewhere in a new report from the Congressional
Research Service. See "Securing U.S. Diplomatic Facilities and Personnel
Abroad: Background and Policy Issues," November 26, 2012:
http://www.fas.org/sgp/crs/row/R42834.pdf
Some other new and updated CRS reports that have not been made publicly
available include the following.
Panama: Political and Economic Conditions and U.S. Relations, November 27,
2012:
http://www.fas.org/sgp/crs/row/RL30981.pdf
The Judgment Fund: History, Administration, and Common Usage, November 26,
2012:
http://www.fas.org/sgp/crs/misc/R42835.pdf
Financing the U.S. Trade Deficit, November 16, 2012:
http://www.fas.org/sgp/crs/misc/RL33274.pdf
Saudi Arabia: Background and U.S. Relations, November 27, 2012:
http://www.fas.org/sgp/crs/mideast/RL33533.pdf
SOME BASIC BUDGET TUTORIALS FROM CRS
In a series of newly updated reports presumably intended for new Members
of Congress who are unfamiliar with basic features of the federal budget,
the Congressional Research Service presented the very rudiments of the
budget process. See:
Basic Federal Budgeting Terminology, November 26, 2012:
http://www.fas.org/sgp/crs/misc/98-410.pdf
Overview of the Authorization-Appropriations Process, November 26, 2012:
http://www.fas.org/sgp/crs/misc/RS20371.pdf
Baselines and Scorekeeping in the Federal Budget Process, November 26,
2012:
http://www.fas.org/sgp/crs/misc/98-560.pdf
Budget Reconciliation Legislation: Development and Consideration, November
26, 2012:
http://www.fas.org/sgp/crs/misc/98-814.pdf
Entitlements and Appropriated Entitlements in the Federal Budget Process,
November 26, 2012:
http://www.fas.org/sgp/crs/misc/RS20129.pdf
Legislative Procedures for Adjusting the Public Debt Limit: A Brief
Overview, November 26, 2012:
http://www.fas.org/sgp/crs/misc/RS21519.pdf
EVOLUTION OF REMOTE SENSING AND NATIONAL SECURITY
A study performed for the National Geospatial-Intelligence Agency (NGA)
"chronicles the policy history of civil and commercial remote sensing from
1960 through 2008."
The study "highlights the difficulties in establishing a consistent
government role in a field where public good and private profit exist
side-by-side, and where business interests have the potential to contribute
to and conflict with national security interests."
See "U.S. National Security and Economic Interests in Remote Sensing: The
Evolution of Civil and Commercial Policy" by James A. Vedda, The Aerospace
Corporation, February 20, 2009:
http://www.fas.org/irp/eprint/remote.pdf
The unclassified study was released yesterday by NGA three years after it
was requested under the Freedom of Information Act.
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
TOP-SECRET – Seattle Police Department Unmanned Aerial System Operations Draft Manual
The following is the draft unmanned aerial system manual released last month by the Seattle Police Department. Thanks to Carlton Purvis for pointing it out to us.
Seattle Police Department Unmanned Aerial System Operations Manual
- Draft
- 14 pages
- October 2012
The following procedures are intended to promote safe, efficient and lawful operation of the Seattle Police Department’s unmanned aerial system (UAS). Safety, above all else, is the primary concern in each and every operation, regardless of the nature of the mission.
2. Philosophy & Mission Statement
It shall be the mission of those personnel of the Seattle Police Department who are trained in the use of unmanned aerial systems (UAS), to use this resource to protect the lives and property of citizens and first responders in a constitutionally and legally sound manner. Use of an aerial system can be utilized in circumstances which would save life and property, as well as being able to detect possible dangers that could not otherwise be seen.
The use of UAS’s is quickly growing but had it been available during large catastrophes such as hurricane Katrina, it would have had a large impact on all aspects of emergency response when personnel were in short supply.
UAS’s can support any responder in any all-hazards incident that would benefit from an aerial perspective, Additionally, the UAS would have suitable uses in locating and apprehending subjects, missing persons, search and rescue operations as well as any task that can best be accomplished from the air in an efficient and effective manner.
It shall be the intent of every UAS operator to make reasonable effort to not invade a person’s reasonable expectation of privacy when operating the UAS. When operating the UAS, the Seattle Police Department will abide by all FAA Regulations for flight and receive the proper authorization for flight. Additionally, the need, availability and use of the UAS will not supersede the issuance of a warrant when needed.
3. Protection of Rights and Privacy
UAS unit Commanders, operators and observers will have the protection of citizens civil rights and reasonable expectations of privacy as a key component of any decision made the to deploy the UAS. UAS operators and observers will ensure and will be held accountable for ensuring that operations of the U AS intrude to a minimal extent upon the citizens of Seattle. To accomplish this primary goal we will:
a) When the UAS is being flown the onboard cameras will be turned so as to be facing away from occupied structures, etc to minimize inadvertent video or still images of uninvolved persons.
b) All video and still images will be maintained in strict compliance with SPD policies and procedures.
c) A website for public input will be maintained and regularly monitored to address citizen concerns and recommendations
d) The SPD UAS unit will not conduct random surveillance activities. The use of the UAS will be tightly controlled and regulated.
e) The authorized missions for the SPD UAS are:
a. Video/photographs for investigative support (TCI, Homicide, ABS)
b. HAZMAT Response
c. Search and Rescue
d. Barricaded persons
e. Traffic collisions
f. Disaster Response (Flood, earthquakes, etc.)All other requested uses will be approved by the Special Operations Bureau Chief prior to accepting the mission.
f) A committee will be formed and meet semi-annually for the purpose of reviewing the existing UAS procedures as well as new technologies and laws and regulations on UAS usage. The committee will consist of personnel from SPD UAS, professional standards section and patrol representatives. The committee will present all proposed policy and procedures changes to the City Council, legal and community groups, and will solicit feedback prior to changing any policy changes,
g) The SPD UAS program will operate,strictly within the law and regulations. If in doubt, prior to operating the UAS we will ensure that warrants are applied for and obtained. We will balance all operations with. the need to accomplish the mission while maintaining public privacy and the freedom from intrusion.
The School of FEMEN in Paris
The Lady from Shanghai Orson Welles & Rita Hayworth – FULL MOVIE
Rita Hayworth and Orson Welles “The Lady from Shanghai” 1948 FULL Movie…
Enjoy =)
FAZ – FRANKFURTER ALLGEMEINE ZEITUNG ÜBER “GoMoPa”
The Stranger (1946) – Full Movie – Edward G. Robinson – Orson Welles
In 1946, Mr. Wilson (Edward G. Robinson) of the United Nations War Crimes Commission is hunting for Nazi fugitive Franz Kindler (Orson Welles). Kindler has effectively concealed his Nazi activities prior to his escape to the United States. He assumes a new identity, Charles Rankin, lands a job as a university professor and marries Mary Longstreet (Loretta Young), who is the daughter of Supreme Court justice Judge Adam Longstreet.
Wilson releases Kindler’s former associate Meinike (Konstantin Shayne) and follows him to Harper, Connecticut, but Meinike is strangled before he can identify Kindler. Wilson must convince Mrs. Rankin, the only person who knows for certain that Meinike came to meet her husband, that her Charles is a war criminal.
The Stranger is a 1946 American film noir/drama film starring Orson Welles, Edward G. Robinson, and Loretta Young. Welles also directed the film, which was based on an Oscar-nominated screenplay written by Victor Trivas. Sam Spiegel was the film’s producer, and the film’s musical score is by Bronisław Kaper. It is believed that this is the first film released after World War II that showed footage of concentration camps. The Stranger was the only film made by Welles to have been a bona fide box office success on the first release (Citizen Kane had made back its budget and marketing, but not enough to make a profit). The copyright was by “The Haig Corporation” and it has been in the public domain for several years.
The Stranger is in the public domain and can be downloaded here for free:
http://www.archive.org/details/TheStranger_0
SECRECY NEWS – CLASSIFICATION DECISIONS ARE REVIEWABLE BY COURTS, GOVT ADMITS
Executive branch decisions to classify national security information are
subject to judicial review in Freedom of Information Act cases, government
attorneys acknowledged in a brief filed yesterday.
That potentially explosive question arose following an extraordinary
ruling by a federal judge ordering the U.S. Trade Representative to release
a one-page classified document that had been requested under the FOIA by
the Center for International Environmental Law. The document's
classification was not "logical," said DC District Judge Richard W. Roberts
last March, and therefore it was not exempt from public disclosure.
http://www.fas.org/blog/secrecy/2012/03/not_logical.html
The government appealed that ruling in September, but stopped short of
asserting that the court had no authority to order release of the
classified document.
Yesterday, in response to arguments presented in an amicus brief from
media organizations, government attorneys made their acceptance of judicial
review explicit in a final reply brief.
"We agree that district courts (and courts of appeals) play an important
role in evaluating the government's compliance with its obligations under
FOIA, in Exemption 1 cases [involving national security classification] as
well as others...."
"We have not sought to diminish the role of courts in FOIA Exemption 1
cases, nor have we suggested that the Executive's determination that a
document is classified should be conclusive or unreviewable," attorneys
wrote in the November 27 brief (at p. 8).
http://www.fas.org/sgp/jud/ciel/112712-ustr-reply.pdf
In other words, the government did not assert that the executive has some
kind of transcendent Article II classification power, nor did government
attorneys contend (a la Egyptian President Morsy) that the judicial review
provisions of FOIA are an unconstitutional infringement on executive
authority.
This was the crucial information policy question that was raised by the
move to appeal Judge Roberts' highly unusual disclosure order, and the
government has more or less resolved it by submitting to the discipline of
judicial review.
What remains is a bona fide dispute: Was the decision to classify the
USTR document well-founded and plausible, as the government insists, and
therefore entitled to judicial deference? Or was it illogical, as the
lower court ruled, nullifying the document's exemption from FOIA?
Oral arguments in the case are scheduled for February of next year.
DOES FOREIGN AID WORK?, AND MORE FROM CRS
New and newly updated reports from the Congressional Research Service
obtained by Secrecy News that have not been made publicly available include
the following.
Does Foreign Aid Work? Efforts to Evaluate U.S. Foreign Assistance,
November 19, 2012:
http://www.fas.org/sgp/crs/row/R42827.pdf
Congressional Redistricting: An Overview, November 21, 2012:
http://www.fas.org/sgp/crs/misc/R42831.pdf
Update on Controlling Greenhouse Gases from International Aviation,
November 19, 2012:
http://www.fas.org/sgp/crs/misc/R42828.pdf
The Federal Acquisition Regulation (FAR): Answers to Frequently Asked
Questions, November 16, 2012:
http://www.fas.org/sgp/crs/misc/R42826.pdf
Gangs in Central America, November 26, 2012:
http://www.fas.org/sgp/crs/row/RL34112.pdf
The Federal Food Safety System: A Primer, November 26, 2012:
http://www.fas.org/sgp/crs/misc/RS22600.pdf
The President's Office of Science and Technology Policy: Issues for
Congress, November 26, 2012:
http://www.fas.org/sgp/crs/misc/RL34736.pdf
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
DIE PLUMPEN STASI-FÄLSCHER DER “GoMoPa”
Juricon über “GoMoPa” inklusive STASI-Verbindung
New – WikiLeaks donations now tax deductible EU wide
Wau-Holland-Stiftung (WHS), named in memory of the German philosopher and net activist Wau Holland, has been collecting donations for WikiLeaks since 2009. In the immediate aftermath of WikiLeaks publication of the US diplomatic cables in 2010, not only did PayPal arbitrarily shut down the WHS donations account, but the tax-exempt status of the Foundation was challenged as well. It took almost two years of negotiations with German tax authorities to strike a deal: Tax exemption (charitable status) will be granted again going forward and going back to 2011, but not for 2010. (See: "Taxing Transparency", Der Spiegel, 13 Nov 2012). Therefore, citizens of EU member states will be able to donate to WikiLeaks operations through WHS and in addition, write the donation off from their income tax. This is because of a ruling of the European Court in 2009 (Decision C-318_07), which mandates that every member state must honour the tax exemption decision of any other member state. And this is how you make a money transfer to support WikiLeaks: Recipient: Wau Holland Stiftung Bank: Commerzbank Kassel, Königsplatz 32-34, 34117 Kassel, Germany IBAN: DE46 5204 0021 0277 2812 04 BIC/SWIFT: COBADEFF520 Reference: WikiLeaks or Project 04 if you prefer add your e-mail or postal address to receive a tax-deductible donation receipt. Hamburg, 26. Nov 2012 Wau-Holland-Stiftung http://www.wauland.de Other methods of donation: https://shop.wikileaks.org/donate
Unveiled – European Commission enabling blockade of WikiLeaks by U.S. hard-right Lieberman/King, contrary to European Parliament’s wishes
European Commission documents released today by WikiLeaks show that hard-right U.S. politicians were directly behind the extrajudicial banking blockade against WikiLeaks. In the heavily redacted documents, MasterCard Europe admits that Senator Joseph Lieberman and Congressman Peter T. King both "had conversations" with MasterCard in the United States. Lieberman, the then-chair of the Senate Intelligence Committee, boasted of instigating Amazon's cutting of service to WikiLeaks - an action condemned by the Council of Europe's Committee of Ministers on 7 December 2011. Senator Lieberman tried to introduce the SHIELD Act into the Senate and advocated for prosecuting the New York Times for espionage in connection with WikiLeaks' releases. Rep. Peter King, chair of the House Homeland Security Committee, tried to formally designate WikiLeaks as a foreign terrorist organization, have its staff listed as 'enemy combatants', and have WikiLeaks put on a U.S. Treasury blacklist. On 13 January 2011 the U.S. Treasury announced it would not do so because there was no evidence that WikiLeaks should be on such a list. While Lieberman and King were unsuccessful in these methods of legally cutting WikiLeaks from its popular donor base, they were successful in doing so extra-legally via VISA and MasterCard, which together hold a monopoly of 97 per cent of the market of EU card payments. VISA Europe is registered in London and is owned by a consortium of European banks. MasterCard Europe is registered in Belgium and has similar ownership, but the Commission papers show that European control of VISA Europe and MasterCard Europe is a fiction. The papers reveal that the instructions to blockade WikiLeaks' operations in Europe came directly from VISA and MasterCard in the United States. Ownership would normally imply control, but VISA and MasterCard Europe are essentially controlled by confidential contracts with their U.S. counterparts, a hidden organizational structure that the Commission calls an "association of undertakings". On Tuesday, 19 November 2012, the European Parliament took an important step towards safeguarding the economic sovereignty of all Europeans. In Article 32 of its resolution, the European Parliament expressed the will that the Commission should prevent the arbitrary refusal of payments by credit card companies, which economically strangles businesses and organizations, notably ours. The resolution is an important step to putting an end to the Lieberman/King blockade, which has wiped out 95 per cent of WikiLeaks' revenues. The Lieberman/King blockade has been directly condemned by, among others, the UN Special Rapporteur of Freedom of Speech and the New York Times Editorial Board. The blockade is a direct infringement of the Article 19 right to receive and impart information, and threatens all donor-funded organizations and the freedom of the press. It comes as a surprise, then, that the European Commission is taking the contrary view in its preliminary decision, of not opening a formal investigation into VISA, MasterCard and AmEx's violations against DataCell, the company that collected donations to the WikiLeaks project until the imposition of the blockade in 2010. The Commission's 16-page preliminary decision has been announced after 15 months of deliberations. The 'normal' waiting time is four months. Yesterday, DataCell and WikiLeaks submitted detailed counter-arguments to the Commission's preliminary decision. Through the leaked documents we learn that VISA and MasterCard have used a false statement by the Australian Prime Minister, Julia Gillard, to mislead the European Commission. The Prime Minister's statement, which she later claimed was made in her "private capacity", was that the WikiLeaks publication of diplomatic cables was "illegal". This was declared to be false by a subsequent investigation by the Australian Federal Police, which declared that WikiLeaks had not broken any Australian law. Earlier this year, the Australian Senate passed a resolution demanding the retraction of the Prime Minister's false statement. The leaked documents reveal MasterCard's political stance to our exposure of the crimes and horrors of military campaigns: "It is evident that any affiliation with an organisation causing damage to the national interests of several nations involved in the wars in Afghanistan and Iraq... will be extremely damaging for the public perception of MasterCard". Julian Assange said: > There is no sovereignty without economic sovereignty. It is concerning that hard-right elements in the United States have been able to pressure VISA and MasterCard, who together hold monopoly over the European market, into introducing a blockade that the U.S. Treasury has rightly rejected. These unaccountable elements are directly interfering in the political and economic freedoms of EU consumers and are setting a precedent for political censorship of the world's media. WikiLeaks will continue to fight the blockade, despite its limited resources, because it is fighting for its survival. Already there have been victories. In June 2012 WikiLeaks won its first court victory in Iceland against the Lieberman-King blockade. Last month WikiLeaks opened a new battle front by filing, together with its partner DataCell, a case against Teller A/S (VISA Denmark). NOTE The movement in Parliament and in the rest of Europe is to support WikiLeaks' publishing rights. The German foundation Wau Holland Stiftung (WHS), which collected donations for WikiLeaks via PayPal had their donations account arbitrarily shut down. The tax-exempt status of the Foundation was challenged as well, as a result of political interference which was exposed this month in Der Spiegel ("Taxing Transparency"). Yesterday, WHS announced that, after almost two years of negotiations with German tax authorities, its tax exemption (charitable status) has been reinstated. Citizens of all EU Member States will now be able to donate to WikiLeaks' operations through WHS and deduct the donation from their income tax. *Additional information*: UN Special Rapporteur on Right to Freedom of Opinion and Expression: http://www.oas.org/en/iachr/expression/showarticle.asp?artID=829&lID=1 Council of Europe - Declaration on online service providers: https://wcd.coe.int/ViewDoc.jsp?id=1883671&Site=CM The Guardian Comment is Free (23 November 2012) by Glenn Greewald: http://www.guardian.co.uk/commentisfree/2012/nov/23/anonymous-trial-wikileaks-internet-freedom Video: U.S. demands to assassinate Assange - http://youtube.com/watch?v=ZuQW0US2sJw *Quote from Visa and MasterCard Submissions to the European Commission* Visa's response to the European Central Bank: > As you will no doubt be aware, in some jurisdictions, various stakeholders have questioned whether WikiLeaks is, in respect of some of the material it publishes, committing criminal acts. Our Operating Regulations prohibit the use of the Visa system for illegal purposes either in the jurisdiction of the merchant (in this case Iceland) or the jurisdiction of the cardholder (which could be anywhere in the world). It is possible that activities that are permitted in one jurisdiction may be illegal in others. Accordingly, the application of the relevant position under the Operating Regulations does not necessarily depend solely on Icelandic law. > This position is appropriate and proportionate in light of the alleged unlawful conduct of WikiLeaks, which, among other sensitive material, in 2010 published and refuses to return large amounts of material stolen from classified US military databases. Further, according to recent press coverage, it appears that the leaking of sensitive information is continuing. MasterCard's arguments to the European Commission: > MasterCard does not hold a collective dominant position with Visa... It is also worth mentioning here that MasterCard does not constitute an 'essential facility', and therefore is under no obligation to provide its services to any particular undertakings. > It is evident that any affiliation with an organisation causing damage to the national interests of several nations involved in the wars in Afghanistan and Iraq, and possibly putting lives needlessly at risk, will be damaging for the public perception of MasterCard and consequently damage MasterCard's goodwill or its [trade]Marks. > By way of example, in 2004 MasterCard requested the Dutch acquirer, then 'Interpay Nederlands B.V.' (now 'Paysquare') to suspend the provision of acquiring services to merchants operating websites offering access to pornographic material including showing sexual acts with animals ('bestiality content'). > ...before taking its decision, MasterCard Incorporated did not have any contacts with public authorities, and therefore did not act upon request from any public authorities. > MasterCard Incorporated had several conversations with the FBI, US Treasury and the Department of Homeland Security (DHS) about the possibility of such DDoS attacks. > MasterCard Incorporated had conversations with certain Congressional staff (i.e. Chairman Lieberman and Chairman King's [Senate and House Homeland Security Chairs] staff)." *European Parliament - on Card, Internet and mobile payments* Towards an integrated European market for card, internet and mobile payments - 20 November 2012 The European Parliament voted that the Commission introduce legislation to determine when credit card companies can deny payments: > 32. Considers it likely that there will be a growing number of European companies whose activities are effectively dependent on being able to accept payments by card; considers it to be in the public interest to define objective rules describing the circumstances and procedures under which card payment schemes may unilaterally refuse acceptance; In his intervention, Swedish MEP Christian Engstrom explained: > Another example is when Visa, Mastercard and Paypal blocked payments to WikiLeaks. There was no legal basis and [it] should be seen as the three companies helped the US government to silence an inconvenient voice. It is not acceptable that private corporations have the power of [controlling] free speech.
TOP-SECRET – U.S. Army Chaplains in Current Operations Leader’s Guide

LEADER’S GUIDE: CHAPLAINS IN CURRENT OPERATIONS
- 64 pages
- For Official Use Only
- January 2008
The United States and our allies are fighting terrorists who have defined this conflict as religiously based. Commanders on both sides have identified the center of gravity as the popular support of the people and understand the value of leveraging the religious aspects of the indigenous culture. Coalition commanders must apply that knowledge to support the overall objectives. Using chaplains, whose expertise includes religion and religious culture, shows great potential for success for enabling operational goals.
Key Lessons:
• Commanders should use chaplains as advisors on religions and religious issues that influence military operations.
• Chaplains must interact with religious leaders from the lowest to the highest levels of government and religious leadership to facilitate mission success.
• Chaplains are a valuable resource to aid the commander when planning and executing operations.This handbook is a valuable tool for leaders to explain how and why religion plays a role in the military decision-making process, how chaplains should interface with local religious leaders, and how chaplains are key members of their commander’s team. Its lessons are applicable to any theater and war.
…
Chaplains are a key resource for commanders. They help commanders understand the religious impact of military operations.
The religious impact picture in the operational area is an important piece of information for commanders as they develop plans, rules of engagement, schemes of maneuver, and operations.
Chaplains can:
• Enhance information operations and public affairs operations.
• Assist with breaking down preconceived notions of liberators versus occupiers.
• Interface with indigenous religious leaders.
• Integrate the commander’s intent to help actualize/fulfill the commander’s critical information requirements and priority intelligence requirements.
• Help commanders better understand the multifaceted capabilities chaplains bring to the battle staff.Chaplains play critical roles during three key operations periods:
Predeployment:
• Provide spiritual/religious support to Soldiers and Families.
• Provide religious and cultural training to Soldiers.
• Train to advise the commander on indigenous religions and religious issues.
• Train to perform religious leader meetings.
• Provide suicide prevention training.Deployment:
• Advise commanders regarding indigenous religions and religious issues and their impact on operations.
• In accordance with the commander’s intent, meet with local religious leaders (religious leader liaison [RLL]).
• Provide spiritual/religious support to Soldiers.
• Provide Post Traumatic Stress Disorder (PTSD) and suicide prevention support to Soldiers.Post-deployment:
• Address PTSD, suicide, and Soldiers’ marital issues.
• Provide spiritual/religious support to Soldiers and Families.…
Section 2.5: Homeland Security and Disaster Response
U.S. military and Canadian Forces’ chaplains have significant experience deploying in support of domestic tragedies all over the world, including hurricane relief; airline disaster search, rescue, recovery, and debris retrieval; earthquake and tidal wave assistance; wildfire support; search and rescue; or other disasters.
An example of a natural disaster response is providing emergency aerial drops of rations to starving refugees. If the rations contain food forbidden by the religious beliefs of the refugees, the intended goodwill gesture could adversely affect the relief effort and the positive press coverage the delivery of emergency supplies was intended to produce. The chaplain has a definite responsibility to advise the commander of religious taboos.
The primary focus of homeland security and disaster response operations is assisting local, state, national, and international agencies in providing humanitarian assistance to survivors. In homeland security operations, military chaplains may provide religious support to civilian disaster victims during emergency operations. The ministry is limited to the designated disaster control area and ceases with the termination of emergency operations. Moreover, the primary focus of military chaplain ministry remains DOD personnel.
Chaplains in foreign humanitarian assistance planning and execution operations, in coordination with civil affairs personnel, may provide pastoral support to refugees and dislocated civilians only when directed by the joint force commander after consultation with the staff judge advocate.
The chaplain’s insignia becomes a powerful restorative and comforting symbol for survivors, rescue workers, families of victims, and the community in general. Chaplains can be invaluable in communicating with civilians and civilian faith communities in a disaster situation.
TMZ – Lindsay Lohan in ‘Liz & Dick’ — The Role of a Lifetime
SECRET – NATO Allied Command Operations Public Affairs Directive

ALLIED COMMAND OPERATIONS (ACO) PUBLIC AFFAIRS DIRECTIVE NUMBER 95-1
- 15 pages
- May 23, 2008
1-1 . Introduction
a. The need to communicate effectively with a wide range of audiences is not just desirable, it is essential to gain understanding and support for NATO’s operations. Public support for NATO’s missions and tasks follows from public understanding of how the Alliance makes a difference to international peace and security. Public confidence, in turn, is enhanced by NATO’s ability to achieve its mandate in a way that is open, transparent. and consistent with member nation values and expectations.
“The Parties to this Treaty reaffirm their faith In … the Charter of the United Nations…. They are determined to safeguard the freedom, common heritage, and civilisation of their peoples, founded on the principles of democracy, individual liberty, and the rule of law.”
-Washington Treaty, 1949b. Military PA policy in NATO and the nations derives from the higher principles of democracy that includes freedom of expression and of the press. Commanders and Public Affairs Officers (PAOs) are in theory bound by NATO policies to inform the public directly, such as through the Internet or through the media, and by international law not to impede the media or freedom of expression.
c. NATO’s adversaries use multiple tools at their disposal to inform and persuade the international community that they have the moral high ground and that NATO does not. They use technology and speed to their advantage, often disregarding truth in the process. This is the public environment in which NATO operational commanders must conduct their missions. In an effects-based approach to operations, enhancing support for the Alliance by maintaining credibility is the effect for the PA function.
1-2. Mission. The mission of ACO PA is to support Alliance aims and objectives through truthful, accurate and timely public release of information about the operations and activities of forces assigned to, or under operational command or control of the Supreme Allied Commander Europe (SACEUR) and ACO headquarters (HQ), consistent with NATO and national policies for operational security, and the privacy of forces and personnel involved.
…
1-6. Strategic Communications in NATO and ACO
a. In concert with other political and military actions, Strategic Communications (StratCom) is used to advance NATO’s aims and operations through the coordinated, appropriate use of Public Diplomacy, PA and Information Operations (Info Ops). This is done at NATO HQ level.
b. Within ACO, StratCom takes in all components of the information campaign, but Public Diplomacy and political guidance are the responsibility of NATO HQ. Therefore, at the ACO level, StratCom will be conducted in concert with other military actions and following NATO political guidance, to advance AGO’s aims and operations through the coordinated, appropriate use of PA and Info Ops, in cooperation with the Public Diplomacy Division. In essence, StratCom is the umbrella under which Info Ops and PA reside.
c. Within ACO, StratCom will be conducted only at the SHAPE level and not by the subordinate operational commands.
1-7. Relationship to Information Operations
a. As outlined in MC 0457/1, PA and Info Ops are separate, but related functions. They directly support military objectives, counter adversary disinformation and deter adversary actions. They both require planning, message development and media analysis, though efforts differ with respect to audience, scope and intent. All military information activities must be closely coordinated with PAin order to ensure consistency in the messages to external audiences and to promote overall effectiveness and credibility of the campaign. Info Ops is a military function to provide advice and coordination of military information activities in order to create desired effects on the will, understanding and capability of adversaries, potential adversaries and other North Atlantic Council (NAC) approved parties in support of Alliance mission objectives. PAis not an Info Ops discipline. While coordination is essential, the lines of authority will remain separate, the PA reporting relationship being direct to the commander. This is to maintain credibility of PA and to avoid creating a media or public perception that PA activities are coordinated by, or are directed by Info Ops. Beyond coordination of efforts, messages, or being informed of these activities, PA will have no role in planning or executing Info Ops, Psy Ops, or deception operations.
b. PA is distinct from Info Ops in that:
(1) PA transcends the theatre of operations- PA speaks to theatre, regional, international, and member-nation audiences.
(2) PA is conducted continually through the war-peace continuum.
(3) PAis targeted at both internal and external audiences.
(4) PA is the only function that is mandated to communicate through the news media.
(5) Info Ops and Psy Ops seek to influence decision makers or the behaviour of target audiences through careful study and targeting.
(6) Using objective words and images, PA seeks to inform broad or target audiences and thus negate the influence of biased or erroneous information. PA may not use deception in its communication.
(7) Info Ops and Psy Ops are often applied in a calculated fashion.
(8) PA is routinely executed within minutes.
The Crazies (2010) – Full Movie
The Crazies 2010 – Horror/Thriller – Rated 15/R
As a toxin begins to turn the residents of Ogden Marsh, Iowa into violent psychopaths, sheriff David Dutton tries to make sense of the situation while he, his wife and two other unaffected townspeople band together in a fight for survival.
Meridian Capital about GoMoPa STASI-FÄLSCHUNGEN DER “GoMoPa”
Sehr geehrte Damen und Herren,
die Betrüger und durch uns inhaftierten Erpresser der GoMoPa versuchen mit einer gefälschten Presse-Mitteilung von sich abzulenken und einen investigativen Journalisten, Bernd Pulch, zu belasten.
Die Presse-Mitteilung auf pressreleaser.org ist eine Fälschung und die gesamte Webseite ist der GoMoPa zu zuordnen.
Hier noch einmal die tatäschlichen Geschehnisse:
Hier der Artikel von “GoMoPa” über Meridian Capital.
 „GoMopa“ schreibt:08.09.2008 „GoMopa“ schreibt:08.09.2008Weltweite Finanzierungen mit WidersprüchenDie Meridian Capital Enterprises Ltd. gibt an, weltweite Finanzierungen anbieten zu können und präsentiert sich hierbei auf aufwendig kreierten Webseiten. GOMOPA hat die dort gemachten Angaben analysiert und Widersprüche entdeckt.Der FirmensitzDer Firmensitz befindet sich laut eigener Aussage in Dubai, Vereinigte Arabische Emirate. In einem GOMOPA vorliegenden Schreiben der Meridian Capital Enterprises Ltd. heißt es jedoch, der Firmensitz sei in London. Auf der Homepage des Unternehmens taucht die Geschäftsadresse in der Londoner Old Broad Street nur als „Kundenabteilung für deutschsprachige Kunden“ auf. Eine weitere Adresse in der englischen Hauptstadt, diesmal in der Windsor Avenue, sei die „Abteilung der Zusammenarbeit mit Investoren“.Die Meridian Capital Enterprises ist tatsächlich als „Limited“ (Ltd.) mit Sitz in England und Wales eingetragen. Aber laut Firmenhomepage hat das Unternehmen seinen „rechtlichen Geschäftssitz“ in Dubai. Eine Abfrage beim Gewerbeamt Dubais (DED) zu dieser Firmierung bleibt ergebnislos.Bemerkenswert ist auch der vermeintliche Sitz in Israel. Auf der Webseite von Meridian Capital Enterprises heißt es: „Die Firma Meridian Capital Enterprises Ltd. ist im Register des israelischen Justizministeriums unter der Nummer 514108471, gemäß dem Gesellschaftsrecht von 1999, angemeldet.“ Hierzu Martin Kraeter, Gomopa-Partner und Prinzipal der KLP Group Emirates in Dubai: „Es würde keinem einzigen Emirati – geschweige denn einem Scheich auch nur im Traum einfallen, direkte Geschäfte mit Personen oder Firmen aus Israel zu tätigen. Und schon gar nicht würde er zustimmen, dass sein Konterfei auch noch mit vollem Namen auf der Webseite eines Israelischen Unternehmens prangt.“Auf der Internetseite sind diverse Fotos mit Scheichs an Konferenztischen zu sehen. Doch diese großen Tagungen und großen Kongresse der Meridian Capital Enterprises werden in den Pressearchiven der lokalen Presse Dubais mit keinem Wort erwähnt. Martin Kraeter: „ Ein ‚britisch-arabisch-israelisches bankfremdes Finanzinstitut sein zu wollen, wie die Meridian Capital Enterprises Ltd. es darstellt, ist mehr als zweifelhaft. So etwas gibt es schlicht und ergreifend nicht! Der Nahostkonflikt schwelt schon seit mehr als 50 Jahren. Hier in den Vereinigten Arabischen Emiraten (VAE) werden Israelis erst gar nicht ins Land gelassen. Israelische Produkte sind gebannt. Es gibt nicht einmal direkte Telefonverbindungen. Die VAE haben fast 70% der Wiederaufbaukosten des Libanon geschultert, nachdem Israel dort einmarschiert ist.“Zwei angebliche Großinvestitionen der Meridian Capital Enterprises in Dubai sind Investmentruinen bzw. erst gar nicht realisierte Projekte. Das Unternehmen wirbt mit ihrer finanziellen Beteiligung an dem Dubai Hydropolis Hotel und dem Dubai Snowdome. Der Aktivitätsstatus der Meridian Capital Enterprises Ltd. ist laut englischen Handelsregister (UK Companies House) „dormant“ gemeldet. Auf der Grundlage des englischen Gesellschaftsrechts können sich eingetragene Unternehmen selbst „dormant“ (schlafend) melden, wenn sie keine oder nur unwesentliche buchhalterisch zu erfassende Transaktionen vorgenommen haben. Dies ist angesichts der angeblichen globalen Investitionstätigkeit der Meridian Capital Ltd. sehr erstaunlich. Der Webauftritt Die Internetseite der MCE ist sehr aufwendig gestaltet, die Investitionen angeblich in Millionen- und Milliardenhöhe. Bei näherer Betrachtung der Präsentationselemente fällt jedoch auf, dass es sich bei zahlreichen veröffentlichen Fotos, die Veranstaltungen der Meridian Capital Enterprises dokumentieren sollen, meist um Fotos von Online-Zeitungen oder frei zugänglichen Medienfotos einzelner Institutionen handelt wie z.B. der Börse Dubai. Auf der Internetpräsenz befinden sich Videofilmchen, die eine frappierende Ähnlichkeit mit dem Werbematerial von NAKHEEL aufweisen, dem größten Bauträger der Vereinigten Arabischen Emirate. Doch den schillernden Videos über die berühmten drei Dubai Palmen „Jumeirah, Jebel Ali und Deira“ oder das Archipel „The World“ wurden offensichtlich selbstproduzierte Trailersequenzen der Meridian Capital Enterprises vorangestellt. Doch könnte es sich bei den Werbevideos um Fremdmaterial handeln. Auch die auf der Webseite wahllos platzierten Fotos von bekannten Sehenswürdigkeiten Dubais fungieren als Augenfang für den interessierten Surfer mit eigenem Finanzierungswunsch. Bei einem Volumen von 10 Millionen Euro oder höher präsentiert sich die Meridian Capital Enterprises Ltd. als der passende Investitionspartner. Das Unternehmen verfügt weltweit über zahlreiche Standorte: Berlin, London, Barcelona, Warschau, Moskau, Dubai, Riad, Tel Aviv, Hong Kong und New York. Aber nahezu alle Standorte sind lediglich Virtual Offices eines global arbeitenden Büroservice-Anbieters. „Virtual Office“ heißt im Deutschen schlicht „Briefkastenfirma“. Unter solchen Büroadressen sollen laut Meridian Capital Enterprises ganze Kommissionen ansässig sein, alles zum Wohle des Kunden.“ Zitatende |
Hier die Hintergründe der Erpressung:
Hier unsere Original-Stellungnahme:
Anfang Oktober 2008 erhielt einer der Arbeiter der Meridian Capital Enterprises Ltd. eine Meldung von einem anonymen Sender, dass in naher Zukunft – zuerst im Internet, dann im Fernsehen, im Radio und in der deutschen Presse – Informationen erscheinen, die die Funktionsweise und Tätigkeiten der Meridian Capital Enterprises Ltd. in einem äußerst negativen Licht darstellen. Der Mitarbeiter der Meridian Capital Enterprises Ltd. wurde also informiert, dass diese Meldungen/Nachrichten zweifelsohne deutlich das Aussehen und den guten Ruf der Firma Meridian Capital Enterprises Ltd. beeinträchtigen.
Der an dieser Stelle erwähnte „Gesprächspartner” hat den Arbeiter der Meridian Capital Enterprises Ltd. informiert, dass die Möglichkeit besteht die peinliche Situation zu vermeiden, indem die Meridian Capital Enterprises Ltd. auf das von der Person gezeigte Konto die Summe von 100.000,00 EUR überweist. Wie sich aber später zeigte, war der Herr Klaus Maurischat – dieser anonyme Gesprächspartner – „Gehirn“ und „Lider des GOMOPA“. Die Ermittlungen wurden angestellt durch die Bundeskriminalpolizei (Verfolgungs- und Ermittlungsorgan auf der Bundesebene) während des Ermittlungsverfahrens wegen einer finanziellen Erpressung, Betrügereien auch wegen der Bedrohungen, welche von Herrn Maurischat und seine Mitarbeiter praktiziert wurden sowie wegen Teilnahme anderer (Leiter der Internetservices und Moderatoren der Blogs) an diesem Prozedere. Diese Straftaten wurden begangen zu Schaden vieler Berufs- und Justizpersonen, darunter auch der Meridian Capital Enterprises Ltd. Die Opfer dieses Verbrechens sind in Deutschland, Österreich, der Schweiz, Spanien, Portugal, Großbritannien, den USA und Kanada sichtbar.
In diesem Moment taucht folgende Frage auf: Wie war die Reaktion der Meridian Capital Enterprises Ltd. auf die Forderungen seitens GOMOPA? Entsprach die Reaktion den Erwartungen von GOMOPA? Hat die Meridian Capital Enterprises Ltd. die geforderte Summe 100.000,00 EUR überwiesen?
Seites der Meridian Capital Enterprises Ltd. gab es überhaupt keine Reaktion auf den Erpressungsversuch von GOMOPA. Ende August 2008 auf dem Service http://www.gompa.net sind zahlreiche Artikel/Meldungen erscheinen, welche die Tätigkeit der Meridian Capital Enterprises Ltd. in einem sehr negativen Licht dargestellt haben. Nachdem die auf http://www.gomopa.net enthaltenen Informationen ausführlich und vollständig analysiert worden waren, ergab es sich, dass sie der Wahrheit nicht einmal in einem Punkt entsprechen und potenzielle und bereits bestehende Kunden der Meridian Capital Enterprises Ltd. in Bezug auf die von diesem Finanzinstitut geführten Geschäftstätigkeit irreführen. Infolge der kriminellen Handlugen von GOMOPA und der mit ihm kooperierenden Services und Blogs im Netz hat die Meridian Capital Enterprises Ltd. beachtliche und messbare geschäftliche Verluste erlitten. Die Meridian Capital Enterprises Ltd. hat nämlich in erster Linie eine wichtige Gruppe von potenziellen Kund verloren. Was sich aber als wichtiger ergab, haben sich die bisherigen Kunden von der Meridian Capital Enterprises Ltd. kaum abgewandt. Diejenigen Kunden haben unsere Dienstleitungen weiterhin genutzt und nutzen die immer noch. In Hinblick auf die bisherige Zusammenarbeit mit der Meridian Capital Enterprises Ltd., werden ihrerseits dem entsprechend keine Einwände erhoben .
GOMOPA hat so einen Verlauf der Ereignisse genau prognostiziert, dessen Ziel beachtliche und messbare geschäftliche durch die Meridian Capital Enterprises Ltd. erlittene Verluste waren. Der Verlauf der Ereignisse hat das Service GOMOPA mit Sicherheit gefreut. GOMOPA hat nämlich darauf gerechnet, dass die Stellung der Meridian Capital Enterprises Ltd. nachlässt und das Finanzinstitut die geforderte Summe (100.000,00 EUR) bereitstellt. Im Laufe der Zeit, als das ganze Prozedere im Netz immer populärer war, versuchte GOMOPA noch vier mal zu der Meridian Capital Enterprises Ltd. Kontakte aufzunehmen, indem es jedes mal das Einstellen dieser kriminellen „Kompanie” versprochen hat, wobei es jedes mal seine finanziellen Forderungen heraufsetzte. Die letzte für das Einstellen der „Kompanie“ gegen die Meridian Capital Enterprises Ltd. vorgesehene Quote betrug sogar 5.000.000,00 EUR (in Worten: fünfmilionen EURO). Die Meridian Capital Enterprises Ltd. konnte sich aber vor den ständig erhöhenden Forderungen seitens des Services GOMOPA behaupten.
Im Oktober 2008 traf die Leitung der Meridian Capital Enterprises Ltd. Entscheidung über die Benachrichtigung der Internationalen Polizei INTERPOL sowie entsprechender Strafverfolgungsorgane der BRD (die Polizei und die Staatsanwaltschaft) über den bestehenden Sachverhalt. In der Zwischenzeit meldeten sich bei der Meridian Capital Enterprises Ltd. zahlreiche Firmen und Korporationen, sogar Berufsperson wie Ärzte, Richter, Priester, Schauspieler und anderen Personen aus unterschiedlichen Ländern der Welt, die der Erpressung von GOMOPA nachgegeben und die geforderten Geldsummen überwiesen haben. Diese Personen gaben bereits Erklärungen ab, dass sie dies getan haben, damit man sie bloß endlich „in Ruhe lässt” und um unnötige Probleme, Schwierigkeiten und einen kaum begründbaren Ausklang vermeiden zu können. Die Opfer dieses kriminellen Vorgehens haben die Meridian Capital Enterprises Ltd. über unterschiedliche Geldsummen, welche verlangt wurden, informiert.
In einem Fall gab es verhältnismäßig kleine (um ein paar tausend EURO), in einem anderen Fall handelte es schon um beachtliche Summen (rund um paar Millionen EURO).
Zusätzlich wendeten sich an die Meridian Capital Enterprises Ltd. Firmen, welche dem GOMOPA noch keine „Gebühr” überweisen haben und bereits überlegen, ob sie dies tun sollen, oder nicht. Diese Firmen erwarteten von der Meridian Capital Enterprises Ltd. eine klare Stellungnahme sowie eine professionelle praktische Beratung, wie man sich in solch einer Lage verhalten soll und wie man diese Geldforderungen umgehen kann. Die Meridian Capital Enterprises Ltd. hat ausnahmslos allen Verbrechensopfern, welche sich bei unserer Firma gemeldet haben, eine Zusammenarbeit vorgeschlagen. Als oberste Aufgabe stellt sich diese Kooperation, gemeinsam entschlossene und wirksame Maßnahmen gegen GOMOPA, gegen andere Services im Netz sowie gegen alle Bloggers zu treffen, die an dem hier beschriebenen internationalen kriminellen Vorgehen mit GOMOPA-Führung teilnehmen.Auf unsere Bitte benachrichtigten alle mitbeteiligten Firmen die Internationale Polizei INTERPOL sowie ihre heimischen Verfolgungsorgane, u. a. die zuständige Staatsanwaltschaft und die Polizeibehörden über den bestehenden Sachverhalt.
In Hinblick auf die Tatsache, dass das verbrecherische Handeln von GOMOPA sich über viele Staaten erstreckte und dass die Anzahl der in der Bundesrepublik Deutschland erstatteten Anzeigen wegen der durch GOMOPA, Internetservices und Bloggers begangenen Straftaten, rasant wuchs – was zweifelsohne von einer weit gehenden kriminellen Wirkungskraft des GOMOPA zeugt – schlug die Internationale Wirtschaftspolizei INTERPOL der Meridian Capital Enterprises Ltd. vor, dass sich ihr Vertreter in Berlin mit dem Vertreter von GOMOPA trifft, um die „Zahlungsmodalitäten“ und Überweisung der Summe von 5.000.000,00 EUR zu besprechen. Dieser Schritt meinte, eine gut durchdachte und durch die Bundeskriminalpolizei organisierte Falle durchzuführen, deren Ziel die Festnahme der unter GOMOPA wirkenden internationalen Straftäter war.
Die koordinierten Schritte und Maßnahmen der Meridian Capital Enterprises Ltd. und anderer Beschädigter, geleitet von der Internationalen Wirtschaftspolizei INTERPOL, dem Bundeskriminalamt und der Staatsanwaltschaft der Bundesrepublik Deutschland haben zur Aus-, Einarbeitung und Durchführung der oben beschriebenen Falle beigetragen. Im November 2008 führte die in Berlin vorbereitete Falle zur Festnahme und Verhaftung des Vertreters des GOMOPA, der nach der Festnahme auf Herrn Klaus Maurichat – als den Hauptverantwortlichen und Anführer der internationalen kriminellen Gruppe GOMOPA verwies. Der Festgenommene benannte und zeigte der Bundeskriminalpolizei zugleich den aktuellen Aufenthaltsort des Herrn Klaus Maurischat. „Gehirn“ und Gründer dieser internationalen kriminellen Gruppe GOMOPA, Herr Klaus Maurischat wurde am selben Tag auch festgenommen und auf Frist verhaftet, wird bald in Anklagezustand gestellt, wird die Verantwortung für eigene Straftaten und die des Forums GOMOPA vor einem zuständigen Bundesgericht tragen. Die Meridian Capital Enterprises Ltd. unternahm bereits alle möglichen Schritte, damit Herr Klaus Maurischat auch auf der Anklagebank des zuständigen Gerichts des Vereinigten Königsreiches Großbritannien erscheint. Unter den beschädigten Berufs- und Justizpersonen aus Großbritannien, neben der Meridian Capital Enterprises Ltd. gibt es noch viele Opfer von GOMOPA…
Die dreisten Verbrecher wagen es unter http://www.pressreleaser.org, einer eigenen “GoMoPa”-Seite unsere Pressemitteilung oben zu verfälschen und unschuldige Personen zu belasten.
“GoMoPa” Boss is Jochen Resch
- May 15, 2011 – 1:15 pm
- Posted in Uncategorized
- Comments Off
Dear Readers,
after a thorough research we are sure that the real “GoMoPa” boss is Jochen Resch, lawyer in Berlin, Germany. He is the brain behind “GoMoPa” and responsable for blackmailing, extortion, racketeering, cybermurder and murder – in the tradition of the East German “Inteeligence” STASI that is why he called “GoMoPa” – Financial “Intelligence” Service .
Webmaster
Meridian Capital about GoMoPa
“GoMoPa” in detention
- May 13, 2011 – 1:02 pm
- Posted in Uncategorized
- Comments Off
Meridian Capital Enterprises Ltd.. unveils new criminal phenomena in network. In recently appeared on the net more often at the same time a new a very worrying phenomenon of criminal nature. Professional criminals groups in the network are taking part, to extortion, fraud, Erschwindeln relating to certain specifically selected companies and businesses are capable of. These criminals developed new methods and means, simply and in a short time to bereichern.Strategien and manifestations, which underlie this process are fairly simple. A criminal is looking to “carefully” on the Internet specific companies and corporations (victims of crime) and informed them in the next step, that of the business activities of such companies and corporations in the near future – first on the Internet then in other available mass media – numerous and very unfavorable information appears. At the same time, the criminals beat their future victims an effective means of reducing unnecessary difficulties and problems to escape the loss of good name and image of the company and corporate sector. These offenders are aware of that reputation, name and appearance of each company is a value in itself. It was therefore a value of what each company is prepared to pay any price. But the reason for difficulties and problems arising from the loss of good name and reputation result. The criminals and their victims are already aware that this loss is devastating consequences might have been the closing down of a particular business can enforce. It takes both to No as well as at large companies regard. The company is concerned that in virtually every industry in each country and cross-border activities sind.Das criminal procedure in the form of a blackmail on money, a fraud is becoming rapidly and globally, ie led cross-border and internationally. Among the victims of extortion, fraud is now looking both at home (domestic) and international corporations, the major emphasis on conservation, keeping and maintaining their reputation in the business according to their credibility lay. The criminals in the network have understood that maintaining an unassailable reputation and name of a company the unique ability to provide fast and easy enrichment forms. The above-mentioned criminal procedure is difficult to track because it is international in nature, and by overlapping or even nonexistent (fictional) professional and judicial persons in various countries and operated company wird.Diese offenders in the network publish it and disseminate false information about your victims on remote servers, which are not uncommon in many exotic countries. There are those countries in which serious gaps in the legal system, investigative and prosecution procedures are visible. As an example, at this point mention India werden. Mit criminals working in the network grid portals known leader of blogs with your seat-consciously or unconsciously, even in highly developed countries. For example, at this point, countries such as Germany, Austria, Switzerland, the United States, Britain, Spain or Portugal are mentioned. The below listed criminals were able to act unpunished today. As a symptom of such action appears here the activity and “effectiveness” of the company GOMOPA, which is on countries such as Germany, Switzerland, Austria, the United States, Britain, Spain and India. A good example of such an action is Mr. Klaus Mauri Chat – the leader and “brain” of the company GOMOPA with many already in force and criminal judgments “on his account”, which in this way for years and funded its maintenance in the industry almost unlimited activity. This status will change dramatically, however, including far and wide thanks to discontinued operations of the firm Meridian Capital Enterprises Ltd.. who would oppose such offenses addressed in the network. Other companies and corporations, in which the crime network and outside of this medium have fallen victim to contribute to combating such crimes bei.Die situation is changing, thanks to effective steps and the successful cooperation of the firm Meridian Capital Enterprises Ltd.. with the international police Interpol, with the federal agency (FBI) in the U.S., the Federal Criminal Police in Germany, with Scotland Yard in Britain, as well as with the Russian secret service FSB.Die Meridian Capital Enterprises Ltd.. – Together with other companies and cooperations, the victim of criminal activities of the network of crime have fallen – has undeniably already started to yield results. The fact that in recent weeks (November 2008) on the territory of the Federal Republic of Germany of the above-mentioned leaders and “brain” of the company GOMOPA, Mr Klaus Maurishat was arrested should not be ignored. The Meridian Capital Enterprises Ltd.. information available results clearly show that the next arrests of persons participating in this process in such countries as: Austria, Switzerland, Russia, Ukraine, Poland, Spain, Mexico, Portugal, Brazil, the USA, Canada, UK, Ireland , Australia, New Zealand and made in a.. The ultimate goal of Meridian Capital Enterprises Ltd.. and the other victims of crime in the network is to provide all participants in this criminal procedure before the competent court to lead. All professional and judicial persons, regardless of the seat and out of the business, which the above-described criminal action (fraud, extortion) to have fallen victim can of Meridian Capital Enterprises Ltd.. led company to join the goal set at all at this point the procedure described those associated in the public and the economic life out. II blacklist blackmail and with international fraudsters and their methods (opus operandi) in the following countries: 1 The Federal Republic Deutschland2. Dubai 3rd Russia 1st The Federal Republic of Germany GmbH GOMOPA, Goldman Morgenstern & Partners LLC., Goldman Morgenstern & Partners Consulting LLC, Wottle collection. In these firms are quite active following persons: – Klaus Mauri Chat ( “Father” and “brain” of the criminal organization responsible for countless final judgments have been achieved (arrested in Germany in November 2008) – Josef Rudolf Heckel ( “right hand “when Mr Klaus Mauri chat, denounced former banker who is excessive in many Bankschmuggeleien was involved.
The study of 900 pages named Toxdat by Ehrenfried Stelzer is the “Stasi Killer Bible”. It lists all kind of murder methods and concentrates on the most effective and untraceable.
“The toxdat study was ordered by Stasi Vice-President Gerhard Neiber, the second man in rank after boss Erich Mielke. The toxdat study was also the theoretical “story book” for the murder of the famous German watchdog and journalist Heinz Gerlach by former Stasi member under the guidance of “GoMoPa”,” an informer stated. “Ehrenfried stelzer” was nicknamed “Professor Murder” by his victims. Even close co-worker now compare him with the German SS”doctor” Mengele, “Dr. Death” from Auschwitz.
Only two articles let the German audience believe that the famous journalist and watchdog Heinz Gerlach died on natural courses by blood pollution.
For more Information the victims have launched a new site: http://www.victims-opfer.com
The first one, published only hours after the death of Mr Heinz Gerlach by the notorious “GoMoPa” (see article below) and a second 3 days later by a small German local newspaper, Weserbergland Nachrichten.
Many people including the hostile Gerlach website “Akte Heinz Gerlach” doubted that this man who had so many enemies and friends would die of natural causes without any previous warning. Rumours occured that Mr. Gerlach’s doctor doubted natural courses at all. After many critical voices discussed the issue a small website of a small German local newspaper – which never before had reported about Mr. Heinz Gerlach and which is not even in the region of Mr Gerlachs home – published that Mr Gerlach died of blood pollution. Weserbergland-Nachrichten published a long article about the deadly consequences of blood pollution and did not even name the source of such an important statement. It claimed only that somebody of Gerlachs inner circle had said this. It is a proven fact that after the collpase of the Eastern German Communist Regime many former Communist propaganda agents went to regional newspapers – often in Western Germany like Günther Schabowski did the man who opened the “Mauer”.
The theatre stage was set: One day later the hostile Gerlach website “Akte Heinz Gerlach” took the agenda publishing that Mr Gerlach had died for natural causes without any further research at all.
This was done by a website which for months and months and months reported everything about Mr. Gerlach.
Furthermore a research proves that the technical details regarding the website hosting of this hostile website “Akte Heinz Gerlach” proves that there are common details with the hosting of “GoMoPa” and their affiliates as proven by the SJB-GoMoPa-victims (see http://www.sjb-fonds-opfer.com)
Insiders believe that the murderers of Mr. Heinz Gerlach are former members of the Eastern German Terror Organisation “Stasi” with dioxins. They also believe that “GoMoPa” was part of the plot. At “GoMoPa”’ a person named Siegfried Siewers was officialy responsible for the press but never appeared in public. “GoMoPa”-victims say that this name was a cameo for “GoMoPa” frontrunner Klaus Maurischat who is controlled by the Stasi Top Agent Ehrenfried Stelzner, Berlin.
Siegfried Sievers, a former Stasi member is responsible for the pollution of millions Germanys for many years with dioxins. This was unveiled at 5th of January 2011 by German prosecutors.
The victims say that Maurischat (probably also a Stasi cameo) and Sievers were in contact as Sievers acted as Stasi Agent and was in fact already a specialist in dioxins under the Communist Terror Regime in Eastern Germany.
Furthermore the Stasi Top Agent Ehrenfried Stelzer disguised as Professor for Criminal studies during the Communist Regime at the Eastern Berlin Humboldt University.
Background:
The man behind the Berlin lawyer Jochen Resch and his activities is Ehrenfried Stelzer, former Stasi Top officer in Berlin and “Professor for Criminal Studies” at the Eastern Berlin Humboldt University during the Communist regime, the SJB-GoMoPa-victims say (www.sjb-fonds-opfer.com) is responsable for the killing of German watchdog and journalist Heinz Gerlach.
These informations stem from various sources who were close to the criminal organization of GoMoPa in the last years. The SJB-GoMoPa say that the well-known German watchdog and journalist Heinz Gerlach was killed by former Stasi members with dioxins. Polychlorinated dibenzodioxins (PCDDs), or simply dioxins, are a group of organic polyhalogenated compounds that are significant because they act as environmental pollutants. They are commonly referred to as dioxins for simplicity in scientific publications because every PCDD molecule contains a dioxin skeletal structure. Typically, the p-dioxin skeleton is at the core of a PCDD molecule, giving the molecule a dibenzo-p-dioxin ring system. Members of the PCDD family have been shown to bioaccumulate in humans and wildlife due to their lipophilic properties, and are known teratogens, mutagens, and confirmed (avered) human carcinogens. They are organic compounds.
Dioxins build up primarily in fatty tissues over time (bioaccumulate), so even small exposures may eventually reach dangerous levels. In 1994, the US EPA reported that dioxins are a probable carcinogen, but noted that non-cancer effects (reproduction and sexual development, immune system) may pose an even greater threat to human health. TCDD, the most toxic of the dibenzodioxins, is classified as a Group 1 carcinogen by the International Agency for Research on Cancer (IARC).
In 2004, a notable individual case of dioxin poisoning, Ukrainian politician Viktor Yushchenko was exposed to the second-largest measured dose of dioxins, according to the reports of the physicians responsible for diagnosing him. This is the first known case of a single high dose of TCDD dioxin poisoning, and was diagnosed only after a toxicologist recognized the symptoms of chloracne while viewing television news coverage of his condition.
German dioxin scandal: In January 2011 about 4700 German farms were banned from making deliveries after tests at the Harles und Jentzsch plant in the state of Schleswig-Holstein showed high levels of dioxin. Again this incident appears to involve PCBs and not PCDDs at all. Dioxin were found in animal feed and eggs in many farms. The person who is responsible for this, Siegfried Sievert is also a former Stasi Agent. At “GoMoPa” the notorious Eastern-Berlin press agency (see article below) one of the henchmen acted under the name of “Siegfried Siewert”.
Further evidence for the killing of Mr.Heinz Gerlach is provided by the SJB-GoMoPa-victims by analyzing the dubious role of former Stasi-Top-agent Ehrenfried Stelzer, also a former “Professor for Crime Studies” under the Communist regime in Eastern Germany and the dubious role of “detective” Medard Fuchsgruber. Both are closely tied to the dubious “GoMoPa” and Berlin lawyer Jochen Resch.
According to the SJB-GoMoPa-victims is Berlin lawyer Jochen Resch the mastermind of the criminal organization “GoMoPa2. The victims state that they have a source inside “GoMoPa” who helped them discover the shocking truth. The so-called “Deep Throat from Berlin” has information that Resch had the idea to found the criminal organization “GoMoPa” and use non-existing Jewish lawyers named Goldman, Morgenstern & Partner as camouflage. Their “office” in Madison Avenue, New York, is a mailbox. This is witnessed by a German Ex-Patriot, a lawyer, whose father, Heinz Gerlach, died under strange circumstances.
Resch seems to use “GoMoPa” as an instrument to blackmail parts of the German Property and Investment.
German authorities are under growing pressure to reopen investigations into at least a dozen suspicious deaths after the arrest of an alleged East German assassin cast new light on the communist regime. Stasi victims quoted a source saying “isolated units” had conducted operations that were “extremely well organised” and had “100 per cent logistical support” from the East German state.
A statement from prosecutors read: “The accused [Jurgen G] is suspected, as a member of a commando of the former DDR, of killing a number of people between 1976 and 1987 who from the point of view of the DDR regime had committed treason or were threatening to do so.”
Details of his Jurgen G’s arrest have been described in suitably florid terms, with the mass circulation tabloid Bild saying he was working at the Wolfsbruch marina near Rheinsberg in north-eastern Germany when a woman approached him. “Excuse me, is that your yellow Trabant in the car park? I just ran into it with my car,” she is said to have asked.
When he followed her to the car park, masked officers jumped out of vans and bushes and overpowered him in an operation worthy of the Stasi itself.
An eyewitness told Bild: “They blindfolded him and raced off in an unmarked car.”
Police across Germany are reported to be sifting through files to see who the victims may have been, and some intelligence officers are greeting the arrest of Jurgen G as a breakthrough.
Thomas Auerbach, who works for the Stasi file authority in Berlin and has written a book based on the death squad files, said: “These people were trained to make such murders look like accidents or suicides, even as ‘ordinary’ crimes such as robberies. They were real terror experts.”
The cases said to be linked to Jurgen G or his unit include many people involved with the commercial arm of the East German ruling socialist party, the SED (Socialist Unity Party).
Uwe Harms, the head of a Hamburg-based haulage firm which was part of a network of companies secretly owned by the SED, disappeared in March 1987 after conversations with various DDR functionaries. Six weeks later, his body was found in a plastic bag.
Weeks before his death he told friends that he felt he was being followed. After reunification, one of the other SED company heads said Mr Harms had been liquidated for refusing to allow his firm to be used to transport arms into East Germany.
Dieter Vogel, a businessman who had been jailed for life for spying for the CIA, was found suffocated in his cell in the East German prison Bautzen on March 9, 1982. The fact that he was due to be taken to the West in a spy swap arrangement just a few weeks later cast doubt on the suicide theory.
He had passed the names of several Stasi moles to the BND, West Germany’s heavily penetrated counter-intelligence service.
The Christian Democrat Union politician Uwe Barschel, 43, was found dead by magazine reporters in his bathtub in a hotel room in Geneva in October, 1987. He died of poisoning, but rumours that he was involved somehow in arms deals and the Stasi have clung to the case.
One of the more high-profile and enduring mysteries is that of Lutz Eigendorf, an East German footballer from the Stasi-backed Dynamo Berlin.
He fled to the West in 1979 amid great publicity. Four years later, he died after crashing his car into a tree on a straight stretch of road with blood alcohol levels way over the limit. Witnesses who had seen him earlier in the evening said he had not been drinking.
Most controversial though is the suggestion that the assassination squad was linked to the murder of a Swedish television reporter and her friend in 1984.
Cats Falk and her friend Lena Graens went missing on Nov 19, 1984. Their bodies were fished out of a Stockholm canal six months later.
Reports suggested a three-man assassination squad killed them, spiking their drinks with drugs, putting them into their car and pushing it into the Hammarby canal.
Shortly before her death, Cats Falk had reportedly uncovered a deal between an arms dealer and an East German firm.
Germany has recently undergone a wave of nostalgia for all things East German, dubbed Ostalgie, with colourful television shows featuring former DDR stars such as the ice skater Katerina Witt talking wistfully about socialist pop music.
A reassessment may be coming in the wake of the revelations.
Victims: The DDR-STASI MURDER GANG “GoMOPa” in murderoplot against Joerg Berger
The Stasi Murder Gang of „GoMoPa“ was involved in many trials to kill the popular East German soccer trainer Joerg Berger, Stasi victims tell in postings on their hompage http://www.sjb-fonds-opfer.com. Berger stated before his early death in his biography that they tried to pollute him with arsenic.
Arsenic and many of its compounds are especially potent poisons. Many water supplies close to mines are contaminated by these poisons. Arsenic disrupts ATP production through several mechanisms. At the level of the citric acid cycle, arsenic inhibits lipoic acid which is a cofactor for pyruvate dehydrogenase; and by competing with phosphate it uncouples oxidative phosphorylation, thus inhibiting energy-linked reduction of NAD+, mitochondrial respiration and ATP synthesis. Hydrogen peroxide production is also increased, which might form reactive oxygen species and oxidative stress. These metabolic interferences lead to death from multi-system organ failure, probably from necrotic cell death, not apoptosis. A post mortem reveals brick red coloured mucosa, owing to severe haemorrhage. Although arsenic causes toxicity, it can also play a protective role.[
Elemental arsenic and arsenic compounds are classified as “toxic” and “dangerous for the environment” in the European Union under directive 67/548/EEC. The International Agency for Research on Cancer (IARC) recognizes arsenic and arsenic compounds as group 1 carcinogens, and the EU lists arsenic trioxide, arsenic pentoxide and arsenate salts as category 1 carcinogens.
Arsenic is known to cause arsenicosis owing to its manifestation in drinking water, “the most common species being arsenate [HAsO42- ; As(V)] and arsenite [H3AsO3 ; As(III)]”. The ability of arsenic to undergo redox conversion between As(III) and As(V) makes its availability in the environment more abundant. According to Croal, Gralnick, Malasarn and Newman, “[the] understanding [of] what stimulates As(III) oxidation and/or limits As(V) reduction is relevant for bioremediation of contaminated sites (Croal). The study of chemolithoautotrophic As(III) oxidizers and the heterotrophic As(V) reducers can help the understanding of the oxidation and/or reduction of arsenic.
Treatment of chronic arsenic poisoning is easily accomplished. British anti-lewisite (dimercaprol) is prescribed in dosages of 5 mg/kg up to 300 mg each 4 hours for the first day. Then administer the same dosage each 6 hours for the second day. Then prescribe this dosage each 8 hours for eight additional days. However the Agency for Toxic Substances and Disease Registry (ATSDR) states that the long term effects of arsenic exposure cannot be predicted. Blood, urine, hair and nails may be tested for arsenic, however these tests cannot foresee possible health outcomes due to the exposure. Excretion occurs in the urine and long term exposure to arsenic has been linked to bladder and kidney cancer in addition to cancer of the liver, prostate, skin, lungs and nasal cavity.[
Occupational exposure and arsenic poisoning may occur in persons working in industries involving the use of inorganic arsenic and its compounds, such as wood preservation, glass production, nonferrous metal alloys and electronic semiconductor manufacturing. Inorganic arsenic is also found in coke oven emissions associated with the smelter industry.
THE DDR GESTAPO-STASI MURDER GANG responsable for the murder of Lutz Eigendorf
The talented Eigendorf played for East German side Dynamo Berlin.
He made his debut for the GDR in an August 1978 match against Bulgaria, immediately scoring his first two goals in a 2–2 draw. He went on to collect six caps, scoring three goals.[1] His final international was a February 1979 friendly match against Iraq.
On 20 March 1979, after a friendship match between Dynamo and West German club 1. FC Kaiserslautern in Gießen he fled to the west hoping to play for that team. But because of his defection he was banned from play for one year by UEFA and instead spent that time as a youth coach with the club.
This was not the first time an East German athlete had fled to the west, but it was a particularly embarrassing defection. Eigendorf’s club Dynamo was under the patronage of the Stasi, East Germany’s secretive state police, and subject to the personal attentions of the organisation’s head, Erich Mielke. He ensured that the club’s roster was made up of the country’s best players, as well as arranging for the manipulation of matches in Dynamo’s favour. After his defection Eigendorf openly criticised the DDR in the western media.
His wife Gabriele remained behind in Berlin with their daughter and was placed under constant police surveillance. Lawyers working for the Stasi quickly arranged a divorce and the former Frau Eigendorf re-married. Her new husband was eventually revealed as a Lothario – an agent of the state police whose role it was to spy on a suspect while romancing them.
In 1983 Eigendorf moved from Kaiserslautern to join Eintracht Braunschweig, all the while under the scrutiny of the Stasi who employed a number of West Germans as informants. On 5 March that year he was badly injured in a suspicious traffic accident and died within two days. An autopsy indicated a high blood alcohol level despite the testimony of people he had met with that evening indicating that Eigendorf had only a small amount of beer to drink.
After German re-unification and the subsequent opening of the files of the former East Germany’s state security service it was revealed that the traffic accident had been an assassination attempt orchestrated by the Stasi, confirming the longtime suspicions held by many. A summary report of the events surrounding Eigendorf’s death was made on German television on 22 March 2000 which detailed an investigation by Heribert Schwan in the documentary “Tod dem Verräter” (“Death to the Traitor”).
On 10 February 2010, a former East German spy revealed the Stasi ordered him to kill Eigendorf, which he claimed not to have done
MfS has been accused of a number of assassinations against political dissidents and other people both inside and outside the country. Examples include the East German football player Lutz Eigendorf and the Swedish journalist Cats Falck.
The terrorists who killed Alfred Herrhausen were professionals. They dressed as construction workers to lay a wire under the pavement of the road along Mr. Herrhausen’s usual route to work. They planted a sack of armor-piercing explosives on a parked bicycle by the roadside. An infrared beam shining across the road triggered the explosion just when the limousine, one of three cars in a convoy, sped by.
The operation, from the terrorists’ point of view, was flawless: Mr. Herrhausen, the chairman of one of Europe’s most powerful companies, Deutsche Bank, was killed in the explosion along that suburban Frankfurt road on Nov. 30, 1989.
But was everything what it seemed?
Within days, the Red Army Faction — a leftist terrorist group that had traumatized West Germany since 1970 with a series of high-profile crimes and brazen killings of bankers and industrialists — claimed responsibility for the assassination. An intense manhunt followed. In June 1990, police arrested 10 Red Army Faction members who had fled to East Germany to avoid arrest for other crimes. To the police’s surprise, they were willing to talk. Equally confounding to authorities: All had solid alibis. None was charged in the Herrhausen attack.
Now, almost two decades later, German police, prosecutors and other security officials have focused on a new suspect: the East German secret police, known as the Stasi. Long fodder for spy novelists like John le Carré, the shadowy Stasi controlled every aspect of East German life through imprisonment, intimidation and the use of informants — even placing a spy at one point in the office of West German Chancellor Willy Brandt.
According to documents reviewed by The Wall Street Journal, the murders of Mr. Herrhausen and others attributed to the Red Army Faction bear striking resemblance to methods and tactics pioneered by a special unit of the Stasi. The unit reported to Stasi boss Erich Mielke and actively sought in the waning years of the communist regime to imitate the Red Army Faction to mask their own attacks against prominent people in Western Germany and destabilize the country.
“The investigation has intensified in recent months,” said Frank Wallenta, a spokesman for the Federal Prosecutor. “And we are investigating everything, including leads to the Stasi.”
If those leads turn out to be true, it would mean not only rewriting some of the most dramatic episodes of the Cold War, but would likely accelerate a broader soul-searching now under way in Germany about the communist past.
In building a reunified country, many Germans have ignored discussion of the brutal realities of its former communist half. When the former East Germany is discussed, it’s often with nostalgia or empathy for brothers hostage to Soviet influence.
Stasi boss Erich Mielke, middle, with unnamed associates
That taboo is slowly being broken. Last year’s Oscar-winning movie, “The Lives of Others,” chronicled in dark detail a Stasi agent’s efforts to subvert the lives of ordinary people. Material in the Stasi archives shows that senior leaders had a shoot-to-kill order against those fleeing from East to West — a controversial order that contradicts East German leaders’ claims that they never ordered any shootings.
This story is based on more than a dozen interviews with police, prosecutors and other security officials. Several policemen and prosecutors confirmed that the allegation of extensive Stasi involvement with the Red Army Faction is a key part of the current investigation.
Court cases in West Germany in the 1990s established that members of the Red Army Faction were granted free passage to other countries in the 1970s and refuge in East Germany in the 1980s. But the current investigation and documents from Stasi archives suggest far deeper involvement — that members of the Red Army Faction were not only harbored by the Stasi but methodically trained in sophisticated techniques of bombing and murder.
Traudl Herrhausen, Mr. Herrhausen’s widow, is one of those pushing for further investigation. She says she long suspected involvement by the Stasi or other intelligence service such as the KGB, but never spoke publicly because she didn’t have evidence and didn’t want to interfere in the investigation. She says she is now breaking an 18-year silence in her desire to see justice done. “Now I want to look my husband’s killers in the eye,” she said in an interview.
The Red Army Faction was founded about 1970 by a band of leftists who justified their terrorism based on opposition to West Germany’s ruling elite. Killing members of this elite would provoke the West German state to take repressive measures that would show its true fascist face, Red Army Faction leaders believed.
In its early years, the group, also known as the Baader-Meinhof band, made headlines with prison breaks, bank robberies, bomb attacks and deadly shootouts. Four gang members led by Ulrike Meinhof freed Red Army Faction leader Andreas Baader from a Berlin jail a month after his arrest.
Red Army Faction violence in West Germany intensified in 1977 when Jürgen Ponto, then head of Dresdner Bank, was shot and killed at his home. Five weeks later, the group killed four people and abducted the chairman of the German employer association, Hans-Martin Schleyer, one of West Germany’s most prominent businessmen. It was the start of a six-week ordeal in which neither government nor terrorists would compromise. To support the Red Army Faction cause, Palestinian terrorists hijacked a Lufthansa jet in Spain, forcing it to land in Mogadishu, Somalia. After the plane was rushed by West German commandos, top Red Army Faction leaders in West Germany committed suicide and Mr. Schleyer was executed by his captors.
Red Army Faction violence began to abate in the late 1970s after the Lufthansa incident. Many in Germany thought the group — whose attacks were often crude — lost its will to kill after the arrest of its senior leaders in 1982. So when the group appeared to renew its terror campaign with a series of high-profile attacks in 1985, police were stunned by the level of their sophistication and determination.
This time, the group dazzled police with its ability to hit targets and leave little substantial evidence behind. They used high-tech devices no one thought they possessed. Their marksmen killed with military precision.
Weapons used by terrorists during the 1977 kidnapping of German industrialist Hanns-Martin Schleyer.
Surprisingly, members of the Red Army Faction so-called third generation had a policeman’s understanding of forensic science. From 1985 onward, the Red Army Faction rarely left a fingerprint or other useful piece of evidence at a crime scene, according to court records. The murder cases from this era are still open. Some suspected Stasi involvement, but no one could ever prove it, according to a senior police official.
The 1989 car-bomb murder of Mr. Herrhausen particularly stunned police with its audacity and sophistication. Mr. Herrhausen was the head of Deutsche Bank, Germany’s largest bank. He was part of the political-business elite that helped turn West Germany from a war-ravaged rump state into an economic powerhouse — all while East Germany languished in frustration. Mr. Herrhausen was a vocal proponent of a united Germany.
In November 1989, Mr. Herrhausen was following the fall of the Berlin wall and events in the Soviet Union closely, conferring frequently with Mikhail Gorbachev, according to his wife and friends. Then on Nov. 27, Mr. Herrhausen announced a plan to acquire the investment banking firm Morgan Grenfell — at the time a record-breaking bank acquisition.
Also during November, a spot along Mr. Herrhausen’s usual route to work was closed because of construction. Terrorists, dressed as construction workers, laid an electric wire under the road’s pavement. On Nov. 29, the stretch reopened.
On the morning of Nov. 30, like every workday morning, Mr. Herrhausen stepped into his limousine at about 8:30. Mr. Herrhausen’s driver waited about one minute to allow the first of the three-car entourage to drive ahead and survey the road.
“It was the route they hadn’t used in weeks,” Mrs. Herrhausen said.
As Mr. Herrhausen sped down the road, a team of terrorists waited. Beside the road, a parked bicycle held a sack of armor-piercing explosives. The detonator was connected by the electric wire under the road to a trigger activated by an interruption in an infrared beam shining across the road.
A terrorist activated the detonator after the first car of bodyguards drove past the bomb. Mr. Herrhausen died at the scene.
As they had during previous attacks, police set up dragnets to round up Red Army Faction cadre. But the June 1990 arrests of 10 members of the group who had earlier been granted political asylum in East Germany produced no leads. All the seized Red Army Faction members had solid alibis.
In July 1991, prosecutors believed they had a breakthrough when an informant claimed he had allowed two members of the Red Army Faction to stay at his home near the Herrhausen residence. Prosecutors followed that trail 13 years before dropping charges in 2004.
Frustrated with the inability of prosecutors to solve the Herrhausen case and believing that prosecutors were ignoring other leads including possible Stasi involvement, German officials replaced the prosecutor overseeing the case.
Police acknowledge that part of the reason for their focus on possible Stasi involvement was that all other leads had dried up. But they say they also knew that over the years the Stasi had worked with and given explosives to other terrorists, including “Carlos the Jackal” and the Basque group ETA in Spain. And in 2001 to 2003, an undercover police officer met with a man who claimed he had been a killer for the Stasi operating in Western Germany, although police were never able to tie him to specific murders.
German investigators turned their attention to Wartin, a small eastern German village nestled in yellow-brown fields of grain near the Polish border. Today, sheep graze in a field spotted with wooden posts.
In the 1980s, however, Wartin was home to the Stasi’s AGM/S — “Minister Working Group/Special Operations.” It got its name because it reported to Mr. Mielke, the minister who headed the Stasi for almost all of East Germany’s 40-year history.
The Wartin unit’s peacetime duties included the kidnapping and murder of influential people in the West, according to Stasi records reviewed by The Wall Street Journal in the Stasi archives in Berlin.
The documents say the unit’s activities included “intimidating anti-communist opinion leaders” by “liquidation,” and “kidnapping or hostage taking, connected with the demand that political messages be read,” according to a description of the unit’s activities written by a senior Wartin official in 1982.
Based on these documents, German investigators increasingly believe that the Stasi played a more active role than previously believed in Red Army Faction terrorism. After years of not being able to draw parallels between the Stasi unit in Wartin and the Red Army Faction killings, police are now focusing closely on such a link. Joachim Lampe, who assisted the successful prosecution of the first wave of Red Army Faction terrorists up until 1982 and was then assigned to prosecute Stasi-related crimes in West Germany, says it’s time to compare the activities of Wartin with the activities of the Red Army Faction to see where they overlap. “It is an important line of investigation,” he said.
A year after the Red Army Faction’s first generation collapsed in 1972, an internal Wartin report said cooperation with terrorists is possible if the individuals could be trusted to maintain secrecy and obey orders. Initial contacts, however, may not have taken place until later in the decade. Disillusionment gripped many of the terrorists living on the lam, according to court records citing witness statements by accused terrorists. Beginning about 1980, the Stasi granted refuge to 10 members of the Red Army Faction in East Germany and gave them assumed identities.
The Stasi sympathized with the anti-capitalist ideals of the Red Army Faction, but Stasi leaders were concerned about placing their trust in a group of uncontrollable leftist militants, a review of Stasi records shows. Stasi officials did not want to tarnish East Germany’s international reputation, so they toyed with different concepts for cooperation with terrorist groups, according to a prosecutor who has investigated Stasi involvement with terrorism.
One suggestion, contained in a document prepared for new officers assigned to the unit, was to emulate Romanian intelligence, which successfully worked with the terrorist “Carlos” to bomb the Radio Free Europe office in Munich, Germany, in 1981. To assist in such operations, the Wartin unit developed highly specialized explosives, poisons and miniature firearms.
About 1980 the Stasi also proposed a second strategy: instead of using a terrorist group directly — such cooperation always contained risk of discovery — they could simply execute attacks so similar to those of known terrorists that police would never look for a second set of suspects, according to Wartin records. The Wartin leadership called this strategy the “perpetrator principle,” according to Stasi records. The unit’s progress in implementing the steps to imitate terrorist attacks is described in a series of progress reports by Wartin officials between 1980 and 1987.
In September 1981, Red Army Faction terrorists attempted to kill U.S. Gen. James Kroesen in Heidelberg, Germany, shooting a bazooka at his car. About the same time, members of the same Red Army Faction team visited East Germany, where they were asked by the Stasi to shoot a bazooka at a car containing a dog. The dog died, according to court records.
In Wartin, officials wrote up a detailed description of the Red Army Faction members’ re-enactment of the Kroesen attack. “It is important to collect all accessible information about the terrorist scene in imperialist countries, to study and analyze their equipment, methods and tactics, so we can do it ourselves,” a senior Wartin official wrote in February 1982, according to the report.
In 1982, West German police discovered two troves of Red Army Faction weapons and documents buried in German forests. Three terrorists, including Red Army Faction leader Christian Klar, were arrested when they approached the sites. The troves were buried in locations easy to find at night, a tactic used by Wartin’s own agents to store operational equipment in West Germany, according to an investigator who viewed the troves and Stasi records.
That same year, a Wartin official described the staged bombing of a moving vehicle. According to the report, several Stasi officers shed “tears of joy” when electronic sensors detected the approaching car and ignited the detonator.
A spokesman at Germany’s federal police investigative agency, the equivalent of the U.S. Federal Bureau of Investigation, declined to comment on the close similarity between the detonator used in the demonstration and the device that killed Mr. Herrhausen, saying this is part of their investigation.
Wartin officers continued their preparations for imitating terrorist attacks in West Germany, according to a 1985 internal Wartin report. They created a special archive profiling the characteristics of known terrorists and terrorist groups, and taught staff members to execute nearly identical attacks, according to Stasi records. Each year, the unit’s officers detailed the unit’s success in teaching these techniques in their annual reports, according to the reports.
Then, in 1987, the AGM/S stopped offensive operations. The unit was disbanded.
Werner Grossmann, a former three-star Stasi General and former head of foreign intelligence operations, says the AGM/S was responsible for planning attacks in West Germany, but was dissolved “because it didn’t produce results.” Mr. Grossmann assumed control of part of the AGM/S after most of the unit was dissolved.
Mr. Grossmann says he took control of part of the AGM/S because he wanted to run intelligence operations against West Germany’s civil defense infrastructure.
“I refused to have anything to do with terrorism and terrorists,” Mr. Grossmann said in an interview. He said he didn’t have any influence over the AGM/S activities before 1987 and wasn’t informed about the unit’s activities before it came under his control.
Olaf Barnickel, a career Stasi officer who served at Wartin, says his unit planned murders in West Germany, but never committed one. “It was all theory and no practice,” Mr. Barnickel said in an interview.
But some German police are unpersuaded. They believe the seeds may have been planted for future violent attacks.
In November 1989, as East Germany disintegrated, groups of citizens forced their way into Stasi installations, seizing control. In Wartin, a local church minister led a group of demonstrators to the main entrance of the Stasi base. The base closed.
Within the Stasi as a whole, the chain of command began to disintegrate. Links to organizations in West Germany, including the Red Army Faction, were broken.
Sixteen months after Mr. Herrhausen’s murder, the Red Army Faction claimed its last victim, killing Detlev Karsten Rohwedder, the head of the Treuhandanstalt, the powerful trust that controlled most state-owned assets in the former East Germany and was overseeing their privatization. Mr. Rohwedder was killed while he was standing by the window of his house in Düsseldorf.
The murder was performed by a trained sharpshooter, according to a police official familiar with the investigation. The Stasi trained members of the Red Army Faction in sharpshooting skills and had its own teams of sharpshooters, according to witness statements by Stasi officials to a Berlin prosecutor and Stasi records.
In 1998, the Red Army Faction issued the last of its communiques, announcing it was disbanding. German police attribute the group’s disappearance to changing times, which made the group seem a relic of the past. Indeed, the Red Army Faction today is largely seen by the German public as part of the social upheaval that plagued West Germany in the 1970s and 1980s. More than one in four Germans consider former Red Army Faction members to have been misguided idealists. More than half now think the investigations should be closed for good in the coming decade when the current group of Red Army Faction prisoners finish serving their prison sentences.
German prosecutors say their investigation of the Stasi’s role is continuing.
Since last month, Mrs. Herrhausen has been in contact with the next of kin of victims in the other unsolved Red Army Faction murder cases, looking for support to push the investigation. The bomb that killed her husband nearly 18 years ago exploded soon after he left for work, within earshot of their home in suburban Frankfurt.
“I still hear that bomb every day,” she says.
Only two articles let the German audience believe that the famous journalist and watchdog Heinz Gerlach died on natural courses by blood pollution.
The first one, published only hours after the death of Mr Heinz Gerlach by the notorious “GoMoPa” (see article below) and a second 3 days later by a small German local newspaper, Weserbergland Nachrichten.
Many people including the hostile Gerlach website “Akte Heinz Gerlach” doubted that this man who had so many enemies and friends would die of natural causes without any previous warning. Rumours occured that Mr. Gerlach’s doctor doubted natural courses at all. After many critical voices discussed the issue a small website of a small German local newspaper – which never before had reported about Mr. Heinz Gerlach and which is not even in the region of Mr Gerlachs home – published that Mr Gerlach died of blood pollution. Weserbergland-Nachrichten published a long article about the deadly consequences of blood pollution and did not even name the source of such an important statement. It claimed only that somebody of Gerlachs inner circle had said this. It is a proven fact that after the collpase of the Eastern German Communist Regime many former Communist propaganda agents went to regional newspapers – often in Western Germany like Günther Schabowski did the man who opened the “Mauer”.
The theatre stage was set: One day later the hostile Gerlach website “Akte Heinz Gerlach” took the agenda publishing that Mr Gerlach had died for natural causes without any further research at all.
This was done by a website which for months and months and months reported everything about Mr. Gerlach.
Furthermore a research proves that the technical details regarding the website hosting of this hostile website “Akte Heinz Gerlach” proves that there are common details with the hosting of “GoMoPa” and their affiliates as proven by the SJB-GoMoPa-victims (see http://www.sjb-fonds-opfer.com)
Insiders believe that the murderers of Mr. Heinz Gerlach are former members of the Eastern German Terror Organisation “Stasi” with dioxins. They also believe that “GoMoPa” was part of the plot. At “GoMoPa”’ a person named Siegfried Siewers was officialy responsible for the press but never appeared in public. “GoMoPa”-victims say that this name was a cameo for “GoMoPa” frontrunner Klaus Maurischat who is controlled by the Stasi Top Agent Ehrenfried Stelzner, Berlin.
Siegfried Sievers, a former Stasi member is responsible for the pollution of millions Germanys for many years with dioxins. This was unveiled at 5th of January 2011 by German prosecutors.
The victims say that Maurischat (probably also a Stasi cameo) and Sievers were in contact as Sievers acted as Stasi Agent and was in fact already a specialist in dioxins under the Communist Terror Regime in Eastern Germany.
Furthermore the Stasi Top Agent Ehrenfried Stelzer disguised as Professor for Criminal studies during the Communist Regime at the Eastern Berlin Humboldt University.
Background:
The man behind the Berlin lawyer Jochen Resch and his activities is Ehrenfried Stelzer, former Stasi Top officer in Berlin and “Professor for Criminal Studies” at the Eastern Berlin Humboldt University during the Communist regime, the SJB-GoMoPa-victims say (www.sjb-fonds-opfer.com) is responsable for the killing of German watchdog and journalist Heinz Gerlach.
These informations stem from various sources who were close to the criminal organization of GoMoPa in the last years. The SJB-GoMoPa say that the well-known German watchdog and journalist Heinz Gerlach was killed by former Stasi members with dioxins. Polychlorinated dibenzodioxins (PCDDs), or simply dioxins, are a group of organic polyhalogenated compounds that are significant because they act as environmental pollutants. They are commonly referred to as dioxins for simplicity in scientific publications because every PCDD molecule contains a dioxin skeletal structure. Typically, the p-dioxin skeleton is at the core of a PCDD molecule, giving the molecule a dibenzo-p-dioxin ring system. Members of the PCDD family have been shown to bioaccumulate in humans and wildlife due to their lipophilic properties, and are known teratogens, mutagens, and confirmed (avered) human carcinogens. They are organic compounds.
Dioxins build up primarily in fatty tissues over time (bioaccumulate), so even small exposures may eventually reach dangerous levels. In 1994, the US EPA reported that dioxins are a probable carcinogen, but noted that non-cancer effects (reproduction and sexual development, immune system) may pose an even greater threat to human health. TCDD, the most toxic of the dibenzodioxins, is classified as a Group 1 carcinogen by the International Agency for Research on Cancer (IARC).
In 2004, a notable individual case of dioxin poisoning, Ukrainian politician Viktor Yushchenko was exposed to the second-largest measured dose of dioxins, according to the reports of the physicians responsible for diagnosing him. This is the first known case of a single high dose of TCDD dioxin poisoning, and was diagnosed only after a toxicologist recognized the symptoms of chloracne while viewing television news coverage of his condition.
German dioxin scandal: In January 2011 about 4700 German farms were banned from making deliveries after tests at the Harles und Jentzsch plant in the state of Schleswig-Holstein showed high levels of dioxin. Again this incident appears to involve PCBs and not PCDDs at all. Dioxin were found in animal feed and eggs in many farms. The person who is responsible for this, Siegfried Sievert is also a former Stasi Agent. At “GoMoPa” the notorious Eastern-Berlin press agency (see article below) one of the henchmen acted under the name of “Siegfried Siewert”.
Further evidence for the killing of Mr.Heinz Gerlach is provided by the SJB-GoMoPa-victims by analyzing the dubious role of former Stasi-Top-agent Ehrenfried Stelzer, also a former “Professor for Crime Studies” under the Communist regime in Eastern Germany and the dubious role of “detective” Medard Fuchsgruber. Both are closely tied to the dubious “GoMoPa” and Berlin lawyer Jochen Resch.
According to the SJB-GoMoPa-victims is Berlin lawyer Jochen Resch the mastermind of the criminal organization “GoMoPa2. The victims state that they have a source inside “GoMoPa” who helped them discover the shocking truth. The so-called “Deep Throat from Berlin” has information that Resch had the idea to found the criminal organization “GoMoPa” and use non-existing Jewish lawyers named Goldman, Morgenstern & Partner as camouflage. Their “office” in Madison Avenue, New York, is a mailbox. This is witnessed by a German Ex-Patriot, a lawyer, whose father, Heinz Gerlach, died under strange circumstances.
Resch seems to use “GoMoPa” as an instrument to blackmail parts of the German Property and Investment.
The name of Benno Ohnesorg became a rallying cry for the West German left after he was shot dead by police in 1967. Newly discovered documents indicate that the cop who shot him may have been a spy for the East German secret police.
It was one of the most important events leading up to the wave of radical left-wing violence which washed over West Germany in the 1970s. On the evening of June 2, 1967, the literature student Benno Ohnesorg took part in a demonstration at West Berlin’s opera house. Mohammad Reza Pahlavi, the shah of Iran, was to attend and the gathered students wanted to call attention to his brutal regime.
The protests, though, got out of hand. Pro-shah demonstrators, some of them flown in from Iran for the occasion, battled with the student protestors. West Berlin police also did their part, brutally beating back the crowd. At 8:30 p.m., a shot was fired, and a short time later the 26-year-old Ohnesorg, having been hit in the back of the head, became the left wing’s first martyr.
Now, though, the history of the event may have to be re-written. New documents discovered in the Stasi archive — the vast collection of files left behind by the East German secret police — reveal that the policeman who shot Ohnesorg, Karl-Heinz Kurras, could in fact have been a spy for East Germany’s communist regime.
In an article that will appear in late May in Deutschlandarchiv, a periodical dedicated to the ongoing project of German reunification, Helmut Müller-Enbergs and Cornelia Jabs reveal that documents they found in the Stasi papers show that Kurras began working together with the Stasi in 1955. He had wanted to move to East Berlin to work for the East German police. Instead, he signed an agreement with the Stasi to remain with the West Berlin police force and spy for the communist state.
As a result of the new information, criminal charges have once again been filed against Kurras, who was acquitted twice, once in 1967 and again in 1970, of negligent homicide charges related to Ohnesorg’s death. Kurras told the Berlin paper Tagesspiegel on Friday that he had never worked together with the Stasi.
But in addition to finding the agreement between Kurras and the Stasi, the two researchers also discovered numerous documents indicating that the East Germans were pleased with the information Kurras passed along — particularly given that he was posted to a division responsible for rooting out moles within the West German police force.
Immediately after Ohnesorg’s death, Kurras received a Stasi communication ordering him to destroy his records and to “cease activities for the moment.” Kurras responded with his acquiescence and wrote “I need money for an attorney.”
The exact circumstances surrounding the death of Ohnesorg have never been completely clarified. Kurras himself, now 81, gave conflicting versions of the story during the investigation but the official version has long been that Kurras fired in self defense. Many others point to witness accounts whereby the police were beating Ohnesorg when the shot was fired.
It is still unclear how the new evidence might play into history’s understanding of the tragic event. The day was one full of violence, with demonstrators and police battling each other with pipes, wooden clubs and stones. Police were further incited by rumors that an officer had been stabbed earlier in the evening. Ohnesorg himself, however, was not directly involved in the violence.
West Berlin in the 1960s and 70s became a focal point of German left wing radicalism. The city had long been left-leaning, and the fact that Berliners were exempt from military service meant that it became a magnate for pacifists and anti-state activists.
Ohnesorg’s death gave them an immediate rallying cry. As the left-wing movement became more radical, many justified their violent activities by pointing to the police brutality that led to the student’s death. A letter written by Ulrike Meinhof announcing the founding of the Red Army Faction, which appeared in SPIEGEL in the fall of 1967, explicitly mentioned the Ohnesorg incident. The RAF went on to terrorize Germany for decades, ultimately killing over 30 people across the country. The radical “June 2 Movement” used the date of the incident in its name.
Kurras, for his part, seems to have been a highly valued Stasi agent. In his files, it is noted that “he is prepared to complete any task assigned to him.” It also mentions that he is notable for having the “courage and temerity necessary to accomplish difficult missions.”
Now it seems the STASI is back again in business after transforming it in to the CYBER-STASI of the 21st Century.
The serial betrayer and cyberstalker Klaus Maurischat is on the run again. The latest action against him (see below) cause him to react in a series of fake statements and “press releases” – one more absurd than the other. Insider analyze that his criminal organisation “GoMoPa” is about to fade away.
On our request the German criminal police (Kriminalpolizei) has opened new cases against the notorious “GoMoPa” organisation which already fled in the underground. Insiders say they have killed German journalist and watchdog Heinz Gerlach and their criminal record is bigger than the Encyclopedia – Britannica
The case is also directed against Google, Germany, whilst supporting criminal action of “GoMoPa” for years and therefore give them the chance to blackmail successfull businessman. This case is therefore an example and will be followed by many others as far as we can project. Furthermore we will bring the case to the attention of the German lawyers community which will not tolerate such misconduct by Googles German legal representative Dr. Arndt Haller and we will bring the case to the attention ofGoogle Inc in Mountain View, USA, and the American ministry of Justice to stop the Cyberstalkers once and for all.
Besides that many legal institutions, individuals and firms have already contacted us to help to clarify the death of Mr. Heinz Gerlach and to prosecute his murderers and their backers.
The case number is ST/0148943/2011
In a series of interviews beginning 11 months before the sudden death of German watchdog Heinz Gerlach Berlin lawyer Joschen Resch unveilved secrets of Gerlach, insiders say. Secret documents from Mr Gerlachs computer were published on two dubious hostile German websites. Both have a lot of similarities in their internet registration. One the notorious “GoMoPa” website belongs to a n Eastern German organization which calls itself “
Numerous attempts have been made to stop our research and the publication of the stories by “GoMoPa” members in camouflage thus confirming the truth and the substance of it in a superior way.
Only two articles let the German audience believe that the famous journalist and watchdog Heinz Gerlach died on natural courses by blood pollution. The first one, published only hours after the death of Mr Heinz Gerlach by the notorious “GoMoPa” (see article below) and a second 3 days later by a small German local newspaper, Weserbergland Nachrichten.
Many people including the hostile Gerlach website “Akte Heinz Gerlach” doubted that this man who had so many enemies and friends would die of natural causes without any previous warning. Rumours occured that Mr. Gerlach’s doctor doubted natural courses at all. After many critical voices discussed the issue a small website of a small German local newspaper – which never before had reported about Mr. Heinz Gerlach and which is not even in the region of Mr Gerlachs home – published that Mr Gerlach died of blood pollution. Weserbergland-Nachrichten published a long article about the deadly consequences of blood pollution and did not even name the source of such an important statement. It claimed only that somebody of Gerlachs inner circle had said this. It is a proven fact that after the collpase of the Eastern German Communist Regime many former Communist propaganda agents went to regional newspapers – often in Western Germany like Günther Schabowski did the man who opened the “Mauer”.
The theatre stage was set: One day later the hostile Gerlach website “Akte Heinz Gerlach” took the agenda publishing that Mr Gerlach had died for natural causes without any further research at all.
This was done by a website which for months and months and months reported everything about Mr. Gerlach.
Furthermore a research proves that the technical details regarding the website hosting of this hostile website “Akte Heinz Gerlach” proves that there are common details with the hosting of “GoMoPa” and their affiliates as proven by the SJB-GoMoPa-victims (see http://www.sjb-fonds-opfer.com)
Insiders believe that the murderers of Mr. Heinz Gerlach are former members of the Eastern German Terror Organisation “Stasi” with dioxins. They also believe that “GoMoPa” was part of the plot. At “GoMoPa”’ a person named Siegfried Siewers was officialy responsible for the press but never appeared in public. “GoMoPa”-victims say that this name was a cameo for “GoMoPa” frontrunner Klaus Maurischat who is controlled by the Stasi Top Agent Ehrenfried Stelznr, Berlin.
Siegfried Sievers, a former Stasi member is responsible for the pollution of millions Germanys for many years with dioxins. This was unveiled at 5th of January 2011 by German prosecutors.
The victims say that Maurischat (probably also a Stasi cameo) and Sievers were in contact as Sievers acted as Stasi Agent and was in fact already a specialist in dioxins under the Communist Terror
The Stasi murder:
„GoMoPa“ & Backers: Blackmailing, Extortion, Racketeering, Internet Murder and Murder. These are the weapons of the East-German “NACHRICHTENDIENST” “GoMoPa”, a renegate confesses.
Deep Throat, Berlin; confesses: „Since months the „GoMoPa“ keyfigures like Klaus-Dieter Maurischat< are in hide-aways because the German police is hunting them for the wirecard fraud and a lot of other criminal actions. I left the group when I noticed that. The found and former Stasi-Colonel Ehrenfried Stelzer died under strange circumstances in Berlin. This has been told to us. But it is also possible that his death was staged. In any case the criminal organization of “GoMoPa” is responsible for the murder of Heinz Gerlach by dioxin. Now my life is also in danger that is why I hide myself.”
According to Deep Throat, Hans J. the murder was done with the help of the old Stasi-connections of the “NACHRICHTENDIENST” “GoMoPa”.
The renegate says that computer hacker Thomas Promny and Sven Schmidt are responsible for the computer crimes and he states that the crime organization of “GoMoPa” has also helpers inside internet companies like Go-Daddy, Media-on and even in Google, Hamburg..
THE “NACHRICHTENDIENST”:New criminal police action against “GoMoPa”:
German criminal police (Kriminalpolizei) has opened new cases against the notorious “GoMoPa” organisation which already fled in the underground.
On our request the German criminal police (Kriminalpolizei) has opened new cases against the notorious “GoMoPa” organisation which already fled in the underground. Insiders say they have killed German journalist and watchdog Heinz Gerlach and their criminal record is bigger than the
Encyclopedia – Britannica
The case is also directed against Google, Germany, whilst supporting criminal action of “GoMoPa” for years and therefore give them the chance to blackmail successfull businessman. This case is therefore an example and will be followed by many others as far as we can project. Furthermore we will bring the case to the attention of the German lawyers community which will not tolerate such misconduct by Googles German legal representative Dr. Arndt Haller and we will bring the case to the attention of Google Inc in Mountain View, USA, and the American ministry of Justice to stop the Cyberstalkers once and for all.
Besides that many legal institutions, individuals and firms have already contacted us to help to clarify the death of Mr. Heinz Gerlach and to prosecute his murderers and their backers.
The case number is
ST/0148943/2011
Stasi-Dioxin: The “NACHRICHTENDIENST” searching for the perfect murder:
Viktor Yushchenko was running against Prime Minister Viktor Yanukovych. Yanukovych was a political ally of outgoing president Leonid Kuchma. Kuchma’s administration depended upon corruption and dishonesty for its power. Government officials ruled with a sense of terror rather than justice. For the powerful and wealthy few, having Yanukovych elected president was important. Should Yushchenko win, Ukraine’s government was sure to topple. Yushchenko’s campaign promises included a better quality of life for Ukrainians through democracy. His wife, Katherine, told CBS in a 2005 interview, “He was a great threat to the old system, where there was a great deal of corruption, where people were making millions, if not billions.”
On September 6, 2004, Yushchenko became ill after dining with leaders of the Ukrainian secret police. Unlike other social or political engagements, this dinner did not include anyone else on Yushchenko’s team. No precautions were taken regarding the food. Within hours after the dinner, Yushchenko began vomiting violently. His face became paralyzed; he could not speak or read. He developed a severe stomachache and backache as well as gastrointestinal pain. Outwardly, Yushchenko developed what is known as chloracne, a serious skin condition that leaves the face scarred and disfigured.
By December 2004, doctors had determined that Yushchenko had been the victim of dioxin poisoning. Dioxin is a name given to a group of related toxins that can cause cancer and even death. Dioxin was used in the biochemical weapon called Agent Orange during the Vietnam War controversial war in which the United States aidedSouth Vietnam in its fight against a takeover by Communist North Vietnam). Yushchenko had a dioxin level six thousand times greater than that normally found in the bloodstream. His is the second-highest level ever recorded.
Yushchenko immediately suspected he had been poisoned, though Kuchma’s camp passionately denied such allegations. Instead, when Yushchenko showed up at a parliamentary meeting shortly after the poisoning incident, Kuchma’s men teased him, saying he must have had too much to drink or was out too late the night before.
Dioxin can stay in the body for up to thirty-five years. Experts predict that his swelling and scars will fade but never completely disappear. John Henry, a toxicologist at London’s Imperial Hospital, told RedNova.com, “It’ll be a couple of years, and he will always be a bit pockmarked. After damage as heavy as that, I think he will not return to his film star looks.” And Yushchenko will live with the constant threat of cancer.
At first it was believed the poison must have come from a Russian laboratory. Russia was a strong supporter of Kuchma and lobbied against Yushchenko in the 2004 election. But by July 2005, Yushchenko’s security forces were able to trace the poison to a lab in Ukraine. Though not entirely ruling out Russia’s involvement, Yushchenko is quoted on his Web site as saying “I’m sure that even though some people are running from the investigation, we will get them. I am not afraid of anything or anybody.”
Evidence shows that such a perfect murder plotted by former Stasi agents is the cause of the death of German watchdog and journalist Heinz Gerlach.
The Ministry for State Security (German: Ministerium für Staatssicherheit (MfS), commonly known as the Stasi (IPA: [‘?tazi?]) (abbreviation German: Staatssicherheit, literally State Security), was the official state security service of East Germany. The MfS was headquartered in East Berlin, with an extensive complex in Berlin-Lichtenberg and several smaller facilities throughout the city. It was widely regarded as one of the most effective and repressive intelligence and secret police agencies in the world. The MfS motto was “Schild und Schwert der Partei” (Shield and Sword of the Party), that is the ruling Socialist Unity Party of Germany (SED).
According to the confessions of an informer, Berlin lawyer Jochen Resch writes most of the “articles” of the communist “STASI” agency “GoMoPa” himself or it is done by lawyers of his firm. The whistleblower states that lawyer Resch is the mastermind behind the “CYBER-STASI” called “NACHRICHTENDIENST” “GoMoPa”. Bizarre enough they use Jewish names of non-existing Jewish lawyers by the name of “Goldman, Morgenstern and Partner” to stage their bogus “firm”. Further involved in their complots are a “detective” Medard Fuchsgruber and “STASI”-Colonel Ehrenfried Stelzer, “the first crime expert” in the former communist East-Germany.
According to London based Meridian Capital hundreds and thousands of wealthy people and companies have paid to the “NACHRICHTENDIENST” to avoid their cyberstalking (see article below).
Finally the German criminal police started their investigations (case number ST/0148943/2011).
The “NACHRICHTENDIENST” is also involved in the death of the well-known German watchdog and journalist Heinz Gerlach who died under strange circumstances in July 2010.
Only hours after his death the “NACHRICHTENDIENST” was spreading the news that Mr Gerlach died of blood pollution and set the stage for a fairy tale. Months before his death the “NACHRICHTENDIENST” started a campaign to ruin his reputation and presumably was also responsable for cyberattacks to bring his website down. In fact they presumably used the same tactics also against our servers. Therefore we investigated all internet details of them and handed the facts to the FBI and international authorities.
Story background:
Now it seems the STASI is back again in business after transforming it in to the CYBER-STASI of the 21st Century.
The serial betrayer and cyberstalker Klaus Maurischat is on the run again. The latest action against him (see below) cause him to react in a series of fake statements and “press releases” – one more absurd than the other. Insider analyze that his criminal organisation “GoMoPa” is about to fade away.
On our request the German criminal police (Kriminalpolizei) has opened new cases against the notorious “GoMoPa” organisation which already fled in the underground. Insiders say they have killed German journalist and watchdog Heinz Gerlach and their criminal record is bigger than the Encyclopedia – Britannica
The case is also directed against Google, Germany, whilst supporting criminal action of “GoMoPa” for years and therefore give them the chance to blackmail successfull businessman. This case is therefore an example and will be followed by many others as far as we can project. Furthermore we will bring the case to the attention of the German lawyers community which will not tolerate such misconduct by Googles German legal representative Dr. Arndt Haller and we will bring the case to the attention of Google Inc in Mountain View, USA, and the American ministry of Justice to stop the Cyberstalkers once and for all.
Besides that many legal institutions, individuals and firms have already contacted us to help to clarify the death of Mr. Heinz Gerlach and to prosecute his murderers and their backers.
The case number is ST/0148943/2011
In a series of interviews beginning 11 months before the sudden death of German watchdog Heinz Gerlach Berlin lawyer Joschen Resch unveilved secrets of Gerlach, insiders say. Secret documents from Mr Gerlachs computer were published on two dubious hostile German websites. Both have a lot of similarities in their internet registration. One the notorious “GoMoPa” website belongs to a n Eastern German organization which calls itself “
Numerous attempts have been made to stop our research and the publication of the stories by “GoMoPa” members in camouflage thus confirming the truth and the substance of it in a superior way.
Only two articles let the German audience believe that the famous journalist and watchdog Heinz Gerlach died on natural courses by blood pollution. The first one, published only hours after the death of Mr Heinz Gerlach by the notorious “GoMoPa” (see article below) and a second 3 days later by a small German local newspaper, Weserbergland Nachrichten.
Many people including the hostile Gerlach website “Akte Heinz Gerlach” doubted that this man who had so many enemies and friends would die of natural causes without any previous warning. Rumours occured that Mr. Gerlach’s doctor doubted natural courses at all. After many critical voices discussed the issue a small website of a small German local newspaper – which never before had reported about Mr. Heinz Gerlach and which is not even in the region of Mr Gerlachs home – published that Mr Gerlach died of blood pollution. Weserbergland-Nachrichten published a long article about the deadly consequences of blood pollution and did not even name the source of such an important statement. It claimed only that somebody of Gerlachs inner circle had said this. It is a proven fact that after the collpase of the Eastern German Communist Regime many former Communist propaganda agents went to regional newspapers – often in Western Germany like Günther Schabowski did the man who opened the “Mauer”.
The theatre stage was set: One day later the hostile Gerlach website “Akte Heinz Gerlach” took the agenda publishing that Mr Gerlach had died for natural causes without any further research at all.
This was done by a website which for months and months and months reported everything about Mr. Gerlach.
Furthermore a research proves that the technical details regarding the website hosting of this hostile website “Akte Heinz Gerlach” proves that there are common details with the hosting of “GoMoPa” and their affiliates as proven by the SJB-GoMoPa-victims (see http://www.sjb-fonds-opfer.com)
Insiders believe that the murderers of Mr. Heinz Gerlach are former members of the Eastern German Terror Organisation “Stasi” with dioxins. They also believe that “GoMoPa” was part of the plot. At “GoMoPa”’ a person named Siegfried Siewers was officialy responsible for the press but never appeared in public. “GoMoPa”-victims say that this name was a cameo for “GoMoPa” frontrunner Klaus Maurischat who is controlled by the Stasi Top Agent Ehrenfried Stelzner, Berlin.
Siegfried Sievers, a former Stasi member is responsible for the pollution of millions Germanys for many years with dioxins. This was unveiled at 5th of January 2011 by German prosecutors.
The victims say that Maurischat (probably also a Stasi cameo) and Sievers were in contact as Sievers acted as Stasi Agent and was in fact already a specialist in dioxins under the Communist Terror Regime in Eastern Germany.
Furthermore the Stasi Top Agent Ehrenfried Stelzer disguised as Professor for Criminal studies during the Communist Regime at the Eastern Berlin Humboldt University.
Background:
The man behind the Berlin lawyer Jochen Resch and his activities is Ehrenfried Stelzer, former Stasi Top officer in Berlin and “Professor for Criminal Studies” at the Eastern Berlin Humboldt University during the Communist regime, the SJB-GoMoPa-victims say (www.sjb-fonds-opfer.com) is responsable for the killing of German watchdog and journalist Heinz Gerlach.
These informations stem from various sources who were close to the criminal organization of GoMoPa in the last years. The SJB-GoMoPa say that the well-known German watchdog and journalist Heinz Gerlach was killed by former Stasi members with dioxins. Polychlorinated dibenzodioxins (PCDDs), or simply dioxins, are a group of organic polyhalogenated compounds that are significant because they act as environmental pollutants. They are commonly referred to as dioxins for simplicity in scientific publications because every PCDD molecule contains a dioxin skeletal structure. Typically, the p-dioxin skeleton is at the core of a PCDD molecule, giving the molecule a dibenzo-p-dioxin ring system. Members of the PCDD family have been shown to bioaccumulate in humans and wildlife due to their lipophilic properties, and are known teratogens, mutagens, and confirmed (avered) human carcinogens. They are organic compounds.
Dioxins build up primarily in fatty tissues over time (bioaccumulate), so even small exposures may eventually reach dangerous levels. In 1994, the US EPA reported that dioxins are a probable carcinogen, but noted that non-cancer effects (reproduction and sexual development, immune system) may pose an even greater threat to human health. TCDD, the most toxic of the dibenzodioxins, is classified as a Group 1 carcinogen by the International Agency for Research on Cancer (IARC).
In 2004, a notable individual case of dioxin poisoning, Ukrainian politician Viktor Yushchenko was exposed to the second-largest measured dose of dioxins, according to the reports of the physicians responsible for diagnosing him. This is the first known case of a single high dose of TCDD dioxin poisoning, and was diagnosed only after a toxicologist recognized the symptoms of chloracne while viewing television news coverage of his condition.
German dioxin scandal: In January 2011 about 4700 German farms were banned from making deliveries after tests at the Harles und Jentzsch plant in the state of Schleswig-Holstein showed high levels of dioxin. Again this incident appears to involve PCBs and not PCDDs at all. Dioxin were found in animal feed and eggs in many farms. The person who is responsible for this, Siegfried Sievert is also a former Stasi Agent. At “GoMoPa” the notorious Eastern-Berlin press agency (see article below) one of the henchmen acted under the name of “Siegfried Siewert”.
Further evidence for the killing of Mr.Heinz Gerlach is provided by the SJB-GoMoPa-victims by analyzing the dubious role of former Stasi-Top-agent Ehrenfried Stelzer, also a former “Professor for Crime Studies” under the Communist regime in Eastern Germany and the dubious role of “detective” Medard Fuchsgruber. Both are closely tied to the dubious “GoMoPa” and Berlin lawyer Jochen Resch.
According to the SJB-GoMoPa-victims is Berlin lawyer Jochen Resch the mastermind of the criminal organization “GoMoPa2. The victims state that they have a source inside “GoMoPa” who helped them discover the shocking truth. The so-called “Deep Throat from Berlin” has information that Resch had the idea to found the criminal organization “GoMoPa” and use non-existing Jewish lawyers named Goldman, Morgenstern & Partner as camouflage. Their “office” in Madison Avenue, New York, is a mailbox. This is witnessed by a German Ex-Patriot, a lawyer, whose father, Heinz Gerlach, died under strange circumstances.
Resch seems to use “GoMoPa” as an instrument to blackmail parts of the German Property and Investment section.
-”Worse than the Gestapo.” —Simon Wiesenthal, Nazi hunter said about the notorious “Stasi”.
Less than a month after German demonstrators began to tear down the Berlin Wall on November 9, 1989, irate East German citizens stormed the Leipzig district office of the Ministry for State Security (MfS)—the Stasi, as it was more commonly called. Not a shot was fired, and there was no evidence of “street justice” as Stasi officers surrendered meekly and were peacefully led away. The following month, on January 15, hundreds of citizens sacked Stasi headquarters in Berlin. Again there was no bloodshed. The last bit of unfinished business was accomplished on May 31 when the Stasi radioed its agents in West Germany to fold their tents and come home.
The intelligence department of the Nationale Volksarmee (NVA), the People’s Army, had done the same almost a week earlier, but with what its members thought was better style. Instead of sending the five-digit code groups that it had used for decades to message its spies in West Germany, the army group broadcast a male choir singing a children’s ditty about a duck swimming on a lake. There was no doubt that the singing spymasters had been drowning their sorrow over losing the Cold War in schnapps. The giggling, word-slurring songsters repeated the refrain three times: “Dunk your little head in the water and lift your little tail.” This was the signal to agents under deep cover that it was time to come home.
With extraordinary speed and political resolve, the divided nation was reunified a year later. The collapse of the despotic regime was total. It was a euphoric time for Germans, but reunification also produced a new national dilemma. Nazi war crimes were still being tried in West Germany, forty-six years after World War II. Suddenly the German government was faced with demands that the communist officials who had ordered, executed, and abetted crimes against their own people—crimes that were as brutal as those perpetrated by their Nazi predecessors—also be prosecuted.
The people of the former Deutsche Demokratische Republik (DDR), the German Democratic Republic, as the state had called itself for forty years, were clamoring for instant revenge. Their wrath was directed primarily against the country’s communist rulers—the upper echelon of the Sozialistische Einheitspartei (SED), the Socialist Unity Party. The tens of thousands of second-echelon party functionaries who had enriched themselves at the expense of their cocitizens were also prime targets for retribution.
Particularly singled out were the former members of the Stasi, the East German secret police, who previously had considered themselves the “shield and sword” of the party. When the regime collapsed, the Stasi had 102,000 full-time officers and noncommissioned personnel on its rolls, including 11,000 members of the ministry’s own special guards regiment. Between 1950 and 1989, a total of 274,000 persons served in the Stasi.
The people’s ire was running equally strong against the regular Stasi informers, the inoffizielle Mitarbeiter (IMs). By 1995, 174,000 had been identified as IMs, or 2.5 percent of the total population between the ages of 18 and 60. Researchers were aghast when they found that about 10,000 IMs, or roughly 6 percent of the total, had not yet reached the age of 18. Since many records were destroyed, the exact number of IMs probably will never be determined; but 500,000 was cited as a realistic figure. Former Colonel Rainer Wiegand, who served in the Stasi counterintelligence directorate, estimated that the figure could go as high as 2 million, if occasional stool pigeons were included.
“The Stasi was much, much worse than the Gestapo, if you consider only the oppression of its own people,” according to Simon Wiesenthal of Vienna, Austria, who has been hunting Nazi criminals for half a century. “The Gestapo had 40,000 officials watching a country of 80 million, while the Stasi employed 102,000 to control only 17 million.” One might add that the Nazi terror lasted only twelve years, whereas the Stasi had four decades in which to perfect its machinery of oppression, espionage, and international terrorism and subversion.
To ensure that the people would become and remain submissive, East German communist leaders saturated their realm with more spies than had any other totalitarian government in recent history. The Soviet Union’s KGB employed about 480,000 full-time agents to oversee a nation of 280 million, which means there was one agent per 5,830 citizens. Using Wiesenthal’s figures for the Nazi Gestapo, there was one officer for 2,000 people. The ratio for the Stasi was one secret policeman per 166 East Germans. When the regular informers are added, these ratios become much higher: In the Stasi’s case, there would have been at least one spy watching every 66 citizens! When one adds in the estimated numbers of part-time snoops, the result is nothing short of monstrous: one informer per 6.5 citizens. It would not have been unreasonable to assume that at least one Stasi informer was present in any party of ten or twelve dinner guests.
THE STASI OCTOPUS
Like a giant octopus, the Stasi’s tentacles probed every aspect of life. Full-time officers were posted to all major industrial plants. Without exception, one tenant in every apartment building was designated as a watchdog reporting to an area representative of the Volkspolizei (Vopo), the People’s Police. In turn, the police officer was the Stasi’s man. If a relative or friend came to stay overnight, it was reported. Schools, universities, and hospitals were infiltrated from top to bottom. German academe was shocked to learn that Heinrich Fink, professor of theology and vice chancellor at East Berlin’s Humboldt University, had been a Stasi informer since 1968. After Fink’s Stasi connections came to light, he was summarily fired. Doctors, lawyers, journalists, writers, actors, and sports figures were co-opted by Stasi officers, as were waiters and hotel personnel. Tapping about 100,000 telephone lines in West Germany and West Berlin around the clock was the job of 2,000 officers.
Stasi officers knew no limits and had no shame when it came to “protecting the party and the state.” Churchmen, including high officials of both Protestant and Catholic denominations, were recruited en masse as secret informers. Their offices and confessionals were infested with eavesdropping devices. Even the director of Leipzig’s famous Thomas Church choir, Hans-Joachim Rotch, was forced to resign when he was unmasked as a Spitzel, the people’s pejorative for a Stasi informant.
Absolutely nothing was sacred to the secret police. Tiny holes were bored in apartment and hotel room walls through which Stasi agents filmed their “suspects” with special video cameras. Even bathrooms were penetrated by the communist voyeurs.8 Like the Nazi Gestapo, the Stasi was the sinister side of deutsche Gründlichkeit (German thoroughness).
After the Berlin wall came down, the victims of the DDR regime demanded immediate retribution. Ironically, their demands were countered by their fellow Germans in the West who, living in freedom, had diligently built einen demokratischen Rechtsstaat, a democratic state governed by the rule of law. The challenge of protecting the rights of both the victims and the accused was immense, given the emotions surrounding the issue. Government leaders and democratic politicians recognized that there could be no “quick fix” of communist injustices without jeopardizing the entire system of democratic jurisprudence. Moving too rapidly merely to satisfy the popular thirst for revenge might well have resulted in acquittals or mistrials. Intricate jurisdictional questions needed to be resolved with both alacrity and meticulousness. No German government could afford to allow a perpetrator to go free because of a judicial error. The political fallout from any such occurrence, especially in the East, could prove fatal to whatever political party occupied the chancellor’s office in Bonn at the time.
Politicians and legal scholars of the “old federal states,” or West Germany, counseled patience, pointing out that even the prosecution of Nazi criminals had not yet been completed. Before unification, Germans would speak of Vergangenheitsbewältigung (“coming to grips with the past”) when they discussed dealing with Nazi crimes. In the reunited Germany, this word came to imply the communist past as well. The two were considered comparable especially in the area of human rights violations. Dealing with major Nazi crimes, however, was far less complicated for the Germans: Adolf Hitler and his Gestapo and Schutzstaffel (SS) chief, Heinrich Himmler, killed themselves, as did Luftwaffe chief and Vice Chancellor Hermann Göring, who also had been the first chief of the Gestapo. The victorious Allies prosecuted the rest of the top leadership at the International War Crimes Tribunal in Nürnberg. Twelve were hanged, three received life terms, four were sentenced to lesser terms of imprisonment (up to twenty years), and three were acquitted.
The cases of communist judges and prosecutors accused of Rechtsbeugung (perversion of justice) are more problematic. According to Franco Werkenthin, a Berlin legal expert charged with analyzing communist crimes for the German parliament, those sitting in judgment of many of the accused face a difficult task because of the general failure of German justice after World War II. Not a single judge or prosecutor who served the Nazi regime was brought to account for having perverted justice—even those who had handed down death sentences for infringements that in a democracy would have been considered relatively minor offenses. Werkenthin called this phenomenon die Jauche der Justiz, the cesspool of justice.
Of course, the crimes committed by the communists were not nearly as heinous as the Nazis’ extermination of the Jews, or the mass murders in Nazi-occupied territories. However, the communists’ brutal oppression of the nation by means including murder alongside legal execution put the SED leadership on a par with Hitler’s gang. In that sense, Walter Ulbricht or Erich Honecker (Ulbricht’s successor as the party’s secretary-general and head of state) and secret police chief Erich Mielke can justifiably be compared to Hitler and Himmler, respectively.
Arrest warrants were issued for Honecker and Mielke. The Soviet government engineered Honecker’s escape to Moscow, where he became the ward of Soviet President Mikhail S. Gorbachev. When the Soviet Union crumbled, the new Russian President Boris Yeltsin expelled Honecker. He was arrested on his return to Germany, but a court decided against a trial when he was diagnosed with liver cancer. Honecker flew to Chile with his wife Margot to live with their daughter, a Chilean citizen by marriage. His exile was short, and he died in 1994. Mielke was not so fortunate: His KGB friends turned their backs on him. He was tried in Germany for the 1931 murder of two police officers, found guilty, and sentenced to six years in prison. Other charges, including manslaughter, were dismissed because of his advanced age and poor health.
Three other members of the twenty-one-member ruling Politburo also have been tried. Former Defense Minister Heinz Kessler was convicted of manslaughter in connection with the order to kill people who were trying to escape to the West. He received a seven-and-a-half-year term. Two others, members of the Central Committee and the National Defense Council, were tried with Kessler and sentenced to seven and a half years and five years, respectively. Politburo member Harry Tisch, who was also head of the communist trade union, was found guilty of embezzlement and served eighteen months. Six others, including Egon Krenz (Honecker’s successor as party chief), were charged with manslaughter. Krenz was found guilty, and on August 25, 1997, was sentenced to six and a half years in prison.
However, eight years after reunification, many of the 165 members of the Central Committee have not yet been put under investigation. In 1945, Nazis holding comparable or lesser positions were subject to automatic arrest by the Allies. They spent months or even years in camps while their cases were adjudicated. Moreover, the Nürnberg Tribunal branded the Reich and its Corps of Political Leaders, SS, Security Service (SD), Secret State Police (Gestapo), SA (Storm Troopers), and Armed Forces High Command criminal organizations. Similarly sweeping actions against communist leaders and functionaries such as Stasi officers were never contemplated, even though tens of thousands of political trials and human rights abuses have been documented. After the East German regime fell, German judicial authorities scrupulously avoided the appearance of waging witch-hunts or using the law as a weapon of vengeance. Prosecutors and judges made great efforts to be fair, often suspending legal action while requesting rulings from the supreme court on possible constitutional conflicts.
The victims of oppression clamored for revenge and demanded speedy prosecution of the erstwhile tyrants. They had little patience for a judicial system that was handicapped by a lack of unblemished and experienced criminal investigators, prosecutors, and judges. Despite these handicaps, the Berlin Central Police Investigations Group for Government Criminality, mindful that the statute of limitations for most communist crimes would expire at the end of 1999, made significant progress under its director Manfred Kittlaus, the able former director of the West Berlin state police. Kittlaus’s major task in 1998 was to investigate wrongful deaths, including 73 murders, 30 attempted murders, 583 cases of manslaughter, 2,938 instances of attempted manslaughter, and 425 other suspicious deaths. Of the 73 murders, 22 were classified as contract murders.
One of those tried and convicted for attempted contract murder was former Stasi collaborator Peter Haak, who was sentenced to six and a half years in prison. The fifty-two-year-old Haak took part in the Stasi’s 1981 Operation Scorpion, which was designed to pursue people who helped East Germans escape to the West. Proceedings against former General Gerhard Neiber, whose Stasi directorate was responsible for preventing escapes and for wreaking vengeance, were still pending in 1998.
Peter Haak’s murder plot was hatched after he befriended Wolfgang Welsch and his family. Welsch was a thorn in the side of the Stasi because of his success in smuggling people out of the DDR. Haak joined Welsch and the latter’s wife and seven-year-old daughter on a vacation in Israel, where he mixed a gram of thallium, a highly poisonous metallic chemical element used in rat poison, into the hamburgers he was preparing for a meal. Welsch’s wife and daughter vomited immediately after ingesting the poison and recovered quickly. Welsch suffered severe aftereffects, but eventually recovered: He had consumed a large amount of beer with the meal, and an expert testified that the alcohol had probably flushed the poison from his system.
Berlin Prosecutor General Christoph Schäfgen revealed that after the DDR’s demise 15,200 investigations had been launched, of which more than 9,000 were still active at the beginning of 1995. Indictments were handed down in 153 cases, and 73 perpetrators were convicted. Among those convicted were the aforementioned Politburo members as well as a number of border guards who had killed people who were trying to escape to the West.
Despite widespread misgivings about the judicial failures in connection with some Nazi crimes, a number of judges and prosecutors were convicted and jailed for up to three years for perversion of justice. In collusion with the Stasi, they had requested or handed down more severe sentences in political cases so that the state could collect greater amounts when the “convicts” were ransomed by the West German government. {The amount of ransom paid was governed by the time a prisoner had been sentenced to serve.)
The enormity of the task facing judicial authorities in reunified Germany becomes starkly evident when one examines the actions they have taken in all five former East German provinces and in East Berlin. From the end of 1990 to July 1996, 52,050 probes were launched into charges of murder, attempted murder, manslaughter, kidnapping, election fraud, and perversion of justice. A total of 29,557 investigations were halted for various reasons including death, severe illness, old age, or insufficient evidence. In those five and a half years, there were only 139 convictions.
The problem is even more staggering when cases of espionage are included. Between 1990 and 1996, the office of the federal prosecutor general launched 6,641 probes, of which 2,431 were terminated before trial—most due to the statute of limitations. Of 175 indictments on charges of espionage, 95 resulted in convictions. In addition to the cases handled at the federal level, the prosecutor general referred 3,926 investigations to state authorities, who terminated 3,344 without trial. State courts conducted 356 trials, resulting in 248 convictions. Because the statute of limitations for espionage is five years, the prosecutor general’s office told me in 1997 it was unlikely that more espionage trials would be conducted.
It is important to emphasize the difference between the statute’s application to so-called government crimes committed in East Germany before the collapse and to crimes, such as espionage, committed in West Germany. The Unification Treaty specifically permits the belated prosecution of individuals who committed acts that were punishable under the East German criminal code and who due to official connivance were not prosecuted earlier. There is no statute of limitations for murder. For most other crimes the limit is five years; however, due to the obstacles created by previous government connivance, the German parliament in 1993 doubled this time limit for prosecution of the more serious crimes. At the same time, the parliament decreed that all cases must be adjudicated by the end of 2002. For less serious offenses, the statute would have run out on December 31, 1997, but the parliament extended it to 2000.
A number of politicians, jurists, and liberal journalists pleaded for a general amnesty for crimes committed by former DDR leaders and Communist Party functionaries. A former West German supreme court judge, Ernst Mahrenholz, said the “sharp sword of justice prevents reconciliation.” Schäfgen, the Berlin prosecutor general, had this answer for the former high court judge and other amnesty advocates:
I cannot agree. We are raising no special, sharp sword against East Germans. We must pursue state-sponsored injustice in exactly the same manner as we do when a thief steals or when one human being kills another. If one wants to change that, then we would have to do away with the entire criminal justice system, because punishment always hurts. We are not criminalizing an entire people but only an ever shrinking, small portion.
German Foreign Minister Klaus Kinkel, who was West Germany’s minister of justice when the nation was unified, said this at a session of parliament in September 1991: “We must punish the perpetrators. This is not a matter of a victor’s justice. We owe it to the ideal of justice and to the victims. All of those who ordered injustices and those who executed the orders must be punished; the top men of the SED as well as the ones who shot [people] at the wall.” Aware that the feelings against communists were running high among their victims, Kinkel pointed to past revolutions after which the representatives of the old system were collectively liquidated. In the same speech before parliament, he said:
Such methods are alien to a state ruled by law. Violence and vengeance are incompatible with the law in any case. At the same time, we cannot tolerate that the problems are swept under the rug as a way of dealing with a horrible past, because the results will later be disastrous for society. We Germans know from our own experience where this leads. Jewish philosophy formulates it in this way: “The secret of redemption is called remembering.”
Defense attorneys for communist officials have maintained that the difficulty lies in the fact that hundreds of thousands of political opponents were tried under laws of the DDR. Although these laws were designed to smother political dissent and grossly violated basic human rights and democratic norms, they were nonetheless laws promulgated by a sovereign state. How could one justly try individual Stasi officers, prosecutors, and judges who had simply been fulfilling their legal responsibility to pursue and punish violators of the law?
Opinions varied widely on whether and how the Stasi and other perpetrators of state-sponsored crimes should be tried. Did the laws of the DDR, as they existed before reunification, still apply in the east? Or was the criminal code of the western part of the country the proper instrument of justice in reunified Germany? However, these questions were moot: As Rupert Scholz, professor of law at the University of Munich and a Christian Democratic member of parliament, pointed out, the Unification Treaty specifies that the penal code of the DDR and not that of the Federal Republic of Germany (FRG) shall be applied to offenses committed in East Germany. Scholz’s view was upheld by the Bundesverfassungsgericht, the supreme court. Most offenses committed by party functionaries and Stasi officers—murder, kidnapping, torture, illegal wiretapping, mail robbery, and fraud—were subject to prosecution in reunified Germany under the DDR’s penal code. But this would not satisfy the tens of thousands of citizens who had been sent to prison under East German laws covering purely political offenses for which there was no West German equivalent.
Nevertheless, said Scholz, judicial authorities were by no means hamstrung, because West Germany had never recognized the East German state according to international law. “We have always said that we are one nation; that the division of Germany led neither to full recognition under international law nor, concomitantly, to a recognition of the legal system of the DDR,” Scholz said. Accordingly, West German courts have consistently maintained that West German law protects all Germans equally, including those living in the East. Therefore, no matter where the crimes were committed, whether in the East or the West, all Germans have always been subject to West German laws. Applying this logic, East German border guards who had either killed or wounded persons trying to escape to the West could be tried under the jurisdiction of West Germany.
The “one nation” principle was not upheld by the German supreme court. Prior to the court’s decision, however, Colonel General Markus Wolf, chief of the Stasi’s foreign espionage directorate, and some of his officers who personally controlled agents from East Berlin had been tried for treason and convicted. Wolf had been sentenced to six years in prison. The supreme court ruling overturned that verdict and those imposed on Wolf’s cohorts, even though they had obtained the most closely held West German secrets and handed them over to the KGB. The maximum penalty for Landesverrat, or treason, is life imprisonment. In vacating Wolf’s sentence, the court said he could not be convicted because he operated only from East German territory and under East German law.
However, Wolf was reindicted on charges of kidnapping and causing bodily harm, crimes also punishable under East German law. The former Stasi three-star general, on March 24, 1955, had approved in writing a plan to kidnap a woman who worked for the U.S. mission in West Berlin. The woman and her mother were tricked by a Stasi agent whom the woman had been teaching English, and voluntarily got into his car. He drove them into the Soviet sector of the divided city, where they were seized by Stasi officers. The woman was subjected to psychological torture and threatened with imprisonment unless she signed an agreement to spy for the Stasi. She agreed. On her return to the American sector, however, the woman reported the incident to security officials. Wolf had committed a felony punishable by up to fifteen years’ imprisonment in West Germany. He was found guilty in March 1977 and sentenced to two years’ probation.
Those who have challenged the application of the statute of limitations to communist crimes, especially to the executions of citizens fleeing to the West, have drawn parallels to the notorious executive orders of Adolf Hitler. Hitler issued orders mandating the summary execution of Soviet Army political commissars upon their capture and initiating the extermination of Jews. An early postwar judicial decision held that these orders were equivalent to law. When that law was declared illegal and retroactively repealed by the West German Bundestag, the statute of limitations was suspended—that is, it never took effect. Many of those convicted in subsequent trials of carrying out the Führer’s orders were executed by the Allies. The German supreme court has ruled the same way as the Bundestag on the order to shoot people trying to escape to West Germany, making the statute of limitations inapplicable to such cases. The ruling made possible the trial of members of the National Defense Council who took part in formulating or promulgating the order. A number of border guards who had shot would-be escapees also have been tried and convicted.
Chief Prosecutor Heiner Sauer, former head of the West German Central Registration Office for Political Crimes, was particularly concerned with the border shootings. His office, located in Salzgitter, West Germany, was established in 1961 as a direct consequence of the Berlin Wall, which was erected on August 13 of that year. Willy Brandt, at the time the city’s mayor (later federal chancellor) had decided that crimes committed by East German border guards should be recorded. At his behest, a central registry of all shootings and other serious border incidents was instituted. Between August 13, 1961 and the opening of the borders on November 9, 1989, 186 border killings were registered. But when the Stasi archives were opened, investigators found that at least 825 people had paid with their lives for trying to escape to the West. This figure was reported to the court that was trying former members of the National Defense Council. In addition to these border incidents, the registry also had recorded a number of similar political offenses committed in the interior of the DDR: By fall 1991, Sauer’s office had registered 4,444 cases of actual or attempted killings and about 40,000 sentences handed down by DDR courts for “political offenses.”
During the early years of Sauer’s operation, the details of political prosecutions became known only when victims were ransomed by West Germany or were expelled. Between 1963 and 1989, West Germany paid DM5 billion (nearly US$3 billion) to the communist regime for the release of 34,000 political prisoners. The price per head varied according to the importance of the person or the length of the sentence. In some cases the ransom amounted to more than US$56,000. The highest sum ever paid to the East Germans appears to have been DM450,000 (US$264,705 using an exchange rate of US$1.70 to the mark). The ransom “object” in this case was Count Benedikt von Hoensbroech. A student in his early twenties, von Hoensbroech was attending a West Berlin university when the wall went up. He was caught by the Stasi while trying to help people escape and was sentenced to ten years at hard labor. The case attracted international attention because his family was related to Queen Fabiola of Belgium, who interceded with the East Germans. Smelling money, the East German government first demanded the equivalent of more than US$1 million from the young man’s father as ransom. In the end, the parties settled on the figure of DM450,000, of which the West German government paid DM40,000 (about $23,529). Such ransom operations were fully controlled by the Stasi.
Political prisoners released in the DDR could not be registered by the West Germans because their cases remained secret. The victims were admonished to keep quiet or face another prison term. Nonetheless, in the first year after reunification, Sauer’s office added another 20,000 documented cases, for a total of 60,000. Sauer said he believed the final figure of all political prosecutions would be somewhere around 300,000. In every case, the Stasi was involved either in the initial arrest or in pretrial interrogations during which “confessions” were usually extracted by physical or psychological torture, particularly between the mid-1940s and the mid-1960s.
Until 1987, the DDR imposed the death penalty for a number of capital crimes, including murder, espionage, and economic offenses. But after the mid-1950s, nearly all death sentences were kept quiet and executions were carried out in the strictest secrecy, initially by guillotine and in later years by a single pistol shot to the neck. In most instances, the relatives of those killed were not informed either of the sentence or of the execution. The corpses were cremated and the ashes buried secretly, sometimes at construction sites. In reporting about one executioner who shot more than twenty persons to death, the Berlin newspaper Bildzeitung said that a total of 170 civilians had been executed in East Germany. However, Franco Werkenthin, the Berlin official investigating DDR crimes, said he had documented at least three hundred executions. He declined to say how many were for political offenses, because he had not yet submitted his report to parliament. “But it was substantial,” he told me. The true number of executions may never be known because no complete record of death sentences meted out by civil courts could be found. Other death sentences were handed down by military courts, and many records of those are also missing. In addition, German historian Günther Buch believes that about two hundred members of the Stasi itself were executed for various crimes, including attempts to escape to the West.
SAFEGUARDING HUMAN DIGNITY?
The preamble to the East German criminal code stated that the purpose of the code was to “safeguard the dignity of humankind, its freedom and rights under the aegis of the criminal code of the socialist state,” and that “a person can be prosecuted under the criminal code only in strictest concurrence with the law.” However, many of the codified offenses for which East German citizens were prosecuted and imprisoned were unique to totalitarian regimes, both fascist and communist.
Moreover, certain sections of the code, such as those on “Treasonable Relaying of Information” and “Treasonable Agent Activity,” were perversely applied, landing countless East Germans in maximum security penitentiaries. The victims of this perversion of justice usually were persons who had requested legal exit permits from the DDR authorities and had been turned down. In many cases, their “crime” was having contacted a Western consulate to inquire about immigration procedures. Sentences of up to two and a half years’ hard labor were not unusual as punishment for such inquiries.
Engaging in “propaganda hostile to the state” was another punishable offense. In one such case, a young man was arrested and prosecuted for saying that it was not necessary to station tanks at the border and for referring to border fortifications as “nonsense.” During his trial, he “admitted” to owning a television set on which he watched West German programs and later told friends what he saw. One of those “friends” had denounced him to the Stasi. The judge considered the accused’s actions especially egregious and sentenced him to a year and a half at hard labor.
Ironically, another part of this section of the criminal code decreed that “glorifying militarism” also was a punishable offense, although the DDR itself “glorified” its People’s Army beyond any Western norm. That army was clad in uniforms and insignia identical to those of the Nazi Wehrmacht, albeit without eagles and swastikas. The helmets, too, were differently shaped, but the Prussian goose step was regulation during parades.
A nineteen-year-old who had placed a sign in an apartment window reading “When justice is turned into injustice, resistance becomes an obligation!” was rewarded with twenty-two months in the penitentiary. Earlier, the youth had applied for an exit visa and had been turned down. A thirty-four-year-old father of two who also had been denied permission to leave the “workers’ and peasants’ state” with his family similarly advertised that fact with a poster reading “We want to leave, but they won’t let us.” The man went to prison for sixteen months. The “crimes” of both men were covered by a law on “Interference in Activities of the State or Society.”
Two letters—one to a friend in West Germany, seeking assistance to legally emigrate to the West, and another containing a similar appeal to Chief of State Honecker—brought a four-year sentence to their writer, who was convicted under two laws: those on “establishing illegal contacts” (writing to his friend) and on “public denigration” (writing to Honecker). The Stasi had illegally intercepted both letters.
The East German party chiefs were not content to rely only on the Stasi’s millions of informers to ferret out antistate sentiments. Leaving nothing to chance, they created a law that made the failure to denounce fellow citizens a crime punishable by up to five years’ imprisonment. One man was sentenced to twenty-three months for failing to report that a friend of his was preparing to escape to the West. The mandatory denunciation law had its roots in the statutes of the Socialist Unity Party, which were published in the form of a little red booklet. I picked up a copy of this booklet that had been discarded by its previous owner, a Stasi chauffeur, who had written “Ha, Ha” next to the mandate to “report any misdeeds, regardless of the person responsible, to leading party organs, all the way up to the Central Committee.”
Rupert Scholz, member of parliament and professor of law at the University of Munich, said many East Germans feel there is little determination among their Western brethren to bring the Stasi criminals to trial. “In fact, we already have heard many of them say that the peaceful revolution should have been a bloody one instead so they could have done away with their tormentors by hanging them posthaste,” Scholz told me.
The Reverend Joachim Gauck, minister to a Lutheran parish in East Germany, shared the people’s pessimism that justice would be done. Following reunification, Gauck was appointed by the Bonn government as its special representative for safeguarding and maintaining the Stasi archives. “We must at least establish a legal basis for finding the culprits in our files,” Gauck told me. “But it will not be easy. If you stood the millions of files upright in one line, they would stretch for 202 kilometers [about 121 miles]. In those files you can find an unbelievable number of Stasi victims and their tormentors.”
Gauck was given the mandate he needed in November 1991, when the German parliament passed a law authorizing file searches to uncover Stasi perpetrators and their informants. He viewed this legislation as first step in the right direction. With the evidence from Stasi files, the perpetrators could be removed from their public service jobs without any formal legal proceedings. Said Gauck: “We needed this law badly. It is not reasonable that persons who served this apparatus of oppression remain in positions of trust.”
See more at the journalist Bernd Pulch website http://www.berndpulch.org
TMZ – Emmy Rossum — Meat and Boobs!
TOP-SECRET – ISAF Media Spokesperson Training Presentation
Secrecy News – WHITE HOUSE ADVANCES INSIDER THREAT POLICY
In a memorandum to agency heads last week, President Obama transmitted
formal requirements that agencies must meet in order "to deter, detect, and
mitigate actions by employees who may represent a threat to national
security."
Along with espionage and acts of violence, the National Insider Threat
Policy notably extends to the "unauthorized disclosure of classified
information, including the vast amounts of classified data available on
interconnected United States Government computer networks." To combat such
unauthorized disclosures, agencies are required to "monitor employee use of
classified networks."
http://www.fas.org/sgp/obama/nitp.pdf
The new standards, which have not been made publicly available, were
developed by an interagency Insider Threat Task Force that was established
by President Obama in the October 2011 executive order 13587, and they
reflect the ongoing tightening of safeguards on classified information in
response to the voluminous leaks of the last few years.
http://www.fas.org/irp/offdocs/eo/eo-13587.htm
But the latest issuance also illustrates the superfluousness (or worse) of
current congressional action concerning leaks. Executive branch agencies
do not need Congress to tell them to develop "a comprehensive insider
threat program management plan," as would be required by the Senate version
of the pending FY2013 Intelligence Authorization Act (section 509). Such
plans will go forward in any case.
http://www.fas.org/irp/congress/2012_cr/ssci-leaks.pdf
Sen. Ron Wyden has placed a hold on the pending intelligence bill, citing
objections to several of the proposed anti-leak provisions contained in
Title V of the bill. He said the proposed steps were misguided or
counterproductive.
"I am concerned that they will lead to less-informed public debate about
national security issues, and also undermine the due process rights of
intelligence agency employees, without actually enhancing national
security," he said on November 14.
http://www.fas.org/irp/congress/2012_cr/wyden-hold.html
The most problematic measures in the Senate bill are those intended to
restrict contacts between reporters and government officials.
Senator Wyden said that legislative actions to limit the ability of the
press to report on classified matters could undermine or cripple the
intelligence oversight process.
"I have been on the Senate Intelligence Committee for 12 years now, and I
can recall numerous specific instances where I found out about serious
government wrongdoing--such as the NSA's warrantless wiretapping program,
or the CIA's coercive interrogation program--only as a result of
disclosures by the press," he said.
* * *
The record of a July 2012 House Judiciary Committee hearing on National
Security Leaks and the Law has recently been published.
http://www.fas.org/irp/congress/2012_hr/leaks-hjc.pdf
IG REVIEW OF FISA COMPLIANCE COMPLETED BUT NOT RELEASED
The Office of the Inspector General (OIG) of the Department of Justice
said it had recently completed a review of the Department's use of Section
702 of the Foreign Intelligence Surveillance Act (FISA) Amendments Act
(FAA), but the report is classified and its findings have not been
released.
"The OIG examined the number of disseminated FBI intelligence reports
containing a reference to a U.S. person identity, the number of U.S. person
identities subsequently disseminated in response to requests for identities
not referred to by name or title in the original reporting, the number of
targets later determined to be located in the United States, and whether
communications of such targets were reviewed. The OIG also reviewed the
FBI's compliance with the required targeting and minimization procedures,"
according to a November 7 OIG memorandum on Top Management and Performance
Challenges in the Department of Justice.
http://www.justice.gov/oig/challenges/2012.htm
A copy of the classified report has been requested under the Freedom of
Information Act.
Earlier this year, Sen. Ron Wyden placed a hold on reauthorization of the
FISA Amendments Act "because I believe that Congress does not have enough
information about this law's impact on the privacy of law-abiding American
citizens, and because I am concerned about a loophole in the law that could
allow the government to effectively conduct warrantless searches for
Americans' communications."
http://www.fas.org/irp/congress/2012_cr/wyden-fisa.html
AUTONOMY IN WEAPON SYSTEMS
The Department of Defense issued a new Directive last week establishing
DoD policy for the development and use of autonomous weapons systems.
http://www.fas.org/irp/doddir/dod/d3000_09.pdf
An autonomous weapon system is defined as "a weapon system that, once
activated, can select and engage targets without further intervention by a
human operator."
The new DoD Directive Number 3000.09, dated November 21, establishes
guidelines that are intended "to minimize the probability and consequences
of failures in autonomous and semi-autonomous weapon systems that could
lead to unintended engagements."
"Failures can result from a number of causes, including, but not limited
to, human error, human-machine interaction failures, malfunctions,
communications degradation, software coding errors, enemy cyber attacks or
infiltration into the industrial supply chain, jamming, spoofing, decoys,
other enemy countermeasures or actions, or unanticipated situations on the
battlefield," the Directive explains.
An "unintended engagement" resulting from such a failure means "the use of
force resulting in damage to persons or objects that human operators did
not intend to be the targets of U.S. military operations, including
unacceptable levels of collateral damage beyond those consistent with the
law of war, ROE [rules of engagement], and commander's intent."
The Department of Defense should "more aggressively use autonomy in
military missions," urged the Defense Science Board last summer in a report
on "The Role of Autonomy in DoD Systems."
http://www.fas.org/blog/secrecy/2012/09/dsb_autonomy.html
The U.S. Army issued an updated Army Field Manual 3-36 on Electronic
Warfare earlier this month.
http://www.fas.org/irp/doddir/army/fm3-36.pdf
INDIA-US SECURITY RELATIONS, AND MORE FROM CRS
New and updated reports from the Congressional Research Service that have
not been made readily available to the public include the following.
India-U.S. Security Relations: Current Engagement, November 13, 2012:
http://www.fas.org/sgp/crs/row/R42823.pdf
A Guide to China's Upcoming Leadership Transitions, October 16, 2012:
http://www.fas.org/sgp/crs/row/R42786.pdf
U.S. Trade and Investment Relations with sub-Saharan Africa and the
African Growth and Opportunity Act, November 14, 2012:
http://www.fas.org/sgp/crs/row/RL31772.pdf
Roles and Duties of a Member of Congress, November 9, 2012:
http://www.fas.org/sgp/crs/misc/RL33686.pdf
The Congressional Research Service made a humorous appearance in the
Doonesbury comic strip on November 24, in connection with the report on tax
cuts that was withdrawn in response to criticism from some Republican
Senators.
http://doonesbury.slate.com/strip/archive/2012/11/24
In fact, as often noted, members of Congress of both parties consistently
withhold public access to most CRS reports.
http://www.fas.org/blog/secrecy/2012/11/crs_withdrawal.html
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
THE SECRET OF MY SUCCESS – FULL MOVIE – Michael J Fox – Helen Slater
MERIDIAN CAPITAL ÜBER DIE SERIEN-RUFMÖRDER, FÄLSCHER UND GEWOHNHEITSVERBRECHER DER STASI-”GoMoPa”
http://www.meridiancapital.wordpress.com/
Gerne können Sie auch Meridian Capital direkt in New York kontaktieren:
www.meridiancapital.com/
HIER NOCH EINMAL DIE BILD-BELEGE ZUM THEMA STASI “GoMoPa” UND KOMPLIZEN BZGL. MERIDIAN CAPITAL
UND HIER DIE STASI-”GoMoPa”-FÄLSCHUNG – PEINLICH-PEINLICH -PEINLICH UND SUPER-DUMM-DREIST
TMZ – Rihanna’s Dressing Room — A Stoner’s Heaven!
Twister – FULL MOVIE
Original STELLUNGNAHME VON MERIDIAN CAPITAL ZU “GoMoPa”
Liebe Leser,
hier die Original-Stellungnahme von Meridian Capital:
http://meridiancapital.wordpress.com
Hier der Artikel von “GoMoPa” über Meridian Capital.
Hier die Hintergründe der Erpressung:
Mit Ihren STASI-MEthoden wollen die “GoMoPa”-STASI-Verbrecher die Wahrheit unterdrücken.
Das wird Ihnen nicht gelingen.
Asterix and the Twelve Tasks – FULL MOVIE
So wollte “GoMoPa” mich erpressen
Unser Bildtext: Klaus Maurischat: There is no Place like home
So wollte der Serienbetrüger Klaus Maurischat uns zwingen die Berichterstattung über den “NACHRICHTENDIENST” “GoMoPa” einzustellen
Meine Anmerkung: Sie lesen
den Original-Text mit den Original-Rechtschreibfehlern von Maurischat in chronologischer Reihenfolge von unten nach oben. “Unter den Linden” ist die Regus-Tarnadresse für den untergetauchten Serienbetrüger und Stasi-Ganoven. “SUMA” steht im Sprach-Jargon des “GoMoPa”-”NACHRICHTENDIENSTLERS” für Suchmaschine.
Zitat:
HAHAHAHAHAHAHAHAHAHAHAHAHAHAHA (MEINE ANTWORT)
> Was anderes fällt einem Hilfsschüler auch nicht ein! Wenn ich dich
> schnappe, dann haue ich dir die Fresse ein – mein Lieber! Merk dir
> das gut, du Kinderficker!
>
> Was sagt denn dein Freund Dr. XXX zu deinem handeln, Schwuchtel?
>
> > HAHAHAHAHAHAHAHAHAHAHAHAHAHAHA (MEINE ANTWORT)
> >
> > > Geiles Google Suchergebniss hast du mittlerweile. Das ist sowas von
> > > geil. Am besten ist dieser Beitrag zu Deiner Magisterarbeit, du
> > > Spinner:
> > >
> > > http://scheisshausfliege.wordpress.com/2011/01/29/die-diplomarbeit-des-magisters-bernd-pulch-ein-haufen-scheisse/
> > >
> > > Wenn du nicht aufhörst, wird niemand mehr ein Stück Brot von dir
> > > nehmen. Dein Name ist dan absolut durch. Glaub mir, wir verstehen da
> > > mehr von als du Schwachkopf!
> > >
> > > Im Übrigen kannst du mich stets gern persönlich treffen. Unter den
> > > Linden 21, Berlin – habe immer für dich Feigling Zeit! (TARN-ADRESSE)
> > >
> > > So – und nun überle wann du die Artikel über uns löschen willst,
> > > sonst mache ich die erste Seite der SUMA Ergebnisse mit deinen
> > > Einträgen voll.
So wollte SJB-Bennewirtz für die fingierte STASI-”GoMoPa” Artikel bei uns löschen – So eng arbeiten SJB und “GoMoPa” zusammen
| Subject: | Request |
| From: | “P. Schmitz” <p.schmitz@deinguterruf.de> |
| Date: | Fri, July 1, 2011 12:18 pm |
| To: | office@ebizz.tv |
| Priority: | Normal |
| Options: | View Full Header | View Printable Version | Download this as a file |
Dear madams, dear sirs, by order of our customer SJB Fonds Skyline OHG we are kindly asking you to remove some entries on your website thetvnet.com. The topicality and the correctness of these entries are no longer up to date. It is a major concern of our customer to see them removed: immobilien-vertraulich.com/law/7279-die-killer-bibel-toxdat--die-900-seiten-stasi-mordstudie-von-gomopa-mastermind-ehrenfried-stelzer.html immobilien-vertraulich.com/law/7277-sjb-fonds-opfer-sven-babyface-schmidt-als-chef-terrorist-von-europas-gefaehrlichster-internet-kriminellen-bande-enttarnt-.html immobilien-vertraulich.com/law/7268-der-beweis-tatsaechlich-vorbestrafter-serienbetrueger-klausmaurischat-gomopa-hat-eigenes-kinder-portal-.html immobilien-vertraulich.com/law/7264-die-killer-bibel-toxdat--die-900-seiten-stasi-mordstudie-von-gomopa-mastermind-ehrenfried-stelzer.html immobilien-vertraulich.com/law/7262-sjb-fonds-opfer-sven-babyface-schmidt-als-chef-terrorist-von-europas-gefaehrlichster-internet-kriminellen-bande-enttarnt-.html immobilien-vertraulich.com/law/7224-die-killer-bibel-toxdat-die-900-seiten-stasi-mordstudie-von-gomopa-mastermind-ehrenfried-stelzer.html immobilien-vertraulich.com/law/7223-opfer-sven-schmidt-als-chef-terrorist-von-europas-gefaehrlichster-internet-kriminellen-bande-enttarnt.html immobilien-vertraulich.com/law/7217-der-beweis-tatsaechlich-vorbestrafter-serienbetrueger-klausmaurischat-gomopa-hat-eigenes-kinder-portal-.html immobilien-vertraulich.com/law/7212-die-killer-bibel-toxdat-die-900-seiten-stasi-mordstudie-von-gomopa-mastermind-ehrenfried-stelzer.html immobilien-vertraulich.com/law/7210-opfer-sven-schmidt-als-chef-terrorist-von-europas-gefaehrlichster-internet-kriminellen-bande-enttarnt.html immobilien-vertraulich.com/law/7203-der-beweis-tatsaechlich-vorbestrafter-serienbetrueger-klausmaurischat-gomopa-hat-eigenes-kinder-portal-.html immobilien-vertraulich.com/law/7200-opfer-die-killer-bibel-toxdat-die-900-seiten-stasi-mordstudie-von-gomopa-mastermind-ehrenfried-stelzer.html immobilien-vertraulich.com/law/7189-opfer-die-killer-bibel-toxdat--die-900-seiten-stasi-mordstudie-von-gomopa-mastermind-ehrenfried-stelzer.html immobilien-vertraulich.com/law/7120--klaus-maurischats-gomopa-cybermoerder-leichen-und-falschmeldungen-plastern-ihren-weg--nicht-nur-im-internet.html immobilien-vertraulich.com/boerse-ipo-reit/7119--der-mehrfach-vorbestrafte-serienbetrueger-und-mutmassliche-paederast-klaus-maurischat-und-seine-neue-qwirecard-enteq.html We hope you can manage the removal of these entries according to the wish of our customer contemporarily.These entries and similar ones cause major problems for our customer. We wanna thank you for your appreciation, for further information please visit our website deinguterruf.de. (the english version is still under construction). In case you are not the right receipt for this request, it would be very kind if you can name the correct person in charge. If you have further questions concerning this case or our services in general, please contact me. It would be a great pleasure to receive a positive feedback. With kind regards, -- Mit freundlichen Grüßen, P. Schmitz DEIN GUTER RUF.DE Ein Projekt der MoveVision GmbH Alfredstraße 341 45133 ESSEN Tel: 0201-2489452 E-mail: p.schmitz (at) deinguterruf.de MoveVision – GmbH - HRB 22121 Geschäftsführer: Martin Lux - Steuernummer: DE228746207 INTERESSANT - BENEWIRTZ WOLLTE HIERMIT AUSSCHLIESSLICH "GoMoPa"-KRITISCHE ARTIKEL LÖSCHEN
Invisible Ghost – Bela Lugois – Full Movie
THE PHANTOM KILLER STRIKES! Only a terrified woman knows the secret of this ghostly murderer…who strikes in the night and leaves no clues—but his victims! With Bela Lugosi.
Invisible Ghost is far from the best of Bela Lugosi’s Monogram vehicles (if indeed there is such a thing), but with Joseph H. Lewis at the controls it is far and away the best directed. Lugosi is cast as Kessler, an otherwise normal gentleman who goes balmy whenever he thinks about his late wife (Betty Compson). It gets worse when Kessler is transformed via hypnosis into an unwitting murderer, apparently at the behest of his wife’s ghost. An innocent man (John McGuire) is executed for Kessler’s first murder, but the victim’s twin brother (also John McGuire) teams with Kessler’s daughter (Polly Ann Young) to determine the identity of the true killer. Though cheaply made, The Invisible Ghost maintains an appropriately spooky atmosphere throughout, with Lugosi delivering a full-blooded performance as a basically decent man controlled by homicidal impulses beyond his ken. Best of all is the non-stereotypical performance by african-american actor Clarence Muse as Lugosi’s articulate, take-charge butler.
Video – Sports Illustrated Swimsuit – Tori Praver
Travel to Hawaii with Ford model Tori Praver for SI Swimsuit.
For more pictures and videos go to http://www.si.com/swimsuit!
TMZ – Kim Kardashian — Putting the A** in Ambassador!
TOP-SECRET – JIEDDO Attack the Network Field Guide Afghanistan

ATTACK THE NETWORK FIELD GUIDE AFGHANISTAN
- Version 1
- 35 pages
- April 2011
The Attack the Network (AtN) and tactical actions listed in this field guide are from interviews with battalion, company, and platoon warfighters successful in reducing the employment of improvised explosive devices (IEDs) in Afghanistan during 2007-2010. The primary intent of this field guide is to provide a collection of field-tested actions that enabled mission success in a counterinsurgency (COIN) environment with an IED threat.
Background: Recent tactical operations have US forces conducting counterinsurgency against adversaries with improvised explosive device capabilities. The best units quickly realized commonality between COIN and Counter-IED (C-IED) best practices in Afghanistan. Operating effectively along the C-IED Attack the Network line of operations led to COIN success as well as a reduction in the effectiveness of IED attacks.
Intent: This field guide provides small unit leaders and individual Soldiers and Marines a proven collection of actions to focus their efforts while attacking networks. Primarily, these actions consist of mission analysis, briefing, and execution and are adapted for use by these small unit leaders in a population-centric operating environment.
Scope: The operating environment noted here is COIN. The actions noted in this document should be coordinated with doctrine, theater guidance, and unit standard operating procedures (SOP). Attack the Network is an operational approach that consists of building and enabling friendly networks as well as countering threat networks. The development and coordination of these friendly networks might actually become the focus of main effort.
…
Minimize Negative Actions
Reduce collateral damage, understand and mitigate the negative effects of your actions
When conducting kinetic actions, use the most precise weapons available to avoid civilian deaths, injuries and other collateral damage.
No matter what, we will always act with honor, and we will always do what is right.
o Minimize collateral damage. Be prepared to make immediate reparations for collateral damage and do so as necessary.
o Treat the Afghans’ houses well – respect their property.
o Make your troops aware of cultural and religious taboos, and how violating such taboos feeds the adversary’s IO campaign. Provide your troops with a simple list of taboos that to avoid and regularly train them on these taboos.
o Be careful and use discretion when interacting with women. Afghan culture considers women as “people who belong to the home.” Men’s dominant attitude will make it hard for you to ensure female contribution.Ask Afghans about the operations conducted by previously deployed units, and their opinions of those operations. Do not repeat mistakes. Ensure that you record all of your operations for the next turnover.
Remember that interacting with one person or group may offend another. Gain knowledge of and consider the human terrain before making alliances.
Do not increase corruption by forming alliances or otherwise empowering corrupt persons.
o Use relationships with local contacts to vet local or national security force commanders for corruption before allying with them.
o Understand that Afghans have a higher tolerance for (and a different definition of) official corruption.
o Watch for corruption by host nation military, police, or civilians and report it to trustworthy local/regional authorities.…
Build Relationships with Local Influencers
Understand the power base in your village to focus relationship building
Build a trusted network involving personal relationships between Coalition leaders at the tactical level and the civilian and host nation leaders of the population they secure.
Choose which warfighters interact with the locals based on aptitude and abilities.
o Remember which of your troops interacted best with Afghan role players during pre-deployment training. Put them out front and put those that interacted poorly in physical security roles.
o Identify the former farmers, craftsmen, and tradesmen among your troops and leverage their knowledge when dealing with Afghan farmers, craftsmen, and tradesmen.
o Have someone in your unit create a relationship with every key member of the local Shura.Determine who has influence in the area, and understand the traditional and current roles they now play in Afghan societies.
Determine why the person has influence and how he uses it. If that person is friendly to the Coalition mission, determine how we can promote that person’s influence. If that person is not friendly (neutral or adversary), then determine if he can be persuaded to have a more positive government position. People who have influence may include:
o A local mullah, malik, or khan.
o A village elder who has lived within the same 15 kilometers of his house for 60 years.
o An insurgent leader whom the people know will send his subordinates into the village at night to kill them if they do not cooperate.
o A local police chief who is respected for the performance of his duties.
o A local doctor who is constantly treating people.
o A respected Mujahedin warrior who fought the Soviets.
o The local who controls the water distribution.Conduct Key Leader Engagements (KLE) to build relationships with people and entities of influence in your village. The KLE fosters and expands effective communications and cooperation between Coalition forces and local Afghans. Night KLEs are an effective way to talk privately and anonymously with a key leader, and should be arranged in advance so the person knows you are coming. If you live in the village, it is easy to conduct a night KLE unnoticed. The KLE is a cyclic process with 7 steps:
o Step 1, Joint Intelligence Preparation of the Operational Environment (JIPOE): Confirm/deny key leader’s capability in relation to desired effects. Leverage their tribal background, tribal code, religious background, political affiliation, alliances, and/or resources.
o Step 2, Identify Key Leaders: Identify persons or entities of influence, and determine their potential for long term influence.
o Step 3, Identify desired effects: Determine what you want to achieve, identify supporting objectives.
o Step 4, Prepare: Determine who will take the lead, and discuss social nuances.
o Step 5, Execute: Demonstrate mutual respect and Afghan meeting etiquette. Be patient, be an active listener, focus on objective, instill local ownership in solutions.
o Step 6, Debrief/Report: Conduct after action review (AAR), establish continuity of all KLEs at all levels of command.
o Step 7, Re-Engage: Sustain/maintain relationship, maximize civil-military cooperation, and monitor key leader development and protection.…
Build Trust Through Actions
Conduct activities to address the needs of the local power base
Consider the possible unintended consequences of your actions before engaging the local leaders. Does support for one person or group, marginalize another and drive them to the adversary? Be seen as impartial until you are certain of the situation.
Establish combat outposts near local power brokers and initiate patrols with the locals under legitimate GIRoA authority/influence.
Give the Afghan people a reason to support their government, the ANSF and us.Protect the Afghan people. Do whatever you can to prevent Afghan civilian casualties of any type, from any source.
o Take ownership over knowing and protecting the local populace, as the police would do in the US.
o Not all locals are guilty! You must protect the people and leverage them in finding the guilty ones.Provide medical aid to locals through tailgate or pre-planned Medical Civic Action Programs (MEDCAPs) or Veterinary Civil Action Programs (VETCAPs). Some locals will only approach US warfighters during a medical emergency. While treating them or their family member, ask them about their home and other aspects of their daily life to begin building a relationship. To the maximum extent possible, local medical aid should be delivered through the local medical providers in order to manage long-term expectations of GIRoA medical care.
Live and train with your ANSF counterparts, incorporating them directly into your formations. Only linking up for operations is not good enough.
Demonstrate personal bravery, commitment, and hardship when providing physical security to Afghans.
o Act in accordance with US military professionalism.
o Learn when to remove body armor.
o Do not automatically jump to using direct fire that may kill innocent civilians; instead close on the adversary with the weapons, tactics and leadership possessed by your unit or by the ANSF unit you are partnered with.
o Provide security at day and night. The populace will appreciate the security you provide. In some cases, attacks may lessen because the elders will not allow them in that area.Reward Afghan bravery.
o Reward bravery through GIRoA when opportunities allow.
o Create an award and award ceremony to reward ANA/ANSF bravery, such as a “Certificate of Accommodation” to Afghan individuals/units assigned to work with Coalition units. One local Afghan Commander has a 1-inch binder, of which he is quite proud: It is full of paper certificates of recognition signed by previous US Commanders.…
Collect on the Human Terrain
Gather and record data on individuals’ relationships to each other and to the adversary networks
Refine intelligence collection from the bottom-up by soliciting input from subordinate units to validate, invalidate, or refine the intelligence picture created.When questioning Afghans, never use the term “Taliban” in reference to the adversary. The term holds admirable connotations to the Afghan people as its true meaning, “Student of Religion.”
Take a camera everywhere you go. With their permission, take pictures of everyone and build this information into a local ‘phonebook.’ Play into their bias of you being a dumb American who knows nothing: ask everything about people. Have a process for downloading the photos every day, and capturing names and other information associated with the person. Create relevant intelligence questions for your troops to ask tomorrow about specific people. Share important information on who’s who (elders, suspected adversary, criminals, friends, etc.).
o Always ask village elders for permission to take pictures and record information in the village. Explain why (so that they can be identified by name and to help build better relationship between the village and the unit). Most village elders will allow this to prove they have nothing to hide.
o Collect a photo, name, friends’ names, brother’s name, etc. for every house in your village. For every person who lives there, take biometrics. Eventually you will have 4,000 pictures of locals that you can use to stimulate dialogues. (“Please tell me about him.”)
When conducting tactical questioning, ask Afghans questions in indirect ways:
o Example: To find the location of fuel stores that could be used for IEDs, ask about how the crops are doing, where they are getting supplies from, and do they have enough fuel for that, etc.; instead of asking the question directly.
o Example: When lights are on in a house at night, check it out. One squad found a wedding celebration. They stayed and built relationships that later led to good intelligence.
o Example: Do not ask, “Who are the adversaries?” They will not say, but they will see increased vehicle traffic, strangers, operations, and hear about injured people. If you gain their trust, ask about new people coming into the area, or ask how and where their child was hurt. Indirectly, they can tell you who is causing harm in the area.
The 13th Warrior – Full Movie
STASI-EXPERTE: RUFMORD AN JUSTIZMINISTER IST STASI-RACHE-AKT
Video – Pompes, self-defense et seins nus : bienvenu à l’école des femen
Elles n’ont que pour seule arme… leurs seins. Depuis 2008, les Femen se sont fait un nom en manifestant un peu partout en Europe, la poitrine à l’air. Nées en Ukraine, ces féministes activistes d’un nouveau genre ont ouvert récemment un centre d’entraînement dans le XVIIIe arrondissement à Paris, dans une petite salle perchée au 1er étage du Lavoir moderne.
STASI-Opfer dokumentieren die Morde und die Mordstudie von STASI-Oberst Ehrenfried Stelzer
TMZ – Kim Kardashian — Making America Proud!
DHS-FBI Suspicious Activity Reporting Bulletin: Misrepresentation – SECRET

(U//FOUO) Terrorists might use disguises, fraudulent or stolen credentials, and cloned or repurposed vehicles to gain access to restricted areas, to blend in with their surroundings when conducting surveillance, or to conceal other activities while planning or executing an attack. Anders Breivik, the gunman who was sentenced to 21 years in prison for the July 2011 attack on the Workers’ Youth League summer camp in Norway, wore a police uniform and displayed false identification to gain unauthorized access to the camp. Depending on the target, disguises might be aimed at impersonating law enforcement, emergency services, or officials of an institution who have legitimate access to secured/restricted sites.
(U//FOUO) The following SAR incidents from the NSI shared space demonstrate types of behavior terrorists might exhibit during planning or actual attacks. Although none were linked to terrorist activity, we consider the examples relevant for situational awareness and training:
— (U) A security officer at a critical infrastructure site approached two individuals who displayed badges and holstered hand guns and claimed to be “homeland security” personnel conducting an investigation. The individuals refused to identify themselves and directed the officer to stay back. Subsequent investigation revealed the individuals were not authorized homeland security/law enforcement officials.
— (U) A subject, who falsely claimed to be an undercover FBI agent, contacted a security officer at an indoor concert arena in an attempt to obtain security plans for the building. He presented a fake business card that identified him as a special agent with the FBI and was later arrested and charged with impersonating a police officer.
(U) Possible Indicators of Misrepresentation
(U//FOUO) The following activities might indicate attempts at misrepresentation and fraudulent impersonation. Depending on the context—time, location, personal behaviors, and other indicators—suspicious persons who attempt to access restricted areas under disguise or using questionable credentials should be reported to appropriate authorities.
— (U//FOUO) Presentation of outdated, expired, tampered with, or otherwise invalid credentials, including documents displaying photographs that don’t match the individual.
— (U//FOUO) Display of uniform without proper identification, or use of partial uniforms and props such as mock weapons to access restricted areas.
— (U//FOUO) Attempt to gain entry by using stolen access cards or special keys.
— (U//FOUO) Attempt to discourage security personnel from requesting proof of identification by evoking authority or displaying intimidating behavior.
— (U//FOUO) Use of one’s legitimate credentials to access areas outside his or her scope of responsibilities (insider threat).
— (U//FOUO) Use of cloned emergency vehicles where the identifiers (decals, markings, logos) differ slightly from the official government or industry vehicles.
Born of Hope – Full Movie
Born of Hope is an independent feature film inspired by the Lord of the Rings and produced by Actors at Work Productions in the UK.
http://www.bornofhope.com
Thanks to Chris Bouchard and the H4G team for putting the film here. For more films by the makers of this and BoH extras please visit.
ActorsatWork
http://www.youtube.com/actorsatwork
Check them out for more videos regarding the film including the audio commentary.
http://www.youtube.com/watch?v=elt_l8zisik
A scattered people, the descendants of storied sea kings of the ancient West, struggle to survive in a lonely wilderness as a dark force relentlessly bends its will toward their destruction. Yet amidst these valiant, desperate people, hope remains. A royal house endures unbroken from father to son.
This 70 minute original drama is set in the time before the War of the Ring and tells the story of the Dúnedain, the Rangers of the North, before the return of the King. Inspired by only a couple of paragraphs written by Tolkien in the appendices of the Lord of the Rings we follow Arathorn and Gilraen, the parents of Aragorn, from their first meeting through a turbulent time in their people’s history.
EANS-News: Statement of Magister Bernd Pulch
Company Information/bernd pulch
London (euro adhoc) – My name is Bernd Pulch, I have studied and
acquired the title Master (Magister) according to the academic laws.
Link to my Master´s thesis
http://www.kepplinger.de/search/node/pulch
and
http://www.kepplinger.de/node/50
I am the heir of the family bible and can therefore represent our
family based on this authority.
My family, my friends and I have be stalked in the internet and real
life, blackmailed and threatened by the serial criminals of “GoMoPa” which is an anonymous company with no real persons responsable and a fake impressum.
Even the name Goldman, Morgenstern & Partners is a fake. These persons have never existed as members of “GoMoPa”, the criminal organisation. All news of them are fakes.
Therefore we have informed the police. The relevant cases are in
Wiesbaden ( ST/0148943/2011), Hamburg (2100 Js 1108 / 10) and Berlin
(110228-0831-037199)
All activities seem to be in connection with the so called Finance
Agency of “GoMoPa” which has already been sued by many persons and
companies for example by Wirecard and Meridian Capital.
Our family has and had many members who work and worked successfully
as entrepreneurs, secretaries of state, banker, lawyers, farmers,
politicians and also journalists.
We will prevent that our family name is violated.
I will therefore prosecute these criminals with the help of the
police. Magister Bernd Pulch London
end of announcement euro adhoc
——————————————————————————–
Further inquiry note:
Bernd Pulch
General Global Media Ltd
London
office@generalglobalmedia.com
Branche: Economy, Business & Finance
ISIN:
WKN:
Börsen: London Stock Exchange (LSE) / Open Market / Entry Standard
See the press release of me in the media
Cryptome – Did Jill Kelley Breakfast at the White House?
|
TMZ – The Hottest Olympian EVER…in a Bikini!
Unveiled – Pentagon Forgets to BCC Bradley Manning Journos
|
The Client List (2010) – Full Movie – Jennifer Love Hewitt
Confidential – DHS-FBI Bulletin: Indicators of Suspicious Behaviors at Hotels

(U//FOUO) Known or possible terrorists have displayed suspicious behaviors while staying at hotels overseas—including avoiding questions typically asked of hotel registrants; showing unusual interest in hotel security; attempting access to restricted areas; and evading hotel staff. These behaviors also could be observed in U.S. hotels, and security and law enforcement personnel should be aware of the potential indicators of terrorist activity.
(U//FOUO) Possible indicators of terrorist behaviors at hotels: The observation of multiple indicators may represent—based on the specific facts or circumstances—possible terrorist behaviors at hotels:
— (U//FOUO) Not providing professional or personal details on hotel registrations—such as place of employment, contact information, or place of residence.
— (U//FOUO) Using payphones for outgoing calls or making front desk requests in person to avoid using the room telephone.
— (U//FOUO) Interest in using Internet cafes, despite hotel Internet availability.
— (U//FOUO) Non-VIPs who request that their presence at a hotel not be divulged.
— (U//FOUO) Extending departure dates one day at a time for prolonged periods.
— (U//FOUO) Refusal of housekeeping services for extended periods.
— (U//FOUO) Extended stays with little baggage or unpacked luggage.
— (U//FOUO) Access or attempted access to areas of the hotel normally restricted to staff.
— (U//FOUO) Use of cash for large transactions or a credit card in someone else’s name.
— (U//FOUO) Requests for specific rooms, floors, or other locations in the hotel.
— (U//FOUO) Use of a third party to register.
— (U//FOUO) Multiple visitors or deliveries to one individual or room.
— (U//FOUO) Unusual interest in hotel access, including main and alternate entrances, emergency exits, and surrounding routes.
— (U//FOUO) Use of entrances and exits that avoid the lobby or other areas with cameras and hotel personnel.
— (U//FOUO) Attempting to access restricted parking areas with a vehicle or leaving unattended vehicles near the hotel building.
— (U//FOUO) Unusual interest in hotel staff operating procedures, shift changes, closed-circuit TV systems, fire alarms, and security systems.
— (U//FOUO) Leaving the property for several days and then returning.
— (U//FOUO) Abandoning a room and leaving behind clothing, toiletries, or other items.
— (U//FOUO) Noncompliance with other hotel policies.
FEMEN uncensored – Video
Strafanzeigen gegen “GoMoPa” in der Presse
Downloaden Sie die Dokumentation hier:
SECRET – Defense Security Service Guide to Marking Classified Information

efense Security Service Center for Development of Security Excellence
- 43 pages
- October 2012
Marking is the principal way of letting holders of information know the specific protection requirements for that information. Markings and designations serve several purposes; specifically, they:
• Alert holders to the presence of classified information, information protected under the Freedom of Information Act (FOIA), and technical information with restrictions on its dissemination
• Identify, as specifically as possible, the exact information needing protection
• Indicate the level of classification and any other markings for control of the information
• Provide guidance on information sharing
• Provide guidance on downgrading (if any) and declassification
• Give information on the source(s) and reason(s) for classification or other restrictions
• Warn holders of special access, control, or safeguarding requirementsThis guide gives Department of Defense (DoD) staff and contractors an overview of the kinds of marking required to protect classified and unclassified controlled information that cannot be disseminated to all audiences. The guide offers an integrated approach to the major requirements for marking and control of information, briefly explaining the reasons for marking and providing examples of correctly marked information. To facilitate information sharing and declassification processes, whenever practicable a classified attachment, addendum, annex, enclosure, or similar section shall be used when classified information constitutes only a small portion of an otherwise unclassified document.
…
TMZ – Heidi Montag — Showin’ Off the Beach Body
Heidi Montag must be absolutely desperate for attention again because she’s back on the beach frolicking in a tiny bikini. Not that we’re complaining or anything…
TOP-SECRET – JIEDDO Attack the Network Field Guide Afghanistan

ATTACK THE NETWORK FIELD GUIDE AFGHANISTAN
- Version 1
- 35 pages
- April 2011
The Attack the Network (AtN) and tactical actions listed in this field guide are from interviews with battalion, company, and platoon warfighters successful in reducing the employment of improvised explosive devices (IEDs) in Afghanistan during 2007-2010. The primary intent of this field guide is to provide a collection of field-tested actions that enabled mission success in a counterinsurgency (COIN) environment with an IED threat.
Background: Recent tactical operations have US forces conducting counterinsurgency against adversaries with improvised explosive device capabilities. The best units quickly realized commonality between COIN and Counter-IED (C-IED) best practices in Afghanistan. Operating effectively along the C-IED Attack the Network line of operations led to COIN success as well as a reduction in the effectiveness of IED attacks.
Intent: This field guide provides small unit leaders and individual Soldiers and Marines a proven collection of actions to focus their efforts while attacking networks. Primarily, these actions consist of mission analysis, briefing, and execution and are adapted for use by these small unit leaders in a population-centric operating environment.
Scope: The operating environment noted here is COIN. The actions noted in this document should be coordinated with doctrine, theater guidance, and unit standard operating procedures (SOP). Attack the Network is an operational approach that consists of building and enabling friendly networks as well as countering threat networks. The development and coordination of these friendly networks might actually become the focus of main effort.
…
Minimize Negative Actions
Reduce collateral damage, understand and mitigate the negative effects of your actions
When conducting kinetic actions, use the most precise weapons available to avoid civilian deaths, injuries and other collateral damage.
No matter what, we will always act with honor, and we will always do what is right.
o Minimize collateral damage. Be prepared to make immediate reparations for collateral damage and do so as necessary.
o Treat the Afghans’ houses well – respect their property.
o Make your troops aware of cultural and religious taboos, and how violating such taboos feeds the adversary’s IO campaign. Provide your troops with a simple list of taboos that to avoid and regularly train them on these taboos.
o Be careful and use discretion when interacting with women. Afghan culture considers women as “people who belong to the home.” Men’s dominant attitude will make it hard for you to ensure female contribution.Ask Afghans about the operations conducted by previously deployed units, and their opinions of those operations. Do not repeat mistakes. Ensure that you record all of your operations for the next turnover.
Remember that interacting with one person or group may offend another. Gain knowledge of and consider the human terrain before making alliances.
Do not increase corruption by forming alliances or otherwise empowering corrupt persons.
o Use relationships with local contacts to vet local or national security force commanders for corruption before allying with them.
o Understand that Afghans have a higher tolerance for (and a different definition of) official corruption.
o Watch for corruption by host nation military, police, or civilians and report it to trustworthy local/regional authorities.…
Build Relationships with Local Influencers
Understand the power base in your village to focus relationship building
Build a trusted network involving personal relationships between Coalition leaders at the tactical level and the civilian and host nation leaders of the population they secure.
Choose which warfighters interact with the locals based on aptitude and abilities.
o Remember which of your troops interacted best with Afghan role players during pre-deployment training. Put them out front and put those that interacted poorly in physical security roles.
o Identify the former farmers, craftsmen, and tradesmen among your troops and leverage their knowledge when dealing with Afghan farmers, craftsmen, and tradesmen.
o Have someone in your unit create a relationship with every key member of the local Shura.Determine who has influence in the area, and understand the traditional and current roles they now play in Afghan societies.
Determine why the person has influence and how he uses it. If that person is friendly to the Coalition mission, determine how we can promote that person’s influence. If that person is not friendly (neutral or adversary), then determine if he can be persuaded to have a more positive government position. People who have influence may include:
o A local mullah, malik, or khan.
o A village elder who has lived within the same 15 kilometers of his house for 60 years.
o An insurgent leader whom the people know will send his subordinates into the village at night to kill them if they do not cooperate.
o A local police chief who is respected for the performance of his duties.
o A local doctor who is constantly treating people.
o A respected Mujahedin warrior who fought the Soviets.
o The local who controls the water distribution.Conduct Key Leader Engagements (KLE) to build relationships with people and entities of influence in your village. The KLE fosters and expands effective communications and cooperation between Coalition forces and local Afghans. Night KLEs are an effective way to talk privately and anonymously with a key leader, and should be arranged in advance so the person knows you are coming. If you live in the village, it is easy to conduct a night KLE unnoticed. The KLE is a cyclic process with 7 steps:
o Step 1, Joint Intelligence Preparation of the Operational Environment (JIPOE): Confirm/deny key leader’s capability in relation to desired effects. Leverage their tribal background, tribal code, religious background, political affiliation, alliances, and/or resources.
o Step 2, Identify Key Leaders: Identify persons or entities of influence, and determine their potential for long term influence.
o Step 3, Identify desired effects: Determine what you want to achieve, identify supporting objectives.
o Step 4, Prepare: Determine who will take the lead, and discuss social nuances.
o Step 5, Execute: Demonstrate mutual respect and Afghan meeting etiquette. Be patient, be an active listener, focus on objective, instill local ownership in solutions.
o Step 6, Debrief/Report: Conduct after action review (AAR), establish continuity of all KLEs at all levels of command.
o Step 7, Re-Engage: Sustain/maintain relationship, maximize civil-military cooperation, and monitor key leader development and protection.…
Build Trust Through Actions
Conduct activities to address the needs of the local power base
Consider the possible unintended consequences of your actions before engaging the local leaders. Does support for one person or group, marginalize another and drive them to the adversary? Be seen as impartial until you are certain of the situation.
Establish combat outposts near local power brokers and initiate patrols with the locals under legitimate GIRoA authority/influence.
Give the Afghan people a reason to support their government, the ANSF and us.Protect the Afghan people. Do whatever you can to prevent Afghan civilian casualties of any type, from any source.
o Take ownership over knowing and protecting the local populace, as the police would do in the US.
o Not all locals are guilty! You must protect the people and leverage them in finding the guilty ones.Provide medical aid to locals through tailgate or pre-planned Medical Civic Action Programs (MEDCAPs) or Veterinary Civil Action Programs (VETCAPs). Some locals will only approach US warfighters during a medical emergency. While treating them or their family member, ask them about their home and other aspects of their daily life to begin building a relationship. To the maximum extent possible, local medical aid should be delivered through the local medical providers in order to manage long-term expectations of GIRoA medical care.
Live and train with your ANSF counterparts, incorporating them directly into your formations. Only linking up for operations is not good enough.
Demonstrate personal bravery, commitment, and hardship when providing physical security to Afghans.
o Act in accordance with US military professionalism.
o Learn when to remove body armor.
o Do not automatically jump to using direct fire that may kill innocent civilians; instead close on the adversary with the weapons, tactics and leadership possessed by your unit or by the ANSF unit you are partnered with.
o Provide security at day and night. The populace will appreciate the security you provide. In some cases, attacks may lessen because the elders will not allow them in that area.Reward Afghan bravery.
o Reward bravery through GIRoA when opportunities allow.
o Create an award and award ceremony to reward ANA/ANSF bravery, such as a “Certificate of Accommodation” to Afghan individuals/units assigned to work with Coalition units. One local Afghan Commander has a 1-inch binder, of which he is quite proud: It is full of paper certificates of recognition signed by previous US Commanders.…
Collect on the Human Terrain
Gather and record data on individuals’ relationships to each other and to the adversary networks
Refine intelligence collection from the bottom-up by soliciting input from subordinate units to validate, invalidate, or refine the intelligence picture created.When questioning Afghans, never use the term “Taliban” in reference to the adversary. The term holds admirable connotations to the Afghan people as its true meaning, “Student of Religion.”
Take a camera everywhere you go. With their permission, take pictures of everyone and build this information into a local ‘phonebook.’ Play into their bias of you being a dumb American who knows nothing: ask everything about people. Have a process for downloading the photos every day, and capturing names and other information associated with the person. Create relevant intelligence questions for your troops to ask tomorrow about specific people. Share important information on who’s who (elders, suspected adversary, criminals, friends, etc.).
o Always ask village elders for permission to take pictures and record information in the village. Explain why (so that they can be identified by name and to help build better relationship between the village and the unit). Most village elders will allow this to prove they have nothing to hide.
o Collect a photo, name, friends’ names, brother’s name, etc. for every house in your village. For every person who lives there, take biometrics. Eventually you will have 4,000 pictures of locals that you can use to stimulate dialogues. (“Please tell me about him.”)
When conducting tactical questioning, ask Afghans questions in indirect ways:
o Example: To find the location of fuel stores that could be used for IEDs, ask about how the crops are doing, where they are getting supplies from, and do they have enough fuel for that, etc.; instead of asking the question directly.
o Example: When lights are on in a house at night, check it out. One squad found a wedding celebration. They stayed and built relationships that later led to good intelligence.
o Example: Do not ask, “Who are the adversaries?” They will not say, but they will see increased vehicle traffic, strangers, operations, and hear about injured people. If you gain their trust, ask about new people coming into the area, or ask how and where their child was hurt. Indirectly, they can tell you who is causing harm in the area.
Point of No Return (1993) – aka the Assassin – Bridget Fonda – Full Movie
Maggie Hayward (Bridget Fonda) is a drug addict found guilty of murdering a police officer, and is sentenced to death by lethal injection. However, her death is faked, and a secret government agent named Bob (Gabriel Byrne) informs her that she is to become an operative. Maggie, having little choice, agrees to cooperate and she begins a regimen of intensive training that includes etiquette and computer use.
Operative Amanda (Anne Bancroft) transforms her into a refined, beautiful woman. She is taken on a dinner date with Bob, who informs her about the first job: an assassination of a VIP eating at the same restaurant. Maggie completes the task, and escapes pursuit by fleeing down a laundry chute. This task was her final test, and she has now completed her training.
The following morning she leaves for Venice, California, where she enters into a romantic relationship with apartment house manager J.P. (Dermot Mulroney). While her first assignments, both hit jobs, are ultimately successful, Maggie quickly comes to hate her work and tries to quit her job as a professional killer. As things progress between her and J.P., she asks for help in leaving the agency. Her request is denied, but Bob agrees to get her out of the agency if she completes the next task.
The new job is to masquerade as Angela (Olivia d’Abo), the girlfriend of Fahd Bakhtiar (Richard Romanus), an Iranian trading in nuclear weapons. However, taking out Angela proves problematic and results in the deaths of Angela’s two bodyguards and the injury of Maggie’s partner, Beth (Lorraine Toussaint). Director Kaufman then sends in Victor, a ‘cleaner’ (Harvey Keitel) to get rid of the bodies. Unknown to Maggie, however, he has also been ordered to kill both agents as well. After killing the wounded Beth in front of Maggie, he drives her to Fahd’s home. At gunpoint she gets Fahd to unlock his computer and reveal his secrets, but he avoids execution and she is forced to flee.
As they purportedly drive back to her residence, Maggie sees a gun in Victor’s waistband and correctly suspects he’s going to kill her. This leads to a struggle and the car spins out of control. Finally, Victor is dragged over a ravine and killed. Maggie makes her way back to her apartment, but leaves sometime during the night. Bob subsequently learns of her disappearance from J.P. As Bob is leaving, he sees Maggie watching him through the mist. Instead of reporting her, though, he calls Kaufman and informs him, after some hesitation, that the cleaner and Maggie are both dead.
WIE MICH DIE “GoMoPa”-SCHEISSHAUSFLIEGEN MIT GOOGLE-EINTRÄGEN ERPRESSEN WOLLTEN
ERPRESSUNG VON MERIDAN CAPITAL DURCH DIE ANONYMEN “GoMoPa”-Scheisshausfliegen (Eigenbezeichnung)
DIE SÜDDEUTSCHE ZEITUNG, DAS HANDELSBLATT UND DIE FAZ ÜBER DIE ERPRESSUNGEN DER “GoMoPa”-Scheisshausfliegen (Eigenbezeichnung) BEISPIEL WIRECARD ETC
TMZ – Petraeus Scandal — The Porn Star Connection
Unveiled – Greek HSBC Swiss Account Holders “Lagarde List”
The following is a list of 2,059 names of Greek citizens that have bank accounts with HSBC’s branch in Geneva, Switzerland. The list was originally published by a Greek magazine called Hot Doc on October 27, 2012 resulting in the arrest of its editor Kostas Vaxevanis for “breach of privacy”. These scanned images of the magazine were originally posted on the website of the Greek television program Zougla. We have taken the images and converted them into a PDF file for easier viewing. The original scanned images of the magazine are also available in a ZIP archive. Thanks to Darker Net for pointing out the scanned images.
| List of 2,059 names in PDF format | 19 pages | Download (5.58 MB) |
| Scanned images of original publication in ZIP archive | Download (48 MB) |
Red Heat – English – Full Movie
Red Heat is a 1988 buddy cop film directed by Walter Hill. The film stars Arnold Schwarzenegger, as Moscow narc Ivan Danko, and James Belushi, as Chicago detective Art Ridžić. Finding themselves on the same case, Danko and Ridžić work as partners to catch a cunning and deadly Soviet Georgian drug kingpin, Viktor Rostavili (Ed O’Ross), who also happens to be the killer of Danko’s previous partner back in Soviet Russia.
The film was released with the tagline “Moscow’s toughest detective. Chicago’s craziest cop. There’s only one thing more dangerous than making them mad: making them partners.” It was the first American film given permission to shoot in Moscow’s Red Square – however, most of the scenes set in the USSR (with the exceptions of the establishing shots under the main titles and the final lengthy shot in Red Square behind the end credits) were actually shot in Hungary. Schwarzenegger was paid a salary of $8 million for his role in the film.[2] It has found a cult audience amongst fluent Russian speakers because of the movie’s weak portrayal of the Russian language and stereotypes.
ZDF:”STASI – GAUCK UND DAS OFFIZELLE ENDE DER STASI
TOP-SECRET – NATO/ISAF Afghanistan Strategic Communications Framework

NATO/ISAF engagement in Afghanistan in 2010 was characterised by a refreshed, comprehensive civ-mil strategy as reflected in a substantial force uplift, significant progress in the growth and development of the Afghan National Security Forces, and discernable campaign progress in priority districts. These were reflected in the NATO/ISAF Strategic Communications Framework 2010 (Ref A). In parallel, political events, including the London Conference, the Consultative Peace Jirga, the Kabul Conference, Afghan Parliamentary elections and the NATO Summit in Lisbon, helped define a clear political roadmap for Afghanistan. These developments are reflected in the Lisbon Summit Declaration which provides political guidance for the focus of our efforts in 2011(Ref B) and reaffirms that NATO’s mission in Afghanistan remains the Alliance’s key priority. Reference B also reflects the priorities outlined in the Kabul Conference (Ref C), including: setting conditions for and beginning Transition, as expressed in the Joint Inteqal/transition paper (Ref D); and developing an enduring NATO and Afghanistan partnership demonstrating the Alliance’s longer-term commitment beyond ISAF’s current mission (ref E). At Lisbon, the Nations also strongly reaffirmed the necessity of a comprehensive and regional approach, fully supported by the international community, to achieve a successful outcome.
Aim. This paper sets out the NATO/ISAF Strategic Communications Framework, based on the Lisbon Summit political guidance, providing the top-level political-military context and guidance to steer NATO/ISAF activities in the communications and information environment in 2011.
StratCom Objectives. The NATO/ISAF StratCom objectives are to:
a. Communicate that stability in Afghanistan is crucial to global security and that NATO/ISAF will never again allow Afghanistan to become a launching pad for international terrorism.
b. In coordination with the Government of the Islamic Republic of Afghanistan (GIRoA), explain and gain support for Transition.
c. Generate the active support of the Afghan people, the GIRoA, Troop Contributing Nations’ (TCNs) populations and International Community for the ISAF mission.
d. Promote NATO’s long-term commitment to Afghanistan in close coordination with GIRoA (ref E).
e. Communicate progress against ISAF campaign objectives and priorities, articulated in theatre-defined measures of effect.
f. Diminish support for the insurgents and criminal patronage networks that are detrimental to the ISAF mission and effective Afghan governance that commands public confidence.
4. StratCom Core Message. The guiding core message for the NATO/ISAF campaign is: “This mission is essential for our shared security. Our strategy is sound, our longterm commitment is solid and with our Afghan partners we will succeed. “
5. StratCom Themes. The following themes are to be promoted to help achieve our StratCom objectives. These themes will, in turn, be reinforced by communications focus topics. Local circumstances will determine the precise manner in which the themes are promoted, but the aim is to leave audiences with the understanding that our mission reflects the following:
Resolve – We are realistic about the challenges we face and our goals. At the Lisbon summit NATO/ISAF reaffirmed a resolve that has been demonstrated over the last year by increased forces, resilience in the face of casualties and a high and effective pace of operations.
Maintain momentum – The effective implementation of our strategy has enabled ISAF and its Afghan partners to increasingly recapture the initiative creating momentum towards success that we will sustain.
Partnership – NATO’s support for Afghanistan will continue beyond the end of the current mission through an enduring partnership. The Afghan people can have confidence in the long-term support of their international partners. NATO/ISAF will work closely with Afghan and international stakeholders, both civilian and military to achieve a stable Afghanistan within a stable region.
Afghan Lead – The clear and sustained strategy of NATO-ISAF and its partners will enable an irreversible transition to Afghan lead. As transition is implemented, the Afghan Government must take increasing responsibility in all areas, including being responsive and accountable to its public.
DOWNLOAD THE ORIGINAL DOCUMENT HERE:
THE RUNNING MAN (1987) Arnold Schwarzenegger – Full Movie
Was sind eigentlich Cyber-Stalker wie “GoMoPa” ?
Unveiled – Paula (Dean) Kranz (Broadwell)
|
SECRET – NATO/KFOR Kosovo Strategic Communications Framework
The following is NATO’s strategic communications framework for operations in Kosovo in both 2011 and 2010. Though unclassified, NATO doctrine and policy documents are not released to the public.
| Kosovo Strategic Communications Framework 2011 | February 21, 2011 | 8 pages | Download |
| Kosovo Strategic Communications Framework 2010 | April 20, 2010 | 8 pages | Download |
1. The mission of KFOR as authorised by the North Atlantic Council (NAC) is to contribute to a safe and secure environment in Kosovo and to support the development of security institutions capable of operating without NATO assistance.
2. In recognition of the improved security situation in Kosovo, KFOR in 2010 began to gradually reduce its force levels and posture by moving to a “Deterrent Presence” (DP) posture. The first phase of KFOR’s move to Deterrent Presence, so-called “Gate One”, was achieved on 31 January 2010. The transition to Gate 2 was approved by the NAC on 26 October 2010 with achievement by March 2011. With the move through Deterrent Presence, NATO will gradually adjust the number of troops deployed in Kosovo. By the time Gate 2 is achieved, KFOR troop levels will be around 5,000 in total.
3. In 2010, the NAC approved the transfer of lead guarding responsibility for a number of Properties with Designated Special Status (PrDSS) from KFOR to the Kosovo Police. Subsequently, the responsibility for four out of the nine PrDSS was transferred to the Kosovo Police. This “unfixing” process is expected to continue, as conditions permit and subject to NAC approval, during 2011.
4. KFOR is assisting in the stand-up and training of the Kosovo Security Force (KSF), an all-volunteer, multi-ethnic, lightly-armed security force under democratic, civilian control. The KSF’s mission is to conduct civil protection operations and to assist civil authorities in responding to natural disasters and other emergencies. KFOR’s training role is limited to assistance and advice in these areas. Initial KSF operating capability was declared on 15 September 2009. As recruitment and training of KSF members proceeds, expectations of a declaration of KSF Full Operational Capability will continue to grow.
5. The adaptation of KFOR’s force posture during 2010 and its unfixing from Properties with Designated Special Status have been supported by an effective strategic communications (StratCom) approach which has been closely coordinated at all stages throughout the NATO chain of command and NATO HQ. Continued StratCom efforts will be required to complement and support military and civilian activities during 2011 as KFOR’s footprint and posture continues to adapt and as progress is made toward mission achievement.
Aim
6. The aim of this framework is to establish NATO’s StratCom objectives, themes and messages in Kosovo for 2011, which will guide all NATO/KFOR activities in the communications and information environment.
Stratcom Core Message
7. The guiding core message is that:
“NATO is committed to contributing to a safe and secure environment within Kosovo, according to its mandate.”
StratCom Objectives
8. NATO’s StratCom objectives in Kosovo are to:
a. secure and maintain the understanding and support of the Kosovo population, regional actors, Troop Contributing Nations’ populations and the International Community for NATO’s mission in Kosovo;
b. dissuade and deter those that might wish to conduct or support destabilizing activities, and isolate them from public support;
c. engage and enlist support from those who, by their actions or implicit authority, can prevent destabilizing activities;
d. engage and encourage support from non-NATO organisations and entities for the continued development of Kosovo as a stable entity within the Balkans region;
e. demonstrate sustainable progress in the overall security situation and in the capability of local security institutions to effectively play their respective roles in the security sector;
f. build trust in local security institutions and EULEX in line with KFOR’s role as third responder.
StratCom Themes
9. The following themes are to be promoted to help our StratCom objectives. These themes will, in turn, be reinforced by communications focus topics. Local circumstances will determine the precise manner in which the themes are promoted, but the aim is to leave audiences with the understanding that our mission reflects the following:
Commitment – The Alliance’s continued commitment to stability, security and multi-ethnicity in Kosovo through political dialogue and democratic processes which, in turn, will contribute to security of the wider Western Balkans region;
Confidence and Trust – NATO’s support to building confidence and trust within all communities in the impartiality and capability of local security institutions in Kosovo, allowing NATO-led forces to hand over lead responsibility for specific tasks to those institutions where conditions permit;
Cooperation – NATO’s determination to work in close cooperation with International Community partners and civil authorities, including other international actors and the institutions in Kosovo, with KFOR as the third responder, and in accordance with its UN mandate, to ensure a safe and secure environment in Kosovo;
Capacity-Building – NATO/KFOR’s support for the development of civil protection capacity by the Kosovo Security Force as a multi-ethnic, lightly-armed, all-volunteer security force under democratic civilian control. In addition, NATO/KFOR support to the Kosovo Police to facilitate handover of border and boundary responsibilities and guarding duties at PrDSS;
Create Conditions – NATO’s role is to contribute to a safe and secure environment Kosovo-wide, thus creating conditions for dialogue amongst all stakeholders to support broader democratic, economic and social progress.
TMZ – Star Wars & Rosa Parks — Together at Last
SECRET – NATO Operation Ocean Shield Counter-Piracy Strategic Communications Framework

1. OPERATION OCEAN SHIELD was launched by the North Atlantic Council on 17 August 2009. NATO is conducting counter-piracy activities as part of an internationally recognised and supported effort in a region of strategic interest to the Alliance. NATO’s commitment is as a complementary player in coordination with the other international counter-piracy actors including the EU’s Operation ATALANTA, CTF-151, and individual nations.
2. In 2010, Allies agreed to prolong OPERATION OCEAN SHIELD to the end of 2012. In addition, they agreed to extend the Joint Operations Area, to increase the scope of port visits by deployed forces and to escort UN vessels to the harbour entrance of Mogadishu. Improved adoption of Best Management Practices (BMP) and the use self-protection measures by the merchant shipping industry has also had a positive effect. However, notwithstanding these initiatives and the combined efforts of the international counter-piracy actors, the scope and intensity of pirate activity off the Horn of Africa has continued to grow. While the incidence of piracy within the Gulf of Aden/Internationally Recognised Transit Corridor (IRTC) has been reduced to a low level, the total number of attacks has grown and the pirates’ increasing use of mother ships is allowing them to act with impunity.
3. The operational challenges facing NATO and its international partners are further compounded by increasing levels of frustration on the part of the shipping industry and regional actors. At the end of 2010, NATO Allies agreed to conduct a strategic review of all aspects of NATO’s counter-piracy efforts within the context of NATO’s overall maritime operations. A final report with recommendations should be endorsed by NATO Defence Ministers at their June 2011 meeting. The outcome of this review may lead to subsequent amendment to this framework document.
StratCom Core Message
4. The guiding StratCom Core Message for OPERATION OCEAN SHIELD is that: “NATO is committed to a collaborative response to counter-piracy off the Horn of Africa in response to the UN request for protecting the safety of the commercial maritime routes and international navigation.”
StratCom Objectives
5. Faced with a growing piracy challenge and the potential for critical media reporting of NATO’s contribution to international counter-piracy action, the 2011 OPERATION OCEAN SHIELD StratCom objectives are to:
a. clearly explain the scope and limitations of NATO’s OPERATION OCEAN SHIELD counter-piracy mission, and win the understanding and active support of the population of the Joint Operations Area, Somalia and neighbouring states, Troop Contributing Nations’ populations and the international community;
b. demonstrate and illustrate the contribution being made to OPERATION OCEAN SHIELD in contributing to international efforts to disrupt acts of piracy off the Horn of Africa;
c. dissuade audiences in the Joint Operations Area, Somalia and neighbouring states from conducting and supporting acts of piracy and armed robbery.
StratCom Themes
6. To be effective, messages, images and actions must be clear, coordinated and synchronized. Four themes are to be promoted during 2011. The ways in which these themes are articulated and demonstrated is to be determined on the basis of local circumstances, but the aim is to leave the audiences with an impression that our mission reflects the following:
a. NATO Responsiveness and Commitment – Within the context of an international collaborative response, NATO has the resolve, capability and commitment to confront threats to international security. Piracy is a threat to regional maritime trading activities, and the strategic interests of NATO Allies, which must be vigorously countered;
b. Cooperation – Maritime cooperation, coordination and complementarities with the other maritime Task Forces and individual navies are essential to fight piracy. The level of cooperation between these forces, and with merchant shipping organisations, is at an unprecedented high;
c. Capacity Building – within means, and subject to the agreement of Allies, NATO is receptive to requests for support from regional states to build regional counter-piracy capacity over the mid- to long-term in complementarity with other international efforts;
d. Realism – piracy off the Horn of Africa is one symptom of deeper political, developmental and security issues in the region. Solutions to these deeper problems lie beyond the means of NATO and require a comprehensive approach by the international community. Moreover, the geographic extent over which acts of piracy are attempted and limited number of assets available means that while NATO ships are proving to be effective at disrupting acts of piracy, the threat itself remains an international concern.
…
KEY MESSAGES – JANUARY 2011
– The root causes of piracy off the Horn of Africa lie ashore and will require a determined effort from the international community to address.
– In close coordination with other international organisations and individual nations, NATO is engaged in countering the piracy threat.
– NATO is conducting counter-piracy operations in support of UN Security Council Resolutions in order to deter piracy activities off the Horn of Africa.
– OPERATION OCEAN SHIELD is a clear sign of the Alliance’s determination to play a role in the international efforts in the maritime field, and its flexibility in meeting the variety of challenges posed in today’s security environment.
– NATO coordinates and complements its efforts with other nations and organisations engaged in counter-piracy activities in and around the Horn of Africa.
– NATO engages at the local, regional and international level in order to deter, prevent and disrupt piracy activities off the Horn of Africa.
– NATO’s Standing Naval Maritime Groups are a multinational force that possesses the expertise, professionalism and experience to accomplish the mission. NATO welcomes contributions by other nations to join in NATO’s counter-piracy efforts.
– NATO supports efforts to develop counter-piracy capacity in and around the Horn of Africa in order to enhance maritime security in the region within the framework of the Contact Group on Piracy off the Coast of Somalia.
– NATO provides an effective and value-added contribution to counter-piracy efforts off the Horn of Africa, in coordination with and complementary to other nations and organisations.
– This operation continues the valuable contribution to maritime security made by NATO in support of World Food Programme humanitarian assistance activities during its earlier OPERATION ALLIED PROVIDER and OPERATION ALLIED PROTECTOR. NATO is open to further requests to provide similar support.
– NATO, through its activities and visible presence, is disrupting an increasing number of pirate attacks, although the total number of attacks continues to increase.
TOP-SECRET-NATO Libyan Military Intervention Strategic Communications Framework

1. Following the popular uprising which began in Benghazi on 17 Feb 2011, Libya remains highly unstable and violent. The UN Security Council adopted Resolution 1970 imposing sanctions, instituting an arms embargo, freezing personal assets of Libya’s leaders, and imposing a travel ban on senior figures. This was followed on 17 March with UNSC Resolution 1973 calling for the implementation of a No-Fly-Zone and authorizing all necessary means to protect civilians.
2. NATO has established 24/7 airborne surveillance of the central Mediterranean and deployed maritime assets to the central Mediterranean. On 22 March, the NAC approved an execution directive allowing NATO forces to interdict violations of the arms embargo. On 24 March, the NAC agreed to start operations to establish a no-fly-zone over Libya, and on 27 March, the NAC agreed to launch operations to protect civilians and civilian-populated areas under threat of attack in Libya. At the meeting of NATO Foreign Ministers in Berlin on 14 April, Allies laid down conditions for an acceptable ceasefire, including regime withdrawal of all its military forces from populated areas they have forcibly entered. It also strongly endorsed the international Contact Group’s call for Qadhafi to leave power.
3. A coordinated and integrated StratCom approach to support NATO action in response to events in Libya is key to achieving the Alliance’s overall objective. Managing the information domain will be critical to NATO’s efforts being understood – and ultimately supported – by the audiences. It will require the use of the full range of information and communication capabilities, in line with NATO policies and authorities establishing an appropriate level of NATO visibility will be important to ensure unity of message, to manage and shape perceptions, to counter potential misinformation and to build public support.
Aim
4. This paper sets out the NATO Strategic Communications Framework, based on political guidance, providing top-level political-military context and guidance to steer NATO’s activities in the communications and information environment during NATO activities in support of UNSCRs 1970, 1973 and Operation UNIFIED PROTECTOR (OUP).
5. StratCom Objectives
a) All audiences clearly understand NATO’s mandate and the scope of its actions, which are seen as a positive contribution to help mitigate the crisis, in support of UNSCRs 1970 and 1973.
b) Support for NATO’s actions is fostered and sustained, regionally and more widely within the International Community.
c) Communications activities and messages by NATO are seen as integrated with other players, including partner nations that are taking an active role.
d) StratCom activities contribute to enhancing cohesion in the Alliance and the wider coalition.
e) Those actors which may contribute to a worsening of the humanitarian situation and/or seek to undermine NATO actions are deterred from doing so. StratCom Core Message
6. The guiding core message for NATO operations and activities in and around Libya is :
“NATO’s operations are taking place in support of the UNSCRs 1970 and 1973 as part of the broad international effort. All NATO allies are committed to meet their responsibilities under the UN Security Council Resolution to stop the violence against the Libyan people and in support of their legitimate aspirations.”
StratCom Themes
7. The following themes are to be promoted to help achieve our StratCom objectives. These themes will, in turn, be reinforced by communications focus topics. Local circumstances will determine the precise manner in which the themes are promoted, but the aim is to leave audiences with the understanding that our mission reflects the following:
a) Responsibility – NATO is a responsible international actor and takes its obligations seriously. There is a clear and unambiguous responsibility to protect the Libyan people. NATO, as a multinational military alliance whose core tasks include crisis management, is best placed to help.
b) Legitimacy & Support – NATO is operating under a clear international legal mandate, in coordination with the Contact Group on Libya, and with broad regional support.
c) Commitment – NATO Allies are committed to use all necessary measures to protect Libyan civilians from violence or threat of violence, and to uphold the strong and clear mandate from the United Nations.
d) Resolve – NATO has the means and political resolve to sustain the effort against the regime until the will of the international community is obeyed by Qadhafi.
e) Cooperation & Realism – NATO is cooperating with a broad range of other actors, locally and regionally, and within the context of a larger international response. The crisis cannot be resolved by military action alone.
f) NATO as a Crisis Manager – NATO’s action is in line with NATO’s New Strategic Concept that commits NATO “to prevent crises, manage conflicts” in close consultation with its international partners, as they may affect Alliance security.
DOWNLOAD THE ORIGINAL DOCUMENT HERE:
MISSION TO MARS – FULL MOVIE
Bonner Presseblog warnt vor Cyber-Stalkern im Internet
TMZ – Courtney Stodden — She Has a Mom!?
Unveiled – UNODC Report: The Use of the Internet for Terrorist Purposes

UNITED NATIONS OFFICE ON DRUGS AND CRIME THE USE OF THE INTERNET FOR TERRORIST PURPOSES
- 158 pages
- September 2012
Technology is one of the strategic factors driving the increasing use of the Internet by terrorist organizations and their supporters for a wide range of purposes, including recruitment, financing, propaganda, training, incitement to commit acts of terrorism, and the gathering and dissemination of information for terrorist purposes. While the many benefits of the Internet are self-evident, it may also be used to facilitate communication within terrorist organizations and to transmit information on, as well as material support for, planned acts of terrorism, all of which require specific technical knowledge for the effective investigation of these offences.
It is a commonly accepted principle that, despite the heinous nature of their acts, alleged terrorists should be afforded the same procedural safeguards under criminal law as any other suspects. The defence of human rights is a core value of the United Nations and a fundamental pillar of the rule-of-law approach to the fight against terrorism. The present publication accordingly highlights the importance of respect for the principles of human rights and fundamental freedoms at all times and, in particular, in the context of the development and implementation of legal instruments related to countering terrorism.
…
7. The Internet may be used not only as a means to publish extremist rhetoric and videos, but also a way to develop relationships with, and solicit support from, those most responsive to targeted propaganda. Terrorist organizations increasingly use propaganda distributed via platforms such as password-protected websites and restricted-access Internet chat groups as a means of clandestine recruitment. The reach of the Internet provides terrorist organizations and sympathizers with a global pool of potential recruits. Restricted access cyberforums offer a venue for recruits to learn about, and provide support to, terrorist organizations and to engage in direct actions in the furtherance of terrorist objectives. The use of technological barriers to entry to recruitment platforms also increases the complexity of tracking terrorism-related activity by intelligence and law enforcement personnel.
…
15. Online payment facilities may also be exploited through fraudulent means such as identity theft, credit card theft, wire fraud, stock fraud, intellectual property crimes and auction fraud. An example of the use of illicit gains to finance acts of terrorism can be seen in the United Kingdom case against Younis Tsouli (see para. 114 below). Profits from stolen credit cards were laundered by several means, including transfer through e-gold online payment accounts, which were used to route the funds through several countries before they reached their intended destination. The laundered money was used both to fund the registration by Tsouli of 180 websites hosting Al-Qaida propaganda videos and to provide equipment for terrorist activities in several countries. Approximately 1,400 credit cards were used to generate approximately £1.6 million of illicit funds to finance terrorist activity.
…
17. In recent years, terrorist organizations have increasingly turned to the Internet as an alternative training ground for terrorists. There is a growing range of media that provide platforms for the dissemination of practical guides in the form of online manuals, audio and video clips, information and advice. These Internet platforms also provide detailed instructions, often in easily accessible multimedia format and multiple languages, on topics such as how to join terrorist organizations; how to construct explosives, firearms or other weapons or hazardous materials; and how to plan and execute terrorist attacks. The platforms act as a virtual training camp. They are also used to share, inter alia, specific methods, techniques or operational knowledge for the purpose of committing an act of terrorism.
18. For example, Inspire is an online magazine allegedly published by Al-Qaida in the Arabian Peninsula with the stated objective of enabling Muslims to train for jihad at home. It contains a large amount of ideological material aimed at encouraging terrorism, including statements attributed to Osama Bin Laden, Sheikh Ayman al-Zawahiri and other well-known Al-Qaida figures. The fall 2010 edition included practical instructional material on how to adapt a four-wheel-drive vehicle to carry out an attack on members of the public and how a lone individual could launch an indiscriminate attack by shooting a gun from a tower. The publication even suggested a target city for such an attack, in order to increase the chances of killing a member of the Government.
…
1. Systematic approach to investigations involving the Internet
202. There is a vast range of data and services available via the Internet which may be employed in an investigation to counter terrorist use of the Internet. A proactive approach to investigative strategies and supporting specialist tools, which capitalizes on evolving Internet resources, promotes the efficient identification of data and services likely to yield the maximum benefit to an investigation. In recognition of the need for a systematic approach to using technological developments relating to the Internet for investigative purposes, the Raggruppamento Operativo Speciale of the Carabinieri of Italy developed the following guidelines, which have been disseminated through the University College Dublin, master’s programme in forensic computing and cybercrime (see section IV.G below) and implemented by domestic enforcement authorities of many member States of the International Criminal Police Organization (INTERPOL) and the European Police Office (Europol):
Protocol of a systematic approach
- Data collection: This phase involves the collection of data through traditional investigative methods, such as information relating to the suspect, any co-inhabitants, relevant co-workers or other associates and information compiled through conventional monitoring activities of channels of communication, including in relation to fixed-line and mobile telephone usage.
- Research for additional information available via Internet-based services: This phase involves requests to obtain information collected and stored in the databases of webbased e-commerce, communications and networking services, such as eBay, PayPal, Google and Facebook, as well as using dedicated search engines such as http://www.123people.com. Data collected by these services through commonly used Internet “cookies” also provide key information regarding multiple users of a single computer or mobile device.
- The activities in phases (a) and (b) above provide information that may be combined and cross-referenced to build a profile of the individual or group under investigation and made available for analysis during later stages of the investigation.
- VoIP server requests: In this phase, law enforcement authorities request information from VoIP service providers relating to the persons under investigation and any known affiliates or users of the same networking devices. The information collected in this phase may also be used as a form of “smart filter” for the purposes of verifying the information obtained in the two prior phases.
- Analysis: The large volume of data obtained from VoIP servers and the providers of various Internet services are then analysed to identify information and trends useful for investigative purposes. This analysis may be facilitated by computer programs, which may filter information or provide graphic representations of the digital data collected to highlight, inter alia, trends, chronology, the existence of an organized group or hierarchy, the geolocation of members of such group, or factors common among multiple users, such as a common source of financing.
- Identification of subjects of interest: In this phase, following smart analysis of the data, it is common to identify subjects of interest based, for example, on subscriber information linked to a financial, VoIP or e-mail account.
- Interception activity: In this phase, law enforcement authorities employ interception tactics similar to those used for traditional communication channels, shifting them to a different platform: digital communication channels. Interception activity may be undertaken in connection with telecommunications services, such as fixed-line broadband, mobile broadband and wireless communications, as well as with regard to services provided by ISPs, such as e-mail, chat and forum communication services. In particular, in recent years experience has revealed vulnerabilities in new communications technologies which may be exploited for investigative or intelligence-gathering purposes. Due care should be taken with respect to ensuring the forensic integrity of the data being gathered and the corroboration, to the extent possible, of any intelligence gathered with objective identifiers such as GPS coordinates, time stamps or video surveillance.
Where permitted by domestic law, some law enforcement authorities may also employ digital monitoring techniques facilitated by the installation of computer hardware or applications such as a virus, a “Trojan Horse” or a keystroke logger on the computer of the person under investigation. This may be achieved through direct or remote access to the relevant computer, taking into consideration the technical profile of the hardware to be compromised (such as the presence of antivirus protections or firewalls) and the personal profile of all users of the device, targeting the least sophisticated user profile.
…
428. Public-private partnerships specifically targeting terrorist use of the Internet could also provide a means to promote clear guidelines regarding information-sharing between the private and public sector, consistent with applicable data protection regulations. A good basis for information-sharing guidelines is provided by the Council of Europe “Guidelines for the cooperation between law enforcement and Internet service providers against cybercrime”. The focus of these guidelines is the establishment of relationships of mutual trust and cooperation between public and private sector stakeholders as a foundation for cooperation. The guidelines also emphasize the need to promote efficient and cost-effective cooperation procedures. Law enforcement authorities and Internet service providers are encouraged to engage in information exchange to strengthen their capacity to identify and combat cybercrime through regular meetings and the sharing of good practices and feedback. The guidelines also encourage the establishment of formal partnerships and written procedures as a basis for longer-term relationships, to ensure, inter alia, that appropriate protections are provided that the partnership will not infringe upon the legal rights of industry participants or the legal powers of law enforcement authorities.
429. Recommended measures to be taken by law enforcement authorities pursuant to the guidelines include:
- Engaging in broad strategic cooperation with ISPs, including by conducting regular technical and legal training seminars, as well as providing feedback on investigations conducted or intelligence gathered, based on ISP-initiated reports/complaints
- Providing explanations and assistance to ISPs regarding investigation techniques not directly related to the case at hand, in order to facilitate an understanding of how ISP cooperation will result in more efficient investigations
- Prioritizing requests for large volumes of data while avoiding unnecessary cost and disruption of business operations.
430. Recommended measures to be taken by Internet Service providers pursuant to the guidelines include:
- Cooperating to minimize the use of services for illegal purposes
- Reporting criminal activity to law enforcement authorities
- When possible, providing a list, upon request, of which types of data could be made available for each service to law enforcement, upon receipt of a valid disclosure request.
431. Public-private partnerships may also provide a forum to promote minimum standards for the secure retention of data by private sector stakeholders and enhance the channels of communication for the provision of information by private sector stakeholders regarding suspicious activities.
A.I. Artificial Intelligence – Steven Spielberg – Stanley Kubrick – Full Movie
Opfer fragen: VON RUFMÖRDERN u. Serienbetrügern erfundene “GoMoPa-SJB”: “Wer stoppt Google-Rufmord für Resch, Bennewirtz und Ehlers ?”
TOP-SECRET – NATO Military Concept for Strategic Communications

MILITARY CONCEPT FOR NATO STRATEGIC COMMUNICATIONS
- 15 pages
1-1. Strategic Communications (StratCom) has emerged as an increasingly vital field of Alliance endeavour in recent years. There have been several attempts to address Strategic Communications in an Alliance context, including the publication of a North Atlantic Council endorsed NATO Strategic Communications Policy, the publication of Strategic Command directives, and the establishment of positions in various headquarters to lead its implementation.
1-2. Despite the high level of interest and attention, Strategic Communications is still a field in its initial stages of development, both for the Alliance and the Nations.
1-3. All aspects of NATO activities have a critical information and communications component. This concept proposes that Strategic Communications is not an adjunct activity, but should be inherent in the planning and conduct of all military operations and activities. As part of the overarching political-military approach to Strategic Communications within NATO, the vision is to put Strategic Communications at the heart of all levels of military policy, planning and execution, and then, as a fully integrated part of the overall effort, ensure the development of a practical, effective strategy that makes a real contribution to success.
1-4. The aim of NATO Strategic Communications is to ensure that NATO’s audiences, whether in the Nations or in a region where a NATO operation is taking place, either friendly or adversarial, receives truthful, accurate and timely information that will allow them to understand and assess the Alliance’s actions and intentions. This will deter aggression and promote NATO’s alms and objectives.
…
4-6. Empowerment.
a. In NATO military structures, the authority to communicate or release information, including imagery and other communication products, has traditionally been restricted to high levels within the command structure. Effective support to Strategic Communications is enhanced by military commanders choosing to delegate communication authority widely, empowering more personnel to communicate the NATO narrative through actions, words and imagery.
b. This requires military leaders to maintain awareness of information released and the ability to refine this information as necessary to ensure its accuracy. Commanders must balance the requirement for speed in the release of information with legitimate concerns for its accuracy and the demands of operational security. In the current and foreseeable future global information environment, the use of new and emerging technology such as internet or mobile telephone based Social Media has resulted In a requirement to release information in as close to real time as possible; as events unfold, not minutes or hours later. By empowering more of our people to communicate, NATO will help ensure that it Is not only the best source of information about the Alliance that gets out, but the first. best source as we”. The willingness of leaders to empower is dependent upon their confidence in the community of interest achieved through successful training and education.
…
b. The ability to coordinate NATO and coalition information and communications activities with the efforts of other agencies and partners within the context of a broader NATO strategy, in accordance with the Comprehensive Approach Action Plan1on the aspects it addresses.
(1) Identify potential outside agencies with influence efforts in the operational area.
(2) Establish robust liaison, support and working agreements, to include structures, processes and permissions for Sharing information with partners.
(3) Coordinate with outside agencies in assessing the perceptions, attitudes, behaviours and beliefs of potential audiences.
(4) Coordinate with outside agencies to establish objectives, determine courses of action, and deliver messages.
(5) Collaborate with other agencies and mission partners in detecting, monitoring, translating and assessing the effects of NATO and others’ influence efforts.c. The ability to access, produce and maintain updated information and knowledge on the perceptions attitudes, behaviours and beliefs of potential audiences.
(1) Identify and segment potential audiences.
(2) Access, collect, produce and maintain existing knowledge databases on perceptions, attitudes and beliefs of the selected audience(s).
(3) Establish close coordination with existing intelligence assets.
(4) Conduct social network analysis of selected audiences.
(5) Collect market research information on the perceptions, attitudes, behaviours and beliefs of the selected audiences from external organizations, or hire external organizations to perform such research.d. The ability to access, produce and maintain updated information and knowledge on complex social communication systems, to include the characteristics of various media agencies.
(1) Identify relevant communication channels, social communication systems and media agencies affecting the NATO and coalition operations area.
(2) Analyse the flow and change of information through relevant communication channels, social communication systems and media agencies.
TMZ – Marc Anthony’s SUPER HOT New GF
Marc Anthony’s new girlfriend looks amazing in a bikini… but her fashion choices won’t even come close to be as harshly criticized as Dax’s t-shirt selection during the morning meeting.
TOP-SECRET – NATO Strategic Communications Policy

1. Today’s information environment, characterized by a 24/7 news cycle, the rise of social networking sites, and the interconnectedness of audiences in and beyond NATO nations territory, directly affects how NATO actions are perceived by key audiences. That perception is always relevant to, and can have a direct effect on the success of NATO operations and policies. NATO must use various channels, including the traditional media, internet-based media and public engagement, to build awareness, understanding, and support for its decisions and operations. This requires a coherent institutional approach, coordination of effort with NATO nations and between all relevant actors, and consistency with agreed NATO policies, procedures and principles.
2. An effective strategic communications policy therefore requires clear definitions of a) the main aims of NATO strategic communications; b) the key principles guiding NATO strategic communications; c) interrelationships between the various information disciplines within NATO (Public Diplomacy, Public Affairs (civilian), Military Public Affairs, Information Operations and Psychological Operations); and d) the roles and authorities of the actors within NATO with communications responsibilities.
…
10. NATO strategic communications aim, as appropriate to circumstances and theatres, to:
a. Contribute positively and directly in achieving the successful implementation of NATO operations, missions, and activities by incorporating strategic communications planning into all operational and policy planning;
b. Build, in close and lasting coordination with NATO nations, public awareness, understanding, and support for specific NATO policies, operations, and other activities in all relevant audiences; and
c. Contribute to general public awareness and understanding of NATO as part of a broader and on-going public diplomacy effort.
…
17. The following guidelines will apply to the use of social media by all NATO civilian and military staff, including all NATO personnel deployed on NATO operations :
a. The use of social media is permitted for all NATO military and civilian staff.
b. Social media can be used to discuss and portray the profession and day-day activities of NATO civilian and military staff
c. NATO civilian and military staff should not, however, use social media in ways that:
i. Compromise operational and / or organisational security, or put the safety of anyone at risk
ii. Reveal confidential discussions, or compromise ongoing negotiations
iii. Comment on the policies of the Alliance and of NATO nations as they relate to security issues
iv. Violate the national laws of the country of origin of the staff member
18. Violation of these guidelines by personnel under NATO authority will be subject to appropriate sanction.
The Sixth Sense HD – Full Movie – Bruce Willis
A boy who communicates with spirits that don’t know they’re dead seeks the help of a disheartened child psychologist.
Malcom Crowe is a child psychologist who receives an award on the same night that he is visited by a very unhappy ex-patient. After this encounter, Crowe takes on the task of curing a young boy with the same ills as the ex-patient. This boy “sees dead people”. Crowe spends a lot of time with the boy (Cole) much to the dismay of his wife. Cole’s mom is at her wit’s end with what to do about her son’s increasing problems. Crowe is the boy’s only hope. Written by Jeff Mellinger.
Discover the secret of ‘The Sixth Sense’!!!!
THE STASI Press Release published by Wikileaks
Sports Illustrated Swimsuit – Oluchi
SECRET – FDNY Presentation: The Transient Hazard of Food Trucks
TMZ – Did Carly Rae Jepsen Steal ‘Call Me Maybe?’
The Meaning of Life by John C. Maxwell
On the first day God created the dog. God said, “Sit all day by the door of your house and bark at anyone who comes in or walks past. I will give you a life span of twenty years.” The dog said, “That’s too long to be barking. Give me ten years and I’ll give you back the other ten.”
So God agreed.
On the second day God created the monkey. God said, “Entertain people, do monkey tricks and make them laugh. I’ll give you a twenty-year life span.” The monkey said, “Monkey tricks for twenty years? I don’t think so. Dog gave you back ten, so that’s what I’ll do too, okay?”
And God agreed.
On the third day God created the cow. “You must go to the field with the farmer all day long and toil under the sun, have calves, and give milk to support the farmer. I will give you a life span of sixty years.”
The cow said, “That’s kind of a tough life you want me to live for sixty years. Let me have twenty and I’ll give back the other forty.”
And God agreed again.
On the fourth day God created man. God said, “Eat, sleep, play, marry and enjoy your life. I’ll give you twenty years.”
Man said, “What? Only twenty years? Tell you what, I’ll take my twenty, and the forty the cow gave back, and the ten the monkey gave back, and the ten the dog gave back, that makes eighty, okay?”
Okay,” said God, “You’ve got a deal.”
So that is why the first twenty years we eat, sleep, play, and enjoy ourselves; the next forty years we slave in the sun to support our family; the next ten years we do monkey tricks to entertain the grandchildren; and the last ten years we sit on the front porch and bark at everyone.
Life has now been explained to you.
TOP-SECRET-NATO Public Diplomacy Strategy 2010-2011

1. The Committee for Public Diplomacy (CPD) has finalised its work on the 2010/2011 NATO Public Diplomacy Strategy and approved the document under a silence procedure on 2 December 2009.
2. The strategy identifies a number of critical communications challenges that the Alliance is facing and proposes two priority areas that deserve special attention in NATO’s communication efforts over the next two years: NATO’s role and achievements in operations and missions and the Alliance’s identity and strategic direction. Against this background the strategy lays out a broad range of communication approaches and tools that will help the Alliance to generate public support for its policies, operations and missions and ultimately improve NATO’s public image and reputation.
…
II. THE PUBLIC ENVIRONMENT
A. NATO’s Communication Challenges
2.1. The current transatlantic environment will continue to challenge NATO’s ability to carry its messages proactively and engagingly to diverse audiences across the globe, but it also entails a number of positive trends on which NATO’s future communication efforts should build. From a broader perspective, the public climate in Europe and North America has recently become more supportive of a close transatlantic security relationship compared to previous years. As the 2009 Transatlantic Trends survey shows, the Alliance has regained public support in many, albeit not all Allied countries. Moreover, NATO’s 60th anniversary, the NATO Summit in Strasbourg/Kehl, the arrival of a new Secretary General in late summer and the launching of a public debate about NATO’s new Strategic Concept have spurred broader public attention and interest in the Alliance.
2.2. But notwithstanding growing European and North American support for transatlantic security cooperation, the public in NATO nations remains highly concerned with the situation in Afghanistan. Compounding the effects of an increasingly challenging security situation, a lack of good governance and the damaging fraud of the recent elections, is the continuing struggle to counterbalance this with effective communications of significant progress across a wide range of areas in the country. As a result, misunderstanding about the real status of mission progress is evident amongst key International Community partners and within some ISAF member nations. The prevailing wish among the public in many European countries is to see the number of their troops reduced or to have them entirely withdrawn, since they fail to see a credible political perspective in Afghanistan. Given the growing number of NATO casualties in the country, large majorities in Europe oppose the use of military ‘hard’ power in general, and consequently of combat troops in Afghanistan. Furthermore, public interest in the Alliance’s successful operations in the Balkans and in combating terrorism in the Mediterranean remains limited, thus adding to doubts about the Allies’ resolve in providing security and stability beyond NATO’s borders.
2.3. In general, as social and economic security has increasingly replaced national security as a major public concern, interest in and understanding of the Alliance’s roles and policies have become significantly weaker. National and international surveys continue to demonstrate that the post-Cold-War generation knows very little about NATO’s concrete activities and its raison d’être as well as the transatlantic values that NATO stands for. The lack of appreciation for the Alliance often coincides with stereotypes and misperceptions of it in broader parts of the public in both Allied and partner countries. Hence explaining NATO’s strategic rationale to the public at large, and specifically to young audiences, must remain a top communication priority in the future in order to strengthen NATO’s identity and reputation. Ultimately, we need to convince our public that the Alliance is relevant to their security concerns and pursues an effective strategy to meet current and future security challenges in close co-ordination with other international organisations.
…
III. KEY COMMUNICATION PRIORITIES IN 2010-2011
3.1. Explaining the values and principles that NATO stands for, first and foremost the principle of Allied solidarity, will feature prominently in NATO’s communication and outreach efforts, in particular towards the young generation. In 2010-2011, PDD will pro-actively support the Alliance’s policies across the transformation agenda and towards partner countries, international organisations and international actors. Within the broad spectrum of themes and messages that NATO will communicate in the next two years, a special emphasis will be given to two priority areas that deserve a dedicated effort.
A. Explain and promote NATO’S role and achievements in areas of operations and missions
3.2. The successful execution of the Alliance’s objectives in Afghanistan depends on strong public support in NATO nations. To counteract declining support and lack of understanding for the ISAF operation and NATO’s wider engagement in Afghanistan, NATO will increase its efforts to acquaint audiences in Member countries, and where possible partner and troop-contributing nations, with the full range of the Alliance’s roles and activities in Afghanistan. It will aim to explain why the success of these efforts matters at home and what more is needed to succeed, with a view to generating support for NATO’s continued engagement in order to achieve a successful transition, where the Afghan authorities will assume full responsibility for protecting their country’s citizens. Ultimately, NATO’s strategic communication efforts should help shape a clearer public understanding that the Allies remain fully committed to the ISAF operation until all requirements for the successful transition to Afghan ownership and leadership have been met in both military and civilian spheres.
3.3. Building on NATO’s current media operations and public diplomacy efforts in support of the operation in Afghanistan, NATO will pursue more targeted and expanded communication activities to generate broader and more comprehensive reporting on what NATO’s operation has already achieved in Afghanistan in all relevant areas, and in particular in the field of training the Afghan security forces. In order to counter continued misperceptions and doubts about the success of NATO’s engagement, a stronger narrative will be elaborated to explain to our public that the Alliance and the international community need to stay engaged in Afghanistan, not only to provide support for stability and reconstruction in the country but primarily for the sake of our own security. NATO’s new narrative should stress that the way forward is linked to the development of conditions allowing for the successful transition to Afghans taking the lead, which NATO will continue to support in multiple ways, and in particular through the NATO Training Mission – Afghanistan (NTM-A). The narrative will have to be resilient and robust, especially against undermining and adverse events.
3.4. Consequently, NATO’s communication activities will focus on making its concrete support for Afghan capacity-building known to the wider public, including through visual material. Moreover, in order to demonstrate the importance of the regional dimension of NATO’s engagement in Afghanistan, we will increasingly explain the Allies’ evolving relationship with Pakistan, which is based on a three-pronged strategy. Last but not least, NATO will expand its programmes to explain that NATO’s military and civilian engagement is embedded in a wider international effort, and that the Allies remain committed to improving cooperation with other international organisations/actors and partners as part of the Comprehensive Approach.
…
IV. TARGET AUDIENCES AND COMMUNICATION PARTNERS
4.1. Building renewed understanding and support for the transatlantic Alliance among the young generation of Europeans and North Americans is vital for NATO. Our emphasis should be on explaining what NATO concretely does and will continue to do in the years to come to meet current and future security challenges. Likewise, we should stress the continued importance of transatlantic values as well as the benefits of addressing the multifarious threats and challenges to our security within a multilateral, transatlantic framework. The latter implies that PDD and Allied nations should jointly develop and apply a dedicated narrative for young people in a modern and appealing language.
4.2. In 2010, PDD projects such as Summit-related Youth Forums, the NATO-Afghan Student Forum, established summer schools and university courses, conferences, workshops for students, essay and film competitions as well as NATO-sponsored online discussions will be merged under a unified brand called ‘Young Network NATO’, which will allow NATO to engage these audiences in a more systematic and sustained fashion. ‘Young Network NATO’ will have professionally designed web modules, including links to the Secretary General’s Corner, on Facebook, Linked-In and other social media, and will regularly offer reports about upcoming events, NATO stories, as well as a portal for online discussions.
4.3. Wherever possible, NATO will seek to give young political leaders a prominent role in discussing NATO and its policies directly with the Secretary General, senior civilian and military NATO representatives and Alliance leaders. The 2010 NATO Summit, forthcoming ministerial meetings as well as the discussion about a new Strategic Concept are excellent opportunities to demonstrate that NATO is keen to take the views of young audiences on board, be it though special events or web-based programmes that can be linked to NATO meetings.
4.4. Generating broader interest in NATO among young people will only be successful if their school education includes background information on transatlantic security issues and educators have sufficient knowledge of and material on NATO. To this end, NATO will work closely with the respective national authorities and the Atlantic Treaty Associations (ATAs) to engage educators through special programmes such as summer schools and virtual training programmes for educators, and to identify the best ways to improve curricula at schools. The NATO Defence College and the NATO School in Oberammergau will be invited to join this particular outreach effort towards educators.
4.5. NATO will continue to survey and monitor public trends in Member and partner nations to be able to identify the most important and suitable target audiences in the respective countries. Taking into account the specifics of the political and public environment in each country, NATO programmes will aim to be as tailored and efficient as possible. Prime movers of information such as political leaders, parliamentarians, think-tankers, security experts, journalists, academics and representatives of influential NGOs will be first on NATO’s list of target audiences across Allied and partner countries. In particular, PDD will seek to reach out to critical voices as well as to young women who, according to the results of the focus study conducted in 2008, represent an important target group for NATO. In addition, PDD will use new media applications to reach out to broader segments of the public.
DOWNLOAD THE ORIGINAL DOCUMENT HERE:
The Orphanage – Full Movie
Pan’s official entry to the 2008 Academy Awards, this multi-award winning thriller screened at the 2007 Cannes Film Festival. Produced by hotshot Latin American director Guillermo del Toro (Guillermo del Toro). A rare film that’s both frightening and moving.
STASI-EXPERTE: RUFMORD AN JUSTIZMINISTER IST STASI-RACHEAKT
Unveiled by Cryptome – Romney Tax Files Plot Search Warrant-Seizure
TMZ – Hot Foreign Models!
Thank goodness for these super hot, foreign models going topless all the time and wearing tiny, skimpy clothing. What would we ever do without them?
Unveiled by Public Intelligence – NATO Military Policy on Psychological Operations
The following are two versions of NATO’s military policy on psychological operations. The most recent version from 2012 shows significant differences from the previous version from 2003, allowing for analysis of the evolution of NATO’s PSYOPS in recent years. Though unclassified, NATO doctrine documents like those below are not released to the public.
| NATO MILITARY POLICY ON PSYCHOLOGICAL OPERATIONS MC 0402/2 | June 22, 2012 | 13 pages | Download |
| NATO MILITARY POLICY ON PSYCHOLOGICAL OPERATIONS MC 0402/1 | March 19, 2003 | 16 pages | Download |
1. The role of Psychological Operations (PSYOPS) is to induce or reinforce the perceptions. attitudes and behaviour of North Atlantic Council (NAC) approved audiences in support of Alliance political and military objectives. Additionally, PSYOPS can mitigate the effective use of hostile propaganda against friendly forces, local civilian audiences and other audiences of importance to NATO.
2. The pervasive and ubiquitous nature of today’s global Information Environment (IE). including the importance of virtual and physical social networks and new media has increased the demand and importance of effective PSYOPS. This has been exacerbated by NATO’s involvement in Non-Article 5 Crisis Response Operations and information attacks against NATO and its member nations. In today’s IE, NATO can expect to operate for an extended period of time with limited resources in areas where sophisticated indigenous media, traditional communication and information from external sources compete to influence the perceptions of local audiences. The organisation, state, or entity more able to effectively and rapidly influence the understanding of a crisis or conflict, especially inducing or reinforcing the perceptions of particular influential audiences, will likely be the most successful.
3. PSYOPS are an indispensable part of the broad range of modern Military, Political, Economic, Civilian and Information (MPEC(I)) activities aimed at conflict prevention and crisis response. PSYOPS may multiply the effects of military capabilities by communicating messages directly through all available means, thus influencing the perceptions, attitudes and behaviour of their intended audiences.
4. The application of PSYOPS can have a significant impact in the long and short term to influence behaviour and act as a force multiplier and enabler to enhance NATO military capabilities. The principles of developing a PSYOPS plan apply across the full spectrum of operational themes (combat, security, and peace support) as discussed in AJP-1 and military activities (offensive, defensive, stability and enabling) as discussed in AJP-3. Although the complexity of the methodology varies with the audiences, basic considerations for the development of all PSYOPS actions are the same.
5. In order to preserve Alliance and PSYOPS credibility, PSYOPS are based on true and factual information, and are generally attributed to NATO or a concurring partner nation or organization.
Days Of Glory – Full Movie
Days Of Glory was nominated for Best Foreign Language Film Oscar at the 2007 Academy Awards, and the Palme d’Or at the 2006 Festival de Cannes.The year is 1943. France is at war. Four Algerian men – Saïd, Abdelkader, Messaoud and Yassir -like 1,30,000 others, enlist in the French Army to save a country they have never seen. A country that discriminates against them. The story of the forgotten North African “indigenous” heroes and their loyalty to an ungrateful fatherland.
SPIEGEL über die STASI-Connection des mutmasslichen “GoMoPa”-Chefs Jochen Resch
TMZ-Now YOU Can Bang Tiger Wood’s Mistress!
In the Name of the King: A Dungeon Siege Tale (2007) INTERNATIONAL CUT – Full Movie
Set in the kingdom of Ehb, the story follows Farmer (Jason Statham), who was adopted by his village. When Farmer’s wife, Solana (Claire Forlani), and his son leave to sell vegetables at the town of Stonebridge, Farmer’s farm is attacked by creatures called Krugs. With the help of his friend and neighbor Norrick (Ron Perlman), he travels to Stonebridge where his wife and son are. Before he arrives, the Krugs, controlled by the wizard Gallian (Ray Liotta), kill his son and capture his wife. Farmer, with the help of Bastian (Will Sanderson), his brother-in-law, and Norrick sets out to find and rescue his wife. The King’s nephew Fallow (Matthew Lillard) is conspiring with the wizard Gallian to take over the kingdom led by King Konreid (Burt Reynolds).
SPIEGEL über die Giftstudie des “GoMoPa”-Masterminds und Resch-Protege´s STASI-Oberst Ehrenfried Stelzer
TOP-SECRET-NATO Allied Joint Doctrine for Psychological Operations

The purpose of Allied Joint Publication (AJP)-3.10.1 Allied Joint Doctrine for Psychological Operations is to address the planning and conduct of military PSYOPS in support of NATO activities. PSYOPS, as one of the key contributors to most information operations (INFO OPS) activities, will achieve their greatest effect when coordinated within the larger INFO OPS plan and supporting a much broader information strategy. The new construct of INFO OPS is focused on affecting will, understanding, and capability through the three activities of influence, counter-command, and information protection. It must be noted that PSYOPS has influence activity as its mission; and by influencing target audiences (TA) directly, PSYOPS, in turn, has indirect effects on understanding and capability.
…
0104. The psychological dimension of conflict is as important as the physical. Conflict is a struggle of wills, that takes place in people’s minds as well as on the battlefield. The attitudes and behaviour of people (friend, foe and the undecided or uncommitted) may be central to determining the outcome of conflict and the nature of the post-conflict environment. Therefore it is necessary to understand the motivation of various target audiences — leaders, military forces, populations — in order to shape their perceptions, affect their will and to persuade them to accept the outcome desired by NATO. The employment of any element of power projection, particularly the military element, has always had a psychological dimension. PSYOPS, as a key element of most INFO OPS activity, are a vital part of the broad range of NATO diplomatic, military, economic, and informational activities.
0105. PSYOPS are enhanced by the expansion of mass communication capabilities. NATO may multiply the effects of its military capabilities by communicating directly to its intended targets. The effectiveness of this communication depends on the perception of the communicator’s credibility and capability to carry out promises or threatened actions in a manner that will be significant to the cultural norms and attitude of the individuals targeted. The employment of any NATO element has a psychological dimension. Perceptions of NATO capabilities are fundamental to strategic deterrence. The effectiveness of deterrence and other strategic concepts hinges on the ability to influence the perceptions of others. It is important not to confuse psychological impact of military operations with planned psychological operations, although the two can be mutually supporting and should be anticipated and coordinated.
0106. PSYOPS constitute a planned process of conveying messages to selected groups, known as target audiences, to promote particular themes that result in desired attitudes and behaviour that affect the achievement of political and military objectives. A target audience is defined by NATO as “an individual or group selected for influence or attack by means of psychological operations” (AAP-6). Given the potential benefit of PSYOPS as an effective force multiplier and combat reducer, commanders at all levels should always consider its use in support of their military aims and objectives. The three basic aims of PSYOPS are to:
a. Weaken the will of the adversary or potentially adversary target audiences.
b. Reinforce the commitment of friendly target audiences.
c. Gain the support and cooperation of uncommitted or undecided audiences.
…
B106. Principles of visual media design. Whilst the design of a visual product is heavily dependent upon the message content and the imagination and skill of the artist, it is nevertheless possible to identify basic components to develop effective PSYOPS products, based on the knowledge about human perception and the differences between discernment and insight. The human perception can be represented with six stages as a process. The following stages are based on each other:
a. Value orientation. The first task of a product is to gain and maintain the attention and interest of the target audience. The single way to activate somebody is to key in on his already existing needs and motives. Therefore, the PSYOPS product has to consider the current hierarchy of needs and level of need satisfaction of the selected target audience.
b. Activation. Activation is only possible if it triggers a response to existing needs. Needs of the target audience must be identified by PSYOPS, who then develop themes and messages which are aimed at meeting these established needs. The recipient must be able to recognise a personal benefit from action demanded from him. The product design should amplify and canalise already existing motives and needs.
The perception of a person can be affected by three kinds of stimuli:
(1) Emotional stimuli. They cause an immediate emotional response (Love, peace, little child image).
(2) Physical stimuli (size, colour and shapes of symbols). They cause no activation alone. However, they amplify the message.
(3) Intellectual stimuli (surprise, necessity or contradiction). They draw the observer into the product.
c. Reception. “A picture is worth a thousand words.” The PSYOPS statement should be understandable in a look and should be immediately credible. Long text passages and box sentences inhibit fast consumption of information. slogans, headings, headlines and/or other succinct, clear messages should be used wherever possible.
d. Comprehension. The messages of a product must not become misunderstood and should be easy to recognise. The message or picture should activate perception and motivate the recipient to act. Pictures and text must be quickly understandable by themselves and should provide common information. Therefore, passive voice, vague or confusing language, ideological or religious discussion, and abstract statements and symbols are to be avoided.
e. Memory. In addition to the initial impact of a visual PSYOPS product, the memory of that product by the target audience is an additional meaningful factor that requires attention. The level of memory increases through: Information emphasised in colour, concrete photos, positive statements, pictorial language and concise text. They may have to be modified considerably in the light of local communication style.
f. Impact. A significant precondition might be that the product appears as non-threatening and stimulates a positive feeling. The effect becomes amplified through a positive image of the sender, the plausibility of the message and if a way out of a personal conflict situation is offered to the recipient. The observer must be able to recognise a personal benefit from action demanded by it. The product design should amplify and canalise already existing motives and needs.
…
B112. Selection of announcers
a. An announcer should be chosen primarily on the basis of his or her clarity of voice and correct colloquial pronunciation of the language in use, although a foreign audience will not expect native speaker qualification from a NATO source. It is also desirable that his or her voice should carry conviction and suggest a personality appropriate to the material being transmitted. While not essential, much benefit will result if the announcer has sufficient local knowledge and creative insight to contribute to the drafting of his/her own scripts.
b. The use of indigenous personnel, possibly including defectors, is a simple and effective way of meeting the problem of language or dialect. However, if this method is employed, special attention must be paid to the question of security, including the physical security of locals working for NATO. In particular, all recorded material must be checked for accuracy of content by a trusted interpreter. Live transmissions should only be made by local nationals of proven loyalty. Every effort should be taken to provide at least one military interpreter for a PSYOPS unit for checking samples of translations and for interpreting in sensitive situation.
…
B119. Internet. The Internet differs from the other media described mainly on two accounts. First it is in principle unlimited in reach. Second it is a medium where the target audience has to actively seek information, and where PSYOPS messages will compete for attention with a lot of other information, including information provided by adversaries. This leads to a strong requirement for making the material published interesting. At present there are in general three ways of using the Internet in PSYOPS: Operating a home page, sending e-mails, addressed to specific and selected targets, and having a chat room. A home page will be generally available to a large audience, whereas targets for e-mail can be groups or individual persons. Chat rooms will normally be directed at groups.
a. Advantages
(1) Reach. Due to the virtually unlimited reach of the Internet it is possible to readily access target audiences worldwide.
(2) Speed. An important characteristic of the Internet is the virtual instantaneous availability of the messages worldwide. This makes it easy and quick to produce messages far away from the target audience. However, an adversary is likewise able to publish over long distances quickly.
(3) Cheap. As a means of dissemination the Internet is cheap. However, the editorial skills and facilities of the required quality may not be.
b. Limitations. When using websites NATO units has to take the relationship to Press & Information activities in to consideration, according to “Guidelines for PSYOPS websites”.
c. Disadvantages
(1) Reach. Due to the unlimited reach of the Internet it is virtually impossible to limit the availability of information published to selected audiences, unless it is sent directly to the target audience as e-mail. This increases the requirement to minimise the negative impact of messages on unintended target audiences.
(2) Computer availability and literacy. Since the target audience has to be able to access the Internet; computers, network access and the ability to exploit the technology have to be available, there are at present limits in the reach in less developed areas. However, target audiences in the NATO countries are easily accessible by adversaries.
(3) Anonymity. On the Internet it is easy to hide the true identity of the originator of a message.
(4) Competition. With a lot of very different information being readily available on the Internet, the PSYOPS messages have to appeal to the target audiences much more than in most other media.
(5) Manipulation. This electronic medium may be easily modified by adversaries and other parties.
…
ANNEX C ATTITUDES AND BEHAVIOUR
Section I – The motivation of the individual
C101. General. Motivation, in general, represents a direct and dynamic component of behaviour, which is determined by a combination of biological, social, and learning factors. Motivation activates behaviour in pursuit of a goal. Current motivational needs influence perception, reasoning, learning and other psychological processes. Its main characteristics are:
a. Motivation is tied to inner conditions and processes, which can only be observed indirectly, through its behavioural outputs.
b. Motivation is not always equal to behaviour, as behaviour tends also to be determined by biological, social, and cultural factors along with perception, reasoning, learning and other psychological processes.
c. The result of motivation is almost always some kind of activity.
d. Motivated behaviour can be described by energy mobilization; persistent, intensive and effective behaviour; direction towards an objective; and change in behaviour dependant upon consequences.
e. Human behaviour is directed towards an objective. As soon as the objective is achieved, this need is satisfied.
f. As soon as one need is satisfied, others occur; therefore, motivation and the requirement to satisfy needs is a never-ending process.
C102. Hierarchy of needs/motives. From an individual’s point of view, the most important drive (which also determines behaviour) is the desire to satisfy his or her individual needs. These range from simple physical requirements of the body (hunger, thirst, etc.) to complex psychological demands such as the desire for recognition and self-esteem. These various needs can be represented as a hierarchy, with the most fundamental and primitive at the bottom of the scale, and the most complex and abstract at the top (see Figure C-1 below). The theory of motivation suggests that individual needs can be described by a scale of satisfaction. However, not all target audiences rate.
…
C127. PSYOPS and communication
a. Means. The means used for the transfer of PSYOPS messages encompass all the usual means of human communication like word-of-mouth, books, newspapers, loudspeakers, radio, TV, etc. They also include emerging technologies that allow messages to be transferred from senders to receivers (such as mobile phones, e-mail, etc.)
b. When conducting PSYOPS, planners should emphasize the use of key communicators as they are the ones who can transfer messages to the TA most effectively. Key elements when considering the use of key communicators are authority, group belonging, and the attraction of the source. For maximum effectiveness of PSYOPS, a credible source of information is necessary. In the minds of the TA, a key communicator should be “one of them”: a persuasive and powerful speaker.
c. Messages. The following should be taken into consideration when crafting PSYOPS messages: message visibility, accessibility, appeal, clarity, simplicity, persuasiveness, the principal of need (i.e., promising the TA you will fulfil their needs), and the principle of unpredictability (i.e., using “soft” methods of persuasion, which allow for adaptation to possible changes).
d. PSYOPS communication techniques. The following are examples of messaging techniques that have been shown to be successful:
(1) Emotional sandwich (emotions – message – emotions).
(2) Emotional transfer (e.g., a flyer with an emotional component like nice pictures, overwritten by the PSYOPS message).
(3) Use of emotionally loaded words.
(4) Use of stereotypes.
…
ANNEX D COUNTER PSYOPS TECHNIQUES AND PROCEDURES
Section I – Analysis
D101. Aim of counter PSYOPS. The aim of counter PSYOPS is to counter or exploit the effects of adversary propaganda or psychological activities. Counter PSYOPS are directed at approved target audiences that are affected by the adversary propaganda, less our own forces and citizents, who are the responsibility of troop information and PI.
D102. Definition. Actions designed to detect and counteract adversary psychological activities.
D103. Analysis of adversary’s psychological activities. Analysis of an adversary’s psychological activity involves the detailed examination of the source, content, audience, media and effects (SCAME) of his messages to obtain intelligence that supplements the conventional forms of intelligence. The audience and the effects can be unintended as well as intended. The primary purpose of the analysis of an adversary’s psychological activity is to collect PSYOPS-related intelligence information. This is in order to evaluate its effect on own troops as well as on friendly and uncommitted civilian audiences within the AOR, in order to be able to eliminate or diminish the negative consequences, and to exploit any contradiction in that adversary psychological activity. The analysis also involves a systematic study of foreign mass communications intended for domestic and/or international audiences.
D104. Source analysis. Identifies the individual, organisation or government that sponsors and disseminates a particular item of an adversary psychological activity. The three components of source analysis are: actor, authority and author. Sources are further subdivided into:
a. White. An acknowledged source.
b. Grey. An unacknowledged source.
c. Black. Originates from a source other than the one that is claimed.
DOWNLOAD THE ORIGINAL DOCUMENT HERE:
Breach (2007) – Full Movie
SPIEGEL -“GELIEBTER GENOSSE”-WIE STASI-OBERST STELZER BND-CHEF HELLENBROICH FÜR “GoMoPa” ANWARB
Cryptome unveils USA v. Appelbaum et al Documents
|
TMZ – Wayne Gretzky’s Daughter — Sexiest Halloween Costume EVER
Unveiled – Quazi Mohammad Rezwanul Ahsan Nafis New York Federal Reserve Bomb Plot Criminal Complaint

4. In or about early July 2012, NAFIS first contacted an FBI confidential human source (the “CHS”) and subsequently attempted to recruit the CHS into a jihadist cell to carry out a terror attack on U.S. soil. On or about July 5, 2012, the CHS received a call from NAFIS wherein NAFIS advised, in sum and substance, that NAFIS is from Bangladesh but came to the United States to wage “jihad.” NAFIS told the CHS that all Muslims and Muslim sheikhs in the United States are “Talafi,” meaning not true Muslims. NAFIS also told the CHS that NAFIS admired Sheikh “O,” whom the CHS understood to be Osama bin Laden. In addition, NAFIS told the CHS that he admired the magazine starting with “I,” which the CHS understood to be the al-Qaeda-affiliate-sponsored publication “Inspire.”
…
7. During the period between July 6, 2012 and July 8, 2012, NAFIS, the CO-CONSPIRATOR and the CHS began to communicate via Facebook, an internet social-media website. During these communications, which were consensually recorded by the CHS, the three discussed certain Islamic legal rulings that advise that it is unlawful for a person who enters a country with a visa to wage jihad there. NAFIS stated that he had conferred with another individual in Bangladesh and was advised that he was not bound by such rulings. Accordingly, NAFIS indicated that he believed that he was free to continue with his plan to conduct a terrorist attack on U.S. soil.
8. On or about July 11, 2012, the CO-CONSPIRATOR told the CHS, in sum and substance, that NAFIS had previously told the CO-CONSPIRATOR that NAFIS wanted to attack and kill a high-ranking government official (the “high-ranking official”). This communication was consensually recorded.
9. A few hours later, on or about July 12, 2012 in the early morning, NAFIS told the CO-CONSPIRATOR and the CHS, in sum and substance, that NAFIS had contacts with al-Qaeda members overseas who could assist the group in planning and executing an attack on the high-ranking official. This communication was consensually recorded.
10. On or about July 14, 2012, NAFIS told the CHS, in sum and substance, that NAFIS intended to return to Bangladesh, likely in December 2012, to obtain training from al-Qaeda. This communication was also consensually recorded.
…
16. On or about August 11, 2012, NAFIS met with the UC in a hotel room in Queens, New York. During that meeting, which was consensually recorded, NAFIS confirmed that he wanted to target the financial district of Manhattan — specifically, the New York Stock Exchange. NAFIS told the UC, in sum and substance, that he wanted to use explosives as part of a suicide attack, either contained in one or more cars, or strapped to his person. NAFIS explained, “We are going to need a lot of TNT or dynamite.” NAFIS also provided the UC with a handwritten map of the area that NAFIS had apparently prepared while scouting the area around the Stock Exchange on or about August 9, 2012.
17. During that same meeting, NAFIS asked the UC whether approval for NAFIS’s proposed attack would come from the “top” of the al-Qaeda leadership. The UC responded, in sum and substance, that he was going to meet with al-Qaeda leadership and advise them about NAFIS’s plan.
18. NAFIS and the UC then traveled to the financial district in Manhattan, and NAFIS took several photographs of prospective targets in that area.
…
On or about October 12, 2012, NAFIS and the UC met and transported what NAFIS believed to be explosive material to the Warehouse. This meeting was consensually recorded. Upon arriving at the Warehouse, NAFIS and the UC offloaded approximately twenty fifty-pound bags of this purported explosive material into a trailer. NAFIS also gave the UC a tarp that he had previously purchased with his own money to cover the purported explosive device when it was placed in the van. NAFIS also provided the UC with a thumb drive containing an article NAFIS had written about his motivations for his attack. NAFIS believed that this article would be published by Inspire magazine. In that article, NAFIS included quotations from “[o]ur beloved Sheikh Osama bin Laden” to justify the fact that his plot likely involved the killing of women and children. NAFIS also stated the following:
all I had in my mind are how to destroy America . . . I came up to this conclusion that targeting America’s economy is most efficient way to draw the path of obliteration of America as well as the path of establishment of Khilapha.
I decided to attack the Federal Reserve bank of New York which is by far the largest (by assets), most active (by volume) and most influential of the 12 regional Federal Reserve Banks. New York Federal Reserve Bank implements monetary policy, supervises and regulates financial institutions and helps maintain the nation’s payment systems.
DOWNLOAD THE ORIGINAL DOCUMENT HERE:
Spy Game – Full Movie – Brad Pitt and Robert Redford
Robert Redford and Brad Pitt. Retiring CIA agent Nathan Muir recalls his training of Tom Bishop while working against agency politics to free him from his Chinese captors.
Süddeutsche Zeitung über die kriminellen Machenschaften der “GoMoPa”
TMZ – Want to See Joanna Krupa’s AWESOME Bikini?
Unveiled – NARA Leaks WikiLeaks Citations – Block Lifted
|
Batman: Arkham Asylum – The Full Movie
“On a routine trip returning The Joker to Arkham Asylum, the Dark Knight himself must deal with traps set within its inner sanctums, purposely set by the now escaped Joker, along with the rest of his rogues’ gallery that are now free within the premises.”
Here is ‘Batman: Arkham Asylum’ presented as a full-length feature game-movie.
Secrecy News – Document Collector Charged under Espionage Statute
In a new case of alleged mishandling of classified materials, a Navy
contract linguist who served in Bahrain until earlier this year was charged
with unlawful retention of national defense information after several
classified documents were found in his possession.
But although James F. Hitselberger, an experienced Arabic translator, was
charged under an Espionage Act statute (18 USC 793e), he is not suspected
of espionage. The government "concedes that Defendant... did not
disseminate the classified information to a 'foreign power'," a Magistrate
Judge noted on Monday when the case was unsealed.
http://www.fas.org/sgp/jud/hitsel/index.html
Rather, Mr. Hitselberger told NCIS agents that "his sole purpose was to
take the materials to his quarters to read" and he "claimed not to know
that the documents... were classified, notwithstanding their clear
markings."
http://www.fas.org/sgp/jud/hitsel/complaint.pdf
The case has a number of unusual features, beginning with the defendant
himself, who is a peripatetic collector of rare documents. While at the
University of Texas at Austin in the 1990s, he was said to have been
"working on an open-ended Ph.D. in an unknown subject." His living
quarters in Bahrain, in which a classified document was allegedly found in
April of this year, were "extremely cluttered and contained hundreds of
newspapers [and] numerous books."
Remarkably, Mr. Hitselberger had donated many of his most valuable
documentary discoveries over the years to the Hoover Institution at
Stanford University, which actually maintains a "James F. Hitselberger
Collection." It notably includes political posters and leaflets that he
gathered in pre-revolutionary Iran.
http://www.oac.cdlib.org/findaid/ark:/13030/kt909nf448/
Unfortunately, according to a newly unsealed complaint, Hoover's
Hitselberger Collection also contained classified records that he had
contributed.
"Agents visited the Hoover Archives and reviewed the collection. In an
area open to the public, the agents found a classified document titled
Bahrain Situation Update dated February 13, 2012.... In a secure,
non-public area of the Archives, agents also discovered two other documents
marked SECRET."
A disconcerted Hoover Institution archivist told Mr. Hitselberger in May
by email that "in light of the FBI investigation of your collection here at
Hoover, we will no longer accept additions to the collection, as we don't
want to risk receiving more classified material."
In April of this year, Mr. Hitselberger was dismissed from his post in
Bahrain and was expected to return to the United States. Instead, however,
he traveled for months through Germany, Sweden, Malta, Bulgaria and the
United Kingdom, and was beyond the reach of U.S. authorities.
"Although the government was aware of Defendant's whereabouts during that
time, the countries would not extradite him [to the U.S.] because the
offense charged was characterized as a 'political offense'," according to a
November 5 memorandum of findings of fact by DC District Magistrate Judge
Deborah A. Robinson.
But last month, when it was learned that he was traveling to Kuwait, the
Government of Kuwait agreed to expel him into U.S. custody if he arrived
there without a valid passport. So the U.S. suspended his passport, and
upon arrival placed him under arrest.
In traditional espionage cases, a suspected spy is sometimes identified by
unexplained affluence or ostentatious behavior. But, as noted, this is not
an espionage case and there is no question of affluence.
To the contrary, the government and the court seemed disturbed by Mr.
Hitselberger's extraordinary frugality which, they suggested, might enable
him to quietly vanish.
"Defendant has demonstrated his ability to live abroad and survive on his
apparently modest means," wrote Judge Robinson. "Defendant's pattern of
residing in, and relocating to, various countries without ascertainable
income bespeaks his ability to live abroad undetected with limited
resources."
http://www.fas.org/sgp/jud/hitsel/findings.pdf
Mr. Hitselberger was ordered detained without bond.
NATURAL GAS IN THE US ECONOMY, AND MORE FROM CRS
New and updated reports from the Congressional Research Service that
Congress has not made available to the public include the following.
Natural Gas in the U.S. Economy: Opportunities for Growth, November 6,
2012:
http://www.fas.org/sgp/crs/misc/R42814.pdf
The Dodd-Frank Wall Street Reform and Consumer Protection Act: Title VII,
Derivatives, November 6, 2012:
http://www.fas.org/sgp/crs/misc/R41398.pdf
Same-Sex Marriages: Legal Issues, November 5, 2012:
http://www.fas.org/sgp/crs/misc/RL31994.pdf
Mayo v. Prometheus: Implications for Patents, Biotechnology, and
Personalized Medicine, November 6, 2012:
http://www.fas.org/sgp/crs/misc/R42815.pdf
U.S. Direct Investment Abroad: Trends and Current Issues, October 26,
2012:
http://www.fas.org/sgp/crs/misc/RS21118.pdf
Foreign Direct Investment in the United States: An Economic Analysis,
October 26, 2012:
http://www.fas.org/sgp/crs/misc/RS21857.pdf
Employment for Veterans: Trends and Programs, October 23, 2012:
http://www.fas.org/sgp/crs/misc/R42790.pdf
Yemen: Background and U.S. Relations, November 1, 2012:
http://www.fas.org/sgp/crs/mideast/RL34170.pdf
Bahrain: Reform, Security, and U.S. Policy, November 6, 2012:
http://www.fas.org/sgp/crs/mideast/95-1013.pdf
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
TOP-SECRET-NATO Bilateral Strategic Command Information Operations Reference Book

The aim of this reference book is to provide the additional information needed by Information Operations (Info Ops) practitioners to better understand and implement the advising and coordinating function of Info Ops in the staffs throughout all levels of command. The reference book covers the experiences and lessons learned on principles, procedures, and techniques in current operations as well as some basic understanding on how to best integrate the Info Ops function in the new evolving structures (new Peacetime Establishment) and procedures within NATO with respect to effects based thinking and the new Comprehensive Operations Planning Directive.
…
In the information age, the strategic, operational and tactical levels are more interrelated than in the past, which demands a different quality of co-ordination and command & control across the levels of engagement. Today’s military operations to counter the complex challenges of the global security environment require consideration and integration of the information factor throughout all processes – analysis, planning, execution and assessment. This integration demands that all decision-makers at all times appropriately understand the (possible) effects of their actions in the information environment; it is not just about deliberate activity using information through means of communication, it is the combination of words and deeds that delivers the ultimate effect. A respective systemic understanding of the information environment should result in a consistent and coherent orchestration of all available means, comparable to the military concept of ‘combined arms combat’ or the philosophy of ‘jointness’ in operational art. This is a new mind-set, which requires comprehensive education and training rather than restructuring military organisations.
Information Operations (Info Ops) is a military function to provide advice and coordination of military information activities in order to create desired effects on the will, understanding and capability of adversaries, potential adversaries and other NAC approved parties in support of Alliance mission objectives.
The Info Ops function is understood as an integrating process rather than a capability in its own right. It provides advice to the commander and his1 staff on effects and possible information activities, and proposes solutions from a generalist’s perspective, based on a comprehensive and systemic understanding of the information environment, including cross-cultural communication. This includes the preparation, integration, monitoring and assessment of capability contributions, and the co-ordination of actions to create synchronised effects considering their relationships and interdependencies and associated resources as a function of time and space.
The Information Environment is the virtual and physical space in which information is received, processed and conveyed. It consists of the information itself and information systems.
The Info Ops understanding of ‘socio-technical information systems’ differs from the traditional, technical understanding of ‘information systems’. The term is used in a broader context of Systems Theory (where ‘systems’ basically consist of actors, processes, structures and supporting technology/tools) in order to introduce the human factor into communication within modern information societies.
An actor’s effectiveness is a function of will, understanding and capability. In other words, actors must have the will to act, an understanding of the situation to act, and possess the capability to act. If any one of these elements is not in place, their ability to act as they desire will be affected. Generally conflict-focused, military campaigns have, in the past, aimed primarily at affecting an adversary’s capability, with the secondary aim of affecting his will. Activities advised by, and coordinated through, Info Ops addressed all three dimensions, i.e., influencing will, affecting understanding, and targeting those capabilities that promote understanding or the application of will – ultimately in order to change behaviour.
Information Activities are actions designed to affect information and/or information systems. They can be performed by any actor and include protection measures.
Effects in the information environment can be created by a variety of military activities, the close co-ordination of which will contribute to the achievement of Information Objectives. Info Ops advice and co-ordination will integrate military activities to: exploit information and information systems; protect own information and information systems; and counter adverse information activities.
‘Targets’ for kinetic information activities could be within the information infrastructure, and/or the IT and information-based processes of (potential) adversaries. In addition, Info Ops will contribute to maintaining the functionality of, and exploiting, own and friendly information systems. Ultimately, humans may become kinetic targets, if nonkinetic action is ineffective.
‘Audiences’ for non-kinetic information activities could be (potential) adversary decisionmakers, supporting opinion leaders and opinion formers, and their followers. However, to be able to support the full spectrum of possible operations/missions, information activities may be conducted to reinforce behaviour of friendly audiences and/or to consolidate and modify behaviour of neutrals – to prevent them from becoming adversary or hostile.
…
4.13 Key Leader Engagement (KLE)
Key Leaders Engagement activities include:
a. Bilateral talks (BILAT) of senior leaders with military and civilian counterparts at their level of influence;
b. Speeches held at various occasions in the presence of the media and/or key decision makers;
c. Featured interviews to selected media with wide influence; and
d. Conferences arranged to discuss specific items of interest with influential characters.
As such, commanders and leaders at all levels are encouraged to conduct “engagements” with decision makers at their respective levels (strategic, operational, tactical) and create an influence that will be beneficial for the NATO goals and objectives.
…
4.13.4 Influence Briefing Package (IBP)
The IBP is a summary of all the necessary information that the commander will require to achieve the desired influence over the key decision maker. The IBP is developed by the Info Ops staff officer and provides three (3) essential elements: messages for influence; assessment considerations; and background information on the key decision maker. All three elements combine to give the commander the essential elements of how the “influencing” activities are tied to the ongoing operations and the desired effects.
DOWNLOAD THE ORIGINAL DOCUMENT HERE:
VIDEO-Election Results 2012: Nate Silver on How He Got It Right
NYT-Obama Wins the 2012 Election: Obama’s Complete Presidential Victory Speech
Von “GoMoPa” verleumdete Journalisten – NDR berichtet
Victor Erevia, Obama Protection Head – Unveiled
A sends:
http://www.facebook.com/vic.erevia
Special Agent in Charge of Obama’s PPD (US Secret Service Presidential Protection Detail).
Pictures of family, location. Not very clever.
Victor Erevia
(540) 288-8382
1108 John Paul Jones Dr
Stafford, VA 22554-2129
Concerning that someone so close to POTUS would have such publicly available details.
Have confirmed by calling number and asking that it is Vic Erevia of USSS.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/victor-erevia/victor-erevia.jpg)
Unveiled – Michelle Obama Protection
Michelle Obama Protection
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict5.jpg)
Lots of supporters take photographs of First lady Michelle Obama, bottom center during a campaign stop at Hampton University, Virginia, November 2, 2012. AP
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict1.jpg)
U.S. First Lady Obama meets with supporters during a get-out-the-vote tour, November 1, 2012. Reuters.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict2.jpg)
First Lady Michelle Obama addressed a crowd of several hundred supporters in Sioux City, Iowa, Monday, Oct. 29, 2012,at the Sioux City COnvention Center in the downtown area. Jerry Mennenga
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict3.jpg)
First Lady Michelle Obama greets a child while talking with supporters after speaking at a campaign rally, Friday, Oct. 26, 2012, in Las Vegas. AP
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict8.jpg)
First lady Michelle Obama returns to the White House after watching her daughter Sasha’s basketball game in Washington, Sunday, March 11, 2012. AP
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict9.jpg)
In this undated image released by Nickelodeon, first lady Michelle Obama. seated second left, interacts with Jerry Trainor, left, as Miranda Cosgrove, center, Nathan Kress and Jennette McCurdy, right, look on during Obama’s guest appearance on the popular children’s show, “iCarly,” premiering Monday, Jan. 16, 2012 at 8 p.m EST on Nickelodeon. AP
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict10.jpg)
First lady Michelle Obama, wearing a hat and sunglasses, stands in line at a Target department store in Alexandria, Va., Thursday, Sept. 29, 2011, after doing some shopping. AP [Secret Service at right.]
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict11.jpg)
First lady Michelle Obama works the crowd while participating during the taping of Extreme Makeover Home Edition in Fayetteville, N.C., Thursday, July 21, 2011. AP
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict12.jpg)
US first lady Michelle Obama steps out of a vehicle, prior to boarding her plane, in Gaborone, Botswana, at the end of her week long trip to Africa, Sunday, June 26, 2011.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict13.jpg)
U.S. first lady Michelle Obama and daughters Sasha and Malia depart Cape Town, South Africa, as they travel to Gaborone, Botswana, Friday, June 24, 2011. AP
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict14.jpg)
U.S. first lady Michelle Obama embraces an audience member after she speaks at Regina Mundi Church and addresses the Young African Women Leaders Forum, in a Soweto township, Johannesburg, South Africa, Wednesday, June 22, 2011. AP
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict15.jpg)
First lady Michelle Obama greets people after speaking at a ceremony to dedicate the first of three new Fisher houses,Thursday, Dec. 2, 2010, at the Bethesda Naval Medical Center in Bethesda, Md. AP
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict16.jpg) U.S. first lady Michelle Obama, center left, walks with friends and security during a visit to Ronda in southern Spain, Saturday, Aug. 7, 2010. AP
U.S. first lady Michelle Obama, center left, walks with friends and security during a visit to Ronda in southern Spain, Saturday, Aug. 7, 2010. AP
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict17.jpg)
Security officers escort a convoy of cars, one believed to be transporting U.S. First Lady Michelle Obama, on arrival at the Villa Padierna Hotel in Marbella, southern Spain, Wednesday, Aug. 4, 2010. AP
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict18.jpg)
First lady Michelle Obama, center, greets Marines after a speech at Camp Pendleton Marine Corps Base in San Diego, Sunday, June 13, 2010. AP
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict19.jpg)
First Lady Michelle Obama, center, examines vegetables grown by Somali immgrant Khadija Musame, second from right, as interpreter Bilal Muya, right, farm coordinator Amy Lint, second from left, and Dr. Robert Ross, President and CEO of The California Endowment, look on Thursday April 15, 2010 in San Diego. AP
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict20.jpg)
U.S. first lady Michelle Obama, second left, shakes hands with UN and NGO workers during a visit to the United Nations base in Port-au-Prince, Tuesday, April 13, 2010. Obama is on a one-day visit to Haiti. AP
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict6.jpg)
Florida, January 2010.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/michelle-protection/pict4.jpg)
Michelle Obama at Latin American Montessori Bilingual Public Charter School, May 4, 2009. Wikipedia
Katy Perry Performs At A Milwaukee Rally For President Barack Obama
![[Image]](https://i0.wp.com/cryptome.org/katy-perry-milwaukee.jpg)
TOP-SECRET – NATO Military Policy on Information Operations

The Information Environment (IE) comprises the information itself, the individuals, organizations and systems that receive, process and convey the information, and the cognitive, virtual and physical space in which this occurs. This environment has seen significant changes in recent years. The importance of worldwide distributed information, the speed at which information is communicated, the role of social media and the reliability of information systems have created a situation in which no Alliance decision or action can be taken without considering its potential impact on the IE. The ubiquitous nature of information and the potential strategic ramifications of tactical actions add to the challenge faced by NATO Commanders. In this new IE it is more difficult to distinguish between the strategic, operational and tactical levels. The coordination, synchronisation and execution of information activities (IA) that deliberately create desired effects in the IE is essential to the Alliance’s successful functioning in peace, crisis and conflict.
Info Ops is a staff function to analyze, plan, assess and integrate activities focused on the IE rather than a capability in its own right. As a staff function, Info Ops provides the Commander with an assessment of the IE and a mechanism to plan and coordinate Information Activities on a continuous basis to achieve Information Effects in support of operational objectives.
At the Political-Military (Pol-Mil) level, the North Atlantic Council (NAC) and the Military Committee (MC), establish mission specific guidance, including StratCom guidance, to enable and maximize the effects of all information-related aspects of NATO’s operations and activities. Throughout the full spectrum of operations, peace, crisis and conflict, the integration and implementation of IA at every level of command is essential to overall success. The early application of IA can save resources, improve force protection and the effectiveness and efficiency of military capabilities through the establishment of planning and targeting priorities, and deconfliction and synchronization of activities.
…
The focus of Info Ops is on preserving and protecting alliance activities in the IE at all times while addressing, during military operations, NAC approved audiences, whose effectiveness is a function of their will, understanding and capabilities. As part of the operational and tactical planning, Info Ops plans, coordinates IA to reinforce or affect changes in behaviour, influence the will, shape perceptions, improve or degrade capabilities, and affect information and information systems.
Info Ops is comprised of three inter-related activity areas:
a. Preserve and protect Alliance freedom of manoeuvre in the IE at all times;
b. Induce, reinforce, influence, convince and encourage perceptions, attitudes and behaviours of NAC-approved audiences as part of NATO’s military missions;
c. Counter adversary’s propaganda as well as command functions and capabilities which support his opinion-forming and decision making processes.
…
Counter-Propaganda is a multidiscipline effort led and coordinated by Info Ops to analyse an adversary’s counter command and propaganda activities, to develop approaches and synchronize actions to counter these as appropriate. NATO PSYOPS forces and assets, supported by other functions, take a lead role in the analysis of adversary’s propaganda and support a variety of IA to counter it.
DOWNLOAD THE ORIGINAL DOCUMENT HERE:
Spider Man 4 – Full Movie
Die STASI am Ball
DOWNLOAD THE ORIGINAL DOCUMENT HERE
Meridian Capital: Klaus Dieter Maurischat „GoMoPa“ in Detention
Meridian Capital über die Verhaftung von GoMoPa-Chef Klaus Maurischat durch das BKA in Berlin wg. Erpressung, Betruges & Cyberstalking
Almost sure – Obama will will Election 2012
The Clash – Safe European Home – Live Uncut Movie
The Clash – London Calling – Uncensored Movie
TMZ – Khloe Kardashian on ‘X Factor’ — Showin’ Off the Nipples!
Spider-Man 2 – Full Movie
TOP-SECRET- NATO Allied Joint Doctrine for Information Operations

Information in the Global Security Environment. The changing global security situation has seen a shift in emphasis from the certainties of super-power confrontation towards more complex interactions of state and non-state actors. Globalisation, competition for resources and tensions in political and social structures combine with ideological, religious and cultural distinctions to increase uncertainty. Furthermore, terrorism, along with the spread of weapons of mass destruction, are likely to remain principal threats. There is also an expectation in some societies, reinforced by media exposure of global issues, that conflict and confrontation will be constrained by increasingly moral codes and regulated by progressively more extensive legal obligations. Concurrently, there has been an ‘information revolution’ (the Internet and mobile telephones) that has ushered in an age of computer-based decision-making. This evolving Information Environment1 comprises information, actors and systems that enable the use of information. The actors include leaders, decision-makers, individuals, and organizations. Information systems2 include the materials and systems employed to collect, apply, or disseminate information. The information environment itself is where humans and automated systems observe, orientate, decide and act upon information, and is therefore the principal environment of decision-making. To address both the changing global security situation and the emergence of a new information environment, NATO is in the process of developing concepts, processes and doctrine, including Information Operations (Info Ops), to deal with these new challenges.
…
Non-Lethal Activities. While Information Objectives may be accomplished through lethal or non-lethal means, there is likely to be an increased focus on non-lethal activity. A large element of Info Ops is non-lethal and recent operations have shown its significance by increasing the commander’s choice of means, by which effects can be created or generated at all stages of a crisis to support achievement of objectives. Increased attention on Info Ops is also due to the realisation that we now live in an information-dominated environment as described in paragraph 0101. There is an increased reliance on, and desire for, information. In addition, the impact of real-time media coverage of crises, the exploitation and manipulation of the media by some parties and the ever-increasing use of technologies such as the Internet have resulted in a world where information plays an increasingly important role.
The Impact of the Media. All crises occur under the spotlight of the international media. The maintenance of understanding and support of public opinion is crucial for democratically accountable governments, and this influences the options they can take, including military action, and the presentation of these options to different audiences. In order to gain and maintain public support, national governments and international organisations/agencies need to show a degree of transparency in their actions, and these actions must be in accordance with international law. The influence of the media has increased as access to regional and international media has increased. This has been brought about by technologies such as satellite broadcasting and global connectivity through the Internet. In addition, the availability of relatively cheap printing and copying equipment has brought newspapers and other printed material to a much wider audience. Consequently, there is a need to be proactive in ensuring that the presentation of NATO actions is accurate and reflects NATO’s messages, while at the same time countering an adversary’s or detractor’s attempts to undermine public support.
…
Information activities coordinated through Info Ops are an integral part of the campaign plan aimed specifically at affecting the will and understanding of decision-makers and affecting those capabilities that directly enable the application of their will or aid their understanding. Effects in the information environment can be created by a variety of military activities, the close coordination of which will contribute to the achievement of the overall objective. Info Ops comprises three inter-related activity areas:
a. Information activities that focus on changing, influencing, or reinforcing perceptions and attitudes of adversaries and other NAC approved parties.
b. Information activities that focus on preserving and protecting Alliance freedom of manoeuvre in the information environment by defending the data and information that supports Alliance decision-makers and decision-making processes.
c. Information activities that focus on countering command functions and capabilities, by affecting the data and information that support adversaries and other NAC approved parties, and are used in command and control, intelligence, surveillance and target acquisition, and weapon systems.
While information operations focussing on preserving and protecting Alliance freedom of manoeuvre in the information environment should take place at all times, information operations activities focussed on influence (paragraph 0119 a) and counter command (paragraph 0119 c) may only take place as part of an OPLAN and thus with NAC approval, including definition by the NAC of adversaries and potential adversaries.
DOWNLOAD THE ORIGINAL DOCUMENT HERE:
MERIDIAN CAPITAL ÜBER DIE SERIEN-RUFMÖRDER, FÄLSCHER UND GEWOHNHEITSVERBRECHER DER STASI-”GoMoPa”
http://www.meridiancapital.wordpress.com/
Gerne können Sie auch Meridian Capital direkt in New York kontaktieren:
www.meridiancapital.com/
HIER NOCH EINMAL DIE BILD-BELEGE ZUM THEMA STASI “GoMoPa” UND KOMPLIZEN BZGL. MERIDIAN CAPITAL
UND HIER DIE STASI-”GoMoPa”-FÄLSCHUNG – PEINLICH-PEINLICH -PEINLICH UND SUPER-DUMM-DREIST
TMZ – Sexy Chicks Invade Hollywood for Halloween
Cryptome unveils WikiLeaks-Wau Holland Tax-Exemption Revoked
German original:
http://www.wauland.de/index.html
English translation:
ON OUR OWN – November 5, 2012
Public benefit of
Wau Holland Foundation
History of withdrawal
End of 2010, the Wau Holland Foundation (WHS) was intervention by the Hessian Ministry of Interior ( [1] , [2] , [3] , [4] ,) the exempt status by the then competent tax office Kassel denied [5] . This decision was taken so that the foundation had with the fundraising and the associated project financing WikiLeaks violated the “principle of selflessness.”
Under the principle of selflessness (§ 55 AO), a foundation may not primarily pursue economic purposes, eg commercial purposes or other commercial purposes, but can only use the money to further their own goals. The withdrawal of exempt status by the IRS is already difficult to understand why, for two reasons: First, lay the tax office has not received accounting records from the year 2010 which would justify such a decision. Second, the regional council has Kassel as supervisory authority early December in a press release made it clear that the promotion of WikiLeaks very well according to the statutes of the Foundation to purchase.
Perhaps this is why the reasoning by the tax office in Hamburg, after the relocation of the Foundation inherited the controversial procedure was changed, and as a “violation of the principle of immediacy” (§ 57 AO) pursued.
During the test
The WHS commissioned a specialized foundation and tax law firm to represent their interests and put an objection against the decision [6] . In subsequent proceedings, there was a test of whether the Foundation had in 2010 met the “requirement of immediacy” and the statutes according to the donations it was no longer in dispute.
The “principle of immediacy,” requires that a nonprofit organization can indeed engage helpers to achieve their goals, it must be a traceable control procedures are set binding.
End of 2009 / early 2010 the WHS had met with the “WikiLeaks” only oral agreements, until the end of 2010, these arrangements were also fixed in a written contract with a project manager, in addition to the objectives and responsibilities and control processes are defined. Although the guidelines were already out of the contract throughout 2010, lived by all parties accordingly, did the tax office does not recognize that the immediacy was preserved and declined after 18 months of testing our appeal against the decision from [7] .
To the process after all this time to finally bring to a conclusion, the WHS agreed with the tax office to Hamburg to complain against a rejection of the opposition does not [8] and to obtain the profit for 2011 and subsequent years back.
Of present state
We have learned through this process, what contractual conditions, we need to encourage charitable can. All donors from 2010, we unfortunately have to say that these donations are not tax deductible. Nevertheless, these donations were used for the purposes of the donor.
When we are presented by the tax office promised exemption notification has been received, we can exhibit for the years 2011 and 2012 donation receipts upon request. For donations to 200, – Euro for the donor, the payment document is sufficient, together with the notice of exemption, which can then be downloaded from http://www.wauland.de.
The projects that promote Wau Holland Foundation, also here to inform.
We appreciate every donation, here you can see the form in which you can donate. For donations, large donations and inheritance rules please contact us at the contact form available.
Explanatory documents
[1] Emails between the Interior and Regional Council
[2]Innenminster of foundation supervision (2010-12-10)
[3] Foundation supervision of Interior Minister (2010-12-16)
[4] Interior Minister of Supervision of the Foundation (2011-01-05)
[5] Revocation of exempt status by the FA Kassel (2011-01-07)
[6] Objection to the tax office decision (2011-01-11)
[7] Objection decision of the Tax Office Hamburg-Nord (2012-10-25)
SECRET-JIEDDO Global IED Monthly Summary Report
The Incredible Hulk – Full Movie
DIE WELT ÜBER DIE DIFFAMIERUNGSMETHODEN DER STASI – VORBILD FÜR “GoMoPa”
SI Swimsuit – Jackie Moon and Heidi Klum – Video
TMZ – Liberty Ross — The Smokin’ Hot Halloween Ensemble
The Prestige – Full Movie
The Prestige is a 2006 British-American mystery thriller.
The story follows Robert Angier and Alfred Borden, rival stage magicians in London at the end of the 19th century. Obsessed with creating the best stage illusion, they engage in competitive one-upmanship with tragic results.
DAS BETRUGSURTEIL GEGEN “BENNEWIRTZ” UND “PETER EHLERS” “GoMoPa”-PARTNER “MAURISCHAT” UND “VORNKAHL” WG BETRUGES AM EIGENEN ANLEGER
Über eine selbstgebaute Blogseite verbreiten die GoMoPa-Gangster eine gefälschte Stellung von Meridian Capital, um Verwirrung zu stiften.
Diese Blogseite existiert erst seit Dezember 2010.
Beweis:
http://www.hypestat.com/pressreleaser.org
Die Meridian Capital-Seite, das Original,
http://othergomopa.blogspot.com/
ist dagegen bereits seit2009 online
Beweis: Aussage Meridian Capital – das Unternehmen können Sie auch gerne direkt kontaktieren.
und
KLAUS DIETER MAURISCHAT IN DETENTION
Source: http://klaus-dieter-maurischat.blogspot.com/2009/01/klaus-dieter-maurischat-in-haft.html
Hintergrund: Die Verurteilung von Klaus Maurischat und Mark Vornkahl wegen Betruges am eigenen Anleger
Klaus Maurischat und Mark Vornkahl, Betreiber vonwww.gomopa.net: Am 24. April 2006 war die Verhandlung am Amtsgericht Krefeld in der Betrugssache: Mark Vornkahl / Klaus Maurischat ./. Dehnfeld. Aktenzeichen: 28 Ls 85/05 Klaus MaurischatLange Straße 3827313 Dörverden.Das in diesem Verfahren ausschließlich diese Betrugsache verhandelt wurde, ist das Urteil gegen Klaus Maurischat recht mäßig ausgefallen.Zusammenfassung der Verhandlung vom 24.04.2006 vor dem Schöffengericht des AG Krefeld in der Sache gegen Klaus Maurischat und Mark Vornkahl.Zur Hauptverhandlung erschienen:Richter Dr. Meister, 2 Schöffen,Staatsanwalt, Angeklagter Klaus Maurischat, vertr. durch RA Meier, Berlin; aus der U-Haft zur Verhandlung überführt.1. Eine Gerichtsvollzieherin stellt unter Ausschuss der Öffentlichkeit eine Urkunde an den Angeklagten Maurischat zu.2. Bei Mark Vornkahl wurde im Gerichtssaal eineTaschenpfändung vorgenommen.Beginn der HauptverhandlungDie Beklagten verzichten auf eine Einlassung zu Beginn.Nach Befragung des Zeugen Denfeld zum Sachverhalt wurde dieVerhandlung auf Wunsch der Staatsanwaltschaft und den Verteidigern unterbrochen.Der Angeklagte Maurischat gab nach Fortsetzung derHauptverhandlung Folgendes zu Protokoll:Er sähe ein, dass das Geld auf das falsche Konto gegangen sei und nicht dem eigentlichen Verwendungszweck zugeführt wurde. Das Geld sei aber zurückgezahlt worden und er distanziere sich ausdrücklich von einem Betrug.Schließung der BeweisaufnahmeDer Staatsanwalt verließt sein PlädoyerEr halte am Vorwurf des Betruges fest. Mit Hinweis auf die einschlägigen Vorstrafen des Angekl. Maurischatund auf laufende Ermittlungsverfahren, beantrage er ein Strafmaß von 1 Jahr und 6 Monaten.Er halte dem Angeklagten zu Gute, dass dieserWiedergutmachung geleistet habe, und dass dieser geständig war. Zudem läge die letzte Verurteilung wegen Betruges 11 Jahre zurück. Auch sei der Geschädigte nicht in existentielle Not geraten, wobei der Staatsanwalt nicht über noch laufende Verfahren hinweg sehen könne. Er läge aber dem Angeklagten Maurischat nahe, keine weiteren Aktivitäten im Bezirk der Staatsanwaltschaft Krefeld auszuüben, insbesondere möchte er, dass keine weiteren Anleger im Bezirk der Staatsanwaltschaft Krefeld durch GoMoPa akquiriert werden.Die Freiheitsstrafe soll zur Bewährung ausgesetzt werden.Plädoyer des Verteidigers des Angekl. Maurischat, Herrn RA MeierEr schließe sich, wie (in der Unterbrechung) vereinbart, dem Staatsanwalt an.Es stimme, dass sein Mandant Fehler in seiner Vergangenheit gemacht habe, und dass er auch diesmal einen Fehler begangen haben könnte, jedoch sei der Hinweis wichtig, dass sein Mandant aus diesen Fehlern gelernt habe.Der Angeklagte haben das letzte Wort.Maurischat sagt, es sei bereits alles gesagt worden.Unterbrechung zu Hauptverhandlung. Der Richter zieht sich mit den Schöffen zur Beratung zurück.Urteilsverkündung:Der Angeklagte wird des gemeinschaftlichen Betrugs für schuldig befunden.Der Angeklagte Klaus Maurischat wird zu einerFreiheitsstrafe von 1 Jahr und 6 Monaten verurteilt. Diese wird zur Bewährung ausgesetzt.Die Bewährungszeit wird auf 3 Jahre festgesetzt.Der Haftbefehl gegen Klaus Maurischat wird aufgehoben.Der Angeklagte trage die Kosten des Verfahrens.UrteilsbegründungDer Richter erklärt, dass eine Täuschung des Geschädigtenvorliegt und somit keine Untreue in Betracht kommen kann.Die Fragen, ob es sich um einen Anlagebetrug handele sei irrelevant. Er hält den Angeklagten die geleistete Wiedergutmachung zu Gute.Ebenso ist das Geständnis für die Angeklagten zu werten. Zudem liegt die letzte Verurteilung des Angeklagten Maurischat 11 Jahre zurück.Die Parteien verzichten auf Rechtsmittel. Das Urteil ist somit rechtskräftig.Mit dem heutigen Urteil endet ein Kapitel in derBetrugssache Goldman Morgenstern & Partners, Klaus Maurischat und Mark Vornkahl.Alle GoMoPa.net Verantwortlichen, Maurischat, Vornkahl und Henneberg sind nun vorbestrafte Abzocker und Betrüger und die Zukunft der Pseudoklitsche GoMoPa.net sieht duster aus.Mir dem Geständnis der beiden ABZOCKER MAURISCHAT UND VORNKAHL vor Gericht bricht ein jahrelangaufrechterhaltenes Lügengeflecht von einigen primitiven Betrügern zusammen. Gewohnheitsverbrecher und Denunzianten,die rechtschaffene Personen und Firmen in ihren Verbrecherforen kriminalisierten.
SECRET-U.S. Customs and Border Protection Security Policy and Procedures Handbook

The following is the complete U.S. Customs and Border Protection Security Policy and Procedures handbook from August 2009. An incomplete version of the document was previously released by Cryptome in 2010
that contained only “minimum security requirements” for architects and engineers. This version is more than 600 pages longer and contains information on everything from document control to the use of the Homeland Security Advisory System. The handbook was obtained from a publicly-accessible website associated with a prominent construction company.
1.1.1. U.S. Customs and Border Protection (CBP) Internal Affairs, Security Management Division is responsible for providing operating policies, procedures, and practices for the physical protection of personnel, infrastructures, and assets from deliberate or unforeseen threats.
1.1.2. These standards shall be applied to all CBP facilities, owned, leased or occupied space. Compliance is mandatory for all new construction, renovation, and relocation projects. Existing CBP facilities are not required to be upgraded unless risk assessment determines otherwise.
1.1.3. These standards shall be used by the Office of Internal Affairs, Security Management Division (SMD) to serve as a guide for: Conducting security surveys for the development of threat assessments; evaluating security conditions during real estate market surveys and using the requirements guide for architectural and engineering (A&E) design efforts. Nothing in this policy handbook shall be construed as contrary to the provisions of any statute or other Federal regulation. In the event of conflict, specific statutory provisions shall apply.
1.1.4. Physical Security Programs shall be administered within each Region, District, and field activity based on the policy set forth in this handbook to ensure the protection of CBP assets. These programs shall be continually and effectively administered and monitored to ensure their integrity. At a minimum, a Physical Security Program shall include those items outlined in Chapter 2.1: Policy.
…
I. Hold Rooms
A. General
1. A hold room is a secure facility for the detention of aliens encountered and processed by operational components of CBP.
2. The hold room is used for detainees and is located within the access-controlled secure and violator processing area. All access control equipment will be HSPD-12/FIPS 201 compliant systems and will only be installed by approved GSA Schedule 70 vendors.
3. Hold rooms for detainees must be constructed to hardened construction standards and must be situated in a secure area to ensure the safety of both officers and the traveling public. Hold rooms should be co-located and rectangular in shape with no dividing walls or partitions. All fixtures must meet detention-grade standards.
4. Hold Rooms are located in the following CBP facilities:
(a) Border Patrol Stations
(b) Border Patrol Sector Headquarters
(c) Border Patrol Check Points
(d) District Offices
(e) Service Processing Centers
(f) Ports of Entry (Air, Land, Sea)
(g) Anti-Smuggling Units
(h) Staging and Alien Detention Removal Facilities5. The nature and circumstances of detentions are governed by existing CBP policy, including CBP Directives No. 3340-030 and 3340-030B:
6. Minimum square footage per occupant of hold rooms is determined by the following method:
(a) 25 sq. ft of common space for wheelchair turnaround circulation as required by ADA
(b) 5 sq. ft for toilet and lavatory fixtures
(c) 7 sq. ft of unencumbered for each detainee (Unencumbered is usable space that is not encumbered by fixtures or furnishings)
(d) A single occupant hold room for detainees is therefore a minimum of 37 Sq. ft. Multiple occupancy rooms shall be 37 Sq. ft for the first occupant and 7 sq. ft of unencumbered space for each additional occupant.7. Other space related requirements include:
(a) 1 toilet per 15 detainees
(b) Males and females must be kept in separate hold rooms (including juveniles)
(c) Young children must remain with their mothers8. Associated spaces include:
(a) Interview Rooms must be located adjacent to the hold rooms, and either within or outside a secure perimeter zone. They must be under 24X7 surveillance and detainees are required to be secured with handcuffs. If located within the violator processing area, the interview room must have the same construction criteria as the hold room. Asylum seekers must be placed in a separate interview room.
(b) Search Rooms must be located adjacent to hold rooms within a secure perimeter zone. It has the same specifications as a hold room, except there are no windows, toilets and floor drains.
(c) Alien Property Storage Rooms must be located within a security perimeter, securely constructed for high attack resistance and they require a door lock and an Intrusion Detection System.…
B. Physical Security Requirements of a Hold Room
1. In general, all hold rooms must have the following requirements:
(a) Located within a security perimeter
(b) Securely constructed for high attack resistance
(c) Minimum space as defined above
(d) No beds; a hold room is not designed for sleeping
(e) Furniture must be of solid construction and secure to wall or floor2. According to the Service Processing Center Detention Construction Standards (SPC Detention Construction Standards, Dated 01 November 2004), hold rooms are classified as having a Medium Security Level.
C. “Medium” security walls shall be constructed using one of the following methods:
1. Concrete masonry unit walls shall be a minimum nominal 8” (200 mm) wide units reinforced with #4 (No. 13 metric) vertical reinforcing bar at 16” (400 mm) on center. All cells of concrete masonry units shall be fully grouted with 3,000 psi (21 Mpa) grout.
2. Pre-cast concrete panel walls shall be a minimum nominal 4” (100 mm) wide, minimum strength of 5,000 psi (35 Mpa) and reinforced with minimum W4 (MW26) welded wire fabric at 4” (100 mm) on center in both directions, conforming to ASTM A185.
3. Cast-in-place concrete walls shall be a minimum 6” (150 mm) wide, minimum strength of 3,000 psi (21 Mpa) reinforced with #4 (No. 13 metric) reinforcing bars at 8” (200 mm) on center in one direction. Cast-in-place concrete walls that are less than 6” (150 mm) wide, but no less than 4” (100 mm) wide shall have a minimum strength of 5,000 psi (35 Mpa) reinforced with W4 (MW26) welded wire fabric at 4” (100 mm) on center in both directions.
4. Steel wall panels shall be 0.093 in. (12-gauge) minimum thickness A-60 galvanneal steel conforming to ASTM A 653-CS requirements. All structural or stiffening members shall be 0.058 in. (16-gauge) minimum thickness A-60 galvanneal steel conforming to ASTM A 653-LFQ requirements. All structural tubing stall be 0.115 in. (11-gauge) minimum thickness steel conforming to ASTM A 653-CS and ASTM A-525, G-90 galvanized requirements.
DOWNLOAD THE ORIGINAL DOCUMENT HERE:
Men in Black III – Full Movie – Will Smith – Tommy Lee Jones
DIE STASI FÄLSCHER a la “GoMoPa” fälschten sogar “BILD”
You are the Judge – Obama Wore an Ear-Piece During Debates?
A news report speculates that Obaman wore an ear-piece during the debates with Romney.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-earpiece/pict9.jpg)
The debate photos below show no ear-piece.
The Last Of The Mohicans – Daniel Day-Lewis & Madeleine Stow – Full Movie
Public Intelligence – Hamid Karzai Decree on Fighting Afghan Corruption
UNCLASSIFIED//FOR OFFICIAL USE ONLY
This product may contain copyrighted material; authorized use is for national security purposes of the United States Government only. Any reproduction, dissemination, or use is subject to the OSC usage policy and the original copyright.
Afghanistan: Karzai’s Recent Decree on Fighting Against Corruption
[SAP20120727457007 Kabul Office of the President of the Islamic Republic of Afghanistan in Pashto; OSC Translated Text; 26 Jul 12]
——————————————
The Office of the President of Islamic Republic of Afghanistan
Decree
On the execution of content of the historical speech of June 21, 2012 in the special session of National Assembly
After years of political isolation, wars, and destruction, we, the people of Afghanistan, have witnessed great political, social, and economic success; we have established our appropriate position in the international community. Along with establishing broad international relations, we have been able to sign important strategic agreements with countries in the region and in the world.
Alongside those achievements, unfortunately, we were faced with challenges in the areas of governance, fights against corruption, law enforcement, and economic self sufficiency.
For this reason, on June 21 of the current year, in a speech to a special session of the National Assembly [parliament], I laid out existing shortcomings and problems, and talked about measures to be taken for the elimination of those problems.
For the purpose of succeeding in those areas, for eliminating existing problems, and for bringing necessary reforms in the three branches of the government, I am approving the following measures:
1st– Joint discussions among government organs:
1. Based on the framework of the constitution and with consideration for separation of powers, the three branches of the government are responsible for the implementation of duties and authorities. They should work and cooperate in such a way that at the end of every fiscal year their developmental expenses should not be less than 50 percent of the allocated budget. The executive branch is accountable to the president for its activities, and should report to him for its actions.
2. I request the Supreme Court of the Islamic Republic of Afghanistan to, in the course of six months, complete and finalize all dossiers currently in process within the judicial system, especially dossiers related to corruption, land usurpation, and chain-assassination.
3. I request the Supreme Court of the Islamic Republic of Afghanistan to, in the course of nine months, activate all inactive courts in the provinces and districts, and staff them with professional personnel.
4. I request the Supreme Court of the Islamic Republic of Afghanistan to, based on the timeframe determined in the law, simplify the judicial procedures for determining the destiny of the accused and suspects, and that the people should be informed of the results through media.
5. I am requesting the National Assembly, the highest legislative organ of the country, to consider the national interests of the Afghan nation and to exercise their duties and authorities in giving priority to a speedy implementation of realistic and legitimate proposals presented to them by the government. While watching the actions of the members of the government, they should help and cooperate with the government in the enforcing of law and timely implementation of developmental projects.
6. I request the National Assembly to, in the course of four and half months, rectify drafts of laws, executive orders, and agreements sent to them by the government.
7. High ranking government officials should separate themselves from supporting law breakers, criminals, and corrupt and guilty individuals. Judicial and law enforcement offices are ordered to take firm legal actions against those who get in the way of justice without considering their official position.
8. Within five months, members of the Cabinet must visit related regional centers at provincial and district levels in order to meet these areas’ needs. They must take measures to attend to their shortages and operational deficiencies. Then, they must report their findings to the Cabinet.
9. During the process of appointing qualified personnel, high ranking government officials must refrain from hiring based on intermediary recommendations. Administerial and state establishments are ordered to follow the rule of law when hiring civil servants in the judiciary, the prosecutors’ office, and universities.
10. Ministries and government administrations, including the judiciary organizations, are charged with the goal of attending to the problems [needs] of the people. They must prepare complete information, especially in provinces and districts, for the implementation of plans and procedures for completed tasks, major achievements, and the quality of their organization and personnel. Present the written report after confirmation and certification by the highest ranking authority in the center, and the verification of provincial governors, on the 28th and 29th of every month to the General Directorate of Administrative Affairs, and through the Cabinet Secretariat to the office of the president.
11. Judiciary agencies are ordered that no individual should be imprisoned, arrested, or placed under investigation without lawful rationale, or remain in prison for a longer period than his/her actual sentenced imprisonment. The Ministry of Interior, the Ministry of Justice, and the office of the Attorney General are ordered to present a report of their actions to the office of the president every three months through the General Directorate of Administrative Affairs and the Cabinet Secretariat.
12. The existence of unlawful weapons has caused the occurrence of bloodshed, bullying, illegal land confiscation, violations of human rights, breach of the decisions made by official organizations, and disturbances of order and justice. In order to eliminate these negative phenomena, under the disarmament program, the Defense and Interior Ministries and the General Directorate of National Security are charged with taking serious action throughout Afghanistan for collecting weapons. Introduce the violators and usurpers to the related agencies for further investigation. They must send their report to the office of the president through the General Directorate of Administrative Affairs and the Cabinet Secretariat.
13. The Ministries of Defense, Interior, Labor, Social Affairs Martyrs and Disabled, and the National Security Directorate are ordered to urgently pay serious attention to observing the rights of their patrons, immediate treatment of the injured, and the preservation of the rights of the Afghan National Police, National Army, and national security martyrs. Every three months, provide a report about their operations to the Cabinet.
14. Within a month, the General Directorate of Administrative Affairs, Ministry of Finance, the Ministry of Economy, the Cabinet Secretariat, the Independent Commission for Administrative Reform and Social Services, and the office of the president are charged with investigating parallel institutions such as (PAD/PMU/PIU) and other structures that are temporarily operating per project basis. They must provide an explanation for these entities’ existence along with the original ministries and directorates, and present it to the Cabinet.
15. Once again, all state organizations and agencies are ordered to refrain from signing contracts for provision of services, with high ranking state officials and those appointed and supported by them. Such conduct would be considered a crime, and those committing it will be legally investigated by the office of the Attorney General.
16. As the provider of security and social order, the Attorney General must gain the trust of the entire population. Therefore, all prosecutors in the country are ordered to fulfill their duties in such a manner that it will demonstrate reform. Their conduct must become the impetus for reform among government employees and members of the society. In this regard, it is the duty of the High Office of Oversight and Anticorruption, ANP’s Department of Criminal Investigation, National Security Directorate, and the Financial Inspection Directorate to help with the Office of the Attorney General. They must do so, not only as a parallel institution, but as an assistant. They must help concerning criminal documents, providing evidence, and in the process of obtaining elucidations. They must identify the violators of law and introduce them to the Attorney General for judicial investigation.
17. For the purpose of providing proper public services to the citizens, until election conditions are provided for municipalities, from now on, the process of appointing mayors will be conducted through the procedure for the selection of high-ranking positions, and by the recommendation of the Special Board of Councils and the Independent Directorate of Local Governance (IDLG). Within three months, IDLG is ordered to appoint provincial and major district chiefs by introducing eligible, honest, and professional individuals through the Board of Appointments.
18. The Interior, Higher Education, Information and Culture, Hajj and Pilgrimage, and the Education Ministries–with cooperation by the Council of Scholars, Imams of mosques, religious scholars, students, and intellectuals–are ordered to invite people for helping to achieve national unity, social consensus, friendship, brotherhood, peace and reconciliation, as well as virtue. They must seriously prevent those propaganda and programs which are contrary to social etiquette and order, causing the youth to deviate, creating negative perceptions within the society.
19. Advisors to the president play the role of a bridge between the office of the president and the people. Therefore, they must work to convey the opinions and suggestions of the people to the government, and strengthen this relationship. On a monthly basis, they must send a report about their operations to the office of the president through the General Directorate of Administrative Affairs and the Cabinet Secretariat.
2nd– The Ministry of Defense is charged with the following:
1. Within two months, with assistance by the Ministries of Finance, Economy, and Justice, it must revisit its provisional affairs. Clear and complete mechanisms must be organized and presented to the Cabinet.
2. Within three months, clarify and organize a just policy concerning promotions, appointments, and transfers; then report to the office of the president.
3. Within three months, foreign foundations that are included in the transition process, prepare an explanation, documentation, and registration of their properties, tools, and weapons. Following ratification by the Cabinet, practice it when taking over the responsibilities.
4. Within three months, in accordance with international agreements, engage in discussions with the United States, and with NATO members concerning Air Force Armament needs; present a report about achievements to the National Security Council and to the Cabinet.
5. Within six months, reexamine the plan for the settlement of forces in light of a detailed arrangement. Every two months, provide a report about the results of this operation to the National Security Council, and to the Cabinet.
6. Include the transition of the Bagram prisoners in operational priorities, and properly complete [the transition] prior to the predetermined deadline.
7. In accordance with proper conditions, promotions of staff, up to the rank of Colonel, must take place prior to 18 Aug 2012.
3rd– The Interior Ministry is Ordered to:
1. Within two months, act on those orders of the court regarding the confiscation of the public and private properties that are finalized, and conveyed to the Ministry of Interior. Send a report about its achievements to the General Directorate of Administrative Affairs and the Cabinet Secretariat.
2. Reassess the organization of the regional police within three months. In accordance with the former [existing] resolutions of the National Security Council, integrate parallel groups and structures with the regional police. Present a report to the Cabinet.
3. Within three months, should report to the Cabinet about living conditions in the country’s prisons and detention centers, and about human rights.
4. Within three months, should report to the Cabinet about information technology and with help of the Ministry of Communication the application of the first phase of electronic ID.
5. Within six months, should present a plan about the improvement of the operations of Kabul traffic police to the Cabinet, with the cooperation of Kabul municipality.
6. Within six months, in light of the detailed plan for transition process, review the plan of settling forces and report every two months to the National Security Council and the Cabinet.
7. The promotion of personnel to the rank of Colonel according to conditions outlined should be finalized before 18th of August.
8. According to the former presidential orders and decisions, the complete dissolving of private security companies and send a report about their belongings to the Ministry of Interior, in the quickest time.
4th–The Foreign Ministry is Ordered to:
1. Within three months, should present to the Cabinet the list of those Ministries who have disobeyed international treaties, and tangible legal violations of all laws, more than two times.
2. Within three months, should present to the office of the president a decision and mechanism for employing diplomats, reassess their qualifications, and particular proposals for improvement.
3. Within six months, should present to the office of the president of the Islamic Republic of Afghanistan to assess the cooperation of all political offices outside the country (educational, cultural, transportation, military and all related offices) with connected organs.
5th–The Ministry of Justice is Ordered to:
1. Within two months, activate the legal translation board for contracts, treaties, and other international documents.
2. Within three months, with the cooperation of Directorate of the Administrative Affairs and Cabinet Secretariat and the Civil Services Administrative Improvements’ Independent Commission should review the law of the Government Fundamental Organizations and send their report to the Cabinet.
3. Within two months, the procurement law should complete the reviewed plan processes.
4. Within two months, the election law should be completed and should be sent to the Cabinet for approval. 5. Within six months, the municipalities’ law and the Office of the Attorney General law should be completed and presented to the Cabinet.
6th–The Office of the Attorney General is Ordered to:
1. Within one month, all the detainees should be assessed by their prosecutor’s offices, detentions without tangible reasons should be stopped and in the detention centers the list of the detainees together with the explanation for accusations be prepared and sent to the Judiciary Committee.
2. From the date of the promulgation of this decree, the proposal for the provincial prosecutor’s director’s appointments, like the appointments of the Ministries and other offices, should be presented to the office of the president of the Islamic Republic of Afghanistan.
3. Within two months, with the help of the Ministry of Justice, the Attorney General’s office and the Ministry of Justice, in order to attend to the dossiers, should distinguish their duties and send their report to the Cabinet.
4. Within two months, the supervisory office of the prosecutor should be formed, or this authority should be passed to the supervisory office of the High Court and a special plan should be presented to the Cabinet.
5. Within six months, with the cooperation of the Ministry of Justice, the alternative to imprisonment plan should be prepared and presented to the Cabinet.
6. Within six months, the inactive prosecution offices in the districts should be activated by employment of professional personnel.
7. Within six months, the Prosecutor General’s office should assess all professional and supportive personnel, recognize the corrupt cadres, employ separate measures, and report to the office of the president.
7th–The High Office of Oversight and Anti-corruption is Ordered to:
1. Within two months, governmental offices and private sectors should take the criterion of the strategy for fight against corruption under supervision, and present their results to the office of the president.
2. Within six months, private institutions’ and government official’s suspicious wealth should be assessed and the report of their findings sent to the office of the president of the Islamic Republic of Afghanistan every two months.
3. Within six months, assess all professional and supportive personnel offices, recognize corrupt officials, make specific recommendations, and present their results to the office of the president.
8th–The Independent Directorate of Local Governance is Ordered to:
1. Within a month, the posts of the governors should be assessed and their necessary improvements and specific proposals should be presented to the office of the president.
2. Within two months, the posts of the deputies to the provinces, with help of the Independent Commission for Administrative Improvement and Civilian Services, should be opened for free competition and hence patriotic, sincere, well qualified and suitable cadres employed.
3. Within three months, the draft of municipalities law and other legislative documents with the aim of traversing the stages, should be sent to the Ministry of Justice.
4. Within six months, the shortage of provincial organizations should be completed with suitable cadres from the Ministries and governmental offices.
5. Within six months, with help of the Ministries of Economic, Home Affairs, and Finance Ministry and other related foundations outline a mechanism so that the provincial reconstruction teams’ activities should be replaced with the present governmental organizations, and presented to the Cabinet.
6. During the years 2013 and 2014, with the cooperation of the Home Affairs and Finance Ministries, the administrative buildings for district officers and security commanders should be completed.
9th–The Directorate of the Administrative Affairs and the Secretariat of the Cabinet is Ordered to:
1. Within two months, prepare and organize the plan for the government official trips and should present it to the Cabinet.
2. Make a list of unimplemented resolutions and presidential decrees and orders from the era of the transitional government to the present, specified by offices and Ministries and present it to the Cabinet within two months.
3. In cooperation with the Ministry of Economic Affairs, assess the professional coordination between the Ministry of Agriculture and Irrigation and the Ministry of Energy and Power on the issue of water and present a specific plan to the Cabinet within two months.
4. Assess professional collaboration between the Ministry of Water and Energy and Afghanistan Power Corporation, in cooperation with the Ministry of Economic Affairs, and present the results about the solution for saving electricity together with a specific plan to the cabinet within two months.
5. Reassess the government organizational structure in cooperation with the Independent Commission for Administrative Reforms and Public Services, and present the draft proposal of parallel organizations’ reform, mentioning the deletions, mergers, and specific instances to the office of the president of the Islamic Republic of Afghanistan within three months.
6. Prepare a list of the individuals who have earned a Master’s degree and degrees higher than Master’s abroad, and are ready to serve in the government, and take appropriate action after obtaining instructions from the office of the president of the Islamic Republic of Afghanistan within three months.
7. In cooperation with the Ministry of Justice, create the policy of obtaining continued benefits for the government officials who retire after serving in the government, and present it to the cabinet within three months.
10th– Ministry of Hajj and Pilgrimage is Assigned to:
1. Arrange at least ten educational courses for increasing the capacity of Imams and improving guidance affairs, and present its report to the Cabinet within two months.
2. Submit a plan for determining, returning, and developing endowed properties, and the process of utilizing its revenue to the Cabinet within three months.
3. Make efforts to better organize the process of obligatory and Umrah [can be performed anytime during the year] Hajj.
11th– The Independent Commission of Administrative Reforms and Public Services is assigned to:
1. Present a report about the details of implementation and need for CBR [Community Based Rehabilitation] and similar projects to the Cabinet within one month.
2. Reassess the structure of the commission and the appointment of the entire staff, including the appointing board commissioners and the High Directorate of Public Services, and present
specific plans about the internal reforms in the Independent Commission of Administrative Reforms and Public Services considering high standards and minimum requirements of employment in the key positions of the commission to the office of the president of the Islamic Republic of Afghanistan within one month.
3. Determine the date of the first general examination aimed at recruiting young cadre, and announce the mechanism for the examination through the media.
4. Within three months, present a comprehensive plan for adding the office of Deputy Minister for Professional Immunity and Public Services for Government Employees to the Cabinet.
12th– Independent Elections Commission is Assigned to:
1. Prepare the plan for registering names [of candidates] for presidential elections in the year 2014, and present it to the Cabinet within one month.
2. Prepare an organized and transparent election platform that guarantees people’s participation, and create a comprehensive schedule for presidential, parliamentary and provincial council elections within three months.
13th– The Ministry of Education is assigned to:
1. Arrange at least four short-term courses aimed at increasing the capacity of 40 thousand teachers, and present the report to the Cabinet within three months.
2. Expand the sustainment and monitoring policies of foundations of education on national and local levels, and present them to the Cabinet within three months.
3. Start evaluating all private and public schools and take serious action against schools that violate the educational polices of the country, or whose instructional qualities are substandard, within six months.
4. Present to the Cabinet the plan for creating a specific administrative unit for the purpose of promoting all the affairs of vocational education, including the foundations of secondary instruction and technical colleges in cooperation with the Ministries of Labor and Social Affairs Martyrs and Disabled, and Higher Education within six months.
5. Take action regarding recruiting 11,000 new teachers and staff through free competition and talent acquisition among qualified teachers and professors in the capital of the nation and the provinces, and present a monthly report to the Cabinet within six months.
6. Within six months, increase the number of teacher support centers for teacher training at district level from 111 to 180 in order to provide training opportunities to female teachers in rural areas.
7. In order to boost patriotism, with the commencement of the 2013 academic year include the subject of love of country to the curriculum of all public and private schools and monitor its proper instruction.
14th– The Ministry of Higher Education is assigned to:
1. Complete the mechanism for taking the college entrance examination and present it to the Cabinet for approval within three months.
2. In cooperation with the Ministry of Foreign Affairs, address the problems of Afghan students abroad, and present its specific proposal for providing practical solutions to their problems within three months.
3. Within six months, start evaluating all private higher education institutions, and take action for the purpose of standardization regarding those who are operating against the higher education policies, or whose quality of instruction is substandard.
4. Present a specific plan to the Cabinet within six months for starting English language instruction in medicine and engineering schools of all universities starting the academic year 2013.
5. Examine the need for taking a government exam for graduates of private universities; provide a specific plan if required, and if not required, provide reasons to the Cabinet. within six months.
15th– The Ministry of Information and Culture is Assigned to:
1. Within two months, present a practical plan to the cabinet that is coordinated amongst relevant organizations, including the governor of Ghazni Province, for the improvement of the Affairs of the Islamic Heritage Center in Ghazni City.
2. Present a specific plan to the Cabinet about the quality control of public and private media and devise minimum standards within two months.
3. Within three months, present an action plan and report to the cabinet regarding national languages, dialects, national terminologies, omitting strange and unfamiliar terminologies from established literature, strengthening national unity, and observing and amplifying established Afghan traditions. To enrich Afghan culture, utilize public and private social media.
4. Present a policy for preserving and repairing historical monuments and ancient sites to the Cabinet, within six months.
16th– The Public Health Ministry is Required to:
1. Within six months, assess public and private hospitals, and take serious steps to standardize those hospitals which provide lower quality or operate contrary to the policies of the Public Health Ministry.
2. Investigate and assess the quality and quantity of all imported and produced medicine in the markets, and present its specific reform proposals to the Cabinet, within six months.
3. Take action for standardizing provincial and district hospitals, and to institutionalize public services.
17th– The Finance Ministry is Ordered to:
1. Present a finished proposal of “Golden Hand Shake” with the help of the Independent Administrative Reform and Civil Service Commission to the Cabinet, within six months.
2. Complete the Kabul Bank affairs assigned to Kabul Bank Audit Delegation, and present its report to the office of the President, within one month.
3. Make a proposal to pursue and implement the pledges of the Tokyo Conference within two months, and inform the Cabinet about its progress on a monthly basis.
4. Present a report to the Cabinet about those officials within the ministry who are either paid by the international organizations or their salaries are regulated by international organizations. Provide information about the level of their salaries and their contracts within two months.
5. Within three months, determine the future of food enterprises, silos, and the national buses [transportation]; and provide a specific plan for determining the future of all enterprises to the Cabinet.
6. Present a plan to the cabinet to equalize the salaries of civil servants within three months, with the cooperation of the Independent Administrative Reform and Civil Service Commission.
7. Within three months, develop a plan for improving the entire state revenues and the capacity of the related ministries based on national priorities, and present a plan for introducing new sources of revenues.
8. Within six months, develop a plan to spend the budget, which is provided by the United Nations, through the national budget for the 2014 election.
9. Assess and investigate the legality, fairness, and activities of all insurance companies, and present its report to the Cabinet within six months.
18th– The Ministry of Commerce and Industry is Ordered to:
1. Within a month, present a plan to the cabinet on the nature of appointments of commerce attachés in different countries, based on the needs and volume of commerce of each specific country.
2. Within two months, present a specific plan to the Cabinet on standardizing and resolving the problems of industrial parks.
3. Within three months, present a plan to the Cabinet on strengthening export and national economy, and on expanding small and medium sized businesses, and reinforcing domestic industries.
4. Devise a policy for national commerce, and present it to the Economic Committee of the Cabinet, within three months.
5. Complete a study of strategic gas reserves and the mechanism of their sustainability, and present it to the Cabinet within six months.
19th– The Ministry of Economy is Ordered to:
1. Within one month, present specific plans for observation of the municipalities’ projects, including developmental projects, to the Cabinet.
2. Publish all contracts with all details (the summary of contracts should not be considered as sufficient) that were signed in the past three years with national and international companies, on the internet and other media outlets, with the cooperation of the Ministries of Finance and Telecommunication and InformationTechnology.
3. Within three months, present a specific plan to the Economic Committee of the Cabinet about the necessary definitions of national economic policies and trade.
4. Within six months, present a specific developmental plan, in coordination with the Ministry of Finance, to the cabinet for the upcoming four years.
5. Within six months, present a plan about infrastructure and other major projects to the cabinet based on the recommendations of the Tokyo Conference (2012), and in coordination with related agencies.
20th– The Afghanistan Bank is Ordered to:
1. Within one month, present a report to the office of the president of the Islamic Republic of Afghanistan about outflow from the country through airports, and on how to oversee the process.
2. Within two months, present a report to the office of the president of the Islamic Republic of Afghanistan on how to popularize the use of afghani (Afs) in the markets during daily business, and how to prevent the use of foreign currency in the markets.
3. Present a complete report to the office of the president of the Islamic Republic of Afghanistan about manners and functions of private banks and consider the oversight of private banks as a top priority.
21st — The Ministry of Mines is Ordered to:
1. Present within one month, and in written form, a complete list of foreign advisors; the reasons for and the sources of their hiring, along with a list of their Afghan employees who are funded by foreign sources or receive additional benefits from them to the Directorate of Administrative Affairs and the Cabinet Secretary.
2. Complete the Mining and Petroleum Law and present it to the Cabinet within two months.
3. Present its plan for the prevention of unauthorized and non-professional extraction and for mine security within two months.
4. Publicize the list of individuals and companies who engage in unauthorized and illegal mining extraction through international media within two months.
5. Finalize a specific plan to provide for transparency regarding mining contracts in the country and present it to the Cabinet within three months. Contract transparency provisions will be based, above all, on agreed international principles and with considerations of the future of the country. It must publicize all contract details (not contract summaries) through the websites of the Ministries of Mines, Finance, and Economy.
22nd — The Ministry of Communications and Information Technology is Ordered to:
1. Ensure improvement in communication companies’ services and report the immunity and confidentiality of telephone subscribers’ conversations and means to prevent the use of mobile phones in terrorist attacks to the National Security Council within three months.
2. Present to the Cabinet a report regarding the feasibility of the implementation of an e-government.
23rd — The Ministry of Water and Energy is Ordered to:
1. Present a report to the Cabinet within one month regarding work progress in Machalgho, Pashdan, Shah-wa-Aroos, Salmah, Almar, and Kamal Khan electric dams and regarding the feasibility of electricity transmission from Naghlu and Sarubi [Dams] to the city of Jalalabad.
2. In cooperation from the outset with the Afghan Electricity Company, present a report to the Cabinet within three months regarding erecting an electricity network in the city of Kabul and in other major cities of the country.
3. Present to the Cabinet within six months the means for long-term self-sufficiency of electricity production in the country.
4. Subject the issue of electricity transmission to the country’s south, east and central regions, including Bamyan and Daykundi, to expert and technical assessment and present specific plans in this regard to the Cabinet within six months.
24th — The Ministry of Public Works is charged to:
1. Embark on establishing and determining the future of a railroad administration in Afghanistan within one month.
2. Begin repair of the Salangs [north and south highways] with the use of the five million dollar commitment of the international coalition forces and present a coherent report to the Cabinet within one month about these repairs as well as the building of Doshi-Pul-e Khumri road.
3. Prepare and present to the Cabinet within one month a list of all incomplete projects along with a description of reasons for their falling behind, stoppage, or delay.
4. Prepare and present to the Cabinet within two months a plan for the protection and monitoring of highways. The Ministry of Public Works is charged to place the protection and monitoring of highways and control over their construction at the top of its priorities.
25th — The Ministry of Transportation and Aviation is charged to:
1. Prepare transparent, comprehensive, and revised mechanisms for the collection of transportation revenues and present them to the Cabinet within three months.
2. Present a plan for the improvement of urban transportation to the Cabinet within six months.
3. Review the establishment and number of transportation offices abroad with a view to the transportation volumes and report to the Cabinet within three months.
4. Present to the Cabinet a specific plan for the building, expansion, and rebuilding of airports specified by province and district within three months.
5. Review the entire organizational structure and personnel of the ministry, identify corrupt officials, employ specific measures and report to the presidential office within six months.
26th — The Ministry of Urban Development is charged to:
1. Study the organizational structure and master plan for New Kabul and present a specific plan to the Cabinet within one month.
2. In cooperation with the Ministry of Justice, the Independent Commission for the Administrative Reform and Civil Service Commission, and presidential advisors, prepare and present to the Cabinet within two months a plan for the refinement of duties between municipalities and the Ministry of Urban Development.
3. To review master plans for Kabul and other provinces within three months and present it to the Cabinet.
4. To precisely and professionally assess documents of all townships [developments], identify existing construction violations as well as problems related to land ownership in those developments with the cooperation of the commission registered in Presidential Decree Number 2232, dated 27 June 2012.
27th — The Ministry of Agriculture and Irrigation is charged to:
1. Present to the Cabinet within three months a specific plan regarding finding markets for agricultural products and strengthening the financial and technical bases of the country’s farmers.
2. In cooperation with the Ministries of Justice, Interior, the Attorney General’s Office, and the High Office of Oversight and Anti-Corruption, to collect precise information about the seizure of government and private land across the country, initially in first rank and later in other provinces.
3. Take action regarding the creation of cold storage rooms in accordance with decision of Cabinet third resolution of the year 1391 [ 2012]
4. Organize and present a practical achievement report to the Cabinet concerning the use of barren and arable lands within six months in accordance with former guidance and instructions of the office of the president of the Islamic Republic of Afghanistan and Cabinet’s decision.
5. Organize a specific plan about the development of agricultural farms, include its practical programs in the 2013 budget year, and present a progress report to the Cabinet within six months.
6. Take appropriate measures regarding forests, especially the development and conservation of pistachio and pine trees, and present a report to the Cabinet.
28th — The Ministry of Rural Rehabilitation and Development is Ordered to:
1. Present a report to the Cabinet about the second phase of national reconciliation projects, mentioning the budget, exact place, the process of financing, and the officials responsible within one month, specified by provinces and districts.
2. Present a report to the Cabinet within two months about the repair and reconstruction of bridges and other facilities which were damaged as a result of flooding and natural disaster this year, specified by provinces and districts.
3. Present a specific plan to the Cabinet within three months about utilizing the provincial and district level developmental councils as unified councils, replacing multiple councils such as Council ofFfight Against Narcotics and other councils.
29th — The Ministry of Counter Narcotics is Ordered to:
1. Make a specific plan for this ministry, within a month, to come out with a policy making status where it can take practical steps to fight narcotics, and present it to the Cabinet.
2. Present a specific report in coordination with the Interior Ministry within two months to consider the merging among similar agencies, such as the office of the Deputy Minister of Counter Narcotics and other agencies.
3. Prepare a plan with the participation and cooperation of other Ministries in the fight against narcotics within three months, and present it to the Cabinet.
30th –The Ministry of Labor, Social Affairs, Martyrs and Disabled is Ordered to:
1. Implement a new retirement system and create bank accounts for retirees within six months.
2. Place the process for distributing funds to martyrs under its investigation with the help of High Office of Oversight and Anti-Corruption within six months, and present a final report to the Cabinet.
3. Create a national employment policy in coordination with job creating agencies within six months, and present it to the Cabinet.
4. Finish distributing electronic work permits to foreigners within six months, and present a report to the Cabinet
5. Create a program for skill development and job creation within six months, and present a report to the Cabinet.
6. Take measures on the country’s zone level to create institutes and training centers for vocational teachers within six months, and present a report to the Cabinet every month about work progress.
31st — Ministry of Refugees and Repatriation Must:
1. Present a report to the Cabinet about the just distribution of township developments for returning refugees in the 34 provinces of the country within three months.
2. Present a specific plan to the Cabinet about finding employment, building townships, and providing education for returning refugees within six months.
3. Devise a policy about the return of Afghan refugees with dignity from Iran and Pakistan within six months, and present it to the Cabinet.
32nd — The Ministry of Women’s Affairs Must:
1. Conduct a public awareness campaign to reduce violence against women through mass media, pulpits, takya khana [Shi’a worship place], and other news media sources within three months.
2. Implement a national working plan, devise a monitoring system within six months, and present the first report to the Cabinet.
33rd — The Kabul Municipality Must:
1. With the help of the Ministry of Communication and Information Technology, create a specific plan for naming all the places in Kabul City and for determining the fate of unplanned areas within two months, and present it to the Cabinet.
2. Prepare a plan for creating canalization and other city networks in Kabul City within four months, and present it to the Cabinet.
This decree and its addenda, which will be published later, do not interfere with the daily work of agencies and ministries. All ministries and government agencies are responsible for implementing this decree and its addenda. The secretariat of the General Directorate of Administrative Affairs and the Cabinet are charged to reinforce the current monitoring mechanism and to accurately observe the duties in this decree and its addenda. By appointing provincial monitoring teams, they should gather the specific information and present a report to the Cabinet and to the office of the president of the Islamic Republic of Afghanistan.
Hamid Karzai
President of the Islamic Republic of Afghanistan
Unternehmenswarnung vor Cyber Mobbing und Erpressung
Life Forestry Switzerland AG: Wie seriös ist Gomopa? Life Forestry warnt
EquityStory AG-News: Life Forestry Switzerland AG / Schlagwort(e): Marktbericht/Stellungnahme Life Forestry Switzerland AG: Wie seriös ist Gomopa? Life Forestry warnt Unternehmen vor Cyber Mobbing und Erpressung
23.07.2012 / 11:42
———————————————————————
Life Forestry warnt Unternehmen vor Cyber Mobbing und Erpressung
Stans, CH, 23. Juli 2012: In Deutschland werden jährlich Tausende von Unternehmen Opfer von Online-Verleumdung und Erpressung. Viele Unternehmen zahlen im Stillen das geforderte ‘Schutzgeld’, um größere Image-Schäden abzuwehren. Das Unternehmen Life Forestry wehrt sich – und macht anderen Unternehmen Mut, seinem Beispiel zu folgen.
Die Life Forestry Switzerland AG aus dem eidgenössischen Stans zählt zu den führenden Anbietern von Direktinvestments in Teakholz und betreut seit 2006 in Zentralamerika Aufforstungsprojekte der höchsten Qualitätsstufe. Seit einigen Wochen ist das Mittelstandsunternehmen Opfer einer gezielten Verleumdungskampagne des vermeintlichen Online-Nachrichtendienstes ‘Gomopa’.
Wie Berichte in der FAZ, dem Handelsblatt, Börse-Online, der Süddeutsche Zeitung und der Financial Times aufzeigen, steckt hinter Gomopa ein Netzwerk von Anwälten, Wirtschaftsdetektiven und Investmentprofis, die seit einigen Jahren in Deutschland immer wieder wegen fragwürdiger Geschäftspraktiken aufgefallen sind. Der Gomopa-Gründer und Unternehmenskopf Klaus Maurischat wurde bereits 2006 wegen Betrugs verurteilt, 2009 wurden Mitarbeiter von Gomopa wegen Insiderhandels und Aktienkursmanipulation im Zusammenhang mit dem Unternehmen WireCard angeklagt. Heute benutzt Gomopa sein gleichnamiges Nachrichtenportal dazu, um Unternehmen mit falschen Fakten und Anschuldigungen anzugreifen und zu erpressen. Zu ihren ‘Opfern’ zählen neben der Life Forestry AG die Immovation AG aus Kassel, die CPA Capital Partners AG und andere Mittelstandsunternehmen.
Die Life Forestry hat bereits vor Wochen Maßnahmen ergriffen, die zur Abwehr von Cyber Mobbing-Attacken beitragen: Zum Beispiel wurde beim Landgericht Frankfurt a.M. eine Unterlassungsverfügung erwirkt, die es Gomopa untersagt, seine ungerechtfertigten Anschuldigungen weiter im Internet zu verbreiten. Auch der Internet-Konzern Google wurde kontaktiert und gebeten, die betreffenden Aussagen aus den Suchmaschinen zu entfernen. Lambert Liesenberg, Geschäftsführer bei der Life Forestry AG, kommentiert die Abwehrmaßnahmen seines Unternehmens: ‘Wir tun, was wir können, um den Schaden zu minimieren. Aber die Cyber Mobber von Gomopa brauchen lediglich neue Anschuldigungen zu erfinden oder auf einen anderen Blog auszuweichen, und schon fängt der Kreislauf von vorne an.’
Aus diesem Grund hält es die Life Forestry AG für immens wichtig, die Öffentlichkeit und vor allem andere Unternehmen über Gomopas rufschädigende Methoden zu informieren. ‘Mafiöse Organisationen wie Gomopa leben davon, dass Unternehmen aus Angst vor Imageschäden ihren Forderungen nachgeben. Wenn bekannter wäre, wie Gomopa arbeitet, dann würde der Einfluss dieser Organisation sehr schnell schrumpfen,’ glaubt Lambert Liesenberg.
Auch im Hinblick auf ihre Kunden hält Life Forestry es für unverzichtbar, über die geschäftsschädigenden Praktiken der Cyber Mobber und ihre Anschuldigungen aufzuklären. Seit der Gründung gehört es zur Unternehmensphilosophie der Life Forestry Switzerland AG, das Vertrauen ihrer Kunden mit maximaler Qualität und – Transparenz – zu verdienen. Geschäftsführer Lambert Liesenberg: ‘Vom Geschäftsmodell über die präzise GPS-Erfassung aller Teakbaumbestände bis zur Herleitung unserer Ertragsprognosen verfolgen wir ein Ziel: für unsere Kunden ein Höchstmaß an Sicherheit und Nachvollziehbarkeit herauszuholen. Wenn Sie Fragen haben, dann zögern Sie nicht uns jederzeit zu kontaktieren.’ Die Life Forestry Switzerland AG bewirtschaftet Teakholz-Pflanzungen der höchsten Qualitätsstufe in Costa Rica und Ecuador. Die Kunden erwerben Eigentum an den Baumbeständen , die nach 20-jähriger Pflege geerntet und verkauft werden. Durch strengste professionelle Standards bei der Auswahl der Anbaugebiete und dem forstwirtschaftlichen Anbau wird eine Holzqualität erreicht, die sich im internationalen Holzmarkt mit Teakholz aus Naturwäldern messen kann. Jeder Teak-Forst wird vom FSC (Forest Stewardship Council) zertifiziert und die Bäume individuell gekennzeichnet. Über eine GPS-Vermessung aller Plantagen und der einzelnen Parzellen kann der Standort der Bäume jederzeit bestimmt und nachgeprüft werden. Teakholzinvestments von Life Forestry stehen für eine hohe finanzielle Performance in Verbindung mit einem messbaren ökologischen und sozialen Mehrwert.
Life Forestry Switzerland AG Mühlebachstrasse 3 CH – 6370 Stans NW
Carl-Lambert Liesenberg Geschäftsführer/CEO
Tel: +41 (0) 41 632 63 00 Fax: +41 (0) 41 632 63 01
info@lifeforestry.com http://www.lifeforestry.com
Ende der Medienmitteilung
———————————————————————
23.07.2012 Veröffentlichung einer Pressemitteilung, übermittelt durch EQS CORPORATE COMMUNICATIONS. http://www.eqs.com – Medienarchiv unter http://www.eqs.com/ch/pressemappen
Für den Inhalt der Mitteilung ist der Herausgeber verantwortlich.
FEMEN femenists occupied Venus de Milo in Louvre
“PETER EHLERS” “DAS INVESTMENT”: “BUNDESKANZLERIN ANGELA MERKEL UND BUNDESFINANZMINISTER WOLFGANG SCHÄUBLE SIND DEUTSCHLANDS BEKANNTESTE HEHLER!”
“Sind Bundeskanzlerin Angela Merkel und Finanzminister Wolfgang Schäuble Deutschlands bekannteste Hehler ?” „Sicher nein“, werden Sie jetzt sagen und fragen: „Wer behauptet diesen staatszersetzenden Schwachsinn ?“„Fonds & Friends-Herausgeber“ Peter Ehlers (wenn der Name stimmt ?) und der Ost-Berliner NACHRICHTENDIENST” “GoMoPa” bezeichneten die deutsche Bundeskanzlerin Angela Merkel und den deutschen Bundesfinanzminister Wolfgang Schäuble als “kriminelle Hehler” und als Deutschlands „bekannteste Hehler“. Original-Zitat Peter Ehlers (wenn denn wengistens der Name stimmt ?) : „Wolfgang Schäuble, Finanzminister unter Kanzlerin Angela Merkel. Beide sind sich nicht immer einig. Jetzt schon: Sie wollen als Staat, von deutschen Steuergeldern bezahlt, ein neues staatliches Geschäft eröffnen: Hehlerei.Peter Ehlers,Herausgeber DAS INVESTMENTEin Kommentar von Peter Ehlers, Herausgeber DAS INVESTMENTEin durchaus einträgliches Geschäft, das nur einen Haken hat: Es ist illegal. Schäuble hat dafür eine lustige Rechtsauffassung: Er sieht den Deal, den der damalige Finanzminister Peer Steinbrück („das beste Geschäft meines Lebens“) machte, für sich als Rechtfertigung. Frei nach dem billigen Motto: Wenn mein Vorgänger kriminell war, darf ich das ja wohl auch sein.“Das heisst nicht nur Schäuble handelt illegal und kriminell – im ganz grossen Stil, sondern auch die Vorgänger Ex-Bundes-Finanzminister Peer Steinbrück und Ex-Bundeskanzler gerhard Schröder…Und mich bezeichnet Peter Ehlers (wenn denn wengistens der Name stimmt ?) als “Internet-Terroristen”, „Erpresser“, „Gewohnheitsverbrecher“ und „Idioten“, ach ja meinen akademischen Titel Magister Artium täusche ich auch vor, sagen Peter Ehlers und GoMoPa, unisono..
Dies ist bezeichnet für die psychotische Wahnwelt dieser mutmasslich kommunistischen Delinquenten aus dem Osten Deutschlands.
Zum Tatbestand:
Im deutschen Strafrecht ist die Beamtenbeleidigung kein eigener Tatbestand. Ein Beamter ist hier nicht anders gestellt als ein anderer Bürger. Es handelt sich also um eine „normale“ Beleidigung gemäß § 185StGB.
Dennoch gibt es bei der Beleidigung eines Amtsträgers, der nicht zwingend Beamter sein muss, eine verfahrensrechtliche Besonderheit: Während die Straftat grundsätzlich nur auf Antrag des Verletzten verfolgt wird, kann gemäß § 194 Abs. 3 StGB bei Amtsträgern auch der Dienstvorgesetzte des Beleidigten den Strafantrag stellen:
„Ist die Beleidigung gegen einen Amtsträger, einen für den öffentlichen Dienst besonders Verpflichteten oder einen Soldaten der Bundeswehr während der Ausübung seines Dienstes oder in Beziehung auf seinen Dienst begangen, so wird sie auch auf Antrag des Dienstvorgesetzten verfolgt. Richtet sich die Tat gegen eine Behörde oder eine sonstige Stelle, die Aufgaben der öffentlichen Verwaltung wahrnimmt, so wird sie auf Antrag des Behördenleiters oder des Leiters der aufsichtführenden Behörde verfolgt. Dasselbe gilt für Träger von Ämtern und für Behörden der Kirchen und anderen Religionsgesellschaften des öffentlichen Rechts.“
Außerdem wird von der Staatsanwaltschaft in der Regel das öffentliche Interesse an der Strafverfolgung bejaht, so dass es weitaus seltener zur Verweisung auf den Privatklageweg oder zur Einstellung des Verfahrens nach § 153, 153a StPO kommt.
In der Praxis zieht die Beleidigung vor allem von (Polizei-)Beamten meist Geldstrafen nach sich. Bei mehrfach wegen solcher Delikte vorbestraften Personen sind in der Praxis schon kurze Freiheitsstrafen von z. B. 3 Monaten ohne Bewährung vorgekommen.
Fallbeispiel:
Beleidigung von Amtsträgern”Prozesse-Dieter” verurteilt“Prozesse-Dieter”, prozessfreudiger Sozialhilfeempfänger aus Ratingen, ist zu einem Jahr Haft verurteilt worden. Das Amtsgericht in Ratingen bei Düsseldorf sprach den als “König der Kläger” bekannt gewordenen ehemaligen 73-jährigen Sportlehrer wegen 44 Beleidigungen von Amtsträgern wie Beamten, Richtern und Rechtspflegern schuldig.
Per Postkarten hatte sie der Senior mit Fäkalausdrücken überzogen. Das Gericht setzte sich über den psychiatrischen Gutachter hinweg, der den Angeklagten als schuldunfähig eingestuft hatte, weil dieser an einer paranoiden Persönlichkeitsstörung leide.
Dies trifft möglicherweise auch auf die Delinquenten Peter Ehlers/”GoMoPa” zu.Zum Thema Wirecard und “GoMoPa” schreibt das “Handelsblatt:Finanzaufsicht untersucht Kursachterbahn bei Wirecard07.04.2010, 07:01 Uhrexklusiv Die Bundesanstalt für Finanzdienstleistungsaufsicht BaFin hat aufgrund der merkwürdigen Kursturbulenzen der Wirecard-Aktie eine förmliche Untersuchung des Falles eingeleitet. BaFin prüft mögliche Marktmanipulationen nach Falschbericht des Internetdienstes Gomopa. Zwei der Gomopa-Gründer wurden schon 2006 wegen Betrugs verurteilt.von Sönke Iwersen Der Kurs von Wirecard, einem Anbieter für elektronische Zahlungslöungen, ist am am vergangenen Dienstag nach Marktgerüchten heftig eingebrochen. Die BaFin prüft mögliche Manipulationen. Quelle: PressebildFRANKFURT. Die Bundesanstalt für Finanzdienstleistungsaufsicht BaFin hat aufgrund der merkwürdigen Kursturbulenzen der Wirecard-Aktie eine förmliche Untersuchung des Falles eingeleitet. “Wir prüfen, ob es Anhaltspunkte für Marktmanipulation in Aktien der Wirecard AG gibt”, sagte eine BaFin-Sprecherin. Zu Details könne sie sich jedoch nicht äußern.Der Kurs des Münchener Zahlungsabwicklers Wirecard war am vergangenen Dienstag um mehr als 30 Prozent eingebrochen. Am Abend zuvor hatte der Internetdienst Goldman, Morgenstern & Partners (Gomopa) berichtet, der in den USA wegen illegalen Online-Glücksspiels verhaftete Deutsche Michael Schütt habe in einem Geständnis Wirecard schwer belastet. Gomopa bezog sich auf einen Bericht der Lokalzeitung “Naples News”. Schütt habe ausgesagt, er sei bei illegalen Geldgeschäften direkt vom Wirecard-Vorstand beauftragt worden.Das Problem an dem Gomopa-Bericht: Er war falsch. Wie Nachfragen des Handelsblattes ergaben, hat die Reporterin, die für die “Naples News” über Schütt schreibt, Wirecard nie erwähnt. Gomopa reagierte auf Nachfragen zögerlich. Erst löschte der Dienst den Hinweis auf die Lokalzeitung, hielt aber den Vorwurf aufrecht, Schütt habe Wirecard belastet. Danach änderte man den Bericht erneut. Nun hieß es, ein Informant von Gomopa verfüge über die fraglichen Details aus Schütts Geständnis.Dem Handelsblatt liegt inzwischen das amtliche Protokoll von Schütts Geständnis am 23. März vor. Schütt bekennt sich darin schuldig, illegale Geldgeschäfte im Zusammenhang mit Online-Glücksspiel abgewickelt zu haben. Das Wort Wirecard kommt nicht vor. Gomopa hatte zu Wochenbeginn seinen Text erneut geändert und nun behauptet, Schütt belaste “eine Bank”. Auf erneute Nachfragen des Handelsblattes war der Bericht dann ganz verschwunden.Der Kurs von Wirecard hat sich inzwischen fast vollständig erholt. Ein Frankfurter Analyst sagte, für ihn sei klar, dass die Aktie seit Wochen manipuliert werde. Erst verteure sich die Leihe der Aktie, dann komme es zu außergewöhnlichem Handel, danach tauchten plötzlich desaströse Gerüchte auf. Dazu gehöre auch die Anzeige, die vor kurzem bei der Staatsanwaltschaft München einging und Wirecard der Geldwäsche bezichtigt. Es sei offensichtlich, dass Short Seller mit der Wirecard-Aktie Jojo spielen.Mark Vornkahl, einer der Gründer von Gomopa wies den Vorwurf der Kursmanipulation gestern zurück. Man wolle nur die Wahrheit aufdecken. Es ist allerdings nicht das erste Mal, dass Gomopa-Vertreter ins Zwielicht geraten. 2006 wurden Vornkahl und Mitgründer Klaus Maurischat wegen Betrugs an einem Anleger verurteilt. Maurischat gab gestern gegenüber dem Handelsblatt weitere Verurteilungen zu. Es habe sich dabei jedoch nicht um Anlagebetrug gehandelt.http://www.handelsblatt.com/finanzen/boerse-maerkte/boerse-inside/finanzaufsicht-untersucht-kursachterbahn-bei-wirecard/3406252.htmlUND SOLCHE TYPEN VERBREITEN WEITERE ENTEN AUS IRGENDEINEM SADDAM – ERDLOCH WÄHREND IN IHREM “VIRTUELLEN BÜRO” NUR EIN LEERER STUHL STEHT.Ich bin der Erbe unseres Familienbuches und damit das Oberhaupt unserer Familie Pulch. Unsere Familie hat seit Jahrunderten in Deutschland, USA und vielen anderen Ländern, erfolgreiche Unternehmer, Staatssekretäre, Banker, Richter, Anwälte, Politiker und auch Journalisten hervorgebracht. Wir lassen unseren guten Namen nicht durch vorbestrafte Anlagebetrüger, Cybermörder undStasi/NS-Kriminelle verunglimpfen. Deren Taten und Fäkalsprache sprechen für sich und bedürfen keiner ernsthaften Auseinandersetzung.Die bezahlten Betrüger sollen die Kapitalanlage-Verbrecher schützen.Darum geht es im Kern. Wie auch schon unterhttp://www.victims-opfer.comundhttp://sjb-fonds-opfer.com/?page_id=11764klar ersichtlich.Hier ist der Original-Bericht von MeridianCapitalhttp://webcache.googleusercontent.com/search?q=cache:8jmni-h2e_4J:www.maurischatinhaft.wordpress.com/+verhaftung+klaus+maurischat&cd=2&hl=de&ct=clnk&gl=de&source=www.google.deIchwerde die kriminellen Verantwortlichen und ihre kriminellen Helfershelfer bis zur letzten Konsequenz zur Verantwortung ziehen.Magister Bernd PulchPS Ich bedanke mich bei investment-on.com sowie allen anderen Medien für die Möglichkeit, die Dinge gerade zu rücken.
Unternehmensinformation / Kurzprofil: INVESTMENT (das Original) erscheint mit einer deutschen Ausgabe, einer globalen Ausgabe und einer Asien-Ausgabe seit mehr als 10 Jahren als unabhängiges Magazin fürInvestoren und Finanzprofis. Dabei stehen die sogenannten “HNWI im Fokus”. Unterstützt durch das Wachstum der Börsenkapitalisierungen in den Schwellenländern stieg das Gesamtvermögen der weltweiten High Net Worth Individuals (HNWI – Privatpersonen mit Nettofinanzvermögen > 1 Mio. US-Dollar ohne Verbrauchsgüter und eigengenutzte Immobilien) im Jahr um 9,4% auf 40,7 Billionen US-Dollar. Dies geht aus dem von Merrill Lynch und Capgemini veröffentlichten zwölften, jährlich erscheinenden, World Wealth Report hervor. Die weltweite Anzahl der HNWI nahm 2007 um 6% auf 10,1 Millionen zu. Gleichzeitig stieg die Zahl der besonders wohlhabenden Personen (Ultra High Net Worth Individuals – UHNWI – Privatpersonen mit Nettofinanzvermögen > 30 Mio. US-Dollar ohne Verbrauchsgüter und eigengenutzte Immobilien) um 8,8%. Erstmals seit Bestehen dieses Reports wurde beim durchschnittlichen Finanzvermögen der HNWI die Schwelle von 4 Millionen US-Dollar überschritten.INVESTMENT gehört zu EBIZZ.TV.Über EBIZZ.TV: EBIZZ TV ist im Veoh-Verbund mit über 600 eigenen Internet-TV-Kanälen und 100.000 assoziierten Kanälen eines der global reichweitenstärksten aber auch zielgruppengenauesten Portale. Im Februar erzielte das Netzwerk laut Nielsen Net Ratings über 28 Mio. Unique User, an Page Views über 350 Millionen (210 Millionen an Video Streams).(Reporting Sandra Lowe ; Editing George Highbottom, Magister Bernd Pulch* und Kim Halburton)
Aus sicherheitstechnischen Gründen geben wir zu unseren Mitarbeitern keine weiteren persönlichen Daten bekannt.
siehe unseren Kreuzzug gegen Cyber Stalking
*Magister Bernd M. Pulch (MA – Magister Artium)
Abschluss des Studiums der Publizistik (Note 2) , Komparatistik (Note 1) und Germanistik (Note 1-2) 1988
Universität Mainz
Magisterarbeit bei Professor Kepplinger über Dolf Zillmanns “Emotional Arousal Theory”1987, Mainz, 400 Seiten
Sie können die Magisterarbeit bei uns zum Preis von nur € 99,- über das Kontaktformular bestellen.
Die Zahlung erfolgt per Vorkasse. Die Lieferzeit beträgt ca. 14 Tage in Deutschland.
© 2011 für Texte und gestaltete Anzeigen beim Verlag. Nachdruck, Vervielfältigung und elektronische Speicherung nur unter Quellenangabe und mit schriftlicher Genehmigung gestattet.
Investment Magazin, Investment, Das Investment
TMZ – Hawaiian Deer Runs Amok on the Beach
Crying Freeman – Full Movie
Crying Freeman is a 1995 French and Canadian produced action film, directed by Christophe Gans, based on the “Portrait of a Killer” arc of the best-selling manga of the same name by Kazuo Koike and Ryoichi Ikegami.
Despite being heavily promoted by Viz Media on Animerica magazine and reprints of the Crying Freeman graphic novel, the film was never released in the United States.
A lethal assassin for a secret Chinese organisation, who sheds tears of regret each time he kills, is seen swiftly and mercilessly executing three Yakuza gangsters by a beautiful artist. She is captivated by the grace of his kill and later falls in love with him. An intense power struggle for the leadership of the Yakuza Clans ensues as they seek vengeance for the death of their leader. They soon realise the fatal mistake of underestimating the deadly skills of the Crying Freeman.
Starring;
Mark Dacascos
Julie Condra
Tchéky Karyo
Byron Mann
Yoko Shimada
Masaya Kato
Rae Dawn Chong
Mako
Secrecy News – Intelligence Spending drops for a second year
For the second year in a row and for only the second time in the post-9/11
era, total intelligence spending declined last year to $75.4 billion,
according to figures released yesterday by the Director of National
Intelligence and the Department of Defense.
http://www.fas.org/irp/budget/index.html
Total spending had peaked in FY2010 at $80.1 billion, and declined in
FY2011 to $78.6 billion.
"We are looking at some pretty steep budget cuts across the board in the
Intelligence Community," DNI James Clapper told the Senate Intelligence
Committee last January.
"Never before has the Intelligence Community been called upon to master
such complexity on so many issues in such a resource-constrained
environment," he said then. "We're rising to the challenge by continuing to
integrate the Intelligence Community, ... taking advantage of new
technologies, implementing new efficiencies, and, as always, simply working
hard. But, candidly, maintaining the world's premier intelligence
enterprise in the face of shrinking budgets will be difficult. We'll be
accepting and managing risk more so than we've had to do in the last
decade."
http://www.fas.org/irp/congress/2012_hr/threat.pdf
But while intelligence budgets are shrinking, they remain very high by
historical standards, having more than doubled over the past decade.
Total intelligence spending is comprised of two budget constructs: the
National Intelligence Program (NIP) and the Military Intelligence Program
(MIP). The large defense intelligence agencies -- including NSA, NRO, and
NGA -- receive funding through both budget programs.
For the first time ever in FY2012, both the budget request for the NIP
($55 billion) and the subsequent budget appropriation ($53.9 billion) have
been disclosed. (The MIP request was disclosed for FY2013, but not for
FY2012.) This is something of a breakthrough in intelligence
classification policy.
Hypothetically (or so it was long asserted), a hostile intelligence
analyst could derive valuable insight from the gap between each year's
budget appropriation, or between the appropriation and the request, to the
detriment of U.S. security.
"Disclosure of the budget request or the total appropriation reasonably
could be expected to cause damage to the national security in several
ways," wrote Director of Central Intelligence George Tenet in 1999 in a
successful effort to keep the budget secret at that time. "First,
disclosure of the budget request reasonably could be expected to provide
foreign governments with the United States' own assessment of its
intelligence capabilities and weaknesses. The difference between the
appropriation for one year and the Administration's budget request for the
next provides a measure of the Administration's unique, critical assessment
of its own intelligence programs. A requested budget decrease reflects a
decision that existing intelligence programs are more than adequate to meet
the national security needs of the United States. A requested budget
increase reflects a decision that existing intelligence programs are
insufficient to meet our national security needs. A budget request with no
change in spending reflects a decision that existing programs are just
adequate to meet our needs."
http://www.fas.org/sgp/foia/tenet499.html
But this longstanding official position has now lost any semblance of
cogency.
"In my view, this argument does not stand up to even a few minutes of
serious analysis," wrote former 9/11 Commission executive director (and
Romney campaign adviser) Philip Zelikow in the latest issue of the CIA
journal Studies in Intelligence.
But with serious analysis evidently in short supply, total intelligence
budget secrecy remained the norm for many decades until recently.
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
Wie die “GoMoPa”-Fälschungen die eigentlichen Täter enttarnen
ANONYME STASI-SCHEI**HAUS-FLIEGEN – NOMEN EST OMEN
Liebe Leser,
trotz serienmässiger Vorstrafen wegen Betruges und der zahlreicher anderer LKA, Kripo-,FBI-Ermittlungen werden die organisierten GoMoPa-STASI-Gangster Ihre unwahren Lügen gegen mich nicht löschen und stellen diese immer wieder neu ins Netz: Kein Wunder, denn ich habe die Verbrechen dieser organisierten Kriminellen aufgedeckt und werde dies weiter tun – im Interesse aller anständigen Mitglieder der menschlichen Gesellschaft !
Wie dumm diese STASI-Verbrecher zeigt sich in deren eigenen Texten: “Wie kann ein Magister eine Diplomarbeit schreiben” ? – wie in deren “Shithouse Fly Blog auf mich falsch dargelegt und natürlich haben die STASI-Kriminellen nicht den Hauch eines Beweises für irgendeine Behauptung – wir dagegen jede Menge und auch jede Menge Aktenzeichen gegen sie:
Zum Beispiel:
Klaus Maurischat ( Aktenzeichen Krefeld vom 24. April 2006; AZ: 28 Ls 85/05 – Am 24. April 2006 war die Verhandlung am Amtsgericht Krefeld in der Betrugssache: Mark Vornkahl / Klaus Maurischat ./. Dehnfeld. Aktenzeichen: 28 Ls 85/05, Klaus Maurischat, Lange Straße 38, 27313 Dörverden)
FAKT IST: Klaus Maurischat ist vorbestraft
Aktenzeichen Krefeld vom 24. April 2006; AZ: 28 Ls 85/05 – Am 24. April 2006 war die Verhandlung am Amtsgericht Krefeld in der Betrugssache: Mark Vornkahl / Klaus Maurischat ./. Dehnfeld. Aktenzeichen: 28 Ls 85/05, Klaus Maurischat, Lange Straße 38, 27313 Dörverden)
Sie wollen mich zwingen, mit ihren Lügen meine Berichterstattung gegen sie einzustellen – wie hier ersichtlich:
So wollte der Serienbetrüger Klaus Maurischat uns zwingen, die Berichterstattung über “GoMoPa” zu stoppen
Unser Bildtext: Klaus Maurischat: There is no Place like home
So wollte der Serienbetrüger Klaus Maurischat uns zwingen die Berichterstattung über den “NACHRICHTENDIENST” “GoMoPa” einzustellen
Meine Anmerkung: Sie lesen
den Original-Text mit den Original-Rechtschreibfehlern von Maurischat in chronologischer Reihenfolge von unten nach oben. “Unter den Linden” ist die Regus-Tarnadresse für den untergetauchten Serienbetrüger und Stasi-Ganoven. “SUMA” steht im Sprach-Jargon des “GoMoPa”-”NACHRICHTENDIENSTLERS” für Suchmaschine.
Zitat:
HAHAHAHAHAHAHAHAHAHAHAHAHAHAHA (MEINE ANTWORT)
> Was anderes fällt einem Hilfsschüler auch nicht ein! Wenn ich dich
> schnappe, dann haue ich dir die Fresse ein – mein Lieber! Merk dir
> das gut, du Kinderficker!
>
> Was sagt denn dein Freund Dr. XXX zu deinem handeln, Schwuchtel?
>
> > HAHAHAHAHAHAHAHAHAHAHAHAHAHAHA (MEINE ANTWORT)
> >
> > > Geiles Google Suchergebniss hast du mittlerweile. Das ist sowas von
> > > geil. Am besten ist dieser Beitrag zu Deiner Magisterarbeit, du
> > > Spinner:
> > >
> > > http://scheisshausfliege.wordpress.com/2011/01/29/die-diplomarbeit-des-magisters-bernd-pulch-ein-haufen-scheisse/
> > >
> > > Wenn du nicht aufhörst, wird niemand mehr ein Stück Brot von dir
> > > nehmen. Dein Name ist dan absolut durch. Glaub mir, wir verstehen da
> > > mehr von als du Schwachkopf!
> > >
> > > Im Übrigen kannst du mich stets gern persönlich treffen. Unter den
> > > Linden 21, Berlin – habe immer für dich Feigling Zeit! (TARN-ADRESSE)
> > >
> > > So – und nun überle wann du die Artikel über uns löschen willst,
> > > sonst mache ich die erste Seite der SUMA Ergebnisse mit deinen
> > > Einträgen voll.
Weitere Info zu den Verbrechen der organisierten Kriminellen der STASI “GoMoPa” aus Erich Mielkes Kloake auf http://www.victims-opfer.com
Und natürlich können die STASI-“GoMoPa” auch dumm-dreist fälschen:
Sports Illustrated Swimsuit: Marisa Miller Cover Model
TMZ – Paris Hilton Caught in Halloween Brawl!
Charlies Angels (HD) – Full Movie
Die Presselounge der “GoMoPa”-Opfer
TOP-SECRET – California State Prisons Mexican Mafia (La eMe) Membership Chart
The Enforcer – Jet Li – Full Movie
Die absurd-lächerlichen Fälschungen der STASI-“GoMoPa”
Hier sind die Links
TMZ- Kate Upton — Responsible for Tigers’ Blowout Loss?
Fans of the Detroit Tigers are pretty bummed that their team got BLOWN OUT in Game 1… and it probably won’t help their morale to learn that is was all Kate Upton’s fault!!!
Cryptome unveils – NRC Tightens Access to Radioactive Material
|
6. Has been convicted of a crime(s) which, in the Reviewing
Official's opinion, indicate poor judgment, unreliability, or
untrustworthiness.
These indicators are not meant to be all inclusive nor intended
to be disqualifying factors. Licensees can also consider how recent
such indicators occurred and other extenuating or mitigating factors
in their determinations. Section 149.c.(2)(B) of the AEA requires
that the information obtained as a result of fingerprinting be used
solely for the purposes of making a determination as to unescorted
access suitability. Unescorted access suitability is not a hiring
decision, and the NRC does not intend for licensees to use this
guidance as such. Because a particular individual may not be
suitable for unescorted access does not necessarily mean that he is
not suitable for escorted access or some other position that does
not involve NRC-regulated activities.
Process To Challenge NRC Denials or Revocations of Unescorted Access to
Certain Radioactive Material
1. Policy.
This policy establishes a process for individuals whom NRC
licensees nominate
[[Page 65231]]
as Reviewing Officials to challenge and appeal NRC denials or
revocations of access to certain radioactive material. Any
individual designated as a licensee Reviewing Official whom the NRC
has determined may not have unescorted access to certain radioactive
material shall, to the extent provided below, be afforded an
opportunity to challenge and appeal the NRC's determination. This
policy shall not be construed to create a liberty or property
interest of any kind in the unescorted access of any individual to
certain radioactive material.
2. Applicability.
This policy applies solely to those employees of licensees who
are designated as a Reviewing Official, and who are thus to be
considered by the NRC for initial or continued unescorted access to
certain radioactive material in that position.
3. Unescorted Access Determination Criteria.
Determinations for granting a designated Reviewing Official
unescorted access to certain radioactive material will be made by
the NRC staff. Unescorted access shall be denied or revoked whenever
it is determined that an individual does not meet the applicable
standards. Any doubt about an individual's eligibility for initial
or continued unescorted access to certain radioactive material shall
be resolved in favor of national security and result in denial or
revocation of unescorted access.
4. Procedures to Challenge the Contents of Records Obtained from
the FBI.
Prior to a determination by the NRC Facilities Security Branch
Chief that an individual designated as a Reviewing Official is
denied or revoked unescorted access to certain radioactive material,
the individual shall:
a. Be provided the contents of records obtained from the FBI for
the purpose of assuring correct and complete information. If, after
reviewing the record, an individual believes that it is incorrect or
incomplete in any respect and wishes to change, correct, or update
the alleged deficiency, or to explain any matter in the record, the
individual may initiate challenge procedures. These procedures
include either direct application by the individual challenging the
record to the agency (i.e., law enforcement agency) that contributed
the questioned information, or direct challenge as to the accuracy
or completeness of any entry on the criminal history record to the
Assistant Director, Federal Bureau of Investigation Identification
Division, Washington, DC 20537-9700 (as set forth in 28 C.F.R. Sec.
16.30 through 16.34). In the latter case, the FBI forwards the
challenge to the agency that submitted the data and requests that
agency to verify or correct the challenged entry. Upon receipt of an
official communication directly from the agency that contributed the
original information, the FBI Identification Division makes any
changes necessary in accordance with the information supplied by
that agency.
b. Be afforded 10 days to initiate an action challenging the
results of an FBI criminal history records check (described in (a),
above) after the record is made available for the individual's
review. If such a challenge is initiated, the NRC Facilities
Security Branch Chief may make a determination based upon the
criminal history record only upon receipt of the FBI's ultimate
confirmation or correction of the record.
5. Procedures to Provide Additional Information.
Prior to a determination by the NRC Facilities Security Branch
Chief that an individual designated as a Reviewing Official is
denied or revoked access to certain radioactive material, the
individual shall be afforded an opportunity to submit information
relevant to the individual's trustworthiness and reliability. The
NRC Facilities Security Branch Chief shall, in writing, notify the
individual of this opportunity, and any deadlines for submitting
this information. The NRC Facilities Security Branch Chief may make
a determination of unescorted access to certain radioactive material
only upon receipt of the additional information submitted by the
individual, or, if no such information is submitted, when the
deadline to submit such information has passed.
6. Procedures to Notify an Individual of the NRC Facilities
Security Branch Chief Determination to Deny or Revoke Access to
Certain Radioactive Material.
Upon a determination by the NRC Facilities Security Branch Chief
that an individual nominated as a Reviewing Official is denied or
revoked access to certain radioactive material, the individual shall
be provided a written explanation of the basis for this
determination.
7. Procedures to Appeal an NRC Determination to Deny or Revoke
Access to Certain Radioactive Material.
Upon a determination by the NRC Facilities Security Branch Chief
that an individual nominated as a reviewing official is denied or
revoked access to certain radioactive material, the individual shall
be afforded an opportunity to appeal this determination to the
Director, Division of Facilities and Security. The determination
must be appealed within 20 days of receipt of the written notice of
the determination by the Facilities Security Branch Chief, and may
either be in writing or in person. Any appeal made in person shall
take place at the NRC's headquarters, and shall be at the
individual's own expense. The determination by the Director,
Division of Facilities and Security, shall be rendered within 60
days after receipt of the appeal.
8. Procedures to Notify an Individual of the Determination by
the Director, Division of Facilities and Security, Upon an Appeal.
A determination by the Director, Division of Facilities and
Security, shall be provided to the individual in writing and include
an explanation of the basis for this determination. A determination
by the Director, Division of Facilities and Security, to affirm the
Facilities Branch Chief's determination to deny or revoke an
individual's access to certain radioactive material is final and not
subject to further administrative appeals.
[FR Doc. 2012-26299 Filed 10-24-12; 8:45 am]
BILLING CODE 7590-01-P
[Federal Register Volume 77, Number 207 (Thursday, October 25, 2012)] [Notices] [Pages 65210-65215] From the Federal Register Online via the Government Printing Office [www.gpo.gov] [FR Doc No: 2012-26292] ----------------------------------------------------------------------- NUCLEAR REGULATORY COMMISSION [NRC-2012-0255; EA-12-148] In the Matter of Licensee Identified in Attachment 1 and all Other Persons Who Seek or Obtain Access to Safeguards Information Described Herein; Order Imposing Fingerprinting and Criminal History Records Check Requirements for Access to Safeguards Information (Effective Immediately) I The Licensee identified in Attachment 1\1\ to this Order, holds a license issued in accordance with the Atomic Energy Act (AEA) of 1954, as amended, by the U.S. Nuclear Regulatory Commission (NRC or the Commission), authorizing them to engage in an activity subject to regulation by the Commission or Agreement States. In accordance with Section 149 of the AEA, fingerprinting and a Federal Bureau of Investigation (FBI) identification and criminal history records check are required of any person who is to be permitted to have access to Safeguards Information (SGI).\2\ The AEA permits the Commission by rule to except certain categories of individuals from the fingerprinting requirement, which the Commission has done (see 10 CFR 73.59, 71 FR 33989; June 13, 2006). Individuals relieved from fingerprinting and criminal history records checks [[Page 65211]] under the relief rule include Federal, State, and local officials and law enforcement personnel; Agreement State inspectors who conduct security inspections on behalf of the NRC; members of Congress and certain employees of members of Congress or Congressional Committees, and representatives of the International Atomic Energy Agency (IAEA) or certain foreign government organizations. In addition, individuals who have a favorably-decided U.S. Government criminal history records check within the last five (5) years, or individuals who have active Federal security clearances (provided in either case that they make available the appropriate documentation), have satisfied the AEA fingerprinting requirement and need not be fingerprinted again. Therefore, in accordance with Section 149 of the AEA the Commission is imposing additional requirements for access to SGI, as set forth by this Order, so that affected licensees can obtain and grant access to SGI. This Order also imposes requirements for access to SGI by any person, from any person,\3\ whether or not a Licensee, Applicant, or Certificate Holder of the Commission or Agreement States. --------------------------------------------------------------------------- \1\ Attachment 1 contains sensitive information and will not be released to the public. \2\ Safeguards Information is a form of sensitive, unclassified, security-related information that the Commission has the authority to designate and protect under section 147 of the AEA. \3\ Person means (1) any individual, corporation, partnership, firm, association, trust, estate, public or private institution, group, government agency other than the Commission or the Department of Energy, except that the Department of Energy shall be considered a person with respect to those facilities of the Department of Energy specified in section 202 of the Energy Reorganization Act of 1974 (88 Stat. 1244), any State or any political subdivision of, or any political entity within a State, any foreign government or nation or any political subdivision of any such government or nation, or other entity; and (2) any legal successor, representative, agent, or agency of the foregoing. --------------------------------------------------------------------------- II The Commission has broad statutory authority to protect and prohibit the unauthorized disclosure of SGI. Section 147 of the AEA grants the Commission explicit authority to issue such Orders as necessary to prohibit the unauthorized disclosure of SGI. Furthermore, Section 149 of the AEA requires fingerprinting and an FBI identification and a criminal history records check of each individual who seeks access to SGI. In addition, no person may have access to SGI unless the person has an established need-to-know the information and satisfies the trustworthy and reliability requirements described in Attachment 3 to Order EA-12-147. In order to provide assurance that the Licensee identified in Attachment 1 to this Order is implementing appropriate measures to comply with the fingerprinting and criminal history records check requirements for access to SGI, the Licensee identified in Attachment 1 to this Order shall implement the requirements of this Order. In addition, pursuant to 10 CFR 2.202, I find that in light of the common defense and security matters identified above, which warrant the issuance of this Order, the public health, safety and interest require that this Order be effective immediately. III Accordingly, pursuant to Sections 81, 147, 149, 161b, 161i, 161o, 182 and 186 of the Atomic Energy Act of 1954, as amended, and the Commission's regulations in 10 CFR 2.202, 10 CFR Parts 30 and 73, it is hereby ordered, effective immediately, that the licensee identified in attachment 1 to this order and all other persons who seek or obtain access to safeguards information, as described above, shall comply with the requirements set forth in this order. A. 1. No person may have access to SGI unless that person has a need-to-know the SGI, has been fingerprinted or who has a favorably- decided FBI identification and criminal history records check, and satisfies all other applicable requirements for access to SGI. Fingerprinting and the FBI identification and criminal history records check are not required, however, for any person who is relieved from that requirement by 10 CFR 73.59 (71 Fed. Reg. 33,989 (June 13, 2006)), or who has a favorably-decided U.S. Government criminal history records check within the last five (5) years, or who has an active Federal security clearance, provided in the latter two cases that the appropriate documentation is made available to the Licensee's NRC- approved reviewing official described in paragraph III.C.2 of this Order. 2. No person may have access to any SGI if the NRC has determined, based on fingerprinting and an FBI identification and criminal history records check, that the person may not have access to SGI. B. No person may provide SGI to any other person except in accordance with Condition III.A. above. Prior to providing SGI to any person, a copy of this Order shall be provided to that person. C. The Licensee identified in Attachment 1 to this Order shall comply with the following requirements: 1. The Licensee shall, within twenty (20) days of the date of this Order, establish and maintain a fingerprinting program that meets the requirements of Attachment 2 to this Order. 2. The Licensee shall, within twenty (20) days of the date of this Order, submit the fingerprints of one (1) individual who a) the Licensee nominates as the ``reviewing official'' for determining access to SGI by other individuals, and b) has an established need-to-know the information and has been determined to be trustworthy and reliable in accordance with the requirements described in Attachment 3 to Order EA- 12-147. The NRC will determine whether this individual (or any subsequent reviewing official) may have access to SGI and, therefore, will be permitted to serve as the Licensee's reviewing official.\4\ The Licensee may, at the same time or later, submit the fingerprints of other individuals to whom the Licensee seeks to grant access to SGI or designate an additional reviewing official(s). Fingerprints shall be submitted and reviewed in accordance with the procedures described in Attachment 2 of this Order. --------------------------------------------------------------------------- \4\ The NRC's determination of this individual's access to SGI in accordance with the process described in Enclosure 5 to the transmittal letter of this Order is an administrative determination that is outside the scope of this Order. --------------------------------------------------------------------------- 3. The Licensee shall, in writing, within twenty (20) days of the date of this Order, notify the Commission, (1) if it is unable to comply with any of the requirements described in this Order, including Attachment 2 to this Order, or (2) if compliance with any of the requirements is unnecessary in its specific circumstances. The notification shall provide the Licensee's justification for seeking relief from or variation of any specific requirement. Licensee responses to C.1., C.2., and C.3. above shall be submitted to the Director, Office of Federal and State Materials and Environmental Management Programs, U.S. Nuclear Regulatory Commission, Washington, DC 20555. In addition, Licensee responses shall be marked as ``Security-Related Information--Withhold Under 10 CFR 2.390.'' The Director, Office of Federal and State Materials and Environmental Management Programs, may, in writing, relax or rescind any of the above conditions upon demonstration of good cause by the Licensee. IV In accordance with 10 CFR 2.202, the Licensee must, and any other person adversely affected by this Order may, submit an answer to this Order within twenty (20) days of the date of this Order. In addition, the Licensee and any other person adversely affected by this Order may request a hearing of this Order within twenty (20) days of the [[Page 65212]] date of the Order. Where good cause is shown, consideration will be given to extending the time to request a hearing. A request for extension of time must be made, in writing, to the Director, Office of Federal and State Materials and Environmental Management Programs, U.S. Nuclear Regulatory Commission, Washington, DC 20555-0001, and include a statement of good cause for the extension. The answer may consent to this Order. If the answer includes a request for a hearing, it shall, under oath or affirmation, specifically set forth the matters of fact and law on which the Licensee relies and the reasons as to why the Order should not have been issued. If a person other than the Licensee requests a hearing, that person shall set forth with particularity the manner in which his interest is adversely affected by this Order and shall address the criteria set forth in 10 CFR 2.309(d). All documents filed in the NRC adjudicatory proceedings, including a request for hearing, a petition for leave to intervene, any motion or other document filed in the proceeding prior to the submission of a request for hearing or petition to intervene, and documents filed by interested governmental entities participating under 10 CFR 2.315(c), must be filed in accordance with the NRC's E-Filing rule (72 FR 49139; August 28, 2007). The E-Filing process requires participants to submit and serve all adjudicatory documents over the internet, or in some cases to mail copies on electronic storage media. Participants may not submit paper copies of their filings unless they seek an exemption in accordance with the procedures described below. To comply with the procedural requirements of E-Filing, at least 10 days prior to the filing deadline, the participant should contact the Office of the Secretary by email at hearing.docket@nrc.gov, or by telephone at 301-415-1677, to request (1) a digital identification (ID) certificate, which allows the participant (or its counsel or representative) to digitally sign documents and access the E-Submittal server for any proceeding in which it is participating; and (2) advise the Secretary that the participant will be submitting a request or petition for hearing (even in instances in which the participant, or its counsel or representative, already holds an NRC-issued digital ID certificate). Based upon this information, the Secretary will establish an electronic docket for the hearing in this proceeding if the Secretary has not already established an electronic docket. Information about applying for a digital ID certificate is available on the NRC's public Web site at http://www.nrc.gov/site-help/ e-submittals/apply-certificates.html. System requirements for accessing the E-Submittal server are detailed in the NRC's ``Guidance for Electronic Submission,'' which is available on the NRC's public Web site at http://www.nrc.gov/site-help/e-submittals.html. Participants may attempt to use other software not listed on the Web site, but should note that the NRC's E-Filing system does not support unlisted software, and the NRC Meta System Help Desk will not be able to offer assistance in using unlisted software. If a participant is electronically submitting a document to the NRC in accordance with the E-Filing rule, the participant must file the document using the NRC's online, Web-based submission form. In order to serve documents through the Electronic Information Exchange System, users will be required to install a Web browser plug-in from the NRC's Web site. Further information on the Web-based submission form, including the installation of the Web browser plug-in, is available on the NRC's public Web site at http://www.nrc.gov/site-help/e-submittals.html. Once a participant has obtained a digital ID certificate and a docket has been created, the participant can then submit a request for hearing or petition for leave to intervene. Submissions should be in Portable Document Format (PDF) in accordance with the NRC guidance available on the NRC's Web site at http://www.nrc.gov/site-help/e- submittals.html. A filing is considered complete at the time the documents are submitted through the NRC's E-Filing system. To be timely, an electronic filing must be submitted to the E-Filing system no later than 11:59 p.m. Eastern Time on the due date. Upon receipt of a transmission, the E-Filing system time-stamps the document and sends the submitter an email notice confirming receipt of the document. The E-Filing system also distributes an email notice that provides access to the document to the NRC's Office of the General Counsel and any others who have advised the Office of the Secretary that they wish to participate in the proceeding, so that the filer need not serve the documents on those participants separately. Therefore, applicants and other participants (or their counsel or representative) must apply for and receive a digital ID certificate before a hearing request/petition to intervene is filed so that they can obtain access to the document via the E-Filing system. A person filing electronically using the agency's adjudicatory E- Filing system may seek assistance by contacting the NRC Meta System Help Desk through the ``Contact Us'' link located on the NRC's Web site at http://www.nrc.gov/site-help/e-submittals.html, by email at MSHD.Resource@nrc.gov, or by a toll-free call at 1-866-672-7640. The NRC Meta System Help Desk is available between 8 a.m. and 8 p.m., Eastern Time, Monday through Friday, excluding government holidays. Participants who believe that they have a good cause for not submitting documents electronically must file an exemption request, in accordance with 10 CFR 2.302(g), with their initial paper filing requesting authorization to continue to submit documents in paper format. Such filings must be submitted by: (1) First class mail addressed to the Office of the Secretary of the Commission, U.S. Nuclear Regulatory Commission, Washington, DC 20555-0001, Attention: Rulemaking and Adjudications Staff; or (2) courier, express mail, or expedited delivery service to the Office of the Secretary, Sixteenth Floor, One White Flint North, 11555 Rockville Pike, Rockville, Maryland 20852, Attention: Rulemaking and Adjudications Staff. Participants filing a document in this manner are responsible for serving the document on all other participants. Filing is considered complete by first-class mail as of the time of deposit in the mail, or by courier, express mail, or expedited delivery service upon depositing the document with the provider of the service. A presiding officer, having granted an exemption request from using E-Filing, may require a participant or party to use E-Filing if the presiding officer subsequently determines that the reason for granting the exemption from use of E-Filing no longer exists. Documents submitted in adjudicatory proceedings will appear in the NRC's electronic hearing docket which is available to the public at http://ehd1.nrc.gov/ehd/, unless excluded pursuant to an order of the Commission, or the presiding officer. Participants are requested not to include personal privacy information, such as social security numbers, home addresses, or home phone numbers in their filings, unless an NRC regulation or other law requires submission of such information. With respect to copyrighted works, except for limited excerpts that serve the purpose of the [[Page 65213]] adjudicatory filings and would constitute a Fair Use application, participants are requested not to include copyrighted materials in their submission. If a hearing is requested by the Licensee or a person whose interest is adversely affected, the Commission will issue an Order designating the time and place of any hearing. If a hearing is held the issue to be considered at such hearing shall be whether this Order should be sustained. Pursuant to 10 CFR 2.202(c)(2)(i), the Licensee may, in addition to requesting a hearing, at the time the answer is filed or sooner, move the presiding officer to set aside the immediate effectiveness of the Order on the ground that the Order, including the need for immediate effectiveness, is not based on adequate evidence but on mere suspicion, unfounded allegations, or error. In the absence of any request for hearing, or written approval of an extension of time in which to request a hearing, the provisions specified in Section III above shall be final twenty (20) days from the date of this Order without further order or proceedings. If an extension of time for requesting a hearing has been approved, the provisions specified in Section III shall be final when the extension expires if a hearing request has not been received. AN ANSWER OR A REQUEST FOR HEARING SHALL NOT STAY THE IMMMEDIATE EFFECTIVENESS OF THIS ORDER. Dated at Rockville, Maryland, this 16th day of October, 2012. For the Nuclear Regulatory Commission. Mark A. Satorius, Director, Office of Federal and State Materials and Environmental Management Programs. Attachment 1: Applicable Materials Licensees Redacted Attachment 2: Requirements for Fingerprinting and Criminal History Records Checks of Individuals When Licensee's Reviewing Official is Determining Access to Safeguards Information General Requirements Licensees shall comply with the requirements of this attachment. A. 1. Each Licensee subject to the provisions of this attachment shall fingerprint each individual who is seeking or permitted access to Safeguards Information (SGI). The Licensee shall review and use the information received from the Federal Bureau of Investigation (FBI) and ensure that the provisions contained in the subject Order and this attachment are satisfied. 2. The Licensee shall notify each affected individual that the fingerprints will be used to secure a review of his/her criminal history record and inform the individual of the procedures for revising the record or including an explanation in the record, as specified in the ``Right to Correct and Complete Information'' section of this attachment. 3. Fingerprints need not be taken if an employed individual (e.g., a Licensee employee, contractor, manufacturer, or supplier) is relieved from the fingerprinting requirement by 10 CFR 73.59, has a favorably-decided U.S. Government criminal history records check within the last five (5) years, or has an active Federal security clearance. Written confirmation from the Agency/employer which granted the Federal security clearance or reviewed the criminal history records check must be provided. The Licensee must retain this documentation for a period of three (3) years from the date the individual no longer requires access to SGI associated with the Licensee's activities. 4. All fingerprints obtained by the Licensee pursuant to this Order must be submitted to the Commission for transmission to the FBI. 5. The Licensee shall review the information received from the FBI and consider it, in conjunction with the trustworthy and reliability requirements included in Attachment 3 to NRC Order EA- 08-161, in making a determination whether to grant access to SGI to individuals who have a need-to-know the SGI. 6. The Licensee shall use any information obtained as part of a criminal history records check solely for the purpose of determining an individual's suitability for access to SGI. 7. The Licensee shall document the basis for its determination whether to grant access to SGI. B. The Licensee shall notify the NRC of any desired change in reviewing officials. The NRC will determine whether the individual nominated as the new reviewing official may have access to SGI based on a previously-obtained or new criminal history check and, therefore, will be permitted to serve as the Licensee's reviewing official. Prohibitions A Licensee shall not base a final determination to deny an individual access to SGI solely on the basis of information received from the FBI involving: An arrest more than one (1) year old for which there is no information of the disposition of the case, or an arrest that resulted in dismissal of the charge or an acquittal. A Licensee shall not use information received from a criminal history check obtained pursuant to this Order in a manner that would infringe upon the rights of any individual under the First Amendment to the Constitution of the United States, nor shall the Licensee use the information in any way which would discriminate among individuals on the basis of race, religion, national origin, sex, or age. Procedures for Processing Fingerprint Checks For the purpose of complying with this Order, Licensees shall, using an appropriate method listed in 10 CFR 73.4, submit to the NRC's Division of Facilities and Security, Mail Stop T-6E46, one completed, legible standard fingerprint card (Form FD-258, ORIMDNRCOOOZ) or, where practicable, other fingerprint records for each individual seeking access to Safeguards Information, to the Director of the Division of Facilities and Security, marked for the attention of the Division's Criminal History Check Section. Copies of these forms may be obtained by writing the Office of Information Services, U.S. Nuclear Regulatory Commission, Washington, DC 20555- 0001, by calling 301-415-7232, or by email to forms.resource@nrc.gov. Practicable alternative formats are set forth in 10 CFR 73.4. The Licensee shall establish procedures to ensure that the quality of the fingerprints taken results in minimizing the rejection rate of fingerprint cards due to illegible or incomplete cards. The NRC will review submitted fingerprint cards for completeness. Any Form FD-258 fingerprint record containing omissions or evident errors will be returned to the Licensee for corrections. The fee for processing fingerprint checks includes one re-submission if the initial submission is returned by the FBI because the fingerprint impressions cannot be classified. The one free re-submission must have the FBI Transaction Control Number reflected on the re-submission. If additional submissions are necessary, they will be treated as initial submittals and will require a second payment of the processing fee. Fees for processing fingerprint checks are due upon application. Licensees shall submit payment with the application for processing fingerprints by corporate check, certified check, cashier's check, or money order, made payable to ``U.S. NRC.'' [For guidance on making electronic payments, contact the Facilities Security Branch, Division of Facilities and Security, at 301-415-7404.] Combined payment for multiple applications is acceptable. The application fee (currently $36) is the sum of the user fee charged by the FBI for each fingerprint card or other fingerprint record submitted by the NRC on behalf of a Licensee, and an NRC processing fee, which covers administrative costs associated with NRC handling of Licensee fingerprint submissions. The Commission will directly notify Licensees who are subject to this regulation of any fee changes. The Commission will forward to the submitting Licensee all data received from the FBI as a result of the Licensee's application(s) for criminal history records checks, including the FBI fingerprint record. Right To Correct and Complete Information Prior to any final adverse determination, the Licensee shall make available to the individual the contents of any criminal records obtained from the FBI for the purpose of assuring correct and complete information. Written confirmation by the individual of receipt of this notification must be maintained by the Licensee for a period of one (1) year from the date of the notification. If, after reviewing the record, an individual believes that it is incorrect or incomplete in any respect and wishes to change, correct, or update the alleged deficiency, or to explain any matter in the record, the individual may initiate challenge procedures. These procedures include either direct application by the individual challenging the record to [[Page 65214]] the agency (i.e., law enforcement agency) that contributed the questioned information, or direct challenge as to the accuracy or completeness of any entry on the criminal history record to the Assistant Director, Federal Bureau of Investigation Identification Division, Washington, DC 20537-9700 (as set forth in 28 CFR 16.30 through 16.34). In the latter case, the FBI forwards the challenge to the agency that submitted the data and requests that agency to verify or correct the challenged entry. Upon receipt of an official communication directly from the agency that contributed the original information, the FBI Identification Division makes any changes necessary in accordance with the information supplied by that agency. The Licensee must provide at least ten (10) days for an individual to initiate an action challenging the results of an FBI criminal history records check after the record is made available for his/her review. The Licensee may make a final SGI access determination based upon the criminal history record only upon receipt of the FBI's ultimate confirmation or correction of the record. Upon a final adverse determination on access to SGI, the Licensee shall provide the individual its documented basis for denial. Access to SGI shall not be granted to an individual during the review process. Protection of Information 1. Each Licensee who obtains a criminal history record on an individual pursuant to this Order shall establish and maintain a system of files and procedures for protecting the record and the personal information from unauthorized disclosure. 2. The Licensee may not disclose the record or personal information collected and maintained to persons other than the subject individual, his/her representative, or to those who have a need to access the information in performing assigned duties in the process of determining access to Safeguards Information. No individual authorized to have access to the information may re- disseminate the information to any other individual who does not have a need-to-know. 3. The personal information obtained on an individual from a criminal history record check may be transferred to another Licensee if the Licensee holding the criminal history record check receives the individual's written request to re-disseminate the information contained in his/her file, and the gaining Licensee verifies information such as the individual's name, date of birth, social security number, sex, and other applicable physical characteristics for identification purposes. 4. The Licensee shall make criminal history records, obtained under this section, available for examination by an authorized representative of the NRC to determine compliance with the regulations and laws. 5. The Licensee shall retain all fingerprint and criminal history records received from the FBI, or a copy if the individual's file has been transferred, for three (3) years after termination of employment or determination of access to SGI (whether access was approved or denied). After the required three (3) year period, these documents shall be destroyed by a method that will prevent reconstruction of the information in whole or in part. Guidance for Licensee's Evaluation of Access to Safeguards Information With the Inclusion of Criminal History Records (Fingerprint) Checks When a Licensee submits fingerprints to the NRC pursuant to an NRC Order, it will receive a criminal history summary of information, provided in Federal records, since the individual's eighteenth birthday. Individuals retain the right to correct and complete information and to initiate challenge procedures described in Attachment 2 of Enclosure 1. The Licensee will receive the information from the criminal history records check of those individuals requiring access to Safeguards Information, and the reviewing official should evaluate that information using the guidance below. Furthermore, the requirements of all Orders which apply to the information and material to which access is being granted must be met. The Licensee's reviewing official is required to evaluate all pertinent and available information in making a determination of access to SGI, including the criminal history information pertaining to the individual as required by the NRC Order. The criminal history records check is used in the determination of whether the individual has a record of criminal activity that indicates that the individual should not have access to SGI. Each determination of access to SGI, which includes a review of criminal history information, must be documented to include the basis for the decision made. (i) If negative information is discovered that was not provided by the individual, or which is different in any material respect from the information provided by the individual, this information should be considered, and decisions made based on these findings, must be documented. (ii) Any record containing a pattern of behaviors which indicates that the behaviors could be expected to recur or continue, or recent behaviors which cast questions on whether an individual should have access to SGI, should be carefully evaluated prior to any authorization of access to SGI. It is necessary for a Licensee to resubmit fingerprints only under two conditions: (1) the FBI has determined that the fingerprints cannot be classified due to poor quality in the mechanics of taking the initial impressions; or (2) the initial submission has been lost. If the FBI advises that six sets of fingerprints are unclassifiable based on conditions other than poor quality, the licensee may submit a request to NRC for alternatives. When those search results are received from the FBI, no further search is necessary. Process To Challenge NRC Denials or Revocations of Access to Safeguards Information 1. Policy. This policy establishes a process for individuals whom NRC licensees nominate as reviewing officials to challenge and appeal NRC denials or revocations of access to Safeguards Information (SGI). Any individual nominated as a licensee reviewing official whom the NRC has determined may not have access to SGI shall, to the extent provided below, be afforded an opportunity to challenge and appeal the NRC's determination. This policy shall not be construed to require the disclosure of SGI to any person, nor shall it be construed to create a liberty or property interest of any kind in the access of any individual to SGI. 2. Applicability. This policy applies solely to those employees of licensees who are nominated as a reviewing official, and who are thus to be considered by the NRC for initial or continued access to SGI in that position. 3. SGI Access Determination Criteria. Determinations for granting a nominated reviewing official access to SGI will be made by the NRC staff. Access to SGI shall be denied or revoked whenever it is determined that an individual does not meet the applicable standards. Any doubt about an individual's eligibility for initial or continued access to SGI shall be resolved in favor of the national security and access will be denied or revoked. 4. Procedures to Challenge the Contents of Records Obtained from the FBI. a. Prior to a determination by the NRC Facilities Security Branch Chief that an individual nominated as a reviewing official is denied or revoked access to SGI, the individual shall: (i) Be provided the contents of records obtained from the FBI for the purpose of assuring correct and complete information. If, after reviewing the record, an individual believes that it is incorrect or incomplete in any respect and wishes to change, correct, or update the alleged deficiency, or to explain any matter in the record, the individual may initiate challenge procedures. These procedures include either direct application by the individual challenging the record to the agency (i.e., law enforcement agency) that contributed the questioned information, or direct challenge as to the accuracy or completeness of any entry on the criminal history record to the Assistant Director, Federal Bureau of Investigation Identification Division, Washington, DC 20537-9700 (as set forth in 28 CFR 16.30 through 16.34). In the latter case, the FBI forwards the challenge to the agency that submitted the data and requests that agency to verify or correct the challenged entry. Upon receipt of an official communication directly from the agency that contributed the original information, the FBI Identification Division makes any changes necessary in accordance with the information supplied by that agency. (ii) Be afforded 10 days to initiate an action challenging the results of an FBI criminal history records check (described in (i), above) after the record is made available for the individual's review. If such a challenge is initiated, the NRC Facilities Security Branch Chief may make a determination based upon the criminal history record only upon receipt of the FBI's ultimate confirmation or correction of the record. 5. Procedures to Provide Additional Information. [[Page 65215]] a. Prior to a determination by the NRC Facilities Security Branch Chief that an individual nominated as a reviewing official is denied or revoked access to SGI, the individual shall: (i) Be afforded an opportunity to submit information relevant to the individual's trustworthiness and reliability. The NRC Facilities Security Branch Chief shall, in writing, notify the individual of this opportunity, and any deadlines for submitting this information. The NRC Facilities Security Branch Chief may make a determination of access to SGI only upon receipt of the additional information submitted by the individual, or, if no such information is submitted, when the deadline to submit such information has passed. 6. Procedures to Notify an Individual of the NRC Facilities Security Branch Chief Determination to Deny or Revoke Access to SGI. a. Upon a determination by the NRC Facilities Security Branch Chief that an individual nominated as a reviewing official is denied or revoked access to SGI, the individual shall be provided a written explanation of the basis for this determination. 7. Procedures to Appeal an NRC Determination to Deny or Revoke Access to SGI. a. Upon a determination by the NRC Facilities Security Branch Chief that an individual nominated as a reviewing official is denied or revoked access to SGI, the individual shall be afforded an opportunity to appeal this determination to the Director, Division of Facilities and Security. The determination must be appealed within 20 days of receipt of the written notice of the determination by the Facilities Security Branch Chief, and may either be in writing or in person. Any appeal made in person shall take place at the NRC's headquarters, and shall be at the individual's own expense. The determination by the Director, Division of Facilities and Security, shall be rendered within 60 days after receipt of the appeal. 8. Procedures to Notify an Individual of the Determination by the Director, Division of Facilities and Security, Upon an Appeal. a. A determination by the Director, Division of Facilities and Security, shall be provided to the individual in writing and include an explanation of the basis for this determination. A determination by the Director, Division of Facilities and Security, to affirm the Facilities Branch Chief's determination to deny or revoke an individual's access to SGI is final and not subject to further administrative appeals. [FR Doc. 2012-26292 Filed 10-24-12; 8:45 am] BILLING CODE 7590-01-P [Federal Register Volume 77, Number 207 (Thursday, October 25, 2012)] [Notices] [Pages 65215-65220] From the Federal Register Online via the Government Printing Office [www.gpo.gov] [FR Doc No: 2012-26288] ----------------------------------------------------------------------- NUCLEAR REGULATORY COMMISSION [NRC-2012-0254; EA-12-147] In the Matter of Licensee Identified in Attachment 1 and all Other Persons Who Obtain Safeguards Information Described Herein; Order Imposing Requirements for the Protection of Certain Safeguards Information (Effective Immediately) I The Licensee, identified in Attachment 1 \1\ to this Order, holds a license issued in accordance with the Atomic Energy Act of 1954, as amended, (AEA) by the U.S. Nuclear Regulatory Commission (NRC or the Commission), authorizing it to possess, use, and transfer items containing radioactive material quantities of concern. The NRC intends to issue a security Order to this Licensee in the near future. The Order will require compliance with specific Additional Security Measures to enhance the security for certain radioactive material quantities of concern. The Commission has determined that these documents will contain Safeguards Information, will not be released to the public, and must be protected from unauthorized disclosure. Therefore, the Commission is imposing the requirements, as set forth in Attachments 2 and 3 to this Order and in Order EA-12-148, so that the Licensee can receive these documents. This Order also imposes requirements for the protection of Safeguards Information in the hands of any person,\2\ whether or not a licensee of the Commission, who produces, receives, or acquires Safeguards Information. --------------------------------------------------------------------------- \1\ Attachment 1 contains sensitive information and will not be released to the public. \2\ Person means (1) any individual, corporation, partnership, firm, association, trust, estate, public or private institution, group, government agency other than the Commission or the Department of Energy, except that the Department of Energy shall be considered a person with respect to those facilities of the Department of Energy specified in section 202 of the Energy Reorganization Act of 1974 (88 Stat. 1244), any State or any political subdivision of, or any political entity within a State, any foreign government or nation or any political subdivision of any such government or nation, or other entity; and (2) any legal successor, representative, agent, or agency of the foregoing. --------------------------------------------------------------------------- II The Commission has broad statutory authority to protect and prohibit the unauthorized disclosure of Safeguards Information. Section 147 of the AEA grants the Commission explicit authority to ``* * * issue such orders, as necessary to prohibit the unauthorized disclosure of safeguards information * * *.'' This authority extends to information concerning the security measures for the physical protection of special nuclear material, source material, and byproduct material. Licensees and all persons who produce, receive, or acquire Safeguards Information must ensure proper handling and protection of Safeguards Information to avoid unauthorized disclosure in accordance with the specific requirements for the protection of Safeguards Information contained in Attachments 2 and 3 to this Order. The Commission hereby provides notice that it intends to treat violations of the requirements contained in Attachments 2 and 3 to this Order, applicable to the handling and unauthorized disclosure of Safeguards Information, as serious breaches of adequate protection of the public health and safety and the common defense and security of the United States. Access to Safeguards Information is limited to those persons who have established the need-to-know the information and are considered to be trustworthy and reliable, and meet the requirements of Order EA-12- 148. A need-to-know means a determination by a person having responsibility for protecting Safeguards Information that a proposed recipient's access to Safeguards Information is necessary in the performance of official, contractual, or licensee duties of employment. The Licensee and all other persons who obtain Safeguards Information must ensure that they develop, maintain and implement strict policies and procedures for the proper handling of Safeguards Information to prevent unauthorized disclosure, in accordance with the requirements in Attachments 2 and 3 to this Order. The Licensee must ensure that all contractors whose employees may have access to Safeguards Information either adhere to the Licensee's policies and procedures on Safeguards Information or develop, or maintain and implement their own acceptable policies and procedures. The Licensee remains responsible for the conduct of their contractors. The policies and procedures necessary to ensure compliance with applicable requirements contained in Attachments 2 and 3 to this Order must address, at a minimum, the following: the general performance requirement that each person who produces, receives, or acquires Safeguards Information shall ensure that Safeguards Information is protected against unauthorized disclosure; protection of Safeguards Information at fixed sites, in use and in storage, and while in transit; correspondence containing Safeguards [[Page 65216]] Information; access to Safeguards Information; preparation, marking, reproduction and destruction of documents; external transmission of documents; use of automatic data processing systems; removal of the Safeguards Information category; the need-to-know the information; and background checks to determine access to the information. In order to provide assurance that the Licensee is implementing prudent measures to achieve a consistent level of protection to prohibit the unauthorized disclosure of Safeguards Information, the Licensee shall implement the requirements identified in Attachments 2 and 3 to this Order. In addition, pursuant to Attachments 2 and 3 to this Order, I find that in light of the common defense and security matters identified above, which warrant the issuance of this Order, the public health, safety and interest require that this Order be effective immediately. III Accordingly, pursuant to Sections 81, 147, 161b, 161i, 161o, 182 and 186 of the Atomic Energy Act of 1954, as amended, and the Commission's regulations in 10 CFR 2.202, 10 CFR Part 30, 10 CFR Part 32, 10 CFR Part 35, 10 CFR Part 70, and 10 CFR Part 73, it is hereby ordered, effective immediately, that the licensee identified in attachment 1 to this order and all other persons who produce, receive, or acquire the additional security measures identified above (whether draft or final) or any related safeguards information shall comply with the requirements of attachments 2 and 3. The Director, Office of Federal and State Materials and Environmental Management Programs, may, in writing, relax or rescind any of the above conditions upon demonstration of good cause by the Licensee. IV In accordance with 10 CFR 2.202, the Licensee must, and any other person adversely affected by this Order may, submit an answer to this Order within twenty (20) days of the date of this Order. In addition, the Licensee and any other person adversely affected by this Order may request a hearing of this Order within twenty (20) days of the date of the Order. Where good cause is shown, consideration will be given to extending the time to request a hearing. A request for extension of time must be made, in writing, to the Director, Office of Federal and State Materials and Environmental Management Programs, U.S. Nuclear Regulatory Commission, Washington, DC 20555-0001, and include a statement of good cause for the extension. The answer may consent to this Order. If the answer includes a request for a hearing, it shall, under oath or affirmation, specifically set forth the matters of fact and law on which the Licensee relies and the reasons as to why the Order should not have been issued. If a person other than the Licensee requests a hearing, that person shall set forth with particularity the manner in which his interest is adversely affected by this Order and shall address the criteria set forth in 10 CFR 2.309(d). Pursuant to 10 CFR 2.202(c)(2)(i), the Licensee or any other person adversely affected by this Order may, in addition to requesting a hearing, at the time the answer is filed or sooner, move the presiding officer to set aside the immediate effectiveness of the Order on the ground that the Order, including the need for immediate effectiveness, is not based on adequate evidence but on mere suspicion, ungrounded allegations or error. All documents filed in the NRC adjudicatory proceedings, including a request for hearing, a petition for leave to intervene, any motion or other document filed in the proceeding prior to the submission of a request for hearing or petition to intervene, and documents filed by interested governmental entities participating under 10 CFR 2.315(c), must be filed in accordance with the NRC's E-Filing rule (72 FR 49139; August 28, 2007). The E-Filing process requires participants to submit and serve all adjudicatory documents over the internet, or in some cases to mail copies on electronic storage media. Participants may not submit paper copies of their filings unless they seek an exemption in accordance with the procedures described below. To comply with the procedural requirements of E-Filing, at least 10 days prior to the filing deadline, the participant should contact the Office of the Secretary by email at hearing.docket@nrc.gov, or by telephone at 301-415-1677, to request (1) a digital identification (ID) certificate, which allows the participant (or its counsel or representative) to digitally sign documents and access the E-Submittal server for any proceeding in which it is participating; and (2) advise the Secretary that the participant will be submitting a request or petition for hearing (even in instances in which the participant, or its counsel or representative, already holds an NRC-issued digital ID certificate). Based upon this information, the Secretary will establish an electronic docket for the hearing in this proceeding if the Secretary has not already established an electronic docket. Information about applying for a digital ID certificate is available on the NRC's public Web site at http://www.nrc.gov/site-help/ e-submittals/apply-certificates.html. System requirements for accessing the E-Submittal server are detailed in the NRC's ``Guidance for Electronic Submission,'' which is available on the NRC's public Web site at http://www.nrc.gov/site-help/e-submittals.html. Participants may attempt to use other software not listed on the Web site, but should note that the NRC's E-Filing system does not support unlisted software, and the NRC Meta System Help Desk will not be able to offer assistance in using unlisted software. If a participant is electronically submitting a document to the NRC in accordance with the E-Filing rule, the participant must file the document using the NRC's online, Web-based submission form. In order to serve documents through the Electronic Information Exchange System, users will be required to install a Web browser plug-in from the NRC's Web site. Further information on the Web-based submission form, including the installation of the Web browser plug-in, is available on the NRC's public Web site at http://www.nrc.gov/site-help/e-submittals.html. Once a participant has obtained a digital ID certificate and a docket has been created, the participant can then submit a request for hearing or petition for leave to intervene. Submissions should be in Portable Document Format (PDF) in accordance with the NRC guidance available on the NRC's Web site at http://www.nrc.gov/site-help/ e-submittals.html. A filing is considered complete at the time the documents are submitted through the NRC's E-Filing system. To be timely, an electronic filing must be submitted to the E-Filing system no later than 11:59 p.m. Eastern Time on the due date. Upon receipt of a transmission, the E-Filing system time-stamps the document and sends the submitter an email notice confirming receipt of the document. The E-Filing system also distributes an email notice that provides access to the document to the NRC's Office of the General Counsel and any others who have advised the Office of the Secretary that they wish to participate in the proceeding, so that the filer need not serve the documents on those participants separately. Therefore, applicants and other participants (or their counsel or representative) must [[Page 65217]] apply for and receive a digital ID certificate before a hearing request/petition to intervene is filed so that they can obtain access to the document via the E-Filing system. A person filing electronically using the agency's adjudicatory E- Filing system may seek assistance by contacting the NRC Meta System Help Desk through the ``Contact Us'' link located on the NRC Web site at http://www.nrc.gov/site-help/e-submittals.html, by email at MSHD.Resource@nrc.gov, or by a toll-free call at 1-866-672-7640. The NRC Meta System Help Desk is available between 8 a.m. and 8 p.m., Eastern Time, Monday through Friday, excluding government holidays. Participants who believe that they have a good cause for not submitting documents electronically must file an exemption request, in accordance with 10 CFR 2.302(g), with their initial paper filing requesting authorization to continue to submit documents in paper format. Such filings must be submitted by: (1) First class mail addressed to the Office of the Secretary of the Commission, U.S. Nuclear Regulatory Commission, Washington, DC 20555-0001, Attention: Rulemaking and Adjudications Staff; or (2) courier, express mail, or expedited delivery service to the Office of the Secretary, Sixteenth Floor, One White Flint North, 11555 Rockville Pike, Rockville, Maryland, 20852, Attention: Rulemaking and Adjudications Staff. Participants filing a document in this manner are responsible for serving the document on all other participants. Filing is considered complete by first-class mail as of the time of deposit in the mail, or by courier, express mail, or expedited delivery service upon depositing the document with the provider of the service. A presiding officer, having granted an exemption request from using E-Filing, may require a participant or party to use E-Filing if the presiding officer subsequently determines that the reason for granting the exemption from use of E-Filing no longer exists. Documents submitted in adjudicatory proceedings will appear in NRC's electronic hearing docket which is available to the public at http://ehd1.nrc.gov/EHD/, unless excluded pursuant to an order of the Commission, or the presiding officer. Participants are requested not to include personal privacy information, such as social security numbers, home addresses, or home phone numbers in their filings, unless an NRC regulation or other law requires submission of such information. With respect to copyrighted works, except for limited excerpts that serve the purpose of the adjudicatory filings and would constitute a Fair Use application, participants are requested not to include copyrighted materials in their submission. If a hearing is requested by the Licensee or a person whose interest is adversely affected, the Commission will issue an Order designating the time and place of any hearing. If a hearing is held the issue to be considered at such hearing shall be whether this Order should be sustained. Pursuant to 10 CFR 2.202(c)(2)(i), the Licensee may, in addition to requesting a hearing, at the time the answer is filed or sooner, move the presiding officer to set aside the immediate effectiveness of the Order on the ground that the Order, including the need for immediate effectiveness, is not based on adequate evidence but on mere suspicion, unfounded allegations, or error. In the absence of any request for hearing, or written approval of an extension of time in which to request a hearing, the provisions specified in Section III above shall be final twenty (20) days from the date of this Order without further order or proceedings. If an extension of time for requesting a hearing has been approved, the provisions specified in Section III shall be final when the extension expires if a hearing request has not been received. An answer or a request for hearing shall not stay the immediate effectiveness of this order. Dated at Rockville, Maryland, this 16th day of October, 2012. For the Nuclear Regulatory Commission. Mark A. Satorius, Director, Office of Federal and State Materials and Environmental Management Programs. Attachment 1: Applicable Materials Licensees Redacted Attachment 2--Modified Handling Requirements for the Protection of Certain Safeguards Information (SGI-M) General Requirement Information and material that the U.S. Nuclear Regulatory Commission (NRC) determines are safeguards information must be protected from unauthorized disclosure. In order to distinguish information needing modified protection requirements from the safeguards information for reactors and fuel cycle facilities that require a higher level of protection, the term ``Safeguards Information--Modified Handling'' (SGI-M) is being used as the distinguishing marking for certain materials licensees. Each person who produces, receives, or acquires SGI-M shall ensure that it is protected against unauthorized disclosure. To meet this requirement, licensees and persons shall establish and maintain an information protection system that includes the measures specified below. Information protection procedures employed by State and local police forces are deemed to meet these requirements. Persons Subject to These Requirements Any person, whether or not a licensee of the NRC, who produces, receives, or acquires SGI-M is subject to the requirements (and sanctions) of this document. Firms and their employees that supply services or equipment to materials licensees would fall under this requirement if they possess facility SGI-M. A licensee must inform contractors and suppliers of the existence of these requirements and the need for proper protection. (See more under Conditions for Access) State or local police units who have access to SGI-M are also subject to these requirements. However, these organizations are deemed to have adequate information protection systems. The conditions for transfer of information to a third party, i.e., need-to-know, would still apply to the police organization as would sanctions for unlawful disclosure. Again, it would be prudent for licensees who have arrangements with local police to advise them of the existence of these requirements. Criminal and Civil Sanctions The Atomic Energy Act of 1954, as amended, explicitly provides that any person, ``whether or not a licensee of the Commission, who violates any regulations adopted under this section shall be subject to the civil monetary penalties of section 234 of this Act.'' Furthermore, willful violation of any regulation or order governing safeguards information is a felony subject to criminal penalties in the form of fines or imprisonment, or both. See sections 147b. and 223 of the Act. Conditions for Access Access to SGI-M beyond the initial recipients of the order will be governed by the background check requirements imposed by the order. Access to SGI-M by licensee employees, agents, or contractors must include both an appropriate need-to-know determination by the licensee, as well as a determination concerning the trustworthiness of individuals having access to the information. Employees of an organization affiliated with the licensee's company (e.g., a parent company), may be considered as [[Page 65218]] employees of the licensee for access purposes. Need-to-Know Need-to-know is defined as a determination by a person having responsibility for protecting SGI-M that a proposed recipient's access to SGI-M is necessary in the performance of official, contractual, or licensee duties of employment. The recipient should be made aware that the information is SGI-M and those having access to it are subject to these requirements as well as criminal and civil sanctions for mishandling the information. Occupational Groups Dissemination of SGI-M is limited to individuals who have an established need-to-know and who are members of certain occupational groups. These occupational groups are: A. An employee, agent, or contractor of an applicant, a licensee, the Commission, or the United States Government; B. A member of a duly authorized committee of the Congress; C. The Governor of a State or his designated representative; D. A representative of the International Atomic Energy Agency (IAEA) engaged in activities associated with the U.S./IAEA Safeguards Agreement who has been certified by the NRC; E. A member of a State or local law enforcement authority that is responsible for responding to requests for assistance during safeguards emergencies; or F. A person to whom disclosure is ordered pursuant to Section 2.744(e) of Part 2 of Part 10 of the Code of Federal Regulations. G. State Radiation Control Program Directors (and State Homeland Security Directors) or their designees. In a generic sense, the individuals described above in (A) through (G) are considered to be trustworthy by virtue of their employment status. For non-governmental individuals in group (A) above, a determination of reliability and trustworthiness is required. Discretion must be exercised in granting access to these individuals. If there is any indication that the recipient would be unwilling or unable to provide proper protection for the SGI-M, they are not authorized to receive SGI-M. Information Considered for Safeguards Information Designation Information deemed SGI-M is information the disclosure of which could reasonably be expected to have a significant adverse effect on the health and safety of the public or the common defense and security by significantly increasing the likelihood of theft, diversion, or sabotage of materials or facilities subject to NRC jurisdiction. SGI-M identifies safeguards information which is subject to these requirements. These requirements are necessary in order to protect quantities of nuclear material significant to the health and safety of the public or common defense and security. The overall measure for consideration of SGI-M is the usefulness of the information (security or otherwise) to an adversary in planning or attempting a malevolent act. The specificity of the information increases the likelihood that it will be useful to an adversary. Protection While in Use While in use, SGI-M shall be under the control of an authorized individual. This requirement is satisfied if the SGI-M is attended by an authorized individual even though the information is in fact not constantly being used. SGI-M, therefore, within alarm stations, continuously manned guard posts or ready rooms need not be locked in file drawers or storage containers. Under certain conditions the general control exercised over security zones or areas would be considered to meet this requirement. The primary consideration is limiting access to those who have a need- to-know. Some examples would be: Alarm stations, guard posts and guard ready rooms; Engineering or drafting areas if visitors are escorted and information is not clearly visible; Plant maintenance areas if access is restricted and information is not clearly visible; Administrative offices (e.g., central records or purchasing) if visitors are escorted and information is not clearly visible. Protection While in Storage While unattended, SGI-M shall be stored in a locked file drawer or container. Knowledge of lock combinations or access to keys protecting SGI-M shall be limited to a minimum number of personnel for operating purposes who have a ``need-to-know'' and are otherwise authorized access to SGI-M in accordance with these requirements. Access to lock combinations or keys shall be strictly controlled so as to prevent disclosure to an unauthorized individual. Transportation of Documents and Other Matter Documents containing SGI-M when transmitted outside an authorized place of use or storage shall be enclosed in two sealed envelopes or wrappers. The inner envelope or wrapper shall contain the name and address of the intended recipient, and be marked both sides, top and bottom with the words ``Safeguards Information--Modified Handling.'' The outer envelope or wrapper must be addressed to the intended recipient, must contain the address of the sender, and must not bear any markings or indication that the document contains SGI-M. SGI-M may be transported by any commercial delivery company that provides nation-wide overnight service with computer tracking features, US first class, registered, express, or certified mail, or by any individual authorized access pursuant to these requirements. Within a facility, SGI-M may be transmitted using a single opaque envelope. It may also be transmitted within a facility without single or double wrapping, provided adequate measures are taken to protect the material against unauthorized disclosure. Individuals transporting SGI-M should retain the documents in their personal possession at all times or ensure that the information is appropriately wrapped and also secured to preclude compromise by an unauthorized individual. Preparation and Marking of Documents While the NRC is the sole authority for determining what specific information may be designated as ``SGI-M,'' originators of documents are responsible for determining whether those documents contain such information. Each document or other matter that contains SGI-M shall be marked ``Safeguards Information--Modified Handling'' in a conspicuous manner on the top and bottom of the first page to indicate the presence of protected information. The first page of the document must also contain (i) the name, title, and organization of the individual authorized to make a SGI-M determination, and who has determined that the document contains SGI-M, (ii) the date the document was originated or the determination made, (iii) an indication that the document contains SGI-M, and (iv) an indication that unauthorized disclosure would be subject to civil and criminal sanctions. Each additional page shall be marked in a conspicuous fashion at the top and bottom with letters denoting [[Page 65219]] ``Safeguards Information Modified Handling.'' In additional to the ``Safeguards Information--Modified Handling'' markings at the top and bottom of each page, transmittal letters or memoranda which do not in themselves contain SGI-M shall be marked to indicate that attachments or enclosures contain SGI-M but that the transmittal does not (e.g., ``When separated from SGI-M enclosure(s), this document is decontrolled''). In addition to the information required on the face of the document, each item of correspondence that contains SGI-M shall, by marking or other means, clearly indicate which portions (e.g., paragraphs, pages, or appendices) contain SGI-M and which do not. Portion marking is not required for physical security and safeguards contingency plans. All documents or other matter containing SGI-M in use or storage shall be marked in accordance with these requirements. A specific exception is provided for documents in the possession of contractors and agents of licensees that were produced more than one year prior to the effective date of the order. Such documents need not be marked unless they are removed from file drawers or containers. The same exception applies to old documents stored away from the facility in central files or corporation headquarters. Since information protection procedures employed by state and local police forces are deemed to meet NRC requirements, documents in the possession of these agencies need not be marked as set forth in this document. Removal From SGI-M Category Documents containing SGI-M shall be removed from the SGI-M category (decontrolled) only after the NRC determines that the information no longer meets the criteria of SGI-M. Licensees have the authority to make determinations that specific documents which they created no longer contain SGI-M information and may be decontrolled. Consideration must be exercised to ensure that any document decontrolled shall not disclose SGI-M in some other form or be combined with other unprotected information to disclose SGI-M. The authority to determine that a document may be decontrolled may be exercised only by, or with the permission of, the individual (or office) who made the original determination. The document shall indicate the name and organization of the individual removing the document from the SGI-M category and the date of the removal. Other persons who have the document in their possession should be notified of the decontrolling of the document. Reproduction of Matter Containing SGI-M SGI-M may be reproduced to the minimum extent necessary consistent with need without permission of the originator. Newer digital copiers which scan and retain images of documents represent a potential security concern. If the copier is retaining SGI-M information in memory, the copier cannot be connected to a network. It should also be placed in a location that is cleared and controlled for the authorized processing of SGI-M information. Different copiers have different capabilities, including some which come with features that allow the memory to be erased. Each copier would have to be examined from a physical security perspective. Use of Automatic Data Processing (ADP) Systems SGI-M may be processed or produced on an ADP system provided that the system is assigned to the licensee's or contractor's facility and requires the use of an entry code/password for access to stored information. Licensees are encouraged to process this information in a computing environment that has adequate computer security controls in place to prevent unauthorized access to the information. An ADP system is defined here as a data processing system having the capability of long term storage of SGI-M. Word processors such as typewriters are not subject to the requirements as long as they do not transmit information offsite. (Note: if SGI-M is produced on a typewriter, the ribbon must be removed and stored in the same manner as other SGI-M information or media.) The basic objective of these restrictions is to prevent access and retrieval of stored SGI-M by unauthorized individuals, particularly from remote terminals. Specific files containing SGI-M will be password protected to preclude access by an unauthorized individual. The National Institute of Standards and Technology (NIST) maintains a listing of all validated encryption systems at http://csrc.nist.gov/ cryptval/1401/1401val.htm. SGI-M files may be transmitted over a network if the file is encrypted. In such cases, the licensee will select a commercially available encryption system that NIST has validated as conforming to Federal Information Processing Standards (FIPS). SGI-M files shall be properly labeled as ``Safeguards Information--Modified Handling'' and saved to removable media and stored in a locked file drawer or cabinet. Telecommunications SGI-M may not be transmitted by unprotected telecommunications circuits except under emergency or extraordinary conditions. For the purpose of this requirement, emergency or extraordinary conditions are defined as any circumstances that require immediate communications in order to report, summon assistance for, or respond to a security event (or an event that has potential security significance). This restriction applies to telephone, telegraph, teletype, facsimile circuits, and to radio. Routine telephone or radio transmission between site security personnel, or between the site and local police, should be limited to message formats or codes that do not disclose facility security features or response procedures. Similarly, call-ins during transport should not disclose information useful to a potential adversary. Infrequent or non-repetitive telephone conversations regarding a physical security plan or program are permitted provided that the discussion is general in nature. Individuals should use care when discussing SGI-M at meetings or in the presence of others to insure that the conversation is not overheard by persons not authorized access. Transcripts, tapes or minutes of meetings or hearings that contain SGI-M shall be marked and protected in accordance with these requirements. Destruction Documents containing SGI-M should be destroyed when no longer needed. They may be destroyed by tearing into small pieces, burning, shredding or any other method that precludes reconstruction by means available to the public at large. Piece sizes one half inch or smaller composed of several pages or documents and thoroughly mixed would be considered completely destroyed. Attachment 3--Trustworthiness and Reliability Requirements for Individuals Handling Safeguards Information In order to ensure the safe handling, use, and control of information designated as Safeguards Information, each licensee shall control and limit access to the information to only those individuals who have established the need-to-know the information, and are considered to be trustworthy and reliable. Licensees shall document the basis for concluding that there is reasonable assurance that individuals [[Page 65220]] granted access to Safeguards Information are trustworthy and reliable, and do not constitute an unreasonable risk for malevolent use of the information. The Licensee shall comply with the requirements of this attachment: 1. The trustworthiness and reliability of an individual shall be determined based on a background investigation: (a) The background investigation shall address at least the past three (3) years, and, at a minimum, include verification of employment, education, and personal references. The licensee shall also, to the extent possible, obtain independent information to corroborate that provided by the employee (i.e., seeking references not supplied by the individual). (b.) If an individual's employment has been less than the required three (3) year period, educational references may be used in lieu of employment history. The licensee's background investigation requirements may be satisfied for an individual that has an active Federal security clearance. 2. The licensee shall retain documentation regarding the trustworthiness and reliability of individual employees for three years after the individual's employment ends. In order for an individual to be granted access to Safeguards Information, the individual must be determined to be trustworthy and reliable, as describe in requirement 1 above, and meet the requirements of NRC Order EA-12-148. DG-SGI-1, Designation Guide for Safeguards Information Redacted [FR Doc. 2012-26288 Filed 10-24-12; 8:45 am] BILLING CODE 7590-01-P |
Jet Li – Born To Defense – Full Movie
TOP-SECRET-U.S. Special Operations Command Terms of Reference

This directive provides Terms of Reference (TOR) for United States Army Special Operations Command (USASOC); Naval Special Warfare Command (NAVSPECWARCOM); Air Force Special Operations Command (AFSOC), Marine Forces Special Operations Command (MARSOC), Joint Military Information Support Command (JMISC), and Joint Special Operations University (JSOU). The TOR for Joint Special Operations Command (JSOC) is addressed in SM 801-88, JSOC Charter.
…
DOWNLOAD THE ORIGINAL DOCUMENT HERE:
FEMEN storm the French Ministry of Justice – Video – UNCUT and UNCENSORED
DER BEWEIS AUS DEM JAHR 2000: SO REGTE GRUNER und JAHR-TOCHTER, IPV, MICH AN, DEN TITEL “INVESTMENT” ZU LANCIEREN
TOP-SECRET – US National Spy Budget FY2013: $52.6 Billion
DOWNLOAD THE ORIGINAL DOCUMENT HERE:
Rob-B-Hood – Jackie Chan – Full Movie
TOP-SECRET – U.S. Marine Corps Infantry Battalion Operations in Afghanistan

The 2nd Battalion, 7th Marines (Task Force 2/7) deployed to southern Afghanistan from April to October 2008, on short notice in order to fill a critical request for forces in support of U.S. Central Command.
Bottom Line Up Front: The mission of training and mentoring Afghani police was complicated by (1) the need to establish and occupy nine forward operating bases (FOBs) spread over an area of approximately 28,700 square kilometers, while (2) simultaneously maintaining a level of security that (3) permitted identification of suitable candidates for police and training them, since a police force did not exist yet in the areas in which 2/7 operated and (4) accomplishing this without any established support network. The operational environment was more kinetic and austere than conditions generally experienced by recent veterans of Operation Iraqi Freedom (OIF). Companies and platoons were widely dispersed and follow-on units deploying to such areas in Afghanistan must be prepared to operate in a semi-autonomous manner. Training and organization need to be tailored to those conditions and their specific area of operations (AO), and consideration should be given to the proven utility of the MAGTF in such an environment. Battalion operations were viewed as effective in establishing a foundation for follow-on units in the following areas: FOB construction, logistics processes, communications infrastructure, initiation of civil military operations, a mentoring and training process, and disrupting insurgent control of areas previously unoccupied by coalition forces.
…
Police mentoring and training efforts were hampered by ongoing anti-coalition activities. “It’s like doing Fallujah before Al Fajr. We’re in the midst of it and trying to fight Taliban while doing civil-military operations (CMO) and while trying to train police and mentor them, because they’re learning as they go. You’re doing everything concurrently. The mantra is ‘clear, hold, build.’ We’re trying to do it all at the same time. …We should be clearing. … certainly to a point of creating a stable, more secured, environment. When you bring in a police force, that’s the building piece. When you’re doing CMO, that’s building, but you’ve got to hold your ground. We don’t really hold much ground outside of our FOB. We go out there and influence it. We disrupt, but we don’t hold it. And the reason we don’t hold it is because we haven’t cleared it, and by providing that security buffer through clearing and then establishing the security footprint to hold it, you’re more able to effectively build. However, during that transition piece, you’re going to get the willing assistance of the people themselves. … I use the term, ‘turning four into forty’, and a four-man fire team now become 40 local citizens in addition to them, that’s now enabling security and taking an interest in their own prosperity.”
The command relationship for 2/7 was in line with their mentoring mission, which placed them under Afghan Regional Security Integration Command (ARSIC) who is under TF Phoenix which reported to CSTC-A, who in turn reported to CENTCOM. This command structure was outside International Security and Assistance Force (ISAF) control. Most of the warfighting capabilities in Afghanistan resided with ISAF, which reported to NATO. The CSTC-A command relationship had significant consequences for 2/7 and impacted on their operations and logistics. “ISAF has the ability to source equipment. ISAF has the priority for all the capabilities whether it is air support, air assets in particular, ISR assets; they are the operational arm. CSTCA is … a train and mentor organization and there is a mindset – because of how they’ve operated in the last few years – that CSTCA will go to established FOBs. They will benefit from the battle space manager’s generosity to host them at their FOBs and then they will take the mission of training that Army and police force. That hasn’t been 2/7’s experience. …. We went to the most austere location of the country … and established a footprint where there wasn’t one previously. That puts us in kind of a problem there because … the equipment, the air support, the war fighting capabilities – exist in ISAF and we were not an ISAF unit, we were a CSTCA unit. A lot of people in the beginning felt ‘You’re just training and mentoring Army and police. Why do you need close air support? Why do you need Predator feeds? Why do you need ISR capabilities? Why do you need all this ammo? This doesn’t make sense. This isn’t how CSTCA has operated’ …We turned to our higher headquarters and said ‘I need you to be a source of supply for me for ammunition, for more equipment, for better force protection measures’ – camera systems, new technologies whatever it may be – as we determined our requirements.” The logistics officer stated that they quickly learned that TF Phoenix and CSTCA had little of the support capabilities needed, and approached the U.S. Army Combat Service Support Battalion (CSSB) 189 at Kandahar, part of Combined Joint Task Force 101 in the ISAF chain of command, who provided them common item support such as water, fuel, construction materials, and medical supplies. The Army CSSB also served as an ammunition supply point for USMC provided ammunition, but the CSSB did not have other USMC unique items, which in many cases had to be ordered from CONUS.
DOWNLOAD THE ORIGINAL DOCUMENT HERE:
Secrecy News – Court orders FBI to release withheld information
COURT ORDERS FBI TO RELEASE WITHHELD INFORMATION
As often happens, the Federal Bureau of Investigation invoked national
security a few years ago to justify withholding certain information from a
Freedom of Information Act requester named Deirdre McKiernan Hetzler.
But as rarely happens, a court last month critically assessed the FBI
national security claim and ordered the Bureau to release some of the
withheld information.
Ms. Hetzler, acting pro se (i.e. without an attorney), had requested
records concerning her deceased father, who had once been the subject of an
FBI investigation. The FBI provided her with some records but withheld
others, stating that they remained classified in order to protect an
intelligence activity.
But after reviewing the withheld records in camera, Judge Michael A.
Telesca of the Western District of New York determined that some of the
information contained in them was not exempt from disclosure under FOIA.
The FBI had been withholding it under the FOIA's national security
exemption even though it was actually unclassified or declassified.
"The Court is not persuaded that Defendants [the FBI and the Justice
Department] have carried their burden of showing that disclosure of this
information could cause serious damage to national security," Judge Telesca
wrote in a September 6, 2012 opinion. He therefore ordered the FBI to
reprocess the request and to release the information to Ms. Hetzler as
specified in his ruling.
http://www.fas.org/sgp/jud/hetzler.pdf
The Court here acted as a check on the normally unconstrained official
tendency to classify and withhold information. That is what judicial
review is supposed to do, though it doesn't happen very often.
Earlier this year, Judge Richard W. Roberts of the DC District ordered the
U.S. Trade Representative to release a classified document to the Center
for International Environmental Law (CIEL) because he found that the
document was not properly classified.
The USTR "failed to provide a plausible or logical explanation of why
disclosure of [the document] reasonably could be expected to damage United
States foreign relations," he wrote in his opinion ordering release.
http://www.fas.org/blog/secrecy/2012/03/not_logical.html
The government has appealed that ruling. Judge Roberts "inappropriately
second-guessed the Executive's expertise in the uniquely sensitive area of
foreign relations," the government said in its September 17 appeals brief.
http://www.fas.org/blog/secrecy/2012/09/ciel_appeal_brief.html
No, on the contrary, CIEL responded in its own brief to the appeals court
this week, Judge Roberts did exactly what the FOIA requires.
"A district court reviewing [an agency claim that a document is classified
and exempt from disclosure] must give substantial weight to the agency's
explanations, but must not simply acquiesce in the agency's determination,"
CIEL attorneys wrote.
http://www.fas.org/sgp/jud/ciel/102412-app.pdf
"Congress explicitly 'stressed the need for an objective, independent
judicial determination, and insisted that judges could be trusted to
approach the national security determinations with common sense, and
without jeopardy to national security'," they wrote, citing prior FOIA case
law.
The document that is being contested in this case is a one-page memorandum
that presents the US government's legal interpretation of the phrase "in
like circumstances."
The government says that because the document was shared confidentially
with other governments as part of a (now-concluded) free trade negotiation,
its involuntary disclosure would undermine the confidentiality of
diplomatic negotiations.
Judge Roberts said this argument was not compelling "since the United
States would be revealing its own position only" and would not be
disclosing foreign government information that had been provided in
confidence.
Indeed, "There is no expectation that a government is required to keep its
own negotiating positions confidential from its own citizens," said former
US trade negotiator Daniel Magraw in a statement cited by CIEL.
CIEL said that "Under USTR's interpretation, USTR could withhold any
document -- even a document whose release would otherwise cause absolutely
no harm -- simply by entering into a confidentiality arrangement and
arguing that the breach of that arrangement would undermine trust and cause
damage to US foreign relations; the withholding would be insulated from
judicial review."
"Fortunately, FOIA limits what an agency can make confidential," CIEL
wrote in its appeals brief.
A date for oral argument before the DC Circuit Court of Appeals has not
yet been set.
AN UPDATED CATALOG OF ARMY WEAPON SYSTEMS
The U.S. Army has just published the 2013 edition of its annual Weapon
Systems Handbook, which is filled with updated information on dozens of
weapon systems, the military contractors who produce them, and the foreign
countries that purchase them.
http://www.fas.org/man/dod-101/sys/land/wsh2013/index.html
So one learns, for example, that the RQ-11B Raven Small Unmanned Aircraft
System is marketed to Denmark, Estonia, Lebanon, and Uganda, while the
United States sells artillery ammunition both to Israel and to Lebanon.
An appendix provides an informative breakdown of military industry
contractors by weapon system and by the state where the contractor is
located.
http://www.fas.org/man/dod-101/sys/land/wsh2013/app.pdf
"The systems listed in this book are not isolated, individual products.
Rather, they are part of an integrated Army system of systems designed to
equip the Army of the future to successfully face any challenges,"
according to the Handbook introduction.
"After 10 years of combat, today's Army is significantly more capable than
the Army of 2001. As we draw down from Iraq and Afghanistan, we must remain
flexible, adaptable, and agile enough to respond and meet the needs of the
combatant commanders."
"Our objective is to equip and maintain an Army with the latest most
advanced weaponry to win and return home quickly."
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
DIE BESTEN DAS INVESTMENT- DAS ORIGINAL Cover seit dem Jahre 2000
The Story of FEMEN – Full Movie
Die “GoMoPa”-Wirecard-Lüge
The FBI – Whiteagle Sentenced to 10 Years in Federal Prison in Ho-Chunk Bribery Case
MADISON, WI—John W. Vaudreuil, United States Attorney for the Western District of Wisconsin, announced that Timothy Whiteagle, 61, Black River Falls, Wisconsin, was sentenced today by Chief U.S. District Judge William M. Conley to 10 years in federal prison for his central role in a bribery and scheme involving contracts awarded by the Ho-Chunk Nation. He was also ordered to serve three years of supervised release following his prison sentence and to pay $162,854 in taxes to the IRS.
On August 1, 2012, following a jury trial on bribery, tax, and obstruction charges, Whiteagle was convicted on all 12 counts.
According to the evidence presented at the trial, the Ho-Chunk Nation, an Indian tribal government, operates casinos in the Western District of Wisconsin and annually receives federal grants well in excess of $10,000. Whiteagle is a Ho-Chunk tribal member. From 2002 to 2009, Whiteagle, at times with the assistance of Deborah H. Atherton, 55, Black River Falls, acted covertly as a behind-the-scenes consultant for clients seeking to do business with the Ho-Chunk Nation. The clients included companies that provided cash access services (such as check cashing and ATMs) at Ho-Chunk casinos and a company that sought to provide mortgages and housing for tribal members. Whiteagle received over $3 million dollars from the clients.
Whiteagle gave Clarence Pettibone, an elected legislator of the Ho-Chunk Nation, money and valuables, and Whiteagle and Atherton solicited clients seeking Ho-Chunk business to do the same. The valuables included checks; money orders; payments to a martial arts studio operated by Pettibone; a Pontiac Firebird; contributions for Pettibone’s re-election campaign; a job for a relative of Pettibone; golf outings; tickets to an NFL football game; visits to adult entertainment venues; auto body work on a car owned by a relative of Pettibone; and vacations for Pettibone and his family members.
Whiteagle and Atherton offered and gave the money and valuables to Pettibone to influence and reward him for helping certain clients do business with the Nation. Pettibone knew the money and valuables were given to him to influence and reward him for assisting the clients. Whiteagle and Pettibone consulted with each other about how to use Pettibone’s official position to assist the clients in obtaining and keeping contracts with the Ho-Chunk Nation; and Pettibone, in his official capacity as an elected legislator, took steps to help the clients do business with the Ho-Chunk Nation, such as scheduling of clients’ proposals on the legislature’s agenda, making motions for the nation to enter into contracts with the clients, delaying legislative action, and opposing proposed contracts between the nation and competitors of the clients.
Co-defendants Pettibone and Atherton were previously convicted and sentenced. Pettibone pleaded guilty to a bribery offense based on his receipt of the Firebird, along with money and other valuables, and was sentenced to five years in federal prison on July 11, 2012. Atherton was sentenced on October 10, 2012, to four years and two months in prison for her role in the bribery scheme and a separate loan fraud scheme. In a related case, Brian Johnson, 42, Shakopee, Minnesota, was sentenced to four months in prison for lying to federal agents during the course of the bribery investigation.
Whiteagle argued at trial, and again at sentencing, that the money and other things of value that he gave to Pettibone were not bribes but merely gifts given in the Ho-Chunk tradition. Judge Conley found that Whiteagle was “the center” of the scheme and profited immensely from businesses wanting to do business with the Ho-Chunk Nation. The judge found that Whiteagle showed a “willingness to engage in any behavior to benefit himself,” including bribery, telling a witness to lie, failing to pay taxes, and lying under oath. In rejecting Whiteagle’s arguments, Judge Conley said, “It is offensive to the court and to the Ho-Chunk Nation to suggest that bribery was part of ‘the Ho-Chunk way.’…Bribery and blatant lying is not the Ho-Chunk way; it is the farthest thing from the Ho-Chunk way.”
United States Attorney Vaudreuil stated, “This prosecution demonstrates the commitment by this office and the U.S. Department of Justice to vigorously investigate and prosecute corruption in tribal governments.”
The charges against Atherton, Whiteagle, Pettibone, and Johnson resulted from a joint investigation conducted by the Federal Bureau of Investigation and IRS Criminal Investigation, with assistance from the Ho-Chunk Nation, the Wisconsin Department of Administration-Division of Gaming, and the U.S. Department of Interior-Bureau of Indian Affairs, Office of Inspector General. The prosecutions have been handled by Assistant U.S. Attorneys Stephen P. Sinnott and Laura Przybylinski Finn.
Cryptome unveils CIA Proprietary Agencies & Agents Worldwide
|
DAS “GoMoPa”-“KINDERPORTAL” MIT “SEXUALAUFKLÄRUNG”
Secret – Historical Pre-Election Terrorist Attacks Analysis

In light of the upcoming 2012 US presidential election, NYSIC is providing a snapshot of four historical cases where terrorists conducted attacks in conjunction with upcoming local or national elections, including the tactics, techniques, and procedures (TTP) used and how the attacks met or failed to meet the terrorists’ goals of altering the outcome of the election.
Studies have highlighted possible theories, most often supported by historical cases, of why terrorists attempt to use attacks to influence the outcome of the election:
- Terrorist attacks greatly increase the probability that the incumbent government will lose re-election.
- Rightist parties are viewed as less conciliatory toward terrorist demands, while leftist parties are viewed as more likely to negotiate or give concessions. In general, relative support for rightist parties is expected to increase after terrorist attacks and to decrease after periods of inactivity.
Historically, terrorist violence has been used more often to extract direct concessions through negotiations after an attack. One such example is the February 9, 1996, Docklands Bombing in Northern Ireland: the Irish Republican Army (IRA) put an end to its 17-month ceasefire experiment by detonating an explosives-laden truck near a plaza where three office towers, a light-railway station and a hotel converge. The bombing successfully forced the British government back to the negotiating table without the precondition that the Provisional Irish Republican Army decommission all its weapons.
In 2004, al-Qa’ida was able to indirectly extract concessions from the Spanish government by influencing the election outcome after the Madrid train bombings, securing a Spanish withdrawal of troops from Iraq.
Implications for New York:
At this time, there is no known credible intelligence suggesting an attack against New York State during the 2012 election period. However, considering the overall security environment, threats could emanate from a variety of actors wanting to influence US policy, including: al-Qa’ida and affiliates; state-sponsored groups; homegrown violent extremists; or anti-government domestic terrorists. Law enforcement and first responders throughout New York State should remain vigilant and consider proactive outreach regarding suspicious activity at or near potential targets in their jurisdictions, including campaign facilities, upcoming political event venues, and previously targeted locations such as shopping centers, recruiting centers, transportation hubs, and social/recreation venues.
DOWNLOAD THE ORIGINAL DOCUMENT HERE:
Collateral Murder – Wikileaks – Iraq – Video
Wikileaks has obtained and decrypted this previously unreleased video footage from a US Apache helicopter in 2007. It shows Reuters journalist Namir Noor-Eldeen, driver Saeed Chmagh, and several others as the Apache shoots and kills them in a public square in Eastern Baghdad. They are apparently assumed to be insurgents. After the initial shooting, an unarmed group of adults and children in a minivan arrives on the scene and attempts to transport the wounded. They are fired upon as well. The official statement on this incident initially listed all adults as insurgents and claimed the US military did not know how the deaths ocurred. Wikileaks released this video with transcripts and a package of supporting documents on April 5th 2010 onhttp://collateralmurder.com
STERN zu Cyberstalking – Wer verfolgt wird, muss sich wehren
FAZ über die kriminellen Cyberstalker der “GoMoPa” und deren Auftraggeber
TMZ – Sofia Vergara’s SEXY Halloween Costume
Former CIA Officer John Kirakou Pleads Guilty to Disclosing Classified Information About CIA Officer
ALEXANDRIA, VA—Former CIA Officer John Kiriakou, 48, of Arlington, Virginia, pleaded guilty today to disclosing to a journalist the name of a covert CIA officer and also admitted to disclosing information revealing the role of another CIA employee in classified activities.
Neil H. MacBride, U.S. Attorney for the Eastern District of Virginia, and James W. McJunkin, Assistant Director in Charge of the FBI’s Washington Field Office, made the announcement after the plea was accepted by U.S. District Judge Leonie M. Brinkema.
Kiriakou pleaded guilty today to one count of intentionally disclosing information identifying a covert agent. As part of the plea agreement, the United States and Kiriakou agree that a sentence of 30 months in prison is the appropriate disposition of this case. Sentencing has been scheduled for January 25, 2013.
“The government has a vital interest in protecting the identities of those involved in covert operations,” said U.S. Attorney MacBride. “Leaks of highly sensitive, closely held, and classified information compromise national security and can put individual lives in danger.”
“Disclosing classified information, including the names of CIA officers, to unauthorized individuals is a clear violation of the law,” said Assistant Director in Charge McJunkin. “Today’s plea would not be possible without the hard work of the prosecutors and FBI special agents and analysts who brought this case to justice and who will continue to pursue those who ignore their obligations to protect national security secrets.”
According to court records, the case is a result of an investigation triggered by a classified filing in January 2009 by defense counsel for high-value detainees at Guantanamo Bay, Cuba. This filing contained classified information the defense had not been given through official government channels, including photographs of certain government employees and contractors. The investigation revealed that on multiple occasions, one of the journalists to whom Kiriakou illegally disclosed classified information, in turn, disclosed that information to a defense team investigator. This information was reflected in the classified defense filing and enabled the defense team to take or obtain surveillance photographs of government personnel. The government has made no allegations of criminal activity by any members of the defense team for the detainees.
Kiriakou was a CIA intelligence officer between 1990 and 2004, serving at headquarters and in various classified overseas assignments. Upon joining the CIA in 1990 and on multiple occasions in following years, Kiriakou signed secrecy and non-disclosure agreements not to disclose classified information to unauthorized individuals. In a statement of facts filed with his plea agreement, Kiriakou admitted that he made illegal disclosures about two CIA employees and their involvement in classified operations to two journalists (referenced as “Journalist A” and “Journalist B” in court records) on multiple occasions between 2007 and 2009.
Kiriakou admitted that, through a series of e-mails with Journalist A, he disclosed the full name of a CIA officer (referred to as “Officer A” in court records) whose association with the CIA had been classified for more than two decades. In addition to identifying the officer for the journalist, Kiriakou also provided information that helped the journalist link the officer to a particular classified operation.
In addition, Kiriakou admitted that he disclosed to Journalists A and B the name and contact information of a CIA analyst, identified in court records as “Officer B,” along with his association with an operation to capture terrorism subject Abu Zubaydah in 2002. Kiriakou knew that the association of Officer B with the Abu Zubaydah operation was classified. Based in part on this information, Journalist B subsequently published a June 2008 front-page story in The New York Times disclosing Officer B’s alleged role in the Abu Zubaydah operation.
Without Kiriakou’s knowledge, Journalist A passed the information he obtained from Kiriakou to an investigator assisting in the defense of high-value detainees at Guantanamo Bay.
Kiriakou also admitted that he lied to the CIA regarding the existence and use of a classified technique, referred to as a “magic box,” while seeking permission from the CIA’s Publications Review Board to include the classified technique in a book.
This case was investigated by the FBI’s Washington Field Office, with assistance from the CIA and the Air Force Office of Special Investigations. Assistant U.S. Attorneys Iris Lan of the Southern District of New York; Mark E. Schneider and Ryan Fayhee of the Northern District of Illinois; and W. Neil Hammerstrom, Jr. of the Eastern District of Virginia are prosecuting the case on behalf of the United States.
Movie -Cold Case Files – One Night on the Bayou/The Buckeye Misdemeanor
SECRET-Joint Publication 3-13.3 Operations Security January 2012

The following Joint Publication is unavailable from the Defense Technical Information Center (DTIC) website. Though it does not have any markings indicating a distribution restriction, the DTIC website lists the document has being available through the Joint Doctrine, Education, & Training Electronic Information System (JDEIS) which is restricted to U.S. military personnel.
Joint forces often display personnel, organizations, assets, and actions to public view and to a variety of adversary intelligence collection activities, including sensors and systems. Joint forces can be under observation at their peacetime bases and locations, in training or exercises, while moving, or when deployed to the field conducting actual operations. In addition, the adversary could compile and correlate enough information to facilitate predicting and countering US operations.
The purpose of operations security (OPSEC) is to reduce the vulnerability of US and multinational forces from successful adversary exploitation of critical information. OPSEC applies to all activities that prepare, sustain, or employ forces. The OPSEC process is a systematic method used to identify, control, and protect critical information and subsequently analyze friendly actions associated with military operations.
Tailored to the OPSEC process, joint intelligence preparation of the operational environment is a useful methodology for intelligence professionals to support the OPSEC planner. The intelligence professional will perform mission analysis on friendly operations. This provides great insight into potential areas where the adversary could collect information and the identity of essential elements of friendly information (EEFIs). Identification of EEFIs will assist the OPSEC planner in ensuring all OPSEC-related critical unclassified information is included in the critical information list.
OPSEC’s most important characteristic is that it is a process. It is an analytical process that can be applied to any operation or activity for the purpose of denying critical information to an adversary. Unlike security programs that seek to protect classified information and controlled unclassified information, OPSEC is concerned with identifying, controlling, and protecting unclassified information that is associated with specific military operations and activities.
…
3. Purpose of Operations Security
a. The purpose of OPSEC is to reduce the vulnerability of US and multinational forces from successful adversary exploitation of critical information. OPSEC applies to all activities that prepare, sustain, or employ forces.
b. The OPSEC process is a systematic method used to identify, control, and protect critical information and subsequently analyze friendly actions associated with military operations and other activities to:
(1) Identify those actions that may be observed by adversary intelligence systems.
(2) Determine what specific indications could be collected, analyzed, and interpreted to derive critical information in time to be useful to adversaries.
(3) Select countermeasures that eliminate or reduce vulnerability or indicators to observation and exploitation.
(4) Avoid patterns of behavior, whenever feasible, and thus preclude the possibility of adversary intelligence constructing an accurate model.
(5) Prevent the display or collection of critical information, especially during preparation for and execution of actual operations.
(6) Avoid drastic changes as OPSEC countermeasures are implemented. Changes in procedures alone will indicate to the adversary that there is an operation or exercise starting.
…
6. Operations Security and Information Operations
OPSEC as a capability of information operations (IO) denies the adversary the information needed to correctly assess friendly capabilities and intentions. It is also a tool, hampering the adversary’s use of its own information systems and processes and providing the necessary support to all friendly IO capabilities. In particular, OPSEC complements military deception (MILDEC) by denying an adversary information required to both assess a real plan and to disprove a deception plan. OPSEC and MILDEC have the same ultimate goal—affecting the adversary’s decision-making process and leading it to an erroneous decision. OPSEC does it by concealing important information, and MILDEC does it by putting misleading information into the environment. These are two related processes. For IO capabilities that exploit new opportunities and vulnerabilities, such as electronic warfare and computer network attack, OPSEC is essential to ensure friendly capabilities that might be easily countered are not compromised. The process of identifying critical information and applying measures to mask them from disclosure to adversaries is only one part of a defense in-depth approach to securing friendly information. To be effective, other types of security must complement OPSEC. Examples of other types of security include physical security, programs in IA, computer network defense, and personnel programs that screen personnel and limit authorized access. In particular, COMSEC plays a vital role in OPSEC. While COMSEC’s primary purpose is to protect classified materials, it can assist with identifying vulnerabilities to loss of critical information through monitoring communications within legal constraints.
…
5. Risk Assessment
a. This action has three components. First, planners analyze the vulnerabilities identified in the previous action and identify possible OPSEC countermeasures for each vulnerability. Second, the commander and staff estimate the impact to operations such as cost in time, resources, personnel or interference with other operations associated with implementing each possible OPSEC countermeasure versus the potential harmful effects on mission accomplishment resulting from an adversary’s exploitation of a particular vulnerability. Third, the commander and staff select specific OPSEC countermeasures for execution based upon a risk assessment done by the commander and staff.
b. OPSEC countermeasures reduce the probability of the adversary either observing indicators or exploiting vulnerabilities, being able to correctly analyze the information obtained, and being able to act on this information in a timely manner.
(1) OPSEC countermeasures can be used to prevent the adversary from detecting an indicator or exploiting a vulnerability, provide an alternative analysis of a vulnerability or an indicator (prevent the adversary from correctly interpreting the indicator), and/or attack the adversary’s collection system.
(2) OPSEC countermeasures include, among other actions, cover, concealment, camouflage, deception, intentional deviations from normal patterns, and direct strikes against the adversary’s intelligence system.
(3) More than one possible measure may be identified for each vulnerability. Conversely, a single measure may be used for more than one vulnerability. The most desirable OPSEC countermeasures are those that combine the highest possible protection with the least adverse effect on operational effectiveness. Chapter III, “Operations Security Planning,” provides a detailed discussion of OPSEC countermeasures.
DOWNLOAD THE ORIGINAL DOCUMENT HERE:
Secrecy News – Liberties Oversight Board invites Public Input
The long-dormant Privacy and Civil Liberties Oversight Board (PCLOB)
announced that it will hold its first public meeting next week and it
invited members of the public to provide input to help shape the Board's
near-term agenda.
"In anticipation of setting the agenda of issues on which the Board will
focus its attention, the Board would welcome the views of nongovernmental
organizations and members of the public," stated a notice in the October 23
Federal Register.
http://www.fas.org/sgp/news/2012/10/pclob.html
The PCLOB was created in response to a recommendation of the 9/11
Commission that "there should be a board within the executive branch to
oversee... the commitment the government makes to defend our civil
liberties."
By statute, the PCLOB is mandated to "(1) analyze and review actions the
executive branch takes to protect the Nation from terrorism, ensuring that
the need for such actions is balanced with the need to protect privacy and
civil liberties; and (2) ensure that liberty concerns are appropriately
considered in the development and implementation of laws, regulations, and
policies related to efforts to protect the Nation against terrorism."
In response to the announcement of next week's meeting, we wrote in to
propose that the PCLOB should review the government's problematic use of
Section 215 of the USA Patriot Act. "The use of Section 215, the so-called
'business records' provision, is the subject of intense and unresolved
controversy that warrants the Board's attention," we suggested.
http://www.fas.org/sgp/news/2012/10/pclob-let.pdf
Senators Ron Wyden and Mark Udall have stated that "most Americans would
be stunned to learn the details of how these secret court opinions have
interpreted section 215 of the Patriot Act." If so, the members of the
PCLOB can be stunned on behalf of most Americans by virtue of the security
clearances and right of access that they possess.
For background on the origins and development of the PCLOB, see "Privacy
and Civil Liberties Oversight Board: New Independent Agency Status,"
Congressional Research Service, August 27, 2012:
http://www.fas.org/sgp/crs/misc/RL34385.pdf
FEDERAL SUPPORT FOR ACADEMIC RESEARCH, AND MORE FROM CRS
Newly updated reports from the Congressional Research Service that
Congress has not made publicly available include the following.
Federal Support for Academic Research, October 18, 2012:
http://www.fas.org/sgp/crs/misc/R41895.pdf
Unfunded Mandates Reform Act: History, Impact, and Issues, October 22,
2012:
http://www.fas.org/sgp/crs/misc/R40957.pdf
Terrorism and Transnational Crime: Foreign Policy Issues for Congress,
October 19, 2012:
http://www.fas.org/sgp/crs/terror/R41004.pdf
Managing the Nuclear Fuel Cycle: Policy Implications of Expanding Global
Access to Nuclear Power, October 19, 2012:
http://www.fas.org/sgp/crs/nuke/RL34234.pdf
U.S. Sanctions on Burma, October 19, 2012:
http://www.fas.org/sgp/crs/row/R41336.pdf
Burma's Political Prisoners and U.S. Sanctions, October 19, 2012:
http://www.fas.org/sgp/crs/row/R42363.pdf
Navy DDG-51 and DDG-1000 Destroyer Programs: Background and Issues for
Congress, October 18, 2012:
http://www.fas.org/sgp/crs/weapons/RL32109.pdf
Navy Ohio Replacement (SSBN[X]) Ballistic Missile Submarine Program:
Background and Issues for Congress, October 18, 2012:
http://www.fas.org/sgp/crs/weapons/R41129.pdf
Navy Shipboard Lasers for Surface, Air, and Missile Defense: Background
and Issues for Congress, October 19, 2012:
http://www.fas.org/sgp/crs/weapons/R41526.pdf
Navy Irregular Warfare and Counterterrorism Operations: Background and
Issues for Congress, October 18, 2012:
http://www.fas.org/sgp/crs/natsec/RS22373.pdf
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
Opfer: DIE STASI-FÄLSCHER UND DER BEWEIS: WIE MERIDIAN CAPITAL VON “GoMoPa” ERPRESST WURDE
BILD: Studie zum Tatort Internet :Jeder Dritte wurde schon gemobbt
Sports Illustrated Swimsuit : SI Swimsuit – Jeisa
SECRET-Joint Publication 3-13.2 Military Information Support Operations

The following Joint Publication is unavailable from the Defense Technical Information Center (DTIC) website. Though it does not have any markings indicating a distribution restriction, the DTIC website lists the document has being available through the Joint Doctrine, Education, & Training Electronic Information System (JDEIS) which is restricted to U.S. military personnel.
Today’s global information environment is complex, rapidly changing, and requires integrated and synchronized application of the instruments of national power to ensure responsiveness to national goals and objectives. In the current operational environment, effective influence is gained by unity of effort in what we say and do, and how well we understand the conditions, target audiences (TAs), and operational environment. Within the military and informational instruments of national power, the Department of Defense (DOD) is a key component of a broader United States Government (USG) communications strategy. To be effective, all DOD communications efforts must inherently support the credibility, veracity, and legitimacy of USG activities.
Military information support operations (MISO) play an important role in DOD communications efforts through the planned use of directed programs specifically designed to support USG and DOD activities and policies. MISO are planned operations to convey selected information and indicators to foreign audiences to influence their emotions, motives, objective reasoning, and ultimately the behavior of foreign governments, organizations, groups, and individuals in a manner favorable to the originator’s objectives. Military information support (MIS) professionals follow a deliberate process that aligns commander’s objectives with an analysis of the environment; select relevant TAs; develop focused, culturally, and environmentally attuned messages and actions; employ sophisticated media delivery means; and produce observable, measurable behavioral responses.
…
b. Within the military and informational instruments of national power, the Department of Defense (DOD) is a key component of a broader United States Government (USG) communications strategy. DOD communications strategy and the separate and unique capabilities of military information support operations (MISO), public affairs (PA) (to include visual information), and defense support to public diplomacy (DSPD) address a variety of communication roles and specific audiences as permitted by operational parameters and policy. DOD informational activities can be used to inform, direct, or persuade. To be effective, all DOD communications efforts must inherently support the credibility, veracity, and legitimacy of USG activities.
c. MISO play an important role in DOD communications efforts through the planned use of directed programs specifically designed to support USG and DOD activities and policies. MISO are planned operations to convey selected information and indicators to foreign audiences to influence their emotions, motives, objective reasoning, and ultimately the behavior of foreign governments, organizations, groups, and individuals in a manner favorable to the originator’s objectives. Military information support (MIS) professionals follow a deliberate process that aligns commander’s objectives with an analysis of the environment; select relevant TAs; develop focused, culturally, and environmentally attuned messages and actions; employ sophisticated media delivery means; and produce observable, measurable behavioral responses. It is important not to confuse psychological impact with MISO. Actions of the joint force, such as strikes or shows of force, have psychological impact but they are not MISO unless their primary purpose is to influence the perceptions and subsequent behavior of a TA. Regardless of the mission set, all MISO are conducted within carefully reviewed and approved programs and under mission-tailored product approval guidelines that flow from national-level authorities.
d. MISO contribute to the success of both peacetime engagements and major operations. The combatant commander (CCDR) receives functional and theater strategic planning guidance from the Joint Strategic Capabilities Plan (JSCP), Unified Command Plan (UCP), and Guidance for Employment of the Force (GEF). These documents are derived from the Secretary of Defense (SecDef) National Defense Strategy, which interprets the President’s national security policy and strategy, and the Joint Chiefs of Staff National Military Strategy.
(1) In peacetime, MISO are planned and integrated to further national defense strategies through the geographic combatant commander’s (GCC’s) theater campaign plan (TCP). CCDRs incorporate MISO programs and integrate them into the broad range of activities required for military engagement, security cooperation, and deterrence (i.e., Phase 0). For example, in steady-state geographic combatant command TCPs, MIS units can deploy to support approved counterinsurgency (COIN), demining, or foreign humanitarian assistance (FHA) programs under either a joint force commander (JFC) or US diplomatic control.
(2) MISO reinforce US policies that center on preventing hostilities and advocating peaceful resolutions when possible. MISO are key in furthering US endeavors to deter aggression and to maximize the JFC’s efforts to shape the operational environment. MIS units communicate well-orchestrated and planned information to international audiences to clarify intent, prevent escalation of tension, ease concerns, and mitigate the potential effects and capabilities of adversary information activities.
…
4. Support of Irregular Warfare
a. General. Irregular warfare (IW) is defined as “a violent struggle among state and non-state actors for legitimacy and influence over the relevant populations. IW favors indirect and asymmetric approaches, though it may employ the full range of military and other capabilities, in order to erode an adversary’s power, influence, and will.”
(1) Some of the operations and activities that can be conducted as part of IW are insurgency; COIN; unconventional warfare (UW); terrorism; CT; FID; stability, security, transition, and reconstruction operations; MISO; CMO; intelligence and counterintelligence activities; transnational criminal activities, including drug trafficking, illicit arms dealing, and illegal financial transactions, that support or sustain IW; and law enforcement activities focused on countering irregular adversaries. (Some IW activities, such as terrorism and transnational crime, violate international law. US law and national policy prohibit US military forces or other government departments and agencies from engaging in or supporting such activities. However, since our adversaries employ terrorism and transnational criminal activities against the interests of the US and its partners, these activities are included below as examples of the range of operations and activities that can be conducted as part of IW.) IW provides a logical, long-term framework for analyzing the
irregular threat and is both a form of armed conflict and warfare.(2) IW is complex and focuses on the control or influence of populations, not on the control of an adversary’s forces or territory. Ultimately, IW is a political struggle for control or influence over, and the support of, a relevant population. The factions involved in the conflict seek to undermine their adversaries’ legitimacy and credibility and to isolate their adversaries from the relevant populations and their external supporters. At the same time, they also seek to strengthen their own legitimacy and credibility to exercise authority over that same population.
(3) When MISO occur in IW, their role usually is much greater than during major operations and campaigns. They impact directly on the operational focus of IW in ways unlike that of combat operations.
b. Approaches. Conducting IW focuses on two approaches—direct and indirect. A JFC will often conduct both approaches simultaneously to defeat our adversaries and those of our partners.
(1) Direct Approach. The direct approach addresses the requirement to pursue adversaries and their infrastructure and resources. Some adversaries, such as terrorists and insurgents fighting for a religious or tribal cause, may be so committed that they simply cannot be persuaded or coerced into laying down their arms; these individuals must be either killed or captured.
(2) Indirect Approach. MISO are key supporting operations to each contextual application of indirect approaches to executing IW.
(a) Focus on addressing the underlying economic, political, cultural, or security conditions that fuel the grievances of the population, rather than on applying military power directly against the military and paramilitary forces of adversaries. Both approaches are necessary, but the direct application of military power is unlikely to be decisive.
(b) Disturb, disrupt, and displace adversaries by attacking them physically and psychologically where they are most vulnerable and unsuspecting, rather than attacking where they are strongest or in the manner they expect.
(c) Empower, enable, and leverage interagency and other partners to attack adversaries militarily or confront them nonmilitarily, rather than relying on direct and unilateral military confrontation by US joint forces.
(d) Take actions with or against third-party states or armed groups to influence adversaries, rather than taking actions to influence adversaries directly.
(e) Attack adversaries using a combination of conventional and nonconventional methods and means rather than relying only on conventional military forces. Nonconventional methods and means might include clandestine or covert actions, operations in combination with irregular forces, or the nonconventional use of conventional capabilities.
(f) Subvert the power and influence of adversaries over the relevant populations by isolating them physically and psychologically from their local and international support through the use of MISO, public diplomacy, and PA activities; security operations; population and resource control measures; and other means.
c. Military Information Support Operations and IW. The ideological and political factors associated with IW create a fertile field for MISO. Examples of MISO applications to selected activities within IW are:
(1) FID. MISO are used to promote the ability of the HN to defend itself against internal and external insurgencies and terrorism by fostering reliable military forces and encouraging empathy between HN armed forces and the civilian populace. MISO also may be used to modify the behavior of selected TAs toward US and multinational capabilities. The main objectives of MISO during FID are to build and maintain support for the host government while decreasing support for insurgents.
(2) CT. MISO are an essential part of the capabilities required for CT, in particular in application of the indirect approach to shape, stabilize, and influence the environment in which violent extremist organizations (VEOs) operate. CT focuses on populations, and in some operational areas, the information presented can determine which side will gain the favor of public opinion. Terrorist groups have gained sympathy and support of moderate audiences through disinformation partly based on their propaganda focusing on miscues of the friendly forces. In CT operations, TA identification and the use of MISO to influence the TAs’ behavior are important. Within an operational area there may be several TAs and multiple synchronized themes, messages, and means of delivery required for each. The intent of MISO in CT operations is to shape and influence the terrorist network’s informational environment.
(3) Stability Operations. Successful execution of stability operations tasks depends on informing the local populace and influencing attitudes to secure the trust and confidence of the population. MISO exerts significant influence on foreign TAs.
(4) COIN Operations. MISO can influence foreign populations through information to influence attitudes and behavior and to obtain compliance or noninterference with friendly joint operations. In addition, MIS units may conduct information activities such as recruit for security forces, legitimize HN governments, and establish and maintain popular support for the HN programs and activities. MISO can provide public information to support humanitarian activities, ease suffering, and restore or maintain civil order. MISO can serve as the supported commander’s voice to foreign populations by conveying the JFC’s intent.
(5) UW. UW involves ideological, religious, political, economic, and social factors which promote intense, emotional partisanship. These human factors, associated with armed resistance activity, create a situation that MIS units are uniquely suited to engage. MIS units support all phases of UW; therefore, MISO planning is immediately integrated into the planning process.
DOWNLOAD THE ORIGINAL DOCUMENT HERE:
TMZ – Christina Aguilera — Targeted by Fatty Website
Kiriakou pleads guilty in leak case
KIRIAKOU PLEADS GUILTY IN LEAK CASE
This morning former CIA officer John Kiriakou pleaded guilty to one count
of disclosure of information identifying a covert agent, a violation of the
Intelligence Identities Protection Act.
"When KIRIAKOU disclosed the identity of Officer A to Journalist A,
KIRIAKOU acted willfully in that defendant knew the disclosure was
illegal," according to a Statement of Facts approved and signed by Mr.
Kiriakou today.
http://www.fas.org/sgp/jud/kiriakou/facts.pdf
Under the terms of a plea agreement, the parties agreed that a prison term
of 30 months would be "the appropriate sentence in this case." Other
charges against him, including several counts under the Espionage Act,
would be dismissed.
http://www.fas.org/sgp/jud/kiriakou/plea.pdf
By foregoing a trial, Mr. Kiriakou loses an opportunity to try and
persuade a jury that his motives were benign, and that the harm to national
security resulting from his disclosure was negligible and insignificant.
But he gains an early resolution of the case, which could otherwise drag on
for months and years, as well as a sentence that would likely be much
shorter than if he were to be found guilty at trial.
"NEGATIVE RECIPROCITY" EMERGES IN THE SECURITY CLEARANCE SYSTEM
In the world of security clearances for access to classified information,
the term "reciprocity" is used to indicate that one executive branch agency
should ordinarily recognize and accept a security clearance that has been
granted by another executive branch agency.
This is not just a nice, cost-efficient thing to do, it is actually a
requirement of law. Under the 2004 intelligence reform law, "all security
clearance background investigations and determinations... shall be accepted
by all agencies."
This requirement for mutual recognition and acceptance applies equally to
the higher order clearances of the intelligence community, where
reciprocity is intended to promote employee "mobility" throughout the
intelligence system, according to the 2009 Intelligence Community Directive
709.
http://www.fas.org/irp/dni/icd/icd-709.pdf
So possessing a clearance from one agency should simplify the process of
access approval at another agency. But the opposite is not supposed to be
true. If an agency refuses for some reason to recognize the clearance
granted by another agency, that refusal is not supposed to incur loss of
clearance in the original agency.
Officially, such "negative reciprocity" is not an authorized, legitimate
security clearance practice. And yet there are signs that it is being
adopted within the Department of Defense Office of Hearings and Appeals
(DOHA), which rules on contested security clearance cases.
A new paper by attorney Sheldon I. Cohen describes a series of DOHA
rulings in which a perverse form of negative reciprocity has been used to
justify the denial or revocation of a security clearance, to the obvious
detriment of due process.
http://www.sheldoncohen.com/
"While the burden of proof has always been placed on the employee by the
DOHA Appeal Board to show why he or she should be granted a security
clearance, until now there was a modicum of a right to confrontation, and a
right to challenge the evidence presented by the government," Mr. Cohen
wrote.
But in a ruling he describes, "anonymous redacted reports and other
agency's decision are enough to deny or revoke a DoD clearance regardless
of contrary evidence."
In a series of recent decisions, the DOHA Appeal Board "has accepted
unsigned, unsworn, summary statements from unidentified persons in
government agencies [that are] in direct conflict with live testimony at a
hearing to deprive or revoke security clearances of government contractor
employees."
To avoid or limit the fallout of negative reciprocity, Mr. Cohen advises
DoD employees and contractors to immediately appeal any adverse clearance
decision, "at least to get [their] side of the issues on the record." Left
unchallenged, it appears that adverse decisions by other agencies will be
presumed reliable by DOHA and that any later attempt to rebut them "will
most probably be rejected."
See "Has the Defense Office of Hearings and Appeals Become a Star Chamber
Court?" by Sheldon I. Cohen, October 19, 2012.
http://www.fas.org/sgp/eprint/doha-cohen.pdf
The Department of Defense last week published a three-volume "DoD
Sensitive Compartmented Information (SCI) Administrative Security Manual,"
DoD Manual 5105.21, October 19, 2012. A copy is available here:
http://www.fas.org/sgp/othergov/dod/index.html
CONGRESSIONAL OVERSIGHT, AND MORE FROM CRS
Newly updated reports from the Congressional Research Service which
Congress has not made publicly available include the following.
Congressional Oversight, October 17, 2012:
http://www.fas.org/sgp/crs/misc/97-936.pdf
Contemporary Developments in Presidential Elections, October 18, 2012:
http://www.fas.org/sgp/crs/misc/R42139.pdf
U.S. International Trade: Trends and Forecasts, October 19, 2012:
http://www.fas.org/sgp/crs/misc/RL33577.pdf
President of the United States: Compensation, October 17, 2012:
http://www.fas.org/sgp/crs/misc/RS20115.pdf
Peru in Brief: Political and Economic Conditions and Relations with the
United States, October 18, 2012:
http://www.fas.org/sgp/crs/row/R42523.pdf
Libya: Transition and U.S. Policy, October 18, 2012:
http://www.fas.org/sgp/crs/row/RL33142.pdf
China Naval Modernization: Implications for U.S. Navy Capabilities --
Background and Issues for Congress, October 17, 2012:
http://www.fas.org/sgp/crs/row/RL33153.pdf
Navy Force Structure and Shipbuilding Plans: Background and Issues for
Congress, October 18, 2012:
http://www.fas.org/sgp/crs/weapons/RL32665.pdf
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
FEMEN concquer Paris – Uncensored Video
DOC – Cold Case Files – Death to a Deacon/A Wifes Mission
Börse-Online berichtet über die Organisierten Kriminellen der “GoMoPa” und wie sie die Finanzbranche bedrohen
DOWNLOAD THE ORIGINAL DOCUMENT HERE:
Sports Illustrated – Swimsuit – Sneak Peak
Unveiled by Cryptome – CIA Camp Peary 2012
BÖRSE ONLINE warnt vor den wegen Betruges am eigenen Anleger vorbestraften “GoMoPa”
Secrecy News – Intelligence Imagery set to be disclosed
A massive quantity of historical intelligence satellite imagery from the
KH-9 HEXAGON program is being declassified and will be made public in a
series of releases that are scheduled over the coming year, intelligence
community officials say.
Declassification of intelligence satellite imagery languished for years
after President Clinton ordered the release of product from the Corona,
Argon and Lanyard missions in the 1995 executive order 12951. Although the
Clinton order also required the periodic review of imagery from other
missions, that requirement was effectively ignored by intelligence agencies
and neglected by congressional oversight.
But in a May 2010 memorandum Director of National Intelligence Dennis C.
Blair ordered the "re-establishment" of the declassification review of
intelligence imagery -- though it had never been officially disestablished
-- with a particular focus on imagery from satellite systems that were
deemed obsolete.
http://www.fas.org/sgp/othergov/intel/imagery.pdf
In January 2011, DNI James R. Clapper formally declared that the KH-9
HEXAGON program was obsolete, and that declassification review of all
program imagery should therefore commence. KH-9 HEXAGON was operational
from 1971 to 1984.
http://www.fas.org/sgp/othergov/intel/dni012011.pdf
"The process to declassify imagery pursuant to EO 12951 began shortly
after DNI Blair's May 26, 2010 memorandum and has been ongoing, in earnest,
with the goal of releasing as much imagery as possible to the public,
consistent with national security," said Michael G. Birmingham of the
Office of the Director of National Intelligence. "Accordingly, The
KH-9/HEXAGON system was declared obsolete in January 2011 and a phased
declassification of its imagery has ensued."
More than two years after the Blair memorandum, however, next to nothing
has yet been made public.
"The notable challenges to this effort are the sheer volume of imagery and
the logistics involved in cataloging the imagery and moving it to archive,"
Mr. Birmingham told Secrecy News.
"For context, and to grasp the scope of the project, the KH-9/HEXAGON
system provided coverage over hundreds of millions of square miles of
territory during its 19 successful missions spanning 1971-1984. It is a
daunting issue to address declassification of the program specifics
associated with an obsolete system such as the KH-9, which involves the
declassification of huge volumes of intelligence information gathered on
thousands of targets worldwide during a 13 year time period."
Daunting or not, the large bulk of the KH-9 imagery is expected to be
released, with only perhaps 5% or so remaining classified.
"There is a schedule of multiple deliveries with final delivery of imagery
scheduled for September 2013," Mr. Birmingham said.
Within the intelligence community, the National Geospatial-Intelligence
Agency is the executive agent for imagery declassification. NGA public
affairs did not respond to questions about its declassification program.
HISTORIAN ANNA K. NELSON, RIP
We were sad to learn that Professor Anna K. Nelson, a tenacious and
effective advocate for improved public access to national security records,
passed away last month.
For decades, Prof. Nelson argued for improved declassification practices
in almost every venue imaginable, from congressional hearings to the most
obscure and transient advisory bodies. As a professor of history at
American University, she insisted that government records were public
property and that access to such records was one of the foundations of good
citizenship.
http://www.american.edu/cas/faculty/anelson.cfm
Among many other posts, she served as a presidentially-appointed member of
the JFK Assassination Records Review Board, which was tasked to oversee the
declassification of records concerning the assassination of President
Kennedy. Because of the perseverance of Dr. Nelson and her colleagues,
that Board was uniquely productive in overcoming longstanding barriers to
declassification, particularly those pertaining to intelligence agency
records.
Nevertheless, she was habitually pessimistic about the prospects for
meaningful secrecy reform.
"Given past performance, it is highly unrealistic to assume that agencies,
particularly Defense and the CIA, will be completely forthcoming or that
the Archives will ever question agency decisions," she wrote in a 2000
letter to Congress. "Agency declassification of selected, heavily redacted
records will not serve the public interest. It will only breed more
suspicion."
http://www.fas.org/sgp/news/2000/02/nelson.html
Prof. Nelson also spoke out in defense of robust investigative reporting
on national security matters. In 2008, for example, she submitted a
declaration of behalf of New York Times reporter James Risen, arguing that
a grand jury subpoena against him in the pending leak case against former
CIA officer Jeffrey Sterling should be quashed.
http://www.fas.org/sgp/jud/sterling/risen-nelson.pdf
"If Mr. Risen and other investigative journalists are unable to report
effectively on matters of intelligence, the historical record will be
incomplete, if not erroneous," Dr. Nelson wrote.
"Although our own books and articles are stuffed with footnotes, we
historians understand that investigative journalists, as observers of the
present, must protect their sources. If they do not, the American people
will never learn about corruption, incompetence, excessive government
secrecy, flaws in homeland security, or disastrous decisions made by policy
makers who are advised by their intelligence chiefs," she wrote. "We must
depend upon journalists and journalists must be permitted to depend upon
confidential sources."
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
TMZ – Paris Hilton’s Sexy Halloween!
Public Intelligence – Joint Publication 3-13.1 Electronic Warfare February 2012

The following Joint Publication is unavailable from the Defense Technical Information Center (DTIC) website. Though it does not have any markings indicating a distribution restriction, the DTIC website lists the document as being available through the Joint Doctrine, Education, & Training Electronic Information System (JDEIS) which is restricted to U.S. military personnel. A previous version of this publication from January 2007 was made available by the Federation of American Scientists
All modern forces depend on the electromagnetic spectrum (EMS). The military requirement for unimpeded access to, and use of, the EMS is the key focus for joint electromagnetic spectrum operations (JEMSO), both in support of military operations and as the focus of operations themselves. Electronic warfare (EW) is essential for protecting friendly operations and denying adversary operations within the EMS throughout the operational environment.
JEMSO are the coordinated efforts of EW and joint electromagnetic spectrum management operations (JEMSMO) to exploit, attack, protect, and manage the electromagnetic operational environment (EMOE). The impact of an EMOE upon the operational capability of military forces, equipment, systems, and platforms is referred to as electromagnetic environmental effects. It encompasses all electromagnetic (EM) disciplines to include electromagnetic compatibility; electromagnetic interference; EM vulnerability; electromagnetic pulse (EMP); electronic protection (EP); hazards of EM radiation to personnel, ordnance, and volatile materials; and natural phenomena effects such as sunspots, lightning, and precipitation static.
…
At the national level, organizations and agencies such as the Central Intelligence Agency, National Security Agency/Central Security Service, National Geospatial-Intelligence Agency, and Defense Intelligence Agency are constantly seeking to identify, catalog, and update the electronic order of battle (EOB) of identified or potential adversaries. The joint intelligence operations center responds to theater-level EW-related intelligence requirements and forwards requests that require national level assets to the defense collection coordination center or other national-level organizations according to established procedures. The intelligence directorate of a joint staff (J-2) [at the subordinate joint force level] normally assigns one or more members of the staff to act as a liaison between the J-2 section and the IO cell where EW planners are normally assigned.
…
At combatant commands and subordinate unified commands, the J-3 is primarily responsible for the EW coordination function. The EW division of the J-3 staff should engage in the full range of EW functions to include deliberate planning; day-to-day planning and monitoring of routine theater EW activities in conjunction with the combatant command’s theater campaign plan; and crisis action planning in preparation for EW as part of emergent joint operations. Since EW is concerned with attacking personnel, facilities, or equipment (EA); protecting capabilities and EMS access (EP); and monitoring, exploiting, and targeting use of the EMS (ES), EW staff personnel have a role in the dynamic management of the EMS, via tools and processes, during operations. A comprehensive and well-thought-out joint restricted frequency list and emission control plan are two significant tools that permit flexibility of EW actions during an operation without compromising friendly EMS use. The electronic warfare control authority, the senior EA authority in the operational area, develops guidance for performing EA on behalf of the JFC.
…
Military operations are executed in an environment complicated by increasingly complex demands on the electromagnetic spectrum (EMS). All modern forces depend on the EMS. The EMS is the entire range of electromagnetic (EM) radiation. At one end of the spectrum are gamma rays, which have the shortest wavelengths and high frequencies. At the other end are radio waves, which have the longest wavelengths and low frequencies. The EMS is used to organize and explain the types of EM energy that exist in our world and throughout the universe. Devices whose functions depend upon the EMS are used by both civilian and military organizations and individuals for intelligence; communications; positioning, navigation, and timing (PNT); sensing; command and control (C2); attack; ranging; data transmission; and information storage and processing. The military requirement for unimpeded access to, and use of, the EMS is the key focus for joint electromagnetic spectrum operations (JEMSO), both in support of military operations and as the focus of operations themselves. Electronic warfare (EW) is essential for protecting friendly operations and denying adversary operations within the EMS throughout the operational environment (OE).
…
DOWNLOAD THE ORIGINAL DOCUMENT HERE:
Sports Illustrated Swimsuit Video – Bar Refaeli Swimsuit
TMZ Invades a Playboy Casting Call – Video
Unveiled by Cryptome – AU Foreign Affairs Declassified WikiLeaks Cables
TOP-SECRET – Joint Publication 3-13.4 Military Deception January 2012

The following Joint Publication is unavailable from the Defense Technical Information Center (DTIC) website. Though it does not have any markings indicating a distribution restriction, the DTIC website lists the document as being available only through the Joint Doctrine, Education & Training Electronic Information System (JDEIS) which is restricted to U.S. military personnel.
Specific guidance from the joint force commander (JFC) or higher authority during planning will determine the military deception (MILDEC) role in a joint operation. MILDEC is intended to deter hostile actions, increase the success of friendly defensive actions, or to improve the success of any potential friendly offensive action. Use of
MILDEC during any phase of an operation should help to mislead adversaries as to the strength, readiness, locations, and intended missions of friendly forces. In combat situations, the focus is on driving the adversary to culmination and achieving the objectives defined by the JFC. In noncombat situations, the JFC seeks to dominate the situation with decisive operations designed to establish conditions for an early, favorable conclusion.…
The MILDEC goal is the commander’s statement of the purpose of the MILDEC as it contributes to the successful accomplishment of the assigned mission. It is important for the commander to first envision the deception goal in terms of its specific contribution to accomplishing the designated mission. The MILDEC objective is a concise statement of what the MILDEC will cause the adversary to do or not do. It is expressed in terms of the adversary’s action or inaction that directly leads to the purpose or condition stated in the MILDEC goal.
MILDEC Targets
The deception target is the adversary decision maker with the authority to make the decision that will achieve the deception objective. The deception target or targets are the key individuals on whom the entire deception operation will be focused.
…
Function of MILDEC include:
• Causing ambiguity, confusion, or misunderstanding in adversary perceptions of friendly critical information.
• Causing the adversary to misallocate personnel, fiscal, and material resources in ways that are advantageous to the friendly force.
• Causing the adversary to reveal strengths, dispositions, and future intentions.
• Conditioning the adversary to particular patterns of friendly behavior to induce adversary perceptions that can be exploited by the joint force.
• Causing the adversary to waste combat power with inappropriate or delayed actions.…
The MILDEC Planning Process
Deception planning is an iterative process that requires continual reexamination of its objectives, target, stories, and means throughout the planning and execution phases. A key factor that must be considered during MILDEC planning is risk. The overriding consideration in risk analysis is the comparison between the risk taken and the possible benefits of the deception. The MILDEC planning process consists of six steps: deception mission analysis, deception planning guidance; staff deception estimate; commander’s deception estimate; Chairman of the Joint Chiefs of Staff estimate review; deception plan development; and deception plan review and approval.
…
DOWNLOAD THE ORIGINAL DOCUMENT HERE:
Veronika Varekova Swimsuit Video
TMZ – Hulk Hogan’s Sex Tape Partner Gets Around!
Cold Case Files – Snatched/A Detectives Promise – Full Movie
Gauck und das OFFIZIELLE Ende der Stasi
Bowery at Midnight – Bela Lugosi – Full Movie
A criminology professor (Lugosi) operates a charitable mission by day, and leads a gang of master thieves by night. Anyone who dares get in his way ends up buried in his cellar—until a mad doctor reanimates the corpses to exact their revenge!
Bowery at Midnight casts Bela Lugosi as Professor Brenner, a psychology instructor at New York University (which looks a lot like Berkeley in the exterior shots!). When not enlightening his students — most of them buxom Monogram starlets — Brenner is engaged in charitable work, running a mission in the Bowery. In truth, however, the kindly professor is a fiend in human form, who uses his mission as a front for a vast criminal empire. When Judy (Wanda McKay), one of Brenner’s students, stumbles onto the truth, she’s targeted for extermination by the Dr. Jekyll-and-Mr. Hyde prof.
Yamila Swimsuit Video
TMZ – Arnold Schwarzenegger’s Maid Reads the Tell-All Book!
TMZ – The Zumba Class Brothel with Famed NY Madam Kristin Davis
TOP-SECRET-Los Angeles Fusion Center: Liquid Carbon Dioxide Leaks Pose Risks to Public

(U) Within the past year, first responders and members of the public have died of asphyxiation, or fallen ill, following accidental inhalation of concentrated carbon dioxide (CO2) gas in public locations. At least two recent incidents are connected with significant gas leaks caused by the failure of liquid CO2 lines connected to beverage dispensers in commercial facilities. Emergency personnel responding to medical or service calls can use signs and symptoms to determine possible CO2 exposure and correspondent risks to first responders.
(U) Dangers Result from Change in Technology
(U) In the past, compressed CO2 tanks were generally stored close to the point of use, and connected directly to equipment via short pipes or hoses (lines). New technologies make it possible to store liquid CO2 tanks at external servicing points, in basements, or other locations far from the point of use, delivering gas via long lines concealed within walls and ceilings. Leaks in these lines can place patrons, employees, and first responders at risk for exposure to the gas.
(U) Leaking liquid CO2 evaporates into a rapidly expanding gas that is heavier than air; it can displace enough oxygen in small, poorly ventilated rooms, basements, and other low-lying areas to create “Immediately Dangerous Life Hazard” (IDLH) environments. (See the accompanying appendix for specific/technical aspects.) Building codes require sensors near CO2 tanks to monitor oxygen levels; however, if these are not present along delivery lines, leaks in locations away from the tanks may go undetected. Sensors may be susceptible to failure or tampering.
…
(U) Indicators of Possible CO2 Exposure
(U) Obvious shortness of breath with visible symptoms will occur as the body compensates for lack of oxygen. The effects of oxygen deficiency, combined with the effects of CO2 toxicity, may cause an individual to feel ill, potentially showing signs such as headache, nausea, dizziness, or mental confusion. Most individuals will begin to show signs and symptoms when exposed to concentrations of CO2, starting as low as seven percent, for approximately 15 minutes; symptoms may vary according to the level of CO2 concentration and length of exposure.
(U) Signs and symptoms indicating possible exposure to CO2 include:
- (U) Shortness of breath
- (U) Dizziness
- (U) Headaches and drowsiness
- (U) Stinging of nose and throat
- (U) Nausea and vomiting
- (U) Excitation, excess salivation, rapid breathing
- (U) Confusion
- (U) Unconsciousness
- (U) Frostbite or frozen skin from contact with escaping liquid or vapor cloud
DOWNLOAD THE ORIGINAL DOCUMENT HERE:
Cold Case Files – Rear Window/The Peeper – Full Movie
Experten in Wikipedia über Cyberstalking
28.000 people disappeared in Syria

Human rights groups working in Syria say at least 28,000 people have disappeared after being abducted by soldiers or militia.
They say they have the names of 18,000 people missing since anti-government protests began 18 months ago and know of another 10,000 cases.
Online activist group Avaaz says “nobody is safe” from a deliberate government campaign of terror.
It intends to give the UN Human Rights Council a dossier for investigation.
The Syrian government has so far not commented on the claims but has in the past strenuously denied reports of human rights abuses.
Avaaz said it had gathered testimony from Syrians who say husbands, sons and daughters were forcibly abducted by pro-government forces.
They include Fayzeh al-Masri, from a suburb of Homs, whose 26-year-old son Ahmad Ghassan Ibrahim disappeared in February – the last number he called them from was traced to a military security branch.
The family were told by someone who answered his phone that he had died, but they have been unable to confirm this.
Counting the disappeared in the real time of a conflict is extremely difficult. It’s almost impossible for outsiders to double-check claims independently.
Recent history shows that accurate counts of those kidnapped and abducted can only begin once a conflict has finished.
Activists in Iraq are still trying work out how many people were killed or went missing during the country’s peak years of violence after 2003. In Latin America, it took Chile almost 20 years to count the exact number of its disappeared during the military coup of 1973.
But the numbers currently suggested by Syrian opposition activists do give a sense of both the scale of the country’s conflict and the uncertainty surrounding the fate of many of its citizens.
“We are certain that he would not have left us or his wife – who is expecting twins. We only want to know his fate,” Mrs Masri told Avaaz.
The brother of Hussein Eisso, a 62-year-old Syrian-Kurdish activist, said he was taken from outside his home in Hasaka after attempting to stage a sit-in over the arrest of other activists.
He said his brother had since been moved between security branches, and had had serious health problems, including a stroke.
The BBC’s James Reynolds, close to the Syrian border in Turkey, says it is often hard to establish real disappearance figures until a conflict is over, but the scale of the figures is an indication of the severity of the conflict in Syria.
‘Breeding fear’
Alice Jay, campaign director at Avaaz, said Syrians were being “plucked off the street by security forces and paramilitaries and being ‘disappeared’ into torture cells”.
“Whether it is women buying groceries or farmers going for fuel, nobody is safe.”
She said it was a deliberate strategy to “terrorise families and communities”, and that each case must be investigated.
“The panic of not knowing whether your husband or child is alive breeds such fear that it silences dissent,” she said.
Other Syrian rights groups backed the allegations. Fadel Abdulghani, of the Syrian Network for Human Rights, estimated that 28,000 people had disappeared since unrest against the government of President Bashar al-Assad began last year.
Muhannad al-Hasani, of human rights organisation Sawasya, said the figure could be as high as 80,000.
“People are being snatched at night, on the street and when no-one is looking,” he said.
Muhammad Khalil, a human rights lawyer from the Syrian city of Hassaka, said the Syrian government had two reasons for carrying out the abductions: “To directly get rid of the rebels and activists, and to intimidate the society so that it won’t oppose the regime.”
Avaaz collected its statistics through a network of independent human rights lawyers and local activist groups in Syria.
The scale of the work and the current instability meant the organisation could not independently verify each disappearance, but it confirmed to the BBC that none of the detentions listed had been official arrests.
Most of the people Avaaz spoke to had personally witnessed a friend or relative being taken from home or the street
The UN says more than 18,000 people have been killed in the conflict with 170,000 fleeing abroad and 2.5 million in need of aid within the country. Opposition and human rights activists put the death toll at more than 30,000.
As violence continues, UN and Arab League envoy Lakhdar Brahimi is due to arrive in Syria on Saturday for talks with Foreign Minister Walid Muallem, Damascus told AFP news agency.
Mr Brahimi has proposed a truce over the Islamic holiday of Eid al-Adha, which starts on 25 October, to “allow a political process to develop”.
The Syrian government has recently indicated that it is interested in exploring a temporary ceasefire – and opposition groups have said they would match this.
Calls for the truce come as the conflict threatens to spill over Syria’s borders.
Turkey’s armed forces have several times returned fire across the border into Syria after Syrian mortar shells landed inside its territory.
Turkish TV reported further cross-border exchanges on Thursday morning. Our correspondent says smoke could be seen rising from the Syrian border village of Haram, while explosions and small arms fire could be heard.
Presse warnt vor Cyberstalkern wie der dubiosen “GoMoPa”
The NSA – The Alexeyeva File
 Translation: A land / Where the air / Is like honey, / You can leave / And speed away carefree, — / But a land, / With which / You suffered together / Is in your heart permanently. [Vladimir Mayakovsky, “Good”] Happy Birthday! Translation: A land / Where the air / Is like honey, / You can leave / And speed away carefree, — / But a land, / With which / You suffered together / Is in your heart permanently. [Vladimir Mayakovsky, “Good”] Happy Birthday! |
 Sergei Kovalev with Alexeyeva, 2011.  Arsenii Roginsky of the Memorial Society with Alexeyeva.
Photos by Svetlana Savranskaya. Related Links
The Moscow Helsinki Group 30th Anniversary |
Moscow, Russian Federation, October 17, 2012 – Marking the 85thbirthday of Russian human rights legend Lyudmila Alexeyeva, the National Security Archive today published on the Web a digital collection of documents covering Alexeyeva’s brilliant career, from the mid-1970s founding of the Moscow Helsinki Group (which she now heads) to the current challenges posed by the Putin regime’s crackdown on civil society.Today’s posting includes declassified U.S. documents from the Carter Presidential Library on Soviet dissident movements of the 1970s including the Moscow Helsinki Group, and KGB and Soviet Communist Party Central Committee documents on the surveillance and repression of the Group.
With the generous cooperation of the Memorial Society’s invaluable Archive of the History of Dissent, the posting also features examples of Alexeyeva’s own letters to officials (on behalf of other dissidents) and to friends, her Congressional testimony and reports, scripts she produced for Radio Liberty, and numerous photographs. Also highlighted in today’s publication are multiple media articles by and about Alexeyeva including her analysis of the current attack on human righters in Russia. As Alexeyeva’s colleagues, friends, and admirers gather today in Moscow to celebrate her 85th birthday, the illustrious history documented in today’s posting will gain a new chapter. The party-goers will not only toast Lyudmila Alexeyeva, but also debate the appropriate responses to the new Putin-inspired requirement that any civil society group receiving any international support should register as a “foreign agent” and undergo frequent “audits.” No doubt Alexeyeva will have something to say worth listening to. She has seen worse. BiographyLyudmila Mikhailovna Alexeyeva was born on July 20, 1927 in Yevpatoria, a Black Sea port town in the Crimea (now in Ukraine). Her parents came from modest backgrounds, but both received graduate degrees; her father was an economist and her mother a mathematician. She was a teenager in Moscow during the war, and she attributes her decision to come back and live in Russia after more than a decade of emigration to the attachment to her country and her city formed during those hungry and frozen war years. Alexeyeva originally studied to be an archaeologist, entering Moscow State University in 1945, and graduating with a degree in history in 1950. She received her graduate degree from the Moscow Institute of Economics and Statistics in 1956. She married Valentin Alexeyev in 1945 and had two sons, Sergei and Mikhail. Already in the university she began to question the policies of the regime, and decided not to go to graduate school in the history of the CPSU, which at the time would have guaranteed a successful career in politics. She did join the Communist Party, hoping to reform it from the inside, but very soon she became involved in publishing, copying and disseminating samizdat with the very first human rights movements in the USSR. In 1959 through 1962 she worked as an editor in the academic publishing house Nauka of the USSR Academy of Sciences. In 1966, she joined friends and fellow samizdat publishers in protesting the imprisonment and unfair trial of two fellow writers, Andrei Sinyavsky and Yuli Daniel. For her involvement with the dissident movement, she lost her job as an editor and was expelled from the Party. Later, in 1970, she found an editorial position at the Institute of Information on Social Sciences, where she worked until her forced emigration in 1977. From 1968 to 1972, she worked as a typist for the first dissident periodical in the USSR, The Chronicle of Current Events. As the 1960s progressed, Alexeyeva became more and more involved in the emerging human rights movement. Her apartment in Moscow became a meeting place and a storage site for samizdat materials. She built up a large network of friends involved in samizdat and other forms of dissent. Many of her friends were harassed by the police and later arrested. She and her close friends developed a tradition of celebrating incarcerated friends’ birthdays at their relatives’ houses, and they developed a tradition of “toast number two” dedicated to those who were far away. Her apartment was constantly bugged and surveilled by the KGB. Founding the Moscow Helsinki GroupIn the spring of 1976, the physicist Yuri Orlov – by then an experienced dissident surviving only by his connection to the Armenian Academy of Sciences– asked her to meet him in front of the Bolshoi Ballet. These benches infamously served as the primary trysting site in downtown Moscow, thus guaranteeing the two some privacy while they talked. Orlov shared his idea of creating a group that would focus on implementing the human rights protections in the Helsinki Accords – the 1975 Final Act was published in full in Pravda, and the brilliant idea was simply to hold the Soviet government to the promises it had signed and was blatantly violating. Orlov had the idea, but he needed someone who could make it happen – a typist, an editor, a writer, a historian – Lyudmila Alexeyeva. In May 1976, she became one of the ten founding members of the Moscow Helsinki Group with the formal announcement reported by foreign journalists with some help from Andrei Sakharov, despite KGB disruption efforts. The government started harassment of the group even before it was formally announced, and very quickly, the group became a target for special attention by Yuri Andropov and his organization – the KGB. Alexeyeva produced (typed, edited, wrote) many early MHG documents. One of her early – and characteristically remarkable – assignments was a fact-finding mission to investigate charges of sexual harassment against a fellow dissident in Lithuania. Several high school boys who would not testify against their teacher were expelled from school. She arranged a meeting with the Lithuanian Minister of Education, who did not know what the Moscow Helsinki Group was but anything from Moscow sounded prestigious enough to command his attention, and convinced him to return the boys to school. It was only when some higher-up called the Minister to explain what the Helsinki Group really was that he reconsidered his decision. As one of ten original members of the Moscow Helsinki Group, Alexeyeva received even greater scrutiny from the Soviet government, including the KGB. Over the course of 1976, she was under constant surveillance, including phone taps and tails in public. She had her apartment searched by the KGB and many of her samizdat materials confiscated. In early February 1977, KGB agents burst into her apartment searching for Yuri Orlov, saying “We’re looking for someone who thinks like you do.” A few days later, she and her second husband, the mathematician Nikolai Williams, were forced to leave the Soviet Union under the threat of arrest. Her departure was very painful – she was convinced that she would never be able to return, and her youngest son had to stay behind. Alexeyeva in ExileAlexeyeva briefly stopped over in the UK, where she participated in human rights protests, before she eventually settled in northern Virginia, and became the Moscow Helsinki Group spokesperson in the United States. She testified before the U.S. Congressional Helsinki Commission, worked with NGOs such as the International Helsinki Federation, wrote reports on the CSCE conferences in Belgrade, Madrid and Vienna, which she attended, and became actively involved in the issue of political abuse of psychiatry in the USSR. She soon met her best-friend-to-be, Larisa Silnicky of Radio Liberty (formerly from Odessa and Prague), who had founded the prominent dissident journal Problems of Eastern Europe, with her husband, Frantisek Silnicky. Alexeyeva started working for the journal as an editor in 1981 (initially an unpaid volunteer!). Meanwhile, she returned to her original calling as a historian and wrote the single most important volume on the movements of which she had been such a key participant. Her book, Soviet Dissent: Contemporary Movements for National, Religious and Human Rights, which was published in the United States in 1984 by Wesleyan University Press, remains the indispensable source on Soviet dissent. The book was not the only evidence of the way Alexeyeva’s talents blossomed in an atmosphere where she could engage in serious research without constant fear of searches and arrest. She worked for Voice of America and for Radio Liberty during the 1980s covering a wide range of issues in her broadcasts, especially in the programs “Neformalam o Neformalakh” and “Novye dvizheniya, novye lyudi,” which she produced together with Larisa Silnicky. These and other programs that she produced for the RL were based mainly on samizdat materials that she was getting though dissident channels, and taken together they provide a real encyclopedia of developments in Soviet society in the 1980s. The depth and perceptiveness of her analysis are astounding, especially given the fact that she was writing her scripts from Washington. Other U.S. institutions ranging from the State Department to the AFL-CIO Free Trade Union Institute also asked her for analyses of the Gorbachev changes in the USSR, among other subjects. In the late 1980s-early 1990s, she was especially interested in new labor movements in the Soviet Union, hoping that a Solidarity-type organization could emerge to replace the old communist labor unions. Back in the USSRThe Moscow Helsinki Group had to be disbanded in 1982 after a campaign of persecution that left only three members free within the Soviet Union. When the Group was finally reestablished in 1989 by Larisa Bogoraz, Alexeyeva was quick to rejoin it from afar, and she never stopped speaking out. She had longed to return to Russia, but thought it would never be possible. She first came back to the USSR in May 1990 (after being denied a visa six times previously by the Soviet authorities) with a group of the International Helsinki Federation members to investigate if conditions were appropriate for convening a conference on the “human dimension” of the Helsinki process. She also attended the subsequent November 1991 official CSCE human rights conference in Moscow, where the human righters could see the end of the Soviet Union just weeks away. She was an early supporter of the idea of convening the conference in Moscow – in order to use it as leverage to make the Soviet government fulfill its obligations – while many Western governments and Helsinki groups were skeptical about holding the conference in the Soviet capital. In 1992-1993 she made numerous trips to Russia, spending more time there than in the United States. She and her husband Nikolai Williams returned to Russia to stay in 1993, where she resumed her constant activism despite having reached retirement age. She became chair of the new Moscow Helsinki Group in 1996, only 20 years after she and Yuri Orlov discussed the idea and first made it happen; and in that spirit, in the 1990s, she facilitated several new human rights groups throughout Russia. When Vladimir Putin became president in 2000, Lyudmila Alexeyeva agreed to become part of a formal committee that would advise him on the state of human rights in Russia, while continuing her protest activities. The two did not go well together in Putin’s mind, and soon she was under as much suspicion as ever. By this time, though, her legacy as a lifelong dissident was so outsized that it was harder to persecute her. Even state-controlled television felt compelled to give her air-time on occasion, and she used her standing as a human rights legend to bring public attention to abuses ranging from the mass atrocities in the Chechen wars to the abominable conditions in Russian prisons. When the Moscow Helsinki Group celebrated its 30th anniversary in 2006, with Lyudmila Alexeyeva presiding, Yuri Orlov came back from his physics professorship at Cornell University to join her on stage. Also paying tribute were dozens of present and former public officials from the rank of ex-Prime Minister on down, as well the whole range of opposition politicians and non-governmental activists, for whom she served as the unique convenor and den mother. The Challenge in Russia TodayIn 2009, Alexeyeva became an organizer of Strategy 31, the campaign to hold peaceful protests on the 31st of every month that has a 31st, in support of Article 31 of the Russian constitution, which guarantees freedom of assembly. Everyone remembers the protest on December 31, 2009, when Lyudmila Alexeyeva went dressed as the Snow Maiden (Snegurochka in the fairy tales) where dozens of other people were also arrested. But when officials realized they had the Lyudmila Alexeyeva in custody, they returned to the bus where she was being held, personally apologized for the inconvenience and offered her immediate release from custody. She refused until all were released. The video and photographs of the authorities arresting the Snow Maiden and then apologizing went viral on the Internet and made broadcast news all over the world. The “31st” protests have ended in arrests multiple times, but that has yet to deter the protesters, who provided a key spark for the mass protests in December 2011. The darker side of the authorities’ attitude was evident in March 2010, when she was assaulted at the Park Kultury metro station where she was paying her respects to the victims of the subway bombings a few days earlier. She had been vilified by the state media so often that the attacker called himself a “Russian patriot” and asserted (correctly, so far) that he would not be charged for his actions. In 2012, the chauvinistic assault became institutional and government-wide, with a new law proposed by the Putin regime and approved by the Duma, requiring any organization that received support from abroad to register as a “foreign agent” and submit to multiple audits by the authorities. The intent was clearly to stigmatize NGOs like the Moscow Helsinki Group that have international standing and raise money from around the world. Earlier this month, Lyudmila Alexeyeva announced that the Group would not register as a foreign agent and would no longer accept foreign support once the law goes into effect in November 2012. Other Russian human righters say they are used to being tagged as foreign agents. In fact, humorous signs appeared at the mass protests in late 2011 asking the U.S. Secretary of State, Hillary Rodham Clinton, “Hillary! Where’s my check? I never got my money!” So the debate over strategy, over how best to deal with and to push back against the new repression, will likely dominate the conversation at Lyudmila Mikhailovna’s 85th birthday party today (July 20). Yet again, when she is one of the few original Soviet dissidents still alive, she is at the center of the storm, committed to freedom in Russia today, and leading the discussion about how to achieve human rights for all. DocumentsDocument 1: Lyudmila Alexeyeva, “Biography,” November 1977. This modest biographical note presents Alexeyeva’s own summary of her life as of the year she went into exile. She prepared this note as part of her presentation to the International Sakharov Hearing in Rome, Italy, on 26 November 1977, which was the second in a series named after the distinguished Soviet physicist and activist (the first was in Copenhagen in 1975) that brought together scholars, analysts and dissidents in exile to discuss human rights in the Soviet bloc. [Source: Memorial Society, Moscow, Archive of History of Dissent, Fond 101, opis 1, Box 2-3-6] Document 2: Lyudmila Alexeyeva to Senator Jacob K. Javits, 4 July, 1975. Even before she co-founded the Moscow Helsinki Group, Lyudmila Alexeyeva actively worked to defend dissidents and political prisoners in the USSR. In this 1975 letter preserved in the Archive of the History of Dissent, the irreplaceable collections of the Memorial Society in Moscow, she is writing from Moscow to a prominent U.S. Senator, Jacob Javits, a Republican from New York and himself Jewish, who was outspoken in supporting not only the right of Jews to emigrate from the USSR to Israel, but also the Soviet dissident cause in general. The case she presents to Javits is that of Anatoly Marchenko, who asked for political emigration (not to Israel) and as punishment was sent to Siberia for four years’ exile – on top of the 11 years he had already spent as a political prisoner on trumped-up charges. Tragically, Marchenko would die in prison in the fall of 1986, just as Gorbachev began releasing the political prisoners. [Source: Memorial Society, Moscow, Archive of History of Dissent, Fond 101, opis 1, Box 2-3-6] Document 3: Yuri Andropov, Chairman of the KGB, Memorandum to the Politburo, 29 December, 1975. Yuri Andropov gives the Politburo an alarming report on dissent in the USSR in connection with criticism of Soviet human rights abuses by the French and Italian Communist parties. The main thrust of Andropov’ report is how to keep the internal opposition in check in the aftermath of the signing of the Helsinki agreement and the following increase of international pressure on the USSR. He gives the number of political prisoners as 860, people who received the “prophylactic treatment” in 1971-74 as 63,108 and states that there are many more “hostile elements” in the country, and that “these people number in the hundreds of thousands.” Andropov concluded that the authorities would have to continue to persecute and jail the dissidents notwithstanding the foreign attention. This document sets the stage and gives a good preview of what would happen after the Moscow Helsinki Group was founded in May 1976. [Source: U.S. Library of Congress, Manuscript Division, Dmitrii A. Volkogonov Papers, Reel 18, Container 28] Document 4: Moscow Helsinki Monitoring Group, “Evaluation of the Influence of the Conference on Security and Co-operation in Europe on the Quality of Human Rights in the U.S.S.R.,” 1 August 1975-1 August 1976. (Summary of the document) This document was written during a time of relative calm, when surprisingly, for the first six months of the existence of the MHG, the authorities did not undertake any repressions against members of the group, and allowed it to function. The document sounds more positive and optimistic than the group’s subsequent assessments of the effect of the Helsinki Accords. The report points out that the Soviet government was sensitive to pressure from foreign governments and groups and that several other objective factors such as the end of the war in Vietnam and increasing Soviet grain purchases made the USSR more open to external influences. Under such pressure, the Soviet government released the mathematician Leonid Plyusch, allowed some refuseniks to emigrate and generally relaxed the restrictions somewhat. The report also lists continuing violations of human rights but concludes that the Helskinki Accords did and probably would play a positive role. [See the Russian page for the original] [Source: Memorial Society, Moscow, Archive of History of Dissent, Fond 101, opis 1, Box 2-3-6] Document 5: KGB Memorandum to the CC CPSU, “About the Hostile Actions of the So-called Group for Assistance of Implementation of the Helsinki Agreements in the USSR,” 15 November 1976. The KGB informed the Politburo about the activities of the MHG for the first time six months after its founding. The report gives a brief history of the human rights movement in the USSR as seen from the KGB. Andropov names each founding member of the group and charges the group with efforts to put the Soviet sincerity in implementing the Helsinki Accords in doubt. The document also alleges MHG efforts to receive official recognition from the United States and reports on its connections with the American embassy. [Source: U.S. Library of Congress, Manuscript Division, Dmitrii A. Volkogonov Papers, Reel 18, Container 28] Document 6: Helsinki Monitoring Group, “Special Notice,” 2 December, 1976. This notice, one of a series by the MHG publicizing official misconduct, testifies to the increasing harassment of members of the group by the KGB. This time it is the son of Malva Landa who has been warned that he might lose his job. The document is signed by Alexeyeva, Orlov and other leading MHG members. [Source: Memorial Society, Moscow, Archive of History of Dissent, Fond 101, opis 1, Box 2-3-6] Document 7: KGB Memorandum to the CC CPSU, “On the Provocative Demonstration by Antisocial Elements on Pushkin Square in Moscow and at the Pushkin Monument in Leningrad,” 6 December, 1976. This KGB report informs the Politburo about silent rallies in Moscow and Leningrad to celebrate Constitution Day by dissidents including members of the MHG. Nobody was arrested. [Source: U.S. Library of Congress, Manuscript Division, Dmitrii A. Volkogonov Papers, Reel 16, Container 24] Document 8: Moscow Helsinki Monitoring Group, “On the Exclusion of Seven Students From the Vienuolis Middle School (Vilnius),” 8 December, 1976. This is a report of the first fact-finding mission undertaken by Lyudmila Alexeyeva with Lithuanian human rights activist and member of the Helsinki Group Thomas Ventslov to investigate charges of sexual harassment against a member of the Lithuanian Helsinki Group Viktoras Petkus. Seven boys were expelled from the school and pressured by the KGB to say that they had spent time at Petkus’ apartment, where he engaged in illegal activities with them. The boys’ families were told that they were expelled on the basis of a school board decision that the parents were not allowed to see. The report concludes that the KGB was behind the charges and that the only reason for the expulsions was the refusal of the boys to give false testimony against their teacher. Alexeyeva met with the Lithuanian Minister of Education to discuss the situation, and he initially agreed to remedy it but then changed his mind upon finding out who his visitor was. [Source: Memorial Society, Moscow, Archive of History of Dissent, Fond 101, opis 1, Box 2-3-6] Document 9: Memo from Andropov to CC CPSU, “About Measures to End the Hostile Activity of Members of the So-called “Group for Assistance in the Implementation of the Helsinki Agreements in the USSR,” 5 January, 1977. After the two informational reports above, the KGB started to get serious about terminating the activities of the MHG. This report charges that the group was capable of inflicting serious damage to Soviet interests, that in recent months group members have stepped up their subversive activities, especially through the dissemination of samizdat documents (and particularly the MHG reports), undermining Soviet claims to be implementing the Helsinki Final Act. The Procuracy would later develop measures to put an end to these activities. [Source: U.S. Library of Congress, Manuscript Division, Dmitrii A. Volkogonov Papers, Reel 18, Container 28] Document 10: Resolution of Secretariat of CC of CPSU, “On Measures for the Curtailment of the Criminal Activities of Orlov, Ginsburg, Rudenko and Ventslova,” 20 January, 1977. Following the recommendations of the KGB report above, and another report submitted by Andropov on January 20, the CC CPSU Secretariat decides to “intercept and curtail the activities” of Orlov, Ginzburg, Rudenko and Ventslov of the MHG, Ukrainian and Lithuanian Helsinki groups. All four would be arrested soon after the resolution. [Source: The Bukovsky Archive, Soviet Archives at INFO-RUSS http://psi.ece.jhu.edu/~kaplan/IRUSS/BUK/GBARC/buk.html, Folder 3.2] Document 11: Extract from CC CPSU Politburo Meeting, “About the Instructions to the Soviet Ambassador in Washington for His Conversation with Vance on the Question of “Human Rights,” 18 February, 1977. After Orlov and Ginzburg are arrested and Lyudmila Alexeyeva goes into exile, and anticipating the visit of U.S. Secretary of State Cyrus Vance to Moscow in March, the Politburo discusses a rebuff to the Carter administration on human rights issues. Ambassador Anatoly Dobrynin is instructed to meet with Vance and inform him of Soviet “bewilderment” regarding Carter administration attempts to raise the issue of Ginsburg’s arrest. Dobrynin should explain to administration officials that human rights is not an issue of inter-state relations but an internal matter in which the United States should not interfere. [Source: TsKhSD (Central Archive of Contemporary Documents) Fond 89, Opis list 25, Document 44] Document 12: “Dignity or Death: How they Plant Dirty Pictures and Dollars on Men Who Fight for Freedom,” The Daily Mail, London, 21 March, 1977, by Lyudmila Alexeyeva and Nicholas Bethell. Documents 12-16 comprise a series of articles in the Western media printed soon after Lyudmila Alexeyeva’s emigration from the USSR. In interviews she described the deteriorating human rights situation in the Soviet Union, including the increased repression and arrests of Helsinki groups members in Russia, Ukraine, Lithuania and Georgia, and calls on the West to put pressure on the Soviet government to comply with the Helsinki Accords. Document 13: “Dignity or Death: My Phone was Dead and All Night the KGB Waited Silently at My Door,” The Daily Mail, London, 22 March, 1977, by Lyudmila Alexeyeva and Nicholas Bethell. Document 14: “Why Brezhnev Must Never be Believed,” The Daily Mail, London, 23 March, 1977, by Lyudmila Alexeyeva and Nicholas Bethell. Document 15: “Soviet Human Rights from Mrs. Lyudmila Alexeyeva and others,” The Times, London, 26 April, 1977, by Lyudmila Alexeyeva, Andrey Amalrik, Vadimir Bukovsky. Document 16: “Soviet Dissidents on the Run,” The Washington Post, 2 June, 1977, by Joseph Kraft. Document 17: “Basket III: Implementation of the Helsinki Accords,” Hearings before the Commission on Security and Cooperation in Europe; Ninety-Fifth Congress, First Session; on the Implementation of the Helsinki Accords; Volume IV: Soviet Helsinki Watch Reports on Repression June 3, 1977; U.S. Policy and the Belgrade Conference, 6 June, 1977. Document 18: National Security Council, Global Issues [staff], to Zbigniew Brzezinski, U.S. National Security Advisor, “Evening Report,” June 7, 1977. This report to their boss by the staff of the Global Issues directorate of the National Security Council on their daily activities includes a remarkable initial paragraph describing internal U.S. government discussions of the Moscow Helsinki Group (called here “the Orlov Committee”). Staffer Jessica Tuchman says a State Department-hosted group of experts all agreed that “the hidden bombshell in the whole human rights debate with the USSR” was the fact that the nationalist movements in the Soviet Union all saw human rights activism as just the “first step” to autonomy – thus the real threat to the Soviet government. [Source: Carter Presidential Library, FOIA case NLC 10-3-2-7-8, 2008] Document 19: Central Intelligence Agency, “The Evolution of Soviet Reaction to Dissent,” 15 July, 1977. This document traces the Soviet government’s response to dissident activity especially in light of their agreement to the human rights provisions outlined in Basket III of the Helsinki Accords. The CIA notes that the Soviet Union signed the accords assuming it would not result in an increase in internal opposition, but that instead the Basket III provisions have provided a rallying point for dissent. It also suggests that internal protests sparked by food shortages and open criticism of the Eurocommunists, including the French and Spanish communist parties, are further causes for the current Soviet crackdown on the opposition. It also mentions political unrest in Eastern Europe and the Unites States new human rights campaign, which has prompted dissidents to make their appeals directly to the U.S. government as reasons for Soviet anxiety. Next, it outlines the Soviet government’s much harsher measures against dissidents in the wake of the Helsinki Accords. These include arrests of members of the Helsinki group, cutting off Western access, and accusing dissidents of espionage. Further, it concludes that the Soviet government’s increased apparent anxiety over dissent is the result of a variety of factors, including the approach of the Belgrade conference and their general fears of increased Western contact leading to discontent and a variety of social vices. [Source: The Carter Presidential Library] Document 20: American Embassy Belgrade to Cyrus Vance, Secretary of State, Text of Speech Given by Ambassador Arthur Goldberg at the Belgrade Conference on Security and Co-operation in Europe Meeting, November 1977 (excerpt). This text, the second half of the U.S. Embassy Belgrade cable reporting the speech made by U.S. ambassador Arthur Goldberg to the Belgrade review conference, specifically raises the cases of Orlov, Scharansky and Ginsberg – three of the founding members, with Alexeyeva, of the Moscow Helsinki Group – in the face of major objections from the Soviet delegation, and no small amount of disquiet from other diplomats present. While considered “timid” by the outside human righters like Alexeyeva, this initiative by the U.S. delegation created a breakthrough of sorts that would heighten the human rights dialogue at upcoming Helsinki review conferences and in the media. [Source: The Carter Presidential Library] Document 21: Secretary of State, to American Embassy Moscow, “Statement on Orlov,” 18 May, 1978. This public statement from the State Deparment’s noon press briefing, sent by cable to the U.S. Embassy Moscow and Consulate Leningrad, uses the strongest language to date on the Orlov case, no doubt informed by Alexeyeva and other Orlov colleagues in exile. Here, the U.S. “strongly deplores” Orlov’s conviction and calls it a “gross distortion of internationally accepted standards,” since the activities for which he was being punished were simply the monitoring of Soviet performance under the Helsinki Final Act. [Source: The Carter Presidential Library] Document 22: Joseph Aragon, to Hamilton Jordan, “Carter on Human Rights,” 7 July, 1978. This memorandum from White House staff member Joe Aragon to the president’s chief of staff, Hamilton Jordan, discusses the Soviet Union’s treatment of dissidents, as monitored by another White House staffer, Joyce Starr. Aragon notes that the overall Soviet campaign against dissidents continues despite Carter’s forceful public stance on human rights. He notes that if anything dissidents have become further shut out of Soviet society since Carter came to office. He specifically mentions the Helsinki group, and Slepak, Orlov, Scharansky, Nadel and Ginzburg as dissidents in need of United States help. He goes in depth into the Slepak case and the state of his family, characterizing Slepak as the Soviet equivalent of a Martin Luther King Jr. However, he writes that the administration so far has made public statements in support of the dissidents, but failed to act on the diplomatic level. Aragon concludes that Carter cares deeply about human rights, but that his reputation is at risk due to the failure of low-level officials to follow through the initiatives outlined in the Helsinki Final Act. Aragon calls for a meeting in which he and other will discuss a course of action for the president. [Source: The Carter Presidential Library] Document 23: Central Intelligence Agency, “Human Rights Review,” 18-31 August, 1978. This document contains a general overview of human rights throughout the world, but begins with a discussion of the condition of dissidents in the Soviet Union and Eastern Europe. It notes that the most recent dissident activity has been in their statements of support for the Czech Charter 77 dissident movement. It also discusses the Soviet Union’s fear of East European and Soviet dissidents forming a united front of opposition. It also mentions an incident in which dissident Aleksandr Lyapin attempted to commit suicide by self-immolation in protest of Helsinki group leader Yuri Orlov’s court sentence, and that he has since been confined to a mental institution. [Source: The Carter Presidential Library] Document 24: Senator Henry M. Jackson, Remarks at the Coalition for a Democratic Majority Human Rights Dinner, September 30, 1978. Document 25: “Basket III: Implementation of the Helsinki Accords,” Hearings before the Commission on Security and Cooperation in Europe; Ninety-Fifth Congress, First Session; on the Implementation of the Helsinki Accords; Volume X: Aleksandr Ginzburg on the Human Rights Situation in the U.S.S.R., 11 May, 1979. Document 26: “A Helsinki Clue to Moscow’s Salt II Intentions,” The New York Times, June 18, 1979, by Lyudmila Alexeyeva, Aleksandr Ginzberg, Petr Grigorenko, Yuri Mnyukh, and Valentin Turchin. Document 27: Jimmy Carter and Cyrus Vance, “Major Executive Statements on Behalf of Anatoliy Scharanskiy,” 16 July, 1979. Document 28: Peter Tarnoff, Department of State, to Zbigniew Brzezinski, “U.S. Government Initiatives on Behalf of Human Rights in the U.S.S.R.” 17 April, 1980. This memorandum from State Department Executive Secretary Peter Tarnoff to Zbigniew Brzezinski contains a list of actions and statements by the U.S. government on human rights and protection of dissidents in the USSR. The list covers the years 1977 through 1980. The actions include reports on the Soviet Union’s implementation of the human rights provisions of the Helsinki Final Act, as well as discussions of these matters at international conferences. Another area of action has to do with investigating denials of exit visas to Jews and prisoners of conscience attempting to leave the Soviet Union. It also comprises various efforts to help imprisoned dissidents by sending observers to attend their trials and providing special aid to some families, including the Ginzburg/Shibayev and Sakharov/Yankelevich families. The document also includes a list of Carter’s addresses in which he voices concerns over human rights or the treatment of Soviet dissidents. Document 29: Helsinki Monitoring Group [members of the Moscow Helsinki group in exile], “On the Madrid Conference on Security and Co-operation in Europe,” c. summer 1980. These recommendations were prepared by members of Helsinki groups in exile before the Madrid review conference of November 1980. The dissidents call the efforts of Western delegations at the earlier Belgrade conference “timid” and chide the lack of pressure on Moscow to observe the human rights provisions of the Helsinki Accords. The report describes the worsening human rights situation in the USSR after the Belgrade conference of 1977-78, arrests of the Helsinki Group members, persecution of religious believers, and restrictions on emigration. Recommendations include that the Madrid conference delegates demand that political prisoners, including Helsinki group members, be released, and that an international commission be created consisting of representatives of member-states to keep the pressure on the Soviets between the review conferences. Similar concerns, the report indicates, were raised by the MHG in its recommendations for the Belgrade conference in 1977. Document 30: Lyudmila Alexeyeva, letter to friends in Moscow, undated, circa summer 1984. This extraordinary personal letter provides a unique vista of Alexeyeva’s life in exile and her thinking about dissent. Here she describes how she found her calling as a historian (a “personal harbor” which is essential for enduring exile), came to write the book on Soviet dissent, and struggled to reform the radios (Liberty, Free Europe, Voice of America) against the nationalist-authoritarian messages provided from “Vermont and Paris” – meaning Aleksandr Solzhenitsyn and Vladimir Bukovsky, respectively – or, the Bolsheviks versus her own Mensheviks within the dissident movement, in her striking analogy. Also here are the personal details, the open window in the woods for the cats, the ruminations on the very process of writing letters (like cleaning house, do it regularly and it comes easily, otherwise it’s never done or only with great difficulty). Here she pleads for activation as opposed to liquidation of the Helsinki Groups, because “we have nothing else to replace them.” [Source: Memorial Society, Moscow, Archive of History of Dissent, Fond 101, opis 1, Box 2-3-6] Document 31: Liudmila Alexeyeva, edited by Yuri Orlov, Documents and People, “What Gorbachev took from samizdat.” In this draft script prepared for a Radio Liberty show in 1987 together with Yuri Orlov, Alexeyeva traces the roots of Gorbachev’s new thinking to samizdat materials as far back as the 1960s. She finds an amazing continuity in terms of ideals and goals, especially in foreign policy-thinking about the primacy of human rights and an interdependent world. [Source: Memorial Society, Moscow, Archive of History of Dissent, Fond 101, opis 1, Box 2-3-2] Document 32: Lyudmila Alexeyeva’s handwritten draft paper on informal associations in the USSR. This unique handwritten draft written for Alexeyeva on the emergence of informal organizations – the first NGOs – in the Soviet Union. The draft is undated but was most likely written in 1990 or early 1991. The main question is whether Gorbachev will stay in power and therefore whether the changes he brought about will stick. She sees the importance of informal organizations in reviving civil society in the Soviet Union and creating conditions for democratization. [Source: Memorial Society, Moscow, Archive of History of Dissent, Fond 101, opis 1, Box 2-3-2] Document 33: Lyudmila Alexeyeva, Trip to Nizhny Novgorod, 9 November, 1992. Lyudmila Alexeyeva visited Nizhny Novgorod on August 29, 1992, and met with members of Dialogue Club and the independent trade union at the ship-building plant Krasnoe Sormovo. Semen Bulatkin, her main contact, talked to her about the political club they founded at the plant, whose outside member was governor Boris Nemtsov, and the difficulties of organizing a free trade union there. The independent trade union was founded in February 1992, with an initial membership of about 250-300 people. Two weeks later, threatened by the plant’s administration with the loss of jobs or social benefits, membership declined to 157. Alexeyeva also met with Governor Nemtsov – a radical reformer and close supporter of President Boris Yeltsin – who told her he had read her book on Soviet dissent and was an active listener of Radio Liberty. [Source: Memorial Society, Moscow, Archive of History of Dissent, Fond 101, opis 1, Box 2-3-2] Document 34: Lyudmila Alexeyeva, Trip to Moscow Report, 10-20 December, 1992. Alexeyeva visited Russia in December 1992, just a year after the Soviet collapse, at the behest of the AFL-CIO Free Trade Union Institute, which had been a key international backer of Solidarity in Poland and sought to support similar independent union development in post-Soviet Russia. Alexeyeva’s trip report does not provide much cause for optimism. In it, she describes democratic reformers’ complaints about President Yeltsin and the lack of alternative progressive leadership; the resistance to change by older Party-dominated union structures; the lack of access to television by new, more democratic unions to make their case; and the effective transformation of Communist Party elites into quasi-capitalist owners and managers of the means of production – not because they are true reformers or effective producers, but because they know how to boss. Dozens of intriguing details and provocative conversation summaries fill the report, including a newspaper story alleging that Yeltsin was now privatizing his own appointment schedule with an outside company, selling access at $30,000 per meeting. [Source: Memorial Society, Moscow, Archive of History of Dissent, Fond 101, opis 1, Box 2-3-2] |
TMZ-Paul Ryan’s SHAMELESS Photo Op
Unveiled – Cuban Missile Crisis Communications
Cuban Missile Crisis Communications
A response to the National Security Archive release on October 12, 2012: “Cuban Missile Crisis Reveleations: Kennedy’s Secret Approach to Castro — Declassified RFK Documents Yield New Information on Back-Channel to Fidel Castro to Avoid Nuclear War.”
http://www.gwu.edu/~nsarchiv/NSAEBB/NSAEBB395/
Related on Russian SIGINT:
http://cryptome.org/jya/rusigint.htm
http://cryptome.org/conus-sigint.htm
To: coldwarcomms[at]yahoogroups.com
From: “OZOB99” <ozob99[at]yahoo.com>
Date: Sun, 14 Oct 2012 13:54:33 -0000
Subject: [coldwarcomms] Cuban Missile Crisis Comms
As the 50th anniversery of this event approaches, here is an update to a post I made 10 years ago,with anecdotes of activities at the AT&T Norfolk Central Office, arguably the epicenter of military telco circuit activity for this crisis.
“Norfolk probably had more involvment in telecommunications than Washington because it was the STC (serving test center) for CINCLANT/SACLANT, TAC HQ Langley AFB, and CONARC Ft. Monroe; with augmented circuits to their subordinate commands and bases, as well to the NCA and other NS/EP entities.
An unusual increase in expedited new circuits,mainly to Southern bases, was evident in the week or so prior to 10-22-62; but we had no way of knowing the nature or gravity of the situation, just that South Florida was a “hotspot”, & Cuba was likely involved due to previous sabre rattling in the news.
By the time Kennedy made his announcement we had established a hand-picked 24/7 “task force” of tech’s (including many additional brought in) expediting circuit provisioning (C&P Telco had similar groups installing on local channels and the customer premises). Circuits that normally had a 3-5 week interval were being established in 3 days or less!; all circuit info & engineering (with the Government Communications sales & engineering folks on an unprecedented 24/7 schedule also) was phoned/TTY in day & night, & posted on a large status chalk board, with the various workgroups copying their portion & running with it; an unbelievable beehive of activity that actually worked well considering the confusion, because we all knew now this was possibly a doomsday scenario without being told so specifically.
The small AT&T office at Key West, along with Homestead, were overwhelmed with circuits from TAC & CINCLANT; these normally “sleepy” little offices had never seen anything like this! The quantities of circuits weren’t as great as Norfolk but the intensity of activities certainly was. Naturally there were additional employees brought in to handle the workload.
In the space of a few weeks hundreds of new circuits were established radiating out of Norfolk, most to Southeastern military bases. A large number of the voice circuits were “C2” conditioned (amplitude & envelope delay) for KY9 encryption, utilizing strings of delay equalizers at various points on the layout. Despite lengthy & detailed calculations for these equalizers many circuits would not support encrypted voice (going green) due to having to use any channel available and many sections in tandem. These were re-engineered by trial & error/SWAG on the spot as they were being installed, some would only work with no equalization! (an anomaly explained by a chance combo of facilities that happened to have the right characteristics of delay. There were a few circuits on C carrier(open wire) that never could be conditioned for encryption.
Many existing voice circuits were upgraded to C2 conditioning for encryption; some of the voice grade data circuits required C2 conditioning but were more forgiving.
Many of the telegraph grade circuits were encrypted for KW-8 et al; these didn’t require conditioning but were difficult to trouble shoot.
A portable “Quick Start” package of Lenkurt 76 radio and 45B carrier was shipped in for additional local channels to the Norfolk Naval Base in case cable pairs ran out; also a wide band Quick Start package of LMX modems & 303 data sets for additional wide band channels to the Naval Base, presumably for KY-3 encryption.
AT&T also loaned DOD (Army I believe) some transportable microwave to fill in some gaps in their networks. (I’ve never found out whether it was TD-2,TE or the Lenkurt Quick start; nor where it was needed.)
In the course of implementing & troubleshooting these circuits we overheard some scary dialog, along with some intense salty curses & oaths.
Being “insiders” to a degree, we were more scared than the general public, and more relieved than most when the Russians blinked.
If asked ahead of time if that quantity of circuits could be established in those few days I think everyone would have said “no way”!; it seems even a stodgy heirarchy can do anything when you have to, replacing the bell shaped heads with virtual helmets.”
Public Intelligence – Obama and Romney 2012 Debates Memorandum of Understanding
The following is the memorandum of understanding between the Obama and Romney campaigns detailing rules and standards for the four arranged Presidential and Vice Presidential debates.
.
Secrecy News – The Purpose of National Security Policy declassified
THE PURPOSE OF NATIONAL SECURITY POLICY, DECLASSIFIED
The most fundamental purpose of national security policy is not to keep
the nation safe from physical attack but to defend the constitutional
order. At least, that is what President Reagan wrote in a Top Secret 1986
directive.
"The primary objective of U.S. foreign and security policy is to protect
the integrity of our democratic institutions and promote a peaceful global
environment in which they can thrive," President Reagan wrote in National
Security Decision Directive 238 on "Basic National Security Strategy,"
which was partially declassified in 2005.
http://www.fas.org/irp/offdocs/nsdd/nsdd-238.pdf
In a list of national security objectives, the directive does note the
imperative "to protect the United States... from military, paramilitary, or
terrorist attack."
But that is not the primary objective, according to the Reagan directive.
Defense of the Constitution evidently takes precedence.
The first purpose of national security policy is "to preserve the
political identity, framework and institutions of the United States as
embodied in the Declaration of Independence and the Constitution,"
President Reagan wrote.
This is a remarkable statement, for several reasons. First, it recognizes
that the political identity and institutions of the United States are not
simply a given, but that they are vulnerable to many types of threats and
must be actively defended and sustained. This task is not normally
assigned the urgency or the priority given to "national security."
Second, the directive distinguishes between constitutional governance and
physical security. Not every measure intended to promote security is
constitutional. And not every act in defense of democratic self-governance
is likely to promote public safety. (The American Revolution was not
calculated to increase "homeland security." Quite the opposite.) Sometimes
a choice between the two is required. President Reagan indicated what he
thought the choice should be.
And third, the directive is remarkable because its rhetoric was so
imperfectly realized by the Reagan Administration (and egregiously defied
in the Iran-Contra Affair) and has been largely abandoned by its
successors.
"Defending our Nation against its enemies is the first and fundamental
commitment of the Federal Government," wrote President George W. Bush in
his 2002 National Security Strategy, skipping over President Reagan's
"primary" objective.
Likewise, "As President, I have often said that I have no greater
responsibility than protecting the American people," President Obama wrote
in his National Strategy for Counterterrorism.
The Reagan directive invites reflection on what U.S. national security
policy would look like if it were truly structured above all "to protect
the integrity of our democratic institutions."
In a section of the directive that was only classified Confidential,
President Reagan contrasted the U.S. with the Soviet Union, which was
described as its polar opposite.
"Our way of life, founded upon the dignity and worth of the individual,
depends on a stable and pluralistic world order within which freedom and
democratic institutions can thrive. Yet, the greatest threat to the Soviet
system, in which the State controls the destiny of the individual, is the
concept of freedom itself."
"The survival of the Soviet system depends to a significant extent upon
the persistent and exaggerated representation of foreign threats, through
which it seeks to justify both the subjugation of its own people and the
expansion of Soviet military capabilities well beyond those required for
self-defense," President Reagan wrote.
Numerous Presidential directives from the Reagan Administration have been
declassified in recent years and have released by the Reagan Library,
though others still remain partially or completely classified.
Many of the declassified directives provide a fascinating account that
enlarges and enriches the public record of events of the time.
http://www.fas.org/irp/offdocs/nsdd/index.html
Only last year, for example, a 1985 directive (NSDD-172) on "Presenting
the Strategic Defense Initiative" was finally declassified.
http://www.fas.org/irp/offdocs/nsdd/nsdd-172.pdf
This year, NSDD 159 on "Covert Action Policy Approval and Coordination
Procedures" (1985) was declassified.
http://www.fas.org/irp/offdocs/nsdd/nsdd-159.pdf
NSDD 207 on "The National Program for Combatting Terrorism" (1986) was
declassified in 2008.
http://www.fas.org/irp/offdocs/nsdd/nsdd-207.pdf
Among other things, that directive ordered the Attorney General to "Review
the Freedom of Information Act (FOIA) and determine whether terrorist
movements or organizations are abusing its provisions."
JOB GROWTH DURING THE RECOVERY, AND MORE FROM CRS
New and updated reports from the Congressional Research Service that
Congress has not made available to the public include the following.
Job Growth During the Recovery, updated October 16, 2012:
http://www.fas.org/sgp/crs/misc/R41434.pdf
The President's Emergency Plan for AIDS Relief (PEPFAR): Funding Issues
After a Decade of Implementation, FY2004-FY2013, October 10, 2012:
http://www.fas.org/sgp/crs/misc/R42776.pdf
Statutes of Limitation in Federal Criminal Cases: An Overview, updated
October 1, 2012:
http://www.fas.org/sgp/crs/misc/RL31253.pdf
Venezuela: Issues for Congress, updated October 16, 2012:
http://www.fas.org/sgp/crs/row/R40938.pdf
Georgia's October 2012 Legislative Election: Outcome and Implications,
October 15, 2012:
http://www.fas.org/sgp/crs/row/R42777.pdf
Iran Sanctions, updated October 15, 2012:
http://www.fas.org/sgp/crs/mideast/RS20871.pdf
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
Cold Case Files – Rear Window/The Peeper – Full Documentary Movie
Opfer berichten über die mutmaßlichen Rufmordtatktiken der GoMoPa
The Devil Bat – Full Movie – Bela Lugosi
Dr. Carruthers plots his revenge on his employers who are making a profit off of his invention. He electrically enlarges bats and sends them out to kill his employers’ family by instilling in the bats a hatred for a particular perfume he has discovered, which he gets his victims to apply before going outdoors. Johnny Layton, a reporter, eventually figures out Carruthers is the killer. He puts the perfume on himself and Carruthers in the hopes he will reveal himself, but the bats swoop on in before he get a confession.
This campy, entertaining cheapie from PRC Pictures features Bela Lugosi as a chemist who plots an elaborate revenge scheme on his business partners, whom he feels have cheated him out of his share. To this end he develops a mutant breed of vicious, oversized bats and trains several of this breed to home in on a special chemical which he then blends with shaving lotion. Presenting gifts of the lotion to his partners as a peace offering (and browbeating them into splashing it on themselves while in his presence), he subsequently unleashes his monstrous pets to tear them to pieces. Believe it or not, this was one of PRC’s more successful horror programmers, spawning a the sequel Devil Bat’s Daughter.
SI Swimsuit Ana Paula Video
Revealed – Fordow Nuclear Plant Qom, Iran in Winter
|
![[Image]](https://i0.wp.com/cryptome.org/2012-info/fordow-ir/pict16.jpg) |
Bing.com/maps![[Image]](https://i0.wp.com/cryptome.org/2012-info/fordow-ir/pict7.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/fordow-ir/pict8.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/fordow-ir/pict9.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/fordow-ir/pict10.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/fordow-ir/pict11.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/fordow-ir/pict12.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/2012-info/fordow-ir/pict13.jpg) |
TMZ-NFL Reporter NAILED with Football… while ON AIR!
SECRET-U.S. Army Regulation 190–13 Physical Security Program
This regulation implements DOD 5200.08–R and DODI 3224.03. It prescribes policies, procedures, and guidance to plan and implement the Department of the Army Physical Security Program. It provides guidance concerning requirements for and use of physical security equipment; the appointment of physical security officers and inspectors; the conduct of physical security inspections and surveys; the management of physical security credentials; the management and use of identification cards and badges; restricted areas; access control for installations and stand-alone facilities; and security forces.
…
6–7. National Defense Areas
a. A restricted area may be established on non-Federal lands within the United States and its possessions and territories to protect classified defense information and DOD equipment or material. When this type of area is established, it will be referred to as a National Defense Area (NDA). Examples of a NDA would include nuclear and chemical event sites and aircraft crash sites.
b. Establishing a NDA temporarily places such non-Federal lands under the effective control of DOD and results only from an emergency event.
c. The senior DOD representative at the scene will define the boundary, mark it with a physical barrier, and post warning signs. Every reasonable attempt will be made to obtain the landowner’s consent and cooperation in establishing of the NDA. Military necessity, however, will determine the final decision regarding NDA location, shape, and size.
d. The authority to establish a NDA includes the authority to deny access to it. It also includes the authority to remove persons who threaten the orderly administration of the NDA. Any use of force employed to enforce this authority will be per AR 190–14.
…
8–11. Installation access control point security forces
a. The IACPs will be manned by armed security force personnel (Soldiers, DA civilian police, DA security guards, or contract guards) as permitted by applicable Federal, state, and territorial statutes, and SOFA.
b. Commanders will use HQDA (DAPM–MPP–PS) IACP staffing guidance for manpower considerations to determine the appropriate manpower for primary and secondary IACPs.
c. Security forces will be provided with—
(1) Adequate means of communications.
(2) Appropriate weapons and ammunition and trained in their care and use per AR 190–14.
(3) Personal protective equipment.
d. Procedures will be established for each IACP, and will be reviewed at least annually and revised, as necessary.
e. Training and weapons qualification of security force personnel will be in accordance with applicable directives, AR 190–56 for all assigned DA police and DA guards, and the statement of work for contract security guards.
f. Training will also include—
(1) Recognition of sabotage-related devices and equipment that might be used against the installation.
(2) Use of devices to identify sabotage-related devices and equipment such as hand-held vapor tracers and vehicle and cargo inspection systems.
(3) Authorized forms of identification for access to the installation.
DOWNLOAD THE ORIGINAL DOCUMENT HERE:
Cold Case Files – Caught on Tape/A Son Remembers – Full Movie
THE STASI Press Release published by Wikileaks
SI Swimsuit Video – Brooklyn
TMZ – Lindsay Lohan: I LIED about My Mom Doing Coke!
PI unveils Investigations Federal Support for Fusion Centers Report

Sharing terrorism-related information between state, local and federal officials is crucial to protecting the United States from another terrorist attack. Achieving this objective was the motivation for Congress and the White House to invest hundreds of millions of taxpayer dollars over the last nine years in support of dozens of state and local fusion centers across the United States.
The Subcommittee investigation found that DHS-assigned detailees to the fusion centers forwarded “intelligence” of uneven quality – oftentimes shoddy, rarely timely, sometimes endangering citizens’ civil liberties and Privacy Act protections, occasionally taken from already-published public sources, and more often than not unrelated to terrorism. Congress directed the Department of Homeland Security (DHS) to lead this initiative. A bipartisan investigation by the Permanent Subcommittee on Investigations has found, however, that DHS’ work with those state and local fusion centers has not produced useful intelligence to support federal counterterrorism efforts.
The Subcommittee investigation also found that DHS officials’ public claims about fusion centers were not always accurate. For instance, DHS officials asserted that some fusion centers existed when they did not. At times, DHS officials overstated fusion centers’ “success stories.” At other times, DHS officials failed to disclose or acknowledge non-public evaluations highlighting a host of problems at fusion centers and in DHS’ own operations.
Since 2003, over 70 state and local fusion centers, supported in part with federal funds, have been created or expanded in part to strengthen U.S. intelligence capabilities, particularly to detect, disrupt, and respond to domestic terrorist activities. DHS’ support for and involvement with these state and local fusion centers has, from the beginning, centered on their professed ability to strengthen federal counterterrorism efforts.
…
Despite reviewing 13 months’ worth of reporting originating from fusion centers from April 1, 2009 to April 30, 2010, the Subcommittee investigation could identify no reporting which uncovered a terrorist threat, nor could it identify a contribution such fusion center reporting made to disrupt an active terrorist plot. Instead, the investigation found:
• Nearly a third of all reports – 188 out of 610 – were never published for use within DHS and by other members of the intelligence community, often because they lacked any useful information, or potentially violated department guidelines meant to protect Americans’ civil liberties or Privacy Act protections.
• In 2009, DHS instituted a lengthy privacy and civil liberties review process which kept most of the troubling reports from being released outside of DHS; however, it also slowed reporting down by months, and DHS continued to store troubling intelligence reports from fusion centers on U.S. persons, possibly in violation of the Privacy Act.
• During the period reviewed, DHS intelligence reporting suffered from a significant backlog. At some points, hundreds of draft intelligence reports sat for months before DHS officials made a decision about whether to release them to the intelligence community. DHS published many reports so late – typically months late, but sometimes nearly a year after they were filed – that many were considered “obsolete” by the time they were released.
• Most reporting was not about terrorists or possible terrorist plots, but about criminal activity, largely arrest reports pertaining to drug, cash or human smuggling.
• Some terrorism-related “intelligence” reporting was based on older news releases or media accounts.
• Some terrorism-related reporting also appeared to be a slower-moving duplicate of information shared with the National Counter Terrorism Center through a much quicker process run by the Federal Bureau of Investigation’s Terrorist Screening Center.The Subcommittee investigation also examined DHS’ management of the fusion center counterterrorism intelligence reporting process. The investigation discovered:
• DHS required only a week of training for intelligence officials before sending them to state and local fusion centers to report sensitive domestic intelligence, largely concerning U.S. persons.
• Officials who routinely authored useless or potentially illegal fusion center intelligence reports faced no sanction or reprimand.The Subcommittee investigation also reviewed how the Federal Emergency Management Agency (FEMA), a component of DHS, distributed hundreds of millions of taxpayer dollars to support state and local fusion centers. DHS revealed that it was unable to provide an accurate tally of how much it had granted to states and cities to support fusion centers efforts, instead producing broad estimates of the total amount of federal dollars spent on fusion center activities from 2003 to 2011, estimates which ranged from $289 million to $1.4 billion.
…
The Subcommittee conducted a more detailed case study review of expenditures of DHS grant funds at five fusion centers, all of which lacked basic, “must-have” intelligence capabilities, according to assessments conducted by and for DHS. The Subcommittee investigation found that the state and local agencies used some of the federal grant money to purchase:
• dozens of flat-screen TVs;
• Sport Utility Vehicles they then gave away to other local agencies; and
• hidden “shirt button” cameras, cell phone tracking devices, and other surveillance equipment unrelated to the analytical mission of a fusion center.All of those expenditures were allowed under FEMA’s rules and guidance, DHS officials told the Subcommittee. Yet none of them appeared to have addressed the deficiencies in the centers’ basic information analysis and sharing capabilities, so they could better contribute to federal counterterrorism efforts.
…
IV. DHS SUPPORT FOR AND INVOLVEMENT IN STATE AND LOCAL FUSION CENTERS DOES NOT GENERATE TIMELY, USEFUL INTELLIGENCE FOR FEDERAL COUNTERTERRORISM EFFORTS
• Reporting from fusion centers was often flawed, and unrelated to terrorism.
• Some reports had “nothing of value.”
• If published, some draft reporting could have violated the Privacy Act.
• Most fusion center reporting related to drug smuggling, alien smuggling or other criminal activity.
• Terrorism-related reporting was often outdated, duplicative and uninformative.
• DHS intelligence reporting officials who repeatedly violated guidelines faced no sanction.
• DHS did not sufficiently train its fusion center detailees to legally and effectively collect and report intelligence.
• Short-staffing and reliance on contract employees hampered reporting efforts.
• Reporting officials aren’t evaluated on the quality of their reporting.
• A hastily-implemented and poorly coordinated review process delayed reporting by months.
• Retaining inappropriate records is contrary to DHS policies and the Privacy Act.• Problems with DHS reporting are acknowledged, but unresolved
DOWNLOAD THE ORIGINAL DOCUMENT HERE:
Secrecy News – Kiriakou not allowed to argue lack of intent to harm U.S.
A court ruled this month that former CIA officer John Kiriakou, who is
charged with unauthorized disclosures of classified information to the
media, will not be permitted to argue at trial that he intended no harm to
the United States, or that his entire career testifies to a deep commitment
to national security.
Instead, the central question at trial will be whether Kiriakou "had
reason to believe" that the information he allegedly released would cause
injury to the United States.
The court ruling, which favors the prosecution's conception of the case,
was issued during a sealed hearing on October 1. The hearing transcript
has not been released, but the ruling was disclosed in two footnotes in an
October 3 defense pleading that was unsealed last week.
http://www.fas.org/sgp/jud/kiriakou/100312-reply98.pdf
The defense said it would have demonstrated at trial "that Mr. Kiriakou
had no intent to harm the United States, and that he had no motive to do so
had the Court not ruled such arguments inadmissible" (footnote 7).
Similarly, the defense indicated that "this Court's October 1, 2012 ruling
precludes arguments regarding Mr. Kiriakou's intent to harm the United
States or a defense resting on Mr. Kiriakou's lack of bad faith" (footnote
4).
The defense said it would continue to "note where information would be
relevant to such arguments in order to preserve its ability to appeal the
issue should that become necessary."
Meanwhile, two reporters who were subpoenaed by the Kiriakou defense filed
motions to quash the subpoenas.
Attorneys for Matthew Cole, designated "Journalist A" in the Kiriakou
indictment, said that the information sought by the Kiriakou defense was
protected by a reporter's First Amendment privilege and that there was no
basis to overrule the privilege.
Not only that, but Cole attorneys George Doumar and Mark Zaid added that
Mr. Cole would assert a Fifth Amendment right to refuse to testify to avoid
self-incrimination. They said that the government's past move to prosecute
unauthorized receipt and transmission of classified information in the
AIPAC case (US v. Rosen) raises the possibility that Cole's testimony
"could subject him to a subsequent federal criminal proceeding. Therefore,
he will invoke his Fifth Amendment right to remain silent."
http://www.fas.org/sgp/jud/kiriakou/101112-Aquash.pdf
Washington Post researcher Julie Tate also moved to quash a subpoena for
her testimony. She was identified as the "Researcher 1" sought by the
defense in an article by Josh Gerstein of Politico last week.
Ms. Tate possesses exceptional news gathering skills. But she has nothing
to do with the charges against Mr. Kiriakou, her attorneys said in their
October 11 motion to quash.
"The testimony defendant seeks from Ms. Tate has no conceivable relevance
to this case. Defendant has been charged with unlawfully disclosing
classified information to Journalist A and Journalist B--not to Ms. Tate.
Ms. Tate is not mentioned in the Indictment, and there is no evidence in
the record that Ms. Tate has ever met or communicated with Mr. Kiriakou....
The law places the burden on the defendant to establish that he has a need
for Ms. Tate's testimony that is so compelling that it outweighs the First
Amendment interests at stake. That burden has not been met."
http://www.fas.org/sgp/jud/kiriakou/101112-tate-quash.pdf
Scott Shane of the New York Times, who is "Journalist B" in the Kiriakou
indictment, is also believed to have been subpoenaed. But that subpoena is
said to have been withdrawn for reasons that are unclear. In any case, Mr.
Shane and the New York Times did not file a motion to quash.
The pending motions to quash the subpoenas will be argued before Judge
Leonie M. Brinkema at an October 18 hearing.
SECRECY CONFERENCE AT FORDHAM LAW SCHOOL
A day-long conference on national security secrecy will be held tomorrow,
October 16, at Fordham Law School in New York City.
The conference brings together a promising mix of former government
officials, journalists, litigators, academics and others, including myself.
For more information on the conference, which is open to the public, see
here:
http://www.fas.org/sgp/news/2012/10/fordham.pdf
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
Cold Case Files – Innocence Stolen/Danger at the Door – Full Movie
Stasi-Experte Rufmord an Ex-Berliner Justizminister ist Stasi-Racheakt
http://www.morgenpost.de/berlin/article1845985/Hubertus-Knabe-vermutet-Stasi-Seilschaften.html
Vorwürfe gegen Braun: Knabe vermutet Stasi-Seilschaften |
White Zombie – Full Movie – Starring Bela Lugosi
When a wealthy plantation owner becomes obsessed with a beautiful but unattainable woman, he strikes a devil’s bargain with a sinister voodoo master (Lugosi)!
In this haunting low-budgeter, Bela Lugosi stars as Murder Legendre, a shadowy character who exercises supernatural powers over the natives in his Haitian domain. Coveting Madge Bellamy as his bride, wealthy Robert Frazier enters into an unholy agreement with Lugosi, whereby Madge will die, then be resurrected as a zombie.
SI Swimsuit Video – Irina
Revealed – US Government Publications Citing WikiLeaks
|
|
|
TMZ – Jenny McCarthy — Naked & Making Out with Chicks!
Jenny McCarthy isn’t trying to hide the fact that she got naked and made out with a bunch of models while high on drugs. Sounds like a pleasant time, no?
TOP-SECRET – U.S. State Department Operations Center Overview Presentation by Public Intelligence
Serial Killer – Glen Edward Rogers – Full Movie
A charming, handsome and volatile individual, Glen was the focus of an all-points national manhunt after a cross-country rampage that left at least four women dead in four separate states. The consummate ladies man, Glen liked to pick up blond and redheaded women in bars and ask them for a ride home. Then he would try to spend the night with them. All those charmed by his redneck good looks are now stretched out in the morgue. The killings came usually as a drunken afterthought. Glen is an example of a spree killer who, unlike serial killers, does not have cooling off periods between kills. His killings were the consequence of impromptu bursts of rage.
His first victim is believed to be a former house mate whose corpse was found in January 1993 under a pile of furniture in an abandoned house owned by the Rogers family. His next known kill was a woman he met at a bar in Van Nuys, California. On September, 1995, she was found raped and strangled inside her burning pickup truck. The third victim, another barfly, was found stabbed to death in her bathtub in Jackson, Mississippi on November 3. Yet another woman’s body was found in a bathtub in Tampa, Florida on November 5. His last victim was found stabbed to death in her bedroom on November 11 in Bossier City, Louisiana.
“He’s getting to be like one of your serial killers,” said a Hamilton, Ohio, police detective. Rogers, a construction worker, grew up in Hamilton where he had frequent run-ins with the law. Once he poked a lit blowtorch through the peephole of his front door when police came in response to a domestic violence call. Authorities believe that he might be linked to as many as twelve deaths. In California, Rogers is a suspect in four unsolved killings in Ontario and Port Hueneme. Two days before his arrest he told his sister that he was responsible for more than 70 deaths. Later he recanted the number and said he was merely joking. According to authorities Glen was being cooperative during a six-hour interview after his arrest on November 13.
On May 7, 1997 Glen was convicted of murder in a Tampa court for killing a woman he had met in a bar. The jury took eight hours to find him guilty of the murder of Tina Marie Cribbs and the next day, just three hours to recommend the death penalty. After the Tampa trial, Rogers faces three more trials in separate states. However, none of these states have filled charges yet.
Rogers and the victim met at a bar where Ms. Cribbs was waiting for her mother, Mrs. Mary Dicke. Mrs. Dicke was late, and Ms. Cribbs left a beer at the bar and asked friends to tell her mother she would be back shortly. She drove Rogers to a motel in Tampa and the two went inside and had sex. In a fit of rage the ex-carnival worker stabbed Ms. Cribbs twice, twisting the knife as he pulled it out from eight- and nine-inch wounds in her chest and buttocks before leaving her to a slow, agonizing death in a motel bathtub.
During the seven-day trial the defense maintained that Rogers wasn’t the murderer. Furthermore Hamilton, Ohio Police Sgt. Tom Kilgore testified that Rogers had worked for the department as a paid undercover narcotics informant, making hundreds of cases over the years without ever breaking his cover. In his closing argument, defense attorney Nick Sinardi said the state rushed to judgment. “Glen Rogers is a thief, not a murderer.” A thief, it seems, with a nasty habit of leaving a trail of bodies in his wake.
Stalking-Studie des Weißen Ring
Crime Stories – Fire and Ice – Full Movie
Crime Stories was a television series on TruTV, hosted by Bill Courage. The series featured biographies and famous exploits of criminals and notorious people such as Al Capone, Adolph Eichmann, the Scottsboro Boys, Sam Sheppard, and the Night Stalker.
Unveiled – DHS Privacy Policy for Operational Use of Social Media

The following is an instruction accompanying DHS Policy Directive 110-01 “Privacy Policy for Operational Use of Social Media” that was enacted in June 2012. The policy directive itself is only three pages and provides little information, whereas this instruction for the policy is ten pages and includes rules for compliance with the directive. The policy was enacted following congressional hearings earlier this year that criticized DHS’ monitoring of social media. However, this privacy policy specifically exempts the use of social media for “situational awareness by the National Operations Center” which was the focus of the hearings.
This Instruction applies throughout DHS regarding the access to and collection, use, maintenance, retention, disclosure, deletion, and destruction of Personally Identifiable Information (PII) in relation to operational use of social media, with the exception of operational use of social media for: (a) communications and outreach with the public authorized by the Office of Public Affairs; (b) situational awareness by the National Operations Center; (c) situational awareness by Components other than the National Operations Center, upon approval by the Chief Privacy Officer following completion of a Social Media Operational Use Template; and (d) the conduct of authorized intelligence activities carried out by the Office of Intelligence and Analysis, the intelligence and counterintelligence elements of the United States Coast Guard, or any other Component performing authorized foreign intelligence or counterintelligence functions, in accordance with the provisions of Executive Order 12333, as amended. This Instruction does not apply to the Office of the Inspector General; however, the OIG will comply with the spirit of the Instruction.
…
D. Rules of Behavior: Component Privacy Officers or PPOCs, in coordination with counsel and Program Managers, or System Managers as appropriate, draft Rules of Behavior for operational use of social media (either separately or as part of a broader policy document) and submit them with the Template to the Chief Privacy Officer for review and approval. Personnel granted access to use social media certify annually that they have read and understand the Component Rules of Behavior. Where certification is not practicable, Component Privacy Officers and PPOCs maintain records of employee attendance at privacy training that includes training on Rules of Behavior.
Rules of Behavior include requirements for operational use of social media and the consequences of failure to adhere to those requirements. Where a federal policy establishes guidelines that apply to a Component’s operational use of social media, the Component’s Rules of Behavior incorporate that policy and that fact is noted in the Template. Unless otherwise noted in the Template adjudication process, the Rules of Behavior provide, at a minimum, that DHS employees:
1. Use social media for operational purposes only when activities are authorized by statute, executive order, regulation, or policy;
2. Use only government-issued equipment, government accounts, and only government email addresses when engaging in the operational use of social media;
3. Use online screen names or identities that indicate an official DHS affiliation and use DHS email addresses to open accounts used when engaging in social media in the performance of their duties;
4. Access publicly available information through social media only by reviewing posted information without interacting with any individual who posted the information;
5. Respect individuals’ privacy settings and access only information that is publicly available unless the individual whose information the employee seeks to access has given consent to access it;
6. Collect the minimum PII necessary for the proper performance of their authorized duties;
7. Protect PII as required by the Privacy Act and DHS privacy policy; and
8. Document operational use of social media, including date, site(s) accessed, information collected, and how it was used in the same manner that the Department would document information collected from any source in the normal course of business. For instance, where information obtained through authorized operational use of social media is used in whole or in part to make decisions regarding an individual’s rights, benefits or privileges, employees document that fact in relevant records.
DOWNLOAD THE ORIGINAL DOCUMENT HERE:
SPIEGEL über die STASI-Connection des mutmasslichen “GoMoPa”-Chefs Jochen Resch
VIDEO – Britney Spears Chats with TMZ!
Britney Spears not only surprised a TMZ camera guy to stop and talk to him… but she was a straight up Chatty Cathy!



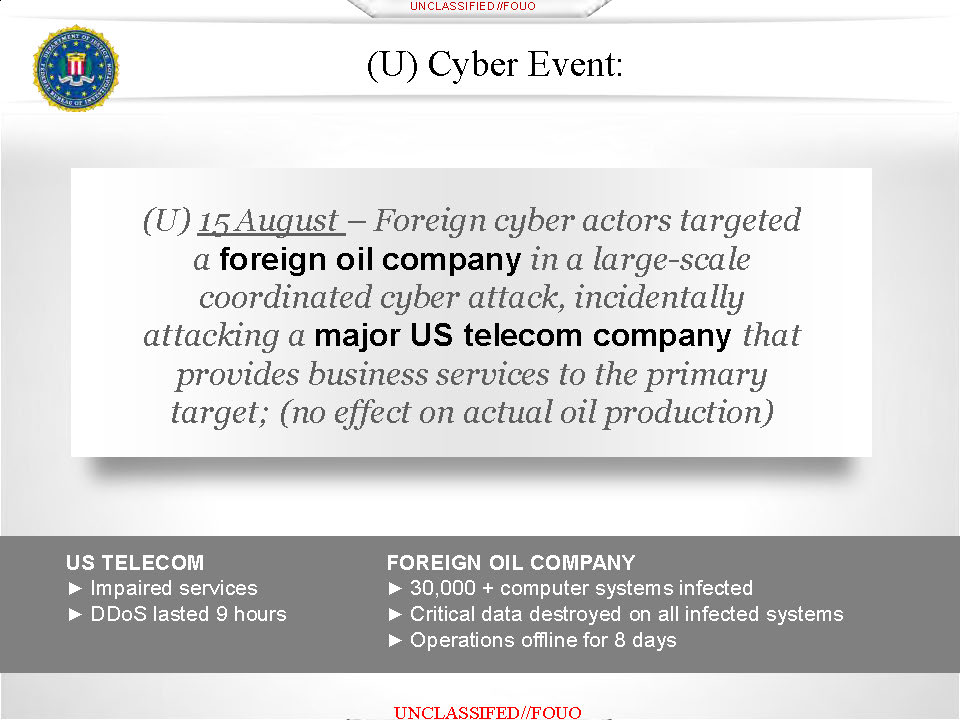

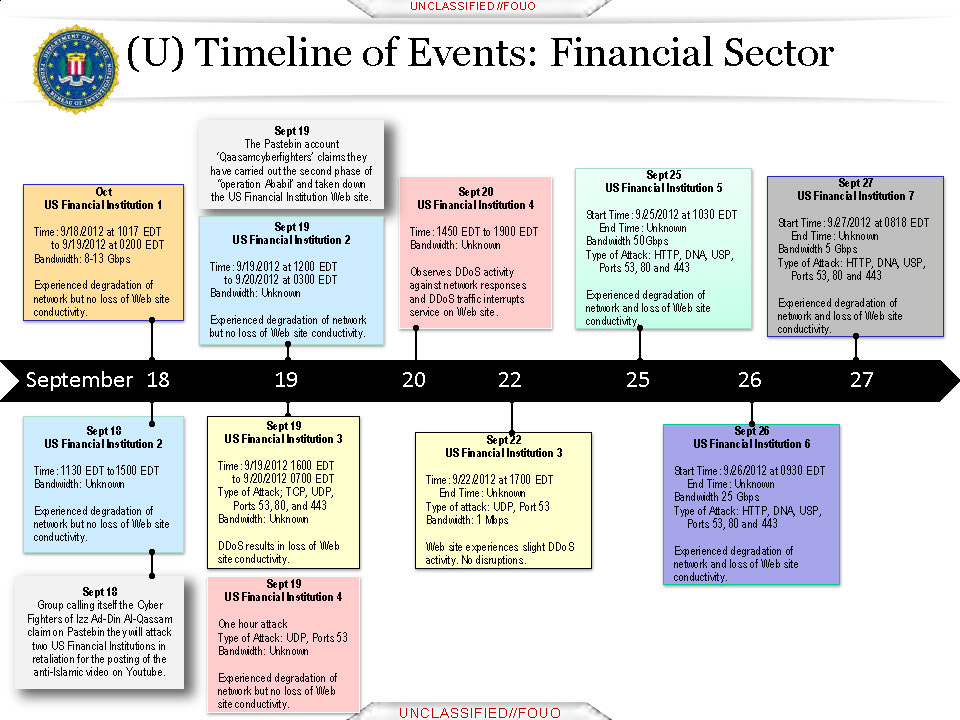
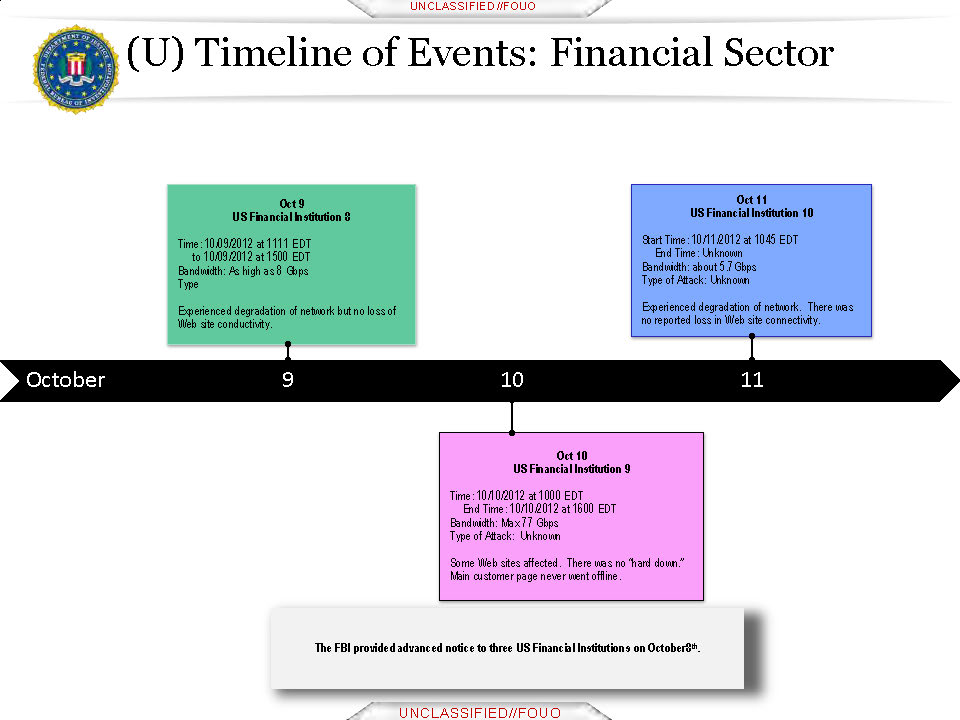



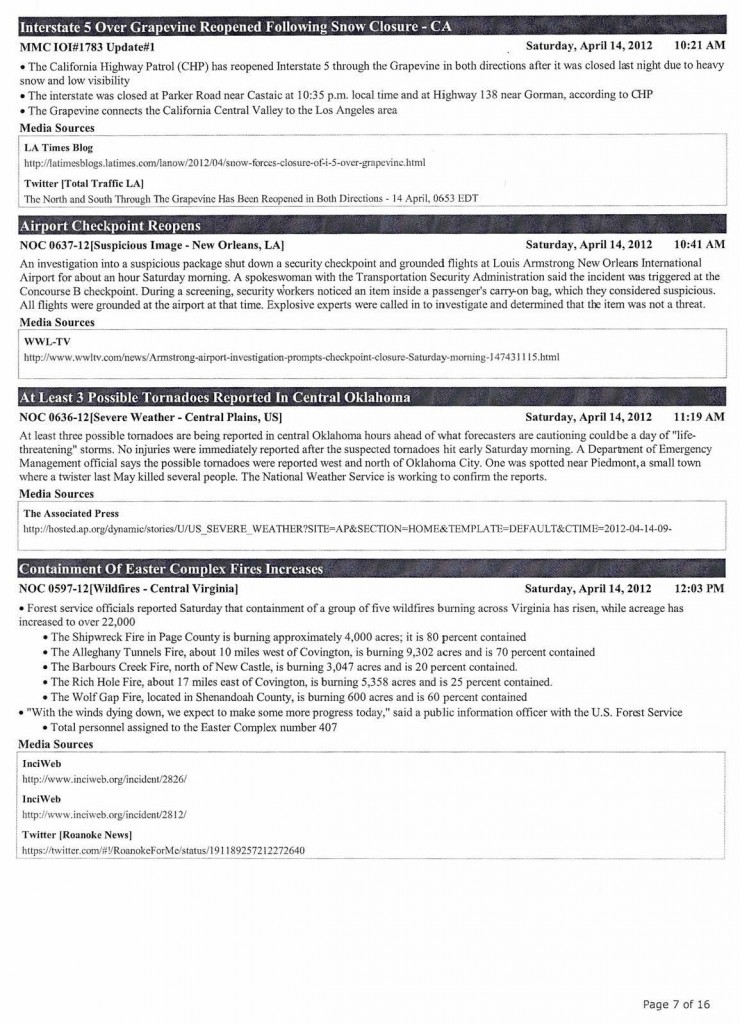


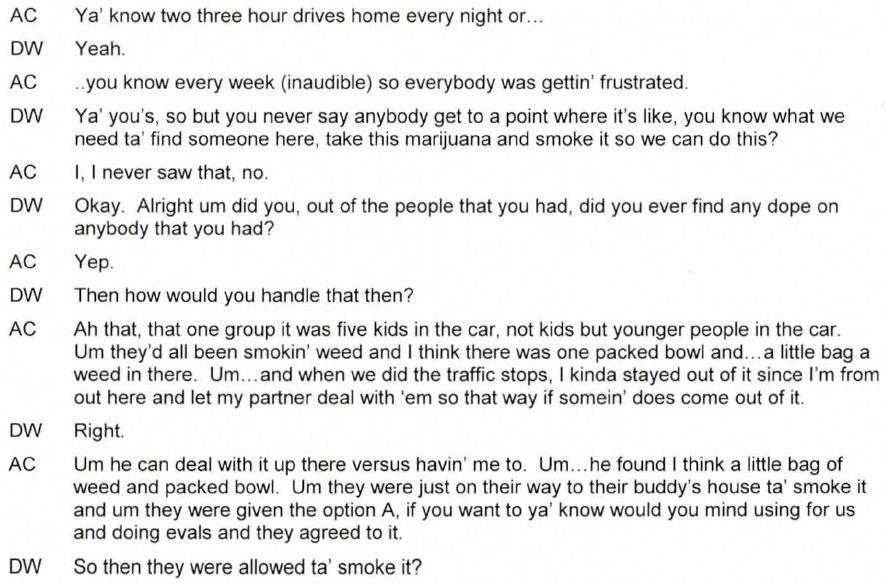
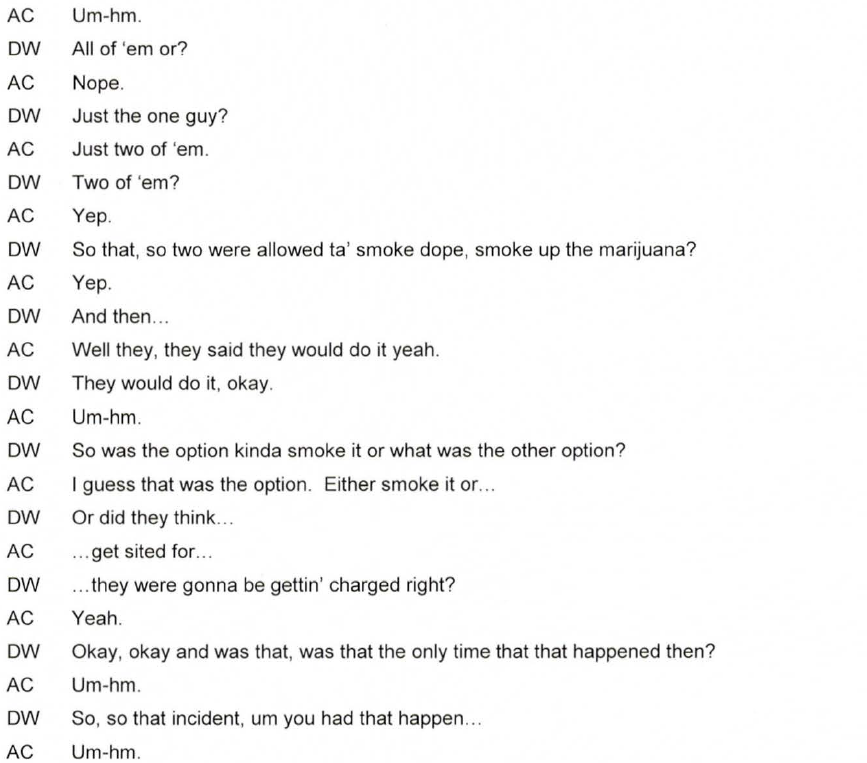
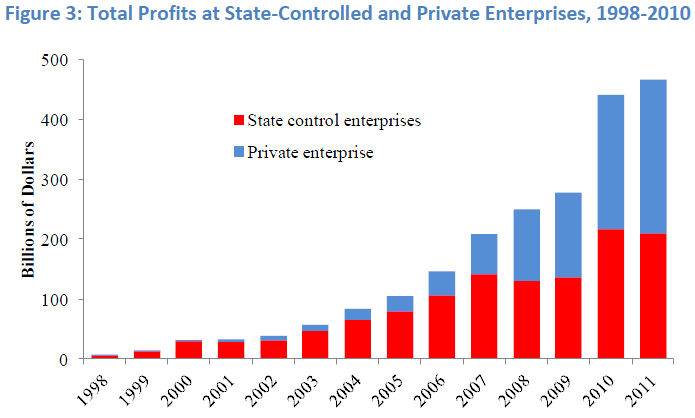
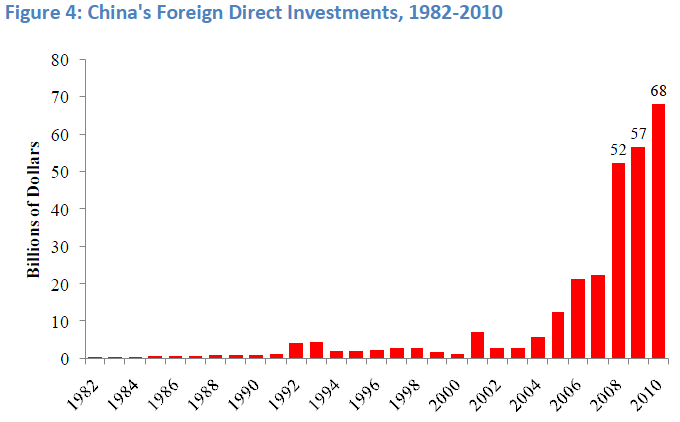






























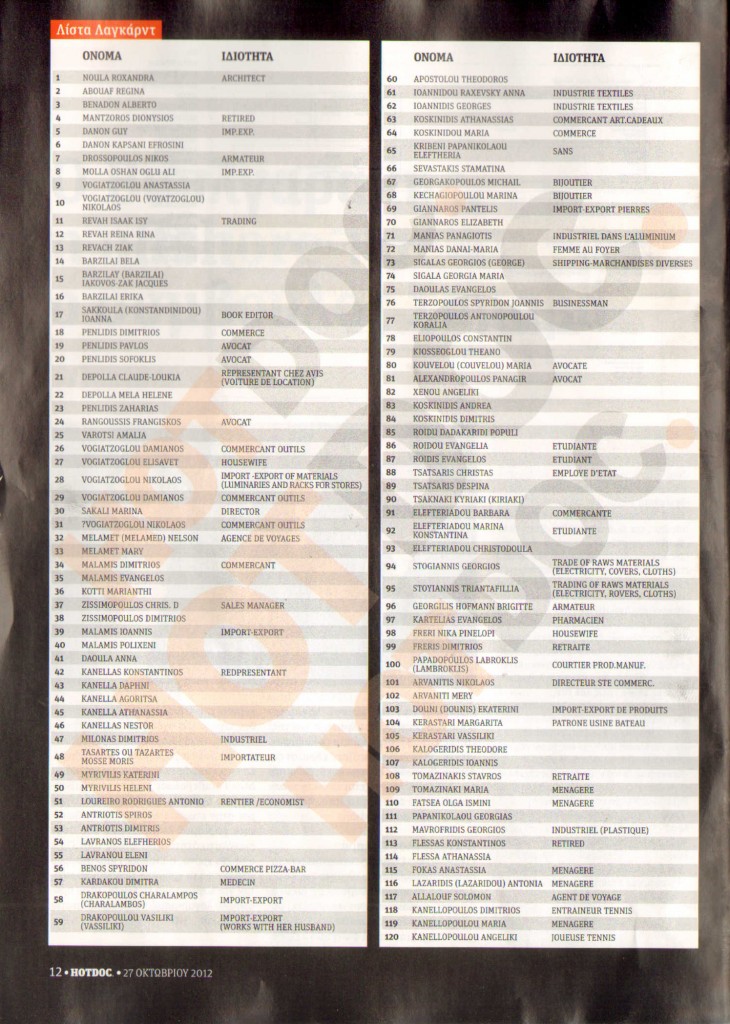
![[Image]](https://i0.wp.com/cryptome.org/2012/11/paula-kranz/pict22.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012/11/paula-kranz/pict24.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012/11/paula-kranz/pict23.jpg)












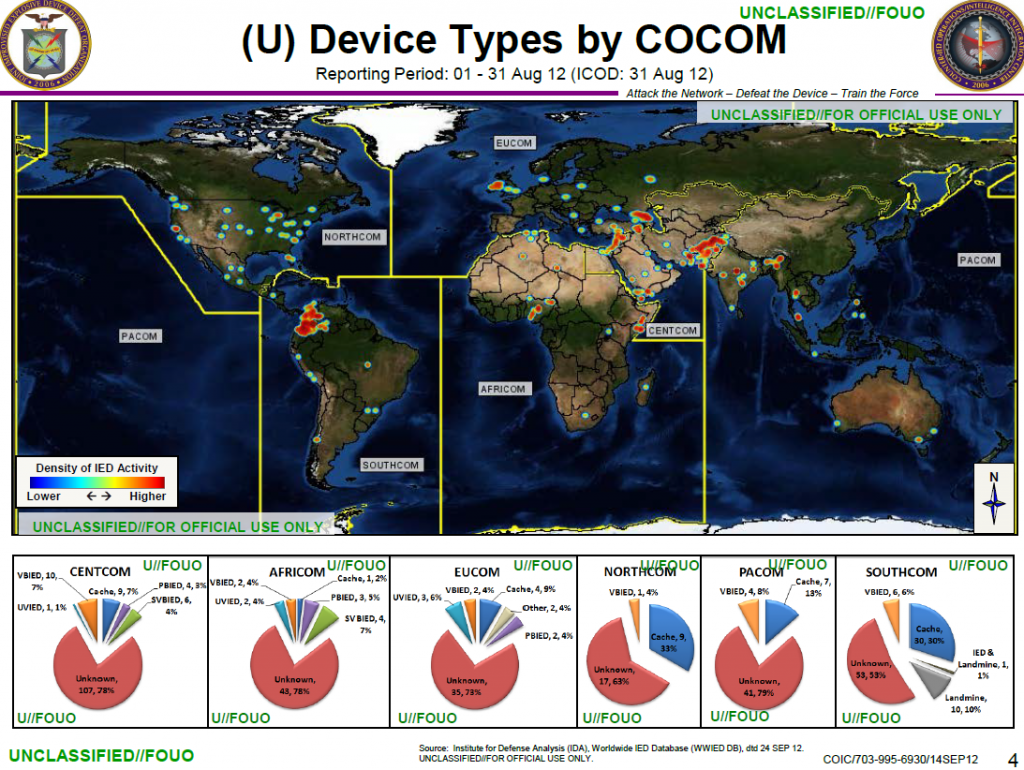
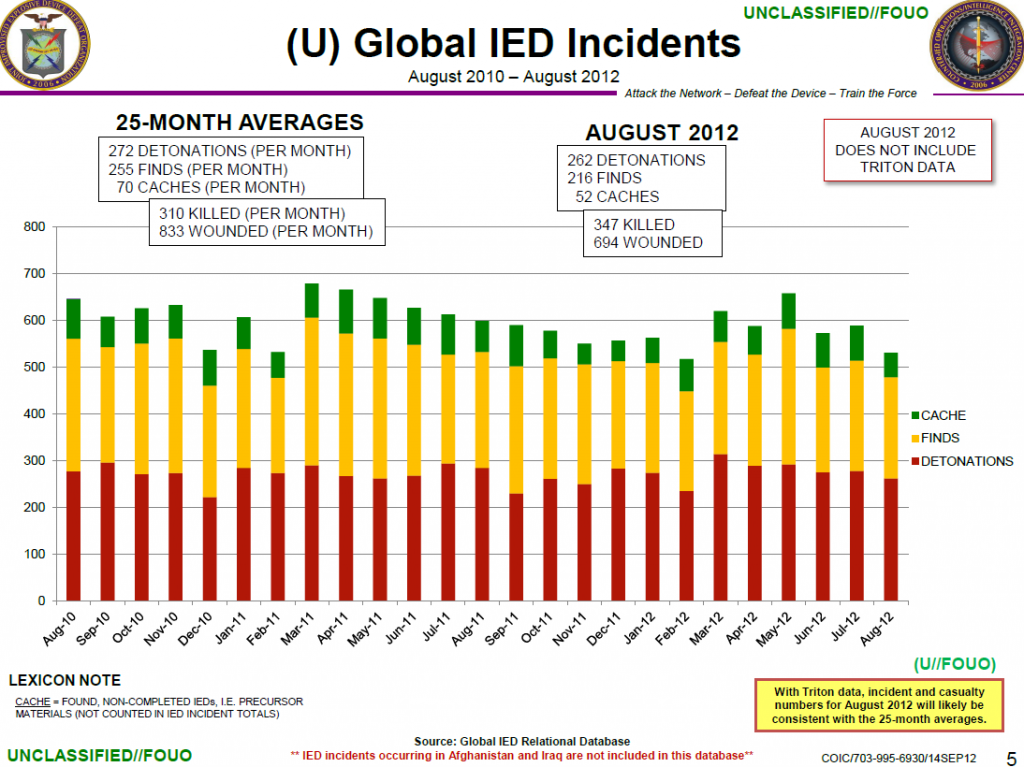
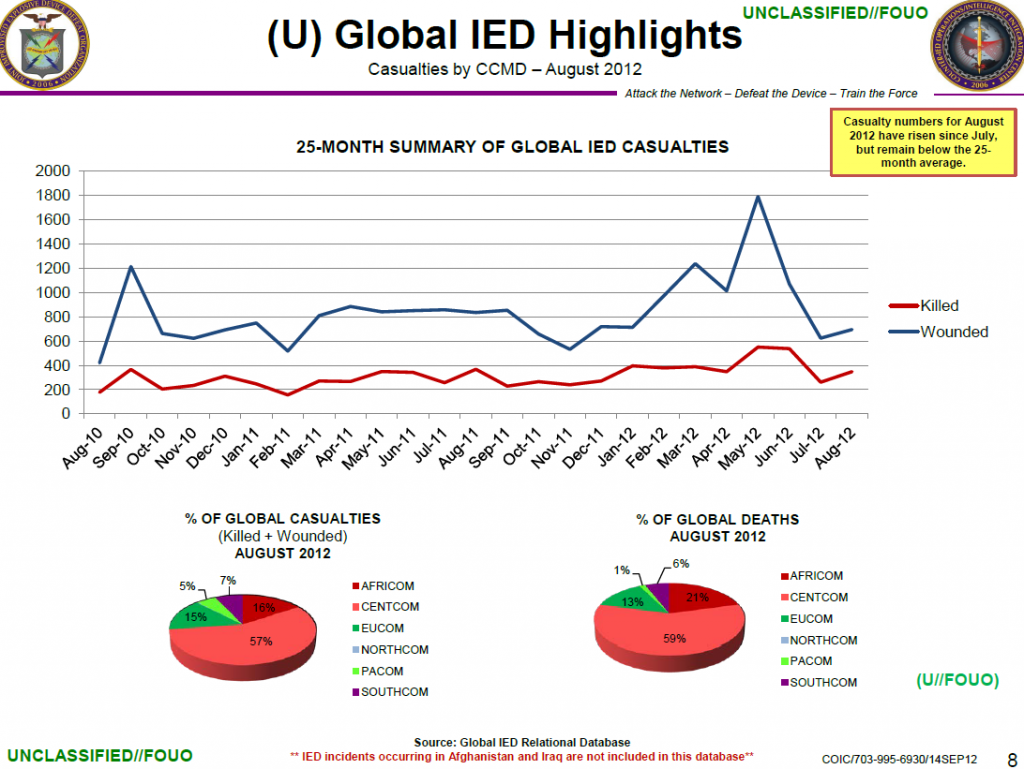
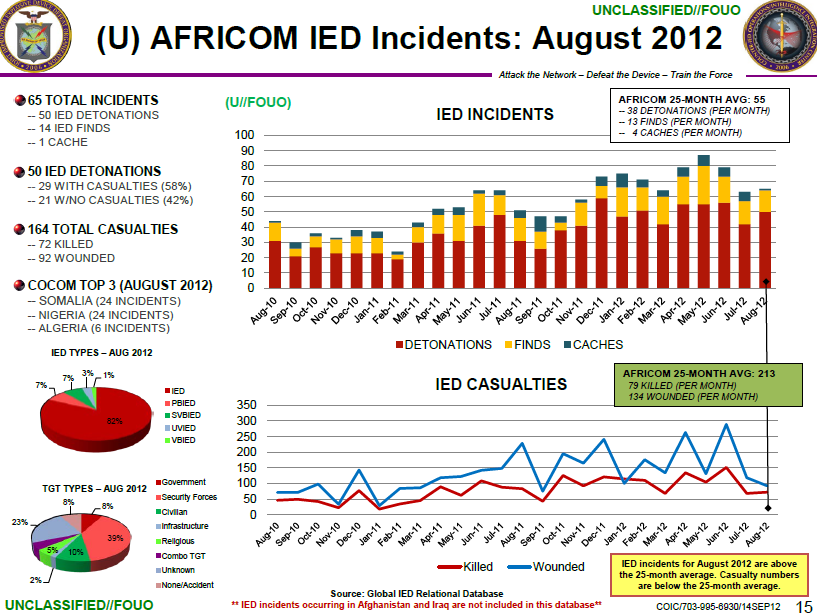
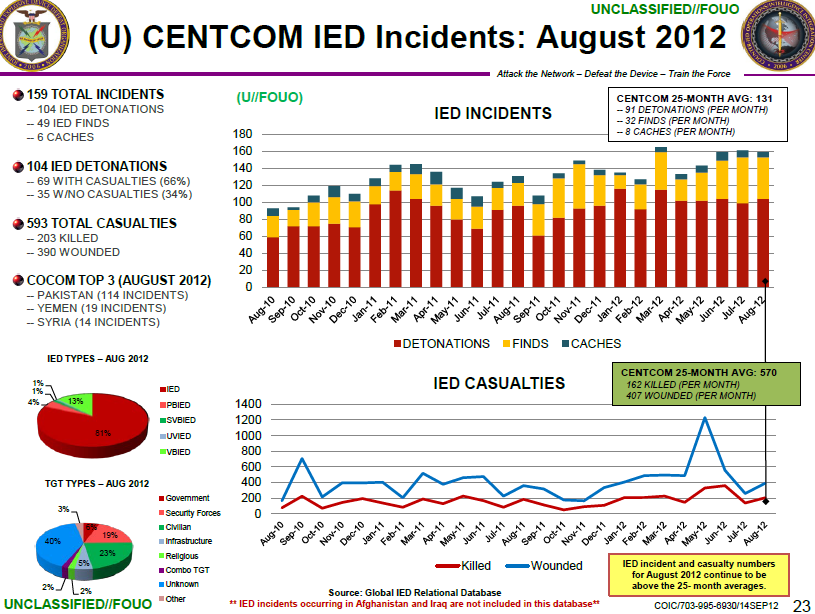
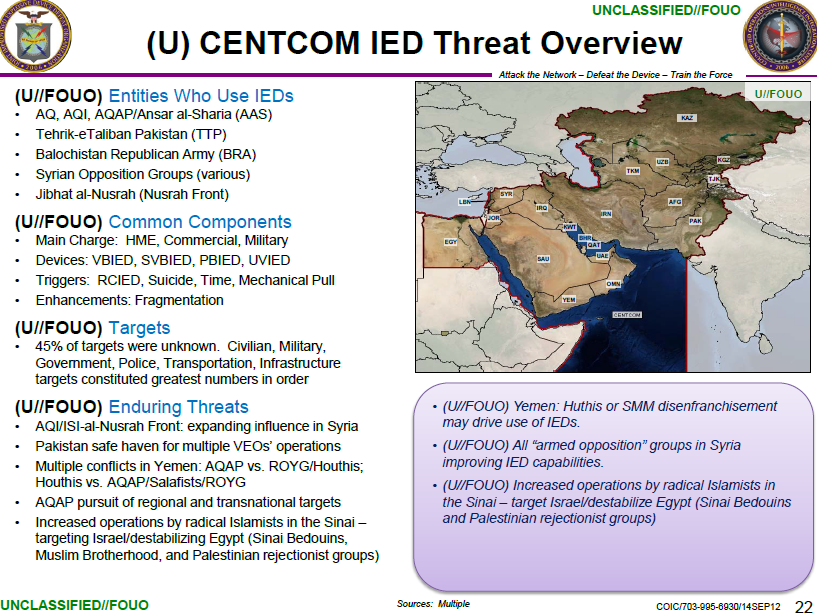

![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-earpiece/pict8.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-earpiece/pict7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-earpiece/pict6.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-earpiece/pict5.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-earpiece/pict4.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-earpiece/pict3.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-earpiece/pict2.jpg)



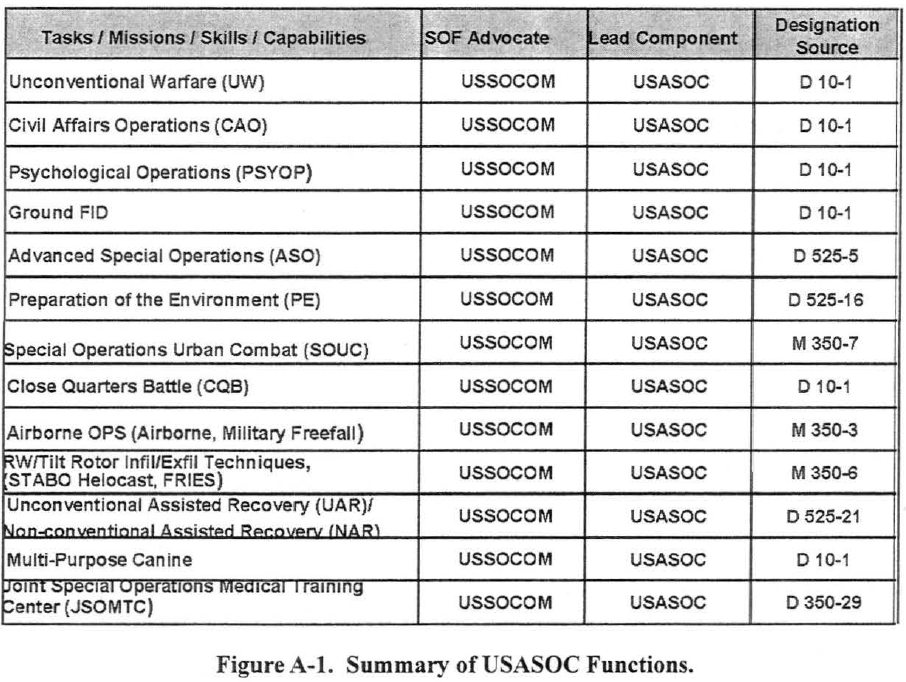
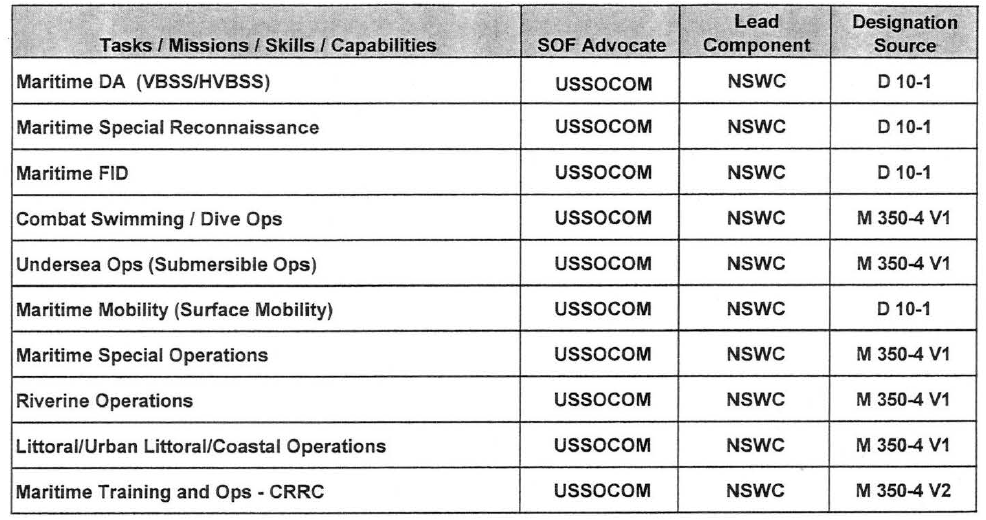
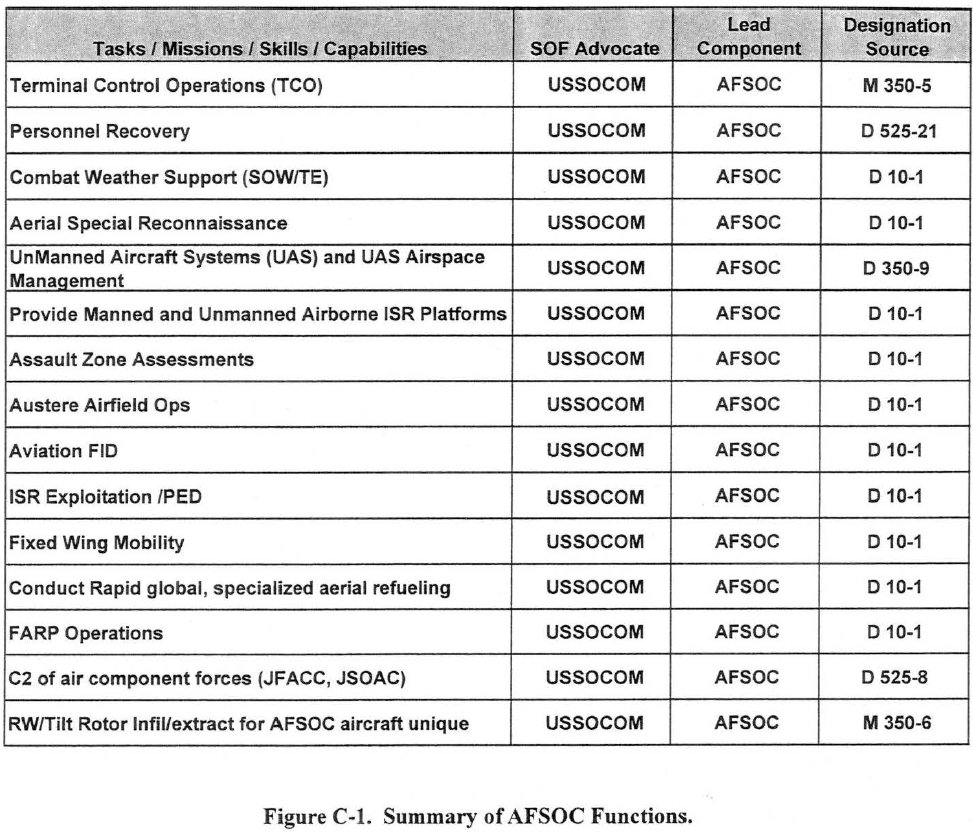



 (Nachfolgend bringen wir eine Original-Pressemeldung von „GoMoPa“, dem „NACHRICHTENDIENST“ mit dem Meridian Capital, London, erpresst werden sollte. Der Artikel strotzt nur von Fehlern. Damit ist deutlich, dass „GoMoPa“ tatsäch Meridian Capital erpresst hat und die Aktionen von Meridian Capital sich gegen „GoMoPa“ gerichtet haben.
(Nachfolgend bringen wir eine Original-Pressemeldung von „GoMoPa“, dem „NACHRICHTENDIENST“ mit dem Meridian Capital, London, erpresst werden sollte. Der Artikel strotzt nur von Fehlern. Damit ist deutlich, dass „GoMoPa“ tatsäch Meridian Capital erpresst hat und die Aktionen von Meridian Capital sich gegen „GoMoPa“ gerichtet haben.![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict58.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict62.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict51.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict52.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict63.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict54.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict53.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict64.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict35.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict36.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict37.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict38.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict39.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict50.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict65.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict44.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict43.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict42.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict40.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict41.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict45.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict46.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict47.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict48.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict49.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict61.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict34.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict33.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict30.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict29.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict32.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict31.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict60.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/cia-peary-2012/pict59.jpg)
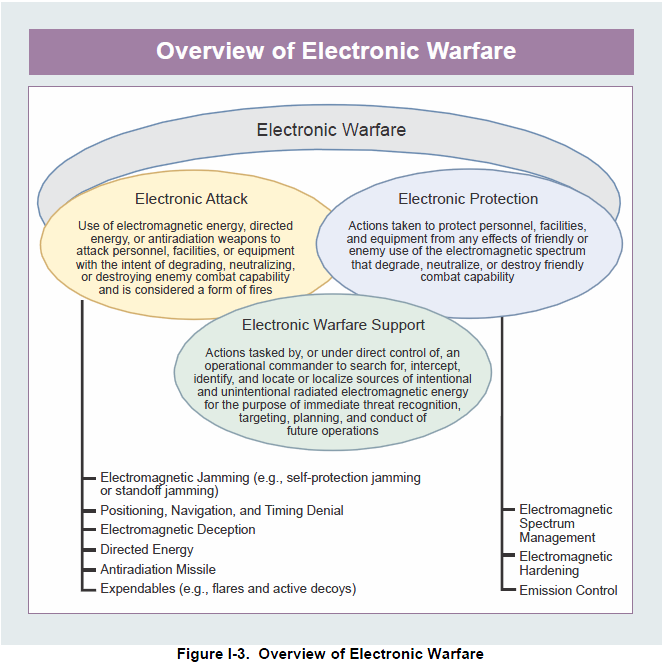
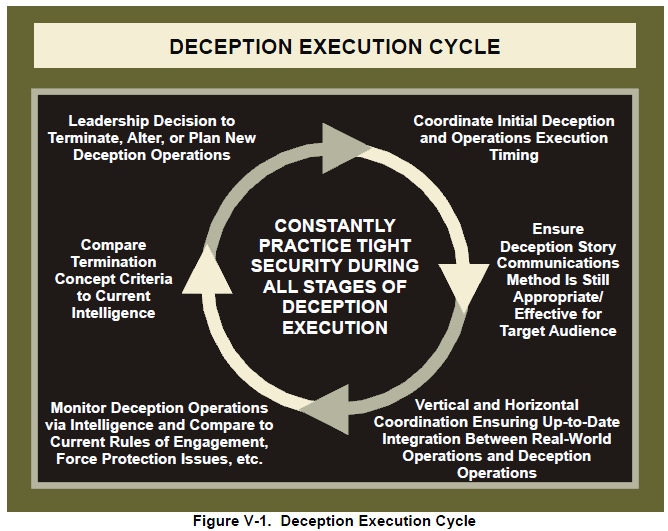













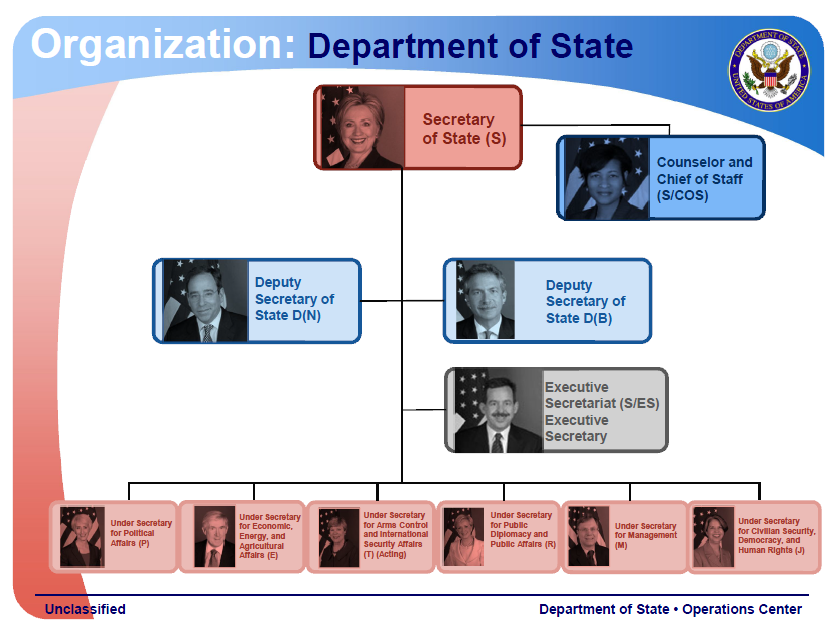
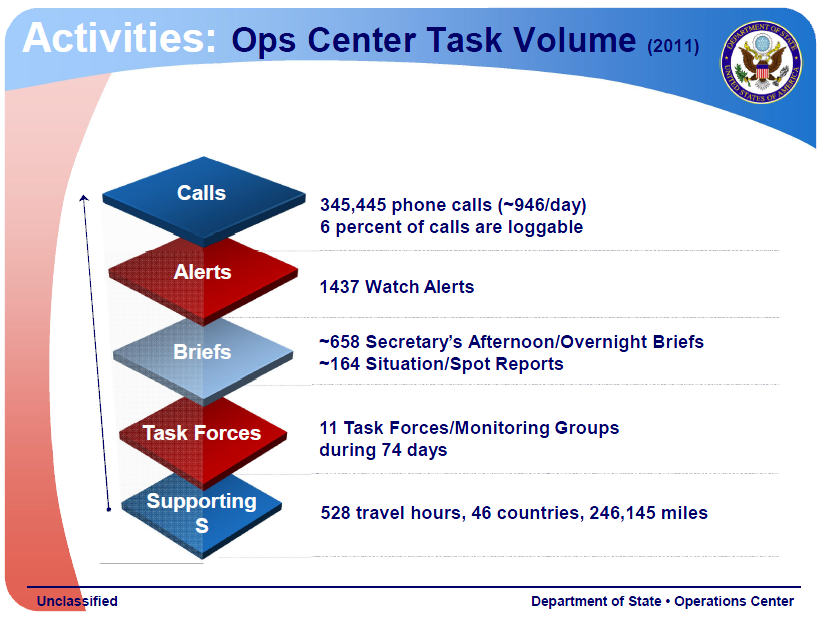
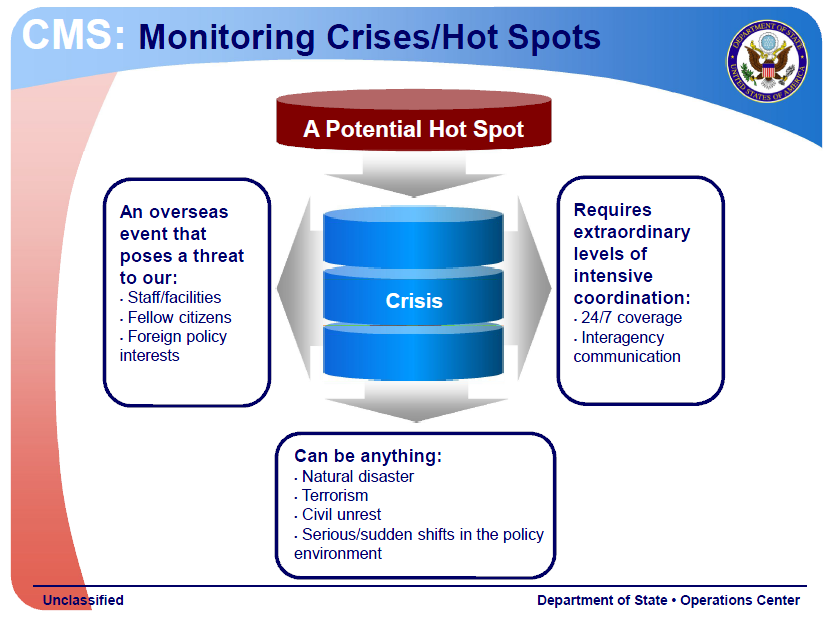

You must be logged in to post a comment.