M&C Corporate Service Limited P.O. Box 309GT Ugland House; South Chuch Street; George Town; Grand Cayman; Cayman Islands,243F3BFC26309BAB69A5EBDB5E4D4D99,The Panama Papers data is current through 2015,CYM,Cayman Islands,14049165,Panama Papers
M&C CORPORATE SERVICES LIMITED; P O BOX 309; UGLAND HOUSE; SOUTH CHURCH STREET; GEORGE TOWN; GRAND CAYMAN; CAYMAN ISLANDS.,3B4CFCD32E51D84E75D5D01C50CC6BAD,The Panama Papers data is current through 2015,CYM,Cayman Islands,14049166,Panama Papers
M/F.; 16 Cheung Fat Street; Cheung Sha Wan; Kowloon; Hong Kong.,FEBF0DBA61B94EF532F22E8957C7C503,The Panama Papers data is current through 2015,HKG,Hong Kong,14049167,Panama Papers
M/F.; 18 APLIU STREET SHAMSHUIPO; KOWLOON; HONG KONG; CHINA.,B6A24E45582F2CEB3BCB8CDF89C4B52C,The Panama Papers data is current through 2015,CHN,China,14049168,Panama Papers
M/F; HENG HING IND. BUILDING 8; YIP CHEONG STREET; FANLING; NEW TERRITORIES.,F8A40CA43E51F75AECDC13AAD0AC5203,The Panama Papers data is current through 2015,HKG,Hong Kong,14049169,Panama Papers
M/F.; Sun House; 181 Des Voeux Road; Central; Hong Kong,4AB967D2B9FE4BB1B154C74C33A9FAB5,The Panama Papers data is current through 2015,HKG,Hong Kong,14049170,Panama Papers
M/Irufoheyge; Maaveyo Magu; Male’ 2-03; Republic of Maldives,3869064F27DB9BA38589302249C8C848,The Panama Papers data is current through 2015,MDV,Maldives,14049171,Panama Papers
M/Sakkeyogasdoshuge; Male’; Republic of Maldives,80BD1E12D41A8E44D837038D9CB13B0A,The Panama Papers data is current through 2015,MDV,Maldives,14049172,Panama Papers
M/S Heirs Abdullah bin Shaiban; Gulf ArabicStreet; Villa No. 1; P.O. Box 709; Abu Dhabi; United Arab Emirates,F9E5B9011367553FC8154E55EA7A13DA,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049173,Panama Papers
M/s Private Affairs Bureau; Fujairah Trade Center; 9th Floor-Suite #902; PO Box 2000; Fujairah United Arab Emirates,94C7C2769B16F0E038F8606ED674844B,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049174,Panama Papers
M:van Oosternrijklaan 32; 2325 EN Leiderdorp; The Netherlands,E86495F2488A8FD93ED75AE7B35596BF,The Panama Papers data is current through 2015,NLD,Netherlands,14049175,Panama Papers
M107 Mezzanine Floor; Best Homes Business Center; Sheikh Zayed Road Dubai UAE,AA04BC6A6B4F442B008738578FB1E8EF,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049176,Panama Papers
“M14 Costa Azul, Cabarete Dominican Republic”,06834ACC576801687CBDA11D6E44605E,The Panama Papers data is current through 2015,DMA,Dominica,14049177,Panama Papers
M-1 Sheikh SAaud Bldg; M-01; Salauddin Rd; Opp. Reef Mall; P.O. Box 22489; Dubai; UAE,2FCED57ED0FF3E539BBE78EC9A11D1ED,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049178,Panama Papers
M-1; SHEIKH SAND BUILDING; SALAHUDDIN ROAD; P.O. BOX 22489; DUBIA; UNITED ARAB EMIRATES,24260AF2E47BEB9794468BBBD9D8AAB6,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049179,Panama Papers
M-1 Sheikh Saud Bldg; M-01; Salauddin Rd; Opp. Reef Mall; P.O. Box 22489; Dubai; UAE,8B86DB47D7B2FD11860826D3DB287320,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049180,Panama Papers
“M-1 SHEIKH SAUD BLDG. M-01 SALAUDDIN ROAD, OPP. REEF MALL P.O. BOX 22489 DUBAI UNITED ARAB EMIRATES”,AC6104BDE201F09B91B499CB2BA127A8,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049181,Panama Papers
M1 SHEIKH SAUD BUILDING; (GULF AIR BUILDING) SALAHDDIN ROAD P.O. BOX 22489; DUBAI; U.A.E,4871FDE7E17727FAFD4D643808ABE89A,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049182,Panama Papers
M1; SHEIKH SAUD BUILDING (GULF AIR BUILDING) SALAHUDDIN ROAD; PO BOX22439; DUBAI; UNITED ARAB EMIRATES,F8007A4E8F1674C80F939BDADC5A4627,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049183,Panama Papers
M1; Sheikh Saud Building (Gulf Air Building); Salahuddin Road; P.O. Box 22489; Dubai; United Arab Emirates,EDC1019067829446976F244B333F03CD,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049184,Panama Papers
M-1; Sheikh; Saud Building; (Gulf Air Building) Salahuddin Road; P.O. Box 22489; Dubai; United Arab Emirates,E0ACF2AA552EBD806A2CD58C31E128B9,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049185,Panama Papers
M-1 SHEIKH SAUD BUILDING; SALHUDDIN ROAD; P.O.BOX 22489; DUBAI (UAE),D3334498E96490CD39DF316DF5D05D6D,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049186,Panama Papers
M1Y PELORUS; KROEGER WERFT; HUTTENSTRASSEE 35; 24790; SCHACHT – AUDORF; GERMANY,7547F519DE2F3AC5B8BD6D06B01D7D49,The Panama Papers data is current through 2015,DEU,Germany,14049187,Panama Papers
M20-108; No. 1; Hua Nan Main Road; Pinghu; Longgang District; Shenzhen; PRC,FD18773CADB381458772FD4F81FB9FE0,The Panama Papers data is current through 2015,CHN,China,14049188,Panama Papers
M-3-19 PLAZA DAMAS; SRI HARLAMAS; 50480 KUALA LUMPUR; MALAYSIA,3897B4B767C1CEAED279FD2F05D646F7,The Panama Papers data is current through 2015,MYS,Malaysia,14049189,Panama Papers
M-3-19; Plaza Damas; Sri Hartamas; 50480 Kuala Lumpur; Malaysia,02F7870C06B27256CE2F65377EF38CE9,The Panama Papers data is current through 2015,MYS,Malaysia,14049190,Panama Papers
M46; Mezzanine Floor; Central Market; Jalan Hang Kasturi; 50050; Kuala Lumpur; Malaysia,810A59F6287AFF8387B2FBDBE274FE48,The Panama Papers data is current through 2015,MYS,Malaysia,14049191,Panama Papers
M4-M5; General Commercial Building; No. 156-164 Des Voeux Road; Central Hong Kong.,C08C42C52F0374AEA3098B4EAD86EF65,The Panama Papers data is current through 2015,HKG,Hong Kong,14049192,Panama Papers
M 540796 Pamulang Estat; E.9/11; Pamulang Timur; Pamulang; Tangerang,B3643F6C1FB04FCE785524B6C725DF40,The Panama Papers data is current through 2015,IDN,Indonesia,14049193,Panama Papers
“M5T 2Y5280 SIMCOE ST., #707 TORONTO ON CANADA”,10C831A6947803C5EE9C93EC5E6770F3,The Panama Papers data is current through 2015,CAN,Canada,14049194,Panama Papers
“M607-1600 BEACH AVE, VANCOUVER.BC. CANADA V6G. 1Y7”,E07AA8CD7102F00C12EE77897915D5FB,The Panama Papers data is current through 2015,CAN,Canada,14049195,Panama Papers
MA¿AN SHAN TUN; SHANGFA CUN; PINGMA ZHEN; TIANDONG XIAN; GUANGXI; CHINA,85B9D357AF0551ACA0BB910802A4D9C9,The Panama Papers data is current through 2015,CHN,China,14049196,Panama Papers
MAALE ABINIM 3; ST-RAMAT-GAN; 52381; ISRAEL,EB7155B57FE38612E6B23DD61C0809B5,The Panama Papers data is current through 2015,ISR,Israel,14049197,Panama Papers
“Maamonlahdentie 1 B 11- 00210 Helsinki, Finland”,05CEC92423873AB76626A99501C320DB,The Panama Papers data is current through 2015,FIN,Finland,14049198,Panama Papers
MA AN SHAN VILLAGE; QIUBIN STREET; WUCHENG DISTRICT; JINHUA CITY; ZHEJIANG PROVINCE; CHINA.,273889221A72715AAF5B7D92CC5845FD,The Panama Papers data is current through 2015,CHN,China,14049199,Panama Papers
Maarad Street; Bulbul bld 3rd; Beirut; Lebanon,7D1B6755DB687069F522CF9F02924A0C,The Panama Papers data is current through 2015,LBN,Lebanon,14049200,Panama Papers
Maassluisstraat 416A; 1062GS; Amsterdam; The Netherlands,DECF9E75413965C68B74840B544FB99E,The Panama Papers data is current through 2015,NLD,Netherlands,14049201,Panama Papers
MA AVENUE; 6-53; ZONE 4; EL TRIANGULO; GUATEMALA CITY; GUATEMALA; GUATEMALA,39D7B907A4A63A16B089423F8886BEB1,The Panama Papers data is current through 2015,GTM,Guatemala,14049202,Panama Papers
MABELLA COURT; 8 ACROPOLEOS AVENUE; O; O. BOX 24533; NICOSOA 1300; CYPRUS,016A5C4417F4F8BDEA8340019A241DD8,The Panama Papers data is current through 2015,CYP,Cyprus,14049203,Panama Papers
“(Macacha Guemes 330, 21-CP 1108-Buenos Aires-Argentina”,0023FACF9D24CF46DB7781F3DE8040C8,The Panama Papers data is current through 2015,ARG,Argentina,14049204,Panama Papers
Macao; China; palillos Quito Bao Bao Ding Garden Court 1B,42C4AC4B6D54C4B9425133EA3199E1B4,The Panama Papers data is current through 2015,CHN,China,14049205,Panama Papers
Macau; Av. da Praia Grande nr. 429; Centro Comercial Praia Grande; 9/F; “A”,16E5D78FC225915FA19F13FD0E30BBBC,The Panama Papers data is current through 2015,MAC,Macao,14049206,Panama Papers
Macau; Cal. da Vitorio; Ed. Kam Long Kok; 27/F; “F”,8F457925AC283870685B368C222A0984,The Panama Papers data is current through 2015,MAC,Macao,14049207,Panama Papers
Macdonald Road; Westville 3629; Durban; South Africa,D04155B9E8F1E968261E6D1383596055,The Panama Papers data is current through 2015,ZAF,South Africa,14049208,Panama Papers
Machaira 40 Pano Deftera; 2460; Nicosia; Cyprus,8BB622FC4660D55550DF90E09B085397,The Panama Papers data is current through 2015,CYP,Cyprus,14049209,Panama Papers
Macharia 40; Pano Deftera; 2460 Nicosia; Cyprus,D95B8E775CDC88C1DD6840D8DBC42FEB,The Panama Papers data is current through 2015,CYP,Cyprus,14049210,Panama Papers
Ma. Cl. Juan Montarela 210; INt. 202; Chorrillos; Lima – Perú,F77F086A5D1E82C5266B41C27D67AFB1,The Panama Papers data is current through 2015,PER,Peru,14049211,Panama Papers
Ma Constance; Mahe; Seychelles,31276962B8B3F8264308289EAE1063B0,The Panama Papers data is current through 2015,SYC,Seychelles,14049212,Panama Papers
MACPHAIL & CO.; rue Pierre-Fatio 12; Case Postale 3453; 1211 Geneve 3; Switzerland,50B24480740A8779D172955A4A43A8E0,The Panama Papers data is current through 2015,CHE,Switzerland,14049213,Panama Papers
Madame Curie Street; Minkara Centre; 3rd Floor; Beirut- Lebanon,CD8AB29AED98A5C8CA9E4FC46B1B5725,The Panama Papers data is current through 2015,LBN,Lebanon,14049214,Panama Papers
Madame Curie Street; Minkara Centre; 3rd Floor; P.O. Box 5584; Beirut; Lebanon,917065BD393D0A9AC2130E0EEF4E64D2,The Panama Papers data is current through 2015,LBN,Lebanon,14049215,Panama Papers
Madame Kouri Street; White Tower; Block A; 14th Floor; Beirut; Lebanon,7536B0D1618BB6210556F859E31A2425,The Panama Papers data is current through 2015,LBN,Lebanon,14049216,Panama Papers
Madaotou Villige; Qiligang Town; Yueqing City; Zhejiang Province; China,5455BB4D38B7D7C7A9197F4609C434E3,The Panama Papers data is current through 2015,CHN,China,14049217,Panama Papers
Mada Wang Chengguan; Xinchang; Zheijian; China,519DD51023320E0B5C509A22C08115DC,The Panama Papers data is current through 2015,CHN,China,14049218,Panama Papers
Madawang Chengguan Xinchang Zhejiang China,51C29FADCA68A91CC7EBAFABCE4C1302,The Panama Papers data is current through 2015,CHN,China,14049219,Panama Papers
Madebosyan Str.; 10; Yerevan; Armenia,46A8F6F109C5C28B549D409F7662E9C8,The Panama Papers data is current through 2015,ARM,Armenia,14049220,Panama Papers
made by lux office,3AB857E980F0C2D3B99D73DE43294D63,The Panama Papers data is current through 2015,BLR,Belarus,14049221,Panama Papers
Maden mahallesi; Gürgensu evleri; no.: 70; Sariyer Istanbul; Turquie,E3BC521EDAD0931247F4DF4FB991BA7E,The Panama Papers data is current through 2015,TUR,Turkey,14049222,Panama Papers
Madhav Co-Op Housing Society; SBS Road; Sagar Sangeet Bldg.; Flat 6D; Colaba; Mumbai 400 005 India,96BDC618ADB3EEE029FF41738AF04FE5,The Panama Papers data is current through 2015,IND,India,14049223,Panama Papers
Madhvani Foundation; Plot 96-98; 5th Street Industrial Estate; PO Box 6361 Kampala Uganda,C43BE7B20A686553AB47ED347FD0A050,The Panama Papers data is current through 2015,UGA,Uganda,14049224,Panama Papers
MADINAH ROAD; P.O.BOX 1049; JEDDAH 21431; KINGDOM OF SAUDI ARABIA.,8D552A7F831E99F326B01CC01A284E90,The Panama Papers data is current through 2015,SAU,Saudi Arabia,14049225,Panama Papers
MADINAH ROAD.; SULTAN CENTER-3RD FLOOR; OFFICE # 304-JEDDAH; KINGDOM OF SAUDI ARABIA,6AF025B1090D533BCDA67DBBB207EC76,The Panama Papers data is current through 2015,SAU,Saudi Arabia,14049226,Panama Papers
MADINA ROAD; JEDDAH; 21471; KSA,A5BF95C355128D15EA2FCD2F39034C50,The Panama Papers data is current through 2015,SAU,Saudi Arabia,14049227,Panama Papers
Madrid; Calle Ayala 15; Escalera derecha; 1-F; 28001; Spain,561BC810E3A6821732F9C4615A59E87B,The Panama Papers data is current through 2015,ESP,Spain,14049228,Panama Papers
Madrid E3-203 y Alfonso Lamina; Cumbaya; Quito; Ecuador,BA9F95A415B20089EFEA1B0A07F8593D,The Panama Papers data is current through 2015,ECU,Ecuador,14049229,Panama Papers
“MADRID, SPAIN”,9191870EB9951C75675B8D8FF78A62FD,The Panama Papers data is current through 2015,ESP,Spain,14049230,Panama Papers
Maduma Discretionary Trust c/o Buccleuch Holdings Limited; Omar Hodge Building; Wickham’s Cay 1; Road Town; Tortola; British Virgin Islands,B5E6348184A9C58414ACF46955D45A1B,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14049231,Panama Papers
M. Advisory FZE; Office No.12; 11th Floor; Rakia Amenity Centre; Building No.2; Al Jazeera Al Hamra; Ras Al Khaimah; U.A.E.,C31868C43C1EF8904F8CB533D9F4EB77,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049232,Panama Papers
Madytou 8-10 Nea Smyrni Athens 171 23Greec,2C45F57BAD18091AEC15933D0DE53BB6,The Panama Papers data is current through 2015,GRC,Greece,14049233,Panama Papers
Madytou 8-10 Nea Smyrni Athens 171 23Greece,79554374A70468528DABFF499A75B6C6,The Panama Papers data is current through 2015,GRC,Greece,14049234,Panama Papers
MAESTRO JOAO DE TULLIO; 140-84; CAMBUI; CAMPINAS; SAO PAULO; SP; BRASIL; CEP:13024-160,86BFB902525F5EB2BE7FA6EFBDB348BA,The Panama Papers data is current through 2015,BRA,Brazil,14049235,Panama Papers
“Magal Hashalom 3 Rishon Leizon, Israel”,97697F144AC41DCFE023A283DE0F0381,The Panama Papers data is current through 2015,ISR,Israel,14049236,Panama Papers
MAGANA FARM; NAIRBI; KENYA,C28B3F07E8CB9B9F8B589162BF97C84C,The Panama Papers data is current through 2015,KEN,Kenya,14049237,Panama Papers
Magdalena 140; Piso 21; Las Condes; Santiago; Chile,B9A16D0EFFC5F1BE20E6A861EA5E90D5,The Panama Papers data is current through 2015,CHL,Chile,14049238,Panama Papers
MAGINI HAGALIL 51 RECHOVOT ISRAEL,9918F36744A120D525C1C125E5EC8C5E,The Panama Papers data is current through 2015,ISR,Israel,14049239,Panama Papers
Maglemosevej 57 2920 Charlottenlund Denmark,7B41EB4853094C6DEB72E372B43BF22A,The Panama Papers data is current through 2015,DNK,Denmark,14049240,Panama Papers
Magnevägen 6; S-131 46 Nacka; Stockholm; SWEDEN,2423DD26CEB6712BA93499AEDD94EB7A,The Panama Papers data is current through 2015,SWE,Sweden,14049241,Panama Papers
MAGNOLIA CHAMBERS; HARBOUR HOUSE; WATERFRONT DRIVE; PO BOX 431; ROAD TOWN; TORTOLA; BVI,E82C1EEB01BADC9BFEC05B47ADAE2715,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14049242,Panama Papers
Magnolia Vila Magnolia Gardens St Lawrence Jersey,B91FE402AEFFA1BBD1048AA53196A2BE,The Panama Papers data is current through 2015,JEY,Jersey,14049243,Panama Papers
Magnusdottir; Mavanesi 6; IS-210 Gardabaer; Iceland,975F3F941B28A4A21C048C46A3ED8232,The Panama Papers data is current through 2015,ISL,Iceland,14049244,Panama Papers
Magracorp Building; 50th St East; Office 613; Manuel Maia de Ycaza,62C129BAF51D7914CB6DAD2A9B26C6A7,The Panama Papers data is current through 2015,,,14049245,Panama Papers
Mahaaiweg 3; Willemstad; Curaçao,BF5F09EC7B87170FABC1C7A3CF801366,The Panama Papers data is current through 2015,CUW,Curaçao,14049246,Panama Papers
“Mah Ambarlidere SK-Dostlar St; Dostlar St C BL No: 3; Abesiktas 34349-01; Istanbul, Turkey”,26484AB691B49E6455A86A2DA9E75920,The Panama Papers data is current through 2015,TUR,Turkey,14049247,Panama Papers
Mah Dr. Mehmet; OZ SK Rizzo K:5/8; 34433; Turkey; Mueyyetzade Mah.Serdar’i Ekrem; 34425; Turkey; Gornaya St 470/20; M.D. Almaty. Rest in Files.,5033625BFAF0022A87CBFCCD7C31BE60,The Panama Papers data is current through 2015,TUR,Turkey,14049248,Panama Papers
Mah Dr. Mehmet; OZ SK Rizzo; K:5/8; 34433; Turkey; Mueyyetzade Mah.Serdar’i E. Sok.Ka; 34425; T.; Gornaya St 470/20; Medeu D.; Almaty; K. Rest in File,7554B4CB72D35D87CC13D867FCEDB12C,The Panama Papers data is current through 2015,TUR,Turkey,14049249,Panama Papers
Mah Dr.Mehmet; OZ SK Rizzo K:5/8; Cihangir 34433; Turkey; Mueyyetzade Mah. Serdar’ Ekrem Sok.Kamondo; Is 34425; Turkey; Gornaya St. 470/20; In Files.,BB059B67A43AD6EB203C904960C8A28A,The Panama Papers data is current through 2015,TUR,Turkey,14049250,Panama Papers
“Mahe, Seychelles”,FA688A0DE6DC93A56F35184E6E0D1A44,The Panama Papers data is current through 2015,SYC,Seychelles,14049251,Panama Papers
Mahé Victoria Seychelles.,418F5984B2CA0B382A429BB0B4C2BC00,The Panama Papers data is current through 2015,SYC,Seychelles,14049252,Panama Papers
Mahirstr.8; D-91925 Munich; Germany.,A09F724ED13BDEB86D184304F4E2FB78,The Panama Papers data is current through 2015,DEU,Germany,14049253,Panama Papers
Mahmood Ahmad Abdulla Al Mudhareb Villa 214. 17c Str Al Garhoud Dubai,490996FFE45030781860B368084E410F,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049254,Panama Papers
Mahmood Ahmad Abdulla Al Mudhareb Villa; 214. 17c Str Al Garhoud; Dubai; UAE,4468296500AB4C5747E1BC768EA6EA96,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049255,Panama Papers
Mahmood Ahmed Abdulla Mudhared Villa; 214/17 C Street; Al Garhoud; Dubai,8A54E03BCFA387D3F9B8C7AFEF637195,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049256,Panama Papers
Mahmutbey Mah; Dilmenler cad.; no. 26; Bagcilar 34217 Istanbul; turkey,E49D55FF614E72CC9EBDB85BE90CE6DC,The Panama Papers data is current through 2015,TUR,Turkey,14049257,Panama Papers
Mahoma 4372; Montevideo; 61211; Uruguay,5E8C3AA902B0558B75AE1941E116B262,The Panama Papers data is current through 2015,URY,Uruguay,14049258,Panama Papers
“MA, HON FONG JOSEPH”,F58BCF72EE69F044C74CE8D415FEF356,The Panama Papers data is current through 2015,USA,United States,14049259,Panama Papers
MAH Tanner; c/o le Chateau du Cheseaux; 1033 Vaud.; Switzerland,BCC318937D935577E47DED884E1B2D87,The Panama Papers data is current through 2015,CHE,Switzerland,14049260,Panama Papers
MAICO Building; The Valley,08BFE9D530AF0D32EFB89C20BA03FDFC,The Panama Papers data is current through 2015,,,14049261,Panama Papers
MAICO Building; The Valley; Anguilla,7A6F074BC5B26B771F982C92D878CF22,The Panama Papers data is current through 2015,AIA,Anguilla,14049262,Panama Papers
– Mail Box 133; Local 6y7; Plaza de los Faroles; San Pedro de Alcantara; Malaga 29670; Spain,64138F14EFF1707FEC002CA6C8CAE3B1,The Panama Papers data is current through 2015,ESP,Spain,14049263,Panama Papers
MAIL BOXES ETC #507. 1710 TESCO LOTUS; SUKHUMIT 50; PRAKANONG KLONGTOEY; BANGKOK 10260; THAILAND,C70AAD8BE31B378271BA74F3F1298969,The Panama Papers data is current through 2015,THA,Thailand,14049264,Panama Papers
MAILING JIASHU YUAN; CHENGGUAN TOWN; DAWU COUNTY; HUBEI PROVINCE,8ED60D9FCAF06381F30A655D65977EFD,The Panama Papers data is current through 2015,TWN,”Taiwan, Province of China”,14049265,Panama Papers
Mai Mian Qiao Cun; Ji Shi Gang; Yin Xian; Zhe Jiang Sheng; People’s Republic of China.,57779292F689A283B385146A779483A3,The Panama Papers data is current through 2015,CHN,China,14049266,Panama Papers
Main Road; Mahaut; Dominica,1C139DB782C678173EDD4E9B8329D9C3,The Panama Papers data is current through 2015,DMA,Dominica,14049267,Panama Papers
Mainstr. 19; D-64390 Erzhausen; Germany,643E22E2B3A77B82DA16EE142DF7175F,The Panama Papers data is current through 2015,DEU,Germany,14049268,Panama Papers
MAIN STREET 90; ROAD TOWN; TORTOLA; BRITISH VIRGIN ISLANDS,447880C974EAC58702930F15D0C7A708,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14049269,Panama Papers
Main Street; Charlestownm Nevis; West Indies.,B48B9EDA210CC5EE1D027ADFB9F0734A,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049270,Panama Papers
MAIN STREET CHARLESTOWN NEVIS,15454BF2A7AECDEC1C568A19939A82CD,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049271,Panama Papers
Main Street; Charlestown; Nevis/West Indies,A9E71AFA4F087796359615D8ECBDEABE,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049272,Panama Papers
Main Street; Charlestown; Nevis; West Indies,7ACF13B3AF2455197A44EB5F202C2CDD,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049273,Panama Papers
MAIN STREET; P.O. BOX 556; CHARELESTOWN; NEVISM WEST INDIES,C7660048583B4D30C23A6C4C6435E95E,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049274,Panama Papers
Main Street; P.O. Box 556; Charlestown; Nevis,2E702257584665F9684C03B7978FC31E,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049275,Panama Papers
Main Street; Road Town; Tortola; British Virgin Islands,5B638EDE5FC61FE8B1D4336981054862,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14049276,Panama Papers
“Main Street Road Town, Tortola BVI”,9A1866512F6A656DFA0F5F9D05FAEFE4,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14049277,Panama Papers
Main Street; St. Joseph; Commonwealth of Dominica,D42E5B4D52DB32F4D35D0E1BE005C485,The Panama Papers data is current through 2015,DMA,Dominica,14049278,Panama Papers
Maint Street; P.O Box 556; Charlestown; Nevis.,2DBFDDFFB7428ED771E397C8E4BC70CF,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049279,Panama Papers
Maipú 1210 Capital Federal; Buenos Aires; Argentina,FA79D18B14E156DB7A28714DEC393ED5,The Panama Papers data is current through 2015,ARG,Argentina,14049280,Panama Papers
Maipú 231 piso 3º of. 58 CABA,527E720778205BAB4D116F917F3AC1B6,The Panama Papers data is current through 2015,IMN,Isle of Man,14049281,Panama Papers
Maipu 232; 4th Floor; Buenos Aires; Argentina,E8CCD1A12631192CF2B6A555457AF9CF,The Panama Papers data is current through 2015,ARG,Argentina,14049282,Panama Papers
“MAIPU 378-RAMOS MEJIA-PROVINCIA DE BUENOS AIRES, ARGENTINA”,D4781764C9F70D4A30749FFE15835CF1,The Panama Papers data is current through 2015,ARG,Argentina,14049283,Panama Papers
MAIS EL JABAL LEBANON,1CCC85F186565E2767AFD8707D6F82FE,The Panama Papers data is current through 2015,LBN,Lebanon,14049284,Panama Papers
Maison de Devier; Cornet Street; SPP; Guernsey GY1 1LF; Channel Islands,59A89B85FC307CAAAA6D4CFF105BF3AA,The Panama Papers data is current through 2015,GGY,Guernsey,14049285,Panama Papers
Maison de Houmet; Houmet du Nord Vale; Guernsey; Channel Islands,832D10B513364895069CBAB8B1932EFB,The Panama Papers data is current through 2015,GGY,Guernsey,14049286,Panama Papers
“Maison La Rochiere, Victoria Mahe Seychelles”,5423A0F9563BAA0D889CD6E65A349736,The Panama Papers data is current through 2015,SYC,Seychelles,14049287,Panama Papers
MAISON LA ROSIERE VICTORIA; MAHE; SEYCHELLES,93DE410C17B91F1F47BB068CAFDE0230,The Panama Papers data is current through 2015,SYC,Seychelles,14049288,Panama Papers
MAISON POMMIER; SARK; CHANNEL ISLANDS,ABAD7A0E9B2DE5974C6A87A6DCD52C79,The Panama Papers data is current through 2015,GGY,Guernsey,14049289,Panama Papers
Maitha Suhail Rashed Alabbar; Villa; DM 46; 357.4B St; Um Saqeem; Dubai,44734DCF1225C02103C4AB98BB235A55,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049290,Panama Papers
“MAITLAND SERVICES LIMITED FALCON HOUSE FALCON CLIFF PALACE ROAD DOUGLAS ISLE OF MAN, BRITISH ISLES *S.I.* IM2 4LB”,A19ABC679790131AFF4B27B0F25547F6,The Panama Papers data is current through 2015,IMN,Isle of Man,14049291,Panama Papers
M.A.J. Food Distribution Systems Road 414 Street 412 Industrial area Phase IV Jeddah – Saudi Arabia,8C31D270C49FABA4B27503564201D5DA,The Panama Papers data is current through 2015,SAU,Saudi Arabia,14049292,Panama Papers
Majia Tang; Team 7; Xinsheng Village; Xinzhuang Industrial Zone; Minhang District; Shanghai City; P.R. China,10ABAF83A018E73975C529CE3E82E37D,The Panama Papers data is current through 2015,CHN,China,14049293,Panama Papers
“Majuro, Marshall Islands”,73FDDE1DEA8C99E7BB6E8E2B57196BC6,The Panama Papers data is current through 2015,MHL,Marshall Islands,14049294,Panama Papers
MAKALI AV CORNER PASEO DO ROXAS MAKATI CITY MERO MANILA,8D52223E4B2565EF4D9C1824E723C8A1,The Panama Papers data is current through 2015,DOM,Dominican Republic,14049295,Panama Papers
Makaliwe l No.8; Jakarta 11650; Indonesia,ECE8657643BA0039AE20DB2056911F98,The Panama Papers data is current through 2015,IDN,Indonesia,14049296,Panama Papers
Makarenko Str. 2/21-5; Moscow; Russia,3B157C78E7939C2DAA2783AF754FAA85,The Panama Papers data is current through 2015,RUS,Russian Federation,14049297,Panama Papers
Makarenko Street; Bldg. 1/19; Apt. 46; Moscow city; Russian Federation,494C2E17D14065284452C46A1D46ABB4,The Panama Papers data is current through 2015,RUS,Russian Federation,14049298,Panama Papers
Makarevskogo Str.5; Apt. 97; Moscow; Russian Federation,4A5F76B2DE1155EF8B3633B0379EE617,The Panama Papers data is current through 2015,RUS,Russian Federation,14049299,Panama Papers
Makariou 3; Apollo Cort; Office 302; 3030 Limasso; l Cyprus,DA6D471F9A738C37763A408745318C5F,The Panama Papers data is current through 2015,CYP,Cyprus,14049300,Panama Papers
Makariou III; 223 Avenue Court; 2nd Floor; PC 3105 Limassol; Cyprus,AE4D324A3ACFDE185B7618BEB120998B,The Panama Papers data is current through 2015,CYP,Cyprus,14049301,Panama Papers
Makataeva Str. 128; Apt 1; Alma-Aty; Kazakhstan,4D46E3DE45AD87D5D8FA0ECE97B4BE84,The Panama Papers data is current through 2015,KAZ,Kazakhstan,14049302,Panama Papers
MAKATI AV CORNER PASEO DE ROXAS MAKATI CITY METRO MANILA,7DD50F313A505B5B1B872003D408DD35,The Panama Papers data is current through 2015,PHL,Philippines,14049303,Panama Papers
Makati; Metro Manila; Philippines,277604391A06BC6D650B13DEB339A131,The Panama Papers data is current through 2015,PHL,Philippines,14049304,Panama Papers
MAKEDONIAS 3; ORAIKOKASTRO; THESSALONIKI; GREECE.,029CC4EAFDFE1C327E9A74CE6C5B6CD9,The Panama Papers data is current through 2015,GRC,Greece,14049305,Panama Papers
Makedonias Street; Filothei Attikis; Greece,D065739ACF1F989360F71FBA98D079A4,The Panama Papers data is current through 2015,GRC,Greece,14049306,Panama Papers
MAKEEVSKAYA Street 19; Ukraine; Kiev 04114,93D64B27522EDCC0EDFD1995DE877336,The Panama Papers data is current through 2015,UKR,Ukraine,14049307,Panama Papers
Makovskogo Street; Bldg. 10; Apt. 80; Odintsovo Town; Moscow Region; Russian Federation,7913E491D907F05DAFE06D6677773EF1,The Panama Papers data is current through 2015,RUS,Russian Federation,14049308,Panama Papers
MAKTOUM ROAD; P.O. BOX 41691; SHARJAH; UNITED ARAB EMIRATES,0AAE84E5FDFFB2B34FCC615A69713430,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049309,Panama Papers
“Malabia 689 Piso 6. Capital Federal, Argentina”,99B183E0C4B36DE9FF7475CDAF282127,The Panama Papers data is current through 2015,ARG,Argentina,14049310,Panama Papers
MALAJA BRONNAJA 12 KORP. 4 APT. 11 MOSCOW 123001 RUSSIA,3DD16C1E158EA1D95128685637D0776A,The Panama Papers data is current through 2015,RUS,Russian Federation,14049311,Panama Papers
MALARÁSI 14; 110. REYKJAVÍK; ICELAND,FF12A67D95B3A0AEEB03E6F3053EF5B5,The Panama Papers data is current through 2015,ISL,Iceland,14049312,Panama Papers
MALATH INSURANCE & REINSURANCE COMPANY,A1BB14EEA05FD0A5F054C25F1D196AE7,The Panama Papers data is current through 2015,,,14049313,Panama Papers
Malaya Bronnaya Street; 21/13 apartment 5; Moscow; Russia,99EEC220C1F7DC16ED7EF1732ACD0E58,The Panama Papers data is current through 2015,RUS,Russian Federation,14049314,Panama Papers
Malaya Bronnaya Street; Bldg. 12- 4; Apt 11; 123001 Moscow city; Russian Federation,A36EB1D6AF4F40815DD510A4258D8351,The Panama Papers data is current through 2015,RUS,Russian Federation,14049315,Panama Papers
Malaya Bronnaya Street; Bldg. 20-2; Apt. 28; City of Moscow; Russian Federation,5313BD0315B49CDE595CB2CDEF781BD7,The Panama Papers data is current through 2015,RUS,Russian Federation,14049316,Panama Papers
“Malaya Filevaskaya Str., Bld. Moscow”,DBEFC04D9E22834177D770E04DE30B88,The Panama Papers data is current through 2015,RUS,Russian Federation,14049317,Panama Papers
Malaya Filevskaya str.38 apt.108; 121433 Moscow; RF,7B97EC5C36E6E5F49CBC2F2E94896B07,The Panama Papers data is current through 2015,RUS,Russian Federation,14049318,Panama Papers
Malaya Nikitskaya Str.; 16-1; Moscow; Russia,4DF7E9FCBCC7642F482520D0485FFD71,The Panama Papers data is current through 2015,RUS,Russian Federation,14049319,Panama Papers
Malaya Polyanka Street; Bldg. 2; Apt. 58; Moscow city; Russian Federation,0A4FDCCDF51917AD7206DB1317B8305F,The Panama Papers data is current through 2015,RUS,Russian Federation,14049320,Panama Papers
MALAYA SUKHAREVSKAYA; 6 BLD 1; MOSCOW 127051; RUSSIA,F1B4FB3A25C383D6B421ECC669836EF7,The Panama Papers data is current through 2015,RUS,Russian Federation,14049321,Panama Papers
MALAYA SUKHAREVSKAYA SQ.; 6 BLD1; MOSCOW 127051,4120488F86CC697535E99A635C7D3227,The Panama Papers data is current through 2015,RUS,Russian Federation,14049322,Panama Papers
Malbahova str.; 17; 55; Nalchik; Russia,19795B8FD03A9B35A6B3CF6E3AC5B9D8,The Panama Papers data is current through 2015,RUS,Russian Federation,14049323,Panama Papers
MALBOROUGH & QUEENS STREET; P O BOX N-10429; NASSAU; BAHAMAS,97CC44C0238DE4ACA4C5618723DB843E,The Panama Papers data is current through 2015,BHS,Bahamas,14049324,Panama Papers
Malborough & Queen Streets; P.O. Box N-10429; Bahamas,AE01C077CDEFA1C92184B6CC0130B1FE,The Panama Papers data is current through 2015,BHS,Bahamas,14049325,Panama Papers
Malborough & Queen Streets; P.O. Box N-10429; Nassau; Bahamas,7972675D565F2157AF8D5907CE6F60C9,The Panama Papers data is current through 2015,BHS,Bahamas,14049326,Panama Papers
Maldonado 1133/102; Montevideo; Uruguay,97AE5FA6ABACB29444490DCE3C820E77,The Panama Papers data is current through 2015,URY,Uruguay,14049327,Panama Papers
Maldonado 1133/2; Montevideo; Uruguay,BC68C70DFD84189076B542843D315C17,The Panama Papers data is current through 2015,URY,Uruguay,14049328,Panama Papers
Maldonado 1133; Apto 2 Montevideo; Uruguay,671F08502751B59C6B11DCD4CC40490E,The Panama Papers data is current through 2015,URY,Uruguay,14049329,Panama Papers
Maldonado Allende 1919; Valle del Cerro; 5009; Argentina,55E954E425833219C129E66EA03B0E02,The Panama Papers data is current through 2015,ARG,Argentina,14049330,Panama Papers
Malecón 28 de julio 257; dpto. 509; Miraflores; Lima; Perú,9AF822A1EFD5DF7CF1AA4EA35FBA8112,The Panama Papers data is current through 2015,PER,Peru,14049331,Panama Papers
Malecon 28 de Julio 685; Dpto. 1601; Miraflores; Lima; Peru.,4B3AB5BC37BBB3A8D766B84392B6B5BC,The Panama Papers data is current through 2015,PER,Peru,14049332,Panama Papers
Malecon Armendariz 175 – dpto. 1001- Miraflores –Lima -Perú,CCE9194F4151E5A3BCF654442753217C,The Panama Papers data is current through 2015,PER,Peru,14049333,Panama Papers
Malecón Balta 720; dpto.. 1-F Miraflores; Lima; Perú,BA515230EC8A15797D3C49B58565D522,The Panama Papers data is current through 2015,PER,Peru,14049334,Panama Papers
Malecon Central 1079; Punta Hermosa; Lima Peru,EF374E1106162ED18DE2404FAF906090,The Panama Papers data is current through 2015,PER,Peru,14049335,Panama Papers
Malecón Cisneros 1268; Depto. 903; Miraflores; Lima; Perú,DD1E0D290352C6A33D7732BAEDC2FFF3,The Panama Papers data is current through 2015,PER,Peru,14049336,Panama Papers
Malecón Cisneros 238; dpto.1102; Miraflores; Lima; Perú,49331FE2D76EF2202A61455638BE2013,The Panama Papers data is current through 2015,PER,Peru,14049337,Panama Papers
“Malecon Clsneros 1070 Apr 901, Lima 18 Peru”,A2D16B0AA2E7D24E32FBFE0B101E2D37,The Panama Papers data is current through 2015,PER,Peru,14049338,Panama Papers
Malecon de Entrerios 161 y Av. Rio Vinces Edificio Jardines de Entrerios 2do Piso. Dep. 5; Guayaquil; Ecuador,2A0656B7D49AB2C9C25971CA150503BE,The Panama Papers data is current through 2015,ECU,Ecuador,14049339,Panama Papers
“Malecón de la Marina, Edificio Costa Mar 538- dpto 1302-Miraflores-Lima-Perú”,0AC6E0691EB558B2F18B18BA02B4DFC1,The Panama Papers data is current through 2015,PER,Peru,14049340,Panama Papers
MALECON DE LA RESERVA 473 DEPTO.701; LIMA; MIRAFLORES,4253D129353F060AF56871FD4F7AFE3E,The Panama Papers data is current through 2015,PER,Peru,14049341,Panama Papers
MALECON DE LA RESERVA 473 DPTO. 701; LIMA; MIRAFLORES,D29728D673815EE2CC0558BE5A8BDE79,The Panama Papers data is current through 2015,PER,Peru,14049342,Panama Papers
Malecon Manuel Seoane 306-B-2; Pimentel; Chiclayo; Lambayeque; Perú,F470EFB5ED822A92E443BD260E8498A9,The Panama Papers data is current through 2015,PER,Peru,14049343,Panama Papers
Malecón Paul Harris 200 dpto. 103; Barranco; Lima; Perú,C5FF16407C9C663F1358C3363413313C,The Panama Papers data is current through 2015,PER,Peru,14049344,Panama Papers
Malecon Paul Harris 398-dpto.103-Barranco-Lima-Perú,F15FD9A635610C0FC5DC9AC1B7F7525A,The Panama Papers data is current through 2015,PER,Peru,14049345,Panama Papers
Malecon Pedro de Osma 205-Barranco-Lima-Peru,558F289D094895E59652ACC8FEBB378C,The Panama Papers data is current through 2015,PER,Peru,14049346,Panama Papers
MALECON SANTA MARIA MZ K LOTE 1 – SANTA MARIA DEL MAR-LIMA -PERÚ,0BB29829CB150A024390B4083ECF8CCF,The Panama Papers data is current through 2015,PER,Peru,14049347,Panama Papers
Malecon Souza 108-dpto.502-piso 5-Barranco-Lima-Perú,95A538074176EA7B0639CC7C63B7B4D1,The Panama Papers data is current through 2015,PER,Peru,14049348,Panama Papers
Maleewan Villa; 119/7 M-2; T.Bankoh; Ayutthaya 13000; Thailand,D9B4ADE06EA3263547E11F7F59A92717,The Panama Papers data is current through 2015,THA,Thailand,14049349,Panama Papers
Malenkovskaya 24-3-10; Moscow; Russia,89F86975848951EEB1F1E0517D48EFD3,The Panama Papers data is current through 2015,RUS,Russian Federation,14049350,Panama Papers
MALENKOVSKAYA STR. 14/2; FLAT 14; 107113 MOSCOW; RUSSIA,5ECB05684BDB8D76977534D28A49D51C,The Panama Papers data is current through 2015,RUS,Russian Federation,14049351,Panama Papers
“MALENKOVSKAYA STR. APT 1 MOSCOW, RUSSIAN FEDERATION”,CD5973C400F1531A7D4AC5EF6BA12F9F,The Panama Papers data is current through 2015,RUS,Russian Federation,14049352,Panama Papers
“M. Alexandrou 92, 18120 Koridallos.”,DB603C555725E4A858C4EEF12A5E8A31,The Panama Papers data is current through 2015,GRC,Greece,14049353,Panama Papers
MALGARD HOUSE; 15 UNION HOUSE STREET; ST HELIER JERSEY; C.I.,AEA7E6FBF50DC58A19C19B333B894D61,The Panama Papers data is current through 2015,JEY,Jersey,14049354,Panama Papers
Malgard House; 15 Union Street; St. Helier; Jersey.,5EAA0F3A28A18613D1DECD30C609FAE0,The Panama Papers data is current through 2015,JEY,Jersey,14049355,Panama Papers
Malhada De Cima Muda CCI 3945; 7570-337 Grandola; Portugal,C4C5EFAB89AF0EDD3E24673367CDE2E8,The Panama Papers data is current through 2015,PRT,Portugal,14049356,Panama Papers
MA LIAN DAO EAST STREET; 15 BLOCK; HONG LIAN QING YUAN BUILDING 6; ROOM 901; XUAN WU DISTRICT; 100055 BEIJING; CHINA,261C47DCA75474ECD03AB4C388D53EED,The Panama Papers data is current through 2015,CHN,China,14049357,Panama Papers
MALIKOVA STREET 25; S; KOKZHAR; ALAMUDUNSKIY REGION; CHUISKAYA OBLAST; KYRGYZ REPUBLIC,E43346F526CB7FC0E5FA0FBB2BCA3A0C,The Panama Papers data is current through 2015,IRN,”Iran, Islamic Republic of”,14049358,Panama Papers
Malik Road; Al Maliki’s Center 3rd Floor; Jeddah; Kingdom of Saudi Arabia,21A50031C3E228C1FAD1ACCF474CF2AD,The Panama Papers data is current through 2015,SAU,Saudi Arabia,14049359,Panama Papers
Malindi; 4 Rue de la Douzaine; Fort George; St. Peter Port; Guernsey,FFDCF39FFAD2F03A54AE9D95F4A1FCCE,The Panama Papers data is current through 2015,GGY,Guernsey,14049360,Panama Papers
“Malinova 9/1661, Praha 10”,B6CC2A4383E3C8CB03E308B8D3B7E5A4,The Panama Papers data is current through 2015,CZE,Czech Republic,14049361,Panama Papers
Malk Hfney Street; Abrag Misr El Tamir; Borg H – Flat 24; Montaza; Alexandria; Egypt,655F7C9FDC952E0F0DBE07B5504CA6DD,The Panama Papers data is current through 2015,EGY,Egypt,14049362,Panama Papers
Malki Al-Bezem Street; Damascus; Syrian Arab Republic.,E524118671F2E1AEA052722505FD71D0,The Panama Papers data is current through 2015,SYR,Syrian Arab Republic,14049363,Panama Papers
Malki Bazem Farouk Building; PO Box 3934; Damascus; Syria,C728BB357E51EE2A93769537212BD261,The Panama Papers data is current through 2015,SYR,Syrian Arab Republic,14049364,Panama Papers
Malkie Israel 27 Ashkelon Israel,69708E642F1A195EE24C5A36A49F32E3,The Panama Papers data is current through 2015,ISR,Israel,14049365,Panama Papers
Malki; Misr St. N°123; Damascus; Syria.,3001D82D170BAE6D513BA294359FFAF1,The Panama Papers data is current through 2015,SYR,Syrian Arab Republic,14049366,Panama Papers
Malki; Shilong; East Khasi Hills; Dist; Meghalaya 793 009; India,57D4347CA607C0795C0CD73A13C8E723,The Panama Papers data is current through 2015,IND,India,14049367,Panama Papers
MALLARD MARITIME MANAGEMENT LIMITED,865D888C7C4378582D679D7CBACAC754,The Panama Papers data is current through 2015,,,14049368,Panama Papers
MALLARD MARITIME MANAGEMENT LTD; SAFFREY SQUARE; SUITE 205; BANK LANE; PO BOX N-8188; NASSAU; BAHAMAS,429A286987E4799AE0CA53FA77FC9B63,The Panama Papers data is current through 2015,BHS,Bahamas,14049369,Panama Papers
Mall Cottage; Grove Park; Wanstead; London; E11 2DL,9730FD53928D392AD09835A819ADD031,The Panama Papers data is current through 2015,GBR,United Kingdom,14049370,Panama Papers
Mall Multiplaza Pacific; Planta baja; Local Party; Crafts & More Corp.,9E9B6E1CBABA1427E46186CCF2DC7824,The Panama Papers data is current through 2015,,,14049371,Panama Papers
Maloohtinskiy Prospect; Bld. 16; Corp. 1; Apt. 376; Saint-Petersburg; Russia,D291C1B897E73D87E75CAEC12EDC409F,The Panama Papers data is current through 2015,RUS,Russian Federation,14049372,Panama Papers
Maloohtisnskiy Pr.; Bld. 16; Corp. 1; Apt. 376; Saint Peter- Peyetsburg; Russia,A3A900903CE28EA02F31FD48B795B8FE,The Panama Papers data is current through 2015,RUS,Russian Federation,14049373,Panama Papers
MALTA; SAN GULJAN STJ4016; PORTOMASO; BLK 18; FLAT 61,39AAFDD44B8E73C08EA8EB9D7EA55626,The Panama Papers data is current through 2015,MLT,Malta,14049374,Panama Papers
“MALUAGA, NIUE”,A12A30FE1CB1353A3C2D4416BF0FBA97,The Panama Papers data is current through 2015,NIU,Niue,14049375,Panama Papers
MALYARD HOUSE 15 UNION STREET ST HELIER JERSEY C 8,686BE8FE39015991AE58E1D9BD60453F,The Panama Papers data is current through 2015,JEY,Jersey,14049376,Panama Papers
MALZARA HOUSE; 15 UNION STREET; ST. HELIER; JERSEY; CHANNEL ISLANDS,8612AE521BCC3E9A8913B1B2BC24AF69,The Panama Papers data is current through 2015,JEY,Jersey,14049377,Panama Papers
MALZARARD HOUSE; 15 UNION STREET; ST HELIER; JERSEY; C.I.,C9DB594A2AD34A399791DBDA9CC12F9B,The Panama Papers data is current through 2015,JEY,Jersey,14049378,Panama Papers
Malzard House,8A9B6E713A3B1E527EA2803909E9C11F,The Panama Papers data is current through 2015,,,14049379,Panama Papers
Malzard HOuse; 15 Orion Street; St. Helier; Jerse,C566B5FED6B1689F3E1D12C1795B19AA,The Panama Papers data is current through 2015,JEY,Jersey,14049380,Panama Papers
MALZARD HOUSE; 15 UNION; ST. HELIER; JERSEY; C.I.,E31FAA84FA81F6E94B08BAD4EA76060C,The Panama Papers data is current through 2015,JEY,Jersey,14049381,Panama Papers
MALZARD HOUSE; 15 UNION STREE; ST HELIER; JERSEY; C.I.,B9AA1170A69E0E7363A48755F6499422,The Panama Papers data is current through 2015,JEY,Jersey,14049382,Panama Papers
MALZARD HOUSE 15 UNION STREET; 8T HELIER; JERSEY,C38C5EF3FB84085EEE4572D4FC875973,The Panama Papers data is current through 2015,JEY,Jersey,14049383,Panama Papers
MALZARD HOUSE; 15 UNION STREET; 8T HELIER JERSEY CI,2334010DC5EF5321C173AFFDF12D0E83,The Panama Papers data is current through 2015,JEY,Jersey,14049384,Panama Papers
MALZARD HOUSE; 15 UNION STREET; 8T HELIER JERSEY CL,54F5DA16DE8A1BE20CB2130A9849CDD8,The Panama Papers data is current through 2015,JEY,Jersey,14049385,Panama Papers
MALZARD HOUSE; 15 UNION STREET; HELIER JERSEY,66D12483C70FBBFF9FB1A5883D47E96E,The Panama Papers data is current through 2015,JEY,Jersey,14049386,Panama Papers
MALZARD HOUSE; 15 UNION STREET; ST.HELIAR JERSEY,07EE3B3AC7703A14DA2E1AEC25E30FFB,The Panama Papers data is current through 2015,JEY,Jersey,14049387,Panama Papers
Malzard House; 15 Union Street; St. Helie; Jersey C.I,974047E8D513D07AF9B9F4F62CCA3D4C,The Panama Papers data is current through 2015,JEY,Jersey,14049388,Panama Papers
MALZARD HOUSE; 15 UNION STREET; ST. HELIER,4807CB82764FBEE1BA4E46DF5FDE33B8,The Panama Papers data is current through 2015,JEY,Jersey,14049389,Panama Papers
MALZARD HOUSE 15 UNION STREET ST HELIER JERSEU,769DF88F2329A946752A0D77EC10DBC7,The Panama Papers data is current through 2015,JEY,Jersey,14049390,Panama Papers
MALZARD HOUSE; 15 UNION STREET; ST.HELIER; JERSEY,70D4638E6E1F6CDE53DFC3D219D1CCD9,The Panama Papers data is current through 2015,JEY,Jersey,14049391,Panama Papers
MALZARD HOUSE; 15 UNION STREET; ST HELIER; JERSEY C1,B299274A1C0FA156876DAE7FCCC5CCED,The Panama Papers data is current through 2015,JEY,Jersey,14049392,Panama Papers
MALZARD HOUSE; 15 UNION STREET; ST-HELIER; JERSEY C1,49F6CA9B6B99FCA63BF0CDE15AF74452,The Panama Papers data is current through 2015,JEY,Jersey,14049393,Panama Papers
MALZARD HOUSE; 15 UNION STREET; ST HELIER; JERSEY; CHANNEL ISLANDS,8B7469DB62F6CFE49A9DBBB50E0EFB1B,The Panama Papers data is current through 2015,JEY,Jersey,14049394,Panama Papers
MALZARD HOUSE; 15 UNION STREET; ST. HELIER; JERSEY; CHANNEL ISLANFDS,DFF9DEBD6F3A0F0CCA15CC6BB477E55F,The Panama Papers data is current through 2015,JEY,Jersey,14049395,Panama Papers
MALZARD HOUSE; 15 UNION STREET; ST. HELIER; JERSEY C.I.,084587F38A06A36CB95DC7C3BDA59F0E,The Panama Papers data is current through 2015,JEY,Jersey,14049396,Panama Papers
MALZARD HOUSE; 15 UNIONSTREET; ST HELIER; JERSEY C.I.1,D37A003983854149E926B818D2181164,The Panama Papers data is current through 2015,JEY,Jersey,14049397,Panama Papers
Malzard House; 15 Union Street; St. Helier Jersey CI I,96247F7174605C139169443A3F2B1E70,The Panama Papers data is current through 2015,JEY,Jersey,14049398,Panama Papers
Malzard House; 15 Union Street; St Helier Jersey CI JE4 8TY,D702489EFACCD99286DF1BE80DB2F253,The Panama Papers data is current through 2015,JEY,Jersey,14049399,Panama Papers
MALZARD HOUSE; 15 UNION STREET; ST. HELIER; JERSEY CL,3E8B5D75C1CA5BA630E622B36E535804,The Panama Papers data is current through 2015,JEY,Jersey,14049400,Panama Papers
MALZARD HOUSE; 15 UNION STREET ST. HELIER JERSEY; CT,E7416874A3AA3F76CC69A7D4FD69B259,The Panama Papers data is current through 2015,JEY,Jersey,14049401,Panama Papers
Malzard House; 15 Union Street; St. Helier; Jersey; JE4 8TY.,59B463A0FE55805E1DAAD1AC9F2F2ECD,The Panama Papers data is current through 2015,JEY,Jersey,14049402,Panama Papers
MALZARD HOUSE; 15 UNION STREET; ST. HELIER; JERSEY JE4 ETY,12BCFA27B27B6F7C1A933C78BA469CDA,The Panama Papers data is current through 2015,JEY,Jersey,14049403,Panama Papers
MALZARD HOUSE 15 UNION STREET ST HELIER JERSY C.I.,9E60331AC59B4E3577F1E9DAE26ECF2D,The Panama Papers data is current through 2015,JEY,Jersey,14049404,Panama Papers
MALZARD HOUSE; 15 UNION STREET; ST. HELIER; JESEY CI,AE7C0D89FB21A8293381527A2E273565,The Panama Papers data is current through 2015,JEY,Jersey,14049405,Panama Papers
MALZARD HOUSE; 15 UNION STREET; ST HELIERM JERSEY; CHANNEL ISLANDS,9C1C81910645F757FB8A9608B5E08178,The Panama Papers data is current through 2015,JEY,Jersey,14049406,Panama Papers
MALZARD HOUSE; 15 UNION STREET; ST HELIR; JERSEY,A4F5EFD9A40B849D6F7F602D18DB37CD,The Panama Papers data is current through 2015,JEY,Jersey,14049407,Panama Papers
Malzard House; 15 Union Street; St. Helis; Jersey C.I.,6DAEEA4C5D1D67A45011C2A6B4914FD1,The Panama Papers data is current through 2015,JEY,Jersey,14049408,Panama Papers
MALZARD HOUSE; 15 UNION STRE; ST HELIER; JERSEY; C.I,FACD30B6E952A2073745DF70E43F5EB0,The Panama Papers data is current through 2015,JEY,Jersey,14049409,Panama Papers
Malzard House; 15 Union Strret; St Helier; Jersey C.I.,2B39317A0A39B0257CFF3B1B4460FFAD,The Panama Papers data is current through 2015,JEY,Jersey,14049410,Panama Papers
MALZARD HOUSE 15 UNION ST ST HELIER JERSEY,80D86C71ADF4CBF3F15C54B65DE9BA2C,The Panama Papers data is current through 2015,JEY,Jersey,14049411,Panama Papers
MALZARD HOUSE; 15 UNON STREET; ST. HELIER; JERSEY; CHANNEL ISLANDS.,0674F7E2A25E6B3B5B89413EB5C3600B,The Panama Papers data is current through 2015,JEY,Jersey,14049412,Panama Papers
MALZARD HOUSE 16 UNION STREET ST HELIER JERSEY,61FED1ABEEADF76D16F6BCAE83A13AC1,The Panama Papers data is current through 2015,JEY,Jersey,14049413,Panama Papers
MALZARD HOUSE; IS UNION STREET; ST.HELIE JERSEY,3CBCDC796E30D051C2A5C1029F69BE45,The Panama Papers data is current through 2015,JEY,Jersey,14049414,Panama Papers
MALZARD HOUSE; IS UNION STREET; ST.HELIER; JERSEY,42F738116FB1312B0B509E22579486D5,The Panama Papers data is current through 2015,JEY,Jersey,14049415,Panama Papers
MALZARD HOUSE; ISUNION STREET; ST HELIER JERSEY CI,605F4D040DC7878A8511DAE23C023747,The Panama Papers data is current through 2015,JEY,Jersey,14049416,Panama Papers
MALZARD HOUSE; ST HELIER; JERSEY; CHANNEL ISLANDS,1B08B68A218D77CD95EBAD879EB83414,The Panama Papers data is current through 2015,JEY,Jersey,14049417,Panama Papers
MALZARD HOUSE; ST. HELIER; JERSEY C.I.,74806D4E999C9BD0F7707D55455B534C,The Panama Papers data is current through 2015,JEY,Jersey,14049418,Panama Papers
Malzard House; Union Street; St. Helier; Jersey C.I.,B7E4E67455D393E88BCC5F74F13FDB04,The Panama Papers data is current through 2015,JEY,Jersey,14049419,Panama Papers
Malzard Houuse 15 Union Street; St Helier; Jerseyt,2A4F85FCE5CEC61F04BCCD2612BEA19C,The Panama Papers data is current through 2015,JEY,Jersey,14049420,Panama Papers
MALZARD HSE; 15 UNION STREET; ST. HELIER; JERSEY; CHANNEL ISLANDS,A0208A1EA707C7292804033D7EA1F11D,The Panama Papers data is current through 2015,JEY,Jersey,14049421,Panama Papers
MALZARD HSE; 15 UNION STR.; ST HELIER; JERSEY; CI,2B30D5BE01F3EA931A45945525A53418,The Panama Papers data is current through 2015,JEY,Jersey,14049422,Panama Papers
MALZARD VHOUSE; 15 UNION STREET; ST. HELIER; JERSEY,4DB9C985130761D008F686D5FE9800F4,The Panama Papers data is current through 2015,JEY,Jersey,14049423,Panama Papers
Malzarn House; 15 Union Street; St Helier; Jersey,2B6C27C56975AFC3D31E7B953F84FDA9,The Panama Papers data is current through 2015,JEY,Jersey,14049424,Panama Papers
Mamiao Village; Lilaojiaxiang Country; Yucheng Town; Henan Province; China,623D33B0CE8C8EF6088E48A1EC05A3B2,The Panama Papers data is current through 2015,CHN,China,14049425,Panama Papers
Mammad Rahim 20; AZ1073 Baku; Azerbaijan,E61FDF1847BFC8991B093408E58758FC,The Panama Papers data is current through 2015,AZE,Azerbaijan,14049426,Panama Papers
MANAGEMENT LTD.; 60 Market Square; Belize City; Belize,C637C6320639A87DBFC6A29CB01A6177,The Panama Papers data is current through 2015,BLZ,Belize,14049427,Panama Papers
Manager; Business Relationship; Dubai Branch; Dubai UAE,C412C56B62E3F2CF15267E1170749442,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049428,Panama Papers
Managua 2222 Depto.221; Ñuñoa; Santiago; Chile,006CF52659EC5BEF2201192D42FD0B45,The Panama Papers data is current through 2015,CHL,Chile,14049429,Panama Papers
“Man A Hing Jerrystraat #23 Paramaribo, Suriname”,80E68A24EF61CE20ECDF71B2D445F3B9,The Panama Papers data is current through 2015,SUR,Suriname,14049430,Panama Papers
“Manama, Bahrain”,3B2854026332000B9D93881C7A8C6BBB,The Panama Papers data is current through 2015,BHR,Bahrain,14049431,Panama Papers
“MANASTIGUR 60, 220 HAFNARFJORDUR”,625DB3B1955CB865C042A47E5275E35C,The Panama Papers data is current through 2015,ISL,Iceland,14049432,Panama Papers
Manastigur 6; Hafnarfjordur 220; Iceland,B12D9F3932DAD9FCB95DC9B1998C78D7,The Panama Papers data is current through 2015,ISL,Iceland,14049433,Panama Papers
Manavgat R2 Blok; D. 20; Bahcesehir; Istanbul – Turkey,D3F03BBE8AD2E0A40A18088CABE601F9,The Panama Papers data is current through 2015,TUR,Turkey,14049434,Panama Papers
Manawi Basha; Basra; Iraq,FC2A2479A5A585CD19E7900B954880D3,The Panama Papers data is current through 2015,IRQ,Iraq,14049435,Panama Papers
Manazil Tower No. 2; Flat No. 2003 Al Taawoun Area; Al Taawoun Road; Sharjah United Arab Emirates,3CA90E44FB20BF7B011E1F20E19C39AF,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049436,Panama Papers
“Manchester, UK”,E1ECDC152C4C0D9A5B761D4B6D85EF52,The Panama Papers data is current through 2015,GBR,United Kingdom,14049437,Panama Papers
Manderley; Lower S Park; South Godstone; RH9 8LF; England,F6C1754455830AEFFEF31FF9D216990C,The Panama Papers data is current through 2015,GBR,United Kingdom,14049438,Panama Papers
“Mandlgasse 5, A-5200 Salzburg”,2AC3BFC6AA9450915BA3FFF22E989E2F,The Panama Papers data is current through 2015,AUT,Austria,14049439,Panama Papers
Mandolingrand 2 SE-332 31 Gislaved Sweden,4C1EFA084F1FE728C15E70283F0DF0DB,The Panama Papers data is current through 2015,SWE,Sweden,14049440,Panama Papers
Manduva Shanti 33A West Coast Park; #06-40; Singapore-127727,38E8A26D9CA706570585316C3E3A7C07,The Panama Papers data is current through 2015,SGP,Singapore,14049441,Panama Papers
Manerba de Garda Corso Europa Italy,C5DA8DC6C599BA4D8E739EF8A55D67B3,The Panama Papers data is current through 2015,ITA,Italy,14049442,Panama Papers
Manfield House; 1 Southampton Street; London WC2R 0LR,6AB40923EA7772B4F44754345976C81E,The Panama Papers data is current through 2015,GBR,United Kingdom,14049443,Panama Papers
MANFIELD HOUSE; 2ND FLOOR; 1 SOUTHAMPTON STREET; LONDON; UNITED KINGDOM; WC2R 0LR,84ED9F915AD4E5E626CD11DEAA79813B,The Panama Papers data is current through 2015,GBR,United Kingdom,14049444,Panama Papers
MANGGA BESAR; BLK 4E – 26 JAKARTA; INDONESIA,DF5422FE046B8530685CD25181EF57B7,The Panama Papers data is current through 2015,IDN,Indonesia,14049445,Panama Papers
Mangga Dua Court Apartment Unit W 1501; Jakarta Pusat; Indonesia,DB7EEECDB708B74BF92572008C9D8E23,The Panama Papers data is current through 2015,IDN,Indonesia,14049446,Panama Papers
Mangga Dua Plaza; Blok E15; Haroo Mangga Dua; Jakarta 10730; Indonesia,754D07590C0A66CA5A6D0CB46050CC55,The Panama Papers data is current through 2015,IDN,Indonesia,14049447,Panama Papers
MANGROVE VILLAGE; VILLA 4141; 4 ABU DHABI; UAE,277662B3B4776A427EB83679D88E3DDD,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049448,Panama Papers
MANIS 3; GERMASOGEIA; P.C. 4044; LIMASSOL; CYPRUS,AADC173E94A13B4C17EA29CC103FEC39,The Panama Papers data is current through 2015,CYP,Cyprus,14049449,Panama Papers
Manor Farm House; Manor Park Road; La Pouquelaye; St. Helier; JE2 3J,B08C1B36F2F5A566319180E446AB1F21,The Panama Papers data is current through 2015,JEY,Jersey,14049450,Panama Papers
“Manor Lawn 15 Norman Place altrincham Cheshire, WA142AB”,6A8FDB83EB22FC37A2A221B63567A2AF,The Panama Papers data is current through 2015,GBR,United Kingdom,14049451,Panama Papers
MANOR PARK; MANOR HOUSE LANE; LEEDS; LS17 93D; UK,9B3FBC6D490C1C9F346B9A92C25763B1,The Panama Papers data is current through 2015,GBR,United Kingdom,14049452,Panama Papers
Manpower Inc. 100 Manpower Place; Milwaukee; Wisconsin United States; 53212,E921B864271312B8E213EC6A9DA30C6C,The Panama Papers data is current through 2015,USA,United States,14049453,Panama Papers
Mansell House; 9-11 Mansell Street; St. Peter Port; Guernsey,29F79F8EC3CBB0ED43E90A2ECF0EA29A,The Panama Papers data is current through 2015,GGY,Guernsey,14049454,Panama Papers
Mansion of Talent Resources Market; Baoan Northern Rd; Luohu District; Shenzhen; Guangdong; China,70443C8EE5F76959C138AB3EF4FC30FC,The Panama Papers data is current through 2015,CHN,China,14049455,Panama Papers
Manson House; 143 Main Street; Gibbraltar,1AE1E6E9B1D72FC69EB215F7276CE7D6,The Panama Papers data is current through 2015,GIB,Gibraltar,14049456,Panama Papers
Manston; Ramsey Road; Laxey IM4 7PT; Isle of Man,335A3F4C0D4501A98FF4EE66DCD9196C,The Panama Papers data is current through 2015,IMN,Isle of Man,14049457,Panama Papers
Mantua 6681 /Montevideo – Uruguay,AB7045F54B67677CEAD8DBF78A31844E,The Panama Papers data is current through 2015,URY,Uruguay,14049458,Panama Papers
Mantua 6842 11500 Montevideo,E2B8544829302E8A282C050539380241,The Panama Papers data is current through 2015,URY,Uruguay,14049459,Panama Papers
Mantua 6842; Montevideo; Uruguay.,730431D54AA22209C8950996B9D6A9DA,The Panama Papers data is current through 2015,URY,Uruguay,14049460,Panama Papers
Mantua 6883; Montevideo; Uruguay,3E4201ADBCE0B824C913D362088DBEDE,The Panama Papers data is current through 2015,URY,Uruguay,14049461,Panama Papers
Manuel Ambrosi E6-178 y Av. Eloy Alfaro; Quito; Ecuador,2B75B8DF73E6272F508BEB7C91E6BE65,The Panama Papers data is current through 2015,ECU,Ecuador,14049462,Panama Papers
Manuela Sáenz N35-122 y Hernández de Girón. Quito-Ecuador,34B18B6D14663DB30168F1002085CBBD,The Panama Papers data is current through 2015,ECU,Ecuador,14049463,Panama Papers
Manuel Borreo E17-150 y Abel Gilbert. Quito-Ecuador,3E7AC6B72A0B2DD4C836A4BFA5299DB6,The Panama Papers data is current through 2015,ECU,Ecuador,14049464,Panama Papers
Manuel Fernandez; Apartado De Correro #4. Apartado Postal 33560; Ribadesella; Asturias; Spain,F30970EBBF0C3F110DB1642218059968,The Panama Papers data is current through 2015,ESP,Spain,14049465,Panama Papers
Manuel Fuentes 530; San Isidro; Lima; Perú,7D3B43CE5695DDD6C68B47BD0CBB4DD1,The Panama Papers data is current through 2015,PER,Peru,14049466,Panama Papers
Manuel Gonzales de la Rosa 228; San Isidro; Peru,425CD48393D8A191CD77ACB1DD0B1918,The Panama Papers data is current through 2015,PER,Peru,14049467,Panama Papers
Manuel J calle 2-100 y Cornelio Merchan Edif. Vitefama; 3er piso Cuenca; Ecuador,6A4997D58EFFA70A3C0B8B87FD642CEB,The Panama Papers data is current through 2015,ECU,Ecuador,14049468,Panama Papers
Manuel María Izaga No.765-of 303-Chiclayo-Lambayeque-Perú,A52FC3FE8DDA56C6000DAFE3C54D6CED,The Panama Papers data is current through 2015,PER,Peru,14049469,Panama Papers
Manuel Montt 2461; Depto.801 Torre A; Ñuñoa Santiago; Chile,ECD28966664C659C11D072A979EA40B1,The Panama Papers data is current through 2015,CHL,Chile,14049470,Panama Papers
Manuel Olguin 373; dpto. 501; Surco; Lima; Peru,A806B4BB43FC80950219149951628E76,The Panama Papers data is current through 2015,PER,Peru,14049471,Panama Papers
Manuel Tovar 540- Int. 203 – Urb.Sta.Cruz- Miraflores-Lima-Perú,056AE95D18A799F2639228A5024E6E6C,The Panama Papers data is current through 2015,PER,Peru,14049472,Panama Papers
Manuel Ugarte 2158; Piso 9 Departamento C; Buenos Aires; Argentina (C1428BSF),98E37AA424C3963EBEEEEF5651E559A0,The Panama Papers data is current through 2015,ARG,Argentina,14049473,Panama Papers
Manuel V. Pagola 3003-Montevideo – Uruguay,5A6753A26620AB999A631AE8450F7C9C,The Panama Papers data is current through 2015,URY,Uruguay,14049474,Panama Papers
Manuel V. Pagola 3003 – Montevideo – Uruguay,62871442487898F7E170CE45C95D9EF9,The Panama Papers data is current through 2015,URY,Uruguay,14049475,Panama Papers
Manu Smruti; Opp Mental Hospital Karelibaug Baroda Gujarat; India,C29201ED92DD730487857F12B3F16FAB,The Panama Papers data is current through 2015,IND,India,14049476,Panama Papers
MANXINGBING YIYUAN; BUXIN LU; SHENZHEN; GUANGDONG; CHINA,56C0F8F24E25B6FCD6147CE8E58BB7DC,The Panama Papers data is current through 2015,CHN,China,14049477,Panama Papers
Manzana “B” Casa #20; Plazuela EI Conquistador. Antigua; Guatemala. Guatemala Centro America,C35E928272F46A6C30DB25E2110D34DC,The Panama Papers data is current through 2015,GTM,Guatemala,14049478,Panama Papers
Manzana E-1; Lote 1; Urb. El Silencio; Playa Señoritas; Lima 24; Perú,1C22D7A5D32DBC9339E82B2867B3C778,The Panama Papers data is current through 2015,PER,Peru,14049479,Panama Papers
Manzana M Lote 1D – Las Vertientes Tablada de Lurín- Villa El Salvador – Lima- Perú,0C3BF8F220F8A597797D65492A88EB8F,The Panama Papers data is current through 2015,PER,Peru,14049480,Panama Papers
Manzana M Lote 1D – Urb.Las Vertientes Tablada de Lurín- Villa El Salvador -Lima- Perú,5522A41823149C87A77D704D0163E2F6,The Panama Papers data is current through 2015,PER,Peru,14049481,Panama Papers
Manzana M Lote 1D – Urb.Las Vertientes Tablada de Lurín- Villa El Salvador – Lima- Perú,024BD4A8950336916C359F612A77D85E,The Panama Papers data is current through 2015,PER,Peru,14049482,Panama Papers
MANZANARES OESTE; EDIFICIO RESIDENCIAS CASA GRANDE; PISO 12; APTO 123A. MANZANARES. CARACAS-VENEZUELA,28118413D4C2EE88FF87A26B500ABC38,The Panama Papers data is current through 2015,VEN,”Venezuela, Bolivarian Republic of”,14049483,Panama Papers
“Mapasingue Este Calle 5TA y Av Las Aguas Guayaquil, Ecuador.”,B5B2671B2526C9ADCD4361FEAD794EF2,The Panama Papers data is current through 2015,ECU,Ecuador,14049484,Panama Papers
Maple Lawn; Beaulieu Road; Lyndhurst; SO43 7DA,6F470E1B3005F916C1C5E84C9E93B071,The Panama Papers data is current through 2015,GBR,United Kingdom,14049485,Panama Papers
(MAPLES & CALDER INTERNATIONAL TRUST BUILDING; P.O. BOX 309; GEORGE TOWN; GRAND CAYMAN; CAYMAN ISLANDS),C37D5C7205B7865D2837C22C0670ABAA,The Panama Papers data is current through 2015,CYM,Cayman Islands,14049486,Panama Papers
MAPLES & CALDER; P.O. BOX 309 UGLAND HOUSE; SOUTH CHURCH ST; GRAND CAYMAN; CAYMAN ISLANDS.,116EFF66EB2AAF15DE3F487090AC3828,The Panama Papers data is current through 2015,CYM,Cayman Islands,14049487,Panama Papers
MAPLES AND CALDER; ATTORNEYS-AT-LAW; UGLAND HOUSE; PO BOX 309; GEORGE TOWN; GRAND CAYMAN; CAYMAN ISLANDS; BRITISH WEST INDIES,7B543446BDA78A50D7FA42C8F75CF797,The Panama Papers data is current through 2015,CYM,Cayman Islands,14049488,Panama Papers
“Maples Corporate Services Limited (“”MCS””); PO Box 309; Ugland House; Grand Cayman; KY1-1104; Cayman Islands”,8CF34B3B3426490475515925B4E60D4D,The Panama Papers data is current through 2015,CYM,Cayman Islands,14049489,Panama Papers
MAPLES CORPORATE SERVICES LIMITED (MCS); PO BOX 309; UGLAND HOUSE; GRAND CAYMAN; KY1-1104; CAYMAN ISLANDS,19085F8FD0C4BF188BD005F31B3800EA,The Panama Papers data is current through 2015,CYM,Cayman Islands,14049490,Panama Papers
Maples Corporate Services Limited; PO Box 309; Ugland House; Grand Cayman; KY1-1104; Cayman Islands,771FDBE73037DE70407506CC5EDA6478,The Panama Papers data is current through 2015,CYM,Cayman Islands,14049491,Panama Papers
Maplese Corporate Services Limited,C33F7BD2C2F7465F8137A9EC007A7D59,The Panama Papers data is current through 2015,CHN,China,14049492,Panama Papers
MAPLES FINANCE BVI LTD; SEA MEADOW HOUSE; P.O. BOX 173; ROAD TOWN; TORTOLA; BVI,990E029CE00EDDAD4B1B1E80BC100F29,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14049493,Panama Papers
Mapstone 50 Shillingford Road Doornkloof 391 Centurion Pretoria South Africa,D2ABD6A1558198DB31DA881826D03040,The Panama Papers data is current through 2015,ZAF,South Africa,14049494,Panama Papers
Mapstown; Dungarvan; Co Waterford,314D7C0ABC09D05E66F232F297D32AA6,The Panama Papers data is current through 2015,IRL,Ireland,14049495,Panama Papers
Marañon 162; Santa Luisa; La Perla; Callao; Perú,4D775C81289ED621C5C52ADF9318E959,The Panama Papers data is current through 2015,PER,Peru,14049496,Panama Papers
Mar Artico 1234 Apto. 101; 11400; Montevideo; Uruguay,709909AFCB723E9F74ADAB2E714A11F3,The Panama Papers data is current through 2015,URY,Uruguay,14049497,Panama Papers
Mar Artico 1245; Montevideo; Uruguay,3B68C4B107F8DDDD86BEB156EE3B279A,The Panama Papers data is current through 2015,URY,Uruguay,14049498,Panama Papers
MARASOVICA 7; 21000 SPLIT; CROATIA,1951F4F4CF2FAF5E8ED23A3F2239C02C,The Panama Papers data is current through 2015,HRV,Croatia,14049499,Panama Papers
MA. Raufathuge; Male 20-02; Republic of Maldives,3281BE3D0CFC3557F3510B28974996C2,The Panama Papers data is current through 2015,MDV,Maldives,14049500,Panama Papers
MAR AZUL; 600 GRAPETREE DRIVE; Apt. 8FS; KEY BISCAYNE; 33149 FLORIDA; USA,06DD99CA058C20D2C28D7E9DFD9F8EF7,The Panama Papers data is current through 2015,USA,United States,14049501,Panama Papers
Marbella; 54 East Street; #3A; City of Panama; Republic of Panama,710B67CD9F0A4A236CDE41AE5BBFBFB4,The Panama Papers data is current through 2015,PAN,Panama,14049502,Panama Papers
Marbella; 54th East Street #3A; City of Panama; Republic of Panama,6CF0C89C8657E54BF687517B300DE008,The Panama Papers data is current through 2015,PAN,Panama,14049503,Panama Papers
Marbella; 54th East Street; #3A; Panama; Rep. of Panama,80FB5B0D727135AB0F416FD4AC2BB70E,The Panama Papers data is current through 2015,PAN,Panama,14049504,Panama Papers
Marbella; 54th East Street; #3A; Panama; Republic of Panama.,7F2B69E5E4103890289B058CB7CE4A97,The Panama Papers data is current through 2015,PAN,Panama,14049505,Panama Papers
Marbella; 54th East Street; Panama City; Republic of Panama,1C2CB9A4EC28098517978A1FA05B0AF1,The Panama Papers data is current through 2015,PAN,Panama,14049506,Panama Papers
Marbella; 54th East Street; Panama; Republic of Panama.,0861AABFA5A126D76D2A509513C29276,The Panama Papers data is current through 2015,PAN,Panama,14049507,Panama Papers
MARBELLA; 54th E. STREET; CITY OF PANAMA; REPUBLIC OF PANAMA,ADF040972815E3928C1B699502495630,The Panama Papers data is current through 2015,PAN,Panama,14049508,Panama Papers
Marbella; 54th E. Street; Panama; Republic of Panama,04CC6172FFBACAD70BD423202E7294D5,The Panama Papers data is current through 2015,PAN,Panama,14049509,Panama Papers
Marbella 54th Street # 3A; City of Panama; Republic of Panama,00DDC0C07FA20475A12FDA798D0DD083,The Panama Papers data is current through 2015,PAN,Panama,14049510,Panama Papers
Marbella; Ave. Balboa; Edificio Bahia Balboa; Mezanine; Ciudad de Panama; Republic of Panama,8B069FBB22E5BA8327ED704208DE9C41,The Panama Papers data is current through 2015,PAN,Panama,14049511,Panama Papers
Marbella Calle 53 MMG Tower Piso 16; Cuidad de Panamá; Repíblica de Panamá,B0902D89D7A20641ECAB03D4DEA8D4C8,The Panama Papers data is current through 2015,PAN,Panama,14049512,Panama Papers
Marbella; Calle 54 Este #3ª; Ciudad de Panamá; República de Panamá,F6D644F0C747CD2A726C936E6FE7CF13,The Panama Papers data is current through 2015,PAN,Panama,14049513,Panama Papers
Marbella; Calle 54 Este #3A; Ciudad de Panamá; República de Panamá,9CF2D0C32CF739C120EC802C071B2B09,The Panama Papers data is current through 2015,PAN,Panama,14049514,Panama Papers
Marbella Calle 54 Este #3A; Cuidad de Panamá; República de Panamá,0361037CB11A9B0CD3CFBB4E28AF448C,The Panama Papers data is current through 2015,PAN,Panama,14049515,Panama Papers
Marbella; Calle 54 Este; 3a; Ciudad de Panamá; Panamá.,131E5D94EF3F354C7F4EBE20CABE1995,The Panama Papers data is current through 2015,PAN,Panama,14049516,Panama Papers
MARBELLA; CALLE 54 ESTE; 3A; CIUDAD DE PANAMA; REPUBLICA DE PANAMA,2B82DA73336C8ABB63DA3A18CA435F01,The Panama Papers data is current through 2015,PAN,Panama,14049517,Panama Papers
MARBELLA; CALLE 54; ESTE 3A; PANAMA; REPUBLIC OF PANAMA,4D24C0BF774F1686237DE2507751312B,The Panama Papers data is current through 2015,PAN,Panama,14049518,Panama Papers
MARBELLA CALLE 54 ESTE PANAMA REP DE PANAMA,35BCD7BF9EDA6946D00486679ACFA190,The Panama Papers data is current through 2015,PAN,Panama,14049519,Panama Papers
Marbella; Condominio Marbella Tower I; apartamento 18-B; Ciudad de Panamá; República de Panamá,218FBA349E31253A2DC0968D222EA15A,The Panama Papers data is current through 2015,PAN,Panama,14049520,Panama Papers
Marbella; East 54th St.; #3A; Panama City; Republic of Panama,A04C4E936DA789D5451E8B2FA5E83E1F,The Panama Papers data is current through 2015,PAN,Panama,14049521,Panama Papers
Marbella; East 54th Street; Panama; Republic of Panama,714C6E612815B083781BFD05C53AB638,The Panama Papers data is current through 2015,PAN,Panama,14049522,Panama Papers
Marbella; Edificio Rio Mar; Apto. 5; Panama; Republic of Panama,9E28BC6916610597D9038CAAFCD4A1CC,The Panama Papers data is current through 2015,PAN,Panama,14049523,Panama Papers
“Marborough & Queens Street, P.O. Box N-10429”,747D8210BA25F6959423AA74F3A5EBA1,The Panama Papers data is current through 2015,,,14049524,Panama Papers
“Marcelino Onieva 1046 c/ Tte. Velázquez, Asunción – Paraguay”,5FBE653D7888B4CEFAD1DD0D36B6B753,The Panama Papers data is current through 2015,PRY,Paraguay,14049525,Panama Papers
Marclo Aurelio 20; Barcelona; SPAIN,9AAA2E40585AF1DC38F556A5BCF5113F,The Panama Papers data is current through 2015,ESP,Spain,14049526,Panama Papers
Marco and Moira Ricco; 1 Fynbos Street; Hermanus Heights; Hermianus; South Africa 7200,E603A2D65B32F09638AB9584C595B53F,The Panama Papers data is current through 2015,ZAF,South Africa,14049527,Panama Papers
Marco Aurelio Street 3862; 36 AP. A401; Montevideo; Uruguay,C9FFDBE78381CF8CC3CB0894432DF6E7,The Panama Papers data is current through 2015,URY,Uruguay,14049528,Panama Papers
MARCO BRUTO; 1005; MONTEVIDEO; URUGUAY,AF336B908719C814468184F91116560A,The Panama Papers data is current through 2015,URY,Uruguay,14049529,Panama Papers
“Marco Bruto 1062, ap 002 Montevideo – Uruguay”,1203BCAB47C774BB5FEA3411EF69B63D,The Panama Papers data is current through 2015,URY,Uruguay,14049530,Panama Papers
“MARCO BRUTO 1125 CP 11300-Montevideo, Uruguay”,AA0C71D39B3A6EFADF5DBDD9AF8AE885,The Panama Papers data is current through 2015,URY,Uruguay,14049531,Panama Papers
Marco Bruto 1144 A,AC659E22BB4259EC2656DFCA11A762CE,The Panama Papers data is current through 2015,URY,Uruguay,14049532,Panama Papers
MARCO BRUTO; 1144 A; 11300 MONTEVIDEO; URUGUAY,19625939EE8D5C1D7B5944A754206E48,The Panama Papers data is current through 2015,URY,Uruguay,14049533,Panama Papers
“Marco Bruto 1144 A, Montevideo (11300) Uruguay”,9C08155EF848F9D9FFABD3B394009182,The Panama Papers data is current through 2015,URY,Uruguay,14049534,Panama Papers
Marco Bruto 1144 A; Montevideo; CP 11300; Uruguay,7A2B4AC7F0FEF69ECCCE259F27AC279F,The Panama Papers data is current through 2015,URY,Uruguay,14049535,Panama Papers
“Marco Bruto 1144A Montevideo, Uruguay”,EE99E4BAEA43BE004C65347803BBE28A,The Panama Papers data is current through 2015,URY,Uruguay,14049536,Panama Papers
Marco Bruto 1144 A; Montevideo; Uruguay; CP 11300,E289517D3250616266876CFE06FB2E1E,The Panama Papers data is current through 2015,URY,Uruguay,14049537,Panama Papers
“MARCO BRUTO 144A , MONTEVIDEO (11300) URUGUAY”,0D96F857C815D652AD67E820BD3BD581,The Panama Papers data is current through 2015,URY,Uruguay,14049538,Panama Papers
Marconi 165-San Isidro-Lima-Perú,C48A80DF2632631F20D197FFDC09913A,The Panama Papers data is current through 2015,PER,Peru,14049539,Panama Papers
“Marcos Riglos 520 (C1424AFL) Buenos Aires, Argentina.”,75D1F72CBE29A0227DC996C116C0698D,The Panama Papers data is current through 2015,ARG,Argentina,14049540,Panama Papers
MARCY BUILDING / 2ND FLOOR PURCELL ESTATE ROAD TOWN TORTOLA BVI,A672D99E945A2A42F477DD594D4B3747,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14049541,Panama Papers
Marcy Building; 2nd Floor; Purcell Estate; P.O. Box 2416; Road Town; Tortola; British Virgin Islands,A5F349538B41CE8F7119B12F7BA29DA2,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14049542,Panama Papers
Marcy Building; 2nd Floor; Purcell Estate; Road Town; Tortola; BVI,C4A304B94A4312A3390ED59A43DD388C,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14049543,Panama Papers
Marcy Building; Purcelle Estate PO BX 2416; Tortola (BVI),B332DF4EBADAD10D9553863621411A5F,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14049544,Panama Papers
Mar de Java 148; Urb. Neptuno; Santiago de Surco; Lima; Perú,73ECC4E1C8EB47238D708A787764BB49,The Panama Papers data is current through 2015,PER,Peru,14049545,Panama Papers
MAR DEL PLATA; CALLE ALTE BROWN 2376; BUENOS AIRES ARGENTINA,3EF0C55B58C6F51A1F6F85E493B5FE76,The Panama Papers data is current through 2015,ARG,Argentina,14049546,Panama Papers
Mar del Sur; Torre I; Apto. 9-C; San Francisco; Ciudad de Panamá,EB975C1999E4A5559B175FFF44691BF5,The Panama Papers data is current through 2015,PAN,Panama,14049547,Panama Papers
Mare Anglaise; Mahe; Seychelles.,D6C9264763A2D1D294DD8B98FC979D26,The Panama Papers data is current through 2015,SYC,Seychelles,14049548,Panama Papers
Marechal Koutouzov Str. 6; Corp. 1; apt 47; MOSCOW; RUSSIA,04355C46060C9E8C0377A19F8DF87FCE,The Panama Papers data is current through 2015,RUS,Russian Federation,14049549,Panama Papers
Marechal Zakharov Street; 18 – Pt 280; Moscow; RUSSIA,E477FF2FAC2817D86A3366F200B2C436,The Panama Papers data is current through 2015,RUS,Russian Federation,14049550,Panama Papers
Mareva House; 4 George Street; Nassau; Bahamas,A784582388E3A2FE064B2414F3041903,The Panama Papers data is current through 2015,BHS,Bahamas,14049551,Panama Papers
Marfa’a 1202; Uruguay St.; Mecattaf Building; 2nd Floor PO Box 11-1982 Riad El Solh; Beirut; Lebanon.,7A178780CA8AA44B3C184881D8D1E8CB,The Panama Papers data is current through 2015,LBN,Lebanon,14049552,Panama Papers
MARFA’A 1202; URUGUAY ST. MECATTAF BUILDING; 2ND FLOOR; RIAD EL SOLH; BEYROUTH; LEBANON,7E890ED8ACAC641E513C0E872B868566,The Panama Papers data is current through 2015,LBN,Lebanon,14049553,Panama Papers
Marfa’a 1202; Uruguay Street; Mecattaf Building; 2nd Floor; Beirut Central District; Beirut; LEBANON,2846FDBC6492450A77C0575F6EDE8F3F,The Panama Papers data is current through 2015,LBN,Lebanon,14049554,Panama Papers
Margaretha van Oostenrijklaan # 32 2353 EN Leiderdorp The Netherlands,643287A7A0EE2D5257E0A166A7CE7C0F,The Panama Papers data is current through 2015,NLD,Netherlands,14049555,Panama Papers
Margaret Kadagwe Residence; Admarc HQ; P.O. Box 5052; Limbe; Malawi,31F90BAF8C499EDD7B536ECF167FCBCA,The Panama Papers data is current through 2015,MWI,Malawi,14049556,Panama Papers
Marga von Etzdorf Weg 13 D- 71034 Böblingen Flugfeld,ABDFAA669C0AE60A26D3463EC5E43851,The Panama Papers data is current through 2015,DEU,Germany,14049557,Panama Papers
MARGOREJO INDAH; C 207-208 SURABAYA; INDONESIA,B048F0B1266FB09EAED4D2F21DEABB7F,The Panama Papers data is current through 2015,IDN,Indonesia,14049558,Panama Papers
“Margot Appartments A01, Jl Haji Batong Raya No. 4 Cilandak Barat Jakarta Indonesia”,E40FC20AD8D5403E5C157FFECBB7B3FC,The Panama Papers data is current through 2015,IDN,Indonesia,14049559,Panama Papers
Margrethe Alle6; 2950 Vedback; Denmark,7D77A38C23B5E796881334CFE89787FE,The Panama Papers data is current through 2015,DNK,Denmark,14049560,Panama Papers
Maria Burgman Rua Cahora Bassa 98 Maputo Mozambique,C5FE106A4C79F0A2F57A7D16FF2AC777,The Panama Papers data is current through 2015,MOZ,Mozambique,14049561,Panama Papers
Maria House; 8 Samou Street; St. Omologites; 1086 Nicosia,F8144A9CDCFB41B5079FFB944E81EF03,The Panama Papers data is current through 2015,CYP,Cyprus,14049562,Panama Papers
“Mariamen Temple Road, Cap”,A38896E96A760C79490162734653ECB1,The Panama Papers data is current through 2015,MUS,Mauritius,14049563,Panama Papers
Mariamen Temple; Road; Cap Malheureux; Mauritius,9880362F35E1F24FB6B0FD0C91F1F848,The Panama Papers data is current through 2015,MUS,Mauritius,14049564,Panama Papers
Mariamen Temple Road; Pave Cap Malheureux; Republic of Mauritius,B4C9EA2A49BAA314555DE1E8B5F12B97,The Panama Papers data is current through 2015,MUS,Mauritius,14049565,Panama Papers
“MARIA MOKOLOMBAN 357 OPIHIKAO PL HONOLULU HI 96825, USA”,C9FC28123A52ED8A0D78CE56F8BF0638,The Panama Papers data is current through 2015,USA,United States,14049566,Panama Papers
Mariano Odisio 432-Miraflores-Lima-Perú,082413A27546CD3905CC11ED67D3E3F7,The Panama Papers data is current through 2015,PER,Peru,14049567,Panama Papers
MARIANO SOLER 3332 DE MONTEVIDEO URUGUAY,6B5F8767769834B3FBC63CEEDD9A6371,The Panama Papers data is current through 2015,URY,Uruguay,14049568,Panama Papers
Mariano Uriarte 6578,E549D6B6FA357C43F6338843C677F43C,The Panama Papers data is current through 2015,,,14049569,Panama Papers
MARIE EDDE ST. AREEJ 2000 BLDG BEIRUT LEBANON,E9DAA4CBDF3022060532846ACD3EB0C4,The Panama Papers data is current through 2015,LBN,Lebanon,14049570,Panama Papers
MARIE EDDE ST. AREJ 2000 BLDG BEIRUT LEBANON,80EB4004D3F4BD40EDA52858CCFD3F1F,The Panama Papers data is current through 2015,LBN,Lebanon,14049571,Panama Papers
Mariehallsvagen 17C; 2544; 50 Helsingborg; Sweden,9A74E88BDB4244F08D92E131851E3D77,The Panama Papers data is current through 2015,SWE,Sweden,14049572,Panama Papers
Marie Kuderikove 3492/5; Brno 636 00; Czech Republic,AF025DDB3D42D4BCAB49065B532B63A7,The Panama Papers data is current through 2015,CZE,Czech Republic,14049573,Panama Papers
MARIENUBIC SHAURIN LANE; ROSE BELLE; MAURITIUS,45AFEA8E959A170B2F8A03AE6B718C07,The Panama Papers data is current through 2015,MUS,Mauritius,14049574,Panama Papers
MARIERUBIC SHAURIN LANE; ROSE BELLE; MAURITIUS,7B3401FD8D9491B21ADF246F4D215E99,The Panama Papers data is current through 2015,MUS,Mauritius,14049575,Panama Papers
MARIERUBIC SHAURIN LANE ROSE BELLE; ROSE BELLE; MAURITIUS,49D8E21A5C2766FABF20120C4B8D641C,The Panama Papers data is current through 2015,MUS,Mauritius,14049576,Panama Papers
“Marii Ulianovoy Street 21 Korp.2 Apt 55, Moscow Russia”,BAE37B11845DDF2F9D5A210B216B2848,The Panama Papers data is current through 2015,RUS,Russian Federation,14049577,Panama Papers
Marina AL Hamra Village; Building MD – 701; Ras Al Khaimah; UAE,3EAC2367927B36343E752B0F39CF4F5B,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049578,Panama Papers
Marina – North Abhur 1 Jeddah 21481 Kingdom of Saudi Arabia,FF3F59C425A859F0E353352858339AC1,The Panama Papers data is current through 2015,SAU,Saudi Arabia,14049579,Panama Papers
Marina Office Park Compound; Villa # A02; PO Box 47800; Abu Dhabi; U.A.E,8196D17DB36991D7BE8A4EFF6FF979B0,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049580,Panama Papers
Marina Promenad; Atessa #1502 Dubai; U.A.E.,8A4D15F01BD26A8E288184563CA1F7E4,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049581,Panama Papers
“Marina Promenade Beauport Apt 1302 P.O. Box 8203 Dubai Marina, U.A.E.”,603D794C5E8623206E604D3AA1FF846F,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049582,Panama Papers
“Marina Promenade Beauport Apt. 1302 P.O. Box 8203 Dubai Marina, United Arab Emirates”,2ED7C663BB2658BADEAA314D3777CCA4,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049583,Panama Papers
Marina Promenade Delphine 1202; Sheikh Zayed Road; Duabi UAE,C843E0A7ED613EDBFB3C8AE253C3F9D7,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049584,Panama Papers
“Marina Residence – Tower A FLAT A – 1001 Dubai Marina Dubai, UAE”,7FE7796643F1332C96B26F6BE0FC7030,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049585,Panama Papers
Marinascape; Avant Tower; Unit 1003; Dubai Marina; Dubai; United Arab Emirates,1C61A2CEFB1288455624BA5079C9FA88,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049586,Panama Papers
Marina Towers; Suite 302; Newton Barracks; Belize City; Belize,8113C3DF2D06C80A1990F0A26EED5976,The Panama Papers data is current through 2015,BLZ,Belize,14049587,Panama Papers
Marina Towers; Suite 303; Newtown Barracks; Belize City; Belize,8E78F0B5A9EC88529862F9F4D75E60A5,The Panama Papers data is current through 2015,BLZ,Belize,14049588,Panama Papers
Marine Parade Road; P.O. Box 0632; Singapore 914405,05B67F0AC2079B894494890FD0AB670E,The Panama Papers data is current through 2015,SGP,Singapore,14049589,Panama Papers
Mariner House; London; EC3N 4DA; UK,333A4C569ADE8C399A2202E030AD5653,The Panama Papers data is current through 2015,GBR,United Kingdom,14049590,Panama Papers
Mariner House; Pepys Street; London EC3N 4DA,3A4154BB08D815F5631547C7B0C82B1A,The Panama Papers data is current through 2015,GBR,United Kingdom,14049591,Panama Papers
MARINERS COVE; 70/29 BENELONG ROAD; HOMEBUSH BAY; SYDNEY; NSW; AUSTRALIA 2127,E2C541861F17AF63C238DEE464541D98,The Panama Papers data is current through 2015,AUS,Australia,14049592,Panama Papers
MARINO; LE CLOS DE LA MARE; LA RUE DE MAUPERTUIS; ST CLEMENT; JERSEY JE2 6NH,F960A045CE446242579FCA39532B1A01,The Panama Papers data is current through 2015,JEY,Jersey,14049593,Panama Papers
Marinou Geroulanou 82; Kato Polemidia; 4153 Limassol; Cyprus,C810AECF6D5FA672ECDEDCAABE3B3EAB,The Panama Papers data is current through 2015,CYP,Cyprus,14049594,Panama Papers
Mariscal Blas Cerdeña 337-dpto.101-San Isidro-Lima-Perú,746317CEC0FEFD83DCCF132095650698,The Panama Papers data is current through 2015,PER,Peru,14049595,Panama Papers
Mariscal Blas Heredia 337; depto. 101; San Isidro; Lima – Perú,8822A7A8186A3AE83187F071954CCB93,The Panama Papers data is current through 2015,PER,Peru,14049596,Panama Papers
Mariscal Castilla 394; Dpto. 402; Aurora; Miraflores; Lima; Perú,88DF0B9FC651F2EC22C25EE552276A20,The Panama Papers data is current through 2015,PER,Peru,14049597,Panama Papers
MARISCAL SUCRE 198; MIRAFLORES; LIMA 18- PERU,B45F4F62EA9B96106391471080C1F301,The Panama Papers data is current through 2015,PER,Peru,14049598,Panama Papers
MARISCAL SUCRE Y JHON F. KENEDY (C.C. CONDADO); QUITO; ECUADOR,E6036CBE6745DC57503625A26A14E054,The Panama Papers data is current through 2015,ECU,Ecuador,14049599,Panama Papers
Maritzdaal Farm Dargle South Africa,EB3E7017DDA4975124323A751C476488,The Panama Papers data is current through 2015,ZAF,South Africa,14049600,Panama Papers
Marka Shamaliah; Ben Roshd Street; Building 77; Apartment 202 Amman; Jordan,363D9A1636E592C01CB0849ED1B6AECD,The Panama Papers data is current through 2015,JOR,Jordan,14049601,Panama Papers
Market Area 50/ Block 3; Ali Al Salem Street; Kuwait,57479101825D5E5B54969983901BC233,The Panama Papers data is current through 2015,KWT,Kuwait,14049602,Panama Papers
MARKETING OFFICE; G/F.; VEGA SUITES; 3 TONG TAK STREET; TSEUNG KWAN O; HONG KONG,5EA6A296746729FE3151C51A66E2D3CC,The Panama Papers data is current through 2015,HKG,Hong Kong,14049603,Panama Papers
MARKET SQUARE; BELIZE CITY; BELIZE,15F149B43F0AE53B9F828A9665DCDAC4,The Panama Papers data is current through 2015,BLZ,Belize,14049604,Panama Papers
MARKET SQUARE; PO BOX 364; BELIZE CITY; BELIZE,7852F0DBE86048BA21BFD7F5A43A0E3B,The Panama Papers data is current through 2015,BLZ,Belize,14049605,Panama Papers
“Markou Drakou 21,1040 Nicosia”,717C207D2D860AA9E98EF009B1BFF42F,The Panama Papers data is current through 2015,CYP,Cyprus,14049606,Panama Papers
Marksa St. 15; Korolevo Village; Vinogradov District; Zakarpatskya Region; Ukraine,B1BAB0B37734C763F4E152264F2BC637,The Panama Papers data is current through 2015,UKR,Ukraine,14049607,Panama Papers
Marksistskaia Str. 1-1-275; Russia; Moscow,265C0CE5B816128DE11D074098838103,The Panama Papers data is current through 2015,RUS,Russian Federation,14049608,Panama Papers
Marksistskaya Str. 9-231RF-109147 Moscow,A46ACDEC8C7225593B3F28A223A92104,The Panama Papers data is current through 2015,RUS,Russian Federation,14049609,Panama Papers
“Marlborough & Queens Street PO Box N-10249, Nassau Bahamas”,92FE988DE6B3A52A09DAEEBDC3D67ED0,The Panama Papers data is current through 2015,BHS,Bahamas,14049610,Panama Papers
MARLBOROUGH & QUEEN STREET; P.O. BOX N-10429; NASSAU; BAHAMAS,2B9972B6585CCD6E8AFEE8EB75255268,The Panama Papers data is current through 2015,BHS,Bahamas,14049611,Panama Papers
“Marlborough & Queen Streets PO Box N-10429, Nassau Bahamas”,92AED564DC635967B43ADF8F9734AC18,The Panama Papers data is current through 2015,BHS,Bahamas,14049612,Panama Papers
MARLBOROUGH AND QUEEN STREETS; PO BOX N-10429; NASSAU; BAHAMAS,3E41E54B930B47D7D5213706A218620E,The Panama Papers data is current through 2015,BHS,Bahamas,14049613,Panama Papers
Marl House; Dove Cote; Sheep Hill Lane; Clayton Le Woods; Chorley; PR6 7AU,DE97000F473950023B3F664E7005BDCF,The Panama Papers data is current through 2015,GBR,United Kingdom,14049614,Panama Papers
MARLPIT HOUSE; BELAUGH GREEN LANE; COLTISHALL; NORFOLK; UK; NR12 7AJ,3997748D71D7249711D139E07E602FD9,The Panama Papers data is current through 2015,GBR,United Kingdom,14049615,Panama Papers
Marmara; 2 Gozo Street; Quawra; SPB 05; Malta,42F9A5D9E259BF782109A93800E1824D,The Panama Papers data is current through 2015,MLT,Malta,14049616,Panama Papers
Mar Maroun Street; Saifi 605 bldg; Saifi; Beirut; Lebanon,CA89C4228CC297A9061046D1BE541167,The Panama Papers data is current through 2015,LBN,Lebanon,14049617,Panama Papers
Mar Maroun str.; Saifi 605 bldg; 3rd floor; Saifi; Beirut; Lebanon,4D5660D112FF50611BA8569E7FB980D7,The Panama Papers data is current through 2015,LBN,Lebanon,14049618,Panama Papers
Mar Maroun Str.; Saifi 605 bldg; Saifi; Beirut; Lebanon,43F4D6FB133874854A27577D7231C285,The Panama Papers data is current through 2015,LBN,Lebanon,14049619,Panama Papers
MAR MEDITERRANEO 5530; Montevideo; Uruguay.,0BA2D7188A70D2462545F624274DF2DE,The Panama Papers data is current through 2015,URY,Uruguay,14049620,Panama Papers
Mar Mediterrano 5812; Montevideo; Uruguay,B5BB5CA229C6717A301F62F550CD7E93,The Panama Papers data is current through 2015,URY,Uruguay,14049621,Panama Papers
Mar Mikael; Nicholas el Turk Street; PSLAB Bldg; Beirut; Lebanon,3D1AFE67D22A097676399620DD10878E,The Panama Papers data is current through 2015,LBN,Lebanon,14049622,Panama Papers
Marokkanergasse 20/11; 1030 Wien; Austria,19143C8CD6735FE598EF02563C329310,The Panama Papers data is current through 2015,AUT,Austria,14049623,Panama Papers
Maros u. 11; Budapest 1125; Hungary,848F50E50FF03FC646BEC103B4CBE012,The Panama Papers data is current through 2015,HUN,Hungary,14049624,Panama Papers
Mar Peruano 220; Urb.Neptuno; Surco; Lima; Perú,86BFC06AB397A54882E44C97F17958AE,The Panama Papers data is current through 2015,PER,Peru,14049625,Panama Papers
Mar Peruano 220-Urb-Neptuno-Surco-Lima-Perú,A71DB84E3D2BC9043D5DA72CD39A4E0E,The Panama Papers data is current through 2015,PER,Peru,14049626,Panama Papers
“MARPUTCULAR CAD. YARPUZ ISANI NO:15/13 EMINONU/ISTANBUL, TURKEY”,3FE493C3BC6D7BEEB0ECB237332E6873,The Panama Papers data is current through 2015,TUR,Turkey,14049627,Panama Papers
Marquee Place; Suite 300; 430 West Bay Road; P.O. Box 30691; Grand Cayman KY1-1203; Cayman Islands,059F0EAAD4374E55DCB082496DE954C6,The Panama Papers data is current through 2015,CYM,Cayman Islands,14049628,Panama Papers
Marques de Valladares; 2 Bajo 36201; Vigo; Pontevedra; España,6B8AB58860207F5D905C01D20EBC7D59,The Panama Papers data is current through 2015,ESP,Spain,14049629,Panama Papers
“Marronwood 4 Kelvedon Avenue Walton on Thames, Surrey KT12 5E”,6DC4DB6555D4F91F7246C79CBC30C1FF,The Panama Papers data is current through 2015,GBR,United Kingdom,14049630,Panama Papers
MAR ROUKOZ STREET; CHRISTY BLDG; BLOC A; 1ST FLOOR; DEKWANEH; BEIRUT; LEBANON,D79A095F05096F7A8011AEBA91A4D5D3,The Panama Papers data is current through 2015,LBN,Lebanon,14049631,Panama Papers
MARSHALA CHUYKOVA ST. 36/56; THE CITY OF ZAPAROZHZHYA; UKRAINE 69121,EDC0087CE19F0E214976FBE5FD08689B,The Panama Papers data is current through 2015,UKR,Ukraine,14049632,Panama Papers
MARSHALA CHUYKOVA ST. 36/56; THE CITY OF ZAPORIZHZHYA; UKRAINE; 69121,E31A862CAD61EA62D6B135BDEA2A0EAE,The Panama Papers data is current through 2015,UKR,Ukraine,14049633,Panama Papers
MARSHALA KATUKOVA STR. 25; BLDG. 1; APP. 456; MOSCOW; RUSSIAN FEDERATION,9AC42119AA29FD8DEBBFC7B204CA70E4,The Panama Papers data is current through 2015,RUS,Russian Federation,14049634,Panama Papers
Marshala Meretskogo str 5; App 52; Moscow; Russia,CD35524E352807037649E10F062F22D5,The Panama Papers data is current through 2015,RUS,Russian Federation,14049635,Panama Papers
Marshala Timoshenko Street; Building 17/2; Apt. 278; Moscow City; Russian Federation,4F31775BEF0F5BF1D7FED81DE5B5BE1E,The Panama Papers data is current through 2015,RUS,Russian Federation,14049636,Panama Papers
MARSHALA ZAKHAROVA; ST. 9-252; ST. PETERSBURG; RUSSIA,A5ACB6F4A0E610529BC956A7043223E6,The Panama Papers data is current through 2015,RUS,Russian Federation,14049637,Panama Papers
MARSHALA ZUKOVA 35/3-6; ST.PETERSBURG; RUSSIA,7E3A5BD0C5E8A035980CB88CFCEF5323,The Panama Papers data is current through 2015,RUS,Russian Federation,14049638,Panama Papers
MARSHAL KATUKOV STREET; 19-1-213/ 123181; RUSSIA MOSCOW,8B5BB91F94491F033B0F9A07569C5A35,The Panama Papers data is current through 2015,RUS,Russian Federation,14049639,Panama Papers
Marshall Islands,30F339BB1A471145380BECF625E21F68,The Panama Papers data is current through 2015,MHL,Marshall Islands,14049640,Panama Papers
MARSWEG 18; WILLEMSTAD; CURACAO,DE8A7D2189DF35B638CE170173E22718,The Panama Papers data is current through 2015,CUW,Curaçao,14049641,Panama Papers
Martell Court Admiral Park ST. Peter Port Guernsey GY1 3HB,A6A7FE2AFEC53CC8A4D4A41F349EABA5,The Panama Papers data is current through 2015,GGY,Guernsey,14049642,Panama Papers
Martello Court,2882CDCD1ED9D9DAE3681B98BAC6BBC6,The Panama Papers data is current through 2015,IRL,Ireland,14049643,Panama Papers
MARTELLO COURT; ADMIRAL PARK,F9319000264A602D2573BE73F2889BEC,The Panama Papers data is current through 2015,,,14049644,Panama Papers
Martello Court; Admiral Park; St. Peter Port; Guernesey; GY1 3HB,E34D520865AF40B1A6D408AADB681529,The Panama Papers data is current through 2015,GGY,Guernsey,14049645,Panama Papers
Martello Court; Admiral Park; St Peter Port; Guernsey,1B240BA00D463DD12E4F0CC39B1F3E61,The Panama Papers data is current through 2015,GGY,Guernsey,14049646,Panama Papers
Martello Court; Admiral Park; St. Peter Port; Guernsey GY1 3HB,388F0550E07576D1FD2FF171C2C768FC,The Panama Papers data is current through 2015,GGY,Guernsey,14049647,Panama Papers
Martello Court; Admiral Park; St Peter Port; Guernsey GY1 3Q,DF6A33B44872C9D802198591896F1837,The Panama Papers data is current through 2015,GGY,Guernsey,14049648,Panama Papers
MARTELLO COURT; ADMIRAL PARK; ST PETER PORT; GUERNSEY; GY1 3QJ,58C86ABDBE0C4EE5D6A2A836D6403F1F,The Panama Papers data is current through 2015,GGY,Guernsey,14049649,Panama Papers
“M ARTHUR HOYEAU 116 RUE CARNOT, 92150 SURENESS FRANCE”,D3A861794A1B66CF8C7623D1AD5C90D9,The Panama Papers data is current through 2015,FRA,France,14049650,Panama Papers
Martín Alonso de Meza 210; Urb. La Mar; Pueblo Libre; Lima; Perú,F00627A3651FEF90E03392B6DFAA5F0E,The Panama Papers data is current through 2015,PER,Peru,14049651,Panama Papers
“MARTIN CORONADO 3260, AR-1425 BUENOS AIRES”,11394CF396CA035A69391CFC3DBFE6FE,The Panama Papers data is current through 2015,ARG,Argentina,14049652,Panama Papers
Martin Coronado 755; San Isidro; Buenos Aires; Argentina.,3CC9081F360BC4104298707FC6914C8E,The Panama Papers data is current through 2015,ARG,Argentina,14049653,Panama Papers
MARTIN FIERRO 2227 VICTORIA; BUENOS AIRES; ARGENTINA,EE7FB902BD28EDABA8C4B4978F6CE557,The Panama Papers data is current through 2015,ARG,Argentina,14049654,Panama Papers
MARTINS BANK CHAMBERS; HALKETT PLACE; ST. HELIER; JERSEY,55B83C062C3E4C537E60CB4AA6FDA03C,The Panama Papers data is current through 2015,JEY,Jersey,14049655,Panama Papers
Mártires de Ilapacoyan 55-4; Col. Centro; Veracruz; México,806CDCACF01086CE06542E55FC6280C9,The Panama Papers data is current through 2015,MEX,Mexico,14049656,Panama Papers
MARTIR OLAYA 201 OF 501; Miraflores; Lima; Perú,F07CD23EB5EBC07A16ADEF40D1AE1D14,The Panama Papers data is current through 2015,PER,Peru,14049657,Panama Papers
Mar Tirreno 0012; Punta del Este; Maldonado – URUGUAY,BEF5731E9145418915BF38009733BF13,The Panama Papers data is current through 2015,URY,Uruguay,14049658,Panama Papers
Martkopi; Gardabani; Georgia,C940D5AECDA4967BB58EE6AA514E2441,The Panama Papers data is current through 2015,GEO,Georgia,14049659,Panama Papers
“MARTN DE PAZ, 114 – VALLE HERMOSO – MONTERRICO – SURCO -LIMA – PERÚ”,EF8F66C2A171879E87146E0AF5DBE6B4,The Panama Papers data is current through 2015,PER,Peru,14049660,Panama Papers
MARWAR RAJASTHAN INDIA,209FB2B9ACF8388F1069D75BD30BA03F,The Panama Papers data is current through 2015,IND,India,14049661,Panama Papers
Maryino Village 4; apt. 58; Leninskiy District of Moscow Region; Russian Federation,F9E6CAD2313B2793275442D4D305B5E1,The Panama Papers data is current through 2015,RUS,Russian Federation,14049662,Panama Papers
Maryville; Carrigaline Road; Douglas Cork.,0B4674F827152978929BDC8254D02D67,The Panama Papers data is current through 2015,IRL,Ireland,14049663,Panama Papers
Maseela Area 1 Plot: 800001; Type of Unit: House; Kuwait,1A6AC3539FCA8059EEC971885FEC7532,The Panama Papers data is current through 2015,KWT,Kuwait,14049664,Panama Papers
Maseela Area 6 Plot: 800001; Type of Unit: House; Kuwait,7C531D618FC37C137764D4EA56C38F5B,The Panama Papers data is current through 2015,KWT,Kuwait,14049665,Panama Papers
MASERA III; VILLA NO 99; MARAKESH,681E7B29E02730301F4090BFBCFC4CFB,The Panama Papers data is current through 2015,MAR,Morocco,14049666,Panama Papers
Masera III; Villa No 99; Marakesh; Morocco,4283591446CF9DDEF654A4A49F5FA686,The Panama Papers data is current through 2015,MAR,Morocco,14049667,Panama Papers
MASHELA STREET; MOSCOW; RUSSIAN FEDERATION.,F4A0B82D19661A355E17DDDF49A8DAC7,The Panama Papers data is current through 2015,RUS,Russian Federation,14049668,Panama Papers
Masra Plaza North Appt. 806 Dubai United Arab Emirates,4F70F8F6AFA4BF7F37BAD0E4E23624F0,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049669,Panama Papers
MASSACHUSETTS INSTITUTE OF TECHNOLOGY/MIT; 30 WARREN STREET; BROOKLINE; MA 02445; U.S.A.,B6E65234CAB0784E5C392969AA9279C1,The Panama Papers data is current through 2015,USA,United States,14049670,Panama Papers
“Massachusetts, U.S.A.”,BCC7409967A408A788FB1C7A804B13D3,The Panama Papers data is current through 2015,USA,United States,14049671,Panama Papers
“MASSAU, BAHAMAS”,396CF2064C2A95BB13F983EAA5E60C5D,The Panama Papers data is current through 2015,BHS,Bahamas,14049672,Panama Papers
Massimo’s Address: Via Carlo Pedrotti 39; Roma; Italy Carlo’s Address: Via Giustiniano Imperatore 16; Roma; Italy,771AF5F2B77227E75656AEE6EAAF23E6,The Panama Papers data is current through 2015,ITA,Italy,14049673,Panama Papers
Massini 3358/801; Montevideo; Uruguay,BFD9642E0B9451763A8CAD8AA47F6BDD,The Panama Papers data is current through 2015,URY,Uruguay,14049674,Panama Papers
“Massira 3 No. 6 P Kasba 2 Marrakech 40000, Morroco”,49F5B4389945A7AE2BA10C1876B2DFA6,The Panama Papers data is current through 2015,CHN,China,14049675,Panama Papers
MASTER 2000; NO. 11; XUEYUAN RD; KUANGYE COLLEGE; HAIDIAN DISTRICT; BEIJING CITY; CHINA,C96FB96FF06179A244EFDAE00A399572,The Panama Papers data is current through 2015,CHN,China,14049676,Panama Papers
Masurenweg 12; 30163 Hannover; Germany,FBD9273C42B053AF11130A9CB0BFD998,The Panama Papers data is current through 2015,DEU,Germany,14049677,Panama Papers
“Masyra 3B No. 99 Marrakesh, Morocco”,044BD14DDEC24D27C33FB003AE6C442A,The Panama Papers data is current through 2015,MAR,Morocco,14049678,Panama Papers
“MATALON 33 TEL AVIV, ISRAEL”,E3E9C4F7B931E2658AA07468DE24E822,The Panama Papers data is current through 2015,ISR,Israel,14049679,Panama Papers
Matco Limited; 11th Floor; Tower 1; NeXTeracom Building; Ebene Cybercity; Mauritius,AA97A90F0503598AF5DAA1FC09D32C0C,The Panama Papers data is current through 2015,MUS,Mauritius,14049680,Panama Papers
Matechova 390/8; 14000 Pargue; Czech Republic,C5282A2FED7B81F26365A3E3416C59F7,The Panama Papers data is current through 2015,CZE,Czech Republic,14049681,Panama Papers
“Mateo Vidal 3234, Montevideo Uruguay.”,3BEC1022F40CE493E3A716091C24AEDB,The Panama Papers data is current through 2015,URY,Uruguay,14049682,Panama Papers
MATERIALES MATURIN C.A.; CENTRO INDUSTRIAL DEL ESTE; 1ERA. AV. ESQ. CON 2DA. TRANSVERSAL; APARTADO 100; CODIGO POSTAL 1.220; CARACAS; VENEZUELA,BC7D6EACE8DC8BAD149B659599DDE750,The Panama Papers data is current through 2015,VEN,”Venezuela, Bolivarian Republic of”,14049683,Panama Papers
MATERIALS SCIENCE & ENGINEERING; NO 1; QING HUA YUAN ROAD; HAIDIAN; BEIJING; CHINA,9DED34E3475AB6152E8C68AAABF6E808,The Panama Papers data is current through 2015,CHN,China,14049684,Panama Papers
Matheson Trust Company(BVI)LimitedRoad Town; Tortola; British Virgin Islands,726AA6207FDE772EAACE2418C8FFBAA0,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14049685,Panama Papers
Mathysen-Gerst Unit A 20th Floor 9 Queens Road Central Hong Kong,F53779BB650E363DAFF6390FDA22B789,The Panama Papers data is current through 2015,HKG,Hong Kong,14049686,Panama Papers
Matinus Nijhoffstraat 52-1; 1064 HK; Amsterdam.,14FB6FC17F18665525F2920D4225546C,The Panama Papers data is current through 2015,NLD,Netherlands,14049687,Panama Papers
Matlapaneng Ward Maun Botswana,A973383793FAC1917F5DEFA35F46EB30,The Panama Papers data is current through 2015,BWA,Botswana,14049688,Panama Papers
Matonsweg 5; 6833 Fraxen; Austria,87D8A5384BDC024C83AA7C86BA08708A,The Panama Papers data is current through 2015,AUT,Austria,14049689,Panama Papers
MATSUMOTO IN 15; FOURTH FLOOR; NO.351 CHANGCHUN ROAD; SONGSHAN DISTRICT; TAIPEI; TAIWAN,D88FE5AA37CB9F63605373C0DA626F15,The Panama Papers data is current through 2015,TWN,”Taiwan, Province of China”,14049690,Panama Papers
Matsuri Trust of Fiman House; St George’s Place; St Peter Port; Guernsey; GY1 2BH,5B11AB6C19DC39E090372F0425B378A6,The Panama Papers data is current through 2015,GGY,Guernsey,14049691,Panama Papers
Matsuri Trust of Fiman House; St George’s Place; St Peter Port; Guersney; GY1 2BH,BB597851509E64BF01E16D077695EA86,The Panama Papers data is current through 2015,GGY,Guernsey,14049692,Panama Papers
Mattstrasse 18; 6052 Hergiswil; Switzerland,A3E059FF95BFA75A8562D2DB64DEABED,The Panama Papers data is current through 2015,CHE,Switzerland,14049693,Panama Papers
“MATVEEVSKAYA STR. 10-2-159 MOSCOW, 119517 RUSSIA”,4820894A9F5DA76988692F998EDC32DA,The Panama Papers data is current through 2015,RUS,Russian Federation,14049694,Panama Papers
MATVEEVSKAYA STREET.; h.10; BUILDING 2; APARTMENT 284; MOSCOW,F0162E903E927F421965EDA69C4FC9A3,The Panama Papers data is current through 2015,RUS,Russian Federation,14049695,Panama Papers
MATZARD HOUSE; 15 UNION STREET; ST. HELIER; JERSEY,8E6732ADA69F1342559856069389519F,The Panama Papers data is current through 2015,JEY,Jersey,14049696,Panama Papers
Mauerbachstrasse 50/3; A-1140 Vienna; Austria,0FA3FD157767155037B0E344BCE316C3,The Panama Papers data is current through 2015,AUT,Austria,14049697,Panama Papers
MAULANA YUSUF 14; BANDUNG 40115; INDONESIA,A83B1945B03BF8E23495FC8283D3A5F8,The Panama Papers data is current through 2015,IDN,Indonesia,14049698,Panama Papers
“Maure 2595 #5 Buenos Aires, Argentina”,9A466B77E3555BE18F8C60FB829F3A23,The Panama Papers data is current through 2015,ARG,Argentina,14049699,Panama Papers
MAURE 2595; PISO5; BUENOS AIRES; ARGENTINA,F81F709FDFE4B8706E7C67E9E6DB0E11,The Panama Papers data is current through 2015,ARG,Argentina,14049700,Panama Papers
Maureen Wiley 86 Ennisclare Dr Oakville On L6J 4N2,05637427CA0A2DA32846BF7B8C1037D1,The Panama Papers data is current through 2015,CAN,Canada,14049701,Panama Papers
Maurikios Court 2; Flat 001; Messinias 7; 3111 Limassol; Cyprus,D8B59A3793B3896A9A5E3852CEC50AE0,The Panama Papers data is current through 2015,CYP,Cyprus,14049702,Panama Papers
“Mavahlio, 47/P.O Box 5975/105-Reykjavik/Iceland”,BF0373E16DB1E9BB6FD65DF9267F7F13,The Panama Papers data is current through 2015,ISL,Iceland,14049703,Panama Papers
Mavahlio 47; P.O. Box 5975; 105 Reyjavick; Iceland,7ED6E61A44D0621214FC3E25C96E39E1,The Panama Papers data is current through 2015,ISL,Iceland,14049704,Panama Papers
Mavanesi 10; IS-210 Gardabaer; Iceland,A8C3B5767FE641DD07643C9681230FFD,The Panama Papers data is current through 2015,ISL,Iceland,14049705,Panama Papers
“Mavi Halic Sitesi Acelya Sok. A2 Block D:11 Maslak, Istanbul”,D97B600233E55A2E8863FD3BA92A937D,The Panama Papers data is current through 2015,TUR,Turkey,14049706,Panama Papers
MAVROVOUNIOTI 10; GERAKAS; ATHENS; GREECE,7ABD562AE73BF8FB477655DFF455C54D,The Panama Papers data is current through 2015,GRC,Greece,14049707,Panama Papers
MAWLANA NUR MOHAMMED NO.9-4 JALAN 2/27 F PUSAT BANDAR WANGSA MAJU 53300 KUALA LUMPUR MALAYSIA,17602291D42EDB13EBB88FBBDEFBE646,The Panama Papers data is current through 2015,MYS,Malaysia,14049708,Panama Papers
Maxell Chambers 35-39 La Colomberie St. Helier Jersey JE2 4QB,0F7F4F845037858EAB61027316886146,The Panama Papers data is current through 2015,JEY,Jersey,14049709,Panama Papers
Maxell Chanmeber; 35-39 La Colomberie; St. Helier; Jersey; Channel Islands JE2 4QB,12545EB393CD2680305A4A4AACF474D2,The Panama Papers data is current through 2015,JEY,Jersey,14049710,Panama Papers
Max Henrique Ureña No. 46; Sergio Pantini; Santo Domingo; Republica Dominicana,30A7937A2BC34FBDDA5D3713B08350B5,The Panama Papers data is current through 2015,DOM,Dominican Republic,14049711,Panama Papers
Max Henriquez Urena No. 34; Ensanche Piantini; Santo Domingo; Republica Dominicana,75E1EAB753226C879B3CD9C93144A1E9,The Panama Papers data is current through 2015,DOM,Dominican Republic,14049712,Panama Papers
Max Henriquez Ureña No. 34 Esq. Lope de Vega; Santo Domingo; Rep. Dominicana.,2632BAF545F3E13CB56083D05BF82AD8,The Panama Papers data is current through 2015,DMA,Dominica,14049713,Panama Papers
MAX HENRIQUEZ UREÑA NO. 34; PIANTINI; DOMINICAN REPUBLIC.,FEFF06244D0A6D1193E9A6D01580427D,The Panama Papers data is current through 2015,DOM,Dominican Republic,14049714,Panama Papers
MAX HENRIQUEZ UREÑA NO.34 PIANTINI; SANTO DOMINGO; REPUBLICA DOMINICANA,256C6A0E5A426903FCDFFDCC2ECC62FA,The Panama Papers data is current through 2015,DOM,Dominican Republic,14049715,Panama Papers
“Max Herniquez Urena #2 Sector Naco Santo Domingo, Dominican Republic”,0B0E95DC83CCC3757215CCE112781849,The Panama Papers data is current through 2015,DOM,Dominican Republic,14049716,Panama Papers
Maximino Perez 402; San Fernando; Buenos Aires; Argentina,7BEEED935F30B158D2B97ED06DE43AE3,The Panama Papers data is current through 2015,ARG,Argentina,14049717,Panama Papers
Maximo Jeria 733; Ñuñoa; Santiago; Chile.,BA05134E32F1D695A98A26D244CCE92A,The Panama Papers data is current through 2015,CHL,Chile,14049718,Panama Papers
Maximo Tajes 6539; Montevideo; Uruguay,73F2FD0BCC7C3CEF8C1B05AAA9B82AF0,The Panama Papers data is current through 2015,URY,Uruguay,14049719,Panama Papers
Maxim Pvt Ltd; 12 km Sheikhupura Road; Sheikhupura; Pakistan,AF02765D00AF2317DB1C6F2695DAE18B,The Panama Papers data is current through 2015,PAK,Pakistan,14049720,Panama Papers
“Max-Planck-Ring 21, Wiesbaden; Germany”,22F3465C5846E751612B5E9666427365,The Panama Papers data is current through 2015,DEU,Germany,14049721,Panama Papers
Max-Planck-Ring 21; Wiesbaden; Germany,F732F373CD12938BFC8270383A37EB3E,The Panama Papers data is current through 2015,DEU,Germany,14049722,Panama Papers
Maxwell Chambers; 35-39 La Colomberie; St. Helier; JE2 4QB,F6A13EF7EB61083B134CA2BE980155DD,The Panama Papers data is current through 2015,JEY,Jersey,14049723,Panama Papers
MAXWELL CHAMBERS; 35-39 LA COLOMBERIE; ST HELIER; JE2 4QB; JERSEY,922E37390F6510E0C89DDC7EA7909803,The Panama Papers data is current through 2015,JEY,Jersey,14049724,Panama Papers
MAXWELL CHAMBERS; 35-39 LA COLOMBERIE; ST. HELIER; JERSEY,A3F113646EF724E5A1490543DECF4BD6,The Panama Papers data is current through 2015,JEY,Jersey,14049725,Panama Papers
Maxwell Chambers 35-39 La Colomberie; St Helier Jersey; Channel Islands,BBD0A8B9645EA85869BFF0856E24FEDC,The Panama Papers data is current through 2015,JEY,Jersey,14049726,Panama Papers
MAXWELL CHAMBERS; 35-39 LA COLOMBERIE; ST HELIER; JERSEY; JE2 4QB,497B1A2903F44BA08D5A0FC7E482F411,The Panama Papers data is current through 2015,JEY,Jersey,14049727,Panama Papers
Maxwell Chambers; 35-39 La Colomberie; St Helier; Jersey JE2 4QB; Jersey,7F50A32CF855A092068506FC712714CB,The Panama Papers data is current through 2015,JEY,Jersey,14049728,Panama Papers
Maxwell Chambers 35-39 La Colomberie St Helier Jersey Jersey JE2 4QB,305B3BA92BF9E4794B613230B62B7E7B,The Panama Papers data is current through 2015,JEY,Jersey,14049729,Panama Papers
MAXWELL CHAMBERS; 35-39 LA COLOMBERlE; ST. HELlER; JERSEY.,CAB2AEB853DAC2B8AD97F058DEF26EBD,The Panama Papers data is current through 2015,JEY,Jersey,14049730,Panama Papers
Maxwell Chambers; 35-39 Le Colomberie; St Helier; Jersey,6D146E5DD585AE0F67C889B16CFC7F33,The Panama Papers data is current through 2015,JEY,Jersey,14049731,Panama Papers
Maxwell Chambers 3s 3g Colomberie; St. Helier; Jersey,344CB6A808C0B5F9EDC173E5D7586C22,The Panama Papers data is current through 2015,JEY,Jersey,14049732,Panama Papers
Maxwell Chmabers 35-39 La Colomberier St Helier Jersey JE2 4QB,B57F415633887DD67EBFBBFA7F768382,The Panama Papers data is current through 2015,JEY,Jersey,14049733,Panama Papers
Mayakovskogo St; . Apt 3; Samara; Russia,D4FD638731ED0D04AD101D8F92E8EFA1,The Panama Papers data is current through 2015,RUS,Russian Federation,14049734,Panama Papers
Mayakovskogo Str. 9/15-14; Kirovsk; Leningradskaya Obl. Russia,A8C1ED70E41507A310CFF89EB11F34CC,The Panama Papers data is current through 2015,RUS,Russian Federation,14049735,Panama Papers
“MAYAN INVESTMENT PROPERTIES, APARTADO 105 CUIDAD CANCUN QUINTANA ROO MEXICO”,2790246D1E74ABAE58196DDE6907C3CB,The Panama Papers data is current through 2015,MEX,Mexico,14049736,Panama Papers
MAYAN IVESTMENT PROPERTIES APARTADO 105 CUIDAD CANCUN QUINTANA ROO MEXICO,F0345F51BB8398D76FDCF84836A53569,The Panama Papers data is current through 2015,MEX,Mexico,14049737,Panama Papers
MAYA RESIDENCES; K. BLOK; DAIRE 11; OTLUKBELI CADDESI; 80600 ETILER; ISTANBUL; TURKEY,F81A906386C9FCFFE288FB5EA4612514,The Panama Papers data is current through 2015,TUR,Turkey,14049738,Panama Papers
Mayfair Drive South 340 Brooklyn; 11234 New York; United States of America,9114DC33BA3E58EBAAB11670E86F1BAC,The Panama Papers data is current through 2015,USA,United States,14049739,Panama Papers
MAYFAIR GARDEN HOUSE #106 5-16-38 ROPPONGI; MINATO-KU TOKYO 106-0032; JAPAN,99A743715D466A5A6AA7039314424E1C,The Panama Papers data is current through 2015,JPN,Japan,14049740,Panama Papers
Mayfair Trust Company Ltd; Second Floor; Capital City; Independence Avenue; PO Box 1312; Victoria; Mahw Seychelles,0A1B7C0638820C88BAB7D0C56F8BA1B8,The Panama Papers data is current through 2015,SYC,Seychelles,14049741,Panama Papers
Mayfair Trust Group Limited; Second Floor; Capital City; Independence Avenue P.O. Box 1312 Victoria; Mahé; Republic of Seychelles,ABFB30DDBC17B44B5BC112995BB7FF6F,The Panama Papers data is current through 2015,SYC,Seychelles,14049742,Panama Papers
Mayfair Trust Group Limited; Second floor; Capital City; Independence Avenue; P.O. Box 1312; Victoria; Mahe; Seychelles,550D891DFF4D04F7458FCD5A1B9BC597,The Panama Papers data is current through 2015,SYC,Seychelles,14049743,Panama Papers
Mayfair Trust Group Limited; Second Floor; Capital City; Independence Avenue; Victoria; Mahe; Seychelles,088CB0BDDB7EC100606CFF98DF2C637D,The Panama Papers data is current through 2015,SYC,Seychelles,14049744,Panama Papers
MAYFIELD FARM; RUE DES CHATAINIERS; ST. JOHN; JERSEY; CHANNEL ISLANDS,B924ADD25139B220C7C62E48DF3845DF,The Panama Papers data is current through 2015,JEY,Jersey,14049745,Panama Papers
Mayfield Grange; Rochdale Road East; Heywood; Lancashire OL10 1SD,7C46B9CD46F1E28994E08BBA1F68E5CF,The Panama Papers data is current through 2015,,,14049746,Panama Papers
MAYFIELD LA RUE BELIN ST MARTIN JERSEY JE3 6BH,D60C4F76AC805116EE0C81F4CAF1C653,The Panama Papers data is current through 2015,JEY,Jersey,14049747,Panama Papers
May Gar Commercial Bldg.; 288 Reclamation Street; kin; HK,526CB825256B11227554CD13BC1E637C,The Panama Papers data is current through 2015,HKG,Hong Kong,14049748,Panama Papers
MAYOR 2; 2000 NEUCHATEL; SWITZERLAND,0656C8858D35D108F5523F5E6546A210,The Panama Papers data is current through 2015,CHE,Switzerland,14049749,Panama Papers
Mayor Arruabarrena 1934; Cerro de las Rosas; Cordoba 5009; Argentina,6CE1CECA0F366127D923EBEE878D6A01,The Panama Papers data is current through 2015,ARG,Argentina,14049750,Panama Papers
MAYO SERVICES SÀRL 42,E13F637CB0304E92E9783D82509BD099,The Panama Papers data is current through 2015,,,14049751,Panama Papers
“MAYO SERVICES SÀRL 42, RUE DU 31-DÉCEMBRE CASE POSTALE 6487 1211 GENEVA 6 SWITZERLAND”,A39A7264D8C3E2CA9972048F3204A192,The Panama Papers data is current through 2015,CHE,Switzerland,14049752,Panama Papers
May Tree House; 128 Ash Lane; Wells; Somerset; BAS 2LU,39E206942733BF10286D8B476AE4ABB5,The Panama Papers data is current through 2015,GBR,United Kingdom,14049753,Panama Papers
Mazard House; 15 Union Street; St. Helier JERSEY,53E44AA55EB5445B89E594492334BDEC,The Panama Papers data is current through 2015,JEY,Jersey,14049754,Panama Papers
“Maza Smilsu Str. 12-10, LV 1050 Riga Latvia”,6045825A40F29F5C9447C515026A9A24,The Panama Papers data is current through 2015,LVA,Latvia,14049755,Panama Papers
Mazroiyah Area; Eastern Province; Dammam 31471; Saudi Arabi,BA0A2E48F28E46384C9DBA1984333ADA,The Panama Papers data is current through 2015,SAU,Saudi Arabia,14049756,Panama Papers
Mazroiyah Area; Eastern Province; Dammam 31471; Saudi Arabia,58D2361C02C3C95660B54453989A5AD1,The Panama Papers data is current through 2015,SAU,Saudi Arabia,14049757,Panama Papers
MBA GRADUATE STUDENT; GRADE 2011; BUSINESS COLLEGE; NO.25; XITUCHENG ROAD; HAIDIAN DISTRICT; BEIJING; CHINA,26BA869B57C0A135E1C253AFEBB42B6B,The Panama Papers data is current through 2015,CHN,China,14049758,Panama Papers
MBC BUILDING; BUBAI MEDIA CITY; DUBAI; UAE,556DD9966AAEC275D8E73501651A1A21,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049759,Panama Papers
MBE 423 E. 5-11-3 Sukhumvit Road; Klongton; Klontoey; Bangkok 10110; Thailand,11ED51BD23CADDD07E6028EED1BD7CA4,The Panama Papers data is current through 2015,THA,Thailand,14049760,Panama Papers
M. BRONNAYA STR. 31/13-25; MOSCOW; RUSSIA,CF1733A07D86F60D9509153BEB489D23,The Panama Papers data is current through 2015,RUS,Russian Federation,14049761,Panama Papers
M.Bruto 1144A Mdeo (11300) Uruguay,9032FB44AD64DF5510921EB2C3F3A9BF,The Panama Papers data is current through 2015,URY,Uruguay,14049762,Panama Papers
M. Ca L’ Hereu SN; Amer; Girona; Spain,D5B2FFAD2C9E2B8D163CC4EF2C34E2D0,The Panama Papers data is current through 2015,ESP,Spain,14049763,Panama Papers
McCallum Trust; La Plaiderie House; La Plaoderie; St. Peter Port; Guernsey GY1 3DQ,1ED71AD1ABD91C7108CD925BB5795E9B,The Panama Papers data is current through 2015,GGY,Guernsey,14049764,Panama Papers
MCG S.A. Rue Faucigny 5 1705 Fribourg,E6D19283EEA39AECC4992F1CD0EB8AE1,The Panama Papers data is current through 2015,CHE,Switzerland,14049765,Panama Papers
“MCG S.A.Rue Faucigny 51705 Fribourg, Switzerland”,985C40EC39597A21E7EE00B7FED184B3,The Panama Papers data is current through 2015,CHE,Switzerland,14049766,Panama Papers
M. Curie Sklodowskej 1512/12; 85104 Bratislava; Slovak Republic,62E3AB9E7BB5CE185D666C62898036FD,The Panama Papers data is current through 2015,IRN,”Iran, Islamic Republic of”,14049767,Panama Papers
MD1/48 President avenue Bompai; Kano; Nigeria,5804FAAA34E85A791212CCF2176642E3,The Panama Papers data is current through 2015,NGA,Nigeria,14049768,Panama Papers
MD1/48 President avenue President avenue Bompai Kano NIGERIA,70191C61397AFE572D8DE922F5814FBC,The Panama Papers data is current through 2015,NGA,Nigeria,14049769,Panama Papers
MEA-2908 PRINCE MOHAMMAD BIN ABDULAZIZ ROA-12241 RIYADH.6055 SAUDIARABIA,D41A59036EA2D7A64398D567FEC9E63C,The Panama Papers data is current through 2015,SAU,Saudi Arabia,14049770,Panama Papers
MEA-2908 PRINCE MOHAMMAD BIN ABDULAZIZ ROAD-OLAYA-RIYDH 12241-SAUDI ARABIA-,C1B92FFE43BF233ACFF3A8EA5396D8EE,The Panama Papers data is current through 2015,SAU,Saudi Arabia,14049771,Panama Papers
Meade Hill; Church Lane; Braishfield; Hampshire; SO51 0QH,169B5C8280EB71C438FA7A59B9006007,The Panama Papers data is current through 2015,GBR,United Kingdom,14049772,Panama Papers
Meade Hill; Church Lane; Braishfield; Hampshire; SO51 OQH,1BBAB94165916D568E279EC2FBC3E09D,The Panama Papers data is current through 2015,GBR,United Kingdom,14049773,Panama Papers
Meadow 5; Street 7; Villa N°2; Dubai; U.A.E.,7E7D86337E7E5242398B829DB9D255B4,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049774,Panama Papers
Meadowbank; La Rue De La Chouquetterie; St Martin; Jersey JE3 6EL,6174248A6097A572DC745A624414FCE9,The Panama Papers data is current through 2015,JEY,Jersey,14049775,Panama Papers
Meadowlea; Pirton Lane; Churchdown; Gloucester; GL3 2QE; United Kingdom,FD8A53B1F98FC01E6DF04A7B411FEF1F,The Panama Papers data is current through 2015,GBR,United Kingdom,14049776,Panama Papers
Meadows 1; St 5; Villa 14; Dubai UAE,C552446C63EBCD6DDEBDB68435E45897,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049777,Panama Papers
MEADOWS 1; VILLA 27; STREET 2; EMIRATES HILLS; DUBAI; UAE,5A299E7FB59F1B8CA14AEDBC70622026,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049778,Panama Papers
Meadows 2; Street 15; Villa 10 Dubai; UAE,4DFC7E1ACBF89E4CE123227512D39330,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049779,Panama Papers
MEADOWS 2; VILLA 18; STREET 16; EMIRATES HILLS DUBAI; UAE,D1F28040A63F58EFEF695E0823BB89FF,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049780,Panama Papers
Meadows 5; Street 8; Villa 31; Dubai; UAE.,7EC4D67A5677EC58B77BC86CCE5384DC,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049781,Panama Papers
Meadows 9; St. 2; Villa 15; Dubai UAE,878A173E5AF39C72A32DC14513618987,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049782,Panama Papers
Meadows 9; Street 2; Villa 3; Dubai; U.A.E.,6ABD566E0F8E312AE552C16B1A72FEAA,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049783,Panama Papers
Meadows 9; Street 6; Villa 26; P.O. Box 17945; Dubai; United Arab Emirates,A724FBC952A6D40B225BBAC9F95A1143,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049784,Panama Papers
Meadows House; 20 Queen Street; W1J 5PR; London; UK,519E62B5C3507F7B7853A4B310D0445D,The Panama Papers data is current through 2015,GBR,United Kingdom,14049785,Panama Papers
MEADOWSIDE LODGE RUE DES BUTTES JE3 3DE JERSEY,2DC885D6A9E5EC493FE57896F606E383,The Panama Papers data is current through 2015,JEY,Jersey,14049786,Panama Papers
Meadowside Lodge Rue Des Buttes St Mary JE3 3DE JERSEY,67F6C05A1ACD3DF559DD9E63839A4390,The Panama Papers data is current through 2015,JEY,Jersey,14049787,Panama Papers
MEADOWSIDE LODGE; RUE DES BUTTES ST.MARY; JERSEY,AF654B9CC5C5ED1793FB32221DE6B387,The Panama Papers data is current through 2015,JEY,Jersey,14049788,Panama Papers
MEADOWSIDE LODGE; RUE DES BUTTES; ST MARY; JERSEY; CHANNEL ISLANDS,938CAE0AC9691C5DE7E1061F8EF73376,The Panama Papers data is current through 2015,JEY,Jersey,14049789,Panama Papers
Meadows; P.O. Box 30871; Dubai; United Arab Emirates,F3A1D05115A8AEDAAEDB2FD47D3EEE2A,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049790,Panama Papers
Measows 9; Street 14; Villa 73; Dubai; U.A.E.,B7C93277A8B05DDEE73E201DB52FDDE5,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049791,Panama Papers
ME BERTHOLET; 13 RUE DE LA SERVETTE; 1210 GENEVE; SWITZERLAND,271B20DF64572B15706BFA7F0303786E,The Panama Papers data is current through 2015,CHE,Switzerland,14049792,Panama Papers
Mebusan Yokusu Basaran Han; K:1 80040 Findikli; Istanbul; Turkey Sandikci-U,C020949BF5668E74DF42DE82EE4CD3D4,The Panama Papers data is current through 2015,TUR,Turkey,14049793,Panama Papers
MECCA STREET; AMMAN; JORDAN,3B7B88387AA356E562A8CF3E618275ED,The Panama Papers data is current through 2015,JOR,Jordan,14049794,Panama Papers
“MECHELSESENNWEG 329, BUS 10 2018 ANVERS”,176DDE308DAAF7A34D3E159FC308BF49,The Panama Papers data is current through 2015,BEL,Belgium,14049795,Panama Papers
MECHELSESTEENWEG 191 2018 ANTWERP BELGIUM,311ABF9F66C59AD603608ED6E9A0503A,The Panama Papers data is current through 2015,BEL,Belgium,14049796,Panama Papers
Meclisi Mebusan Cad. 139A; Atlantik Han K:2; TR-Kabatas; Turkey,BE06E515274DE5EF1EA2BF2C0C1B7C6F,The Panama Papers data is current through 2015,TUR,Turkey,14049797,Panama Papers
Medan mostafa Mahmoud; Mohandeseen; Giza; Egypt,E0169F557DD177A4C6A24C0E7ECC4B0B,The Panama Papers data is current through 2015,EGY,Egypt,14049798,Panama Papers
ME DANTE CANONICA; RUE FRANÇOIS-BELLOT 2; 1206 GENEVA; SWITZERLAND,5B4FE2B67DB619DDE373DEAD29BF4E79,The Panama Papers data is current through 2015,CHE,Switzerland,14049799,Panama Papers
Medawar; Beirut Sehanoui Bldg; 1st Flr; No. 16 P.O. box 11/8985,15482586C3B2BC808EBCC26269BAE322,The Panama Papers data is current through 2015,,,14049800,Panama Papers
Medbury Farm; Box 34 Tengwe; Zimbabwe,86CEAABCDA8DEE57FF6858B7712CABDC,The Panama Papers data is current through 2015,ZWE,Zimbabwe,14049801,Panama Papers
“MEDELLIN, COLOMBIA”,14C4C3A55E63219E7318BDC1E48B689C,The Panama Papers data is current through 2015,COL,Colombia,14049802,Panama Papers
MED ENERGY SAL; ARESCO CENTER; ALKANTARY; JUSTINIAN STREET; PO BOX 11-3516 BEIRUT; LIBANON,B11ACBD5770AF005F1A7D92EA3EDF81A,The Panama Papers data is current through 2015,LBN,Lebanon,14049803,Panama Papers
MED ENERGY S.A.L JUSTINIAN STREET; ARESCO CENTER; 10TH FLOOR P.O.BOX 11-3516 BEIRUT-LEBANON TEL: 01-748 800 FAX: 01-748 700,B4850F6DF3E1CF599F72831415BCA98A,The Panama Papers data is current through 2015,LBN,Lebanon,14049804,Panama Papers
MEDIKOV STR.; BLD. 26; CORP. 3; APT. 156; RUSSIA,6EEE362B72A42DE243E14985F8E0B755,The Panama Papers data is current through 2015,RUS,Russian Federation,14049805,Panama Papers
Medina 1; Triq il Mediterran; San Giljan; Malta EU,8B672E17DDEF9F9057C26CF925999BEC,The Panama Papers data is current through 2015,MLT,Malta,14049806,Panama Papers
Medina Road Jeddah 21471 KSA,47B3051820AFA57F30B813672B3A633A,The Panama Papers data is current through 2015,SAU,Saudi Arabia,14049807,Panama Papers
MEDITERCANEAN VISTA; GRAND OCEAN PLAZA; OCEAN VILLAGE. GIBRALTAR,060EA24084D421F39F494858B5D31FAD,The Panama Papers data is current through 2015,GIB,Gibraltar,14049808,Panama Papers
Mediterranee-Suise3 rue du Mont Blanc1211 Geneva 1 Switzerland,00F9EFE9514E6ED83F1CE4F8585511C5,The Panama Papers data is current through 2015,CHE,Switzerland,14049809,Panama Papers
Mega Kebon Jeruk Blk D 10 No. 6; RT/RW 004/011; Meruya Selatan; Kembangan; Jakarta Barat; Indonesia,887A76339D5EF174A78C30CF9A56A272,The Panama Papers data is current through 2015,IDN,Indonesia,14049810,Panama Papers
Megalou Alexandrou 49; GR 16674 Glyfada; Greece,15AE594C4809EACF6C3998BBD27F8312,The Panama Papers data is current through 2015,GRC,Greece,14049811,Panama Papers
MEGHDOOT; LES NOUVELLES CHARRIERES; ST. JOHN; JE3 4DJ; JERSEY,DDB36347A33D43B300057A46AAB6F7F7,The Panama Papers data is current through 2015,JEY,Jersey,14049812,Panama Papers
MEGHRAI HOUSE; LA MOTTE STREET; ST. HELIER; JERSEY; CI,937FEF2A4D4F3362BD6E7DAD9AECEEFB,The Panama Papers data is current through 2015,JEY,Jersey,14049813,Panama Papers
MEGHRAJ HOUSE; 45 LA MOTTE STREET; JE4 5NP ST. HELIER UNITED KINGDOM,D68546D34564AF0A6FFBE054D34414EA,The Panama Papers data is current through 2015,GBR,United Kingdom,14049814,Panama Papers
MEGHRAJ HOUSE; LA MOTE STREET; ST HELIER; JERSEY; CHANNEL ISLANDS,3AA3D0F0CCD8275F0DB764BD72615D00,The Panama Papers data is current through 2015,JEY,Jersey,14049815,Panama Papers
MEGHRAJ HOUSE; LA MOTTE STREET; ST HELEIR; JERSEY; CHANNEL ISLANDS,CC7B08A00C1283A1BB0554A12A02F6D5,The Panama Papers data is current through 2015,JEY,Jersey,14049816,Panama Papers
Meghraj House; La Motte Street; St Helier Jersey,5D36CB7A57D5C6574312FB506122D845,The Panama Papers data is current through 2015,JEY,Jersey,14049817,Panama Papers
MEGHRAJ HOUSE; LA MOTTE STREET; ST HELIER; JERSEY; CHANNEL ISLAND,260A0E8CDBC78F6BC0877792CD9CB17F,The Panama Papers data is current through 2015,JEY,Jersey,14049818,Panama Papers
MEGHRAJ HOUSE; LA MOTTE STREET; ST HELIER; JERSEY; CHANNEL ISLANDS,6D770F13B74767AAA46C48575F288C79,The Panama Papers data is current through 2015,JEY,Jersey,14049819,Panama Papers
MEGHRAJ HOUSE; LA MOTTE STREET; ST HELIER; JERSEY; CHANNEL ISLANDS; 9E4 9WA,589A885B9232F745677D17706E559D18,The Panama Papers data is current through 2015,JEY,Jersey,14049820,Panama Papers
MEGHRAJ HOUSE; LA MOTTE STREET; ST HELIER; JERSEY; CHANNEL ISLANDS; JE4 9WA,92B45FDEA247425455A15239918D956C,The Panama Papers data is current through 2015,JEY,Jersey,14049821,Panama Papers
MEGHRAJ HOUSE; LA MOTTE STREET; ST HELIER; JERSEY. CI,D7FB135F6AA2ECE461281C935A55B79B,The Panama Papers data is current through 2015,JEY,Jersey,14049822,Panama Papers
MEGHRAJ HOUSE; LA MOTTE STREET; ST HELIER; JERSEY JE4 9WA,87C299E6879E084EC14DE6B27B23BC86,The Panama Papers data is current through 2015,JEY,Jersey,14049823,Panama Papers
MEGHRAT HOUSE; LA MOTTE STREET; ST HELIER; JERSEY; CHANNEL ISLANDS; JE4 9WA,44F066273D90103124930E2276DB4C42,The Panama Papers data is current through 2015,JEY,Jersey,14049824,Panama Papers
Megraj House; PO Box 481; La Motte Street; St Helier; Jersey JE4 9WA,774B502F00B798100EC0F7EE57C198F3,The Panama Papers data is current through 2015,JEY,Jersey,14049825,Panama Papers
Mehdi Zadegan; Flat 4-T7-22-02 392/ Marsa; Dubai UAE,BF9A92FF9284613CFBE9B9B8CD271EDE,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049826,Panama Papers
Mehmet Pasa Sok; Aycibin Ap No. 14/14 Etiler; Istanbul; Turkey,543551E08873FF075AC501FCDD70515F,The Panama Papers data is current through 2015,TUR,Turkey,14049827,Panama Papers
MEHTAO SOKAK OKTAS APT. NO. 29 DAIRE:4 CADDEBOSTAN ISTANBUL,0AF4AC848F7EDE7E642677D8531B6D7E,The Panama Papers data is current through 2015,TUR,Turkey,14049828,Panama Papers
Meichuan Japanese Food Teppanyaki; No. 131 Shanhu Road; Houjie; Dongguan City; Guangdong Province; P.R. China,58980672335D7B0C3B8FD0867B87397E,The Panama Papers data is current through 2015,CHN,China,14049829,Panama Papers
Meierhofstr 2; Vaduz; PO Box 184 Liechtenstein; FL 9490,260935063D7D5E6FB12700DC73B1E5A6,The Panama Papers data is current through 2015,LIE,Liechtenstein,14049830,Panama Papers
“Meierhofstrasse 2 Vaduz ,Liechtenstein”,A2E0EF752EE2E08C15DDC398FB1D8D13,The Panama Papers data is current through 2015,LIE,Liechtenstein,14049831,Panama Papers
“Meierhofstrasse 5, FL-9490 Vaduz”,71E71644A1DC4CB962B6350001C93D79,The Panama Papers data is current through 2015,LIE,Liechtenstein,14049832,Panama Papers
Meierhofstrasse 5 FL-9490 VADUZ LIECHTENSTEIN,59E9E374DD4FD1EEA35CDA0178E50A23,The Panama Papers data is current through 2015,LIE,Liechtenstein,14049833,Panama Papers
MEILANXIN INDUSTRIAL PARK; XUEGANG SOUTH ROAD No.1; BUJI; LONGGANG DISTRICT; SHENZHEN; CHINA,8A008F137DBD03530EF1EEA1984D11EE,The Panama Papers data is current through 2015,CHN,China,14049834,Panama Papers
MEI SI TEAM; YAO MEI VILLAGE; NAN KOU TOWN; MEI COUNTY; GUANG DONG CHINA,97FD470791E12D4E2D1564AE8300F8BE,The Panama Papers data is current through 2015,CHN,China,14049835,Panama Papers
“MEISTRAAT 25 2000, ANTWERPEN”,FEA72FB2B4262CBB861FA36F62CC5440,The Panama Papers data is current through 2015,BEL,Belgium,14049836,Panama Papers
Meizhu Industry; Xinchang County; Zhejiang Province; P.R. China,F7ACBF104873FD551C8A43F3DBCADAF7,The Panama Papers data is current through 2015,CHN,China,14049837,Panama Papers
MEJERHOFSTRASSE 5; FL 9490; VADUZ,51B5536F43CB077C2A19AC8660C98615,The Panama Papers data is current through 2015,LIE,Liechtenstein,14049838,Panama Papers
Mektep Cad; Dirsek Sok. No. 4 D. 4; Florya; Istanbul; Turkey,440BFA69E1C1F001A48FAA81FAC53F94,The Panama Papers data is current through 2015,TUR,Turkey,14049839,Panama Papers
Mektep Sokak; Mimosa Apt 22/4 Istanbul; Turkey,B6D4AE7F3CF3E1C605F448CE10BB453D,The Panama Papers data is current through 2015,TUR,Turkey,14049840,Panama Papers
MELAMRKT 41; B-2000 ANTWERPEN; BELGIUM,A60D14B1E8B4A7158B558B70B611F1F4,The Panama Papers data is current through 2015,BEL,Belgium,14049841,Panama Papers
Melanii 31; Chyliczki; 05-500 Piaseczno; Poland,F51C134791FABB8AE9E125C1F54FD990,The Panama Papers data is current through 2015,POL,Poland,14049842,Panama Papers
“Melchor Ocampo 193 Torre A Piso 11, 11300 México”,E700F73E29590B84FB9194D540B85D9A,The Panama Papers data is current through 2015,MEX,Mexico,14049843,Panama Papers
Melchrutistr 45; 8304 Wallisellen; Suisse,8881A086ADC247A79F2471A0B093742B,The Panama Papers data is current through 2015,CHE,Switzerland,14049844,Panama Papers
“Melchrutistrasse 41, 8304 Wallisellen.”,D6E2AFC0052398CF4AB4F590E2501E96,The Panama Papers data is current through 2015,CHE,Switzerland,14049845,Panama Papers
Melia White House Apt 366,3716B3A2DC6D95F9A0FA7EC44C60DDDE,The Panama Papers data is current through 2015,AUS,Australia,14049846,Panama Papers
Melia White House Apt 366 Albany Street; London; NS1 3UP,4CF52E919C6DBF0DFE85FD7B75E8FBA1,The Panama Papers data is current through 2015,GBR,United Kingdom,14049847,Panama Papers
“Meliton González 1189, Montevideo Uruguay”,8088AB58A92CBB67EC5A63CDBF7C30BD,The Panama Papers data is current through 2015,URY,Uruguay,14049848,Panama Papers
MELKMARKT 41; 2000 ANTWERPEN; BELGIUM,06A71CB12AE5301F67C68857A688B640,The Panama Papers data is current through 2015,BEL,Belgium,14049849,Panama Papers
“MELLBY PRASTGARDM KIVID , SWEDEN SE-277 35”,EF84974CE44D31D8AF372A75738968DE,The Panama Papers data is current through 2015,SWE,Sweden,14049850,Panama Papers
MELMARK 41; B-2000 ANTWERPEN; BELGIUM,AC6D0D487D580FF0EE97CE91ED61FC91,The Panama Papers data is current through 2015,BEL,Belgium,14049851,Panama Papers
MELMARKT 41; 8-2000 ANTWERPEN; BELGIUM,CF56D403DA786E3F1F337EBFEDED7873,The Panama Papers data is current through 2015,BEL,Belgium,14049852,Panama Papers
MELMARKT 41; B-2000 ANTWERPEN; BELGIUM,7F369A0B259896B0CECB63D1684FEFB1,The Panama Papers data is current through 2015,BEL,Belgium,14049853,Panama Papers
MELNIKOVA STR. APPT.62; MOSCOW; RUSSIA,9A6CC54B68A832312853627B25EF4B3D,The Panama Papers data is current through 2015,RUS,Russian Federation,14049854,Panama Papers
ME MACROBIOTICS FOUNDATION – P.O.BOX 5107 HAWAII 32082 KUWAIT,7EA0B2625CB530454C38A054142B592C,The Panama Papers data is current through 2015,KWT,Kuwait,14049855,Panama Papers
ME MACROBIOTICS FOUNDATION – P.O. BOX 5107 – HAWAII 32082 – KUWAIT,ABF0012FBADC507713FD1ED293000CDE,The Panama Papers data is current through 2015,KWT,Kuwait,14049856,Panama Papers
MEMEORIAL SQUARE; P.O.BOX 556; CHARLESTONE; NEVIS; WEST INDIES,47F2A8DA109D0E119239E2E85B1D6086,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049857,Panama Papers
MEMMO CENTER; 4AVENUE DES GUEFES; MC98000 MONACO,7FB2F3DE6B1144CA72A6E5AEE98DD077,The Panama Papers data is current through 2015,MCO,Monaco,14049858,Panama Papers
MEMMO CENTER; 4 AVENUE DES ORCHIDEES; MC98000 MONACO,E75F237286218C270A8BF342C257840D,The Panama Papers data is current through 2015,MCO,Monaco,14049859,Panama Papers
MEMMO CENTRE; 4 AVENUE DES GUELFES; MC98000 MONACO,0A3B2B79E8BC69ECA5078DE821FA885E,The Panama Papers data is current through 2015,MCO,Monaco,14049860,Panama Papers
MEMMO CENTRE; 4 AVENUE DES GUELFES; MC98000; MONACOS,97FEDF65E02326FAB634D68E28C9C0D9,The Panama Papers data is current through 2015,MCO,Monaco,14049861,Panama Papers
MEMMO CENTRE; 4 AVENUE DES GUELFES; MONACO,BBE188D9D447B1F718C71B19047FB637,The Panama Papers data is current through 2015,MCO,Monaco,14049862,Panama Papers
Memorail Square; PO Box 556; Charlestone; Nevis; West Indies,50D210D493812EC498F19985CD96A8C8,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049863,Panama Papers
MEMORIAL SQARE; P.O. BOX 556; CHARLESTONE; NEVIS; WEST INDIES,D95A23E6F1581471E15A895238B690CF,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049864,Panama Papers
MEMORIAL SQ BOX 556 CHARLESTONE NEVIS W.I.,E8C800B438E1B3A3DE46880729224456,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049865,Panama Papers
Memorial Sq.; P.O. Box 556; Charlestone; Nevis; West Indies,B6A5AE94116B09CA26A4E2565CB9DAFD,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049866,Panama Papers
MEMORIAL SQ P O BOX 556 CHARLESTONE NEVIS W.I.,2717587F2A28679F95A10CE8A1696E03,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049867,Panama Papers
Memorial Squae; PO Box 556; Charlestone; Nevis; West Indies,BBD833A51F77DDA7881144A2E4CD1182,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049868,Panama Papers
“MEMORIAL SQUARE 556, CHARLESTONE NEVIS WEST INDIES”,EEAA889540E679F5A8D077F0F7767434,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049869,Panama Papers
MEMORIAL SQUARE BOX 556 CHARLESTONE NEVIS WEST INDIES,707CB968986682EAD9A90ABE012C08B7,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049870,Panama Papers
Memorial Square; Charlestone Nevis; West Indies,B0586CB0F81EBB49D3589706745574D4,The Panama Papers data is current through 2015,CMR,Cameroon,14049871,Panama Papers
Memorial Square; Charlestone; Nevis; W.I.,3C6F31192C57711F3AAEE0CCC8BC979F,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049872,Panama Papers
MEMORIAL SQUARE; P.O. 556; CHARLESTONE NEVIS; WEST INDIES,D9649B1BBF51D503A722A7ED794C4BD1,The Panama Papers data is current through 2015,CMR,Cameroon,14049873,Panama Papers
Memorial Square; POB 556; Charlestone; Nevis; West Indies,BE490EEE38068FF66143CB3F563D08F3,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049874,Panama Papers
Memorial Square; P.O. BHox 556; Charlestone; Nevis West Indies,5FCC67355C6291CD0F1C72D80FC158BE,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049875,Panama Papers
MEMORIAL SQUARE; PO BO 556; CHARLESTONE; NEVIS; WEST INDIES,B6A10BBB1C1405A64914F4D37976A09E,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049876,Panama Papers
Memorial Square; PO Box 336; Charlestone; Nevis; West Indies,129FDC65AC4A27F06BBFBA23C2C4964D,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049877,Panama Papers
Memorial Square; PO BOX 536; Charlestone; Nevis; West Indies,E4C555CAD04990D63097E10BFFA9BF59,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049878,Panama Papers
Memorial Square; PO BOX 556,102F4B81D8F168E8BD36B6B85F375927,The Panama Papers data is current through 2015,NZL,New Zealand,14049879,Panama Papers
Memorial Square P.O. Box 556 Chalestown NEVIS,DB6E410CA10CE8347400242D44D61CAC,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049880,Panama Papers
MEMORIAL SQUARE; P.O. BOX 556; CHARELESTONE; NEVIS; WEST INDIES,98F5A17143A9D12D9810289500F18EDF,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049881,Panama Papers
Memorial Square; PO Box 556; Charestone; Nevis; West Indies,5C5CEC2833CF1FF0135BCAEDDC9F6AD9,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049882,Panama Papers
Memorial Square; P.O. Box 556; Charlestone; Neivs; West Indies,C1BF9A9F4309CB29A4FFC7961AC574DB,The Panama Papers data is current through 2015,CMR,Cameroon,14049883,Panama Papers
MEMORIAL SQUARE; P.O.BOX 556 CHARLESTONE; NEVBIS WEST INDIES,3A46D377D6638D02BF0A69177285FD8E,The Panama Papers data is current through 2015,CMR,Cameroon,14049884,Panama Papers
MEMORIAL SQUARE; PO BOX 556; CHARLESTONE; NEVIA; WEST INDIES,C8B846E46FD1F7E9BA3779852F6EC8D1,The Panama Papers data is current through 2015,CMR,Cameroon,14049885,Panama Papers
Memorial Square; PO Box 556; Charlestone; Nevis,5343534DCE91382D91FB24673C86B8F5,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049886,Panama Papers
MEMORIAL SQUARE; PO BOX 556; CHARLESTONE NEVISE; WEST INDIES,71EF3107F553D7ED69F7C211BCADD3BD,The Panama Papers data is current through 2015,CMR,Cameroon,14049887,Panama Papers
MEMORIAL SQUARE PO BOX 556 CHARLESTONE NEVIS INDIES,CBB3466129D9E97406395E030FD240BB,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049888,Panama Papers
Memorial Square; PO Box 556; Charlestone; Nevis; West Indie,7E73B4F54E0D53BB2CA55B0A639D825F,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049889,Panama Papers
MEMORIAL SQUARE; P.OBOX 556; CHARLESTONE; NEVIS WEST INDIES,99090740AD678AAA21803FFB08248C4A,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049890,Panama Papers
Memorial Square; P.O. Box 556; Charlestone; Nevis; West Indiies,0B61D4EF706929A7EC3CAA76870C6BCC,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049891,Panama Papers
Memorial Square; PO BOX 556; Charlestone; Nevis; West Inides,1642D7209FEAF3CAB5B335C82A51EDB5,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049892,Panama Papers
Memorial Square; PO Box 556; CHarlestone; Nevis; Wet Indies,F6B60E29DB08723B5C99931F1919DA96,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049893,Panama Papers
MEMORIAL SQUARE; P. O. BOX 556; CHARLESTONE; NEVIS; WETS INDIES,DE4880988EF7B24EAD4C6EBEBEC4CEB5,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049894,Panama Papers
MEMORIAL SQUARE P O BOX 556 CHARLESTONE NEVIS W.I.,FAE2D890CFBB47B45F3B5EFF5DF83EB2,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049895,Panama Papers
MEMORIAL SQUARE; P.O. BOX 556; CHARLESTONE; NEWVIS; WEST INDIES,94A087DC20410AE996D3F6C5A0EBB168,The Panama Papers data is current through 2015,CMR,Cameroon,14049896,Panama Papers
Memorial Square; PO Box 556; Charlestone; west Indies,84A464B307DC96FBE12DA5D41C3FB120,The Panama Papers data is current through 2015,CMR,Cameroon,14049897,Panama Papers
Memorial Square; P.O. Box 556; Charleston; Nevis,33D0525051623538CA9603DDA0462FEA,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049898,Panama Papers
Memorial Square PO Box 556; Charleston Nevis; West Indies,45DBF4AC7EC84DEF752E3605AA624ECF,The Panama Papers data is current through 2015,CMR,Cameroon,14049899,Panama Papers
MEMORIAL SQUARE; PO BOX 556; CHARLESTOWNE; NEVIS; WEST INDIES,4CCC4C77846F4AFD4213B44D6D7249C7,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049900,Panama Papers
MEMORIAL SQUARE; P.O. BOX 556; CHARLESTOWN; NEVIS,32C4005C6BA0B113DF54F2A3434406C9,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049901,Panama Papers
Memorial Square – P.O. Box 556 – Charlestown – NEVIS,9EA7ED0260DC627BA8282662F873A926,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049902,Panama Papers
MEMORIAL SQUARE; P.O. BOX 556; CHARLESTOWN; NEVIS; WEST INDIES,B835F6E09BF8CECD97B7D6B17EE4500E,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049903,Panama Papers
Memorial Square; PO Box 556; Charlestown; Nevis; Wi,80D5DE493B1117814C2BB386571AE2AF,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049904,Panama Papers
MEMORIAL SQUARE; P.O. BOX 556; CHARLESTTOWN; NEVIS,958941197BC81D9B5224DEF17ED135C2,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049905,Panama Papers
MEMORIAL SQUARE PO BOX 556; CHEARLESTON; NEVIS; WEST INDIES,1DE6188C413EE5A14C286B86D12A8077,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049906,Panama Papers
MEMORIAL SQUARE; P O BOX 55; CHARLESTONE; NEVIS; WEST INDIES,63A4CA192ECB4795EB664DA5B768CD9D,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049907,Panama Papers
“Memorial Square PO Box 566, Charlestone Nevis West Indea”,7F5AA34903B11F879927F42F84688543,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049908,Panama Papers
“MEMORIAL SQUARE P.O. BOX 566 CHARLESTON NEVIS, EST INDIES”,1E3BF4DB8FF6972625D20C8348E11E48,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049909,Panama Papers
MEMORIAL SQUARE; P.O. BOX CHARLESTONE; NEVIS; WEST INDIES.,22798CDA76BA13B25EA002C4B8BD4EBE,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049910,Panama Papers
Memorial Square; P.O. Boxx 556; Charlestone; Nevis; West I,0C124C4705579122E44683FBB033B3C3,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049911,Panama Papers
MEMORIAL SQUARE; PO OX 556; CHARLESTONE; NEVIS; WEST INDIES,7B4CF6F404A9D877A2D071840352F6EF,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049912,Panama Papers
Memorial Squar; PO Box 556; Charlestone Nevis; West indies,217780079E507AC0EE3F278F195C68C9,The Panama Papers data is current through 2015,CMR,Cameroon,14049913,Panama Papers
Memorial Squarre; PO Box 556; Charlestone; Nevis; West Indies,FBE2283B16BA9E2D17A24FE25FE8D669,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049914,Panama Papers
MEMORIAL SQUQRE; PO BOX 556; CHARLESTONE; NEVIS; WEST INDIES,1E5ED7B1B8F8EE8ACC5FC1FC83B676F9,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049915,Panama Papers
Memoria Square PO Box 556 Charlestone; Nevis; West Indies,DD2A7B96DBC91D11BE71C2EB90F93DA2,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049916,Panama Papers
MEMRIAL SQUARE; P.O.BOX 556; CHARLESTONE; NEVIS WEST INDIES.,3A06CCFF7BF74E2200D9234DB6058962,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14049917,Panama Papers
Men 704; Unit 3; Dong 9; Taigu Xiaoqu; No.632 Taigu Street; Daowai District; Haerbin; Heilongjiang; China,31C6C56685F7F5CDE8E531C2AD67D180,The Panama Papers data is current through 2015,CHN,China,14049918,Panama Papers
Menachem Meshiv St 3; Jerusalem; Israel,A931BE7D73AA4A5C423C1333E26F9653,The Panama Papers data is current through 2015,ISR,Israel,14049919,Panama Papers
MENARA BATIVA; 30th FLOOR JL. K.H. MAS MANSYUR KAV. 126; JAKARTA 10220 INDONESIA C/O 8 TEMASEK BOULEVARD #37-02 SUNTEC TOWER 3 SINGAPORE 038988,8F22BEE0F1932120C641AC587B5689AC,The Panama Papers data is current through 2015,SGP,Singapore,14049920,Panama Papers
Menara Imperium Lt. 10 Suite 10/C JI. HR Rasuna Said Kav. 1; Jakarta 12980; Indonesia,9EF6ED5123F94DB47182C740CBDA44E5,The Panama Papers data is current through 2015,IDN,Indonesia,14049921,Panama Papers
MENARA KADIN INDONESIA 21F.; JALAN HR RASUNA SAID BLOK X-5 KAV. 2-3; JAKARTA 12950; INDONESIA,D6D66497383907E368B0A123B6626801,The Panama Papers data is current through 2015,IDN,Indonesia,14049922,Panama Papers
MENARA KUNINGAN 31ST FLOOR; JL. HR RASUNA SAID; BLOCK X-7 KAV 5 JAKARTA 12940; INDONESIA,837950D2D34AE8D406495ED637E87546,The Panama Papers data is current through 2015,IDN,Indonesia,14049923,Panama Papers
“MENARA RAJAWALI, 17th FLOOR MEGA KUNINGAN LOT 5.1 JAKARTA 12950 INDONESIA”,79B0F2DA72B65388ED32BBA724F64B2D,The Panama Papers data is current through 2015,IDN,Indonesia,14049924,Panama Papers
Mendoza 1826 15A; Cap. Fed. Buenos Aires Argentina Negro 627; Colonia; Uruguay,7EE7C0F39E1686EBF21D42BB7895122F,The Panama Papers data is current through 2015,URY,Uruguay,14049925,Panama Papers
Mendoza 1858; 11th Floor; Depto. C; Postal Code C1428DKD Capital Federal; Buenos Aires; Argentina,2AD613AB308C85D9CF2B24F61A9582DA,The Panama Papers data is current through 2015,ARG,Argentina,14049926,Panama Papers
“Mendoza, Argentina.”,AB9D56E240DFF39781CCABFCCCCEDEF6,The Panama Papers data is current through 2015,ARG,Argentina,14049927,Panama Papers
MENEKSE SOK. NURI SESOREN APT. 11/4 ACIBADEM; ISTAMBUL; TURKEY,24B2F4141F592303E9ACFC8ECC3B8CEB,The Panama Papers data is current through 2015,TUR,Turkey,14049928,Panama Papers
MENELAOU; 13A; LAKATAMIA; P.C. 2320; NICOSIA; CYPRUS,CD5E0537328330F9EDEC06CDDA4AACD6,The Panama Papers data is current through 2015,CYP,Cyprus,14049929,Panama Papers
MENGSHIMEN VILLAGE; SHIMEN TOWN; LULONG; QINHUANGDAO; HEBEI; CHINA,9131A8382994CB51DC1A76E55901E6F2,The Panama Papers data is current through 2015,CHN,China,14049930,Panama Papers
MENTE CARLO PLACE 7; BOULEVARD DES MOULINS; MONACO 98000,E73F9FB334B73E49893E72838C944867,The Panama Papers data is current through 2015,MCO,Monaco,14049931,Panama Papers
Menthonis 11; 1070 Nicosia; Cyprus,1F8266E7DF13959F310450CB02E50E1D,The Panama Papers data is current through 2015,CYP,Cyprus,14049932,Panama Papers
Menthonis 11 1070 Nicosi Cyprus,695677C635528CDBB94B30906A992E1F,The Panama Papers data is current through 2015,CYP,Cyprus,14049933,Panama Papers
MERCEDES 1465; MONTEVIDEO; URUGUAY,AD1244FF50F38A19E925A48003A8286C,The Panama Papers data is current through 2015,URY,Uruguay,14049934,Panama Papers
“MERCEDES 1877/701, MONTEVIDEO – URUGUAY”,A8DB77D7B23D9A43C92929DFD31E87E6,The Panama Papers data is current through 2015,URY,Uruguay,14049935,Panama Papers
Mercedes 3225,6766372E9D503EE232A92EE2E7EB417F,The Panama Papers data is current through 2015,,,14049936,Panama Papers
MERCEDES BENZ; GARGOUR BUILDING; DORIA HIGHWAY; BEIRUT; LEBIANON,966C1F0D7DEE5116FC2360C4BBCC1CBA,The Panama Papers data is current through 2015,LBN,Lebanon,14049937,Panama Papers
Merchants House; 24 North Quay; Douglas; Isle of Man; IM1 4LE,4D10FE8E3469BCB1429BA00801888359,The Panama Papers data is current through 2015,IMN,Isle of Man,14049938,Panama Papers
MERCHISTON LODGE PARK ESTATE LA ROUTE DES GENETS ST BRELADE JE3 8EQ JERSEY,FAED8CD1E6CDB6AF525595DAAEF88A32,The Panama Papers data is current through 2015,JEY,Jersey,14049939,Panama Papers
Merdivenköy MH. Bar-baros; Sokagi Serda-roglu Bina No: 9 Daire: 2; Kadiköy; Turkey.,719DAD91E299278638625A5E9949DFA5,The Panama Papers data is current through 2015,TUR,Turkey,14049940,Panama Papers
Merkela Street 8; appt. 6; Riga; LV-1050; Latvia,8434F82413399C60C006DEA98A2350CB,The Panama Papers data is current through 2015,LVA,Latvia,14049941,Panama Papers
MERKEZ BEBEK; BRIKTAR ARALIGI SK. BESIKTAS; ISTANBUL,5398689EA0731E3B2F5E79780EF60D8D,The Panama Papers data is current through 2015,TUR,Turkey,14049942,Panama Papers
Merkez Mah. Ata- Sok. No: 20 Gaziosmanpasa -Istanbul – Turkey,F24416282523787C0AFF0E1BDD785B82,The Panama Papers data is current through 2015,TUR,Turkey,14049943,Panama Papers
MERKURHAUS/JOSEF RHEINBERGERSTRASSE 6/ VADUZ/ LIECHSTENSTEIN,66073F562199DE1E8BBF27C0A27BF1B0,The Panama Papers data is current through 2015,LIE,Liechtenstein,14049944,Panama Papers
MERKURHAUS/ JOSEF RHEINBERGERSTRASSE 6 / VADUZ/ LIECHTENSTEIN,D0EE5CE1EED5D701F273EB34609CEE28,The Panama Papers data is current through 2015,LIE,Liechtenstein,14049945,Panama Papers
Merkurhaus; Josef; Rheinbergerstrasse 6; Vaduz; Leichtenstein,0B9C20B10323D5CEA16FCB773464EE82,The Panama Papers data is current through 2015,LIE,Liechtenstein,14049946,Panama Papers
MERKURHAUS JOSEF; RHEINBERGERSTRASSE 6; VADUZ; LIECHSTENSTEIN,4ACF551B19E8FF4B89DFFD41499A49F7,The Panama Papers data is current through 2015,LIE,Liechtenstein,14049947,Panama Papers
Merkurhaus Josef; Rheinbergerstrasse 6; Vaduz; Liechtenstein,ECE5A80731B51FAA0A61DDBF55D5D12B,The Panama Papers data is current through 2015,LIE,Liechtenstein,14049948,Panama Papers
Merrill Lynch Investment Managers; 33 King William Street; London EC4R 9AS,8D29B90513A674225C2935364B20AFC2,The Panama Papers data is current through 2015,GBR,United Kingdom,14049949,Panama Papers
Merrion Park; Old Castletown Road; Port Soderick; Isle of Man,63409FF143CC77A2A7B1A9079FA5FA89,The Panama Papers data is current through 2015,IMN,Isle of Man,14049950,Panama Papers
Merrion Park Old Castletown Road Port Soderick Isle of Man IM4 1BB,C1B101606951A5F4AC8E74571874FFFE,The Panama Papers data is current through 2015,IMN,Isle of Man,14049951,Panama Papers
MERRY TERRACE; BLOCK L; 3RD FLOOR; 4 SEYMOUR ROAD; MID LEVELS; HONG KONG,11EF62B124E7DD488774B661609192A5,The Panama Papers data is current through 2015,HKG,Hong Kong,14049952,Panama Papers
MERSCHELL RD; EXETER; DOVON EX46LX; UK,48AA8850D5777AB8555540AE90EBF51C,The Panama Papers data is current through 2015,GBR,United Kingdom,14049953,Panama Papers
Merton Croft; The Crofts; Castletown; Isle of Man IM9 1LY,E13BD3F6E486D7D1B0A34F09E5C3B996,The Panama Papers data is current through 2015,IMN,Isle of Man,14049954,Panama Papers
Merton Grounds Farm; Wendlebury; OX6 ONS; England.,8388921BBFB2FB3BC0737B1C2E5A5D6D,The Panama Papers data is current through 2015,GBR,United Kingdom,14049955,Panama Papers
Merton House; 84 Albion Street; Leeds; LS1 6AG,98BFC759264C60047E18F9687C720D4E,The Panama Papers data is current through 2015,GBR,United Kingdom,14049956,Panama Papers
MERTON HOUSE 84 ALBION STREET LEEDS; WEST YORKSHIRE; LS1 6AG UNITED KINGDOM,B8A34CAFBC6258DA3F0666585BE0BB5D,The Panama Papers data is current through 2015,GBR,United Kingdom,14049957,Panama Papers
“Merzlyakovskiy Per. 13/5, 121013 MOSCOW Russian Federation”,A04ADBFF878F875C641279FF86BFDB34,The Panama Papers data is current through 2015,RUS,Russian Federation,14049958,Panama Papers
Mesa Geitonia; P.C. 4007; Limassol; Cyprus,F77865081342C29C4CCD816EBA39F4ED,The Panama Papers data is current through 2015,CYP,Cyprus,14049959,Panama Papers
Mesa Koru Sitesi Sokak; No. 5 Vayyolu; Yenimahalle Ankara; Turkey,2ECC4D3134663503F4A7848F6AA74344,The Panama Papers data is current through 2015,TUR,Turkey,14049960,Panama Papers
Mesarska Street; House 028; Ljubljana; Republic Of Slovenia,B7B4D153BF38F08D37283520454B0247,The Panama Papers data is current through 2015,SVN,Slovenia,14049961,Panama Papers
MESCHANSKAYA STR.; BLD. 1/17; CORP. 1; APT. 17; MOSCOW; RUSSIA,25700727C534F0496493E9A1FB20C4CF,The Panama Papers data is current through 2015,RUS,Russian Federation,14049962,Panama Papers
MESDAGLAAN 10C; BOSCH EN DUIN; 3735 II; NETHERLANDS,31DB9C21B47713D12A888BE7DC01A800,The Panama Papers data is current through 2015,NLD,Netherlands,14049963,Panama Papers
MESDAGLAAN 10C; BOSCH EN DUIN; 3735 LI; NETHERLANDS,719FA49F903D3D6E4C503ED8999949E7,The Panama Papers data is current through 2015,NLD,Netherlands,14049964,Panama Papers
MESELI SOKAK NO.3; 80620; ISTANBUL; TURKEY,8A4E8517BDCFC9BD1FA6F9D70E0227DD,The Panama Papers data is current through 2015,TUR,Turkey,14049965,Panama Papers
mesk-Flat-2601; E-W Sub Meter; 392 Dubai; UAE,8858CC53B504CCD94E73D3E2B9E68940,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049966,Panama Papers
Messabah Arkarbi PoBox 3217 Aon Dhabi UAE. Villa 16 West 50 A Baran Abu Dhabi,1471396E054CF4284084DE567013EC08,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14049967,Panama Papers
Messeila Block 7; Plot 800002; Safat 13019; Kuwait,E962DD00FA8FB7FBA48E0EB5A1B0EF91,The Panama Papers data is current through 2015,KWT,Kuwait,14049968,Panama Papers
Messeila Palace Kuwait,303389C9B03E850EB56B5842C1D674C5,The Panama Papers data is current through 2015,KWT,Kuwait,14049969,Panama Papers
MESSEILA PLACE; MASSILA; KUWAIT,8337891F9E7B8B6E1243F64FBD8A3107,The Panama Papers data is current through 2015,KWT,Kuwait,14049970,Panama Papers
“Messelia Palace, Kuwait”,5D02649866BF81E3C8643AEA55563B3F,The Panama Papers data is current through 2015,KWT,Kuwait,14049971,Panama Papers
Messiano; Kilkis; Greece,93E8DE2BDA7D700DECD55D4E15AFEEF9,The Panama Papers data is current through 2015,GRC,Greece,14049972,Panama Papers
Messilah Palace Kuwait,1C804980F2FB78AC769E33A53D97D9F4,The Panama Papers data is current through 2015,KWT,Kuwait,14049973,Panama Papers
Messinastrasse 30 Postfach 534 9495 Triesen Principality of Liechtenstein,134151C395010584E653A6EE666D10CB,The Panama Papers data is current through 2015,LIE,Liechtenstein,14049974,Panama Papers
“Messinastrasse 30, Postfach 534 Fl-9495 Triesen Lichenstein”,459161AF308789FBBDBE9D8633D524C4,The Panama Papers data is current through 2015,LIE,Liechtenstein,14049975,Panama Papers
Messinastrasse 30; Postfach 534; FL 9495; Triesen; Liechtenstein,3484F76819C7261A817B726D96F091A2,The Panama Papers data is current through 2015,LIE,Liechtenstein,14049976,Panama Papers
MESSINASTRASSE 30; POSTFACH 534; FL-9495; TRIESEN; LIECHTENSTEIN,B5BA751A663A90EE6FA281ADD5B491A6,The Panama Papers data is current through 2015,LIE,Liechtenstein,14049977,Panama Papers
Messter Vanwibsrfrelan 7; B-8531; Hulste; Belgium,FE958A22190D4BC5C9CF250293A62A55,The Panama Papers data is current through 2015,BEL,Belgium,14049978,Panama Papers
Mesto 3rd Floor; Abbassie Nifurcation Street; Tyre Lebanon,9303563F9A1D1B7617B057578899CE99,The Panama Papers data is current through 2015,LBN,Lebanon,14049979,Panama Papers
Metabo-Allee 1; 72622 Nuertingen; Germany,0E635A5EAF5D98F8B5ED14CE543C44AC,The Panama Papers data is current through 2015,DEU,Germany,14049980,Panama Papers
Metallurgov Str. 47b; Quartier 34; 300057 Tula; Russia,FA54A84BA37F7A1A7BD1BFFD1CF8D54D,The Panama Papers data is current through 2015,RUS,Russian Federation,14049981,Panama Papers
“Metallygrov Str 27 ”B” / 34, Tulla Russia”,3245A94FC7B949B47CEA01415F212CD3,The Panama Papers data is current through 2015,RUS,Russian Federation,14049982,Panama Papers
“Metallyrgrov Str. 27 “”B”” / 34 Tula, Russia”,EC0B894A4415EEBBB40FFAC0E7325774,The Panama Papers data is current through 2015,RUS,Russian Federation,14049983,Panama Papers
METALSTOCK HOUSE; VANGUAR WAY; SHOEBURYNESS; ESSEX SS3 9RE; UK.,0627C09B7FE92B951763C0CFCBDD50FC,The Panama Papers data is current through 2015,GBR,United Kingdom,14049984,Panama Papers
METALSTOCK WAY; SHOEBURYNESS; ESSEX SS3 9RE; UK.,48D3AF359FDD6E1BC2B0E7CE748D428E,The Panama Papers data is current through 2015,GBR,United Kingdom,14049985,Panama Papers
Methonis 1; 1070 Nicosia; Cyprus,AE605158425E19FE959BA0FD014FBF24,The Panama Papers data is current through 2015,CYP,Cyprus,14049986,Panama Papers
Methonis 11; 1070 Nicosai; Cyprus,0C57418342AC5E0FCA627BBC7115B88D,The Panama Papers data is current through 2015,CYP,Cyprus,14049987,Panama Papers
Methonis 11; 1070 Nicosia; Cyprus,474DA3978893C8A6DEEA9C5FA259ACAC,The Panama Papers data is current through 2015,CYP,Cyprus,14049988,Panama Papers
Metochiou 73; 2407 Egomi; Nicosia; Cyprus,0A7A8CC29D0109F7B4722F77AF78E799,The Panama Papers data is current through 2015,CYP,Cyprus,14049989,Panama Papers
Metochiou 73; Egkomi; 2407 Nicosia; Cyprus.,C0ECF7C94BB958385FC36D3A8FD94302,The Panama Papers data is current through 2015,CYP,Cyprus,14049990,Panama Papers
METRO ALAM XI PG 1-2; PONDOK INDAH; JAKARTA SELATAN; INDONESIA,663EC91A8603D96998680923F4C6688B,The Panama Papers data is current through 2015,IDN,Indonesia,14049991,Panama Papers
Metrocity residence B blok n° 74; 1. Levent; 34330 Istanbul; Turkey,0083399198BDA7801A0B4A8D0EA21869,The Panama Papers data is current through 2015,TUR,Turkey,14049992,Panama Papers
Metropolitan Ave.; Metropolitan Park; Roxas Boulevard corner EDSA Extension; Pasay City; Metro Manila; Philippines.,874FF5B438E2B74208748A01C4F33266,The Panama Papers data is current through 2015,PHL,Philippines,14049993,Panama Papers
METROPOLITAN AVE.SUITE 2R BROOKLYN.NY.11211,2212B4D63075B0A9B16132BED4961C38,The Panama Papers data is current through 2015,USA,United States,14049994,Panama Papers
Metsavahi 23; Tallinn; Estonia,C6540CD78DA6BA0B4BD65BACA97E6A82,The Panama Papers data is current through 2015,EST,Estonia,14049995,Panama Papers
Mettallurgov prospect 27/156; Yenakiyevo; Ukraine,87C9381A56A4FE599B38F7F6ADE8692B,The Panama Papers data is current through 2015,UKR,Ukraine,14049996,Panama Papers
Mettelenstrasse 22 CH-8142 Uitikon – Waldegg Switzerland,4F51F4D12C8AA488F0B58CB51AFC8F33,The Panama Papers data is current through 2015,CHE,Switzerland,14049997,Panama Papers
Mevo Hayam Street 11 POB 1532 Arsuf 46920,7BCF69D2E5C429F092F335E1FFAA85CB,The Panama Papers data is current through 2015,USA,United States,14049998,Panama Papers
Mevout Street; House 17; Savion; Israel; 56510,7AFFB9A6D67DD459DA267331E6DFDDD2,The Panama Papers data is current through 2015,ISR,Israel,14049999,Panama Papers
MEWS COTTAGE; HIGH STREET; WHITWELL; NOTTINGHAMSHIRE; S80 4RB; UNITED KINGDOM,B9AC7BF3A40DB846B1AB4446573F27DF,The Panama Papers data is current through 2015,GBR,United Kingdom,14050000,Panama Papers
México Distrito Federal,54F9910DBCBDF3D441BDBBD7F36849B8,The Panama Papers data is current through 2015,MEX,Mexico,14050001,Panama Papers
MEZANINE WESTHADFIELD HOUSE LIBRARY STREET GIBRALTAR,86079440D3EDF80AA79892D28D25FF69,The Panama Papers data is current through 2015,GIB,Gibraltar,14050002,Panama Papers
MEZHDUNARODNAYA STR. 18/30; APT.41; MOSCOW; RUSSIA,BA3A93B0B2D268D21C3BA32550179566,The Panama Papers data is current through 2015,RUS,Russian Federation,14050003,Panama Papers
MEZON KURERU #101 4-37-29; TAKADANOBABA; SHINJUKU-KU TOKYO 169-0075 JAPAN,865E9D4A55C96E51D7D2010EE690CB16,The Panama Papers data is current through 2015,JPN,Japan,14050004,Panama Papers
Mezzanine West Hadfield House Library Street Gibraltar,D3289158712A3854654DDD966C254186,The Panama Papers data is current through 2015,GIB,Gibraltar,14050005,Panama Papers
MF & CO. (BELIZE) LIMITED; No. 15 A Street; Belize City,2FA29EAC793029FEC3B4BD29C5C3E8DD,The Panama Papers data is current through 2015,BLZ,Belize,14050006,Panama Papers
MF & CO. (BELIZE) LIMITED; No. 15 A Street; Belize City; Belize,B4C5CF6A0F2BCDC0102F711FBCC0277F,The Panama Papers data is current through 2015,BLZ,Belize,14050007,Panama Papers
MF Akara Bldg. 24 De Castro Street; Wickhams Cay I; Road Town Tortola; BVI,D9DA81B9C1773B81E660862041D4B466,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050008,Panama Papers
“MF, BAHAMAS”,01E689321CFCCD8776460235D05B27DE,The Panama Papers data is current through 2015,BHS,Bahamas,14050009,Panama Papers
MF BIV CO. – File n° 524219,C2728E98E690443A3929D0927B9743EA,The Panama Papers data is current through 2015,,,14050010,Panama Papers
MF BVI CO. – File n° 524219,956DD39CCF9AF7B4AD736FF05565A844,The Panama Papers data is current through 2015,,,14050011,Panama Papers
MF BVI COMPANY,013932F6DA818A6C9EC89FCB5FA3E91D,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050012,Panama Papers
MF BVI – File n° 811644,E8271960A9E722B0FD0E2236F40A06B4,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050013,Panama Papers
MFC Corporate Finance GMBH; Stubbenhuk 7; 20459; Hamburg; Germany,DD33E5744AD7BD7BCCA3C535BCF87026,The Panama Papers data is current through 2015,DEU,Germany,14050014,Panama Papers
“MF CO., FILE N° 20230”,D29CF8378FC16065D155C9F14F6D9743,The Panama Papers data is current through 2015,USA,United States,14050015,Panama Papers
MF CO. – File n° 525507,C911F5D403871258197B60ECAF8E62C7,The Panama Papers data is current through 2015,,,14050016,Panama Papers
MF CO. – FILE N° 538820,7229549F3AED84AA6515DBDF91B375BB,The Panama Papers data is current through 2015,,,14050017,Panama Papers
MF CO. – FILE N° 552086,A34F991477BFA77B3D33B8F5DF6173C0,The Panama Papers data is current through 2015,,,14050018,Panama Papers
“MF CO., FILE N° 555405”,472563C3103AAF1E77360534B176DCCF,The Panama Papers data is current through 2015,,,14050019,Panama Papers
MF co. – File n° 569217,38E0DE25A9B4BAE8DB0EF7FDBC9573C2,The Panama Papers data is current through 2015,,,14050020,Panama Papers
“MF CO., file n° 6470”,37EA914E49E3689C09ED36AF659CBB96,The Panama Papers data is current through 2015,,,14050021,Panama Papers
MF co.- File nr 612285,EBE81781A668754386D77143A7AC1278,The Panama Papers data is current through 2015,NRU,Nauru,14050022,Panama Papers
MF co.- File nr 613778,5F6CAF5F2269AD2A4E93AFE45728E1B1,The Panama Papers data is current through 2015,NRU,Nauru,14050023,Panama Papers
MF CO. N° 524967,43E1DA26621D7B0FC64442D1233A807F,The Panama Papers data is current through 2015,USA,United States,14050024,Panama Papers
M.F. Corporate Services (Nevada) Limited; 520 S 7th Street; Suite 6; Las Vegas NV 89101,470FC0E14FC5FB711FC572F5B4CFB28C,The Panama Papers data is current through 2015,USA,United States,14050025,Panama Papers
MF CORPORATE SERVICES (NIUE) PTE. LTD,1E6E1F9856CF6DFEA928C5741F2AA2F0,The Panama Papers data is current through 2015,NIU,Niue,14050026,Panama Papers
MF FILE N° 535403,D2322F911AD641B887F929234FE740CD,The Panama Papers data is current through 2015,,,14050027,Panama Papers
MF File n° 564150,3CA87752F78B93B41CB953D08D61EFCD,The Panama Papers data is current through 2015,,,14050028,Panama Papers
MF File n° 564410,041641CEF19484D865D5469E953508E4,The Panama Papers data is current through 2015,,,14050029,Panama Papers
MF Fitzgerald; Attn NA Karpusheff; Le Regina; 15 Bd des Moulins; MC 98000,41640A3E5ED1F8BE78957A3C214CBE5D,The Panama Papers data is current through 2015,MAC,Macao,14050030,Panama Papers
M. Filevskaya Str. 62-3; Moscow; Russia,8EBCC7D225CD6E37E2E4941CADAD9A99,The Panama Papers data is current through 2015,RUS,Russian Federation,14050031,Panama Papers
MF Legal Services; Mossfon Building; 2nd Floor; East 54th Street; P.O. Box 0832-0886,479BB5401A66D829E831AD8B88C21F46,The Panama Papers data is current through 2015,,,14050032,Panama Papers
MF NIUE CO. (FILE N° 308314),1121248626EADF8F6AA168D908C36248,The Panama Papers data is current through 2015,NIU,Niue,14050033,Panama Papers
MF PMA Mossfon Bldg.; East 54th Street; Panama; Rep. of Panama,6E3FB96A80E09F85C8432DF68C4FC3ED,The Panama Papers data is current through 2015,PAN,Panama,14050034,Panama Papers
MF SAMOA/SUSCRIBER,E3F69F77F0F87B8C8DC0EB6C0C4A0D47,The Panama Papers data is current through 2015,WSM,Samoa,14050035,Panama Papers
M F’S FOUNDATION,DC4A3890FD275524A8D7AE91E545807C,The Panama Papers data is current through 2015,USA,United States,14050036,Panama Papers
MF’S NIUE COMPANY,9AC31F53C6BE15441B98172657930FBB,The Panama Papers data is current through 2015,NIU,Niue,14050037,Panama Papers
“MF Suite E-2 Union Court Building Elizabeth Avenue and Shirley Street Nassau, Bahamas”,D49CC6662A203F5C94C1D0F6B4692FCF,The Panama Papers data is current through 2015,BHS,Bahamas,14050038,Panama Papers
MF Trustees Panama,5DDC2152C0B59BE16EB44ED4100A9EF3,The Panama Papers data is current through 2015,PAN,Panama,14050039,Panama Papers
MG2-03 L74 Street 8 East Tape Poi; Parana Country Club; Hernandarias-Alto-Paraná-Paraguay,A9E28ACCACAB253D1F0508189CF72B3C,The Panama Papers data is current through 2015,PRY,Paraguay,14050040,Panama Papers
MGM Bahamas Ltd; 50 Shirley Street; P.O. Box CB-13937; Nassau; The Bahamas,61E1D9E4AF4BA8949F5DC4760C5EB123,The Panama Papers data is current through 2015,BHS,Bahamas,14050041,Panama Papers
MGM TOWER 16 th Floor PANAMA Rep of Panama,7C5373ACB1885C5B88D08829C8175DBA,The Panama Papers data is current through 2015,PAN,Panama,14050042,Panama Papers
M.GRUZINSKAYA STR.31-8; MOSCOW; RUSSIA,35BA887E3C39FD3CE9EBFD85CDD30EAD,The Panama Papers data is current through 2015,RUS,Russian Federation,14050043,Panama Papers
Mg Tower; Second Floor; East 53rd Street; Urbanizacion Marbella; Panama,E011DE67D3EE3B86F7E56DBEFBC65322,The Panama Papers data is current through 2015,PAN,Panama,14050044,Panama Papers
MHALA AVRAMOVICA J-0V S19; 11040 BEOGRAD; SERBIA,80DCA202470BE706ED0E6C2CFF9E7B6C,The Panama Papers data is current through 2015,SRB,Serbia,14050045,Panama Papers
“M, Harfon Botsari 16675 Glyfada Greece”,7A441766B85E1115F53CAF56EE906902,The Panama Papers data is current through 2015,GRC,Greece,14050046,Panama Papers
M.H. THAMRIN 62 SURABAYA INDONESIA,BE8D3DA3C78103D376B7FB0447227901,The Panama Papers data is current through 2015,IDN,Indonesia,14050047,Panama Papers
MHZ2043; RM 1007; 10/F.; HO KING CTR; 2-16 FA YUEN ST MONGKOK; KL; HONGKONG,0F40189AB7932BCB2A94A134B4EF8BC2,The Panama Papers data is current through 2015,HKG,Hong Kong,14050048,Panama Papers
Miami 2081; Montevideo; Uruguay,09FF0CB7D73E27714C07D0768F458CBD,The Panama Papers data is current through 2015,URY,Uruguay,14050049,Panama Papers
“MIAMI, FLORIDA. U.S.A.”,BFBA15747DDBA500376C053C1C4B53DB,The Panama Papers data is current through 2015,USA,United States,14050050,Panama Papers
“Miami Shores, FL 331382556”,CD75D8680490E70CBDC5A8B44CD4C131,The Panama Papers data is current through 2015,USA,United States,14050051,Panama Papers
Miane; Via Trento 2; Modena; Italy,60D94849E74DF62EC7494793BF211CE9,The Panama Papers data is current through 2015,ITA,Italy,14050052,Panama Papers
MIANHUA YUANZHONGCHANG; GAIBEI XIANG; SHANGYU; ZHEJIANG; CHINA,8D4A1DA940A87631C29803A8657504B7,The Panama Papers data is current through 2015,CHN,China,14050053,Panama Papers
MIAOLING ROAD; QINGDAO; CHINA.,1DB08A389E7F160299F655FD0EC1DB17,The Panama Papers data is current through 2015,CHN,China,14050054,Panama Papers
MIAO XI; HAI YAN MIAO VILLAGE; FUHAI TOWN; CIXI CITY; ZHEJIANG PROVINCE.,4469911FF1ED3AEC4D3577E34B6E62EB,The Panama Papers data is current through 2015,CHN,China,14050055,Panama Papers
MICHAEL FARADAY 1060- URB.INDUSTRIAL SANTA ROSA- ATE VITARTE-LIMA-PERÚ,371E3CE08235B903A799EE3B65047465,The Panama Papers data is current through 2015,PER,Peru,14050056,Panama Papers
MICHAEL KRASIA NO. 1; KOKKINOTRIMITHIA; P.C. 2660; NICOSIA; CYPRUS,9491706258F343296154BDF73A8B6999,The Panama Papers data is current through 2015,CYP,Cyprus,14050057,Panama Papers
Michael Ronald Kernot,614ED09C7EF5B3F2D3F526E429112032,The Panama Papers data is current through 2015,,,14050058,Panama Papers
Michail Karaoli 17; Flat 101; Livada 7060; Larnaka; Cyprus,42B186EFD8BA7EDA7C6FD65917BB5EF7,The Panama Papers data is current through 2015,CYP,Cyprus,14050059,Panama Papers
MICHAIL KARAOLI; 2; EGKOMI; PC 2404; NICOSIA; CYPRUS,7C0FAEC3FB67C3AAB3C5FA2B0F6E9CAC,The Panama Papers data is current through 2015,CYP,Cyprus,14050060,Panama Papers
Michalakopoulou 12; 4th floor; Flat/Office 401; P.C. 1075; Nicosia; Cyprus,6175C456A7B7523EE48CF10843D321D6,The Panama Papers data is current through 2015,CYP,Cyprus,14050061,Panama Papers
Micheal Faraday; 1060-Urb.Industrial Santa Rosa-Ate-Vitarte; Perú,F7C56EB5261CC9297EC7851CCA62C9F0,The Panama Papers data is current through 2015,PER,Peru,14050062,Panama Papers
Micheal Okpara Street; Wuse 2; Abuja; Nigeria.,D8C62D567E61C069BF24B043799309CA,The Panama Papers data is current through 2015,NGA,Nigeria,14050063,Panama Papers
Michele Shiha Street; Yazre; Baabda,88F866A0CEEA6E204FEAEB85C673F047,The Panama Papers data is current through 2015,LBN,Lebanon,14050064,Panama Papers
Michele Shiha Street; Yazre; Baabda; Beirut; Lebanon,1BF00528B7F069E40006E993D9FE3C45,The Panama Papers data is current through 2015,LBN,Lebanon,14050065,Panama Papers
Michele street; house 17; Haifa; Israel,CDF75A4EA3E065DC482E15AA1EE28F2A,The Panama Papers data is current through 2015,ISR,Israel,14050066,Panama Papers
Michel Faraday 1060-Urb.Industrial Santa Rosa-Ate-Vitarte-Lima-Perú,F41E31C1AE2A1F81FC54EFF15913884C,The Panama Papers data is current through 2015,PER,Peru,14050067,Panama Papers
MICHELL HOUSE; PO BOX 174; THE VALLEY; ANGUILLA; BRITISH WEST INDIES,E9ED1FC48DF8F32A3D3F6FF74D617812,The Panama Papers data is current through 2015,AIA,Anguilla,14050068,Panama Papers
Michourinsky avenue; 29; 59; RF; Moscow; Russia,17A29022941ACB1E258FA97CDDA547E7,The Panama Papers data is current through 2015,RUS,Russian Federation,14050069,Panama Papers
MICHUNNSKY PR.; OLIMPIYSKAYA VILLAGE; BLD. 11; APT. 159; MOSCOW; RUSSIAN FEDERATION,FED47AF5626454AB77C4997074A0CB54,The Panama Papers data is current through 2015,RUS,Russian Federation,14050070,Panama Papers
Michurinskiy avenue; 7; bld. 1; app. 100; Moscow; Russia,5354199B0E0E4F32D84BC5EF6E81E1AF,The Panama Papers data is current through 2015,RUS,Russian Federation,14050071,Panama Papers
Michurinskiy Prospect 29/Korp. 3-112; Moscow; Russia,DA2AF9BD2CA901E5C422FC8951C907EC,The Panama Papers data is current through 2015,RUS,Russian Federation,14050072,Panama Papers
Michurinskiy prospect; bld. 27; corp. 2; apr. 9; Moscow; Russia,F3370642E2574D3AF11246B2D4975E6D,The Panama Papers data is current through 2015,RUS,Russian Federation,14050073,Panama Papers
Michurinskiy Prospekt 11-1-57MoscowRussia,8E76D40D6FBAA7838C09F928E48DFCDC,The Panama Papers data is current through 2015,RUS,Russian Federation,14050074,Panama Papers
Michurinsky Avenue 19; Block 3; flat 49; Moscow; Russia,DAFB02C46E6EE0AC91385217688102E2,The Panama Papers data is current through 2015,RUS,Russian Federation,14050075,Panama Papers
Michurinsky pr-kt 10/3 – 28; Moscow; Russia.,E87C6314BB818EA89EA97C880EF9B90E,The Panama Papers data is current through 2015,RUS,Russian Federation,14050076,Panama Papers
MICHURINSKY PR-KT 11/2-117; 117192 MOSCOW; RUSSIA,C9A858483EA12ADF709A5AA4DE34ACD5,The Panama Papers data is current through 2015,RUS,Russian Federation,14050077,Panama Papers
Michurinsky Prospect; House 31; Block 3; Flat 36; Moscow; 119607 Russia,D39FF6920C7780D4547643765188E1FE,The Panama Papers data is current through 2015,RUS,Russian Federation,14050078,Panama Papers
MICHURINSKY PROSPECT; HOUSE 9; BUILDING 2; APARTM; 21 MOSCOW; RUSSIA,8F27CCA61F247D11EC76B4F1BC3E4E4D,The Panama Papers data is current through 2015,RUS,Russian Federation,14050079,Panama Papers
MICHURINSKY PROSPECT; HOUSE 9; BUILDING 2; APARTM; 22; MOSCOW; RUSSIA,44E25DA1931EBB7223726AA5A3BEDCEC,The Panama Papers data is current through 2015,RUS,Russian Federation,14050080,Panama Papers
“Michurinsky prospekt 31-1, flat 16 Moscow RUSSIA.”,304AA5FF4A2F836EC5CFEE1807BFE39A,The Panama Papers data is current through 2015,RUS,Russian Federation,14050081,Panama Papers
“Microdistrict “”Dzerjinets””; Bld. 9; Apt. 25; Pushkino City; Moscow District; Russian Federation”,1FD357285FFDEED6F2E016DB747961CB,The Panama Papers data is current through 2015,RUS,Russian Federation,14050082,Panama Papers
Micro district “Geolog” 2; Township Zelenogorskiy; Pushkinskiy district; Moscow Region; Russia,7AF59984A0EB91DCF8DE8F6C8B118E05,The Panama Papers data is current through 2015,RUS,Russian Federation,14050083,Panama Papers
Microdistrict 15; Bldg. 2; Apt no. 15 Aktau; Magistau Region 466200; Kazakhstan,22367D9D05C009250D5CD010A646F387,The Panama Papers data is current through 2015,KAZ,Kazakhstan,14050084,Panama Papers
Microdistrict 7; Bldg. 1; Apt no. 23 Aktau; Magistau Region 466200; Kazakhstan,31053E0552EDA0B9FAFA18311EEB5737,The Panama Papers data is current through 2015,KAZ,Kazakhstan,14050085,Panama Papers
Microjack 705297; Document 1801165; Global Bank Tower 18th Floor; 50 Street; P.O. Box 0831-2484; Paitilla; Panama; Republic of Panama,27B6A58109EBD79D854B1D2301716DB1,The Panama Papers data is current through 2015,PAN,Panama,14050086,Panama Papers
Microjacket 32227; Document 1467047 Mossfon Building; 2nd Floor; East 54th Street; P. O. Box 0832-0886 W.T.C.; Panama; Republic of Panama,A761B3A91EE54DF9A9A787B104B3D616,The Panama Papers data is current through 2015,PAN,Panama,14050087,Panama Papers
Microjacket 524267; Document 943429; Global bank tower 18th Floor; 50 Street; P.O. Box 0831-2484; Paitilla; Panama; Republic of Panama,00A5504CE9400B3E8B56307A08416A4B,The Panama Papers data is current through 2015,PAN,Panama,14050088,Panama Papers
Microrayon “G”; Bldg. 33; Apt. 49; Puschino Town; Moscow region; Russian Federation,A2106153AFE1090C261575AC8D168BC7,The Panama Papers data is current through 2015,RUS,Russian Federation,14050089,Panama Papers
MIDDAGKRANS FARM; VERDUN ROAD; FRANSCHHOEK,817721E35E0AAAD09C76EB7EA4CEA08E,The Panama Papers data is current through 2015,ZAF,South Africa,14050090,Panama Papers
MIDDLE AREA; CHANGXING ROAD; ZONGHE TOUZIQU; ZHENGZHOU; CHINA,7407409DFD37878157259E332359018E,The Panama Papers data is current through 2015,CHN,China,14050091,Panama Papers
MIDDLE CHINNOCK TA18 7PN,5872D015AE2504E899F2827E7DBA6E50,The Panama Papers data is current through 2015,GBR,United Kingdom,14050092,Panama Papers
Middle gate; Floor 3; Gate 2; Building 902; Peace Street; Lvyuan District; Changchun City; Jilin Province; China,7179252FA2E2923A88B577E9F423F00C,The Panama Papers data is current through 2015,CHN,China,14050093,Panama Papers
“Middle Street Ringstown, St. Vincent and Grenadines.”,08CE12F1BB40F37A3336A04CC4549843,The Panama Papers data is current through 2015,VCT,Saint Vincent and the Grenadines,14050094,Panama Papers
Midgardi 9 230 Keflavik Iceland,4206DEC841EC40C1B99616E3D8C39217,The Panama Papers data is current through 2015,ISL,Iceland,14050095,Panama Papers
Midland BankTrust Building,C0AC5A1D2C0C3816DA175903D3243E8E,The Panama Papers data is current through 2015,,,14050096,Panama Papers
Midland Bank Trust Building; Main Street; George Town; Grand Cayman; Cayman Islands; B.V.I.,55168348FD8200DE2D54A1F827DED16E,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050097,Panama Papers
Midland Bank Trust Building; Mary Street; Grand Cayman; Cayman Islands; British West Indies,050070DCD223F2785672F272CB345A9D,The Panama Papers data is current through 2015,CYM,Cayman Islands,14050098,Panama Papers
Midland Trust Limited; 177 Main Street; Road Town; Tortola; British Virgin Islands,32C16909C925D89D719D98F8BF165AD5,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050099,Panama Papers
Midocean Chambers; Pelican Drive; Road Town; Tortola; British Virgin Islands,87AFCAB0F67CB9A48EA6C43CEBA124B9,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050100,Panama Papers
MIDOCEAN CHAMBERS P.O. BOX 805; ROAD TOWN; TORTOLA; BRITISH VIRGIN ISLANDS,57C34F14100C42C1C15C02CE3627E134,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050101,Panama Papers
“Midocean Chambers PO Box 805 Road Town, Tortola VG110 BVI”,9E27B24C0A151E6B99F832D3620EA8D0,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050102,Panama Papers
MIDOCEAN CHAMBERS; ROAD TOWN; TORTOLA; BRITISH VIRGIN ISLANDS,2936E60E4EC18764B82AB75C8A071043,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050103,Panama Papers
Midocean Chambers Road Town Tortola BVI,6FEC621CAA0EF1E8BBC6B4160C2B07E7,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050104,Panama Papers
Midocean Management Trust Service(BVI)Ltd.,4849C4C9D64C83587257E4A1F110CBBF,The Panama Papers data is current through 2015,,,14050105,Panama Papers
Midrethstraat 57 3641 CC Mijdrecht,C9477395272BF204CA232C0A2EF0B214,The Panama Papers data is current through 2015,NLD,Netherlands,14050106,Panama Papers
Migadal Neve Tzedek; 61 Eilat Street; Apartment 611; Tel Aviv 66845 – Israel,881A203B0EB6D75C2F755AFA12C6DDFC,The Panama Papers data is current through 2015,ISR,Israel,14050107,Panama Papers
“MIGDAL HAMENORA STREET NO.14/2 MODI’IN Z.C. 71700, ISRAEL”,08C2BE16746A98CD28B087BD23892DEB,The Panama Papers data is current through 2015,ISR,Israel,14050108,Panama Papers
MIGNOT PLATEAU; CORNET STREET; PO BOX 124; ST. PETERPORT GY1 4EG; CHANNEL ISLANDS,87FAE64D22FB5F271D09360678C6E4B8,The Panama Papers data is current through 2015,GGY,Guernsey,14050109,Panama Papers
Mignot Plateau; St. Peter Port; Guernsey; GY1 4EG,30317FD95EEB69C2962C316FB2D13023,The Panama Papers data is current through 2015,GGY,Guernsey,14050110,Panama Papers
Miguel Aljovín Nº 104; El Rosedal; Miraflores; Lima; Perú,03EA499E4E81EA45435D2495139BFD75,The Panama Papers data is current through 2015,PER,Peru,14050111,Panama Papers
“MIGUEL CANÉ 2958- VILLA LUZURIAGA-PROVINCIA DE BUENOS AIRES, ARGENTINA”,2BAB14B7C77E55A663EEF9CBA96F50C5,The Panama Papers data is current through 2015,ARG,Argentina,14050112,Panama Papers
Miguel Claro 1614 depto. 102; Providencia; Santiago; Chile.,E24224372D1BAC8BB87B8E02158D764E,The Panama Papers data is current through 2015,CHL,Chile,14050113,Panama Papers
Miguel Dasso 117; piso 6; San Isidro; Lima; Perú,6EC9692C67CEB23784F4D8EB607A2358,The Panama Papers data is current through 2015,PER,Peru,14050114,Panama Papers
MIGUEL DASSO 117-PISO 6-SAN ISIDRO-LIMA-PERU,C1E651CC7A1AB41E3F7212EE6D682745,The Panama Papers data is current through 2015,PER,Peru,14050115,Panama Papers
Miguel Dasso 139; Oficina 402; San Isidro; Lima; Perú,A034D33E488209924B4CC4C28370FC72,The Panama Papers data is current through 2015,PER,Peru,14050116,Panama Papers
Miguel de Cervantes Saavedra; Col. Irrigación Del Miguel Hidalgo Torre 1 AP. 804; México DF; México,178A5E51289606258B6445E764F00621,The Panama Papers data is current through 2015,MEX,Mexico,14050117,Panama Papers
“MIGUEL DEL CORRO 1471, MONTEVIDEO URUGUAY”,EEC40B8D40AEE893F07562033530D336,The Panama Papers data is current through 2015,URY,Uruguay,14050118,Panama Papers
Migueletes 1130 P.03 D. 19; 1426 Ciudad Autonoma de Buenos Aires; Argentina,DA8D095E3DA0B8A4EE8833909B659EE1,The Panama Papers data is current through 2015,ARG,Argentina,14050119,Panama Papers
“Migueletes 1130, Piso 5o. Ciudad de Buenos Aires (CP 1426)”,4822173F51F29842870CA9597DA04EEF,The Panama Papers data is current through 2015,ARG,Argentina,14050120,Panama Papers
Migueletes 1231; Capital Federal; Argentina.,18115914304D3F11C1829745CCE40ED8,The Panama Papers data is current through 2015,ARG,Argentina,14050121,Panama Papers
“Migueletes 2326 8 B Ciudad Autonoma de Buenos Aires, Argentina”,543293FC829772CB9F244857035BB11D,The Panama Papers data is current through 2015,ARG,Argentina,14050122,Panama Papers
Miguel Grau 255- INT B- Miraflores-Lima-Perú,47B52CF891445FC2FF78CB459EA5BDD7,The Panama Papers data is current through 2015,PER,Peru,14050123,Panama Papers
MIIDLEWOOD; 11 HIGH WOOD LANE; PAGET PG 05; BERMUDA,39CAA170424948B366154B60B5401625,The Panama Papers data is current through 2015,BMU,Bermuda,14050124,Panama Papers
Mikhailovskaya St.; 9; flat 6 A; Kiev; 01001; Ukraine,D603B2A954E06DF3EE2B24579AC7C1CA,The Panama Papers data is current through 2015,UKR,Ukraine,14050125,Panama Papers
MIKHAILYANY VILLAGE; RYSHKANSKIY DISTRICT; REPUBLIC OF MOLDOVA,F7D1C58DAAE5A7D966C26AD0BE4C2DC2,The Panama Papers data is current through 2015,MDA,”Moldova, Republic of”,14050126,Panama Papers
Mikhaylovich; Of Apt. 37; 18 Arkh.Vlasova street; Moscow; Russia,BFBD64EC894BED013F8D88A87832D87B,The Panama Papers data is current through 2015,RUS,Russian Federation,14050127,Panama Papers
Mikinon 21; Chalandri; 15233 North Athens; Greece.,F575D67AE0050EB9810EBF29331BE8F9,The Panama Papers data is current through 2015,GRC,Greece,14050128,Panama Papers
Miklošiceva ulica 1E; 1230 Domžale; Slovenia; Europe,550958CDCBAEB5F4FF1322DE748A7397,The Panama Papers data is current through 2015,SVN,Slovenia,14050129,Panama Papers
Mikov Street; 53-12; 624440 Krasnoturinsk; Sverdlovsk region; Russian Federation,DCE6414B273C1BF86AA25018A91EE064,The Panama Papers data is current through 2015,RUS,Russian Federation,14050130,Panama Papers
Mikov Street; 53-12; 6244440 Krasnoturinsk; Sverdlovsk region; Russian Federation,EDF4ED39A0A12853F0BB8692BA9468DF,The Panama Papers data is current through 2015,RUS,Russian Federation,14050131,Panama Papers
Mikroraion 1; 30-22; Jubileinyi; Moscovskaya Obl.; Russia,1D629783BA9C12C9A380365B15A856B5,The Panama Papers data is current through 2015,RUS,Russian Federation,14050132,Panama Papers
Mikroraion 3; 21-50; Jubileinyi; Moscovskaya Obl.; Russia,DF7F157F2D473519516CE549D983B92F,The Panama Papers data is current through 2015,RUS,Russian Federation,14050133,Panama Papers
Milano Italy,162D790508C4BB261C770345796A419A,The Panama Papers data is current through 2015,ITA,Italy,14050134,Panama Papers
“Milano Piazzale (square) Segesta, 15-Italy”,C84C401D67FC6494D196F4597B11EDAB,The Panama Papers data is current through 2015,ITA,Italy,14050135,Panama Papers
MILANO. VIA F; FERRUCCI; 6; ITALY,42D9B0686075D1D0A4E64EA3FBD3AFA8,The Panama Papers data is current through 2015,ITA,Italy,14050136,Panama Papers
Milan Tankosica 27; 11000 Belgrade; Serbia; Europe,669AEDFDC178146A1FAE98CE9CEEF480,The Panama Papers data is current through 2015,SRB,Serbia,14050137,Panama Papers
Mild Mall; Suite 6; Wickhams Cay I; P.O. Box 3085; Road Town; British Virgin Islands,3189C54B482EED44B566EB8E51C00214,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050138,Panama Papers
Mile Fleurs Ave. Du Manoir Ville Au Roi St. Peter Port Guemsey GY1 1PE,41096C9A96C898F437341EDBAD0B668A,The Panama Papers data is current through 2015,GGY,Guernsey,14050139,Panama Papers
Milenium House; 1st floor; Victoria Road; Isle of Man,6D29AE06DB7F82DF2C8BBEF602CA25A6,The Panama Papers data is current through 2015,IMN,Isle of Man,14050140,Panama Papers
Milimani House; Milamani Road; Kitale; Kenya,49C74B20245F31CFC2FA2FF739CA2493,The Panama Papers data is current through 2015,KEN,Kenya,14050141,Panama Papers
MILIONI STREET 1; 106 73 ATHENS; GREECE,63EA7C28D7F26E8956355C9B81FF8051,The Panama Papers data is current through 2015,GRC,Greece,14050142,Panama Papers
Militopolskoye Shosse 110A-129 332440 Berdiansk; Zaporozhskaya obl; Ukraine.,DC2C26FB9C5888A3F65BDEE66F31258B,The Panama Papers data is current through 2015,UKR,Ukraine,14050143,Panama Papers
Milla 8 Las Cumbres; Panama City; Republic of Panama,51A687632CD25F4C177F3D6C30DCD3E8,The Panama Papers data is current through 2015,PAN,Panama,14050144,Panama Papers
Milla 8; Las Cumbres; Panama; Rep. de Panamá,234739F44370A953307F588A7A2FCC22,The Panama Papers data is current through 2015,PAN,Panama,14050145,Panama Papers
Mill Avenue 2621; Brooklyn 11234 New York; United States of America,E9FD344D17333EDC1DDA0F34DFD53EDA,The Panama Papers data is current through 2015,USA,United States,14050146,Panama Papers
MILL COURT; HOPE STREET; CASTLETOWN; ISLE OF MAN,ECB7C8009F111DF2A3468E6DEAED47BF,The Panama Papers data is current through 2015,IMN,Isle of Man,14050147,Panama Papers
Mill Court; La Charroterie; St Peter port; Guernsey; GY1 4LW,4D770D238A05DF4F5ADFC5EDE7BB23A4,The Panama Papers data is current through 2015,GGY,Guernsey,14050148,Panama Papers
Millefiori 1C1; Rue des Genets; 98000 Monaco,BE572500629E67664250110FB0F7C887,The Panama Papers data is current through 2015,MCO,Monaco,14050149,Panama Papers
MILLENIUM HOUSE; FIRST FLOOR; VICTORIA ROAD; DOUGLAS; ISLE OF MAN; IM2 4RW,96882E35DEA119F6ED2A53D933129E0D,The Panama Papers data is current through 2015,IMN,Isle of Man,14050150,Panama Papers
Millenium House; Victoria Road; Douglas; Isle of Man,F2AB248D7D4CA63E58BC2CA5F10985F0,The Panama Papers data is current through 2015,IMN,Isle of Man,14050151,Panama Papers
MILLENIUM HOUSE; VICTORIA ROAD; FIRST FLOOR; DOUGLAS; ISLE OF MAN IM2 4RW,056D3A0719E862AB523096B446F67F45,The Panama Papers data is current through 2015,IMN,Isle of Man,14050152,Panama Papers
Millennia#16-01; 62 Langsuan Rd; Bangkok; 10330 Thailand,4F926377000A2D802305EF2D1E21CAC4,The Panama Papers data is current through 2015,THA,Thailand,14050153,Panama Papers
MILLENNIUM BRIDGE HOUSE; 2 LAMBETH HILL; LONDON EC4V 4AJ; UK,B8BF35A43D8ACE2470BBBB9A1F07B3EB,The Panama Papers data is current through 2015,GBR,United Kingdom,14050154,Panama Papers
MILLENNIUM HOUSE; DOUGLAS; ISLE OF MAN; IM2 4RW,6813ECAD330725D166E344725333B3BA,The Panama Papers data is current through 2015,IMN,Isle of Man,14050155,Panama Papers
MILLENNIUM HOUSE; FIRST FLOOR; VICTORIA ROAD; DOUGLAS; ISLE OF MAN,4B7EC5A23C68360E41A44B6E2C289287,The Panama Papers data is current through 2015,IMN,Isle of Man,14050156,Panama Papers
MILLENNIUM HOUSE; FIRST FLOOR; VICTORIA ROAD; DOUGLAS; ISLE OF MAN IM2 4 RW,2113C8171AC58B04340FA4A7F848AEF3,The Panama Papers data is current through 2015,IMN,Isle of Man,14050157,Panama Papers
Millennium House; Vicotria Road; First Floor; Douglas; Isle of Man IM2 4RW,783494B4EFFC319F2E8E8A63C9F49FFF,The Panama Papers data is current through 2015,IMN,Isle of Man,14050158,Panama Papers
Millennium House; Victoria Road; Douglas; IM2 4RW; Isle Of Man,9A42277088DAE3DD73EC9DABEBCD14F7,The Panama Papers data is current through 2015,IMN,Isle of Man,14050159,Panama Papers
MILLENNIUM HOUSE; VICTORIA ROAD; DOUGLAS ISLE OF MAN; IM2 4RW,D527550446BAB9856F1197A9E1929921,The Panama Papers data is current through 2015,IMN,Isle of Man,14050160,Panama Papers
MILLENNIUM HOUSE; VICTORIA; ROAD; FIRST FLOOR; DOUGLAS; ISLE OF MAN IM2 4RW,452350FF53A5FA35520077F5B62DB471,The Panama Papers data is current through 2015,IMN,Isle of Man,14050161,Panama Papers
MILLENNIUM HOUSE; VICTORIA ROAD; FIRST FOOR; DOUGLAS; ISLE OF MAN 1IN 4RW,5761E65419DB08AD2C5D2905B59D321A,The Panama Papers data is current through 2015,IMN,Isle of Man,14050162,Panama Papers
Millenuim House; Victoria Road; Daouglas; Isle of Man,BE079A92AAE5EDF40A82D432E12F1821,The Panama Papers data is current through 2015,IMN,Isle of Man,14050163,Panama Papers
MILL HATCH; DUNMOW ROAD; THAXTED; ESSEX; CM6 2LU; UNITED KINGDOM,ECA8B28DFC5B08ED3E51049B15945A8A,The Panama Papers data is current through 2015,GBR,United Kingdom,14050164,Panama Papers
Mill House; Glen Auldyn; Lezayre; Ramsey; Isle of Man; IM7 2AQ,972B73EC2C2101C8F820D0C1EC96DBE7,The Panama Papers data is current through 2015,IMN,Isle of Man,14050165,Panama Papers
Millington Drake 1780/101; Montevideo; Uruguay,0828B42B1D33E7B566481ED714C48249,The Panama Papers data is current through 2015,URY,Uruguay,14050166,Panama Papers
Mill Mall/PO Box 964; Road Town; Tortola; BVI,19A2CD0160441D659CE3ADF86B85A226,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050167,Panama Papers
MILL MALL; P.O. BOX 964; ROAD TOWN; TORTOLA; BRITISH VIRGIN ISLANDS,BCCDF51CE9B2E1BA4A0421D4221783A6,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050168,Panama Papers
Mill Mall; P.O. Box 964; Road Town; Tortola; BVI,B1B31E6F7EFFBEDEF44F90558EEC1886,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050169,Panama Papers
“Mill Mall Road Town, Tortola British Virgin Islands”,42192477C7D19A512EC9D8DD06684C9B,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050170,Panama Papers
MILL MALL STREET; SUITE 6; WICKHAMS CAY I; P.O. BOX 3085; ROAD TOWN; TORTOLA; BVI,6C8654BEE2F43DF45B49B30165A2D133,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050171,Panama Papers
Mill Mall; Suite 6; Road Town; British Virgin Islands,217EF8D2DC1F29D436943E5741BA55ED,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050172,Panama Papers
Mill Mall; Suite 6; Road Town; Tortola; British Virgin Islands Wickhams Cay 1; P.O.Box 3085,0CD6199A2DBD7F9DEA313976FB1C5696,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050173,Panama Papers
MILL MALL SUITE 6; WICHAMS CAY 1; P O BOX 3085; ROAD TOWN; TORTOLA; BRITISH VIRGIN ISLANDS,31F835AB2474D9F1911EEBFD146FED6B,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050174,Panama Papers
Mill Mall; suite 6; Wickhams Can 1; Road Town; Tortola.,CF85A049376A8952E73900B84395C8C9,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050175,Panama Papers
Mill Mall; Suite 6; Wickham’s Cay 1; c/o box 3085; Road Town; Tortola; British Virgin Islands,71183DE3AA5F1F54489E7373D8358519,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050176,Panama Papers
Mill Mall; Suite 6; Wickhams Cay 1; PO Box 3085; Road Town; Tortola; British Virgin Islands,93D9BD1FD1E39181B84ED673372FEE1B,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050177,Panama Papers
Mill Mall; Suite 6; Wickhams Cay 1; P.O. Box 3085; Road Town; Tortola; BVI,5BE0E9A9D5D29F0E4D3B199ED29BE1E5,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050178,Panama Papers
Mill Mall; Suite 6; Wickhams Cay 1; Road Town; Tortola; British Virgin Islands.,1E0073731F7BDBBFDE002BEF75F83DA3,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050179,Panama Papers
Mill Mall; Suite 6; Wickhams Cay 1; Road Town; Tortola; BVI,67E186272B4E8EE1B81BA72C135F4E95,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050180,Panama Papers
MILL MALL; SUITE 6 WICKHAMS CAY 1 VG ROAD TOWN TORTOLA; BRITISH VIRGIN ISLANDS,5CD7EA5A385C691747E963F9287E74A4,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050181,Panama Papers
MILL MALL; SUITE 6; WICKHAMS CAY I; ROAD TOWN; TORTOLA; BRITISH VIRGIN ISLANDS,D3F6864A3C1B7BA44995EF6574D3F285,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050182,Panama Papers
Mill Mall; Suite 6; Wickhams Cay; PO Box 3085; Road Town; Tortola; British Virgin Islands,FFD002C9C80DD8EE0F62D10262EA92BF,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050183,Panama Papers
Mill Mall Tower; 2nd Floor Wickhams Cay 1; PO Box 4406 Road Town British Virgin Islands,CB66FED5E3A34B2FFA879F9B7775505A,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050184,Panama Papers
Mill Mall Tower; 2nd Floor; Wickhams Cay 1; PO Box 4406; Road Town; Tortola; British Virgin Islands,4D63192768B231FB72BD212019673294,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050185,Panama Papers
MILL MAL; SUITE 6; WICKHAMS CAY 1; ROAD TOWN; TORTOLA; BRITISH VIRGIN ISLANDS,E158D5B0EDCCE20790E9B62FC132D0C1,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050186,Panama Papers
Millrace House; The Millrace; Sulby; Ramsey; Isle of Man; IM7 2HT,5E596789CE6844C2FD7169A5B658DBE5,The Panama Papers data is current through 2015,IMN,Isle of Man,14050187,Panama Papers
Mills Mall; Suite 6; Wickhams Cay 1; Road Town; Tortola; British Virgin Islands,2D09957F8227E464514ECA98828E27C8,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050188,Panama Papers
Milner Grove; Magenta; Flat 5 Milner Street Sliema Malta,CD9CCD3F4AC853404E09311F6A30EEB1,The Panama Papers data is current through 2015,MLT,Malta,14050189,Panama Papers
MILNER HOUSE; 18 PARLIAMENT SSTREET HAMILTON HM 12; BERMUDA.,83CDE1760BE290CC85562F020900335A,The Panama Papers data is current through 2015,BMU,Bermuda,14050190,Panama Papers
Milner House; 18 Parliament Street; Hamilton; Bermuda.,C601BF836615950D32A126EBE71E7C83,The Panama Papers data is current through 2015,BMU,Bermuda,14050191,Panama Papers
“MILNER HOUSE 18 PARLIMENT STREET HAMILTON, BERMUDA”,6AD1C6F0EA801E93D1D67BA3B93FC27F,The Panama Papers data is current through 2015,BMU,Bermuda,14050192,Panama Papers
Milner Road; Lytham St Annes; Lancashire UK FY8 4EY,C2A4EA7EAC104D841705EA63DF4A4E1F,The Panama Papers data is current through 2015,GBR,United Kingdom,14050193,Panama Papers
MILTON’S WAY; 11 BELL’S CRESCENT; WESTLAKE; TOKAI; 7945; SOUTH AFRICA,0CB4582D0E9234B1E741CC719FC30820,The Panama Papers data is current through 2015,ZAF,South Africa,14050194,Panama Papers
Minamihorie 4-30-21-306; Nishi Ward; Osaka Prefecture; Japan 5500015,0A5D3D8C5524D7C940141083B443ACAB,The Panama Papers data is current through 2015,JPN,Japan,14050195,Panama Papers
MINCHVAN EAST ROAD SECTION 3; LANE 106 ALLEY 3; NO. 55; 11F; TAIPEI CITY TAIWAN,0130663350DF844D959EFC43C960DC65,The Panama Papers data is current through 2015,TWN,”Taiwan, Province of China”,14050196,Panama Papers
Mindaugo 23-51; Vilniud LT03214; Lithuania,566BBCF13455FC5E493D7B97894322AE,The Panama Papers data is current through 2015,LTU,Lithuania,14050197,Panama Papers
Mindaugo St.; Apt. 44; Trakay; Lithuania,18C6574E2B386F02144008135FBA6E84,The Panama Papers data is current through 2015,LTU,Lithuania,14050198,Panama Papers
Mindvalley; A-23A-13A; Tower A; Menara UOA; 5; Jalan; Bangsar Utama 1; Kuala Lumpur 59000; Malaysia,91BFCD583D67CF47BB82B2499F25E3A9,The Panama Papers data is current through 2015,MYS,Malaysia,14050199,Panama Papers
Mindvalley; A-23A-13A; Tower A; Menara UOA; 5; Jalan; Bangstar Utama 1; Kuala Lumpur 59000; Malaysia,E58B568E93C810FB365AA54D96F834B1,The Panama Papers data is current through 2015,MYS,Malaysia,14050200,Panama Papers
Mindvalley; A-23 A-13A; Tower A; Nenara VOA Bangsar 5; Jalan Bangsar Utama 1; Kuala Lumpur 59000; Malaysia,E92DAC4CABE1F582E5F18E1AAD104EC6,The Panama Papers data is current through 2015,MYS,Malaysia,14050201,Panama Papers
Minerva Financial Services Limited; PO Box 218; 43 La Motte Street; St. Helier; JE4 8SD; Jersey,DEE7B3CFF01FD8CD1BC4175E338AC02F,The Panama Papers data is current through 2015,JEY,Jersey,14050202,Panama Papers
Minerva Financial Services; PO Box 218; 43 La Motte Street; St. Helier; JE4 8SD; Jersey,C4BE306A4C81E08337D1E67E932FC448,The Panama Papers data is current through 2015,JEY,Jersey,14050203,Panama Papers
Ming Chuan Road; Section 2; No. 266. Tainan 70042; Taiwan,D56BA9DBD7577B391CAD93D48EBAD839,The Panama Papers data is current through 2015,TWN,”Taiwan, Province of China”,14050204,Panama Papers
“MING GLOBAL HOLDING CO., LTD.”,954F904A541ABC030222472A2DA9490D,The Panama Papers data is current through 2015,,,14050205,Panama Papers
Mingrui Company; Hetou Village; East Wu Town; Yinzhou Dist.; Ningbo City; China,631A9AFDE990368C09C4F6977414EBAE,The Panama Papers data is current through 2015,CHN,China,14050206,Panama Papers
Mini Farm; Klein Drakenstein; South Africa; 7628,6C2808203F4CC6B97CCD89D2A7899CDA,The Panama Papers data is current through 2015,ZAF,South Africa,14050207,Panama Papers
“Ministry of TourismP.O. Box GP4386Accra, Ghana”,F1FDB0BAF85FA1431C9EB81CD2534F20,The Panama Papers data is current through 2015,GHA,Ghana,14050208,Panama Papers
Minskaya; 104/la; Moscow; Russia,75EB89048457D7263584B4FBE2D4481B,The Panama Papers data is current through 2015,RUS,Russian Federation,14050209,Panama Papers
Minskaya Str. 1g-2-215; 119590 Moskau; Russia,F92DA713FF26BF81F28E14BA78A5BCD8,The Panama Papers data is current through 2015,RUS,Russian Federation,14050210,Panama Papers
MINSKAYA STREET 1-233/MOSCOW RUSSIA,EC10E8BD5CE639146FAC27666DAD0120,The Panama Papers data is current through 2015,RUS,Russian Federation,14050211,Panama Papers
Minskaya street 1-233; Moscou; Russia,9C1A83124A7FE873C18F5F8FD8A8C0DC,The Panama Papers data is current through 2015,RUS,Russian Federation,14050212,Panama Papers
“Minskaya Street, 1-233 MOSCOW RUSSIA”,16C17B9D491E5F9865D8EBC3F7586E9B,The Panama Papers data is current through 2015,RUS,Russian Federation,14050213,Panama Papers
Minskaya street 1g-2-215; 119590 Moscow; Russian Federation,F673AE9D765BF92CBF62E7CACED40A09,The Panama Papers data is current through 2015,RUS,Russian Federation,14050214,Panama Papers
Minskaya Street 20; apartment 48 420140 Kazan; RUSSIA,1378AB3938B9030ACB25939144E91168,The Panama Papers data is current through 2015,RUS,Russian Federation,14050215,Panama Papers
“Mintakert utca 7, Budapest 1224 Hungary”,F59DA21769BD6DC5A518D6DAD1B616D7,The Panama Papers data is current through 2015,HUN,Hungary,14050216,Panama Papers
MIN XING GONG YE YUAN; NO. 59; MIN XING YI ROAD; LANE 3029; HUA XU GONG LU; HUA XIN TOWN; QING PU DISTRICT; SHANG HAI; CHINA,24E3B8B27FFFE9A51D63892DA2861883,The Panama Papers data is current through 2015,CHN,China,14050217,Panama Papers
Minz 18 Tel Aviv Israel,5E4C6A123E4BA2DEA53EE0C267470725,The Panama Papers data is current through 2015,ISR,Israel,14050218,Panama Papers
Miraflores 1398; Montevideo; Republica Oriental de Uruguay,B4B323E1E2B3216CA8DEBBB11B29ABBC,The Panama Papers data is current through 2015,URY,Uruguay,14050219,Panama Papers
“Miramar, Bradley Huddersfield”,011342E2E9A61634A66BE09EF290774C,The Panama Papers data is current through 2015,GBR,United Kingdom,14050220,Panama Papers
Mira Street 51-4; Tiraspol; Moldova,71644BE9AE478E3B168FB3284301D9AF,The Panama Papers data is current through 2015,MDA,”Moldova, Republic of”,14050221,Panama Papers
Mirdiff; P.O. Box 30871; Dubai; United Arab Emirates,404A324A2FDCF613CEF0A965249155E4,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14050222,Panama Papers
Mir-Gasimov St.; Apt. 27; Baku; Azerbaijan R.,FEA5F145192A3FAA4DE92C47735542A4,The Panama Papers data is current through 2015,AZE,Azerbaijan,14050223,Panama Papers
Mirlos; Lote 45C; San Rafael; Quito Ecuador,27A5F37248BE08D609BA3343B0C1F164,The Panama Papers data is current through 2015,ECU,Ecuador,14050224,Panama Papers
MI-ROCA FARM; RUE DES NIEMES; ST PETER; JERSEY; CHANNEL ISLANDS,93766BEDC6BAE4725837EF96E4FC0647,The Panama Papers data is current through 2015,JEY,Jersey,14050225,Panama Papers
Miroquesada 158; dpto.. 1901; San Isidro; Lima; Perú,B9169330A9655013C8DF233D8AEFB811,The Panama Papers data is current through 2015,PER,Peru,14050226,Panama Papers
MIROSLAVA VILLAGE; MIROSLAVA COMMUNE; P.C. 707305; LASI COUNTY; ROMANIA,CD5DABE24C1CD7044E56218F3F44C546,The Panama Papers data is current through 2015,ROU,Romania,14050227,Panama Papers
Mirskoy Per. 8/10-1-9; Moscow; Russia,484D09346F3978E0267DC0BE4ABC14E2,The Panama Papers data is current through 2015,RUS,Russian Federation,14050228,Panama Papers
Mirza Fatali Lane 13; Yasamal District; Baku; Azerbaijan,57A616648E66F23E01B8BDA22FF03687,The Panama Papers data is current through 2015,AZE,Azerbaijan,14050229,Panama Papers
MISCHOSTOS; INVESTMENTS S.A.; C/O POSTSTRASSE 2; FL-9491 RUGGELL; LIECHTENSTEIN,32B0DB80A590C484F7039990C1BDB930,The Panama Papers data is current through 2015,LIE,Liechtenstein,14050230,Panama Papers
Mishmar Hgvul 4 Jerusalem Israel.,07195B26AC78BB2C862E1D64BC412308,The Panama Papers data is current through 2015,ISR,Israel,14050231,Panama Papers
MISHREF; BLOCK 1; STREET; HOUSE 17; KUWAIT,84057CADA1863876B2B220425261982E,The Panama Papers data is current through 2015,KWT,Kuwait,14050232,Panama Papers
MISHREF; BLOCK 6; STREET 6; HOME 40; KUWAIT,E112300AAC6B3C09C6C42D0E20378FAF,The Panama Papers data is current through 2015,KWT,Kuwait,14050233,Panama Papers
Mishrif West; Area 3; Street 306; House 15; Kuwait,443094039285779E48628083ACB448C0,The Panama Papers data is current through 2015,KWT,Kuwait,14050234,Panama Papers
MISIONES 1371; MONTEVIDEO; URUGUAY,58739262D8E4D56B13ECD0E4474F3359,The Panama Papers data is current through 2015,URY,Uruguay,14050235,Panama Papers
Misiones 1379; Oficina 602; Montevideo; Uruguay,A4D70C186047903750B52FF4D742341E,The Panama Papers data is current through 2015,URY,Uruguay,14050236,Panama Papers
Misiones 1486; piso 3; Montevideo; Uruguay,771AC0437544C8AB1BBF77CA64020C83,The Panama Papers data is current through 2015,URY,Uruguay,14050237,Panama Papers
“Misiones 1487, Montevideo Uruguay.”,D18A4B970113AEE27DD3CBC90F0CA762,The Panama Papers data is current through 2015,URY,Uruguay,14050238,Panama Papers
MISIONES 1488; PISO 8; MONTEVIDEO; URUGUAY,5B16553F46036613DA17E005FD108F80,The Panama Papers data is current through 2015,URY,Uruguay,14050239,Panama Papers
“Misiones 940 Manuel Alberti, Provincia de Buenos Aires Argentina”,6F1C4FE71CF46726E752316A55BD95C3,The Panama Papers data is current through 2015,ARG,Argentina,14050240,Panama Papers
Misty Blue; Le Jardin du Couvent; St Mary; Jersey; JE3 3ER; United Kingdom,A759411B51962BEDC3664DAD77B16C2F,The Panama Papers data is current through 2015,JEY,Jersey,14050241,Panama Papers
MITCHEL HOUSE THE VALLEY ANGUILLA,3ADE2039312307516AF7A225E71816CF,The Panama Papers data is current through 2015,AIA,Anguilla,14050242,Panama Papers
Mitchell House PO Box 1321 The Valley Anguilla BWI,5CFF3C6E0AF2347C6FB29C5B76049329,The Panama Papers data is current through 2015,AIA,Anguilla,14050243,Panama Papers
Mitchell House; The Valley; Anguilla; British West Indies,855064E10C251DBAF247EBA17464EF79,The Panama Papers data is current through 2015,AIA,Anguilla,14050244,Panama Papers
Mitchurinskiy pr. 6; build.1; aprt. 67; Moscow; Russian Federation,B00AFB66EDE1308424DC8B9556DE9CB6,The Panama Papers data is current through 2015,RUS,Russian Federation,14050245,Panama Papers
MITINSKAYA ST. 27-1492; 123627 MOSCOW; RUSSIA,FDB28B87440FB057B2F3626749CAA85A,The Panama Papers data is current through 2015,RUS,Russian Federation,14050246,Panama Papers
Mitinskaya str. 27-1-492; 123627 Moscow; Russia,5DA5E9B029118DBEDABFEC6B2CA5A352,The Panama Papers data is current through 2015,RUS,Russian Federation,14050247,Panama Papers
Mitinskaya street 27-1; Flat 492; Moscow; Russia; 125222,C82081A430655E8DF0B8E7A10A972A4D,The Panama Papers data is current through 2015,RUS,Russian Federation,14050248,Panama Papers
Mitre 1236 Avenue; Campana; Buenos Aires; Argentina,164CC3482473C1A93725678574A1509B,The Panama Papers data is current through 2015,ARG,Argentina,14050249,Panama Papers
MITRE 675 MONTES DE OCA DEPARTMENT OF BELGRANO REPUBLIC OF ARGENTINA,BE57F322880A7AFEEB0E71CDA1236759,The Panama Papers data is current through 2015,ARG,Argentina,14050250,Panama Papers
Mitre Emilio 632 1640 Martinez E/C: Gutierrez Ricardo y Goyena Pedro,73222E88D751AF4222A00FF63BB2042B,The Panama Papers data is current through 2015,,,14050251,Panama Papers
MITRE HOUSE 44-46 FLEET STREET; LONDON EC4Y 1BN; ENGLAND,350DFC194E5A6E7B69BD2A3FABB65095,The Panama Papers data is current through 2015,GBR,United Kingdom,14050252,Panama Papers
MITRE HOUSE; 44-46 FLEET STREET; LONDON; UNITED KINGDOM,445CE8C60578E9CC17E1C406898CF6D9,The Panama Papers data is current through 2015,GBR,United Kingdom,14050253,Panama Papers
MITTAL; JL JEMUR; ANDAYAWI 23/25; SURABAYA; INDONESIA,134839D5FB3F3473AC108A6DD6BF201C,The Panama Papers data is current through 2015,IDN,Indonesia,14050254,Panama Papers
Mitteldorf 1; Vaduz; Liechtenstein,C4403705330C1FD9AD24B1F4952B9368,The Panama Papers data is current through 2015,LIE,Liechtenstein,14050255,Panama Papers
Mittelmeer Nominees Limited; Doiranis 10; Egkomi; Nicosia; Cyprus,74364207EA34E88F824839F5A795C233,The Panama Papers data is current through 2015,CYP,Cyprus,14050256,Panama Papers
Mizraa 01; Mizraa 2280700; Israel,C90F211744D35433C5A377769B72C1FB,The Panama Papers data is current through 2015,ISR,Israel,14050257,Panama Papers
MJHAMEDA HADLIJAHICA 3S F1000 SARAJEVO; BOSNIA; HERZEGOVINA,6EDEDA6EA1ABAA64D2DAFAD4ADBCB43C,The Panama Papers data is current through 2015,BIH,Bosnia and Herzegovina,14050258,Panama Papers
Mkr. Aksay-5; bld. 6; apt. 33; Almaty; Republic of Kazakhstan,63269237270C8D89E68CE15E1FE8E22F,The Panama Papers data is current through 2015,KAZ,Kazakhstan,14050259,Panama Papers
M.L. (B.V.I.) Limited-seal imprint,E5BC801146F3C7FB4FAEF6D5E052733E,The Panama Papers data is current through 2015,,,14050260,Panama Papers
M. Lenshinsky 10-11; 119034 Moscow; Russia,4E7FC087D2680FF05A4449632F6167A1,The Panama Papers data is current through 2015,RUS,Russian Federation,14050261,Panama Papers
MLN ML TR 33 12 12 CJ BSA C A SETOR DE H INDIVIDUAIS NO 71540 ¿ 030 LAGO MORTE DF BRAZIL,72DDEAA2D2EAF3CBA366B93157489901,The Panama Papers data is current through 2015,BRA,Brazil,14050262,Panama Papers
MLN ML TR 33 3C 12 A 71540 ¿ 030 LAGO MORTE DF BRAZIL,EB757B711546D9B05414BA523DE72E6F,The Panama Papers data is current through 2015,BRA,Brazil,14050263,Panama Papers
Mln Ml Trecho 33 12 12; Setor de Habitacoes Individuais Norte; Lago Norte; Distrito Federal Brazil,09C5682DC2160E6C1A597ADA03E469C4,The Panama Papers data is current through 2015,BRA,Brazil,14050264,Panama Papers
“M. Majerove 493, CZ-73801 Frydek Mistek”,5615190F1A913C317F7E4309F295BCED,The Panama Papers data is current through 2015,CZE,Czech Republic,14050265,Panama Papers
MMG Bahamas Ltd; 50 Shirley Street; PO Box CB 13937 Nassau; The Bahamas,A8C48B7AD9E7AC2D767F2B4D2BA1A667,The Panama Papers data is current through 2015,BHS,Bahamas,14050266,Panama Papers
MMG Towe; 16th Floor Marbella; Panama City; Panama.,86E1279D29D8B9E78E4472475A2CC137,The Panama Papers data is current through 2015,PAN,Panama,14050267,Panama Papers
MMG Towe; 53rd E Street; Urbanizacion Marbella; Republic of Panama,EFE79395082240A621772E2418E5CAAE,The Panama Papers data is current through 2015,PAN,Panama,14050268,Panama Papers
MMG Tower; 16th Floor; 53E Street; Marbella P.O. Box 0832-00232 World Trade Center Panama City; Republic of Panama,2553F081A9674E7258DA98E0C740015D,The Panama Papers data is current through 2015,PAN,Panama,14050269,Panama Papers
MMG TOWER; 16TH FLOOR; 53RD EAST ST.; URBANIZACION MARBELLA; OBARRIO; PANAMA CITY PANAMA,3737F371BBA234FA4BD6134F0825C3BB,The Panama Papers data is current through 2015,PAN,Panama,14050270,Panama Papers
MMG TOWER; 16TH FLOOR; 53RD E STREET; MARBELLA; PANAMA,B39A820899FB054A04FAF34CDBCDDB04,The Panama Papers data is current through 2015,PAN,Panama,14050271,Panama Papers
MMG Tower; 16th Floor; 53rd E Street; Marbella; Panama 00232WTC PA,42EE541A99AC66D5D05A893B72AD2966,The Panama Papers data is current through 2015,PAN,Panama,14050272,Panama Papers
MMG Tower; 16th Floor; 53rd E Street; Marbella; Panama; Republic of Panama,A32216167565BCC9016B961207315979,The Panama Papers data is current through 2015,PAN,Panama,14050273,Panama Papers
MMG Tower; 16th Floor; 53rd E Street; Urbanizacion Marbella; Panama,F0E3CB383D20878DFCAADE8604EE0EC4,The Panama Papers data is current through 2015,PAN,Panama,14050274,Panama Papers
MMG Tower; 16th Floor 53rd E Street; Urbanizacion Marbella Panama Republic of Panama,4979BE9D081E094A1C910000C53E4ECF,The Panama Papers data is current through 2015,PAN,Panama,14050275,Panama Papers
MMG Tower; 16th Floor; 53rd E Str; Marbella; Panama,05EDC7A1F6E241AA763D38737592BB3D,The Panama Papers data is current through 2015,PAN,Panama,14050276,Panama Papers
MMG Tower 16th Floor; Marbella; Panama,8E3C9BBC4A31B64C04237B6A94D3A4F9,The Panama Papers data is current through 2015,PAN,Panama,14050277,Panama Papers
MMG TOWER; 16TH FLOOR; MARBELLA; PANAMA CITY,88B98A5A1CF4F9A2812EF8C61E49F305,The Panama Papers data is current through 2015,PAN,Panama,14050278,Panama Papers
MMG Tower; 23rd Floor; Avenida del Pacifico and Avenida Paseo del Mar; Costa del Este; Panama City; Republic of Panama,54214C1C2C1C0E1A91F71A2E040C7E18,The Panama Papers data is current through 2015,PAN,Panama,14050279,Panama Papers
MMG Tower; 53rd E Street; Ubanizacion Marbella; Panama; Republic of Panama,B6C1FFB2D19099BF00342D503C79CB31,The Panama Papers data is current through 2015,PAN,Panama,14050280,Panama Papers
MMG Tower; 53rd E street; Urbanizacion Marbella; Panama,C70D23787C1F8C8DA571F8A7179874AB,The Panama Papers data is current through 2015,PAN,Panama,14050281,Panama Papers
“MMG Tower 53rd E Street Urbanizacion Marbella Panama, Rep. of Panama”,EB0408BB26D5CDE4C7348C25B64E94CD,The Panama Papers data is current through 2015,PAN,Panama,14050282,Panama Papers
MMG Tower; 53rd E Street; Urbanizacion Marbella; Panama; Republic of Panama,2AAA606326010EA6EEBB089BBAEF3D29,The Panama Papers data is current through 2015,PAN,Panama,14050283,Panama Papers
MMG Tower; 53rd E Street; Urbanizacion Marbella; Republic of Panama,295B6F41335B3EAE7904F1353F81AC9D,The Panama Papers data is current through 2015,PAN,Panama,14050284,Panama Papers
MMG Tower; 53rd E Street; Urbanization Marbella; Republic of Panama,CF7508F73B0E848FED5AFED8DC8BB347,The Panama Papers data is current through 2015,PAN,Panama,14050285,Panama Papers
MMG Tower; 53rd E Street; Urb. Marbella; Panama,0063B1270CD420994D129C202188566F,The Panama Papers data is current through 2015,PAN,Panama,14050286,Panama Papers
MMG TOWER 53RD E STREET URB. MARBELLA PANAMA REP. OF PANAMA.,A5406D48F6E8DC3B2905851152E0F742,The Panama Papers data is current through 2015,PAN,Panama,14050287,Panama Papers
MMG TOWER 53rd E STREET URB. MARBELLA PANAMA REP. PANAMA,53D73C512E572E56A614A9456CC7E69C,The Panama Papers data is current through 2015,PAN,Panama,14050288,Panama Papers
MMG Tower; 53rd E Street; Urb. Marbella; Panama; Republic of Panama,56121858B40F8D36135007ECAD713F4C,The Panama Papers data is current through 2015,PAN,Panama,14050289,Panama Papers
MMG TOWER; 53RD STREET E; MARBELLA; REP. OF PANAMA,17EF0DF0680D3D8D13704BD50713B4AD,The Panama Papers data is current through 2015,PAN,Panama,14050290,Panama Papers
MMG Tower; 53rd Streetr; Urbanizacion Marbella; Panama; Republic of Panama,B5B35703C758AF148B675D02EFF2156C,The Panama Papers data is current through 2015,PAN,Panama,14050291,Panama Papers
MMG TOWER; 53RD STREET; URBANIZACIOJN MARBELLA; PANAMA REPUBLIC OF PANAMA,C93ECC067522B6C7807F70E2F64AA08F,The Panama Papers data is current through 2015,PAN,Panama,14050292,Panama Papers
MMG TOWER; 53rd Street; Urbanizacion Marbella; Panama Rep of Panama,4F07F37C9BD811A746E10610859CCACF,The Panama Papers data is current through 2015,PAN,Panama,14050293,Panama Papers
MMG Tower; 53rd Street Urbanizacion Marbella; Panama; Republic of Panama,29EFDFC4A3CBA59BEC222FAC0305C677,The Panama Papers data is current through 2015,PAN,Panama,14050294,Panama Papers
MMG Tower; 53rd Street; Urb. Marbella; Panama,9B9ECB294AFF5718250D9E6173AEEF78,The Panama Papers data is current through 2015,PAN,Panama,14050295,Panama Papers
MMG TOWER; 53 STREET; URBANIZACION MARBELLA; PANAMA REP OF PANAMA,A278D91F6E0231B1081B9F4FDA486F59,The Panama Papers data is current through 2015,PAN,Panama,14050296,Panama Papers
MMG TOWER 553RD E STREET URBANIZACION MARBELLA; PANAMA; REPUBLIC OF PANAMA,455DFDF325C2B99D0AD0D43455BC9846,The Panama Papers data is current through 2015,PAN,Panama,14050297,Panama Papers
MMG Tower; 8th Floor; 53rd E Street; Urbanizacion Marbella; Panama; Republic of Panama.,E786D07093D642D639745591B7D86BF3,The Panama Papers data is current through 2015,PAN,Panama,14050298,Panama Papers
MMG Tower; Ave. Paseo del Mar; Costa del Este; Panama City; Republic of Panama,C8F89564A6C8A913FA9F597850EA5E8C,The Panama Papers data is current through 2015,PAN,Panama,14050299,Panama Papers
MMG Tower; East 53rd Street; Marbella; Panama; Rep. of Panama,A45AD8E4E938AFC7BB772AB6B549B7B9,The Panama Papers data is current through 2015,PAN,Panama,14050300,Panama Papers
MMG Tower; Piso 16; Calle 53 E; Marbella Panama; Apartado 0832-00232 WTC.,F5D05EAE5D4DCBA0672AC3F41BD27735,The Panama Papers data is current through 2015,PAN,Panama,14050301,Panama Papers
MMG TOWER; P.O. BOS 0832-00232; WORLD TRADE CENTER; PANAMA REPUBLIC OF PANAMA,3832F52FFB253A1DE3EFC01C832AB198,The Panama Papers data is current through 2015,PAN,Panama,14050302,Panama Papers
MMG TOWER P.O. BOX 0832 00232; WORLD TRADE CENTER; PANAMA; REPUBLIC OF PANAMA,41C979D6338F115E2A9D486E86A3CD87,The Panama Papers data is current through 2015,PAN,Panama,14050303,Panama Papers
MMG TOWER; P.O. BOX 0832-00232; WORLD TRADE CENTER; PANAMA; REPUBLIC OF PANAMA,A9A0C2B3A3727B702DE7CF7EC364565C,The Panama Papers data is current through 2015,PAN,Panama,14050304,Panama Papers
MMG Tower; second floor East 53rd Street; Panama; Republic of Panama,A5696E05BACBBA68FBF28E5936EBA9E4,The Panama Papers data is current through 2015,PAN,Panama,14050305,Panama Papers
MMG Tower; Urbanizacion Marbella; 53rd E Street; 16th Floor Panama City; Panama,9EA5B7C1E5594F1C2371ED9A3DB9AAA8,The Panama Papers data is current through 2015,PAN,Panama,14050306,Panama Papers
M. Musuwo of 18 Bloomfield Road; Greendale North; Harare; Zimbabwe,E3180D3AAF53E40E2347181A1B7A60F1,The Panama Papers data is current through 2015,ZWE,Zimbabwe,14050307,Panama Papers
“MN- 14F Xinbaohui Building Nanyon Bd Nanshan District, 518054 SHENZHEN (Republic of China)”,2A50DEADCD8E714C3931006D415F294C,The Panama Papers data is current through 2015,CHN,China,14050308,Panama Papers
MOARBES LLP,34DC94795AA8EBE223C1AA58499CD3B2,The Panama Papers data is current through 2015,,,14050309,Panama Papers
Móavadi 3; 110 Reykjavik; Iceland.,83043D8A42C3051ADF732350ADDB066D,The Panama Papers data is current through 2015,ISL,Iceland,14050310,Panama Papers
MODERN BLDG.; 6TH FLOOR; EL ARZ STREET; SAIFI; BEIRUT; LEBANON,1AF17C4BEAB95145579FBD477DEF1C3C,The Panama Papers data is current through 2015,LBN,Lebanon,14050311,Panama Papers
Modern Group Office Building; No. 1 Xiangheyuan Road; Dongzhimen; East City District; Beijing PR China,68DEBB02E9C205A3C706FE85D36840FC,The Panama Papers data is current through 2015,CHN,China,14050312,Panama Papers
MODESTOU PENTELI 13; 2407; EGKOMI; NICOSIA; CYPRUS,047460A3948C7B36436E192908121DFF,The Panama Papers data is current through 2015,CYP,Cyprus,14050313,Panama Papers
“Moehlstrasse 16, D-81675 Munich Germany”,B9FED0D2819986E0A0D8C09786704B88,The Panama Papers data is current through 2015,DEU,Germany,14050314,Panama Papers
“Moerasvaren 47 2661 PX Bergschenhoek, The Netherlands”,DD1D831B2F0CF1144583A03C8782408F,The Panama Papers data is current through 2015,NLD,Netherlands,14050315,Panama Papers
“Mohaliver, 9 Bnei Beraq Israel”,78B7618D554B817D5A94FFC810297380,The Panama Papers data is current through 2015,ISR,Israel,14050316,Panama Papers
Mohamed Alhashmi P.O. Box 61133 Abu Dhabi UAE,BE9A161E2FA385BDE3363255859151DE,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14050317,Panama Papers
Mohamed Farid str. PO BOX 15 Bengazi Libya,840F76F438A8B67DDC86D9E8C8B9EAE6,The Panama Papers data is current through 2015,LBY,Libya,14050318,Panama Papers
MOHAMMED AL GAAZ BUILDING 124/110 AL MAKTOUM ROAD P.O. BOX 60200 DUBAI UNITED ARAB EMIRATES,25CE940006C1A781A5CDDFA93F22366D,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14050319,Panama Papers
MOHD IBRAHIM HAMAD OBAIDALLA 317/28 TAWI SAIGH AREADM.26 BHD CITI BANK BLOCK/B FLAT-608,7EBFC7ECFD77866C4599926C79853DAC,The Panama Papers data is current through 2015,,,14050320,Panama Papers
MOJAYSKOE HIGHWAY; BLD. 79; FLAT 89; ODINTSOVO TOWN; MOSCOW; REGION; RUSSIA,6775CE0F9446C99627FEA9BCD32707A7,The Panama Papers data is current through 2015,RUS,Russian Federation,14050321,Panama Papers
Mokolodi Estates P.O. Box 170 Gaborone Botswana,0AB6F673DAE079AE8A82616FE05D1DC9,The Panama Papers data is current through 2015,BWA,Botswana,14050322,Panama Papers
Mokosin 54; Prelouc; Czech Republic,025670215032892A894B81364AE4EDE3,The Panama Papers data is current through 2015,CZE,Czech Republic,14050323,Panama Papers
MOK TSE CHE SUN CHUEN; SAI KUNG; KOWLOON; HONG KONG,44369A1B6A180B8DE7C1B36E293502CC,The Panama Papers data is current through 2015,HKG,Hong Kong,14050324,Panama Papers
“Mole Cottage Snowdenham Lane , Bramley Guldford Surrey GU5 0AS”,28D24870F3AF592CA0EAEA335EA758C8,The Panama Papers data is current through 2015,GBR,United Kingdom,14050325,Panama Papers
Molenberglaan 29; 6416 EK Heerlen; The Netherlands.,C9274E9CD85FE2226266E4E3B44547AD,The Panama Papers data is current through 2015,NLD,Netherlands,14050326,Panama Papers
Molenkampweg 23; 7971 BN Havelte; The Netherlands,4348F37DB8B73D2504518E11FE1BDF3C,The Panama Papers data is current through 2015,NLD,Netherlands,14050327,Panama Papers
Molenkampweg 23; BN Havelte 7971; The Netherlands,6D9A28C51799B8C322374EB30FC5F288,The Panama Papers data is current through 2015,NLD,Netherlands,14050328,Panama Papers
MOLI DE SON FONT; PUIGPUNYENT; MALLORCA-BALEARES; SPAIN,49AB123F90AAABEC1C84C453870E2886,The Panama Papers data is current through 2015,ESP,Spain,14050329,Panama Papers
“Moliere 664 4B, 1407 Cap Federal – Argentina”,71A0BCBCCA16B4A1B2274E452AC23A5D,The Panama Papers data is current through 2015,ARG,Argentina,14050330,Panama Papers
MOLINOS DE EL SALVADOR S.A. DE C.V.; BLVEJERC Y 50 AVE NORTE; SAN SALVADOR; EL SALVADOR,30D3C518940603E367CBF6008E4876C5,The Panama Papers data is current through 2015,SLV,El Salvador,14050331,Panama Papers
MO.LI.YUAN; C 901 WAN KE CITY GARDEN XIANG MEI RD.; FU TIAN DISTRICT; SHENZHEN; P.R.CHINA,F6700DA49BCC4BCE845CCF8525FA1D3D,The Panama Papers data is current through 2015,CHN,China,14050332,Panama Papers
Mollerusweg 74 2031 BZ Haarlem the Netherlands,9AA91D4A925137313851EE0757C6E3B7,The Panama Papers data is current through 2015,NLD,Netherlands,14050333,Panama Papers
MOLOCHNIY PER D1; KV.21; 119034 MOSCOW; RUSSIA,CC59CF9EBEB68E39E1D7EBC0A1AEFE6A,The Panama Papers data is current through 2015,RUS,Russian Federation,14050334,Panama Papers
Molochnoi Pereulok; Bldg. 6; Apt. 6; 119034; Moscow; Russian Federation,07F379CEF70804B4810BC7D0E87549DA,The Panama Papers data is current through 2015,RUS,Russian Federation,14050335,Panama Papers
Molodejnaua Str 4; apt 475; Moscow; Russia,82D520C609BD653D718EF1188D26AC67,The Panama Papers data is current through 2015,RUS,Russian Federation,14050336,Panama Papers
MOLODEZHNAY; 18/11; KRASNY SULIN; ROSTOV PROVINCE; RUSSIA,B7967D36567801AAE4D2D7288F279FED,The Panama Papers data is current through 2015,RUS,Russian Federation,14050337,Panama Papers
Molodezhnaya Street 5-37; Moscow; Russia,1A8550AA839DE8A7B0BFA1C1F5C16AF4,The Panama Papers data is current through 2015,RUS,Russian Federation,14050338,Panama Papers
Molodezhnaya Street; Bld. 42. 16; Odintsovo; Moscow District; Russia,0F3E0A21E499F74E79A9FF4176FE93EA,The Panama Papers data is current through 2015,RUS,Russian Federation,14050339,Panama Papers
“MOLODOGVARDEYSKAYA STR. 4/KORP.1-29,123467 MOSCOW RUSSIA)”,0F40A8C6E2D9DBC63ADF91992010C317,The Panama Papers data is current through 2015,RUS,Russian Federation,14050340,Panama Papers
Molodogvardeytsev Street; Bld. 70/V; Apt. 38; Chelyabinsk; Russia,D1DADF24CF79934B1BD06A0DE54A3D65,The Panama Papers data is current through 2015,RUS,Russian Federation,14050341,Panama Papers
Monaco MC98000,F4220AFC7C4686D647EA548732632D11,The Panama Papers data is current through 2015,MCO,Monaco,14050342,Panama Papers
Monaco – Monaco,1E3E2752495B1869A207537E4F5FCFD0,The Panama Papers data is current through 2015,MCO,Monaco,14050343,Panama Papers
Mona Deena Villas; Villa # 2 Gate 1757; Road 3741; Block 337 Umm Al Hassam; Bahrain,5A7CD952B3A9E5B7507E3F12F12D010C,The Panama Papers data is current through 2015,BHR,Bahrain,14050344,Panama Papers
Monasterio 987. Vicente Lopez; Buenos Aires; Argentina.,2D662E639503F172EE8710264BF2496D,The Panama Papers data is current through 2015,ARG,Argentina,14050345,Panama Papers
MONATAGU PAVILION; 8-10M QUEENSWAY; GIBRALTAR,853C0CEFF68DA0E1CD0A3C5CFBA1667A,The Panama Papers data is current through 2015,GIB,Gibraltar,14050346,Panama Papers
MONATGU PAVILION; 8-10 QUEENSWAY; GIBRALTAR.,3EEF1D5B99D8FDA92E8E87FF1D051998,The Panama Papers data is current through 2015,GIB,Gibraltar,14050347,Panama Papers
MONATGU PAVILLION; 8-10; OUEENSWAY; GIBRALTAR.,F72B9025AD97EF601BFADDF73E3393CC,The Panama Papers data is current through 2015,GIB,Gibraltar,14050348,Panama Papers
MONES ROSES 5941; MONTEVIDEO; URUGUAY,AC51005AEF50BD8D15FBD9638CB1EC65,The Panama Papers data is current through 2015,URY,Uruguay,14050349,Panama Papers
Monet 119; Maravalle II; Cumbaya; Quito; Ecuador,F880D0B40163B07E607EB1FE6632FE50,The Panama Papers data is current through 2015,ECU,Ecuador,14050350,Panama Papers
Mongolia; Dornogovi Province; Saynshand Suom; 1st Bag; Shinezoon 33 Apt 3#43,36D25EC973506FA20ED51746D5FB2900,The Panama Papers data is current through 2015,MNG,Mongolia,14050351,Panama Papers
Mongolia; Orhon aimag; Bayan-Undur soum; Zest bag; 1th khoroolol; 16-28,40E56BAD5F39555B70F3C08EA8DFA86D,The Panama Papers data is current through 2015,MNG,Mongolia,14050352,Panama Papers
MONGOLIA; ULAANBAATAR; BAYANGOL DISTRICT; 19TH KHOROO; 4TH KHOROOLOL; 52-16,B622EB81A069F2D458B02F3C3800C7AF,The Panama Papers data is current through 2015,MNG,Mongolia,14050353,Panama Papers
Mongolia; Ulaanbaatar; Bayangol district; 8th Khoroo; 4th Khoroolol; 13-51,6E160159ED77E9040EE77B25820C078C,The Panama Papers data is current through 2015,MNG,Mongolia,14050354,Panama Papers
Mongolia; Ulaanbaatar; Bayanzurkh district; 18th khoroo; 13th khoroolol; 39G-19,3D1651F53D3A351FC44BED71C179F02C,The Panama Papers data is current through 2015,MNG,Mongolia,14050355,Panama Papers
Mongolska street 1427/14; post code 708 00; Ostrava Poruba; Czech Republic,C5D1DC45EC8A6B752FC8847D4A4E4699,The Panama Papers data is current through 2015,CZE,Czech Republic,14050356,Panama Papers
Monkgarron; West End; Ebbesbourne Wake; Salisbury; Wiltshire; SP5 5JS,908DB22E045D8330D7C51E691114EC2A,The Panama Papers data is current through 2015,GBR,United Kingdom,14050357,Panama Papers
MON SEJOUR; LA RUE ES PHILIPPES; GROUVILLE; JERSEY; JE3 9UZ,80E2B6DDBF2EA8AF74A301A8395FAF38,The Panama Papers data is current through 2015,JEY,Jersey,14050358,Panama Papers
MONTAGUE PAVILLION; 8-10 QUEENSWAY; GIBRALTAR,9599DB353778CEF0E40920F657DCAB13,The Panama Papers data is current through 2015,GIB,Gibraltar,14050359,Panama Papers
Montague Pavillion; 8 to 10 Queensway; Gibraltar,9ACC6E25DAD3D8D0D6EA9C340B21774A,The Panama Papers data is current through 2015,GIB,Gibraltar,14050360,Panama Papers
MONTAGUE PAVILLON; 8-10 QUEENSWAY; GIBRALTAR,0014EF16485B3762E496D48BA0C9BE99,The Panama Papers data is current through 2015,GIB,Gibraltar,14050361,Panama Papers
Montague Sterling Centre,A5FC4453F1A0ACC93083243B6184095F,The Panama Papers data is current through 2015,HTI,Haiti,14050362,Panama Papers
MONTAGUE STERLING CENTRE; EAST BAY STREET; P.O. BOX N 3720; NASSAU; BAHAMAS,6B6F9443902872FCC26D0C9DAEF887D0,The Panama Papers data is current through 2015,BHS,Bahamas,14050363,Panama Papers
Montague Sterling Centre; East Bay Street; PO Box N-3924; Nassau; The Bahamas,B6F40A884EE49E9DE2011B4A7B92534C,The Panama Papers data is current through 2015,BHS,Bahamas,14050364,Panama Papers
“Montague Sterling Centre PO Box N-3924 East Bay Street Nassau, Bahamas”,6AE6C04722D45288B206BCF079612C1F,The Panama Papers data is current through 2015,BHS,Bahamas,14050365,Panama Papers
MONTAGU OAVILION; 8-10 QUEENSWAY; GIBRALTAR,F58969C6254728994924838237B9A1BA,The Panama Papers data is current through 2015,GIB,Gibraltar,14050366,Panama Papers
“MONTAGU PAVILIION 8-10 QUEENSWAY, GIBRALTAR”,064DC32624AC5BB784D965B27B4B454B,The Panama Papers data is current through 2015,GIB,Gibraltar,14050367,Panama Papers
MONTAGU PAVILIION 8-10 QUEENSWAY; MONTAGU PAVILIION 8-10 QUEENSWAY; GIBRALTAR,2594EC4479C3D7898C030908563F4AB4,The Panama Papers data is current through 2015,GIB,Gibraltar,14050368,Panama Papers
“MONTAGU PAVILION,”,1D45E72E193C210D824273FBFC0533F6,The Panama Papers data is current through 2015,USA,United States,14050369,Panama Papers
Montagu Pavilion; 8/10 Queensway; Gibraltar,8B37E4C3D97EE9F5C8F6303B3374FB40,The Panama Papers data is current through 2015,GIB,Gibraltar,14050370,Panama Papers
MONTAGU PAVILION; 8-10; GIBRALTAR,FDE03A4E60A6147EB0668CA4DFE02B54,The Panama Papers data is current through 2015,GIB,Gibraltar,14050371,Panama Papers
“MONTAGU PAVILION,8-10 QUEENSWAY”,3F8E3E9807F8D43CD1F730D64E7F3C31,The Panama Papers data is current through 2015,GIB,Gibraltar,14050372,Panama Papers
“MONTAGU PAVILION 8-10 QUEENSWAY,GIBNRALTAR”,A1842BF413024A595799840C1EE53221,The Panama Papers data is current through 2015,GIB,Gibraltar,14050373,Panama Papers
“MONTAGU PAVILION 8-10 QUEENSWAY,GIBRALATR.”,3888EA3B458ED306AD2D531DFCF9854E,The Panama Papers data is current through 2015,GIB,Gibraltar,14050374,Panama Papers
Montagu Pavilion; 810 Queensway; Gibraltar,CCA576A732DC62A4F6B0B1B9DE97367D,The Panama Papers data is current through 2015,GIB,Gibraltar,14050375,Panama Papers
MONTAGU PAVILION; 8-10; QUEENSWAY; GIBRALTAR,CC8FC4BB28B7846C4C574EF8CB218D52,The Panama Papers data is current through 2015,GIB,Gibraltar,14050376,Panama Papers
MONTAGU PAVILION 8-10 QUEENSWAY GIBRALTARAR,6516EBBAA7AE2BEFE55A52AF737FE1A0,The Panama Papers data is current through 2015,GIB,Gibraltar,14050377,Panama Papers
MONTAGU PAVILION 8-10 QUEENSWAY GIBRALTARAR2,E36A3B67702089A1610C60CD385E9CC6,The Panama Papers data is current through 2015,GIB,Gibraltar,14050378,Panama Papers
MONTAGU PAVILION 8-10 QUEENSWAY; GIBRALTARMONTAGU PAVILION 8-10 QUEENSWAY; GIBRALTAR,40F1DBC61F2E72325931B5020568F619,The Panama Papers data is current through 2015,GIB,Gibraltar,14050379,Panama Papers
Montagu Pavilion; 8-10 Queensway; Gibralter,16E04D3B4F226A2708C11E5E896C407F,The Panama Papers data is current through 2015,GIB,Gibraltar,14050380,Panama Papers
MONTAGU PAVILION; 8-10 QUEENWAY; GIBRALTAR,25BFD77FDA950BFFFA8705FD947BEF41,The Panama Papers data is current through 2015,GIB,Gibraltar,14050381,Panama Papers
MONTAGU PAVILION 8-10 QUEESWAY GIBRALTAR,6006257E0C9BC76D07AEC47414C86EB8,The Panama Papers data is current through 2015,GIB,Gibraltar,14050382,Panama Papers
MONTAGU PAVILION; 8-10 QUENSWAY; GIBRALTAR,313DA9E803DB72053AE42C45B5129EBF,The Panama Papers data is current through 2015,GIB,Gibraltar,14050383,Panama Papers
MONTAGU PAVILION; 8-40 QUEENSWAY; GIBRALTAR,408F600D3770581D43409D1F2831F972,The Panama Papers data is current through 2015,GIB,Gibraltar,14050384,Panama Papers
“MONTAGU PAVILION,GIBRALTAR”,8C150B9C95779958A68697363136FB33,The Panama Papers data is current through 2015,GIB,Gibraltar,14050385,Panama Papers
“MONTAGU PAVILION QUEENSWAY,GIBRALTAR”,E0E3A7C4CCD1044D0571313EB43F3488,The Panama Papers data is current through 2015,GIB,Gibraltar,14050386,Panama Papers
“MONTAGU PAVILLION,8-10 QUEENSWAY GIBRALTAR”,6734333024529742DD4CAC40DB482747,The Panama Papers data is current through 2015,GIB,Gibraltar,14050387,Panama Papers
MONTAGU PAVILLION; 8-10 QUEENSWAY; GILBRALTAR.,5F8E9359A5A8C84238612E100F106413,The Panama Papers data is current through 2015,GIB,Gibraltar,14050388,Panama Papers
MONTAGU PAVILLION; 8-10 QUEENS WAYS; GIBRALTAR,ED1B86A50C5F859F9A3D7CAA7B4A7A1E,The Panama Papers data is current through 2015,GIB,Gibraltar,14050389,Panama Papers
MONTAGU STUART WORTLEY HUNT OF APARTMENT 717; AL ARTA 1; THE GREENS; P.O. BOX 500462; DUBAI; UAE,A4FF9046EFF625C012E97BB87872C2CD,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14050390,Panama Papers
Mont Arthur St Brelade Jersey JE3 8AH CHANNEL ISLANDS,603C66B308B75A70BA1DC0E8E6983AB5,The Panama Papers data is current through 2015,JEY,Jersey,14050391,Panama Papers
Mont Blanc Trustees SA; 17 rue Henri-Mussard; 1208 Geneva; Switzerland,BE90D79216A9599DBB009E0CCCF3BFF1,The Panama Papers data is current through 2015,CHE,Switzerland,14050392,Panama Papers
“MONT BUXTON MAHE, SEYCHELLES”,39A6772961103210C04141F6E92C3B78,The Panama Papers data is current through 2015,SYC,Seychelles,14050393,Panama Papers
Mont Buxton; Mahe; Seyechelles,AE44EE4748C66BE8B01D7BE7DFF2C79B,The Panama Papers data is current through 2015,SYC,Seychelles,14050394,Panama Papers
Mont Crevelt House; South Quary; St. Sampson’s; Guernsey C.I.,901273A6EE64F42512B850C8AC161897,The Panama Papers data is current through 2015,GGY,Guernsey,14050395,Panama Papers
Mont Crevelt House; South Quay; Sampson’s; GUERNSEY; CI.,725E4EE7B5540DE6BC6ED5B7E859BD41,The Panama Papers data is current through 2015,GGY,Guernsey,14050396,Panama Papers
Mont Crevelt House; South Quay; St Jampoon; Guernsey,AFD6A4BB501D99B3FA63278A553CF342,The Panama Papers data is current through 2015,GGY,Guernsey,14050397,Panama Papers
MONT CREVELT HOUSE; SOUTH QUAY; ST. SAMPOSN’S GUERNSEY; C.I.,F05AAEEDDCF8CDF660E05D45AE047B39,The Panama Papers data is current through 2015,GGY,Guernsey,14050398,Panama Papers
Mont Crevelt House; South Quay; St. Sampson; Guernsey,4B11482261CD35CE4CD5FFE041666039,The Panama Papers data is current through 2015,GGY,Guernsey,14050399,Panama Papers
MONT CREVELT HOUSE SOUTH QUAY ST SAMPSON GUERNSEY C.I.,AF5A4EA823A68FB11B85722A17C37B65,The Panama Papers data is current through 2015,GGY,Guernsey,14050400,Panama Papers
Mont Crevelt House; South Quay; St. Sampsons; Giernsey,3985BC22235BE944846C85814BCD1090,The Panama Papers data is current through 2015,GGY,Guernsey,14050401,Panama Papers
MONT CREVELT HOUSE SOUTH QUAY ST SAMPSON’S GUERNSEY,E520D1AF2EFB602EBC28F7DA6B45F4EF,The Panama Papers data is current through 2015,GGY,Guernsey,14050402,Panama Papers
MONT CREVELT HOUSE; SOUTH QUAY; ST. SAMPSON’S; GUERNSEY; C.I.,40CFC8E873A3C7BADEFD41054311DBED,The Panama Papers data is current through 2015,GGY,Guernsey,14050403,Panama Papers
Mont Crevelt House; South Quay; St. Sampson’s Guernsey; CL,9D9E1F42783380BDE5C904D9074D93CB,The Panama Papers data is current through 2015,GGY,Guernsey,14050404,Panama Papers
Mont Crevelt House; South Quay; St. Sampson’s; Guernsey; GY1 3AL,3017B5A33DB460D35EF5D96BDCB1DDF7,The Panama Papers data is current through 2015,GGY,Guernsey,14050405,Panama Papers
MONT CREVELT HOUSE; SOUTH QUAY; ST. SAMPSON’S; GUERNSEY; GY2 4LH,296E5A3538BED90861726B8A7B730EE9,The Panama Papers data is current through 2015,GGY,Guernsey,14050406,Panama Papers
Mont Crevelt House; South Quay; St. Sampson’s; GY2 4LH,EB52BF1B52A65386C337F53095E49D86,The Panama Papers data is current through 2015,USA,United States,14050407,Panama Papers
MONT CREVELT HOUSE SOUTH QUAY ST SAMPSPNS GUERNSEY,5E5A38C90C4A7638B7AC2851066C253E,The Panama Papers data is current through 2015,GGY,Guernsey,14050408,Panama Papers
“MONT CREVELT HOUSE, SOUTH QUAY ST. SMPSON’S GUERNSEY GY2 4LH”,F8783E242FDE4B28DDB6DA22C9FD3742,The Panama Papers data is current through 2015,GGY,Guernsey,14050409,Panama Papers
MONT CREVELT HOUSE; SOUTH QUAY; ST. STAMPSON GUERNSEY GY1 4LH,4D6B3956A7B7EF419B89B0E5A3EBD75C,The Panama Papers data is current through 2015,GGY,Guernsey,14050410,Panama Papers
Mont-de-Sion 3; 1206 Geneve; Switzerland,D60E92745BC58D41B6DCC455033185A3,The Panama Papers data is current through 2015,CHE,Switzerland,14050411,Panama Papers
“Monteagudo 1777 1640¿ Martinez, San Isidro Buenos Aires Argentina”,236588550698341D7679972821F95804,The Panama Papers data is current through 2015,ARG,Argentina,14050412,Panama Papers
MONTEAGUDO 48- MARCOS PAZ- PCIA. BUENOS AIRES. REP. ARGENTINA. CP 1727,A250F565837575E7583019E9643A5EF3,The Panama Papers data is current through 2015,ARG,Argentina,14050413,Panama Papers
Monte Alegre MZ Q – LT 7 – DPTO 402-URB.CHACARILLA DEL ESTANQUE –SURCO-LIMA-PERÚ,8AB61A69EA51FA60C770888FF7F2BDBD,The Panama Papers data is current through 2015,PER,Peru,14050414,Panama Papers
Monte Alverne 105; Santa Monica – Belo Horizonte – MF – CEP 3152509; Brazil,9E1D2BF52B19C6A3F0472A73C2BE06AD,The Panama Papers data is current through 2015,BRA,Brazil,14050415,Panama Papers
Montebello 487; Rinconada Alta; La Molina; Lima; Perú,F36E77F4866A322A0F93FEE06CC74904,The Panama Papers data is current through 2015,PER,Peru,14050416,Panama Papers
Monte Carlo 220 –dpto. 301- Surco-Lima-Perú,3ED13EECBC6A3E1AD99CBE3627526D2B,The Panama Papers data is current through 2015,PER,Peru,14050417,Panama Papers
MONTECARLO; PALACE; 7BLD DES MOULINS; MONACO 98000,B78134A12E42B9DE35CE4EC8FCD692C2,The Panama Papers data is current through 2015,MCO,Monaco,14050418,Panama Papers
Monte-Carlo Palace; Boulevard des Moulins 7; MC 98000 MONACO,57B3A39169AC6B4055AEC009831E8D2C,The Panama Papers data is current through 2015,MCO,Monaco,14050419,Panama Papers
Monte Carmelo 249-dpto 202-Santiago de Surco-Lima-Peru,B832A19889905F1DC59D2652DD8ACAE3,The Panama Papers data is current through 2015,PER,Peru,14050420,Panama Papers
Montecarmelo 35 Providencia; Santiago; Chile.,CA427CBECEBC81AF35A786289F966AF0,The Panama Papers data is current through 2015,CHL,Chile,14050421,Panama Papers
Monte Cassino 11/57; Warsaw; Poland,603EED5D54EFE015D7C482341F87C892,The Panama Papers data is current through 2015,POL,Poland,14050422,Panama Papers
Montecito 38; piso 36; dept 31; México D.F.,0070E393B32750B3160E15F77264AFB1,The Panama Papers data is current through 2015,MEX,Mexico,14050423,Panama Papers
Montecristi 127; Dpto. 302; Surco; Lima – Perú,F0FAF76062969A9BCF64590786FD7AAC,The Panama Papers data is current through 2015,PER,Peru,14050424,Panama Papers
“MONTEFALCO (PG) LOC. PIETRAUTA 1 , Italy.”,D5A51BEBE518893338EF4CE58FEC9E2A,The Panama Papers data is current through 2015,ITA,Italy,14050425,Panama Papers
Monte Libano 235-402; Col. Lomás de Chapultepec; Delegación Benito Juarez; CP 11000 Mexico Distrito Federal,CF44E4CDCE9DFA718C1B5A73F9C5E17C,The Panama Papers data is current through 2015,MEX,Mexico,14050426,Panama Papers
Monte Marina; 31/33 Avenue des Papalins; Monaco,2F04D3E218CBDCADC11D1EB6297F7439,The Panama Papers data is current through 2015,MCO,Monaco,14050427,Panama Papers
MONTE MARINA; 31-33 AV DES PAPALINS; 98000 MONACO,E3D9D236DF8FC4E34756DA233AA66C28,The Panama Papers data is current through 2015,MCO,Monaco,14050428,Panama Papers
MONTE MAYOR 182; SURCO; LIMA; PERÚ,4849619B50BDD9D3B4A92EF7C8DD7BC3,The Panama Papers data is current through 2015,PER,Peru,14050429,Panama Papers
Monte Paraiso Country Club. Apt. 10-5 29600 Marbella (Malaga) SPAIN,88D6560028C39C9D0A1FF17D690B278A,The Panama Papers data is current through 2015,ESP,Spain,14050430,Panama Papers
MONTE PARAISO – ED. PEGASO; CASCADA DE COMOJAN; 29600 MARBELLA; SPAIN,C22256C3D902B8F5990FE3CC214B4965,The Panama Papers data is current through 2015,ESP,Spain,14050431,Panama Papers
Monterrey 341–Surco-Lima-Peru,73777B97A642CEB544CD39E6A3D8784E,The Panama Papers data is current through 2015,PER,Peru,14050432,Panama Papers
MONTES DE OCA SN PEDRO URB MARUZ D E ENTRADA PRINCIPAL 75S. IZQ,5FB3D6A69E149B087E432313066C6881,The Panama Papers data is current through 2015,CIV,Côte d’Ivoire,14050433,Panama Papers
MONTESERRIN CALLE JILGUEROS Y DE LAS GOLONDRINAS LOTE 4. QUITO-ECUADOR,C3A6F845F20CFAFAF0BC10341F883525,The Panama Papers data is current through 2015,ECU,Ecuador,14050434,Panama Papers
Monte Umbroso Street 203-INt 302 – Santiago de Surco – Lima – Peru,63564B96DB5B0794BC19887C0540081B,The Panama Papers data is current through 2015,PER,Peru,14050435,Panama Papers
Montevideo 1520 Piso 4; Of.”A”; Capital Federal; ARGENTINA; CP: 1018,37C60A8C5D9BFDA45CFB28EFDF22571B,The Panama Papers data is current through 2015,ARG,Argentina,14050436,Panama Papers
Montevideo 1573 Piso 4 Departamento B; Ciudad de Buenos Aires; República Argentina; CP 1018,12BC17F125DE5D07ACCF98E815468491,The Panama Papers data is current through 2015,ARG,Argentina,14050437,Panama Papers
MONTEVIDEO 1722; PB; (1021) CABA,541748365F114D9E3D37715F1FC88B57,The Panama Papers data is current through 2015,URY,Uruguay,14050438,Panama Papers
Montevideo 1947; 5º B; Buenos Aires 1021; Argentina,B8C53853AE2F494EA3560E8CD012B644,The Panama Papers data is current through 2015,ARG,Argentina,14050439,Panama Papers
Montevideo 489 – 10 A; Buenos Aires; Argentina,9E64B81E015CD2217FA2E9BB59A545F8,The Panama Papers data is current through 2015,ARG,Argentina,14050440,Panama Papers
“MONTEVIDEO, CALLE CERRITO #461 AP.P.5”,437B27B1D53BBE777058684BC94B118B,The Panama Papers data is current through 2015,URY,Uruguay,14050441,Panama Papers
“Montevideo, Uruguay”,505F10A6A8EAC32268DB3D44385E1626,The Panama Papers data is current through 2015,URY,Uruguay,14050442,Panama Papers
Mont Fleuri; Mahe; Republic of Seychelles,0DD831B1BAE829A8269B3BFDA1F1093F,The Panama Papers data is current through 2015,SYC,Seychelles,14050443,Panama Papers
Mont Fleuri Mahe Seychelles,F69CCACA70083AC914FF23992D253613,The Panama Papers data is current through 2015,SYC,Seychelles,14050444,Panama Papers
MONTGU PAVILION 8-10 QUEENSWAY; P.O BOX 575; GIBRALTAR,16E8DF4E5DB93CFB1C6B5D4F9FD44F00,The Panama Papers data is current through 2015,GIB,Gibraltar,14050445,Panama Papers
MONTGU PAVILLION; QUEENSWAY; GIBRALTAR,AE6A7BEB396031DD755D1655A34AEE91,The Panama Papers data is current through 2015,GIB,Gibraltar,14050446,Panama Papers
MONT KIARA AMAN CONDO BLK B 23A-3 JALAN KIARA2 MONT KIARA; KUALA LUMPUR; MALAYSIA,E36A0587FAFC28909E642880196877A7,The Panama Papers data is current through 2015,MYS,Malaysia,14050447,Panama Papers
Mont Kiara Aman Condo; Block B 23A-3 Jalan Kiara 2; Mont Kiara; Kuala Lumpur; Malaysia,DAD42AB62D59B458E54FA5EDF8E6E516,The Panama Papers data is current through 2015,MYS,Malaysia,14050448,Panama Papers
MONT KIARA AMAN CONDO; BLOCK B 23-A; JALAN KIARA 2; MONT KIARA; KUALA; LUMPUR; MALAYSIA,71F42394233B25D3F1CE3FA9FD85E5F9,The Panama Papers data is current through 2015,MYS,Malaysia,14050449,Panama Papers
Montpelier Street; London SW7 1HD; United Kingdom,2FC8B9F9DC8438FA01806F84DBFF1347,The Panama Papers data is current through 2015,GBR,United Kingdom,14050450,Panama Papers
MONTPELIER (TRUST & CORPORATE) SERVICES LIMITEDFERNLEIGH HOUSEPALACE ROAD; DOUGLAS IM2 4LBISLE OF MAN; BRITISH ISLES,E49DE8AE697F99E663EA37BDE7720469,The Panama Papers data is current through 2015,IMN,Isle of Man,14050451,Panama Papers
MONTPELIER (TRUST AND CORPORATE,AB9E81308D1C5DE6DBD3D2F29AAC46A2,The Panama Papers data is current through 2015,,,14050452,Panama Papers
Mont Plaisir; Mahe; Seychelles,ADFF196C1F473CD449ED1F17B7474A9A,The Panama Papers data is current through 2015,SYC,Seychelles,14050453,Panama Papers
“Montreal H3A 3J6 Canada and Montreal, H3B 4W5 Canada”,87ED1DD6DF78B5484EAF518EC6AFD735,The Panama Papers data is current through 2015,CAN,Canada,14050454,Panama Papers
“Montreal, Quebec; Canada”,B28A2F7AD182454F42ECF50C7219DC4D,The Panama Papers data is current through 2015,CAN,Canada,14050455,Panama Papers
“Montreal Quebec, Canada”,1A3CA6F20883CDEBDD7C4B79A1A5CB2B,The Panama Papers data is current through 2015,CAN,Canada,14050456,Panama Papers
Montreal Quebec; Canada; H3A; 3J6 & Montreal; H3B; 4W5; Canada,2EF09BFA813AE781312812FC05EF83BF,The Panama Papers data is current through 2015,CAN,Canada,14050457,Panama Papers
Montreal Quebec; Canada; H3A; 3J6 & Montreal Quebec; Canada; H3B; 4W5,8ABFF3BD4B76BF39FA2B6A1F55312A90,The Panama Papers data is current through 2015,CAN,Canada,14050458,Panama Papers
MONT ROLAND 39100 DOLE FRANCE,A0B4CFDD0EAD36BB7E836CDC94B44866,The Panama Papers data is current through 2015,FRA,France,14050459,Panama Papers
Montrose Court / Princess gate; London SW7 2QQ,C5FCC716224EA43AA62D5D64A7CE74E0,The Panama Papers data is current through 2015,GBR,United Kingdom,14050460,Panama Papers
“Montrose Place, 7 Montrose Terrace Bishopcourt Cape Town South Africa 7708″,9B5E8E1F70EB4F3ACD7F10E63C2F17AD,The Panama Papers data is current through 2015,ZAF,South Africa,14050461,Panama Papers
Montt Crevelt House; South Quay; St. Sampsons Guernsey; C.I.,AF8DC439F21198C5FA36260BDE55FBF6,The Panama Papers data is current through 2015,GGY,Guernsey,14050462,Panama Papers
MOO BAN MANTANA RANGSIT SOI 38; N711/199 PRACHATIPAT THANYA; BURI PATHUMTHANI 12130; THAILAND,5141B02ACFAE3EF38C58AE32A5C5CC11,The Panama Papers data is current through 2015,THA,Thailand,14050463,Panama Papers
Moohin Road; MS 656; Habana 4740; Queensland; Australia,8275BF4564B89C83B144187332B3081B,The Panama Papers data is current through 2015,AUS,Australia,14050464,Panama Papers
Moon Tower; 45/66 Soi 59; Sukhmvit; Bankok; 10110; Thailand,469D070E741E5B8B2C64CD602298DB0F,The Panama Papers data is current through 2015,THA,Thailand,14050465,Panama Papers
Moon Tower; 45/66 Soi 59; Sukhumvit; Bangkok 10110; Thailand,61FE5DB0CF776377E2E03B39E44CC3F9,The Panama Papers data is current through 2015,THA,Thailand,14050466,Panama Papers
Moore Stephens Trust Company (Isle of Man) Limited,0482643238CFEEC7BED37D717DFC7900,The Panama Papers data is current through 2015,IMN,Isle of Man,14050467,Panama Papers
Moorhouse Development Limited P.O. Box 3175 Road Town Tortola British Virgin Island,9351EBF4C36BCADDDA1FB5E6B79730CA,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050468,Panama Papers
Moorhouse; Moorhouse Road Westerha; Kent; TN16 2ES,F3E6196B686599B5FB3E8A32DDD7F503,The Panama Papers data is current through 2015,GBR,United Kingdom,14050469,Panama Papers
Moorhouse; Westerham; Kent; TN16 2ES,A82CA3B7AA704C4BC22B7BB9A53A852E,The Panama Papers data is current through 2015,GBR,United Kingdom,14050470,Panama Papers
Moosa Group Enterprises JLT; Indigo Tower; Office #207 and 208; Jumeirah Lakes Tower; PO Box 62513; Dubai; United Arab Emirates,903D7030FDCA6D8E49BFE07A8E5D15F0,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14050471,Panama Papers
MORC.80; ILOT ROAD; LONG MOUNTAIN; MAURITIUS,B7980FBB35DD014874B6F86D1412245B,The Panama Papers data is current through 2015,MUS,Mauritius,14050472,Panama Papers
Morc Chetty No 5. Societe Beau Manguier; Pereybere; GPO Box 244; Mauritius,8FCB21B90D2FBA06F3397808268E7002,The Panama Papers data is current through 2015,MUS,Mauritius,14050473,Panama Papers
MORCELLEMENT IIOIS; BAIE DU TOMBEAU; MAURITIUS,36768A274F7E16B63D8FE67E03D931B2,The Panama Papers data is current through 2015,MUS,Mauritius,14050474,Panama Papers
MORC; SWAN; PEREYBERE; MAURITIUS,0CBEDB1CF4BBE7E0BB9B593A9E31CBF3,The Panama Papers data is current through 2015,MUS,Mauritius,14050475,Panama Papers
MORE CHETTY 5; SOCIETE BEAU MANGUIER; BAIN BOEUF; PEREBERE; GPO BOX 244; MAURITIUS,E5D2C3614EE462433750E6933860093E,The Panama Papers data is current through 2015,MUS,Mauritius,14050476,Panama Papers
Moreno 1332; Carhue (6430); Buenos Aires; Argentina,E2520776CC3DCF3091C89924674B63E3,The Panama Papers data is current through 2015,ARG,Argentina,14050477,Panama Papers
Moreno 231; San Lorenzo cp 2200; Santa Fe; Argentina,B3DABD4885CBE37BCA33B138B60F2C99,The Panama Papers data is current through 2015,ARG,Argentina,14050478,Panama Papers
Moreno 421; Quilmes; Argentina,ACCE1DB0B624F28BB5B3A61491C493F3,The Panama Papers data is current through 2015,ARG,Argentina,14050479,Panama Papers
“Moreno 794 7.B.CP.1091 ciudad de Buenos Aires, Argentina”,CFDF9DC3BA37ED12D6A3C71C85335B86,The Panama Papers data is current through 2015,ARG,Argentina,14050480,Panama Papers
MORFOU 13; MATINA COURT; FLAT 101; 3012 LIMASSOL; CYPRUS,1FA7AB8EBA4BE95E09D7D712B933239B,The Panama Papers data is current through 2015,CYP,Cyprus,14050481,Panama Papers
Morfou 25; Mesovounia; 4045; Germasogia; Limassol; Cyprus,E72E03653B0096375DAA94B4060AE52D,The Panama Papers data is current through 2015,CYP,Cyprus,14050482,Panama Papers
Morgan & Morgan; 53d Street; Swiss Tower; 16th Floor; Panama; Republic of Panama,0BB300BE1CA722BB9CC93BD339641564,The Panama Papers data is current through 2015,PAN,Panama,14050483,Panama Papers
Morgan & Morgan; 53rd Street; Urbanización Obarrio; Swiss Tower; 14th Floor; Panama,A74E8788FC1E68E3E6E46EA3233D1FBA,The Panama Papers data is current through 2015,PAN,Panama,14050484,Panama Papers
Morgan & Morgan 53rd Street; Urbanizacion Obarrio Swiss Tower; 16th Floor; Panama,2E1B8BED0B9872904DAC81A749AE4156,The Panama Papers data is current through 2015,PAN,Panama,14050485,Panama Papers
MORGAN & MORGAN- 53 Street Urbanizacion MARBELLA SP,026D78E8FD3533EAC33C299157854E6C,The Panama Papers data is current through 2015,PAN,Panama,14050486,Panama Papers
Morgan & Morgan Building; Pasea Estate; P.O. Box 958; Road Town; Tortola; British Virgin Islands,43D7E105837DEF315DC37D91B0A3E257,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050487,Panama Papers
Morgan & Morgan Building; Pasea Estate; Road Town; British Virgin Islands,7073C6DE9CD3981C68C9D43E52DBD982,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050488,Panama Papers
Morgan & Morgan Building; Pasea Estate; Road Town; Tortola; Birtish Virgin Islands.,3FAE6E7AD1A1AC32D265CEDE0AEECBD8,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050489,Panama Papers
MORGAN & MORGAN BUILDING; PASEA ESTATE; ROAD TOWN; TORTOLA; BRITISH VIRGIN ISLANDS,B9839756E89A953B0C4049627FBF624B,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050490,Panama Papers
Morgan & Morgan Building; Pasea Estate; Road Town; Tortola; B.V.I.,38F8A86FB51BB29E922378A9D78E8D8A,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050491,Panama Papers
Morgan & Morgan Building; Peasea Estate; Road Town; Tortola; British Virgin Islands,5615E2C24D46DFAED3ED9E287941BC7E,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050492,Panama Papers
Morgan & Morgan Building P.O. Box 958; Pasea Estate; Road Town; Tortola; British Virgin Islands.,7ADBF7189255B03E5C3141CF2E82C84A,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050493,Panama Papers
Morgan & Morgan Building; Sir Francis Drake Highway; Pasea Estate; Road Town; Tortola; British Virgin Islands,701AF51BE9CF9DCA04BB7A1DB14F850C,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050494,Panama Papers
Morgan & Morgan Calle 53 Urbanizacion Obarrio Swiss Tower piso 16 Panamá Panamá,DFE1D7DFFC31979AE6C5392FCD52BAA8,The Panama Papers data is current through 2015,PAN,Panama,14050495,Panama Papers
Morgan & Morgan Calle 53 Urb. Obarrio; Swiss Tower; Piso 16 Panama; Panama,50B4AA519D7472727183EF21E2F78681,The Panama Papers data is current through 2015,PAN,Panama,14050496,Panama Papers
Morgan & Morgan; Pasea Estate; Road Town; Tortola; British Virgin Islands,C17DA9BAE3E23148DC5BCDA3DE85F2CE,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050497,Panama Papers
“MORGAN & MORGAN TRUST CO. LTD, ROAD TOWN TORTOLA BVI.”,197F816D59A0DFADA0E6C32B04E18C8A,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050498,Panama Papers
MORGAN & MORGAN TRUST CORPORATION BELIZE LIMITED; P.O. BOX 1777; 35A REGENT STREET; JASMINE COURT; BELIZE CITY; BELIZE,85AB7861170D93F25AB471E793FE2D33,The Panama Papers data is current through 2015,BLZ,Belize,14050499,Panama Papers
MORGAN & MORGAN TRUST CORPORATION (BELIZE) LIMITED Withfield Tower; Third Floor; 4792 Coney Drive; P.O.Box 1777; Belize City; BELIZE,79FFECF762D5D89DDCA1E0CA125A255B,The Panama Papers data is current through 2015,BLZ,Belize,14050500,Panama Papers
MORGAN & MORGAN TRUST CORPORATION LIMITED; PASEA ESTATE; P.O. BOXD 3149; ROAD TOWN; TORTOLA; BRITIS VIRGIN ISLANDS,A974D2921E52F9A5AEDBFF8D4004BF74,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050501,Panama Papers
MORGAN & MORGAN TRUST CORPORATION LIMITED; P.O. BOX 958 PASEA ESTATE; ROAD TOWN; TORTOLA; BRITISH VIRGIN ISLANDS,22E263CB3CC581EE72E4B5C485B0CD37,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050502,Panama Papers
MORGAN & MORGAN Trust Corporation Limited; P.O. Box 958; Pasea Estate; Road Town; Tortola; BVI,65583BED08FBF5C54049E68C7718AD5B,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050503,Panama Papers
Morgan & Morgan Trust Corporation Limited; Road Town; Tortola; British Virgin Islands,FD054C0CE89597C7F82604763DA3ED66,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050504,Panama Papers
MORGAN & MORGAN TRUST CORPORATION LTD. P O BOX 1777 BELIZE CITY BELIZE,669CF9C96C9C037C8BDB4B7ED65A89B9,The Panama Papers data is current through 2015,BLZ,Belize,14050505,Panama Papers
MORGAN & MORGAN TRUST CORPORTATE LIMITED P.O. BOX 958; ROAD TOWN; TORTOLA; BRITISH VIRGIN ISLANDS,F75CC26217D880D6A97B8907702DA6B4,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050506,Panama Papers
Morgan & Morgon Building; P.O. Box 958; Pasea Estate; Road Town; Tortola; British Virgin Islands,D98CC4B8F422EA801D5C612645827D8E,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050507,Panama Papers
Morgan and Morgan Building; Pasea Estate; Road Town; Tortola; British Virgin Islands,CC8E8EA7875888F544FCA0B40471FABB,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050508,Panama Papers
Morgan and Morgan Building; Pase Estate; Road Town; Tortolaa; British Virgin Islands,91499ED2D0DD44DADB5671D5FDE3E125,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050509,Panama Papers
Morgan and Morgan; Calle 53 Urbanizacion Obarrio; Swiss Tower; Piso 16 Panama; Panama,95B0ED0A1D2AFCECF679DFDDD435617C,The Panama Papers data is current through 2015,PAN,Panama,14050510,Panama Papers
MORGAN GRENFELL HOUSE; LEFEBVRE STREET; ST PETER PORT; GUERNSEY,8CBB4981587D158093719C79041E7003,The Panama Papers data is current through 2015,GGY,Guernsey,14050511,Panama Papers
MORGAN GRENFELL HOUSE; LEFEBVRE STREET; ST.PETER PORT.GUERNSEY CHANNEL ISLANDS,0ED3CB751B2D5DF5A2EB89BEF39237C7,The Panama Papers data is current through 2015,GGY,Guernsey,14050512,Panama Papers
Morgan Grenfell House; Lefebvre St; St Peter Port; GY1 4BY; Guernsey; C.I.,2310E0BB870AA26F58B9F97BD842FDFE,The Panama Papers data is current through 2015,GGY,Guernsey,14050513,Panama Papers
“MORGAN STANLEY, 30TH FLOOR THREE EXCHANGE SQUARE CENTRAL HONG KONG”,E35FF39B86CAC5C2FAF4D9C6A7765321,The Panama Papers data is current through 2015,HKG,Hong Kong,14050514,Panama Papers
Morgan Trust Co. of Bahamas Ltd.; The Bahamas Financial Center; 2nd Floor; Charlotte & Shorley Street; P. O. Box N-4899 / Nassau; Bahamas,0ED4FE938DD6E2D8103AB060BD7E93AD,The Panama Papers data is current through 2015,BHS,Bahamas,14050515,Panama Papers
“Morgan y Morgan 53rd E Street Urbanizacion Marbelle MMG Toower, 16th Floor Panama-Republic of Panama”,50C5010EF7E01B424FC6934E44EAE7DD,The Panama Papers data is current through 2015,PAN,Panama,14050516,Panama Papers
Morial Square; P.O. Box 556; Charles; Nevis; West Indies,23C5E205343C25DB1C0490C9D39338E2,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14050517,Panama Papers
MORITO CO.; LTD.; 11-28; 1-CHOME; NISHIKI NAKA-KU; NAGOYA; JAPAN,E90EED77EF5A22118DDB63D759E3CE53,The Panama Papers data is current through 2015,JPN,Japan,14050518,Panama Papers
Mori work group 3; cai street; Yichin city; Yichin street; Hei long jiang Province; China,CC9056C01B2D50BD06C433498EF0C26B,The Panama Papers data is current through 2015,CHN,China,14050519,Panama Papers
Morkurhaus; Josef; Rheinbergerstrasse 6 Vaduz,BC4CF3B7CF5DBE3871400CB19F7584AB,The Panama Papers data is current through 2015,LIE,Liechtenstein,14050520,Panama Papers
MORLEYS; WOODSIDE GREEN; GREAT HALLINGBURY; BISHOP STORTGORD; ENGLAND; CM22 7UQ,C81B0405D9B2A8A66C02CB1CB64018A5,The Panama Papers data is current through 2015,GBR,United Kingdom,14050521,Panama Papers
MORNE LA CROIX; SOUFRIERE; SAINT LUCIA,154A7B66803F3CF0DB77A602AFC5A30F,The Panama Papers data is current through 2015,LCA,Saint Lucia,14050522,Panama Papers
“Morne Proper, Dominica.”,7029C9EE406A8DB8238E318F7602466B,The Panama Papers data is current through 2015,DMA,Dominica,14050523,Panama Papers
“Morne Prospe, Dominica”,1C99FFC1C9518AE3CFBE84638C5D2C71,The Panama Papers data is current through 2015,DMA,Dominica,14050524,Panama Papers
Morne Prosper,BAA71D3F0B09097067EC26296BCE14D7,The Panama Papers data is current through 2015,HTI,Haiti,14050525,Panama Papers
“Morne Prosper, Dominica”,76A9E526F9A4434528A72A7F7291F885,The Panama Papers data is current through 2015,DMA,Dominica,14050526,Panama Papers
“Morne Prosper, Dominicana”,248F2929379D5381871C37CBC8AC61CD,The Panama Papers data is current through 2015,DMA,Dominica,14050527,Panama Papers
“Morne Prosper, Domnica”,7A0BE450706DFC88E18197BAE3ACCA1E,The Panama Papers data is current through 2015,DMA,Dominica,14050528,Panama Papers
MORNING POST CENTRE; 22 DAI FAT STREET; TAI PO INDUSTRIAL ESTATE; NEW TERRITORIES; HONG KONG,11B28B88208CBDB98C7C413F14F740B5,The Panama Papers data is current through 2015,HKG,Hong Kong,14050529,Panama Papers
Morning Post Centre; 22 Dai Fat Stret; Tai Po Industrial Estate; New Territories; Hong Kong,3C905A4C83376B7C6961EAD22A6D2E18,The Panama Papers data is current through 2015,HKG,Hong Kong,14050530,Panama Papers
MORNING STAR HOLDINGS LIMITED; P O BOX 556; MAIN STREET; CHARLESTOWN; NE,A926DAAC89A029C2134226CF4C64B714,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14050531,Panama Papers
MORNING STAR HOLDINGS LIMITED; P.O. BOX 556; MAIN STREET; CHARLESTOWN; NEVIS,C288E415F4B39BD02D1A7411AD611E28,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14050532,Panama Papers
MORNING STAR HOLDINGS LTD. MEMORIAL SQUARE HUMKINS PLAZA BOX 556 CHARLESTOWN NEVIS,8AE17A8155DBC98E505A04C8490D1A76,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14050533,Panama Papers
MORNING STAR HOLDINGS LTD. MEMORIAL SQUARE HUNKINS PLAZA BOX 556 CHARLESTON NEVIS,4F0402688C8D1E790820DF7C14AFF507,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14050534,Panama Papers
“MORNING STAR HOLDINGS LTD., MEMORIAL SQUARE HUNKINS PLAZA BOX 556 CHARLESTOWN NEVIS”,A7462A006D6A1FE6FB3CD493B4668CB1,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14050535,Panama Papers
“MorningView llc, Via Nosedo 26 6900 Lugano – Switzerland”,91BC76068E966C82F5C5A6268CEBC69F,The Panama Papers data is current through 2015,CHE,Switzerland,14050536,Panama Papers
Morozova Street; Build. 117; office/flat 39; Siktivkar; Komi Republic; Russia,80120EC01498592C29CECFFECB5AB3AB,The Panama Papers data is current through 2015,RUS,Russian Federation,14050537,Panama Papers
Morrison 1566; 2000 Rosario; Republica Argentina,9275EC09FCC821EA39B3FAE53E1BA654,The Panama Papers data is current through 2015,ARG,Argentina,14050538,Panama Papers
Morris Paul Drive; Ponds Pasture; Basseterre; St. Kitts,72B2DEF76BC758CB800713985102C803,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14050539,Panama Papers
Morskaya nab; Building 39; korp. 2; office/flat 13; St. Petersburg; Russia,B1AF58E354960AA75BAAB5E0FFC02308,The Panama Papers data is current through 2015,RUS,Russian Federation,14050540,Panama Papers
Morskaya Street; 128; Apartment 98; Volgodonsk; Rostov region; Russian Federation,5A9B9C4820F11E75AF60BA3F5B0BB058,The Panama Papers data is current through 2015,RUS,Russian Federation,14050541,Panama Papers
Morton House; Government Road; Charlestown; Nevis; West Indies.,ACE8CF60E9E3A04040B6E17D400A055B,The Panama Papers data is current through 2015,KNA,Saint Kitts and Nevis,14050542,Panama Papers
MORTON STREET 15; STANFORD; SOUTH AFRICA; 7210,51D30A8E0BA9B0293B0AB2B0B13BFBDF,The Panama Papers data is current through 2015,ZAF,South Africa,14050543,Panama Papers
MORTSJOVAGEN 4; 749 72 FJARDHUNDRA; SWEDEN,579C8A162676AEDC95F163D1AF0E63F9,The Panama Papers data is current through 2015,SWE,Sweden,14050544,Panama Papers
Morvany; Modricka 486/34; Brno; Czech Republic,2F9432CEC1852E05045DA495DA27BBDD,The Panama Papers data is current through 2015,CZE,Czech Republic,14050545,Panama Papers
MORYMOR TRUST CORPORATION LTD.; 50 SHIRLEY STREET; POB N-341; NASSAU; BAHAMAS,A8A53E48EF9DD7F55BDF95F45C76D71B,The Panama Papers data is current through 2015,BHS,Bahamas,14050546,Panama Papers
MOSCOVSKAYA ST. 5-35; NOGINSK; MOSCOW REGION; RUSSIA,E4C2A30459ECB4954CE30D7310CE3B3C,The Panama Papers data is current through 2015,RUS,Russian Federation,14050547,Panama Papers
Moscovskoe Shosse 8-122; St. Petersburg; Russia,C2927CF6434A5920A80EDD996A588DB0,The Panama Papers data is current through 2015,RUS,Russian Federation,14050548,Panama Papers
“Moscow, 1 Ostankinskaya 26-33”,DEEA605EAA7C87FEDFC397380E8D71D2,The Panama Papers data is current through 2015,RUS,Russian Federation,14050549,Panama Papers
Moscow; 21 Olimpisky Prospect; flat 26,1188AAEC72B6DFC157D2BFD5781BA39D,The Panama Papers data is current through 2015,RUS,Russian Federation,14050550,Panama Papers
Moscow; 8-1-59 Academician Korolev Street; Russia,C343829DEFB8FB651D8B938AEB139C5E,The Panama Papers data is current through 2015,RUS,Russian Federation,14050551,Panama Papers
Moscow; Boulevard; Gorozhankinyh b.4; flat 41; Russian Federation,B9837F72D14DD7D668249A90C2B6D6EB,The Panama Papers data is current through 2015,RUS,Russian Federation,14050552,Panama Papers
Moscow; Bronnaya Street 44; apt 27; Russian Federation,3D1FC77F7DD458C25A278DC8F90D8FE5,The Panama Papers data is current through 2015,RUS,Russian Federation,14050553,Panama Papers
“Moscow, Chapayevsky 3-894”,4F2BB42E940EADBE4518786D914B728C,The Panama Papers data is current through 2015,RUS,Russian Federation,14050554,Panama Papers
Moscow; Govorova street; bld 32; apt 118,823E8C0CB8CC602038D6BE01DFECB043,The Panama Papers data is current through 2015,RUS,Russian Federation,14050555,Panama Papers
MOSCOW; LENINGRADSKY PROSPECT 33; BLDG. 1; APP.33; MOSCOW; RUSSIAN FEDERATION,93A883757F896D530DF49F5BA1F78429,The Panama Papers data is current through 2015,RUS,Russian Federation,14050556,Panama Papers
MOSCOW; LOMONOSOVSKIY PROS. 34; FLT. 109,6D65E7B197C1D32E6FC60176B8F604B5,The Panama Papers data is current through 2015,RUS,Russian Federation,14050557,Panama Papers
Moscow; Lukinskaya street 7; apt. 317,43E79206BBD5A68F8A92B5921EDC07ED,The Panama Papers data is current through 2015,RUS,Russian Federation,14050558,Panama Papers
“Moscow, Novosuchevskai 21-23”,B8E408AE2CCF8ECA22DE4FF18703D175,The Panama Papers data is current through 2015,RUS,Russian Federation,14050559,Panama Papers
MOSCOW; PRECHISTENKA STREET; 28; 8 – RUSSIA,C1E28A32B7C873B03AC112A75977476F,The Panama Papers data is current through 2015,RUS,Russian Federation,14050560,Panama Papers
Moscow; Prospect Mira 58; Flat 139; Index 129110,D95C12BE690AC266990C9B8FBDF7D13D,The Panama Papers data is current through 2015,RUS,Russian Federation,14050561,Panama Papers
Moscow Region Odinzovski area Zhukovka village 61-17,2FC45738A23D8887F0C6E896D66663FE,The Panama Papers data is current through 2015,RUS,Russian Federation,14050562,Panama Papers
“MOSCOW, RUSSIA”,9CCE142626CCB0B80C39EBA11CD36E3A,The Panama Papers data is current through 2015,RUS,Russian Federation,14050563,Panama Papers
MOSCOW RUSSIA 115533; 20 NAGATINSKAIA NABEREZHNAIA; APT 13,96264A7C1B7E611B311BDC927A9F0661,The Panama Papers data is current through 2015,RUS,Russian Federation,14050564,Panama Papers
“Moscow, Russian Federation”,1B2AB01E859F4A08E731227BD4A93A29,The Panama Papers data is current through 2015,RUS,Russian Federation,14050565,Panama Papers
Moscow; U1 Tolbukhina; Bldg. 11 #2; Apt; 133; Russian Federation,A70DCAED20CEFB0B4F5818709A6309AD,The Panama Papers data is current through 2015,RUS,Russian Federation,14050566,Panama Papers
Moscow Universitetsky; pr. 21/3; apt 028,9E16E02EA97D4B7FFA798311BAB7F075,The Panama Papers data is current through 2015,RUS,Russian Federation,14050567,Panama Papers
Moscow Universitetsky; pr. 23/3; apt 025,36E765E9864838A9663D2AADD380930E,The Panama Papers data is current through 2015,RUS,Russian Federation,14050568,Panama Papers
Moscow; UÑ Szhorsa; No.2; Flat 229,FF0E7AB214F81385A0930141AFE443CB,The Panama Papers data is current through 2015,RUS,Russian Federation,14050569,Panama Papers
Mosfilmovskaya Street; 78; Apt. 76; Moscow; 117192; Russia,86B6182D51D12A0B06CB9518A8CE949E,The Panama Papers data is current through 2015,RUS,Russian Federation,14050570,Panama Papers
Mosfilmpvskaya Str. 70/3-531; Moscow; Russia,0EAFB9CE505CD50312226CE25F51C2B9,The Panama Papers data is current through 2015,RUS,Russian Federation,14050571,Panama Papers
MOSFON BUILDING; EAST 54TH STREET; PANAMA CITY; PANAMA,9C6B2B2B8838BCDB97A6B23198BF0F88,The Panama Papers data is current through 2015,PAN,Panama,14050572,Panama Papers
Mosfon Building; Second Floor; 54 East Street; Panama; Republic of Panama,D71F2A8F3CC3D4BFB1C2741CE81DBC44,The Panama Papers data is current through 2015,PAN,Panama,14050573,Panama Papers
“Moshav Arugut 291, Israel”,01BE8B7C95B97C814E04D2A8DCE0B94A,The Panama Papers data is current through 2015,ISR,Israel,14050574,Panama Papers
MOSHAVE EIN-AYALA; KHOF-CARMEL; ISRAEL,2CC212A7D30172ED3170FD4E3089F73B,The Panama Papers data is current through 2015,ISR,Israel,14050575,Panama Papers
“MOSHAV LOTEM, ISRAEL”,F9F7F43EAFA3E27E6AE6A2A5130858BD,The Panama Papers data is current through 2015,ISR,Israel,14050576,Panama Papers
“Moshav Mazliah 22, Israel”,94881B9F821D96530600A3D7B801FAB2,The Panama Papers data is current through 2015,ISR,Israel,14050577,Panama Papers
Moshe Rachmilevich 114; Jerusalem; Israel.,5C3E69CABB3C13583063FC0924DFC228,The Panama Papers data is current through 2015,ISR,Israel,14050578,Panama Papers
Moskevska 57; Prague 10; Czech Republic 10000,CD76ED6118B5108E90F87D9E77269A11,The Panama Papers data is current through 2015,CZE,Czech Republic,14050579,Panama Papers
Moskovskaya Oblast; Akedemika; Lavrentyeva street; Russia,48ADEDB3065654BFD168DB52226856B6,The Panama Papers data is current through 2015,RUS,Russian Federation,14050580,Panama Papers
Moskovskaya Oblast; Dolgoprudniy Town; Sportivnaya Street 13; apt 57; 58. Russia,62D901D5A3EA2BBC5D6F1DF90433E4B6,The Panama Papers data is current through 2015,RUS,Russian Federation,14050581,Panama Papers
Moskovskaya oblast; Poselok Zhavoronki; 30 Let Oktyabrya Street; house 50; Russia,8003E2027F0740E8B4F018BE5D4DEB92,The Panama Papers data is current through 2015,RUS,Russian Federation,14050582,Panama Papers
“Moskovskaya obl.; Razdory; PGK; “”Rassvet”” 8; RUSSIA”,3B1477359C42A9175FCA174027CBECF0,The Panama Papers data is current through 2015,RUS,Russian Federation,14050583,Panama Papers
MOSKOVSKIY PR. 151; APP. 25; ST.PETRSBURG; 196128; RUSSIA,1BF6D04C6485AB5D013C257951A081D5,The Panama Papers data is current through 2015,RUS,Russian Federation,14050584,Panama Papers
Moskovskiy pr.; 208; 48; St. Petersburg; Russia,190535B734E881D8D99A336651C0CD8A,The Panama Papers data is current through 2015,RUS,Russian Federation,14050585,Panama Papers
Moskovskoe Shossem Bldg.; 278; Apt. 86; Saint-Petersburg City; 196627; Russian Federation,660ADAF467C7B5647B932A4C9B228F66,The Panama Papers data is current through 2015,RUS,Russian Federation,14050586,Panama Papers
MOSKOVSKOJE SHOSSE; ST. PETERBURG 15-13; RUSKO,BE111C3949444A4E6A5FB55EE0140E85,The Panama Papers data is current through 2015,RUS,Russian Federation,14050587,Panama Papers
MOSKOVSKY PR. 110; APPT 97; NABEREZHNYE CHELNY RUSSIA,F8E2D167D32114A18B4144B975848473,The Panama Papers data is current through 2015,RUS,Russian Federation,14050588,Panama Papers
“MOSKOVSKY PROSPEKT, 208/48ST. PETERSBURGRUSSIA”,BE7186818C455635CA45B973078E9FE3,The Panama Papers data is current through 2015,RUS,Russian Federation,14050589,Panama Papers
Moskovskyy Prospekt 171-98; St. Petersburg; Russian Federation,35CBEBF77077363BCEFA0333FB4376A2,The Panama Papers data is current through 2015,RUS,Russian Federation,14050590,Panama Papers
“MOSLES BUILDING, THIRD FLOOR”,BCDE5CC4CB0F656120D56AFD1203E4C5,The Panama Papers data is current through 2015,,,14050591,Panama Papers
MOSLES BUILDING; THIRD FLOOR; B. POLYANKA STR. 15 109180; MOSCOW,14ABAA6780C48D0A8FC0FE875C91D786,The Panama Papers data is current through 2015,RUS,Russian Federation,14050592,Panama Papers
MOSLES BUILDING; THIRD FLOOR; B. POLYANKA STR. 15 119180 MOSCOW; RUSSIA,59E1ABE8C1A7829A3A725CC02A123726,The Panama Papers data is current through 2015,RUS,Russian Federation,14050593,Panama Papers
MOSLES BUILDING; THIRD FLOOR B. POLYANKA STR. 15 MOSCOW; RUSSIA,78973F7F1D66735E6BE68D49E6F9638F,The Panama Papers data is current through 2015,RUS,Russian Federation,14050594,Panama Papers
“Mosovskeho 13, 811 03 Bratislava 1”,72125C2483CC4D54768DB435D8081C15,The Panama Papers data is current through 2015,AUS,Australia,14050595,Panama Papers
MOSQUE ROAD; SURINAM; MAURITIUS,FE696CDED37906DAF1F7FD64AECD6E8F,The Panama Papers data is current through 2015,MUS,Mauritius,14050596,Panama Papers
“MOSSACK BUILDING 2ND FLOOR, EAST 54TH STREET PANAMA”,172779F782D7C6FF15EC954C4698DC41,The Panama Papers data is current through 2015,PAN,Panama,14050597,Panama Papers
“Mossack Fonseca & Co. Arango-Orillac Bldg, 54th Street PO box 0832-0886 WTC Panama”,9AC664EB2FD92CE7EA589CE65E3D80AD,The Panama Papers data is current through 2015,PAN,Panama,14050598,Panama Papers
Mossack Fonseca & Co; Arango-Orillac Building; 54th St.; P.O. Box 0832-0886 WTC,734431A52841DE867221142C0F901C39,The Panama Papers data is current through 2015,PAN,Panama,14050599,Panama Papers
“MOSSACK FONSECA & CO., ARANGO-ORILLACBUILDING SECOND FLOOR EAST 54TH STREET”,85A8FE30BD29803E5775A30C5A28C392,The Panama Papers data is current through 2015,PAN,Panama,14050600,Panama Papers
MOSSACK FONSECA & CO.; ARANGO ORILLAC BUILDING; SECOND FLOOR; EAST 54TH STREET; P.O. BOX 0832-0886; W.T.C. PANAMA.,13A97E81A32B3EECB70745E8A47E4C0C,The Panama Papers data is current through 2015,PAN,Panama,14050601,Panama Papers
MOSSACK FONSECA & CO. (BAHAMAS) LIMITED; BAHAMAS INTERNATIONAL TRUST BUILDING; BANK LANE; P.O. BOX N-8188; NASSAU; BAHAMAS,61A924F4735FEF0CEB4DA4F57D1A7CCD,The Panama Papers data is current through 2015,BHS,Bahamas,14050602,Panama Papers
Mossack Fonseca & Co. (Bahamas) Limited; Saffrey Square; Bank Lane; P.O. Box N-8188; Nassau; Bahamas.,233C637683CCC30583F5FDB4C2A57DE1,The Panama Papers data is current through 2015,BHS,Bahamas,14050603,Panama Papers
Mossack Fonseca & Co. (Bahamas) Limited; Saffrey Square; Suite 205; Bank Lane; P.O. Box N-8188; Nassau; Commonwealth of the Bahamas,CA880A761E3EFB436E7D356C73B351CA,The Panama Papers data is current through 2015,BHS,Bahamas,14050604,Panama Papers
Mossack Fonseca & Co. (Bahamas) Ltd.; Saffrey Square; Suite 205; Bank Lane; P.O. Box N-8188; Nassau; Bahamas,E0A8313C265A816B8B82D14EA821C8DD,The Panama Papers data is current through 2015,BHS,Bahamas,14050605,Panama Papers
Mossack Fonseca & Co. (Bahamas) Ltd.; Saffrey Square; Suite 205; Bnak Lance; P.O. Box No. 8188; Nassau; Bahamas,CCE9AC83477EEE6AD14A7809F7B3819B,The Panama Papers data is current through 2015,BHS,Bahamas,14050606,Panama Papers
“MOSSACK FONSECA & CO. (BAHAMAS) LTD. Suite E-2 Union Court Building Elizabeth Avenue and Shirley Street Nassau, Bahamas”,21892150C7F41078D8AD9E11CDBEC1B0,The Panama Papers data is current through 2015,BHS,Bahamas,14050607,Panama Papers
MOSSACK FONSECA & CO (BAHAMS) LIMITED SAFFREY SQUARE; SUITE 205; BANK LANE; P.O.BOX N-8188; NASSAU; COMMONWEALTH OF THE BAHAMAS.,68246366905F2E1FECAACBBE1333FC89,The Panama Papers data is current through 2015,BHS,Bahamas,14050608,Panama Papers
MOSSACK FONSECA & CO. (BVI) LTD.; AKARA BLDG.; 24 DE CASTRO STREET; WICKHAMS CAY 1; ROAD TOWN; TORTOLA; BRITISH VIRGIN ISLANDS,8CFE160200D8557DA7278E29FC3FA08F,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050609,Panama Papers
Mossack Fonseca & Co. (BVI) Ltd. Akara Building; 24 De Castro Street; Wickhams Cay 1; Road Town; Tortola British Virgin Islands,B636CBA4D6B2524E0B1798D9951B73E4,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050610,Panama Papers
Mossack Fonseca & Co. (BVI) Ltd; P.O. Box 3136; 24 de Castro Street; Wickhams Cay 1; Road Town; Tortola; BVI.,BE6A1C3667122E188E81C410E4A6A831,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050611,Panama Papers
MOSSACK FONSECA & CO. (B.V.I.) LTD; P.O. BOX 3136; ROAD TOWN; TORTOLA; BRITISH VIRGIN ISLANDS,D11339326DFA34502C9B335162CE26BD,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050612,Panama Papers
MOSSACK FONSECA & CO. (B.V.I.) LTD; P.O. BOX 3136; ROAD TOWN; TORTOLA; BRITISH VIRGIN ISLANDS1,7770643CFFF80FA94743F2A5E7E55C62,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050613,Panama Papers
“Mossack Fonseca & Co. (BVI) Ltd. Tortola, British Virgin Islands”,18ACC2FFC58D24CBD28DFA26EC774579,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050614,Panama Papers
MOSSACK FONSECA & CO. (KUXEMBOURG) S.R.L. 58A; RUE PRINCIPALE; L-6990 RAMELDANGE; LUXMEBOURG; S.I.,52DB9FC804AEE6E7839A0BC53F4F5E5D,The Panama Papers data is current through 2015,LUX,Luxembourg,14050615,Panama Papers
MOSSACK FONSECA & CO. (LUGANO) S.A.G.L.; VIA D. FONTANA 8; PO BOX 5496; CH-6901 LUGANO; SWITZERLAND,9542F30CBC0BE17F979AAF9C588A46EC,The Panama Papers data is current through 2015,CHE,Switzerland,14050616,Panama Papers
MOSSACK FONSECA & CO.; (LUXEMBOURG) S.A.R.L. 58A; RUE PRINCIPALE L-6990 RAMELDANGE; LUXEMBOURG S.I.,6455F1D315E32375579A2C827762FECF,The Panama Papers data is current through 2015,LUX,Luxembourg,14050617,Panama Papers
MOSSACK FONSECA & CO. (LUXEMBOURG) S.A.R.L. 58A; RUE PRINCIPALE; L-6990 RAMNELDANGE; LUXEMBOURG; S.I.,1528342F0DEF92493A4E351774136683,The Panama Papers data is current through 2015,LUX,Luxembourg,14050618,Panama Papers
MOSSACK FONSECA & CO. (LUXEMBOURG) S.R.L. 58A; RUE PRINCIPALE; L-6990 RAMELDANGE; LUXEMBOURG; S.I.,68CA3D5F8EE1B80F91AD6A9D0BCD244B,The Panama Papers data is current through 2015,LUX,Luxembourg,14050619,Panama Papers
MOSSACK FONSECA & CO. (LUXEMBOURG) S.R.L.; 58 RUE PRINCIPALE; L-6990 RAMELDANGE; LUXEMBOURG S.I.,A7DB7073C565DD4FD8D7579493262B18,The Panama Papers data is current through 2015,LUX,Luxembourg,14050620,Panama Papers
Mossack Fonseca &Co.; Mossfon Bldg.; 54th Street; Panama; Republic of Panama,A80AA2F3918B527A53314464C1523CC5,The Panama Papers data is current through 2015,PAN,Panama,14050621,Panama Papers
MOSSACK FONSECA & CO.; MOSSFON BLDG.; 54TH STREET P. O. BOX 0832-0886; W.T.C; PANAMA; REP. OF PANAMA,999DEBEF01BFE53D87DBD56A188F7FE5,The Panama Papers data is current through 2015,PAN,Panama,14050622,Panama Papers
MOSSACK FONSECA & CO. Mossfon Bldg.; 54th Street; REP.OF PANAMA-PANAMA,B18B2977514B4EF84299AF4F842AA574,The Panama Papers data is current through 2015,PAN,Panama,14050623,Panama Papers
“MOSSACK FONSECA & CO. MOSSFON BUILDING 54TH STREET PANAMA, REP. OF PANAMA”,4BD6114059E073A68A7F3117C4C5FF06,The Panama Papers data is current through 2015,PAN,Panama,14050624,Panama Papers
Mossack Fonseca & Co; Mossfon Building; Second Floor; East 54th Street; PO Box 0832-0886 W.T.C.Panama City; Panama,0F1CFD0C083E687230A28CDA4A255F0B,The Panama Papers data is current through 2015,PAN,Panama,14050625,Panama Papers
“Mossack Fonseca & Co. (Panama) Ltd. Mossfon Building Calle 54 Este Panama, Republica De Panama”,39353AB646BB598E357D8C7D824AD0C3,The Panama Papers data is current through 2015,PAN,Panama,14050626,Panama Papers
MOSSACK FONSECA & CO. (PERU) CORP.,8A76254E8DF43459ACAD4D473F17F814,The Panama Papers data is current through 2015,PER,Peru,14050627,Panama Papers
MOSSACK FONSECA & CO (PTY).,8FF5952A233073132B14BA1A54AD2D2E,The Panama Papers data is current through 2015,COL,Colombia,14050628,Panama Papers
MOSSACK FONSECA & CO (PTY). MOSSFON BUILDING; EAST 54TH STREET. PANAMA; REP. OF PANAMA,AC309A0C7A649982B850B1E2876136B6,The Panama Papers data is current through 2015,PAN,Panama,14050629,Panama Papers
MOSSACK FONSECA & CO (PTY). Mossfon Building; East 54th Street; Panama; Republic of Panama,6033FEB53B8CAA80B9162B886A774290,The Panama Papers data is current through 2015,PAN,Panama,14050630,Panama Papers
“MOSSACK FONSECA & CO. (SEYCHELLES) LTD- Suite 13, First Floor-Oliaji Trade Centre- Francis Rachel Street-Victoria Mahe-SEYCHELLES”,FE3FA1862C1F3D1AA3058E56156FB8F8,The Panama Papers data is current through 2015,SYC,Seychelles,14050631,Panama Papers
Mossack Fonseca & Co. (Singapore) Pte Ltd,194097724FB15552F39646FB524CD766,The Panama Papers data is current through 2015,SGP,Singapore,14050632,Panama Papers
MOSSACK FONSECA & CO. (U.K.) LIMITED; Invision House; Wilbury Way; Hitchin; Hertfordshire; SG4 0TW; United Kingdom.,89FCC7F549A289A34E32CFD765ABBB20,The Panama Papers data is current through 2015,GBR,United Kingdom,14050633,Panama Papers
“MOSSACK FONSECA, BAHAMAS”,9FFDB70081430AE29026C30C074D80FA,The Panama Papers data is current through 2015,BHS,Bahamas,14050634,Panama Papers
MOSSACK FONSECA PANAMA,A55DF0E3EED5A48204CAB548A725C244,The Panama Papers data is current through 2015,PAN,Panama,14050635,Panama Papers
MOSSACK FONSECA; PANAMA; REP. OF PANAMA EAST 54TH STREET; MOSSFON BUILDING; & CO (PTY),5D332C9A90874A1EA9178B52C727C03A,The Panama Papers data is current through 2015,PAN,Panama,14050636,Panama Papers
Mossafon Building; 2nd Floor; 54th Street; Panama; Republic of Panama,60B4159C9A8589607C0C1E8A58BB929F,The Panama Papers data is current through 2015,PAN,Panama,14050637,Panama Papers
Mosscak Fonseca & Co (Samoa) Limited; Level 5; Development Bank of Samoa Building; Beach Road; Apia Samoa.,CDE6D580C8EFE64D1B17B879EE5252E7,The Panama Papers data is current through 2015,WSM,Samoa,14050638,Panama Papers
Mossfom bldg; 54th street; panama; repofPanama,BBFC47BF23D57E9D11D617CF4AD4DB27,The Panama Papers data is current through 2015,PAN,Panama,14050639,Panama Papers
mossfom bldg-54th street-panama-repofpanamapa,ED5AA06E2591160AF4F43757C8FFCCD0,The Panama Papers data is current through 2015,PAN,Panama,14050640,Panama Papers
Mossfon Bdlg; 54th Street; Panama; Rep. of Panama,218A8FE9F6E9FD6C425298CA92CB96BA,The Panama Papers data is current through 2015,PAN,Panama,14050641,Panama Papers
Mossfon Bldb; 54th Street; Panama; Rep. of Panama,A4DA4CC12CD26B38B8DD67AF3376AC85,The Panama Papers data is current through 2015,PAN,Panama,14050642,Panama Papers
“Mossfon Bldg.,”,87617AA94772C66EE0CC9F6E09A47F32,The Panama Papers data is current through 2015,,,14050643,Panama Papers
Mossfon Bldg. 24 De Castro Street; Wickhams Cay I; Road Town Tortola; British Virgin Islands,03775B4B378A9C753520D1D50E07AF2F,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050644,Panama Papers
Mossfon Bldg; 2nd Fl.; East 54th Street; P.O. Box 0832-0886 W.T.C.; Panama; Rep. of Panama,36C6C2F945D1E0E7A0C236CB1158BF20,The Panama Papers data is current through 2015,PAN,Panama,14050645,Panama Papers
Mossfon Bldg.; 2nd Floor; 54th East St.; Panama City; Rep. of Panama,E015FE68EBA3A1FB69F416C9B2741C77,The Panama Papers data is current through 2015,PAN,Panama,14050646,Panama Papers
Mossfon Bldg.; 2nd Floor; 54th Street; Panama,60FB9C79FF737456EF917A1749D79772,The Panama Papers data is current through 2015,PAN,Panama,14050647,Panama Papers
Mossfon Bldg. 2nd Floor; 54th Street Panama City; PANAMA,20C8DE5639CCADC0390273BDA3B43458,The Panama Papers data is current through 2015,PAN,Panama,14050648,Panama Papers
Mossfon Bldg.; 2nd Floor 54th Street; Panama; Rep. of Panama,A64614E38AF1CAEC313284AD11CA0C3D,The Panama Papers data is current through 2015,PAN,Panama,14050649,Panama Papers
MOSSFON BLDG; 2ND FLOOR; EAST 54TH STREET; PANAMA CITY; REPUBLIC OF PANAMA,3BE26EBBBCEDE21145A02A1E7FED9486,The Panama Papers data is current through 2015,PAN,Panama,14050650,Panama Papers
Mossfon Bldg.; 2nd Floor; East 54th Street; PanamaP.O. Box 0232-0886Republic of Panama,36D576DD2BBAB919618196DE58D977E1,The Panama Papers data is current through 2015,PAN,Panama,14050651,Panama Papers
Mossfon Bldg; 2nd Floor; East 54 th Street; Panama; Rep. of Panama,C88BD2D767BF7A21FFEBE9657000D8B9,The Panama Papers data is current through 2015,PAN,Panama,14050652,Panama Papers
Mossfon Bldg. 2nd Floor East 54th Street Panama Republic of Panama,E5DD91A0F7D8E451C6549BBE17361E6C,The Panama Papers data is current through 2015,PAN,Panama,14050653,Panama Papers
Mossfon Bldg; 2nd flr; E 54th St; Panama; R of Panama,EFBDA3D2D54EEC59592650FE29F078CD,The Panama Papers data is current through 2015,PAN,Panama,14050654,Panama Papers
MOSSFON BLDG; 54 EAST STREET; PANAMA CITY; REPUBLIC OF PANAMA,BE6675AA16FF91F06E578603E072AF57,The Panama Papers data is current through 2015,PAN,Panama,14050655,Panama Papers
Mossfon Bldg.; 54 East Street; Panama; Rep. of Panama,994F5E27A3722F73E4A42166A02E889A,The Panama Papers data is current through 2015,PAN,Panama,14050656,Panama Papers
Mossfon Bldg; 54 Panama Street; Republic of Panama,468E48D19F75E96B7214503F28BE2BB3,The Panama Papers data is current through 2015,PAN,Panama,14050657,Panama Papers
Mossfon Bldg; 54 Street; Panama City; Rep. of Panama,DC25F17E7E5AD773341BAF8D19D905F6,The Panama Papers data is current through 2015,PAN,Panama,14050658,Panama Papers
Mossfon Bldg; 54 Street; Panama; Rep. of Panama,42D09B5D673E97E331541F46EC229D43,The Panama Papers data is current through 2015,PAN,Panama,14050659,Panama Papers
Mossfon Bldg.; 54 Street; P.O. Box 0832-0886 W.T.C.; Panama; Republic of Panama,AEEBFBF5F34534B833018ADF6B07CD6F,The Panama Papers data is current through 2015,PAN,Panama,14050660,Panama Papers
Mossfon Bldg; 54th East Street; Panama City; Rep. of Panama,A2B03289229842ACBD01E9C363B122C7,The Panama Papers data is current through 2015,PAN,Panama,14050661,Panama Papers
Mossfon Bldg.; 54th East Street; Panama; Rep. of Panama,302F706E828183C75936A1DF42FCA1AA,The Panama Papers data is current through 2015,PAN,Panama,14050662,Panama Papers
“Mossfon Bldg, 54th Street”,4E09A4185386A8F4F02D89C0734195D8,The Panama Papers data is current through 2015,,,14050663,Panama Papers
MOSSFON BLDG.; 54TH STREET; 3RD. FLOOR; PANAMA; REP. OF PANAMA.,5CC752D84ACAB6E8ACB285984C41B26F,The Panama Papers data is current through 2015,PAN,Panama,14050664,Panama Papers
MOSSFON BLDG.; 54TH STREET; PAM,72FDD267D56B854C470234B75A2EA4AB,The Panama Papers data is current through 2015,PAN,Panama,14050665,Panama Papers
Mossfon Bldg.; 54th Street; Panama,313E3179B73C52E6EAFF91B6086B6005,The Panama Papers data is current through 2015,PAN,Panama,14050666,Panama Papers
Mossfon Bldg; 54th Street; Panama City; Panama,21C217647664E08880884ED22850EE09,The Panama Papers data is current through 2015,PAN,Panama,14050667,Panama Papers
Mossfon Bldg.; 54th Street; Panama City; Rep. of Panama,749EB043BB417C25EAA080B9DFB8C6B3,The Panama Papers data is current through 2015,PAN,Panama,14050668,Panama Papers
Mossfon Bldg; 54th Street; Panaman; Rep. of Panama,D5132F17A59E7EB9D142C590DF072DCD,The Panama Papers data is current through 2015,PAN,Panama,14050669,Panama Papers
Mossfon Bldg; 54 th Street; Panama; Rep. of Panam,F28F2743CAB745447315CD2E40301998,The Panama Papers data is current through 2015,PAN,Panama,14050670,Panama Papers
“Mossfon Bldg, 54th Street Panama Rep. of Panama”,DDD8D1409913E47BEB1BB82B0ED4D5F6,The Panama Papers data is current through 2015,PAN,Panama,14050671,Panama Papers
mossfon bldg-54th street-Panama-rep.of.panama,E0B6238E6E97B3F42E50EFDDF760B6E0,The Panama Papers data is current through 2015,PAN,Panama,14050672,Panama Papers
MOSSFON BLDG-54TH STREET-PANAMA-REP.OF.PANAMA-,501714247DD84F99F5A6536B4738A2E0,The Panama Papers data is current through 2015,PAN,Panama,14050673,Panama Papers
“Mossfon Bldg.,54TH Street -Panama-Rep of Panama”,E3861D816F0B7EDE1CCCBCE51A31337D,The Panama Papers data is current through 2015,PAN,Panama,14050674,Panama Papers
Mossfon Bldg.; 54th Street; Panama; Rep. of Panama .,2719FE705A8ECDC31B985E33A48C809E,The Panama Papers data is current through 2015,PAN,Panama,14050675,Panama Papers
Mossfon Bldg.; 54th Street Panama; Republic of Panama,160892764B50B67A741EEA90B445C2B4,The Panama Papers data is current through 2015,PAN,Panama,14050676,Panama Papers
Mossfon Bldg; 54th Street; Paname; Rep. of Panama,15E4A57076AEBCEBB16456C021059680,The Panama Papers data is current through 2015,PAN,Panama,14050677,Panama Papers
Mossfon Bldg; 54th Street; Panamy; Rep. of Panama,15A2CC325151D0F5A09A4D57A52B49B8,The Panama Papers data is current through 2015,PAN,Panama,14050678,Panama Papers
Mossfon Bldg; 54 th Street; Panana; Rep. of Panama,FD5B30B97F71C6537612837934AB0E7D,The Panama Papers data is current through 2015,PAN,Panama,14050679,Panama Papers
MOSSFON BLDG.; 54TH STREET; PANMA,E4F4A5257CB895F1CCE83C07D11DF814,The Panama Papers data is current through 2015,PAN,Panama,14050680,Panama Papers
MOSSFON BLDG; 54TH STREET; PMA,82B8E1864241428C11BEEBA43EF0CA07,The Panama Papers data is current through 2015,PAN,Panama,14050681,Panama Papers
Mossfon Bldg.54th Street; P.O. BOX 0832-0886 W.T.CPanama; Republic of Panama,9C415AA42E6EE21E16639581FF54FC9C,The Panama Papers data is current through 2015,PAN,Panama,14050682,Panama Papers
Mossfon Bldg.; 54th Street; Second Floor; East; Panama City; Republic of Panama.,DB582F1DDD9041BF647BFEF2DCB48217,The Panama Papers data is current through 2015,PAN,Panama,14050683,Panama Papers
MOSSFON BLDG.; 54TH STREET; SECOND FLOOR; EAST; PANAMA-CITY; REPUBLIC OF PANAMA,A265EB8539AF6248DFEAA6B57A0F2DAD,The Panama Papers data is current through 2015,PAN,Panama,14050684,Panama Papers
Mossfon Bldg.; 54th Street; Second Floor; East; Panama; Republic of Panama,939F7F228969CEFA5D5E811018770976,The Panama Papers data is current through 2015,PAN,Panama,14050685,Panama Papers
Mossfon Bldg.; 54th Street; Second Floor; Panama; Rep. of Panama.,FA6F93B664034803B6A1F07F29EFEFF6,The Panama Papers data is current through 2015,PAN,Panama,14050686,Panama Papers
Mossfon Bldg.; 54th Street; Secondo Floor; East; Panama City; Republic of Panama,FBE007240EF5943C8060495F13FE81B0,The Panama Papers data is current through 2015,PAN,Panama,14050687,Panama Papers
Mossfon Bldg.; East 54 Street; Panama City,2241465D4D7C1FF9FBBB31F43B523041,The Panama Papers data is current through 2015,PAN,Panama,14050688,Panama Papers
MOSSFON BLDG- EAST 54TH STREET-2ND FLOOR-PANAMA-REP OF PANAMA-,BDBEBB7384456AC1C53271D02AD26E79,The Panama Papers data is current through 2015,PAN,Panama,14050689,Panama Papers
Mossfon Bldg; east 54th Street; 2nd Floor; Panama; republic of panama,A3E490B1F5B56A4E8FB288B3AA0030CB,The Panama Papers data is current through 2015,PAN,Panama,14050690,Panama Papers
Mossfon Bldg.; East 54th Street; Panama,5D612A0E89F0F9FD0D1078DB25FECFB8,The Panama Papers data is current through 2015,PAN,Panama,14050691,Panama Papers
Mossfon Bldg.; East 54th Street; Panama City; Rep. of Panama,14BE5AB01CCDEA6D8573102D3187DAFA,The Panama Papers data is current through 2015,PAN,Panama,14050692,Panama Papers
Mossfon Bldg.; East 54th Street; Panama city; Republic of Panama,089A80F6EB85D324D591C38495BEF399,The Panama Papers data is current through 2015,PAN,Panama,14050693,Panama Papers
MOSSFON BLDG; EAST 54TH STREET; PANAMA; REP. DE PANAMA,C2F8448E6F16C7236C5AE595C335A370,The Panama Papers data is current through 2015,PAN,Panama,14050694,Panama Papers
Mossfon bldg.; East 54th Street; Panama; Rep. ofPanama,ED215FD1861CB47426655126D96DE11A,The Panama Papers data is current through 2015,PAN,Panama,14050695,Panama Papers
Mossfon Bldg.; East 54th Street; Panama; republic of Panam,8D5292175500C7ED03EB7D032F3A66BE,The Panama Papers data is current through 2015,PAN,Panama,14050696,Panama Papers
Mossfon Bldg.; East 54th Street; Panama Republic of Panama,C403D6907F80C38BB9BBBBD17DBBA2D3,The Panama Papers data is current through 2015,PAN,Panama,14050697,Panama Papers
MOSSFON BLDG.; EAST 54TH STREET; PANAMA- REPUBLIC OF PANAMA,0565554DD4C6B759134572E8A40178CC,The Panama Papers data is current through 2015,PAN,Panama,14050698,Panama Papers
Mossfon Bldg.; East 54th Street; Panama; Republic of Panama MF FILE N°12414,CF8F6366F71E3EF1B48FDD49CECBA227,The Panama Papers data is current through 2015,PAN,Panama,14050699,Panama Papers
Mossfon Bldg.; East 54th Street; Republic of Panama; Panama,C28FBC648ABB913DBA2463DD6E80B98F,The Panama Papers data is current through 2015,PAN,Panama,14050700,Panama Papers
Mossfon Bldg.Mossfon Bldg.; 54th Street; Panama; Rep. of Panama,D53243BA9AC16926CADE9C43E3AB01DC,The Panama Papers data is current through 2015,PAN,Panama,14050701,Panama Papers
Mossfon Bldg.; Second Floor; East 54th Street; Panama City; Republic of Panama,93FACB7A4504A27900130DEB3606F1DC,The Panama Papers data is current through 2015,PAN,Panama,14050702,Panama Papers
Mossfon Bldg.; Second Floor; East 54th Street; Panama; Rep. of Panama,E08E8AAAD557C2182F1B2BF37A423C98,The Panama Papers data is current through 2015,PAN,Panama,14050703,Panama Papers
Mossfon Bldg.; Second Floor; East 54th Street; Panama; Republic of Panama,500C1079CF2277116190A0F8736A2651,The Panama Papers data is current through 2015,PAN,Panama,14050704,Panama Papers
Mossfon Bldn East 54th Street; Panama; Republic of Panama,68DA646E25B34DAF86357E2472748735,The Panama Papers data is current through 2015,PAN,Panama,14050705,Panama Papers
MOSSFON BUIDING EAST 54 STREET PANAMA REP OF PANAMA,3ED431DD5B5ACCBA1167707089BBBEA2,The Panama Papers data is current through 2015,PAN,Panama,14050706,Panama Papers
Mossfon Buidling; 54 East Street; Panama; Rep. of Panama,EB51665D0FBAED679FC6C45C0D0717DD,The Panama Papers data is current through 2015,PAN,Panama,14050707,Panama Papers
Mossfon Buidling; 54th Street; Panama; Republic of Panama,00F86A409CD2367EE131E40C42F0AAA1,The Panama Papers data is current through 2015,PAN,Panama,14050708,Panama Papers
MOSSFON BUIDLING; EAST 54TH STREET; PANAMA; REP. OF PANAMA,F1BAE65498FED84ABB9052CBA2384C8B,The Panama Papers data is current through 2015,PAN,Panama,14050709,Panama Papers
Mossfon Buidling Second Floor; East 5th Street; Panama; Republic de Panama,810796980990325AA724EEF254BE5947,The Panama Papers data is current through 2015,PAN,Panama,14050710,Panama Papers
“Mossfon BuiIding 54 Street, Panama Republic of Panama”,0BB7CB85D87F5EAED408EC52D462AD8B,The Panama Papers data is current through 2015,PAN,Panama,14050711,Panama Papers
Mossfon Build; 2nd Floor; East 54 Street; Panama,D1A2E07FE7460096A6221CD214FFF3D3,The Panama Papers data is current through 2015,PAN,Panama,14050712,Panama Papers
Mossfon Building,4FC3C00D0B45C4DA8FDEFD2C255E4EF0,The Panama Papers data is current through 2015,,,14050713,Panama Papers
Mossfon Building; 2do piso; calle 54 Este; Ciudad de Panamá; República de Panamá,DD839598AA266F41F050F973C1CC2F12,The Panama Papers data is current through 2015,PAN,Panama,14050714,Panama Papers
Mossfon Building; 2do Piso; Calle 54 Este; PO Box 0832-0886 W.T.C.; Panamá; Republica de Panamá,BBA42DA7828EC742BD446E4DEA646A3F,The Panama Papers data is current through 2015,PAN,Panama,14050715,Panama Papers
MOSSFON BUILDING; 2ND FL. 54TH STREET; PANAMA.,19D4405EAE91DD3212BAC31A5C99F568,The Panama Papers data is current through 2015,PAN,Panama,14050716,Panama Papers
Mossfon Building; 2nd Flooe East 54th Street Panama; Republic of Panama,21D98F70EAB8F096EE29830200B510E4,The Panama Papers data is current through 2015,PAN,Panama,14050717,Panama Papers
“MOSSFON BUILDING, 2ND FLOOR”,73EEF95CA6F61EDAF3B228CBF7B6CF1F,The Panama Papers data is current through 2015,,,14050718,Panama Papers
MOSSFON BUILDING; 2nd Floor; 54 East Street; Marbella; Panama,2AD3C094C5B371547C66754DDDA4B8BA,The Panama Papers data is current through 2015,PAN,Panama,14050719,Panama Papers
Mossfon Building; 2nd Floor; 54 East Street; Panama,AE4C33EDEE6D2F03BA163E1773583708,The Panama Papers data is current through 2015,PAN,Panama,14050720,Panama Papers
Mossfon Building; 2nd Floor; 54 East Street; Panama City; Panama,9AE23065D4F0A3B70EAA62028E71541F,The Panama Papers data is current through 2015,PAN,Panama,14050721,Panama Papers
Mossfon Building; 2nd Floor; 54 East Street; Panama; Republic of Panama.,9070C2C66941468577205AD98EB34F75,The Panama Papers data is current through 2015,PAN,Panama,14050722,Panama Papers
MOSSFON BUILDING; 2ND FLOOR; 54 E ST.; PANAMA; REP; OF PANAMA,318175936ACDE7156F176737E681E6BD,The Panama Papers data is current through 2015,PAN,Panama,14050723,Panama Papers
MOSSFON BUILDING; 2nd FLOOR; 54 STREET; MARBELLA; PANAMA; REPUBLIC OF PANAMA,0AD6A5913670ED3A540F12700EA84B84,The Panama Papers data is current through 2015,PAN,Panama,14050724,Panama Papers
Mossfon Building; 2nd Floor; 54th East Street; Marbella; Panama; Republic of Panama,DCE5ADF69DC17431D9C2012577E63620,The Panama Papers data is current through 2015,PAN,Panama,14050725,Panama Papers
Mossfon Building; 2nd Floor; 54th East Street; Panama,A29656A7BFF824EE1FDEC2C577C0D8FB,The Panama Papers data is current through 2015,PAN,Panama,14050726,Panama Papers
Mossfon Building 2nd Floor; 54th East Street; Panama City; Republic of Panama,6AC5B55469A78C3A3D35815F85CC9A8E,The Panama Papers data is current through 2015,PAN,Panama,14050727,Panama Papers
“Mossfon Building 2nd Floor, 54th East Street Panama-City REPUBLIC OF PANAMA.”,26DB12D05A089EA31944A228496753F2,The Panama Papers data is current through 2015,PAN,Panama,14050728,Panama Papers
Mossfon Building; 2nd Floor; 54th East Street; Panama; Rep. of Panamá,2A605FAE3D707D3D5D5142D7CDFC55D6,The Panama Papers data is current through 2015,PAN,Panama,14050729,Panama Papers
Mossfon Building; 2nd Floor; 54th East Street; Panama; Republic of Panama.,6F541E92652214EF0B8106D9AD7205B7,The Panama Papers data is current through 2015,PAN,Panama,14050730,Panama Papers
Mossfon Building; 2nd floor; 54th E Street; Marbella; Panama; Rep. of Panama,8DAA943695C4497C3EA73367EA2D85B3,The Panama Papers data is current through 2015,PAN,Panama,14050731,Panama Papers
Mossfon Building; 2nd Floor; 54th E. Street; Marbella; Panama; Republic of Panama,AEA1854B19A8AB96930C73213E9436A2,The Panama Papers data is current through 2015,PAN,Panama,14050732,Panama Papers
Mossfon Building; 2nd Floor; 54th E. Street; Panama.,DF061DEAFF2E882509C94508BA9D7A56,The Panama Papers data is current through 2015,PAN,Panama,14050733,Panama Papers
Mossfon Building; 2nd Floor; 54th E. Street; Panama City; Republic of Panama,6CE1FDE7297F36C4F170DD6325920F00,The Panama Papers data is current through 2015,PAN,Panama,14050734,Panama Papers
Mossfon Building; 2nd Floor; 54th Stree; Panama; Republic of Panama,5090CA504299482E5D6D377A33412ABB,The Panama Papers data is current through 2015,PAN,Panama,14050735,Panama Papers
Mossfon Building; 2nd Floor; 54th Street East; P.O. 0832-0886 W.T.C.; Panama; Republic of Panama,DB448EED52C1D88912F5D354D85A4D25,The Panama Papers data is current through 2015,PAN,Panama,14050736,Panama Papers
Mossfon Building; 2nd Floor; 54th Street; Marbella; Panama; Republic of Panama.,98AA0862A7E45CEF2A68538C902F77AA,The Panama Papers data is current through 2015,PAN,Panama,14050737,Panama Papers
Mossfon Building; 2nd Floor; 54th Street; Panama,C6C723C3B5C9D12E4E69CB965017289C,The Panama Papers data is current through 2015,PAN,Panama,14050738,Panama Papers
Mossfon building; 2nd floor; 54th Street; Panama city; Republic of Panama,96F008166EA805AC23B1C33E5D64E0D8,The Panama Papers data is current through 2015,PAN,Panama,14050739,Panama Papers
“Mossfon Building 2nd Floor, 54th Street Panama Republic of Panama”,04D074D6D3CFB23EBE2F24591F2FA705,The Panama Papers data is current through 2015,PAN,Panama,14050740,Panama Papers
MOSSFON BUILDING; 2ND FLOOR; EAST 54 ST; PANAMA,748437D0BD6FA4D880E8D68EE66EF30E,The Panama Papers data is current through 2015,PAN,Panama,14050741,Panama Papers
Mossfon Building; 2nd Floor; East 54 Street; Marbella; Panama; Republic of Panama,CDBDBA3F8C36AFE88FB056F8C828583C,The Panama Papers data is current through 2015,PAN,Panama,14050742,Panama Papers
Mossfon Building 2nd floor East 54 Street Panama,13A424BDE50E32EE0E812F996AEEF3AA,The Panama Papers data is current through 2015,PAN,Panama,14050743,Panama Papers
Mossfon Building; 2nd Floor; East 54 Street; Panama; Republic of Panama,9E019C6201695CB41376E2BA40CA8255,The Panama Papers data is current through 2015,PAN,Panama,14050744,Panama Papers
Mossfon Building; 2nd Floor; East 54 Street; P.O. Box 0832-0886 W.T.C.; Panama; Republic of Panama,AB864950B280B33E315CD85D04B20375,The Panama Papers data is current through 2015,PAN,Panama,14050745,Panama Papers
Mossfon Building 2nd Floor; East 54th St. Marbella Panama; Rep. Of Panama,F797195847FEBF6361859B592402651A,The Panama Papers data is current through 2015,PAN,Panama,14050746,Panama Papers
Mossfon Building; 2nd Floor; East 54th Street; Marbella; Panama,D3999704AE055124A8C54AB5C45167FC,The Panama Papers data is current through 2015,PAN,Panama,14050747,Panama Papers
Mossfon Building; 2nd Floor; East 54th Street; Marbella; Panama; Rep.Of Panama,0983C01AD47DAF116689C16609FC4861,The Panama Papers data is current through 2015,PAN,Panama,14050748,Panama Papers
Mossfon Building; 2nd Floor; East 54th Street; Panama,BBAAD470CD29226C01171F3E0B2405E2,The Panama Papers data is current through 2015,PAN,Panama,14050749,Panama Papers
Mossfon Building; 2nd Floor; East 54th Street; Panama City; Panama.,6E7A0107838895634C42BD38C3C8C0C6,The Panama Papers data is current through 2015,PAN,Panama,14050750,Panama Papers
Mossfon Building 2nd floor East 54th Street Panama City Republic of Panama,092CEE24AB124DA57C70B63EFE912238,The Panama Papers data is current through 2015,PAN,Panama,14050751,Panama Papers
Mossfon Building; 2nd Floor; East 54th Street; Panama; Panama City; Republic of Panama,653F3E968DE8F84B7E2E8425A6FA1E87,The Panama Papers data is current through 2015,PAN,Panama,14050752,Panama Papers
MOSSFON BUILDING; 2ND FLOOR; EAST 54TH STREET; PANAMA; REP. OF PANAMA,8E59DD585CC2B7445689A3E1996BDA21,The Panama Papers data is current through 2015,PAN,Panama,14050753,Panama Papers
“MOSSFON BUILDING, 2ND FLOOR EAST 54TH STREET PANAMA REPUBLIC OF MPANAMA”,BE91B70BB5BBCE5A597BAC86EDAC9DD1,The Panama Papers data is current through 2015,PAN,Panama,14050754,Panama Papers
MOSSFON BUILDING; 2ND FLOOR EAST 54TH STREET; PANAMA REPUBLIC OF PANAMA,EF1962A9A5882AEDD3469794C21381B7,The Panama Papers data is current through 2015,PAN,Panama,14050755,Panama Papers
Mossfon Building; 2nd Floor; East 54th Street; PO Box 0832-0886 W.T.C,1A87BC855572854083DEF96AFD9CA145,The Panama Papers data is current through 2015,,,14050756,Panama Papers
“MOSSFON BUILDING 2ND FLOOR, EAST 54TH STREET P.O. BOX 08320886 W.T.C. PANAMA”,7B4D124977F1FFB28EC4C690B128AF8A,The Panama Papers data is current through 2015,PAN,Panama,14050757,Panama Papers
Mossfon Building; 2nd floor; East 54th Street; PO Box 0832-0886 W.T.C. Panama,578CF332062E0AFEBD8A1C9E19EF548C,The Panama Papers data is current through 2015,PAN,Panama,14050758,Panama Papers
Mossfon Building; 2nd Floor; East 54th Street; P.O. Box 0832-0886; W.T.C. Panama; Panama; Republic of Panama.,4C8FE446F8650B735C5164C3C6F448FE,The Panama Papers data is current through 2015,PAN,Panama,14050759,Panama Papers
Mossfon Building; 2nd Floor; East 54th Street; P. O. Box 0832-0886 W.T.C.; Panama; Republic of Panama,C43C9496C434217121F4653C9853D343,The Panama Papers data is current through 2015,PAN,Panama,14050760,Panama Papers
Mossfon building; 2nd Floor; East 54th Street; P.O. Box 0832-08886 W.T.C.; Panama; Republic of Panama,C96323E4A2BDCEF5EA62EE51E2179D8B,The Panama Papers data is current through 2015,PAN,Panama,14050761,Panama Papers
Mossfon Building; 2nd Floor; East 54th Street; P.O. Box 0832; W.T.C.; Republic of Panama.,3028DDA98D5FD88A599E6ADAA3716ED9,The Panama Papers data is current through 2015,PAN,Panama,14050762,Panama Papers
Mossfon Building; 2nd Floor; East 54t Street; Marbella; Panama City; Panama,8CB8DC3862B6AC65023C90FCCEF22678,The Panama Papers data is current through 2015,PAN,Panama,14050763,Panama Papers
MOSSFON BUILDING; 2ND FLOOR; EAST STREET; PANAMA; REPUBLIC OF PANAMA,946411E507766DC2C1BBBA618647D14A,The Panama Papers data is current through 2015,PAN,Panama,14050764,Panama Papers
Mossfon Building; 2nd Floor; Est 54th Street; Panama; Republic of Panama,B902BFC6A572D3BD039AB4DD0A8C5FCE,The Panama Papers data is current through 2015,PAN,Panama,14050765,Panama Papers
MOSSFON BUILDING; 2ND FLOOR; MARBELLA; PANAMA,B0B8EDBCB69558A4624B9712E264171A,The Panama Papers data is current through 2015,PAN,Panama,14050766,Panama Papers
Mossfon Building; 2nd floor; Panama,5A4299F78410BFDE31036F2913CB344B,The Panama Papers data is current through 2015,PAN,Panama,14050767,Panama Papers
Mossfon Building; 2o Floor; 54 Street; Marbella; Panama; Republic of Panama,9575D3C0F603F0FE9F571F05805F6B0F,The Panama Papers data is current through 2015,PAN,Panama,14050768,Panama Papers
Mossfon Building; 2o. Floor; East 54 Street; Panama; Republic of Panama.,0DD86D184CDF3B2926AF9A1AB948B0AF,The Panama Papers data is current through 2015,PAN,Panama,14050769,Panama Papers
Mossfon Building; 3rd Flloor; 54th Street; Marbella; Panama; Republic of Panama,9EF798C49699B68D45D795D30E8AC6E4,The Panama Papers data is current through 2015,PAN,Panama,14050770,Panama Papers
MOSSFON BUILDING; 3RD FLOOR 54TH E. STREET; PANAMA,902E4135C1C7789BE5AF71637F0DE9CD,The Panama Papers data is current through 2015,PAN,Panama,14050771,Panama Papers
Mossfon Building; 3rd Floor; 54th E. Street; Panama Rep of Panama,963E5566C23B302C5407C1B17E97BF21,The Panama Papers data is current through 2015,PAN,Panama,14050772,Panama Papers
MOSSFON BUILDING; 3RD FLOOR; 54TH STREET EAST; PANAMA,E82636587F6C0ED42FAC75B0CEEA294F,The Panama Papers data is current through 2015,PAN,Panama,14050773,Panama Papers
Mossfon Building; 3rd Floor; East 54th Street; Panama; Republic of Panama,997D87B091CB87712471B748300532A5,The Panama Papers data is current through 2015,PAN,Panama,14050774,Panama Papers
Mossfon Building; 3rd Floor; East 54th Street; PO Box 0832-0886 W.T.C.; Panama; Republic of Panama,C8C3038D316A81BA243CE0B06BF536CC,The Panama Papers data is current through 2015,PAN,Panama,14050775,Panama Papers
Mossfon Building; 54 East Street; Marbella; Panama; Republic of Panama,8499B5BDE30D8F9BFA36FC500385B428,The Panama Papers data is current through 2015,PAN,Panama,14050776,Panama Papers
MOSSFON BUILDING; 54 EAST STREET; PANAMA REPUBLIC OF PANAMA,7CF24AB8C21F484809620EB3242EBF4C,The Panama Papers data is current through 2015,PAN,Panama,14050777,Panama Papers
MOSSFON BUILDING 54 ST. MARBELLA PANAMA REPUBLIC OF PANAMA,40604A0B8D6FC8B6261B81A361607392,The Panama Papers data is current through 2015,PAN,Panama,14050778,Panama Papers
“MOSSFON BUILDING 54, STREET PANAMA”,33AC45D6B4FEE914E0E3F7F1AA28569D,The Panama Papers data is current through 2015,PAN,Panama,14050779,Panama Papers
Mossfon Building; 54 Street; P.O. Box 0832-0886; WTC Panama; Rep of Panama,FC3D67AA8E3F4DAB15484FAAAA2D0B1C,The Panama Papers data is current through 2015,PAN,Panama,14050780,Panama Papers
Mossfon Building; 54th East Street; City of Panama; Republic of Panama,23FE0C1B7E0FAAAC2E27377BD873B454,The Panama Papers data is current through 2015,PAN,Panama,14050781,Panama Papers
Mossfon Building; 54th East Street; Floor 3; Panama; Republic of Panama,5F8D10BBF3CD185A0FB8EE0DCE86A7B5,The Panama Papers data is current through 2015,PAN,Panama,14050782,Panama Papers
Mossfon Building; 54th East Street; Panama City; Republic of Panama,E38C4A3C68626D53E99AC34FA271056E,The Panama Papers data is current through 2015,PAN,Panama,14050783,Panama Papers
Mossfon Building; 54th East Street; Panama; Replublic of Panama,D8560186FFDF0227EA0E2593233E6AB2,The Panama Papers data is current through 2015,PAN,Panama,14050784,Panama Papers
Mossfon Building; 54th East Street; Panama; Rep. of Panama,F560C24D13EFCBA224ADB98018B84B74,The Panama Papers data is current through 2015,PAN,Panama,14050785,Panama Papers
Mossfon Building; 54th East Street; Panama; Republic of Panama,DBCC2A8CC266EFC8DBC3F55436EDB5B5,The Panama Papers data is current through 2015,PAN,Panama,14050786,Panama Papers
Mossfon Building; 54th E Street; 3rd Floor; Marbella; Panama; Rep. of Panama,8327381111F7417F16A504A97CBBD0FE,The Panama Papers data is current through 2015,PAN,Panama,14050787,Panama Papers
Mossfon Building; 54th E Street; 3rd Floor; Marbella; Panama; Republic of Panama,C1217A3A7E8129A614EF1E43FCFB7C5C,The Panama Papers data is current through 2015,PAN,Panama,14050788,Panama Papers
“Mossfon Building 54th E. Street, Panama”,65359A99647909DE814CAC238D019406,The Panama Papers data is current through 2015,PAN,Panama,14050789,Panama Papers
Mossfon Building; 54th E. Street; Panama City; Republic of Panama,AB66DC570E56B289B07C7BDBCA90FE07,The Panama Papers data is current through 2015,PAN,Panama,14050790,Panama Papers
Mossfon Building; 54th; E. Street Panama; Republic of Panama,62BE6FB5192FC25A41D5511E726AD9CE,The Panama Papers data is current through 2015,PAN,Panama,14050791,Panama Papers
Mossfon Building; 54th E. Street; Republic of Panama; Panama,E8578AA5F4BE6367FB3A7DEFC4FBC933,The Panama Papers data is current through 2015,PAN,Panama,14050792,Panama Papers
Mossfon Building; 54th Street; City of Panama; Panama,345B4AAC4F160184E0A89898A69FF1DF,The Panama Papers data is current through 2015,PAN,Panama,14050793,Panama Papers
Mossfon Building; 54th Street East; Panama City; Republic of Panama,1A39E071DCCC060FBEFBA51C00090322,The Panama Papers data is current through 2015,PAN,Panama,14050794,Panama Papers
Mossfon Building; 54th Street East; Second floor; Panama; Republic of Panama,5001EA61D838011454F23ABBB76BC779,The Panama Papers data is current through 2015,PAN,Panama,14050795,Panama Papers
Mossfon Building; 54th Street E; Marbella; Panama; Republic of Panama,2395C27DC7EB938E5DAF507A4498F200,The Panama Papers data is current through 2015,PAN,Panama,14050796,Panama Papers
Mossfon Building; 54th Street; Marbella; Panamá,41A0CA20B601AECAE92EF2DEE5715B6D,The Panama Papers data is current through 2015,PAN,Panama,14050797,Panama Papers
Mossfon Building; 54th Street Marbella; Panama; Rep. of Panama,2E9430148EF1A121CBA969CE39429A6A,The Panama Papers data is current through 2015,PAN,Panama,14050798,Panama Papers
Mossfon Building; 54th Street Marbella; Panama; Republic of Panama,164D40ADBEE16F1D4EDAB57113565457,The Panama Papers data is current through 2015,PAN,Panama,14050799,Panama Papers
“Mossfon Building 54th Street Marbella P.O. Box 0832-0886 W.T.C. Panama Panama, Republic of Panama”,32BA0DC2A6730181110991C3AE6464F8,The Panama Papers data is current through 2015,PAN,Panama,14050800,Panama Papers
Mossfon Building; 54th Street; Marbella; P.O. Box 0832-0886; W.T.C. Panama; Republic of Panama,E0D3F8C2163804388C891ECA593D6ECF,The Panama Papers data is current through 2015,PAN,Panama,14050801,Panama Papers
Mossfon building; 54th Street; Panama,6D5BE3AD834200D67BB5A2A8D0A91320,The Panama Papers data is current through 2015,PAN,Panama,14050802,Panama Papers
MOSSFON BUILDING; 54TH STREET; PANAMA CITY; PANAMA,04E1ADBDE5CB97B8A2F41ADA2C88D9C9,The Panama Papers data is current through 2015,PAN,Panama,14050803,Panama Papers
Mossfon Building; 54th Street; Panama City; Panama W.T.C. PANAMA.,8B3B87E78971143492B9770404DBF017,The Panama Papers data is current through 2015,PAN,Panama,14050804,Panama Papers
Mossfon Building 54th Street Panama City Republic of Panama,52579FE424651864CFF114DF61F8AA0E,The Panama Papers data is current through 2015,PAN,Panama,14050805,Panama Papers
Mossfon Building; 54th Street; Panamá; Panamá,7EE37F59787CE9B0A6B1668562474A8D,The Panama Papers data is current through 2015,PAN,Panama,14050806,Panama Papers
Mossfon Building; 54th Street; Panama; Rep. of Panama,01FA8BA949A8955254028C3FD4B6E0C3,The Panama Papers data is current through 2015,PAN,Panama,14050807,Panama Papers
Mossfon Building; 54th Street; Panama; Repubic of Panama,A583C06FDD981E3771A230D1089FD619,The Panama Papers data is current through 2015,PAN,Panama,14050808,Panama Papers
Mossfon Building; 54th Street; Panama; Republic of Panam,5EFF1E888E3E89DE8149D80632476846,The Panama Papers data is current through 2015,PAN,Panama,14050809,Panama Papers
“MOSSFON BUILDING 54TH STREET, PANAMA REPUBLIC OF PANAMA”,8B2F01834841D7FB4309514BE6852B26,The Panama Papers data is current through 2015,PAN,Panama,14050810,Panama Papers
Mossfon Building54th StreetPananaRepublic of Panama,37EFA831002028C1DAA1E7279F7B2E9E,The Panama Papers data is current through 2015,PAN,Panama,14050811,Panama Papers
Mossfon Building; 54th Street; P.O. Box 0332-0886 W.T.C.; Panama; Republic of Panama,F7EF60B3C6831BDC5A548907E3FDF7FD,The Panama Papers data is current through 2015,PAN,Panama,14050812,Panama Papers
Mossfon Building; 54th Street; P.O. Box 0832-0886; W.T.C.; Panama,7AB261A606B1E7D370B5F50F25252603,The Panama Papers data is current through 2015,PAN,Panama,14050813,Panama Papers
Mossfon Building; 54th Street; P.O. Box 0832-0886; W.T.C.; Panama City; Republic of Panama,39854FBE98EE2F459F4C3E2ACE25AB52,The Panama Papers data is current through 2015,PAN,Panama,14050814,Panama Papers
Mossfon Building; 54th street; P.O. box 0832-0886 WTC; Panama; Rep of Panama,FCB137E0D7A71300F015C1A3A5B36599,The Panama Papers data is current through 2015,PAN,Panama,14050815,Panama Papers
Mossfon Building; 54th Street; P.O. Box 0832-0886; W.T.C.; Panama; Republic of Panama,98C98D83EA384DBDC04F803C08F08F60,The Panama Papers data is current through 2015,PAN,Panama,14050816,Panama Papers
Mossfon Building; 54th Street; P.OL Box 0832-0886; W.T.C.; Panama Rep de Panama,D8334DBA4456835DFFA4ABC7EBD69287,The Panama Papers data is current through 2015,PAN,Panama,14050817,Panama Papers
Mossfon Building; 54th Street; WTC; Panama; Republic of Panama,C13C32BF31F024E54DF79911991F308B,The Panama Papers data is current through 2015,PAN,Panama,14050818,Panama Papers
Mossfon Building Bldg.; 2nd Floor 54th East Street; Panama Republic of Panama,988274513C458F7E00ECCDB670BD3DD7,The Panama Papers data is current through 2015,PAN,Panama,14050819,Panama Papers
Mossfon Building Bldg.; 54th Street; Panama; Rep. of Panama,C902D8506A7EFE2B69349BE664ABA5EE,The Panama Papers data is current through 2015,PAN,Panama,14050820,Panama Papers
Mossfon Building Bldg.; second floor; 54th Street; Panama; Rep. of Panama,966E4921A902DE4B9413E1710DFC33CA,The Panama Papers data is current through 2015,PAN,Panama,14050821,Panama Papers
MOSSFON BUILDING; CALLE 54 ESTE; PANAMA REPUBLICA DE PANAMA,31C3F44CE7AB21F862CAA7897E4EFB8D,The Panama Papers data is current through 2015,PAN,Panama,14050822,Panama Papers
Mossfon Building; East %4th Street; Panama City; Republic of Panama,8F863CB329C4E669D8890EE974F233AB,The Panama Papers data is current through 2015,PAN,Panama,14050823,Panama Papers
“MOSSFON BUILDING, EAST 54 ST. PANAMA”,8CBD16A91B75178197CBE76B48D85243,The Panama Papers data is current through 2015,PAN,Panama,14050824,Panama Papers
MOSSFON BUILDING; eAST 54 STREET; PANAMA,134964ADF73B462215D243FA2E046494,The Panama Papers data is current through 2015,PAN,Panama,14050825,Panama Papers
Mossfon Building; East 54 Street; Panama; Republic of Panama.,43767F1345470F575670B63DCB5C08DF,The Panama Papers data is current through 2015,PAN,Panama,14050826,Panama Papers
Mossfon Building; East 54tg Street; Panama; Rep. of Panama,36D85FD0A26C1F61E092C2F2A6B8ED68,The Panama Papers data is current through 2015,PAN,Panama,14050827,Panama Papers
MOSSFON BUILDING; EAST 54TH STREER; P.O. BOX 0832-0886 W.T.C.; PANAMA; REPUBLIC OF PANAMA,91893C86477139BE97061FE5EEAB59DA,The Panama Papers data is current through 2015,PAN,Panama,14050828,Panama Papers
Mossfon Building East 54th Street; 2 Floor Panama City; Republic of Panama,C5A39C4F2C8E532A1D254CACECE6515A,The Panama Papers data is current through 2015,PAN,Panama,14050829,Panama Papers
Mossfon Building; East 54th Street; Marbella; Panama; Republic of Panama,C02B7F85EDF228ABF1366B0C99B187BF,The Panama Papers data is current through 2015,PAN,Panama,14050830,Panama Papers
“Mossfon Building East 54th Street, Panama”,77436827412AD0E47276AE3F8107A03E,The Panama Papers data is current through 2015,PAN,Panama,14050831,Panama Papers
MOSSFON BUILDING EAST 54TH STREET PANAMA CITY,1E3DB22CABC7C603159DBF4B1118E9F0,The Panama Papers data is current through 2015,PAN,Panama,14050832,Panama Papers
MOSSFON BUILDING EAST 54TH STREET; PANAMA CITY; PANAM,3012921FD740735515EC87AB5D03E9DF,The Panama Papers data is current through 2015,PAN,Panama,14050833,Panama Papers
Mossfon Building; East 54th Street; Panama City; Panama,36D4E9C9924558BA3C1D49292C98451E,The Panama Papers data is current through 2015,PAN,Panama,14050834,Panama Papers
MOSSFON BUILDING-EAST 54TH STREET-PANAMA CITY-REP.OF.PANAMA-,B7DDCD89EB0CAEB079F3E273DB491CAF,The Panama Papers data is current through 2015,PAN,Panama,14050835,Panama Papers
Mossfon Building; East 54th Street; Panama City; Republic of Panama,585837FC5CF35B847E7BD615712EE5C2,The Panama Papers data is current through 2015,PAN,Panama,14050836,Panama Papers
Mossfon Building; East 54th Street; Panamá; Rep. de Panamá,DC1CFCC06ADD5D41DBD714E53A057727,The Panama Papers data is current through 2015,PAN,Panama,14050837,Panama Papers
“MOSSFON BUILDING EAST 54TH STREET PANAMA, REP. OF PANAMA.”,124E0EB49A3568C20CFD9EC11AC0B96A,The Panama Papers data is current through 2015,PAN,Panama,14050838,Panama Papers
MOSSFON BUILDING; EAST 54TH STREET; PANAMA; REPUBIC OF PANAMA,88BD9B73148FD0EA56DCA94A1FD1BC8E,The Panama Papers data is current through 2015,PAN,Panama,14050839,Panama Papers
Mossfon Building; East 54th Street; Panama; Republic of Panama,AA492733040759AA4E8EB02CF9C8FC74,The Panama Papers data is current through 2015,PAN,Panama,14050840,Panama Papers
Mossfon Building; East 54th Street; Panama; Republic of Panama§,439AA86747F6CEDBD6676023DD5FAB57,The Panama Papers data is current through 2015,PAN,Panama,14050841,Panama Papers
MOSSFON BUILDING; EAST 54TH STREET; P.O. BOX 0832-0886; PANAMA; REPUBLIC OF PANAMA,38DF023E6C95812E1A36453C1A1CAE56,The Panama Papers data is current through 2015,PAN,Panama,14050842,Panama Papers
Mossfon Building; East 54th Street; P.O. Box 0832-0886 W.T.C.; Panama; Republic of Panama.,5F58E96F8E946C79D5CD1D6CD3731DF9,The Panama Papers data is current through 2015,PAN,Panama,14050843,Panama Papers
Mossfon Building; East 54th Street; P.O. Box 0832088; W.T.C.; Panamá Rep. de Panamá,6BA7C2BB00D2FD128B55E332BC72E341,The Panama Papers data is current through 2015,PAN,Panama,14050844,Panama Papers
Mossfon Building; East 54th Street; second floor; Panama,2E3B3856B752F82C407528FC3C9AFFA9,The Panama Papers data is current through 2015,PAN,Panama,14050845,Panama Papers
Mossfon Building; First floor; East 54th Street; Panama,DE3809F17956135631DA6E398CFC7992,The Panama Papers data is current through 2015,PAN,Panama,14050846,Panama Papers
“Mossfon Building, Panama”,C9419073BB4AA8DFC1A6041420DA4496,The Panama Papers data is current through 2015,PAN,Panama,14050847,Panama Papers
Mossfon Building; Panama City; Panama,ED6A2ED1CB482B47FD33C67684A72434,The Panama Papers data is current through 2015,PAN,Panama,14050848,Panama Papers
Mossfon Building Panama City Republic of Panama,2328B04DED1B1AF24458BE1F574C090D,The Panama Papers data is current through 2015,PAN,Panama,14050849,Panama Papers
Mossfon Building Secodn Floor; East 54 Street; Panama; Republic of Panama,148A043DF0EBB69CDEC139CE1C39007F,The Panama Papers data is current through 2015,PAN,Panama,14050850,Panama Papers
Mossfon Building; second floor; 54 east st.; Marbella; Panama; Republic of Panama,67181D1CDE7161356CDE743092762893,The Panama Papers data is current through 2015,PAN,Panama,14050851,Panama Papers
Mossfon Building; Second Floor; 54 East Street; Panamá; Rep. of Panamá,22F111A0FC968C7922801C5D6640B52B,The Panama Papers data is current through 2015,PAN,Panama,14050852,Panama Papers
MOSSFON BUILDING; SECOND FLOOR; 54 EAST STREET; PANAMA; REPUBLIC OF PANAMA.,4560A9C585EE5DDCF065A5D24197984F,The Panama Papers data is current through 2015,PAN,Panama,14050853,Panama Papers
Mossfon Building; Second Floor; 54 St. E; Marbella; Panama; Republic of Panama,AA4610F69E4E361ABC45699AF14EB7A2,The Panama Papers data is current through 2015,PAN,Panama,14050854,Panama Papers
MOSSFON BUILDING; SECOND FLOOR; 54 STREET EAST; MARBELLA; PANAMA; REPUBLIC OF PANAMA,5132981EAE8711B342646F134590F90F,The Panama Papers data is current through 2015,PAN,Panama,14050855,Panama Papers
MOSSFON BUILDING; SECOND FLOOR; 54 STREET; PANAMA REP OF PANAMA,0EF71270A1A0FDD63B2AE94AC9E053BD,The Panama Papers data is current through 2015,PAN,Panama,14050856,Panama Papers
MOSSFON BUILDING; SECOND FLOOR; 54 STRET EAST; MARBELLA; PANAMA; REPUBLIC OF PANAMA,982139E17048DDDC273CA02601877CB7,The Panama Papers data is current through 2015,PAN,Panama,14050857,Panama Papers
MOSSFON BUILDING; SECOND FLOOR; 54ST STREET EAST; PANAMA; REP. OF PANAMA,5E47BDEA1B0FA327C16B919CBBEEE38E,The Panama Papers data is current through 2015,PAN,Panama,14050858,Panama Papers
Mossfon Building Second Floor; 54th East; Street; Marbella; Panama,AF2C6E414803F1D2784EF145C2E6E07C,The Panama Papers data is current through 2015,PAN,Panama,14050859,Panama Papers
Mossfon Building; Second floor; 54th East Street; Marbella; Rep. of Panama,9AC29248B13B4DBEE05ADB15CB3B4FA5,The Panama Papers data is current through 2015,PAN,Panama,14050860,Panama Papers
Mossfon Building; Second Floor; 54th East Street; Panama,14CE904EDFF4E1285376AADBAF3B2820,The Panama Papers data is current through 2015,PAN,Panama,14050861,Panama Papers
Mossfon Building; Second Floor; 54th East Street; Panama Republic of Panama,E83ED13F0ABF1940E972A5DECA4BEA0E,The Panama Papers data is current through 2015,PAN,Panama,14050862,Panama Papers
Mossfon Building; Second Floor; 54th E Street; Panama,889E3CEEA7B219F557BE1321C3C4A276,The Panama Papers data is current through 2015,PAN,Panama,14050863,Panama Papers
Mossfon Building; Second Floor; 54th Street East; Panama City; Panama,B0B77A422C958832528B7660A338CCE1,The Panama Papers data is current through 2015,PAN,Panama,14050864,Panama Papers
Mossfon Building; Second Floor; 54th Street East; Panama; Republic of Panama,A621AFB9F93B0537B5BD7900A1800580,The Panama Papers data is current through 2015,PAN,Panama,14050865,Panama Papers
Mossfon Building; Second Floor; 54th Street; Panama; Rep. of Panama,869C9788BCADB985E52C49FB7D2B8E3C,The Panama Papers data is current through 2015,PAN,Panama,14050866,Panama Papers
Mossfon Building; Second Floor; 54th Street; Panama; Republic of Panama,01A2B6236B4CF60A4DB9C58406F97464,The Panama Papers data is current through 2015,PAN,Panama,14050867,Panama Papers
MOSSFON BUILDING; SECOND FLOOR; EAST 54 STREET MARBELLA; PANAMA,ECF767738E9F0F83B87916F20E4B3B71,The Panama Papers data is current through 2015,PAN,Panama,14050868,Panama Papers
MOSSFON BUILDING; SECOND FLOOR; EAST 54 STREET; MARBELLA; PANAMA; REPUBLIC OF PANAMA,BD56E427CD8E3CF32D51E5A51C04337B,The Panama Papers data is current through 2015,PAN,Panama,14050869,Panama Papers
MOSSFON BUILDING; SECOND FLOOR; EAST 54 STREET; PANAMA; REPUBLIC OF PANAMA,86F1CF53772BC5DC14BAC675E715A23B,The Panama Papers data is current through 2015,PAN,Panama,14050870,Panama Papers
MOSSFON BUILDING; SECOND FLOOR; EAST 54TH; PANAMA; REPUBLIC OF PANAMA,96B90814CC0FF877F67B87BE39B0FD1B,The Panama Papers data is current through 2015,PAN,Panama,14050871,Panama Papers
MOSSFON BUILDING; SECOND FLOOR; EAST 54TH SREET MARBELLA; PANAMA; REPUBLIC OF PANAMA,709673DC0CB1022DA6BB004D022FB928,The Panama Papers data is current through 2015,PAN,Panama,14050872,Panama Papers
Mossfon Building; Second Floor; East 54th Srtreet; Marbella; Panama; Rep. of Panama,F294A0E9E50EEBB6CA9D92A7B0934EE2,The Panama Papers data is current through 2015,PAN,Panama,14050873,Panama Papers
MOSSFON BUILDING; SECOND FLOOR; EAST 54TH ST; PANAMA; PANAMA,C0EC93AAFA1B27A98374E4CE894DB984,The Panama Papers data is current through 2015,PAN,Panama,14050874,Panama Papers
Mossfon Building; Second Floor; East 54th Street; 7 Panama,AEBE1F0651F8A15C22F385D36F5A27EC,The Panama Papers data is current through 2015,PAN,Panama,14050875,Panama Papers
Mossfon Building; Second Floor; East 54th Street; City Of Panama; Republic Of Panama,B2141AA2725F519DA1BD2B429211CDFF,The Panama Papers data is current through 2015,PAN,Panama,14050876,Panama Papers
MOSSFON BUILDING; SECOND FLOOR; EAST 54TH STREET MARBELLA; PANAMA; REPUBLIC OF O PANAMA,739032C30F5610554EB11046447333CE,The Panama Papers data is current through 2015,PAN,Panama,14050877,Panama Papers
MOSSFON BUILDING; SECOND FLOOR; EAST 54TH STREET MARBELLA; PANAMA; REPUBLIC OF PANAMA,D3436B6431AE937EC507892C2915B7C8,The Panama Papers data is current through 2015,PAN,Panama,14050878,Panama Papers
Mossfon Building; Second floor; East 54th Street; Panama,B100DB1877DC85EE20D8A7FDD4CBFF18,The Panama Papers data is current through 2015,PAN,Panama,14050879,Panama Papers
Mossfon Building; Second floor; East 54th Street; Panama City; Republic of Panama,5AB5DC1C78CEE8B57419476D211CF198,The Panama Papers data is current through 2015,PAN,Panama,14050880,Panama Papers
MOSSFON BUILDING; SECOND FLOOR; EAST 54TH STREET; PANAMA; PANAMA,1198AB90CBCEA6716FB0ACB5DA8E2A60,The Panama Papers data is current through 2015,PAN,Panama,14050881,Panama Papers
MOSSFON BUILDING; SECOND FLOOR; EAST 54TH STREET; PANAMA REP OF PANAMA,02DB7754165ABEF89145402C84FD4E7D,The Panama Papers data is current through 2015,PAN,Panama,14050882,Panama Papers
Mossfon Building; Second Floor; East 54th Street; Panama; Republica of Panama.,6E00C5F3F3736B405CE8117240A20583,The Panama Papers data is current through 2015,PAN,Panama,14050883,Panama Papers
Mossfon Building; Second Floor; East 54th Street; Panama; Republic of Paama,C0F58F310FB00AD9E0FFF7E21AAF68E6,The Panama Papers data is current through 2015,PAN,Panama,14050884,Panama Papers
Mossfon Building; Second Floor; East 54th Street; Panama; Republic of Panam,BB75098BE05B6C444534CAF53520E54E,The Panama Papers data is current through 2015,PAN,Panama,14050885,Panama Papers
Mossfon Building; Second Floor; East 54 th Street; Panama; Republic of Panama,6FC86CBF4F48588FD926ACD07B8FC6D9,The Panama Papers data is current through 2015,PAN,Panama,14050886,Panama Papers
Mossfon Building; Second Floor; East 54th Street; Panama; Republico of Panama,DC2376B6DA4FCE988288235818FC53C1,The Panama Papers data is current through 2015,PAN,Panama,14050887,Panama Papers
MOSSFON BUILDING; SECOND FLOOR; EAST 54TH STREET; PANAMA; REPUBLIC PANAMA,28D1A8B8A89CBBCB0779E01795AD402C,The Panama Papers data is current through 2015,PAN,Panama,14050888,Panama Papers
Mossfon Building; Second Floor; East 54th Street; P.O. Box 0832-0886 W.T.C.; Panama,3D88366E287063942AF26EE0BC574E2B,The Panama Papers data is current through 2015,PAN,Panama,14050889,Panama Papers
Mossfon Building; Second Floor; East 54th Street; PO Box 0832-0886; W.T.C. Panama; Republic of Panama.,F398C417597867C2789B70E410B14F22,The Panama Papers data is current through 2015,PAN,Panama,14050890,Panama Papers
Mossfon Building; Second Floor; East 54th Street; Republic of Panama; Panama,C09D4F0CF702E757D640C45101CF7E6B,The Panama Papers data is current through 2015,PAN,Panama,14050891,Panama Papers
MOSSFON BUILDING; SECOND FLOOR; EAST 5TH STREET; PANAMA CITY REPUBLIC OF PANAMA,AF77AB89D4A219D150E672CC8DEDAAD2,The Panama Papers data is current through 2015,PAN,Panama,14050892,Panama Papers
Mossfon Building; Second Floor; Easth 54 Street; Panama Republic of Panama,DB9B8458F787EAC54B044260506EBAE1,The Panama Papers data is current through 2015,PAN,Panama,14050893,Panama Papers
Mossfon Building; second floor; Easth 54th Street; PO Box 0832-0886 W.T.C. Panama; Republic of Panama,D65D8E32B60A649536C73B385188E6E0,The Panama Papers data is current through 2015,PAN,Panama,14050894,Panama Papers
Mossfon Building; Second Floor; Est 54th Street; Panama City; Republic of Panama.,06A641B09B4E21BD024B8F24AAC877D3,The Panama Papers data is current through 2015,PAN,Panama,14050895,Panama Papers
Mossfon Building; Secon Floor; East 54th Street; Panama; Republic of Panama,3AE5864BEAFBF52EFE8DCE8061526846,The Panama Papers data is current through 2015,PAN,Panama,14050896,Panama Papers
Mossfon Building; Street 54th E Street; Panama City; Republic of Panama,342A21C59F30D5E5D138F80195360B04,The Panama Papers data is current through 2015,PAN,Panama,14050897,Panama Papers
MossFon Building; Third Floor; 54 East Street; Marbella; Panama Rep of Panama,B90AF6F8487B78B442D18F0047939AA4,The Panama Papers data is current through 2015,PAN,Panama,14050898,Panama Papers
Mossfon Building; Third Floor; 54 Street; Panama,DA87B8C81D36D37052EA394725BFB407,The Panama Papers data is current through 2015,PAN,Panama,14050899,Panama Papers
MOSSFON BUILDING; THIRD FLOOR; 54th EAST STREET; MARBELLA; PANAMA; REP OF PANAMA,9FB438E58707B9BF7A32FE212A6BAC1A,The Panama Papers data is current through 2015,PAN,Panama,14050900,Panama Papers
Mossfon Building; Third Floor; East 50th and 54; Republic of Panama,9DEC5B1784E50F746EFF09FB2AE21488,The Panama Papers data is current through 2015,PAN,Panama,14050901,Panama Papers
Mossfon Building; Third Floor East 50th and 54th; Republic of Panama,71DE0B75C65660709246674120B12CF8,The Panama Papers data is current through 2015,PAN,Panama,14050902,Panama Papers
Mossfon Building; Third Floor; East 54th Street; Panama; Republic of Panama,1CA8D5E302578B3617A9A73F76501152,The Panama Papers data is current through 2015,PAN,Panama,14050903,Panama Papers
Mossfon Buildong 54th Street Panama Republic of Panama,4C5E1D8C0998CFC5CE527FDA73E393AF,The Panama Papers data is current through 2015,PAN,Panama,14050904,Panama Papers
Mossfon Bulding; 54 East StreetPanama; Republic of Panama,3EE54E89FD3B100E56B1CDE7305E477D,The Panama Papers data is current through 2015,PAN,Panama,14050905,Panama Papers
Mossfon Bulding; Second Floor; East 54th Street; Panama; Republic Of Panama,015BB6256EC4C5BB2BAC6F1BCAF014B2,The Panama Papers data is current through 2015,PAN,Panama,14050906,Panama Papers
Mossfon Buliding 2nd Floor East 54th Street Panama Republic of Panama,3537075DE02DC3BEEEA858BBBD7D83AB,The Panama Papers data is current through 2015,PAN,Panama,14050907,Panama Papers
MOSSFON BULIDING; 54th; Street; Marbella,00658D6FC606575D08E4F150A9511572,The Panama Papers data is current through 2015,ESP,Spain,14050908,Panama Papers
Mossfon Buliding; East 54th S. Panama; Rep. of Panama,F913204578EB1A1C5A26EE0E0AB19976,The Panama Papers data is current through 2015,PAN,Panama,14050909,Panama Papers
MOSSFON BVI,2C881C46D1F98AA6CF571F399AB5FE1E,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050910,Panama Papers
(Mossfon BVI Cny),5AB4FD4E1D4C06B0085C25CD21038F04,The Panama Papers data is current through 2015,VGB,”Virgin Islands, British”,14050911,Panama Papers
Mossfonfon Buiilding; Panama City; Panama,38BC188C34BE9BBD5CD3E807C5ECDB31,The Panama Papers data is current through 2015,PAN,Panama,14050912,Panama Papers
MOSSFON MANAGERS LTD.,698232FCC5C232F03F6CD165ECBF4B10,The Panama Papers data is current through 2015,,,14050913,Panama Papers
MOSSFON MANAGERS LTD.; SAFFREY SQUARE; SUITE 205; BANK LANE; P.O. BOX N-8188,1FA45A8E923F99F36502F05F6DF74053,The Panama Papers data is current through 2015,,,14050914,Panama Papers
MOSSFON MANAGERS LTD; SAFFREY SQUARE; SUITE 205; BANK LANE; P.O. BOX N-8188; NASSAU,699DED3AC59B9B06BFD3D33F904FDCF2,The Panama Papers data is current through 2015,BHS,Bahamas,14050915,Panama Papers
MOSSFON MANAGERS LTD.; SAFFREY SQUARE; SUITE 205; BANK LANE; P.O. BOX N-8188; NASSAU; BAHAMAS.,88291CE9C399465AC3F15C09F478DF31,The Panama Papers data is current through 2015,BHS,Bahamas,14050916,Panama Papers
MOSSFON MANAGERS LTD.; SAFFREY SQUARE; SUITE 205; BANK LANE; P.O. BOX N-8188; NASSAU; NEW PROVIDENCE ISLAND; BAHAMAS,3D6345D318D2B376A278AD88C00B635F,The Panama Papers data is current through 2015,BHS,Bahamas,14050917,Panama Papers
MOSSFON MANAGERS (SERVICES); Mossfon Building; East 54th Street; Panama; Republic of Panama.,6849F37D76D73BD1F4CB60B1CB0F14B4,The Panama Papers data is current through 2015,PAN,Panama,14050918,Panama Papers
MOSSFON MANAGERS (SERVICES) MOSSFON BUILDING EAST 54TH STREET P.O. BOX 0832-0886; W.T.C. PANAMA; REPUBLIC OF PANAMA,F0D88AFFB48503F1CA67DECB94DAA217,The Panama Papers data is current through 2015,PAN,Panama,14050919,Panama Papers
MOSSFON ORILLAC BLDG-EAST 54TH STREET-2ND FLOOR-PANAMA-REP-OF-PANAMA,3AE8F70B0EADE10D53CCED5CE4A138A7,The Panama Papers data is current through 2015,PAN,Panama,14050920,Panama Papers
Mossfon Trust Corporation; 3rd Floor; 54th East Street; Panama; Republic of Panama.,378C9D78466E8BD00892ACD270CE3874,The Panama Papers data is current through 2015,PAN,Panama,14050921,Panama Papers
MOSSFON TRUST CORPORATION; APARTADO 0832-0886; WORLD TRADE CENTER; PANAMA; REP. DE PANAMA,7DB5FF8F2F2AC488D9477578C6F9B8FB,The Panama Papers data is current through 2015,PAN,Panama,14050922,Panama Papers
MOSSFON TRUST CORPORATION; APARTADO 0832-0886; WORLD TRADE CENTER; PANAMA; REPUBLIC OF PANAMA,8859A60BFDC7BA50C046C54A2BE5C899,The Panama Papers data is current through 2015,PAN,Panama,14050923,Panama Papers
MOSSFON TRUST CORPORATION; Mossfon Building; 3rd floor; 54th E. Street; Panama,15221FB0AB893EBA0F5D347F3974BC02,The Panama Papers data is current through 2015,PAN,Panama,14050924,Panama Papers
Mosson Bldg.; 54th East Street; Panama; Rep. of Panama,BB77F48FBA50D379A88581199C568382,The Panama Papers data is current through 2015,PAN,Panama,14050925,Panama Papers
Mosssfon Building; 54th Street; Panama; Rep. of Panama,260CD2B66EE994B084B2178AD526C04C,The Panama Papers data is current through 2015,PAN,Panama,14050926,Panama Papers
MOSTALINA INVESTMENTS S.A.,FCBFDB04EC5C86A40279F23B7EADBDA7,The Panama Papers data is current through 2015,,,14050927,Panama Papers
MOSTAR HERZEGOWINA,4B97571968184A96362007BE238E7E21,The Panama Papers data is current through 2015,BIH,Bosnia and Herzegovina,14050928,Panama Papers
Moste 40j; 1218 Komenda; Slovenia; Europe,42461788E327154E1034B5244BEBFEA2,The Panama Papers data is current through 2015,SVN,Slovenia,14050929,Panama Papers
“Mota Gur 9 Givat Shmuel, Israel”,ADFA44C82580F5E9E194017E372D638E,The Panama Papers data is current through 2015,ISR,Israel,14050930,Panama Papers
Motionsvagen 3; 61634 Aby; Sweden.,15E811436C50B60B6D5EFD24AC2C6BDE,The Panama Papers data is current through 2015,SWE,Sweden,14050931,Panama Papers
Moudabber Center; Bloc B; 4th Floor; Kaslik Highway; Zouk Mikael; Lebanon.,ED48BCB64BA0F897A78998CFEAE190BE,The Panama Papers data is current through 2015,LBN,Lebanon,14050932,Panama Papers
Moulin-de-Vert 21; 1288 Aire-la-Ville; Switzerland,AC8DA8C7F18FF90CABF17383580B17F4,The Panama Papers data is current through 2015,CHE,Switzerland,14050933,Panama Papers
Mountain Dream; Bowring Road; Isle of Man; IM8 3EU,2E702F20CFD5624118D334C46B55893C,The Panama Papers data is current through 2015,IMN,Isle of Man,14050934,Panama Papers
MOUNTAIN RANGE BOUTIQUE LODGE HERITAGE PARK CARDRONA VALLEY ROAD P.O. BOX 451 WANAKA NEW ZEALAND,4D695BA8CF0E379AE2CCB0C1824CEF60,The Panama Papers data is current through 2015,NZL,New Zealand,14050935,Panama Papers
MOUNTAIN RANGE; HERITAGE PARK; 1 CARDRONA VALLEY ROAD; WANAKA 9192; NEW ZEALAND,73635093BDD676924533CF7A03ADD60B,The Panama Papers data is current through 2015,NZL,New Zealand,14050936,Panama Papers
“MOUNTAIN VALLEY SOKAK 141; OVACIK FETHIYE, MUGLA 48300 TURKEY”,06BF41FC2074F77A0B9624B7AEB7B843,The Panama Papers data is current through 2015,TUR,Turkey,14050937,Panama Papers
MOUNT CREVELT HOUSE; SOUTH QUAY; ST; SAMPSON’S GUERNSEY; C.I.,D783C58A9CC0AEEB79A5DCCFB52A7EA4,The Panama Papers data is current through 2015,GGY,Guernsey,14050938,Panama Papers
MOUNT CREVELT HOUSE; SOUTH QUAY ST. SAMPSON’S QUERNSEY; CI,84F227CB37D1C0399A99FDC65DBD164F,The Panama Papers data is current through 2015,CHN,China,14050939,Panama Papers
MOUNT HERON; ZWAANSWYK ROAD; TOKAI; 7945; SOUTH AFRICA,4B145DFE3FAEBBCB918E32F7D46DC7E3,The Panama Papers data is current through 2015,ZAF,South Africa,14050940,Panama Papers
Mount Kos Estate; Kosmos; Hartbeespoort 0261; South Africa,B8F7D27B77951F9B6A84475C709D3FE8,The Panama Papers data is current through 2015,ZAF,South Africa,14050941,Panama Papers
MOUSAYTBEH – CANARI BLDG – 9TH FLOOR – BEIRUT LEBANON,448CC362E757750F6467D91278803BFD,The Panama Papers data is current through 2015,LBN,Lebanon,14050942,Panama Papers
MO WAN ZHU; DA MIAO CUN; HUAXI XIANG; XIAOCHANG XIAN; HUBEI; CHINA,C1F3B4A47877CA8FF2945805A9EFD0CB,The Panama Papers data is current through 2015,CHN,China,14050943,Panama Papers
MOYNE DRIVE NYALI; MOMBASA; P.O. BOX 80872; MOMBASA; KENYA,6A9F56ED1A8D87E8E79EA323EE323342,The Panama Papers data is current through 2015,KEN,Kenya,14050944,Panama Papers
MOZHAISKOE SHOSSE 84-25; ODINTSOVO; RUSSIA,6EBF12A9EBBB7CA00CE6DA8925062B8A,The Panama Papers data is current through 2015,RUS,Russian Federation,14050945,Panama Papers
Mozhayskoe Shosse; Bldg. 45-2; Apt. 79; Moscow city; Russian Federation,2167F8901EAA0A787ED8EA2015C0CBCC,The Panama Papers data is current through 2015,RUS,Russian Federation,14050946,Panama Papers
“Mozolky 2569/14 Brno, Czech Republic”,C8EA570E97740697AB9DDDB2220666F2,The Panama Papers data is current through 2015,CZE,Czech Republic,14050947,Panama Papers
M. Paco 7-15; Vilnius LT 02309; Lituanie,1AAAF8C662E80D581E49E45FEBDE76BD,The Panama Papers data is current through 2015,LTU,Lithuania,14050948,Panama Papers
M. Peschanyy Per.; Bld. 8; Apt 52; Moscow; Russia,689147DDB660429665784F060190F0F9,The Panama Papers data is current through 2015,RUS,Russian Federation,14050949,Panama Papers
MPIMARI 9; PIREAS; ATHENS 18539; GREECE,0686A2330DD477F2F7F138B186E9765E,The Panama Papers data is current through 2015,GRC,Greece,14050950,Panama Papers
MR1-15-04 Pangsapuri Servis Sri Acapella; Shah Alam; 40100 Selangor; Malaysia,12A1086242AF0EB3D4D6B56A84650A24,The Panama Papers data is current through 2015,MYS,Malaysia,14050951,Panama Papers
MR. A. COOPER; MILLENIUM WEALTH MANAGEMENT LTD.; ALFRED ESCHER STRASSE 9; CH 8027 ZURICH; SWITZERLAND,E5B9390E349AB6DFC33F6DB50A152B92,The Panama Papers data is current through 2015,CHE,Switzerland,14050952,Panama Papers
MR ALEXEI BARANNIKOV OF 50-56 KORNEICHYUK STREET MOSCOW RUSSIA,BDBA04576329553318F5A2C2672CA455,The Panama Papers data is current through 2015,RUS,Russian Federation,14050953,Panama Papers
MR. A.P. WALLIS; INTER-CONTINENTAL MANAGEMENT LIMITED; PROSPECT CHAMBERS; PROSPECT HILL; DOUGLAS; ISLE OF MAN; IM1 1ET,1885F90F057BD623A96DF4EF0B0B9698,The Panama Papers data is current through 2015,IMN,Isle of Man,14050954,Panama Papers
Mr D.J. Sheppard; Esprit; 23 King Street; St Helier; Jersey; JE2 4WF.,86B201F9A95E939AA415B304D0DDA625,The Panama Papers data is current through 2015,JEY,Jersey,14050955,Panama Papers
Mr. Encarnacion domiciled at Municipio Cerro; Ciudad de la Habana; Cuba. Mr. Gonzalez domiciled at Location Sanchez Soto; Camaguey; Ciudad-CUBA,974D51546C08376CC4F1DFDF61179E97,The Panama Papers data is current through 2015,CUB,Cuba,14050956,Panama Papers
MR. ERLING JARSWALL; SIHLSTRASSE 20; 8032 ZURICH,A56C2D535B1CA8AACE332F5B81692AA9,The Panama Papers data is current through 2015,CHE,Switzerland,14050957,Panama Papers
(Mr. Georgy Narbut of Lielvardes Str. 105-41; Riga; Latvia; LV-1084),72984AABE9BB8814F26DD53196B222A8,The Panama Papers data is current through 2015,LVA,Latvia,14050958,Panama Papers
MRIC No.: S0019309G 145 Ceylon Road Singapore 429707,6CD02D64372F579B01E48CAB7B184655,The Panama Papers data is current through 2015,SGP,Singapore,14050959,Panama Papers
MR IERACHMIEL FISCHER and MRS ALICE EISBART – WOLACH STREET 3- KIRYAT ONO- ISRAEL // MR MARC FISCHER- STERSTRAAT 17- 2018 ANTWERPEN-BELGIUM //,61298690C0259CE479B89C7CE2255E43,The Panama Papers data is current through 2015,BEL,Belgium,14050960,Panama Papers
MR I.S. YURYEVVATUTINA ST.; 16 BLD. 2; APARTMENT 70MOSCOW; RUSSIAN FEDERATION,F6A03ED6864497C825DFF92FDE5251E9,The Panama Papers data is current through 2015,RUS,Russian Federation,14050961,Panama Papers
“MR J J WHITTLE MARL HOUSE, DOVE COTE SHEEP HILL LANE CLAYTON LE WOODS CHORLEY PR6 7AU”,EF6556CFA7105C51C0989E9CB18920D2,The Panama Papers data is current through 2015,GBR,United Kingdom,14050962,Panama Papers
MR J LONGWORHT OXFORD HOUSE 20 EUXTON LANE CHORLEY PR7 1PS,62C9A4D7782504C408C6A9B7D13066A2,The Panama Papers data is current through 2015,GBR,United Kingdom,14050963,Panama Papers
MR. JUAN PABLO CAPPELLO; GREENBERG TRAURIG; 1221 BRICKELL AVENUE; MIAMI; FLORIDA 33131; USA,B6D755C41036AA500F59EB22DB9E9299,The Panama Papers data is current through 2015,USA,United States,14050964,Panama Papers
(Mr. KAMIL KHUSNETDINOV of Valovaya Str. 21/125 -24; Moscow; Russia),021AA3CB0B549205D218DE01F2844552,The Panama Papers data is current through 2015,RUS,Russian Federation,14050965,Panama Papers
“MR K WHITTLE MARL HOUSE, DOVE COTE SHEEP HILL LANE CLAYTON LE WOODS CHORLEY PR6 7AU”,A46DACF57AF4AF5AD5167760120AA72B,The Panama Papers data is current through 2015,GBR,United Kingdom,14050966,Panama Papers
MR. LUTHER; 93 SOUTH WATER STREET; EDHARTOWN; MA 02539 USA; MRS. KREMER; 1100 BEECH ROAD; ROSEMONT; PA 19010; USA,45171BAFAD520D67D917004B97E53E7D,The Panama Papers data is current through 2015,USA,United States,14050967,Panama Papers
MR MAZEN MURAD- 5-7 GRAND RUE- 1260 NYON and MR NADER MURAD- 5-7 GRAND RUE- 1260 NYON,FEF20FD99455D093E1730E32DC5936C1,The Panama Papers data is current through 2015,CHE,Switzerland,14050968,Panama Papers
MR. MICHEL ABOUCHALACHE; C/O SIF SOCIETE INTERNATIONAL DE FINANCE; LOEWENSTRASSE 19; PO BOX 7278; 8023 ZURICH,1906B8816F13A6475C0C7E9DBFBAC61D,The Panama Papers data is current through 2015,CHE,Switzerland,14050969,Panama Papers
Mr. Mounir Hamza 5th Floor; Agha Building; Australia Street; Rawche; Beirut – Lebanon,565C33EC22BE9DFAB5EE498F91C7C86B,The Panama Papers data is current through 2015,LBN,Lebanon,14050970,Panama Papers
Mr. Ncorsbhley; 1 Camelia Street; Morningside Ext 40; Sandton; South Africa,D126389E31B1D23A5892CFD0D910DECE,The Panama Papers data is current through 2015,ZAF,South Africa,14050971,Panama Papers
Mr. Palmer; 8 Fairbridge Avenue; Belgravia; Harare; Zimbabwe,FC8DB2E63909108E0AFED6EAB1BF9595,The Panama Papers data is current through 2015,ZWE,Zimbabwe,14050972,Panama Papers
“MR. PATRICK BITTEL C/O BUDIN & ASSOCIES RUE SENEBIER, 20 1211 GENEVE 12 SWITZERLAND”,DC5B32B1FC5325D3D745CD3ED5B01557,The Panama Papers data is current through 2015,CHE,Switzerland,14050973,Panama Papers
MR. RAFAEL JR. DIZON ABIERA 13/F ROYAL MATCH BUILDING 6780 AYALA AVENUE MAKATI CITY PHILIPPINES,3E4E7DE368F8FCB86AC7605E7DC0D412,The Panama Papers data is current through 2015,PHL,Philippines,14050974,Panama Papers
“MR. RENE REYNAUD C´AN PRUAGA E – 07192 ESTELLENCS, MALLORCA ESPAÑA”,A7374C0D3C8E889EF2B42346AAE6B9EE,The Panama Papers data is current through 2015,ESP,Spain,14050975,Panama Papers
Mr. René ReynaudC’An Pruaga E- 07192EstellencsMallorcaSpain,80E73DFEF45A397780EE5D9724F66EC5,The Panama Papers data is current through 2015,ESP,Spain,14050976,Panama Papers
Mrs. Al-Husseini; P.O. Box 1049; Jeddah,4FC50C439951D235E26F1D382FBFB087,The Panama Papers data is current through 2015,SAU,Saudi Arabia,14050977,Panama Papers
MRS. ALLA IVANOVA MRS. DARIA IVANOVA CLOS DE WAGRAM 2 UCCLE BELGIUM,E0F619DB1CAE2F5C9D29ACC9D1AE6210,The Panama Papers data is current through 2015,BEL,Belgium,14050978,Panama Papers
MRS E M LONGWORTH OXFORD HOUSE 20 EUXTON LANE CHORLEY PR7 1PS,0E6218032CE19E413E46811D82D2A4CC,The Panama Papers data is current through 2015,GBR,United Kingdom,14050979,Panama Papers
Mr. S.F. Cairns; Wychwood Trust Limited; 1 Castle Street; Castletown; Isle of Man; IM9 1LF,E8B58A945B177A5B5CFFDF60C1D6CA91,The Panama Papers data is current through 2015,IMN,Isle of Man,14050980,Panama Papers
Mr. S.F. Cairns; Wychwood Trust Limited; 1 Castle Street; Castletown; Isle of Man; IM9 1LF; British Isles,376AAB7B20B7443A29E93F374BD97BE9,The Panama Papers data is current through 2015,IMN,Isle of Man,14050981,Panama Papers
MR S LONGWORTH DELMA HALL LANE WRIGHTINGTON WIGAN WN6 9EL,30A9924966E735B154BB01F5CF5303D8,The Panama Papers data is current through 2015,USA,United States,14050982,Panama Papers
MRS. PENNY MACEWEN; HAYNES & TRIAS; 2/3B HORESE BARRACK LANE; GIBRALTER,09ADD22F2E28A034FC5AC62FA4EB00B5,The Panama Papers data is current through 2015,GIB,Gibraltar,14050983,Panama Papers
Mrs. Susan Richards; Foyle Hill House; Foyle Hill; Shaftesbury; Dorset; England SP7 0PT,E3B3AD3DA24026AC624FEC8C191C89E7,The Panama Papers data is current through 2015,GBR,United Kingdom,14050984,Panama Papers
Mrs Susan Richards; Foyle Hill House; Foyle Hill; Shaftesbury; Dorset; SP7 OPT; United Kingdom,9E37CB695FDCF1A68BA52A20E70EDA62,The Panama Papers data is current through 2015,GBR,United Kingdom,14050985,Panama Papers
MRS SUSAN RICHARDS of FOYLE HILL HOUSE; SHAFTSBURY; DORSET SP7 0PT,20BB08DB7F660244A7A6DEC0C147E563,The Panama Papers data is current through 2015,GBR,United Kingdom,14050986,Panama Papers
Mr. Stephanus Janke,E93D493518C371B46F09D610DC3F40F2,The Panama Papers data is current through 2015,,,14050987,Panama Papers
Mrstikova 3299/30; Prague 10; Czech Republic,370070459227C429B6103D38D94BA0D8,The Panama Papers data is current through 2015,CZE,Czech Republic,14050988,Panama Papers
Mrs. T. Jowett; 593 Pinner Road; Pinner; HA5 SRT; United Kingdom,89330E5D653E186B3E0ECAEA9DFA6C9D,The Panama Papers data is current through 2015,GBR,United Kingdom,14050989,Panama Papers
Mr. Theo Harris Marcopolus; Suite 13; 1st. Floor; Oliaji Trade Centre; Francis Rachel Street; Victoria; Mahe; Seychelles,FB5754917E954B55F248F18D46A783EA,The Panama Papers data is current through 2015,SYC,Seychelles,14050990,Panama Papers
Mr. Vakhtang Pkhakadze,44E56EE5BDF80165BAFE60BA0EB376D5,The Panama Papers data is current through 2015,,,14050991,Panama Papers
(MR. VOLODYMYR BYLYM OF ULITSA GNATA YURY 14-22; KIEV; UKRAINE),FE0E41DA2C8FBD9E3F16D09B5E733450,The Panama Papers data is current through 2015,UKR,Ukraine,14050992,Panama Papers
M. Sakkeyoghasdhoshuge; Male 20-02; Republic of Maldives,345BBA41E3524904E83A9946666945C2,The Panama Papers data is current through 2015,MDV,Maldives,14050993,Panama Papers
MS E. SHIPITSYNAVARSHAVSKOE SHOSSEBUILDING No. 122; APARTMENT 431MOSCOW; RUSSIAN FEDERATION,14A42B6A1FF41FDE1DA5689623AE770A,The Panama Papers data is current through 2015,RUS,Russian Federation,14050994,Panama Papers
M. Sin Kwok Sang Flate 11/F Yenfu Mansion n’137 Hipwo Street Kwuntong Hong Kong,DC8D00069B82EF596B5F9E71F678224E,The Panama Papers data is current through 2015,HKG,Hong Kong,14050995,Panama Papers
Ms. Ngo Chinh Mien,A75D1A73895B65F1B485708088A097B5,The Panama Papers data is current through 2015,,,14050996,Panama Papers
MSOSFON BUILDING; SECOND FLOOR; EAST 54TH STREET; PANAMA; REPUBLIC OF PANAMA,596914A02DA01F60F96703757BD9A9B5,The Panama Papers data is current through 2015,PAN,Panama,14050997,Panama Papers
MTB Clients Nominees Limited c/o Morgan Trust Company (Bahamas) Limited; P.O. Box N-4889; Nassau; Bahamas,82099BDAD4E69E138A23C3876DA3C25B,The Panama Papers data is current through 2015,BHS,Bahamas,14050998,Panama Papers
M. Tomlachovsky Per 8/1/22; Moscow; Russia,ECD656EEF1D9108472251803E0F4C077,The Panama Papers data is current through 2015,RUS,Russian Federation,14050999,Panama Papers
MTS HIMALAYA 745 LOMAS DE CHAPULTEPEC 11000 MEXICO D.F.,867D503F0DEC2FF5B72E03EEA0872F05,The Panama Papers data is current through 2015,MEX,Mexico,14051000,Panama Papers
MUALLIM NACI CAD No.113 ORTAROY – ISTANBUL TURKEY,9A55FA9E04ECAA26EF810AC192DCFE4D,The Panama Papers data is current through 2015,TUR,Turkey,14051001,Panama Papers
Muara karang Blok B8 barat No. 71; Jakarta 14450; Indonesia,649D561DD6372BCDCAFFBE15753D238D,The Panama Papers data is current through 2015,IDN,Indonesia,14051002,Panama Papers
Mu Cheng Yuan Xing Zheng Village; Shi Qua Xiang; Lan Xi City; Zhejiang Province; China,B2C039F4818F4405176288F71757F613,The Panama Papers data is current through 2015,CHN,China,14051003,Panama Papers
MU DAN DE 8A; FAZHANXIN YUAN; MINTIAN LU; FU TIAN DISTRICT SHENZHEN; GUANGDONG PROVINCE PEOPLE’S REPUBLIC OF CHINA,8F8894B4DB37EDEC7B193F916864FF6D,The Panama Papers data is current through 2015,CHN,China,14051004,Panama Papers
Muehlfeldweg 21; 85748 Garching; Germany,ACBFCF06DE9D7C2FEB28372141CA960C,The Panama Papers data is current through 2015,DEU,Germany,14051005,Panama Papers
Mueyyetzade Mah. Serdar¿i Ekrem Sok.Kamondo Apt No: 22; Beyoglu; Istanbul 34425 Turkey,EE92AC93695C37BFA1AFAF5C68C2499A,The Panama Papers data is current through 2015,TUR,Turkey,14051006,Panama Papers
MugungHwa Apt 702-704; 11 Dongan-ro; Dongan-gu; Anyang-si; Gyeonggi-do; South Korea,EEB8E7C6C947A67D899E15147CF67991,The Panama Papers data is current through 2015,KOR,”Korea, Republic of”,14051007,Panama Papers
Muhammad bin Fahd bin Abdulaziz Palace Al Akrabiya Prince Jalawi Bin Adbul Aziz Bin Musayyid Str. Alkhobar SAUDI ARABIA,91E2264A90A385B087ECE4B3F0839540,The Panama Papers data is current through 2015,SAU,Saudi Arabia,14051008,Panama Papers
Muirfield Green Lodge; Duncar Road; Gullan; EH31 2EF; United Kingdom,E6373BE220CEF05334F406CFF650B5FF,The Panama Papers data is current through 2015,GBR,United Kingdom,14051009,Panama Papers
“Mujiaozhai group, Mujiaozhai village Faer Xiang Shuicheng County Guizhou Province China”,7775FC9C95ABC774C4EAC5977A2B8811,The Panama Papers data is current through 2015,CHN,China,14051010,Panama Papers
“MULCASTED, ST HELIER”,12D749E751CADEA9B450BF330007589A,The Panama Papers data is current through 2015,JEY,Jersey,14051011,Panama Papers
MULEBA COTTAGE No.8; LOWER KABETTE RD; WESTLANDS; NAIROBI,5029E390B5E05645C949C433A6119B58,The Panama Papers data is current through 2015,NAM,Namibia,14051012,Panama Papers
Mulford abogados; 56th streer; Sortis Business Tower; office 10-H; Panama.,ADED3979A80FA076F472C4983CCF9035,The Panama Papers data is current through 2015,PAN,Panama,14051013,Panama Papers
Mulford Abogados; 60th Street; Obarrio 60 Building; Of. 11E; Panama; Republic of Panama;,0C775B255FF7929040DF8707E1B26B78,The Panama Papers data is current through 2015,PAN,Panama,14051014,Panama Papers
MULTI GROUP FINANCE; C/O MULTIDUCIAIRE LEMAN; PLACE DE LA RIPONNE 3; 1005 LAUSANNE; SWITZERLAND,47D7C5C4D93B7AD8C7B25BF444B81CA7,The Panama Papers data is current through 2015,CHE,Switzerland,14051015,Panama Papers
MULTI GROUP FINANCE; C/O MULTIFIDUCIAIRE LEMAN; PLACE DE LA RIPONNE 3; 1005 LAUSANNE; SWITZERLAND,B5969FA426799C396F49A27CB187E97E,The Panama Papers data is current through 2015,CHE,Switzerland,14051016,Panama Papers
“Mumbai, India”,05390C5029AB005AC50D6FA76591A465,The Panama Papers data is current through 2015,IND,India,14051017,Panama Papers
“Mun. Brasov Jud. Brasov Str. Toamnei nr. 12 bl.1 sc. F ap.4, Romania”,0BAC6BAC5D7C77A9FB3112A53264F425,The Panama Papers data is current through 2015,ROU,Romania,14051018,Panama Papers
Mun. Bucuresti Str. Valea Ialomitei Nr. 4; bl. C11 sc. D et. 3 ap. 132 Sec. 6; Romania,D04C93A1BE1DACFF58163D346AC5494A,The Panama Papers data is current through 2015,ROU,Romania,14051019,Panama Papers
“Muncinlupa, PH”,EAABF3F3C4E1FE15782905459221AABB,The Panama Papers data is current through 2015,PHL,Philippines,14051020,Panama Papers
Mun. Constanta Jud. Constanta; Prl. 8 Martie nr. 16a; Romania,3507B51B367FCFBB738189D7C0C644D0,The Panama Papers data is current through 2015,ROU,Romania,14051021,Panama Papers
Muñecas 1099; CABA; Argentina,EBC05DA669AC5F04E6F45D739B2D12E3,The Panama Papers data is current through 2015,ARG,Argentina,14051022,Panama Papers
“Munich, Germany”,ABDAAF9198B8B239DBAB0A344F31F553,The Panama Papers data is current through 2015,DEU,Germany,14051023,Panama Papers
Municipio de Franco da Rocha; Estado de Sao Paulo; Rua Marino Tardelli; 240; Vila Martinho; CEP: 07852-030 – Brazil,AE1547C0CD50FB8B69B5561C2D654B31,The Panama Papers data is current through 2015,BRA,Brazil,14051024,Panama Papers
Municipio de Franco da Rocha; Estado de Sao Paulo; Rua Zanela e Alves; 143; Centro; CEP: 07851-071 – Brazil,471A4BE696600BD2A66427A1EF2EA728,The Panama Papers data is current through 2015,BRA,Brazil,14051025,Panama Papers
Munícipio de Jundiaí; Estado de Sao Paulo; em la Rua Colina; 210; Bairro Jardim Paulista,62281C94FB34AA5A4781920D5722B972,The Panama Papers data is current through 2015,BRA,Brazil,14051026,Panama Papers
Municipio de Recife; Estado de Pernambuco; a Rua Silveira Lobo; 32; Poço; Caixa Postal 383. CEP 52.061-030; Brasil.,756EA5B59D24ECCD5ACBB20E4519233D,The Panama Papers data is current through 2015,BRA,Brazil,14051027,Panama Papers
Munícipio de Sao Paulo; Estado de Sao Paulo; em la Rua Eugênio Lorenzetti; 137; apartamento 35; Bairro Jardim Íris,CB01A0A2D059268F6196C1F50BA6A2BC,The Panama Papers data is current through 2015,BRA,Brazil,14051028,Panama Papers
Municipio de Sao Paulo; Estado de Sao Paulo; en la Rua Montesquieu; 100; apto. 111; CEP: 04116-190; Brazil,AE75F4A941B4C078CC1F7355544FAAA4,The Panama Papers data is current through 2015,BRA,Brazil,14051029,Panama Papers
Município de Sao Paulo; Estado de Sao Paulo; na Rua Montesquieu; 100; apto. 111; CEP: 04116-190; Brazil,BF8F61C7A99EC9BD569521C72B2CCE84,The Panama Papers data is current through 2015,BRA,Brazil,14051030,Panama Papers
Municipio Libertador Distrito Federal; Esquina La Marron Edificio General Paez Planta Baja; Local Roliz 12,FE572E9ADB613F88057949BC94B180A1,The Panama Papers data is current through 2015,VEN,”Venezuela, Bolivarian Republic of”,14051031,Panama Papers
“Mun. Slobozia Jud. lalomita Str. Nicolae Balcescu bl. 25B sc. A ap. 1, Romania”,42F212C04D5299AA3ACC955FAF0CC845,The Panama Papers data is current through 2015,ROU,Romania,14051032,Panama Papers
Mun Timisoara Jud Timis Cal Martirilor 1989 no 78 bl 12 et 2 ap 12 Romania,5956C4F044E8DFC76681EC513EADA8D2,The Panama Papers data is current through 2015,ROU,Romania,14051033,Panama Papers
“Muntinnlupa, Philippines”,2624E9E273E9A9F207BF21E54DFE8C3A,The Panama Papers data is current through 2015,PHL,Philippines,14051034,Panama Papers
Murat Susuz O.R.G. Aksalur; Cad. Konaklar Mah. Bassin; Sit. H Blok A. Kapi; D.64. Levent-Istanbul; Turkey,7986CF73C060E2B15091A7FF3585863E,The Panama Papers data is current through 2015,TUR,Turkey,14051035,Panama Papers
Muravskaya Street 24; Aprt. 10; Moscow; Russian Federation,8FB29B8D2C30E140B97A50AF86AB0E7B,The Panama Papers data is current through 2015,RUS,Russian Federation,14051036,Panama Papers
Murdoch House; North Shore Road; Ramsey; Isle of Man; IM8 3DY,E93CAF52DBB1A4E2FD3BC129C0DEEC9E,The Panama Papers data is current through 2015,IMN,Isle of Man,14051037,Panama Papers
MUREX; Fakhreddine Street; Corner Center; 14th Floor; Kantari; Beyrouth-Lebanon,2EE9048CB081311D97D86BCF2EA12450,The Panama Papers data is current through 2015,LBN,Lebanon,14051038,Panama Papers
Murgeon 287 y 10 Agosto; Quito; Ecuador,B057639169759A41C0011A02D640DC8B,The Panama Papers data is current through 2015,ECU,Ecuador,14051039,Panama Papers
Murjan 5; Apartment 2301; Jumeirah Beach Residence; PO Box 72459; Dubai; United Arab Emirates,5E700B2D974DAAC44D68EF78915C3D5C,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14051040,Panama Papers
Muromskaya str 17/20 apt 78; Kiev 03190; Ukraine,2FC642E19D43F6AF55A7336BCAD67092,The Panama Papers data is current through 2015,UKR,Ukraine,14051041,Panama Papers
Murphy’s Lane; Goodwill; Dominica,B278DFE4EDB9EAE1304AC73B6D219F86,The Panama Papers data is current through 2015,DMA,Dominica,14051042,Panama Papers
Murroor Road; Al Zaafarana Area; Villa No. 745; Abu Dhabi; U.A.E.,112A7445CD11BE789ECCDA1D655AEF89,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14051043,Panama Papers
MURSEL ULUC MH. 931 CAD. NO: 10/10 CANKAYA ANKARA TURKEY,F4915B94F5C560C35F598FF1FB9C7CF3,The Panama Papers data is current through 2015,TUR,Turkey,14051044,Panama Papers
Musabbeh Rashid Mesabbeh Al Fatan; Villa 34; 363 Um Suquim; PO Box 122071; Dubai; UAE,09E1B8B5570134C45B515FCEEAB733E5,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14051045,Panama Papers
Musabbeh Rashid Mesabbeh Al Fata; Villa 34; 363 Um Suquim PO Box 122071; Duba; UAE,84C850DEA4BAB13090CC150B30470510,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14051046,Panama Papers
Musa Dzhalil str. 2-1-190; Moscow 115573; Russian Federation,9ED19E625CFA6BBC768D9E7B7985CE94,The Panama Papers data is current through 2015,RUS,Russian Federation,14051047,Panama Papers
Musa Jalil Street; Building 30/1; apt. 158 Moscow Russian Federation.,538E2BE08EA0735F0D6A45400D117240,The Panama Papers data is current through 2015,RUS,Russian Federation,14051048,Panama Papers
Musalla Tower H no.67 Bur Dubai St; Dubai; UAE,23B9DCD7F1AF9D0EF896037AEAF74C4C,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14051049,Panama Papers
Musandam; Dibba House no. 35; Oman,53CE2329C750CBB9AF2C85179E9D6020,The Panama Papers data is current through 2015,OMN,Oman,14051050,Panama Papers
Mushrukova Street; Build. 15; Corpus 1; office/flat 91; Ufa; Bashkortostan Republic; Russia,562BEAF873979A09CD49A0298E06625C,The Panama Papers data is current through 2015,RUS,Russian Federation,14051051,Panama Papers
Muslim Al Kubaissi Villa; House Number 20; Street No.11; Karama Area; West 14; Abu Dhabi; UAE,9EB2449C01767736CD821AE1C264518F,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14051052,Panama Papers
Muslim Al Kubaissi Villa; Street No. 11; Karama Area; West 14; Abu Dhabi; UAE.,4E8A6E3D5A9871E3DC09EBF3975045B0,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14051053,Panama Papers
Muslim Al Kubaissi Villa; Street No. 11; Karama Area; West 14; Abu Dubai; UAE,8D9E5BA49D79CC85CB823C1FCA471B9B,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14051054,Panama Papers
Mussafah – MW4 – 7th and 16th street. Ground floor Abu Dhabi UAE,89D960C188497DC0DC8F65F81F91E3AB,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14051055,Panama Papers
MUSY DZHALILIA STR. 36-173; MOSCOW; RUSSIA,E793130ED165C157C27CFD65E13B56F0,The Panama Papers data is current through 2015,RUS,Russian Federation,14051056,Panama Papers
Muthuku; 5th Drive; Kerarapon Drive; Ngong; Nairobi; Kenya,6DF4F13A48D17A6CE5BF7E6EAF99B4B9,The Panama Papers data is current through 2015,KEN,Kenya,14051057,Panama Papers
MUTIANA GREEN LANE AVE GREEN LANES ST. PETER PORT GUERNSEY,DD12ACFC181FEF728FA509989B5C7CA6,The Panama Papers data is current through 2015,GGY,Guernsey,14051058,Panama Papers
MUTIARA LANES AVENUE; GREEN LANES; ST PETER PORT; GUERNSEY; CHANNEL ISLANDS; GY 1TU,9CB8FFDA77979299A5C97D29C863AB4B,The Panama Papers data is current through 2015,GGY,Guernsey,14051059,Panama Papers
MUURSTRAAT 4; B-9790; WORTEGEM – PETEGEM,06DF39427334385552A0F174249B988B,The Panama Papers data is current through 2015,BEL,Belgium,14051060,Panama Papers
Mu Yu Zu; Ping Tian Village; Yun Xi Country; Yun Xi District; Yue Yang City; Hunan Province; China,438E2BE6CB6EAD4441BD5A9940A5DF4C,The Panama Papers data is current through 2015,CHN,China,14051061,Panama Papers
MUZYCHNA STREET 33; APT. 93; ZAPOROZHYE; UKRAINE,B9ACAB04D0DCB8E5E8F8A176D35AAD02,The Panama Papers data is current through 2015,UKR,Ukraine,14051062,Panama Papers
MVP TECH; OFFICE 21-22 BUILIDNG 13; KNOWLEDGE VILLAGE P O BOX 500704 DUBAI; U.A.E.,D6824749A30470AAFDAEEFF18623E0F2,The Panama Papers data is current through 2015,ARE,United Arab Emirates,14051063,Panama Papers
Mykinon 12; Lavinia Court; 6th Floor; 1065 Nicosia; Cyprus,4A8F5454BF34F75D1342F0730D4BFEDE,The Panama Papers data is current through 2015,CYP,Cyprus,14051064,Panama Papers
My Place Apartments 703; 42/2 Soi 2; Ratchiangsean Road; A. Muang; Chiang Mai 50100; Thailand,BFE85626C52EC349BC6A0964FA00F333,The Panama Papers data is current through 2015,THA,Thailand,14051065,Panama Papers
MYRTLE CHRISTENSEN 24628 11TH AVE S DES MOINES WA 98198-3860,6097B19FEBF2DD027E6A02FA8EA5139E,The Panama Papers data is current through 2015,USA,United States,14051066,Panama Papers
Myrvollveien 9B; 1363 Hovik; Norway,ADEB07F66F5CE3FA7B1FCC6F34D7F50F,The Panama Papers data is current through 2015,NOR,Norway,14051067,Panama Papers
Myvoirrey. Rheast Lane; Peel; Isle of Man; United Kingdom,848BF4662B52BE2FB2115492123EB837,The Panama Papers data is current through 2015,IMN,Isle of Man,14051068,Panama Papers
Mz.0-10; Urb. Miraflores; Castilla; Piura; Perú,4C82E1D7C3A76D7081253856E99C6894,The Panama Papers data is current through 2015,PER,Peru,14051069,Panama Papers
Mz. A; Lt. 21; Centro Industrial Las Praderas; Lurín; Lima; Perú,040020CE869D762A0161B17916943C5E,The Panama Papers data is current through 2015,PER,Peru,14051070,Panama Papers
Mz B; Lote 11; Sublt 5; Urb.Casuarina Alta; Santiago de Surco; Lima; Perú,5DF7BB41DC5F63B77EA5BC649A11F2CF,The Panama Papers data is current through 2015,PER,Peru,14051071,Panama Papers
Mz D. Lote 158 C – Urb.Casa Blanca Pachacamac – Lima –Perú,D3437DE2D7075228676A72976D352D18,The Panama Papers data is current through 2015,CIV,Côte d’Ivoire,14051072,Panama Papers
Mz G – Lote29 – Urb.Santa Rosa de Surco – 2da Etapa – Santiago de Surco – Lima – Perú,D737A00E108A738F8A1BC38EFD41516C,The Panama Papers data is current through 2015,PER,Peru,14051073,Panama Papers
MZ H LT 18 Urb.Rincon de la Planicie- La Molina-Lima-Perú,AE43FA50C37516BC295000C3076558BD,The Panama Papers data is current through 2015,PER,Peru,14051074,Panama Papers
MZ K; LT 7; DPTO. 3; URB. LA ENCANTADA; CHORRILLOS; LIMA; PERÚ,6A3E3E524526A2A89961FB1FBFFE1510,The Panama Papers data is current through 2015,PER,Peru,14051075,Panama Papers
Mz Ñ; Lt 13; Urb. Miraflores; Castilla; Piura; Piura; Perú.,A9B60545AA112F4AF9B0665ABC527915,The Panama Papers data is current through 2015,PER,Peru,14051076,Panama Papers
MZ.P; LT 16; LA PLANICIE; LIMA; PERÚ,FE50F5571B3C88FE026DC42E5505D3AE,The Panama Papers data is current through 2015,PER,Peru,14051077,Panama Papers
Offshore Leaks Database, Offshore Leaks Data, Offshore Leaks Meaning, Offshore Leaks Vs Panama Papers, Offshore Leaks Database Search, Offshore Leaks Adalah, Offshore Leaks Adalah, Offshore Leaks Azerbaijan, Offshore Account Leaks, Offshore Leaks Credit Agricole, Panama Offshore Accounts Leaked, Affaire Offshore Leaks, Offshore Leaks Algerie, Offshore Leaks Bvi, Offshore Bank Leaks, Offshore Leaks Database, Offshore Leaks Bedeutung, Offshore Leaks Belgique Liste, Offshore Leaks Belgen, Offshore Leaks Belgique, Offshore Leaks Canada, Offshore Leaks Credit Agricole, Offshore Leaks China, Offshore Company Leaks, Icij Offshore Leaks China, Offshore Leaks Database, Offshore Leaks Database Search, Offshore Leaks Database Download, Offshore Leaks Download, Offshore Leaks Definition, Offshore Document Leaks, Icij Offshore Leaks Database Download, Icij Offshore Leaks Database China, Icij Offshore Leaks Database India, Icij Releases Offshore Leaks Database, Offshore Leaks Espresso, Offshore Leaks France, Offshore Leaks Paradis Fiscal, Guardian Offshore Leaks, Leaks Offshore Oil And Gas, Offshore Leaks Hsbc, Offshore Leaks Hsbc Mauritius, Icij Offshore Leaks Hsbc, Offshore Tax Haven Leaks, Icij Offshore Leaks Database Http \/\/Offshoreleaks.icij.org\/, Offshore Leaks Hrvatska, Offshore Leaks Icij, Offshore Leaks Investigative Journalism, Offshore Leaks India, Icij Offshore Leaks Database Download, Icij Offshore Leaks Hsbc, Icij Offshore Leaks India, Icij Offshore Leaks Database China, Icij Offshore Leaks Malta, Icij Offshore Leaks Wiki, Icij Offshore Leaks Sri Lanka, Offshore Leaks Investigative Journalism, Offshore Leaks List Of Names, Offshore Leaks Luxemburg, Offshore Leaks Le Monde, Panama Offshore Leaks List, Icij Offshore Leaks Sri Lanka, Lista Offshore Leaks, Offshore Leaks Belgique Liste, Offshore Leaks Meaning, Offshore Leaks Mauritius, Icij Offshore Leaks Malta, Offshore Leaks Hsbc Mauritius, Offshore Leaks Le Monde, Offshore Leaks Mexico, Offshore Leaks Names, Offshore Leaks Swiss Names, Panama Offshore Leaks Names, Offshore Leaks List Of Names, Offshore Leaks Nomi, Offshore Leaks.icij.org\/search, Offshore Leaks Panama Papers, Offshore Leaks Pwc, Offshore Leaks Philippines, Offshore Leaks Portcullis, Offshore Leaks Project, Offshore Leaks Portugal, Icij Offshore Leaks Panama, Panama Offshore Leaks List, Panama Offshore Leaks Names, Panama Offshore Leaks Pakistan, Offshore Leaks Russia, Rothschild Offshore Leaks, Offshoreleaks Romania, Offshore Leaks Report, Offshore Leaks Search, Offshore Leaks Swiss Names, Offshore Leaks Singapore, Offshore Leaks Switzerland, Offshore Leaks Scandal, Offshore Leaks Seychelles, Offshore Leaks Sri Lanka, Offshore Leaks Swiss, Offshore Leaks Suisse, Offshore Leaks Turkey, Offshore Leaks Youtube, Offshore Leaks Ubs, Offshore Leaks Vs Panama Papers, Offshore Leaks Wiki, Offshore Leaks Wikipedia, Offshore Leaks Website, Www.offshore Leaks, Offshore Leaks Youtube. The Panama Papers Book, The Panama Papers Scandal, The Panama Papers Pdf, The Panama Papers Explained, The Panama Papers Netflix, The Panama Papers Leak, The Panama Papers Book Pdf, The Panama Papers Jail, The Panama Papers Movie, The Panama Papers Wiki, The Panama Papers Amazon, The Panama Papers A Torrential Leak, The Panama Papers And Hillary Clinton, The Panama Papers Australia, The Panama Papers Africa, The Panama Papers Are Super Awkward For Beijing, The Panama Papers An Introduction, The Panama Papers Algeria, The Panama Papers Albania, The Panama Papers And Nigeria, The Panama Papers Book, The Panama Papers Book Pdf, The Panama Papers Book Review, The Panama Papers Breaking The Story, The Panama Papers Bbc, The Panama Papers Bernie Sanders, The Panama Papers Bulgaria, The Panama Papers Bangladesh, Why Are The Panama Papers Bad, When Will The Panama Papers Be Released, Panama Paper China, The Panama Papers Clinton, The Panama Papers Canada, The Panama Papers Cnn, The Panama Papers Celebrities, The Panama Papers Conspiracy, The Panama Papers Complete List, The Panama Papers Cartoon, Bbc Panama Papers, The Panama Papers Embarrass China\u2019s Leaders, The Panama Papers Documentary, The Panama Papers Download, The Panama Papers Database, The Panama Papers Donald Trump, The Panama Papers Documents, The Panama Papers Details, The Panama Papers Definition, The Panama Papers Deutsch, The Panama Papers For Dummies, How Were The Panama Papers Discovered, The Panama Papers Explained, The Panama Papers Epub, The Panama Papers Embarrass China\u2019s Leaders, The Panama Papers Explained With Piggy Banks, The Panama Papers For Dummies, The Panama Papers Full List, The Panama Papers Fox News, How Were The Panama Papers Found, The Panama Papers Goodreads, The Panama Papers Guardian, The Panama Papers Greece, The Panama Papers Ghana, How Panama Papers Get Leaked, How Did The Panama Papers Get Leaked, The Panama Papers Here’s What We Know, The Panama Papers How To Hide A Billion Dollars, The Panama Papers Hillary, Who Leaked Panama Papers, The Panama Papers Imdb, The Panama Papers In Perspective, The Panama Papers Icij, The Panama Papers Indonesia, The Panama Papers India, The Panama Papers Iceland, The Panama Papers Ireland, The Panama Papers Interactive, The Panama Papers Indonesian, The Panama Papers Israel, The Panama Papers Jail, The Panama Papers Japan, The Panama Papers Kenya, The Panama Papers Leak, The Panama Papers List, The Panama Papers Libya, Panama Papers India List, The Panama Papers Sri Lanka, Are The Panama Papers Legal, The Panama Papers India List, Wikileaks Panama Papers, How Did The Panama Papers Leak, The Panama Papers Embarrass China\u2019s Leaders, The Panama Papers Movie, The Panama Papers Malaysia, The Panama Papers Morocco, Why The Panama Papers Matter, What The Panama Papers Mean, What Do The Panama Papers Mean, Why Do The Panama Papers Matter, The Panama Papers Netflix, The Panama Papers Names, The Panama Papers News, The Panama Papers New York Times, The Panama Papers Nyt, The Panama Papers Npr, The Panama Papers Najib, The Panama Papers Nz, The Panama Papers Nigeria, The Panama Papers Indian Names, The Panama Papers Obermayer, Panama Newspapers Online, The Panama Papers List Of Names, The Panama Papers Victims Of Offshore, How Were The Panama Papers Obtained, The Panama Papers Pdf, The Panama Papers Pulitzer, The Panama Papers Pakistan, The Panama Papers Pdf Download, The Panama Papers Putin, The Panama Papers Philippines, The Panama Papers Power Players, The Panama Papers Podcast, The Panama Papers Peru, The Panama Papers Portugal, The Panama Papers Que Es, The Panama Papers Review, The Panama Papers Reddit, The Panama Papers Reveal, Are The Panama Papers Real, When Were The Panama Papers Released, What Do The Panama Papers Reveal, What Did The Panama Papers Reveal, What Does The Panama Papers Reveal, The Panama Papers Scandal, The Panama Papers Search, The Panama Papers Secrets Of The Super Rich, The Panama Papers Summary, The Panama Papers South Africa, The Panama Papers Story, The Panama Papers Sri Lanka, The Panama Papers Singapore, The Panama Papers United States, The Panama Papers Are Super Awkward For Beijing, The Panama Papers Thailand, The Panama Papers Trump, The Panama Papers Tempo, The Panama Papers Thai, The Panama Papers Taiwan, The Panama Papers Toronto Star, The Panama Paper Trail, The Panama Papers 7 Things To Know, The Panama Papers A Torrential Leak, The Panama Papers How To Hide A Billion Dollars, Panama Papers Usa, The Panama Papers United States, The Panama Papers Us Politicians, The Panama Papers Us Names, Panama Papers Youtube, The Panama Papers What You Need To Know, The Panama Papers Victims Of Offshore, The Panama Papers Vice, The Panama Papers Vox, The Panama Papers Venezuela, The Panama Papers Wiki, The Panama Papers Wikileaks, The Panama Papers Website, The Panama Papers What You Need To Know, The Panama Papers Explained With Piggy Banks, The Panama Papers Here’s What We Know, How The Panama Papers Were Leaked, How The Panama Papers Work, How Do The Panama Papers Work, The Panama Papers Youtube, The Panama Papers New York Times, The Panama Papers What You Need To Know, The Panama Papers New Zealand, Zimbabweans In The Panama Papers







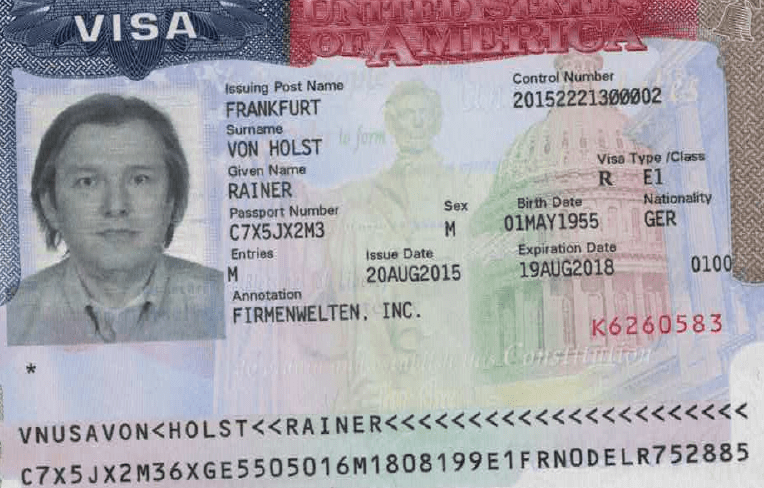

























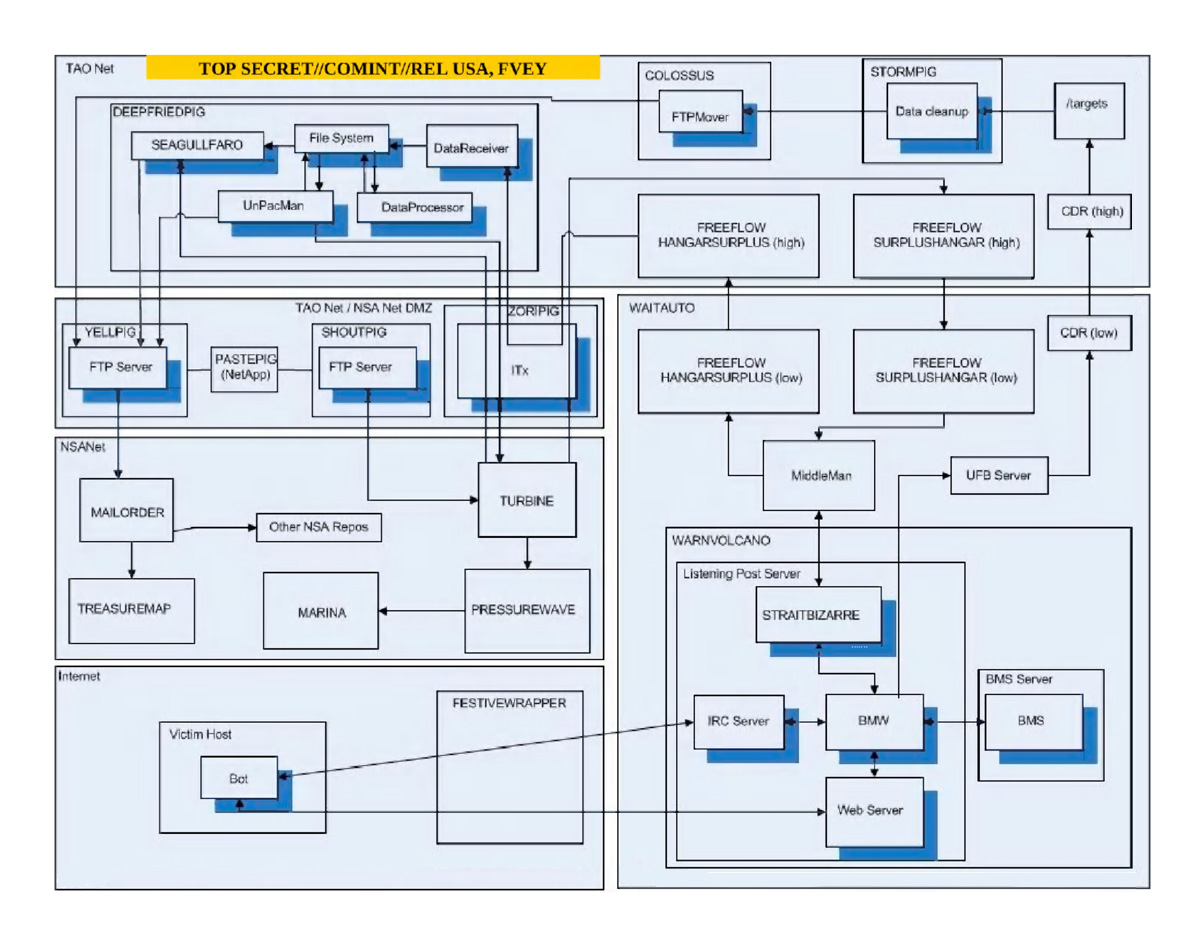




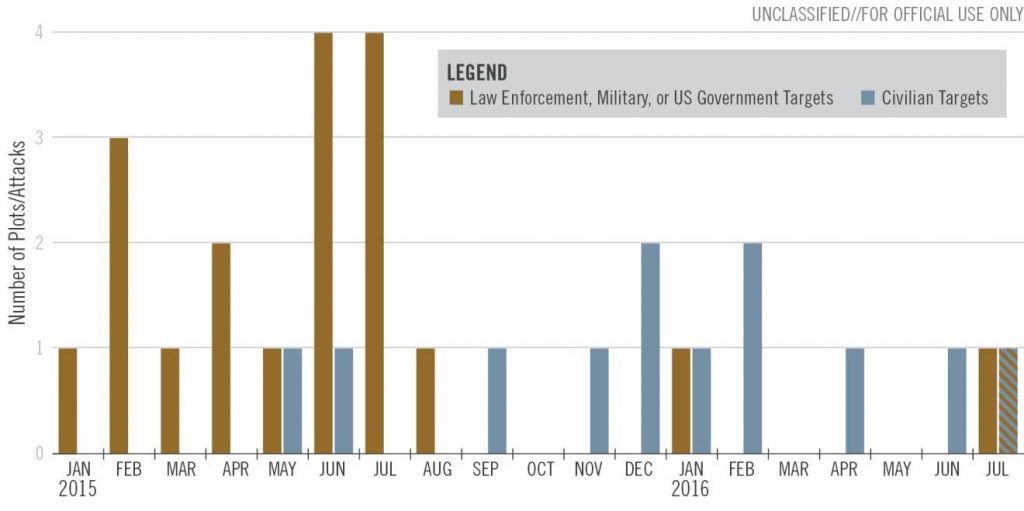




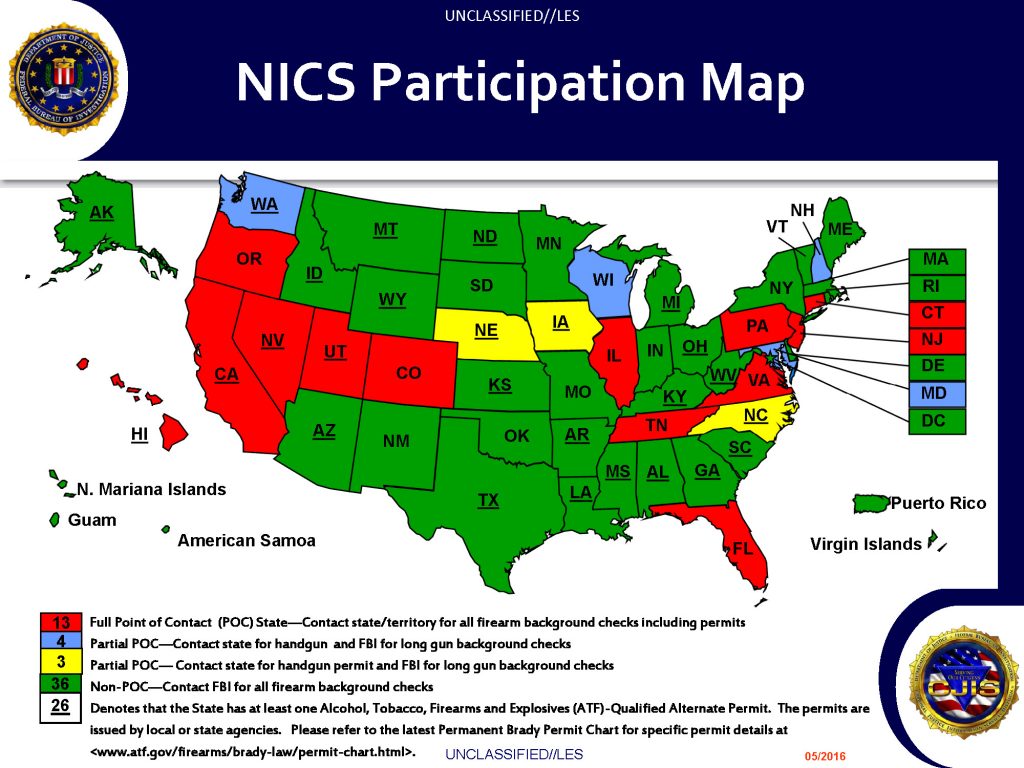

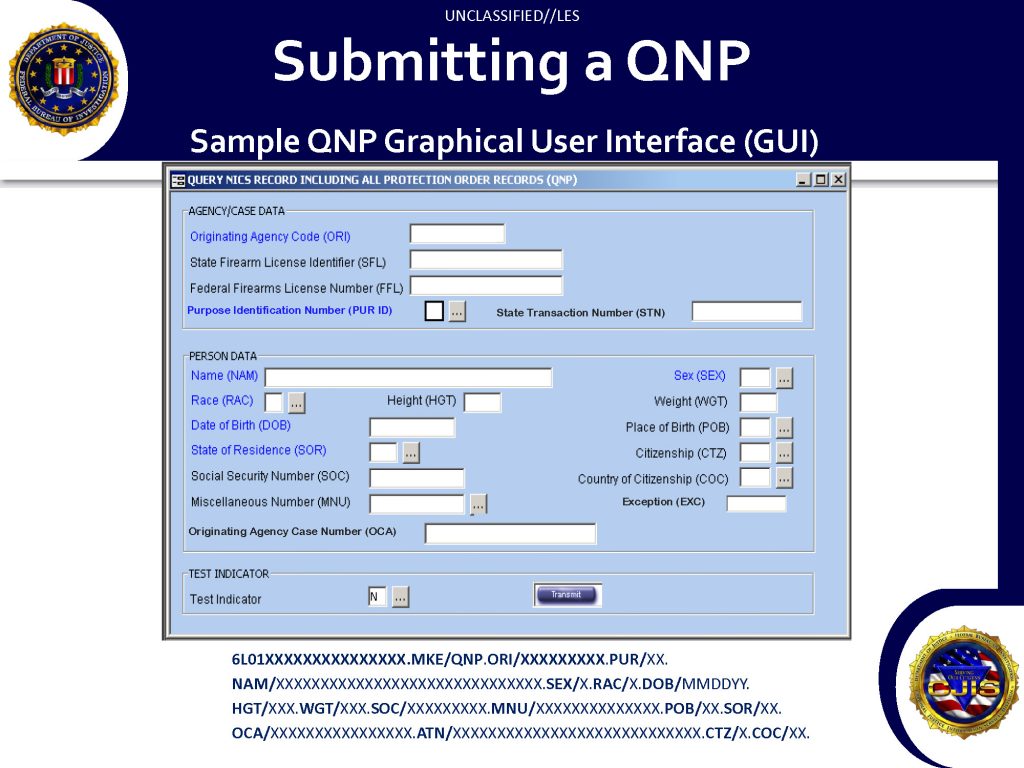
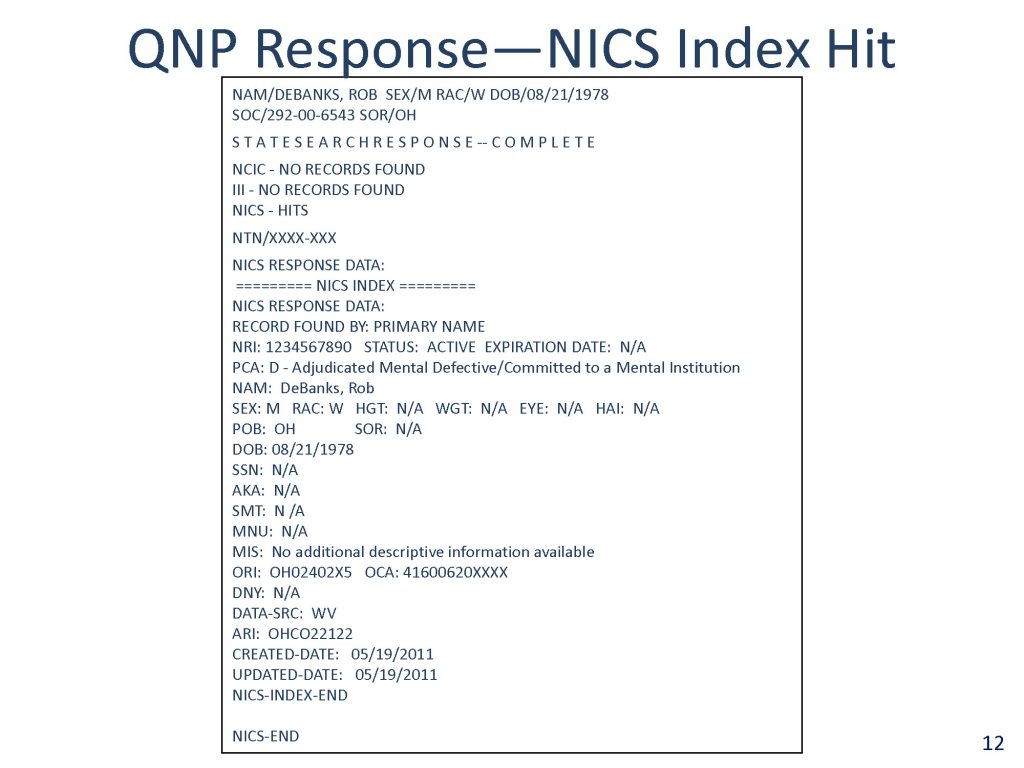



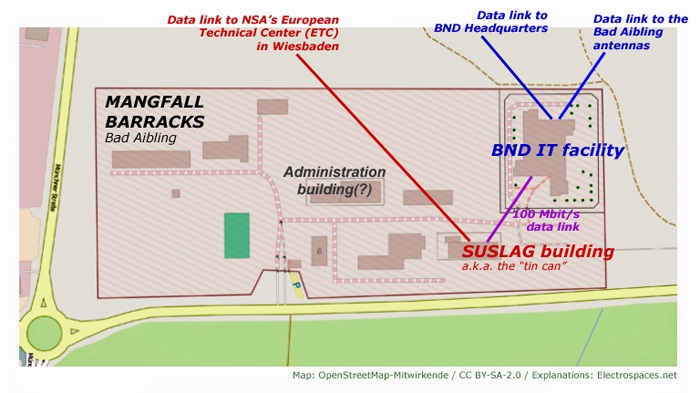
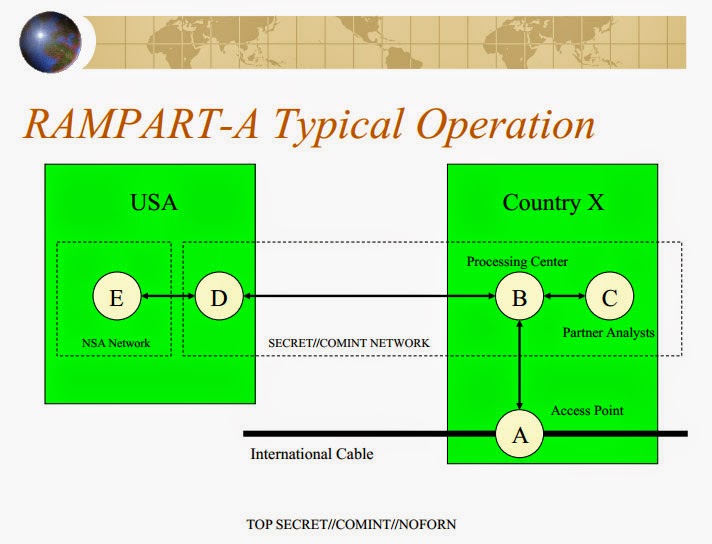
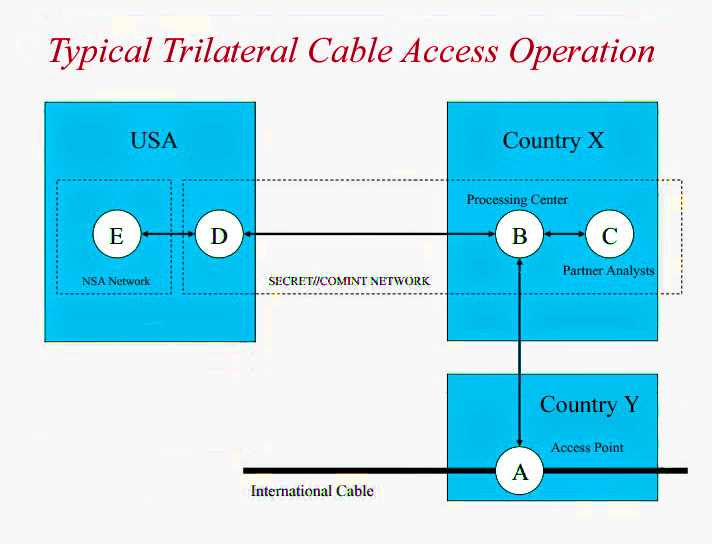
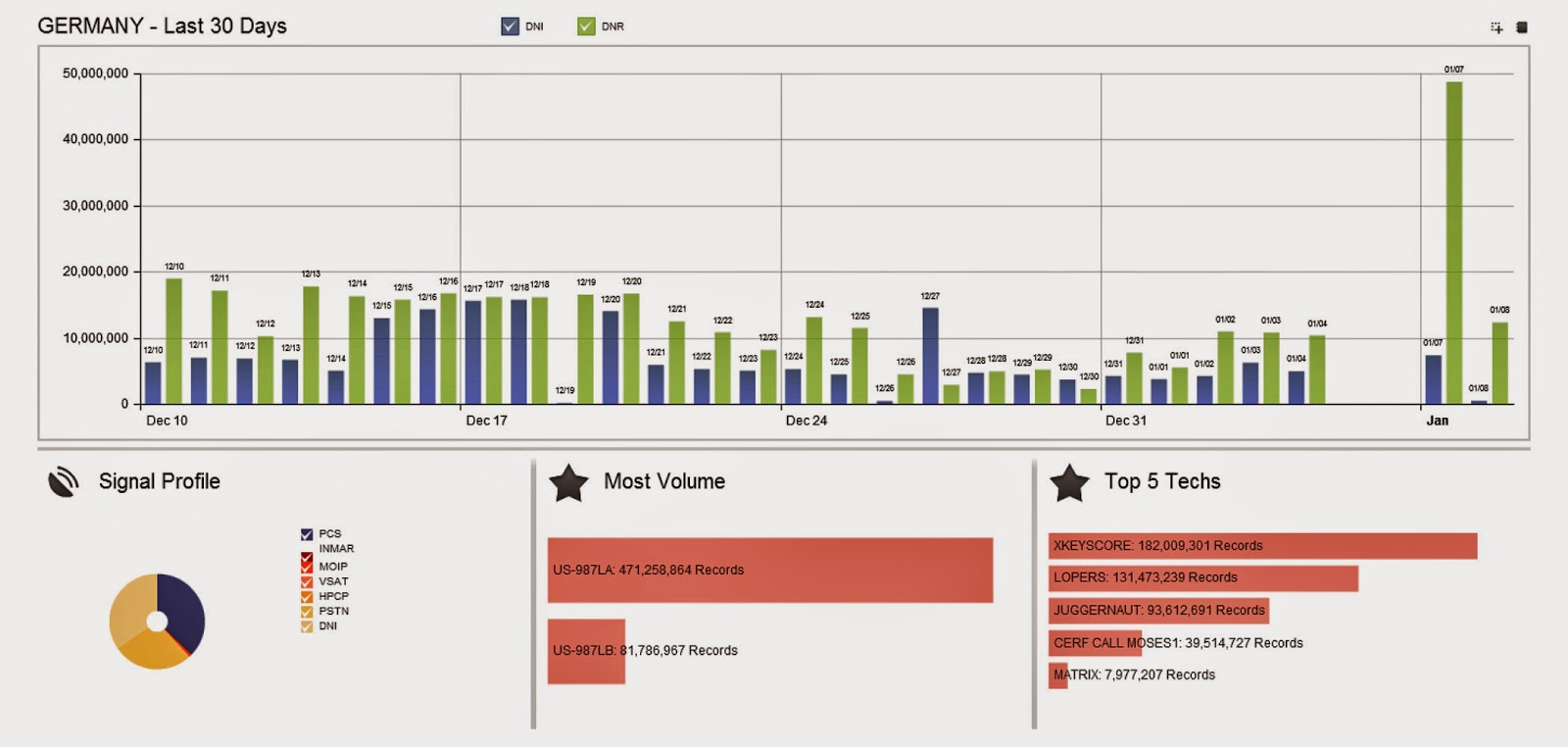
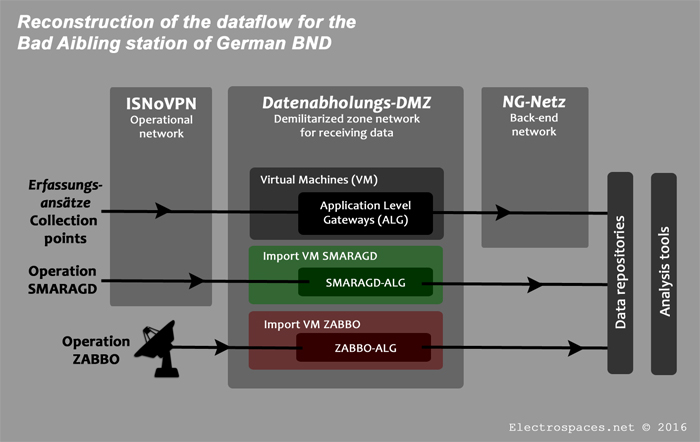
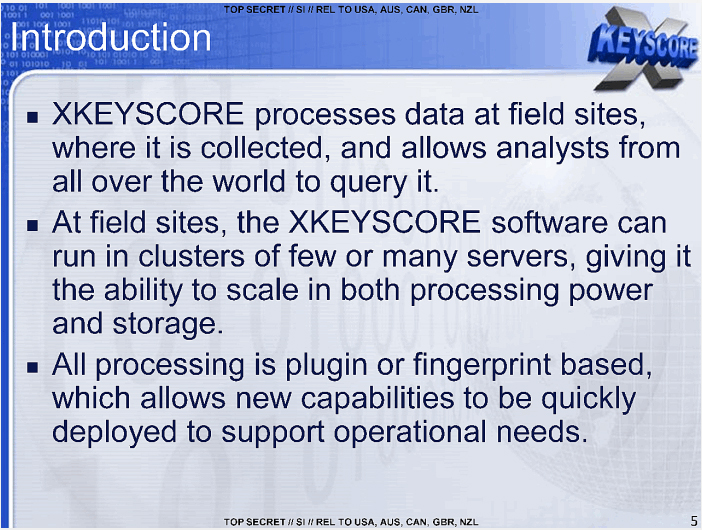
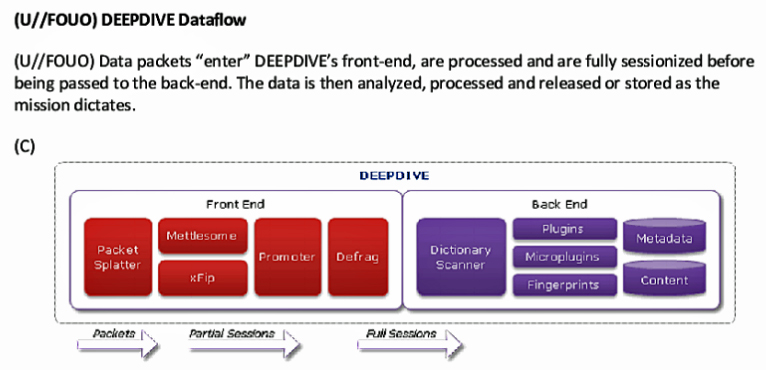

You must be logged in to post a comment.