
THE INVESTMENT – MAGAZINE – THE ORIGINAL – DAS INVESTMENT MAGAZIN – DAS ORIGINAL – Sehr geehrte Damen und Herren,
die Betrüger und durch uns inhaftierten Erpresser der GoMoPa versuchen mit einer gefälschten Presse-Mitteilung von sich abzulenken und einen investigativen Journalisten, Bernd Pulch, zu belasten.
Die Presse-Mitteilung auf pressreleaser.org ist eine Fälschung und die gesamte Webseite ist der GoMoPa zu zuordnen.
Hier noch einmal die tatäschlichen Geschehnisse:
Hier der Artikel von “GoMoPa” über Meridian Capital.
„GoMopa“ schreibt:08.09.2008
Weltweite Finanzierungen mit WidersprüchenDie Meridian Capital Enterprises Ltd. gibt an, weltweite Finanzierungen anbieten zu können und präsentiert sich hierbei auf aufwendig kreierten Webseiten. GOMOPA hat die dort gemachten Angaben analysiert und Widersprüche entdeckt.Der FirmensitzDer Firmensitz befindet sich laut eigener Aussage in Dubai, Vereinigte Arabische Emirate. In einem GOMOPA vorliegenden Schreiben der Meridian Capital Enterprises Ltd. heißt es jedoch, der Firmensitz sei in London. Auf der Homepage des Unternehmens taucht die Geschäftsadresse in der Londoner Old Broad Street nur als „Kundenabteilung für deutschsprachige Kunden“ auf. Eine weitere Adresse in der englischen Hauptstadt, diesmal in der Windsor Avenue, sei die „Abteilung der Zusammenarbeit mit Investoren“.Die Meridian Capital Enterprises ist tatsächlich als „Limited“ (Ltd.) mit Sitz in England und Wales eingetragen. Aber laut Firmenhomepage hat das Unternehmen seinen „rechtlichen Geschäftssitz“ in Dubai. Eine Abfrage beim Gewerbeamt Dubais (DED) zu dieser Firmierung bleibt ergebnislos.Bemerkenswert ist auch der vermeintliche Sitz in Israel. Auf der Webseite von Meridian Capital Enterprises heißt es: „Die Firma Meridian Capital Enterprises Ltd. ist im Register des israelischen Justizministeriums unter der Nummer 514108471, gemäß dem Gesellschaftsrecht von 1999, angemeldet.“ Hierzu Martin Kraeter, Gomopa-Partner und Prinzipal der KLP Group Emirates in Dubai: „Es würde keinem einzigen Emirati – geschweige denn einem Scheich auch nur im Traum einfallen, direkte Geschäfte mit Personen oder Firmen aus Israel zu tätigen. Und schon gar nicht würde er zustimmen, dass sein Konterfei auch noch mit vollem Namen auf der Webseite eines Israelischen Unternehmens prangt.“Auf der Internetseite sind diverse Fotos mit Scheichs an Konferenztischen zu sehen. Doch diese großen Tagungen und großen Kongresse der Meridian Capital Enterprises werden in den Pressearchiven der lokalen Presse Dubais mit keinem Wort erwähnt.
Martin Kraeter: „ Ein ‚britisch-arabisch-israelisches bankfremdes Finanzinstitut sein zu wollen, wie die Meridian Capital Enterprises Ltd. es darstellt, ist mehr als zweifelhaft. So etwas gibt es schlicht und ergreifend nicht! Der Nahostkonflikt schwelt schon seit mehr als 50 Jahren. Hier in den Vereinigten Arabischen Emiraten (VAE) werden Israelis erst gar nicht ins Land gelassen. Israelische Produkte sind gebannt. Es gibt nicht einmal direkte Telefonverbindungen. Die VAE haben fast 70% der Wiederaufbaukosten des Libanon geschultert, nachdem Israel dort einmarschiert ist.“
Zwei angebliche Großinvestitionen der Meridian Capital Enterprises in Dubai sind Investmentruinen bzw. erst gar nicht realisierte Projekte. Das Unternehmen wirbt mit ihrer finanziellen Beteiligung an dem Dubai Hydropolis Hotel und dem Dubai Snowdome.
Der Aktivitätsstatus der Meridian Capital Enterprises Ltd. ist laut englischen Handelsregister (UK Companies House) „dormant“ gemeldet. Auf der Grundlage des englischen Gesellschaftsrechts können sich eingetragene Unternehmen selbst „dormant“ (schlafend) melden, wenn sie keine oder nur unwesentliche buchhalterisch zu erfassende Transaktionen vorgenommen haben. Dies ist angesichts der angeblichen globalen Investitionstätigkeit der Meridian Capital Ltd. sehr erstaunlich.
Der Webauftritt
Die Internetseite der MCE ist sehr aufwendig gestaltet, die Investitionen angeblich in Millionen- und Milliardenhöhe. Bei näherer Betrachtung der Präsentationselemente fällt jedoch auf, dass es sich bei zahlreichen veröffentlichen Fotos, die Veranstaltungen der Meridian Capital Enterprises dokumentieren sollen, meist um Fotos von Online-Zeitungen oder frei zugänglichen Medienfotos einzelner Institutionen handelt wie z.B. der Börse Dubai.
Auf der Internetpräsenz befinden sich Videofilmchen, die eine frappierende Ähnlichkeit mit dem Werbematerial von NAKHEEL aufweisen, dem größten Bauträger der Vereinigten Arabischen Emirate. Doch den schillernden Videos über die berühmten drei Dubai Palmen „Jumeirah, Jebel Ali und Deira“ oder das Archipel „The World“ wurden offensichtlich selbstproduzierte Trailersequenzen der Meridian Capital Enterprises vorangestellt. Doch könnte es sich bei den Werbevideos um Fremdmaterial handeln.
Auch die auf der Webseite wahllos platzierten Fotos von bekannten Sehenswürdigkeiten Dubais fungieren als Augenfang für den interessierten Surfer mit eigenem Finanzierungswunsch. Bei einem Volumen von 10 Millionen Euro oder höher präsentiert sich die Meridian Capital Enterprises Ltd. als der passende Investitionspartner. Das Unternehmen verfügt weltweit über zahlreiche Standorte: Berlin, London, Barcelona, Warschau, Moskau, Dubai, Riad, Tel Aviv, Hong Kong und New York. Aber nahezu alle Standorte sind lediglich Virtual Offices eines global arbeitenden Büroservice-Anbieters. „Virtual Office“ heißt im Deutschen schlicht „Briefkastenfirma“. Unter solchen Büroadressen sollen laut Meridian Capital Enterprises ganze Kommissionen ansässig sein, alles zum Wohle des Kunden.“
Zitatende
Hier die Hintergründe der Erpressung:
http://www.immobilien-vertraulich.com/law/7154-opfer-nach-immovation-und-estavis-versucht-gomopa-nun-dkb-zu-erpressen-gomopa-hintermann-ra-resch.html
Hier unsere Original-Stellungnahme:
Anfang Oktober 2008 erhielt einer der Arbeiter der Meridian Capital Enterprises Ltd. eine Meldung von einem anonymen Sender, dass in naher Zukunft – zuerst im Internet, dann im Fernsehen, im Radio und in der deutschen Presse – Informationen erscheinen, die die Funktionsweise und Tätigkeiten der Meridian Capital Enterprises Ltd. in einem äußerst negativen Licht darstellen. Der Mitarbeiter der Meridian Capital Enterprises Ltd. wurde also informiert, dass diese Meldungen/Nachrichten zweifelsohne deutlich das Aussehen und den guten Ruf der Firma Meridian Capital Enterprises Ltd. beeinträchtigen.
Der an dieser Stelle erwähnte „Gesprächspartner” hat den Arbeiter der Meridian Capital Enterprises Ltd. informiert, dass die Möglichkeit besteht die peinliche Situation zu vermeiden, indem die Meridian Capital Enterprises Ltd. auf das von der Person gezeigte Konto die Summe von 100.000,00 EUR überweist. Wie sich aber später zeigte, war der Herr Klaus Maurischat – dieser anonyme Gesprächspartner – „Gehirn“ und „Lider des GOMOPA“. Die Ermittlungen wurden angestellt durch die Bundeskriminalpolizei (Verfolgungs- und Ermittlungsorgan auf der Bundesebene) während des Ermittlungsverfahrens wegen einer finanziellen Erpressung, Betrügereien auch wegen der Bedrohungen, welche von Herrn Maurischat und seine Mitarbeiter praktiziert wurden sowie wegen Teilnahme anderer (Leiter der Internetservices und Moderatoren der Blogs) an diesem Prozedere. Diese Straftaten wurden begangen zu Schaden vieler Berufs- und Justizpersonen, darunter auch der Meridian Capital Enterprises Ltd. Die Opfer dieses Verbrechens sind in Deutschland, Österreich, der Schweiz, Spanien, Portugal, Großbritannien, den USA und Kanada sichtbar.
In diesem Moment taucht folgende Frage auf: Wie war die Reaktion der Meridian Capital Enterprises Ltd. auf die Forderungen seitens GOMOPA? Entsprach die Reaktion den Erwartungen von GOMOPA? Hat die Meridian Capital Enterprises Ltd. die geforderte Summe 100.000,00 EUR überwiesen?
Seites der Meridian Capital Enterprises Ltd. gab es überhaupt keine Reaktion auf den Erpressungsversuch von GOMOPA. Ende August 2008 auf dem Service http://www.gompa.net sind zahlreiche Artikel/Meldungen erscheinen, welche die Tätigkeit der Meridian Capital Enterprises Ltd. in einem sehr negativen Licht dargestellt haben. Nachdem die auf http://www.gomopa.net enthaltenen Informationen ausführlich und vollständig analysiert worden waren, ergab es sich, dass sie der Wahrheit nicht einmal in einem Punkt entsprechen und potenzielle und bereits bestehende Kunden der Meridian Capital Enterprises Ltd. in Bezug auf die von diesem Finanzinstitut geführten Geschäftstätigkeit irreführen. Infolge der kriminellen Handlugen von GOMOPA und der mit ihm kooperierenden Services und Blogs im Netz hat die Meridian Capital Enterprises Ltd. beachtliche und messbare geschäftliche Verluste erlitten. Die Meridian Capital Enterprises Ltd. hat nämlich in erster Linie eine wichtige Gruppe von potenziellen Kund verloren. Was sich aber als wichtiger ergab, haben sich die bisherigen Kunden von der Meridian Capital Enterprises Ltd. kaum abgewandt. Diejenigen Kunden haben unsere Dienstleitungen weiterhin genutzt und nutzen die immer noch. In Hinblick auf die bisherige Zusammenarbeit mit der Meridian Capital Enterprises Ltd., werden ihrerseits dem entsprechend keine Einwände erhoben .
GOMOPA hat so einen Verlauf der Ereignisse genau prognostiziert, dessen Ziel beachtliche und messbare geschäftliche durch die Meridian Capital Enterprises Ltd. erlittene Verluste waren. Der Verlauf der Ereignisse hat das Service GOMOPA mit Sicherheit gefreut. GOMOPA hat nämlich darauf gerechnet, dass die Stellung der Meridian Capital Enterprises Ltd. nachlässt und das Finanzinstitut die geforderte Summe (100.000,00 EUR) bereitstellt. Im Laufe der Zeit, als das ganze Prozedere im Netz immer populärer war, versuchte GOMOPA noch vier mal zu der Meridian Capital Enterprises Ltd. Kontakte aufzunehmen, indem es jedes mal das Einstellen dieser kriminellen „Kompanie” versprochen hat, wobei es jedes mal seine finanziellen Forderungen heraufsetzte. Die letzte für das Einstellen der „Kompanie“ gegen die Meridian Capital Enterprises Ltd. vorgesehene Quote betrug sogar 5.000.000,00 EUR (in Worten: fünfmilionen EURO). Die Meridian Capital Enterprises Ltd. konnte sich aber vor den ständig erhöhenden Forderungen seitens des Services GOMOPA behaupten.
Im Oktober 2008 traf die Leitung der Meridian Capital Enterprises Ltd. Entscheidung über die Benachrichtigung der Internationalen Polizei INTERPOL sowie entsprechender Strafverfolgungsorgane der BRD (die Polizei und die Staatsanwaltschaft) über den bestehenden Sachverhalt. In der Zwischenzeit meldeten sich bei der Meridian Capital Enterprises Ltd. zahlreiche Firmen und Korporationen, sogar Berufsperson wie Ärzte, Richter, Priester, Schauspieler und anderen Personen aus unterschiedlichen Ländern der Welt, die der Erpressung von GOMOPA nachgegeben und die geforderten Geldsummen überwiesen haben. Diese Personen gaben bereits Erklärungen ab, dass sie dies getan haben, damit man sie bloß endlich „in Ruhe lässt” und um unnötige Probleme, Schwierigkeiten und einen kaum begründbaren Ausklang vermeiden zu können. Die Opfer dieses kriminellen Vorgehens haben die Meridian Capital Enterprises Ltd. über unterschiedliche Geldsummen, welche verlangt wurden, informiert.
In einem Fall gab es verhältnismäßig kleine (um ein paar tausend EURO), in einem anderen Fall handelte es schon um beachtliche Summen (rund um paar Millionen EURO).
Zusätzlich wendeten sich an die Meridian Capital Enterprises Ltd. Firmen, welche dem GOMOPA noch keine „Gebühr” überweisen haben und bereits überlegen, ob sie dies tun sollen, oder nicht. Diese Firmen erwarteten von der Meridian Capital Enterprises Ltd. eine klare Stellungnahme sowie eine professionelle praktische Beratung, wie man sich in solch einer Lage verhalten soll und wie man diese Geldforderungen umgehen kann. Die Meridian Capital Enterprises Ltd. hat ausnahmslos allen Verbrechensopfern, welche sich bei unserer Firma gemeldet haben, eine Zusammenarbeit vorgeschlagen. Als oberste Aufgabe stellt sich diese Kooperation, gemeinsam entschlossene und wirksame Maßnahmen gegen GOMOPA, gegen andere Services im Netz sowie gegen alle Bloggers zu treffen, die an dem hier beschriebenen internationalen kriminellen Vorgehen mit GOMOPA-Führung teilnehmen.Auf unsere Bitte benachrichtigten alle mitbeteiligten Firmen die Internationale Polizei INTERPOL sowie ihre heimischen Verfolgungsorgane, u. a. die zuständige Staatsanwaltschaft und die Polizeibehörden über den bestehenden Sachverhalt.
In Hinblick auf die Tatsache, dass das verbrecherische Handeln von GOMOPA sich über viele Staaten erstreckte und dass die Anzahl der in der Bundesrepublik Deutschland erstatteten Anzeigen wegen der durch GOMOPA, Internetservices und Bloggers begangenen Straftaten, rasant wuchs – was zweifelsohne von einer weit gehenden kriminellen Wirkungskraft des GOMOPA zeugt – schlug die Internationale Wirtschaftspolizei INTERPOL der Meridian Capital Enterprises Ltd. vor, dass sich ihr Vertreter in Berlin mit dem Vertreter von GOMOPA trifft, um die „Zahlungsmodalitäten“ und Überweisung der Summe von 5.000.000,00 EUR zu besprechen. Dieser Schritt meinte, eine gut durchdachte und durch die Bundeskriminalpolizei organisierte Falle durchzuführen, deren Ziel die Festnahme der unter GOMOPA wirkenden internationalen Straftäter war.
Die koordinierten Schritte und Maßnahmen der Meridian Capital Enterprises Ltd. und anderer Beschädigter, geleitet von der Internationalen Wirtschaftspolizei INTERPOL, dem Bundeskriminalamt und der Staatsanwaltschaft der Bundesrepublik Deutschland haben zur Aus-, Einarbeitung und Durchführung der oben beschriebenen Falle beigetragen. Im November 2008 führte die in Berlin vorbereitete Falle zur Festnahme und Verhaftung des Vertreters des GOMOPA, der nach der Festnahme auf Herrn Klaus Maurichat – als den Hauptverantwortlichen und Anführer der internationalen kriminellen Gruppe GOMOPA verwies. Der Festgenommene benannte und zeigte der Bundeskriminalpolizei zugleich den aktuellen Aufenthaltsort des Herrn Klaus Maurischat. „Gehirn“ und Gründer dieser internationalen kriminellen Gruppe GOMOPA, Herr Klaus Maurischat wurde am selben Tag auch festgenommen und auf Frist verhaftet, wird bald in Anklagezustand gestellt, wird die Verantwortung für eigene Straftaten und die des Forums GOMOPA vor einem zuständigen Bundesgericht tragen. Die Meridian Capital Enterprises Ltd. unternahm bereits alle möglichen Schritte, damit Herr Klaus Maurischat auch auf der Anklagebank des zuständigen Gerichts des Vereinigten Königsreiches Großbritannien erscheint. Unter den beschädigten Berufs- und Justizpersonen aus Großbritannien, neben der Meridian Capital Enterprises Ltd. gibt es noch viele Opfer von GOMOPA…
Die dreisten Verbrecher wagen es unter http://www.pressreleaser.org, einer eigenen “GoMoPa”-Seite unsere Pressemitteilung oben zu verfälschen und unschuldige Personen zu belasten.
“GoMoPa” Boss is Jochen Resch
May 15, 2011 – 1:15 pm
Posted in Uncategorized
Comments Off
Dear Readers,
after a thorough research we are sure that the real “GoMoPa” boss is Jochen Resch, lawyer in Berlin, Germany. He is the brain behind “GoMoPa” and responsable for blackmailing, extortion, racketeering, cybermurder and murder – in the tradition of the East German “Inteeligence” STASI that is why he called “GoMoPa” – Financial “Intelligence” Service .
Webmaster
Meridian Capital about GoMoPa
“GoMoPa” in detention
May 13, 2011 – 1:02 pm
Posted in Uncategorized
Comments Off
Meridian Capital Enterprises Ltd.. unveils new criminal phenomena in network. In recently appeared on the net more often at the same time a new a very worrying phenomenon of criminal nature. Professional criminals groups in the network are taking part, to extortion, fraud, Erschwindeln relating to certain specifically selected companies and businesses are capable of. These criminals developed new methods and means, simply and in a short time to bereichern.Strategien and manifestations, which underlie this process are fairly simple. A criminal is looking to “carefully” on the Internet specific companies and corporations (victims of crime) and informed them in the next step, that of the business activities of such companies and corporations in the near future – first on the Internet then in other available mass media – numerous and very unfavorable information appears. At the same time, the criminals beat their future victims an effective means of reducing unnecessary difficulties and problems to escape the loss of good name and image of the company and corporate sector. These offenders are aware of that reputation, name and appearance of each company is a value in itself. It was therefore a value of what each company is prepared to pay any price. But the reason for difficulties and problems arising from the loss of good name and reputation result. The criminals and their victims are already aware that this loss is devastating consequences might have been the closing down of a particular business can enforce. It takes both to No as well as at large companies regard. The company is concerned that in virtually every industry in each country and cross-border activities sind.Das criminal procedure in the form of a blackmail on money, a fraud is becoming rapidly and globally, ie led cross-border and internationally. Among the victims of extortion, fraud is now looking both at home (domestic) and international corporations, the major emphasis on conservation, keeping and maintaining their reputation in the business according to their credibility lay. The criminals in the network have understood that maintaining an unassailable reputation and name of a company the unique ability to provide fast and easy enrichment forms. The above-mentioned criminal procedure is difficult to track because it is international in nature, and by overlapping or even nonexistent (fictional) professional and judicial persons in various countries and operated company wird.Diese offenders in the network publish it and disseminate false information about your victims on remote servers, which are not uncommon in many exotic countries. There are those countries in which serious gaps in the legal system, investigative and prosecution procedures are visible. As an example, at this point mention India werden. Mit criminals working in the network grid portals known leader of blogs with your seat-consciously or unconsciously, even in highly developed countries. For example, at this point, countries such as Germany, Austria, Switzerland, the United States, Britain, Spain or Portugal are mentioned. The below listed criminals were able to act unpunished today. As a symptom of such action appears here the activity and “effectiveness” of the company GOMOPA, which is on countries such as Germany, Switzerland, Austria, the United States, Britain, Spain and India. A good example of such an action is Mr. Klaus Mauri Chat – the leader and “brain” of the company GOMOPA with many already in force and criminal judgments “on his account”, which in this way for years and funded its maintenance in the industry almost unlimited activity. This status will change dramatically, however, including far and wide thanks to discontinued operations of the firm Meridian Capital Enterprises Ltd.. who would oppose such offenses addressed in the network. Other companies and corporations, in which the crime network and outside of this medium have fallen victim to contribute to combating such crimes bei.Die situation is changing, thanks to effective steps and the successful cooperation of the firm Meridian Capital Enterprises Ltd.. with the international police Interpol, with the federal agency (FBI) in the U.S., the Federal Criminal Police in Germany, with Scotland Yard in Britain, as well as with the Russian secret service FSB.Die Meridian Capital Enterprises Ltd.. – Together with other companies and cooperations, the victim of criminal activities of the network of crime have fallen – has undeniably already started to yield results. The fact that in recent weeks (November 2008) on the territory of the Federal Republic of Germany of the above-mentioned leaders and “brain” of the company GOMOPA, Mr Klaus Maurishat was arrested should not be ignored. The Meridian Capital Enterprises Ltd.. information available results clearly show that the next arrests of persons participating in this process in such countries as: Austria, Switzerland, Russia, Ukraine, Poland, Spain, Mexico, Portugal, Brazil, the USA, Canada, UK, Ireland , Australia, New Zealand and made in a.. The ultimate goal of Meridian Capital Enterprises Ltd.. and the other victims of crime in the network is to provide all participants in this criminal procedure before the competent court to lead. All professional and judicial persons, regardless of the seat and out of the business, which the above-described criminal action (fraud, extortion) to have fallen victim can of Meridian Capital Enterprises Ltd.. led company to join the goal set at all at this point the procedure described those associated in the public and the economic life out. II blacklist blackmail and with international fraudsters and their methods (opus operandi) in the following countries: 1 The Federal Republic Deutschland2. Dubai 3rd Russia 1st The Federal Republic of Germany GmbH GOMOPA, Goldman Morgenstern & Partners LLC., Goldman Morgenstern & Partners Consulting LLC, Wottle collection. In these firms are quite active following persons: – Klaus Mauri Chat ( “Father” and “brain” of the criminal organization responsible for countless final judgments have been achieved (arrested in Germany in November 2008) – Josef Rudolf Heckel ( “right hand “when Mr Klaus Mauri chat, denounced former banker who is excessive in many Bankschmuggeleien was involved.
The study of 900 pages named Toxdat by Ehrenfried Stelzer is the “Stasi Killer Bible”. It lists all kind of murder methods and concentrates on the most effective and untraceable.
“The toxdat study was ordered by Stasi Vice-President Gerhard Neiber, the second man in rank after boss Erich Mielke. The toxdat study was also the theoretical “story book” for the murder of the famous German watchdog and journalist Heinz Gerlach by former Stasi member under the guidance of “GoMoPa”,” an informer stated. “Ehrenfried stelzer” was nicknamed “Professor Murder” by his victims. Even close co-worker now compare him with the German SS”doctor” Mengele, “Dr. Death” from Auschwitz.
Only two articles let the German audience believe that the famous journalist and watchdog Heinz Gerlach died on natural courses by blood pollution.
For more Information the victims have launched a new site: http://www.victims-opfer.com
The first one, published only hours after the death of Mr Heinz Gerlach by the notorious “GoMoPa” (see article below) and a second 3 days later by a small German local newspaper, Weserbergland Nachrichten.
Many people including the hostile Gerlach website “Akte Heinz Gerlach” doubted that this man who had so many enemies and friends would die of natural causes without any previous warning. Rumours occured that Mr. Gerlach’s doctor doubted natural courses at all. After many critical voices discussed the issue a small website of a small German local newspaper – which never before had reported about Mr. Heinz Gerlach and which is not even in the region of Mr Gerlachs home – published that Mr Gerlach died of blood pollution. Weserbergland-Nachrichten published a long article about the deadly consequences of blood pollution and did not even name the source of such an important statement. It claimed only that somebody of Gerlachs inner circle had said this. It is a proven fact that after the collpase of the Eastern German Communist Regime many former Communist propaganda agents went to regional newspapers – often in Western Germany like Günther Schabowski did the man who opened the “Mauer”.
The theatre stage was set: One day later the hostile Gerlach website “Akte Heinz Gerlach” took the agenda publishing that Mr Gerlach had died for natural causes without any further research at all.
This was done by a website which for months and months and months reported everything about Mr. Gerlach.
Furthermore a research proves that the technical details regarding the website hosting of this hostile website “Akte Heinz Gerlach” proves that there are common details with the hosting of “GoMoPa” and their affiliates as proven by the SJB-GoMoPa-victims (see http://www.sjb-fonds-opfer.com)
Insiders believe that the murderers of Mr. Heinz Gerlach are former members of the Eastern German Terror Organisation “Stasi” with dioxins. They also believe that “GoMoPa” was part of the plot. At “GoMoPa”’ a person named Siegfried Siewers was officialy responsible for the press but never appeared in public. “GoMoPa”-victims say that this name was a cameo for “GoMoPa” frontrunner Klaus Maurischat who is controlled by the Stasi Top Agent Ehrenfried Stelzner, Berlin.
Siegfried Sievers, a former Stasi member is responsible for the pollution of millions Germanys for many years with dioxins. This was unveiled at 5th of January 2011 by German prosecutors.
The victims say that Maurischat (probably also a Stasi cameo) and Sievers were in contact as Sievers acted as Stasi Agent and was in fact already a specialist in dioxins under the Communist Terror Regime in Eastern Germany.
Furthermore the Stasi Top Agent Ehrenfried Stelzer disguised as Professor for Criminal studies during the Communist Regime at the Eastern Berlin Humboldt University.
Background:
The man behind the Berlin lawyer Jochen Resch and his activities is Ehrenfried Stelzer, former Stasi Top officer in Berlin and “Professor for Criminal Studies” at the Eastern Berlin Humboldt University during the Communist regime, the SJB-GoMoPa-victims say (www.sjb-fonds-opfer.com) is responsable for the killing of German watchdog and journalist Heinz Gerlach.
These informations stem from various sources who were close to the criminal organization of GoMoPa in the last years. The SJB-GoMoPa say that the well-known German watchdog and journalist Heinz Gerlach was killed by former Stasi members with dioxins. Polychlorinated dibenzodioxins (PCDDs), or simply dioxins, are a group of organic polyhalogenated compounds that are significant because they act as environmental pollutants. They are commonly referred to as dioxins for simplicity in scientific publications because every PCDD molecule contains a dioxin skeletal structure. Typically, the p-dioxin skeleton is at the core of a PCDD molecule, giving the molecule a dibenzo-p-dioxin ring system. Members of the PCDD family have been shown to bioaccumulate in humans and wildlife due to their lipophilic properties, and are known teratogens, mutagens, and confirmed (avered) human carcinogens. They are organic compounds.
Dioxins build up primarily in fatty tissues over time (bioaccumulate), so even small exposures may eventually reach dangerous levels. In 1994, the US EPA reported that dioxins are a probable carcinogen, but noted that non-cancer effects (reproduction and sexual development, immune system) may pose an even greater threat to human health. TCDD, the most toxic of the dibenzodioxins, is classified as a Group 1 carcinogen by the International Agency for Research on Cancer (IARC).
In 2004, a notable individual case of dioxin poisoning, Ukrainian politician Viktor Yushchenko was exposed to the second-largest measured dose of dioxins, according to the reports of the physicians responsible for diagnosing him. This is the first known case of a single high dose of TCDD dioxin poisoning, and was diagnosed only after a toxicologist recognized the symptoms of chloracne while viewing television news coverage of his condition.
German dioxin scandal: In January 2011 about 4700 German farms were banned from making deliveries after tests at the Harles und Jentzsch plant in the state of Schleswig-Holstein showed high levels of dioxin. Again this incident appears to involve PCBs and not PCDDs at all. Dioxin were found in animal feed and eggs in many farms. The person who is responsible for this, Siegfried Sievert is also a former Stasi Agent. At “GoMoPa” the notorious Eastern-Berlin press agency (see article below) one of the henchmen acted under the name of “Siegfried Siewert”.
Further evidence for the killing of Mr.Heinz Gerlach is provided by the SJB-GoMoPa-victims by analyzing the dubious role of former Stasi-Top-agent Ehrenfried Stelzer, also a former “Professor for Crime Studies” under the Communist regime in Eastern Germany and the dubious role of “detective” Medard Fuchsgruber. Both are closely tied to the dubious “GoMoPa” and Berlin lawyer Jochen Resch.
According to the SJB-GoMoPa-victims is Berlin lawyer Jochen Resch the mastermind of the criminal organization “GoMoPa2. The victims state that they have a source inside “GoMoPa” who helped them discover the shocking truth. The so-called “Deep Throat from Berlin” has information that Resch had the idea to found the criminal organization “GoMoPa” and use non-existing Jewish lawyers named Goldman, Morgenstern & Partner as camouflage. Their “office” in Madison Avenue, New York, is a mailbox. This is witnessed by a German Ex-Patriot, a lawyer, whose father, Heinz Gerlach, died under strange circumstances.
Resch seems to use “GoMoPa” as an instrument to blackmail parts of the German Property and Investment.
German authorities are under growing pressure to reopen investigations into at least a dozen suspicious deaths after the arrest of an alleged East German assassin cast new light on the communist regime. Stasi victims quoted a source saying “isolated units” had conducted operations that were “extremely well organised” and had “100 per cent logistical support” from the East German state.
A statement from prosecutors read: “The accused [Jurgen G] is suspected, as a member of a commando of the former DDR, of killing a number of people between 1976 and 1987 who from the point of view of the DDR regime had committed treason or were threatening to do so.”
Details of his Jurgen G’s arrest have been described in suitably florid terms, with the mass circulation tabloid Bild saying he was working at the Wolfsbruch marina near Rheinsberg in north-eastern Germany when a woman approached him. “Excuse me, is that your yellow Trabant in the car park? I just ran into it with my car,” she is said to have asked.
When he followed her to the car park, masked officers jumped out of vans and bushes and overpowered him in an operation worthy of the Stasi itself.
An eyewitness told Bild: “They blindfolded him and raced off in an unmarked car.”
Police across Germany are reported to be sifting through files to see who the victims may have been, and some intelligence officers are greeting the arrest of Jurgen G as a breakthrough.
Thomas Auerbach, who works for the Stasi file authority in Berlin and has written a book based on the death squad files, said: “These people were trained to make such murders look like accidents or suicides, even as ‘ordinary’ crimes such as robberies. They were real terror experts.”
The cases said to be linked to Jurgen G or his unit include many people involved with the commercial arm of the East German ruling socialist party, the SED (Socialist Unity Party).
Uwe Harms, the head of a Hamburg-based haulage firm which was part of a network of companies secretly owned by the SED, disappeared in March 1987 after conversations with various DDR functionaries. Six weeks later, his body was found in a plastic bag.
Weeks before his death he told friends that he felt he was being followed. After reunification, one of the other SED company heads said Mr Harms had been liquidated for refusing to allow his firm to be used to transport arms into East Germany.
Dieter Vogel, a businessman who had been jailed for life for spying for the CIA, was found suffocated in his cell in the East German prison Bautzen on March 9, 1982. The fact that he was due to be taken to the West in a spy swap arrangement just a few weeks later cast doubt on the suicide theory.
He had passed the names of several Stasi moles to the BND, West Germany’s heavily penetrated counter-intelligence service.
The Christian Democrat Union politician Uwe Barschel, 43, was found dead by magazine reporters in his bathtub in a hotel room in Geneva in October, 1987. He died of poisoning, but rumours that he was involved somehow in arms deals and the Stasi have clung to the case.
One of the more high-profile and enduring mysteries is that of Lutz Eigendorf, an East German footballer from the Stasi-backed Dynamo Berlin.
He fled to the West in 1979 amid great publicity. Four years later, he died after crashing his car into a tree on a straight stretch of road with blood alcohol levels way over the limit. Witnesses who had seen him earlier in the evening said he had not been drinking.
Most controversial though is the suggestion that the assassination squad was linked to the murder of a Swedish television reporter and her friend in 1984.
Cats Falk and her friend Lena Graens went missing on Nov 19, 1984. Their bodies were fished out of a Stockholm canal six months later.
Reports suggested a three-man assassination squad killed them, spiking their drinks with drugs, putting them into their car and pushing it into the Hammarby canal.
Shortly before her death, Cats Falk had reportedly uncovered a deal between an arms dealer and an East German firm.
Germany has recently undergone a wave of nostalgia for all things East German, dubbed Ostalgie, with colourful television shows featuring former DDR stars such as the ice skater Katerina Witt talking wistfully about socialist pop music.
A reassessment may be coming in the wake of the revelations.
Victims: The DDR-STASI MURDER GANG “GoMOPa” in murderoplot against Joerg Berger
The Stasi Murder Gang of „GoMoPa“ was involved in many trials to kill the popular East German soccer trainer Joerg Berger, Stasi victims tell in postings on their hompage http://www.sjb-fonds-opfer.com. Berger stated before his early death in his biography that they tried to pollute him with arsenic.
Arsenic and many of its compounds are especially potent poisons. Many water supplies close to mines are contaminated by these poisons. Arsenic disrupts ATP production through several mechanisms. At the level of the citric acid cycle, arsenic inhibits lipoic acid which is a cofactor for pyruvate dehydrogenase; and by competing with phosphate it uncouples oxidative phosphorylation, thus inhibiting energy-linked reduction of NAD+, mitochondrial respiration and ATP synthesis. Hydrogen peroxide production is also increased, which might form reactive oxygen species and oxidative stress. These metabolic interferences lead to death from multi-system organ failure, probably from necrotic cell death, not apoptosis. A post mortem reveals brick red coloured mucosa, owing to severe haemorrhage. Although arsenic causes toxicity, it can also play a protective role.[
Elemental arsenic and arsenic compounds are classified as “toxic” and “dangerous for the environment” in the European Union under directive 67/548/EEC. The International Agency for Research on Cancer (IARC) recognizes arsenic and arsenic compounds as group 1 carcinogens, and the EU lists arsenic trioxide, arsenic pentoxide and arsenate salts as category 1 carcinogens.
Arsenic is known to cause arsenicosis owing to its manifestation in drinking water, “the most common species being arsenate [HAsO42- ; As(V)] and arsenite [H3AsO3 ; As(III)]”. The ability of arsenic to undergo redox conversion between As(III) and As(V) makes its availability in the environment more abundant. According to Croal, Gralnick, Malasarn and Newman, “[the] understanding [of] what stimulates As(III) oxidation and/or limits As(V) reduction is relevant for bioremediation of contaminated sites (Croal). The study of chemolithoautotrophic As(III) oxidizers and the heterotrophic As(V) reducers can help the understanding of the oxidation and/or reduction of arsenic.
Treatment of chronic arsenic poisoning is easily accomplished. British anti-lewisite (dimercaprol) is prescribed in dosages of 5 mg/kg up to 300 mg each 4 hours for the first day. Then administer the same dosage each 6 hours for the second day. Then prescribe this dosage each 8 hours for eight additional days. However the Agency for Toxic Substances and Disease Registry (ATSDR) states that the long term effects of arsenic exposure cannot be predicted. Blood, urine, hair and nails may be tested for arsenic, however these tests cannot foresee possible health outcomes due to the exposure. Excretion occurs in the urine and long term exposure to arsenic has been linked to bladder and kidney cancer in addition to cancer of the liver, prostate, skin, lungs and nasal cavity.[
Occupational exposure and arsenic poisoning may occur in persons working in industries involving the use of inorganic arsenic and its compounds, such as wood preservation, glass production, nonferrous metal alloys and electronic semiconductor manufacturing. Inorganic arsenic is also found in coke oven emissions associated with the smelter industry.
THE DDR GESTAPO-STASI MURDER GANG responsable for the murder of Lutz Eigendorf
The talented Eigendorf played for East German side Dynamo Berlin.
He made his debut for the GDR in an August 1978 match against Bulgaria, immediately scoring his first two goals in a 2–2 draw. He went on to collect six caps, scoring three goals.[1] His final international was a February 1979 friendly match against Iraq.
On 20 March 1979, after a friendship match between Dynamo and West German club 1. FC Kaiserslautern in Gießen he fled to the west hoping to play for that team. But because of his defection he was banned from play for one year by UEFA and instead spent that time as a youth coach with the club.
This was not the first time an East German athlete had fled to the west, but it was a particularly embarrassing defection. Eigendorf’s club Dynamo was under the patronage of the Stasi, East Germany’s secretive state police, and subject to the personal attentions of the organisation’s head, Erich Mielke. He ensured that the club’s roster was made up of the country’s best players, as well as arranging for the manipulation of matches in Dynamo’s favour. After his defection Eigendorf openly criticised the DDR in the western media.
His wife Gabriele remained behind in Berlin with their daughter and was placed under constant police surveillance. Lawyers working for the Stasi quickly arranged a divorce and the former Frau Eigendorf re-married. Her new husband was eventually revealed as a Lothario – an agent of the state police whose role it was to spy on a suspect while romancing them.
In 1983 Eigendorf moved from Kaiserslautern to join Eintracht Braunschweig, all the while under the scrutiny of the Stasi who employed a number of West Germans as informants. On 5 March that year he was badly injured in a suspicious traffic accident and died within two days. An autopsy indicated a high blood alcohol level despite the testimony of people he had met with that evening indicating that Eigendorf had only a small amount of beer to drink.
After German re-unification and the subsequent opening of the files of the former East Germany’s state security service it was revealed that the traffic accident had been an assassination attempt orchestrated by the Stasi, confirming the longtime suspicions held by many. A summary report of the events surrounding Eigendorf’s death was made on German television on 22 March 2000 which detailed an investigation by Heribert Schwan in the documentary “Tod dem Verräter” (“Death to the Traitor”).
On 10 February 2010, a former East German spy revealed the Stasi ordered him to kill Eigendorf, which he claimed not to have done
MfS has been accused of a number of assassinations against political dissidents and other people both inside and outside the country. Examples include the East German football player Lutz Eigendorf and the Swedish journalist Cats Falck.
The terrorists who killed Alfred Herrhausen were professionals. They dressed as construction workers to lay a wire under the pavement of the road along Mr. Herrhausen’s usual route to work. They planted a sack of armor-piercing explosives on a parked bicycle by the roadside. An infrared beam shining across the road triggered the explosion just when the limousine, one of three cars in a convoy, sped by.
The operation, from the terrorists’ point of view, was flawless: Mr. Herrhausen, the chairman of one of Europe’s most powerful companies, Deutsche Bank, was killed in the explosion along that suburban Frankfurt road on Nov. 30, 1989.
But was everything what it seemed?
Within days, the Red Army Faction — a leftist terrorist group that had traumatized West Germany since 1970 with a series of high-profile crimes and brazen killings of bankers and industrialists — claimed responsibility for the assassination. An intense manhunt followed. In June 1990, police arrested 10 Red Army Faction members who had fled to East Germany to avoid arrest for other crimes. To the police’s surprise, they were willing to talk. Equally confounding to authorities: All had solid alibis. None was charged in the Herrhausen attack.
Now, almost two decades later, German police, prosecutors and other security officials have focused on a new suspect: the East German secret police, known as the Stasi. Long fodder for spy novelists like John le Carré, the shadowy Stasi controlled every aspect of East German life through imprisonment, intimidation and the use of informants — even placing a spy at one point in the office of West German Chancellor Willy Brandt.
According to documents reviewed by The Wall Street Journal, the murders of Mr. Herrhausen and others attributed to the Red Army Faction bear striking resemblance to methods and tactics pioneered by a special unit of the Stasi. The unit reported to Stasi boss Erich Mielke and actively sought in the waning years of the communist regime to imitate the Red Army Faction to mask their own attacks against prominent people in Western Germany and destabilize the country.
“The investigation has intensified in recent months,” said Frank Wallenta, a spokesman for the Federal Prosecutor. “And we are investigating everything, including leads to the Stasi.”
If those leads turn out to be true, it would mean not only rewriting some of the most dramatic episodes of the Cold War, but would likely accelerate a broader soul-searching now under way in Germany about the communist past.
In building a reunified country, many Germans have ignored discussion of the brutal realities of its former communist half. When the former East Germany is discussed, it’s often with nostalgia or empathy for brothers hostage to Soviet influence.
Stasi boss Erich Mielke, middle, with unnamed associates
That taboo is slowly being broken. Last year’s Oscar-winning movie, “The Lives of Others,” chronicled in dark detail a Stasi agent’s efforts to subvert the lives of ordinary people. Material in the Stasi archives shows that senior leaders had a shoot-to-kill order against those fleeing from East to West — a controversial order that contradicts East German leaders’ claims that they never ordered any shootings.
This story is based on more than a dozen interviews with police, prosecutors and other security officials. Several policemen and prosecutors confirmed that the allegation of extensive Stasi involvement with the Red Army Faction is a key part of the current investigation.
Court cases in West Germany in the 1990s established that members of the Red Army Faction were granted free passage to other countries in the 1970s and refuge in East Germany in the 1980s. But the current investigation and documents from Stasi archives suggest far deeper involvement — that members of the Red Army Faction were not only harbored by the Stasi but methodically trained in sophisticated techniques of bombing and murder.
Traudl Herrhausen, Mr. Herrhausen’s widow, is one of those pushing for further investigation. She says she long suspected involvement by the Stasi or other intelligence service such as the KGB, but never spoke publicly because she didn’t have evidence and didn’t want to interfere in the investigation. She says she is now breaking an 18-year silence in her desire to see justice done. “Now I want to look my husband’s killers in the eye,” she said in an interview.
The Red Army Faction was founded about 1970 by a band of leftists who justified their terrorism based on opposition to West Germany’s ruling elite. Killing members of this elite would provoke the West German state to take repressive measures that would show its true fascist face, Red Army Faction leaders believed.
In its early years, the group, also known as the Baader-Meinhof band, made headlines with prison breaks, bank robberies, bomb attacks and deadly shootouts. Four gang members led by Ulrike Meinhof freed Red Army Faction leader Andreas Baader from a Berlin jail a month after his arrest.
Red Army Faction violence in West Germany intensified in 1977 when Jürgen Ponto, then head of Dresdner Bank, was shot and killed at his home. Five weeks later, the group killed four people and abducted the chairman of the German employer association, Hans-Martin Schleyer, one of West Germany’s most prominent businessmen. It was the start of a six-week ordeal in which neither government nor terrorists would compromise. To support the Red Army Faction cause, Palestinian terrorists hijacked a Lufthansa jet in Spain, forcing it to land in Mogadishu, Somalia. After the plane was rushed by West German commandos, top Red Army Faction leaders in West Germany committed suicide and Mr. Schleyer was executed by his captors.
Red Army Faction violence began to abate in the late 1970s after the Lufthansa incident. Many in Germany thought the group — whose attacks were often crude — lost its will to kill after the arrest of its senior leaders in 1982. So when the group appeared to renew its terror campaign with a series of high-profile attacks in 1985, police were stunned by the level of their sophistication and determination.
This time, the group dazzled police with its ability to hit targets and leave little substantial evidence behind. They used high-tech devices no one thought they possessed. Their marksmen killed with military precision.
Weapons used by terrorists during the 1977 kidnapping of German industrialist Hanns-Martin Schleyer.
Surprisingly, members of the Red Army Faction so-called third generation had a policeman’s understanding of forensic science. From 1985 onward, the Red Army Faction rarely left a fingerprint or other useful piece of evidence at a crime scene, according to court records. The murder cases from this era are still open. Some suspected Stasi involvement, but no one could ever prove it, according to a senior police official.
The 1989 car-bomb murder of Mr. Herrhausen particularly stunned police with its audacity and sophistication. Mr. Herrhausen was the head of Deutsche Bank, Germany’s largest bank. He was part of the political-business elite that helped turn West Germany from a war-ravaged rump state into an economic powerhouse — all while East Germany languished in frustration. Mr. Herrhausen was a vocal proponent of a united Germany.
In November 1989, Mr. Herrhausen was following the fall of the Berlin wall and events in the Soviet Union closely, conferring frequently with Mikhail Gorbachev, according to his wife and friends. Then on Nov. 27, Mr. Herrhausen announced a plan to acquire the investment banking firm Morgan Grenfell — at the time a record-breaking bank acquisition.
Also during November, a spot along Mr. Herrhausen’s usual route to work was closed because of construction. Terrorists, dressed as construction workers, laid an electric wire under the road’s pavement. On Nov. 29, the stretch reopened.
On the morning of Nov. 30, like every workday morning, Mr. Herrhausen stepped into his limousine at about 8:30. Mr. Herrhausen’s driver waited about one minute to allow the first of the three-car entourage to drive ahead and survey the road.
“It was the route they hadn’t used in weeks,” Mrs. Herrhausen said.
As Mr. Herrhausen sped down the road, a team of terrorists waited. Beside the road, a parked bicycle held a sack of armor-piercing explosives. The detonator was connected by the electric wire under the road to a trigger activated by an interruption in an infrared beam shining across the road.
A terrorist activated the detonator after the first car of bodyguards drove past the bomb. Mr. Herrhausen died at the scene.
As they had during previous attacks, police set up dragnets to round up Red Army Faction cadre. But the June 1990 arrests of 10 members of the group who had earlier been granted political asylum in East Germany produced no leads. All the seized Red Army Faction members had solid alibis.
In July 1991, prosecutors believed they had a breakthrough when an informant claimed he had allowed two members of the Red Army Faction to stay at his home near the Herrhausen residence. Prosecutors followed that trail 13 years before dropping charges in 2004.
Frustrated with the inability of prosecutors to solve the Herrhausen case and believing that prosecutors were ignoring other leads including possible Stasi involvement, German officials replaced the prosecutor overseeing the case.
Police acknowledge that part of the reason for their focus on possible Stasi involvement was that all other leads had dried up. But they say they also knew that over the years the Stasi had worked with and given explosives to other terrorists, including “Carlos the Jackal” and the Basque group ETA in Spain. And in 2001 to 2003, an undercover police officer met with a man who claimed he had been a killer for the Stasi operating in Western Germany, although police were never able to tie him to specific murders.
German investigators turned their attention to Wartin, a small eastern German village nestled in yellow-brown fields of grain near the Polish border. Today, sheep graze in a field spotted with wooden posts.
In the 1980s, however, Wartin was home to the Stasi’s AGM/S — “Minister Working Group/Special Operations.” It got its name because it reported to Mr. Mielke, the minister who headed the Stasi for almost all of East Germany’s 40-year history.
The Wartin unit’s peacetime duties included the kidnapping and murder of influential people in the West, according to Stasi records reviewed by The Wall Street Journal in the Stasi archives in Berlin.
The documents say the unit’s activities included “intimidating anti-communist opinion leaders” by “liquidation,” and “kidnapping or hostage taking, connected with the demand that political messages be read,” according to a description of the unit’s activities written by a senior Wartin official in 1982.
Based on these documents, German investigators increasingly believe that the Stasi played a more active role than previously believed in Red Army Faction terrorism. After years of not being able to draw parallels between the Stasi unit in Wartin and the Red Army Faction killings, police are now focusing closely on such a link. Joachim Lampe, who assisted the successful prosecution of the first wave of Red Army Faction terrorists up until 1982 and was then assigned to prosecute Stasi-related crimes in West Germany, says it’s time to compare the activities of Wartin with the activities of the Red Army Faction to see where they overlap. “It is an important line of investigation,” he said.
A year after the Red Army Faction’s first generation collapsed in 1972, an internal Wartin report said cooperation with terrorists is possible if the individuals could be trusted to maintain secrecy and obey orders. Initial contacts, however, may not have taken place until later in the decade. Disillusionment gripped many of the terrorists living on the lam, according to court records citing witness statements by accused terrorists. Beginning about 1980, the Stasi granted refuge to 10 members of the Red Army Faction in East Germany and gave them assumed identities.
The Stasi sympathized with the anti-capitalist ideals of the Red Army Faction, but Stasi leaders were concerned about placing their trust in a group of uncontrollable leftist militants, a review of Stasi records shows. Stasi officials did not want to tarnish East Germany’s international reputation, so they toyed with different concepts for cooperation with terrorist groups, according to a prosecutor who has investigated Stasi involvement with terrorism.
One suggestion, contained in a document prepared for new officers assigned to the unit, was to emulate Romanian intelligence, which successfully worked with the terrorist “Carlos” to bomb the Radio Free Europe office in Munich, Germany, in 1981. To assist in such operations, the Wartin unit developed highly specialized explosives, poisons and miniature firearms.
About 1980 the Stasi also proposed a second strategy: instead of using a terrorist group directly — such cooperation always contained risk of discovery — they could simply execute attacks so similar to those of known terrorists that police would never look for a second set of suspects, according to Wartin records. The Wartin leadership called this strategy the “perpetrator principle,” according to Stasi records. The unit’s progress in implementing the steps to imitate terrorist attacks is described in a series of progress reports by Wartin officials between 1980 and 1987.
In September 1981, Red Army Faction terrorists attempted to kill U.S. Gen. James Kroesen in Heidelberg, Germany, shooting a bazooka at his car. About the same time, members of the same Red Army Faction team visited East Germany, where they were asked by the Stasi to shoot a bazooka at a car containing a dog. The dog died, according to court records.
In Wartin, officials wrote up a detailed description of the Red Army Faction members’ re-enactment of the Kroesen attack. “It is important to collect all accessible information about the terrorist scene in imperialist countries, to study and analyze their equipment, methods and tactics, so we can do it ourselves,” a senior Wartin official wrote in February 1982, according to the report.
In 1982, West German police discovered two troves of Red Army Faction weapons and documents buried in German forests. Three terrorists, including Red Army Faction leader Christian Klar, were arrested when they approached the sites. The troves were buried in locations easy to find at night, a tactic used by Wartin’s own agents to store operational equipment in West Germany, according to an investigator who viewed the troves and Stasi records.
That same year, a Wartin official described the staged bombing of a moving vehicle. According to the report, several Stasi officers shed “tears of joy” when electronic sensors detected the approaching car and ignited the detonator.
A spokesman at Germany’s federal police investigative agency, the equivalent of the U.S. Federal Bureau of Investigation, declined to comment on the close similarity between the detonator used in the demonstration and the device that killed Mr. Herrhausen, saying this is part of their investigation.
Wartin officers continued their preparations for imitating terrorist attacks in West Germany, according to a 1985 internal Wartin report. They created a special archive profiling the characteristics of known terrorists and terrorist groups, and taught staff members to execute nearly identical attacks, according to Stasi records. Each year, the unit’s officers detailed the unit’s success in teaching these techniques in their annual reports, according to the reports.
Then, in 1987, the AGM/S stopped offensive operations. The unit was disbanded.
Werner Grossmann, a former three-star Stasi General and former head of foreign intelligence operations, says the AGM/S was responsible for planning attacks in West Germany, but was dissolved “because it didn’t produce results.” Mr. Grossmann assumed control of part of the AGM/S after most of the unit was dissolved.
Mr. Grossmann says he took control of part of the AGM/S because he wanted to run intelligence operations against West Germany’s civil defense infrastructure.
“I refused to have anything to do with terrorism and terrorists,” Mr. Grossmann said in an interview. He said he didn’t have any influence over the AGM/S activities before 1987 and wasn’t informed about the unit’s activities before it came under his control.
Olaf Barnickel, a career Stasi officer who served at Wartin, says his unit planned murders in West Germany, but never committed one. “It was all theory and no practice,” Mr. Barnickel said in an interview.
But some German police are unpersuaded. They believe the seeds may have been planted for future violent attacks.
In November 1989, as East Germany disintegrated, groups of citizens forced their way into Stasi installations, seizing control. In Wartin, a local church minister led a group of demonstrators to the main entrance of the Stasi base. The base closed.
Within the Stasi as a whole, the chain of command began to disintegrate. Links to organizations in West Germany, including the Red Army Faction, were broken.
Sixteen months after Mr. Herrhausen’s murder, the Red Army Faction claimed its last victim, killing Detlev Karsten Rohwedder, the head of the Treuhandanstalt, the powerful trust that controlled most state-owned assets in the former East Germany and was overseeing their privatization. Mr. Rohwedder was killed while he was standing by the window of his house in Düsseldorf.
The murder was performed by a trained sharpshooter, according to a police official familiar with the investigation. The Stasi trained members of the Red Army Faction in sharpshooting skills and had its own teams of sharpshooters, according to witness statements by Stasi officials to a Berlin prosecutor and Stasi records.
In 1998, the Red Army Faction issued the last of its communiques, announcing it was disbanding. German police attribute the group’s disappearance to changing times, which made the group seem a relic of the past. Indeed, the Red Army Faction today is largely seen by the German public as part of the social upheaval that plagued West Germany in the 1970s and 1980s. More than one in four Germans consider former Red Army Faction members to have been misguided idealists. More than half now think the investigations should be closed for good in the coming decade when the current group of Red Army Faction prisoners finish serving their prison sentences.
German prosecutors say their investigation of the Stasi’s role is continuing.
Since last month, Mrs. Herrhausen has been in contact with the next of kin of victims in the other unsolved Red Army Faction murder cases, looking for support to push the investigation. The bomb that killed her husband nearly 18 years ago exploded soon after he left for work, within earshot of their home in suburban Frankfurt.
“I still hear that bomb every day,” she says.
Only two articles let the German audience believe that the famous journalist and watchdog Heinz Gerlach died on natural courses by blood pollution.
The first one, published only hours after the death of Mr Heinz Gerlach by the notorious “GoMoPa” (see article below) and a second 3 days later by a small German local newspaper, Weserbergland Nachrichten.
Many people including the hostile Gerlach website “Akte Heinz Gerlach” doubted that this man who had so many enemies and friends would die of natural causes without any previous warning. Rumours occured that Mr. Gerlach’s doctor doubted natural courses at all. After many critical voices discussed the issue a small website of a small German local newspaper – which never before had reported about Mr. Heinz Gerlach and which is not even in the region of Mr Gerlachs home – published that Mr Gerlach died of blood pollution. Weserbergland-Nachrichten published a long article about the deadly consequences of blood pollution and did not even name the source of such an important statement. It claimed only that somebody of Gerlachs inner circle had said this. It is a proven fact that after the collpase of the Eastern German Communist Regime many former Communist propaganda agents went to regional newspapers – often in Western Germany like Günther Schabowski did the man who opened the “Mauer”.
The theatre stage was set: One day later the hostile Gerlach website “Akte Heinz Gerlach” took the agenda publishing that Mr Gerlach had died for natural causes without any further research at all.
This was done by a website which for months and months and months reported everything about Mr. Gerlach.
Furthermore a research proves that the technical details regarding the website hosting of this hostile website “Akte Heinz Gerlach” proves that there are common details with the hosting of “GoMoPa” and their affiliates as proven by the SJB-GoMoPa-victims (see http://www.sjb-fonds-opfer.com)
Insiders believe that the murderers of Mr. Heinz Gerlach are former members of the Eastern German Terror Organisation “Stasi” with dioxins. They also believe that “GoMoPa” was part of the plot. At “GoMoPa”’ a person named Siegfried Siewers was officialy responsible for the press but never appeared in public. “GoMoPa”-victims say that this name was a cameo for “GoMoPa” frontrunner Klaus Maurischat who is controlled by the Stasi Top Agent Ehrenfried Stelzner, Berlin.
Siegfried Sievers, a former Stasi member is responsible for the pollution of millions Germanys for many years with dioxins. This was unveiled at 5th of January 2011 by German prosecutors.
The victims say that Maurischat (probably also a Stasi cameo) and Sievers were in contact as Sievers acted as Stasi Agent and was in fact already a specialist in dioxins under the Communist Terror Regime in Eastern Germany.
Furthermore the Stasi Top Agent Ehrenfried Stelzer disguised as Professor for Criminal studies during the Communist Regime at the Eastern Berlin Humboldt University.
Background:
The man behind the Berlin lawyer Jochen Resch and his activities is Ehrenfried Stelzer, former Stasi Top officer in Berlin and “Professor for Criminal Studies” at the Eastern Berlin Humboldt University during the Communist regime, the SJB-GoMoPa-victims say (www.sjb-fonds-opfer.com) is responsable for the killing of German watchdog and journalist Heinz Gerlach.
These informations stem from various sources who were close to the criminal organization of GoMoPa in the last years. The SJB-GoMoPa say that the well-known German watchdog and journalist Heinz Gerlach was killed by former Stasi members with dioxins. Polychlorinated dibenzodioxins (PCDDs), or simply dioxins, are a group of organic polyhalogenated compounds that are significant because they act as environmental pollutants. They are commonly referred to as dioxins for simplicity in scientific publications because every PCDD molecule contains a dioxin skeletal structure. Typically, the p-dioxin skeleton is at the core of a PCDD molecule, giving the molecule a dibenzo-p-dioxin ring system. Members of the PCDD family have been shown to bioaccumulate in humans and wildlife due to their lipophilic properties, and are known teratogens, mutagens, and confirmed (avered) human carcinogens. They are organic compounds.
Dioxins build up primarily in fatty tissues over time (bioaccumulate), so even small exposures may eventually reach dangerous levels. In 1994, the US EPA reported that dioxins are a probable carcinogen, but noted that non-cancer effects (reproduction and sexual development, immune system) may pose an even greater threat to human health. TCDD, the most toxic of the dibenzodioxins, is classified as a Group 1 carcinogen by the International Agency for Research on Cancer (IARC).
In 2004, a notable individual case of dioxin poisoning, Ukrainian politician Viktor Yushchenko was exposed to the second-largest measured dose of dioxins, according to the reports of the physicians responsible for diagnosing him. This is the first known case of a single high dose of TCDD dioxin poisoning, and was diagnosed only after a toxicologist recognized the symptoms of chloracne while viewing television news coverage of his condition.
German dioxin scandal: In January 2011 about 4700 German farms were banned from making deliveries after tests at the Harles und Jentzsch plant in the state of Schleswig-Holstein showed high levels of dioxin. Again this incident appears to involve PCBs and not PCDDs at all. Dioxin were found in animal feed and eggs in many farms. The person who is responsible for this, Siegfried Sievert is also a former Stasi Agent. At “GoMoPa” the notorious Eastern-Berlin press agency (see article below) one of the henchmen acted under the name of “Siegfried Siewert”.
Further evidence for the killing of Mr.Heinz Gerlach is provided by the SJB-GoMoPa-victims by analyzing the dubious role of former Stasi-Top-agent Ehrenfried Stelzer, also a former “Professor for Crime Studies” under the Communist regime in Eastern Germany and the dubious role of “detective” Medard Fuchsgruber. Both are closely tied to the dubious “GoMoPa” and Berlin lawyer Jochen Resch.
According to the SJB-GoMoPa-victims is Berlin lawyer Jochen Resch the mastermind of the criminal organization “GoMoPa2. The victims state that they have a source inside “GoMoPa” who helped them discover the shocking truth. The so-called “Deep Throat from Berlin” has information that Resch had the idea to found the criminal organization “GoMoPa” and use non-existing Jewish lawyers named Goldman, Morgenstern & Partner as camouflage. Their “office” in Madison Avenue, New York, is a mailbox. This is witnessed by a German Ex-Patriot, a lawyer, whose father, Heinz Gerlach, died under strange circumstances.
Resch seems to use “GoMoPa” as an instrument to blackmail parts of the German Property and Investment.
The name of Benno Ohnesorg became a rallying cry for the West German left after he was shot dead by police in 1967. Newly discovered documents indicate that the cop who shot him may have been a spy for the East German secret police.
It was one of the most important events leading up to the wave of radical left-wing violence which washed over West Germany in the 1970s. On the evening of June 2, 1967, the literature student Benno Ohnesorg took part in a demonstration at West Berlin’s opera house. Mohammad Reza Pahlavi, the shah of Iran, was to attend and the gathered students wanted to call attention to his brutal regime.
The protests, though, got out of hand. Pro-shah demonstrators, some of them flown in from Iran for the occasion, battled with the student protestors. West Berlin police also did their part, brutally beating back the crowd. At 8:30 p.m., a shot was fired, and a short time later the 26-year-old Ohnesorg, having been hit in the back of the head, became the left wing’s first martyr.
Now, though, the history of the event may have to be re-written. New documents discovered in the Stasi archive — the vast collection of files left behind by the East German secret police — reveal that the policeman who shot Ohnesorg, Karl-Heinz Kurras, could in fact have been a spy for East Germany’s communist regime.
In an article that will appear in late May in Deutschlandarchiv, a periodical dedicated to the ongoing project of German reunification, Helmut Müller-Enbergs and Cornelia Jabs reveal that documents they found in the Stasi papers show that Kurras began working together with the Stasi in 1955. He had wanted to move to East Berlin to work for the East German police. Instead, he signed an agreement with the Stasi to remain with the West Berlin police force and spy for the communist state.
As a result of the new information, criminal charges have once again been filed against Kurras, who was acquitted twice, once in 1967 and again in 1970, of negligent homicide charges related to Ohnesorg’s death. Kurras told the Berlin paper Tagesspiegel on Friday that he had never worked together with the Stasi.
But in addition to finding the agreement between Kurras and the Stasi, the two researchers also discovered numerous documents indicating that the East Germans were pleased with the information Kurras passed along — particularly given that he was posted to a division responsible for rooting out moles within the West German police force.
Immediately after Ohnesorg’s death, Kurras received a Stasi communication ordering him to destroy his records and to “cease activities for the moment.” Kurras responded with his acquiescence and wrote “I need money for an attorney.”
The exact circumstances surrounding the death of Ohnesorg have never been completely clarified. Kurras himself, now 81, gave conflicting versions of the story during the investigation but the official version has long been that Kurras fired in self defense. Many others point to witness accounts whereby the police were beating Ohnesorg when the shot was fired.
It is still unclear how the new evidence might play into history’s understanding of the tragic event. The day was one full of violence, with demonstrators and police battling each other with pipes, wooden clubs and stones. Police were further incited by rumors that an officer had been stabbed earlier in the evening. Ohnesorg himself, however, was not directly involved in the violence.
West Berlin in the 1960s and 70s became a focal point of German left wing radicalism. The city had long been left-leaning, and the fact that Berliners were exempt from military service meant that it became a magnate for pacifists and anti-state activists.
Ohnesorg’s death gave them an immediate rallying cry. As the left-wing movement became more radical, many justified their violent activities by pointing to the police brutality that led to the student’s death. A letter written by Ulrike Meinhof announcing the founding of the Red Army Faction, which appeared in SPIEGEL in the fall of 1967, explicitly mentioned the Ohnesorg incident. The RAF went on to terrorize Germany for decades, ultimately killing over 30 people across the country. The radical “June 2 Movement” used the date of the incident in its name.
Kurras, for his part, seems to have been a highly valued Stasi agent. In his files, it is noted that “he is prepared to complete any task assigned to him.” It also mentions that he is notable for having the “courage and temerity necessary to accomplish difficult missions.”
Now it seems the STASI is back again in business after transforming it in to the CYBER-STASI of the 21st Century.
The serial betrayer and cyberstalker Klaus Maurischat is on the run again. The latest action against him (see below) cause him to react in a series of fake statements and “press releases” – one more absurd than the other. Insider analyze that his criminal organisation “GoMoPa” is about to fade away.
On our request the German criminal police (Kriminalpolizei) has opened new cases against the notorious “GoMoPa” organisation which already fled in the underground. Insiders say they have killed German journalist and watchdog Heinz Gerlach and their criminal record is bigger than the Encyclopedia – Britannica
The case is also directed against Google, Germany, whilst supporting criminal action of “GoMoPa” for years and therefore give them the chance to blackmail successfull businessman. This case is therefore an example and will be followed by many others as far as we can project. Furthermore we will bring the case to the attention of the German lawyers community which will not tolerate such misconduct by Googles German legal representative Dr. Arndt Haller and we will bring the case to the attention ofGoogle Inc in Mountain View, USA, and the American ministry of Justice to stop the Cyberstalkers once and for all.
Besides that many legal institutions, individuals and firms have already contacted us to help to clarify the death of Mr. Heinz Gerlach and to prosecute his murderers and their backers.
The case number is ST/0148943/2011
In a series of interviews beginning 11 months before the sudden death of German watchdog Heinz Gerlach Berlin lawyer Joschen Resch unveilved secrets of Gerlach, insiders say. Secret documents from Mr Gerlachs computer were published on two dubious hostile German websites. Both have a lot of similarities in their internet registration. One the notorious “GoMoPa” website belongs to a n Eastern German organization which calls itself “
Numerous attempts have been made to stop our research and the publication of the stories by “GoMoPa” members in camouflage thus confirming the truth and the substance of it in a superior way.
Only two articles let the German audience believe that the famous journalist and watchdog Heinz Gerlach died on natural courses by blood pollution. The first one, published only hours after the death of Mr Heinz Gerlach by the notorious “GoMoPa” (see article below) and a second 3 days later by a small German local newspaper, Weserbergland Nachrichten.
Many people including the hostile Gerlach website “Akte Heinz Gerlach” doubted that this man who had so many enemies and friends would die of natural causes without any previous warning. Rumours occured that Mr. Gerlach’s doctor doubted natural courses at all. After many critical voices discussed the issue a small website of a small German local newspaper – which never before had reported about Mr. Heinz Gerlach and which is not even in the region of Mr Gerlachs home – published that Mr Gerlach died of blood pollution. Weserbergland-Nachrichten published a long article about the deadly consequences of blood pollution and did not even name the source of such an important statement. It claimed only that somebody of Gerlachs inner circle had said this. It is a proven fact that after the collpase of the Eastern German Communist Regime many former Communist propaganda agents went to regional newspapers – often in Western Germany like Günther Schabowski did the man who opened the “Mauer”.
The theatre stage was set: One day later the hostile Gerlach website “Akte Heinz Gerlach” took the agenda publishing that Mr Gerlach had died for natural causes without any further research at all.
This was done by a website which for months and months and months reported everything about Mr. Gerlach.
Furthermore a research proves that the technical details regarding the website hosting of this hostile website “Akte Heinz Gerlach” proves that there are common details with the hosting of “GoMoPa” and their affiliates as proven by the SJB-GoMoPa-victims (see http://www.sjb-fonds-opfer.com)
Insiders believe that the murderers of Mr. Heinz Gerlach are former members of the Eastern German Terror Organisation “Stasi” with dioxins. They also believe that “GoMoPa” was part of the plot. At “GoMoPa”’ a person named Siegfried Siewers was officialy responsible for the press but never appeared in public. “GoMoPa”-victims say that this name was a cameo for “GoMoPa” frontrunner Klaus Maurischat who is controlled by the Stasi Top Agent Ehrenfried Stelznr, Berlin.
Siegfried Sievers, a former Stasi member is responsible for the pollution of millions Germanys for many years with dioxins. This was unveiled at 5th of January 2011 by German prosecutors.
The victims say that Maurischat (probably also a Stasi cameo) and Sievers were in contact as Sievers acted as Stasi Agent and was in fact already a specialist in dioxins under the Communist Terror
The Stasi murder:
„GoMoPa“ & Backers: Blackmailing, Extortion, Racketeering, Internet Murder and Murder. These are the weapons of the East-German “NACHRICHTENDIENST” “GoMoPa”, a renegate confesses.
Deep Throat, Berlin; confesses: „Since months the „GoMoPa“ keyfigures like Klaus-Dieter Maurischat< are in hide-aways because the German police is hunting them for the wirecard fraud and a lot of other criminal actions. I left the group when I noticed that. The found and former Stasi-Colonel Ehrenfried Stelzer died under strange circumstances in Berlin. This has been told to us. But it is also possible that his death was staged. In any case the criminal organization of “GoMoPa” is responsible for the murder of Heinz Gerlach by dioxin. Now my life is also in danger that is why I hide myself.”
According to Deep Throat, Hans J. the murder was done with the help of the old Stasi-connections of the “NACHRICHTENDIENST” “GoMoPa”.
The renegate says that computer hacker Thomas Promny and Sven Schmidt are responsible for the computer crimes and he states that the crime organization of “GoMoPa” has also helpers inside internet companies like Go-Daddy, Media-on and even in Google, Hamburg..
THE “NACHRICHTENDIENST”:New criminal police action against “GoMoPa”:
German criminal police (Kriminalpolizei) has opened new cases against the notorious “GoMoPa” organisation which already fled in the underground.
On our request the German criminal police (Kriminalpolizei) has opened new cases against the notorious “GoMoPa” organisation which already fled in the underground. Insiders say they have killed German journalist and watchdog Heinz Gerlach and their criminal record is bigger than the
Encyclopedia – Britannica
The case is also directed against Google, Germany, whilst supporting criminal action of “GoMoPa” for years and therefore give them the chance to blackmail successfull businessman. This case is therefore an example and will be followed by many others as far as we can project. Furthermore we will bring the case to the attention of the German lawyers community which will not tolerate such misconduct by Googles German legal representative Dr. Arndt Haller and we will bring the case to the attention of Google Inc in Mountain View, USA, and the American ministry of Justice to stop the Cyberstalkers once and for all.
Besides that many legal institutions, individuals and firms have already contacted us to help to clarify the death of Mr. Heinz Gerlach and to prosecute his murderers and their backers.
The case number is
ST/0148943/2011
Stasi-Dioxin: The “NACHRICHTENDIENST” searching for the perfect murder:
Viktor Yushchenko was running against Prime Minister Viktor Yanukovych. Yanukovych was a political ally of outgoing president Leonid Kuchma. Kuchma’s administration depended upon corruption and dishonesty for its power. Government officials ruled with a sense of terror rather than justice. For the powerful and wealthy few, having Yanukovych elected president was important. Should Yushchenko win, Ukraine’s government was sure to topple. Yushchenko’s campaign promises included a better quality of life for Ukrainians through democracy. His wife, Katherine, told CBS in a 2005 interview, “He was a great threat to the old system, where there was a great deal of corruption, where people were making millions, if not billions.”
On September 6, 2004, Yushchenko became ill after dining with leaders of the Ukrainian secret police. Unlike other social or political engagements, this dinner did not include anyone else on Yushchenko’s team. No precautions were taken regarding the food. Within hours after the dinner, Yushchenko began vomiting violently. His face became paralyzed; he could not speak or read. He developed a severe stomachache and backache as well as gastrointestinal pain. Outwardly, Yushchenko developed what is known as chloracne, a serious skin condition that leaves the face scarred and disfigured.
By December 2004, doctors had determined that Yushchenko had been the victim of dioxin poisoning. Dioxin is a name given to a group of related toxins that can cause cancer and even death. Dioxin was used in the biochemical weapon called Agent Orange during the Vietnam War controversial war in which the United States aidedSouth Vietnam in its fight against a takeover by Communist North Vietnam). Yushchenko had a dioxin level six thousand times greater than that normally found in the bloodstream. His is the second-highest level ever recorded.
Yushchenko immediately suspected he had been poisoned, though Kuchma’s camp passionately denied such allegations. Instead, when Yushchenko showed up at a parliamentary meeting shortly after the poisoning incident, Kuchma’s men teased him, saying he must have had too much to drink or was out too late the night before.
Dioxin can stay in the body for up to thirty-five years. Experts predict that his swelling and scars will fade but never completely disappear. John Henry, a toxicologist at London’s Imperial Hospital, told RedNova.com, “It’ll be a couple of years, and he will always be a bit pockmarked. After damage as heavy as that, I think he will not return to his film star looks.” And Yushchenko will live with the constant threat of cancer.
At first it was believed the poison must have come from a Russian laboratory. Russia was a strong supporter of Kuchma and lobbied against Yushchenko in the 2004 election. But by July 2005, Yushchenko’s security forces were able to trace the poison to a lab in Ukraine. Though not entirely ruling out Russia’s involvement, Yushchenko is quoted on his Web site as saying “I’m sure that even though some people are running from the investigation, we will get them. I am not afraid of anything or anybody.”
Evidence shows that such a perfect murder plotted by former Stasi agents is the cause of the death of German watchdog and journalist Heinz Gerlach.
The Ministry for State Security (German: Ministerium für Staatssicherheit (MfS), commonly known as the Stasi (IPA: [‘?tazi?]) (abbreviation German: Staatssicherheit, literally State Security), was the official state security service of East Germany. The MfS was headquartered in East Berlin, with an extensive complex in Berlin-Lichtenberg and several smaller facilities throughout the city. It was widely regarded as one of the most effective and repressive intelligence and secret police agencies in the world. The MfS motto was “Schild und Schwert der Partei” (Shield and Sword of the Party), that is the ruling Socialist Unity Party of Germany (SED).
According to the confessions of an informer, Berlin lawyer Jochen Resch writes most of the “articles” of the communist “STASI” agency “GoMoPa” himself or it is done by lawyers of his firm. The whistleblower states that lawyer Resch is the mastermind behind the “CYBER-STASI” called “NACHRICHTENDIENST” “GoMoPa”. Bizarre enough they use Jewish names of non-existing Jewish lawyers by the name of “Goldman, Morgenstern and Partner” to stage their bogus “firm”. Further involved in their complots are a “detective” Medard Fuchsgruber and “STASI”-Colonel Ehrenfried Stelzer, “the first crime expert” in the former communist East-Germany.
According to London based Meridian Capital hundreds and thousands of wealthy people and companies have paid to the “NACHRICHTENDIENST” to avoid their cyberstalking (see article below).
Finally the German criminal police started their investigations (case number ST/0148943/2011).
The “NACHRICHTENDIENST” is also involved in the death of the well-known German watchdog and journalist Heinz Gerlach who died under strange circumstances in July 2010.
Only hours after his death the “NACHRICHTENDIENST” was spreading the news that Mr Gerlach died of blood pollution and set the stage for a fairy tale. Months before his death the “NACHRICHTENDIENST” started a campaign to ruin his reputation and presumably was also responsable for cyberattacks to bring his website down. In fact they presumably used the same tactics also against our servers. Therefore we investigated all internet details of them and handed the facts to the FBI and international authorities.
Story background:
Now it seems the STASI is back again in business after transforming it in to the CYBER-STASI of the 21st Century.
The serial betrayer and cyberstalker Klaus Maurischat is on the run again. The latest action against him (see below) cause him to react in a series of fake statements and “press releases” – one more absurd than the other. Insider analyze that his criminal organisation “GoMoPa” is about to fade away.
On our request the German criminal police (Kriminalpolizei) has opened new cases against the notorious “GoMoPa” organisation which already fled in the underground. Insiders say they have killed German journalist and watchdog Heinz Gerlach and their criminal record is bigger than the Encyclopedia – Britannica
The case is also directed against Google, Germany, whilst supporting criminal action of “GoMoPa” for years and therefore give them the chance to blackmail successfull businessman. This case is therefore an example and will be followed by many others as far as we can project. Furthermore we will bring the case to the attention of the German lawyers community which will not tolerate such misconduct by Googles German legal representative Dr. Arndt Haller and we will bring the case to the attention of Google Inc in Mountain View, USA, and the American ministry of Justice to stop the Cyberstalkers once and for all.
Besides that many legal institutions, individuals and firms have already contacted us to help to clarify the death of Mr. Heinz Gerlach and to prosecute his murderers and their backers.
The case number is ST/0148943/2011
In a series of interviews beginning 11 months before the sudden death of German watchdog Heinz Gerlach Berlin lawyer Joschen Resch unveilved secrets of Gerlach, insiders say. Secret documents from Mr Gerlachs computer were published on two dubious hostile German websites. Both have a lot of similarities in their internet registration. One the notorious “GoMoPa” website belongs to a n Eastern German organization which calls itself “
Numerous attempts have been made to stop our research and the publication of the stories by “GoMoPa” members in camouflage thus confirming the truth and the substance of it in a superior way.
Only two articles let the German audience believe that the famous journalist and watchdog Heinz Gerlach died on natural courses by blood pollution. The first one, published only hours after the death of Mr Heinz Gerlach by the notorious “GoMoPa” (see article below) and a second 3 days later by a small German local newspaper, Weserbergland Nachrichten.
Many people including the hostile Gerlach website “Akte Heinz Gerlach” doubted that this man who had so many enemies and friends would die of natural causes without any previous warning. Rumours occured that Mr. Gerlach’s doctor doubted natural courses at all. After many critical voices discussed the issue a small website of a small German local newspaper – which never before had reported about Mr. Heinz Gerlach and which is not even in the region of Mr Gerlachs home – published that Mr Gerlach died of blood pollution. Weserbergland-Nachrichten published a long article about the deadly consequences of blood pollution and did not even name the source of such an important statement. It claimed only that somebody of Gerlachs inner circle had said this. It is a proven fact that after the collpase of the Eastern German Communist Regime many former Communist propaganda agents went to regional newspapers – often in Western Germany like Günther Schabowski did the man who opened the “Mauer”.
The theatre stage was set: One day later the hostile Gerlach website “Akte Heinz Gerlach” took the agenda publishing that Mr Gerlach had died for natural causes without any further research at all.
This was done by a website which for months and months and months reported everything about Mr. Gerlach.
Furthermore a research proves that the technical details regarding the website hosting of this hostile website “Akte Heinz Gerlach” proves that there are common details with the hosting of “GoMoPa” and their affiliates as proven by the SJB-GoMoPa-victims (see http://www.sjb-fonds-opfer.com)
Insiders believe that the murderers of Mr. Heinz Gerlach are former members of the Eastern German Terror Organisation “Stasi” with dioxins. They also believe that “GoMoPa” was part of the plot. At “GoMoPa”’ a person named Siegfried Siewers was officialy responsible for the press but never appeared in public. “GoMoPa”-victims say that this name was a cameo for “GoMoPa” frontrunner Klaus Maurischat who is controlled by the Stasi Top Agent Ehrenfried Stelzner, Berlin.
Siegfried Sievers, a former Stasi member is responsible for the pollution of millions Germanys for many years with dioxins. This was unveiled at 5th of January 2011 by German prosecutors.
The victims say that Maurischat (probably also a Stasi cameo) and Sievers were in contact as Sievers acted as Stasi Agent and was in fact already a specialist in dioxins under the Communist Terror Regime in Eastern Germany.
Furthermore the Stasi Top Agent Ehrenfried Stelzer disguised as Professor for Criminal studies during the Communist Regime at the Eastern Berlin Humboldt University.
Background:
The man behind the Berlin lawyer Jochen Resch and his activities is Ehrenfried Stelzer, former Stasi Top officer in Berlin and “Professor for Criminal Studies” at the Eastern Berlin Humboldt University during the Communist regime, the SJB-GoMoPa-victims say (www.sjb-fonds-opfer.com) is responsable for the killing of German watchdog and journalist Heinz Gerlach.
These informations stem from various sources who were close to the criminal organization of GoMoPa in the last years. The SJB-GoMoPa say that the well-known German watchdog and journalist Heinz Gerlach was killed by former Stasi members with dioxins. Polychlorinated dibenzodioxins (PCDDs), or simply dioxins, are a group of organic polyhalogenated compounds that are significant because they act as environmental pollutants. They are commonly referred to as dioxins for simplicity in scientific publications because every PCDD molecule contains a dioxin skeletal structure. Typically, the p-dioxin skeleton is at the core of a PCDD molecule, giving the molecule a dibenzo-p-dioxin ring system. Members of the PCDD family have been shown to bioaccumulate in humans and wildlife due to their lipophilic properties, and are known teratogens, mutagens, and confirmed (avered) human carcinogens. They are organic compounds.
Dioxins build up primarily in fatty tissues over time (bioaccumulate), so even small exposures may eventually reach dangerous levels. In 1994, the US EPA reported that dioxins are a probable carcinogen, but noted that non-cancer effects (reproduction and sexual development, immune system) may pose an even greater threat to human health. TCDD, the most toxic of the dibenzodioxins, is classified as a Group 1 carcinogen by the International Agency for Research on Cancer (IARC).
In 2004, a notable individual case of dioxin poisoning, Ukrainian politician Viktor Yushchenko was exposed to the second-largest measured dose of dioxins, according to the reports of the physicians responsible for diagnosing him. This is the first known case of a single high dose of TCDD dioxin poisoning, and was diagnosed only after a toxicologist recognized the symptoms of chloracne while viewing television news coverage of his condition.
German dioxin scandal: In January 2011 about 4700 German farms were banned from making deliveries after tests at the Harles und Jentzsch plant in the state of Schleswig-Holstein showed high levels of dioxin. Again this incident appears to involve PCBs and not PCDDs at all. Dioxin were found in animal feed and eggs in many farms. The person who is responsible for this, Siegfried Sievert is also a former Stasi Agent. At “GoMoPa” the notorious Eastern-Berlin press agency (see article below) one of the henchmen acted under the name of “Siegfried Siewert”.
Further evidence for the killing of Mr.Heinz Gerlach is provided by the SJB-GoMoPa-victims by analyzing the dubious role of former Stasi-Top-agent Ehrenfried Stelzer, also a former “Professor for Crime Studies” under the Communist regime in Eastern Germany and the dubious role of “detective” Medard Fuchsgruber. Both are closely tied to the dubious “GoMoPa” and Berlin lawyer Jochen Resch.
According to the SJB-GoMoPa-victims is Berlin lawyer Jochen Resch the mastermind of the criminal organization “GoMoPa2. The victims state that they have a source inside “GoMoPa” who helped them discover the shocking truth. The so-called “Deep Throat from Berlin” has information that Resch had the idea to found the criminal organization “GoMoPa” and use non-existing Jewish lawyers named Goldman, Morgenstern & Partner as camouflage. Their “office” in Madison Avenue, New York, is a mailbox. This is witnessed by a German Ex-Patriot, a lawyer, whose father, Heinz Gerlach, died under strange circumstances.
Resch seems to use “GoMoPa” as an instrument to blackmail parts of the German Property and Investment section.
-”Worse than the Gestapo.” —Simon Wiesenthal, Nazi hunter said about the notorious “Stasi”.
Less than a month after German demonstrators began to tear down the Berlin Wall on November 9, 1989, irate East German citizens stormed the Leipzig district office of the Ministry for State Security (MfS)—the Stasi, as it was more commonly called. Not a shot was fired, and there was no evidence of “street justice” as Stasi officers surrendered meekly and were peacefully led away. The following month, on January 15, hundreds of citizens sacked Stasi headquarters in Berlin. Again there was no bloodshed. The last bit of unfinished business was accomplished on May 31 when the Stasi radioed its agents in West Germany to fold their tents and come home.
The intelligence department of the Nationale Volksarmee (NVA), the People’s Army, had done the same almost a week earlier, but with what its members thought was better style. Instead of sending the five-digit code groups that it had used for decades to message its spies in West Germany, the army group broadcast a male choir singing a children’s ditty about a duck swimming on a lake. There was no doubt that the singing spymasters had been drowning their sorrow over losing the Cold War in schnapps. The giggling, word-slurring songsters repeated the refrain three times: “Dunk your little head in the water and lift your little tail.” This was the signal to agents under deep cover that it was time to come home.
With extraordinary speed and political resolve, the divided nation was reunified a year later. The collapse of the despotic regime was total. It was a euphoric time for Germans, but reunification also produced a new national dilemma. Nazi war crimes were still being tried in West Germany, forty-six years after World War II. Suddenly the German government was faced with demands that the communist officials who had ordered, executed, and abetted crimes against their own people—crimes that were as brutal as those perpetrated by their Nazi predecessors—also be prosecuted.
The people of the former Deutsche Demokratische Republik (DDR), the German Democratic Republic, as the state had called itself for forty years, were clamoring for instant revenge. Their wrath was directed primarily against the country’s communist rulers—the upper echelon of the Sozialistische Einheitspartei (SED), the Socialist Unity Party. The tens of thousands of second-echelon party functionaries who had enriched themselves at the expense of their cocitizens were also prime targets for retribution.
Particularly singled out were the former members of the Stasi, the East German secret police, who previously had considered themselves the “shield and sword” of the party. When the regime collapsed, the Stasi had 102,000 full-time officers and noncommissioned personnel on its rolls, including 11,000 members of the ministry’s own special guards regiment. Between 1950 and 1989, a total of 274,000 persons served in the Stasi.
The people’s ire was running equally strong against the regular Stasi informers, the inoffizielle Mitarbeiter (IMs). By 1995, 174,000 had been identified as IMs, or 2.5 percent of the total population between the ages of 18 and 60. Researchers were aghast when they found that about 10,000 IMs, or roughly 6 percent of the total, had not yet reached the age of 18. Since many records were destroyed, the exact number of IMs probably will never be determined; but 500,000 was cited as a realistic figure. Former Colonel Rainer Wiegand, who served in the Stasi counterintelligence directorate, estimated that the figure could go as high as 2 million, if occasional stool pigeons were included.
“The Stasi was much, much worse than the Gestapo, if you consider only the oppression of its own people,” according to Simon Wiesenthal of Vienna, Austria, who has been hunting Nazi criminals for half a century. “The Gestapo had 40,000 officials watching a country of 80 million, while the Stasi employed 102,000 to control only 17 million.” One might add that the Nazi terror lasted only twelve years, whereas the Stasi had four decades in which to perfect its machinery of oppression, espionage, and international terrorism and subversion.
To ensure that the people would become and remain submissive, East German communist leaders saturated their realm with more spies than had any other totalitarian government in recent history. The Soviet Union’s KGB employed about 480,000 full-time agents to oversee a nation of 280 million, which means there was one agent per 5,830 citizens. Using Wiesenthal’s figures for the Nazi Gestapo, there was one officer for 2,000 people. The ratio for the Stasi was one secret policeman per 166 East Germans. When the regular informers are added, these ratios become much higher: In the Stasi’s case, there would have been at least one spy watching every 66 citizens! When one adds in the estimated numbers of part-time snoops, the result is nothing short of monstrous: one informer per 6.5 citizens. It would not have been unreasonable to assume that at least one Stasi informer was present in any party of ten or twelve dinner guests.
THE STASI OCTOPUS
Like a giant octopus, the Stasi’s tentacles probed every aspect of life. Full-time officers were posted to all major industrial plants. Without exception, one tenant in every apartment building was designated as a watchdog reporting to an area representative of the Volkspolizei (Vopo), the People’s Police. In turn, the police officer was the Stasi’s man. If a relative or friend came to stay overnight, it was reported. Schools, universities, and hospitals were infiltrated from top to bottom. German academe was shocked to learn that Heinrich Fink, professor of theology and vice chancellor at East Berlin’s Humboldt University, had been a Stasi informer since 1968. After Fink’s Stasi connections came to light, he was summarily fired. Doctors, lawyers, journalists, writers, actors, and sports figures were co-opted by Stasi officers, as were waiters and hotel personnel. Tapping about 100,000 telephone lines in West Germany and West Berlin around the clock was the job of 2,000 officers.
Stasi officers knew no limits and had no shame when it came to “protecting the party and the state.” Churchmen, including high officials of both Protestant and Catholic denominations, were recruited en masse as secret informers. Their offices and confessionals were infested with eavesdropping devices. Even the director of Leipzig’s famous Thomas Church choir, Hans-Joachim Rotch, was forced to resign when he was unmasked as a Spitzel, the people’s pejorative for a Stasi informant.
Absolutely nothing was sacred to the secret police. Tiny holes were bored in apartment and hotel room walls through which Stasi agents filmed their “suspects” with special video cameras. Even bathrooms were penetrated by the communist voyeurs.8 Like the Nazi Gestapo, the Stasi was the sinister side of deutsche Gründlichkeit (German thoroughness).
After the Berlin wall came down, the victims of the DDR regime demanded immediate retribution. Ironically, their demands were countered by their fellow Germans in the West who, living in freedom, had diligently built einen demokratischen Rechtsstaat, a democratic state governed by the rule of law. The challenge of protecting the rights of both the victims and the accused was immense, given the emotions surrounding the issue. Government leaders and democratic politicians recognized that there could be no “quick fix” of communist injustices without jeopardizing the entire system of democratic jurisprudence. Moving too rapidly merely to satisfy the popular thirst for revenge might well have resulted in acquittals or mistrials. Intricate jurisdictional questions needed to be resolved with both alacrity and meticulousness. No German government could afford to allow a perpetrator to go free because of a judicial error. The political fallout from any such occurrence, especially in the East, could prove fatal to whatever political party occupied the chancellor’s office in Bonn at the time.
Politicians and legal scholars of the “old federal states,” or West Germany, counseled patience, pointing out that even the prosecution of Nazi criminals had not yet been completed. Before unification, Germans would speak of Vergangenheitsbewältigung (“coming to grips with the past”) when they discussed dealing with Nazi crimes. In the reunited Germany, this word came to imply the communist past as well. The two were considered comparable especially in the area of human rights violations. Dealing with major Nazi crimes, however, was far less complicated for the Germans: Adolf Hitler and his Gestapo and Schutzstaffel (SS) chief, Heinrich Himmler, killed themselves, as did Luftwaffe chief and Vice Chancellor Hermann Göring, who also had been the first chief of the Gestapo. The victorious Allies prosecuted the rest of the top leadership at the International War Crimes Tribunal in Nürnberg. Twelve were hanged, three received life terms, four were sentenced to lesser terms of imprisonment (up to twenty years), and three were acquitted.
The cases of communist judges and prosecutors accused of Rechtsbeugung (perversion of justice) are more problematic. According to Franco Werkenthin, a Berlin legal expert charged with analyzing communist crimes for the German parliament, those sitting in judgment of many of the accused face a difficult task because of the general failure of German justice after World War II. Not a single judge or prosecutor who served the Nazi regime was brought to account for having perverted justice—even those who had handed down death sentences for infringements that in a democracy would have been considered relatively minor offenses. Werkenthin called this phenomenon die Jauche der Justiz, the cesspool of justice.
Of course, the crimes committed by the communists were not nearly as heinous as the Nazis’ extermination of the Jews, or the mass murders in Nazi-occupied territories. However, the communists’ brutal oppression of the nation by means including murder alongside legal execution put the SED leadership on a par with Hitler’s gang. In that sense, Walter Ulbricht or Erich Honecker (Ulbricht’s successor as the party’s secretary-general and head of state) and secret police chief Erich Mielke can justifiably be compared to Hitler and Himmler, respectively.
Arrest warrants were issued for Honecker and Mielke. The Soviet government engineered Honecker’s escape to Moscow, where he became the ward of Soviet President Mikhail S. Gorbachev. When the Soviet Union crumbled, the new Russian President Boris Yeltsin expelled Honecker. He was arrested on his return to Germany, but a court decided against a trial when he was diagnosed with liver cancer. Honecker flew to Chile with his wife Margot to live with their daughter, a Chilean citizen by marriage. His exile was short, and he died in 1994. Mielke was not so fortunate: His KGB friends turned their backs on him. He was tried in Germany for the 1931 murder of two police officers, found guilty, and sentenced to six years in prison. Other charges, including manslaughter, were dismissed because of his advanced age and poor health.
Three other members of the twenty-one-member ruling Politburo also have been tried. Former Defense Minister Heinz Kessler was convicted of manslaughter in connection with the order to kill people who were trying to escape to the West. He received a seven-and-a-half-year term. Two others, members of the Central Committee and the National Defense Council, were tried with Kessler and sentenced to seven and a half years and five years, respectively. Politburo member Harry Tisch, who was also head of the communist trade union, was found guilty of embezzlement and served eighteen months. Six others, including Egon Krenz (Honecker’s successor as party chief), were charged with manslaughter. Krenz was found guilty, and on August 25, 1997, was sentenced to six and a half years in prison.
However, eight years after reunification, many of the 165 members of the Central Committee have not yet been put under investigation. In 1945, Nazis holding comparable or lesser positions were subject to automatic arrest by the Allies. They spent months or even years in camps while their cases were adjudicated. Moreover, the Nürnberg Tribunal branded the Reich and its Corps of Political Leaders, SS, Security Service (SD), Secret State Police (Gestapo), SA (Storm Troopers), and Armed Forces High Command criminal organizations. Similarly sweeping actions against communist leaders and functionaries such as Stasi officers were never contemplated, even though tens of thousands of political trials and human rights abuses have been documented. After the East German regime fell, German judicial authorities scrupulously avoided the appearance of waging witch-hunts or using the law as a weapon of vengeance. Prosecutors and judges made great efforts to be fair, often suspending legal action while requesting rulings from the supreme court on possible constitutional conflicts.
The victims of oppression clamored for revenge and demanded speedy prosecution of the erstwhile tyrants. They had little patience for a judicial system that was handicapped by a lack of unblemished and experienced criminal investigators, prosecutors, and judges. Despite these handicaps, the Berlin Central Police Investigations Group for Government Criminality, mindful that the statute of limitations for most communist crimes would expire at the end of 1999, made significant progress under its director Manfred Kittlaus, the able former director of the West Berlin state police. Kittlaus’s major task in 1998 was to investigate wrongful deaths, including 73 murders, 30 attempted murders, 583 cases of manslaughter, 2,938 instances of attempted manslaughter, and 425 other suspicious deaths. Of the 73 murders, 22 were classified as contract murders.
One of those tried and convicted for attempted contract murder was former Stasi collaborator Peter Haak, who was sentenced to six and a half years in prison. The fifty-two-year-old Haak took part in the Stasi’s 1981 Operation Scorpion, which was designed to pursue people who helped East Germans escape to the West. Proceedings against former General Gerhard Neiber, whose Stasi directorate was responsible for preventing escapes and for wreaking vengeance, were still pending in 1998.
Peter Haak’s murder plot was hatched after he befriended Wolfgang Welsch and his family. Welsch was a thorn in the side of the Stasi because of his success in smuggling people out of the DDR. Haak joined Welsch and the latter’s wife and seven-year-old daughter on a vacation in Israel, where he mixed a gram of thallium, a highly poisonous metallic chemical element used in rat poison, into the hamburgers he was preparing for a meal. Welsch’s wife and daughter vomited immediately after ingesting the poison and recovered quickly. Welsch suffered severe aftereffects, but eventually recovered: He had consumed a large amount of beer with the meal, and an expert testified that the alcohol had probably flushed the poison from his system.
Berlin Prosecutor General Christoph Schäfgen revealed that after the DDR’s demise 15,200 investigations had been launched, of which more than 9,000 were still active at the beginning of 1995. Indictments were handed down in 153 cases, and 73 perpetrators were convicted. Among those convicted were the aforementioned Politburo members as well as a number of border guards who had killed people who were trying to escape to the West.
Despite widespread misgivings about the judicial failures in connection with some Nazi crimes, a number of judges and prosecutors were convicted and jailed for up to three years for perversion of justice. In collusion with the Stasi, they had requested or handed down more severe sentences in political cases so that the state could collect greater amounts when the “convicts” were ransomed by the West German government. {The amount of ransom paid was governed by the time a prisoner had been sentenced to serve.)
The enormity of the task facing judicial authorities in reunified Germany becomes starkly evident when one examines the actions they have taken in all five former East German provinces and in East Berlin. From the end of 1990 to July 1996, 52,050 probes were launched into charges of murder, attempted murder, manslaughter, kidnapping, election fraud, and perversion of justice. A total of 29,557 investigations were halted for various reasons including death, severe illness, old age, or insufficient evidence. In those five and a half years, there were only 139 convictions.
The problem is even more staggering when cases of espionage are included. Between 1990 and 1996, the office of the federal prosecutor general launched 6,641 probes, of which 2,431 were terminated before trial—most due to the statute of limitations. Of 175 indictments on charges of espionage, 95 resulted in convictions. In addition to the cases handled at the federal level, the prosecutor general referred 3,926 investigations to state authorities, who terminated 3,344 without trial. State courts conducted 356 trials, resulting in 248 convictions. Because the statute of limitations for espionage is five years, the prosecutor general’s office told me in 1997 it was unlikely that more espionage trials would be conducted.
It is important to emphasize the difference between the statute’s application to so-called government crimes committed in East Germany before the collapse and to crimes, such as espionage, committed in West Germany. The Unification Treaty specifically permits the belated prosecution of individuals who committed acts that were punishable under the East German criminal code and who due to official connivance were not prosecuted earlier. There is no statute of limitations for murder. For most other crimes the limit is five years; however, due to the obstacles created by previous government connivance, the German parliament in 1993 doubled this time limit for prosecution of the more serious crimes. At the same time, the parliament decreed that all cases must be adjudicated by the end of 2002. For less serious offenses, the statute would have run out on December 31, 1997, but the parliament extended it to 2000.
A number of politicians, jurists, and liberal journalists pleaded for a general amnesty for crimes committed by former DDR leaders and Communist Party functionaries. A former West German supreme court judge, Ernst Mahrenholz, said the “sharp sword of justice prevents reconciliation.” Schäfgen, the Berlin prosecutor general, had this answer for the former high court judge and other amnesty advocates:
I cannot agree. We are raising no special, sharp sword against East Germans. We must pursue state-sponsored injustice in exactly the same manner as we do when a thief steals or when one human being kills another. If one wants to change that, then we would have to do away with the entire criminal justice system, because punishment always hurts. We are not criminalizing an entire people but only an ever shrinking, small portion.
German Foreign Minister Klaus Kinkel, who was West Germany’s minister of justice when the nation was unified, said this at a session of parliament in September 1991: “We must punish the perpetrators. This is not a matter of a victor’s justice. We owe it to the ideal of justice and to the victims. All of those who ordered injustices and those who executed the orders must be punished; the top men of the SED as well as the ones who shot [people] at the wall.” Aware that the feelings against communists were running high among their victims, Kinkel pointed to past revolutions after which the representatives of the old system were collectively liquidated. In the same speech before parliament, he said:
Such methods are alien to a state ruled by law. Violence and vengeance are incompatible with the law in any case. At the same time, we cannot tolerate that the problems are swept under the rug as a way of dealing with a horrible past, because the results will later be disastrous for society. We Germans know from our own experience where this leads. Jewish philosophy formulates it in this way: “The secret of redemption is called remembering.”
Defense attorneys for communist officials have maintained that the difficulty lies in the fact that hundreds of thousands of political opponents were tried under laws of the DDR. Although these laws were designed to smother political dissent and grossly violated basic human rights and democratic norms, they were nonetheless laws promulgated by a sovereign state. How could one justly try individual Stasi officers, prosecutors, and judges who had simply been fulfilling their legal responsibility to pursue and punish violators of the law?
Opinions varied widely on whether and how the Stasi and other perpetrators of state-sponsored crimes should be tried. Did the laws of the DDR, as they existed before reunification, still apply in the east? Or was the criminal code of the western part of the country the proper instrument of justice in reunified Germany? However, these questions were moot: As Rupert Scholz, professor of law at the University of Munich and a Christian Democratic member of parliament, pointed out, the Unification Treaty specifies that the penal code of the DDR and not that of the Federal Republic of Germany (FRG) shall be applied to offenses committed in East Germany. Scholz’s view was upheld by the Bundesverfassungsgericht, the supreme court. Most offenses committed by party functionaries and Stasi officers—murder, kidnapping, torture, illegal wiretapping, mail robbery, and fraud—were subject to prosecution in reunified Germany under the DDR’s penal code. But this would not satisfy the tens of thousands of citizens who had been sent to prison under East German laws covering purely political offenses for which there was no West German equivalent.
Nevertheless, said Scholz, judicial authorities were by no means hamstrung, because West Germany had never recognized the East German state according to international law. “We have always said that we are one nation; that the division of Germany led neither to full recognition under international law nor, concomitantly, to a recognition of the legal system of the DDR,” Scholz said. Accordingly, West German courts have consistently maintained that West German law protects all Germans equally, including those living in the East. Therefore, no matter where the crimes were committed, whether in the East or the West, all Germans have always been subject to West German laws. Applying this logic, East German border guards who had either killed or wounded persons trying to escape to the West could be tried under the jurisdiction of West Germany.
The “one nation” principle was not upheld by the German supreme court. Prior to the court’s decision, however, Colonel General Markus Wolf, chief of the Stasi’s foreign espionage directorate, and some of his officers who personally controlled agents from East Berlin had been tried for treason and convicted. Wolf had been sentenced to six years in prison. The supreme court ruling overturned that verdict and those imposed on Wolf’s cohorts, even though they had obtained the most closely held West German secrets and handed them over to the KGB. The maximum penalty for Landesverrat, or treason, is life imprisonment. In vacating Wolf’s sentence, the court said he could not be convicted because he operated only from East German territory and under East German law.
However, Wolf was reindicted on charges of kidnapping and causing bodily harm, crimes also punishable under East German law. The former Stasi three-star general, on March 24, 1955, had approved in writing a plan to kidnap a woman who worked for the U.S. mission in West Berlin. The woman and her mother were tricked by a Stasi agent whom the woman had been teaching English, and voluntarily got into his car. He drove them into the Soviet sector of the divided city, where they were seized by Stasi officers. The woman was subjected to psychological torture and threatened with imprisonment unless she signed an agreement to spy for the Stasi. She agreed. On her return to the American sector, however, the woman reported the incident to security officials. Wolf had committed a felony punishable by up to fifteen years’ imprisonment in West Germany. He was found guilty in March 1977 and sentenced to two years’ probation.
Those who have challenged the application of the statute of limitations to communist crimes, especially to the executions of citizens fleeing to the West, have drawn parallels to the notorious executive orders of Adolf Hitler. Hitler issued orders mandating the summary execution of Soviet Army political commissars upon their capture and initiating the extermination of Jews. An early postwar judicial decision held that these orders were equivalent to law. When that law was declared illegal and retroactively repealed by the West German Bundestag, the statute of limitations was suspended—that is, it never took effect. Many of those convicted in subsequent trials of carrying out the Führer’s orders were executed by the Allies. The German supreme court has ruled the same way as the Bundestag on the order to shoot people trying to escape to West Germany, making the statute of limitations inapplicable to such cases. The ruling made possible the trial of members of the National Defense Council who took part in formulating or promulgating the order. A number of border guards who had shot would-be escapees also have been tried and convicted.
Chief Prosecutor Heiner Sauer, former head of the West German Central Registration Office for Political Crimes, was particularly concerned with the border shootings. His office, located in Salzgitter, West Germany, was established in 1961 as a direct consequence of the Berlin Wall, which was erected on August 13 of that year. Willy Brandt, at the time the city’s mayor (later federal chancellor) had decided that crimes committed by East German border guards should be recorded. At his behest, a central registry of all shootings and other serious border incidents was instituted. Between August 13, 1961 and the opening of the borders on November 9, 1989, 186 border killings were registered. But when the Stasi archives were opened, investigators found that at least 825 people had paid with their lives for trying to escape to the West. This figure was reported to the court that was trying former members of the National Defense Council. In addition to these border incidents, the registry also had recorded a number of similar political offenses committed in the interior of the DDR: By fall 1991, Sauer’s office had registered 4,444 cases of actual or attempted killings and about 40,000 sentences handed down by DDR courts for “political offenses.”
During the early years of Sauer’s operation, the details of political prosecutions became known only when victims were ransomed by West Germany or were expelled. Between 1963 and 1989, West Germany paid DM5 billion (nearly US$3 billion) to the communist regime for the release of 34,000 political prisoners. The price per head varied according to the importance of the person or the length of the sentence. In some cases the ransom amounted to more than US$56,000. The highest sum ever paid to the East Germans appears to have been DM450,000 (US$264,705 using an exchange rate of US$1.70 to the mark). The ransom “object” in this case was Count Benedikt von Hoensbroech. A student in his early twenties, von Hoensbroech was attending a West Berlin university when the wall went up. He was caught by the Stasi while trying to help people escape and was sentenced to ten years at hard labor. The case attracted international attention because his family was related to Queen Fabiola of Belgium, who interceded with the East Germans. Smelling money, the East German government first demanded the equivalent of more than US$1 million from the young man’s father as ransom. In the end, the parties settled on the figure of DM450,000, of which the West German government paid DM40,000 (about $23,529). Such ransom operations were fully controlled by the Stasi.
Political prisoners released in the DDR could not be registered by the West Germans because their cases remained secret. The victims were admonished to keep quiet or face another prison term. Nonetheless, in the first year after reunification, Sauer’s office added another 20,000 documented cases, for a total of 60,000. Sauer said he believed the final figure of all political prosecutions would be somewhere around 300,000. In every case, the Stasi was involved either in the initial arrest or in pretrial interrogations during which “confessions” were usually extracted by physical or psychological torture, particularly between the mid-1940s and the mid-1960s.
Until 1987, the DDR imposed the death penalty for a number of capital crimes, including murder, espionage, and economic offenses. But after the mid-1950s, nearly all death sentences were kept quiet and executions were carried out in the strictest secrecy, initially by guillotine and in later years by a single pistol shot to the neck. In most instances, the relatives of those killed were not informed either of the sentence or of the execution. The corpses were cremated and the ashes buried secretly, sometimes at construction sites. In reporting about one executioner who shot more than twenty persons to death, the Berlin newspaper Bildzeitung said that a total of 170 civilians had been executed in East Germany. However, Franco Werkenthin, the Berlin official investigating DDR crimes, said he had documented at least three hundred executions. He declined to say how many were for political offenses, because he had not yet submitted his report to parliament. “But it was substantial,” he told me. The true number of executions may never be known because no complete record of death sentences meted out by civil courts could be found. Other death sentences were handed down by military courts, and many records of those are also missing. In addition, German historian Günther Buch believes that about two hundred members of the Stasi itself were executed for various crimes, including attempts to escape to the West.
SAFEGUARDING HUMAN DIGNITY?
The preamble to the East German criminal code stated that the purpose of the code was to “safeguard the dignity of humankind, its freedom and rights under the aegis of the criminal code of the socialist state,” and that “a person can be prosecuted under the criminal code only in strictest concurrence with the law.” However, many of the codified offenses for which East German citizens were prosecuted and imprisoned were unique to totalitarian regimes, both fascist and communist.
Moreover, certain sections of the code, such as those on “Treasonable Relaying of Information” and “Treasonable Agent Activity,” were perversely applied, landing countless East Germans in maximum security penitentiaries. The victims of this perversion of justice usually were persons who had requested legal exit permits from the DDR authorities and had been turned down. In many cases, their “crime” was having contacted a Western consulate to inquire about immigration procedures. Sentences of up to two and a half years’ hard labor were not unusual as punishment for such inquiries.
Engaging in “propaganda hostile to the state” was another punishable offense. In one such case, a young man was arrested and prosecuted for saying that it was not necessary to station tanks at the border and for referring to border fortifications as “nonsense.” During his trial, he “admitted” to owning a television set on which he watched West German programs and later told friends what he saw. One of those “friends” had denounced him to the Stasi. The judge considered the accused’s actions especially egregious and sentenced him to a year and a half at hard labor.
Ironically, another part of this section of the criminal code decreed that “glorifying militarism” also was a punishable offense, although the DDR itself “glorified” its People’s Army beyond any Western norm. That army was clad in uniforms and insignia identical to those of the Nazi Wehrmacht, albeit without eagles and swastikas. The helmets, too, were differently shaped, but the Prussian goose step was regulation during parades.
A nineteen-year-old who had placed a sign in an apartment window reading “When justice is turned into injustice, resistance becomes an obligation!” was rewarded with twenty-two months in the penitentiary. Earlier, the youth had applied for an exit visa and had been turned down. A thirty-four-year-old father of two who also had been denied permission to leave the “workers’ and peasants’ state” with his family similarly advertised that fact with a poster reading “We want to leave, but they won’t let us.” The man went to prison for sixteen months. The “crimes” of both men were covered by a law on “Interference in Activities of the State or Society.”
Two letters—one to a friend in West Germany, seeking assistance to legally emigrate to the West, and another containing a similar appeal to Chief of State Honecker—brought a four-year sentence to their writer, who was convicted under two laws: those on “establishing illegal contacts” (writing to his friend) and on “public denigration” (writing to Honecker). The Stasi had illegally intercepted both letters.
The East German party chiefs were not content to rely only on the Stasi’s millions of informers to ferret out antistate sentiments. Leaving nothing to chance, they created a law that made the failure to denounce fellow citizens a crime punishable by up to five years’ imprisonment. One man was sentenced to twenty-three months for failing to report that a friend of his was preparing to escape to the West. The mandatory denunciation law had its roots in the statutes of the Socialist Unity Party, which were published in the form of a little red booklet. I picked up a copy of this booklet that had been discarded by its previous owner, a Stasi chauffeur, who had written “Ha, Ha” next to the mandate to “report any misdeeds, regardless of the person responsible, to leading party organs, all the way up to the Central Committee.”
Rupert Scholz, member of parliament and professor of law at the University of Munich, said many East Germans feel there is little determination among their Western brethren to bring the Stasi criminals to trial. “In fact, we already have heard many of them say that the peaceful revolution should have been a bloody one instead so they could have done away with their tormentors by hanging them posthaste,” Scholz told me.
The Reverend Joachim Gauck, minister to a Lutheran parish in East Germany, shared the people’s pessimism that justice would be done. Following reunification, Gauck was appointed by the Bonn government as its special representative for safeguarding and maintaining the Stasi archives. “We must at least establish a legal basis for finding the culprits in our files,” Gauck told me. “But it will not be easy. If you stood the millions of files upright in one line, they would stretch for 202 kilometers [about 121 miles]. In those files you can find an unbelievable number of Stasi victims and their tormentors.”
Gauck was given the mandate he needed in November 1991, when the German parliament passed a law authorizing file searches to uncover Stasi perpetrators and their informants. He viewed this legislation as first step in the right direction. With the evidence from Stasi files, the perpetrators could be removed from their public service jobs without any formal legal proceedings. Said Gauck: “We needed this law badly. It is not reasonable that persons who served this apparatus of oppression remain in positions of trust.”


![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict129.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict128.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict130.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict131.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict132.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict133.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict134.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict135.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict136.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict137.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict138.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict139.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict140.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict141.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict142.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict143.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict144.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict145.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict146.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict114.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict113.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict116.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict120.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict115.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict117.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict119.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict118.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict123.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict122.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict124.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict125.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict126.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict127.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict121.jpg)


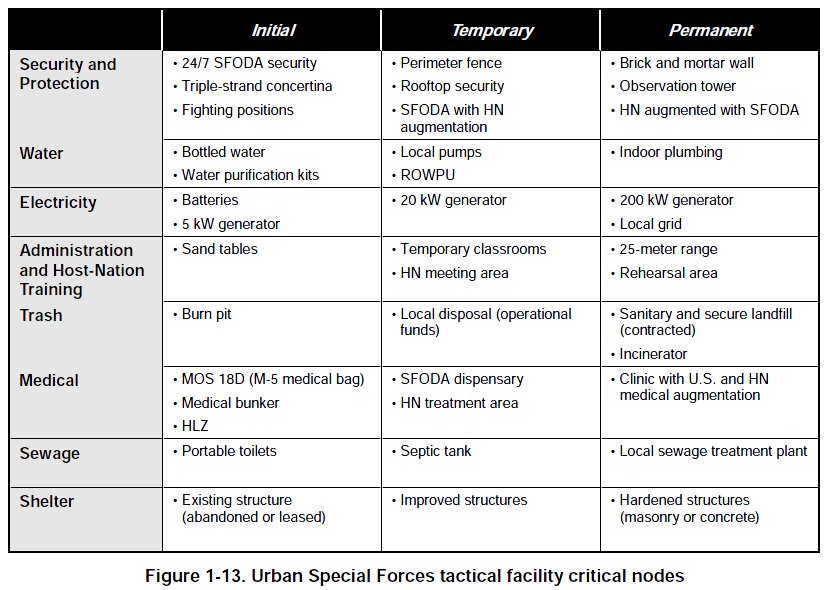
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-dnc-2012/pict27.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-dnc-2012/pict36.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-dnc-2012/pict35.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-dnc-2012/pict34.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-dnc-2012/pict29.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-dnc-2012/pict31.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-dnc-2012/pict30.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-dnc-2012/pict32.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-dnc-2012/pict33.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-dnc-2012/pict28.jpg)




![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict49.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict107.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict108.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict109.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict50.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict51.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict106.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict11.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict15.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict17.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict18.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict19.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict12.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict14.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict2.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict3.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict4.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict1.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict0.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict5.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict6.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict8.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict9.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict13.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict110.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict111.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict104.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict105.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict102.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict96.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict97.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict98.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict99.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict100.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict101.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict103.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict82.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict83.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict84.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict85.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict112.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict86.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict87.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict88.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict89.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict90.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict91.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict93.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict94.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict95.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict92.jpg)


![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict81.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict61.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict63.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict52.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict55.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict53.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict54.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict66.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict60.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict56.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict57.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict58.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict59.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict62.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict67.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict68.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict69.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict70.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict71.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict72.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict73.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict74.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict75.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict76.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict79.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict77.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict78.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict80.jpg)

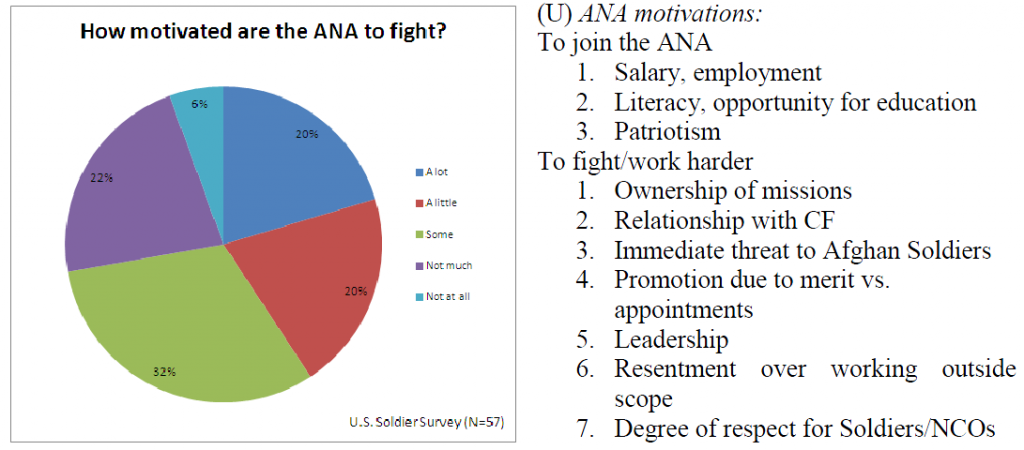

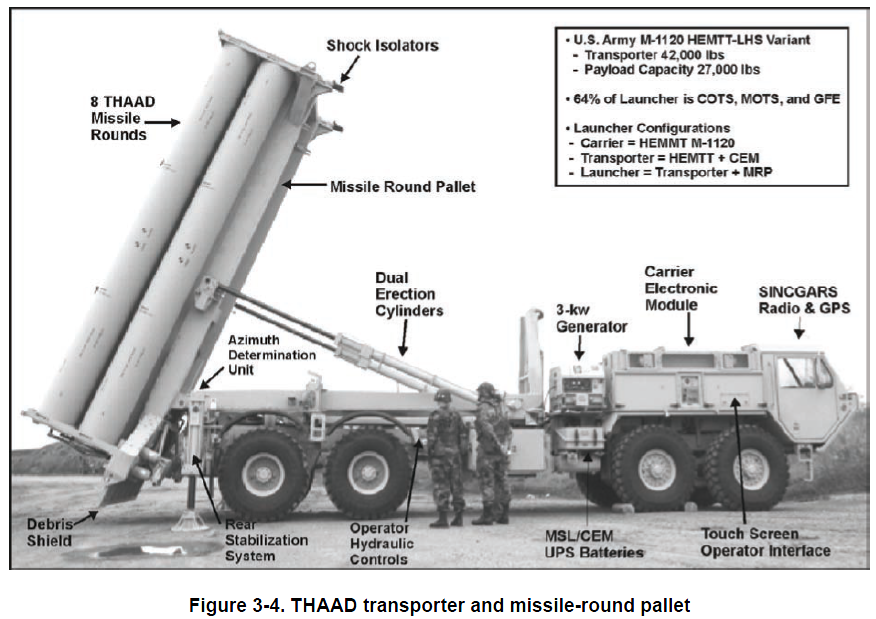
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict26.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict34.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict35.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict33.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict27.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict32.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict28.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict31.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict29.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict30.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict21.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict23.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict20.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict22.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict24.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict25.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict37.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict39.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict38.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict36.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict40.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict43.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict41.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict42.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict45.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict46.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict47.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict48.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/free-syria/pict44.jpg)

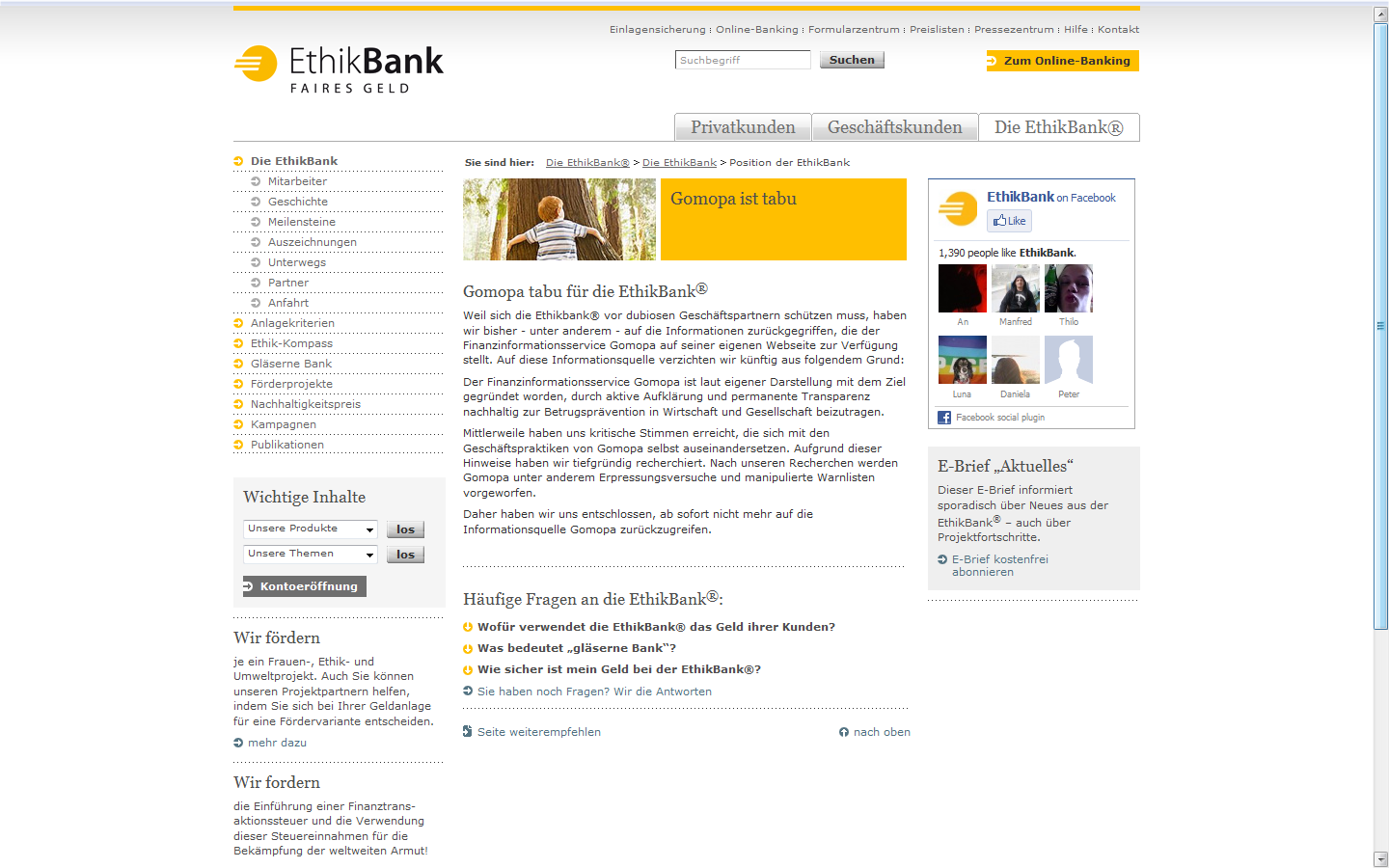

![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-boundary.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-boundary3.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-boundary5.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-boundary4.jpg)

![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-pulpit-13.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-pulpit-12.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-pulpit-11.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-pulpit-09.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-pulpit-10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-pulpit-07.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-pulpit-06.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-pulpit-04.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-pulpit-05.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-pulpit-08.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-pulpit-03.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-juliets/assange-pulpit-02.jpg)









![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict26.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict22.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict27.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict28.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict29.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict30.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict17.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict25.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict20.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict15.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict11.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict16.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict24.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict6.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict8.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict13.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict18.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict12.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict14.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict19.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict23.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-hovel/pict21.jpg)


















![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict173.jpg) Republican presidential candidate and former Massachusetts Governor Mitt Romney (L) and Rep. Paul Ryan (R-WI) (R) greet supporters during a campaign rally on August 11, 2012 in Manassas, Virginia. Mitt Romney kicked off a four day bus tour with an announcement of his running mate, Rep. Paul Ryan (R-WI).
Republican presidential candidate and former Massachusetts Governor Mitt Romney (L) and Rep. Paul Ryan (R-WI) (R) greet supporters during a campaign rally on August 11, 2012 in Manassas, Virginia. Mitt Romney kicked off a four day bus tour with an announcement of his running mate, Rep. Paul Ryan (R-WI).![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict165.jpg) Republican presidential candidate and former Massachusetts Governor Mitt Romney (L) and his running mate Rep. Paul Ryan (R-WI) wave to an overflow crowd before a campaign rally at Absolute Style furniture on August 12, 2012 in High Point, North Carolina. Mitt Romney continues his four day bus tour a day after announcing his running mate, Rep. Paul Ryan (R-WI).
Republican presidential candidate and former Massachusetts Governor Mitt Romney (L) and his running mate Rep. Paul Ryan (R-WI) wave to an overflow crowd before a campaign rally at Absolute Style furniture on August 12, 2012 in High Point, North Carolina. Mitt Romney continues his four day bus tour a day after announcing his running mate, Rep. Paul Ryan (R-WI).![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict162.jpg) Republican U.S. presidential candidate Mitt Romney greets supporters during a campaign stop at Absolute Style furniture store in High Point, North Carolina August 12, 2012.
Republican U.S. presidential candidate Mitt Romney greets supporters during a campaign stop at Absolute Style furniture store in High Point, North Carolina August 12, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict163.jpg) Republican presidential candidate and former Massachusetts Governor Mitt Romney greets an overflow crowd before a campaign rally at Absolute Style furniture on August 12, 2012 in High Point, North Carolina. Mitt Romney continues his four day bus tour a day after announcing his running mate, Rep. Paul Ryan (R-WI).
Republican presidential candidate and former Massachusetts Governor Mitt Romney greets an overflow crowd before a campaign rally at Absolute Style furniture on August 12, 2012 in High Point, North Carolina. Mitt Romney continues his four day bus tour a day after announcing his running mate, Rep. Paul Ryan (R-WI).![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict164.jpg) Republican vice presidential candidate Rep. Paul Ryan (R-WI) greets an overflow crowd before a campaign rally at Absolute Style furniture on August 12, 2012 in High Point, North Carolina. Mitt Romney continues his four day bus tour a day after announcing his running mate, Rep. Paul Ryan (R-WI).
Republican vice presidential candidate Rep. Paul Ryan (R-WI) greets an overflow crowd before a campaign rally at Absolute Style furniture on August 12, 2012 in High Point, North Carolina. Mitt Romney continues his four day bus tour a day after announcing his running mate, Rep. Paul Ryan (R-WI).![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict166.jpg) US Republican presidential candidate and former Massachusetts Governor Mitt Romney greets supporters prior to speaking during a campaign rally at Absolute Style furniture company in High Point, North Carolina, August 12, 2012. Romney and his running mate Wisconsin Representative Paul Ryan continue on the second day of a 4-day bus trip that will take Romney to 4 key swing states, Virginia, North Carolina, Florida and Ohio, and also to Ryan’s home state of Wisconsin.
US Republican presidential candidate and former Massachusetts Governor Mitt Romney greets supporters prior to speaking during a campaign rally at Absolute Style furniture company in High Point, North Carolina, August 12, 2012. Romney and his running mate Wisconsin Representative Paul Ryan continue on the second day of a 4-day bus trip that will take Romney to 4 key swing states, Virginia, North Carolina, Florida and Ohio, and also to Ryan’s home state of Wisconsin.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict167.jpg) Republican presidential candidate and former Massachusetts Governor Mitt Romney (R) looks on as his running mate Republican vice presidential candidate, U.S. Rep. Paul Ryan (R-WI) speaks to an overflow crowd outside of a campaign rally at the NASCAR Technical Institute on August 12, 2012 in Mooresville, North Carolina. Mitt Romney continues his four day bus tour a day after announcing his running mate, Rep. Paul Ryan (R-WI).
Republican presidential candidate and former Massachusetts Governor Mitt Romney (R) looks on as his running mate Republican vice presidential candidate, U.S. Rep. Paul Ryan (R-WI) speaks to an overflow crowd outside of a campaign rally at the NASCAR Technical Institute on August 12, 2012 in Mooresville, North Carolina. Mitt Romney continues his four day bus tour a day after announcing his running mate, Rep. Paul Ryan (R-WI).![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict168.jpg) Republican vice presidential candidate, U.S. Rep. Paul Ryan (R-WI) shakes hands with supporters after speaking with Republican presidential candidate and former Massachusetts Governor Mitt Romney during the Mooresville Victory Rally August 12, 2012 at NASCAR Technical Institute in Mooresville, North Carolina. Mitt Romney will make stops in Florida and Ohio during his four-day bus tour.
Republican vice presidential candidate, U.S. Rep. Paul Ryan (R-WI) shakes hands with supporters after speaking with Republican presidential candidate and former Massachusetts Governor Mitt Romney during the Mooresville Victory Rally August 12, 2012 at NASCAR Technical Institute in Mooresville, North Carolina. Mitt Romney will make stops in Florida and Ohio during his four-day bus tour.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict169.jpg) Republican presidential candidate and former Massachusetts Gov. Mitt Romney shakes hands with supporters after speaking at the Mooresville Victory Rally with his running mate Republican vice presidential candidate, U.S. Rep. Paul Ryan (R-WI) August 12, 2012 at NASCAR Technical Institute in Mooresville, North Carolina. Mitt Romney will make stops in Florida and Ohio during his four-day bus tour.
Republican presidential candidate and former Massachusetts Gov. Mitt Romney shakes hands with supporters after speaking at the Mooresville Victory Rally with his running mate Republican vice presidential candidate, U.S. Rep. Paul Ryan (R-WI) August 12, 2012 at NASCAR Technical Institute in Mooresville, North Carolina. Mitt Romney will make stops in Florida and Ohio during his four-day bus tour.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict170.jpg) Republican presidential candidate Mitt Romney, center, greets supporters at a rally Sunday, Aug. 12, 2012, in Mooresville, N.C. , at the NASCAR Technical Institute.
Republican presidential candidate Mitt Romney, center, greets supporters at a rally Sunday, Aug. 12, 2012, in Mooresville, N.C. , at the NASCAR Technical Institute.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict171.jpg) Republican presidential candidate, former Massachusetts Gov. Mitt Romney, and vice presidential running mate Rep. Paul Ryan, R-Wis. , left, greet supporters during a campaign event at the NASCAR Technical Institute, Sunday, Aug. 12, 2012, in Mooresville, N.C.
Republican presidential candidate, former Massachusetts Gov. Mitt Romney, and vice presidential running mate Rep. Paul Ryan, R-Wis. , left, greet supporters during a campaign event at the NASCAR Technical Institute, Sunday, Aug. 12, 2012, in Mooresville, N.C.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict174.jpg) In this photo provided by the U.S. Coast Guard, Republican Presidential candidate Mitt Romney, second from right, shakes a person’s hand during a campaign rally in Manassas, Va. , Saturday, Aug. 11, 2012. Romney announced Wisconsin Congressman Paul Ryan, second from left, as his running mate during an event in Norfolk, Va. , launching a bus tour promoting The Romney Plan For A Stronger Middle Class in Virginia.
In this photo provided by the U.S. Coast Guard, Republican Presidential candidate Mitt Romney, second from right, shakes a person’s hand during a campaign rally in Manassas, Va. , Saturday, Aug. 11, 2012. Romney announced Wisconsin Congressman Paul Ryan, second from left, as his running mate during an event in Norfolk, Va. , launching a bus tour promoting The Romney Plan For A Stronger Middle Class in Virginia.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict175.jpg) Members of the U.S. Secret Service are seen on the rooftop of a building near the site of a campaign rally for Republican presidential candidate, former Massachusetts Gov. Mitt Romney, in Manassas, Va. , Saturday, Aug. 11, 2012.
Members of the U.S. Secret Service are seen on the rooftop of a building near the site of a campaign rally for Republican presidential candidate, former Massachusetts Gov. Mitt Romney, in Manassas, Va. , Saturday, Aug. 11, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict176.jpg) Wisconsin Representative Paul Ryan greets supporters after US Republican presidential candidate and former Massachusetts Governor Mitt Romney announced Ryan as his vice presidential running mate during a campaign rally at the Nauticus Museum after touring the USS Wisconsin in Norfolk, Virginia, August 11, 2012. Romney and his new running mate embark on the first day of a 4-day bus trip that will take the White House hopefuls to 4 key swing states, Virginia, North Carolina, Florida and Ohio.
Wisconsin Representative Paul Ryan greets supporters after US Republican presidential candidate and former Massachusetts Governor Mitt Romney announced Ryan as his vice presidential running mate during a campaign rally at the Nauticus Museum after touring the USS Wisconsin in Norfolk, Virginia, August 11, 2012. Romney and his new running mate embark on the first day of a 4-day bus trip that will take the White House hopefuls to 4 key swing states, Virginia, North Carolina, Florida and Ohio.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict177.jpg) Republican presidential candidate, former Massachusetts Gov. Mitt Romney (R) and U.S. Rep. Paul Ryan (R-WI) wave as Ryan is announced as his vice presidential running mate aboard the USS Wisconsin August 11, 2012 in Norfolk, Virginia. Ryan, a seven term congressman, is Chairman of the House Budget Committee and provides a strong contrast to the Obama administration on fiscal policy.
Republican presidential candidate, former Massachusetts Gov. Mitt Romney (R) and U.S. Rep. Paul Ryan (R-WI) wave as Ryan is announced as his vice presidential running mate aboard the USS Wisconsin August 11, 2012 in Norfolk, Virginia. Ryan, a seven term congressman, is Chairman of the House Budget Committee and provides a strong contrast to the Obama administration on fiscal policy.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict178.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict179.jpg) US Republican presidential candidate and former Massachusetts Governor Mitt Romney and Wisconsin Representative Paul Ryan(2ndL) greet supporters after announcing Ryan as his vice presidential running mate during a campaign rally at the Nauticus Museum after touring the USS Wisconsin in Norfolk, Virginia, August 11, 2012. Romney and his new running mate embark on the first day of a 4-day bus trip that will take the White House hopefuls to 4 key swing states, Virginia, North Carolina, Florida and Ohio.
US Republican presidential candidate and former Massachusetts Governor Mitt Romney and Wisconsin Representative Paul Ryan(2ndL) greet supporters after announcing Ryan as his vice presidential running mate during a campaign rally at the Nauticus Museum after touring the USS Wisconsin in Norfolk, Virginia, August 11, 2012. Romney and his new running mate embark on the first day of a 4-day bus trip that will take the White House hopefuls to 4 key swing states, Virginia, North Carolina, Florida and Ohio.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict180.jpg) Republican presidential candidate, former Massachusetts Gov. Mitt Romney (C) arrives at the USS Wisconsin August 11, 2012 in Norfolk, Virginia. Mitt Romney will announce Rep. Paul Ryan (R-WI), a seven term congressman, as his Vice President pick. Ryan is Chairman of the House Budget Committee and provides a strong contrast to the Obama administration on fiscal policy.
Republican presidential candidate, former Massachusetts Gov. Mitt Romney (C) arrives at the USS Wisconsin August 11, 2012 in Norfolk, Virginia. Mitt Romney will announce Rep. Paul Ryan (R-WI), a seven term congressman, as his Vice President pick. Ryan is Chairman of the House Budget Committee and provides a strong contrast to the Obama administration on fiscal policy.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict181.jpg) Janna Ryan, wife of newly announced Republican vice presidential candidate, Wisconsin Rep. Paul Ryan, partially visible behind her, greets crowd members after her husband addressed the crowd Saturday, Aug. 11, 2012 in Norfolk, Va.
Janna Ryan, wife of newly announced Republican vice presidential candidate, Wisconsin Rep. Paul Ryan, partially visible behind her, greets crowd members after her husband addressed the crowd Saturday, Aug. 11, 2012 in Norfolk, Va.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict182.jpg) U.S. Secret Service agents guard the campaign bus of Republican presidential candidate and former Massachusetts Gov. Mitt Romney on August 10, 2012 in Norfolk, Virginia. Romney is kicking off a four-day bus tour that in addtion to Viriginia, will see the candidate visit Florida, North Carolina and Ohio.
U.S. Secret Service agents guard the campaign bus of Republican presidential candidate and former Massachusetts Gov. Mitt Romney on August 10, 2012 in Norfolk, Virginia. Romney is kicking off a four-day bus tour that in addtion to Viriginia, will see the candidate visit Florida, North Carolina and Ohio.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict183.jpg) The motorcade of Republican presidential candidate and former Massachusetts Gov. Mitt Romney drives towards Downtown Boston on August 10, 2012 in Belmont, Massachusetts. Mitt Romney visited his campaign headquarters a day before kicking off a four day bus tour that will visit Virginia, Florida, North Carolina and Ohio.
The motorcade of Republican presidential candidate and former Massachusetts Gov. Mitt Romney drives towards Downtown Boston on August 10, 2012 in Belmont, Massachusetts. Mitt Romney visited his campaign headquarters a day before kicking off a four day bus tour that will visit Virginia, Florida, North Carolina and Ohio.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict184.jpg) A U.S. Secret Service agent guards a door before Republican presidential candidate and former Massachusetts Gov. Mitt Romney arrived at his campaign headquarters on August 10, 2012 in Boston, Massachusetts. Mitt Romney visited his campaign headquarters a day before kicking off a four day bus tour that will visit Virginia, Florida, North Carolina and Ohio.
A U.S. Secret Service agent guards a door before Republican presidential candidate and former Massachusetts Gov. Mitt Romney arrived at his campaign headquarters on August 10, 2012 in Boston, Massachusetts. Mitt Romney visited his campaign headquarters a day before kicking off a four day bus tour that will visit Virginia, Florida, North Carolina and Ohio.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict185.jpg) Republican presidential candidate and former Massachusetts Gov. Mitt Romney departs an Upper East Side event in Manhattan on August 9, 2012 in New York City. Mitt Romney is visiting New York for fundraising events today before travelling to Boston.
Republican presidential candidate and former Massachusetts Gov. Mitt Romney departs an Upper East Side event in Manhattan on August 9, 2012 in New York City. Mitt Romney is visiting New York for fundraising events today before travelling to Boston.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict186.jpg) A secret service agent stands posted at a field as Republican presidential candidate and former Massachusetts Governor Mitt Romney meets with Iowa Secretary of Agriculture Bill Northey at a farm in Des Moines, Iowa August 8, 2012.
A secret service agent stands posted at a field as Republican presidential candidate and former Massachusetts Governor Mitt Romney meets with Iowa Secretary of Agriculture Bill Northey at a farm in Des Moines, Iowa August 8, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict187.jpg) Republican presidential candidate and former Massachusetts Governor Mitt Romney (back C) shakes hands with supporters during a campaign event at Central Campus High School in Des Moines, Iowa August 8, 2012.
Republican presidential candidate and former Massachusetts Governor Mitt Romney (back C) shakes hands with supporters during a campaign event at Central Campus High School in Des Moines, Iowa August 8, 2012.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict188.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict189.jpg) Republican presidential candidate and former Massachusetts Gov. Mitt Romney campaigns at Stepto’s BBQ Shack in Evansville, Ind. , Saturday, Aug. 4, 2012.
Republican presidential candidate and former Massachusetts Gov. Mitt Romney campaigns at Stepto’s BBQ Shack in Evansville, Ind. , Saturday, Aug. 4, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict190.jpg) Republican presidential candidate and former Massachusetts Gov. Mitt Romney greets supporters during a campaign event with Republican Governors at Basalt Public High School on August 2, 2012 in Basalt, Colorado. One day after returning from a six-day overseas trip to England, Israel and Poland, Mitt Romney is campaigning in Colorado before heading to Nevada.
Republican presidential candidate and former Massachusetts Gov. Mitt Romney greets supporters during a campaign event with Republican Governors at Basalt Public High School on August 2, 2012 in Basalt, Colorado. One day after returning from a six-day overseas trip to England, Israel and Poland, Mitt Romney is campaigning in Colorado before heading to Nevada.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict191.jpg) Republican presidential candidate and former Massachusetts Gov. Mitt Romney steps off of a picnic table after speaking to an overflow crowd during a campaign event at the Jefferson County Fairgrounds on August 2, 2012 in Golden, Colorado. One day after returning from a six-day overseas trip to England, Israel and Poland, Mitt Romney is campaigning in Colorado before heading to Nevada.
Republican presidential candidate and former Massachusetts Gov. Mitt Romney steps off of a picnic table after speaking to an overflow crowd during a campaign event at the Jefferson County Fairgrounds on August 2, 2012 in Golden, Colorado. One day after returning from a six-day overseas trip to England, Israel and Poland, Mitt Romney is campaigning in Colorado before heading to Nevada.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict193.jpg) U.S. Republican Presidential candidate Mitt Romney takes off his jacket as he walks to his limousine after visiting the Warsaw Uprising Memorial in Warsaw, July 31, 2012.
U.S. Republican Presidential candidate Mitt Romney takes off his jacket as he walks to his limousine after visiting the Warsaw Uprising Memorial in Warsaw, July 31, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict192.jpg) U.S. Republican presidential candidate, former Massachusetts Gov. Mitt Romney (C) talks with participants after his speech in the Hall of the University of Warsaw Library on July 31, 2012 in Warsaw, Poland. After visiting London, Israel, and the polish city of Gdansk, Romney visits the capital of Poland, Warsaw.
U.S. Republican presidential candidate, former Massachusetts Gov. Mitt Romney (C) talks with participants after his speech in the Hall of the University of Warsaw Library on July 31, 2012 in Warsaw, Poland. After visiting London, Israel, and the polish city of Gdansk, Romney visits the capital of Poland, Warsaw.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict194.jpg) U.S. Republican presidential candidate Mitt Romney (C) is surrounded by security as he walks in the center of Gdansk Old Town, July 30, 2012.
U.S. Republican presidential candidate Mitt Romney (C) is surrounded by security as he walks in the center of Gdansk Old Town, July 30, 2012.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict195.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict196.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict197.jpg) Republican presidential candidate and former Massachusetts Gov. Mitt Romney and his wife Ann board their charter plane in Tel Aviv, Israel as they travel to Poland, Monday, July 30, 2012.
Republican presidential candidate and former Massachusetts Gov. Mitt Romney and his wife Ann board their charter plane in Tel Aviv, Israel as they travel to Poland, Monday, July 30, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict198.jpg) U.S. Republican Presidential candidate Mitt Romney (C) arrives surrounded by security to deliver foreign policy remarks at Mishkenot Sha’ananim in Jerusalem, July 29, 2012.
U.S. Republican Presidential candidate Mitt Romney (C) arrives surrounded by security to deliver foreign policy remarks at Mishkenot Sha’ananim in Jerusalem, July 29, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict199.jpg) US Republican presidential candidate Mitt Romney greets people after placing a message, written on paper, in the ancient stones of the Western Wall in Jerusalem’s Old City on July 29, 2012, during the annual Tisha B’Av (Ninth of Av) fasting and a memorial day, commemorating the destruction of ancient Jerusalem temples. Romney is meeting Israeli leaders as he seeks to burnish his foreign policy credentials and portray himself as a better friend to Israel than President Barack Obama.
US Republican presidential candidate Mitt Romney greets people after placing a message, written on paper, in the ancient stones of the Western Wall in Jerusalem’s Old City on July 29, 2012, during the annual Tisha B’Av (Ninth of Av) fasting and a memorial day, commemorating the destruction of ancient Jerusalem temples. Romney is meeting Israeli leaders as he seeks to burnish his foreign policy credentials and portray himself as a better friend to Israel than President Barack Obama.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict200.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict201.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict202.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict203.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict204.jpg) Israeli security is seen after the motorcade of Republican presidential candidate and former Massachusetts Gov. Mitt Romney arrives at the King David Hotel in Jerusalem, Sunday, July 29, 2012.
Israeli security is seen after the motorcade of Republican presidential candidate and former Massachusetts Gov. Mitt Romney arrives at the King David Hotel in Jerusalem, Sunday, July 29, 2012. ![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict205.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict206.jpg) U.S. Republican Presidential candidate Mitt Romney is recognized by pedestrians at Grosvenor Place in London, July 27, 2012, as he was forced by gridlock traffic to walk from his hotel to the Irish Embassy to meet with Irish Prime Minister (Taoiseach) Enda Kenny.
U.S. Republican Presidential candidate Mitt Romney is recognized by pedestrians at Grosvenor Place in London, July 27, 2012, as he was forced by gridlock traffic to walk from his hotel to the Irish Embassy to meet with Irish Prime Minister (Taoiseach) Enda Kenny.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict207.jpg) U.S. Republican Presidential candidate Mitt Romney gets out of his SUV with a team of security as he arrives for a fundraising event in London, July 26, 2012.
U.S. Republican Presidential candidate Mitt Romney gets out of his SUV with a team of security as he arrives for a fundraising event in London, July 26, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict208.jpg) Republican presidential candidate, former Massachusetts Gov. Mitt Romney arrives for a private fundraiser in Buffalo N.Y. , on Friday, June 29, 2012.
Republican presidential candidate, former Massachusetts Gov. Mitt Romney arrives for a private fundraiser in Buffalo N.Y. , on Friday, June 29, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict209.jpg) A U.S. Secret Service agent carries his weapon as he looks out from a motorcade vehicle as Republican presidential candidate Mitt Romney, not pictured, arrives for a private campaign finance event in New York, Thursday, June 28, 2012.
A U.S. Secret Service agent carries his weapon as he looks out from a motorcade vehicle as Republican presidential candidate Mitt Romney, not pictured, arrives for a private campaign finance event in New York, Thursday, June 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/romney-protect01/pict210.jpg) Secret Service vehicles escort the campaign bus of Republican presidential candidate, former Massachusetts Gov. Mitt Romney after leaving Yampa Valley Airport on May 28, 2012 in Yampa, Colorado. Mitt Romney will campaign in Colorado before heading to Las Vegas, Nevada.
Secret Service vehicles escort the campaign bus of Republican presidential candidate, former Massachusetts Gov. Mitt Romney after leaving Yampa Valley Airport on May 28, 2012 in Yampa, Colorado. Mitt Romney will campaign in Colorado before heading to Las Vegas, Nevada.
![[]](https://i0.wp.com/arcticready.com/PR-images/shell.gif)
![[]](https://i0.wp.com/arcticready.com/PR-images/whale_email1.jpg)








![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict154.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict153.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict152.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict135.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict136.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict137.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict138.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict140.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict144.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict139.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict142.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict141.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict143.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict145.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict147.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict148.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict146.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict149.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict150.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/pussy-riot/pict151.jpg)

![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict14.jpg) U.S. President Barack Obama (3rd L) greets an Air Force officer before boarding Marine One helicopter on August 4, 2012 at Joint Base Andrews, Maryland. Obama is spending the weekend at Camp David.
U.S. President Barack Obama (3rd L) greets an Air Force officer before boarding Marine One helicopter on August 4, 2012 at Joint Base Andrews, Maryland. Obama is spending the weekend at Camp David.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict15.jpg) President Barack Obama shakes hands with supporters at the end of a campaign rally at Loudoun County High School on August 2, 2012 in Leesburg, Virginia. The president campaigned earlier in the day in Florida.
President Barack Obama shakes hands with supporters at the end of a campaign rally at Loudoun County High School on August 2, 2012 in Leesburg, Virginia. The president campaigned earlier in the day in Florida.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict16.jpg) President Barack Obama, center, greets supporters after speaking at a campaign event at Loudoun County High School, Thursday, Aug. 2, 2012 in Leesburg, Va. Obama was campaigning in Florida and Northern Virginia today.
President Barack Obama, center, greets supporters after speaking at a campaign event at Loudoun County High School, Thursday, Aug. 2, 2012 in Leesburg, Va. Obama was campaigning in Florida and Northern Virginia today.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict17.jpg) President Barack Obama greets supporters after speaking at a campaign event at Loudoun County High School, Thursday, Aug. 2, 2012 in Leesburg, Va. Obama spent the day campaigning in Florida and Northern Virginia.
President Barack Obama greets supporters after speaking at a campaign event at Loudoun County High School, Thursday, Aug. 2, 2012 in Leesburg, Va. Obama spent the day campaigning in Florida and Northern Virginia.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict19.jpg) A Secret Service Counter Sniper Team prepares to climb down a ladder from on top of a people mover after President Barack Obama aboard Air Force One landed at Dulles International Airport in Sterling, Va.. , Thursday, Aug. 2, 2012.
A Secret Service Counter Sniper Team prepares to climb down a ladder from on top of a people mover after President Barack Obama aboard Air Force One landed at Dulles International Airport in Sterling, Va.. , Thursday, Aug. 2, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict22.jpg) President Barack Obama greets supporters after a campaign event at Rollins College, Thursday, Aug. 2, 2012, in Winter Park, Fla.
President Barack Obama greets supporters after a campaign event at Rollins College, Thursday, Aug. 2, 2012, in Winter Park, Fla.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict21.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict23.jpg) President Barack Obama greets guests on the tarmac upon his arrival at Orlando International Airport, Thursday, Aug. 2, 2012, in Orlando, Fla. Obama is campaigning in Florida and Northern Virginia today.
President Barack Obama greets guests on the tarmac upon his arrival at Orlando International Airport, Thursday, Aug. 2, 2012, in Orlando, Fla. Obama is campaigning in Florida and Northern Virginia today.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict50.jpg) President Barack Obama stops to greet patrons at Lechonera El Barrio, a local restaurant in Orlando, Fla. , Thursday, Aug. 2, 2012. Obama is campaigning in Florida and Northern Virginia today.
President Barack Obama stops to greet patrons at Lechonera El Barrio, a local restaurant in Orlando, Fla. , Thursday, Aug. 2, 2012. Obama is campaigning in Florida and Northern Virginia today.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict53.jpg) President Barack Obama greets eight-year old Olivia Short after he departed from Air Force One upon his arrival in Orlando, Fla. , Thursday, Aug. 2, 2012.
President Barack Obama greets eight-year old Olivia Short after he departed from Air Force One upon his arrival in Orlando, Fla. , Thursday, Aug. 2, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict54.jpg) President Barack Obama is hugged by a supporter after speaking at a campaign event at Mansfield Central Park, Wednesday, Aug. 1, 2012, in Mansfield, Ohio. Obama is campaign in Ohio with stops in Mansfield and Akron today. [Secret Service ready to remove an arm from Obama’s back. Note three agents in the crowd.]
President Barack Obama is hugged by a supporter after speaking at a campaign event at Mansfield Central Park, Wednesday, Aug. 1, 2012, in Mansfield, Ohio. Obama is campaign in Ohio with stops in Mansfield and Akron today. [Secret Service ready to remove an arm from Obama’s back. Note three agents in the crowd.]![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict56.jpg) Marine One helicopter, with President Barack Obama aboard, takes off from Wall Street heliport in New York, Monday, July, 30, 2012. Obama traveled to New York for a private fundraiser. [Decoy helo at rear, fire truck at right, Coast Guard ship in the river.]
Marine One helicopter, with President Barack Obama aboard, takes off from Wall Street heliport in New York, Monday, July, 30, 2012. Obama traveled to New York for a private fundraiser. [Decoy helo at rear, fire truck at right, Coast Guard ship in the river.]![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict55.jpg) US President Barack Obama prepares to land at the Wall Street Helipad in New York on July 30, 2012. Obama is in New York to attend campaign events ahead of the November presidential election. [Two Marine transport at left, Secret Service agent on dock.]
US President Barack Obama prepares to land at the Wall Street Helipad in New York on July 30, 2012. Obama is in New York to attend campaign events ahead of the November presidential election. [Two Marine transport at left, Secret Service agent on dock.]
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict57.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict58.jpg) A Secret Service vehicle, left, and Air Force Security Forces vehicle follow Air Force One on the tarmac as it prepares to take-off with President Barack Obama aboard, at Andrews Air Force Base, Md. , Monday, July 30, 2012.
A Secret Service vehicle, left, and Air Force Security Forces vehicle follow Air Force One on the tarmac as it prepares to take-off with President Barack Obama aboard, at Andrews Air Force Base, Md. , Monday, July 30, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict59.jpg) U.S. First Lady Michelle Obama sits separated from the public during the basketball match between the U.S. and France for the London 2012 Olympic Games at the Basketball Arena in the Olympic Park at Stratford in east London July 29, 2012. [Michelle’s customary Secret Service at her right, and below.]
U.S. First Lady Michelle Obama sits separated from the public during the basketball match between the U.S. and France for the London 2012 Olympic Games at the Basketball Arena in the Olympic Park at Stratford in east London July 29, 2012. [Michelle’s customary Secret Service at her right, and below.]![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict60.jpg) US First Lady Michelle Obama (R) speaks with tennis player Venus Williams (top L) as they attend the women’s singles tennis match between Serbia’s Jelena Jankovic and Serena Williams of the US during the London 2012 Olympic Games at the All England Tennis Club in Wimbledon, southwest London, on July 28, 2012.
US First Lady Michelle Obama (R) speaks with tennis player Venus Williams (top L) as they attend the women’s singles tennis match between Serbia’s Jelena Jankovic and Serena Williams of the US during the London 2012 Olympic Games at the All England Tennis Club in Wimbledon, southwest London, on July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict61.jpg) U.S First Lady Michelle Obama, left, waves an American flag as she cheers on the U.S. swim team during the first day of finals at the 2012 Summer Olympics, Saturday, July 28, 2012, in London. At right is Summer Schlopy, host of Yahoo! Sports’ web series Elite Athlete Workout. [Two Secret Service at left.]
U.S First Lady Michelle Obama, left, waves an American flag as she cheers on the U.S. swim team during the first day of finals at the 2012 Summer Olympics, Saturday, July 28, 2012, in London. At right is Summer Schlopy, host of Yahoo! Sports’ web series Elite Athlete Workout. [Two Secret Service at left.]![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict62.jpg) Agents keep watch as U.S. President Barack Obama (C) walks to the Marine One helicopter before departing from a soccer field at the Madeira School after attending a campaign event at a nearby private residence in McLean, Virginia, July 27, 2012.
Agents keep watch as U.S. President Barack Obama (C) walks to the Marine One helicopter before departing from a soccer field at the Madeira School after attending a campaign event at a nearby private residence in McLean, Virginia, July 27, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict63.jpg) US President Barack Obama walk across a field after stepping off Marine One upon arrival at the Madeira School landing zone July 27, 2012 in McLean, Virginia. Obama is in McLean to attend campaign fundraisers.
US President Barack Obama walk across a field after stepping off Marine One upon arrival at the Madeira School landing zone July 27, 2012 in McLean, Virginia. Obama is in McLean to attend campaign fundraisers.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict64.jpg) President Barack Obama waves as he walks across the football field at Madeira school in McLean, Va. , Friday, July, 27, 2012. Obama Traveled to Northern Virginia for a private fundraiser.
President Barack Obama waves as he walks across the football field at Madeira school in McLean, Va. , Friday, July, 27, 2012. Obama Traveled to Northern Virginia for a private fundraiser.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict65.jpg) US First Lady Michelle Obama plays with children as part of her ‘Let’s Move-London’ event at the Winfield House in London on July 27, 2012, hours before the official start of the London 2012 Olympic Games. [SS at right.
US First Lady Michelle Obama plays with children as part of her ‘Let’s Move-London’ event at the Winfield House in London on July 27, 2012, hours before the official start of the London 2012 Olympic Games. [SS at right.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict66.jpg) U.S. first lady Michelle Obama plays with schoolchildren during a ‘Let’s Move!’ event for about 1,000 American military children and American and British students at the U.S. ambassador’s residence in London, ahead of the 2012 Summer Olympics, Friday, July 27, 2012. [Two Secret Service in suits to hide weapons; at center, female.]
U.S. first lady Michelle Obama plays with schoolchildren during a ‘Let’s Move!’ event for about 1,000 American military children and American and British students at the U.S. ambassador’s residence in London, ahead of the 2012 Summer Olympics, Friday, July 27, 2012. [Two Secret Service in suits to hide weapons; at center, female.]![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict67.jpg) U.S. Secret Service keeps watch as President Barack Obama departs the New Orleans area in Air Force One at Louis Armstrong International Airport in Kenner, La. , Wednesday, July 25, 2012. Obama delivered remarks at the National Urban League 2012 Annual Conference and attended campaign events in New Orleans.
U.S. Secret Service keeps watch as President Barack Obama departs the New Orleans area in Air Force One at Louis Armstrong International Airport in Kenner, La. , Wednesday, July 25, 2012. Obama delivered remarks at the National Urban League 2012 Annual Conference and attended campaign events in New Orleans.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict68.jpg) President Barack Obama walks over to greet people after arriving at Boeing Field in Seattle, Tuesday, July 24, 2012.
President Barack Obama walks over to greet people after arriving at Boeing Field in Seattle, Tuesday, July 24, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict69.jpg) US President Barack Obama greets wellwishers upon arrival on Air Force One at Portland International Airport in Portland, Oregon, July 24, 2012. Obama is traveling to attend campaign events and fundraisers.
US President Barack Obama greets wellwishers upon arrival on Air Force One at Portland International Airport in Portland, Oregon, July 24, 2012. Obama is traveling to attend campaign events and fundraisers.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict70.jpg) Supporters walk in a line across the tarmac to greet President Barack Obama on his arrival at Boeing Field Tuesday, July 24, 2012, in Seattle. Obama is scheduled to attend a pair of campaign fund-raisers in the area.
Supporters walk in a line across the tarmac to greet President Barack Obama on his arrival at Boeing Field Tuesday, July 24, 2012, in Seattle. Obama is scheduled to attend a pair of campaign fund-raisers in the area.![[Image]](https://i0.wp.com/cryptome.org/2012-info/obama-protect48/pict71.jpg) President Barack Obama heads to his limousine after stopping at the Gateway Breakfast House in Portland, Ore. , Tuesday, July 24, 2012.
President Barack Obama heads to his limousine after stopping at the Gateway Breakfast House in Portland, Ore. , Tuesday, July 24, 2012.

![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict78.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict61.jpg) Local residents clash with the police in front of a local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu province July 28, 2012. Chinese officials cancelled an industrial waste pipeline project on Saturday after anti-pollution demonstrators occupied the government office in eastern China, destroying computers and overturning cars. The demonstration was the latest in a string of protests sparked by fears of environmental degradation and highlights the social tensions the government in Beijing faces as it approaches a leadership transition this year.
Local residents clash with the police in front of a local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu province July 28, 2012. Chinese officials cancelled an industrial waste pipeline project on Saturday after anti-pollution demonstrators occupied the government office in eastern China, destroying computers and overturning cars. The demonstration was the latest in a string of protests sparked by fears of environmental degradation and highlights the social tensions the government in Beijing faces as it approaches a leadership transition this year.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict60.jpg) A police officer bleeds after clashing with local residents in front of a local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.
A police officer bleeds after clashing with local residents in front of a local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict30.jpg) A woman, with her face covered in blood, is helped by demonstrators after clashes with police during protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.
A woman, with her face covered in blood, is helped by demonstrators after clashes with police during protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict62.jpg) Local residents, holding banner which reads “Against the Oji Paper Group, protect our homeland”, shout as they gather to protest against plans for a water discharge project in Qidong, China Saturday, July 28, 2012.
Local residents, holding banner which reads “Against the Oji Paper Group, protect our homeland”, shout as they gather to protest against plans for a water discharge project in Qidong, China Saturday, July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict63.jpg) A group of protesters overturn a car near the local government office compound in the coastal city of Qidong, near Shanghai, in the eastern China province of Jiangsu on July 28, 2012.
A group of protesters overturn a car near the local government office compound in the coastal city of Qidong, near Shanghai, in the eastern China province of Jiangsu on July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict64.jpg) Local residents gather around scattered documents and an overturned car during a protest against plans for a water discharge project in Qidong, China Saturday, July 28, 2012.
Local residents gather around scattered documents and an overturned car during a protest against plans for a water discharge project in Qidong, China Saturday, July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict65.jpg) Local residents surround a vehicle after they overturned it, as they gather to protest against plans for a water discharge project in Qidong, China Saturday, July 28, 2012.
Local residents surround a vehicle after they overturned it, as they gather to protest against plans for a water discharge project in Qidong, China Saturday, July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict66.jpg) Armed police officers head to the local government office building where local residents gathered to protest against plans for a water discharge project in Qidong, China Saturday, July 28, 2012.
Armed police officers head to the local government office building where local residents gathered to protest against plans for a water discharge project in Qidong, China Saturday, July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict67.jpg) Local residents stand on smashed cars as they occupy the local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.
Local residents stand on smashed cars as they occupy the local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict52.jpg) Police beat a protestor on the ground (not pictured) outside the local government offices in the coastal city of Qidong, near Shanghai, in the eastern China province of Jiangsu on July 28, 2012.
Police beat a protestor on the ground (not pictured) outside the local government offices in the coastal city of Qidong, near Shanghai, in the eastern China province of Jiangsu on July 28, 2012.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict53.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict81.jpg) This photo taken on July 28, 2012 shows police putting a protester’s T-shirt over his head (C) after they detained him outside the local government offices in Qidong in the eastern China province of Jiangsu. The coastal city of Qidong, near Shanghai, seemed calm on July 29 a day after local officials announced a waste water pipeline project from the paper mill, which belongs to Japanese company Oji Paper, would be ‘permanently cancelled’.
This photo taken on July 28, 2012 shows police putting a protester’s T-shirt over his head (C) after they detained him outside the local government offices in Qidong in the eastern China province of Jiangsu. The coastal city of Qidong, near Shanghai, seemed calm on July 29 a day after local officials announced a waste water pipeline project from the paper mill, which belongs to Japanese company Oji Paper, would be ‘permanently cancelled’.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict47.jpg) A police officer is thrown to the ground by protesters near the local government office building Saturday July 28, 2012 in Qidong, Jiangsu Province, China. Authorities in eastern China dropped plans for a water-discharge project Saturday after thousands of protesters angry about pollution took to the streets, in the latest of many such confrontations in a country where three decades of rapid economic expansion have come at an environmental price.
A police officer is thrown to the ground by protesters near the local government office building Saturday July 28, 2012 in Qidong, Jiangsu Province, China. Authorities in eastern China dropped plans for a water-discharge project Saturday after thousands of protesters angry about pollution took to the streets, in the latest of many such confrontations in a country where three decades of rapid economic expansion have come at an environmental price.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict51.jpg) Protesters and police clash outside the local government offices in Qidong in the eastern China province of Jiangsu on July 28, 2012.
Protesters and police clash outside the local government offices in Qidong in the eastern China province of Jiangsu on July 28, 2012.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict45.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict50.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict44.jpg) A line of paramilitary police makes its way through protesters outside the local government offices in Qidong in the eastern China province of Jiangsu on July 28, 2012.
A line of paramilitary police makes its way through protesters outside the local government offices in Qidong in the eastern China province of Jiangsu on July 28, 2012.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict68.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict69.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict73.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict55.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict41.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict49.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict71.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict72.jpg) Police officers guard the local government office building Saturday July 28, 2012 in Qidong, Jiangsu Province, China.
Police officers guard the local government office building Saturday July 28, 2012 in Qidong, Jiangsu Province, China.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict40.jpg) Protesters stand as police officers guard the local government office building Saturday July 28, 2012 in Qidong, Jiangsu Province, China.
Protesters stand as police officers guard the local government office building Saturday July 28, 2012 in Qidong, Jiangsu Province, China.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict48.jpg) Vehicles damaged by protesters are seen at the local government office building Saturday July 28, 2012 in Qidong, Jiangsu Province, China.
Vehicles damaged by protesters are seen at the local government office building Saturday July 28, 2012 in Qidong, Jiangsu Province, China.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict42.jpg) A protester stands in front of a lines of riot police officers Saturday July 28, 2012 in Qidong, Jiangsu Province, China.
A protester stands in front of a lines of riot police officers Saturday July 28, 2012 in Qidong, Jiangsu Province, China.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict46.jpg) Protesters, right, confront with police officers, left, near the local government office building Saturday July 28, 2012 in Qidong, Jiangsu Province, China.
Protesters, right, confront with police officers, left, near the local government office building Saturday July 28, 2012 in Qidong, Jiangsu Province, China.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict21.jpg) A demonstrator fights with a police officer in front of the local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012. Angry demonstrators occupied a government office in eastern China on Saturday, destroying computers and overturning cars parked outside in a violent protest against an industrial waste pipeline they said would poison their coastal waters. The demonstration was the latest in a string of protests sparked by fears of environment degradation and highlights the social tensions the government in Beijing is having to deal with as it approaches a leadership transition this year. About a 1,000 protesters marched through the coastal city of Qidong, about one hour north of Shanghai by car, shouting slogans against the plan to build a pipeline through the city that would empty waste from a nearby paper factory into the sea.
A demonstrator fights with a police officer in front of the local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012. Angry demonstrators occupied a government office in eastern China on Saturday, destroying computers and overturning cars parked outside in a violent protest against an industrial waste pipeline they said would poison their coastal waters. The demonstration was the latest in a string of protests sparked by fears of environment degradation and highlights the social tensions the government in Beijing is having to deal with as it approaches a leadership transition this year. About a 1,000 protesters marched through the coastal city of Qidong, about one hour north of Shanghai by car, shouting slogans against the plan to build a pipeline through the city that would empty waste from a nearby paper factory into the sea.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict27.jpg) Protesters beat a policeman (C) during a protest outside the local government offices in Qidong in the eastern China province of Jiangsu on July 28, 2012. Thousands of demonstrators protested against alleged pollution from a paper factory in this easten China city and clashed with police after they seized bottles of liquor and wine from the offices along with cartons of cigarettes, items which Chinese officials frequently receive as bribes.
Protesters beat a policeman (C) during a protest outside the local government offices in Qidong in the eastern China province of Jiangsu on July 28, 2012. Thousands of demonstrators protested against alleged pollution from a paper factory in this easten China city and clashed with police after they seized bottles of liquor and wine from the offices along with cartons of cigarettes, items which Chinese officials frequently receive as bribes.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict28.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict26.jpg) Protesters beat a policeman (C) during a protest outside the local government offices in Qidong in the eastern China province of Jiangsu on July 28, 2012. Thousands of demonstrators protested against alleged pollution from a paper factory in this easten China city and clashed with police after they seized bottles of liquor and wine from the offices along with cartons of cigarettes, items which Chinese officials frequently receive as bribes.
Protesters beat a policeman (C) during a protest outside the local government offices in Qidong in the eastern China province of Jiangsu on July 28, 2012. Thousands of demonstrators protested against alleged pollution from a paper factory in this easten China city and clashed with police after they seized bottles of liquor and wine from the offices along with cartons of cigarettes, items which Chinese officials frequently receive as bribes.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict29.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict31.jpg) Local residents occupy a local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.
Local residents occupy a local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict23.jpg) Local residents push over a police vehicle as they gather to protest against plans for a water discharge project in Qidong, China Saturday, July 28, 2012. The government in the city announced on its official website Saturday that the plans were scrapped amid opposition by local residents, who are concerned over potential pollution.
Local residents push over a police vehicle as they gather to protest against plans for a water discharge project in Qidong, China Saturday, July 28, 2012. The government in the city announced on its official website Saturday that the plans were scrapped amid opposition by local residents, who are concerned over potential pollution.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict24.jpg) A police car lies overturned as protesters occupy a government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.
A police car lies overturned as protesters occupy a government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict22.jpg) A local resident squats on a destroyed car after demonstrators occupied the local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.
A local resident squats on a destroyed car after demonstrators occupied the local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict25.jpg) Demonstrators stand inside a destroyed office at the local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012. Angry demonstrators occupied a government office in eastern China on Saturday, destroying computers and overturning cars in a violent protest against an industrial waste pipeline they said would poison their coastal waters.
Demonstrators stand inside a destroyed office at the local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012. Angry demonstrators occupied a government office in eastern China on Saturday, destroying computers and overturning cars in a violent protest against an industrial waste pipeline they said would poison their coastal waters.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict32.jpg) Police officers stands next to a damaged police car after demonstrators occupied the local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.
Police officers stands next to a damaged police car after demonstrators occupied the local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict37.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict20.jpg) A demonstrator smashes a car window during a protest against an industrial waste pipeline under construction in front of the local government building in Qidong, Jiangsu Province July 28, 2012.
A demonstrator smashes a car window during a protest against an industrial waste pipeline under construction in front of the local government building in Qidong, Jiangsu Province July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict19.jpg) Demonstrators smash a car in front of the local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.
Demonstrators smash a car in front of the local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict18.jpg) Local residents gather to protest against plans for a water discharge project in Qidong, China Saturday, July 28, 2012. The government in the city announced on its official website Saturday that the plans were scrapped amid opposition by local residents, who are concerned over potential pollution. AP
Local residents gather to protest against plans for a water discharge project in Qidong, China Saturday, July 28, 2012. The government in the city announced on its official website Saturday that the plans were scrapped amid opposition by local residents, who are concerned over potential pollution. AP![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict17.jpg) Local residents gather to protest against plans for a water discharge project in Qidong, China Saturday, July 28, 2012. The government in the city announced on its official website Saturday that the plans were scrapped amid opposition by local residents, who are concerned over potential pollution.
Local residents gather to protest against plans for a water discharge project in Qidong, China Saturday, July 28, 2012. The government in the city announced on its official website Saturday that the plans were scrapped amid opposition by local residents, who are concerned over potential pollution.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict16.jpg) Local residents protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.
Local residents protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict33.jpg) Local residents marche during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.
Local residents marche during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict36.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict34.jpg) Police officers try to calm the crowd during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.
Police officers try to calm the crowd during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict35.jpg) Local residents occupy the local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.
Local residents occupy the local government building during a protest against an industrial waste pipeline under construction in Qidong, Jiangsu Province July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict54.jpg) Protesters gather on rooftops to shout slogans outside the local government offices in the coastal city of Qidong, near Shanghai, in the eastern China province of Jiangsu on July 28, 2012.
Protesters gather on rooftops to shout slogans outside the local government offices in the coastal city of Qidong, near Shanghai, in the eastern China province of Jiangsu on July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict56.jpg) People standing on cars hold a banner as other protestors shout slogans inside the local government office compound in the coastal city of Qidong, near Shanghai, in the eastern China province of Jiangsu on July 28, 2012.
People standing on cars hold a banner as other protestors shout slogans inside the local government office compound in the coastal city of Qidong, near Shanghai, in the eastern China province of Jiangsu on July 28, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict57.jpg) Protestor shout slogans and hold placards outside the local government offices in the coastal city of Qidong, near Shanghai, in the eastern China province of Jiangsu on July 28, 2012.
Protestor shout slogans and hold placards outside the local government offices in the coastal city of Qidong, near Shanghai, in the eastern China province of Jiangsu on July 28, 2012.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/qidong/2/pict74.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012/07/report-infra-damage-bc.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012/07/report-infra-damage2.jpg)

![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict77.jpg) Nick Warner, director-general of Australia’s Secret Intelligence Service (ASIS), prepares to give a speech at the National Portrait Gallery in Canberra on July 19, 2012. Australia’s top spy warned of the ‘very real threat’ from extremists, in the first public address by the head of the country’s Secret Intelligence Service (ASIS) in its 60-year history.
Nick Warner, director-general of Australia’s Secret Intelligence Service (ASIS), prepares to give a speech at the National Portrait Gallery in Canberra on July 19, 2012. Australia’s top spy warned of the ‘very real threat’ from extremists, in the first public address by the head of the country’s Secret Intelligence Service (ASIS) in its 60-year history.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict76.jpg) Nick Warner (C), director-general of Australia’s Secret Intelligence Service (ASIS), gets wired up before giving a speech at the National Portrait Gallery in Canberra on July 19, 2012. Australia’s top spy warned of the ‘very real threat’ from extremists, in the first public address by the head of the country’s Secret Intelligence Service (ASIS) in its 60-year history.
Nick Warner (C), director-general of Australia’s Secret Intelligence Service (ASIS), gets wired up before giving a speech at the National Portrait Gallery in Canberra on July 19, 2012. Australia’s top spy warned of the ‘very real threat’ from extremists, in the first public address by the head of the country’s Secret Intelligence Service (ASIS) in its 60-year history.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict78.jpg) Nick Warner, director-general of Australia’s Secret Intelligence Service (ASIS), speaks at the National Portrait Gallery in Canberra on July 19, 2012. Australia’s top spy warned of the ‘very real threat’ from extremists, in the first public address by the head of the country’s Secret Intelligence Service (ASIS) in its 60-year history.
Nick Warner, director-general of Australia’s Secret Intelligence Service (ASIS), speaks at the National Portrait Gallery in Canberra on July 19, 2012. Australia’s top spy warned of the ‘very real threat’ from extremists, in the first public address by the head of the country’s Secret Intelligence Service (ASIS) in its 60-year history.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict108.jpg) Director Richard Fadden waits to testify before the Commons public safety committee on Parliament Hill in Ottawa May 31, 2012.
Director Richard Fadden waits to testify before the Commons public safety committee on Parliament Hill in Ottawa May 31, 2012.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict92.jpg) French intelligence national coordinator, Ange Mancini, leaves after a meeting with French Justice on March 29, 2012 in Paris.
French intelligence national coordinator, Ange Mancini, leaves after a meeting with French Justice on March 29, 2012 in Paris.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict93.jpg) French intelligence national coordinator, Ange Mancini arrives at the Elysee presidential palace in Paris, on March 27, 2012 to take part in a meeting with French President, magistrates and policemen who took part in the investigations following the shooting of seven persons and in the siege of self-proclaimed Islamist Mohamed Merah’s flat in Toulouse. Mohamed Merah was killed during the RAID police special forces unit assault after a 32-hour siege on March 21.
French intelligence national coordinator, Ange Mancini arrives at the Elysee presidential palace in Paris, on March 27, 2012 to take part in a meeting with French President, magistrates and policemen who took part in the investigations following the shooting of seven persons and in the siege of self-proclaimed Islamist Mohamed Merah’s flat in Toulouse. Mohamed Merah was killed during the RAID police special forces unit assault after a 32-hour siege on March 21.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict101.jpg) General Director of National Police (DGPN) Frederic Pechenard (L) and his Principal private secretary Robert Martin (C) speak with director of the French Intelligence agency, the Central Directorate of Interior Intelligence (DCRI) Bernard Squarcini (R) as they inaugurate the France’s Milipol global security trade fair on October 18, 2011 in Paris. Milipol Paris 2011, welcoming more than 1,000 exhibiting companies from 43 countries, runs until October 21.
General Director of National Police (DGPN) Frederic Pechenard (L) and his Principal private secretary Robert Martin (C) speak with director of the French Intelligence agency, the Central Directorate of Interior Intelligence (DCRI) Bernard Squarcini (R) as they inaugurate the France’s Milipol global security trade fair on October 18, 2011 in Paris. Milipol Paris 2011, welcoming more than 1,000 exhibiting companies from 43 countries, runs until October 21.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict117.jpg) Director of the NZSIS Warren Tucker reads out a prepared statement regarding Ahmed Zaoui, September 13, 2007.
Director of the NZSIS Warren Tucker reads out a prepared statement regarding Ahmed Zaoui, September 13, 2007.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict96.jpg) Syria’s President Bashar al-Assad (R) meets Russian Foreign Minister Sergei Lavrov (2nd R) with Russian Foreign Intelligence Service chief Mikhail Fradkov (L) in Damascus February 7, 2012, in this handout photograph released by Syria’s national news agency SANA. Lavrov began talks with Syrian President Bashar al-Assad on Tuesday by saying Moscow wants Arab peoples to live in peace and the Syrian leader is aware of his responsibility, Russian news agency RIA reported.
Syria’s President Bashar al-Assad (R) meets Russian Foreign Minister Sergei Lavrov (2nd R) with Russian Foreign Intelligence Service chief Mikhail Fradkov (L) in Damascus February 7, 2012, in this handout photograph released by Syria’s national news agency SANA. Lavrov began talks with Syrian President Bashar al-Assad on Tuesday by saying Moscow wants Arab peoples to live in peace and the Syrian leader is aware of his responsibility, Russian news agency RIA reported.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict81.jpg) The Director General of the British domestic security and counter-intelligence service MI5 Jonathan Evans, right, sits beside the head of the British foreign intelligence service, the Secret Intelligence Service (SIS), MI6, Sir John Sawers, left, as they listen in the front row of the audience during a speech by Britain’s Foreign Secretary William Hague at the Foreign Office in London, Wednesday, Nov. 16, 2011. Hague’s speech was on Secret Intelligence, praising the work of agencies, stressing the importance of framework of law, values and accountability.
The Director General of the British domestic security and counter-intelligence service MI5 Jonathan Evans, right, sits beside the head of the British foreign intelligence service, the Secret Intelligence Service (SIS), MI6, Sir John Sawers, left, as they listen in the front row of the audience during a speech by Britain’s Foreign Secretary William Hague at the Foreign Office in London, Wednesday, Nov. 16, 2011. Hague’s speech was on Secret Intelligence, praising the work of agencies, stressing the importance of framework of law, values and accountability.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict82.jpg) The Director General of the British domestic security and counter-intelligence service MI5 Jonathan Evans, right, chats with the head of the British foreign intelligence service, the Secret Intelligence Service (SIS), MI6, Sir John Sawers, left, as they sit in the front row of the audience before the start of a speech by Britain’s Foreign Secretary William Hague at the Foreign Office in London, Wednesday, Nov. 16, 2011. Hague’s speech was on Secret Intelligence, praising the work of agencies, stressing the importance of framework of law, values and accountability.
The Director General of the British domestic security and counter-intelligence service MI5 Jonathan Evans, right, chats with the head of the British foreign intelligence service, the Secret Intelligence Service (SIS), MI6, Sir John Sawers, left, as they sit in the front row of the audience before the start of a speech by Britain’s Foreign Secretary William Hague at the Foreign Office in London, Wednesday, Nov. 16, 2011. Hague’s speech was on Secret Intelligence, praising the work of agencies, stressing the importance of framework of law, values and accountability.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict83.jpg) The Director General of the British domestic security and counter-intelligence service MI5 Jonathan Evans, second left, sits beside the head of the British foreign intelligence service, the Secret Intelligence Service (SIS), MI6, Sir John Sawers, left, as they listen with other officials in the front row of the audience during a speech by Britain’s Foreign Secretary William Hague at the Foreign Office in London, Wednesday, Nov. 16, 2011. Hague’s speech was on Secret Intelligence, praising the work of agencies, stressing the importance of framework of law, values and accountability.
The Director General of the British domestic security and counter-intelligence service MI5 Jonathan Evans, second left, sits beside the head of the British foreign intelligence service, the Secret Intelligence Service (SIS), MI6, Sir John Sawers, left, as they listen with other officials in the front row of the audience during a speech by Britain’s Foreign Secretary William Hague at the Foreign Office in London, Wednesday, Nov. 16, 2011. Hague’s speech was on Secret Intelligence, praising the work of agencies, stressing the importance of framework of law, values and accountability.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict107.jpg) John Brennan, Assistant to the President for Homeland Security and Counterterrorism, speaks at the Intelligence and National Security Alliance conference in Washington, Wednesday, Sept. 7, 2011.
John Brennan, Assistant to the President for Homeland Security and Counterterrorism, speaks at the Intelligence and National Security Alliance conference in Washington, Wednesday, Sept. 7, 2011.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict89.jpg) Director of National Intelligence James R. Clapper leaves a joint closed door meeting with the Senate and House Intelligence Committee on Capitol Hill, on June 7, 2012 in Wasington, DC. The joint Intelligence committee met with Clapper to discuss administration leaks of classified information.
Director of National Intelligence James R. Clapper leaves a joint closed door meeting with the Senate and House Intelligence Committee on Capitol Hill, on June 7, 2012 in Wasington, DC. The joint Intelligence committee met with Clapper to discuss administration leaks of classified information.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict90.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict91.jpg) James R. Clapper, Director of the National Intelligence Agency, talks with guests during a luncheon hosted by U.S. Secretary of State Hillary Clinton, to honor President of the Republic of the Philippines Benigno S. Aquino III, at the Department of State, on June 8, 2012 in Washington, DC. Later today President Aquino is scheduled to meet with U.S. President Barack Obama at the White House.
James R. Clapper, Director of the National Intelligence Agency, talks with guests during a luncheon hosted by U.S. Secretary of State Hillary Clinton, to honor President of the Republic of the Philippines Benigno S. Aquino III, at the Department of State, on June 8, 2012 in Washington, DC. Later today President Aquino is scheduled to meet with U.S. President Barack Obama at the White House.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict95.jpg) Witnesses are seated as the US Senate Intelligence Committee holds a full committee hearing on ‘World Wide Threats.’ on January 31, 2012 on Capitol Hill in Washington, DC. Witnesses include: Director of National Intelligence James Clapper; CIA Director David Petraeus; FBI Director Robert Mueller; Defense Intelligence Agency Director Lt. Gen. Ronald Burgess; National Counter terrorism Center Director Matthew Olsen; Assistant Secretary of State for Intelligence and Research Philip Goldberg; and Homeland Security Undersecretary for Intelligence and Analysis Caryn Wagner.
Witnesses are seated as the US Senate Intelligence Committee holds a full committee hearing on ‘World Wide Threats.’ on January 31, 2012 on Capitol Hill in Washington, DC. Witnesses include: Director of National Intelligence James Clapper; CIA Director David Petraeus; FBI Director Robert Mueller; Defense Intelligence Agency Director Lt. Gen. Ronald Burgess; National Counter terrorism Center Director Matthew Olsen; Assistant Secretary of State for Intelligence and Research Philip Goldberg; and Homeland Security Undersecretary for Intelligence and Analysis Caryn Wagner.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict98.jpg) FBI Director Robert Mueller, testifies before the US Senate Intelligence Committee during a full committee hearing on ‘World Wide Threats.’ on January 31, 2012 on Capitol Hill in Washington, DC.
FBI Director Robert Mueller, testifies before the US Senate Intelligence Committee during a full committee hearing on ‘World Wide Threats.’ on January 31, 2012 on Capitol Hill in Washington, DC.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict99.jpg) CIA Director David Petraeus, testifies before the US Senate Intelligence Committee during a full committee hearing on ‘World Wide Threats.’ on January 31, 2012 on Capitol Hill in Washington, DC.
CIA Director David Petraeus, testifies before the US Senate Intelligence Committee during a full committee hearing on ‘World Wide Threats.’ on January 31, 2012 on Capitol Hill in Washington, DC.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict110.jpg) Assistant Secretary of State for Intelligence and Research Philip Goldberg testifies before the Senate Select Committee on Intelligence on Capitol Hill January 31, 2012 in Washington, DC. The committee met to hear testimony on the topic of ‘World Wide Threats.’
Assistant Secretary of State for Intelligence and Research Philip Goldberg testifies before the Senate Select Committee on Intelligence on Capitol Hill January 31, 2012 in Washington, DC. The committee met to hear testimony on the topic of ‘World Wide Threats.’![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict112.jpg) Homeland Security Undersecretary for Intelligence and Analysis Caryn Wagner testifies before the Senate Select Committee on Intelligence on Capitol Hill January 31, 2012 in Washington, DC. The committee met to hear testimony on the topic of ‘World Wide Threats.’
Homeland Security Undersecretary for Intelligence and Analysis Caryn Wagner testifies before the Senate Select Committee on Intelligence on Capitol Hill January 31, 2012 in Washington, DC. The committee met to hear testimony on the topic of ‘World Wide Threats.’![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict97.jpg) National Counterterrorism Center Director Matthew Olsen testifies before the Senate Select Committee on Intelligence on Capitol Hill January 31, 2012 in Washington, DC. The committee met to hear testimony on the topic of ‘World Wide Threats.’
National Counterterrorism Center Director Matthew Olsen testifies before the Senate Select Committee on Intelligence on Capitol Hill January 31, 2012 in Washington, DC. The committee met to hear testimony on the topic of ‘World Wide Threats.’![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict116.jpg) Director of Defense Intelligence Agency Army Lt. Gen. Ronald Burgess testifies on Capitol Hill in Washington, Thursday, Feb. 2, 2012, before the House Intelligence Committee hearing on worldwide threats.
Director of Defense Intelligence Agency Army Lt. Gen. Ronald Burgess testifies on Capitol Hill in Washington, Thursday, Feb. 2, 2012, before the House Intelligence Committee hearing on worldwide threats.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict113.jpg) National Security Agency Director Gen. Keith Alexander speaks about cybersecurity and the new threats posed to the U.S. economy and military at the American Enterprise Institute July 9, 2012 in Washington, DC. Alexander is also the commander of the U.S. Cyber Command and chief at the Central Security Service, with responsibility for national foreign intelligence, combat support and U.S. national security information system protection. Alexander said that in cyberspace ‘the probability for crisis is mounting,’ and that now is the time for putting into place strong policies and rules for operations and defense.
National Security Agency Director Gen. Keith Alexander speaks about cybersecurity and the new threats posed to the U.S. economy and military at the American Enterprise Institute July 9, 2012 in Washington, DC. Alexander is also the commander of the U.S. Cyber Command and chief at the Central Security Service, with responsibility for national foreign intelligence, combat support and U.S. national security information system protection. Alexander said that in cyberspace ‘the probability for crisis is mounting,’ and that now is the time for putting into place strong policies and rules for operations and defense.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict87.jpg) National Security Agency Director Gen. Keith Alexander speaks about cybersecurity and the new threats posed to the U.S. economy and military at the American Enterprise Institute July 9, 2012 in Washington, DC. Alexander is also the commander of the U.S. Cyber Command and chief at the Central Security Service, with responsibility for national foreign intelligence, combat support and U.S. national security information system protection. Alexander said that in cyberspace ‘the probability for crisis is mounting,’ and that now is the time for putting into place strong policies and rules for operations and defense.
National Security Agency Director Gen. Keith Alexander speaks about cybersecurity and the new threats posed to the U.S. economy and military at the American Enterprise Institute July 9, 2012 in Washington, DC. Alexander is also the commander of the U.S. Cyber Command and chief at the Central Security Service, with responsibility for national foreign intelligence, combat support and U.S. national security information system protection. Alexander said that in cyberspace ‘the probability for crisis is mounting,’ and that now is the time for putting into place strong policies and rules for operations and defense.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict88.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict100.jpg) John Sano, Deputy Director of the C.I.A’s national clandestine service attends an international conference focused on a solution for Camp Ashraf in Iraq, which is home to thousands of outlawed Iranian regime opponents, on January 20, 2012 in Paris.
John Sano, Deputy Director of the C.I.A’s national clandestine service attends an international conference focused on a solution for Camp Ashraf in Iraq, which is home to thousands of outlawed Iranian regime opponents, on January 20, 2012 in Paris.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict86.jpg) Retired Gen. Michael Hayden, former Central Intelligence Agency and National Security Agency Director, speaks during the launch of the 2012 Failed States Index (FSI), on July 13, 2012 in Washington, DC. The FSI is a report that is released annually and highlights current trends in social, economic and political pressures that affect all states in the international community.
Retired Gen. Michael Hayden, former Central Intelligence Agency and National Security Agency Director, speaks during the launch of the 2012 Failed States Index (FSI), on July 13, 2012 in Washington, DC. The FSI is a report that is released annually and highlights current trends in social, economic and political pressures that affect all states in the international community.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict102.jpg) New York Police Department Commissioner Ray Kelly (C) takes part in his morning intelligence briefing with the Deputy Commissioner for Counterterrorism, Richard Daddario (L), and Deputy Commissioner of Intelligence, David Cohen (R) inside of the Executive Command Center at NYPD headquarters in New York August 5, 2011. The NYPD has worked since 9/11 on a long-term project to permanently increase vigilance in Lower Manhattan and Midtown, home to prominent financial institutions and national landmarks. Picture taken August 5, 2011.
New York Police Department Commissioner Ray Kelly (C) takes part in his morning intelligence briefing with the Deputy Commissioner for Counterterrorism, Richard Daddario (L), and Deputy Commissioner of Intelligence, David Cohen (R) inside of the Executive Command Center at NYPD headquarters in New York August 5, 2011. The NYPD has worked since 9/11 on a long-term project to permanently increase vigilance in Lower Manhattan and Midtown, home to prominent financial institutions and national landmarks. Picture taken August 5, 2011.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict104.jpg) New York Police Department Commissioner Ray Kelly (R) takes part in his morning intelligence briefing with the Deputy Commissioner for Counterterrorism Richard Daddario (C) and Deputy Commissioner of Intelligence David Cohen (L) inside of the Executive Command Center at NYPD headquarters in New York August 5, 2011. The NYPD has worked since 9/11 on a long-term project to permanently increase vigilance in Lower Manhattan and Midtown, home to prominent financial institutions and national landmarks. Picture taken August 5, 2011.
New York Police Department Commissioner Ray Kelly (R) takes part in his morning intelligence briefing with the Deputy Commissioner for Counterterrorism Richard Daddario (C) and Deputy Commissioner of Intelligence David Cohen (L) inside of the Executive Command Center at NYPD headquarters in New York August 5, 2011. The NYPD has worked since 9/11 on a long-term project to permanently increase vigilance in Lower Manhattan and Midtown, home to prominent financial institutions and national landmarks. Picture taken August 5, 2011.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict105.jpg) New York Police Department Commissioner Ray Kelly (L) takes part in his morning intelligence briefing with the Deputy Commissioner of Public Information, Paul Browne, and Deputy Commissioner of Intelligence, David Cohen (R) inside of the Executive Command Center at NYPD headquarters in New York August 5, 2011. The NYPD has worked since 9/11 on a long-term project to permanently increase vigilance in Lower Manhattan and Midtown, home to prominent financial institutions and national landmarks. Picture taken August 5, 2011.
New York Police Department Commissioner Ray Kelly (L) takes part in his morning intelligence briefing with the Deputy Commissioner of Public Information, Paul Browne, and Deputy Commissioner of Intelligence, David Cohen (R) inside of the Executive Command Center at NYPD headquarters in New York August 5, 2011. The NYPD has worked since 9/11 on a long-term project to permanently increase vigilance in Lower Manhattan and Midtown, home to prominent financial institutions and national landmarks. Picture taken August 5, 2011.![[Image]](https://i0.wp.com/cryptome.org/2012-info/spy-chiefs/pict106.jpg) New York Police Department Commissioner Ray Kelly (C) takes part in his morning intelligence briefing with the Deputy Commissioner for Counter-terrorism Richard Daddario (R) and Deputy Commissioner of Intelligence David Cohen (L) inside the Executive Command Center at the NYPD headquarters in New York August 5, 2011. The NYPD has worked since 9/11 on a long-term project to permanently increase vigilance in Lower Manhattan and Midtown, home to prominent financial institutions and national landmarks. Picture taken August 5, 2011.
New York Police Department Commissioner Ray Kelly (C) takes part in his morning intelligence briefing with the Deputy Commissioner for Counter-terrorism Richard Daddario (R) and Deputy Commissioner of Intelligence David Cohen (L) inside the Executive Command Center at the NYPD headquarters in New York August 5, 2011. The NYPD has worked since 9/11 on a long-term project to permanently increase vigilance in Lower Manhattan and Midtown, home to prominent financial institutions and national landmarks. Picture taken August 5, 2011.














![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-07/pict106.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-07/pict103.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-07/pict104.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/daiichi-12-07/pict105.jpg)




 Alle Pläne schon in der Tasche: Titelbild der Doktorarbeit
Alle Pläne schon in der Tasche: Titelbild der Doktorarbeit Ein Ferienhaus von Schalck-Golodkowski. Von mehr als 200 Tarnfirmen ließ sich gut leben.
Ein Ferienhaus von Schalck-Golodkowski. Von mehr als 200 Tarnfirmen ließ sich gut leben. Beschaffte das Geld für 5000 Tonnen Äpfel: Alexander Schalck-Golodkowski
Beschaffte das Geld für 5000 Tonnen Äpfel: Alexander Schalck-Golodkowski
 Der große Devisenbeschaffer endete vor dem Untersuchungsausschuss des Deutschen Bundestages
Der große Devisenbeschaffer endete vor dem Untersuchungsausschuss des Deutschen Bundestages


 Deep Throat, Berlin, berichtet: „Das Mastermind hinter allen „GoMoPa“-Aktionen ist der „Anlegerschutzanwalt“ Jochen Resch. Er hat auch Meridian Capital erpresst, schickt aber immer die Handlanger wie Klaus-Dieter Maurischat vor. Nur vorbestrafte Serienbetrüger wie Maurischat lassen sich zu solchen Straftaten instrumentalisieren. Resch hat auch den Terminus „Cyberstalker“ aus den USA importiert. Maurischat kann das aufgrund mangelnder Bildung sogar nicht einmal korrekt schreiben.“
Deep Throat, Berlin, berichtet: „Das Mastermind hinter allen „GoMoPa“-Aktionen ist der „Anlegerschutzanwalt“ Jochen Resch. Er hat auch Meridian Capital erpresst, schickt aber immer die Handlanger wie Klaus-Dieter Maurischat vor. Nur vorbestrafte Serienbetrüger wie Maurischat lassen sich zu solchen Straftaten instrumentalisieren. Resch hat auch den Terminus „Cyberstalker“ aus den USA importiert. Maurischat kann das aufgrund mangelnder Bildung sogar nicht einmal korrekt schreiben.“
You must be logged in to post a comment.